Wooden horse monitoring and auditing method and system thereof
A Trojan horse and behavior technology, applied in the field of Trojan horse monitoring and auditing methods and systems, can solve the problems of network communication content processing and analysis, frequent update of feature library, response lag, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
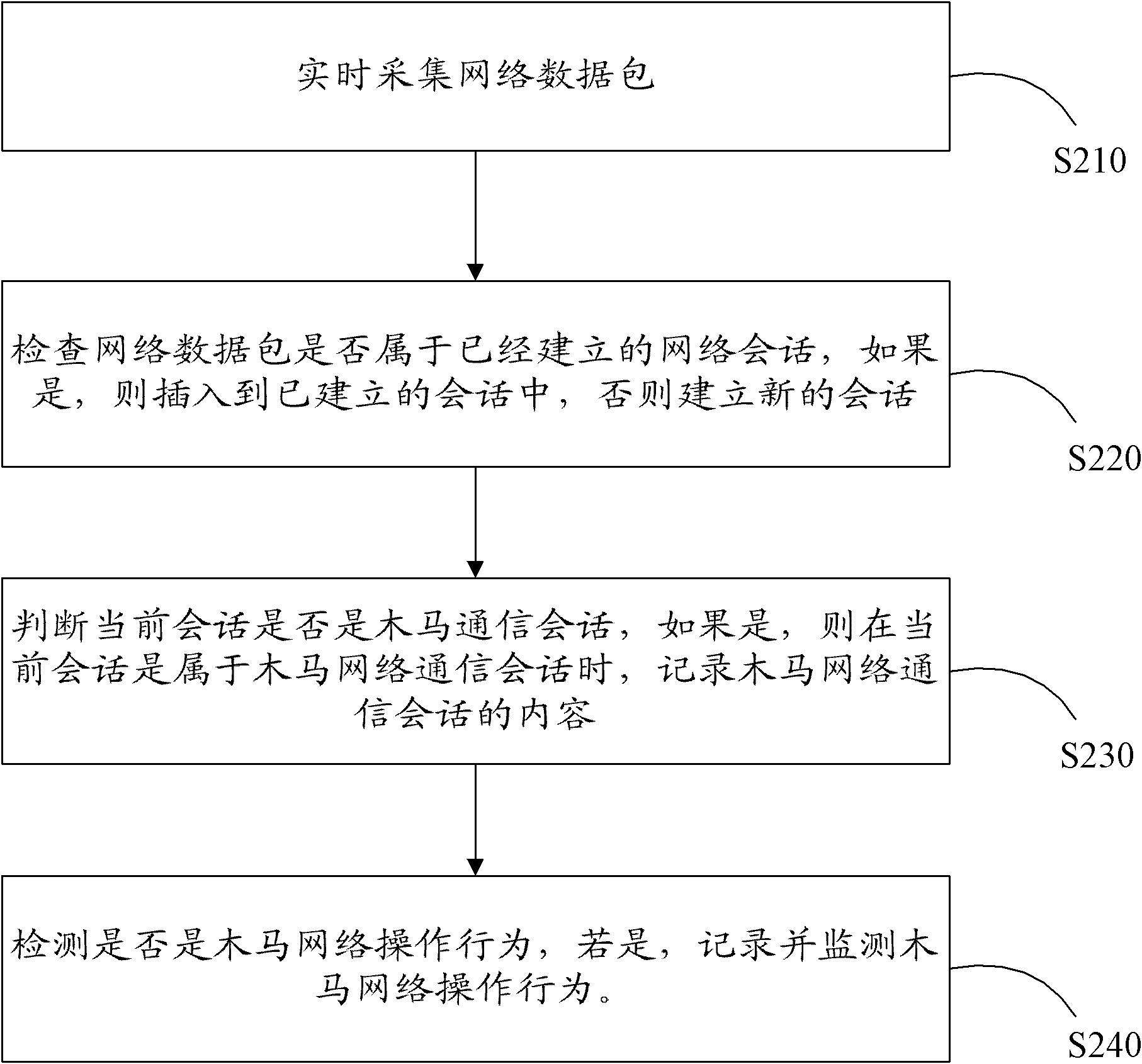
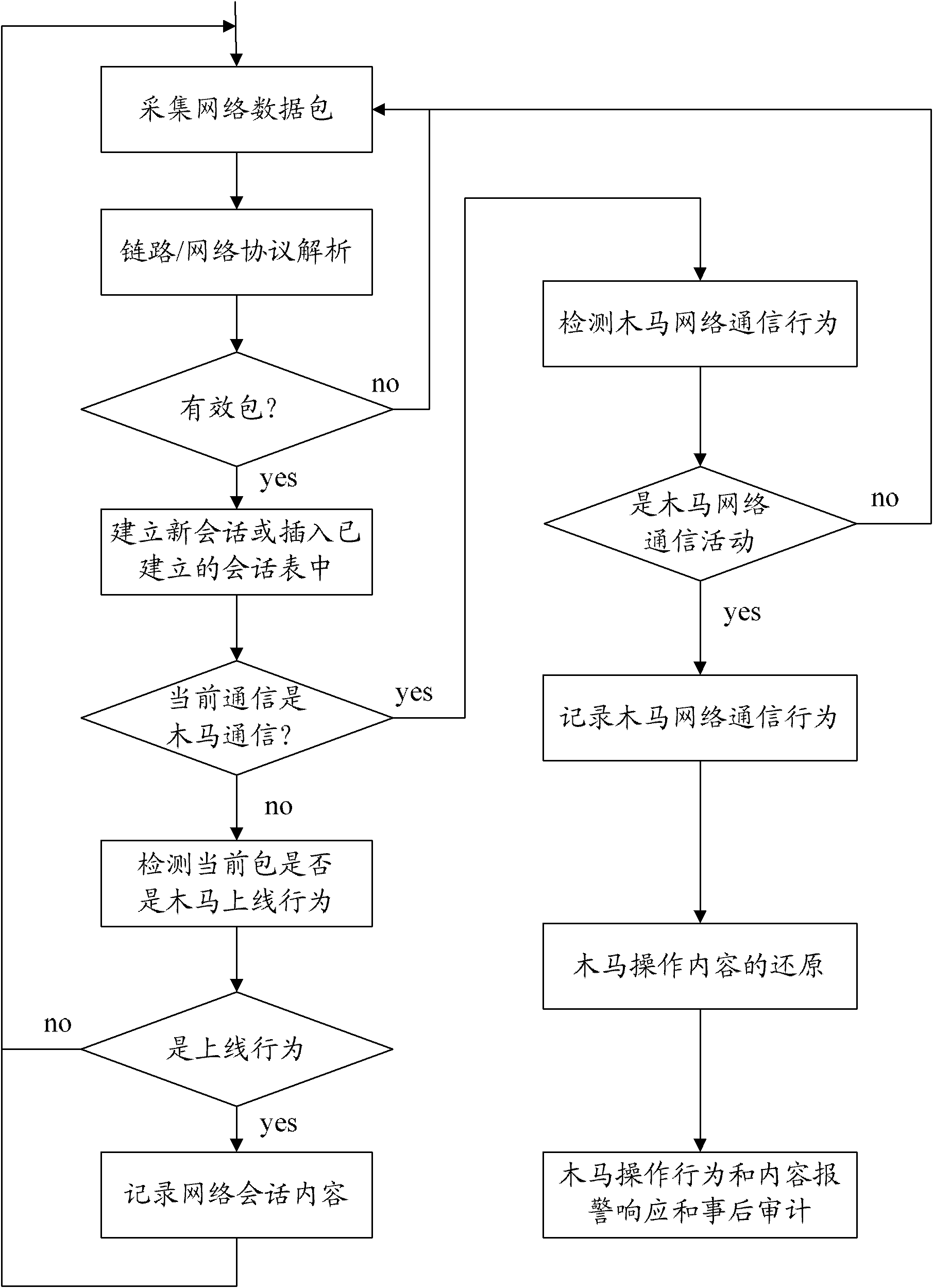
[0049] First introduce the concept and working principle of the Trojan horse:
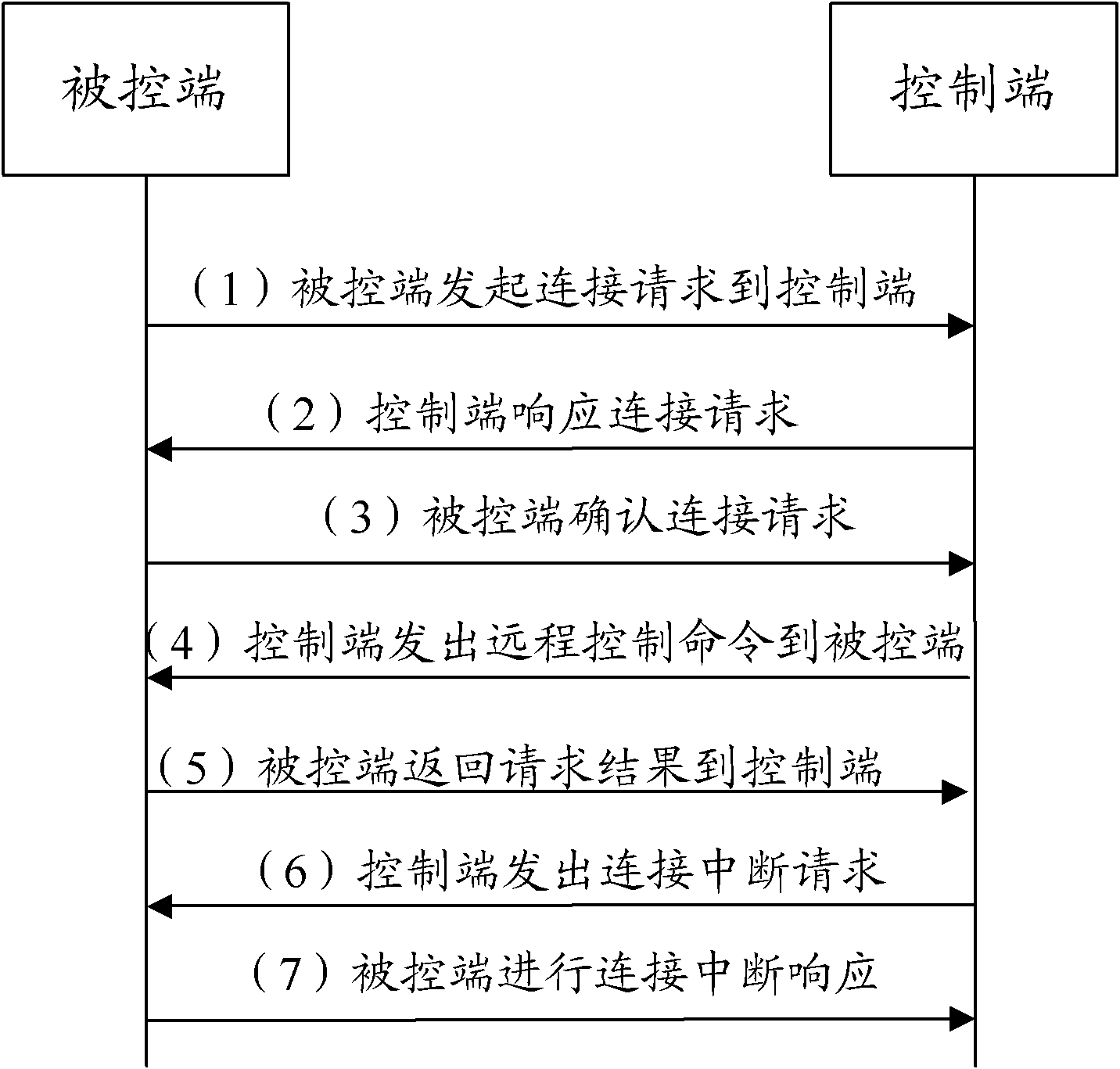
[0050] A Trojan horse is a program that establishes a connection between remote computers so that the remote computer can control the local computer through the network. Its operation complies with the TCP / IP protocol. The back door is very similar to the "Trojan horse" tactic in war, hence the name Trojan horse program.
[0051] The Trojan horse program is composed of two parts, one part is an agent program installed and embedded in the system of the controlled host, and the other part is a control terminal program. After the Trojan agent runs, it needs to establish a network connection (forward connection or reverse connection) with the control term...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com