Method and system for protecting permission of volatile memory bank
A volatile storage and permission technology, applied in internal/peripheral computer component protection, instruments, electrical digital data processing, etc., can solve data security threats and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
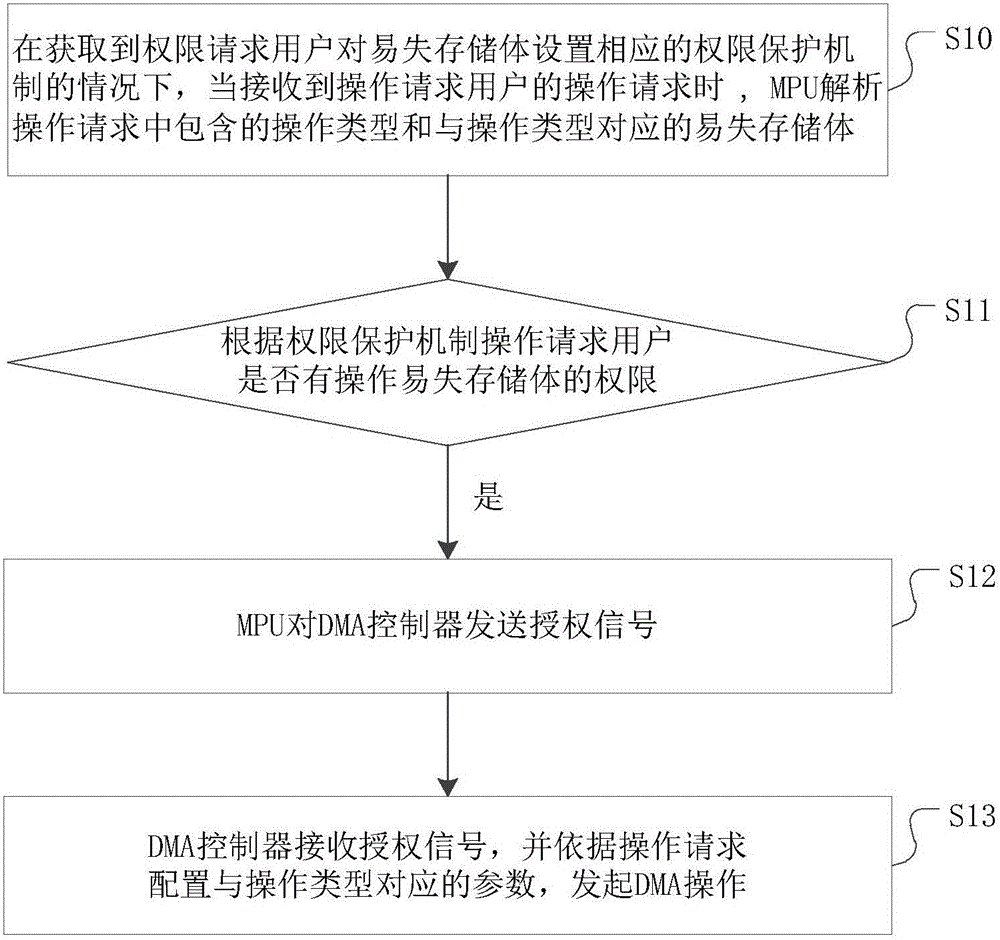
[0031] figure 1 It is a flowchart of a method for protecting volatile storage rights provided by the present invention. Such as figure 1 As shown, the methods for protecting volatile memory permissions include:
[0032] Step S10: In the case of obtaining the permission requesting user to set the corresponding permission protection mechanism for the volatile memory, when receiving the operation request of the operation requesting user, the MPU parses the operation type contained in the operation request and the corresponding operation type Volatile storage.
[0033] Among them, the operation type included in the operation request is a DMA operation, which specifically includes: DMA read operation and DMA write operation, DMA read operation or DMA write operation.
[0034] Step S11: The MPU judges whether the operation requesting user has the authority to operate the volatile memory bank according to the authority protection mechanism.
[0035] If the user is requested to have the auth...
Embodiment 2
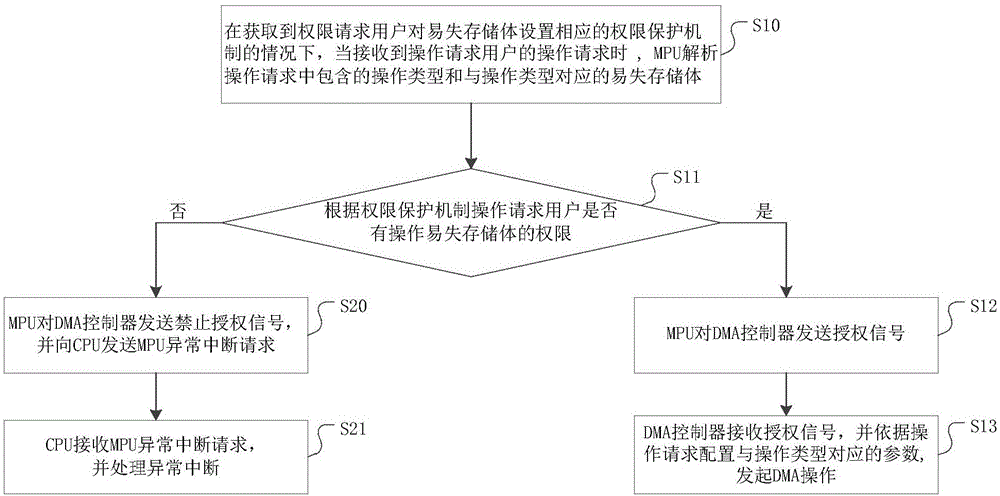
[0040] On the basis of the above embodiment 1, figure 2 It is a flow chart of another method for protecting volatile storage rights provided by the present invention. Such as figure 2 As shown, the method for protecting the rights of the volatile memory also includes:
[0041] If the user does not have the authority to operate the volatile memory bank according to the operation request of the authority protection mechanism, step S20 is entered.
[0042] Step S20: The MPU sends an authorization prohibition signal to the DMA controller, and sends an MPU abnormal interrupt request to the CPU.
[0043] Step S21: The CPU receives the MPU abnormal interrupt request, and processes the abnormal interrupt.
[0044] This embodiment provides another method and system for protecting the authority of volatile memory banks. When the authority requesting user sets a corresponding authority protection mechanism for the volatile memory bank, when the operation request of the operation requesting use...
Embodiment 3
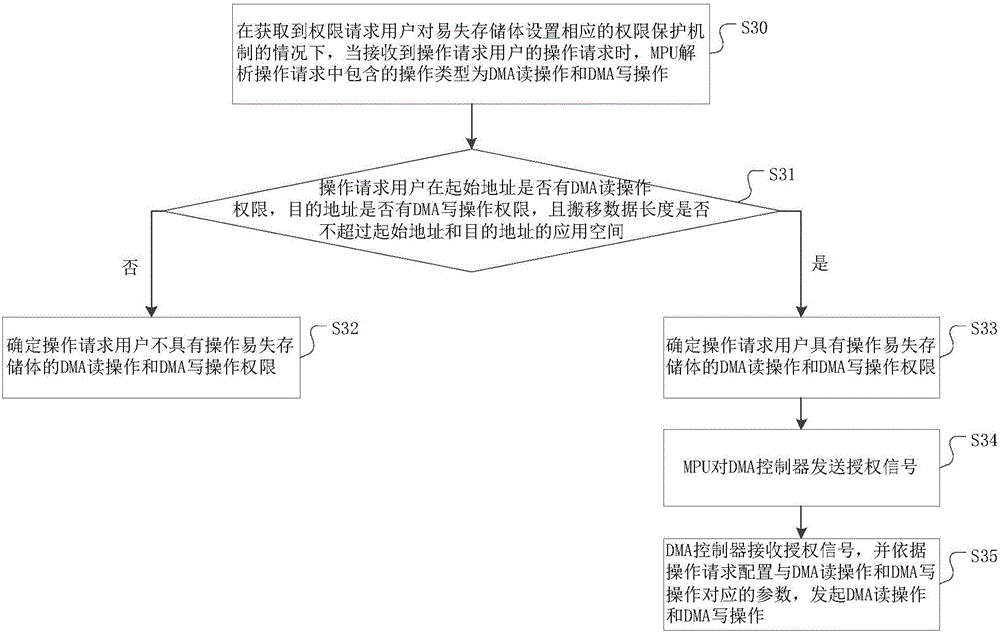
[0047] On the basis of the first embodiment, the operation types specifically include: DMA read operation and DMA write operation, DMA read operation or DMA write operation.
[0048] When the operation type is DMA read operation and DMA write operation, the operation request includes the start address, destination address and the length of the moved data. The flow chart of the method for protecting volatile memory permissions is as follows image 3 Shown
[0049] When the operation type is DMA read operation, the operation request includes the start address and the length of the moved data. The flow chart of the method for protecting the volatile memory bank permissions is as follows Figure 4 Shown
[0050] When the operation type is DMA write operation, the operation request includes the destination address and the length of the moved data. The flow chart of the method for protecting volatile memory permissions is as follows Figure 5 Shown.
[0051] image 3 When the operation type ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com