Security data storage method, computer device and computer readable storage medium
A technology for secure data and computer programs, applied in the field of computer-readable storage media, storage methods, and computer devices for implementing such methods, capable of solving problems such as unsuitability for deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
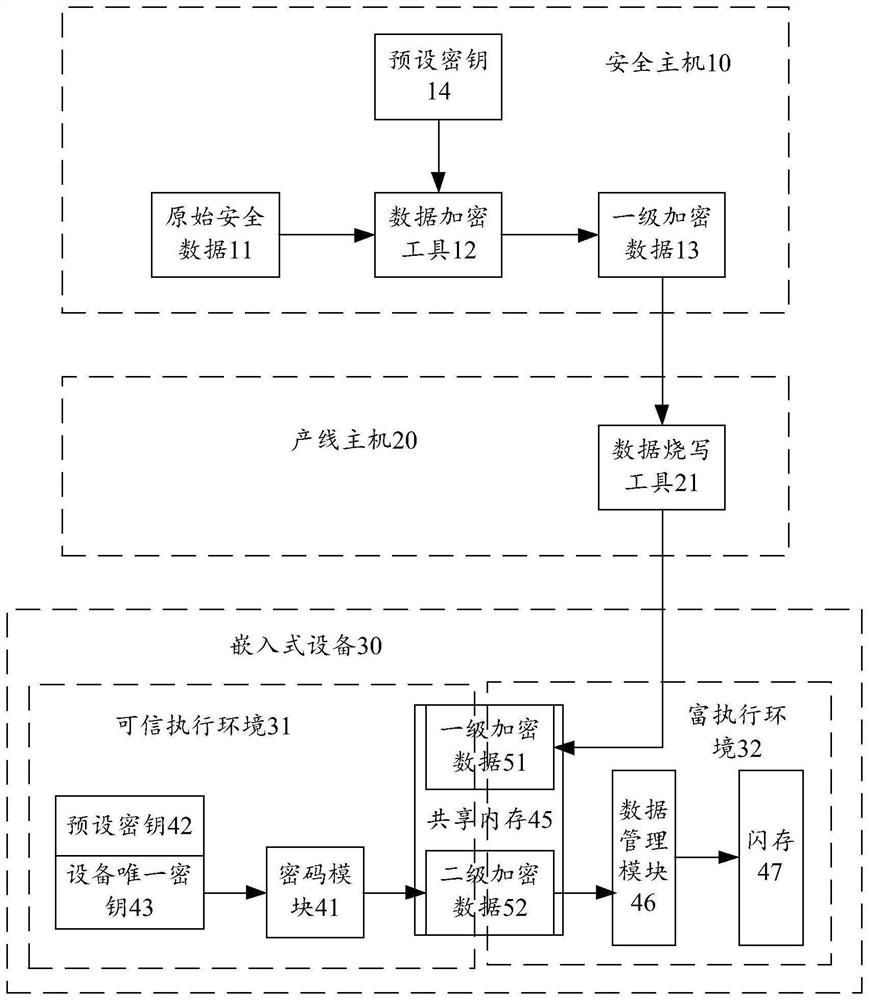
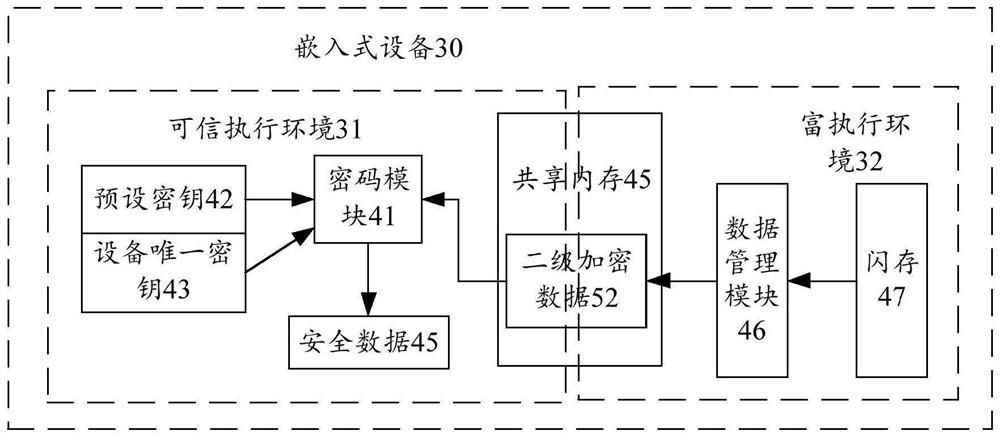
[0034] The method for storing security data of the present invention is applied to an embedded device, and preferably, the embedded device can store security data. Preferably, the embedded device is provided with a processor and a memory, the memory stores a computer program, and the processor implements the above-mentioned storage method of the security data by executing the computer program.
[0035] Embodiments of the storage method of security data:
[0036] This embodiment involves multiple links of writing, reading, and programming of secure data, and ensures secure data storage by encrypting, decrypting, writing, and reading the secure data in the trusted execution environment TEE of the embedded device. security, and low-cost realization of secure data read and write.
[0037] Combine below figure 1 Describes the process of writing secure data. The original security data 11 is important asset data, such as DRM (Digital Rights) certificate, HDCP key (for output prote...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com