Patents
Literature
195results about How to "Avoid illegal operation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
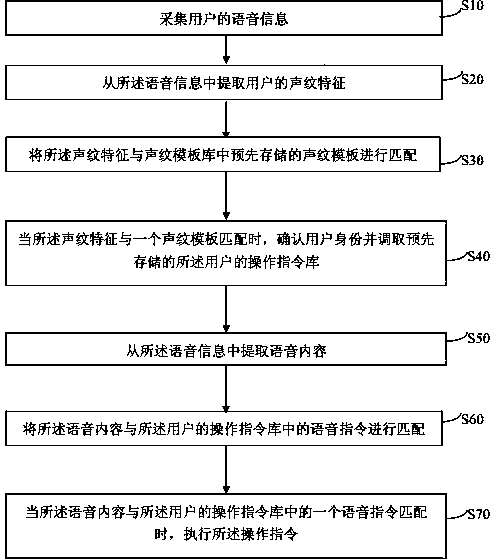
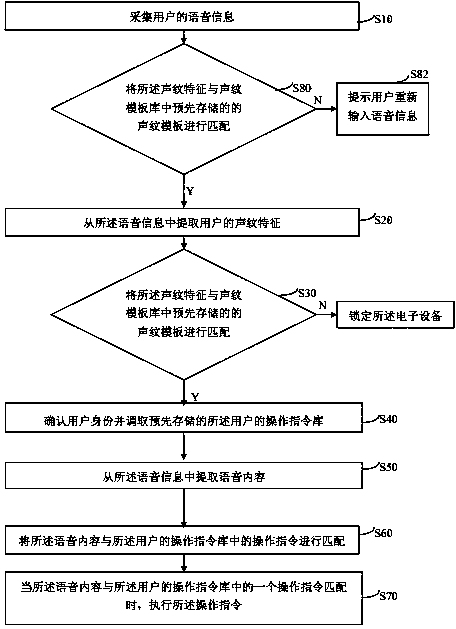
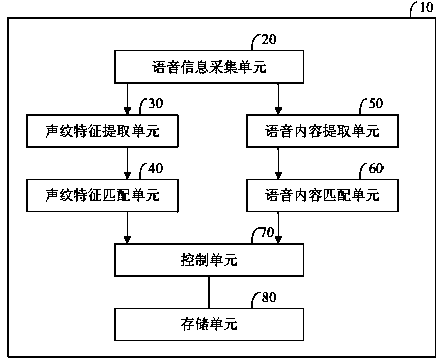
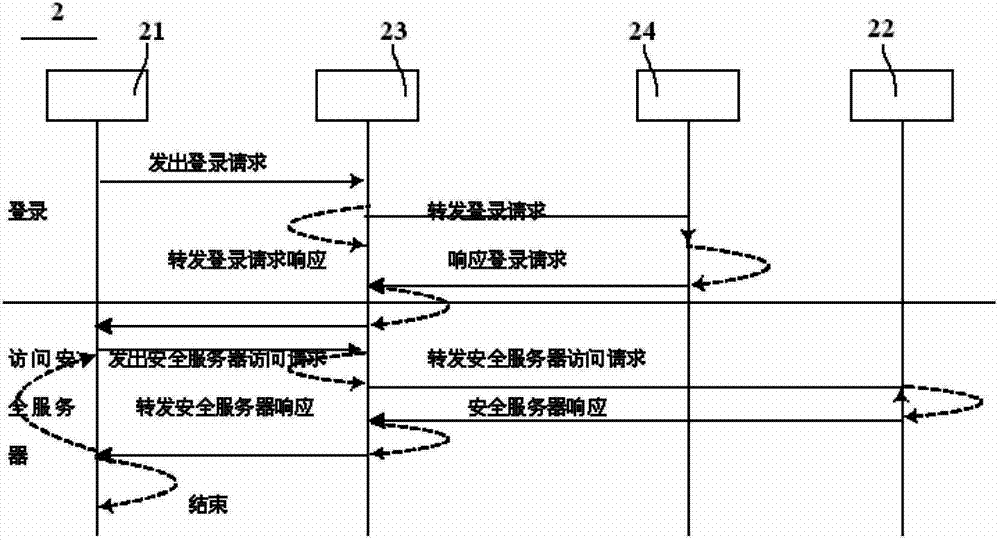
Voice control method and system for electronic device
InactiveCN103730120AImprove securityImprove privacySpeech recognitionTemplate matchingTemplate based
The invention discloses a voice control method and system for an electronic device. The voice control method comprises the following steps: voice information of a user is acquired; a voice print feature of the user is extracted from the voice information; the voice print feature of the user is matched with voice print templates prestored in a voice print template base; when the voice print feature of the user is matched with one voice print template, the identity of the user is determined, and a prestored operation instruction base of the user is called; voice content is extracted from the voice information; the voice content is matched with operation instructions in the operation instruction base of the user; when the voice content is matched with one operation instruction in the operation instruction base of the user, the operation instruction is executed. According to the voice control method and system for the electronic device, the identity of a legal user of the electronic device is verified by matching the voice print feature of the user, so that illegal operation by illegal users is effectively prevented, and the safety and the privacy of the electronic device are improved; the operation instructions are executed by matching the voice content of the user, so that voice control is realized.
Owner:SHENZHEN ARATEK BIOMETRICS TECH CO LTD
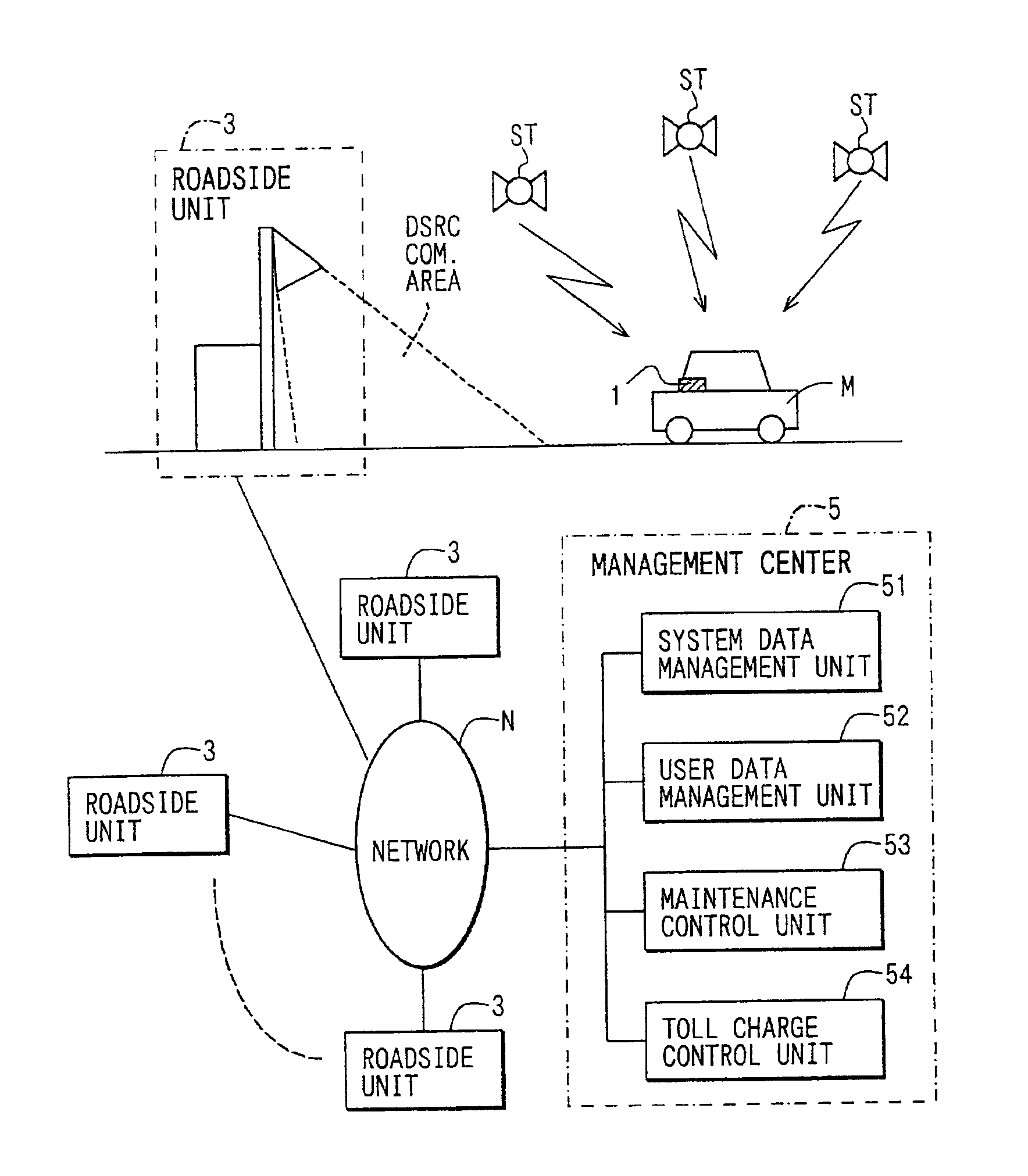
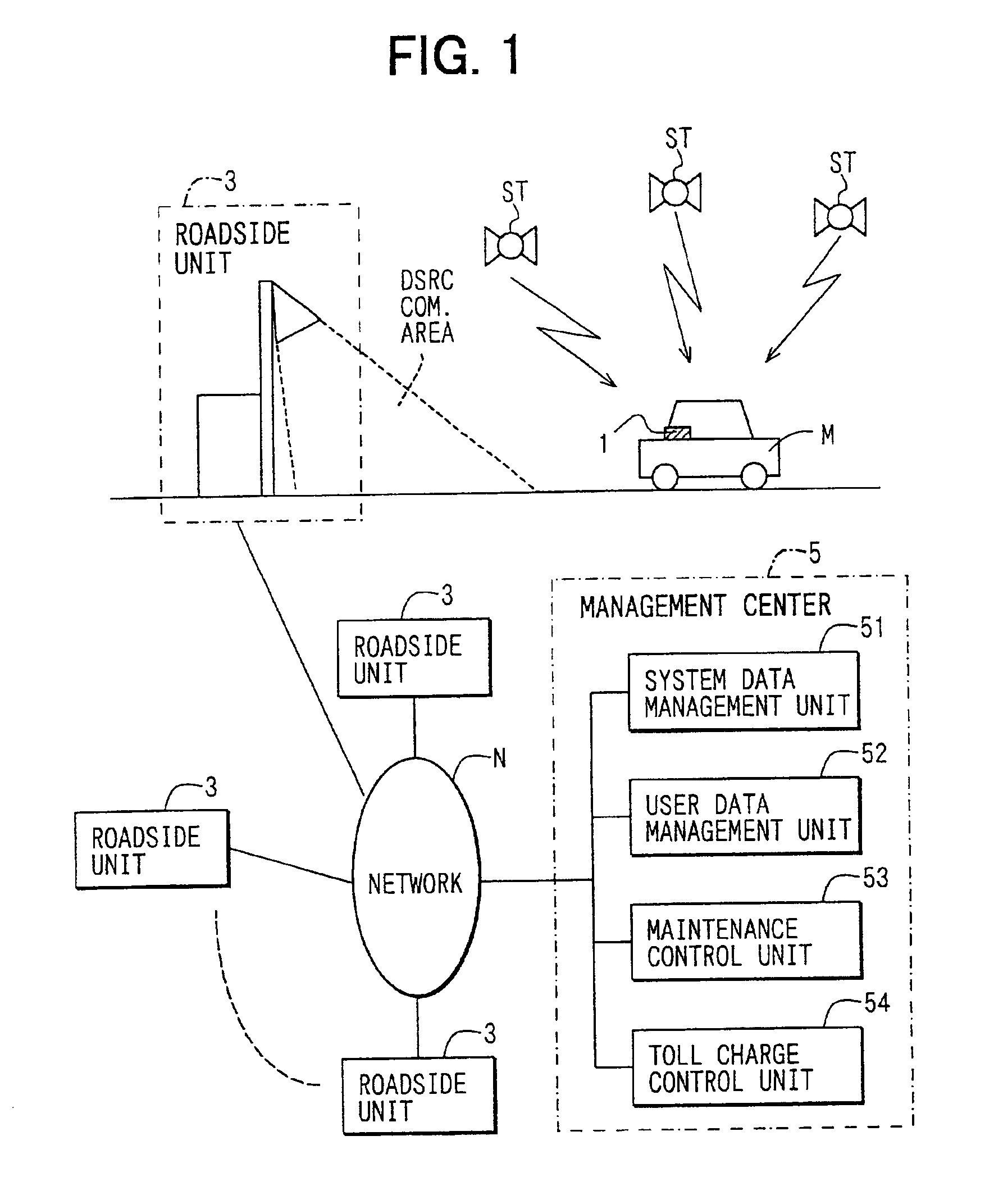
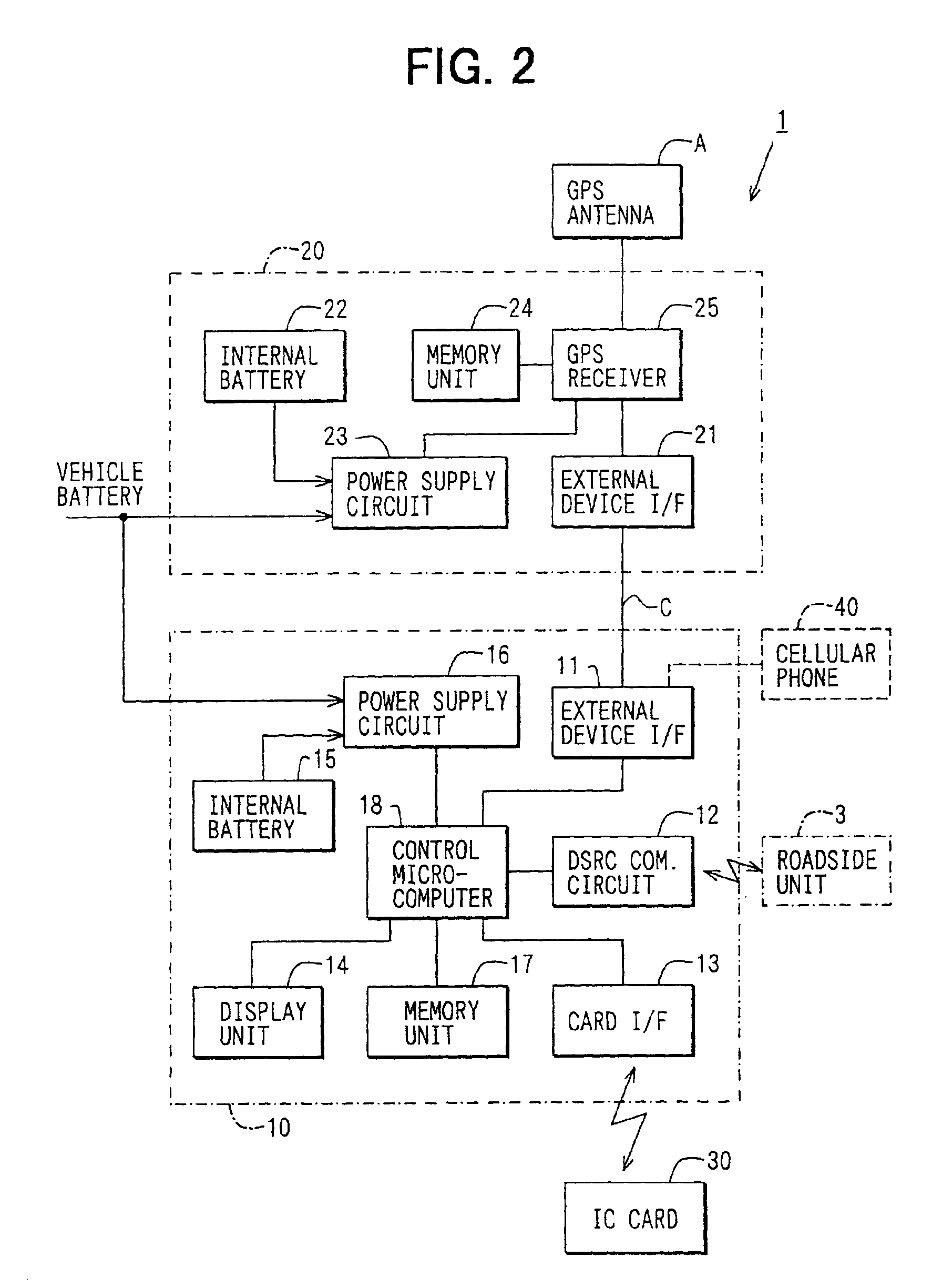
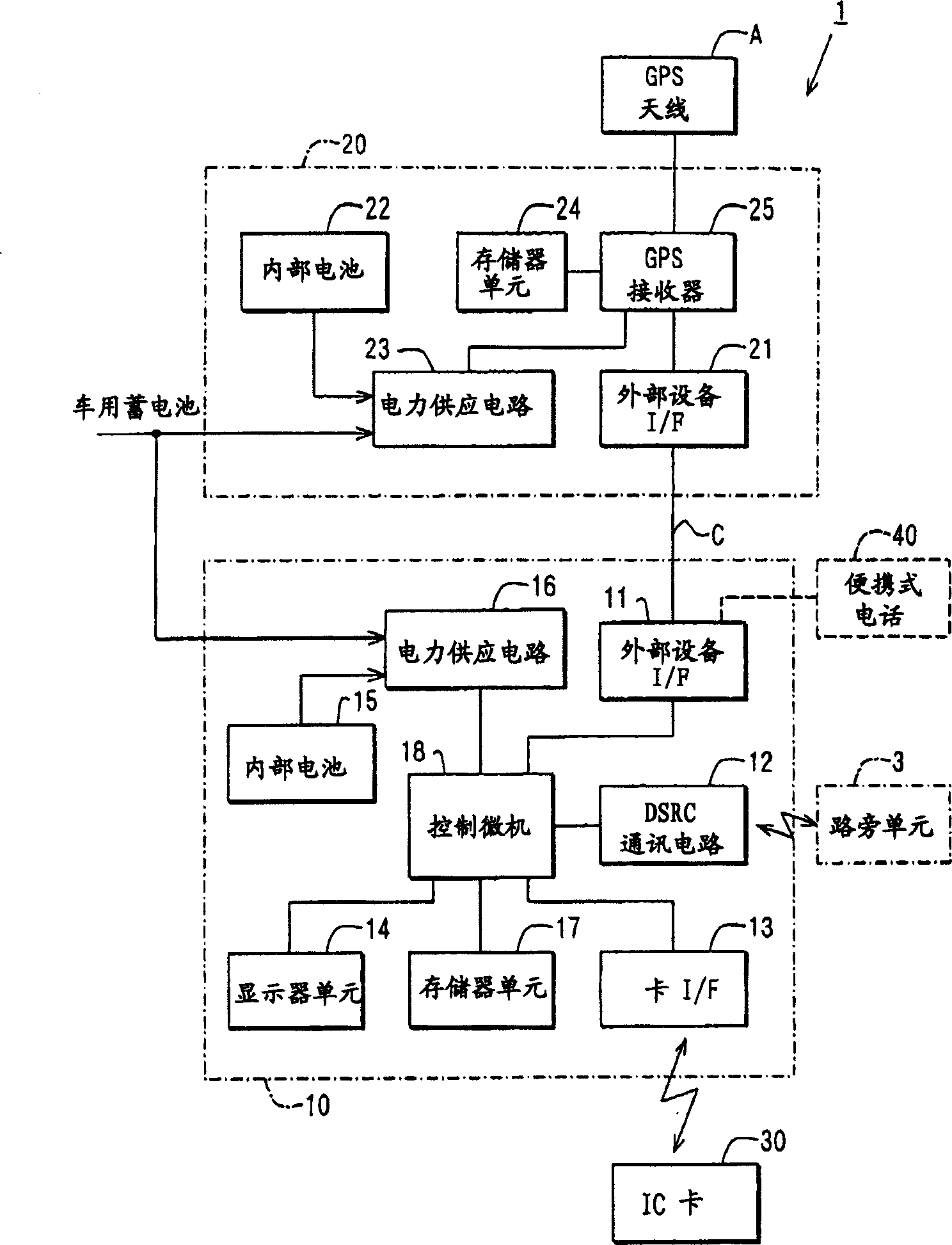
In-vehicle apparatus and service providing system
InactiveUS6937162B2Avoid illegal operationVehicle testingTicket-issuing apparatusLocation detectionService provision
If acquisition of measured position and time data (position / time) from a position detection unit fails, a “GPS OFF mode” is set, and the latest position and time data is stored as start data. Thereafter, when the position and time data is obtained successfully, and the operation is recovered from the “GPS OFF mode”, the “GPS OFF mode” is cancelled. Also, the obtained position and time data (restoration data) is stored. Monitor data is formed from the start data and the restoration data. The monitor data is transmitted to a management center through road-vehicle communication. Also, history data of the position and time stored in the position detection unit during the “GPS OFF mode” is read. If the history data satisfies the toll charging condition, the toll charging data is formed and is transmitted to the management center.
Owner:DENSO CORP
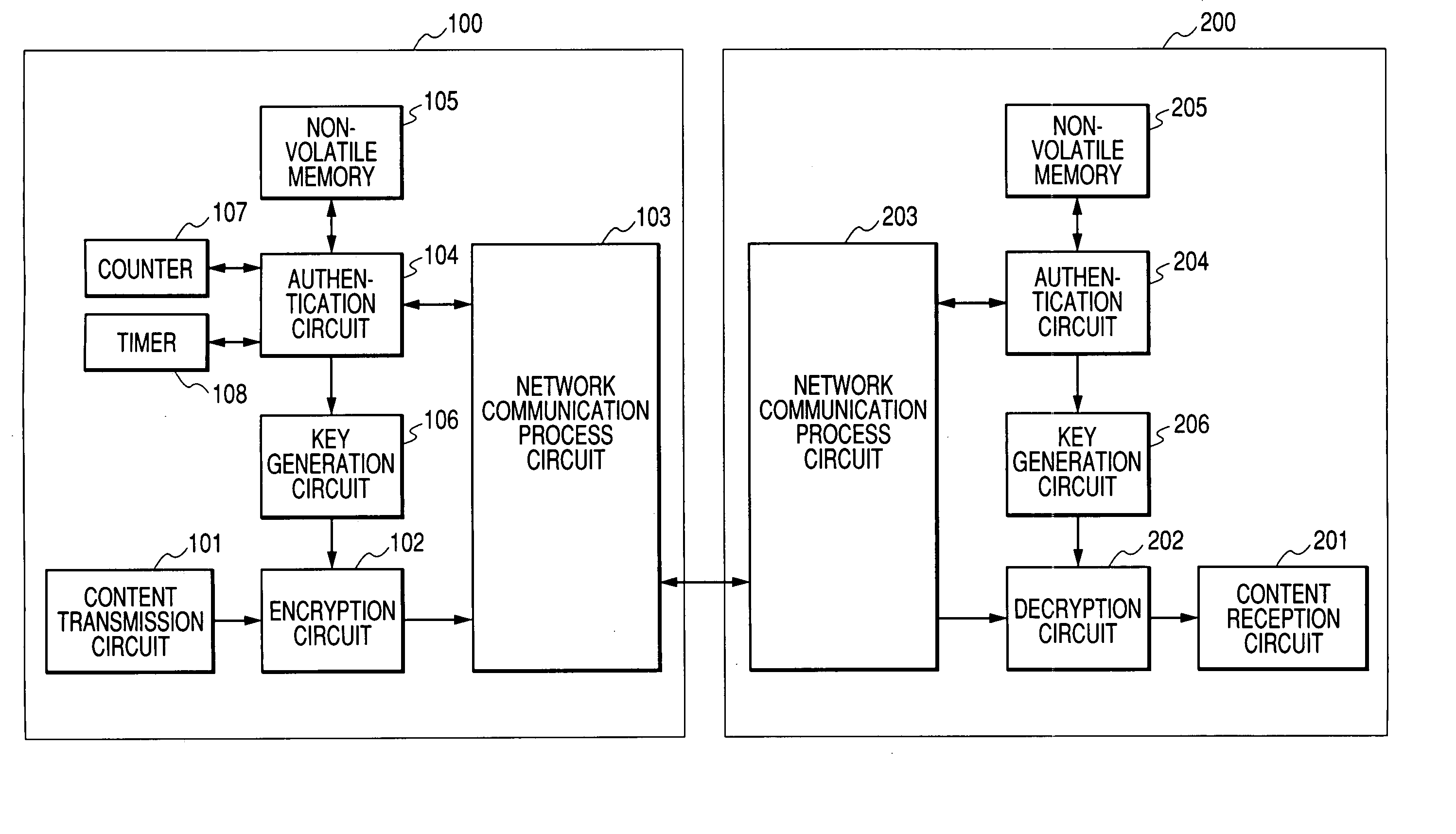
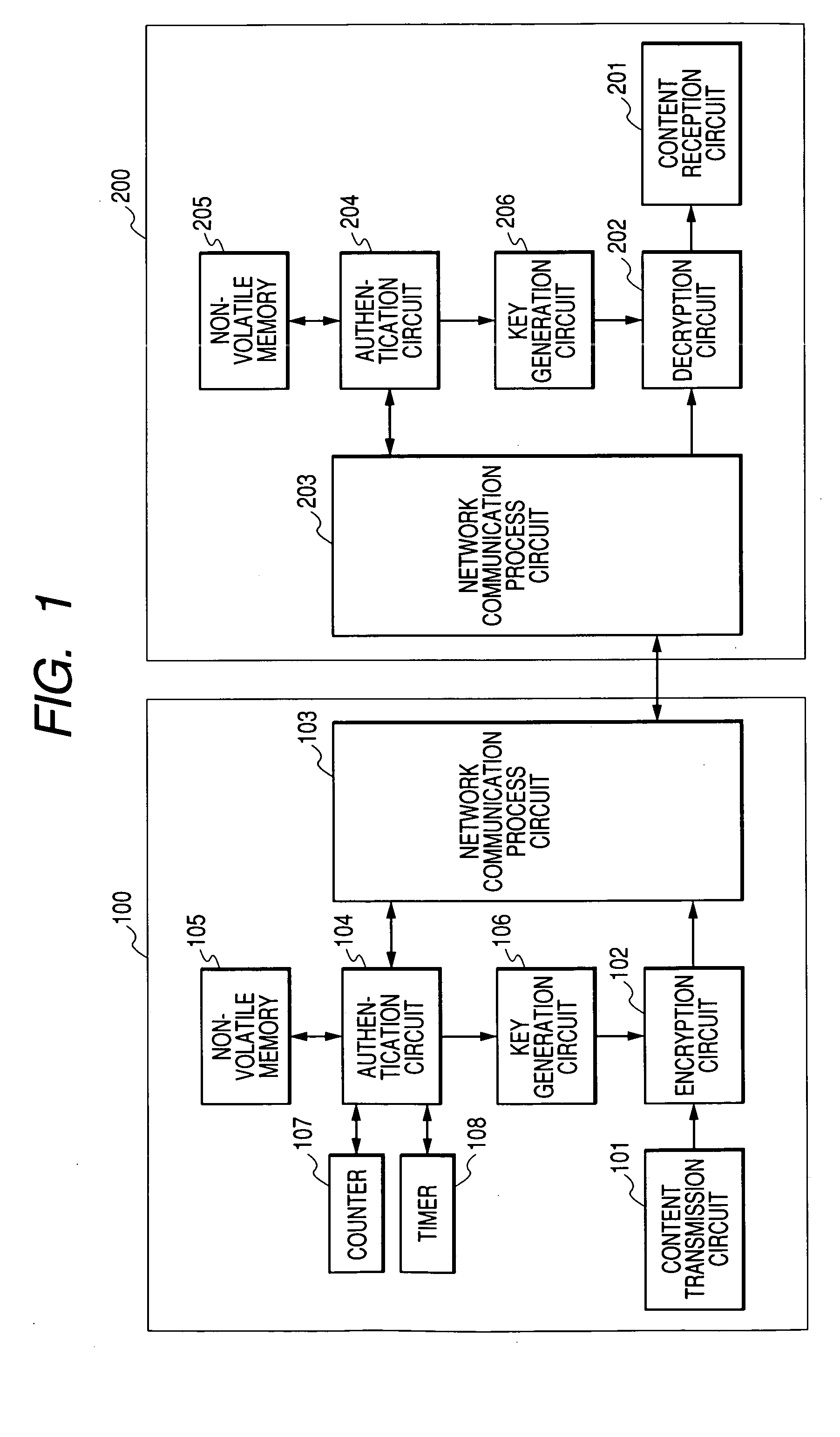
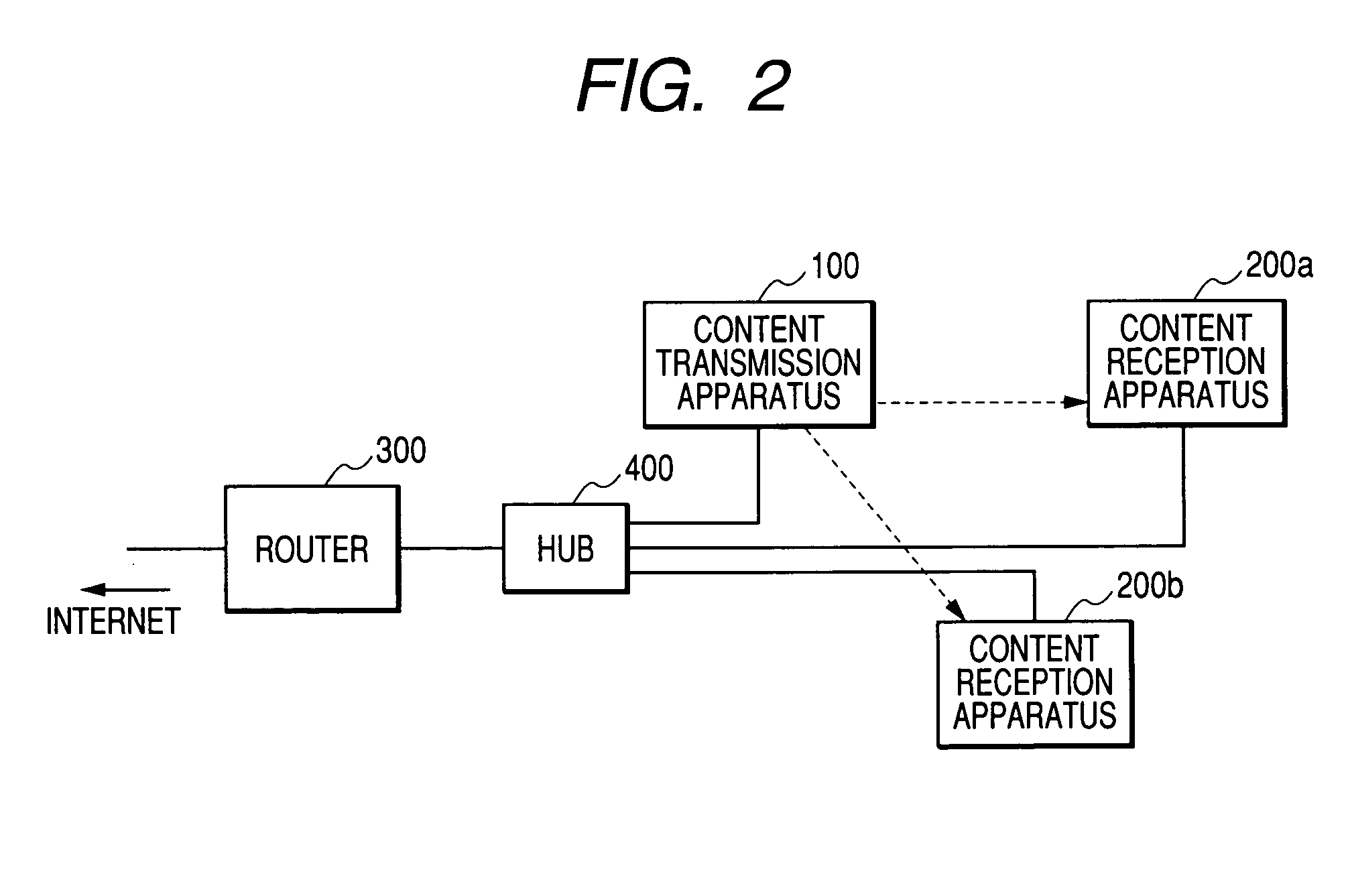
Content transmission apparatus, content reception apparatus and content transmission method
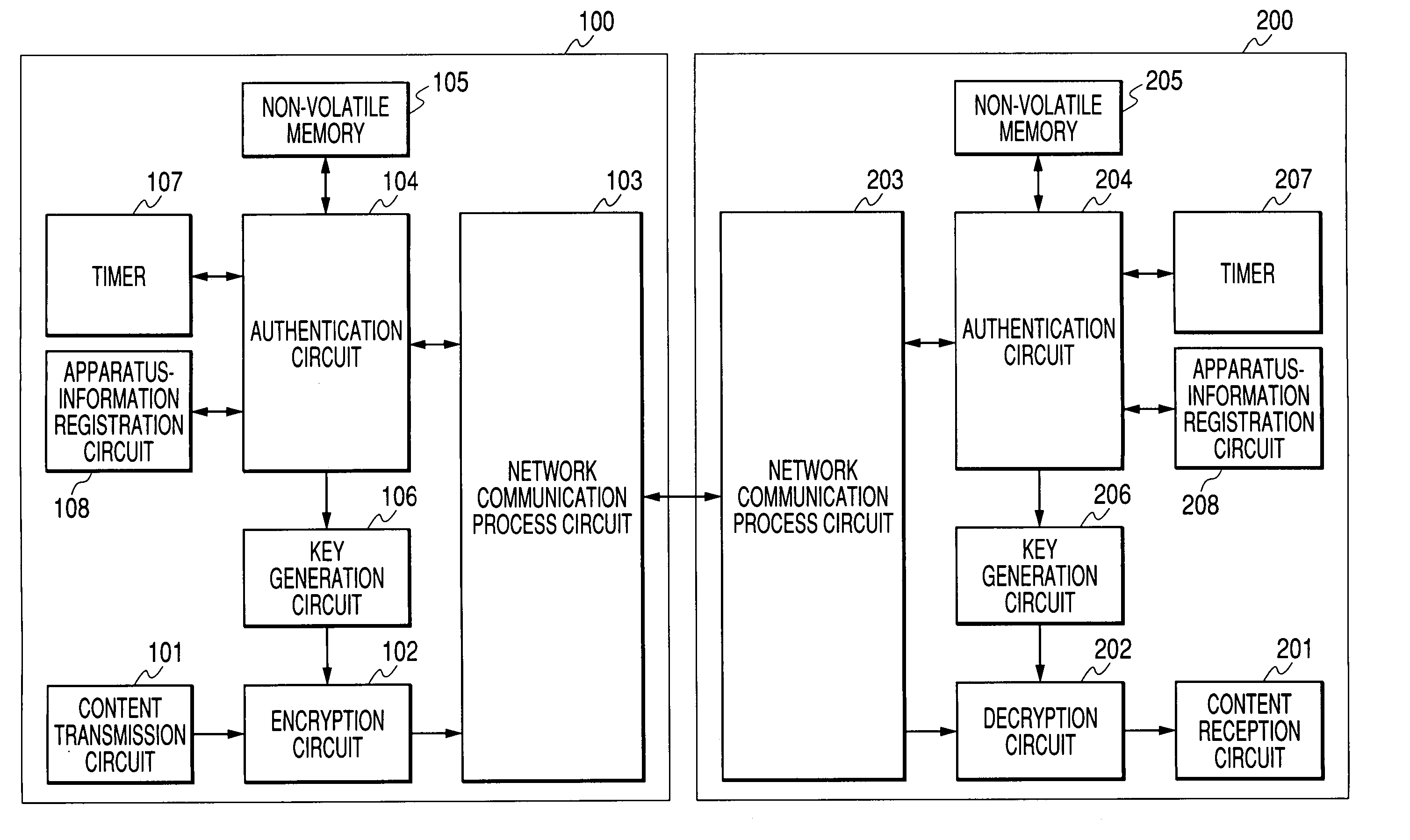
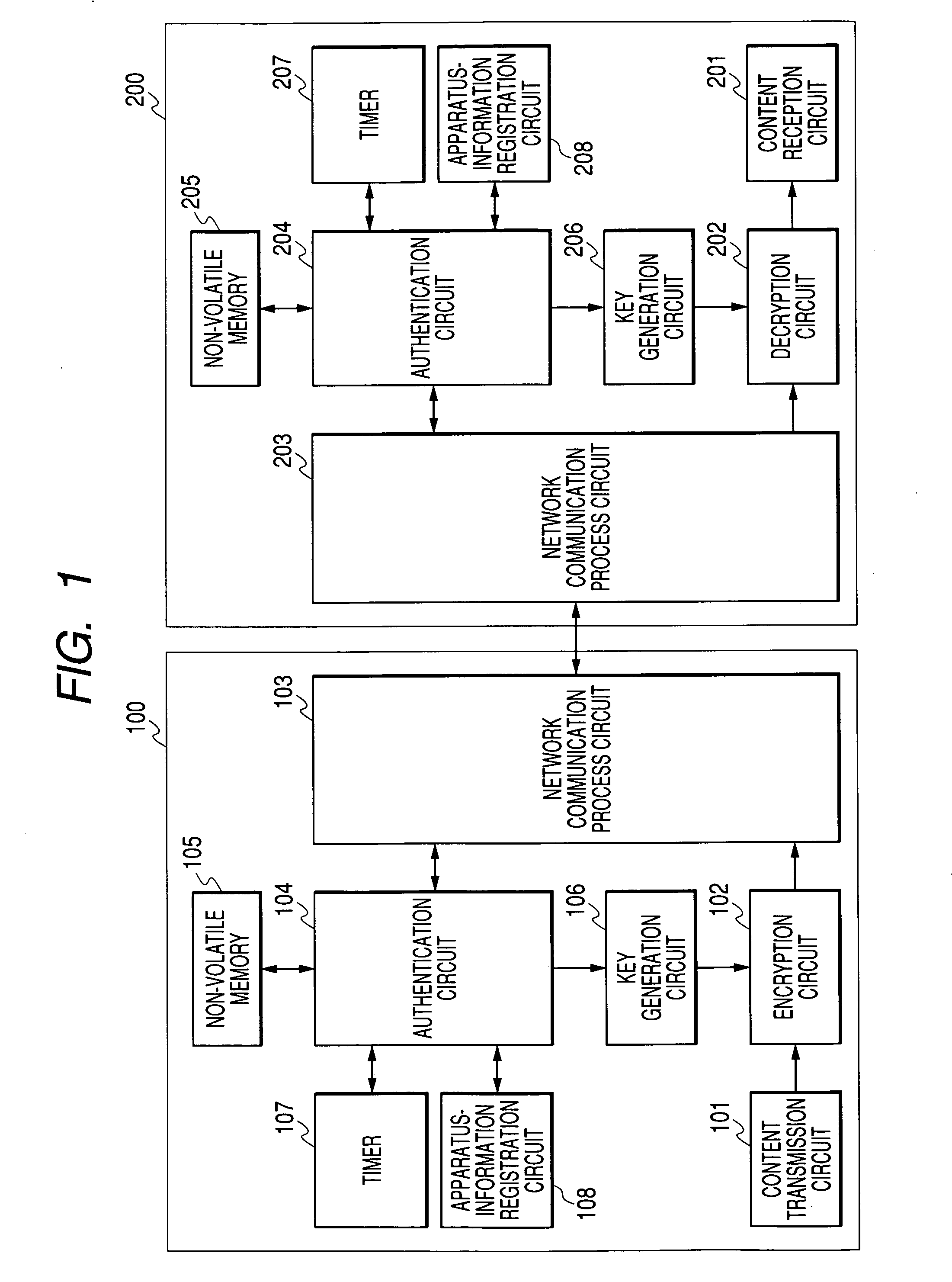
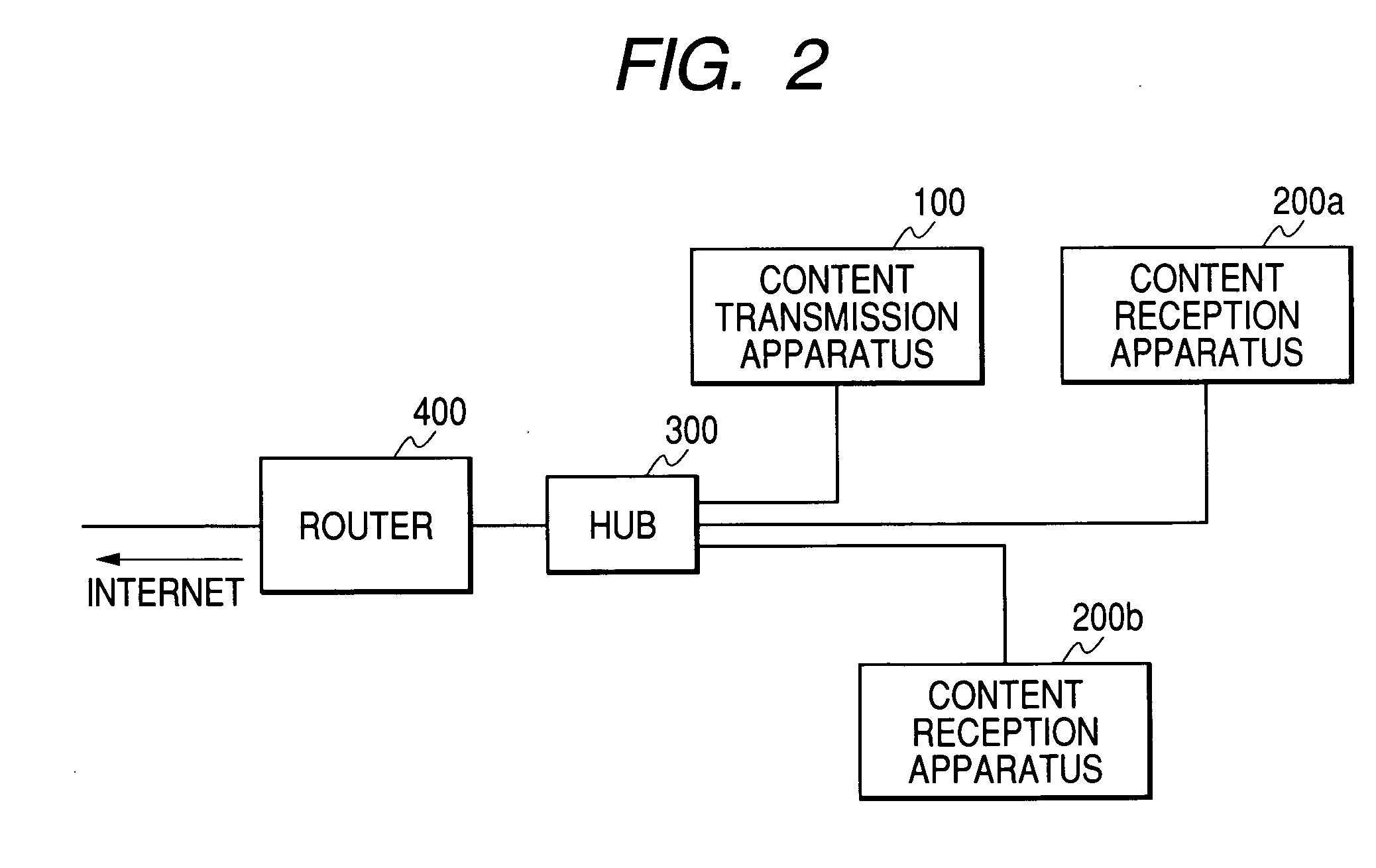
ActiveUS20050160265A1Limit legal operationIncrease heightKey distribution for secure communicationUser identity/authority verificationAuthentication information
A copyright of a content is protected by preventing creation of illegal copies of the content and the content is prevented from being transmitted beyond a range of personal use in a process to transmit the content through a LAN. Before transmission of a content, a content transmission apparatus and a content reception apparatus perform a determination of authentication information available in a predetermined command accompanying authentication information, or an authentication determination based on a time until reception of a response to a predetermined command request accompanying predetermined authentication information. If the authentication is unsuccessful, the requested content is not transmitted to the content reception apparatus. With such arrangement, it is possible to effectively protect a copyright when a content is transmitted by way of a network.
Owner:MAXELL HLDG LTD
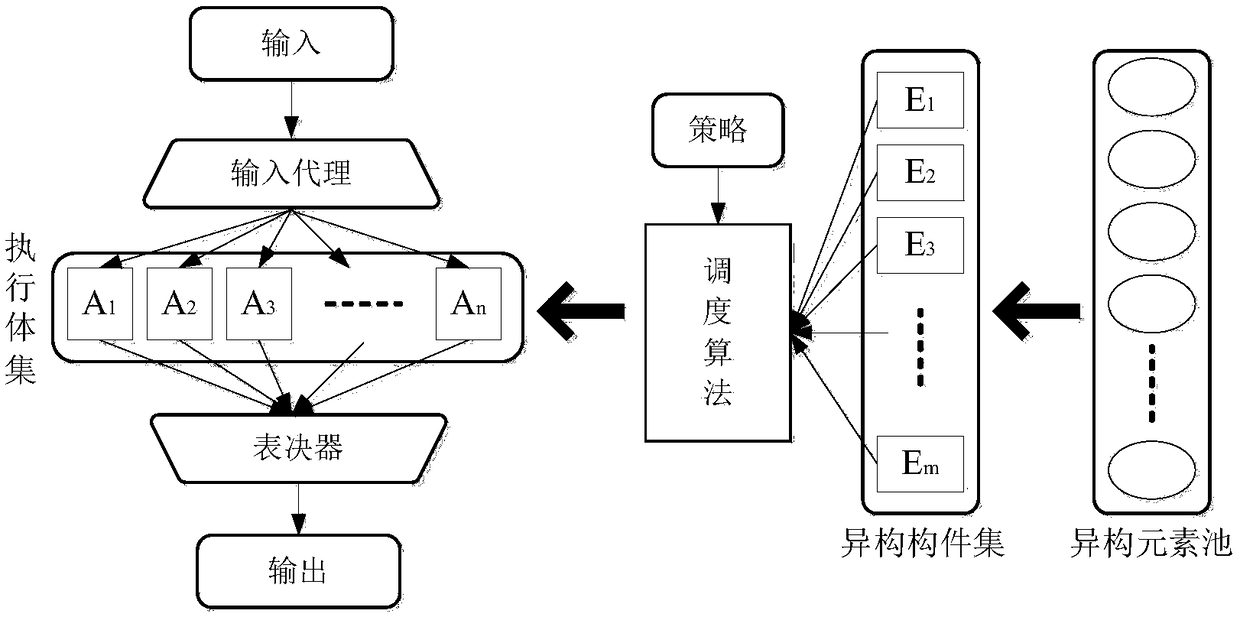
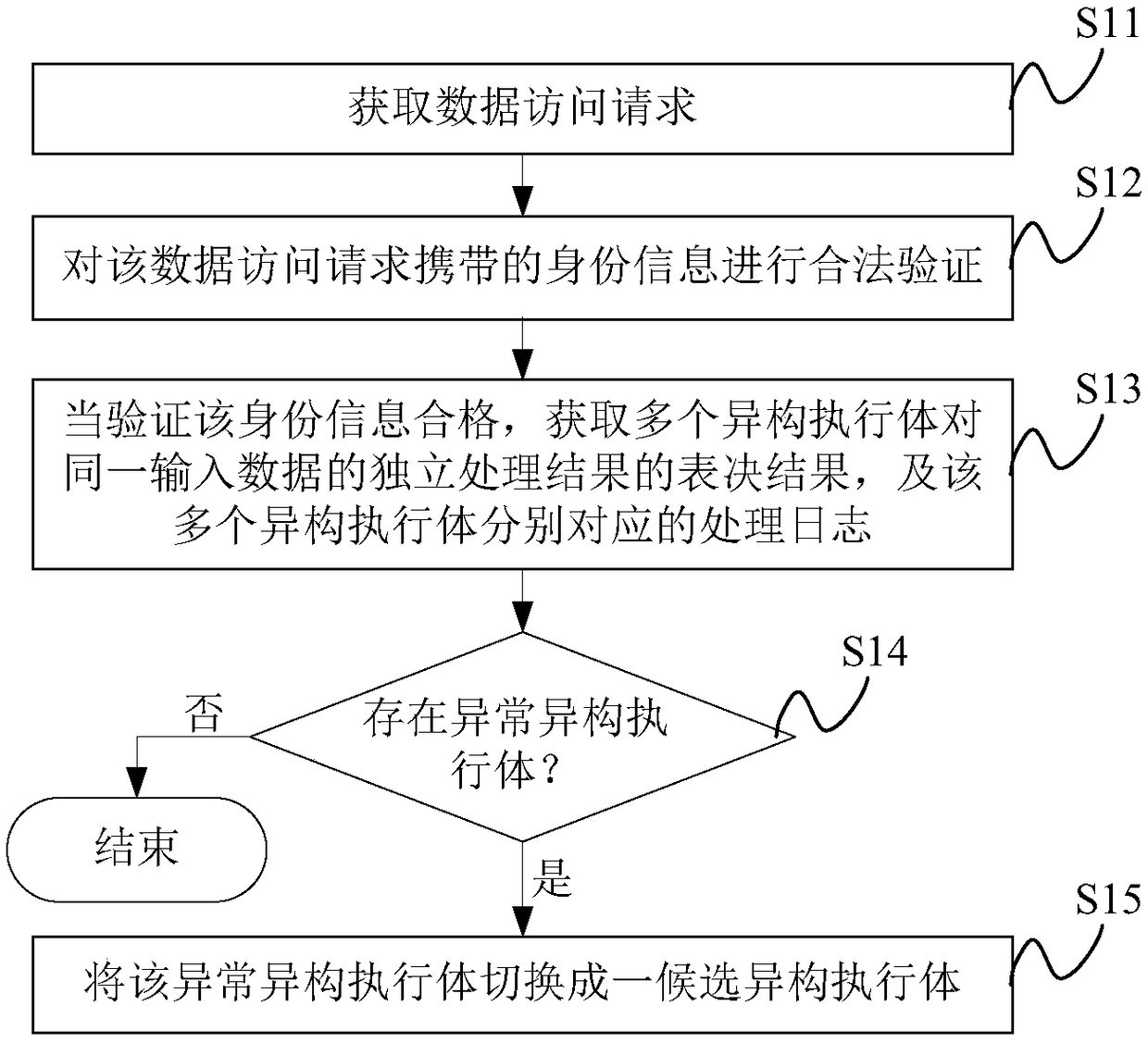
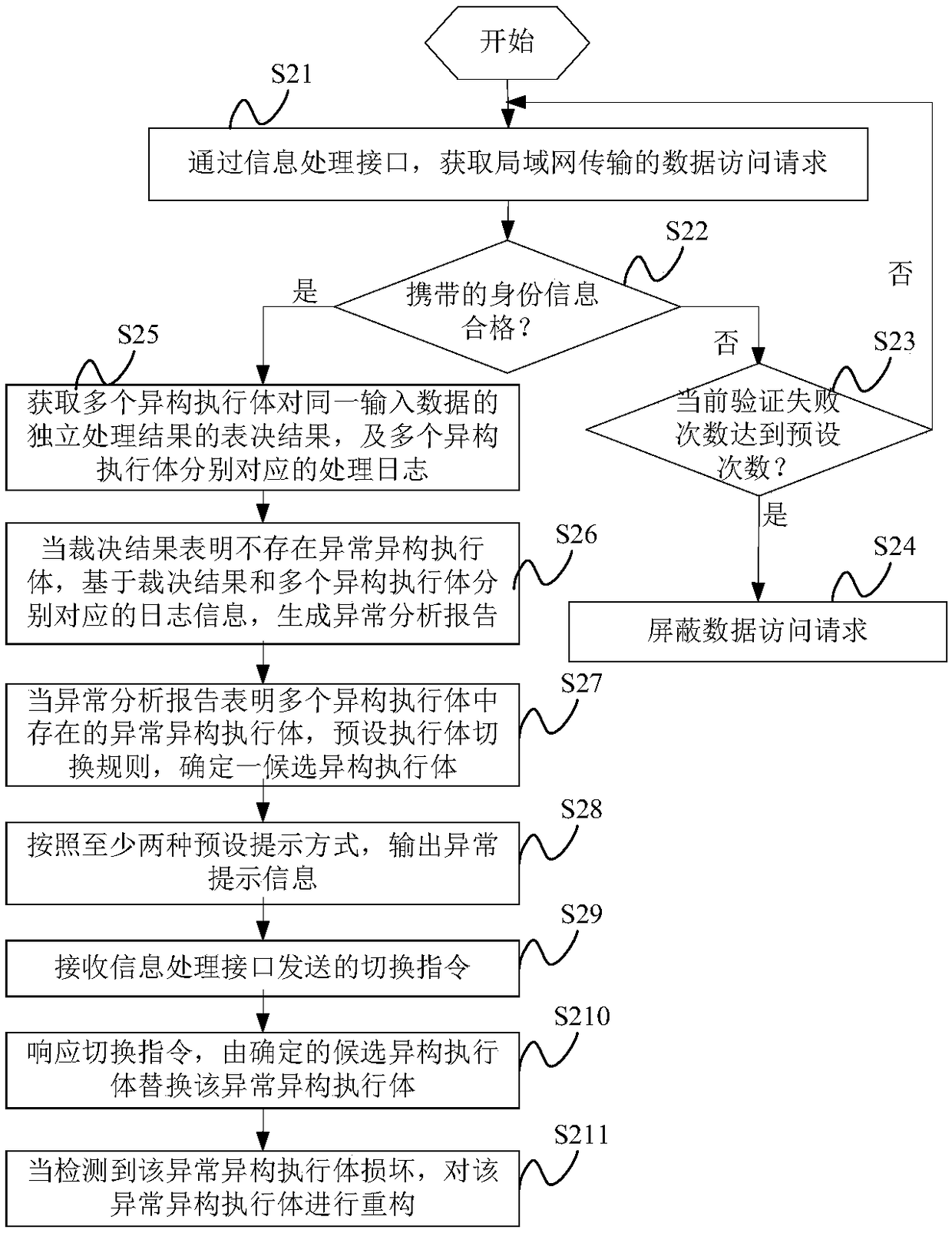
Information processing method and device
ActiveCN108769073AAvoid illegal operationSafe and stable operationData switching networksInformation processingData access
The invention provides an information processing method and device. After a data access request is obtained, whether identity information carried in the data access request is qualified is verified atfirst, after it is confirmed that the identity information is qualified, voting results of multiple heterogeneous executive bodies on an independent processing result of the same input data, and corresponding processing logs of the multiple heterogeneous executive bodies can be obtained, thereby avoiding illegal operations of illegal users, and furthermore, in the embodiment, whether the multipleheterogeneous executive bodies contain an abnormal heterogeneous executive body is analyzed by combining the voting results and the multiple processing logs, and the abnormal heterogeneous executivebody is replaced in time, thereby solving the technical problem in the traditional scheme that, the abnormal heterogeneous executive body is only determined according the voting results, such that coordinated attack vulnerability caused by a system configuration error cannot be solved, and ensuring the safe and stable operation of a computer device.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +2
Content transmission apparatus and content reception apparatus
InactiveUS20050160274A1Avoid creatingData quality of the content hardly deterioratesKey distribution for secure communicationMultiple keys/algorithms usageWireless lanTimer
It is an object of the present invention to protect a copyright of a content by suppressing creation of illegal copies of the content and prevent a content from being transmitted beyond a range of personal use in a process to transmit the content through a wire or wireless LAN. Before transmitting a content from a content transmission apparatus to a content reception apparatus, the content transmission apparatus and the content reception apparatus authenticate each other. In the authentication, a timer measures a time interval between a transmission of an authentication request and a reception of an acknowledgement of a reception of the request or between a transmission of a response to a received authentication request and a reception of an acknowledgement of a reception of the response. If the time interval does not exceed an upper limit, a content encrypted by using a shared key is transmitted from the content transmission apparatus to the content reception apparatus, and the address of the content reception apparatus as well as apparatus information unique to the content reception apparatus are cataloged in the content transmission apparatus. Thus, in order to transmit another content, the content is merely encrypted prior to the transmission without measuring a time interval.
Owner:HITACHI LTD
Authentication method, system, and device
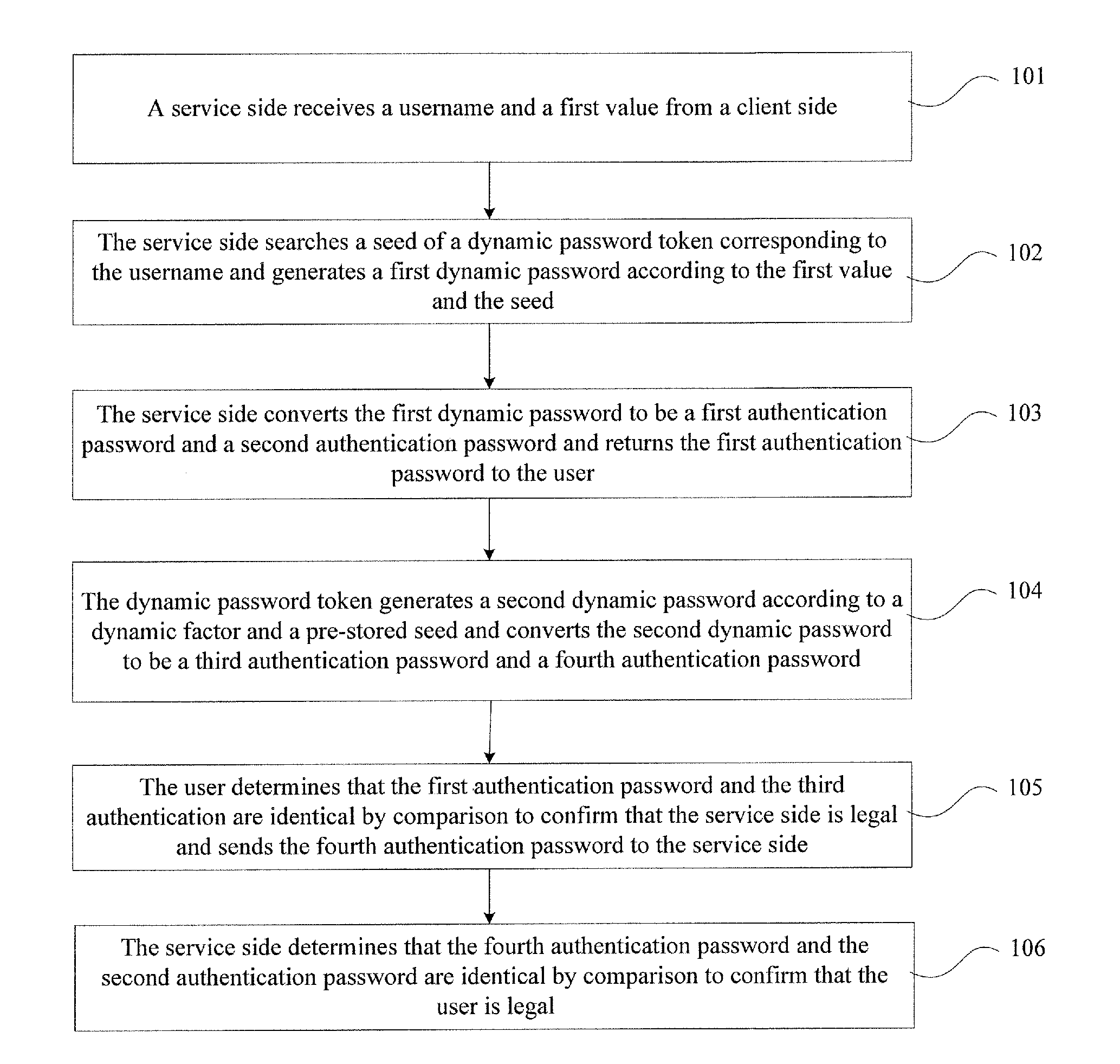
ActiveUS20120137131A1Authentication securityAvoid illegal operationDigital data processing detailsUser identity/authority verificationPasswordClient-side
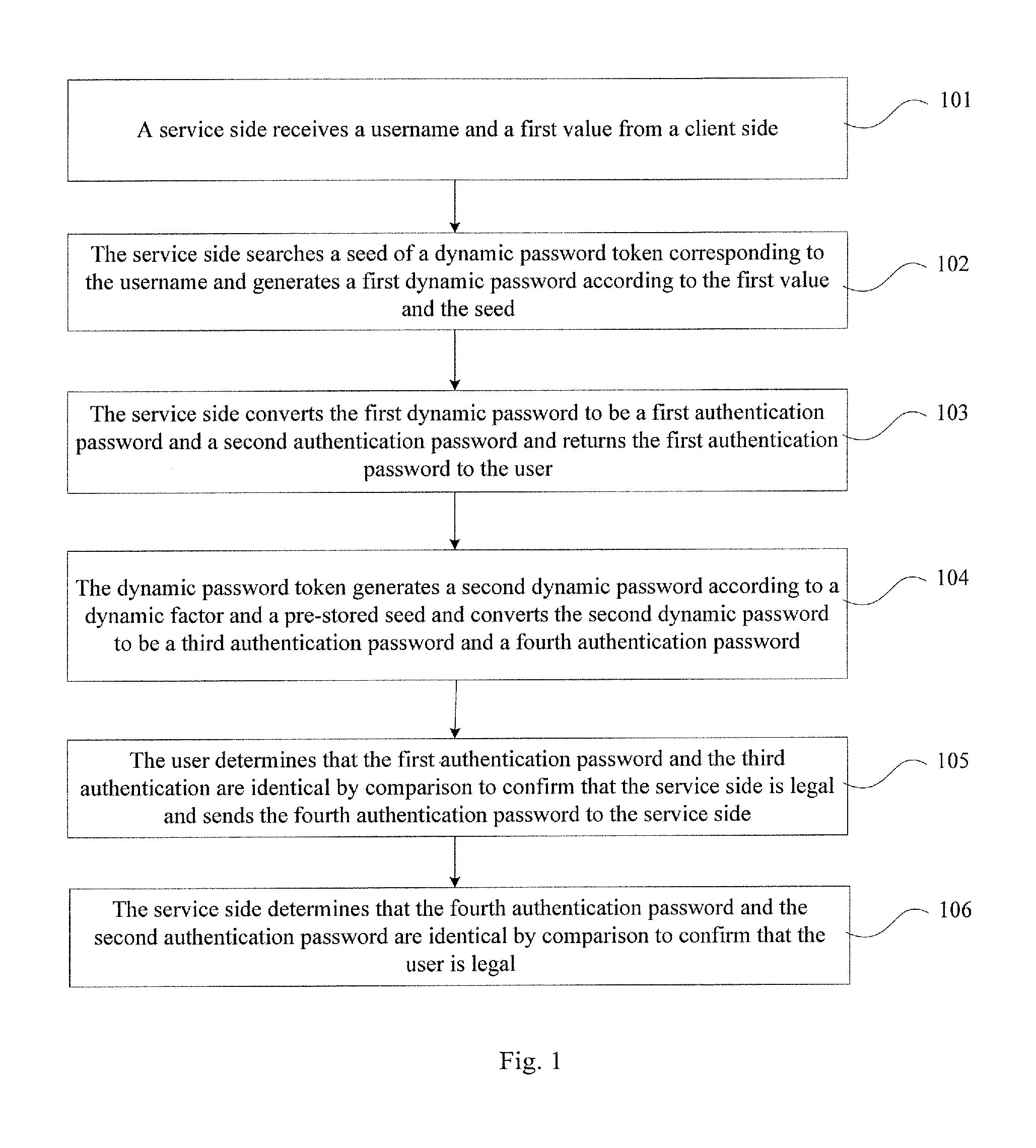
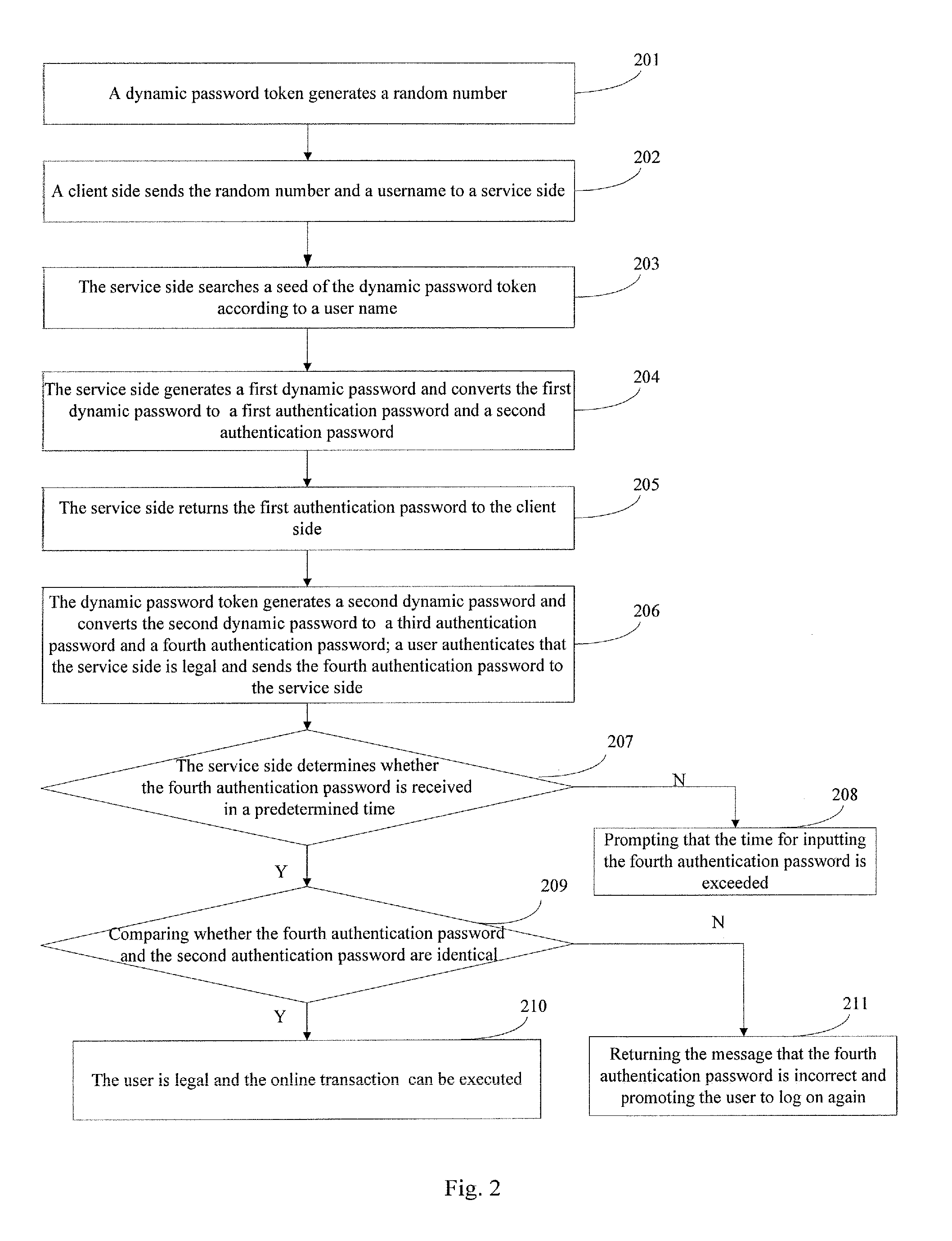
The present invention provides an authentication method, an authentication system, and an authentication device, which is in information security field. The method includes that a service side receives a username and a first value from a client side, searches a seed of a dynamic password token, and generates a first dynamic password according to the first value and the seed, converts the first dynamic password to the first authentication password and the second authentication password, and sends the first authentication password to the user; the dynamic password token generates a second dynamic password and sends the first authentication password to a user; the dynamic password token generates a second dynamic password and converts the second dynamic password to a third authentication password and a fourth authentication password; the user compares the first authentication password and the third authentication password to determine that they are identical, so as to confirm that the user is legal or the transaction is permissible. The invention prevents malicious attack and operation of illegal users, which improves the security of information and property of the users.
Owner:FEITIAN TECHNOLOGIES
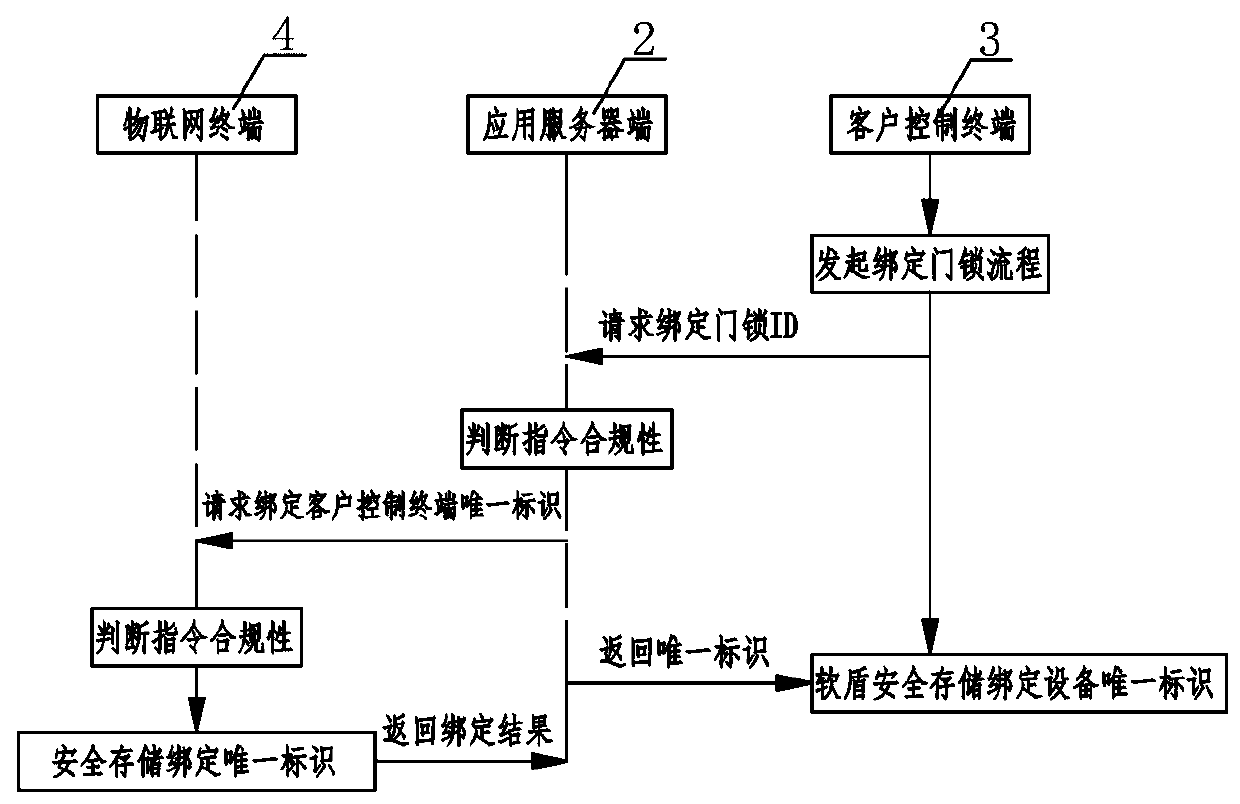
Internet of Things safety management system
ActiveCN110784491AEnsure communication securityAvoid illegal operationTransmissionSafety management systemsThe Internet
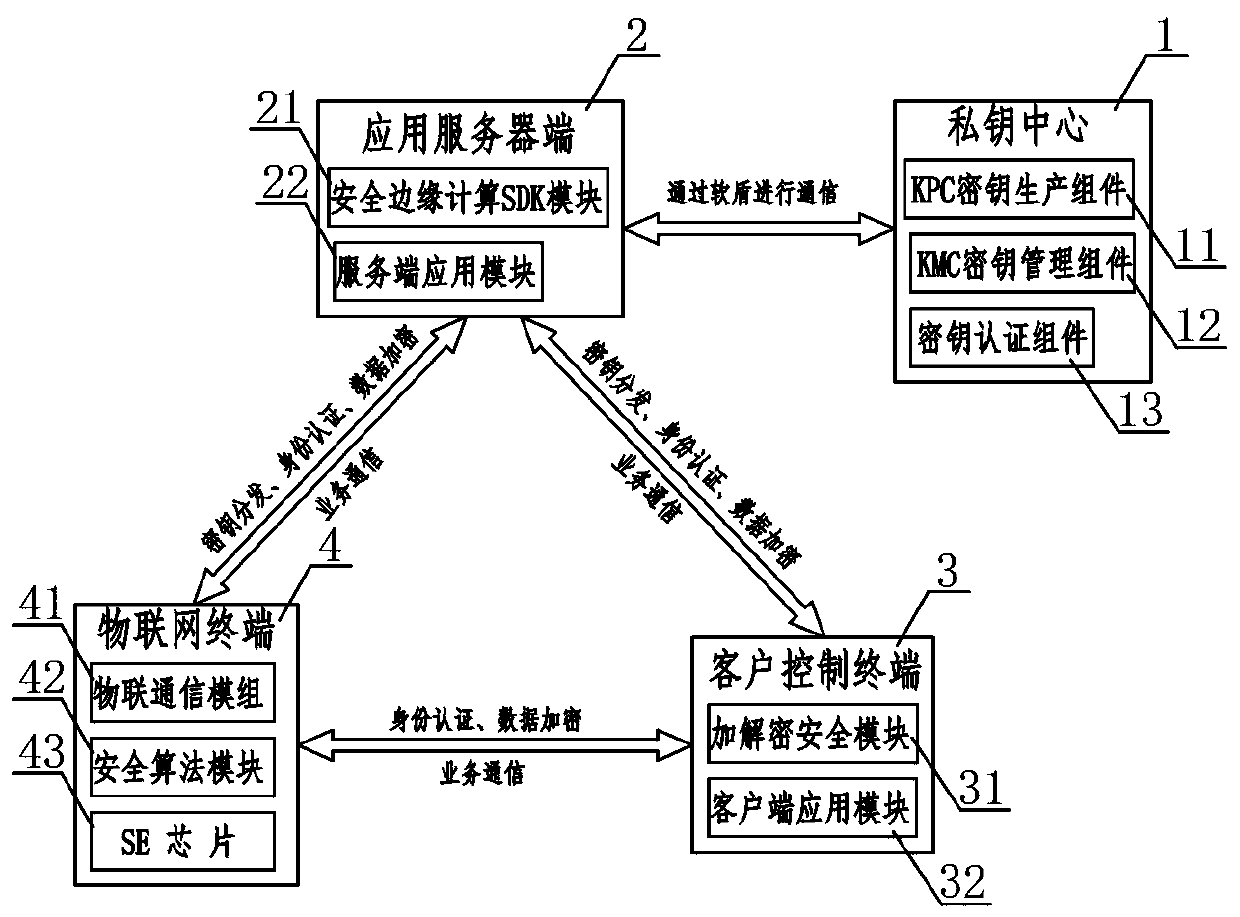
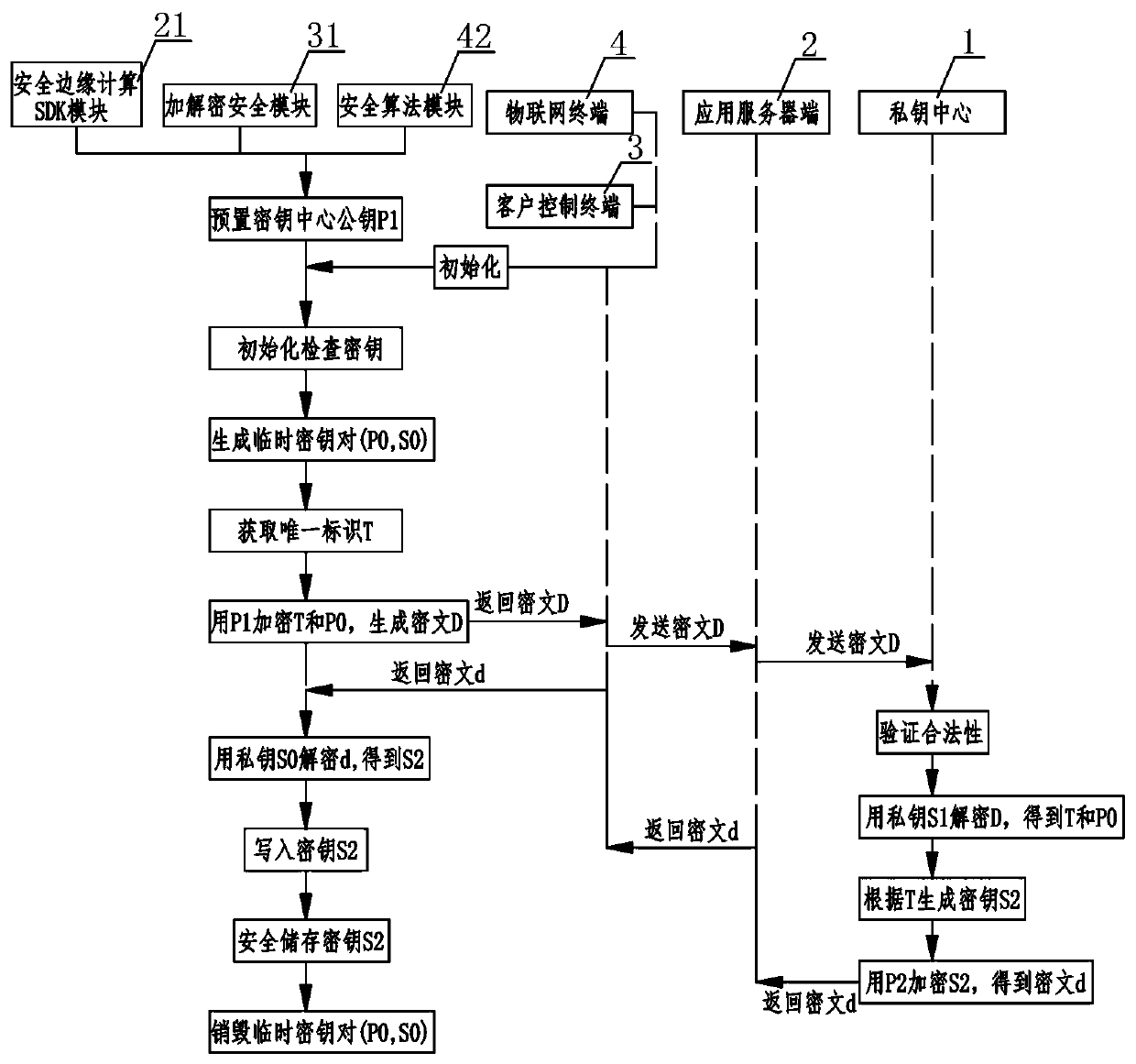
The invention relates to an Internet of Things security management system. A private key center and an application server perform communication authentication data transmission through a soft shield;the application server side performs mutual communication of key distribution, identity authentication and data encryption with the client control terminal and the Internet of Things terminal at the same time; mutual communication of identity authentication and data encryption is carried out between the client control terminal and the Internet of Things terminal, wherein the private key center comprises a KPC key production assembly, a KMC key management assembly and a key authentication assembly, the application server comprises a security edge computing SDK module and a server application module, and the client control terminal comprises an encryption and decryption security module and a client application module, and the Internet of Things terminal comprises an Internet of Things communication module, a security algorithm module and an SE chip. According to the Internet of Things security management system, only the user is completely autonomous and controllable in the Internet of Things system, the cloud system does not have the authority of directly operating the user equipment, and the Internet of Things control security level can be effectively improved.
Owner:深圳前海智安信息科技有限公司
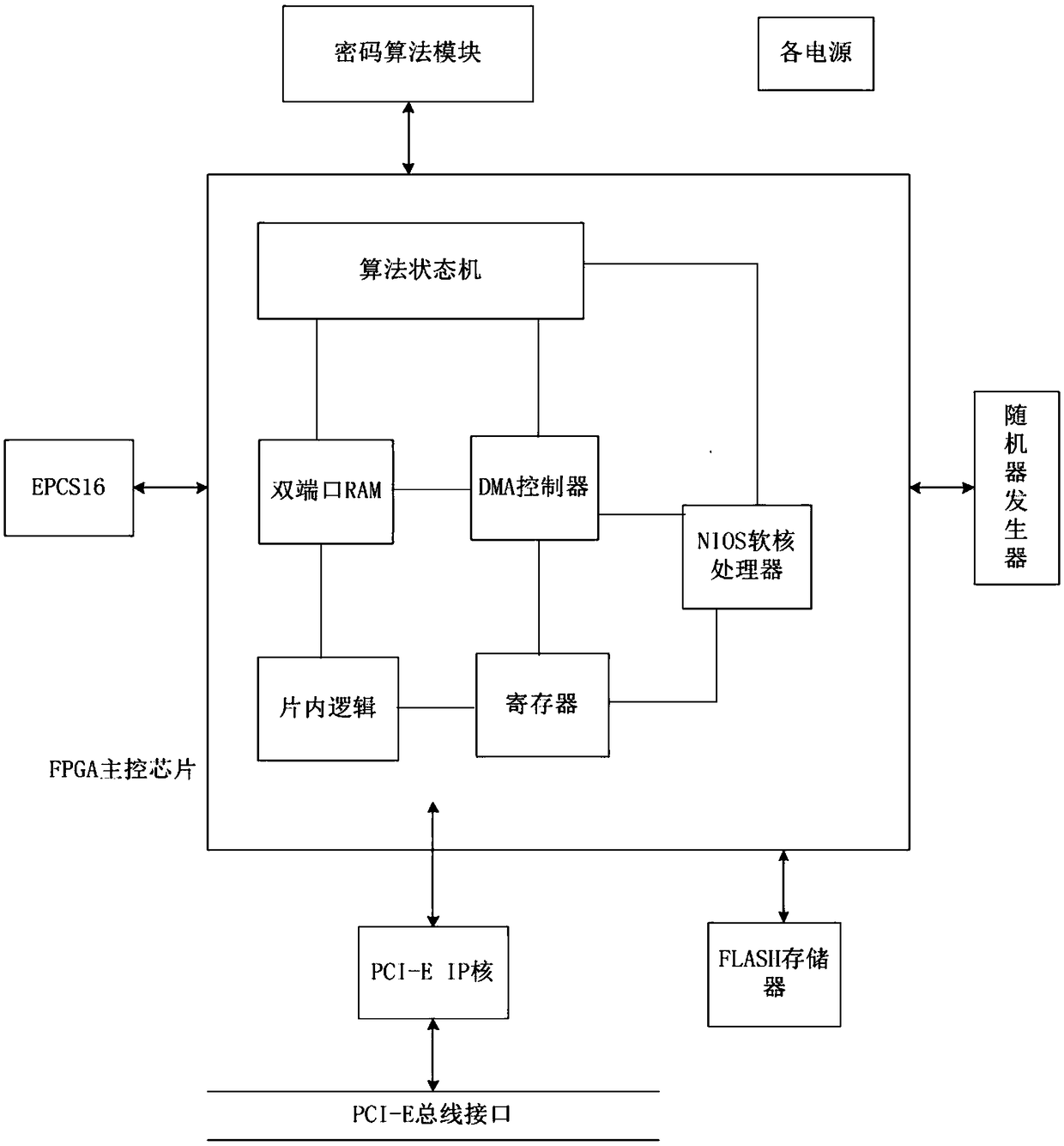
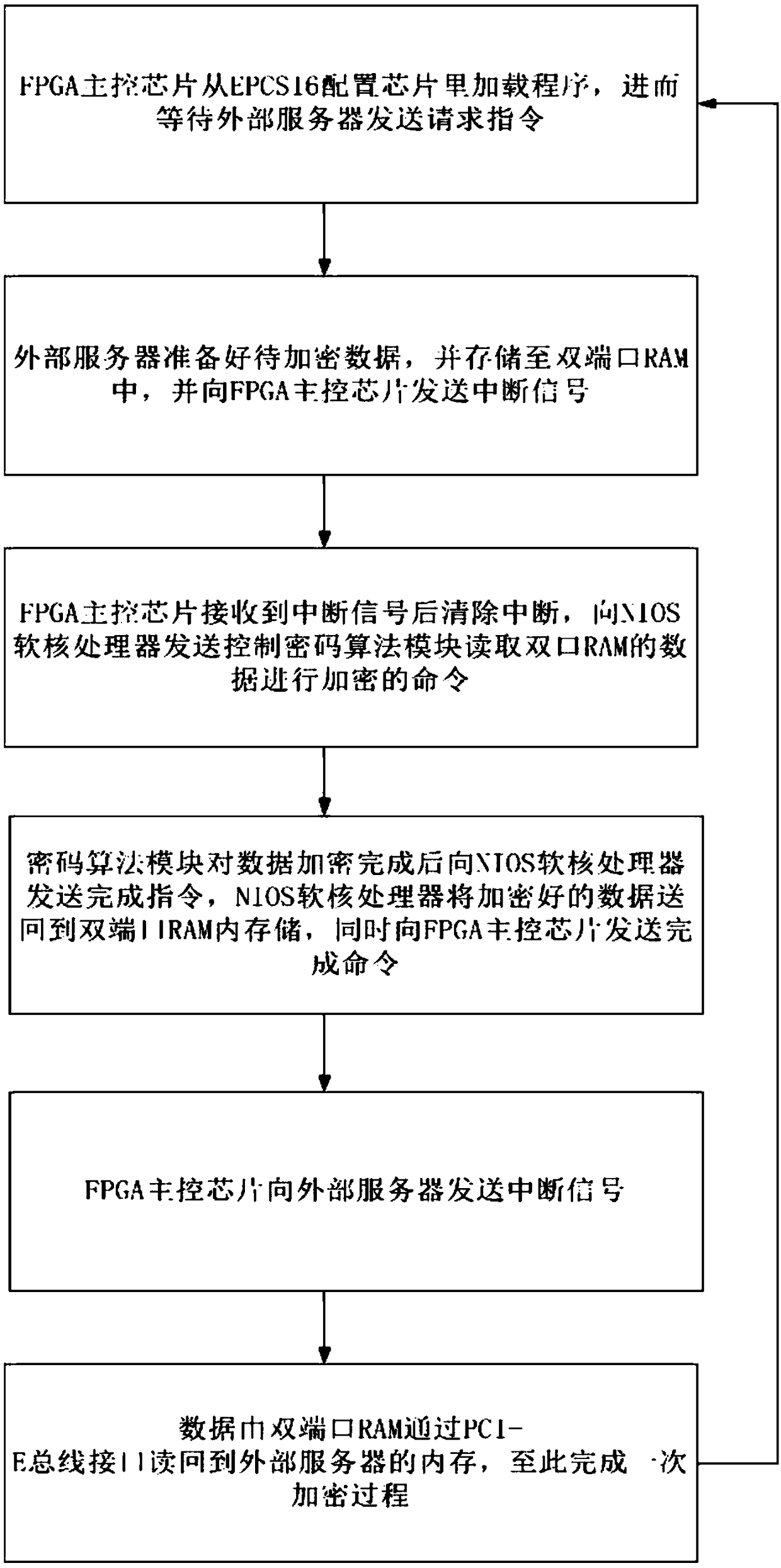
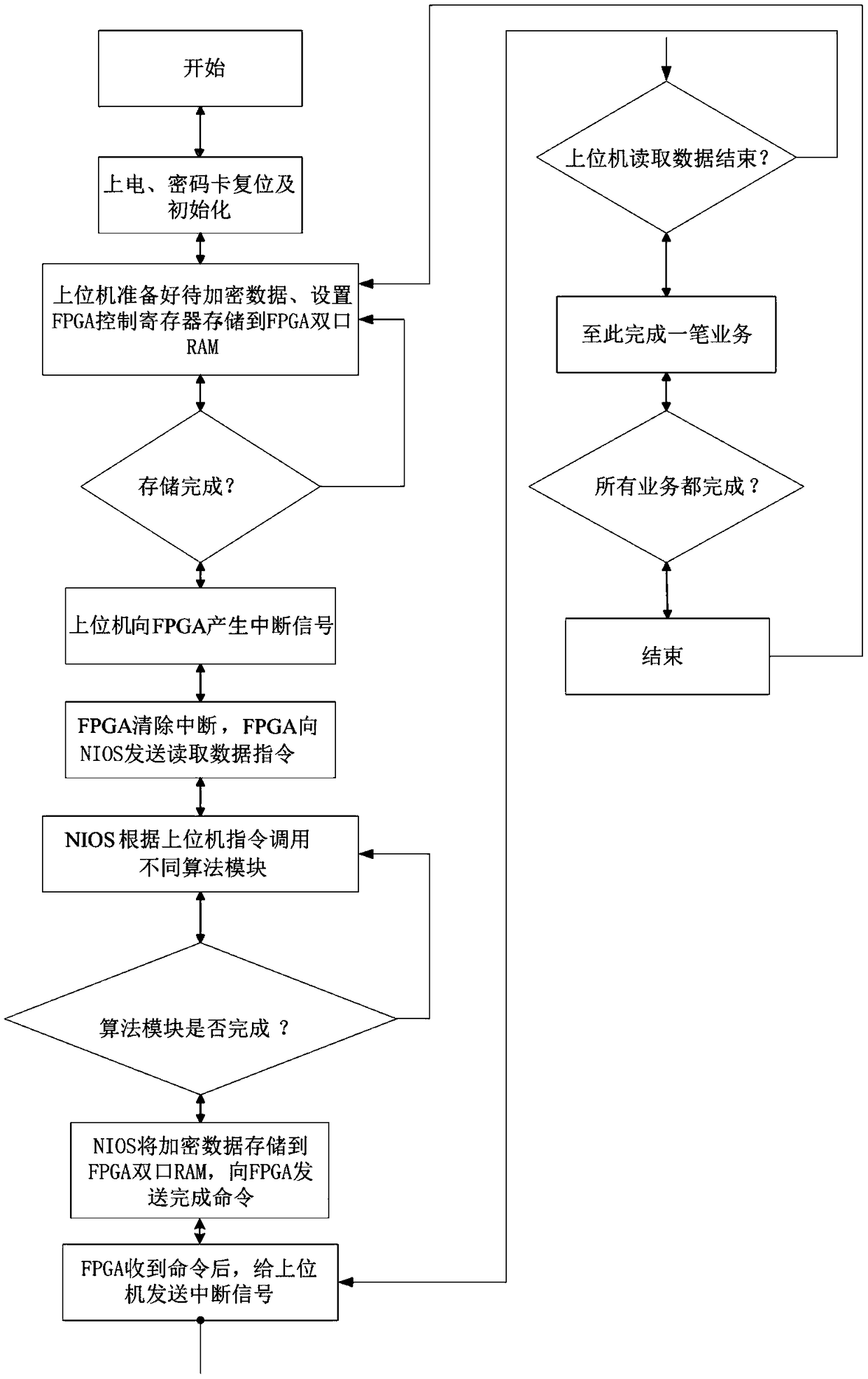
A full algorithm cryptographic card based on PCI-E interface and an encryption method thereof
InactiveCN109145568AImprove security strengthImprove securityDigital data authenticationEnergy efficient computingAlgorithmic State MachineSERCOS interface
The invention discloses a method based on PCI-E interface full algorithm cryptographic card, including: a cryptographic algorithm module, a FLASH memory, a PCI-E bus interface, a random numb generator, and an FPGA master control chip with NIOS soft core processor, wherein a PCI-E IP core and an algorithm state machine are integrated in the FPGA master control chip. The cryptographic algorithm module comprises a symmetric key encryption SM4 algorithm chip, a symmetric key encryption SM1 algorithm chip and an asymmetric key encryption SM2 algorithm chip. The invention also discloses an encryption method of the cipher card. The invention provides a high-performance full-algorithm cryptographic card, which simultaneously reduces the complexity of hardware circuit and energy consumption, improves the key operation speed, and the cryptographic card adopts a home-made cryptographic algorithm, so that the user's key is most securely protected.
Owner:西安得安信息技术有限公司
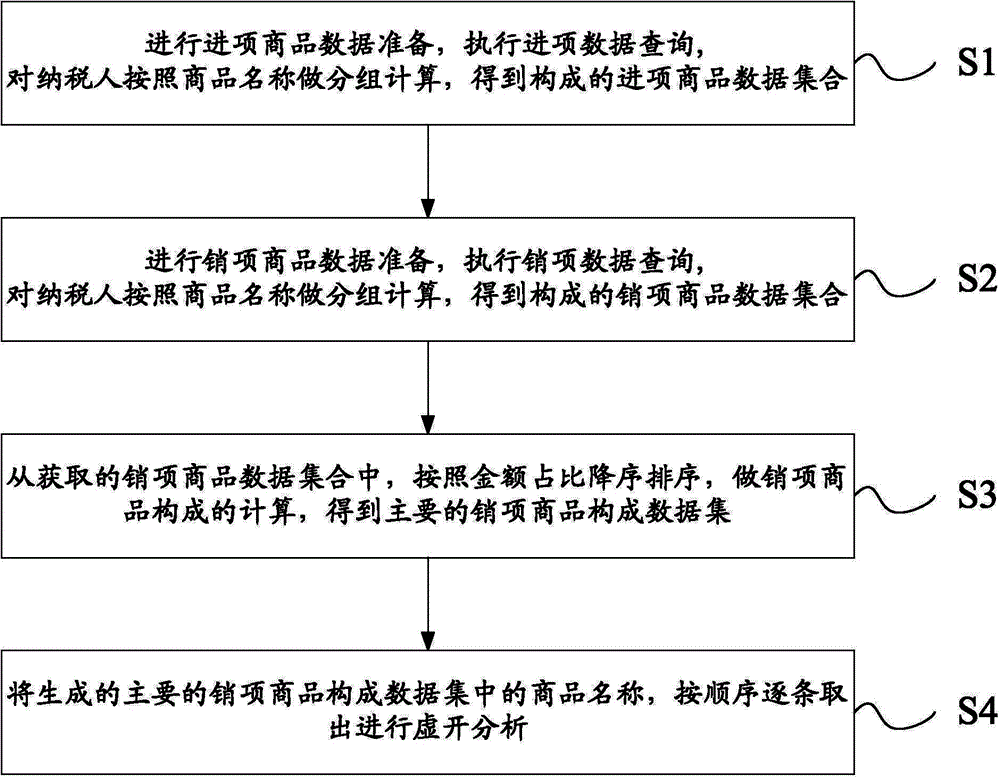
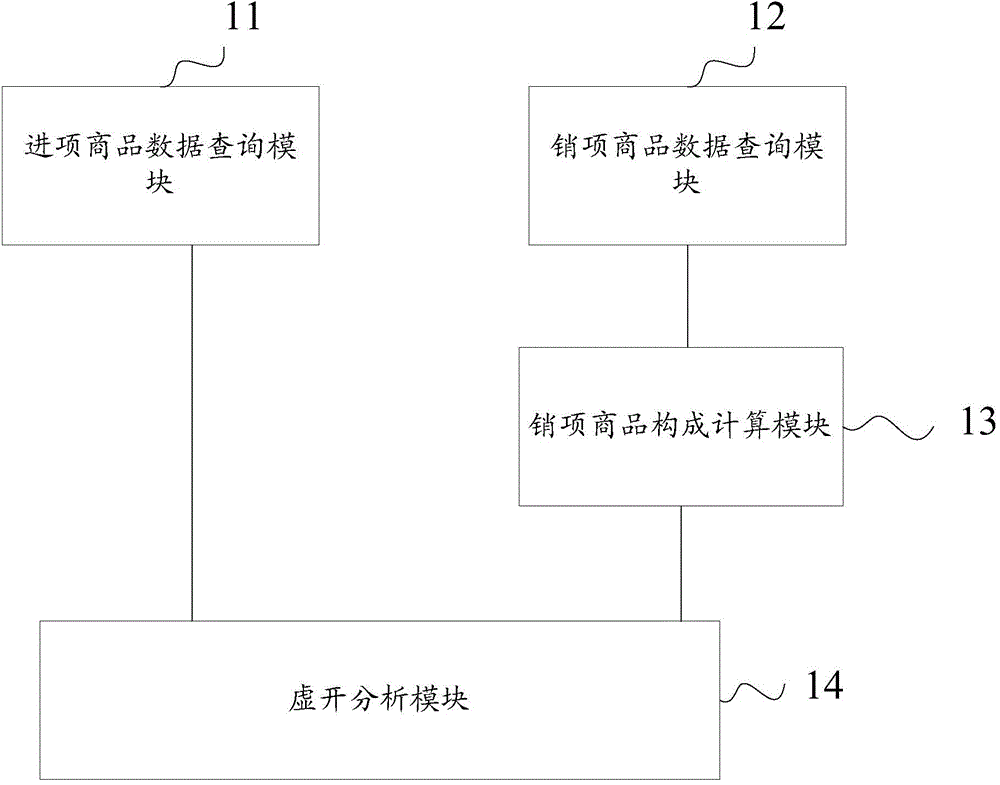
Method of monitoring enterprise false invoice through commodity composition and system thereof
InactiveCN104636973AStandardize normal production and operationAvoid illegal operationFinanceSpecial data processing applicationsData setInvoice
The invention provides a method of monitoring an enterprise false invoice through commodity composition and a system thereof. The method comprises the following steps: input commodity data preparation is carried out, input data query is executed, taxpayers are grouped and calculated according to commodity names, and a composed input commodity data collection is obtained; output commodity data preparation is carried out, output data query is executed, taxpayers are grouped and calculated according to commodity names, and a composed output commodity data collection is obtained; in the obtained output commodity data collection, descending sorting is carried out according to the money sum proportion, calculation of the output commodity composition is carried out, and a main output commodity composition data collection is obtained; and names of commodities in the generated main output commodity composition data collection are sequentially taken out item by item for false issuing analysis. Enterprise false issuing invoice doubts are found, production and operation activities of the enterprise are monitored, normal production and operation of the enterprise are further regulated, and illegal and rule-breaking operation of the enterprise is avoided.
Owner:AEROSPACE INFORMATION
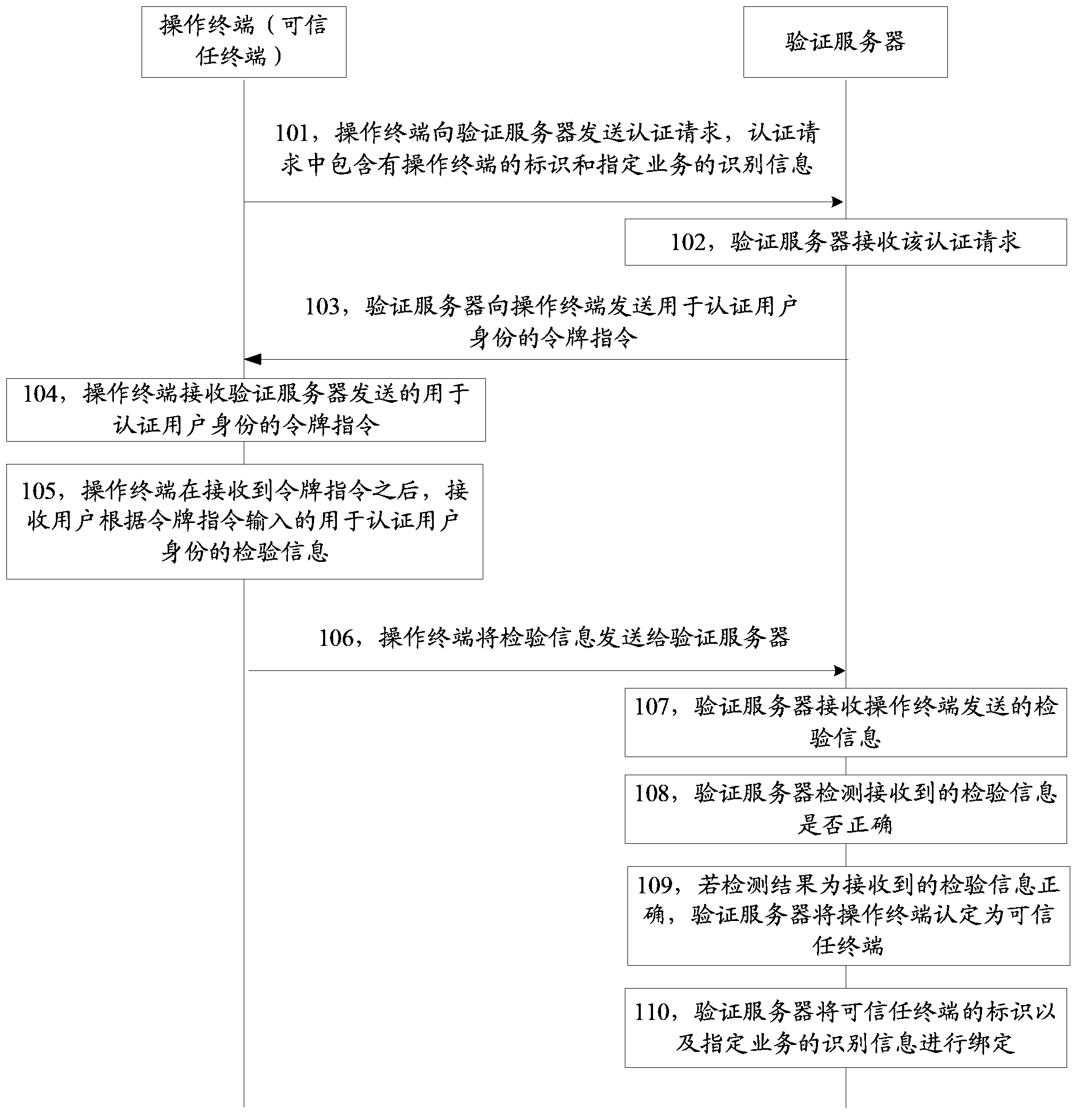
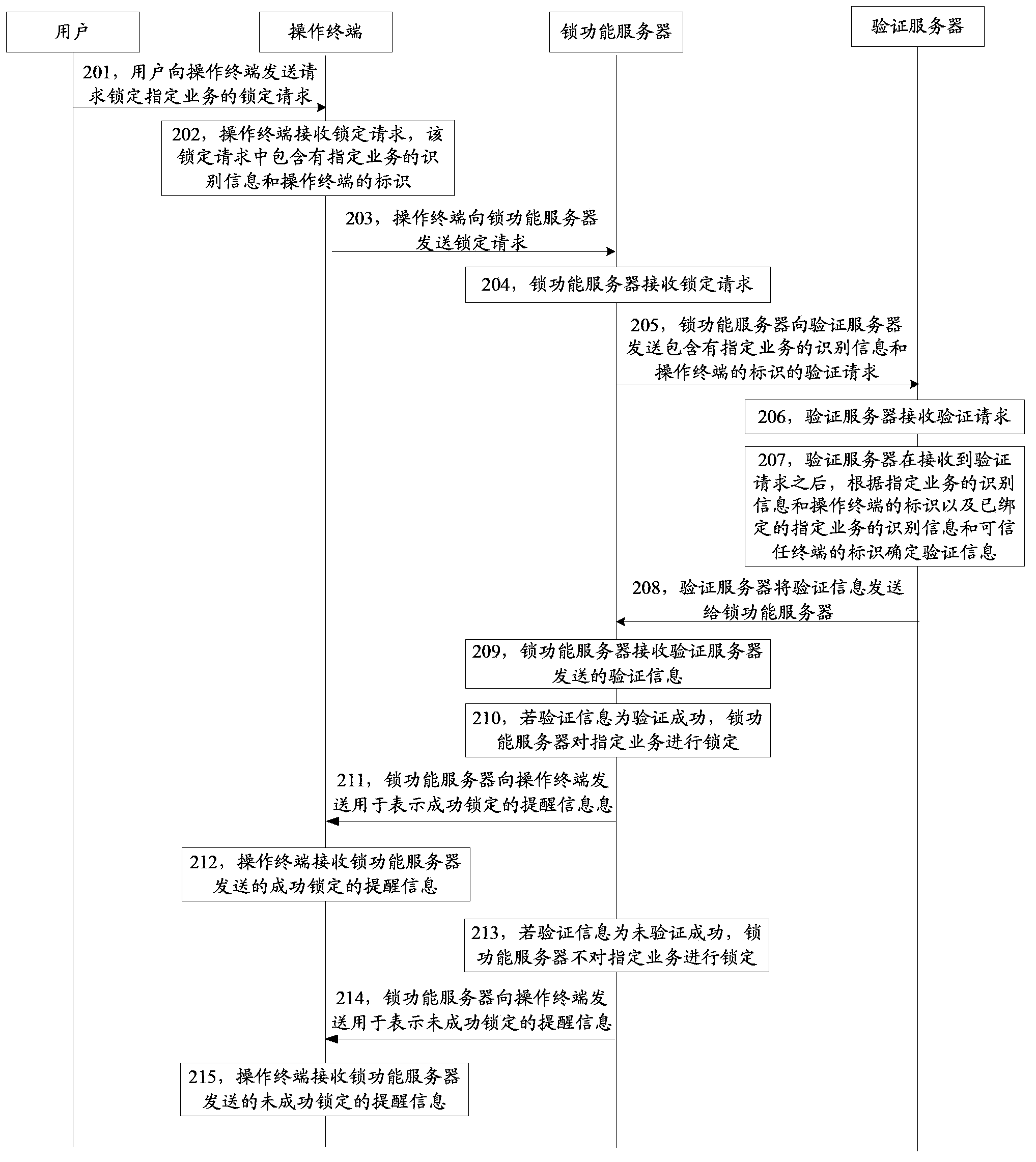
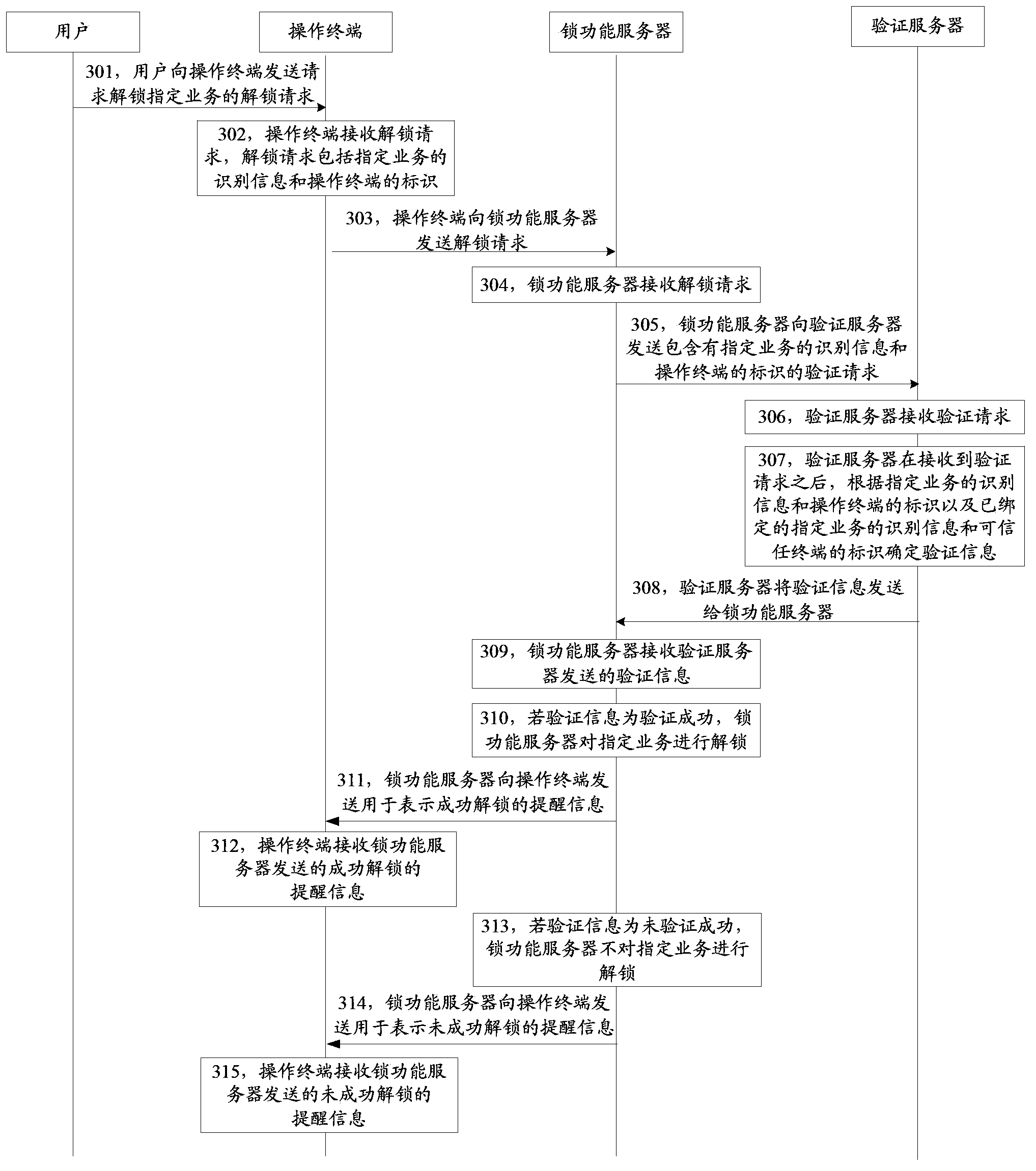
Service locking method, service unlocking method, device and system
ActiveCN104219196AAvoid illegal operationSolve the problem of illegal operationUser identity/authority verificationDigital data authenticationVirtual propertyComputer terminal
The invention discloses a service locking method, a service unlocking method, a device and a system, and belongs to the field of network property safety. The service locking method comprises the following steps: receiving a locking request, wherein the locking request comprises the identification information of a specified service and the identity of an operating terminal, and the specified service is a service for performing sensitive operation on network virtual properties; and transmitting a verification request which comprises the identification information of the specified service and the identity of the operating terminal to a verification server, and locking the specified service after verification success information transmitted by the verification server is received. According to the service locking method, the specified service on the operating terminal is locked after successful verification of the operating terminal by the verification server, so that the problem of illegal operation of the network virtual properties of a legal user in a service operating method in the prior art is solved, any operating terminal cannot directly operate a locked specified service, and the situation of illegal operation of the specified service by an illegal user is avoided.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
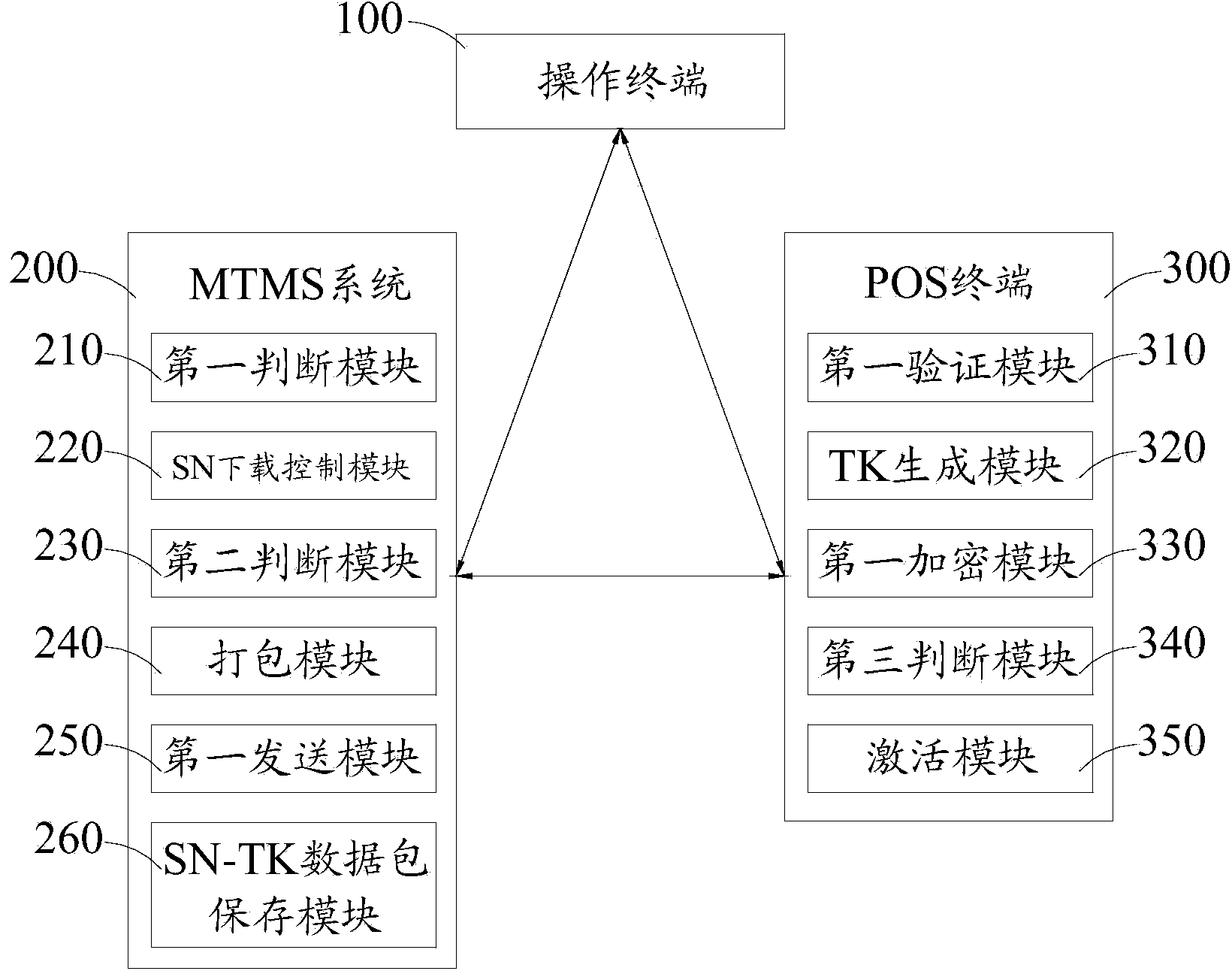
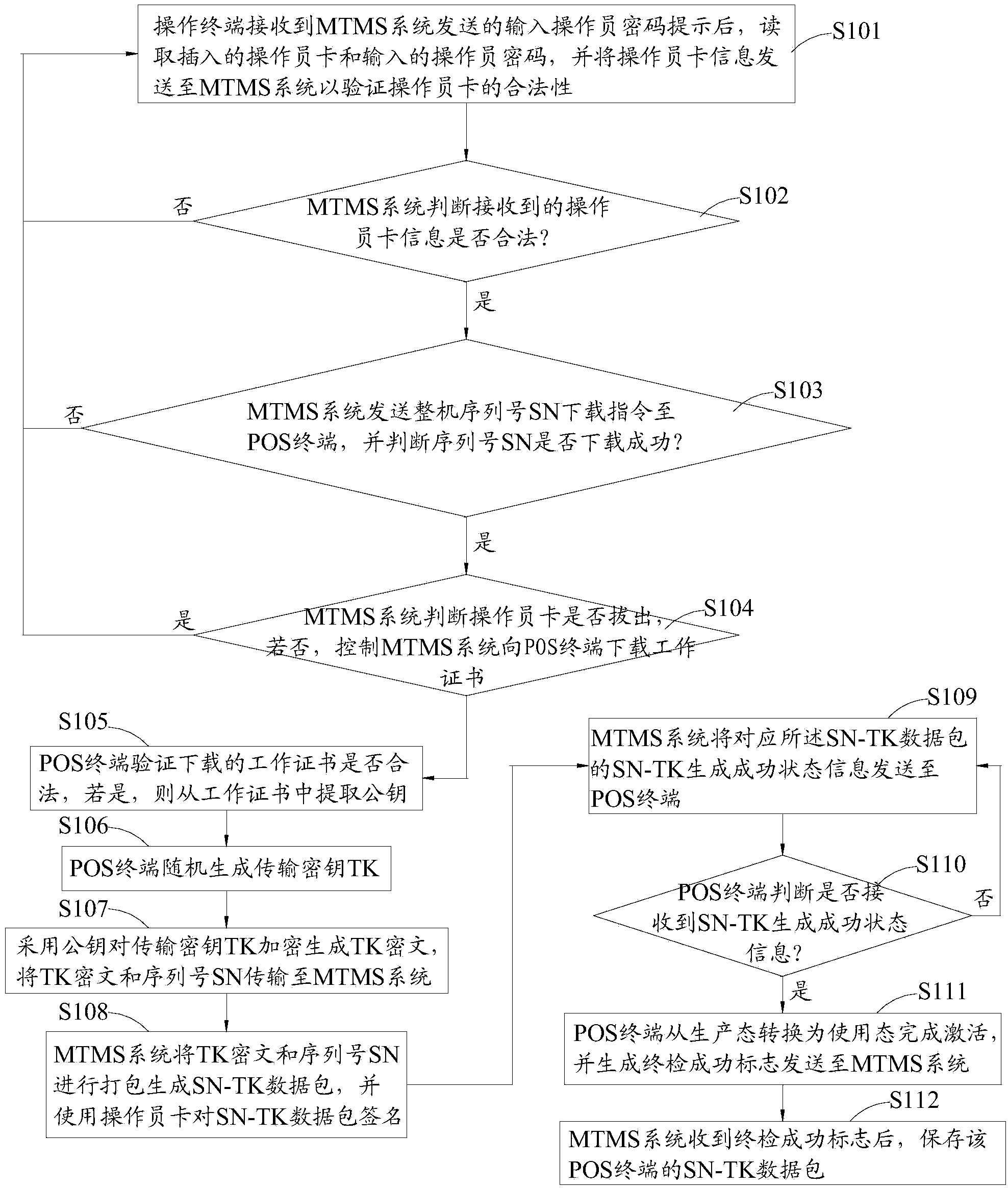
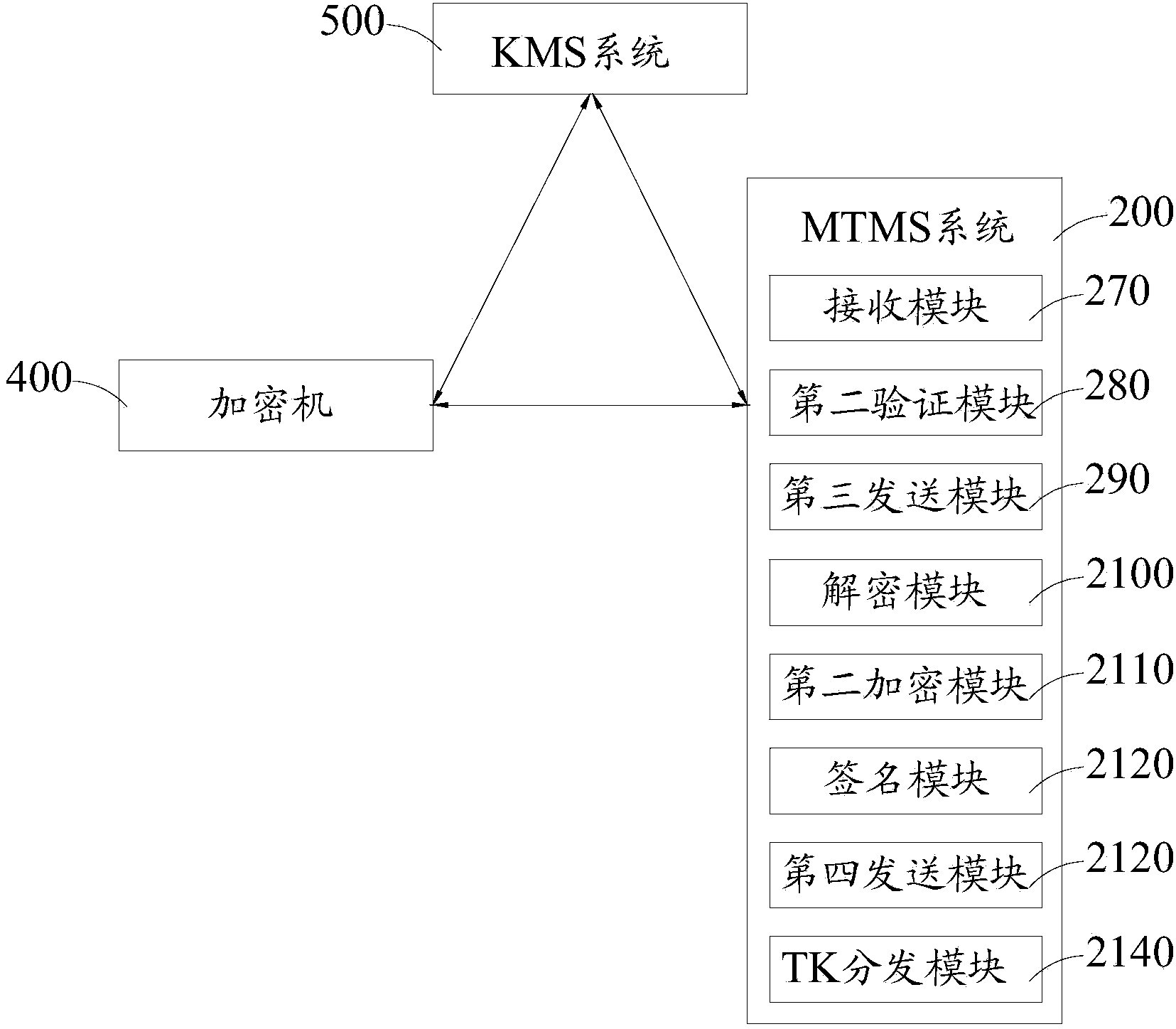
Method and device for safely collecting and distributing transmission keys
ActiveCN103716167AUniqueness guaranteedUniqueKey distribution for secure communicationUser identity/authority verificationNetwork packetComputer terminal
The invention relates to the field of electronic payment terminals and discloses a method and device for safely collecting and distributing transmission keys. The method includes the generation step and the distribution step. The generation step mainly includes the sub-steps that an operator card is authenticated, a complete machine serial number and a working certificate are loaded, and activation operation is performed on a POS terminal. The distribution step mainly includes the subs-steps that encryption equipment performs encryption and signature on SN-TK data packets in an MTMS system again, and then the SN-TK data packets are distributed to a KMS system. The method and device have the advantages that when each POS terminal is produced, a transmission key (TK) is generated at random, and it is guaranteed that TK data collected by each POS terminal have uniqueness; in the process of TK collection, strict permission verification is performed on an operator, so that safety is guaranteed; in the process of distribution, strict valid verification, and secondary switching encryption and signature are performed, so that accuracy of the collected TK data is guaranteed in the production process.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
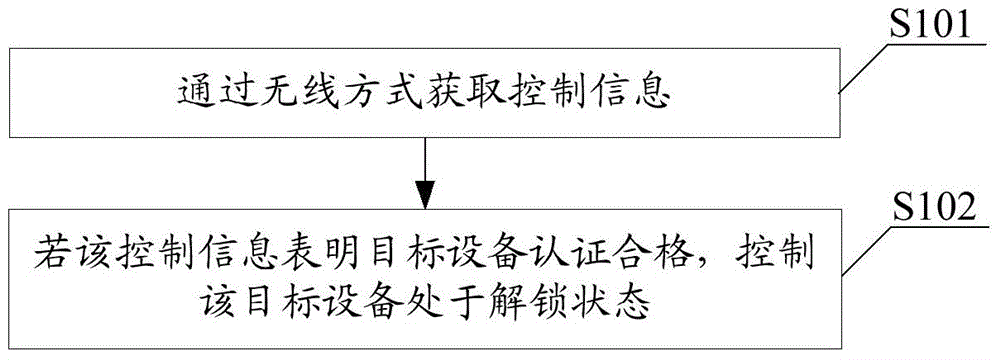
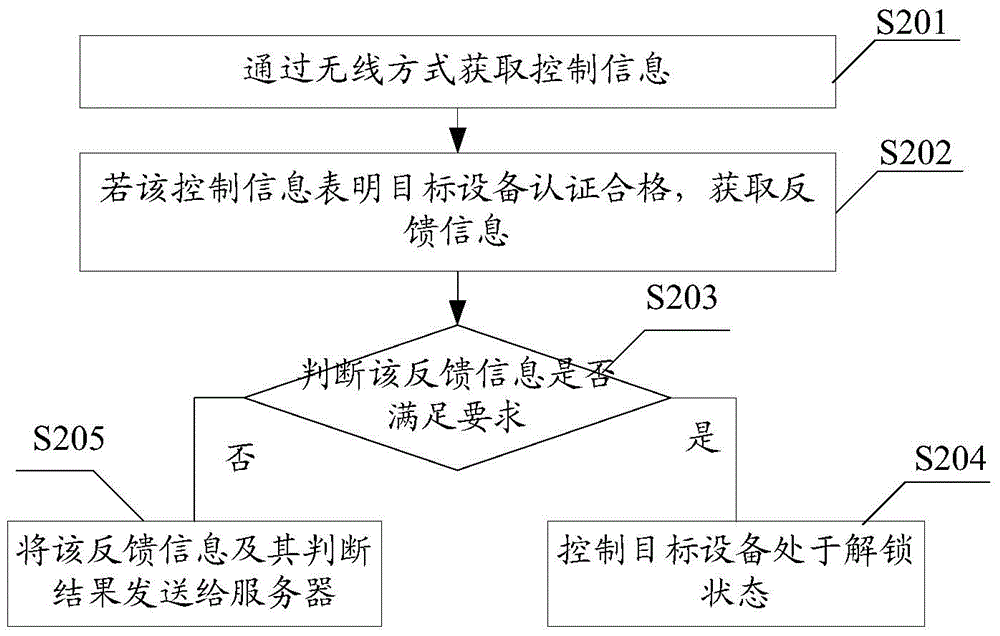
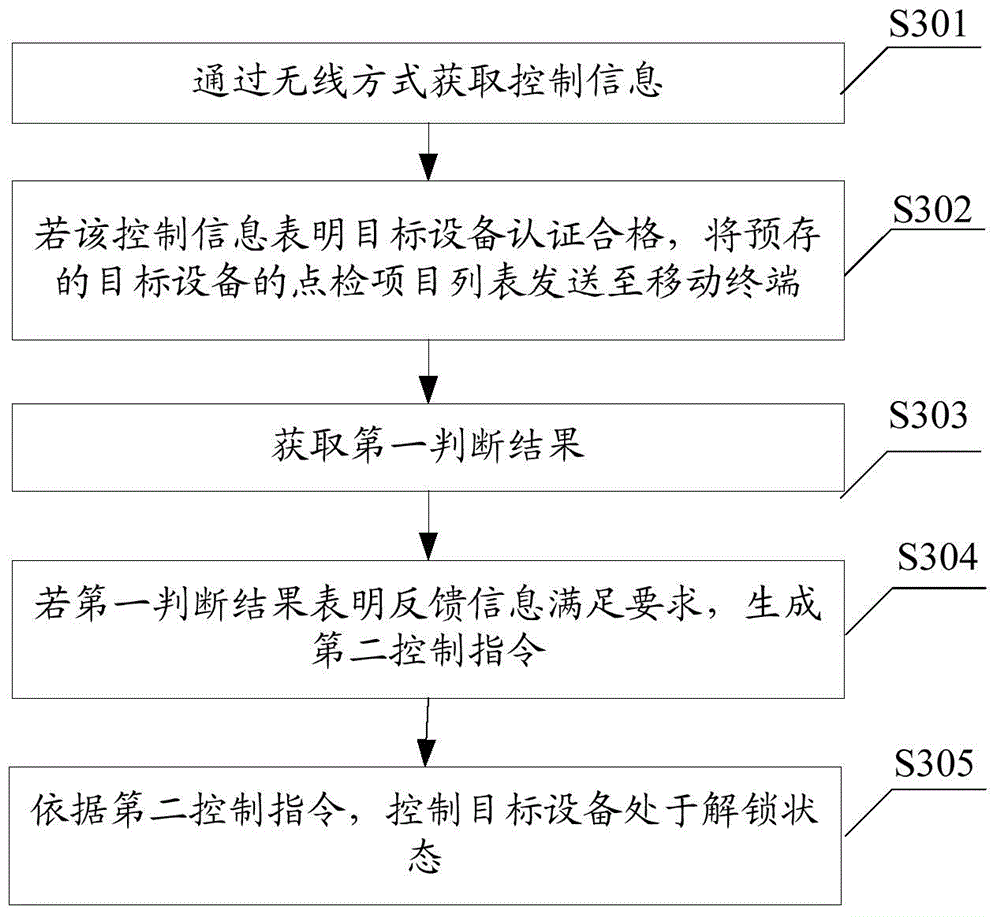
Equipment control method, device and system
ActiveCN104811500AEasy wiringAffect personal safetyTransmission systemsTransmissionDriving safetyEmbedded system
The invention provides an equipment control method, device ad system. The equipment control method is applied to a controller of the system. The controller is used for acquiring control information from a mobile terminal or a server through a wireless manner; if the control information indicates that target equipment is authenticated to be qualified, the controller controls the target equipment to be in an unlocking state, so that an operator can operate the target equipment, and thus the driving safety and reliability of the equipment are improved; furthermore, the mobile terminal is used to substitute for an existing vehicle-mounted card reader or a vehicle-mounted display / input terminal to acquire the authentication information of a user, so that the hardware cost of the equipment per se is reduced; because the mobile terminal and the controller are connected in a wireless manner, wiring in the equipment is simplified; the visual field of a driver cannot be sheltered, and thus the personnel safety of the driver and surrounding personnel thereof, as well as the safety of surrounding goods and equipment cannot be influenced.
Owner:SUZHOU YIXINAN IND TECH CO LTD
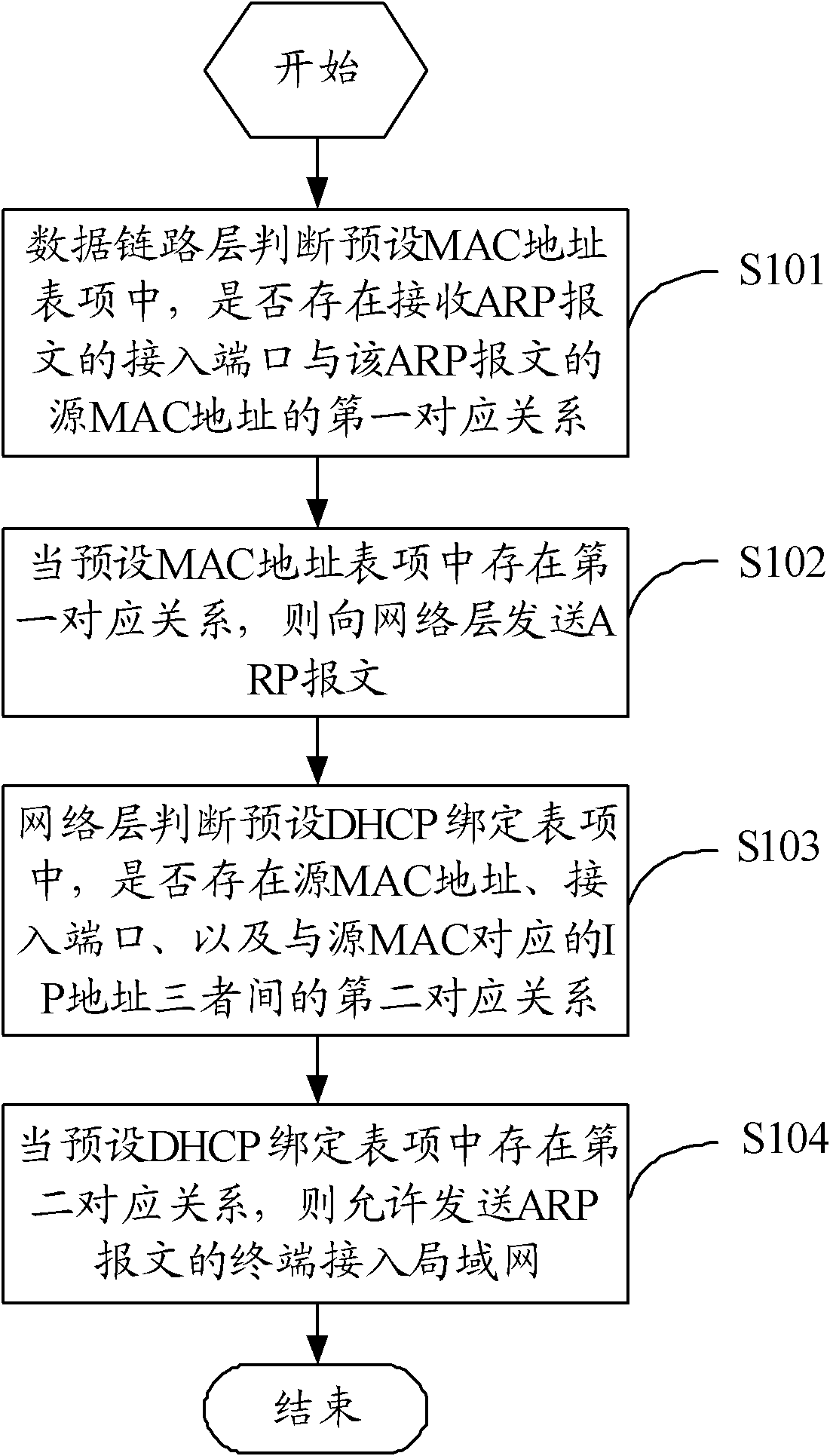
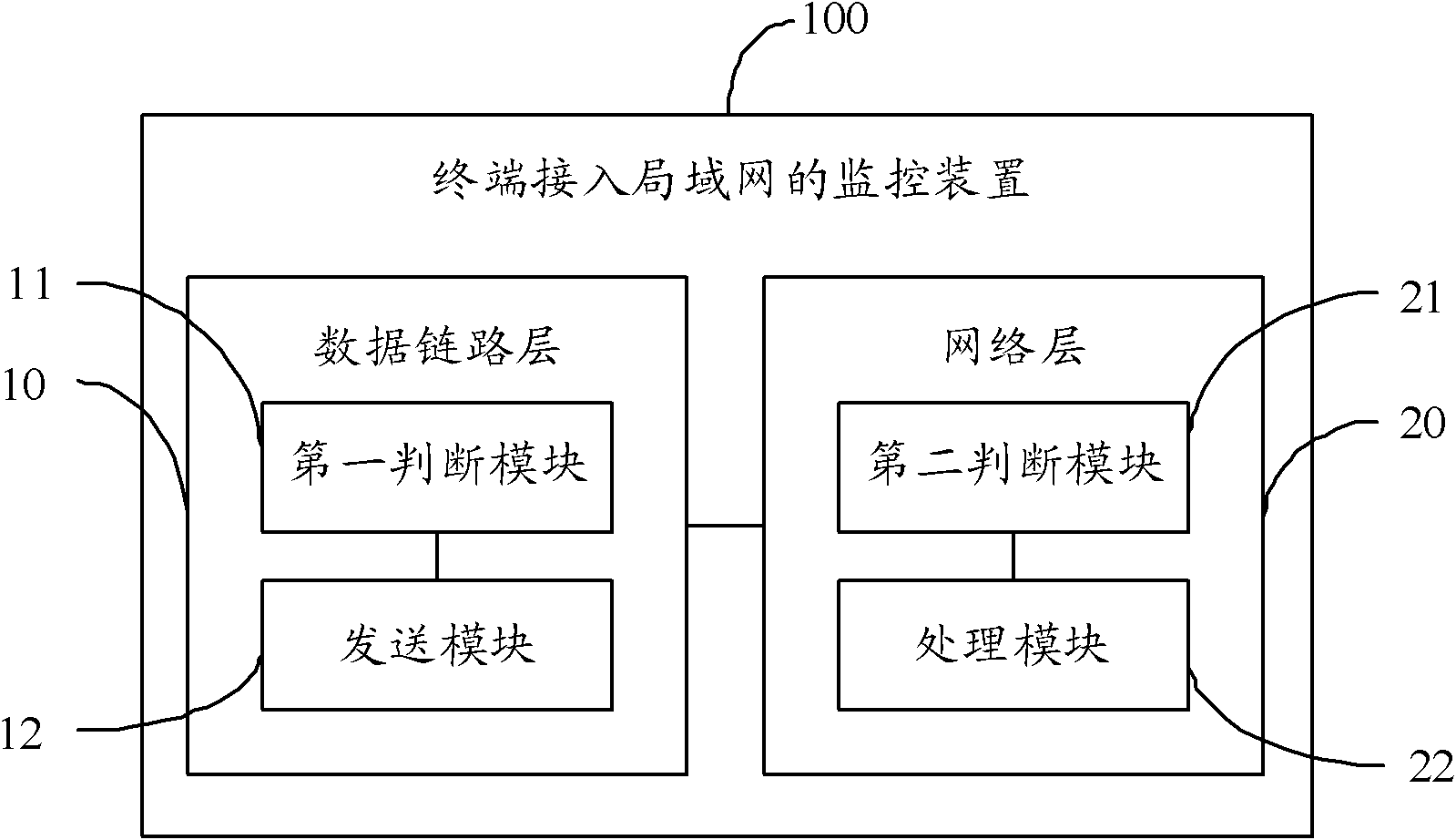
Monitoring method and monitoring device for access of terminal to local area network (LAN)
InactiveCN101984693AImprove reliabilityImprove securitySecurity arrangementAddress Resolution ProtocolIp address
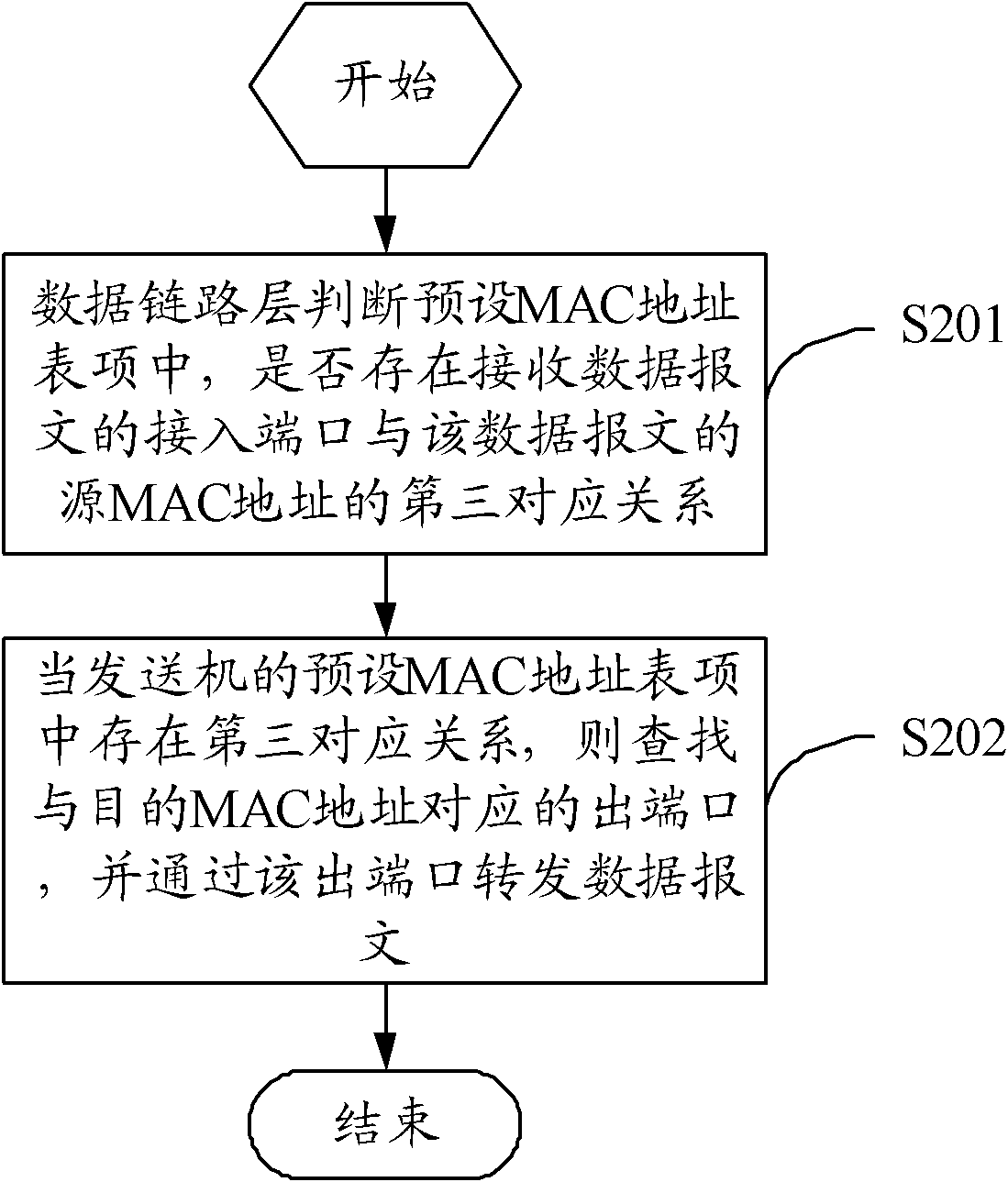
The invention discloses a monitoring method and monitoring device for access of a terminal to a local area network (LAN). The monitoring method comprises the following steps: a data link layer (DLL) judges whether a first congruent relationship between an access port for receiving an address resolution protocol (ARP) message and a source media access control (MAC) address of the ARP message exists in a preset MAC address table; if yes, the ARP message is sent to a network layer; the network layer judges whether a second congruent relationship among the source MAC address, the access port and an IP address corresponding to the source MAC exists in a preset dynamic host configuration protocol (DHCP) bonding table; and if yes, the terminal sending the ARP message is allowed to access to the LAN. The monitoring method and monitoring device for the access of the terminal to the LAN provided by the invention can effectively prevent accesses of illegal terminals and illegal operation of accessing terminals, and improve the reliability and safety of the LAN.
Owner:ZTE CORP
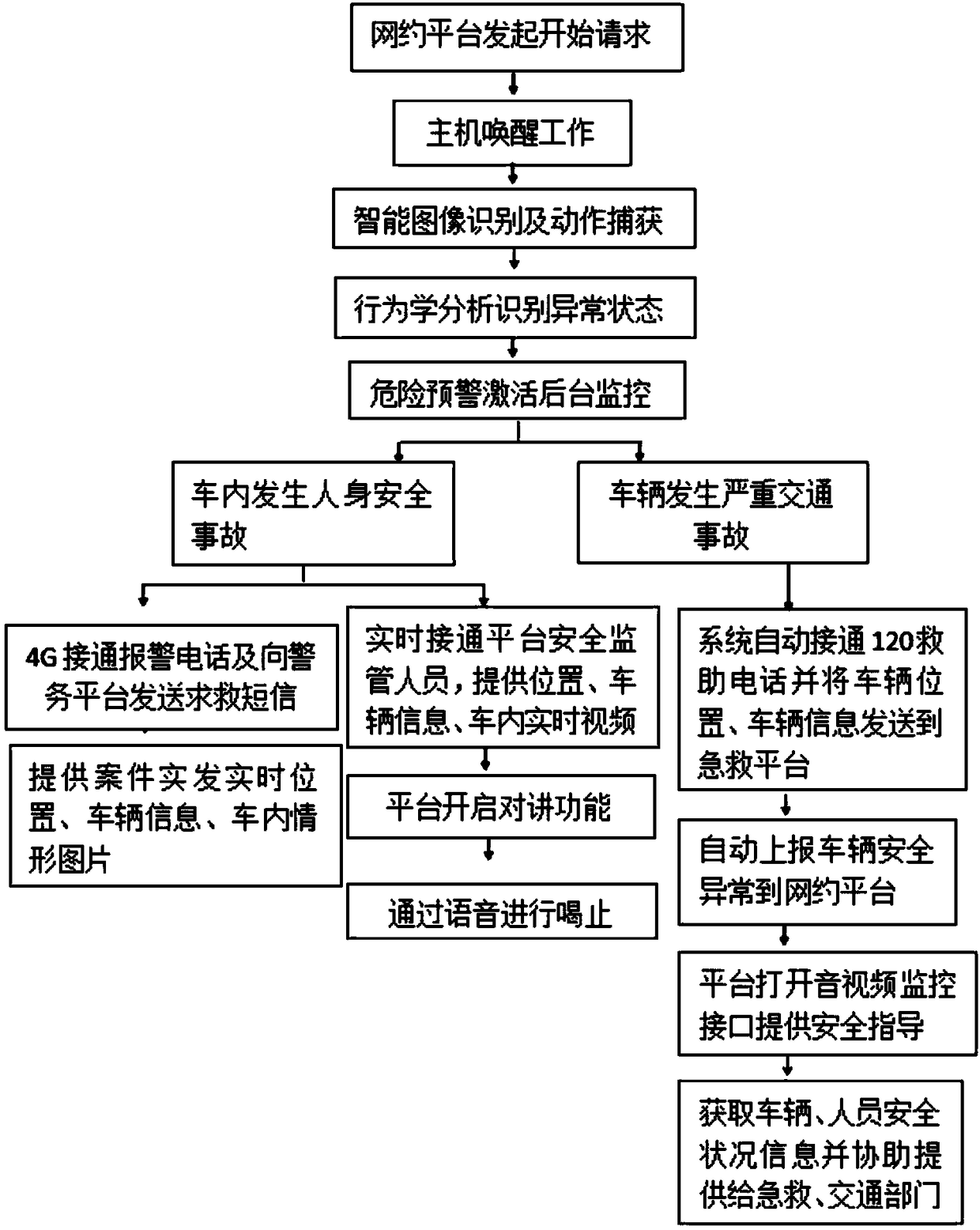
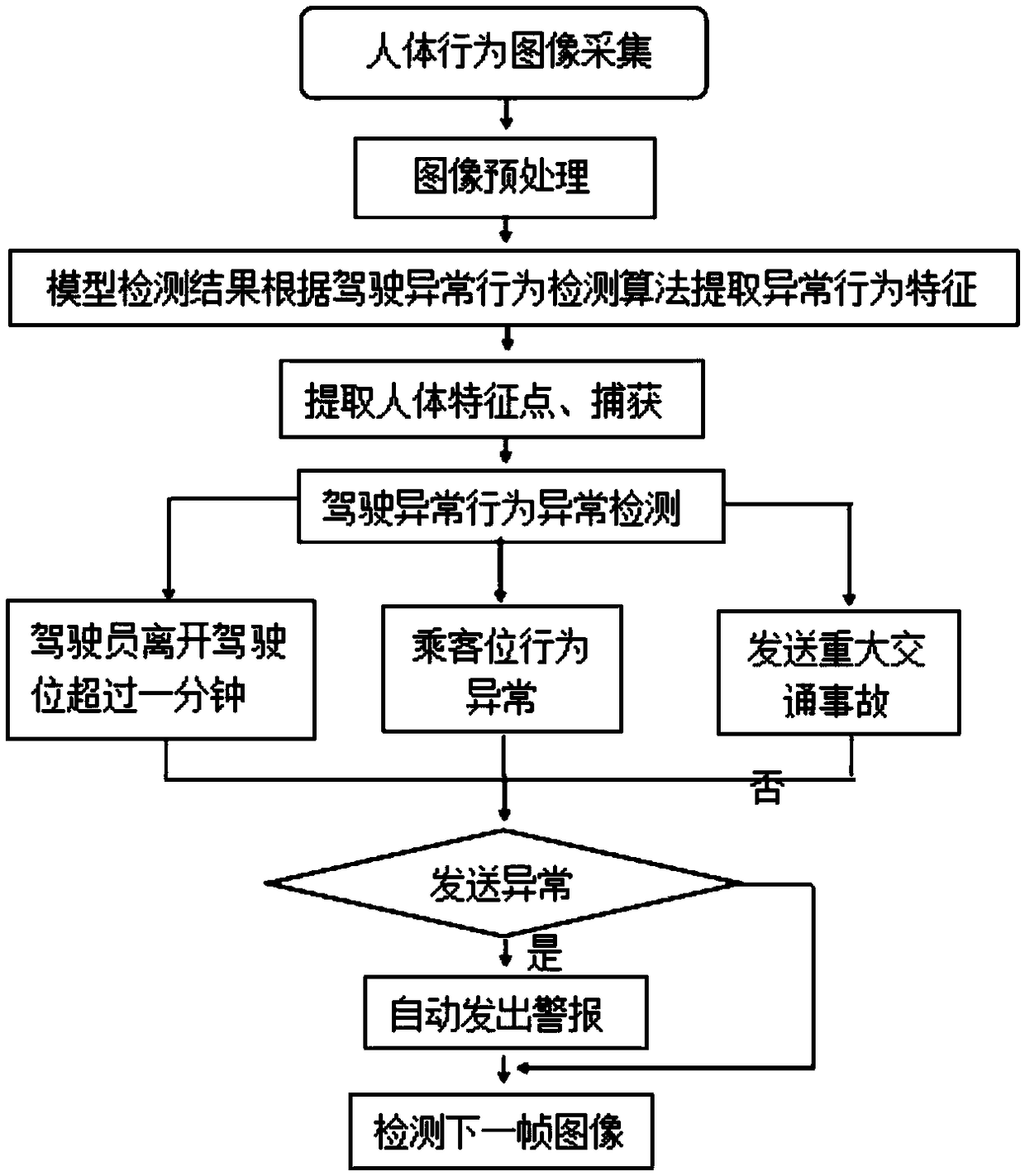
Third-party riding and driving safety automatic alarm method based on image processing
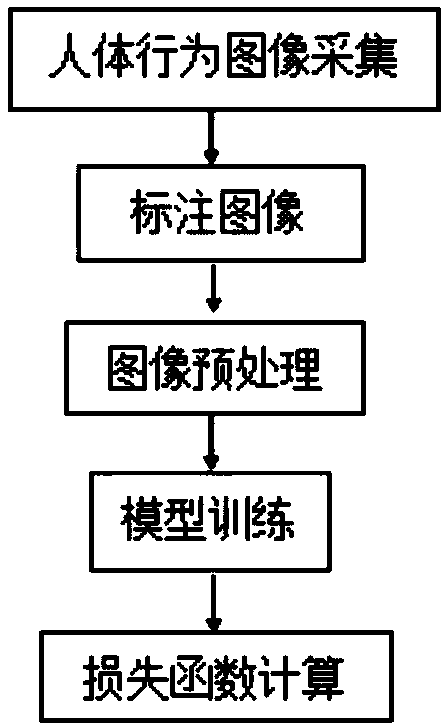
PendingCN108986400AEasy to deal withStop driving without a licenseCharacter and pattern recognitionClosed circuit television systemsDriver/operatorSimulation
The invention discloses a third-party riding and driving safety automatic alarm method based on image processing, and the method comprises two stages: a multi-task deep learning body behavior detection model training stage and a body behavior testing stage. The body behavior testing stage comprises the steps: performing the detection of a dangerous behavior of a body based on a multi-task deep learning body behavior detection model, and calculating a body behavior loss function, a body behavior attitude loss function, a loss function of other feature points of the body and a total loss function according to the multi-task deep learning body behavior detection model. When an online car-hailing service order is generated, a riding and driving safety automatic alarm device installed in a vehicle can be automatically excited, and a built-in wide-angle high-definition camera starts to work: firstly collecting a face image of a driver, comparing with the driver image data stored in an onlinecar-hailing platform, checking the identity information of the driver, and entering the body behavior testing stage. The method can perform the automatic early warning when a driver has an abnormal behavior, can effectively reduce the illegal criminal activities of the online car-hailing services and enables the risk of the life and property safety to be minimized.
Owner:深圳市尼欧科技有限公司
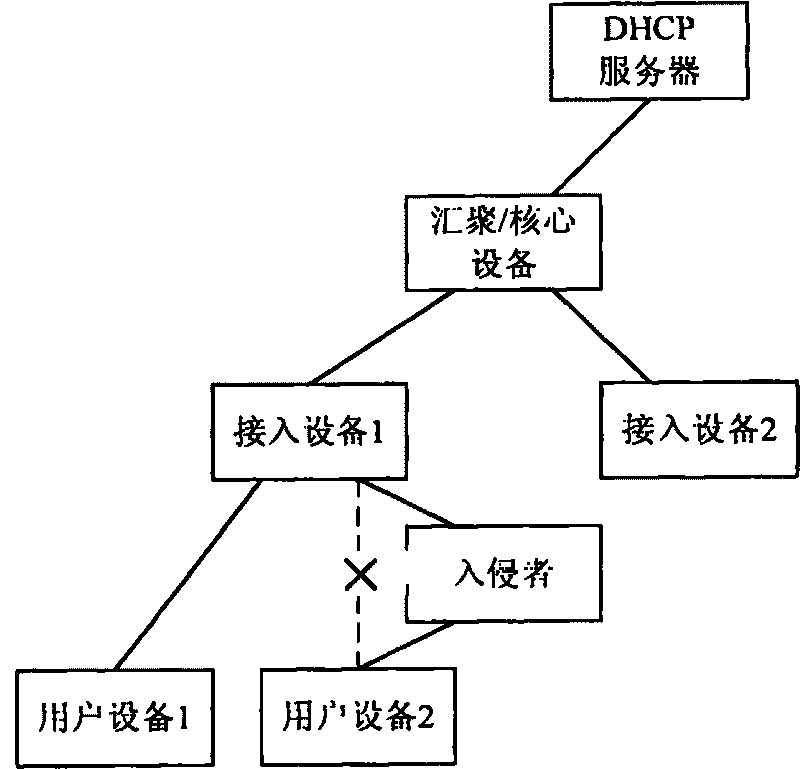
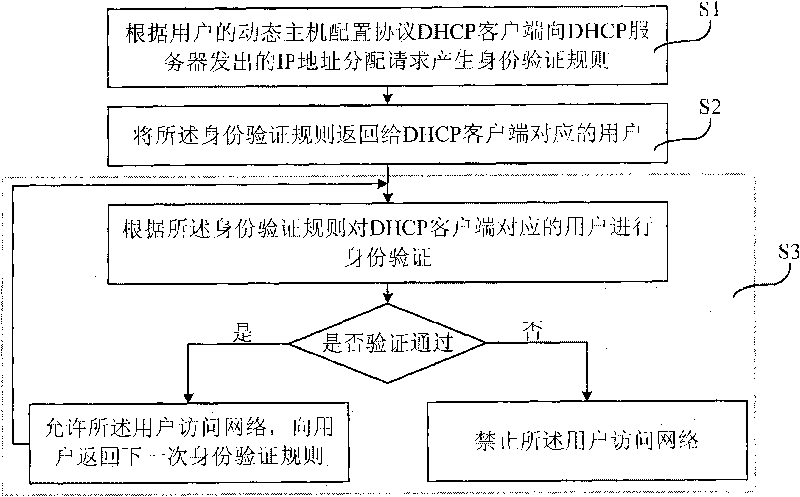
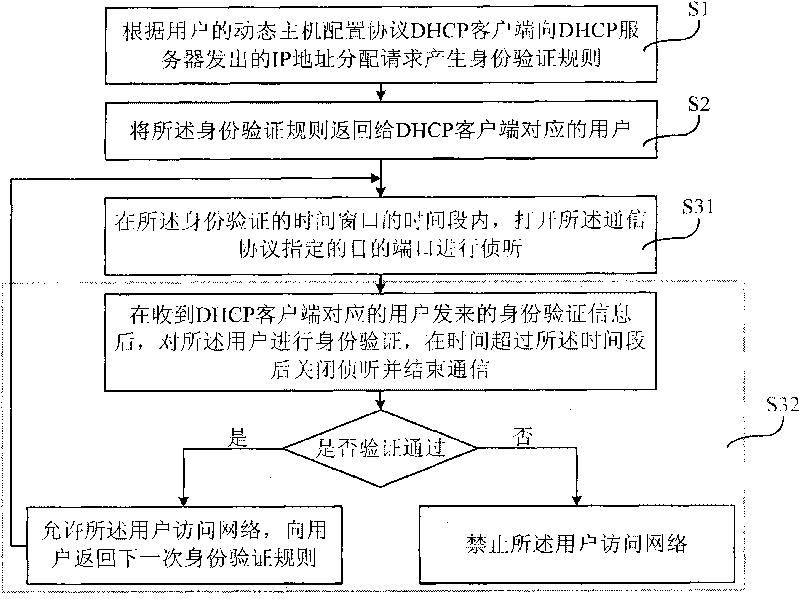
Safe address allocation method, detecting device, detecting equipment and detecting system
The embodiment of the invention provides a safe address allocation method, a detecting device, detecting equipment, user equipment, a DHCP server and a safe address allocation system. By performing regular identity authentication on a user through the detecting device, the embodiment of the invention can use different identity rules in each time of identity authentication to ensure that an illegal user is hard to judge which message is a message for identity authentication and how to authenticate identity, so that the illegal user cannot falsely use the identity of a legal user to access network, and is prevented from embezzling the IP address and the MAC address of the legal user for illegal operation.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Method and system for identity authentication and encryption of industrial user
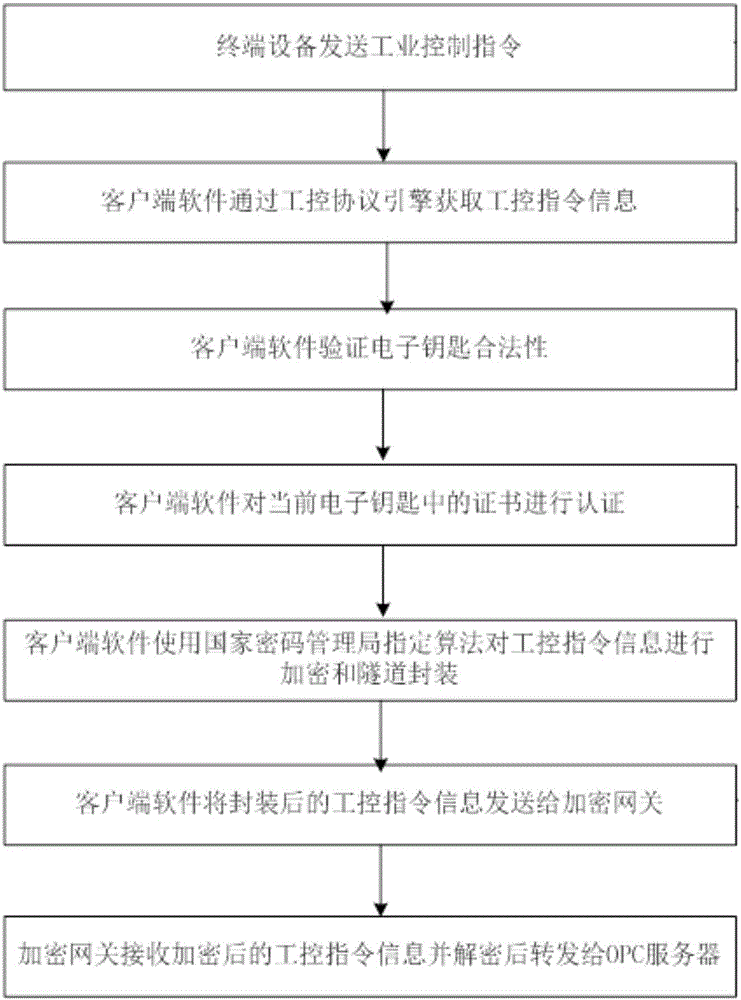
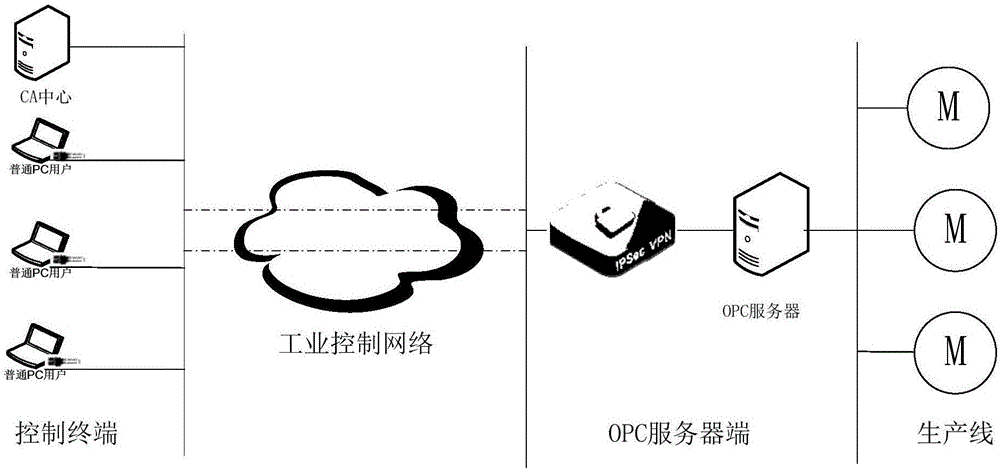
ActiveCN106100836AAvoid illegal operationEnsure safetyKey distribution for secure communicationTerminal equipmentAuthentication server
The invention relates to the field of industrial information security technologies, in particular to a method and a system for identity authentication and encryption of an industrial user. The method comprises the following steps that an electronic key is connected to user terminal equipment through a USB interface and login of a client is realized through the user terminal equipment; a client compares a hardware feature code of the user terminal equipment and a hardware feature code bound with the electronic key, if the hardware feature code of the user terminal equipment and the hardware feature code bound with the electronic key are consistent and an authentication server verifies that a user certificate has legality, the client obtains industrial control command information and carries out encryption and packaging processing to obtain an encrypted data packet; the client transmits the data packet to an encryption gateway; and the encryption gateway carries out unpacking and decryption processing on the data packet to obtain decrypted industrial control command information and transmits the industrial control command information to an OPC server. According to the method and the system, a problem that the truth of the data packet cannot be guaranteed due to the low data transmission security of the industrial information system at the present stage is solved.
Owner:SEATECH TIANYU TECH BEIJING
Security authentication method, security authentication device and security verification system
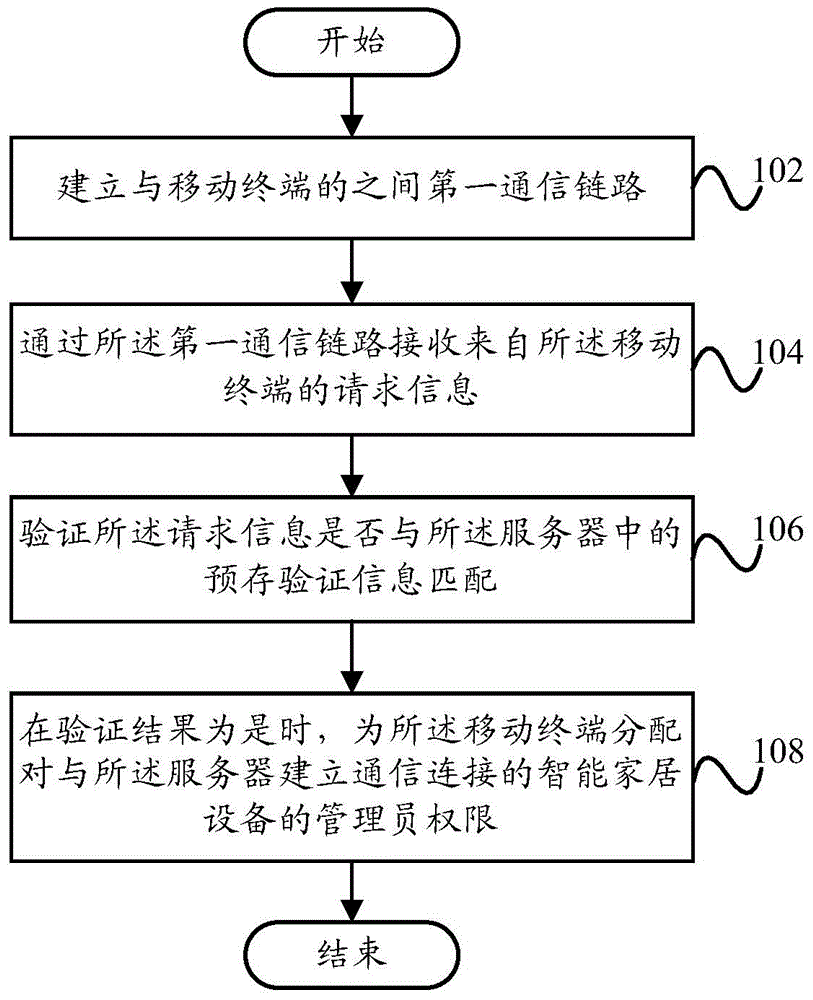
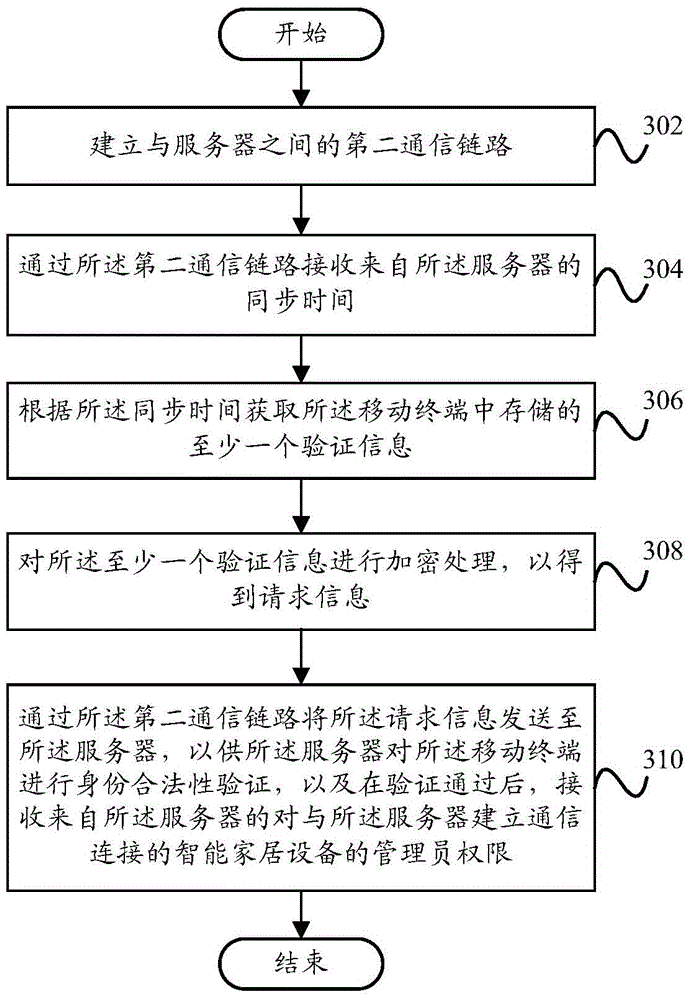
ActiveCN105635094AAvoid illegal operationImprove experienceComputer security arrangementsTransmissionPasswordCommunication link
The invention provides a security authentication method, a security authentication device and a security verification system. The security verification method for a server comprises the following steps: establishing a first communication link with a mobile terminal; receiving request information from the mobile terminal through the first communication link; verifying whether the request information is matched with pre-stored verification information in the server; and when the verification result is yes, allocating manager authority of an intelligent home device that establishes a communication connection with the server to the mobile terminal. By adopting the security verification method provided by the technical scheme of the invention, pointed security authentication is carried out by means of the properties of an intelligent home network, the illegal operation of the intelligent home device resulting from the leakage of a fixed password can be effectively avoided, and the security of the intelligent home network is improved, so that the user experience is improved.
Owner:シェンジェンインムーテクノロジーシーオーエルティーディー
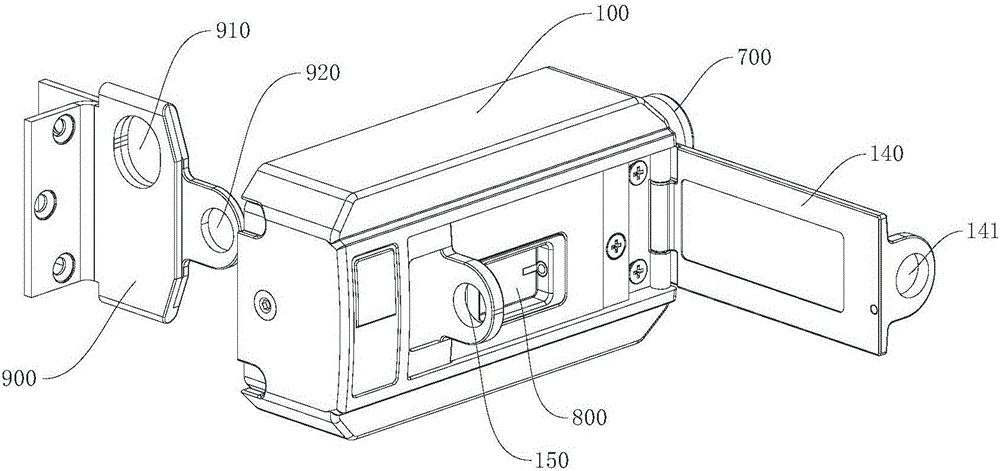
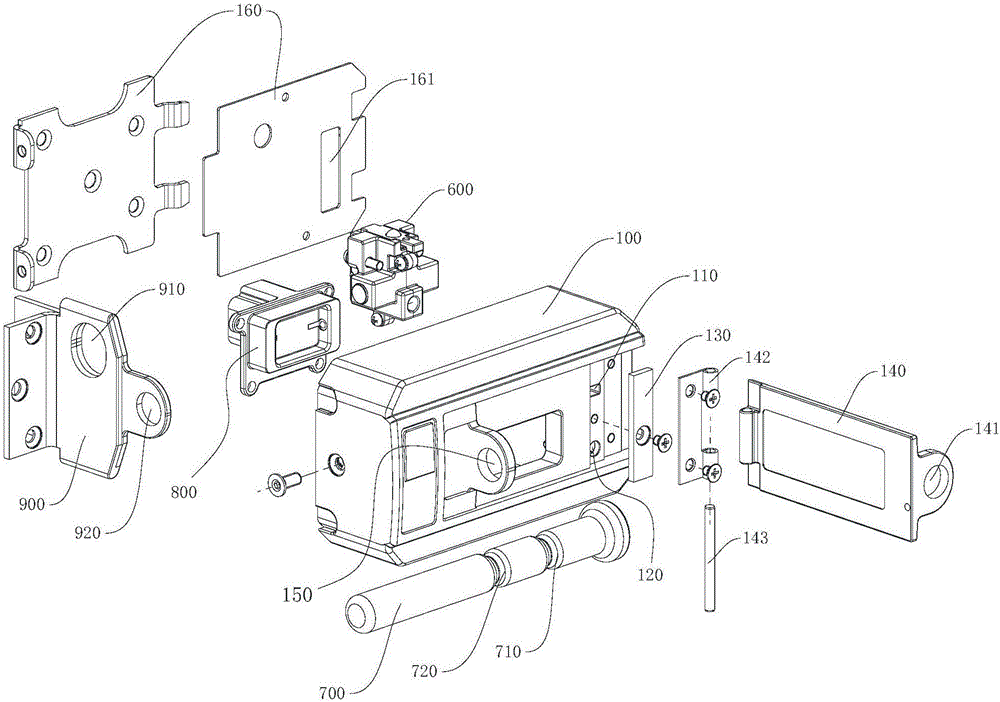
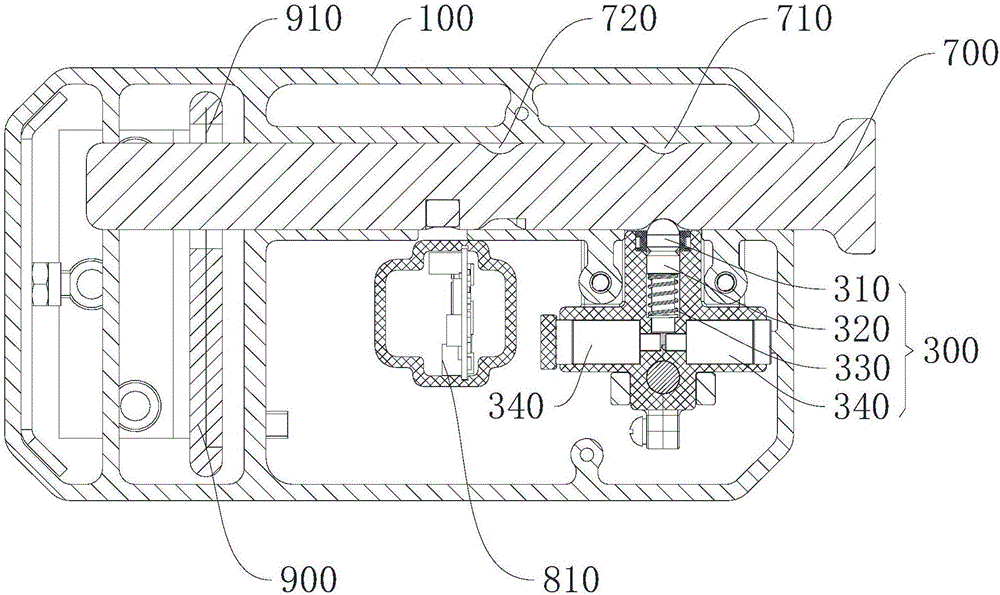
Electronic lock and emergency unlocking method thereof
ActiveCN106522679AEmergency unlock implementationEasy to operateNon-mechanical controlsLocking mechanismEngineering
The invention provides an electronic lock and an emergency unlocking method thereof and relates to the field of locks. The electronic lock is simple in structure and reliable in performance, emergency unlocking can be conducted on the locked lock, and meanwhile, illegal operation of emergency unlocking under the non-emergency situation also can be effectively prevented, so that unified management and monitoring of the lock is ensured. The electronic lock comprises a locking pin and a lock tongue base of a main lock body. An electronic locking mechanism comprises a blocking shaft and a locking block matched with the blocking shaft in a contact mode. The telescopic motion of the blocking shaft drives the locking block to lock or loosen the locking pin. An emergency unlocking mechanism comprises a sliding block and an anti-push mechanism. The sliding block is slidably arranged on the lock tongue base and provided with a locking block hole. The locking block is arranged in the locking block hole. When the locking block locks the locking pin, the sliding block can push the locking block to be away from the blocking shaft. The anti-push mechanism is arranged in a lock tongue base containing cavity and can lock the sliding block, limit sliding of the sliding block and release locking of the sliding block during emergency unlocking.
Owner:ZHUHAI UNITECH POWER TECH CO LTD
Fuel tanker truck transport state monitoring system and method
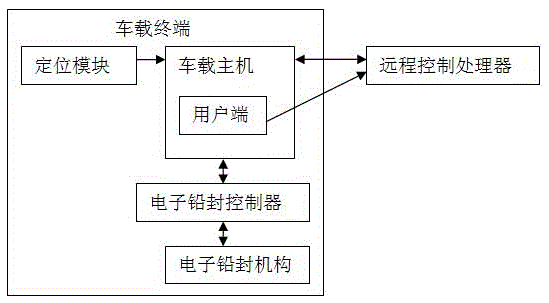
InactiveCN105425763AAvoid illegal operationImprove reliabilityTransmission systemsTotal factory controlRemote controlTank truck
The invention provides a fuel tanker truck transport state monitoring system. The system comprises a vehicle-mounted terminal and a remote control processor, wherein the vehicle-mounted terminal is mounted on a fuel tanker truck, and the vehicle-mounted terminal and the remote control processor are connected through a wireless network. The invention further provides a fuel tanker truck transport state monitoring method. The system and method provided by the invention prevent such phenomena of random parking, private loading and unloading of oil products and the like in the transport process of the fuel tanker truck in the prior art and have the advantages of comprehensive monitoring, high reliability, convenient operation and the like.
Owner:GUIGANG JIATE ELECTRONICS TECH CO LTD
Secure communication method and system of secure server
ActiveCN103036883ASignificant progressAvoid illegal operationTransmissionSecure communicationComputer terminal
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
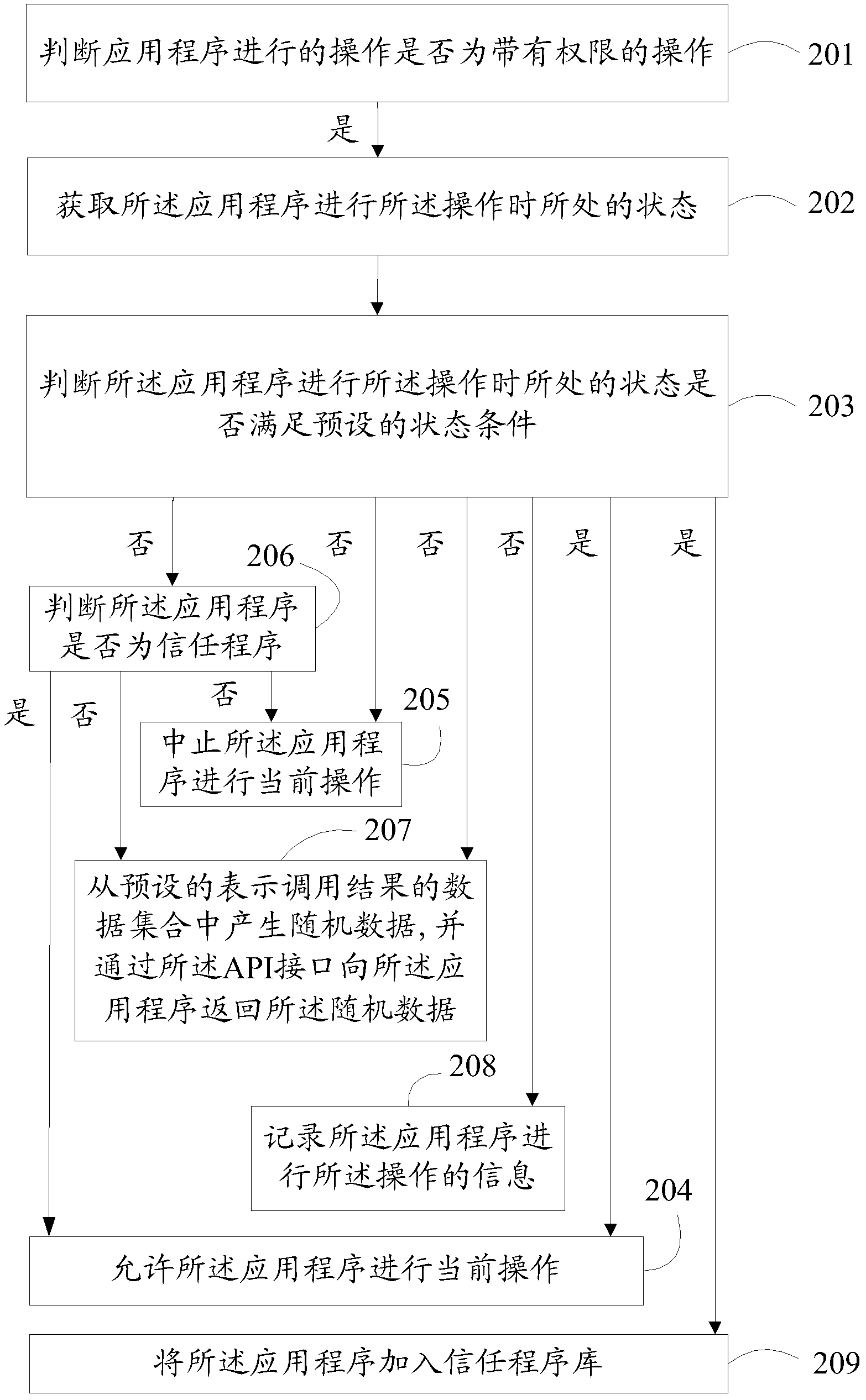
Safety management method and device based on user behavior
ActiveCN103218552AAvoid illegal operationImprove securityDigital data authenticationSubstation equipmentApplication softwareMalware
The embodiment of the invention discloses a safety management method and device based on a user behavior. By judging whether the operation is the user behavior or not, the illegal operation of malicious software is prevented, and loss brought to a user is avoided. The method provided by the embodiment mainly comprises the steps that whether a status meets a preset status condition when the operation is carried out by an application program is judged, the preset status condition is a status condition which accords with the user behavior logic and is required by the operation carried out by the application program, and relevant treatment is carried out according to a judging result. The invention further provides a corresponding safety management device based on the user behavior. By the adoption of the safety management method and device, illegal operation is avoided, and the safety management based on the user behavior is realized.
Owner:HUAWEI DEVICE CO LTD
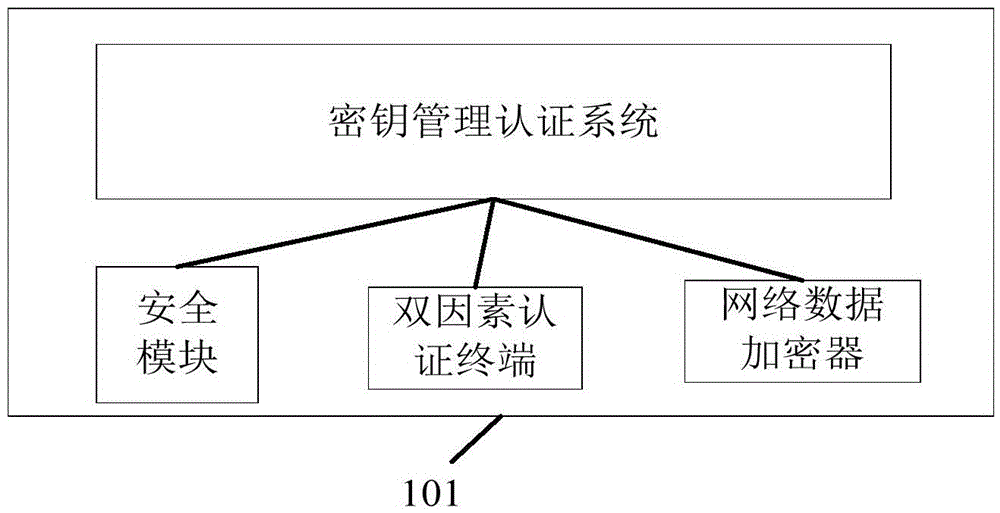
Industrial information security authentication system
InactiveCN105471901AAvoid destructionPrevent illegal theftTransmissionTerminal equipmentNetwork data
The invention provides an industrial information security authentication system, comprising a key management authentication system, a security module, a network data encryption device and a double-factor access authentication terminal. The industrial information security authentication system provided by the invention is mainly used for preventing illegal access, preventing data from being illegally tampered, damaged and stolen, and prevents illegal operation. According to the industrial information security authentication system provided by the invention, registration, authentication and management of terminal equipment are achieved. The aim that the legal terminal accesses the legal network and the legal platform manages the legal device is achieved, and a support effect is provided for preventing the information from being used without authorization or misused.
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
Service processing method and system, network side device and vending machine
InactiveCN106228683AAvoid illegal operationEasy to operateCoin-freed apparatus detailsApparatus for dispensing discrete articlesPasswordCipher
The invention provides a service processing method and system, a network side device and a vending machine. The method includes the steps that when the vending machine detects a service request of a user, the facial image information of the user is collected, wherein the facial image information is used for verifying the identity of the user; the vending machine makes the service request related to the facial image information and sends the service request and the facial image information to the network side; when the vending machine conforms that the user passes the identity verification and the service request is successfully processed according to the feedback of the network side, corresponding service is provided for the user. When the corresponding service is achieved by the user through the vending machine, the identity of the user is verified through the facial image information of the user, operation is easy and convenient, and the security is higher compared with a value card which needs to be used after a password is input.
Owner:河北徐宁机电设备有限公司
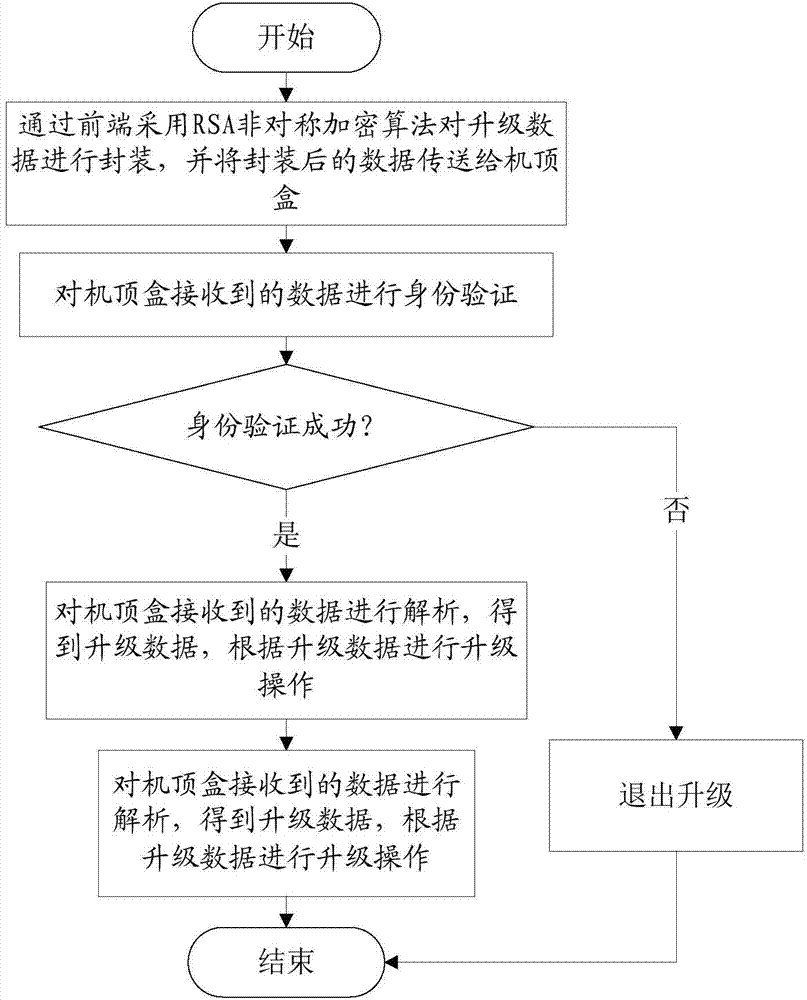
Method and system for preventing set top box software from malicious upgrade
InactiveCN104780445APrevent malicious modificationProtect interestsSelective content distributionEncapsulated dataData shipping
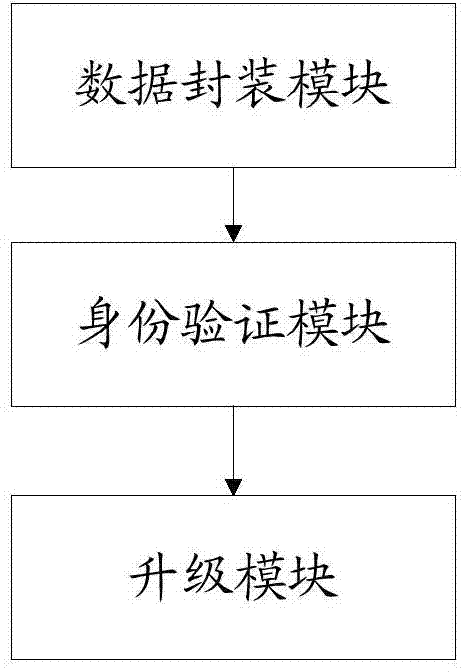
The invention provides a method for preventing set top box software from malicious upgrade, comprising the steps as follows: step 10, encapsulating upgrade data by adopting RSA asymmetric cryptographic algorithm via a front end and transmitting the encapsulated data to a set top box; step 20, authenticating data received by the set top box, and entering a step 30 if the authentication is successful; otherwise, quitting the upgrade; step 30, analyzing the data received by the set top box to obtain upgrade data and performing upgrade according to the upgrade data. The invention further provides a system for preventing set top box software from malicious upgrade, comprising a data encapsulation module, an authentication module and an upgrade module. The method and the system of the invention improve safety of data and effectively prevent illegal operation.
Owner:FUJIAN NEWLAND COMM SCI TECH
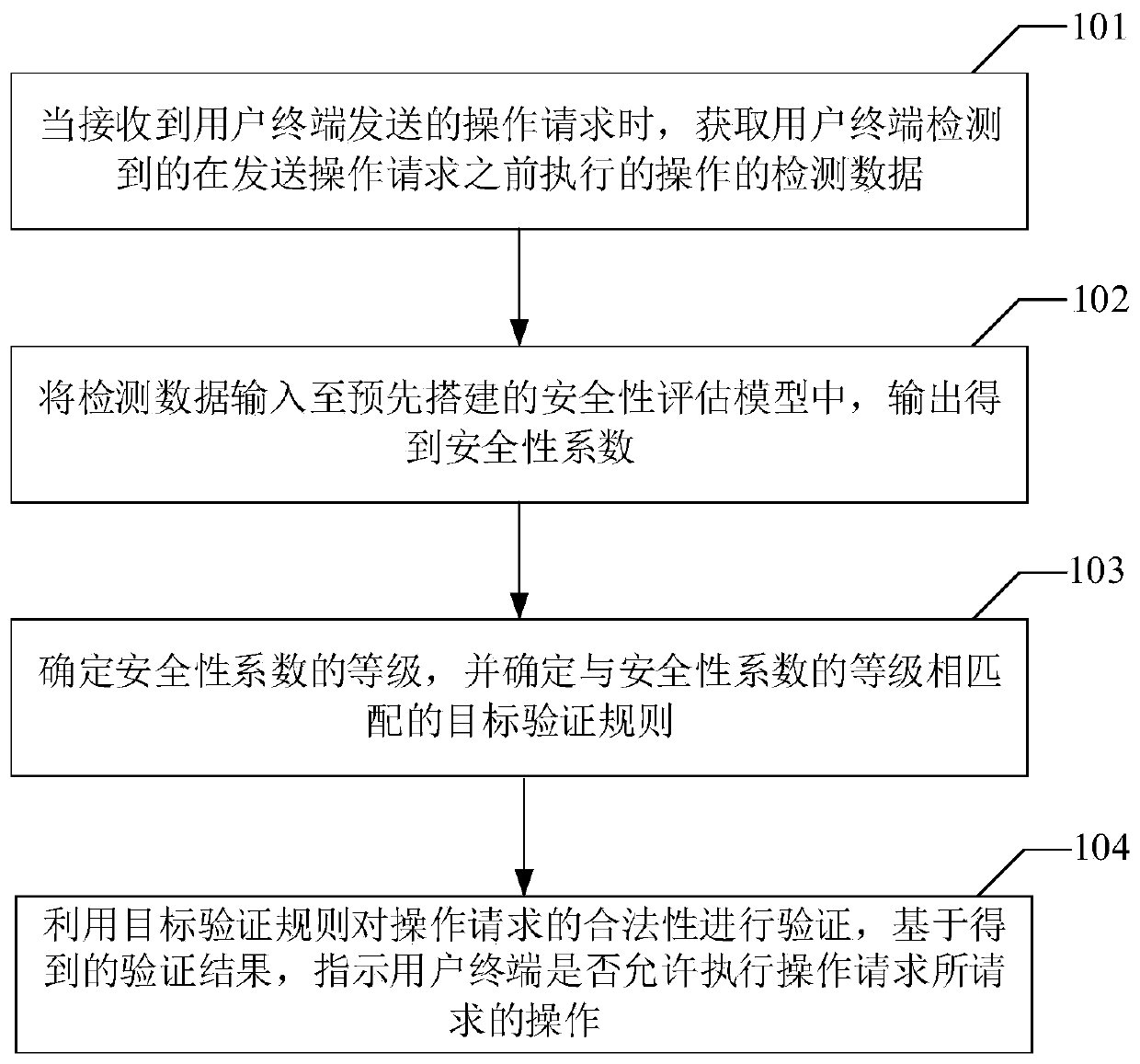
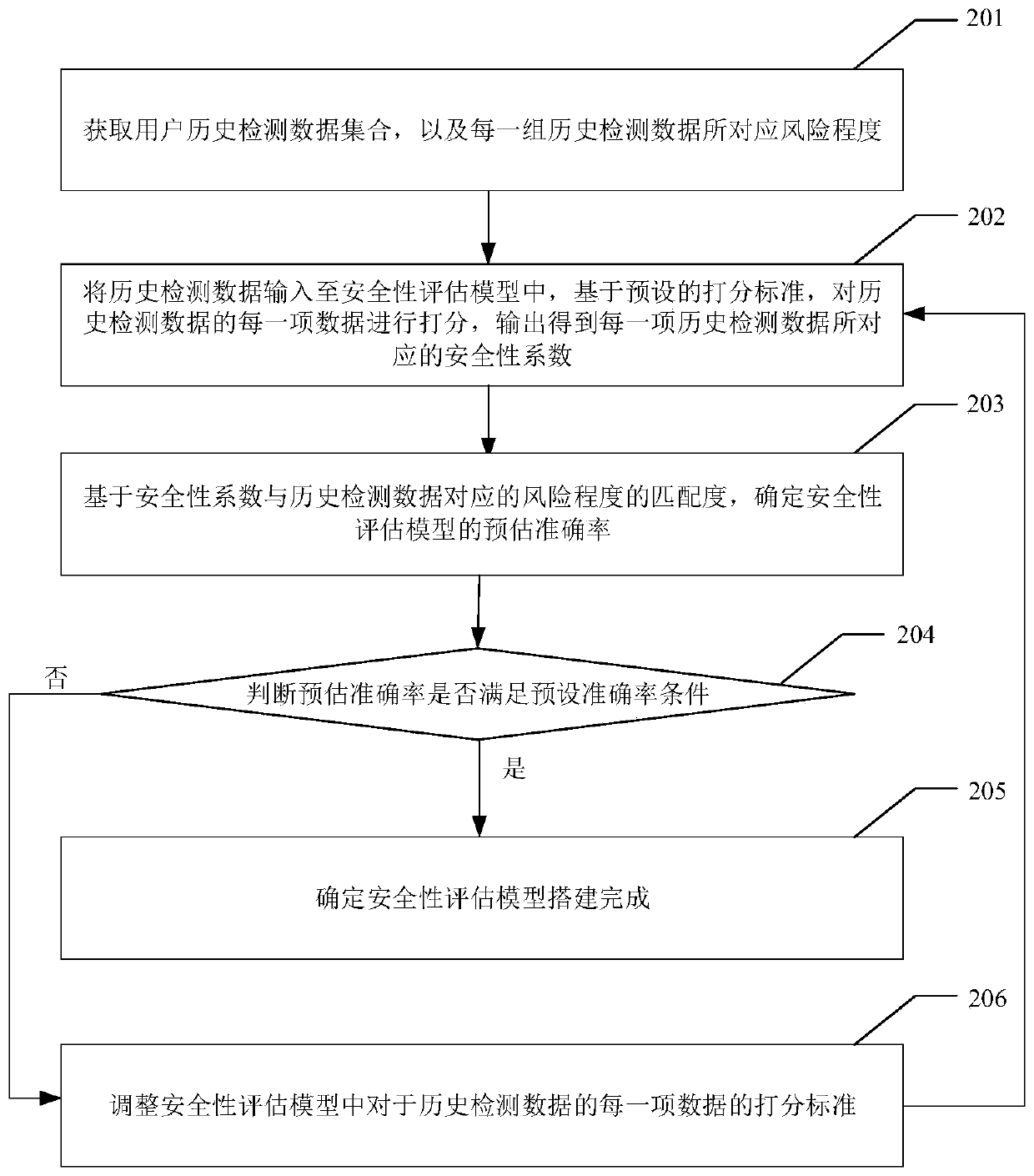
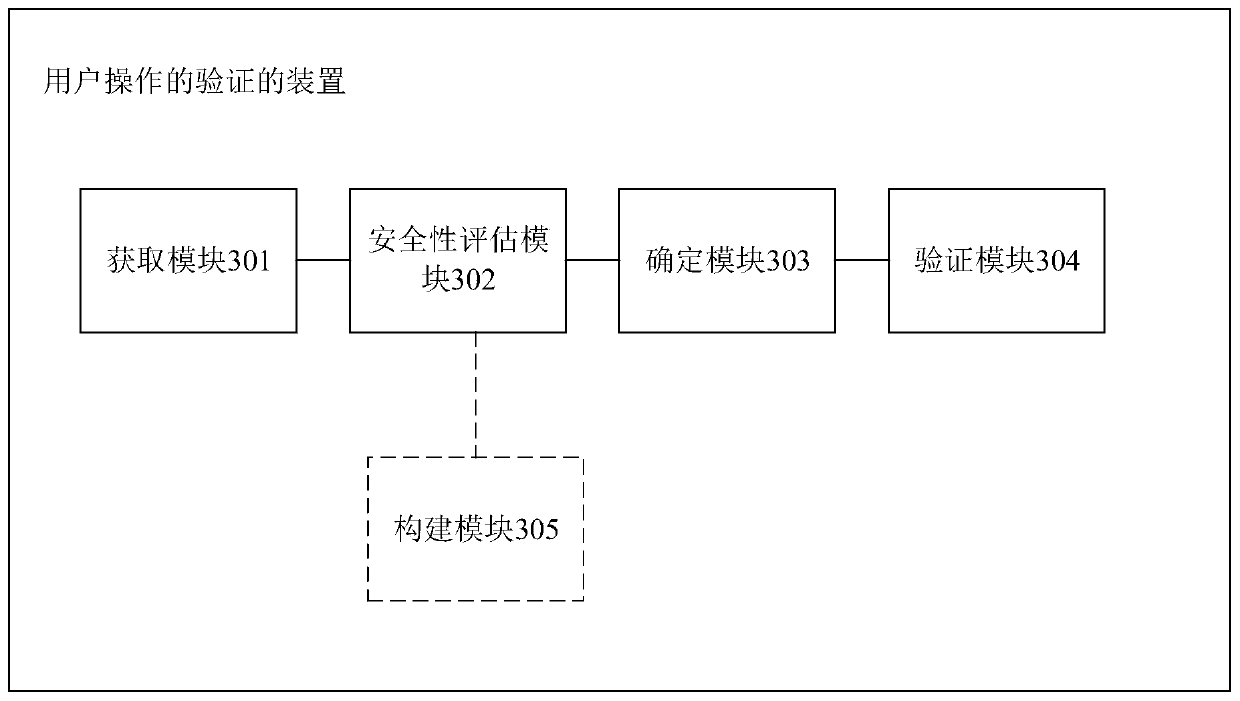
Method and device for verifying user operation
InactiveCN110084011AOperational Behavior MonitoringAvoid illegal operationDigital data authenticationPlatform integrity maintainanceComputer terminalComputer security
The invention provides a user operation verification method and device, and the method comprises the steps: obtaining the detection data of an operation which is detected by a user terminal and executed before an operation request is sent when the operation request sent by the user terminal is received; inputting the detection data into a pre-established security evaluation model, and outputting to obtain a security coefficient which is used for describing the risk of the operation request; determining the level of the security coefficient, and determining a target verification rule matched with the level of the security coefficient; and verifying the legality of the operation request by using the target verification rule, and indicating whether the user terminal is allowed to execute theoperation requested by the operation request based on an obtained verification result. By means of the method, the safety of the user account in the operation execution process of the user can be improved, and the behavior that the user executes illegal operation after logging in maliciously is avoided.
Owner:BEIJING TRUSFORT TECH CO LTD
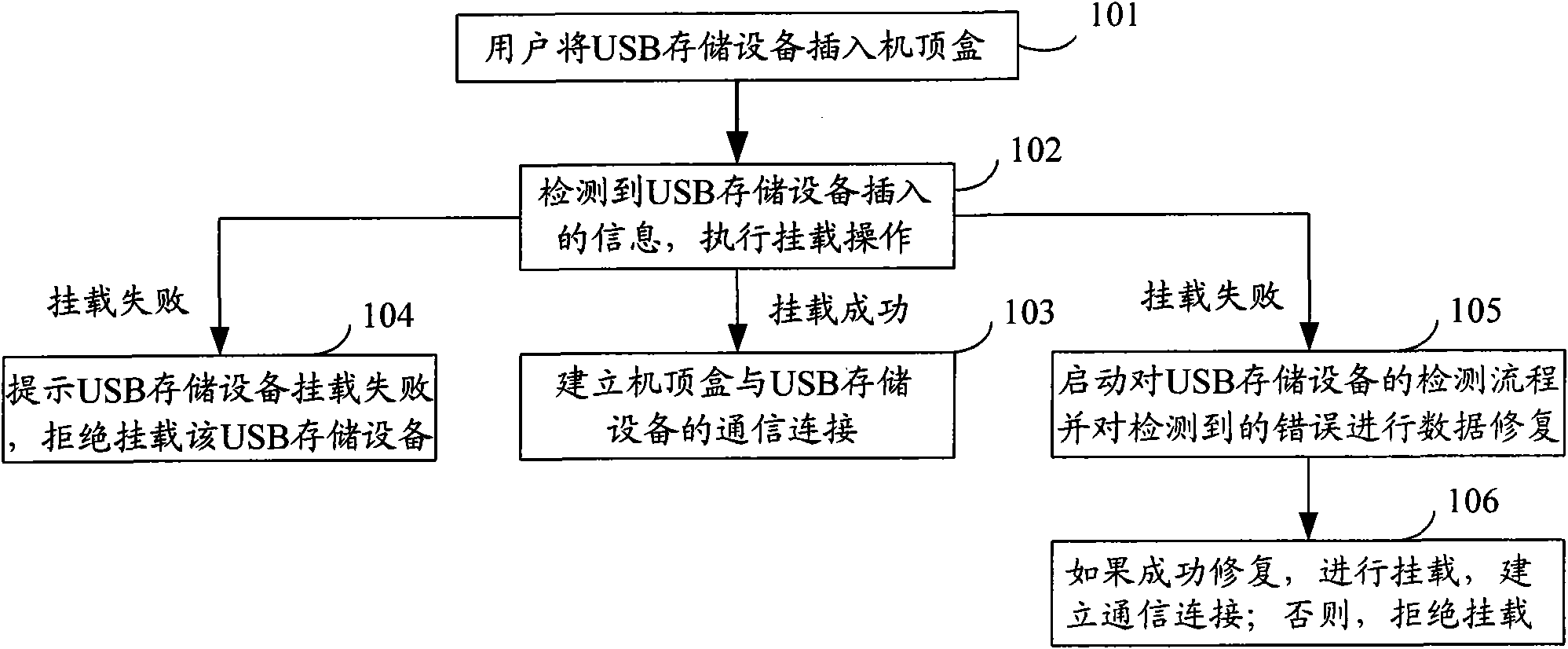
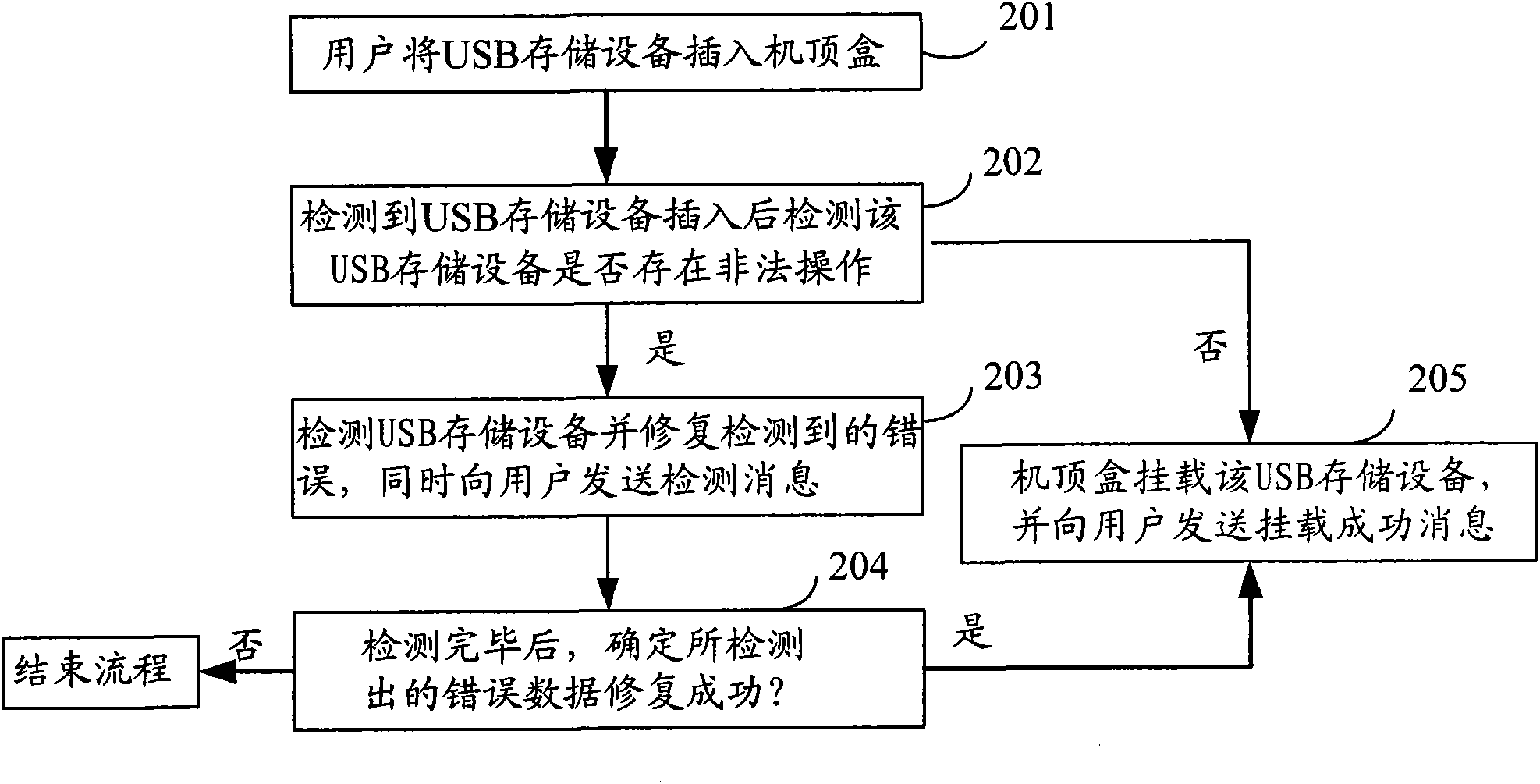
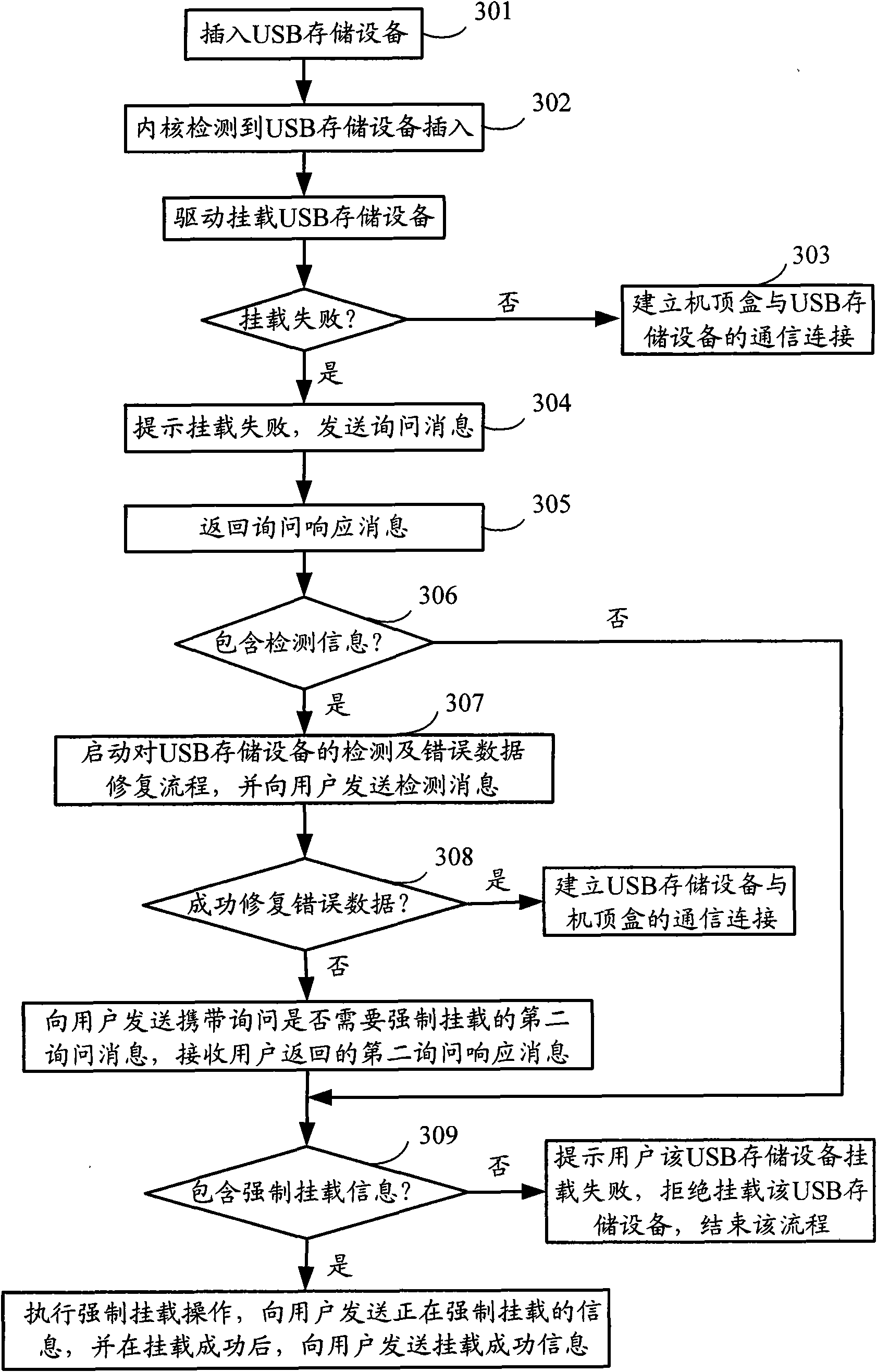
Method and digital TV receiving terminal for mounting storage device
InactiveCN101650695AIncrease success rateKnow the mounting status in real timeTelevision systemsElectric digital data processingEmbedded systemDigital television
The invention discloses a method for mounting a storage device, comprising the following steps: detecting the insertion of the storage device and judging whether the inserted storage device carries out illegal operation or not, if so, entering the next step; detecting the storage device, restoring the detected error data and sending a detected message to a user; confirming that the error data aresuccessfully restored and mounting the storage device. The invention also discloses a digital TV receiving terminal for mounting the storage device. By applying the method and the digital TV receivingterminal for mounting the storage device, the user can know the mounting state of the storage device in real time, thereby avoiding the illegal operation caused by drawing the device out by the userwho considers that the storage device is not identified because no any prompting information appears in a long-term detecting process, and improving the success ratio of mounting the storage device.
Owner:SHENZHEN COSHIP ELECTRONICS CO LTD
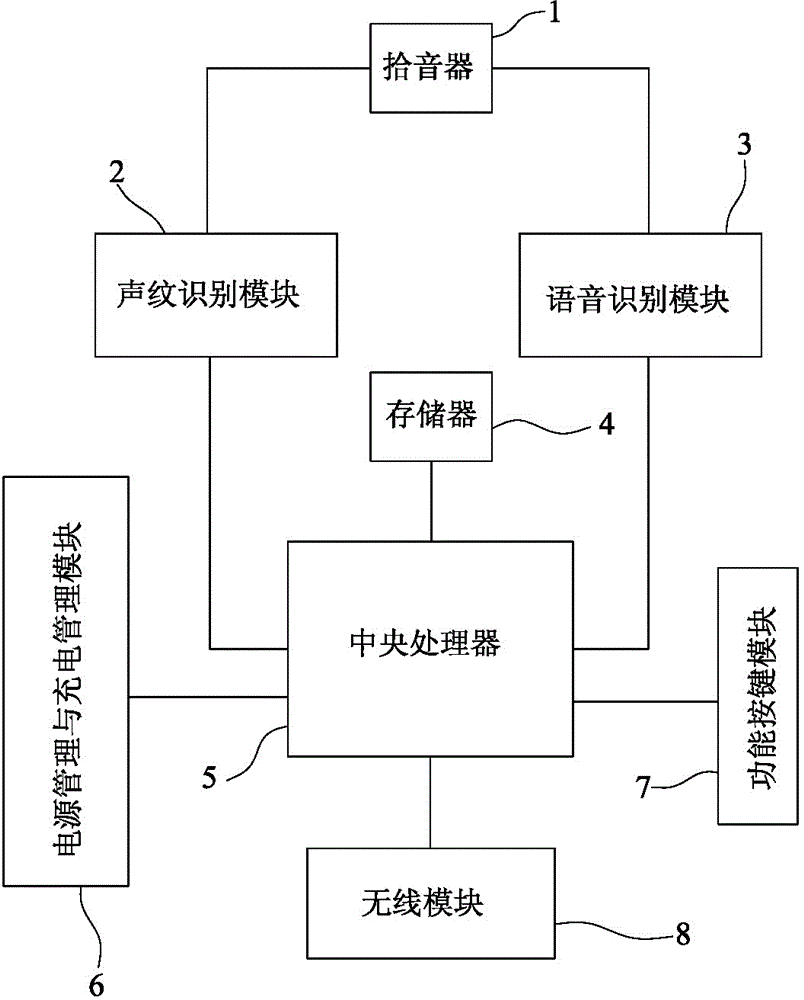
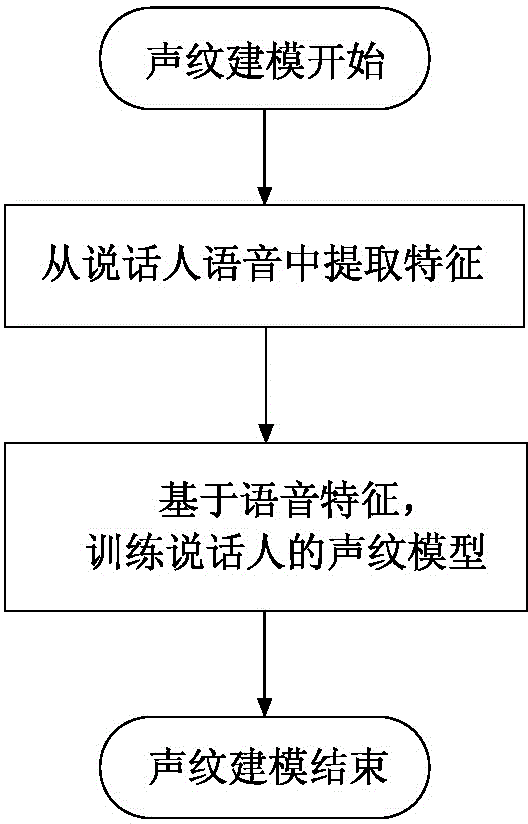
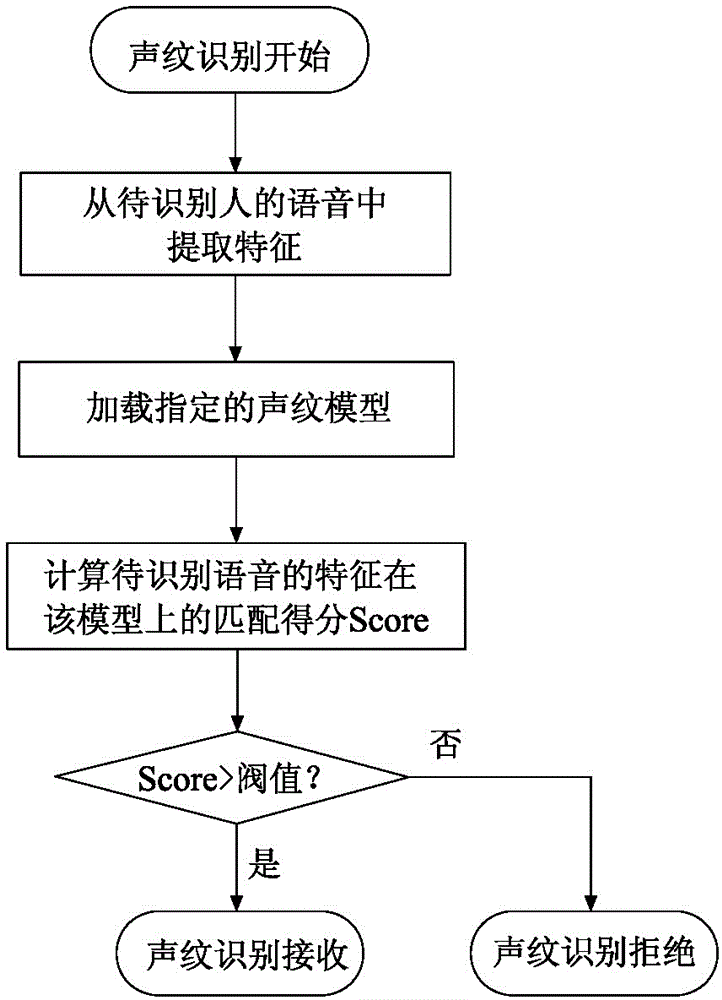
Intelligent home voice management system based on voiceprint recognition
InactiveCN105336328AWith voiceprint recognition functionAvoid illegal operationSpeech recognitionTotal factory controlSpeech soundManagement system
The invention discloses an intelligent home voice management system based on voiceprint recognition, comprising a pickup, a voiceprint recognition module, a voice recognition module, a storage, a central processing unit, a wireless module, a power management and charge management module, and a key functional module. The pickup is connected with the voiceprint recognition module and the voice recognition module. The voiceprint recognition module, the voice recognition module, the storage, the wireless module, the power management and charge management module and the key functional module are connected with the central processing unit. The system is simple in structure, easy to control and convenient to use.
Owner:XIAMEN KONGLE TECH CO LTD
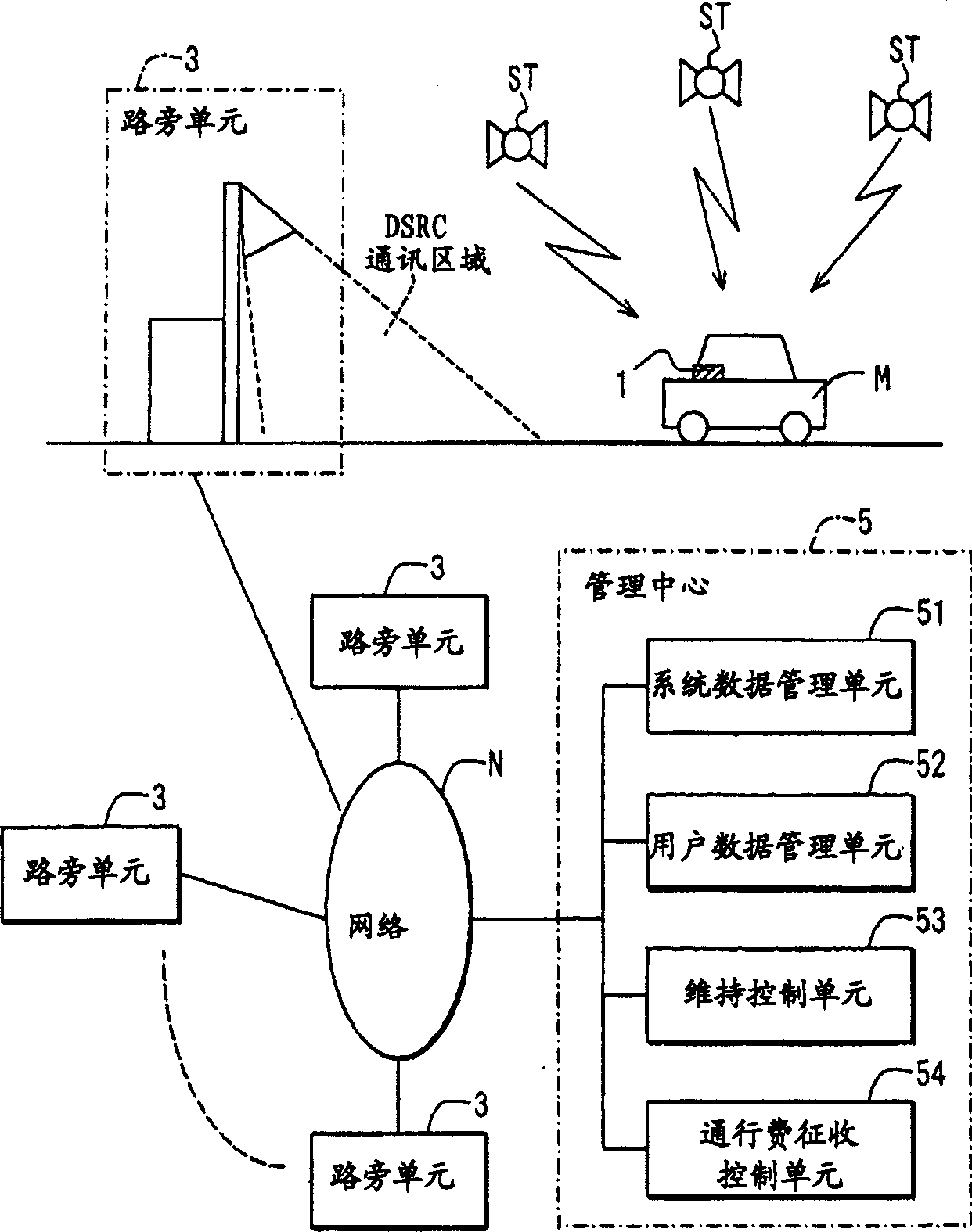
Vehicle device and service supply system
InactiveCN1342571AAvoid illegal operationFair and reliable toll collection operationsTicket-issuing apparatusRegistering/indicating working of vehiclesLocation detectionService provision
If acquisition of measured position and time data (position / time) from a position detection unit fails, a "GPS OFF mode" is set, and the latest position and time data is stored as start data. Thereafter, when the position and time data is obtained successfully, and the operation is recovered from the "GPS OFF mode", the "GPS OFF mode" is cancelled. Also, the obtained position and time data (restoration data) is stored. Monitor data is formed from the start data and the restoration data. The monitor data is transmitted to a management center through road-vehicle communication. Also, history data of the position and time stored in the position detection unit during the "GPS OFF mode" is read. If the history data satisfies the toll charging condition, the toll charging data is formed and is transmitted to the management center.
Owner:DENSO CORP
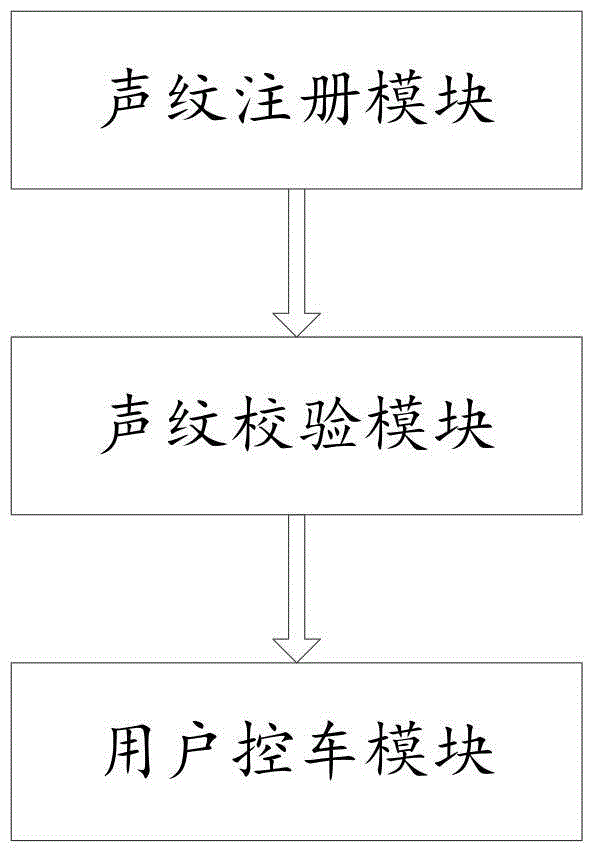
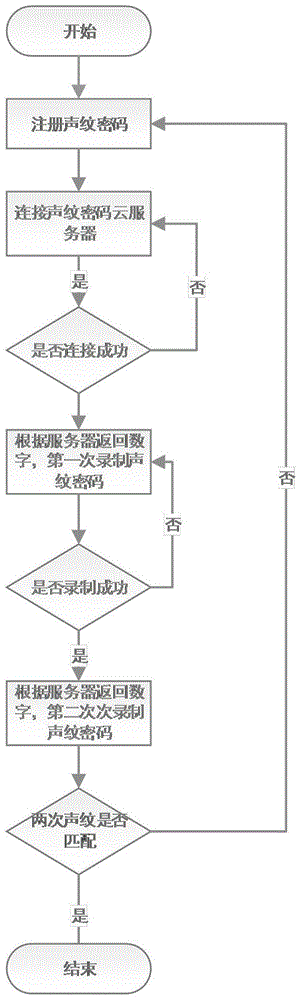
Voiceprint password vehicle control system and method
The present invention provides a voiceprint password vehicle control system and method. The system includes a voiceprint registration module, a voiceprint check module and a user vehicle control module. The voiceprint check module is connected to the voiceprint registration module and the user vehicle control module. The voiceprint registration module is used for collecting a voiceprint password of a user. The voiceprint check module is used for matching transmitted voiceprints. The user vehicle control module is used for vehicle control operation. The user can use the voiceprint password to control the vehicle by using a mobile phone App, and common control functions include ignition, misfire, unlocking, locking, warming, opening and closing of windows, and so on. An App based simple and safe vehicle control manner is provided for an owner of the vehicle.
Owner:DALIAN ROILAND SCI & TECH CO LTD
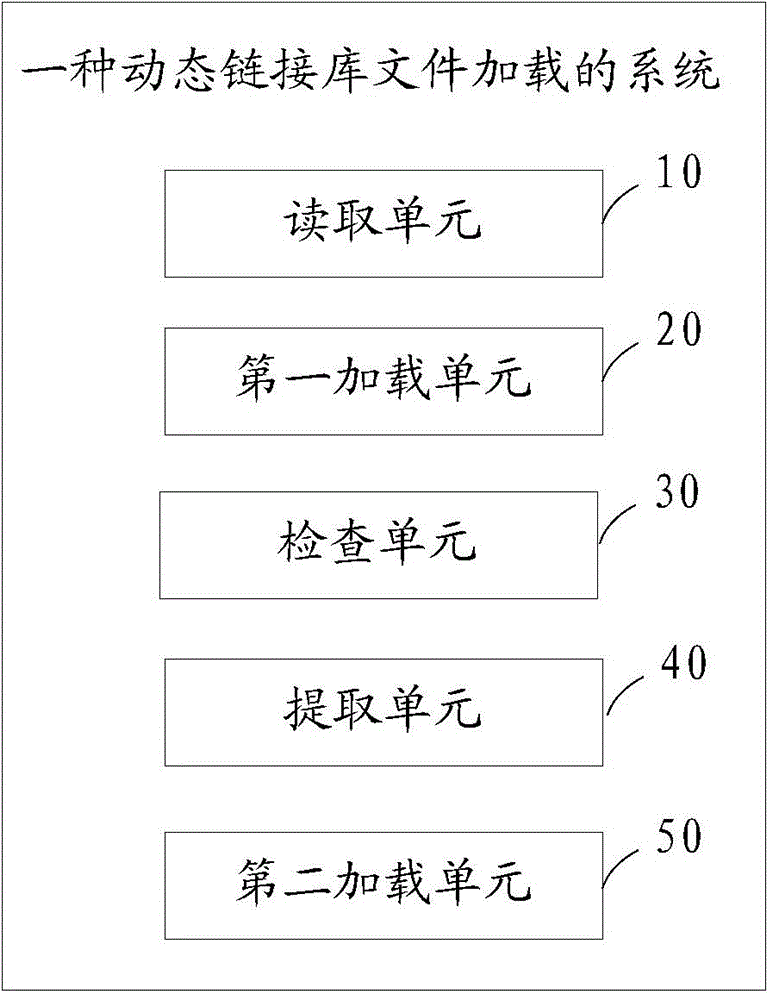
Dynamic link library file loading method and dynamic link library file loading system
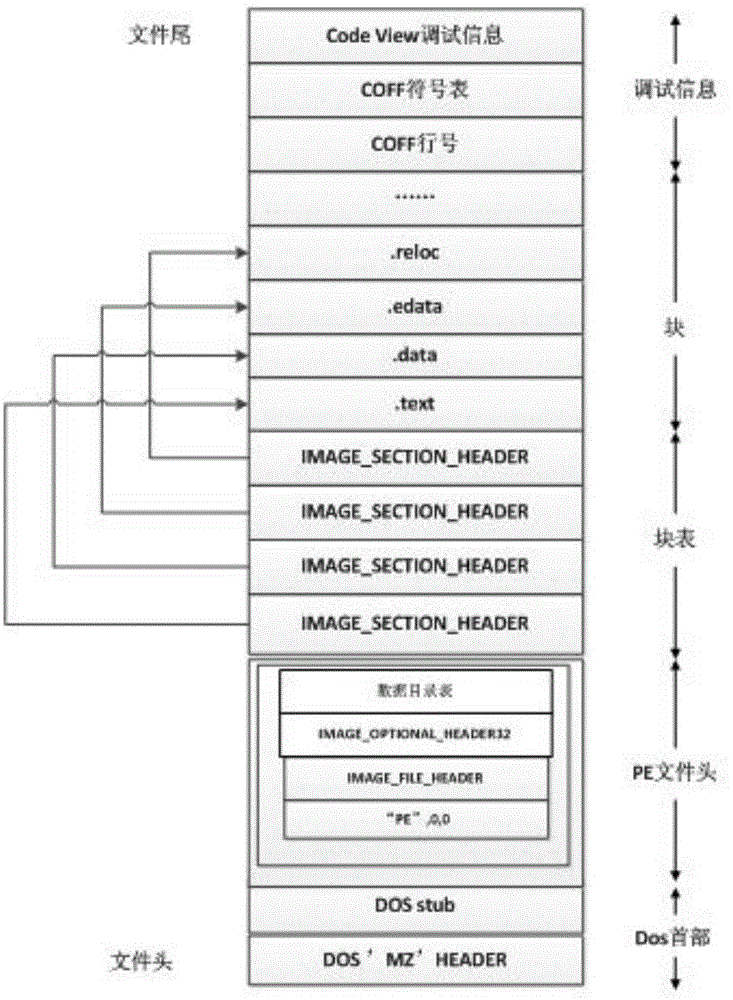
The invention relates to the field of a dynamic link library, and particularly relates to a dynamic link library file loading method and a dynamic link library file loading system. The method comprises the steps: S100, reading a dynamic link library file, and loading the dynamic link library file to a preset first memory; S200, checking whether the dynamic link library file conforms to a PE format or not; executing the step S300 if the dynamic link library file conforms to the PE format; otherwise, ending the step, and feeding back the error of the dynamic link library file; S300, extracting a PE head in the dynamic link library file according to the PE format, and loading the PE head to a preset second memory. According to the method, the dynamic link library file conforming to the PE format is loaded to the first memory, and the PE head of the dynamic link library file is loaded to the second memory, so that the PE loading is realized.
Owner:FUJIAN TQ DIGITAL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com