Method and device for verifying user operation
A user and user terminal technology, applied in the field of information processing, can solve problems such as the inability to realize real-time monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
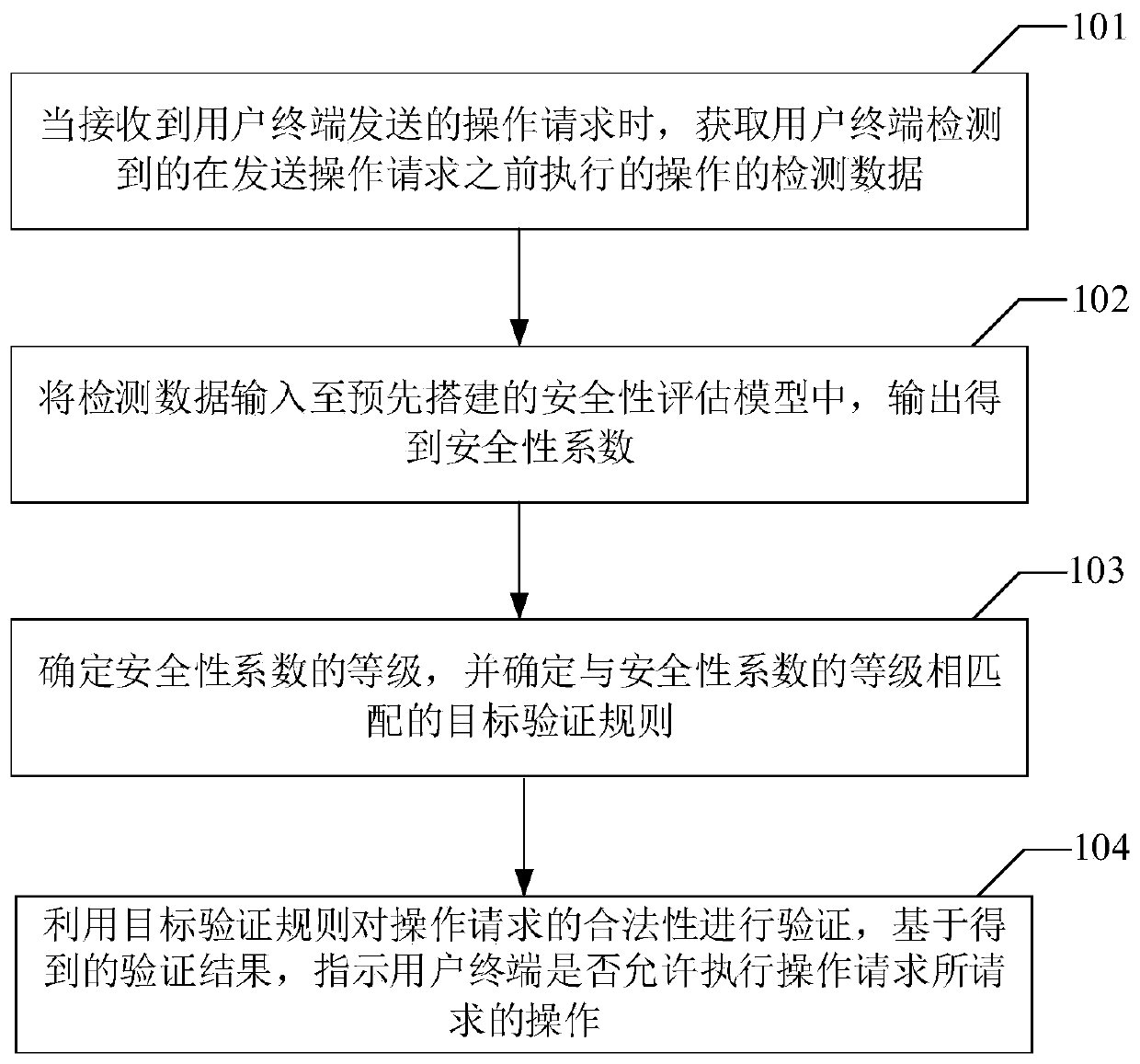
[0062] see figure 1 As shown, it is a schematic flowchart of a user operation verification method provided by the embodiment of the present application, which is executed by the server and includes the following steps:
[0063] Step 101. When receiving an operation request sent by a user terminal, acquire detection data of operations detected by the user terminal performed before sending the operation request.
[0064] When the user performs an operation through the user terminal, the user may send an operation request to the server through the user terminal, and the server may acquire detection data of the user terminal when receiving the operation request sent by the user terminal.
[0065] Wherein, the detection data of the user terminal may be the detection data of the operation performed by the user terminal before sending the operation request, and the user terminal may detect the data through a component installed on the application software.
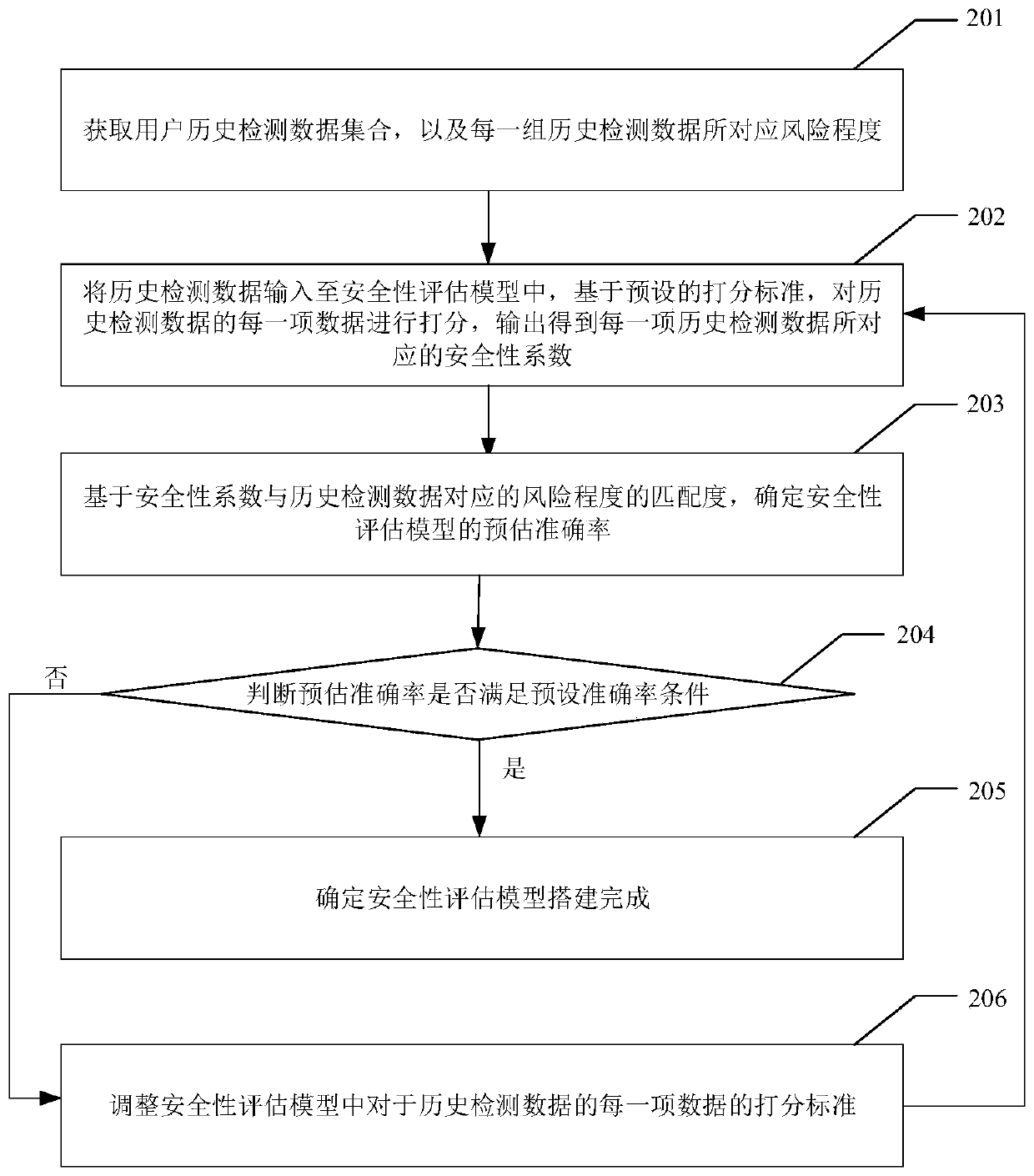
[0066] In a possible imp...
Embodiment 2
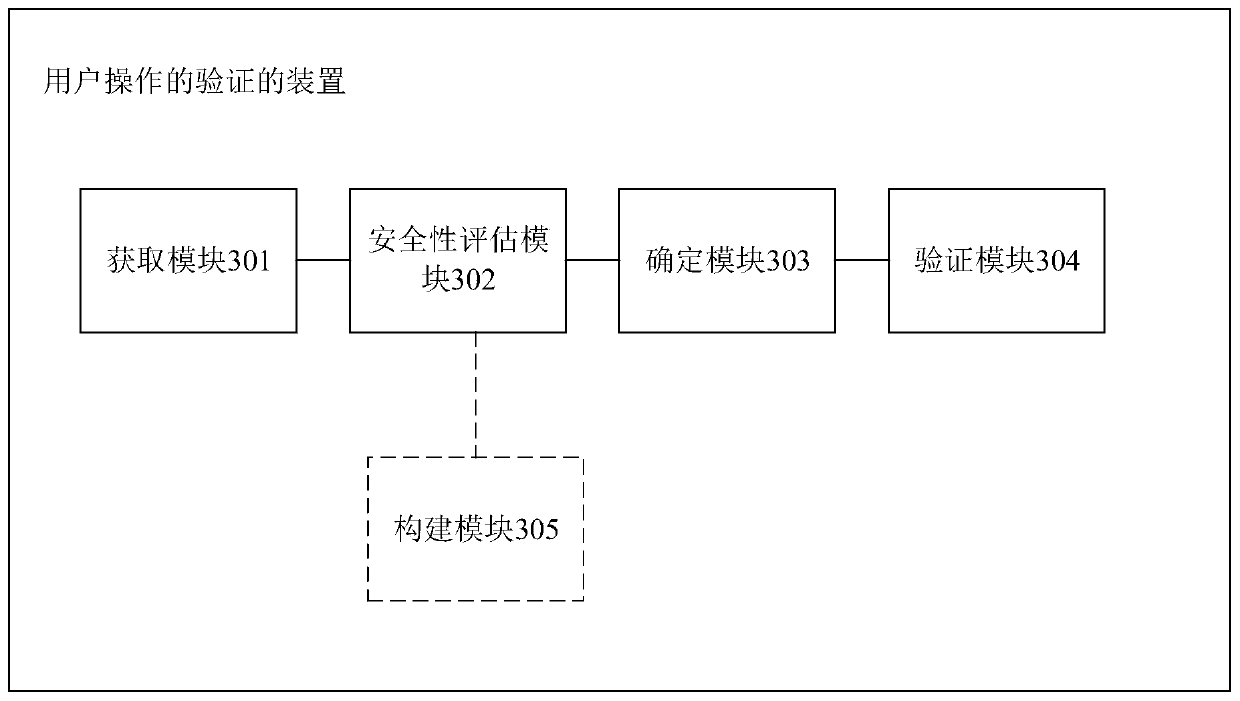
[0100] see image 3 As shown, it is a schematic diagram of the structure of a user-operated verification device provided by the embodiment of the present application, including an acquisition module 301, a security assessment module 302, a determination module 303, a verification module 304, and a construction module 305, specifically:
[0101] The obtaining module 301 is configured to, when receiving the operation request sent by the user terminal, obtain the detection data of the operation performed before sending the operation request detected by the user terminal;
[0102] A safety evaluation module 302, configured to input the detection data into a pre-built safety evaluation model, and output a safety factor, wherein the safety factor is used to describe the level of risk of the operation request;
[0103] A determining module 303, configured to determine the level of the safety factor, and determine a target verification rule matching the level of the safety factor;
...
Embodiment 3
[0123] Based on the same technical idea, an embodiment of the present application also provides an electronic device. refer to Figure 4 As shown, it is a schematic structural diagram of an electronic device 400 provided in the embodiment of the present application, including a processor 401 , a memory 402 , and a bus 403 . Among them, the memory 402 is used to store execution instructions, including a memory 4021 and an external memory 4022; the memory 4021 here is also called an internal memory, and is used to temporarily store calculation data in the processor 401 and exchange data with an external memory 4022 such as a hard disk. The processor 401 exchanges data with the external memory 4022 through the memory 4021. When the electronic device 400 is running, the processor 401 communicates with the memory 402 through the bus 403, so that the processor 401 executes the following instructions:
[0124] When receiving the operation request sent by the user terminal, acquiring...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com