Service locking method, service unlocking method, device and system
A business and unlocking technology, applied in the field of network property security, which can solve problems such as illegal operation of network virtual property
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
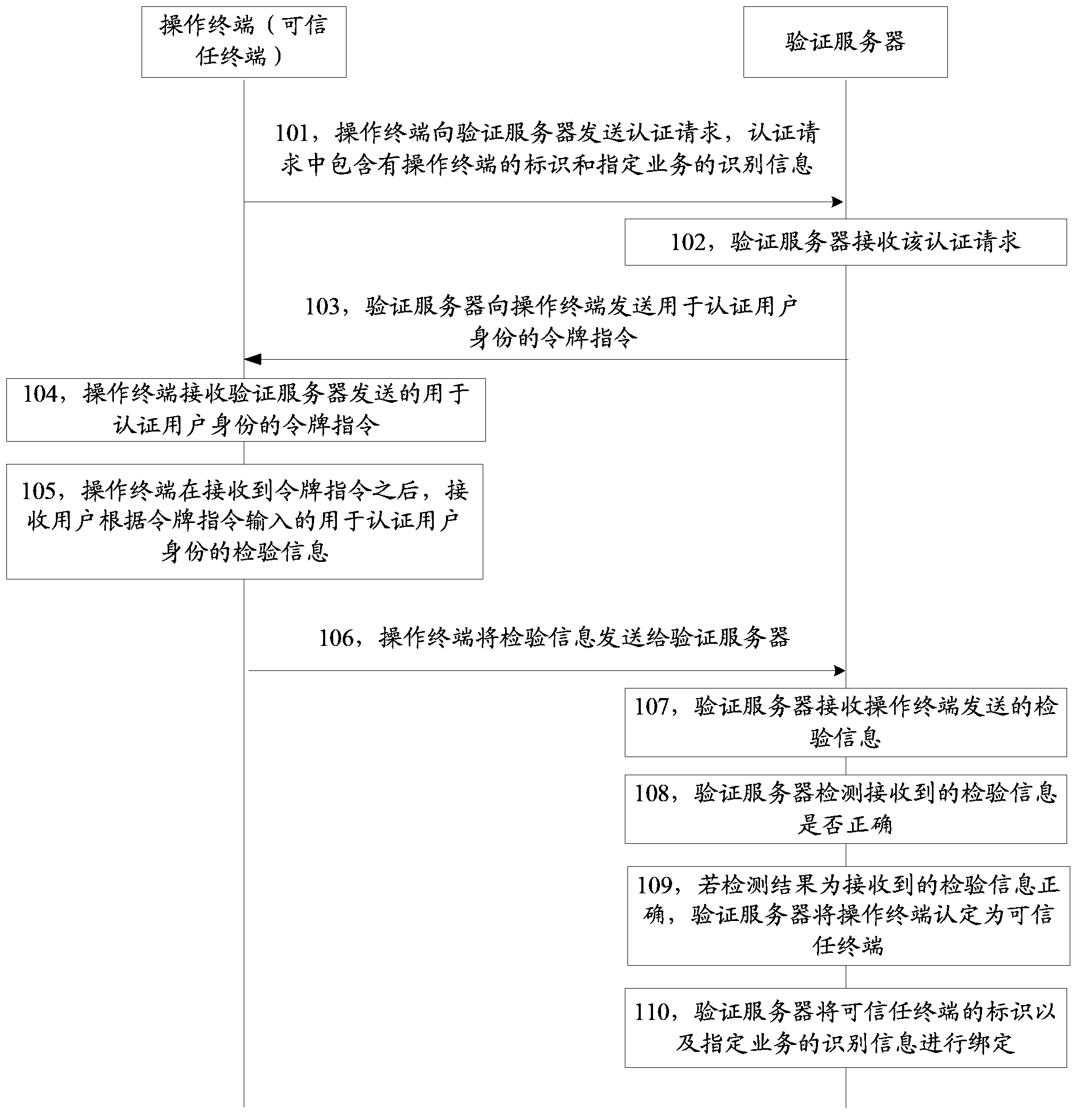
[0084] See figure 1 As shown in FIG. 1 , it shows the method flow chart of the service authentication method provided by Embodiment 1 of the present invention. The service authentication method is completed through the cooperation of the operation terminal and the verification server. The business authentication method may include:
[0085] Step 101, the operating terminal sends an authentication request to the verification server, and the authentication request includes the identification of the operating terminal and the identification information of the designated service;
[0086] The operating terminal here refers to a terminal for a user to perform related operations, such as a mobile phone, a personal computer, a multimedia TV, a multi-function camera, or an e-reader.
[0087] In practical application, the user can download and install an application program interface (app) or plug-in corresponding to the specified service provided by the server corresponding to the s...
Embodiment 2
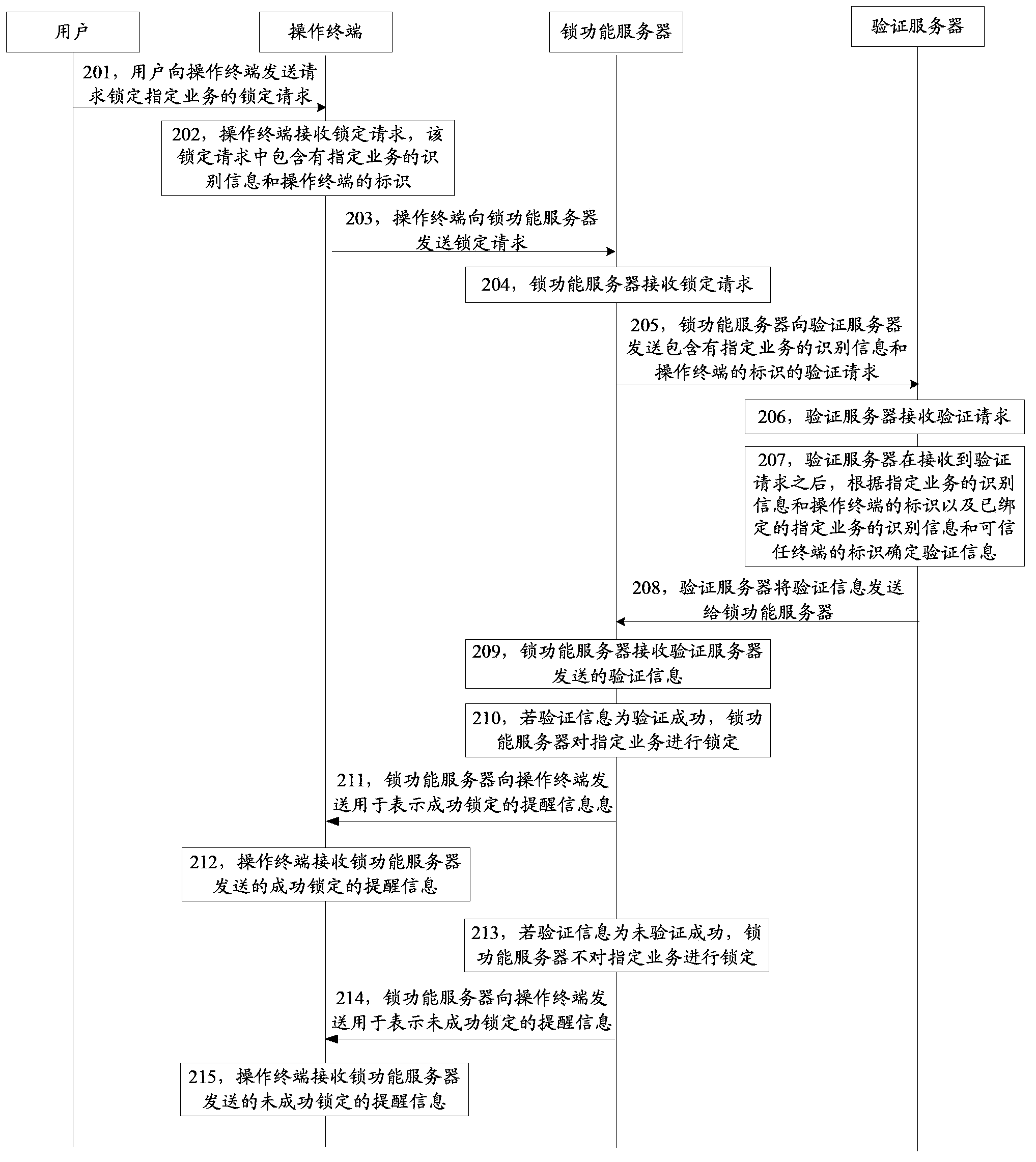
[0112] See figure 2 As shown in FIG. 2 , it shows a method flow chart of the service locking method provided in Embodiment 2 of the present invention. The service locking method can be completed through the cooperation of the operation terminal, the lock function server and the verification server. The business locking method may include:
[0113] Step 201, the user sends a lock request to the operation terminal to request to lock a specified service;
[0114] The designated business here is the business that performs sensitive operations on network virtual property, and sensitive operations can be consumed through network virtual property. For example, these specified businesses may usually include online payment operations, game currency usage operations, and the like. Users can ensure that the important information contained in these services will not be disclosed by locking the specified services.
[0115] It should be noted that the operating terminal here may be a t...
Embodiment 3
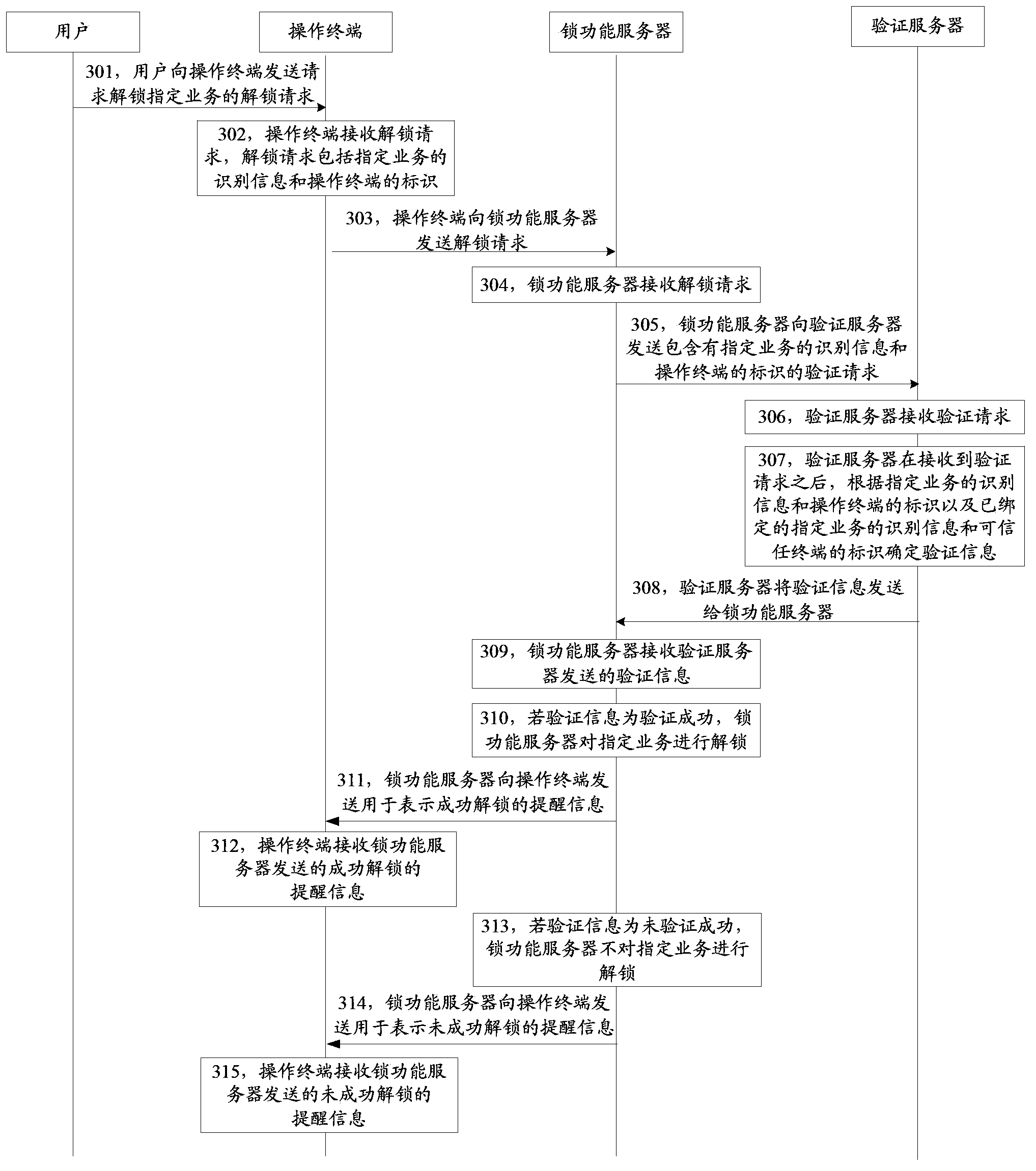
[0168] See image 3 As shown in , it shows the method flowchart of the service unlocking method provided by Embodiment 3 of the present invention. The business unlocking method can be completed by the cooperation of the operation terminal, the lock function server and the verification server. The business unlocking method may include:
[0169] Step 301, the user sends an unlocking request to the operating terminal requesting to unlock a specified service;
[0170] Designated services usually involve network virtual property. For example, these designated services may usually include online payment operations of user accounts, operations of using game currency, and other operations that carry user property information.
[0171] Usually, the user can choose to unlock a locked specified service on the operation terminal, so as to perform related operations through the unlocked specified service.
[0172] The operation terminal here can be a trusted terminal or an ordinary oper...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com