Secure communication method and system of secure server
A security server and communication system technology, applied in transmission systems, electrical components, etc., can solve problems such as unauthorized access by users, threats to security application systems, and difficulty in tracing and tracking, so as to improve security performance, avoid direct operation, and be strong. retroactive effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, but the protection scope of the present invention is not limited thereto.
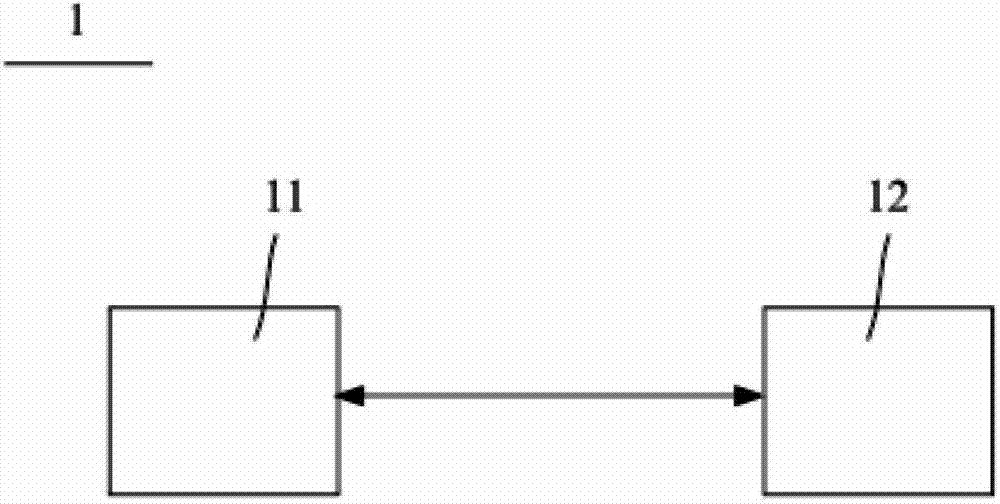
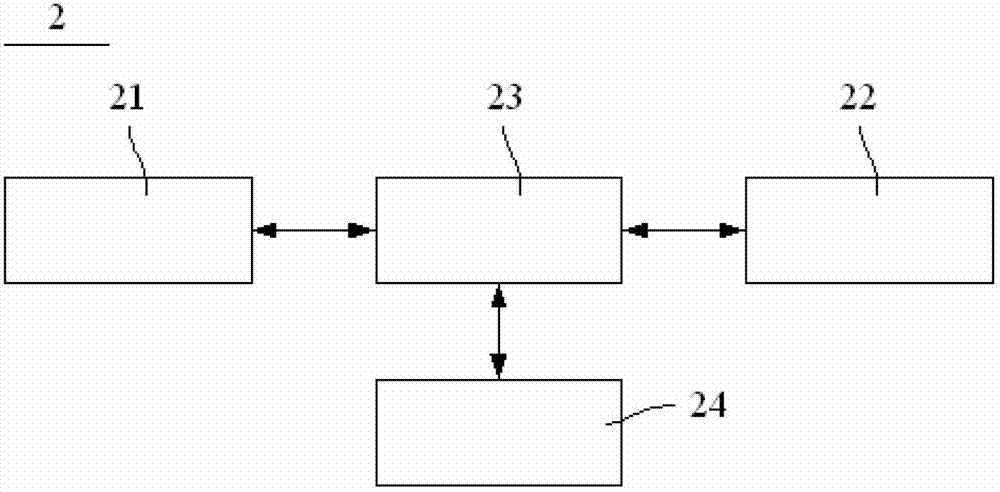
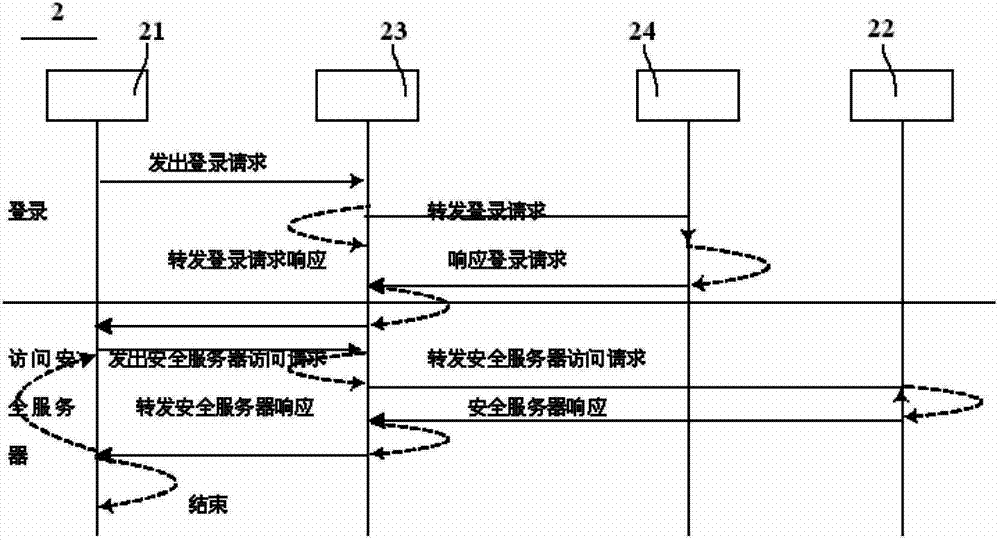
[0047] Such as figure 2 As shown, the security communication system 2 of the security server of the present invention includes a proxy server 23 , a business system operation terminal 21 , an information verification terminal 24 and a security server 22 . Wherein, three network cards are installed in the proxy server 23, and are respectively connected through communication between the business system operation terminal 21, the information verification terminal 24 and the security server 22 through these three network cards, and the business system operation terminal 21, the information verification terminal 24 and the security server The servers 22 are not connected to each other, so that the security server 22 is isolated from the operation terminal 21 of the business s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com