Safety management method and device based on user behavior
A security management and behavior technology, applied in the field of mobile communications, can solve the problems of reduced security and illegal operations, and achieve the effect of preventing illegal operations and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0024] For the basic flowchart of a security management method based on user behavior in Embodiment 1, please refer to figure 1 , including the following steps:
[0025] 101. Determine whether the operation performed by the application program is an operation with permission.
[0026] For applications, authorization is required to obtain security-related system services. Therefore, certain permissions are required to obtain security-related system services. For information security of the communication terminal, the communication terminal can monitor various operations performed by the application program, and determine whether the operation performed by the application program is an operation with authorization. If the operation is an operation with permission, it indicates that the operation is a security-related operation. Specifically, operations with permissions include operations related to information security, such as sending short messages, making calls, sending em...
Embodiment 2
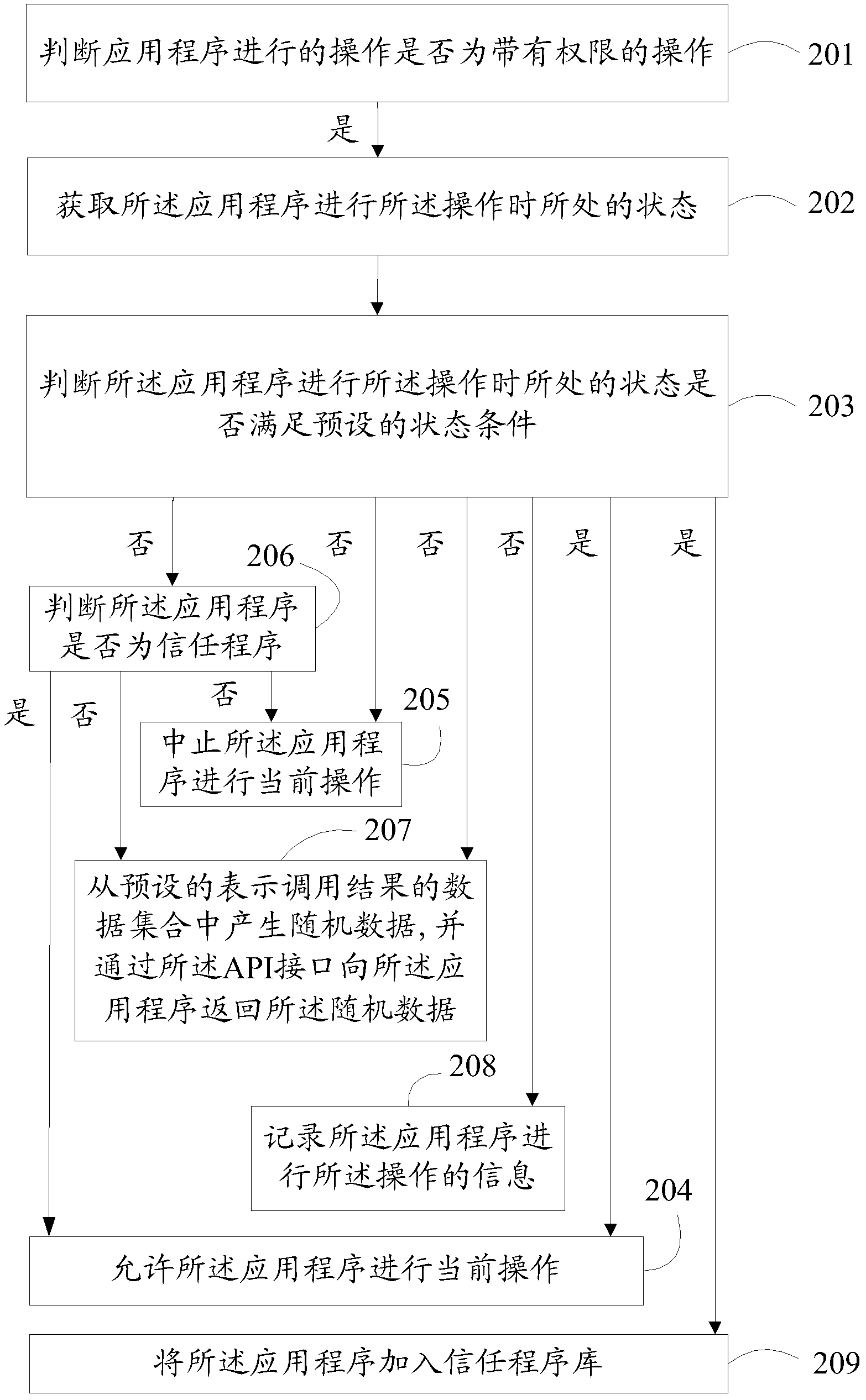
[0040] Embodiment 2, a basic flowchart of a security management method based on user behavior can refer to figure 2 , including the following steps:
[0041] 201. Determine whether the current operation performed by the application program is an operation with permission.
[0042] 202. If the operation performed by the application program is an operation with permission, acquire a state condition of the operation performed by the application program.
[0043] 203 . Determine whether the state of the application program when performing the operation satisfies a preset state condition, where the preset state condition is a state condition that is required to perform the operation and conforms to user behavior logic.
[0044] If the state in which the application program performs the operation satisfies the preset state condition, execute:
[0045] 204. Allow the application program to continue operating.
[0046] For a better understanding of steps 201 to 204, reference may ...
Embodiment 3
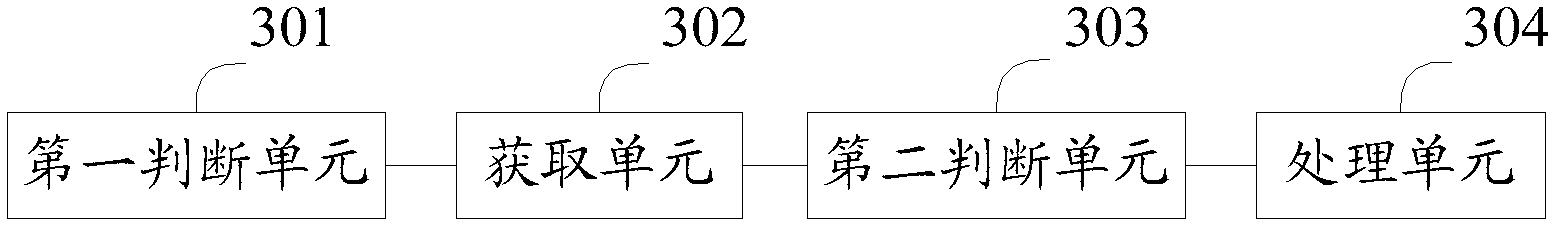
[0066] Embodiment 3, a logical structure diagram of a security management device based on user behavior can refer to image 3 , including: a first judging unit 301 , an acquiring unit 302 , a second judging unit 303 and a processing unit 304 .
[0067] The first judging unit 301 is used to judge whether the operation performed by the application program is an operation with permission.
[0068] The obtaining unit 302 is configured to obtain a status condition for the application program to operate when the judgment result of the first judgment unit 301 is yes.
[0069] The second judging unit 303 is configured to judge whether the state of the application when the operation is in operation satisfies a preset state condition after the acquisition unit acquires the state in which the application is in operation. , the preset state condition is a state condition that conforms to user behavior logic required for performing the operation.
[0070] The processing unit 304 is confi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com