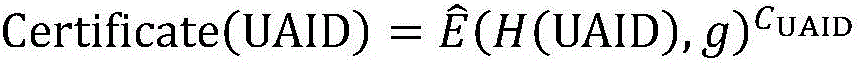Patents
Literature
90results about How to "Prevent illegal theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
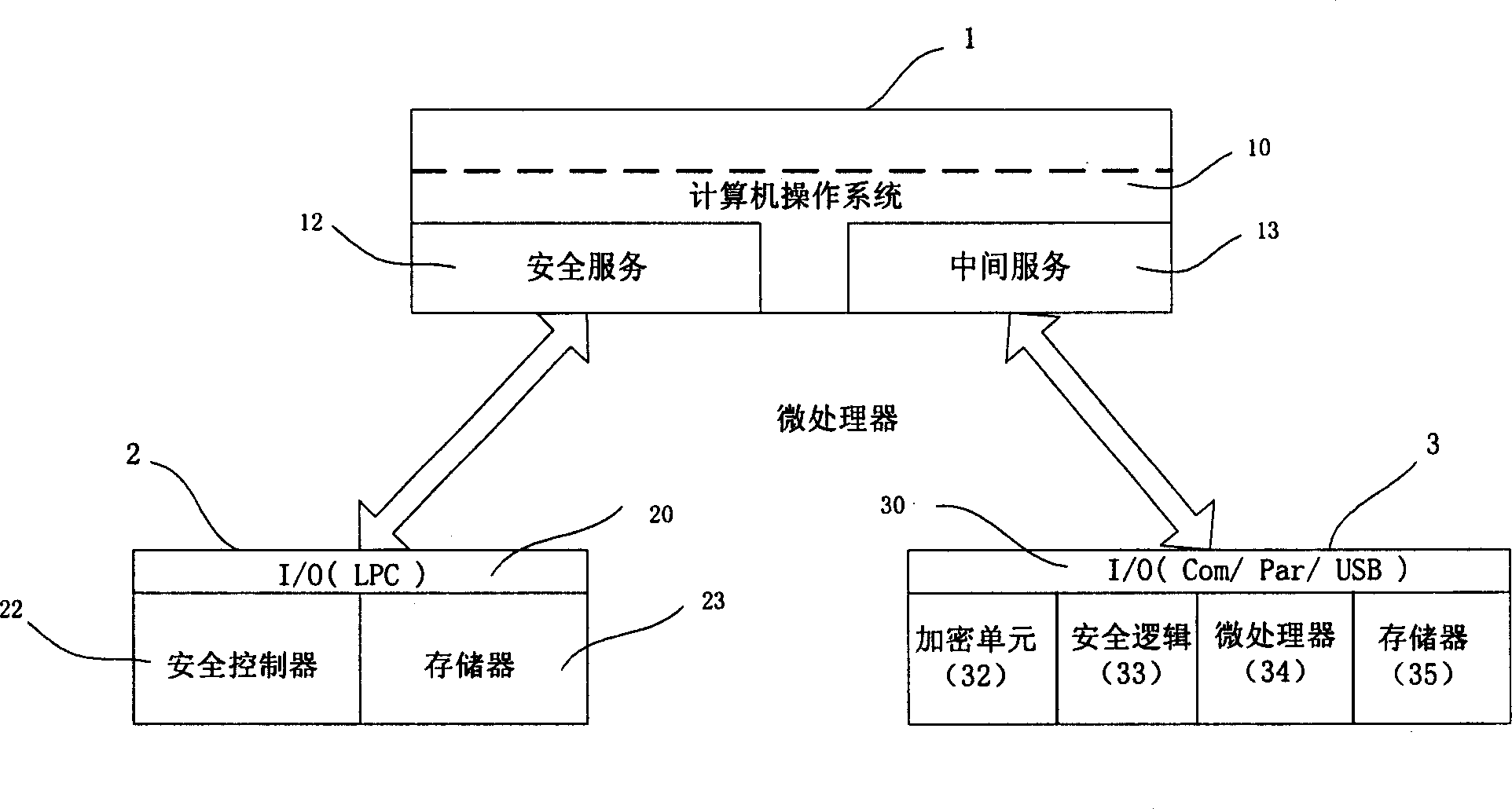
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
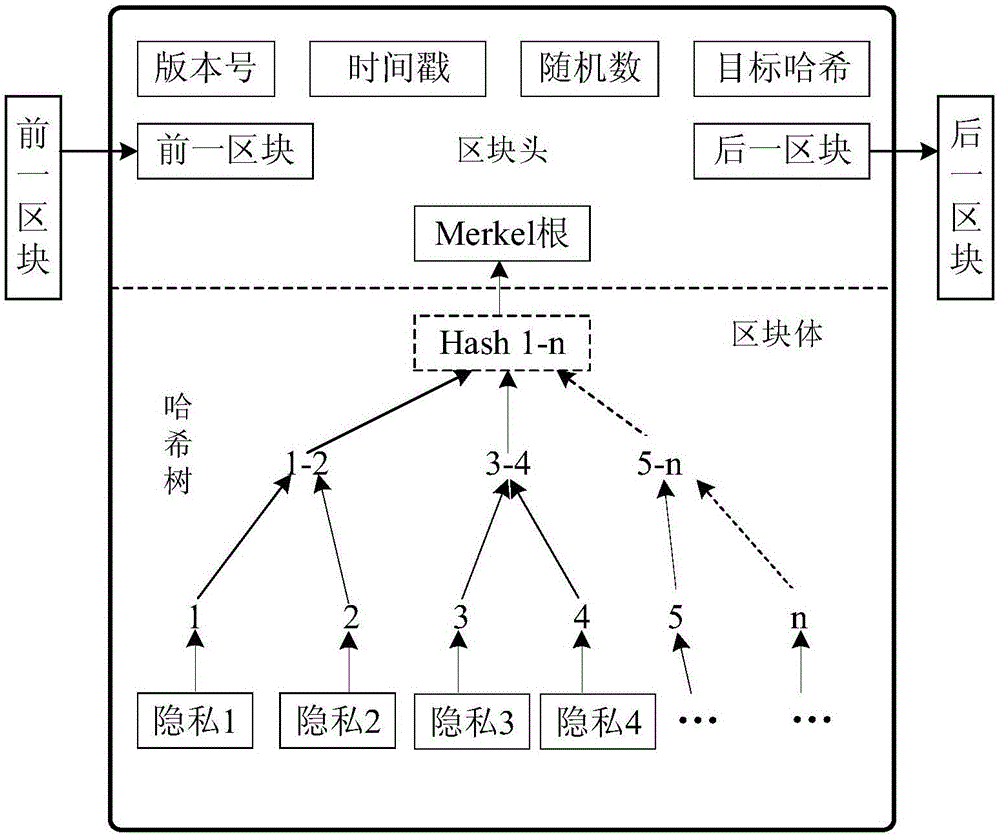
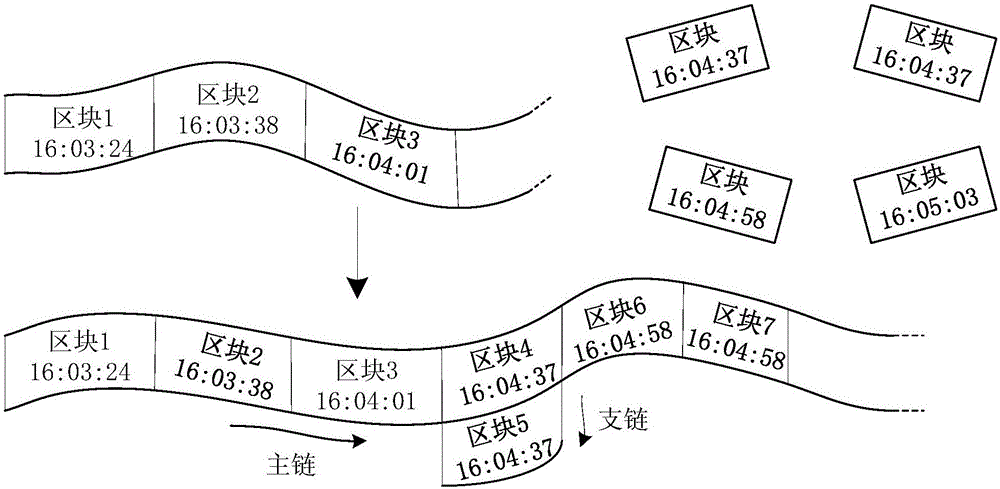
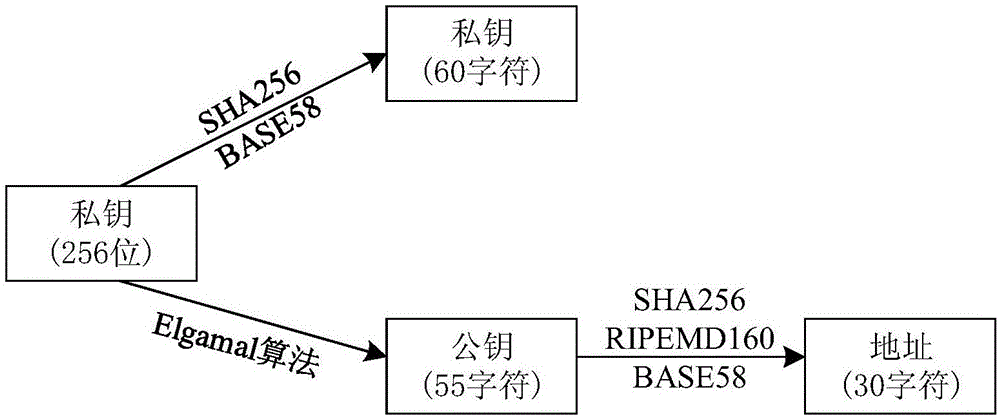
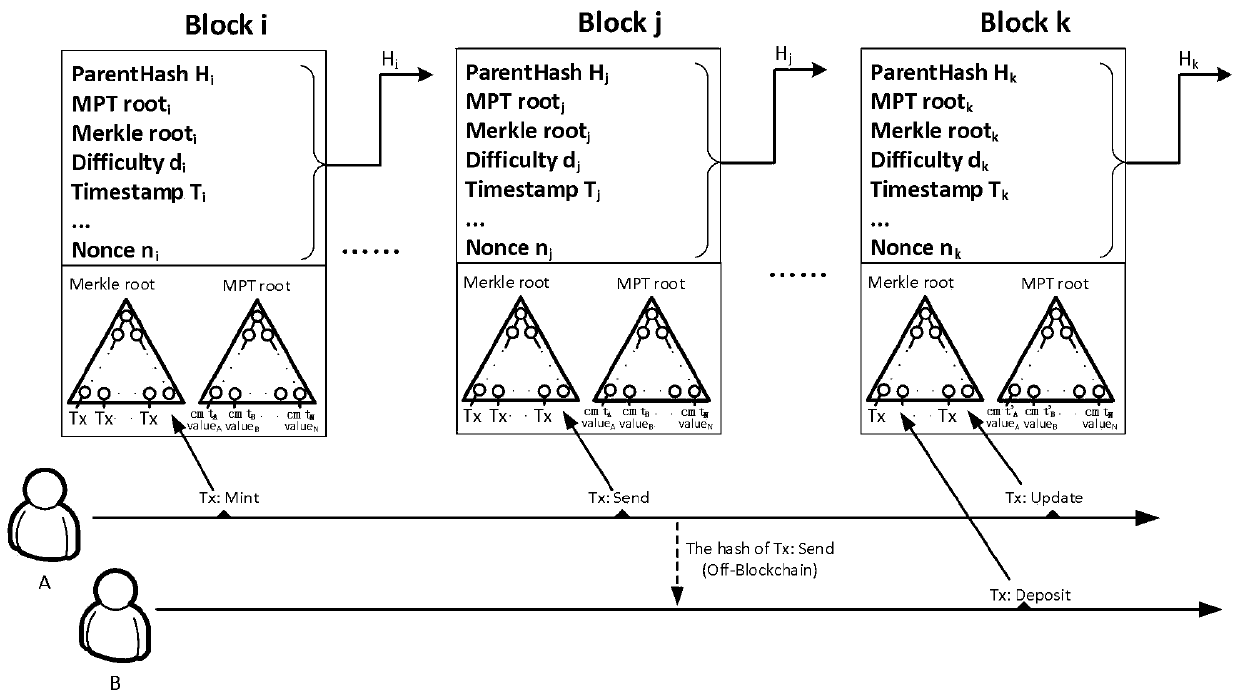
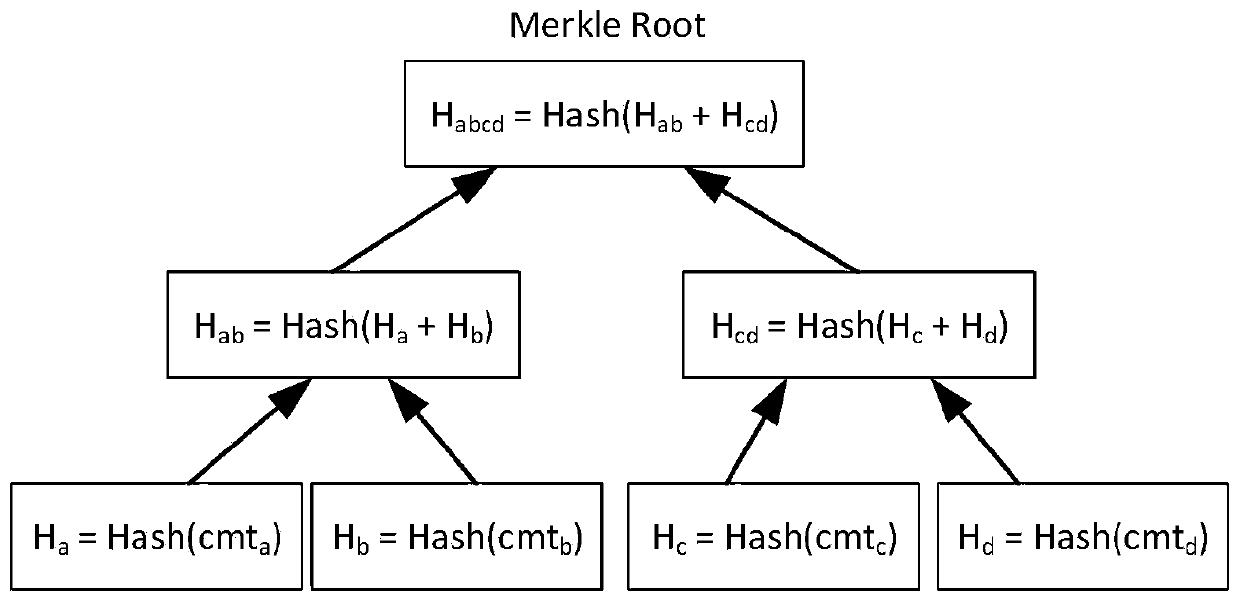
Privacy protection method based on block chain technology
ActiveCN106534085AImprove securityPromote orderlyDigital data protectionTransmissionPasswordPrivacy protection
The invention discloses a privacy protection method based on a block chain technology. The privacy protection method based on a block chain technology is characterized in that a block chain is formed by means of head-tail-connection of a large amount of blocks with similar organization structure; and each independent block can encapsulate privacy data with a time stamp, and can complete distributed networking propagation and a consensus algorithm task of distributed nodes at the same time, thus realizing efficient normal form organization management of the privacy data. Besides, the privacy protection method based on a block chain technology coordinatively uses an asymmetric encryption algorithm-Elgamal in the block chain, wherein a public key password and a private key password are respectively corresponding to encryption and decryption process of data; and the theoretical quantity of the private keys is very great, so that the possibility that the privacy data is stolen by traversing the whole private key space does not exist and then the safety of the privacy data can be guaranteed in cryptography. The complete organization and operating mechanism of the block chain enables the privacy protection method based on a block chain technology to have wide application prospect in the privacy protection field.
Owner:HANGZHOU YUNXIANG NETWORK TECH
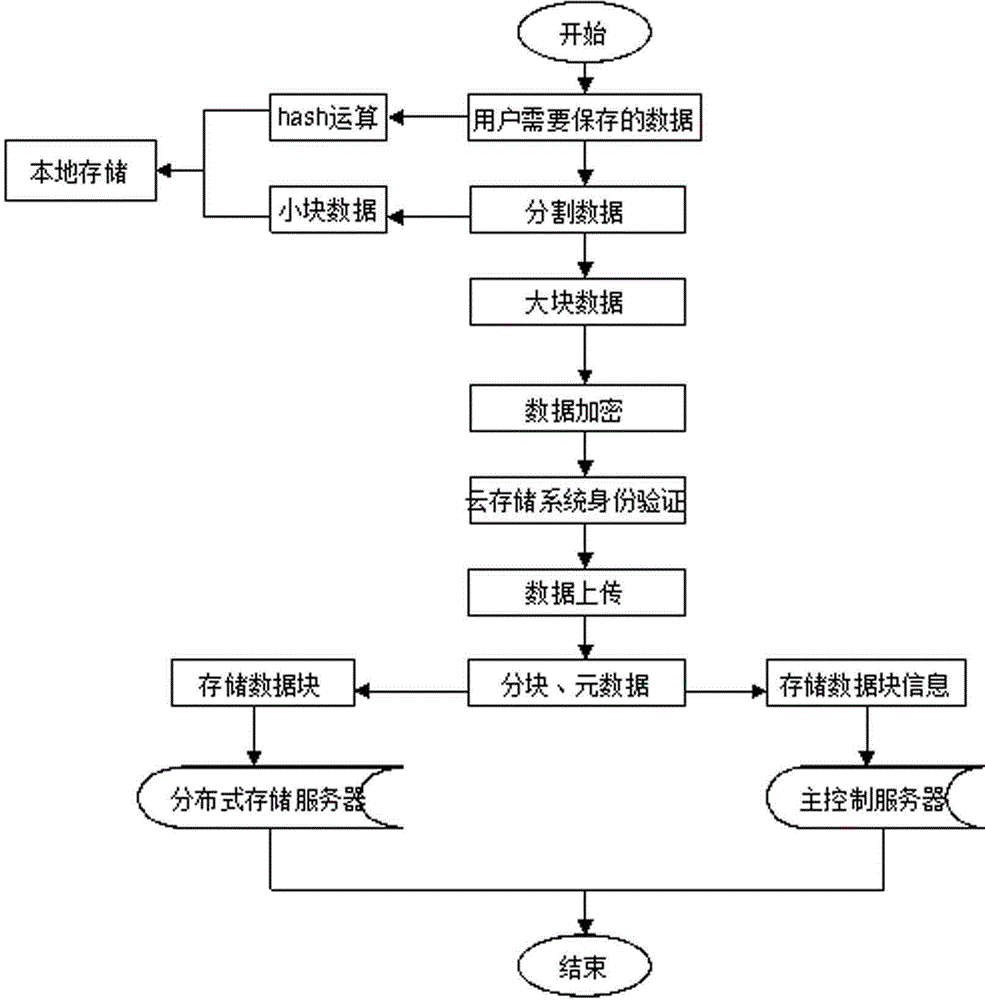
Data safety protection method based on data partitioning
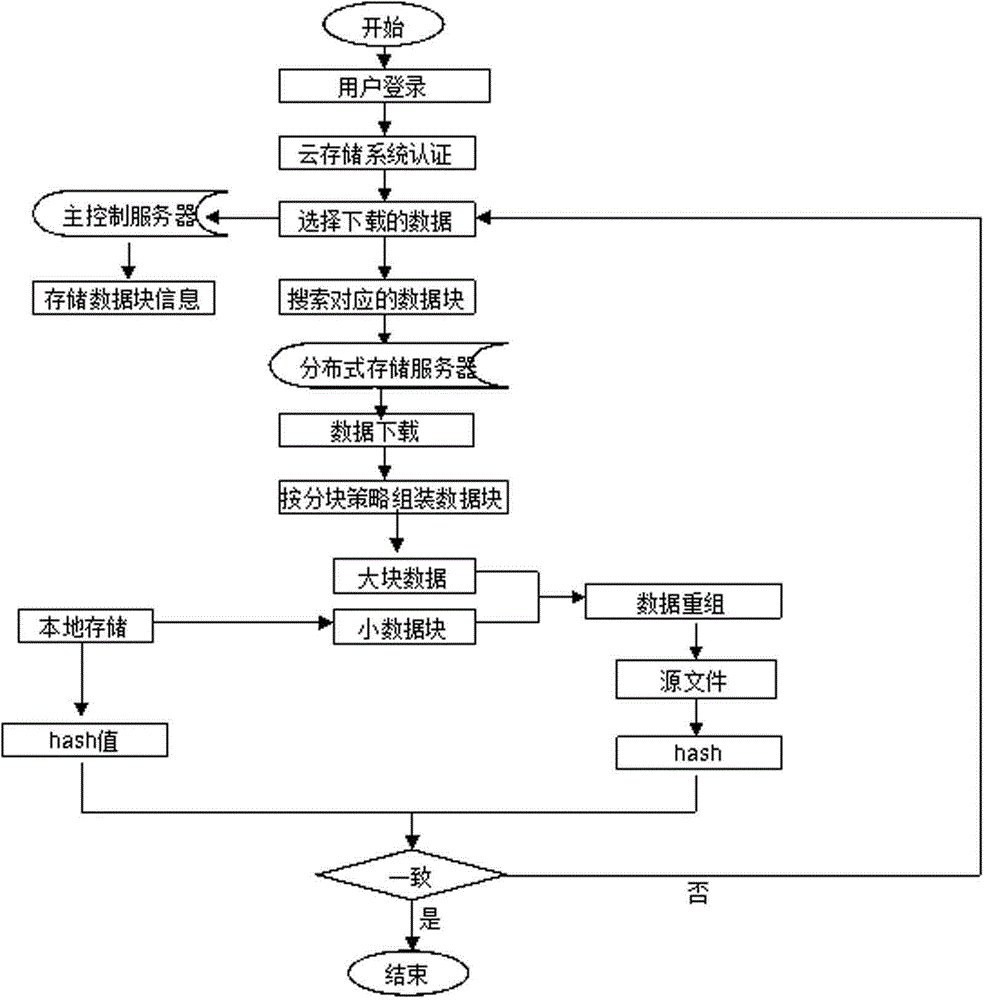
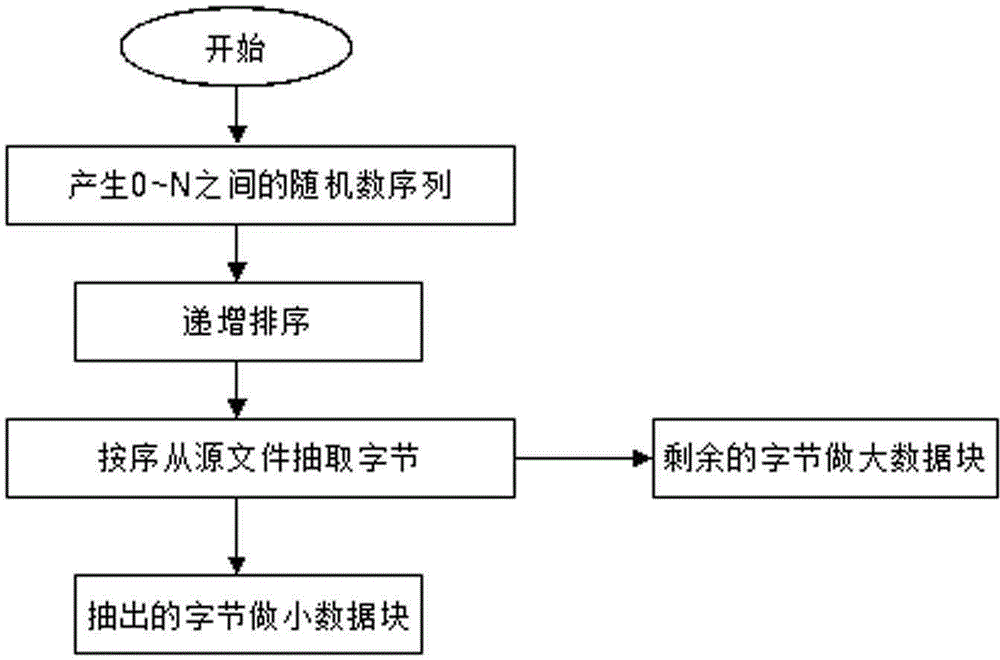
The invention provides a data safety protection method based on data partitioning. According to an employed strategy, different data needing storage at a client end are reasonably partitioned into great and small data blocks, and the great and small data blocks are respectively deployed in local and non-local cloud storage systems. Compared with the prior art, the data safety protection method based on data partitioning can effectively prevent a malicious user or a cloud storage administrator from carrying out illegal stealing and tampering of privacy data of users, provides more choices for safety of different data for users and has advantages of improved system flexibility, strong practicality and easy popularization.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Method and system for remote storing processing of data
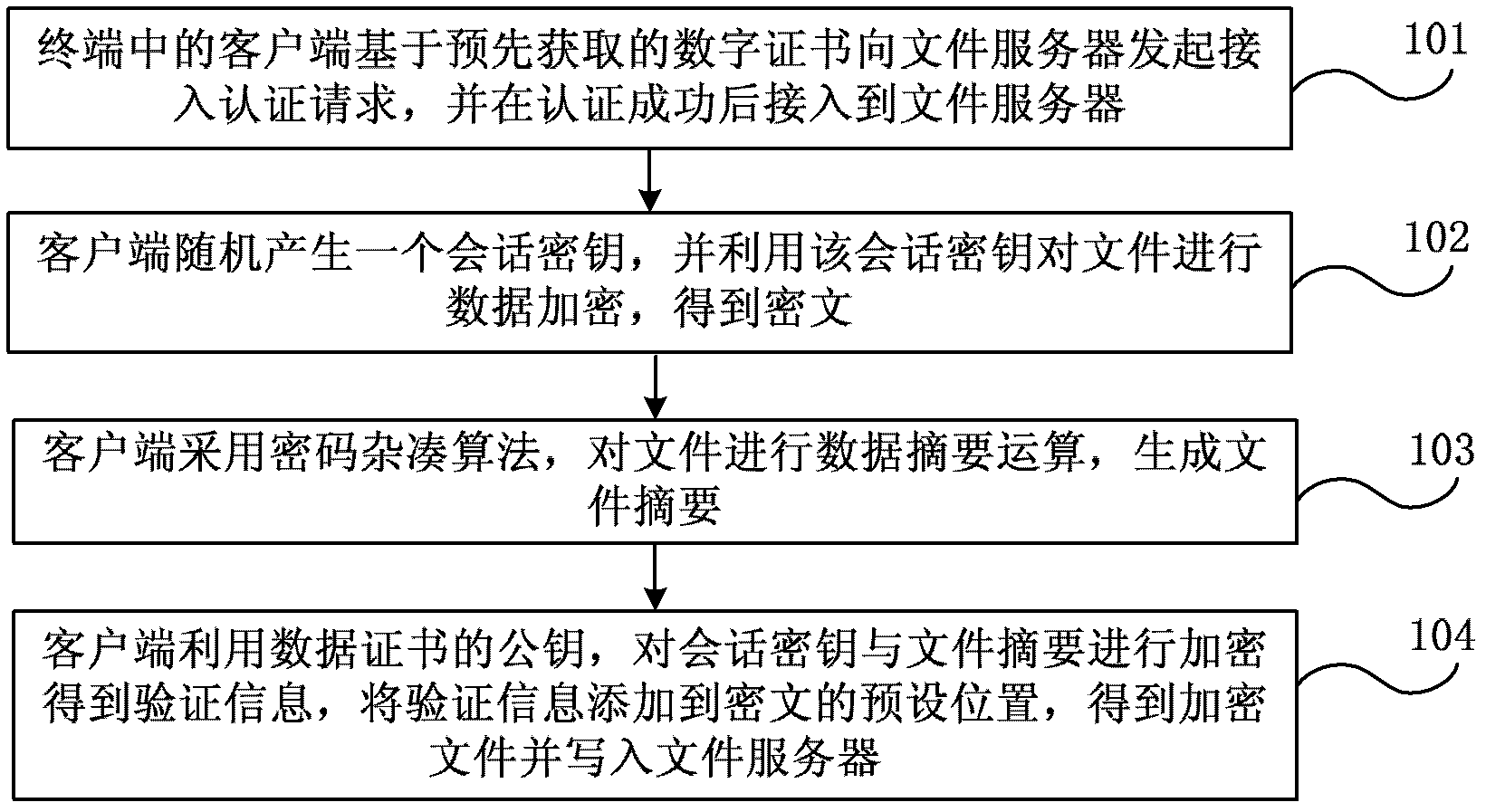
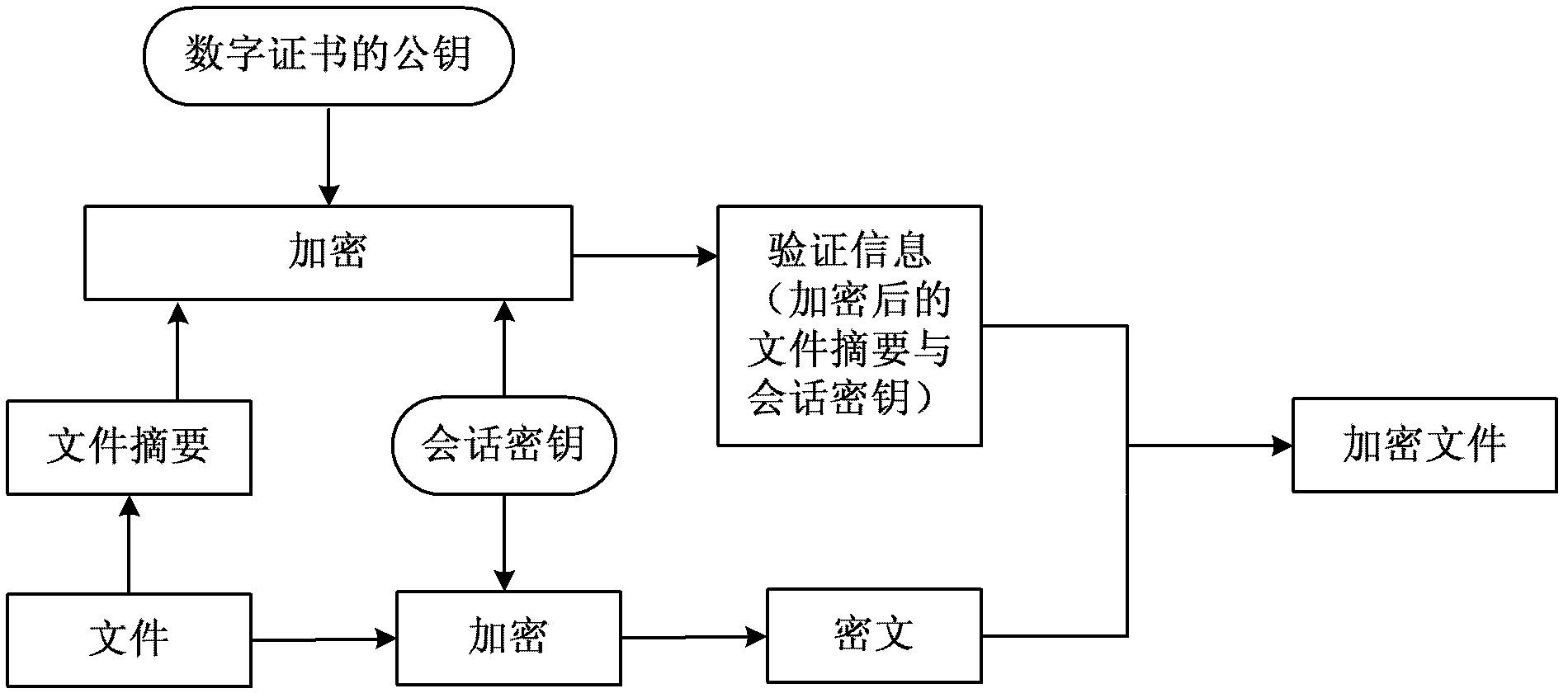
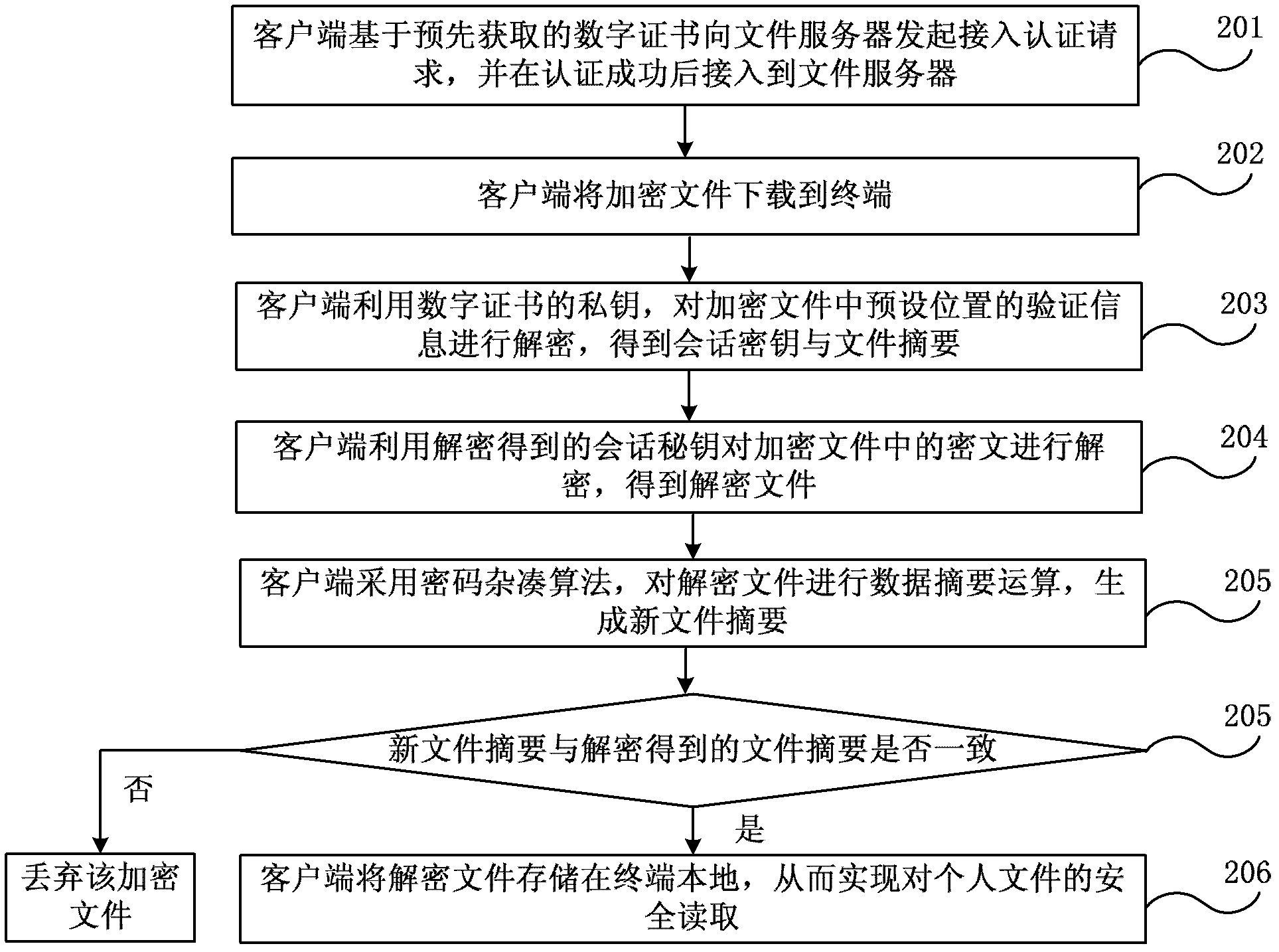
The utility model discloses a method and a system for remote storing processing of data. The method comprises that when a terminal uploads files stored locally to a file server of a network side, a client of the terminal initiates an access authentication request to the file server based on a digital certificate which is acquired in advance, the client accesses the file server after successful authentication, the client generates a dialog key randomly and conducts data encryption to files through the dialog key, a cyphertext is obtained, the client conducts data abstracting mathematical operation by using a cryptographic hash algorithm, the file summary is generated, the client conducts the encryption to the dialog key and the file summary by using a common key of the data certificate, authentication information is obtained, the authentication information is added to a preset position of the cyphertext, and an encryption file is obtained and written to the file server. By the aid of the method and the system, file data of a user is prevented from eavesdropping and stealing illegally during remote store, and the safety of data remote store is improved.
Owner:CHINA TELECOM CORP LTD
Data synchronization system with data security and proxy capabilities
InactiveUS20050138211A1Prevent illegal theftMultiple digital computer combinationsElectric digital data processingData differencingThe Internet
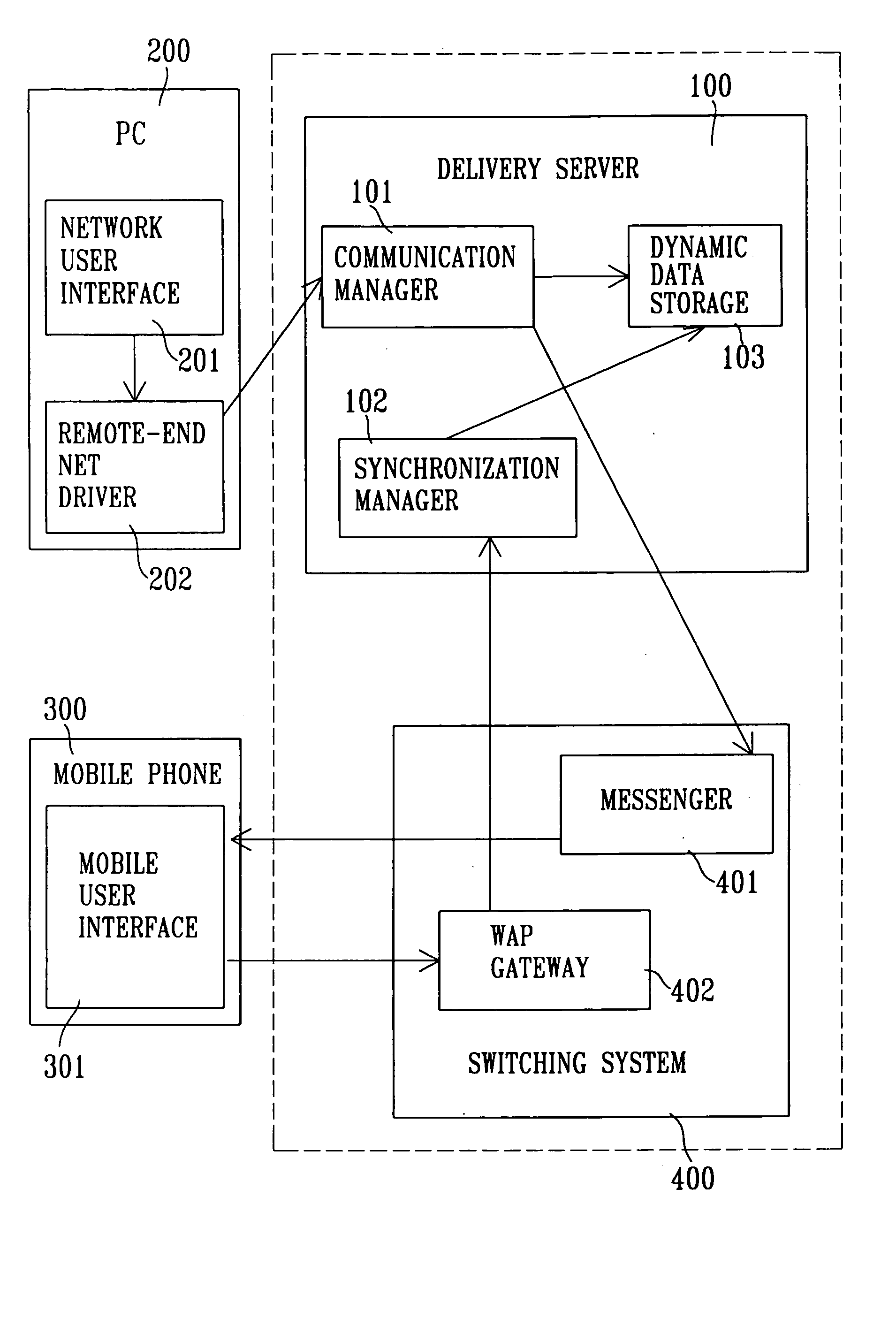
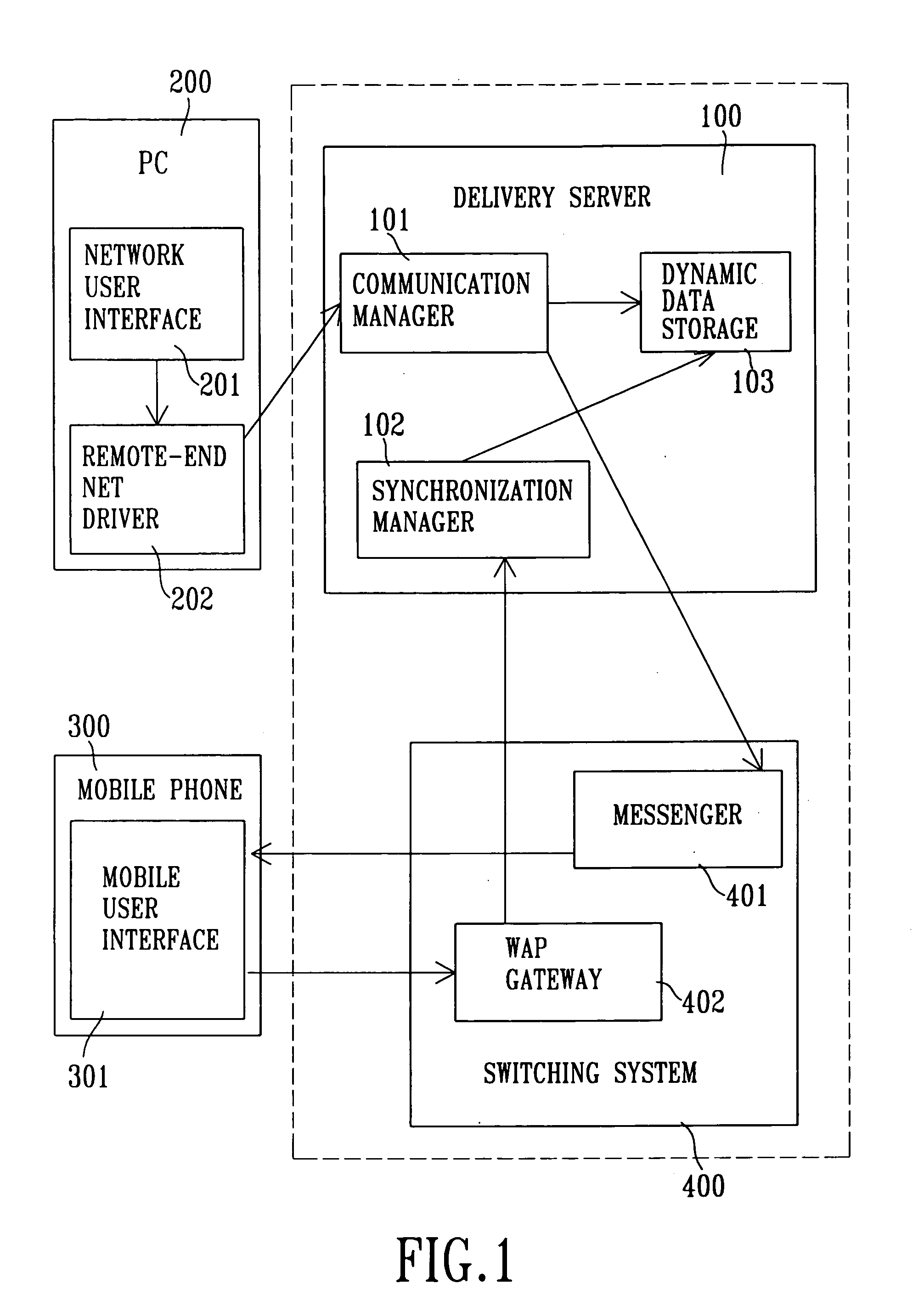
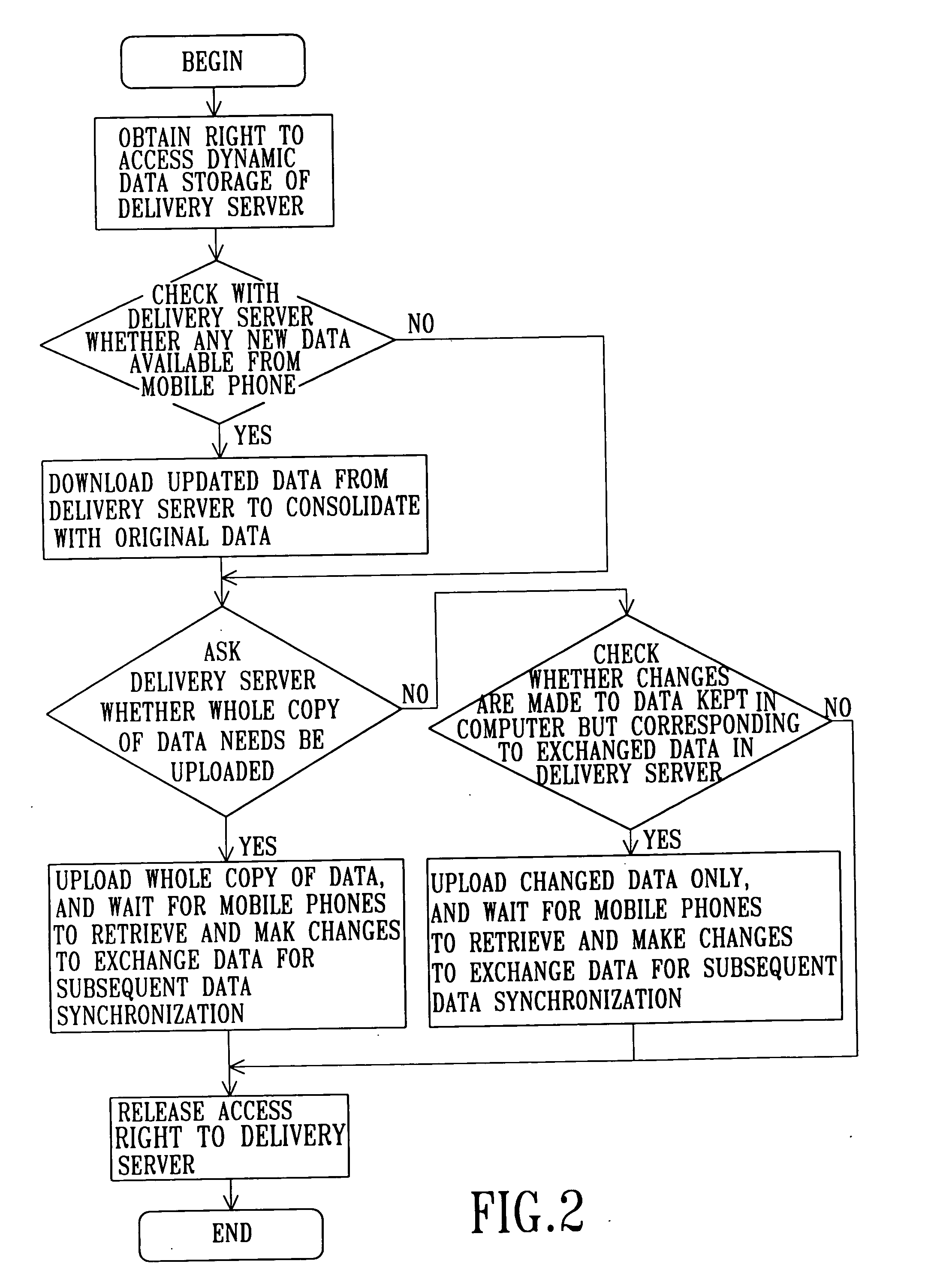
A modified data synchronization system having data security and proxy capabilities has a delivery server, a PC, and at least one mobile phone. The PC sends out the exchange data through the Internet to a remote location where the delivery server is installed, and then one mobile phone compliant with SyncML protocols dials in to conduct data synchronization with the delivery server through wireless means, through which the existing data discrepancy between the mobile phone and the PC can be eliminated. The PC does not need to install a dedicated SyncML server, and data security can be ensured in the synchronization process, as data transfer between the PC and the delivery server through secured protocol over the Internet, and that between the mobile phone and the delivery server is through a dedicated channel.
Owner:MOBILE ACTION TECH
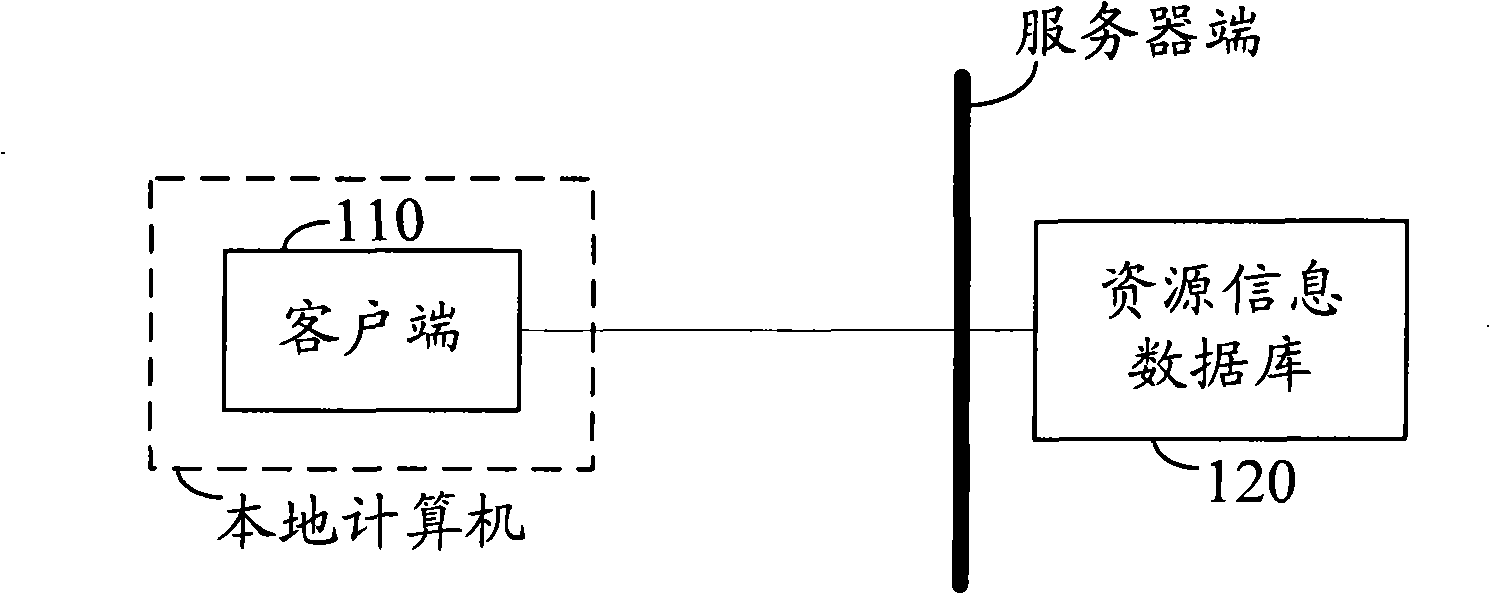
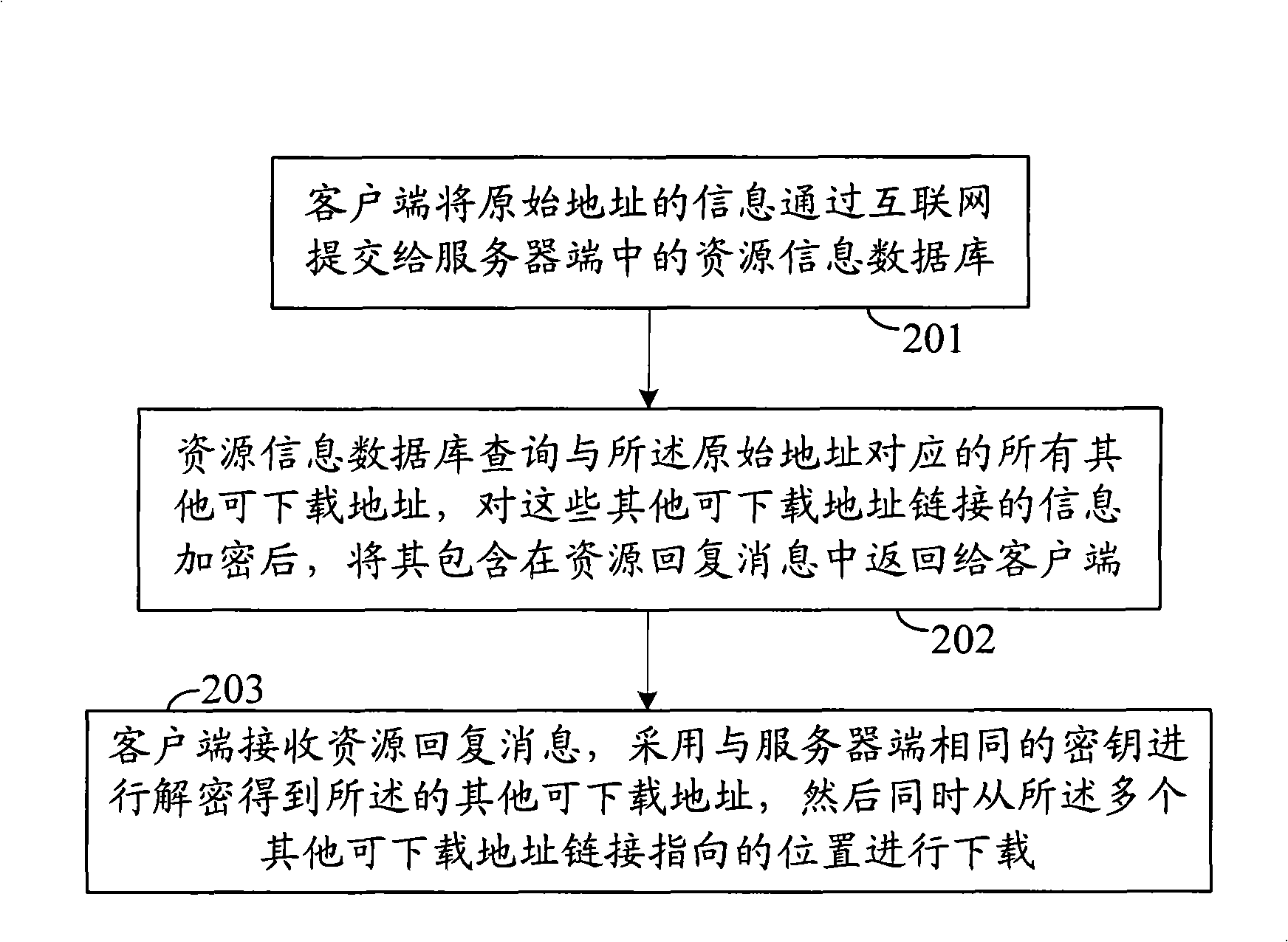
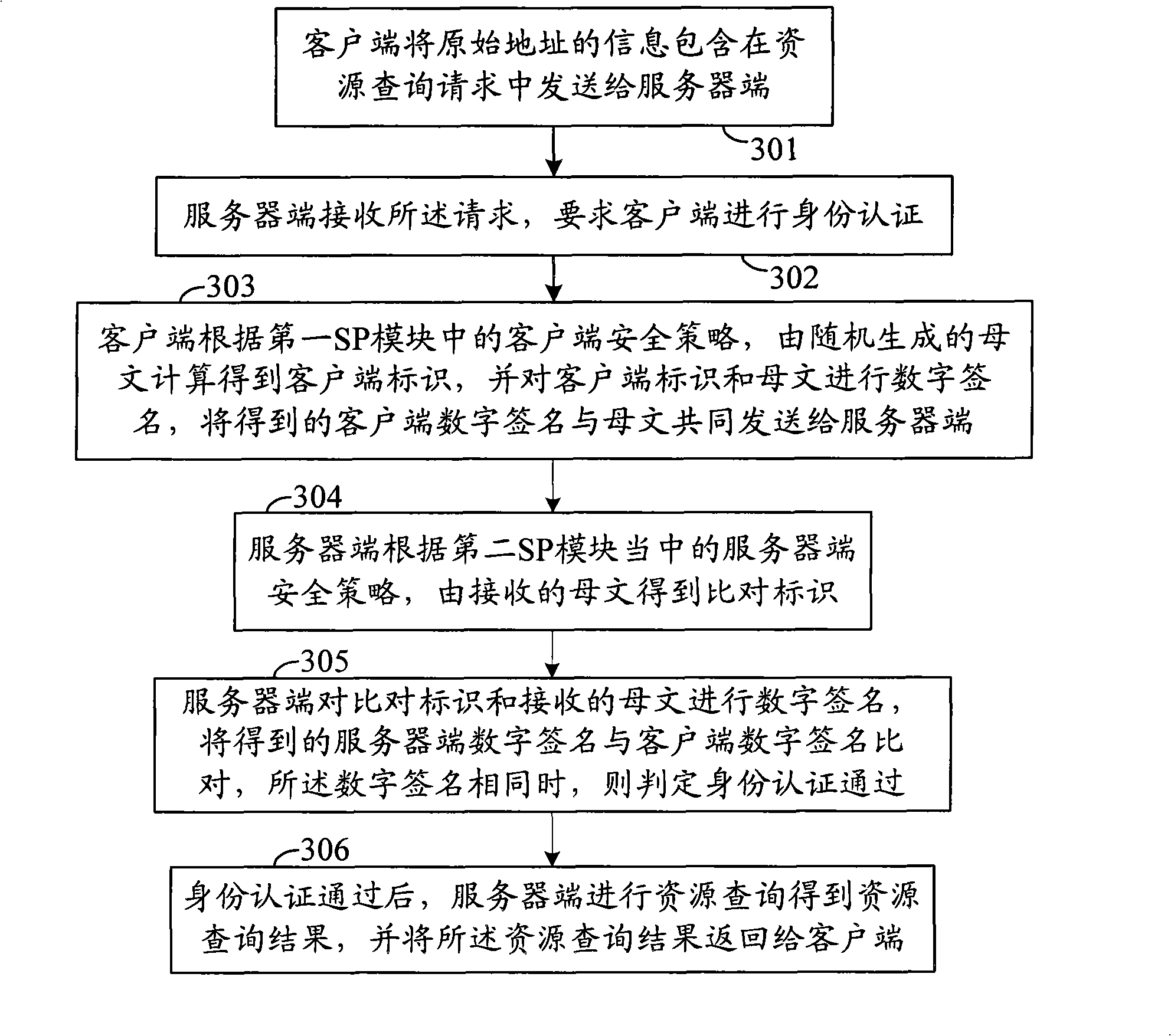
Network resource query method and system
ActiveCN101404576APrevent illegal theftImprove security strengthKey distribution for secure communicationUser identity/authority verificationResource informationClient-side
The invention discloses a network resources inquiry method. A client side and a server side are equipped with the same security policy which is an algorithm used in the whole identity authentication process. The method comprises the following steps: the client side sends a resource inquiry request to the server side, and the server side indicates the client side to authenticate identity after receiving the resources inquiry request; after the identity authentication is passed, the server side inquires resources to obtain a resources inquiry result, and sends back the resources inquiry result to the client side. The invention also further provides a network resources inquiry system. The network resource inquiry method and the system ensure that the valid client side can successfully pass the identity authentication and obtain the resources inquiry result, avoid hackers or rivals from illegally stealing information in the resource information database, and greatly enhances the information security in the resource information database.
Owner:SHENZHEN THUNDER NETWORK TECH
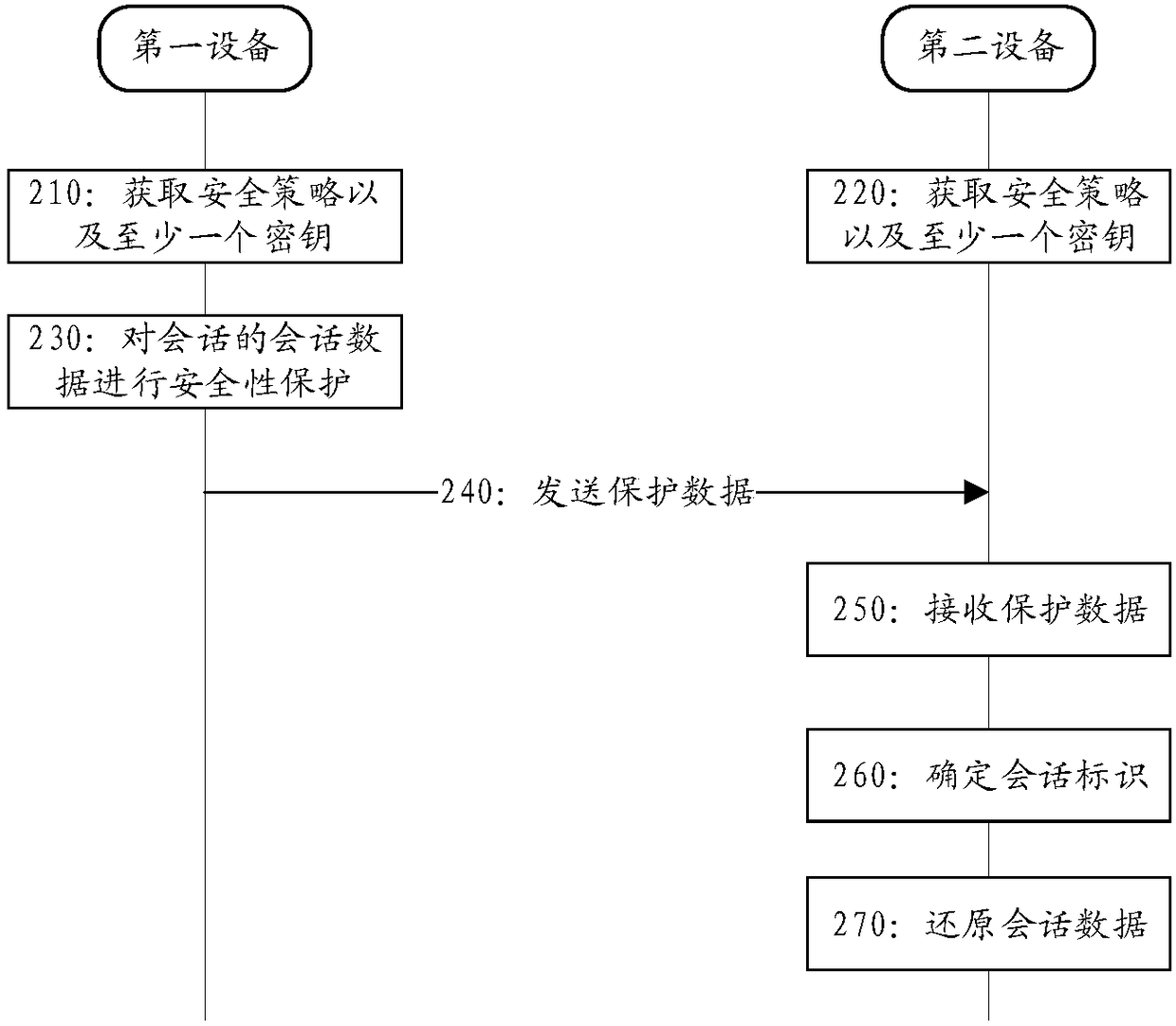
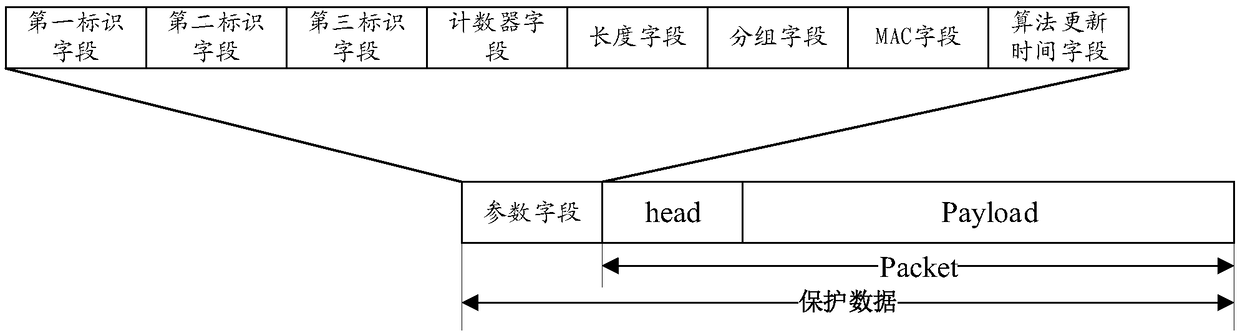
Security realization method, equipment and system
ActiveCN108347410APrevent illegal theftSave resourcesSecurity arrangementSecuring communicationSecurity policyAccess network
The embodiment of the invention discloses a security realization method, equipment and a system. The method comprises the steps that first equipment obtains a security policy and at least one key of asession; and the first equipment sends protection data to second equipment, wherein the protection data is obtained by protecting security of session data of the session through unitization of the atleast key according to the security policy of the session, and the second equipment is used for restoring the protection data through utilization of the at least one key according to the security policy, thereby obtaining the session data, when the first equipment is terminal equipment, the second equipment is an access network node or a user plane node, and when the first equipment is the accessnetwork node or the user plane node, the second equipment is the terminal equipment.
Owner:HUAWEI TECH CO LTD
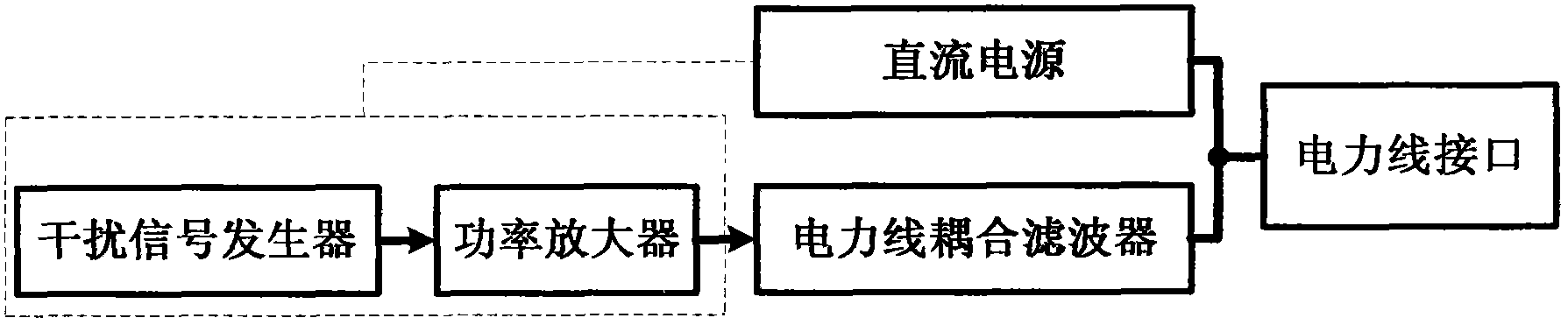
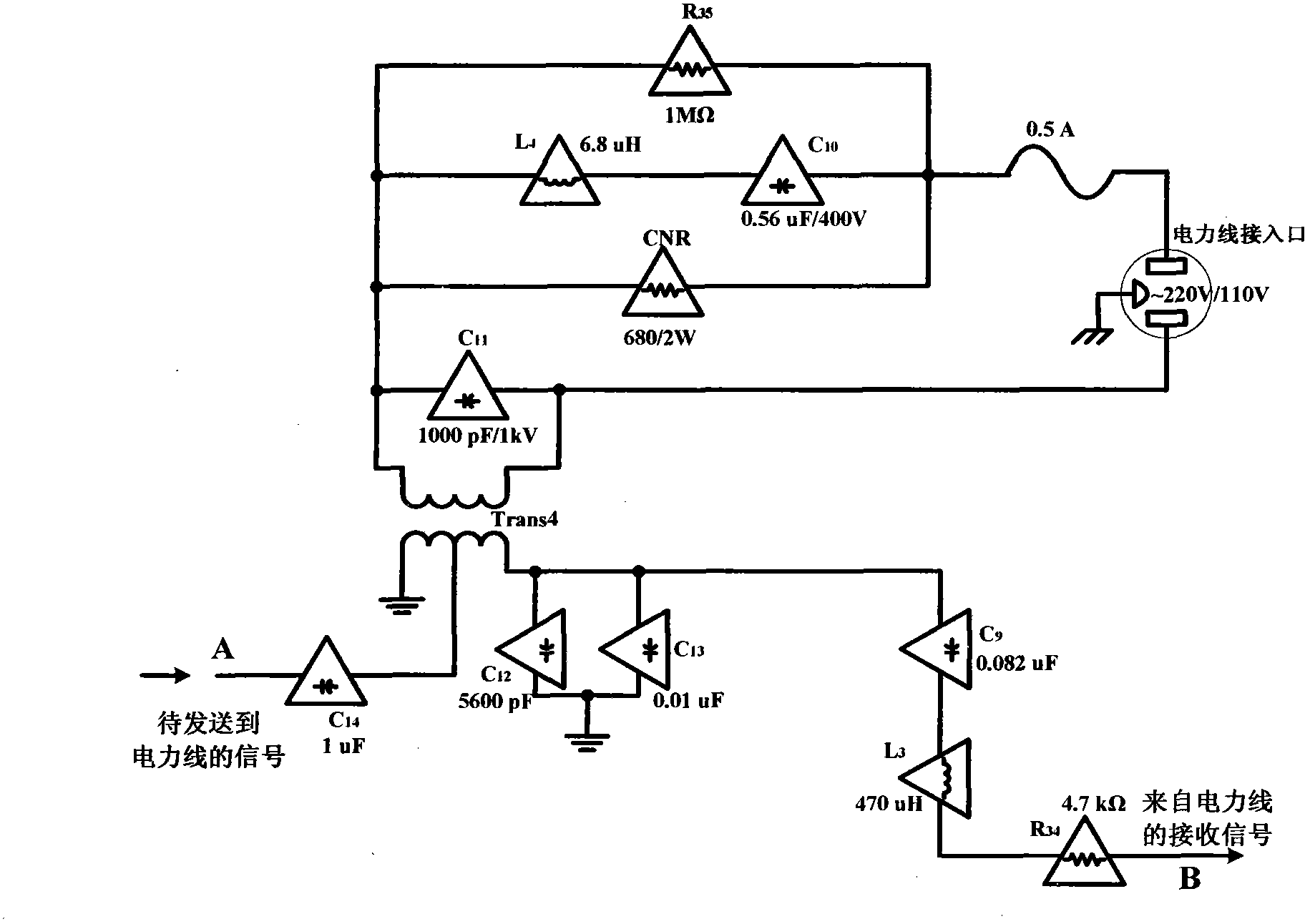
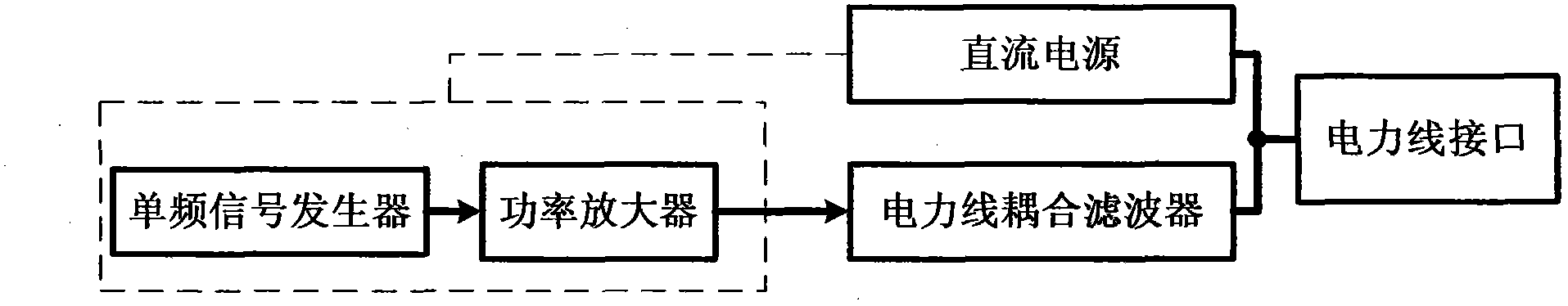
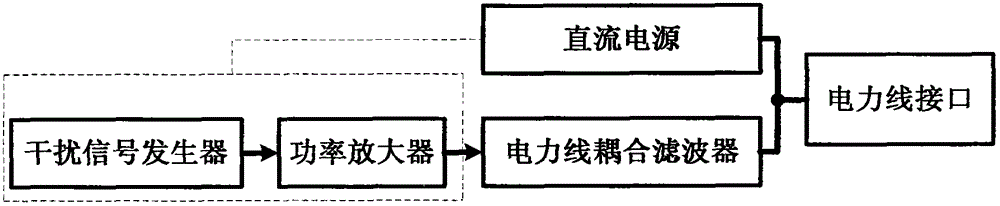
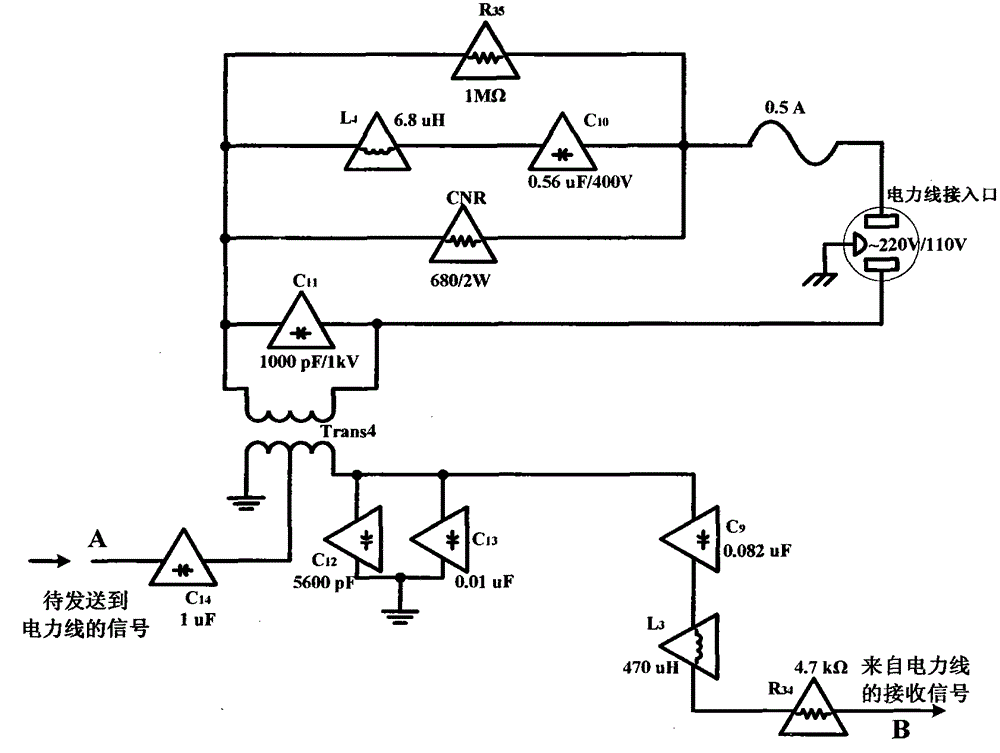
Power-line communication interference devices
InactiveCN103856242AEasy accessReceive and detectPower distribution line transmissionCommunication jammingEngineeringPower line interference
The invention relates to power-line communication interference devices and particularly relates to a plurality of devices which perform communication interference on facilities which use power lines for communication and belongs to the technical field of power-line communication, communication interference and interference resistance and information security. A device specifically includes a power-line interface, a DC power supply, a power-line coupling filter, a power amplifier and an interference signal generator. The invention also provides a power-line communication interference device with a power-line communication signal detection and analysis function, a processing and forwarding power-line communication interference device and a power-line communication signal short circuit / bypassing power-line communication interference device. The power-line communication interference devices are connected with power lines conveniently through forms of power-line insert ports, insert grooves and sockets and the like so that interference signals which interfere power-line communication are generated; an excellent interference effect is achieved through an extra-low interference power and electricity consumption quantity is low so that the power-line communication interference devices are especially suitable for being used in low-power-consumption inference application; and the interference mechanisms are simple in structure, low in realization cost and high in self-adaptive capability.
Owner:李祥明 +2
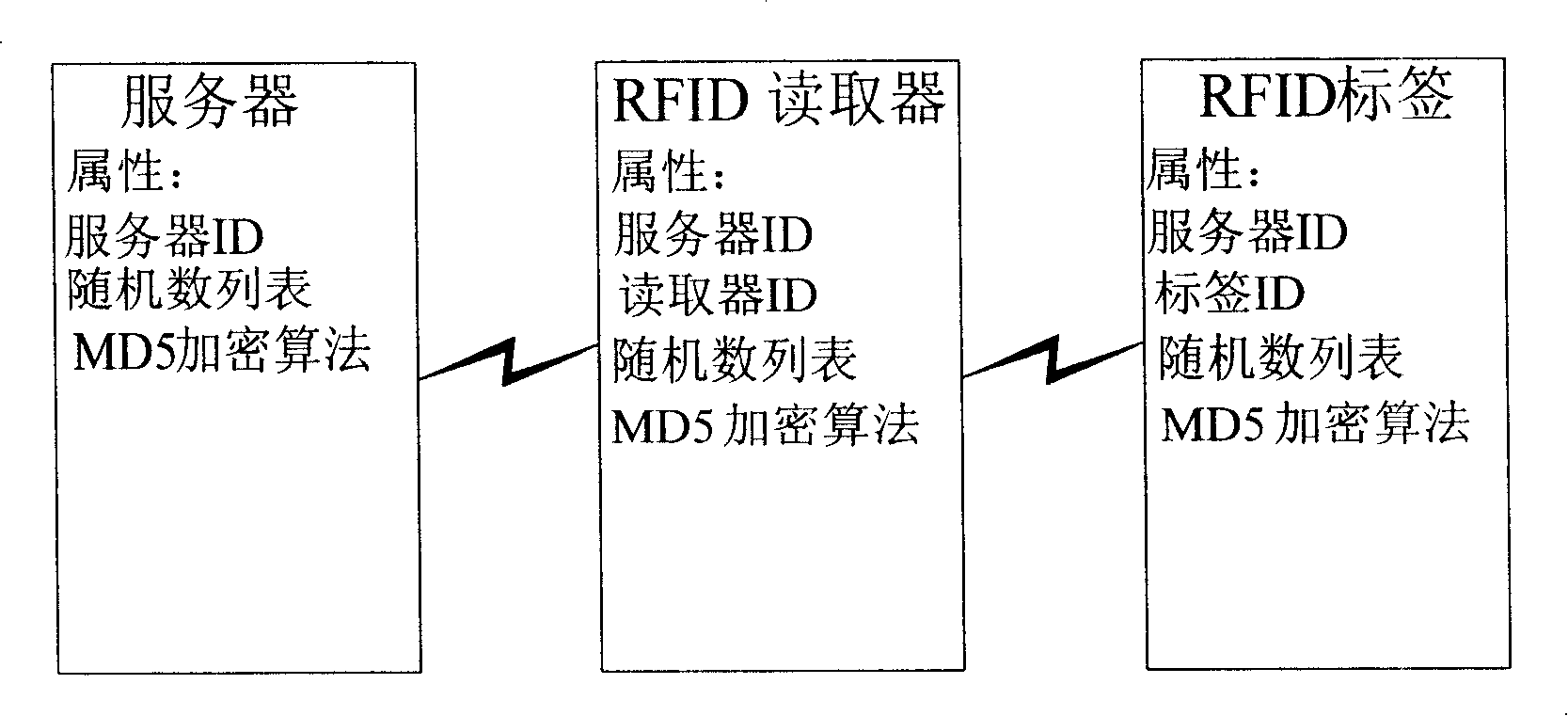
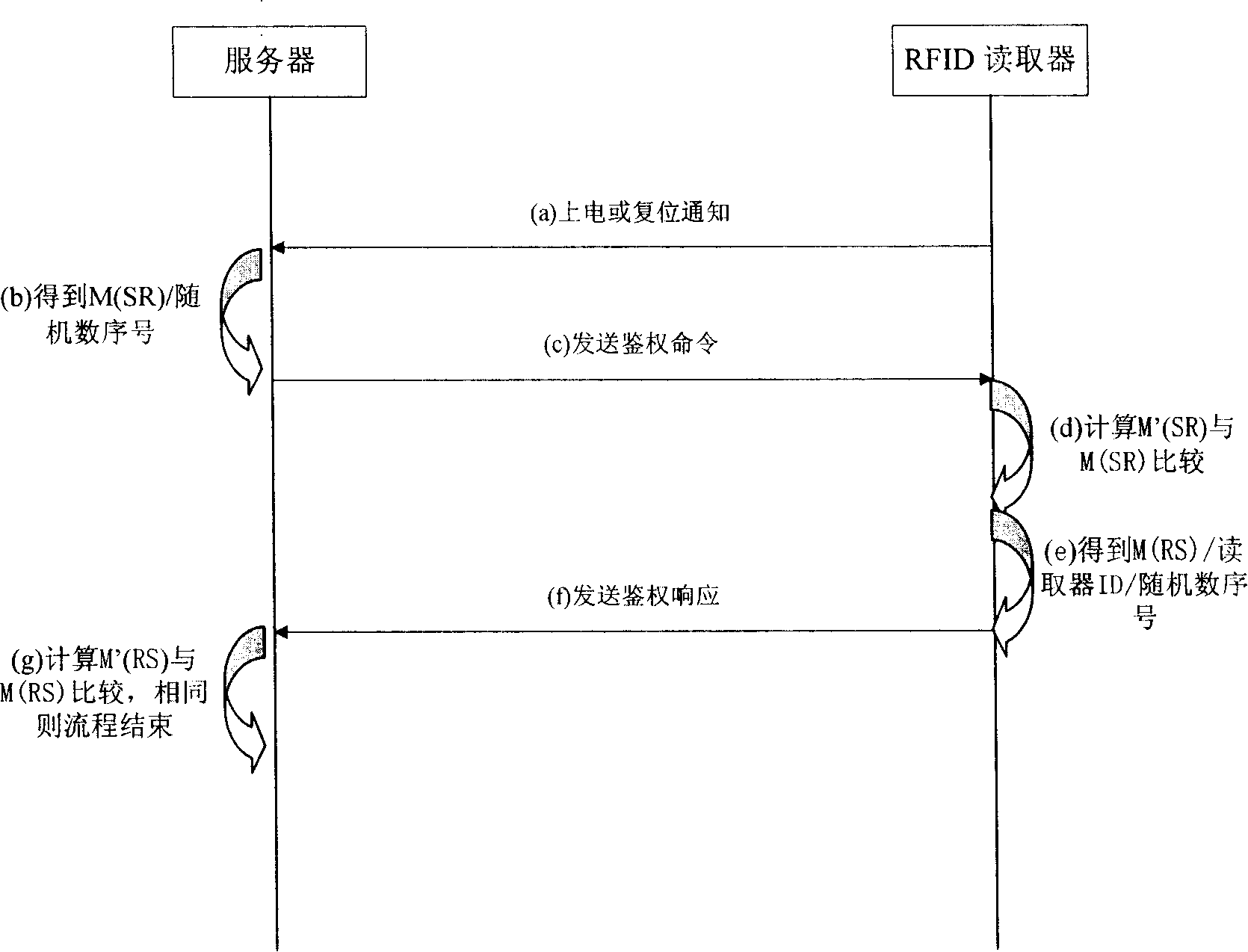
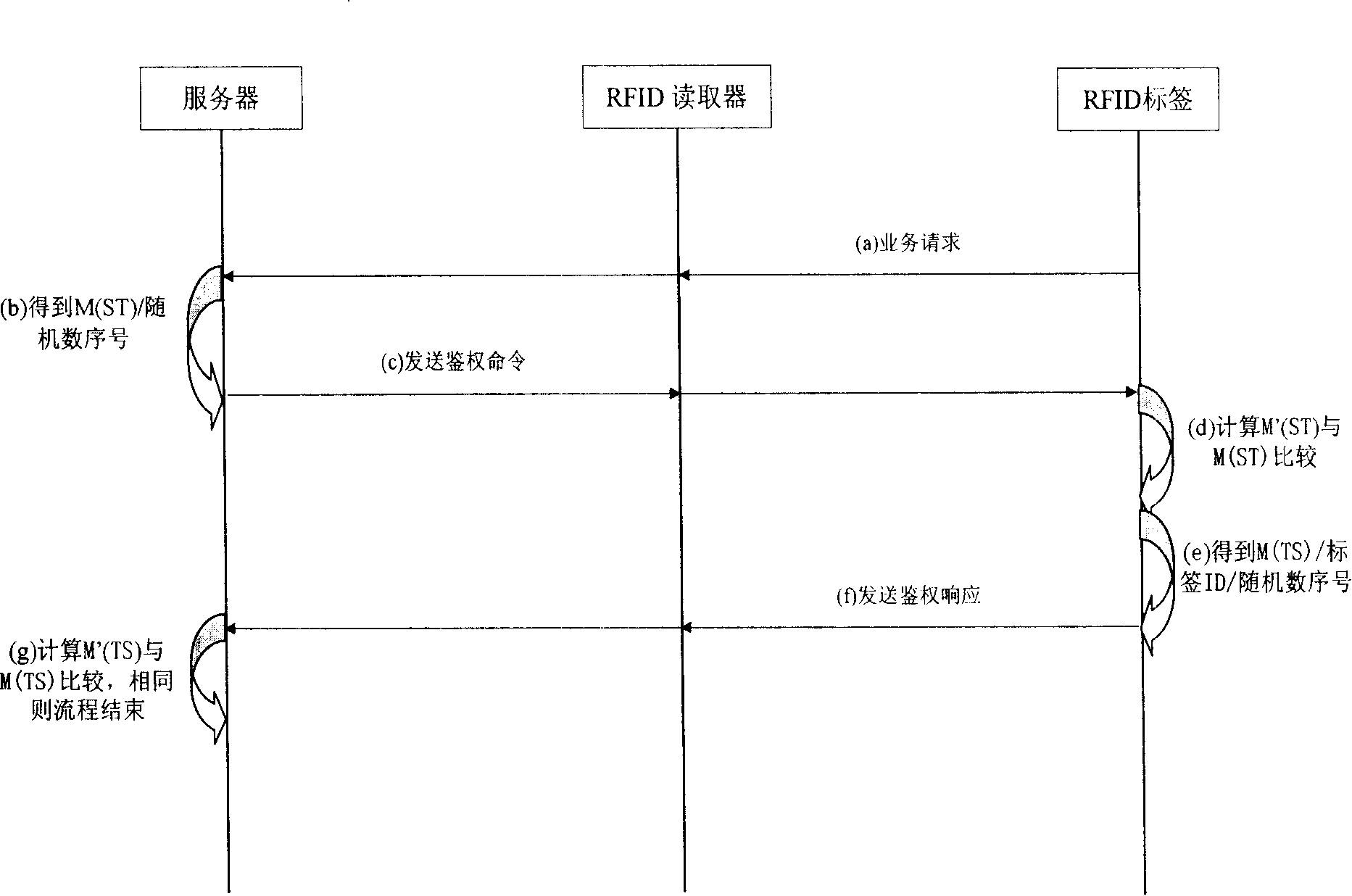
Method and system for protecting radio frequency identification tag and reader data safety
ActiveCN101211401APrevent illegal theftGuarantee data securityUser identity/authority verificationSensing record carriersTelecommunications networkRadio frequency
The invention relates to a method and system to protect data safety of RF identification (RFID) tags and acquisition devices, so as to fulfill bidirectional authority verification between a network server and RFID tags and acquisition devices; therefore, the invention can effectively prevent illegal access on RFID tags and acquisition devices that have not passed safety certification. When effectively using a matured and simple arithmetic structure, the RFID system has no higher requirement for system hardware, so as to effectively lower composition cost between the RFID system and prior telecom network.
Owner:CHINA TELECOM CORP LTD
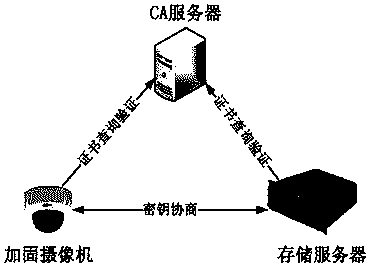
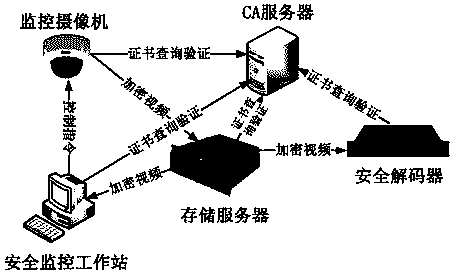
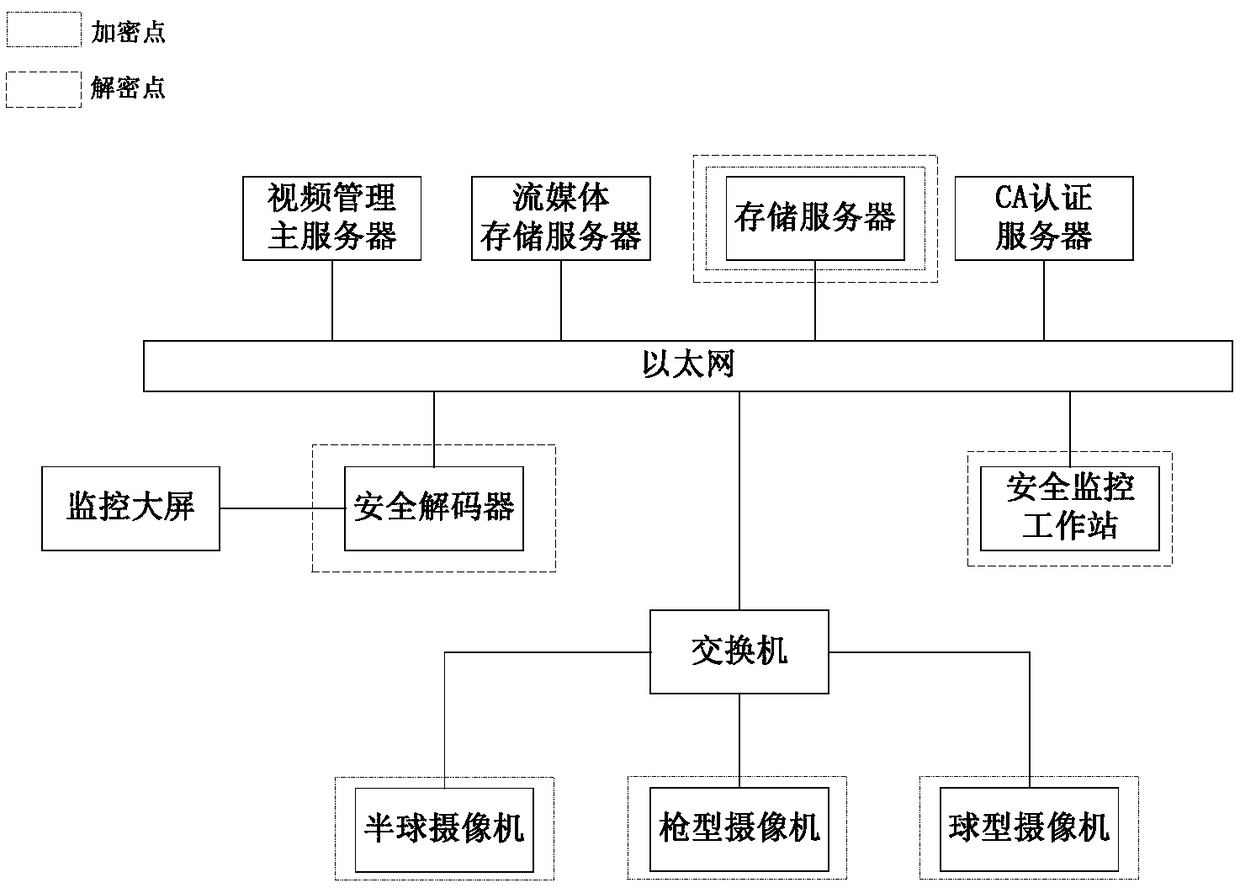
Video encryption system
ActiveCN109218825APrevent illegal theftPrevent counterfeitingKey distribution for secure communicationSelective content distributionPublic key certificateWorkstation
The invention belongs to the technical field related to data encryption and video security, A video encryption system includes two-way authentication module, When the key negotiation module, the videodecryption module, the security decoder and the security monitoring workstation are connected with the storage server, the storage server transmits the video key encryption key and the correspondingversion number of the related reinforced camera to the security decoder through the signaling mode, and the security monitoring workstation executes the key negotiation process once in the forwardingprocess. Device authentication, through the verification of the validity of the public key certificate in the built-in cryptographic module, can verify the validity of the device. When the device is out of control, the device can be revoked in time in the CA server, and the device can be blocked from re-entering the network. Through the encryption scheme of the whole encryption process, the videoinformation is always in a safe state and under strict supervision in all application links, and the possibility of illegal stealing, forgery or alteration of video images is avoided.
Owner:北京京航计算通讯研究所
Blockchain account model privacy protection method based on zero knowledge proof
ActiveCN109858281AFacilitate orderly and paradigm managementThe transaction amount is completely confidentialFinanceDigital data protectionZero-knowledge proofBlockchain
The invention discloses a blockchain account model privacy protection method based on zero knowledge proof. The method comprises the following steps: an account transfer person converts a plaintext balance into a zero knowledge balance; performing transfer operation on the zero-knowledge balance; the account transfer person updates the balance of himself / herself; the payee updates the balance of the payee; and the user converts the zero-knowledge balance into a plaintext balance. According to the method, the zero knowledge proof and the blockchain account model are combined, so that the privacy protection of transaction data is realized, and the data can be effectively prevented from being leaked. According to the technical scheme of the invention, plaintext data transactions are hidden, although both parties know that some unmarked transactions are carried out, a plurality of senders and receivers are generated when many transactions are carried out at the same time, so that both parties of each specific transaction are covered, the two parties of the transaction cannot be corresponded, and the transaction amount is completely confidential.
Owner:HANGZHOU YUNXIANG NETWORK TECH
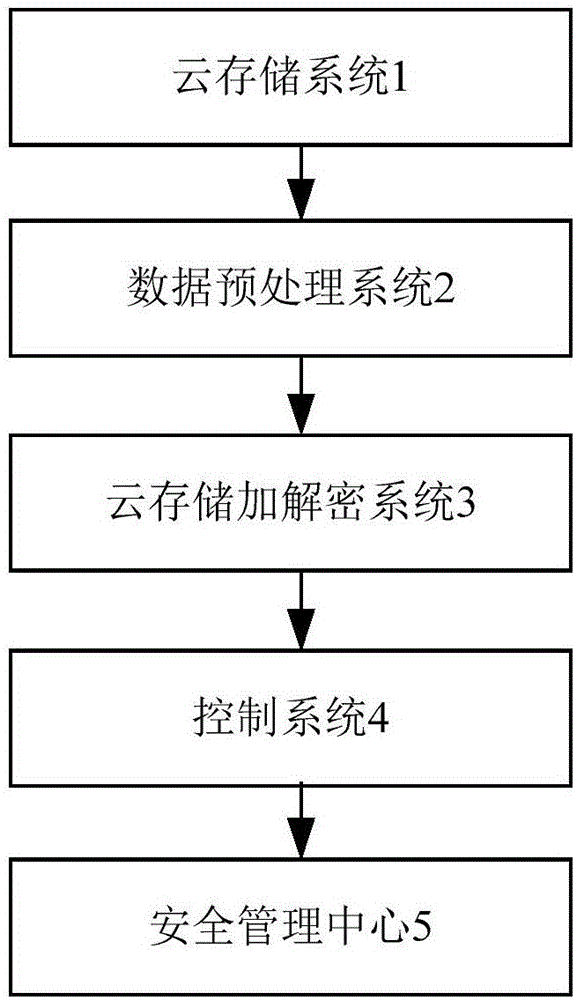
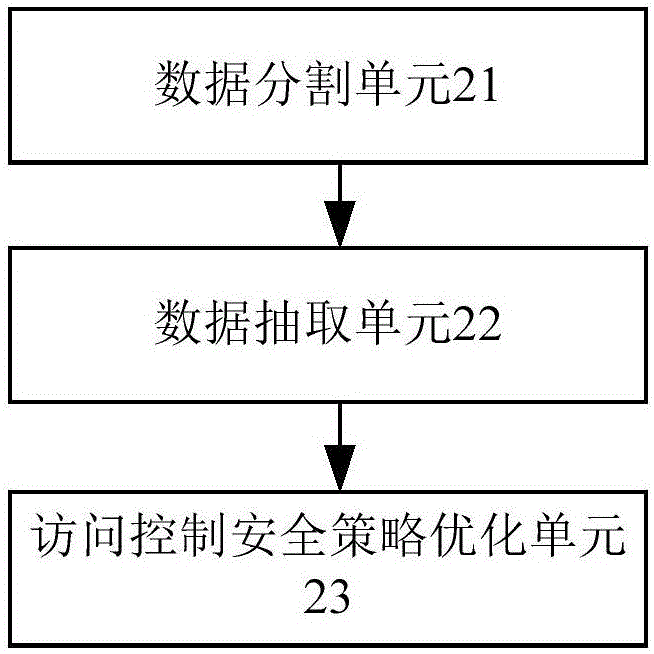
Big data safety management system
ActiveCN106203146AEasy to achieve unified managementEasy accessDigital data protectionControl systemSafety management systems
The invention provides a big data safety management system. The system comprises a cloud storage system, a data pre-processing system, a cloud storage encryption / decryption system, a control system and a safety management center. Through the brand-new module design, the data management level is improved, and the data security is enhanced.
Owner:GUANGDONG GANG XIN SCI & TECH
Video-encryption camera and encryption method thereof
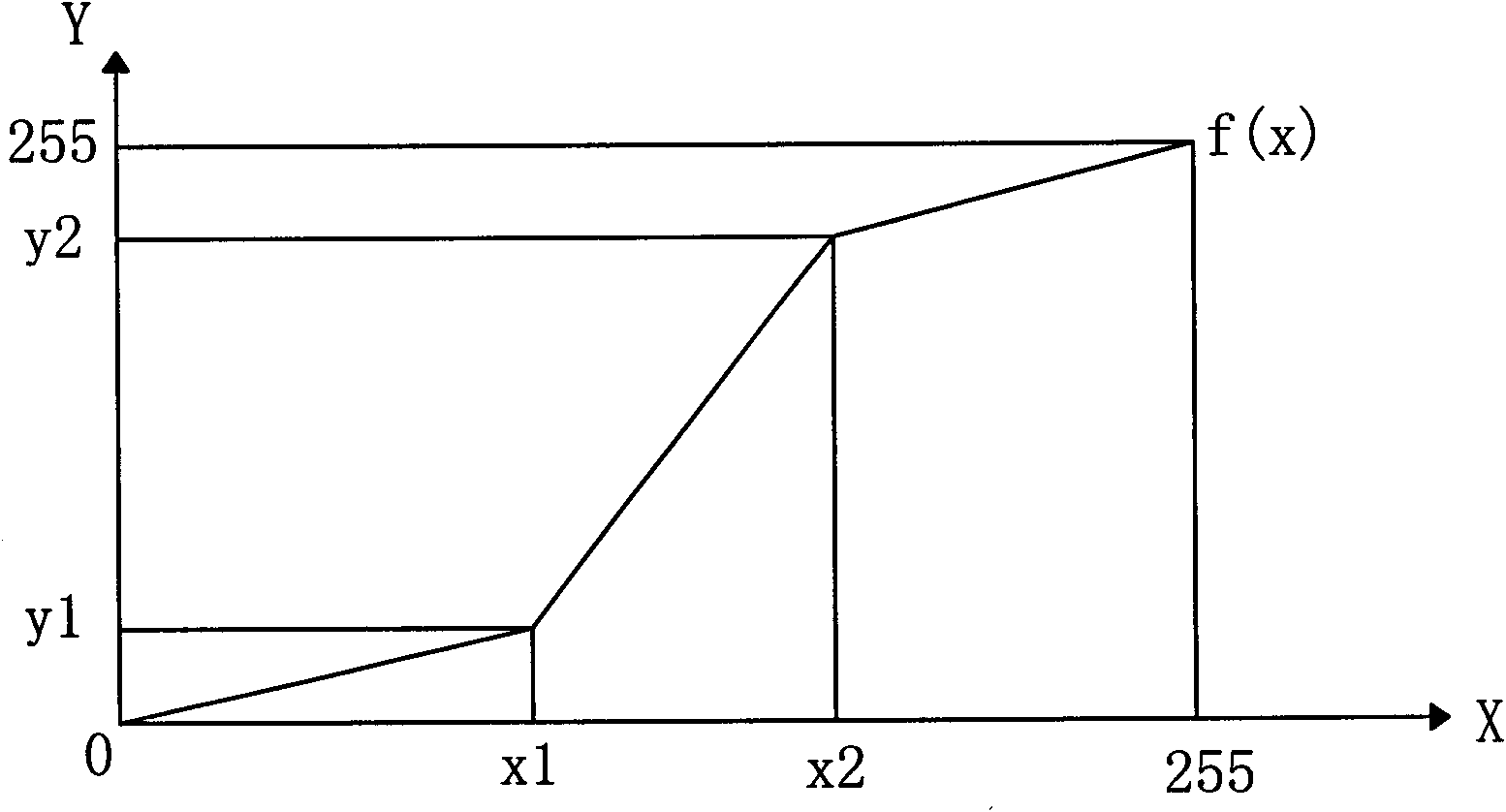
ActiveCN101902576AEasy to crackImprove securityTelevision system detailsColor television detailsVideo storageChaotic encryption
The invention relates to a video-encryption camera comprising a video acquisition module, a video pre-processing and encrypting module and a video storage module, wherein the video acquisition module is used for transmitting video data to the video pre-processing and encrypting module upon the completion of video acquisition; the video pre-processing and encrypting module is used for pre-processing each frame of video data, making calculations by calling a chaotic encryption system in the video storage module to generate chaotic sequences and further carrying out the XOR operations on the chaotic sequences and each frame of video data to encrypt the video data; and the video storage module is used for storing the encrypted video data on a real-time basis. Compared with the prior art, the invention encrypts the video data while acquiring and pre-processing the video data, and stores the encrypted video data in the video storage module on a real-time basis, thus avoiding the consequences that the raw video data are illegally stolen or falsified.
Owner:SOUTH CHINA NORMAL UNIVERSITY
Data protection method and system
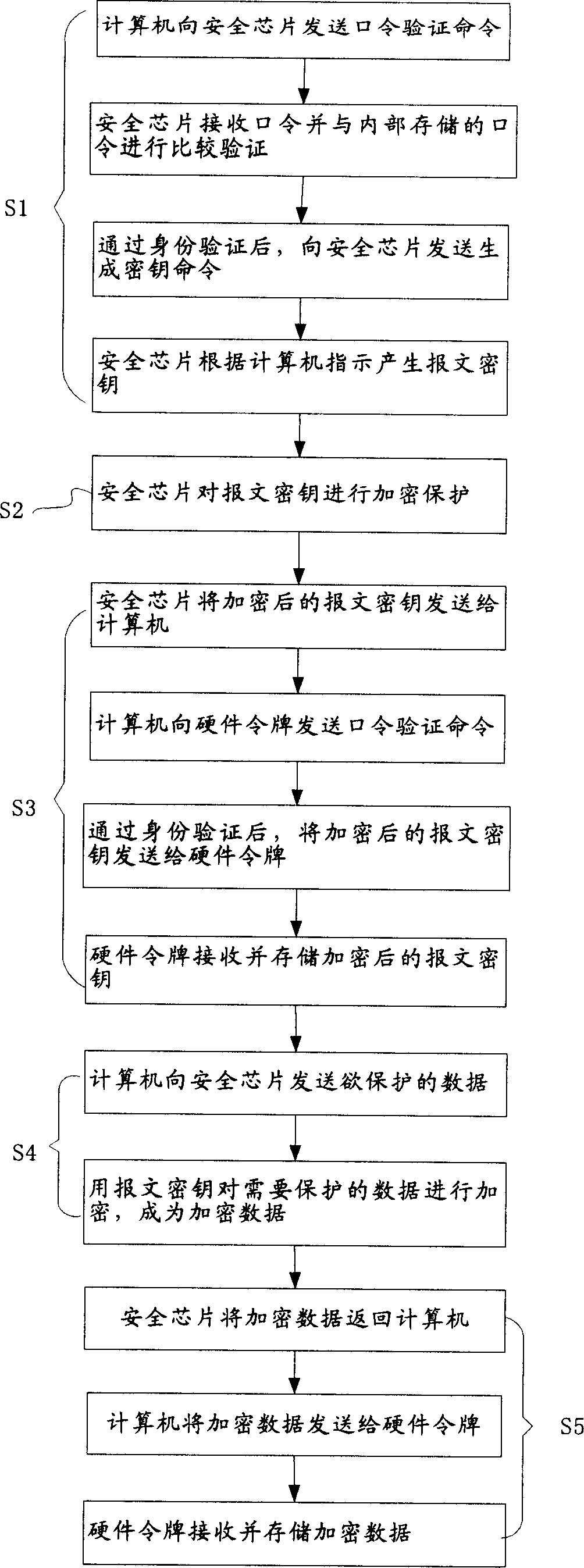
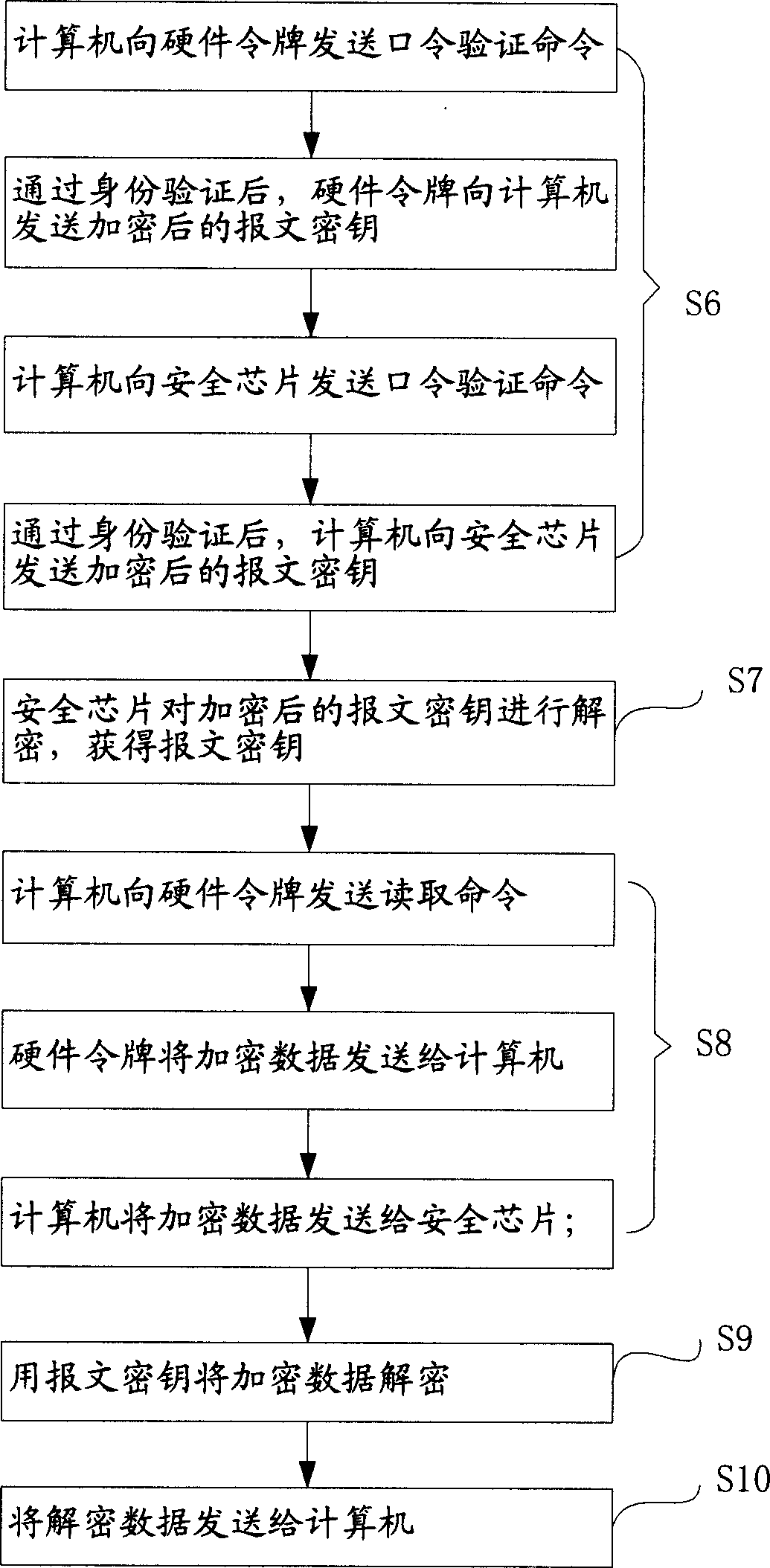
InactiveCN1607511APrevent illegal theftAvoid lossMemory loss protectionUnauthorized memory use protectionDECIPHERKey storage
This invention relates to a data protection method and a protection system. The method includes a cipher flow and a decipher flow, in which, the cipher flow includes the following steps: a safety chip generates a report cryptographic key and ciphers it to store it in hardware token. The data is ciphered with the report cryptographic key to be stored in the hardware token. The deciphering flow includes the following steps: The safety chip gets the ciphered report cryptographic key from the token and deciphers it to get the report key, the safety chip gets ciphered data from a hardware token and deciphers the data with the report cryptographic key. The data protection system includes a safety chip, a hardware token and a computer.
Owner:LENOVO (BEIJING) LTD
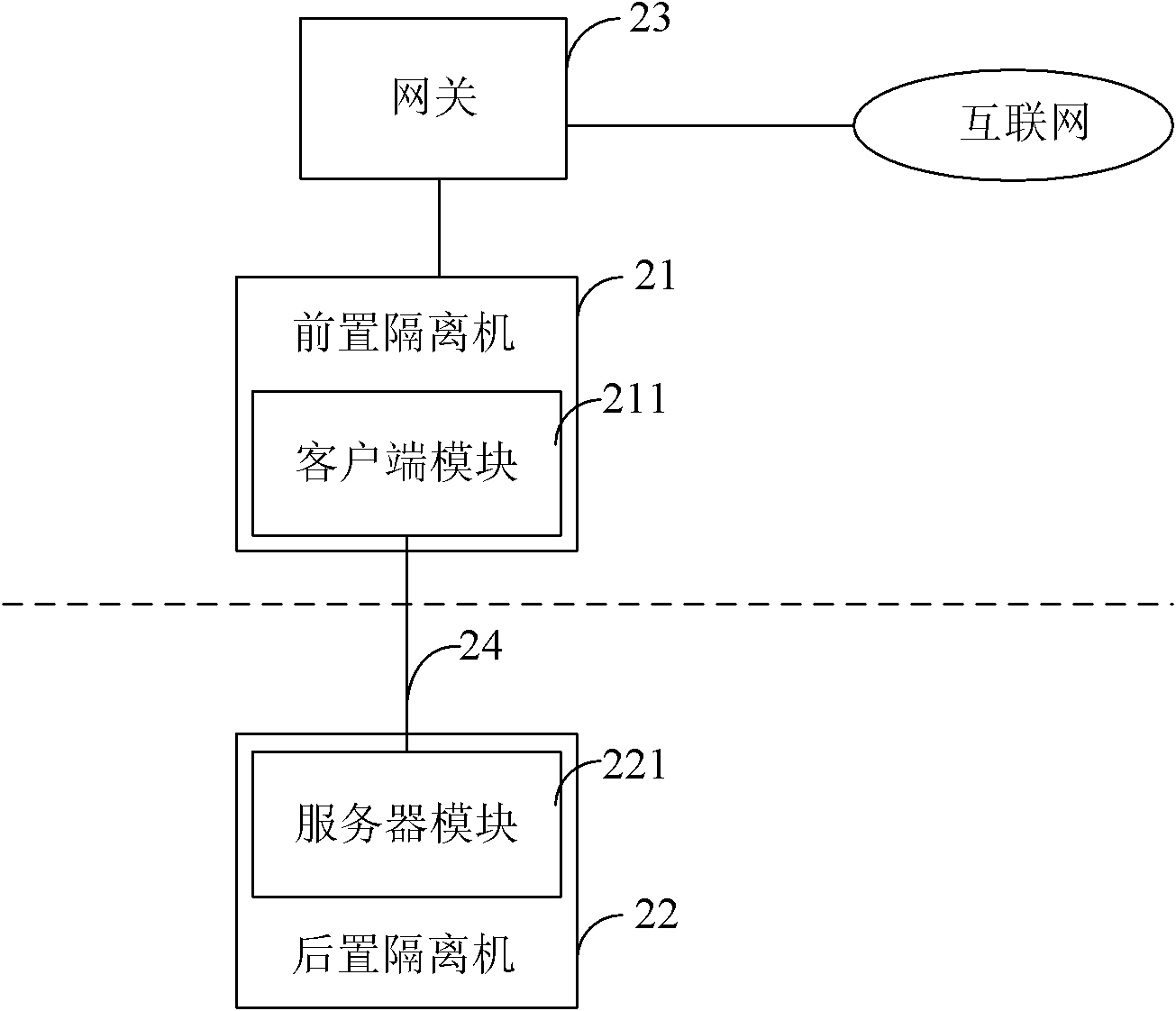
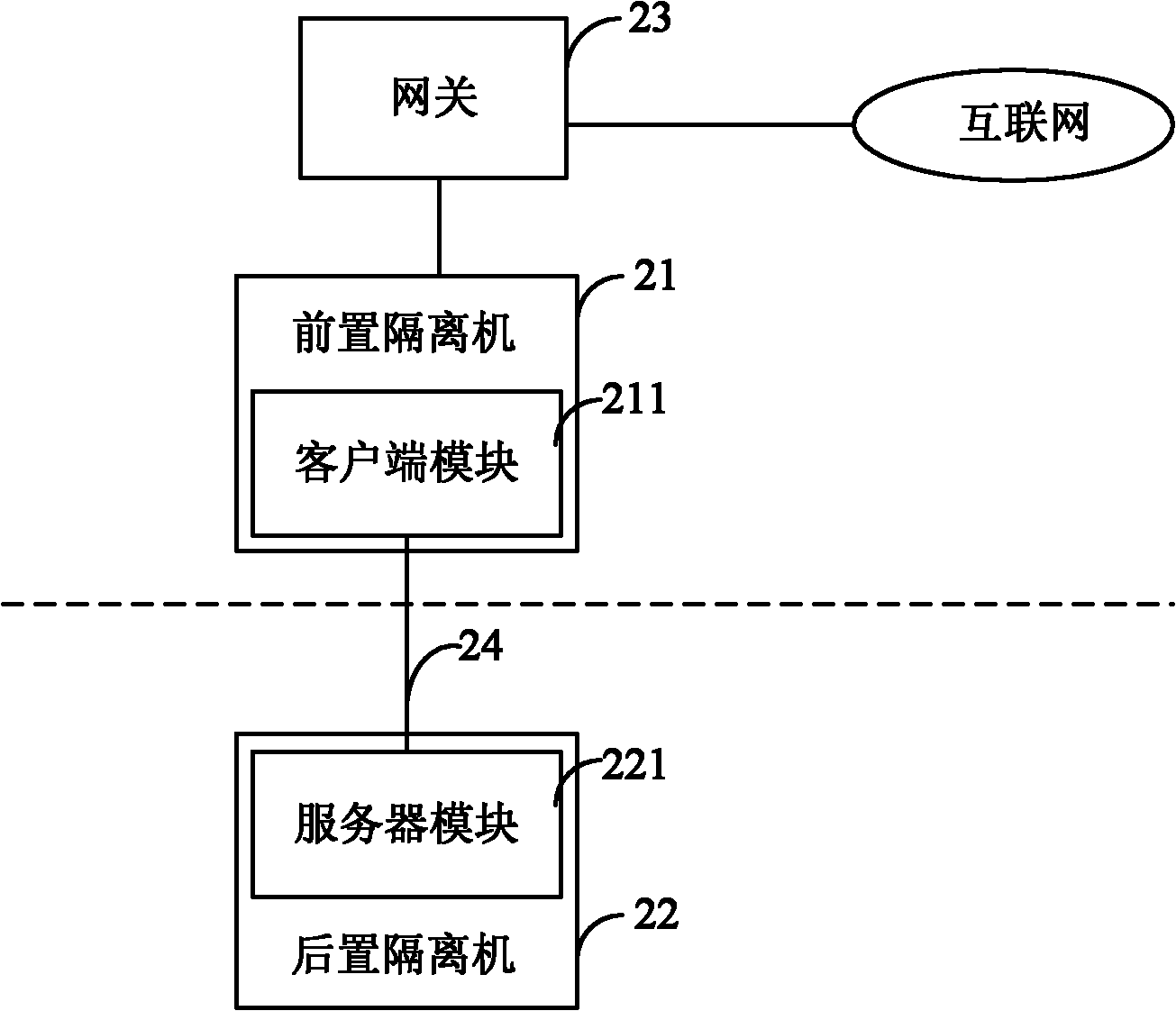
Network communication system
The invention relates to a network communication system. The system is characterized in that the system comprises at least a front isolator in the office network segment and rear isolators in the transaction network segment, wherein the front isolator / isolators is / are connected with the internet; the front isolator / isolators and the rear isolators are connected via USB connection lines; application program interfaces (APIs) are adopted at the two ends of each USB connection line; and the front isolator / isolators and the rear isolators transfer data by adopting private protocols. The system has the following advantages: the computers connected with the internet and the computers connected with the internal local area network (LAN) are separated from each other and are connected with each other via special USB connection lines, the private protocols are adopted for data interaction, and the USB connection lines adopt non-standard APIs and the security is high, thus effectively preventing the information data in the internal LAN from being illegally stolen by the undesirable internet users.
Owner:HUNDSUN TECH
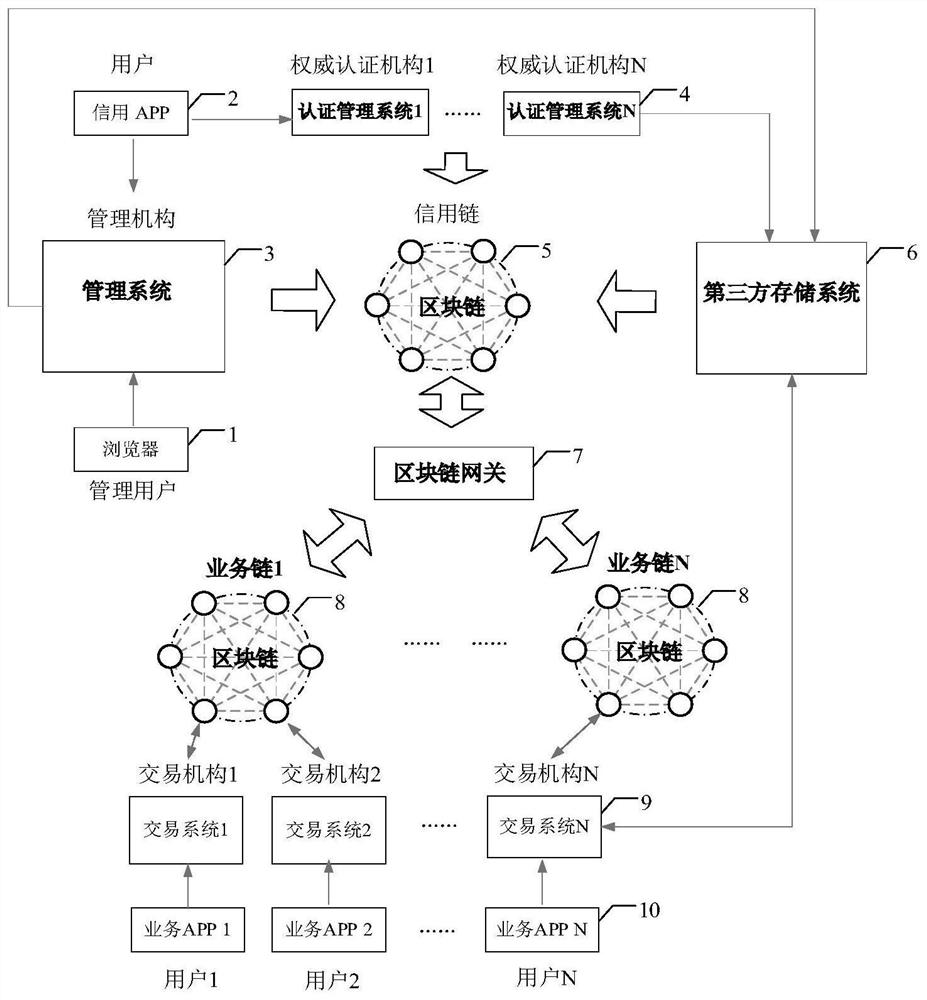
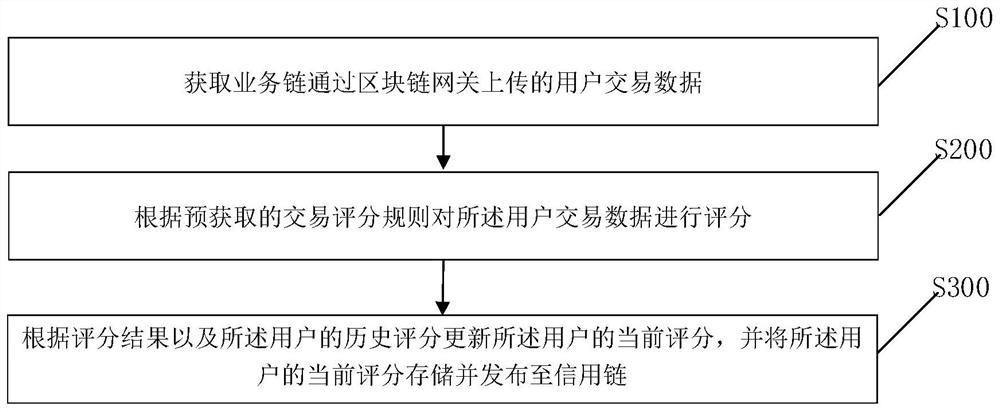
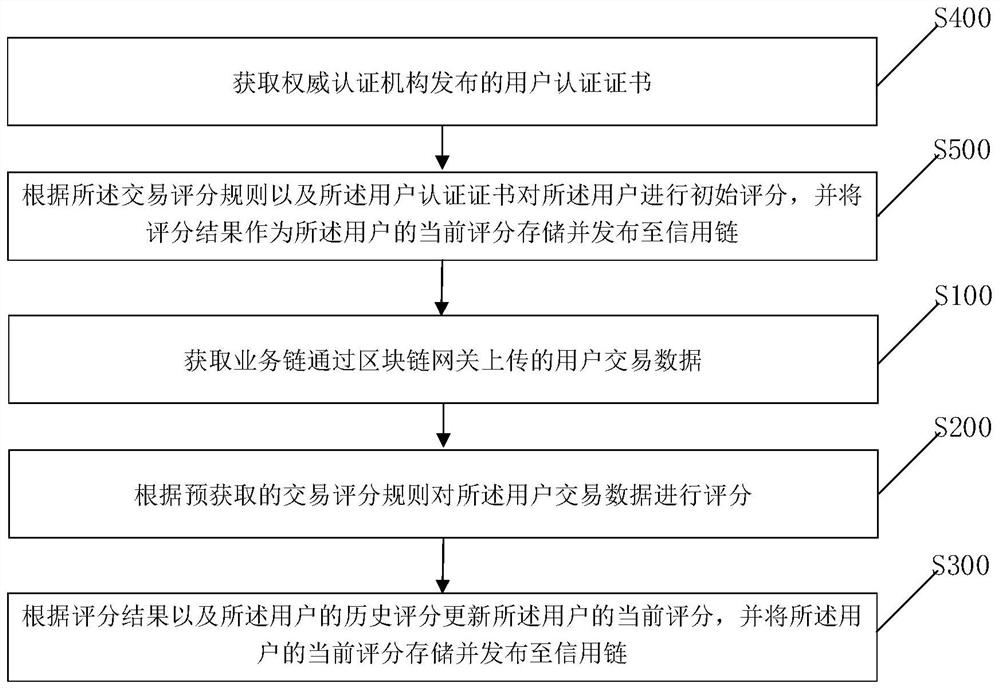
Credit scoring method for block chain, transaction method and related device
PendingCN111681007APrevent illegal theftPrevent tamperingDigital data protectionProtocol authorisationTransaction dataFinancial transaction
The invention provides a credit scoring method for a block chain, a transaction method and a related device, the credit scoring method for the block chain is applied to a credit chain node, and the method comprises the steps: obtaining user transaction data uploaded by a business chain through a block chain gateway; scoring the user transaction data according to a pre-acquired transaction scoringrule; and updating the current score of the user according to the scoring result and the historical score of the user, and storing and publishing the current score of the user to a credit chain. The credit chain and the service chain are communicated through the block chain gateway, credit scoring service is provided through the credit chain, the characteristics of the block chain are effectivelyutilized, data is prevented from being illegally stolen or tampered, credit evaluation scoring rules are accepted by all node mechanisms of the block chain together, and the method is public, transparent and high in rationality.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
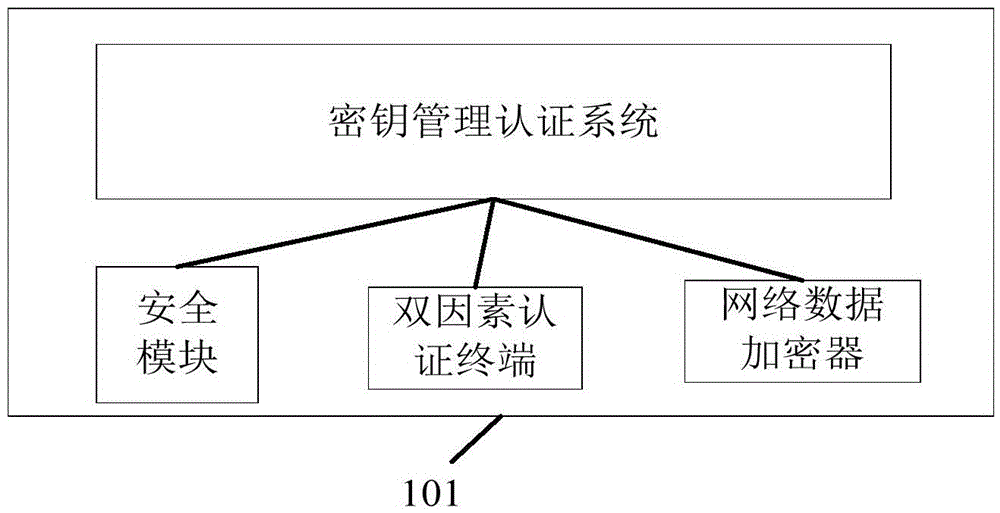
Industrial information security authentication system
InactiveCN105471901AAvoid destructionPrevent illegal theftTransmissionTerminal equipmentNetwork data
The invention provides an industrial information security authentication system, comprising a key management authentication system, a security module, a network data encryption device and a double-factor access authentication terminal. The industrial information security authentication system provided by the invention is mainly used for preventing illegal access, preventing data from being illegally tampered, damaged and stolen, and prevents illegal operation. According to the industrial information security authentication system provided by the invention, registration, authentication and management of terminal equipment are achieved. The aim that the legal terminal accesses the legal network and the legal platform manages the legal device is achieved, and a support effect is provided for preventing the information from being used without authorization or misused.
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
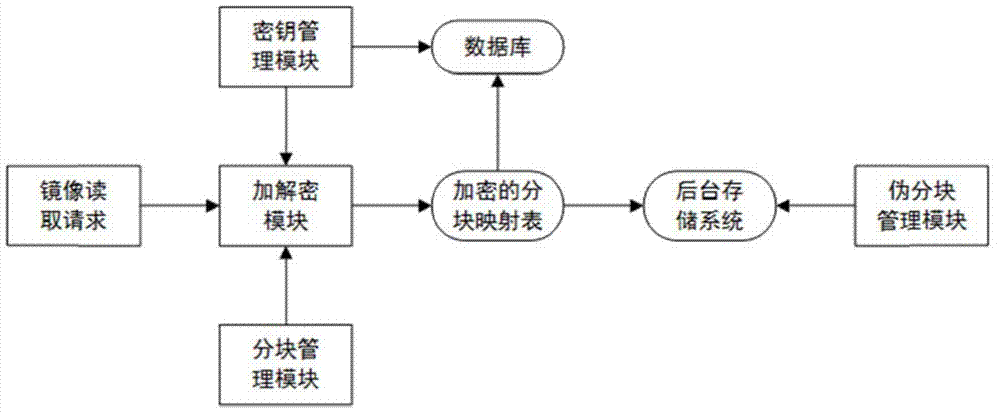
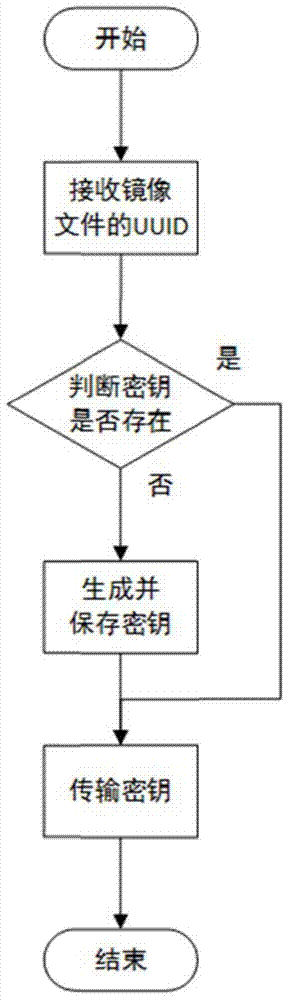
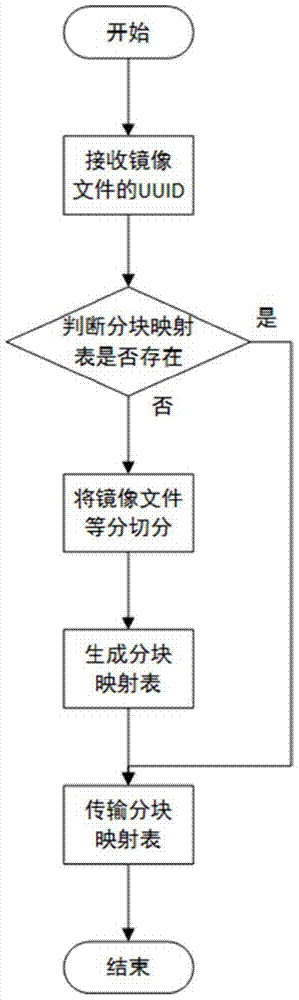
Lightweight mirror image file encryption system and method
ActiveCN104780048APrevent illegal tamperingReduce the possibility of brute-forcingKey distribution for secure communicationUser identity/authority verificationBrute forceMirror image
The invention discloses a lightweight mirror image file encryption system and a lightweight mirror image file encryption method and belongs to the technical field of cloud computing of computers. A mirror image file in a cloud computing system is encrypted, stored and managed. The encryption system comprises a key management module, a mirror image file block management module, an encryption / decryption module, a pseudo partitioning management module, a database and a background storage system. The encryption method comprises a key acquisition stage, a mirror image file partitioning stage, a mirror image file storage stage, a mirror image file reading stage and a pseudo partitioning maintenance stage. The mirror image file block management module is used for equally segmenting all mirror image files and then protecting the mirror image files through an encryption block mapping table. The safety of the mirror image files is ensured, and the encryption / decryption time cost is lower. Meanwhile, by creating and managing pseudo blocks in an idle storage space, the possibility of brute force is further reduced, and the safety is improved. The lightweight mirror image file encryption system and the lightweight mirror image file encryption method are applicable to any cloud computing system relating to mirror image file management.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
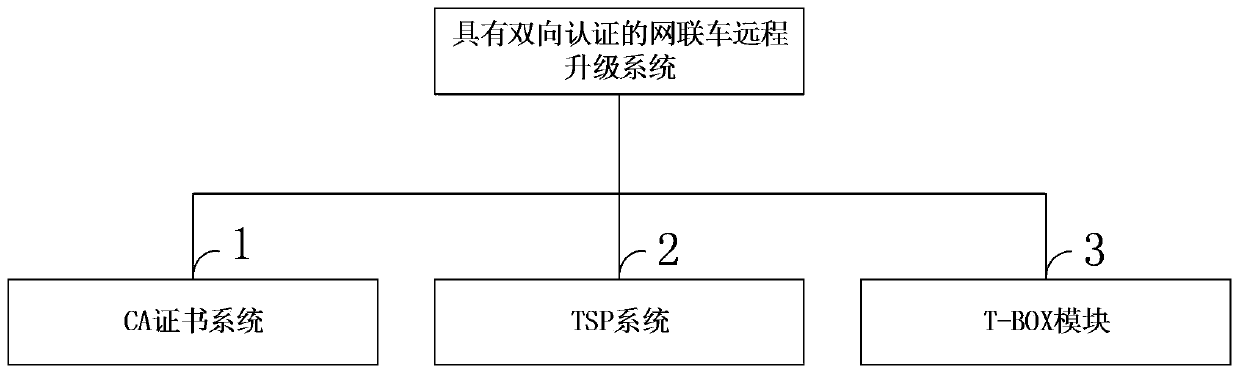
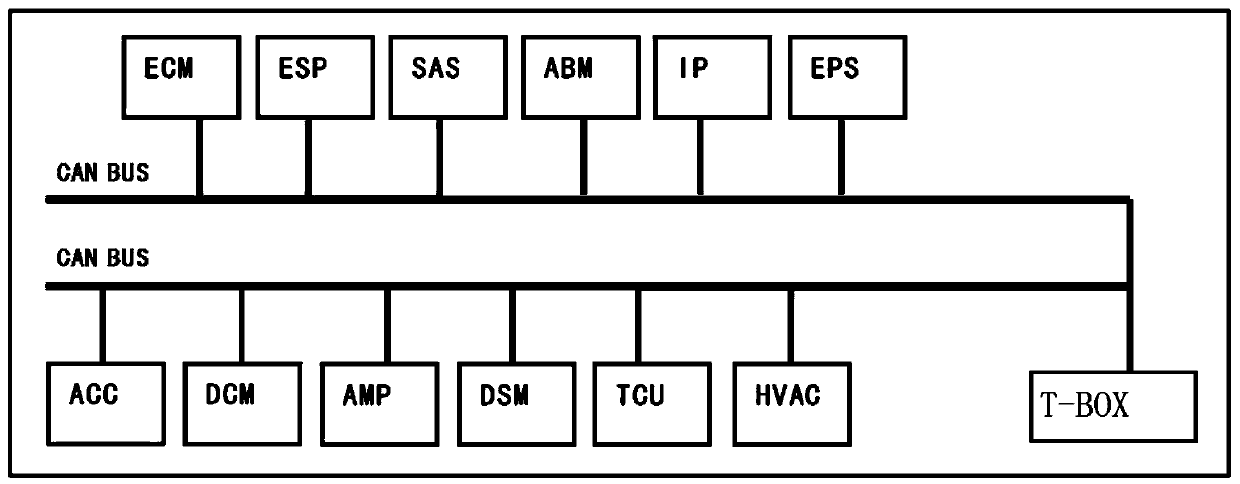
Networked vehicle remote upgrading system and method with anti-attack bidirectional authentication
ActiveCN110891257AAchieving Reliability CertificationPrevent counterfeitingEncryption apparatus with shift registers/memoriesParticular environment based servicesData packSecurity rule
The invention belongs to the technical field of systematic safety of Internet of Vehicles, and discloses a networked vehicle remote upgrading system and method with anti-attack bidirectional authentication, a CA certificate system is used for performing identity authentication on a vehicle through a digital certificate in an Internet of Vehicles network, and supporting bidirectional authenticationbetween a TSP and a networked vehicle. A TSP system is used for supporting remote upgrading of vehicles. A T-BOX system is used for detecting the IP of the TSP during upgrading; wherein the IP is notthe IP of the TSP, and the data packet of the IP is discarded; and in a non-upgrading state, external communication is compared according to rules in the security rule base of the firewall, and rulesof the rule base are updated through TSP real-time operation. According to the invention, the reliability authentication of the bidirectional identity between the networked vehicle T-BOX and the vehicle remote service provider TSP is realized, and the identity counterfeiting is prevented; reliability of data transmission between the T-BOX and the TSP is achieved, and illegal stealing and tampering of automobile upgrading software in the transmission process are prevented.
Owner:CHENGDU UNIV OF INFORMATION TECH
Secure communication method and system based on secure communication module
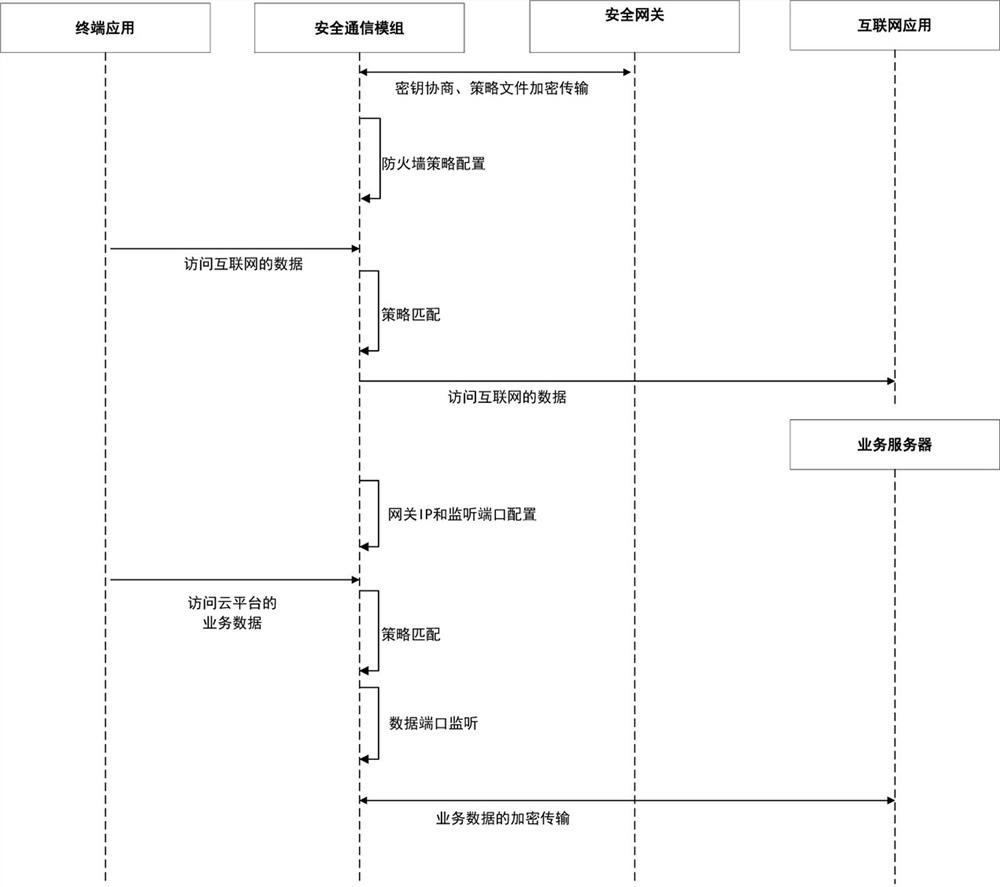
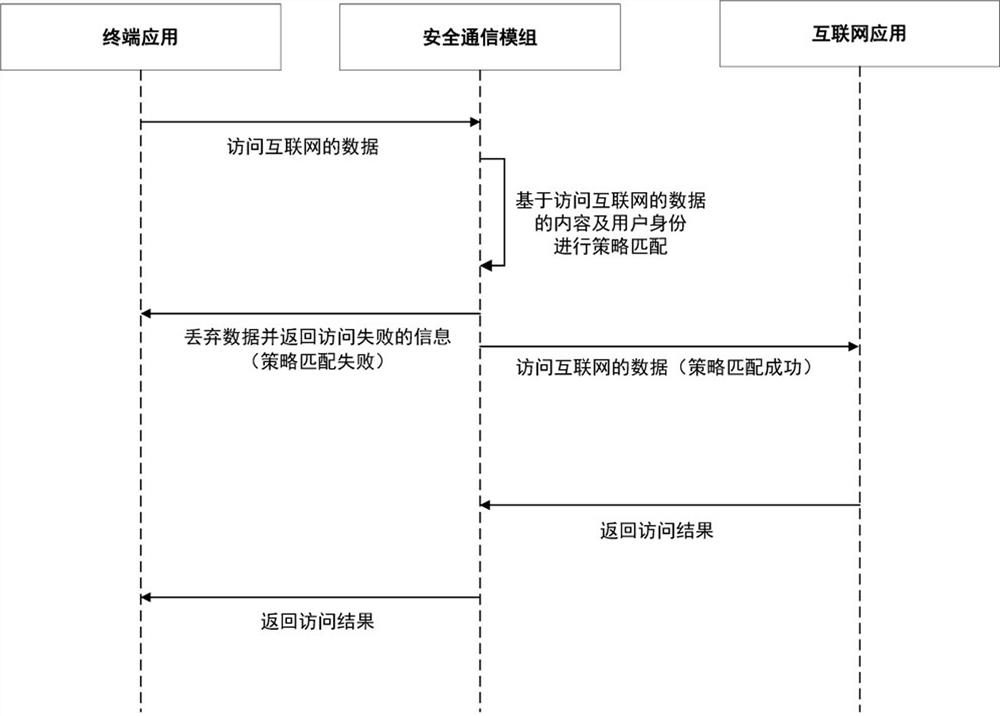
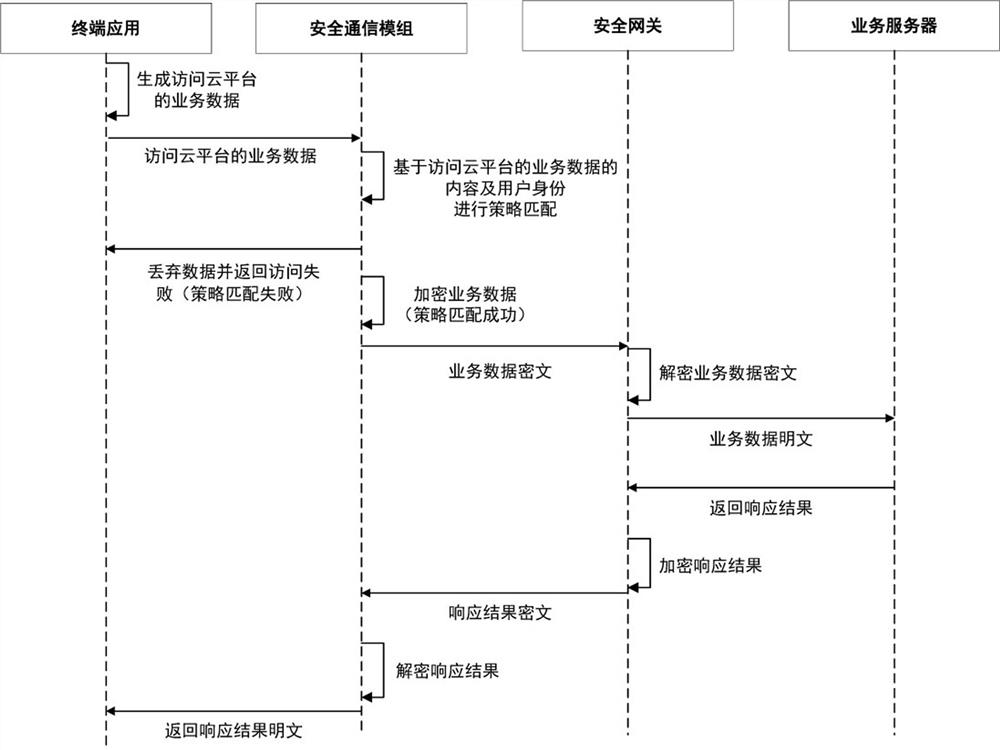
ActiveCN111918284AGuaranteed encrypted transmissionEasy accessKey distribution for secure communicationUser identity/authority verificationSecure communicationInternet privacy
The invention provides a secure communication method and system based on a secure communication module, and the method comprises the steps that a secure mobile terminal obtains a session key after carrying out the key negotiation with a security gateway of a cloud platform through the secure communication module, and carries out the encryption transmission of a strategy file; the security communication module performs firewall policy configuration according to the policy file; when the internet application is accessed, the terminal application sends data for accessing the internet to the safety communication module for strategy matching; if the first strategy is successfully matched, the security communication module sends the data of accessing the Internet to the Internet application fornetworking processing; when the cloud platform service is accessed, the security communication module performs gateway IP and monitoring port configuration according to the strategy file, and sends the service data accessing the cloud platform to the security communication module to perform policy matching and the like with a second policy file. And thus, the secure mobile terminal is ensured to securely access the Internet application or the cloud platform through the secure communication module.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Method and system for protecting mobile storage device
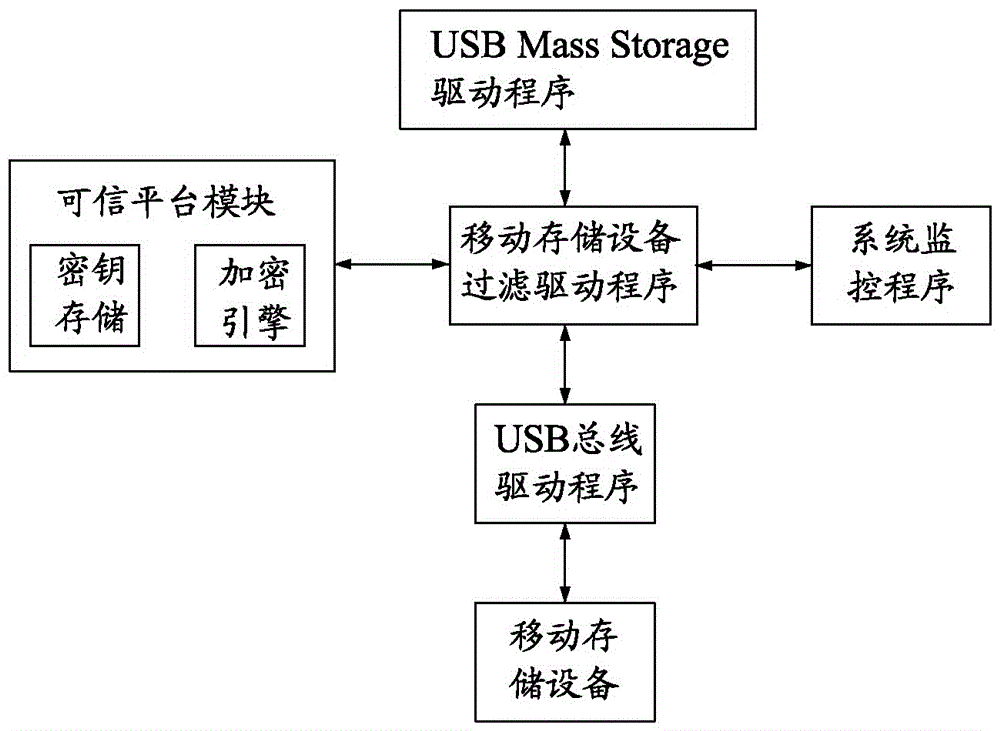
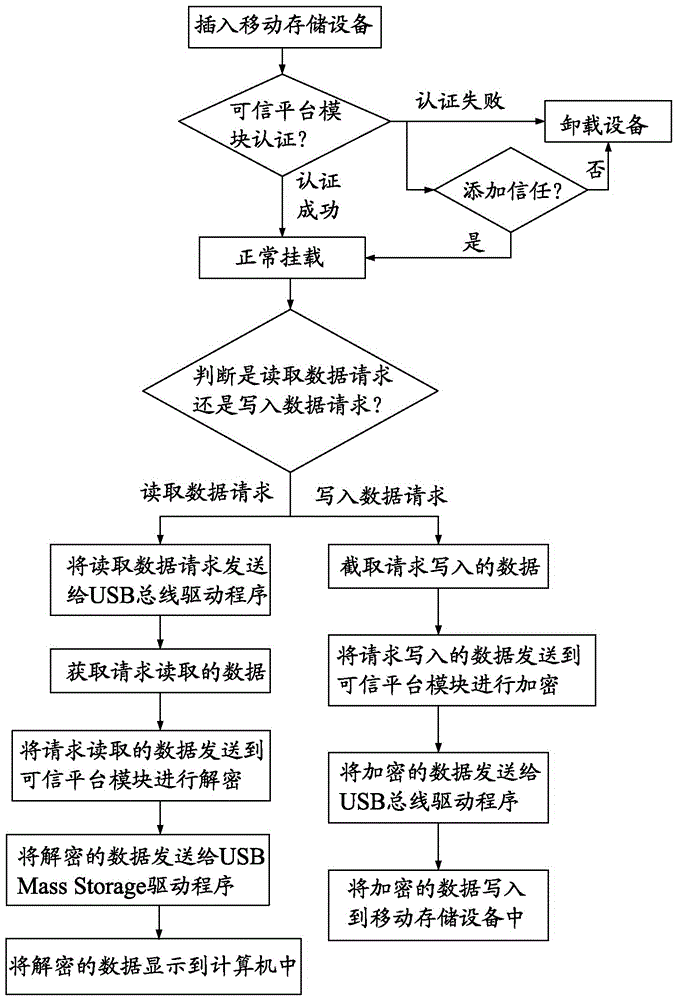
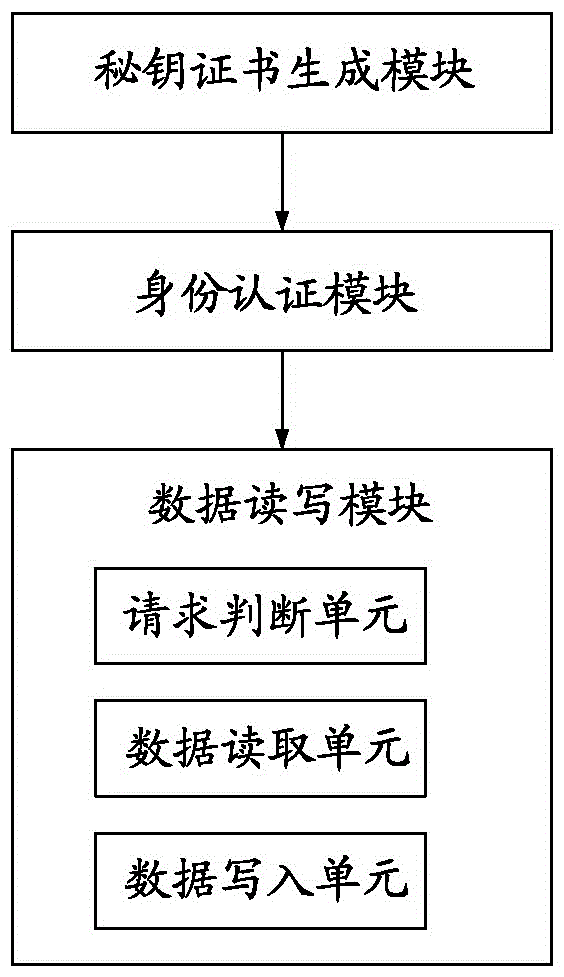
InactiveCN106778326AAccess effective interceptionAccess interceptionDigital data protectionInternal/peripheral component protectionTrusted Platform ModuleRemovable media
The invention provides a method for protecting a mobile storage device. The method includes the steps that a key and a certificate are generated through a credible platform module of a computer, the certificate is written into a separate partition of the mobile storage device, and the key is stored into the credible platform module; the mobile storage device is inserted into the computer for mounting, and the certificate is obtained from the mobile storage device and sent to the credible platform module for identity authentication; read-write operation data in the mobile storage device is sent to the credible platform module for encryption and decryption first, and then read-write operation on the mobile storage device is carried out. The invention further provides a system corresponding to the method. The method has the advantages that the access of an illegal mobile storage device can be effectively intercepted; the key for encryption and decryption of the mobile storage device is protected by the credible platform module, the safety of the key can be ensured, and the key can be prevented from being illegally stolen.
Owner:FUJIAN CENTM INFORMATION
System and method for presetting Widevine Keys in television in batched mode
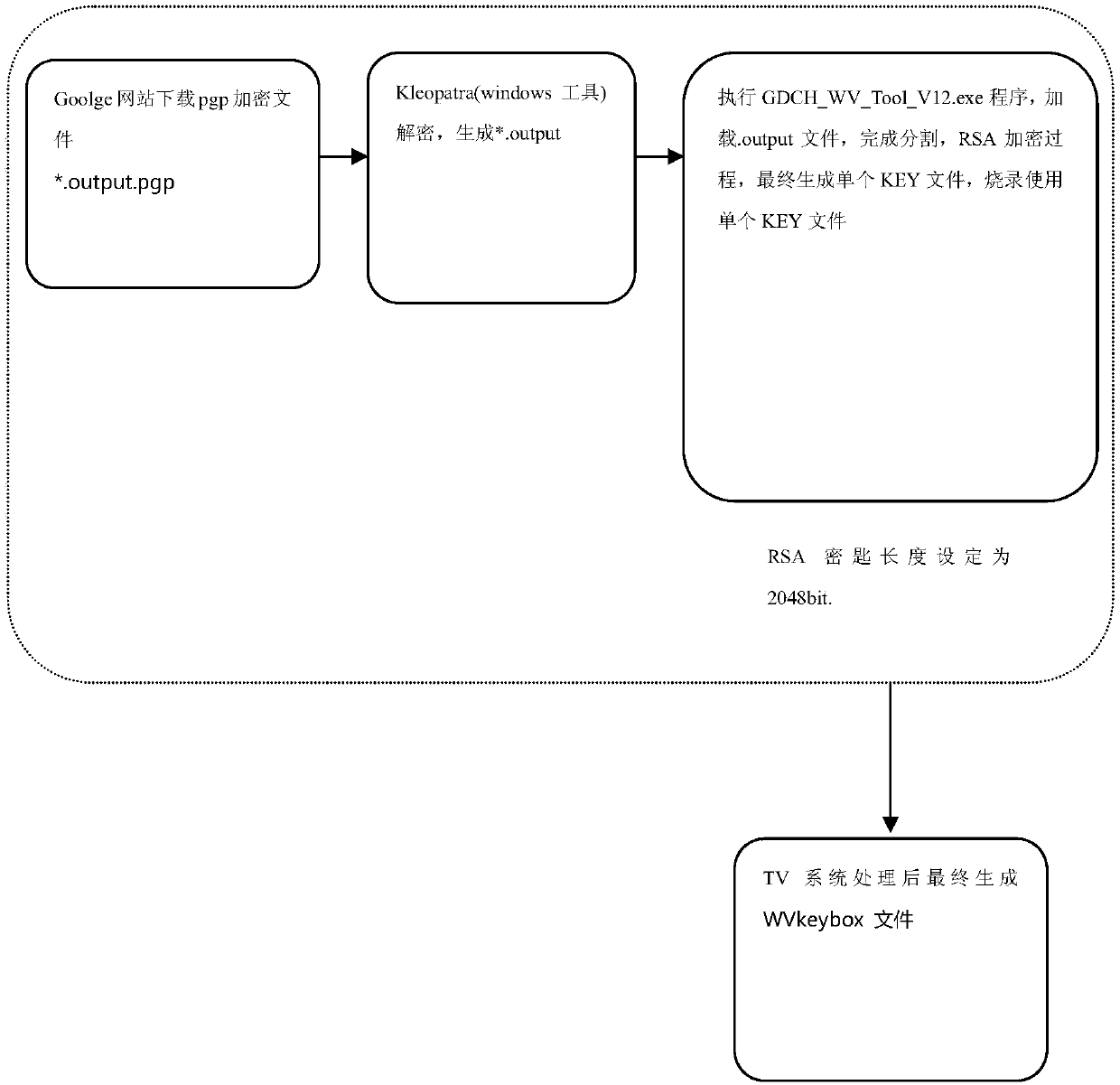
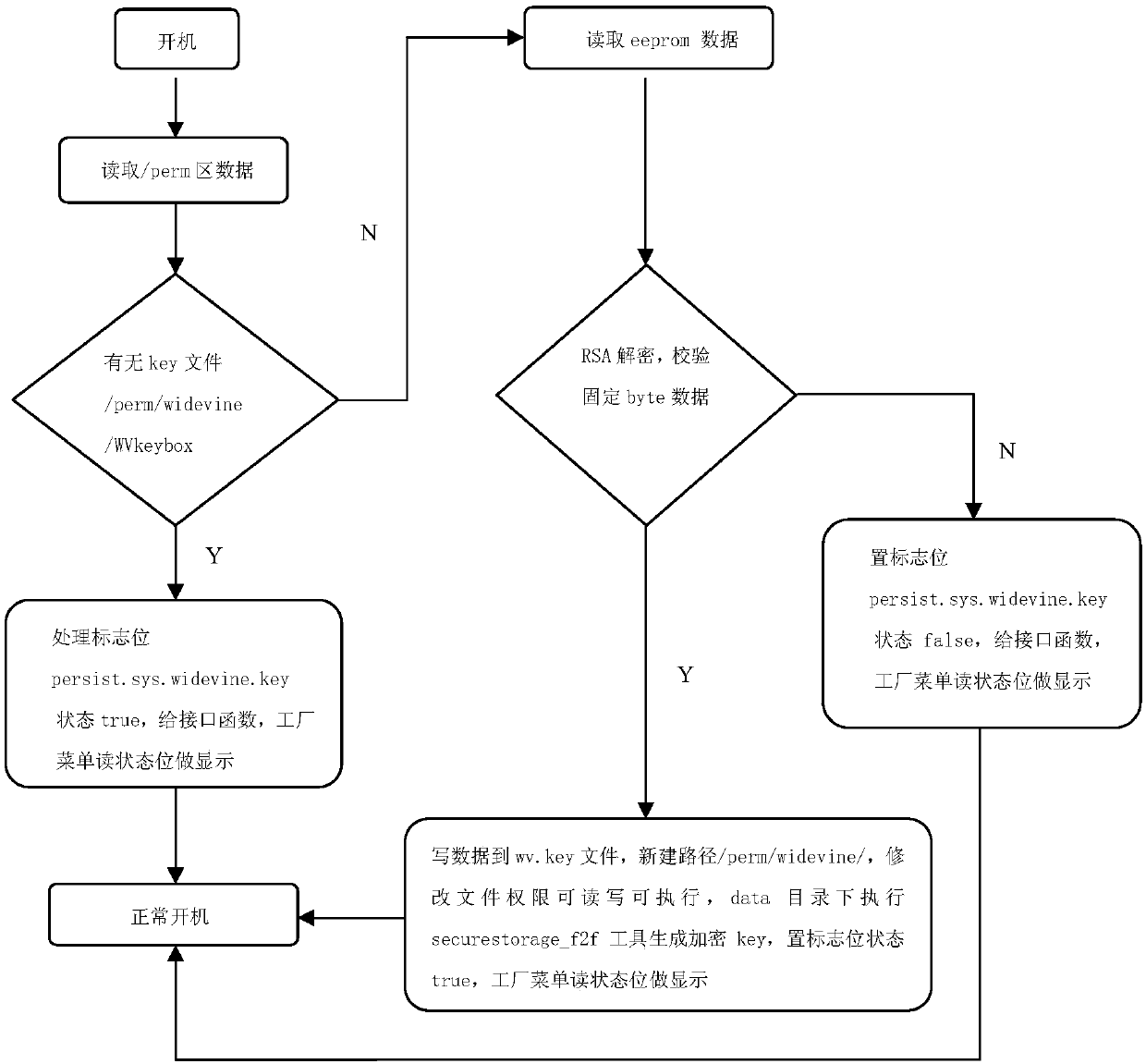
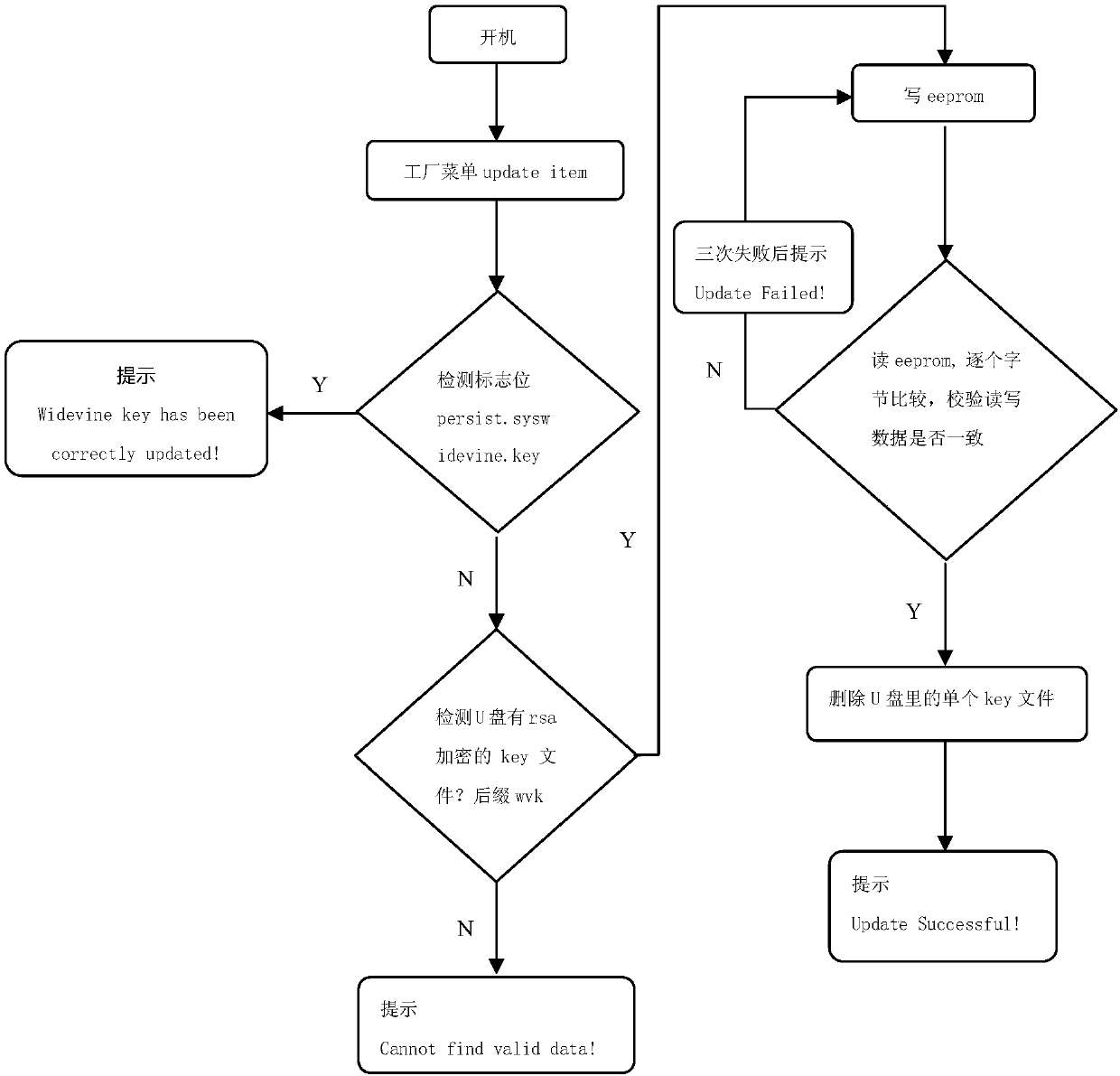
ActiveCN107809677APrevent illegal theft and misappropriationImprove securitySelective content distributionEncryptionCable television
The invention relates to a smart television parameter setting technology, and discloses a system and method for presetting Widevine Keys in a television in a batched mode. The system and method can beapplied to batched presetting of the Widevine Keys in complete television production links, and the security of Key data is improved. The method comprises the steps that 1, an original Key data packet is partitioned, and the partitioned Key data is subjected to encryption processing; 2, burning parameters are configured, and the encrypted Key data is burnt into an eeprom of the television througha burner; 3, the Key data is read from the eeprom of the television, and after the Key data is processed, secret key data used for decryption during network video playing is generated and stored; and4, the television detects whether or not the secret key data used for decryption during network video playing is stored after the television is powered on, and if the secret key data is not stored, the step 3 is conducted.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Method and device for achieving data security of operation system
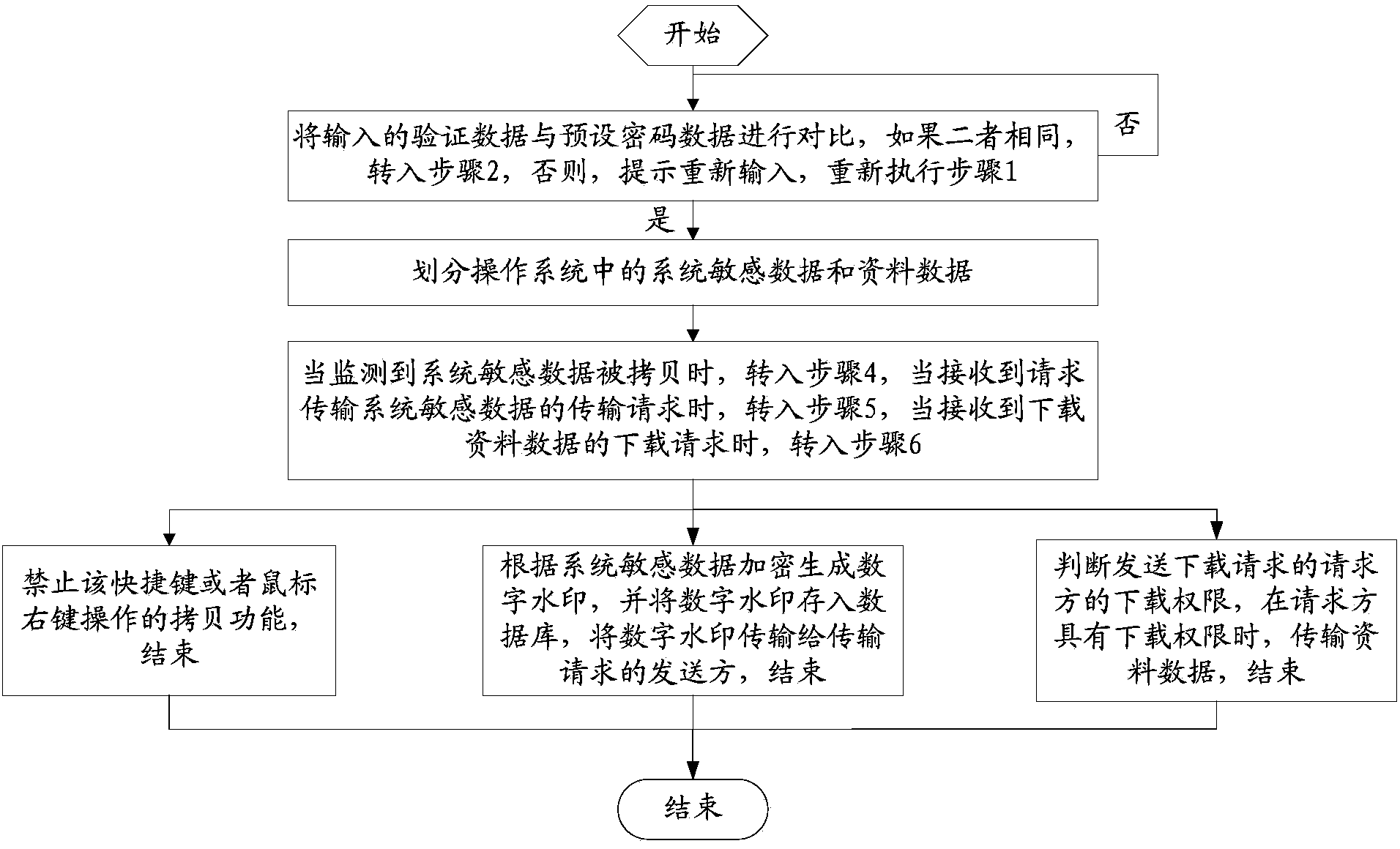
InactiveCN103488948AReduce risk of leakagePrevent tamperingDigital data protectionPlatform integrity maintainanceOperational systemTransport system
The invention relates to a method and a device for achieving data security of an operation system. The method includes the following steps: comparing inputted verification data with preset password data; dividing systematic sensitive data and material data in the operation system; when monitoring that the systematic sensitive data are copied, shifting into a step 4, when receiving a transmission request for transmitting the systematic sensitive data, shifting into a step 5, and when receiving a download request for downloading the material data, shifting into a step 6; prohibiting a copy function of operation of a shortcut key or right mouse button, and finishing; generating digital watermarks by encryption according to the systematic sensitive data, storing the digital watermarks in a database, transmitting the digital watermarks to a sender sending the transmission request, and finishing; judging download permission of a requester sending the download request, transmitting the material data when the requester has the download permission, and finishing. By the method and the device, risk of job number and password disclosure can be reduced, and system login safety is improved.
Owner:北京思特奇信息技术股份有限公司
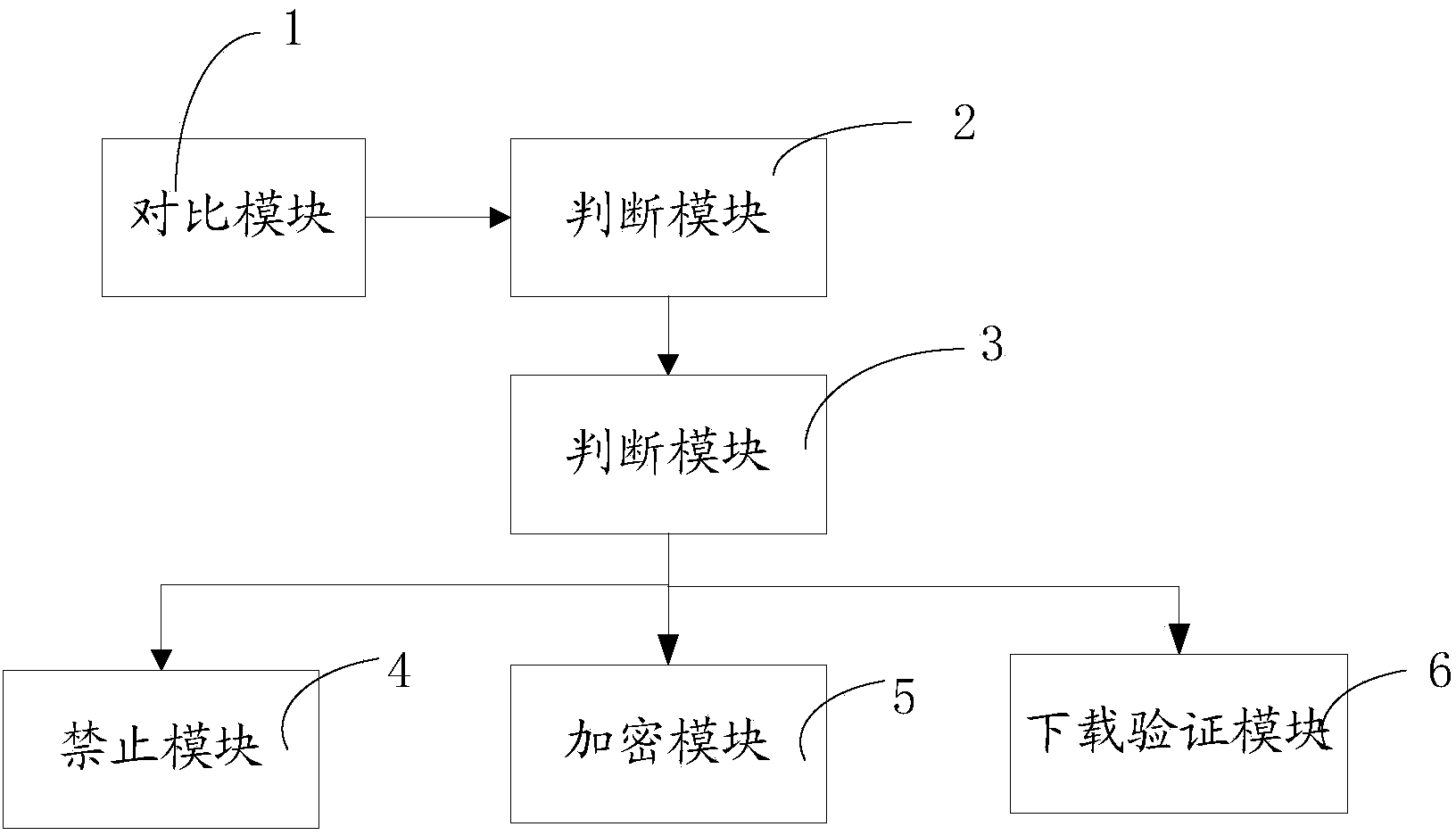
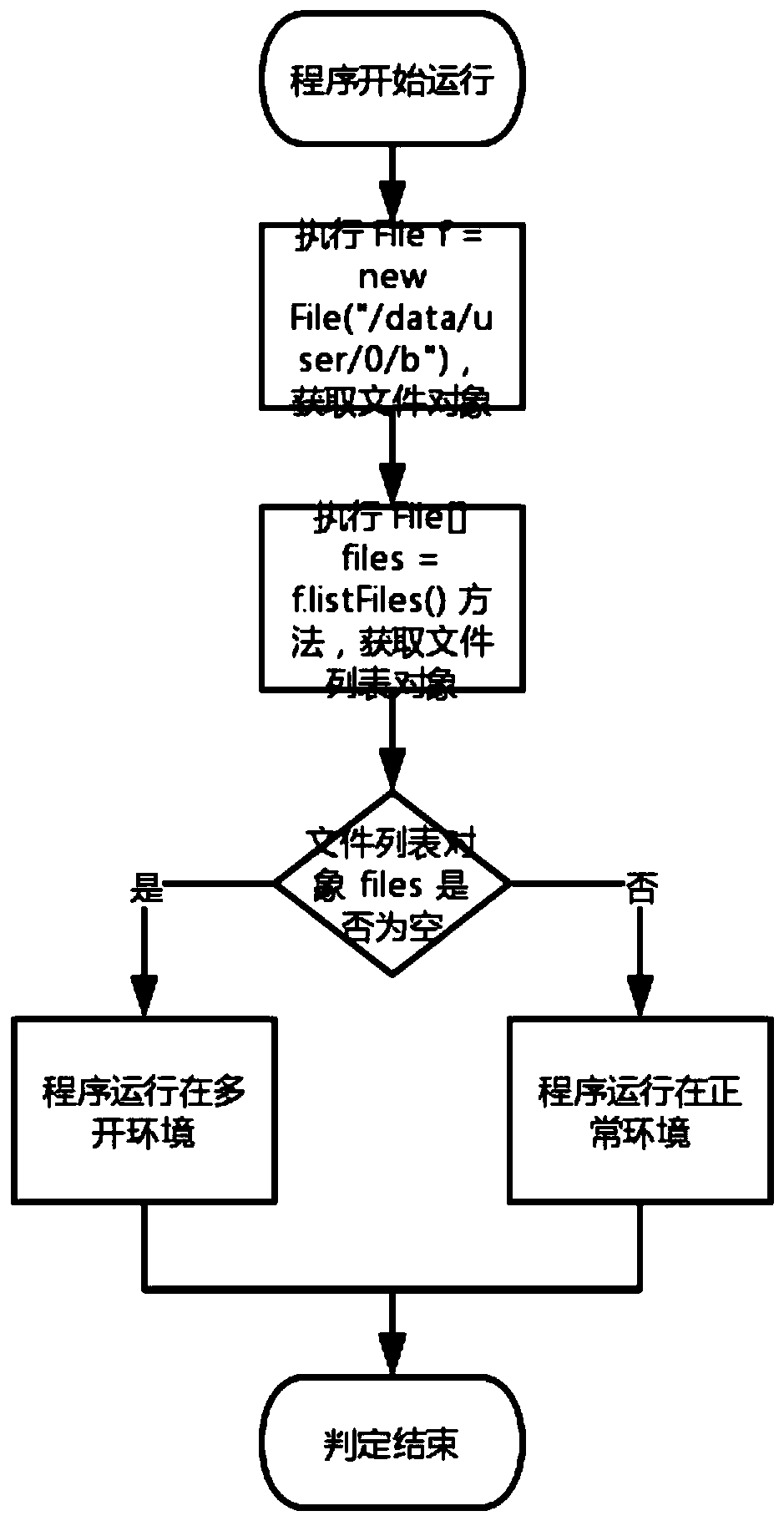
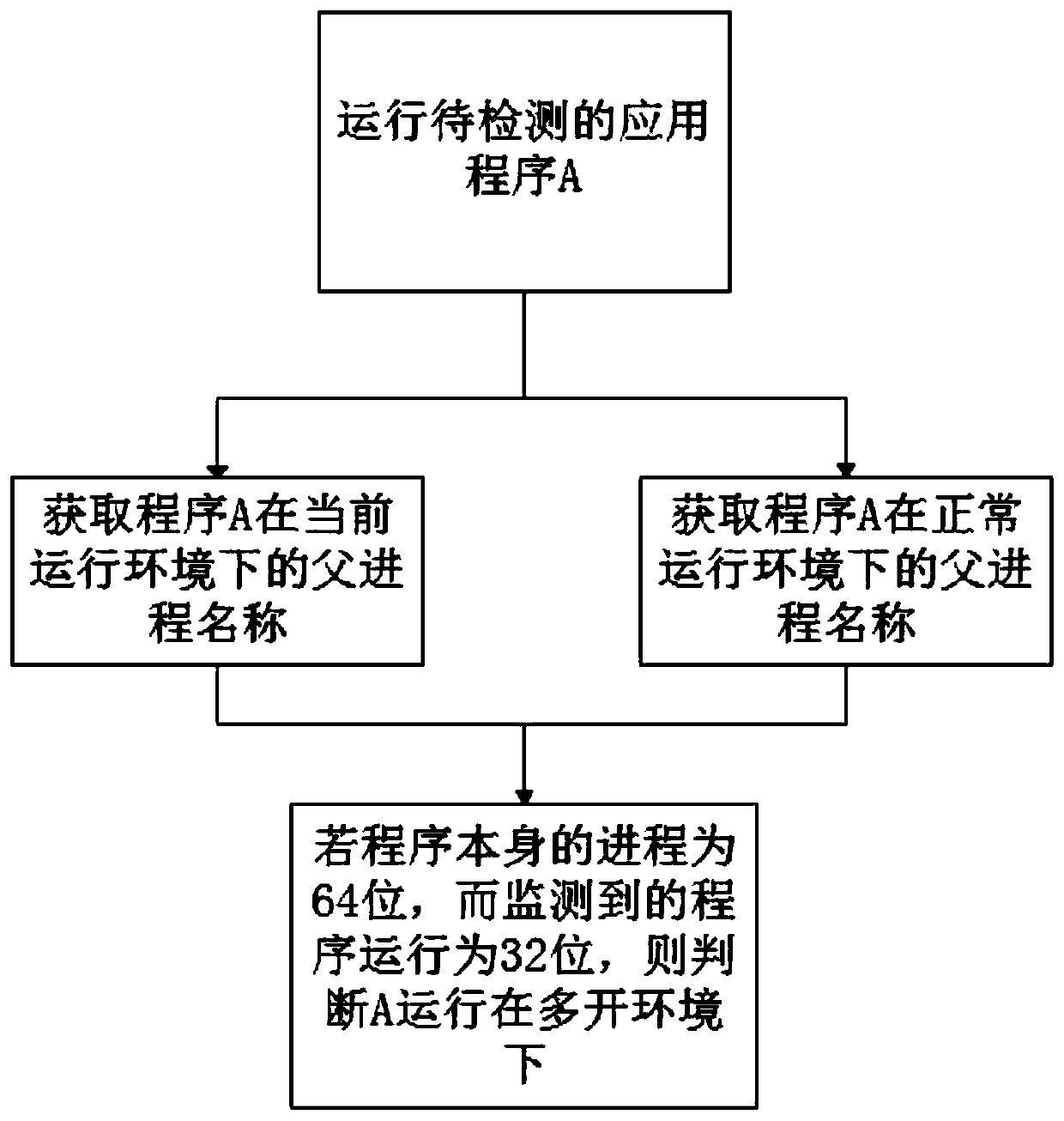
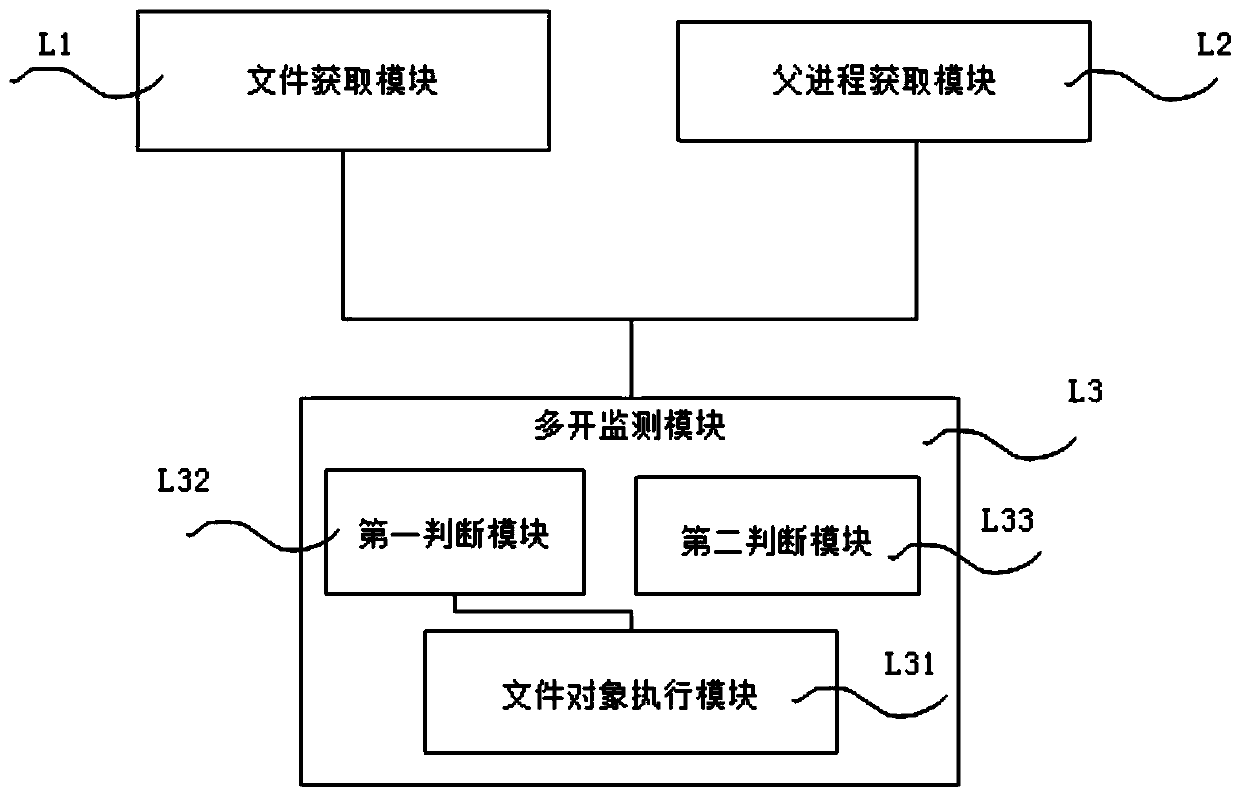
Method and system for judging running of application program in multi-open environment based on Android system
InactiveCN111027054APrevent tamperingPrevent illegal theftPlatform integrity maintainanceSoftware engineeringApplication procedure
The invention discloses a method and system for judging running of an application program in a multi-open environment based on an Android system, and the method comprises the steps: firstly, running ato-be-detected application program A, and sequentially obtaining file objects corresponding to a storage path of the application program A or the name of a parent process of the application program Ain a current running environment; and further judging whether the application program A runs in a multi-open environment or not. The method has the beneficial effects that whether the application process is a 64-bit process or a 32-bit process or whether there is a feedback query result in a file list can be judged based on the name of the parent process in the normal and to-be-detected running environment, and further whether the application runs in the multi-open environment can be determined; according to the system and the method, the compatibility problem of the Android is considered, the detection efficiency is improved, and the system and the method have wide application prospect and application value.
Owner:WUHAN JIYI NETWORK TECH CO LTD
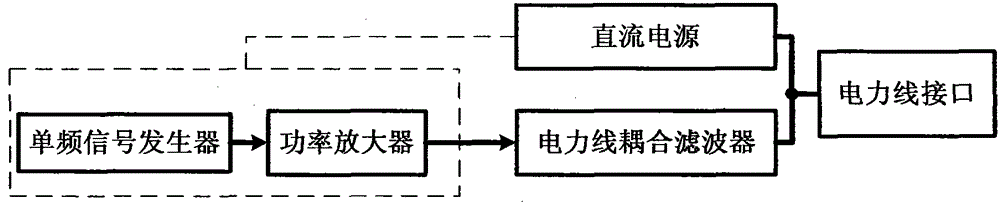
Power Line Communication Jamming Device
InactiveCN103856242BEasy accessReceive and detectPower distribution line transmissionCommunication jammingEngineeringPower line interference
The invention relates to power-line communication interference devices and particularly relates to a plurality of devices which perform communication interference on facilities which use power lines for communication and belongs to the technical field of power-line communication, communication interference and interference resistance and information security. A device specifically includes a power-line interface, a DC power supply, a power-line coupling filter, a power amplifier and an interference signal generator. The invention also provides a power-line communication interference device with a power-line communication signal detection and analysis function, a processing and forwarding power-line communication interference device and a power-line communication signal short circuit / bypassing power-line communication interference device. The power-line communication interference devices are connected with power lines conveniently through forms of power-line insert ports, insert grooves and sockets and the like so that interference signals which interfere power-line communication are generated; an excellent interference effect is achieved through an extra-low interference power and electricity consumption quantity is low so that the power-line communication interference devices are especially suitable for being used in low-power-consumption inference application; and the interference mechanisms are simple in structure, low in realization cost and high in self-adaptive capability.
Owner:李祥明 +2
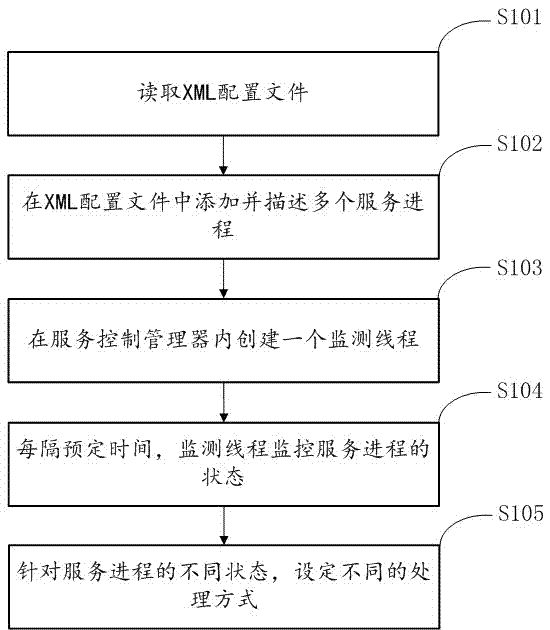
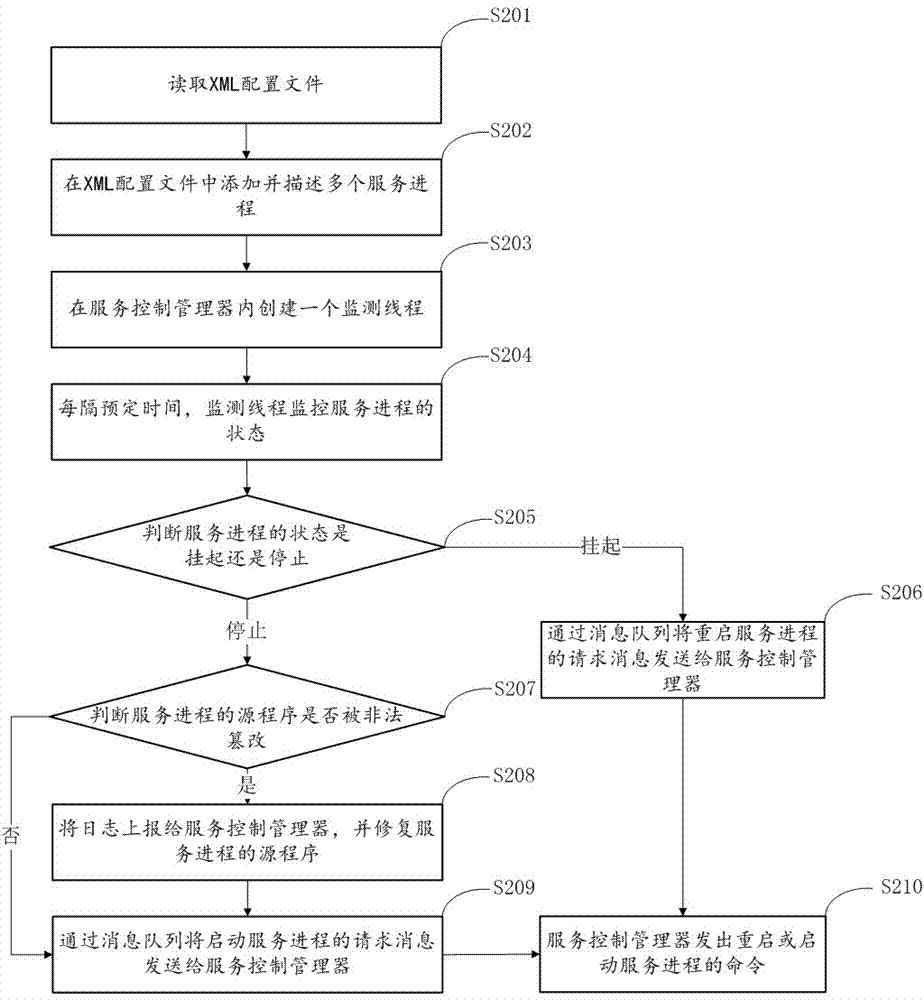
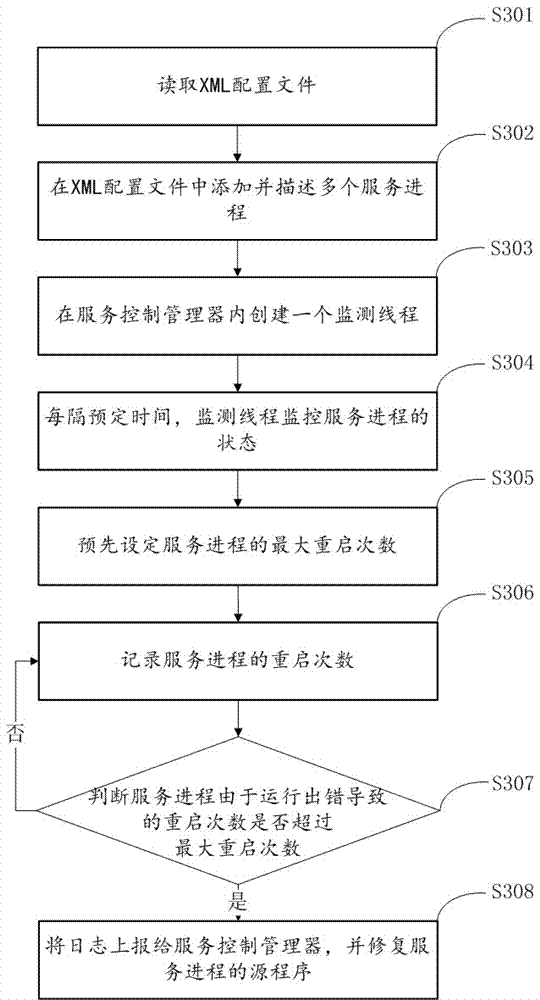
Management method and device for service process of storage server
ActiveCN107423620APrevent illegal theftGuaranteed Integrity and ReliabilityHardware monitoringPlatform integrity maintainanceService controlService process
The invention belongs to the technical field of service process management, and particularly relates to a management method and device for the service process of a storage server. The management method for the service process of the storage server comprises the following steps that: reading an XML (Extensive Markup Language) configuration file; adding and describing a plurality of service processes into the XML configuration file; creating a monitoring thread in the service control manager; at each preset time interval, monitoring the state of the monitoring service process; and aiming at different states of the service process to set different processing ways. The invention also discloses a management device for the service process of the storage server. Different states of the service process can be aimed to set different processing ways, data can be prevented from being illegally stolen, and the integrity and the reliability of storage business are guaranteed.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
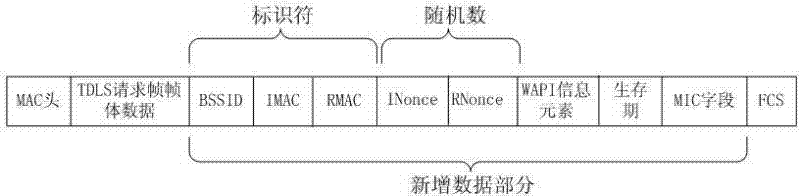
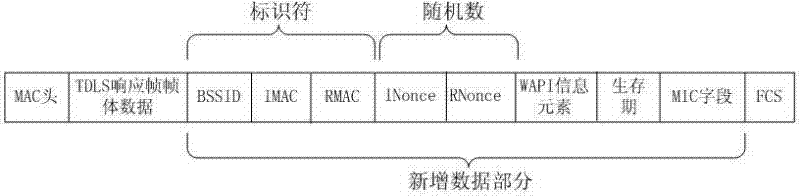
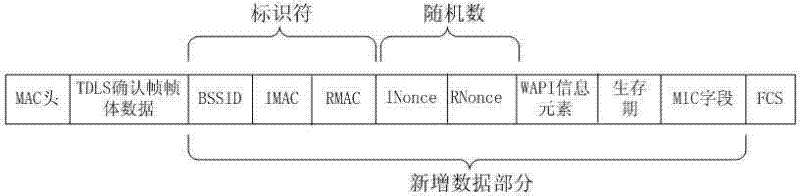
Tunnel direct link setup (TDLS) safety protection method based on Wireless LAN Authentication and Privacy Infrastructure (WAPI)
ActiveCN102595396APrevent illegal theftPrevent tamperingSecurity arrangementSecure communicationWireless lan
The invention provides a method for ensuring safe communication of tunnel direct link setup (TDLS) by using wireless LAN Authentication and Privacy Infrastructure (WAPI). Safe links supplied by WAPI are respectively built between stations (STA) and access points (AP); the safe authentication of each STA is ensured; when a TDLS link needs to be built between two STAs, the STA that establishes the TDLS firstly transmits a TDLS request; the TDLS request comprises the information of the STA and WAPI information elements; after receiving the TDLS request, the STA at the other side generates and saves a key according to a key kit in a negotiation, wherein the key generates two sub-keys, one is used for ensuring the safe communication of a TDLS setting frame, and the other one is used for ensuring the safe communication of the TDLS link; the STA transmits a TDLS response which contains the information of the STA; after receiving the TDLS response, the TDLS initial STA generates a key and transmits a TDLS confirmation, wherein the key also generates two sub-keys, and is same as the key generated by the response of TDLS to STA. Finally the two STA generate the same key to ensure the safety of the data on the TDLS link.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Gunstock for charge gun
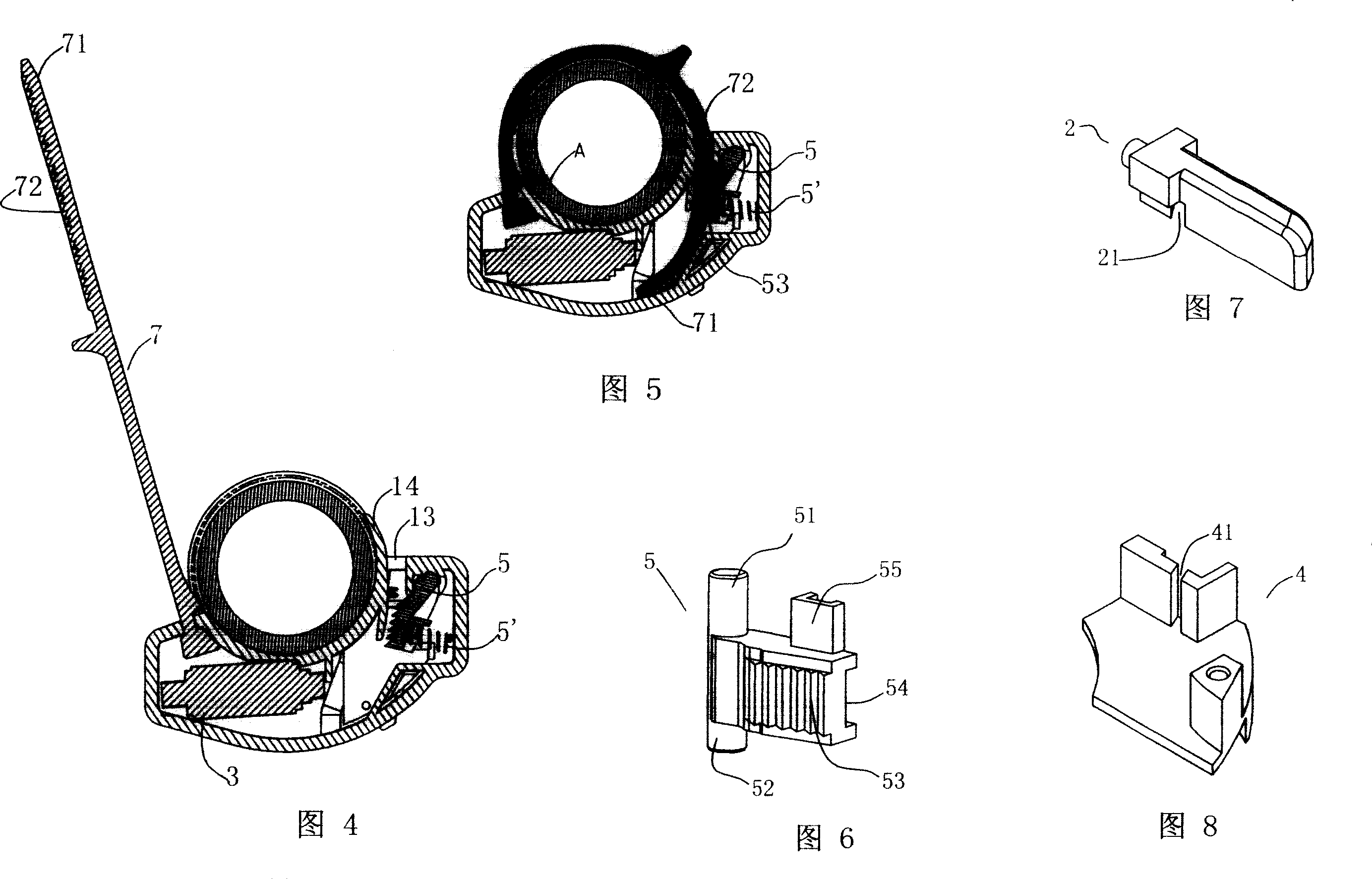
InactiveCN105846497AAvoid lossPrevent random plugging and takingBatteries circuit arrangementsElectric powerEngineeringElectrical and Electronics engineering
The invention discloses a charging gun bracket, the base is provided with an inner cavity for placing the charging gun; an electronic lock device is also provided outside the base, the electronic lock device includes a housing, and The push rod fitted in the housing is further provided with a driving device for driving the push rod to move, and the side wall of the base is provided with a through hole for the push rod to extend into. In the electronic lock device of the present invention, when the charging gun is inserted into the inner cavity of the base, the push rod in the electronic lock device extends in and locks the charging gun and the bracket together, thereby preventing the charging gun from being lost; Random plugging and unplugging of electric vehicle charging guns by non-charging users or illegal theft.
Owner:HAHON ELECTRIC INT CO LTD
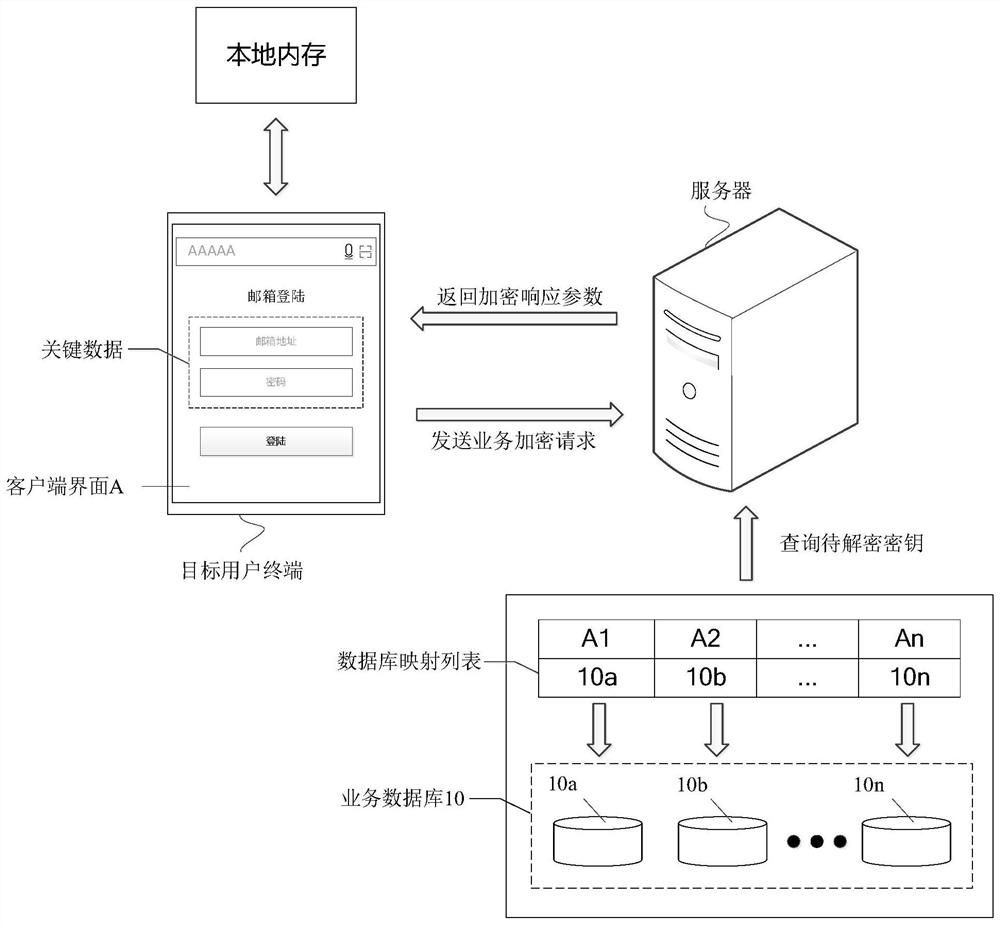
Encrypted data communication method and device, equipment and medium
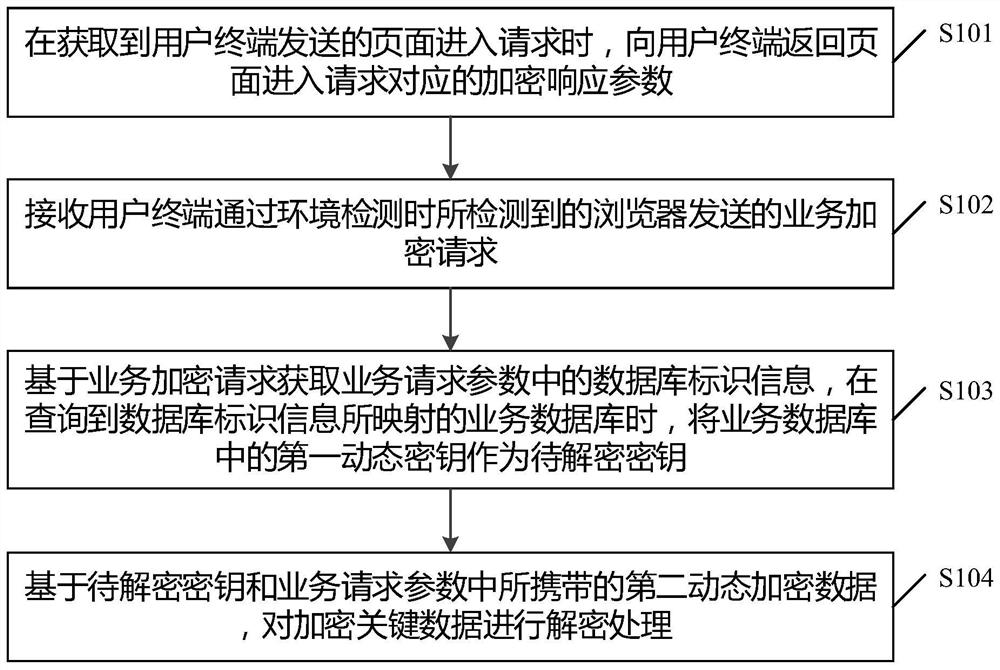
PendingCN112131564APrevent illegal theftImprove securityDigital data protectionDigital data authenticationEngineeringData transmission
The embodiment of the invention provides an encrypted data communication method and device, equipment and a medium, and the method comprises the steps: returning an encryption response parameter corresponding to a page entering request to a user terminal when the page entering request sent by the user terminal is obtained; receiving a service encryption request sent by a browser and detected whenthe user terminal passes the environment detection; acquiring database identification information in the service request parameters based on the service encryption request, and taking a first dynamickey in a service database as a to-be-decrypted key when the service database mapped by the database identification information is queried; and decrypting the encrypted key data based on the to-be-decrypted key and second dynamic encrypted data carried in the service request parameter. By adopting the embodiment of the invention, the security of data transmission can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Bandage type wine bottle burglar preventor and special unlocking device
InactiveCN101135210AThe method of lifting saves effortReduce manufacturing costLocks for portable objectsNon-mechanical controlsBandageAnti theft
The present invention is one kind of strap type anti-theft device for wine bottle and its special unlocking unit. The anti-theft device includes one casing, one strap connected to the casing, and anti-theft EAS label inside the casing. The casing is provided with one strap port for the free end of the strap to pass through, one strap backstop comprising one locking block and one spring, and one unlocking hole for the unlocking unit to be inserted in. The unlocking unit includes one shell, one notch for holding the casing of the anti-theft device, and one shifting fork. The special unlocking unit can unlock the strap type anti-theft device easily and reliably.
Owner:SHENZHEN RONGHUA ELECTRONICS
Archive management method based on block chain
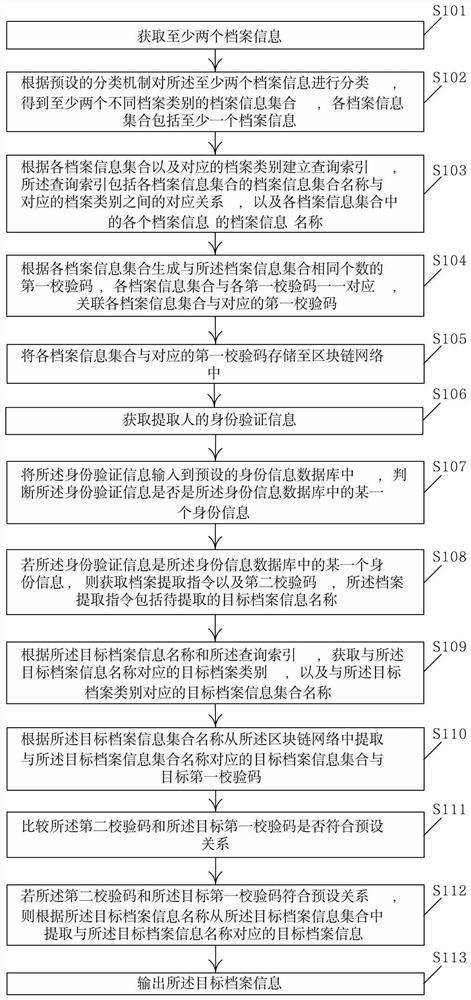
PendingCN111611460AImprove securityReduce the possibility of illegal theftDigital data protectionDigital data authenticationCheck digitEngineering
The invention relates to an archive management method based on a block chain. The method comprises the steps of obtaining at least two pieces of archive information, classifying the archive information and establishing a query index; storing the classified archive information and the generated corresponding first check code into a block chain network; when the archive information is extracted, obtaining identity verification information of an extractor; after the identity verification is passed, obtaining an archive extraction instruction and a second check code; extracting a related target archive information set and a target first check code from the block chain network according to the archive extraction instruction; comparing whether the second check code and the target first check code meet a preset relationship or not; and if yes, obtaining and outputting target archive information. According to the archive management method based on the block chain, the possibility that the archive information is illegally stolen, tampered and damaged can be effectively reduced, and the safety of archive management is effectively improved.
Owner:ZHEJIANG GUANGSHA COLLEGE OF APPLIED CONSTRTECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com