Method and device for achieving data security of operation system
A data security and operating system technology, applied in the field of IT data security, can solve problems such as inapplicability, achieve the effect of improving login security, preventing tampering, and reducing the risk of employee number and password leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
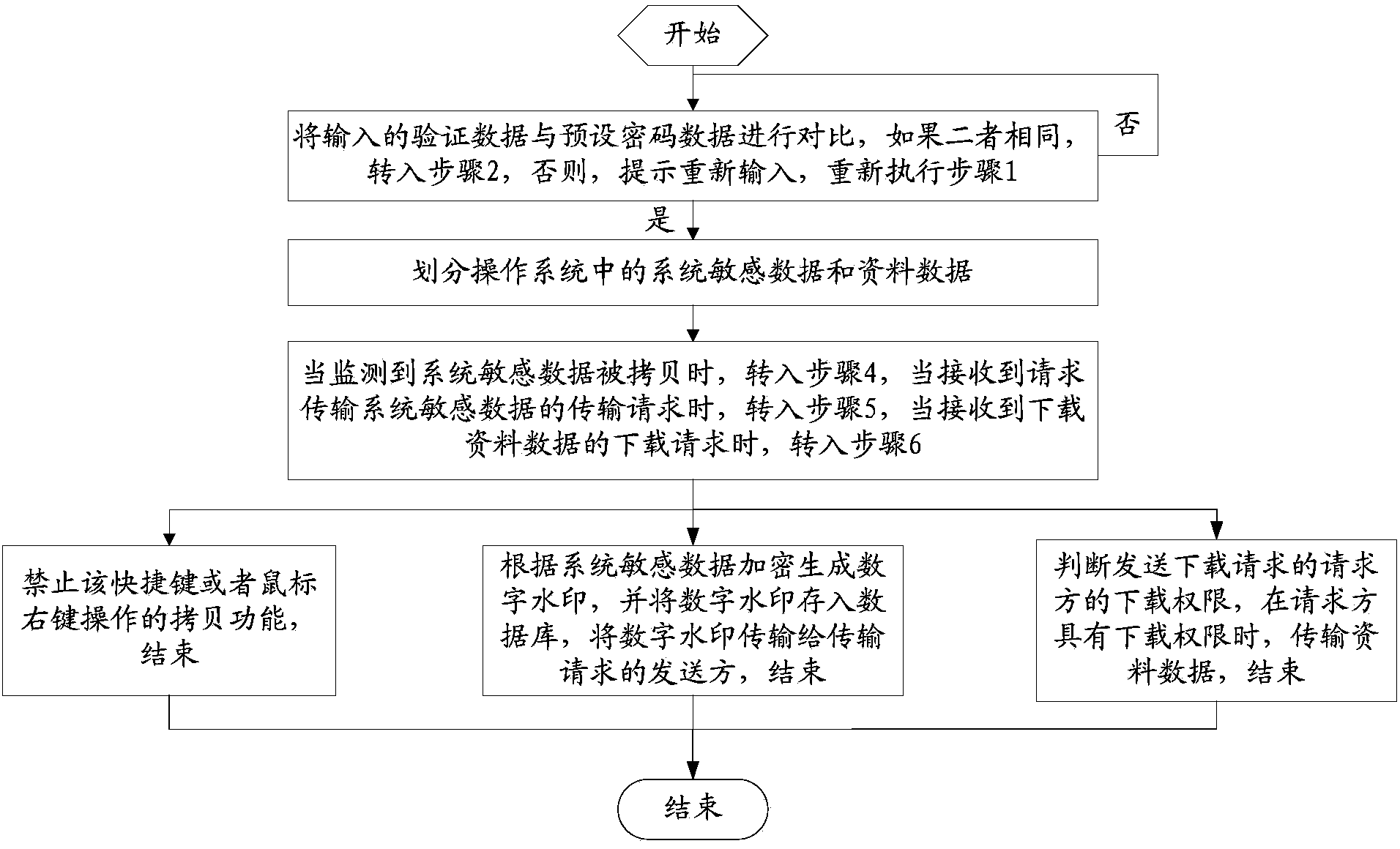
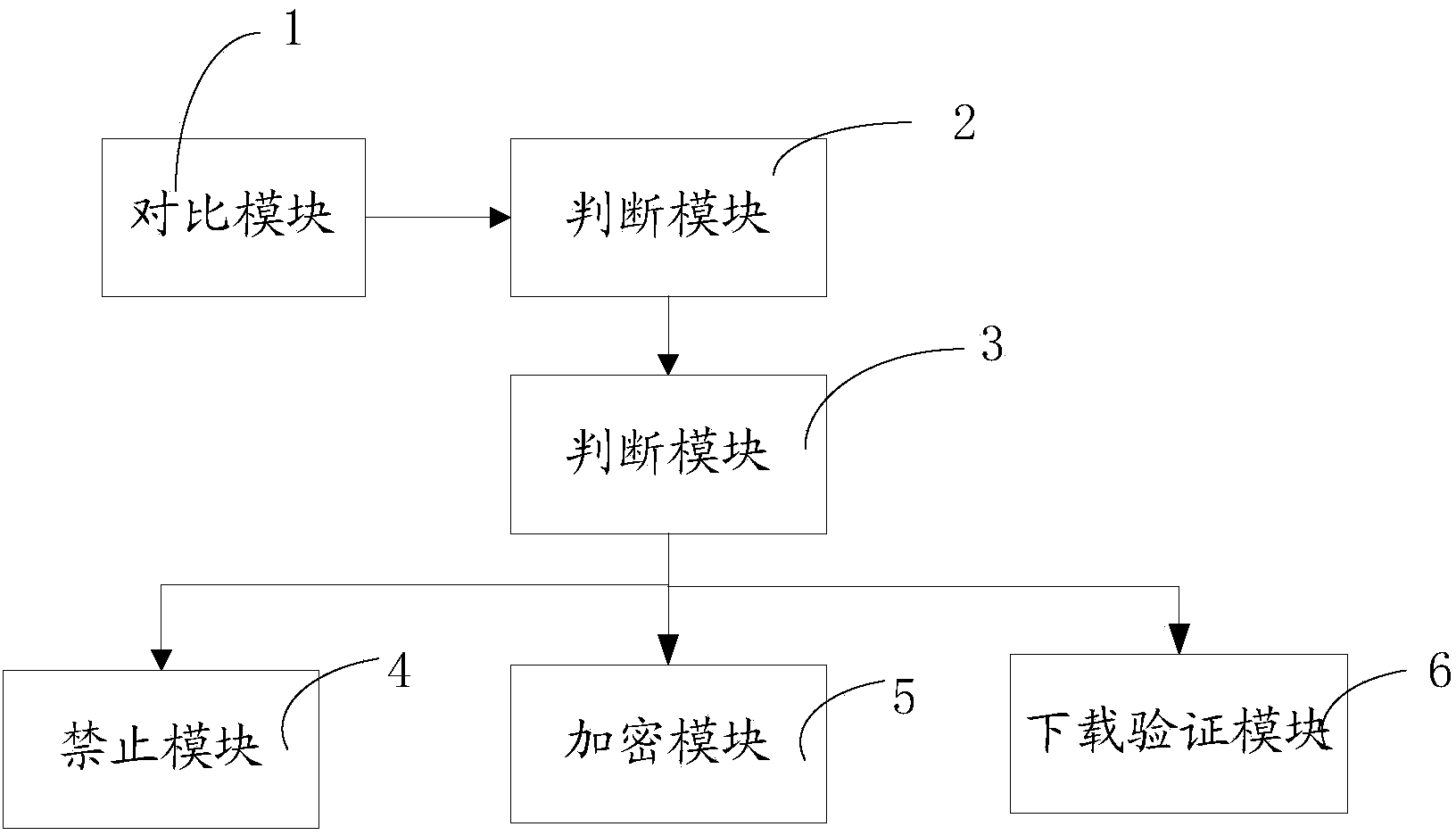
[0041] A method for realizing operating system data security, comprising the following steps:
[0042] Step 1: Compare the input verification data with the preset password data, if they are the same, go to step 2, otherwise, prompt to re-enter, and re-execute step 1;
[0043] Step 2: Divide system sensitive data and data data in the operating system;
[0044] Step 3: When it is detected that the sensitive data of the system is copied, go to step 4. When a transmission request for sensitive data of the system is received, go to step 5. When a download request for downloading data is received, go to step 5. 6;
[0045] Step 4: Prohibit the shortcut key or the copy function of the right mouse button operation, end;
[0046] Step 5: Generate a digital watermark based on system sensitive data encryption, store the digital watermark in the database, transmit the digital watermark to the sender of the transmission request, and end; use the java class to generate a digital watermark...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com