Key generation method, encrypted data analyzing method, devices and key managing center
A key management center, encryption data technology, applied in the field of communication, can solve the problem of low network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
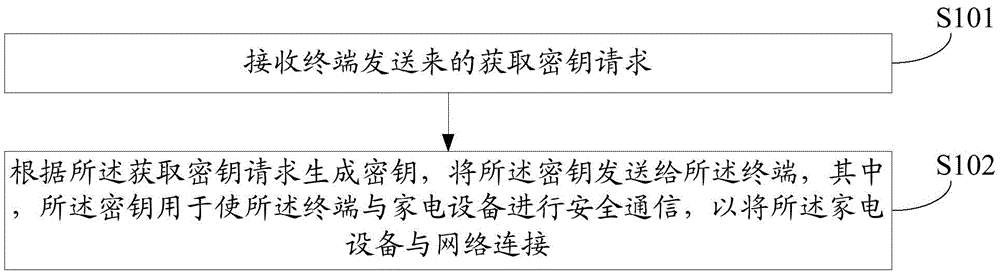
[0082] An embodiment of the present invention provides a method for generating a key, the method is executed by a key management center, see figure 1 , the method includes:
[0083] S101. Receive a key acquisition request sent by a terminal, where the key acquisition request carries a device identifier and a terminal identifier;
[0084] S102. Generate a key according to the key acquisition request, and send the key to the terminal, where the key is used to enable the terminal to securely communicate with the home appliance, so as to connect the home appliance with the home appliance A network connection, wherein the key uniquely corresponds to the key acquisition request.
[0085] The present invention generates the corresponding key according to the key acquisition request sent by the terminal, so that different key acquisition requests correspond to different keys, thereby greatly reducing the risk of key leakage, and effectively solving the problem of the prior art. The ...
Embodiment 2
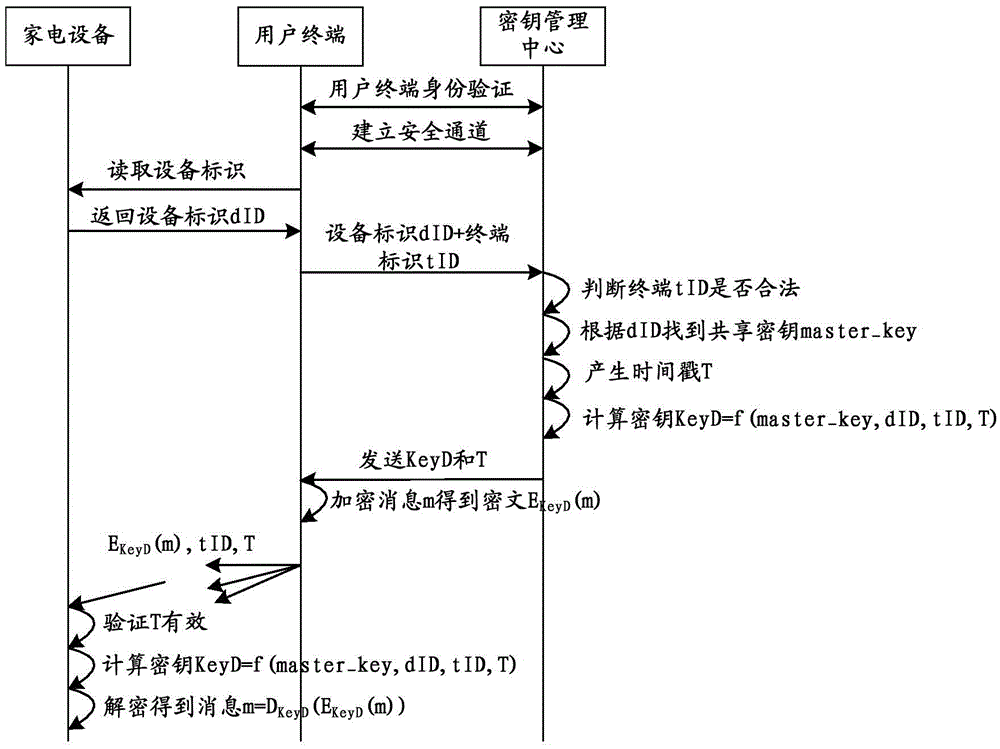
[0169] corresponds to figure 1 The key generation method introduced, this embodiment provides a method for parsing encrypted data, the execution subject of this method is a home appliance, see Image 6 , the execution subject of this method is a home appliance, and this method includes:
[0170] S601. Receive encrypted data sent by the terminal, wherein the encrypted data is data obtained by the terminal encrypting preset networking data according to a key generated by the key management center, and the key is the Generated by the key management center according to the key acquisition request sent by the terminal, the key uniquely corresponds to the key acquisition request, and the key acquisition request carries a device identifier and a terminal identifier;
[0171] S602. Analyze the encrypted data to obtain the networking data, and access a network according to the networking data.
[0172] Since the keys of the present invention are all generated by the key management ce...
Embodiment approach
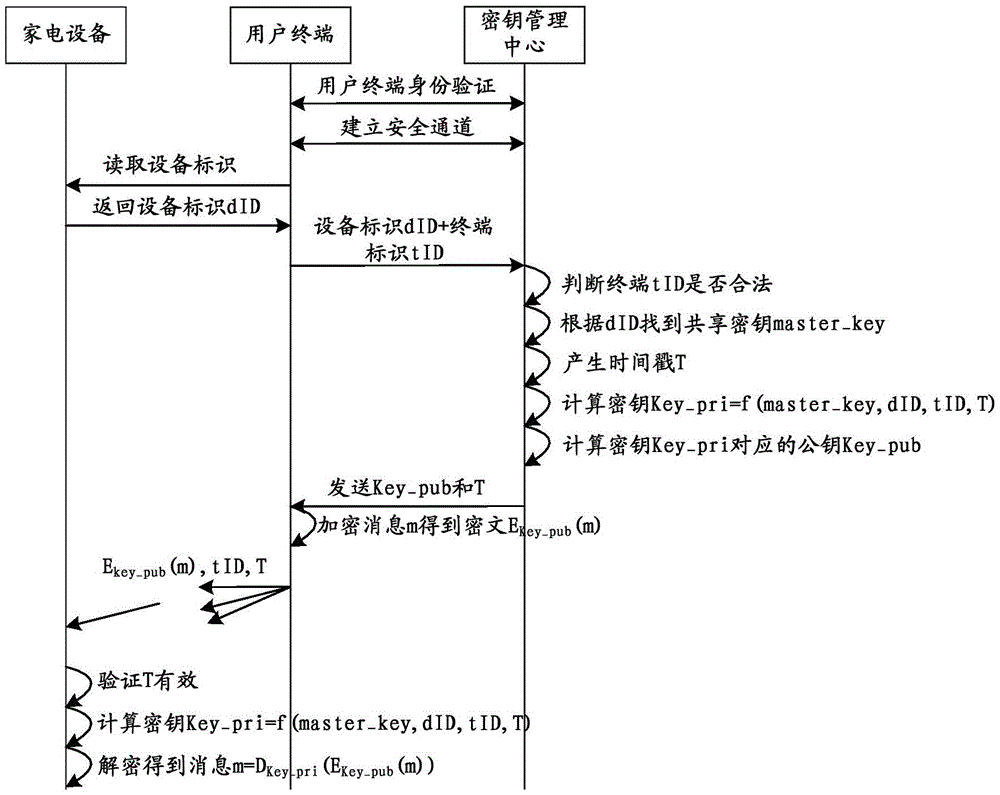
[0206] The embodiment of the present invention also provides a preferred implementation manner, the device further includes: a setting unit;
[0207] The setting unit is configured to pre-set the shared key corresponding to the household electrical appliance according to the household electrical appliance, and set a time stamp after receiving the key acquisition request;
[0208] The generating unit is specifically configured to generate the key according to the device identifier, the terminal identifier, the shared key, and the time stamp, and send the key to the terminal, so that the The terminal uses the key to securely communicate with the home appliance, and connects the home appliance to the network.
[0209] That is, the present invention pre-sets different shared keys according to different household appliances, generates the key with the shared key, the device ID, the terminal ID, and the time stamp, and sends the key to To the terminal, the terminal uses the key to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com