Network resource query method and system
A network resource and resource query technology, which is applied to key distribution, can solve the problems of increased key leakage, no automatic update of keys, and inability to continue to use, so as to achieve the effect of improving the strength of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
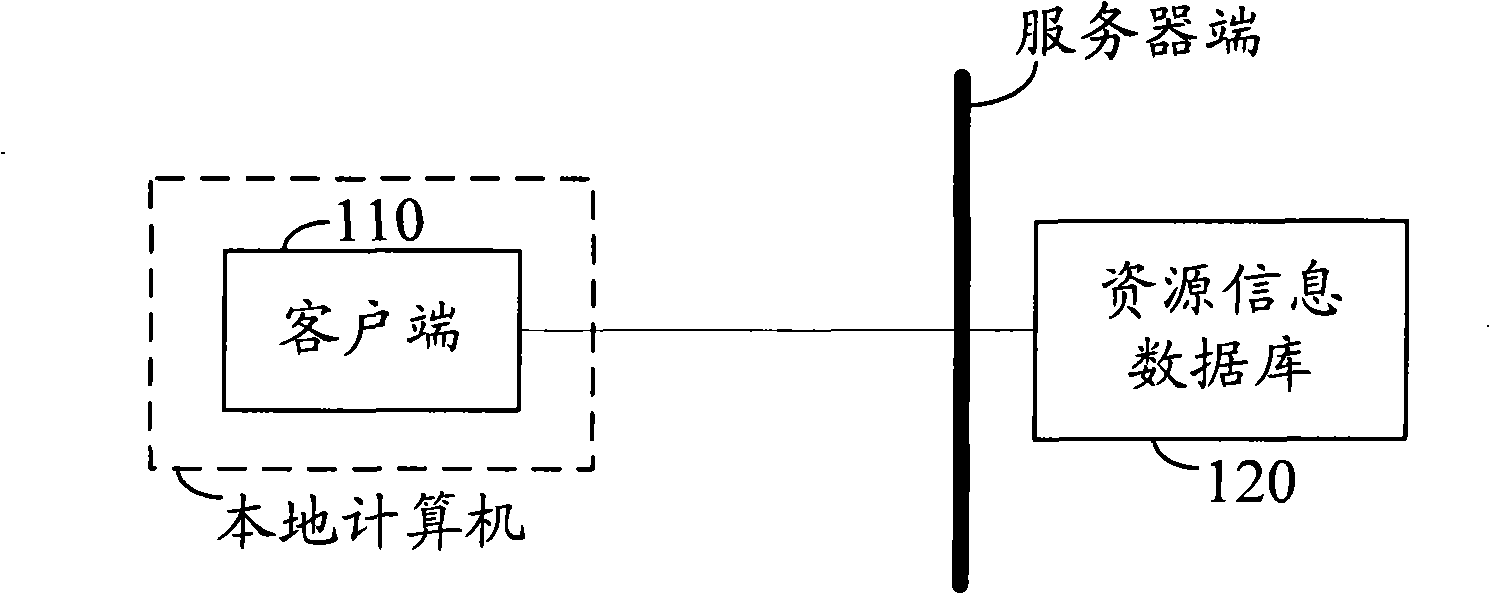
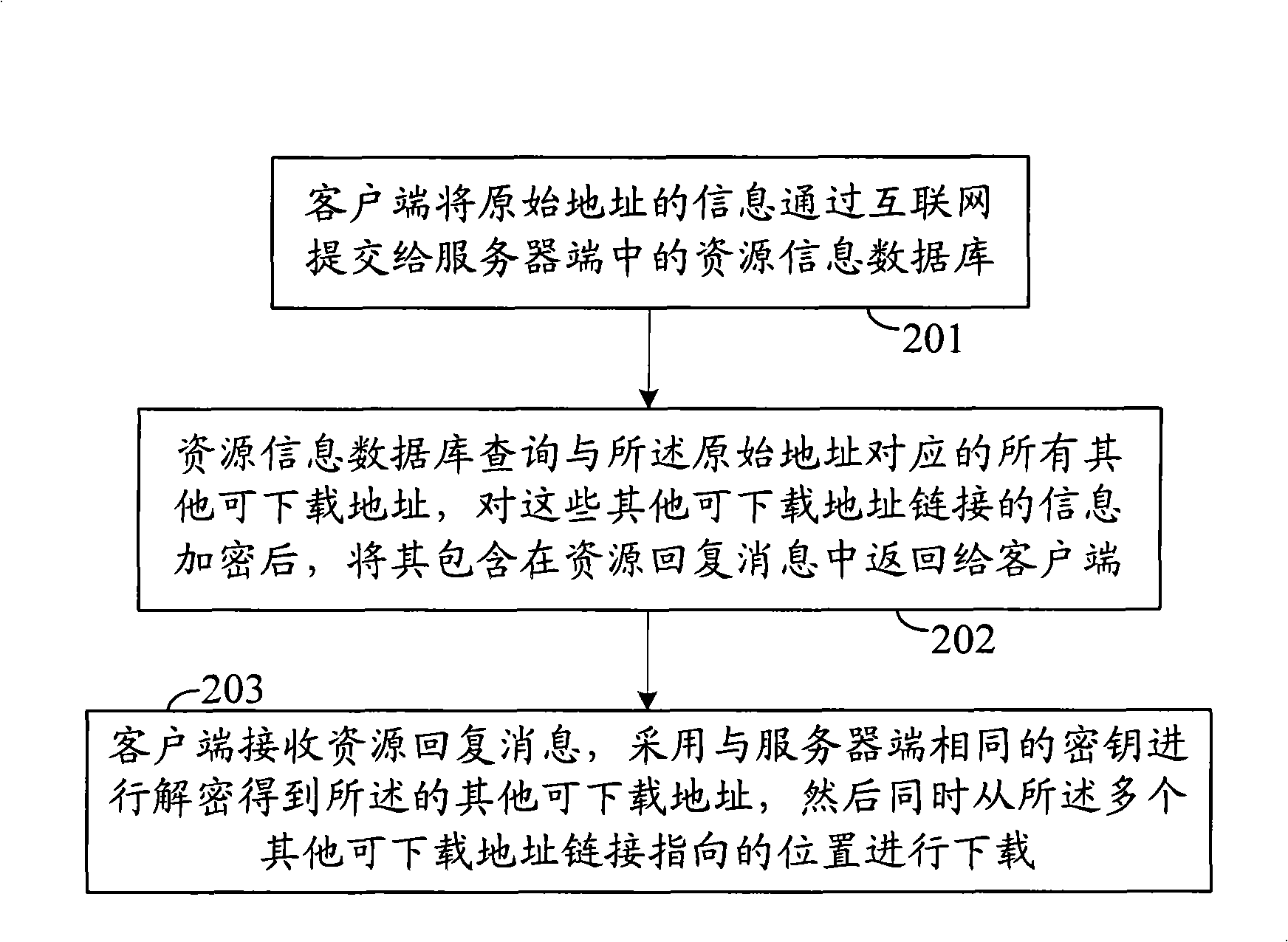
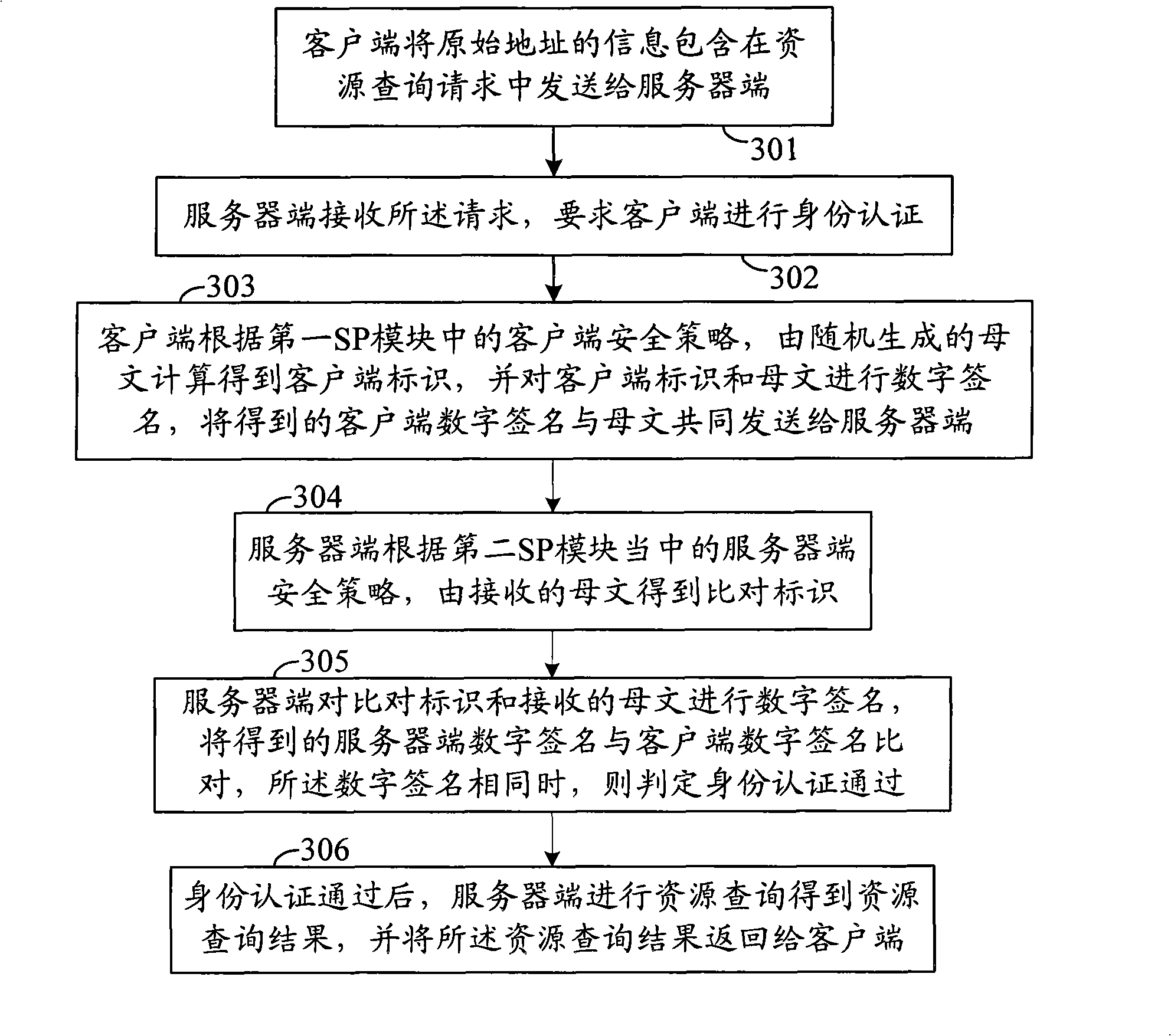
[0023] A method for querying network resources is provided in an embodiment of the present invention, the flow of which is as follows image 3 As shown, wherein after the client is started, it establishes a connection with the server through the network, and the same security policy is preset in the client and the server, and the security policy is an algorithm used in the entire identity authentication process. The method includes:
[0024] Step 301: the client includes the original address information in the resource query request and sends it to the server;
[0025] Step 302: the server side receives the request and requires the client side to perform identity authentication;
[0026] Step 303: The client randomly generates the mother text, accordin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com