Security realization method, equipment and system
A technology for implementing methods and devices, applied in the field of communications, capable of solving problems such as waste of resources and data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
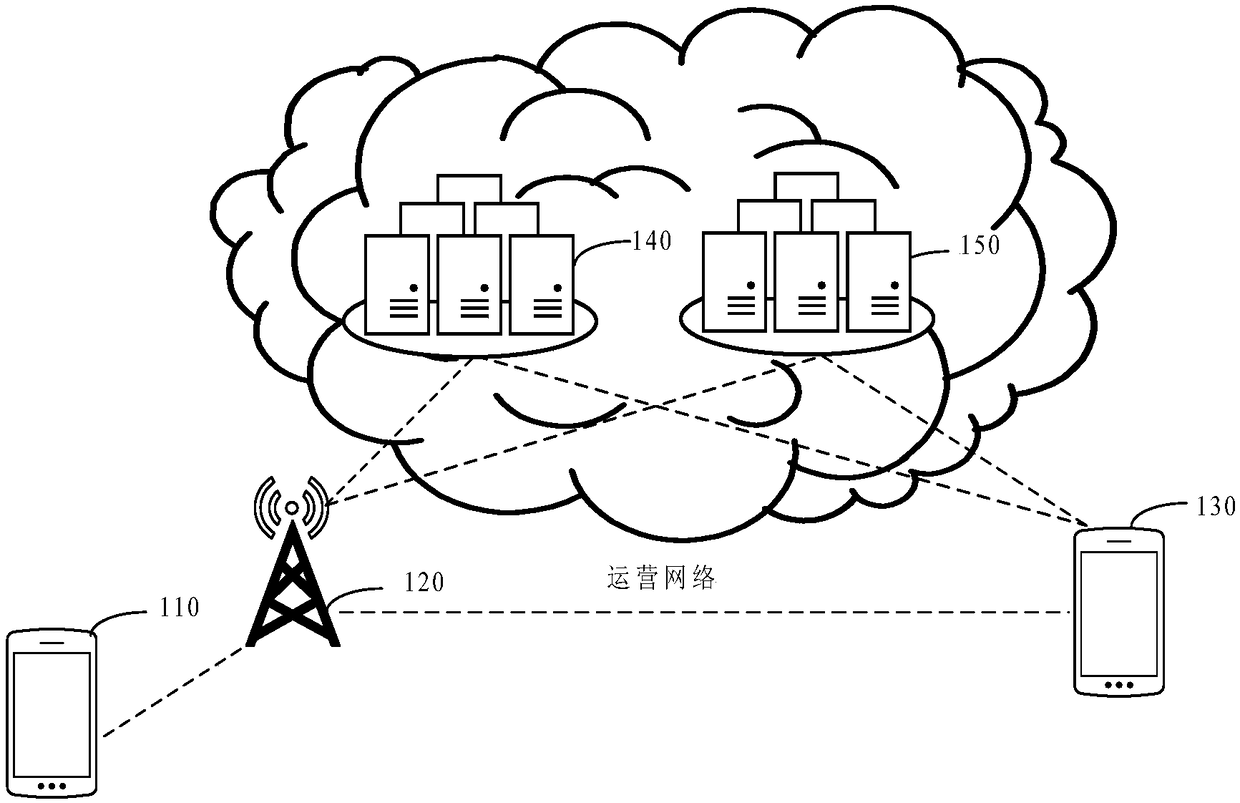
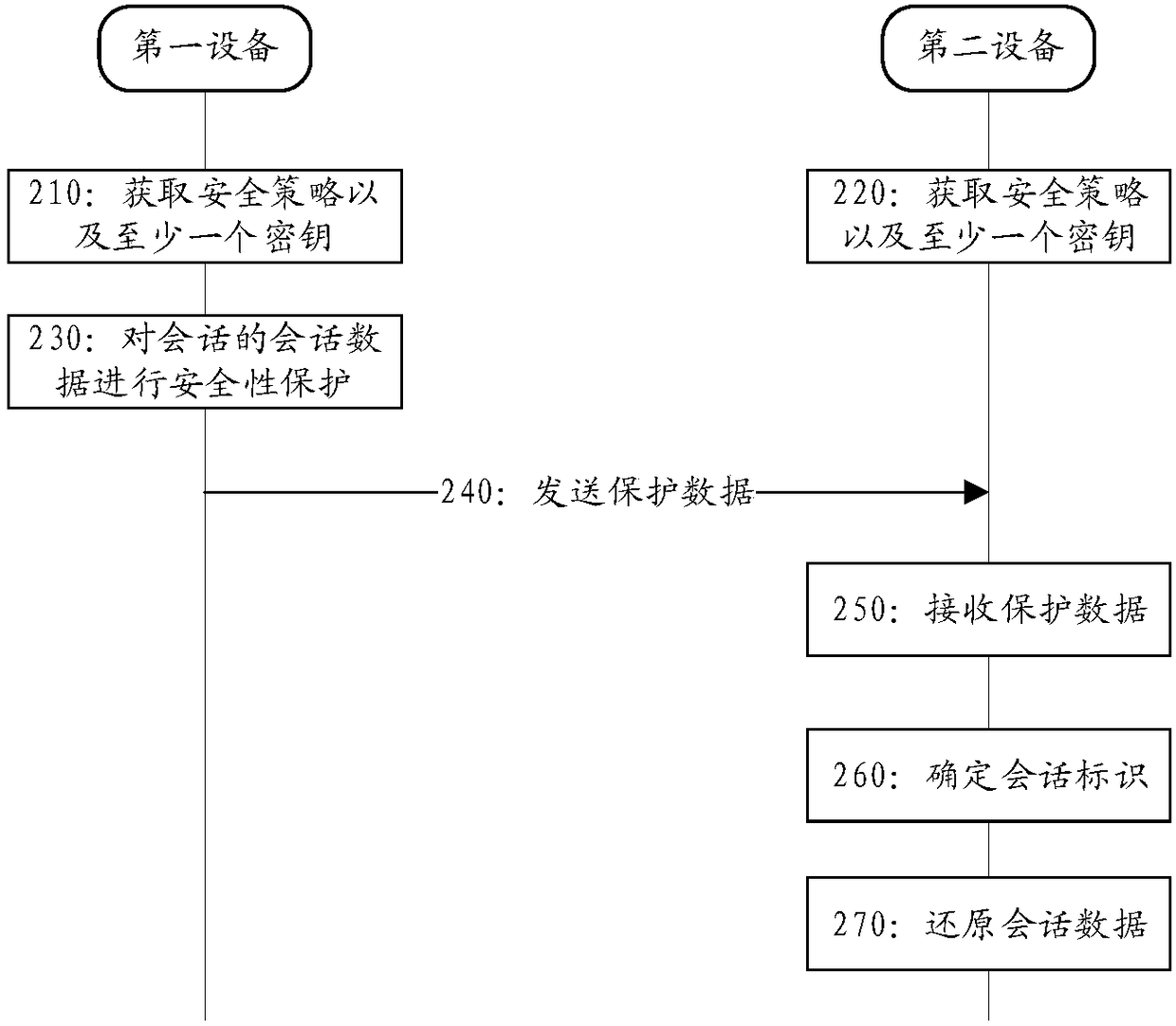
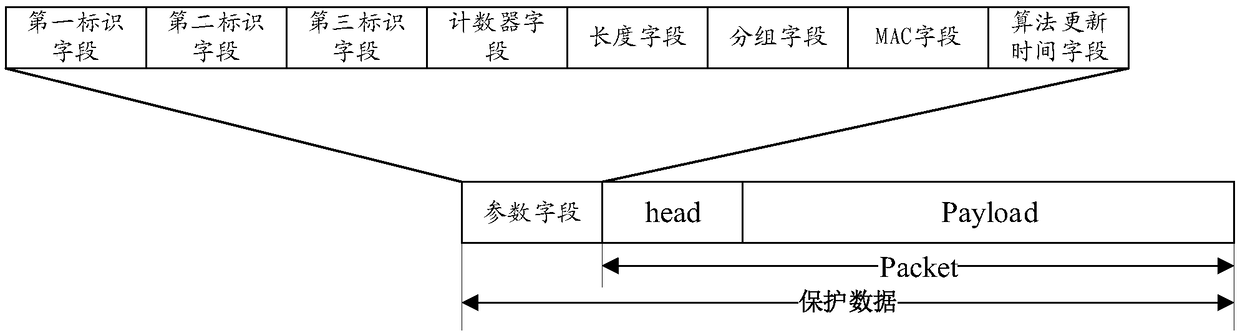
[0144] In order to facilitate understanding of the solution, the network architecture to which the solution of the embodiment of the present application may be applied is firstly introduced below with reference to related drawings. Such as figure 1 As shown, the future mobile communication network architecture includes a terminal device 110 , an access network node 120 and a user plane node 130 . Wherein, the terminal device 110 accesses the operation network through the access network node 120 , so as to implement communication with the user plane node 130 .
[0145] The terminal device 110 is a logical entity, and specifically may be any one of a user equipment (User Equipment), a communication device (Communication Device), and an Internet of Things (Internet of Things, IoT) device. Wherein, the user equipment may be a smart phone (smart phone), a smart watch (smart watch), a smart tablet and so on. The communication device may be a server, a gateway (Gateway, GW), a base...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com