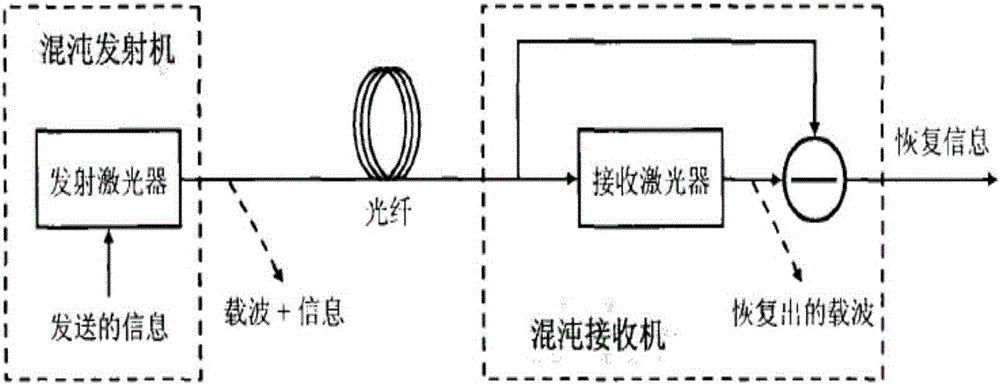
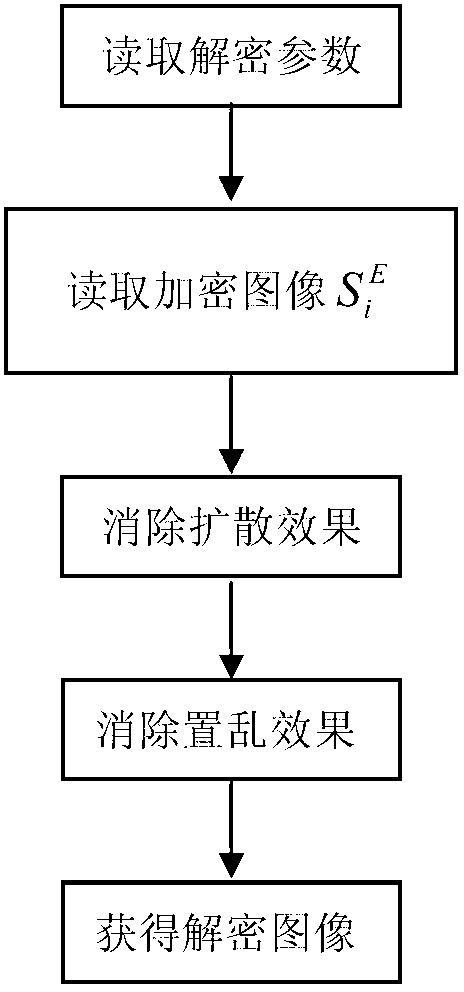
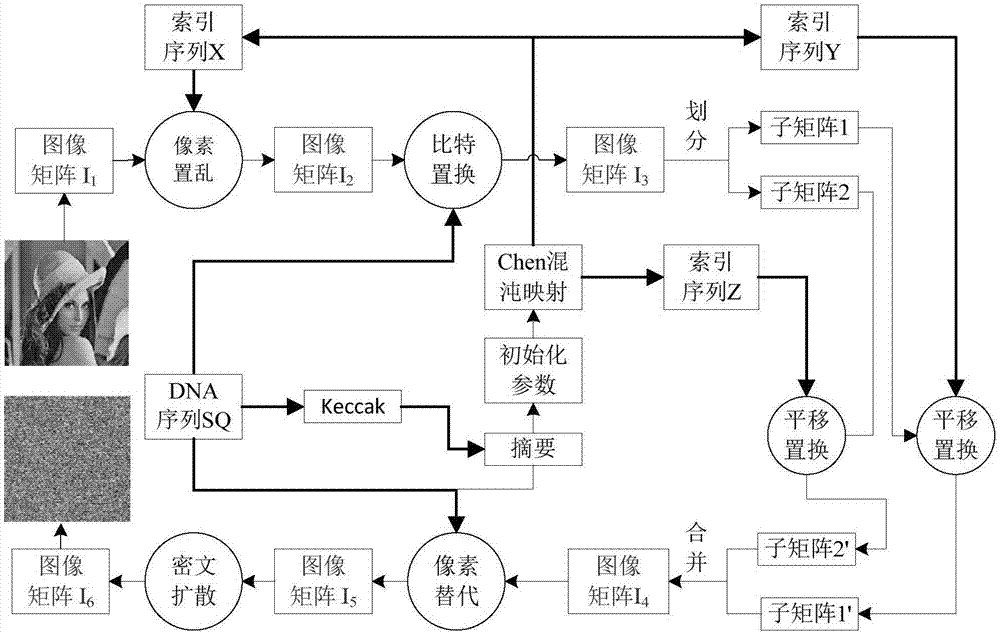
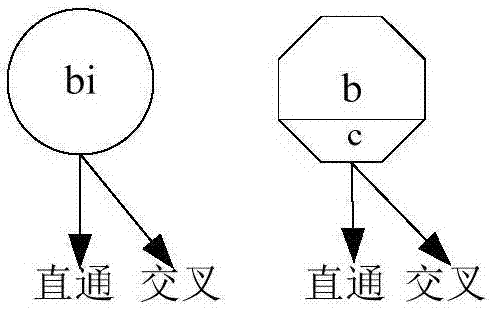
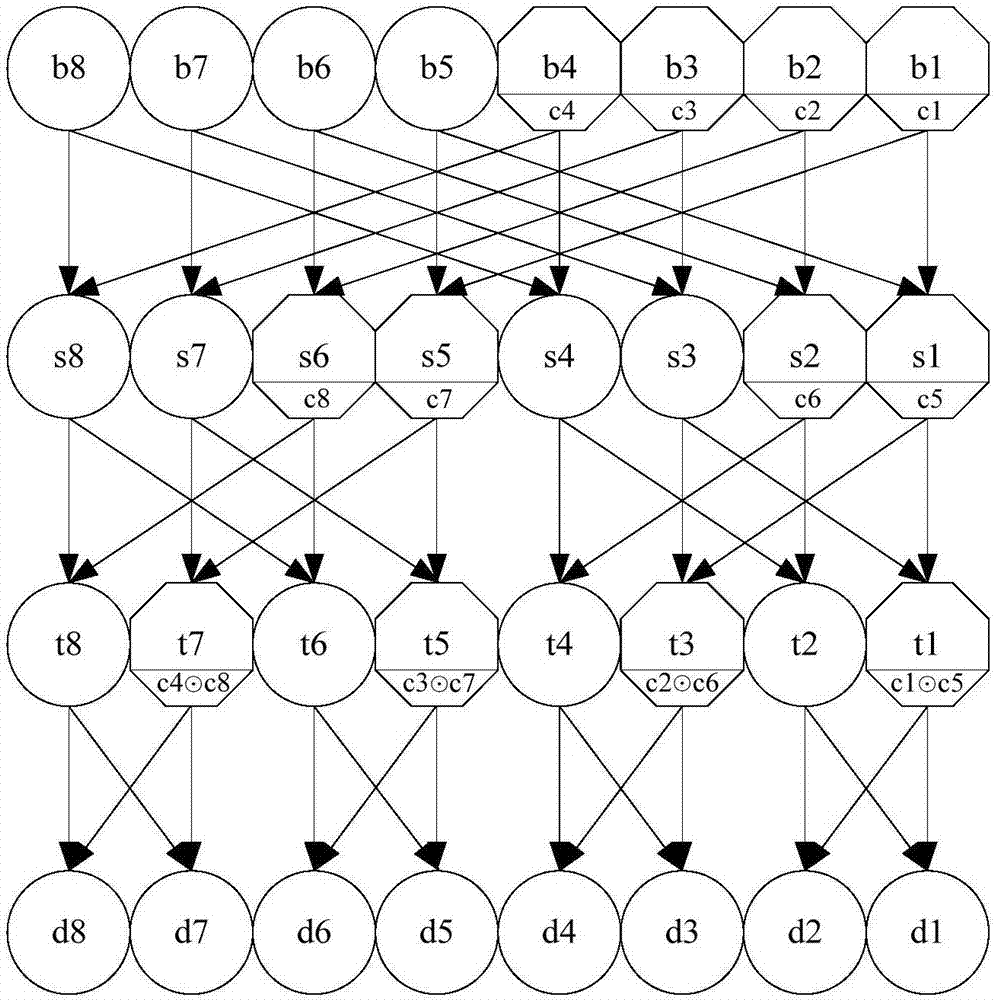
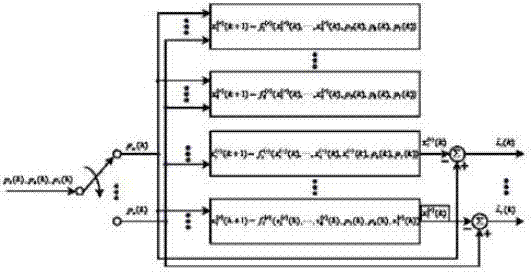
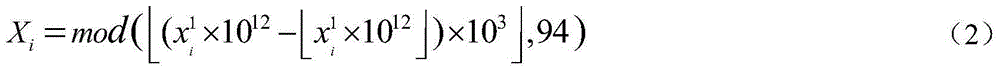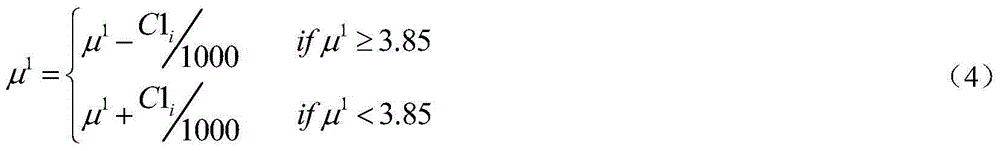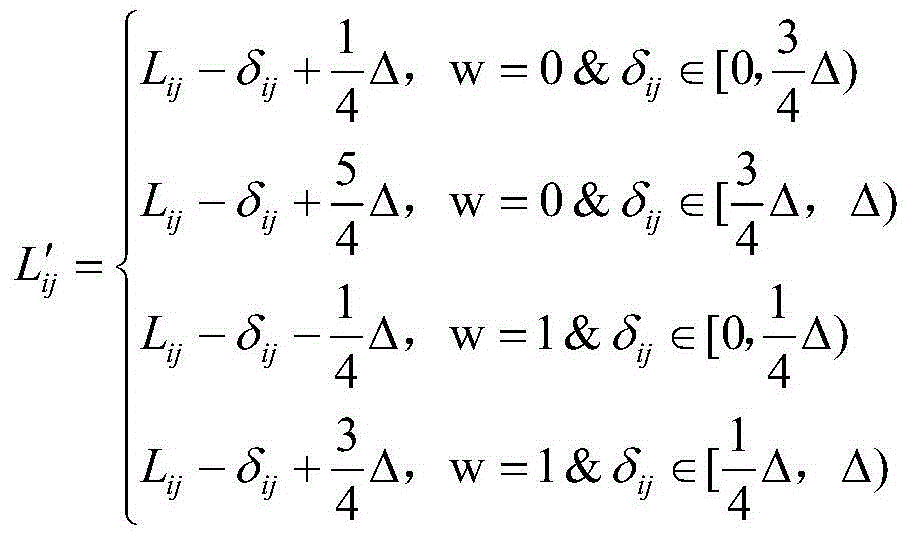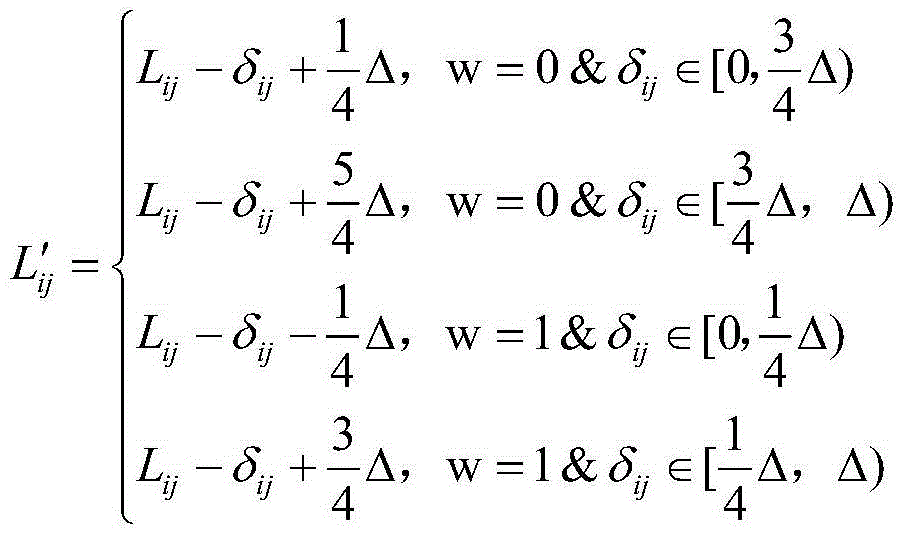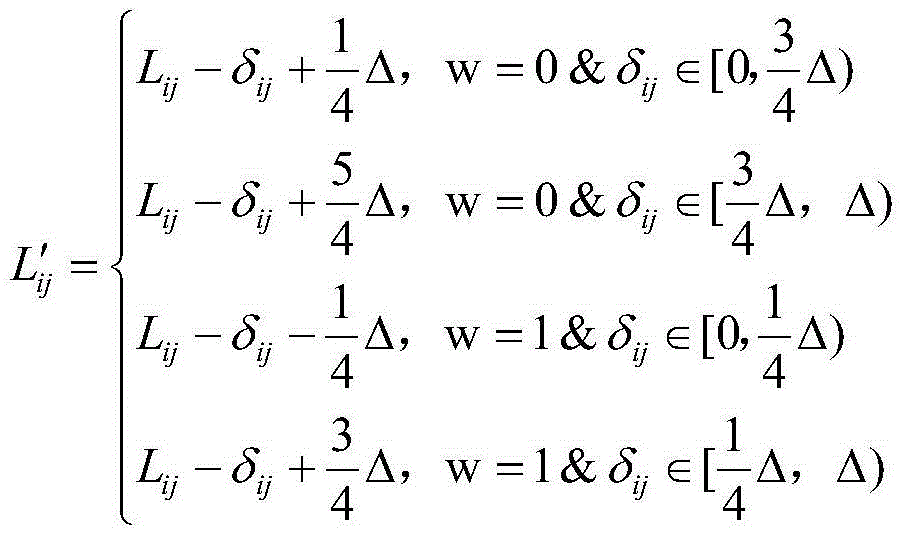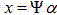Patents
Literature
231 results about "Chaotic encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
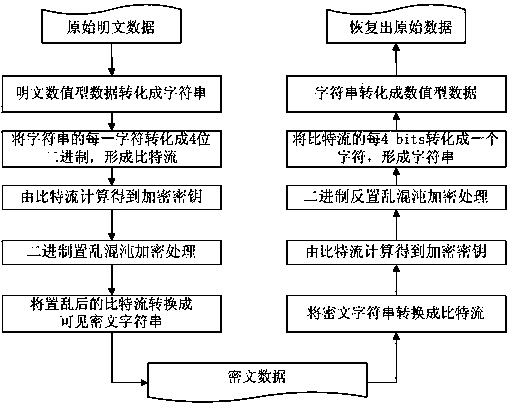
Encryption and decryption method for numeric type data
ActiveCN103532701AEnsure safetyGuaranteed feasibilityEncryption apparatus with shift registers/memoriesOriginal dataCiphertext
The invention discloses an encryption and decryption method for numeric type data. The method comprises the following steps that the numeric type data is converted into character strings; each character is sequentially converted into 4 bits according to the correspondence relationship between the numeric characters and the binary system, and a bit stream is formed; the number of 0 and 1 in the bit stream is counted, and an encryption secret key is obtained through calculation; the encryption secret key is utilized, a chaotic sequence with the pseudo-random property is generated by a chaotic system, in addition, chaotic signals are taken from the chaotic sequence and are sequenced in an ascending sequence, and the bit stream is scrambled according to the positions in accordance with the scrambling rule; the corresponding relationship between the four-digit binary coding mode and the visible ciphertext characters is utilized for converting the scrambled bit stream into the visible ciphertext character strings, and the ciphertext can be decrypted and recovered into the original data type data through adopting the similar method. According to the method provided by the invention, the corresponding table customization is adopted, the numeric type data is subjected to binary scrambling chaotic encryption processing, the safety and the feasibility of the data encryption are ensured, and in addition, the encryption efficiency is also greatly improved.
Owner:南通九盛软件有限公司
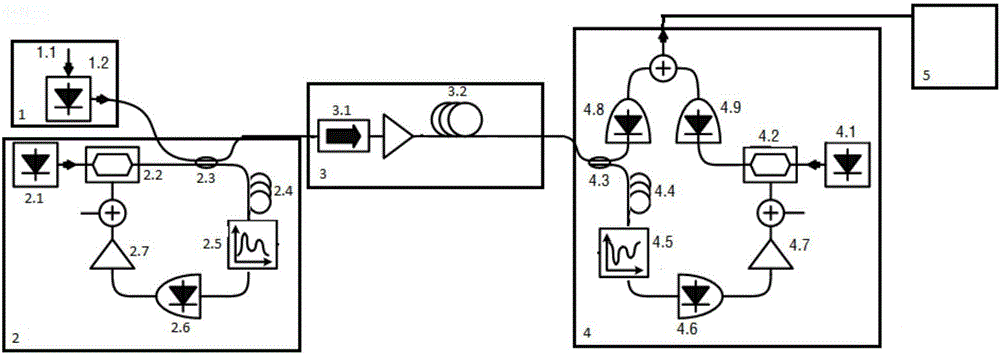
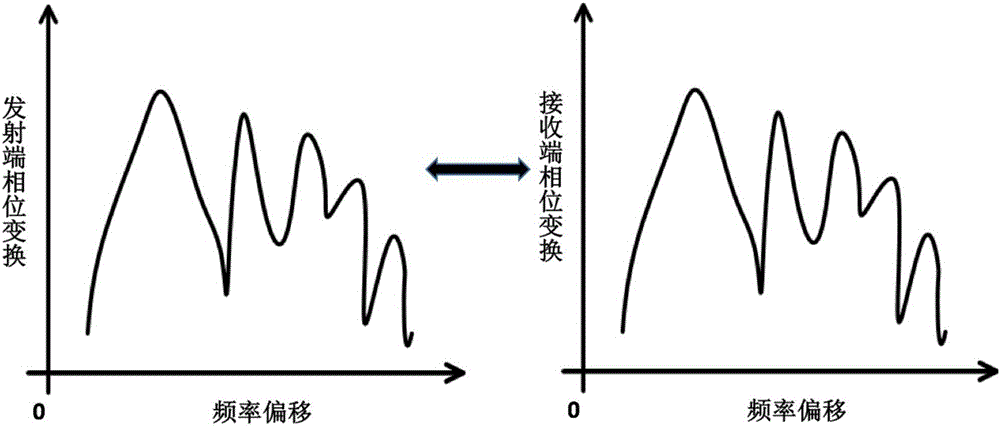
Secondary chaotic encryption optical communication system based on phase transformation
InactiveCN106330428AEasy to adjustThere are many adjustable parameters for encryptionSecuring communication by chaotic signalsElectromagnetic receiversConfidentialityOptical communication
The invention discloses a secondary chaotic encryption optical communication system based on phase transformation. The system comprises an optical signal transmitting device, a chaotic combined phase transformation encryption device, a transmission fiber, a chaotic combined phase transformation decryption device and a signal receiving device. The signal encryption part is a chaotic encryption module added with a phase transformation decryption device in a feedback loop, and the signal decryption device is an open-loop chaotic laser receiving module comprising a phase transformation decryption device. The system overcomes the defect that encryption variables of a chaotic encryption system are few; by combining phase transformation decryption with chaotic encryption, an eavesdropper is difficult in analyzing and attacking the energy; high-speed signals can be supported, and 10 Gb / s high-speed signals can be directly encrypted; a light emitting source of an existing WDM (Wavelength Division Multiplexing) system can be directly used for encrypting, and a special ultra-short pulse light source is not needed; and decryption can be implemented by using the same phase transformation modules at the receiving end as at the transmitting end, so that the adjusting difficulty is reduced without changing the confidentiality.
Owner:SHANGHAI JIAO TONG UNIV
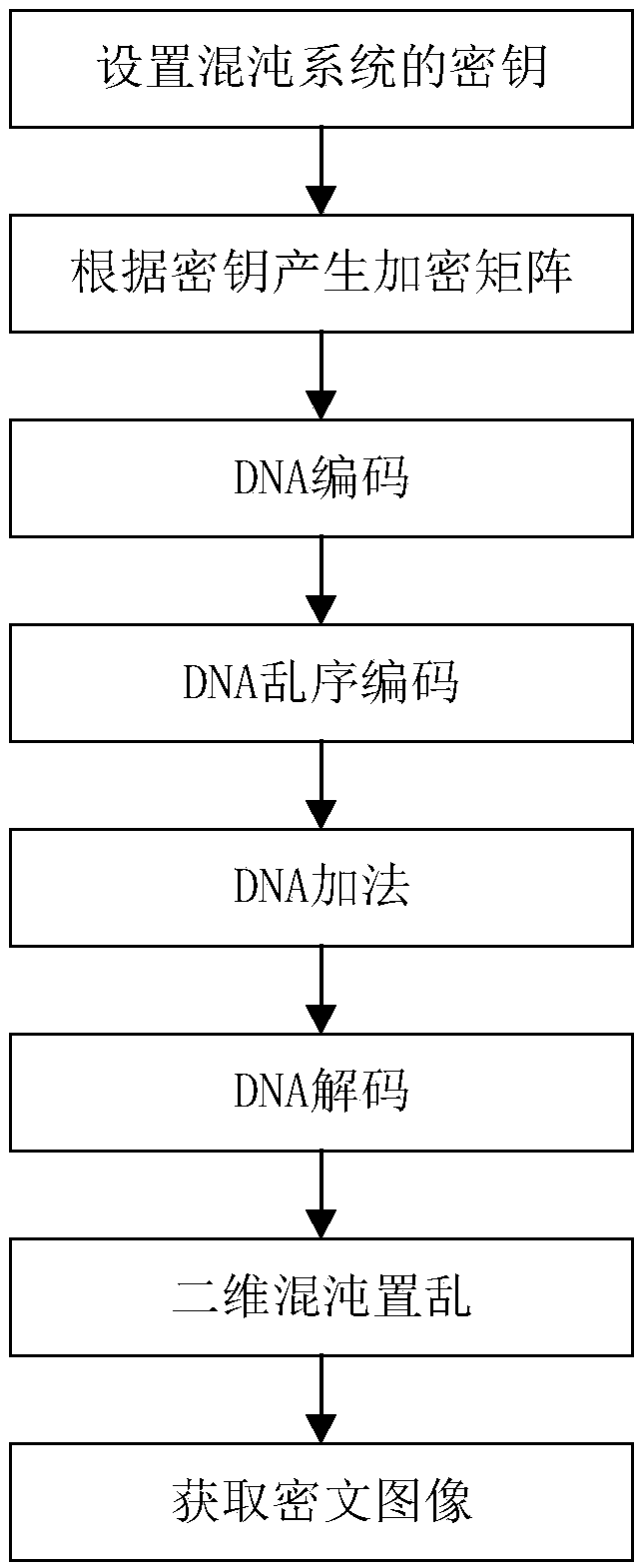
A multi-channel color image chaotic encryption method based on DNA coding
ActiveCN109918923AGood encryptionImprove execution efficiencyImage codingDigital data protectionColor imageHash function
The invention discloses a multi-channel color image chaotic encryption method based on DNA coding, relates to the field of digital image encryption, and aims to solve the problems that an existing image chaotic encryption scheme is insufficient, and a high-dimensional continuous time chaotic system is complex in discrete process algorithm, so that the safety of an encrypted image is low, and the acquisition of a discrete chaotic sequence is time-consuming. A six-dimensional discrete hyper-chaotic system is used for generating six groups of chaotic sequences, and a Hash function SHA-256 is usedfor generating a system iteration initial value; RGB (red, green and blue) components of the color image are extracted, DNA (deoxyribonucleic acid) coding is performed on each component to obtain a DNA matrix, the DNA matrixes is merged, a recombinant DNA matrix is constructed, and row and column scrambling operation is executed; Then, the scrambled DNA matrix is splitted into three matrixes withthe same size, respectively DNA calculation is carried out on the three matrixes and the three chaotic key matrixes subjected to DNA coding, and DNA decoding operation is carried out on the obtainedmatrixes; diffusion encryption operation is performed on the decoding matrix, wherein the encryption round number is determined by SHA-256. The encryption effect is good and the security is high.
Owner:HARBIN UNIV OF SCI & TECH
Design method for chaos digital secret communication system based on FPGA
InactiveCN101345615AIncreased complexityImprove real-time performanceSecuring communicationComputer architectureCommunications system
The invention relates to design method for FPGA based chaos digital secure communication system comprising following steps: executing discrete process for continuous chaos system by FPGA hardware, designing chaos discrete system by FPGA hardware and make it produce digital chaos sequence in a certain accuracy, adopting the digital chaos sequence as key, designing drive response type synchronous secure communication system based on choas discrete system, constructing a closed loop with interior signal, accomplishing two block FPGA development board finite digital voice communication using lattice type Cai chaos and real time voice secure communication system design based on lattice type Cai chaos. The invention is highly secure and accomplishes combination of chaos encryption system and traditional cipher system. The inventive secure communication system not only serve voice secure communication, but transmit confidential binary file. As long as data can be represented as binary data, it can execute secure communication. The inventive system can employ graph encryption / decryption and transmit over Ethernet.
Owner:GUANGDONG UNIV OF TECH
Encryption and decryption method of character data
ActiveCN104486073AEnsure safetyGuaranteed feasibilitySecuring communicationComputer hardwareCiphertext-only attack
The invention discloses an encryption and decryption method of character data. The encryption and decryption method comprises the following steps: converting plaintext character data into a numerical sequence; carrying out bidirectional encryption on all elements in the numerical sequence by utilizing a chaotic signal generated by a variable key chaotic system and obtaining a bidirectional chaotic encryption numerical sequence; self-defining a corresponding relation between numerical data and a visible ciphertext character, converting the bidirectional chaotic encryption numerical sequence into a visible ciphertext character sequence, obtaining a ciphertext string unequal to the plaintext character data in length, and decrypting and restoring a ciphertext into original character data through a similar method. The encryption and decryption method has the benefits that the self-defined corresponding relation is adopted for carrying out bidirectional chaos encryption processing on the character data so as to generate the length-variable ciphertext string, and the ciphertext string has good resistance to known / chosen-plaintext attack, ciphertext-only attack, so that the safety and the feasibility of data encryption and decryption are ensured.
Owner:SHANGHAI TAIYU INFORMATION TECH
High-robustness digital watermarking method making color QR code embedded in color image
InactiveCN105931174APrecise positioningIncrease imperceptibilityImage watermarkingColor imageSingular value decomposition
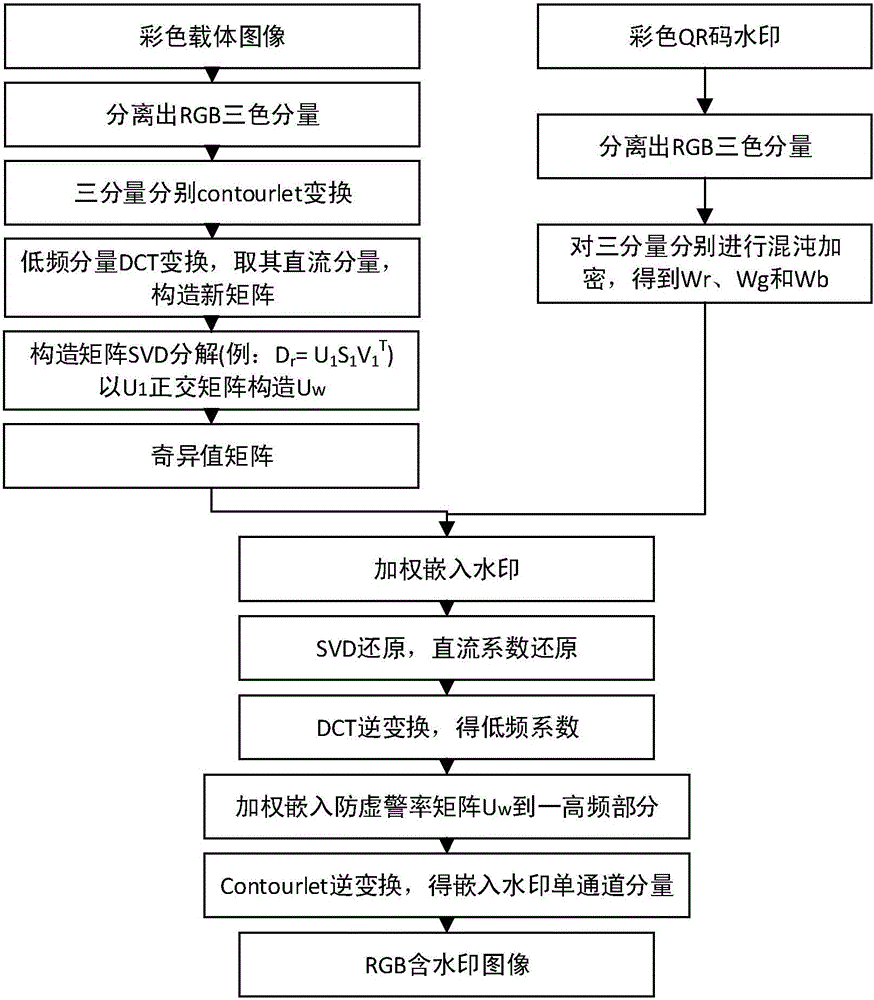
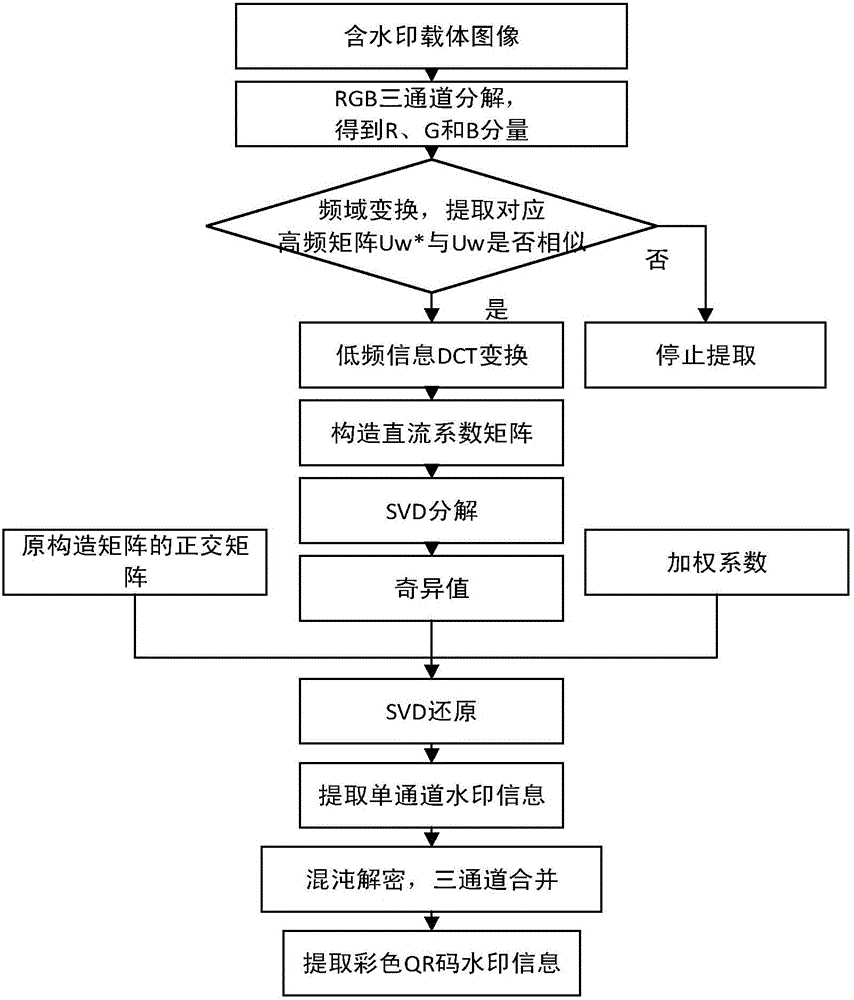
The invention relates to a high-robustness digital watermarking method making a color QR code embedded in a color image. Based on a color QR code, a Contourlet transformation technology, a DCT (discrete cosine transformation) technology and an SVD (singular value decomposition) transformation technology, the color QR code is adopted as original watermark information. The method includes the following steps that: a color host image and the color QR code are water-marked in an RGB space so as to be subjected to three-channel decomposition, and three-channel watermarks obtained after the decomposition are subjected to chaotic encryption separately; Contourlet transformation is performed on each channel image of the color host image, and DCT is performed on the low-frequency components of the channel images, and the direct-current components of the channel images are adopted to construct new matrixes, SVD transformation is performed on the new matrixes, so that singular value matrixes can be obtained; and the watermarks are embedded into corresponding channels, SVD inverse transformation, inverse DCT, and Contourlet inverse transformation are carried out, so that the color image containing the watermarks can be obtained. Compared with an existing algorithm for embedding color watermarks into a color image, the high-robustness digital watermarking method of the invention has the advantages of high imperceptibility and high robustness.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
Internet picture transparent and safe transmission method based on chaotic encryption
ActiveCN103427979AImprove efficiencyImprove encryption securitySecuring communicationUser inputInternet users
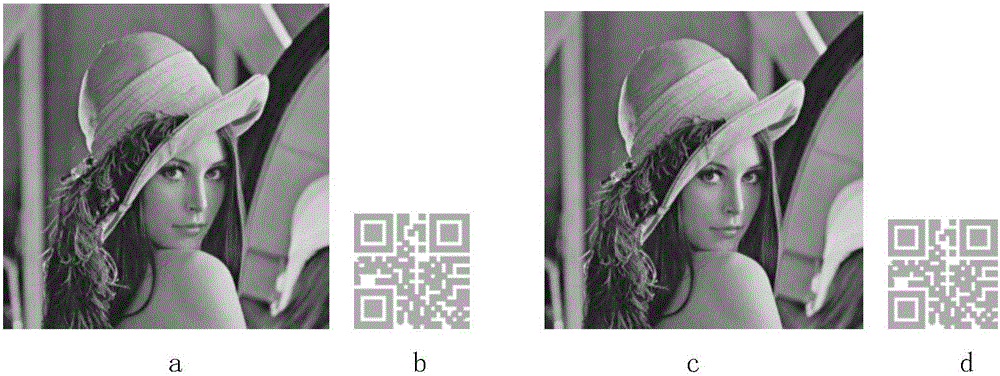
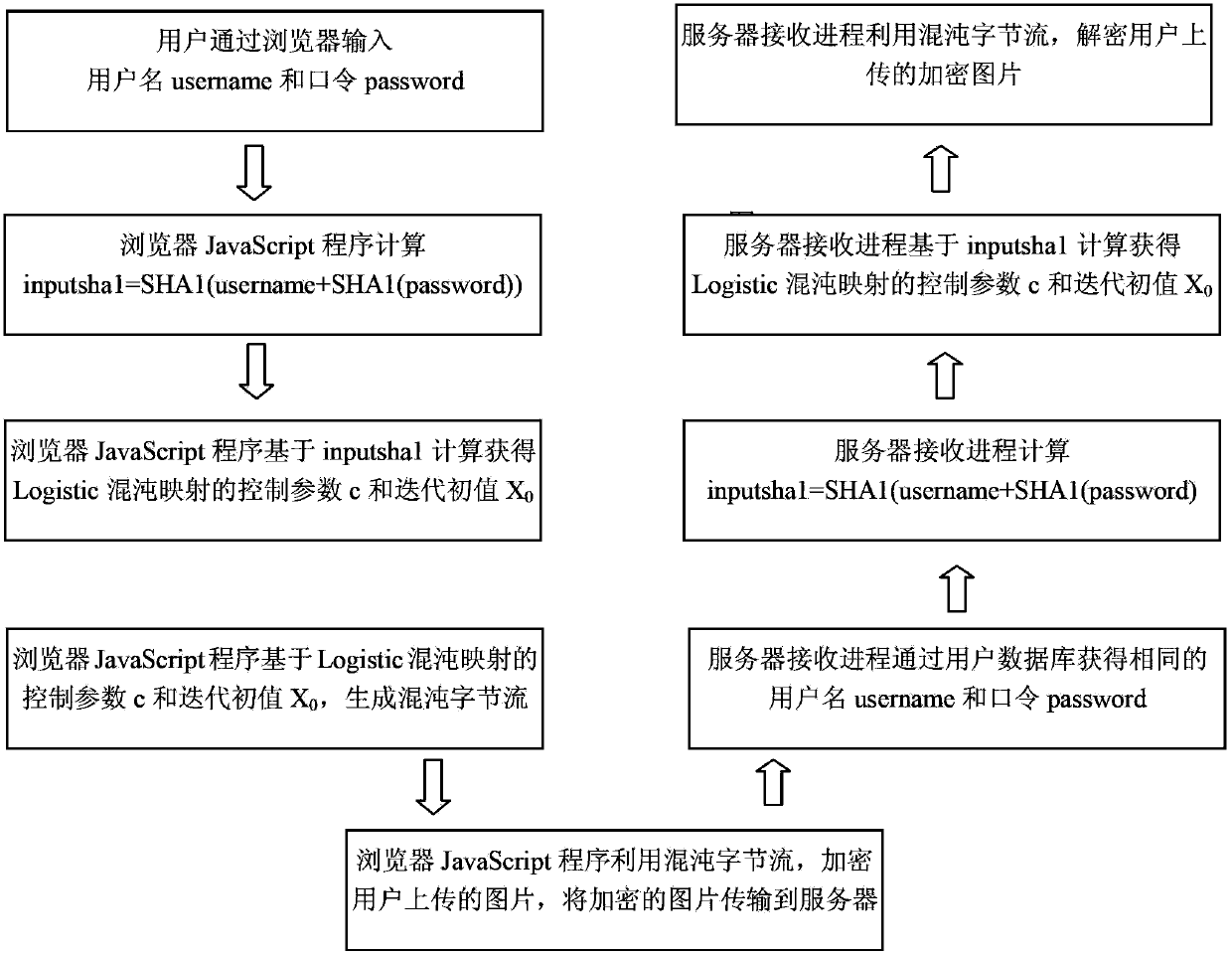
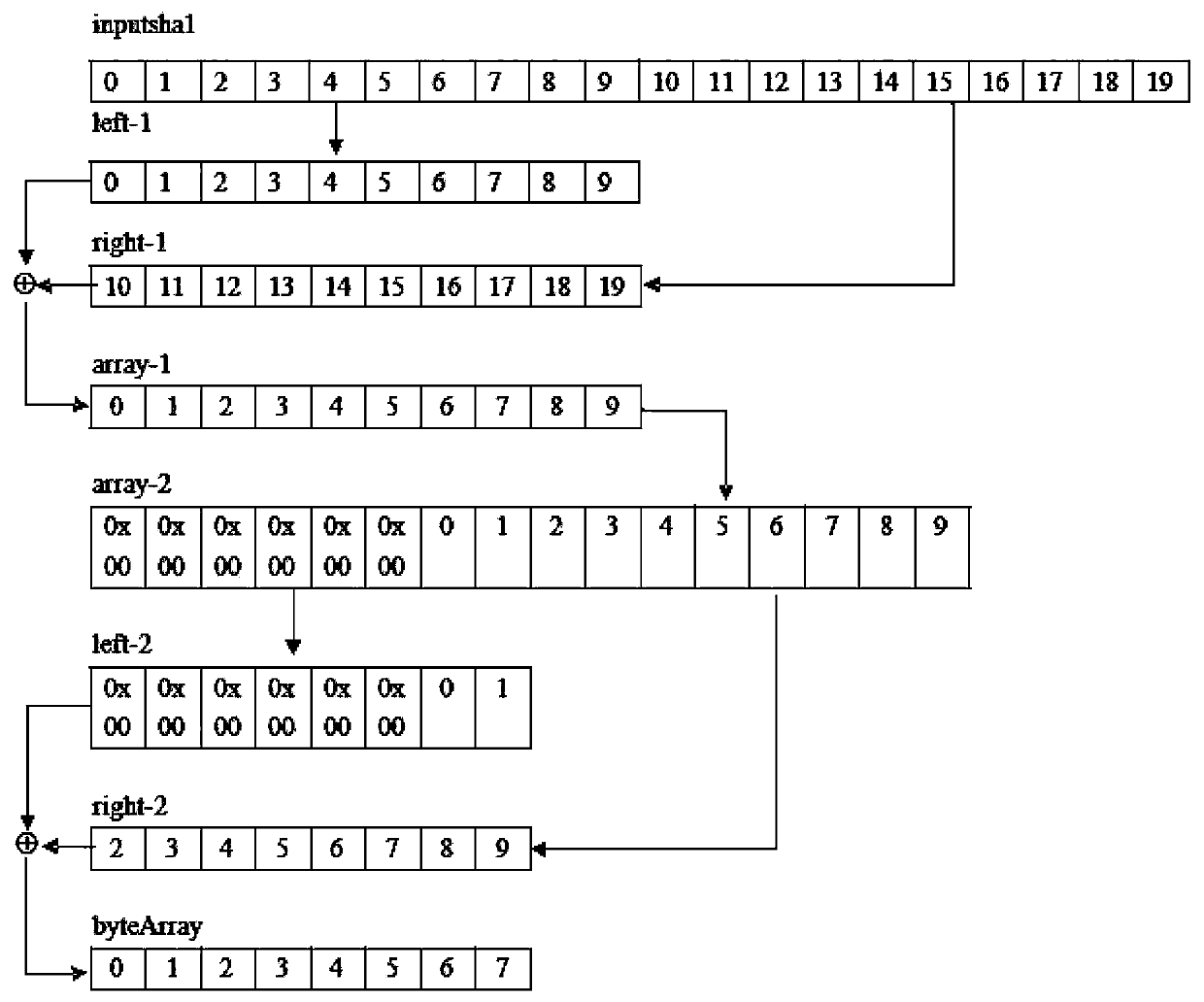
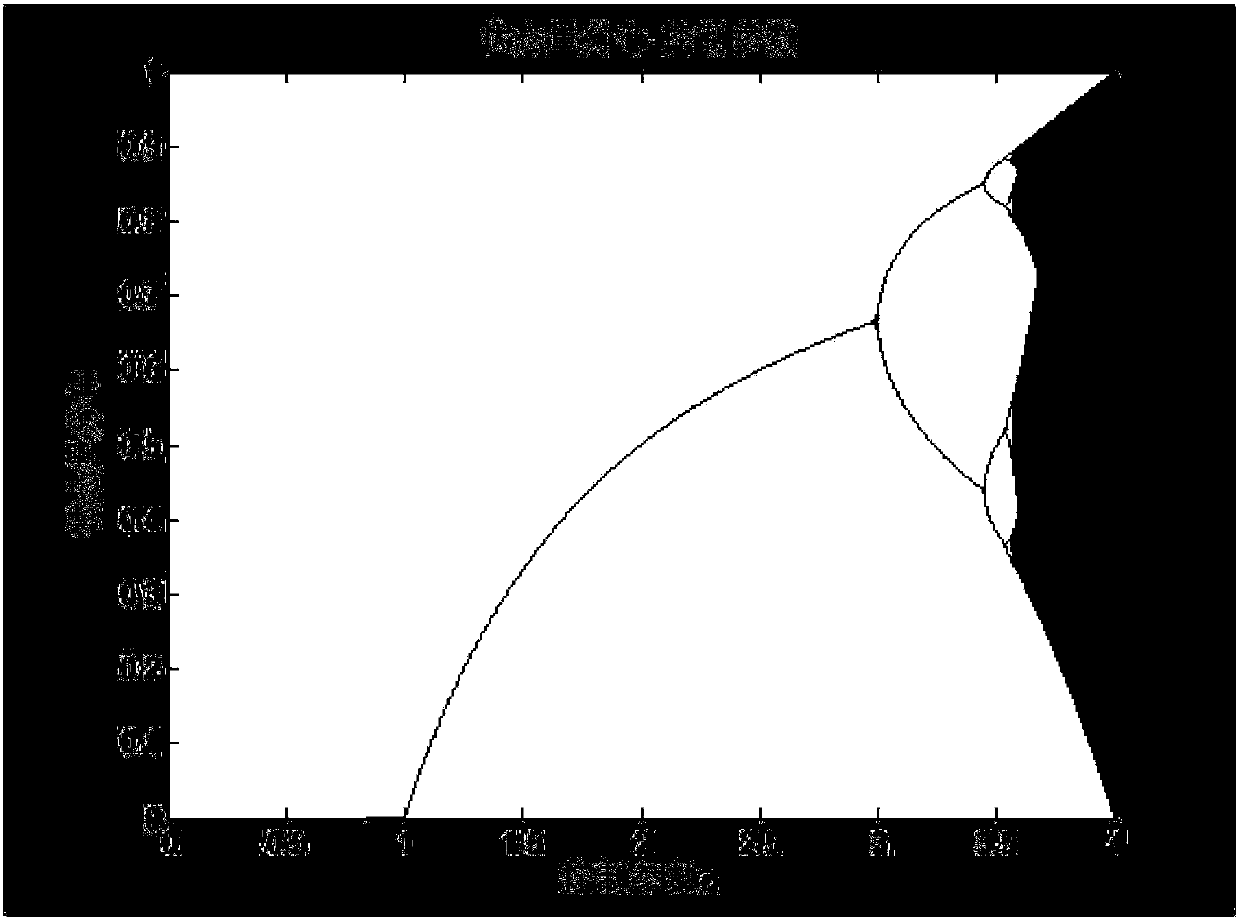
The present invention relates to an internet picture transparent and safe transmission method based on chaotic encryption, and provides a chaotic digital image encryption transmission solution scheme which supports the automatic generation of a secret key and is fully transparent to the internet user operation. According to the internet picture transparent and safe transmission method based on the chaotic encryption, a browser client utilizes a JavaScript program to automatically map, calculate and obtain two key Logistic chaotic secret key parameters according to the information, such as the usernames, password Hash values, etc. inputted by the internet valid users, to realize the safe and transparent encryption and transmission on the to-be-uploaded pictures of users; a server terminal can query a user database according to the registered username to obtain the password Hash value of a user, so that a same chaotic random sequence can be obtained, and finally the encrypted pictures uploaded by the user can be decrypted; on the contrary, when the user registers validly to require the server pictures, the JavaScript program can automatically carry out the chaotic secret key parameter calculation and chaotic decryption operations at a browser terminal. According to the scheme of the present invention, the balance problem among the security, the encryption efficiency, the secret key management and the like of the internet picture transmission can be solved effectively.
Owner:ZHEJIANG UNIV OF TECH
Network video monitoring system based on FPGA chaotic encryption
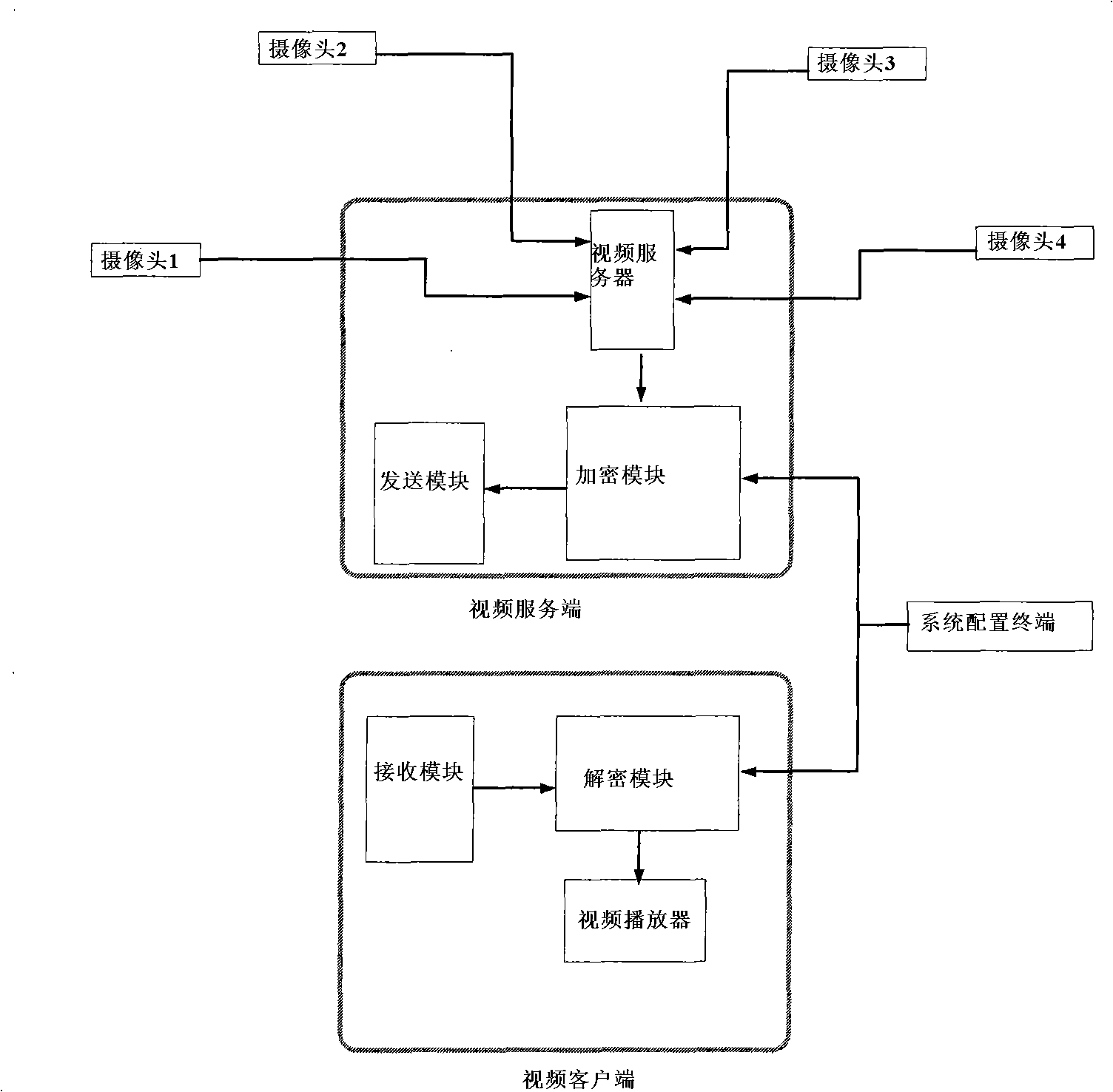
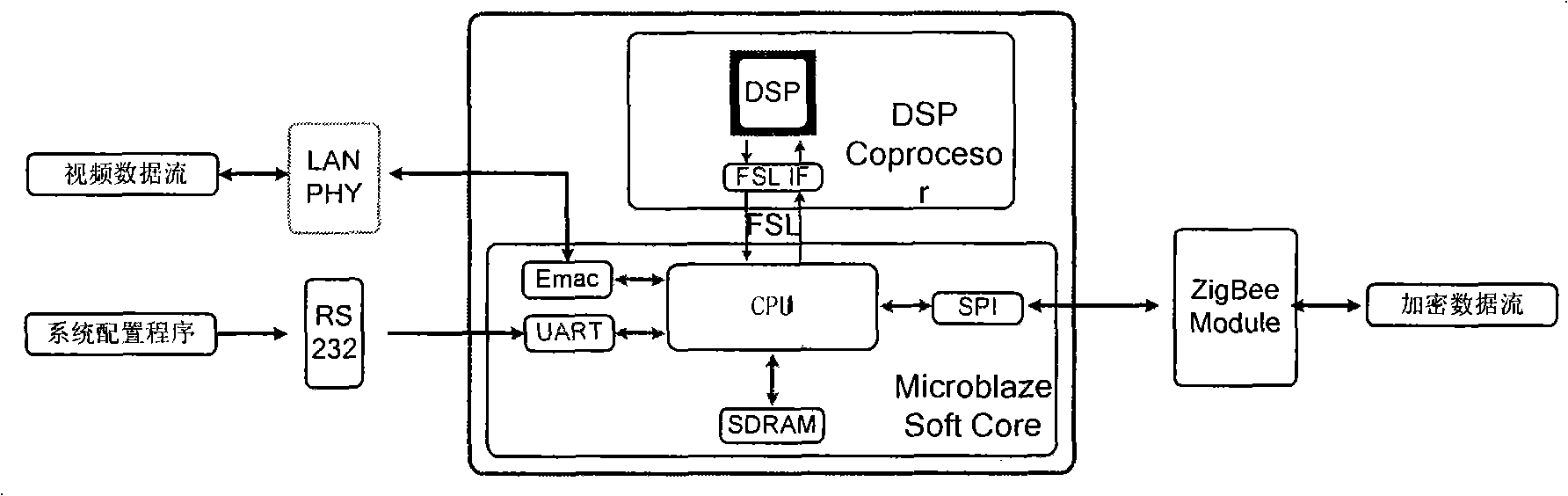
InactiveCN101527823AFunction increaseConsider practicalityAnalogue secracy/subscription systemsClosed circuit television systemsPlaintextVideo monitoring
The invention relates to a network video monitoring system based on FPGA chaotic encryption, comprising a server terminal, a client terminal and a system configuration terminal. The server terminal comprises a plurality of cameras, a video server, an encryption module and a signal sending module; the client terminal comprises a signal receiving module, a decryption module and a client terminal player; video frequency collected by the plurality of cameras is coded by the server, then input into the encryption module via the Ethernet and sent to the client terminal via the signal sending module after encrypted; the signal receiving module of the client terminal receives the encrypted video data and then sends the data to the decryption module for processing and finally the client terminal player plays the video data; the encryption module and the decryption module are respectively an FPGA encryption board and a decryption board; the encryption process and the decryption process of the encryption module to video flow are as follows: the encryption module adopts a CPRS array which is cut and operates with a plain text data module 2, and then sent; and the receiving terminal of the decryption module obtains the same CPRS array, and then operates with a cryptograph module to realize decryption.
Owner:NANJING UNIV
Different-dimensional switchable chaotic system design method and circuit
The invention relates to a different-dimensional switchable chaotic system design method and a circuit; a four-dimensional hyper-chaos system is constructed by adding variables and feeding back control items based on a three-dimensional generalized Lorenz system family; and a switchable different-dimensional chaotic circuit is designed through a plurality of switch controllers in Multisim software. An analog circuit constructed by the invention is convenient to use and easy to realize by hardware, and has relatively lower cost; the designed switchable circuit not only can flexibly realize the switching between a three-dimensional chaotic system and the four-dimensional hyper-chaos system, but also can return to realize the switch among three chaotic systems in the same dimension; and the systems can serve as practical chaotic modulation and chaotic encryption signals, and can be widely applied to the field of information security cryptography with higher requirements on confidentiality and reliability.
Owner:JIANGXI UNIV OF SCI & TECH
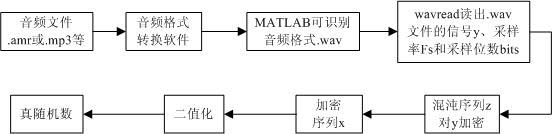
True random number generation method based on chaotic encryption
InactiveCN102541509AIncrease the differenceEasy and convenient to getRandom number generatorsChaotic systemsMATLAB
The invention discloses a true random number generation method based on chaotic encryption. The true random number generation method comprises the following steps of: recording a piece of audio by portable digital voice recording equipment; converting the format of the audio into a wav format, introducing the audio into MATLAB software installed in computer equipment, and reading a signal (y), a sampling rate Fs and sampling bits of the audio; generating a chaotic sequence, of which the length is same as the length of the value sequence of the signal (y), by a chaotic system, wherein an initial value and a system parameter of the chaotic system guarantee that the system generates a chaotic behavior after iteration; encrypting the value sequence of the signal (y) by the chaotic sequence to generate an encrypted true value sequence; and performing binary processing on the encrypted true value sequence, wherein a binary output is a true random number. An audio signal is recorded by a portable device so that a random source is acquired easily and conveniently; the acquired audio sequence is encrypted by the chaotic sequence so that the difference of audio signals recorded at different times is further expanded; and the random number can be generated by using regular audios, such as music with weak background noise.
Owner:HENAN UNIV OF SCI & TECH
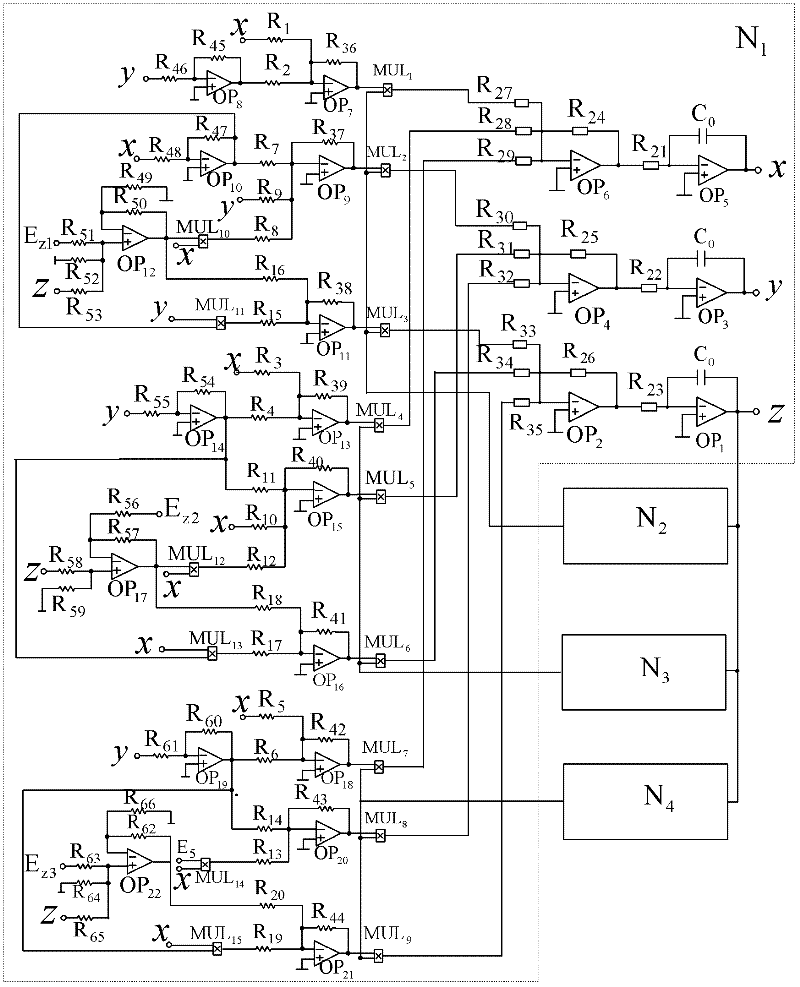
Composite chaotic signal generator
InactiveCN102694643AEasy to implementImprove performanceSecuring communicationChaotic systemsSignal generator
The invention discloses a composite chaotic signal generator which comprises a basic chaotic signal generation circuit N1, a sequence generator N2, a sequence generator N3 and a sequence generator N4, wherein the sequence generator N2, the sequence generator N3 and the sequence generator N4 are used for generating switching control functions. An output end of the basic chaotic signal generation circuit N1 is respectively connected with an input end of the sequence generator N2, an input end of the sequence generator N3 and an input end of the sequence generator N4. An output end of each of the sequence generator N2, the sequence generator N3 and the sequence generator N4 are connected with an input end of the basic chaotic signal generation circuit N1. The sequence generators for generating switching control functions enable hardware of the composite chaotic signal generator to be realized more easily. The composite chaotic signal generator can generate a composite Lorenz-Chen-Lu chaotic system to enhance chaotic encryption.
Owner:GUANGDONG UNIV OF EDUCATION
Classified passive optical network based on synchronization of chaos
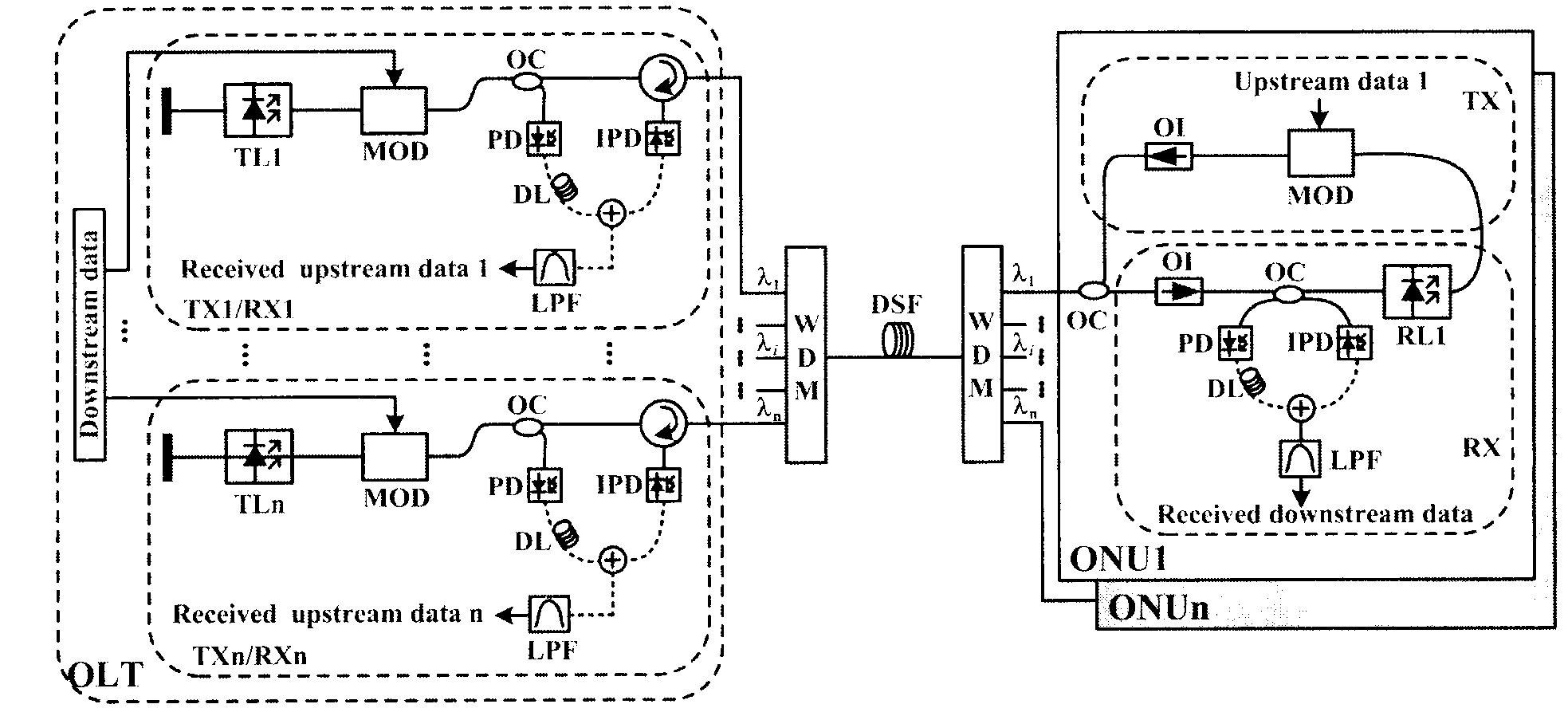
InactiveCN103260095AIncrease system capacityImprove securityMultiplex system selection arrangementsFibre transmissionCarrier signalOptical communication
The invention discloses a classified passive optical network based on synchronization of chaos, and belongs to the technical field of classified optical communication. N pairs of semiconductor lasers with the same operating wavelength are adopted at two ends of an OLT and two ends of an optical network unit to serve as a chaotic carrier wave generator. Uplink information and downlink information are respectively loaded to n chaotic carrier waves with different wavelengths through an optical modulator to achieve information chaotic encryption, up-load and down-load are carried out through optical fibers after combination by adopting a wavelength-division multiplexing technology, and at last information decryption is achieved by adopting a chaotic carrier wave with the same wavelength. An all-optical chaotic signal is used as a carrier wave and combined with the wavelength-division multiplexing technology to carry out classified transmission on uplink information and downlink information, information security of the passive optical network is improved from a physical layer, the classified passive optical network based on synchronization of the chaos is suitable for a communication service with high requirements in information confidentiality, and reference significance is provided to improve safety of the passive optical network.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
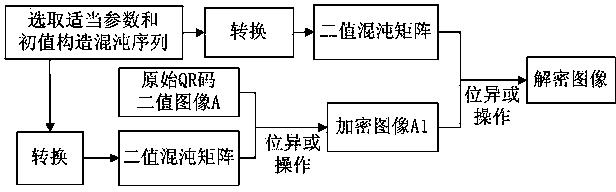
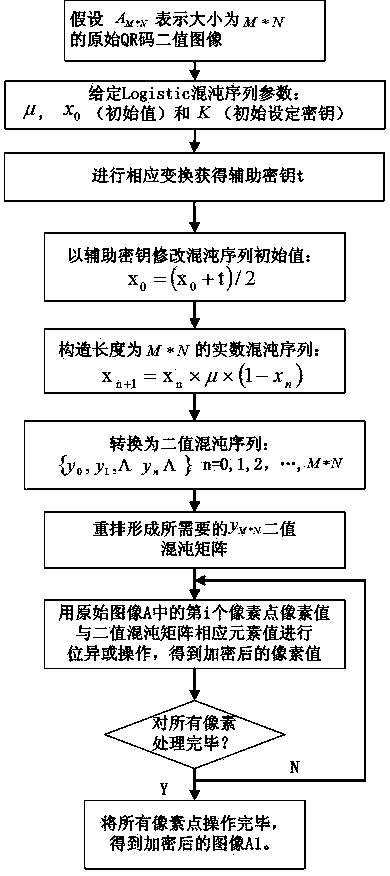
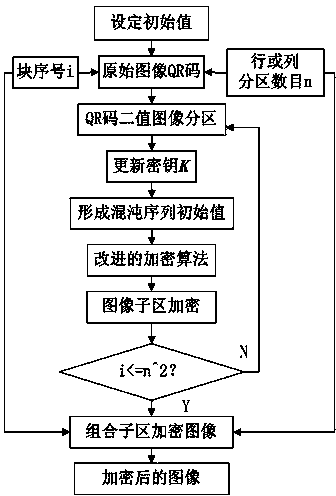
QR two-dimensional code binary image partition-based key varying chaotic encryption method
InactiveCN103414549AAdd auxiliary keyImplement chaotic encryptionRecord carriers used with machinesSecuring communicationComputer hardwareTransfer procedure
The invention relates to a QR two-dimensional code binary image partition-based key-varying chaotic encryption method. The method comprises the following steps that: 1), a traditional logistic chaotic mapping encryption algorithm is improved in a manner that an auxiliary key is added such that a new initial value x0 can be formed; 2), an original QR-code binary image is partitioned, and the total number of sub-region images of which the pixel is 1 is calculated, and therefore, the initial values of random keys of sub-blocks are formed; and 3), the auxiliary key and the random key are combined with partition encryption technology, such that QR code binary image partition-based key-varying chaotic encryption and decryption algorithms can be realized. With the QR two-dimensional code binary image partition-based key-varying chaotic encryption method adopted, random variation of keys can be realized; key space and key paths can be expanded; the reliability and security of encryption can be enhanced; a requirement for QR code information confidentiality in storage and transmission can be satisfied; and at the same time, an encryption effect, encryption speed and cracking difficulty are further improved. The QR two-dimensional code binary image partition-based key-varying chaotic encryption method of the invention is advantageous in convenience, practicability, safety and reliability.
Owner:GUANGDONG UNIV OF TECH
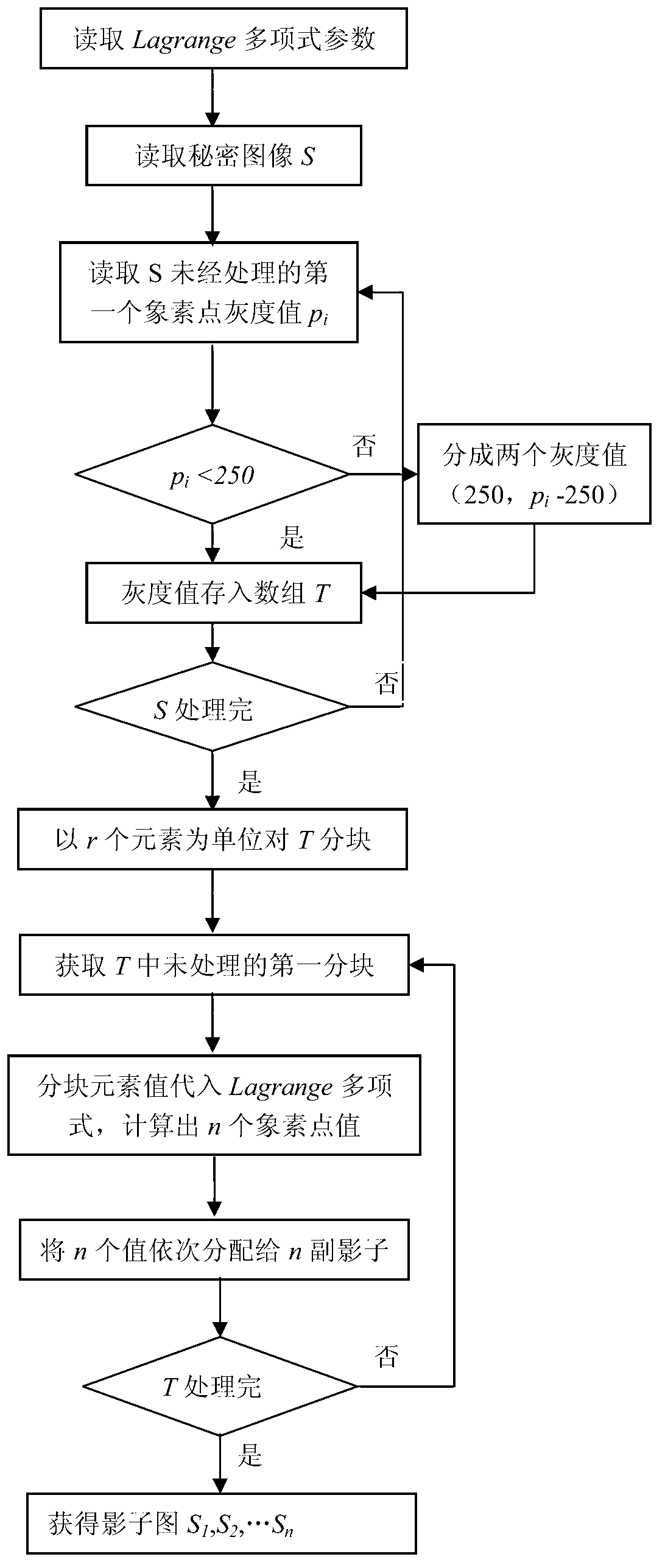
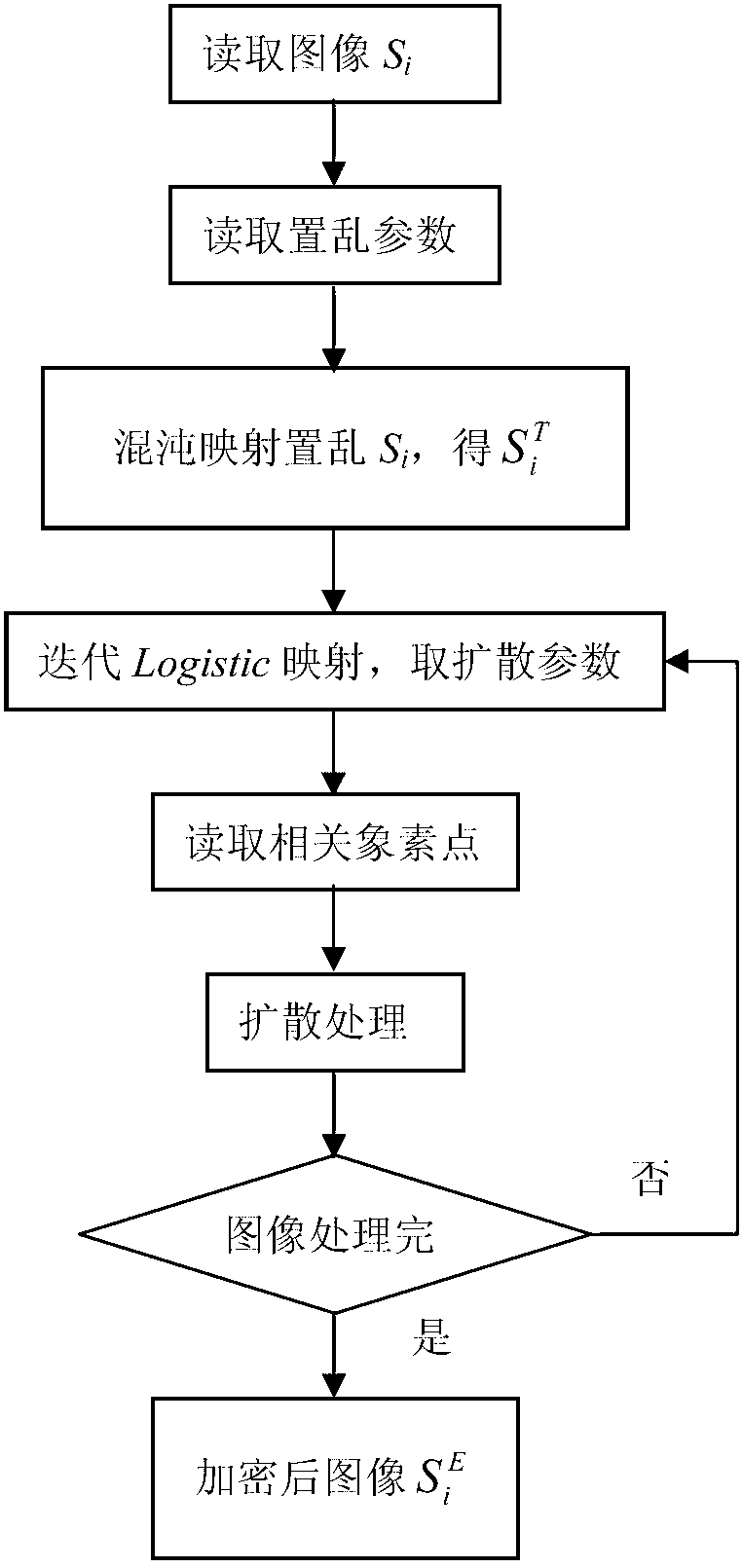
Chaotic-encryption-based medical image share method
ActiveCN103226802AImplement integrity verificationMeet confidentiality requirementsImage data processing detailsSecret shareConfidentiality
The invention discloses a chaotic-encryption-based medical image share method which comprises a secret image breakdown step, a chaotic image encryption step, a chaotic image decryption step and a secret image recovery step. According to the invention, a threshold secret share scheme is utilized to divide an image into n shadow images, the chaos principle is utilized to encrypt the n shadow images, the encrypted shadow images have the statistical property of white noise, and the collected r shadow images are utilized to recover the secret image. The chaotic-encryption-based medical image share method facilitates data storage and transmission, ensures confidentiality and integrity of significant images, and has strong anti-attack capacity.
Owner:CENT SOUTH UNIV
Chaotic image encryption method based on bit replacement and dynamic DNA coding
ActiveCN106952213AAchieve substitutionImprove featuresImage data processing detailsDiffusionCiphertext
The invention provides a chaotic image encryption method based on bit replacement and dynamic DNA coding. The objective of the invention is to solve the problem that security of chaotic encryption is affected by degradation of chaotic dynamics characteristics of an image encryption method based on a chaotic system in the prior art. The chaotic image encryption method comprises steps of firstly using the Keccak algorithm to calculate a hash value of a DNA sequence; based on the hash value, generating an initial state value of the chaotic mapping; by use of a hyperchaotic Chen system, generating a chaotic mapping index to carry out pixel position overall scrambling on an image; combining the Butterfly network to carry out bit position scrambling on each pixel, thereby achieving position grade scrambling; carrying out dynamic DNA coding on the image and combining the given DNA sequence to carry out XOR operation, thereby achieving replacing of the pixels; and finally, through the ciphertext feedback, further enhancing the chaotic and diffusion features. According to the invention, the chaotic image encryption method has big key space and is highly sensitive to a key, and capable of effectively resisting attacking operation of statistical analysis and exhaustion analysis.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
DWT-SVD robust blind watermark method based on multilevel DCT
ActiveCN103955879AIncrease valueGood resistance to attackImage data processing detailsWatermark methodComputer science
The invention relates to a DWT-SVD robust blind watermark method based on multilevel DCT. The method comprises a watermark embedding method and a watermark extraction method. The watermark embedding method includes the steps that discrete waterlet transformation is conducted on an original image, a low-frequency sub-band of the original image is divided into small blocks, multilevel DCT is conducted on each small block, chaotic encryption is conducted on watermarks to be embedded, multilevel DCT coefficients of each small block form a new matrix, and the encrypted watermarks are embedded into a singular value matrix of each new matrix. The watermark extraction method is the inverse process of the watermark embedding method and includes the steps of extraction of the encrypted watermarks and decryption and restoration of the watermarks through secret keys. According to the method, by the combination of the advantages of DWT and SVD on the digital watermark respect and the utilization of the energy concentration characteristic of multilevel DCT, data of which values are large are acquired, the embedded capacity of the watermarks is increased, the characteristic of being good in robustness is still maintained, and the problem of conflicts between the capacity of the watermarks and robustness is well solved.
Owner:HANGZHOU DIANZI UNIV
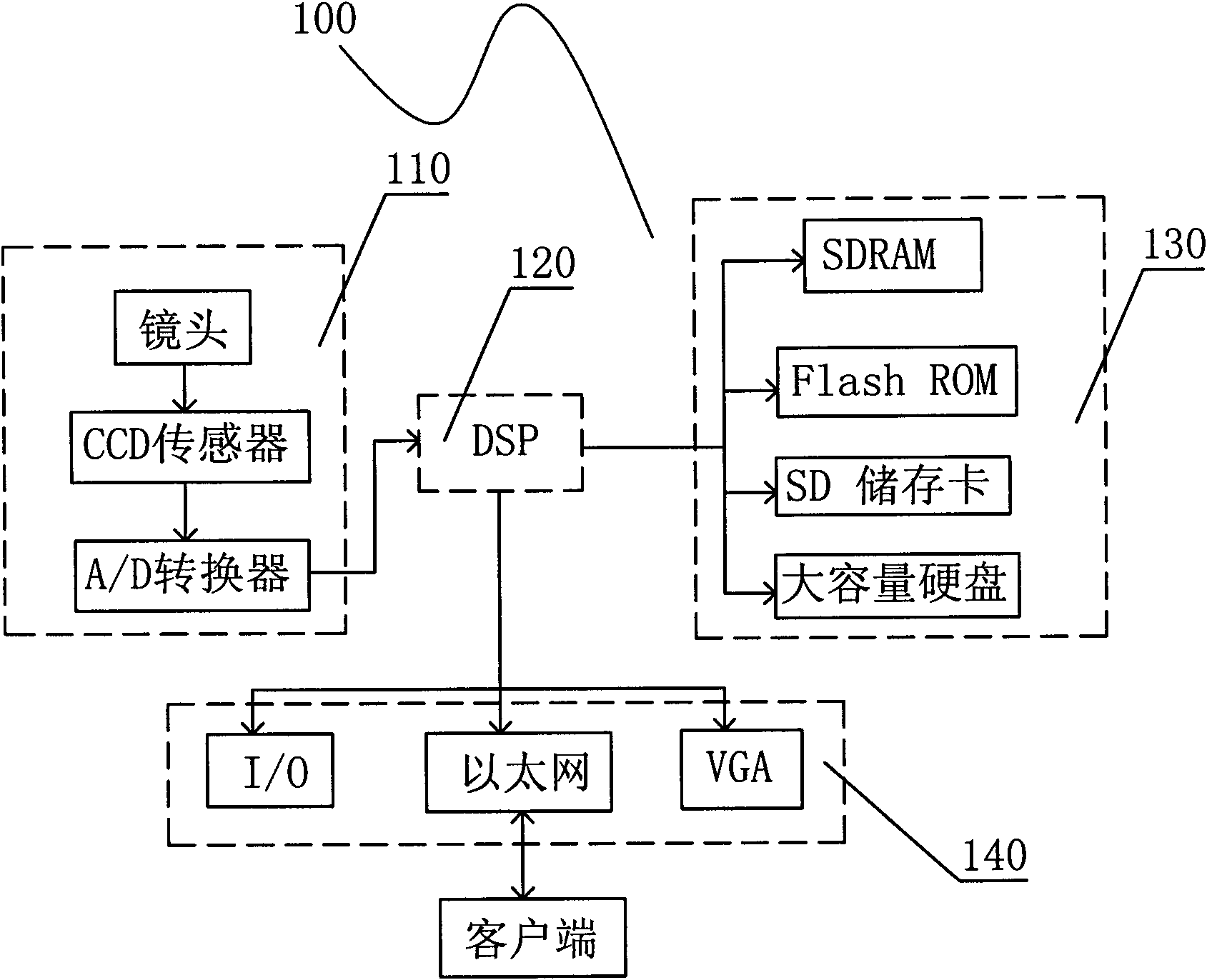
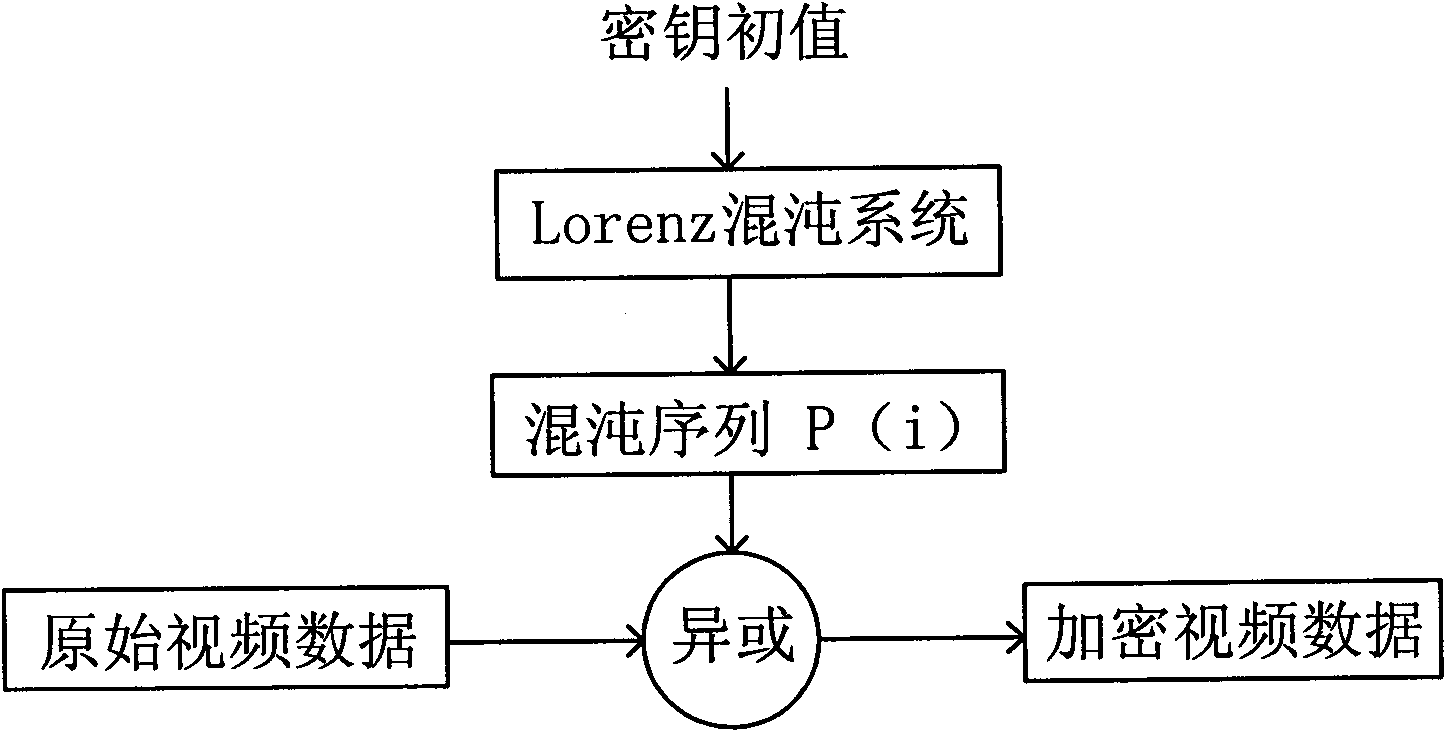
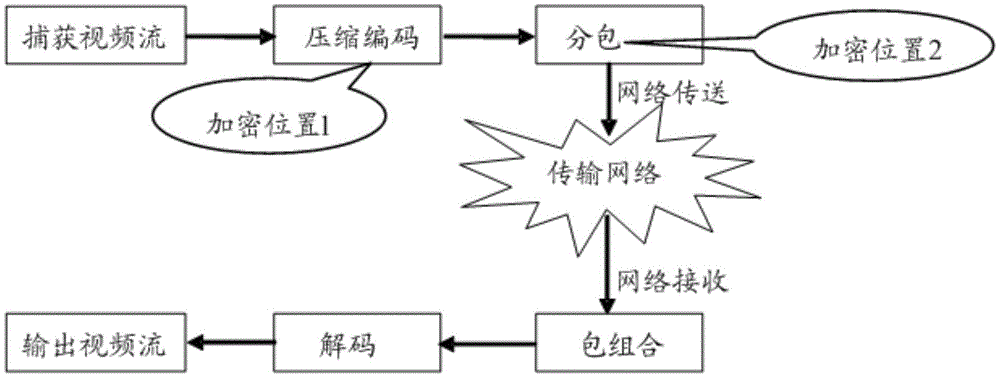
Video-encryption camera and encryption method thereof
ActiveCN101902576AEasy to crackImprove securityTelevision system detailsColor television detailsVideo storageChaotic encryption
The invention relates to a video-encryption camera comprising a video acquisition module, a video pre-processing and encrypting module and a video storage module, wherein the video acquisition module is used for transmitting video data to the video pre-processing and encrypting module upon the completion of video acquisition; the video pre-processing and encrypting module is used for pre-processing each frame of video data, making calculations by calling a chaotic encryption system in the video storage module to generate chaotic sequences and further carrying out the XOR operations on the chaotic sequences and each frame of video data to encrypt the video data; and the video storage module is used for storing the encrypted video data on a real-time basis. Compared with the prior art, the invention encrypts the video data while acquiring and pre-processing the video data, and stores the encrypted video data in the video storage module on a real-time basis, thus avoiding the consequences that the raw video data are illegally stolen or falsified.
Owner:SOUTH CHINA NORMAL UNIVERSITY
Fine particulate matter removal device and method with combined action of acoustic agglomeration and cyclone separation
InactiveCN104128047AEfficient removalDispersed particle separationEnergy based chemical/physical/physico-chemical processesCycloneImaging processing
The invention discloses a fine particulate matter removal device and method with combined action of acoustic agglomeration and cyclone separation. The device is embedded in each terminal workstation in an MIS system, is used for adding an invisible watermark to an acquired new image, and also provides integrity detection and tampering localization analysis for terminal work management and image processing. The technical method is embedded and integrated into a management information system for authenticating image content integrity and locating a tampered image region, and the method can be expressed as integrated external hardware when in concrete realization. The realization of the whole device scheme is divided into two parts: one, image characteristic information as the watermark is generated by the original image, the watermark information is subjected to chaotic encryption and then embedded into the original image, and the invisibility of the watermark information is realized under a condition without increasing the bandwidth; and two, a watermark-containing medical image is subjected to watermark extraction on a receiving end, the image can be subjected to integrity detection, the tampered image region is located, and thus a strong support is provided for further decision.
Owner:CENT SOUTH UNIV
Method for chaotic encryption of multi-path image digital information
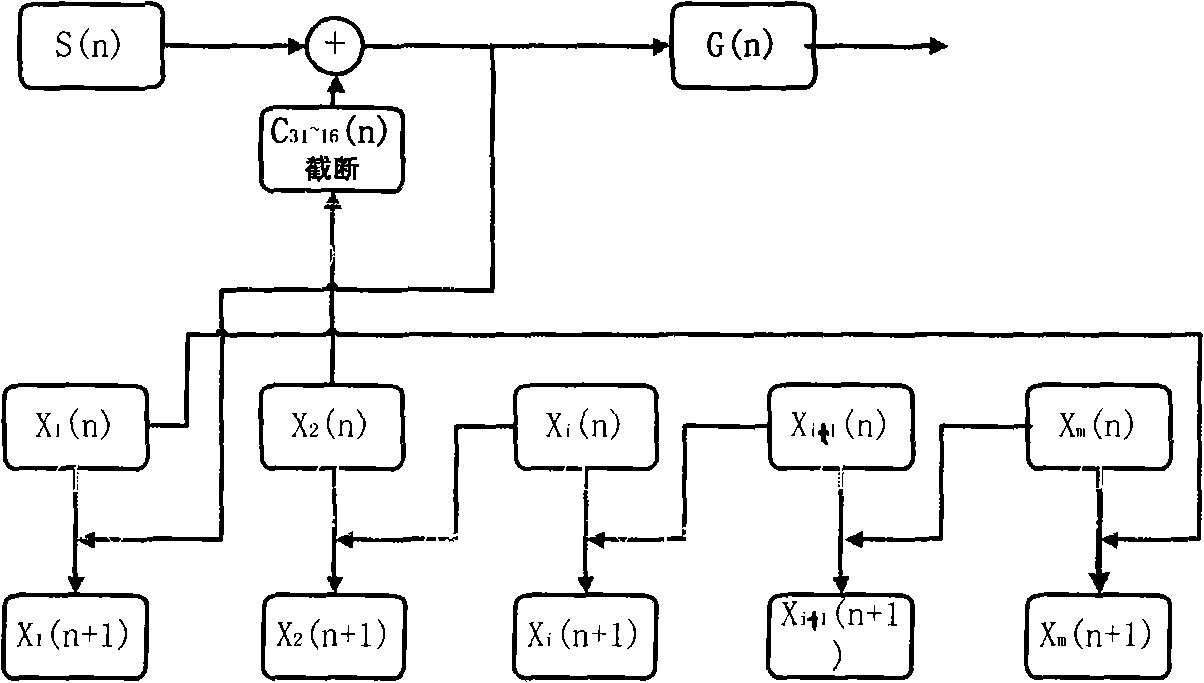
ActiveCN103888637AHigh degree of reductionDigital video signal modificationSecuring communicationAlgorithmEnd system
The invention discloses a method for chaotic encryption of multi-path image digital information. The method comprises the following steps that an n-dimension discrete chaotic system kinetic equation is established; according to the seven-dimension chaotic system kinetic equation, n-m+1 real number chaotic sequences generated through iteration are rounded and then converted into binary digital information through a digital information encipher, and then XOR operation is conducted on the binary digital information and digital information of n-m+1 images, so that cryptograph values of the n-m+1 images are obtained respectively; the cryptograph values are transmitted to a digital information decipher through a digital transmission channel. According to the method, three-path image information is encrypted simultaneously just through one seven-dimension chaotic system; due to the fact that the cascading closed loop principle is adopted, a sending end system and a receiving end system have identical drive signals, strict synchronization can be realized, the influence of modulation of the size of useful information is avoided, and decrypted information has a high reduction degree under the condition that the parameters of the sending end are matched with the parameters of the receiving end.
Owner:GUANGDONG UNIV OF TECH
DWT-SVD geometric attack prevention blind watermark method based on SIFT
ActiveCN103955878AGood resistance to attackGood attackImage data processing detailsSingular value decompositionWatermark method
The invention relates to a DWT-SVD geometric attack prevention blind watermark method based on SIFT. The method comprises a watermark embedding method and a watermark extraction method. The watermark embedding method includes the steps that discrete waterlet transformation is conducted on an original image, a low-frequency sub-band of the original image is divided into small blocks, singular value decomposition is conducted on each small block, chaotic encryption is conducted on watermarks to be embedded, and the watermarks are embedded into the maximum singular value of each small block through an optimal quantitative method, the SIFT feature points of a watermark image are stored as secret keys, the types of geometric attacks are judged according to the secret keys, and correction is conducted. The watermark extraction method is the inverse process of the watermark embedding method and includes the steps of correction of attacked images, watermark extraction and watermark decryption and restoration. According to the method, by the utilization of the rotation, zoom and translation invariance of the SIFT feature points and the combination of the advantages of DWT and SVD in the digital watermark aspect, robustness on geometric attacks is remarkably improved.
Owner:HANGZHOU DIANZI UNIV
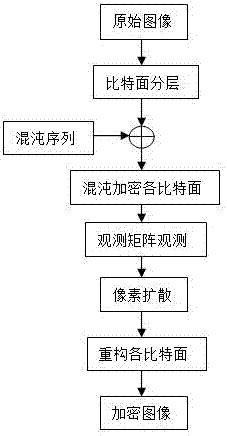
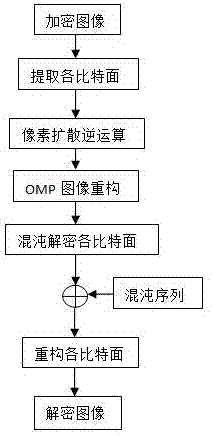
Image bit-plane chaotic encryption method based on compressed sensing
InactiveCN106997607AImplement compression encryptionImprove transmission securityUser identity/authority verificationImage codingConfidentialityChaotic systems
The invention provides a method for image encryption, and a method of performing encryption on bit planes. A chaotic system acquisition interval is used as a secret key, and observation of generated bit planes is performed via a compressed sensing technology, and therefore, sampling compressed encryption of the image is achieved. Firstly, bit planes of an original image and an encrypted matrix are combined to form a scrambling image to undergo compressed sensing, then the encrypted scrambling image is observed via compressed sensing, and pixel diffusion of the observed image is performed via the encrypted matrix, and a final encrypted image is obtained. The chaotic system acquisition interval is used as the secret key, and confidentiality can be enhanced. The method is also advantageous in that, image bit plane scrambling is used, observed matrix features via compressed sensing is used, and the random characteristic of the chaotic system is fully used. When sampling compression of the image is performed, encryption of the image is completed, and transmission security of the image is effectively enhanced.
Owner:SICHUAN UNIV
Image encryption and decryption method employing DNA scrambling coding and chaotic mapping
InactiveCN107798708AReduce complexityImprove performanceImage codingChaos modelsPlaintextComputer hardware
The invention discloses an image encryption and decryption method employing DNA scrambling coding and chaotic mapping, and the encryption method takes the one-dimensional Logistic chaotic mapping in the chaotic encryption technology and DNA coding calculation as the basis, and then integrates the DNA scrambling coding, and is based on a plurality of step-by-step extraction algorithms of one-dimensional Logistic chaotic mapping and two-dimensional chaotic scrambling. According to the invention, a random matrix, generated by a chaotic system according to a text corresponding algorithm, is used for encryption and decryption, and is combined with a plaintext image matrix for DNA scrambling coding. Moreover, the two-dimensional chaotic scrambling is used for the bit-level scrambling of an encrypted image so as to replace DNA base pair complementation and replacement, thereby enabling the encryption algorithm to have a good encryption structure so as to effectively resist various of passwordattack behaviors while reducing the encryption cost.
Owner:SHENZHEN UNIV
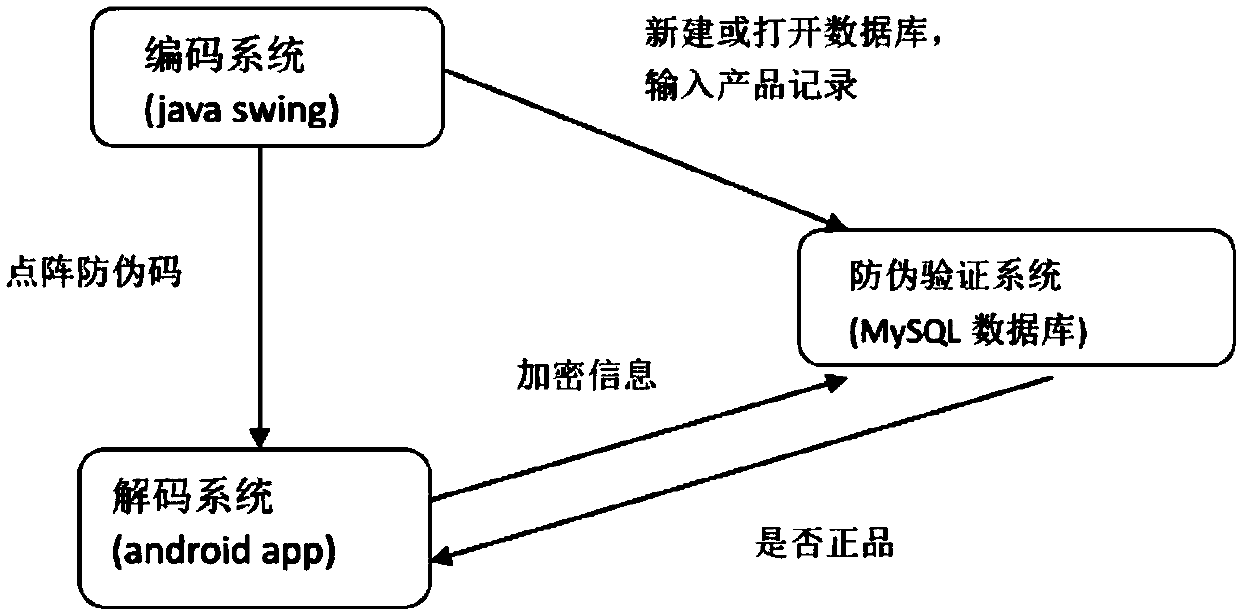
Chaotic encryption-based lattice anti-fake code design method and application system thereof
ActiveCN107609621AImprove securityMake up for the defect of not being able to resist scan-forgery attacksCo-operative working arrangementsCommercePlaintextDiffusion
The invention discloses a chaotic encryption-based lattice anti-fake code design method and an application system thereof. According to the method and the application system, the safety of lattice anti-fake codes is improved by utilizing a chaotic encryption technology, and chaotic encryption sequences are generated by using a worm population model and different initial values and control parameters so as to be applied to the diffusion and scrambling processes of chaotic encryption. According to the method and the application system, a ciphertext of a designed is as long as a plaintext, concise, efficient, high in encryption speed and suitable for commercialized production. The invention furthermore discloses the chaotic encryption-based lattice anti-fake code application system. Accordingto the method and the application system, a counter method is utilized to fill the gap that lattice anti-fake codes cannot resist scanning-counterfeiting attack, and a decryption function is deployedat a server, so that the pressure of an android app client is lightened, benefit is brought to the relative independence of the server, passwords are not easy to leak and the safety coefficient is relatively high.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
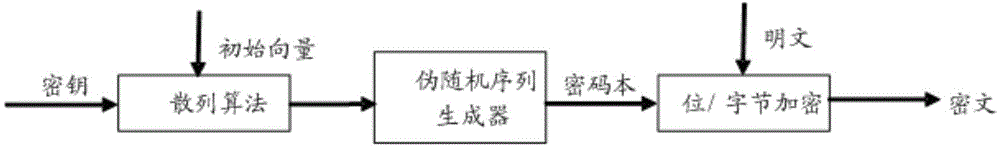
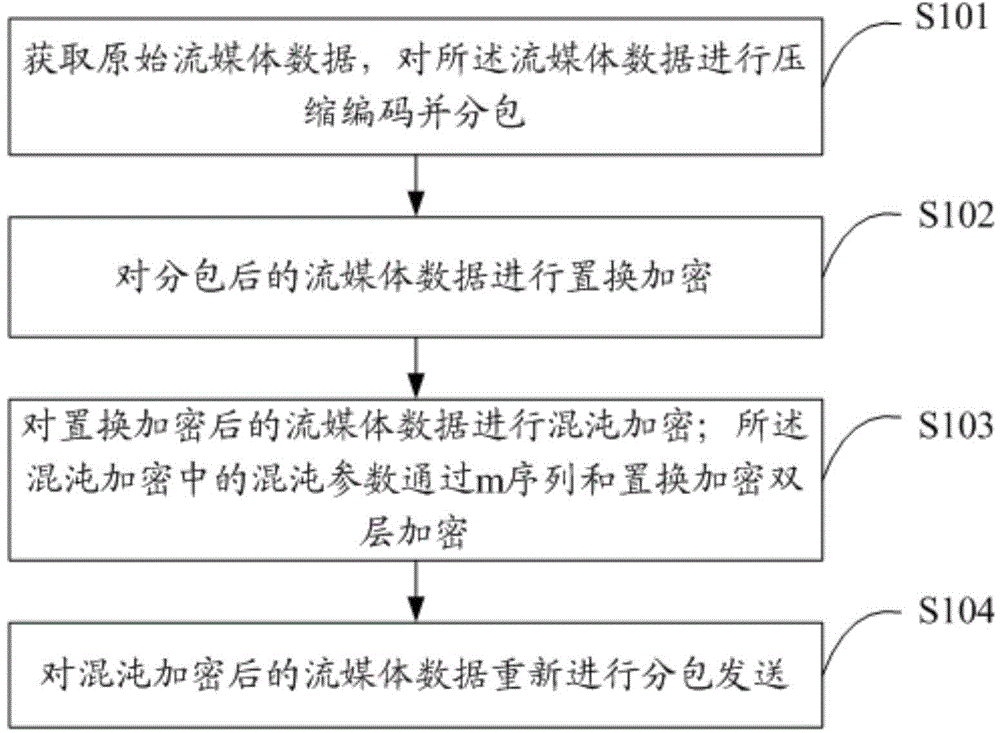
Streaming media encryption and decryption method and device
ActiveCN104580236AOvercoming weak secrecyDoes not affect compression ratioSecuring communication by chaotic signalsConfidentialityChaotic systems
The invention relates to a streaming media encryption and decryption method and device. The encryption method comprises the first step of acquiring original streaming media data, conducting compression encoding on the streaming media data and subpackaging the streaming media data, the second step of conducting substitution encryption on the subpackaged streaming media data, the third step of conducting chaotic encryption on the streaming media data subjected to substitution encryption, the fourth step of conducting double-layer encryption on chaotic parameters during chaotic encryption through m sequences and substitution encryption, and the fifth step of subpackaging and transmitting the streaming media data subjected to chaotic encryption again. The method aims at overcoming the defects of a chaotic system, the m sequences and substitution encryption are combined to improve the anti-decoding capability of parameter sequences, the weak confidentiality of streaming media encryption is overcome, and the compression ratio of streaming media is not affected.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
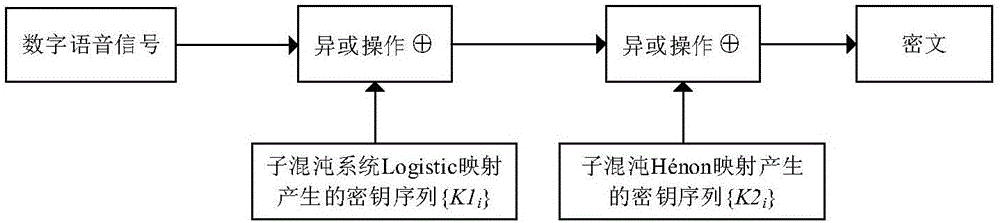
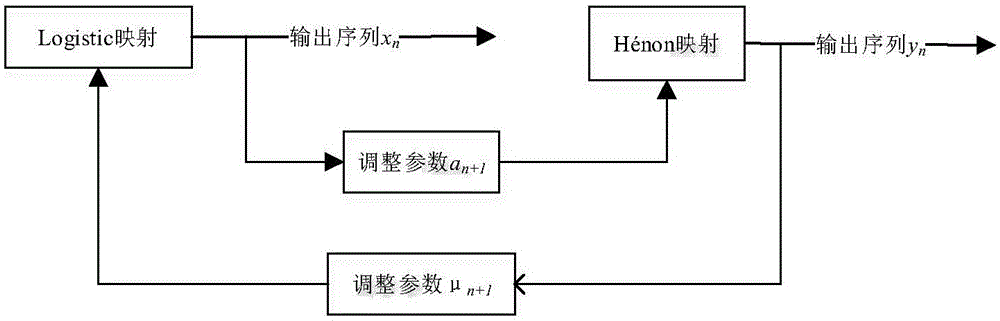
Chaotic encryption method for voice information
ActiveCN106375079AGood pseudorandomnessExtended cycleSecuring communication by chaotic signalsPlaintextComputer hardware
The invention discloses a chaotic encryption method for voice information. The method is characterized in comprising the steps of 1), establishing a dynamic variable parameter composite chaotic system and generating a real-value chaotic sequence of which length is the same to that of a plaintext voice sequence through utilization of the system; 2), carrying out binarization processing on the real-value chaotic sequence, thereby obtaining a chaotic key sequence of which length is the same to that of the plaintext voice sequence; and 3), through combination of the chaotic key sequence, carrying out bit-by-bit exclusive or operation on the plaintext voice sequence, thereby obtaining a ciphertext. According to the method, under limited calculation precision, the chaotic sequence with good pseudo-randomness can be generated, the valid precision effect is reduced, and a chaotic sequence cycle is prolonged; and through adoption of a chaotic system cascading mode, the encryption security is improved, a sufficient key space can be generated, and an exhaustive attack can be resisted effectively.
Owner:HUAQIAO UNIVERSITY
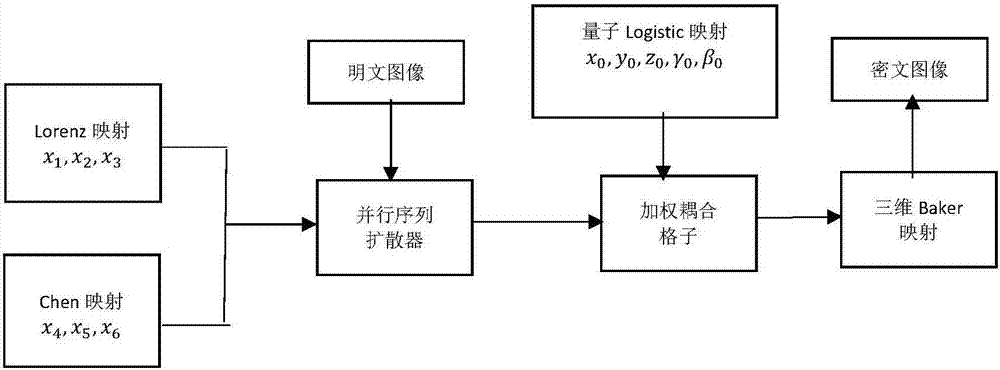
Quantum chaos-based parallel image encryption method
InactiveCN107292802ASmooth connectionResist Differential AttacksImage data processing detailsPlaintextComputer hardware
The invention relates to a quantum chaos-based parallel image encryption method. The invention aims to solve the defects of a current traditional serial chaotic encryption algorithm. According to the method of the invention, a sequence generated by hyperchaotic Lorenz mapping and Chen mapping is used as an input sequence for parallel encryption; a generated intermediate ciphertext is adopted as the input of quantum logistic mapping; three-dimensional Baker scrambling operation is performed; and therefore, plaintext information can be hidden. As indicated by experimental simulation, the encryption speed of the algorithm of the invention is higher than that of the traditional serial encryption algorithm, the algorithm of the invention can effectively resist statistical attacks and differential attacks to achieve a very good encryption effect.
Owner:GUANGDONG UNIV OF TECH
Chaotic optical network physical layer protection method and system, networking method and network
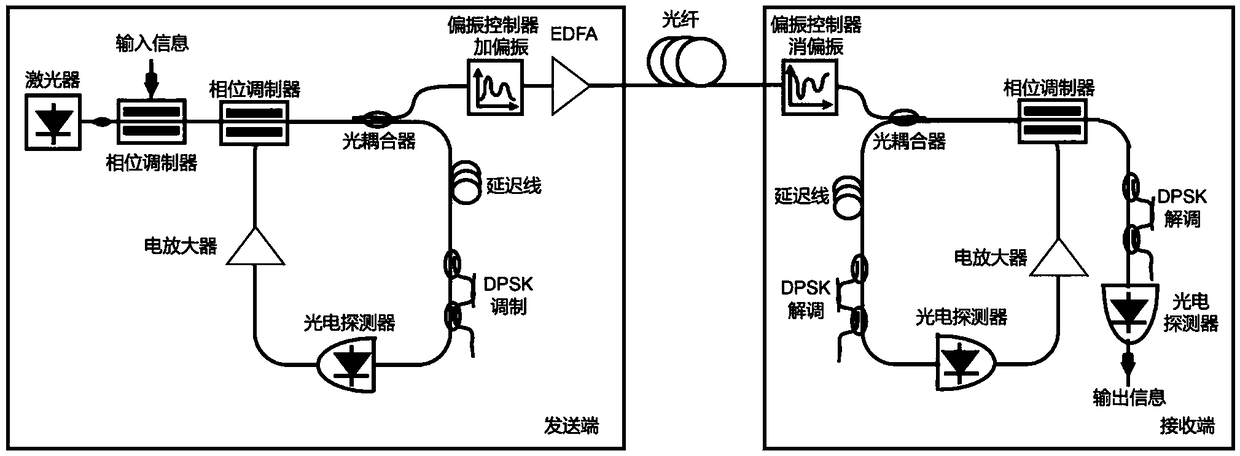
ActiveCN108964873AGood sync qualityHigh securityModulated-carrier systemsWavelength-division multiplex systemsComputer hardwarePhysical layer
The invention discloses a chaotic optical network physical layer protection method and system, a networking method and a network, related to the physical layer protection field of a chaotic optical network. The multi-dimensional physical layer protection method comprises the following steps: a transmitting end performs digital chaotic encryption after performing optical chaotic phase modulation, so as to control the speed of polarization change and the change amount of each time, and realize two-level hardware encryption in the physical layer of the chaotic optical network; and a receiving endfirst performs digital chaos decryption, and then performs optical chaotic phase demodulation, so as to realize two-level hardware decryption in the physical layer of the chaotic optical network. Theinvention encrypts in three dimensions of time, frequency and polarization; the chaotic signal and polarization disturbance obviously enhance the secrecy; and the speed of polarization change and thechange amount of each time are controlled; so that the intercept probability is significantly reduced.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
Three-order non-autonomous nonlinear chaotic circuit
ActiveCN106160998ASimple structureAvoid crackingSecuring communication by chaotic signalsInformation processingEngineering
The invention discloses a three-order non-autonomous nonlinear chaotic circuit which comprises three channels, wherein the first channel corresponds to a first function of a chaotic circuit characteristic equation; the second channel corresponds to a second function of the chaotic circuit characteristic equation; the third channel corresponds to a third function of the chaotic circuit characteristic equation; outputs of a first channel circuit are also used as two input signals of the second channel circuit; outputs of a second channel circuit are fed back to an input end and used as an input signal of the second channel circuit and an input signal of the first channel circuit; outputs of a third channel circuit are also used as an input signal of the second channel circuit, and fed back to the input end and used as an input signal of the third channel circuit. The nonlinear chaotic circuit is more novel and special; chaotic encryption is harder to crack. The circuit is simple in structure and easy to implement; rich and peculiar dynamic behaviors can be generated; the three-order non-autonomous nonlinear chaotic circuit has wide prospect and effect in the fields such as information processing and secret communication.
Owner:XIAN UNIV OF TECH
Hyper-chaotic encryption method based on Josephf traversal and bit plane reconstruction
ActiveCN112422266AImprove securityBit disorderEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsAlgorithmBit plane
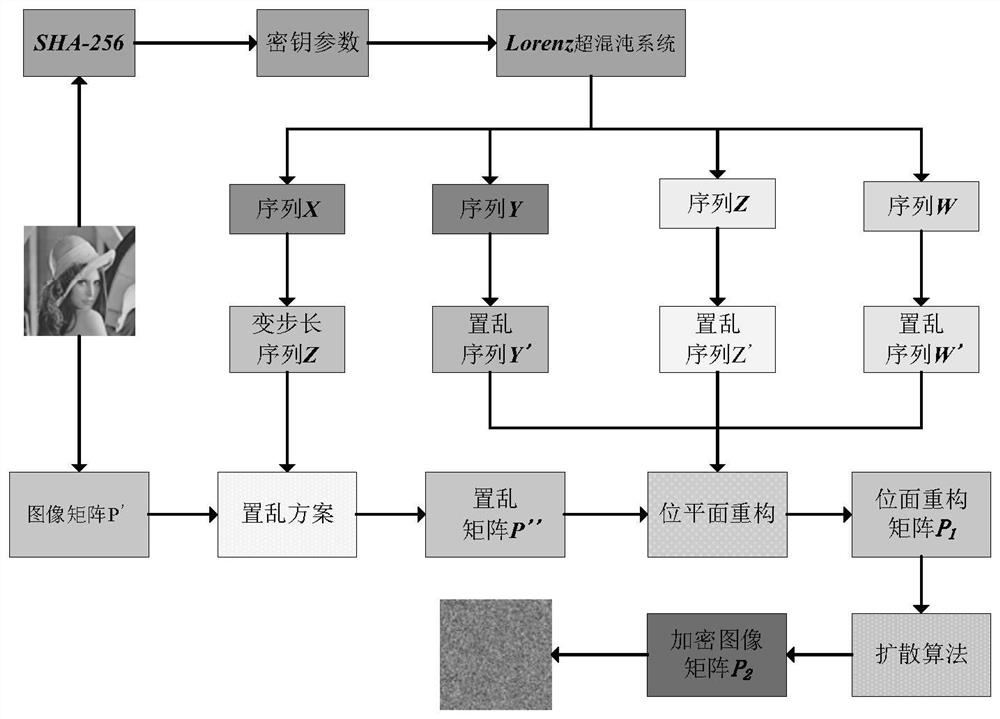
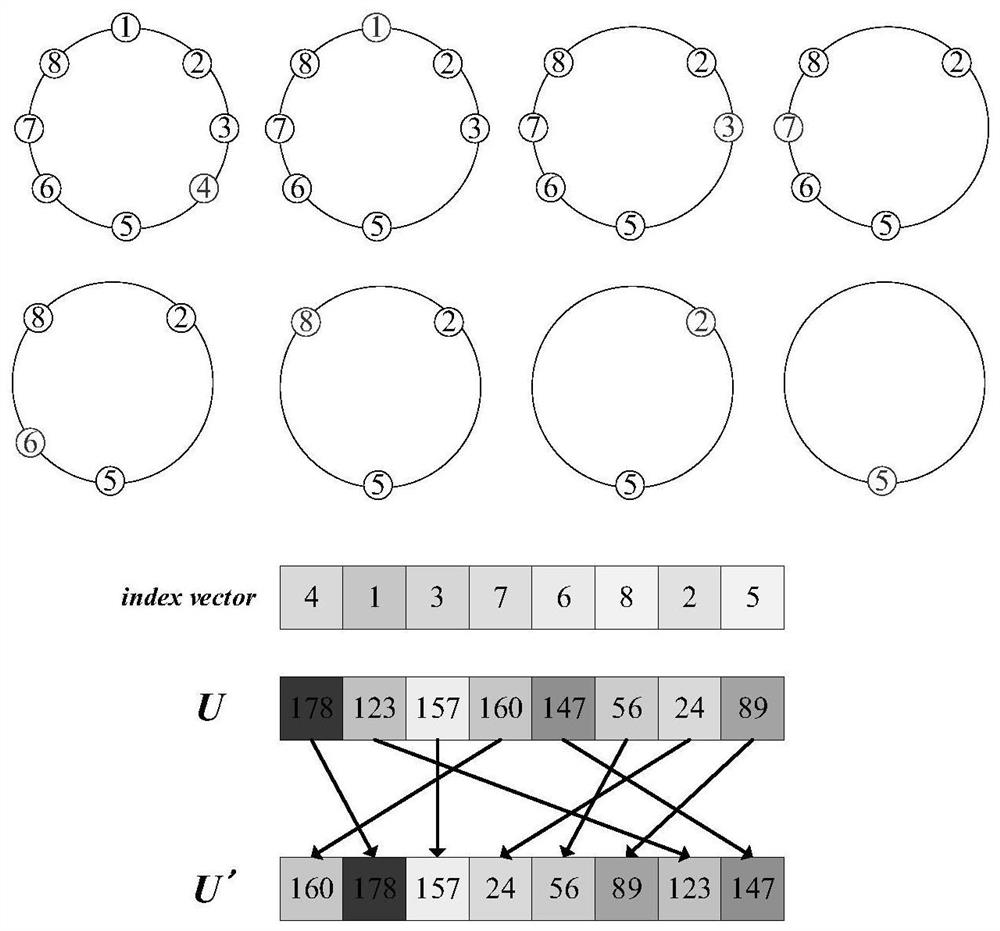
The invention provides a hyper-chaotic encryption method based on Josephf traversal and bit plane reconstruction. The hyper-chaotic encryption method comprises the following steps: converting a grayscale image into an image matrix; inputting the image matrix into an SHA-256 algorithm as a secret key, and obtaining initialization parameters according to the secret key; substituting the initialization parameters into a hyper-chaotic Lorenz system for iteration to generate four chaotic sequences, processing one chaotic sequence to serve as a variable step size sequence, performing pixel positionscrambling on a one-dimensional sequence of an image matrix by utilizing an improved Josephf traversal method, and rearranging a pixel scrambling matrix; dividing the pixel scrambling matrix into eight bit planes, and performing bit plane reconstruction on the pixel scrambling matrix by using the other three chaotic sequences and a bit plane reconstruction method to generate a bit plane reconstruction image matrix; and diffusing the bit plane reconstruction image matrix to generate a final encrypted image. According to the method, different types of images can be encrypted into uniformly distributed encrypted images, and the method has very sensitive key sensitivity and can resist various attacks.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Encrypted medical image robust multi-watermark realizing method in cloud environment
InactiveCN104867100AGuarantee data securityMake up for the shortcomings of not being able to protect the medical image itselfImage data processing detailsFeature vectorExclusive or
The invention discloses an encrypted medical image robust multi-watermark realizing method in cloud environment, and belongs to the field of multimedia signal processing. The method comprises the following major steps that: firstly, an original medical image is encrypted in a transformation domain; binary text watermark pictures are encrypted; then, the encrypted original image is subjected to DCT (Discrete Cosine Transformation) to obtain feature vectors; the feature vectors of the encrypted image and watermarks subjected to chaotic encryption are used for carrying out exclusive-or operation; zero watermarks are embedded to obtain a binary logic sequence; next, watermark extraction and watermark reduction are carried out, and the watermarks are extracted by the binary logic sequence generated during the watermark embedding; the extracted watermarks and the binary logic sequence are subjected to exclusive-or operation, and reduced watermarks are obtained; and finally, encrypted image reduction is carried out. Compared with a conventional method of directly embedding scrambled watermarks into an original image, the method provided by the invention has the advantages that the effect of embedding the watermarks into the encrypted image is achieved, and the security of the original image stored in a cloud end can be guaranteed.
Owner:HAINAN UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com