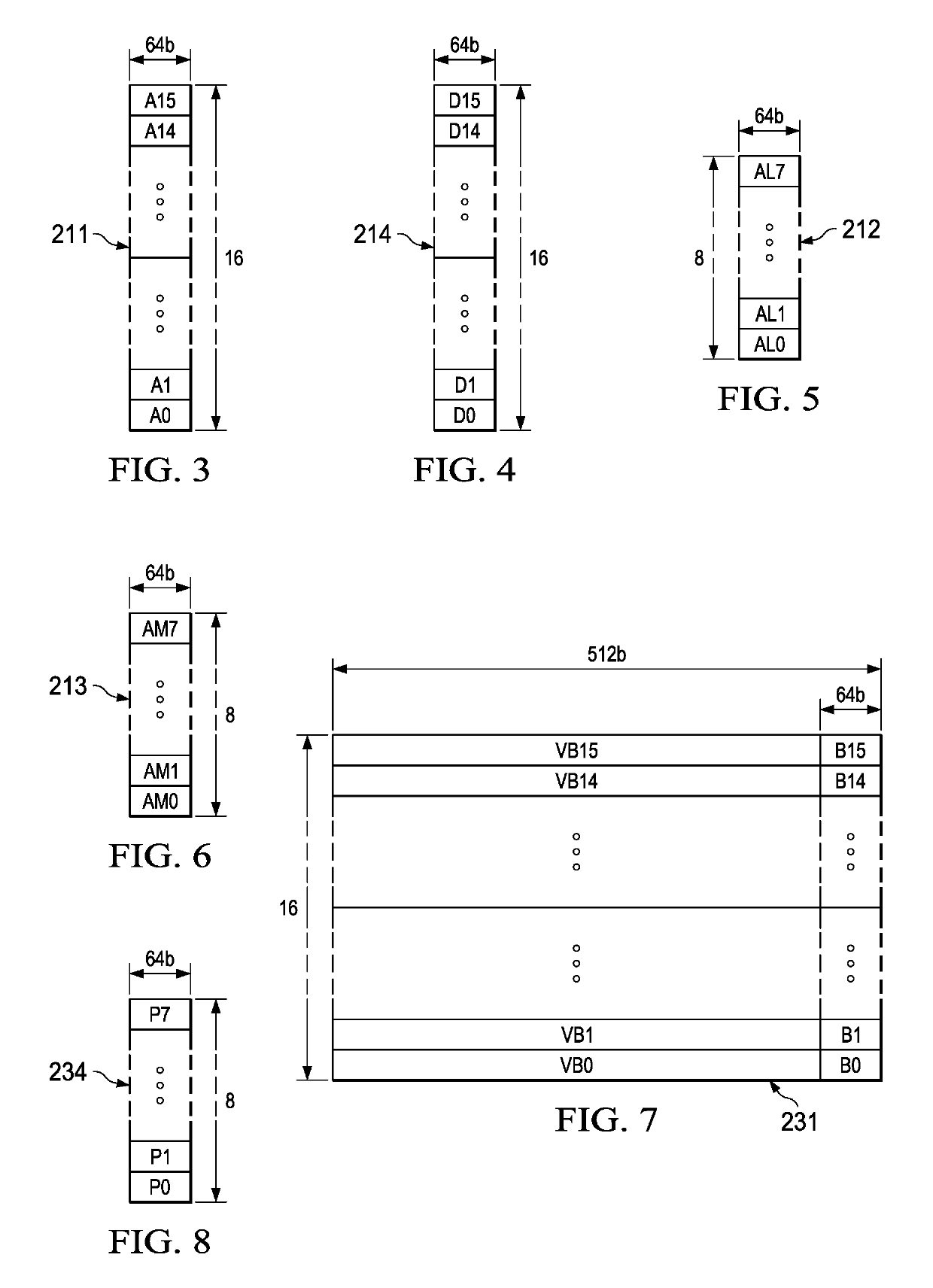
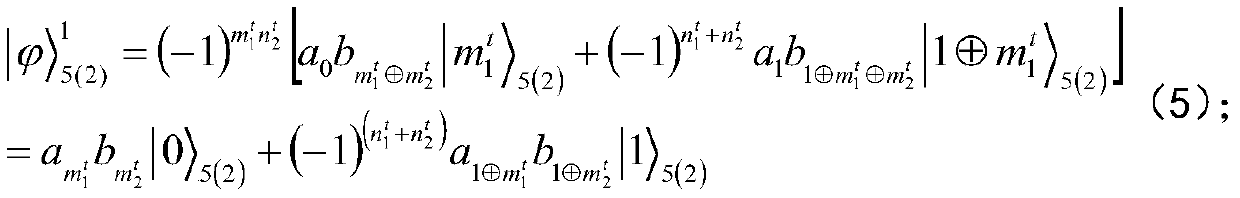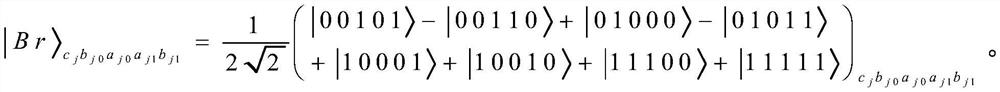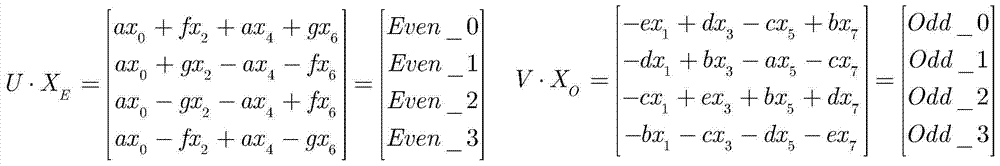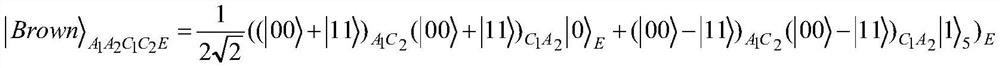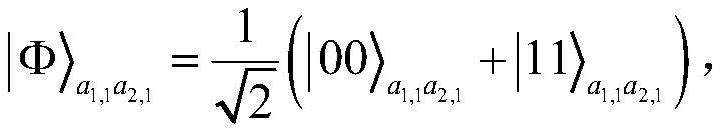Patents
Literature
31 results about "Butterfly network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
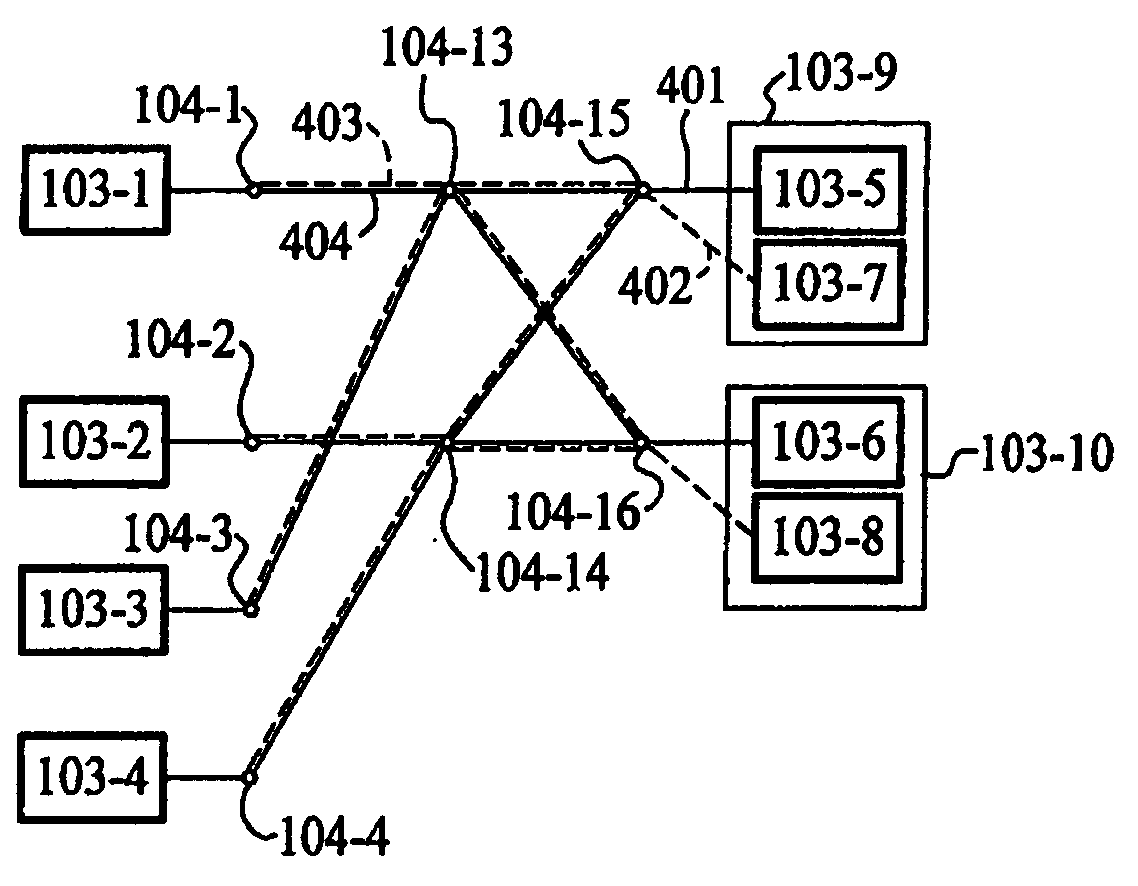
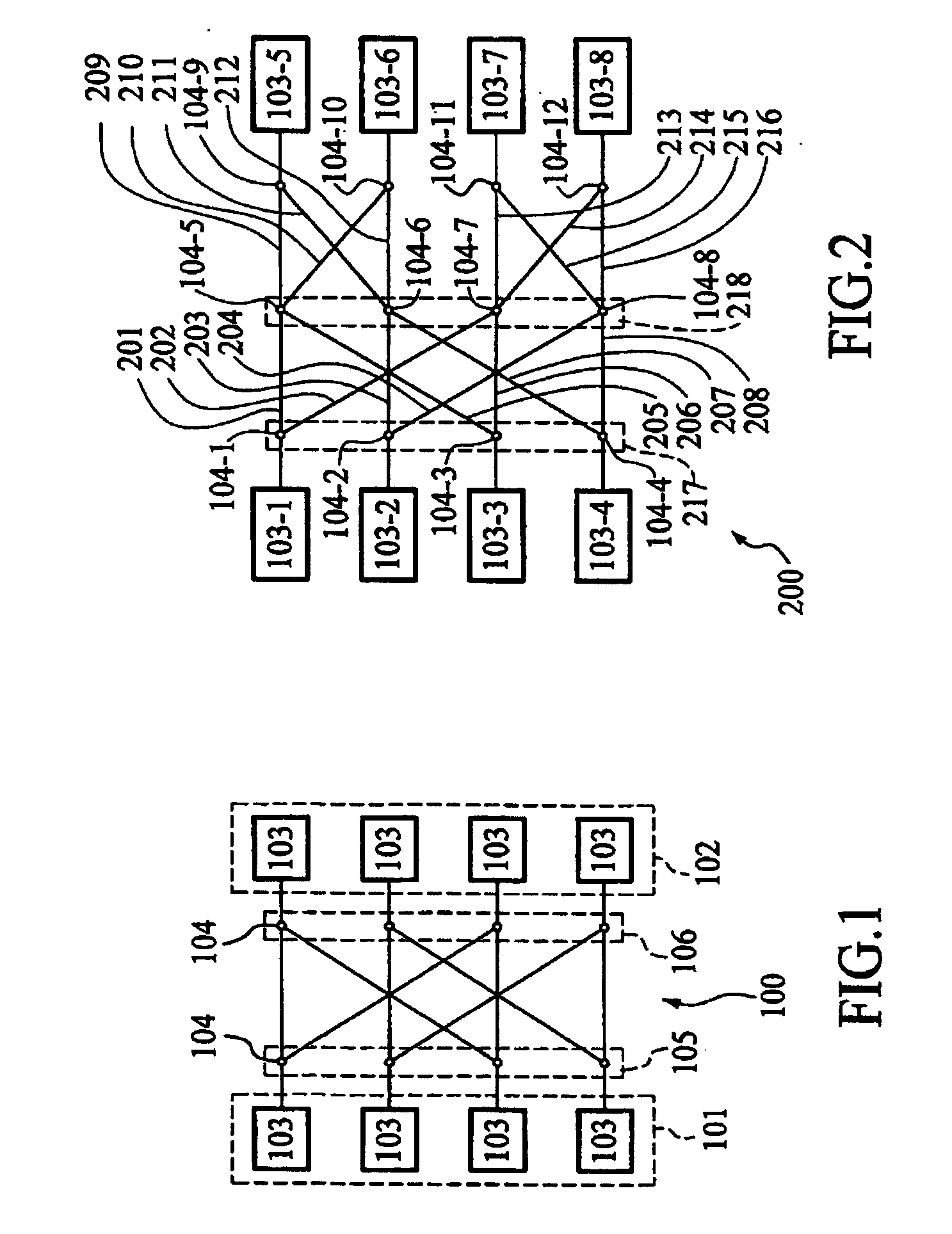
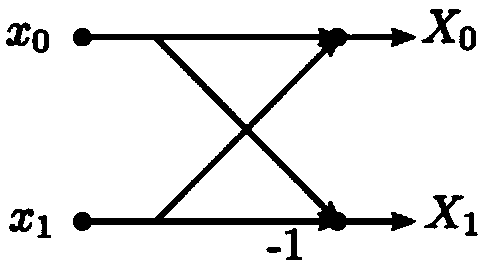
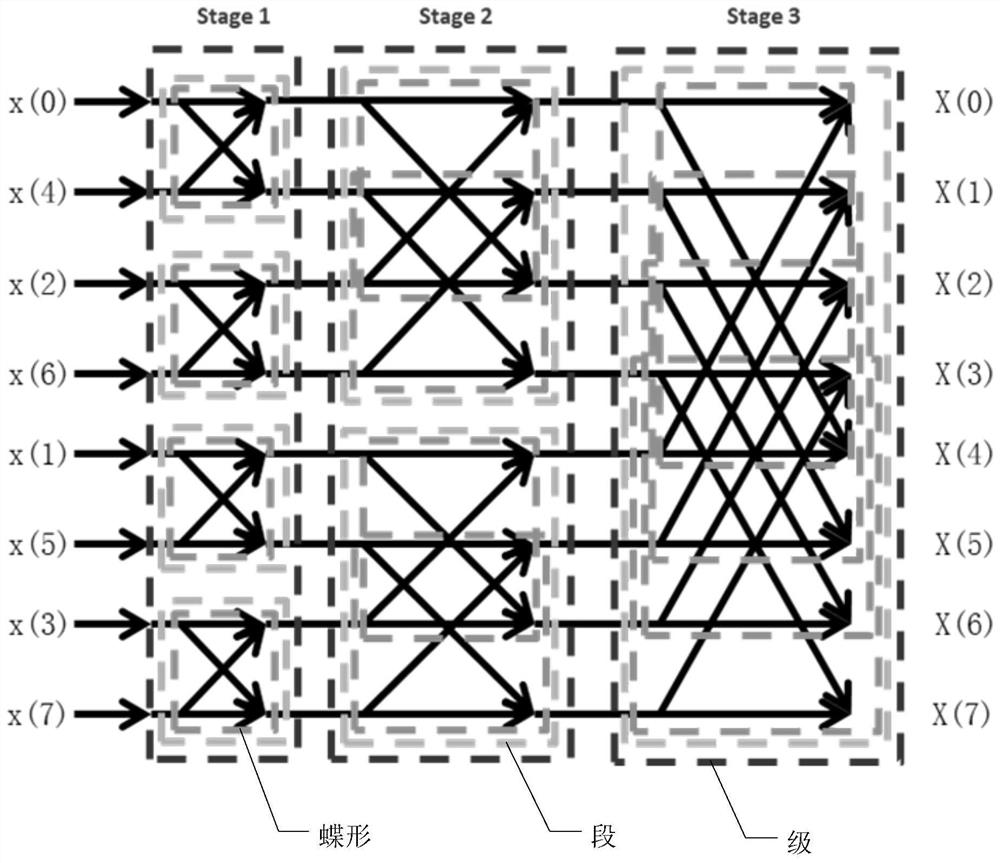
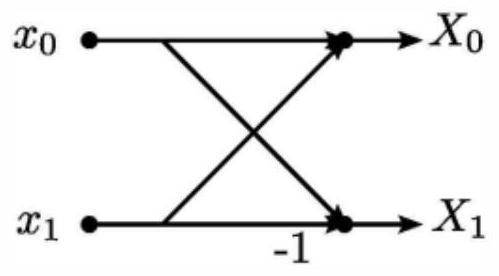
A butterfly network is a technique to link multiple computers into a high-speed network. This form of multistage interconnection network topology can be used to connect different nodes in a multiprocessor system. The interconnect network for a shared memory multiprocessor system must have low latency and high bandwidth unlike other network systems, like local area networks (LANs) or internet for three reasons...
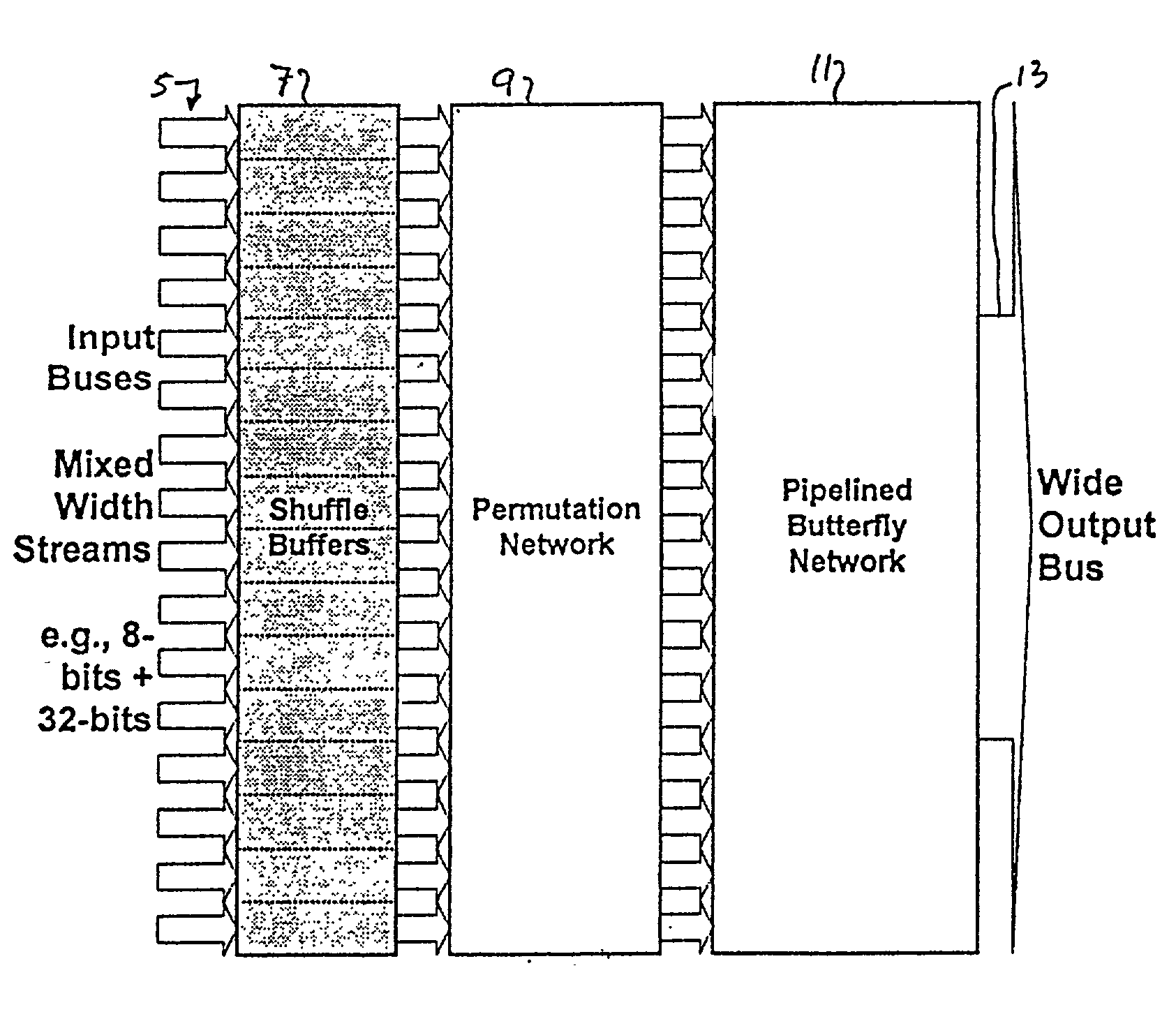
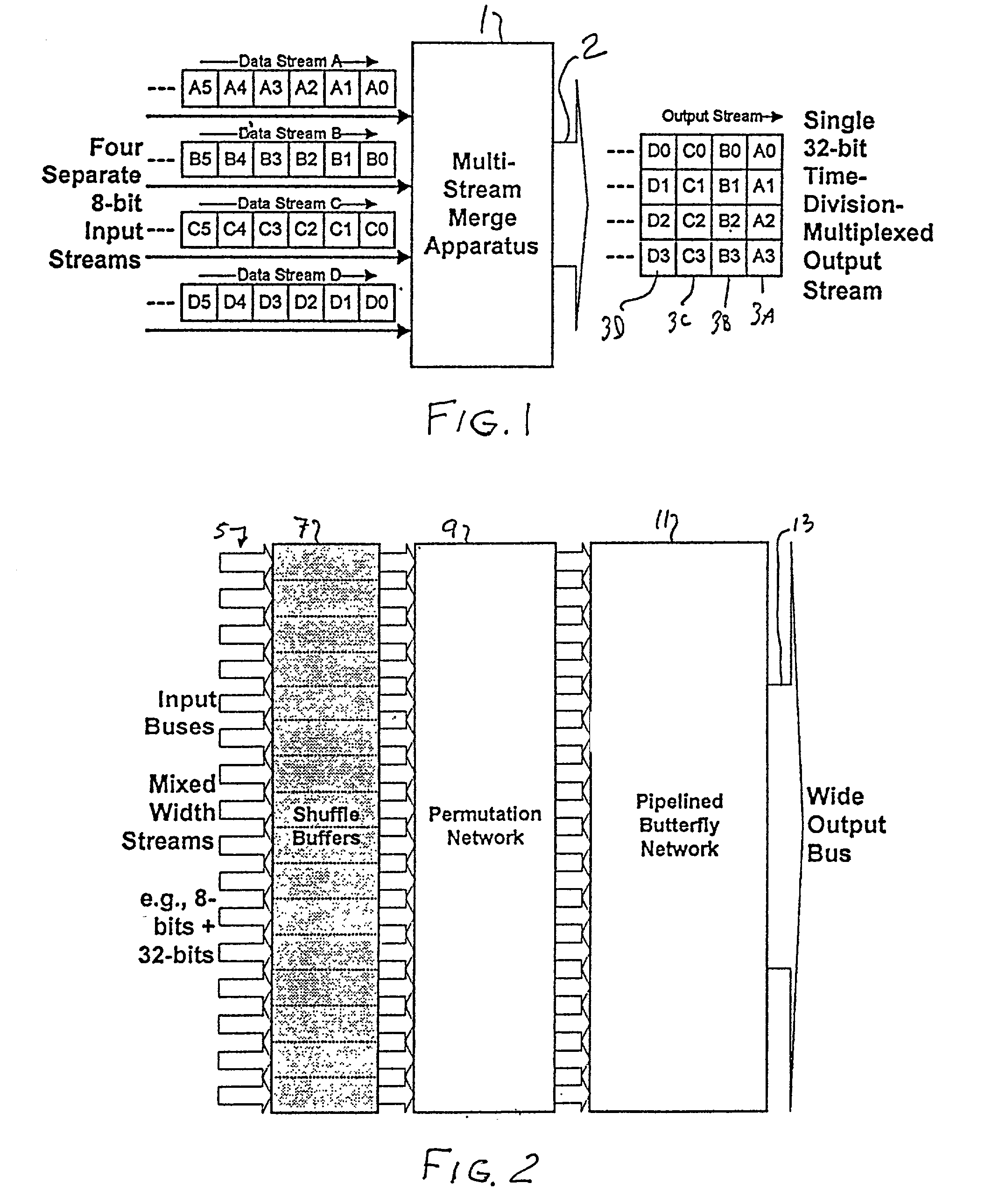
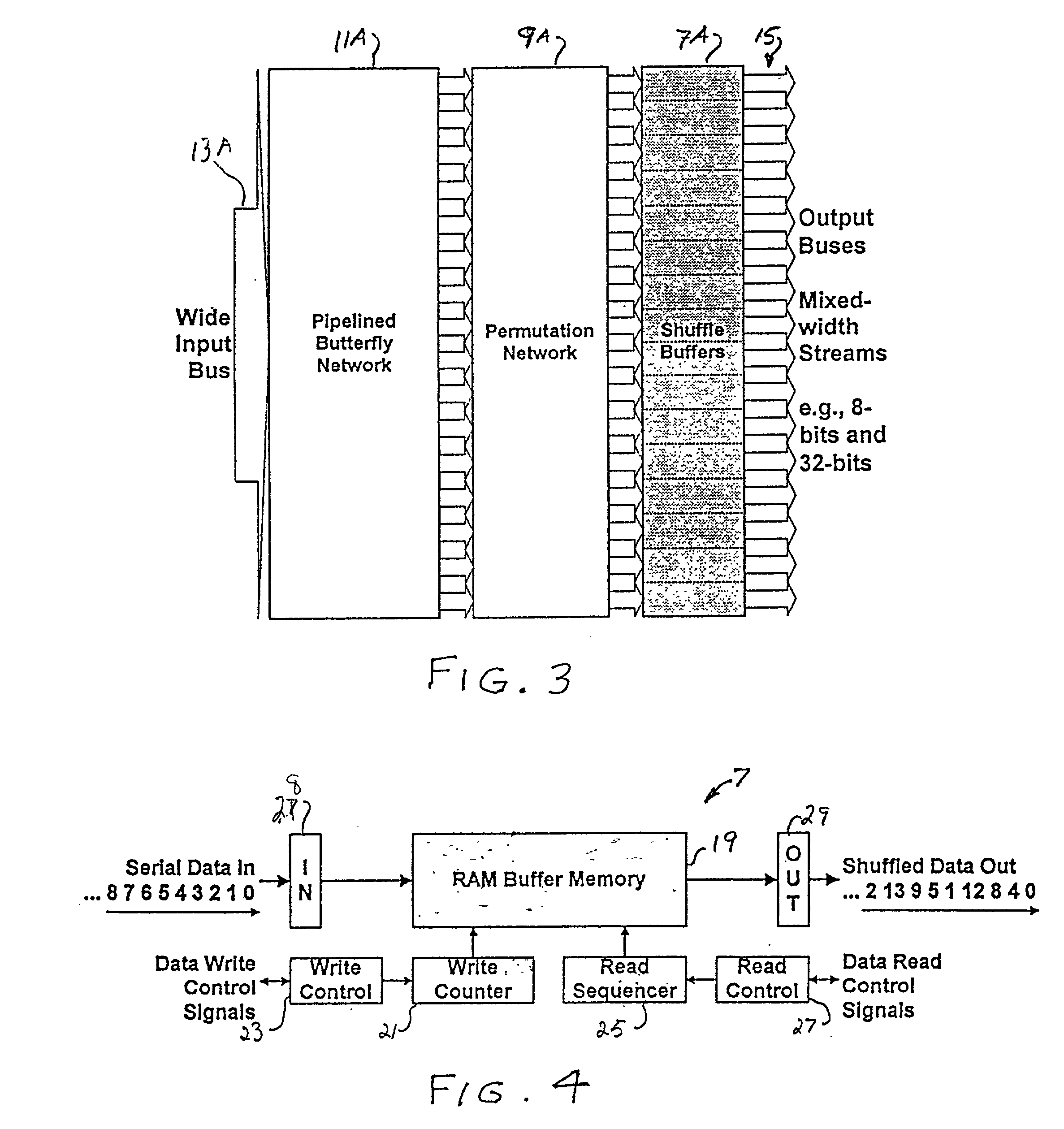
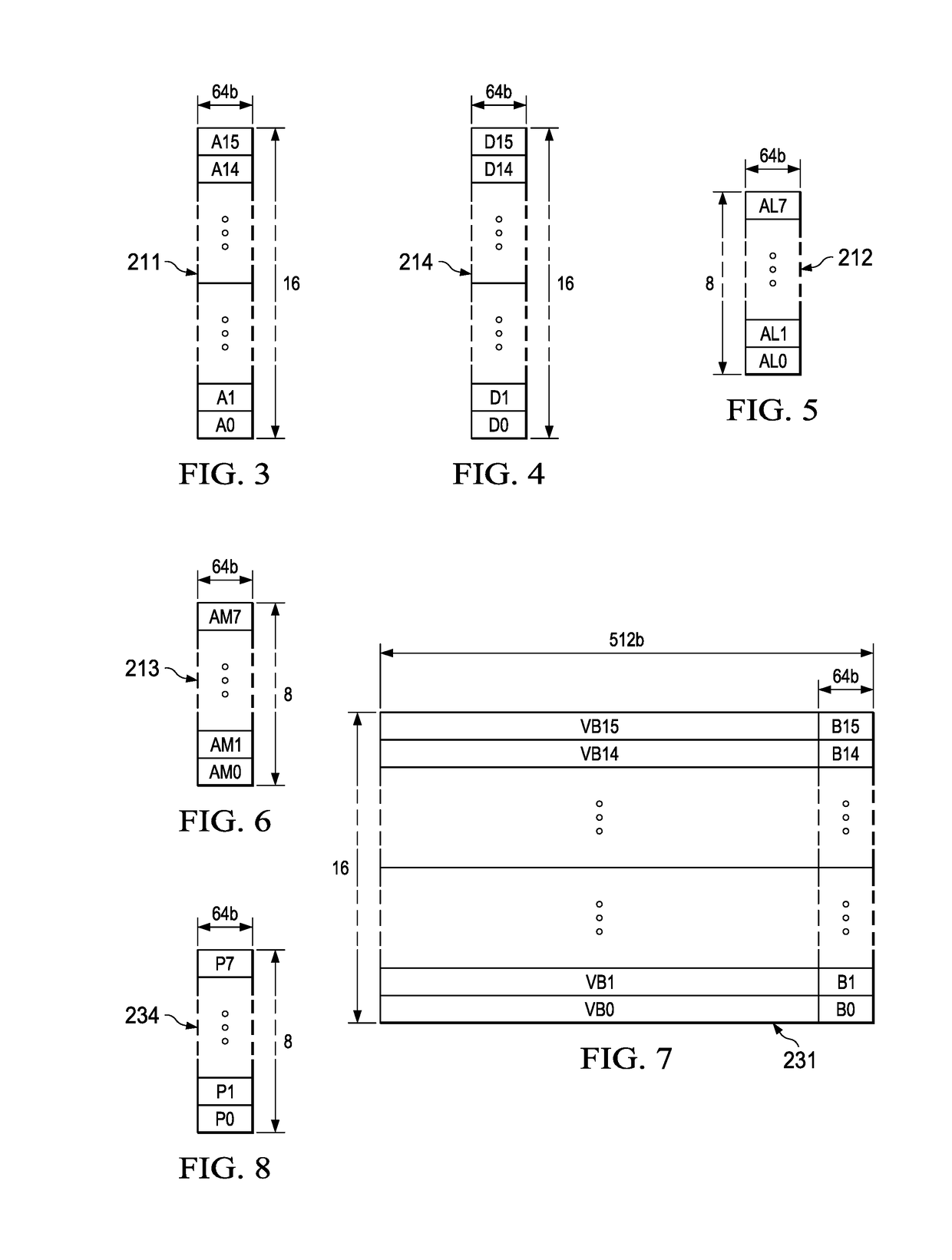
Multi-stream merge network for data width conversion and multiplexing
InactiveUS20030002474A1Less complexParallel/series conversionTime-division multiplexMultiplexingData stream
The present invention relates to a merging network for multiple data streams comprising a pipelined butterfly network. The pipelined butterfly network comprises an input network for receiving a plurality of data streams of mutually constant widths, each data stream having logically related data bits carried on contiguous signal lines, a butterfly network containing suitably interconnected register and multiplexer means for rearranging the received data streams into a time-multiplexed constant-width output data stream, the output data stream having a width equal to or greater than the sum of the widths of the input data streams, and an output network for providing the output data stream interleaved to an output bus.
Owner:PMC-SIERRA
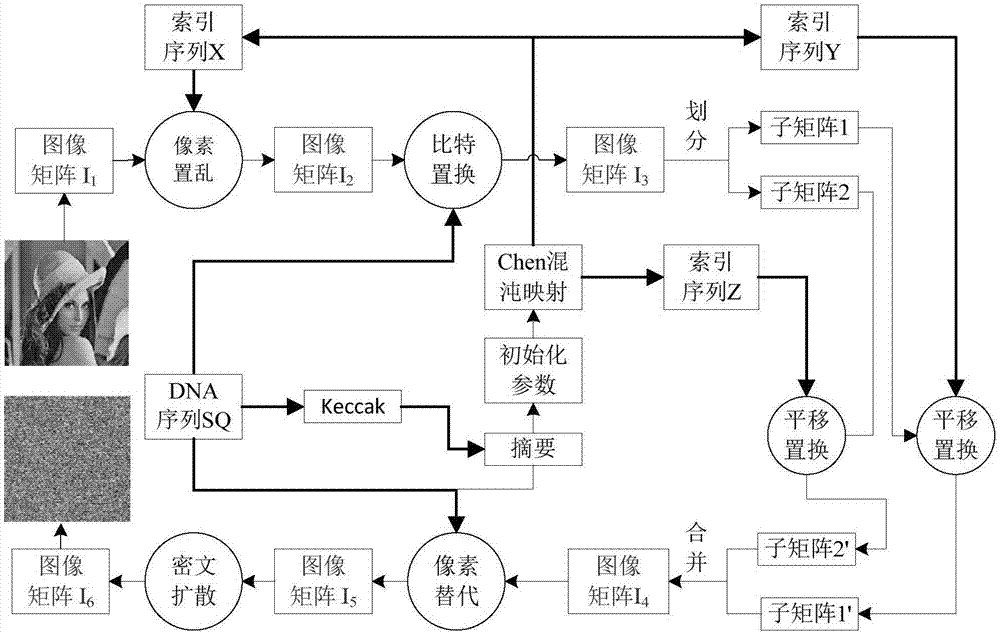
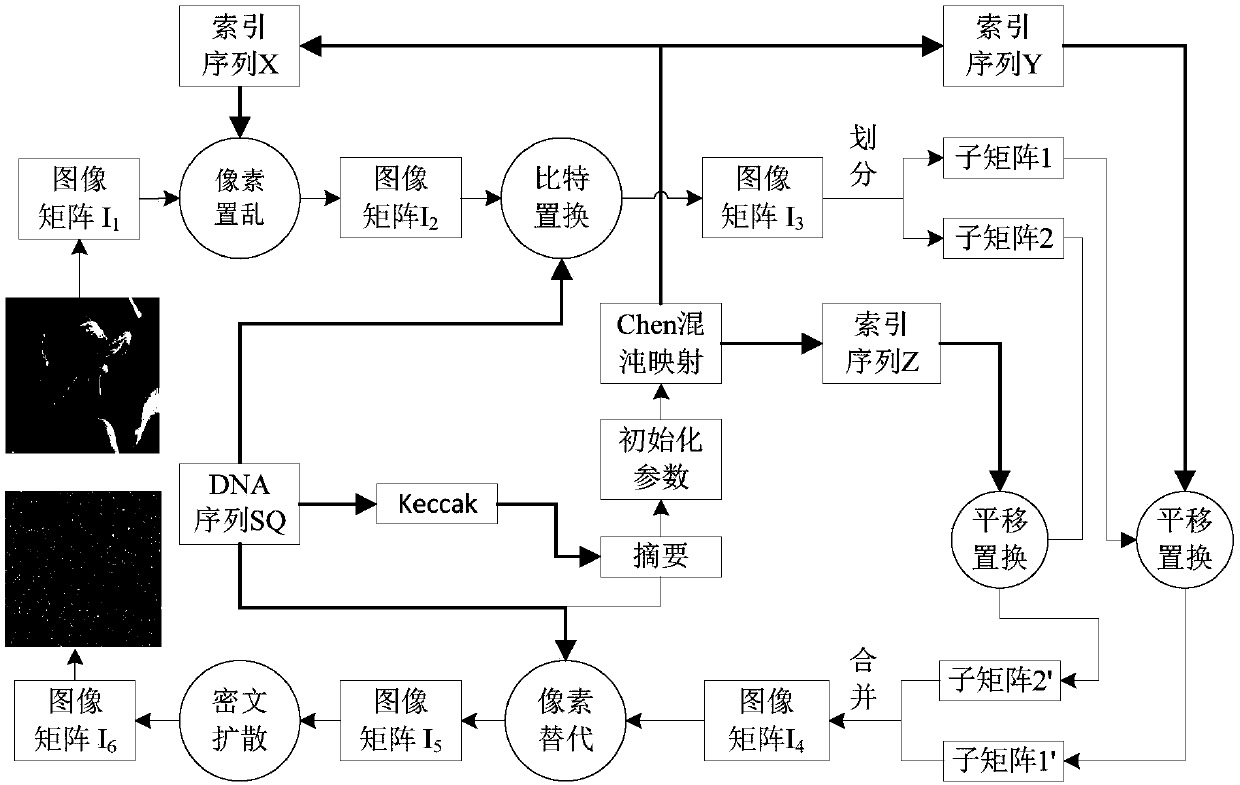
Chaotic image encryption method based on bit replacement and dynamic DNA coding
ActiveCN106952213AAchieve substitutionImprove featuresImage data processing detailsDiffusionCiphertext
The invention provides a chaotic image encryption method based on bit replacement and dynamic DNA coding. The objective of the invention is to solve the problem that security of chaotic encryption is affected by degradation of chaotic dynamics characteristics of an image encryption method based on a chaotic system in the prior art. The chaotic image encryption method comprises steps of firstly using the Keccak algorithm to calculate a hash value of a DNA sequence; based on the hash value, generating an initial state value of the chaotic mapping; by use of a hyperchaotic Chen system, generating a chaotic mapping index to carry out pixel position overall scrambling on an image; combining the Butterfly network to carry out bit position scrambling on each pixel, thereby achieving position grade scrambling; carrying out dynamic DNA coding on the image and combining the given DNA sequence to carry out XOR operation, thereby achieving replacing of the pixels; and finally, through the ciphertext feedback, further enhancing the chaotic and diffusion features. According to the invention, the chaotic image encryption method has big key space and is highly sensitive to a key, and capable of effectively resisting attacking operation of statistical analysis and exhaustion analysis.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Method and system for performing permutations using permutation instructions based on butterfly networks
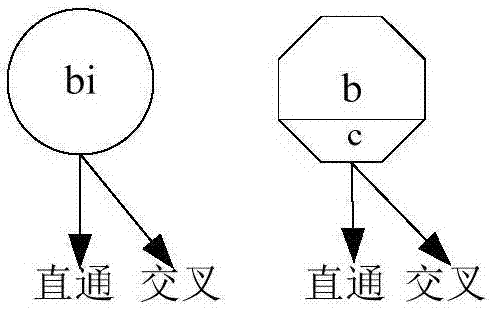
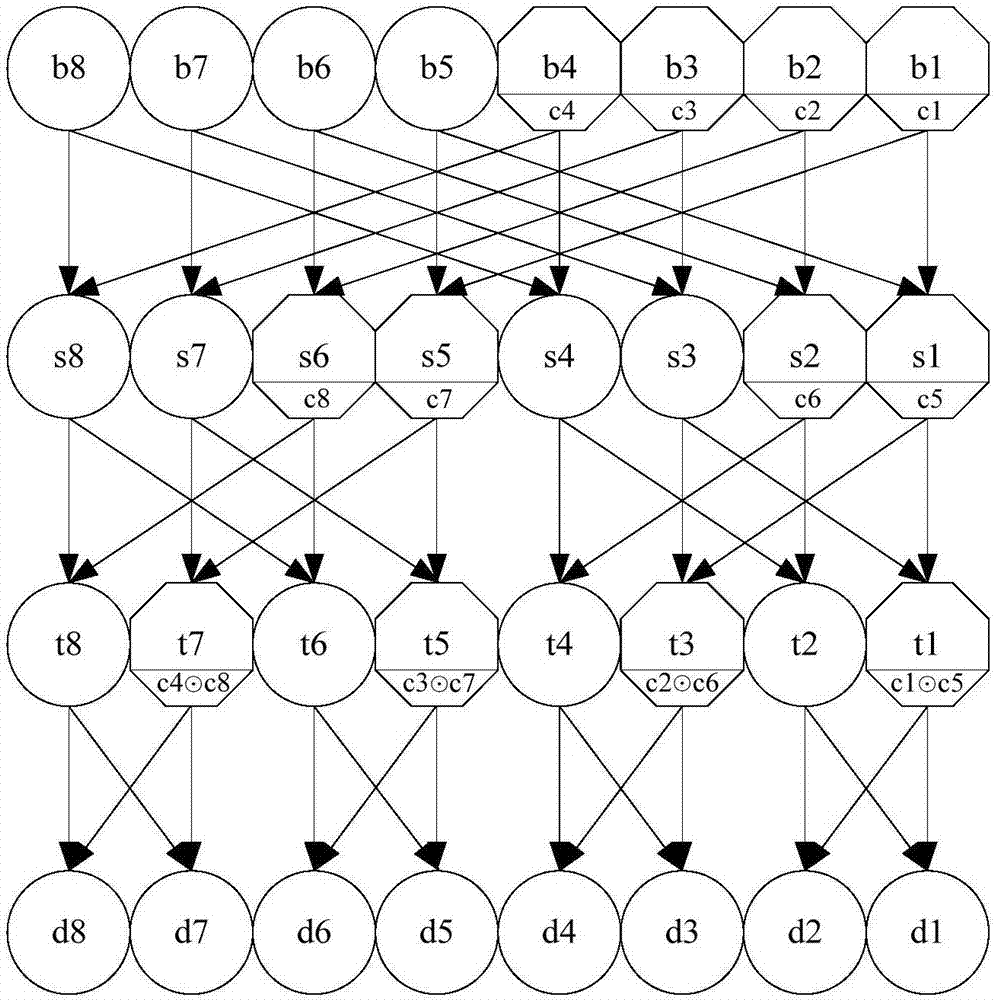
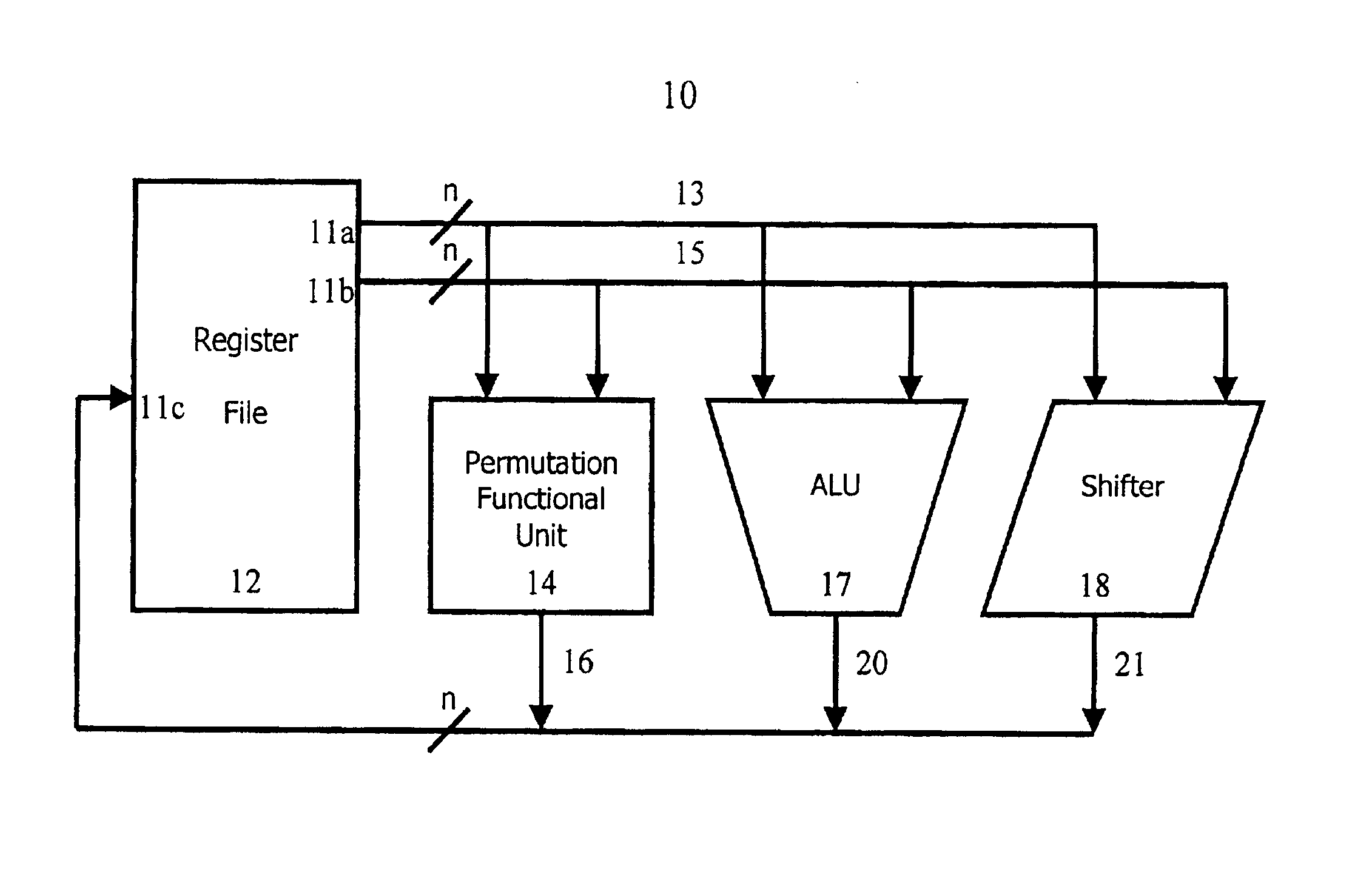
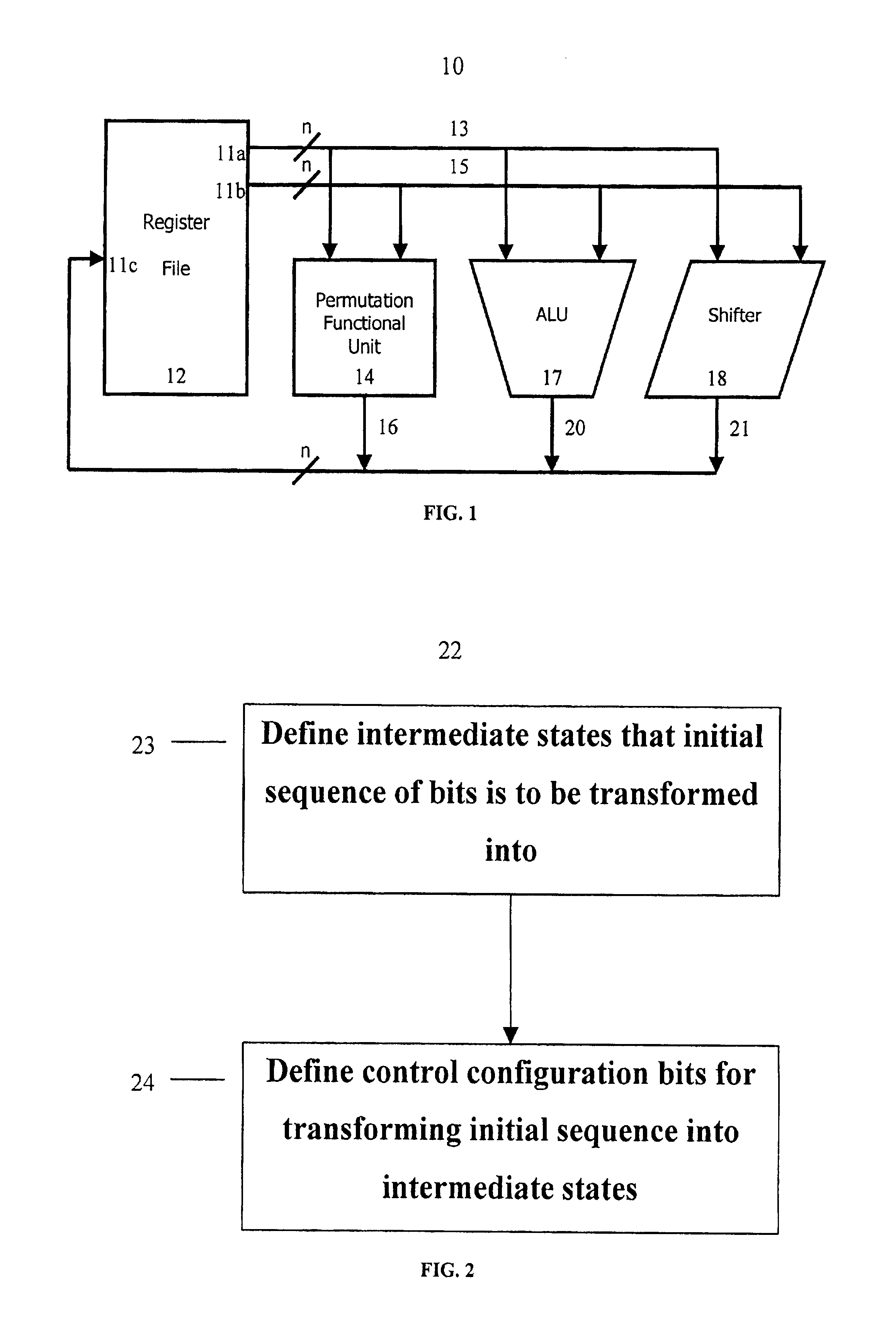
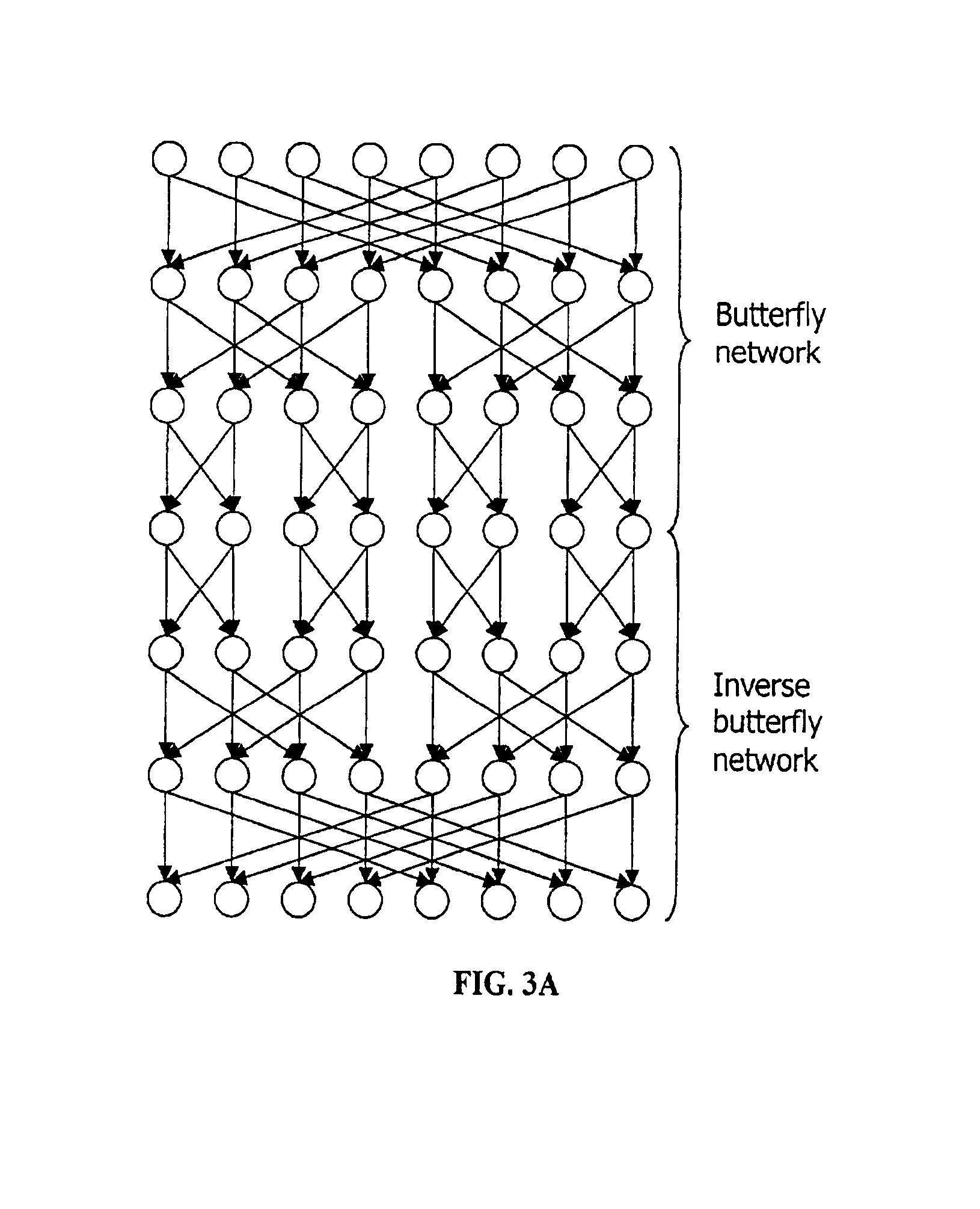
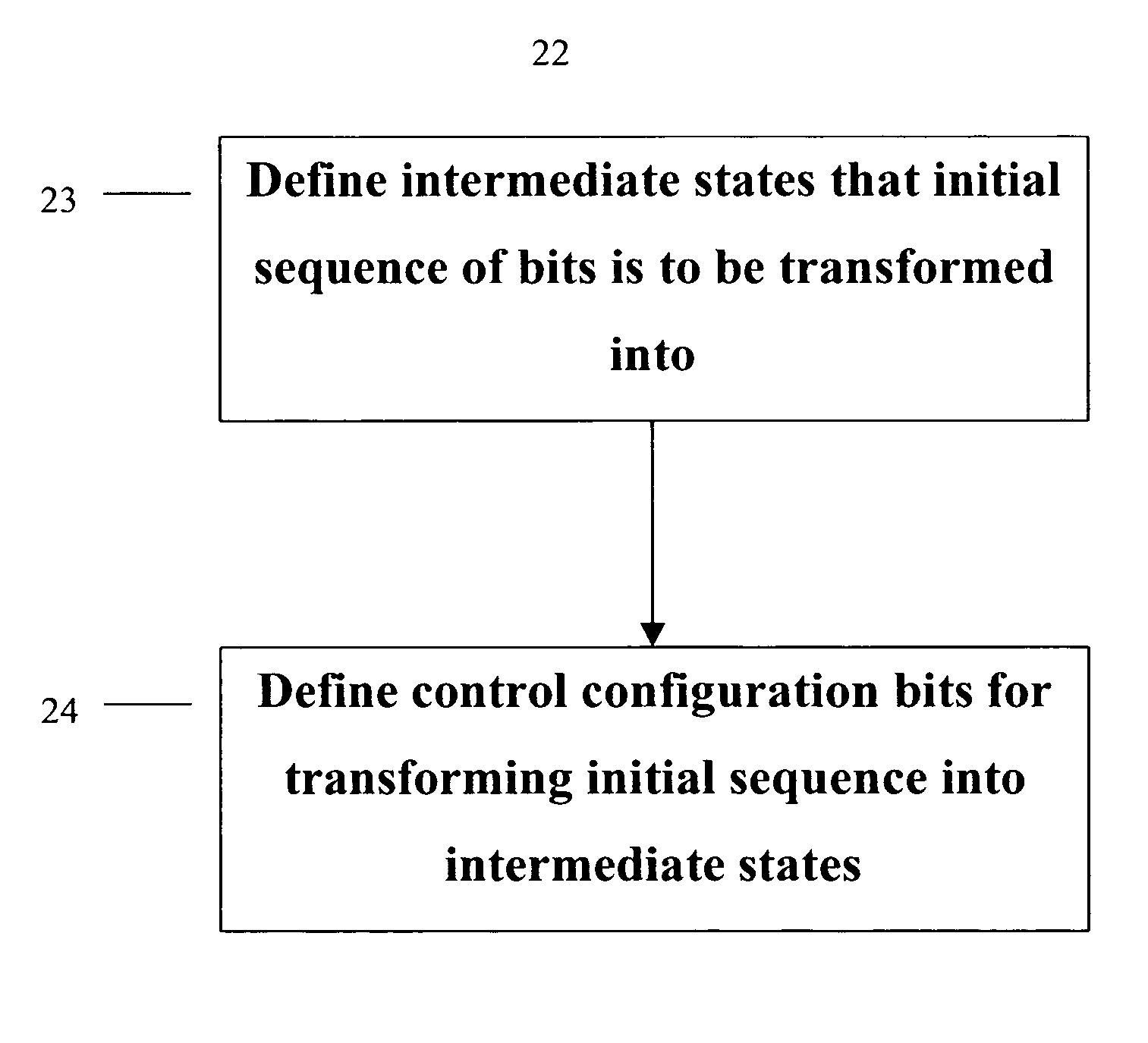
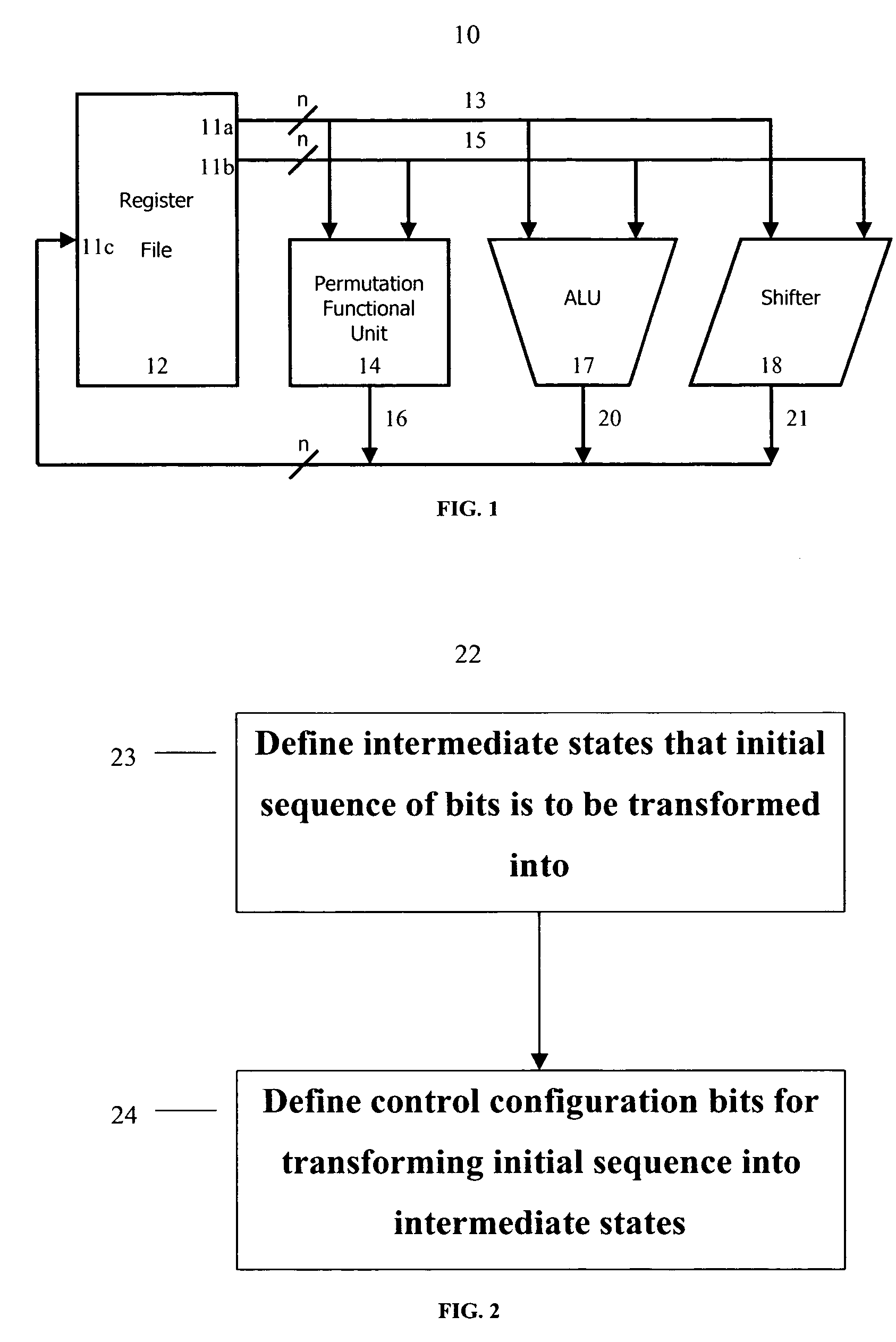
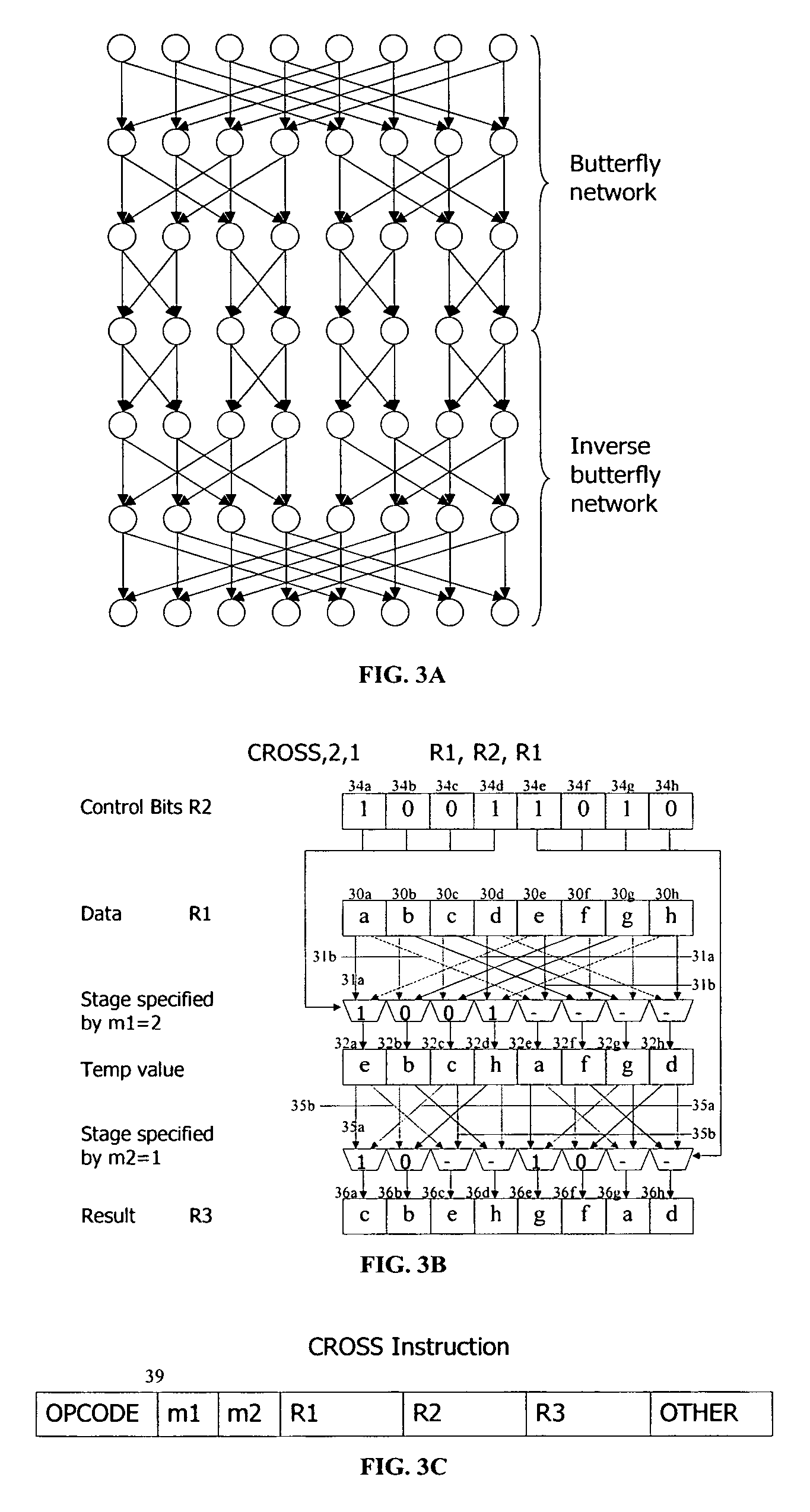
ActiveUS6922472B2Telegraphic message interchanged in timeSecret communicationComputer architectureInitial sequence
The present invention provides permutation instructions which can be used in software executed in a programmable processor for solving permutation problems in cryptography, multimedia and other applications. The permute instructions are based on a Benes network comprising two butterfly networks of the same size connected back-to-back. Intermediate sequences of bits are defined that an initial sequence of bits from a source register are transformed into. Each intermediate sequence of bits is used as input to a subsequent permutation instruction. Permutation instructions are determined for permitting the initial source sequence of bits into one or more intermediate sequence of bits until a desired sequence is obtained. The intermediate sequences of bits are determined by configuration bits. The permutation instructions form a permutation instruction sequence of at least one instruction. At most 21 gr / m permutation instructions are used in the permutation instruction sequence, where r is the number of k-bit subwords to be permuted, and m is the number of network stages executed in one instruction. The permutation instructions can be used to permute k-bit subwords packed into an n-bit word, where k can be 1, 2, . . . , or n bits, and k*r=n.
Owner:TELEPUTERS
Method and system for performing permutations using permutation instructions based on butterfly networks
InactiveUS20060039555A1Telegraphic message interchanged in timeSecret communicationComputer architectureBack-to-back connection
The present invention provides permutation instructions which can be used in software executed in a programmable processor for solving permutation problems in cryptography, multimedia and other applications. The permute instructions are based on a Benes network comprising two butterfly networks of the same size connected back-to-back. Intermediate sequences of bits are defined that an initial sequence of bits from a source register are transformed into. Each intermediate sequence of bits is used as input to a subsequent permutation instruction. Permutation instructions are determined for permitting the initial source sequence of bits into one or more intermediate sequence of bits until a desired sequence is obtained. The intermediate sequences of bits are determined by configuration bits. The permutation instructions form a permutation instruction sequence of at least one instruction. At most 21gr / m permutation instructions are used in the permutation instruction sequence, where r is the number of k-bit subwords to be permuted, and m is the number of network stages executed in one instruction. The permutation instructions can be used to permute k-bit subwords packed into an n-bit word, where k can be 1, 2, . . . , or n bits, and k*r=n.
Owner:LEE RUBY B +2
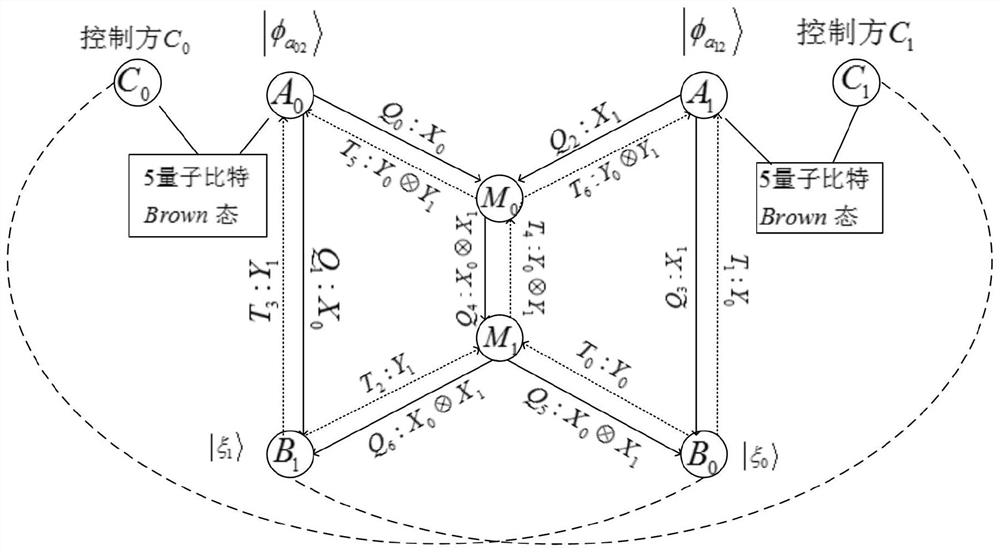
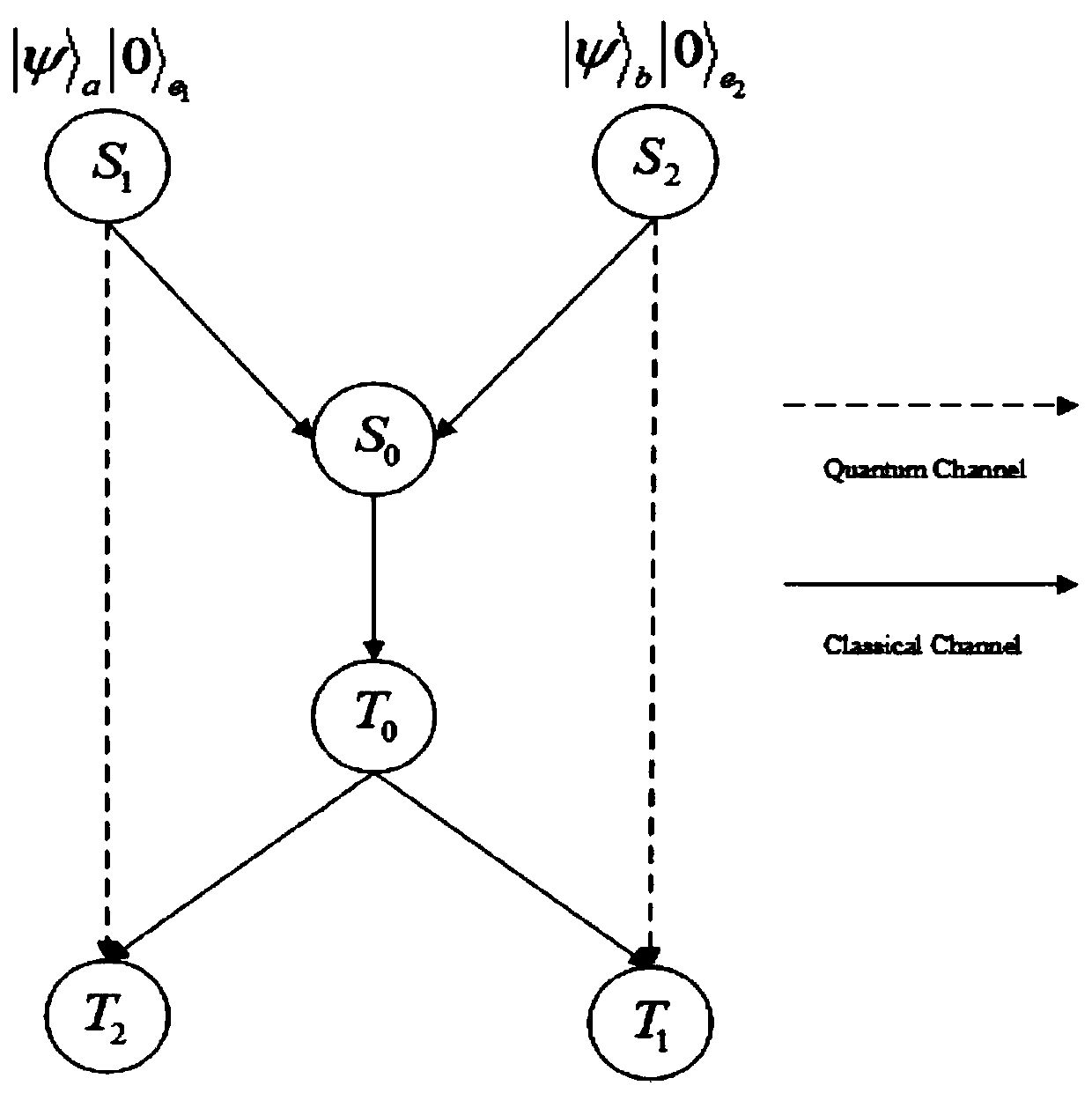
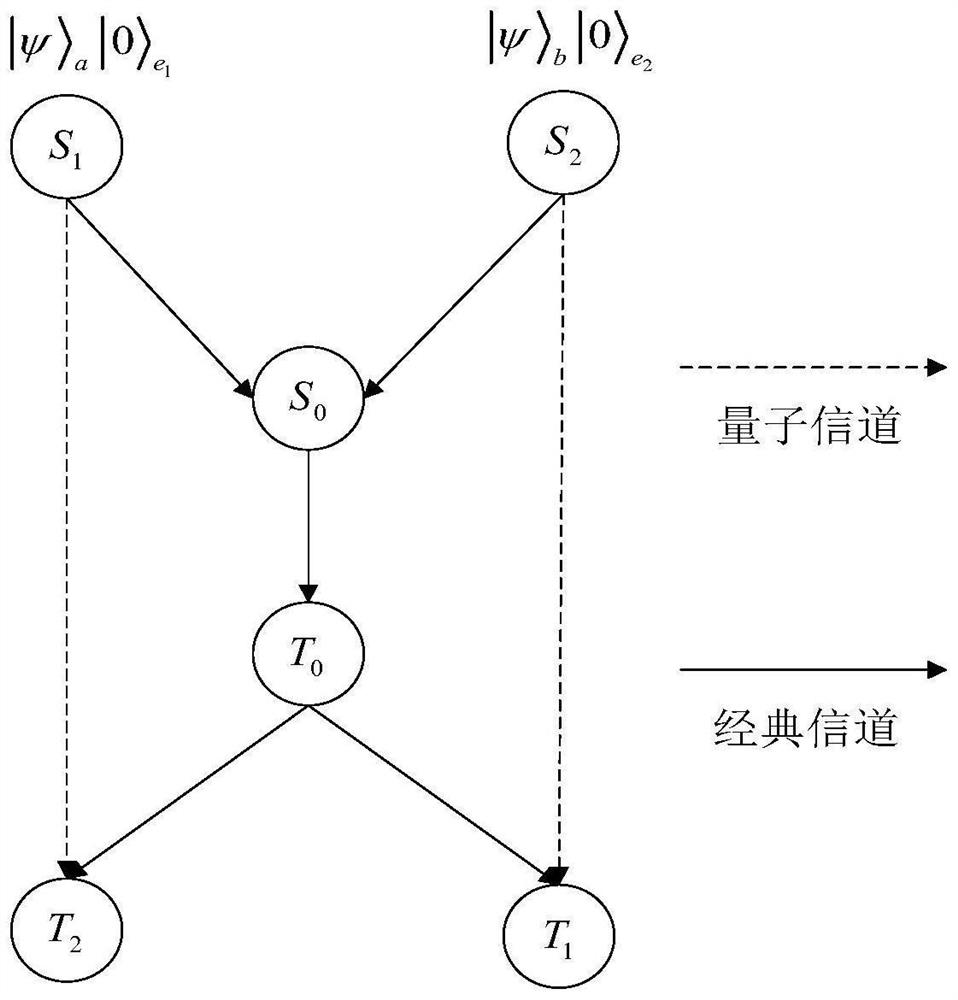
Bidirectional single-bit state preparation method based on Brown state and network coding
ActiveCN111510289AAchieve bidirectional preparationReduce resource consumptionKey distribution for secure communicationTelecommunicationsNetwork code
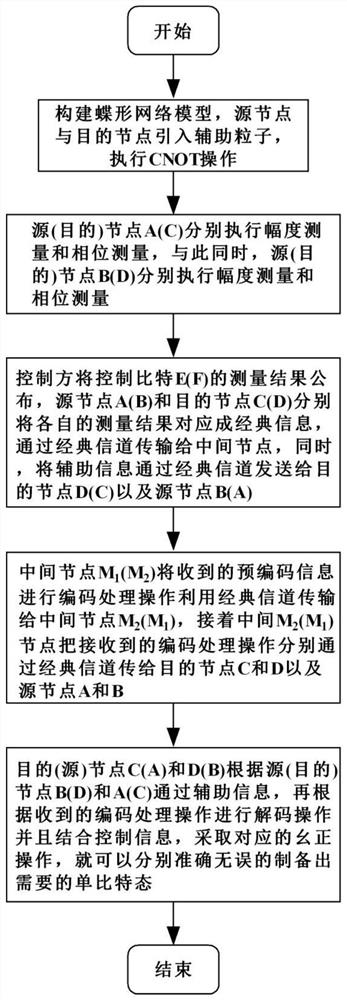
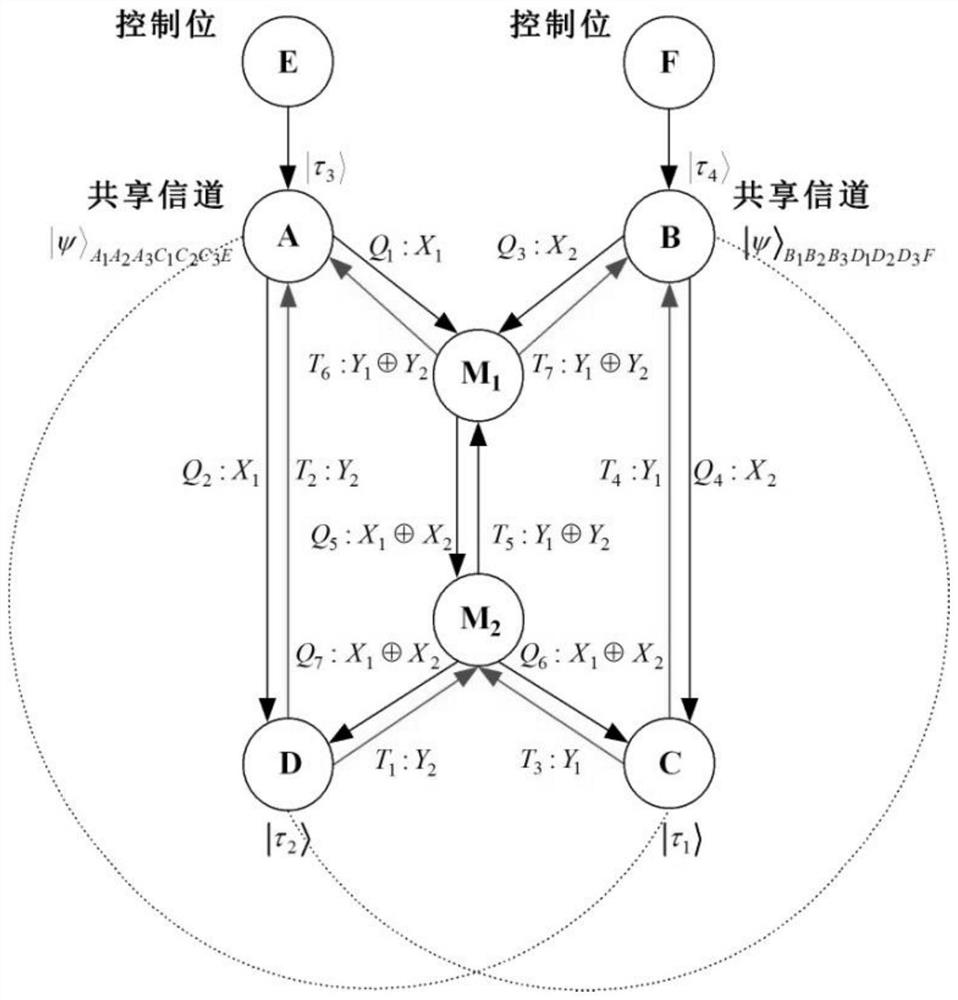
The invention discloses a bidirectional single-bit state preparation method based on a Brown state and network coding. According to the bidirectional single-bit state preparation method, state preparation based on the Brown state and network coding are combined for the first time, cross transmission is carried out between a sender and a receiver through a butterfly network and a five-bit Brown state, and an arbitrary single-bit quantum state scheme is prepared bidirectionally. The bidirectional single-bit state preparation method is mainly characterized in that a quantum network coding model is established through state preparation on the basis of a butterfly network coding protocol. A channel shared by a source node and a destination node is obtained by adding auxiliary particles in the five-bit Brown state and performing channel modulation through CNOT operation. The transmission of known information in the whole network model is realized, compared with a quantum stealth transmissionscheme, the resource consumption is lower, the transmission efficiency reaches a higher level, the bidirectional preparation is innovatively realized, and the communication capacity reaches four bitsper round. The bidirectional single-bit state preparation method has a wide application prospect in the technical field of quantum communication networks.
Owner:SUZHOU UNIV
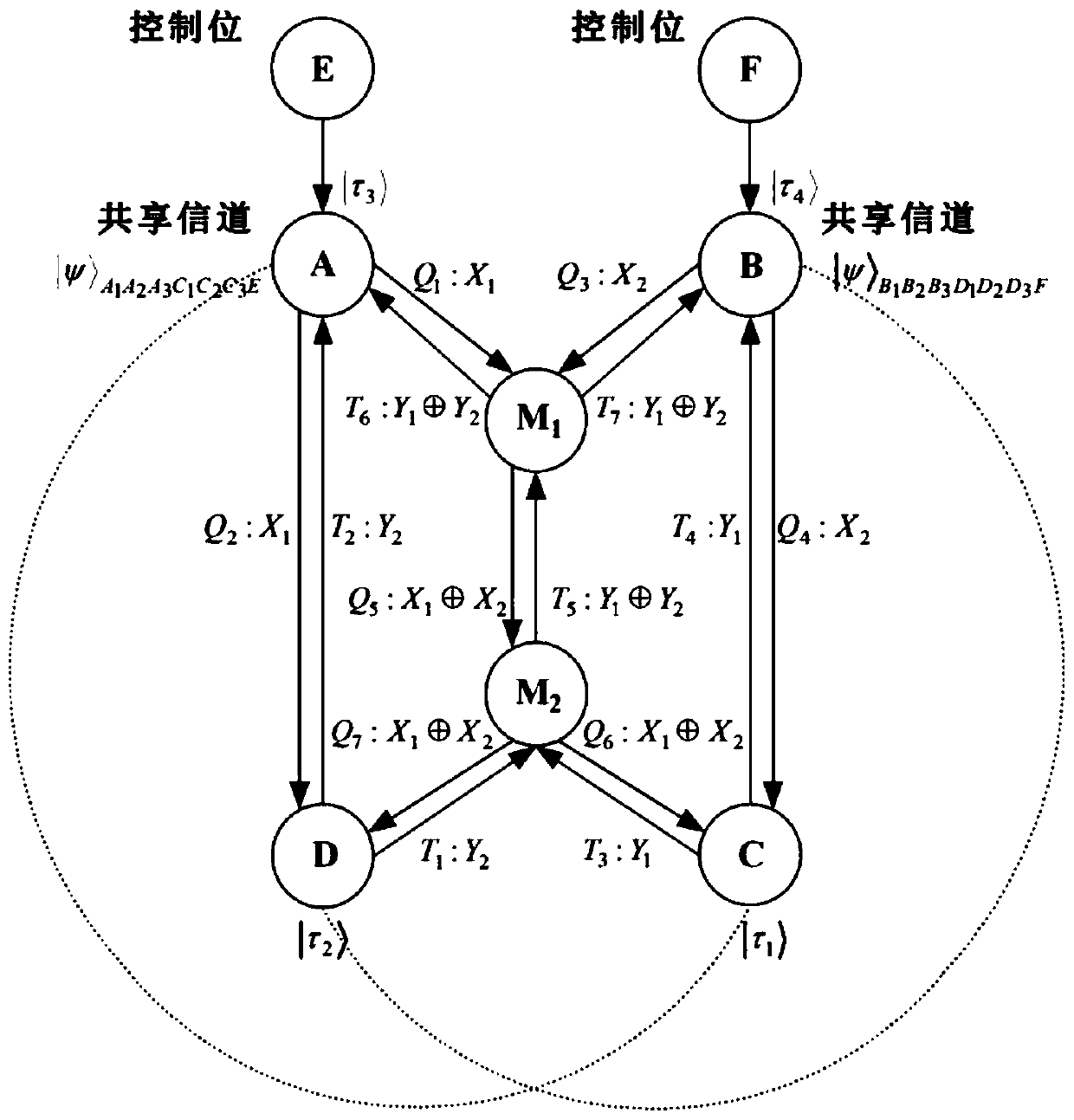
Two-stage quantum state cooperative multicast method based on butterfly network structure
InactiveCN110768793ASave on classic communication costsGuaranteed confidentialityKey distribution for secure communicationSite diversityNetwork structureEngineering
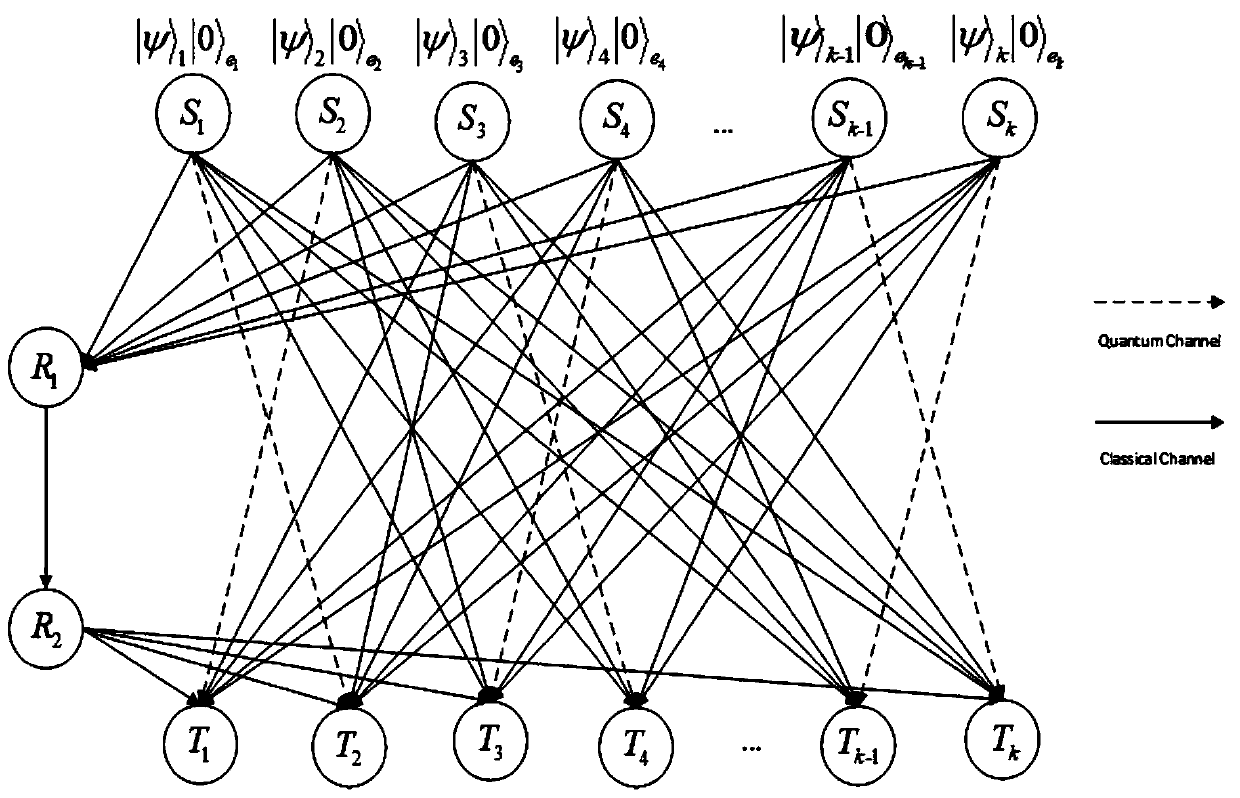
The invention discloses a two-stage quantum state cooperative multicast method based on a butterfly network structure, which belongs to the field of multi-party quantum secret communication. The two-stage quantum state cooperative multicast method comprises the following steps: two source nodes in a sender are measured by using particles with entangled states to obtain a measurement result and anentangled state particle collapse state; the intermediate node C1 corrects the coefficient subscripts of the collapsed state of the entangled state particles by using the measurement result to obtaina corrected state; the source node sends the correction state to a target node through a side channel; the intermediate node C1 sends the measurement result to an intermediate node C2 through a bottleneck channel, and the intermediate node C2 generates a classic bit by using the measurement result and sends the classic bit to a target node; the target node performs unitary operation on a correction state by using the classic bit, so that the target node has the same quantum state, and cooperative multicast of two stages of quantum states is completed; the two target nodes in the butterfly network can obtain the same quantum state with a determined probability.
Owner:国网甘肃省电力公司信息通信公司 +3
Address generation for multiple access of memory
Owner:NOKIA TECHNOLOGLES OY
Multiple access for parallel turbo decoder
ActiveCN101682338ACode conversionError correction/detection by combining multiple code structuresMemory addressMemory bank
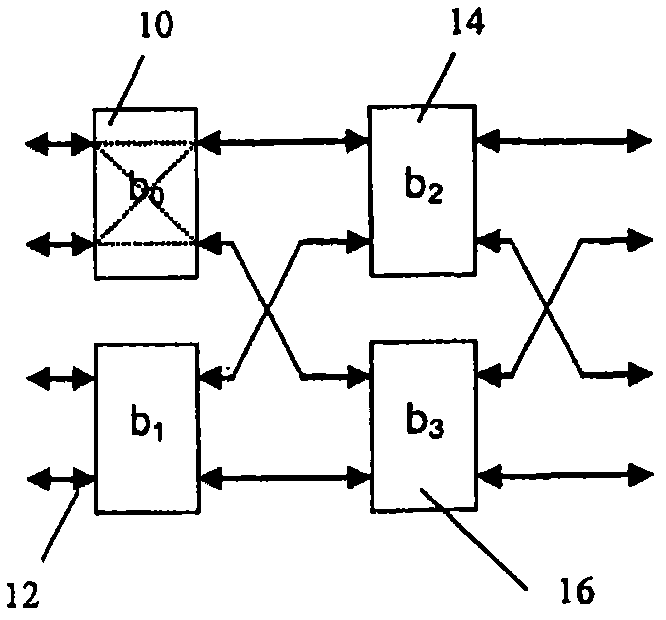
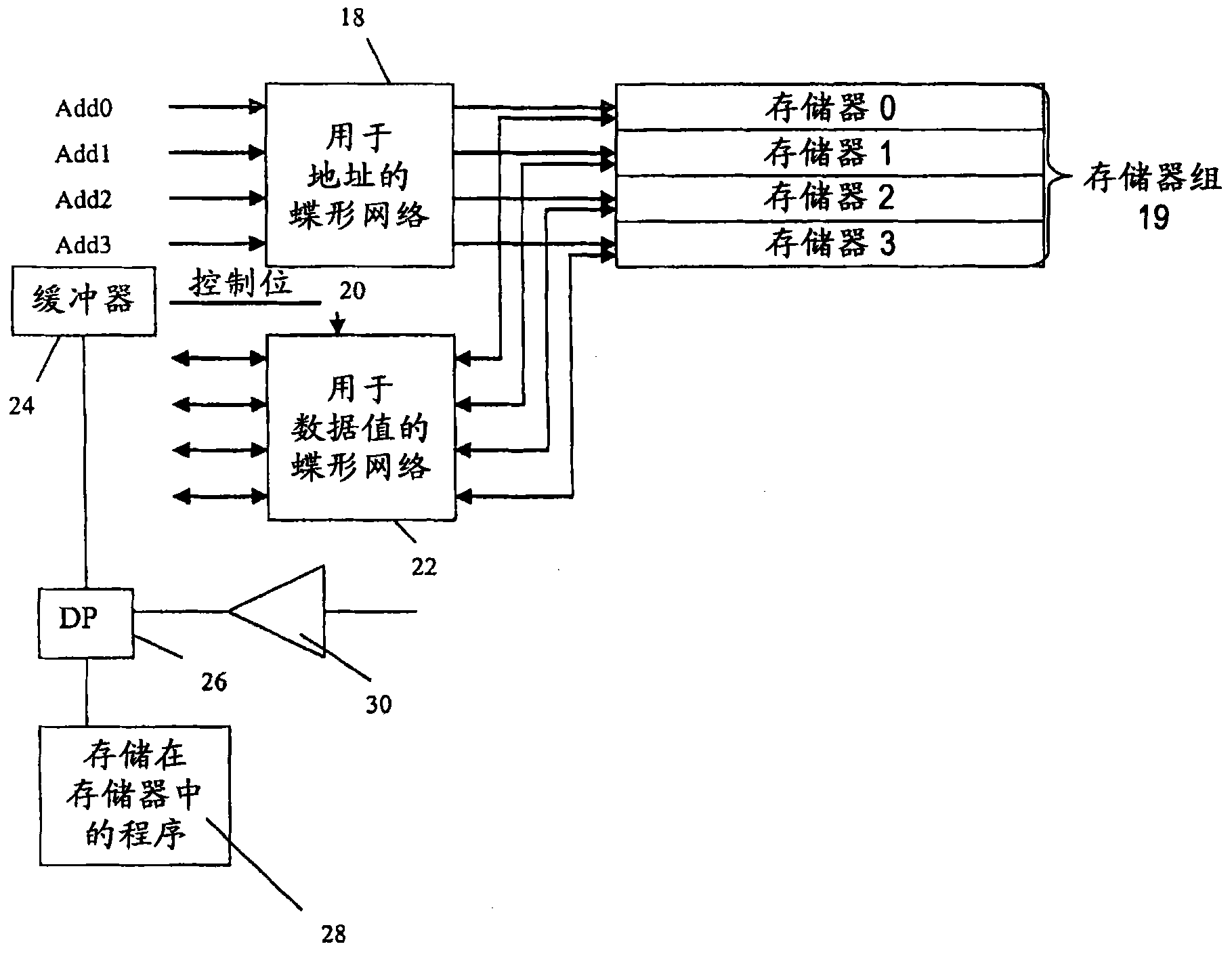
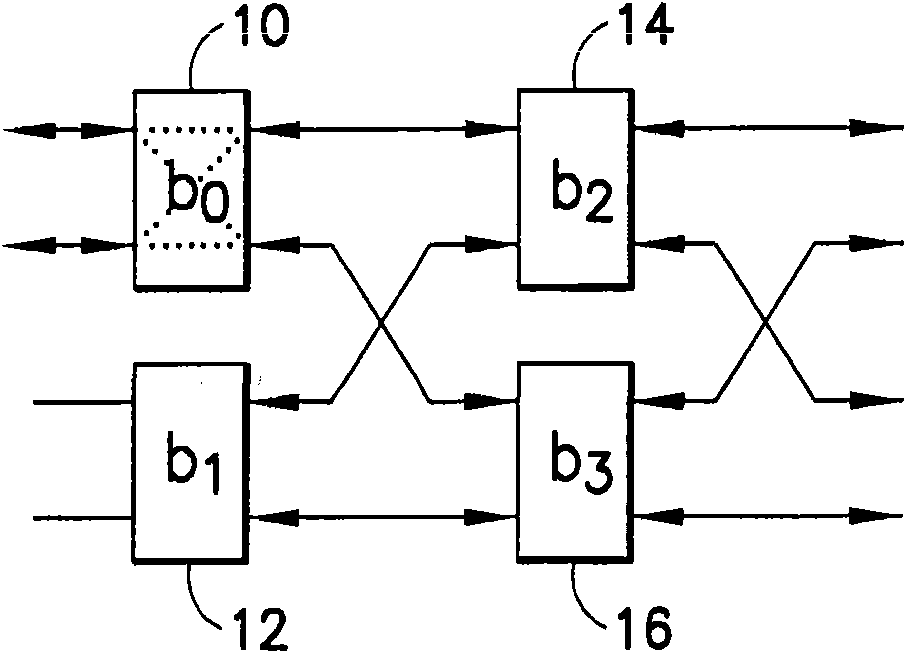
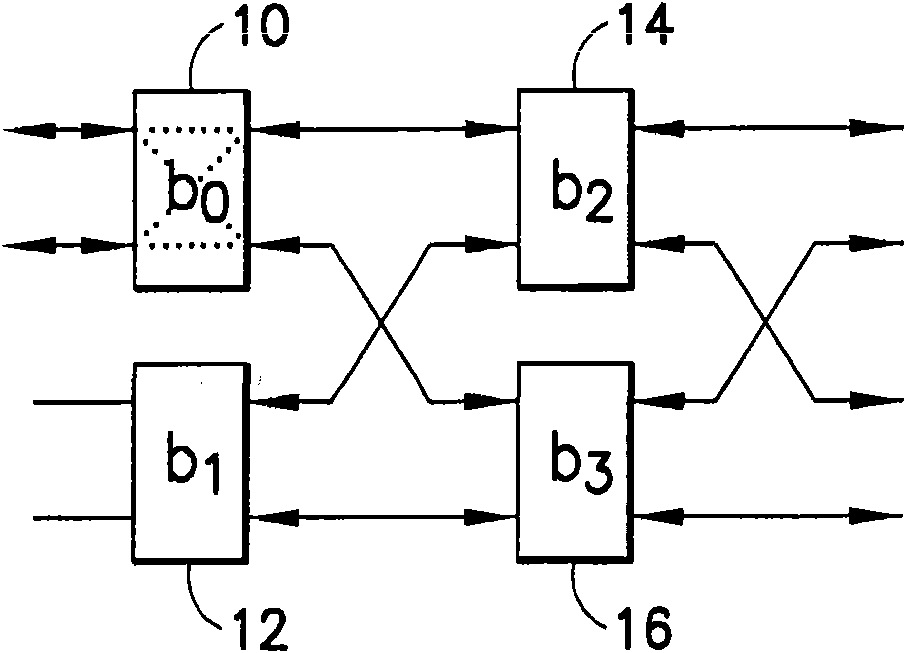
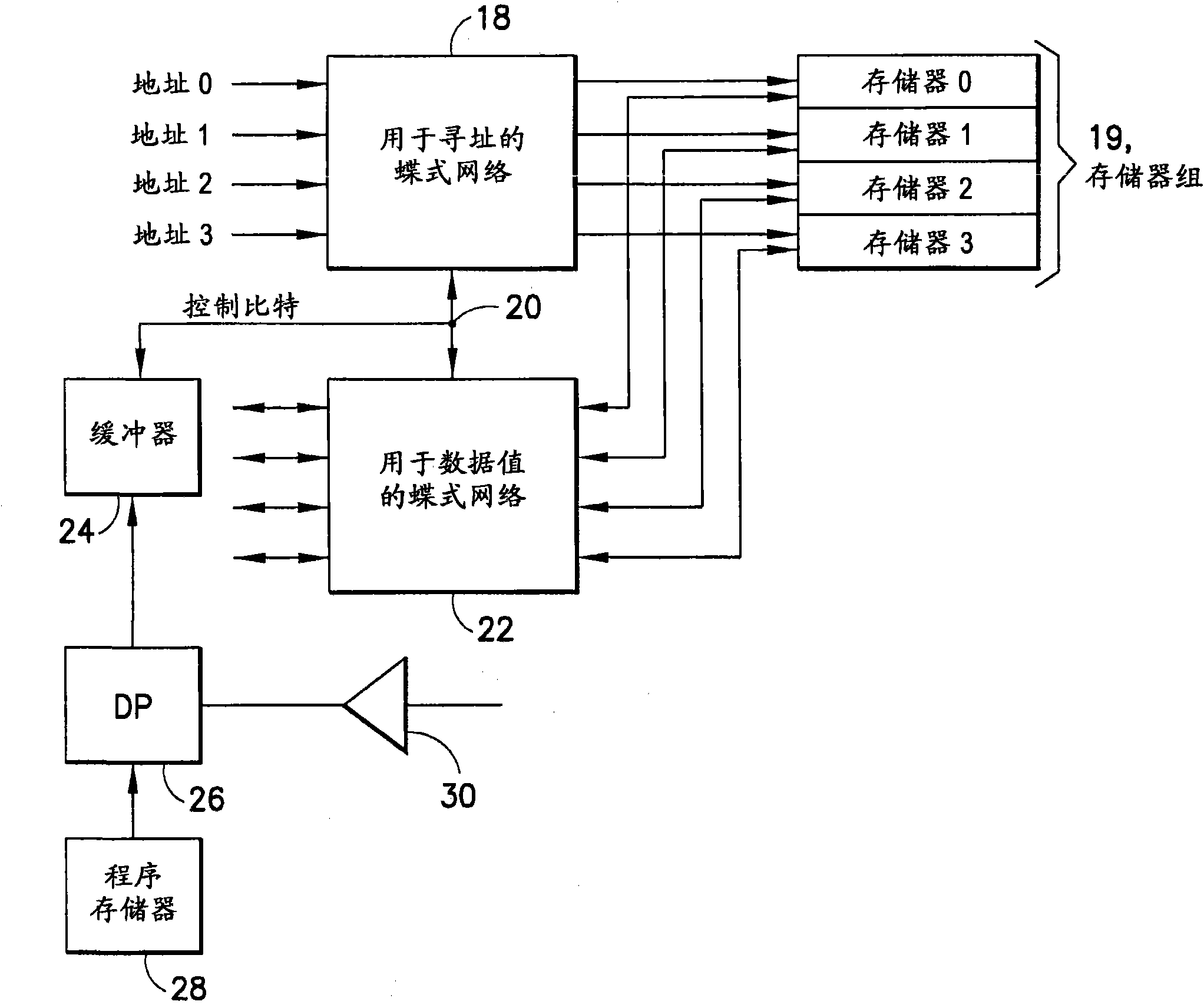
A memory bank contains a plurality of memories, a first Butterfly network is configured to apply memory addresses to the memory bank, and a second Butterfly network is configured to pass data to or from the memory bank. A control signal is generated for the first and second Butterfly networks in accordance with a multiple access rule to enable parallel access to the memory bank, without memory access conflict, for one of a linear order and an interleaved order. The method and apparatus is particularly advantageous for use in turbo decoding.
Owner:NOKIA TECHNOLOGLES OY
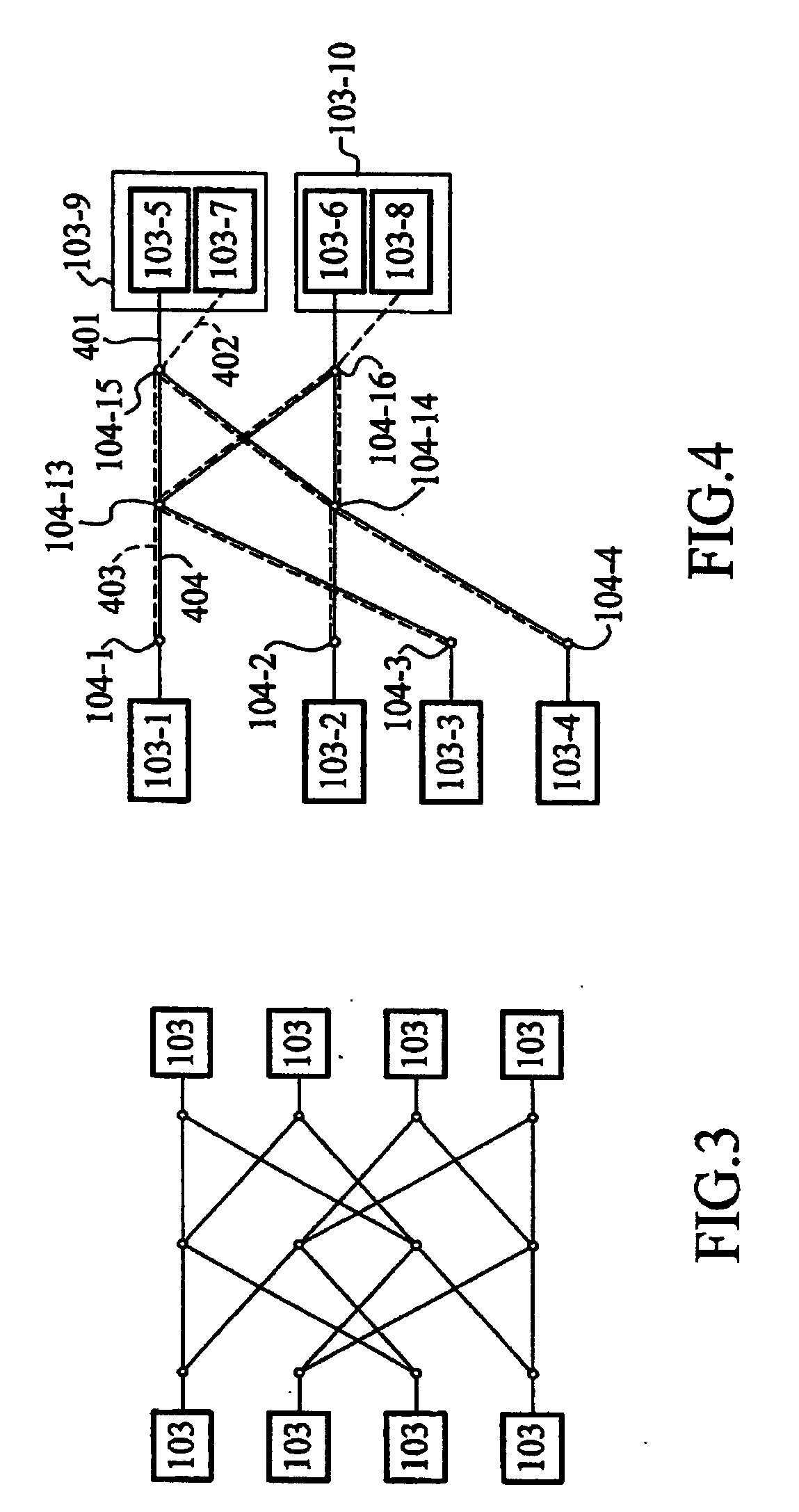
Superimposing butterfly network controls for pattern combinations
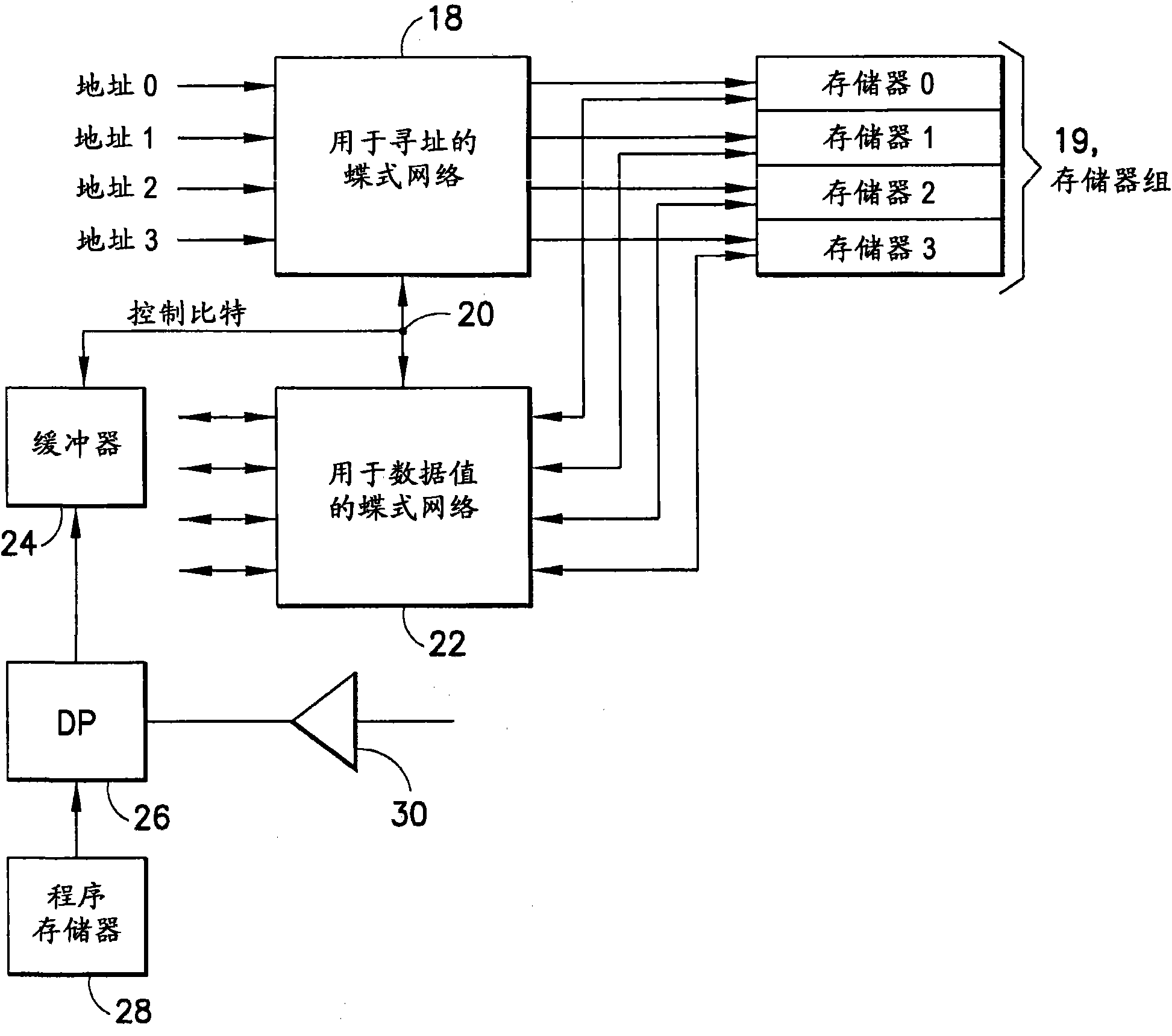
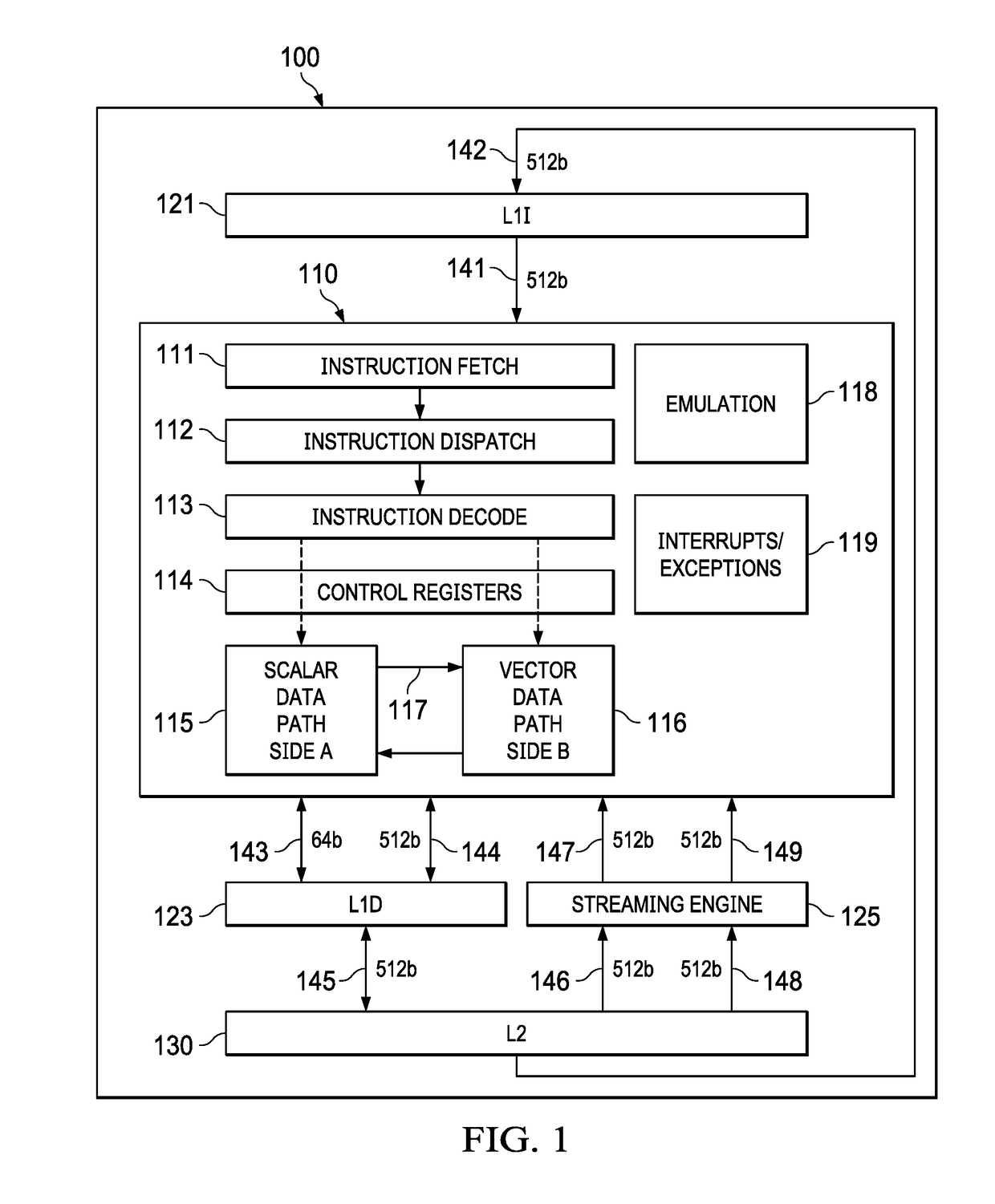
ActiveUS10140239B1Reduce control circuitLimited setMemory architecture accessing/allocationInstruction analysisData streamData transformation
A multilayer butterfly network is shown that is operable to transform and align a plurality of fields from an input to an output data stream. Many transformations are possible with such a network which may include separate control of each multiplexer. This invention supports a limited set of multiplexer control signals, which enables a similarly limited set of data transformations. This limited capability is offset by the reduced complexity of the multiplexor control circuits. This invention used precalculated inputs and simple combinatorial logic to generate control signals for the butterfly network. Controls are independent for each layer and therefore are dependent only on the input and output patterns. Controls for the layers can be calculated in parallel.
Owner:TEXAS INSTR INC
Butterfly network coding method based on bidirectional mixed quantum information exchange
ActiveCN112953648ASolve the transmission bottleneckImprove throughputPhotonic quantum communicationForward error control useInformation transmissionEngineering
The invention discloses a butterfly network coding method based on bidirectional mixed quantum information exchange, and the method comprises the following steps: constructing a butterfly network model, crossing and sharing a five-bit Brown channel by a source node, a destination node and a control party, and carrying out particle distribution; enabling a target node to introduce auxiliary particles, executing CNOT operation, enabling two pairs of dialogue parties to select proper measurement bases to measure the particles, enabling the dialogue parties to send measurement results to the other party, and if a control party agrees with information exchange between the dialogue parties, enabling the control party to execute single particle measurement and send the measurement results to the dialogue parties; enabling the dialogue party to send a measurement result to a corresponding intermediate node; enabling the intermediate node to send the information codes to the four dialogue parties; decoding by each dialogue party, and recovering a target state by executing proper unitary operation. The information transmission rate is greatly improved by adopting the butterfly network, the source node and the destination node have the same status, the application range of the quantum channel is expanded, and the operation difficulty coefficient is reduced.
Owner:SUZHOU UNIV
Butterfly network on load data return
ActiveUS20190020360A1Reduce control circuitLimited setCode conversionConcurrent instruction executionData streamData transformation
A method is shown that is operable to transform and align a plurality of fields from an input to an output data stream using a multilayer butterfly or inverse butterfly network. Many transformations are possible with such a network which may include separate control of each multiplexer. This invention supports a limited set of multiplexer control signals, which enables a similarly limited set of data transformations. This limited capability is offset by the reduced complexity of the multiplexor control circuits.
Owner:TEXAS INSTR INC
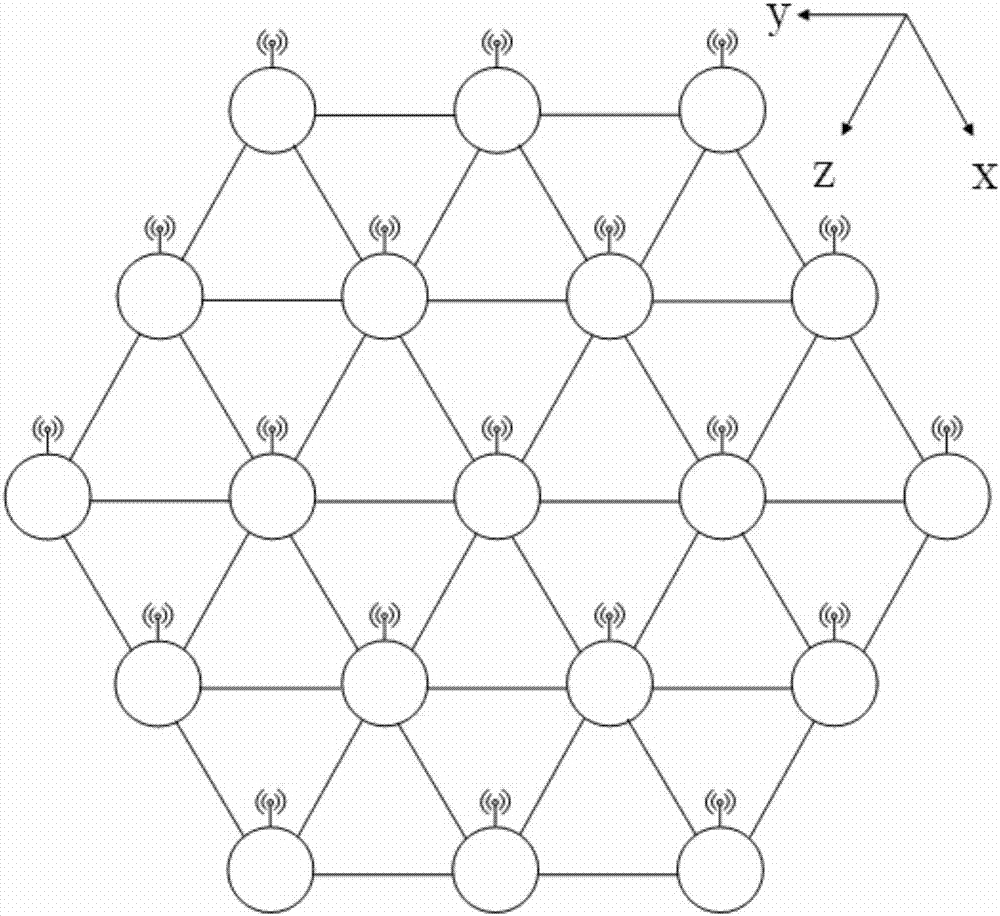
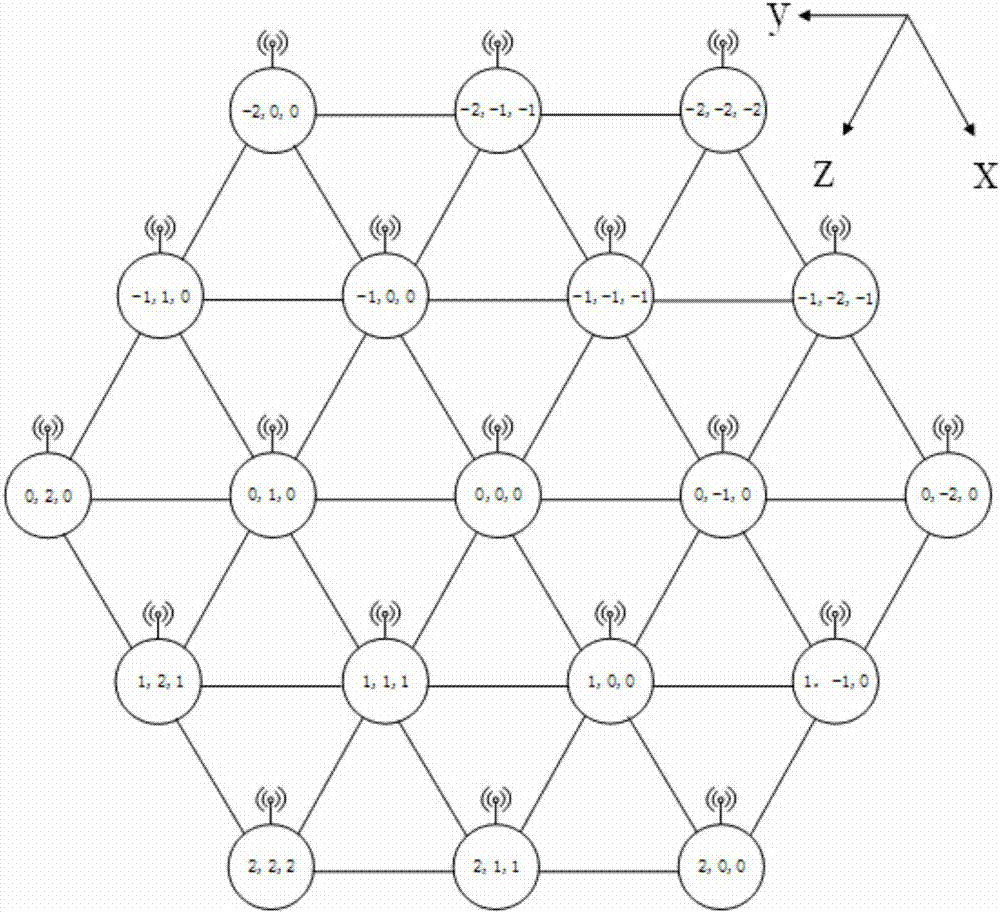
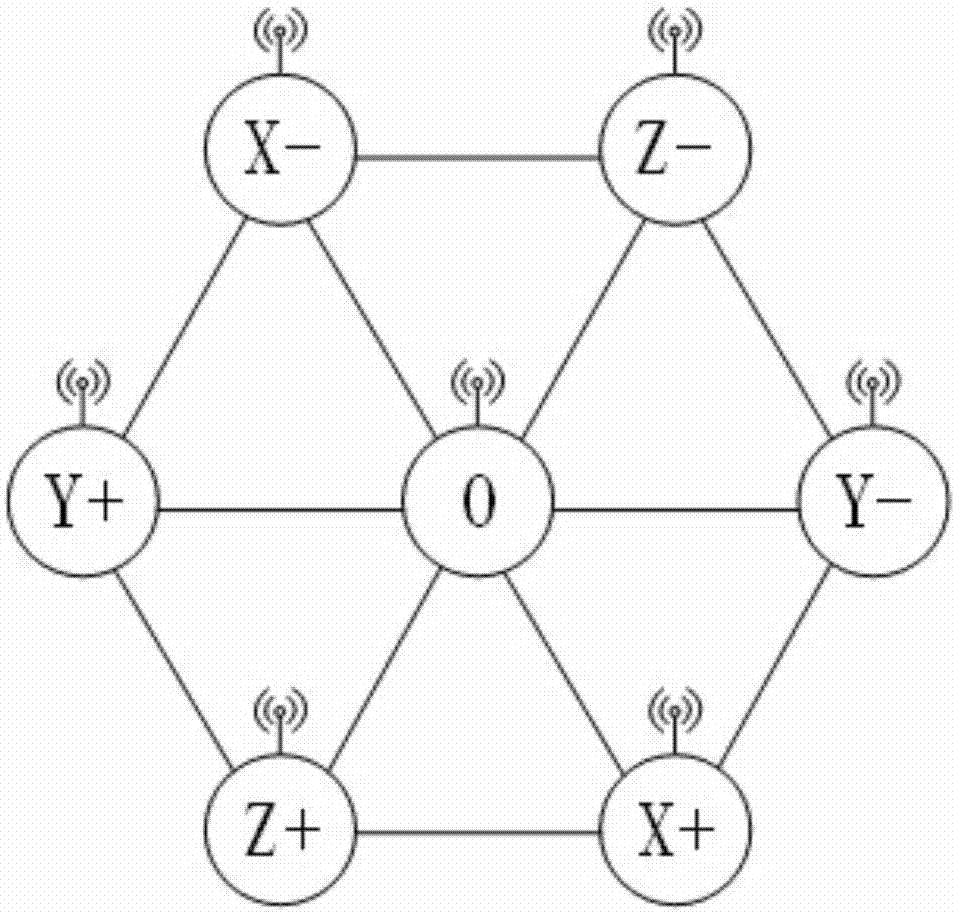
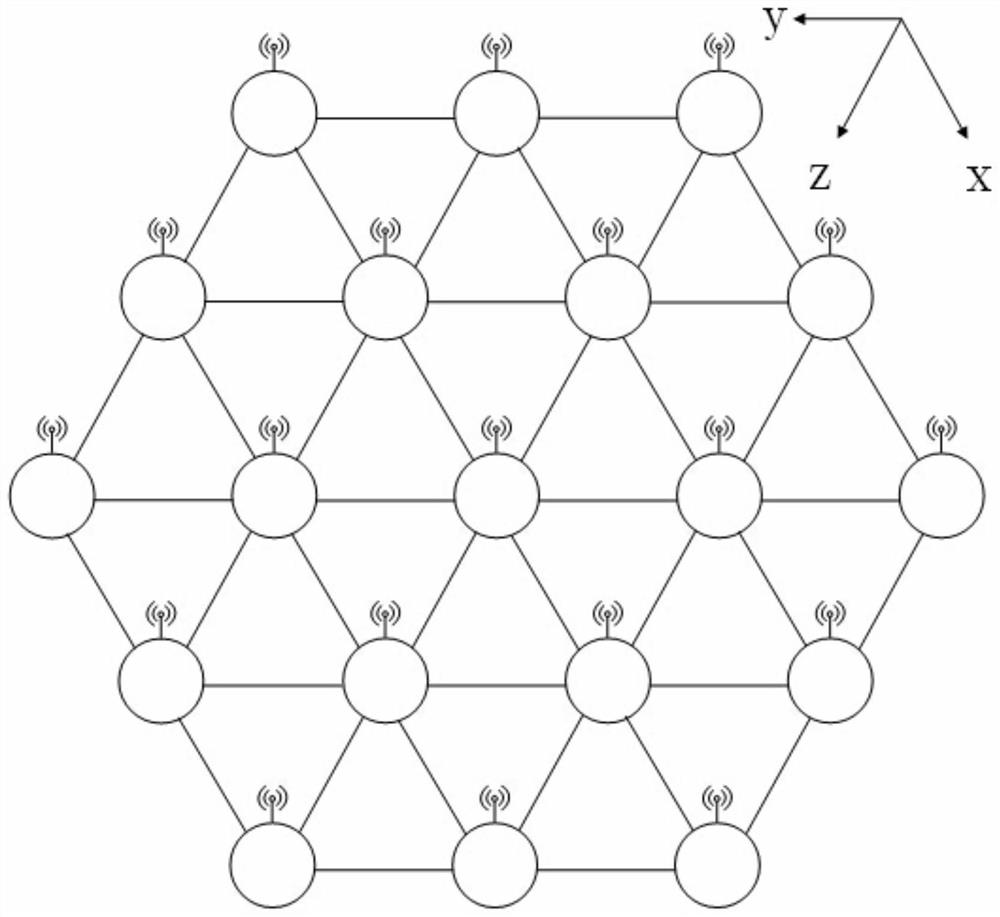
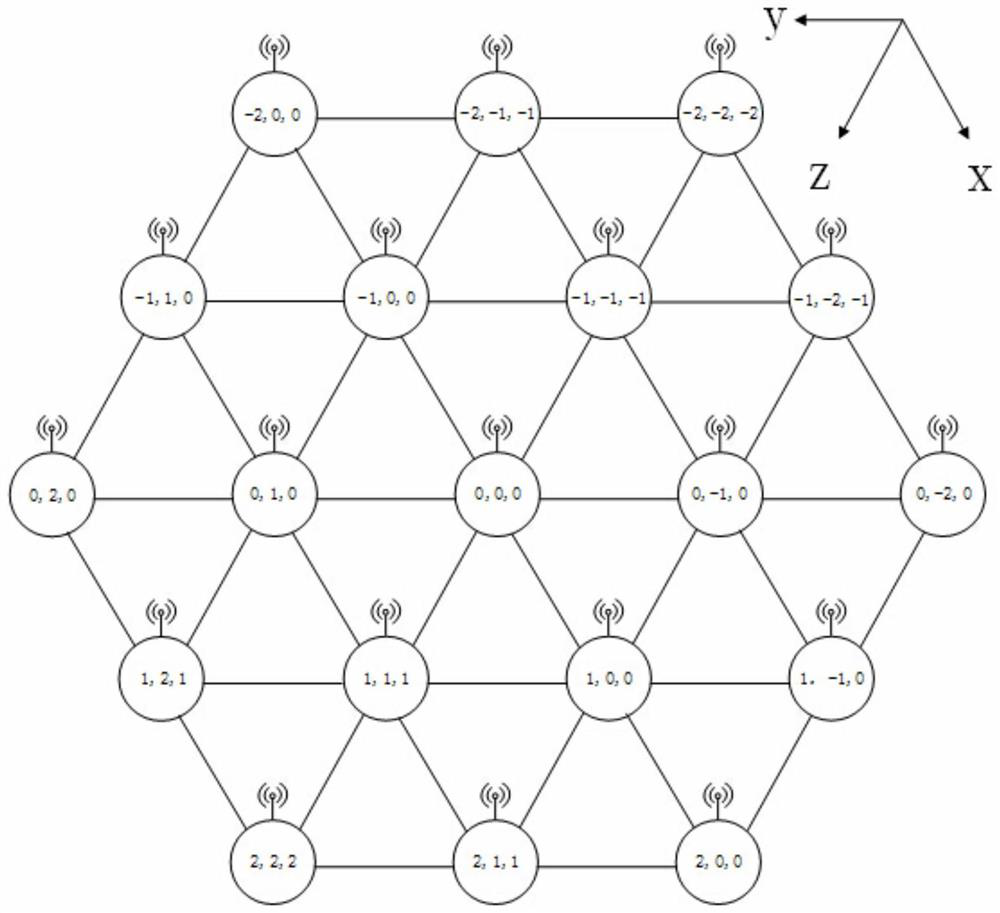
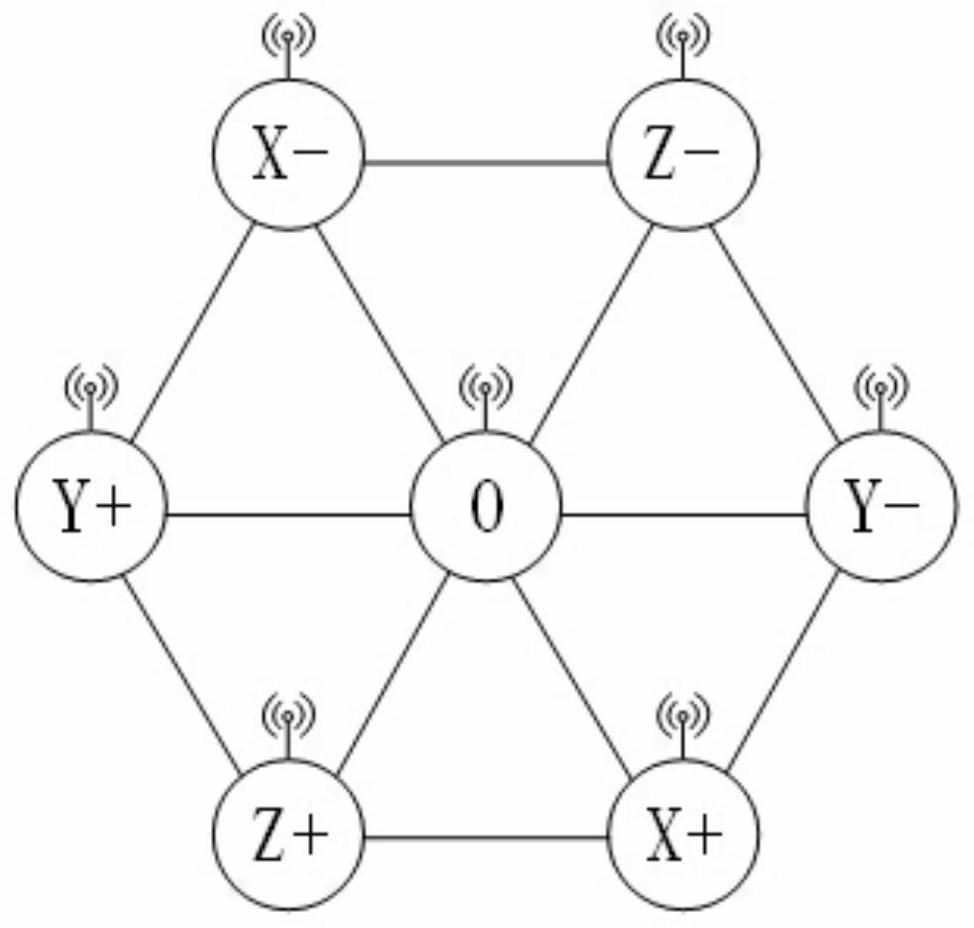
Network-on-chip architecture based on butterfly network coding and shortest path acquiring method of network-on-chip architecture
ActiveCN107517159AShort path routingAvoid deadlockData switching networksIsoetes triquetraCellular topology
The invention relates to the technical field of on-chip communication, in particular to a network-on-chip architecture based on butterfly network coding and a shortest path acquiring method of the network-on-chip architecture. The nodes of the network-on-chip architecture are distributed in a honeycomb manner, and each honeycomb is an equilateral triangle formed by the connecting lines of three adjacent nodes. The network-on-chip architecture has the advantages that the network-on-chip architecture based on butterfly network coding and Z-X-Y shortest-path routing matched with honeycomb topology can avoid deadlock and find out the shortest routing path; compared with traditional topological structures such as mesh topology, the honeycomb topology of the network-on-chip architecture has natural shortcuts and can reduce key link hop count; meanwhile, the network-on-chip architecture uses the butterfly network coding, can greatly eliminate network hot spots and can solve the problem of network congestion; the honeycomb network-on-chip architecture transmits data packets in a wireless manner and transmits control signals in a wired manner, data and the control signals are separated, and high-speed and efficient data transmission can be completed.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
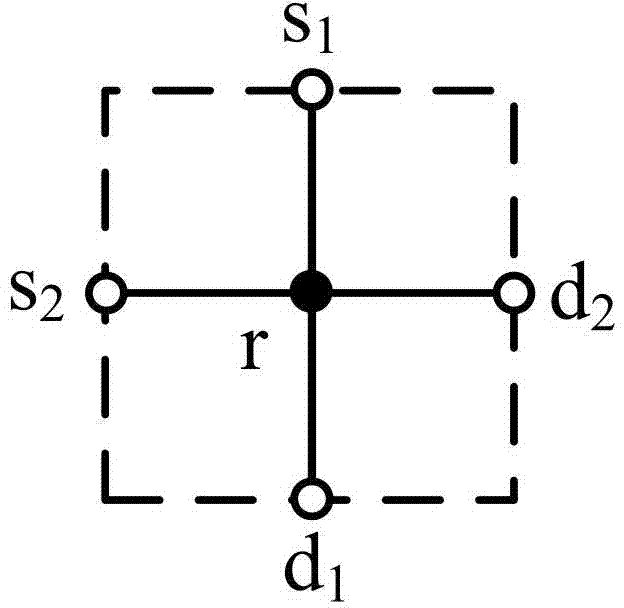
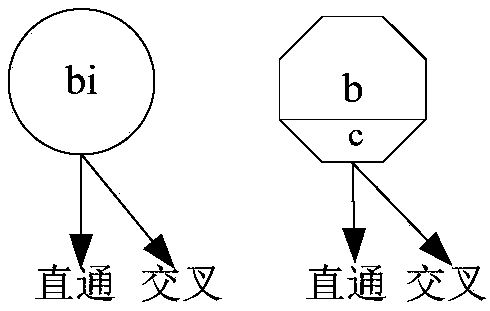
Butterfly network for permutation or de-permutation utilized by channel algorithm
A butterfly network for channel coding permutation and de-permutation. The butterfly network may include a first side and a second side, wherein each of the first side and second side has at least one terminal and two or more columns of nodes located between the first and second sides, wherein a first column of the columns may interface the first side, a second column of the columns may interface the second side and each of the columns comprises at least one node, wherein each node of the columns may be connected to a first number of nodes in each of adjacent columns next to the columns, and said first number may be identical for all the nodes in the network, and wherein the nodes which may be selected as switches are concurrently controlled to perform switching operations.
Owner:NAT CHIAO TUNG UNIV
Superimposing butterfly network controls for pattern combinations
ActiveUS20180341616A1Memory architecture accessing/allocationInstruction analysisData streamData transformation
A multilayer butterfly network is shown that is operable to transform and align a plurality of fields from an input to an output data stream. Many transformations are possible with such a network which may include separate control of each multiplexer. This invention supports a limited set of multiplexer control signals, which enables a similarly limited set of data transformations. This limited capability is offset by the reduced complexity of the multiplexor control circuits. This invention used precalculated inputs and simple combinatorial logic to generate control signals for the butterfly network. Controls are independent for each layer and therefore are dependent only on the input and output patterns. Controls for the layers can be calculated in parallel.
Owner:TEXAS INSTR INC
Wireless multi-core array hot spot eliminating method based on butterfly network codes and framework
ActiveCN104780114AImprove network throughputReduce the number of hotspotsArchitecture with single central processing unitData switching networksParallel processingComplex system
The invention relates to the field of communication, in particular to the field of wireless multi-core parallel processing, and particularly discloses a wireless multi-core array hot spot eliminating method based on butterfly network codes and a framework. The wireless multi-core array framework with the distributed butterfly network codes is provided. The network throughput rate of a wireless multi-core array is improved through the multiple butterfly network codes which are intersected, the number of hot spots in the multi-core array is reduced, and an efficient and parallel multi-core cooperative processing platform is provided for a complex system. Meanwhile, by means of the wireless multi-core array hot spot eliminating method and the framework, a hot-spot minimizing algorithm is provided to carry out optimization design of the wireless multi-core array framework, the maximization of the number of the butterfly network codes serves as the objective, and the maximized coding gains are obtained. It is verified that the framework can achieve at least 4% of throughput rate gains with the small overhead, and at least 43% of hot spots in a network can be eliminated.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
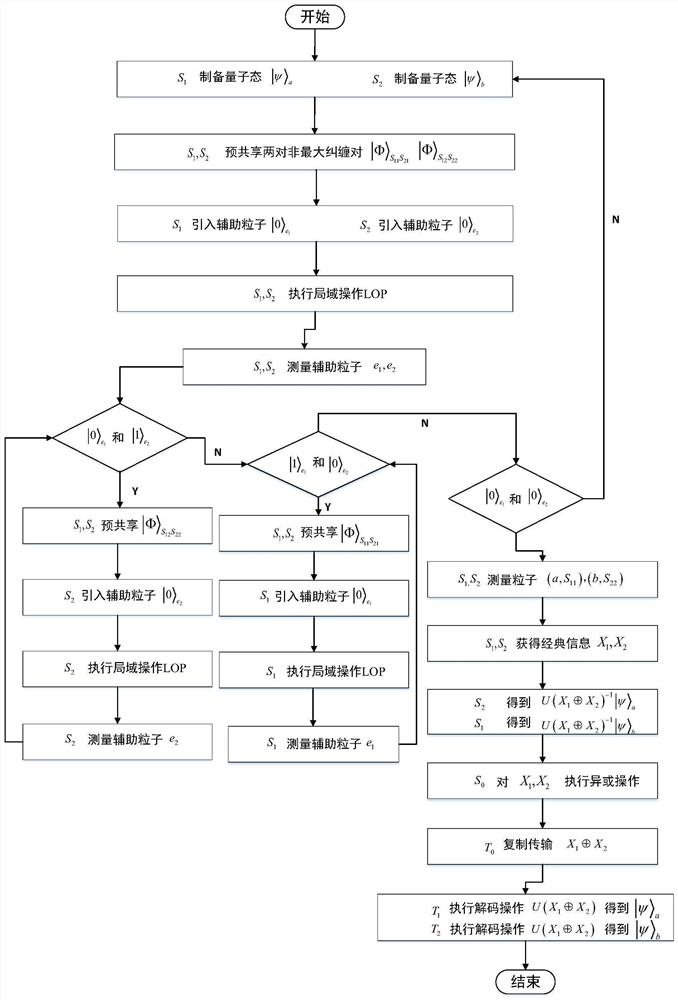
Quantum network coding method based on quantum state non-loss
ActiveCN111130771ASolve communication problemsReduce utilizationKey distribution for secure communicationNetwork communicationQuantum network
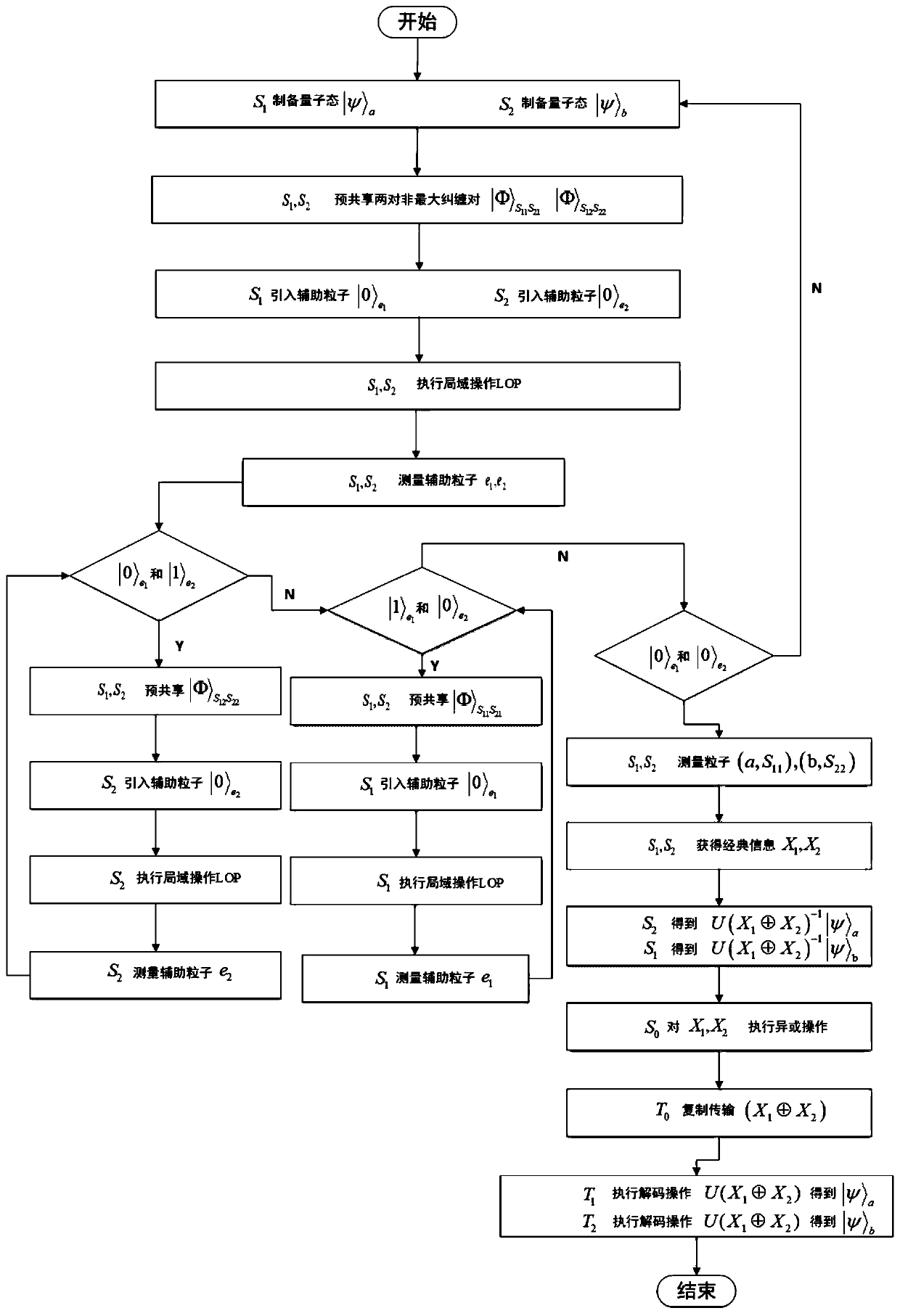
The invention discloses a quantum network coding method based on quantum state non-loss, and belongs to the technical field of network communication. The method is characterized in that two pairs of non-maximum entangled states are pre-shared between senders of the butterfly network, and perfect transmission of quantum states with fidelity of 1 can be realized by performing some local operations on the senders. By adding auxiliary particles to the sender, whether the quantum state is successful or not can be known before the quantum state is transmitted on the quantum network. The quantum state is not lost, that is, when transmission fails, the quantum state to be transmitted by the sender does not collapse to other states, and the quantum state is reproduced at the sender. When the measurement result of the auxiliary particles is | 0 >, | psi > a-| psi > b is realized; and when the measurement result of the auxiliary particles is | 1 >, | psi > a-| psi > a is realized. According to the quantum network coding based on quantum multi-unicast, perfect quantum state cross transmission is realized in a butterfly network model, a solution is provided for quantum 2-pair and k-pair networkcommunication problems, and the quantum network coding based on quantum multi-unicast has certain practical value.
Owner:南京万般上品信息技术有限公司
Butterfly network on load data return
A method is shown that is operable to transform and align a plurality of fields from an input to an output data stream using a multilayer butterfly or inverse butterfly network. Many transformations are possible with such a network which may include separate control of each multiplexer. This invention supports a limited set of multiplexer control signals, which enables a similarly limited set of data transformations. This limited capability is offset by the reduced complexity of the multiplexor control circuits.
Owner:TEXAS INSTR INC
A Quantum Network Coding Method Based on No Loss of Quantum State
ActiveCN111130771BSolve communication problemsReduce utilizationKey distribution for secure communicationQuantum networkNetwork communication
The invention relates to a quantum network encoding method based on quantum state not being lost, which belongs to the technical field of network communication. It is characterized in that two pairs of non-maximally entangled states are pre-shared between the senders of the butterfly network, and the perfect transmission of quantum states with a fidelity of 1 can be achieved by performing a series of local operations on the sender. Adding helper particles on the sender side allows quantum states to be known before they are transmitted across the quantum network. The so-called non-lost quantum state means that when the transmission fails, the quantum state to be transmitted by the sender will not collapse into other states, but the quantum state will be reproduced at the sender. That is to say, when the measurement result of the auxiliary particle is |0>, the realization of |ψ> a →|ψ> b ; When the measurement result of the auxiliary particle is |1>, realize |ψ> a →|ψ> a . The present invention is based on quantum multi-unicast quantum network coding, realizes perfect quantum state cross transmission in the butterfly network model, provides a solution to the problem of quantum 2-pair and k-pair network communication, and has certain practical value .
Owner:南京万般上品信息技术有限公司
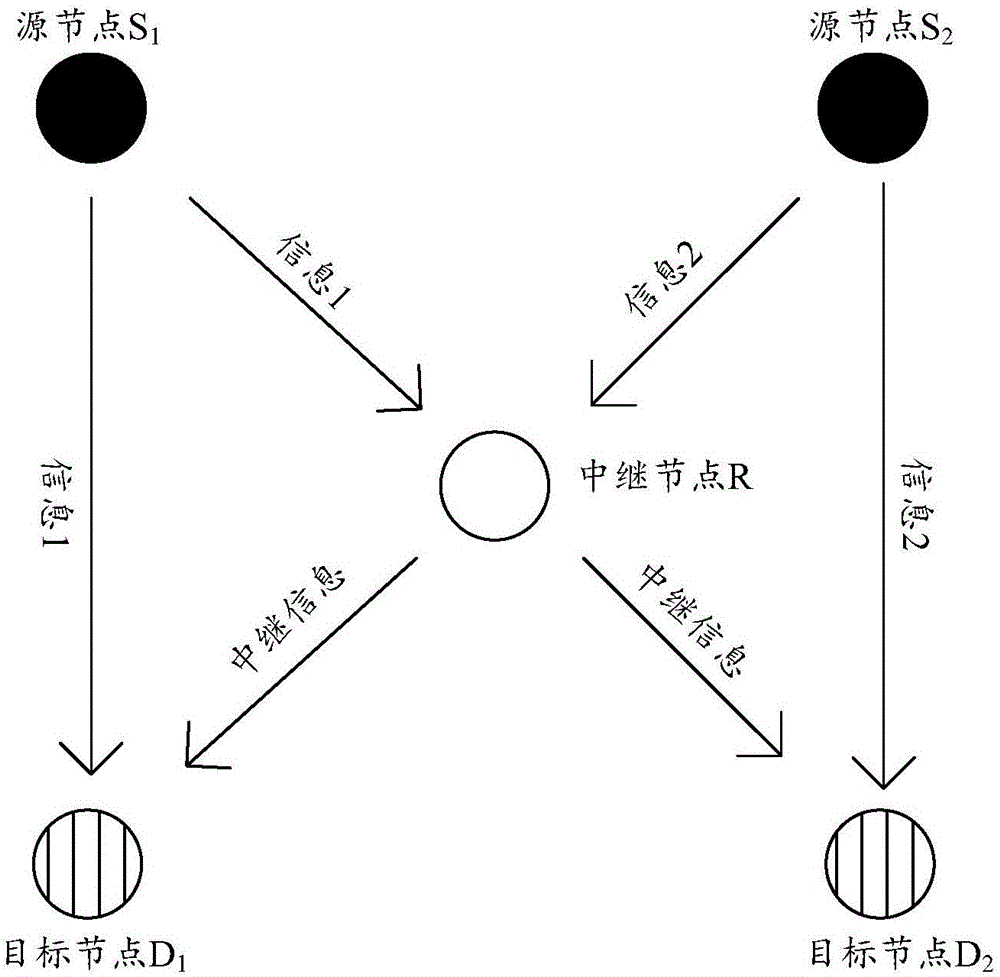
A Network Coding Method Based on Orthogonal Codes
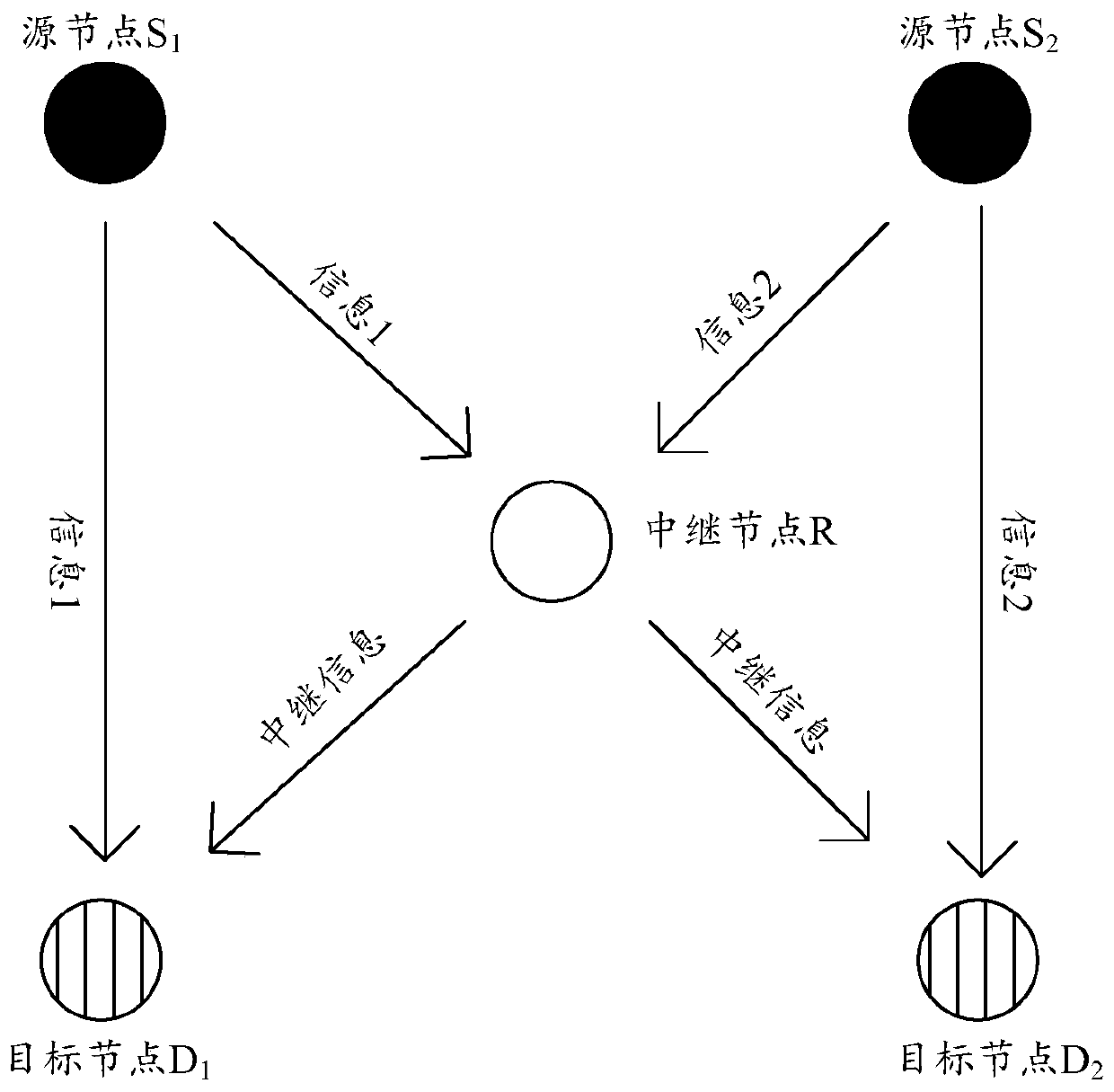
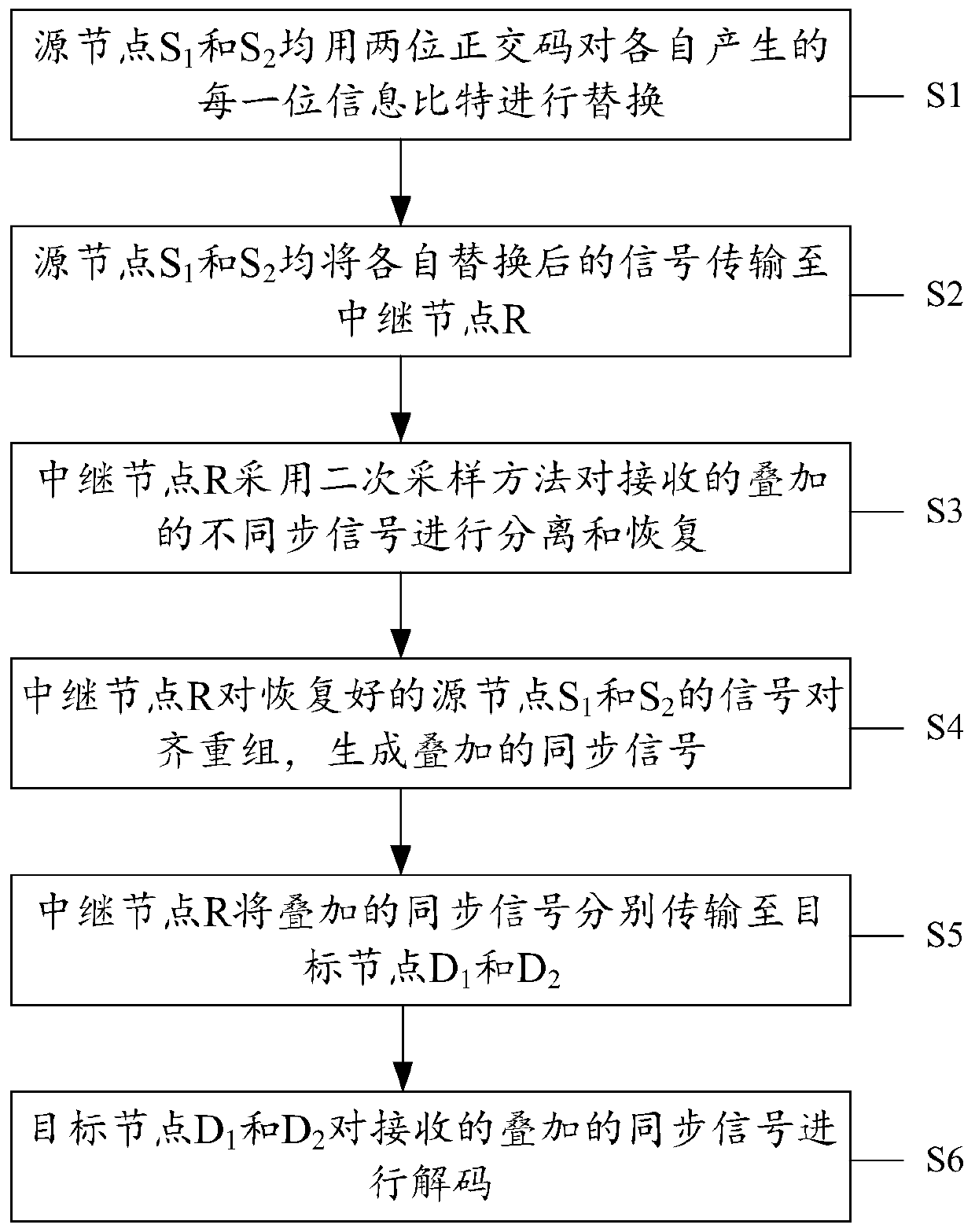
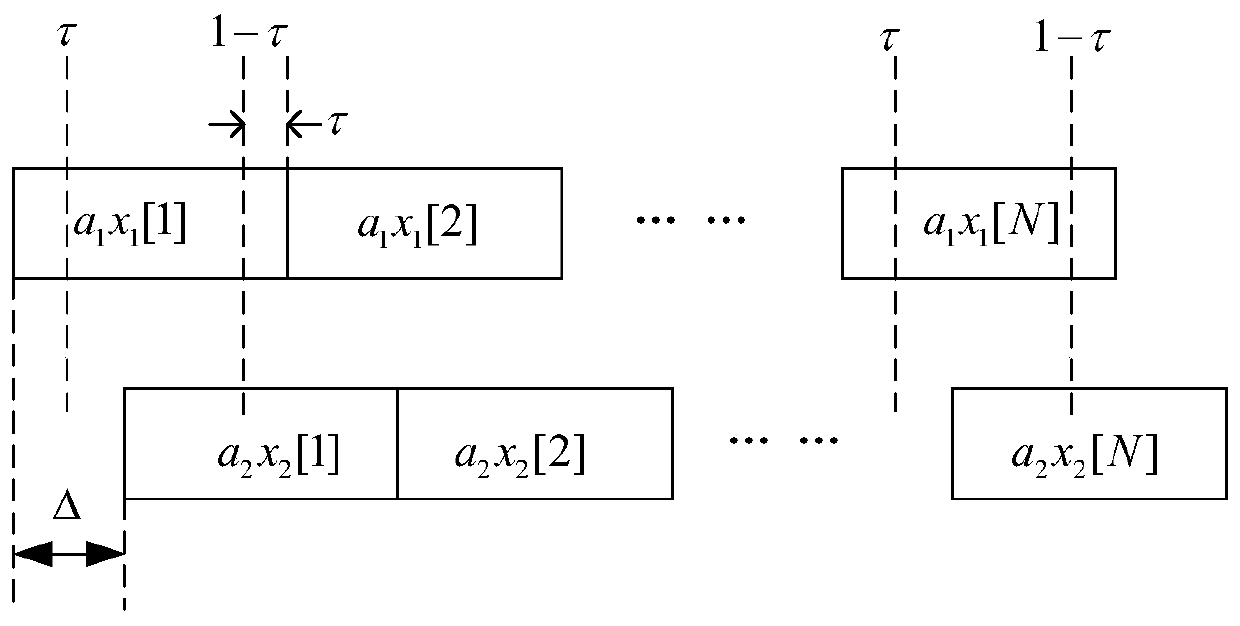
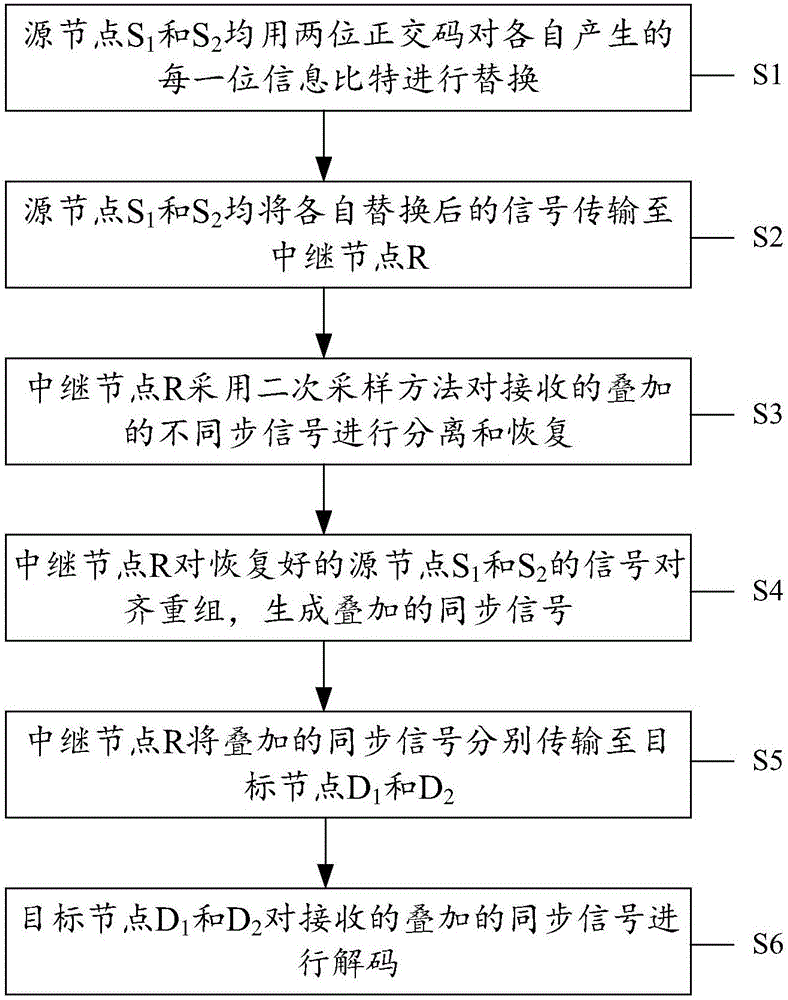
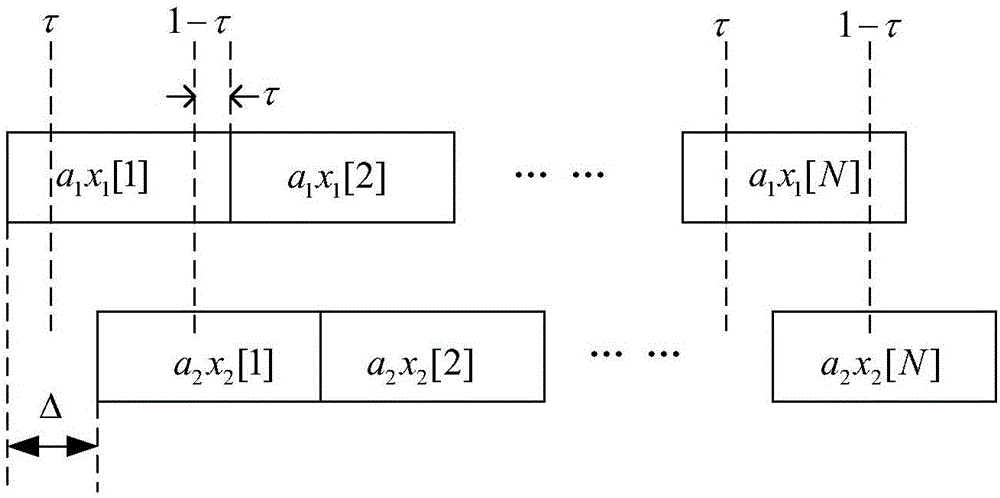
InactiveCN106533626BAchieve synchronizationLow costForward error control useNetwork codeComputer science
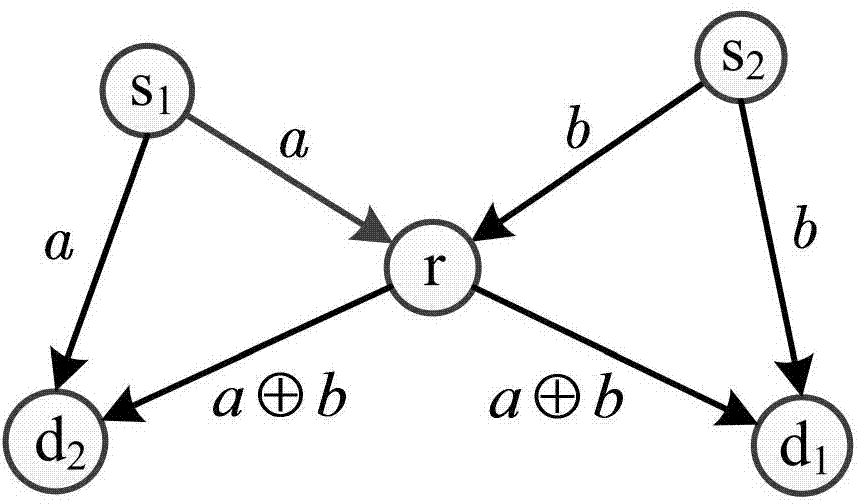
The invention discloses a network coding method based on orthogonal codes and relates to the technical field of wireless communication to reduce the cost during physical layer network coding application. The method includes step S1 of source nodes S1 and S2 replacing respectively generated each information bit through two-bit orthogonal codes, step S2 of the source nodes S1 and S2 sending signals after respective replacement to a relay node R, step S3 of the relay node R separating and recovering the received, superimposed and unsynchronized signals through a secondary sampling method, step S4 of the relay node R aligning and recombining the recovered source nodes S1 and S2 signals to generated superimposed synchronous signals, step S5 of the relay node R respectively transmitting the superimposed synchronous signals to target nodes D1 and D2, step S6 of the target nodes D1 and D2 decoding the received superimposed synchronous signals. The network coding method is applicable to a butterfly network.
Owner:NANCHANG UNIV +1
Network-on-Chip Architecture Based on Butterfly Network Coding and Its Shortest Path Acquisition Method
ActiveCN107517159BShort path routingAvoid deadlockData switching networksCellular architectureCellular topology
The invention relates to the technical field of intra-chip communication, in particular to an on-chip network architecture based on butterfly network coding and a method for obtaining the shortest path. Each node of the network architecture is distributed in a honeycomb shape, and each honeycomb is an equilateral triangle formed by connecting lines of three adjacent nodes. The Z-X-Y shortest path routing based on the butterfly network coding based on-chip network architecture and the cellular topology can find the shortest routing path under the condition of avoiding deadlock; compared with the traditional topology, such as mesh topology, the cellular topology in the architecture provided by the present invention has natural shortcuts, which can shorten the number of hops of key links; at the same time, the architecture provided by the present invention will use butterfly network coding, which can greatly eliminate network hot spots and solve network congestion Problem: The cellular architecture provided by the present invention transmits data packets by wireless, transmits control signals by wire, and separates data from control signals, so that high-speed and high-efficiency data transmission can be accomplished.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
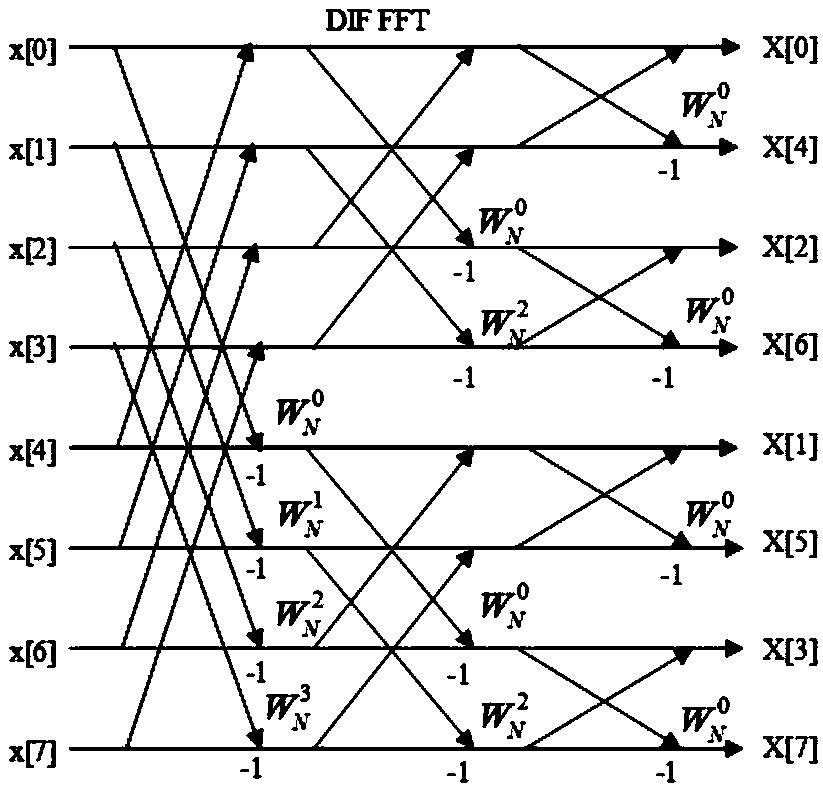
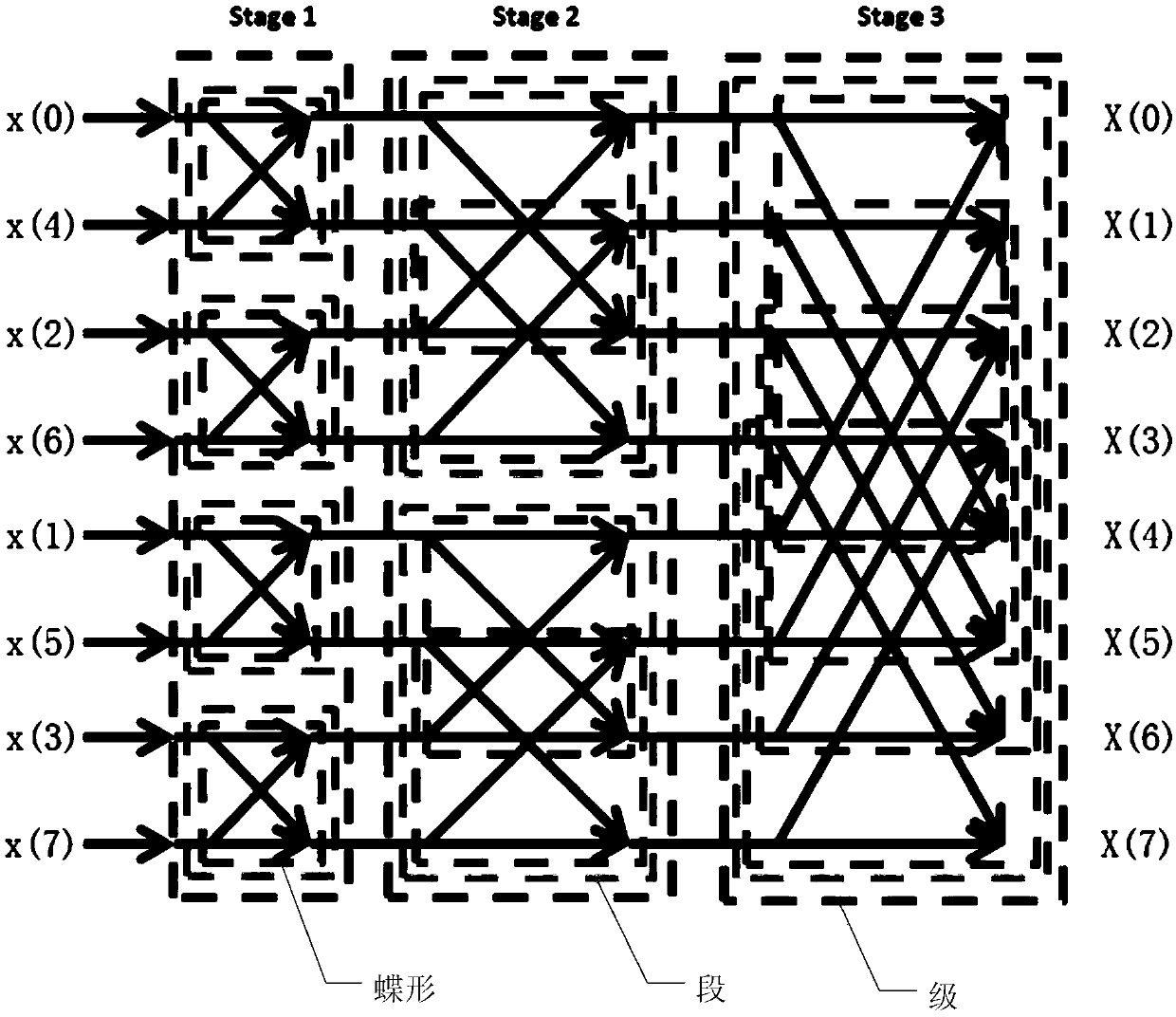
Method and device for generating fast Fourier transform code
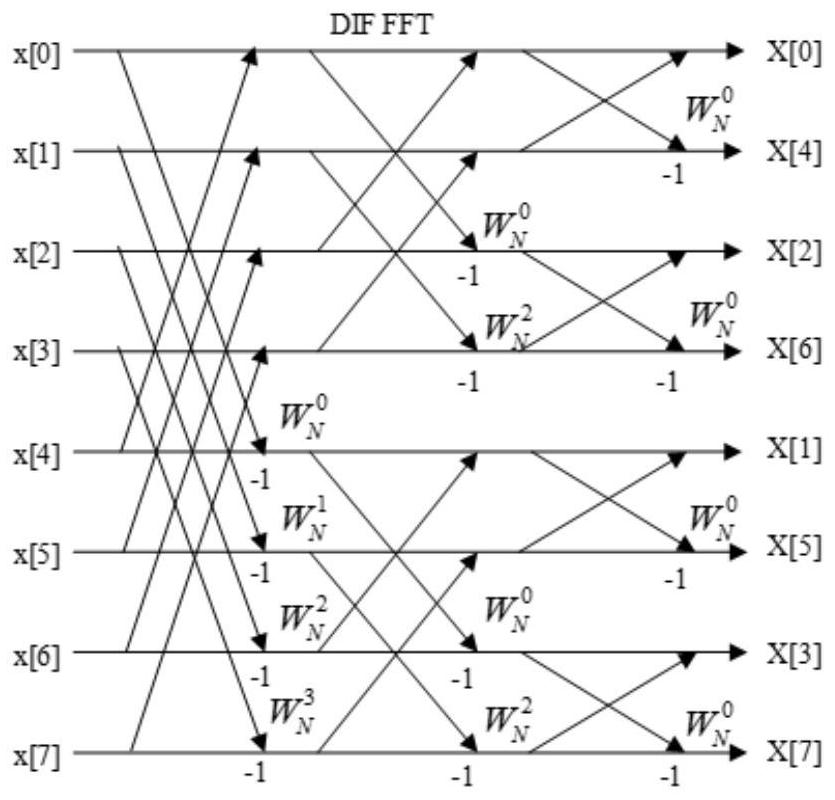
ActiveCN110750249AProgramming languages/paradigmsComplex mathematical operationsFast Fourier transformCode generation
The invention discloses a method and device for generating a fast Fourier transform code, which are used for generating an FFT code and decomposing the FFT code into a plurality of atom templates so as to facilitate subsequent optimization of the atom templates and further improve the performance of the FFT code. The method comprises: acquiring a data sequence needing fast Fourier transform (FFT)and the length of the data sequence; determining an FFT decomposition mode of the data sequence according to the length of the data sequence, and obtaining one or more stages of the butterfly networkcorresponding to the FFT decomposition mode, wherein each stage corresponds to a butterfly base; determining a butterfly-shaped code needing to be called in each level and the calling times of the butterfly-shaped code in each level according to the butterfly-shaped base corresponding to each level; and according to the butterfly code in each level and the calling frequency of calling the butterfly code in each level, generating the code of each level step by step to obtain an FFT code for performing fast Fourier transform on the data sequence.
Owner:XFUSION DIGITAL TECH CO LTD
Biclustering mining method based on butterfly network under synchronous programming model Hama BSP
InactiveCN109243535AIncrease profitReduce trafficBiostatisticsHybridisationBiclusteringComputer science
The invention provides a biclustering mining method based on a butterfly network under a synchronous programming model Hama BSP. The concrete steps are that firstly a Hama platform with an underlyingHDFS and 2n nodes is deployed, then the biclustering mining work is performed on each node on the Hama platform in the local computing stage, only the local source data is used if it is the first overstep, otherwise, only the newly received data is matched with the local data and then the nodes are grouped and communicated by the butterfly network method in the global communication stage, and synchronization of the communication is performed in the barrier synchronization stage. According to the method, all the biclustering can be finally mined after multiple times of iteration. According to the method, the communication traffic is less, the redundancy of the communication data volume and the mining result can be effectively reduced and the utilization rate of the nodes can be improved.
Owner:HENAN UNIV OF ECONOMICS & LAW
Multiple access for parallel turbo decoder
ActiveCN101682338BCode conversionError correction/detection by combining multiple code structuresMemory addressMemory bank
A memory bank contains a plurality of memories, a first Butterfly network is configured to apply memory addresses to the memory bank, and a second Butterfly network is configured to pass data to or from the memory bank. A control signal is generated for the first and second Butterfly networks in accordance with a multiple access rule to enable parallel access to the memory bank, without memory access conflict, for one of a linear order and an interleaved order. The method and apparatus is particularly advantageous for use in turbo decoding.
Owner:NOKIA TECH OY
A method and device for generating fast Fourier transform codes
ActiveCN110750249BProgramming languages/paradigmsComplex mathematical operationsFast Fourier transformCode generation
This application discloses a fast Fourier transform code generation method and device, which are used to generate fast Fourier transform FFT codes, decompose the FFT codes into multiple atomic templates, facilitate subsequent optimization of the atomic templates, and further improve the FFT code performance. The method comprises: obtaining the data sequence that needs to be subjected to fast Fourier transform FFT and the length of the data sequence; determining the FFT decomposition mode of the data sequence according to the length of the data sequence, and obtaining one or more stages of the butterfly network corresponding to the FFT decomposition mode, Each level corresponds to a butterfly base; determine the butterfly code that needs to be called in each level and the calling times of the butterfly code in each level according to the butterfly base corresponding to each level; according to each level The butterfly codes in the stages and the number of times the butterfly codes in each stage are called generate the codes of each stage step by stage to obtain the FFT codes for fast Fourier transforming the data sequence.
Owner:XFUSION DIGITAL TECH CO LTD
Chaotic Image Encryption Method Based on Bit Permutation and Dynamic DNA Coding
ActiveCN106952213BAchieve substitutionImprove featuresImage data processing detailsDiffusionCiphertext
The invention provides a chaotic image encryption method based on bit replacement and dynamic DNA coding. The objective of the invention is to solve the problem that security of chaotic encryption is affected by degradation of chaotic dynamics characteristics of an image encryption method based on a chaotic system in the prior art. The chaotic image encryption method comprises steps of firstly using the Keccak algorithm to calculate a hash value of a DNA sequence; based on the hash value, generating an initial state value of the chaotic mapping; by use of a hyperchaotic Chen system, generating a chaotic mapping index to carry out pixel position overall scrambling on an image; combining the Butterfly network to carry out bit position scrambling on each pixel, thereby achieving position grade scrambling; carrying out dynamic DNA coding on the image and combining the given DNA sequence to carry out XOR operation, thereby achieving replacing of the pixels; and finally, through the ciphertext feedback, further enhancing the chaotic and diffusion features. According to the invention, the chaotic image encryption method has big key space and is highly sensitive to a key, and capable of effectively resisting attacking operation of statistical analysis and exhaustion analysis.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
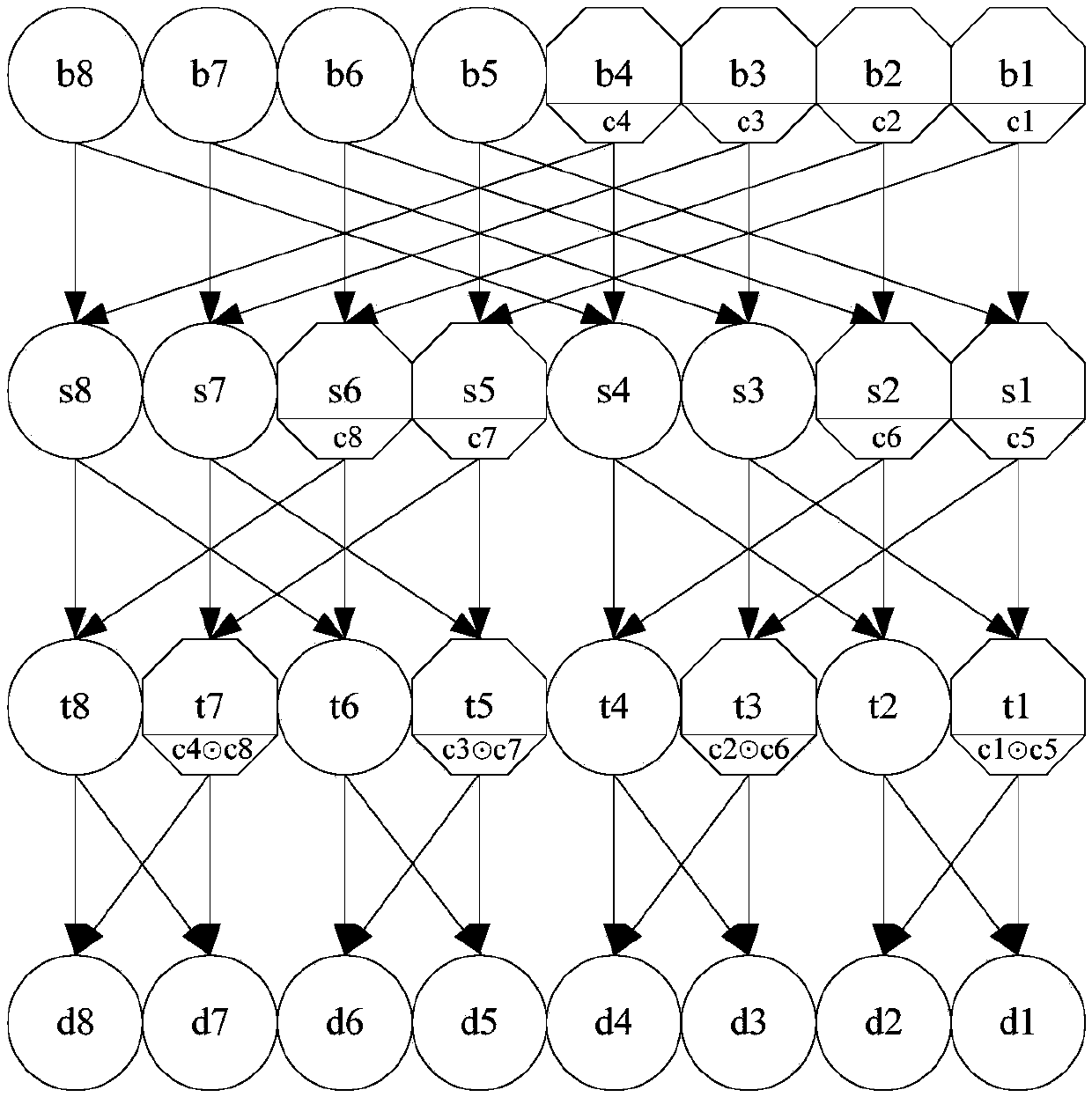
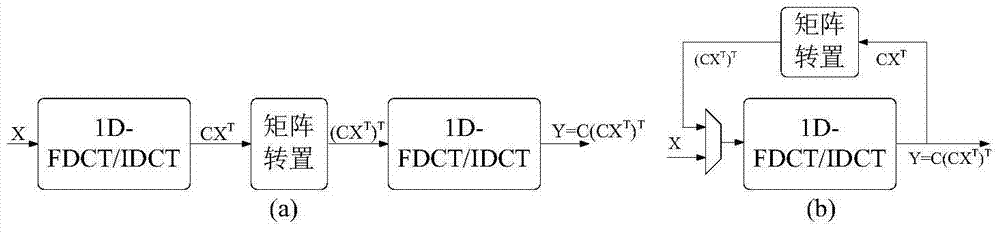
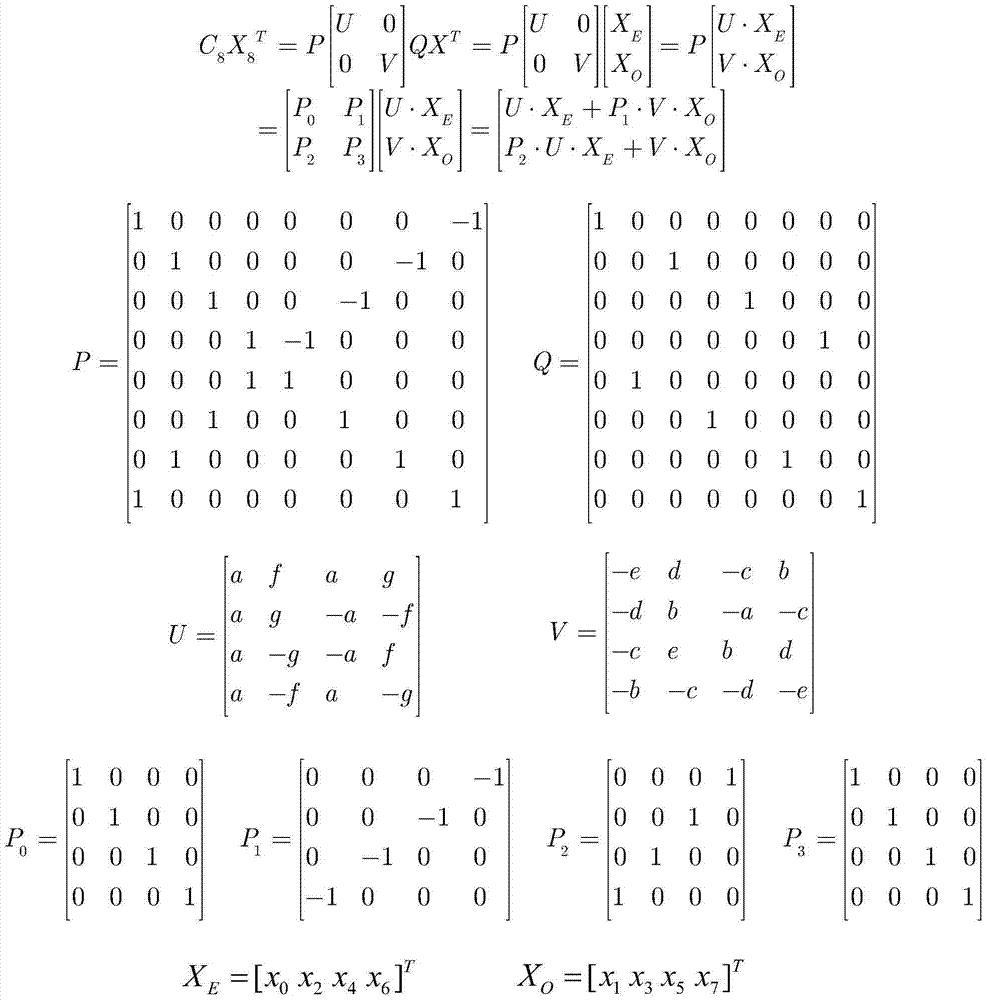
Low-overhead multi-standard 8×8 one-dimensional discrete cosine transform circuit based on resource sharing
ActiveCN104811738BSave logic resourcesImprove performanceDigital video signal modificationProcessor registerResource based
The present invention provides a low-overhead multi-standard 8×8 one-dimensional discrete cosine transform circuit based on hardware resource sharing, which mainly includes four processing units PE and a butterfly transform network; the processing unit includes a constant coefficient multiplier and a data distributor , two sets of accumulating units, two registers, and two selectors; the input data is multiplied by the constant coefficient multiplier to obtain the multiplication result, and the multiplication result is distributed by the data distributor, and the odd and even parts are respectively transferred to the two The group accumulation unit is output to the storage unit after the accumulation calculation of two groups of accumulation units, and then the final calculation result is transferred to the butterfly transformation network after being selected by two two-choice selectors, and received by the butterfly transformation network The signal is processed to realize the design of one-dimensional discrete cosine transform circuit. The object of the present invention is to provide a discrete cosine transform circuit structure that saves circuit logic resources and improves performance, and can quickly complete discrete cosine transform operations.
Owner:INST OF ELECTRONICS CHINESE ACAD OF SCI
Bidirectional single-bit state preparation method based on brown state and network coding
ActiveCN111510289BAchieve bidirectional preparationReduce resource consumptionKey distribution for secure communicationNetwork codeEngineering
The invention discloses a bidirectional single-bit state preparation method based on Brown state and network coding. The present invention combines state preparation based on the Brown state with network coding for the first time, cross-transmits from the sender to the receiver through the butterfly network and the five-bit Brown state, and prepares any single-bit quantum state bidirectionally. Mainly The feature is: on the basis of the butterfly network coding protocol, the quantum network coding model is established through state preparation. The channel shared by the source node and the destination node is obtained by channel modulation through the CNOT operation with five-bit Brown states plus auxiliary particles. Realize the transmission of known information in the entire network model. Compared with the quantum teleportation scheme, the resource consumption is less, and the transmission efficiency reaches a higher level. It also innovatively realizes two-way preparation, and the communication capacity reaches four bits per round. . It has broad application prospects in the field of quantum communication network technology.
Owner:SUZHOU UNIV
Network coding method based on orthogonal codes
InactiveCN106533626AAchieve synchronizationLow costForward error control useNetwork codeComputer science
The invention discloses a network coding method based on orthogonal codes and relates to the technical field of wireless communication to reduce the cost during physical layer network coding application. The method includes step S1 of source nodes S1 and S2 replacing respectively generated each information bit through two-bit orthogonal codes, step S2 of the source nodes S1 and S2 sending signals after respective replacement to a relay node R, step S3 of the relay node R separating and recovering the received, superimposed and unsynchronized signals through a secondary sampling method, step S4 of the relay node R aligning and recombining the recovered source nodes S1 and S2 signals to generated superimposed synchronous signals, step S5 of the relay node R respectively transmitting the superimposed synchronous signals to target nodes D1 and D2, step S6 of the target nodes D1 and D2 decoding the received superimposed synchronous signals. The network coding method is applicable to a butterfly network.
Owner:NANCHANG UNIV +1
Safe quantum network encoding method based on quantum homomorphic encryption
PendingCN113872748AImplement cross transferEnsure safetyKey distribution for secure communicationCommunication with homomorphic encryptionComputer networkEngineering
The invention belongs to the field of quantum communication network technology and quantum cryptography, and particularly relates to a safe quantum network encoding method based on quantum homomorphic encryption. Quantum homomorphic encryption is applied to quantum network encoding, and the quantum state of the measurement result of the sender is encrypted, so that the intermediate node in the butterfly network cannot obtain the quantum state information to be transmitted of the sender, and safe quantum network encoding is realized.
Owner:GUIZHOU UNIV
Method and architecture of wireless multi-core array hotspot elimination based on butterfly network coding
ActiveCN104780114BImprove network throughputReduce the number of hotspotsArchitecture with single central processing unitData switching networksBase codeWireless mesh network
The present invention relates to the field of communication, in particular to the field of wireless multi-core parallel processing, and specifically refers to a wireless multi-core array hotspot elimination method and architecture based on butterfly network coding; a wireless multi-core array architecture using distributed butterfly network coding is proposed, through multiple The disjoint butterfly network coding improves the network throughput of the wireless multi-core array, reduces the number of hotspots in the multi-core array, and provides an efficient and parallel multi-core collaborative processing platform for complex systems. At the same time, the present invention proposes a minimization hotspot algorithm to optimize the design of the wireless multi-core array architecture, aiming at maximizing the number of codes in the butterfly network to obtain the maximum coding gain. Through verification, the architecture proposed by the present invention can achieve at least 4% increase in throughput with less overhead, and eliminate at least 43% of hot spots in the network.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com