Patents
Literature
151 results about "Information confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Confidentiality is the protection of personal information. Confidentiality means keeping a client’s information between you and the client, and not telling others including co-workers, friends, family, etc.
Block chain privacy protection system and method based on homomorphic encryption
InactiveCN109840771AImprove confidentialityCannot be tampered withFinanceDigital data protectionEncrypted functionPrivacy protection
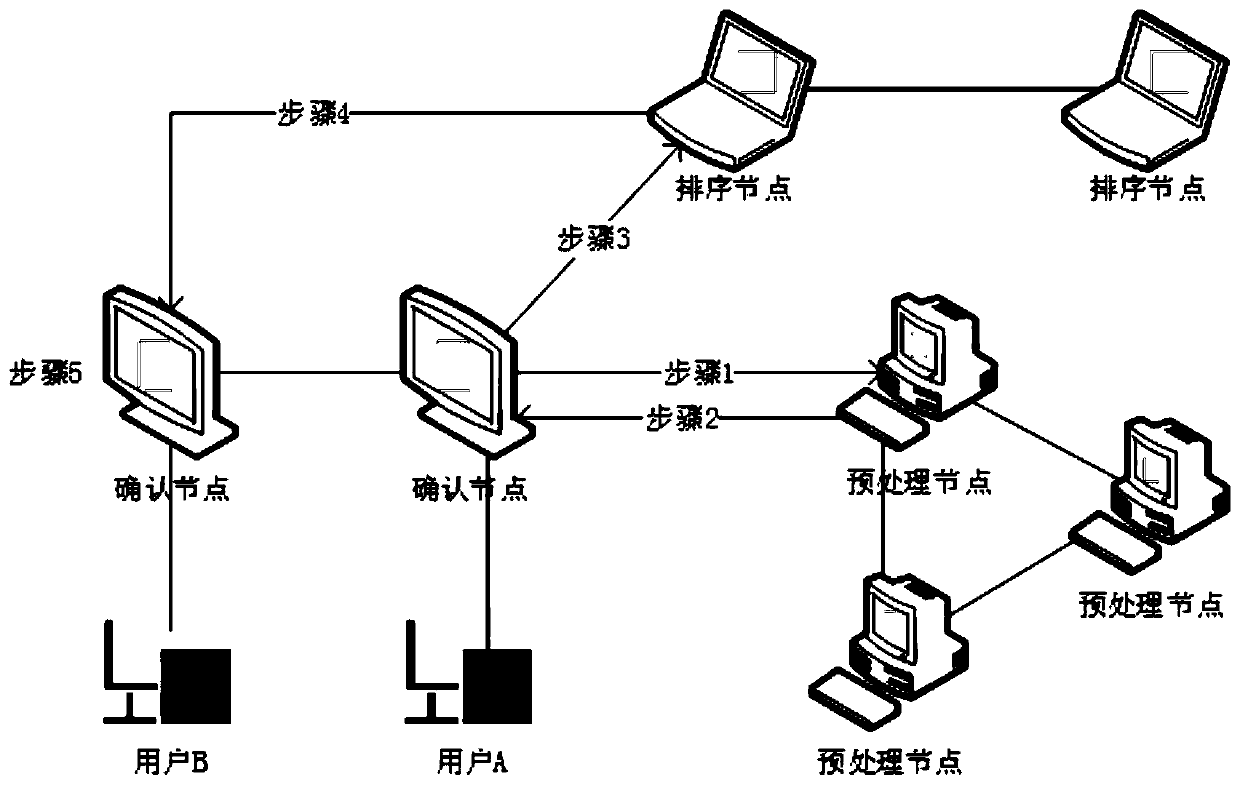
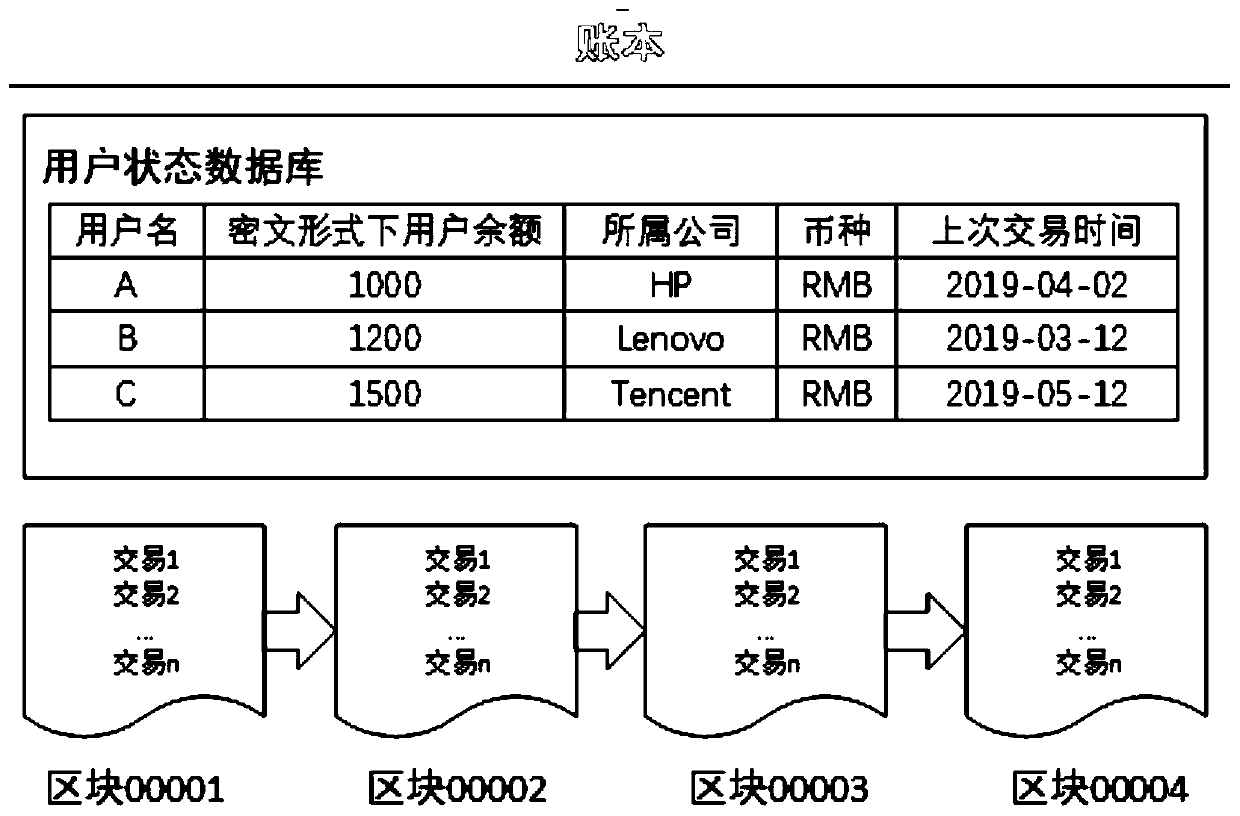
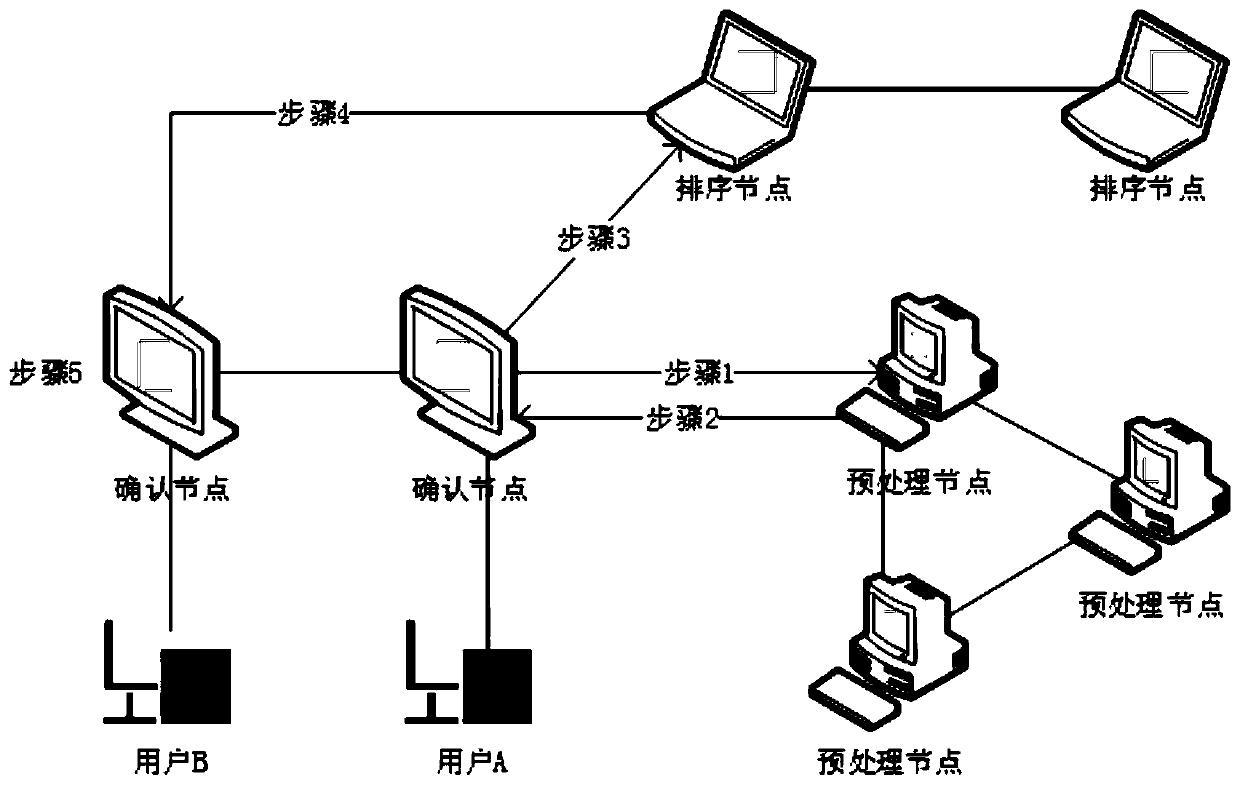
The invention provides a block chain privacy protection system and method based on homomorphic encryption. The privacy protection system comprises an authentication center which is used for carrying out identity verification, issuing a certificate and periodically checking an account book; The block chain nodes are used for collecting transactions, verifying the transactions, sorting the transactions and generating blocks; Wherein the block chain nodes comprise a preprocessing node, a confirmation node and a sorting node; And a user: one user corresponds to one confirmation node. According tothe block chain privacy protection system and method based on homomorphic encryption provided by the invention, the block chain privacy protection scheme can realize transaction information confidentiality; The blockchain privacy protection scheme can ensure that the transaction information cannot be tampered; The blockchain privacy protection scheme can ensure transaction legality; The re-encryption function in the blockchain privacy protection scheme is secure.
Owner:XIDIAN UNIV
An information security method and procedure
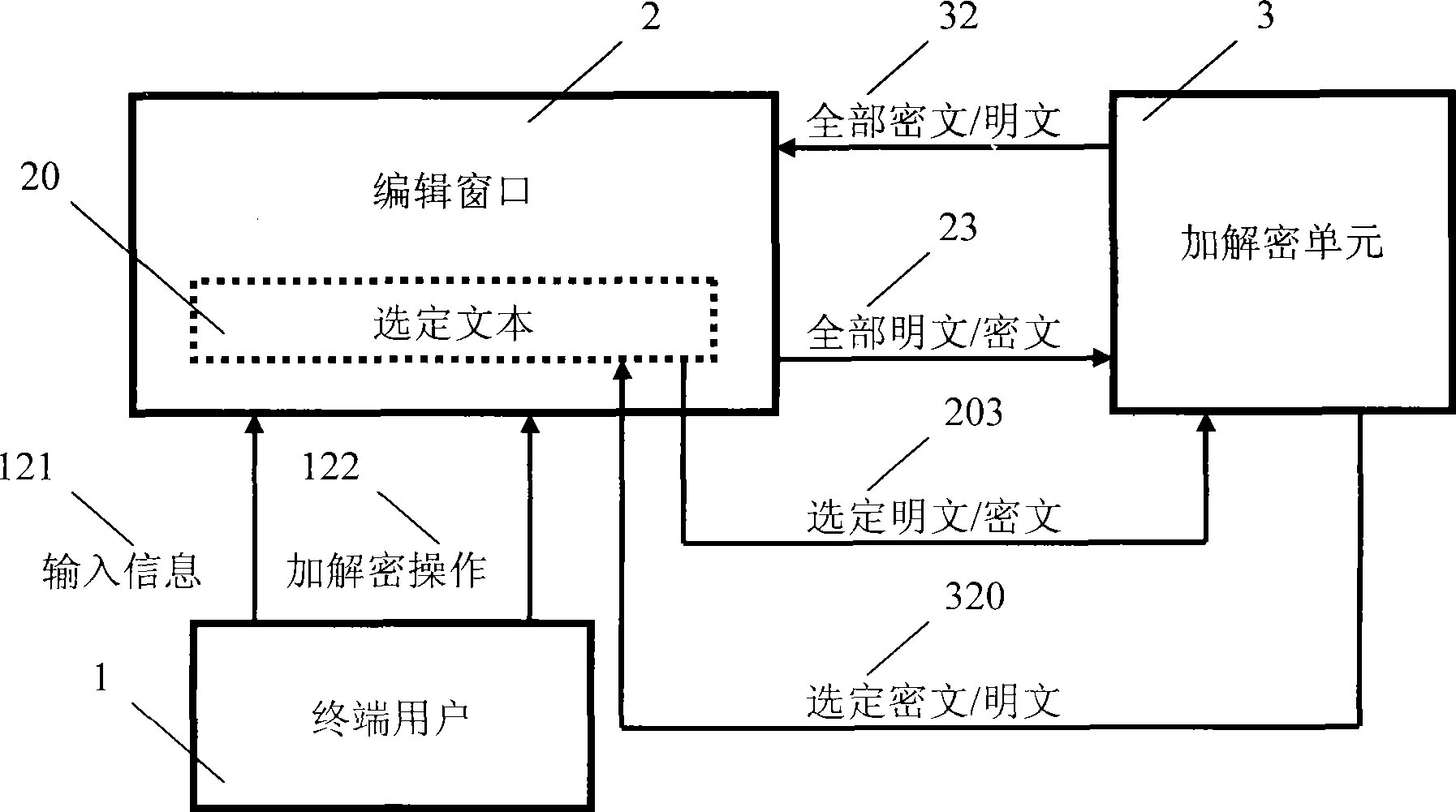
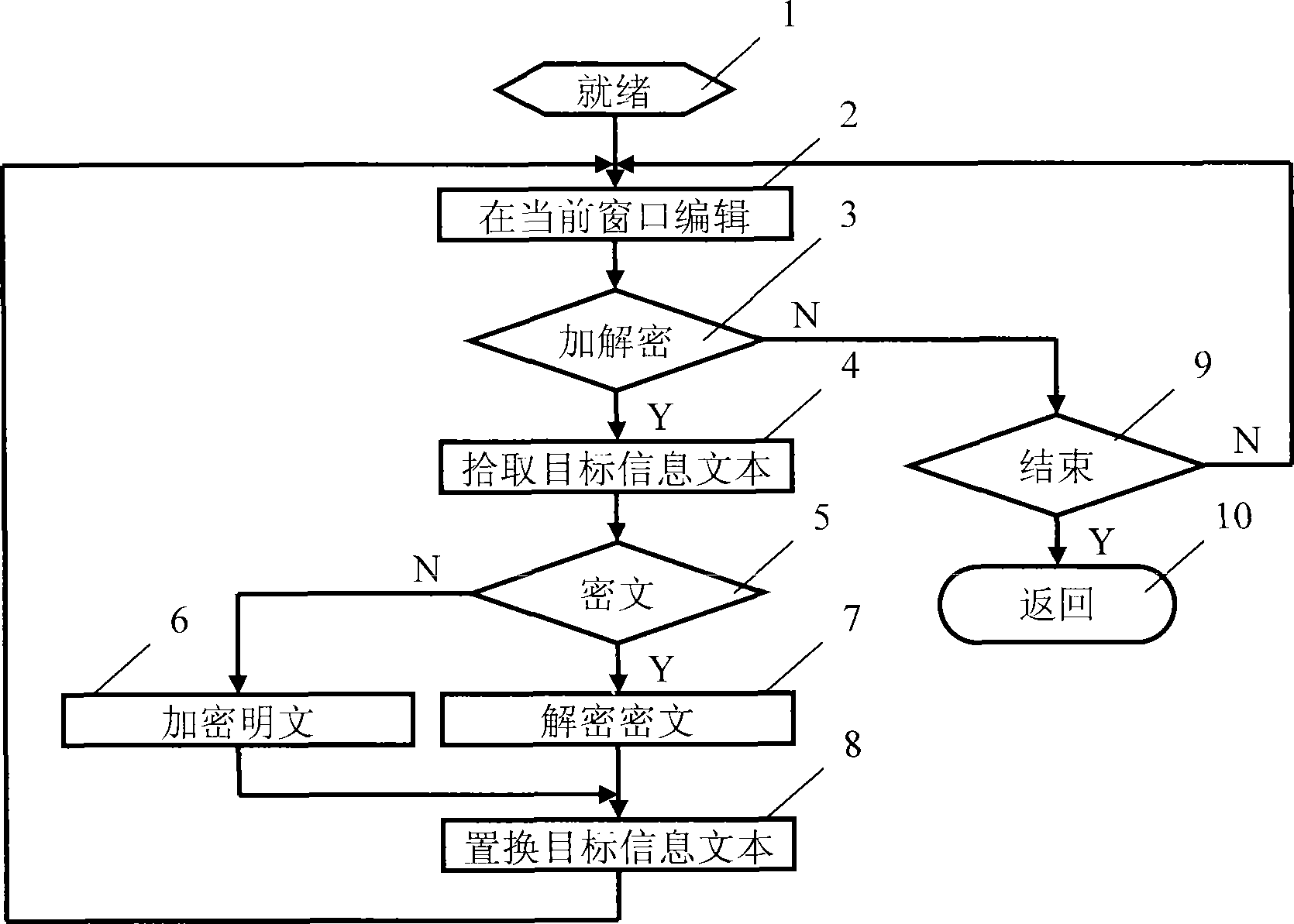
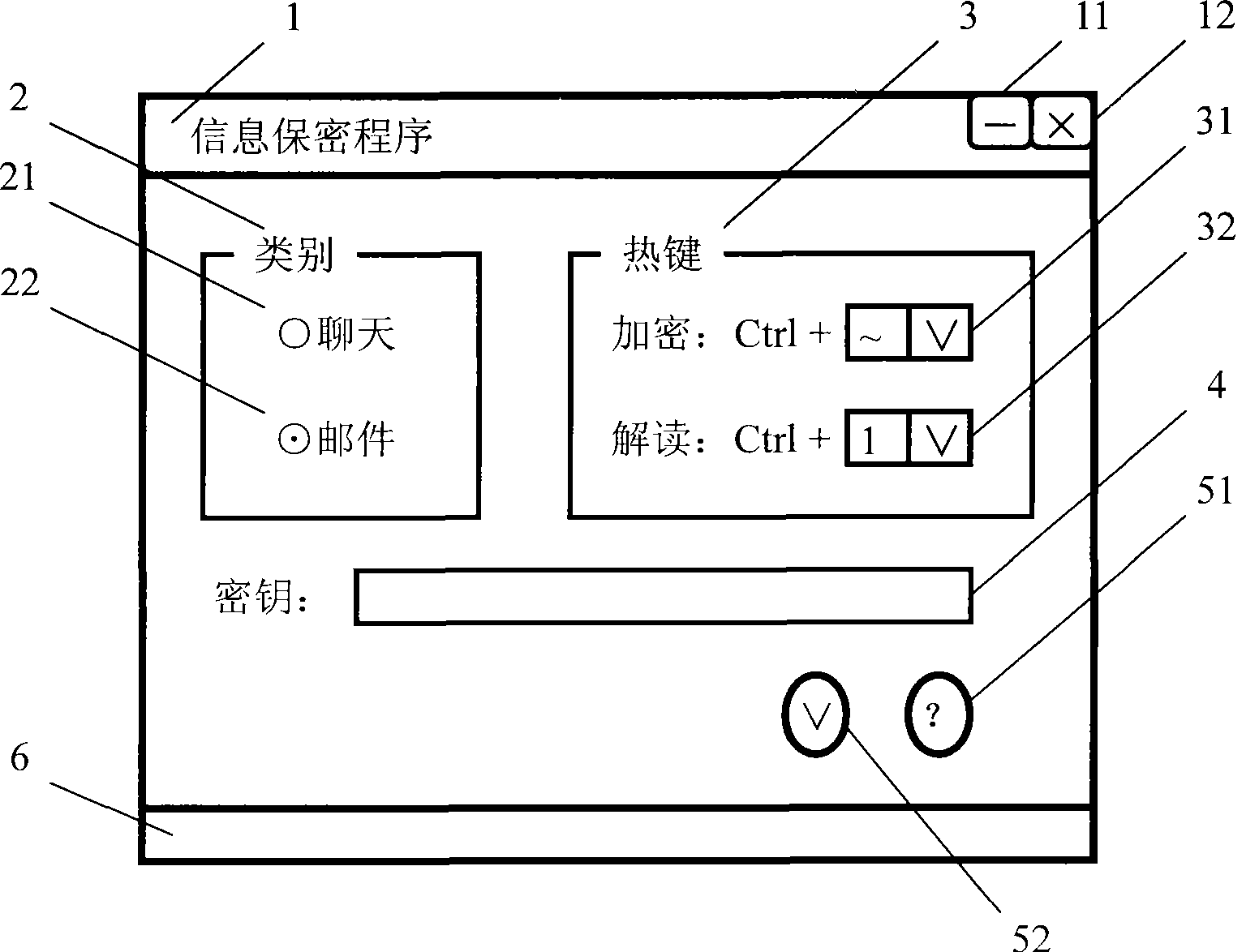
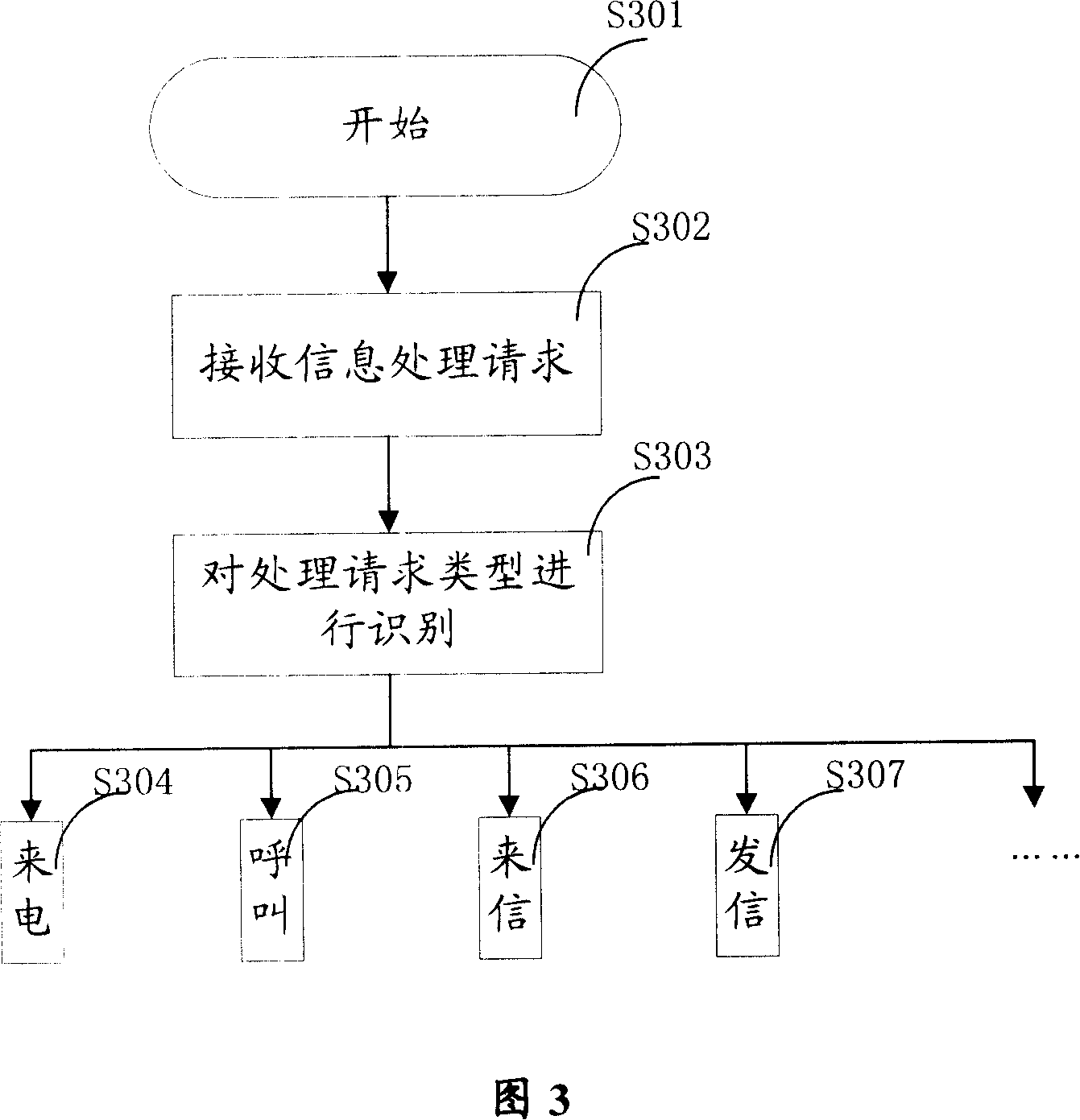
An information security method and procedure relates to the field of computer software, network communications and information security technology, especially used for information security of instant messaging, e-mail and other edited texts. By cipher algorithm procedure and / or by cipher device hardware, complete or selective instant encrypt or instant decipher is performed to text message in the current editing text, so as to instantly replace it from plaintext to ciphertext or from ciphertext to plaintext and present in the same window; when the cursor is stopped at the read-only ciphertext, it can be instant read and the corresponding plaintext can be presented; furthermore, it can be driven by a same shortcut operation, so that the encryption and decryption can be alternately performed, plaintext and ciphertext can be alternately replaced and displayed; a practical information security program is also designed, which is used in synergy with the object program and runs independently, to realize real-time encryption and decryption to information. The invention is general-purpose, convenient, flexible and efficient, and has universality because of its informality in the device hardware and no limitation to the application software.
Owner:杨筑平
Information privacy method and electronic terminal
InactiveCN103177206AAvoid identificationConfidentiality is concealedDigital data protectionDigital data authenticationComputer terminalInformation confidentiality
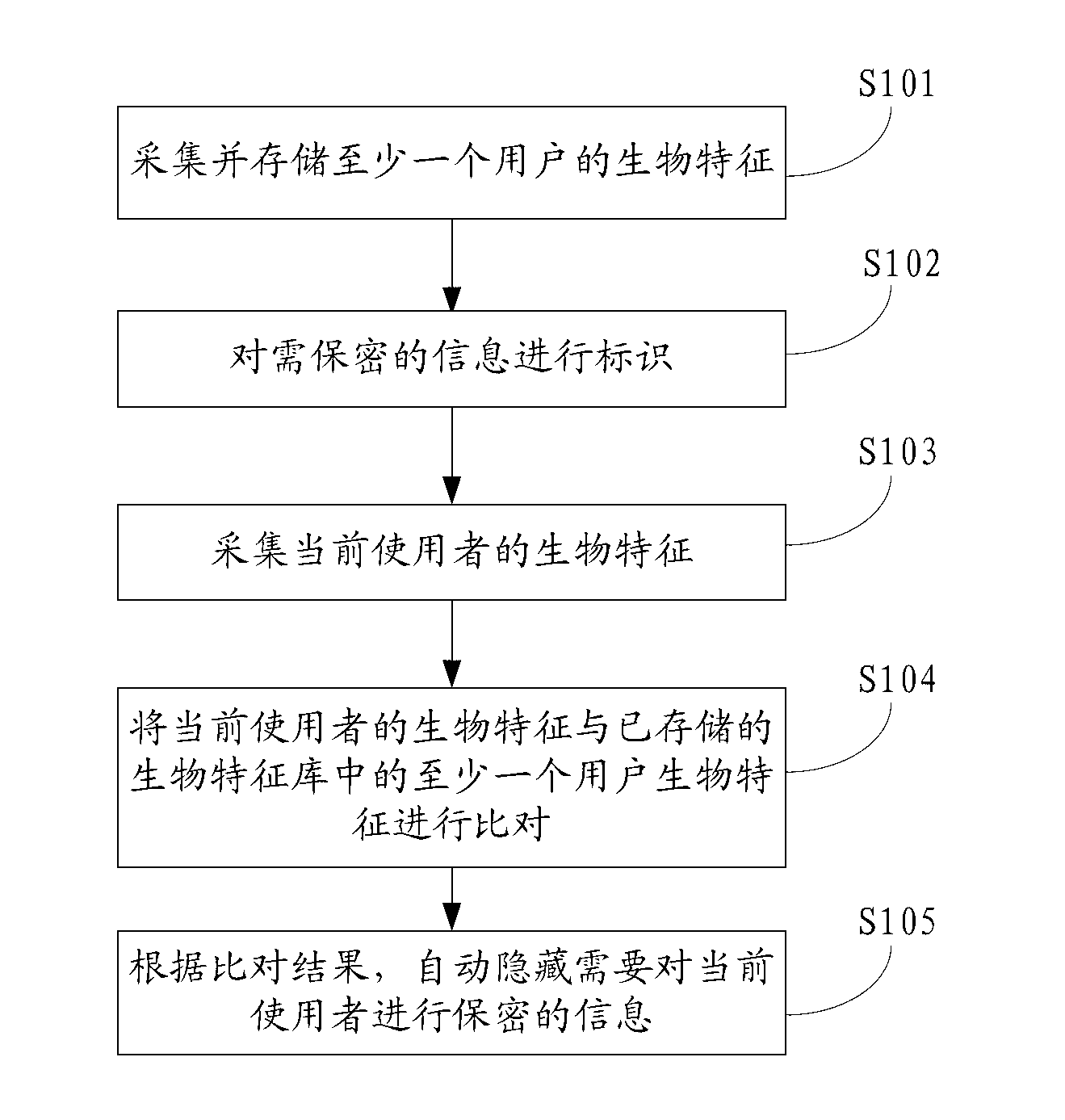
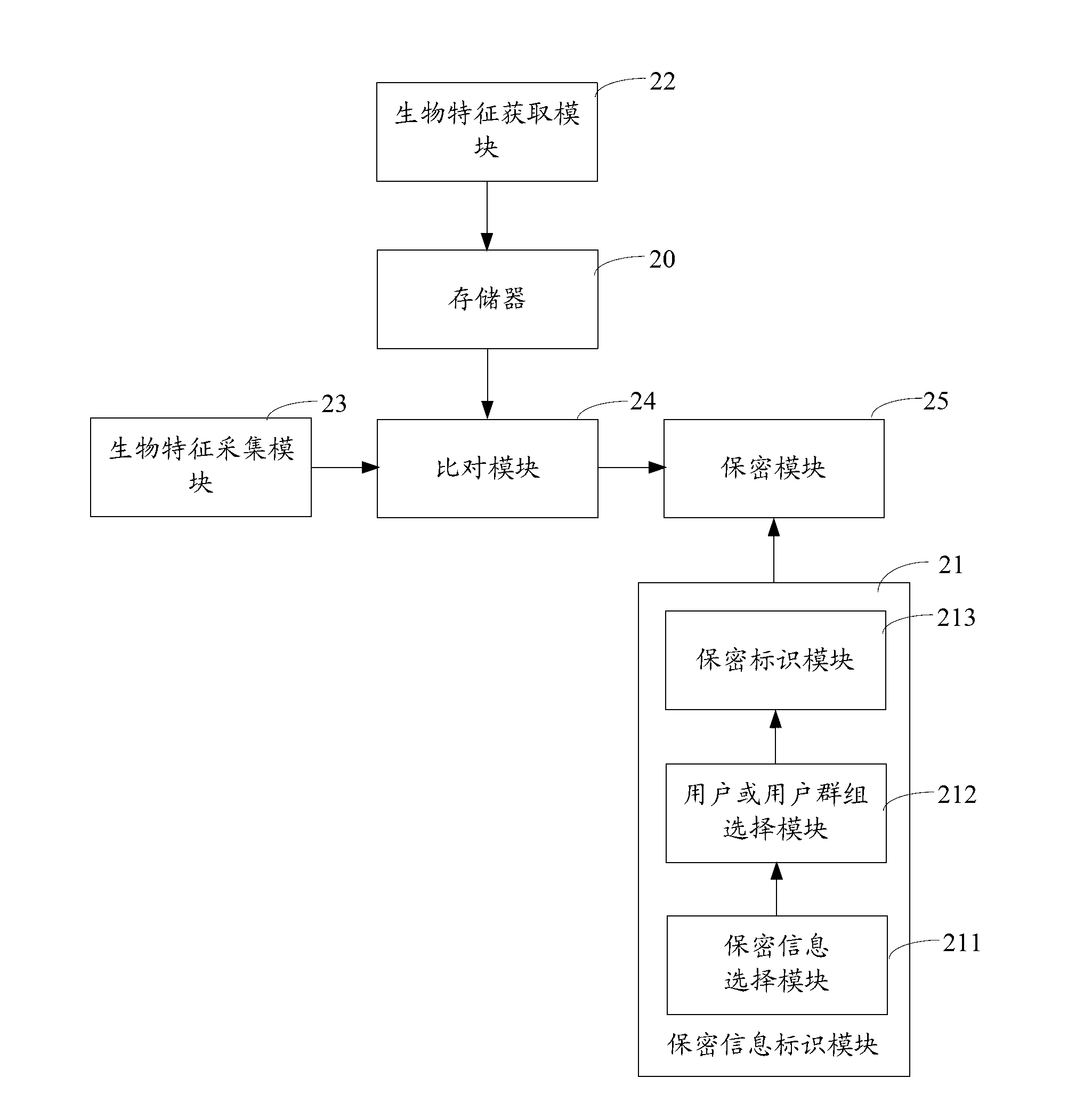
The invention belongs to the field of communication and provides an information privacy method and an electronic terminal. The information privacy method includes the following steps. Biological characteristics of a current user are collected. The biological characteristics of the current user are compared with at least one user biological characteristic stored in a biological characteristic base. The user biological characteristic is correlated with operation authority of information privacy. According to a comparison result, information that the current user is not supposed to know is automatically hidden. The biological characteristics of the current user are collected and compared with the stored biological characteristics. Based on the comparison result, the information that the current user is not supposed to know is automatically hidden. Thus, automatic identification can be performed without tedious log-in and code entering. Private information can be automatically hidden and a privacy manner is invisible and not easily observed by people.
Owner:NUBIA TECHNOLOGY CO LTD
Government affair data exchange method and device based on block chain
InactiveCN109858258AMeet data fusion demandsDatabase distribution/replicationDigital data protectionTamper resistanceData access
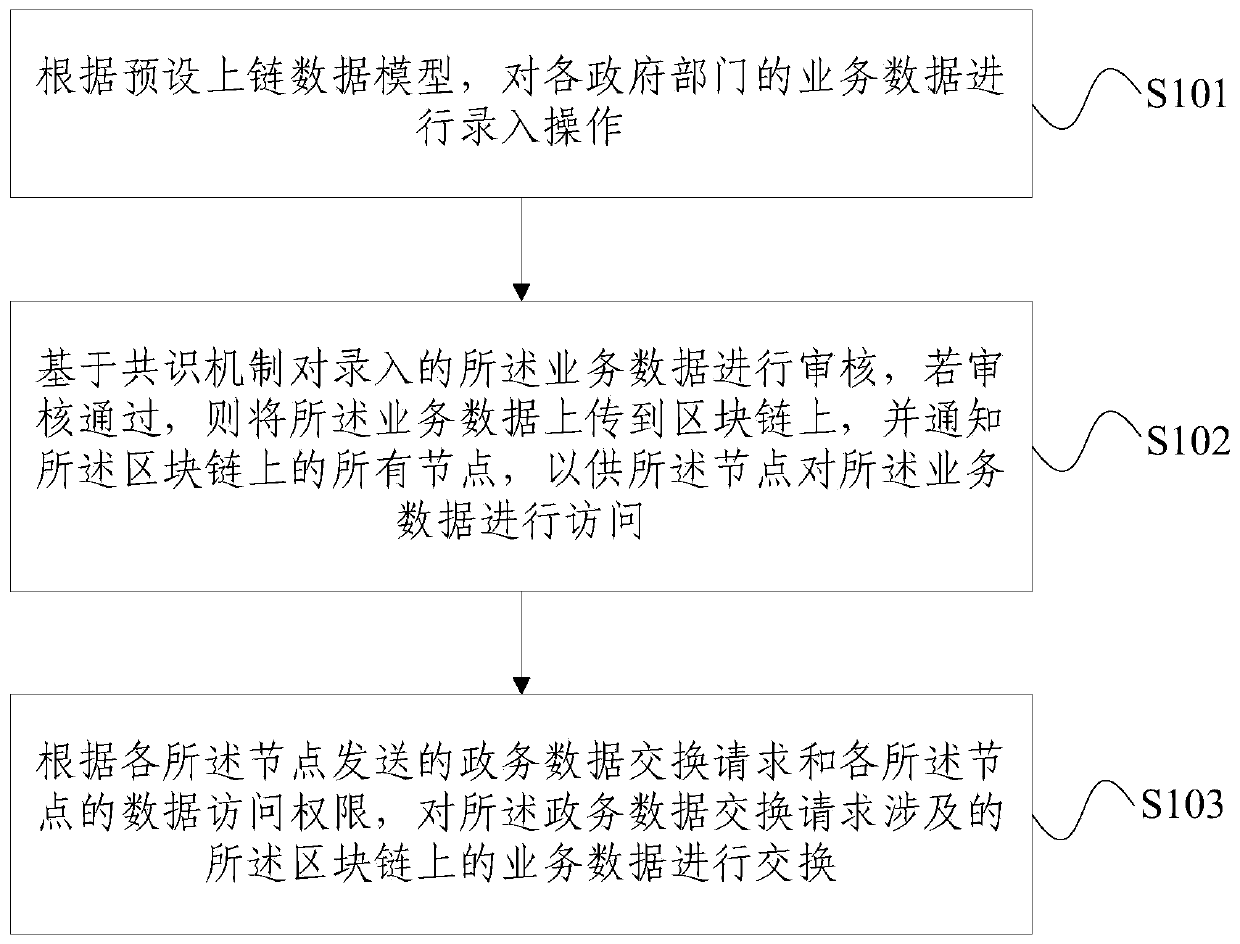
The embodiment of the invention provides a government affair data exchange method and device based on a block chain, and the method comprises the steps: carrying out the input operation of the business data of each government department according to a preset uplink data model; the input service data is audited based on a consensus mechanism, if the audit is passed, the service data is uploaded tothe block chain, and all nodes on the block chain are notified, so that the nodes can access the service data; and according to the government affair data exchange requests sent by the nodes and the data access authorities of the nodes, service data on the block chains related to the government affair data exchange requests are exchanged. According to the embodiment of the invention, the block chain technology is applied to the government affair data exchange scene, the problems of information confirmation, information confidentiality and information tamper-proofing existing in cross-domain data circulation and sharing are solved, cross-domain sharing of government affair data, multi-department communication, power-assisted supervision and collaborative promotion of execution departments are promoted, and the data fusion appeal of smart government affairs is met.
Owner:BEIJING MATARNET TECH
Method for acquiring information, and hand-held mobile communications device for implementing the method
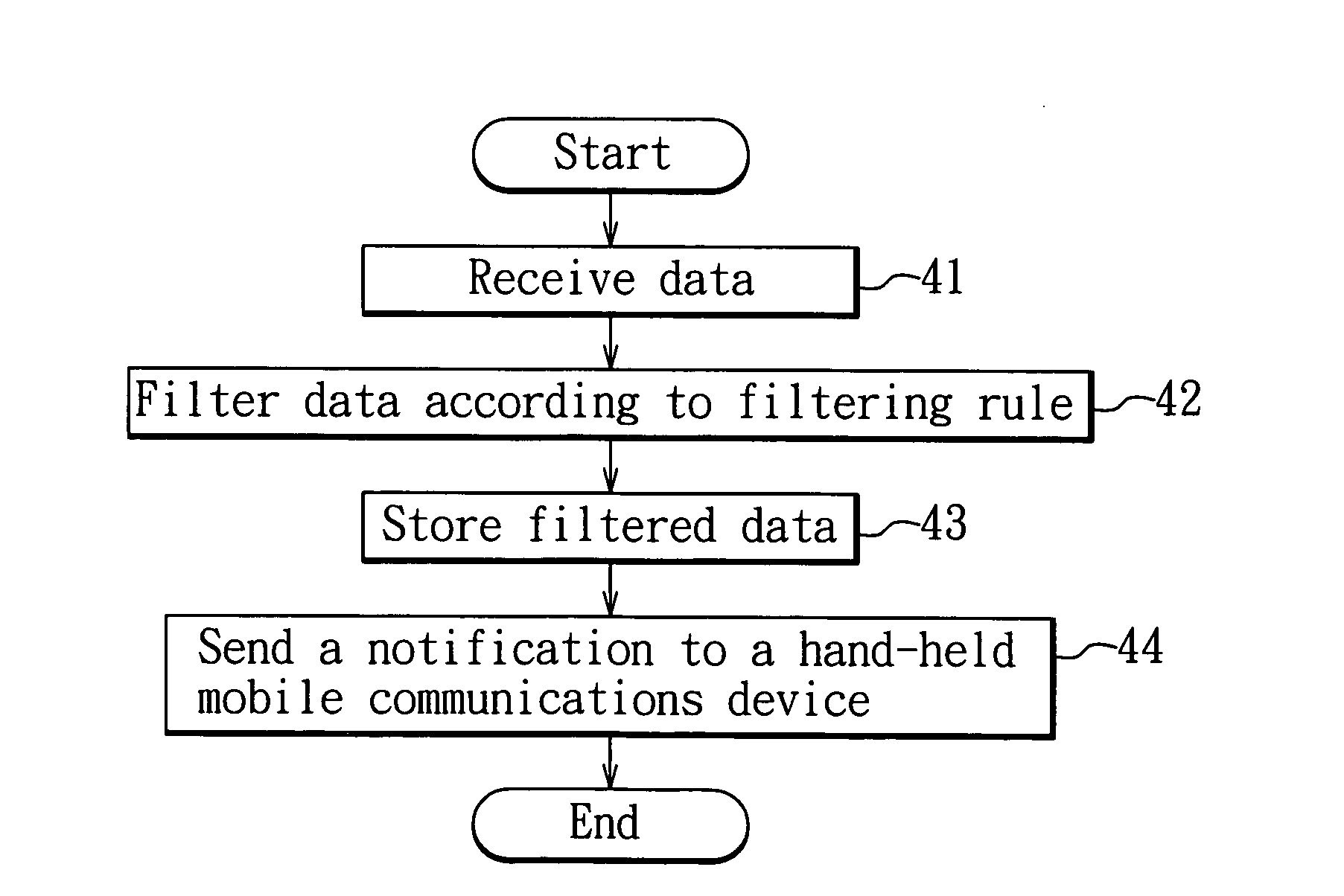
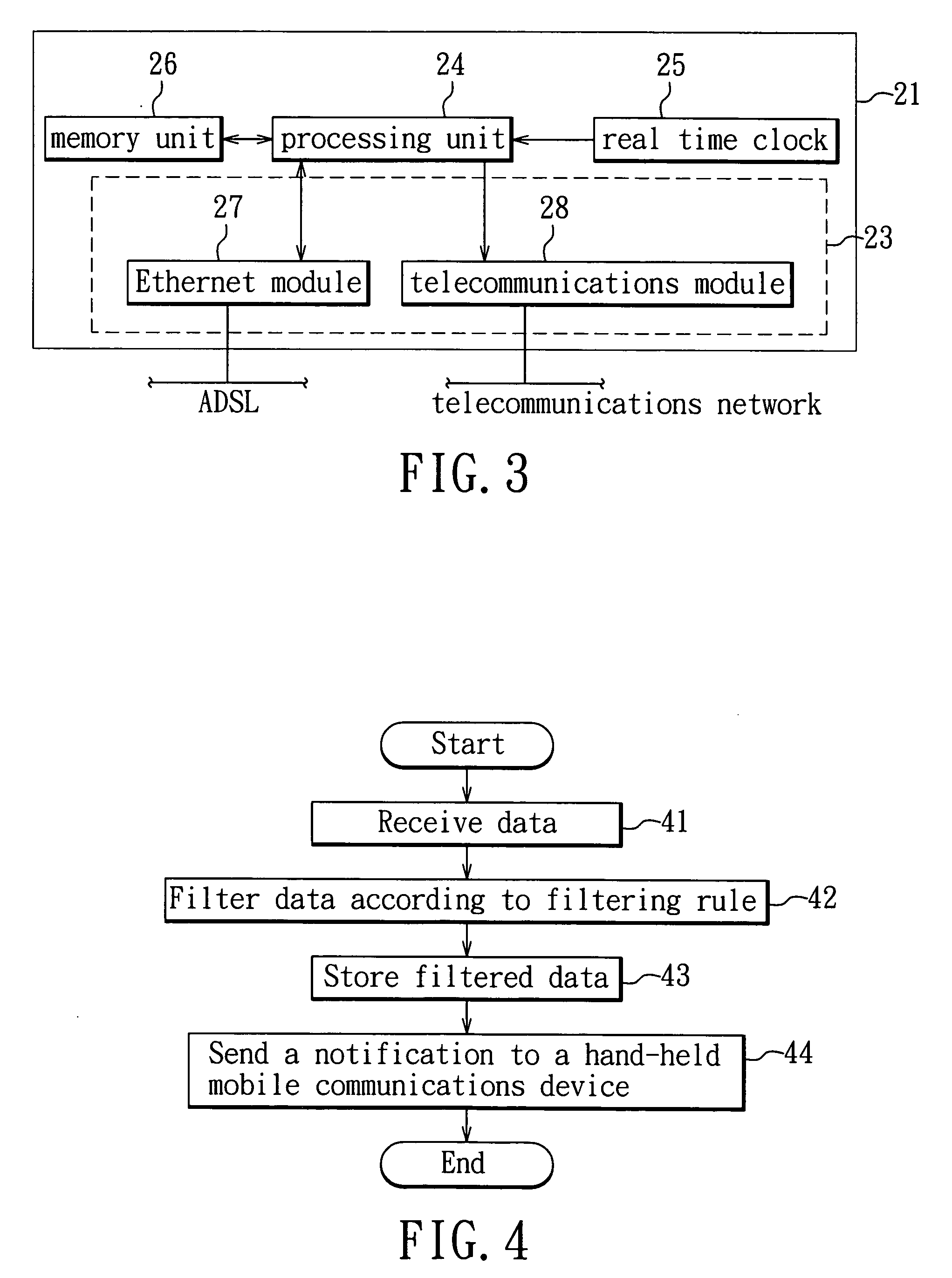
InactiveUS20070204022A1Overcomes drawbackDigital computer detailsData switching networksThe InternetFiltering rules
A method for acquiring information is implemented in a hand-held mobile communications device to access information in a remote information server through the Internet. The method includes enabling the communications device to acquire information from the information server at predetermined times, to filter the acquired information according to a filtering rule, and to display information complying with the filtering rule or a notification message relating to the information complying with the filtering rule according to a user setting. The method and device permits user convenience and ensures information confidentiality, without incurring extra fees.
Owner:ACER INC
Method and apparatus for protecting mobile terminal private information
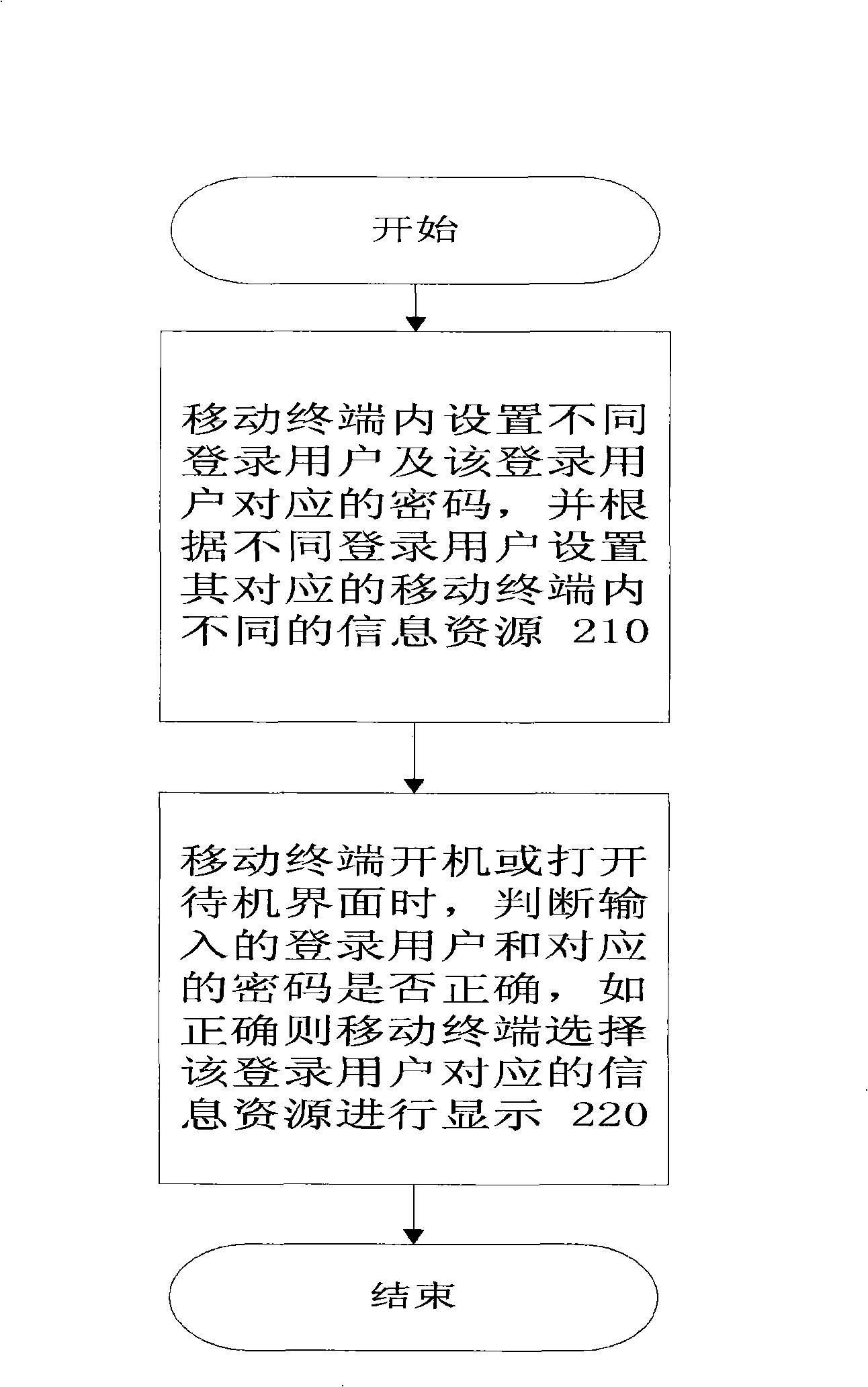
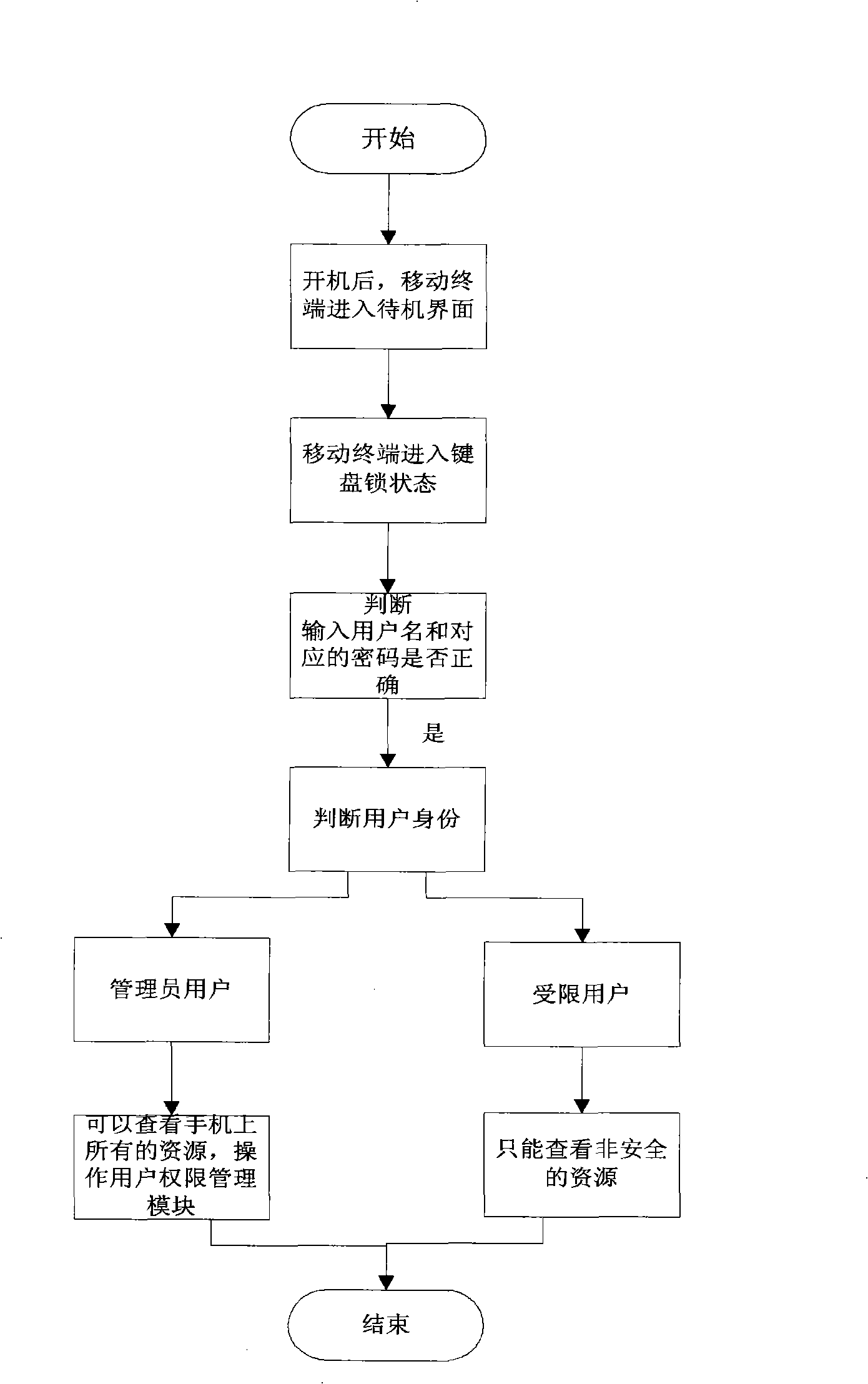
InactiveCN101282535AEliminate concerns about confidentiality of private informationRemove concerns about confidentialitySubstation equipmentRadio/inductive link selection arrangementsPasswordInformation resource
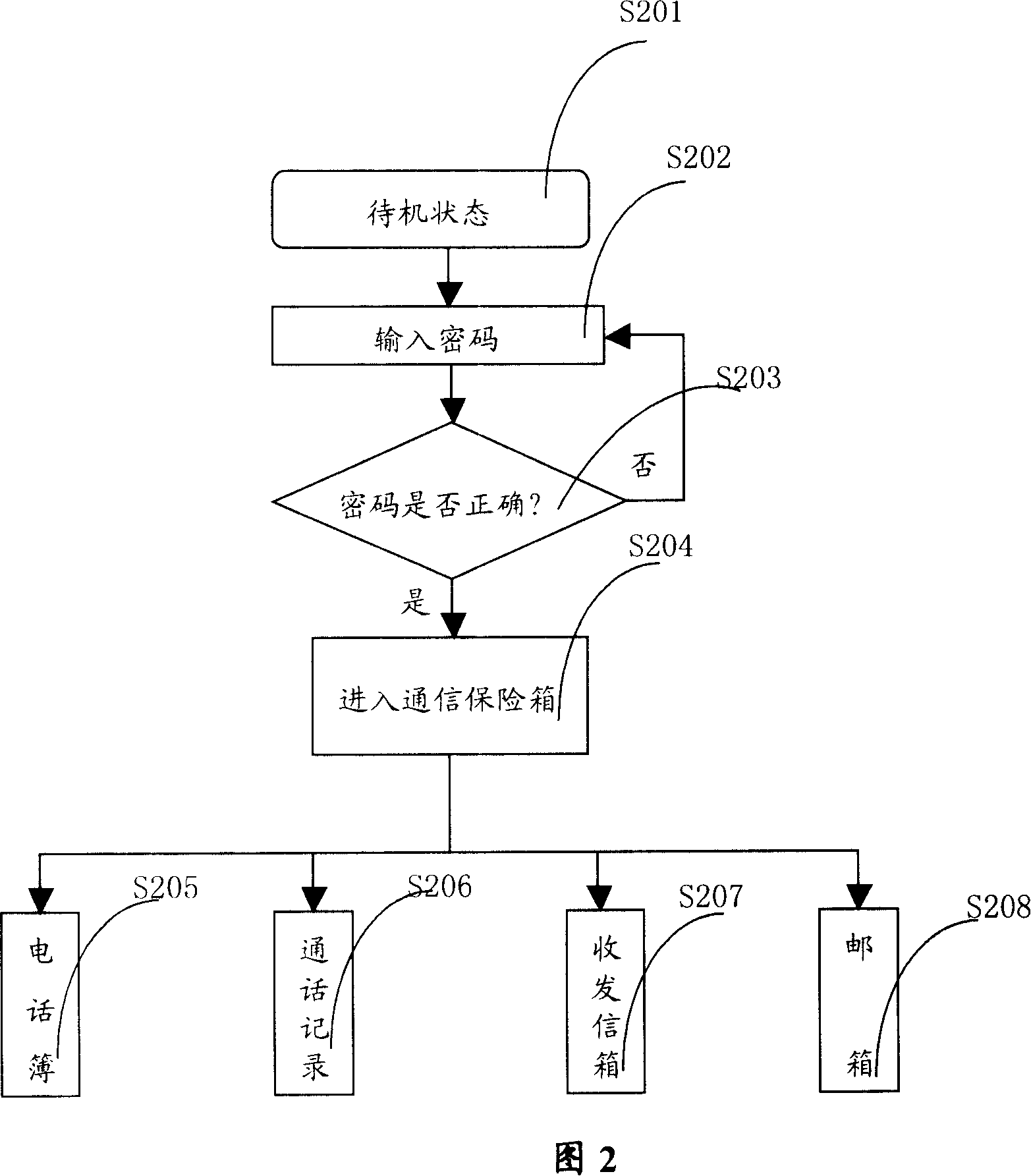
The invention discloses a method and device for protecting the private information of the mobile terminal. The method comprises: setting different login users and the corresponding password for the login user in the mobile terminal, and setting the corresponding different resource of the mobile terminal according to the different login users; when the mobile terminal is opened or in the standby interface, judging whether the corresponding password of the login user is correct; if the password is correct, the mobile terminal selects the corresponding information resource to display of the login user. The invention enables the other people see the corresponding information inclusively; the information which is not allowed to see id hidden, which can completely remove the worries for the private information confidentiality in the mobile terminal.
Owner:ZTE CORP
Method, device and system for mobile information services
InactiveUS20070191034A1Overcomes drawbackRadio/inductive link selection arrangementsMessaging/mailboxes/announcementsHand heldFiltering rules
In a method of mobile information services, a mobile information service device is connected to a remote information server and a telecommunications service provider so as to timely provide information to a hand-held mobile communications device. In the method, the mobile information service device searches the information server according to a filtering rule for information complying with the filtering rule, and sends a notification message to the hand-held mobile communications device through the telecommunications service provider such that the hand-held mobile communications device, after receipt of the notification message, downloads information related to the notification message from the information server, thereby achieving user convenience and ensuring information confidentiality, without incurring extra fees.
Owner:ACER INC
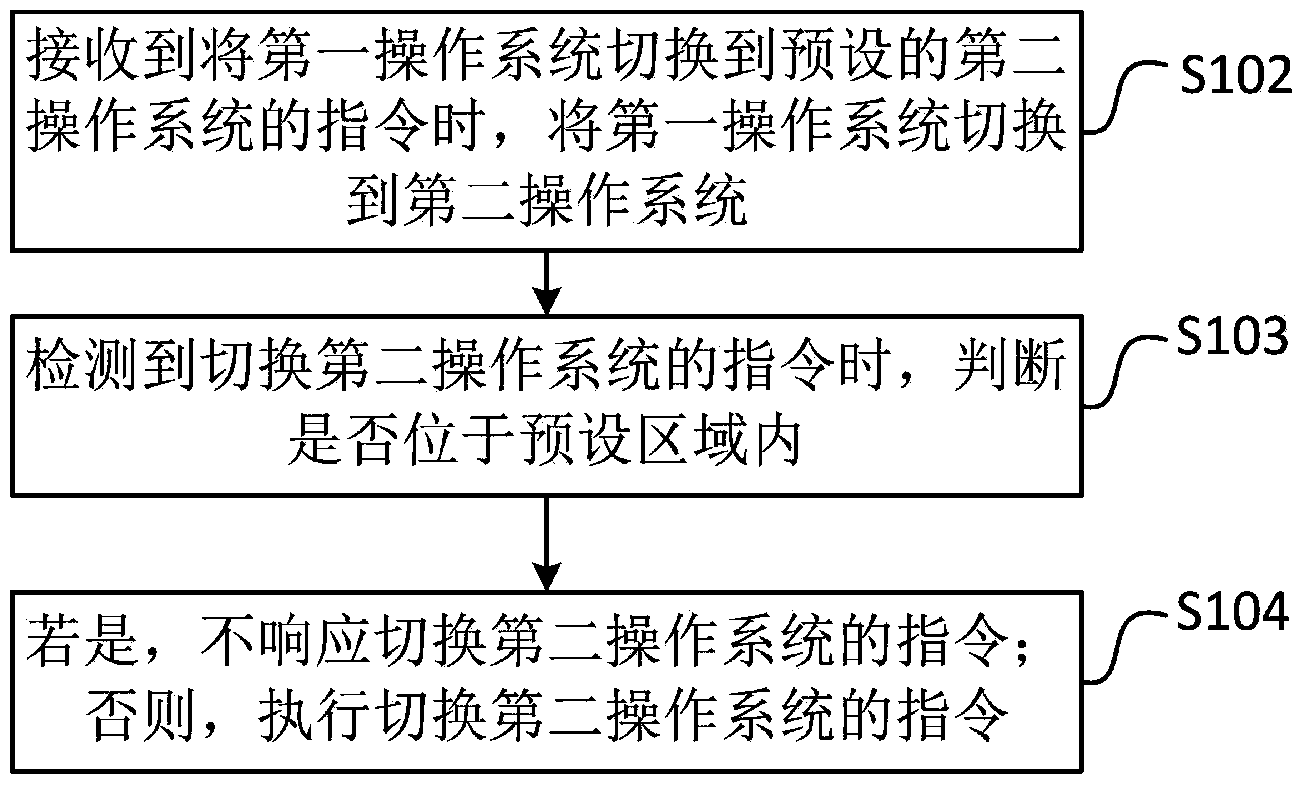
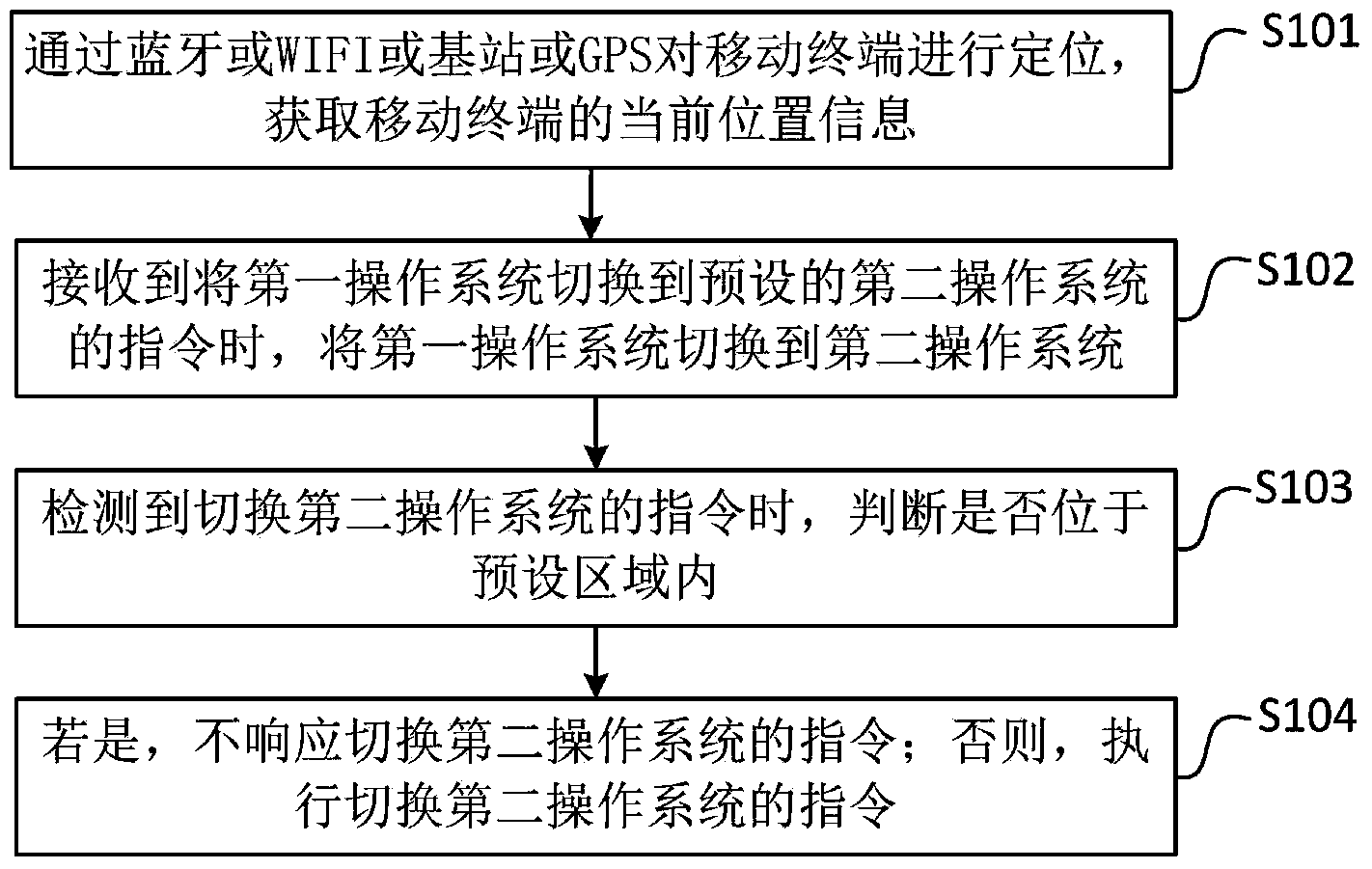
Mobile terminal as well as method and device for controlling switching of operation systems of mobile terminal
InactiveCN104239140AImplement security managementGuaranteed confidentialityProgram initiation/switchingComputer terminalInformation confidentiality
The invention discloses a mobile terminal as well as a method and a device for controlling switching of operation systems of the mobile terminal and belongs to the technical field of mobile terminals. The method comprises the following steps: when receiving an instruction of switching a first operation system to a preset second operation system, switching the first operation system to the second operation system; when detecting an instruction of switching to thse second operation system, judging whether the mobile terminal in positioned in a preset region; if yes, ensuring not to respond to the instruction of switching the second operation system; otherwise, executing the instruction of switching to the second operation system. By adopting the method, when the mobile terminal enters into a preset region which is required to keep confidential, controlling to switch the mobile terminal into the preset operation system, wherein the operation system is a safe operation system, applications or functions, such as photographing and sound recording, which possibly cause information leakage, are restricted, the operation system can not be switched from the preset operation system to another operation system in the preset region, united safety management for the mobile terminal is realized and the information confidentiality is ensured.
Owner:NUBIA TECHNOLOGY CO LTD
Method for acquiring information, and hand-held mobile communications device for implementing the method
A method for acquiring information is implemented in a hand-held mobile communications device to access information in a remote information server through the Internet. The method includes enabling the communications device to acquire partial content of information from the information server at predetermined times, to filter the acquired partial content according to a filtering rule, download information that complies with the filtering rule according to the filtering result, and to display the information complying with the filtering rule or a notification message relating to the information complying with the filtering rule according to a user setting. The method and device permit user convenience and ensure information confidentiality, without incurring extra fees.
Owner:ACER INC
Classified passive optical network based on synchronization of chaos
InactiveCN103260095AIncrease system capacityImprove securityMultiplex system selection arrangementsFibre transmissionCarrier signalOptical communication
The invention discloses a classified passive optical network based on synchronization of chaos, and belongs to the technical field of classified optical communication. N pairs of semiconductor lasers with the same operating wavelength are adopted at two ends of an OLT and two ends of an optical network unit to serve as a chaotic carrier wave generator. Uplink information and downlink information are respectively loaded to n chaotic carrier waves with different wavelengths through an optical modulator to achieve information chaotic encryption, up-load and down-load are carried out through optical fibers after combination by adopting a wavelength-division multiplexing technology, and at last information decryption is achieved by adopting a chaotic carrier wave with the same wavelength. An all-optical chaotic signal is used as a carrier wave and combined with the wavelength-division multiplexing technology to carry out classified transmission on uplink information and downlink information, information security of the passive optical network is improved from a physical layer, the classified passive optical network based on synchronization of the chaos is suitable for a communication service with high requirements in information confidentiality, and reference significance is provided to improve safety of the passive optical network.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
QR two-dimensional code binary image partition-based key varying chaotic encryption method
InactiveCN103414549AAdd auxiliary keyImplement chaotic encryptionRecord carriers used with machinesSecuring communicationComputer hardwareTransfer procedure
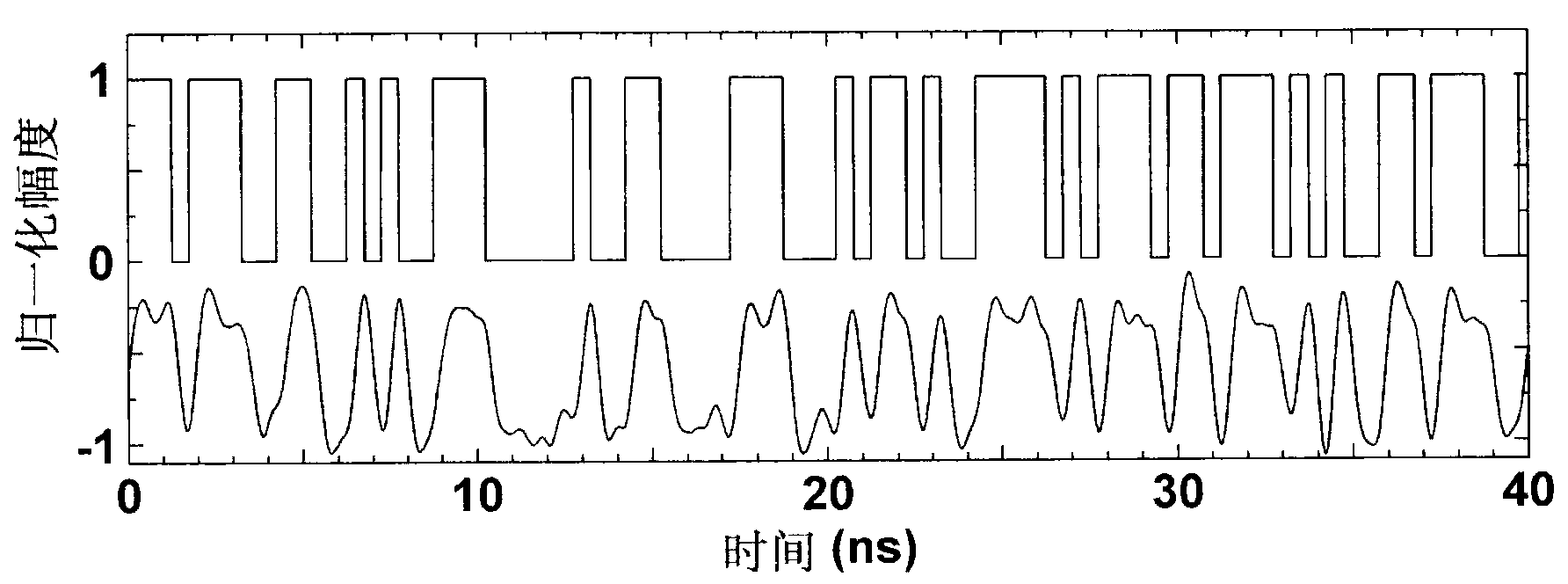
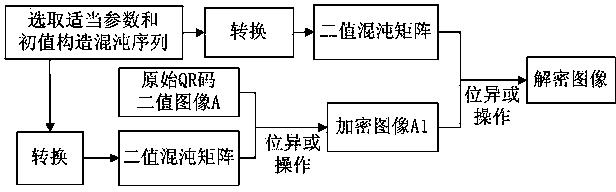
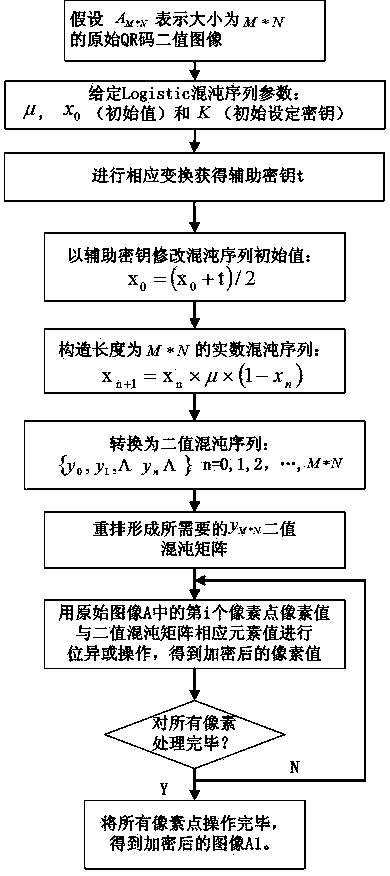
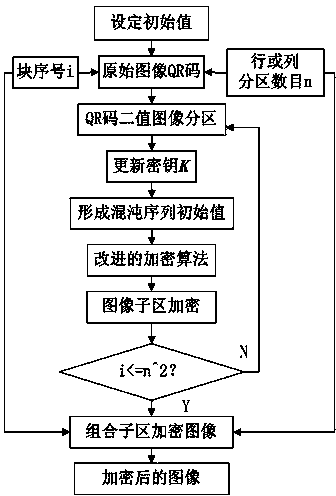
The invention relates to a QR two-dimensional code binary image partition-based key-varying chaotic encryption method. The method comprises the following steps that: 1), a traditional logistic chaotic mapping encryption algorithm is improved in a manner that an auxiliary key is added such that a new initial value x0 can be formed; 2), an original QR-code binary image is partitioned, and the total number of sub-region images of which the pixel is 1 is calculated, and therefore, the initial values of random keys of sub-blocks are formed; and 3), the auxiliary key and the random key are combined with partition encryption technology, such that QR code binary image partition-based key-varying chaotic encryption and decryption algorithms can be realized. With the QR two-dimensional code binary image partition-based key-varying chaotic encryption method adopted, random variation of keys can be realized; key space and key paths can be expanded; the reliability and security of encryption can be enhanced; a requirement for QR code information confidentiality in storage and transmission can be satisfied; and at the same time, an encryption effect, encryption speed and cracking difficulty are further improved. The QR two-dimensional code binary image partition-based key-varying chaotic encryption method of the invention is advantageous in convenience, practicability, safety and reliability.
Owner:GUANGDONG UNIV OF TECH
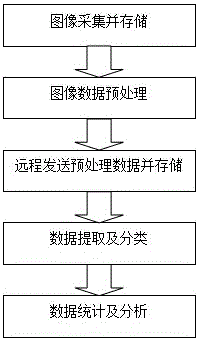
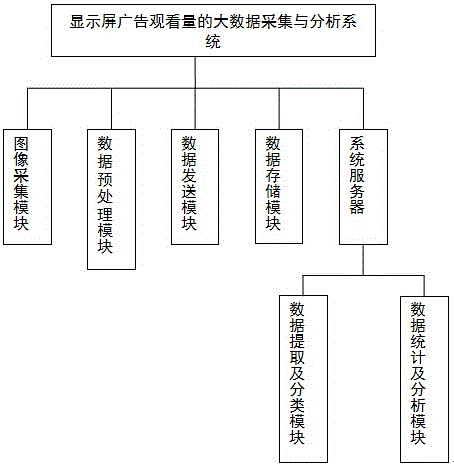
Big data acquisition and processing system and method based on viewing amount of advertisements on display screen
InactiveCN105894333ASolving Data Acquisition ProblemsImprove confidentialityMarketingLong term dataData acquisition
The invention relates to a big data acquisition and processing system and method based on the viewing amount of advertisements on a display screen, and belongs to the technical field of advertisement data acquisition and processing. The invention includes the steps of advertisement file import; image acquisition and storage; image data pre-processing; pre-processed data remote transmission and storage; data extraction and classification; and data statistics and analysis. The invention acquires image data automatically in real time with high acquisition efficiency and information confidentiality, obtains the real-time viewing amount of target advertisements through data classification, statistics and analysis, predicts the viewing amount of advertisements at fixed locations and time through long-term data accumulation, and assists advertisers in putting forward a reasonable advertising program.
Owner:KUNMING UNIV OF SCI & TECH
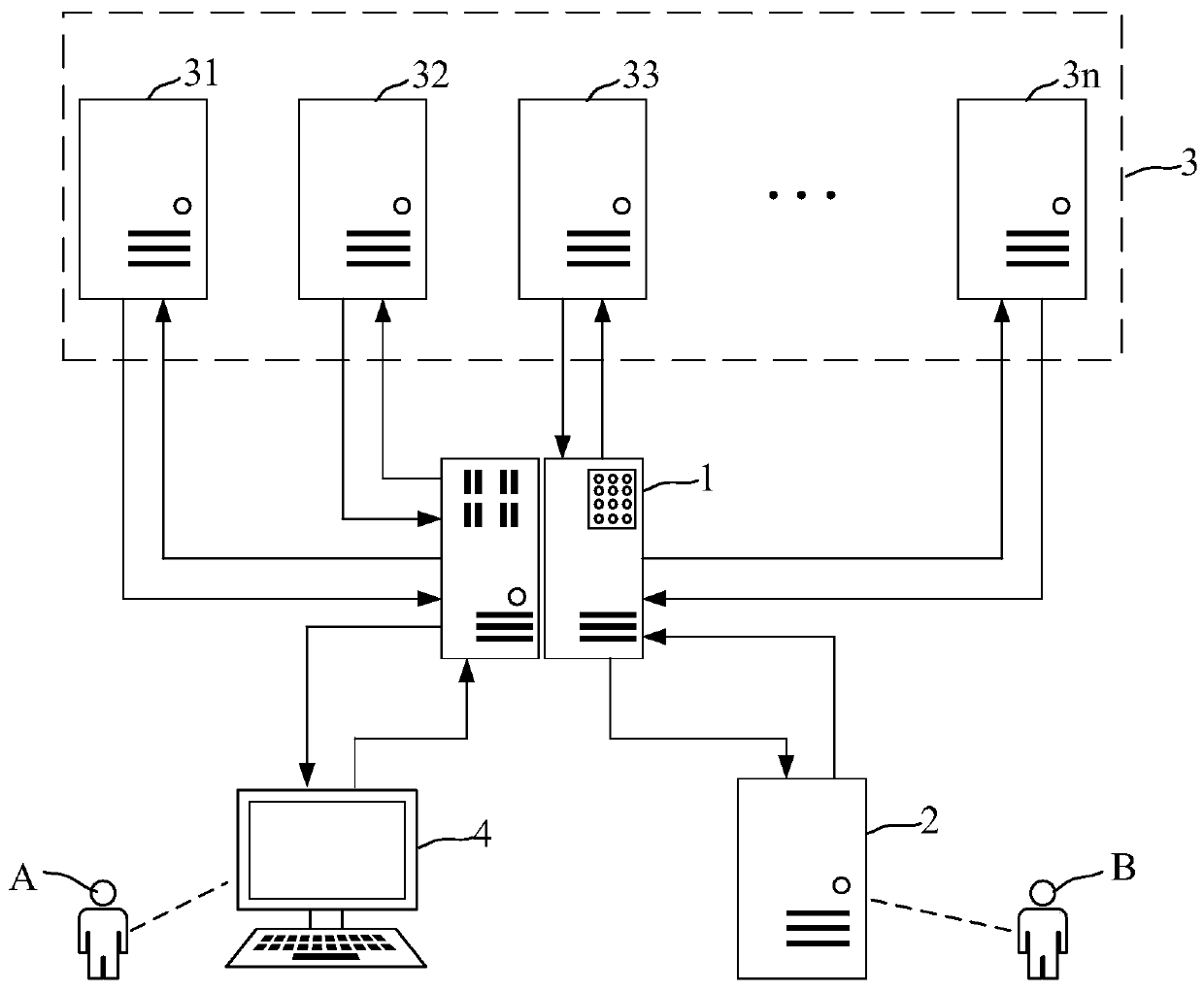
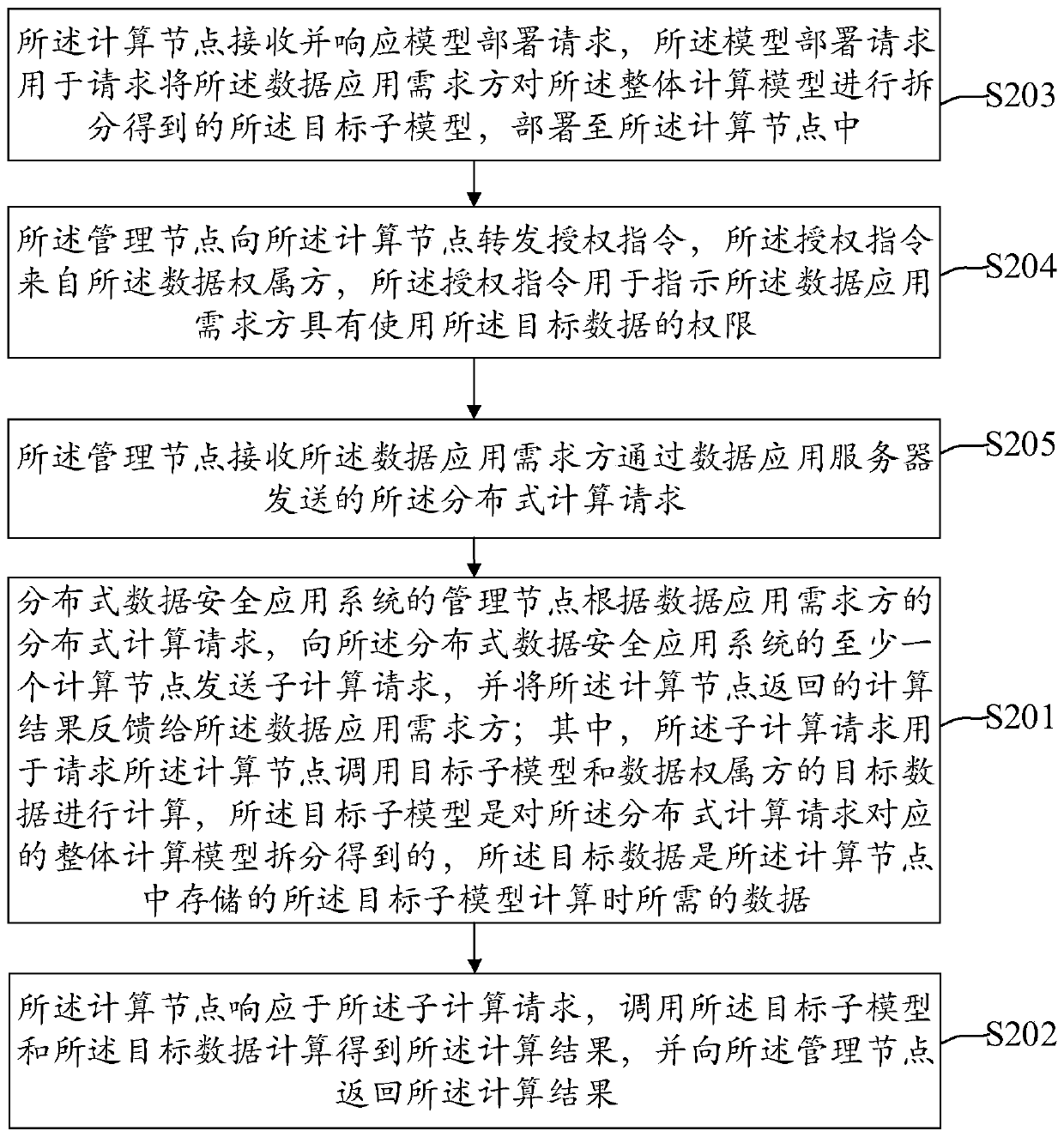
Distributed data security application method and system and electronic device
ActiveCN110222533AInhibit migrationGuarantee data securityDigital data protectionData switching networksDemand sideData application
The invention discloses a distributed data security application method and system and an electronic device. The method comprises the following steps: a management node of the distributed data securityapplication system carrying out data security application according to a distributed computing request of a data application demander; sending a sub-computing request to at least one computing node of the distributed data security application system, feeding back a calculation result returned by the calculation node to the data application demander; wherein the sub-calculation request is used forrequesting a calculation node to call target data of a target sub-model and a data ownership party for calculation, the target sub-model is obtained by splitting an overall calculation model corresponding to the distributed calculation request, and the target data is data required for calculation of the target sub-model stored in the calculation node; and the computing node responding to the sub-computing request, calling the target sub-model and the target data to compute to obtain a computing result, and returning the computing result to the management node. According to the method, data security and information confidentiality in the computing nodes can be strictly and effectively guaranteed.
Owner:英联(厦门)金融技术服务股份有限公司
System and method for cryptographic communications using permutation
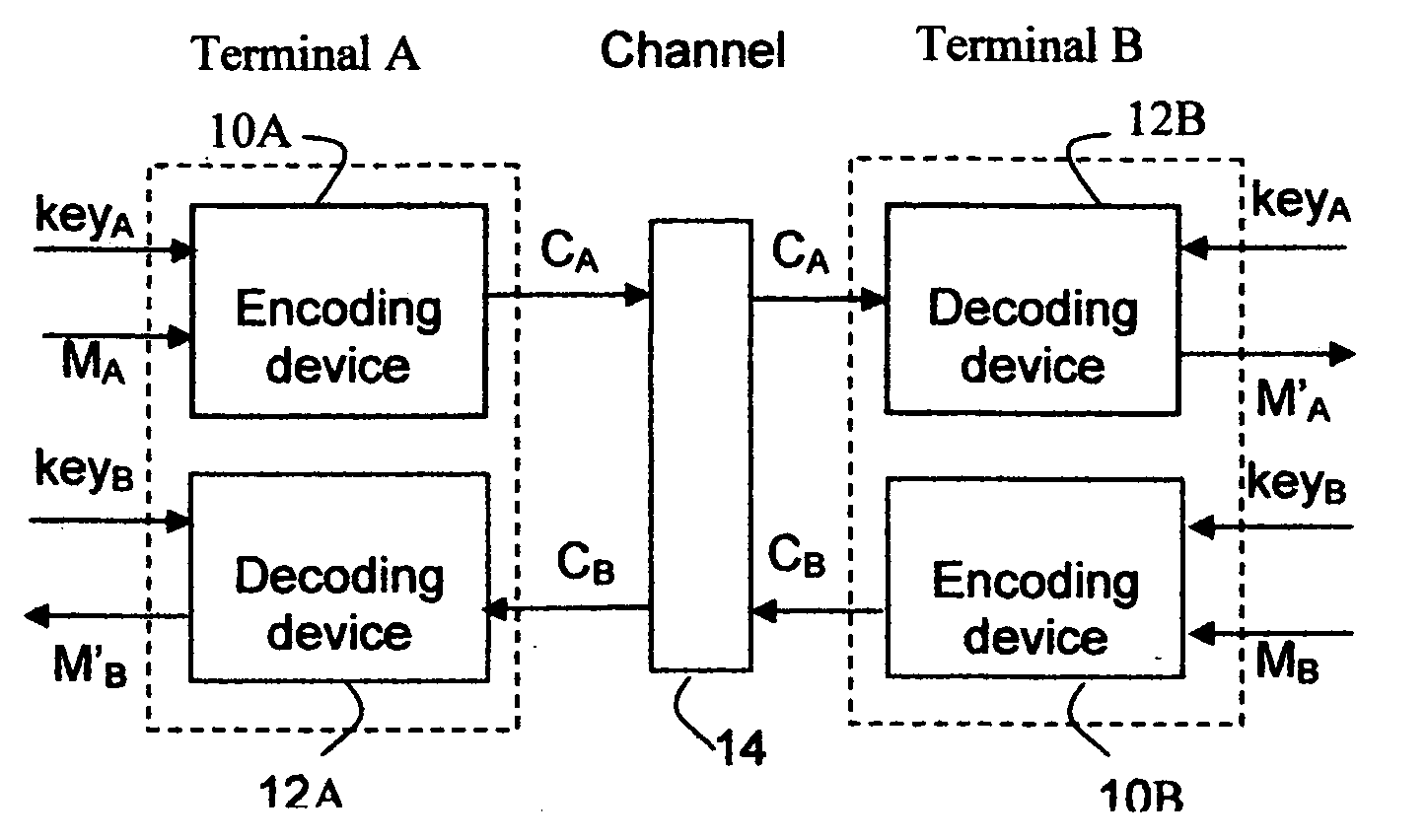
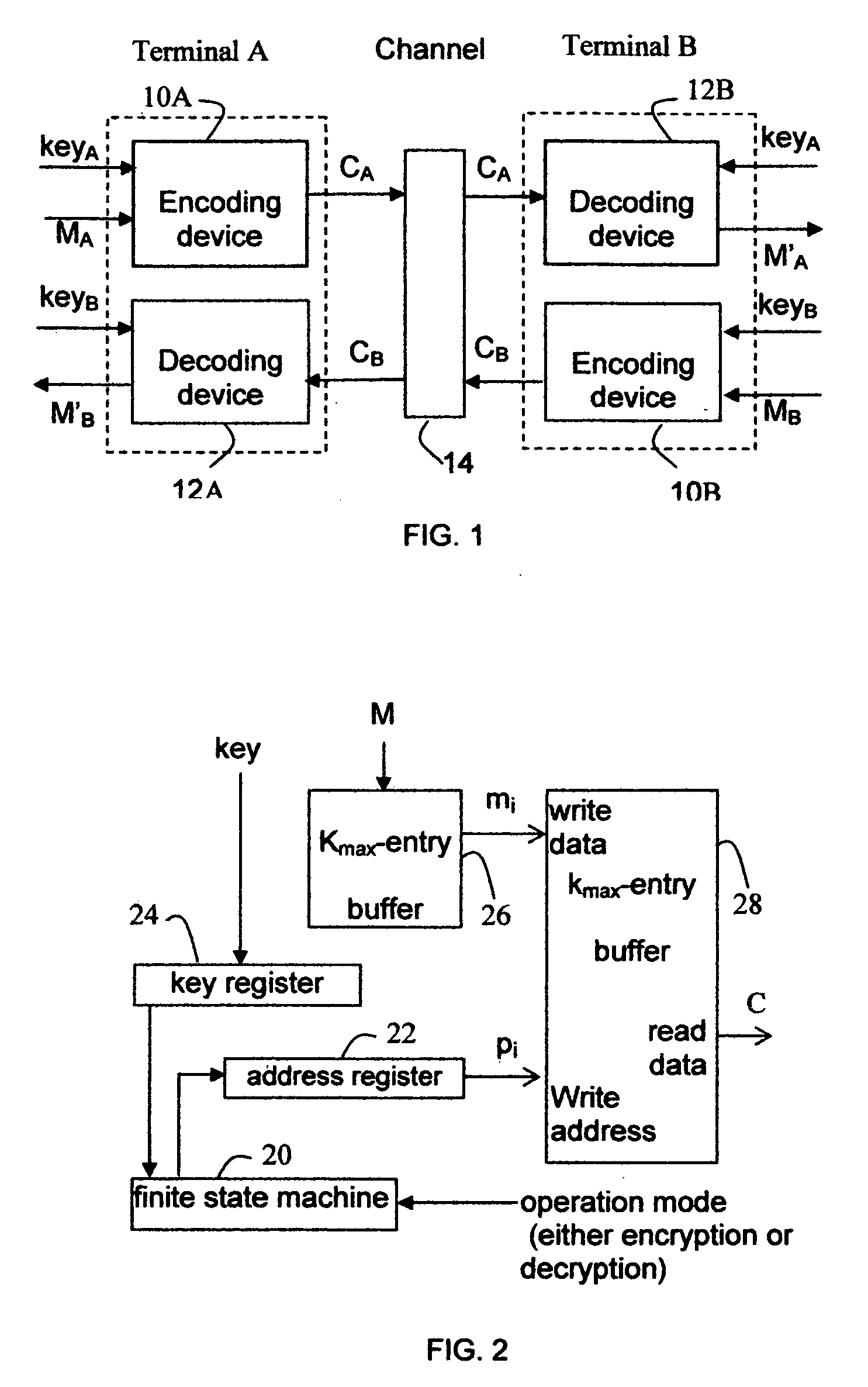
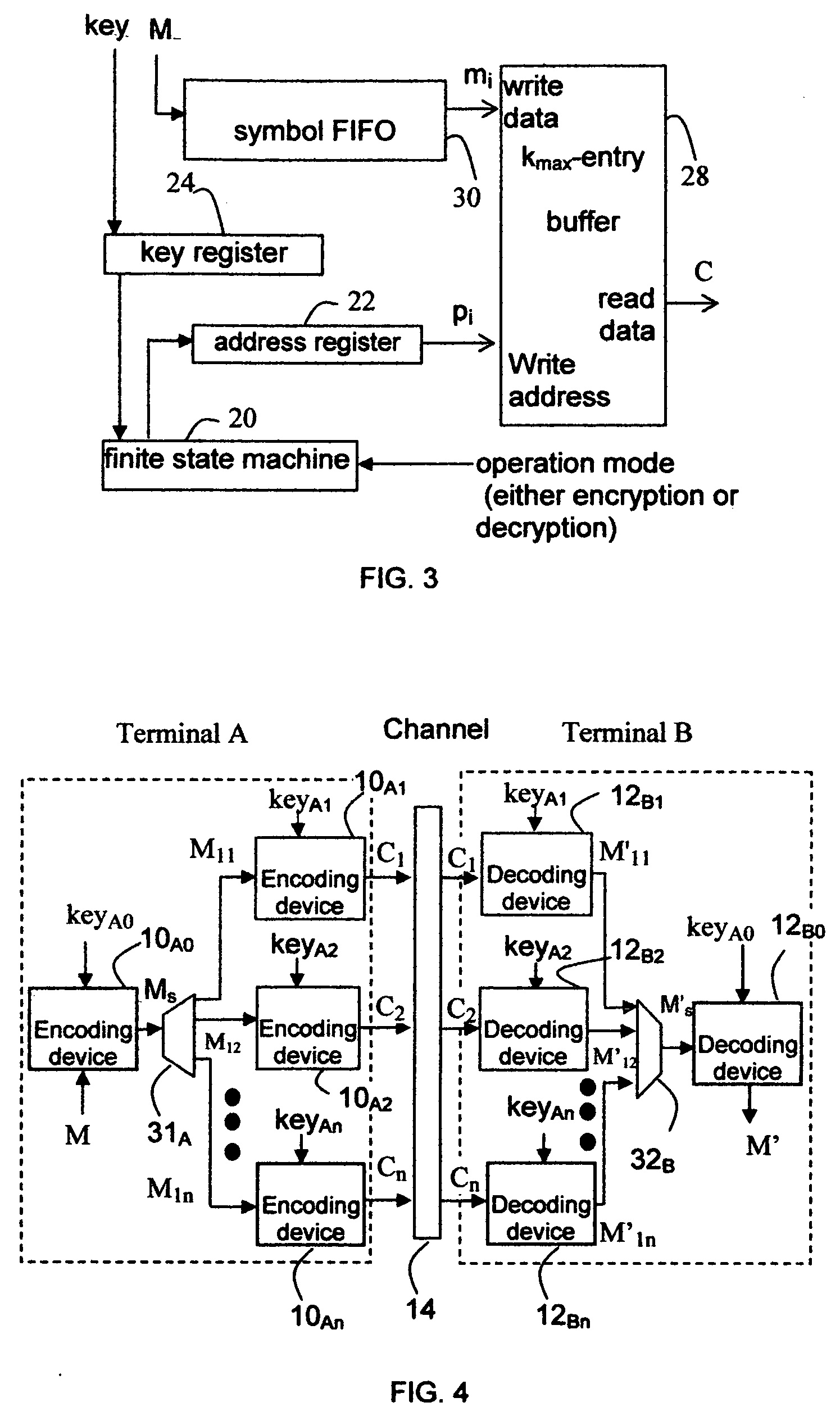
InactiveUS20120027198A1Small sizeComplexity of encryption is further confoundedEncryption apparatus with shift registers/memoriesSecret communicationComputer hardwareCiphertext
The present invention discloses a system and method for cryptographic communications. It may significantly improve operation efficiency of existing symbol level encryption algorithms by permutating at symbol sequence level with significantly less computational requirements. The system includes a communications channel, at least one terminal with encoding device and at least one terminal with decoding device. A message comprising ordered symbols can be partitioned into ordered symbol sequences. Then the order of symbol sequences is permutated by the encoding device. The partition and permutation can be repeated recursively on the resultant symbol sequences to obtain the ciphertext. All the partition and permutating information are characterized by a secret key, used for decoding on the receiving terminal. It is required that the final resultant symbol sequences in the ciphertext should not disclose information confidentiality. The present invention can be also applied to secure distributed data storage.
Owner:HE DR ZHIJIANG
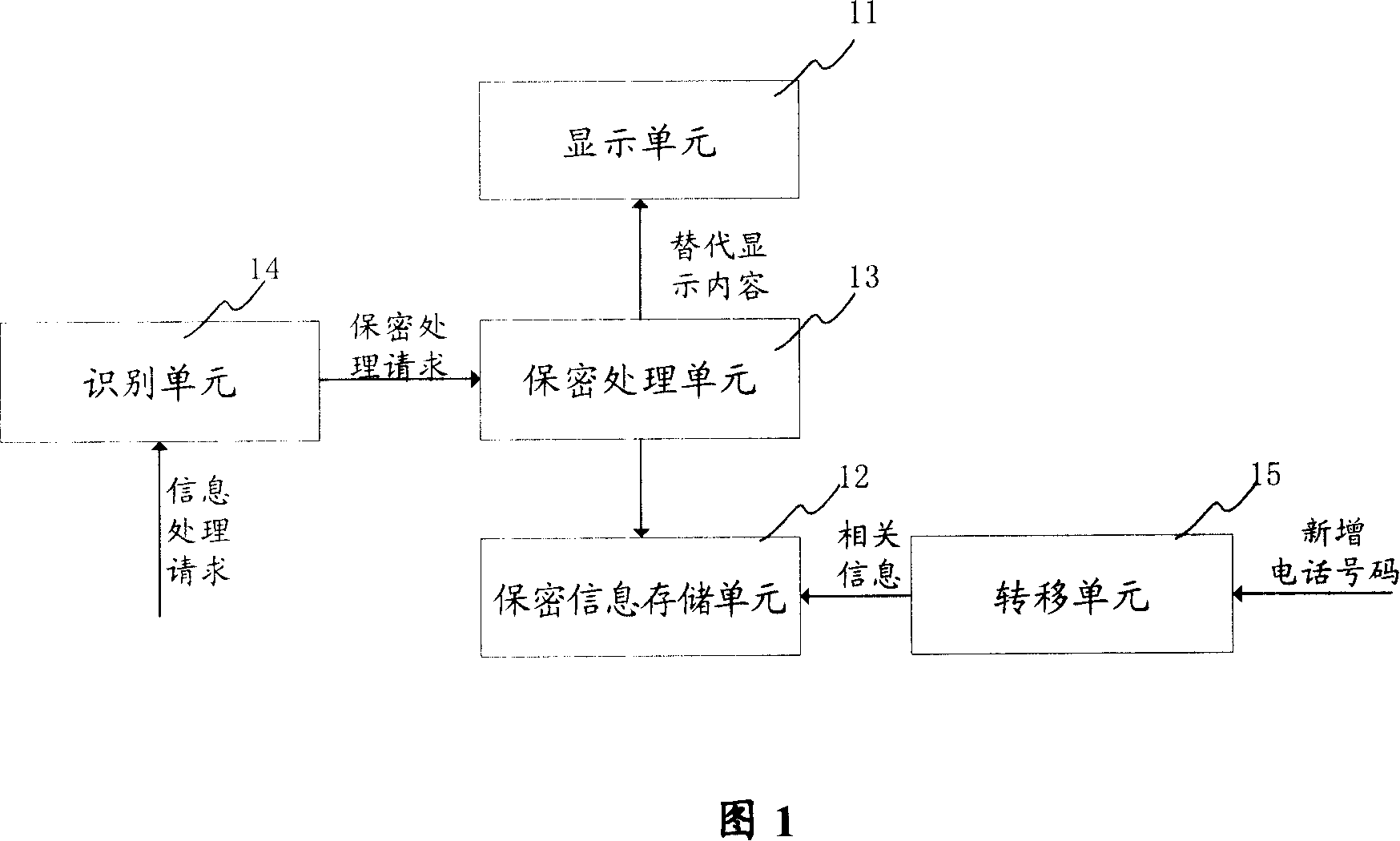
Information secret device for mobile communication terminal and relative method
InactiveCN101052152AImprove confidentialityAvoid attempts to crack passwordsKey distribution for secure communicationDigital data authenticationPasswordComputer terminal
The invention comprises: a display unit; a message storage unit used for saving each kink of secret information; a identifying unit used for identifying the number correlated to the message and deciding if the number was saved in the phone book saved in the storage unit; if yes, then sending a request for starting the secret process; a secret processor used for receiving the secretly-processing quest, and according to the request reading the currently-processing message, and making secret process for the message. The invention provides two secret methods and one secret message reading method. In the invention, only the owner of mobile phone knows the secret entrance and uses the password to access the secret unit.
Owner:HAIER GRP CORP +1
Authority control system and method of logistics information
InactiveCN103489086AImprove confidentialityPrevent leakageLogisticsRecord carriers used with machinesLogistics managementControl system
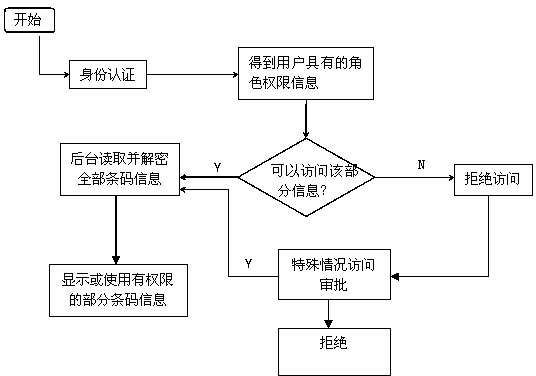
The invention provides an authority control system and method of logistics information, and relates to a logistics system and an information encryption method, in particular to an express system and an information encryption method. The system comprises a fast freight, a bar code identification device and software, wherein the fast freight is provided with encryption bar code identification; after the bar code identification device collects a bar code, the software decodes information of the bar code, and the software only displays or uses part of the information of the bar code. The bar code comprises one or more of addresser information, addressee information, sending time, a serial number and an ID number. The software can be used after login through authentication. The software sets authority according to login identification, decodes all the information in background, and displays or uses part of the information according to the authority. The authority control method of the logistics information mainly comprises the steps that 1, the encrypted bar code is generated by the software and adheres to the fast freight or goods before sending; 2, authentication is needed when the software is logged in; 3, part of the information is displayed or used according to the authority.
Owner:章玺
Computer information privacy detection method based on network
ActiveCN102984128AReach confidentiality checkRaise awareness of confidentialityTransmissionPassive detectionEngineering
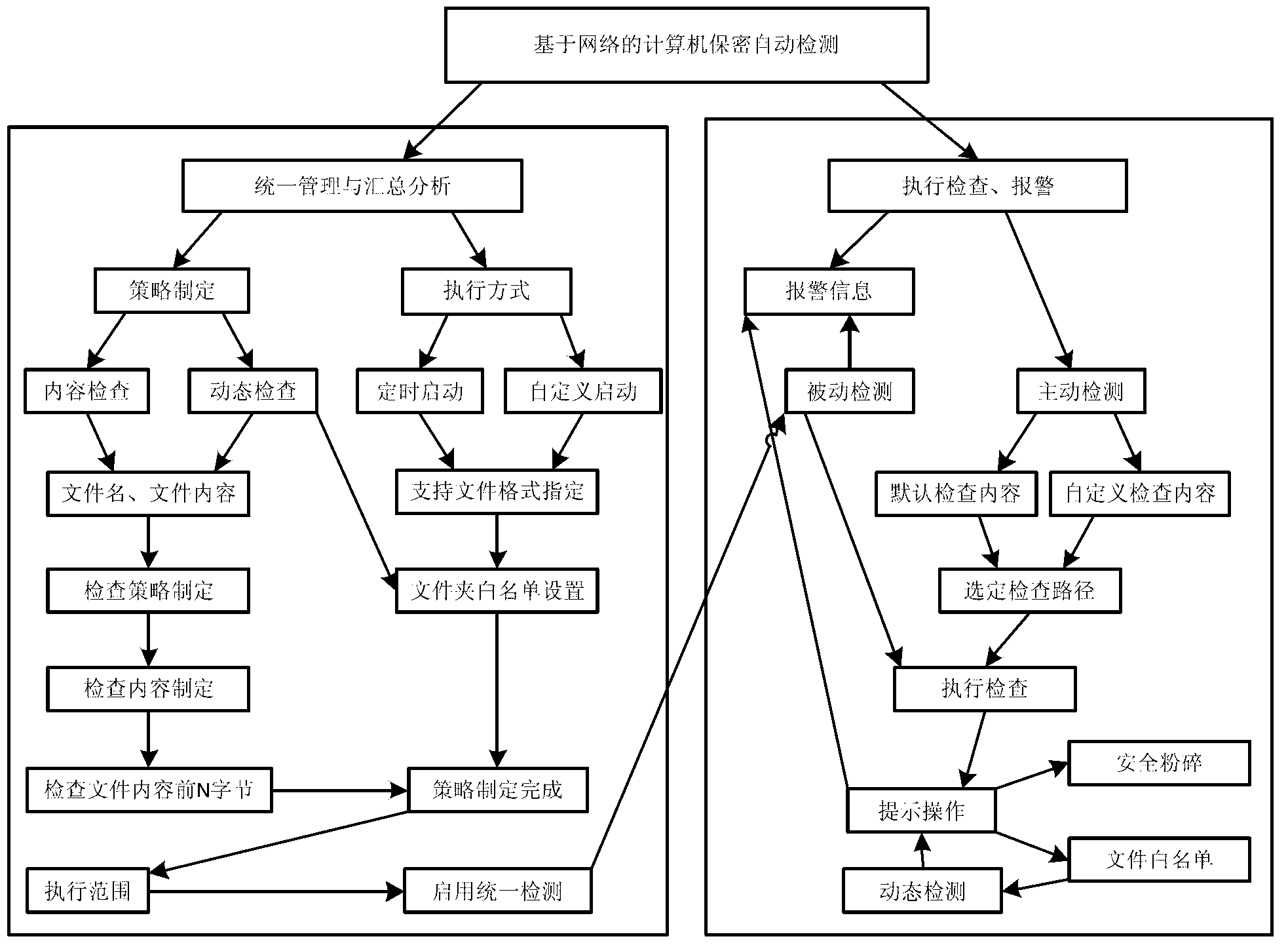
The invention provides a computer information privacy detection method based on a network. The computer information privacy detection method based on the network comprises the following steps. A network server terminal is linked with a computer client terminal. A network server terminal detection strategy is set up. A computer client detection strategy is confirmed. Dynamics of papers are monitored in real time with alarm. Modes of positive detection and passive detection are combined, all detection results are uniformly collected and analyzed and the computer client terminal is prompted to deal correspondingly. A white list which contains sensitive word information set by the computer client terminal is utilized to improve accuracy and search efficiency of privacy detection. Through unified setting and issuing of a privacy detection strategy of the network server terminal, real time monitoring and alarming of dynamics of the papers of the computer client terminal, automatic checking and an early warning mechanism are achieved. The working staff are more aware of secrecy and prevention by a technical method and leakage risks of an enterprise are avoided.
Owner:CHINA ELECTRIC POWER RES INST +1
Authentication method by broadcast signature and ciphering
InactiveCN101505301AHigh strengthUnforgeableSpecial service provision for substationPublic key for secure communicationSigncryptionHigh intensity
The invention discloses a broadcast signcryption authentication method, which comprises the following steps that: 1) system parameters are set; 2) a broadcast center calculates public key signature according to the parameters, and uses a user secret key to encrypt message to be broadcasted; 3) the broadcast center broadcasts the encrypted message acquired in step 2) to a user group; and 4) the user receives the encrypted message broadcasted in the broadcast center, uses a private key to decrypt the signature and verifies the validity of the signature. The method carries out two-layer confidential encapsulation of signature and encryption for the message, and broadcasts and mass-sends different messages to a group of users in once broadcast; and only specific authorized users can receive the designated message; therefore, the method has high-strength information confidentiality, signcryption information unforgeability and signcryption information non-repudiation. The method can regulate legal user groups at any time according to actual demand, but does not need to newly distribute new shared secret keys, has high flexibility, can make full use of communication bandwidth, saves cost, and greatly improves the communication efficiency.
Owner:SHIJIAZHUANG RAILWAY INST
Logistics information receipt using bar codes
InactiveCN103440517AFast printQuick identificationLogisticsRecord carriers used with machinesLogistics managementRapid identification
The invention provides a logistics information receipt using bar codes, and relates to logistics information receipts, in particular to courier receipts. The bar codes are printed on the logistics information receipt. One bar code is generated according to the information of a recipient, namely the bar code is generated according to a delivery address, a contact number and contact information of the recipient. The other bar code is generated according to a shipping address, a contact number and contact information of a sender. The bar codes are one-dimensional codes or two-dimensional codes, wherein numbers are arranged below the bar codes, and the number of the bar codes is more than one. The reverse side of the logistics information receipt is provided with adhesive stickers. The bar codes are generated by specific software. One bar code is generated according to the information including the contact number, the delivery address and the contact person of the recipient. The other bar code is generated according to the information including the shipping address, the contact number and the contact person of the sender. The logistics information receipt is provided with a signature column. The logistics information receipt using the bar codes has the advantages that specified coded information can be printed quickly through a printer to generate information needed by logistics; a machine can be used for rapid identification in a sorting process; the identification rate is high, and identification errors are reduced; the personal information confidentiality of the logistics information receipt is high; paper is saved, and paper size can be reduced substantially.
Owner:章玺
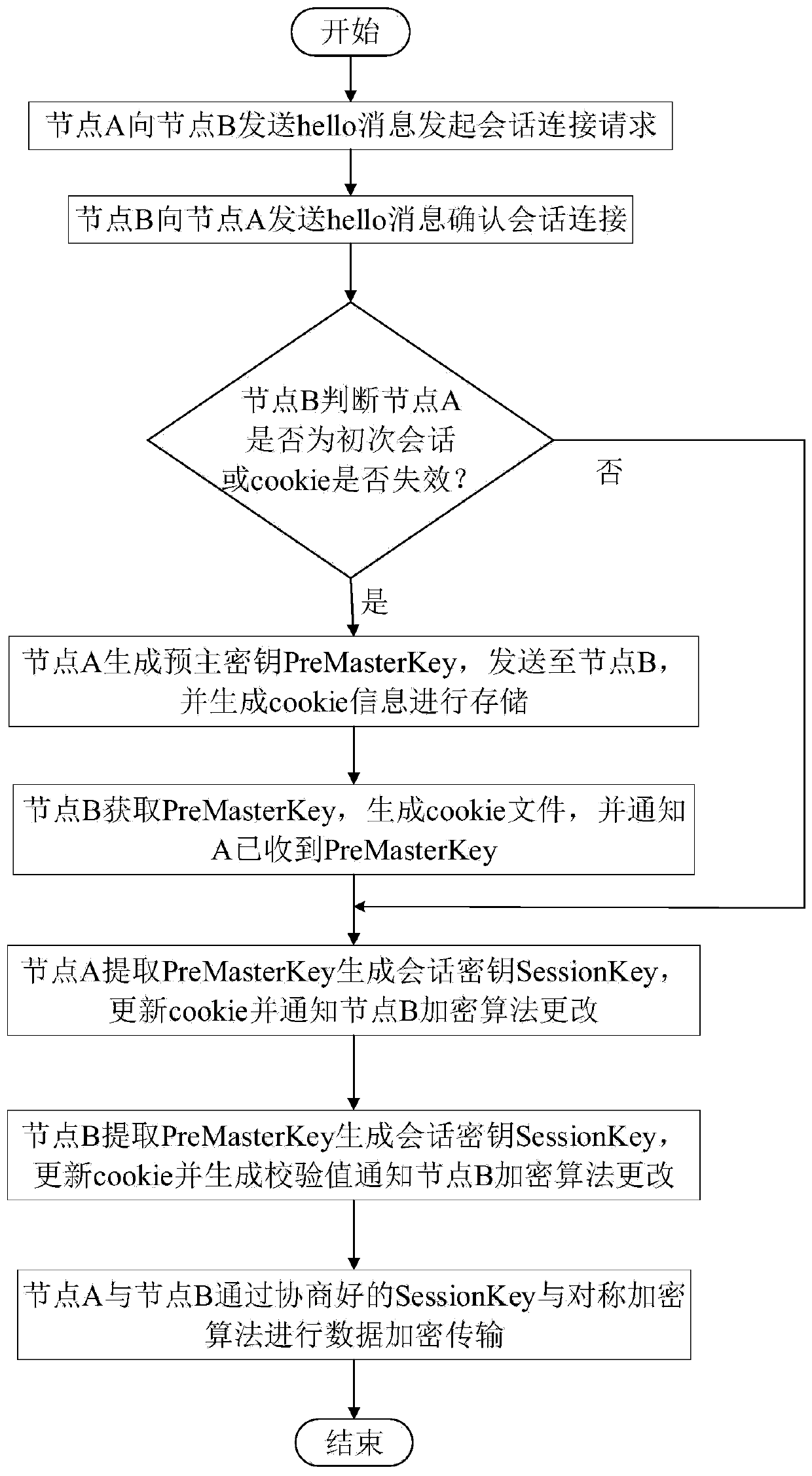
Internet of Vehicles data secure transmission technology based on improved SSL/TLS protocol
InactiveCN110048850AImprove securityImprove efficiencyKey distribution for secure communicationUser identity/authority verificationMan-in-the-middle attackAttack
The invention discloses an Internet of Vehicles data secure transmission technology based on an improved SSL / TLS protocol, and belongs to the field of Internet of Vehicles. Due to the fact that a wireless communication mode is adopted between nodes of the Internet of Vehicles, man-in-the-middle attacks exist in the data transmission process, and information confidentiality and integrity are reduced. Aiming at the requirements of the Internet of Vehicles communication on safety and real-time performance, the invention designs a data safety transmission technology based on an improved SSL / TLS (Secure Sockets Layer / Transport Layer Security) protocol. The technology comprises two stages: in a key negotiation stage, the security of a key is ensured through asymmetric encryption, and in a data encryption transmission stage, the encryption and decryption time of communication data is reduced through symmetric encryption. And then, aiming at the problem that the SSL / TLS protocol is unsafe andtimely delayed in key negotiation due to a single-point fault of a certificate authority and low asymmetric encryption speed, the SSL / TLS protocol is improved by utilizing a block chain and cookie technology. Compared with the prior art, the improved SSL / TLS protocol disclosed by the invention is greatly improved in the aspects of security and efficiency of key negotiation.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
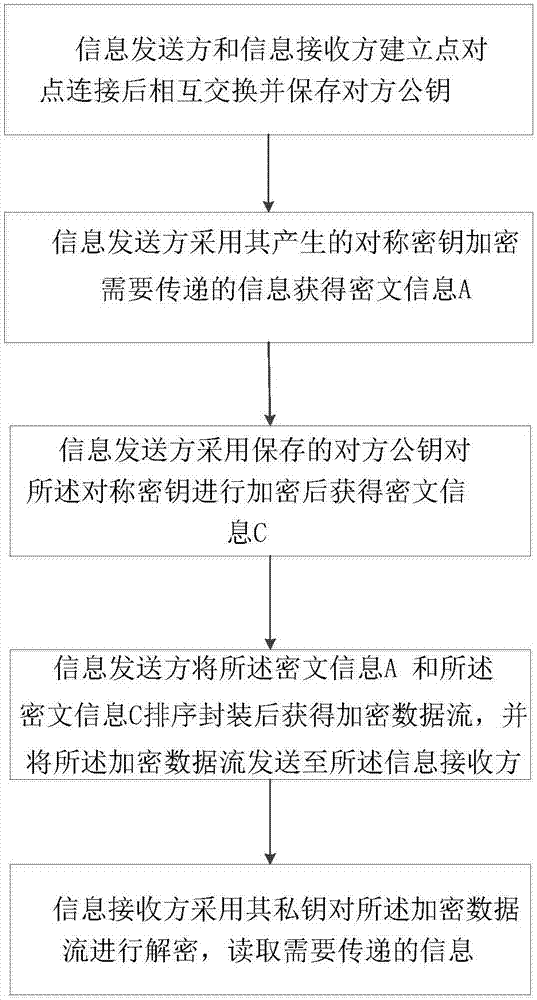
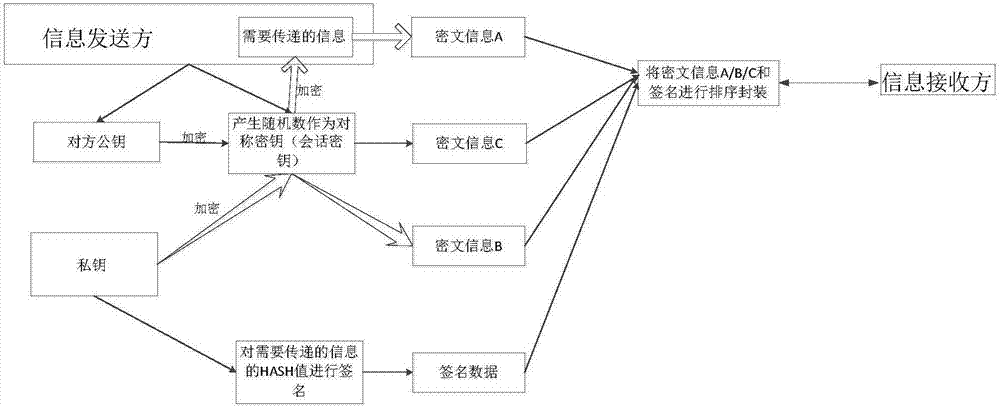
Information secret keeping method applicable to point-to-point instant messaging
InactiveCN107342977AEnsure safetySimplify complexityUser identity/authority verificationData switching networksData streamCiphertext
The invention discloses an information secret keeping method applicable to point-to-point instant messaging. The method comprises the steps that an information sender and an information receiver establish point-to-point connection and then mutually exchange and store opposite public keys; the information sender encrypts information needing to be transmitted through adoption of a symmetric key generated by the information sender, thereby obtaining ciphertext information A; the information sender encrypts the symmetric key through adoption of the stored opposite public key, thereby obtaining the ciphertext information C; the information sender arranges and packages the ciphertext information A and the ciphertext information C to obtain an encryption data stream and sends the encryption data stream to the information receiver; and the information receiver decrypts the encryption data stream through adoption a private key of the information receiver and reads the information needing to be transmitted. The point-to-point transmission information can be encrypted in an asymmetric encryption and symmetric encryption combined mode, the security of a communication process can be ensured, and moreover, the complexity of encryption and decryption operation is simplified.
Owner:河南芯盾网安科技发展有限公司
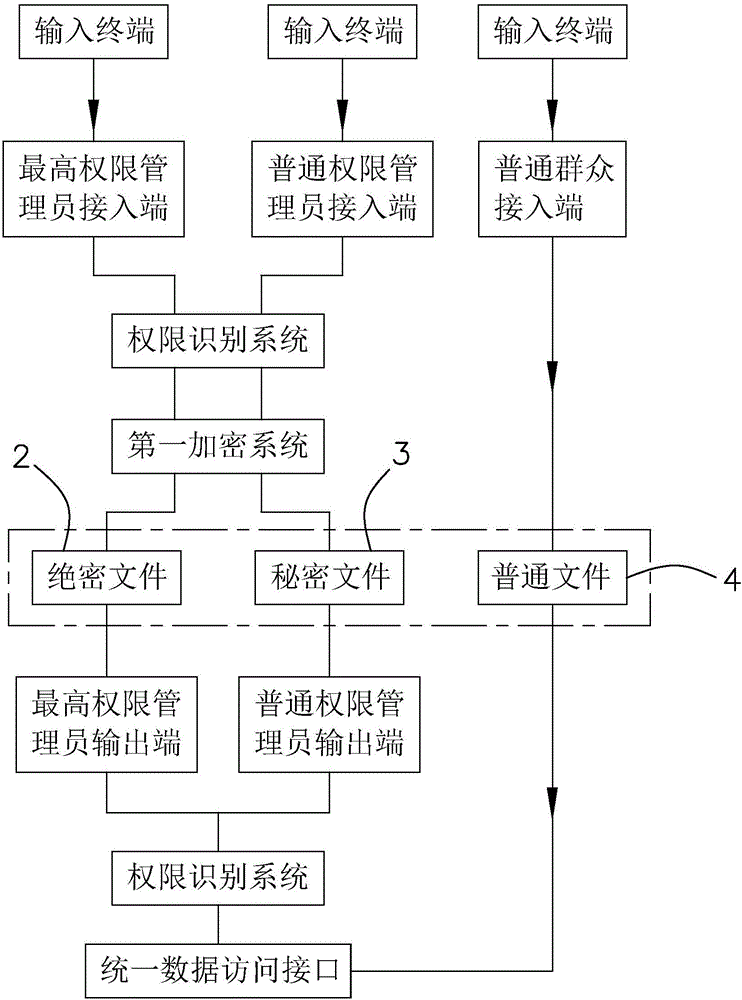
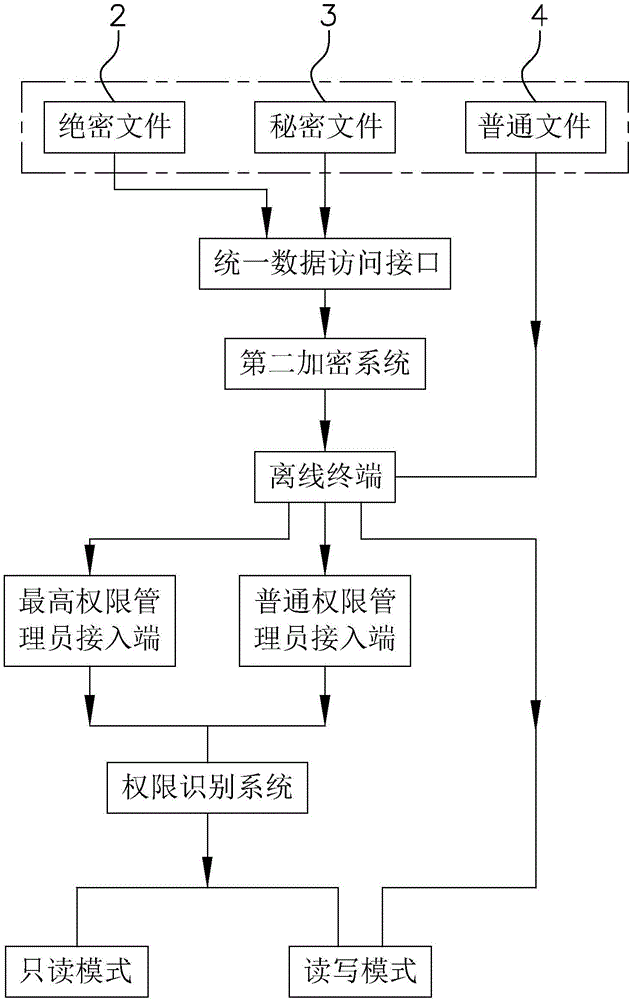
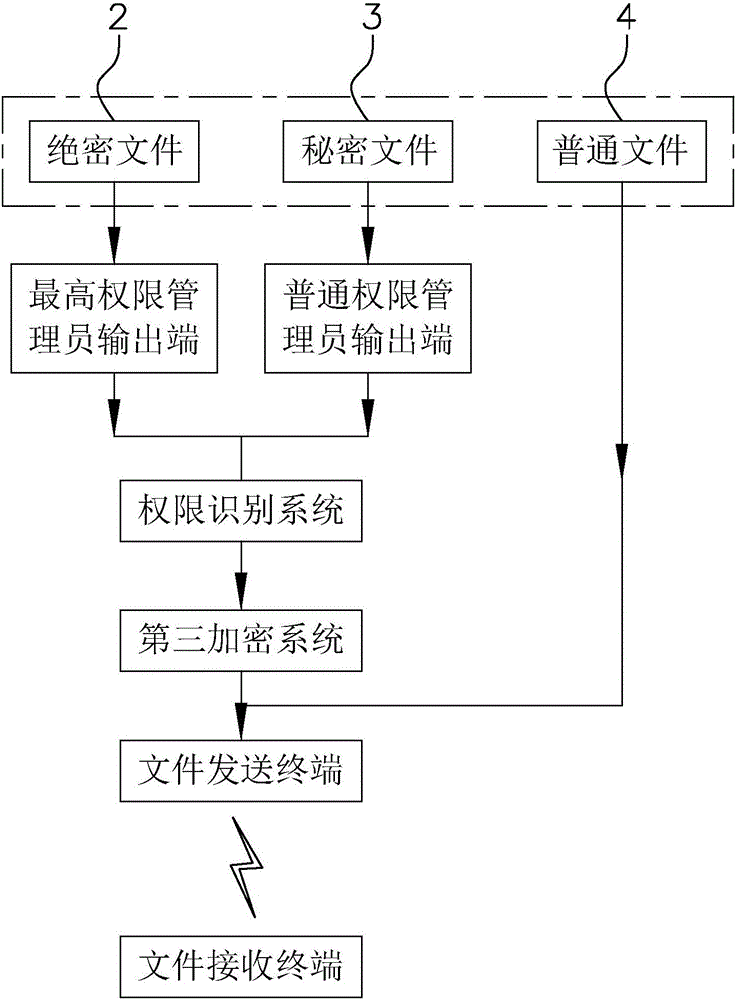
Information privacy system and operation method thereof
ActiveCN106778325AImprove securityDigital data protectionDigital data authenticationData accessRights management
The invention discloses an information privacy system and an operation method of the information privacy system, and solves the problems that the information in a conventional work communication study platform is easily stolen. The technical scheme has a key point that the information privacy system comprises a top-secret paper database, a secret paper database, a common paper database, a supreme authority administrator access end, a common authority administrator access end, a general public access end, an authority recognition system, a first encryption system, a unified data access interface, a supreme authority administrator output end and a common authority administrator output end. According to the information privacy system and the operation method of the information privacy system, the paper data can be stored to the paper databases at different security levels according to the importance grade when stored, the corresponding authority is acquired through the authority recognition system when data in the paper database are checked and read, then the paper information stored in the corresponding paper database is checked through an external connection access device, otherwise, the paper cannot be opened, and the information security is improved.
Owner:杭州领点科技有限公司
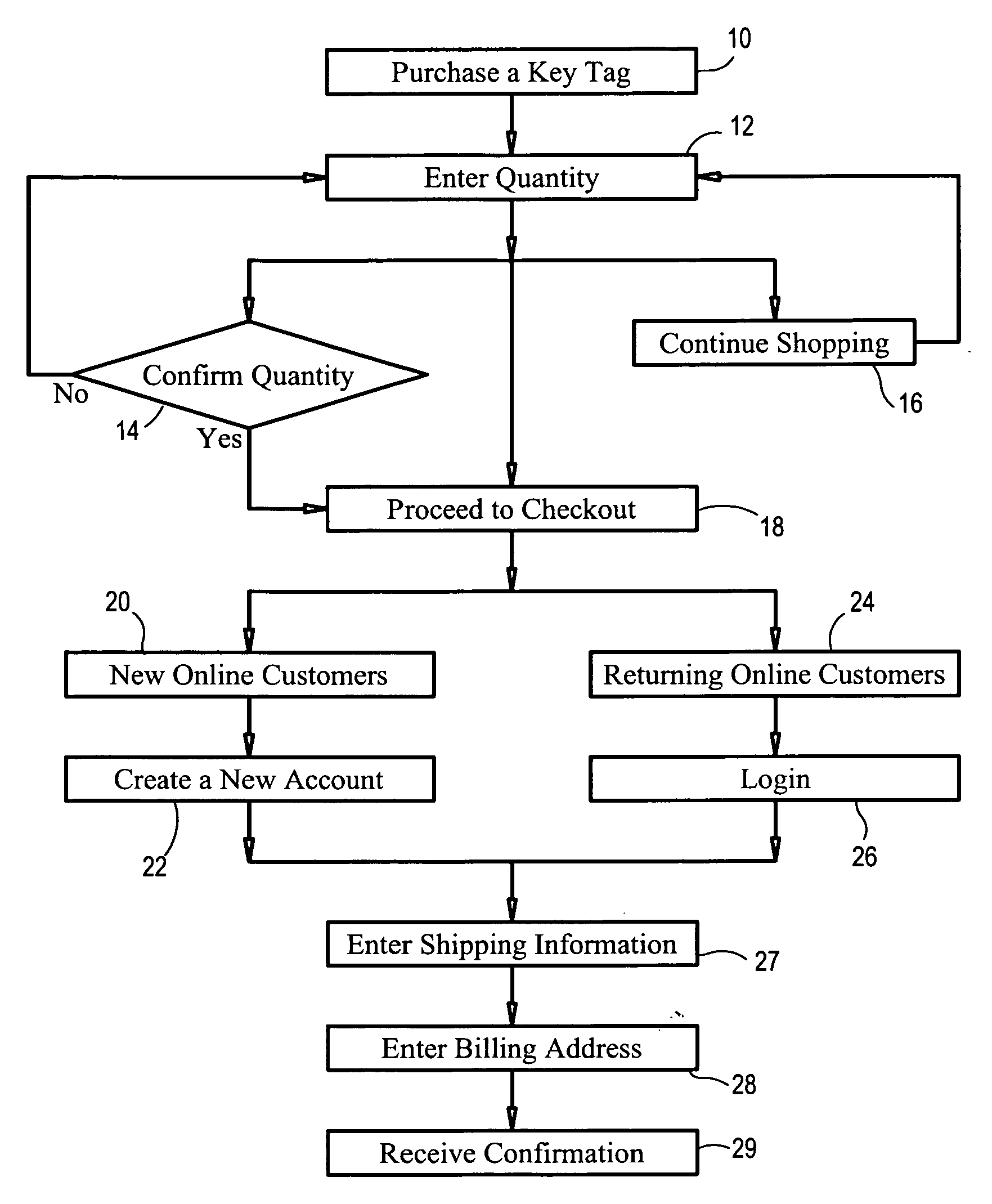
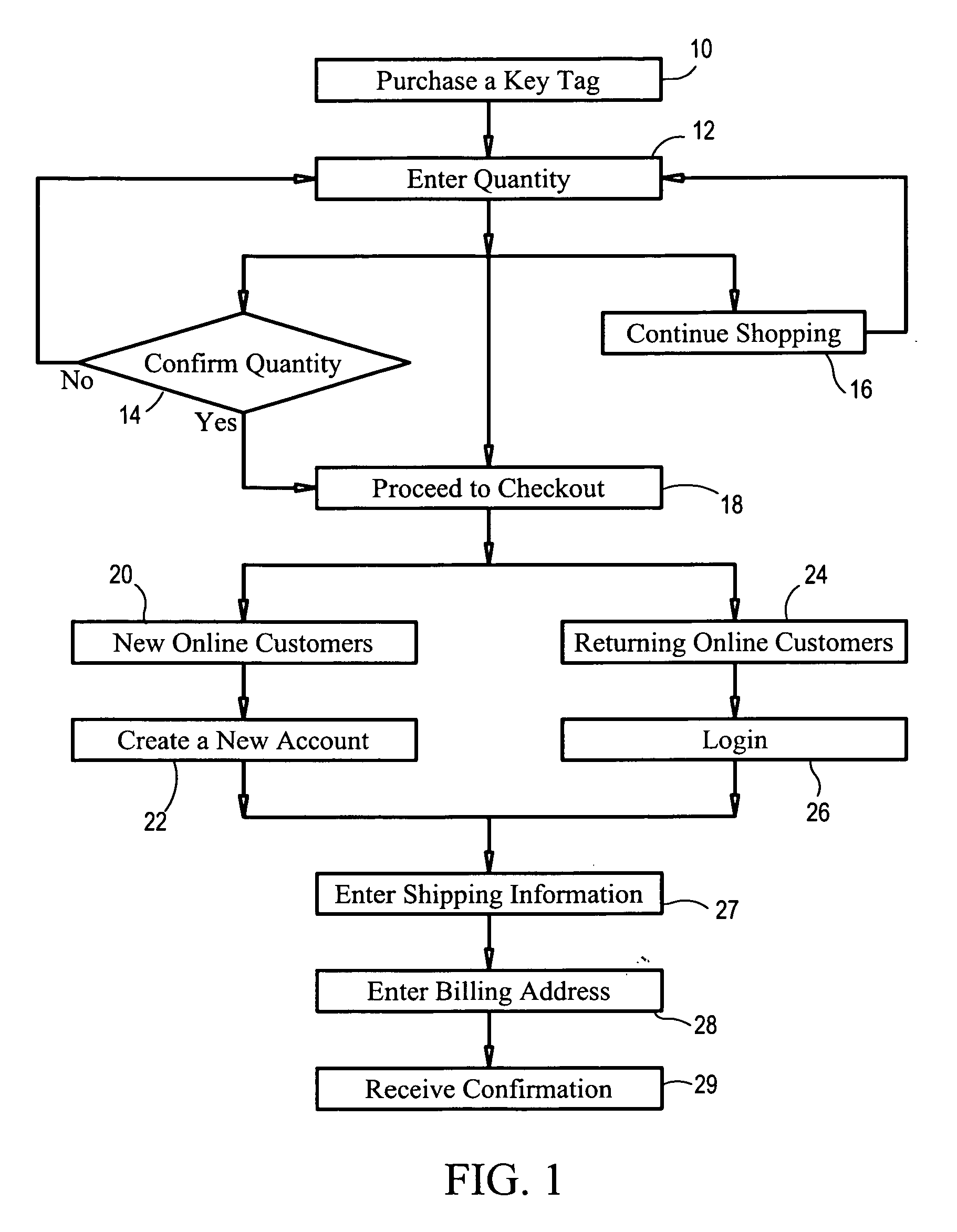
Lost key rewards system and method
A lost key rewards system and method which allows key owners to register their traditional keys as well as “advanced”, programmable key information with a central database accessible by a world wide website portal where the key owner's contact information is kept private and confidential. In particular, the lost key rewards system and method utilize an encoded key tag, each with a unique key tag number that a key tag owner may attach to their keychain or key ring. The key tag also has instructions for accessing a specified website and forwarding the found key tags for a reward. A key tag finder may participate in the program by registering the found keys and its specific key tag with its unique key tag number along with their contact information. Thus, if the key tag owner's keys and key tag are lost and found, the key tag finder has a system and method of returning the keys and / or key tag to the key tag owner and may choose to receive a reward. This lost key rewards system and method also provides the opportunity for large or small corporations to incorporate the key retrieval system as an employee and / or customer reward program and additional advertisement for the company through their logo being placed on a key tag.
Owner:GREEN MY CITY
Message-hidden mobile phone information safety communication method based on JPEG (joint photographic experts group) image
The invention relates to a message-hidden mobile phone information safety communication method based on a JPEG (joint photographic experts group) image. At a sending terminal, privacy message is input, an image with the appropriate size is selected according to the privacy message amount, the privacy message is hidden in a JPEG carrier image to form a privacy-contained image, and the privacy-contained image is sent to a receiving terminal through a mobile phone multimedia message; and at the receiving terminal, the privacy message can be extracted from the privacy-contained image through inputting a correct password. The method utilizes the mobile phone short message service to receive and send message, the confidentiality is strong, and the method is safe.
Owner:GUANGXI NORMAL UNIV
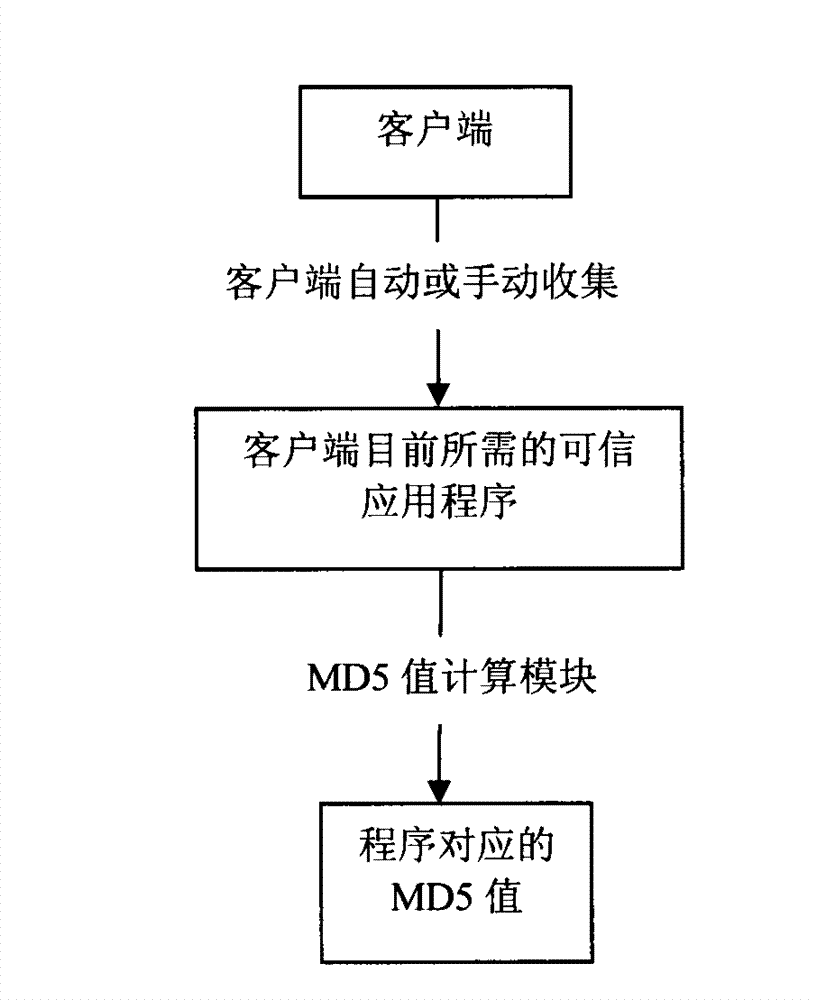
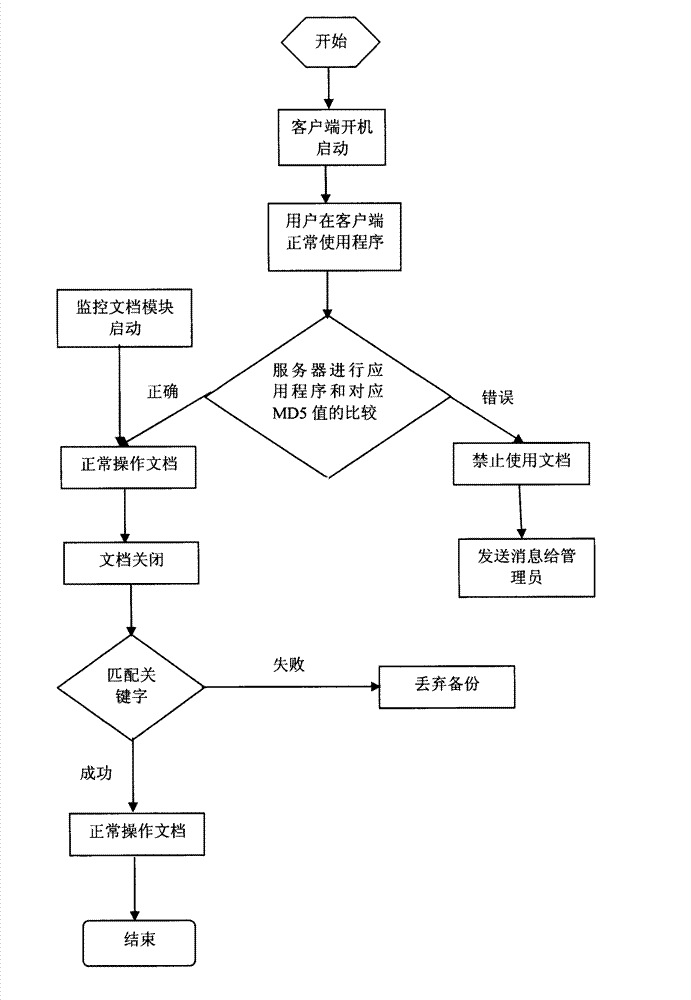
Operation statistics and operation document backup method of trusted program based on cloud storage
ActiveCN102737192AGuaranteed Information Confidentiality RequirementsPrevent leakageComputer security arrangementsRedundant operation error correctionComputer moduleApplication software
The invention discloses an operation statistics and operation document backup method of a trusted program based on cloud storage. The method comprises the steps of establishing cloud servers for each enterprise and institution, setting program data storage modules in each server, and storing and backing up collected application programs uploaded by terminals, wherein the application programs called by the terminals can be normally used through the program data comparison at the cloud servers; and carrying out the backup operation of the documents operated by the trusted program according to a keyword database, protecting the backup of the documents to be backed up and automatically discarding unnecessary or unrelated data. According to the operation statistics and operation document backup method, the trusted processes of clients are artificially or automatically collected, and the trusted processes are measured by MD5 (message digest 5) values and uploaded to the cloud servers together to be stored, recorded and distributed, and then, each client monitors and judges whether the application programs currently used by a user are trusted programs in real time, monitors the operation documents of the trusted program in real time and automatically uploads the documents to be backed up to the cloud servers so as to back up the documents. According to the operation statistics and operation document backup method of the trusted program based on the cloud storage, the information confidentiality requirements of enterprises and institutions can be met, the information leakiness accident caused by the program problem can be prevented effectively, the data backup complexity of the user is reduced, and the data backup efficiency is improved, and the checkability, backup and availability of core documents can be improved.
Owner:JIANGNAN UNIV
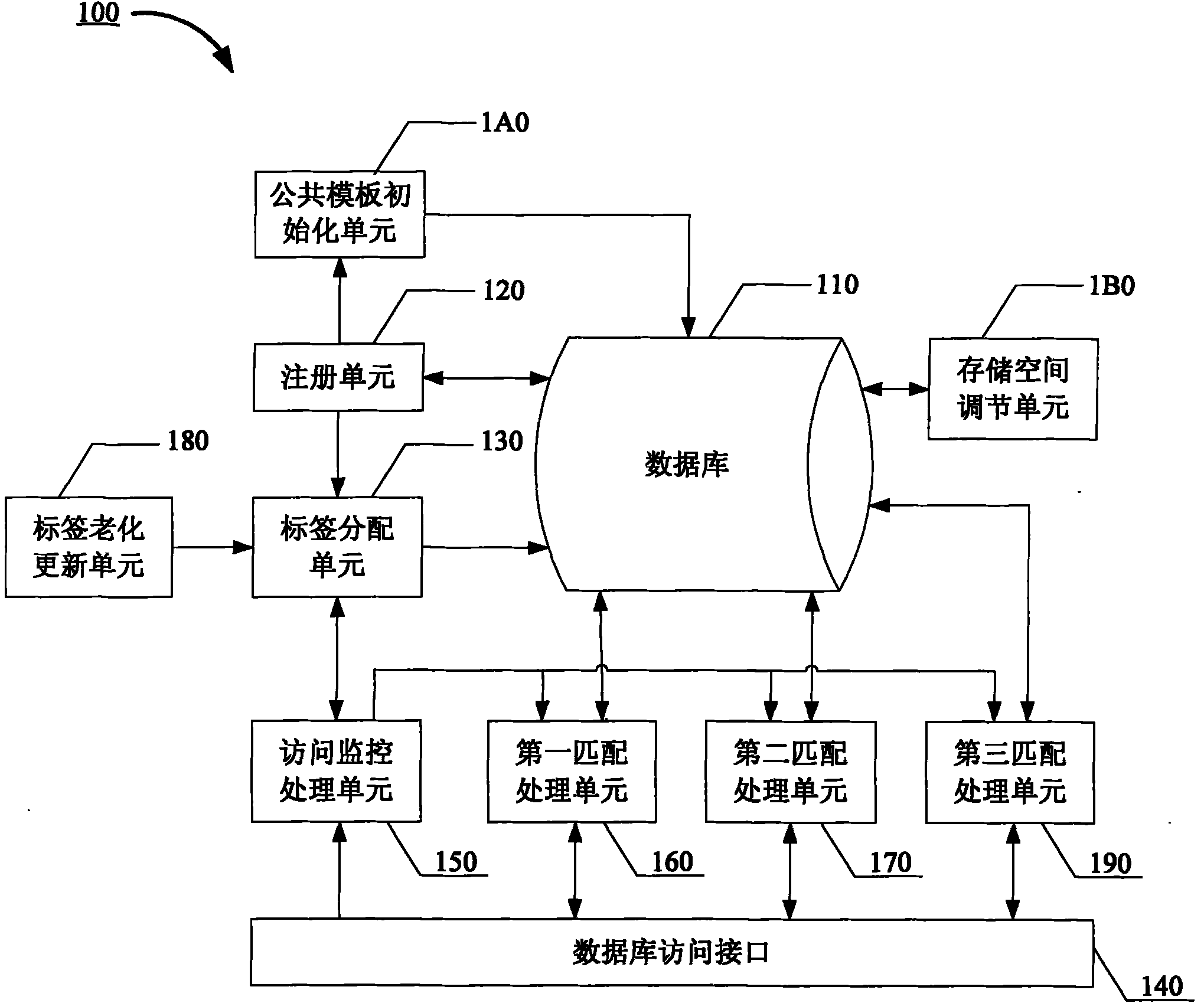
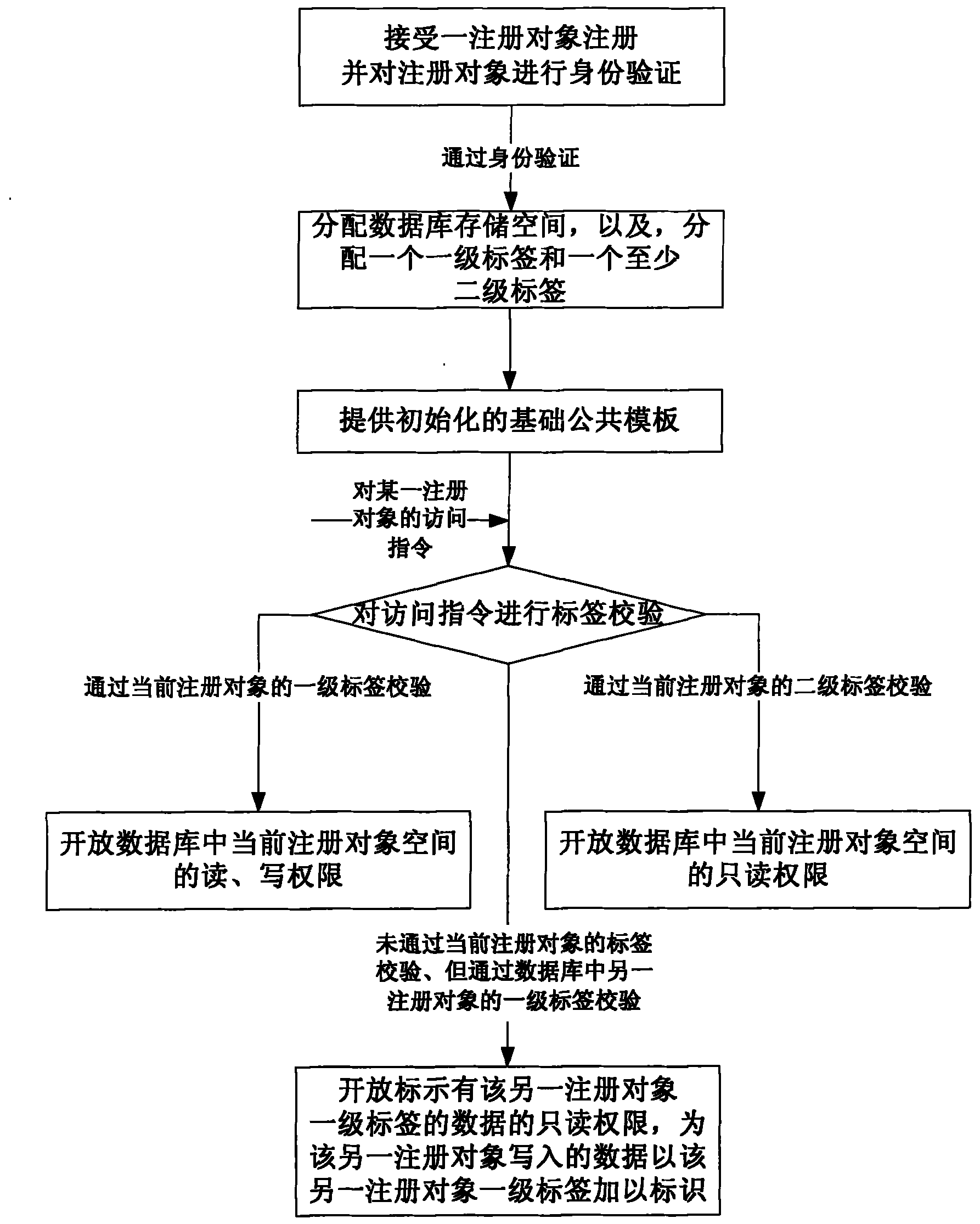
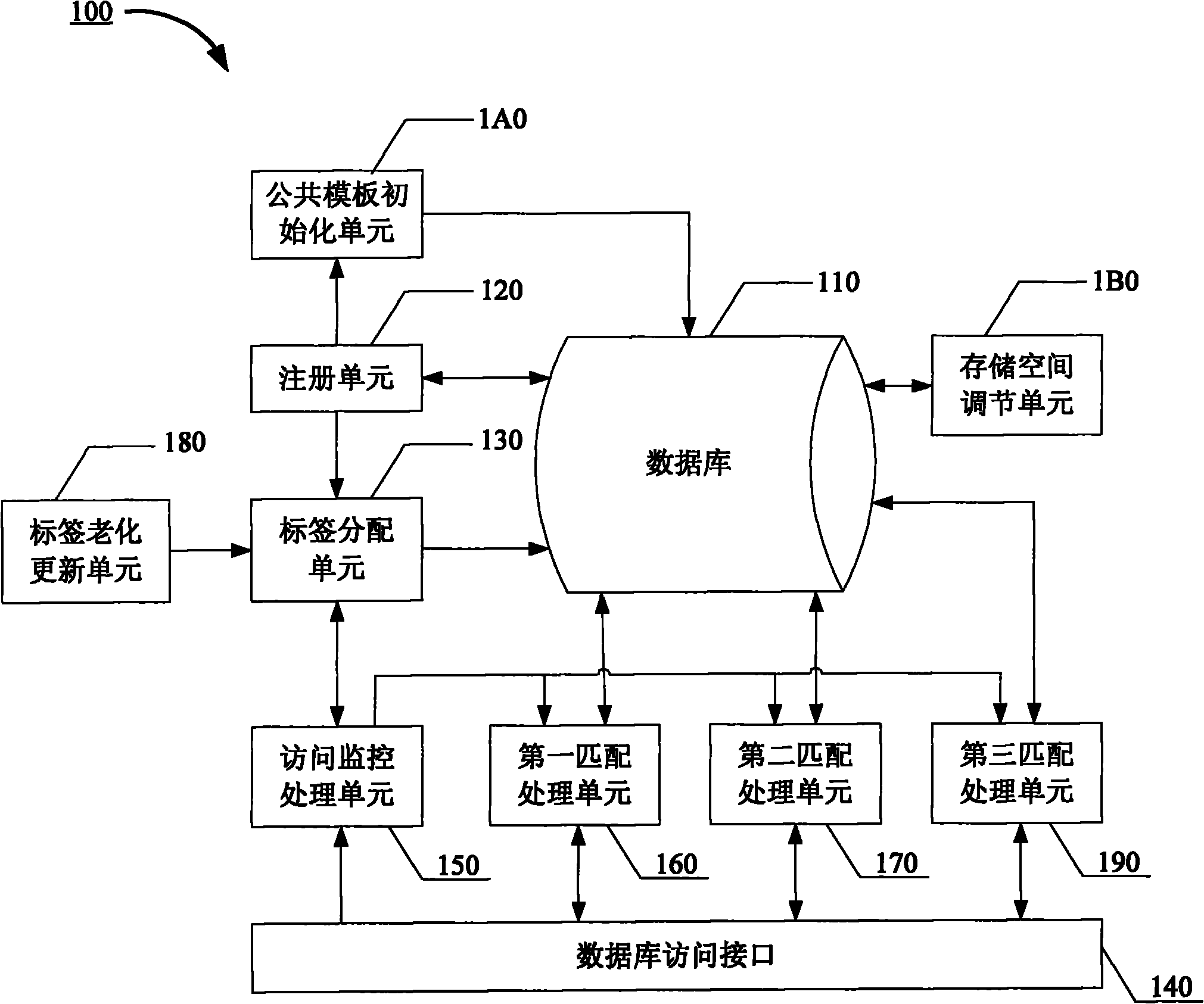
Information database system and access control method thereof
InactiveCN102063431AFlexible sharingSecurity enables sharingDigital data protectionSpecial data processing applicationsInformation confidentialityDatabase
The invention discloses an information database system and an access control method thereof. The access control method of the information database system comprises the following steps: allotting one first-order label and at least one second-order label to each registered object, and checking the labels of for an access command; opening the spacial read and write authority of the currently registered object space in a database to public use under the condition that the access command passes the check of the first-order label of the currently registered object; and opening the spacial read-onlyauthority of the currently registered object space in the database to public use under the condition that the access command passes the check of the second-order label of the currently registered object. Due to the adoption of the invention, the information database information can be kept secret, exchanged and shared flexibly and safely.
Owner:郭承运
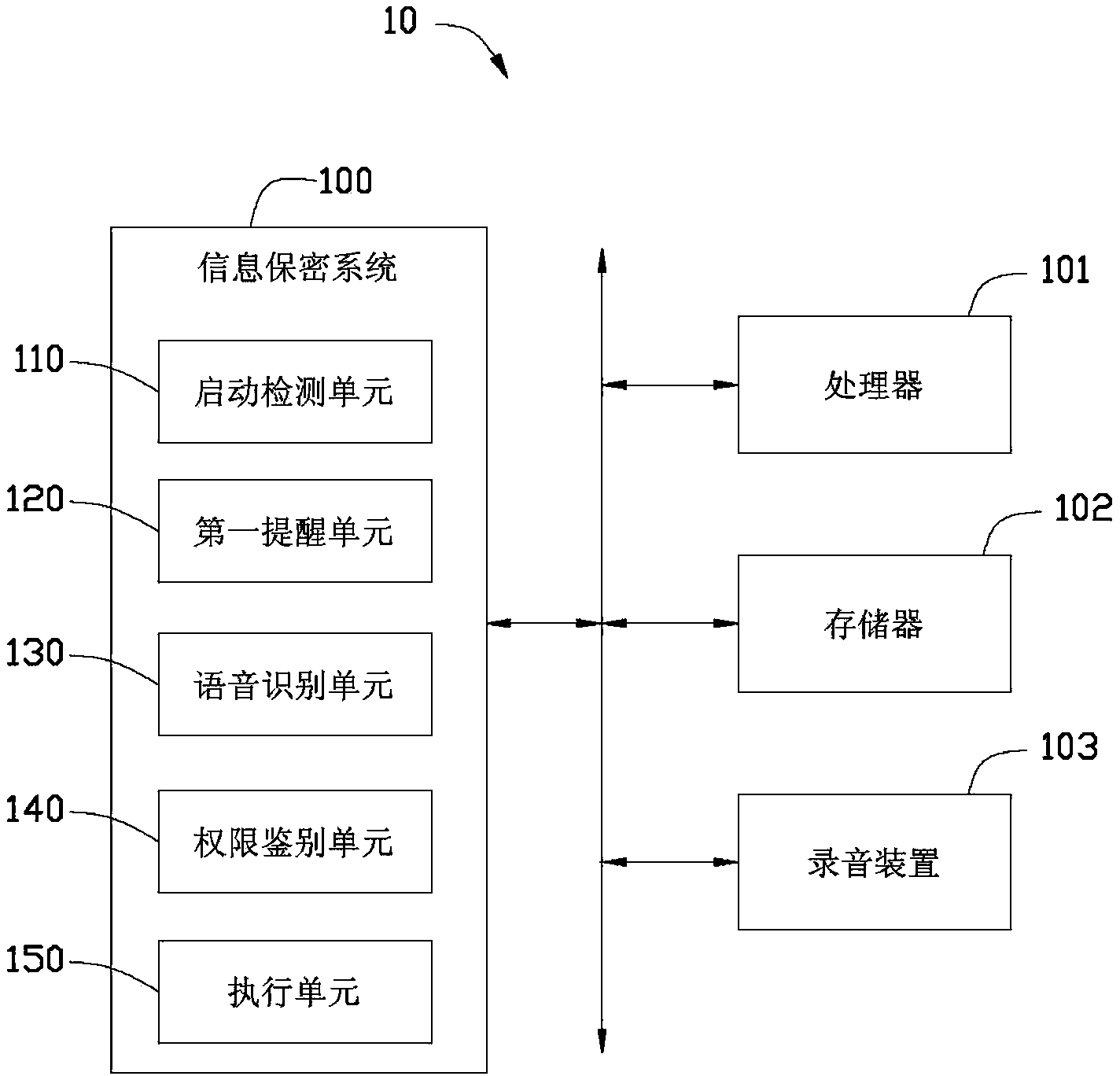
Information security system and information security method
InactiveCN103391354AAvoid churnDigital data authenticationSubstation equipmentExecution unitInformation security
A data secrecy system of an electronic device detects whether a screen unlocking interface of the electronic device is activated. The data secrecy system controls the recorder to record a phrase said by a user after the user is invited to speak. And then the data secrecy system extracts characteristics of the recorded phrase. The data secrecy system determines a privilege level for the user to access all or a part of functions of the electronic device according to the characteristics of the phrase, and controls the electronic device to work according to the determined privilege level of the user.
Owner:FU TAI HUA IND SHENZHEN +1
Method for inputting or presetting passwords for display screen information secrecy product by using one key, and application
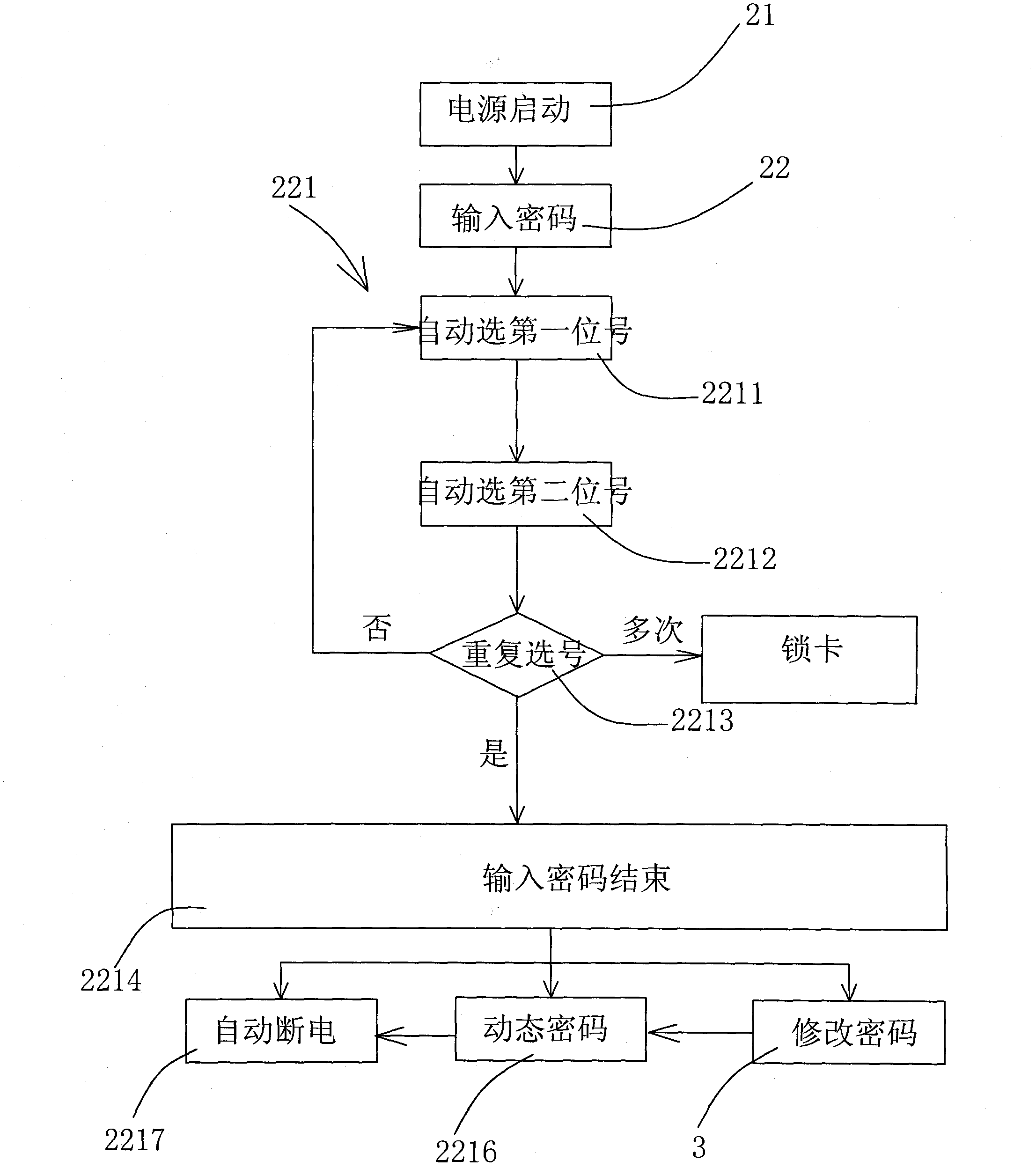
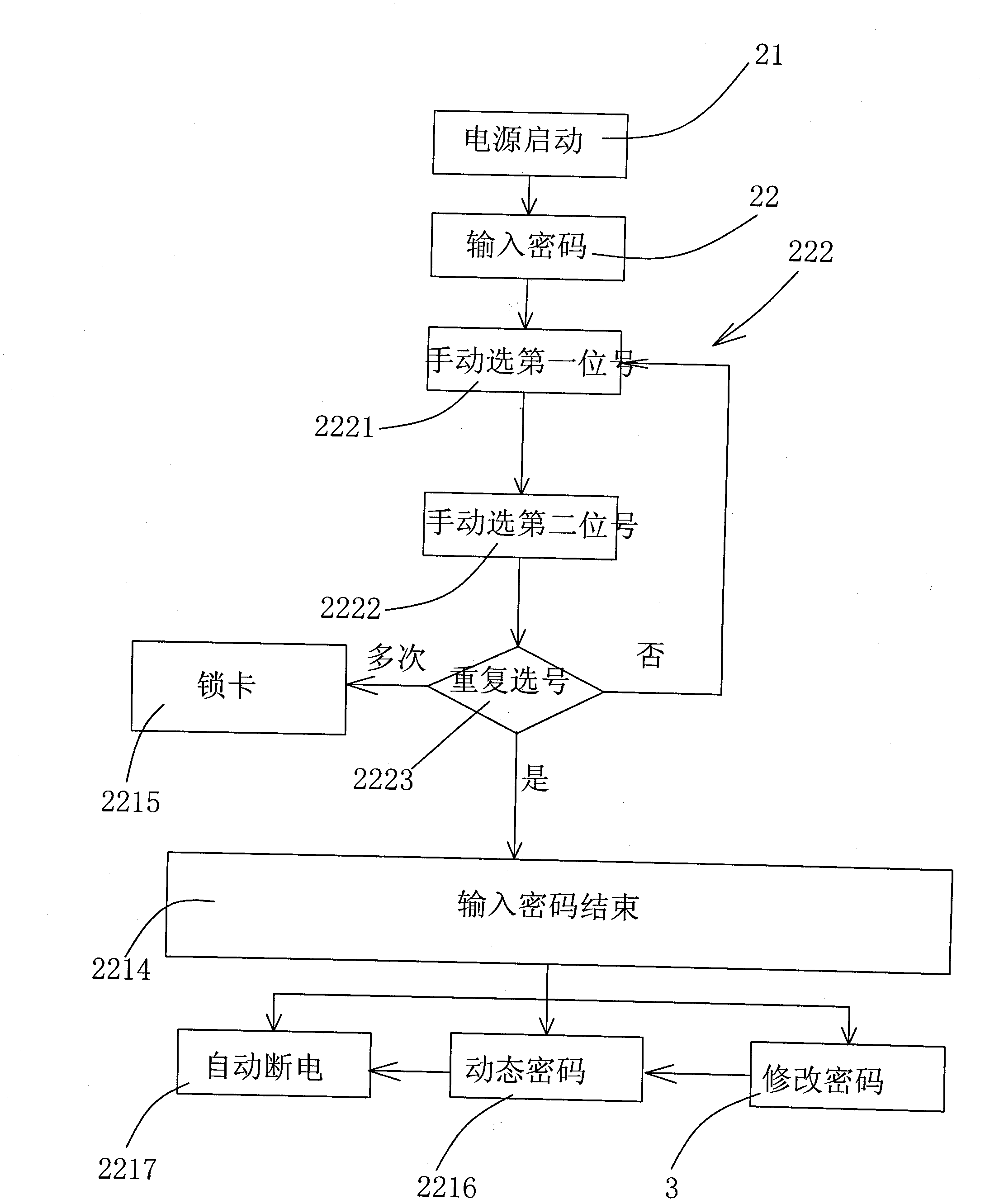
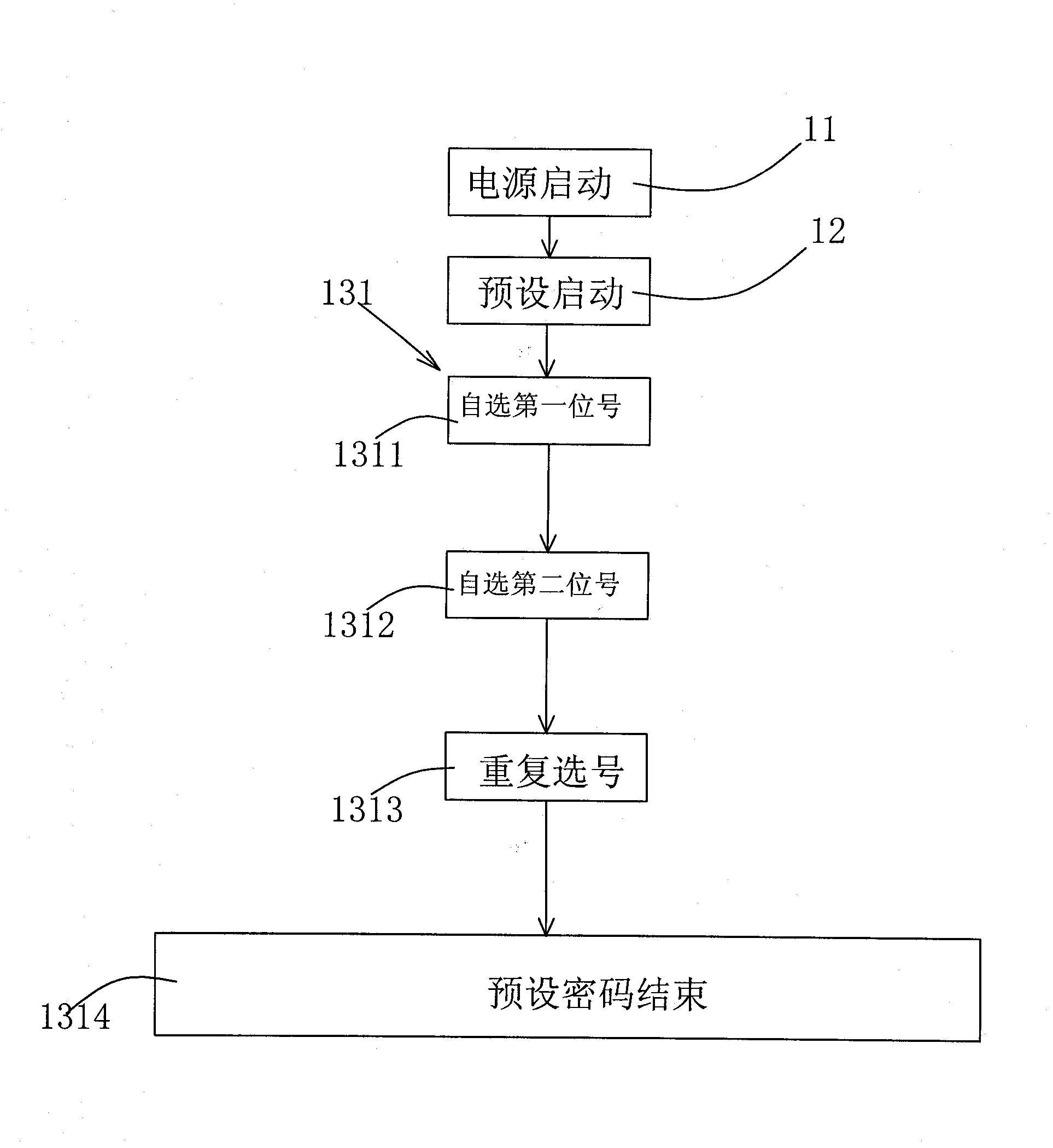
InactiveCN102831337ASimple inputEasy to modifyComputer security arrangementsKey pressingLiquid-crystal display
The invention discloses a method for inputting or presetting passwords for a display screen information secrecy product by using one key, and application. The method for inputting the passwords comprises the steps of: pressing a key for a long time, and starting a power supply; starting from one bit of the leftmost side of a liquid crystal display screen, automatically showing figures of 0-9, selecting the first figure of the preset password by a setter, pressing the key for a short time, and storing the figure; showing the next bit by the liquid crystal display, automatically showing figures of 0-9, selecting a figure of the next preset password by the setter, pressing the key for a short time, and storing the figure; and repeating the steps until all input passwords are selected completely. Because the structure of the traditional information secrecy product is not changed, the information secrecy product is preset by using one key, a power-on password is input or corrected, even if the information secrecy product is lost, the power-on password is not known by other people, and the information secrecy product can not be used, and therefore the benefit of people can be well protected.
Owner:陈国平
Method capable of tracing blabber
InactiveCN103336921AThe responsibility to protect is clearly implementedQuickly track downDigital data authenticationRecord carriers used with machinesEngineeringInformation confidentiality
The invention relates to the field of information confidentiality, in particular to a method capable of tracing a blabber. The invention has the technical scheme that the method comprises an information management system, each login person is given with one different user name, the user name corresponds to real information of the login person, coding or numbering processing can be automatically carried out on the real information or the user name of the login person by the information management system when the login person accesses to the information management system for searching through the user name, information codes capable of being identified can be formed, the information codes and searched result information can be combined and can be displayed in a form of a picture, the information codes are displayed on the picture by being used as watermarks or shades, and the number of the information codes is one or multiple. According to the method disclosed by the invention, the citizen information protection responsibility can be clearly implemented into each person, and a correlative responsible person or blabber can be quickly traced according to the information codes after citizen information is revealed.
Owner:衡阳市劳动保障信息中心
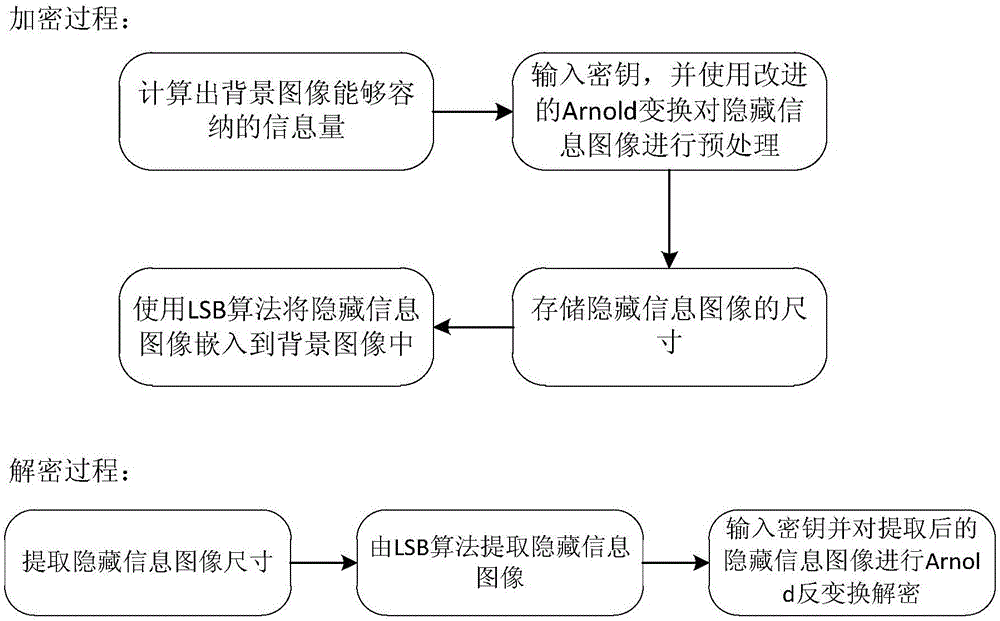
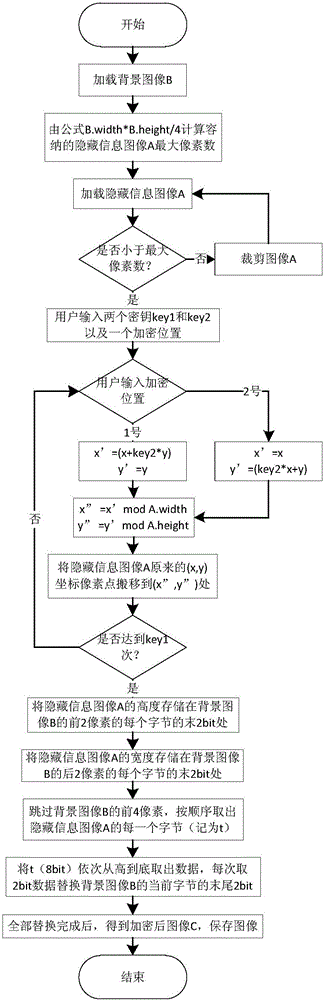
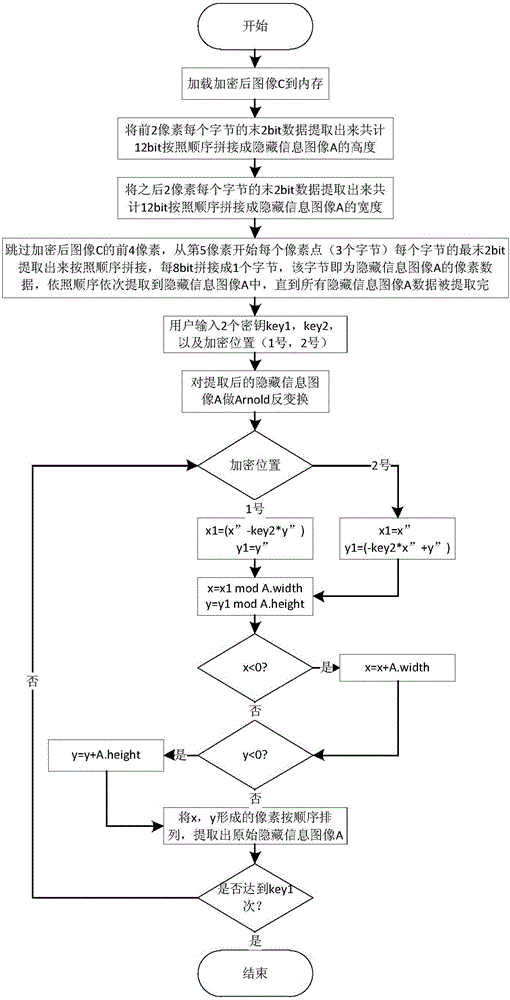
Image information encryption and decryption method based on improved Arnold transformation and LSB
ActiveCN106157231AImprove confidentialityVandal resistantImage watermarkingArnold transformationInformation quantity
The invention discloses an image information encryption and decryption method based on improved Arnold transformation and LSB. The method includes: using the improved Arnold transformation to preprocess an image, and using an LSB algorithm to embed the preprocessed image into a background image to form a new image with the encrypted image. The encryption process mainly includes: calculating the information quantity which can be contained by the background image, inputting a key, using the improved Arnold transformation to preprocess a hidden-information image, saving the size of the hidden-information image, and using the LSB algorithm to embed the hidden-information image into the background image. The decryption process mainly includes: extracting the size of the hidden-information image, using the LSB algorithm to extract the hidden-information image, inputting a key and performing reverse Arnold transformation on the extracted hidden-information image so as to achieve decryption. By the image information encryption and decryption method, information confidentiality is enhanced greatly.
Owner:NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com