Information security system and information security method
A technology of information security and voice information, which is applied in telephone communication, equipment, voice analysis, etc., and can solve the problems that information security cannot meet people's needs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
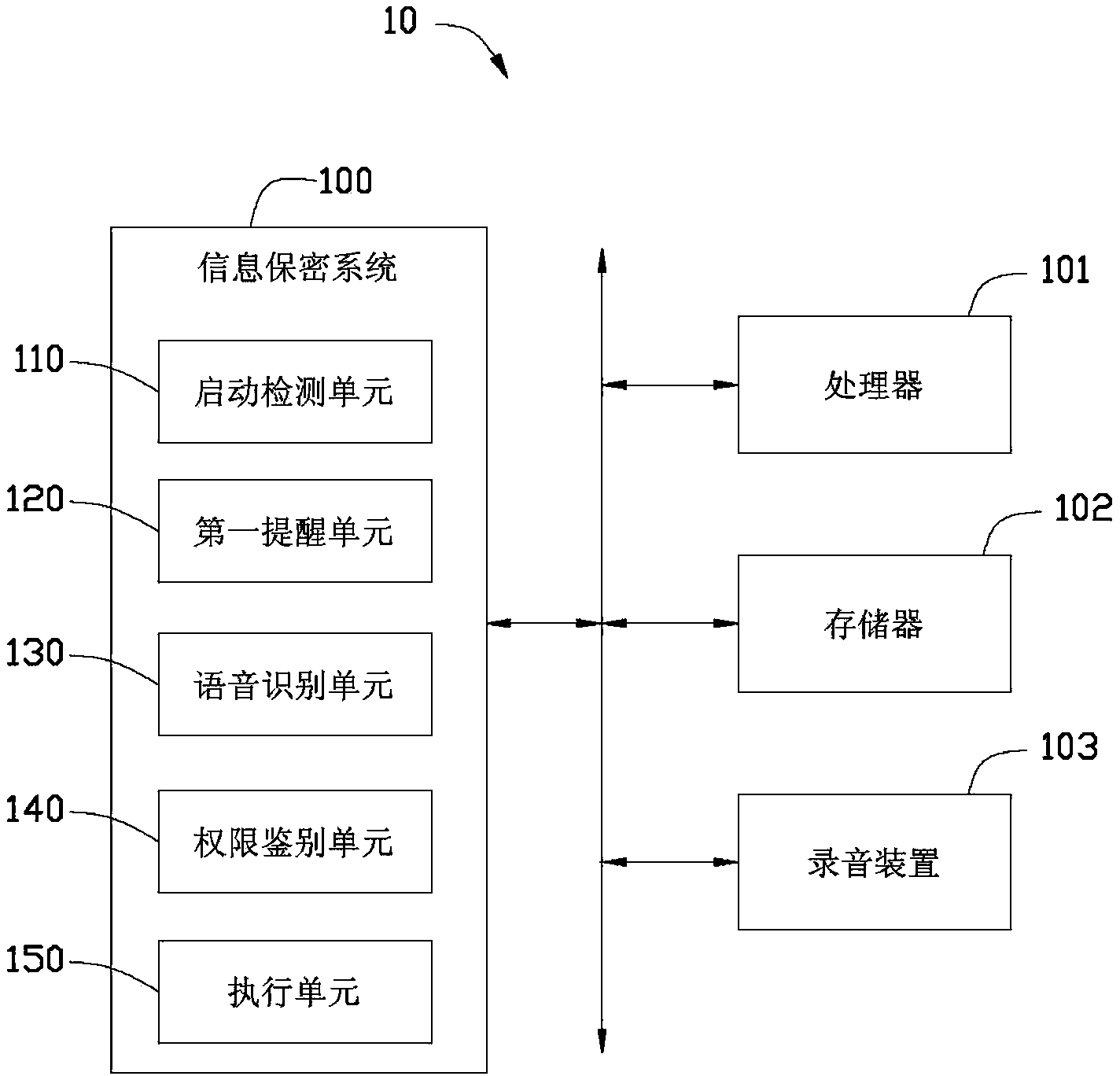
[0030] see figure 1 , which is a schematic block diagram of an implementation of the information security system 100 of the present invention applied to the portable electronic device 10 . The information security system 100 runs in a portable electronic device 10 , and the portable electronic device 10 includes a processor 101 , a memory 102 and a recording device 103 . The recording device 103 is used for recording voice information input by the user into the portable electronic device 10 . The portable electronic device 10 described in this embodiment is described by taking a mobile phone as an example. In other embodiments of the present invention, the portable electronic device 10 may also be a tablet computer, a camera, etc., and is not limited thereto.
[0031] The information security system 100 is used to manage the functions of the portable electronic device 10 that can be used when the portable electronic device 10 releases the lock screen interface to enter the op...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com