Information privacy system and operation method thereof
An information security and encryption system technology, applied in the field of information security systems, can solve problems such as security risks and personal privacy violations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0057] This specific embodiment is only an explanation of the present invention, and it is not a limitation of the present invention. Those skilled in the art can make modifications to this embodiment without creative contribution as required after reading this specification, but as long as they are within the rights of the present invention All claims are protected by patent law.
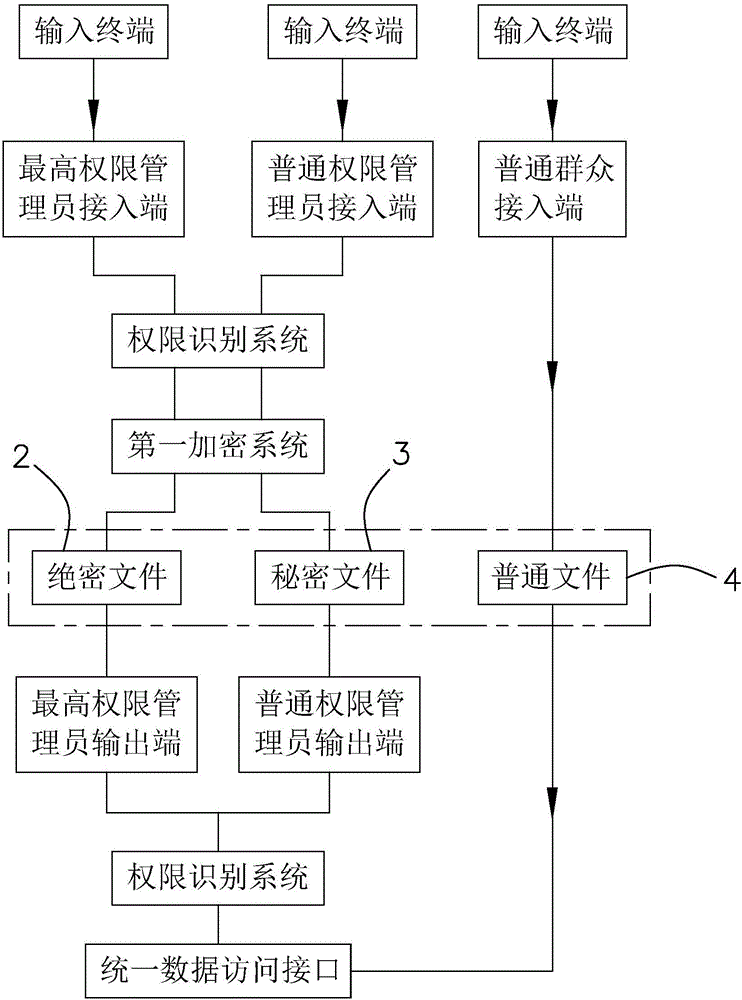
[0058] An information security system disclosed in this embodiment, such as figure 1 As shown, it includes an input terminal 1 for storing files, and the input terminal 1 can be a U disk, a mobile hard disk, a mobile phone, a tablet computer, and the like.
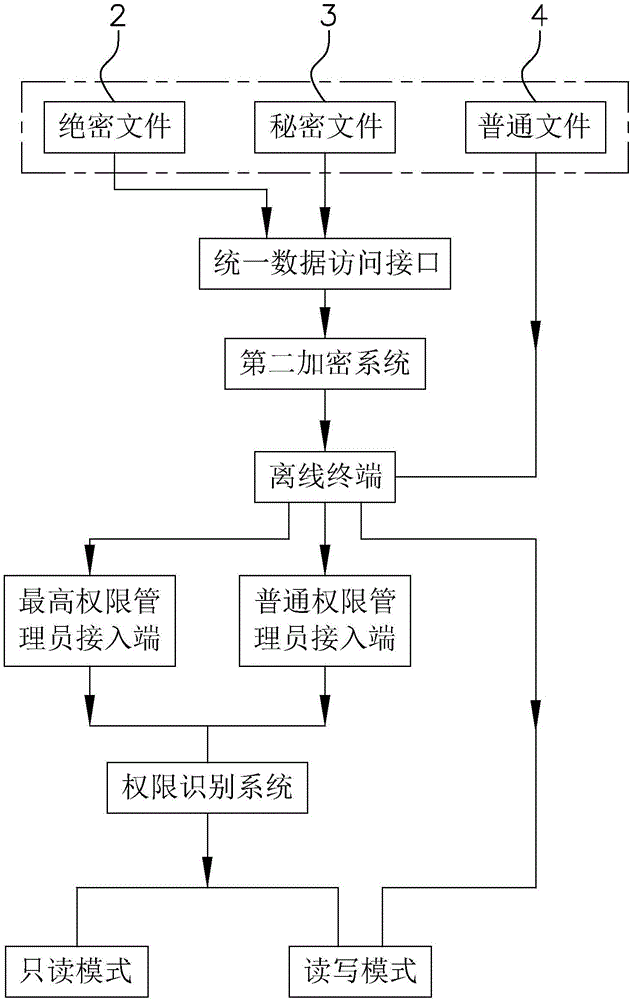
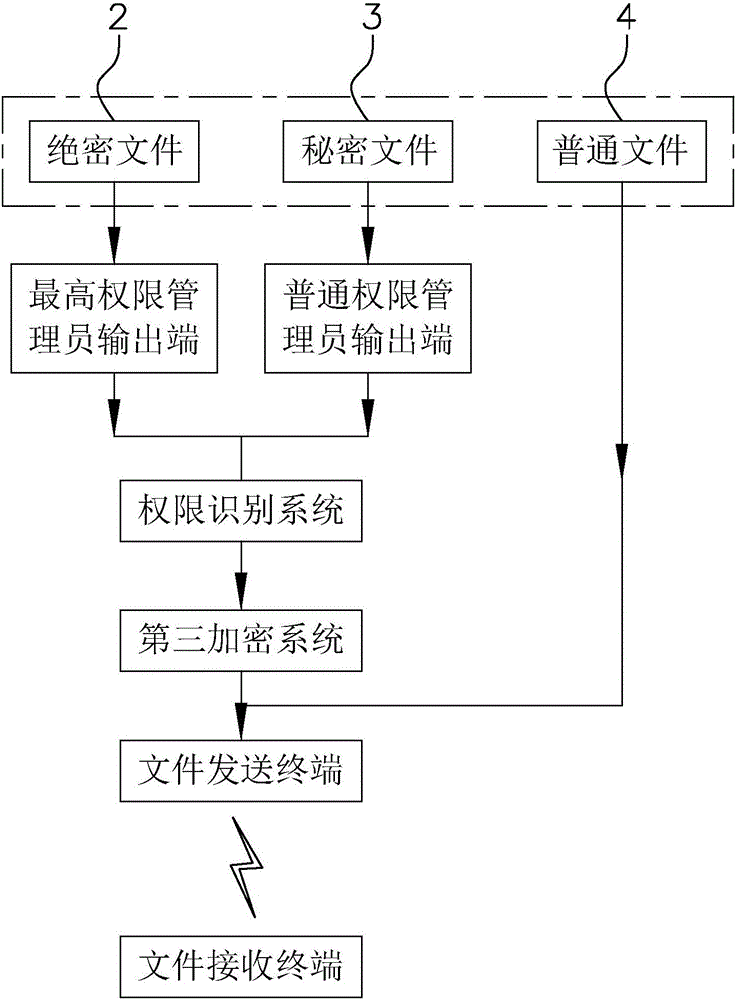
[0059] Such as figure 1 As shown, top secret file database 2, secret file database 3 and common file database 4 are also included. Among them, the top-secret file database 2 is used to store the most important information f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com