Information secret keeping method applicable to point-to-point instant messaging
A kind of information confidentiality, point-to-point technology, applied in secure communication devices, user identity/authority verification, digital transmission systems, etc. security, simplification of complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described in detail below in conjunction with the accompanying drawings, so that those skilled in the art can implement it with reference to the description.
[0032] It should be understood that terms such as "having", "comprising" and "including" as used herein do not entail the presence or addition of one or more other elements or combinations thereof.
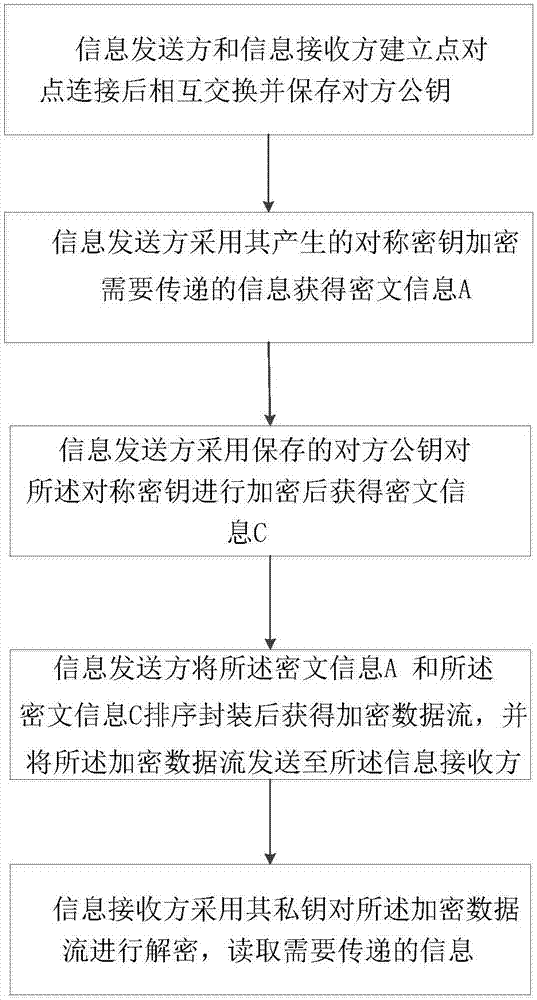
[0033] Such as figure 1 As shown, the present invention provides a kind of information security method suitable for point-to-point instant communication, it is characterized in that, comprises the following steps:
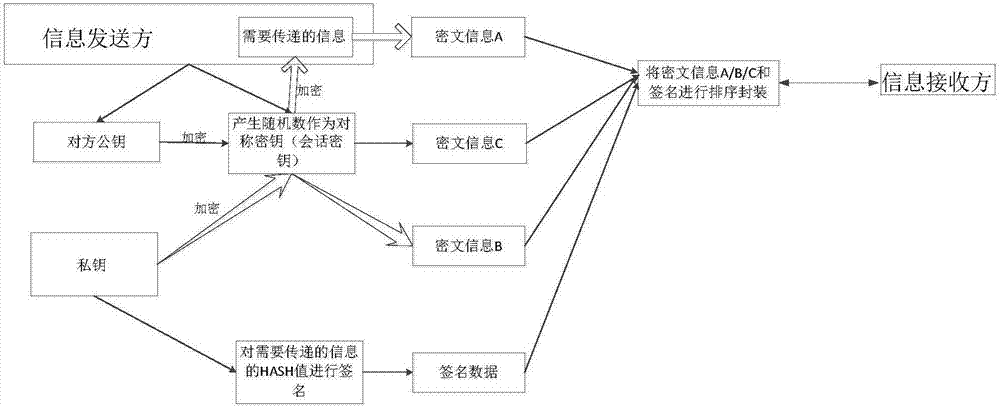
[0034] The information sender and the information receiver establish a point-to-point connection and exchange and save each other's public key; the information sender uses the symmetric key generated by it to encrypt the information to be transmitted to obtain the ciphertext information A; the information sender uses the saved public key pair of the other party The s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com