An information security method and procedure
A technology of information security and procedures, applied in digital data protection, instruments, electrical digital data processing, etc., can solve problems that are not easy to implement, unable to deal with, helpless to cover up input information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
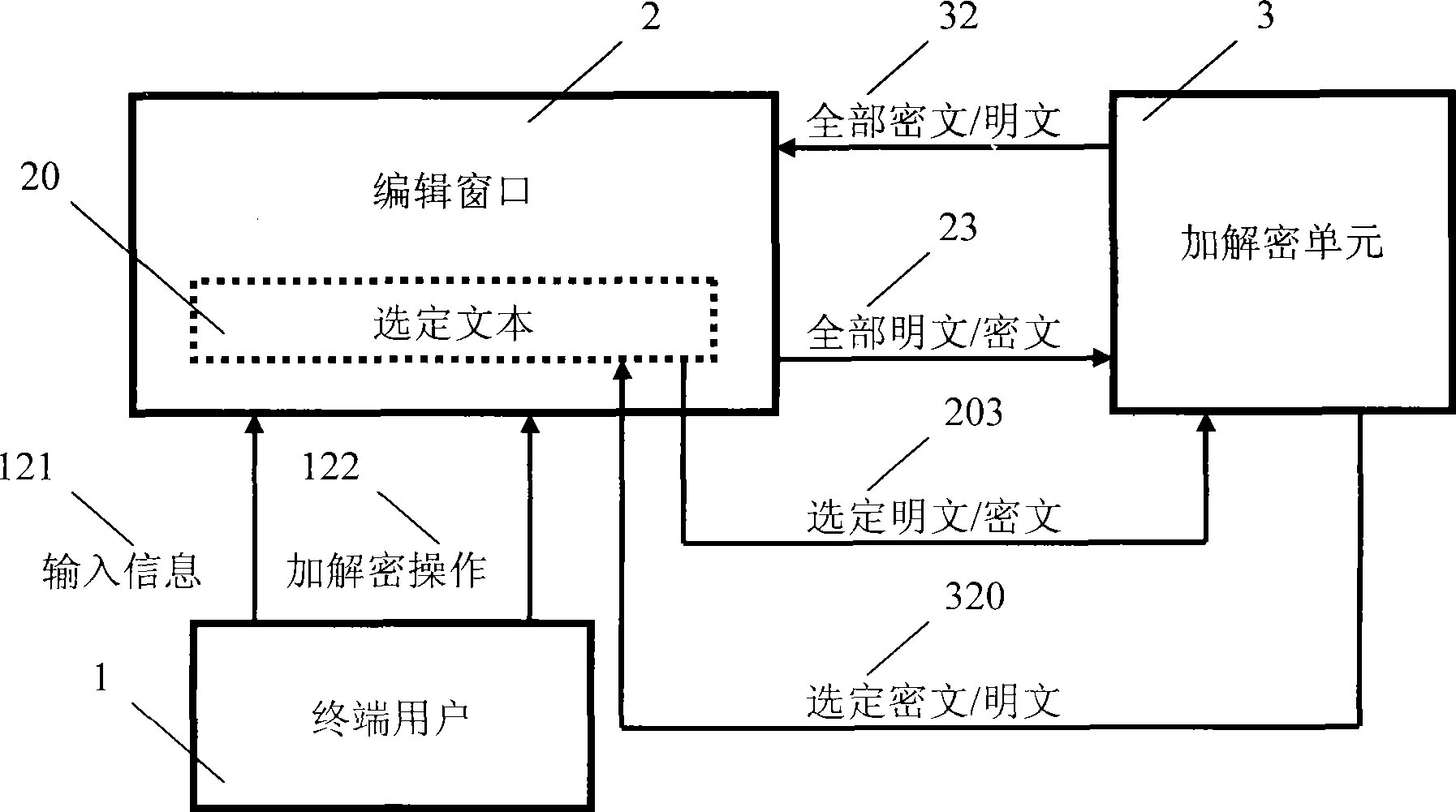
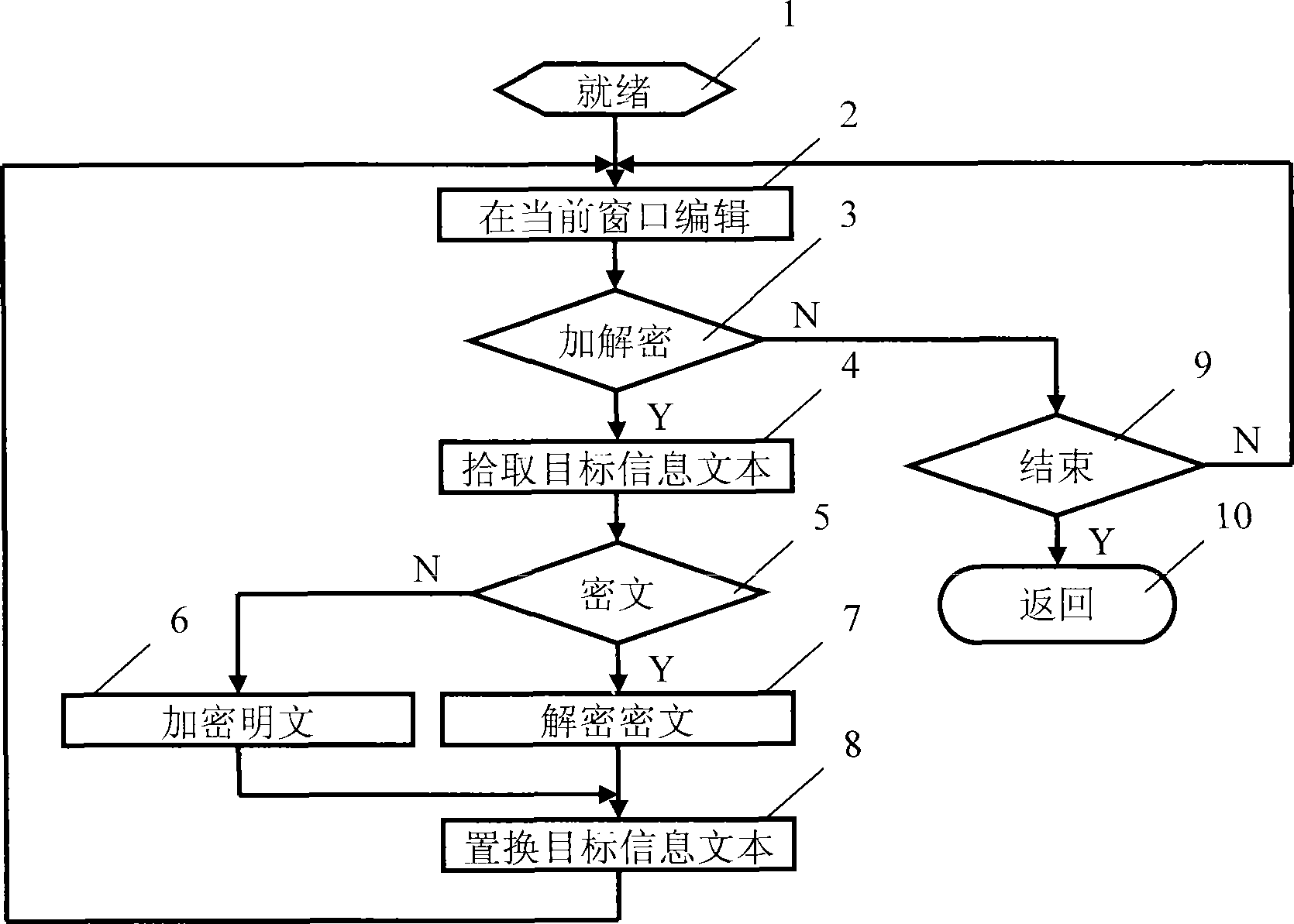
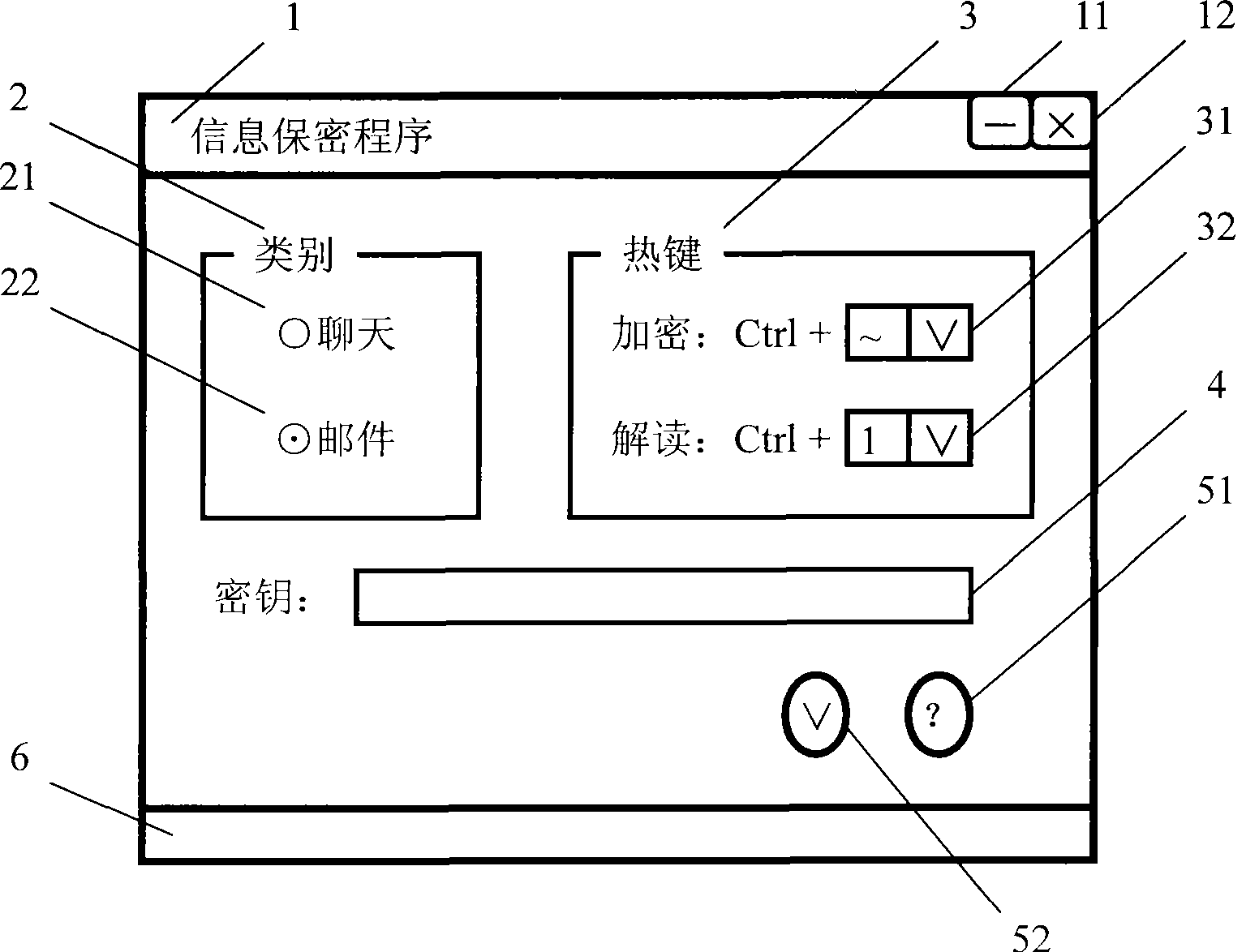
[0017] Compiled a utility program of Windows dialog box structure named "Information Confidentiality Program". The main interface structure of the program, such as image 3 shown. The program integrates a cryptographic device product with a USB interface called "Password Golden Armor", loads its supporting API dynamic link library, and calls its programming interface functions to realize encryption and decryption functions. The program responds to the device change message, automatically detects the access and removal of the cryptographic device, and provides the availability criterion of the cryptographic device for encryption and decryption operations. During program initialization, set and register encryption hotkeys and decryption hotkeys. The program then automatically avoids conflicts and completes the update registration for the user's operation of changing the hotkey. In order to respond to hotkey messages, the program distinguishes between encryption hotkeys and de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com