System and method for cryptographic communications using permutation
a cryptographic communication and permutation technology, applied in the field of cryptographic communication systems and methods, can solve the problems of requiring substantial computing power, data transmitted over communications channels are susceptible to interceptions, eavesdropping and modification, and data storage devices may be accessed undetected, so as to reduce the size of shared secret encryption keys, shorten or reduce the size of secret keys, and simplify encryption. the effect of complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051]Basic Configuration
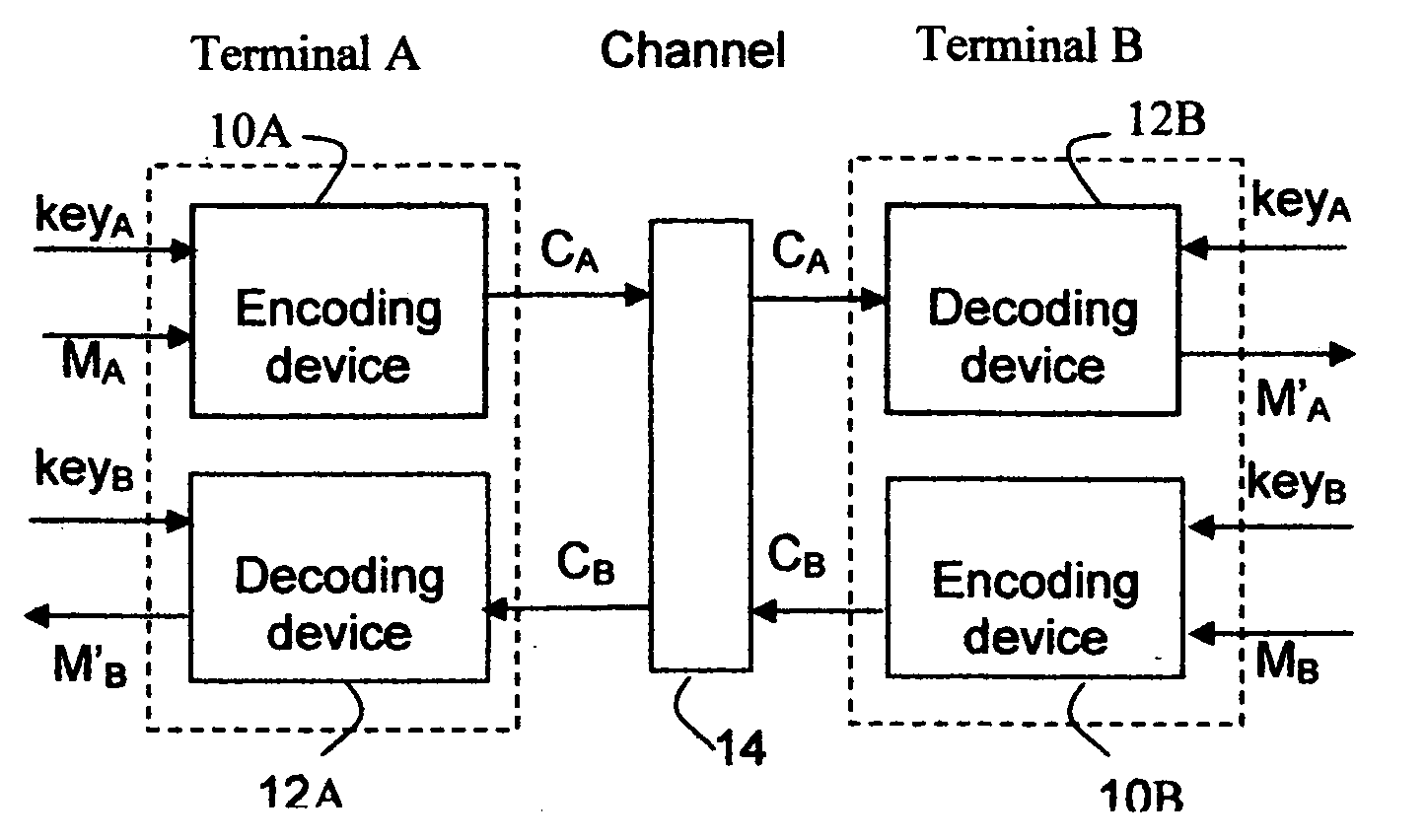
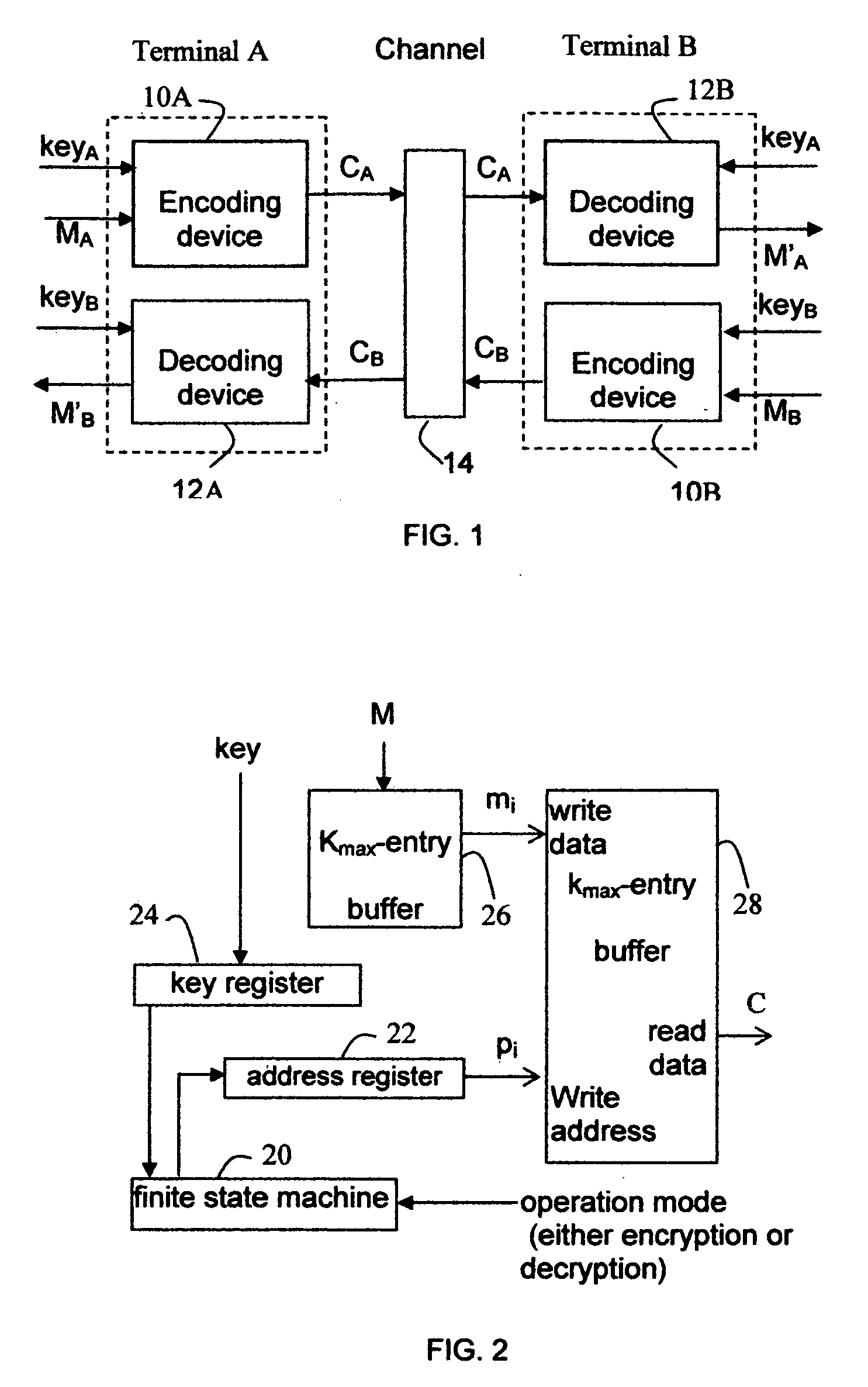
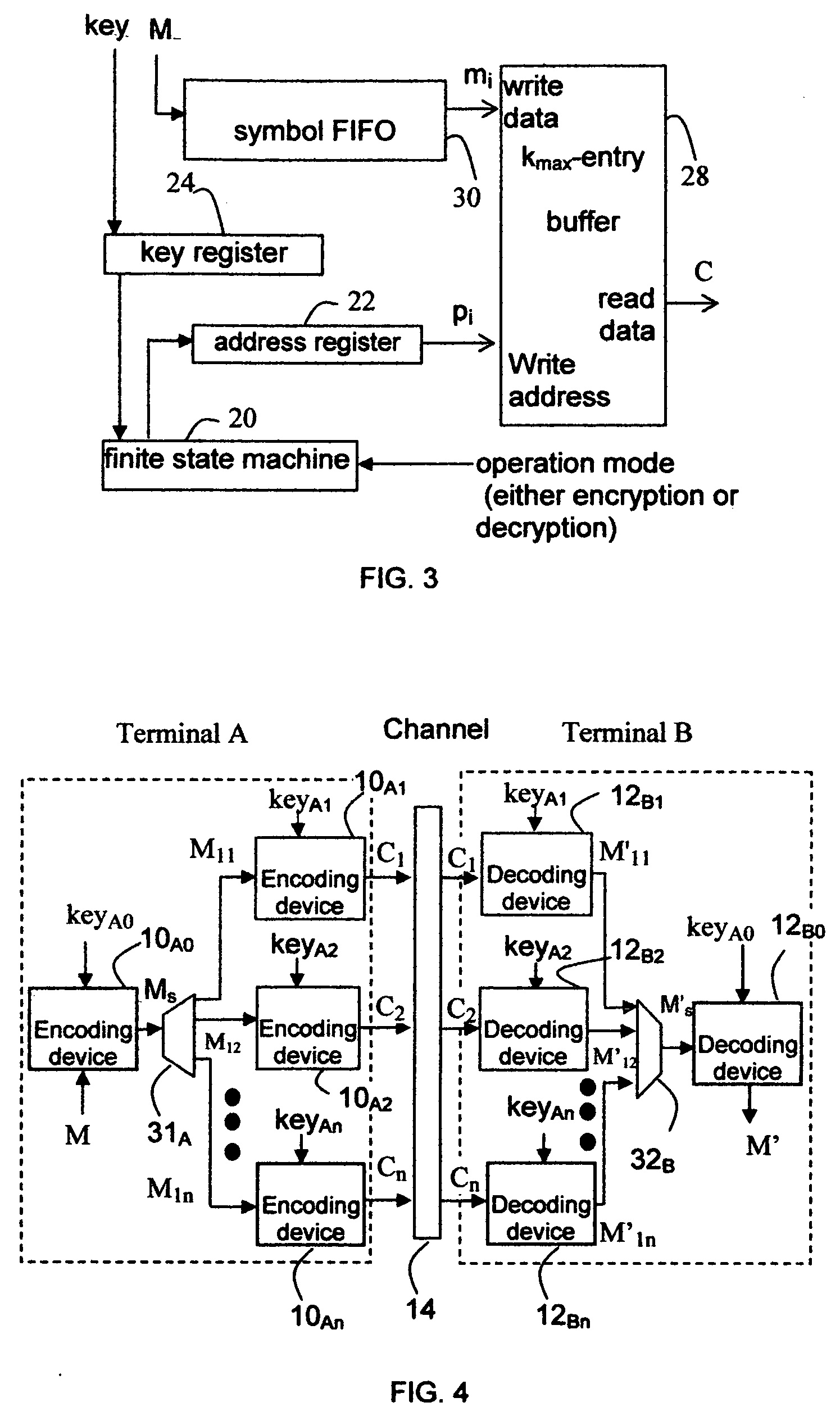
[0052]FIG. 1 shows an embodiment of the present invention in block diagram form. This system comprises a communications channel 14 and two terminals A and B. The communications channel 14 in the embodiment in FIG. 1 is a two-way communications channel. Nonetheless, the communications channel consistent with the present invention may be one-way, 2-way or even multi-way in other embodiments. Each of terminals A and B includes encoding device 10A and 10B, respectively, and decoding device 12A and 12B, respectively. An encryption key keyA is applied on both encoding device 10A, which transforms a message MA to a ciphertext CA, and decoding device 12B, which transforms the received ciphertext CA back to M′A. Similarly, an encryption key keyB is applied on both encoding device 10B, which transforms a message MB to a ciphertext CB, and decoding device 12A, which transforms the received ciphertext CB back to M′B. In other embodiments of one-way communications from t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com