Patents
Literature
459 results about "Encrypted function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An encrypted function is an attempt to provide mobile code privacy without providing any tamper-resistant hardware. Polynomial and rational functions are encrypted such that their transformation can again be implemented as programs consisting of cleartext instructions that a processor or interpreter understands. The processor would not understand the program's function. This field of study is gaining popularity as mobile cryptography.
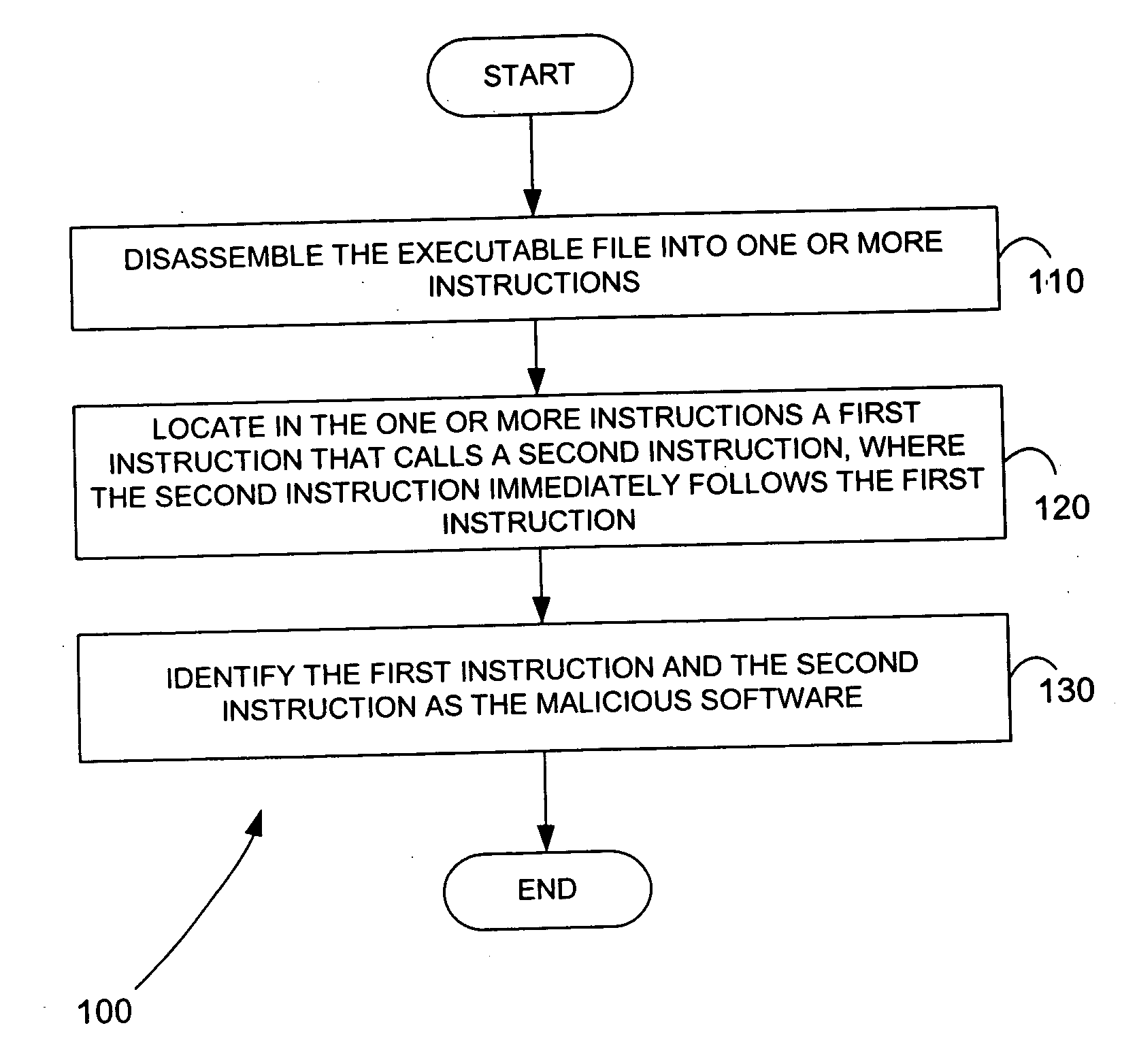
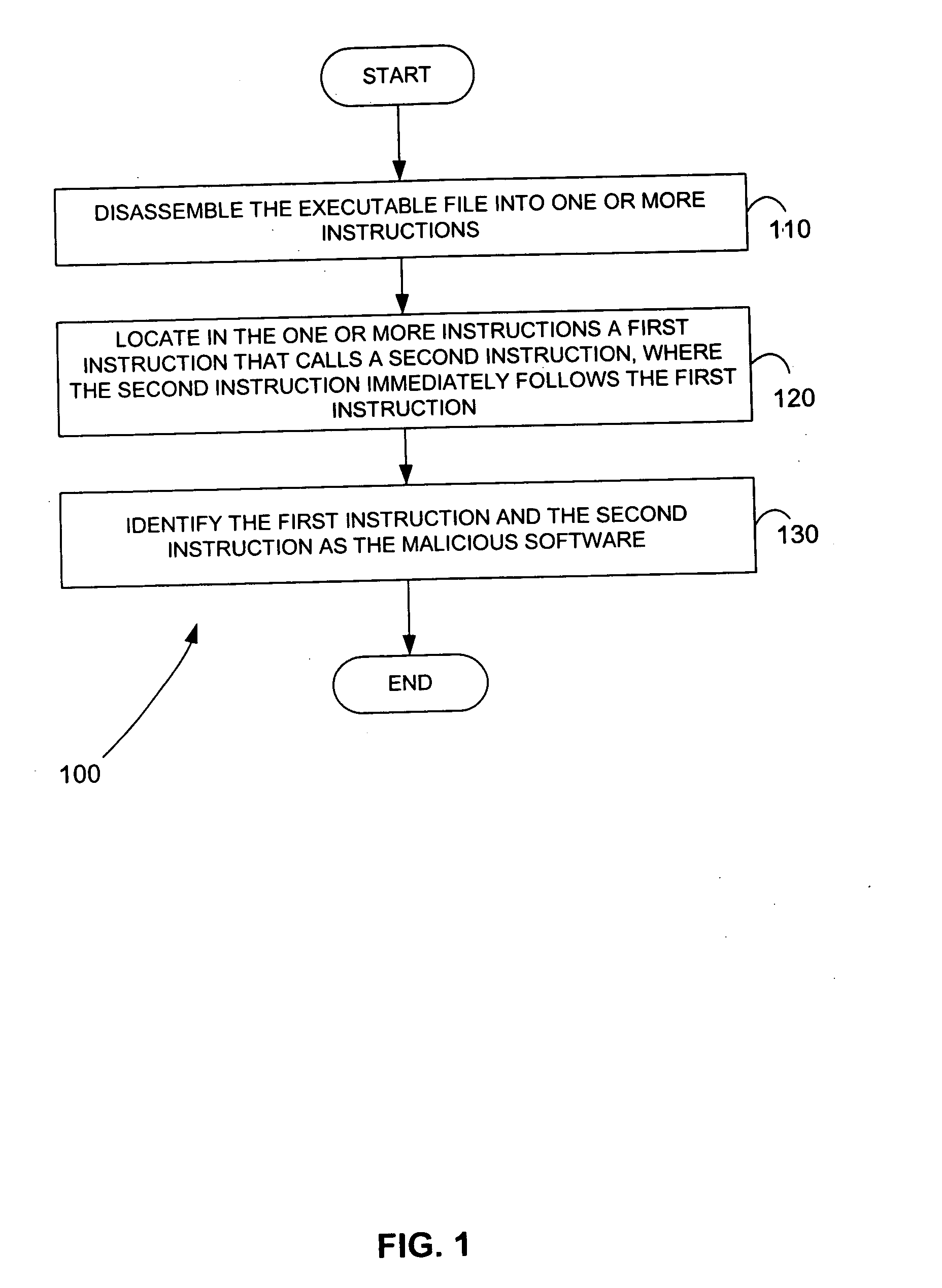
Methods for identifying malicious software
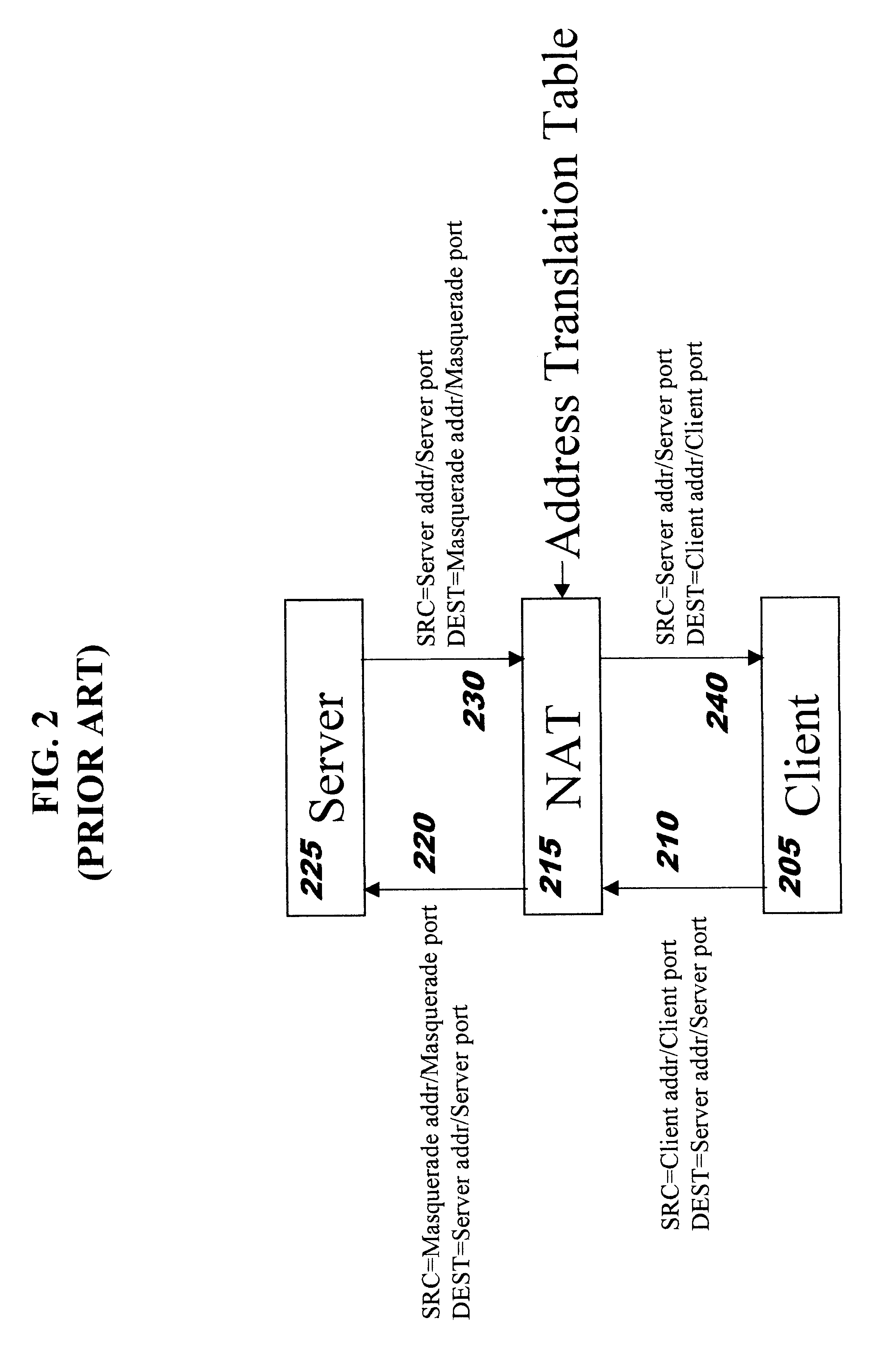
ActiveUS7644441B2Memory loss protectionEncryption apparatus with shift registers/memoriesGraphicsEncrypted function
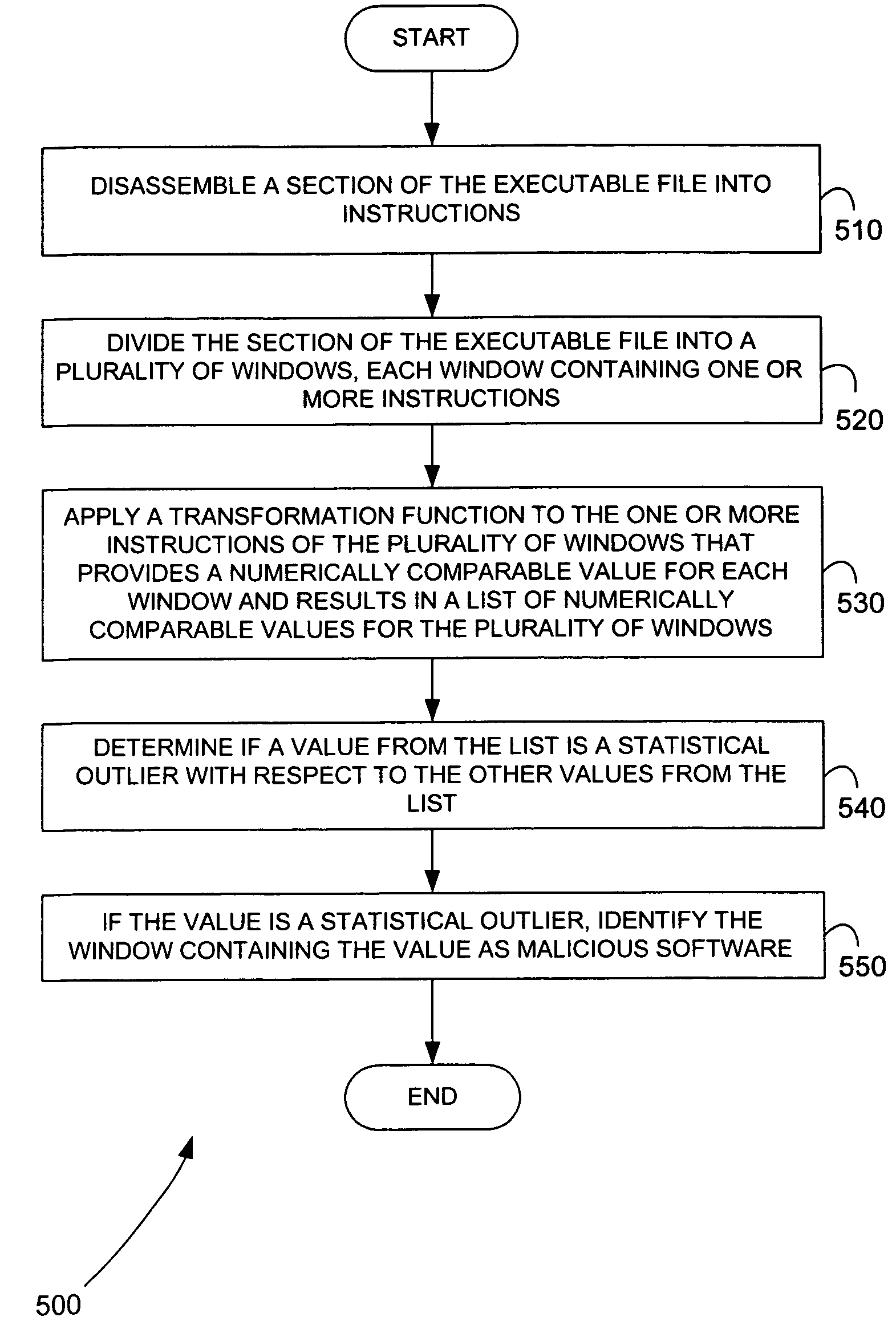
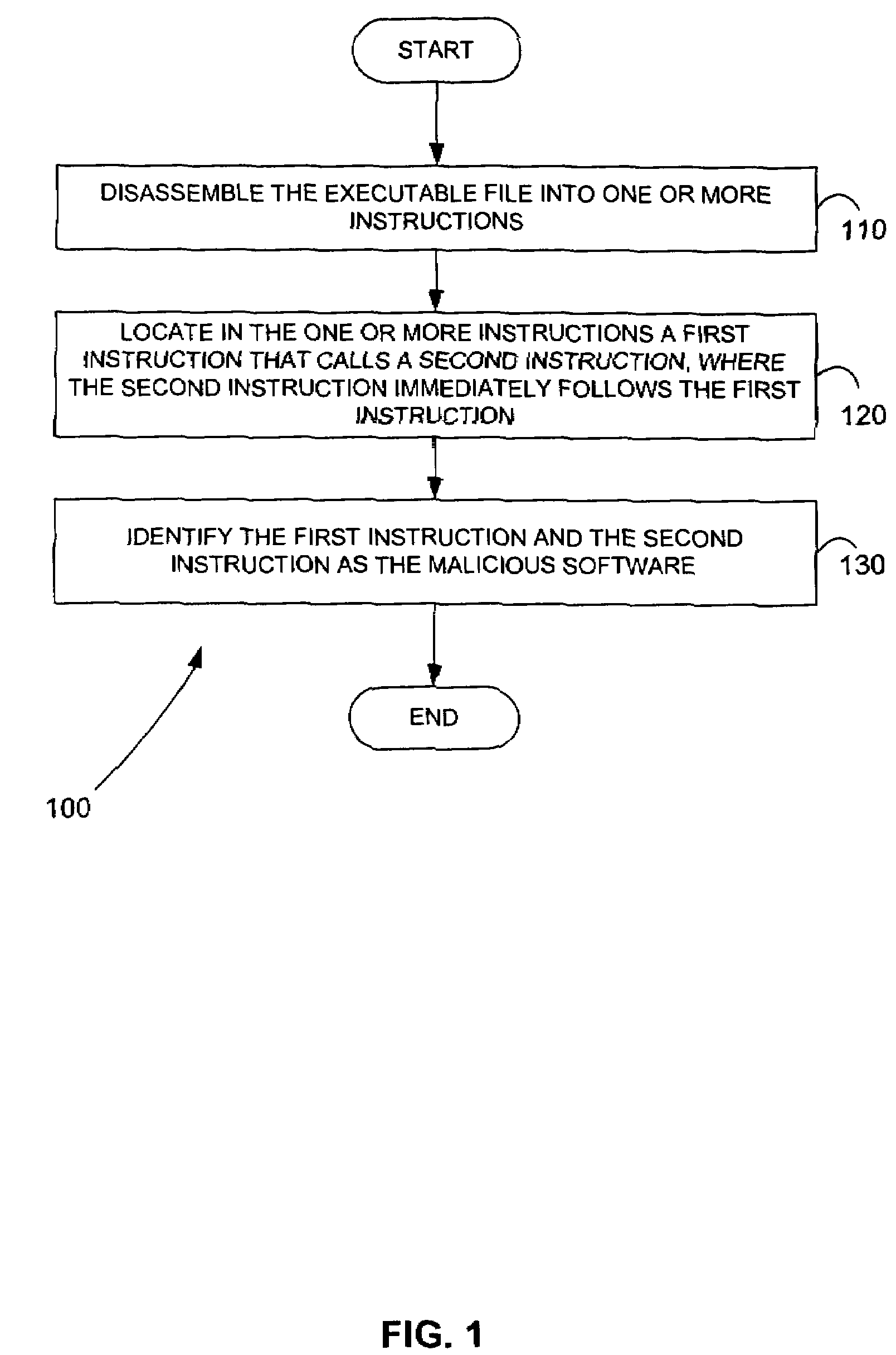
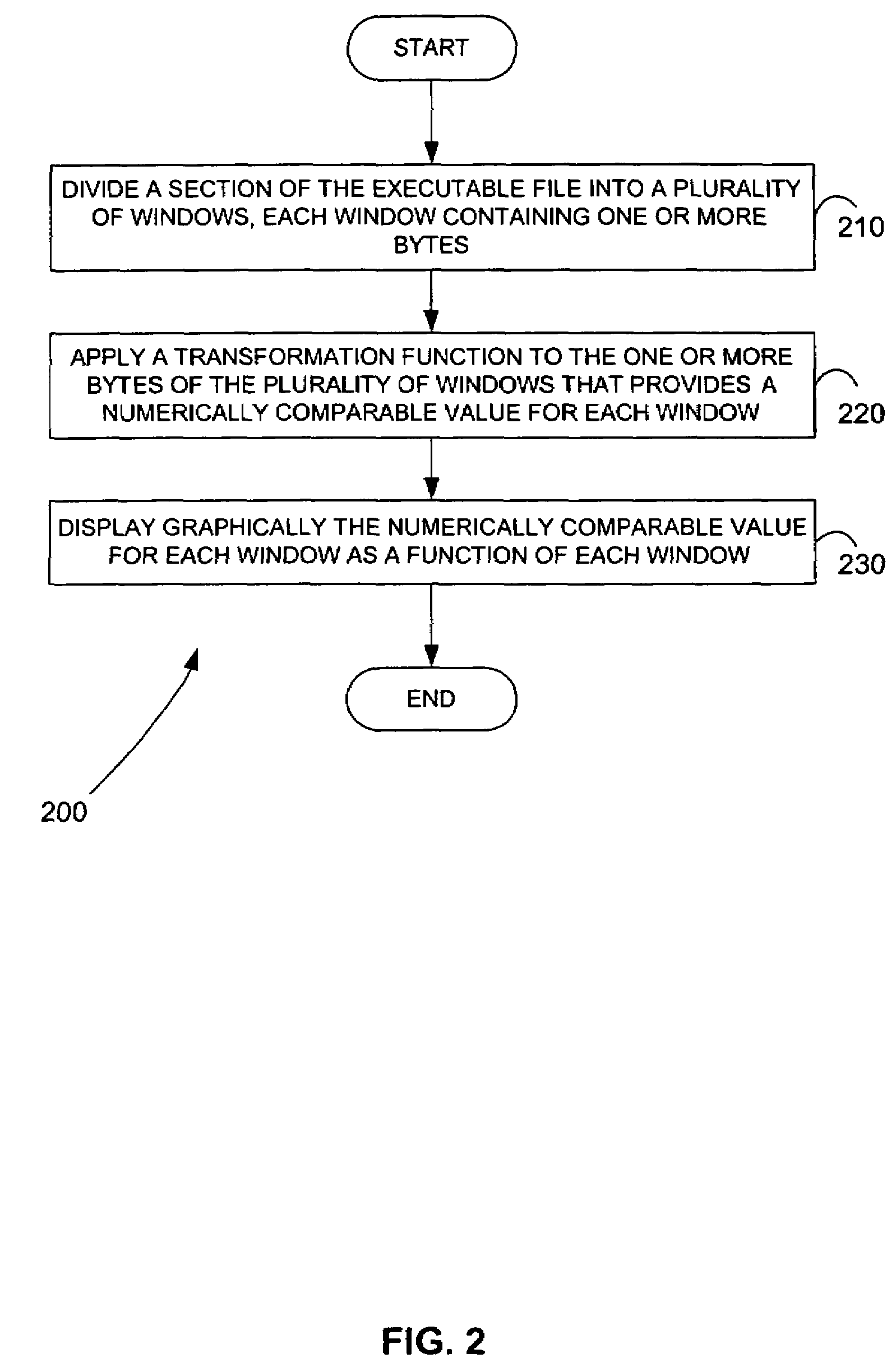
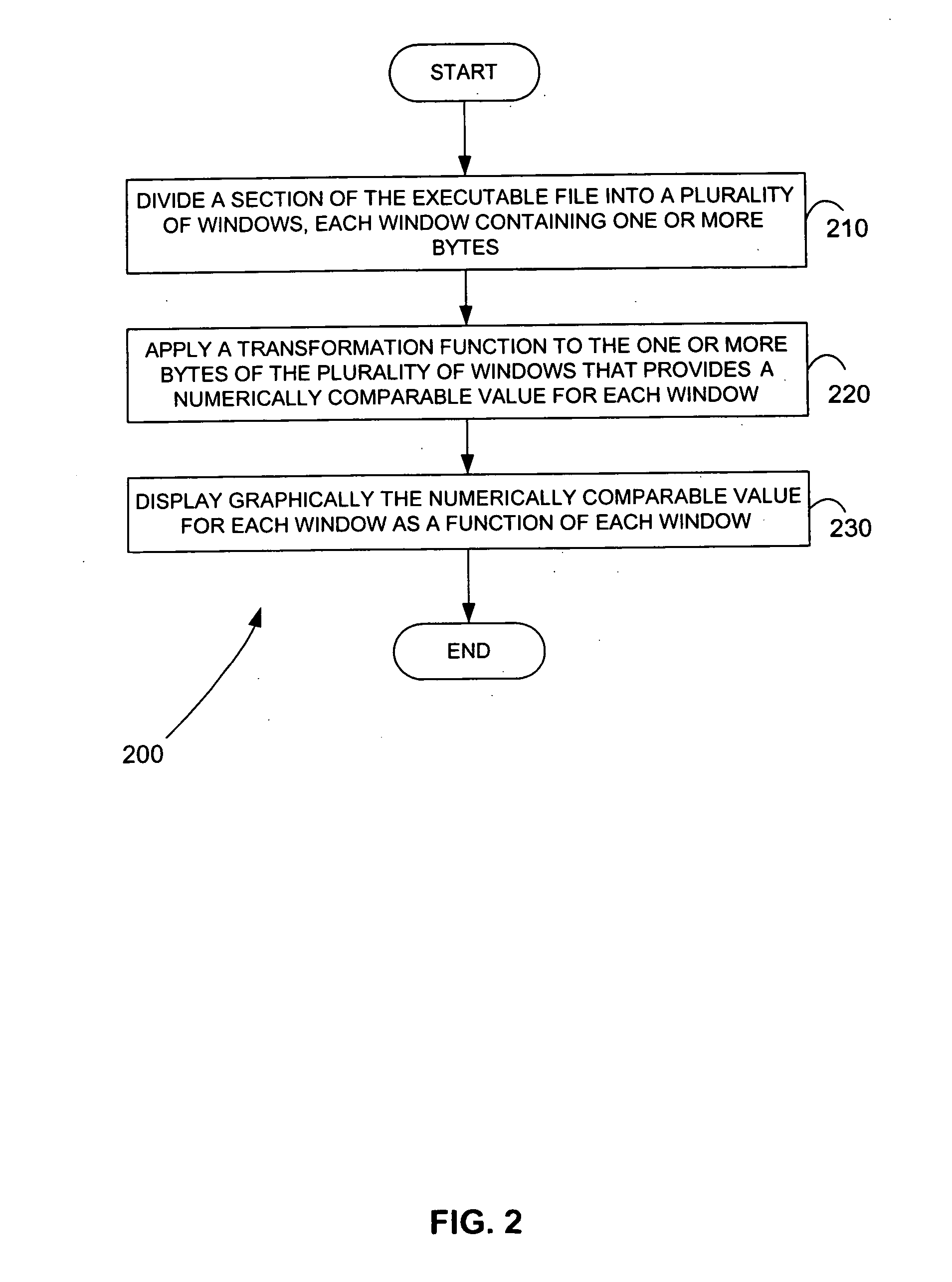
Malicious software is identified in an executable file by identifying malicious structural features, decryption code, and cryptographic functions. A malicious structural feature is identified by comparing a known malicious structural feature to one or more instructions of the executable file. A malicious structural feature is also identified by graphically and statistically comparing windows of bytes or instructions in a section of the executable file. Cryptography is an indicator of malicious software. Decryption code is identified in an executable file by identifying a tight loop around a reversible instruction that writes to random access memory. Cryptographic functions are identified in an executable file be obtaining a known cryptographic function and performing a string comparison of the numeric constants of the known cryptographic function with the executable file.
Owner:SYNOPSYS INC
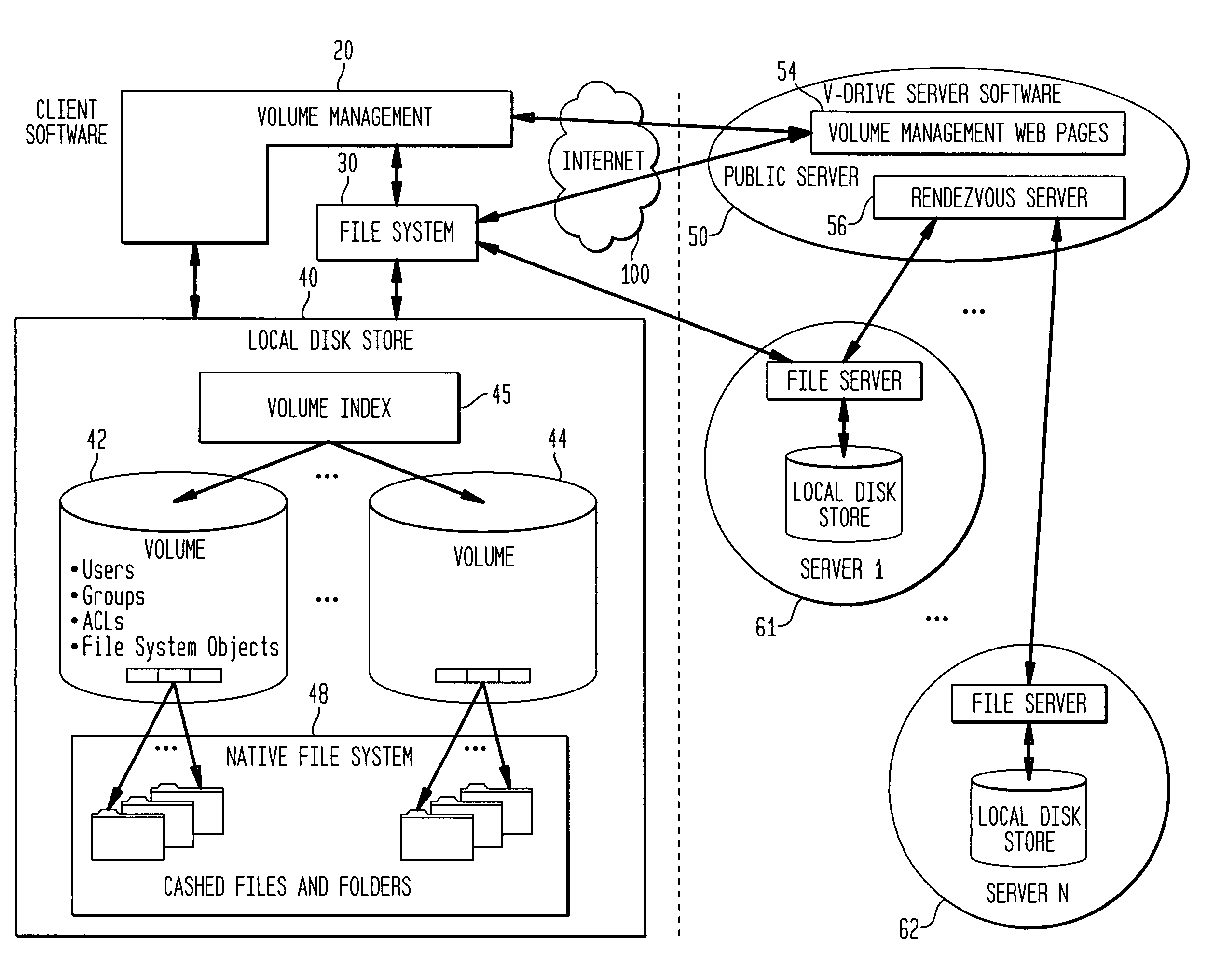
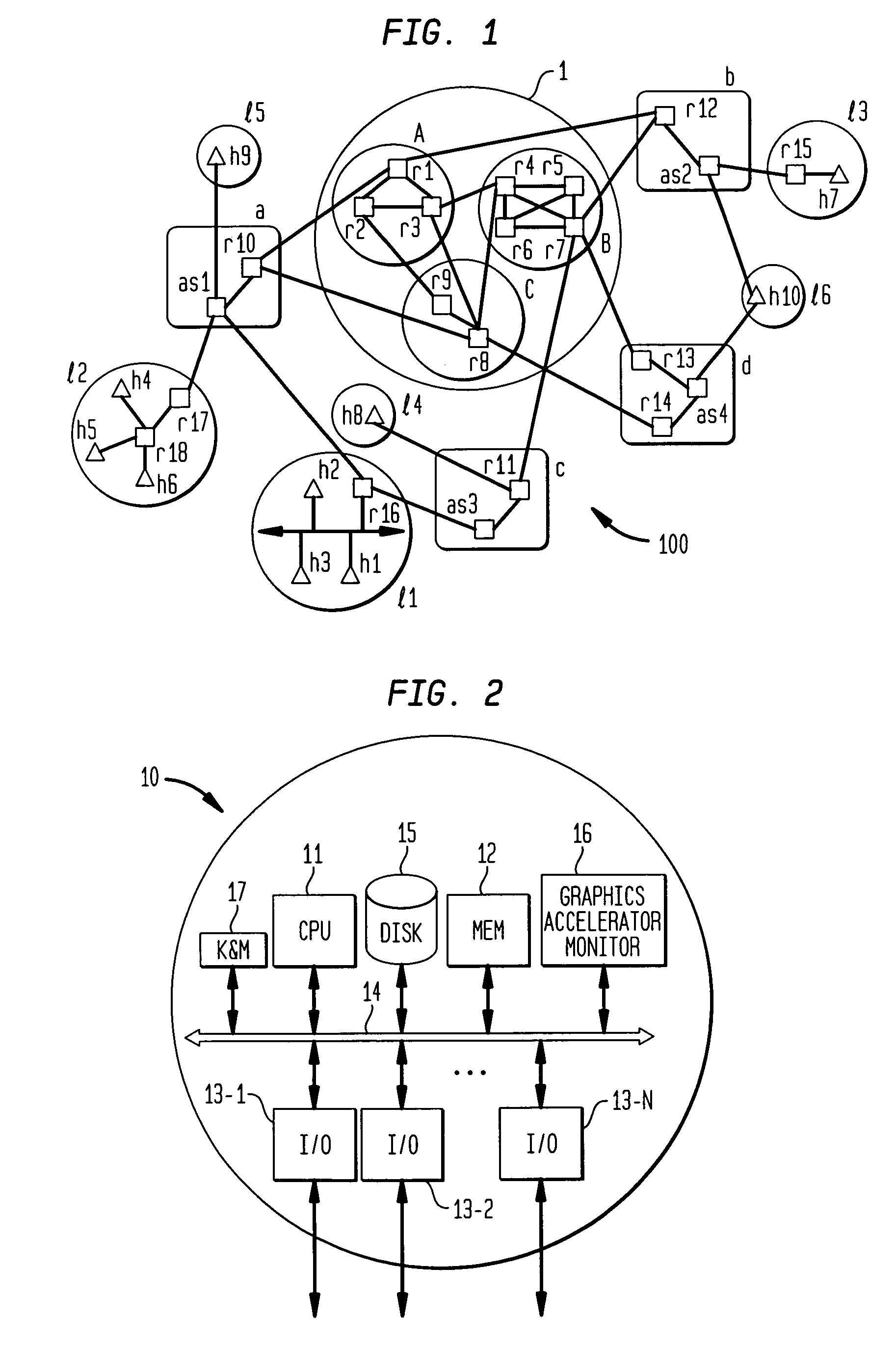
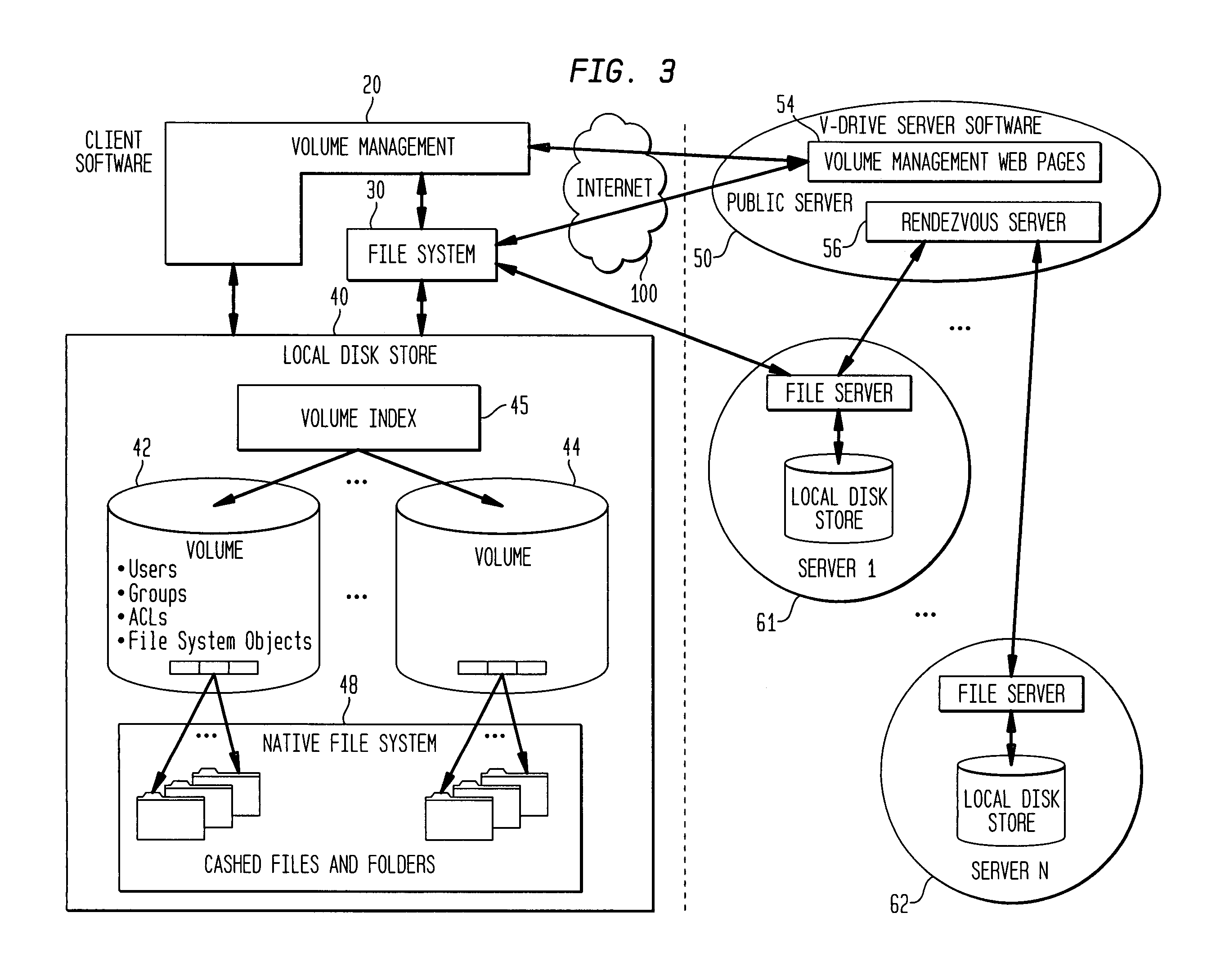
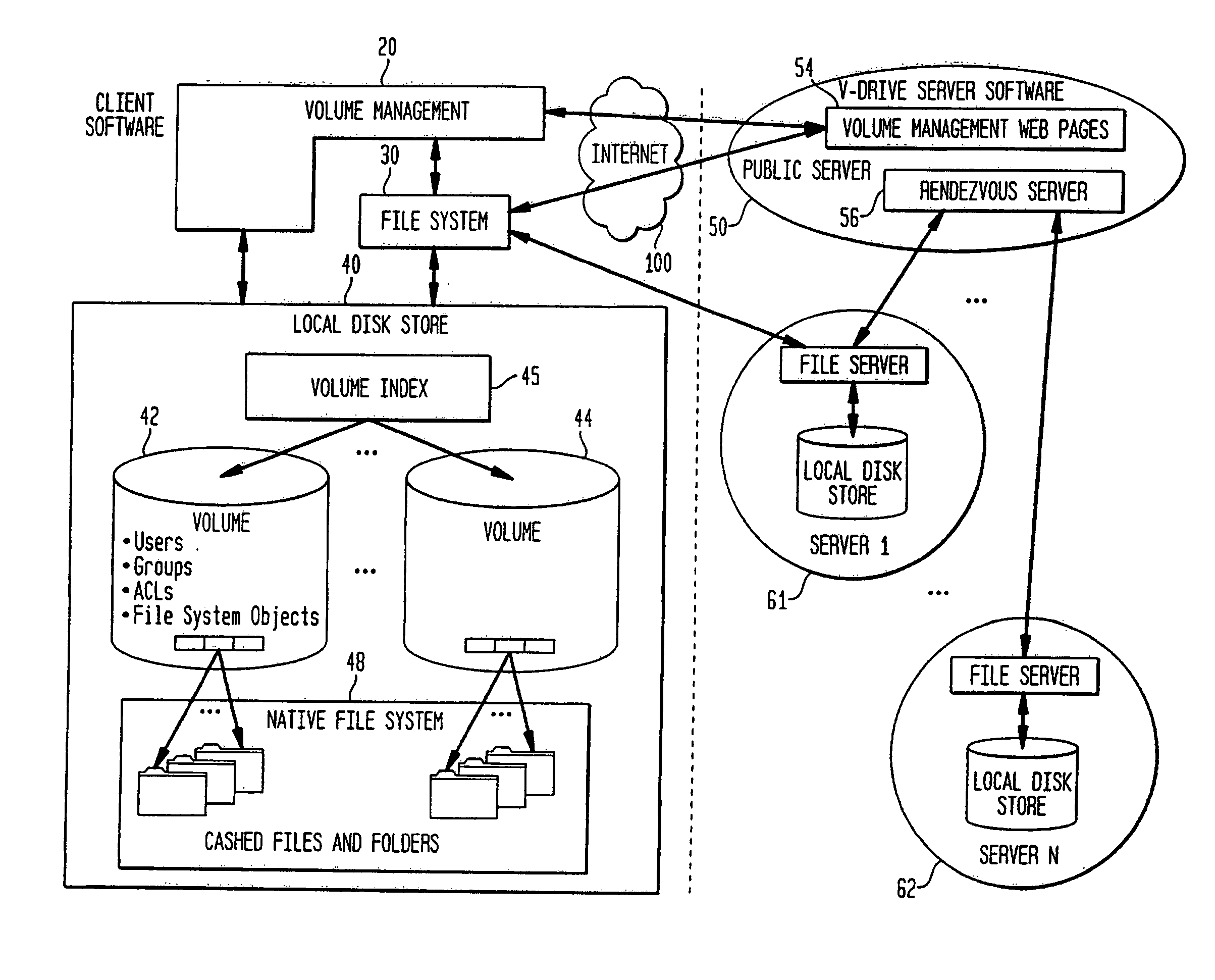
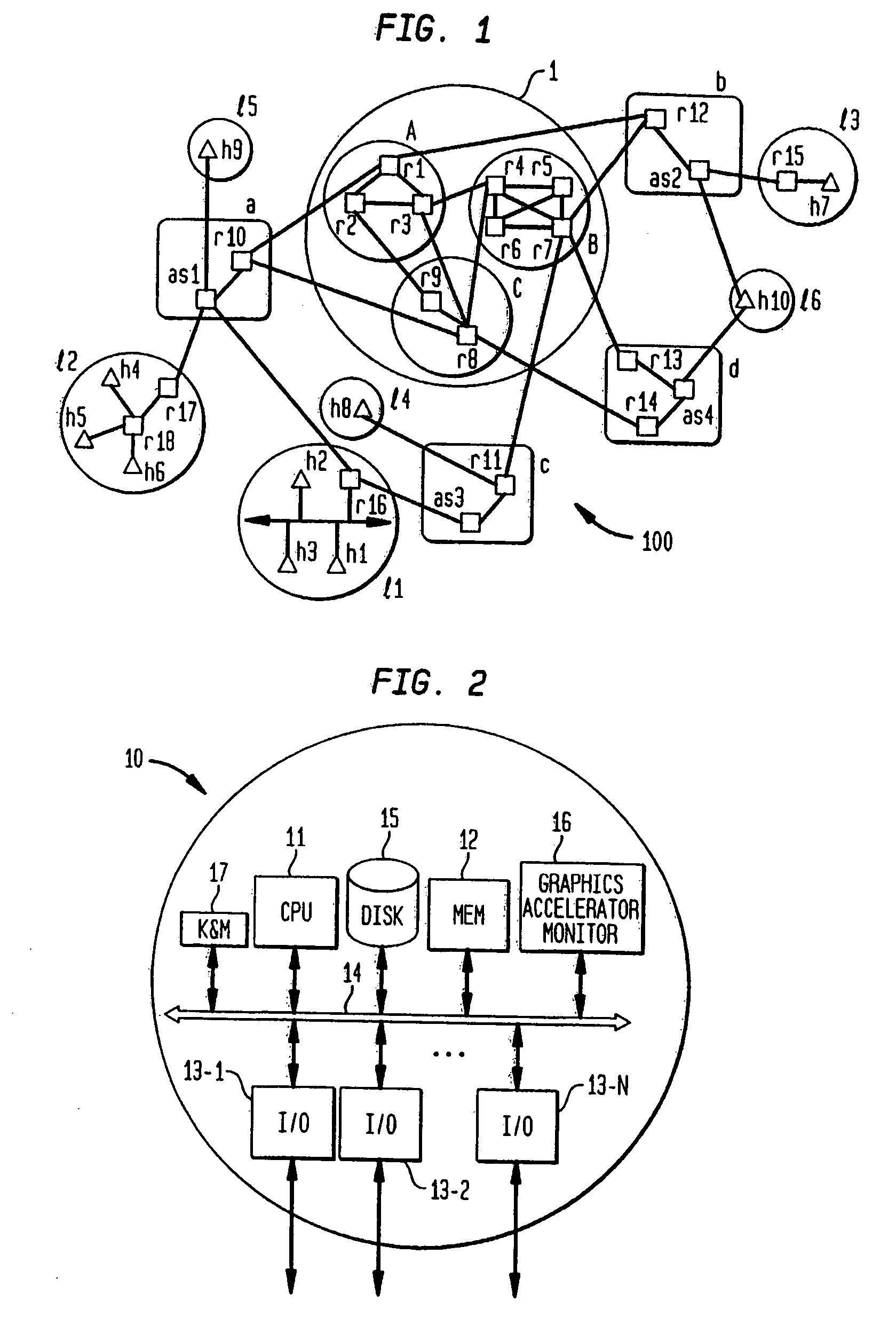
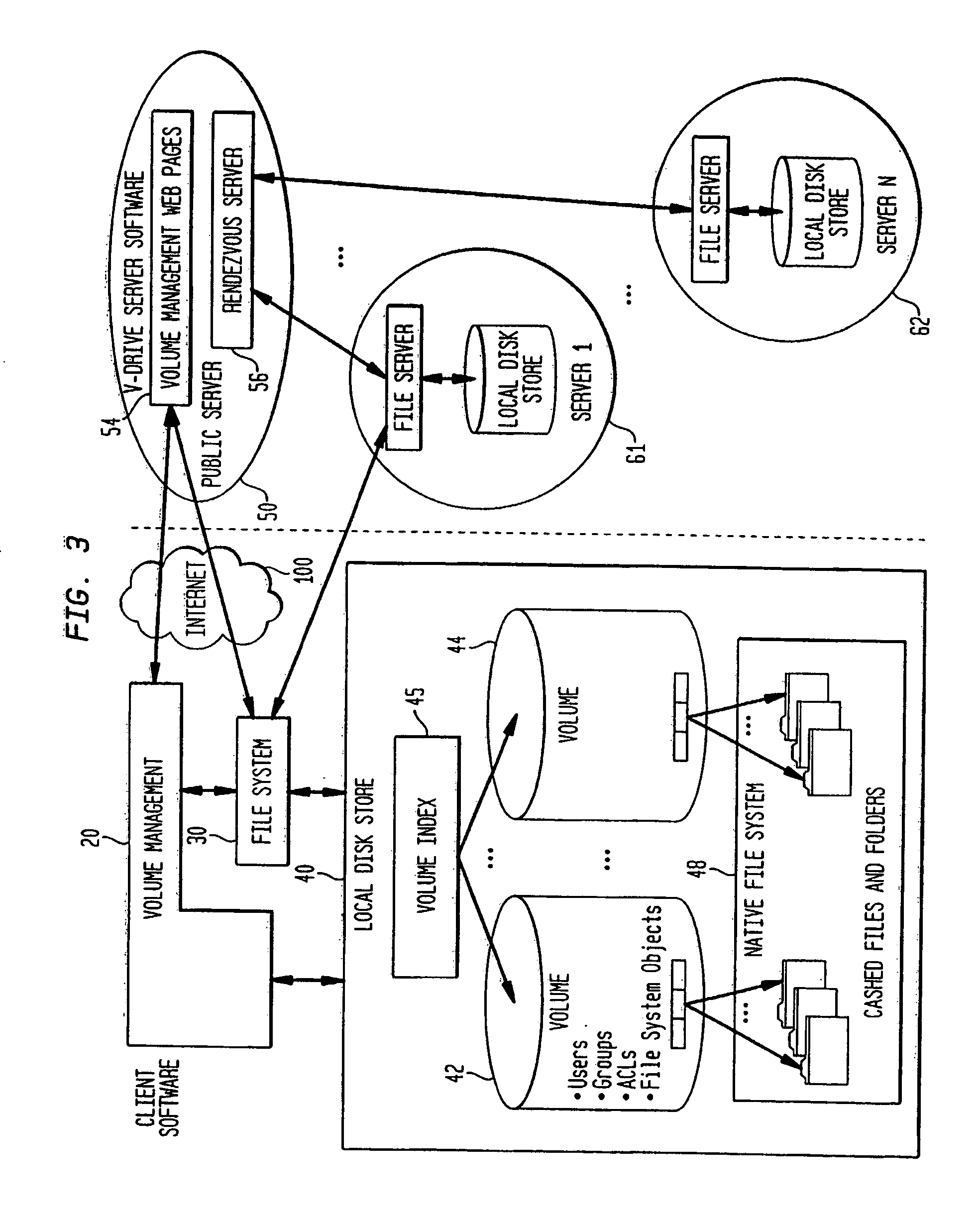
Internet-based shared file service with native PC client access and semantics and distributed access control
InactiveUS7136903B1Web data retrievalPublic key for secure communicationWide area networkAccess control
A multi-user file storage service and system enable each user of a pre-subscribed user group to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Additionally, an encrypted key is transferred from the file server node to a particular client node via a secure channel. The encrypted key uses an encryption function and a decryption function not known locally at the remote file server. Furthermore, both privileged access control rights and file sharing mode access control to a particular file of the group of files are delegated to one or more distributed nodes other than the remote file server node which provides the data.
Owner:GOOGLE LLC
Internet-based shared file service with native PC client access and semantics and distributed version control
InactiveUS20060129627A1Multiple digital computer combinationsTransmissionOperational systemWide area network
A multi-user file storage service and system enable each user of a pre-subscribed user group to operate an arbitrary client node at an arbitrary geographic location, to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node in communication with the remote file server node via the wide area network. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Illustratively, the integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Thus, all native operating system application programming interfaces operate as if all multi-user applications accessing the files function as if the remote server and client nodes were on the same local area network. Illustratively, an interface is provided for adapting file access one of the client nodes. The interface designates at the client node each accessible file of the group as stored on a virtual storage device. The interface enables access to the designated files in a fashion which is indistinguishable, by users of, and applications executing at, the client node, with access to one or more files stored on a physical storage device that is locally present at the client node. Illustratively, an encrypted key is transferred from the remote file server node to one of the client nodes via a secure channel. The key is encrypted using an encryption function not known locally at the remote file server node. The transferred key is decrypted at the client node. The key is used at the client node to decrypt information of the files downloaded from the remote file server node or to encrypt information of the files prior to uploading for storage at the remote file server node. Access control to a particular one of the files of the group can be delegated to an access control node.
Owner:GOOGLE LLC
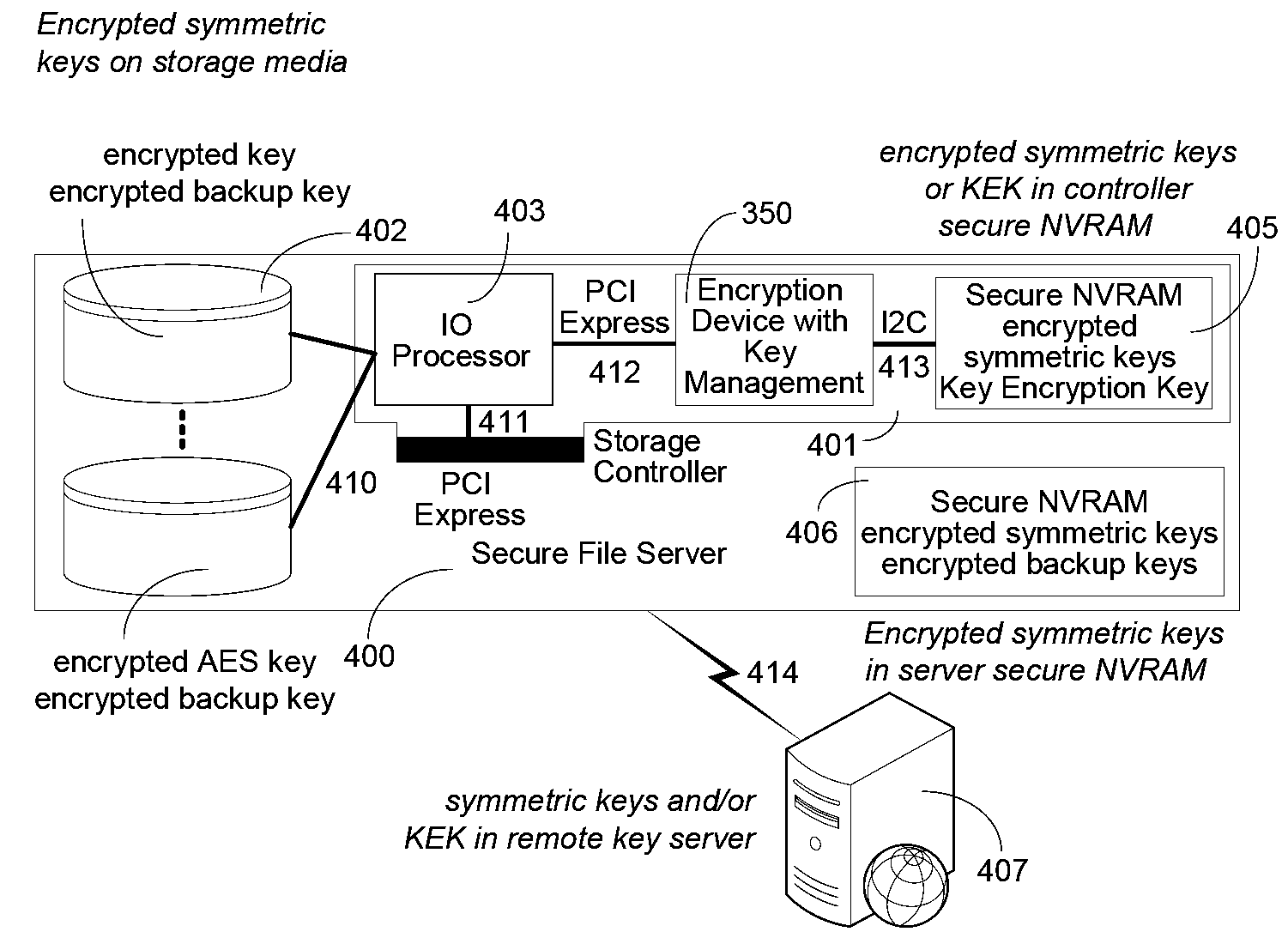
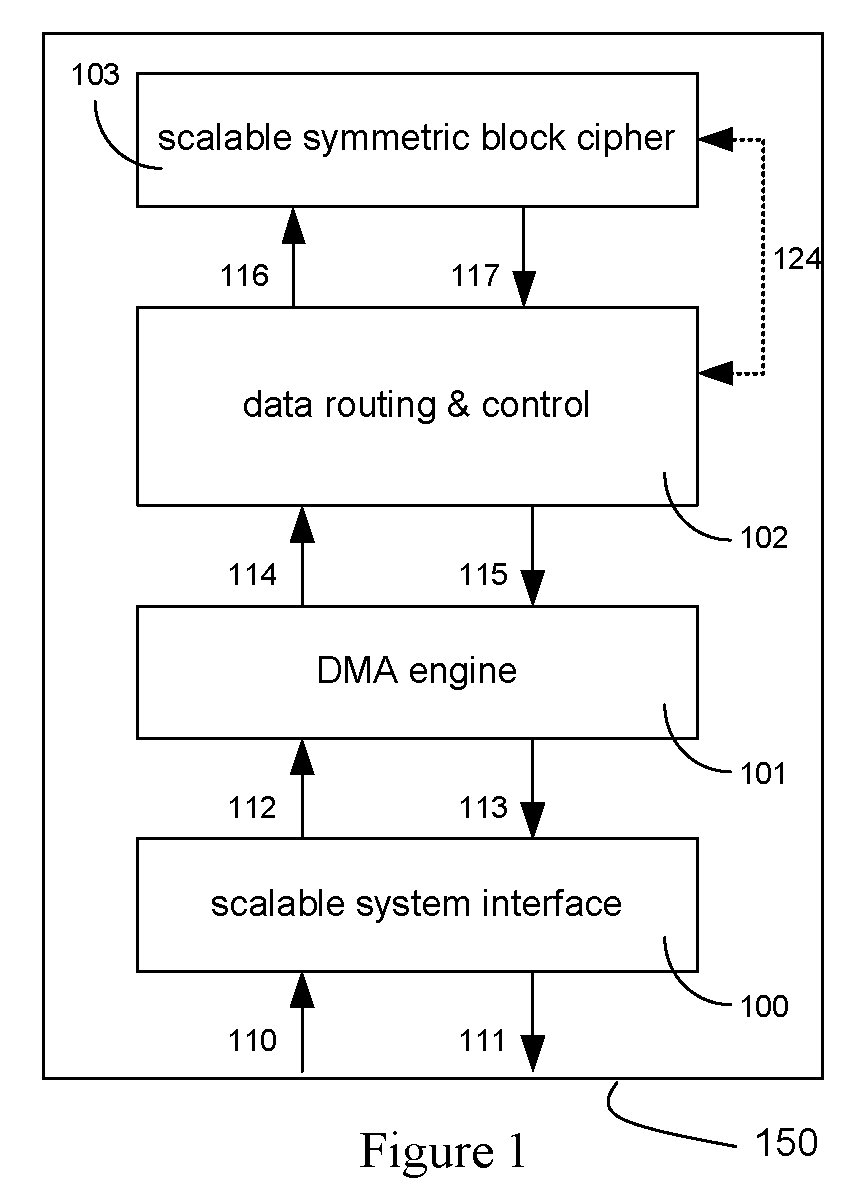
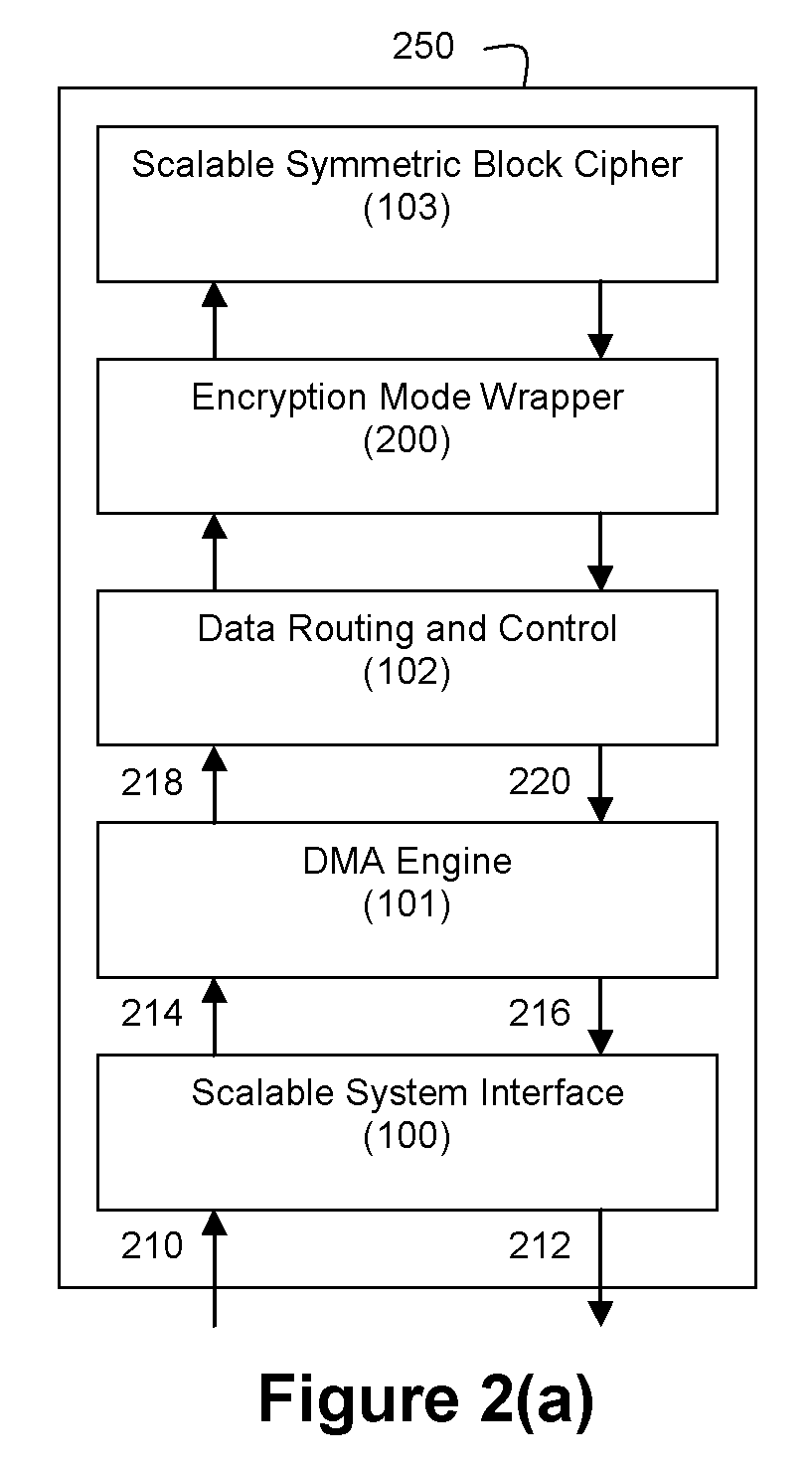
Method and Apparatus for Hardware-Accelerated Encryption/Decryption
ActiveUS20090060197A1Avoid contactMaximize availabilityEncryption apparatus with shift registers/memoriesSecret communicationMultiple encryptionComputer hardware
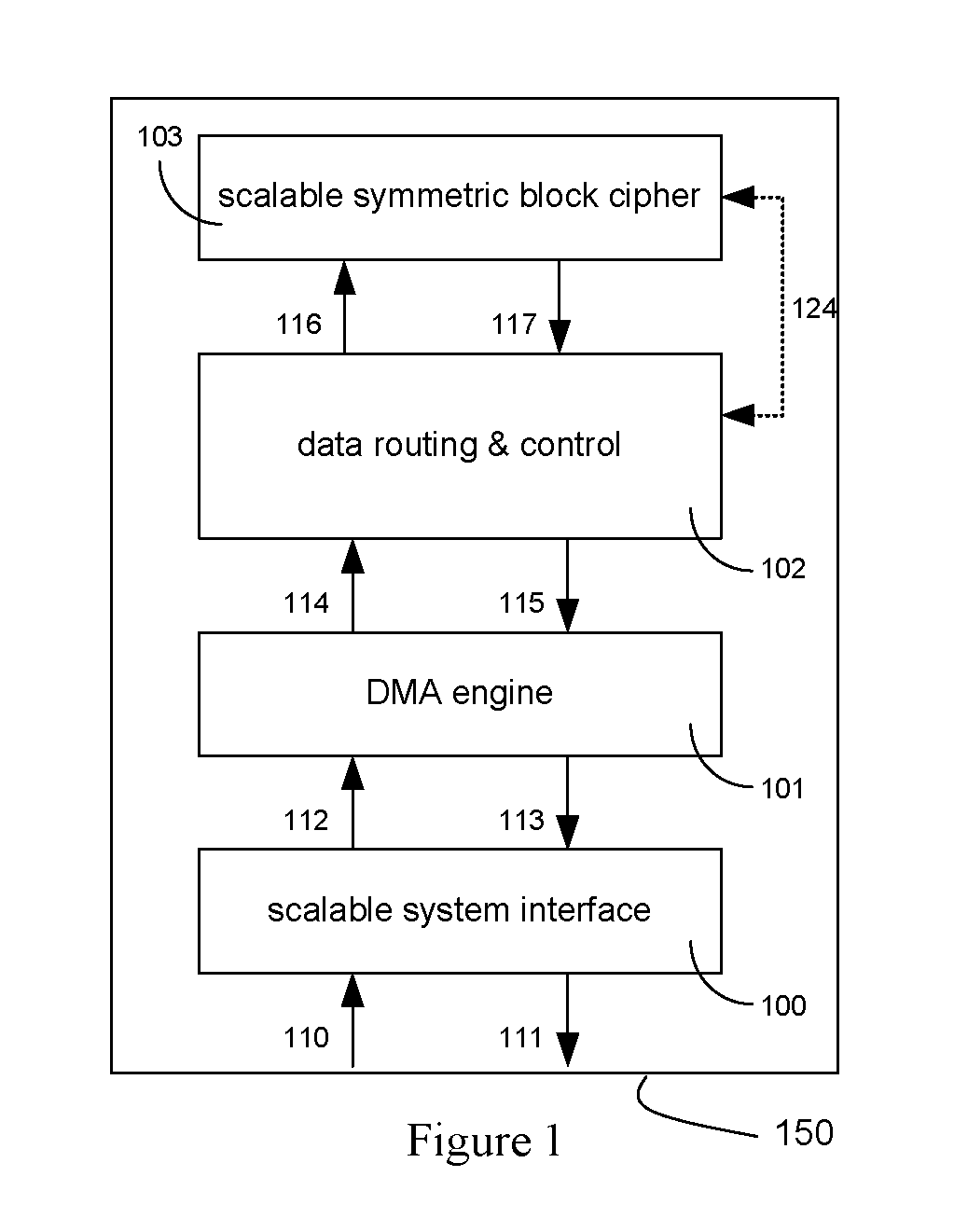
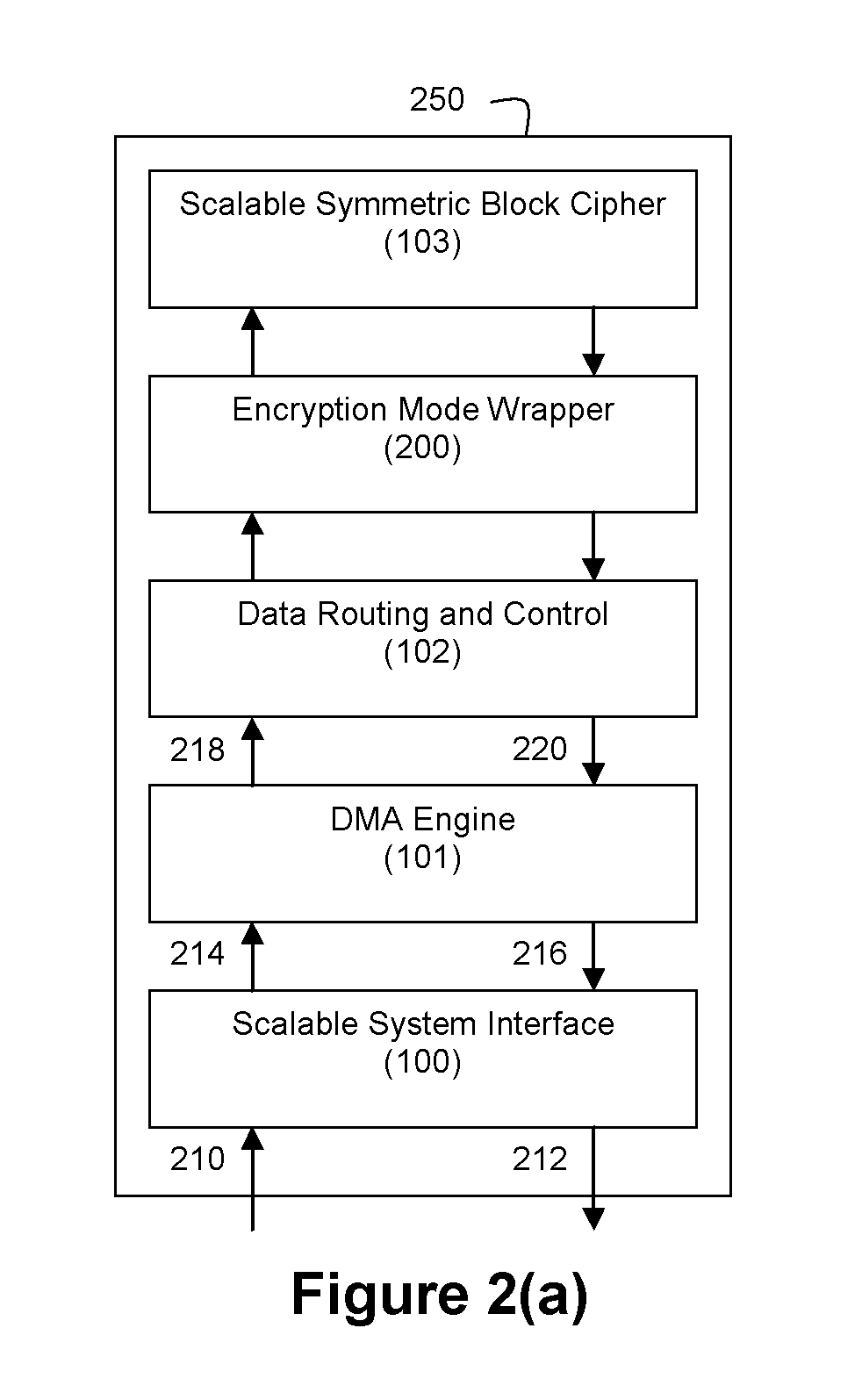
An integrated circuit for data encryption / decryption and secure key management is disclosed. The integrated circuit may be used in conjunction with other integrated circuits, processors, and software to construct a wide variety of secure data processing, storage, and communication systems. A preferred embodiment of the integrated circuit includes a symmetric block cipher that may be scaled to strike a favorable balance among processing throughput and power consumption. The modular architecture also supports multiple encryption modes and key management functions such as one-way cryptographic hash and random number generator functions that leverage the scalable symmetric block cipher. The integrated circuit may also include a key management processor that can be programmed to support a wide variety of asymmetric key cryptography functions for secure key exchange with remote key storage devices and enterprise key management servers. Internal data and key buffers enable the device to re-key encrypted data without exposing data. The key management functions allow the device to function as a cryptographic domain bridge in a federated security architecture.
Owner:IP RESERVOIR
System and method for data management structure using auditable delta records in a distributed environment
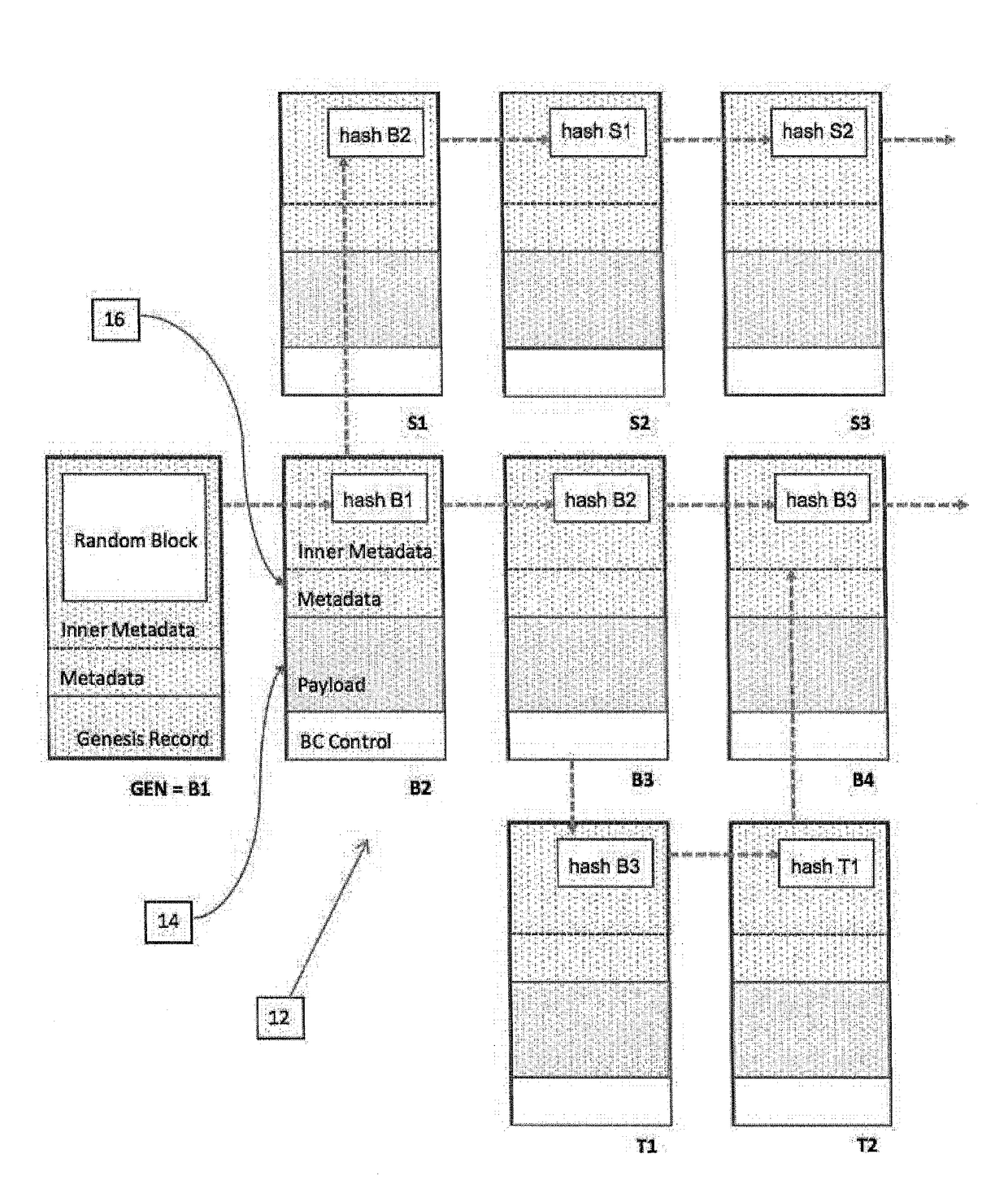
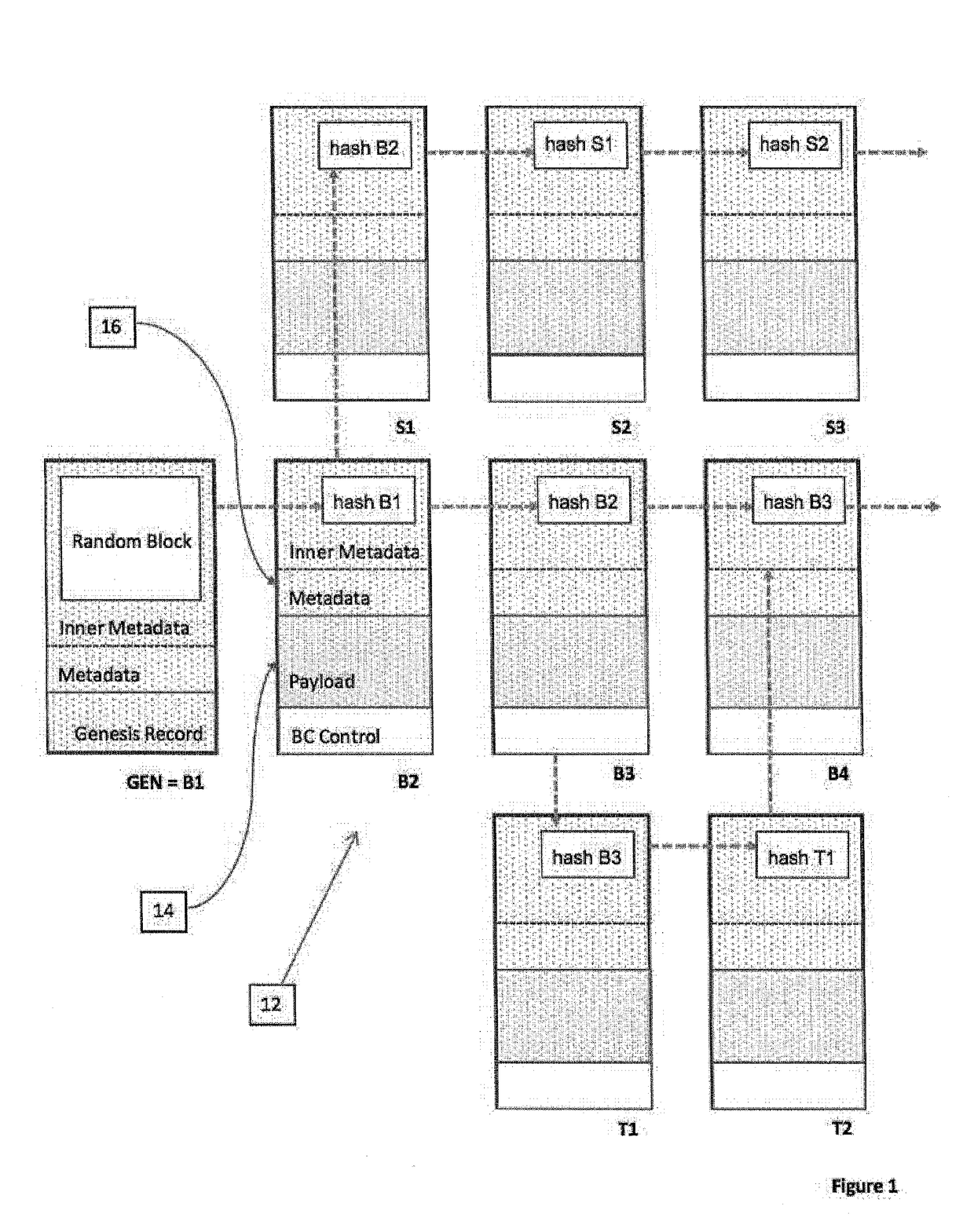
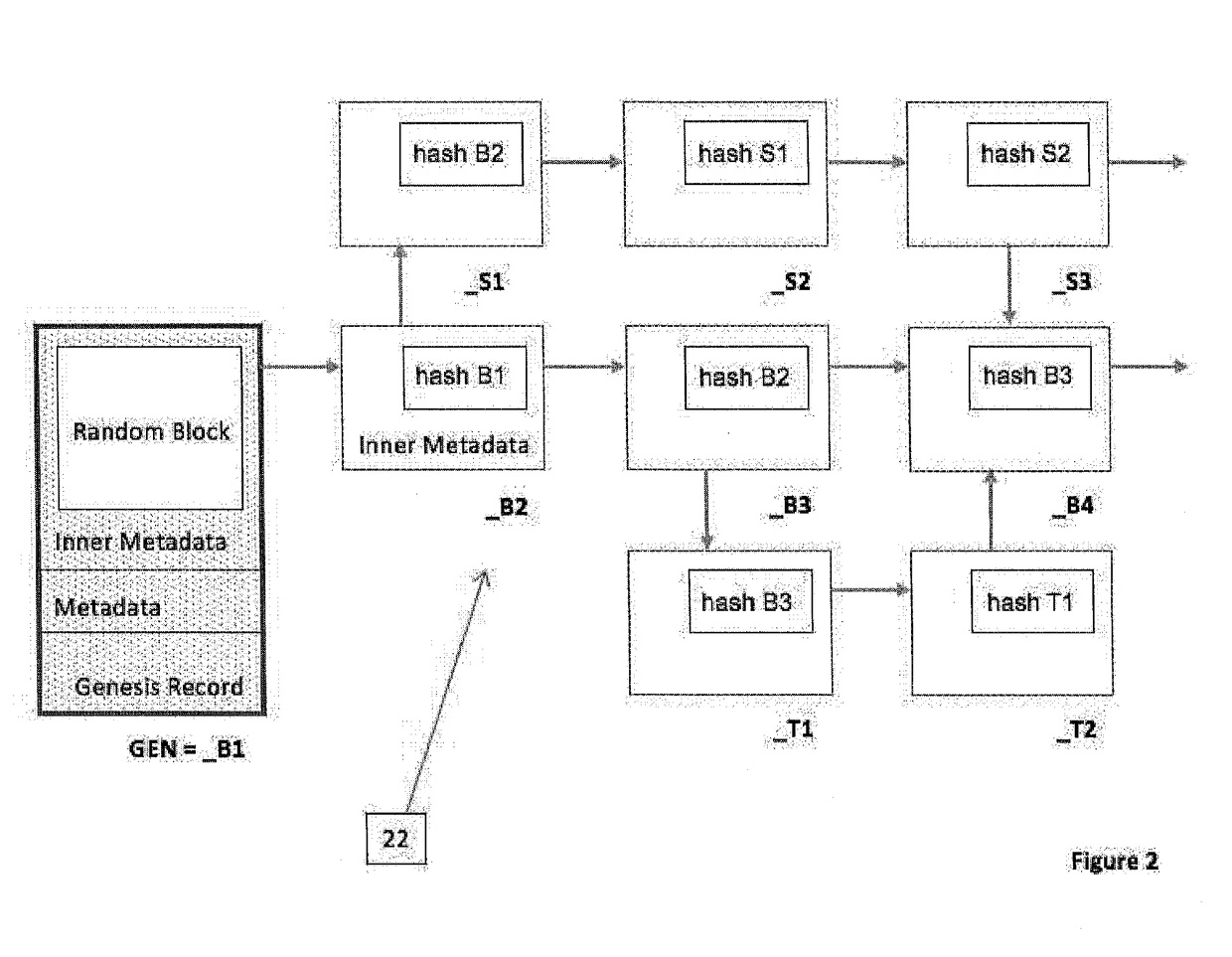
A system and method of recording data from a number of devices in a distributed network system in a manner adaptable for auditing the device output. The devices may include one or more control, sensor, edge, or peripheral computing devices physically separate in the distributed network system and in communication with a control server. Such distributed networks systems are common in SCADA or IoT applications. The content stream of data records output from the devices are recorded; a payload stripped stream of data records which are stripped of the payload are recorded and preferably retained by an escrow service. The metadata of the data records includes the hash value of one or more predecessor data records. The hash values are calculated based on the payload and a linkage function, preferably a cryptographic function. A comparison of hash values of the payload stripped stream and the content stream provides the audit ability.
Owner:OLEA NETWORKS
Method and apparatus for automatic database encryption
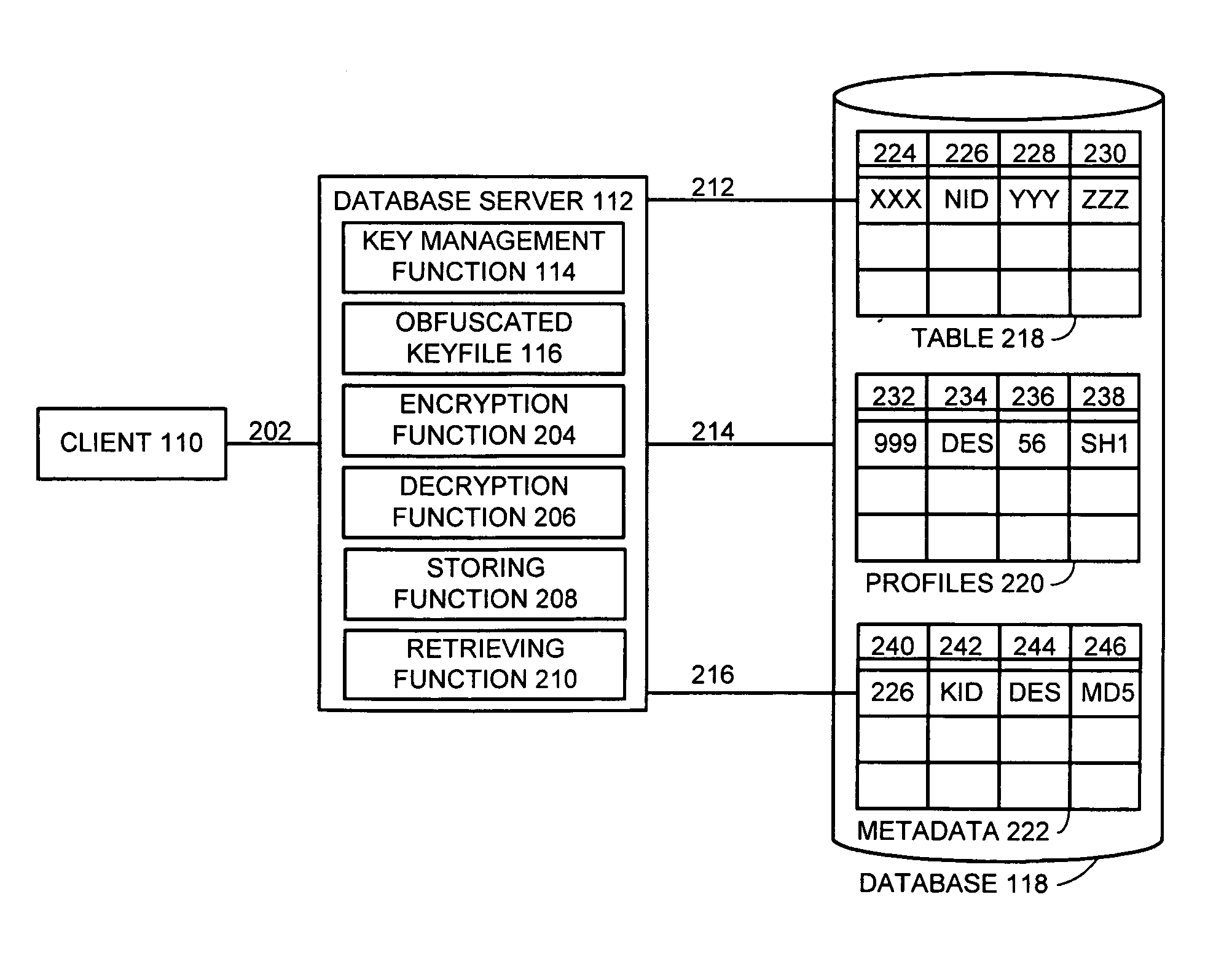
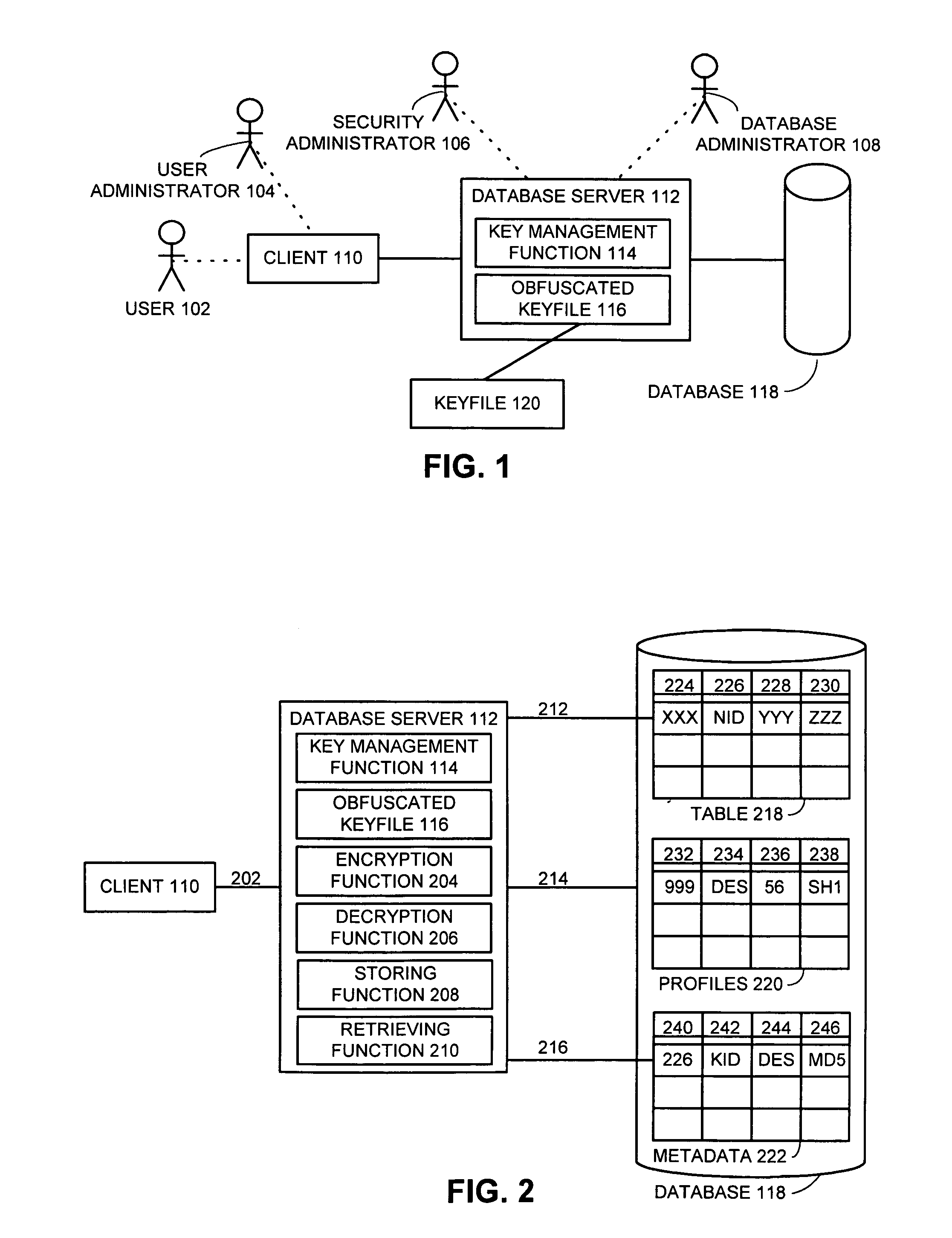
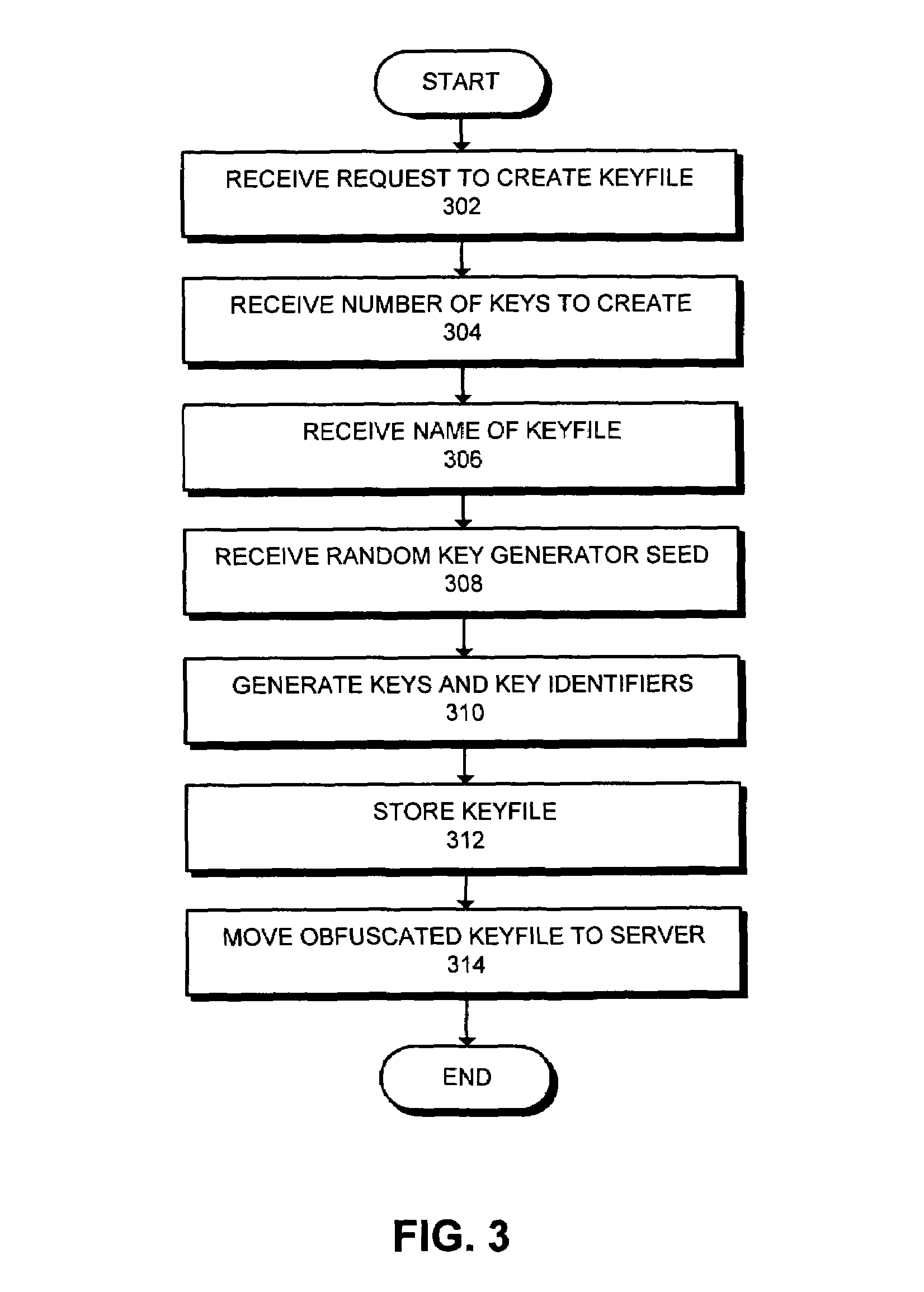
InactiveUS7111005B1Data processing applicationsMultiple keys/algorithms usageEncrypted functionDatabase encryption
One embodiment of the present invention provides a system for managing encryption within a database system that is managed by a database administrator, and wherein a user administrator not otherwise associated with the database system, manages users of the database system. This system performs encryption automatically and transparently to a user of the database system. The system operates by receiving a request to store data in a column of the database system. If a user has designated the column as an encrypted column, the system automatically encrypts the data using an encryption function. This encryption function uses a key stored in a keyfile managed by the security administrator. After encrypting the data, the system stores the data in the database system using a storage function of the database system.
Owner:ORACLE INT CORP
System and method for interfacing a software process to secure repositories
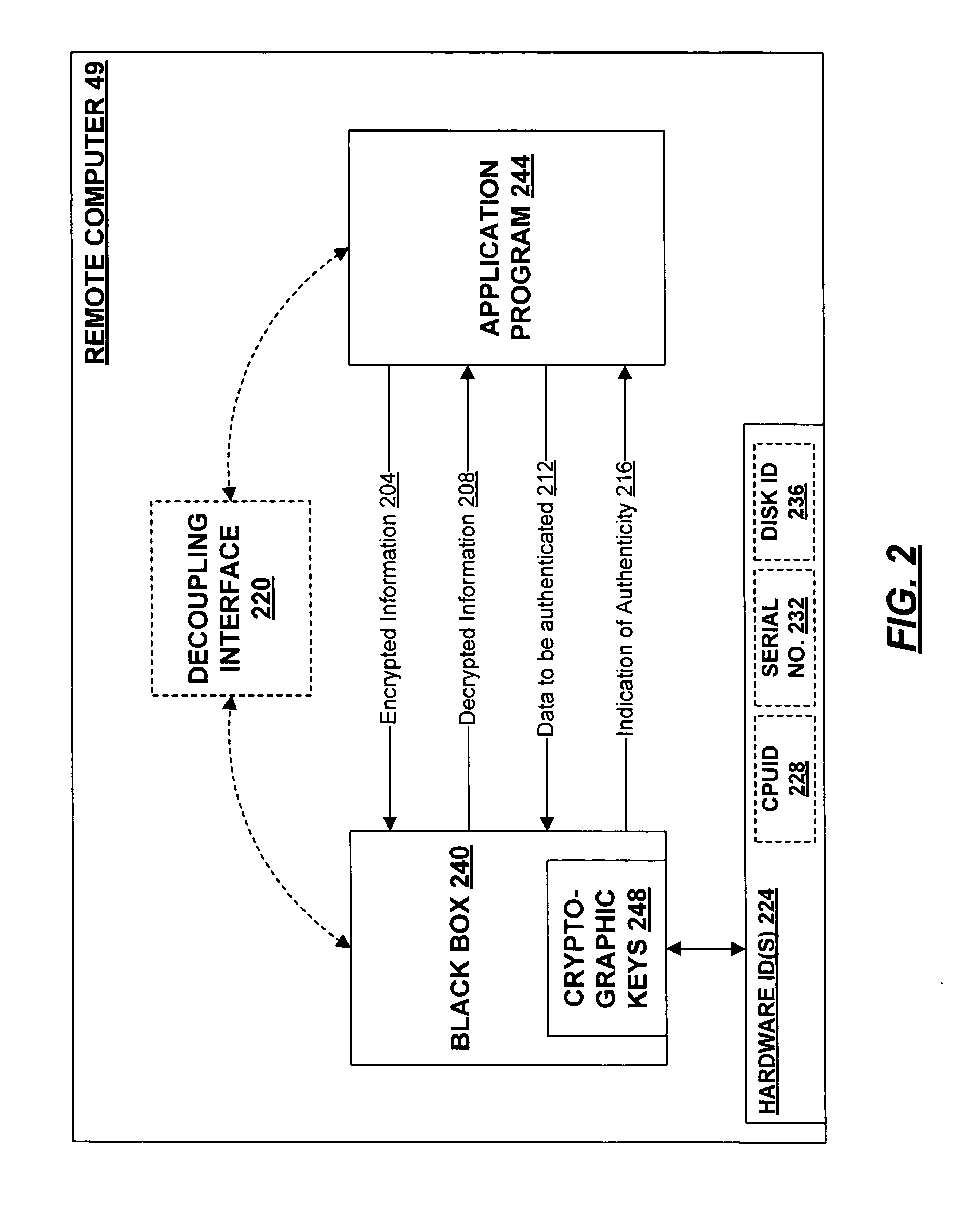
InactiveUS7051200B1Operational safetyDigital data processing detailsUnauthorized memory use protectionPersonalizationEncrypted function
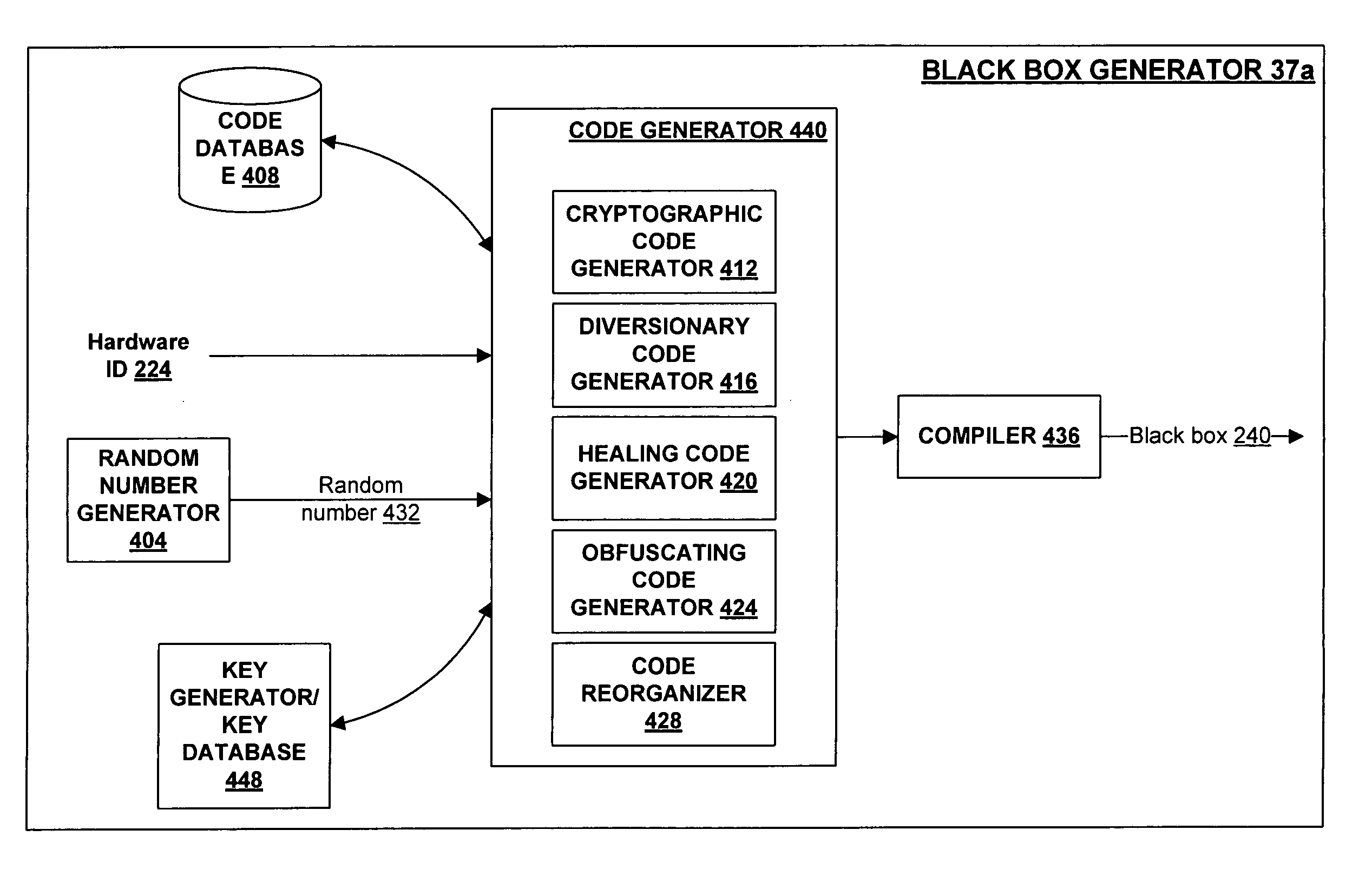
A secure repository individualized for a hardware environment and a method and system for providing the same. The secure repository includes a hidden cryptographic key and code that applies the key without requiring access to a copy of the key. The code that implements the secure repository is generated in a manner that is at least partly based on a hardware ID associated with the hardware environment in which the secure repository is to be installed, and may also be based on a random number. Cryptographic functions implemented by the secure repository include decryption of encrypted information and validation of cryptographically signed information. The secure repository may be coupled to an application program, which uses cryptographic services provided by the secure repository, by way of a decoupling interface that provides a common communication and authentication interface for diverse types of secure repositories. The decoupling interface may take the form of a single application programmer interface (API) usable with multiple dynamically linkable libraries.
Owner:MICROSOFT TECH LICENSING LLC
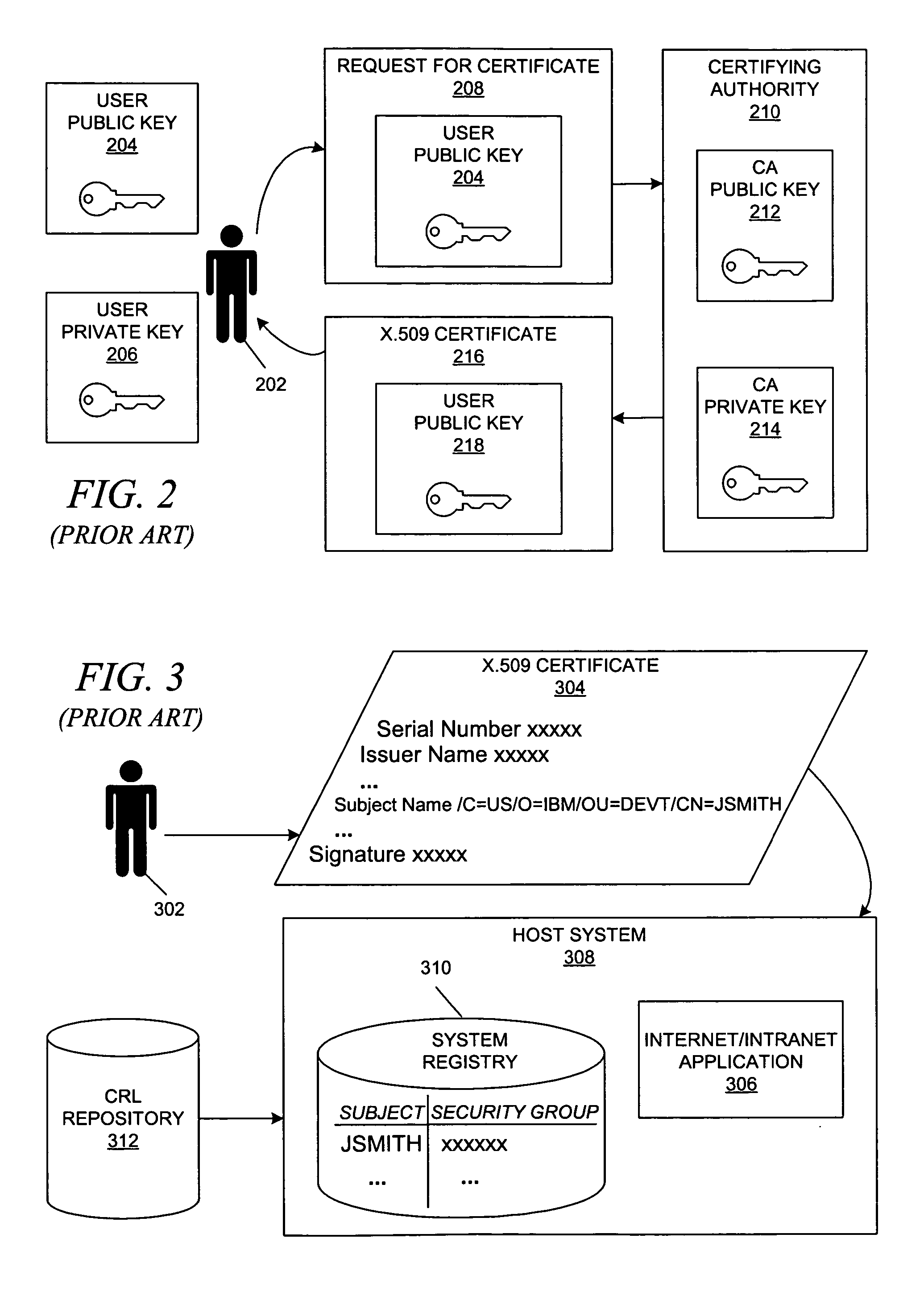
Cryptography system and method for providing cryptographic services for a computer application
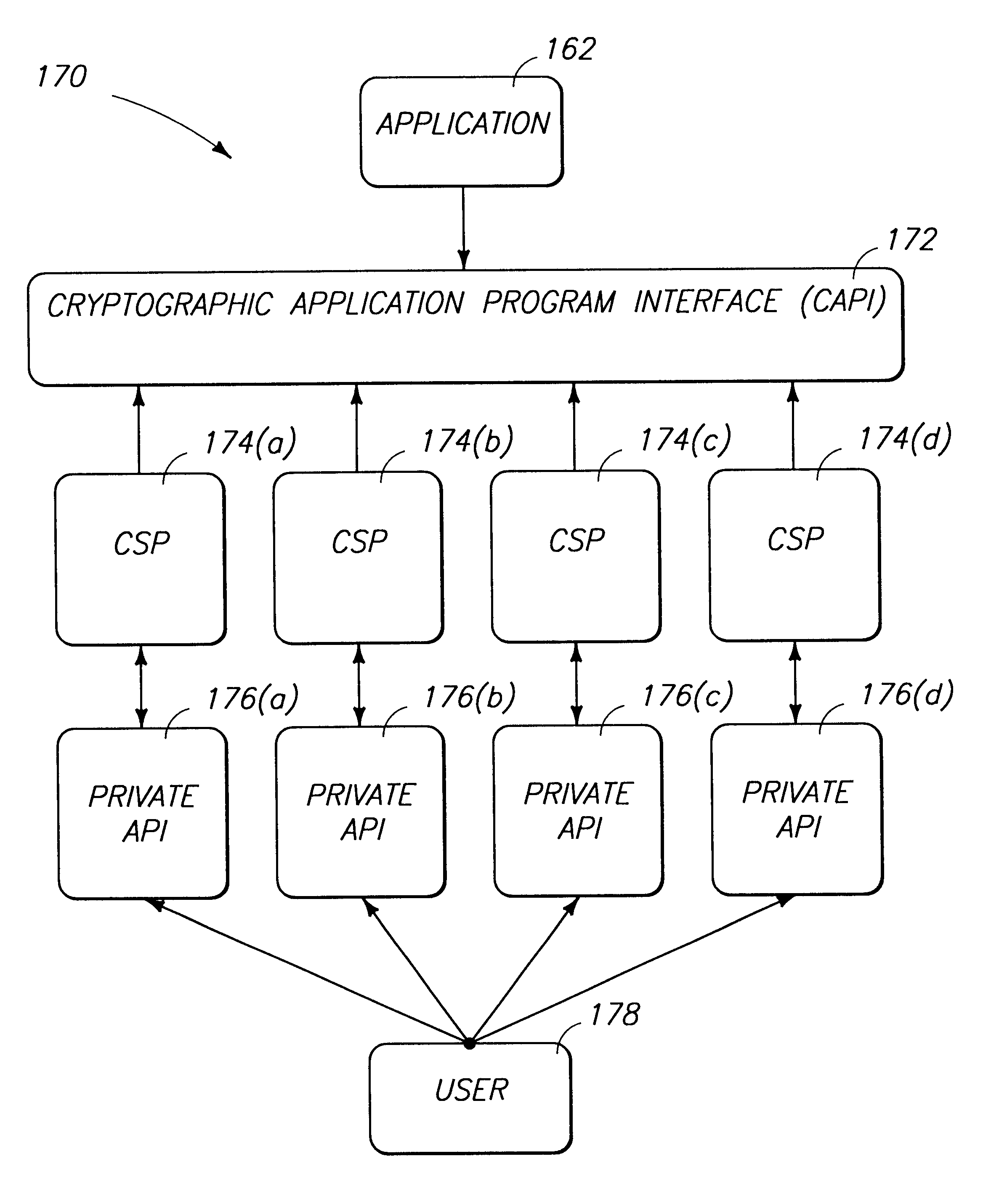
InactiveUSRE38070E1Maximum protectionEasy to modifyKey distribution for secure communicationDigital data processing detailsDigital signatureEncrypted function
A cryptography system architecture provides cryptographic functionality to support an application requiring encryption. decryption, signing, and verification of electronic messages. The cryptography system has a cryptographic application program interface (CAPI) which interfaces with the application to receive requests for cryptographic functions. The cryptographic system further includes at least one cryptography service provider (CSP) that is independent from, but dynamically accessible by, the CAPI. The CSP provides the cryptographic functionality and manages the secret cryptographic keys. In particular, the CSP prevents exposure of the encryption keys in a non-encrypted form to the CAPI or application. The cryptographic system also has a private application program interface (PAPI) to provide direct access between the CSP and the user. The PAPI enables the user to confirm or reject certain requested cryptographic functions, such as digitally signing the messages or exportation of keys.
Owner:MICROSOFT TECH LICENSING LLC
System and method for storage and retrieval of a cryptographic secret from a plurality of network enabled clients
InactiveUS20030204732A1Key distribution for secure communicationUser identity/authority verificationData processing systemPassword
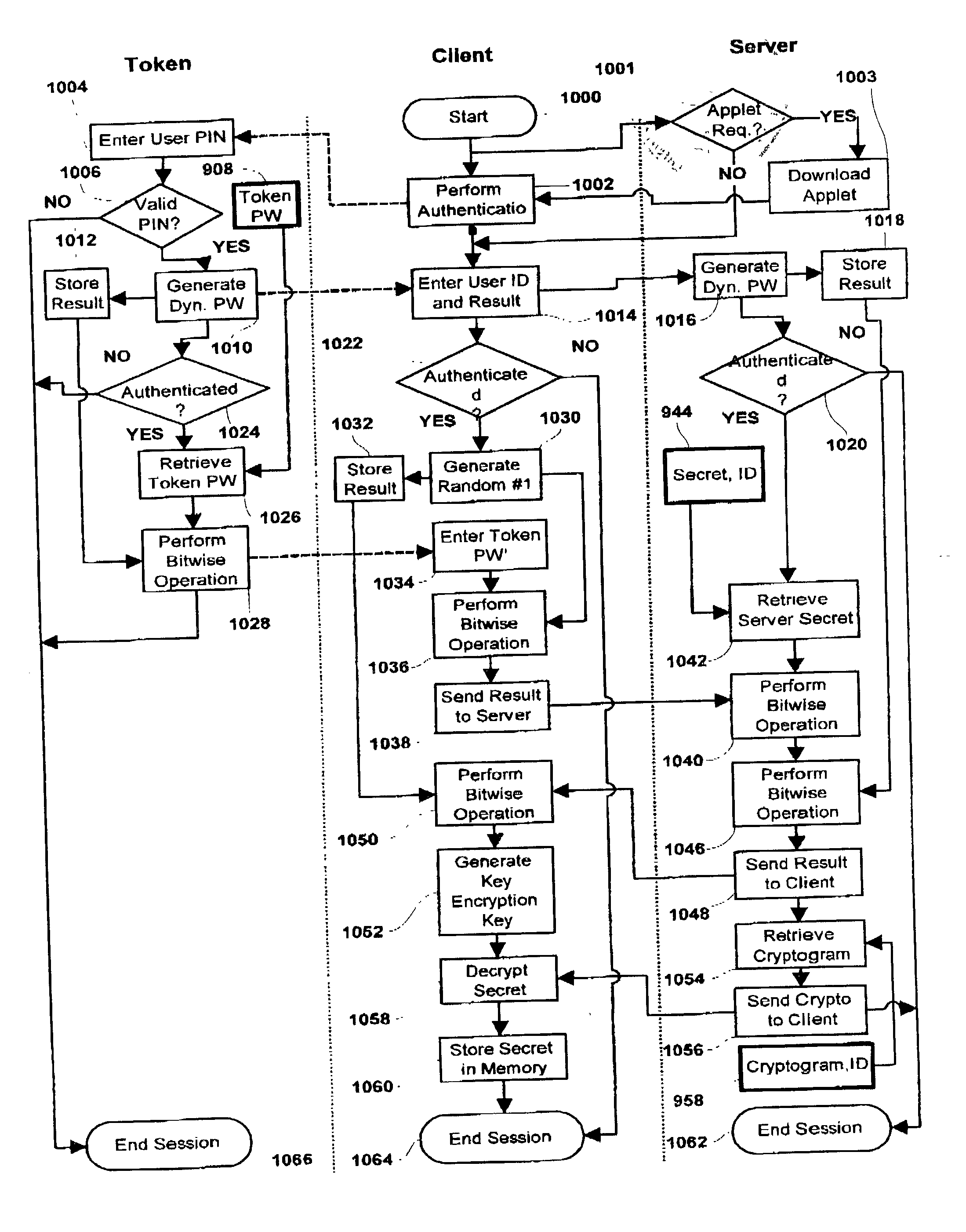
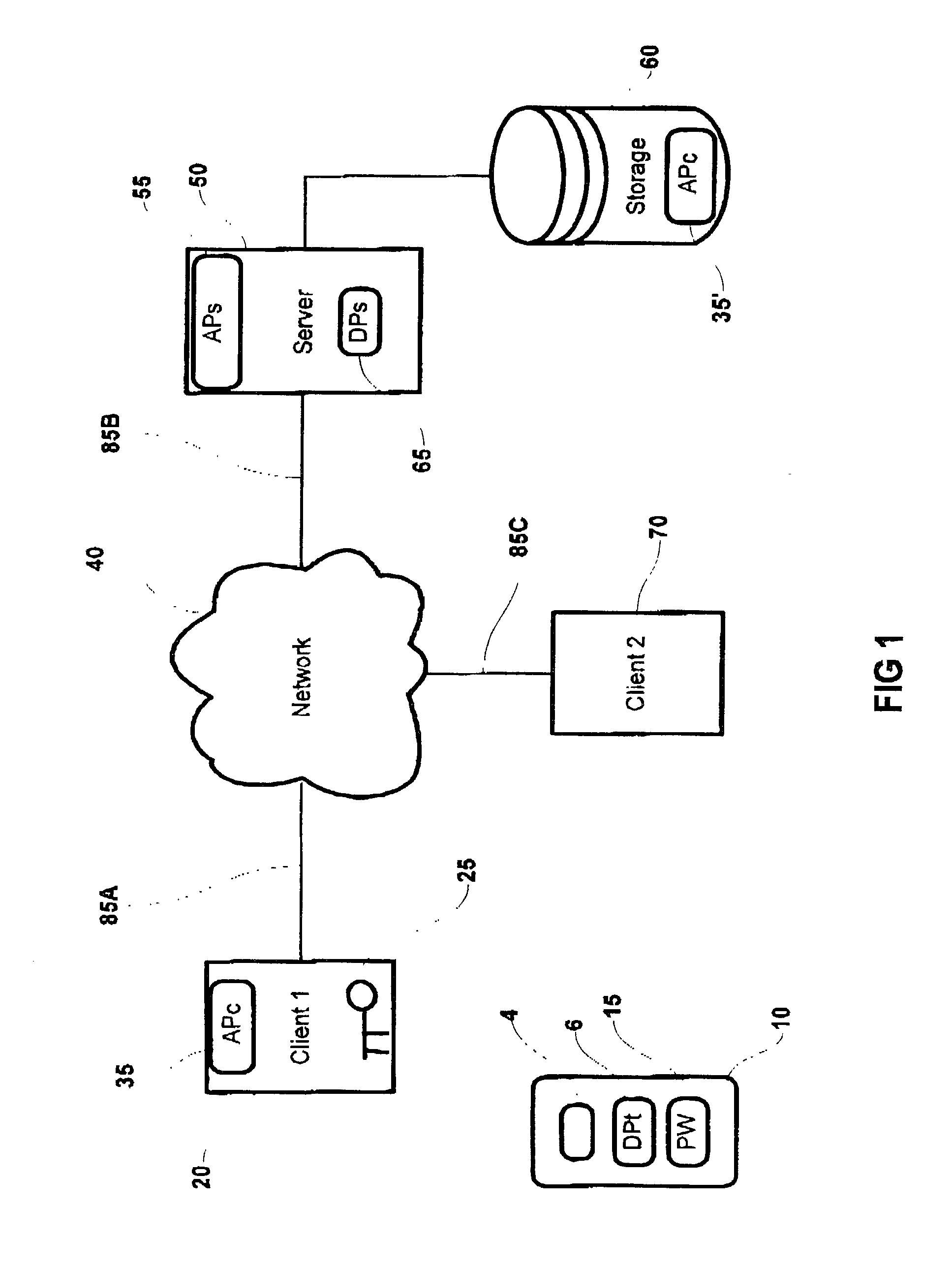
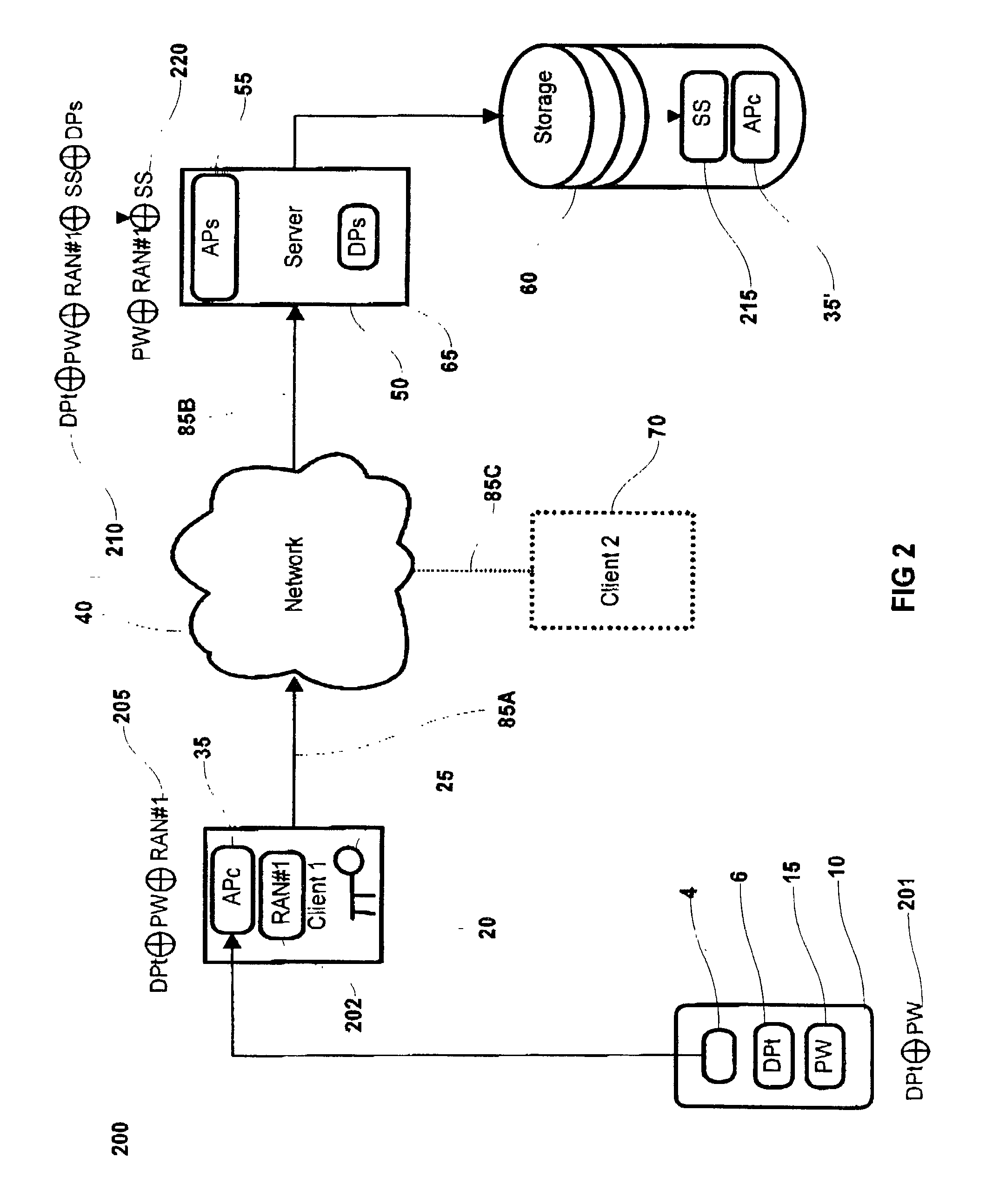
This patent application describes a data processing system and method for securely storing and retrieving a cryptographic secret from a plurality of network-enabled clients. The cryptographic secret is encrypted using a split key arrangement where a first key component is generated and stored inside a hardware security token and a second key component is generated and stored on a server. Random variables and dynamic passwords are introduced to mask the key components during transport. In order to gain access to the first password, the user is required to enter his or her PIN. The key encryption key is generated by performing a series of XOR operations, which unmasks the first and second key components on a client allowing generation of a symmetric key The symmetric key is used to encrypt the cryptographic secret at the user's normal client and decrypt the cryptogram at another client lacking the cryptographic secret. The applications performing the cryptographic functions are intended as browser applets, which remains in transient memory until the user's session has ended. At which time, the key encryption key and cryptographic secret are destroyed.
Owner:ACTIVCARD
Isolated authentication device and associated methods
InactiveUS20060242423A1Easily and accurately authentiDigital data authenticationIndividual entry/exit registersOperational systemEngineering
An isolated authentication device and related methods to provide a reliable means of authenticating the identity of its user to a network resource or server or other resource, and of authenticating the identity of a network resource or server or other resource to the device's user. The isolated authentication device may be attached to or in communication with a host device, such as a mobile telephone, personal digital or data assistant, GPS multifunction device, portable music player, wristband watch, personal computer, or similar device. A constrained operating system provides limited functionality, including authentication, data transfer, and cryptographic functions. Encrypted image, fingerprint, password, and / or personal identification number data is stored in read-only or protected nonvolatile memory. Input may be provided by means of a numeric or alphanumeric keypad, and images and information may be displayed on a screen. The device may be used to digitally sign a document, or a key to a lock.
Owner:KUSUL JOHN WESLEY
Fully Homomorphic Encryption
InactiveUS20130170640A1Reduce noise levelGrowth inhibitionPublic key for secure communicationSecret communicationRoundingNoise level
In one exemplary embodiment of the invention, a method and computer program include: receiving first and second ciphertexts having first and second data encrypted per an encryption scheme, the encryption scheme has public / secret keys and encryption, decryption, operation and refresh functions, the encryption function encrypts data, the decryption decrypts ciphertext, the operation receives ciphertexts and performs operation(s) on them, the refresh operates to prevent growth of the magnitude of noise for a ciphertext while reducing the modulus of the ciphertext without using the secret key, utilizing a modulus switching technique that involves transforming a first ciphertext c modulo q into a second ciphertext c′ modulo p while preserving correctness, the technique includes scaling by p / q and rounding, p<q; using the operation function(s), performing operation(s) on them to obtain a third ciphertext; and reducing a noise level of the third ciphertext using the refresh function.
Owner:IBM CORP
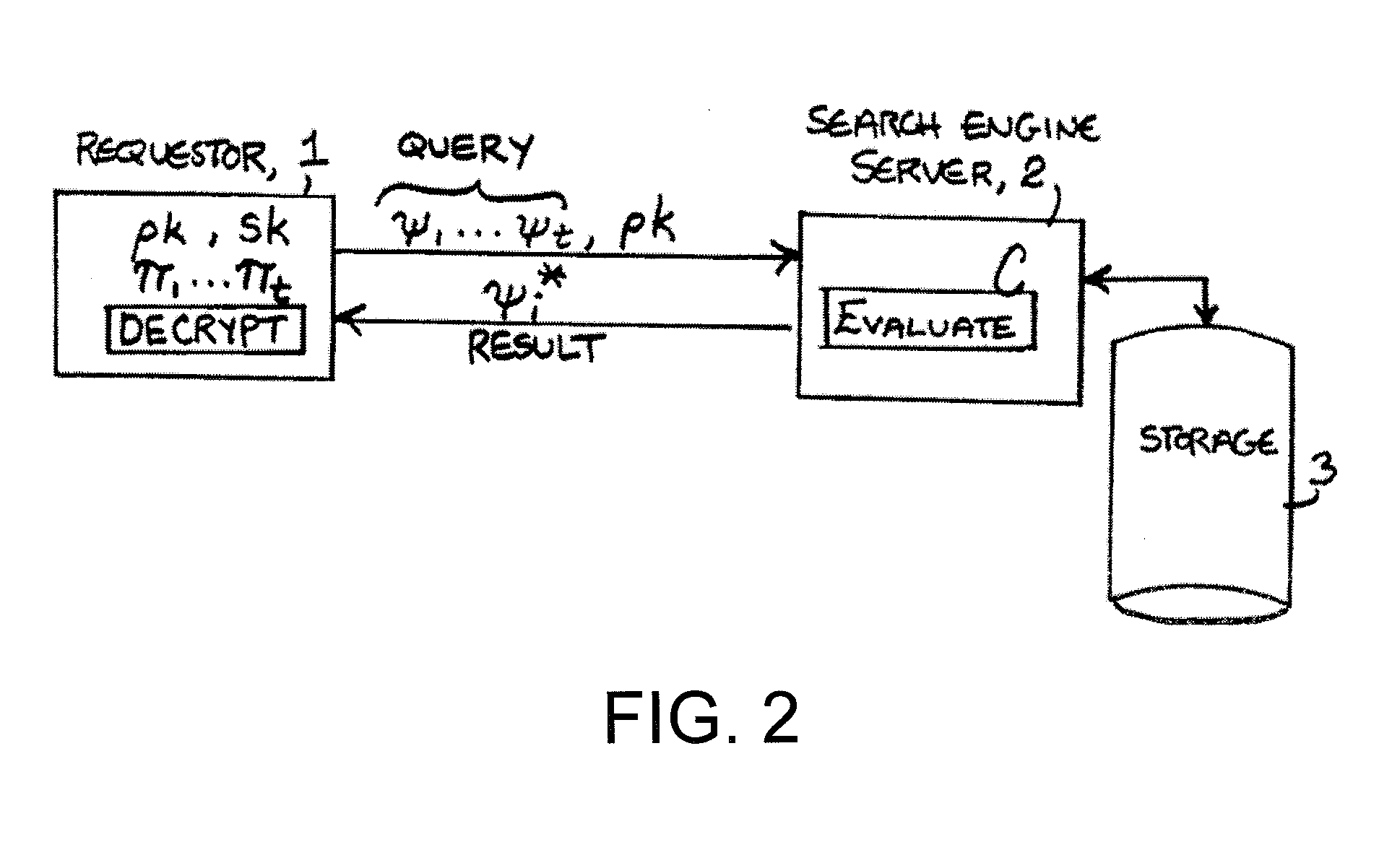
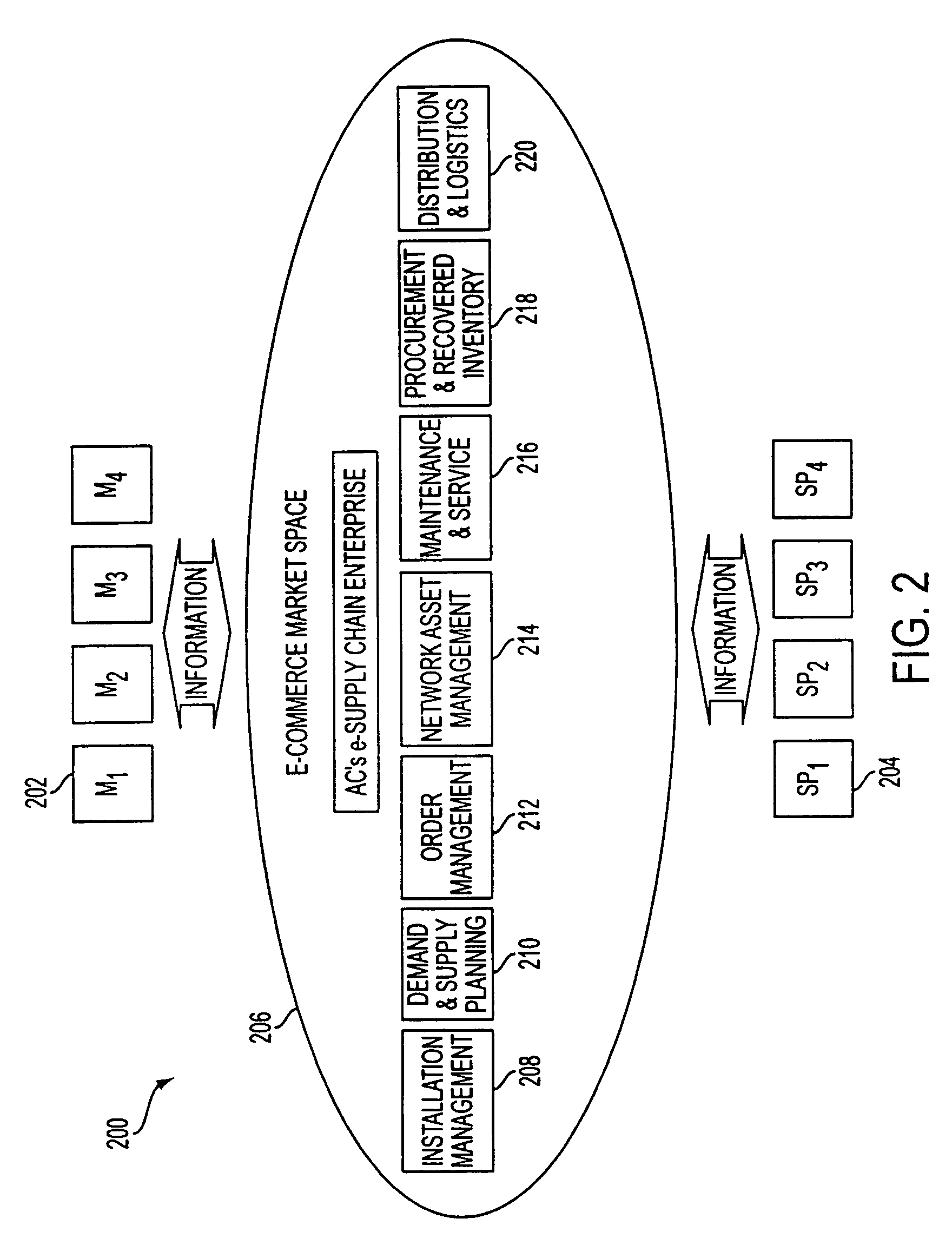
Technology sharing during demand and supply planning in a network-based supply chain environment
A system, method, and article of manufacture are provided for technology sharing during demand and supply planning in a network-based supply chain environment. Steps included are providing locator and mapping capabilities utilizing the network. Technology that includes streaming audio, stereo audio and video data is also shared utilizing the network. Encryption capabilities for the technology are also included. Further, searching capabilities are provided utilizing the network in addition to logging events and passive user profiling. The event logging includes logging network operations. User profile data is automatically received and stored. User profile data includes user identity, state, preferences and interests. User profile data is also automatically exported to an active profile manager which automatically adds additional user profile data. Additional user profile data includes information related to whether the user is a service provider or a manufacturer and the location of user.
Owner:ACCENTURE GLOBAL SERVICES LTD
Methods for identifying malicious software
ActiveUS20050223238A1Design be often employMemory loss protectionEncryption apparatus with shift registers/memoriesGraphicsEncrypted function
Malicious software is identified in an executable file by identifying malicious structural features, decryption code, and cryptographic functions. A malicious structural feature is identified by comparing a known malicious structural feature to one or more instructions of the executable file. A malicious structural feature is also identified by graphically and statistically comparing windows of bytes or instructions in a section of the executable file. Cryptography is an indicator of malicious software. Decryption code is identified in an executable file by identifying a tight loop around a reversible instruction that writes to random access memory. Cryptographic functions are identified in an executable file be obtaining a known cryptographic function and performing a string comparison of the numeric constants of the known cryptographic function with the executable file.
Owner:SYNOPSYS INC
Efficient Homomorphic Encryption Scheme For Bilinear Forms
InactiveUS20110243320A1Public key for secure communicationSecret communicationComputer hardwareCiphertext
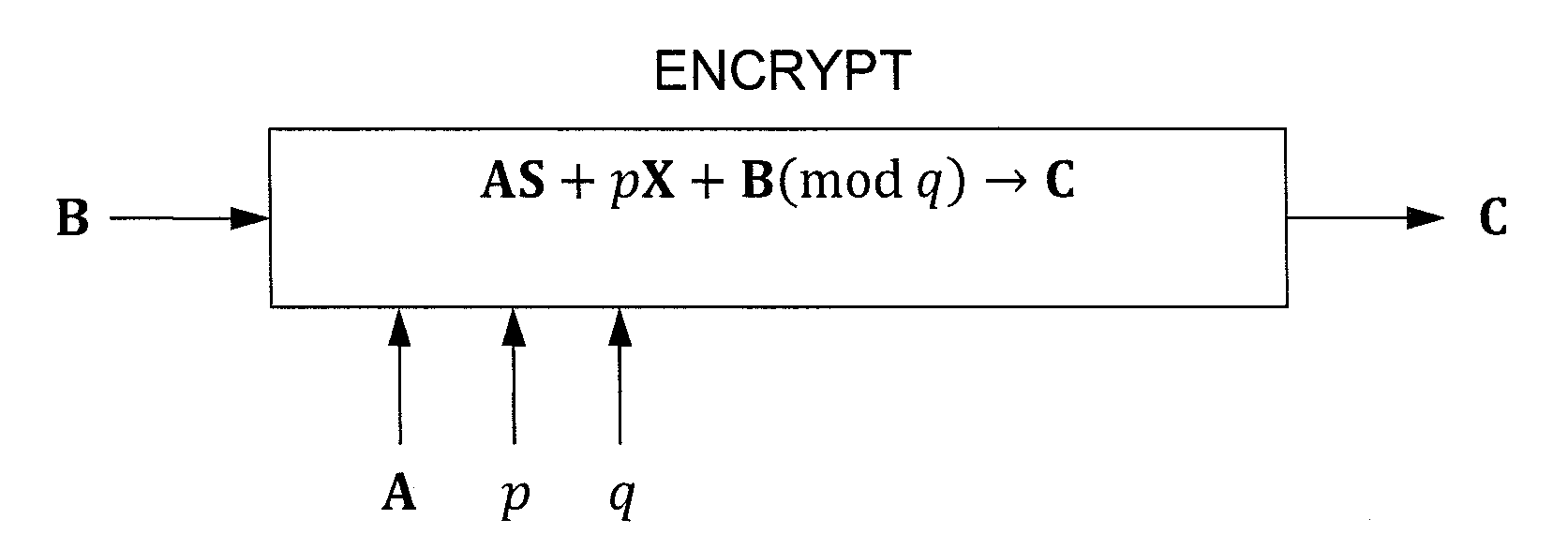
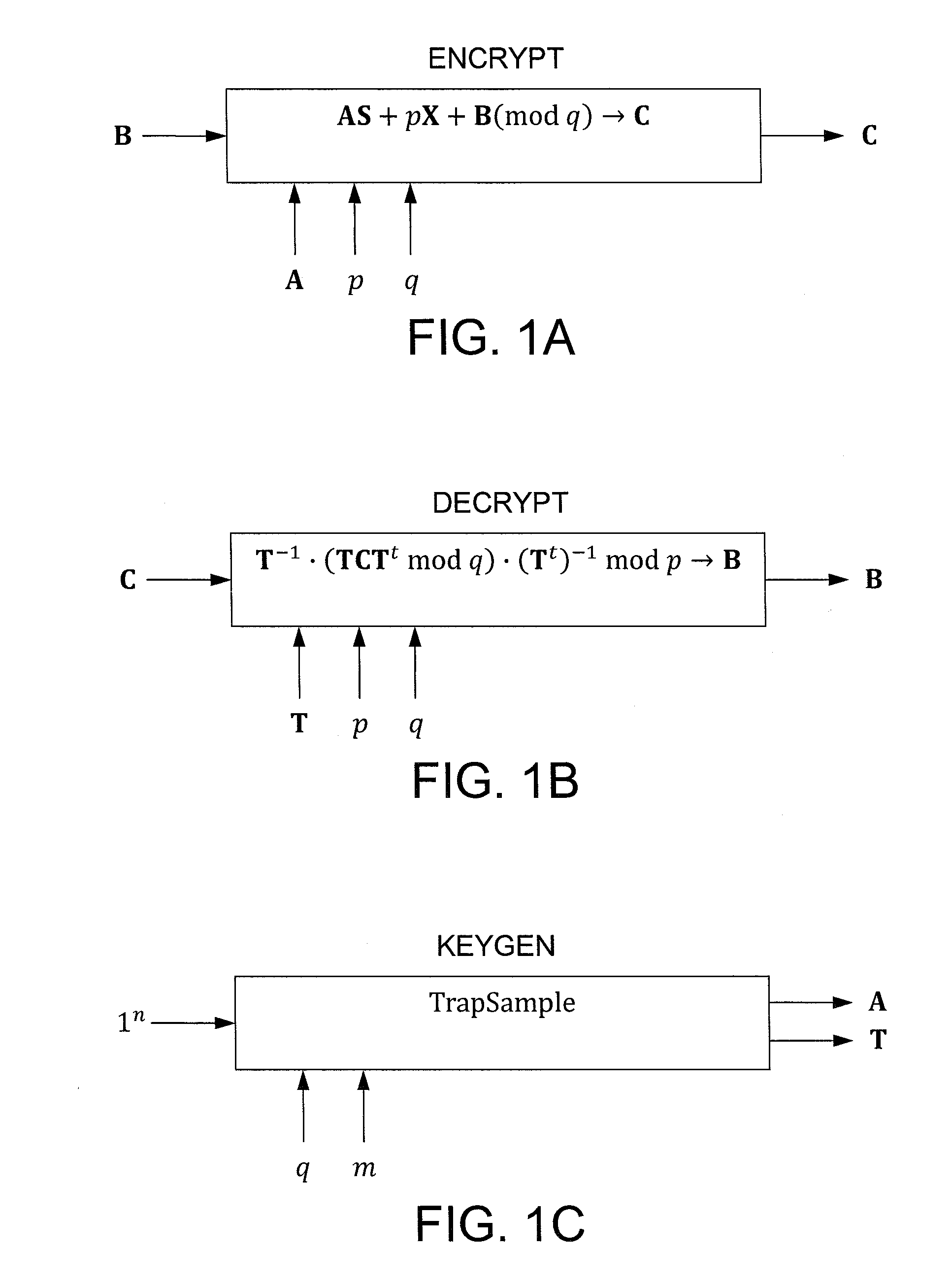
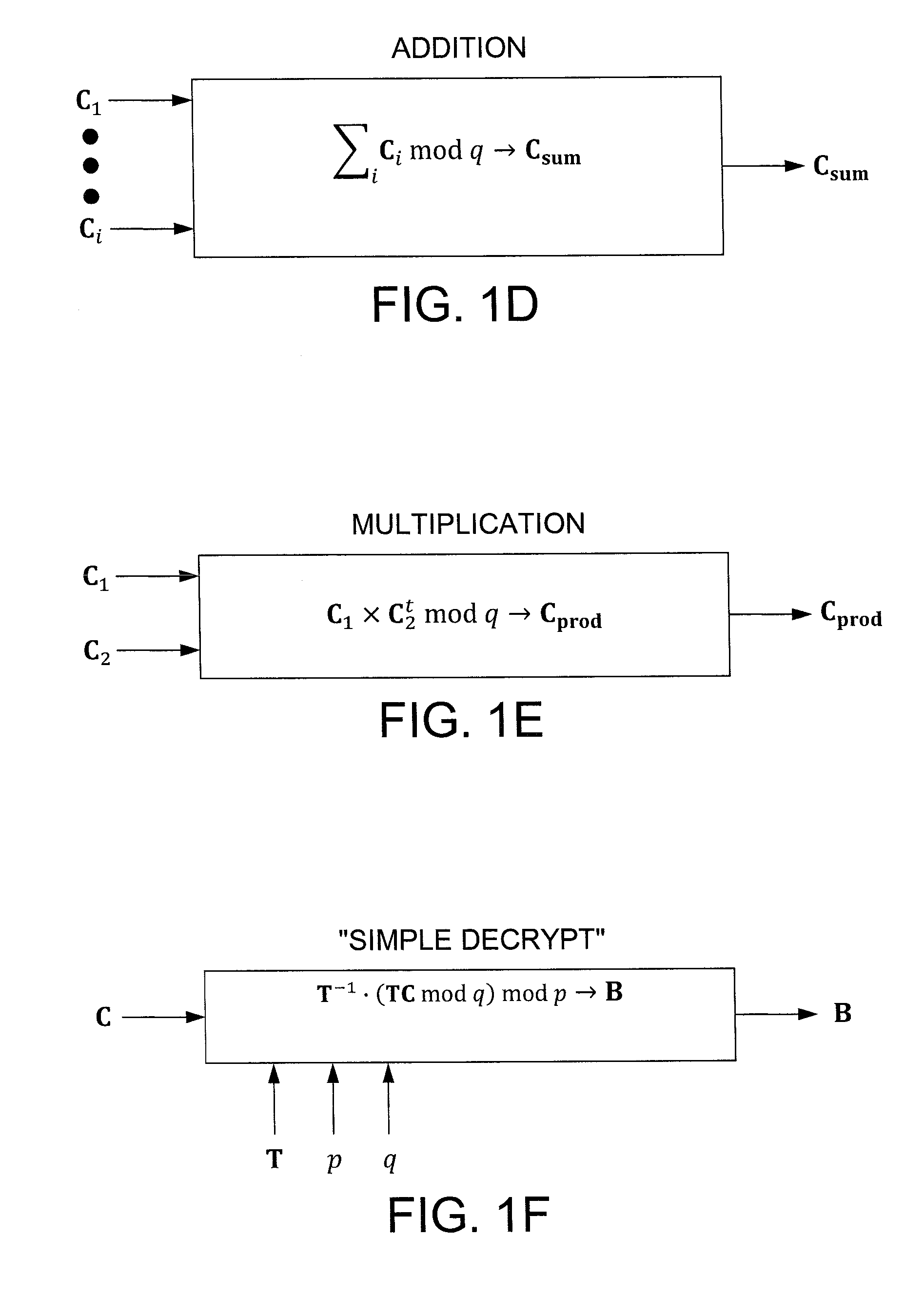
In one exemplary embodiment, a computer readable storage medium tangibly embodying a program of instructions executable by a machine for performing operations including: receiving information B to be encrypted as a ciphertext C in accordance with an encryption scheme having an encrypt function; and encrypting B in accordance with the encrypt function to obtain C, the scheme utilizes at least one public key A, where B, C, and A are matrices, the encrypt function receives as inputs A and B and outputs C as C→AS+pX+B (mod q), S is a random matrix, X is an error matrix, p is in integer, q is an odd prime number. In other exemplary embodiments, the encryption scheme includes a decrypt function that receives as inputs at least one private key T (a matrix) and C and outputs B as B=T−1·(TCTt mod q)·(Tt)−1 mod p.
Owner:IBM CORP
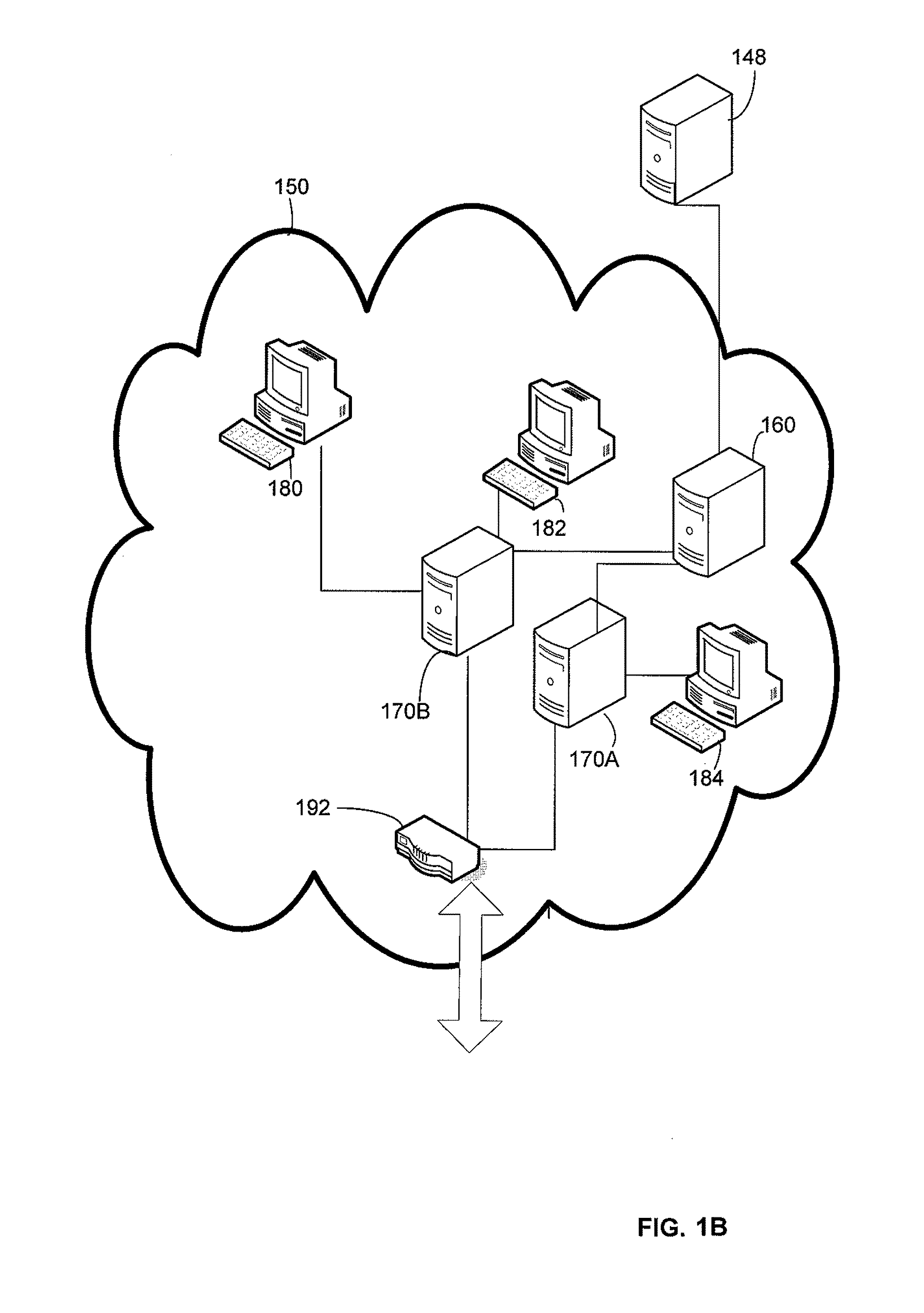
Providing secure network access for short-range wireless computing devices
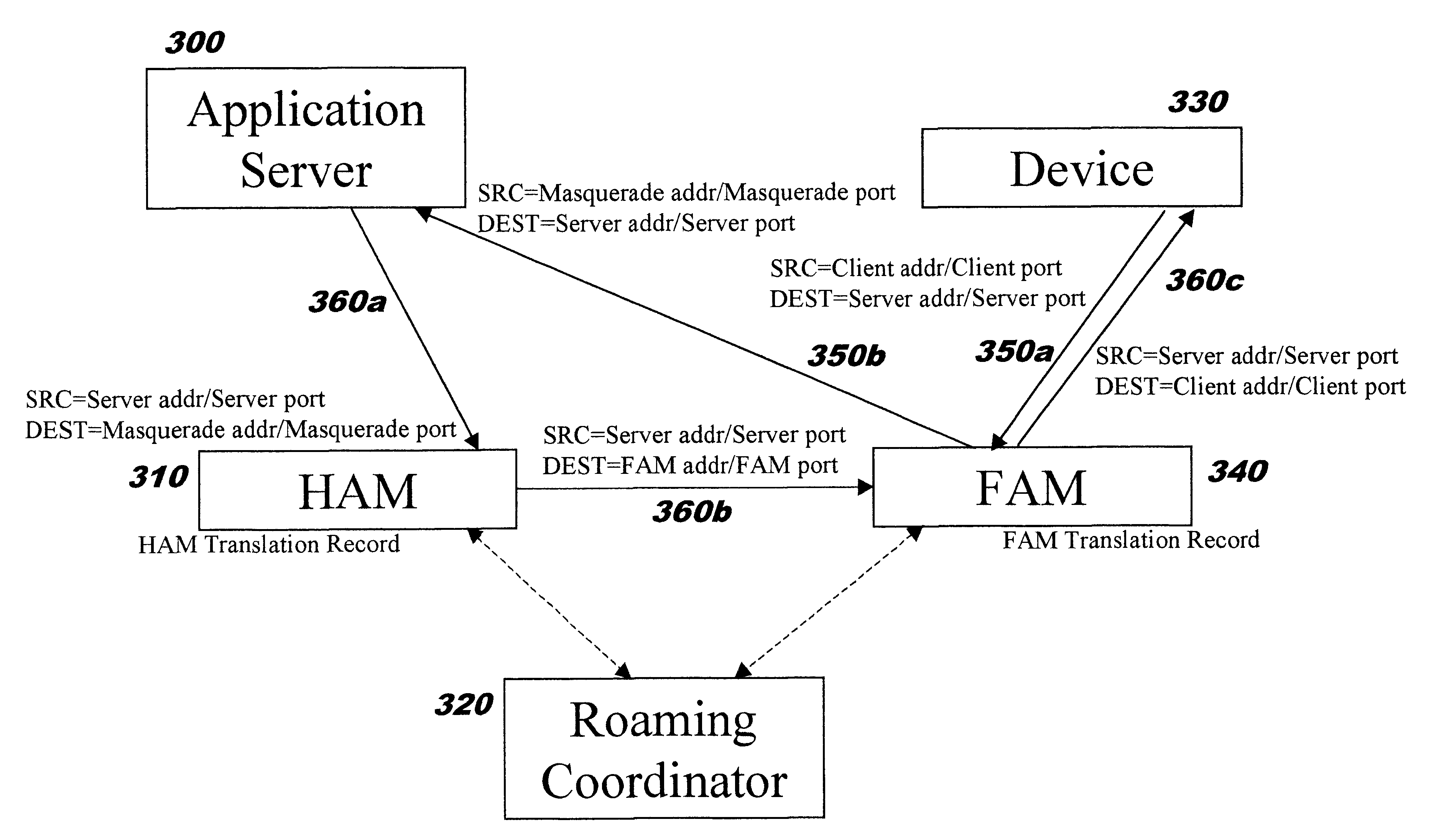
InactiveUS6851050B2Improve system performanceImprove scalabilityKey distribution for secure communicationUser identity/authority verificationEncrypted functionClient-side
The present invention provides methods, systems, and computer program instructions for providing location-independent packet routing and secure access in a wireless networking environment (such as that encountered within a building), enabling client devices to travel seamlessly within the environment. Each client device uses a constant address. An address translation process that is transparent to the client and server is automatically performed as the device roams through the environment, enabling efficient client migration from one supporting access point to another. The secure access techniques provide user-centric authentication and allow policy-driven packet filtering, while taking advantage of encryption capabilities that are built in to the hardware at each endpoint.
Owner:REEFEDGE
Processor including general-purpose and cryptographic functionality in which cryptographic operations are visible to user-specified software
ActiveUS7620821B1Memory loss protectionDigital data processing detailsGeneral purposeComputer hardware
A processor including general-purpose and cryptographic functionality, in which cryptographic operations are visible to user-specified software. According to one embodiment, a processor may include instruction execution logic configured to execute instructions specified by a user of the processor, where the instructions are compliant with a general-purpose instruction set architecture. The processor may further include a cryptographic functional unit configured to implement a plurality of cryptographic operations, and further configured to process the cryptographic operations independently of the instruction execution logic. A subset of the instructions may be executable to cause individual ones of the cryptographic operations to be processed by the cryptographic functional unit.
Owner:ORACLE INT CORP
Encrypted Communication Method
InactiveUS20080235507A1Setting costReduce setup costsMultiple keys/algorithms usageData taking preventionDomain nameNetwork packet
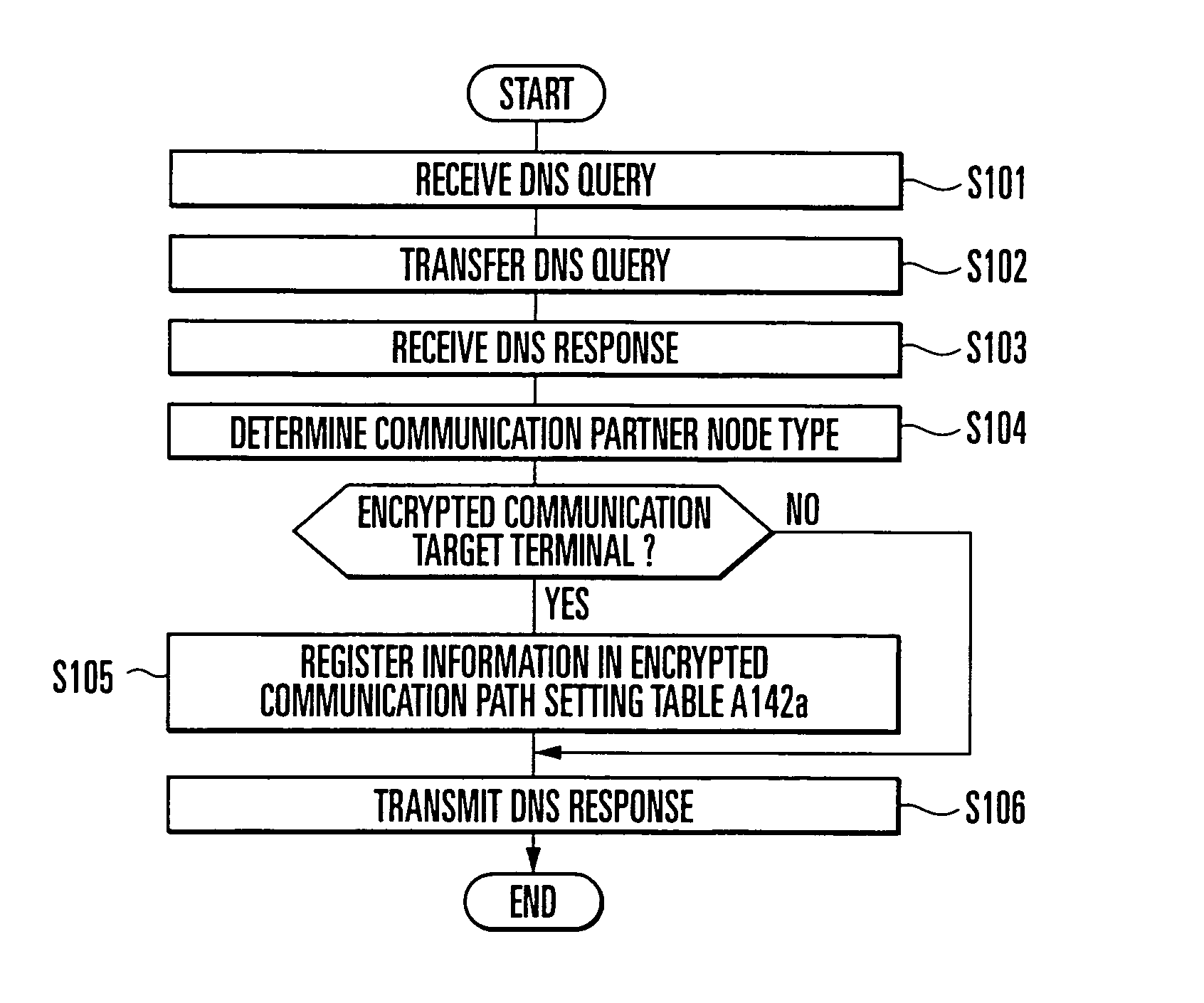
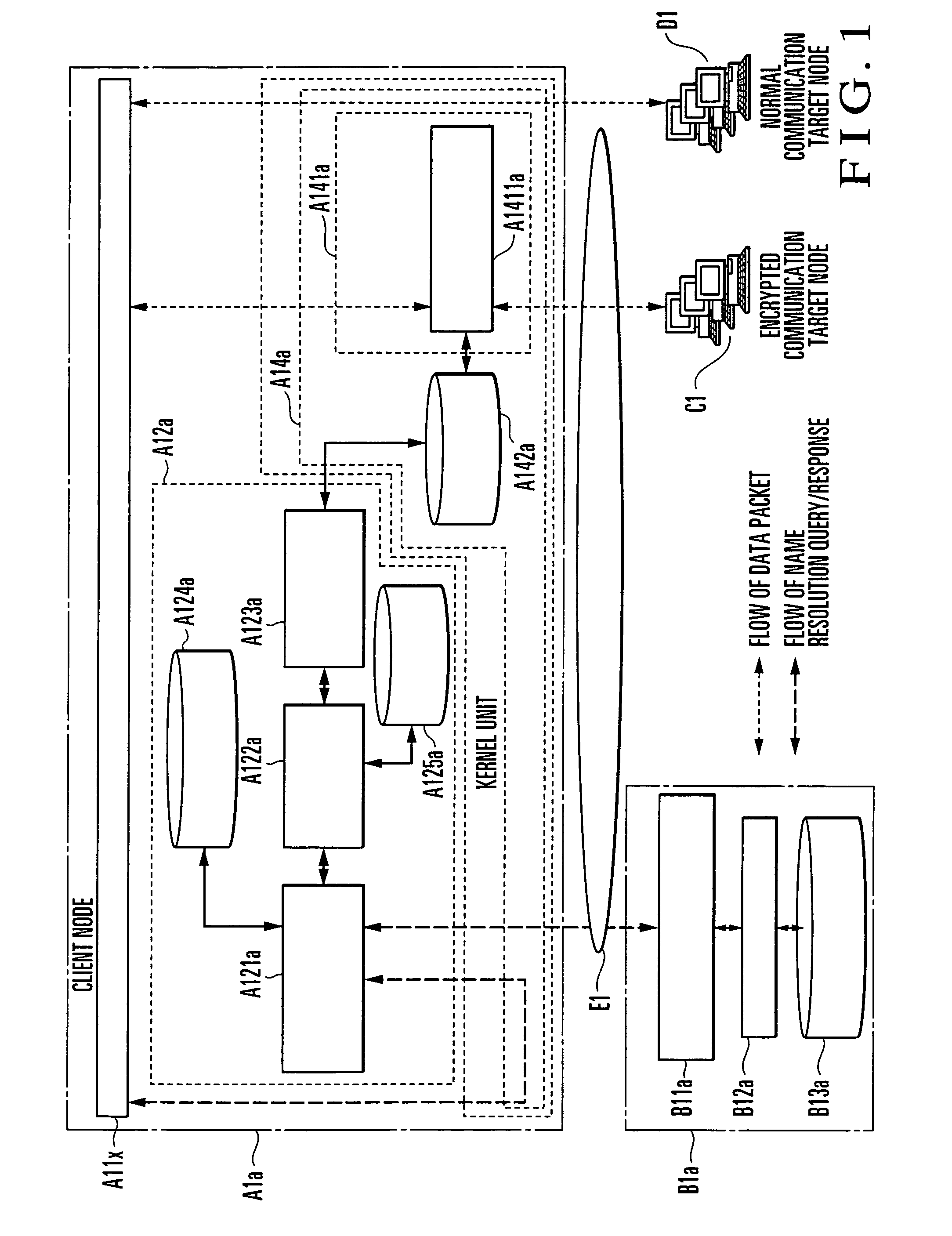
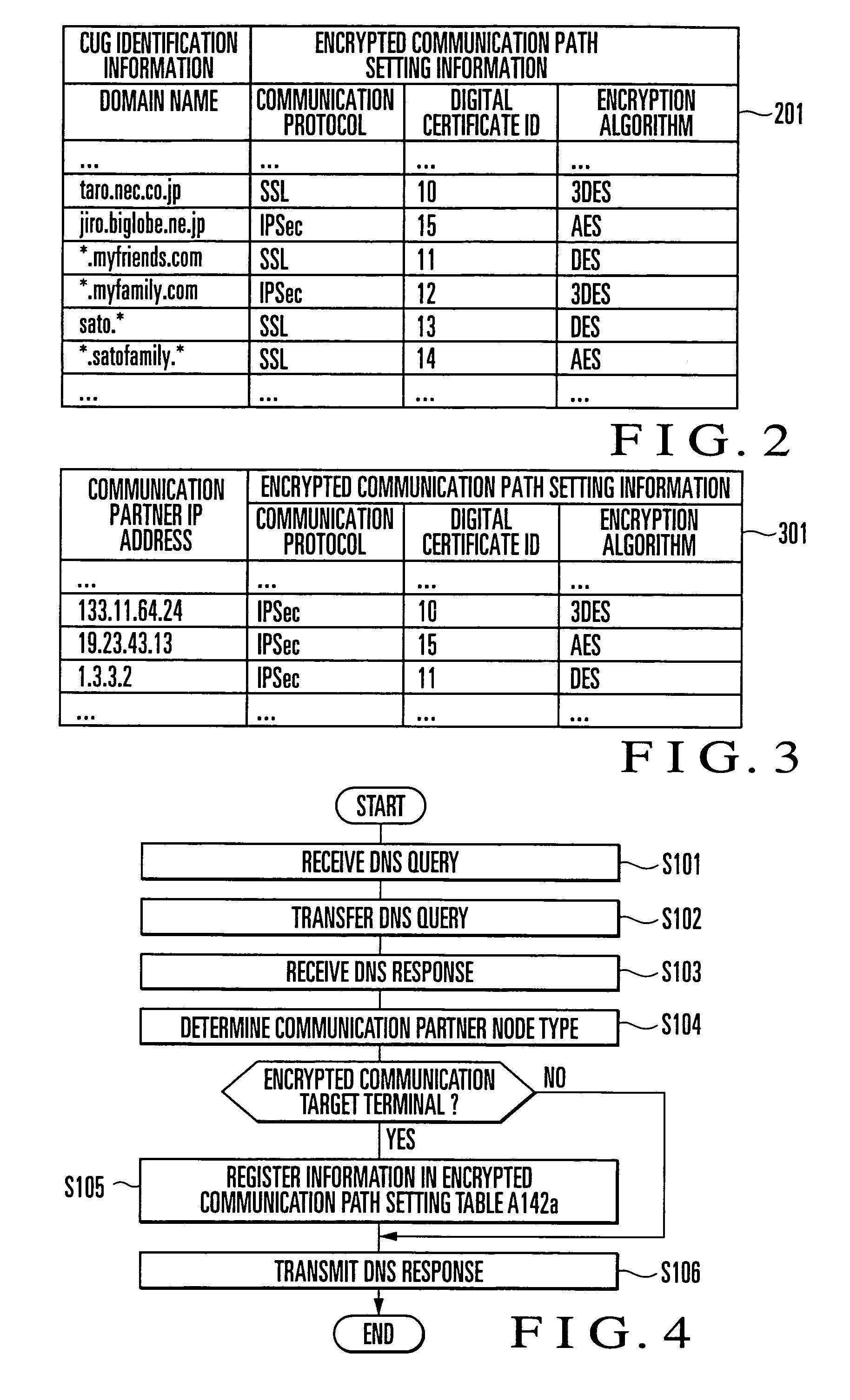
A DNS Proxy unit (A12a) holds the domain name of an encrypted communication target node in a CUG setting table (A125a), intercepts a name resolution request for a communication partner node output from an application (A11x) to a DNS server (B1a), determines by looking up the CUG setting table (A125a) whether the communication partner is an encrypted communication target node, and if the communication partner is an encrypted communication target node, registers the IP address of the name-resolved communication partner in an encrypted communication path setting table (A142a). A data packet sent from the application (A11x) to the IP address is intercepted by a data transmission / reception unit (A14a). A data packet to an IP address registered in the encrypted communication path setting table (A142a) is encrypted by a communication encryption unit (A141a) and transmitted to the communication partner. In this way, in executing encrypted communication with a plurality of communication partners by using a communication encryption function provided by an OS, setting of the encrypted communication target node can be done by using a domain name.
Owner:NEC CORP
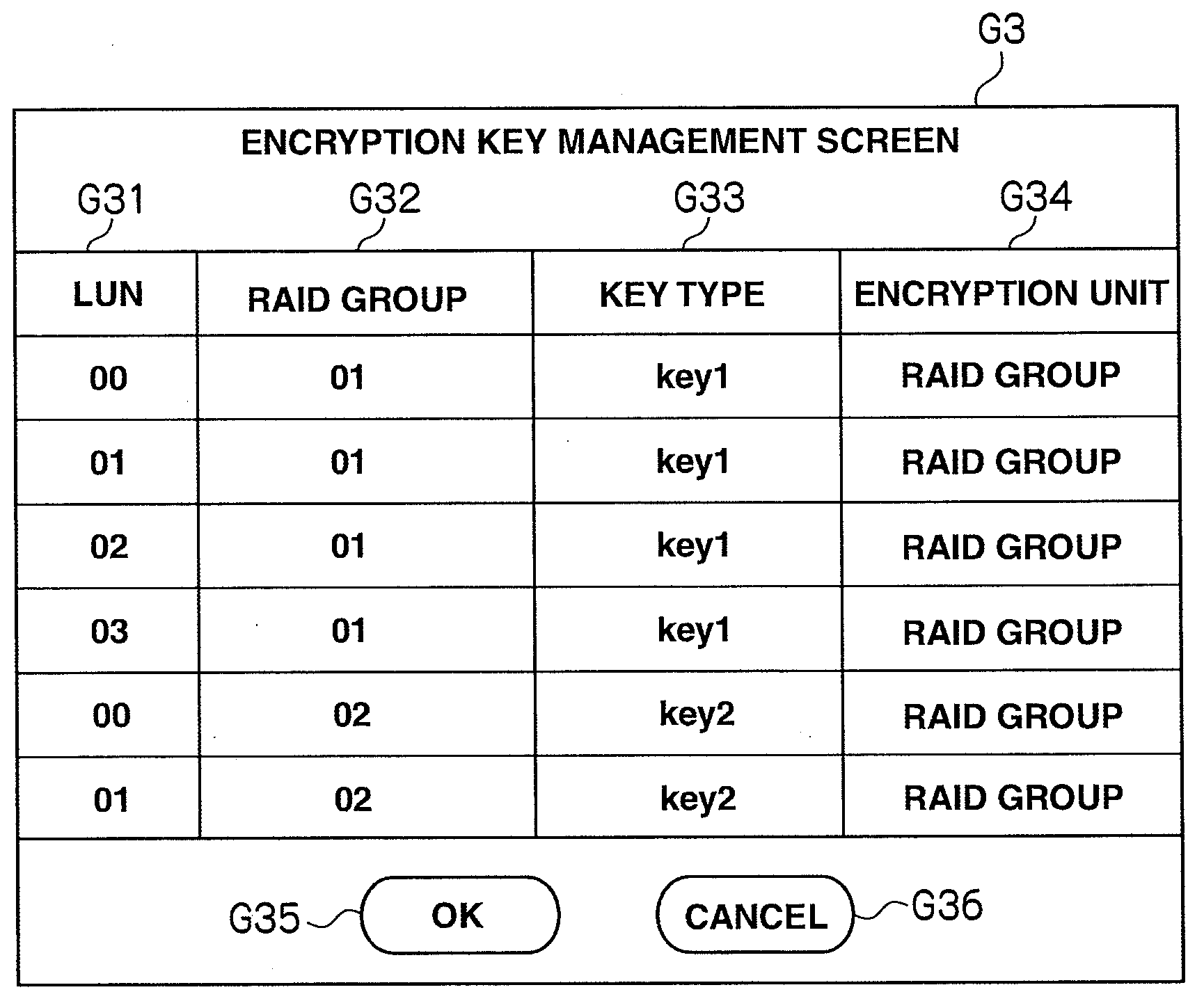
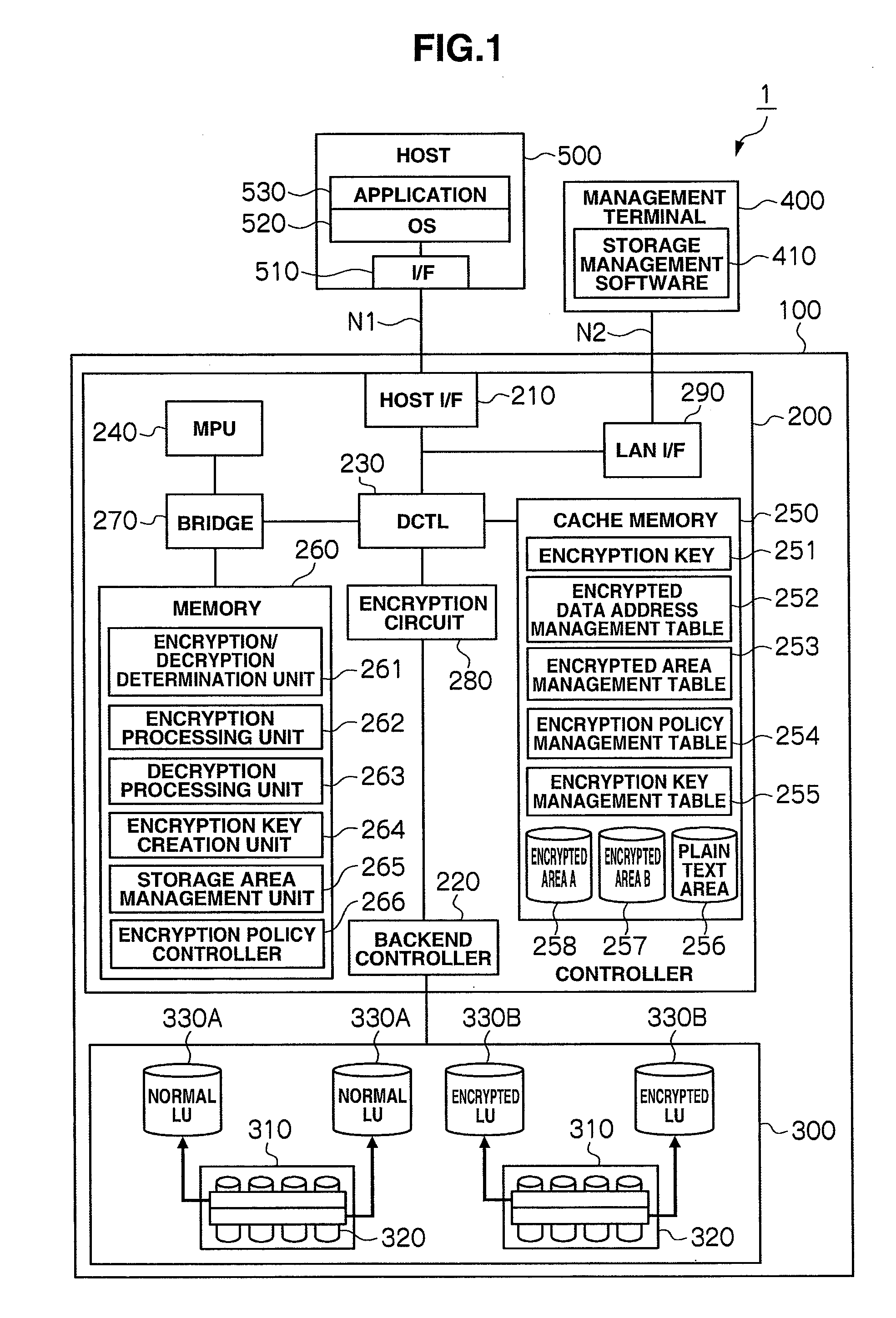
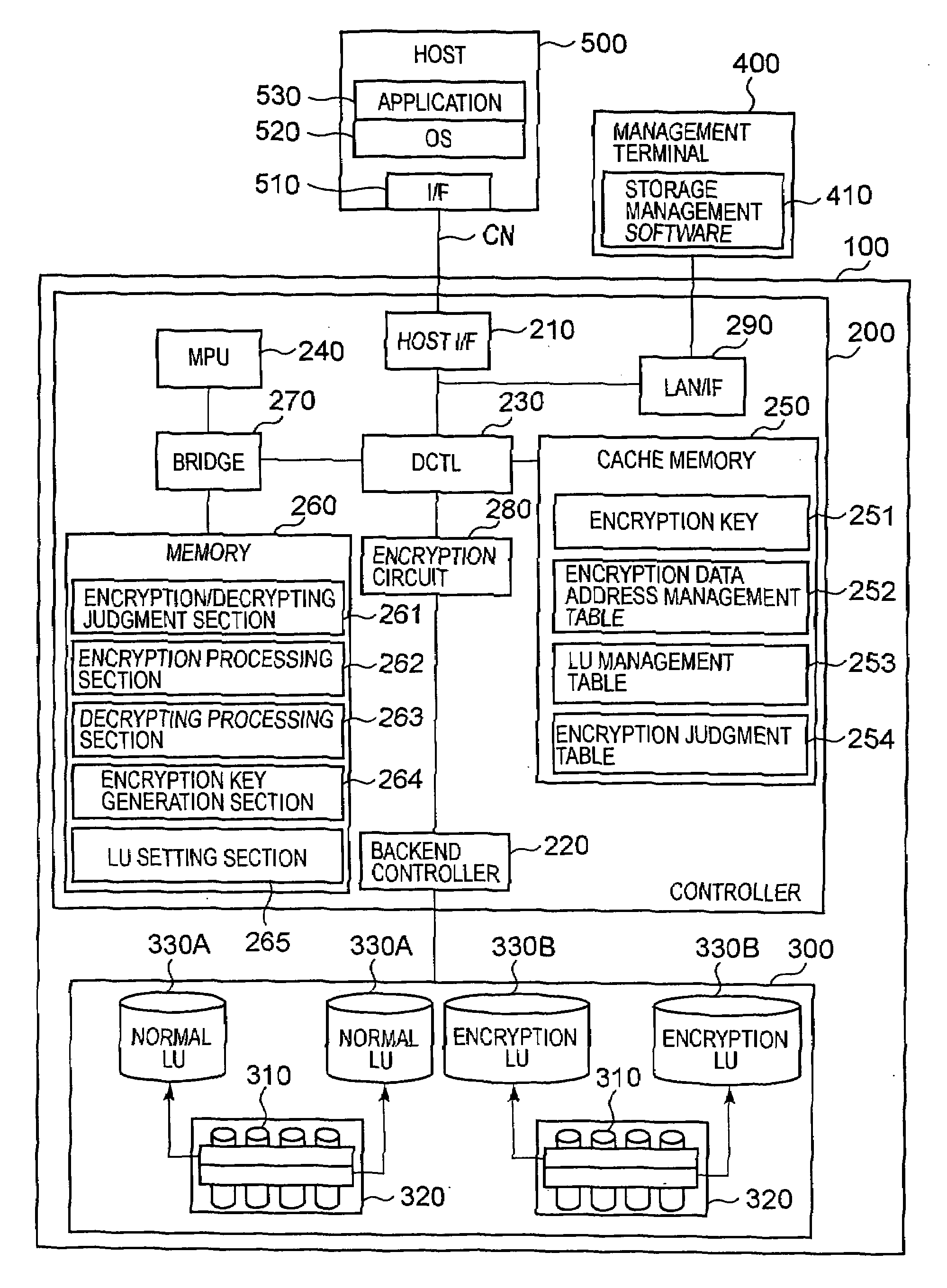
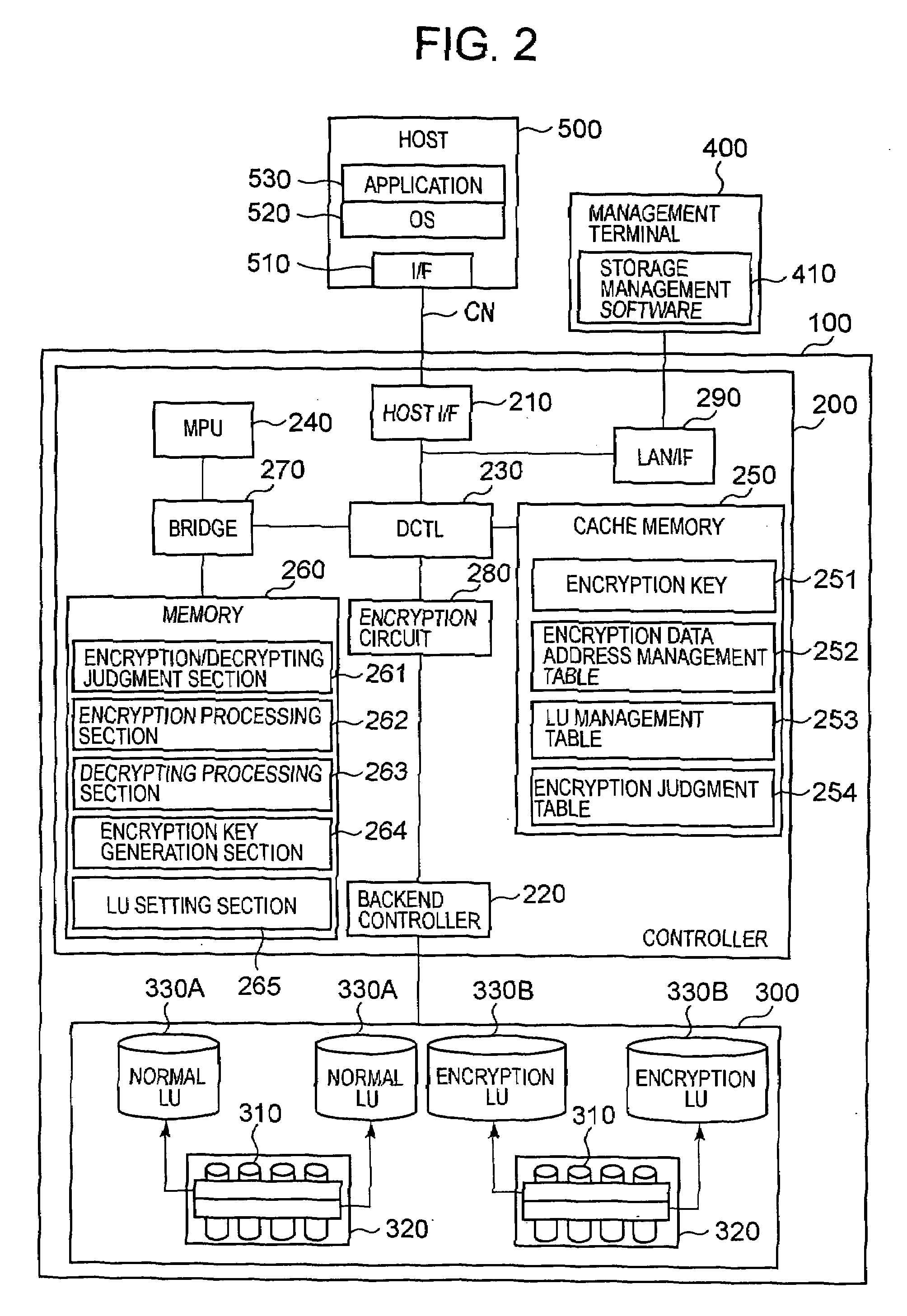
Storage controller comprising encryption function, data encryption method, and storage system
InactiveUS20080240441A1High riskImprove protectionUnauthorized memory use protectionHardware monitoringEncrypted functionControl store
Proposed are a storage controller equipped with an encryption function, a data encryption method, and a storage system enabling a user to apply one's desired encryption policy to data received from a computer or the like. This storage controller includes a storage apparatus for storing data from a computer, and a controller for controlling the input and output of data stored in the storage apparatus. The controller has a configuration information management unit for managing configuration information of attributes concerning an encryption function as information for encrypting data, and an encryption execution unit for performing encryption of data from the computer and data stored in the storage apparatus based on the configuration information of attributes concerning the encryption function.
Owner:HITACHI LTD
Method to assure correct data packet traversal through a particular path of a network
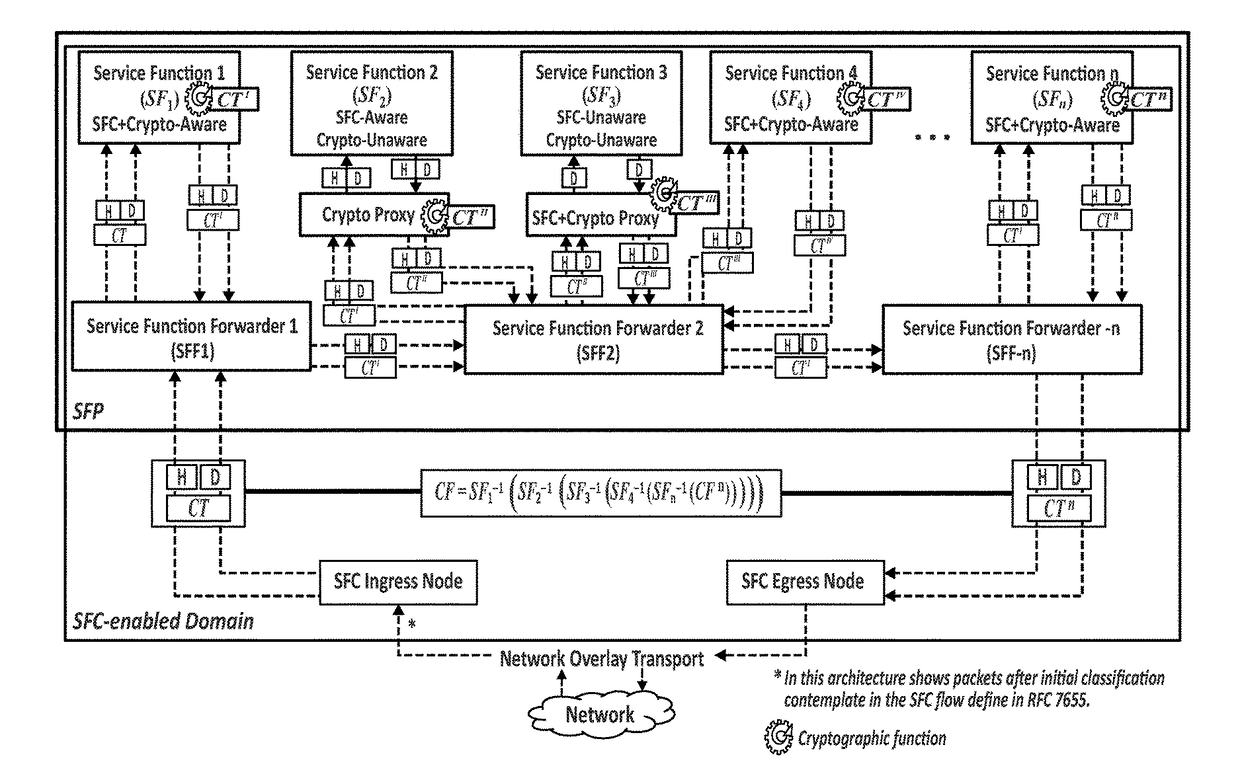
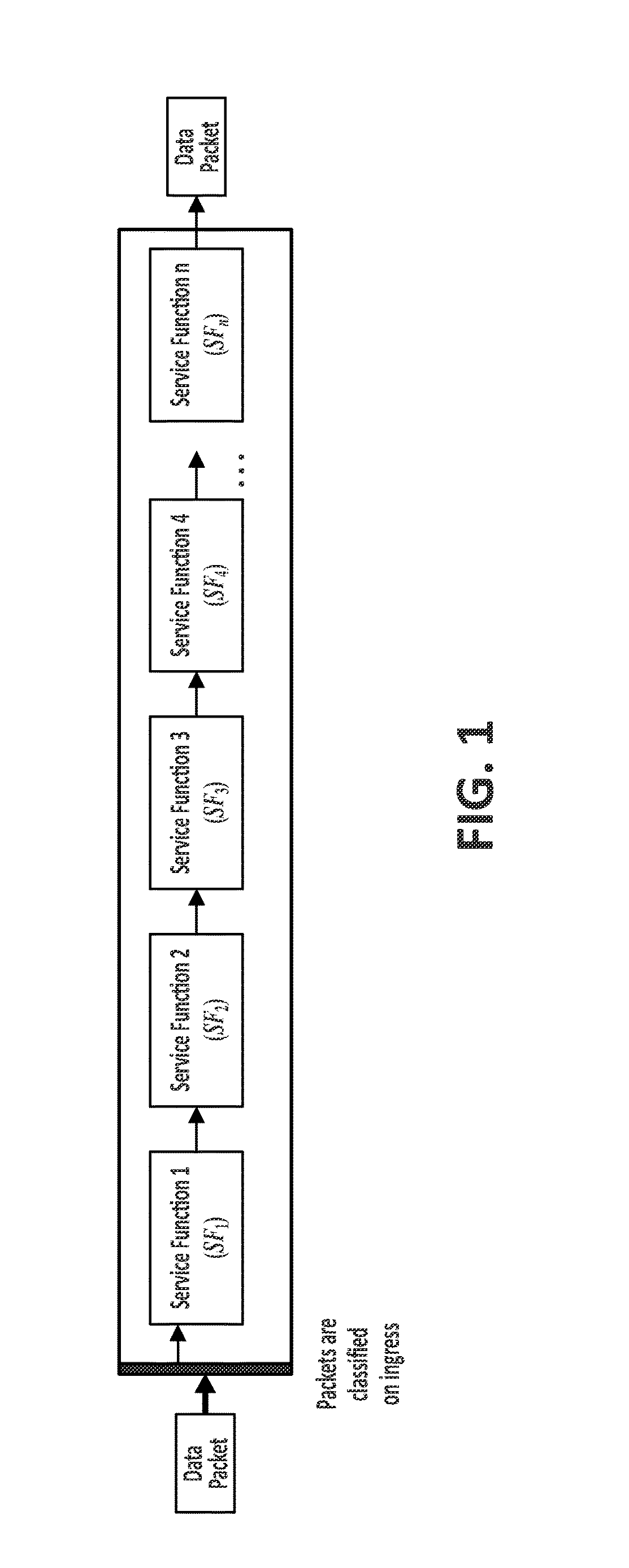
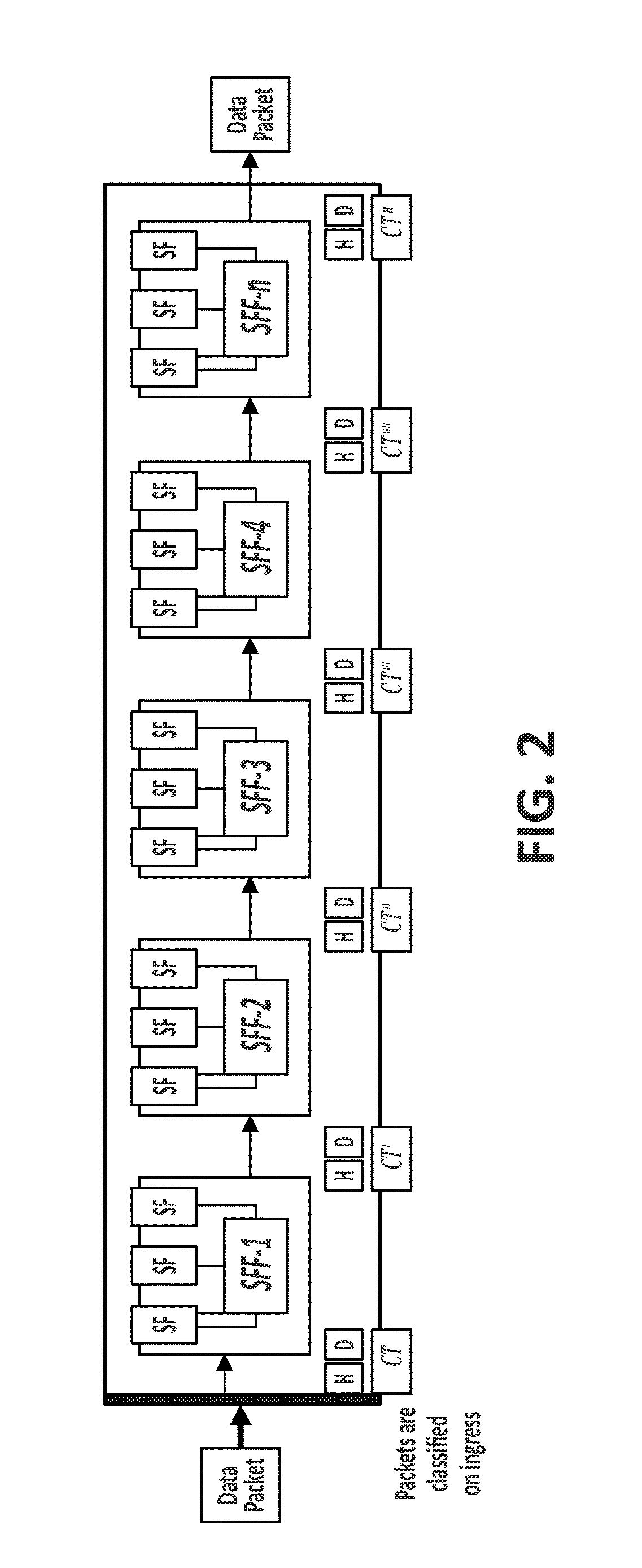
ActiveUS20170295021A1Improve scalabilityImprove reuseMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesNetwork packetEncrypted function
The method comprising, in a network based on a chain of individual Service Functions, SFs, that are composed to implement Network Services, NSs: assigning, at an ingress node of a network architecture, to at least one data packet received by said ingress node from the network, a unique cryptographic tag; processing said assigned unique cryptographic tag using a cryptographic function specific to each Service Function, SF; and verifying, at a given point of the network architecture, said processed unique cryptographic tag by applying a cryptographic verification function composed by the inverse functions of the cryptographic functions associated to the SFs traversed by the at least one data packet.
Owner:TELEFONICA SA
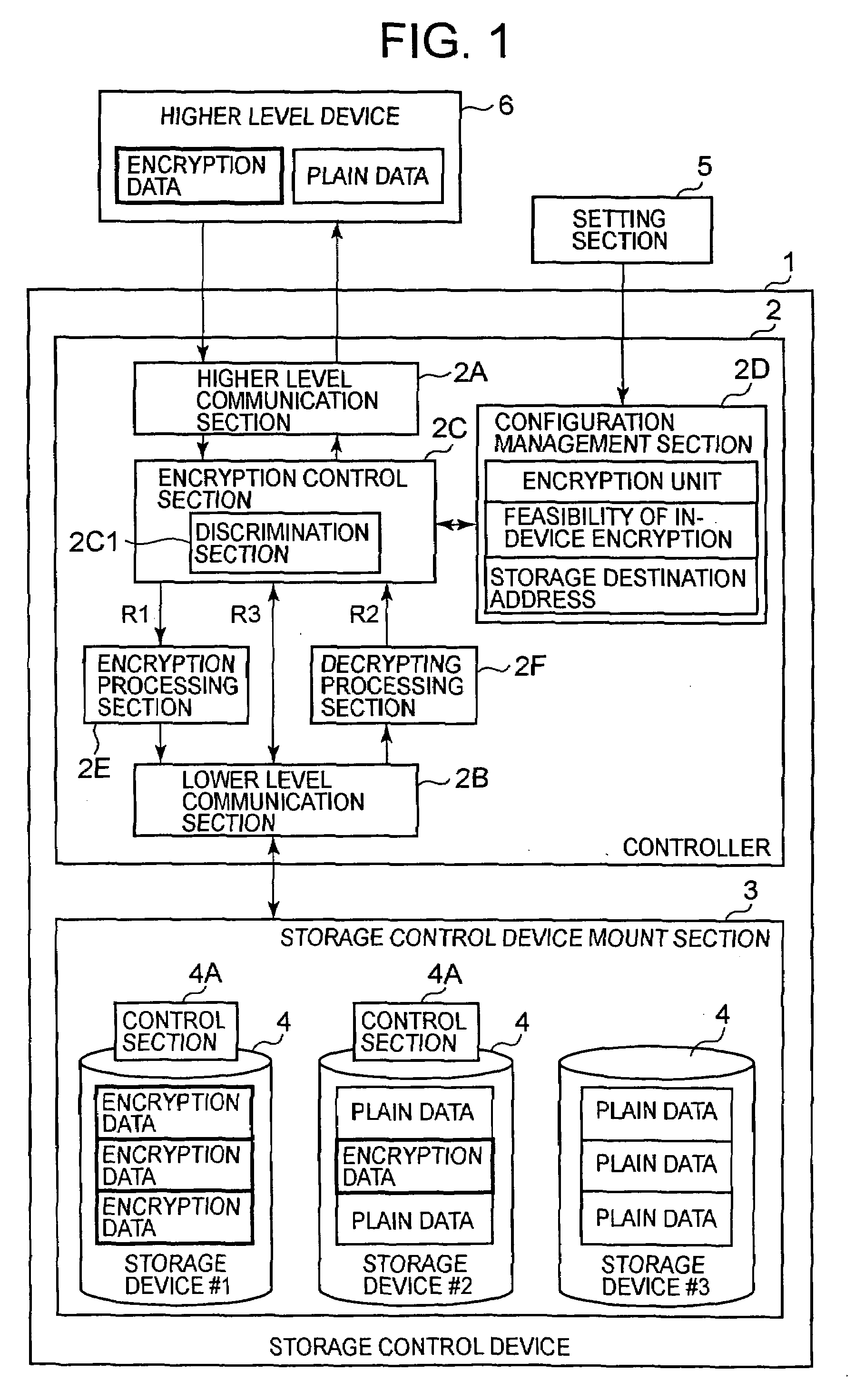
Storage control device and method of controlling encryption function of storage control device
InactiveUS20080126813A1Unauthorized memory use protectionHardware monitoringComputer hardwarePlaintext
The storage control device of the present invention suppresses a drop in the performance of a host and storage control device by preventing the execution of encryption processing in the host and storage control device. The user presets an attribute that relates to the encryption of each storage device by considering the type of data transmitted from a higher order device (encryption data or plain data, for example) and the importance of the data and so forth. Such user operating policies are registered in a configuration management section via a setting section. When the data received from the higher-level device are encryption data, the storage control device stores the data in the storage device as is without performing encryption processing. When the received data are plain data, the storage control device converts the plain data into encryption data by performing encryption processing and stores the encryption data in the storage device.
Owner:HITACHI LTD
User-Space Enabled Virtual Private Network
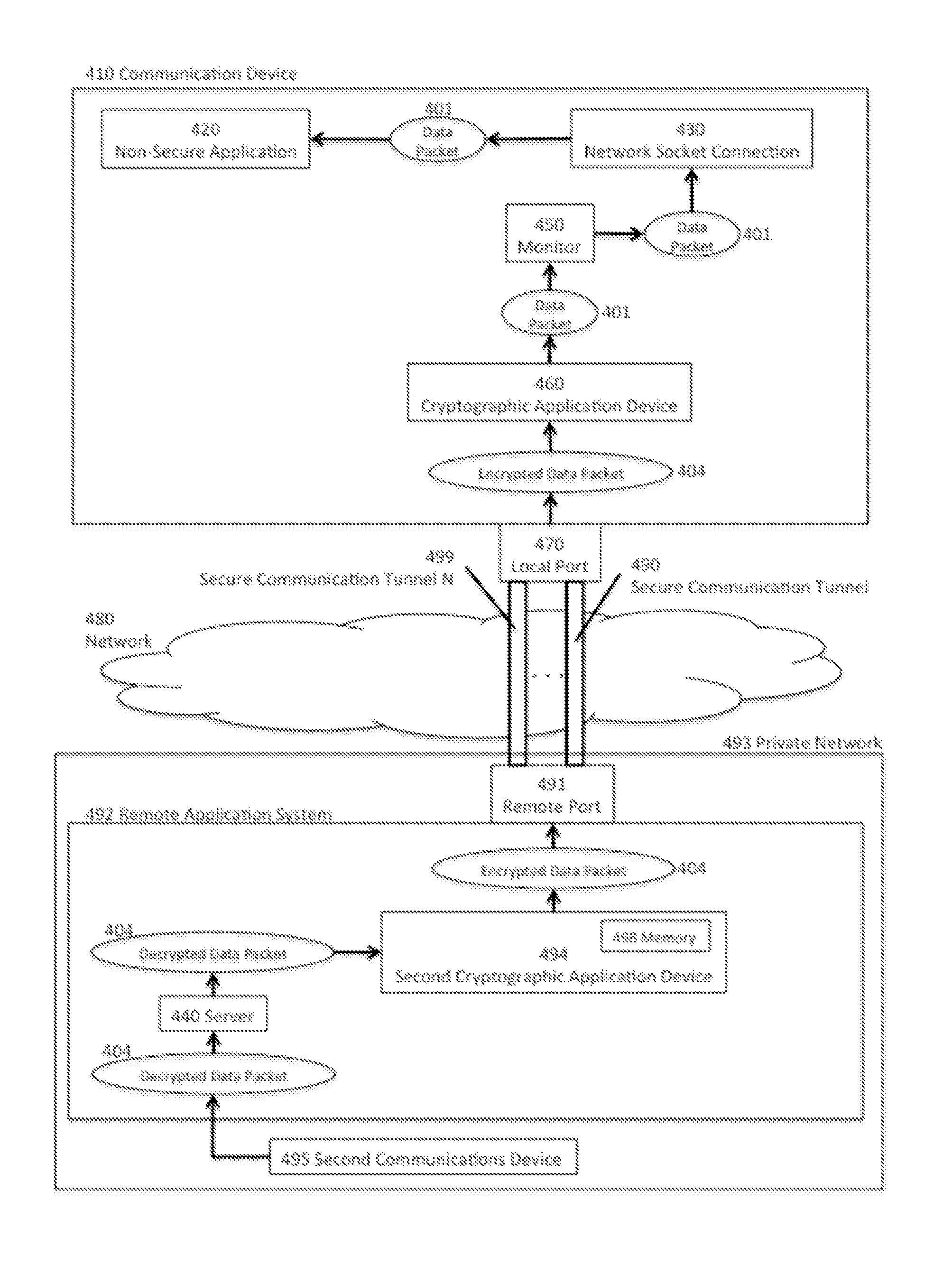
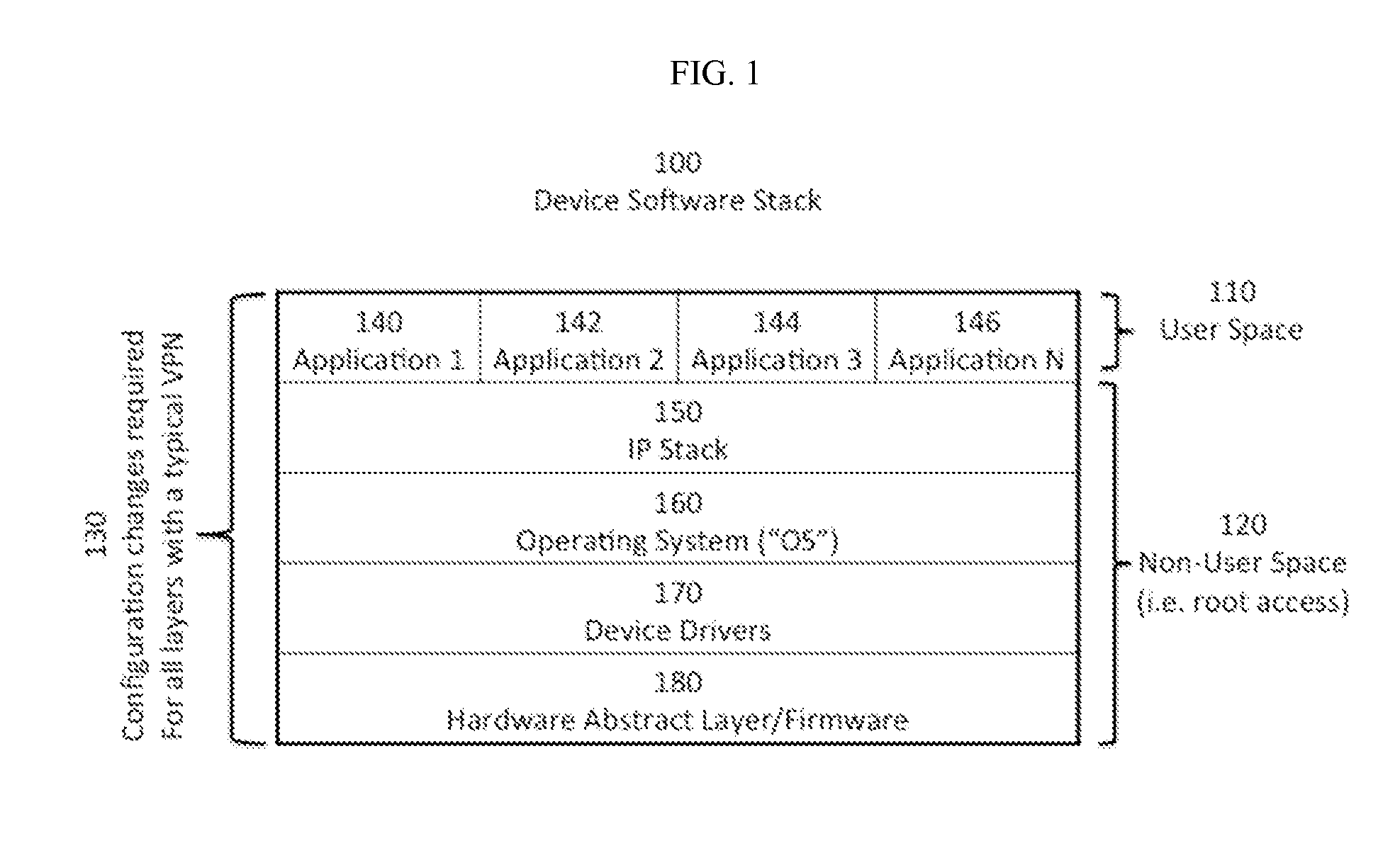
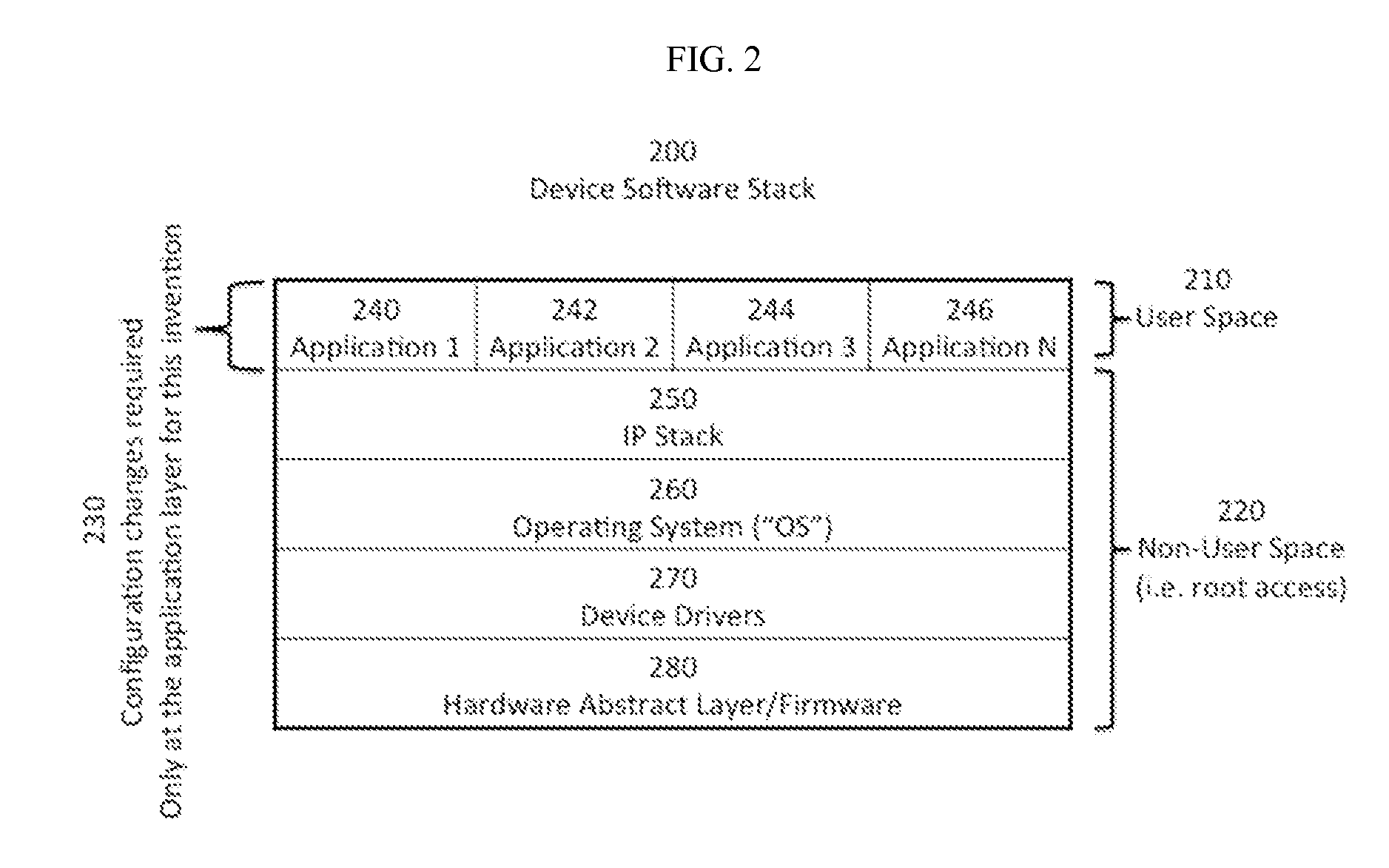
This invention includes apparatus, systems, and methods to establish a virtual private network (“VPN”), or a secured network for authenticated and encrypted data transmission to prevent disclosure of private information to unauthorized parties. This invention provides secure and authenticated data transmission from a communication device to another device over any public or private network while using existing standard applications such as email, VoIP, internet browsers, ISR applications, video conferencing, telecommuting, inventory tracking and control, etc. without the need to secure or add encryption features into each specific application. This invention provides the opportunity to selectively secure one or more existing applications with configuration changes that can be made at the user-space level of the software stack and without need for higher level software stack access, such as root access.
Owner:SAIFE
Secure disposal of storage data
InactiveUS20090196417A1Quickly and securely eraseKey distribution for secure communicationDigital data protectionComputer hardwareCiphertext
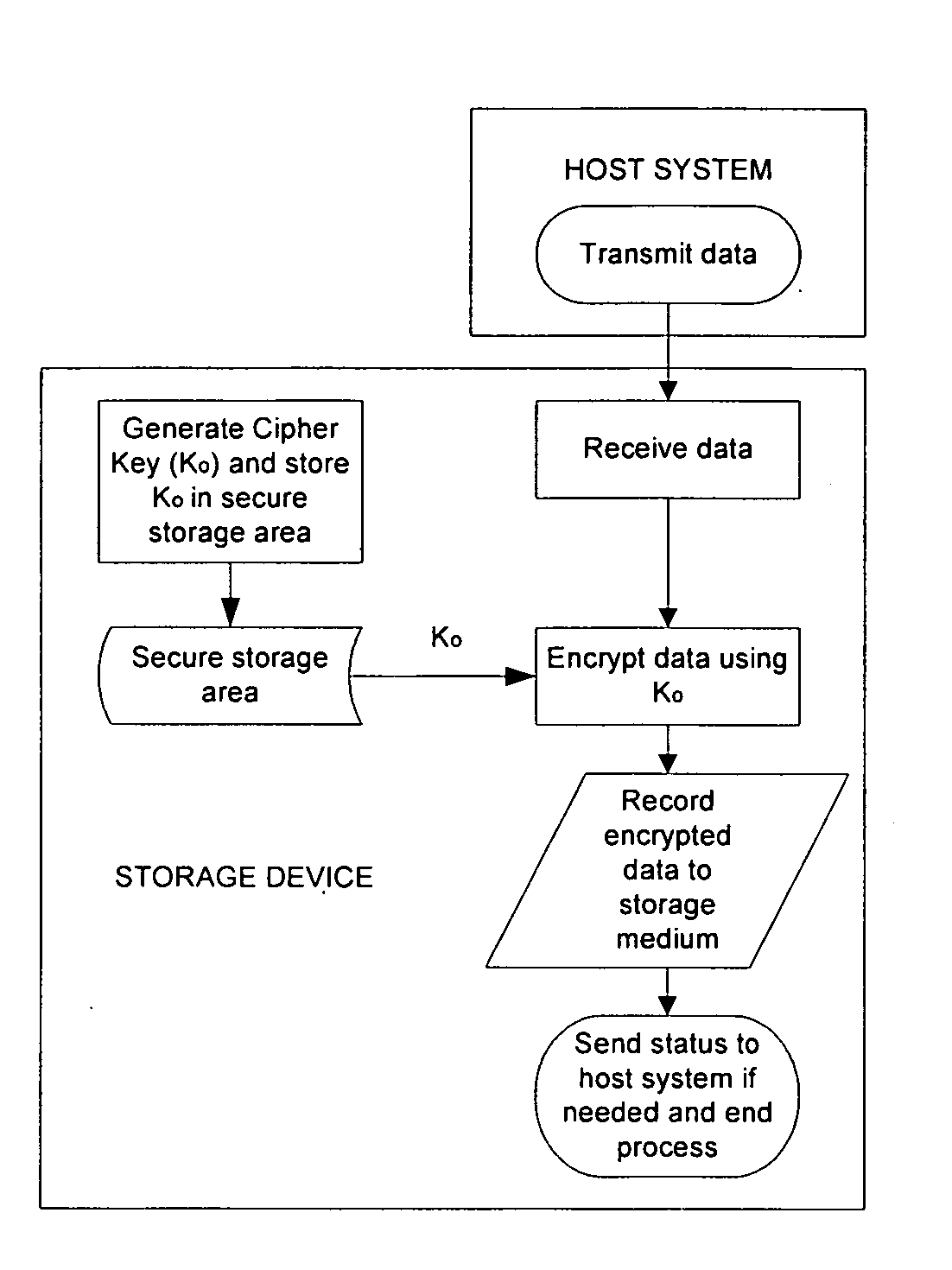
A data storage device (such as a magnetic disk drive), which has a built-in encryption function using a self generated cipher key. The data storage device uses the cipher key to routinely encrypt the incoming data without instruction and / or control by the host system or other components that are external to the device and its dedicated controls (e.g., a disk drive controller card). The encryption function is a built-in function or self-contained function of the drive and / or it dedicated controller. To permanently delete the entire content of the drive, the cipher key is located and erased to render the ciphertext that is stored in the storage device unusable. In another embodiment of the present invention, the data disposal is managed on a file basis through the use of a plurality of internally generated file-specific cipher keys, which are managed through the aid of an internal key library.
Owner:SEAGATE TECH LLC
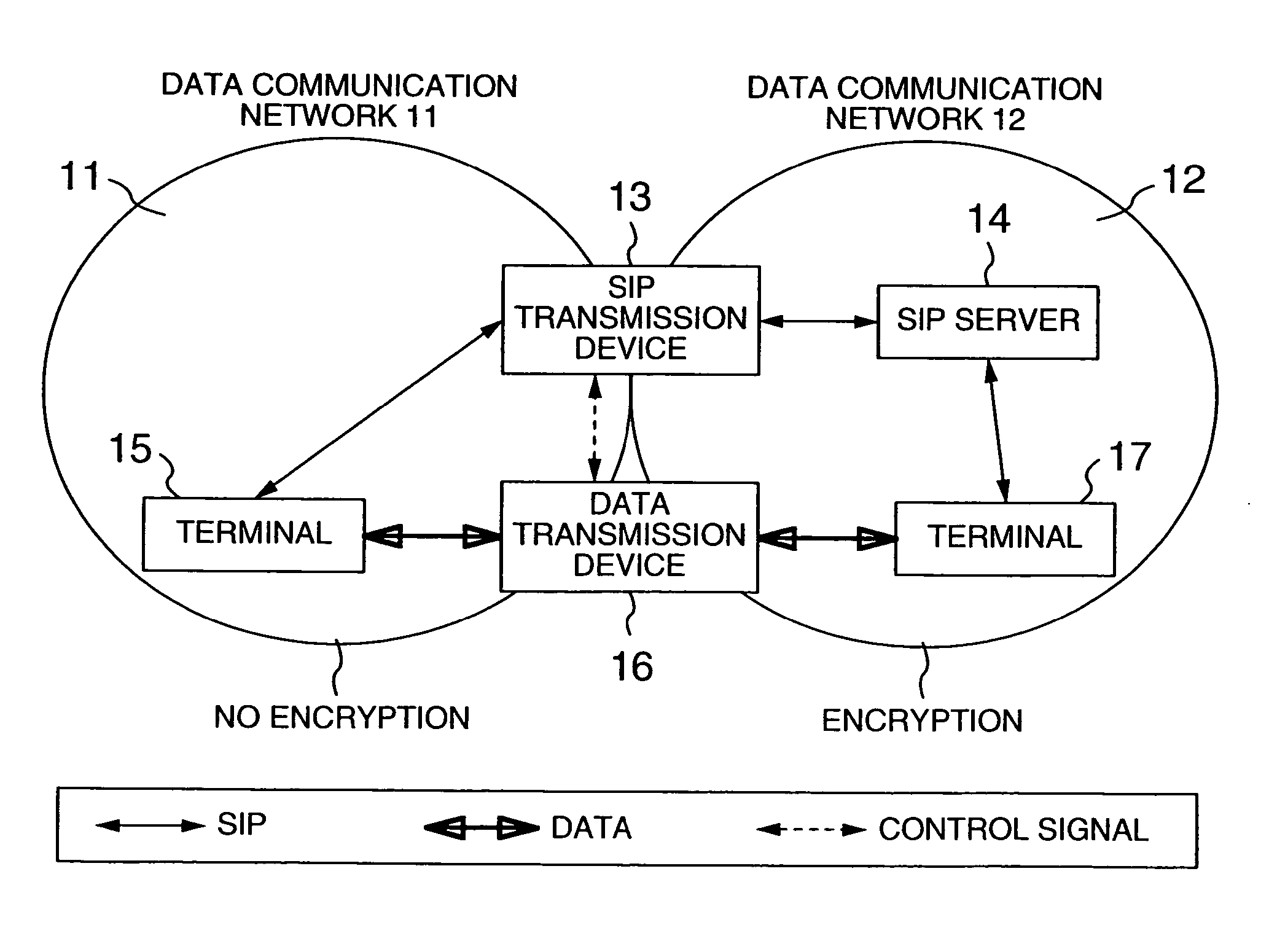
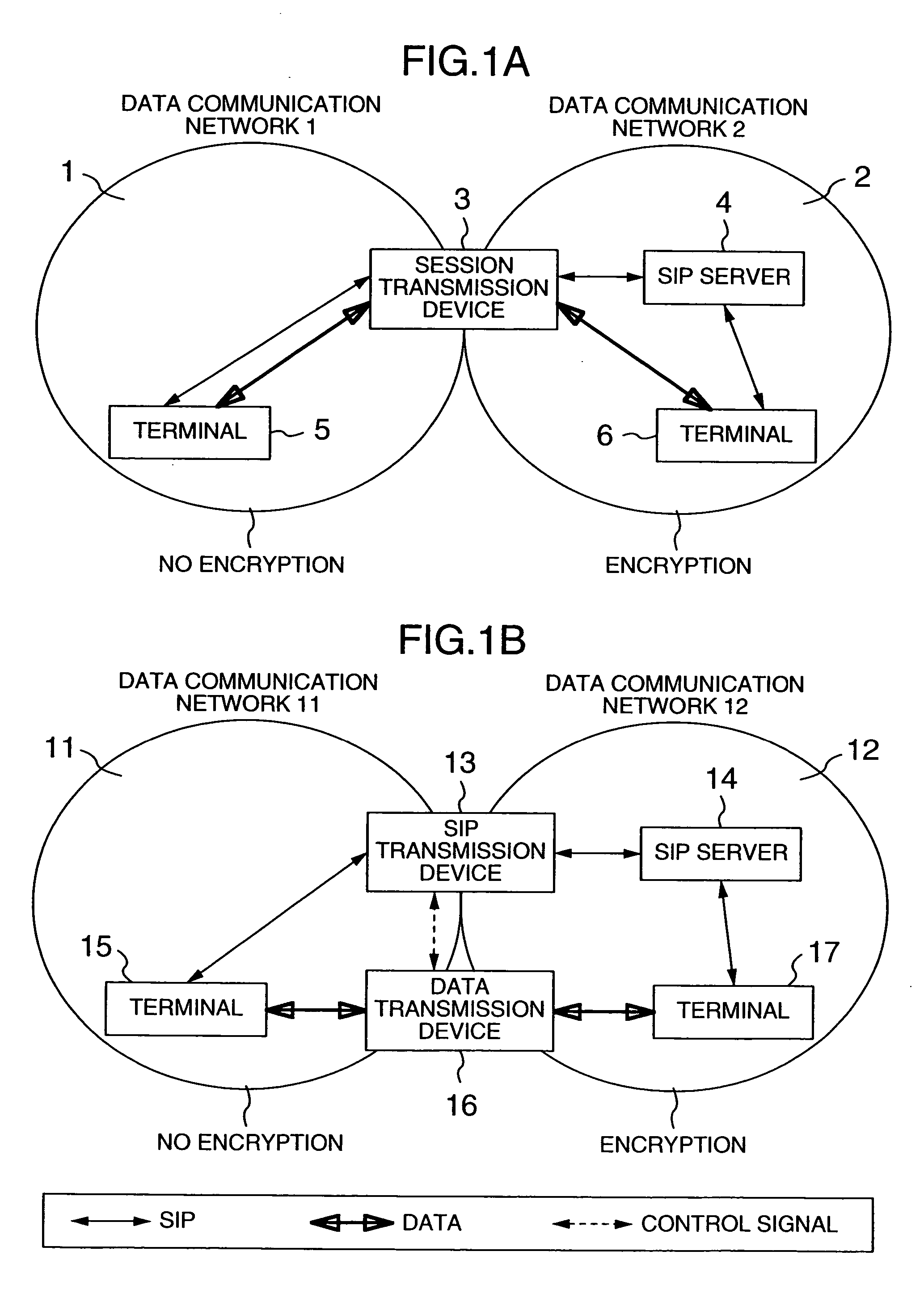
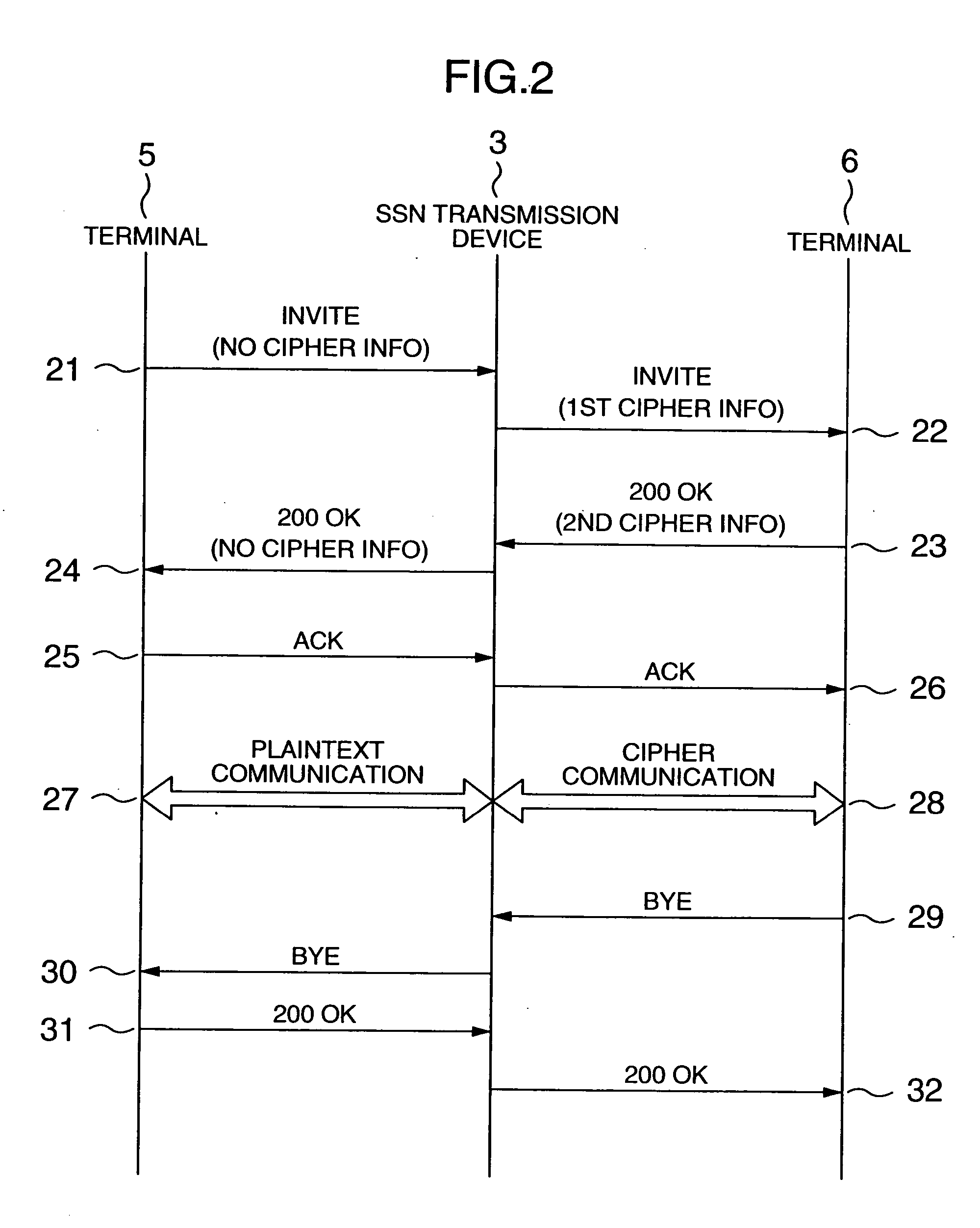
Network system, data transmission device, session monitor system and packet monitor transmission device
InactiveUS20060010321A1Key distribution for secure communicationUser identity/authority verificationEncrypted functionNetworked system
In a network system for communication between a first terminal with an encrypting function and a second terminal without the encrypting function, a control data transmission device includes a receiving unit receiving control data sent from the first terminal to the second terminal, a data processing unit for extracting cipher information of the first terminal from the control data, a memory storing the cipher information of the first terminal, and a sending unit for sending the control data without the cipher information toward the second terminal, or sending to the first terminal the control data with the cipher information, and further sending the cipher information to the user data transmission device; a user data transmission device includes an encryption processing unit for decrypting the data that was sent from the first terminal to the second terminal while encrypting the data as sent from the second terminal to the first terminal.
Owner:HITACHI LTD
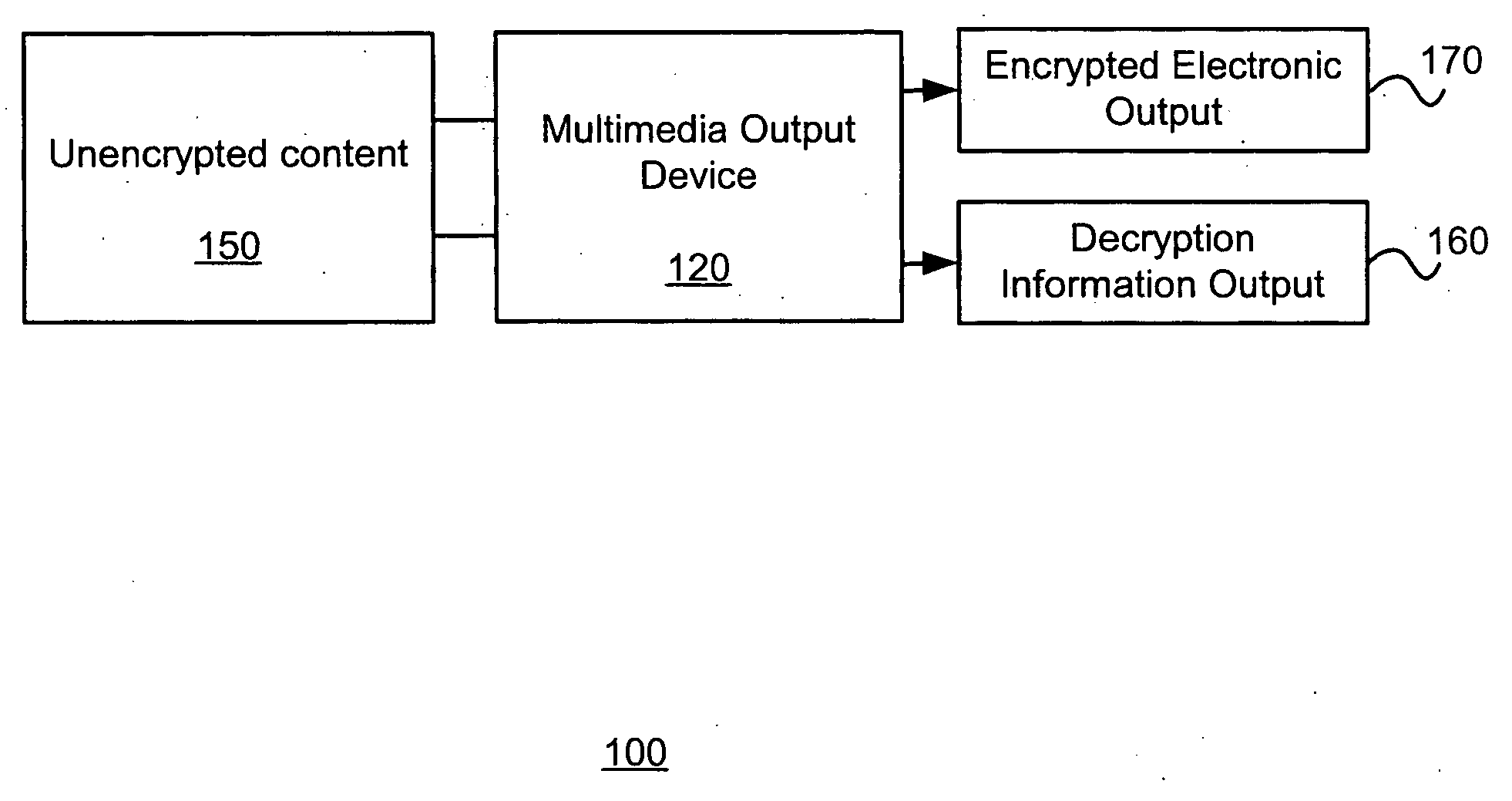
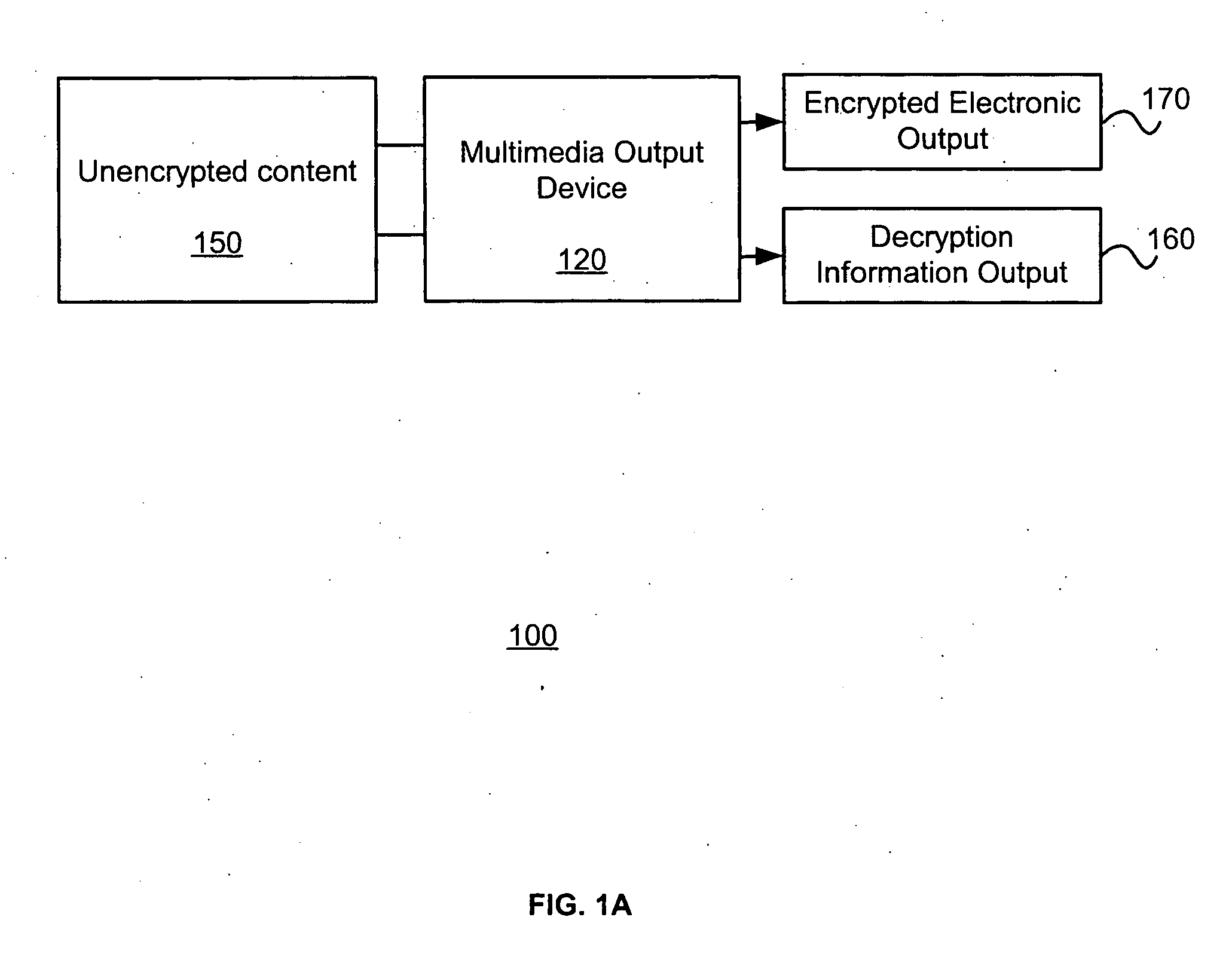
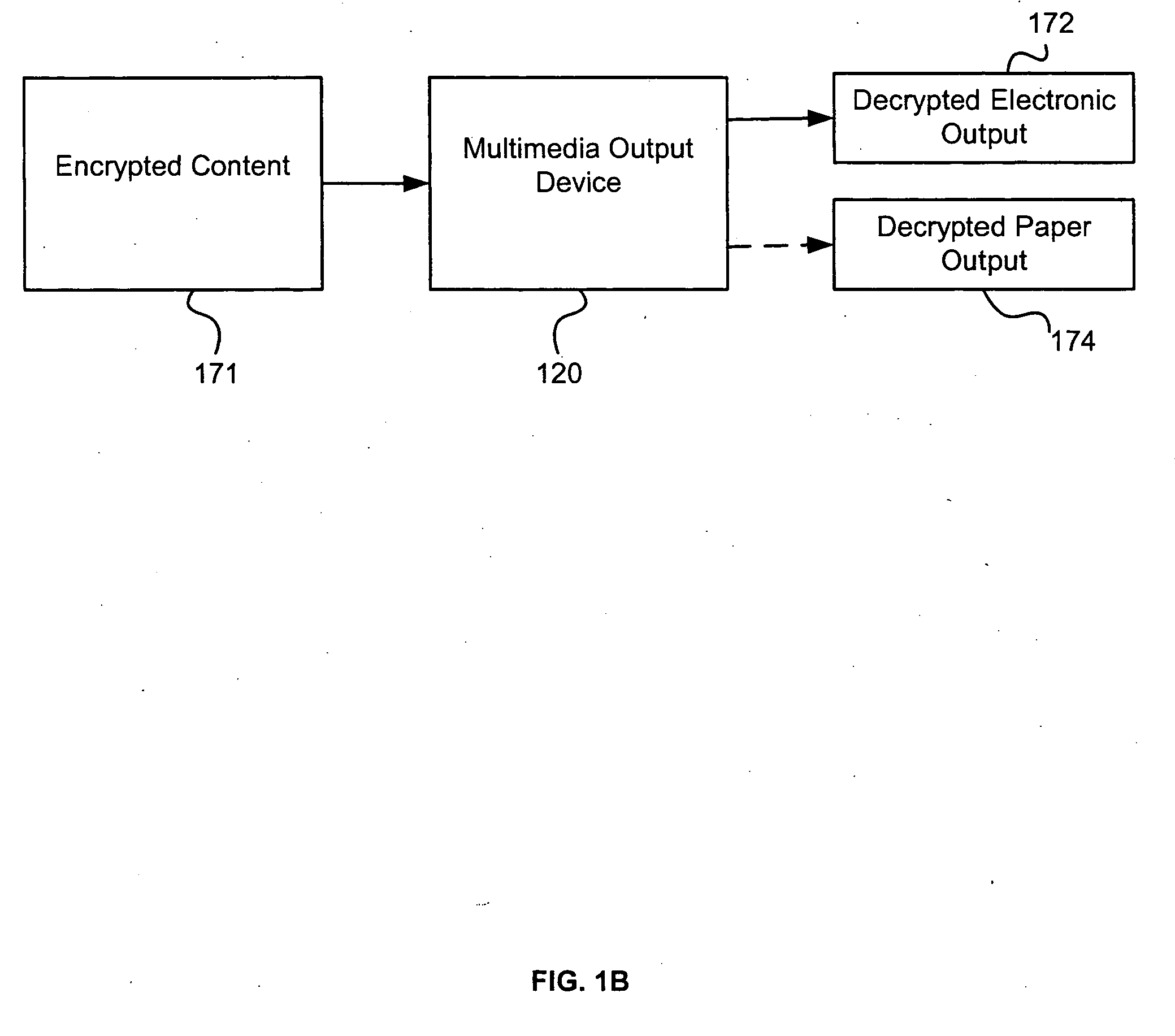
Multimedia output device having embedded encryption functionality
ActiveUS20050050344A1Provide securityAbility to provideElectrophonic musical instrumentsUser identity/authority verificationEncrypted functionOutput device
A multimedia output device having embedded encryption functionality enables the outputting of content in an encrypted form. The multimedia output device receives the content to be encrypted, encrypts the content, and generates an electronic output of the encrypted content. The multimedia output device also generates an associated paper output that provides information about the decryption, such as a key, an identification of the electronic output of the encrypted content, and optionally a description of the contents of the content encrypted.
Owner:RICOH KK
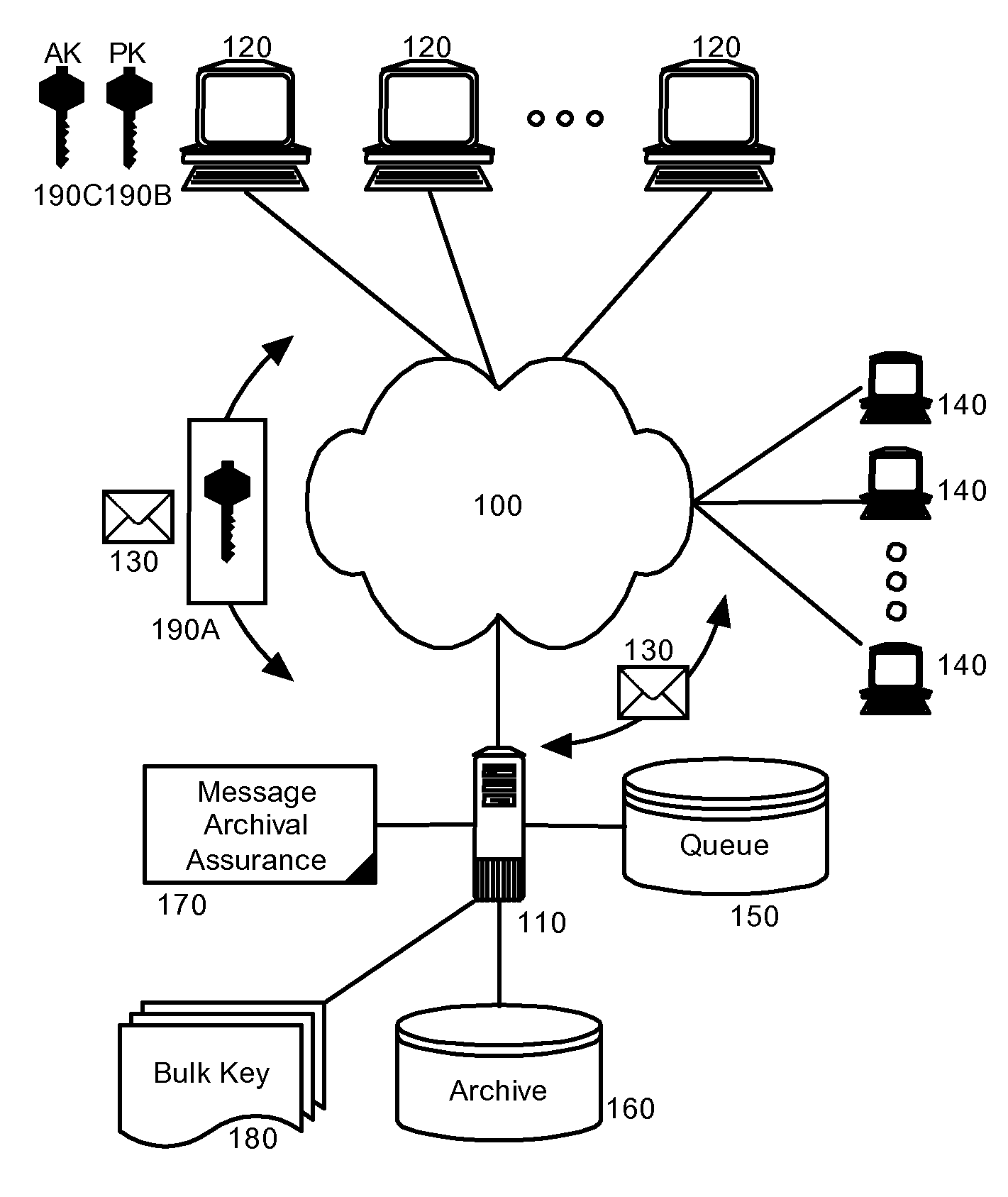
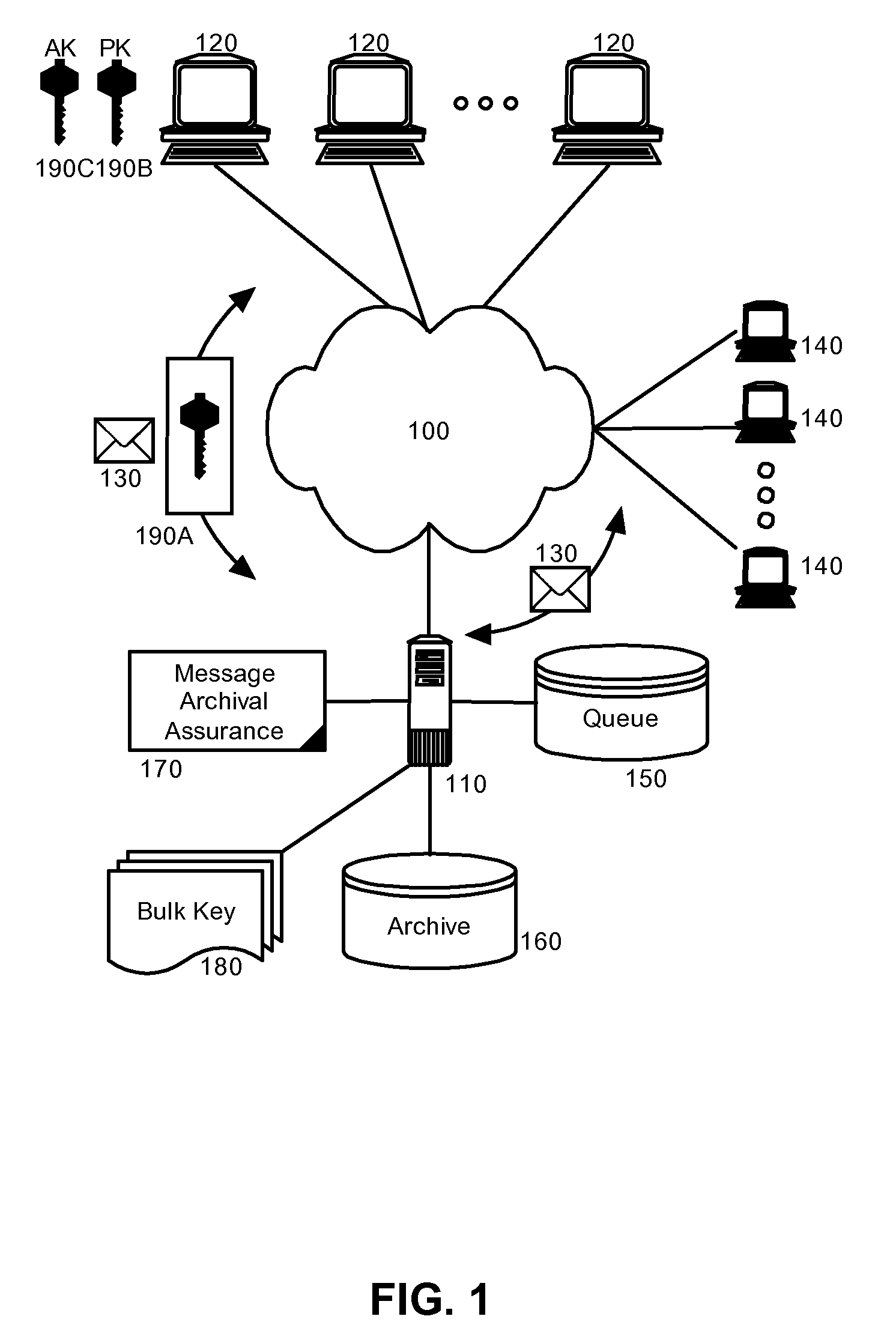
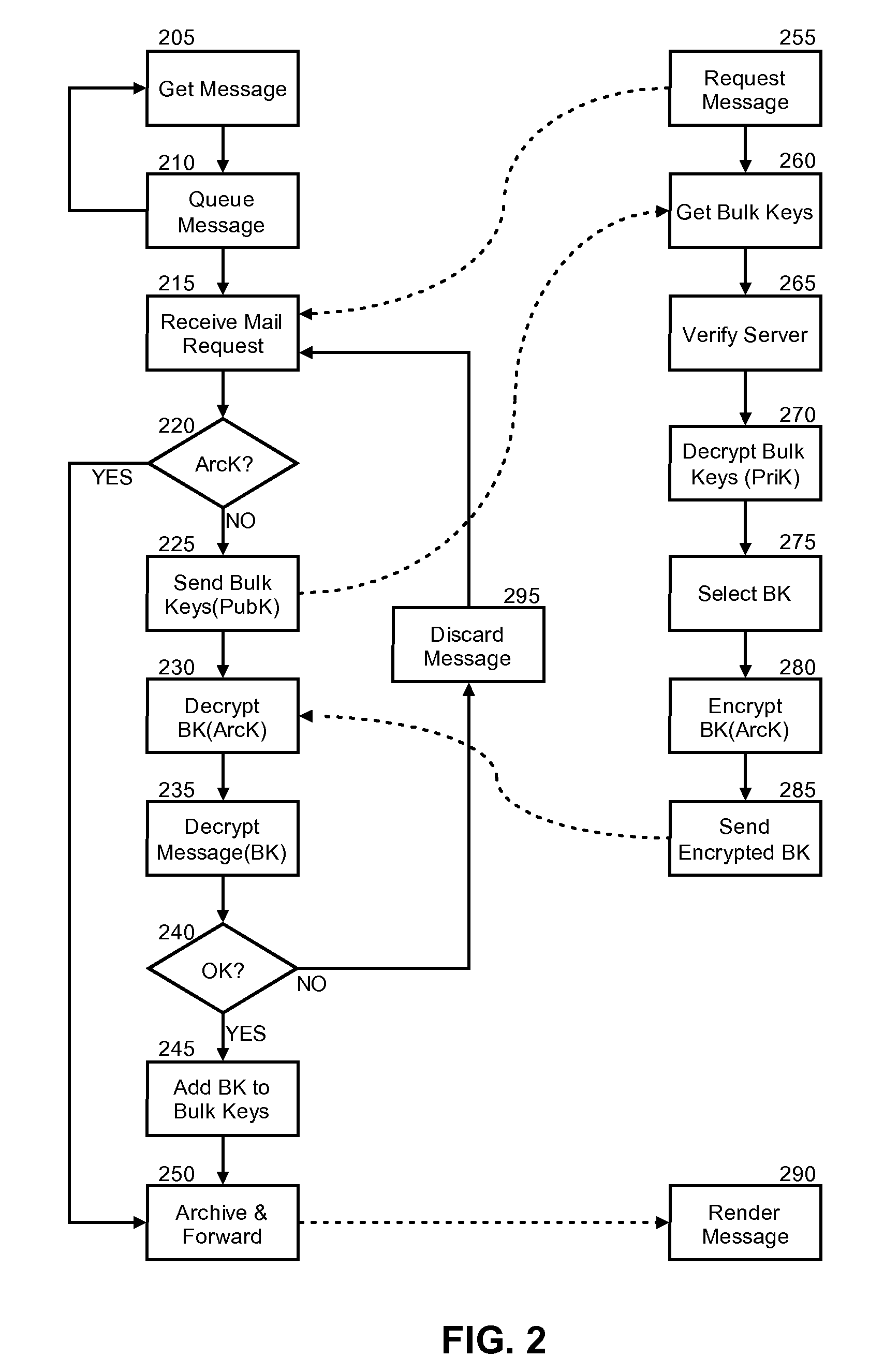
Message archival assurance for encrypted communications
InactiveUS20080019530A1Key distribution for secure communicationMultiple keys/algorithms usageEncrypted functionClient-side
Embodiments of the present invention address deficiencies of the art in respect to encrypted message management in an archival environment, and provide a novel and non-obvious method, system and computer program product for message archival assurance. In one embodiment of the invention, a message archival assurance method can be provided that can include receiving an encrypted message designated for receipt by a messaging client; determining whether the encrypted message is decryptable using one of a set of a bulk keys accessible by the messaging system; and, archiving and forwarding the encrypted message to the messaging client only if the encrypted message is decryptable using one of a set of bulk keys accessible by the messaging system and otherwise discarding the encrypted message.
Owner:IBM CORP
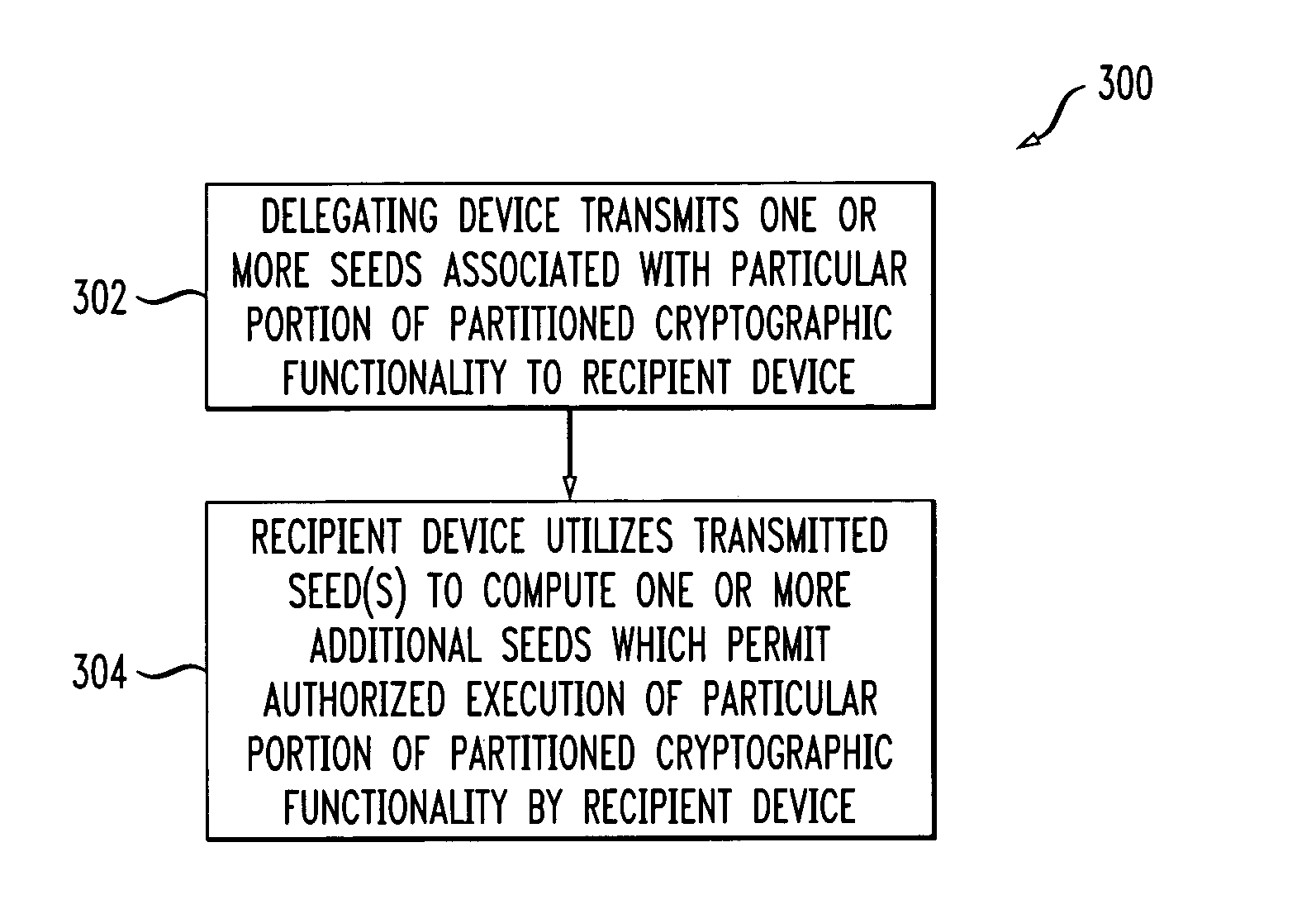
Method and apparatus for graph-based partition of cryptographic functionality
ActiveUS20050036615A1Efficient mechanismReadily apparentSecret communicationSpecial data processing applicationsGraphicsComputer hardware
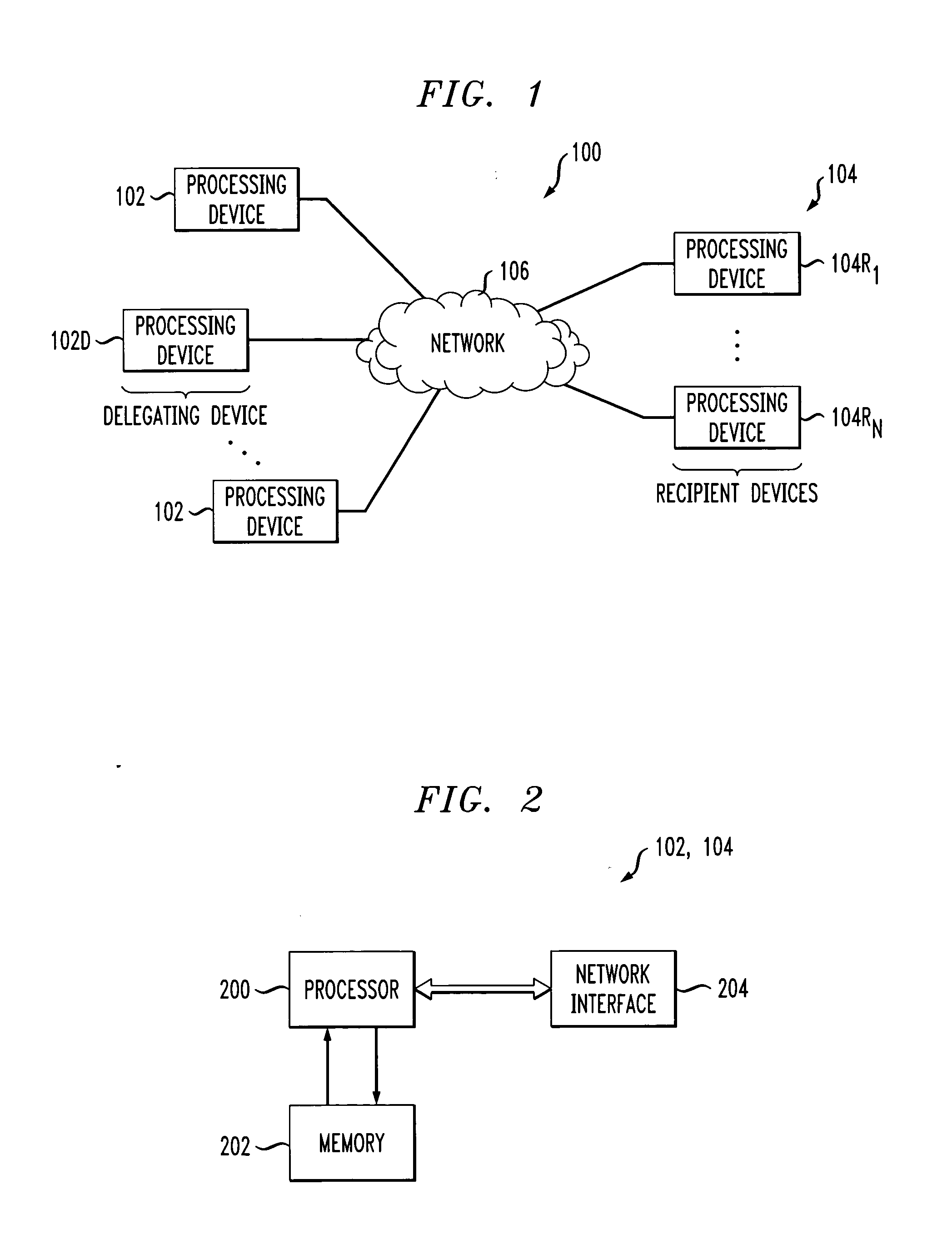
Techniques are disclosed for partitioning of cryptographic functionality, such as authentication code verification or generation ability, so as to permit delegation of at least one of a number of distinct portions of the cryptographic functionality from a delegating device to at least one recipient device. The cryptographic functionality is characterizable as a graph comprising a plurality of nodes, and a given set of the nodes is associated with a corresponding one of the distinct portions of the cryptographic functionality. Information representative of one or more of the nodes is transmitted from the delegating device to the recipient device such that the recipient device is thereby configurable for authorized execution of a corresponding one of the distinct portions of the cryptographic functionality. Advantageously, the invention provides a particularly efficient mechanism for the provision of cryptographic functionality in accordance with a subscription model.
Owner:EMC IP HLDG CO LLC
Method and apparatus for hardware-accelerated encryption/decryption
ActiveUS8879727B2Maximize availabilityLimited operating lifeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMultiple encryptionKey exchange
An integrated circuit for data encryption / decryption and secure key management is disclosed. The integrated circuit may be used in conjunction with other integrated circuits, processors, and software to construct a wide variety of secure data processing, storage, and communication systems. A preferred embodiment of the integrated circuit includes a symmetric block cipher that may be scaled to strike a favorable balance among processing throughput and power consumption. The modular architecture also supports multiple encryption modes and key management functions such as one-way cryptographic hash and random number generator functions that leverage the scalable symmetric block cipher. The integrated circuit may also include a key management processor that can be programmed to support a wide variety of asymmetric key cryptography functions for secure key exchange with remote key storage devices and enterprise key management servers. Internal data and key buffers enable the device to re-key encrypted data without exposing data. The key management functions allow the device to function as a cryptographic domain bridge in a federated security architecture.
Owner:IP RESERVOIR
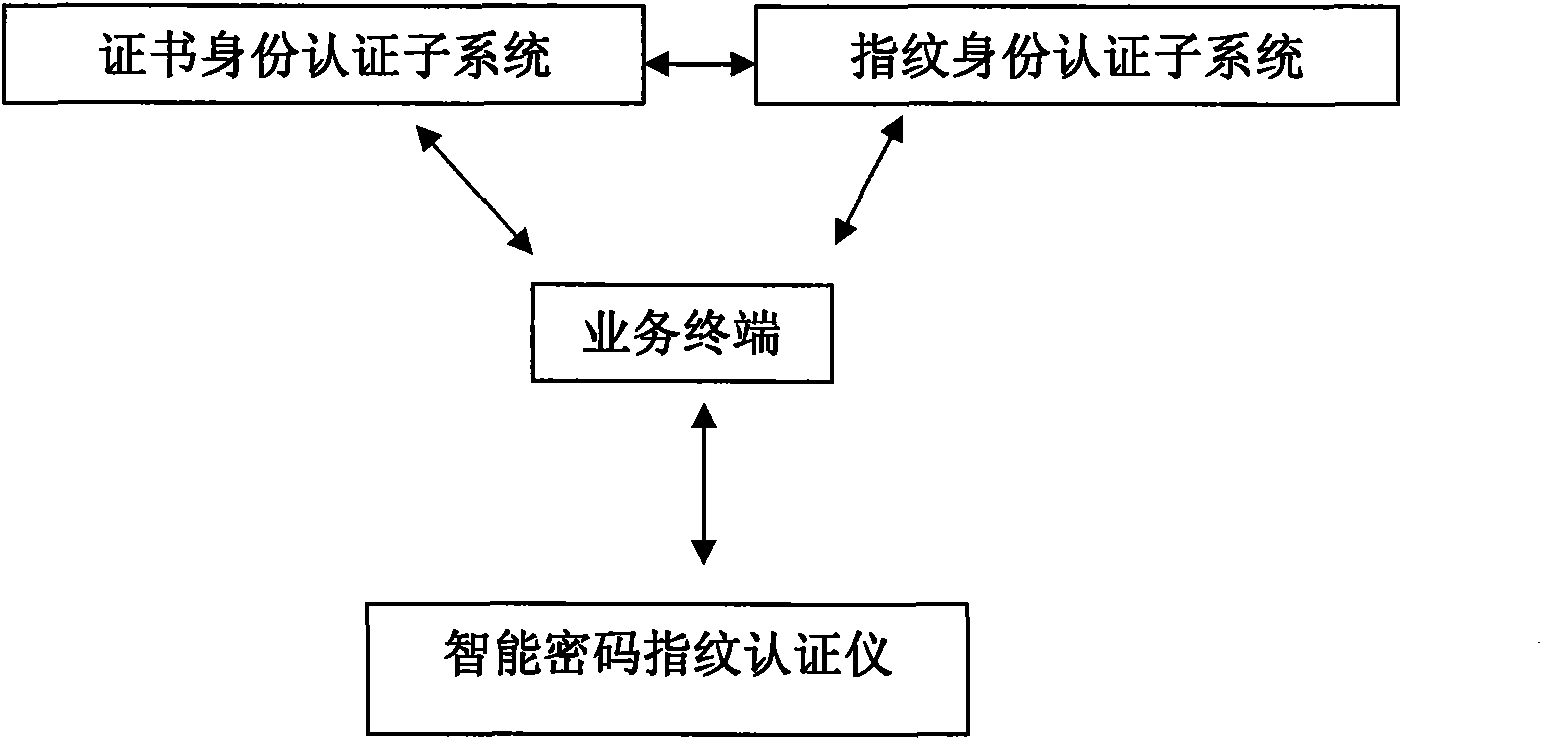
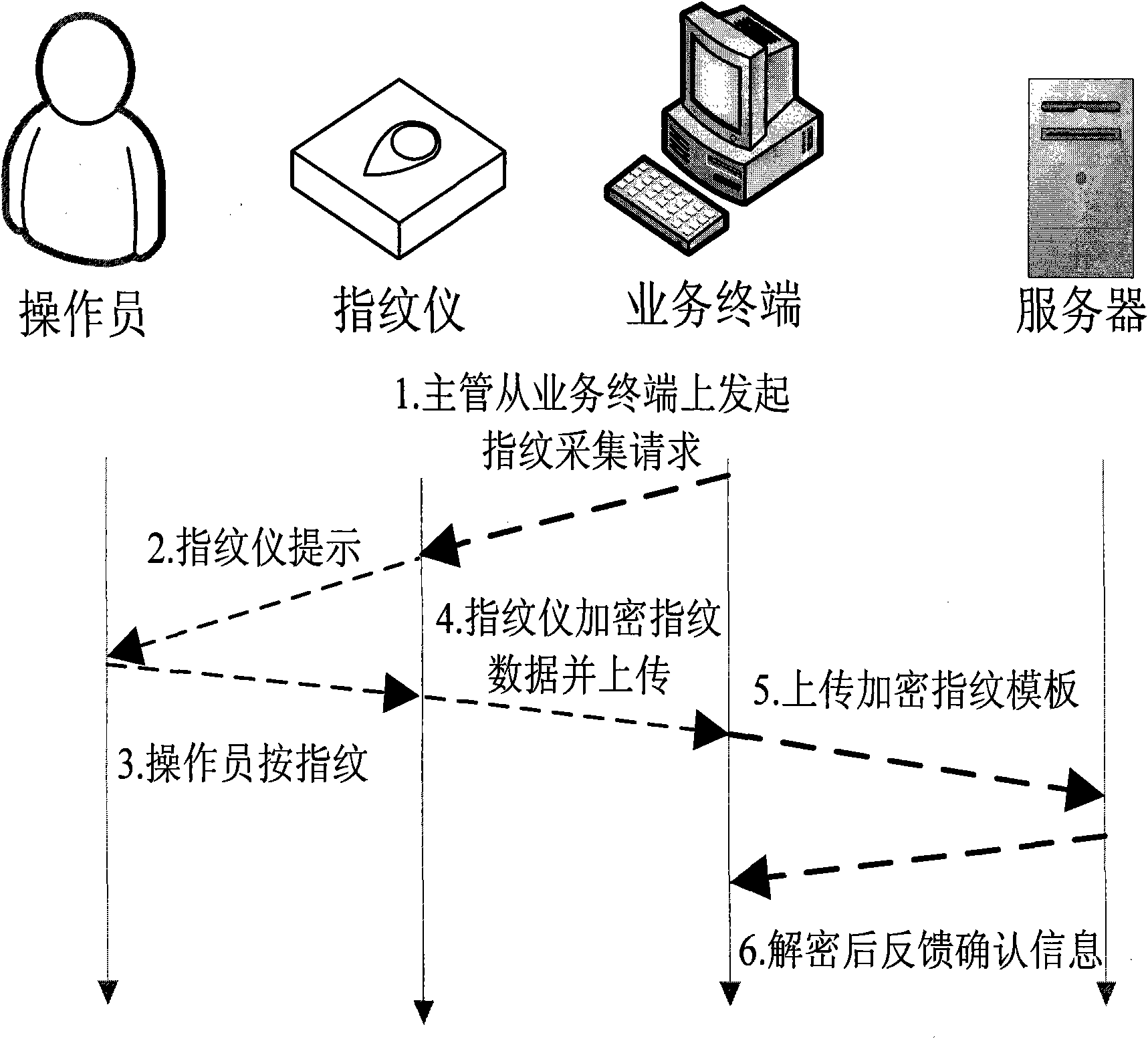
Identity authentication system combining fingerprint identification and PKI system
InactiveCN101631020AEnsure data security communicationImprove securityUser identity/authority verificationSecure communicationNetwork connection
The invention relates to an identity authentication system combining fingerprint identification and a PKI system in the technical field of information security, which comprises a certificate identity authentication subsystem, a fingerprint identity authentication subsystem, a service terminal and an intelligent password fingerprint instrument, wherein the certificate identity authentication subsystem, the fingerprint identity authentication subsystem and the service terminal are connected with one another through a network, the intelligent password fingerprint instrument is directly connected with the service terminal, and the certificate identity authentication subsystem is used for network identity authentications to ensure the data secure communications between each subsystems; and the fingerprint identity authentication subsystem consists of a fingerprint verification server which stores personnel fingerprints and identity information, supports the encryption function and simultaneously can transmit fingerprint templates to the certificate identity authentication subsystem, the service terminal and the intelligent password fingerprint instrument according to requests, and can verify the fingerprint templates and return information on matching or not matching according to the requests. The security strength of the identity authentication system is strengthened greatly.
Owner:SHANGHAI FERLY DIGITAL TECH
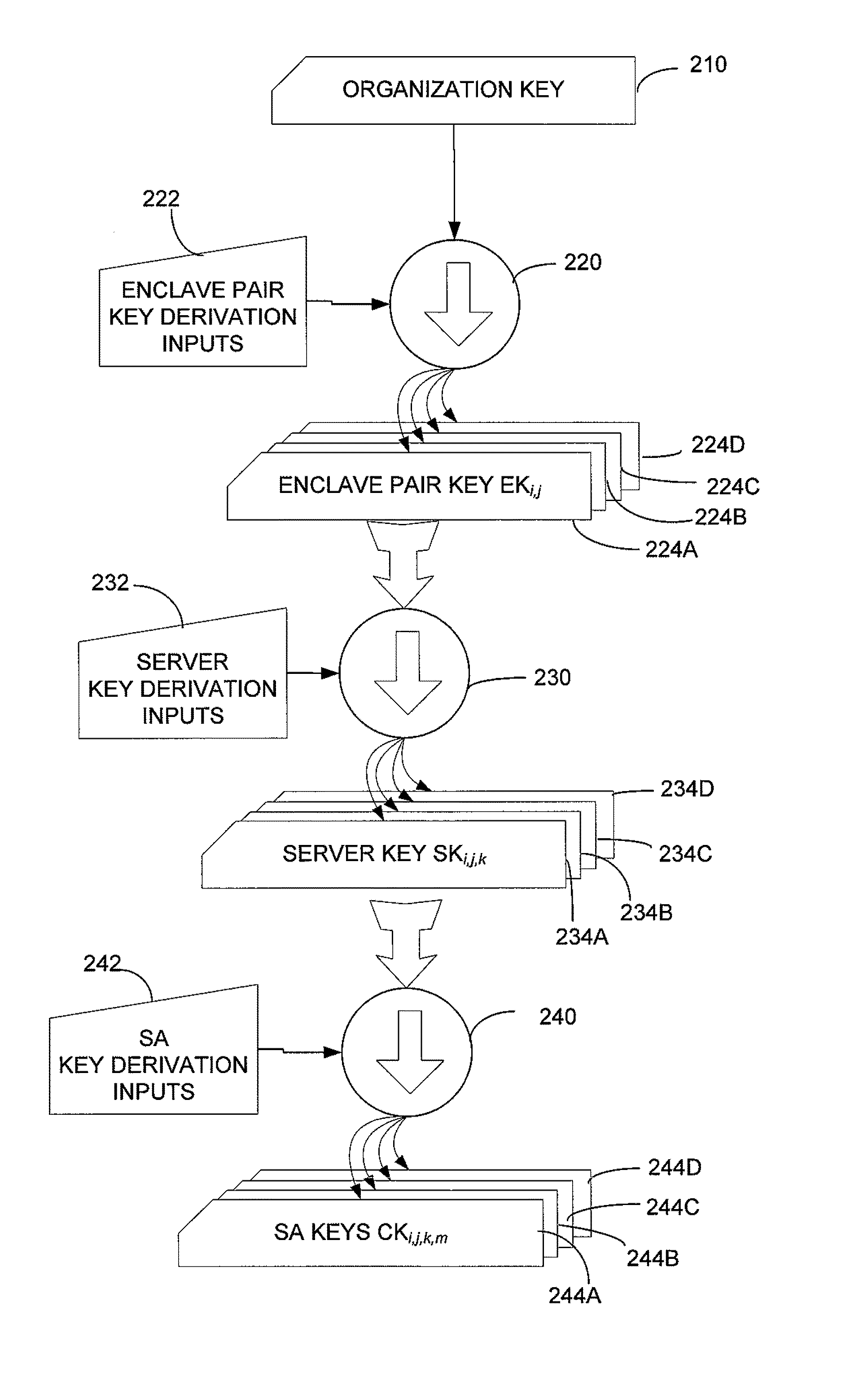
Key management in secure network enclaves
A hierarchical key generation and distribution mechanism for a computer system in which devices are organized into secure enclaves. The mechanism enables network access to be tailored to approximate minimum needed privileges for each device. At the lowest level of the hierarchy, keys are used to form security associations between devices. Keys at each level of the hierarchy are generated from keys at a higher level of the hierarchy and key derivation information. Key derivation information is readily ascertainable, either from identifiers for devices or from within messages, supporting hardware offload of cryptographic functions. Because keys may be generated based on the enclaves in which the hosts participating in a security association are located, the system includes a mechanism by which devices can discover the enclave in which they are located.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for establishing a trust framework based on smart key devices
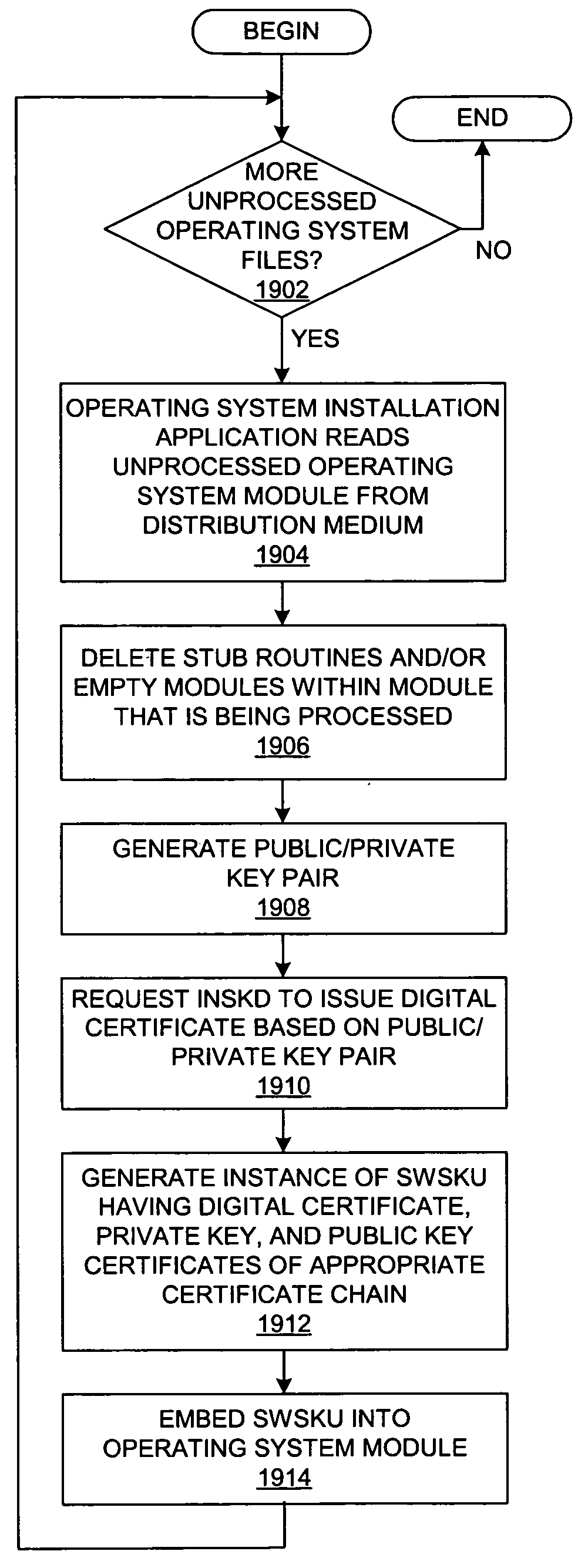
ActiveUS20050154875A1User identity/authority verificationUnauthorized memory use protectionTrust relationshipSecure unit
A mechanism is provided for securing cryptographic functionality within a host system such that it may only be used when a system administrator physically allows it via a hardware security token. In addition, a hardware security unit is integrated into a data processing system, and the hardware security unit acts as a hardware certificate authority. The hardware security unit may be viewed as supporting a trust hierarchy or trust framework within a distributed data processing system. The hardware security unit can sign software that is installed on the machine that contains the hardware security unit. Server processes that use the signed software that is run on the machine can establish mutual trust relationships with the hardware security unit and amongst the other server processes based on their common trust of the hardware security unit.
Owner:META PLATFORMS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com