Patents
Literature
118 results about "Database encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
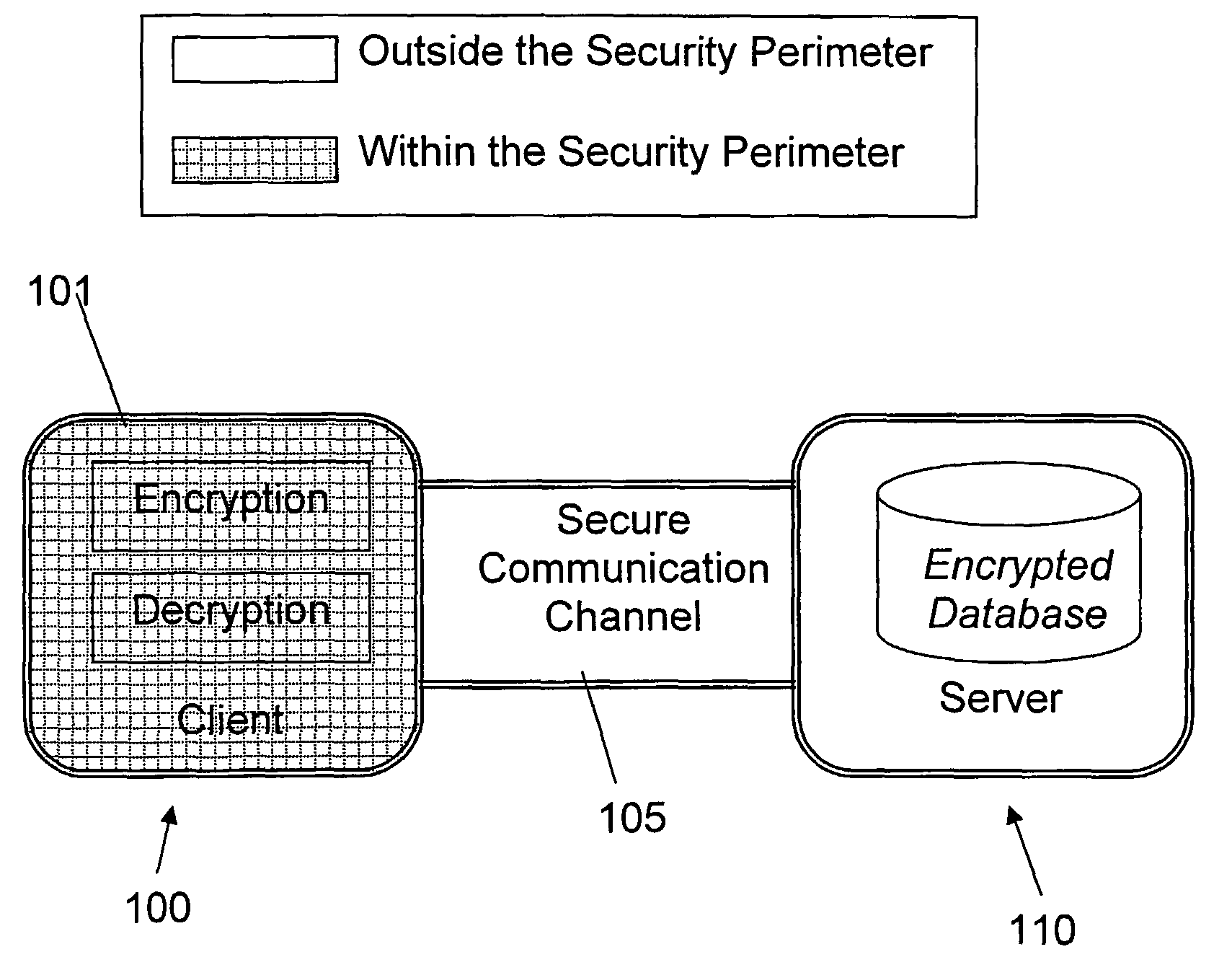
Database encryption can generally be defined as a process that uses an algorithm to transform data stored in a database into "cipher text" that is incomprehensible without first being decrypted. It can therefore be said that the purpose of database encryption is to protect the data stored in a database from being accessed by individuals with potentially "malicious" intentions. The act of encrypting a database also reduces the incentive for individuals to hack the aforementioned database as "meaningless" encrypted data is of little to no use for hackers. There are multiple techniques and technologies available for database encryption, the most important of which will be detailed in this article.
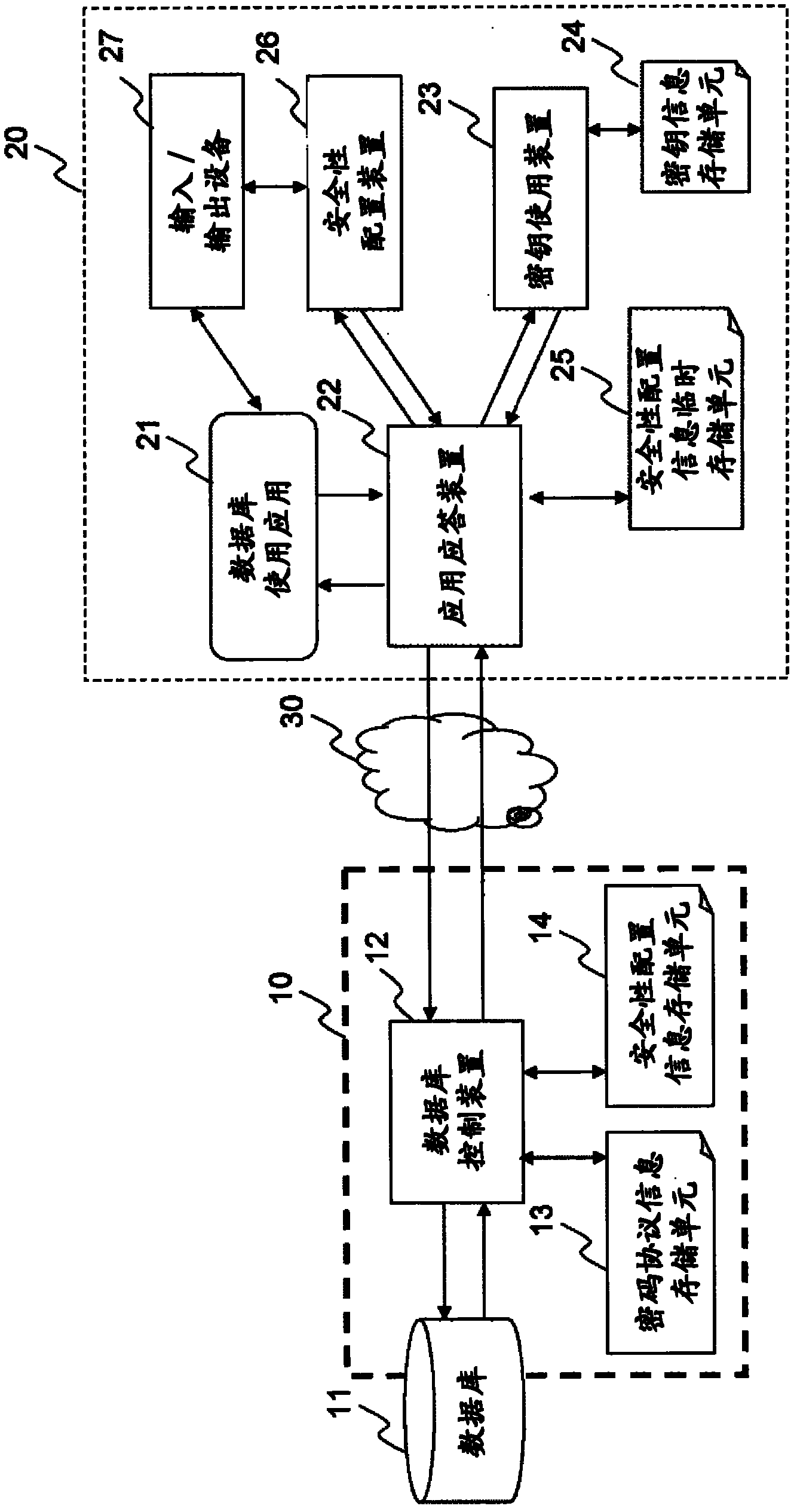
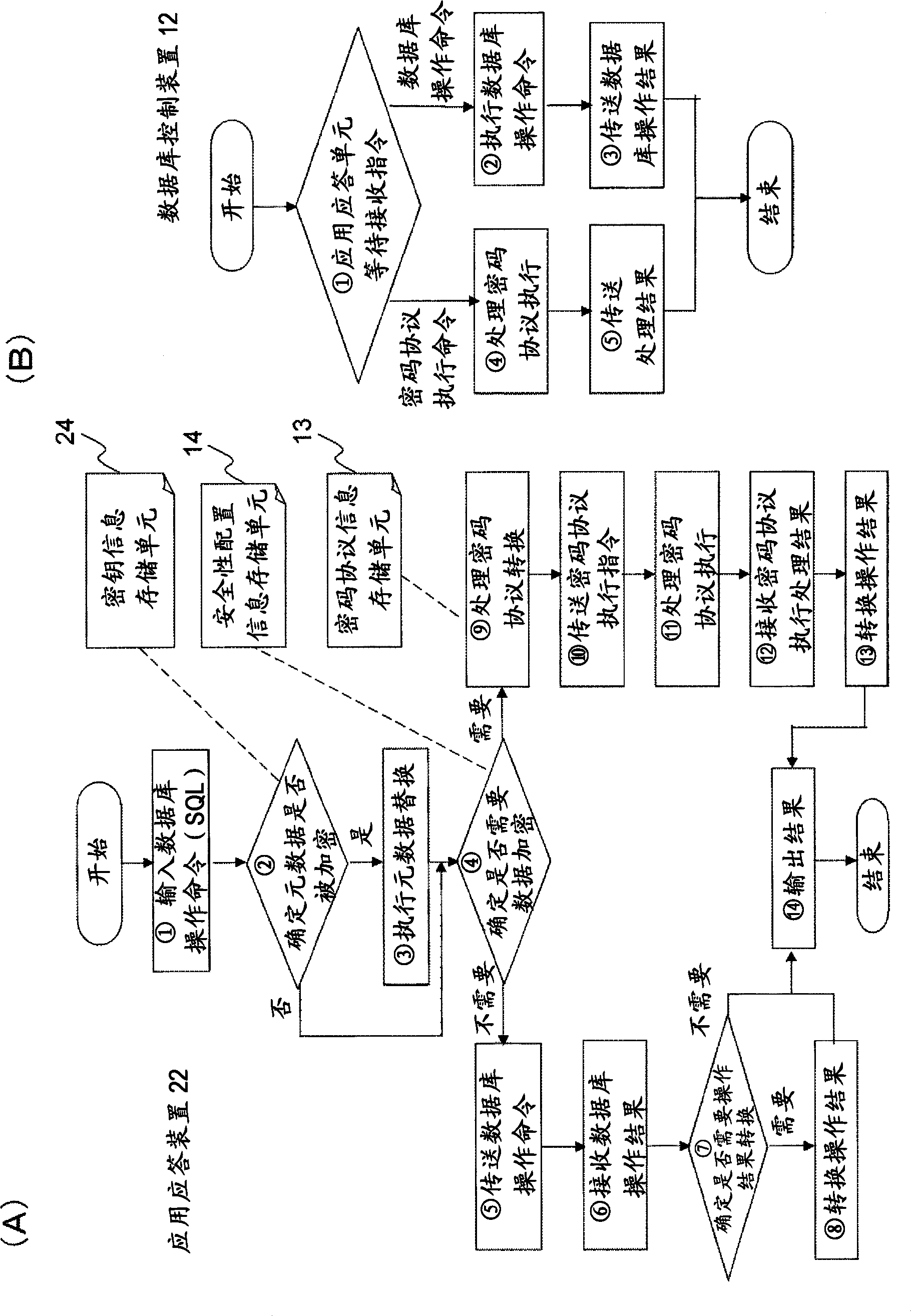
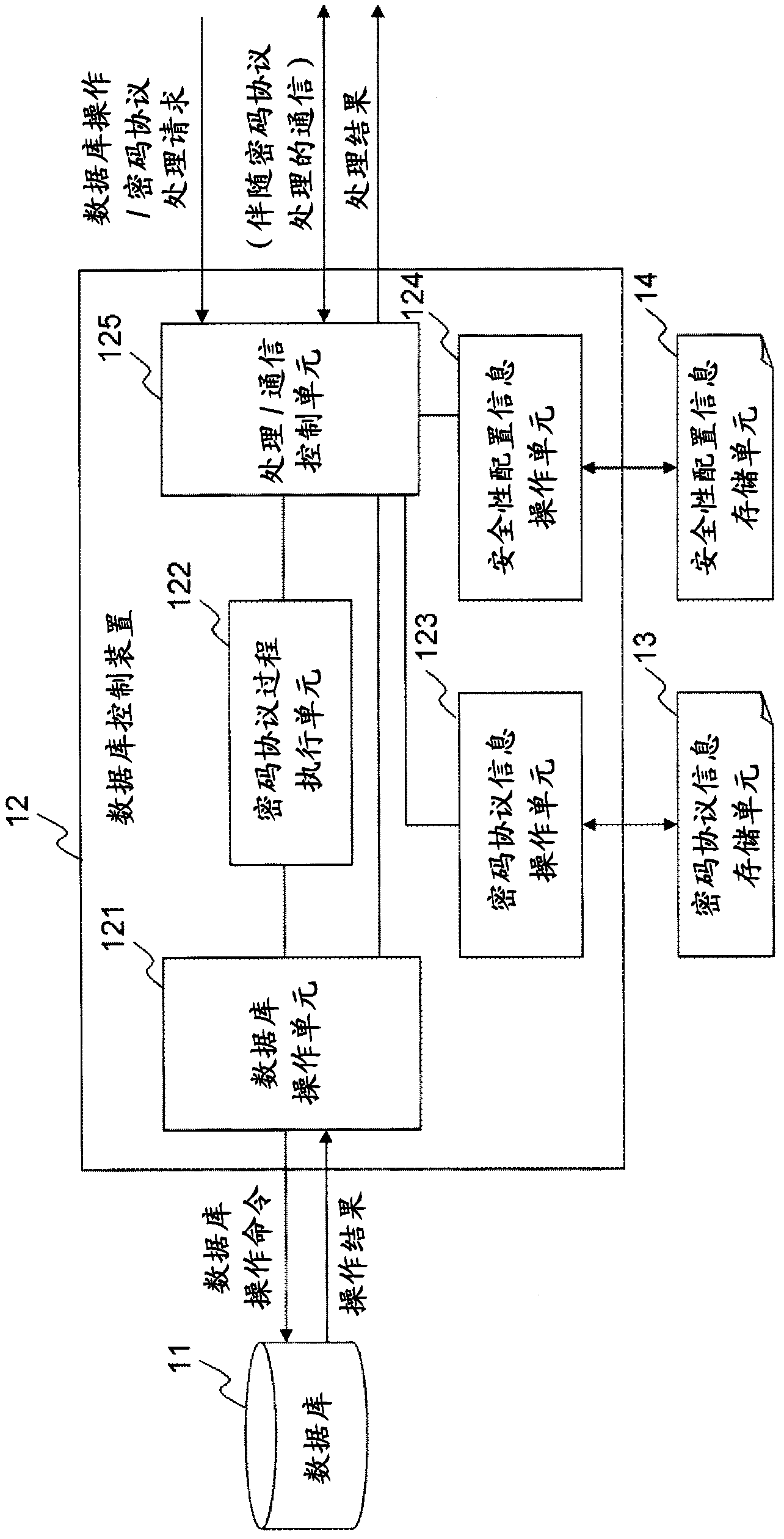
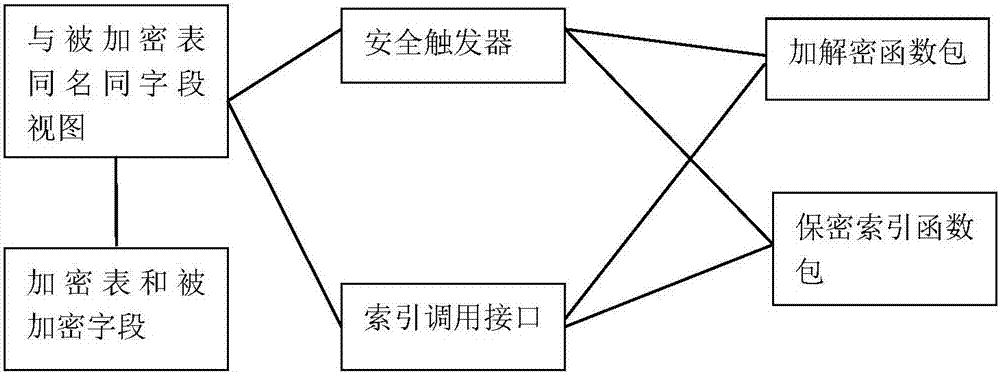
Structure Preserving Database Encryption Method and System
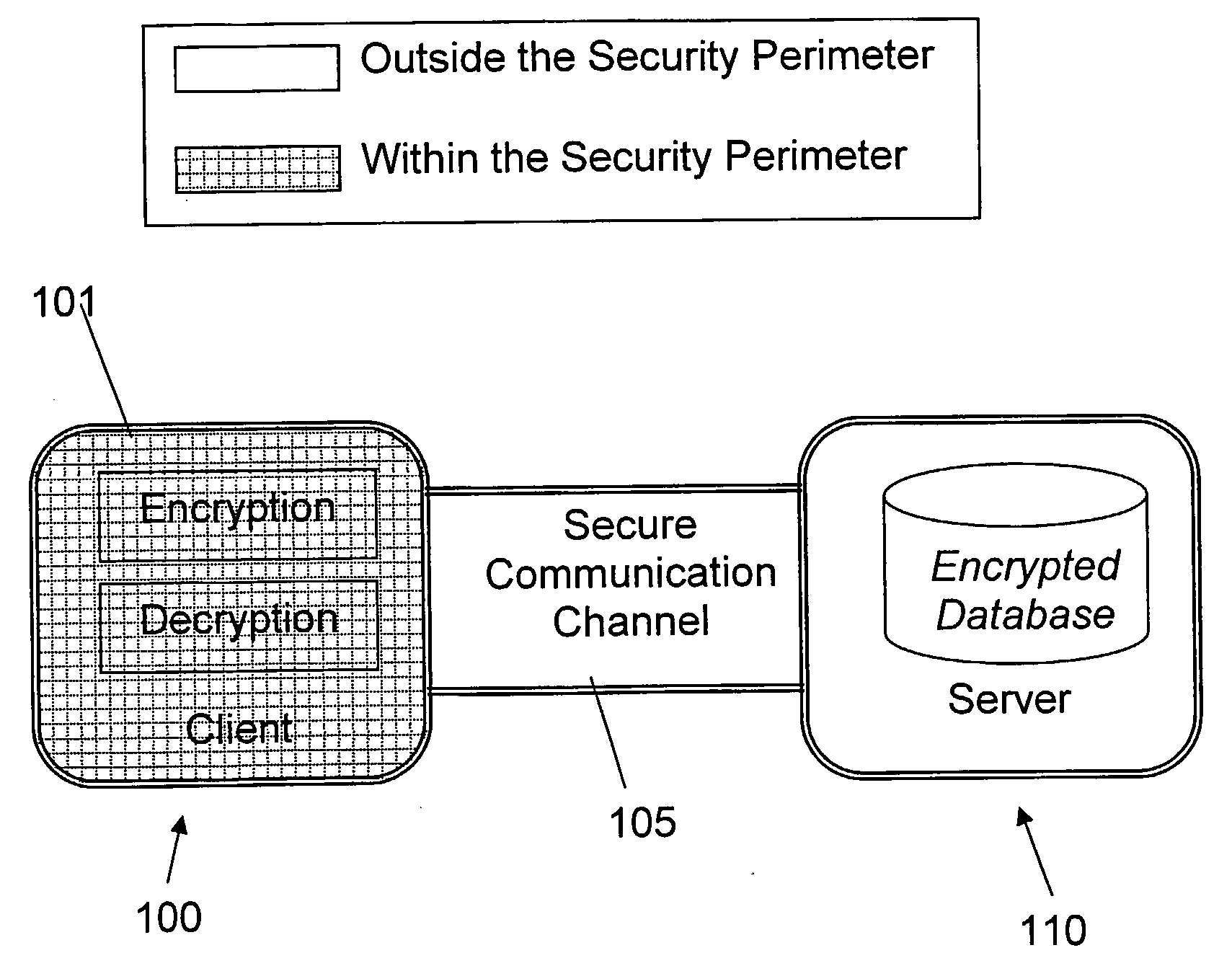
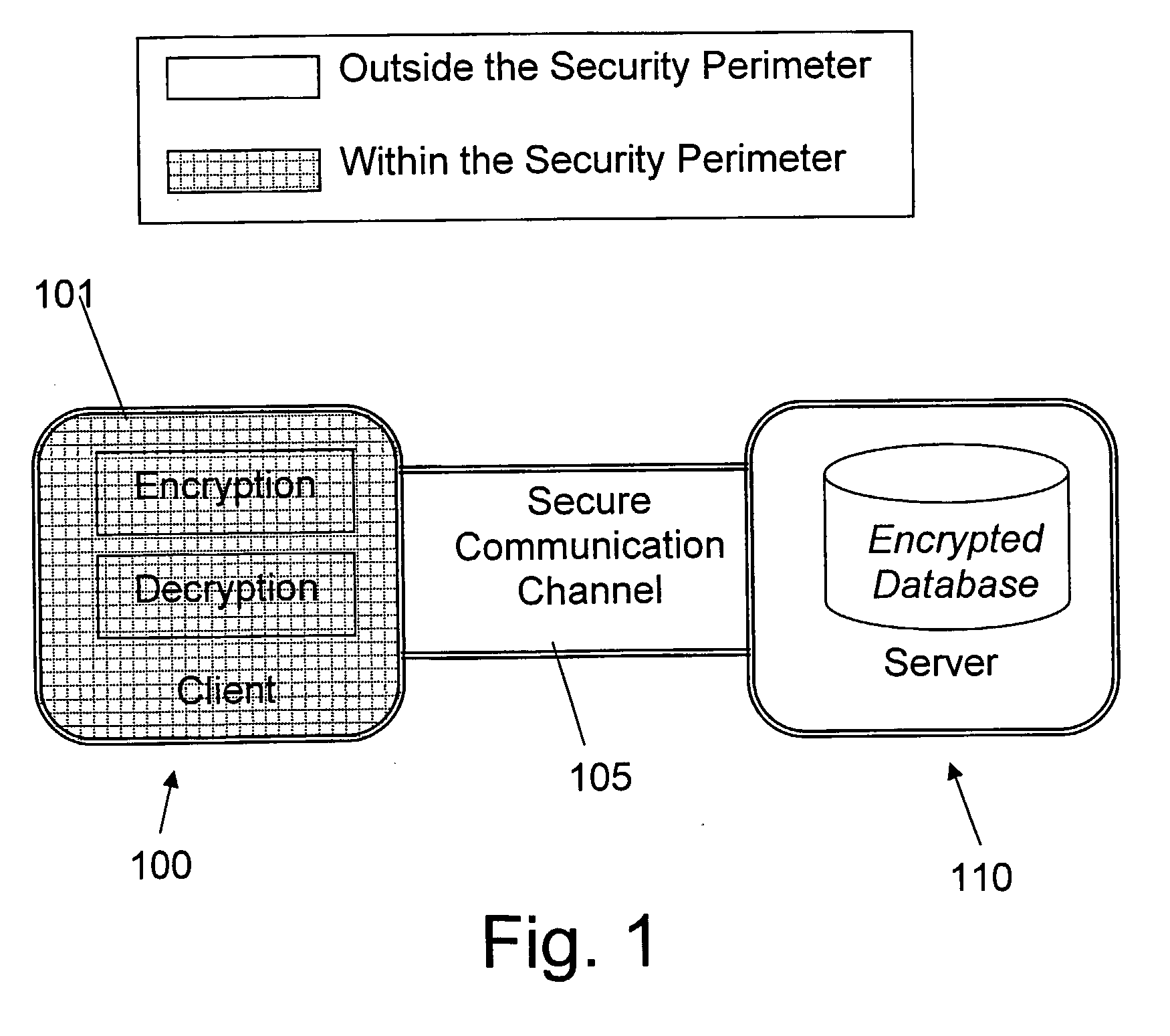
ActiveUS20080133935A1Easy accessAvoid contactKey distribution for secure communicationMultiple keys/algorithms usageDatabase indexMulti user environment
A database encryption system and method, the Structure Preserving Database Encryption (SPDE), is presented. In the SPDE method, each database cell is encrypted with its unique position. The SPDE method permits to convert a conventional database index into a secure one, so that the time complexity of all queries is maintained. No one with access to the encrypted database can learn anything about its content without the encryption key. Also a secure index for an encrypted database is provided. Furthermore, secure database indexing system and method are described, providing protection against information leakage and unauthorized modifications by using encryption, dummy values and pooling, and supporting discretionary access control in a multi-user environment.
Owner:BEN GURION UNIVERSITY OF THE NEGEV
Method and apparatus for automatic database encryption
InactiveUS7111005B1Data processing applicationsMultiple keys/algorithms usageEncrypted functionDatabase encryption
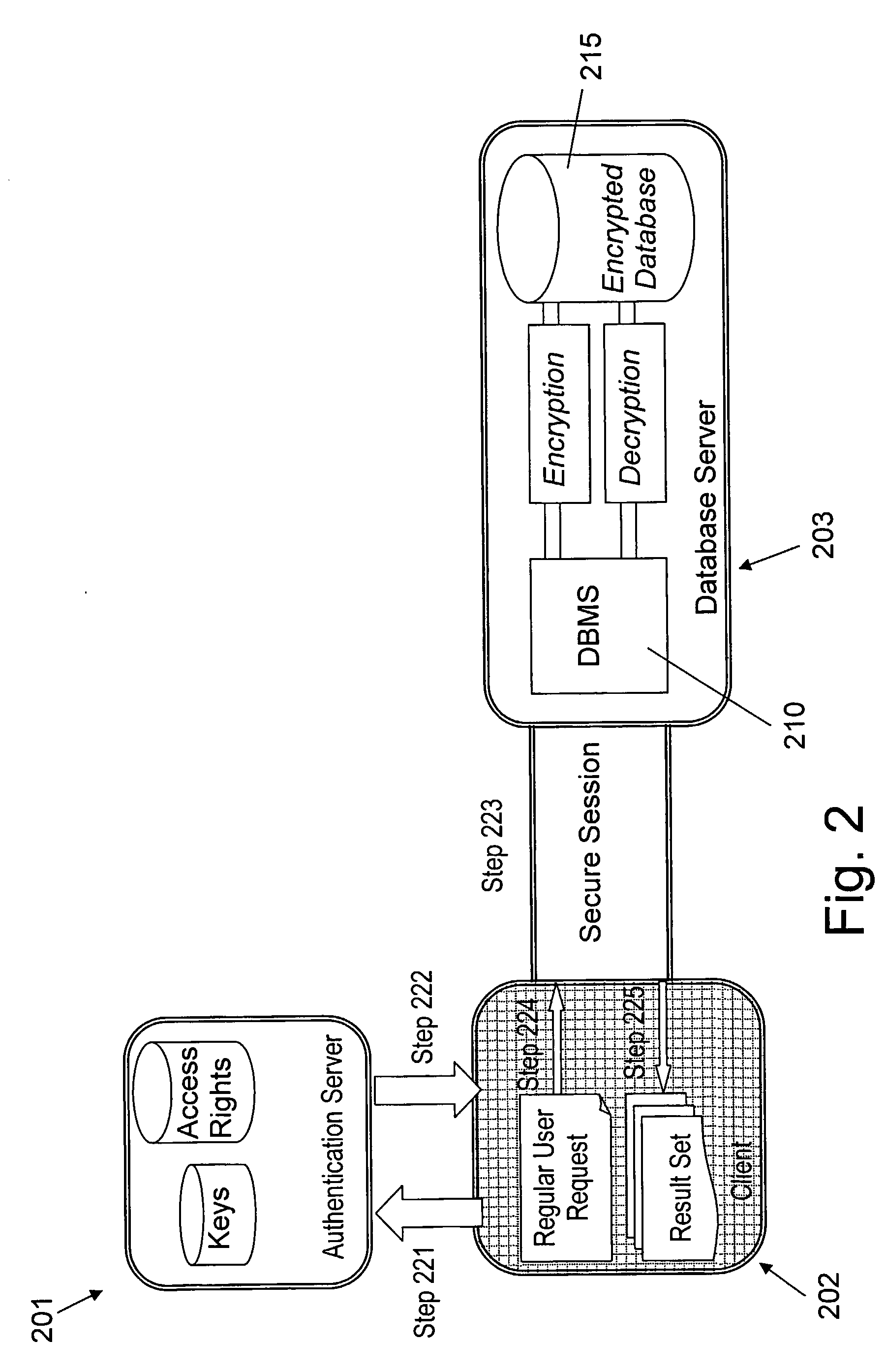
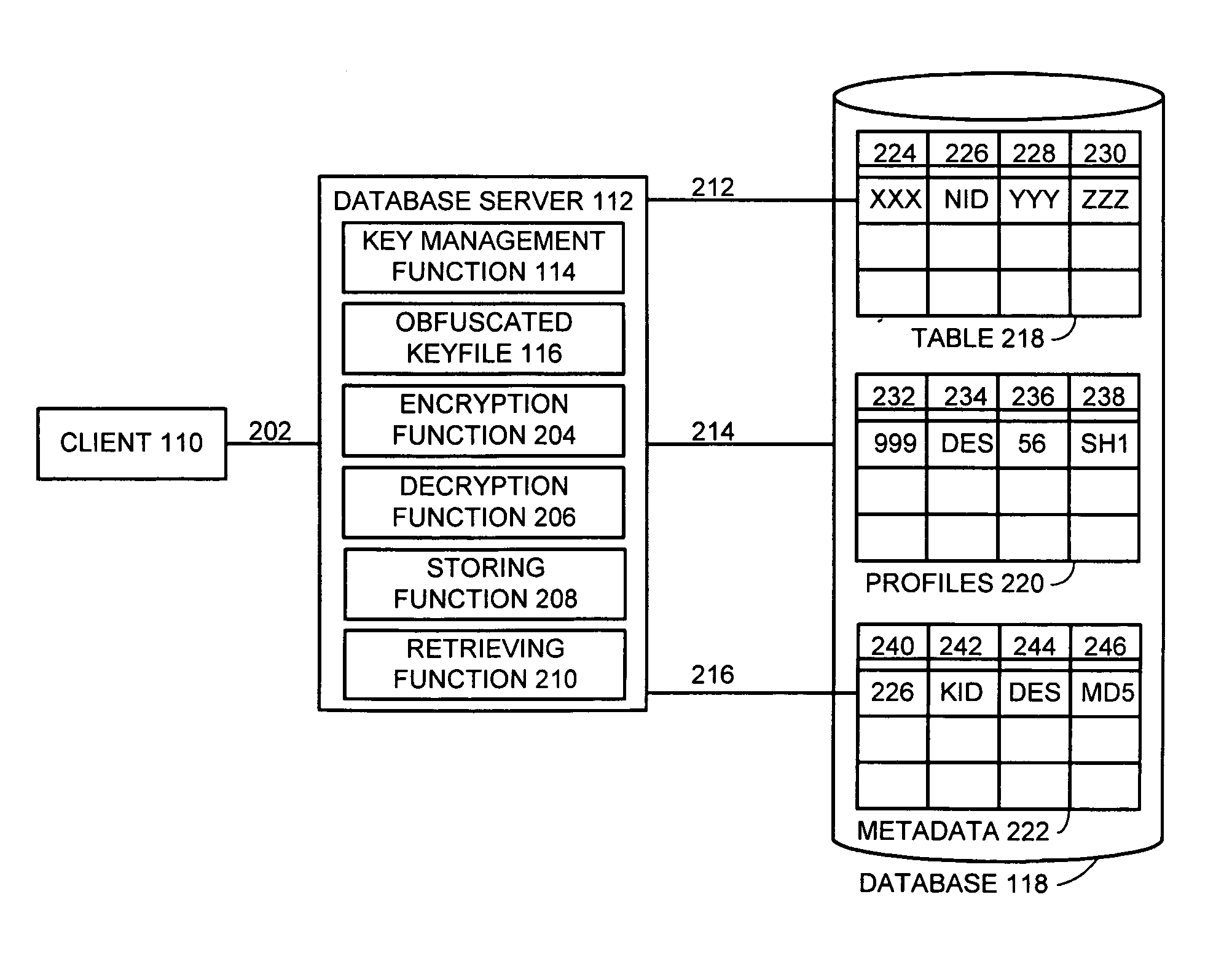
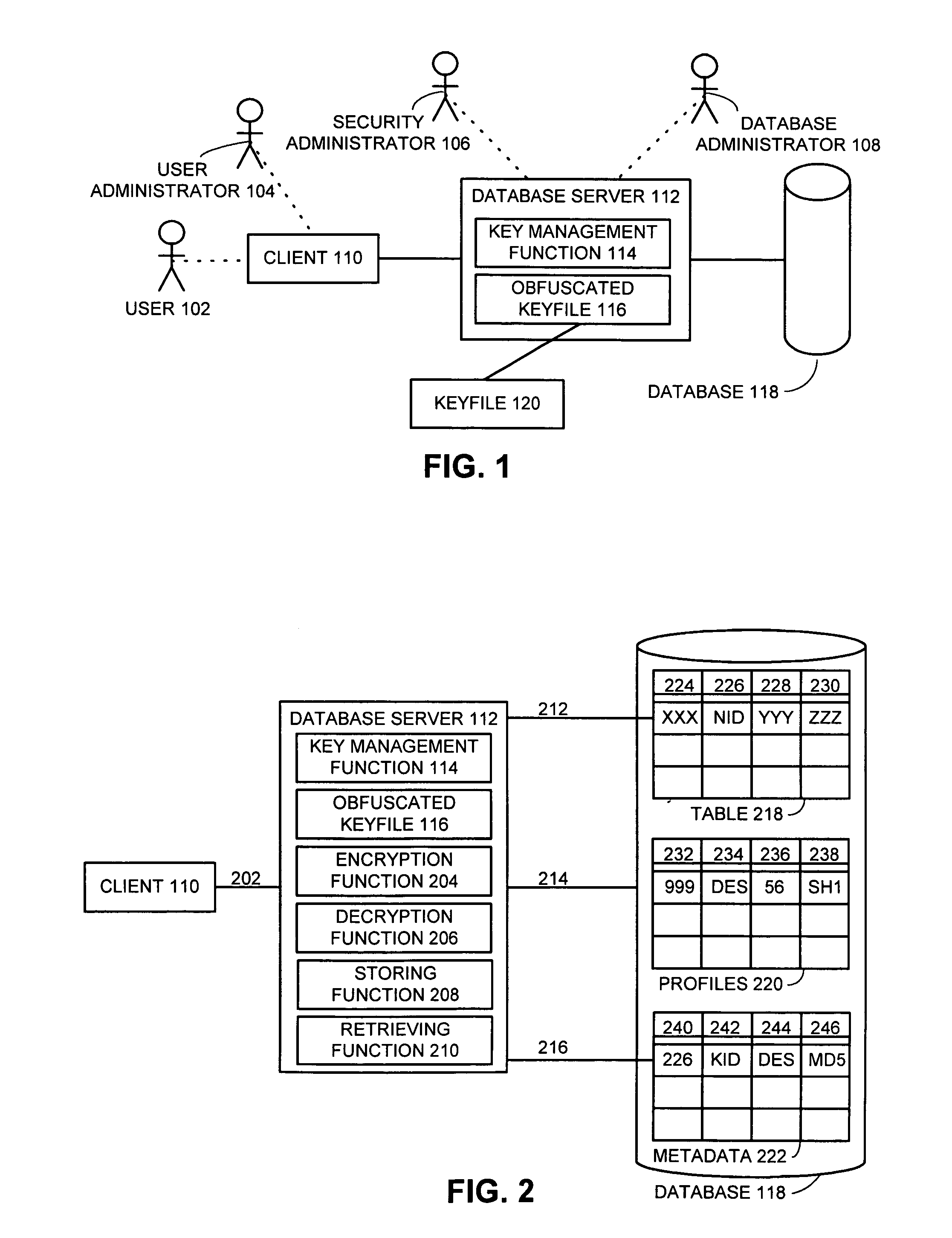
One embodiment of the present invention provides a system for managing encryption within a database system that is managed by a database administrator, and wherein a user administrator not otherwise associated with the database system, manages users of the database system. This system performs encryption automatically and transparently to a user of the database system. The system operates by receiving a request to store data in a column of the database system. If a user has designated the column as an encrypted column, the system automatically encrypts the data using an encryption function. This encryption function uses a key stored in a keyfile managed by the security administrator. After encrypting the data, the system stores the data in the database system using a storage function of the database system.
Owner:ORACLE INT CORP
Combined hardware and software based encryption of databases
InactiveUS6963980B1Increase flexibilityImprove performanceUser identity/authority verificationUnauthorized memory use protectionTamper proof hardwareRelational database
A relational database system for encryption of individual data elements comprising a encryption devices of at least two different types, the types being tamper-proof hardware and software implemented. The encryption processes of the system are of at least two different security levels, differing in the type of encryption device holding the process keys for at least one of the process key categories and also differing in which type of device executing the algorithm of the process. Each data element to be protected is assigned an attribute indicating the usage of encryption process of a certain security level.
Owner:PROTEGRITY CORP
Security data item level database encryption system
ActiveCN102236766ADigital data protectionSpecial data processing applicationsHash functionCiphertext
The invention relates to a security data item level database encryption method. Confidential data is encrypted by a data item level particle size; a hash function is used for deriving an encryption key of each data item according to a derived key and unique positioning information of the data item, even the data item encryption keys for encryption of all integral databases can be derived by using one key to reduce the using amount of the keys and facilitate key management; and a stream cipher algorithm is used for encrypting the data items to avoid filling. A ciphertext index is also encrypted by the stream cipher algorithm; each field (column) is encrypted by using the same key; therefore, searching keywords can be encrypted and then ciphertexts of corresponding fields are matched in spite of precise complete or incomplete searching. The method also has complete security functions of key management, secret sharing, security backup, mandatory access control, security connection and the like.
Owner:WANBANG CHARGING EQUIP CO LTD +1
Management system and method for user safety authority limit
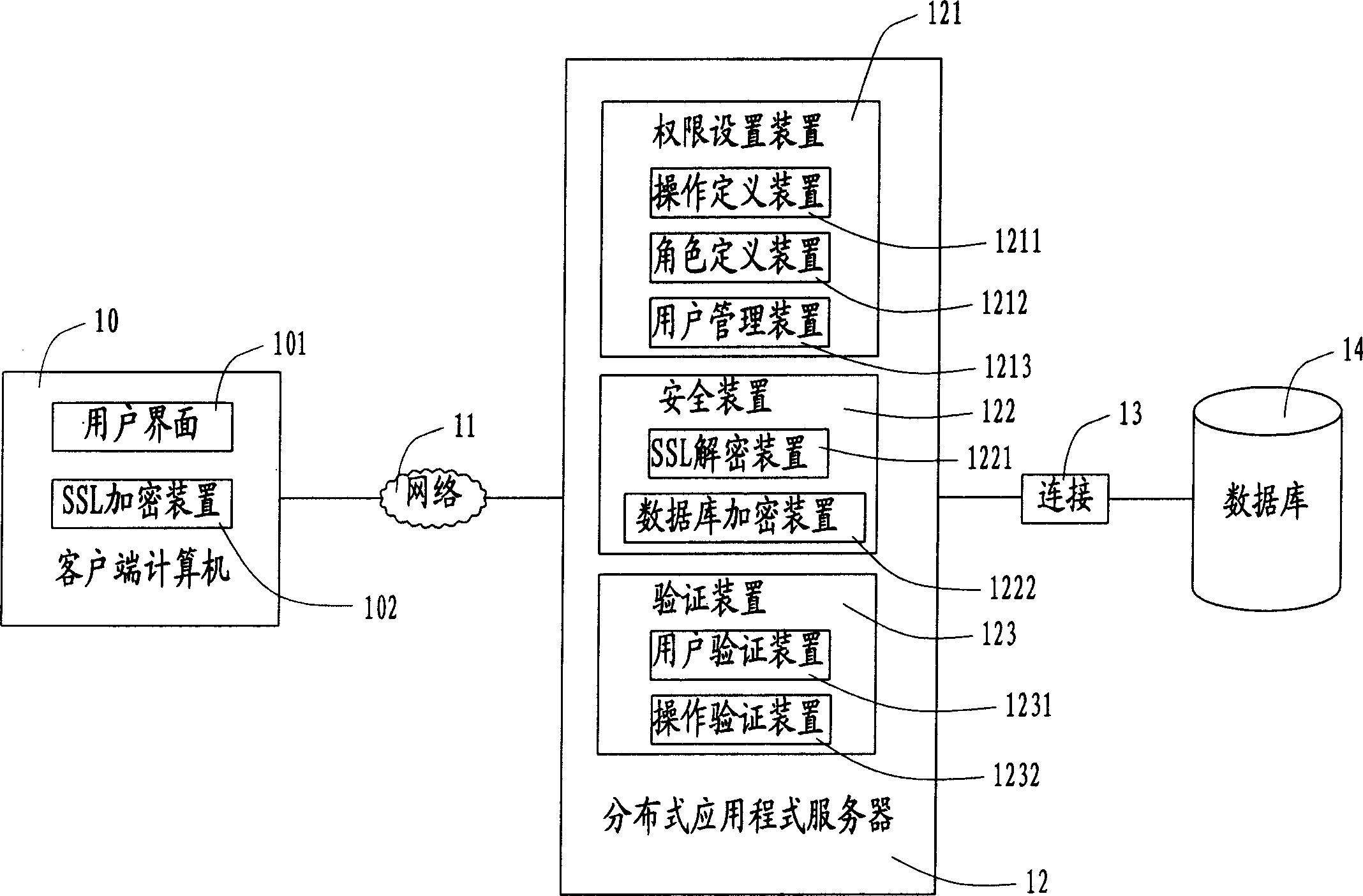
InactiveCN1485746AEnsure safetyGuaranteed scalabilityUnauthorized memory use protectionExtensibilitySafety management systems
The user authority safety management system and method, wherein the system comprises a plurality of client end computers, a distributed application program server and a data base, the user calls the application program device for proceeding operation definition and role definition through the user interface on the client end computer, and store the information into the database. The invention realizes the user authority control based the system operation, thus guaranteeing the expandability of the system.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
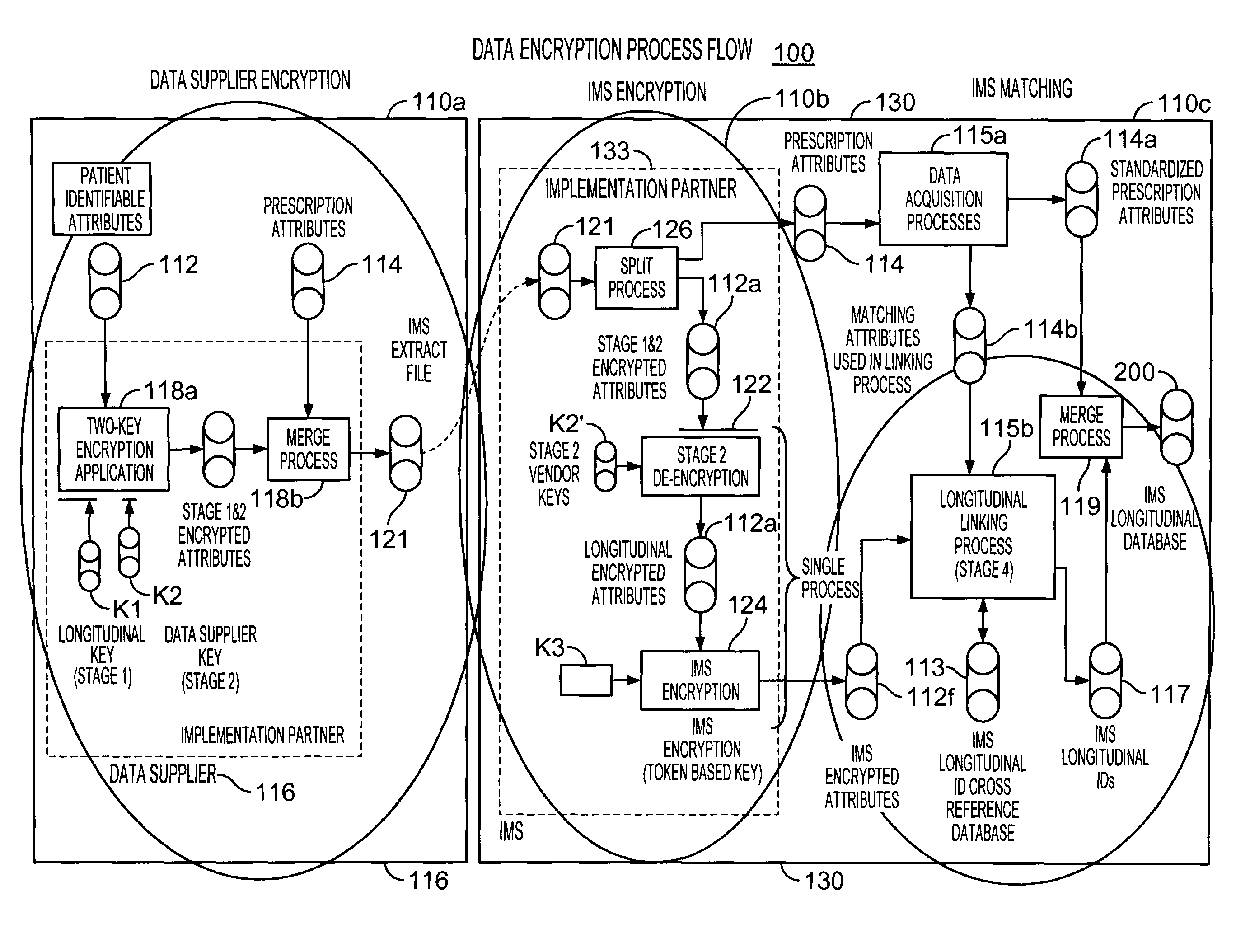
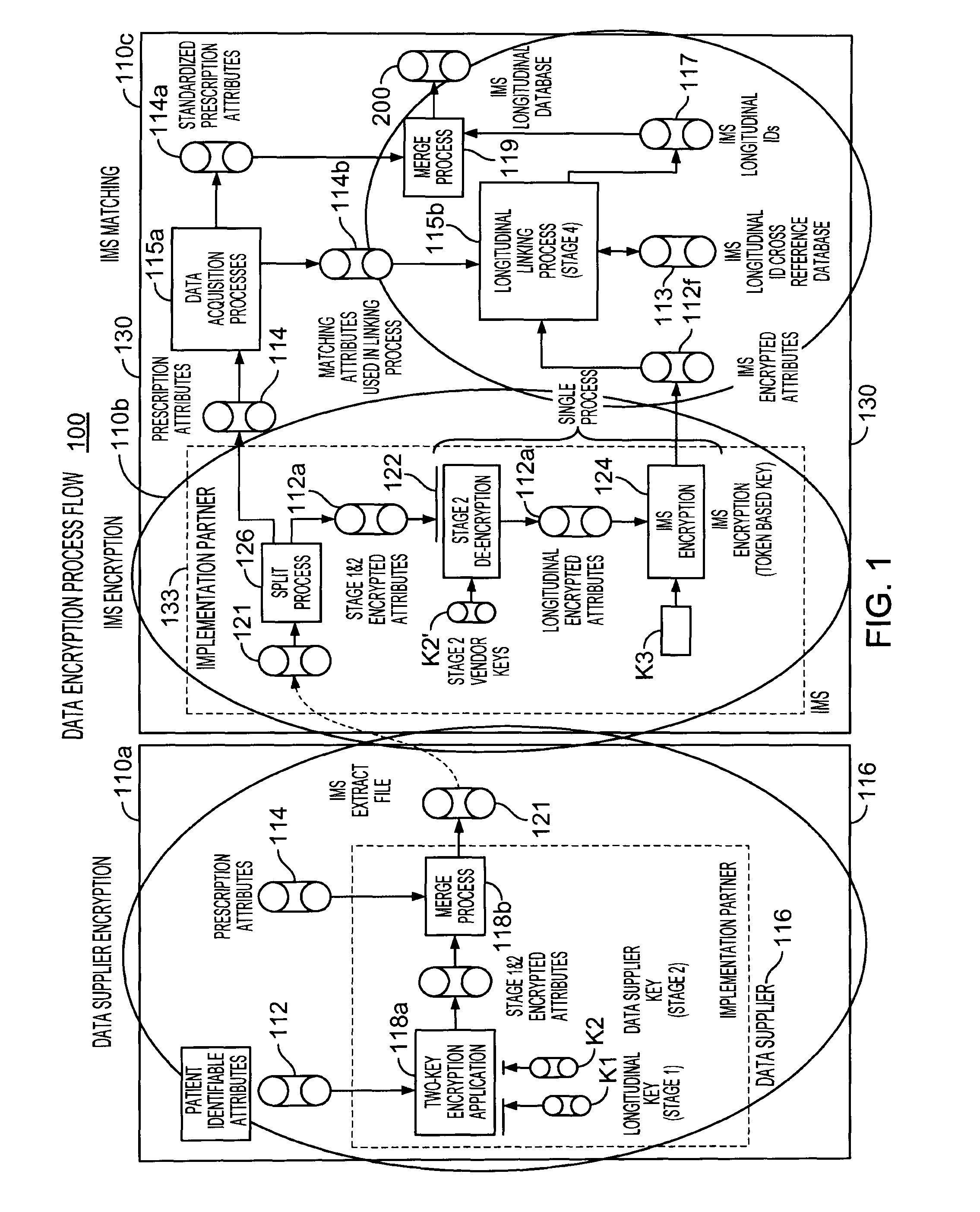
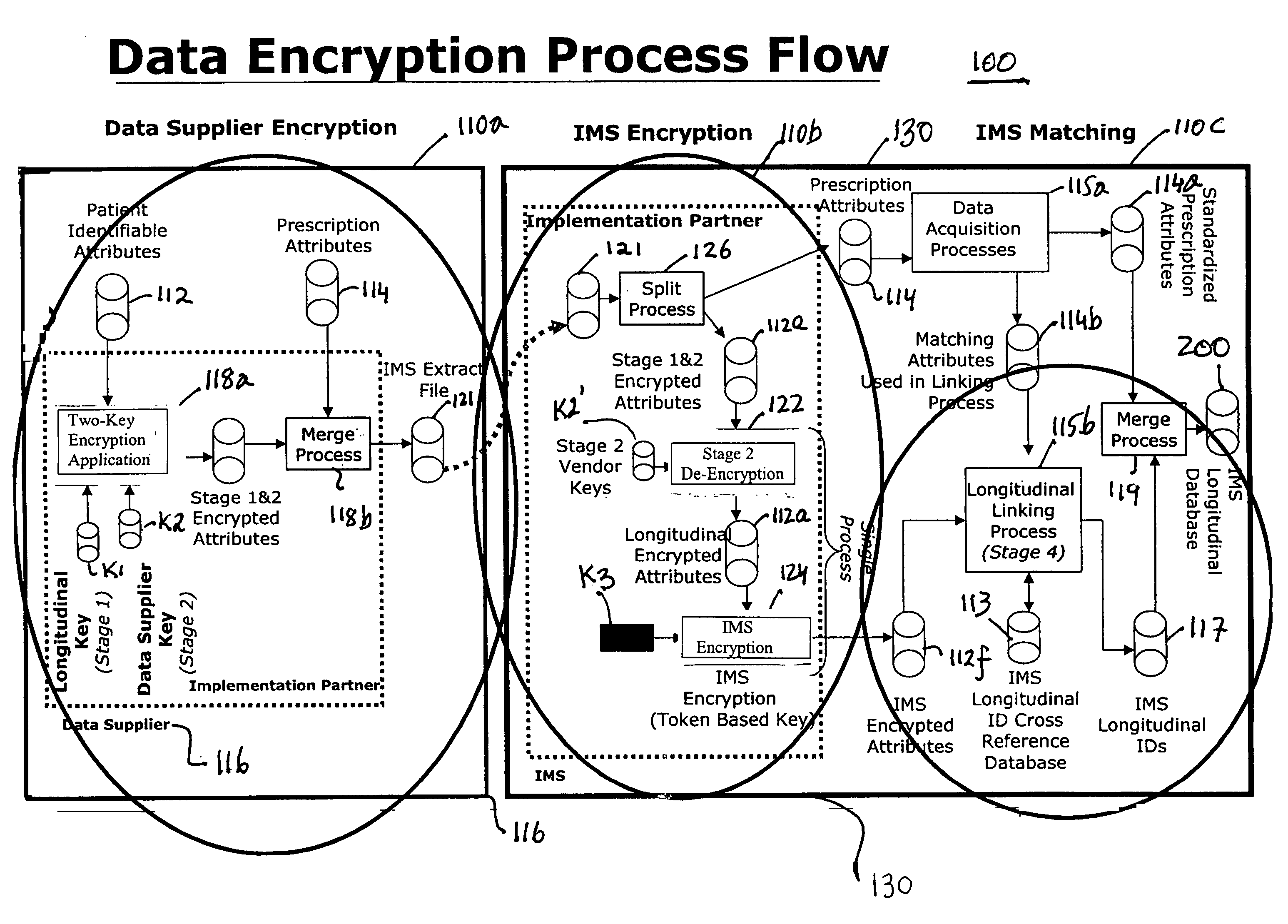
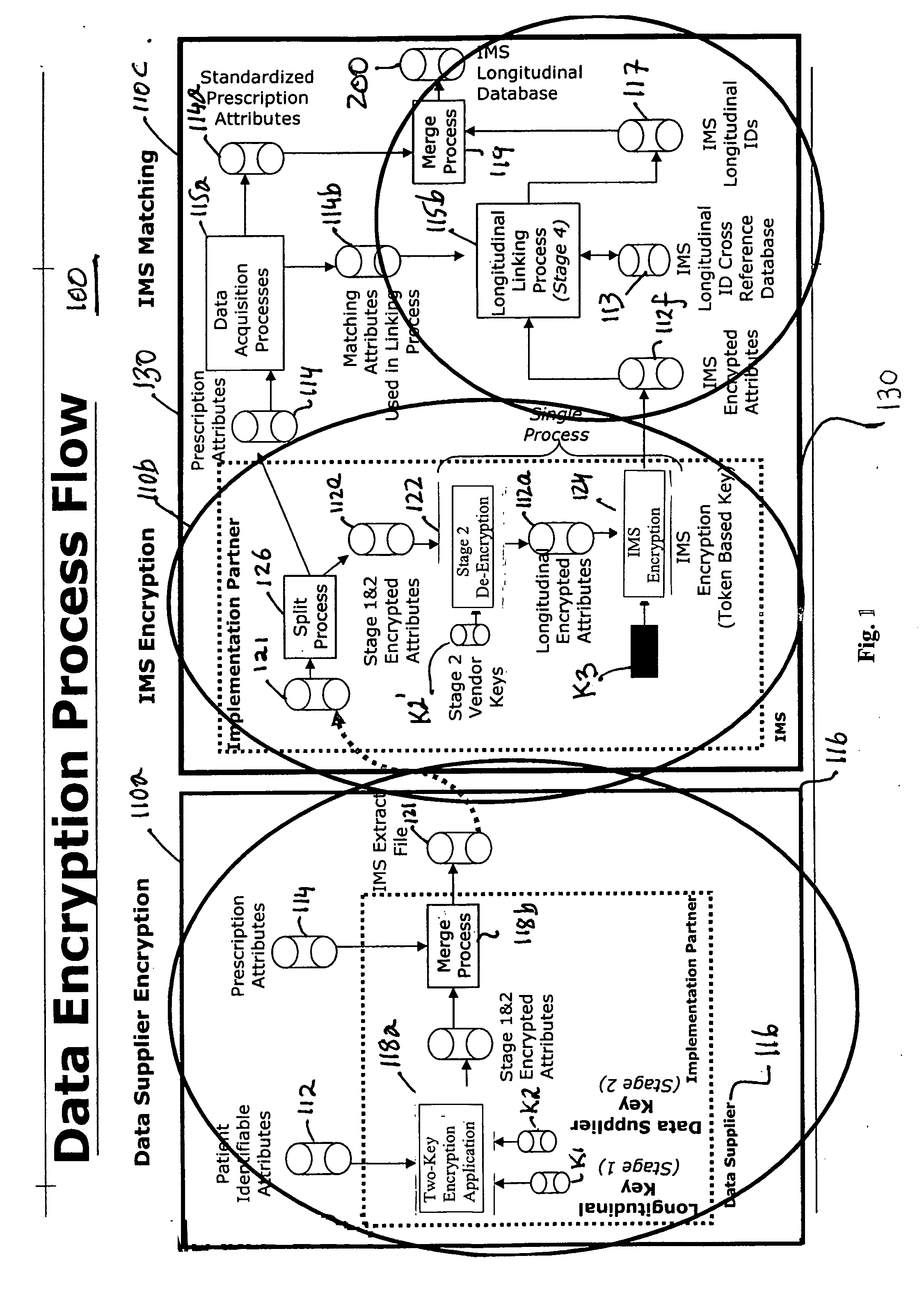
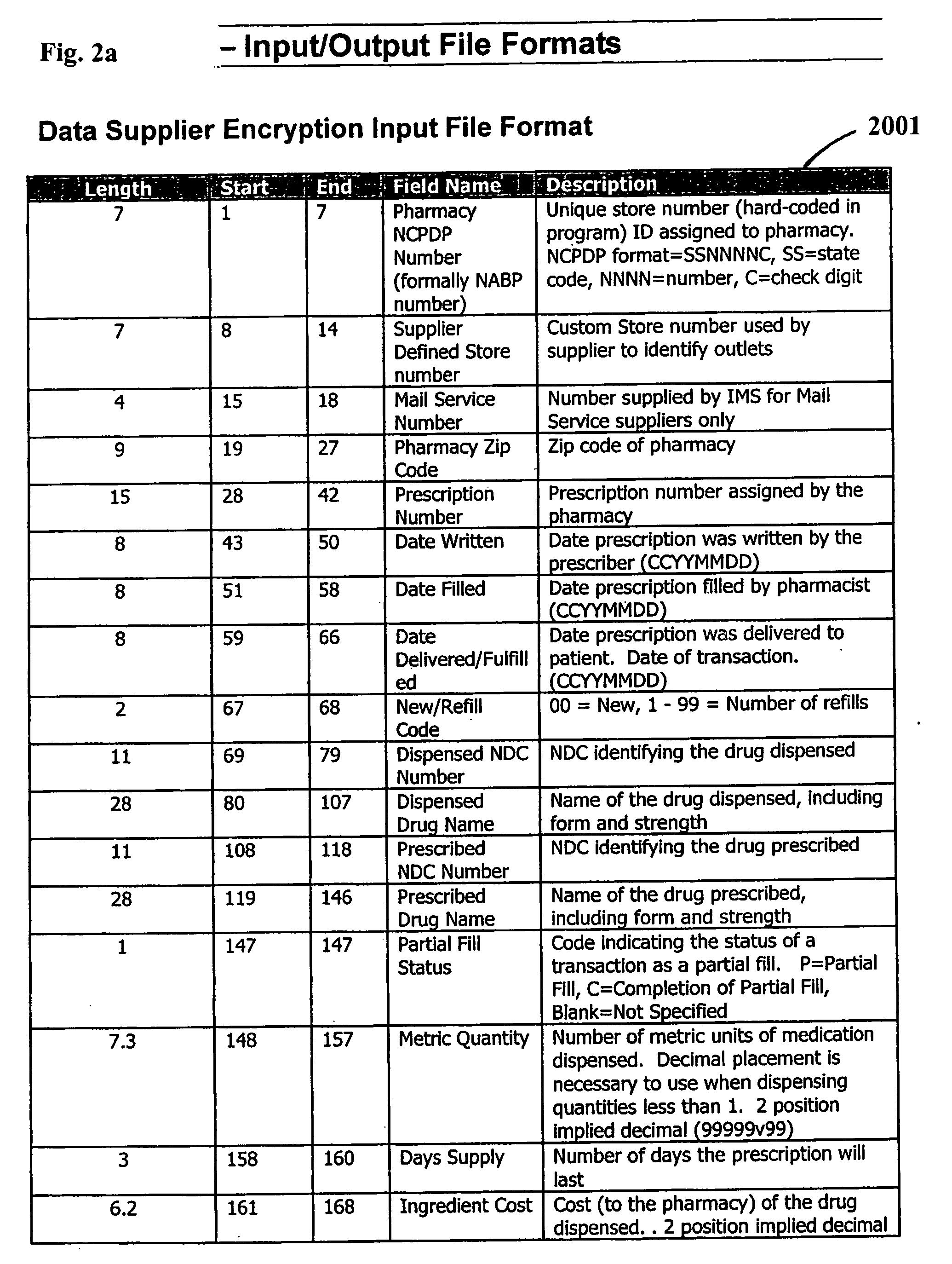
Multi-source longitudinal patient-level data encryption process
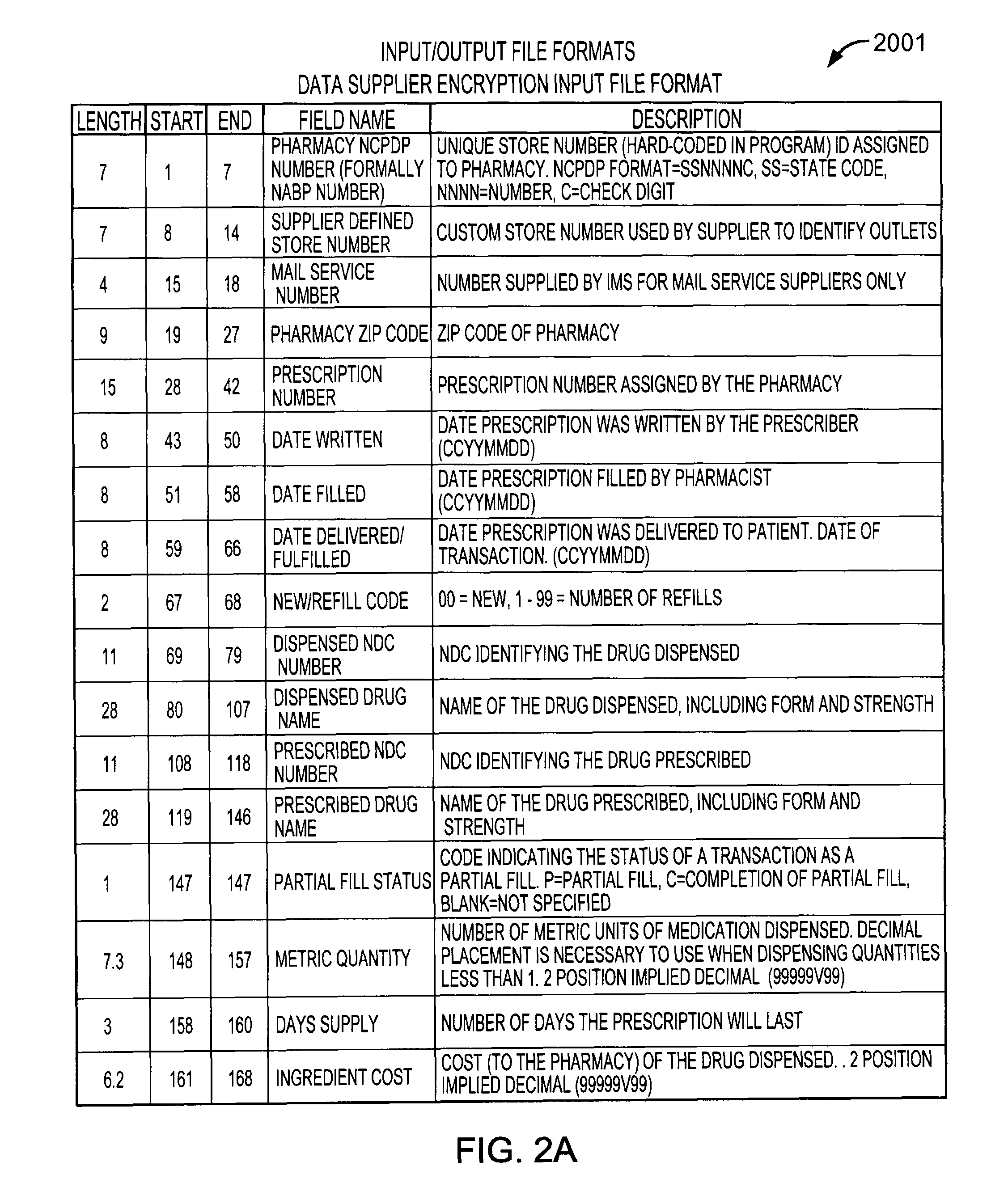
ActiveUS8275850B2Safely analyzeWithout riskDigital computer detailsComputer security arrangementsProcess systemsReference database
Systems and processes for assembling de-identified patient healthcare data records in a longitudinal database are provided. The systems and processes may be implemented over multiple data suppliers and common database facilities while ensuring patient privacy. At the data supplier locations, patient-identifying attributes in the data records are placed in standard format and then doubly encrypted using a pair of encryption keys before transmission to a common database facility. The pair of encryption keys includes a key specific to the data supplier and a key specific to the common database facility. At the common database facility, the encryption specific to the data supplier is removed, so that multi-sourced data records have only the common database encryption. Without direct access to patient identifying-information, the encrypted data records are assigned dummy labels or tags by which the data records can be longitudinally linked in the database. The tags are assigned based on statistical matching of the values of a select set of encrypted data attributes with a reference database of tags and associated encrypted data attribute values.
Owner:IMS SOFTWARE SERVICES
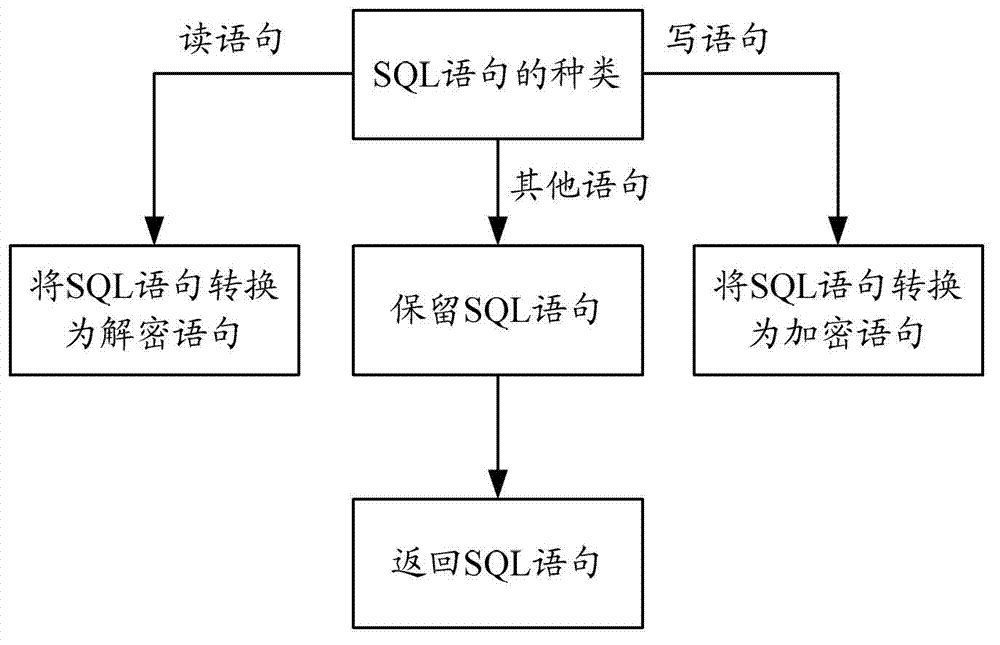
Structured query language (SQL) rewrite based database external encryption/decryption system and usage method thereof
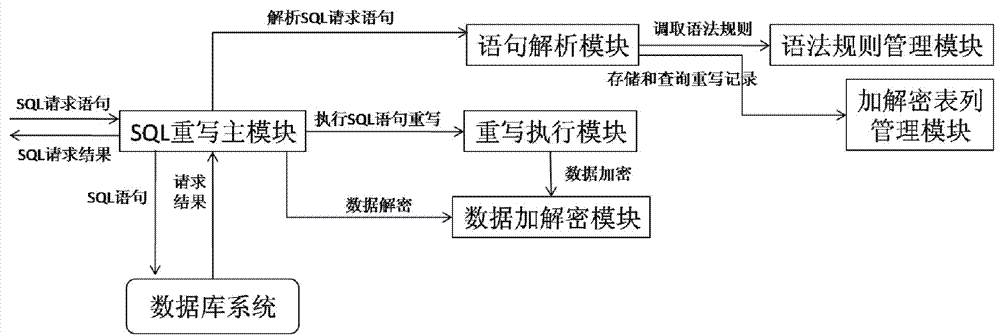
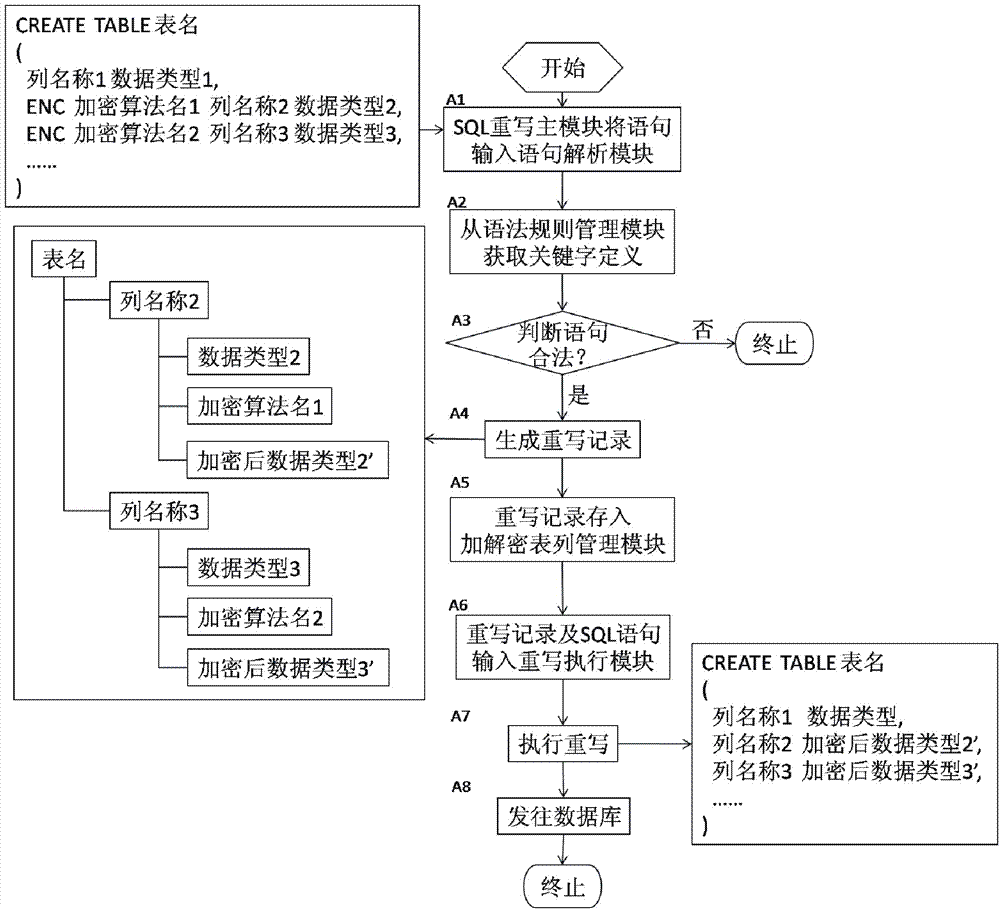
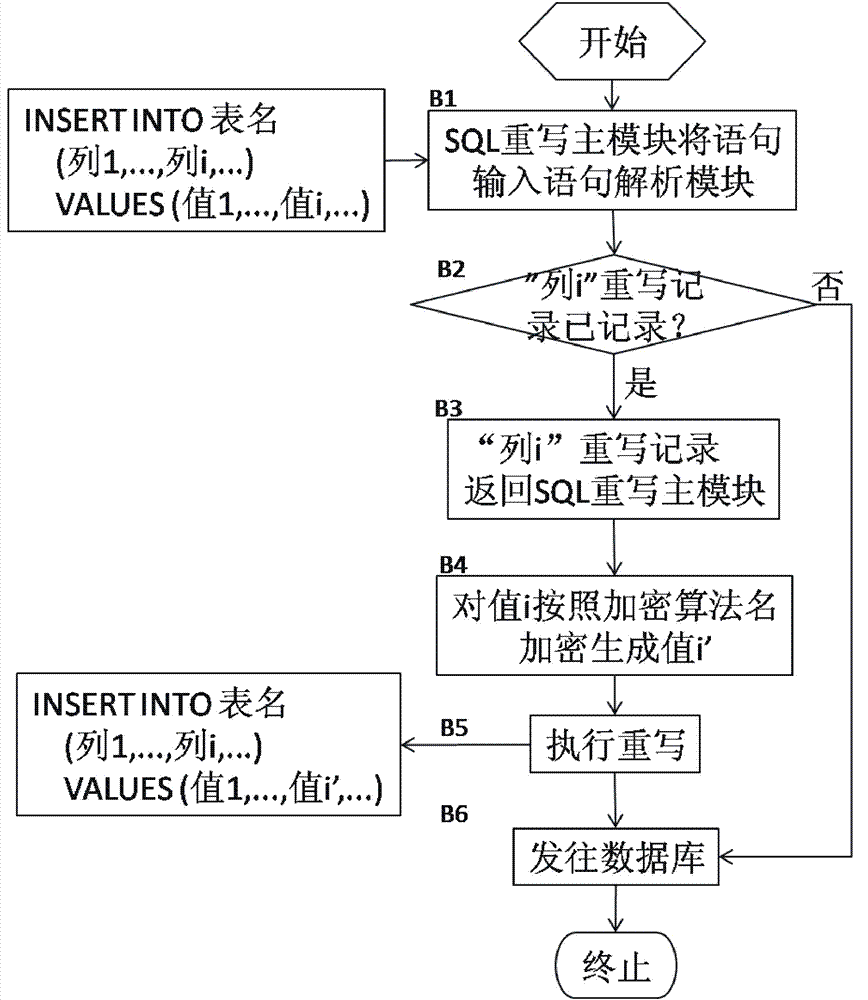
ActiveCN102902932AAvoid encryption and decryption overheadAvoid visitingDigital data protectionSpecial data processing applicationsDatabase encryptionData query
The invention provides an SQL rewrite based database external encryption / decryption system and a usage method thereof. The system comprises an SQL rewrite main module, a statement parsing module, a grammatical rule management module, an encryption / decryption table management module, a rewrite execution module and a data encryption / decryption module. The method comprises the steps of executing a rewritten data sheet creation process, a rewritten data insertion process and a data query process. According to the system and the method, an SQL rewrite technology is used, and data are encrypted and decrypted outside a database system, so that encryption / decryption costs of the database system are avoided.
Owner:武汉华工安鼎信息技术有限责任公司
Multi-source longitudinal patient-level data encryption process
ActiveUS20050268094A1Overcome data source varianceSafely analyzeDigital computer detailsComputer security arrangementsData providerMulti source data
Systems and processes for assembling de-identified patient healthcare data records in a longitudinal database are provided. The systems and processes may be implemented over multiple data suppliers and common database facilities while ensuring patient privacy. At the data supplier locations, patient-identifying attributes in the data records are placed in standard format and then doubly encrypted using a pair of encryption keys before transmission to a common database facility. The pair of encryption keys includes a key specific to the data supplier and a key specific to the common database facility. At the common database facility, the encryption specific to the data supplier is removed, so that multi-sourced data records have only the common database encryption. Without direct access to patient identifying-information, the encrypted data records are assigned dummy labels or tags by which the data records can be longitudinally linked in the database. The tags are assigned based on statistical matching of the values of a select set of encrypted data attributes with a reference database of tags and associated encrypted data attribute values.
Owner:IMS SOFTWARE SERVICES
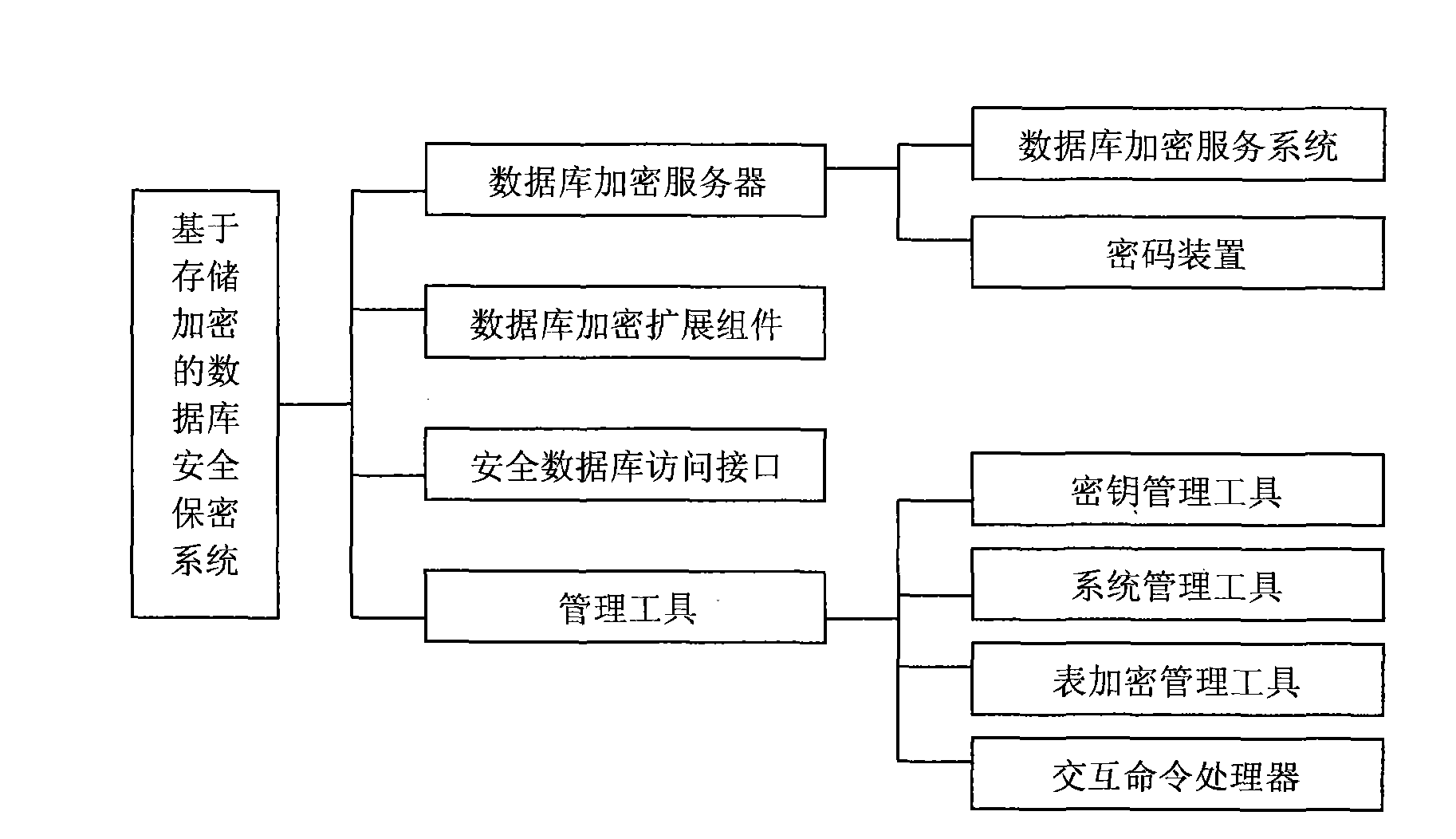
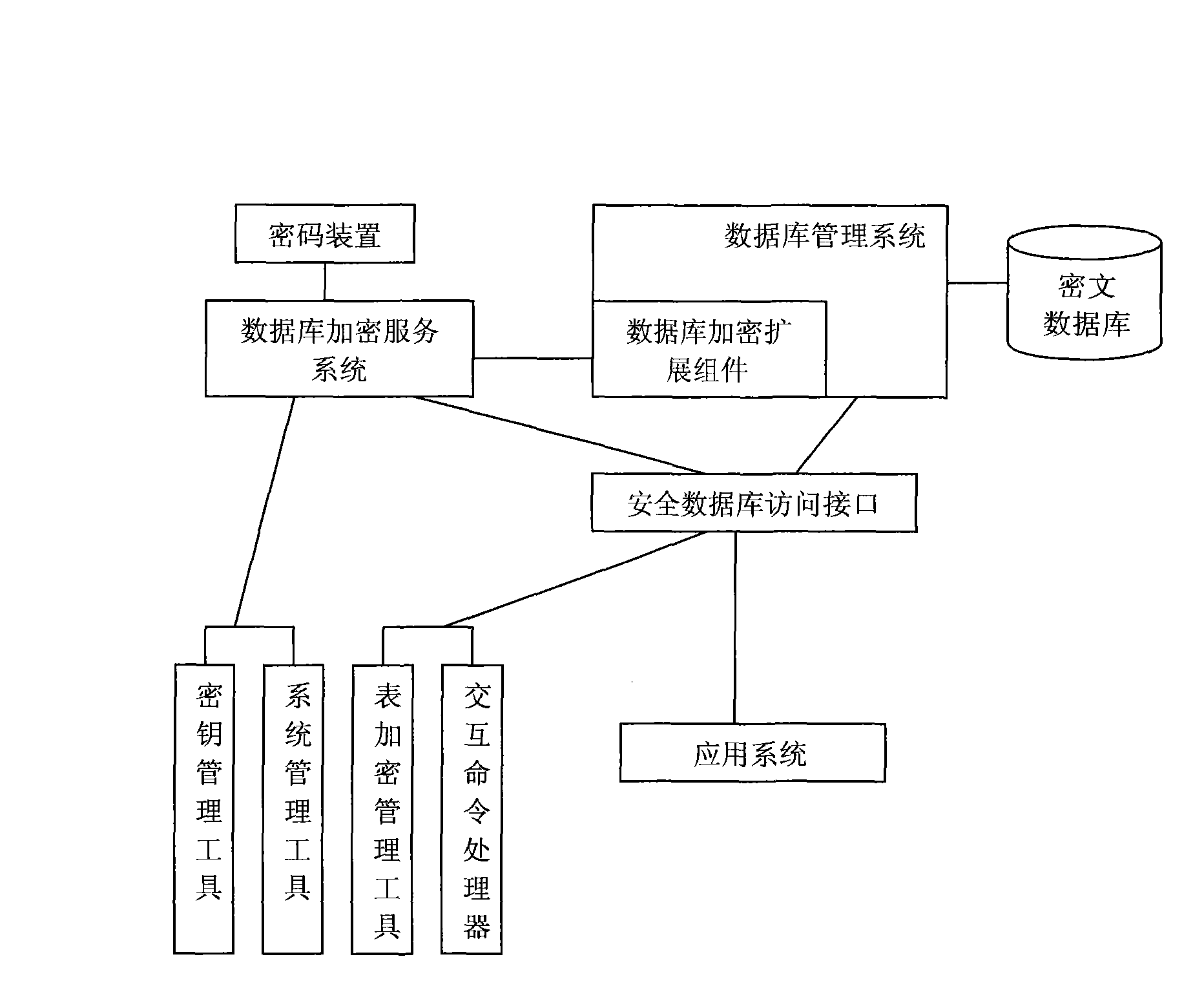
Database security system based on storage encryption
ActiveCN101639882AImplement encapsulationAchieve isolationDigital data protectionSpecial data processing applicationsManagement toolInterface standard
The invention provides a database security system based on storage encryption, comprising a database encryption server, a database encryption expansion component, a safe database access interface anda management tool. A database encryption service system encrypts and decrypts all data in the database security system and intensively applies safety control and management; the database encryption expansion component connects with the database encryption service system and a database management system and calls a cipher service function of the database safety service system to encrypt and decryptroutine data; the safe database access interface provides safe and transparent database access support to an application system; the management tool is used for safety configuration management by management personnel. The database security system provides an interface standard conforming to database access, supports transparent encryption and decryption of routine data and big data object, and screens complex details realizing the security function of the database for the application system.
Owner:HUAZHONG UNIV OF SCI & TECH +1
Structure preserving database encryption method and system
ActiveUS8639947B2Provide protectionKey distribution for secure communicationMultiple keys/algorithms usageDatabase indexMulti user environment
A database encryption system and method, the Structure Preserving Database Encryption (SPDE), is presented. In the SPDE method, each database cell is encrypted with its unique position. The SPDE method permits to convert a conventional database index into a secure one, so that the time complexity of all queries is maintained. No one with access to the encrypted database can learn anything about its content without the encryption key. Also a secure index for an encrypted database is provided. Furthermore, secure database indexing system and method are described, providing protection against information leakage and unauthorized modifications by using encryption, dummy values and pooling, and supporting discretionary access control in a multi-user environment.
Owner:BEN GURION UNIVERSITY OF THE NEGEV
Method and system for database encryption
ActiveUS20150178506A1Unauthorized memory use protectionHardware monitoringDatabase encryptionDatabase caching
A method for encrypting a database, according to which a dedicated encryption module is placed inside a Database Management Software above a database cache. Each value of the database is encrypted together with the coordinates of said value using a dedicated encryption method, which assumes the existence of an internal cell identifier that can be queried but not tampered.
Owner:BEN GURION UNIVERSITY OF THE NEGEV
Database encryption system, method and program
InactiveCN103392178APrevent leakageImprove processing efficiencyMultiple keys/algorithms usageDigital data protectionDatabase encryptionData storing
Owner:NEC CORP
Encipherment protection system and encipherment protection method for database in cloud computing environment
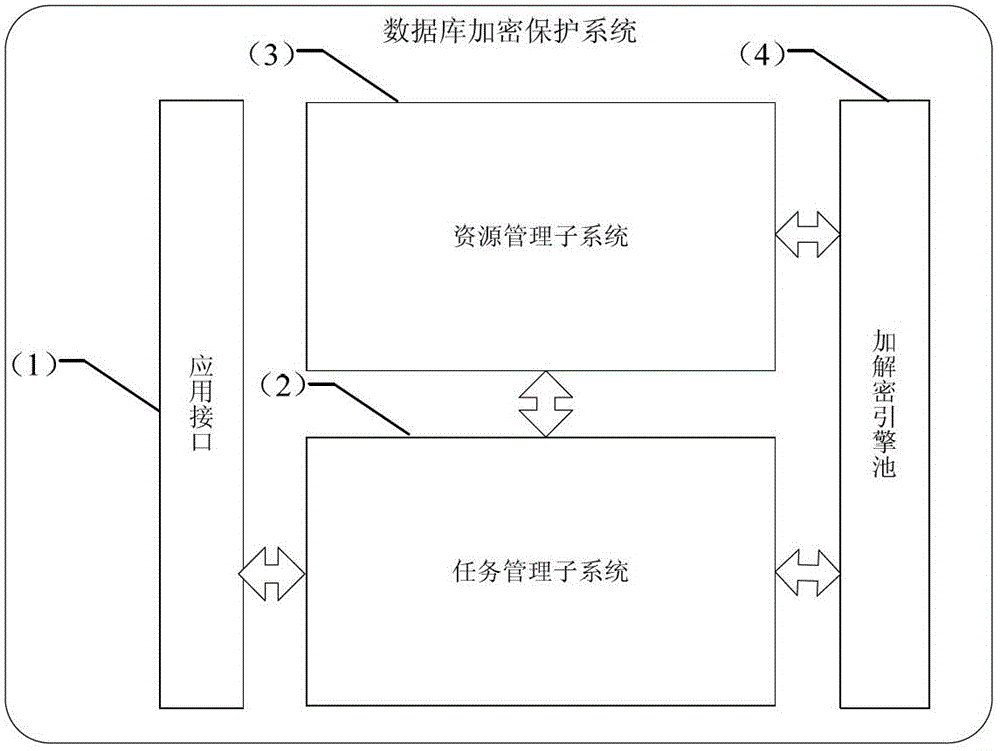
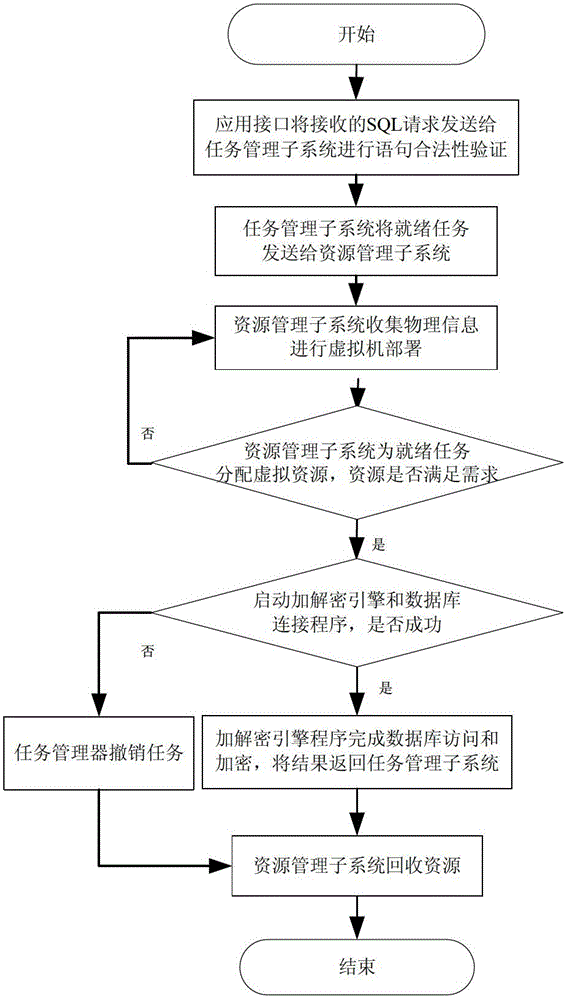
ActiveCN102722576ASolve the encryption protection problemAffect performance degradationComputer security arrangementsTransmissionPlaintextCiphertext
The invention provides an encipherment protection system and an encipherment protection method for a database in a cloud computing environment. The encipherment protection system provided by the invention comprises an application interface, a task management subsystem, a resource management subsystem and an encipherment engine pool. The encipherment protection system provided by the invention has the following advantages that 1. the encipherment protection system adopts the encipherment engine pool so as to avoid that the database performance is reduced by the influence of the overload operation of encipherment and decryption modules; 2. an application system is entirely transparent to final users of the database, so that the conversion between clear test and cipher text can be carried out according to the requirements; 3. the encipherment engine pool is fully independent from the database and the application system, so that the encipherment function of data can be realized without changing the database and the application system; 4. the encipherment engine pool constructed by using virtualization technologies has favorable manageability and elasticity, and can be constructed according to the requirements, the bottleneck problems of the fine granularity and the large concurrency access in the application of a relational database are solved, resources can be reasonably used, and the capability and the efficiency of a database server are enhanced.
Owner:XIAN FUTURE INT INFORMATION CO LTD +1
Ciphertext indexing method for database encryption and in-base encryption system
ActiveCN106934030AImprove reliabilityImprove retrieval performanceDigital data protectionSpecial data processing applicationsComputer hardwareHash function
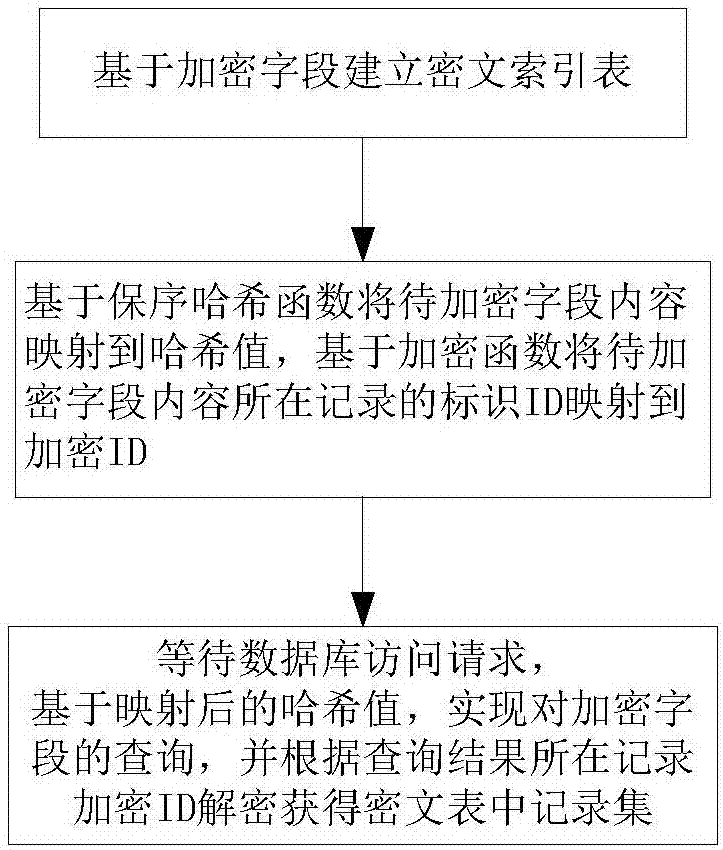
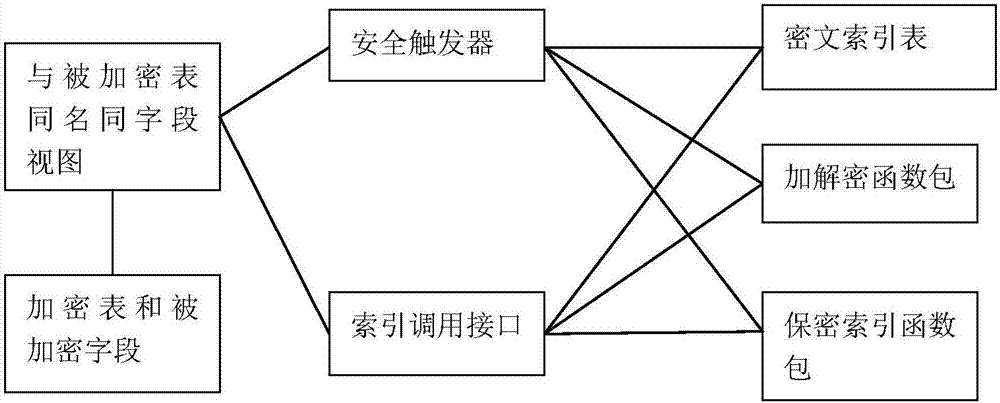
The invention relates to a ciphertext indexing method for database encrypted fields and an in-base encryption system and belongs to the field of information security technology. According to the method, first, identification ID is mapped to encryption ID based on an encrypted field P1, (encryption ID, Hash value) is saved into a T2(ID2, P2), finally, a ciphertext index table T2 is established, and the table where the encrypted field P1 exists is recorded as T1, wherein the table T2 comprises a ciphertext index field P2, and fields ID2 in one-to-one correspondence with records in the T1 are recorded in the T2; and then, content of a to-be-encrypted field is mapped to the Hash value based on an order-preserving Hash function, equivalent query and range query of the encrypted field are realized based on the Hash value obtained after the record of the content of the to-be-encrypted field is mapped to the Hash value based on an encryption function, decryption is performed on the recorded ID2 according to query results to obtain a record set in the T1, and the record set is returned. Compared with the prior art, the method is good in reliability and high in universality, meanwhile has high security and can guarantee extremely high retrieval and storage efficiency.
Owner:戴林
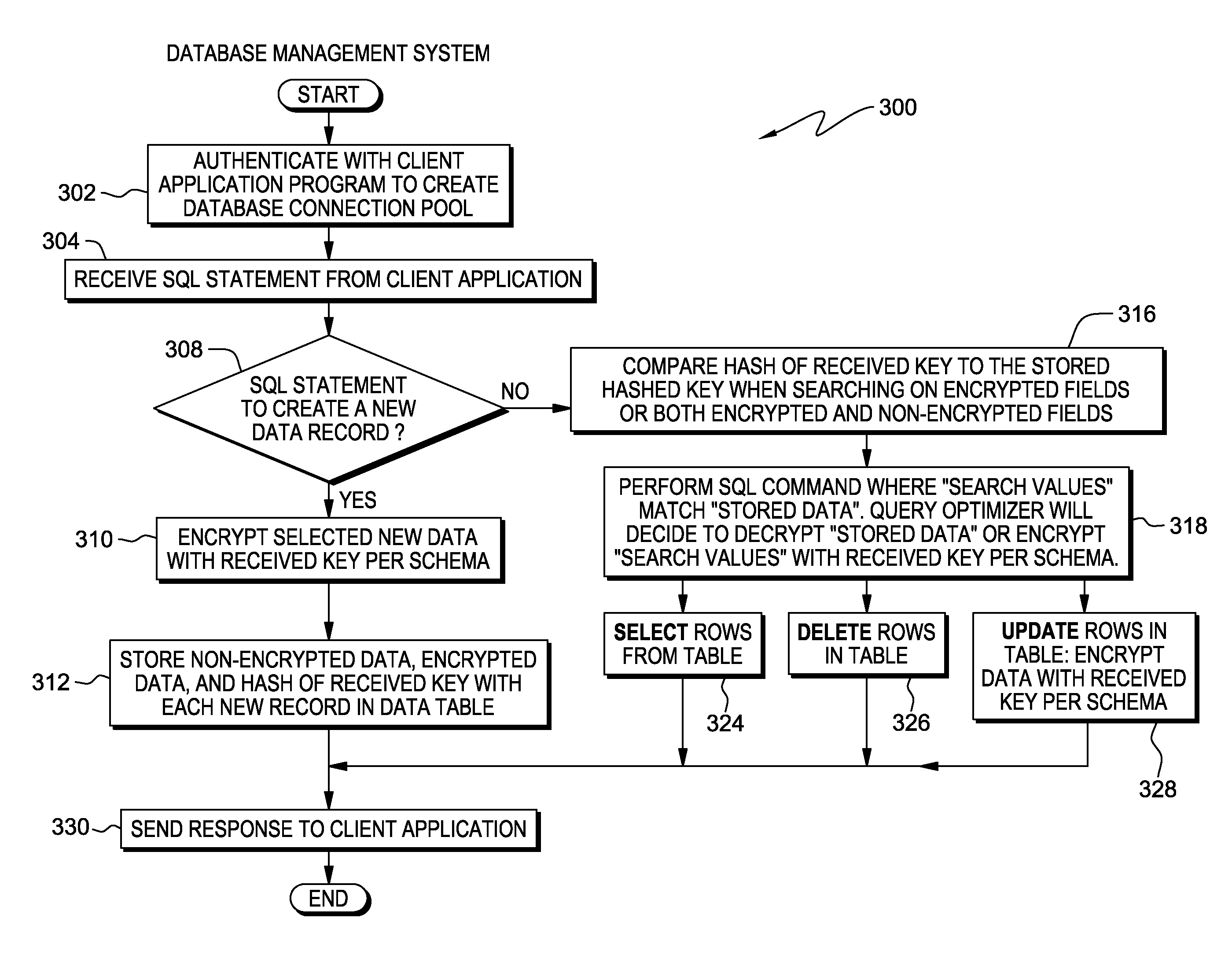
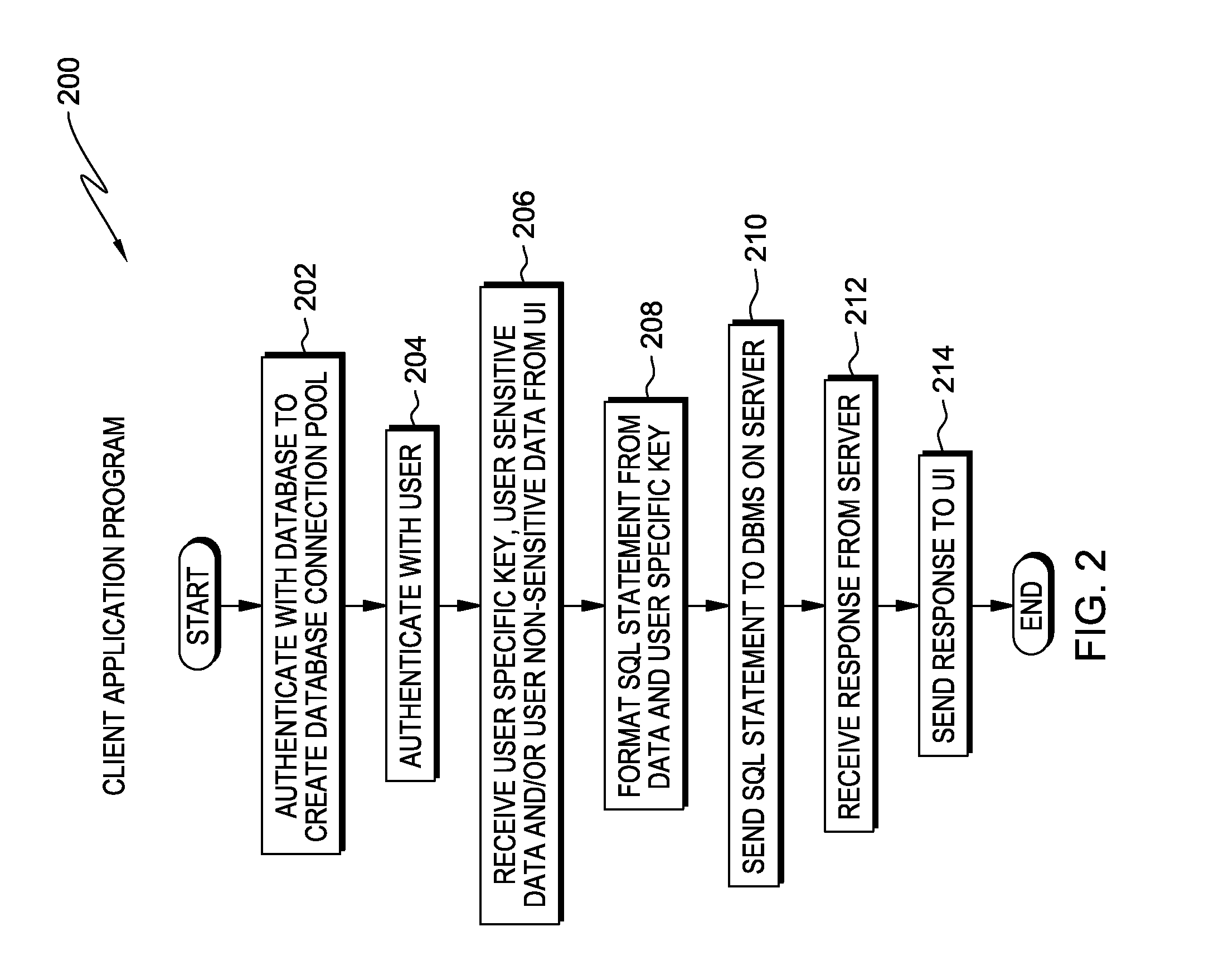
Field level database encryption using a transient key
Embodiments of the present invention disclose a method, system, and computer program product for implementing user specific encryption in a database system. A computer receives a query statement including a user specific key and data, the data including data needing encryption and non-encrypted data. The computer encrypts the data needing encryption using the user specific key. The computer inserts both the encrypted data and the non-encrypted data into a table row in a database. The computer creates a hash of the user specific key, and stores the hash of the user specific key in the table row with the data.
Owner:IBM CORP
Format preserving-based database transparent encryption method
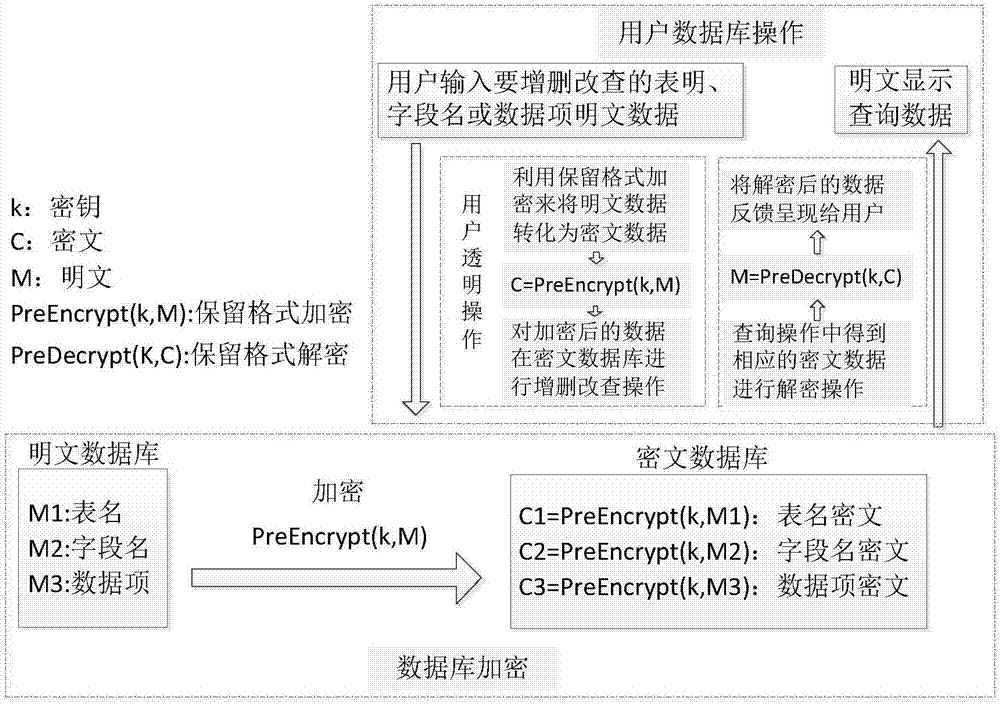
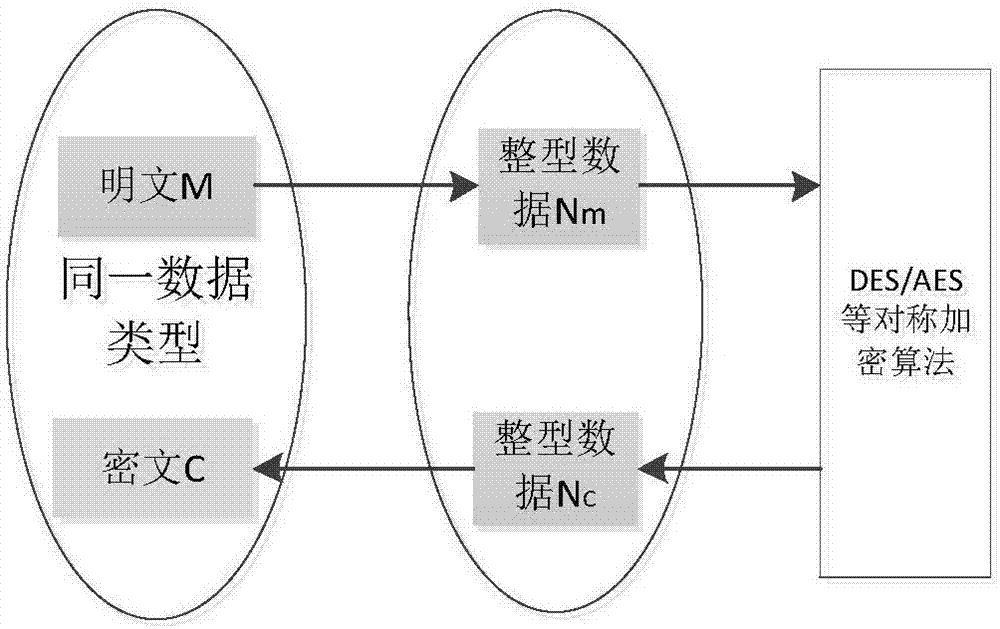
The invention provides a format preserving-based transparent database encryption method. The security of a database can be effectively protected and storage is performed in a ciphertext form. A legal user can be transparentized; the same addition, deletion, modification and query methods as a non encrypted database are provided; and use of the user is not influenced. According to the method, a record in each data item of the database is encrypted in a format preserving encryption manner, so that the record can be stored in the database in the form of a ciphertext with the same data type. When the user needs to perform addition, deletion, modification and query on the encrypted database, a plaintext field input by the user is encrypted and converted into the ciphertext with the same data type, thereby enabling the plaintext field to be consistent with the data in the encrypted database; and a result obtained by a query is decrypted and presented to the user in a plaintext form, so that the user is transparentized.
Owner:GUANGDONG UNIV OF TECH
Field-level database encryption device
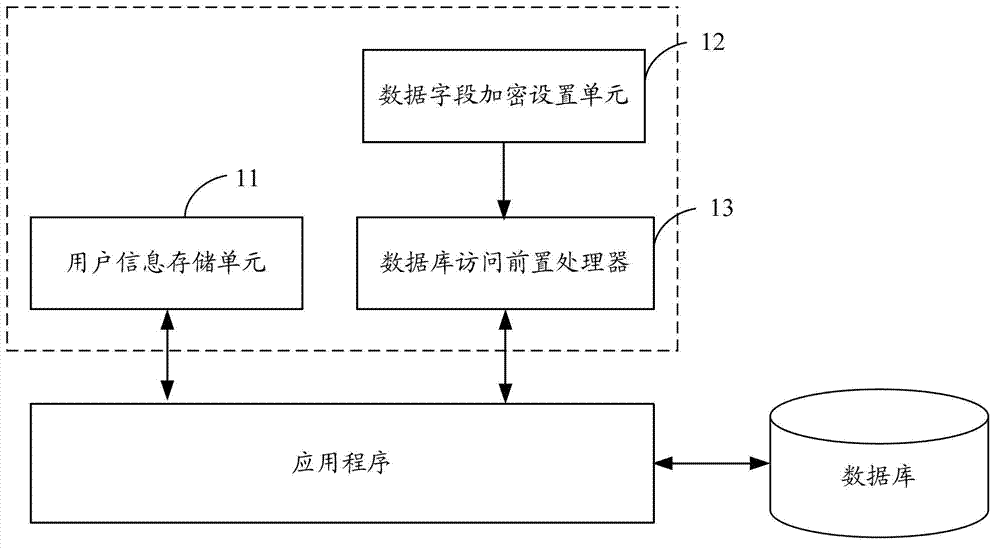
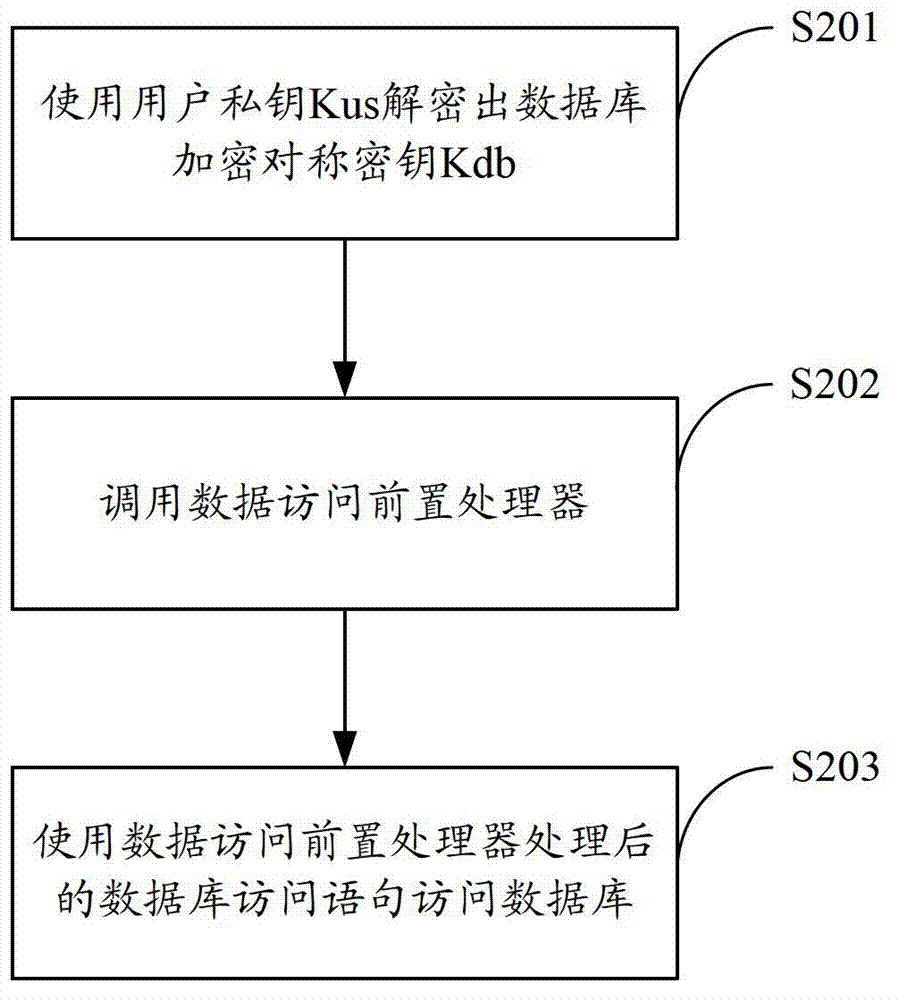
InactiveCN102855448ASupport full-text search functionDigital data protectionSpecial data processing applicationsApplication softwareInformation security
The invention is suitable for the field of information security and provides a field-level database encryption device, which comprises a user information storage unit, a database field encryption setting unit and a database access preprocessor, wherein the user information storage unit is used for storing database encryption symmetric keys which are encrypted through user public keys; the database field encryption setting unit is used for setting whether fields in a database are encrypted or not; and the database access preprocessor is used for conducting encryption conversion or decryption conversion to database access statements according to the decrypted database encryption symmetric keys and field encryption setting information in the database field encryption setting unit. By using the field-level database encryption device, a user can select different symmetric encryption algorithms supported by a database system according to demands for different encryption intensities, an application program does not need to conduct encryption or decryption operation to the database, all data encryption and decryption operations are completed by the database system, a full-text retrieval function of data items can be supported, and the original database access statements are not needed to be changed and can be directly and transparently used.
Owner:SHENZHEN LIMING NETWORK SYST CO LTD +1
Method and system for database encryption
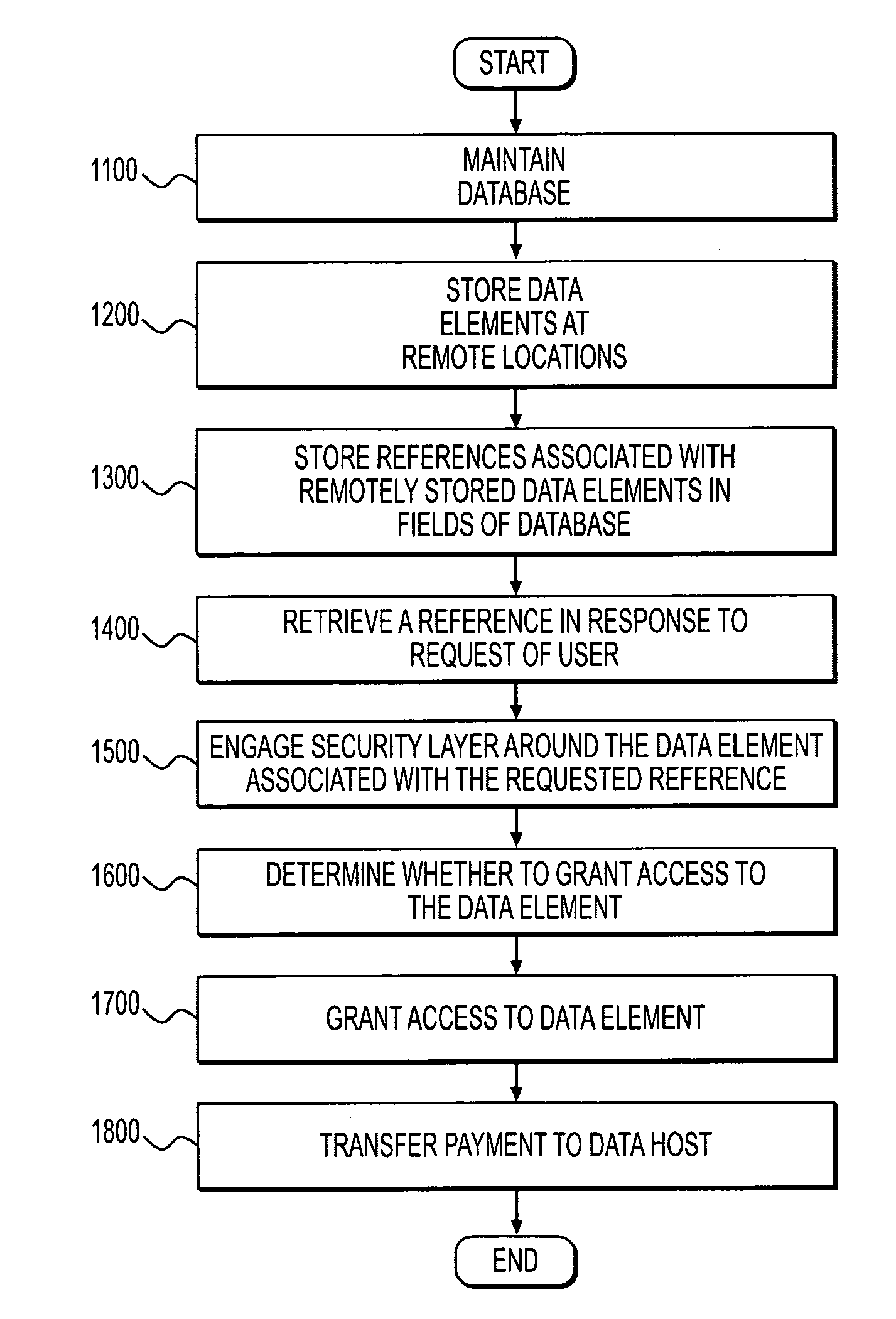
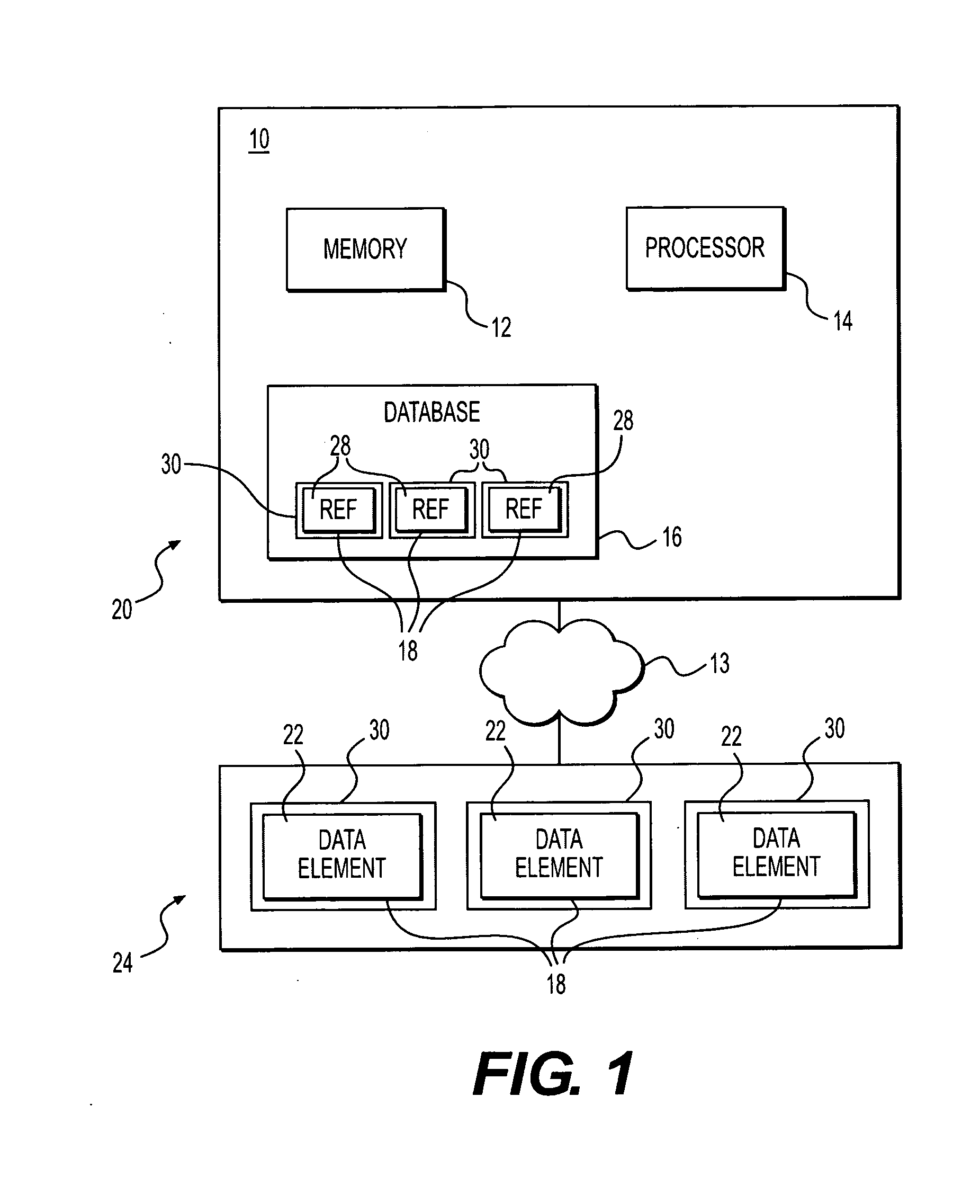
InactiveUS20120054489A1Digital data information retrievalComputer security arrangementsIp addressCryptographic protocol
The present disclosure is directed to a method for database encryption, which includes maintaining a database having fields and storing one or more data elements in a location associated with an IP address, wherein the IP address is 128 bits or greater and wherein the location of the IP address is remote from the location at which the database is maintained. The method may include storing, in at least one field of the database, a reference including an IP address corresponding with at least one of the data elements. In addition, the method may include retrieving the reference responsive to a request received from a user. Further, the method may include engaging a security layer around the data element, including performing at least one security check according to a security protocol, and determining whether to grant access to the at least one data element based on the security protocol.
Owner:UNIV BANK
Method and system for partial matching query of encrypted field in database
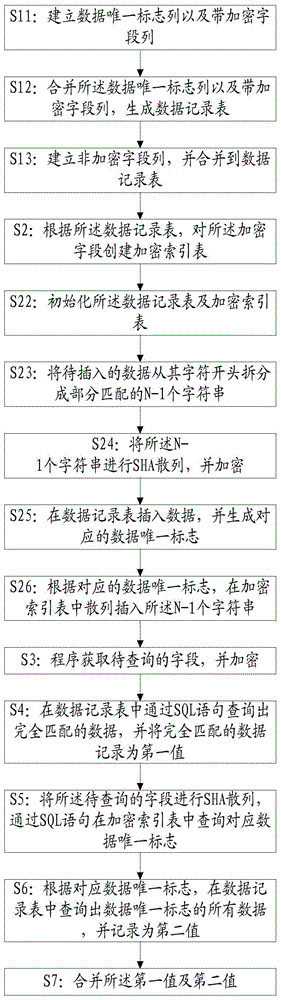
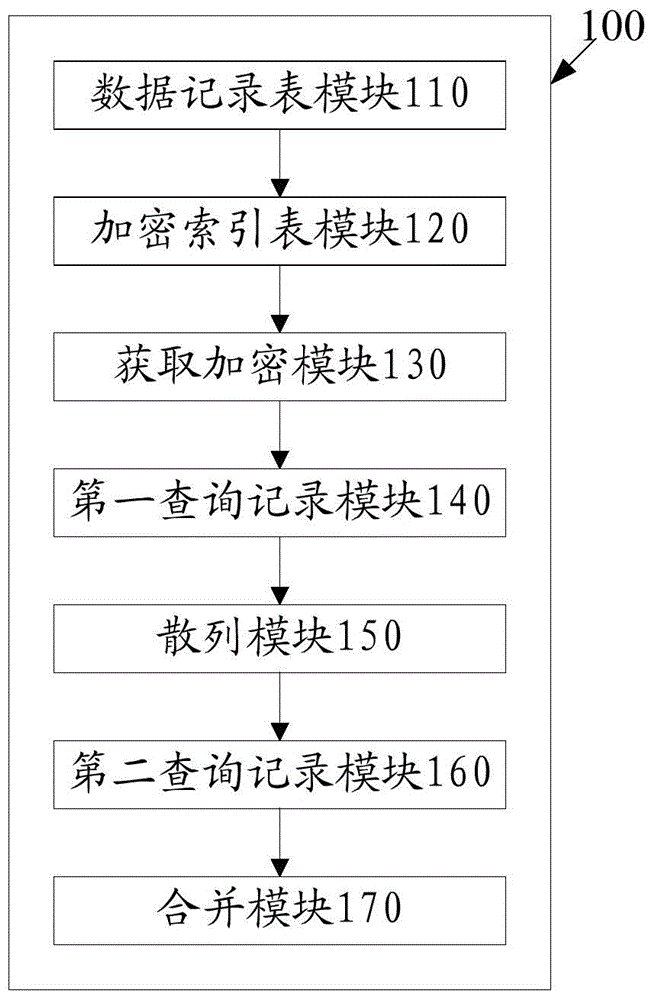
ActiveCN105138585AEasy to operateImprove efficiencySpecial data processing applicationsUsabilityDatabase encryption
The invention discloses a method and a system for partial matching query of an encrypted field in a database. The method comprises the following steps: creating a data record table; creating an encrypted index table for the encrypted field according to the data record table; obtaining and encrypting a to-be-queried field by program; querying completely matched data from the data record table through a structured query language (SQL) sentence, and recording the completely matched data as first values; carrying out secure hash algorithm (SHA) hashing on the to-be-queried field, and querying a corresponding unique data identifier from the encrypted index table through the SQL sentence; and querying all data with the unique data identifier in the data record table according to the corresponding unique data identifier, and recording the data as second values; and merging the first values with the second values. In the manner, an encryption scheme can be used only by partial matching query of the field under the condition of ensuring the performance, so that the safety and the usability of the system are improved.
Owner:FUJIAN TQ DIGITAL
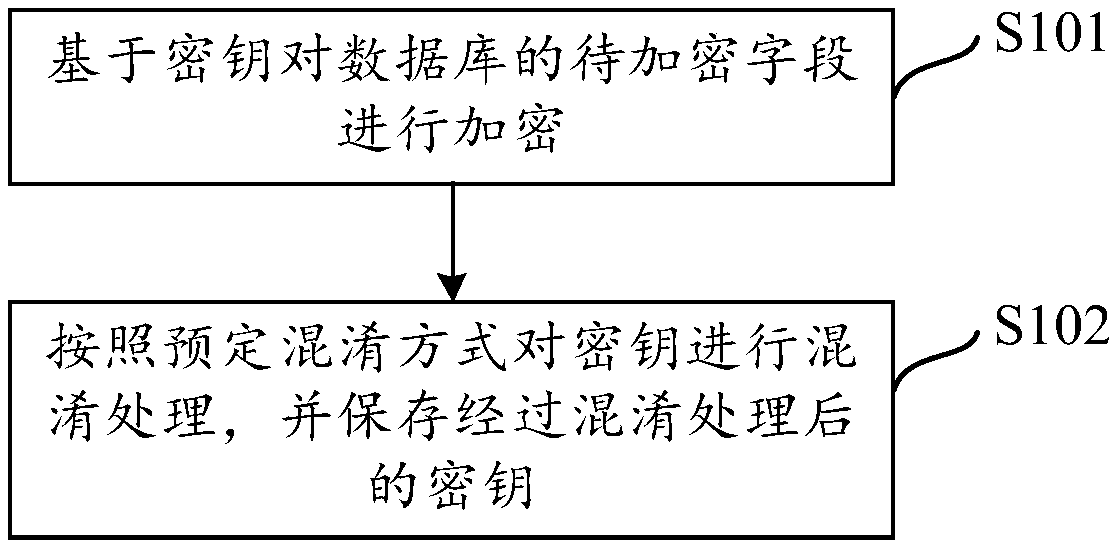
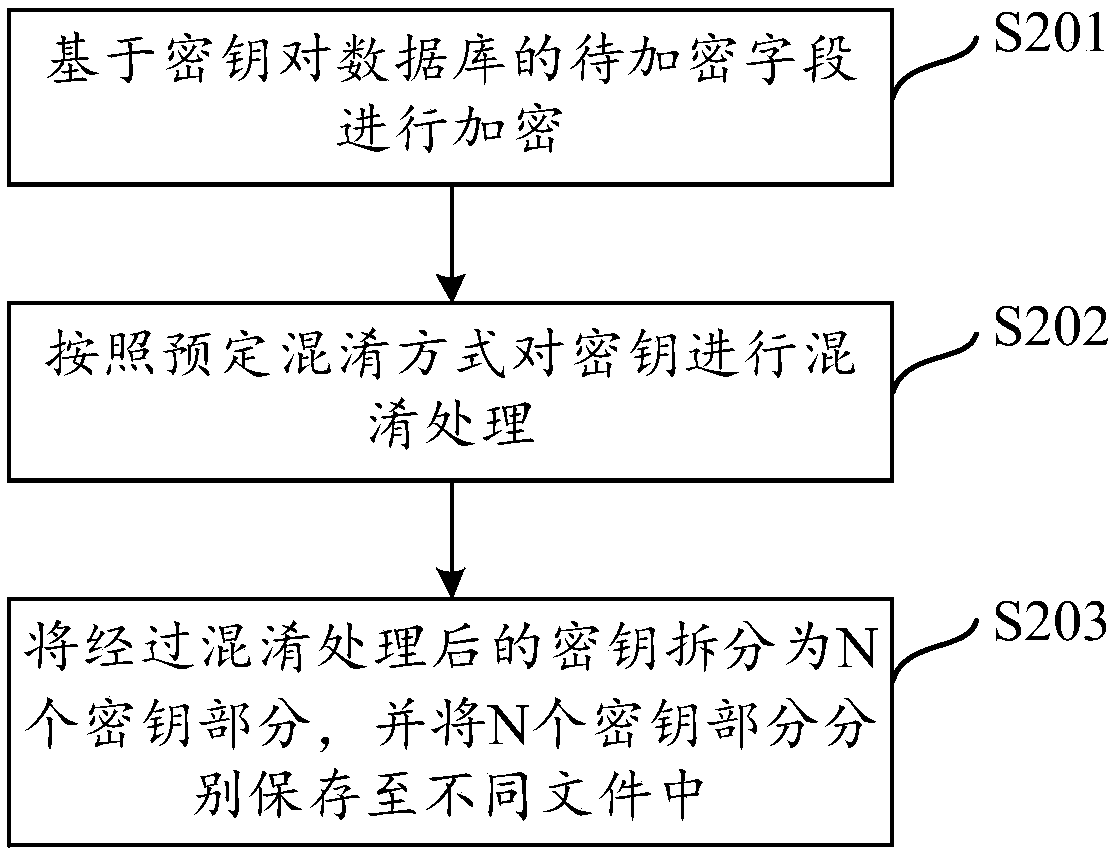
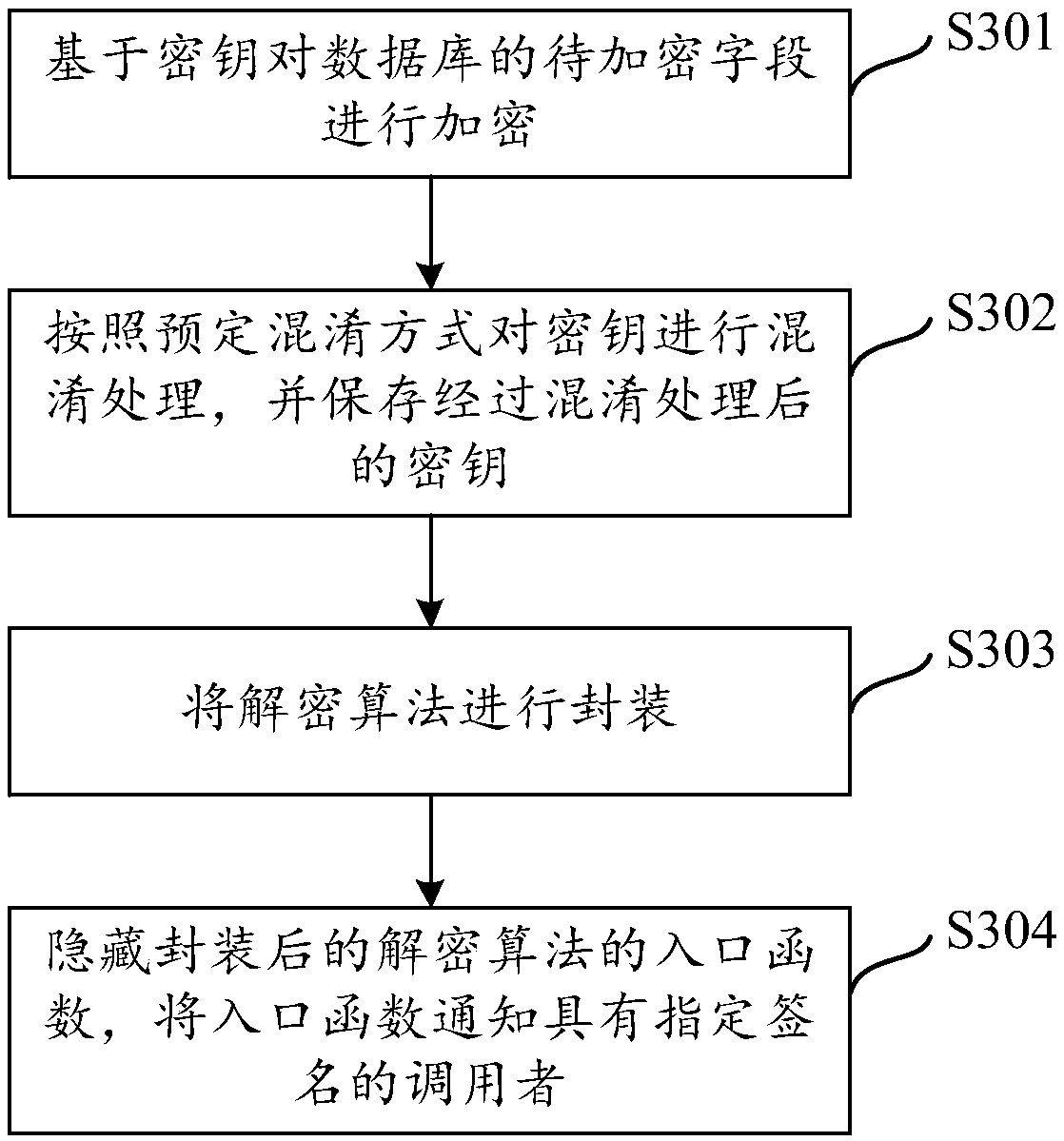
Database encryption and decryption methods and devices, storage medium and terminal
ActiveCN108712412AImprove the safety of useAchieve protectionTransmissionComputer terminalApplication software
The invention discloses a database encryption method and device, a database decryption method and device, a storage medium, and a terminal. The method comprises the steps of encrypting, based on secret keys, to-be-encrypted fields of a database; and mixing the secret keys according to a preset mixing manner, and storing the mixed secret keys. According to the method, the fields of the database areencrypted, and the secret keys are mixed, so that even if an unauthorized user cracks a mobile terminal and acquires database content, the user cannot acquire a correct secret key so as not to decrypt encrypted database fields, therefore, the database content is protected, the operating risk of the application is lowered, and the use safety for the user is improved.
Owner:BEIJING 58 INFORMATION TTECH CO LTD
Database encryption and decryption method and device
ActiveCN104636444AIncrease the difficulty of crackingImprove securityRelational databasesDigital data protectionPasswordDatabase file
The invention provides a database encryption and decryption method and device. The method comprises the steps that version information, a mark and an encryption algorithm corresponding to a database are written into a preset position in a database to be encrypted, an encrypted password is calculated according to the version information and the mark corresponding to the database to be encrypted, and the encrypted password is written into a password verifying position in the database; during decryption, an encryption password in the preset position and the content of the password verifying position in a database to be decrypted are read, and the encryption password and the content of the password verifying position are compared; if the encryption password and the content of the password verifying position are consistent, the database can be opened only when a secret key is obtained according to a secondary encryption algorithm and the password verifying position is backfilled with the secret key; the file loading correctness of the database can be ensured, meanwhile, the cracking difficulty of the database can be improved, and the safety of the encrypted database is improved.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Security protection method and system for light-weight database
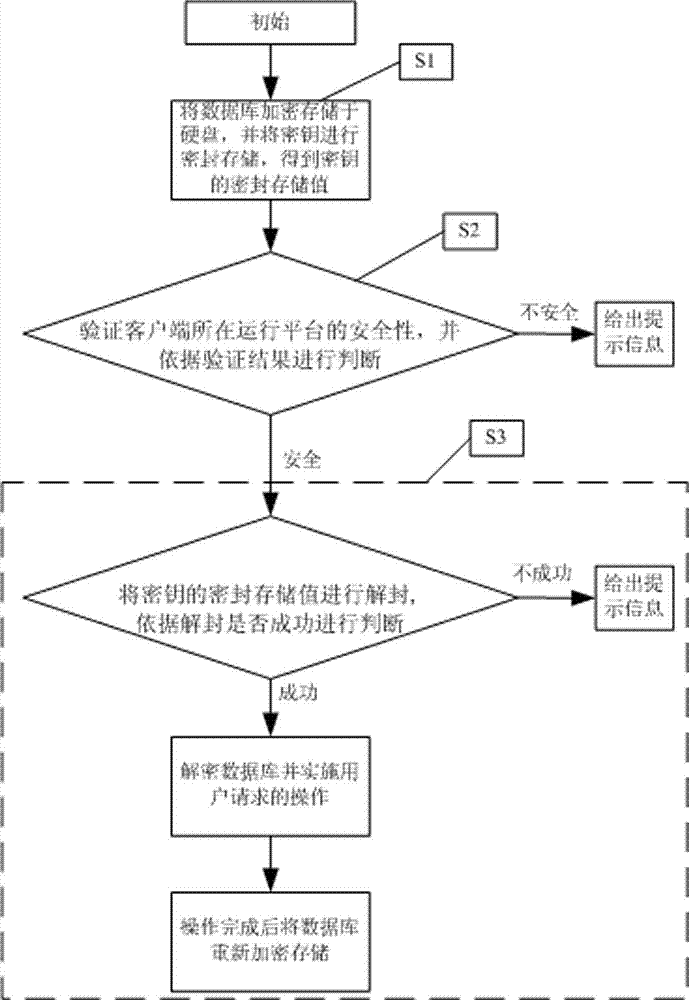
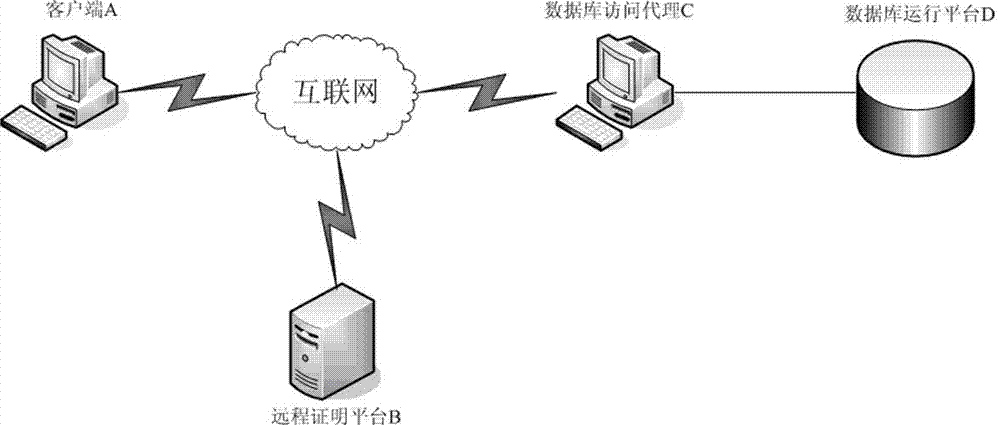
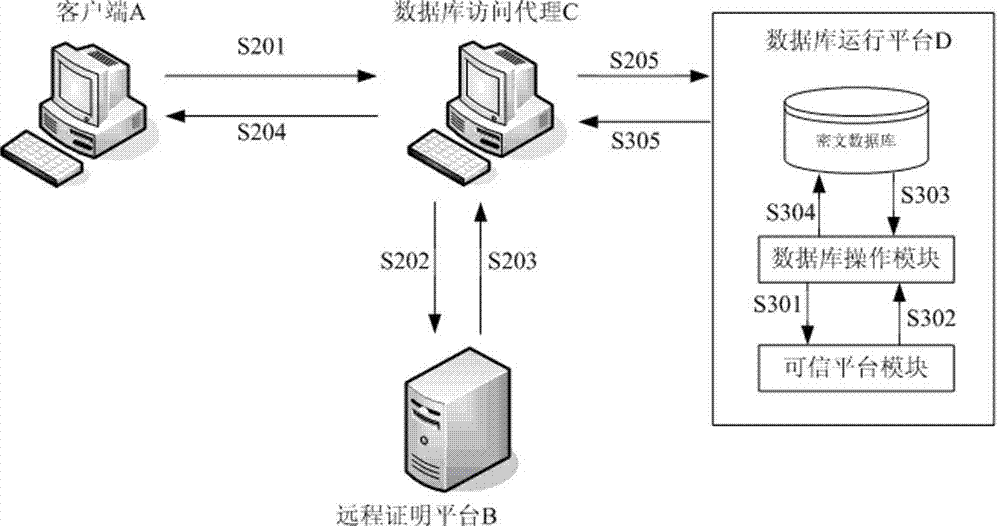
ActiveCN103500202AAvoid safety hazardsDigital data protectionSpecial data processing applicationsCiphertextEngineering
The invention provides a security protection method and system for a light-weight database, and relates to the technical field of information security. The method includes the steps that firstly, a user has access to the database through a database access agency; secondly, the database access agency verifies the security of a running platform where a client-side is located through a remote authentication platform before responding to the operation conducted by the user on the database; thirdly, the database must be decoded before the operation conducted by the user is responded due to the fact that the database is a ciphertext database; fourthly, the running platform where the database is located needs to verify the security of the running platform before the database is decoded, if the running platform is safe, decoding is conducted on the database and the user operation is conducted, and the database is encoded and stored again after the operation is completed. The system comprises a remote authentication subsystem and a database encoding protection subsystem. After the method and system are adopted, the security of the database can be enhanced, the security of the running platform where the client-side is located and the security of the running platform where the database is located are verified before the user has access to the database, and therefore the potential safety hazards caused by undemanding identity authentication and the platforms which may have been broken through can be avoided.
Owner:NO 709 RES INST OF CHINA SHIPBUILDING IND CORP
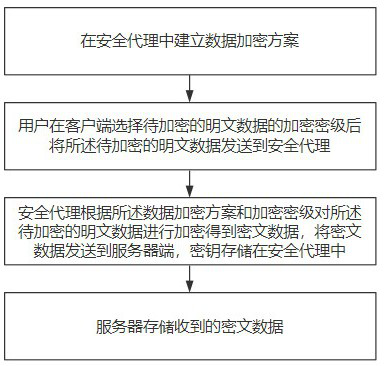
Relational database encryption method and encrypted database query method
ActiveCN112380557AImprove encryption efficiencyImprove storage space utilizationRelational databasesDigital data protectionDatabase queryRelational database
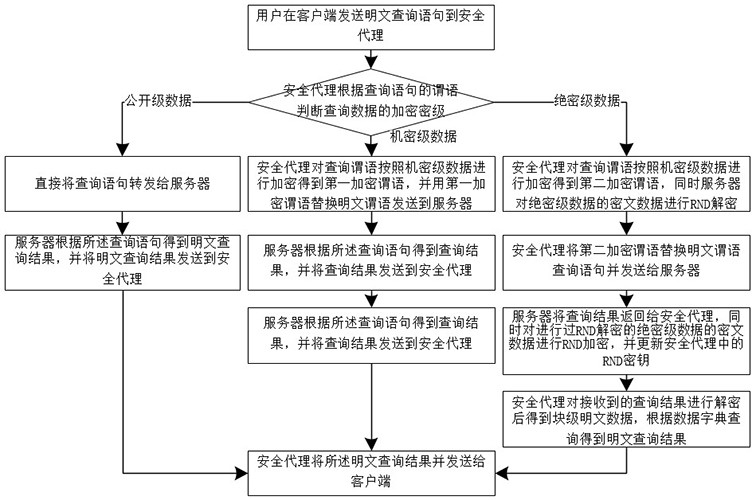
The invention discloses a relational database encryption method and an encrypted database query method, and the method comprises the steps of building a data encryption scheme in a safety agent; enabling a user to select the encryption security level of to-be-encrypted plaintext data at a client and then to send the to-be-encrypted plaintext data to be transmitted to the safety agent; and enablingthe safety agent to encrypt the plaintext data to be encrypted according to the data encryption scheme and the encryption security level to obtain ciphertext data, sendiing the ciphertext data to a server, and storing a key in the security agent. By means of the mode, the encryption time can be greatly shortened, the data encryption efficiency and the storage space utilization rate are improved,the data safety is guaranteed, a safety agent mechanism is introduced, a safety agent only needs to decrypt a query result once during data query, decryption does not need to be conducted at a serverside, and the query efficiency and the data security are improved.
Owner:JIANGXI NORMAL UNIV
Efficient database encryption method based on dictionary mapping
ActiveCN108734024AIncrease the difficultyImprove securityEncryption apparatus with shift registers/memoriesPublic key for secure communicationGeneration processCiphertext
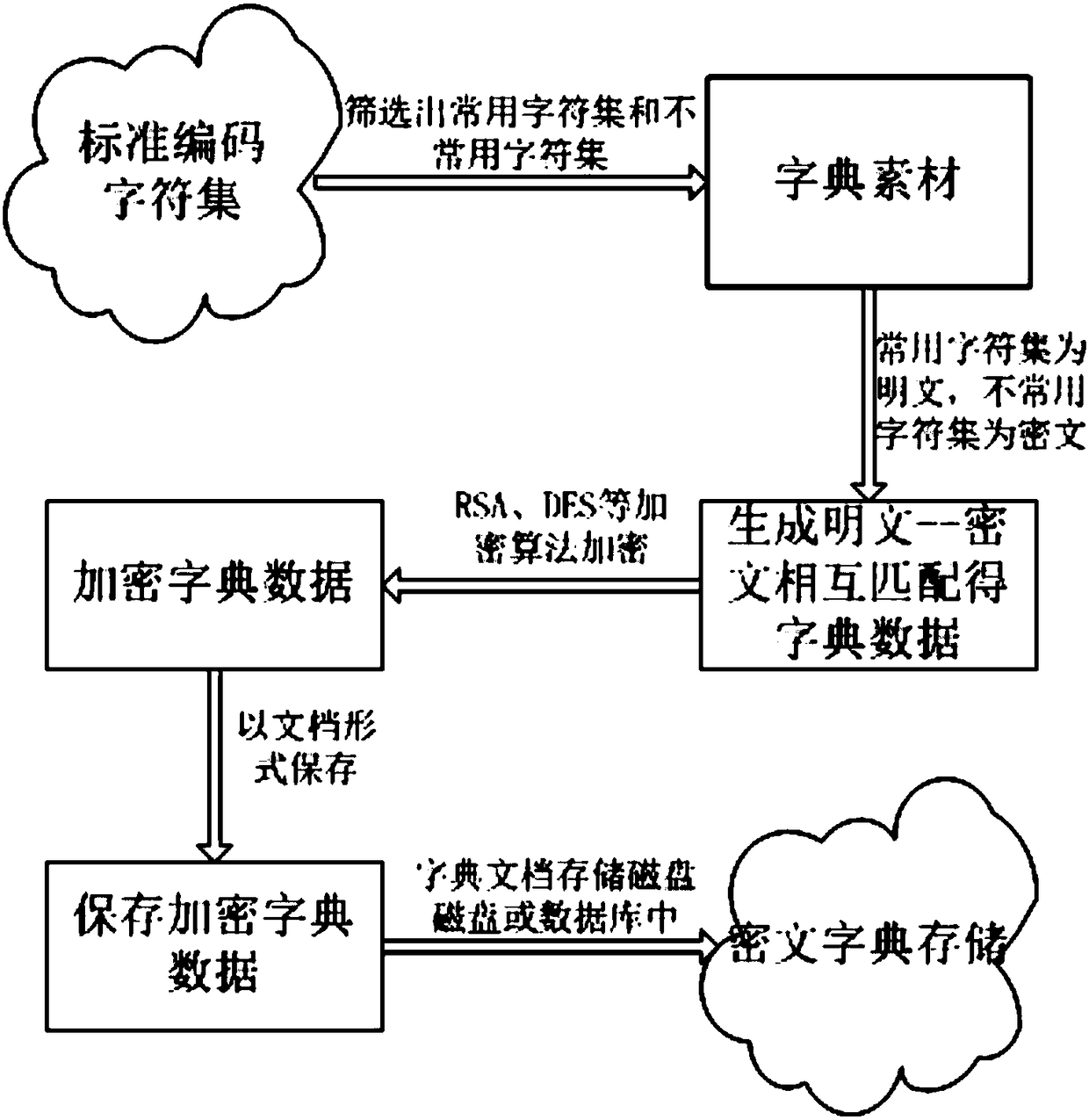
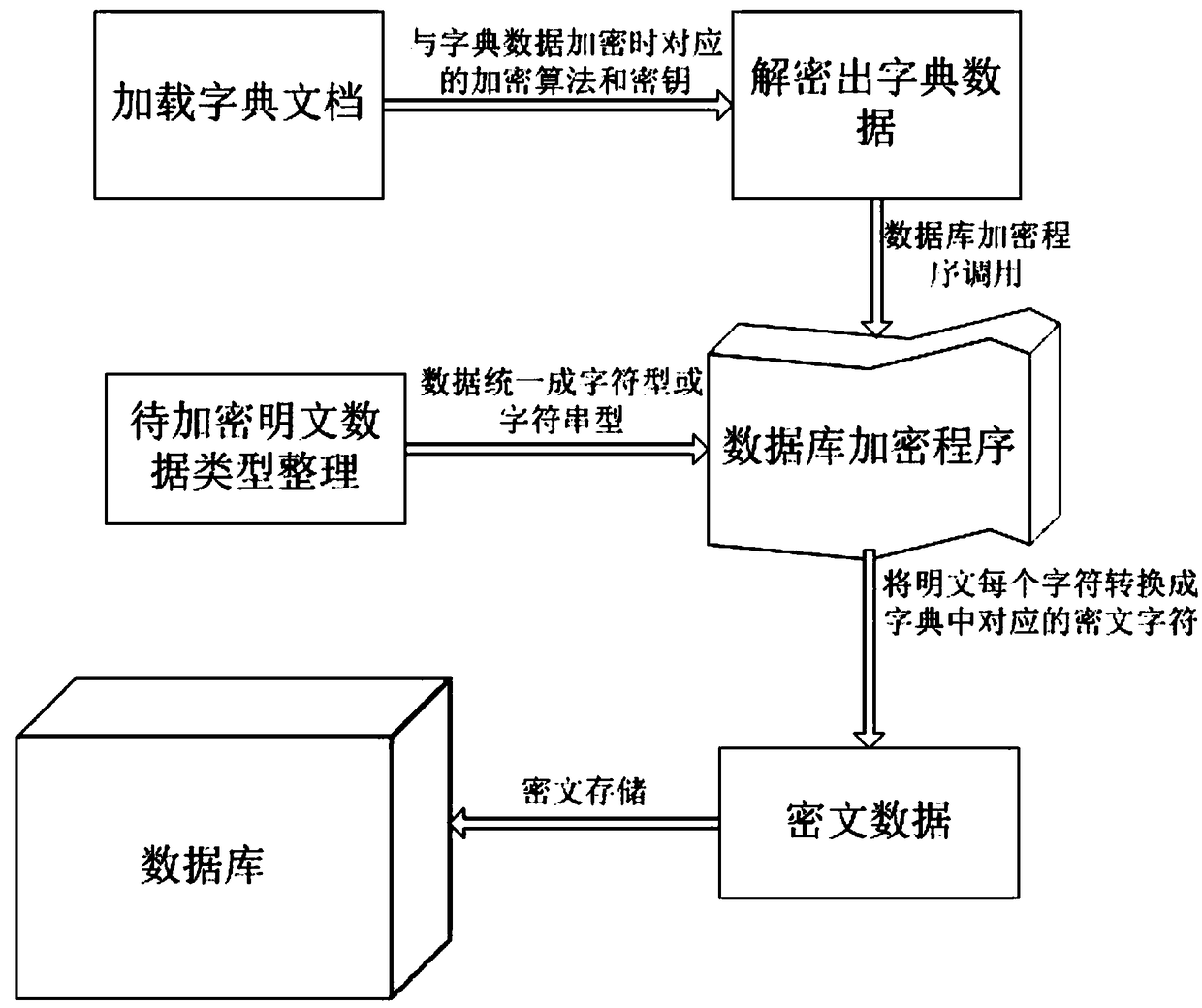
The invention discloses an efficient database encryption method based on dictionary mapping. The method comprises at least a dictionary generation process, a dictionary encryption and storage process,a dictionary calling and decryption process, a ciphertext data generation and storage process, a ciphertext search process, a dictionary update process, and a double-dictionary running process. The efficient database encryption method based on dictionary mapping effectively prevents data information from disclosing after a database is invaded, and makes data break and breach much harder at the cost of small system performance.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
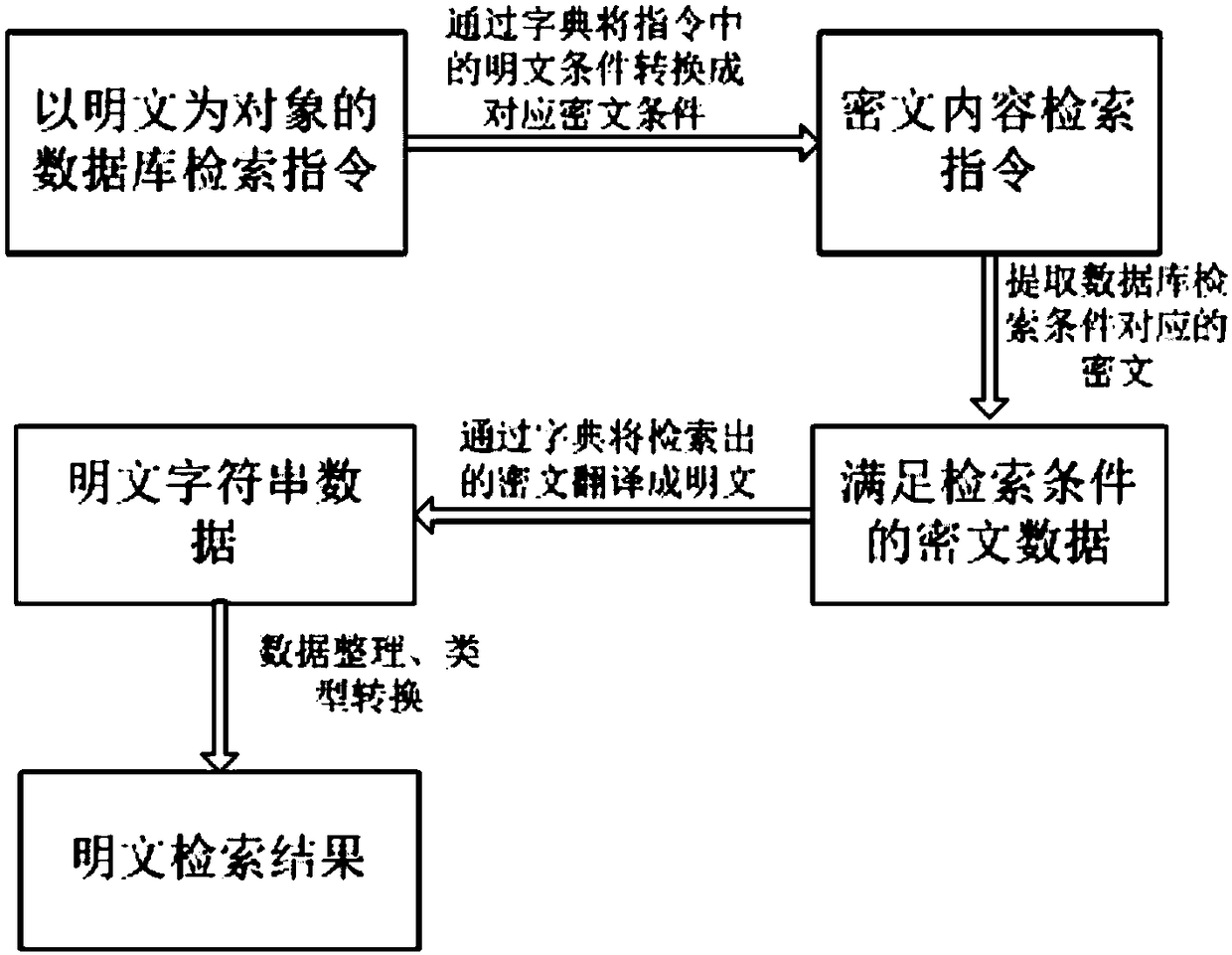
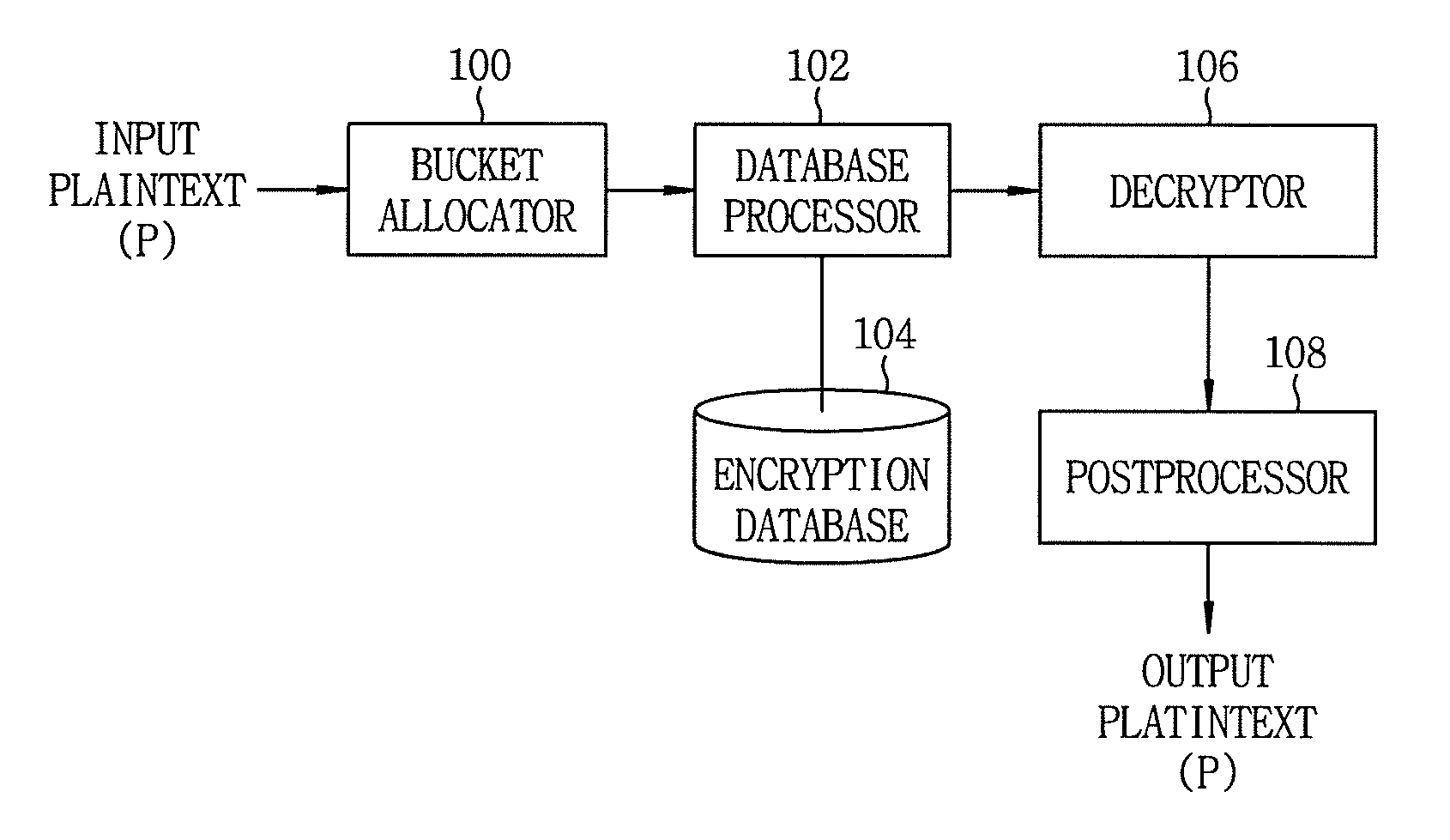
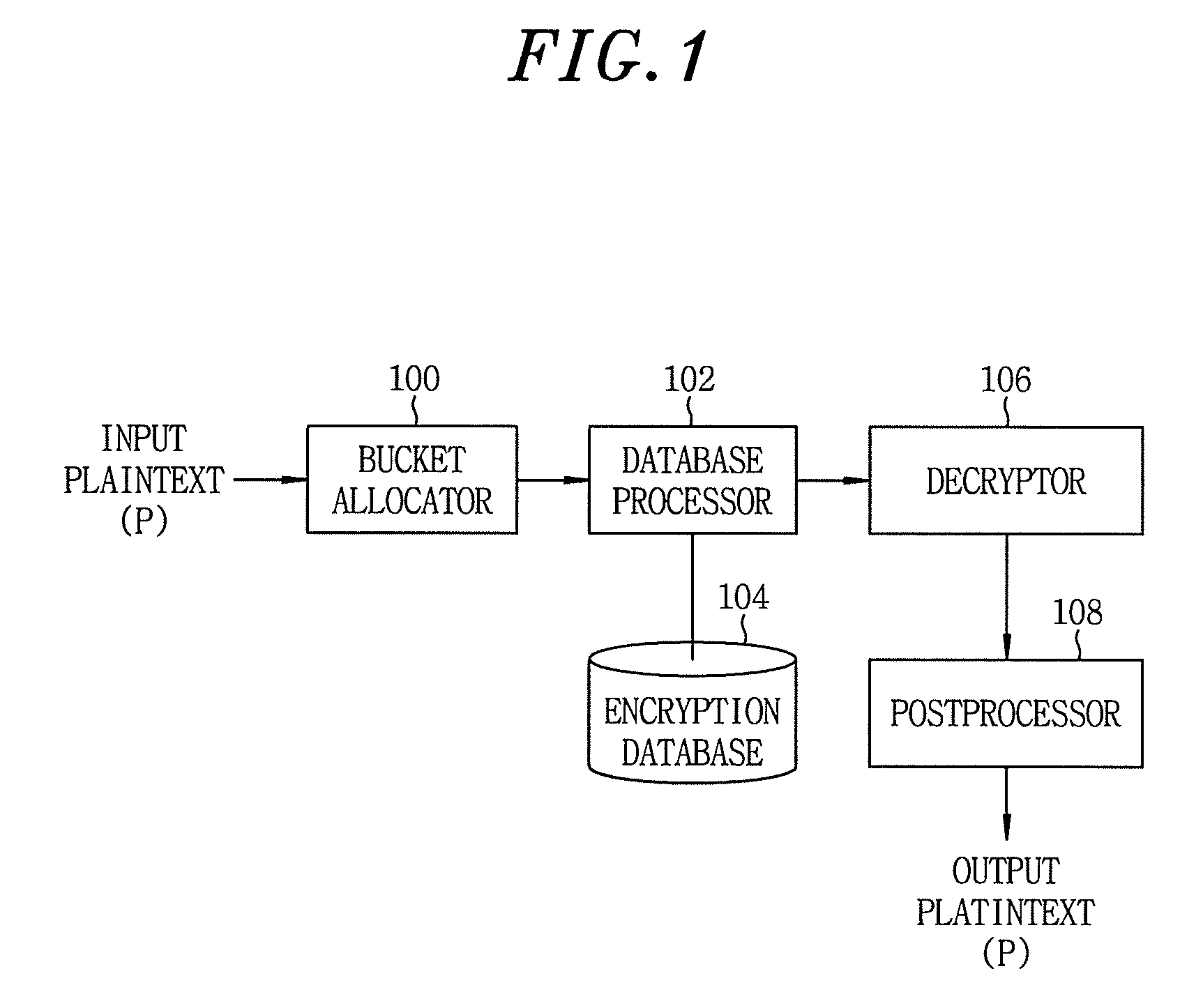
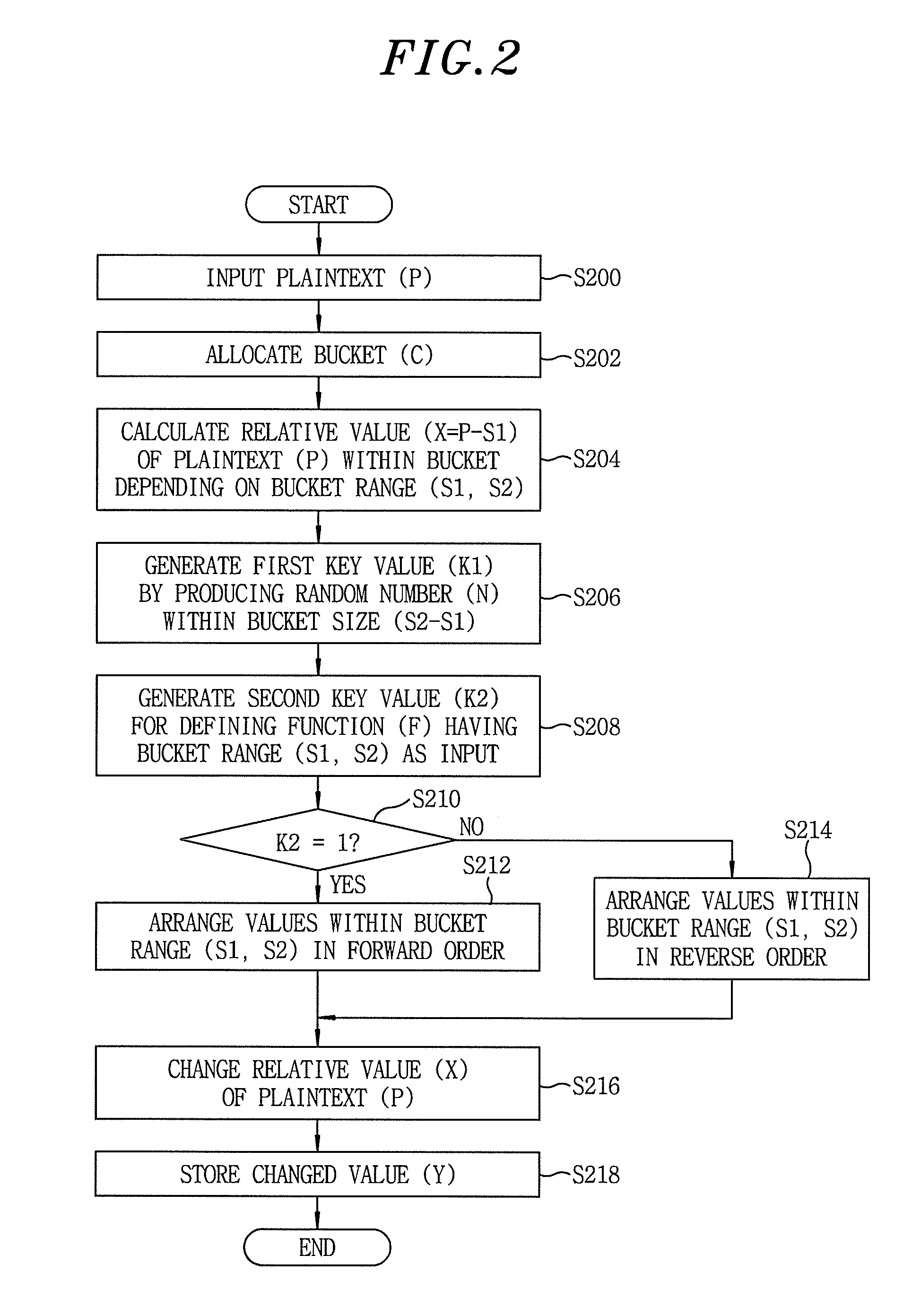
Database encryption and query method keeping order within bucket partially
InactiveUS20090316887A1Safety for stored dataEnsure safetyDigital data information retrievalDigital computer detailsPlaintextComputer hardware
A database encryption and query method keeping an order within a bucket partially, which encrypts and stores numeric data in a database, includes calculating a relative value of a plaintext within a bucket to which the plaintext is allocated; generating a first key value by producing a random number within the bucket; generating a second key value for defining a function having a bucket range of the bucket as an input; and changing the relative value based on the first and the second key value with keeping an order of the relative value partially to store the changed relative value. The first key value may be a value of separating order informations on the relative value. Further, the second key value may be a resultant value obtained by applying a mod 2 operation to the bucket size of the bucket.
Owner:ELECTRONICS & TELECOMM RES INST
Method for encrypting database and database server
ActiveCN106022154AVerify integrityDigital data protectionInternal/peripheral component protectionComputer hardwareDatabase server
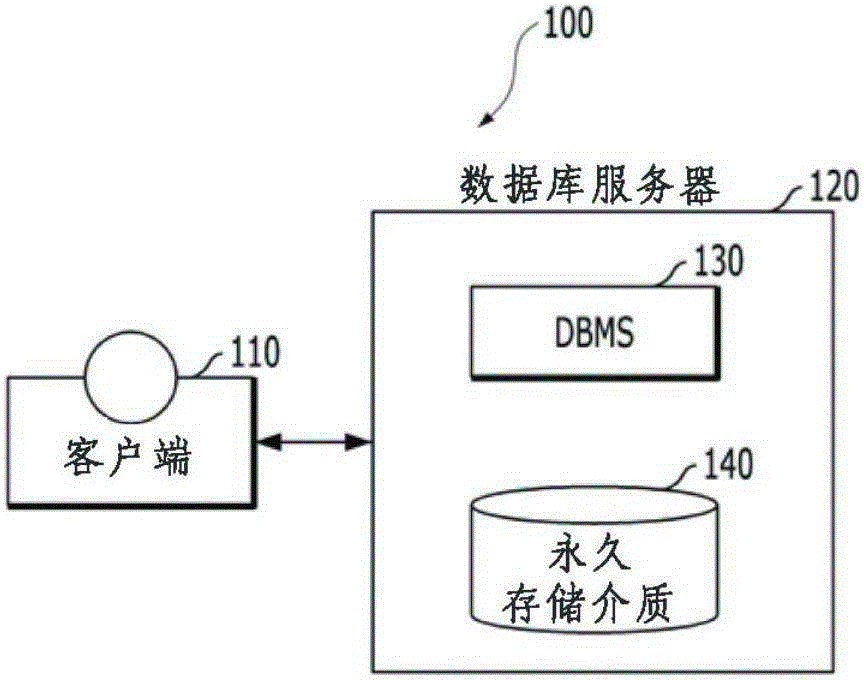
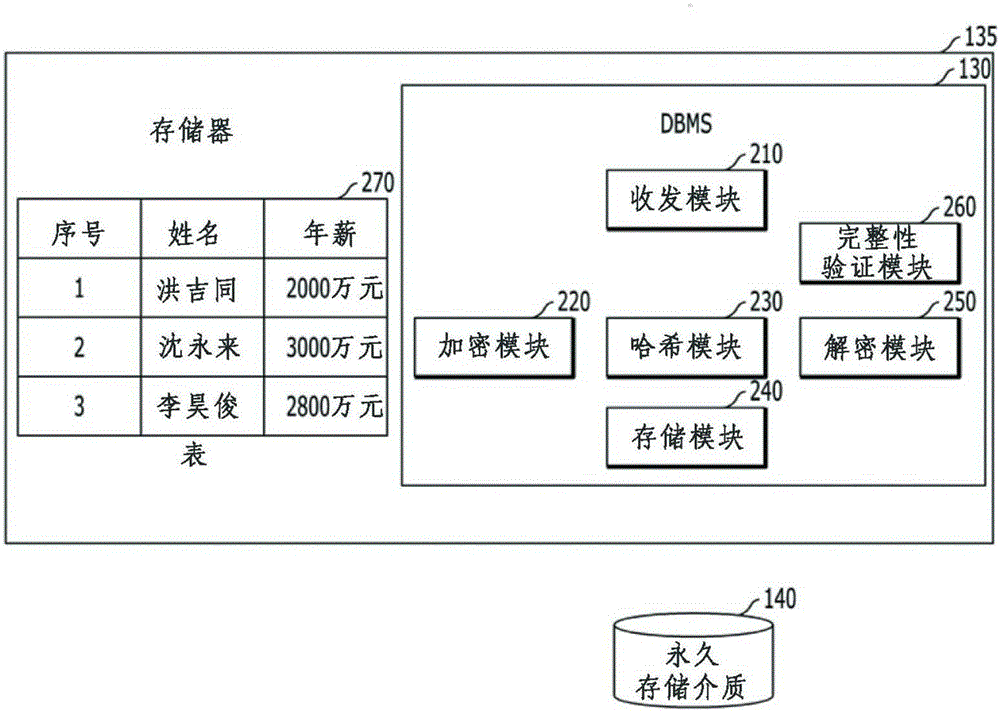
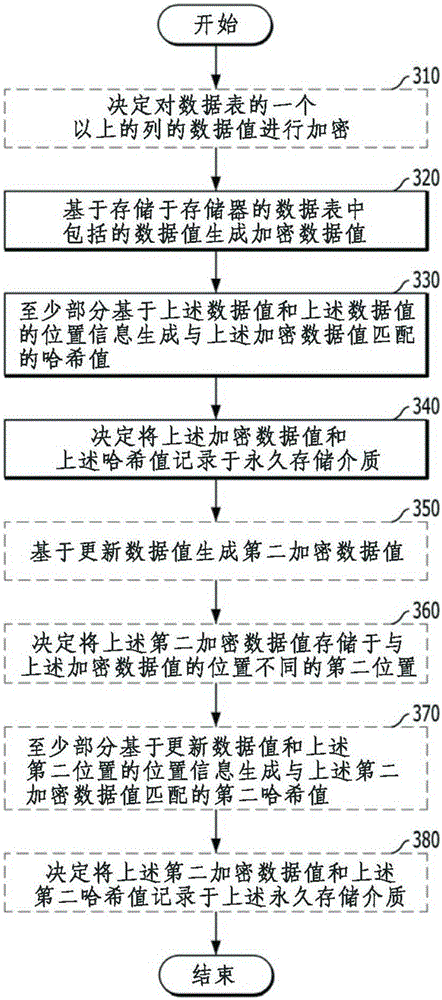
According to an embodiment of the present invention, the invention relates to a method for encrypting a database and a database server. The method comprises encrypting a data value included in a data table stored in a memory and storing the encrypted data value in a persistent storage medium. The method comprises the following steps: a step of generating an encrypted data value based on the data value included in the data table stored in a memory; a step of generating a hash value that matches the encrypted data value at least partially based on the data value and positional information of the data value; and a step of determining to write the encrypted data value and the hash value on a persistent storage medium.
Owner:TMAXTIBERO CO LTD
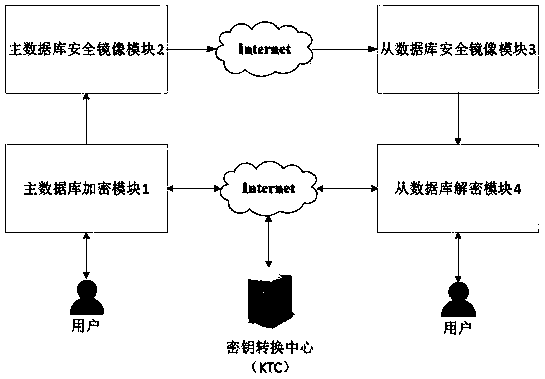
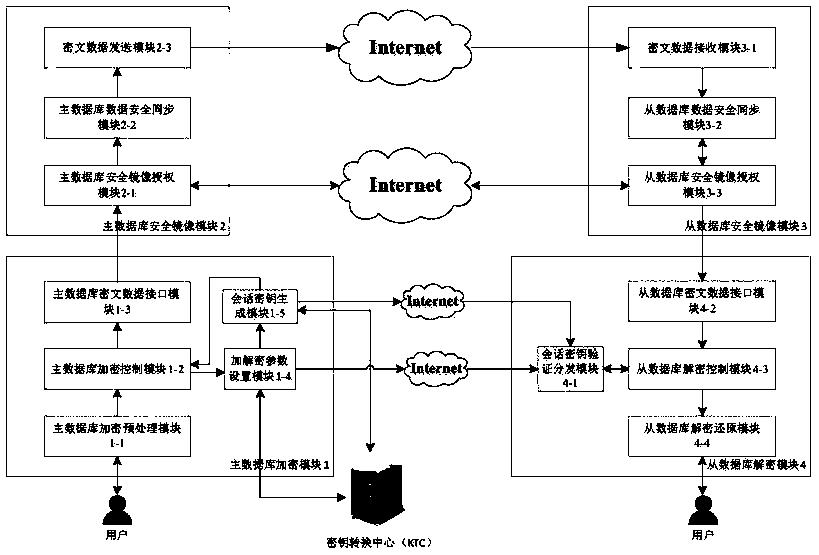
Secure data mirroring method with key negotiation function
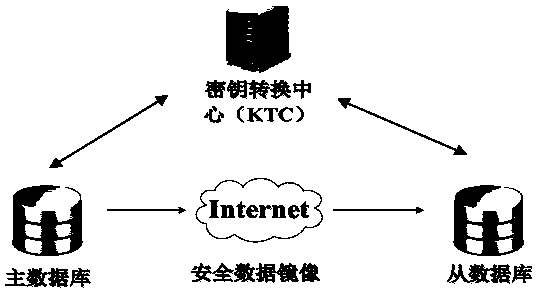
ActiveCN109995522APrevent leakageEnsure safetyKey distribution for secure communicationDatabase distribution/replicationData synchronizationCiphertext
The invention discloses a secure data mirroring method with a key negotiation function. The system comprises a master database encryption module, a master database security mirroring module, a slave database security mirroring module and a slave database decryption module. The main database encryption module is responsible for performing encryption preprocessing and grouping encryption on data ofa main database based on a CBC mode, and transmitting the data in a ciphertext mode to ensure confidentiality; the slave database decryption module is responsible for decrypting and verifying the integrity of the mirror image data and restoring the mirror image data based on the CBC mode, and has the capability of resisting replay attack; the master database encryption module and the slave database decryption module distribute session keys through the key forwarding center to ensure the safety of key distribution; and the master database security mirroring module and the slave database security mirroring module avoid data leakage through authorization and encrypted mirroring data transmission. The invention provides an encrypted data mirroring method which realizes safe data synchronization and is suitable for master-slave replication among all databases.
Owner:SOUTHEAST UNIV
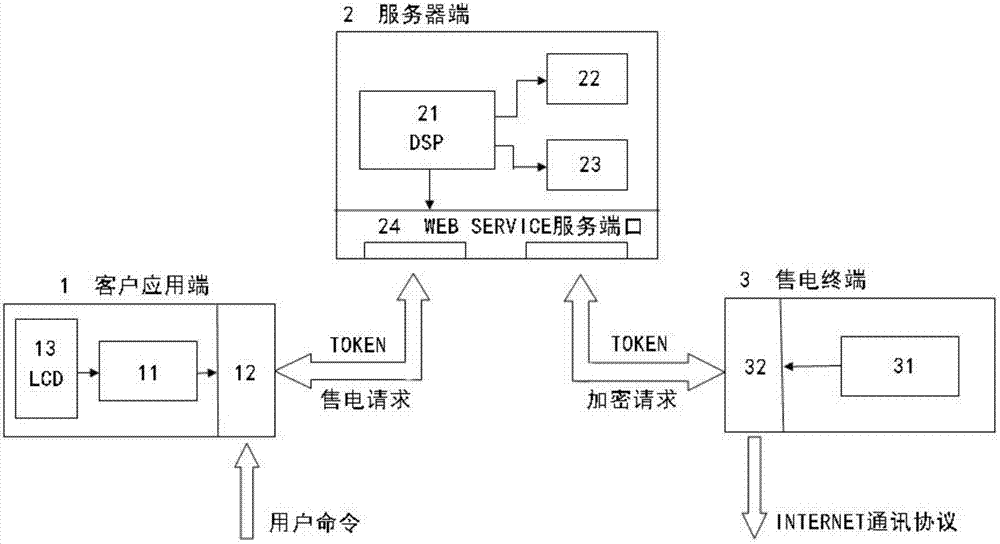
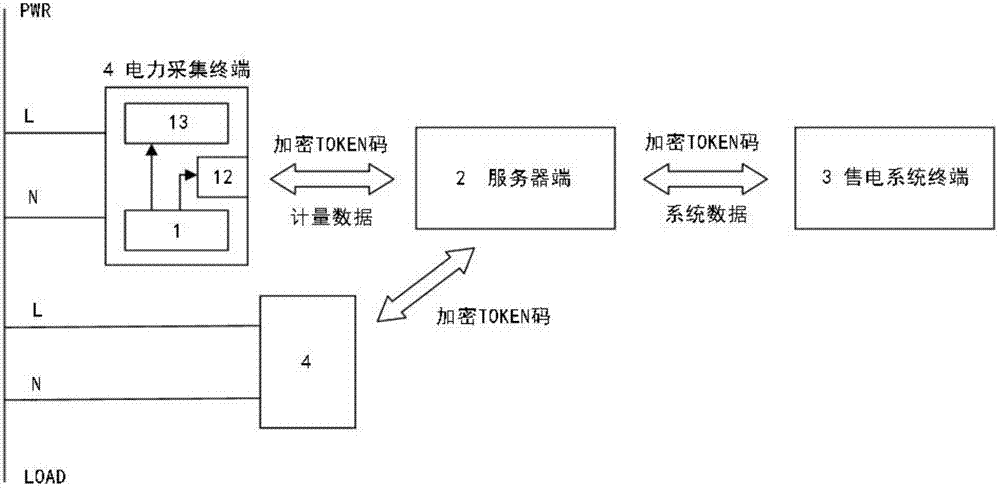
Data acquisition system for electricity vending system, self-upgrade type electricity vending system and upgrading method
ActiveCN102779376AEasy to installEasy to useApparatus for hiring articlesWeb serviceData acquisition
The invention discloses a data acquisition system for an electricity vending system. The data acquisition system comprises a client application end, a server end and an electricity vending terminal, wherein the client application end is in communication and connection with the electricity vending terminal through the server end. The invention further discloses a self-upgrade type electricity vending system utilizing the data acquisition system and an automatic upgrading method thereof. The server end of the data acquisition system disclosed by the invention can provide the access to a main station terminal database, encryption service and the like through a provided WEB-SERVICE interface so as to respond to different requests of a client; and after a server receives the request, corresponding data or parameters can be obtained, and an electricity vending TOKEN code is further required in an encrypted way. According to the data acquisition system disclosed by the invention, mounting and use of the client can be facilitated; and simultaneously, data communication between the client and the server is of required data which is in TOKEN way purely, picture graphs, tables or other unrelated stream media data are not involved, and data traffic and bandwidth are saved.
Owner:WAHLAP TECH CO LTD +1
Database data encryption and decryption method and device, computer equipment and storage medium
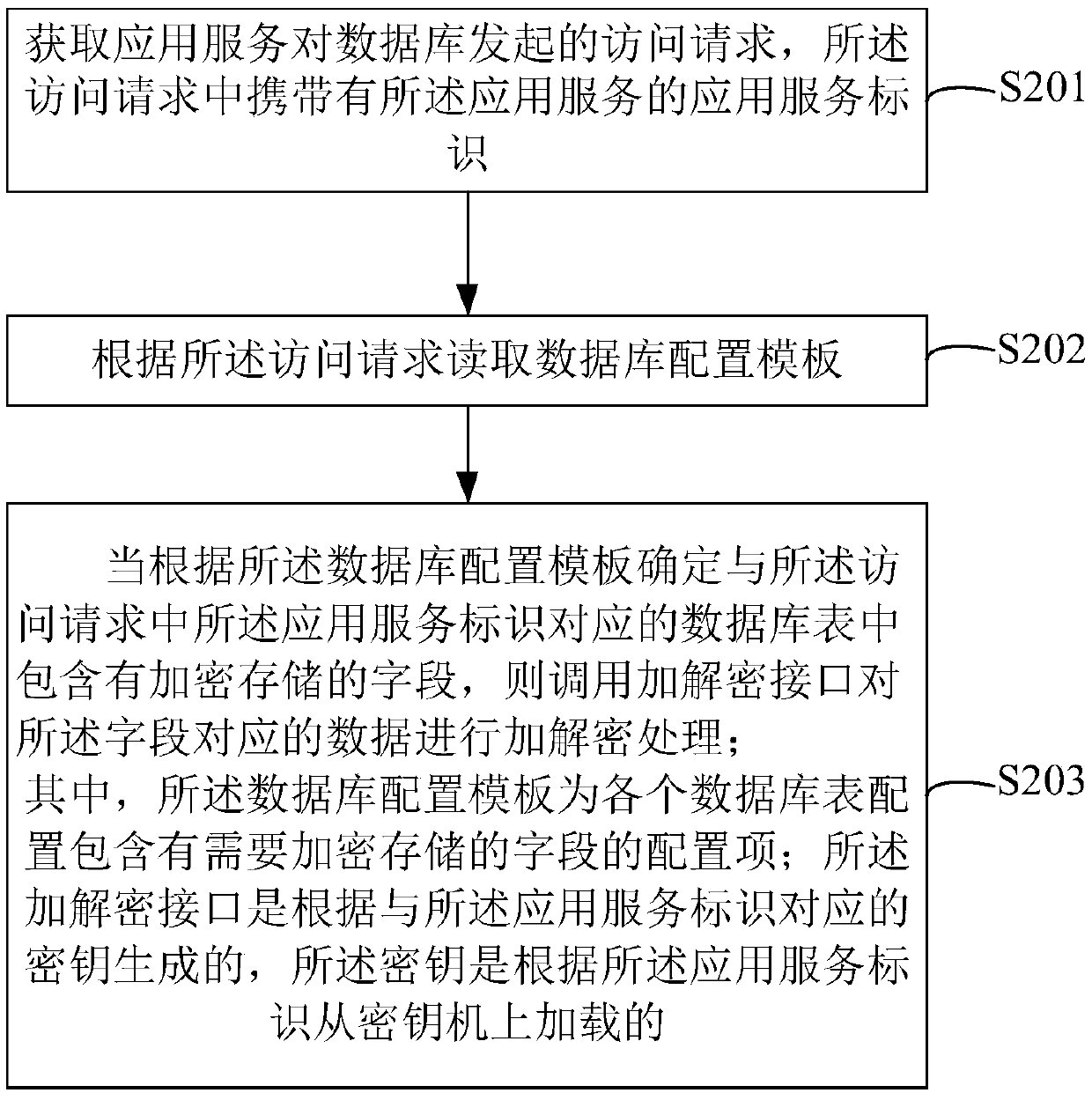
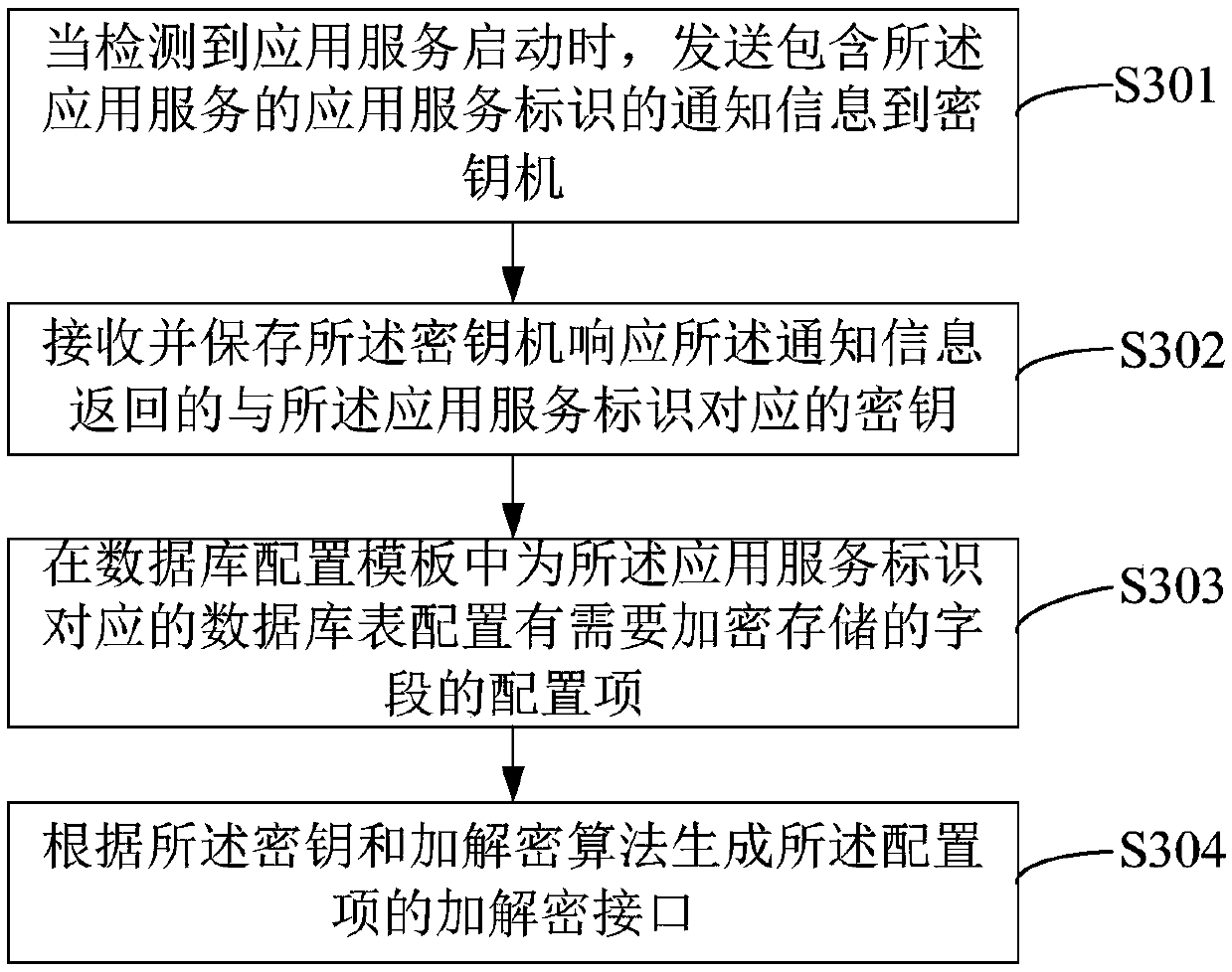
InactiveCN109697370AImprove securityImprove distribution efficiencyDigital data protectionConfiguration itemKey distribution
The invention relates to a database data encryption and decryption method and device, computer equipment and a storage medium. The method comprises the steps that acquiring an access request initiatedby an application service to a database; reading a database configuration template according to the access request; when determining that a database table accessed by the access request contains encrypted and stored fields according to the database configuration template, calling an encryption and decryption interface to encrypt and decrypt data corresponding to the fields; wherein the database configuration template configures a configuration item containing fields needing to be encrypted and stored for each database table; wherein the encryption and decryption interface is generated according to a key corresponding to the application service, and the key is loaded from a key machine according to the application service identifier. The key distribution efficiency and security can be improved.
Owner:深圳采福科技有限公司
Automatic management device of lead-acid power batteries
InactiveCN103746148AImprove securityImplement security managementSecondary cells testingDigital data authenticationComputer hardwarePower battery
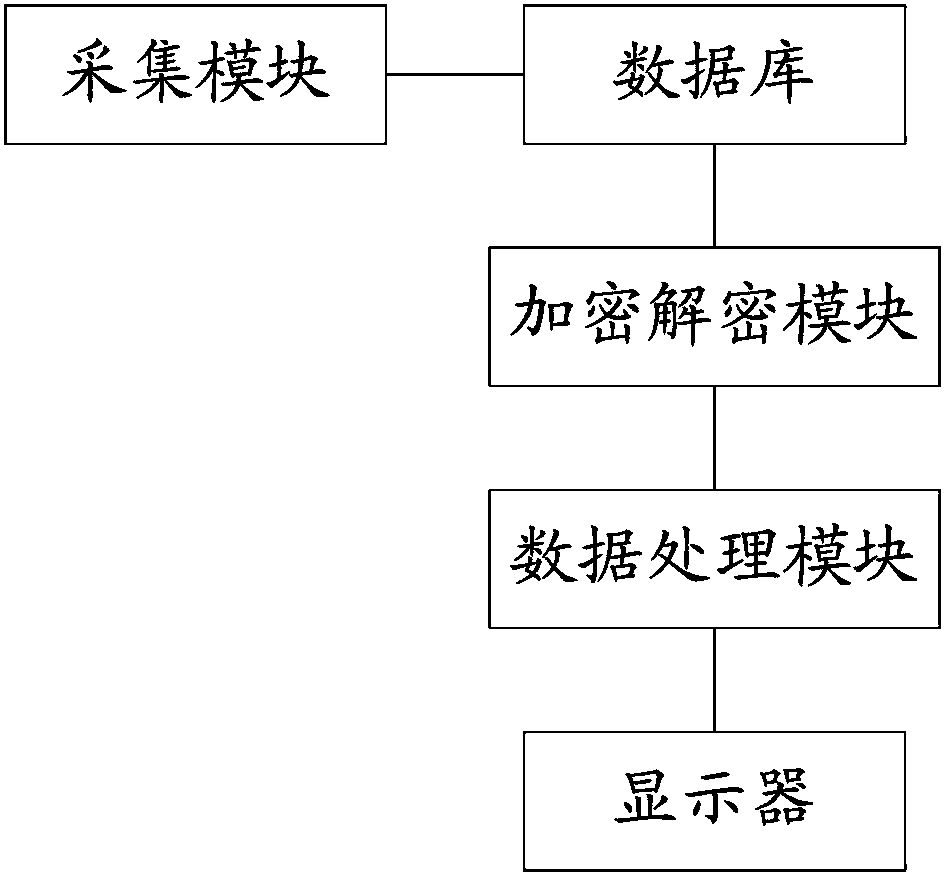
The invention discloses an automatic management device of lead-acid power batteries. The automatic management device comprises a data base, an acquisition module, an encryption and decryption module, a data processing module and a display, wherein the data base is used for storing digital certificates and maintaining the digital certificates in the data base via a management interface; the acquisition module is used for acquiring parameter data of the lead-acid power batteries by a two-wire system and uploading the parameter data to the data base; the encryption and decryption module is used for encrypting and / or decrypting the parameter data by using the digital certificates; the data processing module is used for paying the encryption and decryption module for separate passwords, receiving and processing the parameter data and then sending the processing results to the display; the display is used for receiving and displaying the processing results. The automatic management device has the beneficial effects that the parameter data is encrypted and / or decrypted by using the digital certificates so as to achieve safety management of the device, thus improving the safety of the automatic management device of the lead-acid power batteries.
Owner:GUANGXI UNIVERSITY OF TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com