Patents
Literature
51 results about "Format-preserving encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
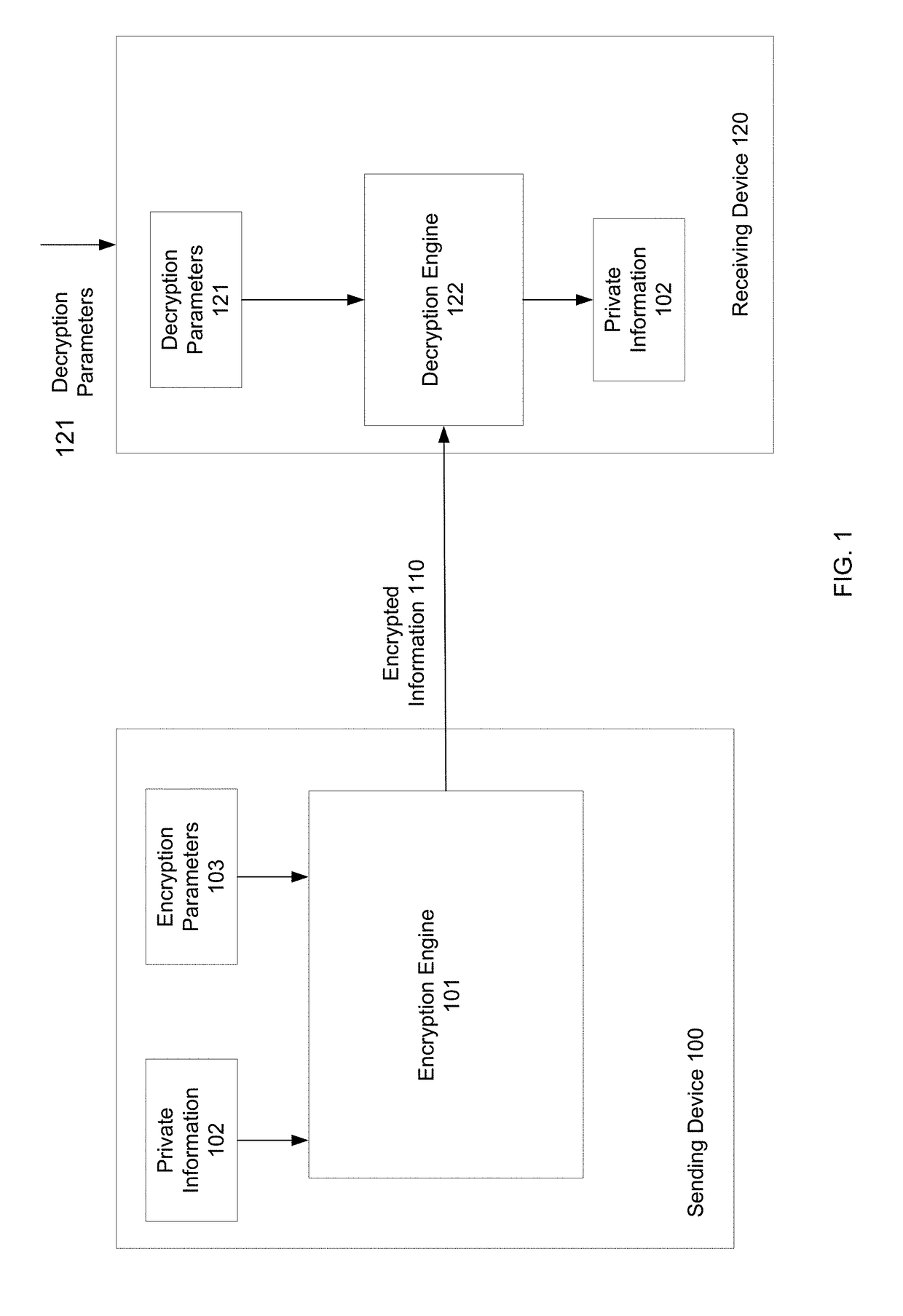
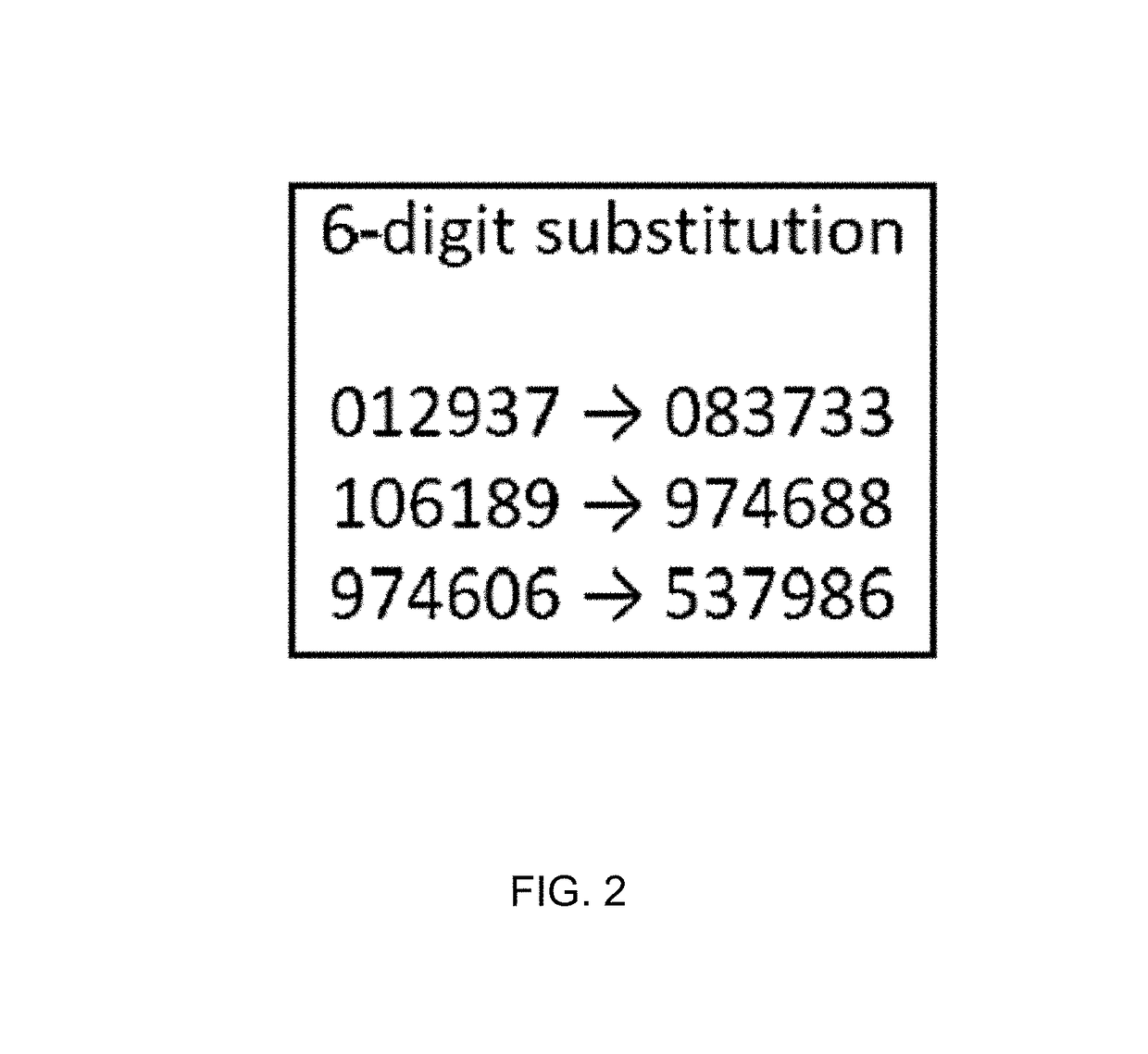
In cryptography, format-preserving encryption (FPE), refers to encrypting in such a way that the output (the ciphertext) is in the same format as the input (the plaintext). The meaning of "format" varies.
Format-preserving cryptographic systems
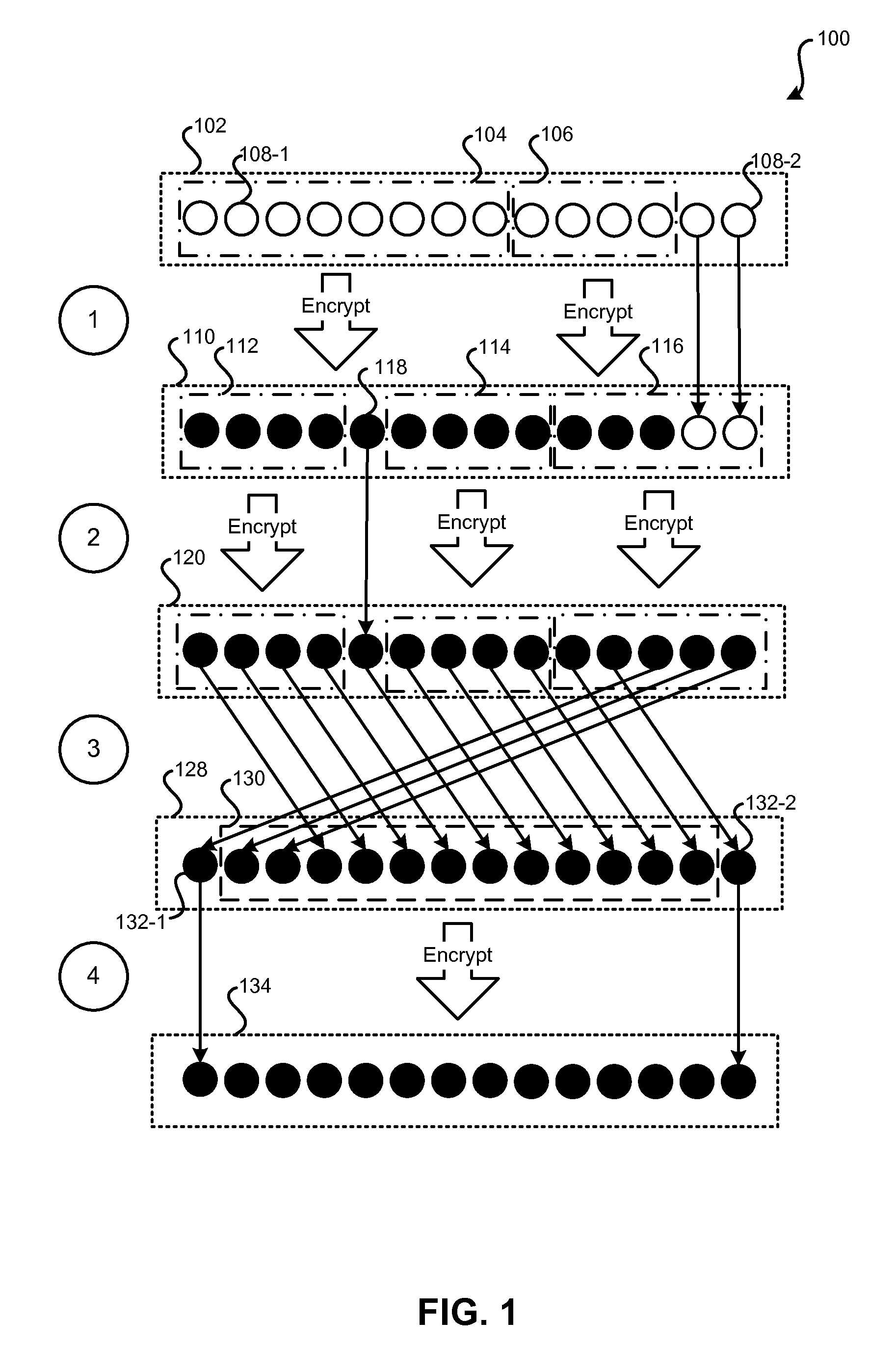
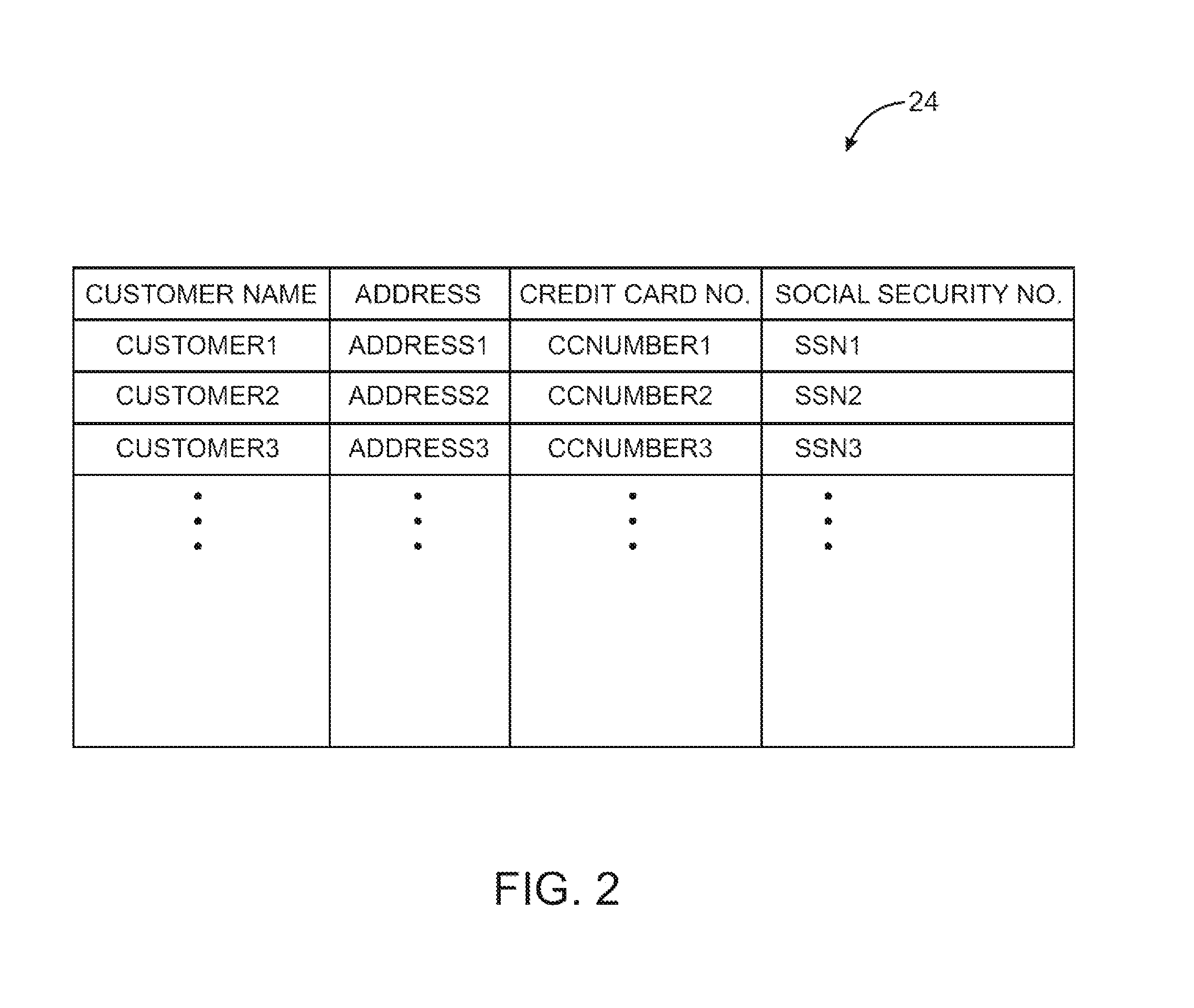
ActiveUS20080170693A1Error detection/correctionCryptography processingData processing systemOne-way function
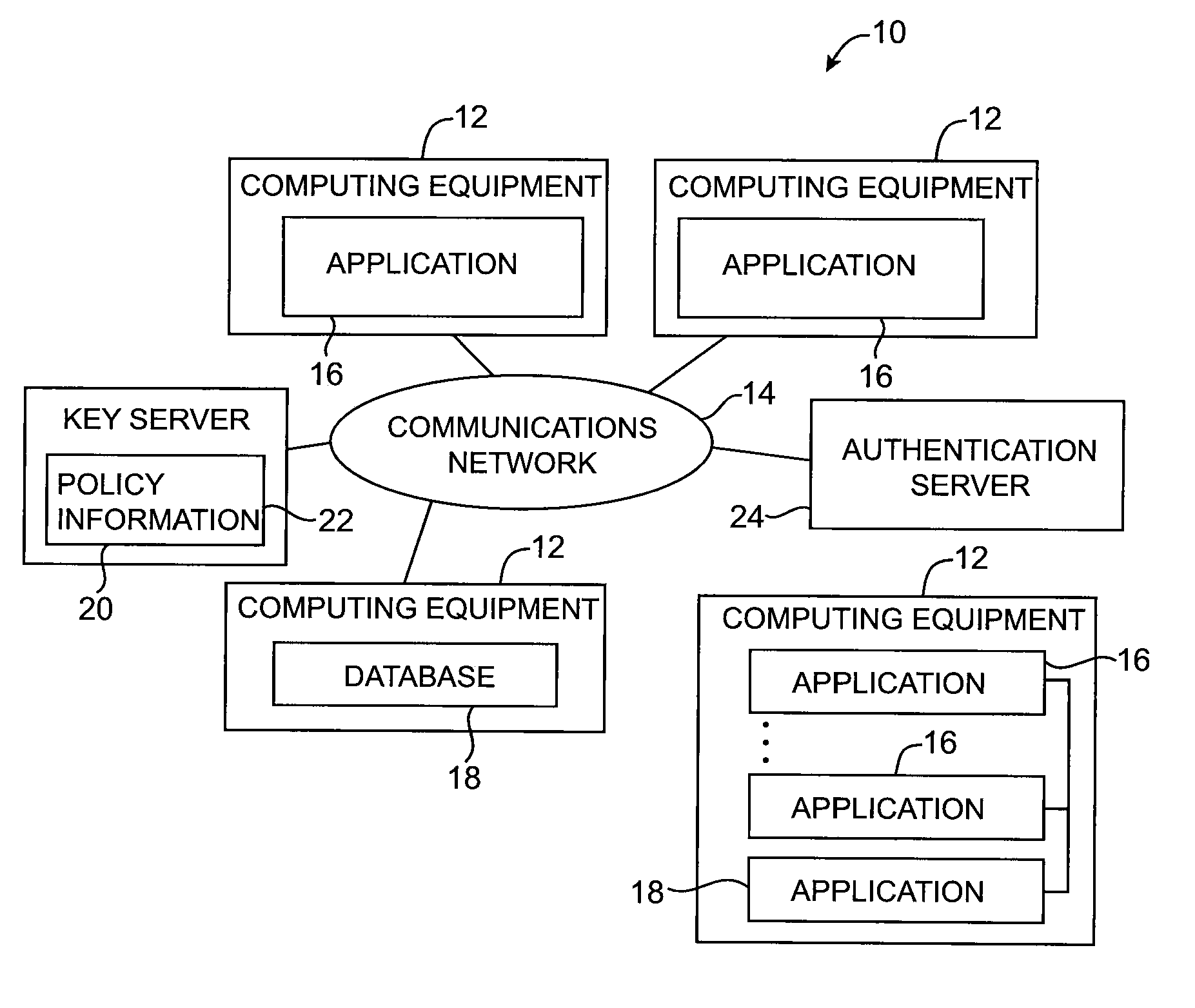
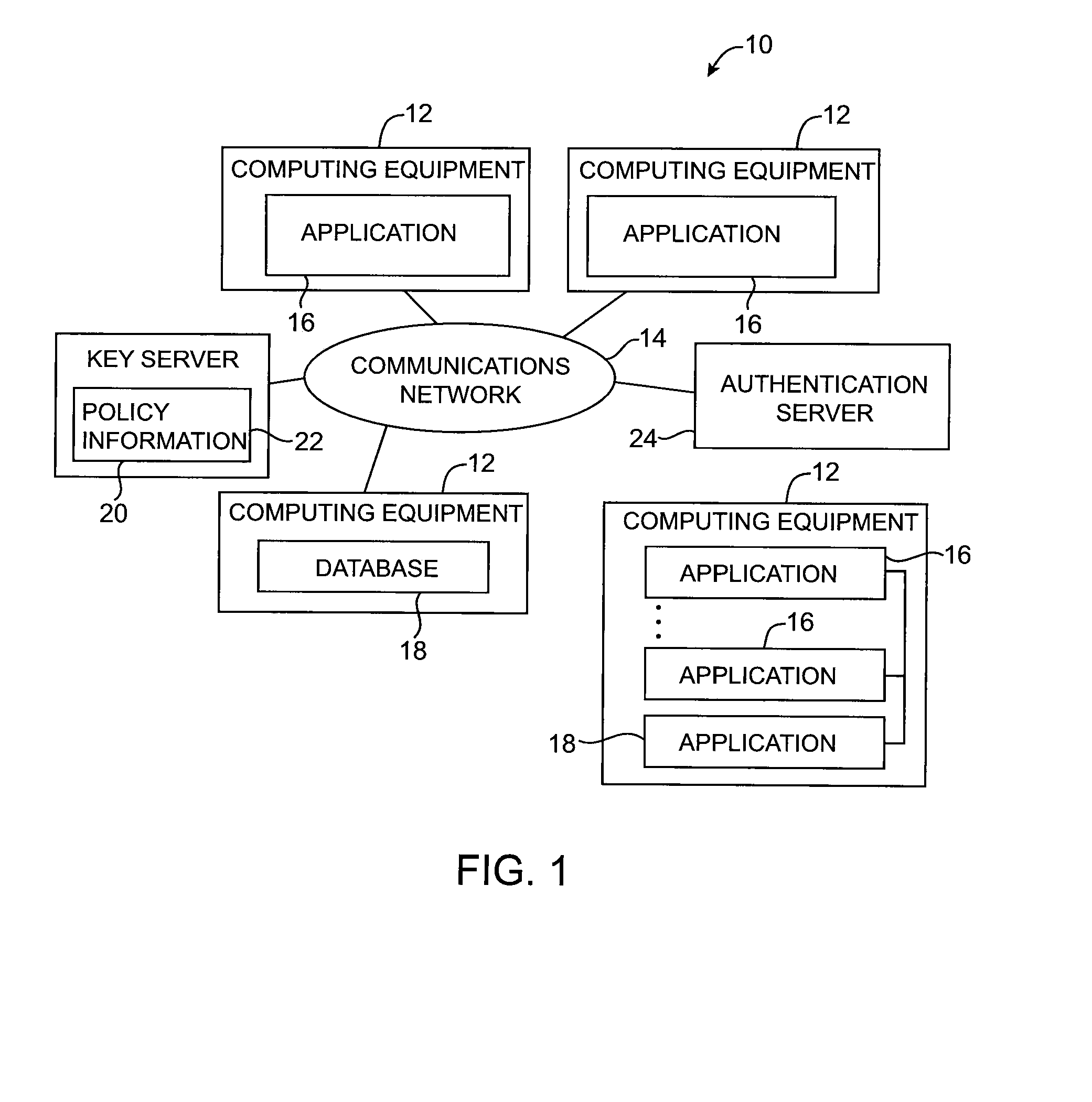
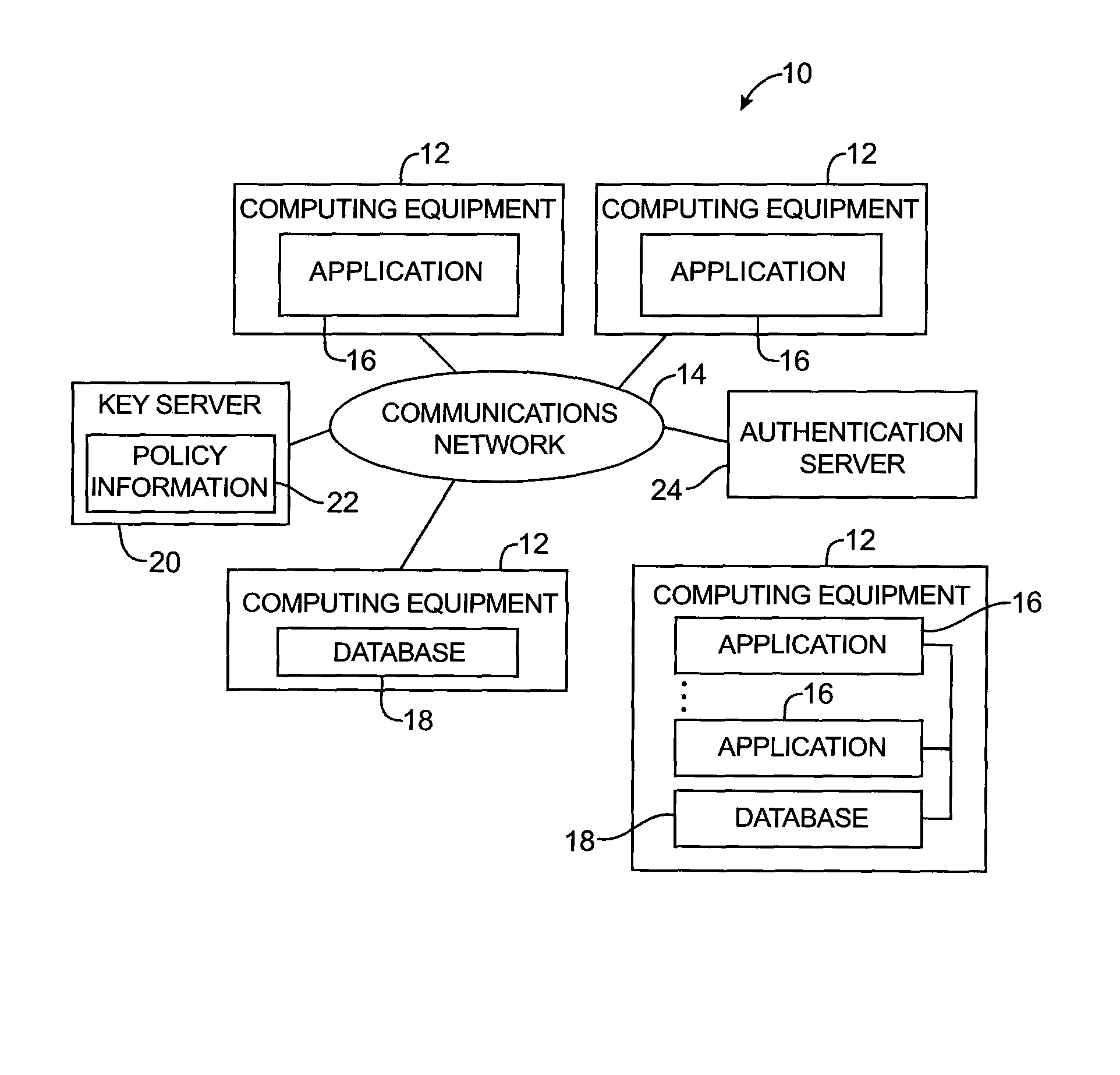
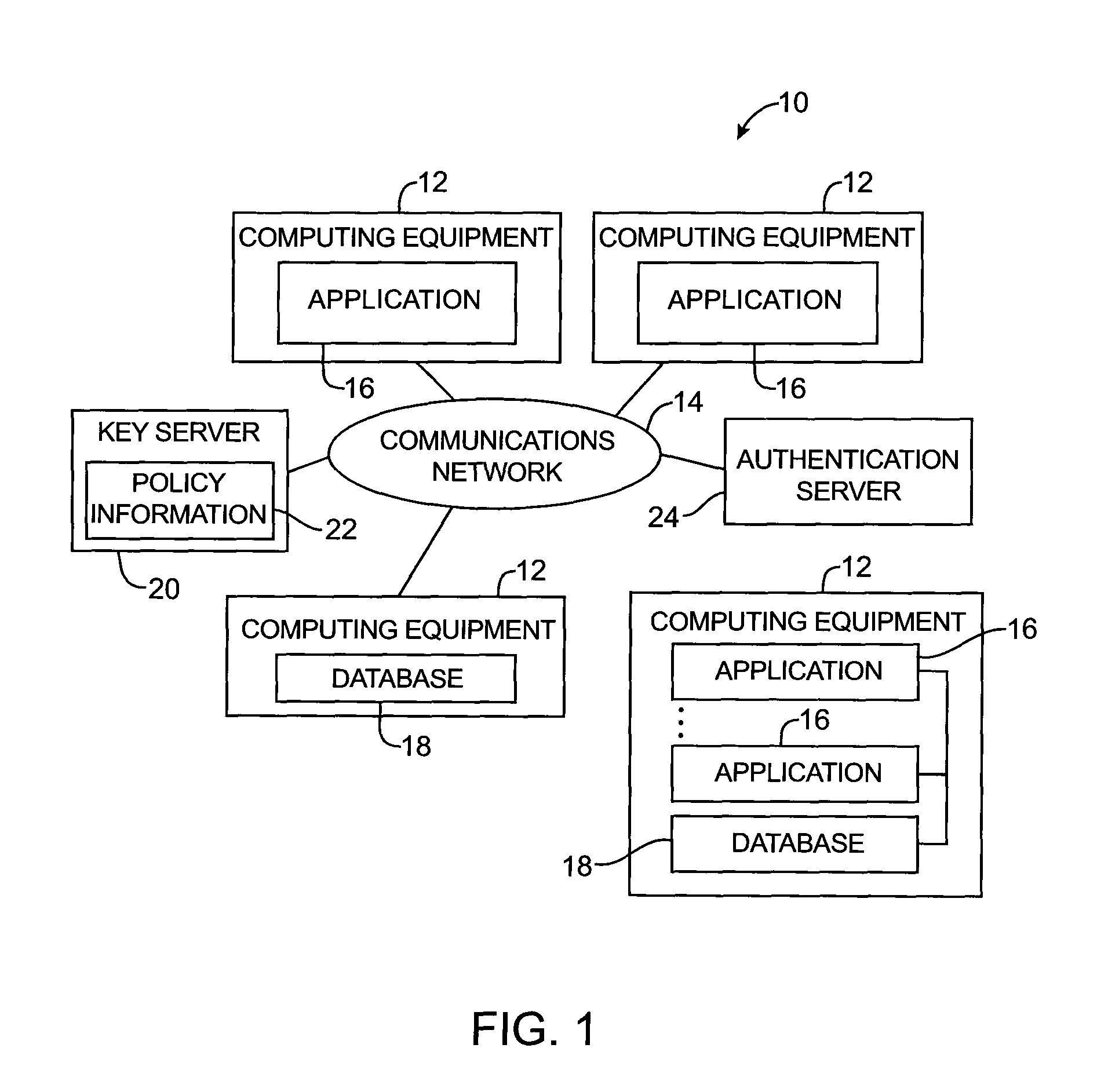
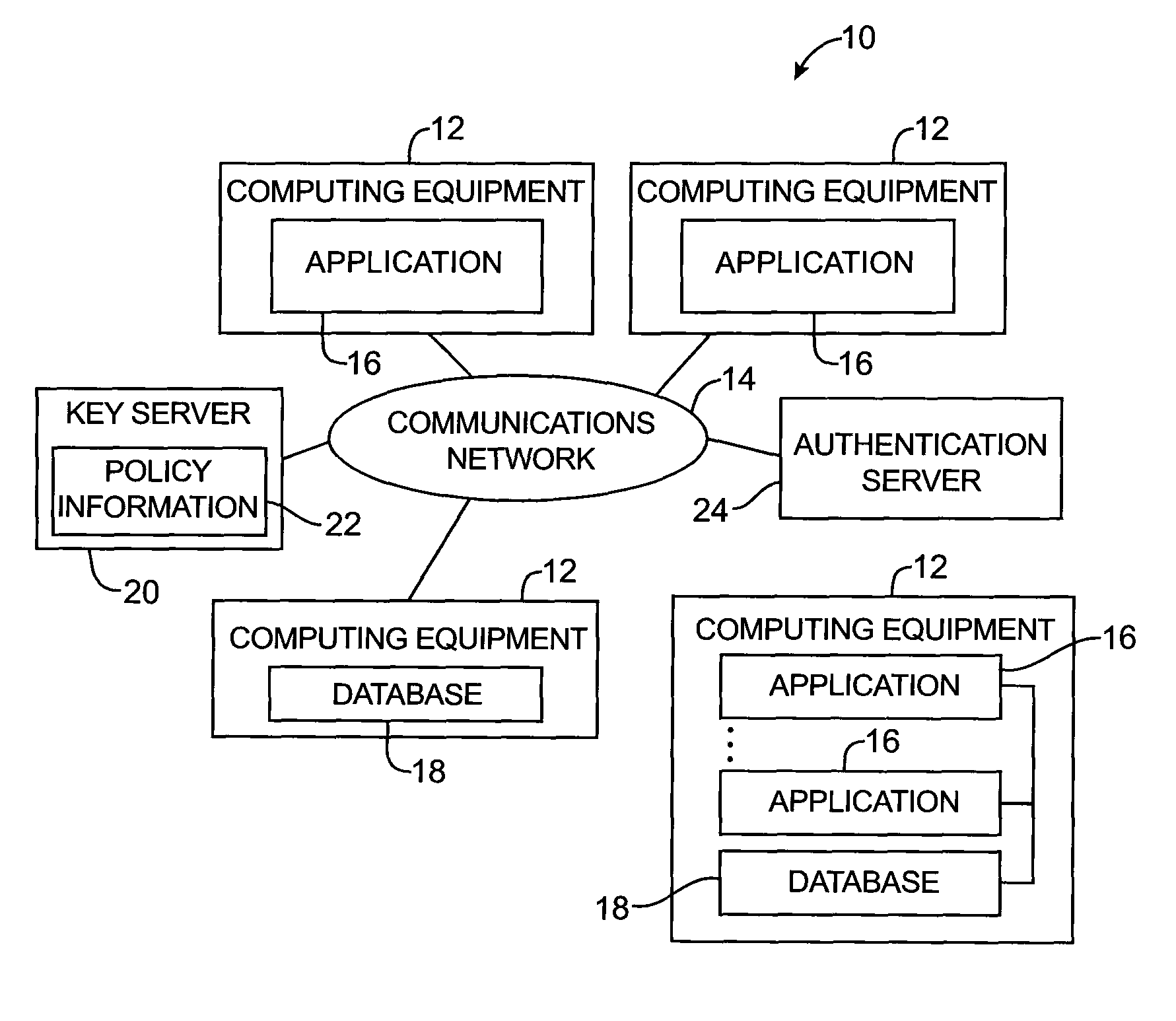
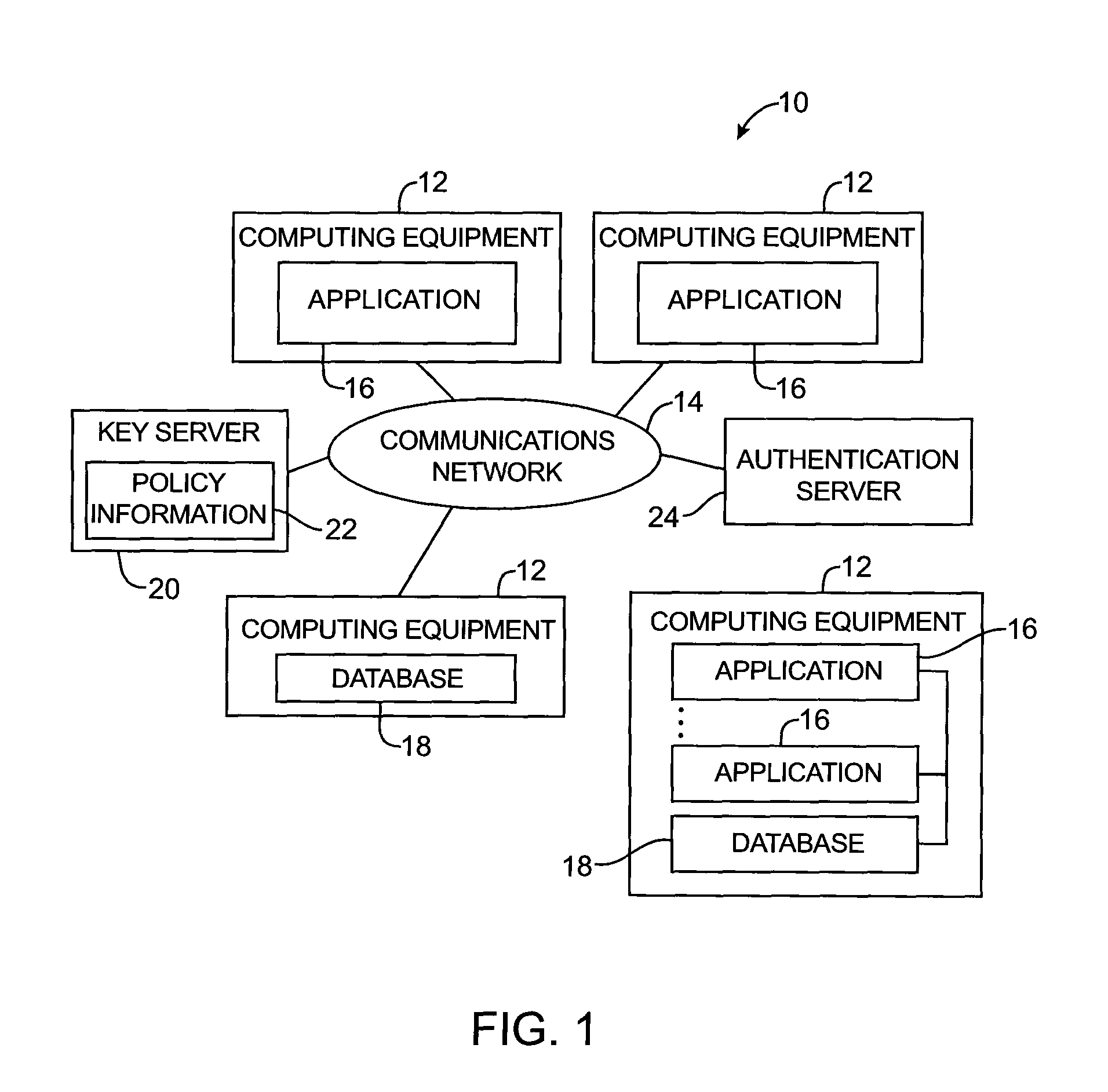
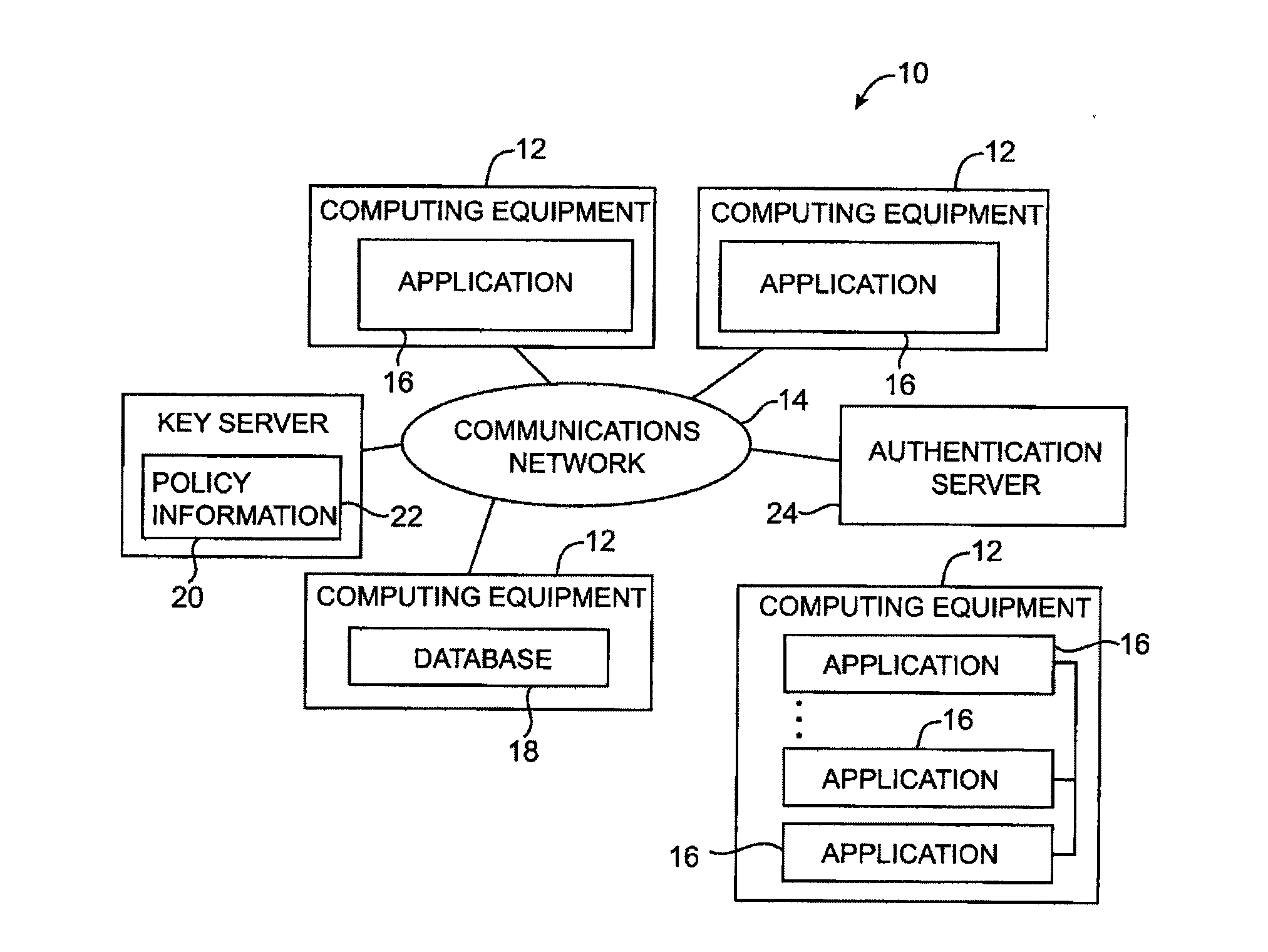
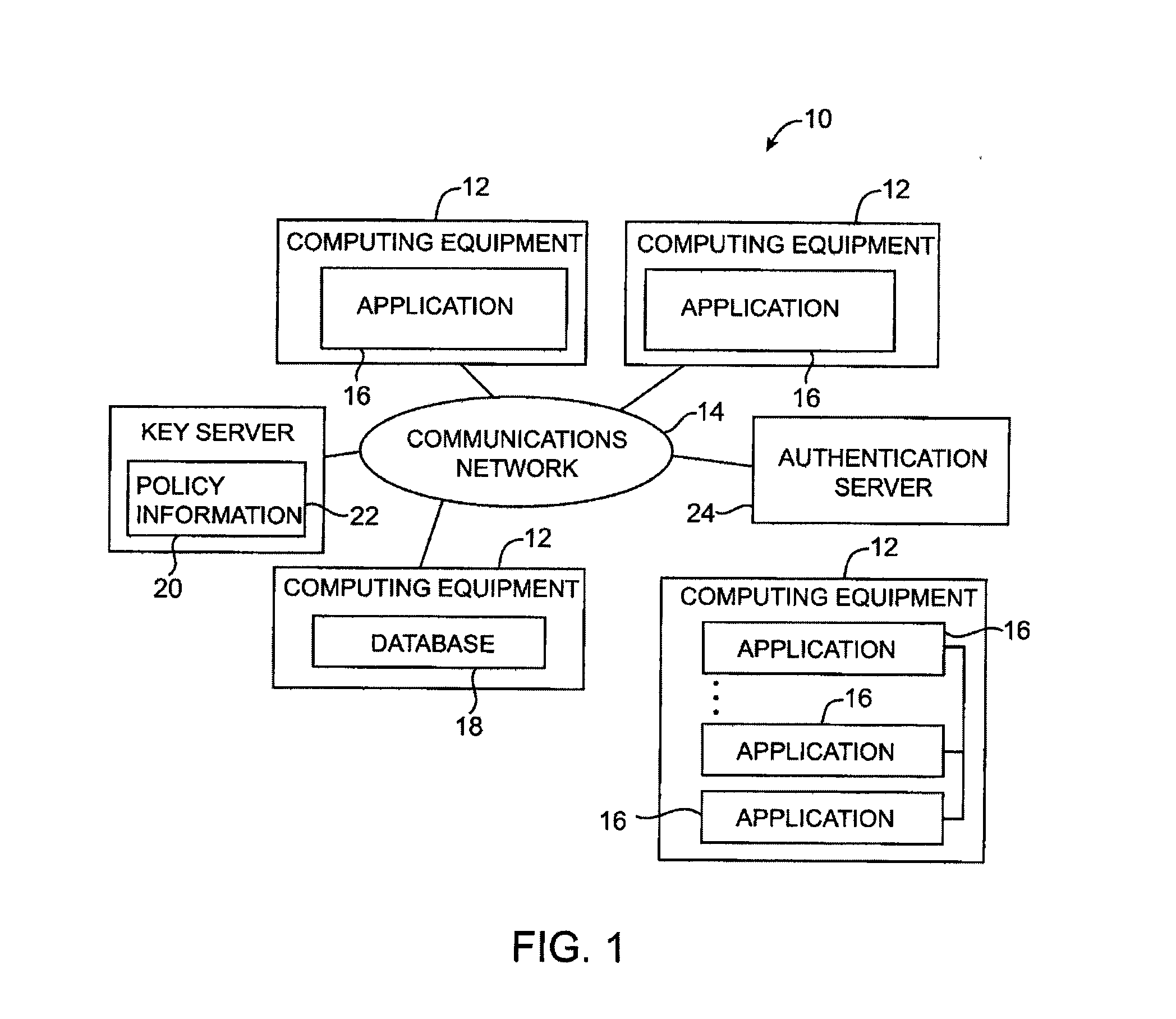
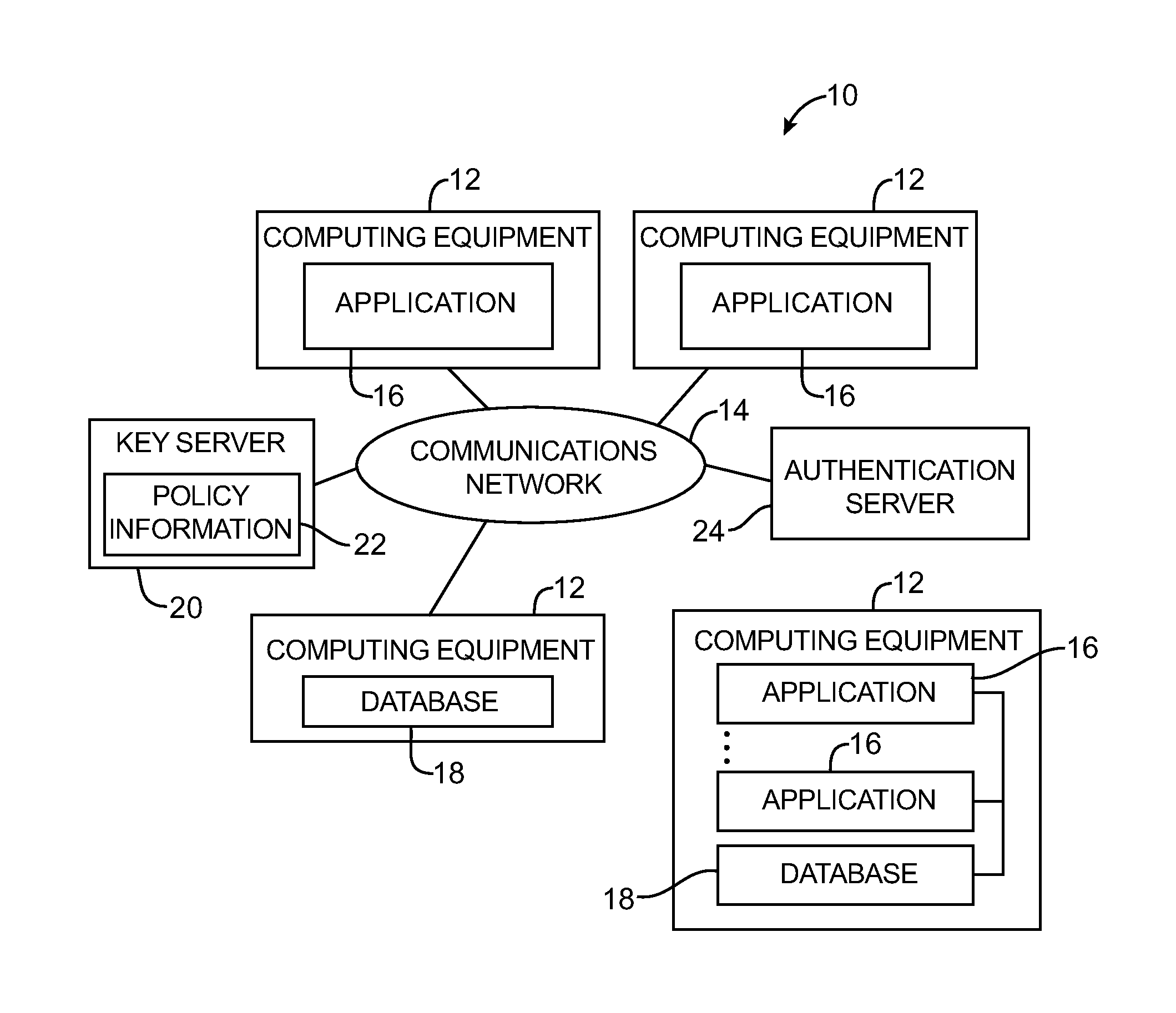
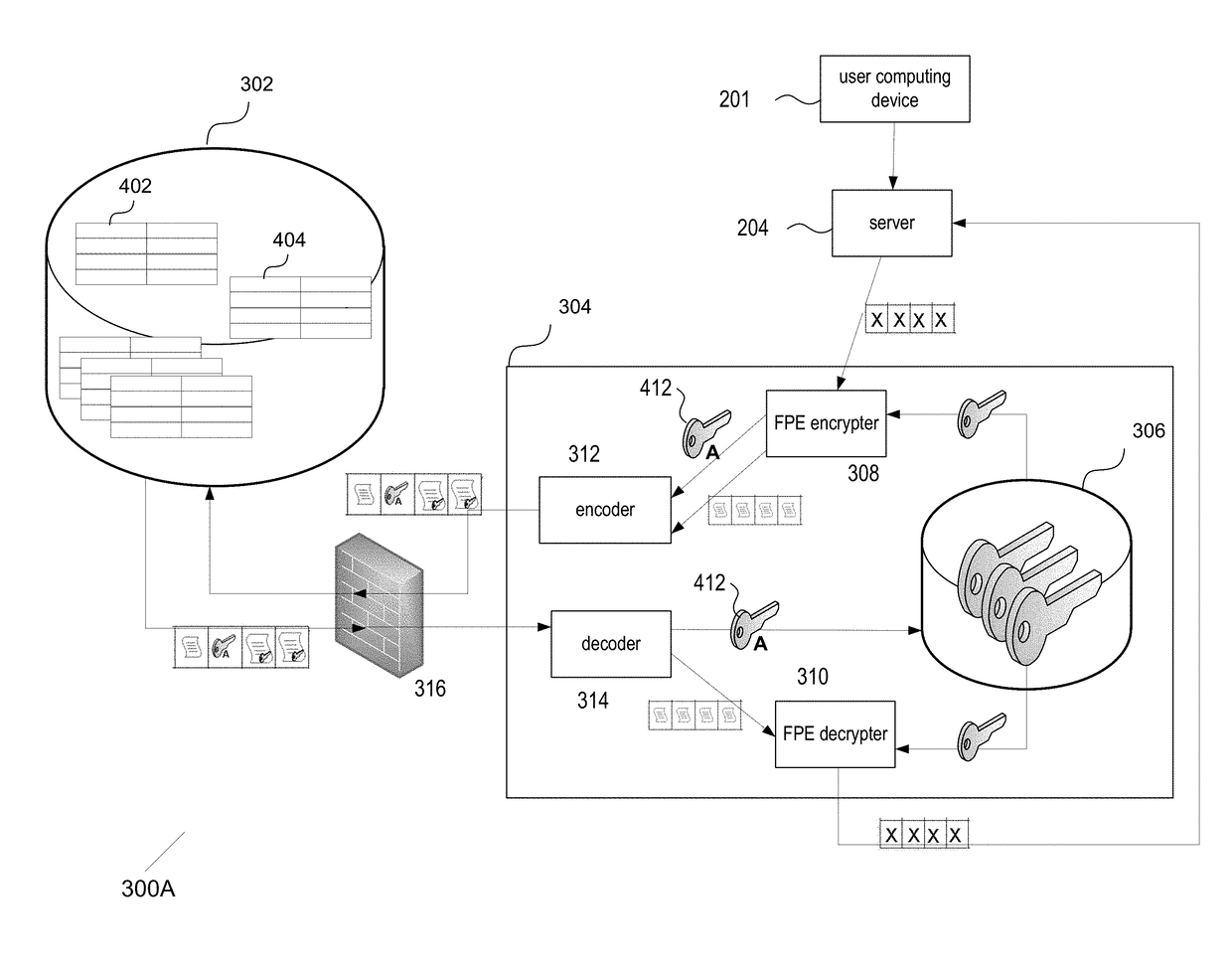
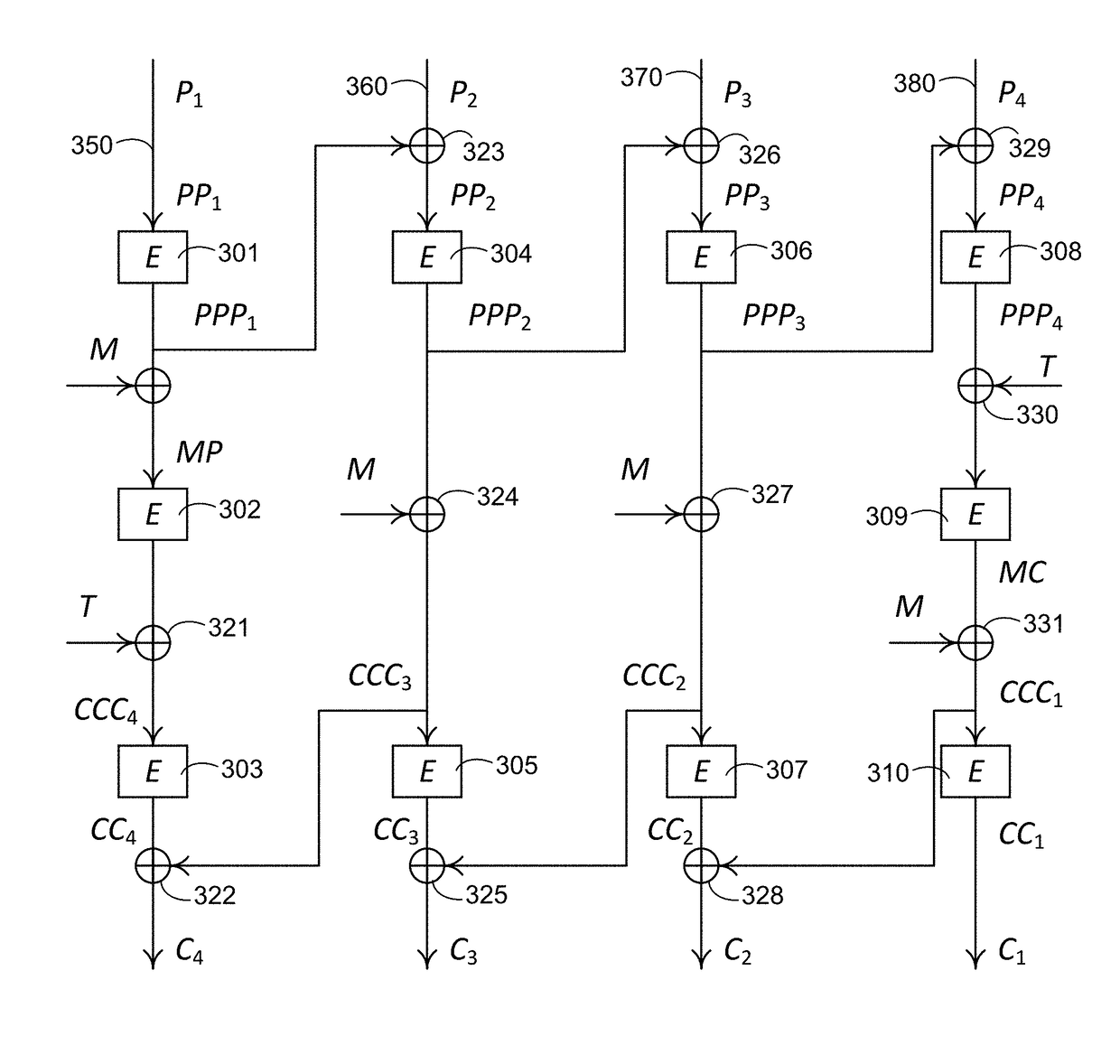
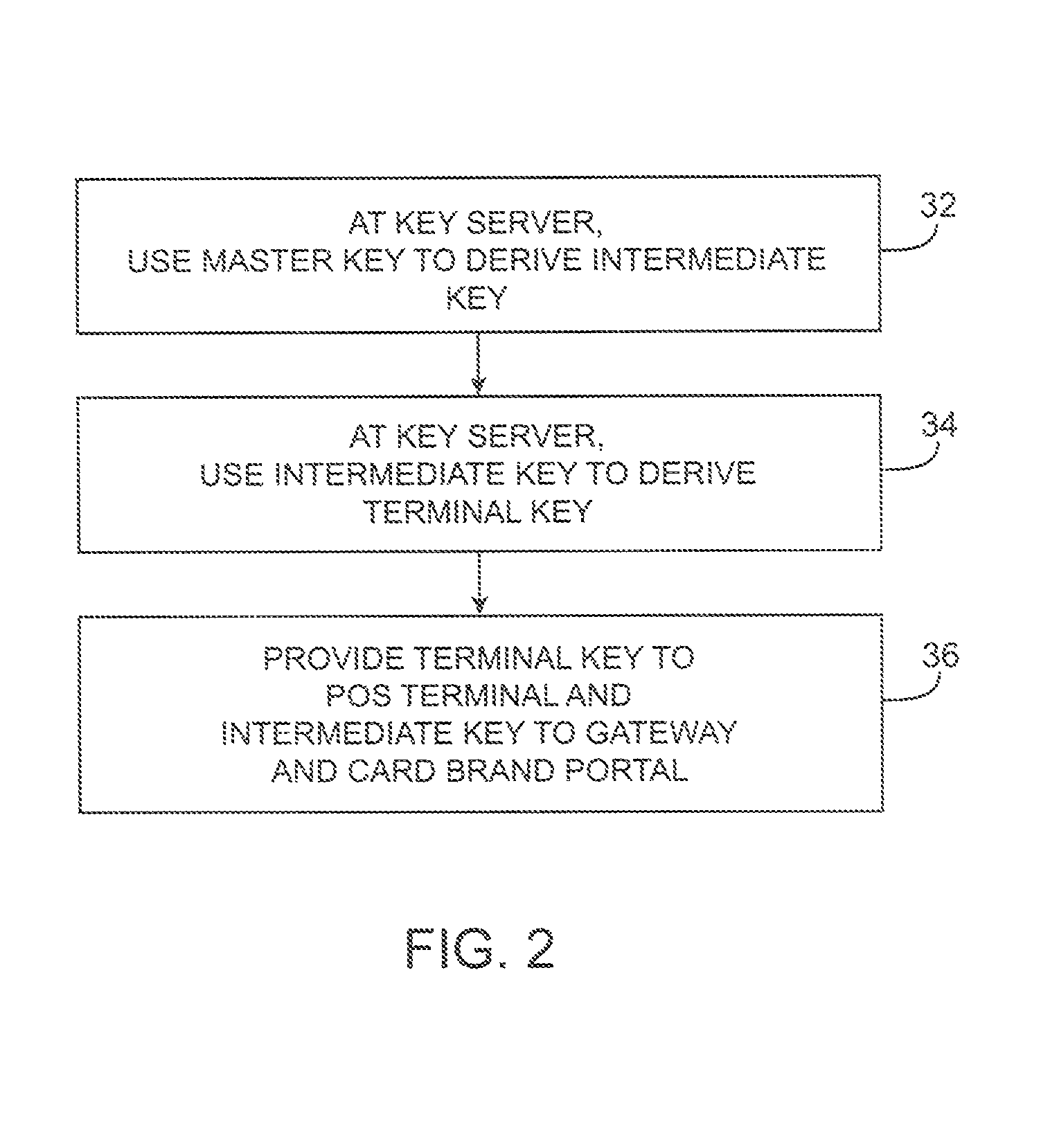
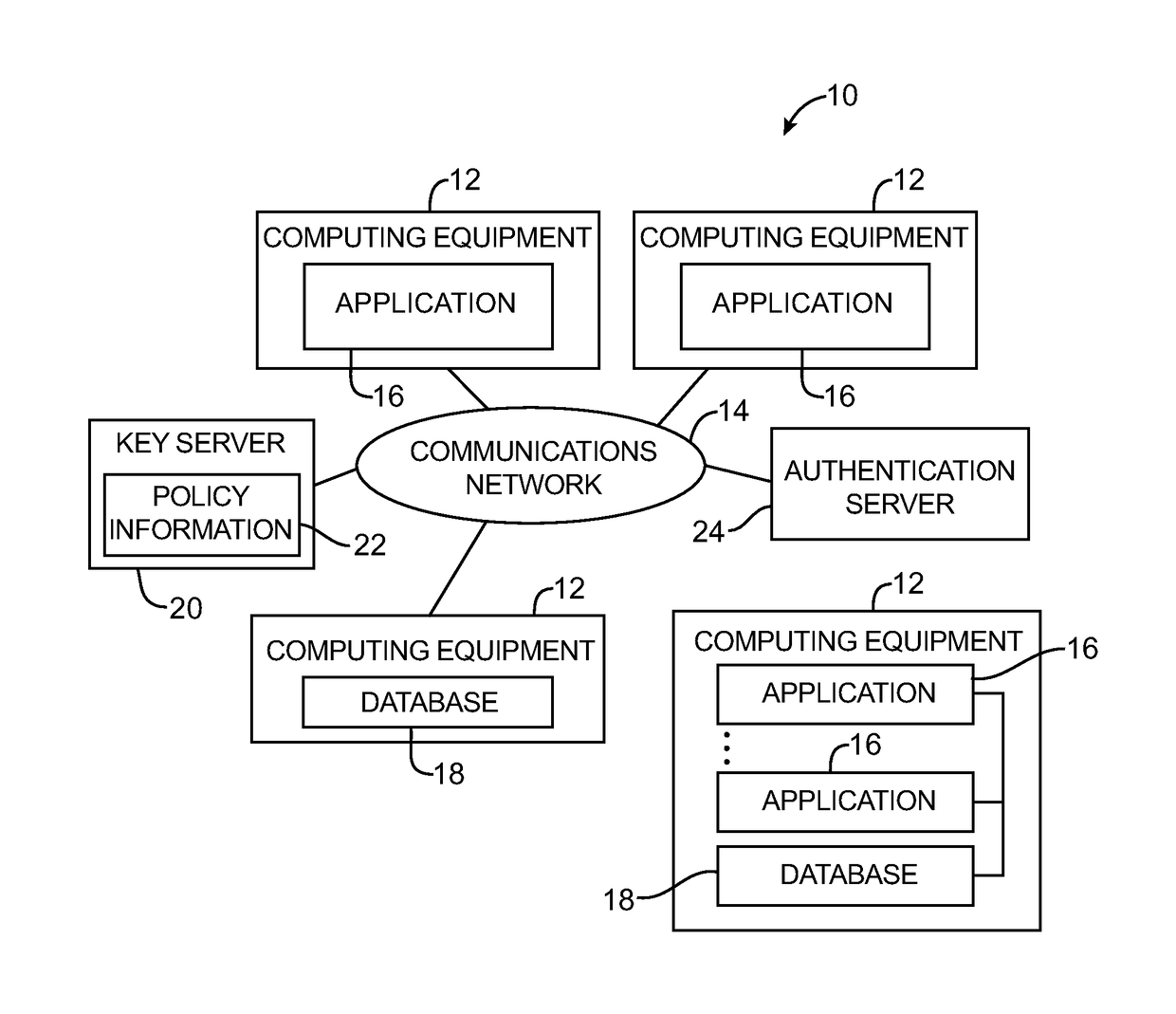
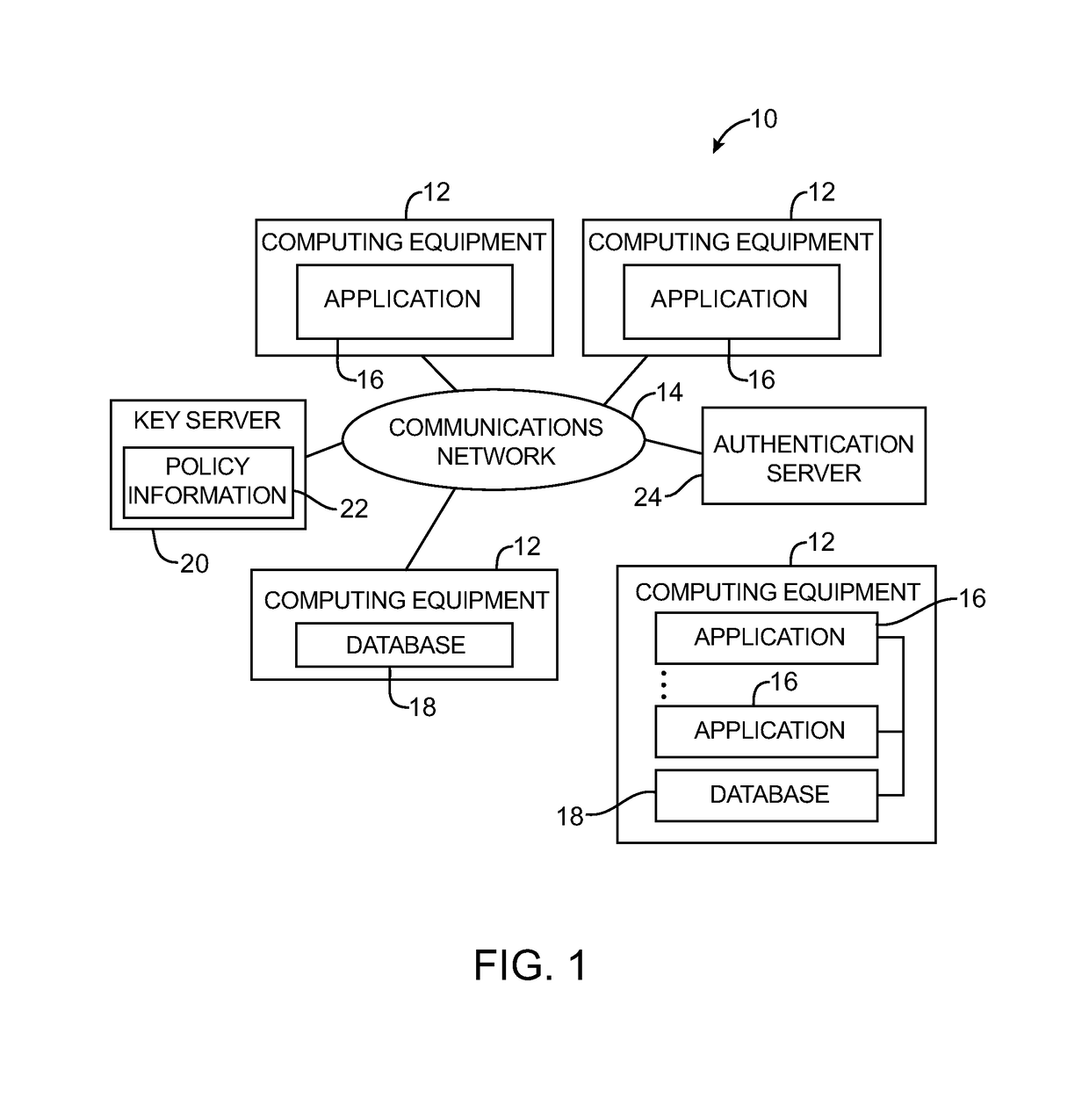
Key requests in a data processing system may include identifiers such as user names, policy names, and application names. The identifiers may also include validity period information indicating when corresponding keys are valid. When fulfilling a key request, a key server may use identifier information from the key request in determining which key access policies to apply and may use the identifier in determining whether an applicable policy has been satisfied. When a key request is authorized, the key server may generate a key by applying a one-way function to a root secret and the identifier. Validity period information for use by a decryption engine may be embedded in data items that include redundant information. Application testing can be facilitated by populating a test database with data that has been encrypted using a format-preserving encryption algorithm. Parts of a data string may be selectively encrypted based on their sensitivity.
Owner:MICRO FOCUS LLC
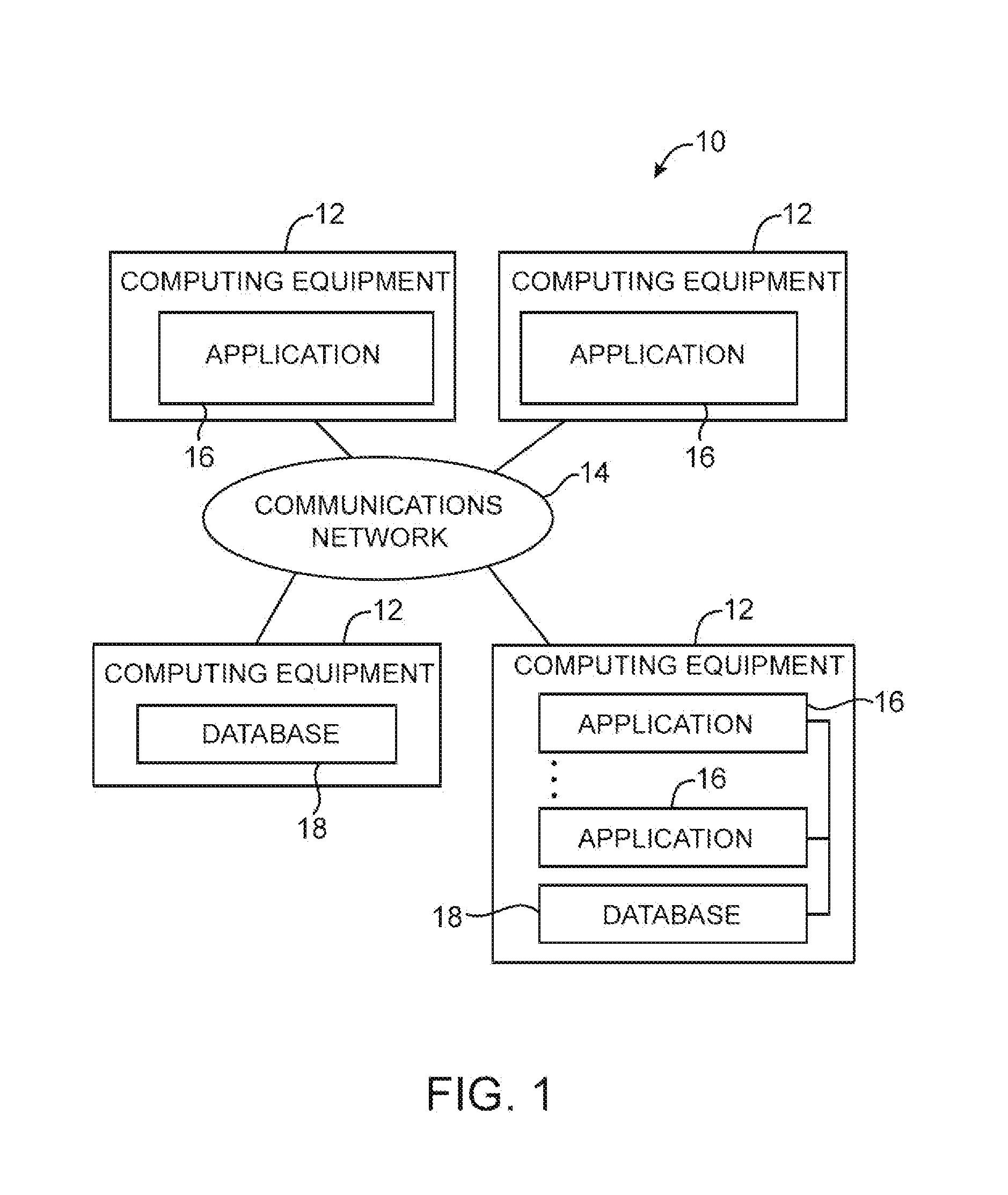
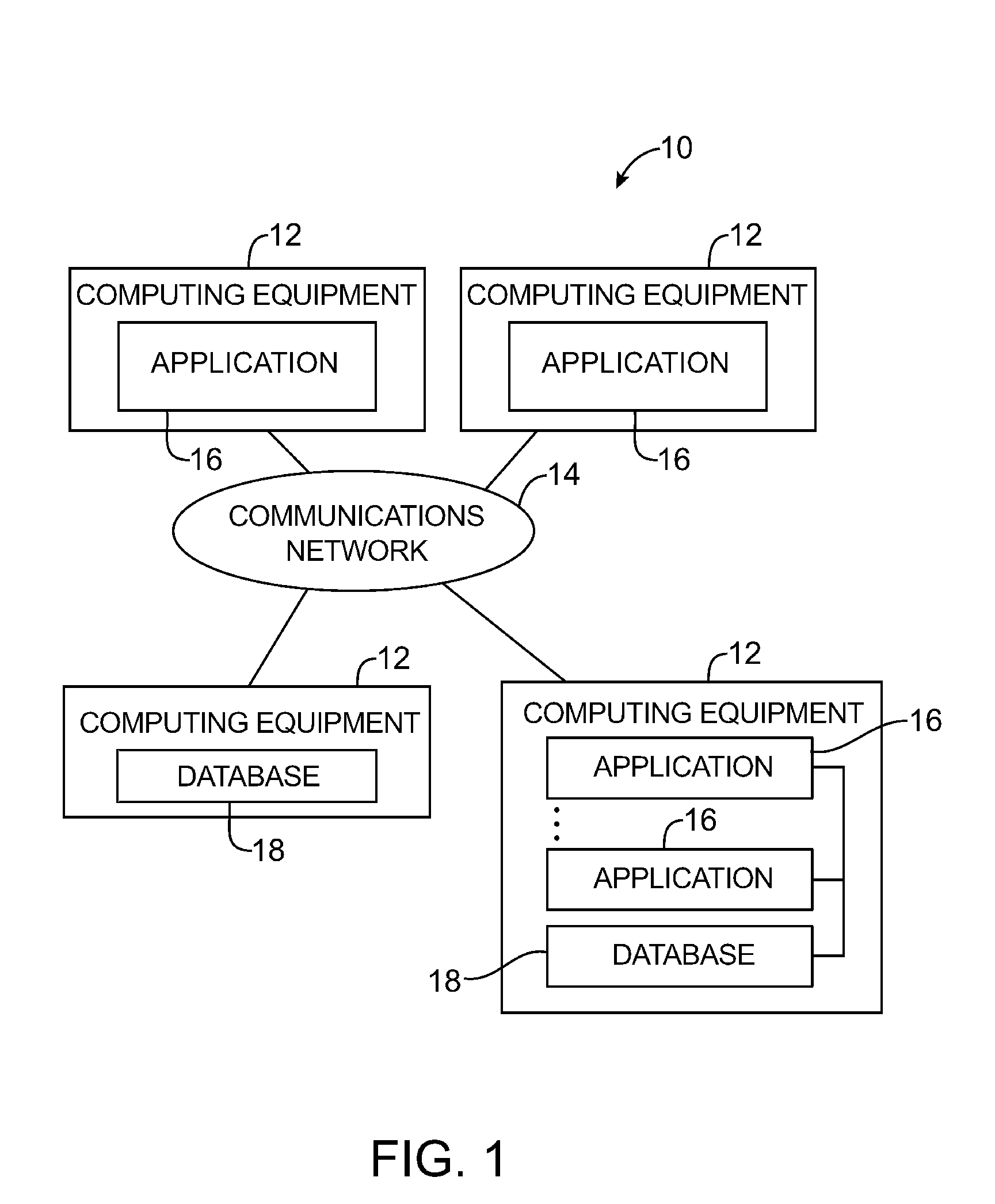
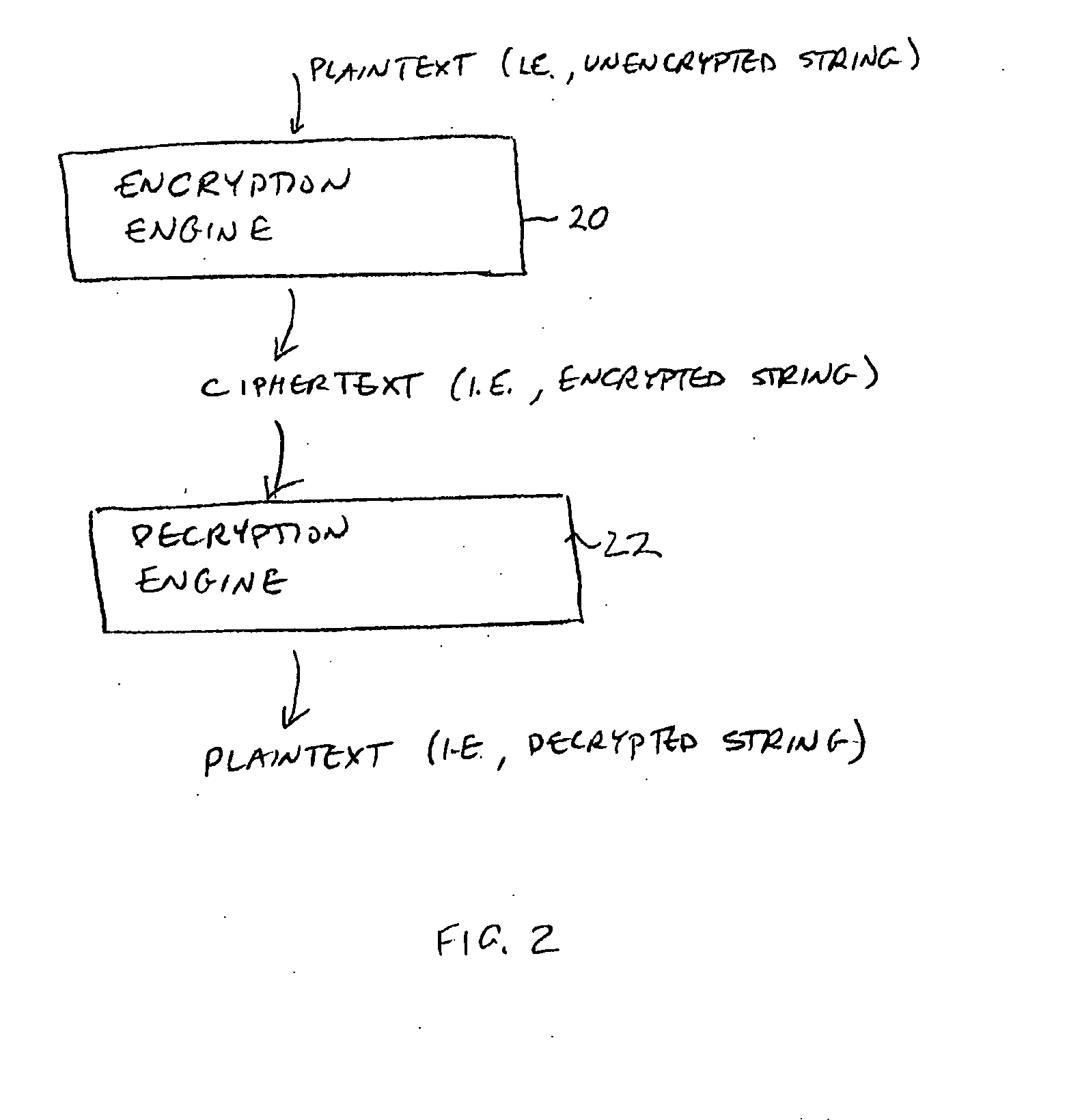
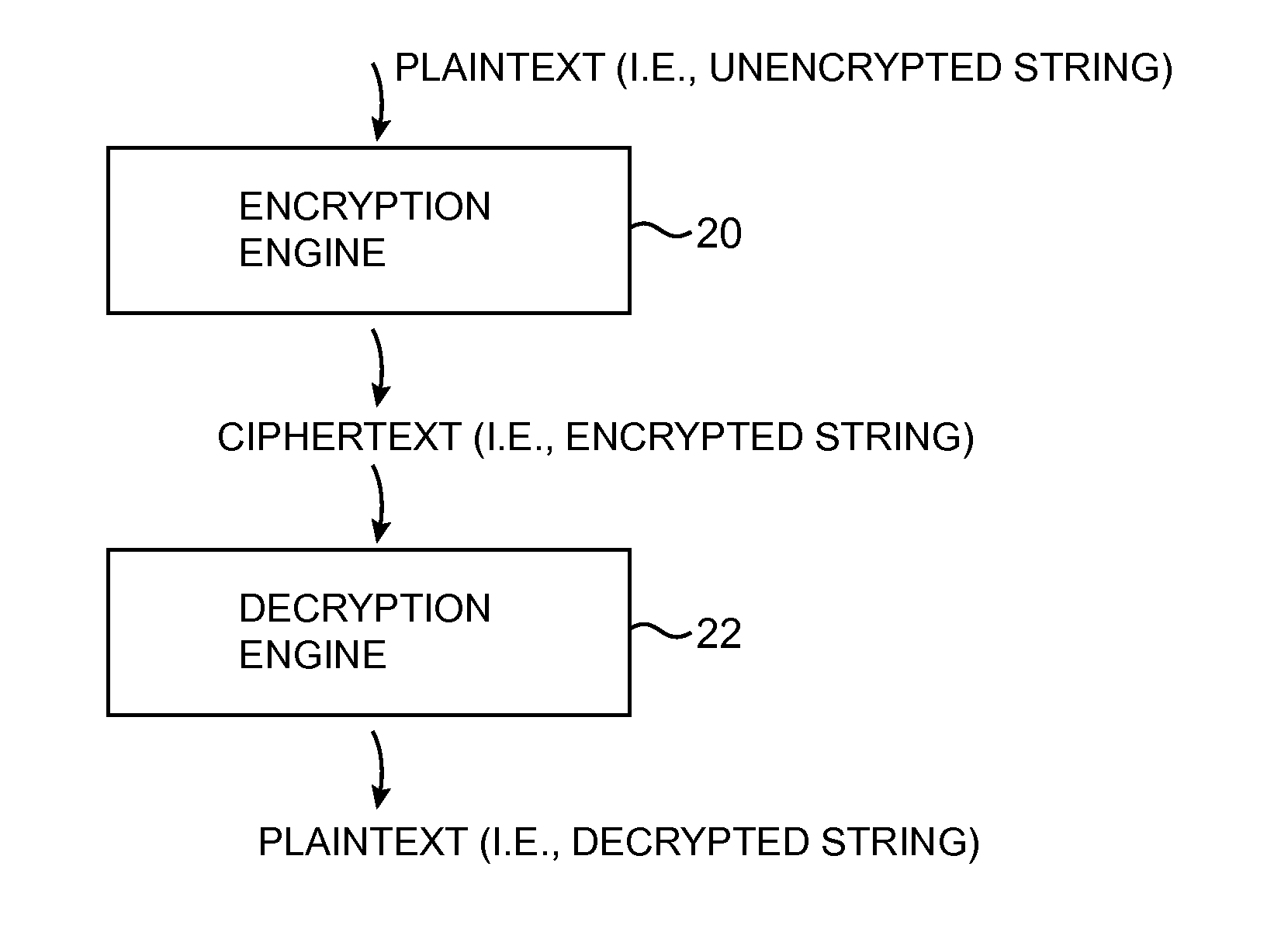
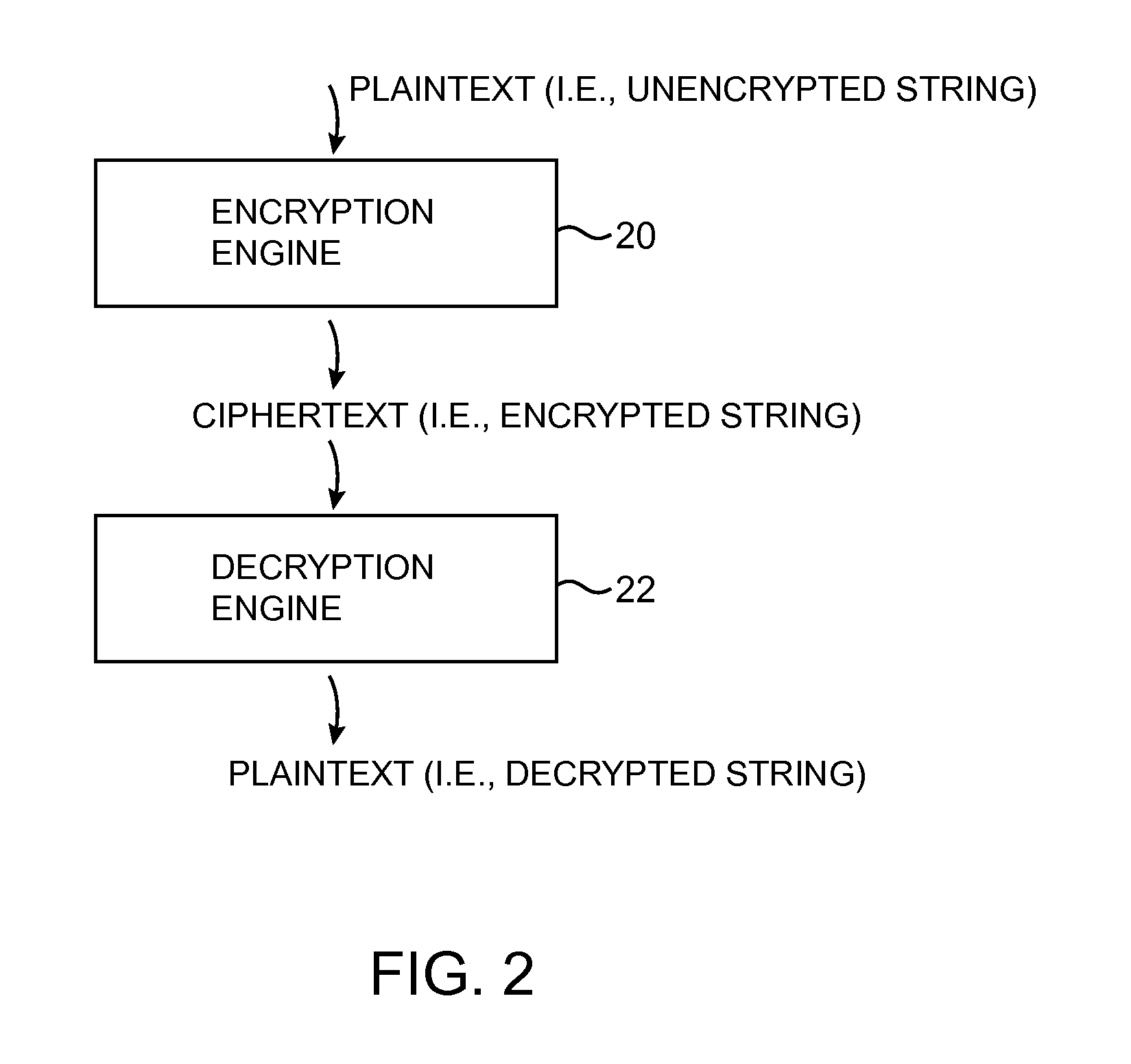
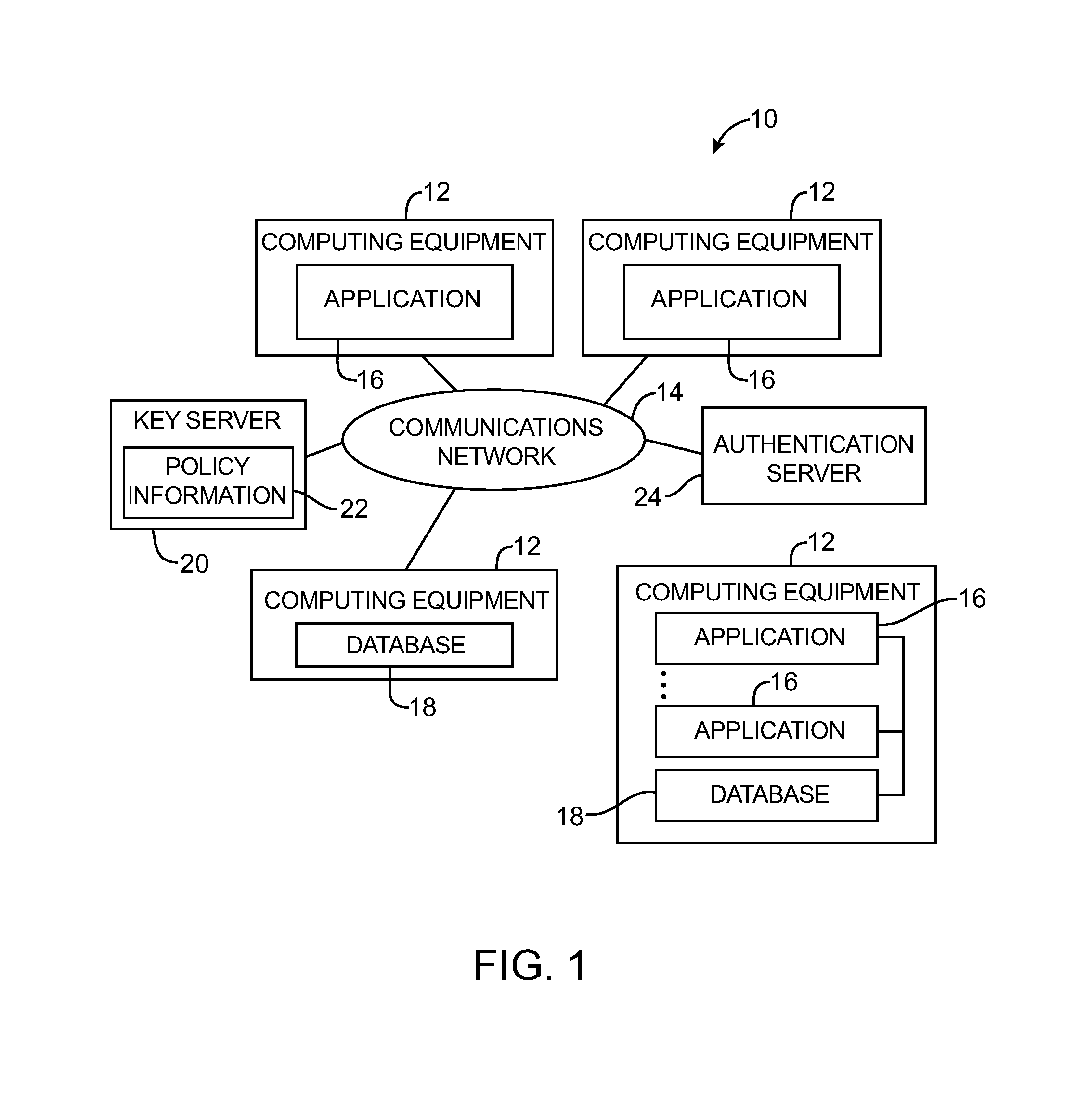
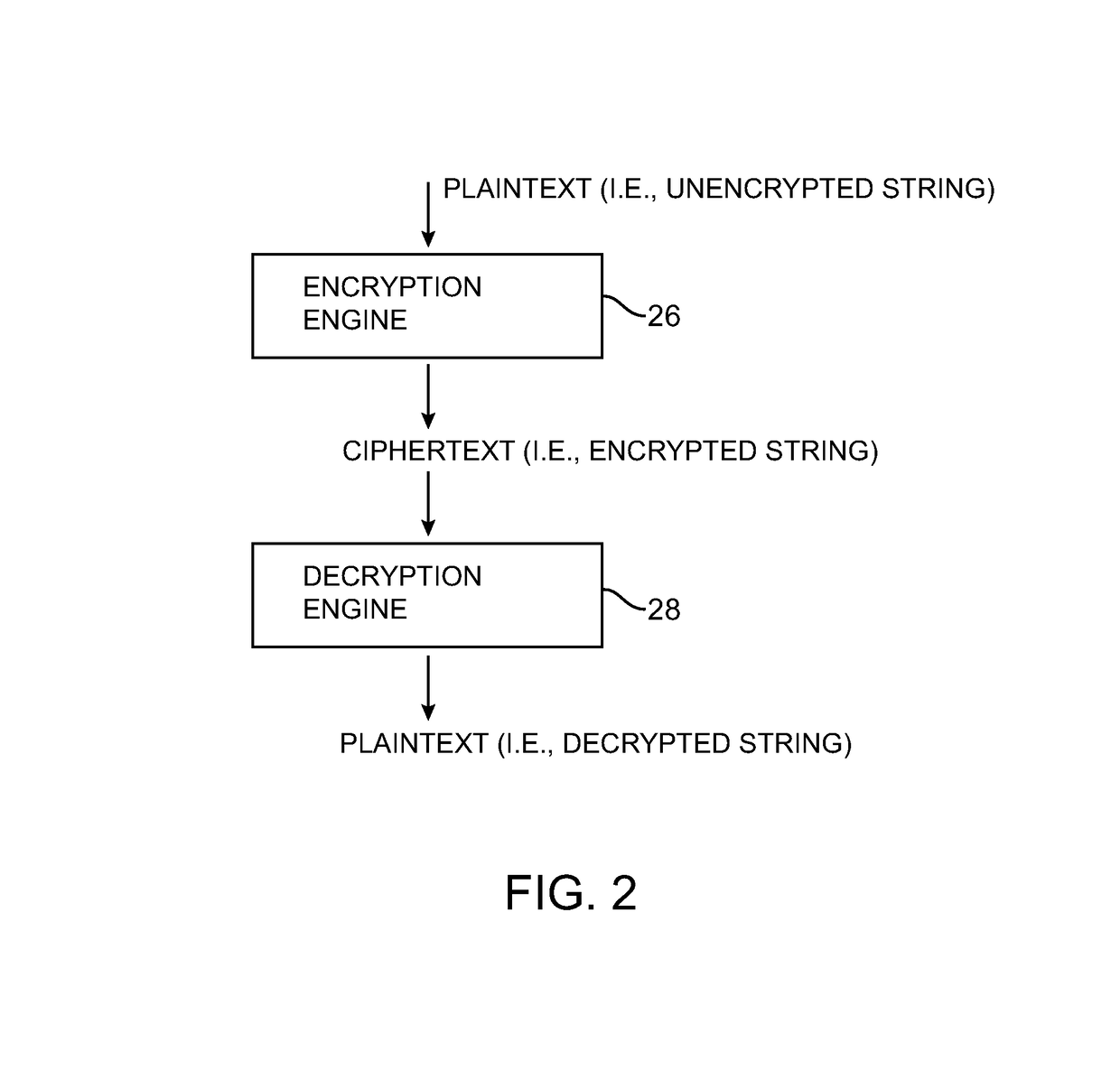
Data processing systems with format-preserving encryption and decryption engines
ActiveUS7864952B2User identity/authority verificationUnauthorized memory use protectionData processing systemBlock cipher
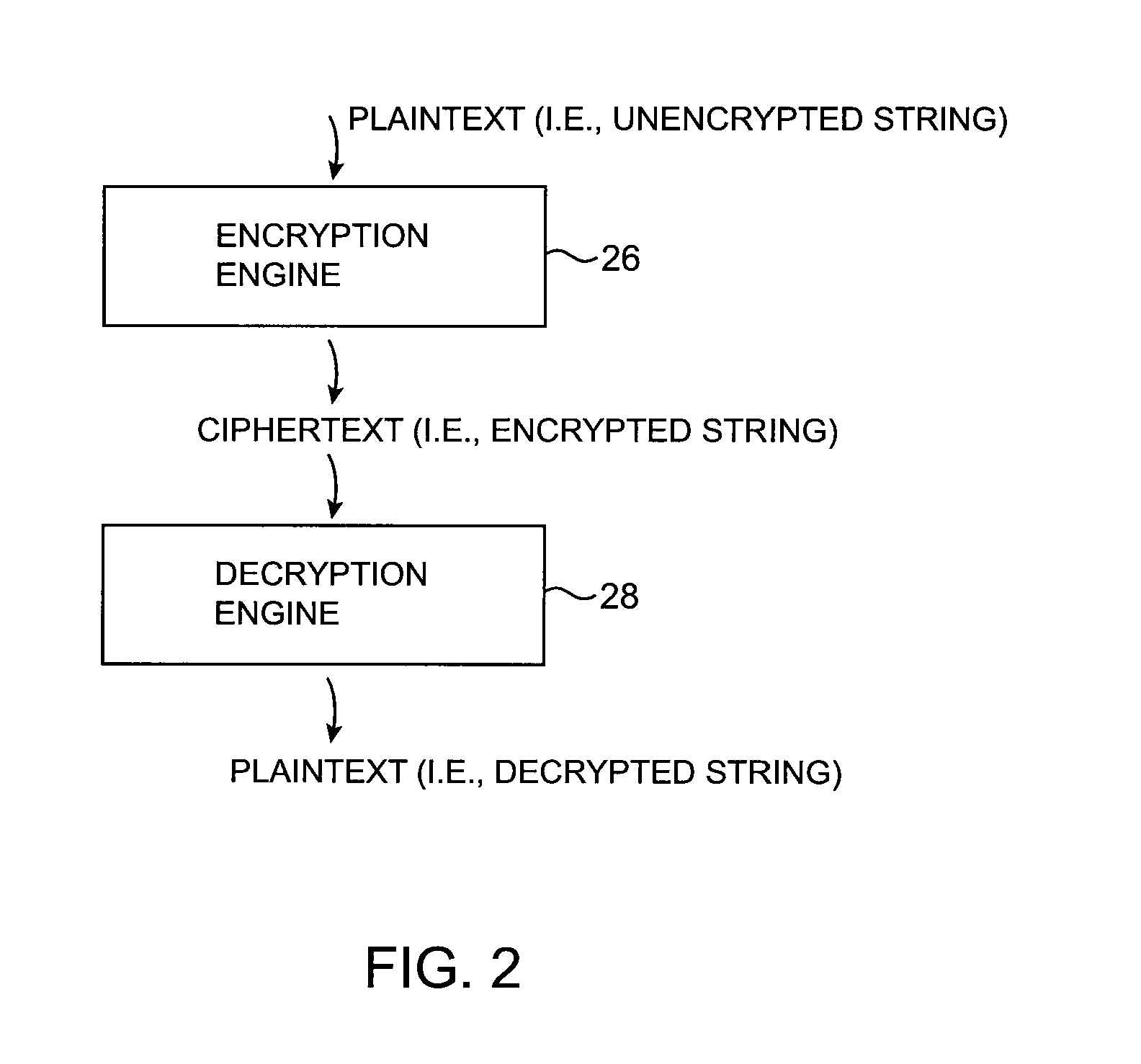
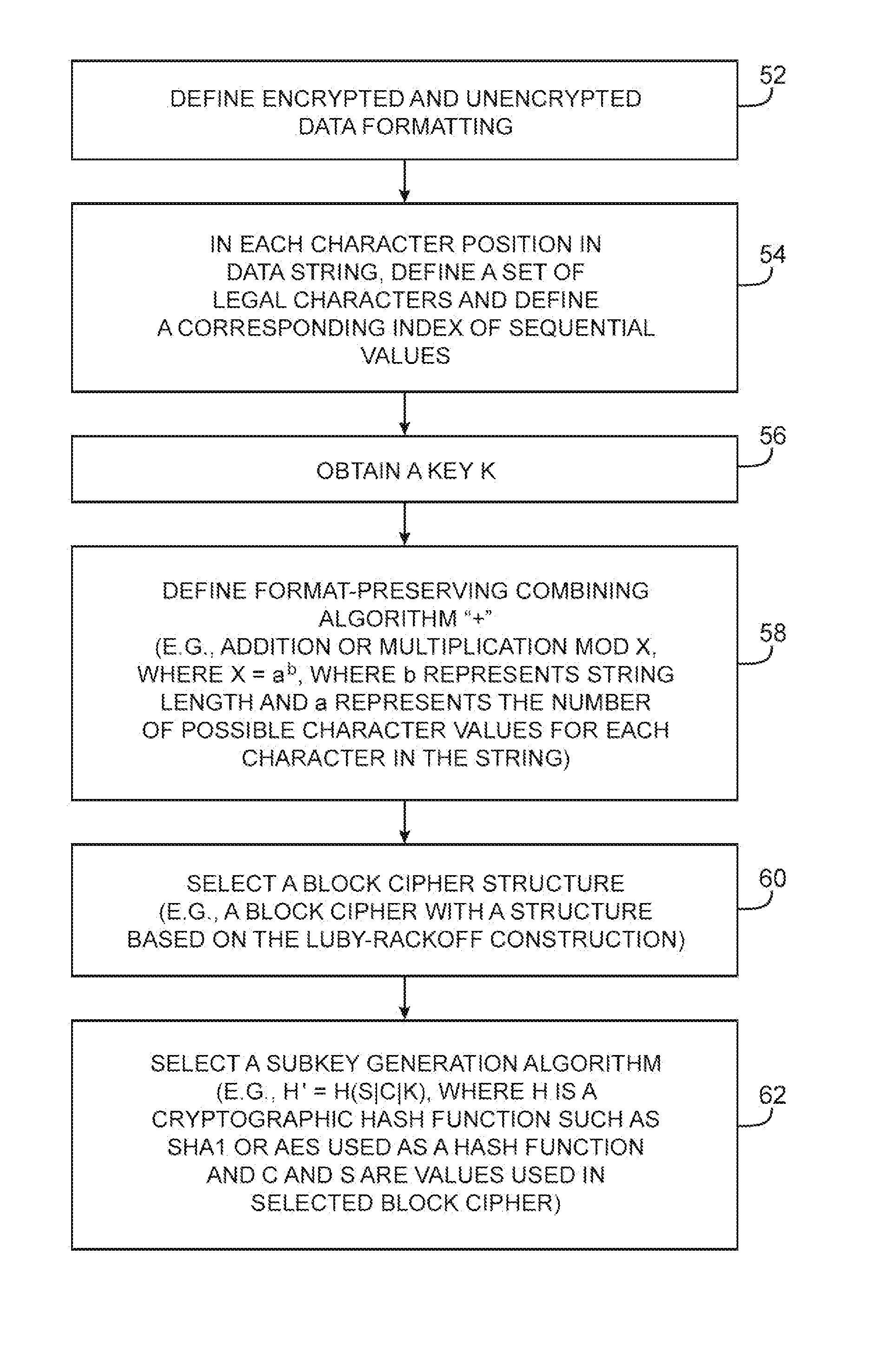
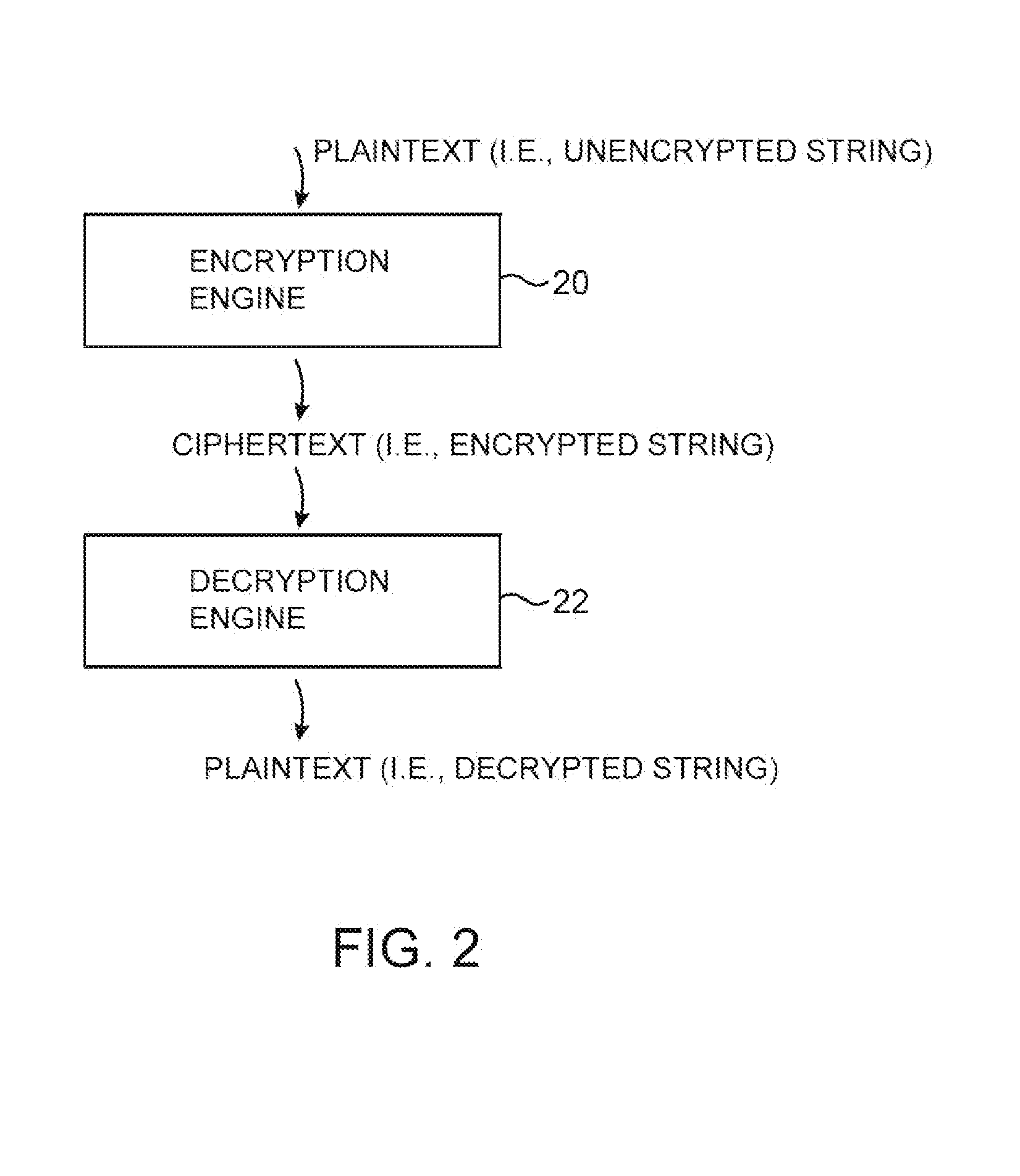
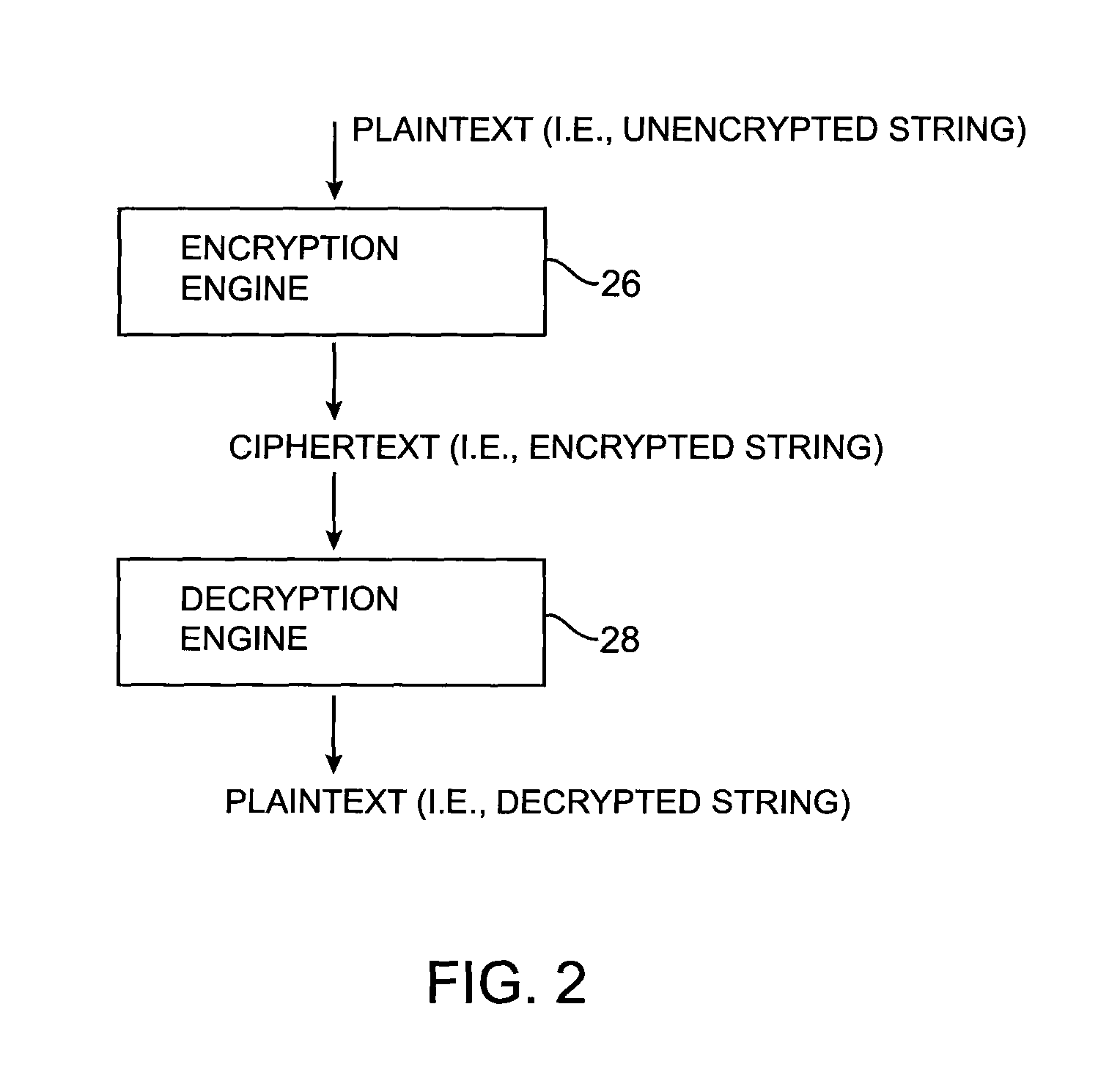
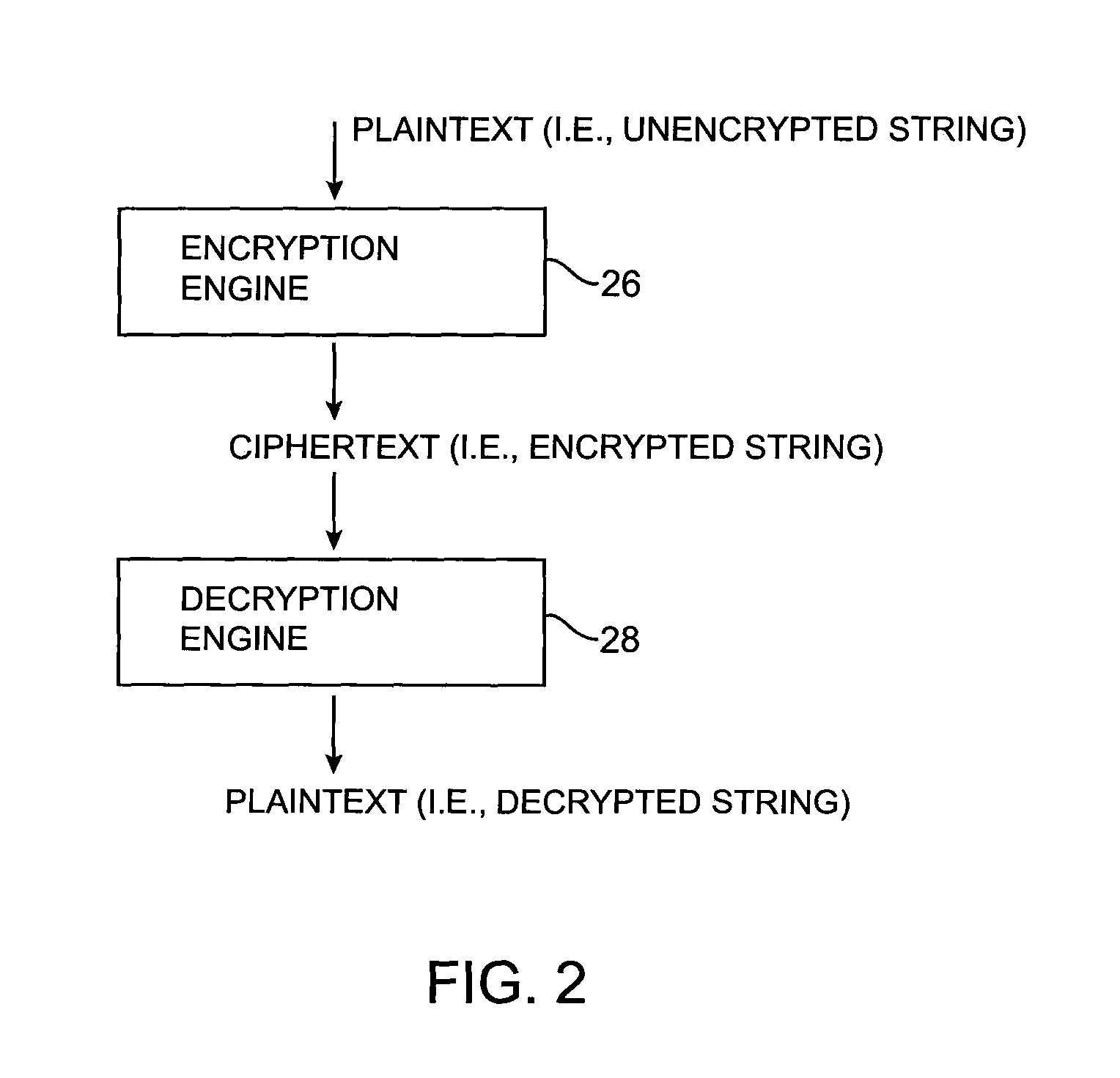
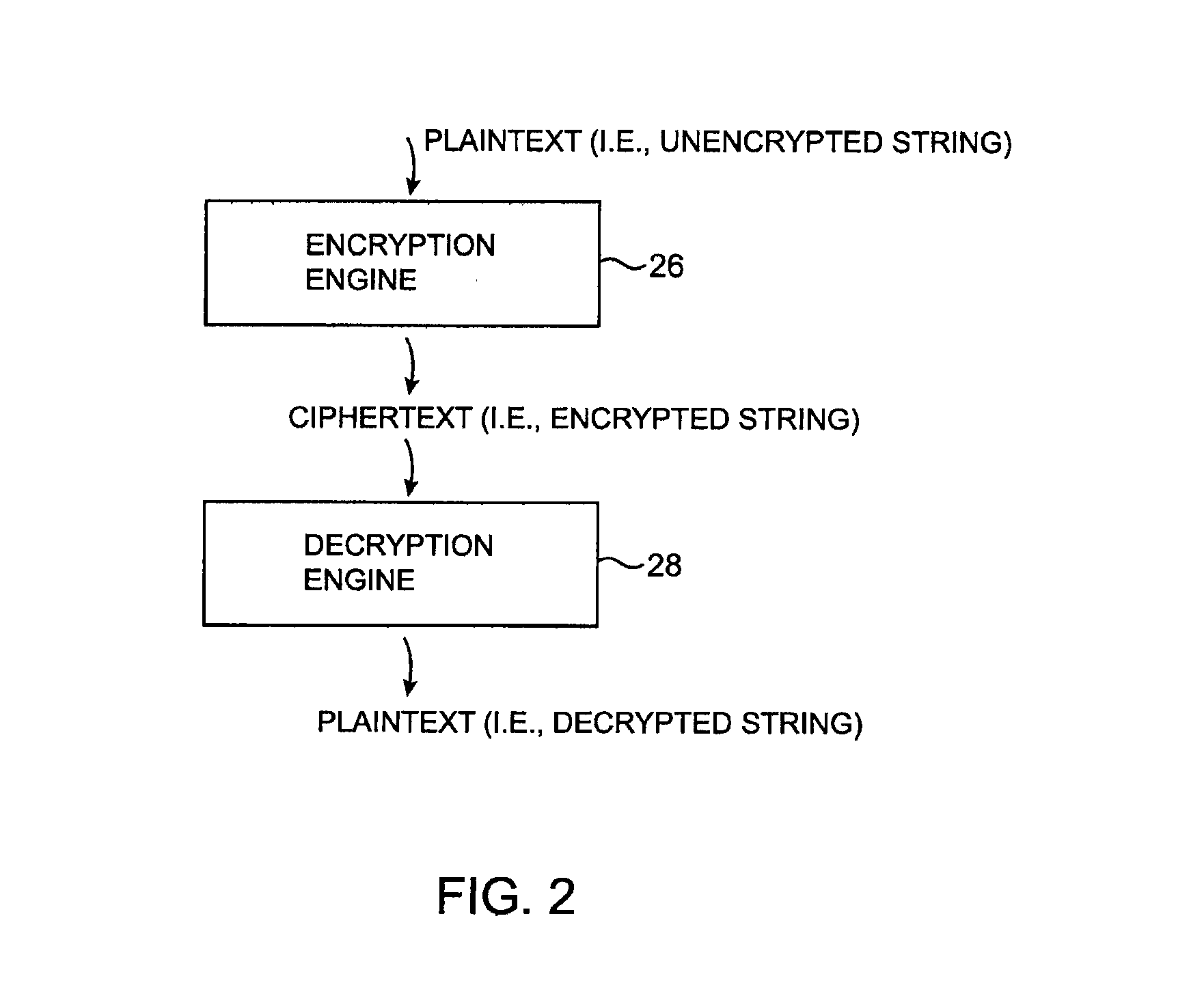
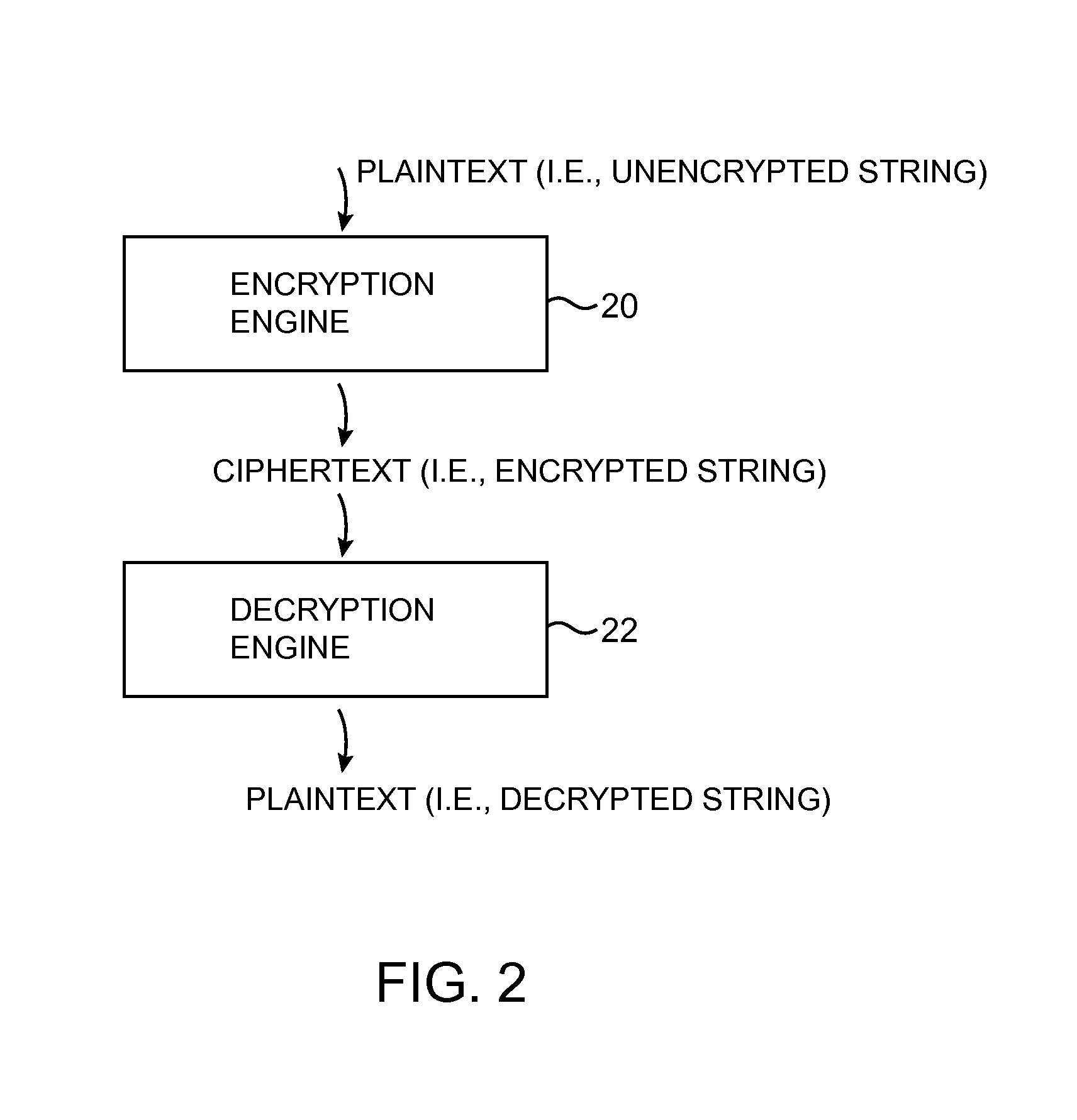
A data processing system is provided that includes format-preserving encryption and decryption engines. A string that contains characters has a specified format. The format defines a legal set of character values for each character position in the string. During encryption operations with the encryption engine, a string is processed to remove extraneous characters and to encode the string using an index. The processed string is encrypted using a format-preserving block cipher. The output of the block cipher is post-processed to produce an encrypted string having the same specified format as the original unencrypted string. During decryption operations, the decryption engine uses the format-preserving block cipher in reverse to transform the encrypted string into a decrypted string having the same format.
Owner:MICRO FOCUS LLC
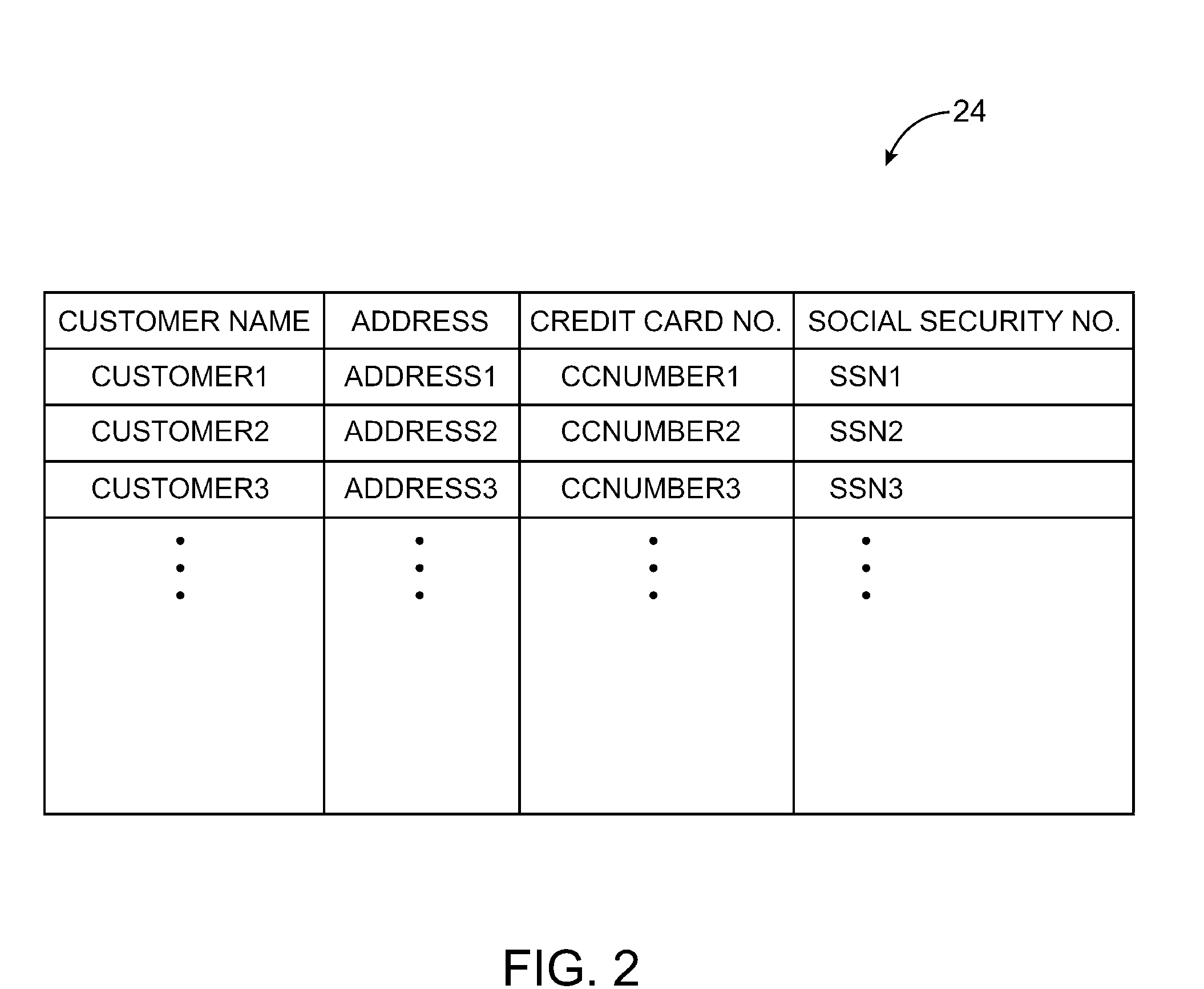
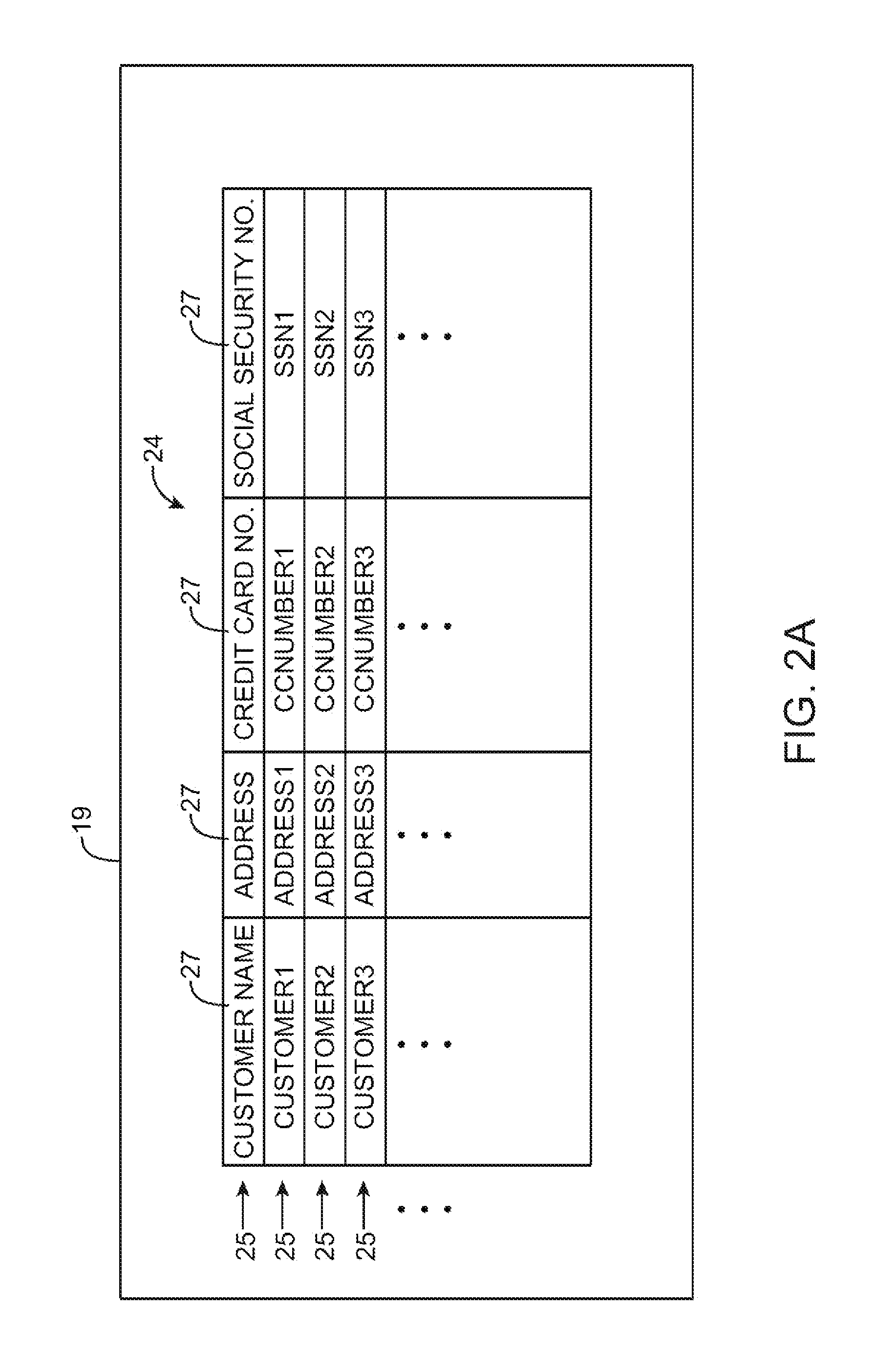
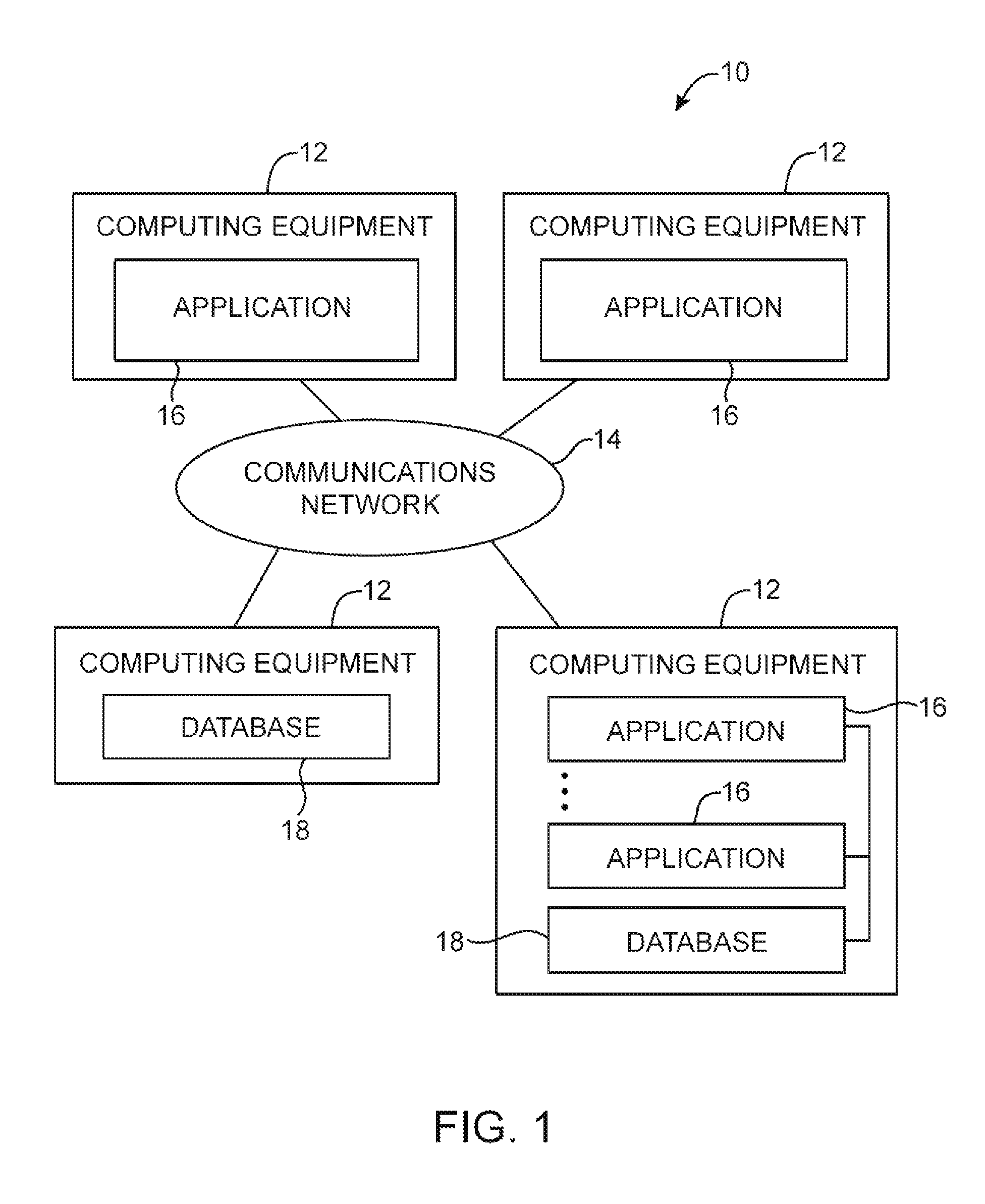
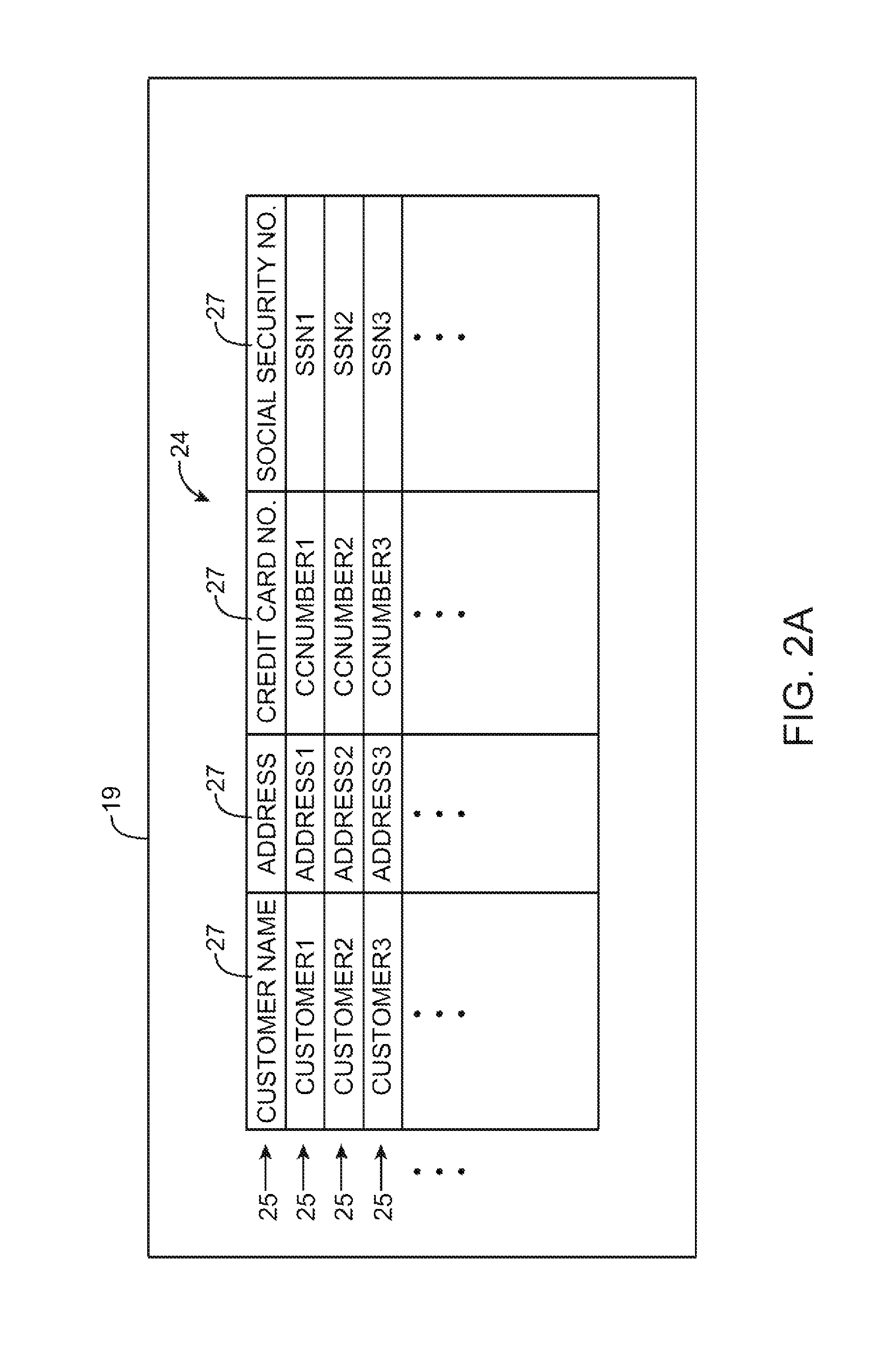
Systems for embedding information in data strings
ActiveUS20100284532A1Information be useCode conversionComputer security arrangementsData processing systemBase Number
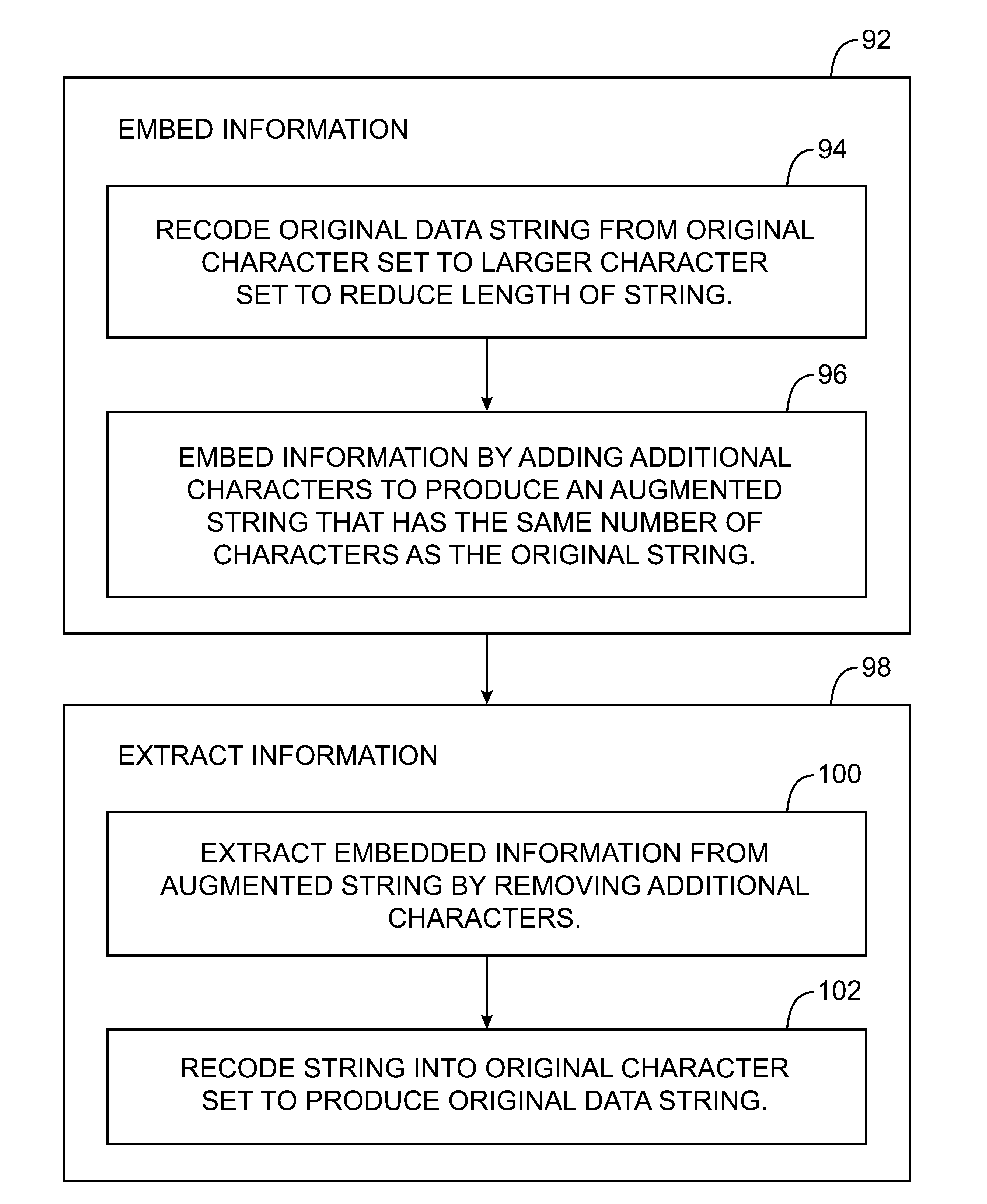
A data processing system is provided that includes applications, databases, encryption engines, and decryption engines. Encryption and decryption engines may be used to perform format-preserving encryption on data strings stored in a database. Applications may be used to embed information in data strings. Information may be embedded by using a character set that is larger than a character set being used by a data string. A data string may be converted into a larger character set, analogous to converting a number from a lower base to higher base. Such a conversion may shorten a data string, allowing information to be embedded as appended characters.
Owner:MICRO FOCUS LLC
Data processing systems with format-preserving encryption and decryption engines
ActiveUS20100074441A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationData processing systemBlock cipher
A data processing system is provided that includes format-preserving encryption and decryption engines. A string that contains characters has a specified format. The format defines a legal set of character values for each character position in the string. During encryption operations with the encryption engine, a string is processed to remove extraneous characters and to encode the string using an index. The processed string is encrypted using a format-preserving block cipher. The output of the block cipher is post-processed to produce an encrypted string having the same specified format as the original unencrypted string. During decryption operations, the decryption engine uses the format-preserving block cipher in reverse to transform the encrypted string into a decrypted string having the same format.
Owner:MICRO FOCUS LLC
Data processing systems with format-preserving encryption and decryption engines
ActiveUS20140108813A1Unauthorized memory use protectionHardware monitoringData processing systemBlock cipher
A data processing system is provided that includes format-preserving encryption and decryption engines. A string that contains characters has a specified format. The format defines a legal set of character values for each character position in the string. During encryption operations with the encryption engine, a string is processed to remove extraneous characters and to encode the string using an index. The processed string is encrypted using a format-preserving block cipher. The output of the block cipher is post-processed to produce an encrypted string having the same specified format as the original unencrypted string. During decryption operations, the decryption engine uses the format-preserving block cipher in reverse to transform the encrypted string into a decrypted string having the same format.
Owner:MICRO FOCUS LLC
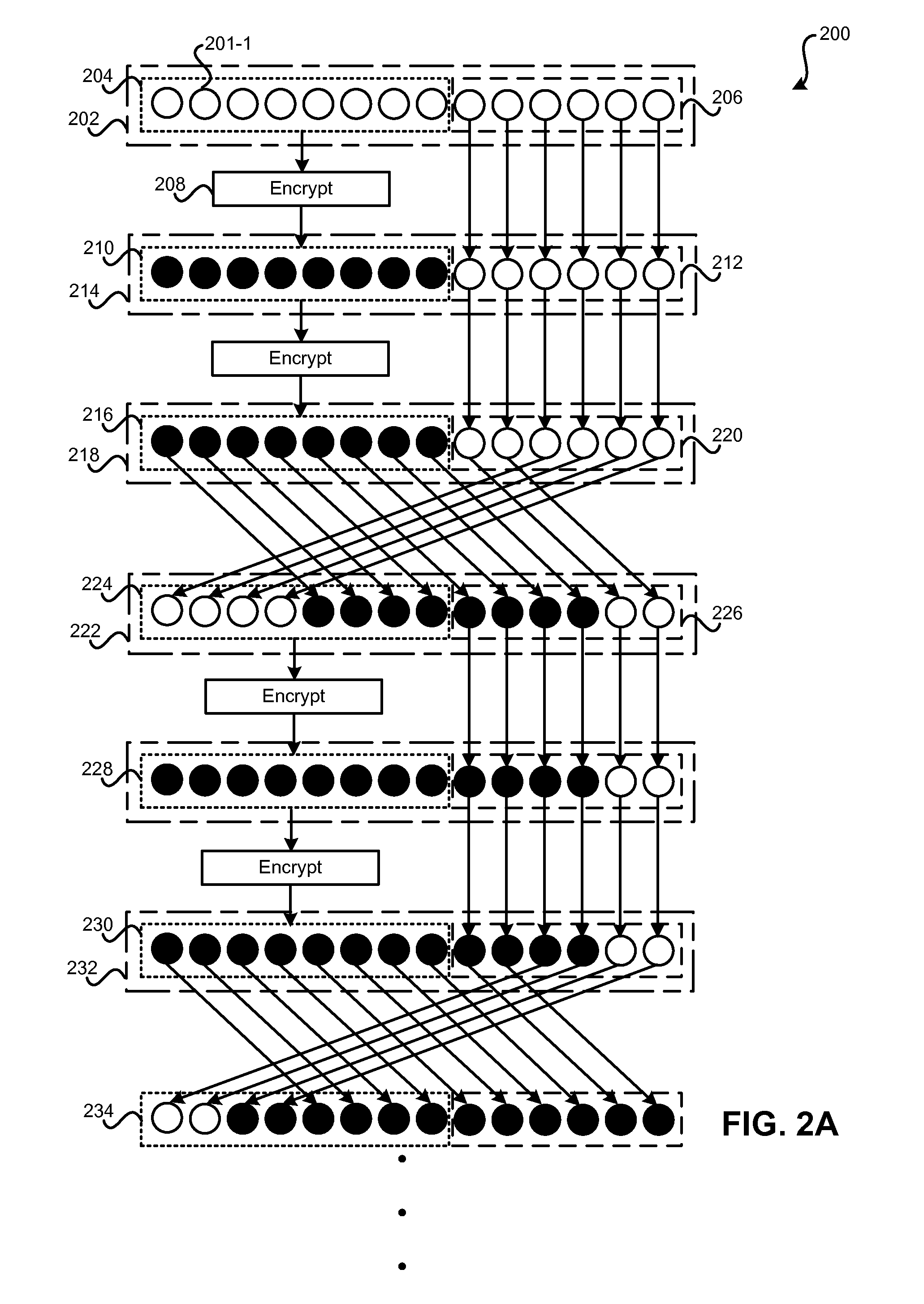
Format-Preserving Encryption Via Rotating Block Encryption
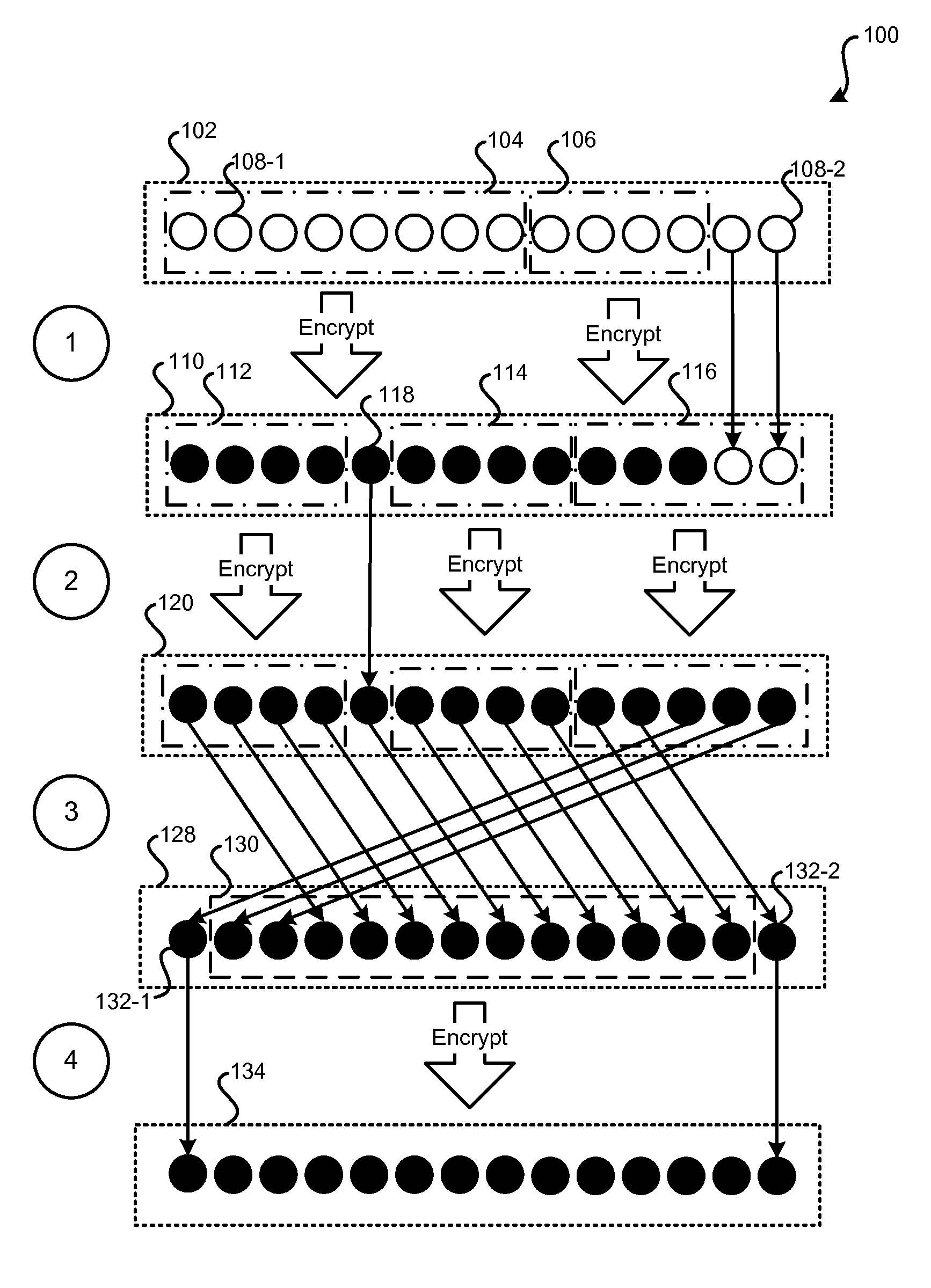
Methods and systems are described for format-preserving encryption. Format-preserving encryption on an entire format F may be achieved by performing format-preserving encryption on one or more subsets of F and then applying one or more permutation rounds in such a way that all elements of F enter a subset to be encrypted. A predetermined number of encryption rounds and a predetermined number of permutation rounds may be interleaved until all elements are thoroughly mixed. The resultant output data may be saved in a database in the same format as the original input data, meet all constraints of the database, and pass all validity checks applied by software supporting the database.
Owner:CA TECH INC
Systems for structured encryption using embedded information in data strings
ActiveUS20130198525A1Unauthorized memory use protectionHardware monitoringData processing systemUsage data
A data processing system is provided that includes applications, databases, encryption engines, and decryption engines. Encryption and decryption engines may be used to perform format-preserving encryption on data strings stored in a database. Encryption and decryption engines may include embedded-format-preserving encryption and decryption engines. Embedded-format-preserving encryption engines may be used to encrypt data strings and embed information in data strings. Information corresponding to a format-preserving encryption operation of a data string may be embedded in an associated data string. The associated data string may be encrypted before or after embedding the information in the associated data string. The embedded information may include key management data that corresponds to a managed encryption key that was used to encrypt the data string.
Owner:MICRO FOCUS LLC
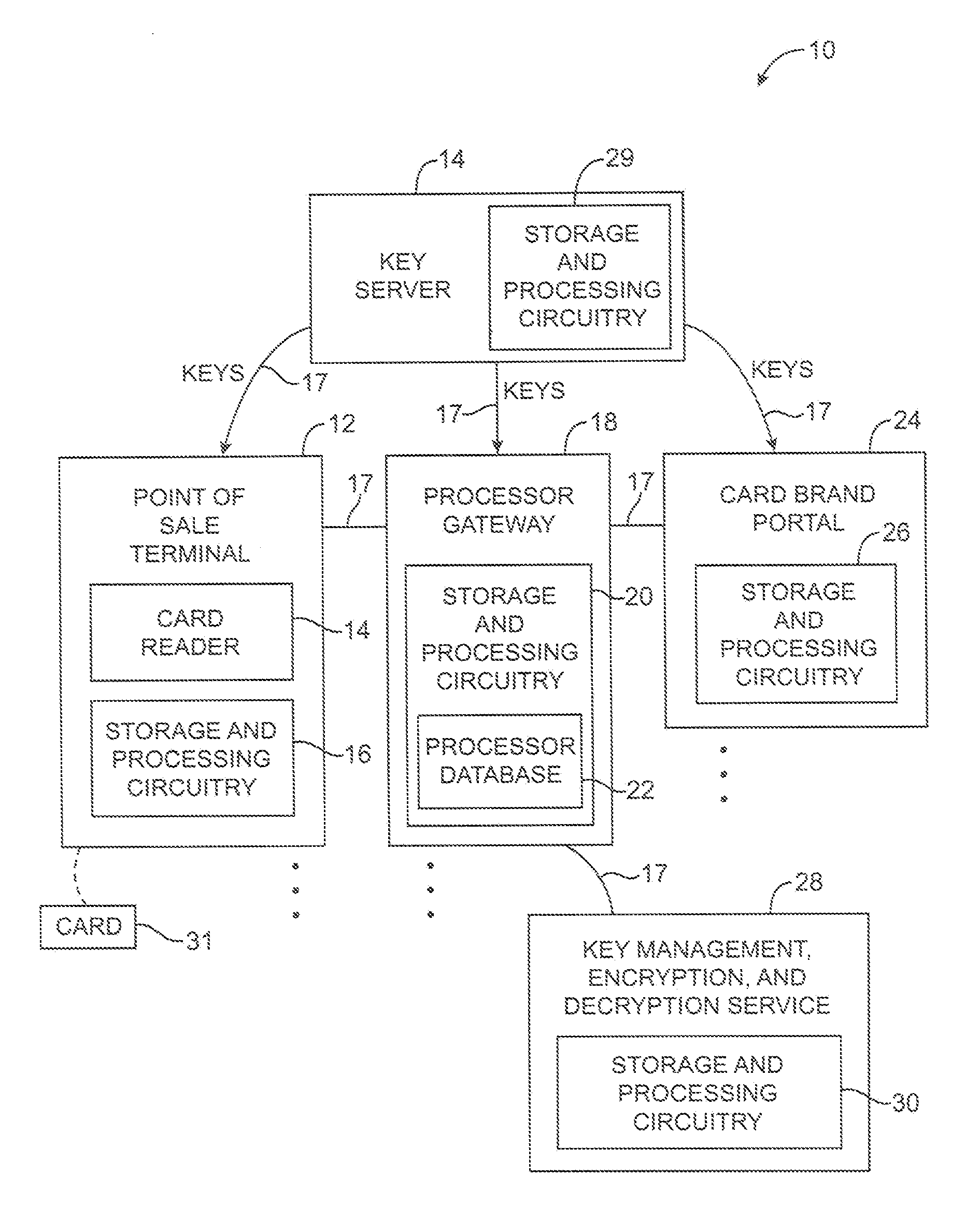
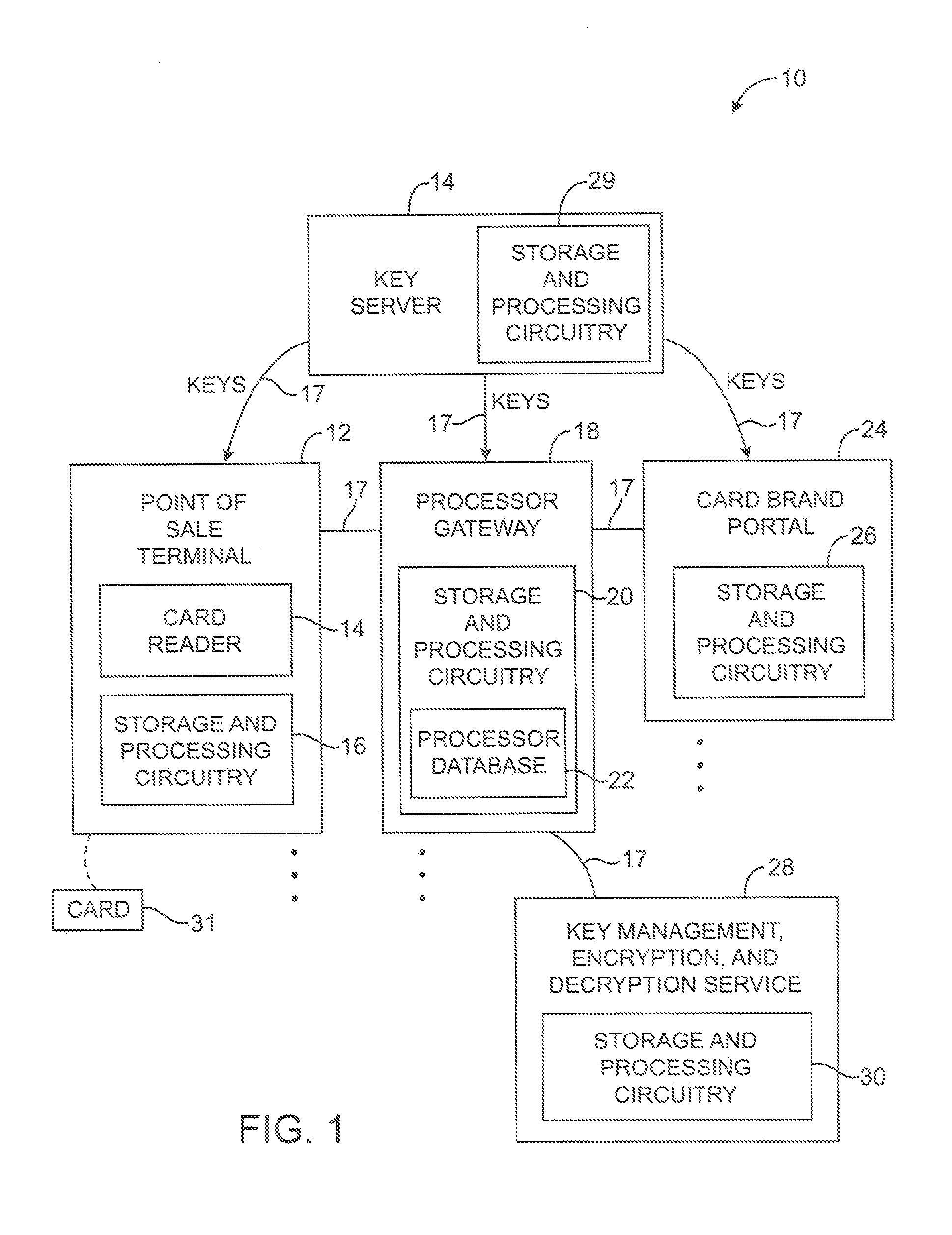
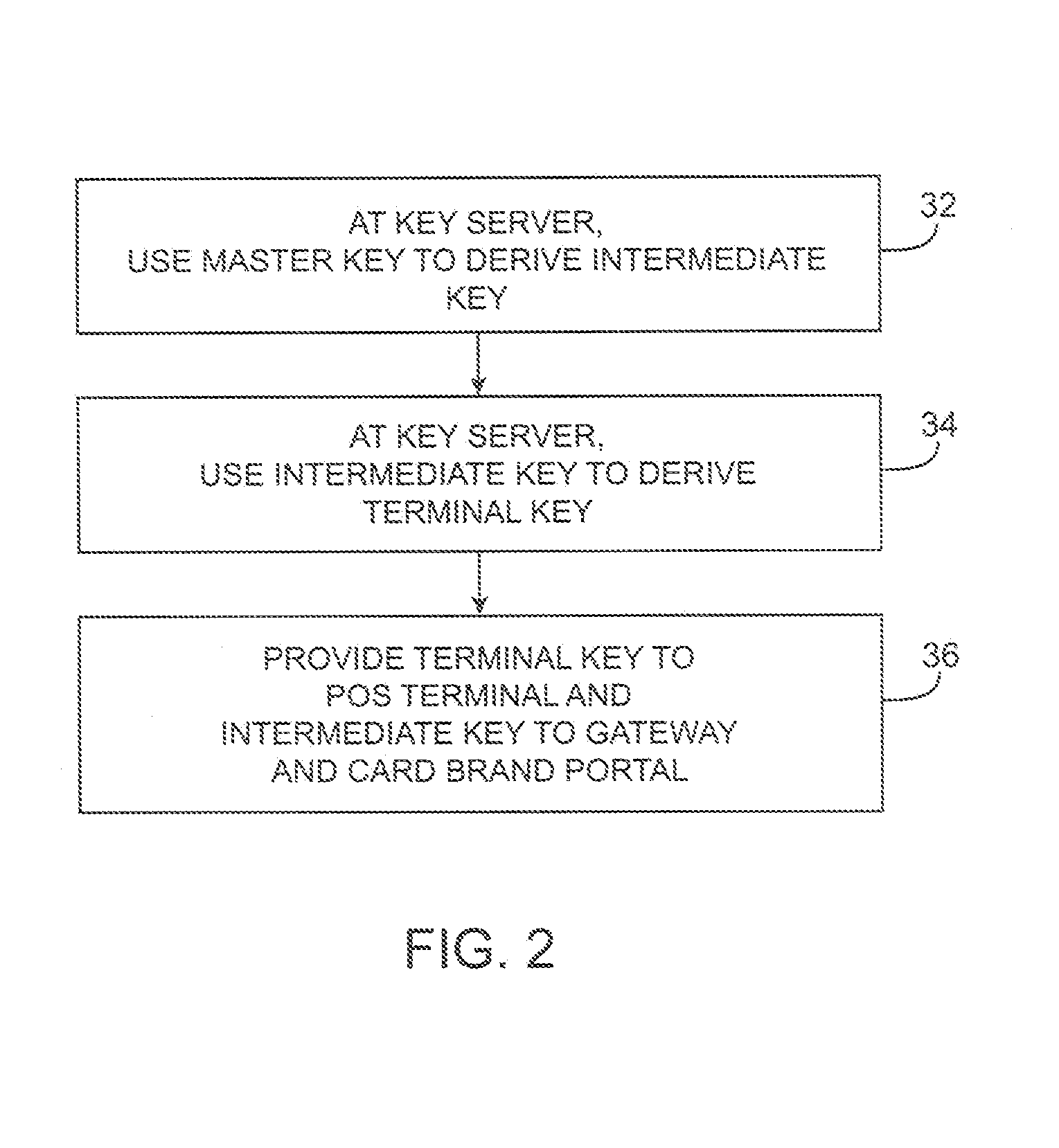
Purchase transaction system with encrypted payment card data
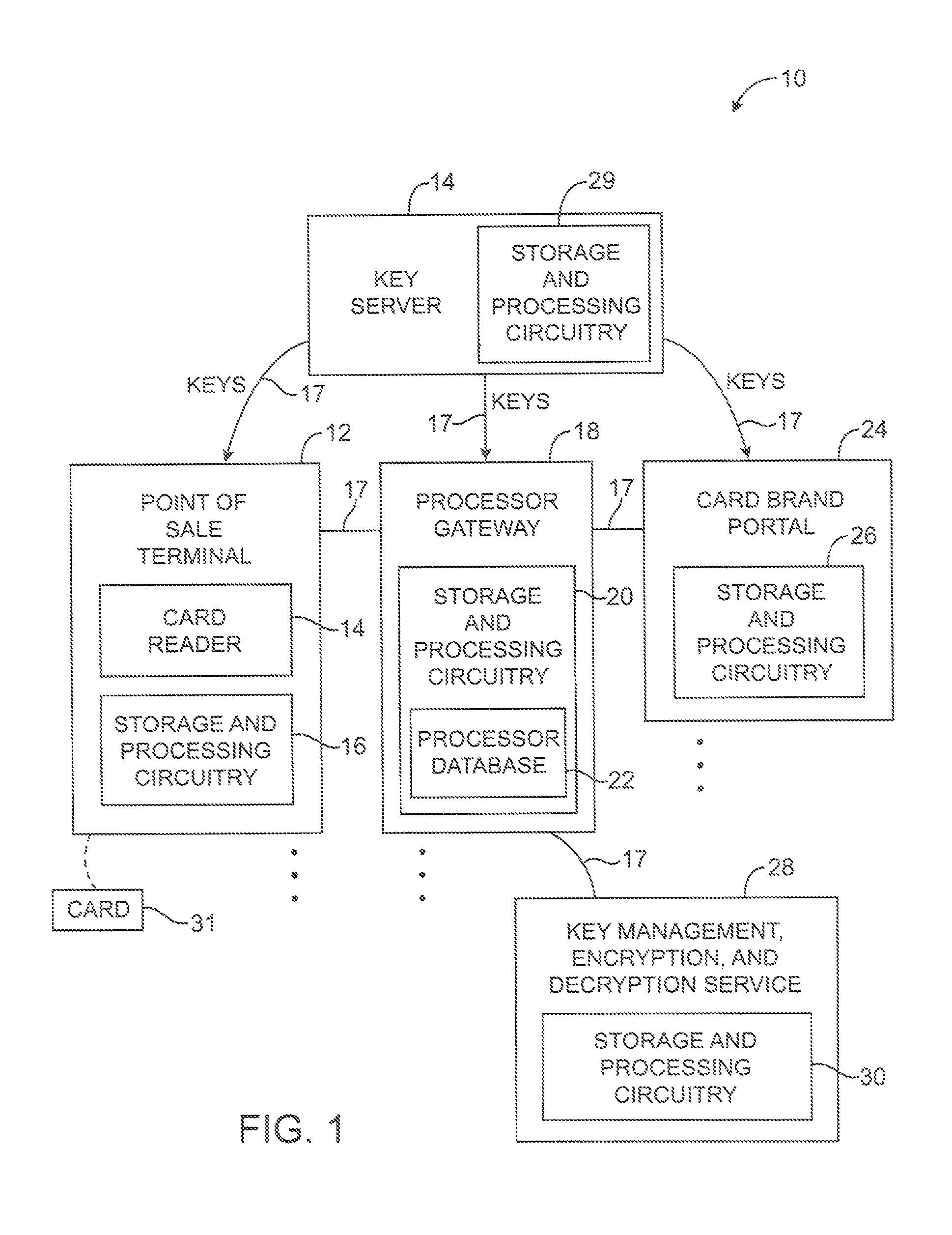
InactiveUS20110137802A1Key distribution for secure communicationAcutation objectsComputer hardwareCredit card
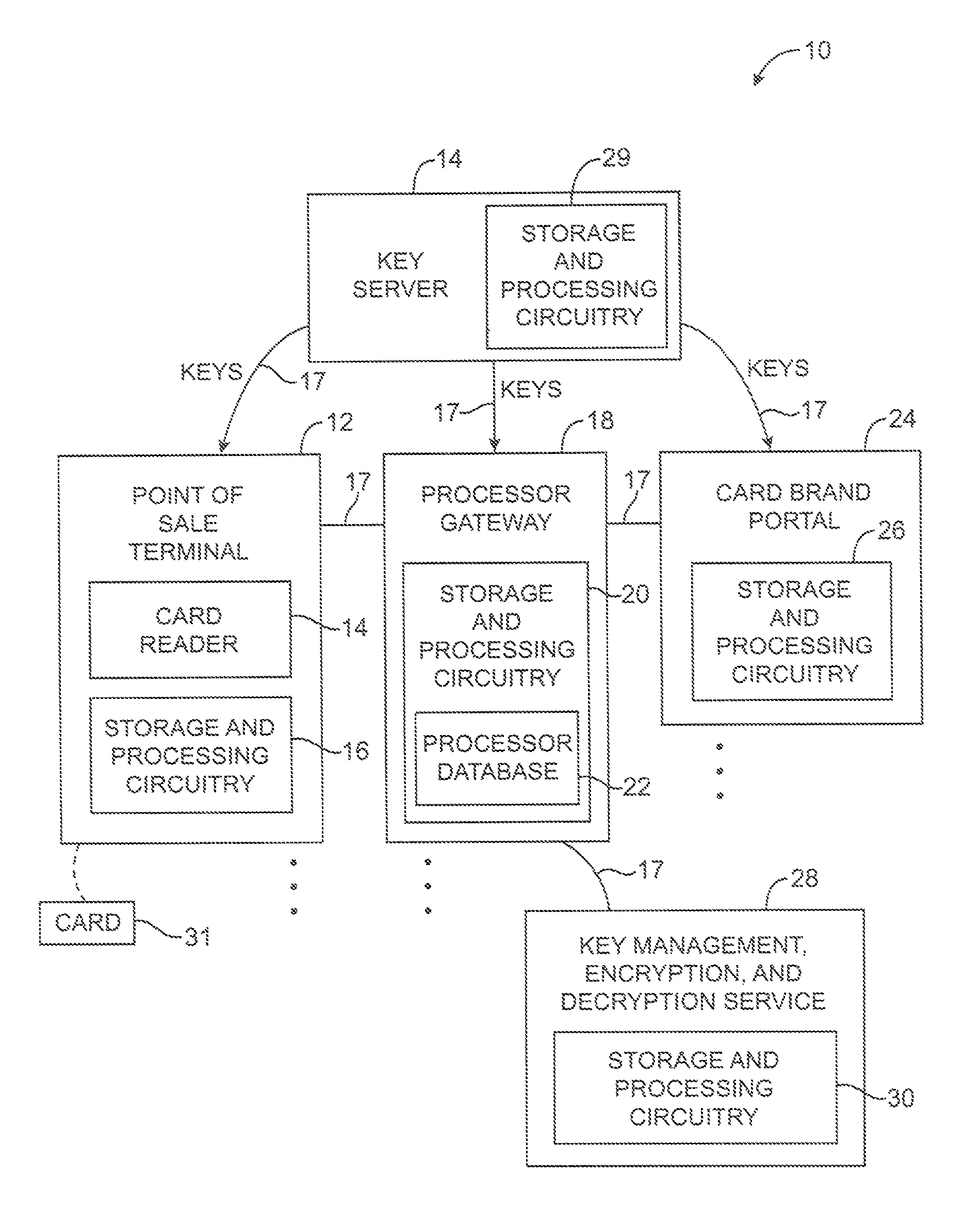
Systems and methods are provided for securing payment card information. A user may present a payment card such as a credit card to point-of-sale equipment. The point-of-sale equipment may encrypt the payment card information. An encryption algorithm may be used that takes as inputs a first part of the payment card information, a tweak formed by a second part of the payment card information, and an encryption key. The encrypted payment card information may be conveyed to a gateway over a communications network. The gateway may identify which encryption algorithm was used in encrypting the payment card information and may re-encrypt the payment card information using a format preserving encryption algorithm. A network-based service may be used to remotely perform functions for the gateway.
Owner:MICRO FOCUS LLC
Format-preserving cryptographic systems
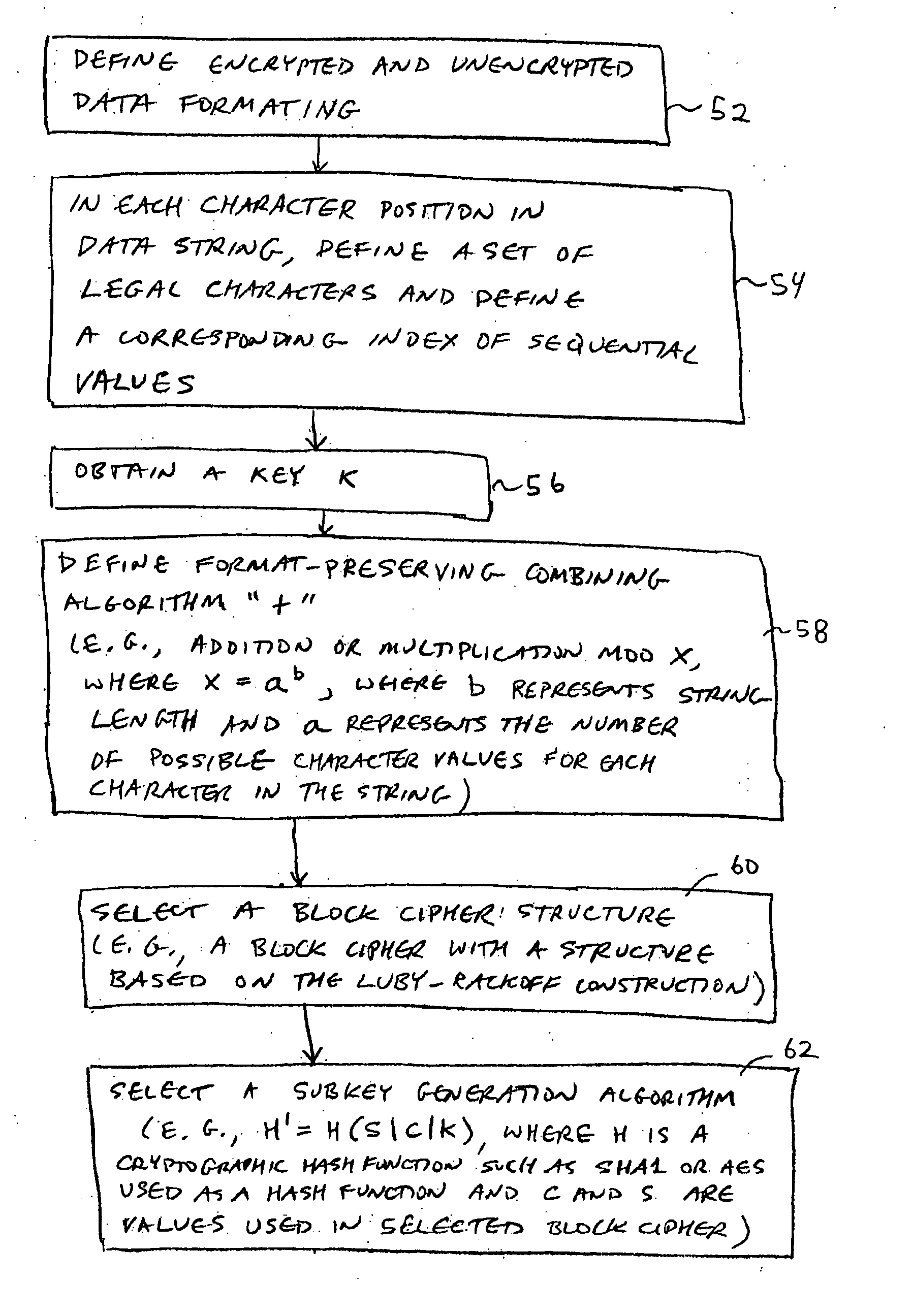
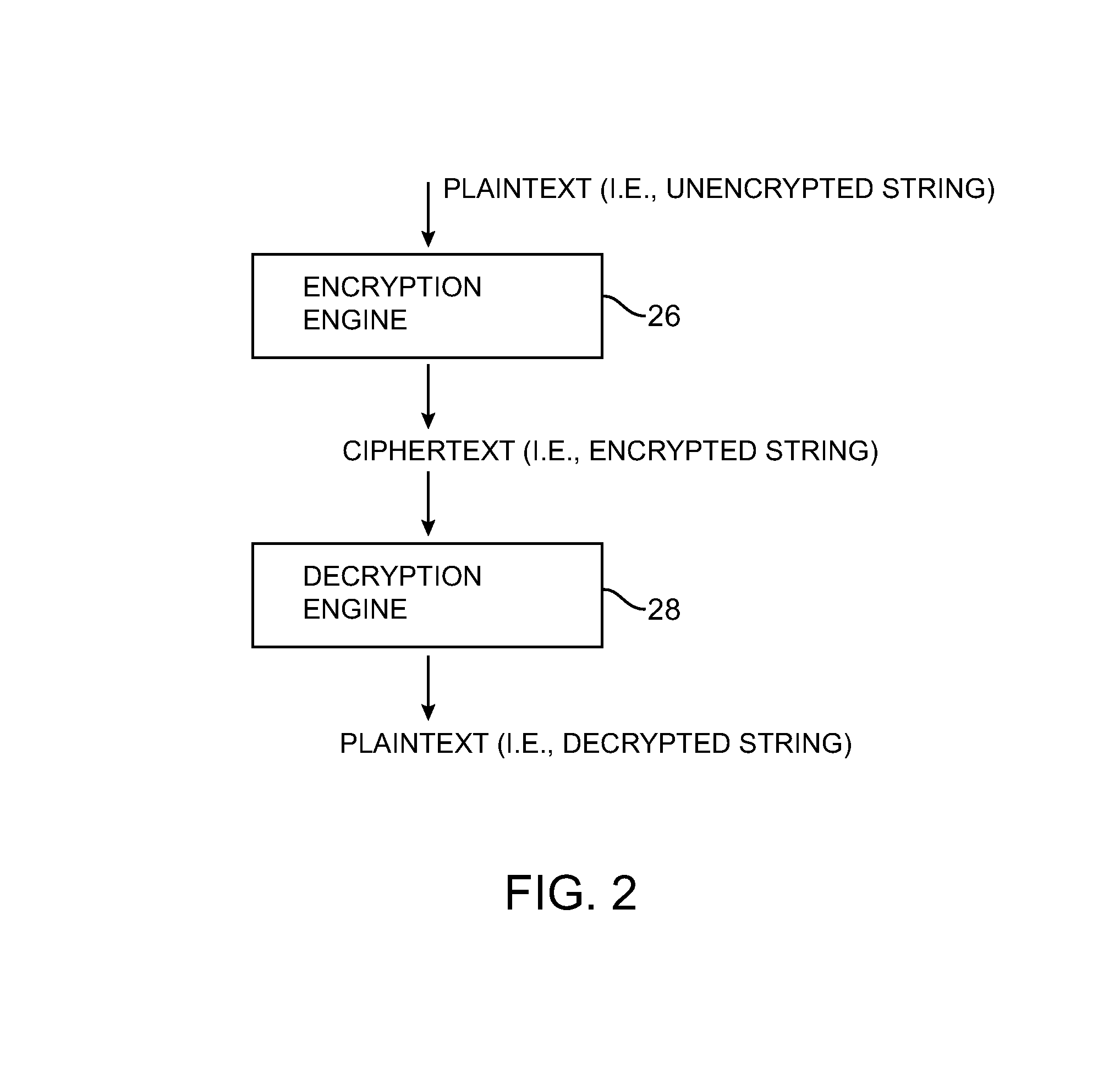
Format-preserving encryption and decryption processes are provided. The encryption and decryption processes may use a block cipher. A string that is to be encrypted or decrypted may be converted to a unique binary value. The block cipher may operate on the binary value. If the output of the block cipher that is produced is not representative of a string that is in the same format as the original string, the block cipher may be applied again. The block cipher may be repeatedly applied in this way during format-preserving encryption operations and during format-preserving decryption operations until a format-compliant output is produced. Selective access may be provided to portions of a string that have been encrypted using format-preserving encryption.
Owner:MICRO FOCUS LLC
Format-preserving cryptographic systems
Format-preserving encryption and decryption processes are provided. The encryption and decryption processes may use a block cipher. A string that is to be encrypted or decrypted may be converted to a unique binary value. The block cipher may operate on the binary value. If the output of the block cipher that is produced is not representative of a string that is in the same format as the original string, the block cipher may be applied again. The block cipher may be repeatedly applied in this way during format-preserving encryption operations and during format-preserving decryption operations until a format-compliant output is produced. Selective access may be provided to portions of a string that have been encrypted using format-preserving encryption.
Owner:MICRO FOCUS LLC
Format-preserving cryptographic systems
InactiveUS20140089204A1Cryptography processingUnauthorized memory use protectionData processing systemOne-way function
Key requests in a data processing system may include identifiers such as user names, policy names, and application names. The identifiers may also include validity period information indicating when corresponding keys are valid. When fulfilling a key request, a key server may use identifier information from the key request in determining which key access policies to apply and may use the identifier in determining whether an applicable policy has been satisfied. When a key request is authorized, the key server may generate a key by applying a one-way function to a root secret and the identifier. Validity period information for use by a decryption engine may be embedded in data items that include redundant information. Application testing can be facilitated by populating a test database with data that has been encrypted using a format-preserving encryption algorithm. Parts of a data string may be selectively encrypted based on their sensitivity.
Owner:MICRO FOCUS LLC
Format preserving encryption
ActiveUS20170214521A1Reduce dataReduce riskEncryption apparatus with shift registers/memoriesDigital data protectionClient-sideInformation security
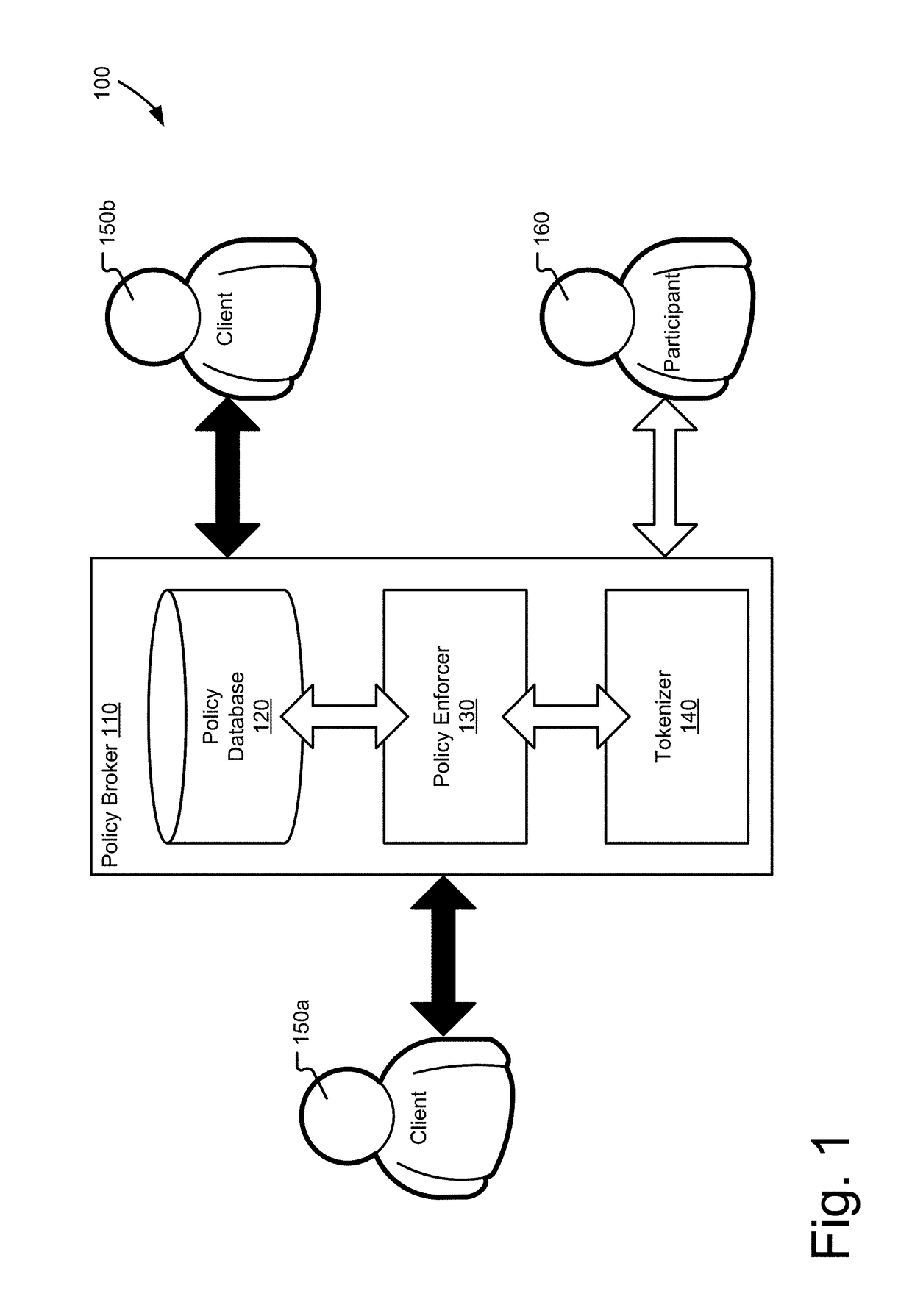
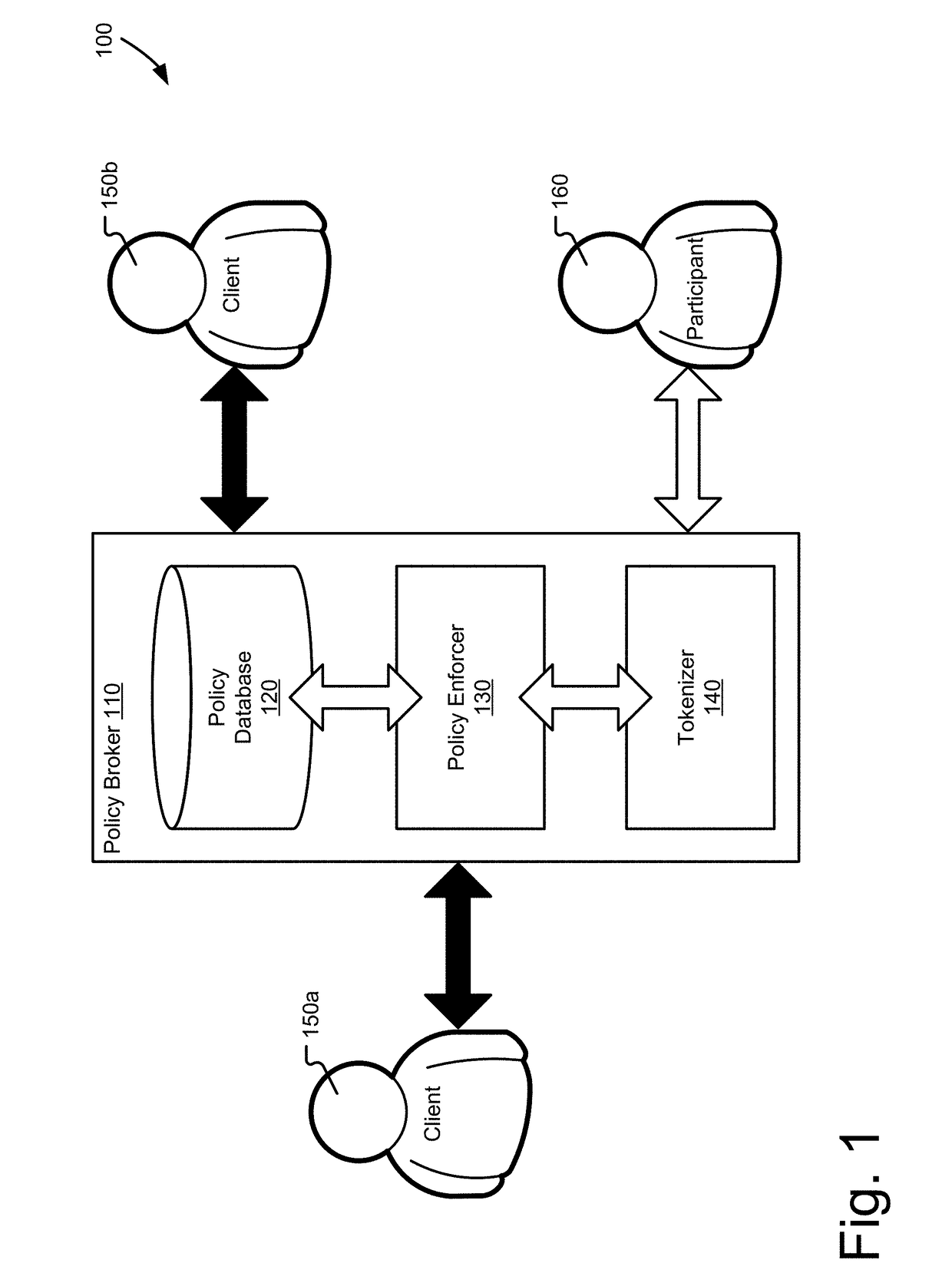
Encrypting data without losing their format is important in computing systems, because many parties using confidential data rely on systems that require specific formatting for data. Information security depends on the systems and methods used to store and transmit data as well as the keys used to encrypt and decrypt those data. A policy broker is disclosed that maintains keys for clients in confidence, while providing cryptographically secure ciphertext as tokens that the clients may use in their systems as though they were the unencrypted data. Tokens are uniquely constructed for each client by the policy broker based on policies set by a receiving client detailing the formatting needs of their systems. Each client may communicate with other clients via the policy broker with the tokens and will send tokens unique to their system that the policy broker will translate into the tokens of the other party.
Owner:EXPERIAN HEALTH INC
Variable-length block cipher apparatus and method capable of format preserving encryption
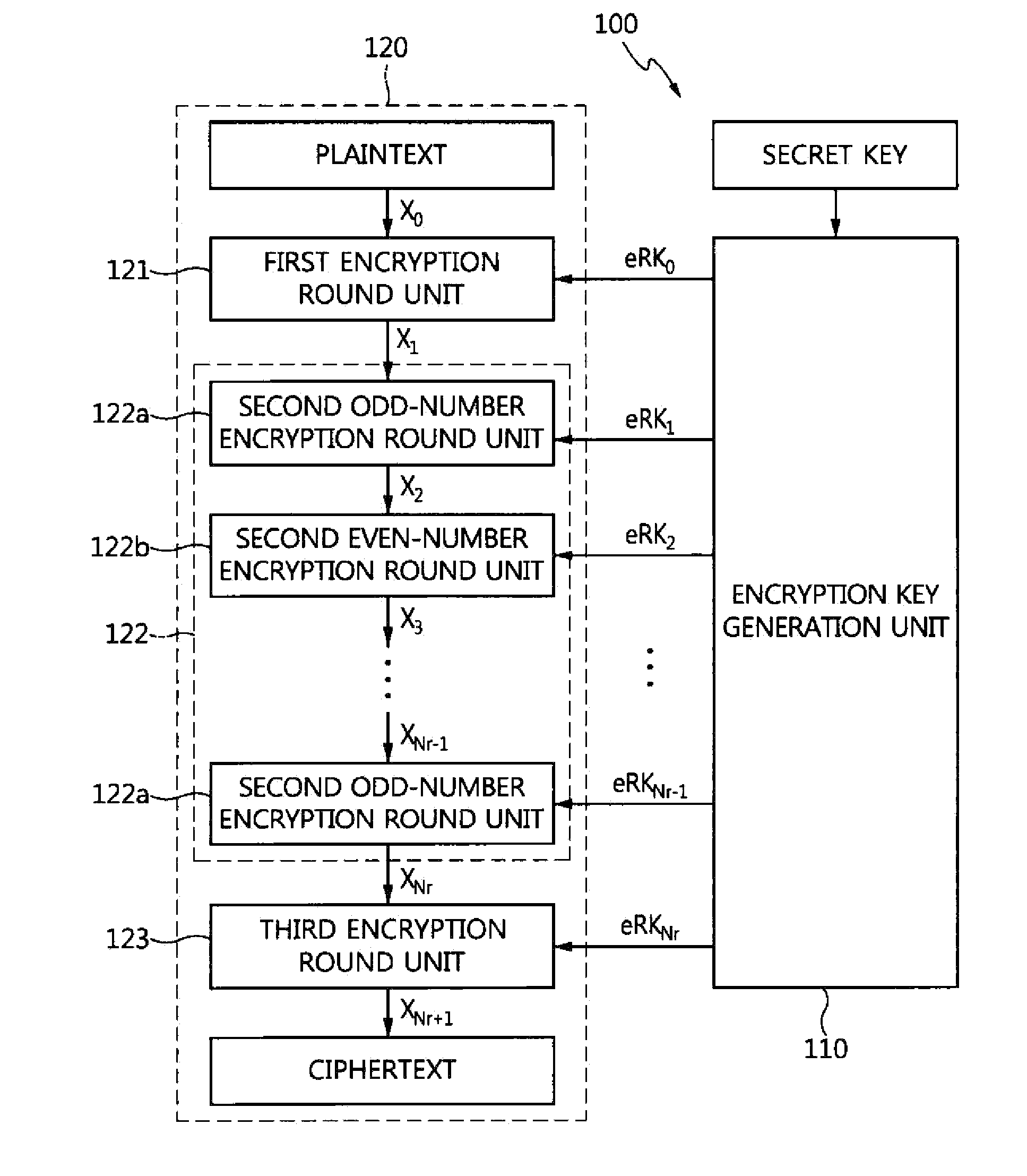
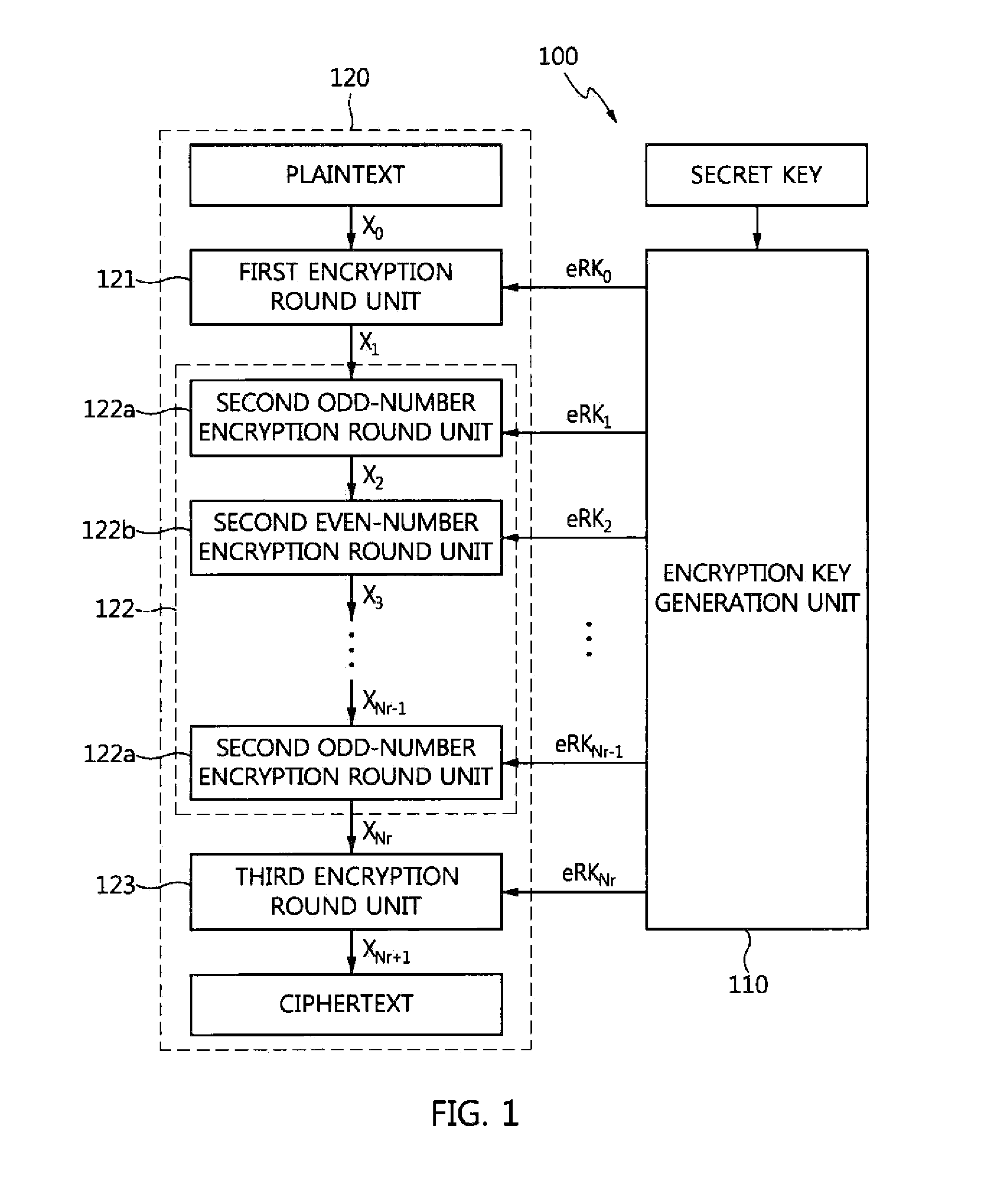
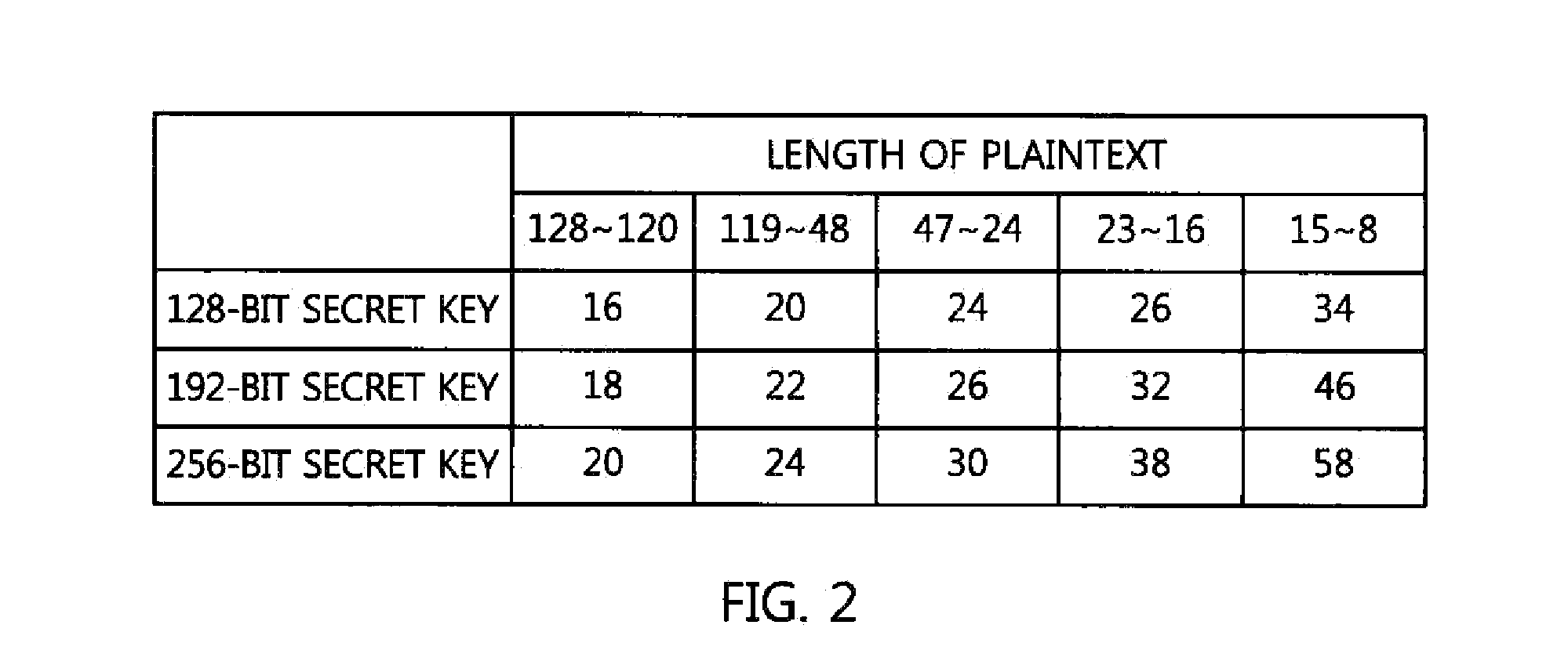
InactiveUS20150244518A1Multiple keys/algorithms usageEncryption apparatus with shift registers/memoriesPlaintextCryptographic key generation
A variable-length block cipher apparatus and method capable of format preserving encryption are provided. An encryption device for a variable-length block cipher apparatus includes an encryption key generation unit configured to generate encryption round keys eRK0, eRK1, . . . , eRKNr using a secret key and the number of rounds Nr, and a ciphertext output unit configured to output ciphertext having a length identical to that of plaintext using the plaintext and the encryption round keys. 7. A decryption device for a variable-length block cipher apparatus includes a decryption key generation unit configured to generate decryption round keys dRK0, dRK1, . . . , dRKNr using a secret key and a number of rounds Nr, and a plaintext restoration unit configured to restore ciphertext into plaintext having a length identical to that of the ciphertext using the ciphertext and the decryption round keys.
Owner:ELECTRONICS & TELECOMM RES INST
Format-preserving cryptographic systems
ActiveUS20130339252A1Computer security arrangementsSecret communicationComputer hardwareBlock cipher
Format-preserving encryption and decryption processes are provided. The encryption and decryption processes may use a block cipher. A string that is to be encrypted or decrypted may be converted to a unique binary value. The block cipher may operate on the binary value. If the output of the block cipher that is produced is not representative of a string that is in the same format as the original string, the block cipher may be applied again. The block cipher may be repeatedly applied in this way during format-preserving encryption operations and during format-preserving decryption operations until a format-compliant output is produced. Selective access may be provided to portions of a string that have been encrypted using format-preserving encryption.
Owner:MICRO FOCUS LLC
Format preserving-based database transparent encryption method
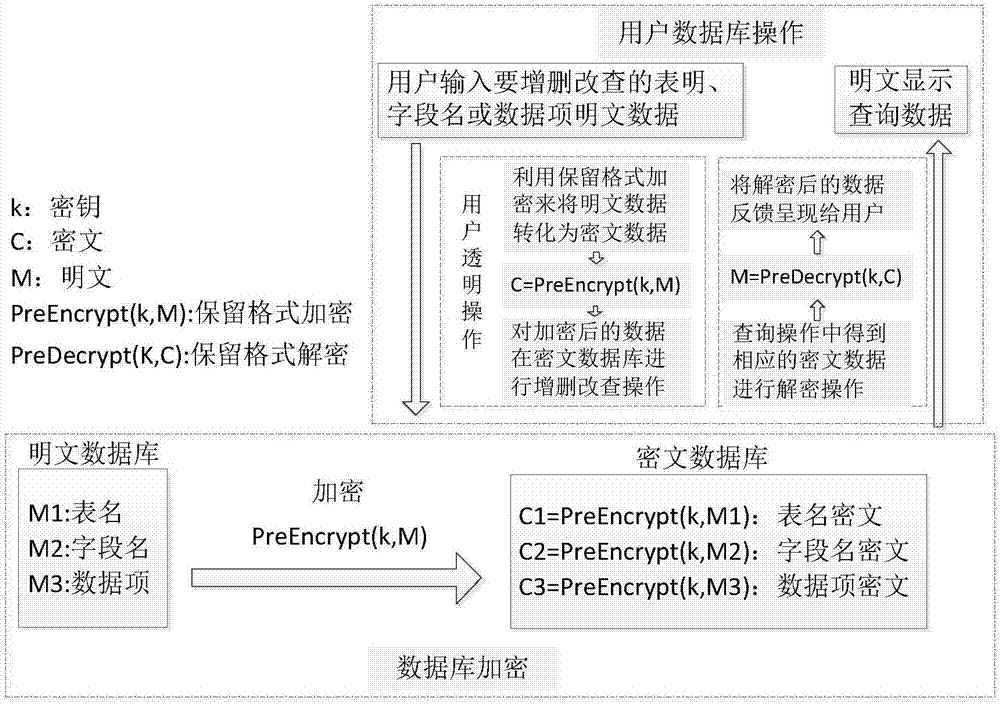
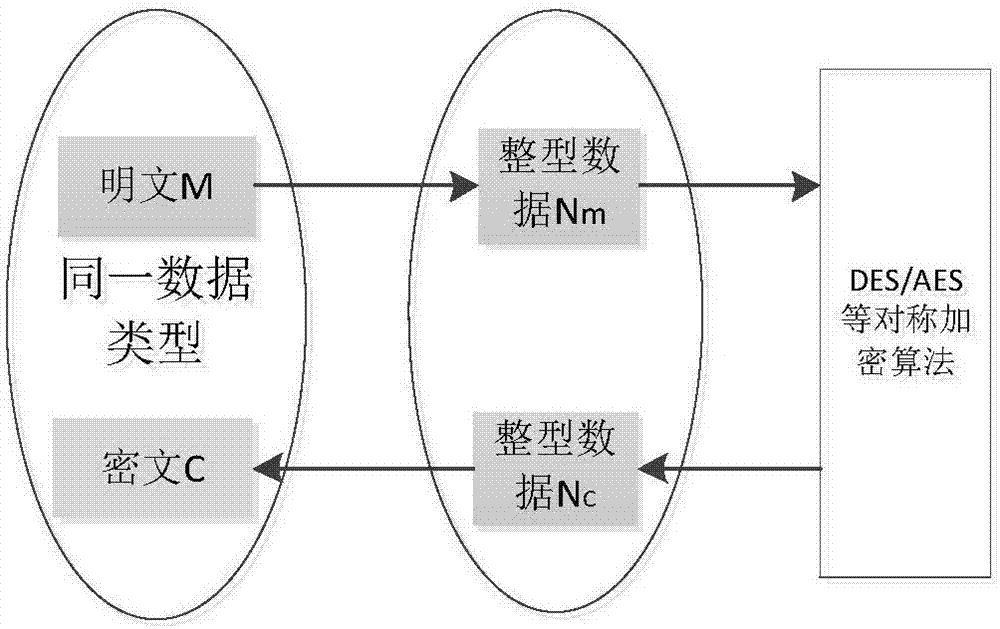
The invention provides a format preserving-based transparent database encryption method. The security of a database can be effectively protected and storage is performed in a ciphertext form. A legal user can be transparentized; the same addition, deletion, modification and query methods as a non encrypted database are provided; and use of the user is not influenced. According to the method, a record in each data item of the database is encrypted in a format preserving encryption manner, so that the record can be stored in the database in the form of a ciphertext with the same data type. When the user needs to perform addition, deletion, modification and query on the encrypted database, a plaintext field input by the user is encrypted and converted into the ciphertext with the same data type, thereby enabling the plaintext field to be consistent with the data in the encrypted database; and a result obtained by a query is decrypted and presented to the user in a plaintext form, so that the user is transparentized.
Owner:GUANGDONG UNIV OF TECH
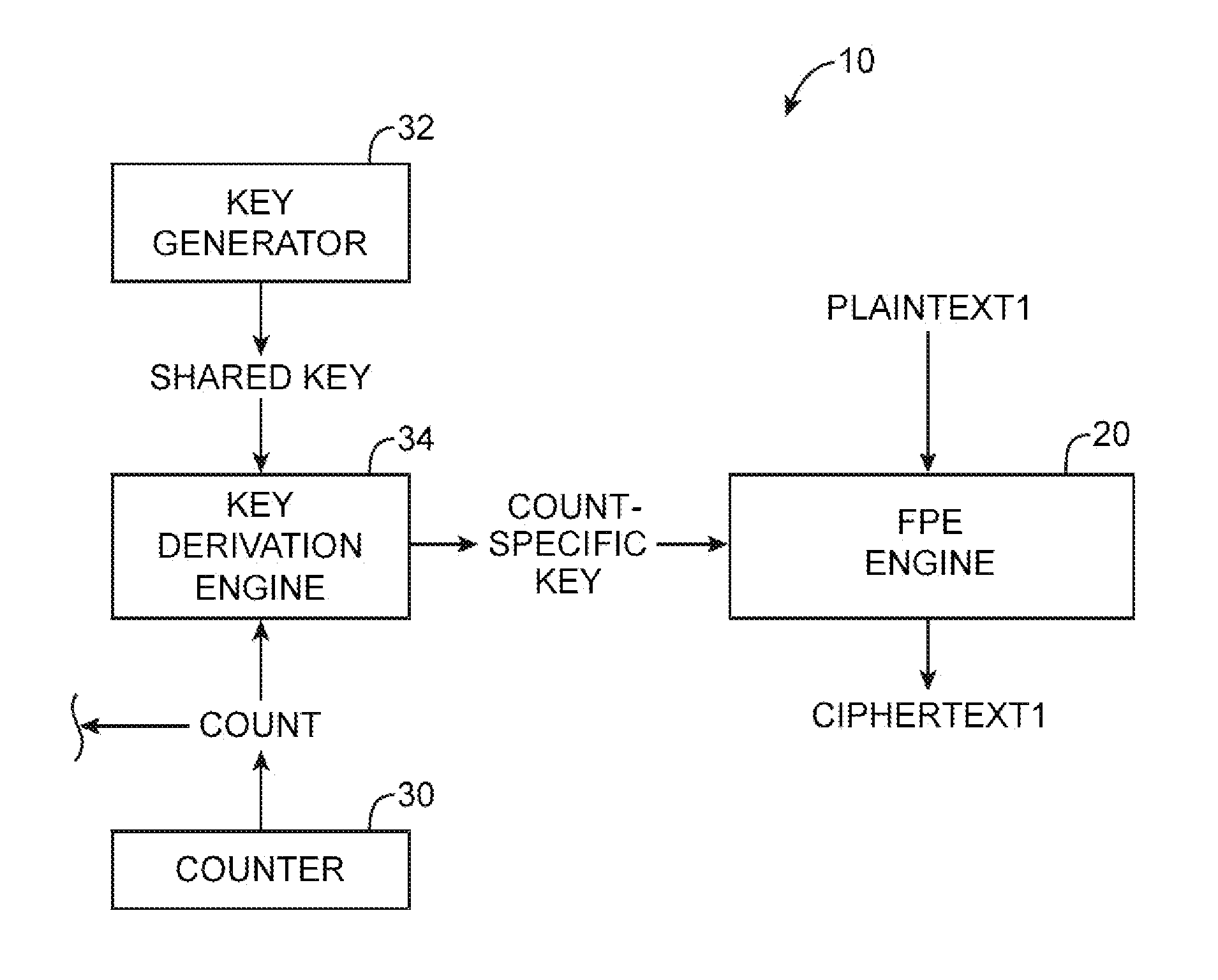
Progressive Key Rotation for Format Preserving Encryption (FPE)
ActiveUS20180089454A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesPlaintextData store
Aspects of the disclosure provide a technological improvement to a cipher by improving data security of format-preserving encryption (FPE), by, inter alia, embedding specific key identifiers for rotating keys directly into ciphertext. Aspects of the disclosure relate to methods, computer-readable media, and apparatuses for improving data security in a format-preserving encryption (FPE) context by using specific methods of rotating and identifying the appropriate encryption key from among numerous rotating keys stored in a key data store. Specific to FPE, a plaintext of the data and its corresponding ciphertext of the data remain the same in length / size; yet the methods, computer-readable media, and / or apparatuses disclosed herein permit embedding of an identification of a specific key among the plurality of rotating keys for the particular ciphertext without compromising the technical requirements of FPE.
Owner:BANK OF AMERICA CORP
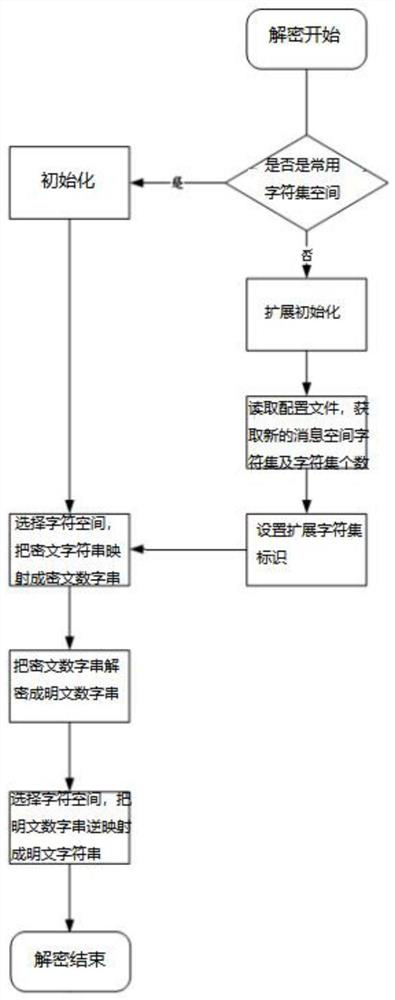
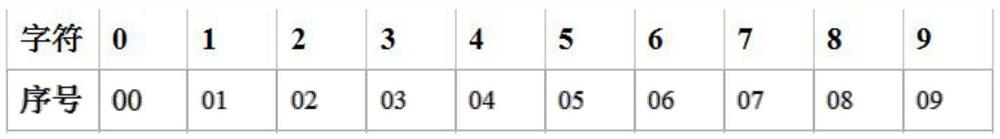
Implementation mode of extensible format preserving encryption method
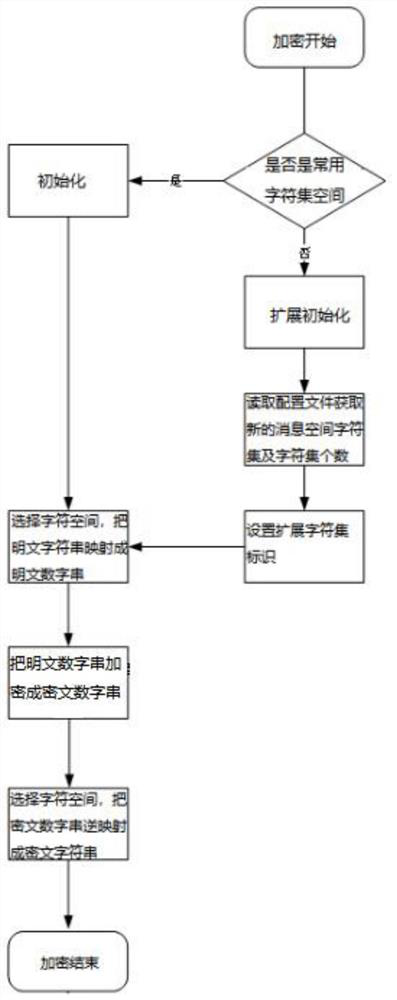
ActiveCN112597480ARealize configurableImprove scalabilityNatural language data processingDigital data authenticationTheoretical computer scienceData bank
The invention provides an implementation mode of an extensible format-preserving encryption method, which comprises the following steps: firstly, judging the type of a field to be encrypted in a usersensitive information database, determining whether the field belongs to a common message space or not, and if so, according to a character set identifier of data, acquiring a specific character set in a common message space defined in the program in advance; and if not, expanding a new message space, and obtaining a newly-added character set; mapping plaintext character strings needing to be encrypted through the character sets obtained respectively, and encoding the plaintext character strings into plaintext numeric strings; encrypting to obtain a ciphertext numeric string; and finally, selecting a character set of the message space according to the character set identifier, and performing inverse mapping on the encrypted ciphertext numeric string to obtain ciphertext character strings with the same format, thereby finishing encryption. By defining and configuring the message space, the configurable and extensible FPE message space is realized, the new message space does not need tobe adapted by modifying a bottom layer code, and the practicability of the FPE encryption method is improved.
Owner:BEIJING LIANSHI NETWORKS TECH CO LTD
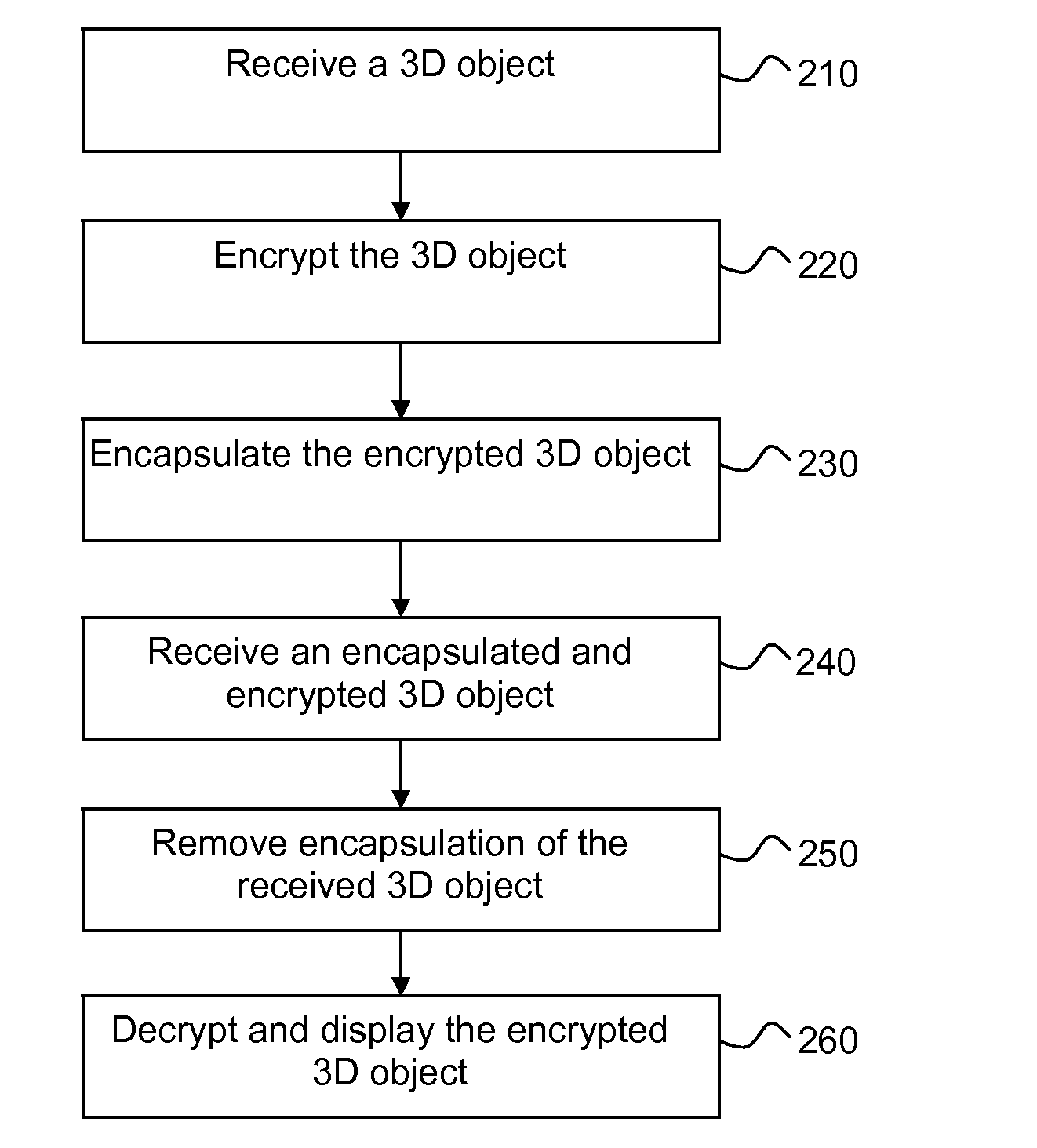
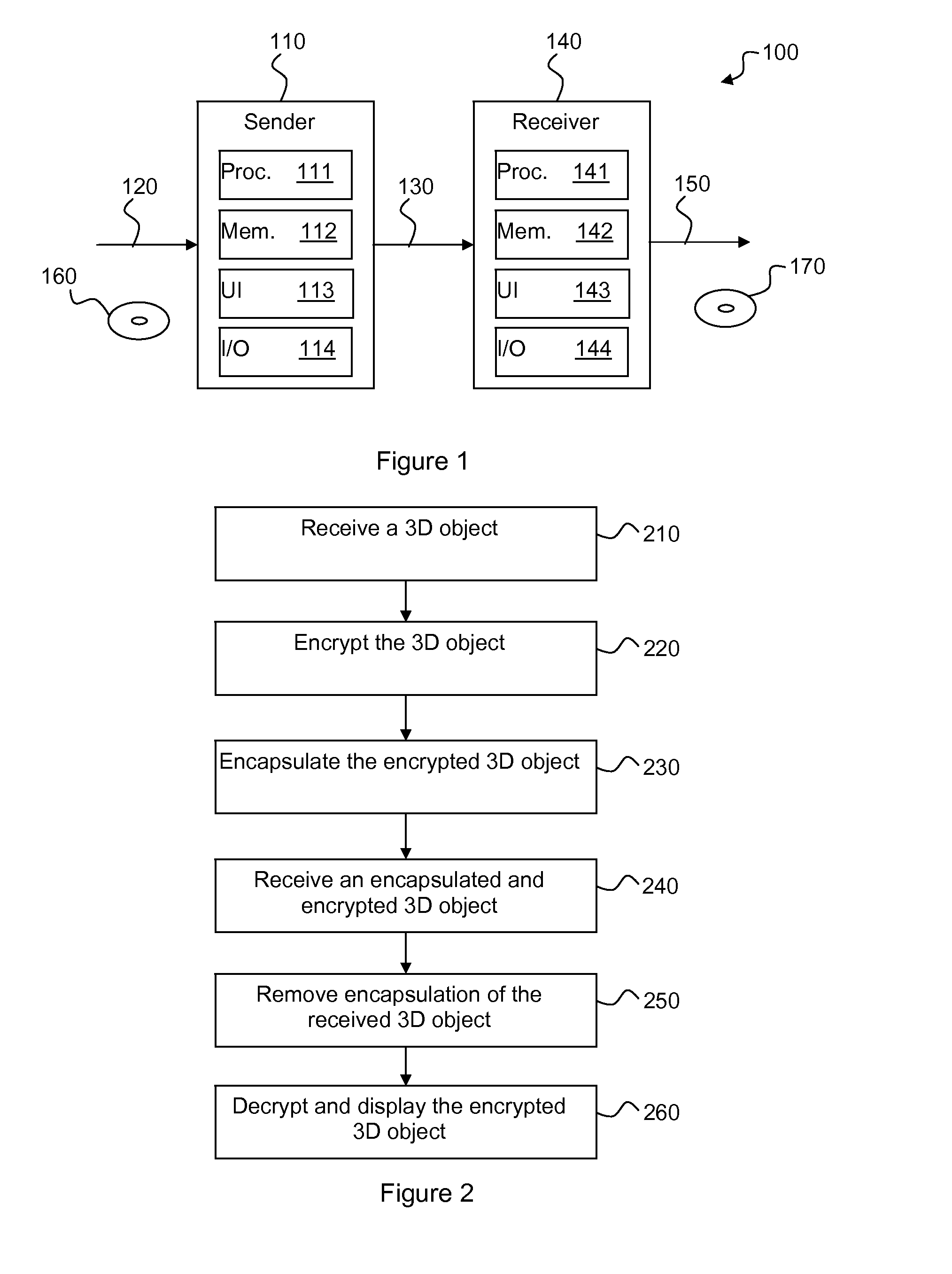
Methods and devices for optimising rendering of an encrypted 3D graphical object
The graphical characteristics of 3D graphical objects encrypted using format-preserving encryption makes rendering of such objects quite inefficient by non-authorized devices. To optimise the rendering of a three-dimensional graphical object represented by a list of points and a list of surfaces defined by points in the list of points, a device receives the graphical object; encrypts the graphical object using a format-preserving encryption method to obtain an encrypted graphical object; encapsulates the encrypted graphical object to obtain an encapsulated graphical object by adding at least one encapsulation by adding for each encapsulation, to the list of surfaces, a plurality of surfaces that together enclose the encrypted graphical object and, in an embodiment, at least one point to the list of points; and outputs the encapsulated graphical object. Decryption is performed by essentially reversing the encryption.
Owner:INTERDIGITAL CE PATENT HLDG
Fast format-preserving encryption for variable length data
ActiveUS20180316491A1Fast and secure FPEKey distribution for secure communicationRandom number generatorsVariable-length codeTheoretical computer science
Systems, apparatuses, and methods are provided for fast format-preserving encryption. An input string can be divided into blocks (potentially of varying length). An arrangement of cryptographic pipelines can perform operations on different blocks, each pipeline providing an output block. The cryptographic pipelines can interact such that the output blocks are dependent on each other, thereby providing strong encryption. The pipelines can operate efficiently on the block and operations can occur partly in parallel.
Owner:VISA INT SERVICE ASSOC
Purchase transaction system with encrypted payment card data
InactiveUS8571995B2Key distribution for secure communicationAcutation objectsComputer hardwareCredit card
Systems and methods are provided for securing payment card information. A user may present a payment card such as a credit card to point-of-sale equipment. The point-of-sale equipment may encrypt the payment card information. An encryption algorithm may be used that takes as inputs a first part of the payment card information, a tweak formed by a second part of the payment card information, and an encryption key. The encrypted payment card information may be conveyed to a gateway over a communications network. The gateway may identify which encryption algorithm was used in encrypting the payment card information and may re-encrypt the payment card information using a format preserving encryption algorithm. A network-based service may be used to remotely perform functions for the gateway.
Owner:MICRO FOCUS LLC
Format-preserving cryptographic systems
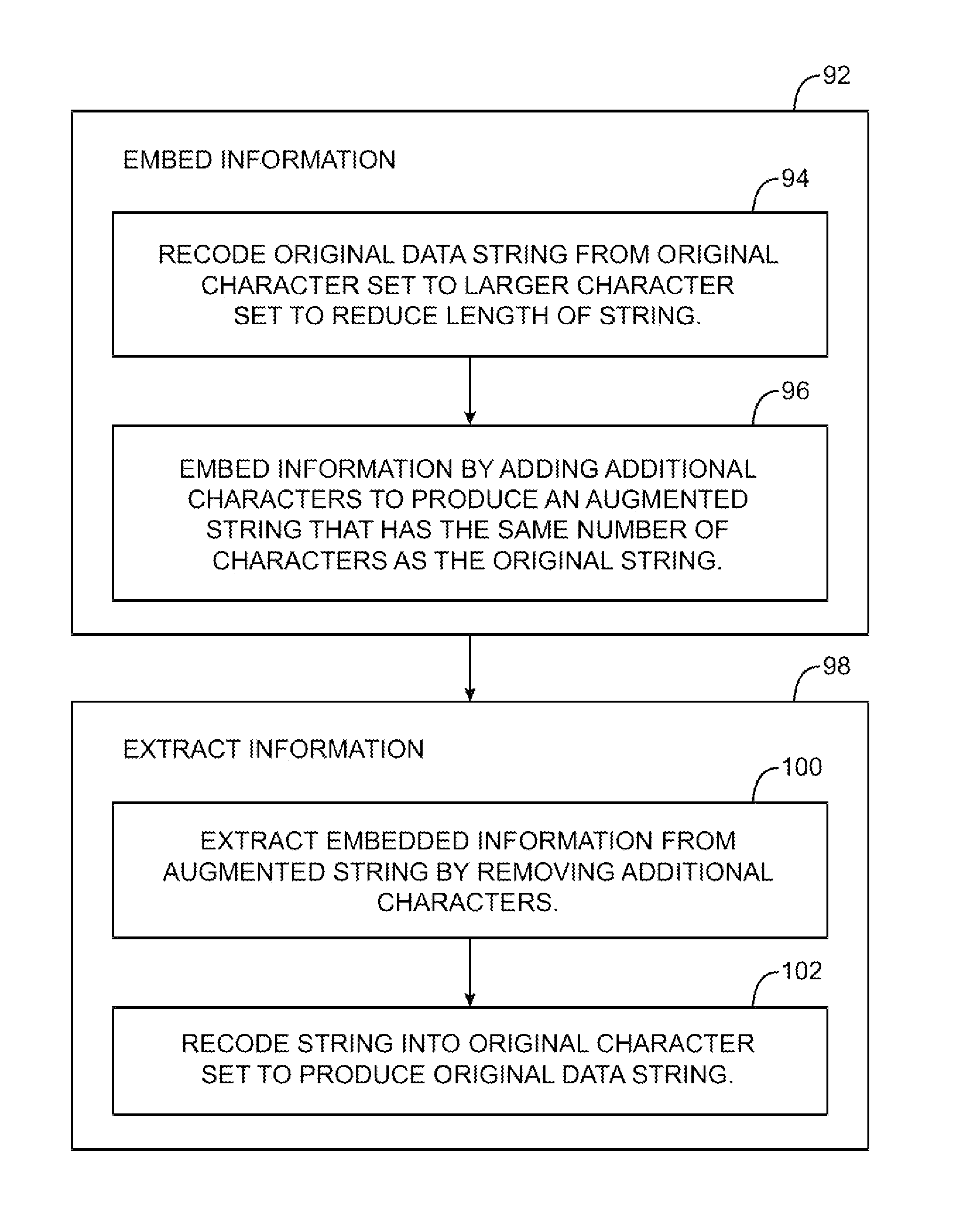
ActiveUS20170149565A9Computer security arrangementsSecret communicationComputer hardwareComputer science
Format-preserving encryption and decryption processes are provided. The encryption and decryption processes may use a block cipher. A string that is to be encrypted or decrypted may be converted to a unique binary value. The block cipher may operate on the binary value. If the output of the block cipher that is produced is not representative of a string that is in the same format as the original string, the block cipher may be applied again. The block cipher may be repeatedly applied in this way during format-preserving encryption operations and during format-preserving decryption operations until a format-compliant output is produced. Selective access may be provided to portions of a string that have been encrypted using format-preserving encryption.
Owner:MICRO FOCUS LLC
Sensitive information identification system and sensitive information identification method
ActiveCN104361489AEnsure safetyImplement encryptionProtocol authorisationPaymentInformation transmission
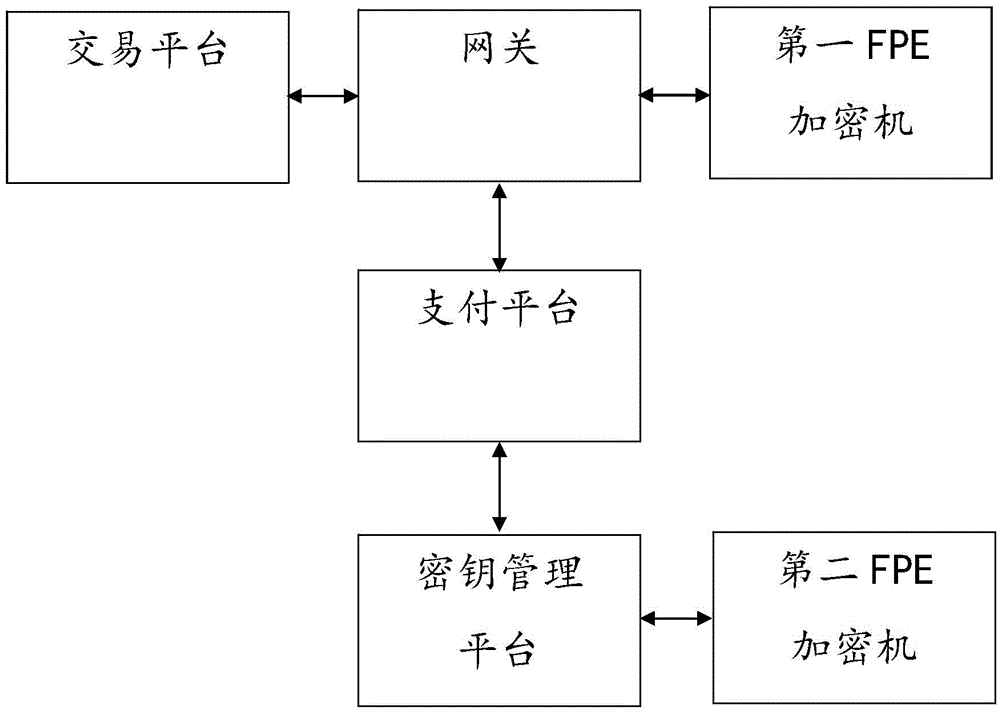
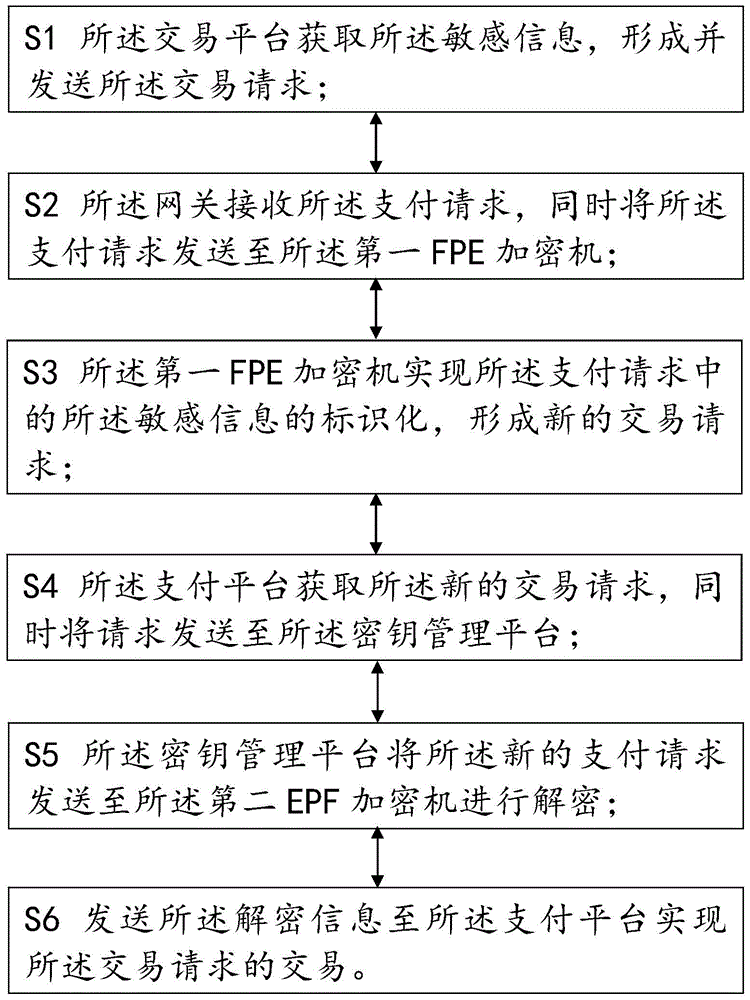
The invention relates to the field of information security, in particular to an information identification system and an information identification method. The information identification system comprises transaction platforms, a gateway, a payment platform, a secret key management platform, a first FPE (format preserving encryption) encryptor and a second FPE encryptor, wherein each transaction platform is used for acquiring sensitive information and generating and sending a transaction request, the gateway is connected with the transaction platforms and used for providing an access port for the transaction platforms, the payment platform is connected with the gateway and used for achieving payment for the transaction request, the secret key management platform is connected with the payment platform and used for managing and assigning secret key information of the transaction platforms, the first FPE encryptor is connected with the gateway and used for achieving identification of the sensitive information in the transaction request, and the second FPE encryptor is connected with the secret key management platform and used for decrypting the sensitive information subjected to identification. The information identification system centers on the secret key management platform, secret keys are distributed to each transaction platform, and the sensitive information is encrypted by FPE, so that no change on data length during sensitive information transmission is guaranteed, and security of the sensitive information is ensured.
Owner:SHANGHAI PEOPLENET SECURITY TECH
Device, method, and program for format-preserving encryption, and device, method, and program for decryption
ActiveUS20150341166A1Efficient and secure encryption/decryptionEfficient and secure processingEncryption apparatus with shift registers/memoriesSecret communicationPlaintextData format
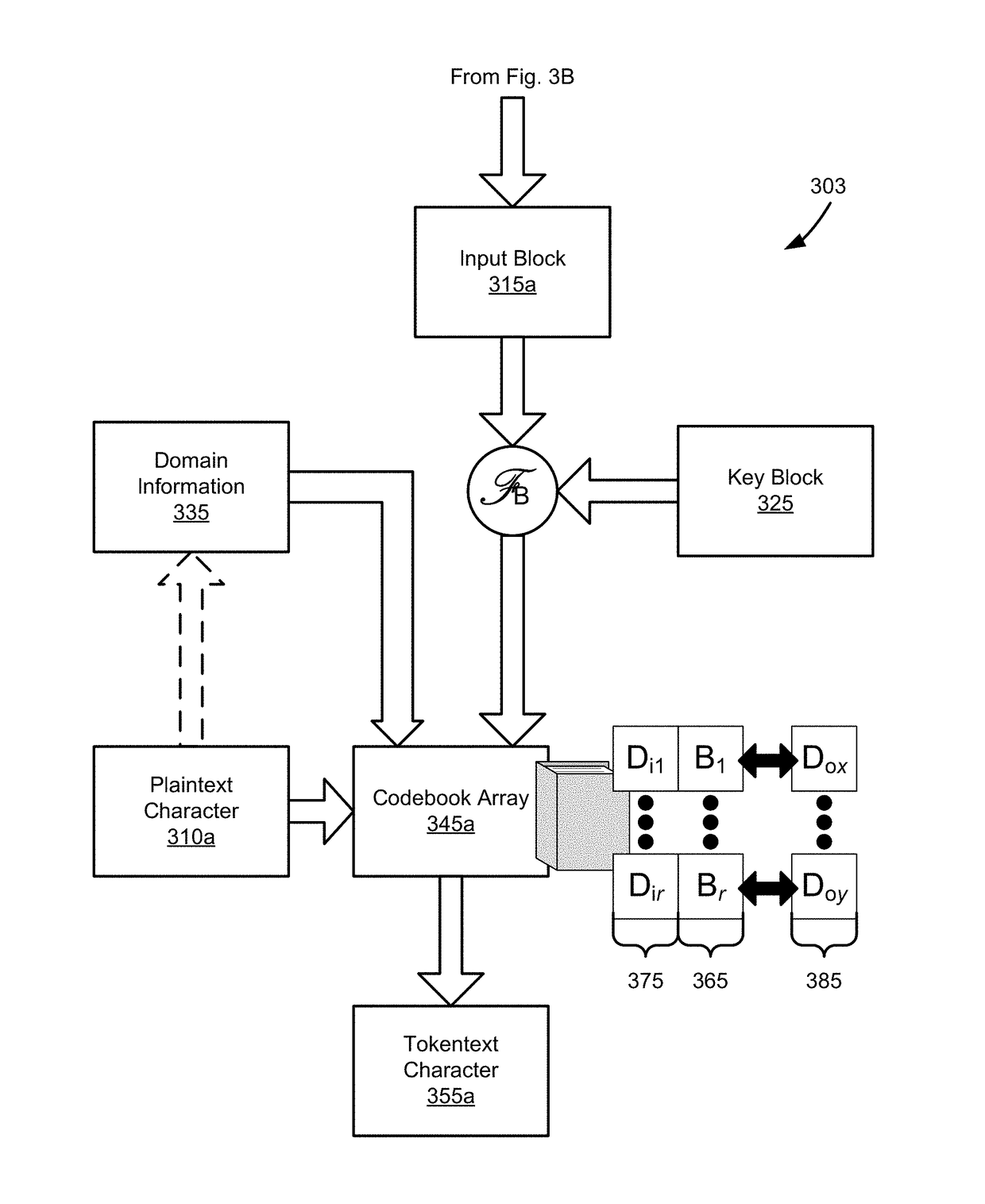
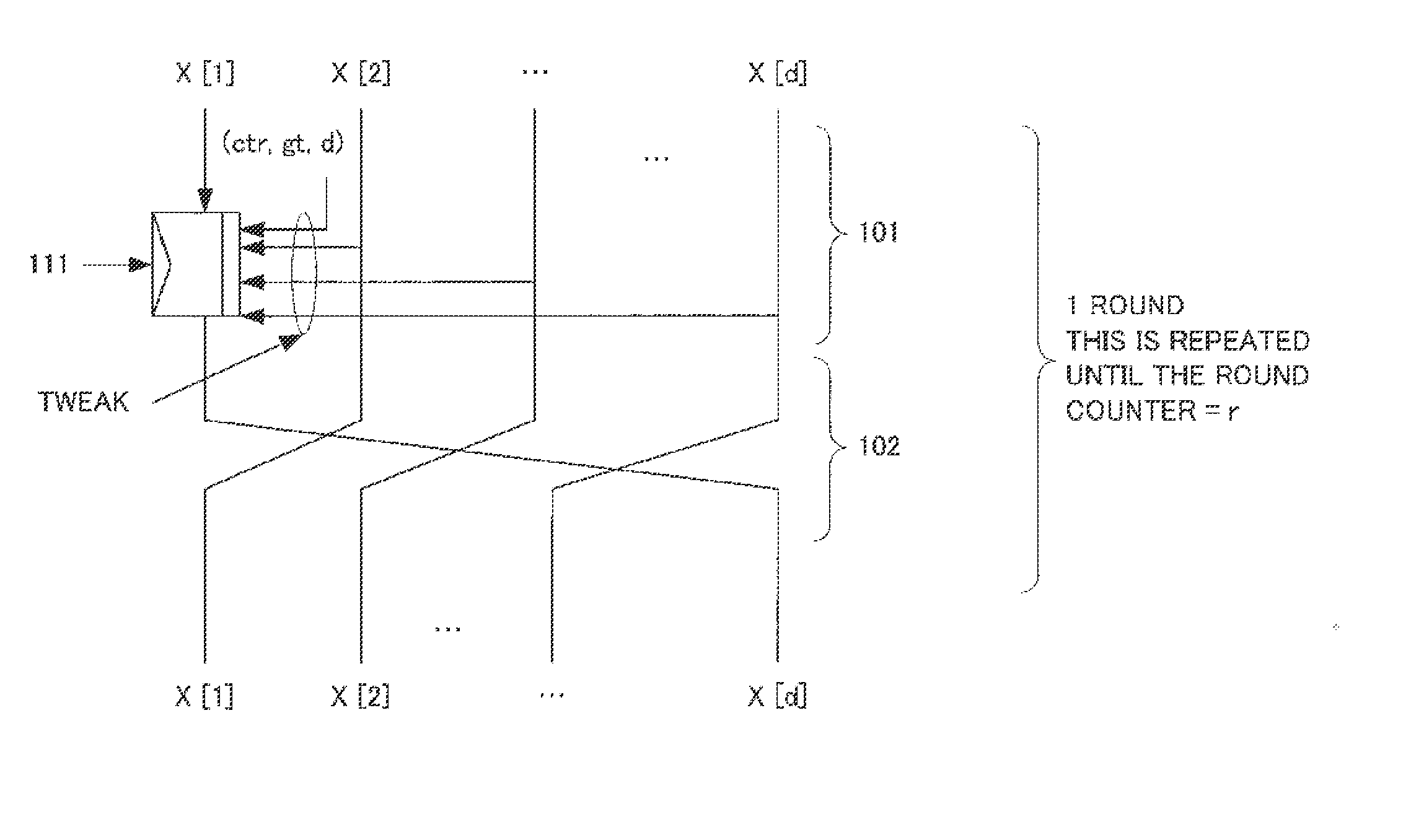
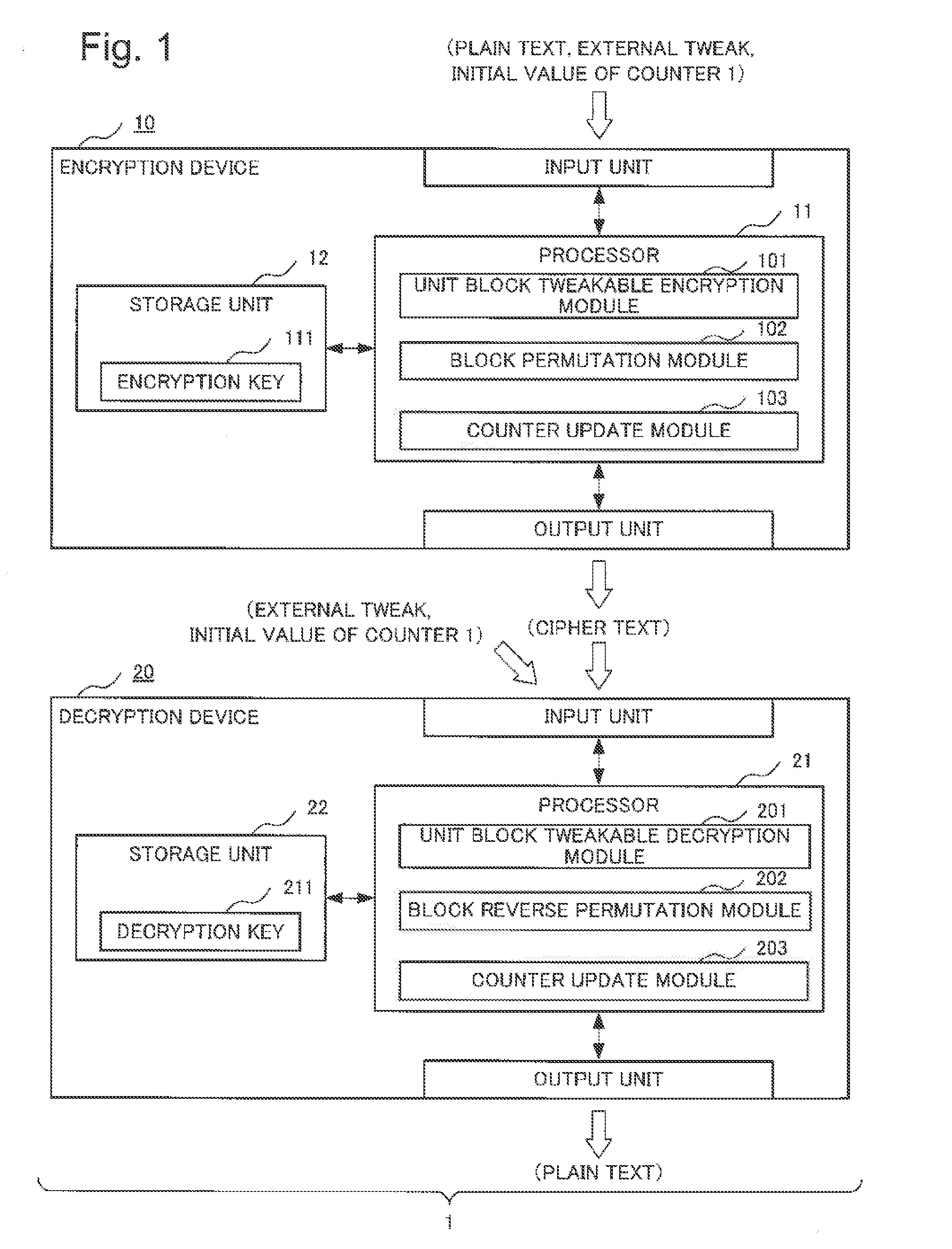
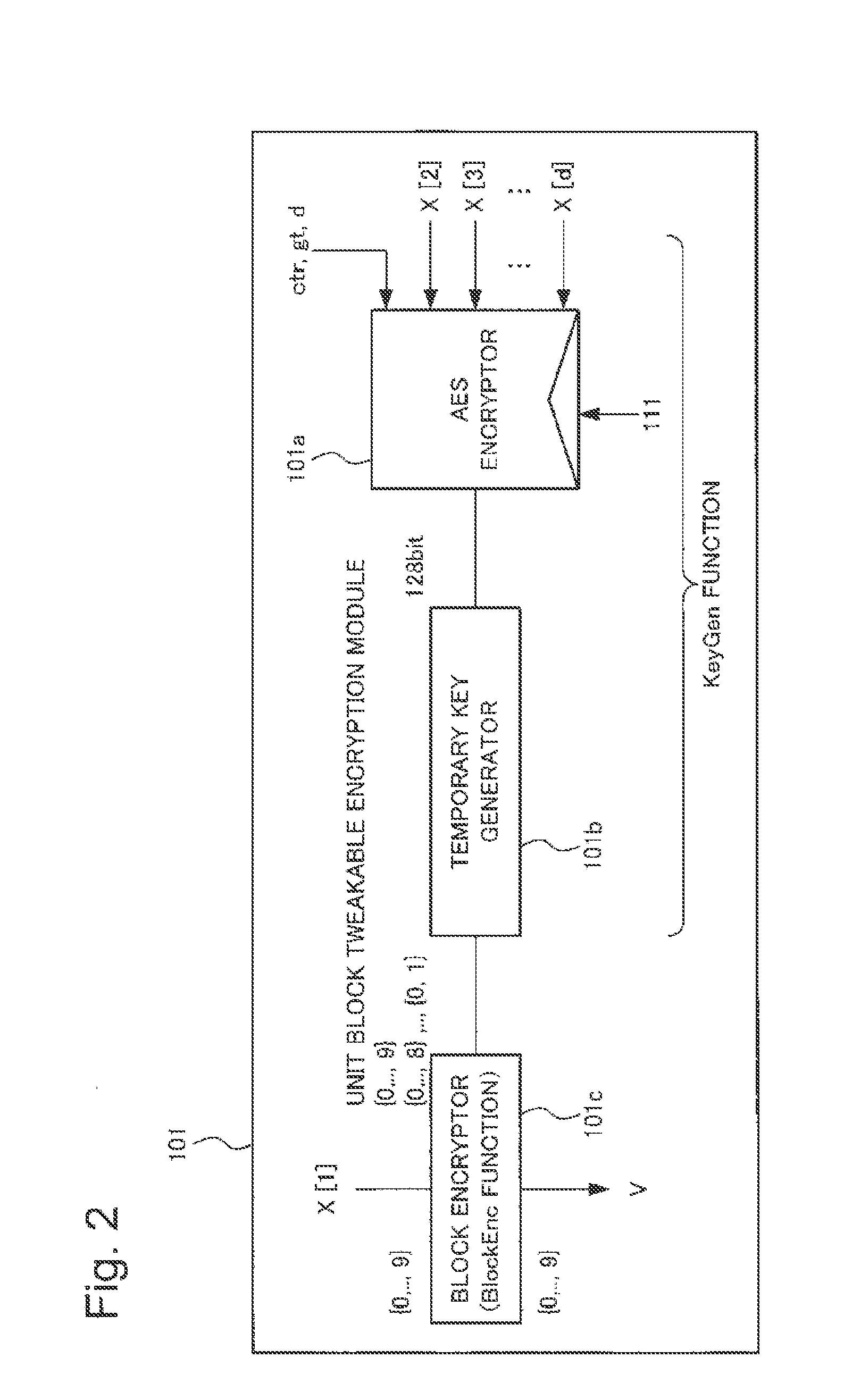
[Subject] To provide a format-preserving encryption device and the like that enables efficient and secure encryption / decryption while maintaining the data format.[Solution] An encryption device 10 includes: an unit block tweakable encryption module 101 that encrypts a specific digit of a plain text by using numerical values of remaining respective digits excluding the specific digit of the plain text and an external tweak that is input concurrently with the plain text; a block permutation module 102 that permutates respective digits including the encrypted specific digit of the plain text per digit based on a predetermined rule; and a counter update module 103 that causes processing by the unit block tweakable encryption unit and the block permutation unit to repeat for a predetermined number of times. A decryption device 20 performs the reverse processing to the encryption device 10.
Owner:NEC CORP
Format preserving encryption
ActiveUS20180053008A1Reduce dataReduce riskEncryption apparatus with shift registers/memoriesDigital data protectionClient-sideInformation security
Encrypting data without losing their format is important in computing systems, because many parties using confidential data rely on systems that require specific formatting for data. Information security depends on the systems and methods used to store and transmit data as well as the keys used to encrypt and decrypt those data. A policy broker is disclosed that maintains keys for clients in confidence, while providing cryptographically secure ciphertext as tokens that the clients may use in their systems as though they were the unencrypted data. Tokens are uniquely constructed for each client by the policy broker based on policies set by a receiving client detailing the formatting needs of their systems. Each client may communicate with other clients via the policy broker with the tokens and will send tokens unique to their system that the policy broker will translate into the tokens of the other party.
Owner:EXPERIAN HEALTH INC
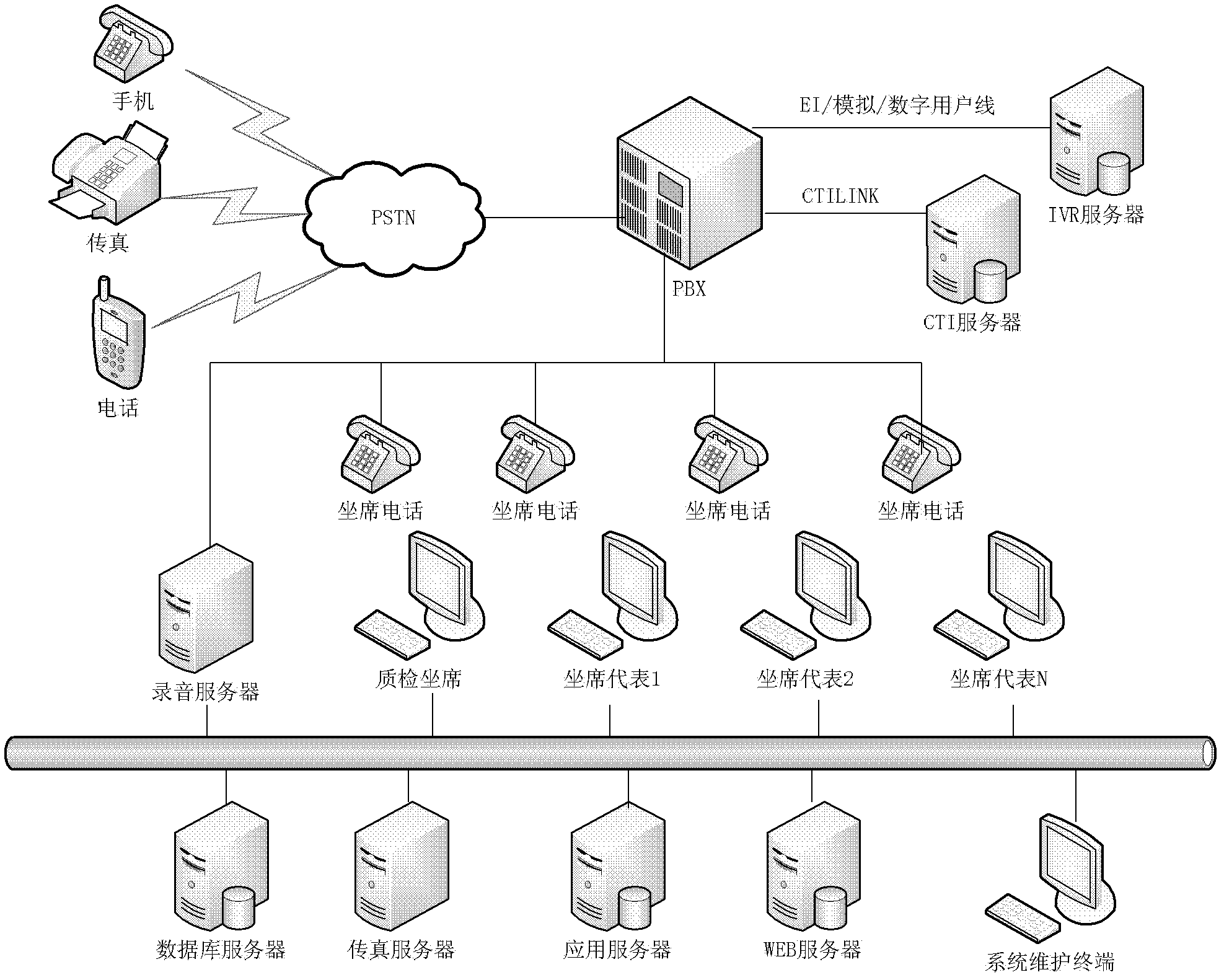
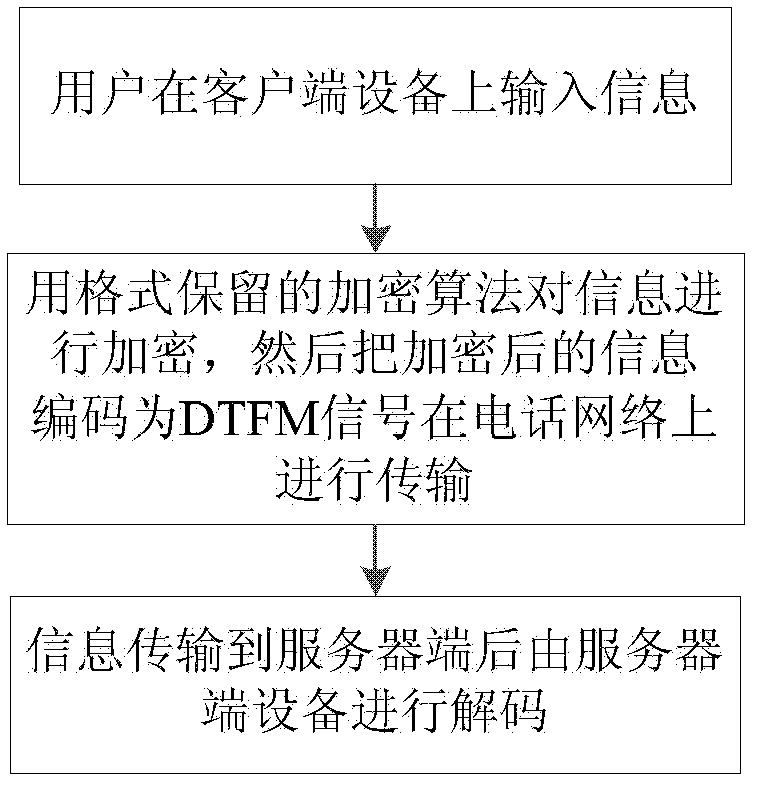
Interactive voice response system and method
InactiveCN102611811ASensitive data encryption protectionKey distribution for secure communicationInterconnection arrangementsUser inputTelephone network
The invention discloses an interactive voice response system. The interactive voice response system comprises a server-end device and a client-end device, wherein the server-end device and the client-end device perform interaction through a telephone network, and a user inputs information on the client-end device; the information is encrypted by a format-preserving encryption algorithm, and then the information after encryption is encoded into a DTFM (dual-tone multi-frequency) signal for transmission on the telephone network; and the information is transmitted to a server end and then decrypted by a server end device. According to the technical scheme disclosed by the invention, sensitive data of the interactive voice response system can be encrypted and protected, so that the system can be safe and reliable.
Owner:PEKING UNIV
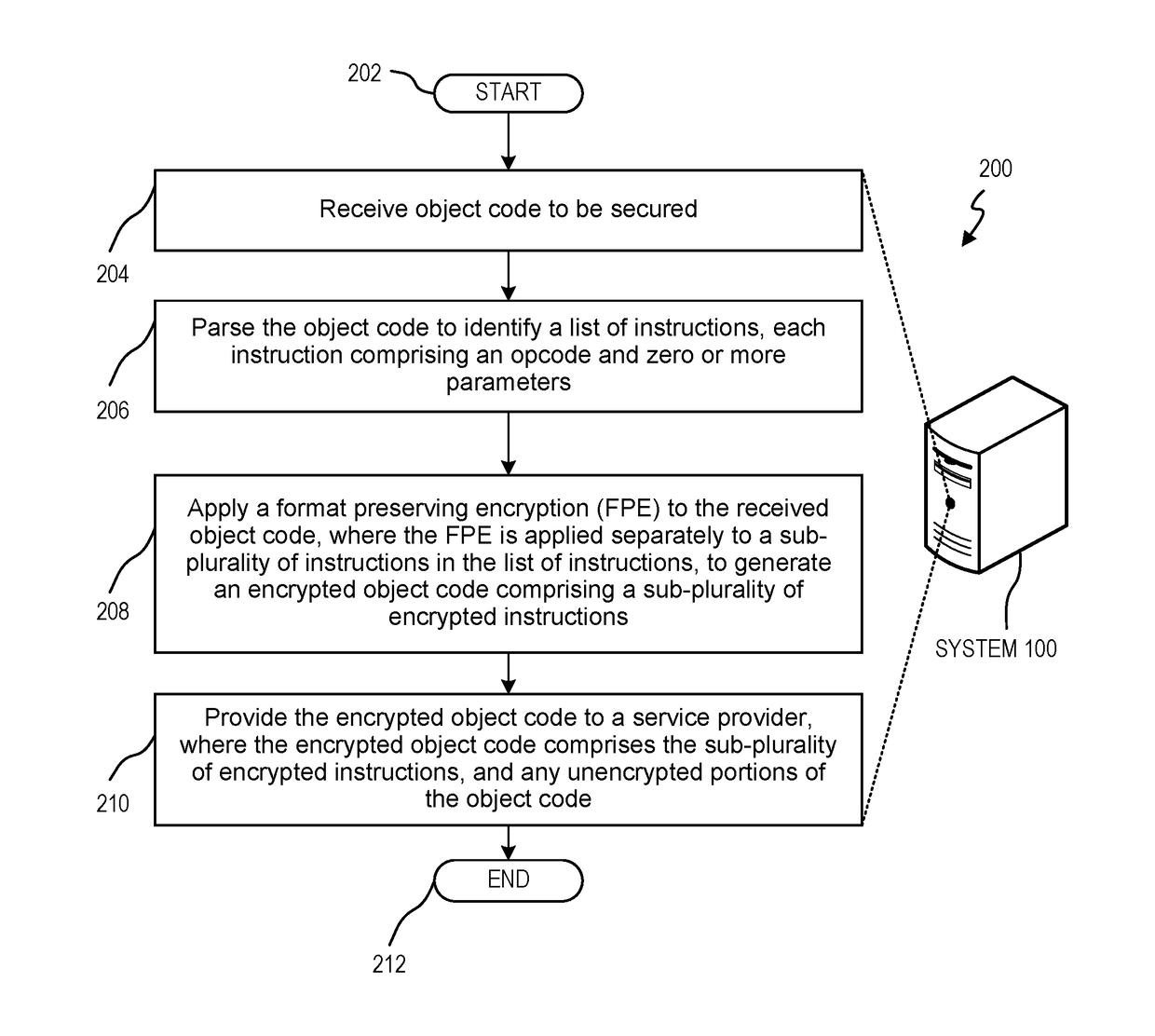
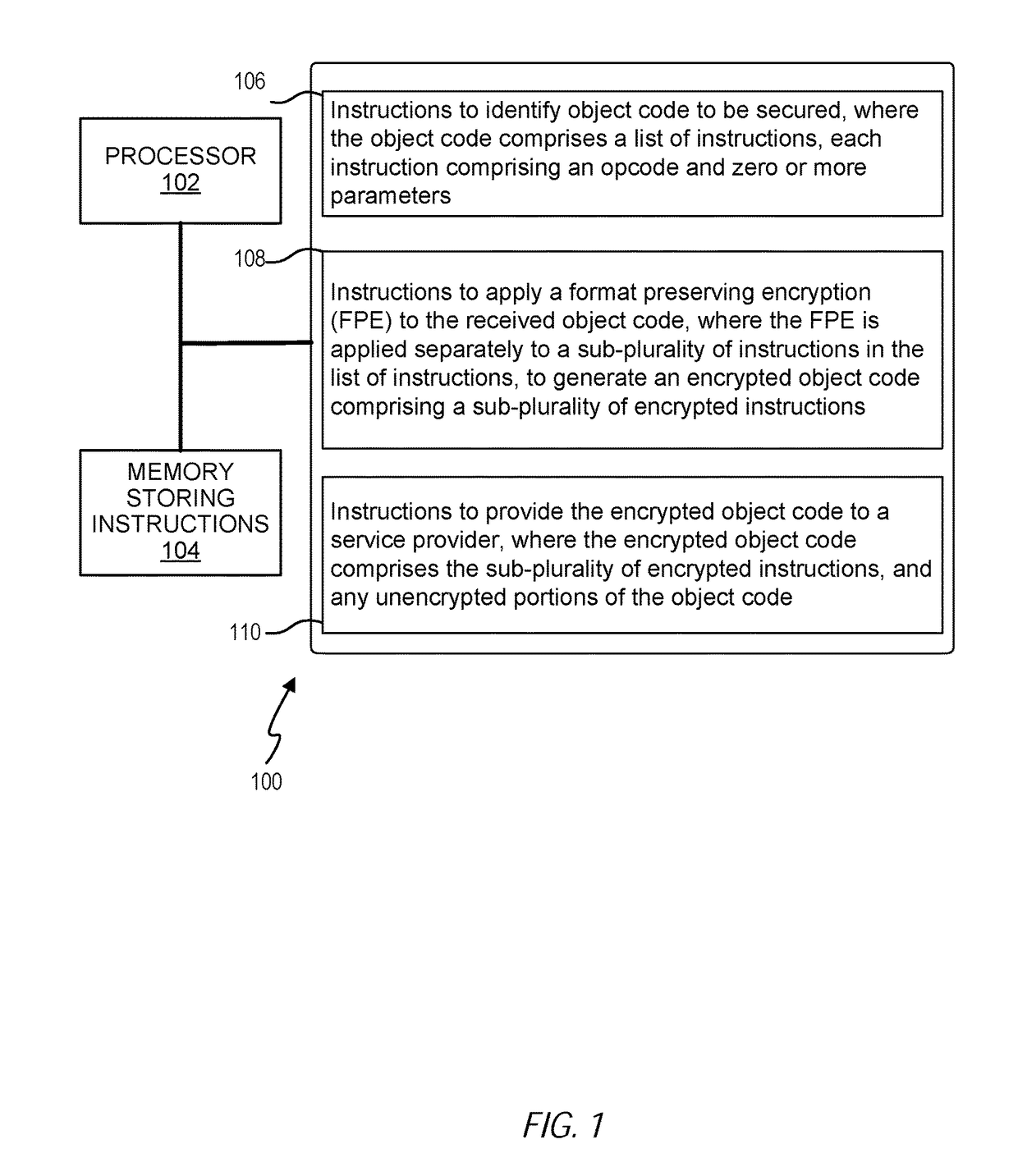
Format preserving encryption of object code
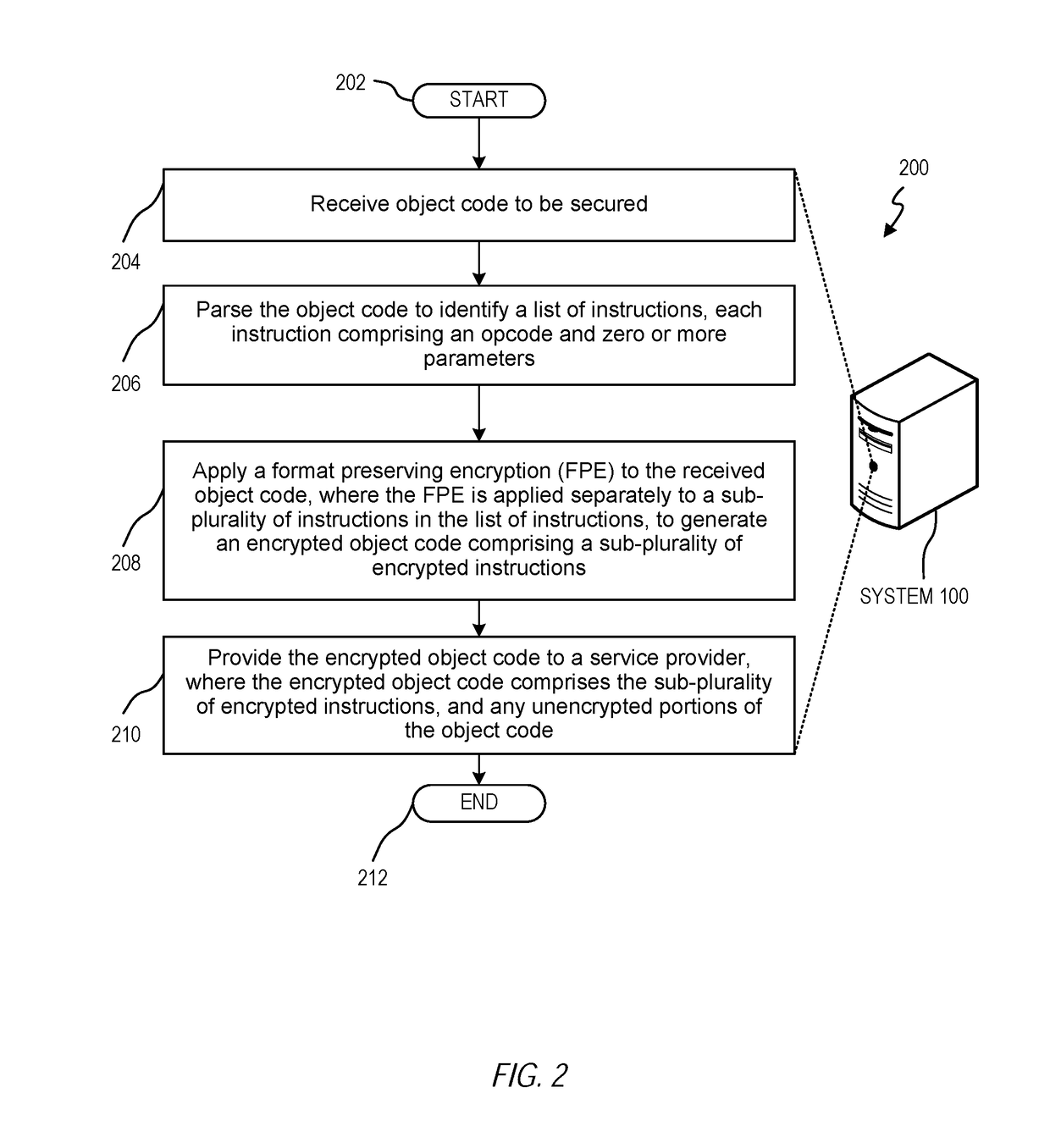
ActiveUS20180309569A1Memory architecture accessing/allocationKey distribution for secure communicationObject codeStore instruction
Format preserving encryption of object code is disclosed. One example is a system including at least one processor and a memory storing instructions executable by the at least one processor to identify object code to be secured, where the object code comprises a list of instructions, each instruction comprising an opcode and zero or more parameters. A format preserving encryption (FPE) is applied to the received object code, where the FPE is applied separately to a sub-plurality of instructions in the list of instructions, to generate an encrypted object code comprising a sub-plurality of encrypted instructions. An encrypted object code is provided to a service provider, where the encrypted object code comprises the sub-plurality of encrypted instructions, and any unencrypted portions of the object code.
Owner:MICRO FOCUS LLC
Data processing systems with format-preserving encryption and decryption engines
ActiveUS8855296B2Digital data processing detailsUser identity/authority verificationData processing systemBlock cipher
A data processing system is provided that includes format-preserving encryption and decryption engines. A string that contains characters has a specified format. The format defines a legal set of character values for each character position in the string. During encryption operations with the encryption engine, a string is processed to remove extraneous characters and to encode the string using an index. The processed string is encrypted using a format-preserving block cipher. The output of the block cipher is post-processed to produce an encrypted string having the same specified format as the original unencrypted string. During decryption operations, the decryption engine uses the format-preserving block cipher in reverse to transform the encrypted string into a decrypted string having the same format.
Owner:MICRO FOCUS LLC
Authentication to authorization bridge using enriched messages
ActiveUS11195173B2User identity/authority verificationProtocol authorisationCommunications systemInternet privacy
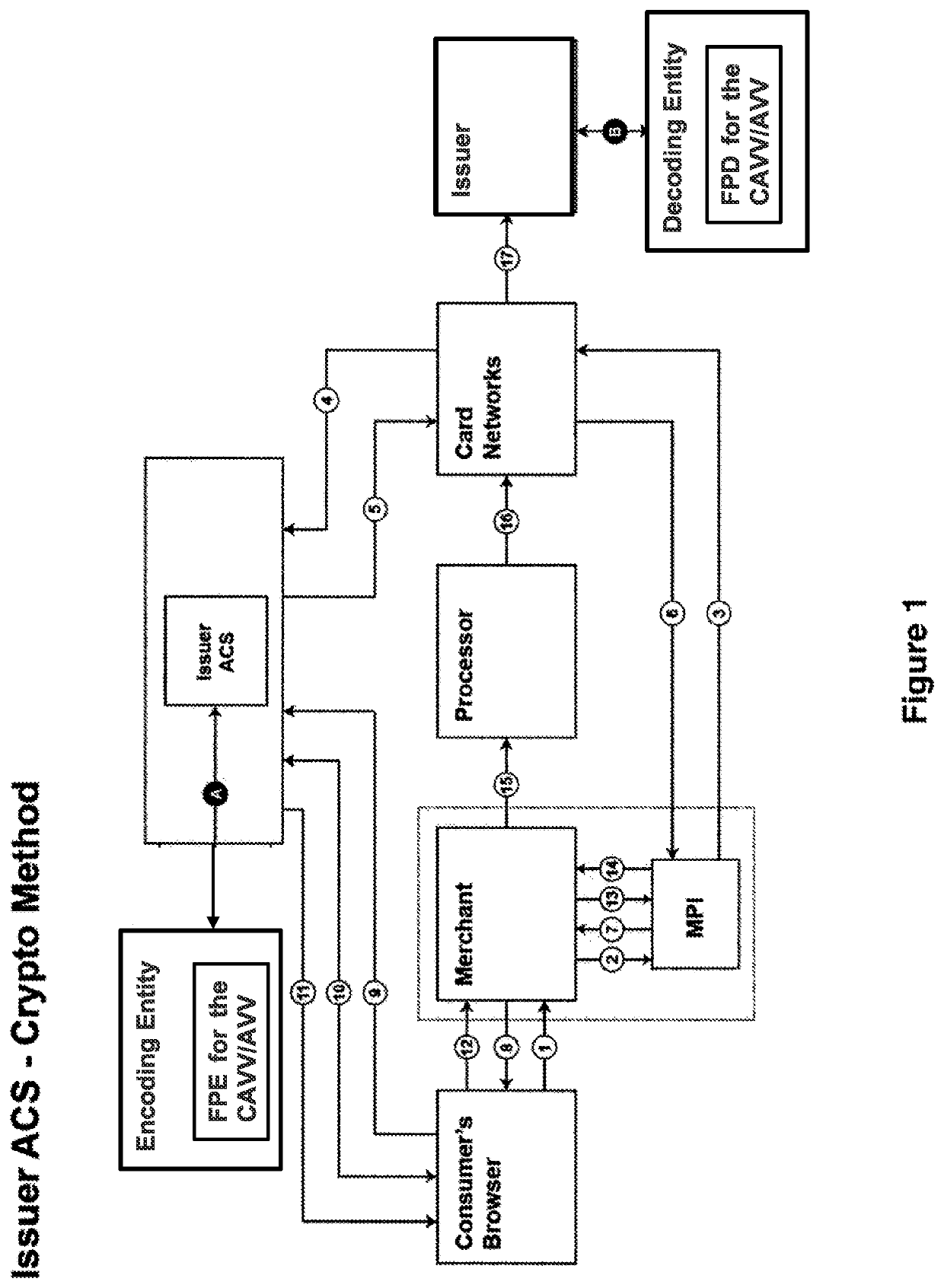
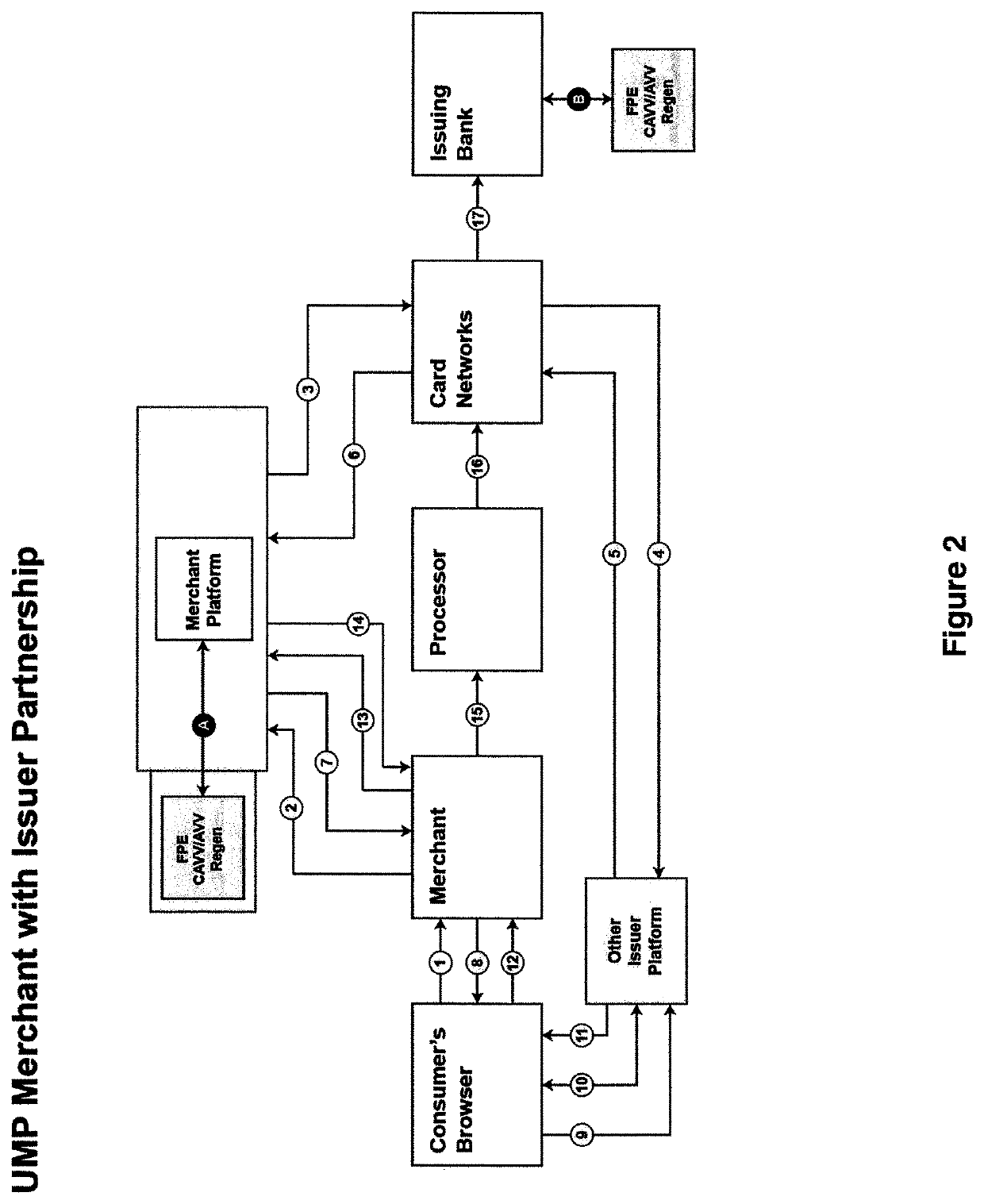
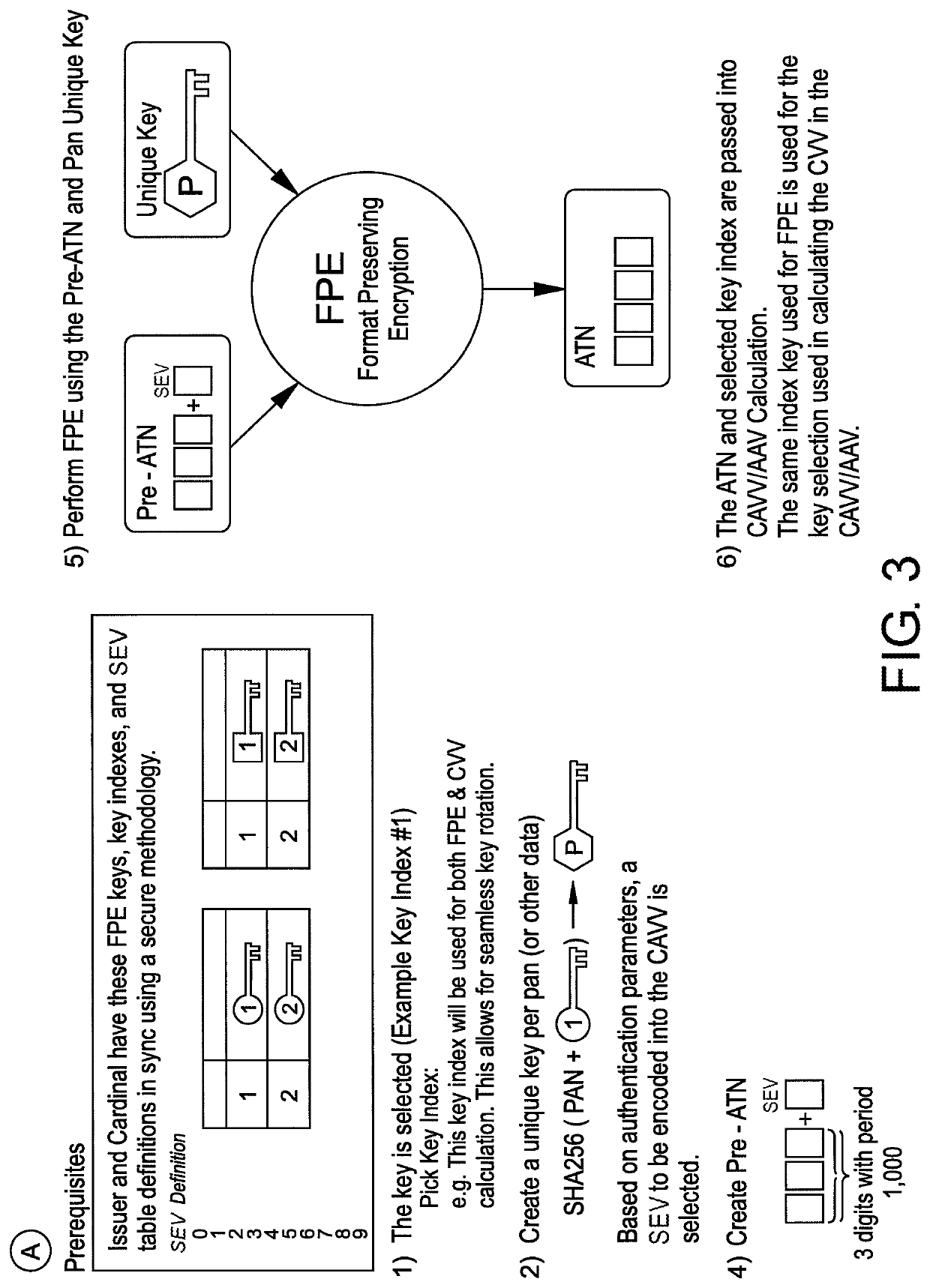
A system of electronic communication is disclosed. The system may: create a Pre-Authentication Transaction Number (Pre-ATN) by combining a number with a Special Encode Value (SEV), wherein the SEV is a single digit integer value; encrypt the Pre-ATN using a Format Preserving Encryption (FPE) to generate an encrypted Authentication Transaction Number (ATN); and send the encrypted ATN to an access control server (ACS) to use the encrypted ATN to generate a cardholder Authentication Verification Value (CAVV) or an Accountholder Authentication Value (AAV).
Owner:CARDINALCOMMERCE CORP
Systems for structured encryption using embedded information in data strings
ActiveUS8949625B2Key distribution for secure communicationUnauthorized memory use protectionData processing systemData library
A data processing system is provided that includes applications, databases, encryption engines, and decryption engines. Encryption and decryption engines may be used to perform format-preserving encryption on data strings stored in a database. Encryption and decryption engines may include embedded-format-preserving encryption and decryption engines. Embedded-format-preserving encryption engines may be used to encrypt data strings and embed information in data strings. Information corresponding to a format-preserving encryption operation of a data string may be embedded in an associated data string. The associated data string may be encrypted before or after embedding the information in the associated data string. The embedded information may include key management data that corresponds to a managed encryption key that was used to encrypt the data string.
Owner:MICRO FOCUS LLC
Systems for embedding information in data strings
A data processing system is provided that includes applications, databases, encryption engines, and decryption engines. Encryption and decryption engines may be used to perform format-preserving encryption on data strings stored in a database. Applications may be used to embed information in data strings. Information may be embedded by using a character set that is larger than a character set being used by a data string. A data string may be converted into a larger character set, analogous to converting a number from a lower base to higher base. Such a conversion may shorten a data string, allowing information to be embedded as appended characters.
Owner:MICRO FOCUS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com