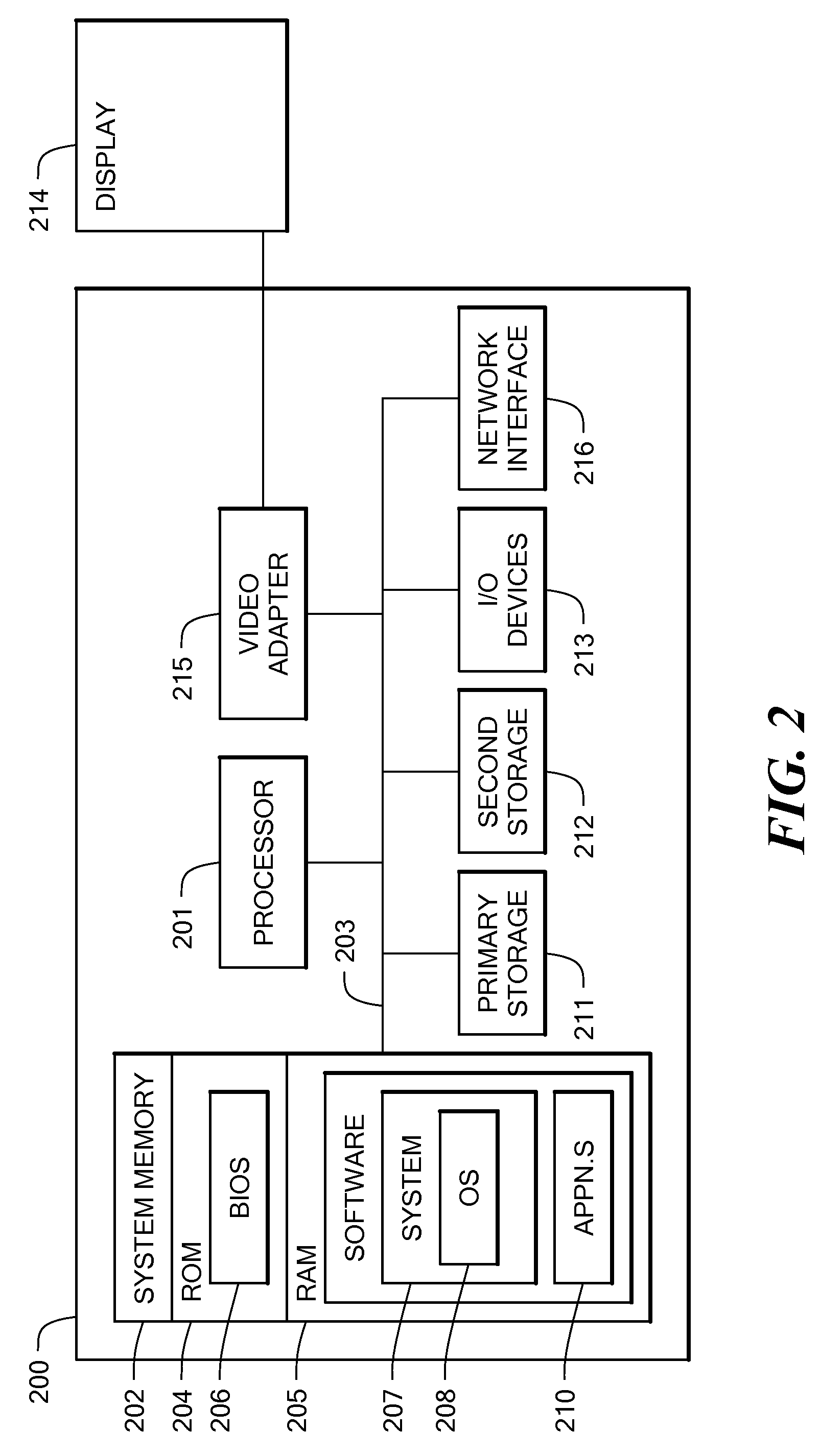
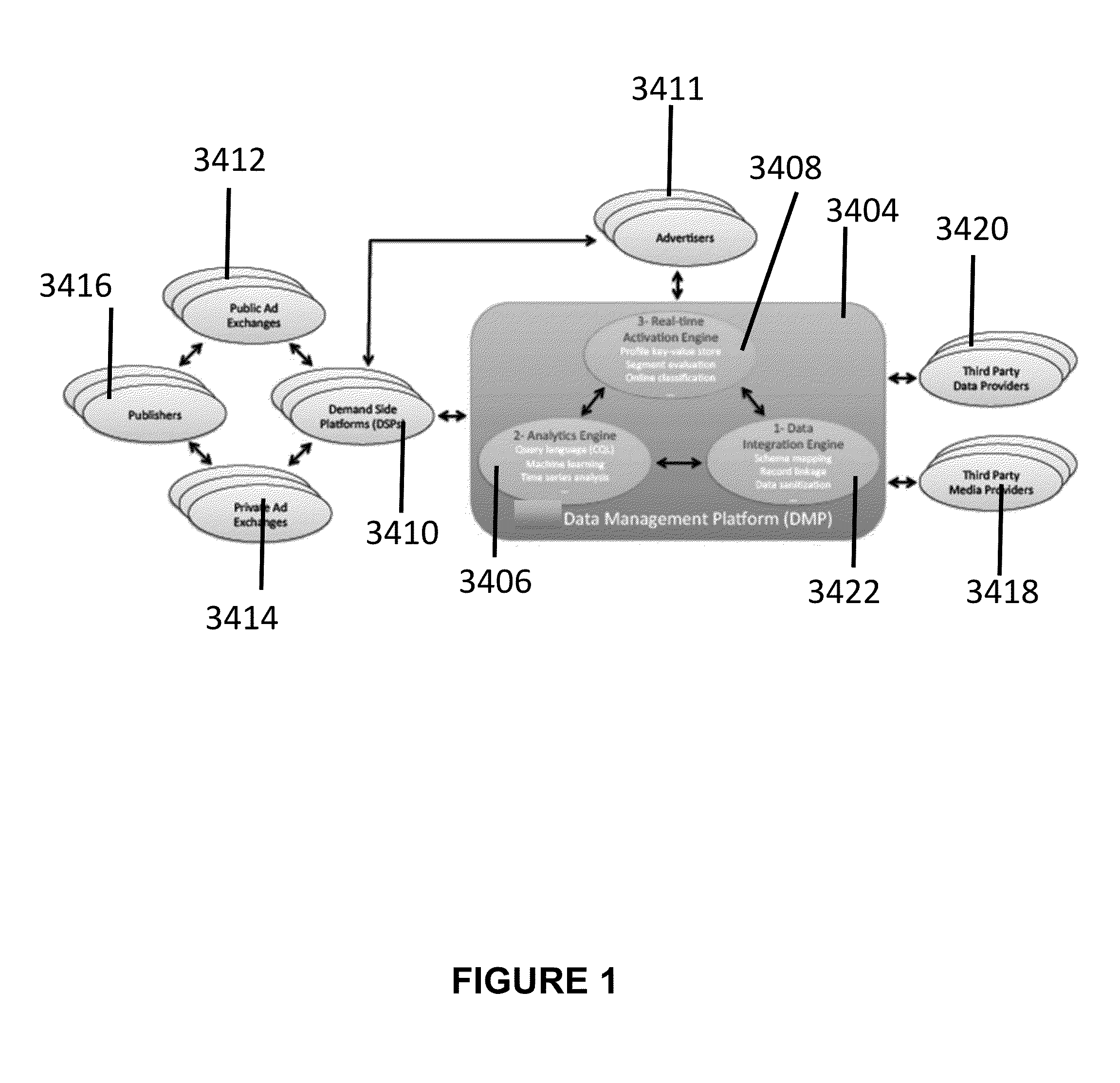
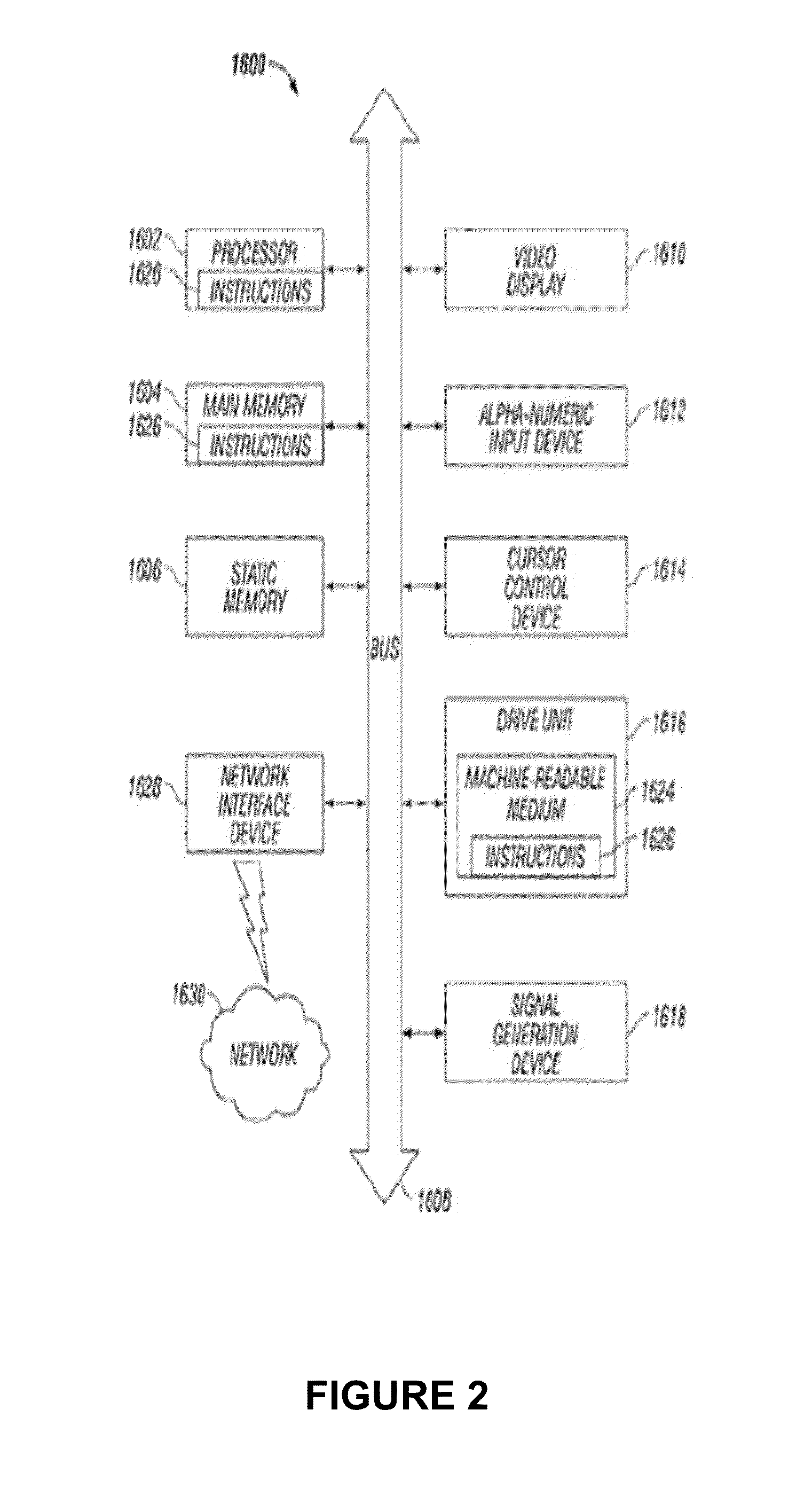
Patents
Literature
438 results about "Validity checking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Validity check. Validity check is a verification performed, either through software or manually, to verify that no errors are present or that it adheres to a standard.
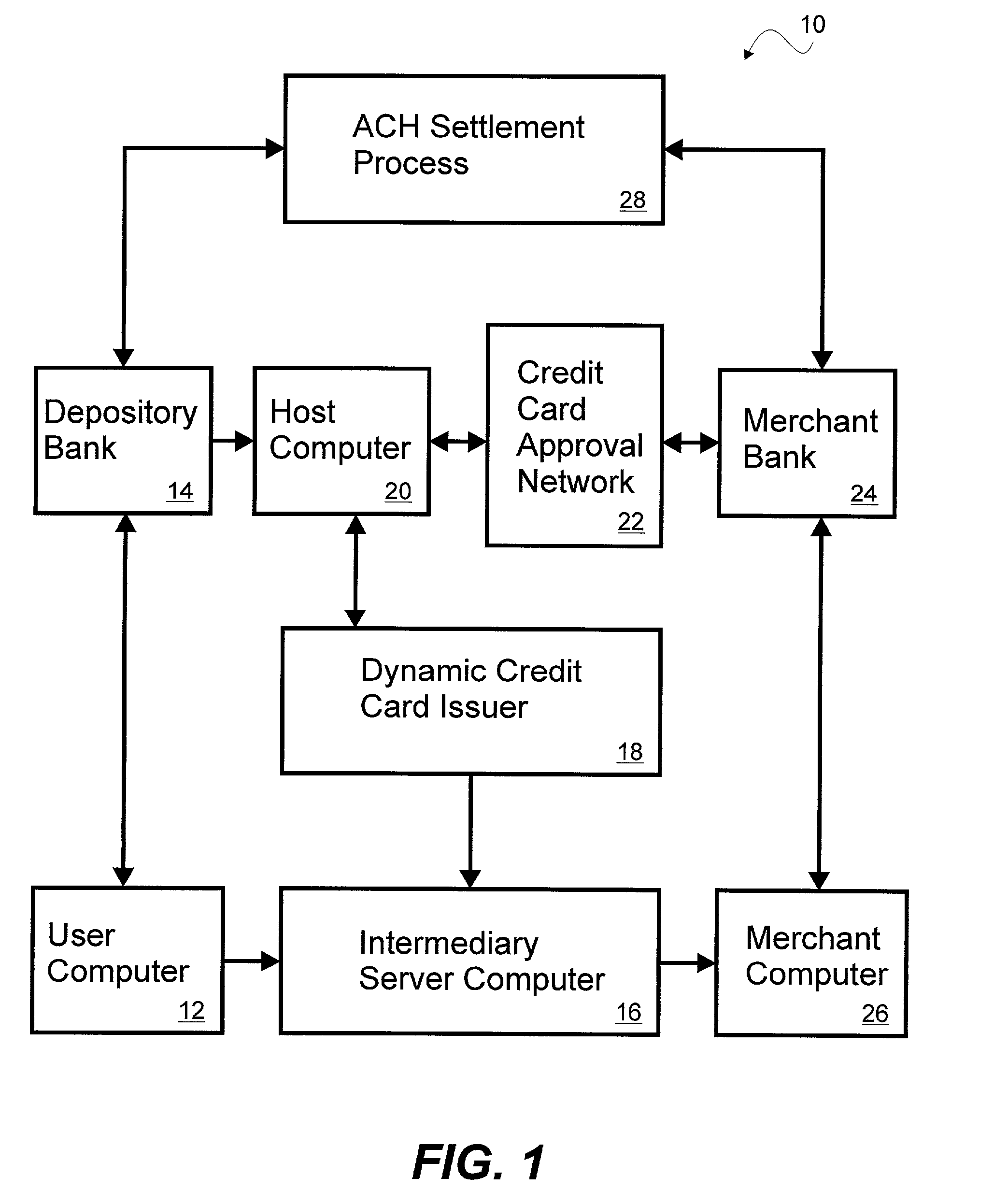
System and method for dynamically issuing and processing transaction specific digital credit or debit cards
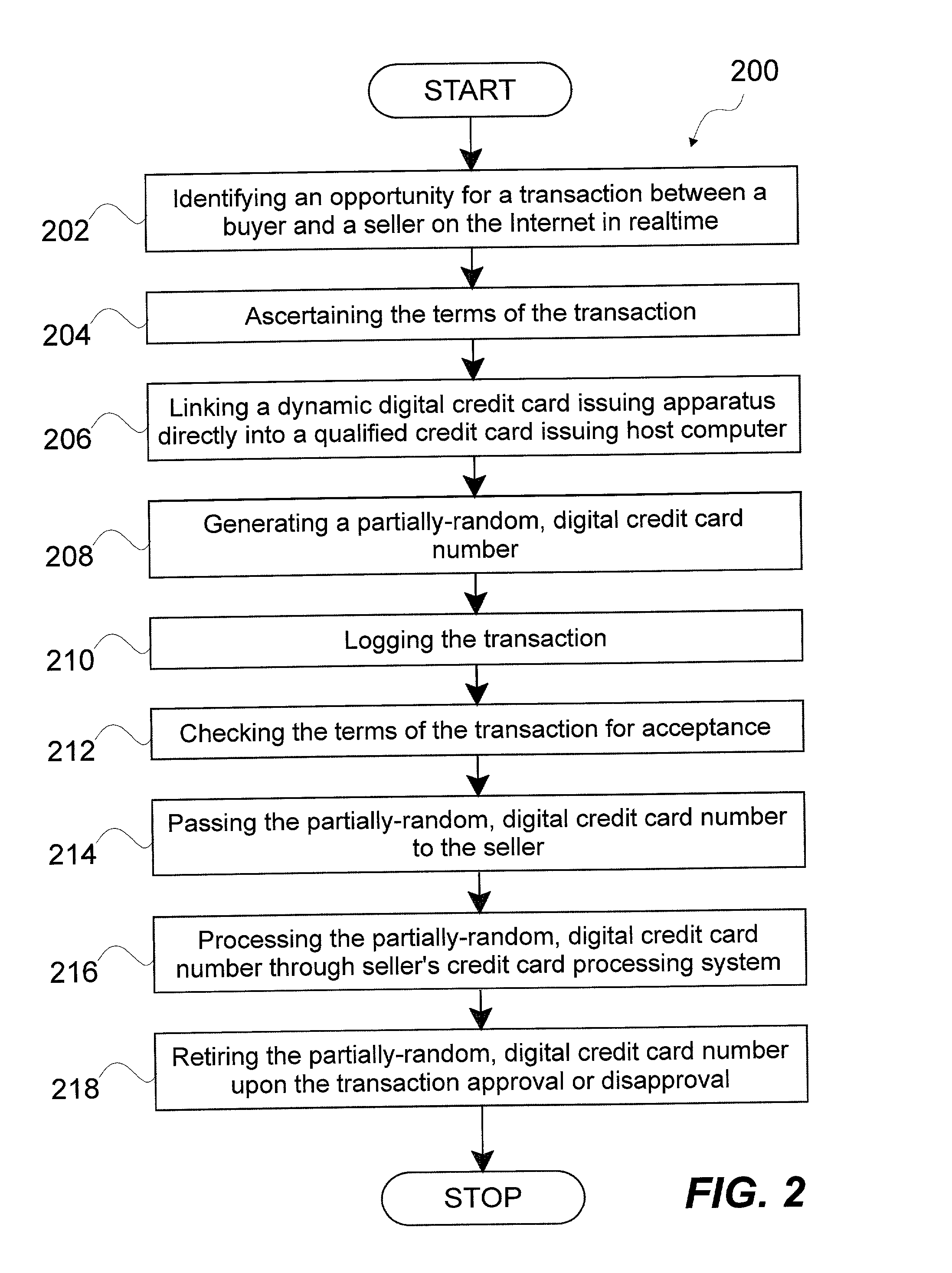
A system and method of dynamically issuing credit card numbers and processing transactions using those credit card numbers is disclosed. A method according to the invention includes digitally recognizing a transaction opportunity on the Internet in real-time, recognizing the terms of the transaction, linking a dynamic digital credit card issuing apparatus directly into a qualified credit card issuing host, generating a partially random digital credit card number, logging the transaction, checking the terms of the transaction for acceptance, passing the dynamically issued digital credit card number to the merchant, processing the digital credit card number through the merchant's card processing system, receiving the transaction approval request, participating in credit card validity checking systems, processing the approval request in real-time, sending the requesting party a legitimate authorization code, and retiring the digital credit card number immediately upon transaction approval or disapproval. A system according to the invention implements the method of the invention.
Owner:ORANGATANGO
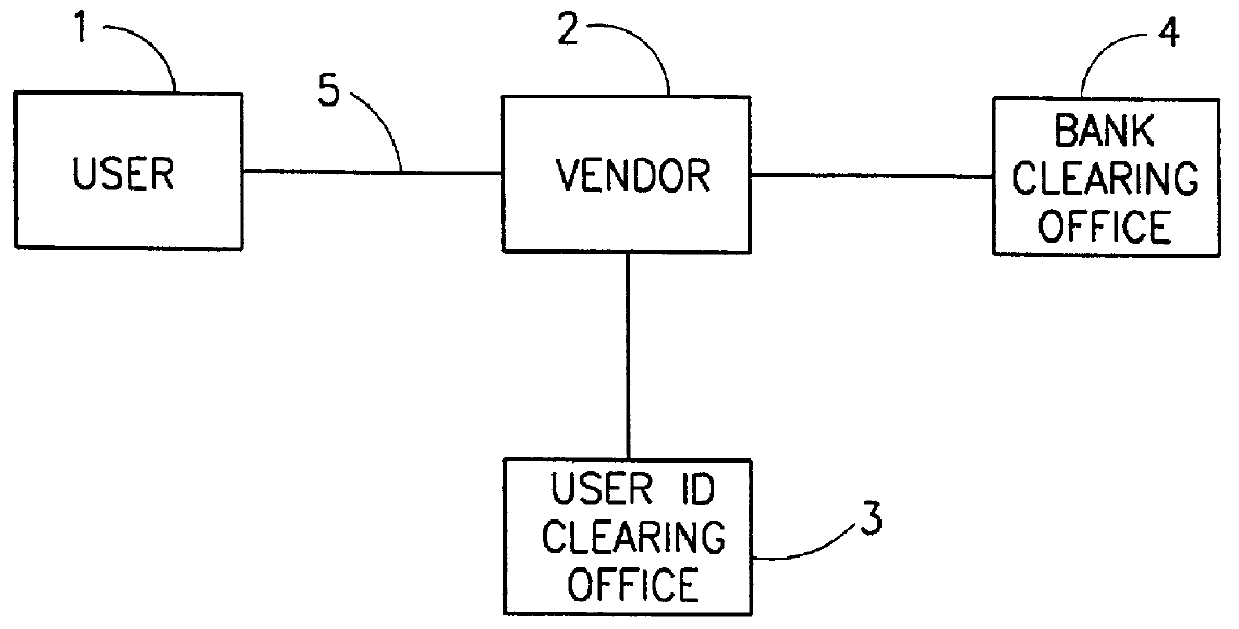
System for transaction over communication network
A method for conducting transaction between first user and a remote second user interlinked through a communication network, by utilizing also a clearing office interlinked to the network. The clearing office storing the user privileged information. The method including the steps of the user and the clearing office establishing a cryptographic secured session, the user transmitting, via the session, a user privileged information and transaction specific data, the transaction specific data being indicative of a transaction identification data. The clearing office activating transaction validity checking procedure by utilizing a user privileged information and the transaction specific data. In response to affirmative result of the transaction validity checking, the clearing office producing a transaction validity indication being indicative of the transaction identification code. The clearing office and the user establishing a communication session and the clearing office transmitting, via the session, the transaction validity indication.
Owner:NUSH MARKETING MANAGEMENT & CONSULTANCE
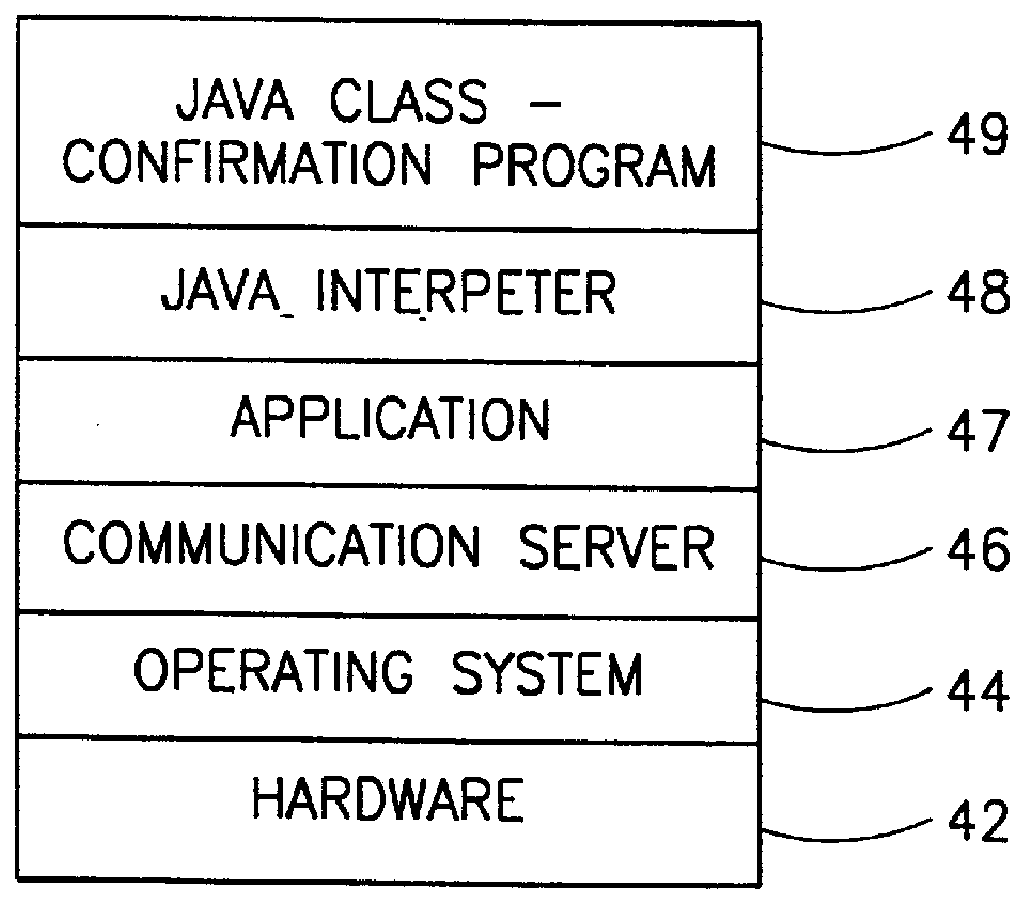
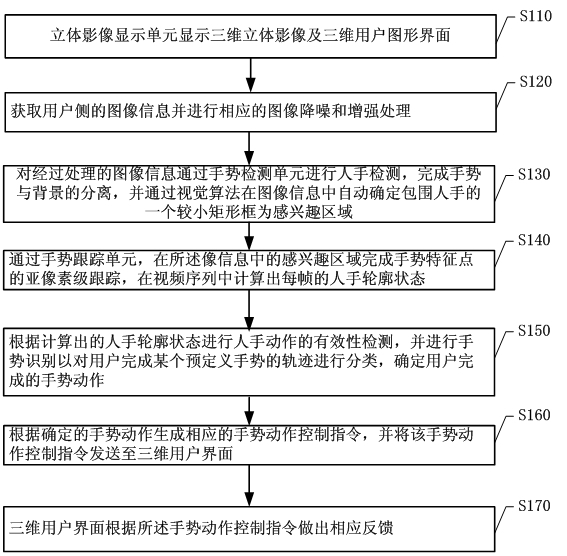
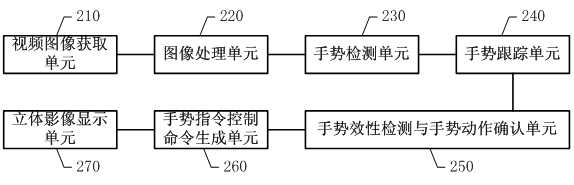
Man-machine interactive system and real-time gesture tracking processing method for same
InactiveCN102426480AReal-time hand detectionReal-time trackingInput/output for user-computer interactionCharacter and pattern recognitionVision algorithmsMan machine
The invention discloses a man-machine interactive system and a real-time gesture tracking processing method for the same. The method comprises the following steps of: obtaining image information of user side, executing gesture detection by a gesture detection unit to finish separation of a gesture and a background, and automatically determining a smaller rectangular frame which surrounds the hand as a region of interest in the image information through a vision algorithm; calculating the hand profile state of each frame in a video sequence by a gesture tracking unit; executing validity check on hand actions according to the calculated hand profile state, and determining the gesture action finished by the user; and generating a corresponding gesture action control instruction according to the determined gesture action, and making corresponding feedbacks by a three-dimensional user interface according to the gesture action control instruction. In the system and the method, all or part of gesture actions of the user are sensed so as to finish accurate tracking on the gesture, thus, a real-time robust solution is provided for an effective gesture man-machine interface port based on a common vision sensor.
Owner:KONKA GROUP
Managing real time access management to personal information
ActiveUS9202026B1High security riskReduce flowDigital data processing detailsDigital data protectionInternet privacyReal time management
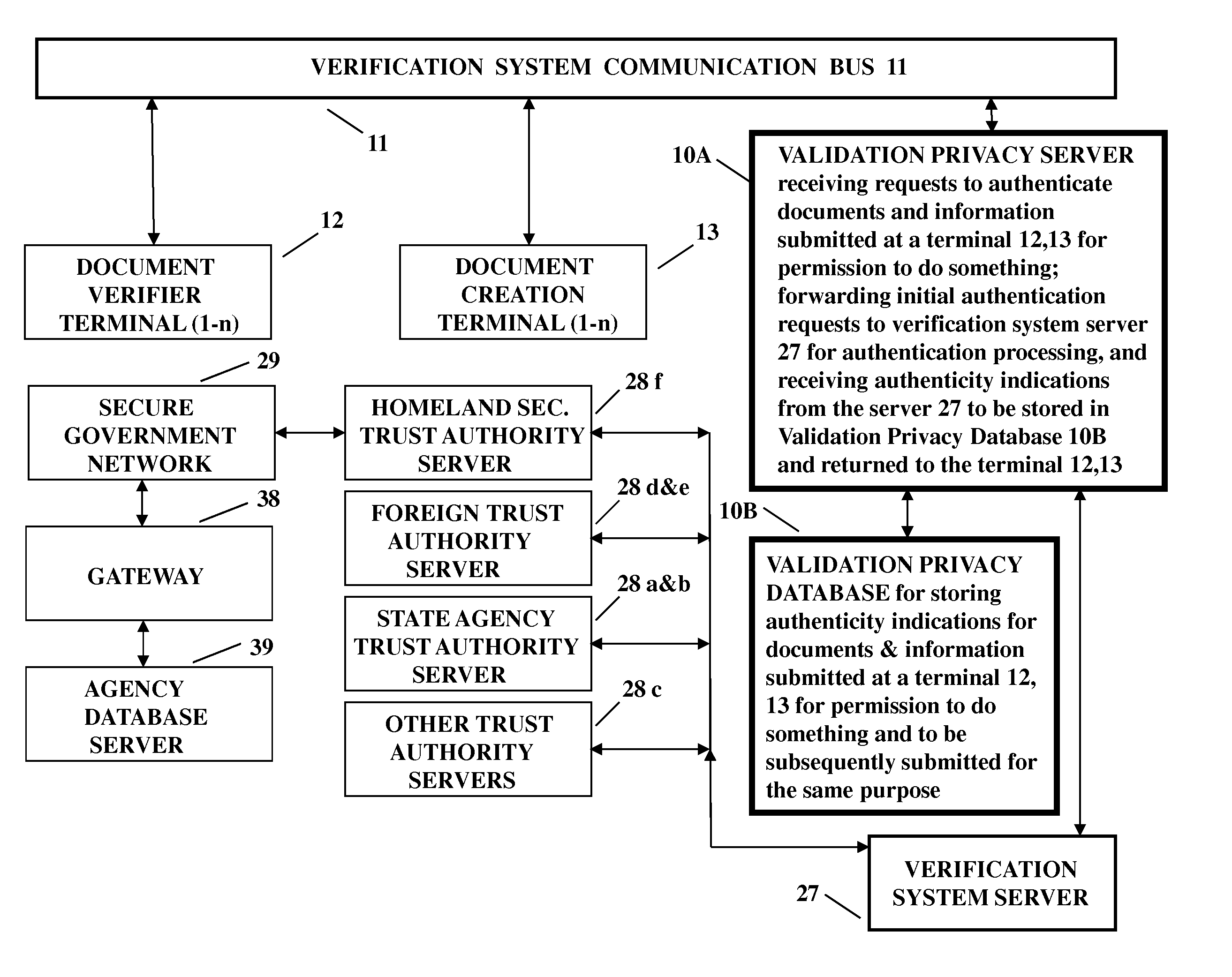
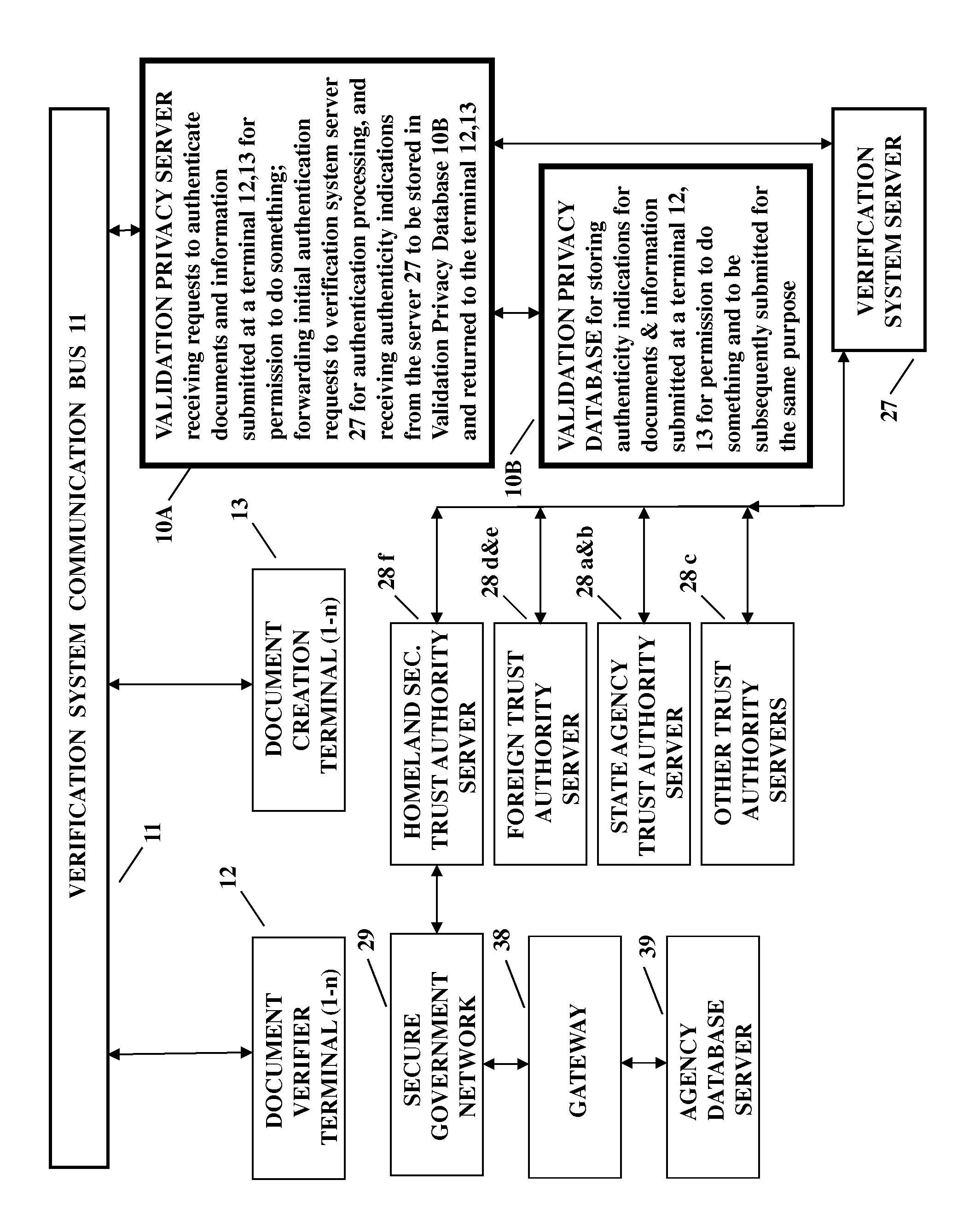
Apparatus is disclosed for verifying the validity of documents and biometrics submitted by individuals at a document verification terminal, or the use of an e-token with appropriate information thereon in an encrypted manner, so they may perform some action such as purchase an alcoholic beverage or enter a highly secure governmental facility. A Validation Privacy Server and its associated Validation Privacy Database store the results of previous document and biometric validity checks using governmental databases, to be used for subsequent submissions of the same document for the same purpose. In this manner governmental databases are not overloaded with mundane document and personal validity checks every time a document is used for the same purpose. The storage of the results of document checking by the Validation Privacy Server and its associated Validation Privacy Database may be performed with or without the approval of the individual depending on privacy determinations as to the accessibility of the information.
Owner:ACUANT
Method and system for file transfer
ActiveUS20080040503A1Reduce transmission delayMultiple digital computer combinationsTransmissionAnti virusConfidentiality
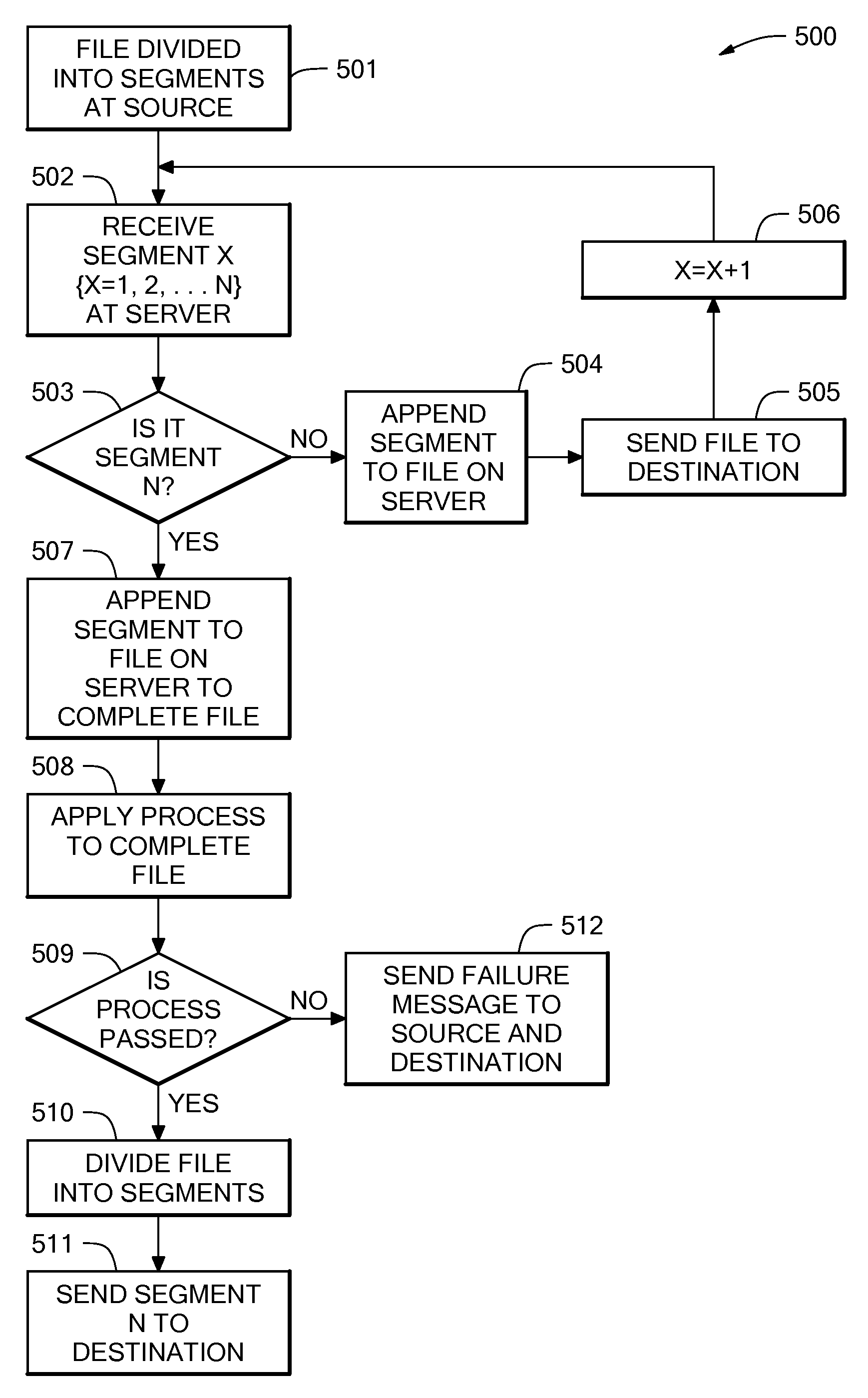
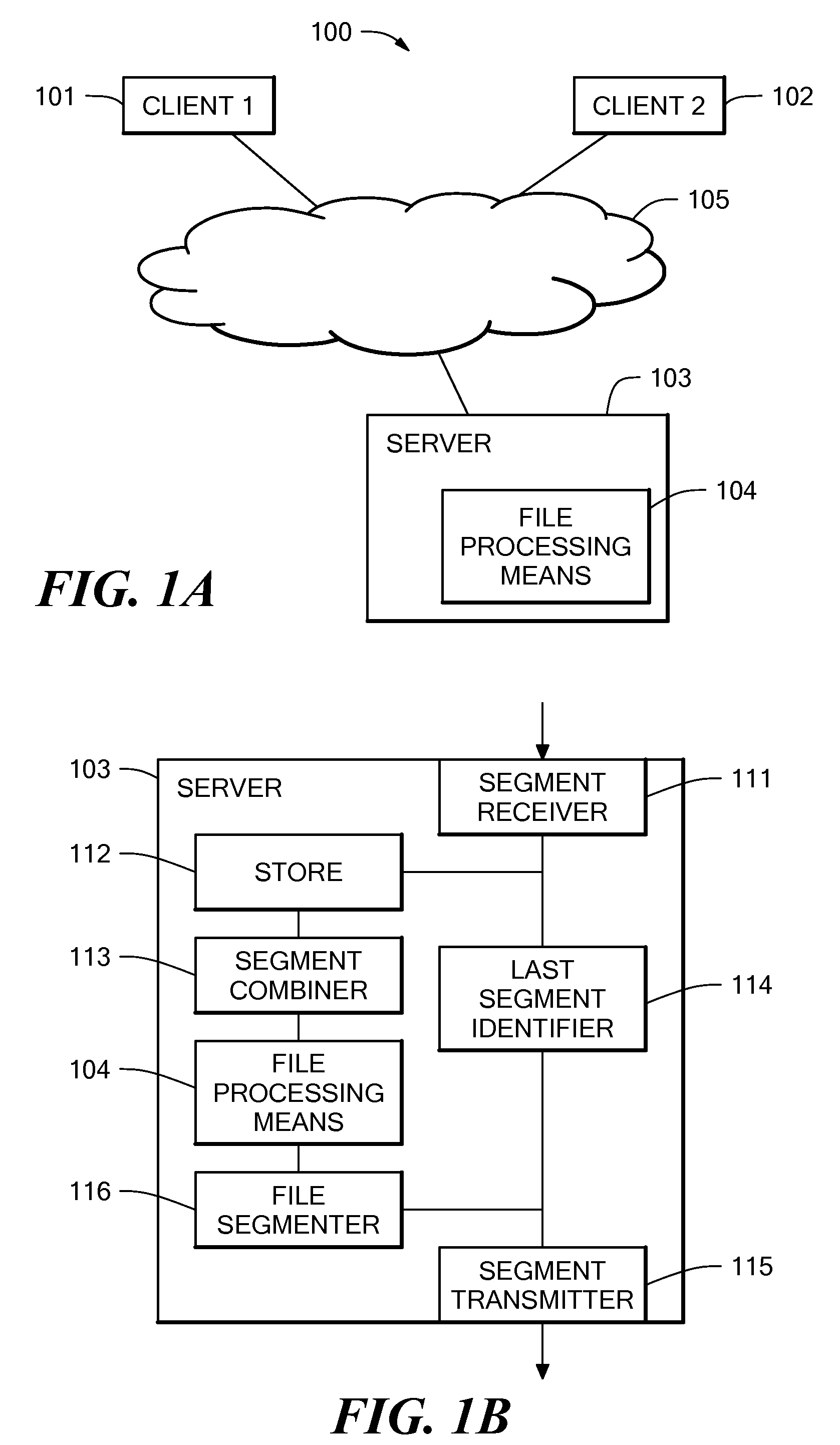
A method and system for file transfer are provided in which a file is transferred between a source client and a destination client via a middle server. The server receives segments of a file from the source client and stores the segments of the file as they are received. The server also forwards the segments of the file to a destination client as they are received, with the exception of one segment. The server combines the segments to form the whole file and applies a process to the whole file. The process may be for example an authorisation process such as an anti-virus check, a confidentiality check, or a content validity check. If the file passes the process, the remaining excepted segment is forwarded to the destination client.
Owner:IBM CORP
Data management platform for digital advertising
InactiveUS20140279074A1Improve customer experienceAdvertisementsNatural language data processingDigital advertisingData management
A data management apparatus for digital advertising includes a data integration processor for collecting and storing data from providers, resolving heterogeneity of the data at schema and data levels, and performing validity checks of the data; an analytics processor for receiving validated data from the data integration processor and providing to users custom, nesting-aware, SQL-like query language and a library of data mining methods, machine learning models, and analytical user profiles (AUP); and an activation processor for encapsulating complex computations performed in real-time, segment evaluation, and online user classification using runtime user profiles (RUP).
Owner:TURN
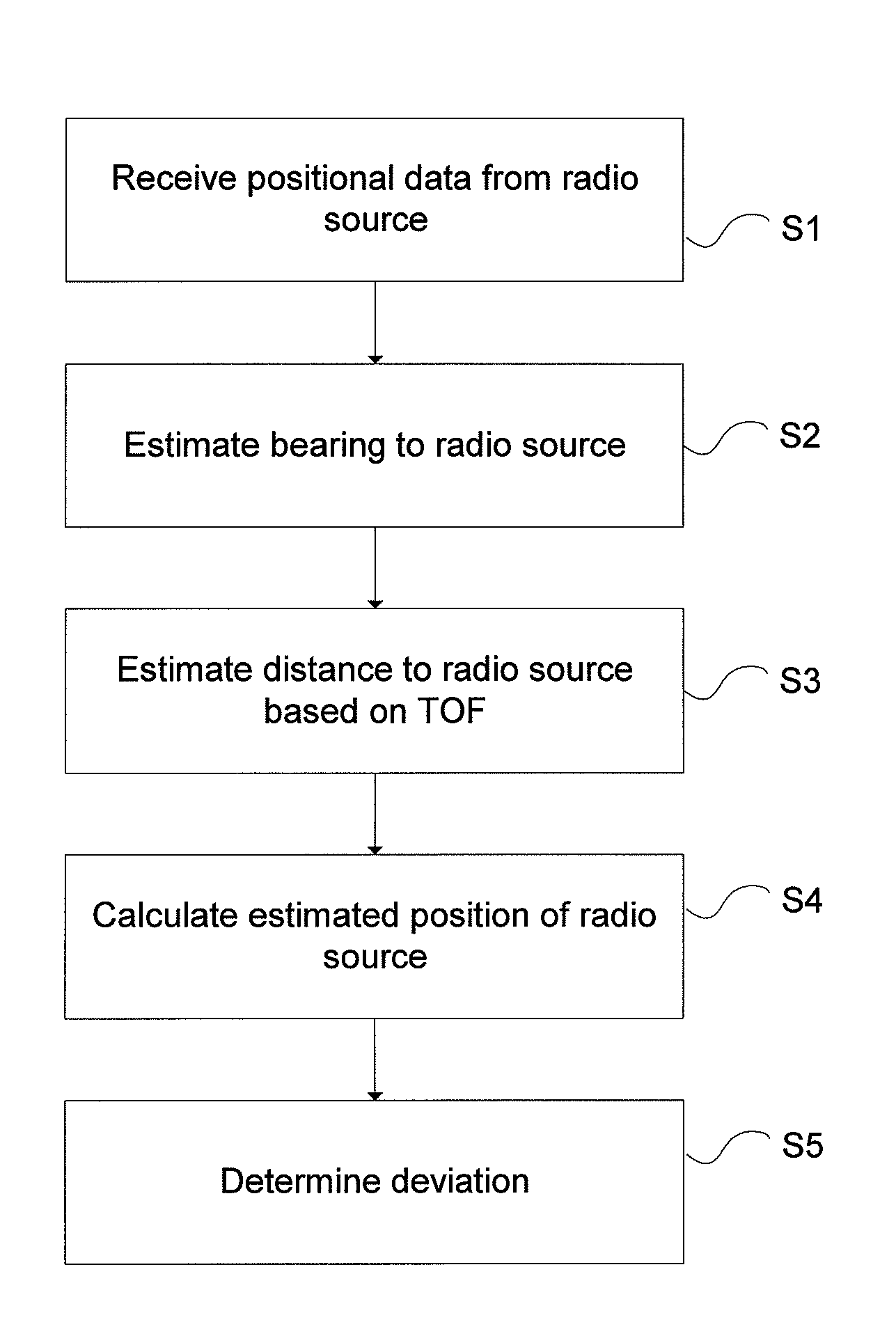
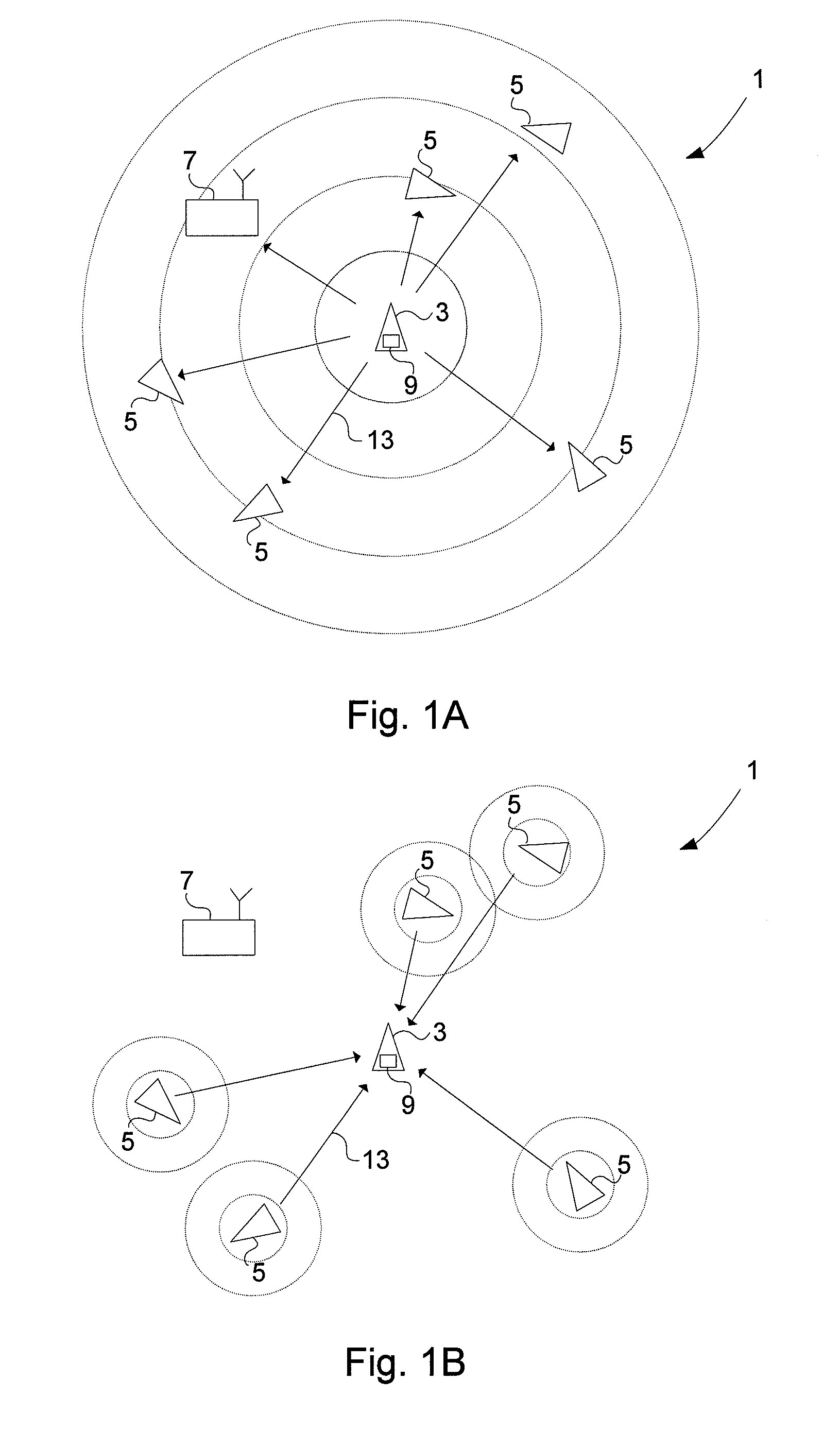
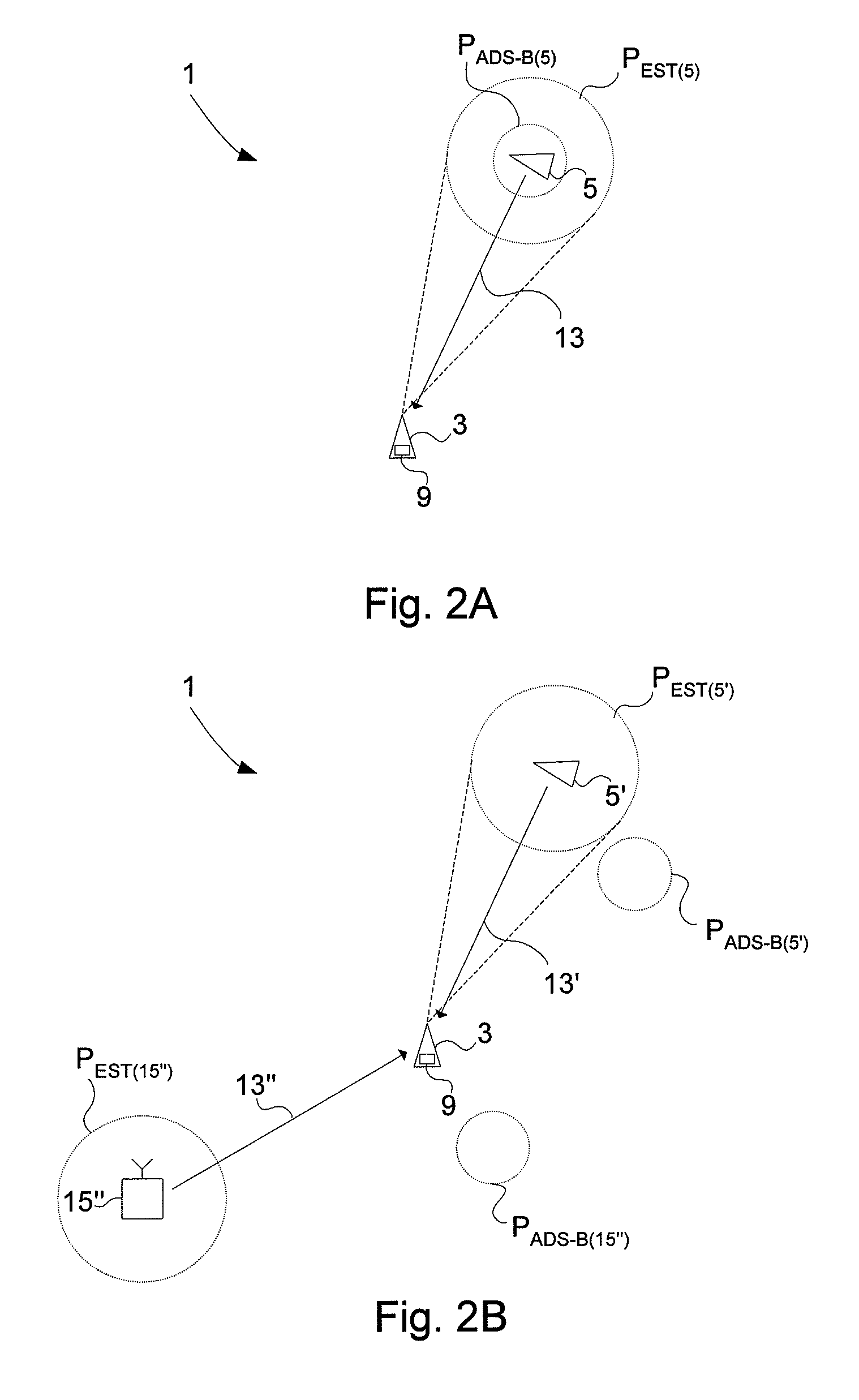
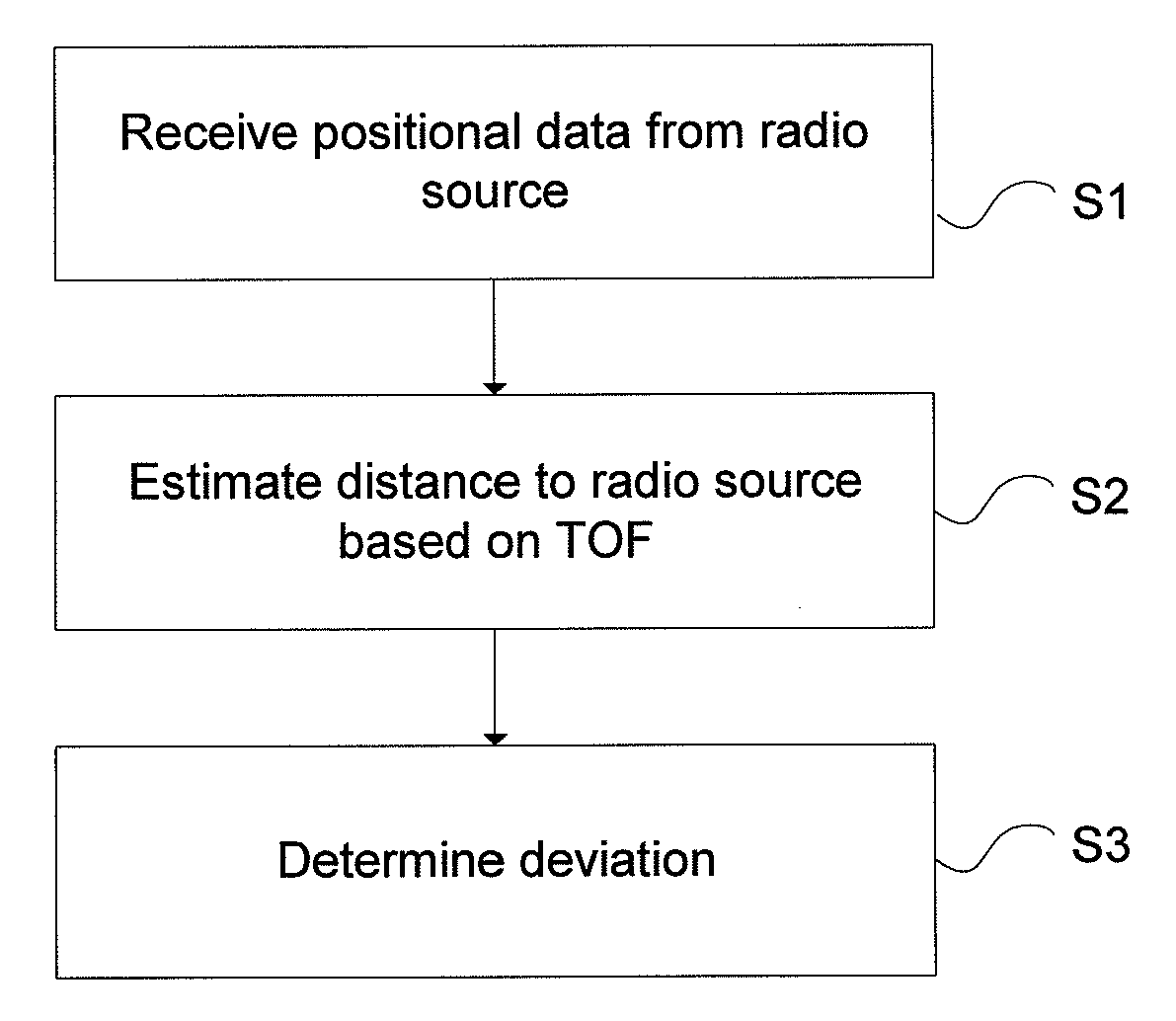
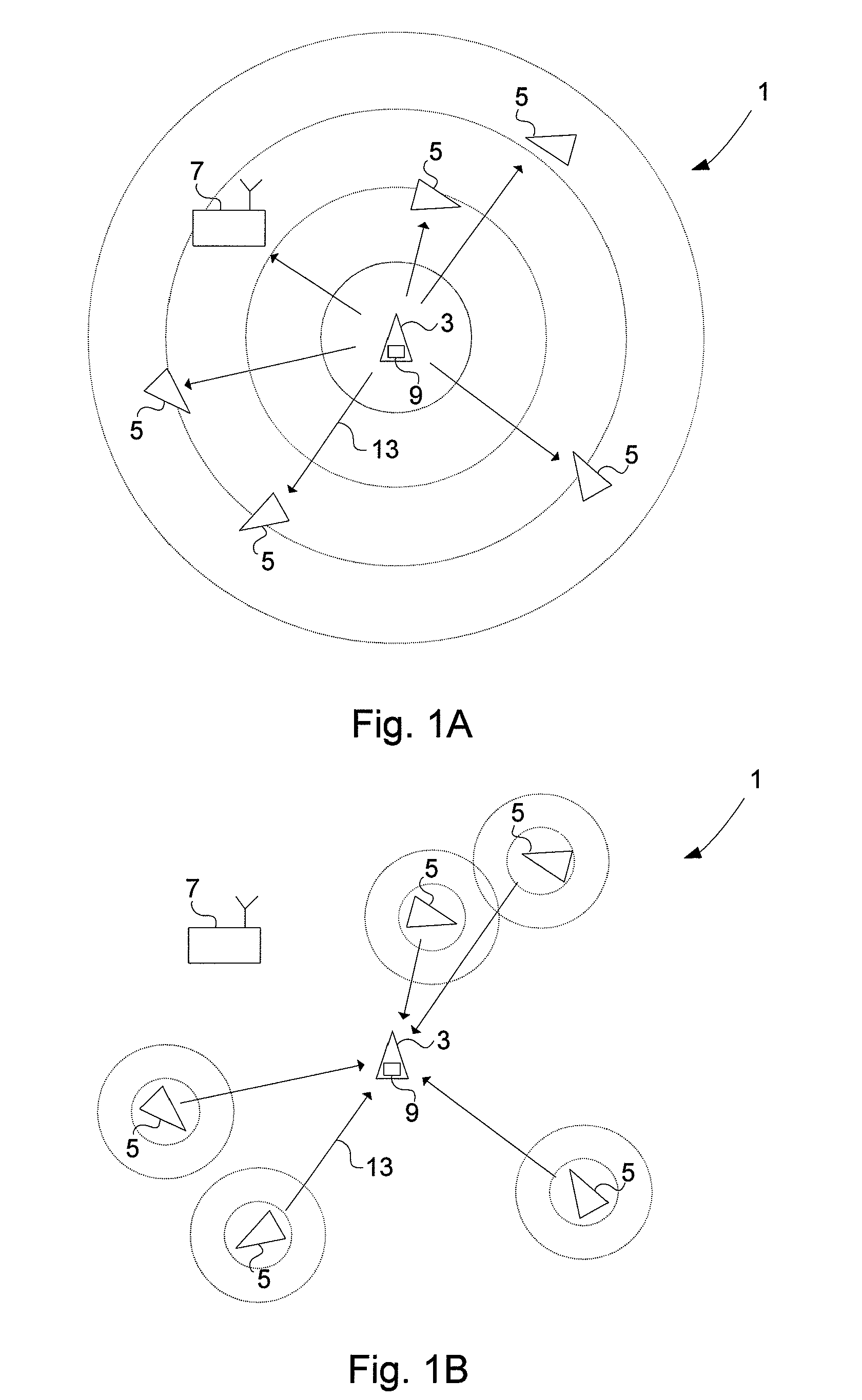
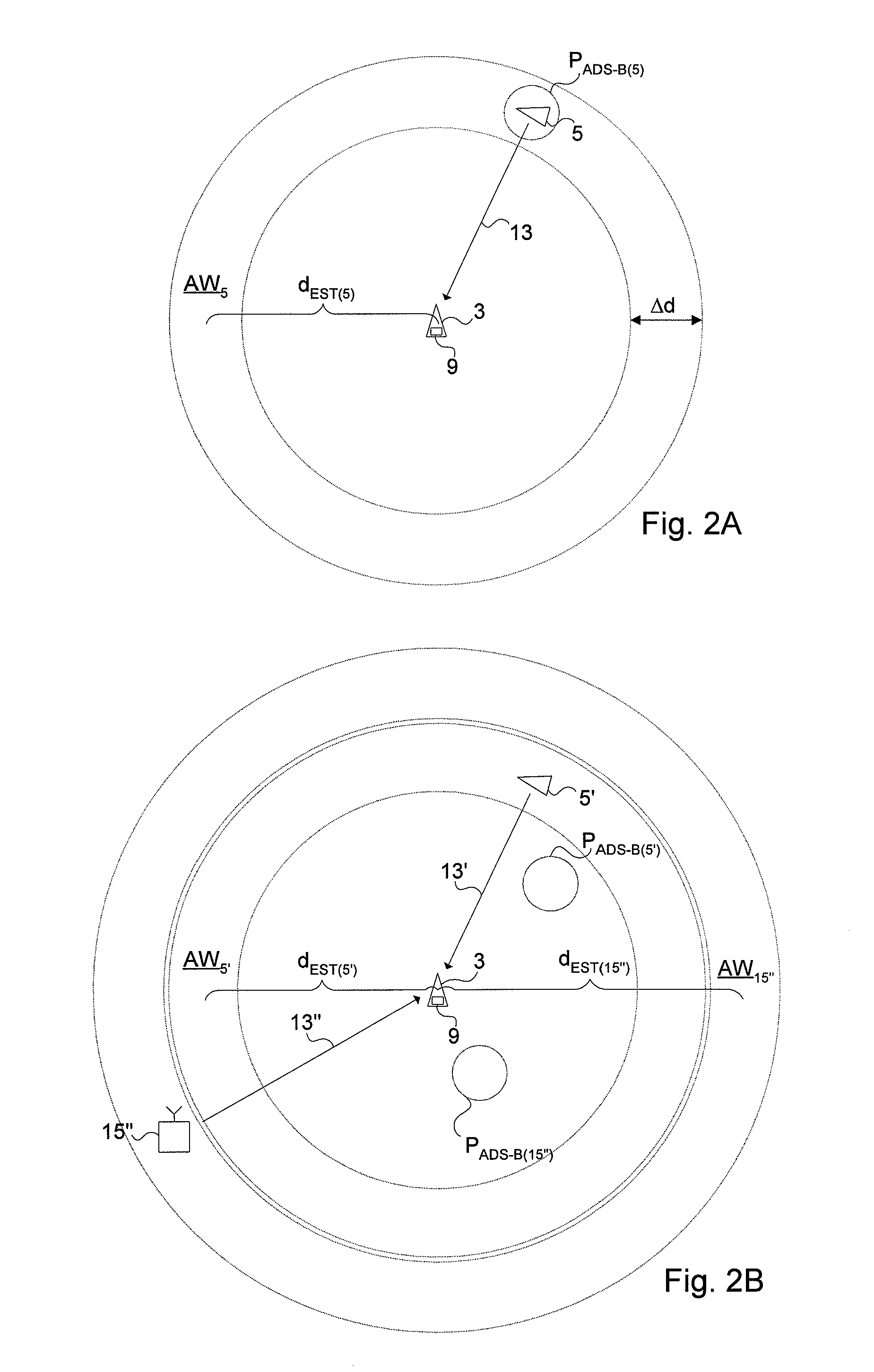
Validity check of vehicle position information
ActiveUS20110163908A1Not easy to make mistakesSensitive to usePosition fixationBeacon systemsIn vehicleEngineering
A method for validating received positional data in vehicle surveillance applications wherein vehicles transmit positional data indicating their own position to surrounding vehicles. A a radio direction finding antenna arrangement of a receiving unit receives a signal carrying positional data indicating an alleged position of a vehicle, transmitted from a radio source. The bearing from the receiving unit to the radio source is estimated utilizing the radio direction finding antenna arrangement and the received signal. The distance between the receiving unit and the radio source is estimated based on the time of flight for a signal travelling there between at known speed. An estimated position of the radio source is calculated based on the estimated bearing and the estimated distance. A deviation value indicating the deviation / coincidence between the alleged position of a vehicle is determined according to the received positional data and the estimated position of the radio source.
Owner:SAAB AB
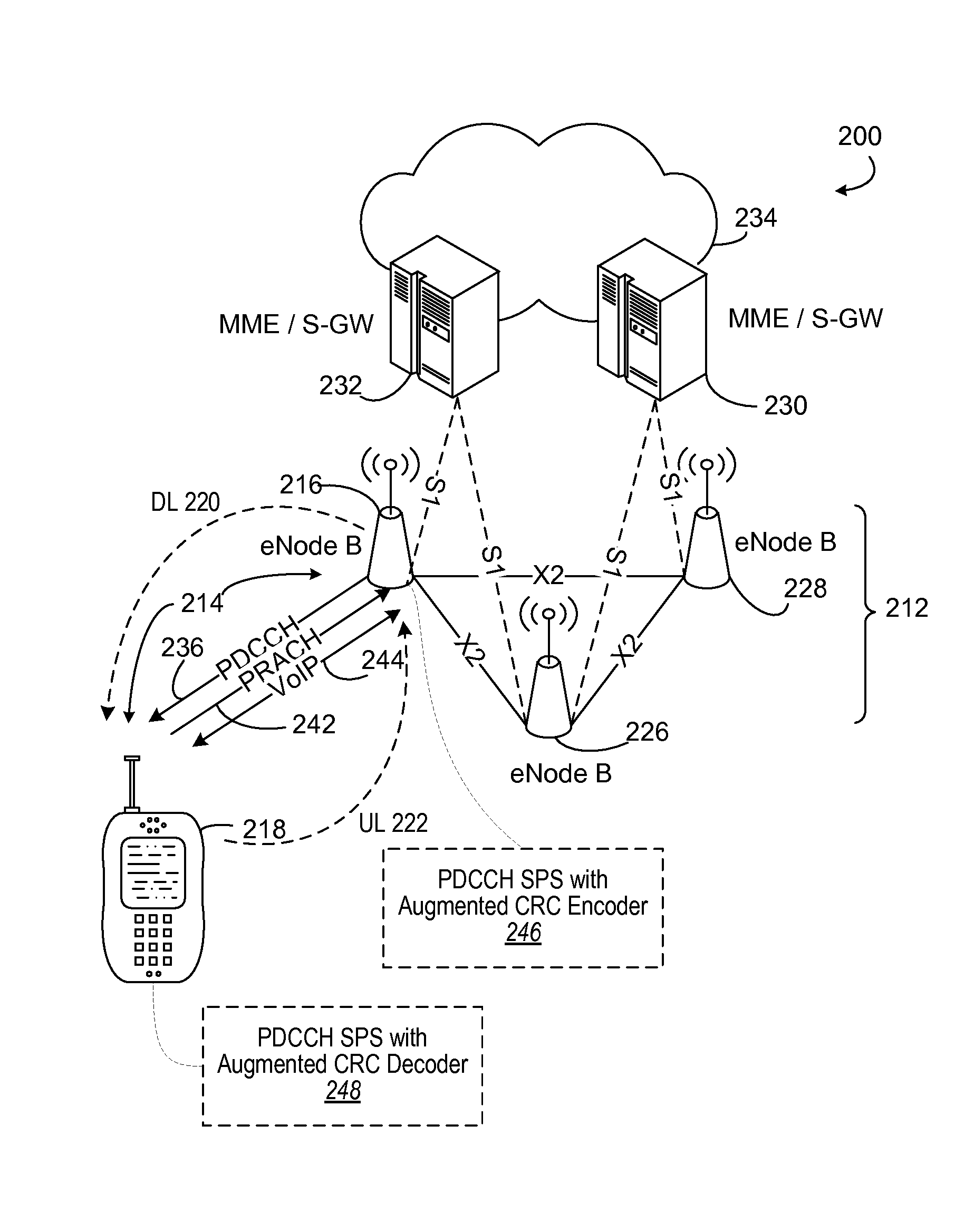
Filtering semi-persistent scheduling false alarms
ActiveUS20090257385A1Network traffic/resource managementForward error control useError checkingCommunications system
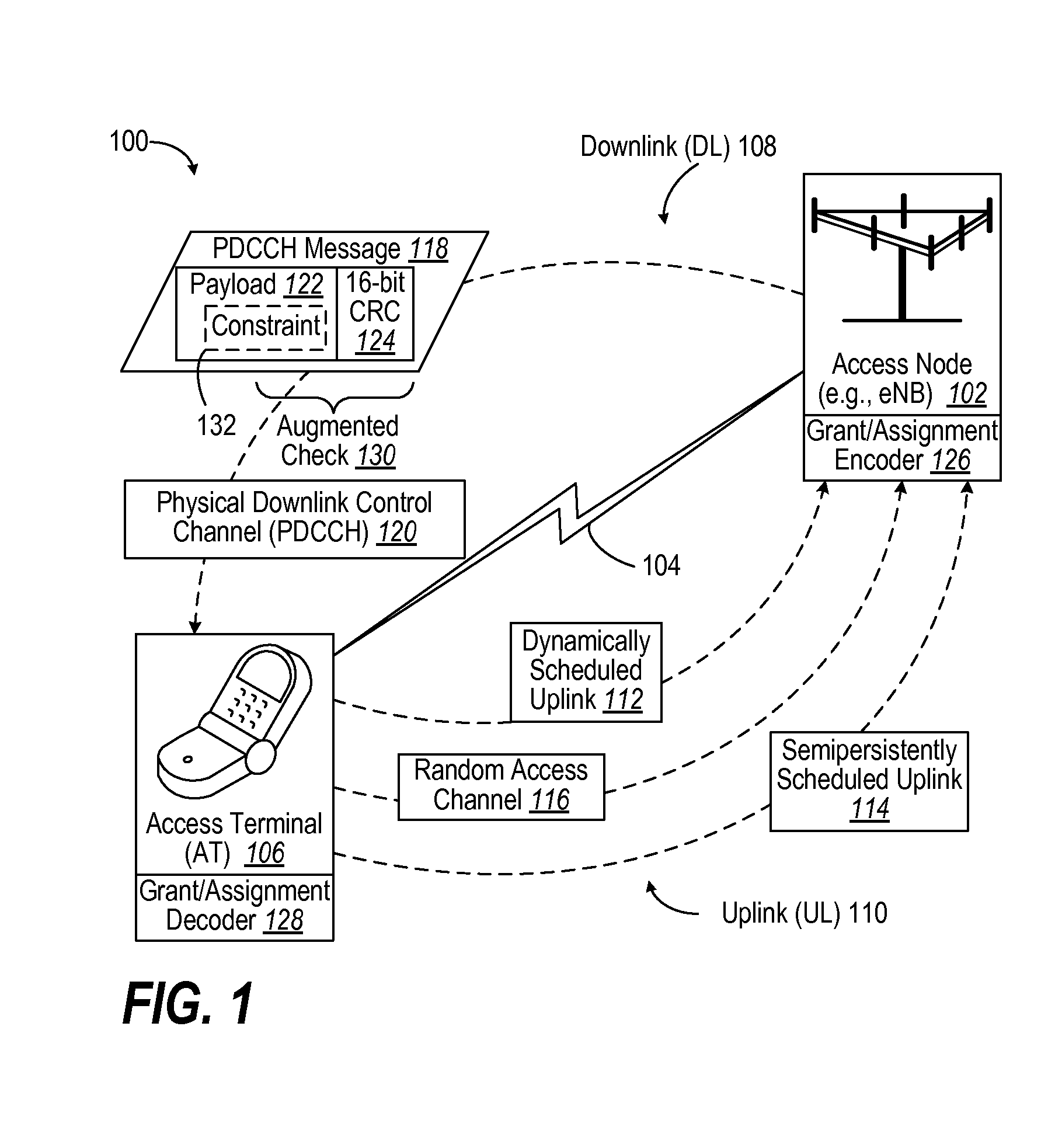
A scheduled data communication system of an access node and terminal supports recurring communications of small data amounts such as Voice over IP (VoIP). In order to make error checking more robust in a random access response (RAR), such as for semi-persistent scheduling (SPS) for VoIP, a portion of a grant or assignment payload has a constraint imposed that can be verified as a condition precedent to determining a valid grant or assignment rather than only relying upon a validity check field, such as a cyclic redundancy check (CRC). Thereby, incorrect validation of a grant or assignment is avoided for dynamic scheduling or for semi-persistent scheduling, the latter causing a persistent error.
Owner:QUALCOMM INC
Systems and methods for validating an address
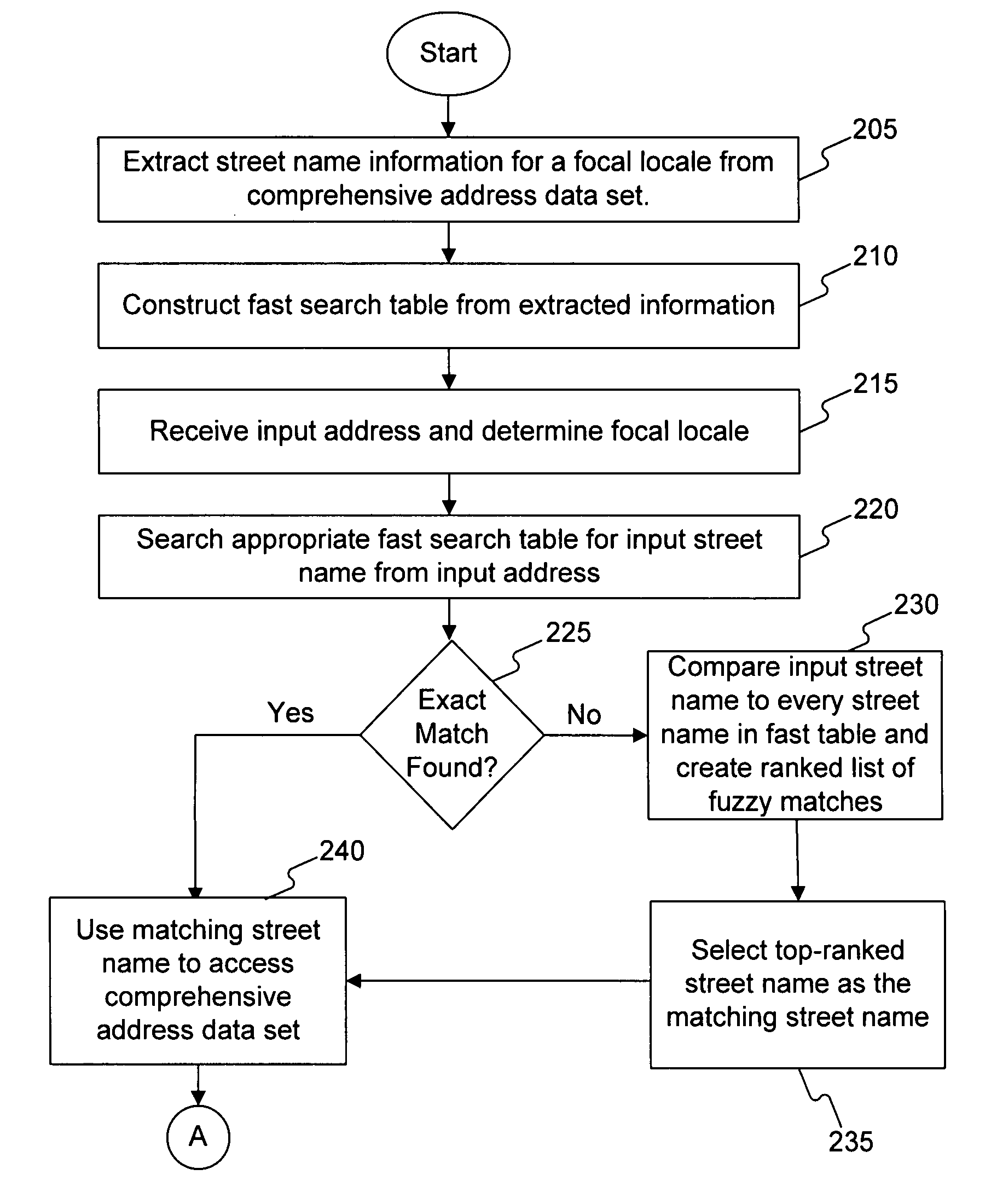
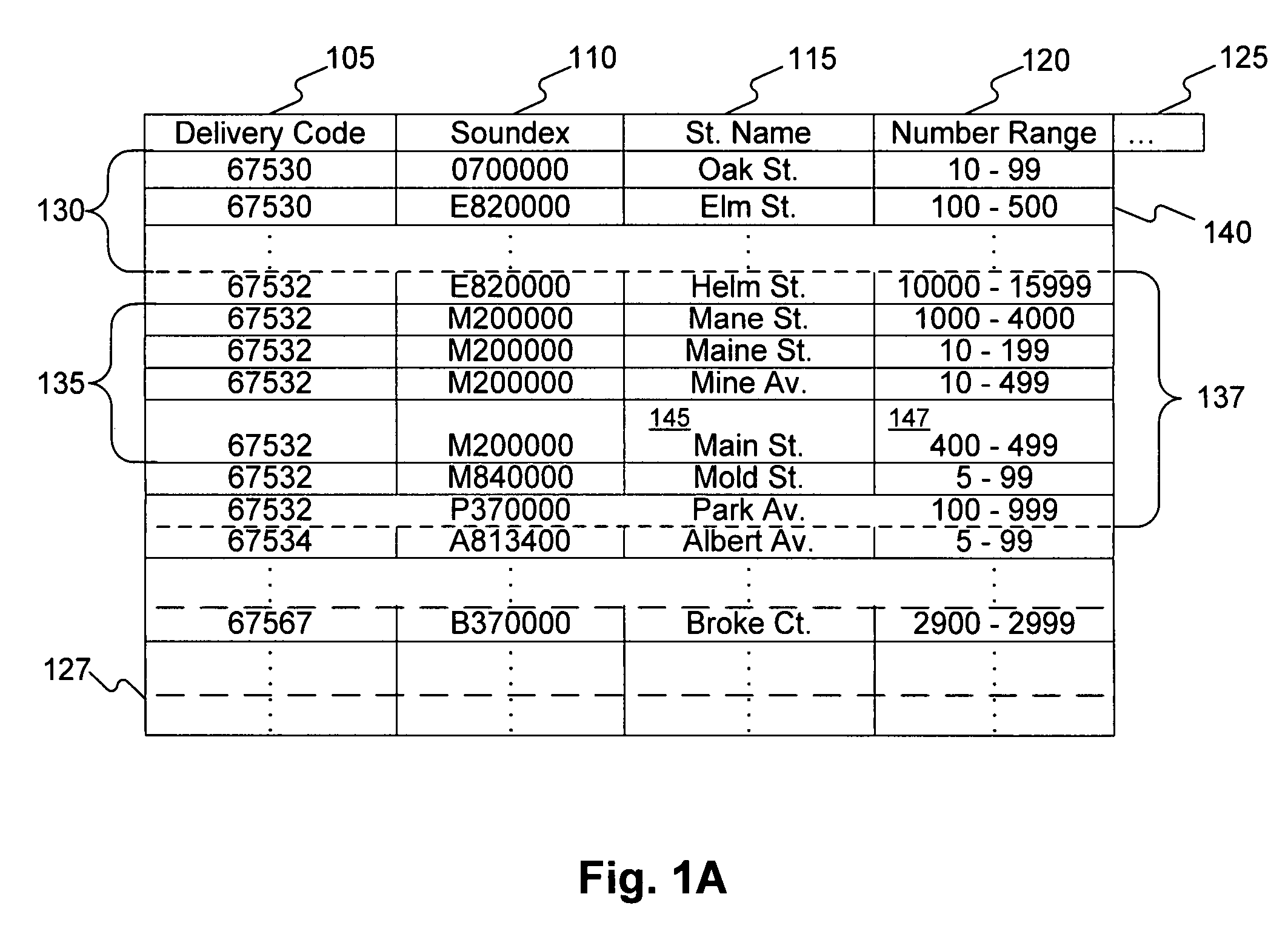
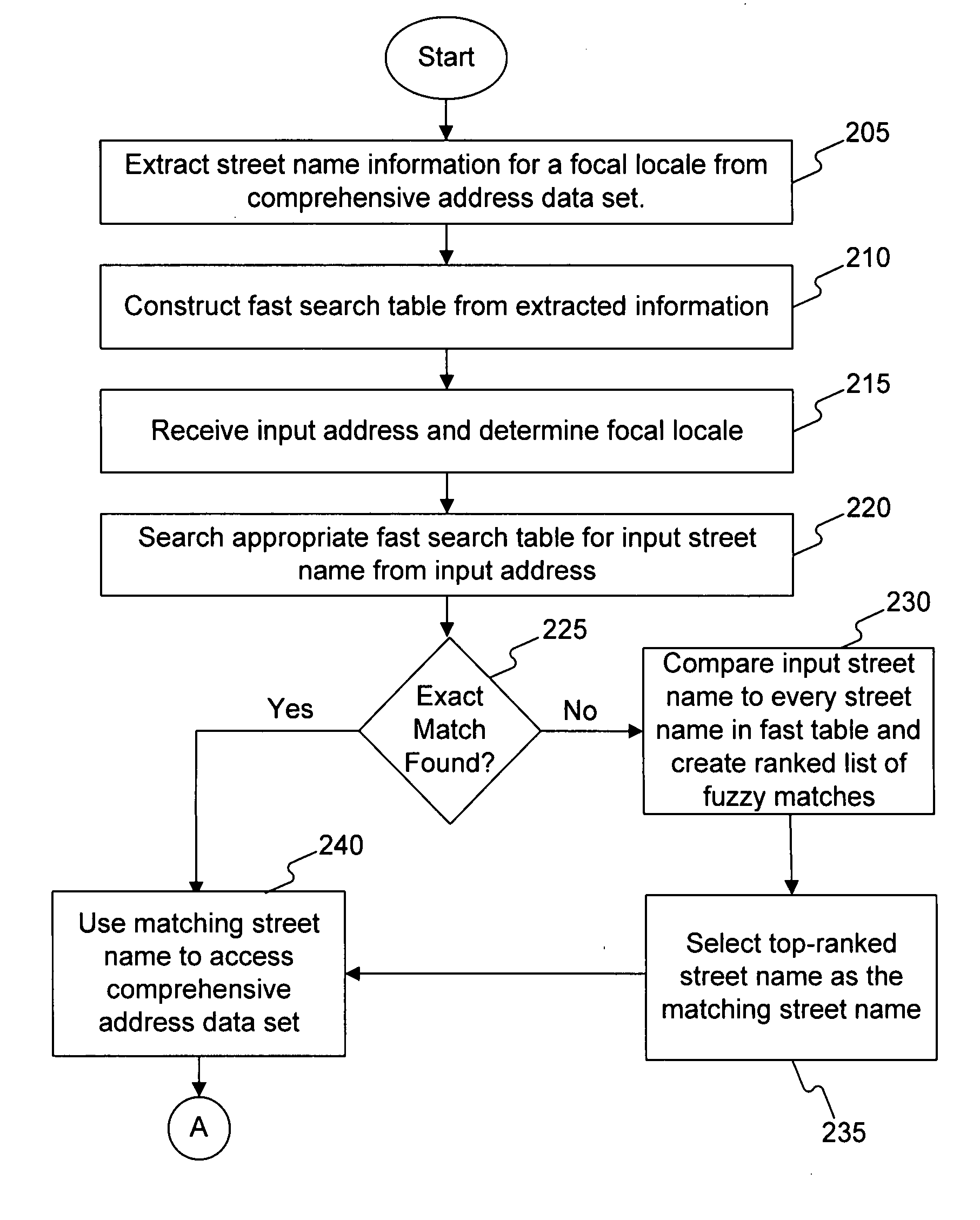
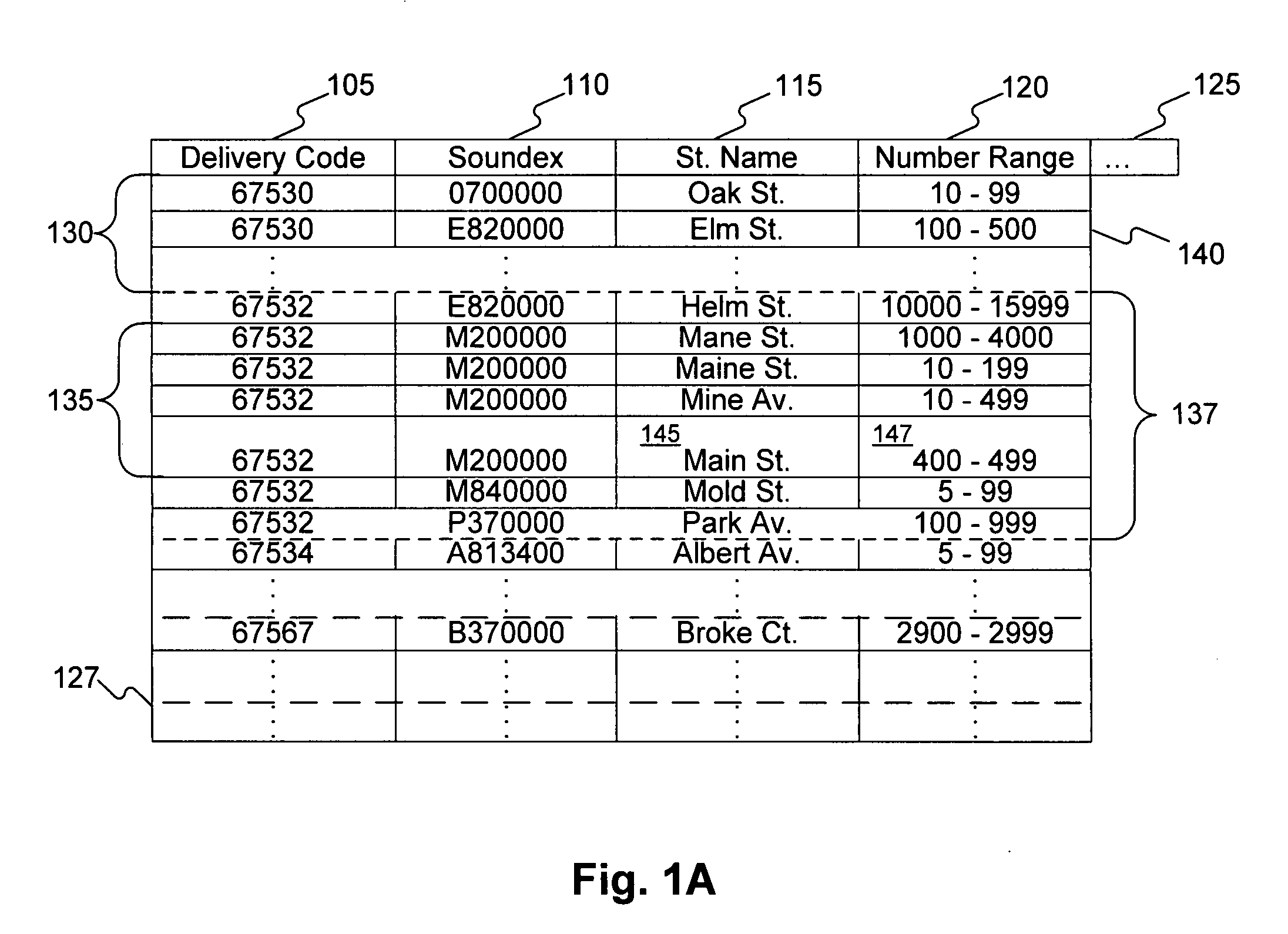
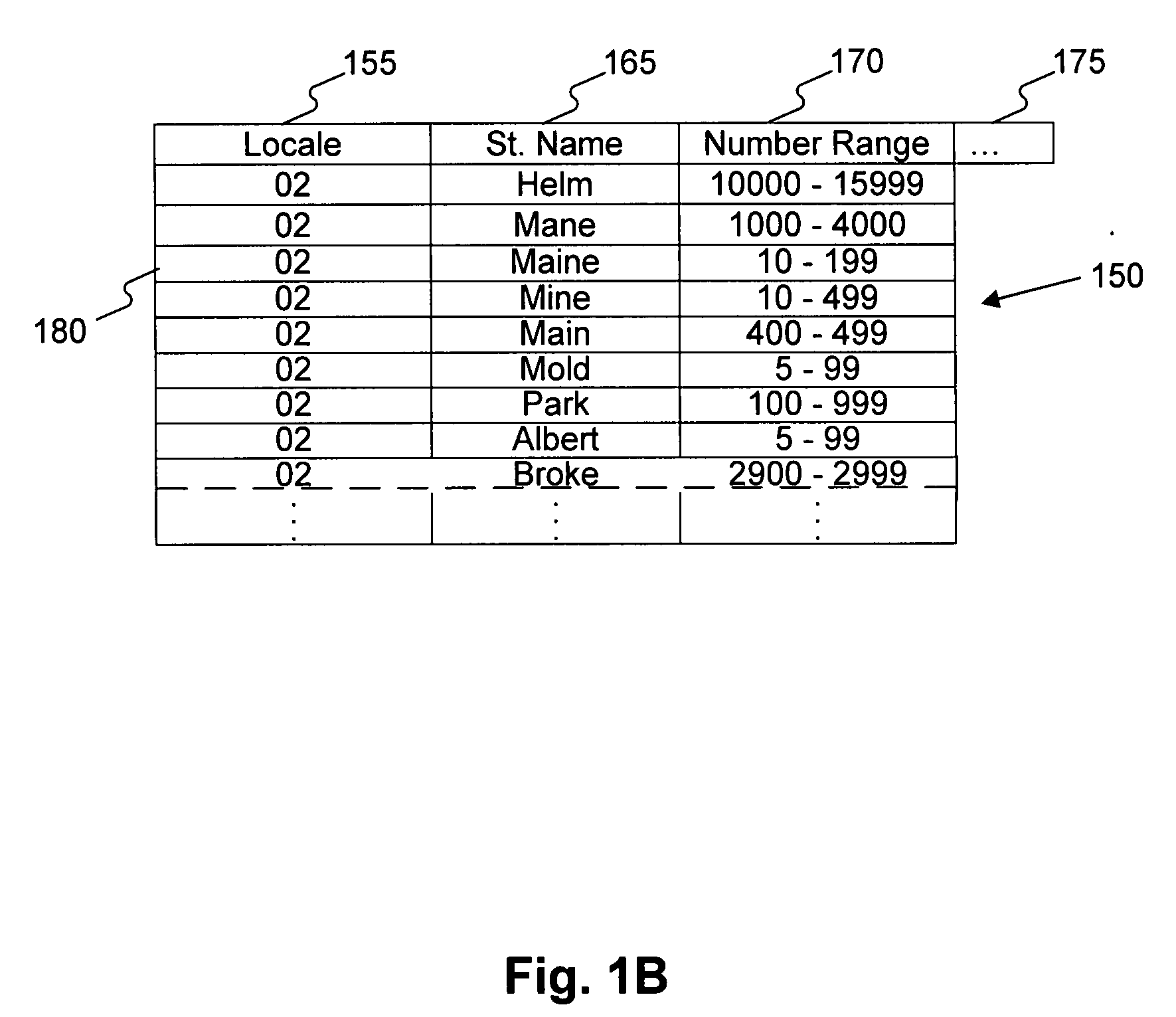
Systems, methods, and software determine whether a field of an input digital representation of information, such as the street name field in an address, is correct by quickly comparing the field to a list of valid choices for that field. The list of valid choices is generated based on information from the input digital representation, such as a character string. If an exact match is not found, a fuzzy match comparison determines the most closely matching valid choice. If a suitable fuzzy match is not found, then the input information is invalid. Otherwise, another field of the input information, such as the building number field of an address, is tested for validity. If the second field passes the validity check, then the fuzzy match (or exact match) for the field is valid. A fuzzy matching field may replace the input field, thereby correcting the input information.
Owner:US POSTAL SERVICE
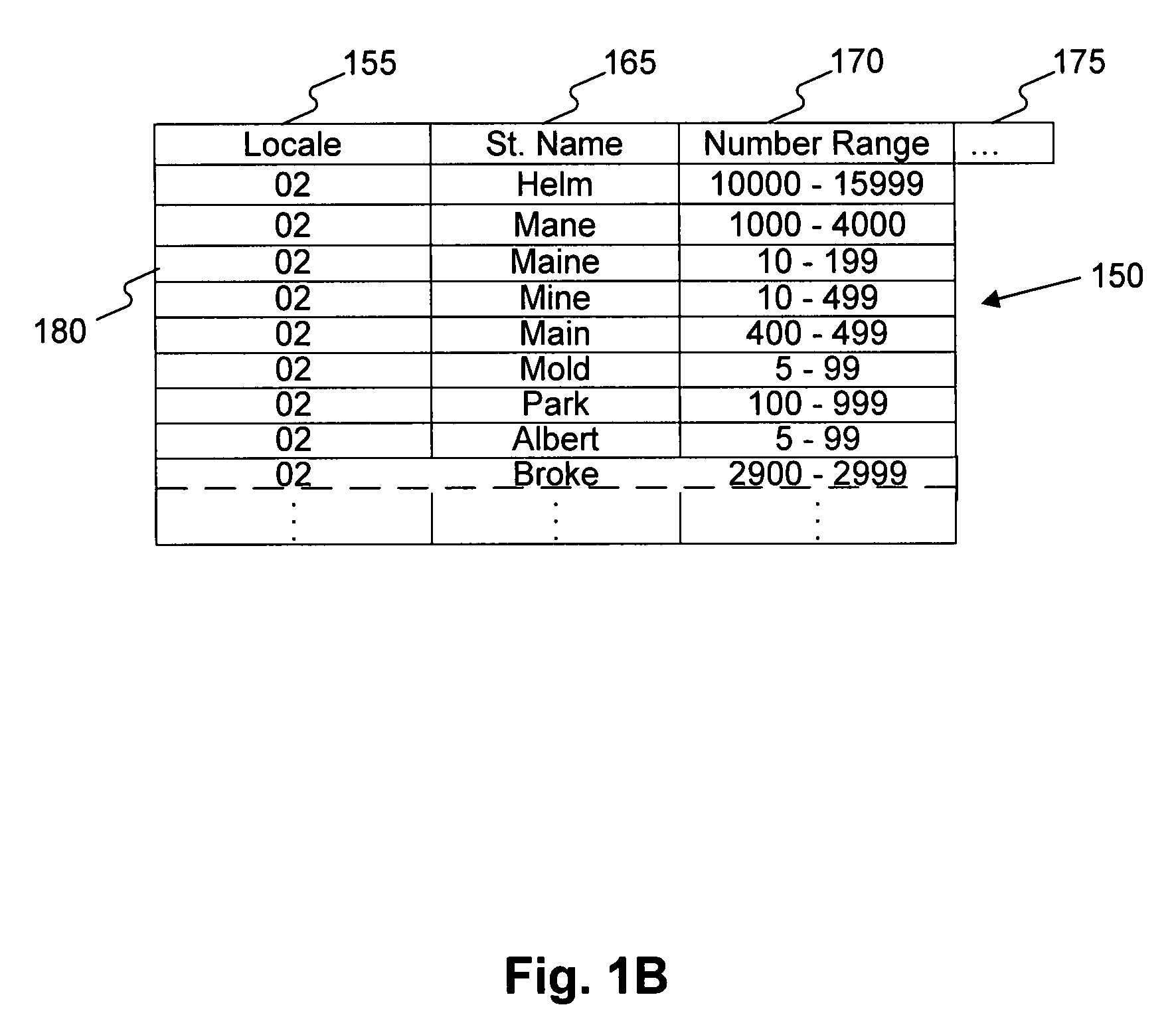
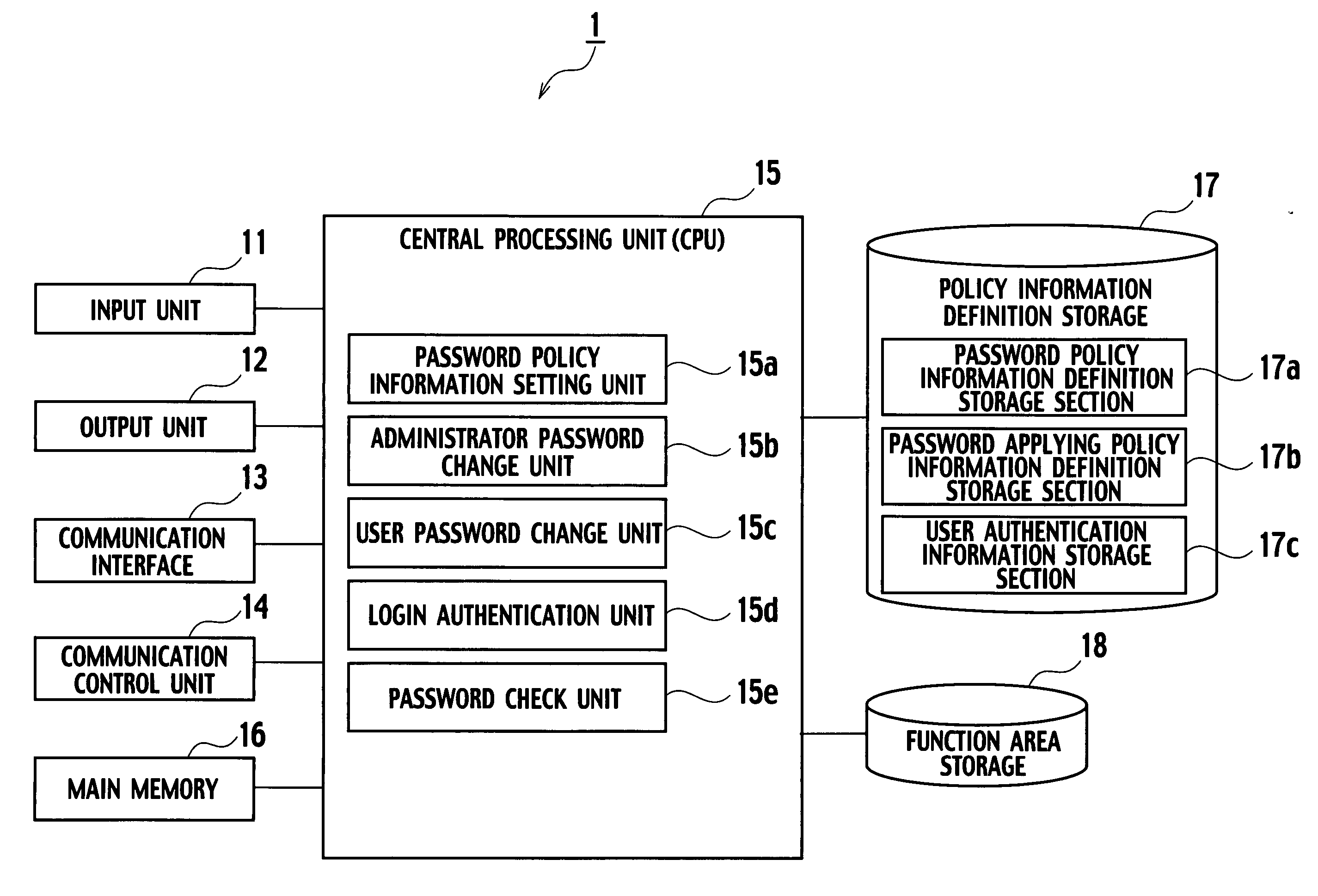
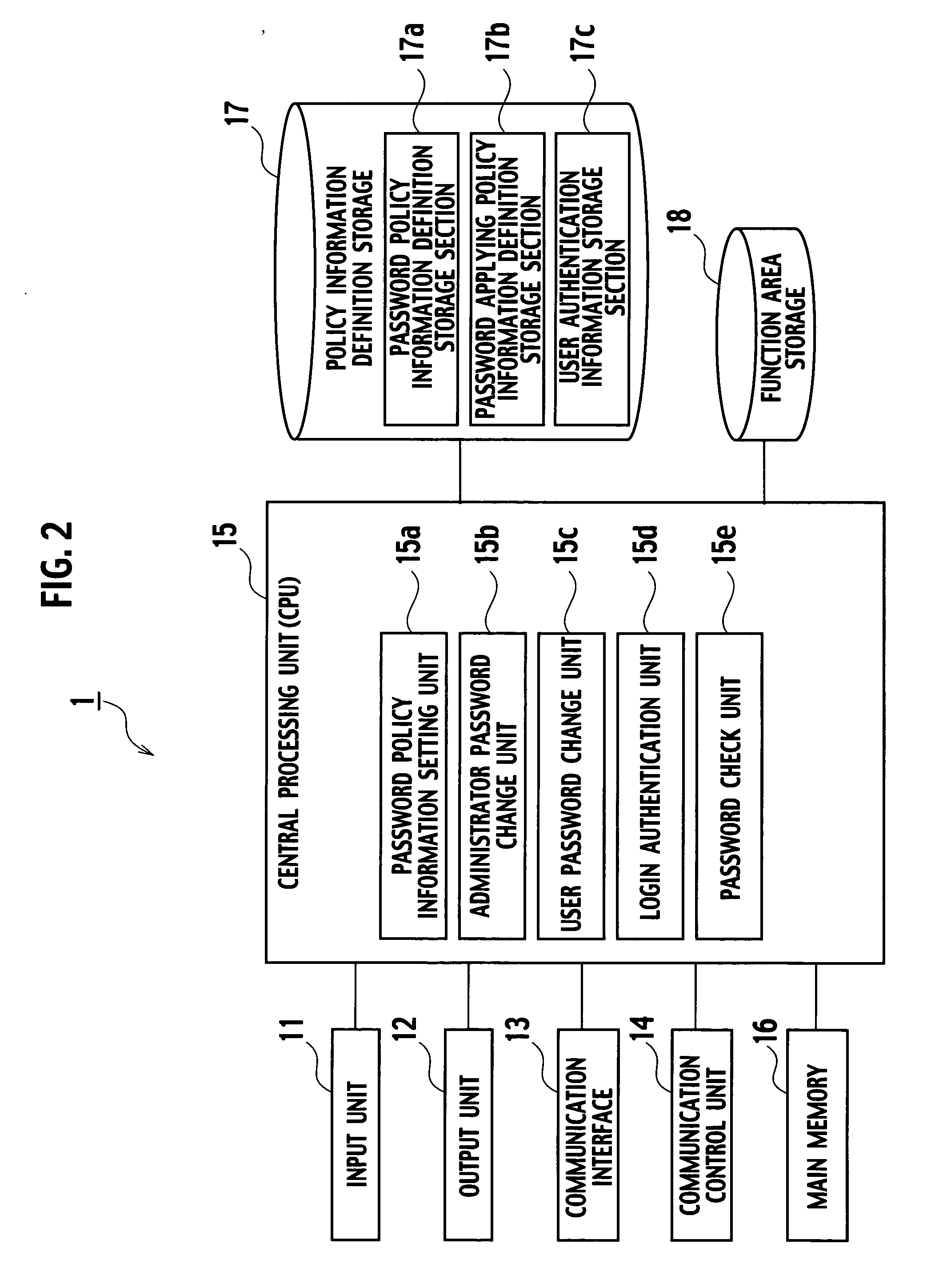
Server, method and program product for management of password policy information
InactiveUS20060259960A1Random number generatorsUser identity/authority verificationPassword policyPassword
A password policy information management server 1 according to an embodiment of the present invention includes: a password policy information definition storage section 17a storing the password policy information; a password applying policy information definition storage section 17b storing password applying policy information including timing information; password policy information setting unit 15a configured to allow the administrator of the information system to set each password policy information; a password check unit 15e configured to check validity of the password; and an administrator password change unit 15b configured to request validity checking of a new password to the password check unit 15e according to timing defined by the password applying policy information stored in the password applying policy information definition storage section 17b.
Owner:KK TOSHIBA +1
System and method of accessing keys for secure messaging
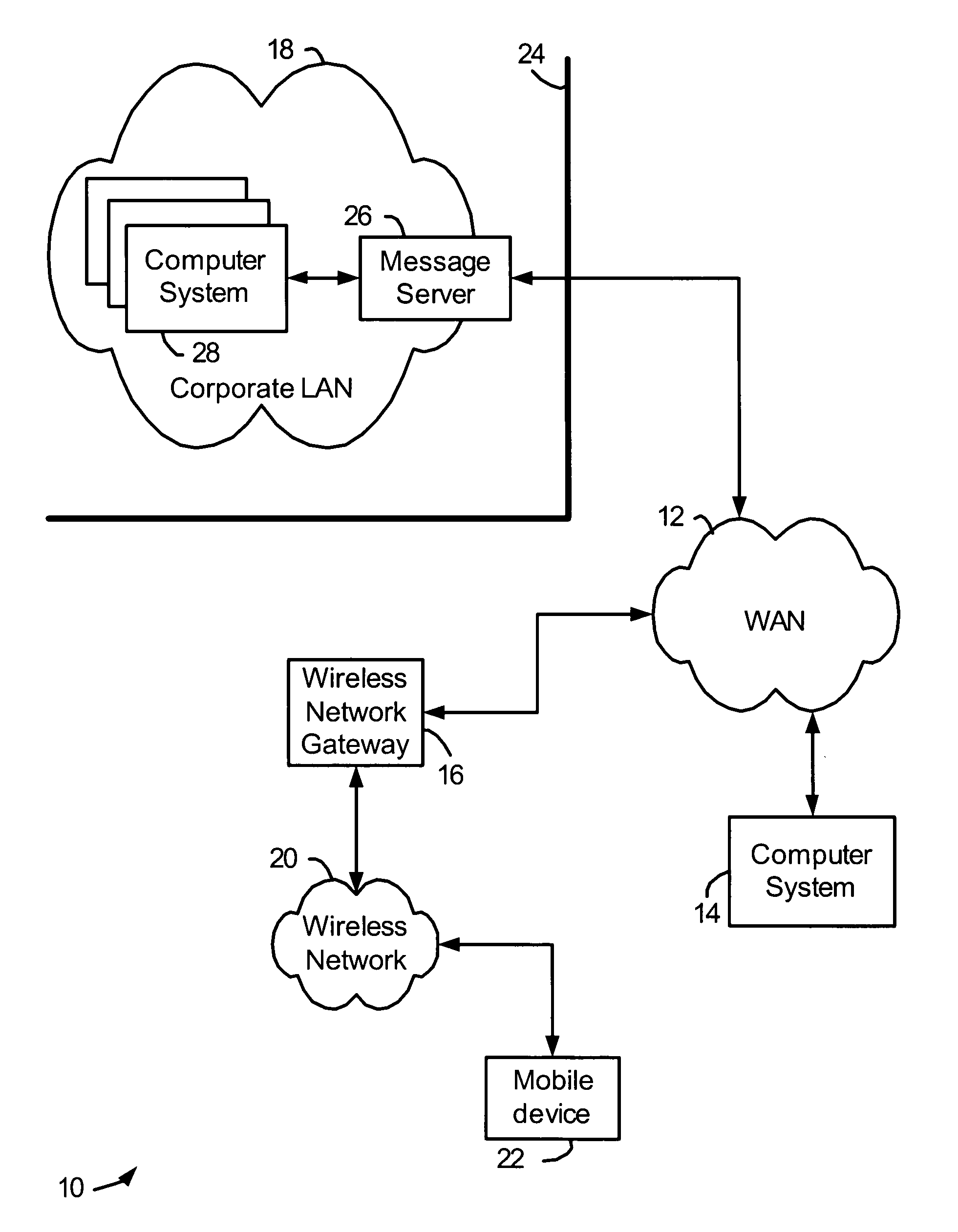
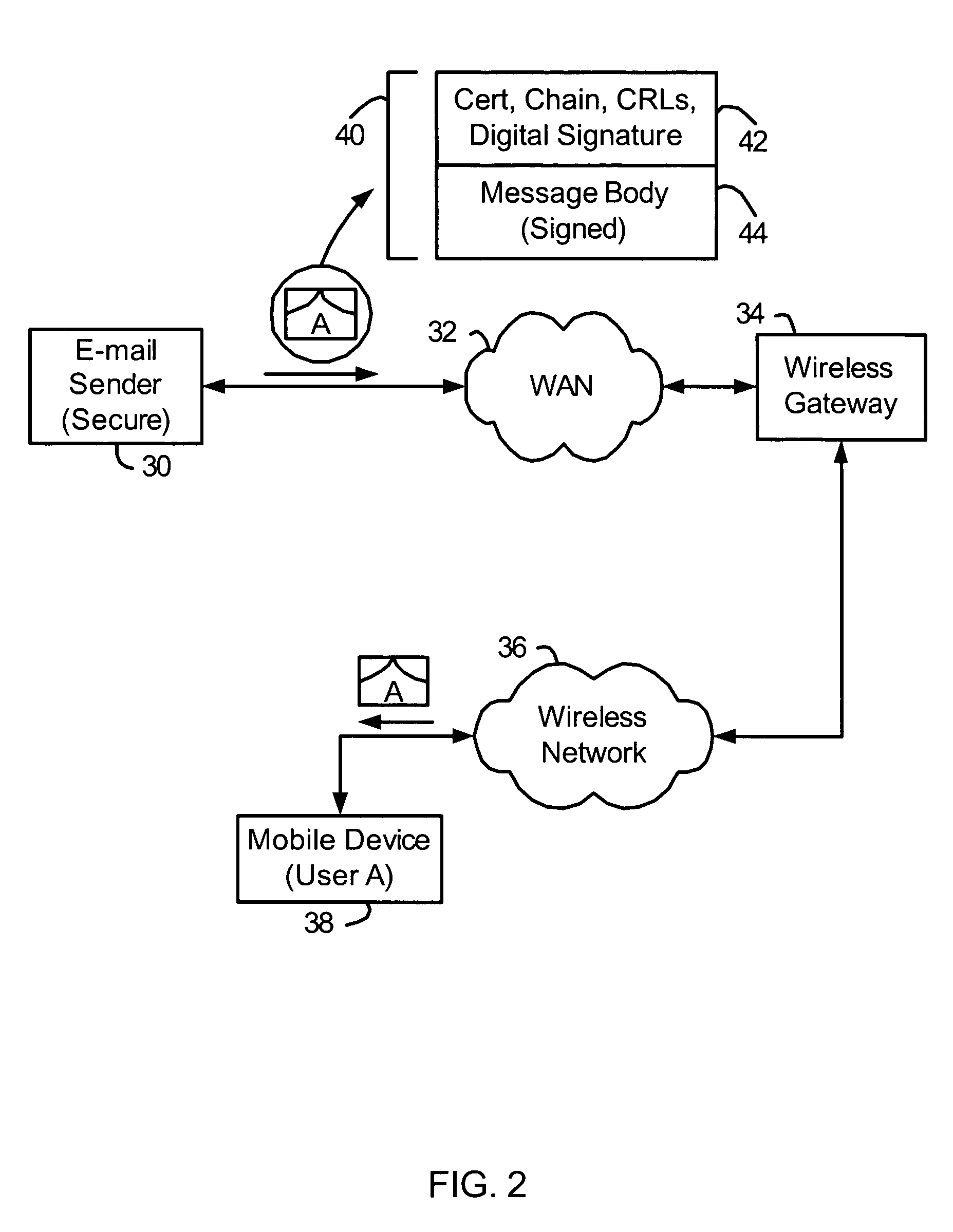
ActiveUS20050038991A1User identity/authority verificationNetwork topologiesMobile deviceSecure messaging
Methods and systems for handling on an electronic device a secure message to be sent to a recipient. Data is accessed about a security key associated with the recipient. The received data is used to perform a validity check related to sending a secure message to the recipient. The validity check may uncover an issue that exists with sending a secure message to the recipient. A reason is determined for the validity check issue and is provided to the mobile device's user.
Owner:MALIKIE INNOVATIONS LTD
Validity check of vehicle position information transmitted over a time-synchronized data link
InactiveUS20110140950A1Not easy to make mistakesSensitive to usePosition fixationBeacon systemsIn vehicleComputer science
A method for validating positional data in vehicle surveillance applications wherein vehicles transmit positional data indicating their own position to surrounding vehicles using a data link over which a transmission is initiated at a given transmission point in time that is known by all users of the data link. A signal transmitted from a radio source over the data link is received at a receiving unit. The signal carries positional data indicating an alleged position of a vehicle. The distance between the receiving unit and the radio source is estimated based on the time of flight and the propagation velocity of the received signal. The time of flight is determined based on the time elapsed from the transmission point in time of the signal to the time of reception of at least a first part of the signal. A deviation value is determined. The deviation value indicates the difference between the distance to the position of a vehicle according to the received positional data and the estimated distance to the radio source.
Owner:SAAB AB
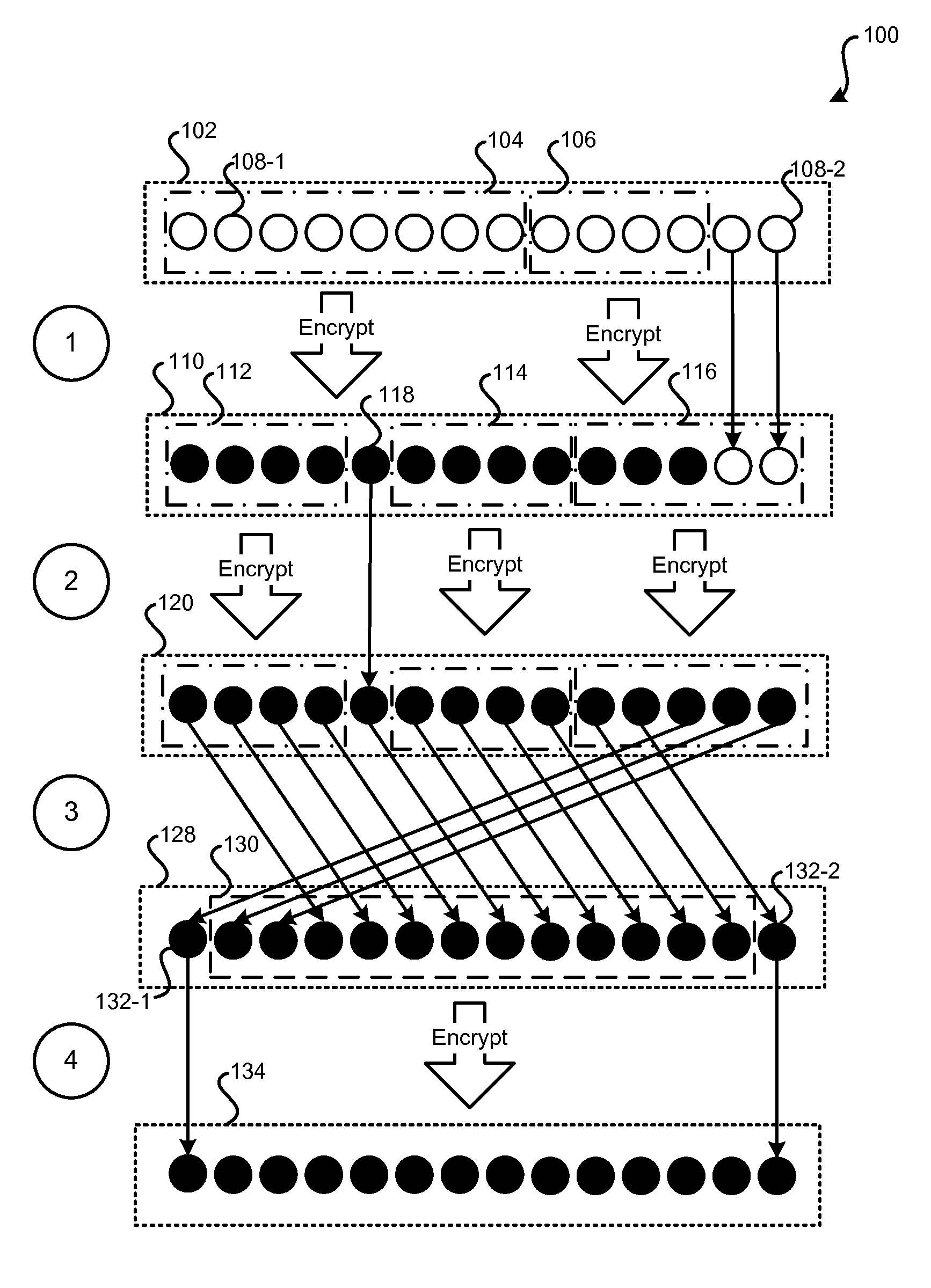
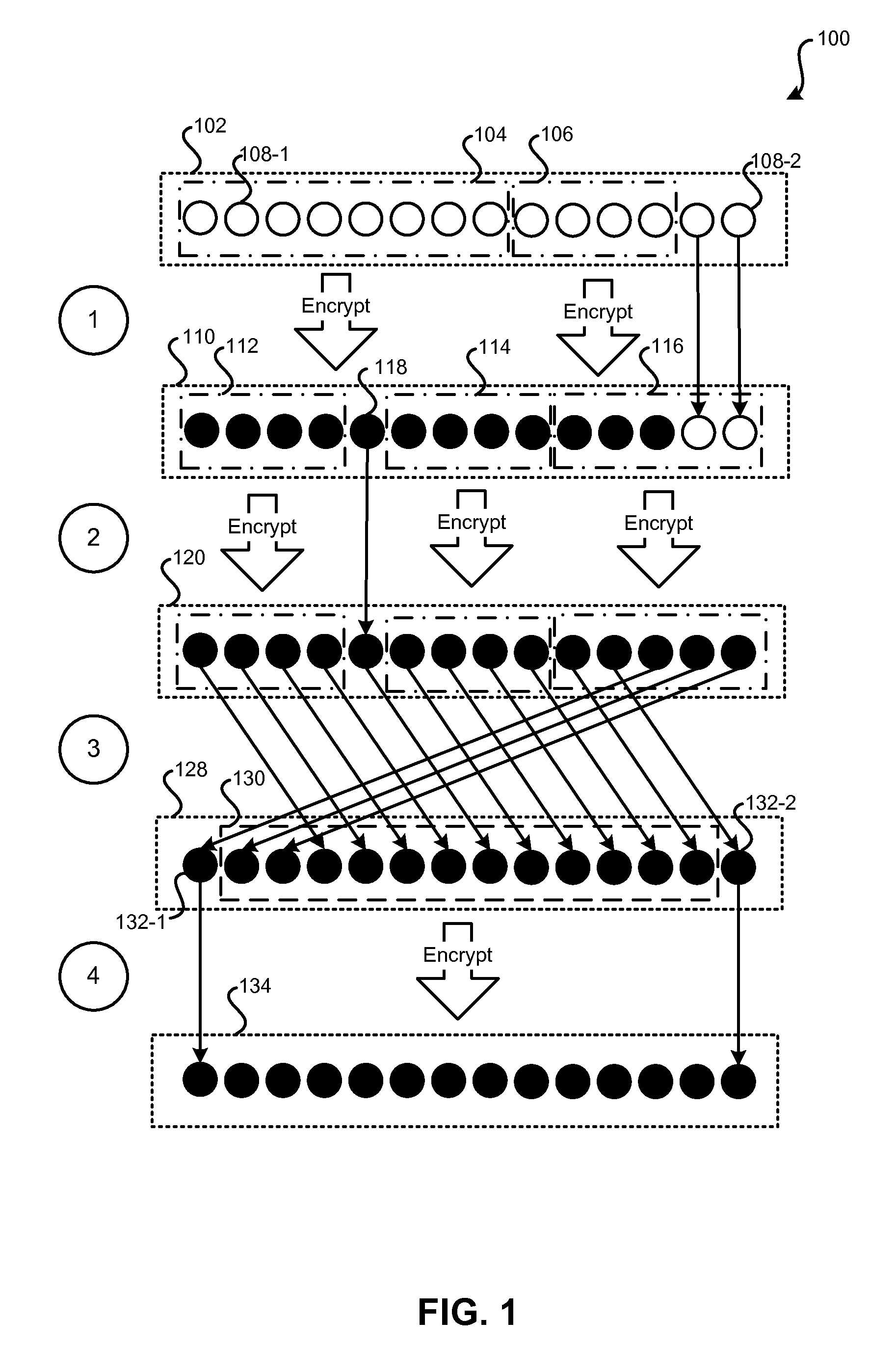
Format-Preserving Encryption Via Rotating Block Encryption
Methods and systems are described for format-preserving encryption. Format-preserving encryption on an entire format F may be achieved by performing format-preserving encryption on one or more subsets of F and then applying one or more permutation rounds in such a way that all elements of F enter a subset to be encrypted. A predetermined number of encryption rounds and a predetermined number of permutation rounds may be interleaved until all elements are thoroughly mixed. The resultant output data may be saved in a database in the same format as the original input data, meet all constraints of the database, and pass all validity checks applied by software supporting the database.
Owner:CA TECH INC
FMCW radar system
InactiveUS6888494B2Pedestrian/occupant safety arrangementAnti-collision systemsRadar systemsContinuous wave
An inventive frequency modulated continuous wave (FMCW) radar system realizes both a quick detection of a higher relative speed provisional target and a sure detection of a smaller relative speed provisional target. The number of detection cycles used for a paring validity check, used to see if a detected target or a pair of frequencies is an actual target or a pair for an actual target, is set in response to the relative velocity enabling the target information for a target of higher relative velocity to be output more quickly.
Owner:DENSO CORP
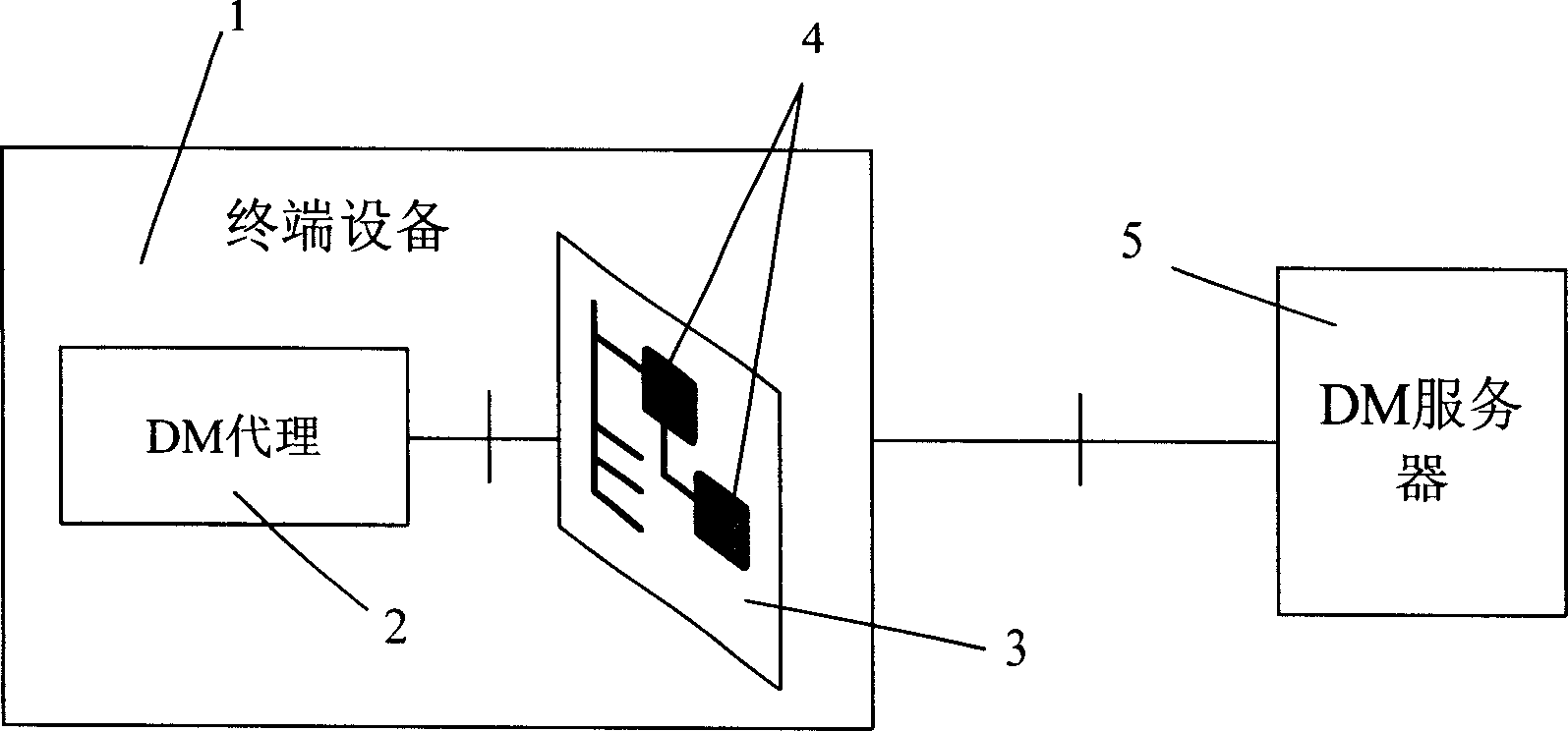
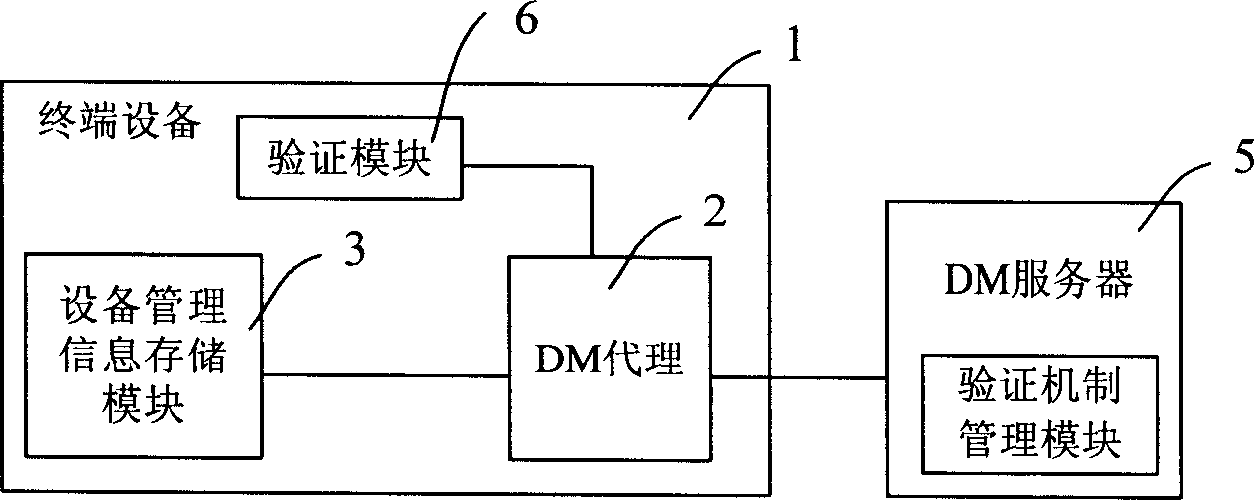
Software validity checking system and method based on device management protocol
InactiveCN1866870AImplementation licenseImprove experienceData switching networksValidation methodsControl system
The invention discloses a software legality checking system of device control system, which consists of device control server and terminal device, wherein terminal device includes device control proxy and device control information memory module for storing checking information and one checking modular. The invention also discloses a software legality checking method based on device control protocol with uniform encryption mode, registration code and digital copyright control mode. The invention is favorable for software provider controlling and managing, which guarantees the legality of software usage.
Owner:HUAWEI TECH CO LTD
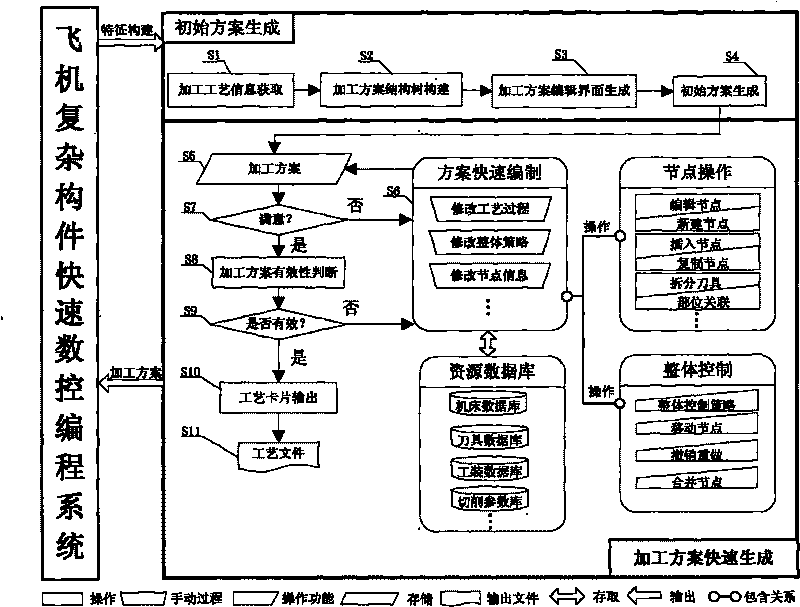
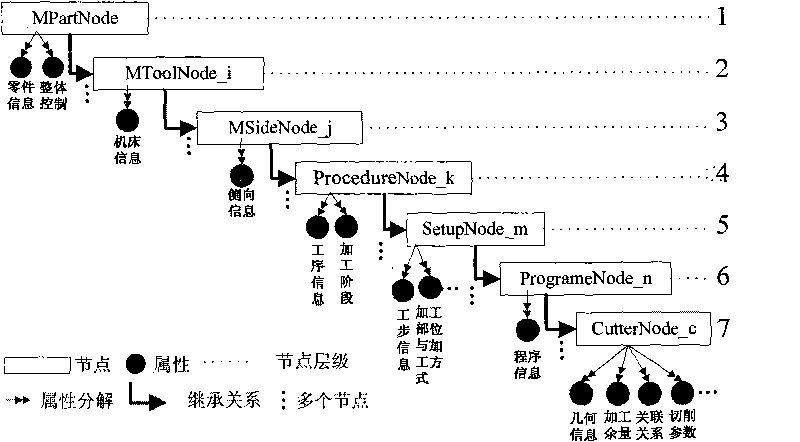
Quick generation method of numerical control machining scheme of complex parts of airplane
InactiveCN101763067AImprove efficiencyImprove accuracyProgramme controlComputer controlNumerical controlReusability
The invention discloses a quick generation method of a numerical control machining scheme of complex parts of an airplane, which mainly comprises the steps of: 1) obtaining machining technology information; 2) building the structural tree of the machining scheme; 3) generating the interaction display of the machining scheme; 4) quickly coding the machining scheme; 5) testing the effectiveness of the machining scheme; and 6) outputting the scheme. The method educates, normalizes and standardizes the machining scheme of the complex parts of the airplane, and improves the unitarity of the machining scheme, the reusability and the programming quickness, thereby shortening the programming period of numerical control machining scheme of the complex parts of the airplane, and improving the numerical control machining preparing efficiency and the machining quality.
Owner:SHENYANG AIRCRAFT CORP +1
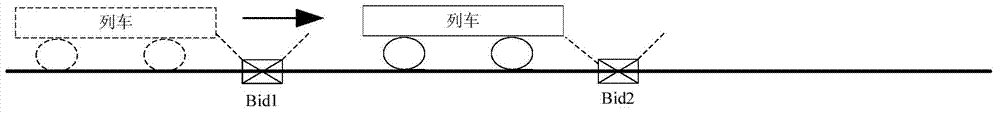
Automatic train wheel diameter correcting method
ActiveCN103707903AReduce workloadWith automatic wheel diameter correction functionVehicle route interaction devicesEngineeringSubway line
The invention relates to the technical field of train wheel diameter correction and discloses an automatic train wheel diameter correcting method. The automatic train wheel diameter correcting method includes the steps of firstly, determining the initial values of wheel diameters; secondly, arranging transponders, selecting two adjacent transponders on a straight line to serve as the basis reference of wheel diameter correction, and measuring the actual distance between the two transponders; thirdly, by a train, obtaining the operation distance in set time according the measured speed, and obtaining the updated wheel diameter values according to the ratio of the operation distance to the measured actual distance and the initial values of the wheel diameters; fourthly, performing validity check on the updated wheel diameter values; fifthly, filtering bad values of the updated wheel diameter values. The method has the advantages that the standard transponder system of a subway line is used as the auxiliary equipment for train wheel diameter automatic correction, and automatic train wheel diameter correction is achieved while system speed measuring and positioning precision is increased.
Owner:TRAFFIC CONTROL TECH CO LTD
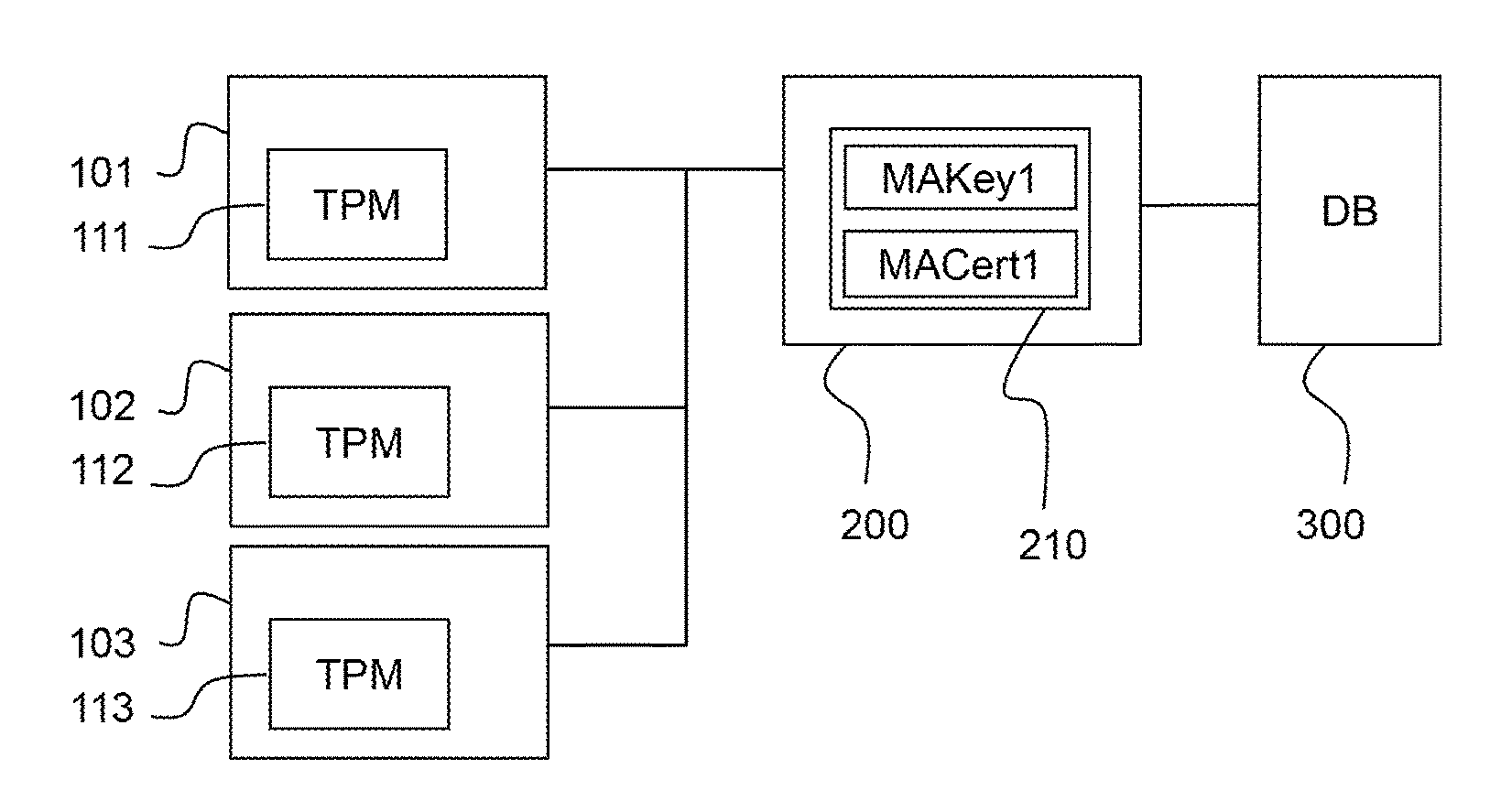
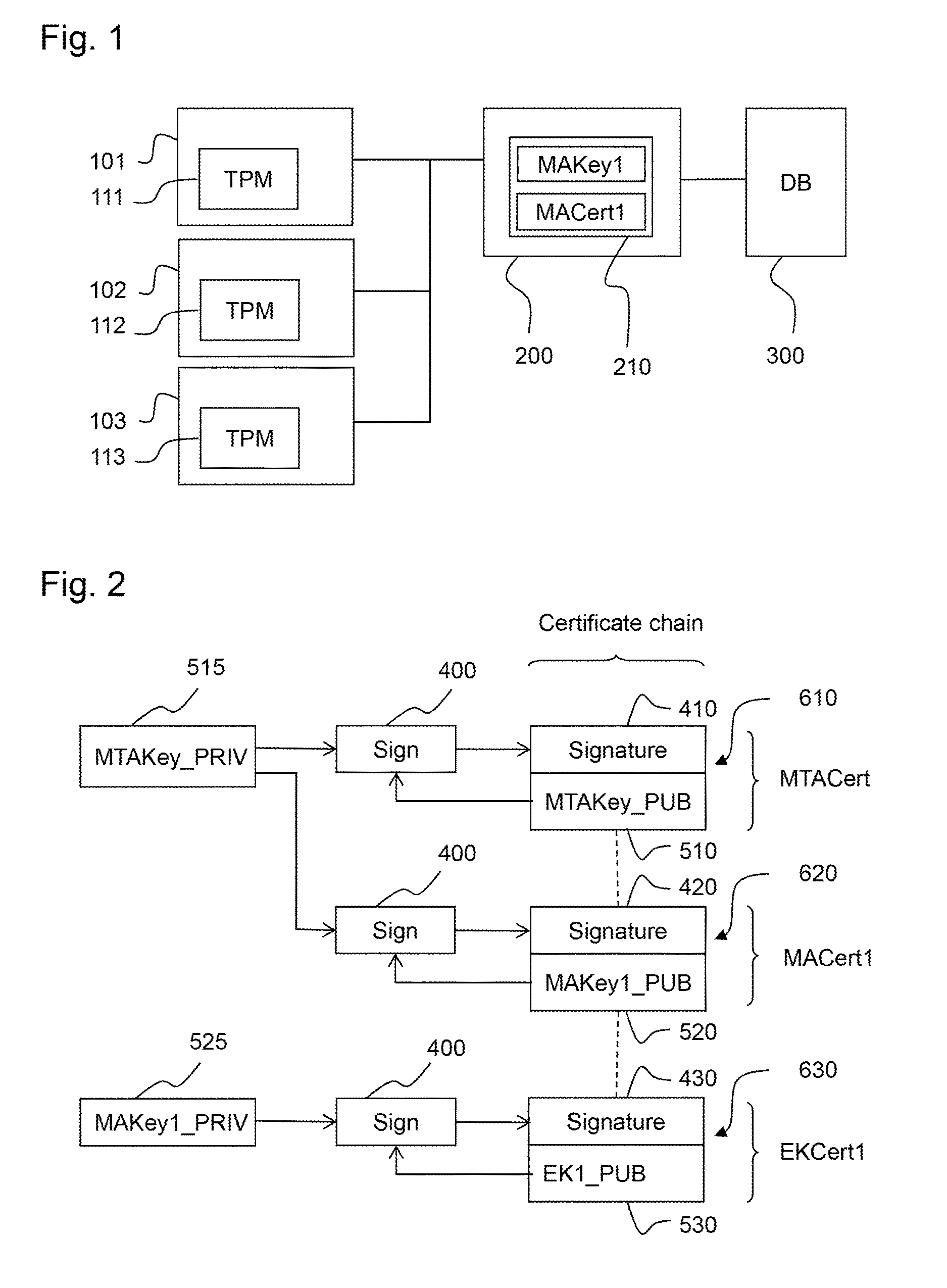
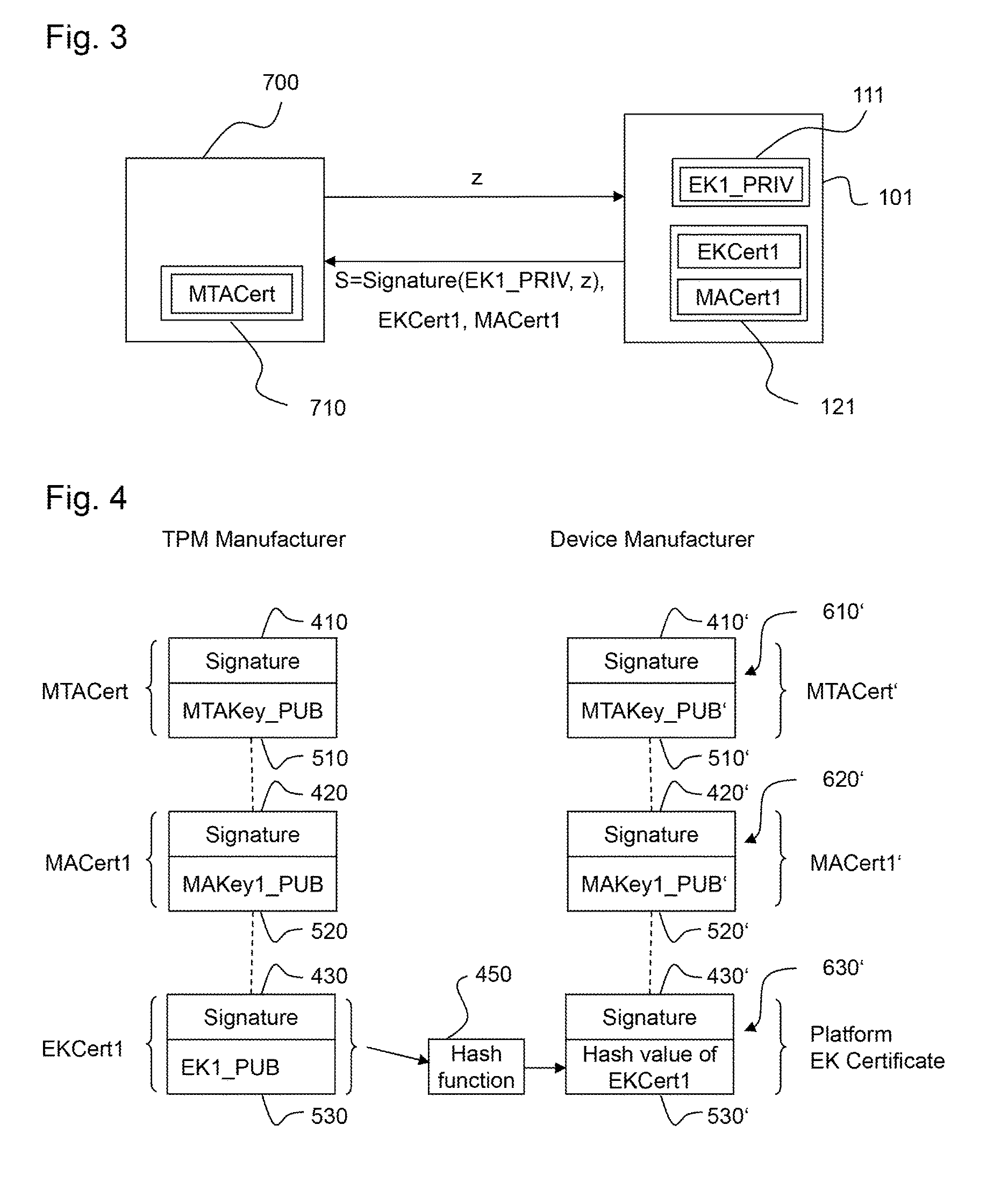
Method and system for creating and checking the validity of device certificates
ActiveUS20170054566A1Creation can be simplified improvedValidity can be simplified improvedUser identity/authority verificationInformation technology support systemTimestampValidity checking
To easily identify an invalid device certificate by means of a validity check when signing keys that are used to create device certificates are compromised, a piece of status information is provided for device certificates that comprises positive evidence of the existence and validity of the device certificate, and alternatively or additionally to apply a special validity model for device certificates, wherein the time of issue of the device certificate is documented by means of a signed electronic timestamp, and wherein a different signing key is used for signing the timestamp than for signing the device certificate. Additionally, all information that is required for the validity check of a device certificate is stored in a memory of the device or in a memory associated with the device, so that an identity check on the device can be performed at any time without fetching additional data.
Owner:PHOENIX CONTACT GMBH & CO KG
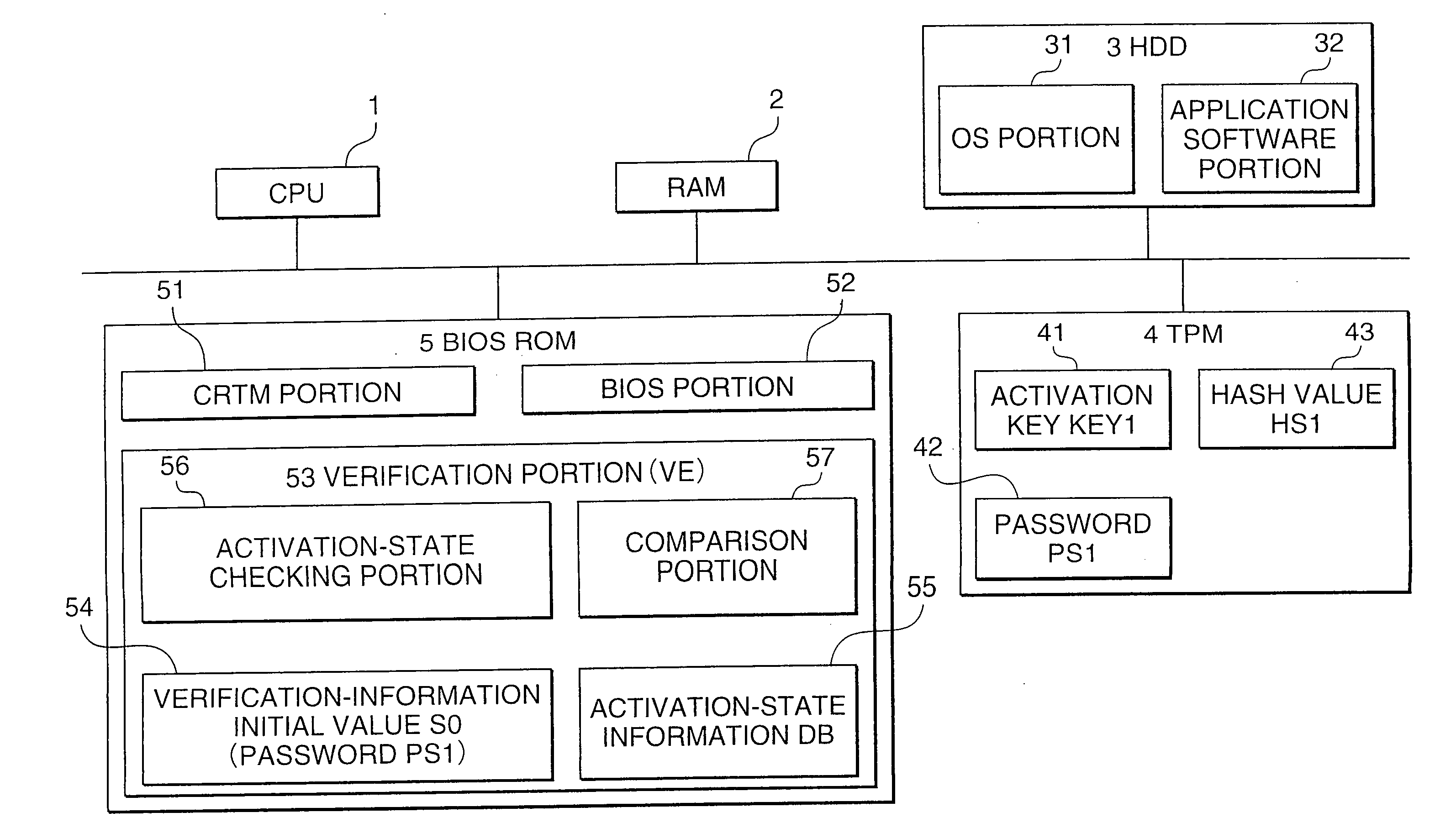
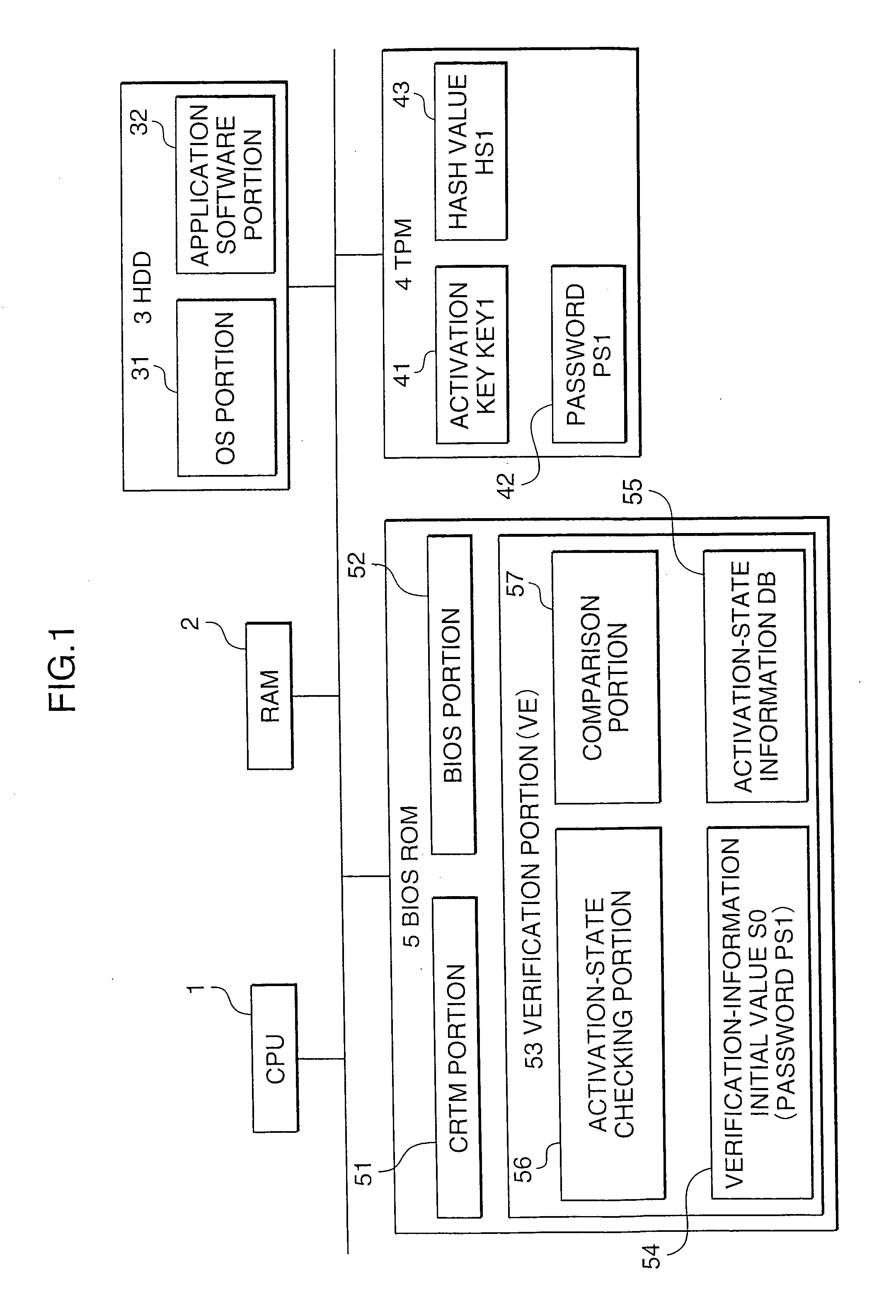
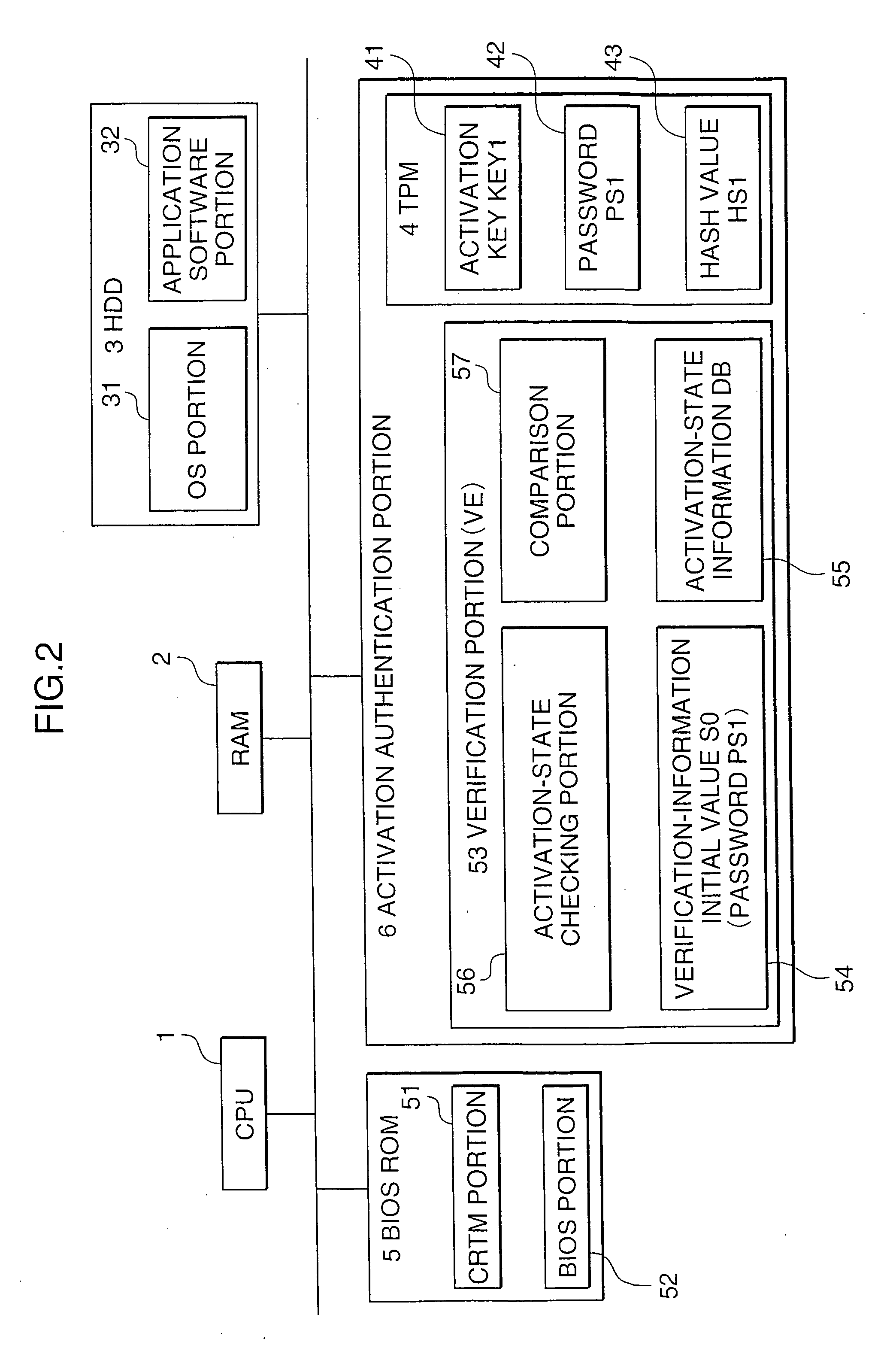
Information processing device having activation verification function
InactiveUS20070226518A1Reduce the burden onProlonged activation processUnauthorized memory use protectionHardware monitoringInformation processingBiological activation
An information processing device having an activation verification function comprises: a module recording portion which stores plural system programs, a security chip having the function of checking the validity of the system programs and a verification portion which inspects the activation states of the system programs. The security chip executes validity checking processing using verification data provided by the system programs. If the security chip cannot confirm the validity of the system programs, the verification portion acquires activation-state information about activated system programs from the activated system programs. If pre-stored verification-information initial values for valid system programs and the acquired activation-state information match with each other, the verification portion determines that the current activation states of the system programs are valid, and the subsequent activation processing for the system programs is advanced.
Owner:FUJITSU LTD
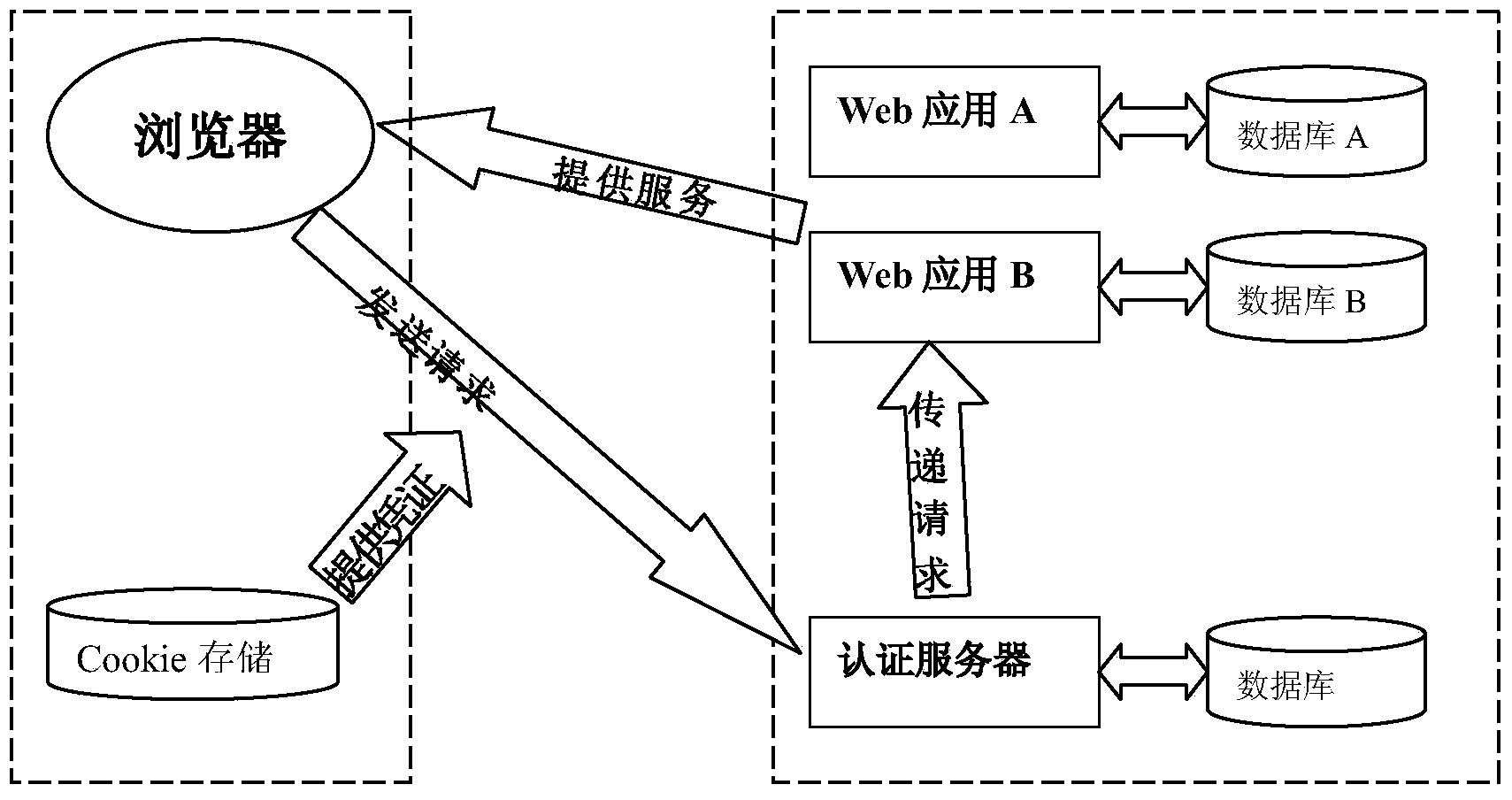
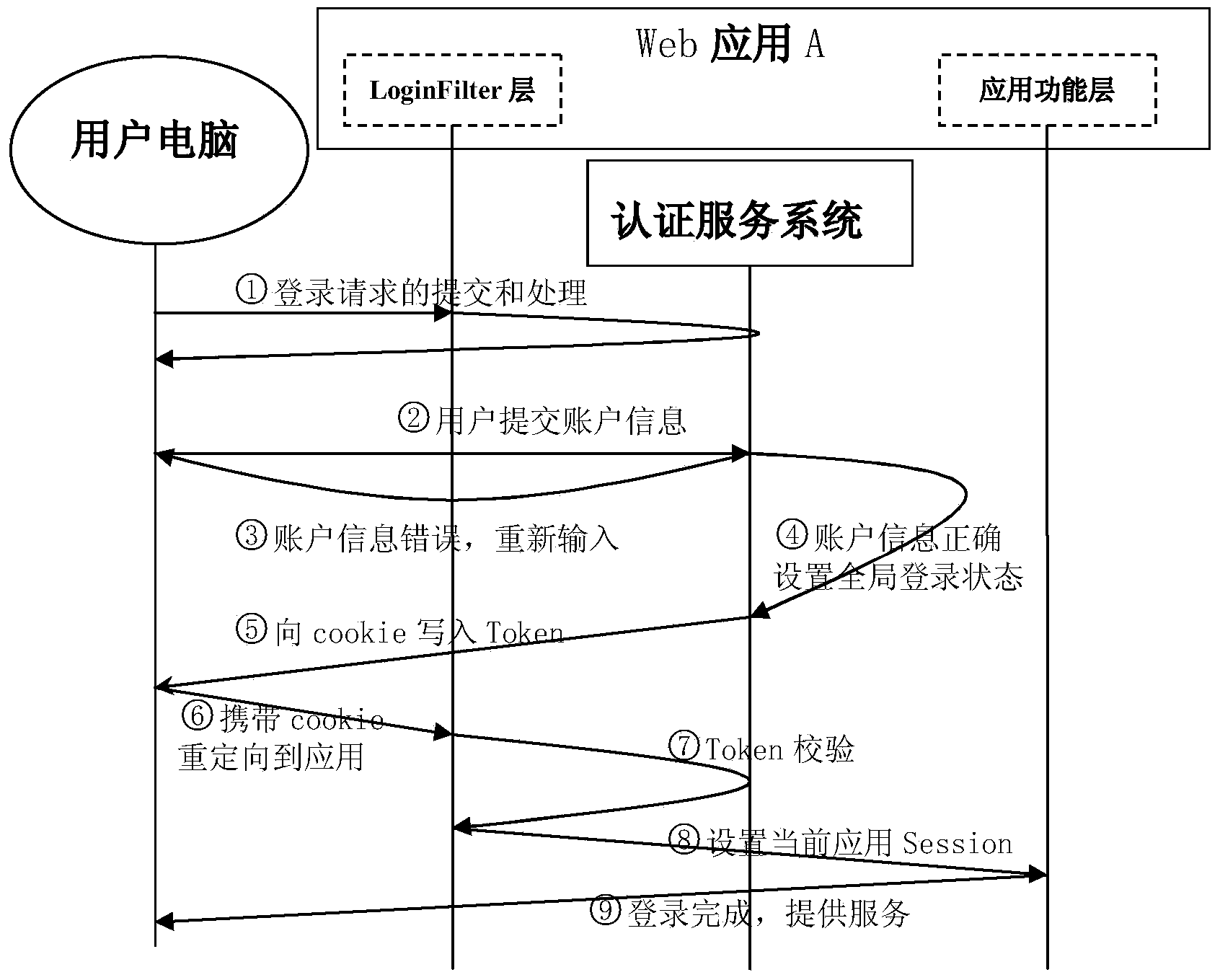
Single sign-on light weight implementation method based on Cookie
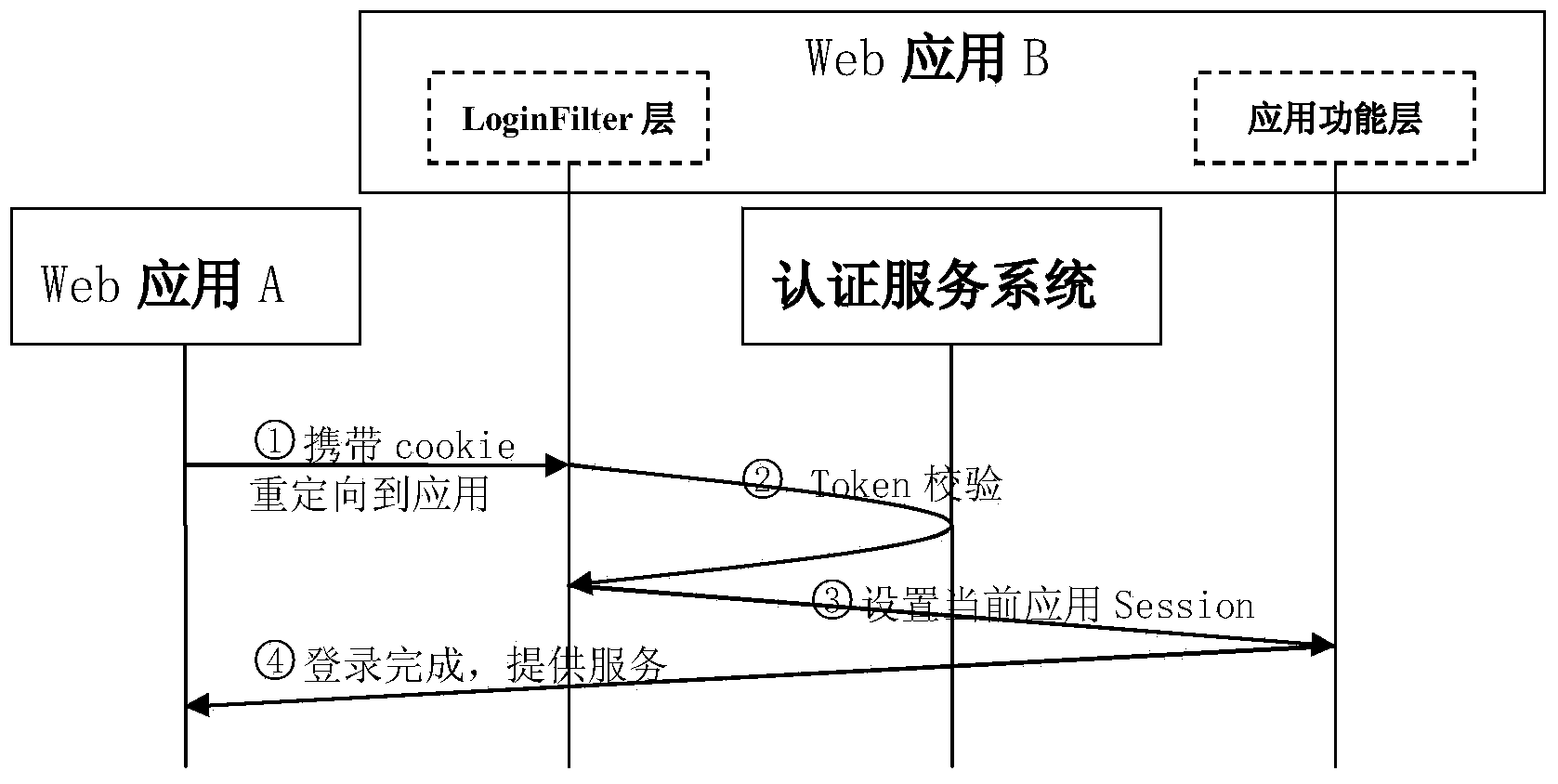
ActiveCN104320423AImprove work efficiencyLow operating costTransmissionWeb applicationAuthentication server
The invention relates to the technical field of computers, and provides a single sign-on method based on Cookie. After a user logs in any application in a system, seamless switching between a plurality of applications can be achieved. When switching is performed by a user between the applications in the system, in other words, when a user browser carrying Cookie is redirected to a target Web application to be switched, the LoginFilter of a target Web application unit reads a trust certificate from the Cookie and carries the trust certificate to request validity check from an authentication server; the authentication server feeds back user login information after performing check, and the LoginFilter completes login authorization setting of the user in the current application according to the fed back information. A light weight single sign-on solution scheme is provided, the single sign-on function is completed with trust evidence sharing as a core, and the method has the advantages of being stable, convenient and fast to use, safe, easy to extend and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Method and system for the authorised decoding of encoded data
InactiveUS20050033956A1Secure and efficient preventionLoss can be avoidedUser identity/authority verificationUnauthorized memory use protectionComputer hardwareValidity checking
The present invention relates to a method and a system for authorized decryption of encrypted data. First, the encrypted data is provided. Then the validity of at least two certificates is verified. If the validity check is positive, a key is provided, which can be used to decrypt the encrypted data.
Owner:VIRTUAL PAPER EMEDIA SOLUTIONS
Method for protecting embedded type device software
ActiveCN102982264ALarge irreversibilityProgram/content distribution protectionValidation methodsMedia access control
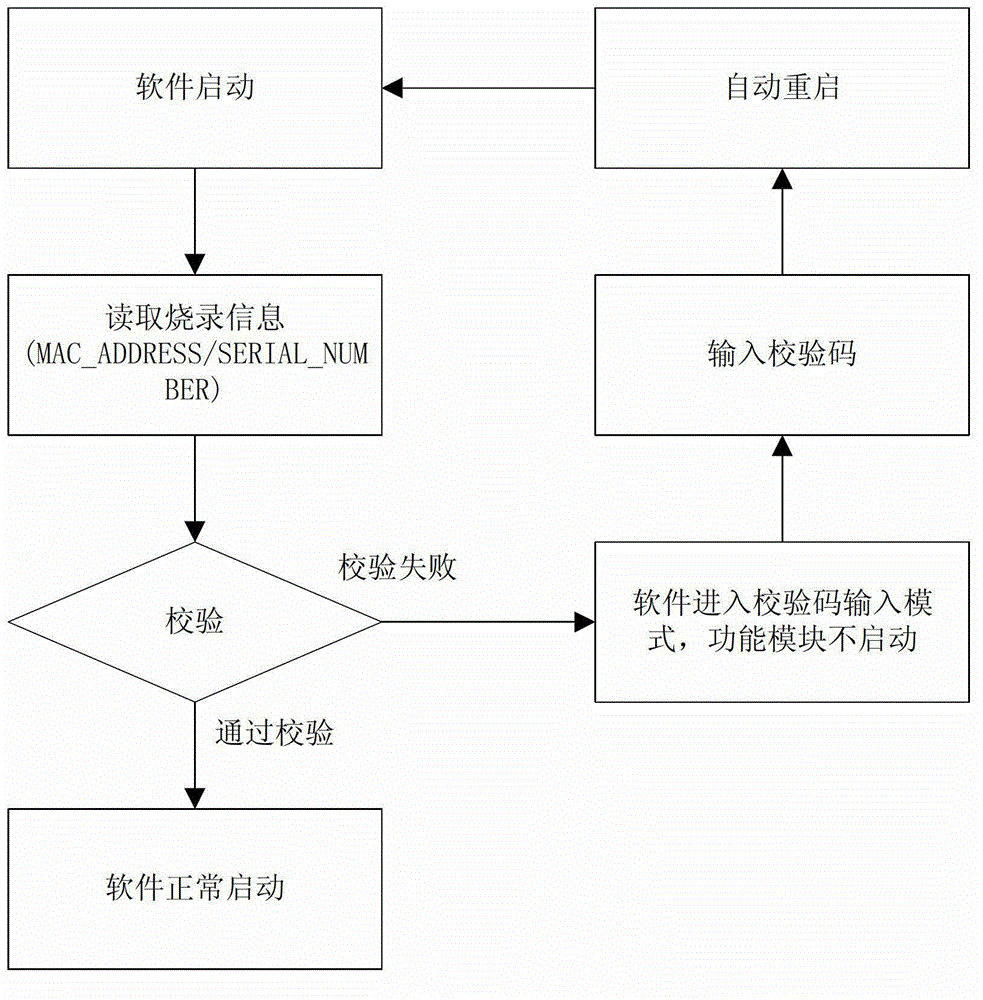
The invention discloses a method for protecting embedded type device software. The method comprises the steps that a piece of storage space is drawn from dynamic memory of a network device to be used for storing check codes; the software is started, burn information is read, and the burn information comprises MAC (media access control) addresses and a serial number; the MAC addresses and the serial number are subjected to checking; if the checking fails, the operation enters a check code input mode, the newly input check codes are written into the dynamic memory, and the software is started again; and if the checking succeeds, the software is started normally. According to the method for protecting the embedded type device software, a check method of the MAC addresses is utilized, characteristics that the network device is required to burn the MAC addresses and the MAC addresses are globally unique are utilized, so that software validity checking and copy protection checking are simultaneously performed during a process of MAC burning; without device networking, the checking can be performed and the MAC addresses are bound; but by means of encryption algorithm calculation, larger irreversibility of the burn information is achieved.
Owner:PHICOMM (SHANGHAI) CO LTD
Systems and methods for validating an address
Systems, methods, and software determine whether a field of an input digital representation of information, such as the street name field in an address, is correct by quickly comparing the field to a list of valid choices for that field. The list of valid choices is generated based on information from the input digital representation, such as a character string. If an exact match is not found, a fuzzy match comparison determines the most closely matching valid choice. If a suitable fuzzy match is not found, then the input information is invalid. Otherwise, another field of the input information, such as the building number field of an address, is tested for validity. If the second field passes the validity check, then the fuzzy match (or exact match) for the field is valid. A fuzzy matching field may replace the input field, thereby correcting the input information.
Owner:US POSTAL SERVICE
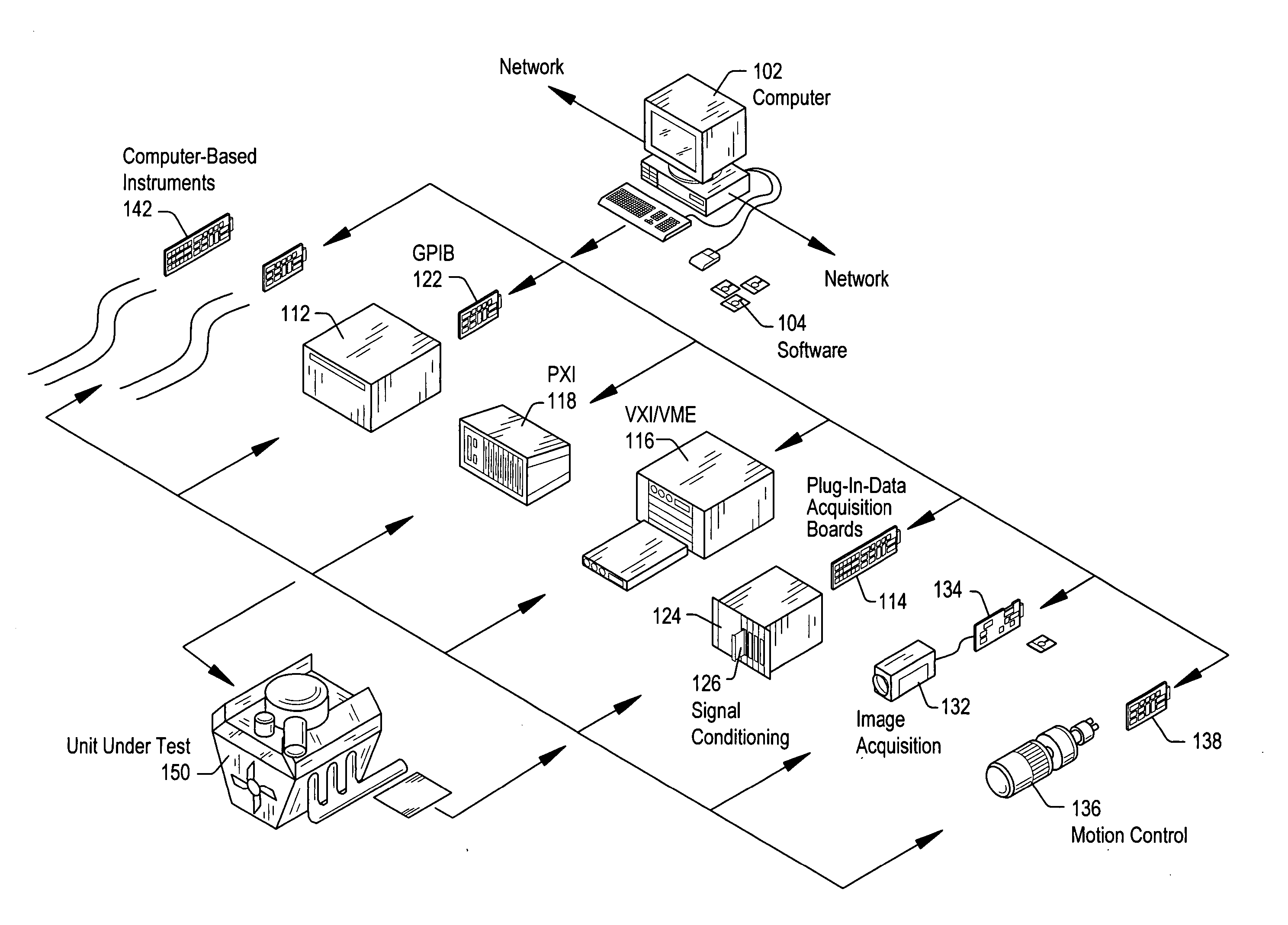
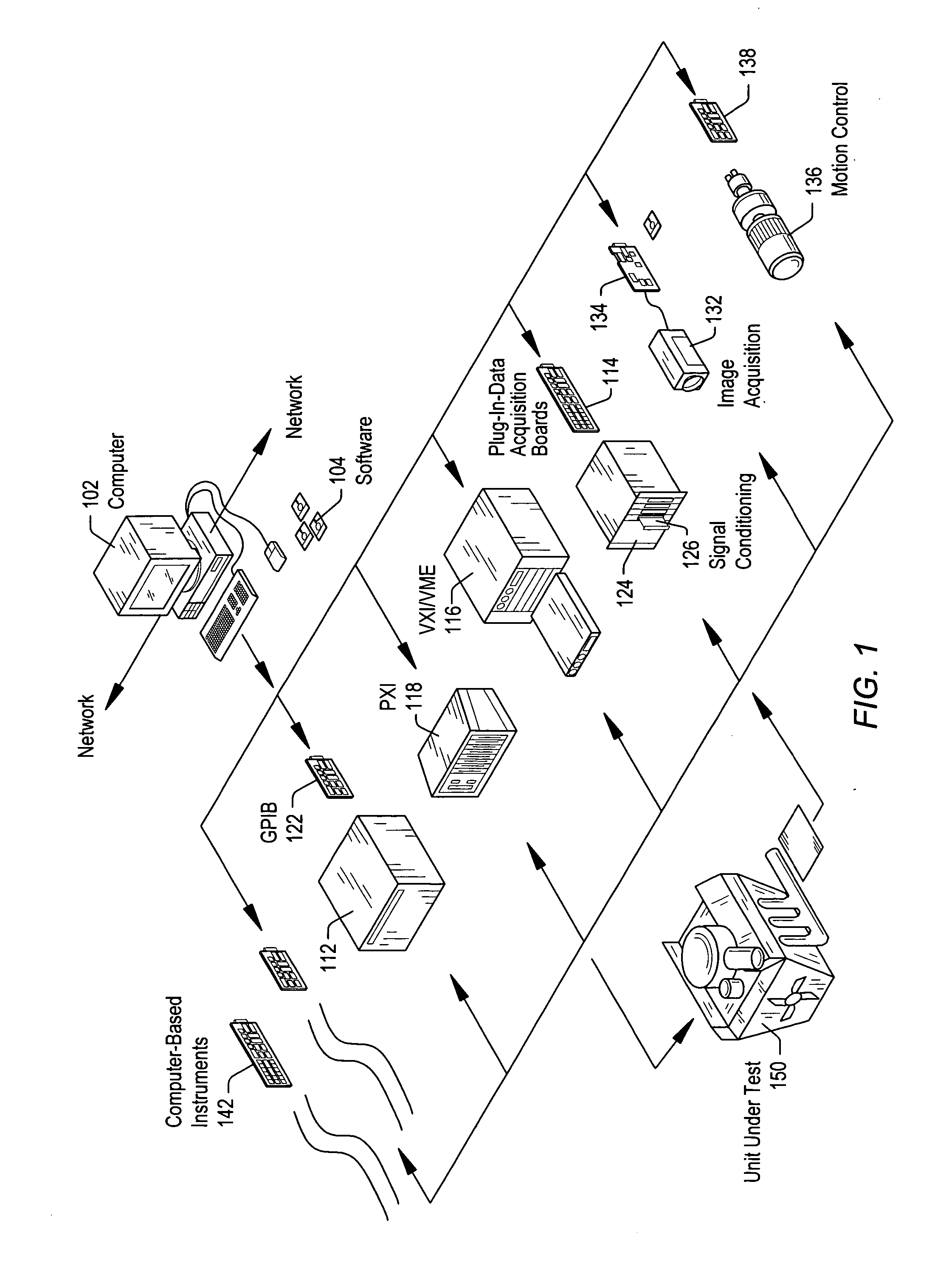
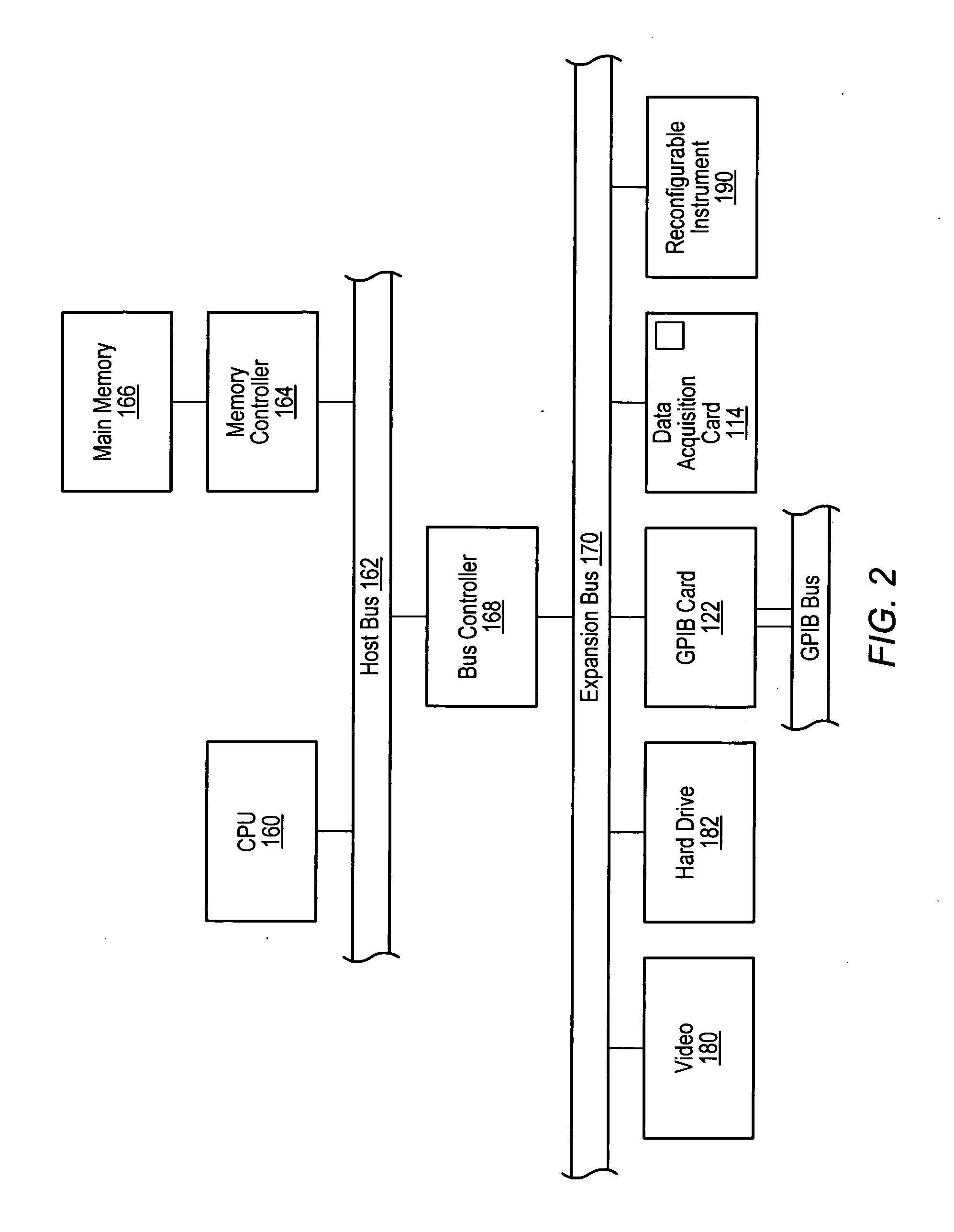
Test executive which provides heap validity checking and memory leak detection for user code modules
ActiveUS20060143537A1Improve executionImprove execution performanceError detection/correctionCode moduleTest execution
A system and method for automatically detecting heap corruption errors and memory leak errors caused by user-supplied code modules that are called by steps of a test executive sequence. The test executive sequence may first be created by including a plurality of test executive steps in the test executive sequence and configuring at least a subset of the steps to call user-supplied code modules. The test executive sequence may then be executed on a host computer under control of a test executive engine. For each step that calls a user-supplied code module, the test executive engine may perform certain actions to automatically detect whether the user-supplied code module causes a heap corruption error and / or automatically detect whether the user-supplied code module causes a memory leak error.
Owner:NATIONAL INSTRUMENTS
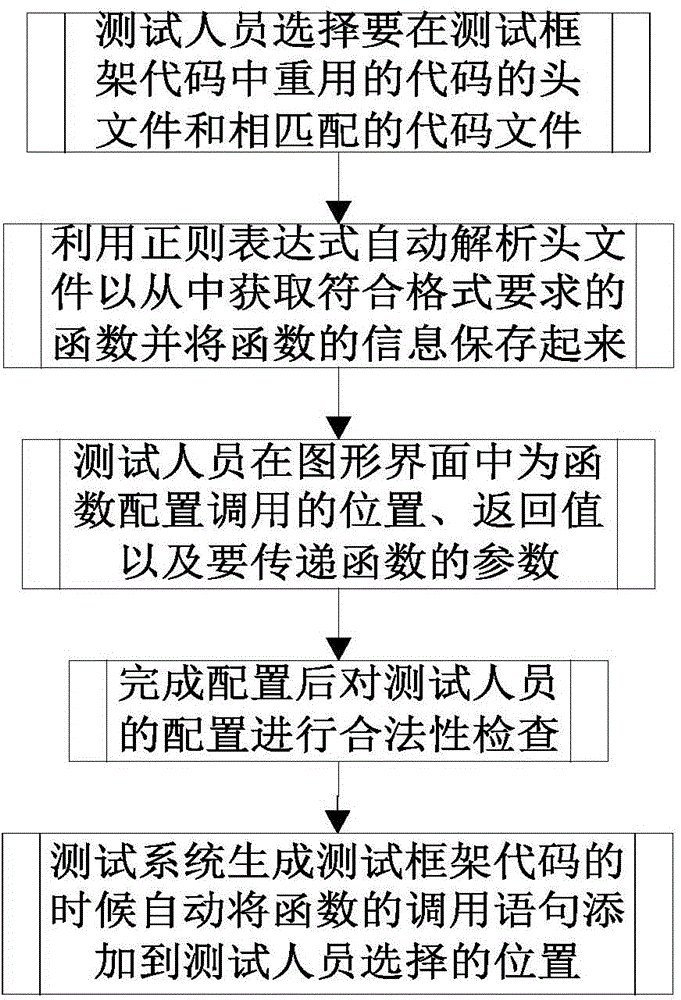
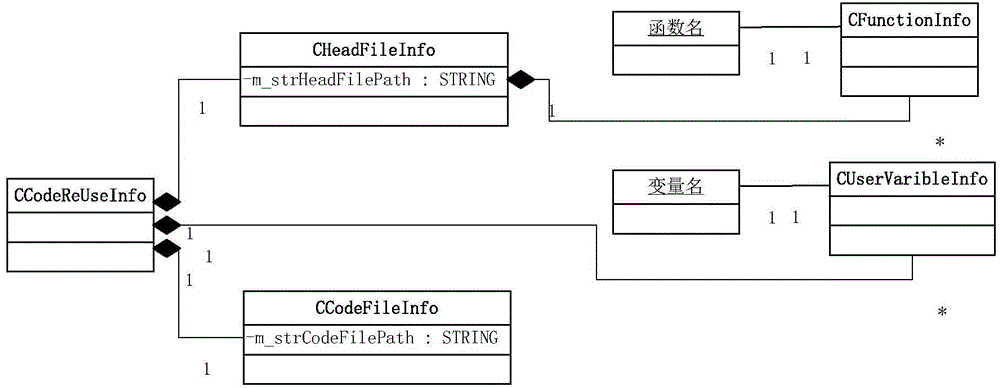
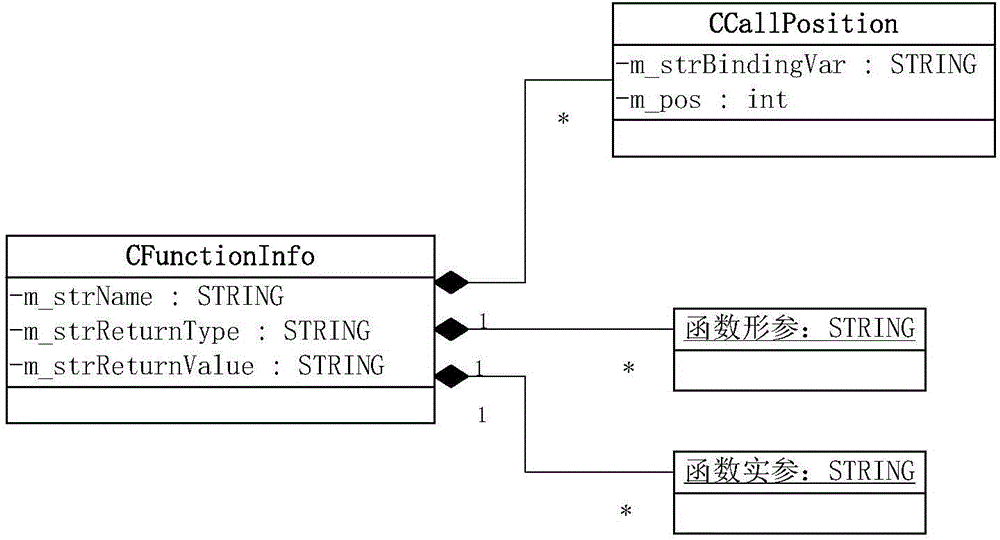
Code reuse method applied to test system
ActiveCN104156314AEasy to packImprove work efficiencySoftware testing/debuggingSpecific program execution arrangementsOperation modeRegular expression
The invention discloses a code reuse method applied to a test system. The method comprises the steps that a header file and a code file matched with the header file of a reused code among test framework codes are selected; the header file is analyzed automatically through a regular expression, and a function meeting format requirements is obtained from the header file; analyzed information is displayed in a graphical interface, and a call position, a return value and parameters to be transmitted to the function are configured for the function in the graphical interface; after configuration is completed, validity check is automatically conducted on the configuration; a call statement of the function is automatically added to the selected position, statements contained in the header file are added to corresponding positions, and the header file, the code file and other generated code files are jointly compiled to generate an executable program. According to the code reuse method, the call statement of the function is generated automatically according to test demands and added to the required position; the codes can be analyzed automatically, and information related to the function can be obtained, so testing personnel can complete configuration of code reuse conveniently in a graphical interface operation mode.
Owner:BEIHANG UNIV
System and method for implementing digital television on-line payment
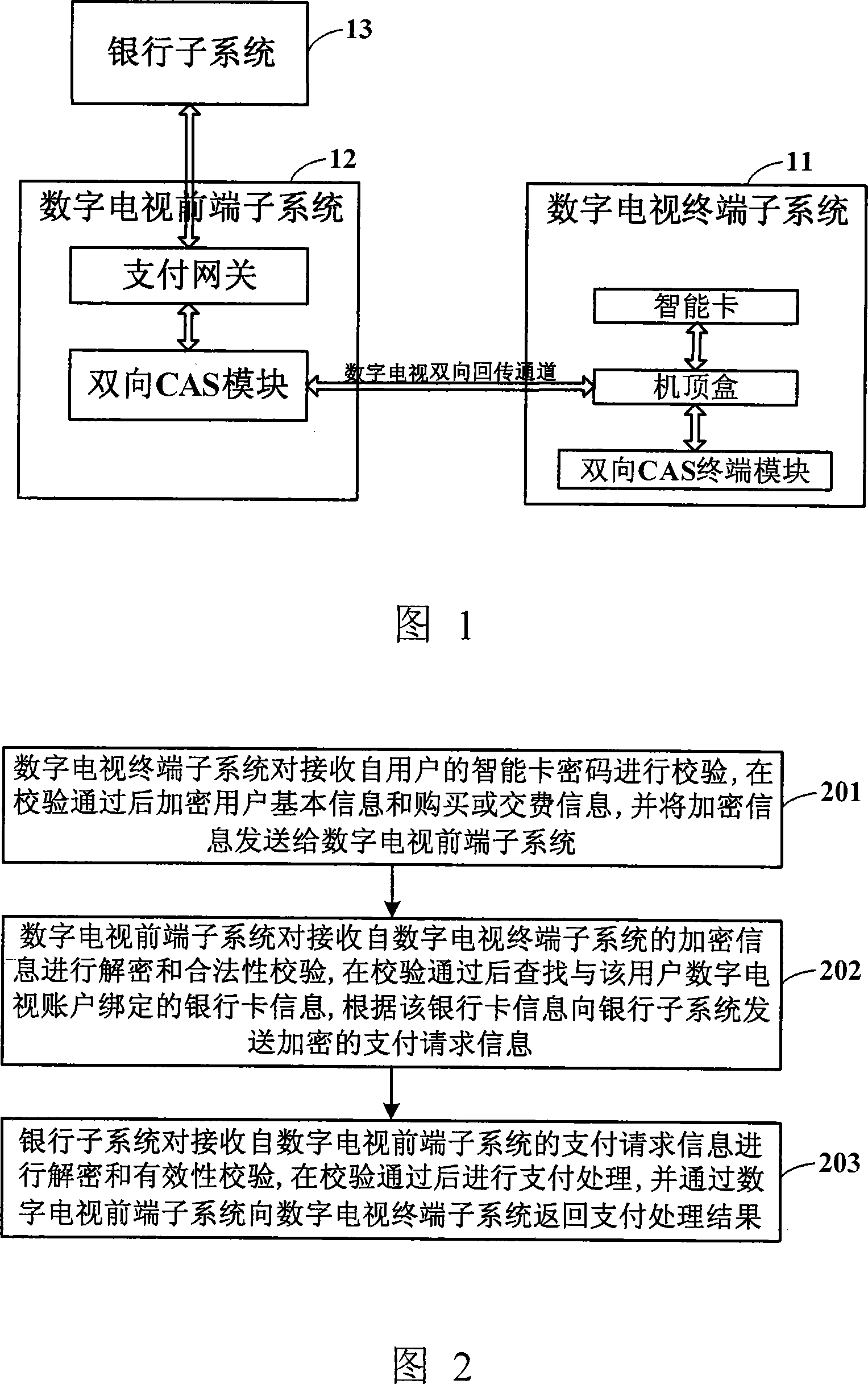
InactiveCN101119471ARealize online paymentLow costTelevision system detailsAnalogue secracy/subscription systemsPaymentPassword
The present invention relates to radiated television technical field and discloses a system to realize on-line payment of digital TV programs and consists of a digital TV terminal system that is used for checking the password of the receiving intelligence card and for encrypting the basic information and purchasing / charging information of subscribers after the check is passed through and for sending the encrypt information to the digital TV front-end sub-system; the digital TV front-end sub-system is used for carrying out decryption and validity check of the received encrypt information and for searching bank card information binding with the digital TV account of the subscribers after the check is passed through and then for sending encrypted payment request information to the sub-system of the bank according to the information of the bank card; the bank sub-system is used for deciphering and to executing validity check on the payment request received, and for conducting payment handling after the check is qualified and then for return the payment handling results to the digital TV terminal system. The present invention further discloses a method to realize on-line payment of digital TV. Utilizing the present invention, the attainable cost is reduced thus is favorable to be promoted and popularized.
Owner:SUMAVISION TECH CO LTD
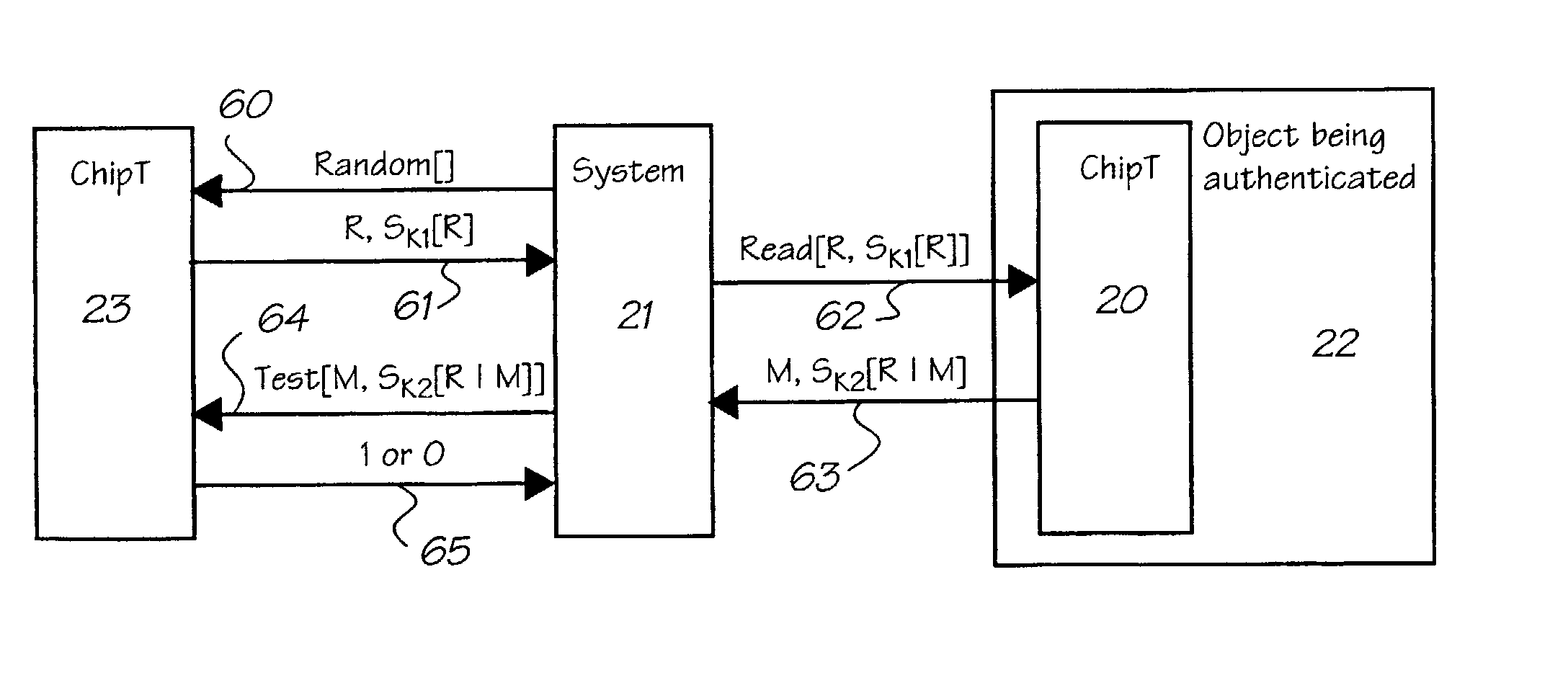
Unauthorized modification of values stored in flash memory
InactiveUS7093139B2Promote recoveryUser identity/authority verificationRead-only memoriesChecksumIntermediate state
The invention is a method and system in which an authentication chip having secret information stored within it, including secret data stored in multi-level flash memory, is protected from unauthorized modification of values stored in the flash memory. The secret information is stored using an internal command and can only be accessed by one or more further commands. Secret data in the information is stored in intermediate states of the multilevel flash memory between the minimum and maximum voltage level states. A validity check is performed on secret data items before allowing them to be read out by a command accessing them. The validity check involves calculation of a checksum and comparison of the result with a checksum stored using the internal command as part of the secret information.
Owner:MEMJET TECH LTD
Automatic train route handling method
InactiveCN109649453AImprove intelligenceReduce parking spotsAutomatic systemsSignal boxes station blockingProgram planningEngineering
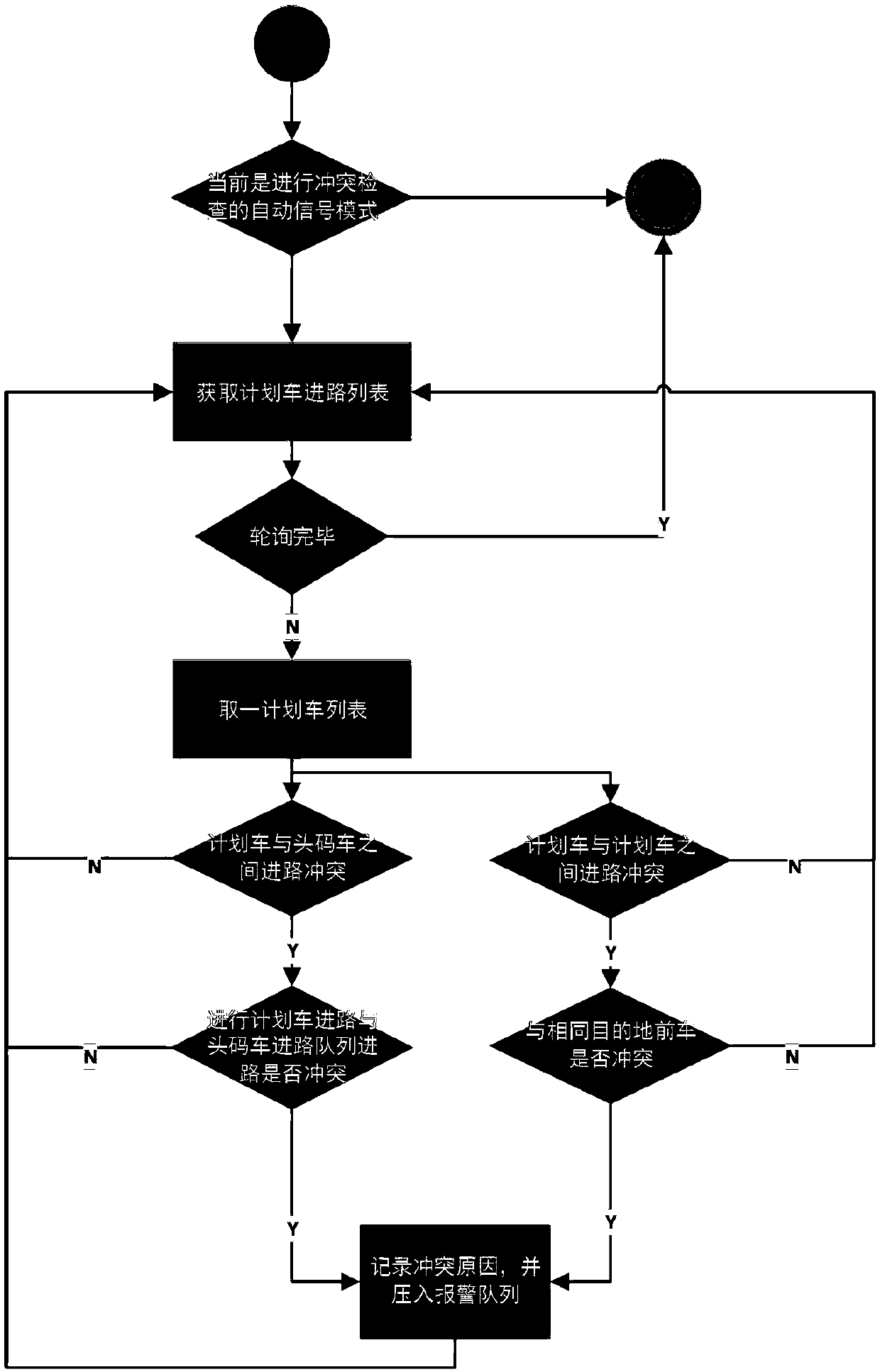
The invention belongs to the field of urban rail traffic, and relates to an automatic train route handling method which includes the steps: inspecting train route validity comprising route connectivity requirements and completeness requirements; inspecting triggering opportunities and conditions; inspecting signal conditions; selecting train routes; inspecting route conflict; selecting train routeprotection turnout positions. According to the automatic train route handling method, route triggering opportunities, route selection and conflict detection of a planning train and a heading train are considered, automatic handling of the routes, selection of protection schemes and restarting of signal can be implemented according to dynamic change of station equipment, the automatic route handling intelligent degree of an ATS (automatic tuning system) is greatly improved, and the method is faster, more accurate and more flexible.
Owner:TIANJIN JINHANG COMP TECH RES INST
Security and ticketing system control and management
InactiveUS20050204140A1User identity/authority verificationPayment circuitsComputer hardwareHash function
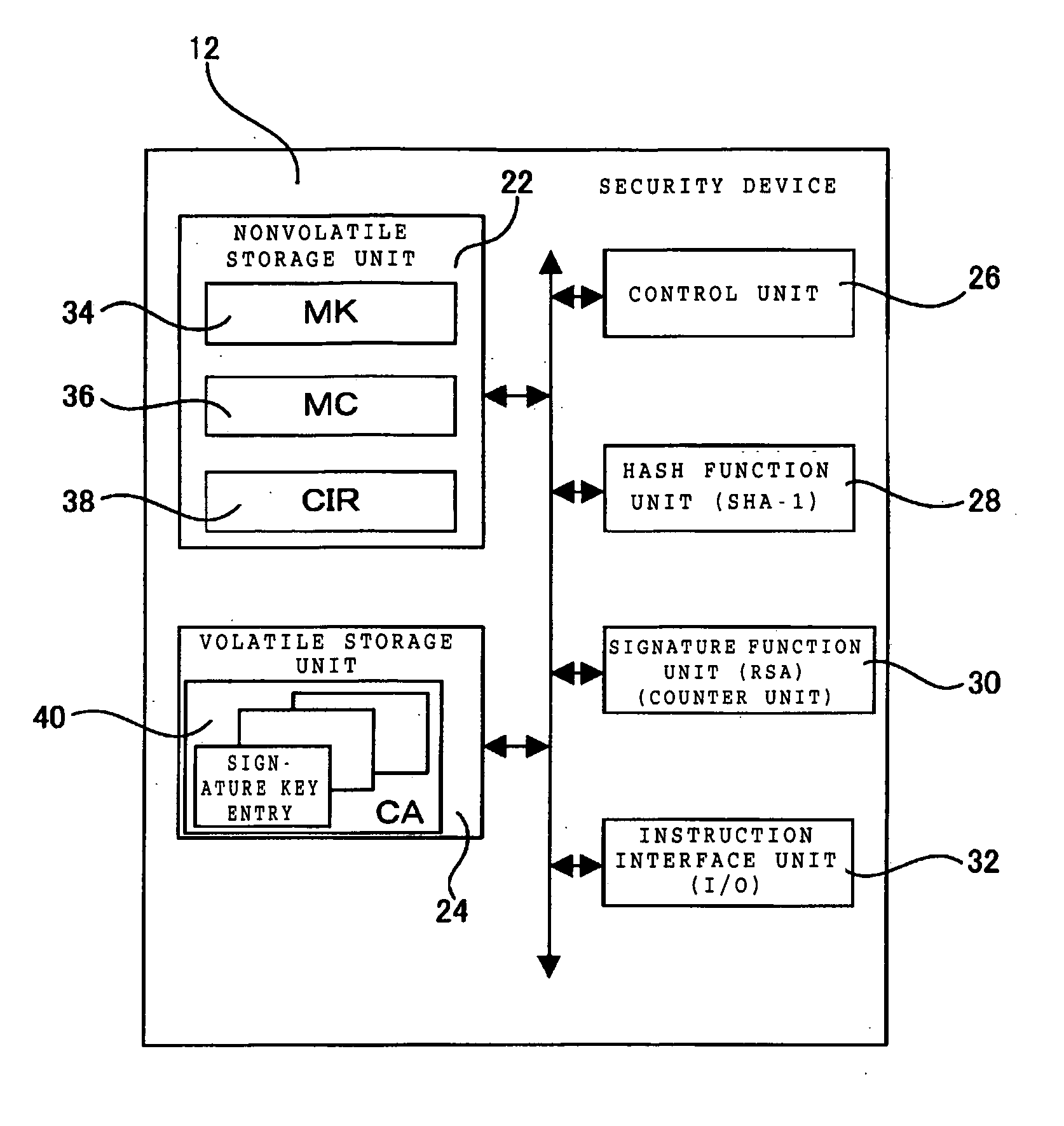
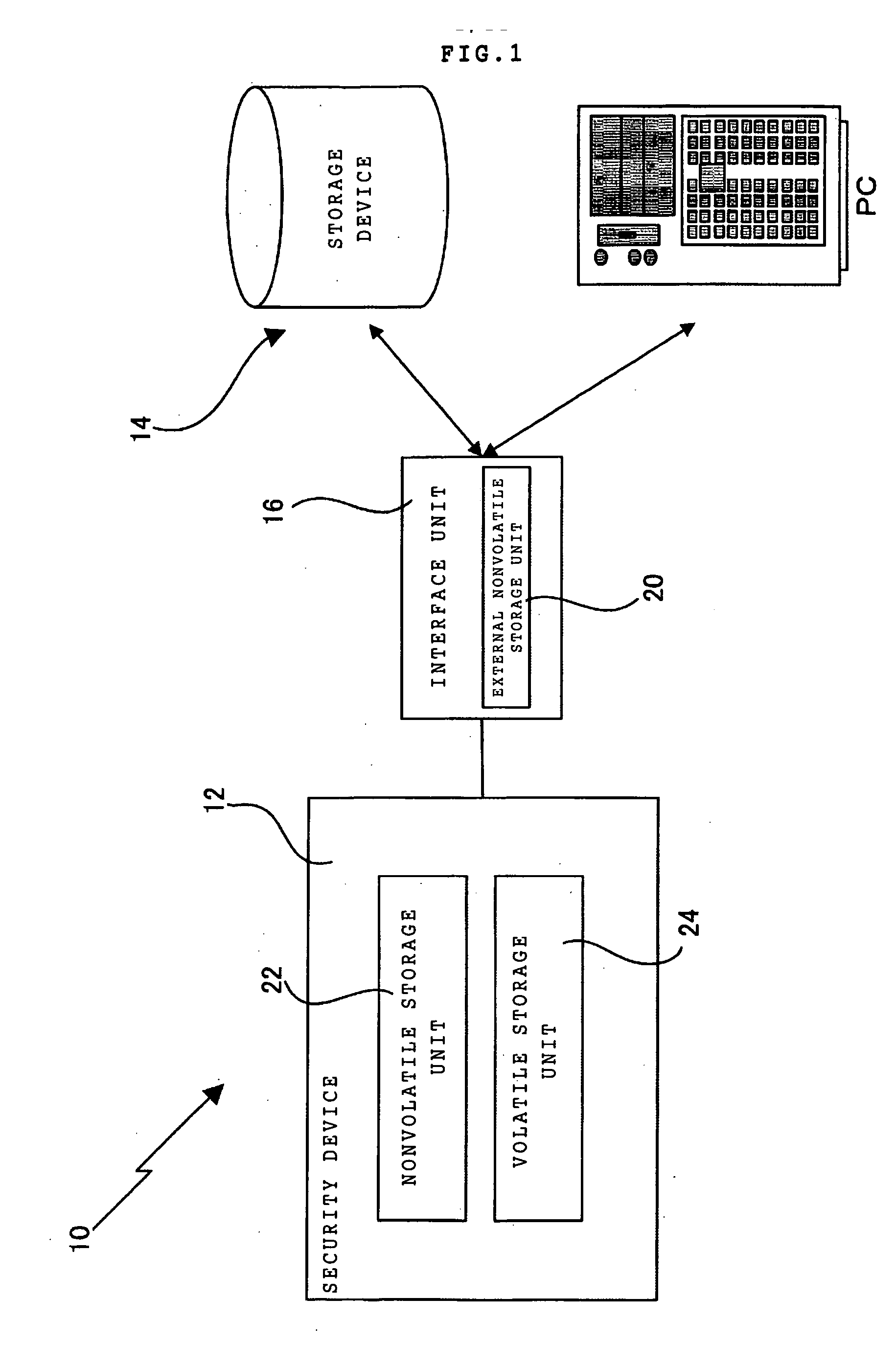
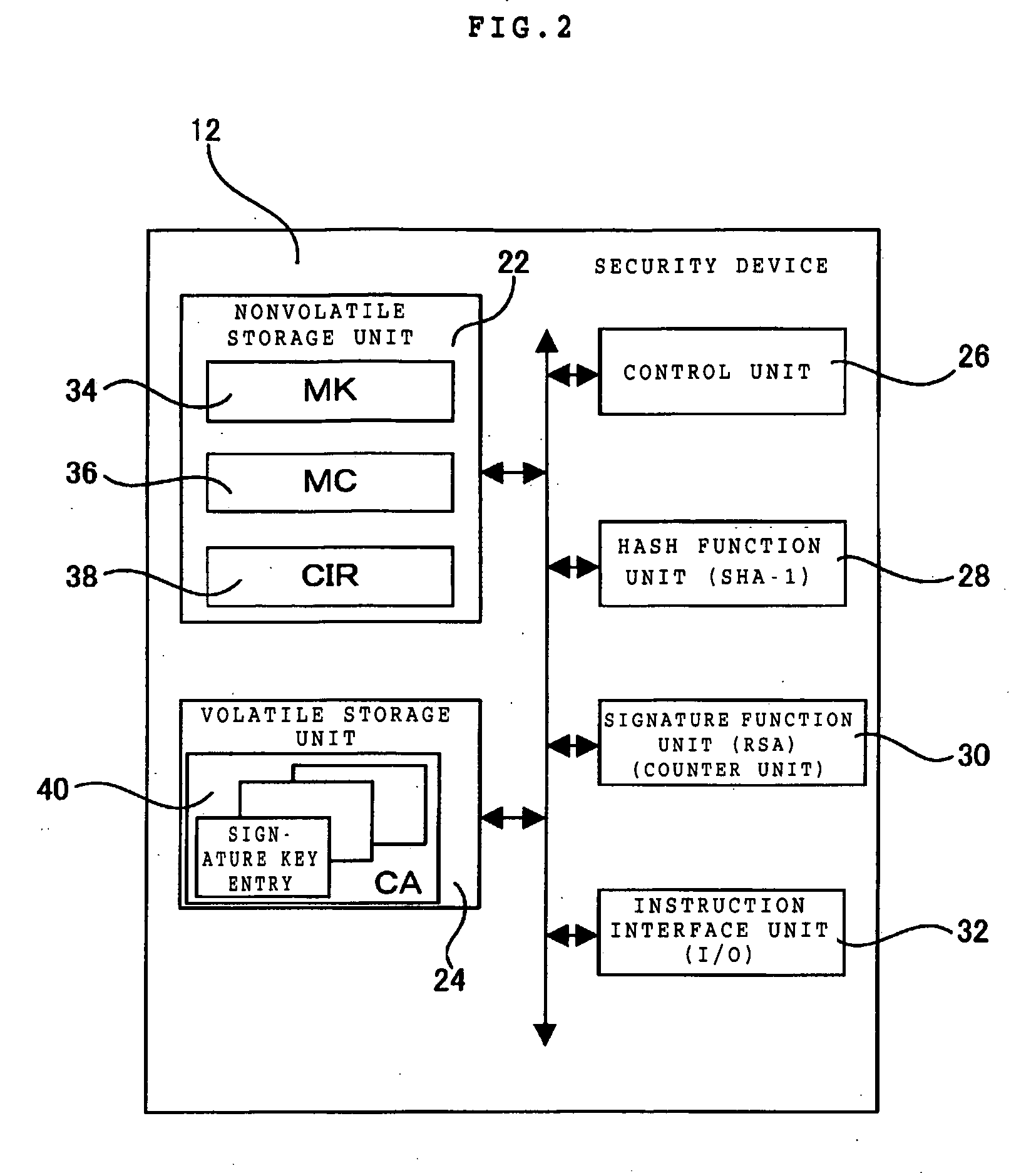
A security device of this invention includes a nonvolatile storage unit 22 for storing a validity check unit including a counter updated every time signature function means 30 is called up, a volatile storage unit 24 for reading and storing a counter array out of an external nonvolatile storage unit storing the counter array, in which the counter array is obtained by coupling a hash value generated for each signature key with a signature number counter for counting the number of signatures performed by use of the signature key, and a hash function unit 28 for reading the counter array out of the volatile storage unit 24, generating the hash value, and transferring the hash value to the validity check unit for a validity check.
Owner:IBM CORP
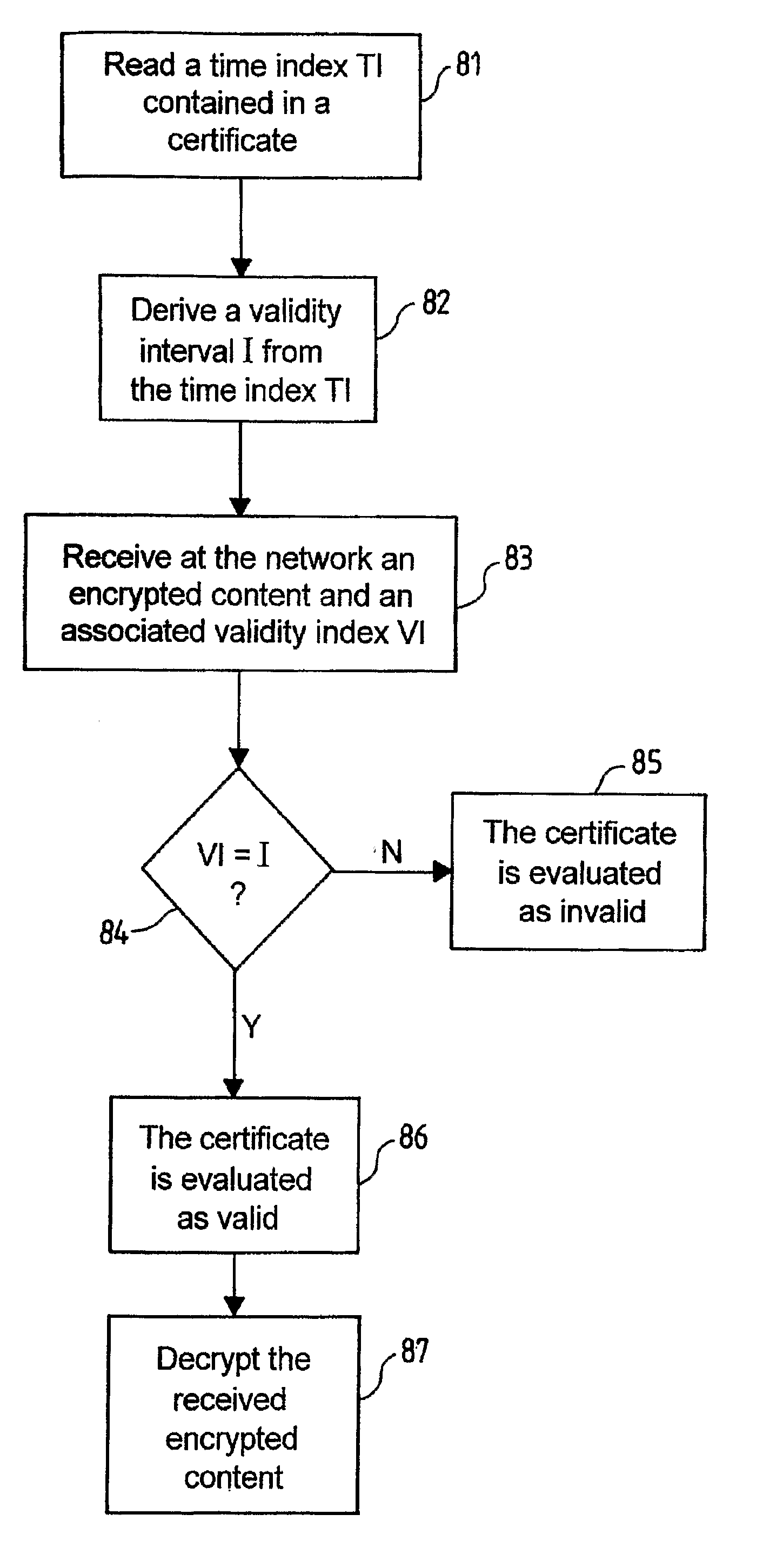
Certificate validity checking
InactiveUS20070186111A1Public key for secure communicationDigital data processing detailsOperating systemTime index
A method for checking a validity of a certificate containing a key associated to a network device in a network, comprises receiving at the network an encrypted content and a validity index associated to the content. The validity of the certificate is evaluated from a time index contained within the certificate, the time index having a value corresponding to a time of issue of the certificate, and from the validity index associated to the encrypted content.
Owner:THOMSON LICENSING SA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com