Method for protecting embedded type device software
A technology for embedded devices and software protection, applied in the direction of program/content distribution protection, etc., can solve the problems of software identification, software verification, and poor security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
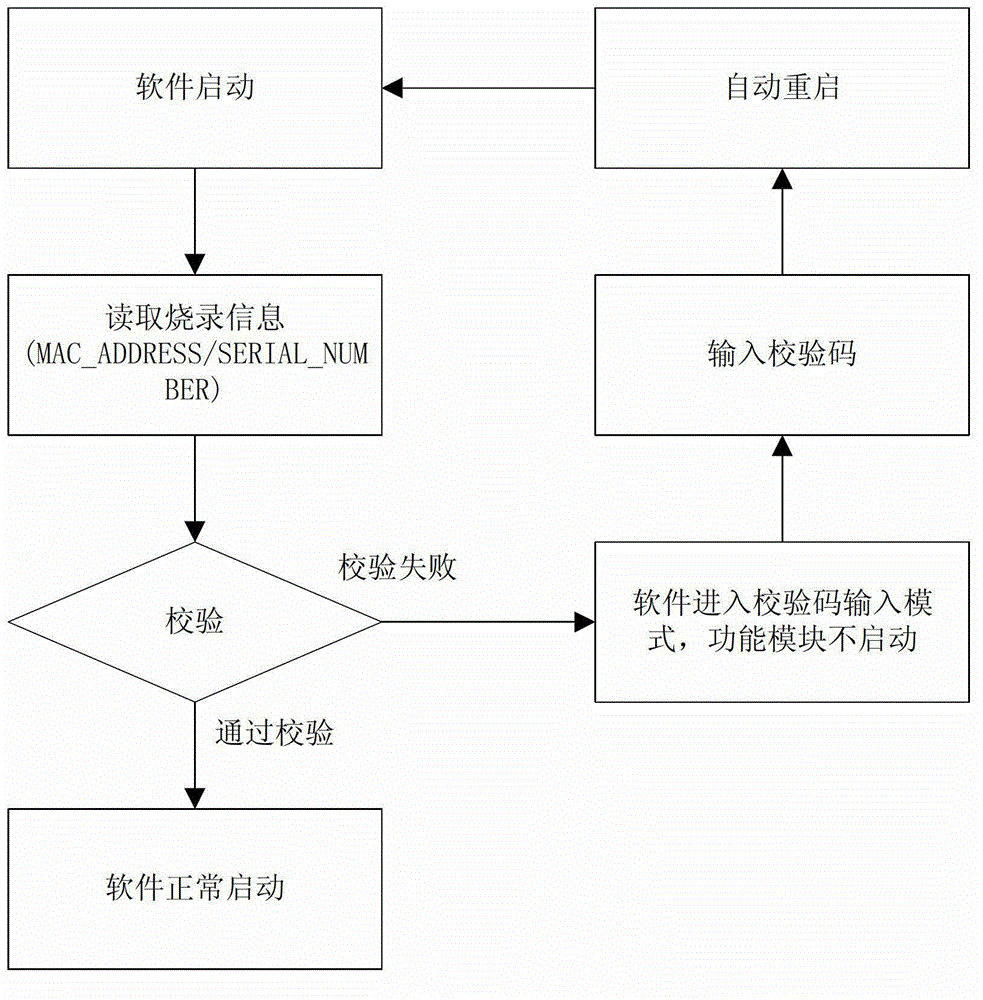
[0027] The present invention will be further described below in combination with principle diagrams and specific operation examples.
[0028] The present invention has a premise assumption: in the network equipment, there must be an action of burning the MAC address before leaving the factory, and there is no less than one block of reserved space in the dynamic memory (Flash). The special physical structure of a block ranges from 4KB to 128KB, accounting for about 0.2%-0.5% of the Flash size. This part of the space is used to store the check code that is burned simultaneously with the MAC address.
[0029] Under this premise, Flash will have an area in the software to store authentication information.
[0030] In the execution structure of the software itself, first of all, corresponding to each version of the embedded software, the software itself will have an 8-digit serial number, corresponding to the number of the software version itself, defined here as FIRMWARE_NUMBER, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com