Patents
Literature
193 results about "Software verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Software verification is a discipline of software engineering whose goal is to assure that software fully satisfies all the expected requirements.
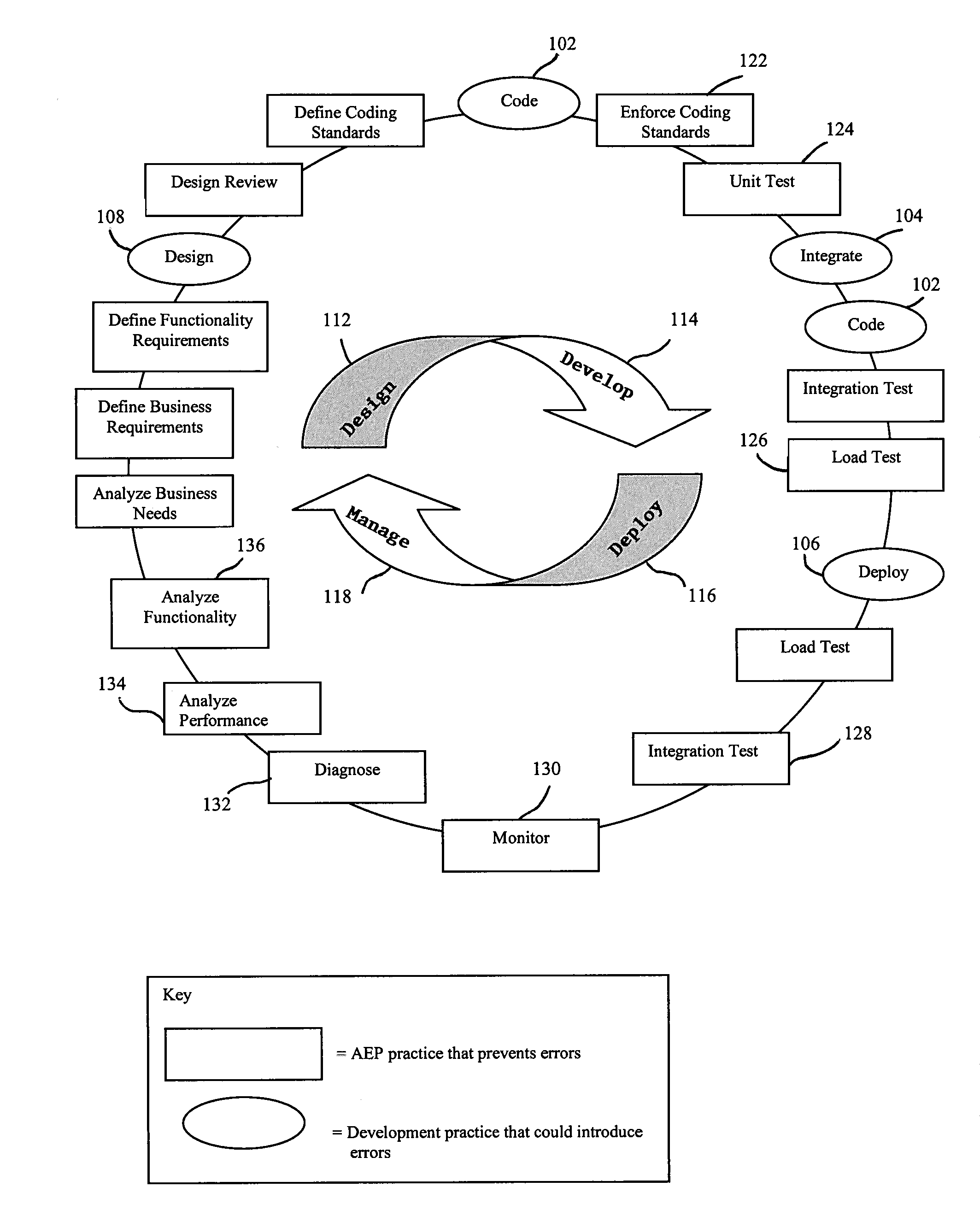
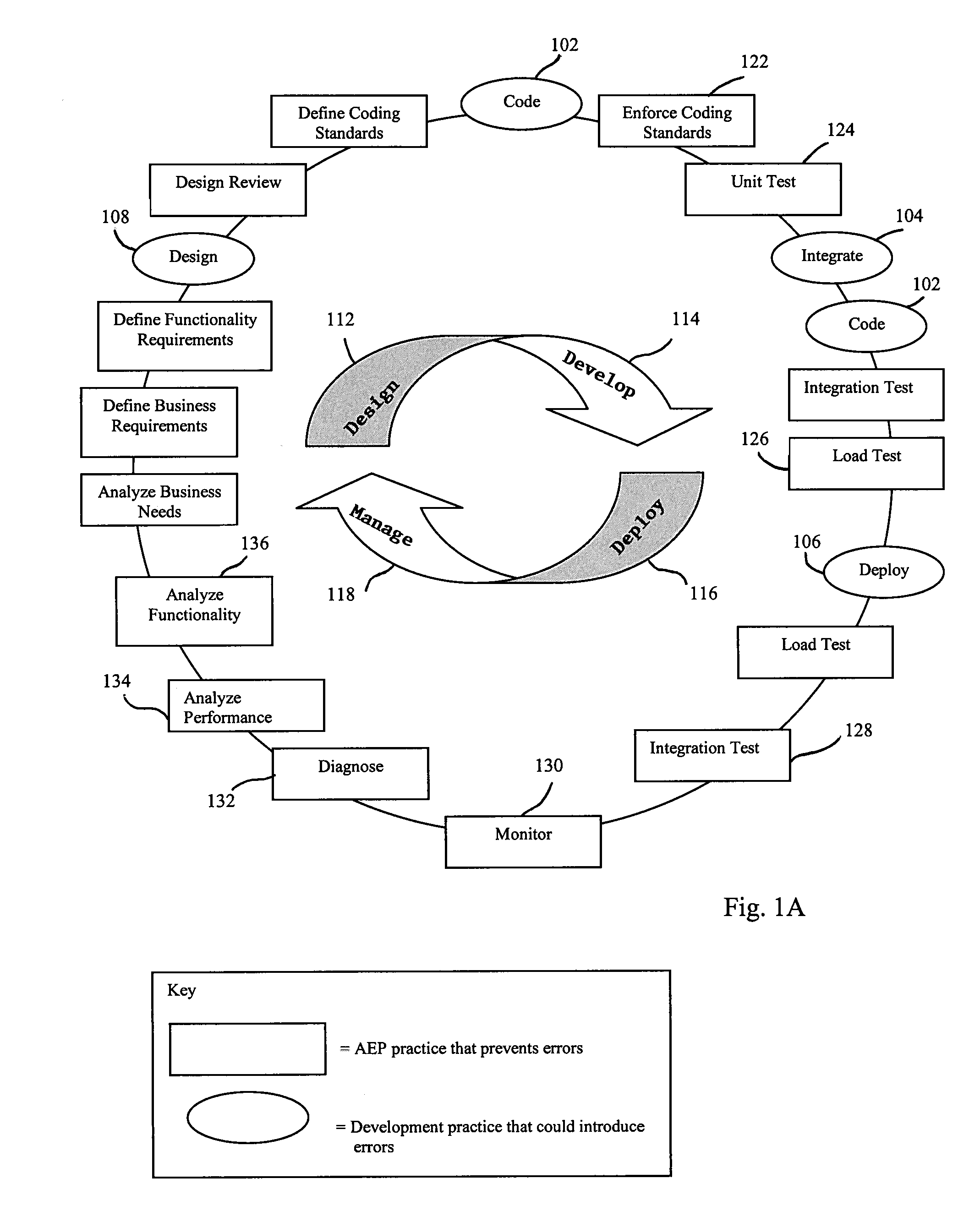
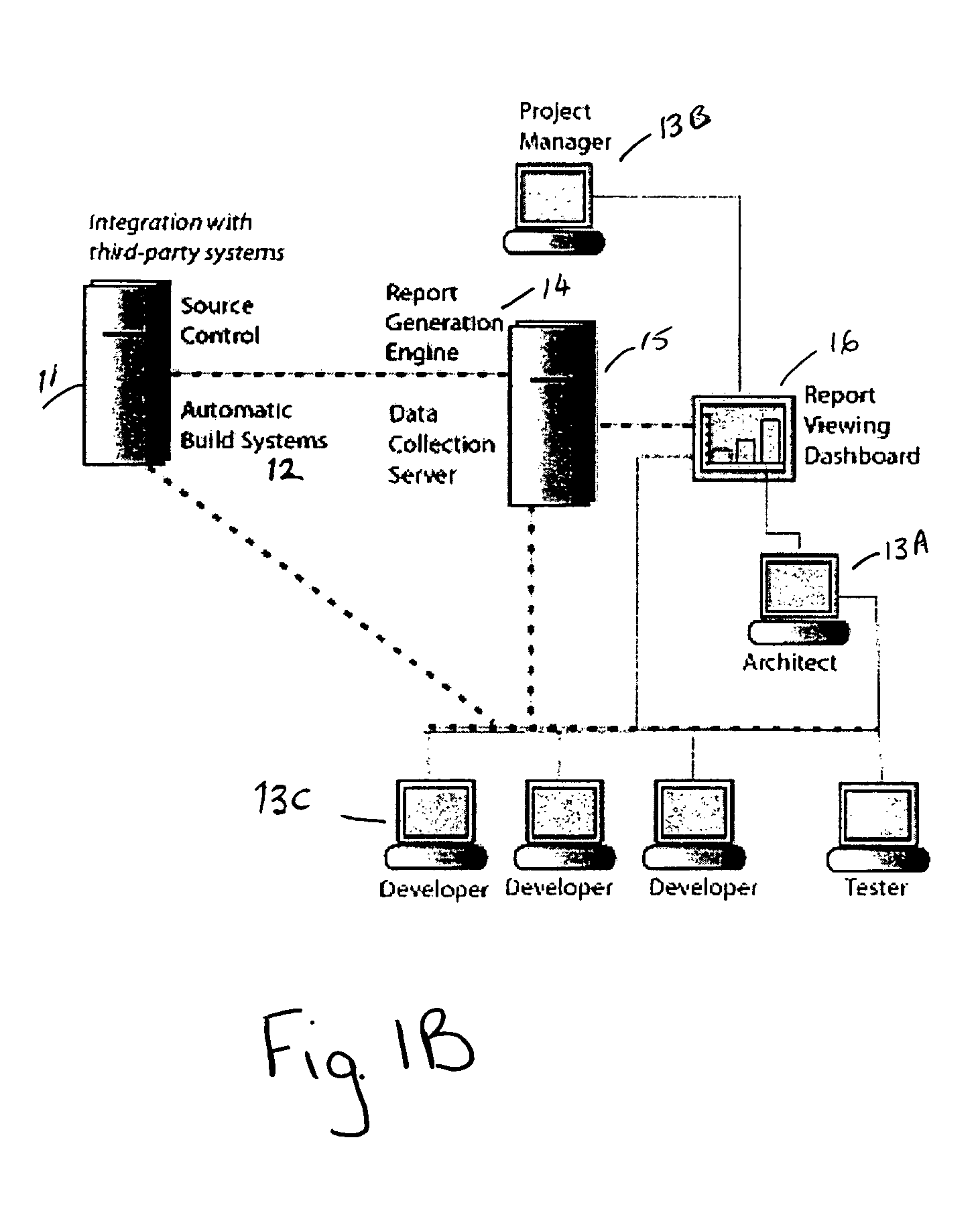
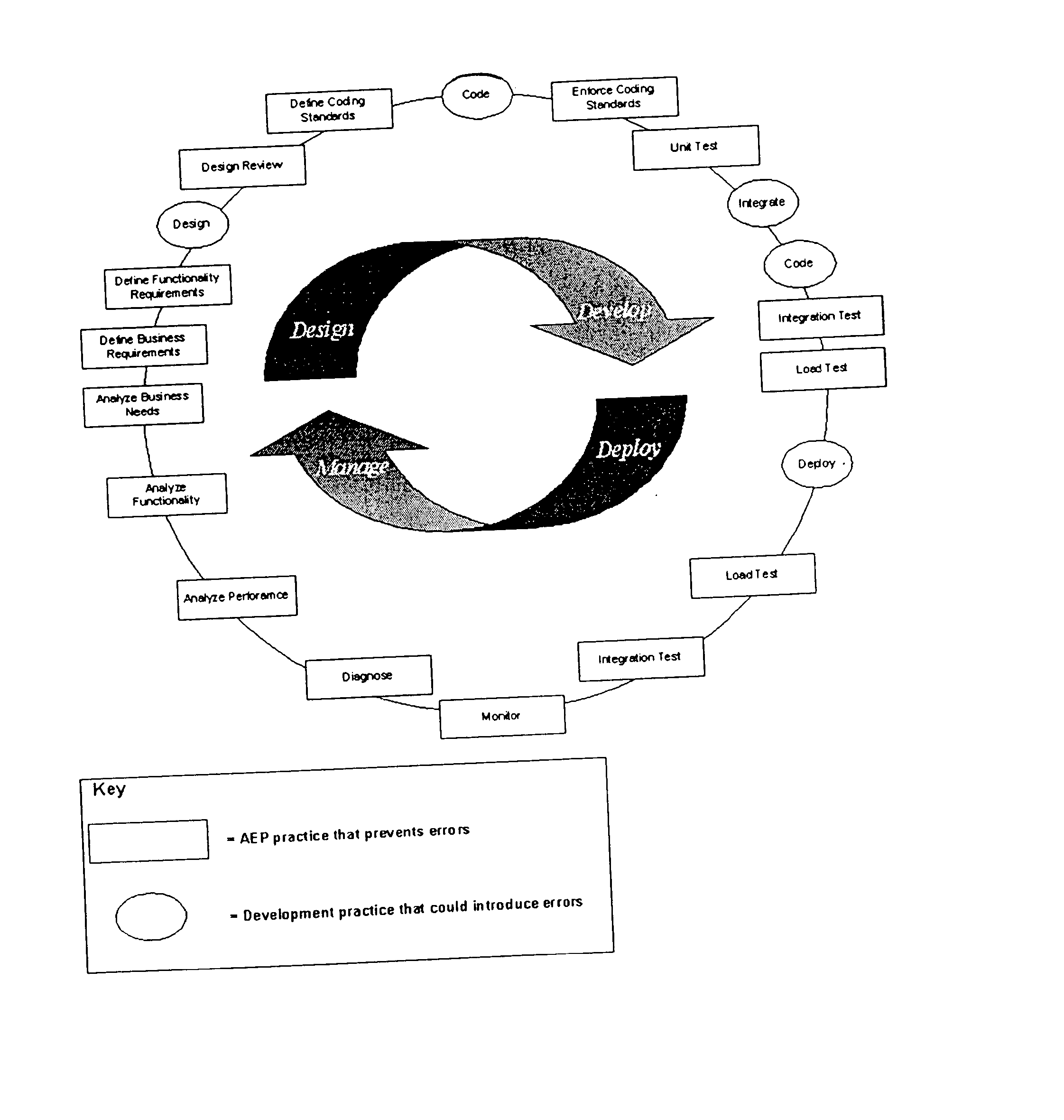
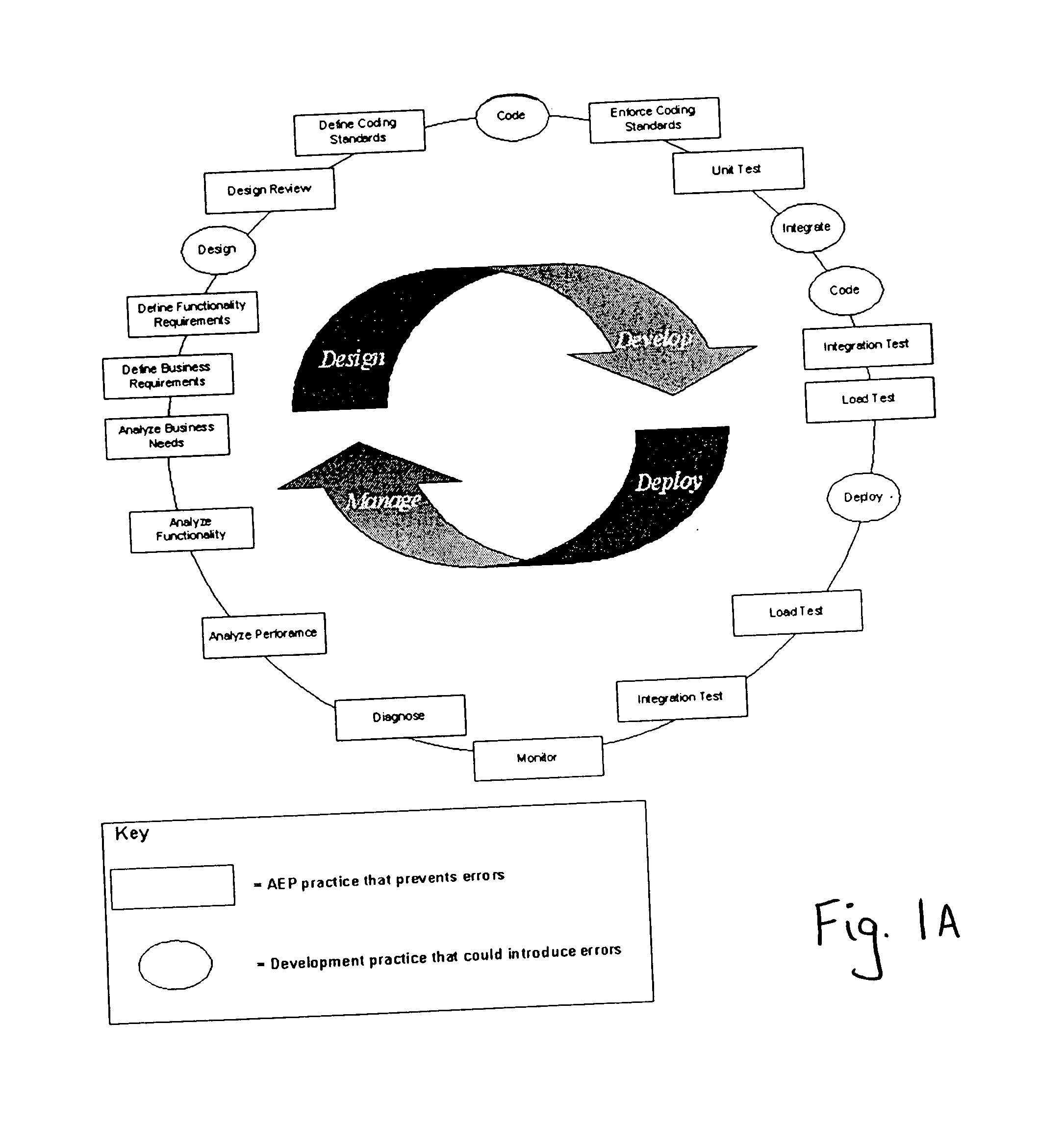
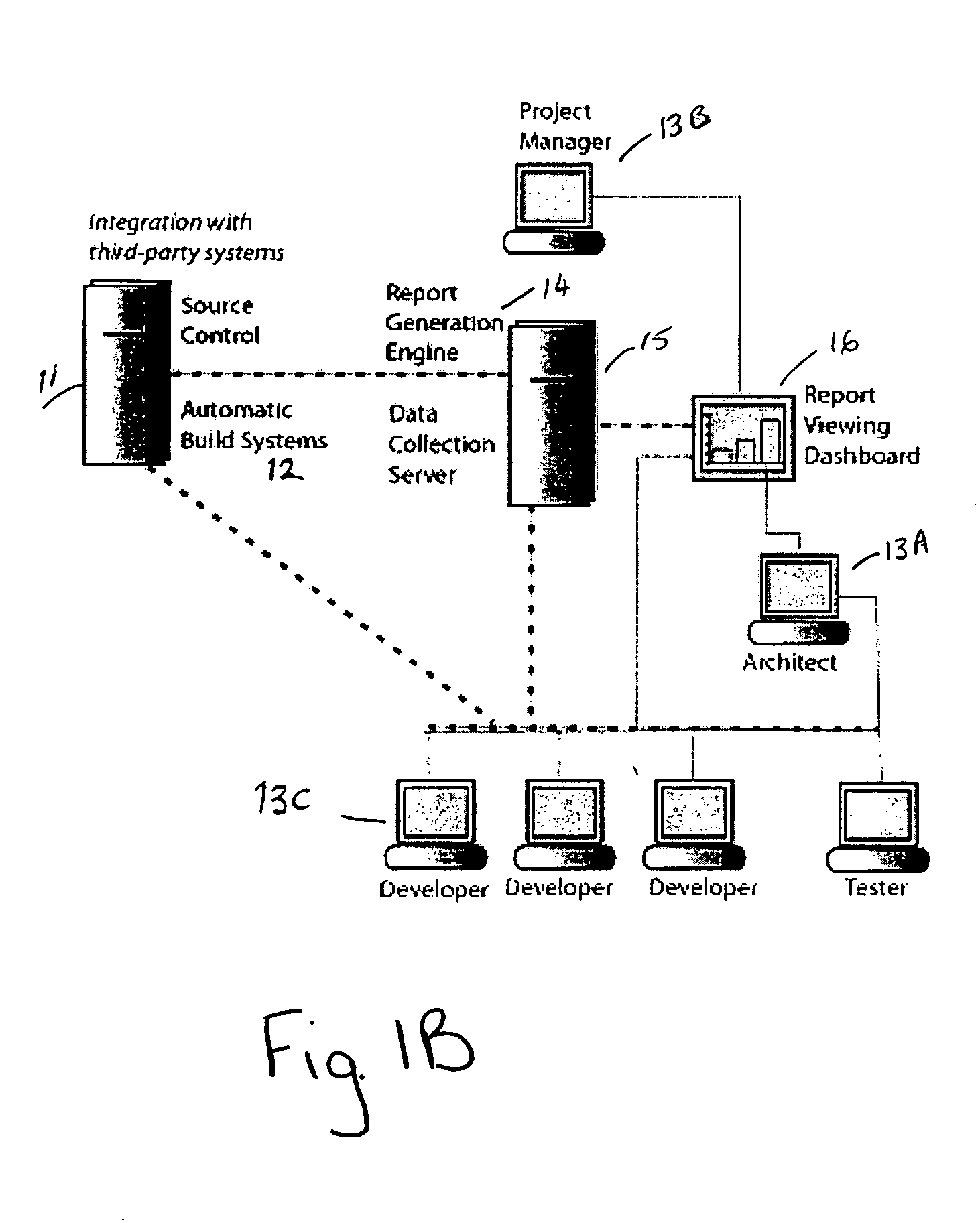
Method and system for automatic error prevention for computer software
ActiveUS7596778B2Automatically preventing errorError detection/correctionEmergency protective arrangements for automatic disconnectionError preventionComputer software
In one embodiment, the present invention is a method for automatically preventing errors in computer software. The method includes storing the computer software in a code repository; executing a plurality of software verification tools to verify the computer software, wherein each of the plurality of software verification tools automatically generates one or more test cases; generating verification results responsive to executing the plurality of software verification tools and the automatically generated test cases; processing the verification results for generating an objective criterion of quality of the computer software; and customizing the scope of one or more of the plurality of verification tools responsive to the objective criterion of quality of the computer software.
Owner:PARASOFT
Method and system for automatic error prevention for computer software
ActiveUS20050015675A1Automatically preventing errorError detection/correctionEmergency protective arrangements for automatic disconnectionError preventionComputer software
In one embodiment, the present invention is a method for automatically preventing errors in computer software. The method includes storing the computer software in a code repository; executing a plurality of software verification tools to verify the computer software, wherein each of the plurality of software verification tools automatically generates one or more test cases; generating verification results responsive to executing the plurality of software verification tools and the automatically generated test cases; processing the verification results for generating an objective criterion of quality of the computer software; and customizing the scope of one or more of the plurality of verification tools responsive to the objective criterion of quality of the computer software.
Owner:PARASOFT
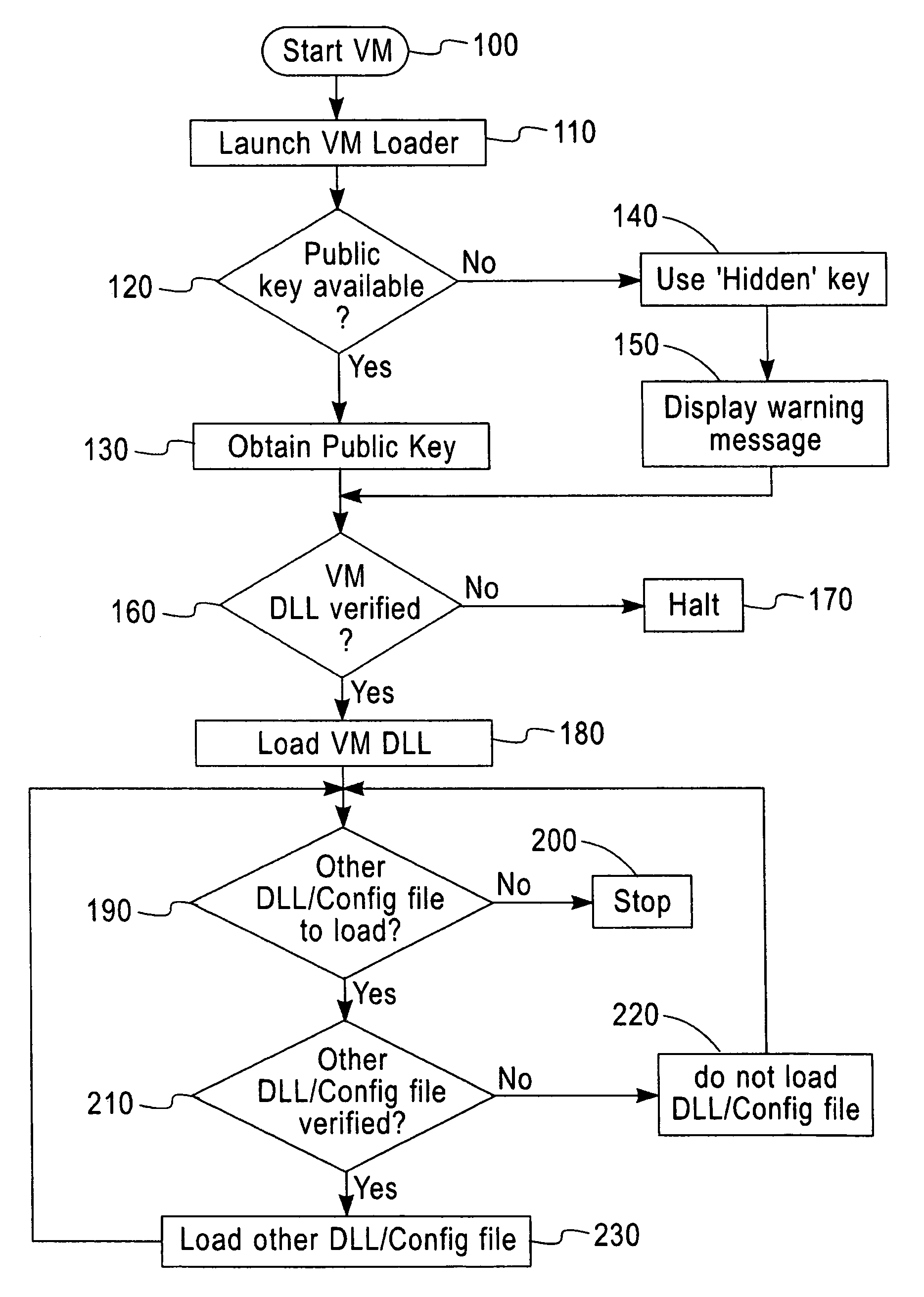
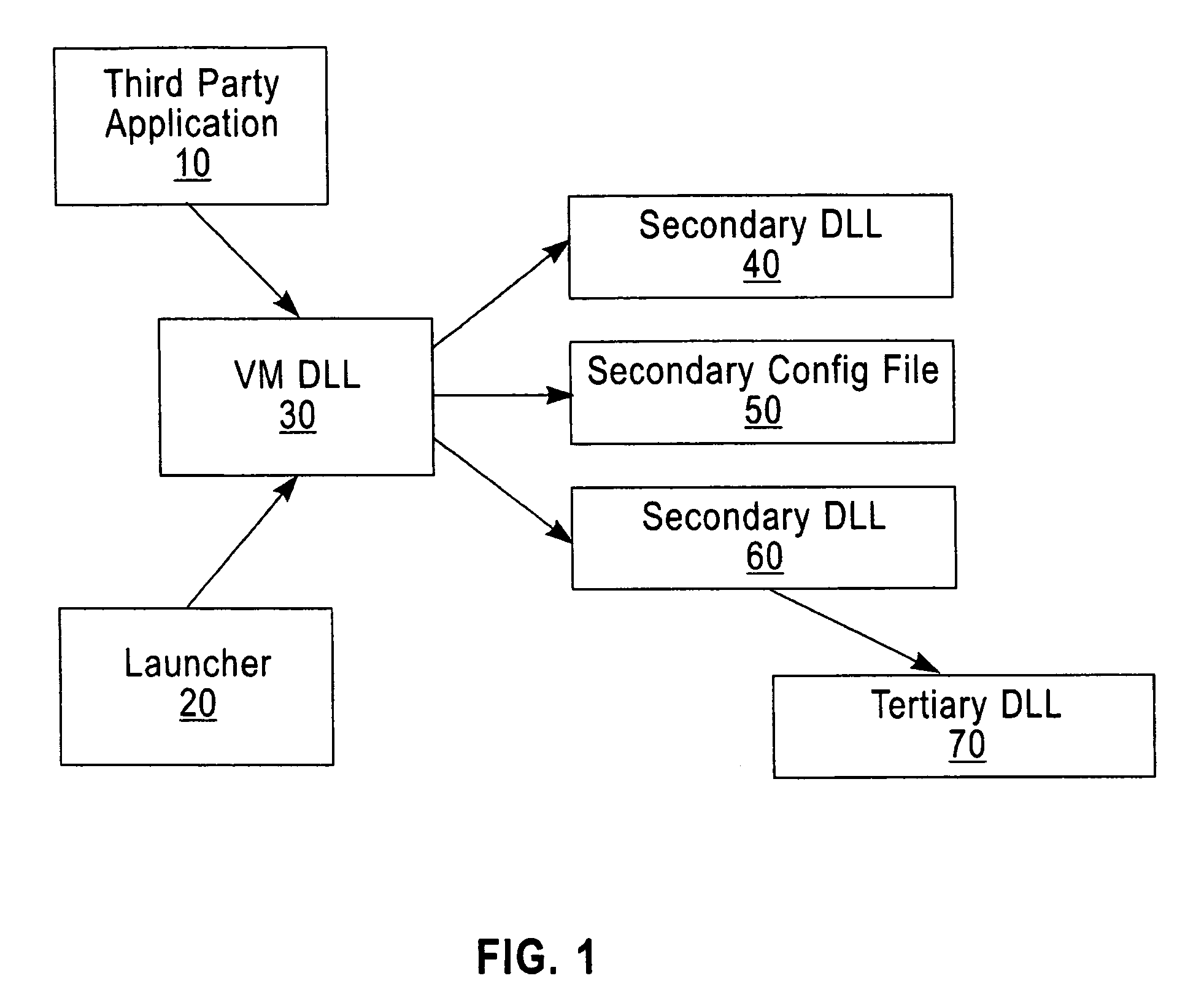
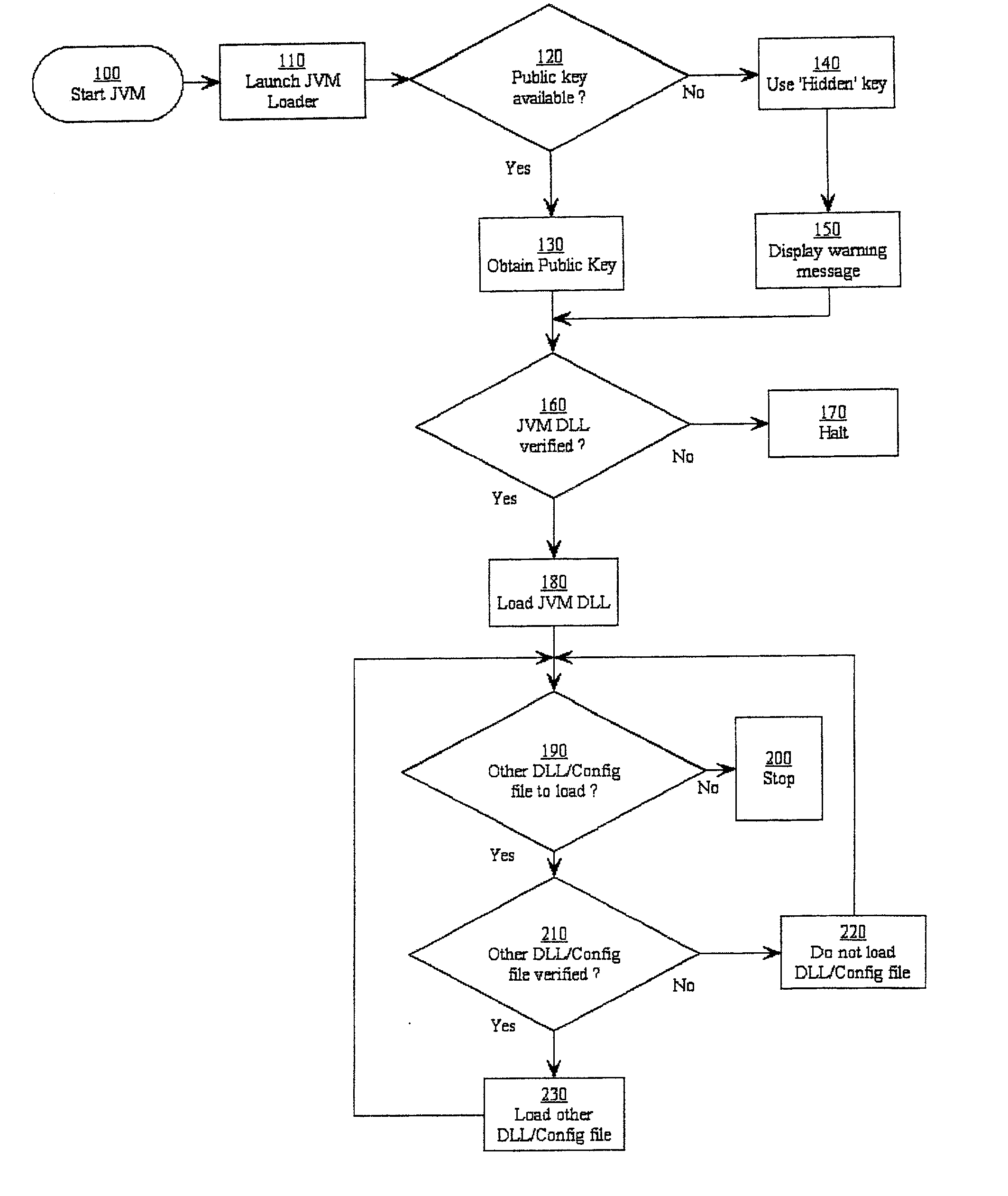
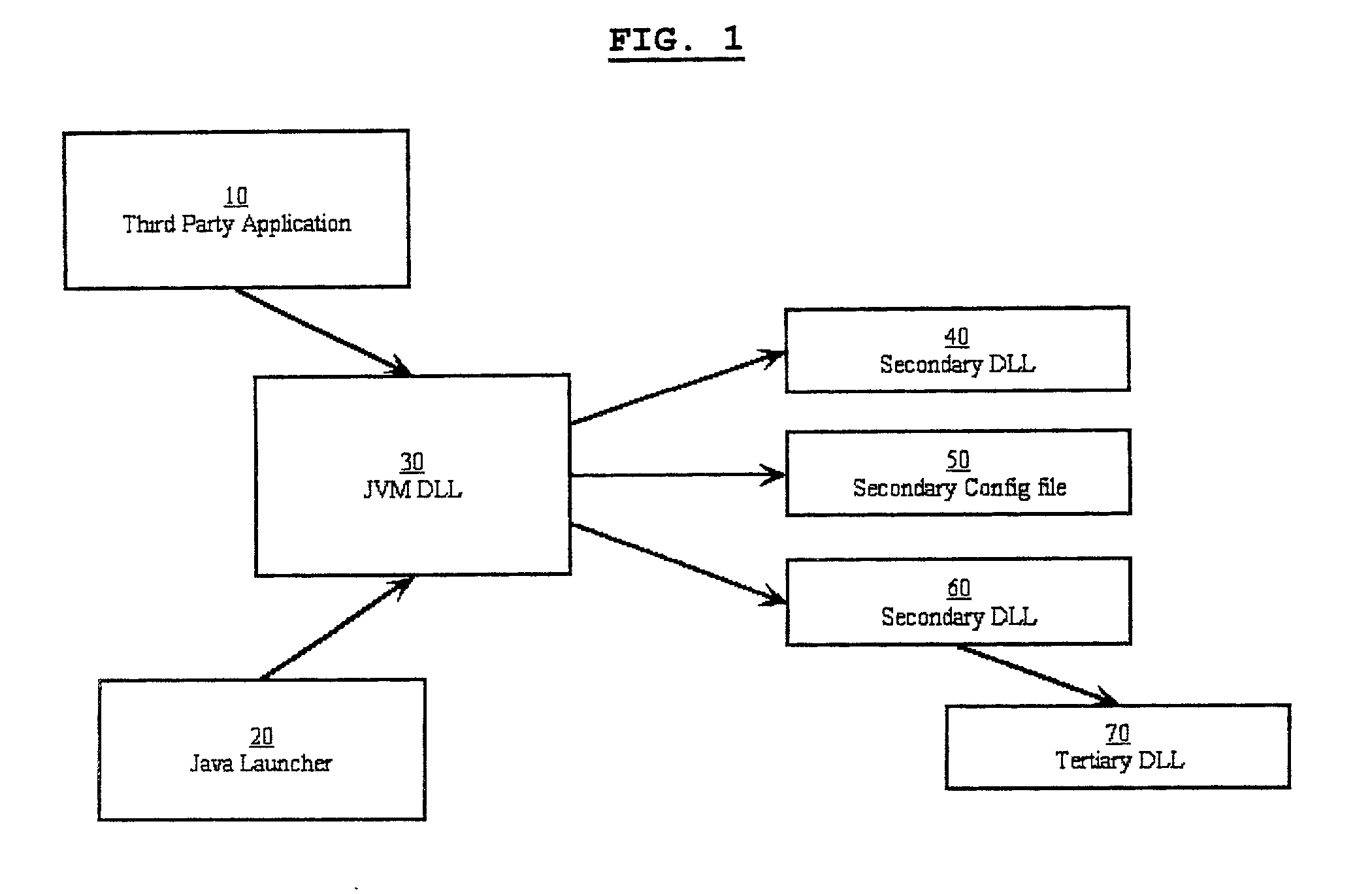
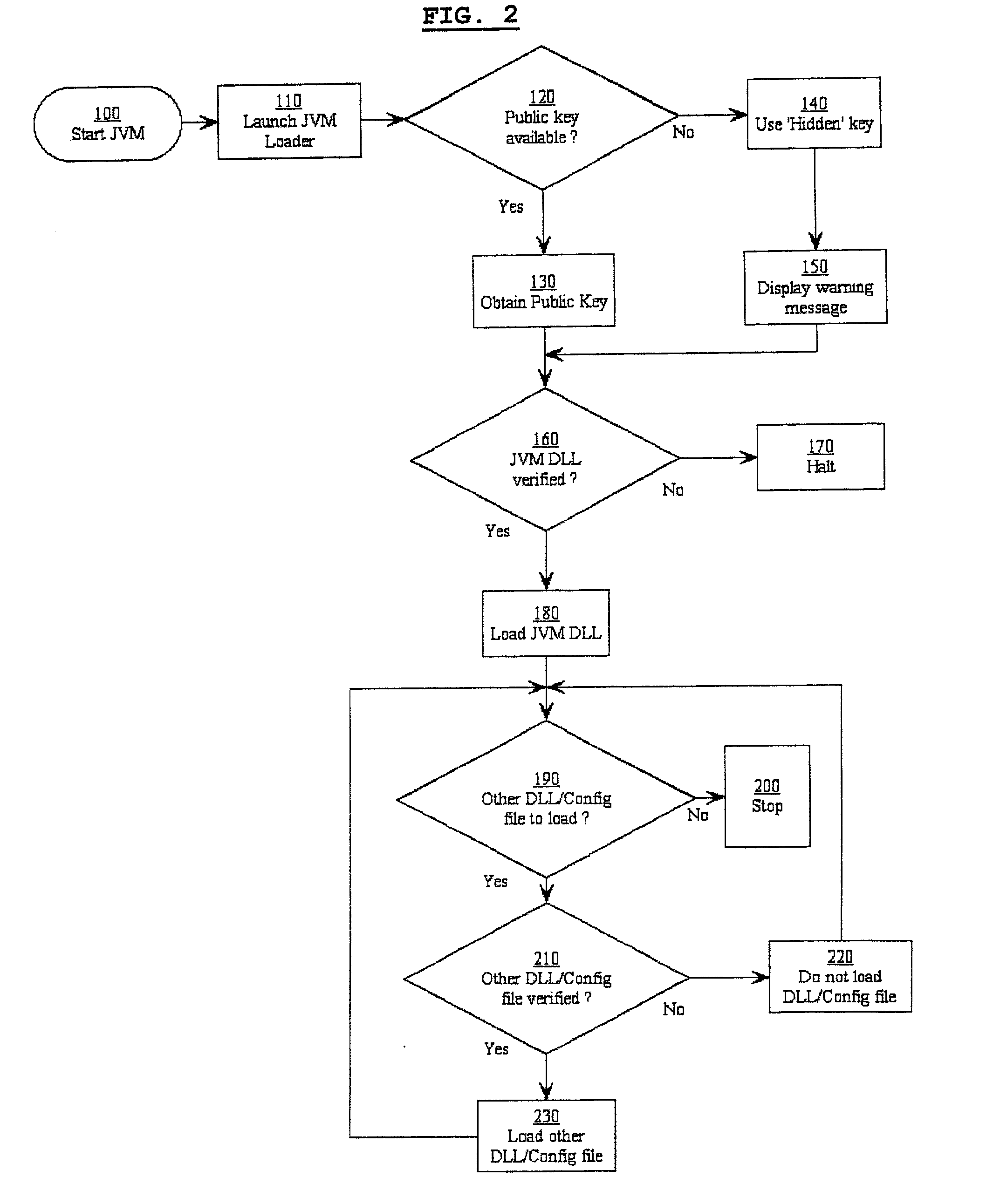
Software verification system, method and computer program element
InactiveUS7496757B2Improve securityGreat confidenceUser identity/authority verificationUnauthorized memory use protectionDigital signatureApplication software
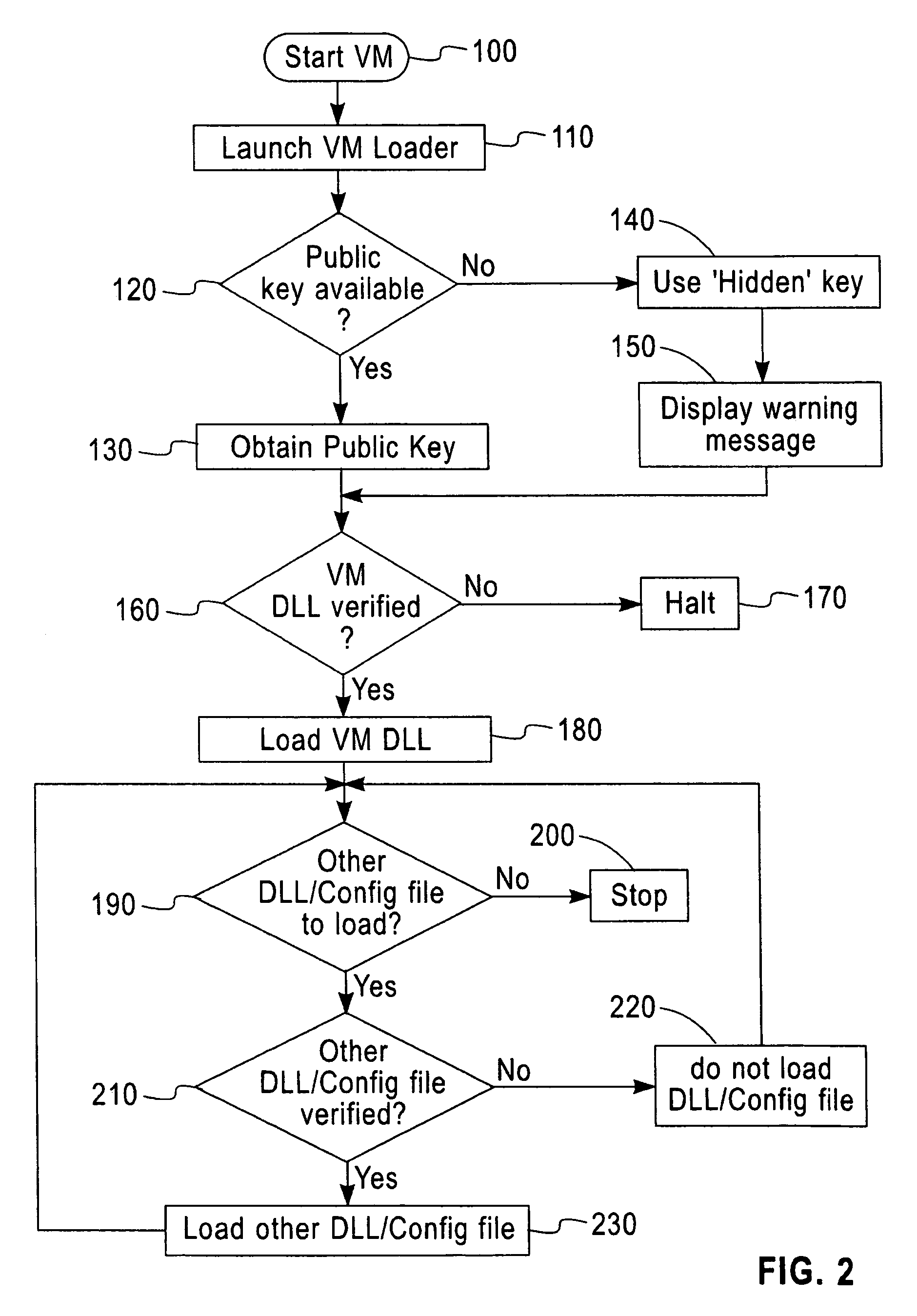
A software security system is arranged to verify the authenticity of each element of a Java Virtual Machine installation. A digital signature is attached to each file of the JVM installation. A loader (20) verifies the digital signature of the JVM DLL (30). The JVM DLL 30 then verifies the digital signature of each other DLL and configuration file to be loaded (40, 50, 60, 70), and only loads those files which have successfully verified digital signatures. In this way the security of the JVM is enhanced, a user has greater confidence that the Java applications will function correctly, and the detection of incorrect or damaged JVM installations is improved.
Owner:TREND MICRO INC
Credit and transaction systems
An Internet-coupled transaction service has a link to a computer appliance coupled to a merchant site, the computer appliance operated by a person who has selected one or more products or services to purchase at the merchant site, and who has selected, through the merchant site, the transaction service to arrange payment, and software executing from a computer-readable medium accessible to the service. The transaction service, via the software verifies the identity of the person, determines a credit worthiness for the person, and the score being sufficient, arranges payment to be made to the merchant on behalf of the person, and arranges repayment terms with the person for the payment to the merchant.
Owner:INTELLECTUAL ADVANCE
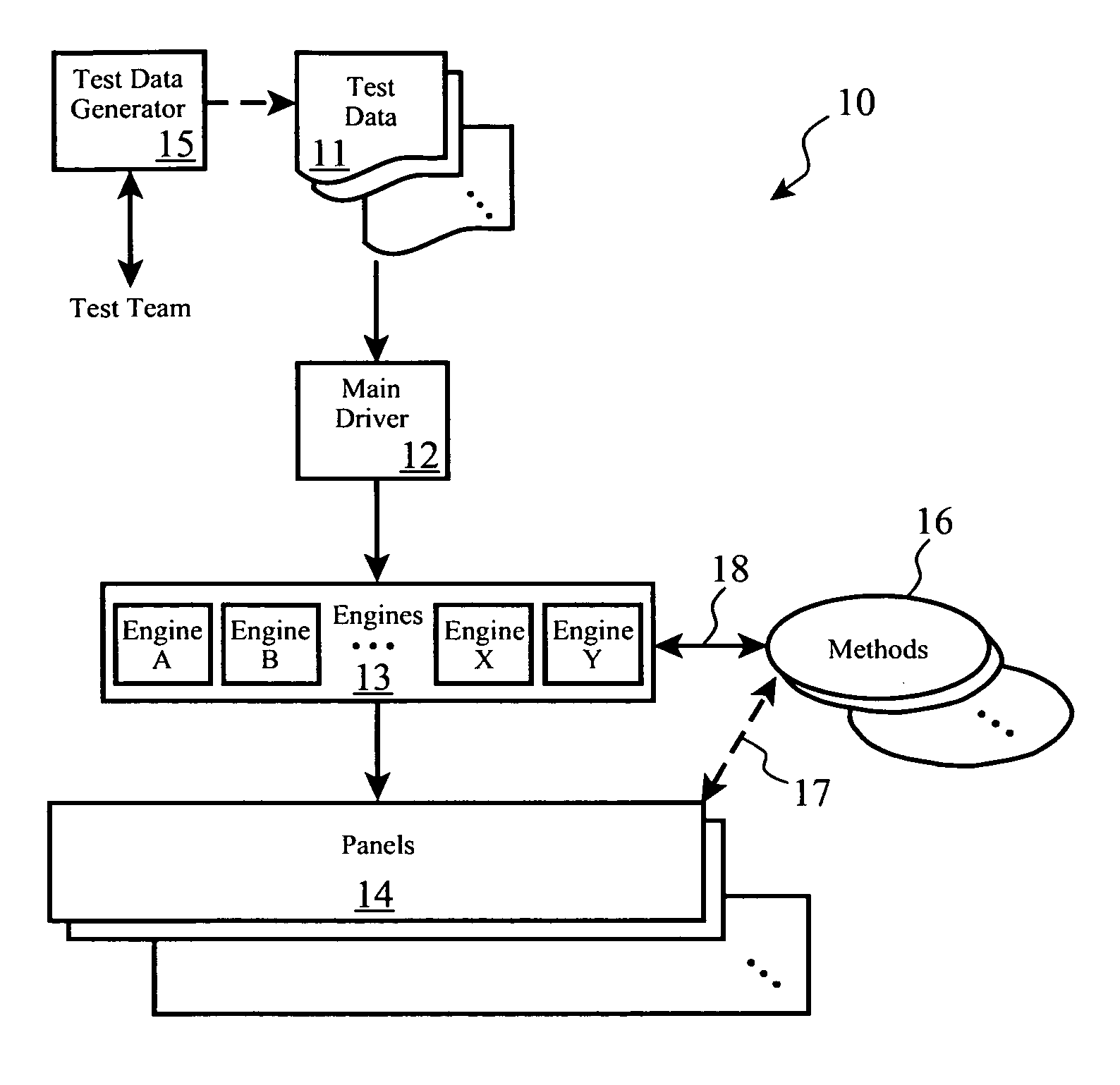
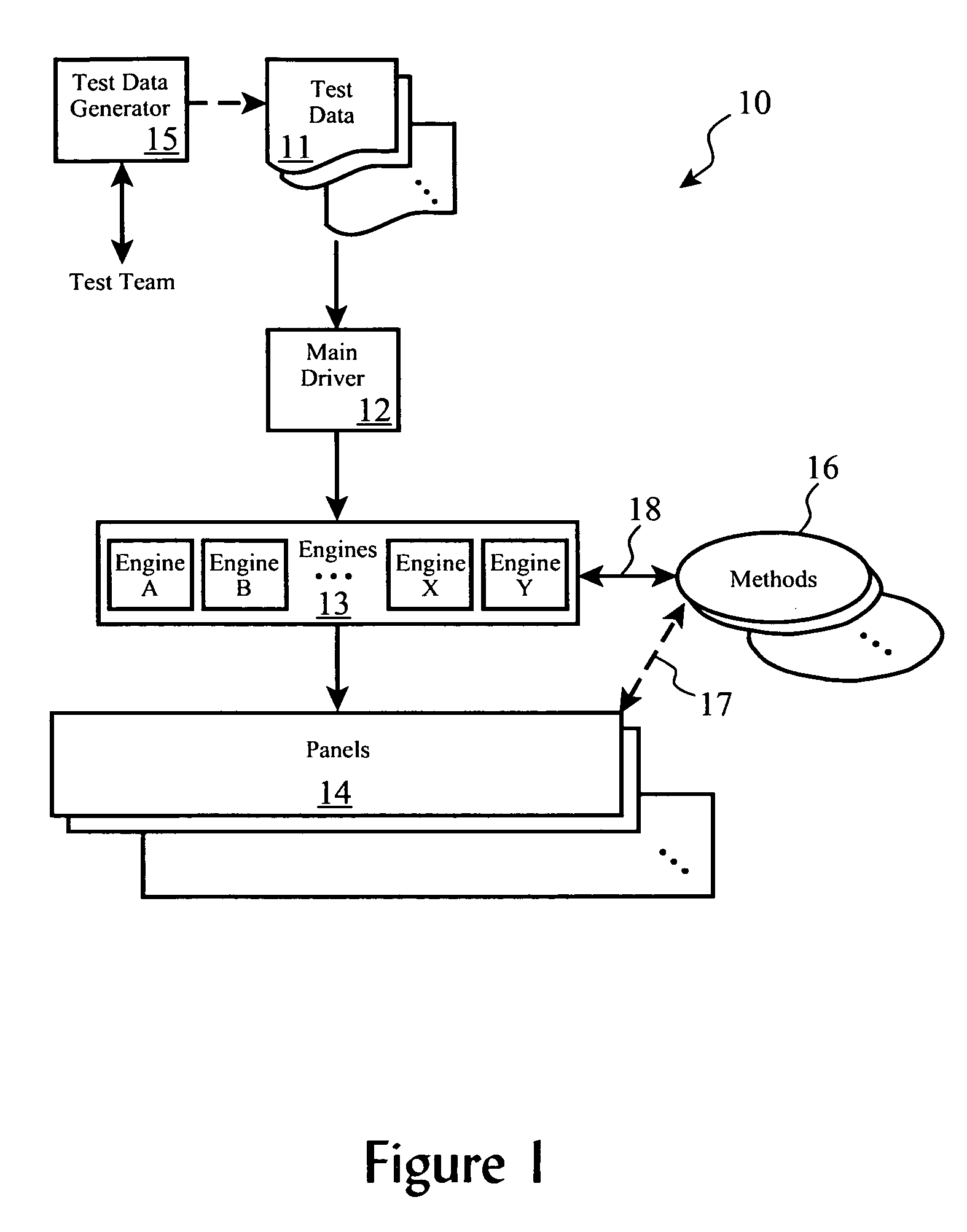
Automation structure for software verification testing
Functional testing of application software through exercising graphical user interface functions of the application software is automated and enhanced by providing one or more test data sets, one or more classes of panels in which each panel is described according to a set of graphical user interface objects and a set of corresponding methods, and one or more engines which encapsulate one or more test method calls or invocations. During testing and in cooperation with a functional test system, the test data sets are parsed to obtain individual test operations, which are then acting upon by invoking one or more of the engines in order to subject the application program to one or more test conditions. Results are logged, summarized, and optionally emailed to test personnel.
Owner:IBM CORP
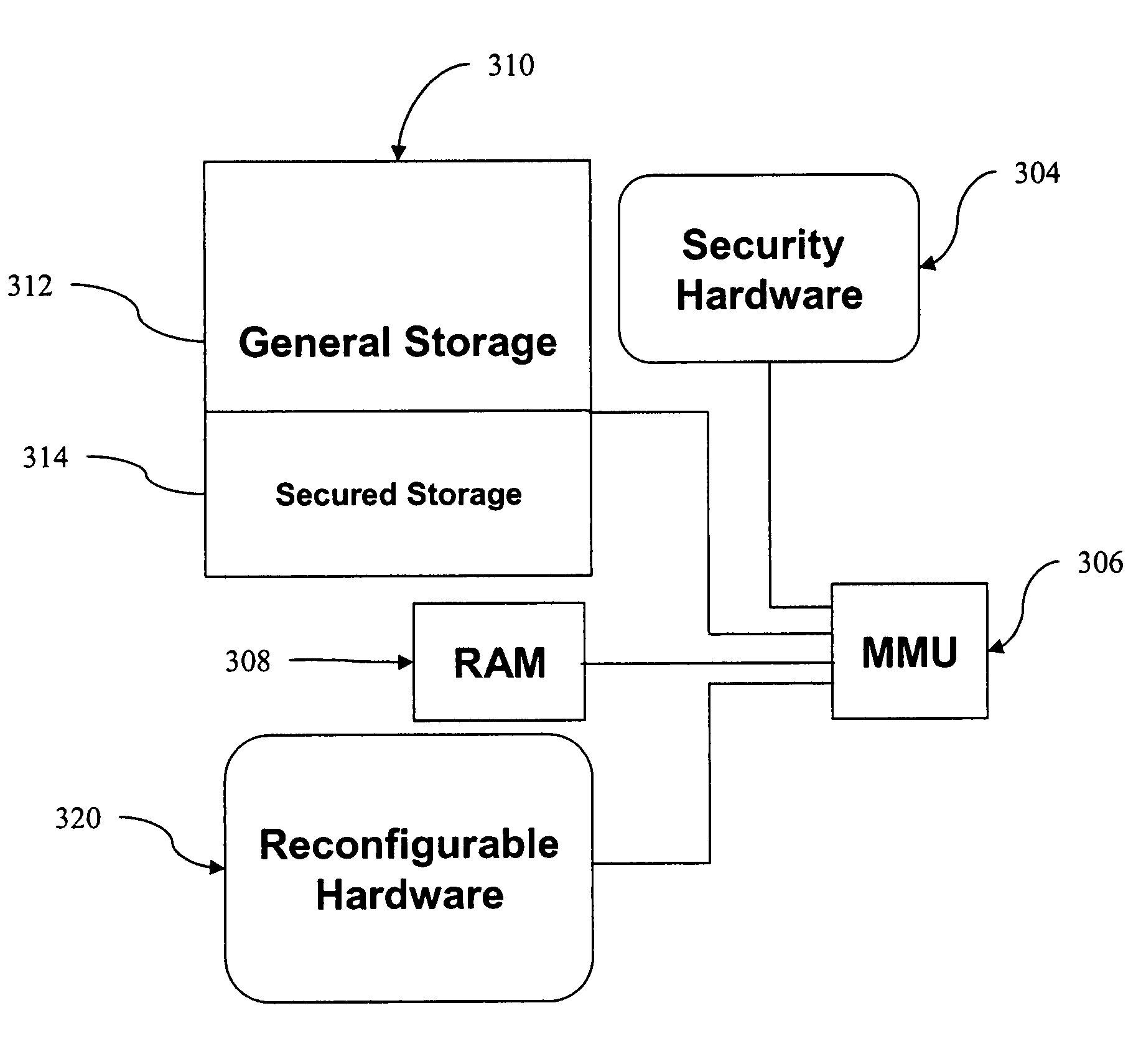
Using hardware to secure areas of long term storage in CE devices
InactiveUS7502946B2Digital data processing detailsUnauthorized memory use protectionOperational systemAuthorization
A system includes long-term storage (e.g., flash memory) for storing sensitive data and critical components of a consumer electronic (CE) device such as an operating system (OS) kernel, private cryptographic key values, security applications, and firmware configurations, for example. Security hardware / software designates and restricts access to secured portions of long-term storage that contain the critical components. Requests for access to these secured portions are addressed by the security hardware / software, which authenticates a cryptographic authorization code received with the request. Read-write access to the secured portions is allowed for download and installation of, for example, a software or firmware upgrade if the cryptographic authorization code is authenticated.
Owner:SOVEREIGN PEAK VENTURES LLC
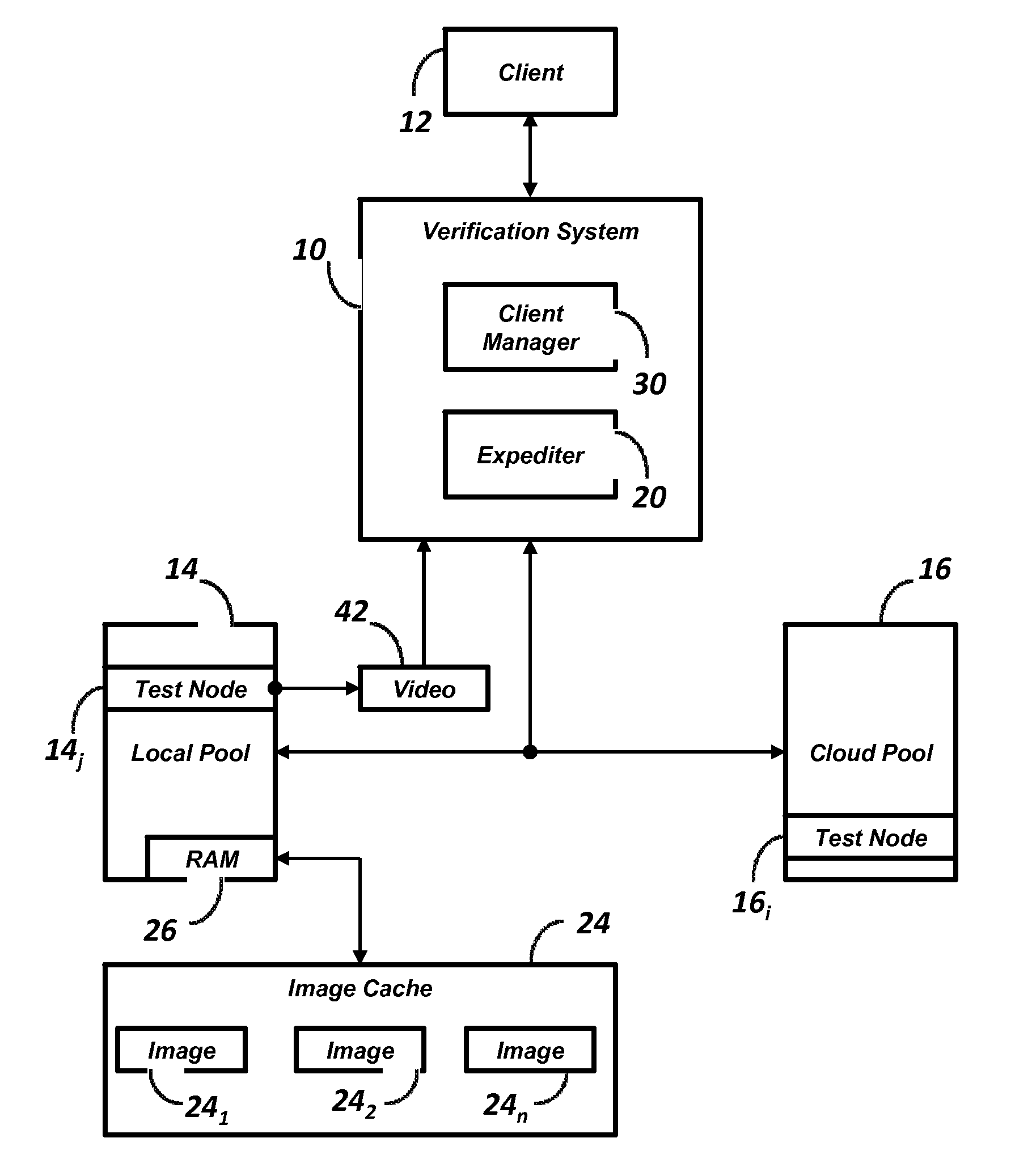
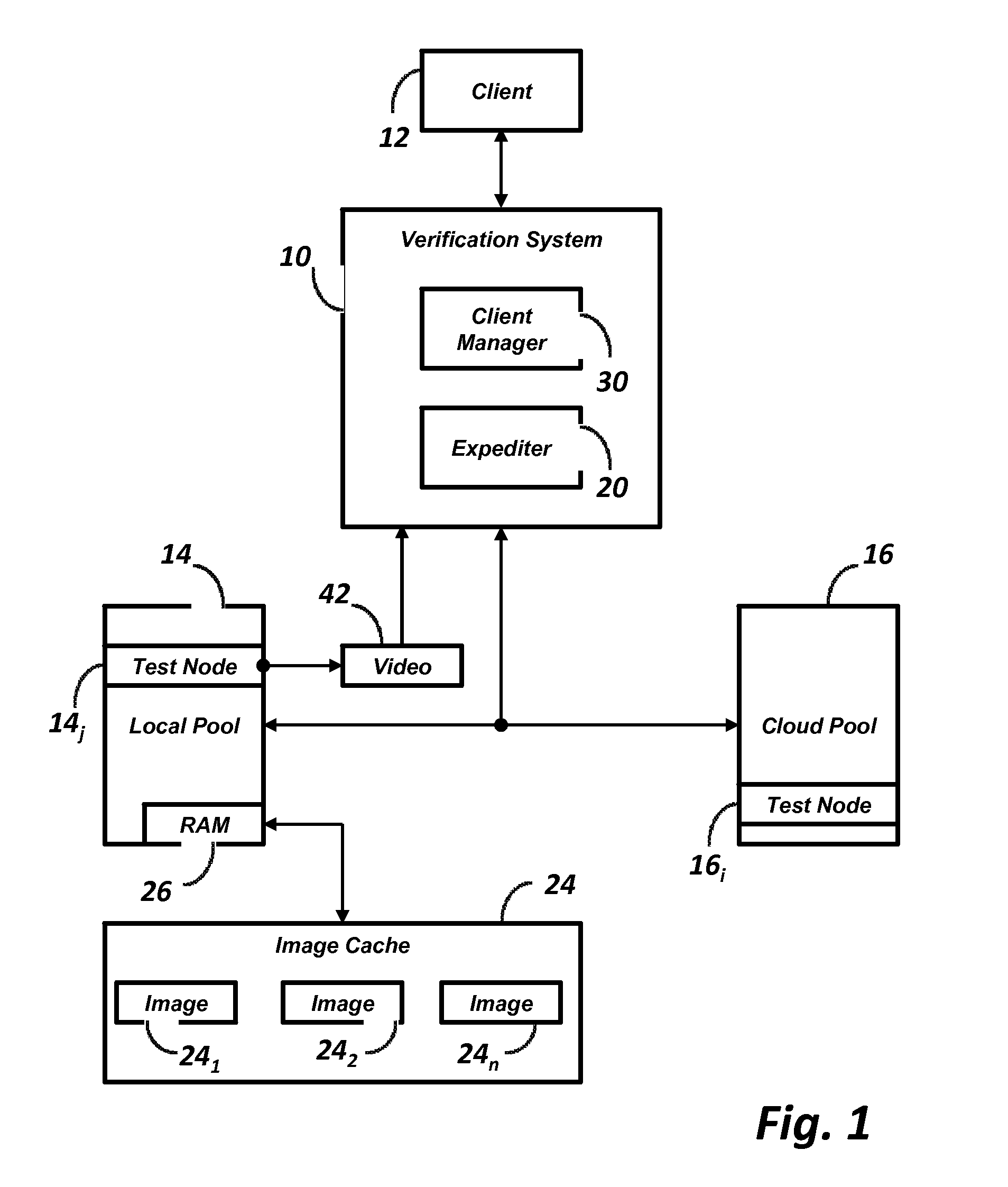
Real Time Verification of Web Applications
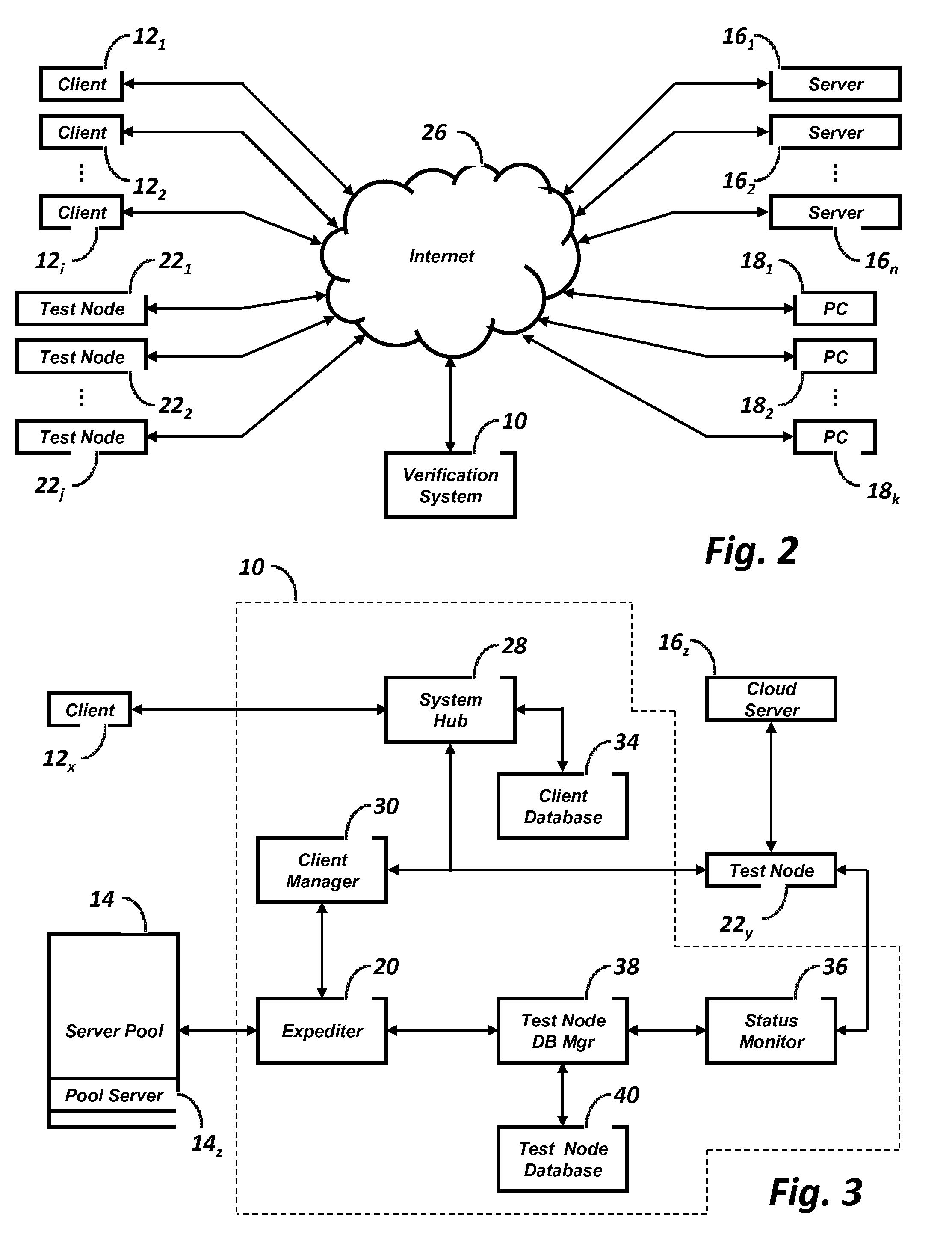
ActiveUS20120017210A1Reduce delaysEliminate needMultiple digital computer combinationsPlatform integrity maintainanceReal time validationWeb application
A software verification system including a cloud service, a plurality of test nodes, a client manager, and an expediter is disclosed. The cloud service is a commercially available shared resource service having two or more physical machines, each of which is configured to host a plurality of virtual machines. Each test node is one virtual machine running a platform. The client manager manages a verification session between one of the clients and the verification system. The expediter recognizes the available platforms for use by the test nodes in a cloud service pool of servers and a local pool of servers. When a clients requests the verification session to use a specific platform, the expediter obtains a network address of an available test node running the specified platform and connects the requesting client to the available test node running the requested platform. If the requested platform is not available, a new virtual machine, located in the local pool of servers, having the requested platform is started and connected with the requesting client.
Owner:SAUCE LABS
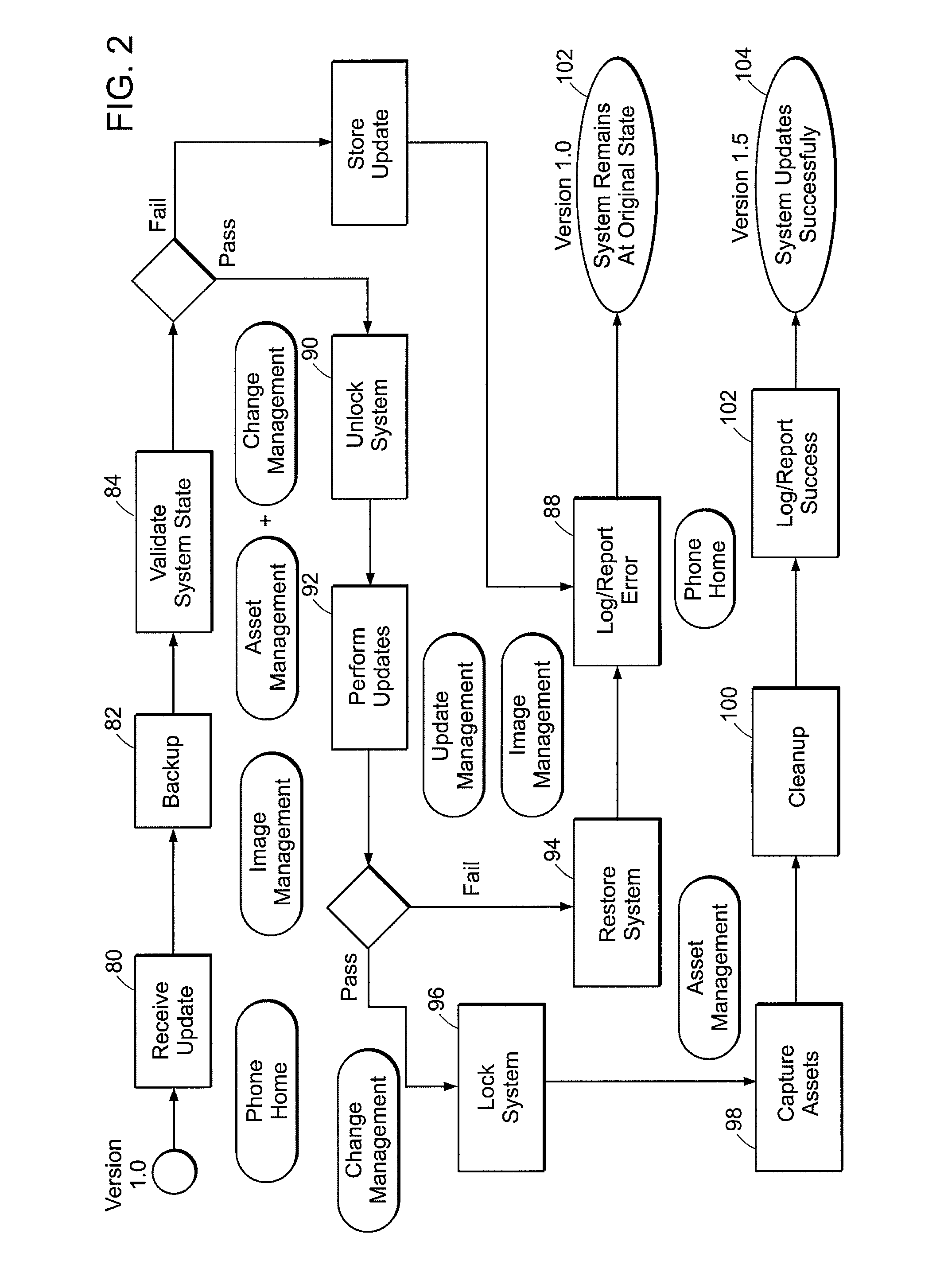
Methods and apparatus for life-cycle management
InactiveUS20080222604A1Preventing minimizing riskReduce stepsPlatform integrity maintainanceResourcesDigital dataSoftware update
The invention provides in some aspects a digital data processor executing management software that controls overall operation of the device, including, installation, configuration, updating, and / or other modifications of its software, hardware and configuration files and other “assets.” The management software validates changes to those assets (e.g., software updates and configuration file edits) requested by system administrators and others and can propagate related changes to other assets. As a result, it keeps the digital data processor in a consistent, working state, avoiding operational interruption that might otherwise result from corruption of assets (e.g., lost files) and / or attempts to install inconsistent assets. The management software can serve as an agent for one or more external digital data processing devices that are in communications coupling with the managed digital data processing device, which one or more external digital data processing devices mediate installation, configuration, updating, modification and / or use of the one or more assets.
Owner:UNICOM ENG INC
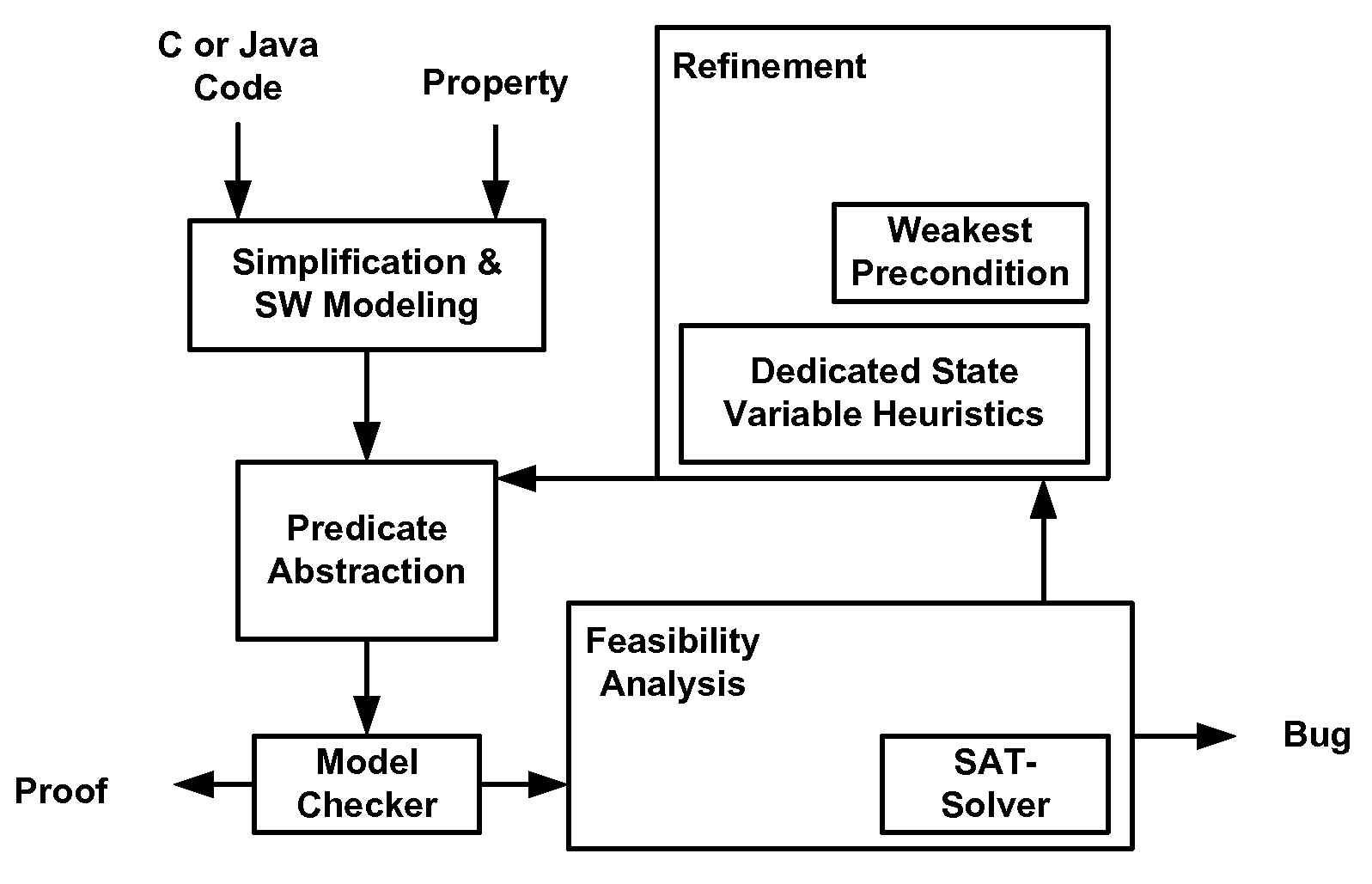
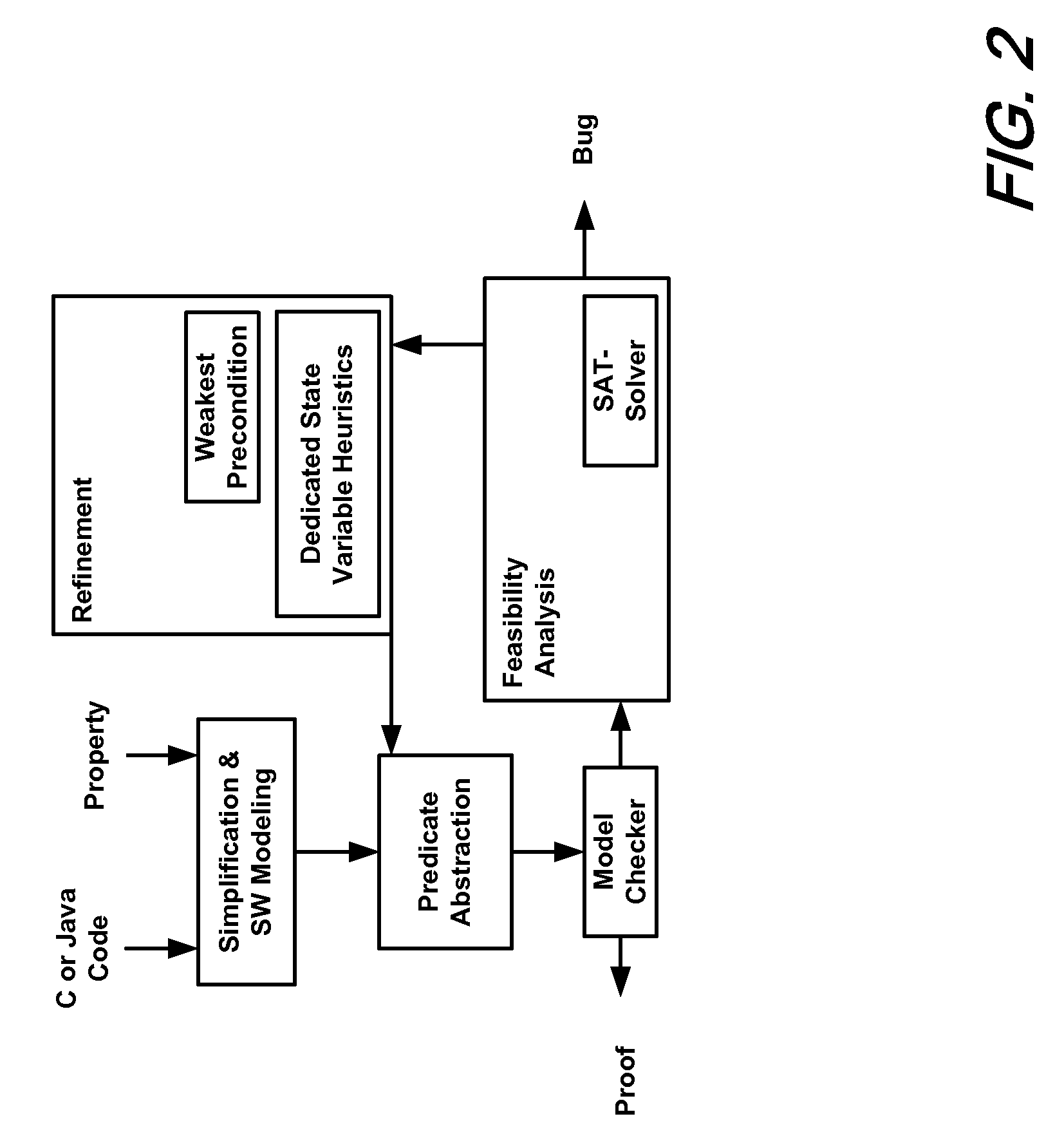
Software verification
InactiveUS20060282807A1Improve performanceEfficiency of the abstraction computation is advantageously increasedError detection/correctionSoftware simulation/interpretation/emulationVerification systemSoftware
A system and method is disclosed for formal verification of software programs that advantageously improves performance of an abstraction-refinement loop in the verification system.
Owner:NEC CORP
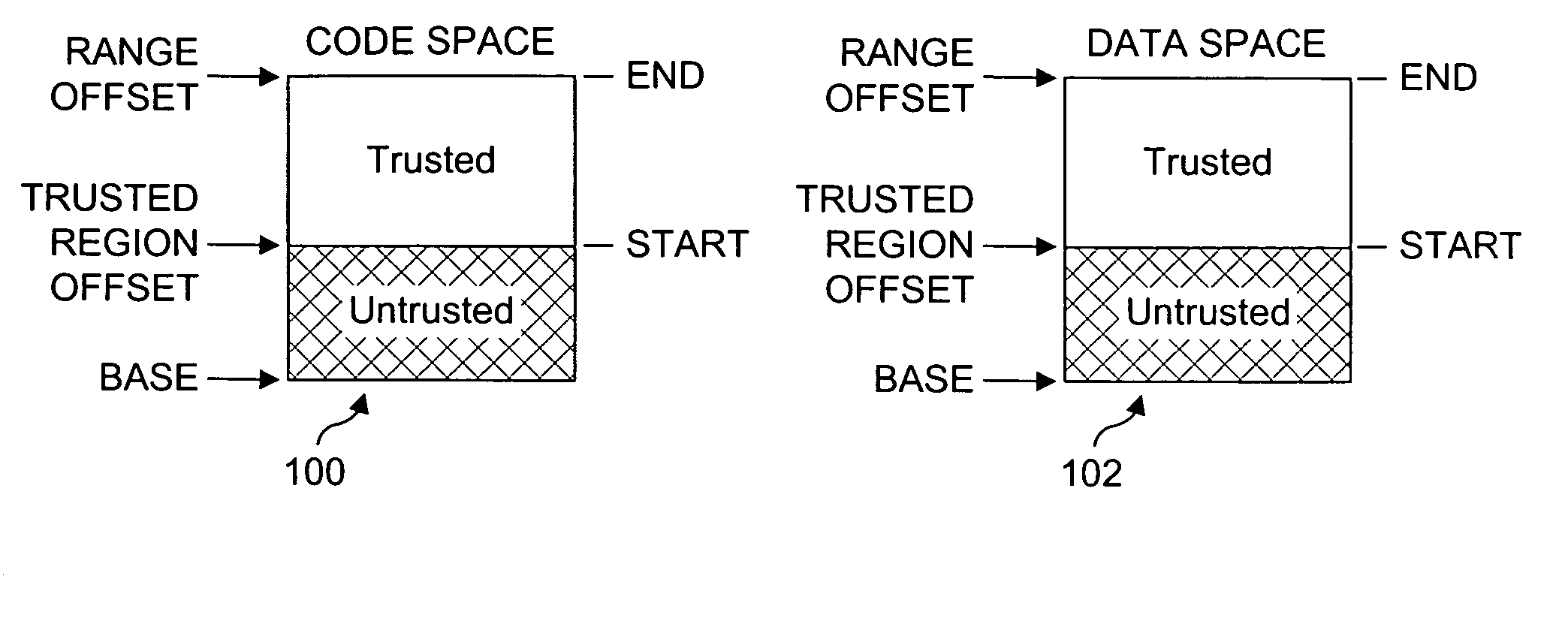
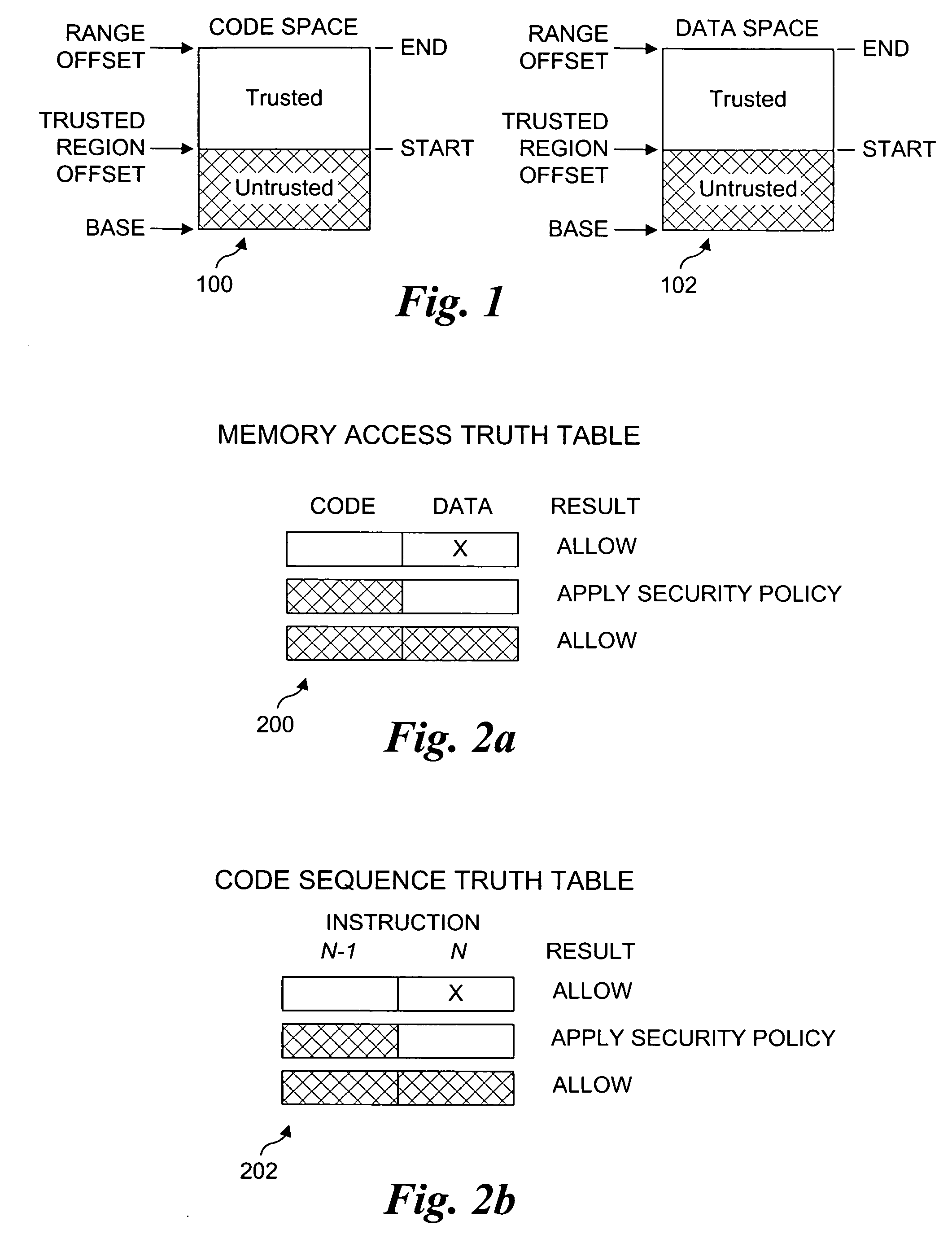
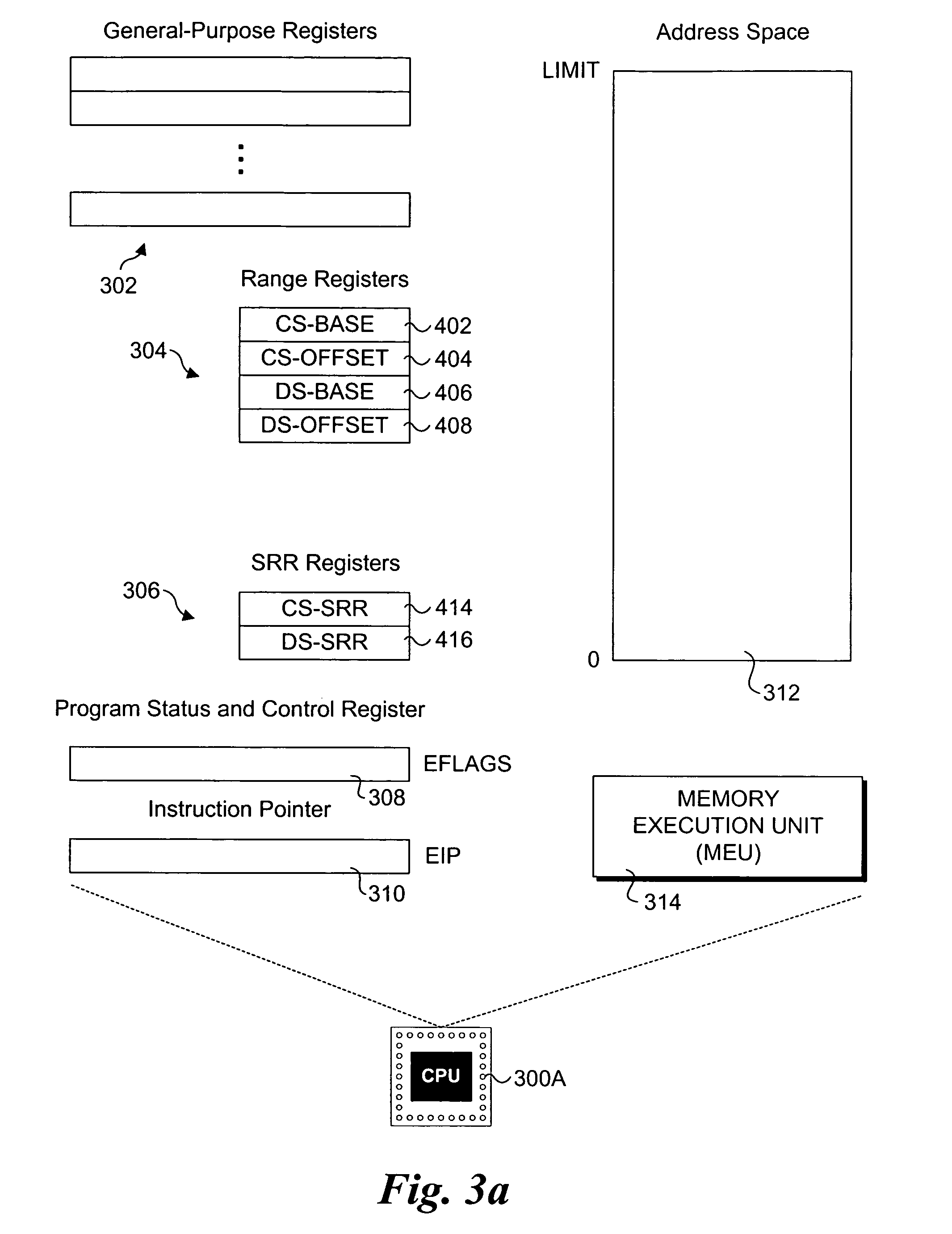
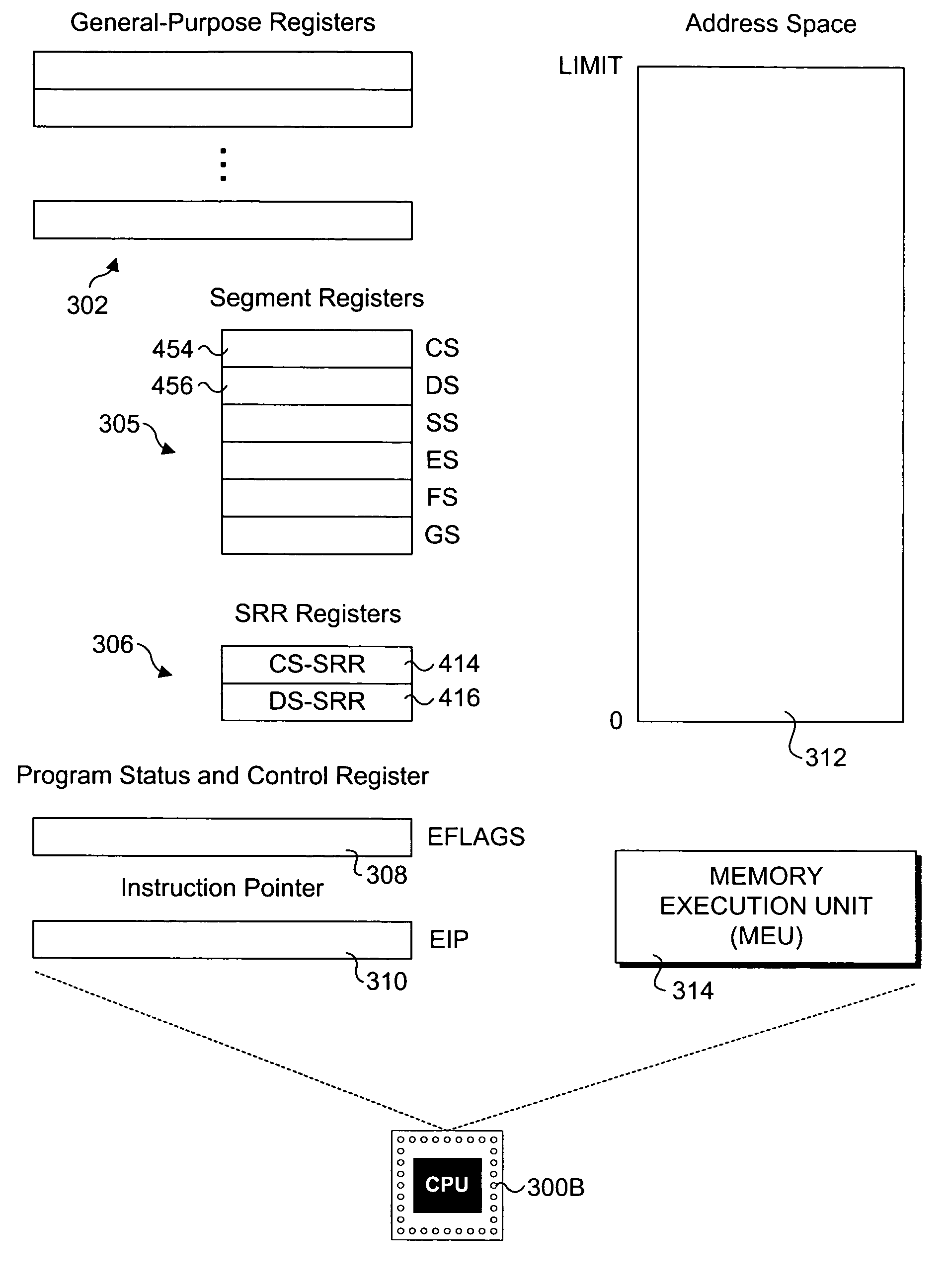
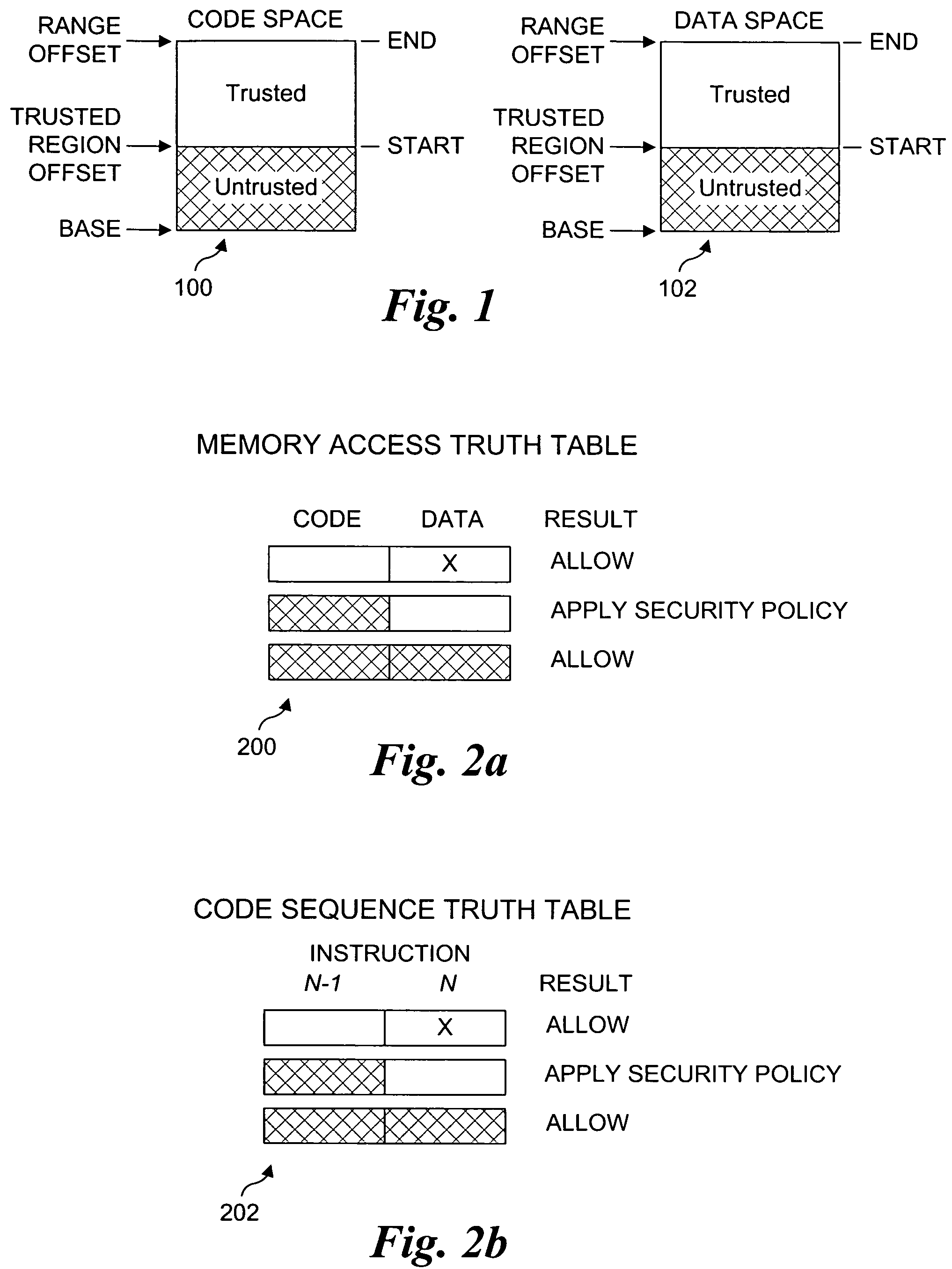
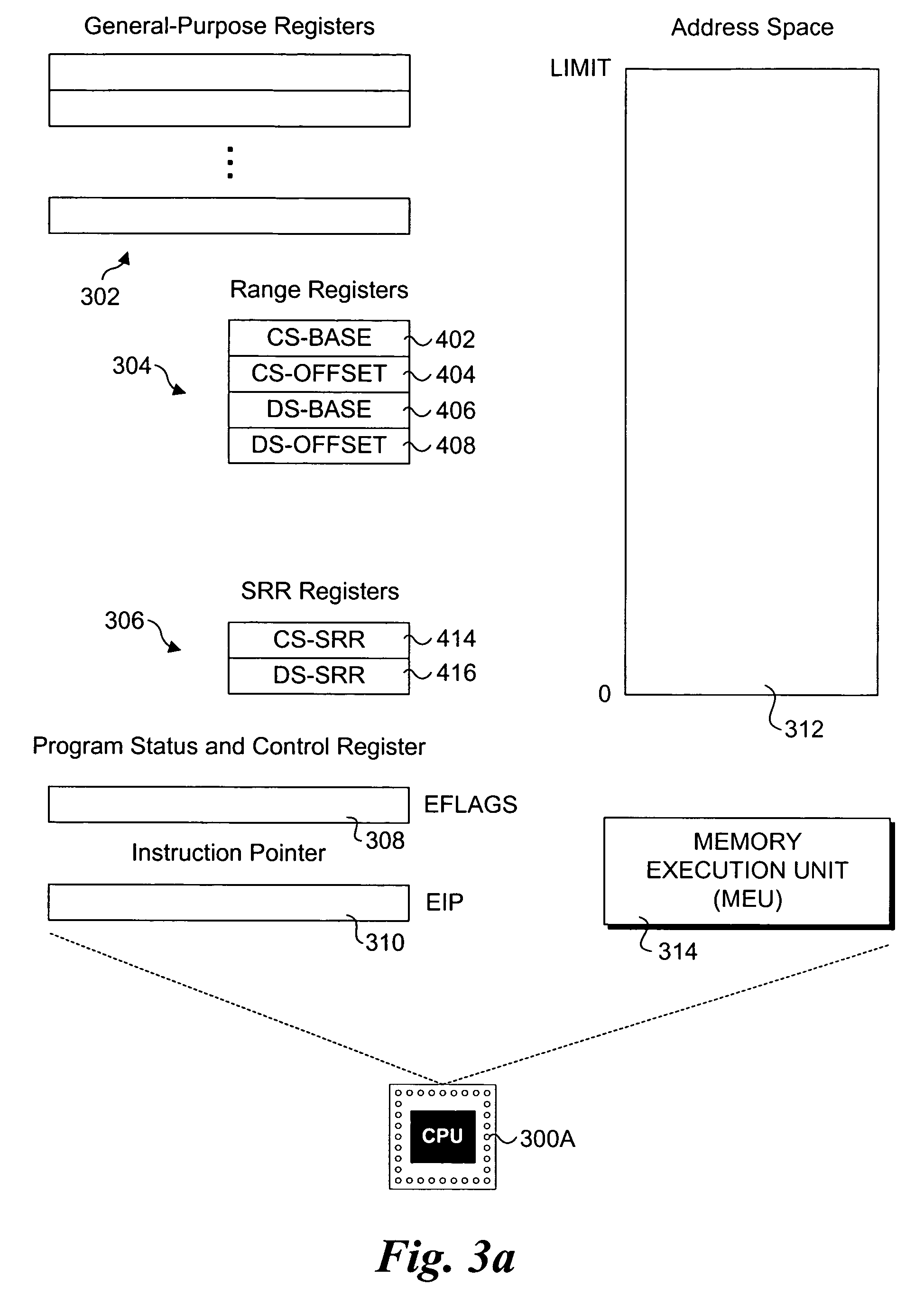
Processor extensions and software verification to support type-safe language environments running with untrusted code
Processor extensions and software verification to support type-safe language environments running with untrusted code. Code and data spaces are partitioned into trusted and untrusted regions. Type-safe code is loaded into the trusted region of the code space, while non-type-safe code is loaded into the untrusted region of the code space. The trusted region of the data space is allocated to the type-safe code. The untrusted region of the data space is allocated to the non-type-safe code. Hardware-based truth tables are employed for defining allowable and disallowable code sequences and memory access operations. For code sequences, allowable operations are based on the location (i.e., region) of a code sequence including a current instruction and a prior instruction. For memory access, the location of the requesting instruction and data requested are considered. Disallowed code sequence or memory access operations cause the processor to generate a safe access protection trap. In response to the safe access protection trap, a software-based dynamic verifier applies a security policy to determine whether to allow the operation to proceed.
Owner:INTEL CORP
Software verification system, method and computer program element
InactiveUS20030135746A1Great confidenceImprove securityUser identity/authority verificationUnauthorized memory use protectionDigital signatureApplication software
A software security system is arranged to verify the authenticity of each element of a Java Virtual Machine installation. A digital signature is attached to each file of the JVM installation. A loader (20) verifies the digital signature of the JVM DLL (30). The JVM DLL 30 then verifies the digital signature of each other DLL and configuration file to be loaded (40, 50, 60, 70), and only loads those files which have successfully verified digital signatures. In this way the security of the JVM is enhanced, a user has greater confidence that the Java applications will function correctly, and the detection of incorrect or damaged JVM installations is improved.
Owner:TREND MICRO INC
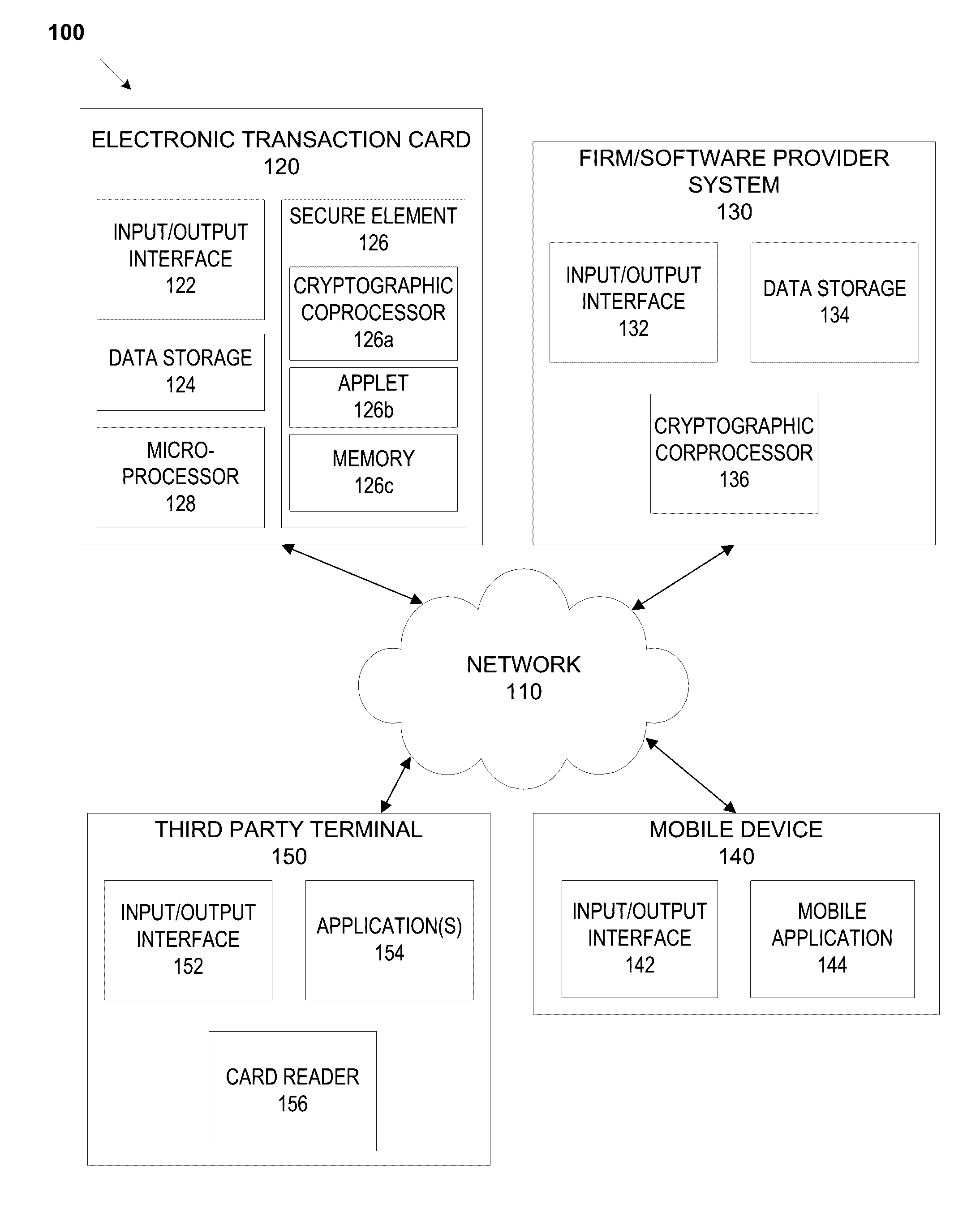
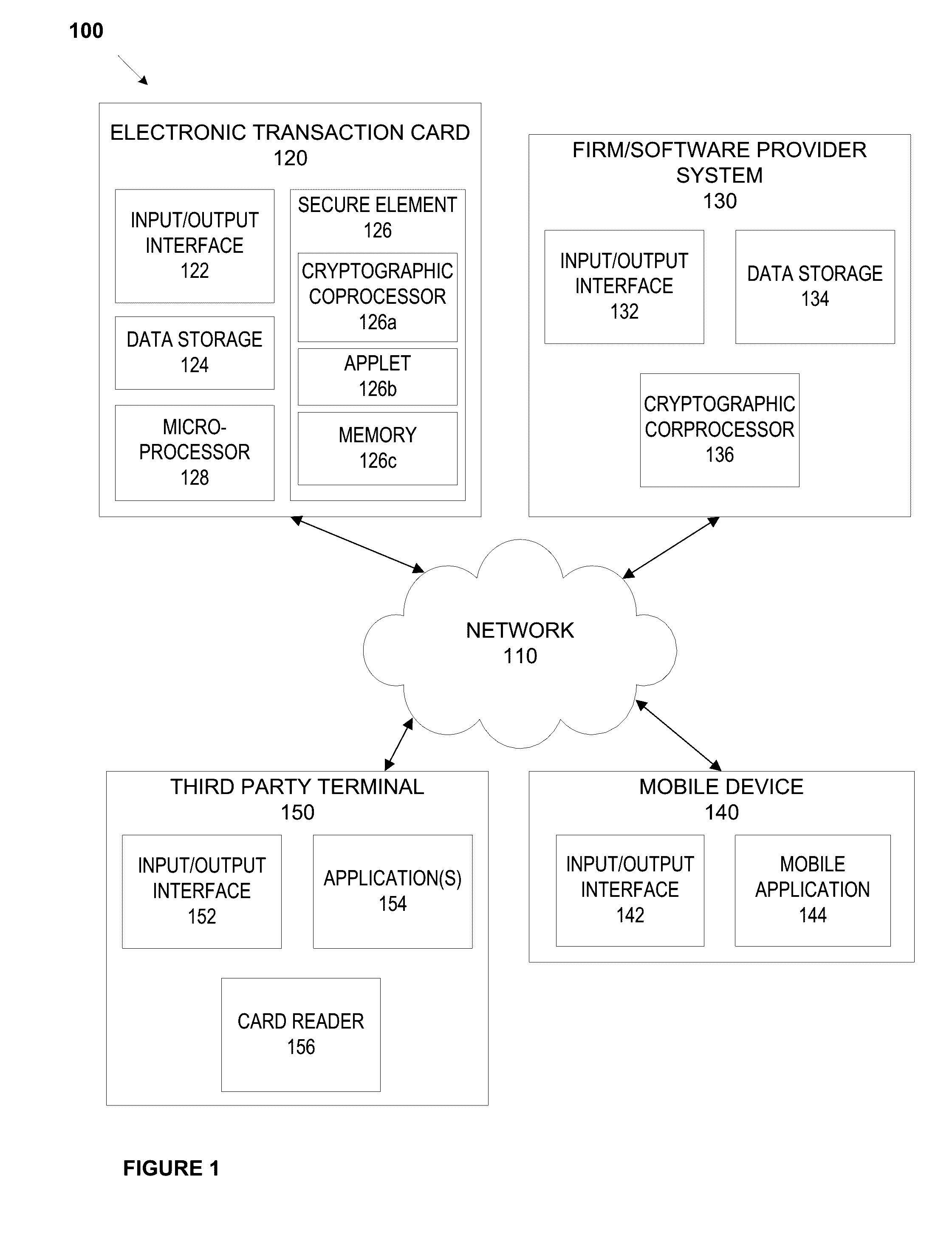
System and methods for secure firmware validation
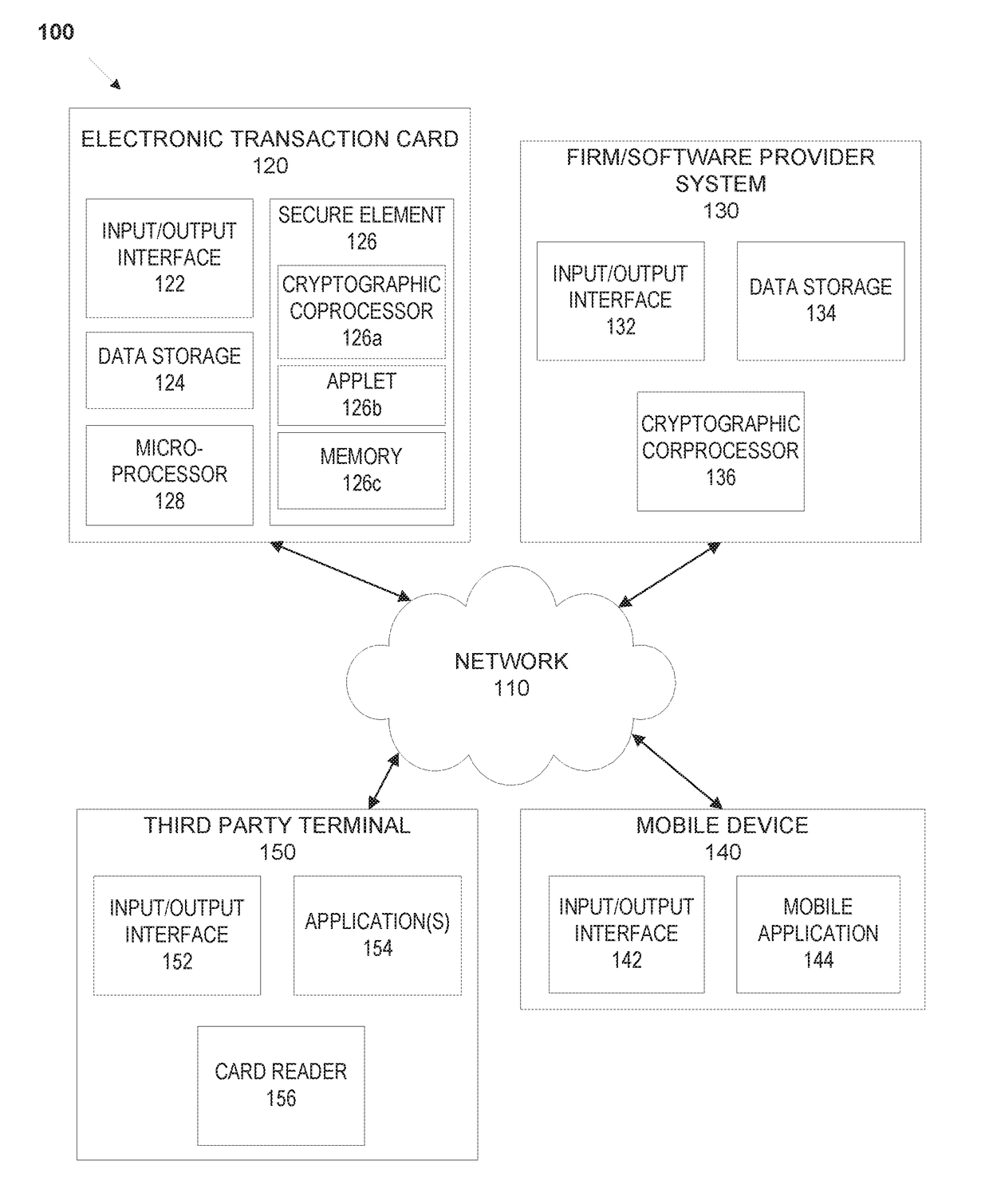
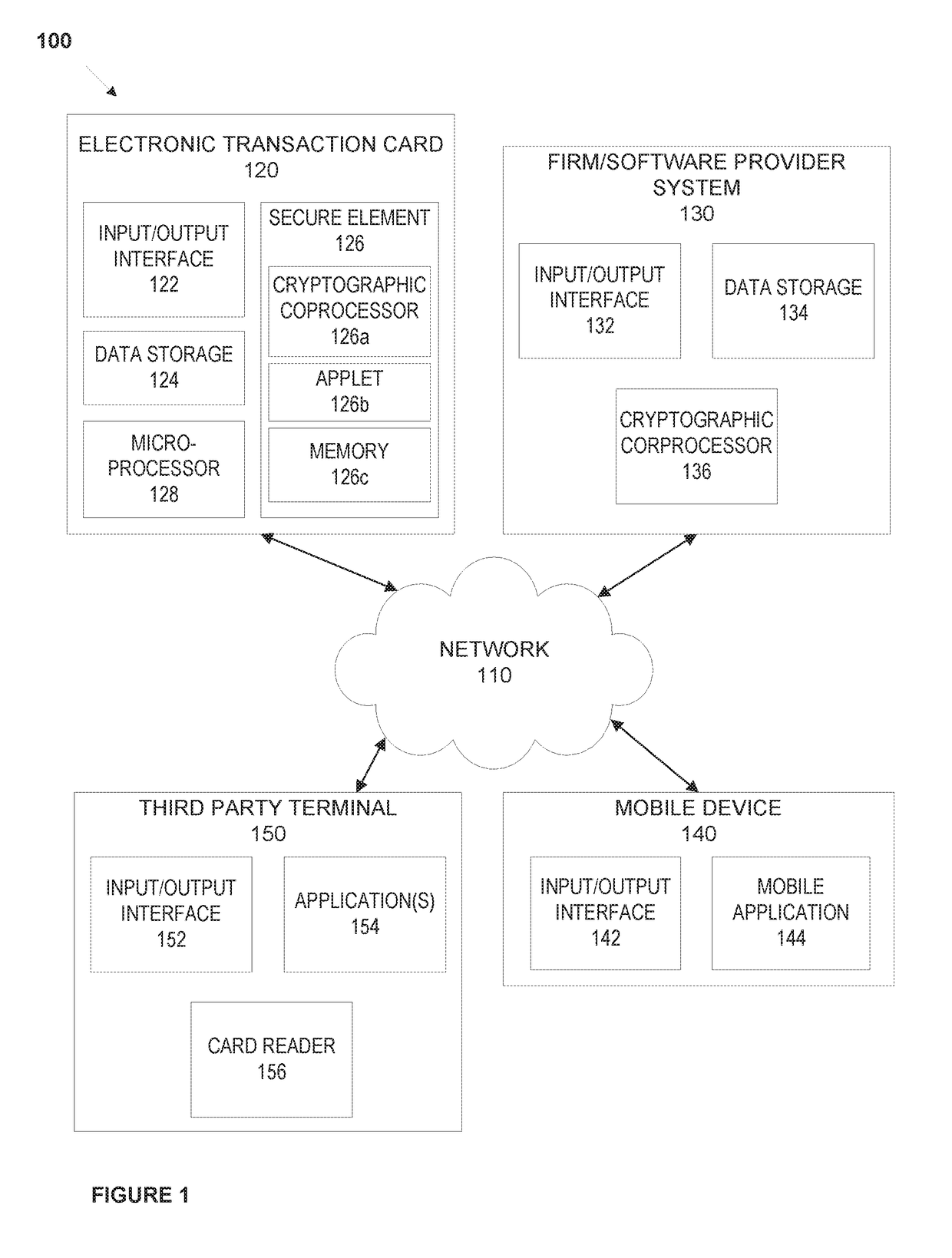
ActiveUS20160306977A1Internal/peripheral component protectionBootstrappingCoprocessorSoftware update
An electronic device, such as a dynamic transaction card having an EMV chip, that acts as a TPM having a memory, an applet, and a cryptographic coprocessor performs secure firmware and / or software updates, and performs firmware and / or software validation for firmware and / or software that is stored on the electronic device. Validation may compare a calculated checksum with a checksum stored in EMV chip memory. If a checksum calculated for firmware and / or a software application matches a checksum stored in EMV chip memory of the transaction card, the transaction card may operate normally. If a checksum calculated for firmware and / or a software application does not match a checksum stored in EMV chip memory of the transaction card, the transaction card may freeze all capabilities, erase the memory of the transaction card, display data indicative of a fraudulent or inactive transaction card, and / or the like.
Owner:CAPITAL ONE SERVICES
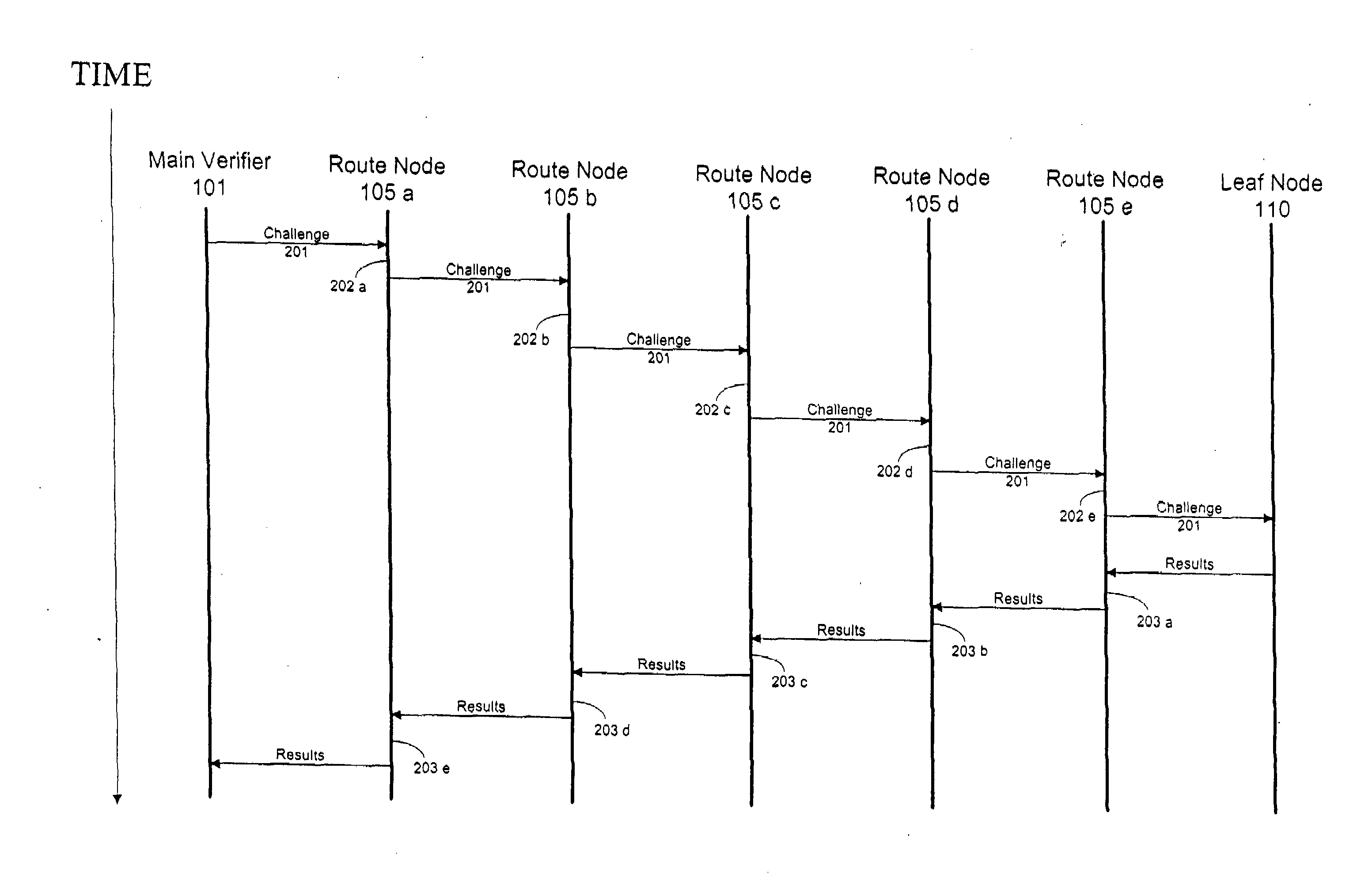
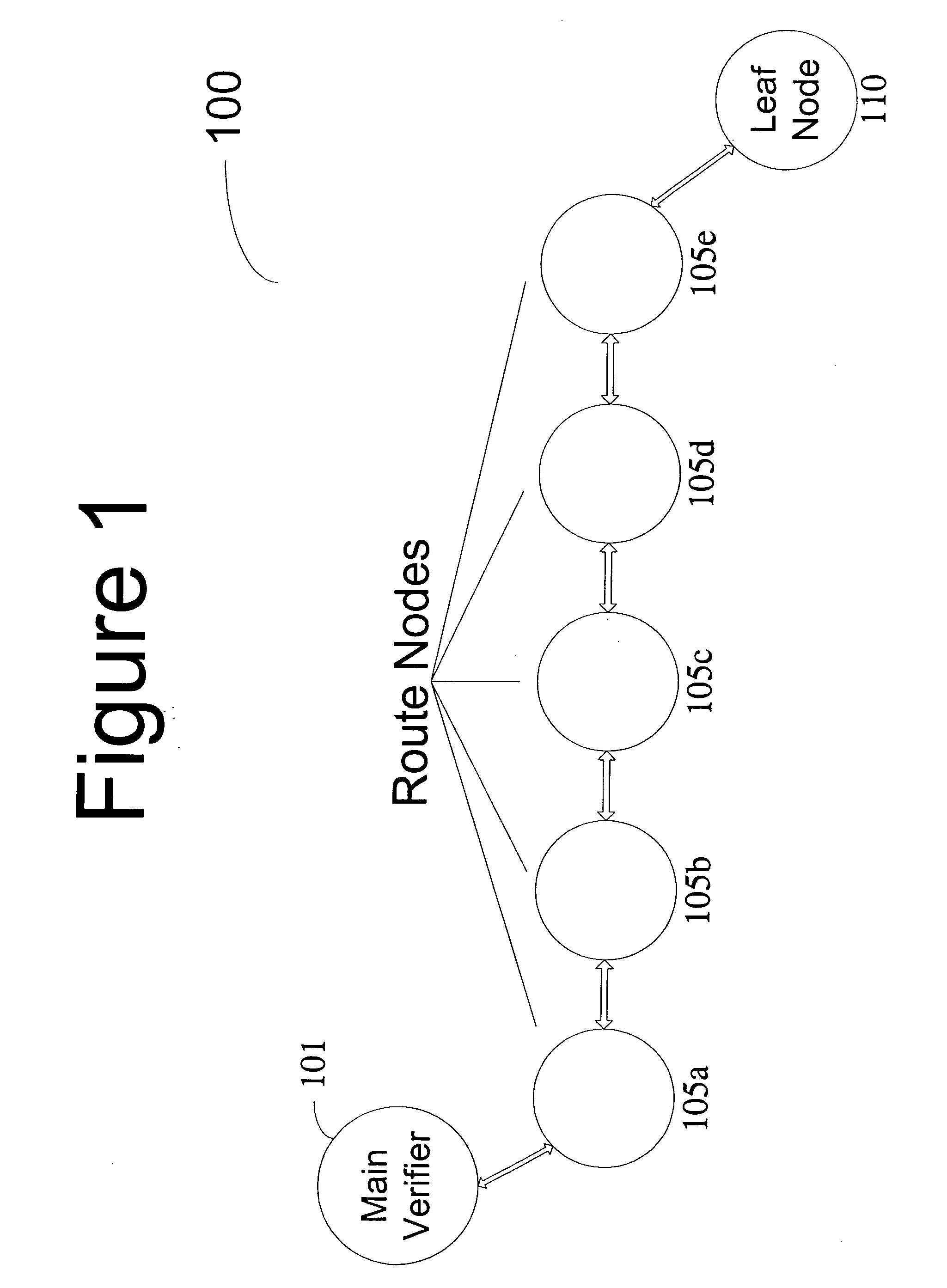
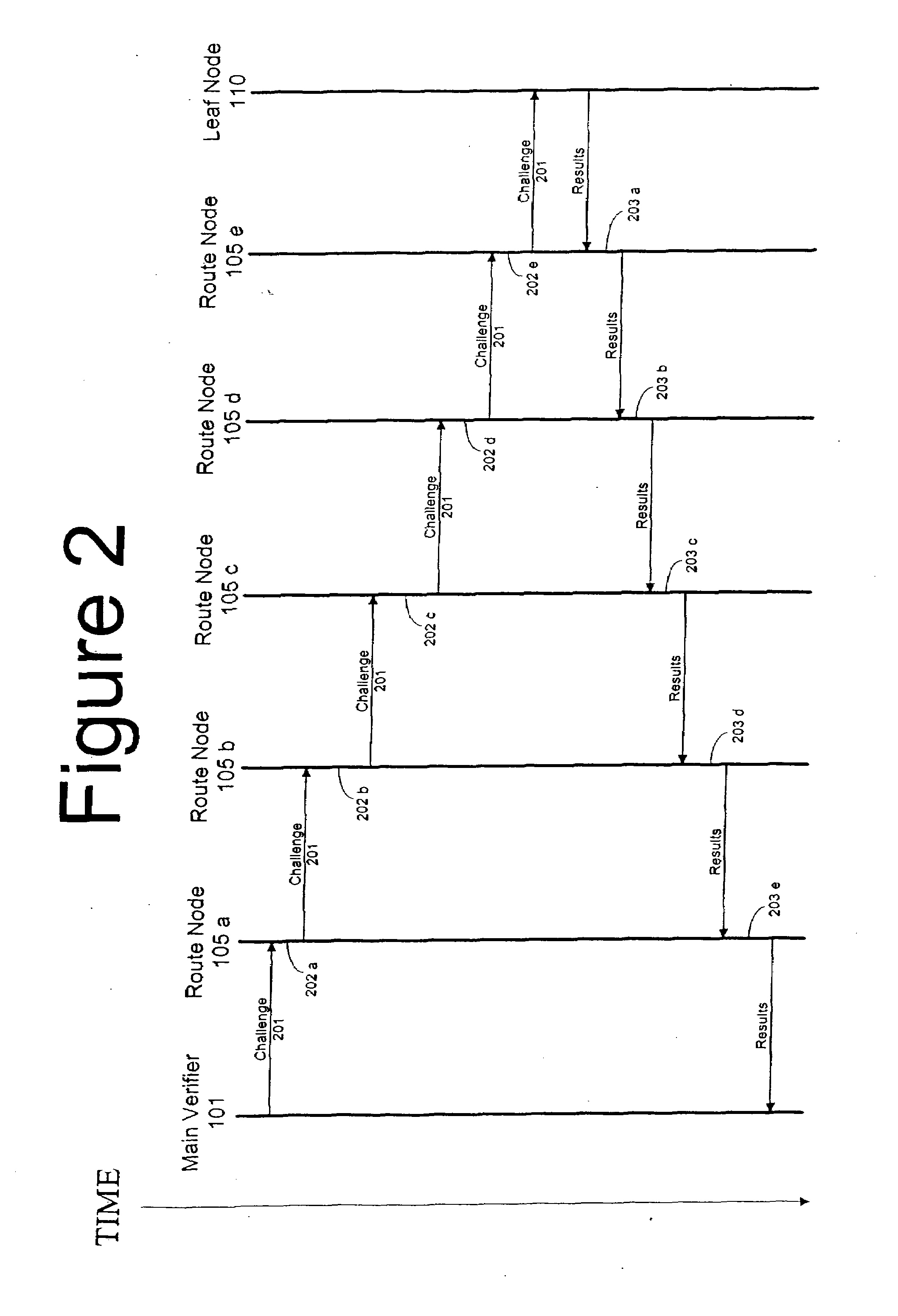
Method and computer product to increase accuracy of time-based software verification for sensor networks
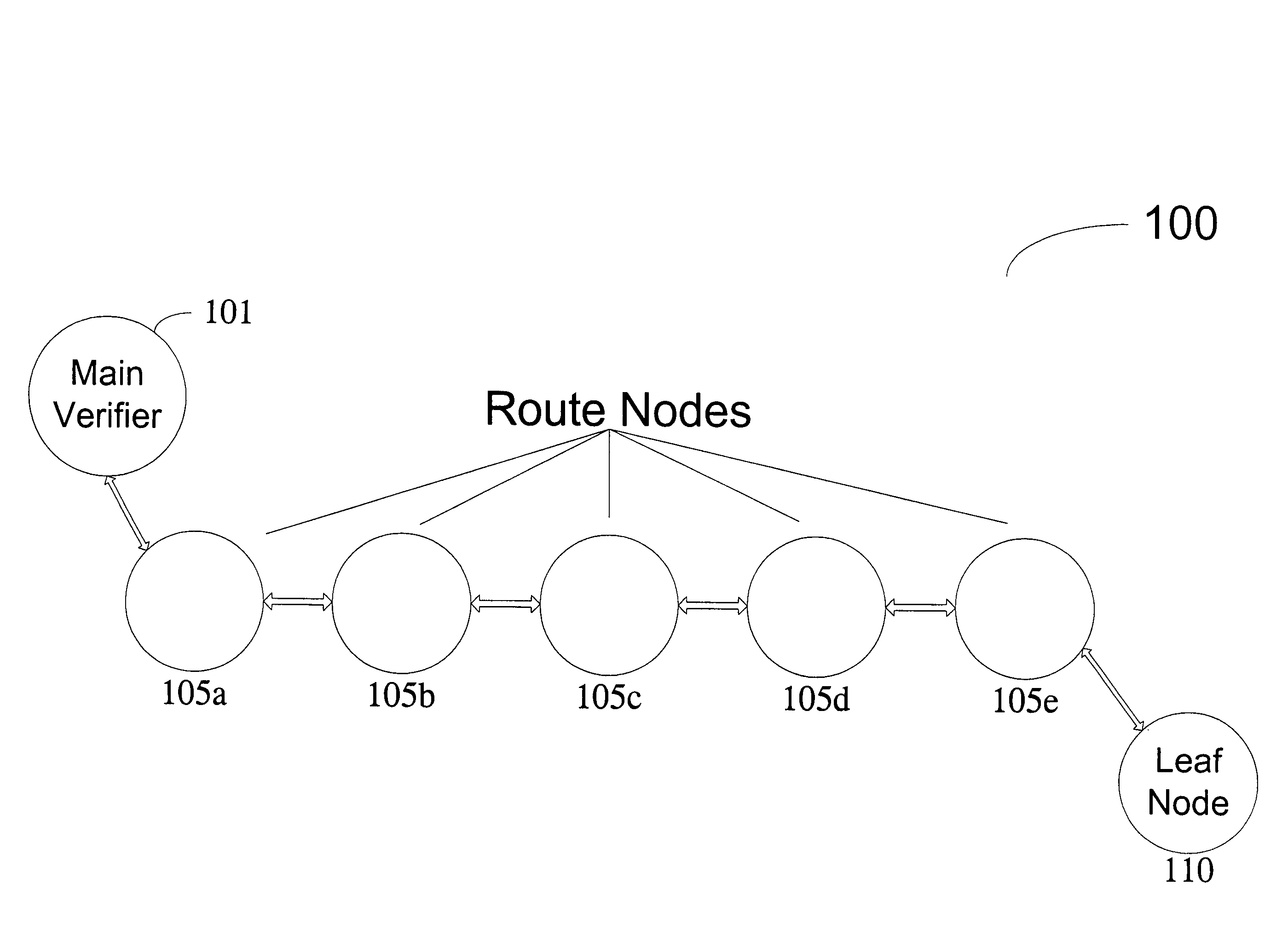
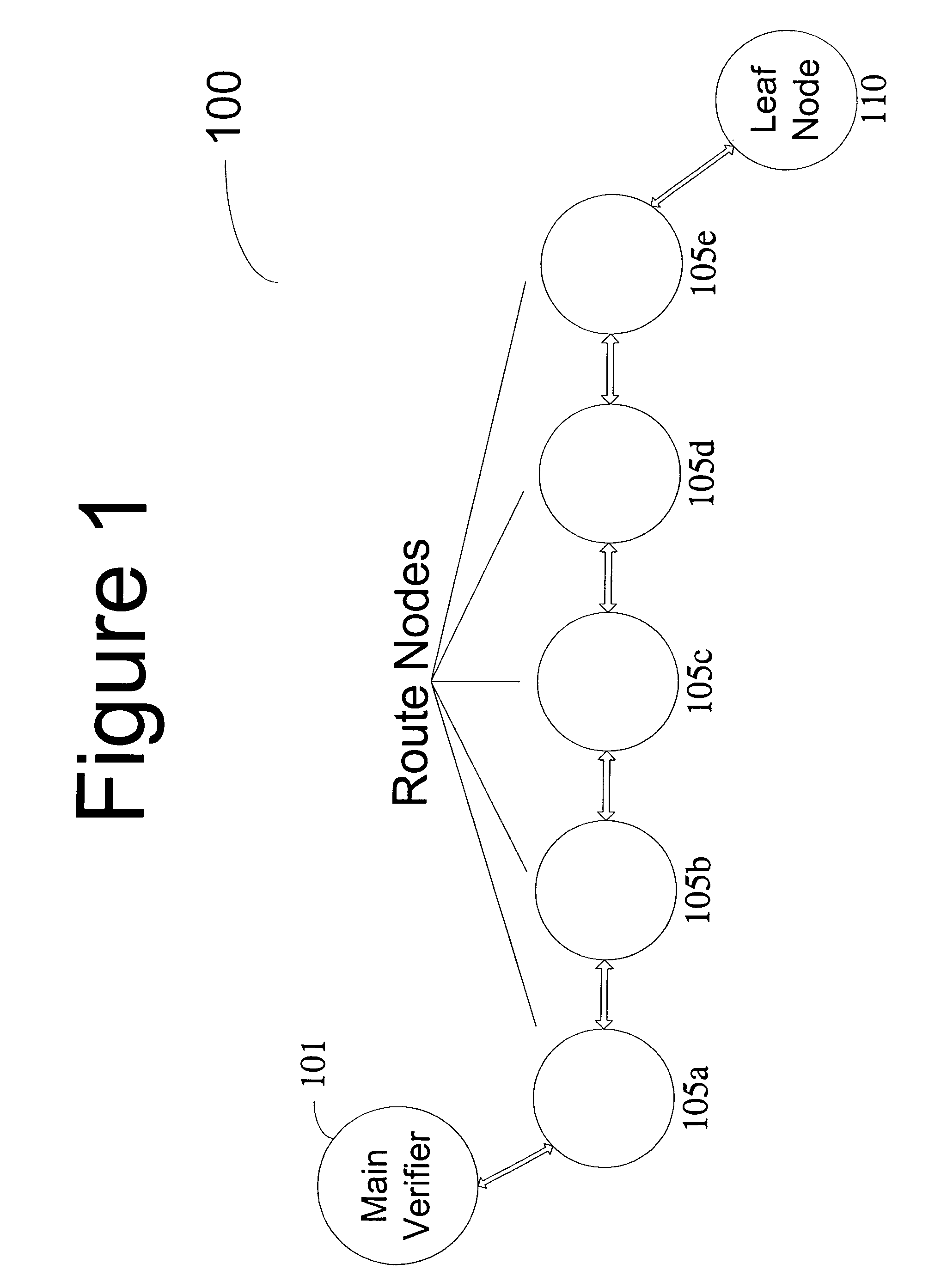
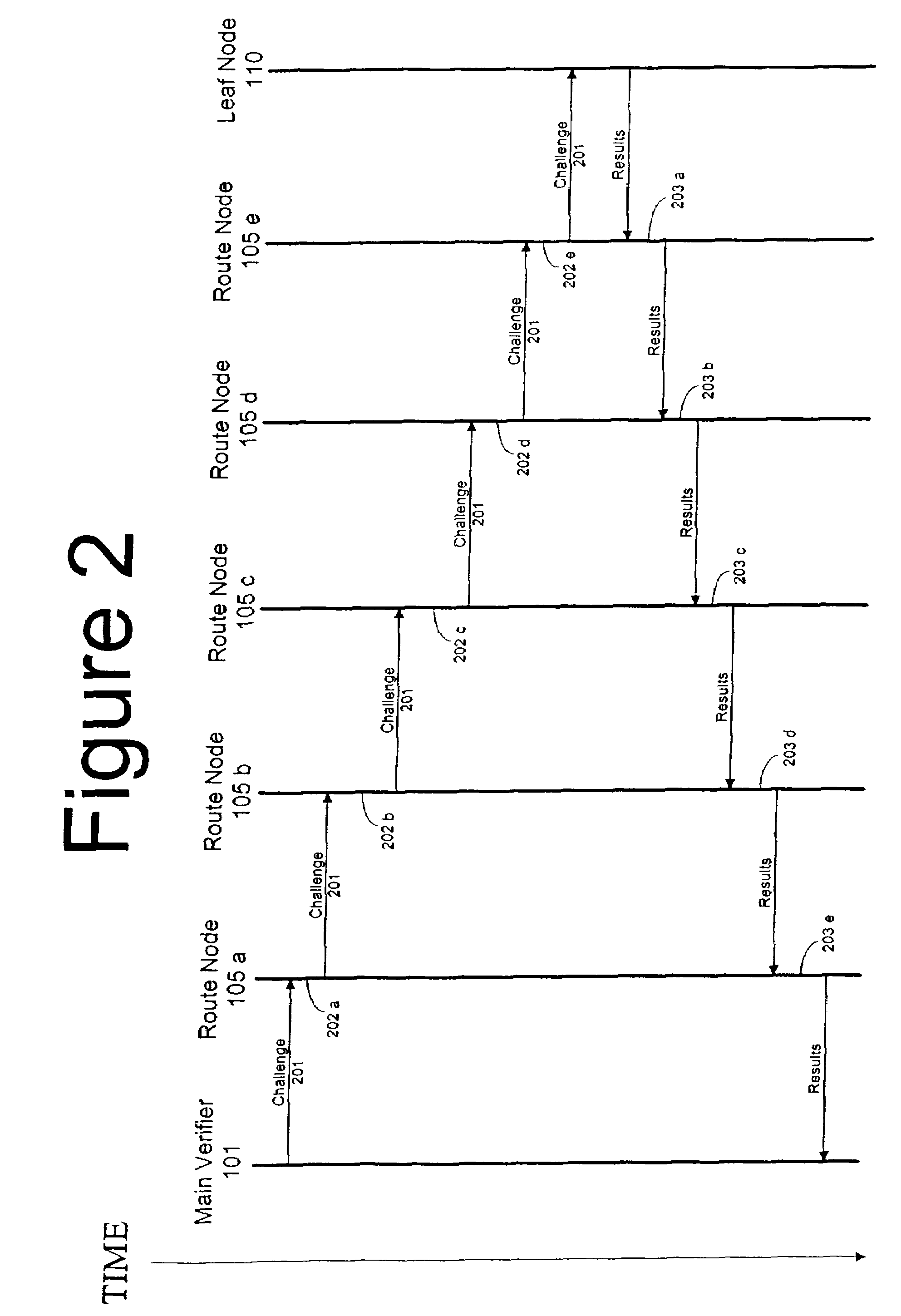
InactiveUS7877596B2Accurate verificationMinimum time delayUser identity/authority verificationMultiple digital computer combinationsLine sensorMinimum time
A recursive verification protocol to reduce the time variance due to delays in the network by putting the subject node at most one hop from the verifier node provides for an efficient manner to test wireless sensor nodes. Since the software signatures are time based, recursive testing will give a much cleaner signal for positive verification of the software running on any one node in the sensor network. In this protocol, the main verifier checks its neighbor, who in turn checks its neighbor, and continuing this process until all nodes have been verified. This ensures minimum time delays for the software verification. Should a node fail the test, the software verification downstream is halted until an alternative path (one not including the failed node) is found. Utilizing techniques well known in the art, having a node tested twice, or not at all, can be avoided.
Owner:HONEYWELL INT INC
System and method for realizing software protection
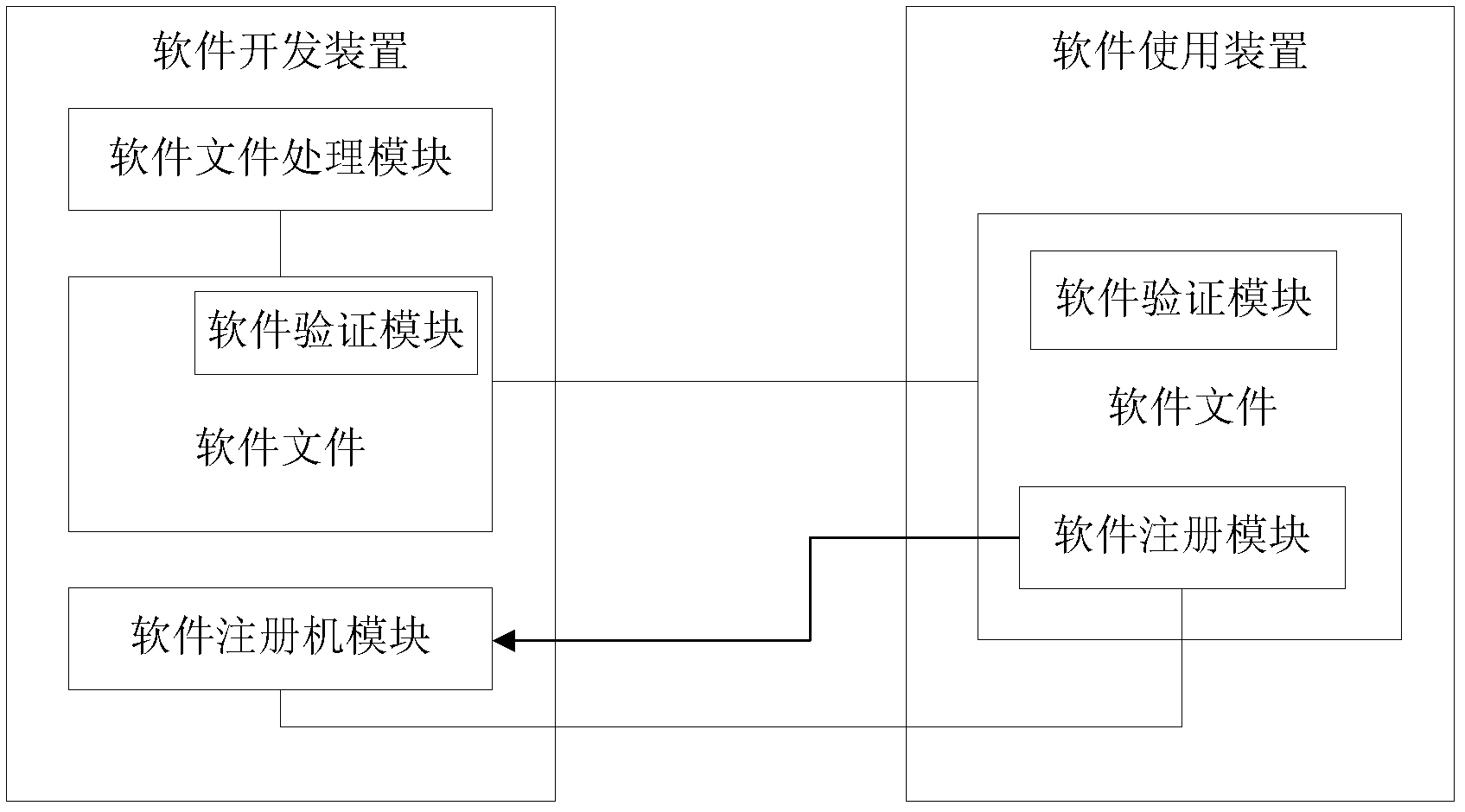
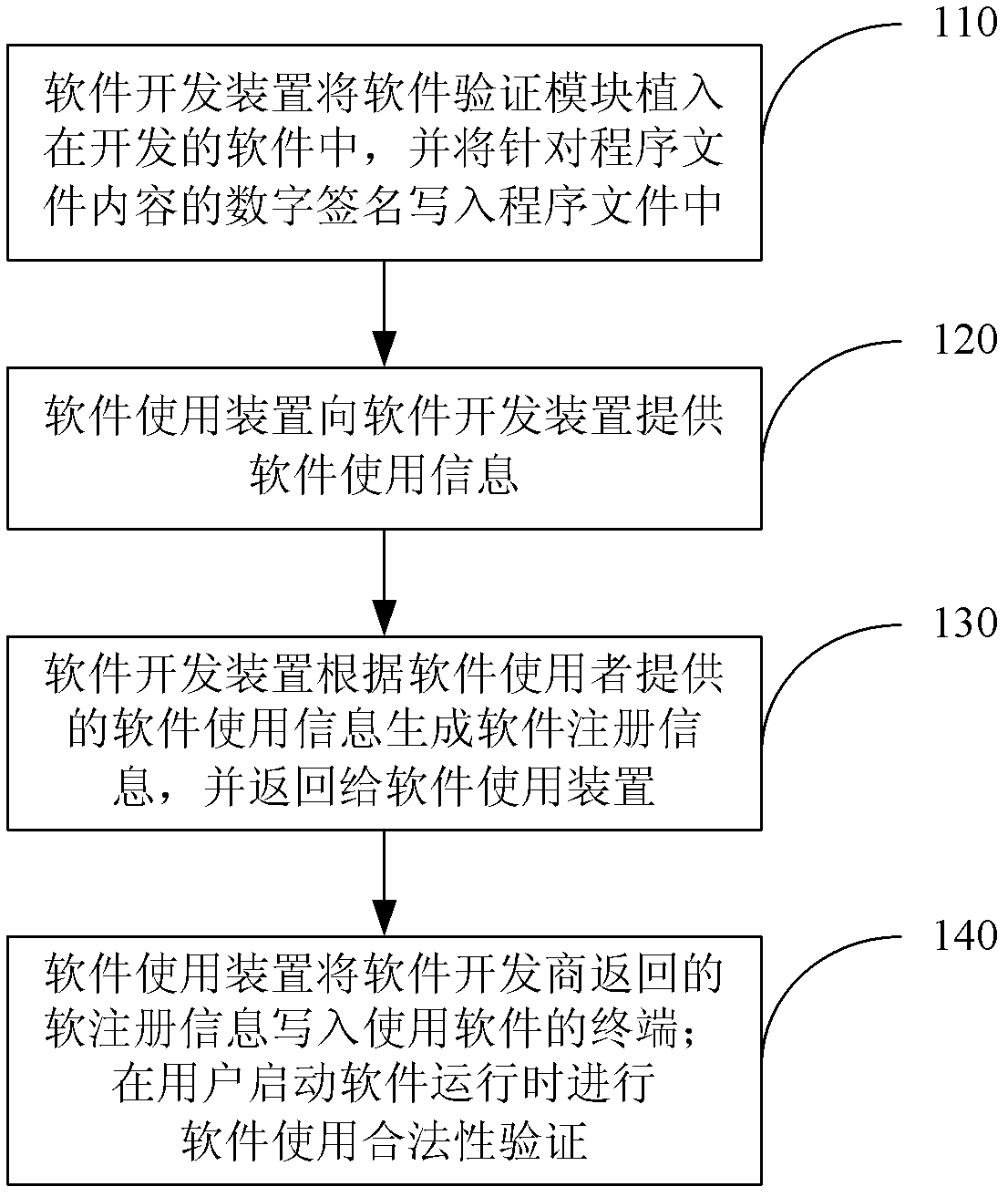
ActiveCN102314578AProtect interestsAvoid using effectsProgram/content distribution protectionDigital signatureComputer module
The invention provides a system and a method for realizing software protection, wherein the system comprises a software development device and a software application device; the software development device is used for implanting a software verification module into developed software and for writing a digital signature which is generated aiming at the content of a program file in the developed program file; and the software application device is used for carrying out authorization verification on the software through the implanted software verification module when the software is started to run by a user. With the adoption of the system and the method for realizing the software protection provided by the invention, the software can be greatly protected so as to prevent unauthorized users from using and unlocking the software, so that the benefit of software developers is greatly protected, and the software industry of China develops towards the healthy direction.
Owner:广西浪潮云计算服务有限公司
Processor extensions and software verification to support type-safe language environments running with untrusted code
Processor extensions and software verification to support type-safe language environments running with untrusted code. Code and data spaces are partitioned into trusted and untrusted regions. Type-safe code is loaded into the trusted region of the code space, while non-type-safe code is loaded into the untrusted region of the code space. The trusted region of the data space is allocated to the type-safe code. The untrusted region of the data space is allocated to the non-type-safe code. Hardware-based truth tables are employed for defining allowable and disallowable code sequences and memory access operations. For code sequences, allowable operations are based on the location (i.e., region) of a code sequence including a current instruction and a prior instruction. For memory access, the location of the requesting instruction and data requested are considered. Disallowed code sequence or memory access operations cause the processor to generate a safe access protection trap. In response to the safe access protection trap, a software-based dynamic verifier applies a security policy to determine whether to allow the operation to proceed.
Owner:INTEL CORP
Method and computer product to increase accuracy of time-based software verification for sensor networks
InactiveUS20070271452A1Reduce time varianceAccurate verificationUser identity/authority verificationMultiple digital computer combinationsLine sensorMinimum time
A recursive verification protocol to reduce the time variance due to delays in the network by putting the subject node at most one hop from the verifier node provides for an efficient manner to test wireless sensor nodes. Since the software signatures are time based, recursive testing will give a much cleaner signal for positive verification of the software running on any one node in the sensor network. In this protocol, the main verifier checks its neighbor, who in turn checks its neighbor, and continuing this process until all nodes have been verified. This ensures minimum time delays for the software verification. Should a node fail the test, the software verification downstream is halted until an alternative path (one not including the failed node) is found. Utilizing techniques well known in the art, having a node tested twice, or not at all, can be avoided.
Owner:HONEYWELL INT INC
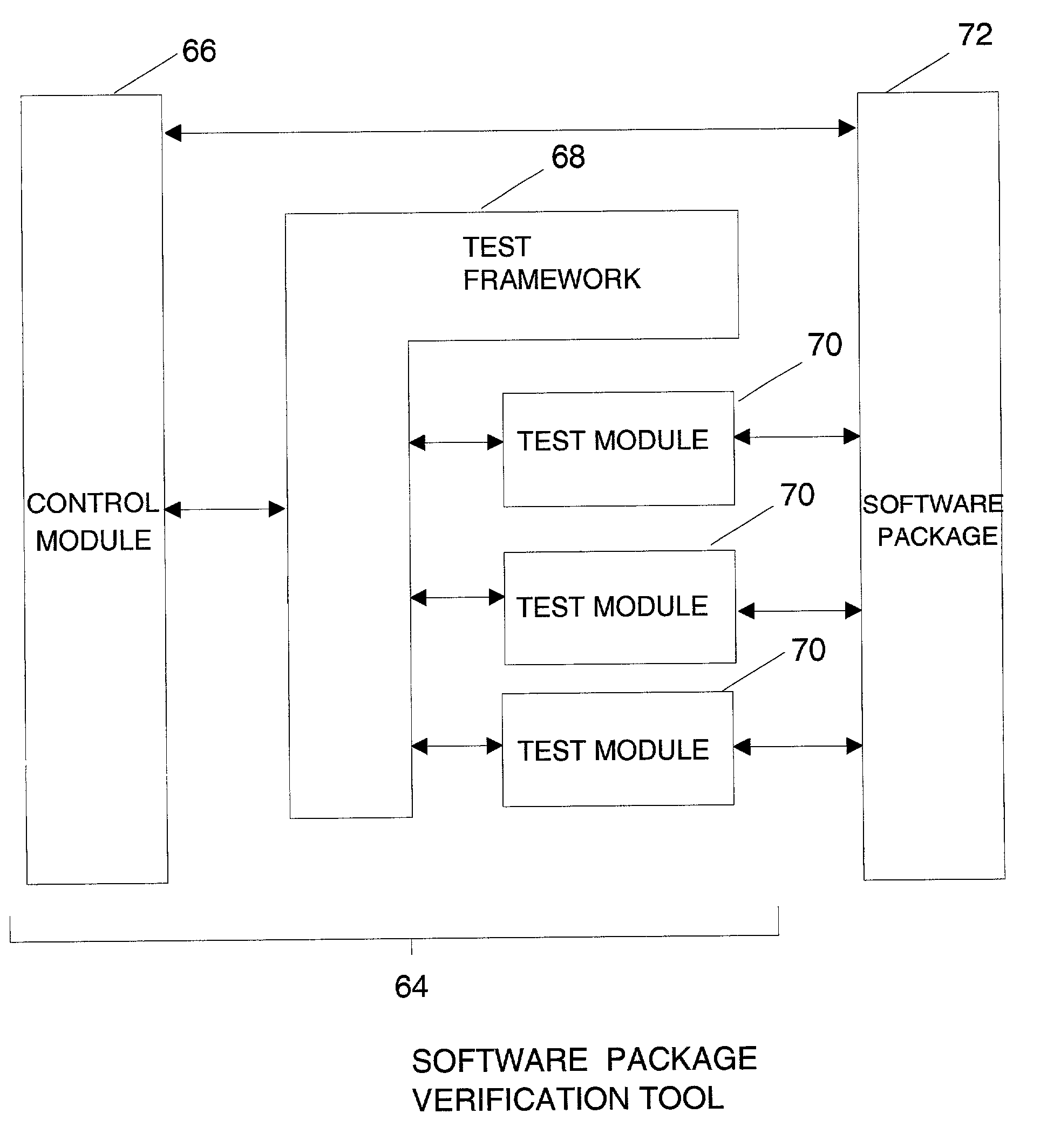
Software package verification
InactiveUS7080357B2Avoid timeData processing applicationsSoftware testing/debuggingComputer hardwareSoftware package
A software package verification tool enables verifying a software package that includes at least one software component. The tool includes at least one test module defining a test of at least one parameter of a software component of the package. It also includes a control module operable to access a framework that identifies each test module and to cause at least one test module to perform the test defined thereby for verifying the package. The framework, within which individual test modules may be added or deleted as required, provides a flexible test structure for software packages. Typically, the framework identifies a plurality of test modules for verifying the correctness of a particular software package. In such a case, the framework can identify a priority for each test module for effecting an ordering of the tests. This enables the performance of the tests to be efficient, avoiding, for example, unnecessary tests that are redundant if the software package fails a more fundamental test.
Owner:ORACLE INT CORP
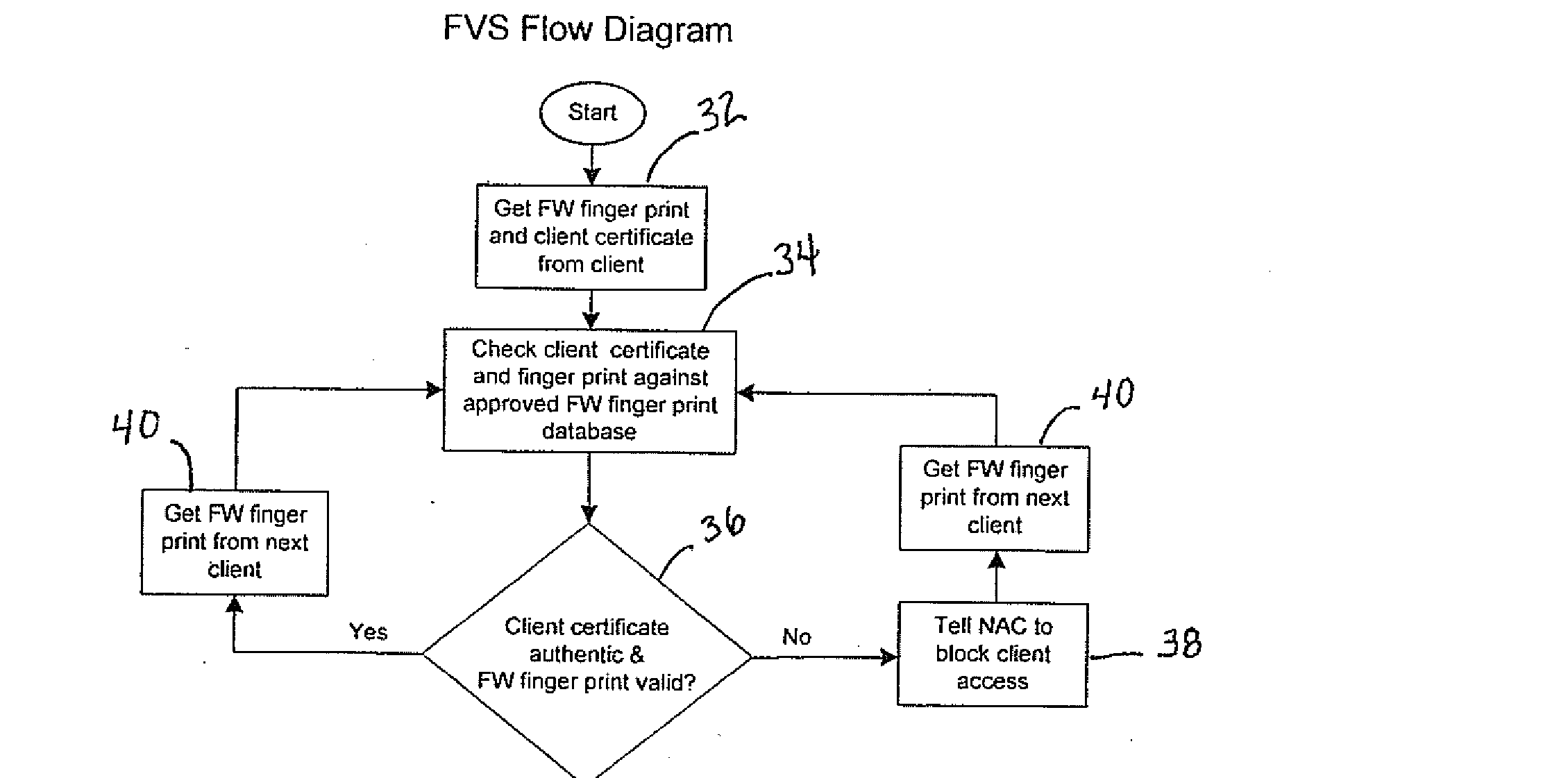
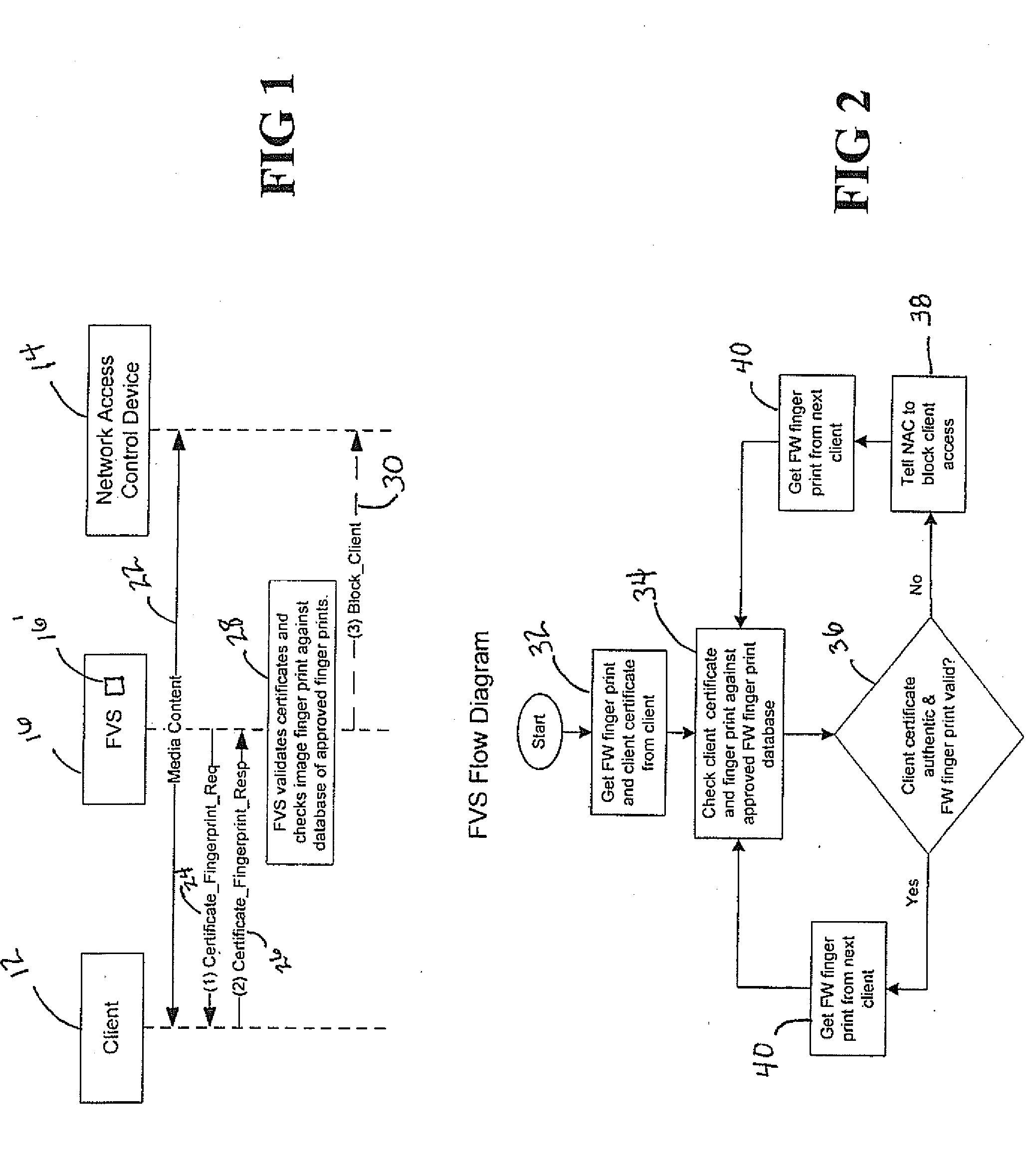
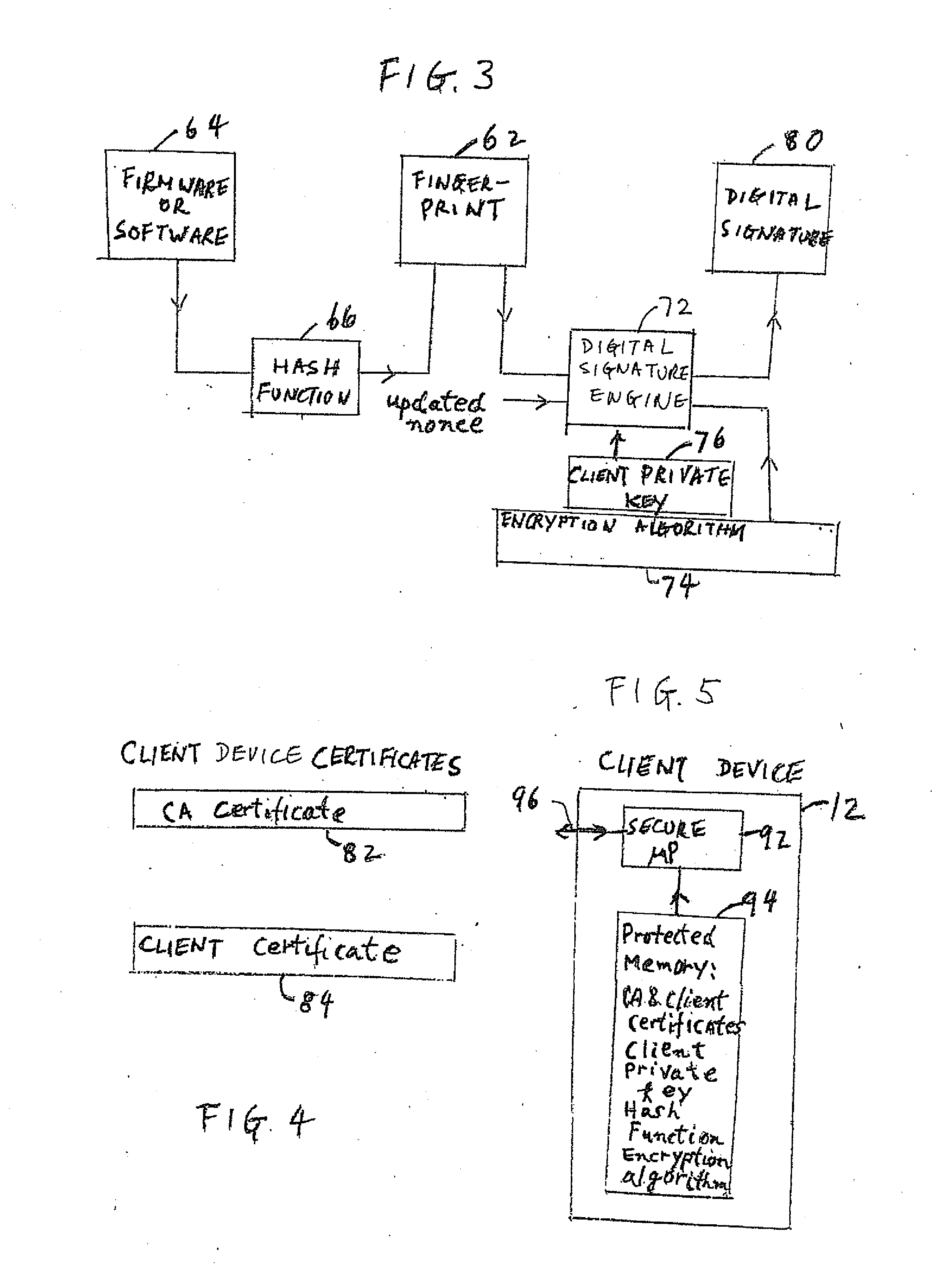
Firmware/software validation
InactiveUS20100064048A1Computer security arrangementsMultiple digital computer combinationsClient-sideNetwork Access Control
The fingerprint value of the firmware or software of a client device is received and the validity of the fingerprint is verified. Network access control device is notified when the fingerprint of the firmware or software from the client device is determined to be not authorized.
Owner:CABLELABS
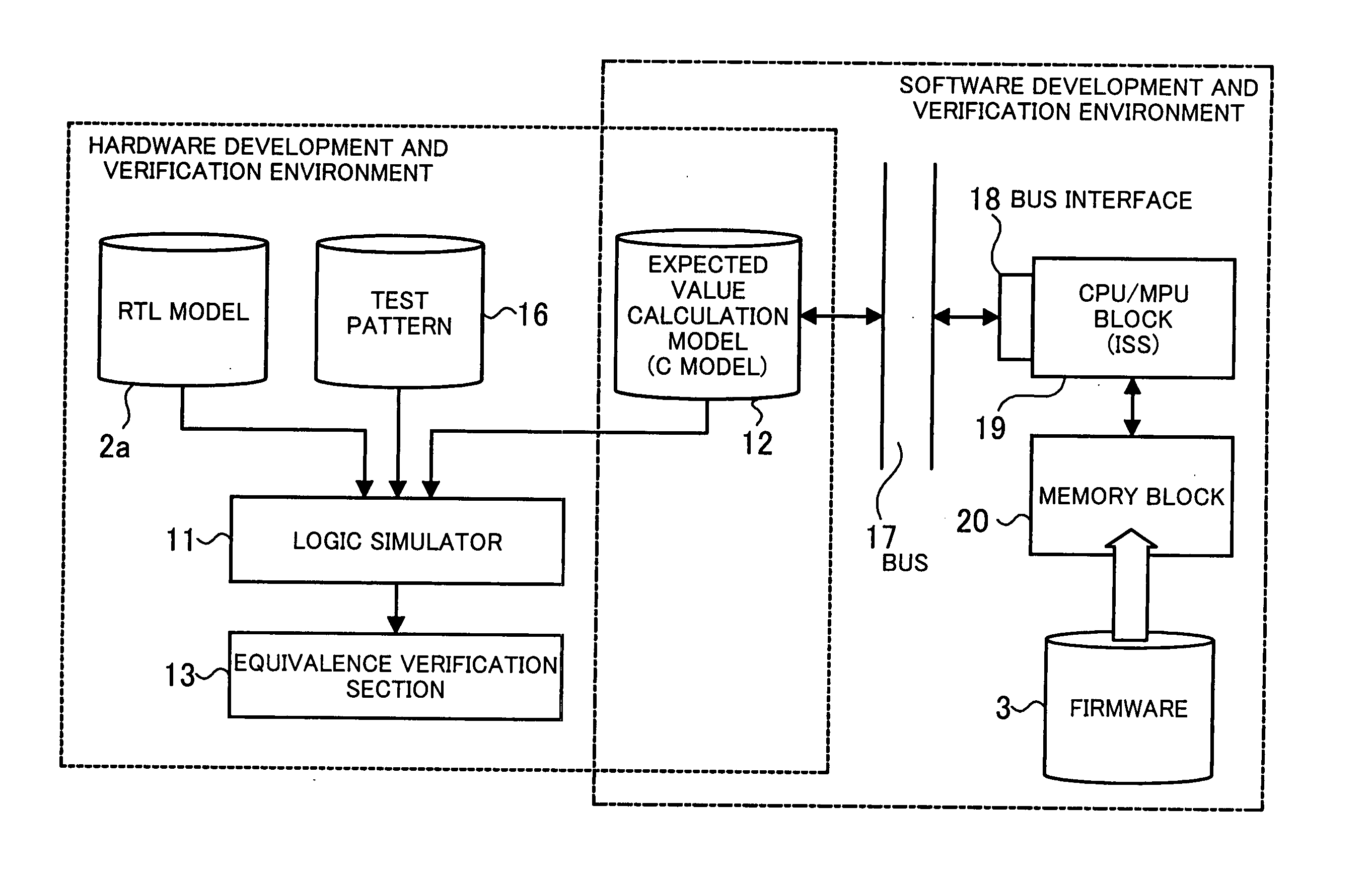
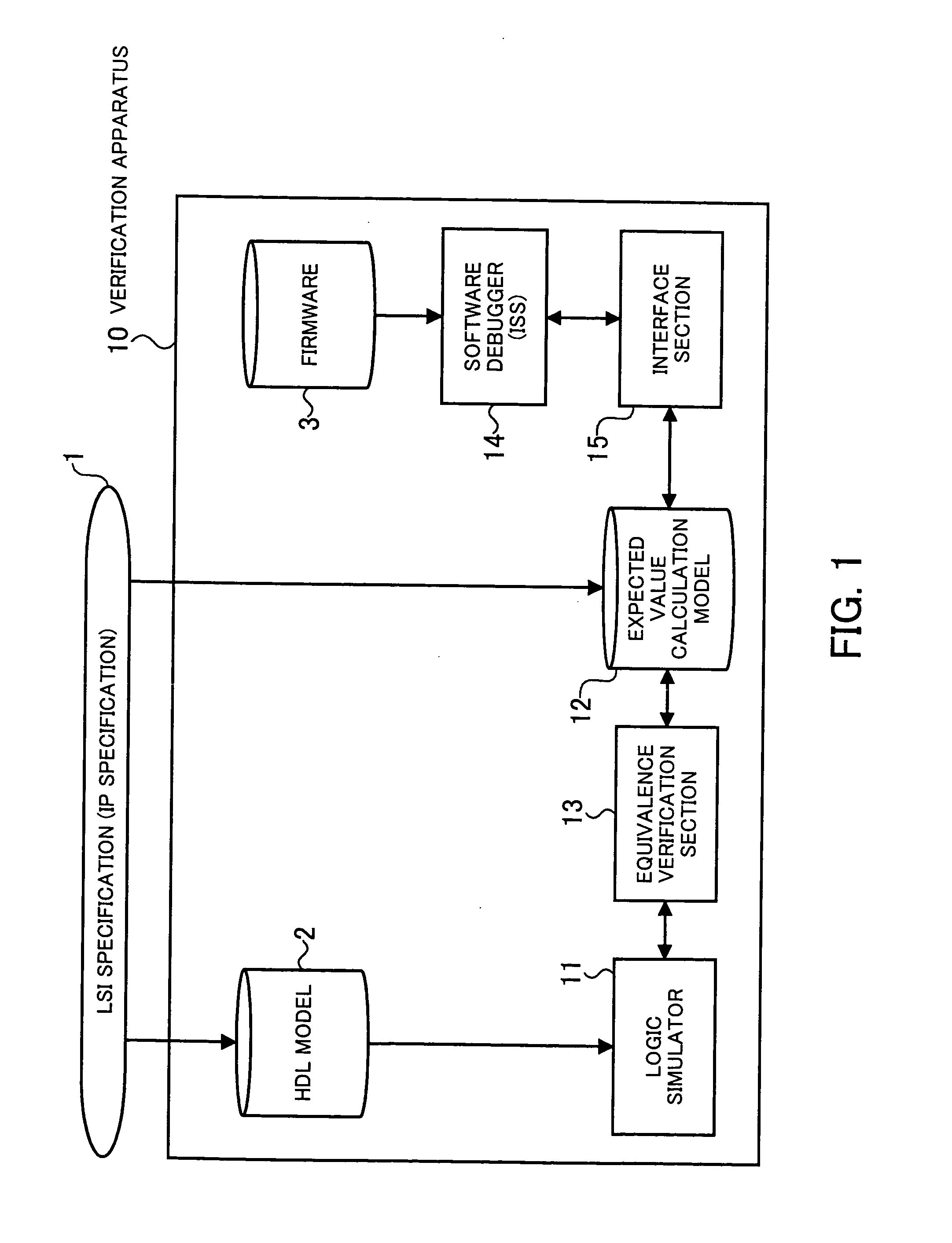
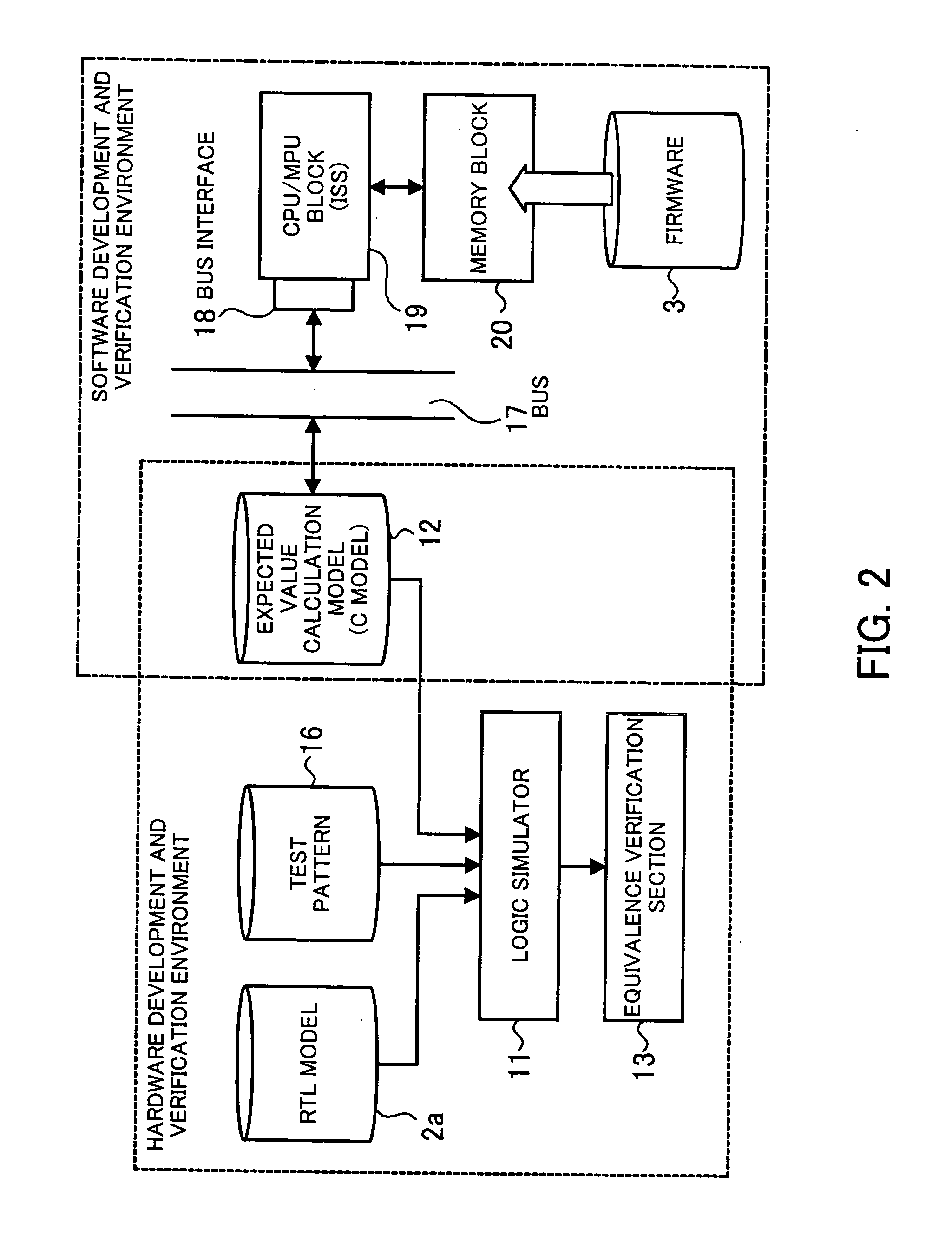
Verification apparatus, verification method, and program
InactiveUS20050102640A1Error detection/correctionAnalogue computers for electric apparatusValidation methodsComputer science
A verification apparatus that efficiently performs hardware verification and software verification in the development of a system LSI with great accuracy. At the hardware verification, an equivalence verification section compares the result of the simulation of an HDL model by a logic simulator and an expected value generated from an expected value calculation model and verifies whether there is equivalence between them. At the software verification, the expected value calculation model is used via an interface section and a firmware is verified by a software debugger. The expected value calculation model is used as an expected value generation model at hardware verification time and is used as a C model of hardware at software verification time. By using the expected value calculation model both for the hardware verification and for the software verification in this way, verification can efficiently be performed with great accuracy.
Owner:SOCIONEXT INC
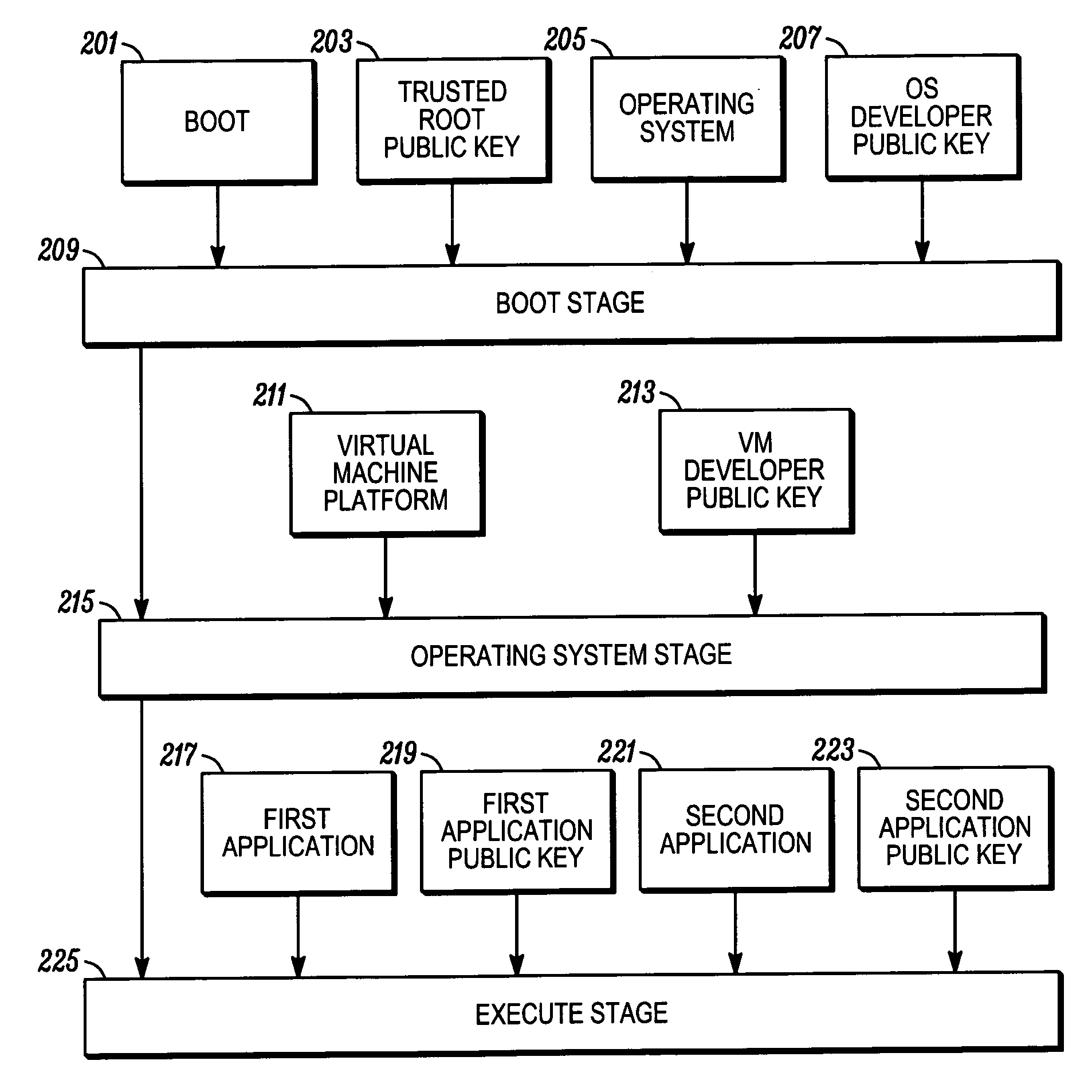
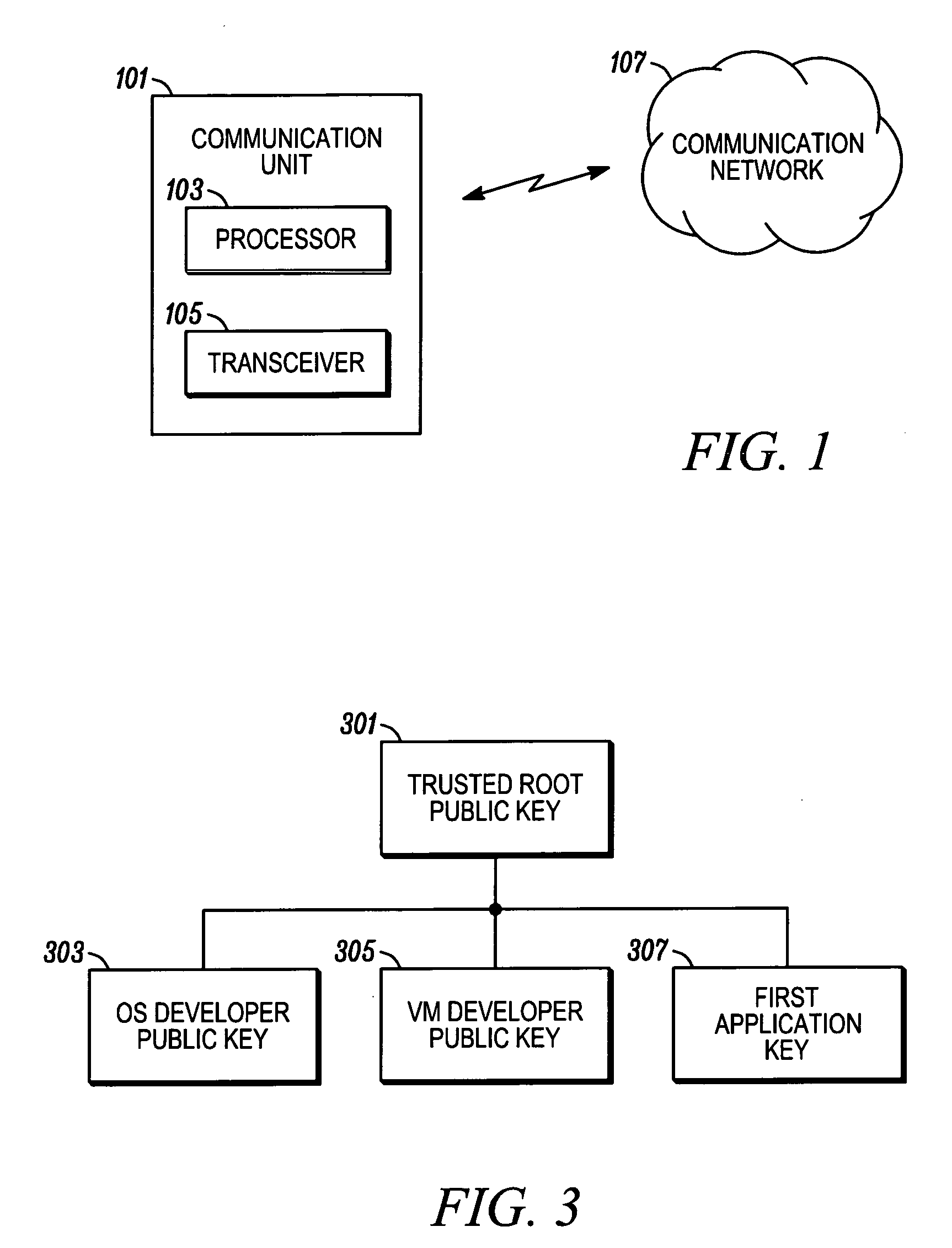
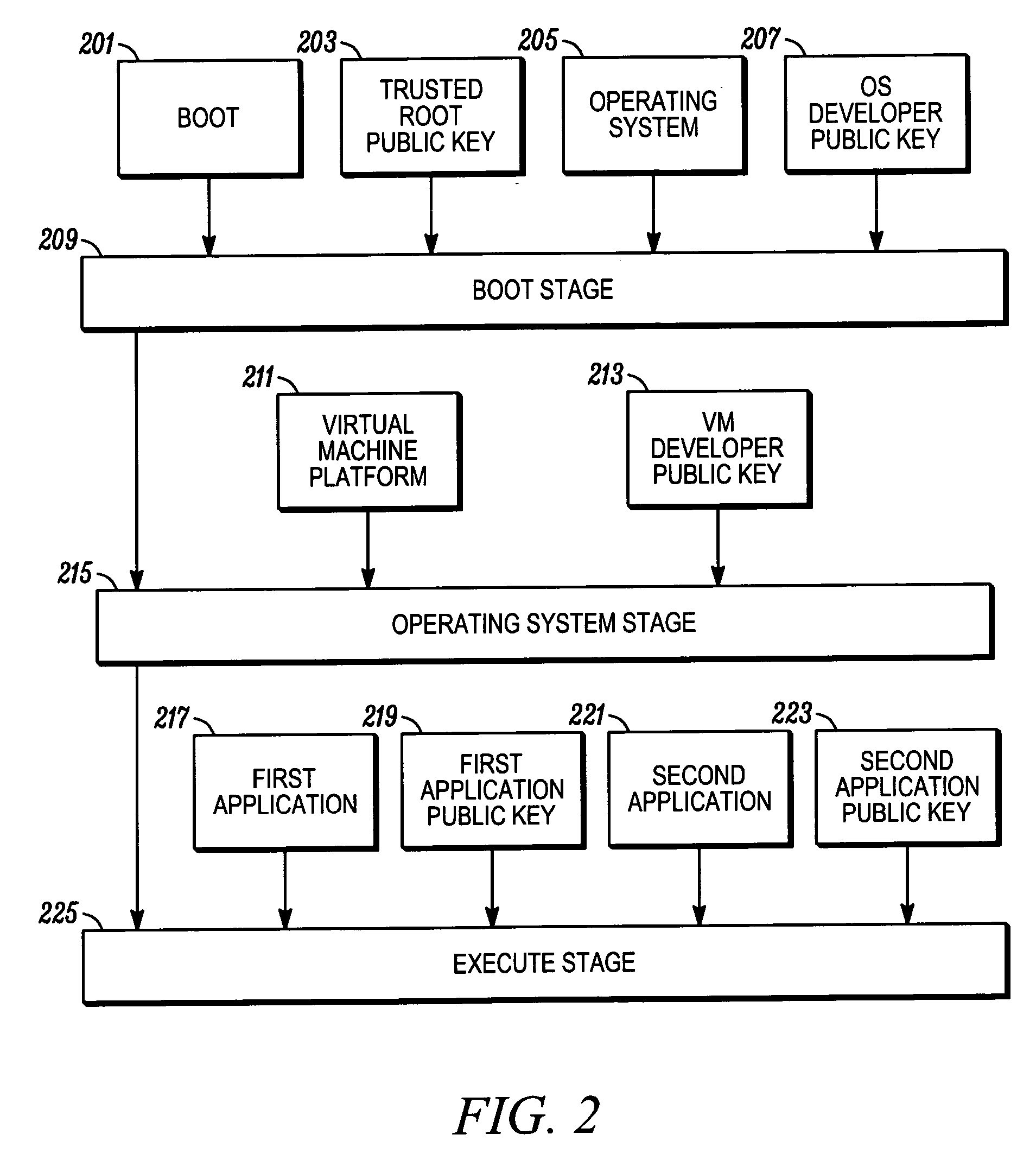
Multiple stage software verification
A communication unit (101) includes a transceiver (105) for communication over a communication network (107), and a processor (103). The processor (103) can install software components, including a first software component and a second software component. Responsive to a boot, the processor (103) can verifying the first software component against a first pre-determined value corresponding to at least the first software component; and subsequent to completion of the boot, verify the second software component against a second pre-determined value corresponding to at least the second software component.
Owner:MOTOROLA INC
Software verification method for control units and verification system
InactiveUS20050022166A1Development risk can be minimizedLow costProgramme controlComputer controlComputer architectureExperimental control
A method and system for the verification of software functions for a control unit, using a simulation model to simulate the software functions and the control unit, the software code for the software functions being generated automatically from the identical simulation model, firstly for a first experimental control unit and secondly for a second standard control unit, identical input variables for the software functions being used on both control units and the output variables of both control units resulting therefrom being detected synchronized in time, i.e., simultaneously, the software functions being verified through comparison of the output variables of both control units.
Owner:ROBERT BOSCH GMBH
Pre-boot software verification
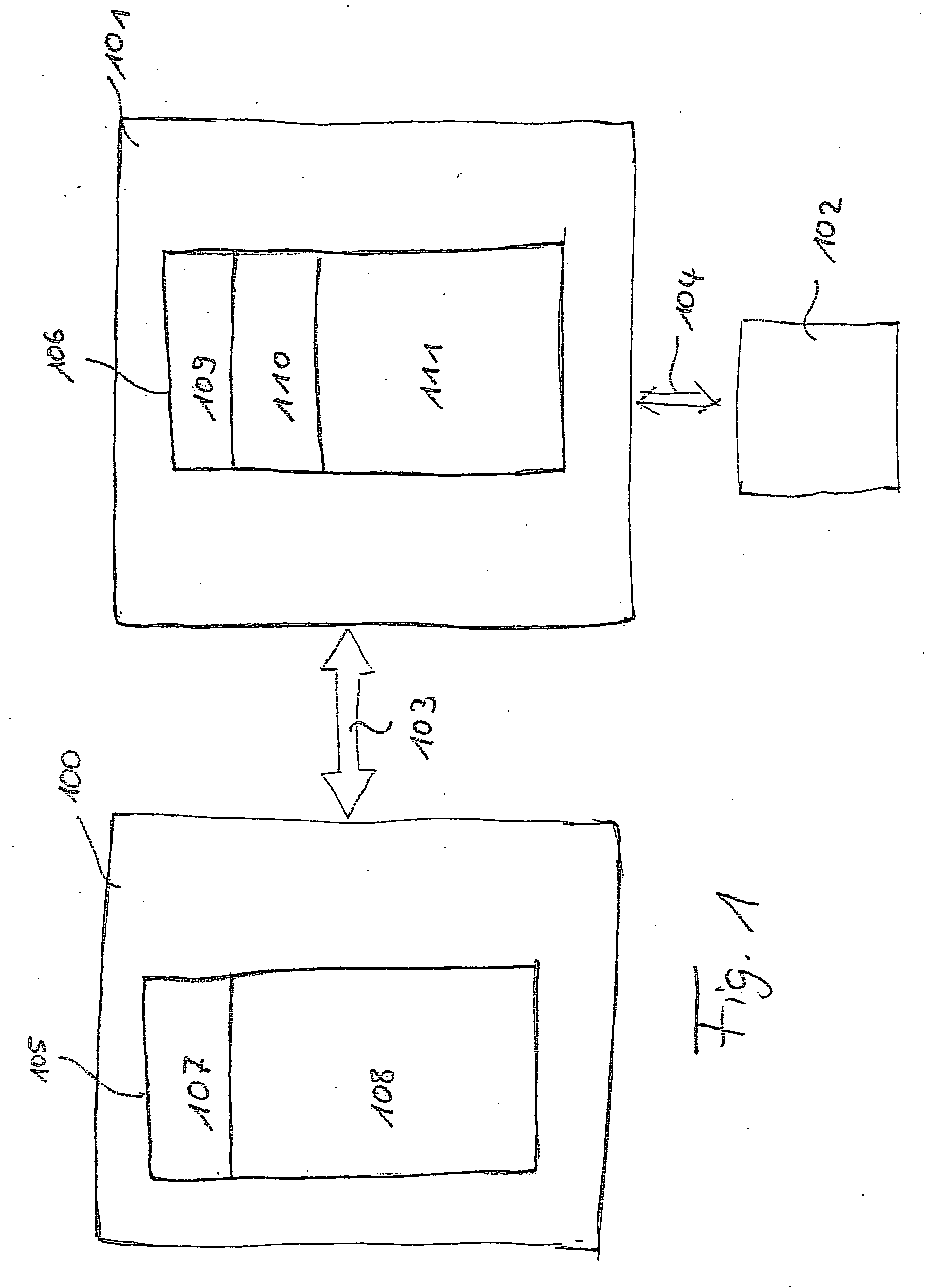
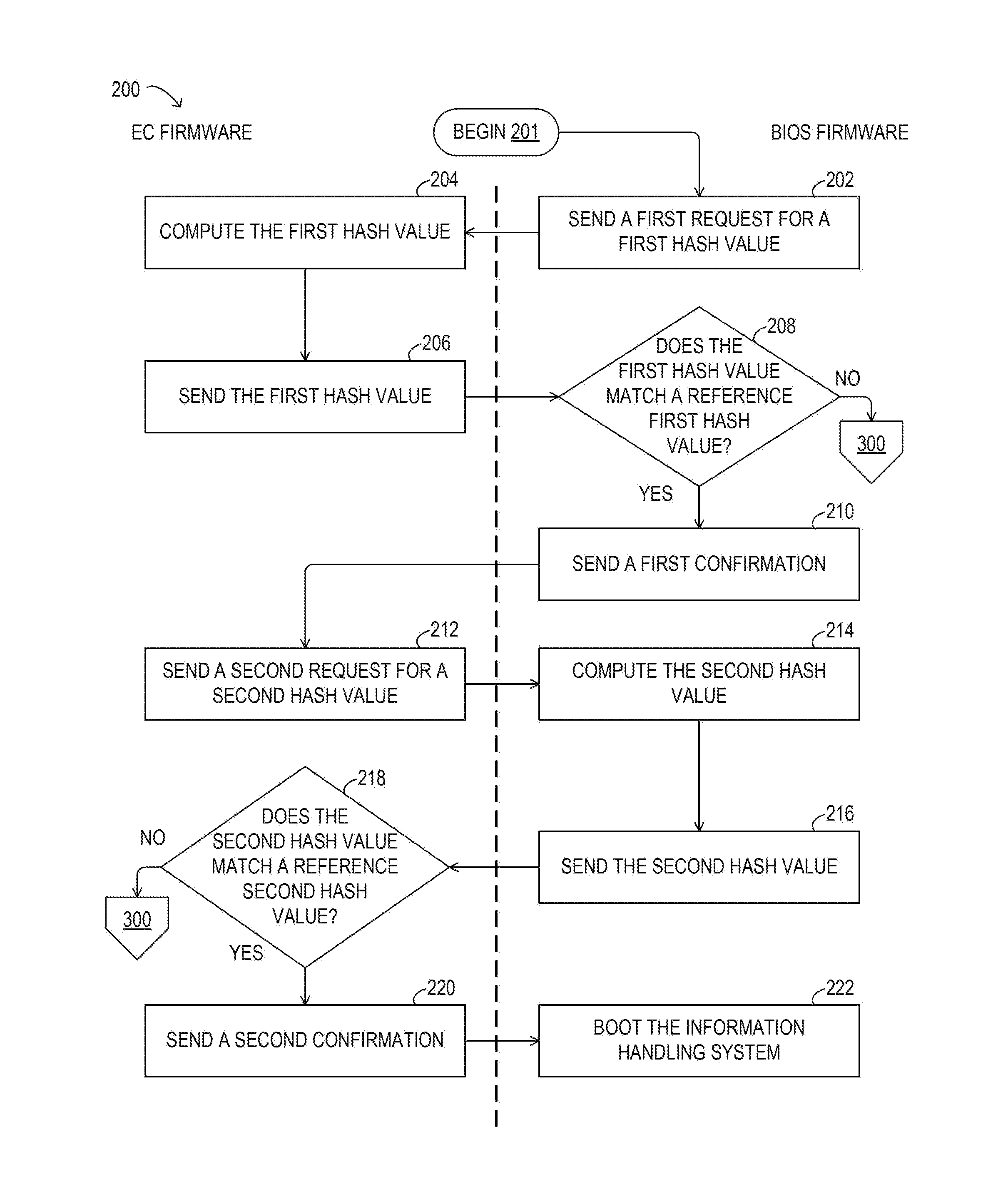
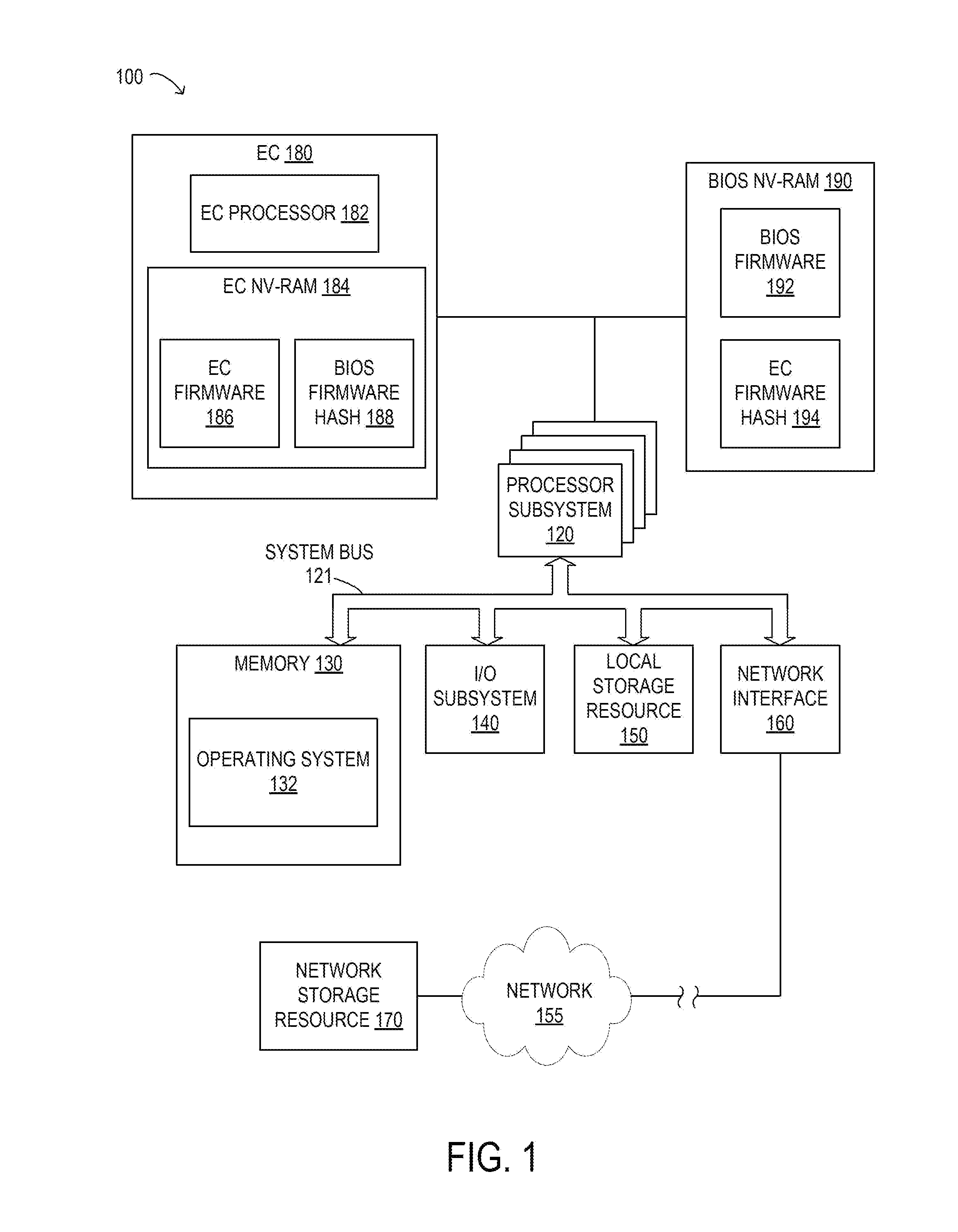
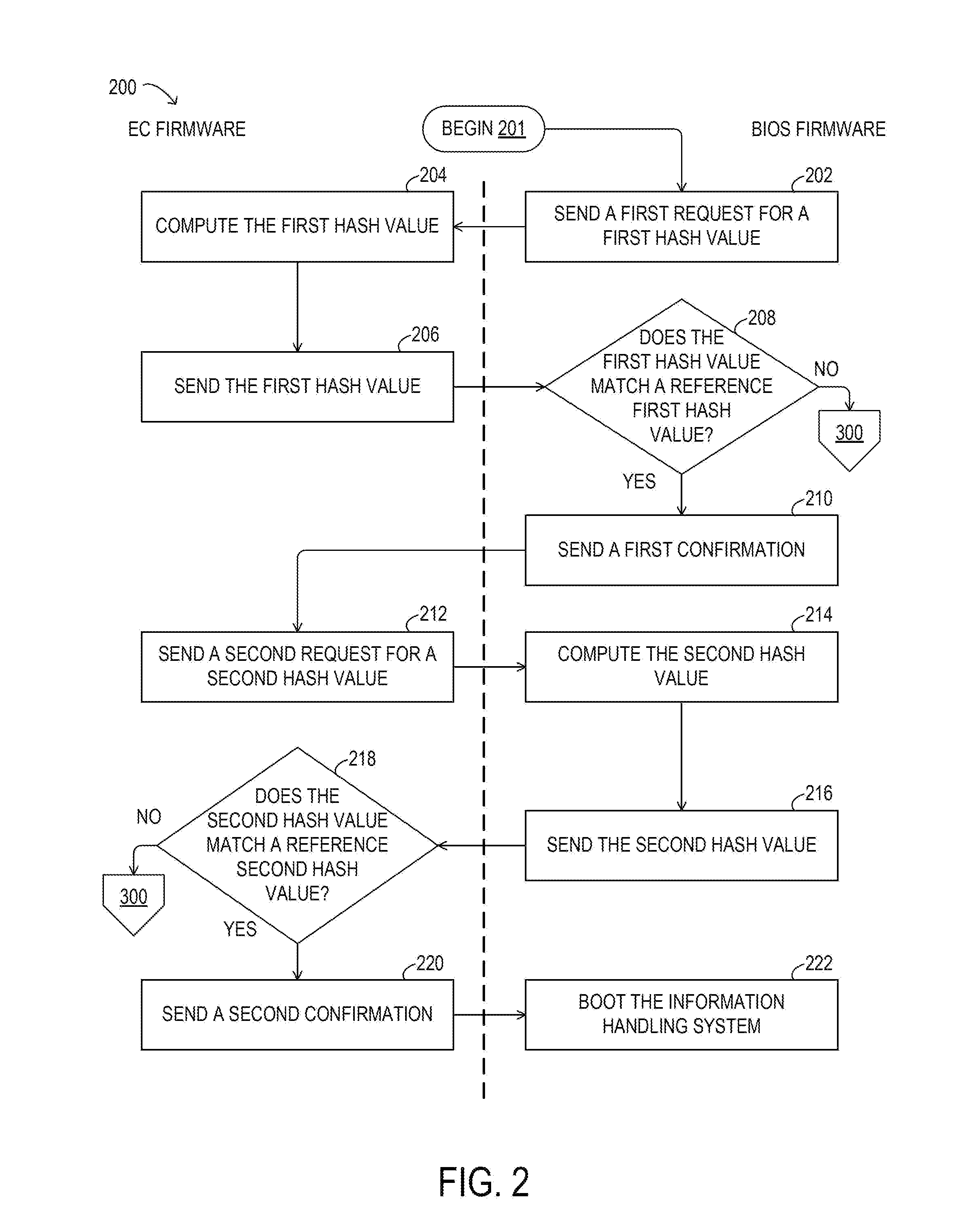
ActiveUS20150324588A1Digital computer detailsPlatform integrity maintainanceFirmware versionEmbedded controller
Methods and systems for implementing pre-boot software verification may involve using an embedded controller (EC) and a basic input / output system (BIOS) to confirm each other's firmware using hash values. The hash values may be generated from certain portions of the firmware, which may overlap and may be specific to a particular firmware version.
Owner:DELL PROD LP
Control microcomputer verification device and vehicle-mounted control device
InactiveUS20080147949A1Improve verification efficiencyImprove quality and reliabilityHardware monitoringRedundant operation error correctionMicrocomputerFinite-state machine
The present invention offers an advanced control software verification technology, particularly, an assertion-based verification technology, by providing a control microcomputer verification device and vehicle-mounted control device that exhibit improved verification efficiency. Assertion-based verification is performed with a verification device that has a hardware configuration in which the verification device is independent of a CPU core of a microcomputer but operates in parallel with the CPU core of the microcomputer, which sequentially executes control software. The hardware to be employed to achieve the above purpose is a finite state machine based on microprogrammed control. An interrupt factor is branched immediately before an interrupt controller for the microcomputer and used as a transition input. When an abnormal transition is detected, a warning is output to the microcomputer as an interrupt or output to the outside in the form of a signal.
Owner:HITACHI LTD
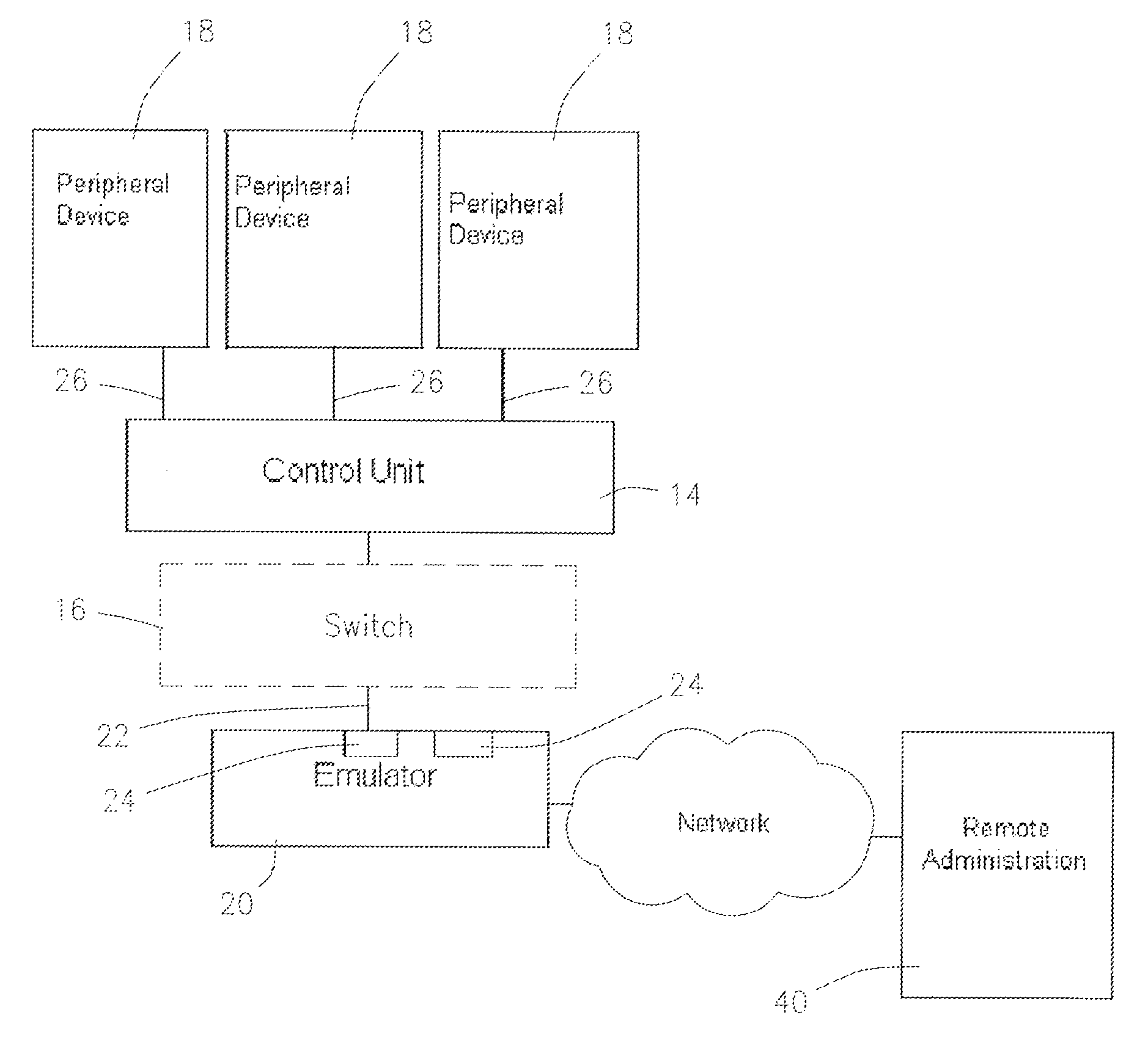
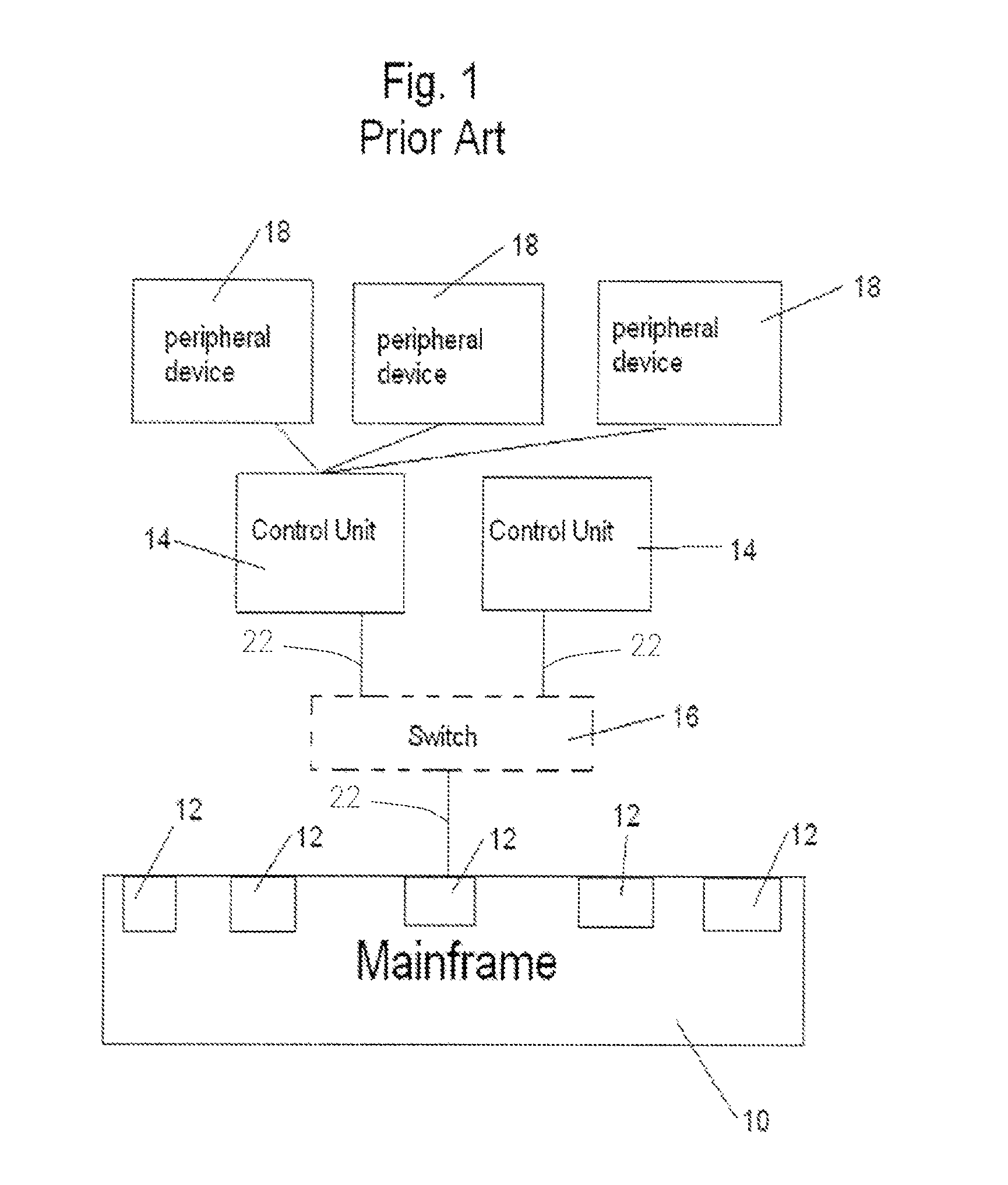
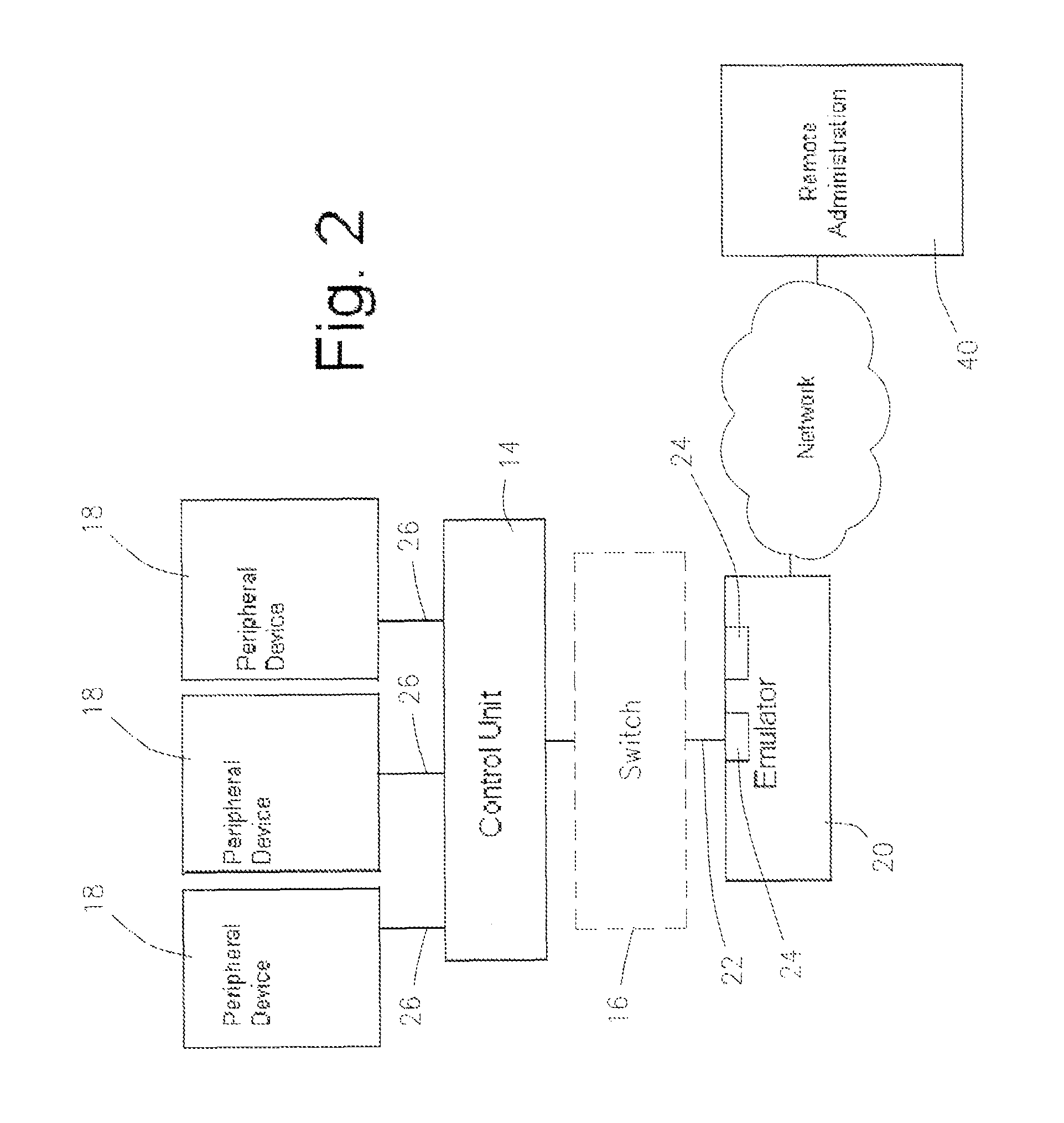
Remotely controlled channel emulator for testing of mainframe peripherals
A method and a system to emulate a mainframe data channel for testing and diagnostics of mainframe peripheral devices and for remote control and configuration of the testing and diagnostics. The system includes an emulator central processing unit communicably attached to at least one of the mainframe peripheral devices. First driver software is resident in the emulator central processing unit to initialize and start an adaptor for at least one mainframe peripheral device. Second channel program software is resident in the emulator central processing unit having commands to the emulator central processing unit and to the mainframe peripheral devices. Third application software is resident in the emulator central processing unit to test and diagnose the mainframe peripheral devices. Fourth software resident in the emulator central processing unit validates remote access to the emulator central processing unit.
Owner:GLOBAL INTERFACE SOLUTIONS INC D B A SECUREAGENT SOFTWARE
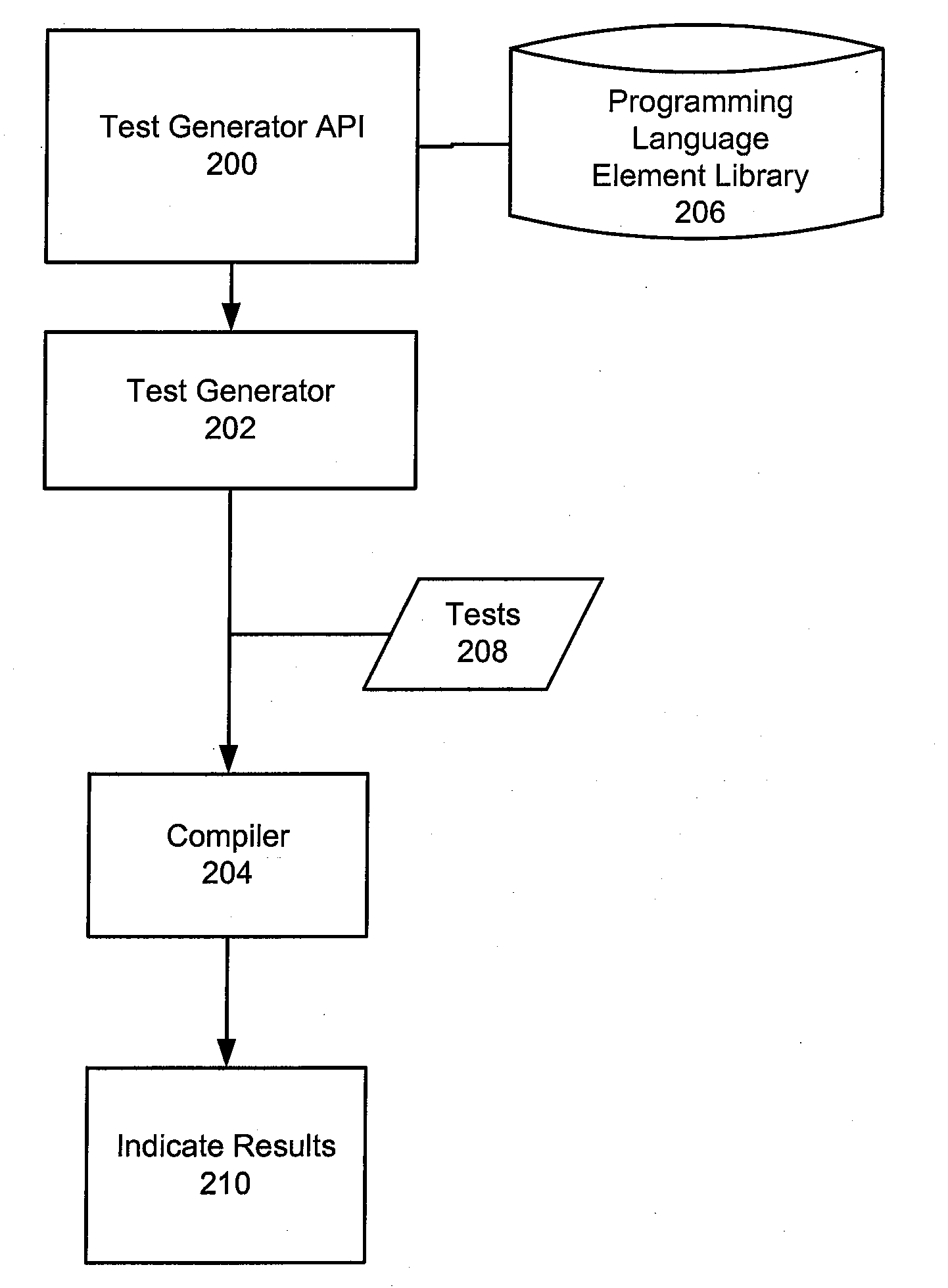
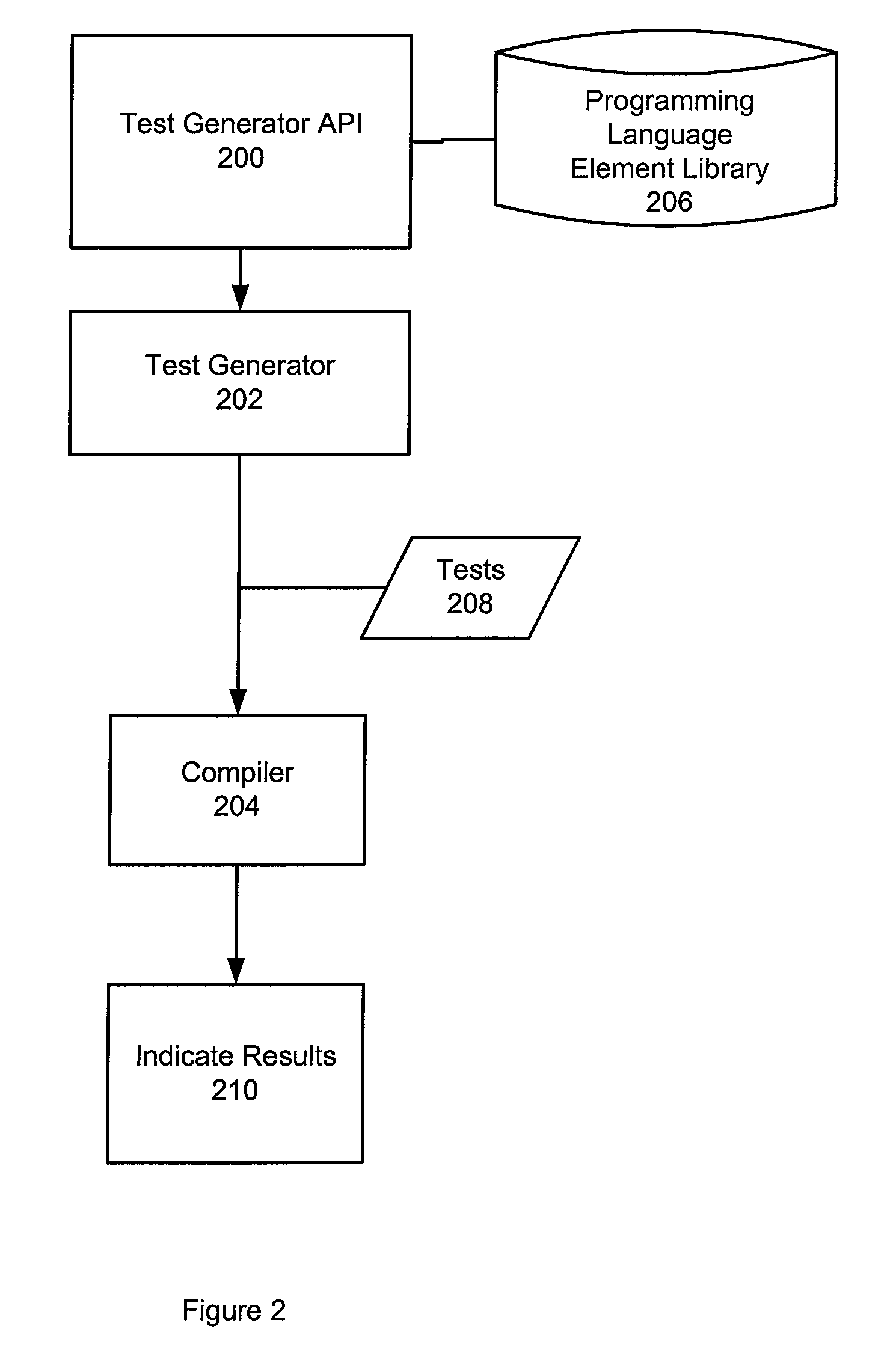
Automation of software verification
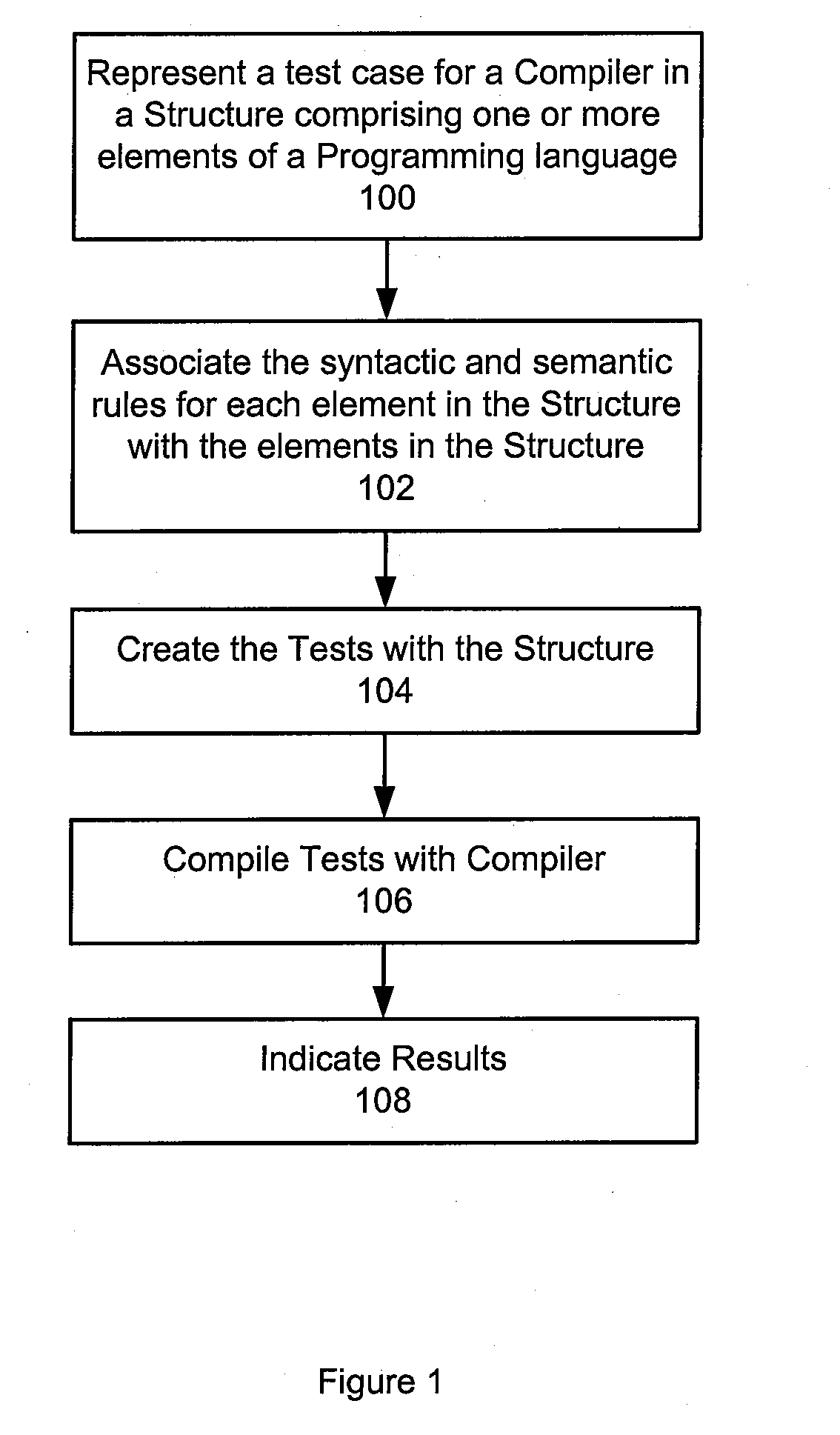
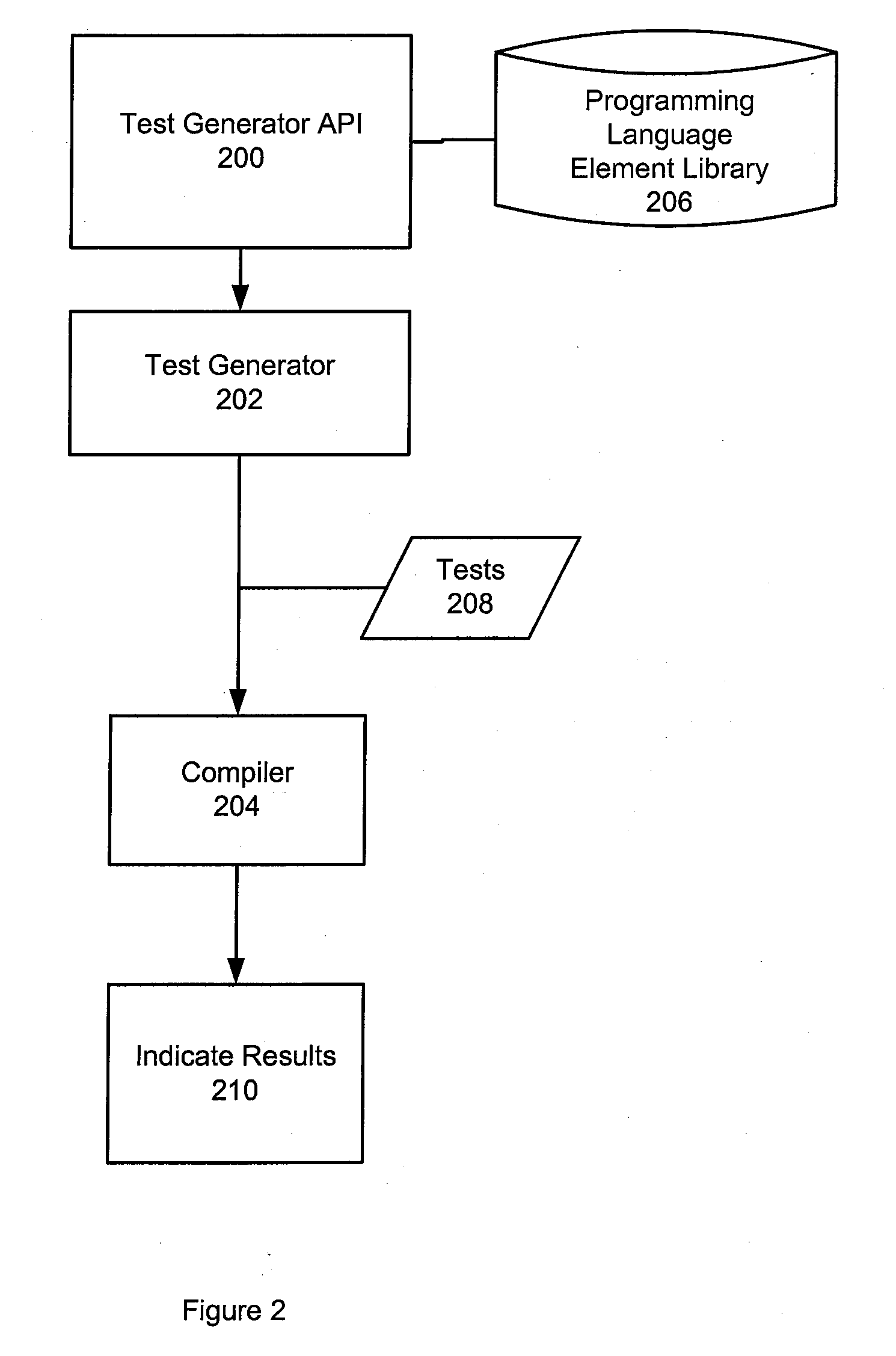
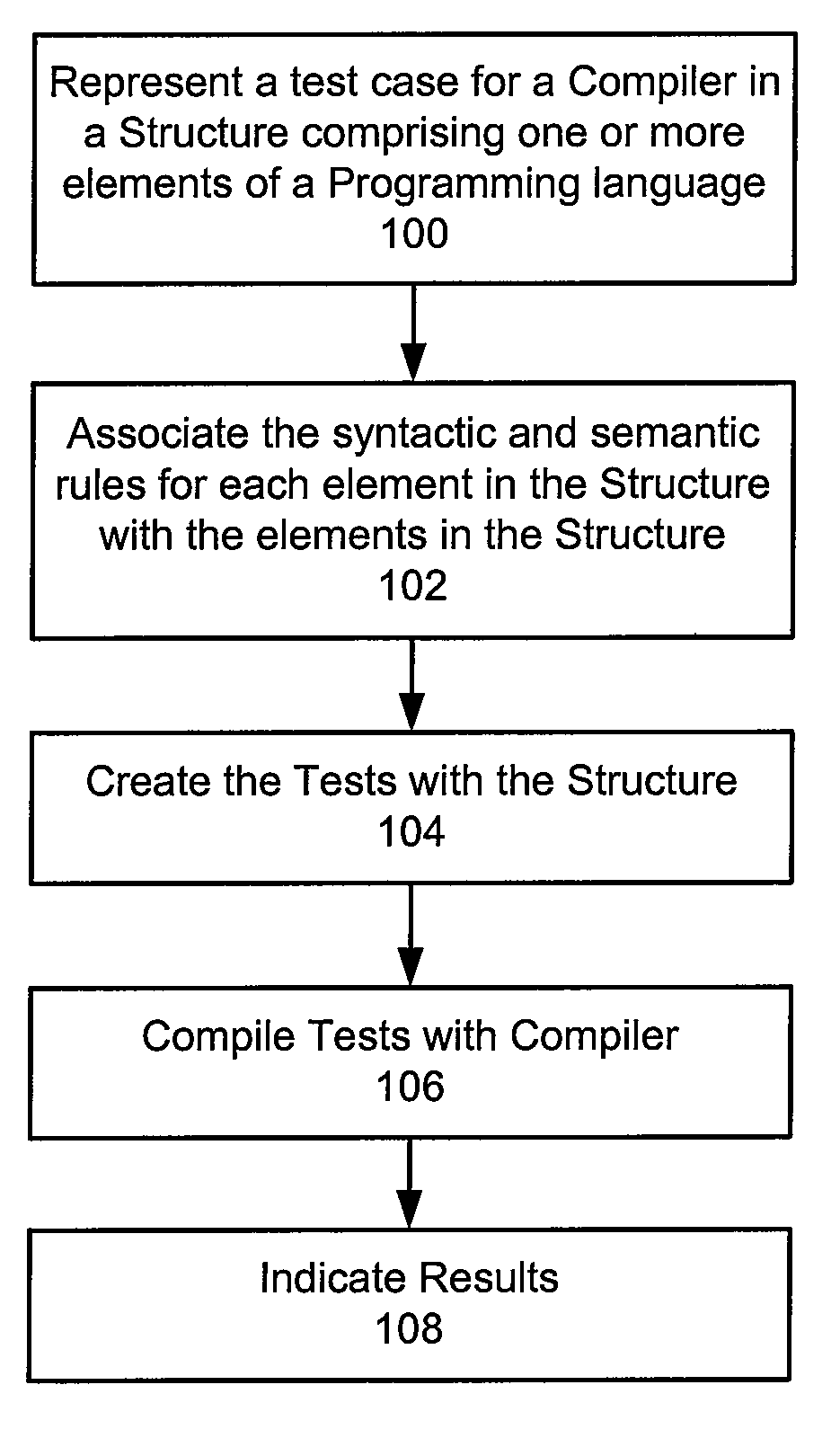
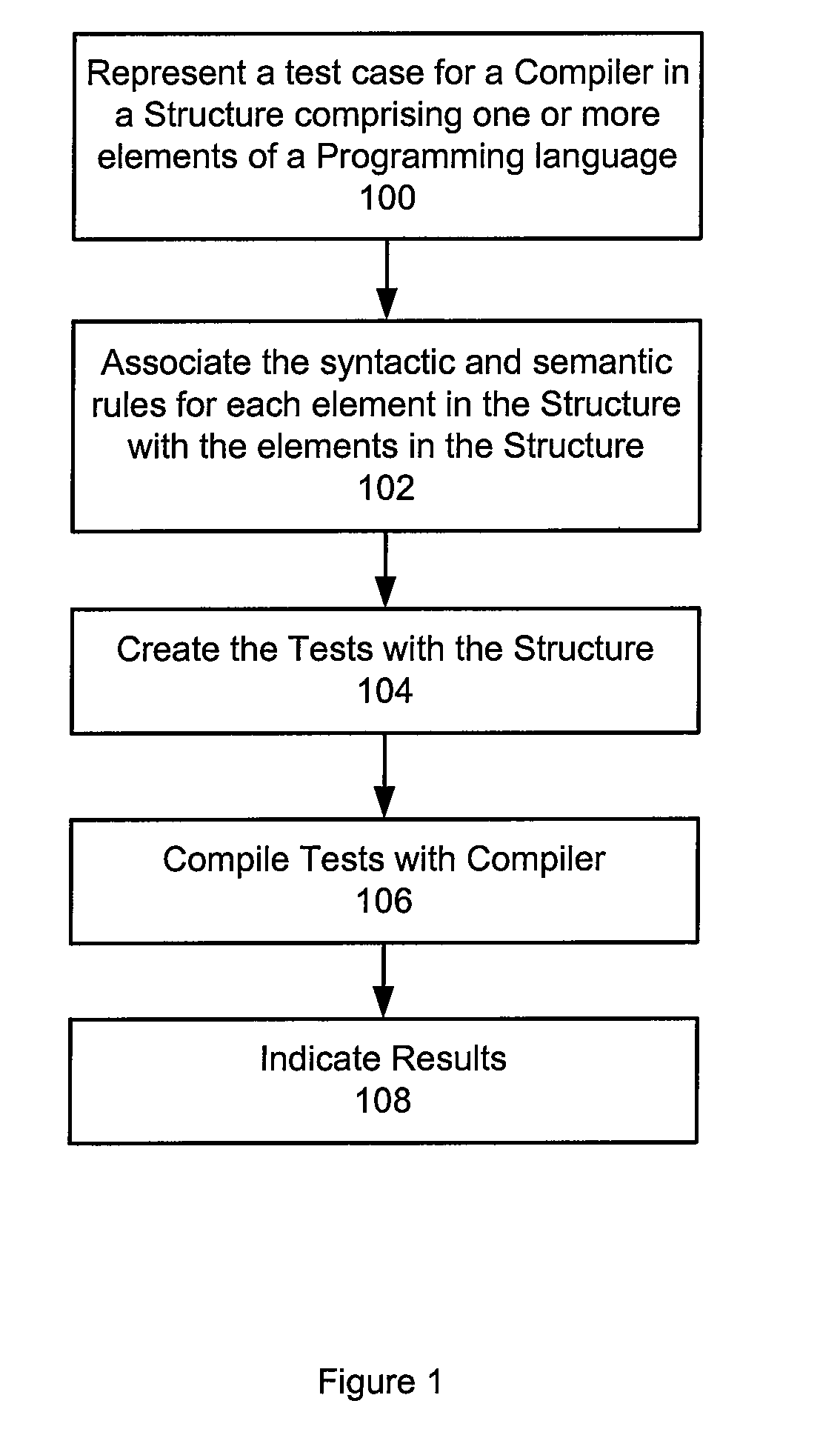
InactiveUS20090172649A1Error detection/correctionSpecific program execution arrangementsAutomatic test generationHuman language
A method, system, and computer program product are disclosed for automatic test generation for a compiler. In one approach, the method, system and computer program product represent a test case for the compiler in a structure with one or more elements of a programming language, associate at least one syntactic rule and semantic rule with the one or more elements in the structure, create a test with the structure compiling the test with the compiler, and display results of the test.
Owner:CADENCE DESIGN SYST INC
Automation of software verification
InactiveUS8156474B2Error detection/correctionSpecific program execution arrangementsComputer scienceAutomatic test generation
A method, system, and computer program product are disclosed for automatic test generation for a compiler. In one approach, the method, system and computer program product represent a test case for the compiler in a structure with one or more elements of a programming language, associate at least one syntactic rule and semantic rule with the one or more elements in the structure, create a test with the structure compiling the test with the compiler, and display results of the test.
Owner:CADENCE DESIGN SYST INC
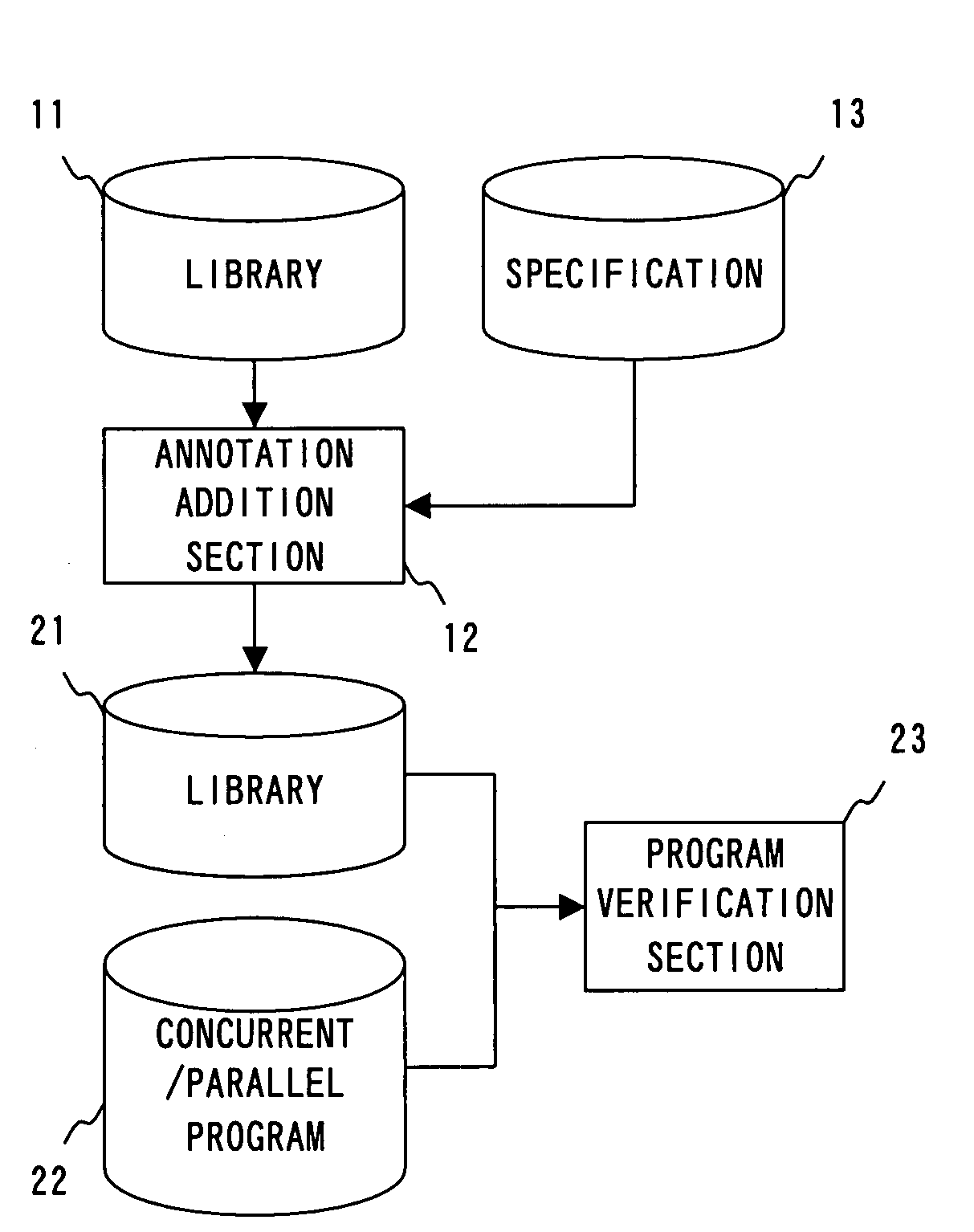
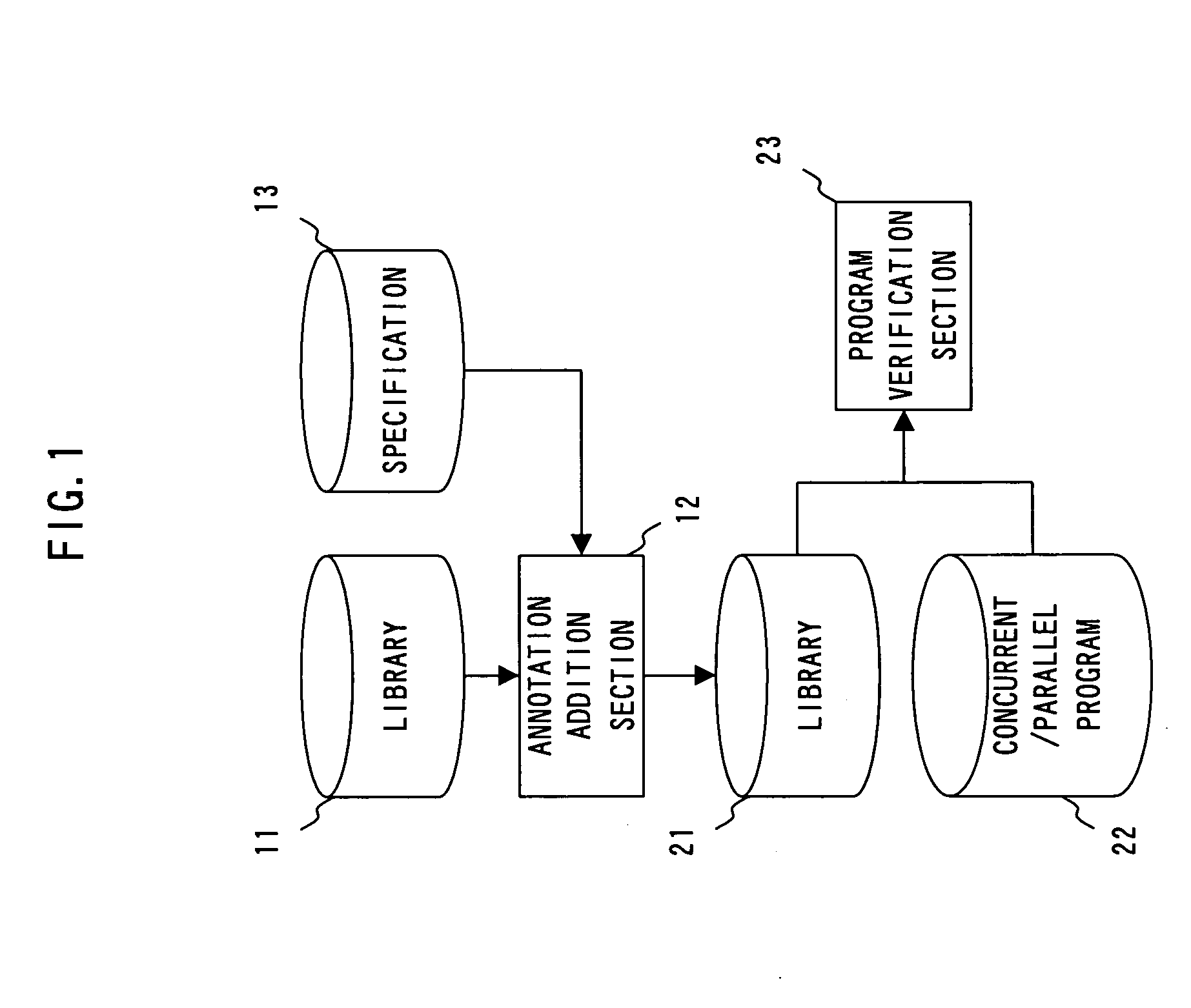
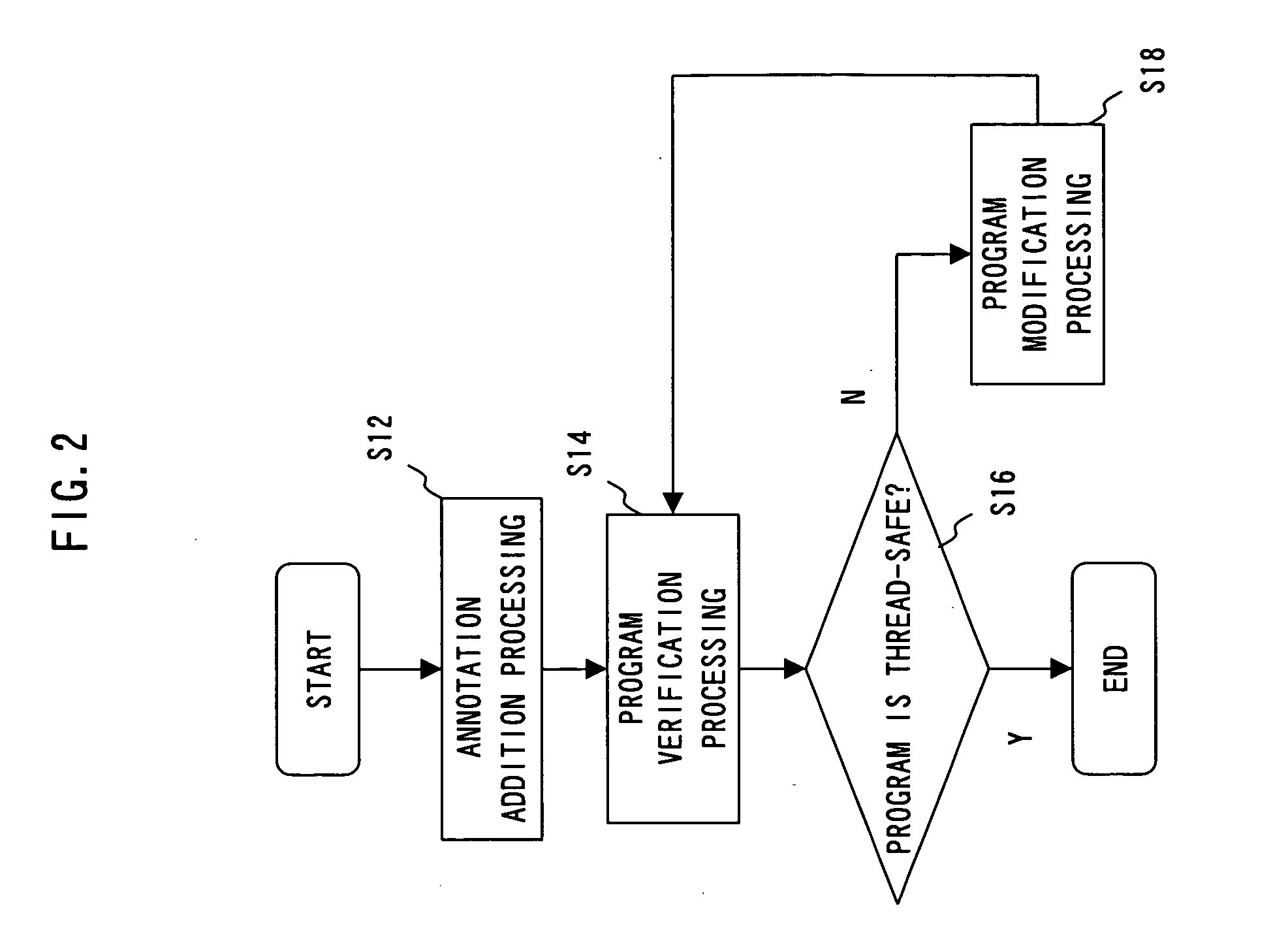
Recording medium, software verification apparatus and software verification method
InactiveUS20070220493A1Reduce verification costsSoftware engineeringSpecific program execution arrangementsSoftware engineeringParallel software
The present invention has been made to provide a software verification program, a software verification apparatus, and a software verification method capable of reducing verification cost of concurrent / parallel software.A software verification program allowing a computer to execute verification of software including a library 11 and a program that uses a library 21 to operate in a concurrent or parallel manner, comprises: a shared element utilizing part extraction step that extracts a part at which a shared element, which is an element that is defined in the library 21 and which can be used by the program 22, is used in the program 22; and a condition verification step that verifies based on a thread-safe condition defined in the library 21 for the each shared element whether a shared element in the shared element utilizing part extracted by the shared element utilizing part extraction step satisfies the thread-safe condition.
Owner:FUJITSU LTD
System and methods for secure firmware validation
ActiveUS20180225459A1Software engineeringSemiconductor/solid-state device detailsCoprocessorSoftware update
An electronic device, such as a dynamic transaction card having an EMV chip, that acts as a TPM having a memory, an applet, and a cryptographic coprocessor performs secure firmware and / or software updates, and performs firmware and / or software validation for firmware and / or software that is stored on the electronic device. Validation may compare a calculated checksum with a checksum stored in EMV chip memory. If a checksum calculated for firmware and / or a software application matches a checksum stored in EMV chip memory of the transaction card, the transaction card may operate normally. If a checksum calculated for firmware and / or a software application does not match a checksum stored in EMV chip memory of the transaction card, the transaction card may freeze all capabilities, erase the memory of the transaction card, display data indicative of a fraudulent or inactive transaction card, and / or the like.
Owner:CAPITAL ONE SERVICES
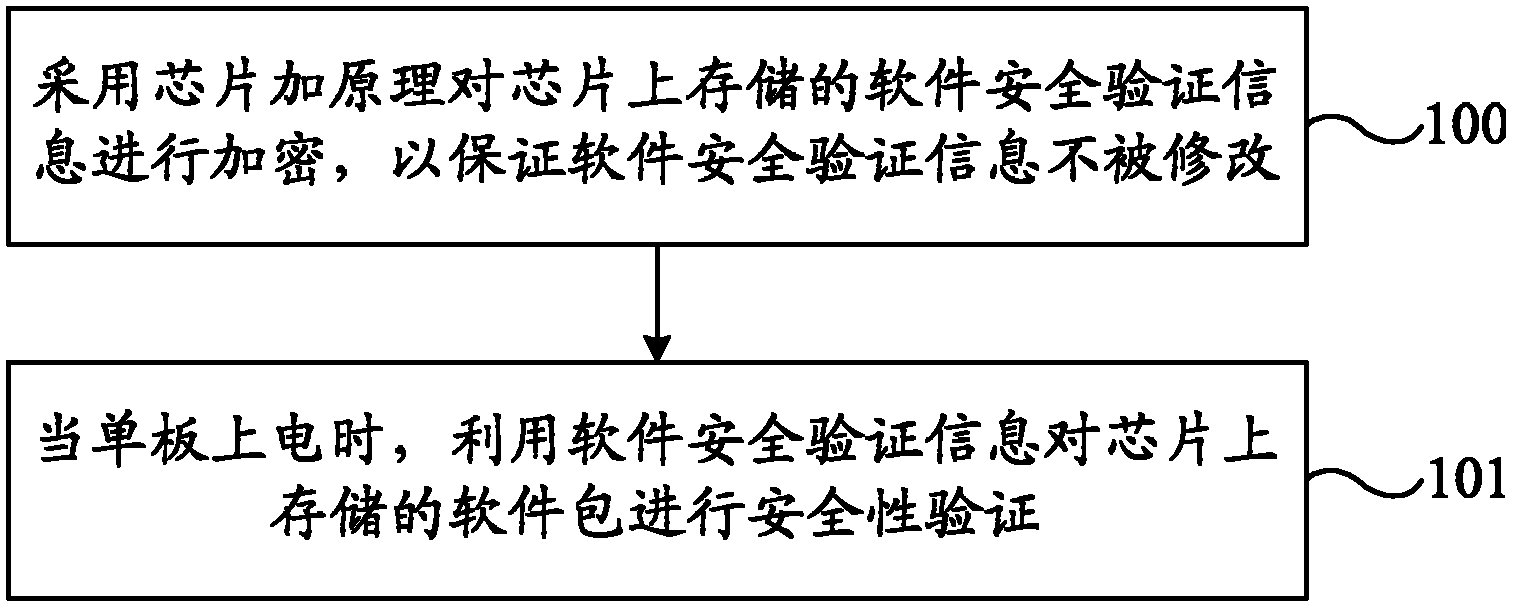
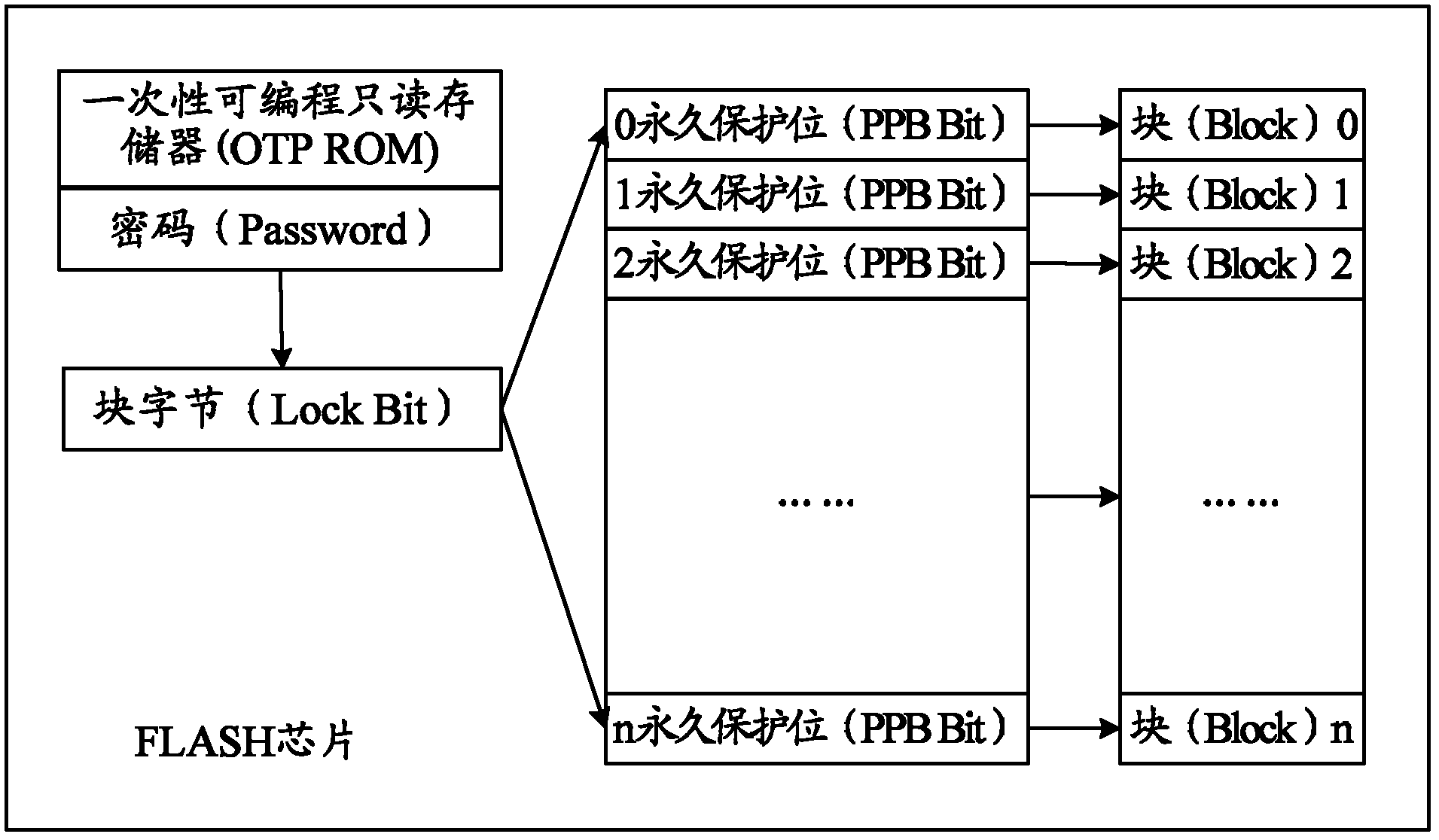
Protection method of chip and chip itself
InactiveCN102317948AEnsure safetySolve the problem of random tamperingInternal/peripheral component protectionMemory systemsElectricitySingle plate
This embodiment of the invention provides a protection method of chip and chip itself. The method includes: encrypting security verification information of software stored in chip by means of chip add principle to prevent the modification of the mentioned software security verification information; verifying the security of the mentioned software package stored in the chip by employing the software security verification information as soon as the single plate is connected to power. The technical proposal of this invention can guarantee the security of software verification information, effectively solve the problem of modification of chip contents, and also effectively assure the security of software that is operated on the single plate.
Owner:HUAWEI TECH CO LTD
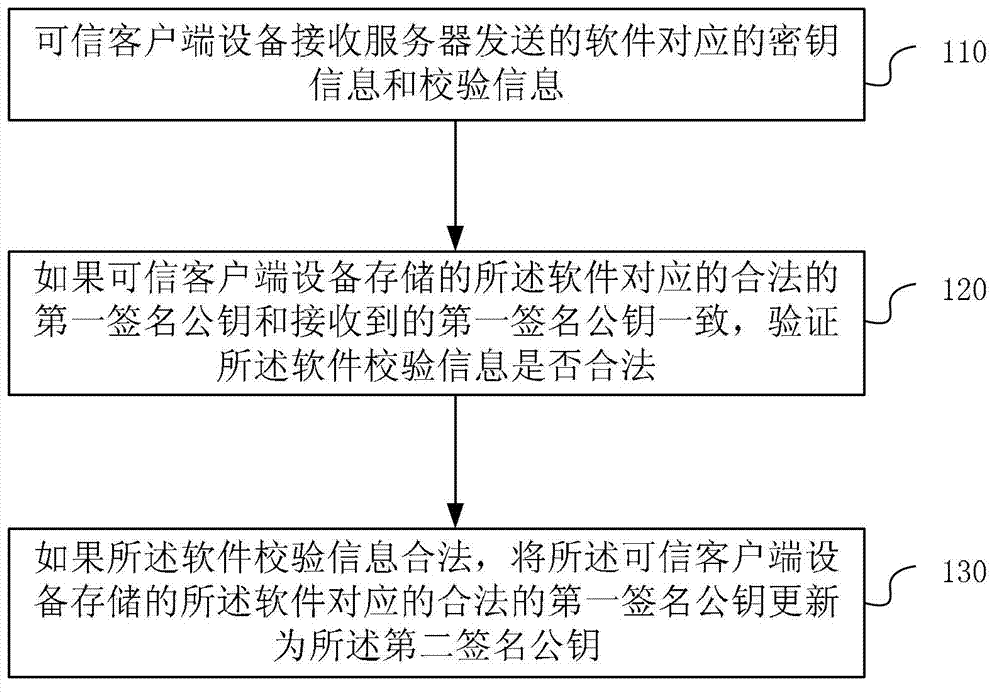
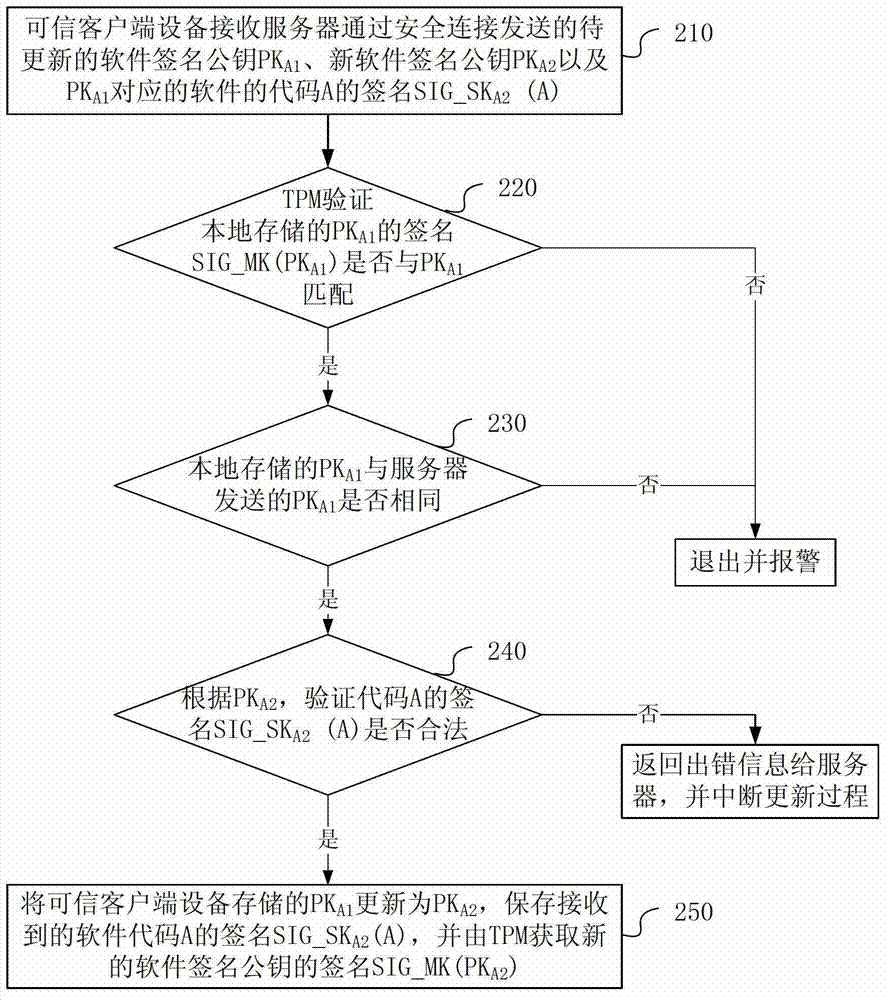
Software secret key updating method and device
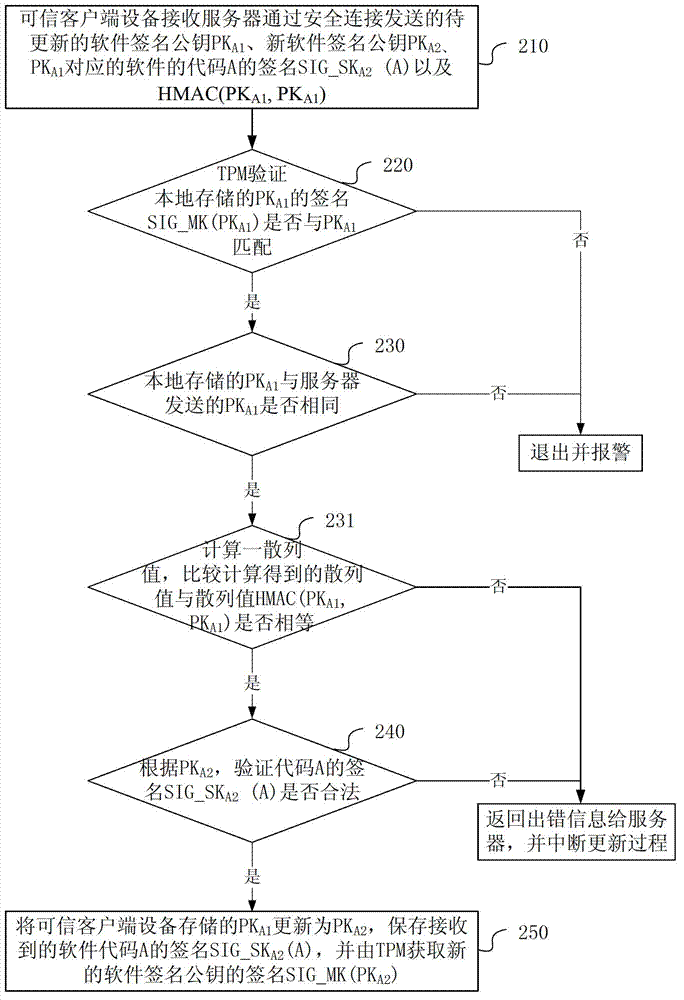
ActiveCN103595530APrevent unable to update issuesKey distribution for secure communicationUser identity/authority verificationComputer hardwareTrusted client
Provided in an embodiment of the present invention are a software key updating method and device. A trusted client device receives key information and verification information corresponding to the software and transmitted by a server, the key information containing a to-be-updated first software public key signature and a new second software public key signature, and the verification information containing software verification information; if a valid first software public key signature corresponding to the software and stored in the trusted client device is consistent with the received first software public key signature, then checking whether the software verification information is valid; and if the software verification information is valid, then updating the valid first software public key signature corresponding to the software and stored in the trusted client device as a second software public key signature. With the above solution, the present invention can remotely update a software key signature on a trusted client device, thus preventing the problem of being unable to update an invalid key.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com