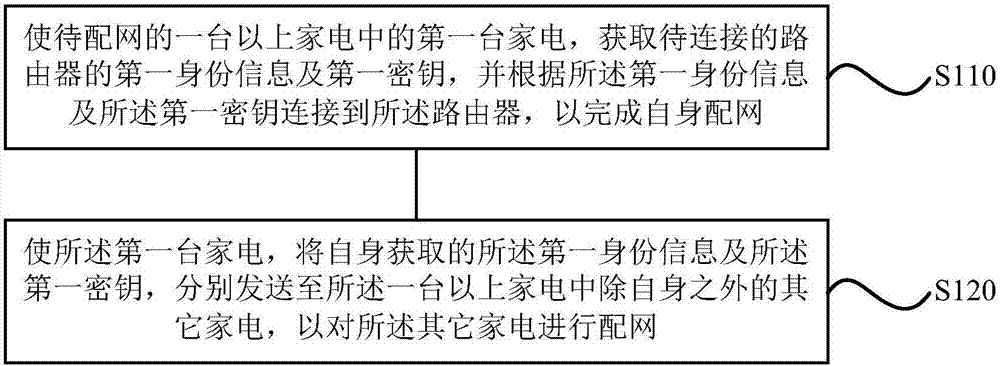
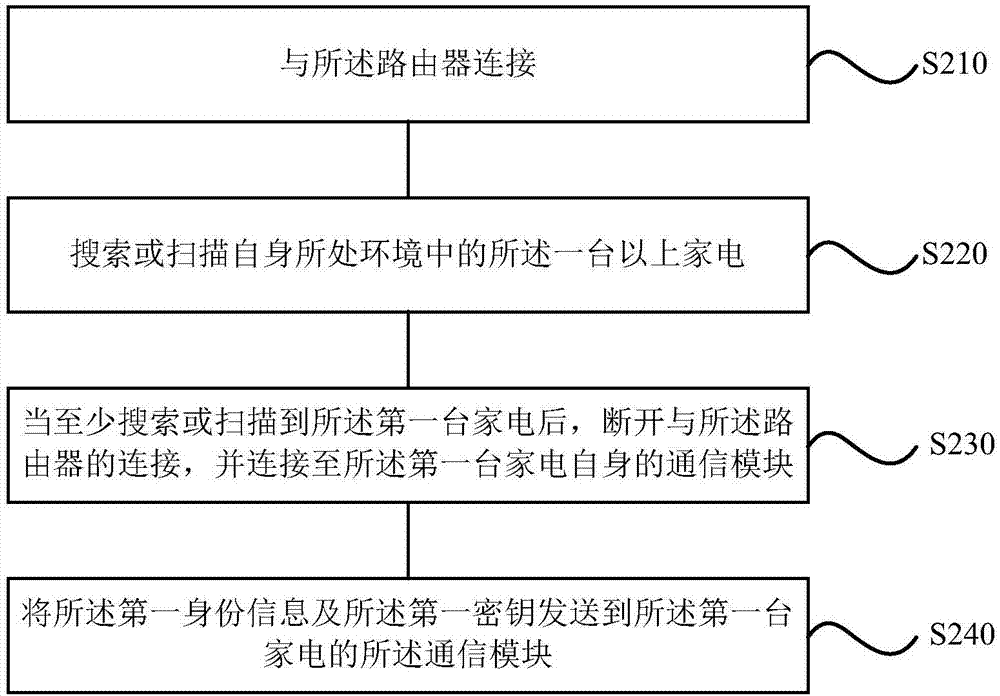
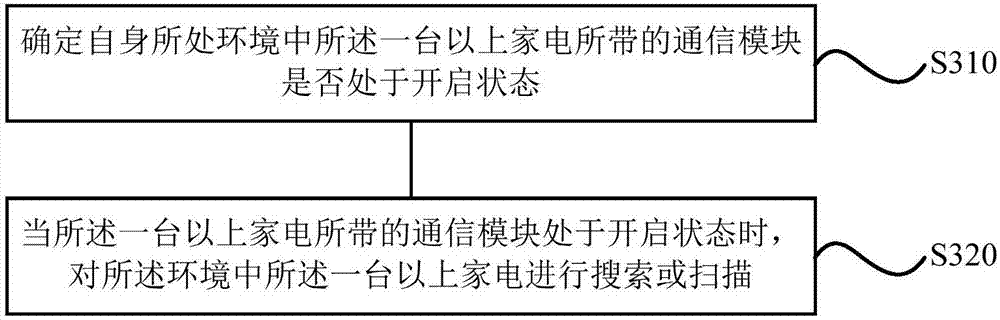
Patents
Literature
189 results about "Computer appliance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A computer appliance is a computer with software or firmware that is specifically designed to provide a specific computing resource. Such devices became known as appliances because of the similarity in role or management to a home appliance, which are generally closed and sealed, and are not serviceable by the user or owner. The hardware and software are delivered as an integrated product and may even be pre-configured before delivery to a customer, to provide a turn-key solution for a particular application. Unlike general purpose computers, appliances are generally not designed to allow the customers to change the software and the underlying operating system, or to flexibly reconfigure the hardware.
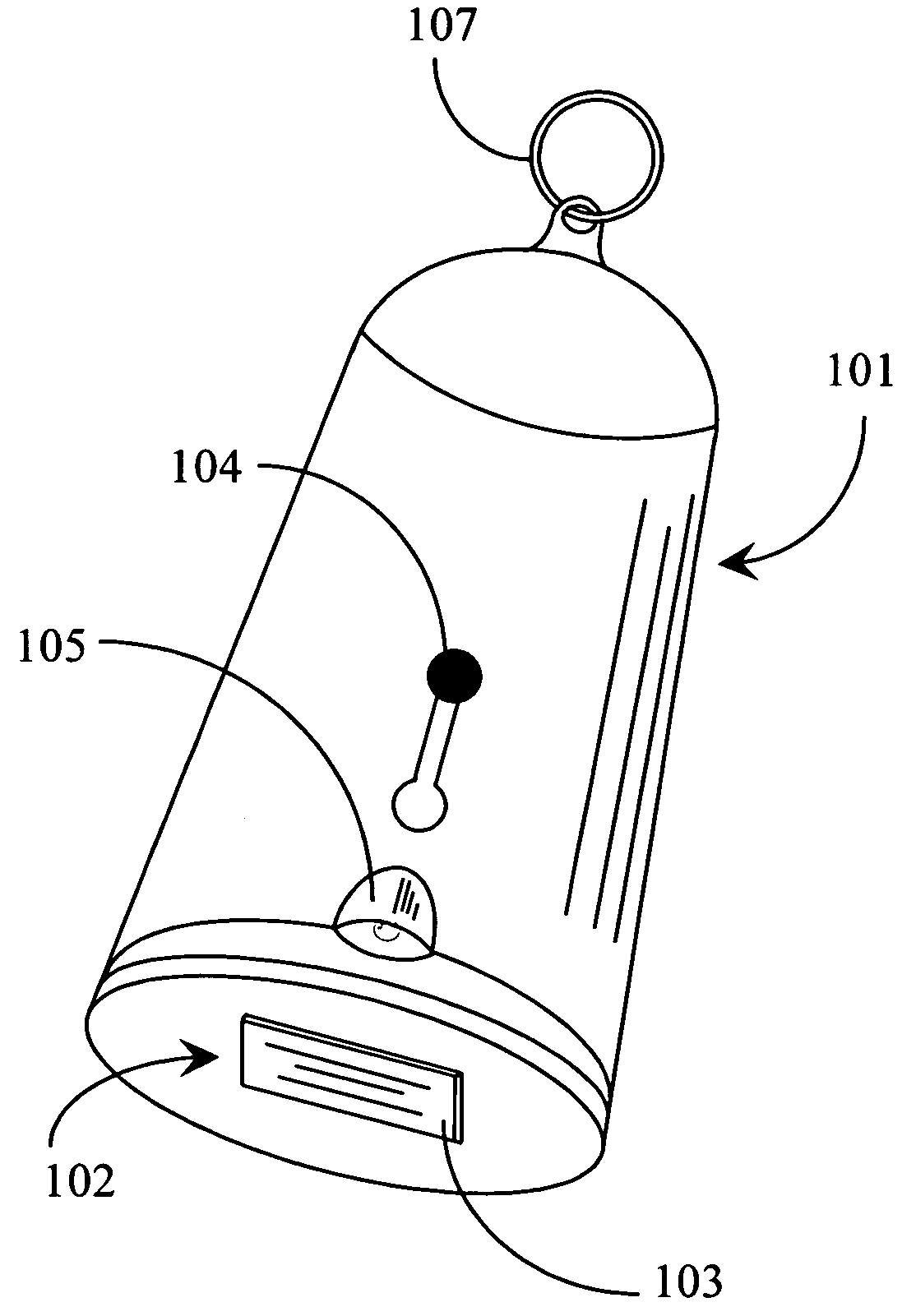
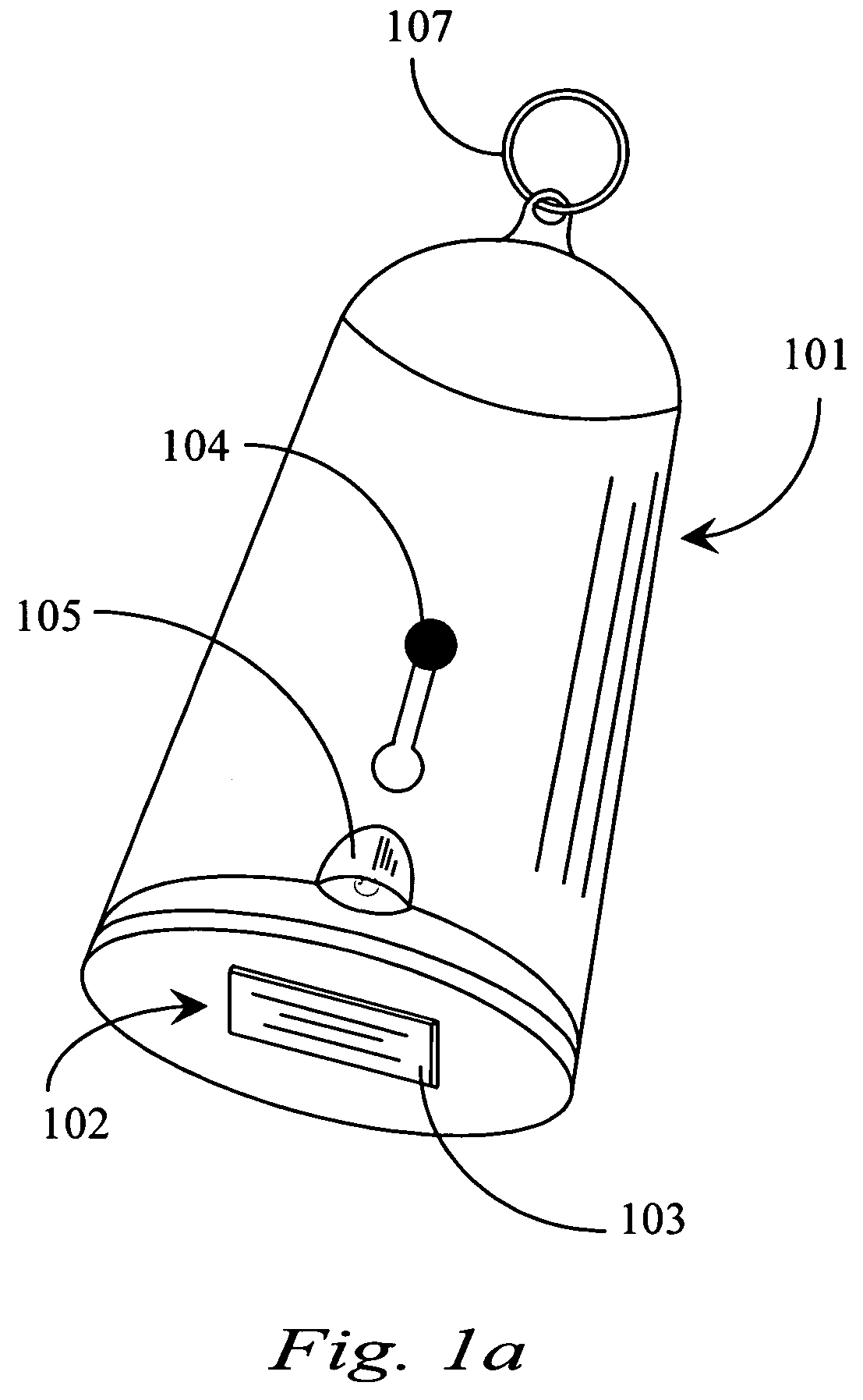
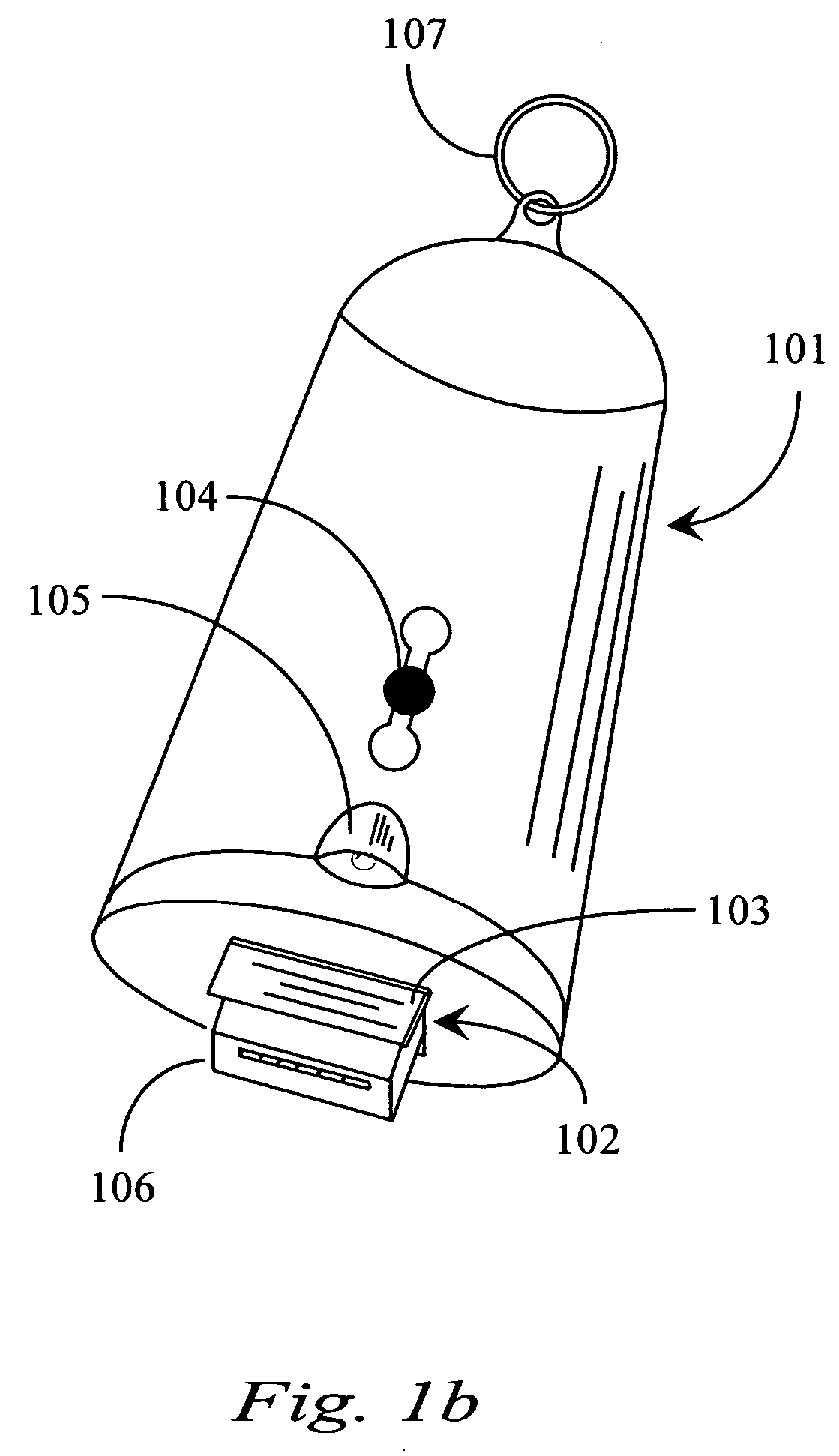
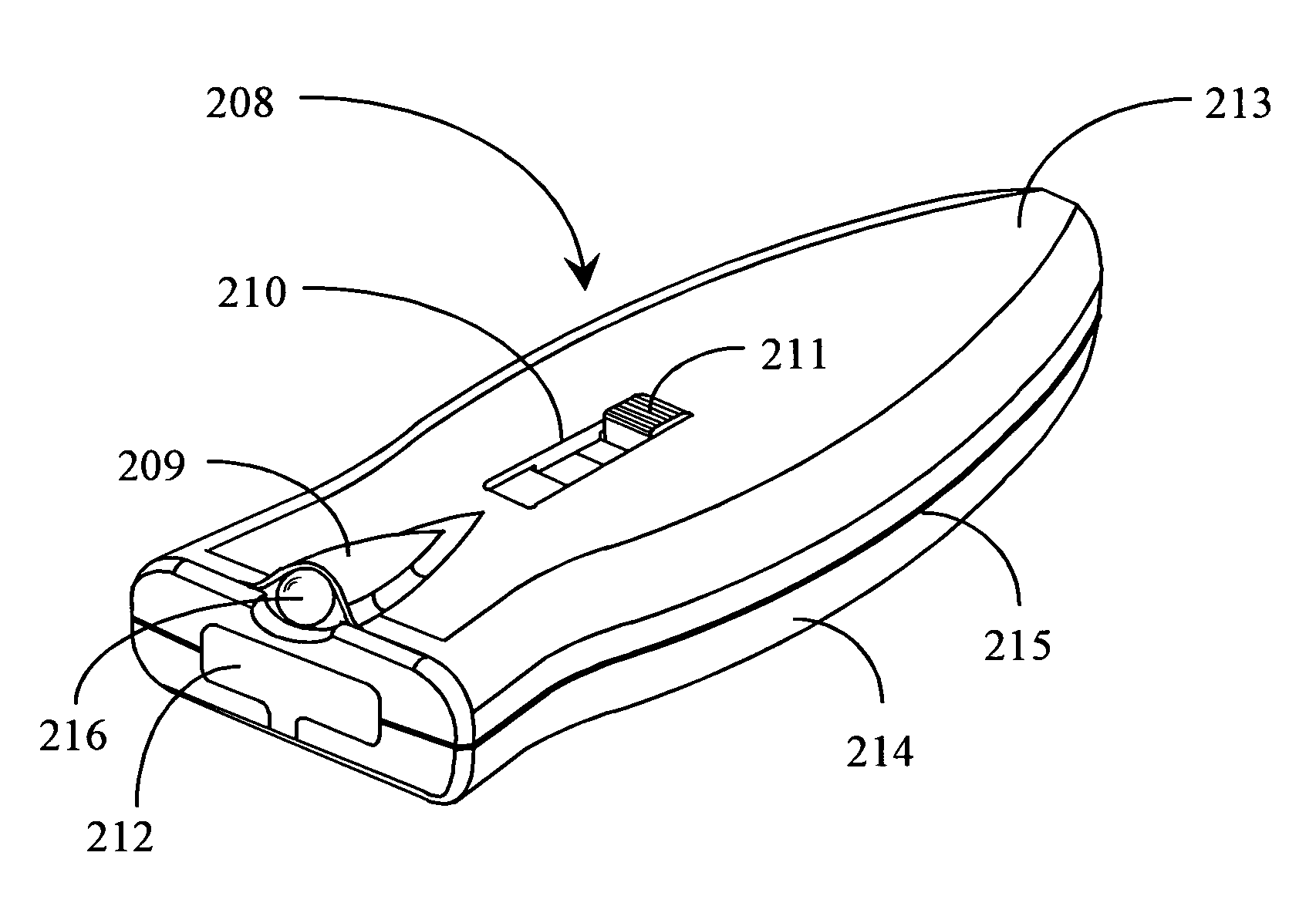
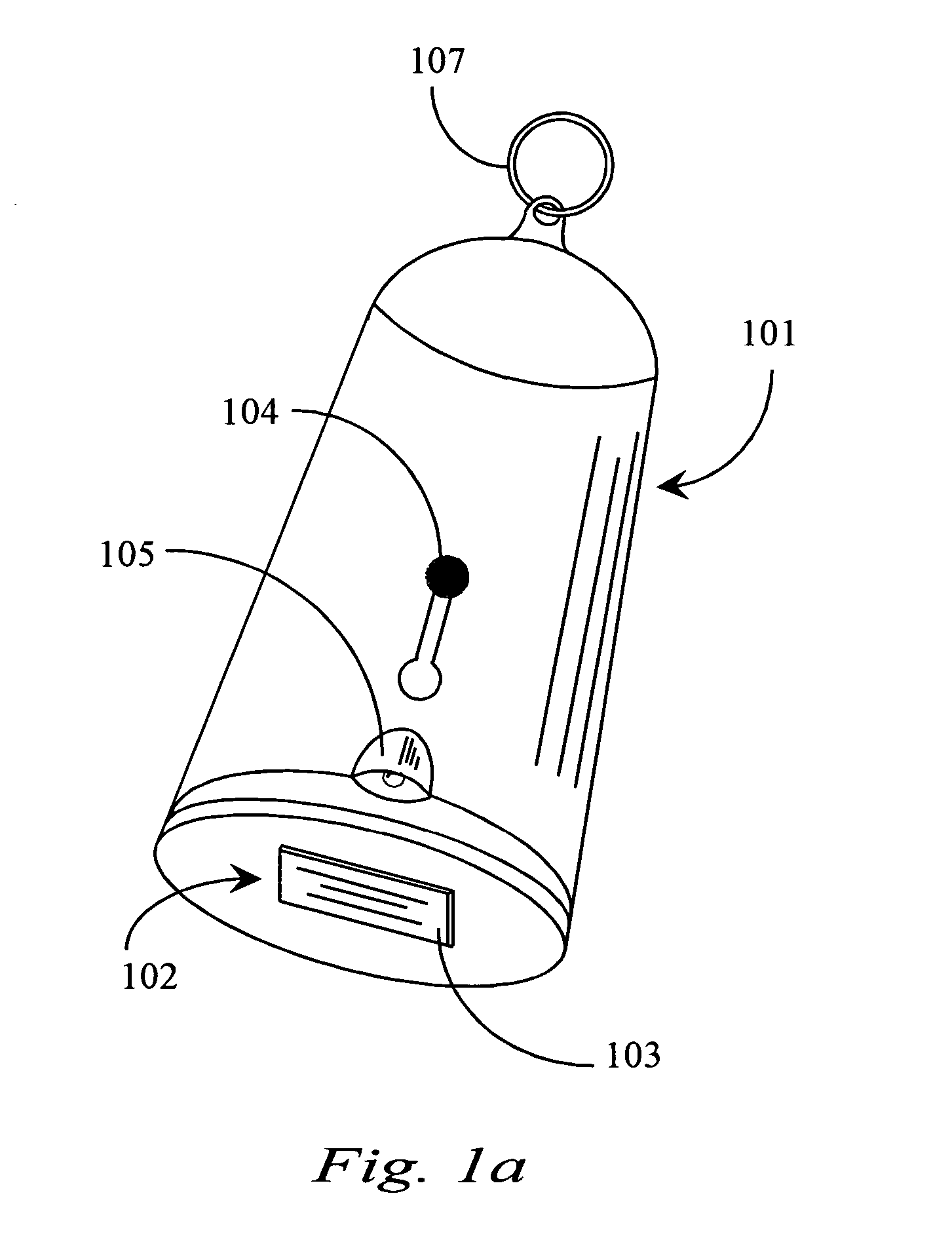
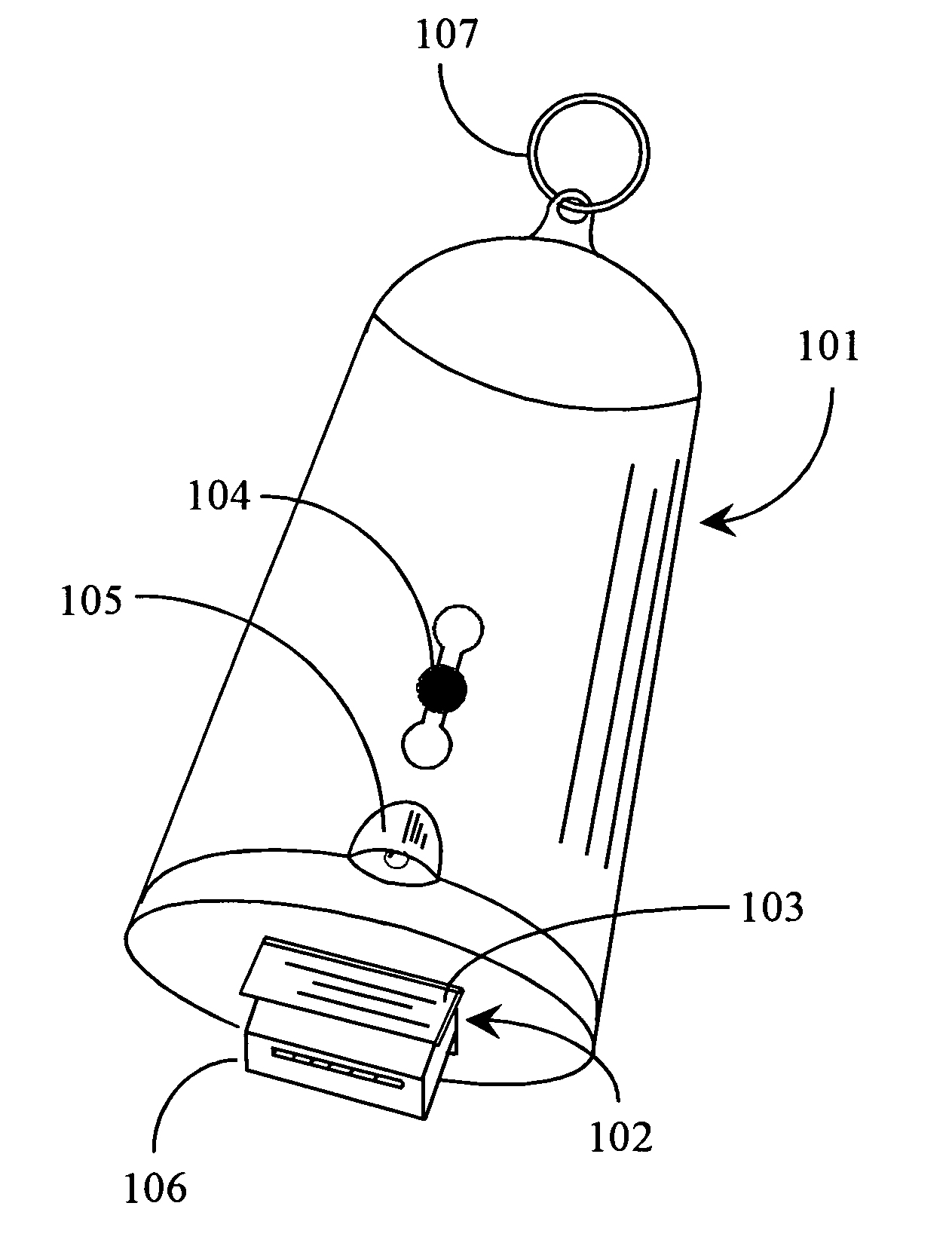
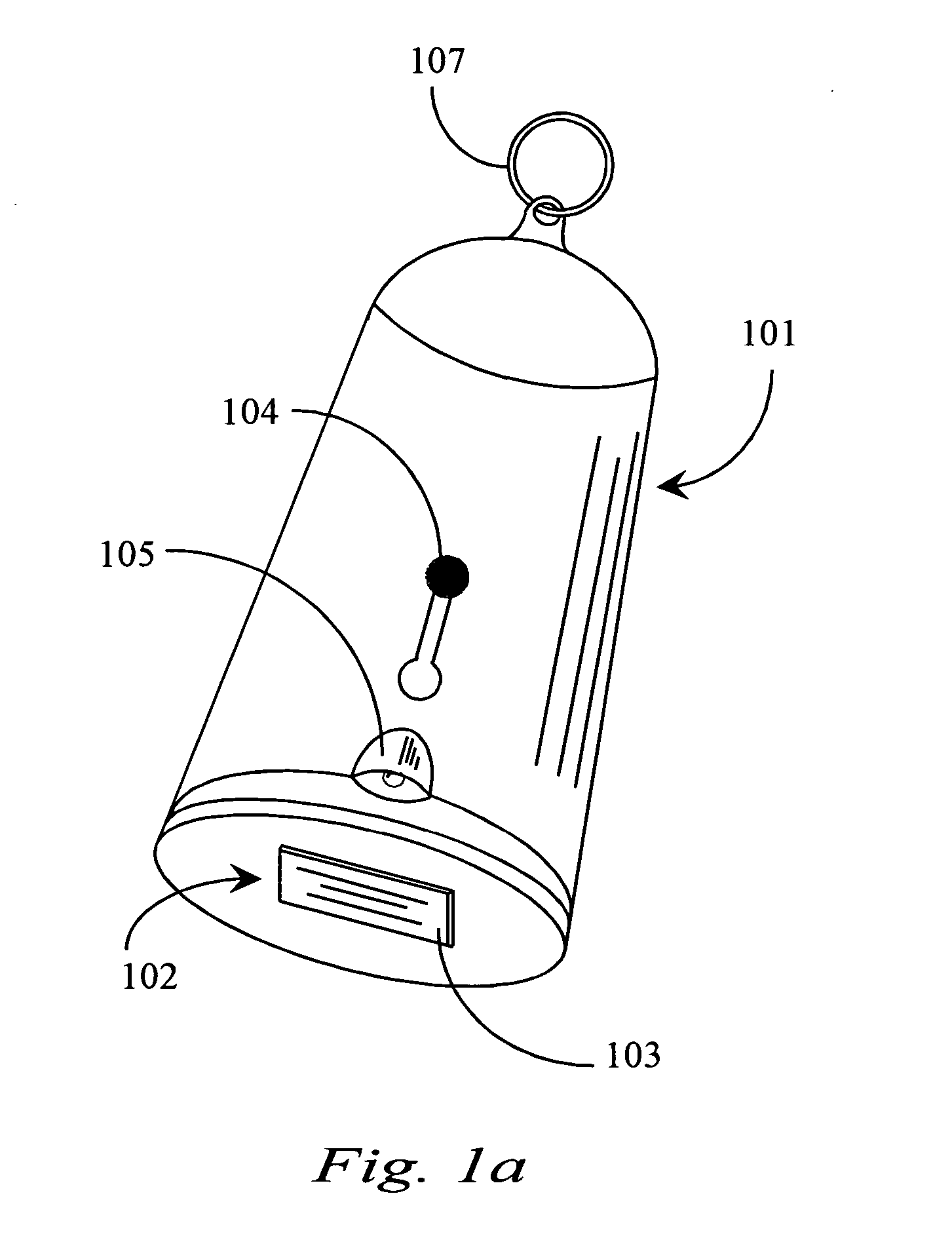
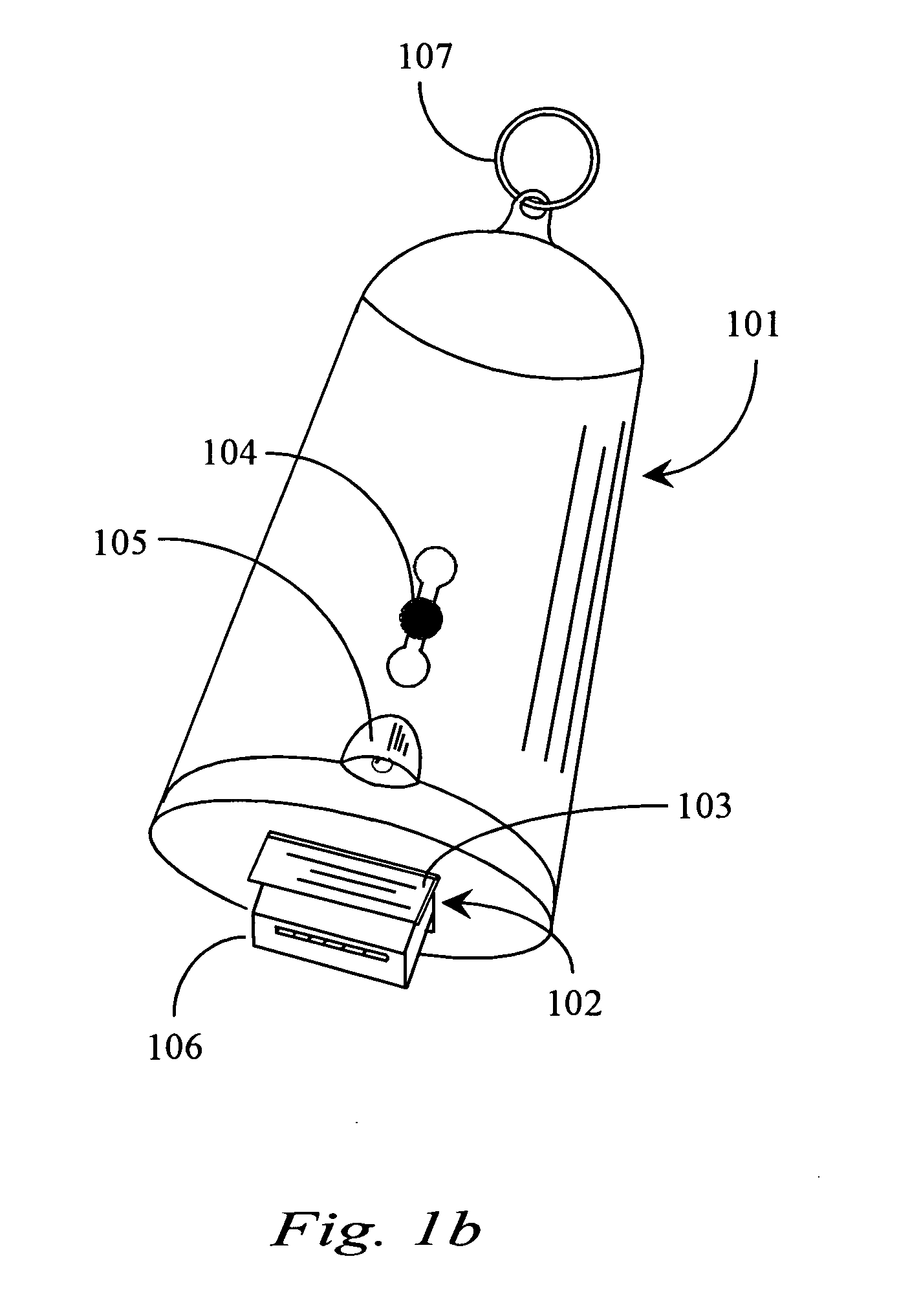
Thumb drive with retractable USB connector
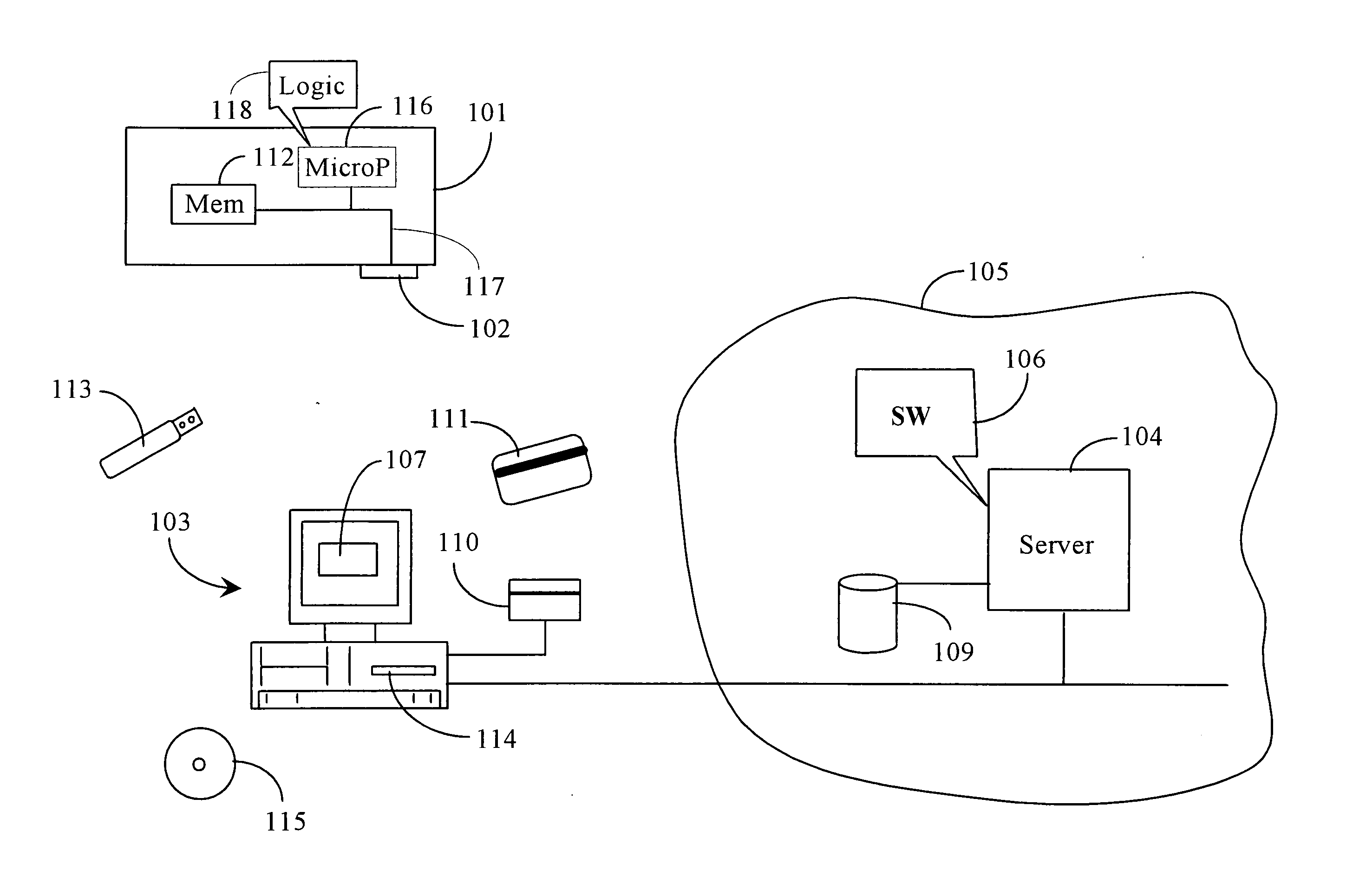
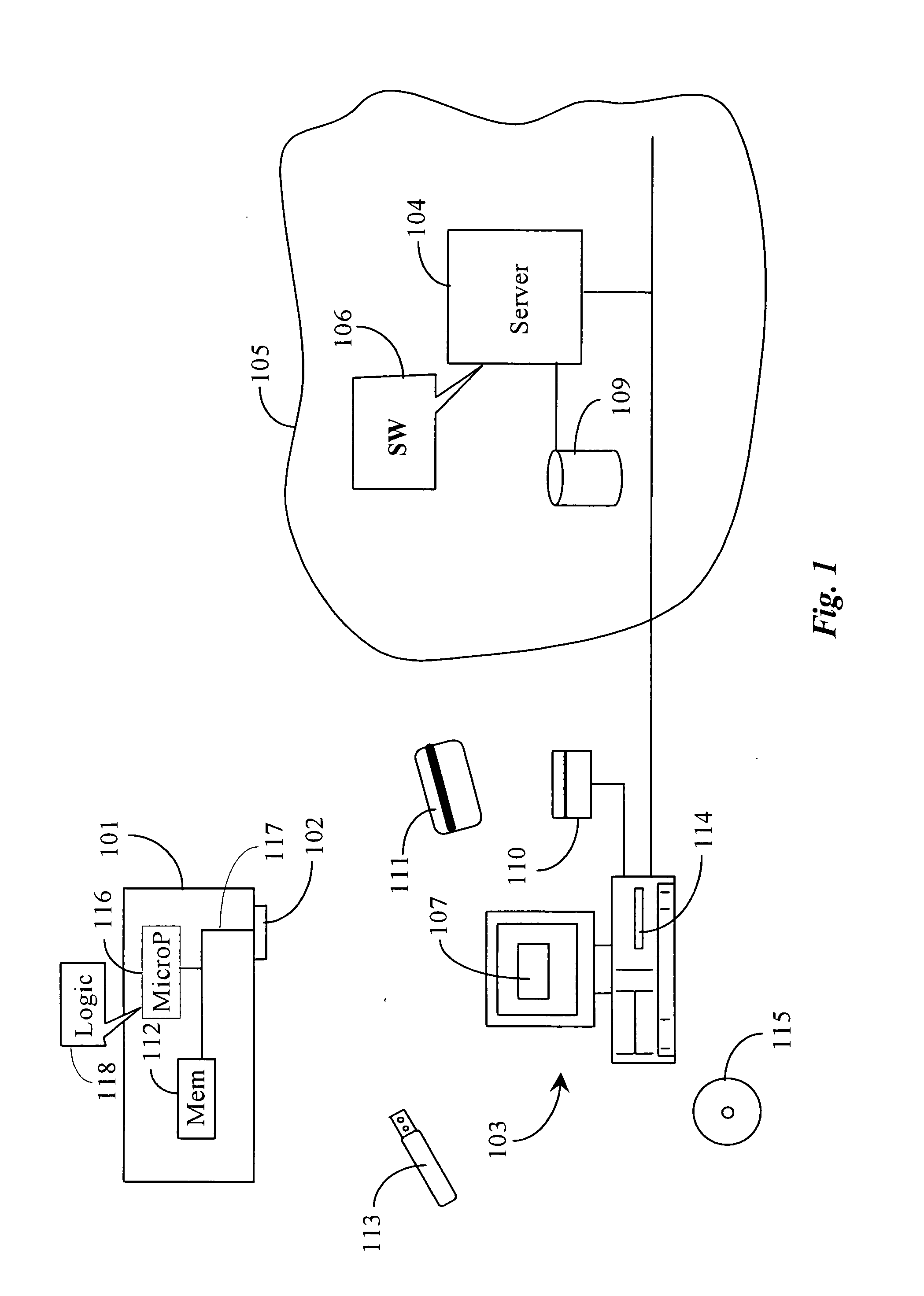
A thumb drive has an on-board memory for storing digital information, a male USB connector coupled to the on-board memory for connecting to a USB port of a computer appliance, and an extension / retraction mechanism coupled to the connector and on-board memory for extending the connector from an enclosure of the drive and for retracting the connector when not in use. In various embodiments a light is also provided for use with finding female USB ports for connection, and as a utility light.
Owner:ANU IP
Thumb drive with retractable USB connector
InactiveUS7070425B2Live contact access preventionElectrical apparatus casings/cabinets/drawersOn boardDisplay device
A thumb drive comprises on-board memory for storing digital information, a male USB connector coupled to the on-board memory for connecting to a USB port of a computer appliance, internal control elements for managing MP3 player functions for the thumb drive, a display for displaying downloaded song titles, user-operable controls for selecting and playing songs recorded as audio files in the on-board memory as audio output at an output connector, a Bluetooth™ compatible transmitter for transmitting selected data and audio output to external Bluetooth™ compatible devices, and an extension / retraction mechanism coupled to the connector for extending the connector from an enclosure of the drive and for retracting the connector when not in use.
Owner:ANU IP
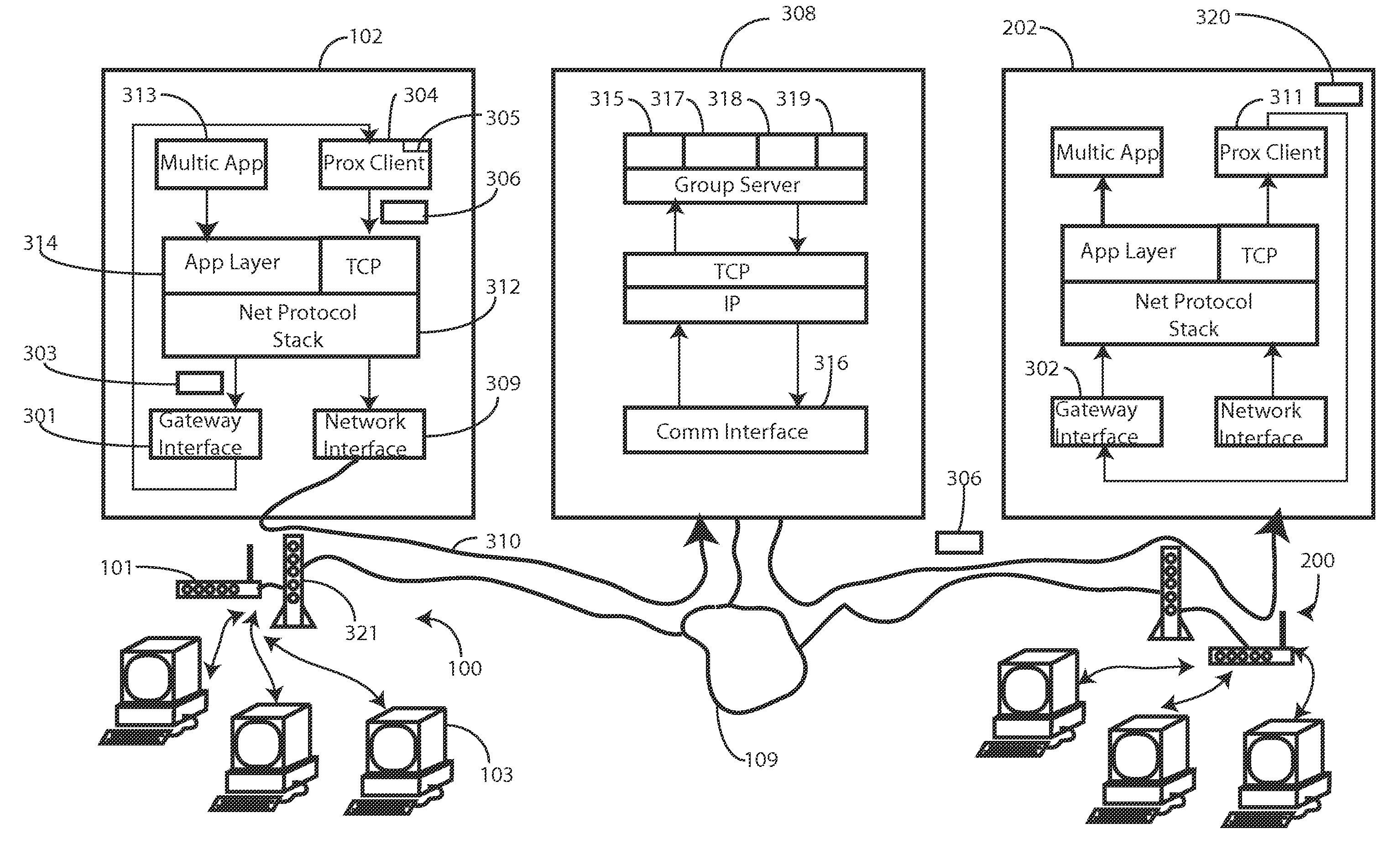
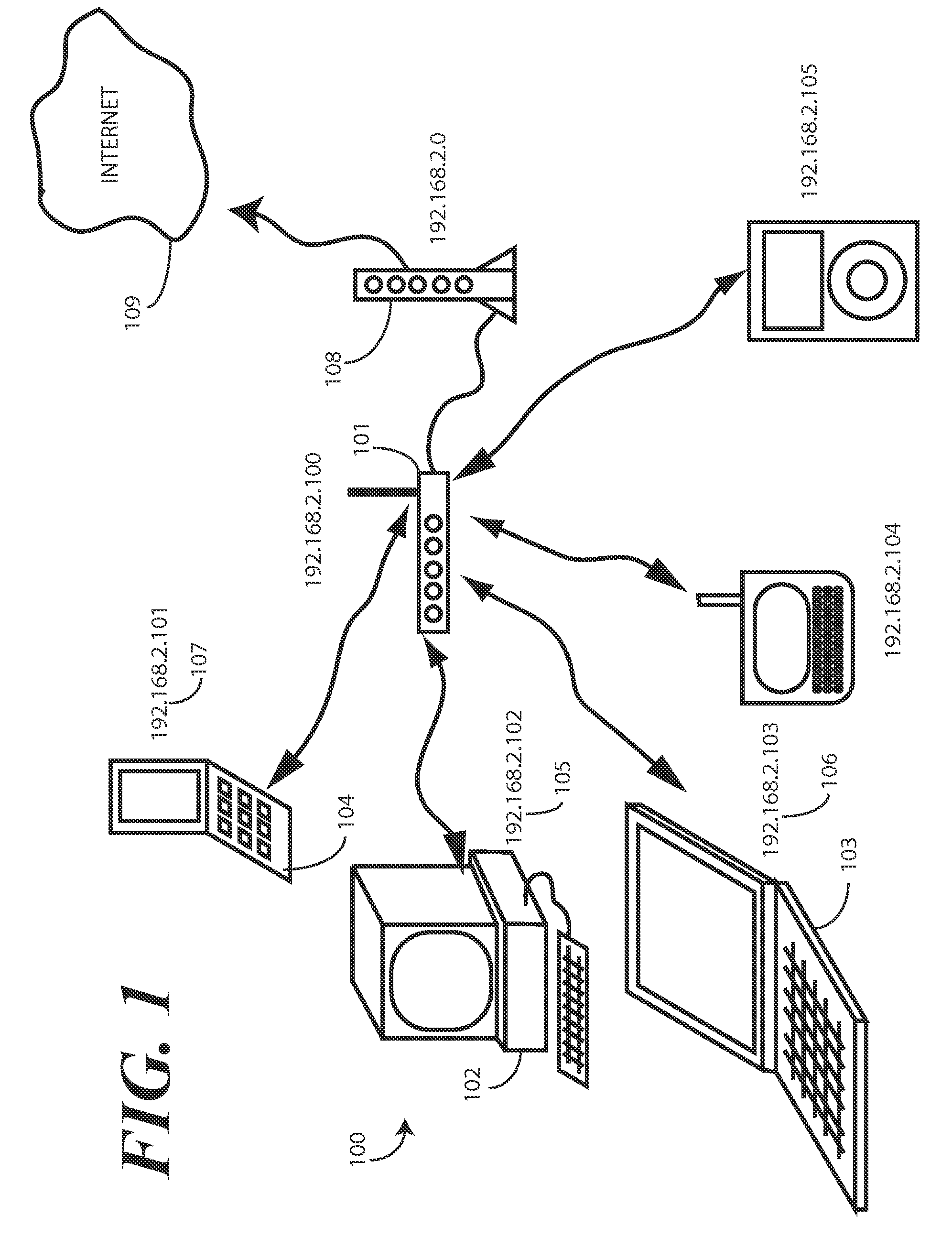
Method and system for service discovery across a wide area network
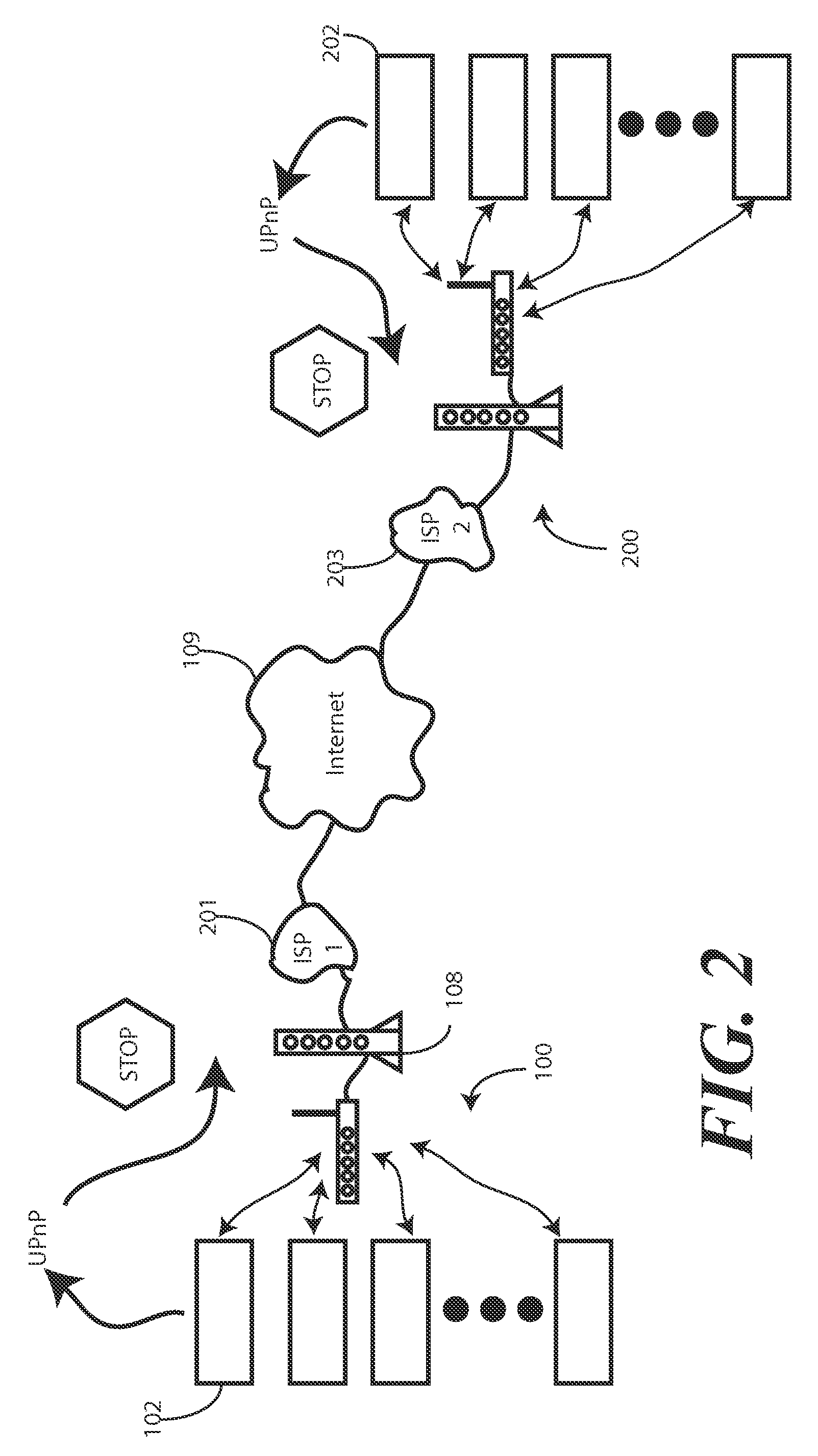
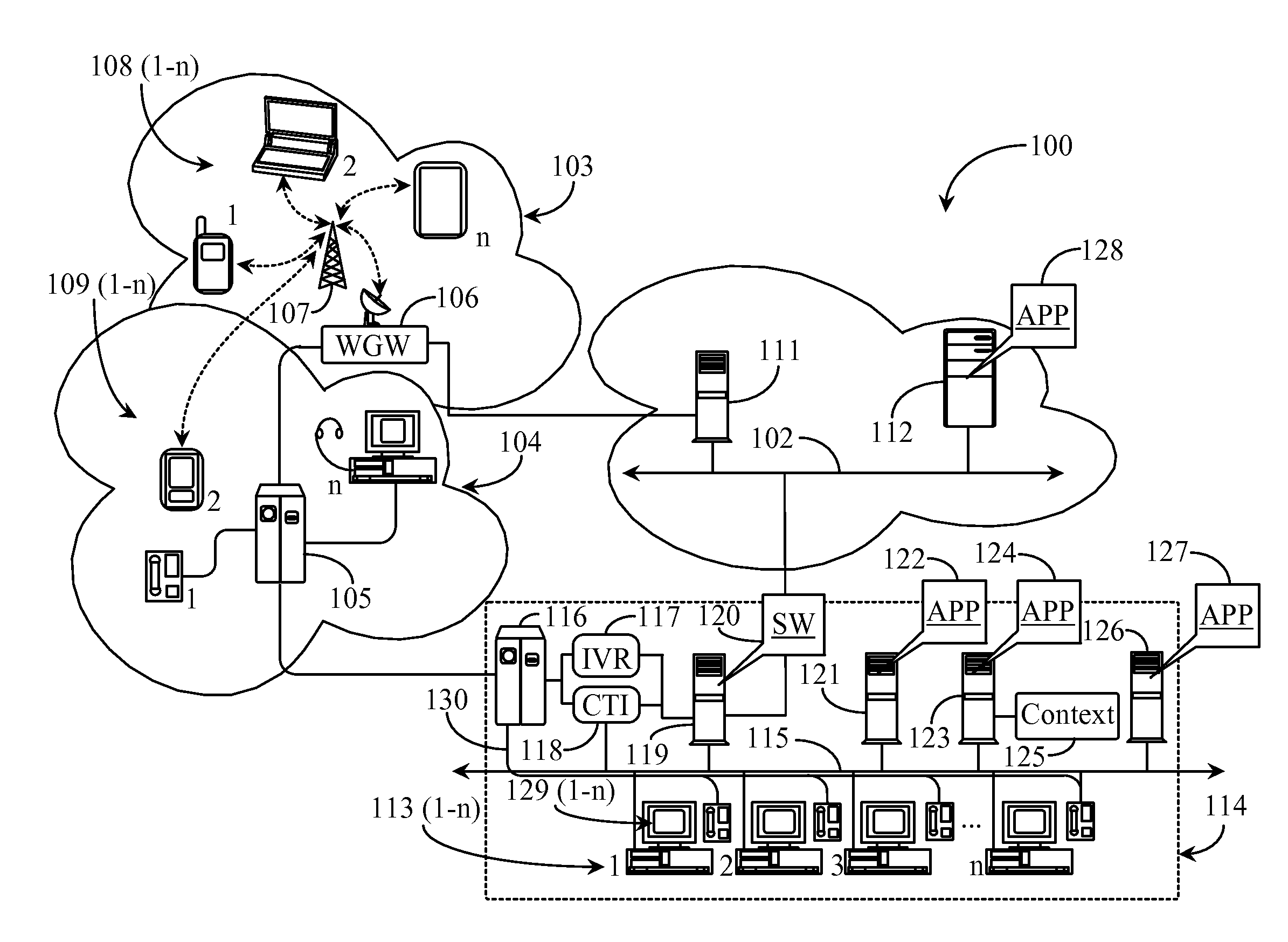
A method and system for simulating a local area network across a wide area network (109) is provided. The method and system facilitate delivery of multicast communications (303), such as search messages from plug and play applications, from one local area network (100) to another (200), despite the fact that these local area networks (100,200) may be spread distally across a wide area network (109). The system utilizes a trusted group server (308) to forward encapsulated unicast communications (306) to member networked computer devices (202), even when in different domains. Each networked computer device (102,202) includes a gateway interface (301,302) and a local proxy client (304,311). The gateway interface (301) receives multicast communications (306) from multicast applications (313) and delivers them to the local proxy client (304). The local proxy client (304) encapsulates the multicast communications (306) and delivers them to the group server (308), where they are replicated and delivered to all members of the group.
Owner:MOTOROLA MOBILITY LLC
Credit and transaction systems
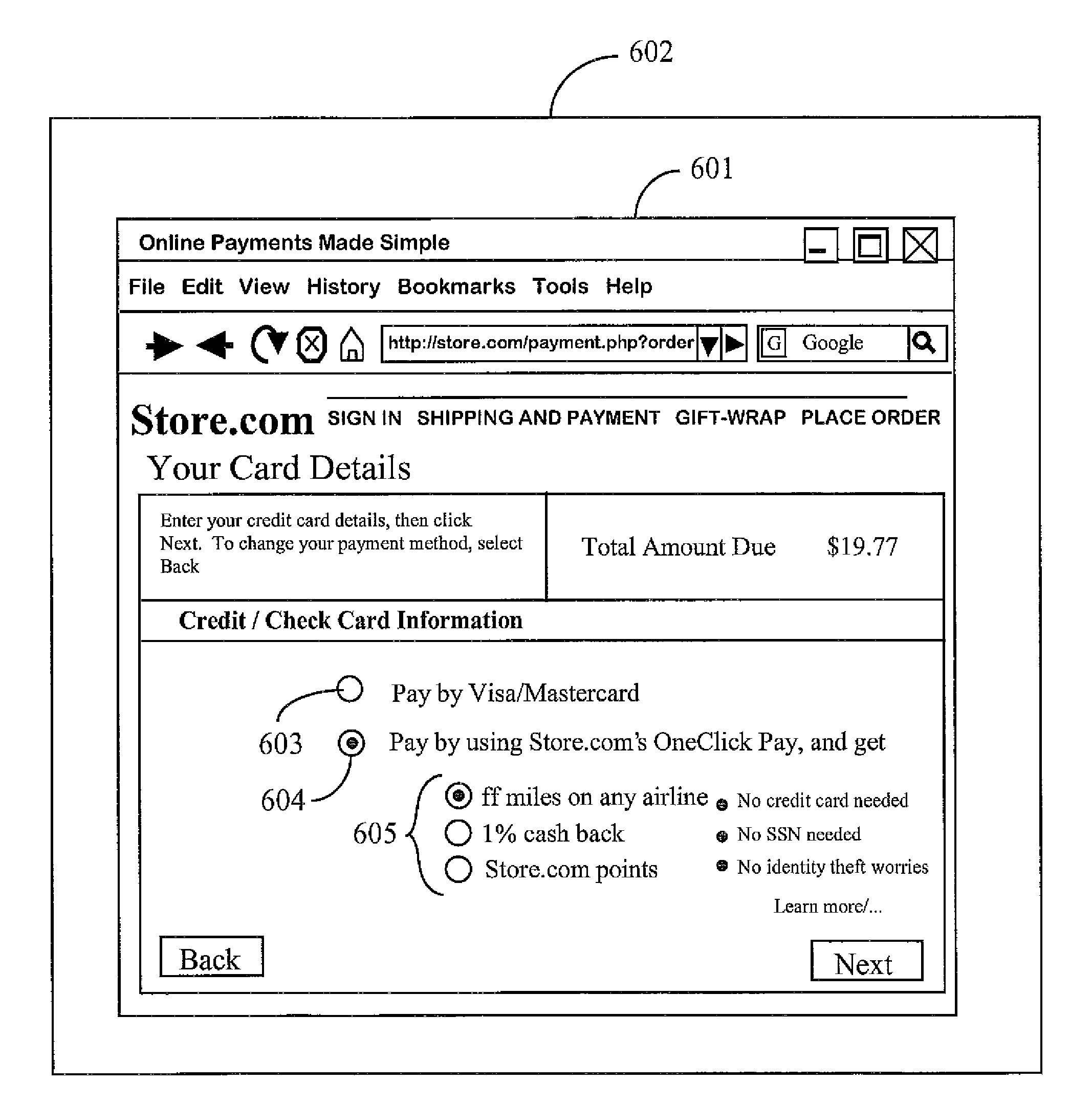
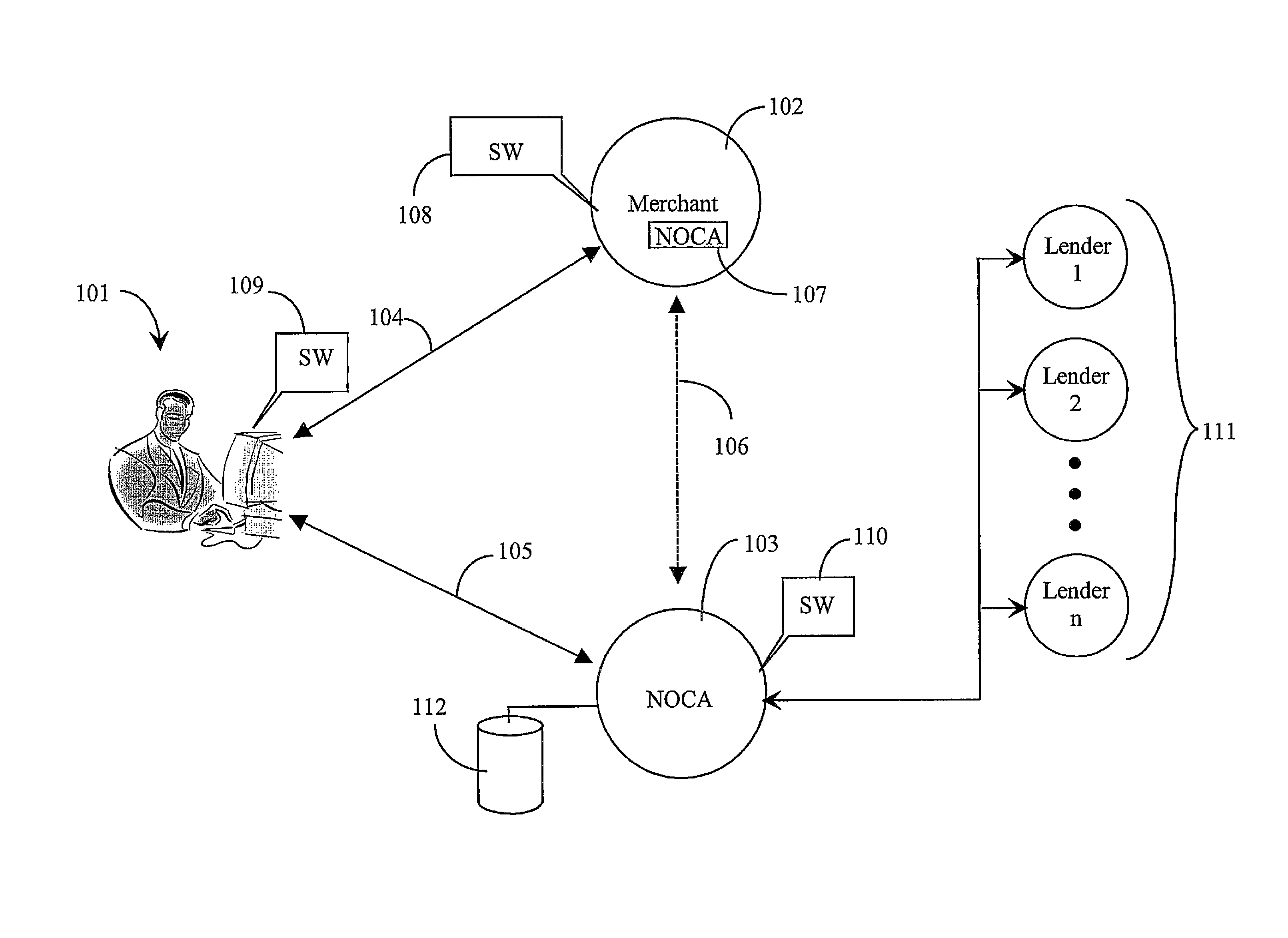
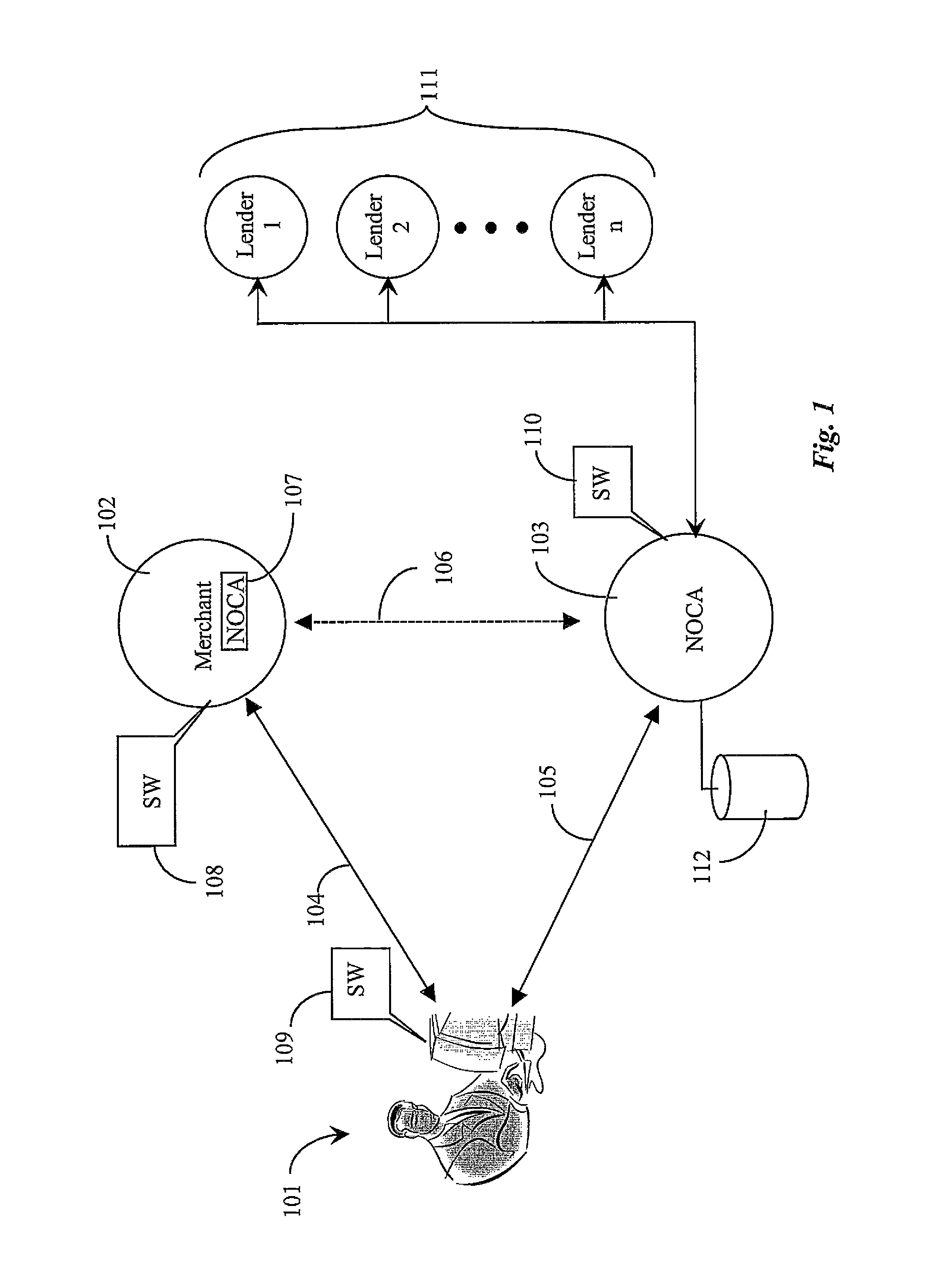
An Internet-coupled transaction service has a link to a computer appliance coupled to a merchant site, the computer appliance operated by a person who has selected one or more products or services to purchase at the merchant site, and who has selected, through the merchant site, the transaction service to arrange payment, and software executing from a computer-readable medium accessible to the service. The transaction service, via the software verifies the identity of the person, determines a credit worthiness for the person, and the score being sufficient, arranges payment to be made to the merchant on behalf of the person, and arranges repayment terms with the person for the payment to the merchant.
Owner:INTELLECTUAL ADVANCE
Link annotation for keyboard navigation
ActiveUS7689924B1Input/output for user-computer interactionMultiple digital computer combinationsUser inputDisplay device
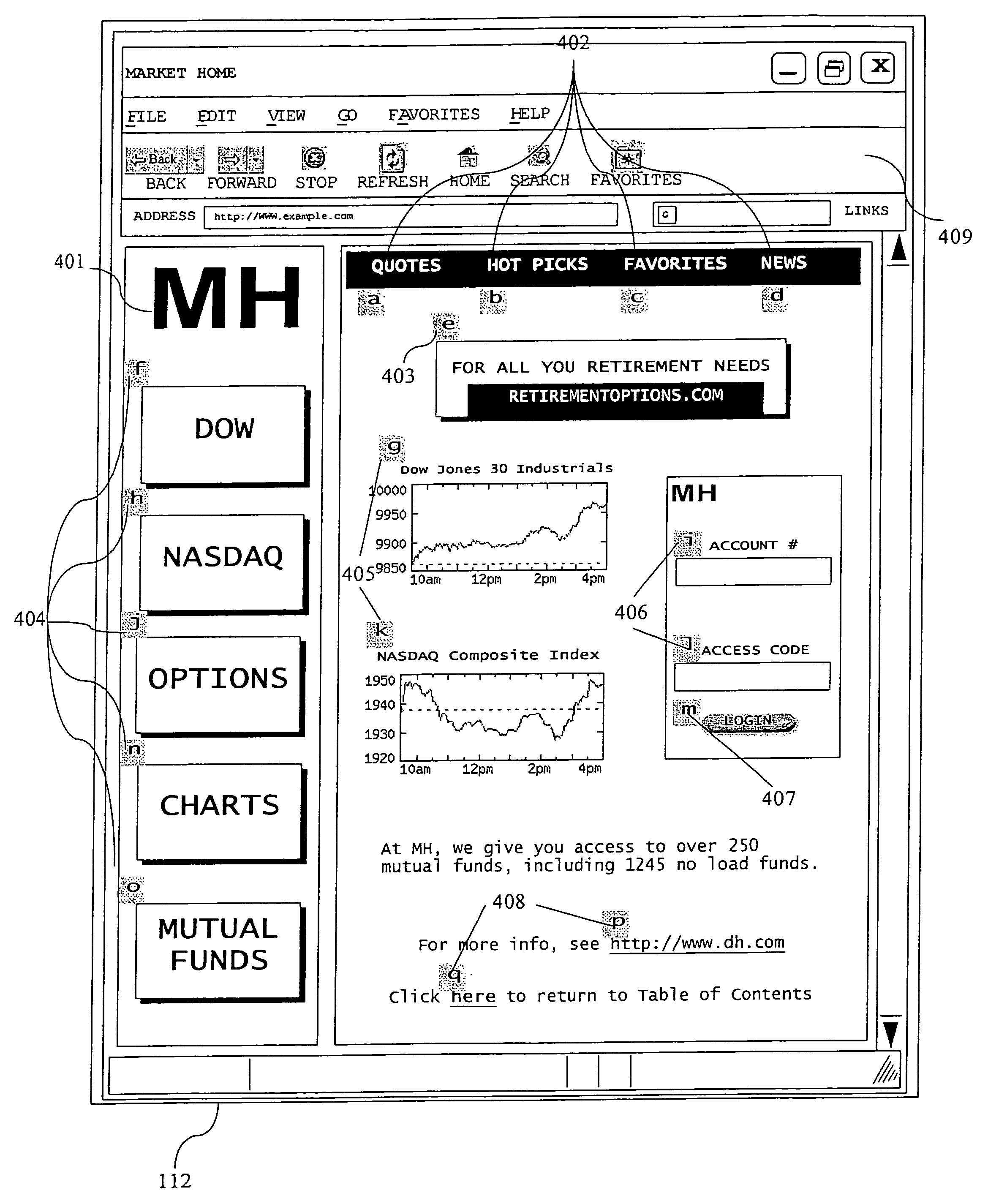
A computer navigation system and method has one or more interactive links displayed on a display connected to a computer appliance, and one or more visual linktags associated with individual ones of the one or more interactive links, the linktags displaying one or more numbers, characters or symbols, the system enabled to initiate an interactive link in the display upon user input of one of the numbers, characters or symbols in a linktag.
Owner:GOOGLE LLC
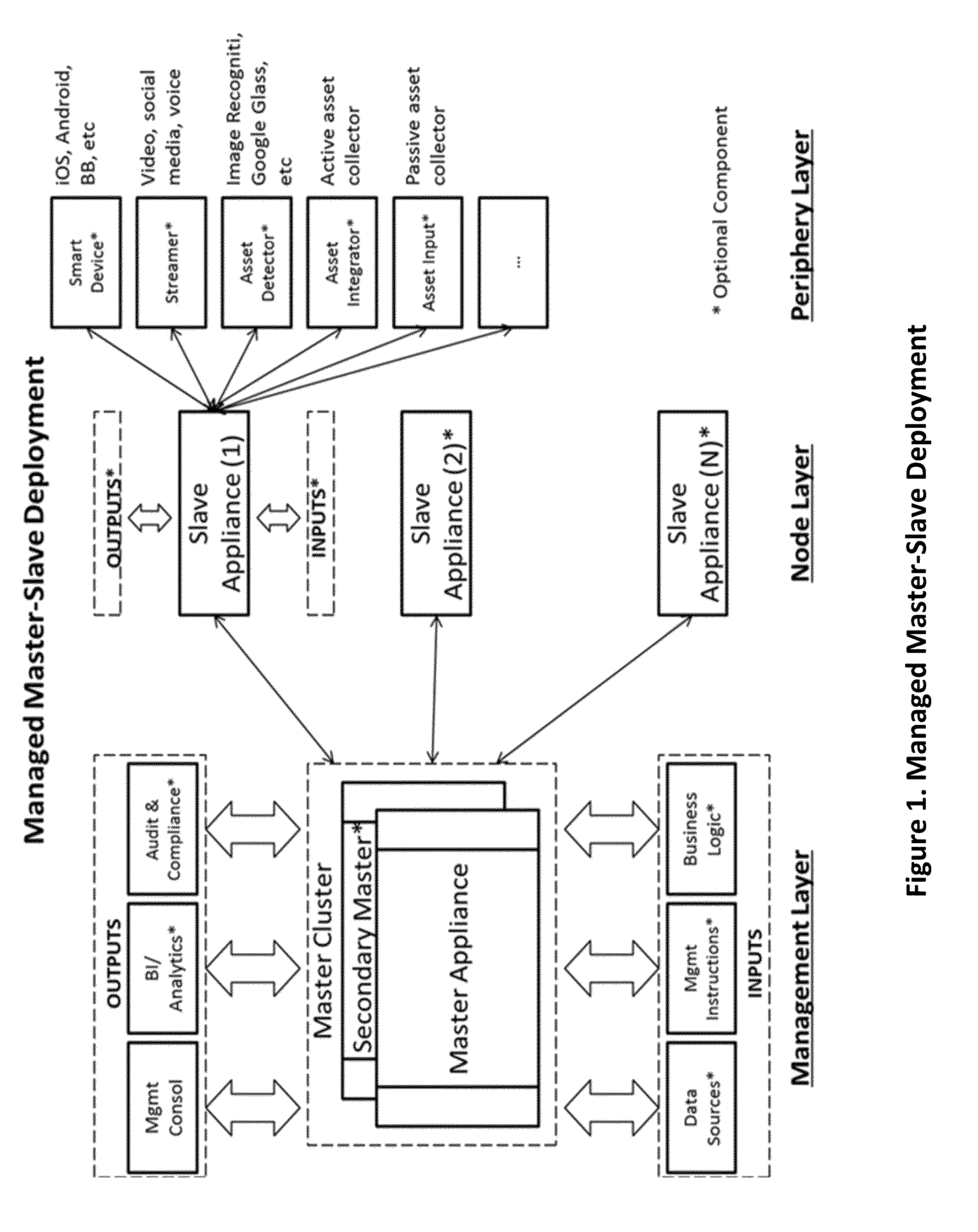
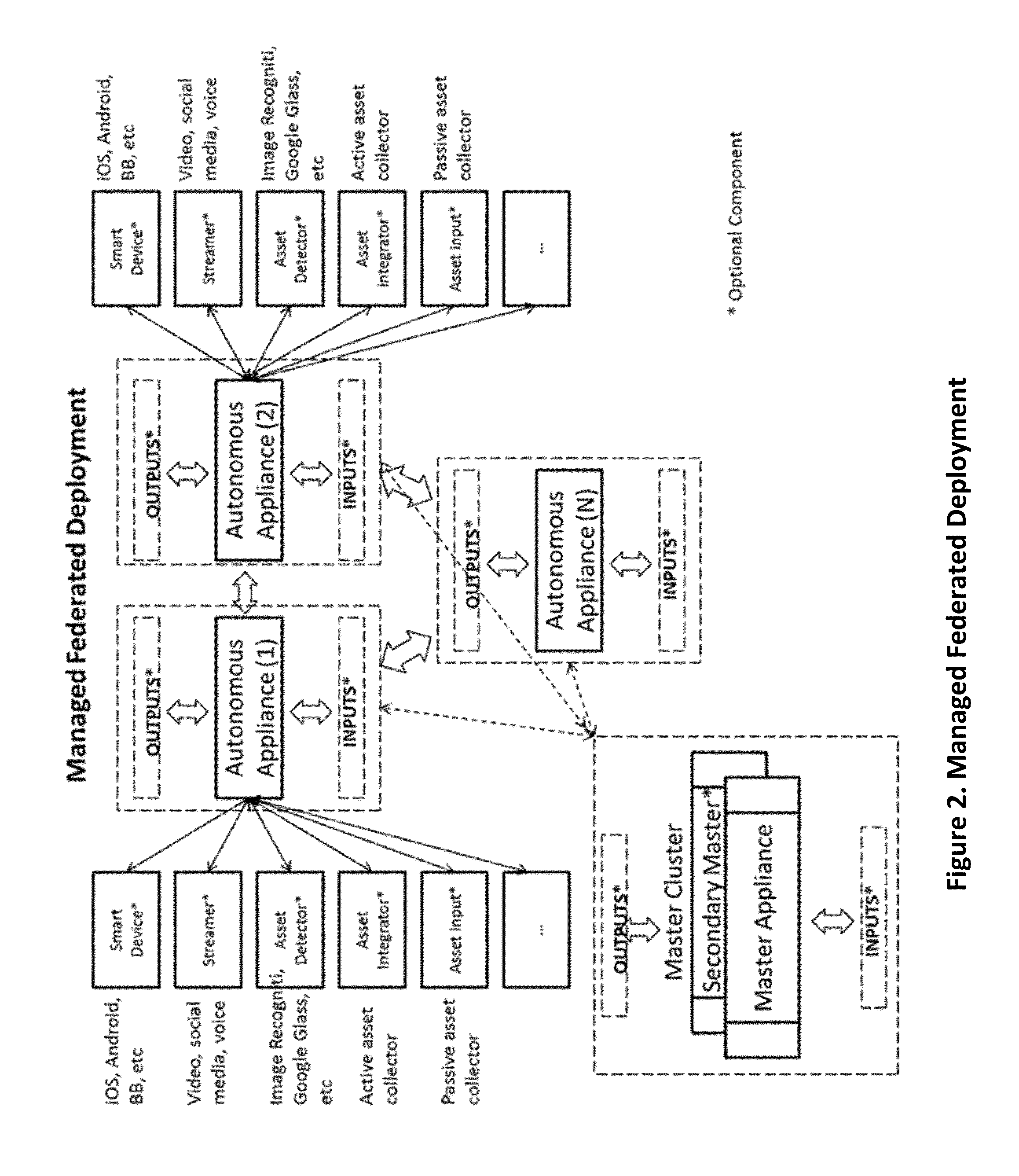
Appliance clearinghouse with orchestrated logic fusion and data fabric - architecture, system and method
InactiveUS20160006629A1Facilitate acquisitionEasy to manageDigital computer detailsInternal/peripheral component protectionUnstructured dataNetworked control system
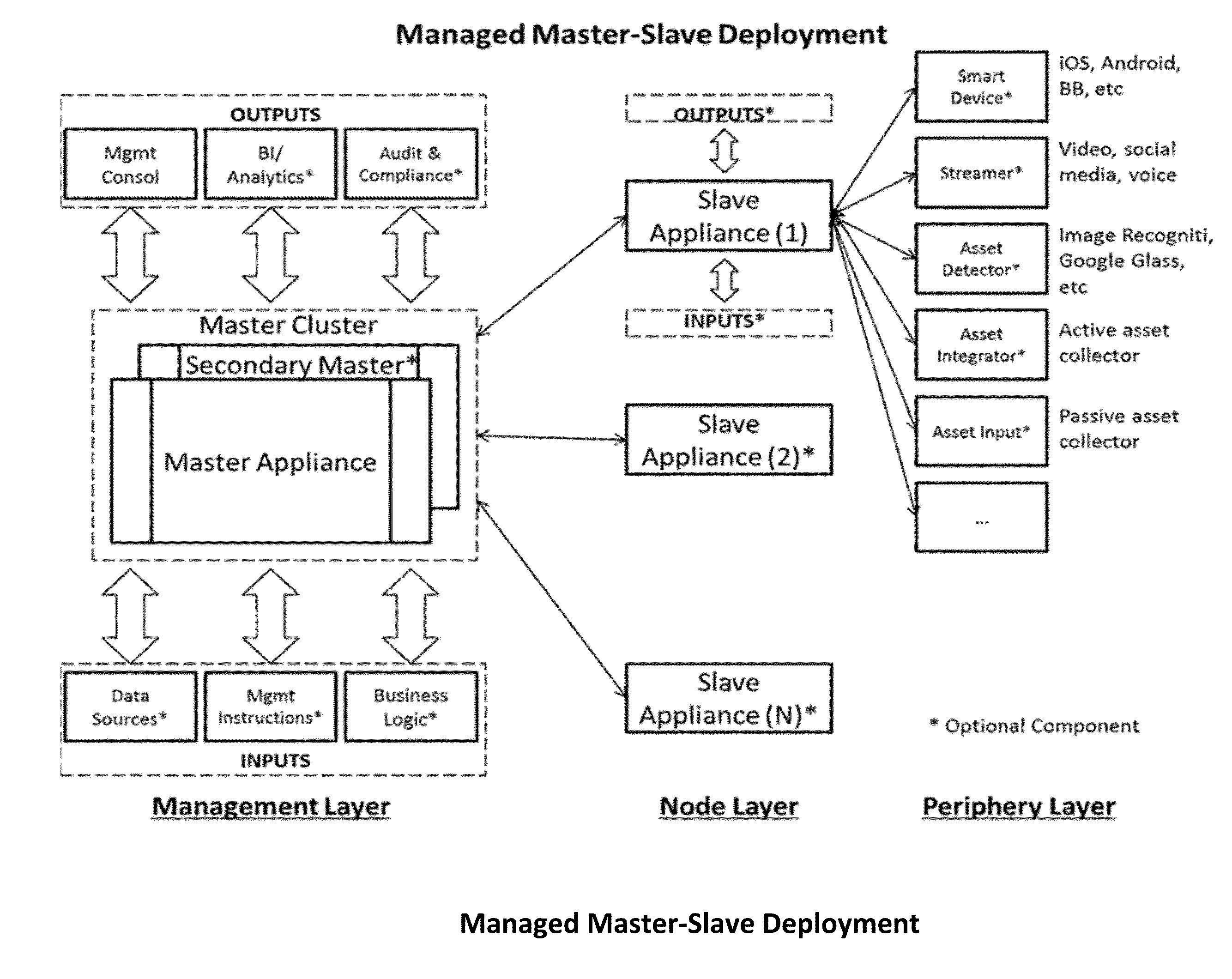
A computerized method for controlling or connecting a plurality of computer appliances in a networked control system comprised of control center, computer appliance and peripherals for the purposes of establishing an automated framework and technical devices for intelligent integration of two or more applications, logic rules, data repositories and / or services together to automate, manage, synchronize or monitor knowledge or business solutions in real-time. The control center, computer appliances or peripherals can store and process structured or unstructured data; the control center is communicating with each appliance or periphery across a communication network; the control center can determine when an appliances or peripheral requires maintenance or update; the control center controls the current inventory of computer appliances and peripherals; the control center can add or reinitialize a new computer appliance or peripheral; the computer appliance can also add peripherals. A user can interact with the control center, computer appliance or a peripheral to perform monitoring, management or analysis functions.
Owner:IANAKIEV GEORGE +1
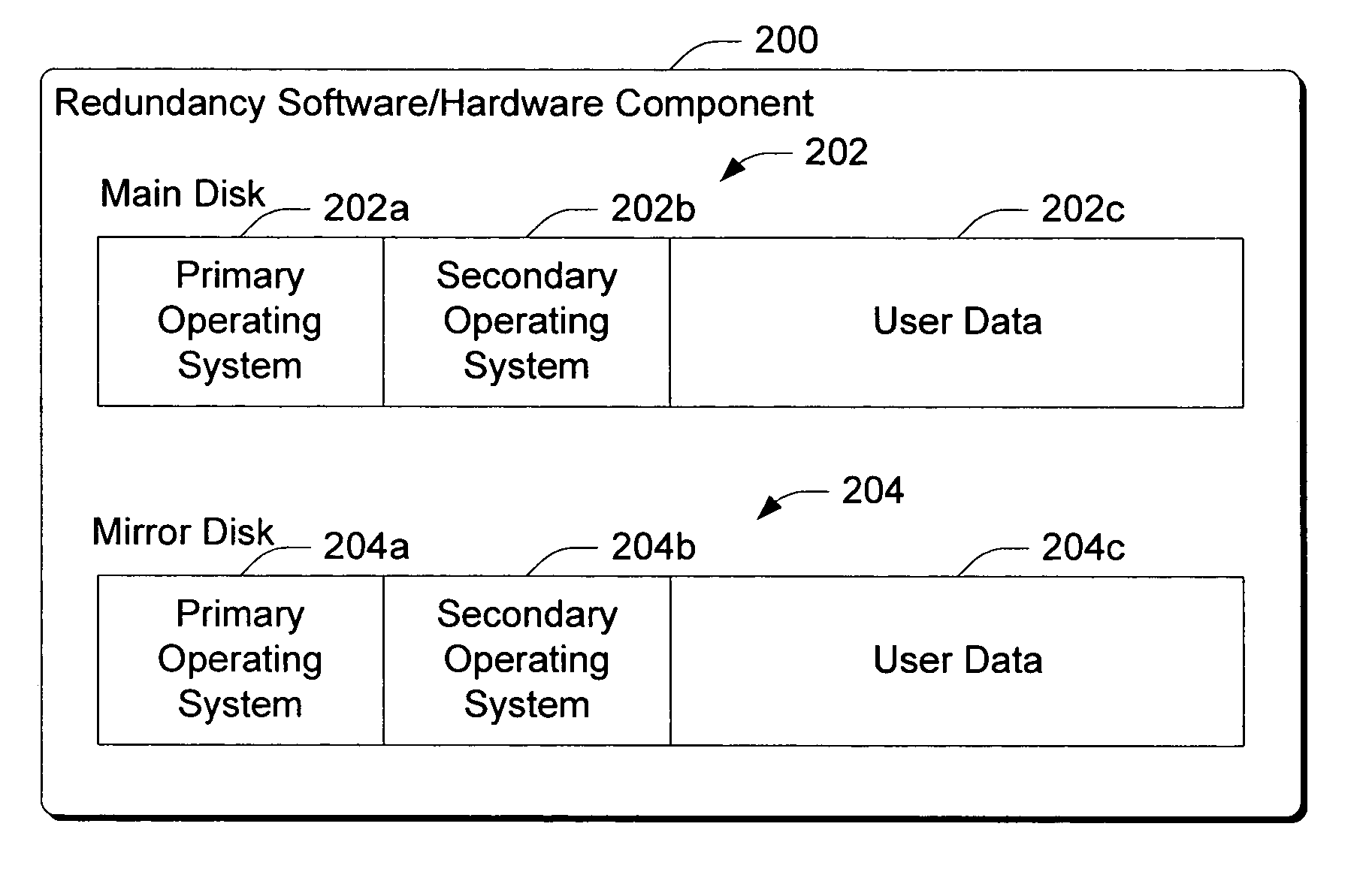
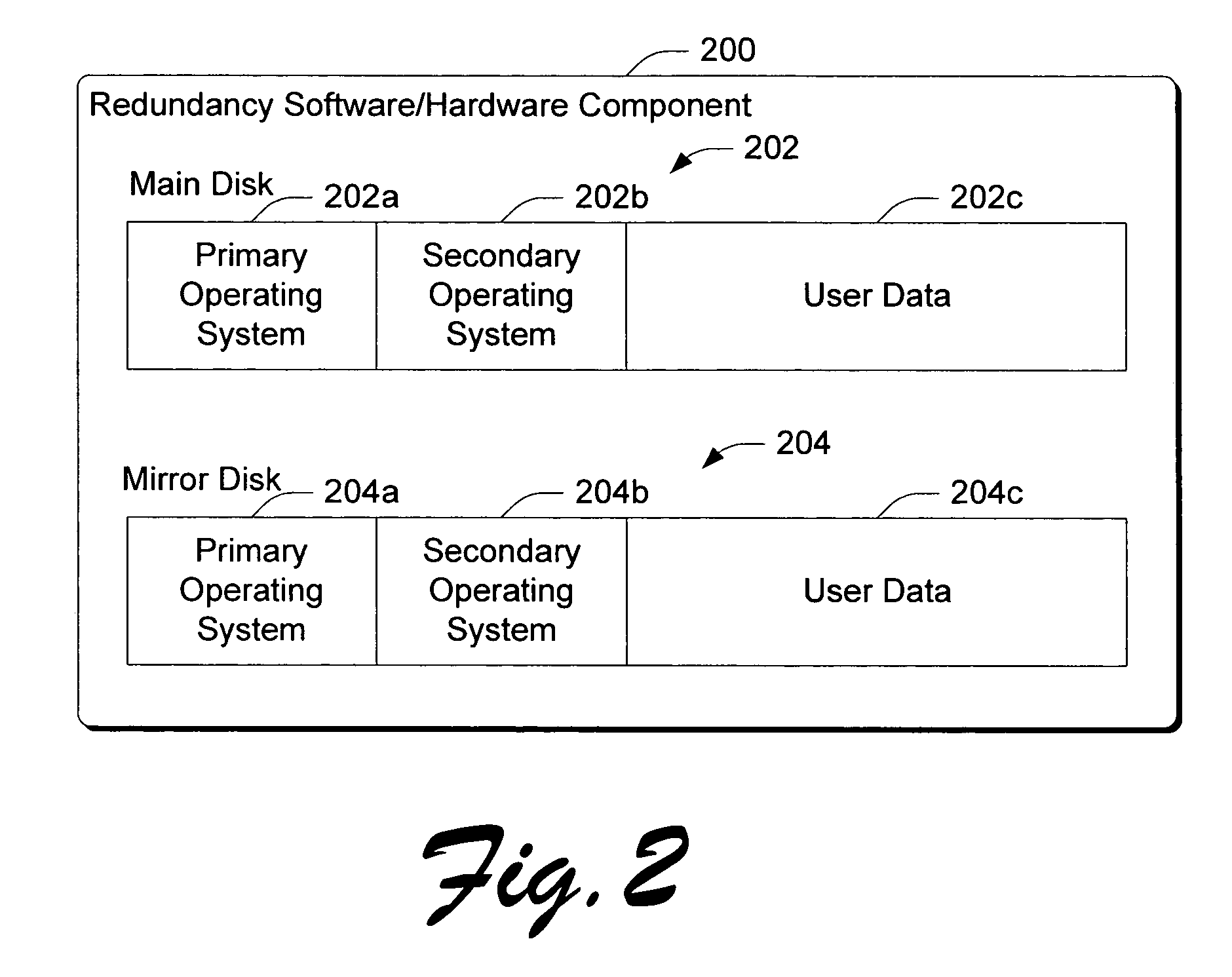
Automated recovery of computer appliances
InactiveUS7131026B2Improve reliabilityReduce the possibilityBootstrappingNon-redundant fault processingHard disc driveSystem failure
Aspects of the invention provide methods and architectures for enhancing the reliability of computer appliances and reducing the possibilities that human intervention is necessary in the event of a system failure or failure condition. The provided architecture is extensible and provides a generalized framework that is adaptable to many different types of computer appliances. One aspect of the invention provides a boot up redundancy component to ensure that a computer appliance can be appropriately booted. In the described embodiment, the appliance hard drive is configured with multiple partitions that can be utilized to boot the appliance thereby reducing the chances that the appliance will not boot. In addition, an architecture is disclosed that comprises one or more resource monitoring components that monitor an associated appliance resource for a failure condition. The resource monitoring components are programmed to attempt to remedy certain failure conditions that they detect. An appliance monitoring service is also provided and is programmed to attempt to remedy failure conditions that are not remedied by one or more of the resource monitoring objects.
Owner:MICROSOFT TECH LICENSING LLC
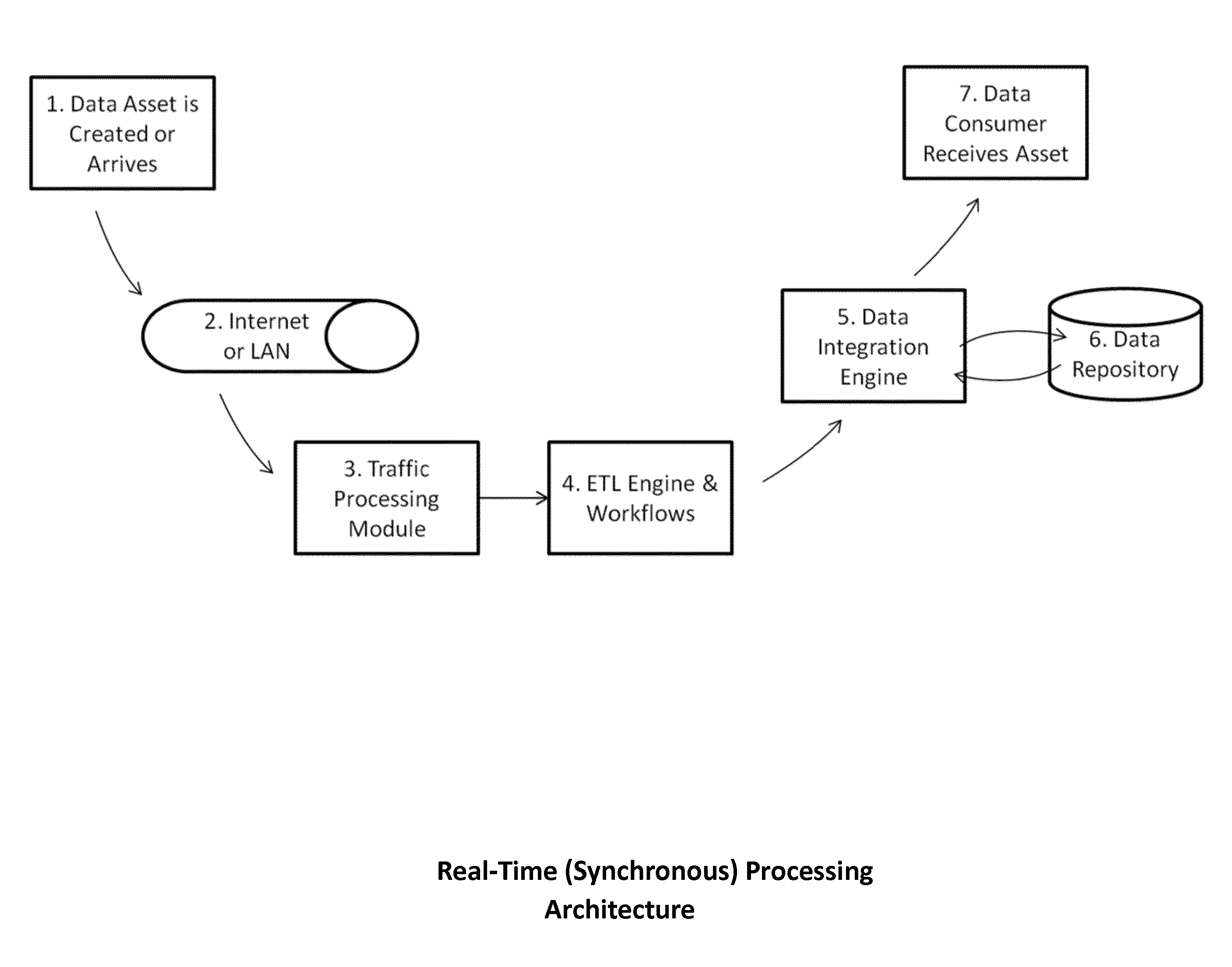
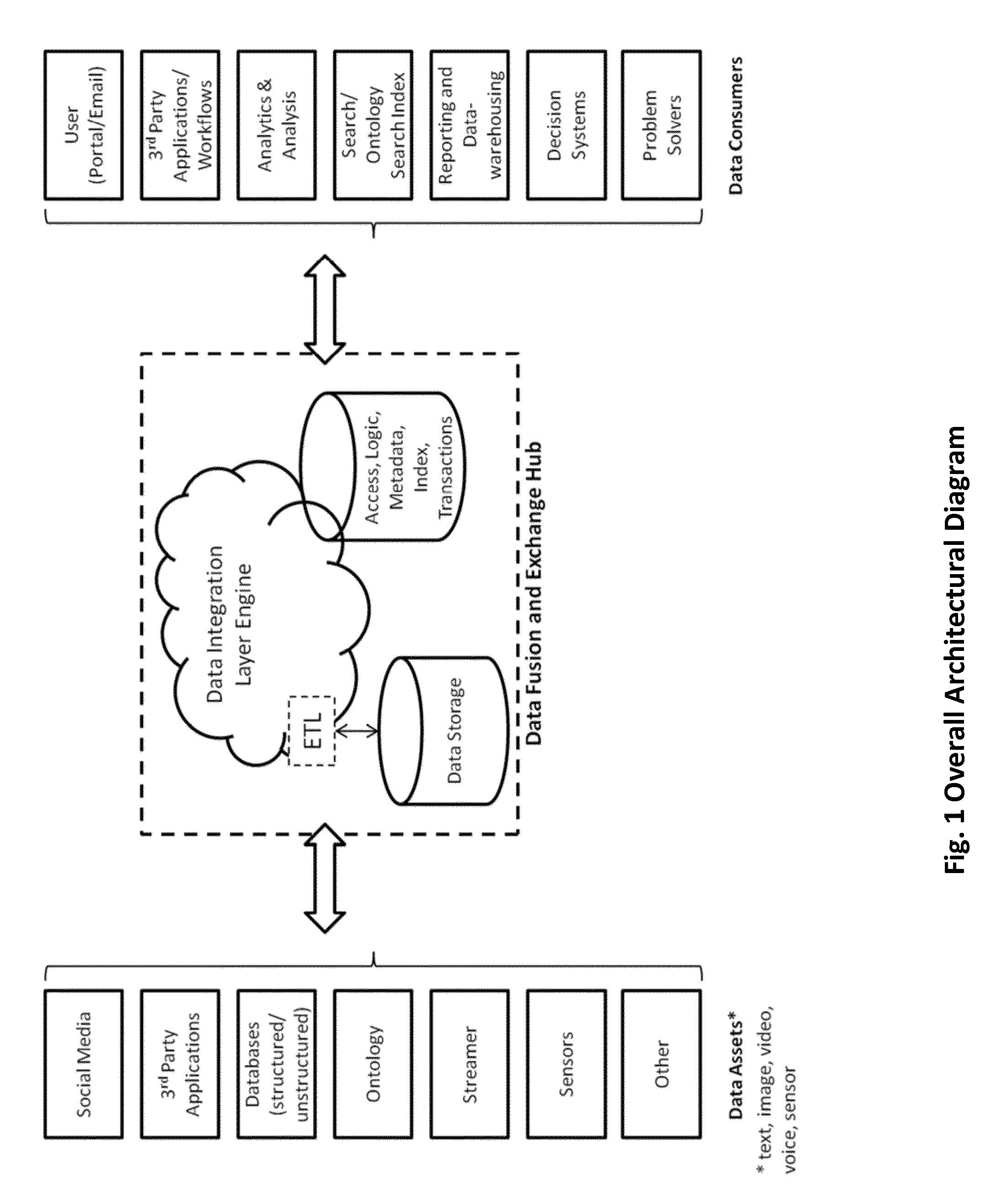
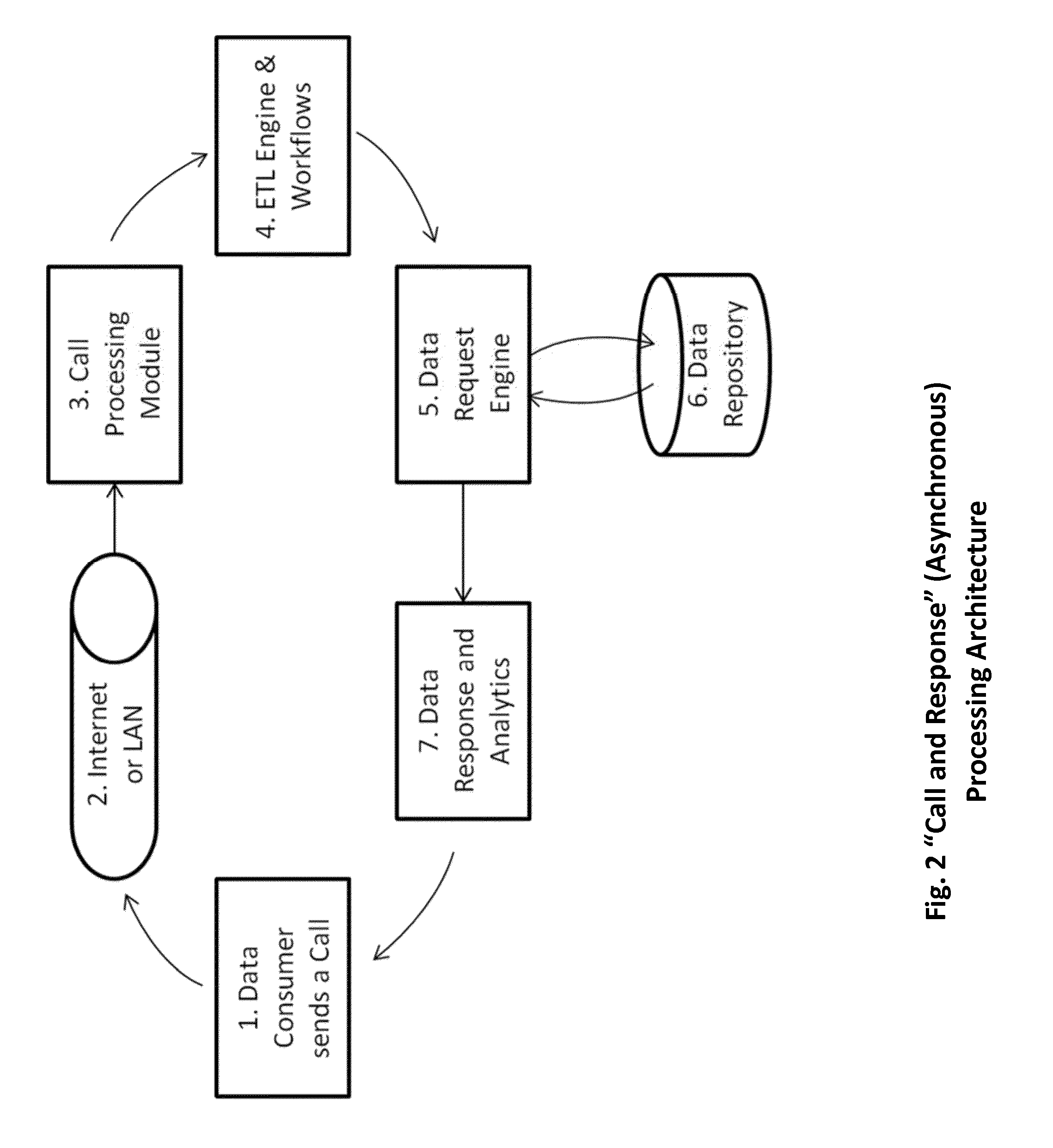
Data fusion and exchange hub - architecture, system and method
InactiveUS20160021181A1Reduce the valueFlexible processPayment architectureOffice automationApplication softwareWearable computer
A computerized method for facilitate and orchestrate the exchange and integration of data assets and data consumers, with or without computer appliances, automated framework comprised of technical devices for enabling integration of one or more of data assets including data streamer, structured data repository, unstructured data repository, 3rd party application, ontology, sensor, service provider, text, image, video, voice, and data consumers including human user, web portal, email, repository of data, reporting warehouse, 3rd party application, workflow, analytics process, model, ontology index, problem solver, decision system, mobile device, sensor, wearable computer. The automated framework can be one of asynchronous messaging-based, asynchronous near real-time, synchronous real-time; computer memory is used for storing applications for distribution to data consumers. The framework provides encryption, authentication, rights and roles controlling data assets, or data consumers. A user can interact with the framework to perform monitoring, management or analysis functions.
Owner:IANAKIEV GEORGE +1
System and Method Identifying a User to an Associated Device
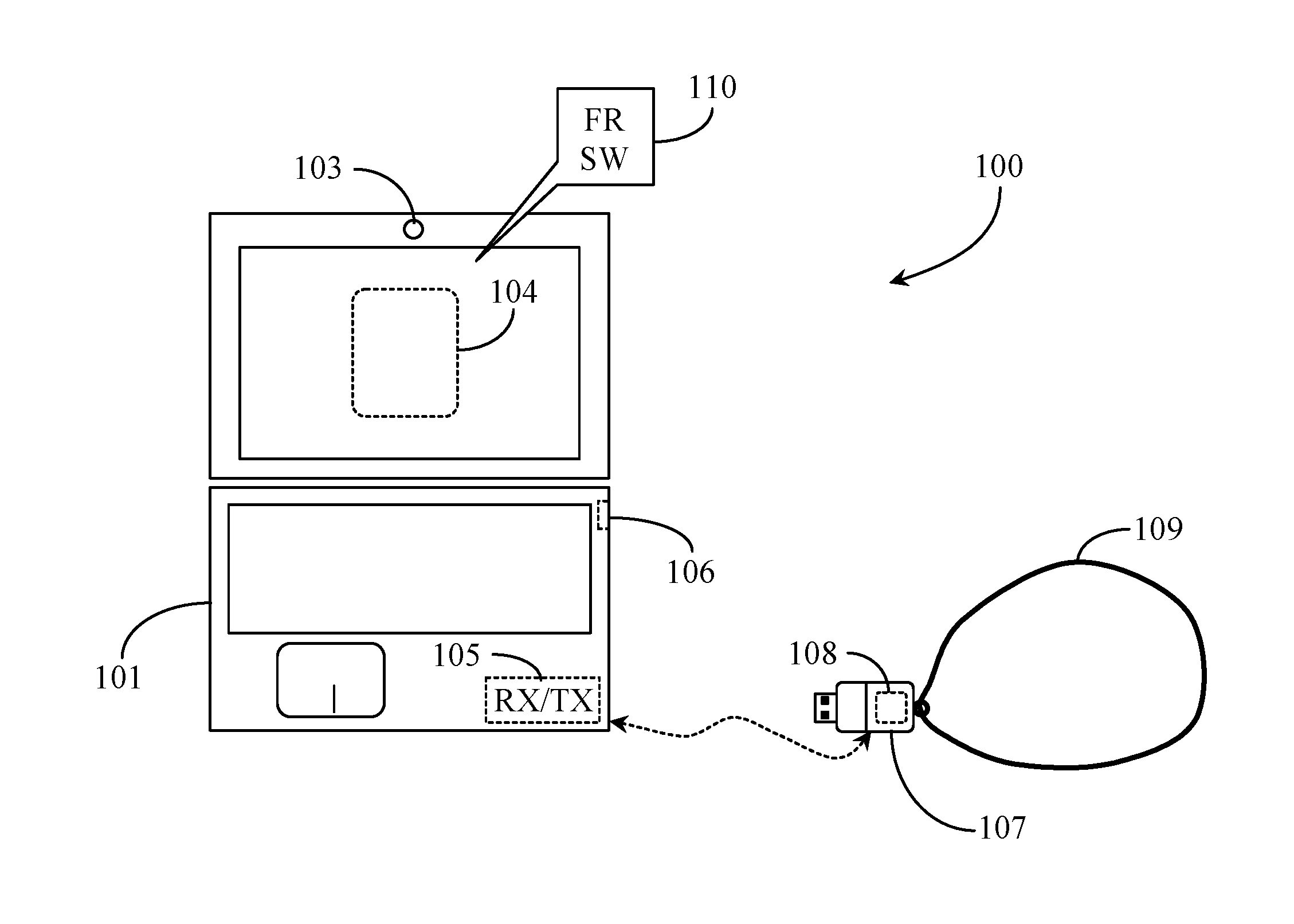
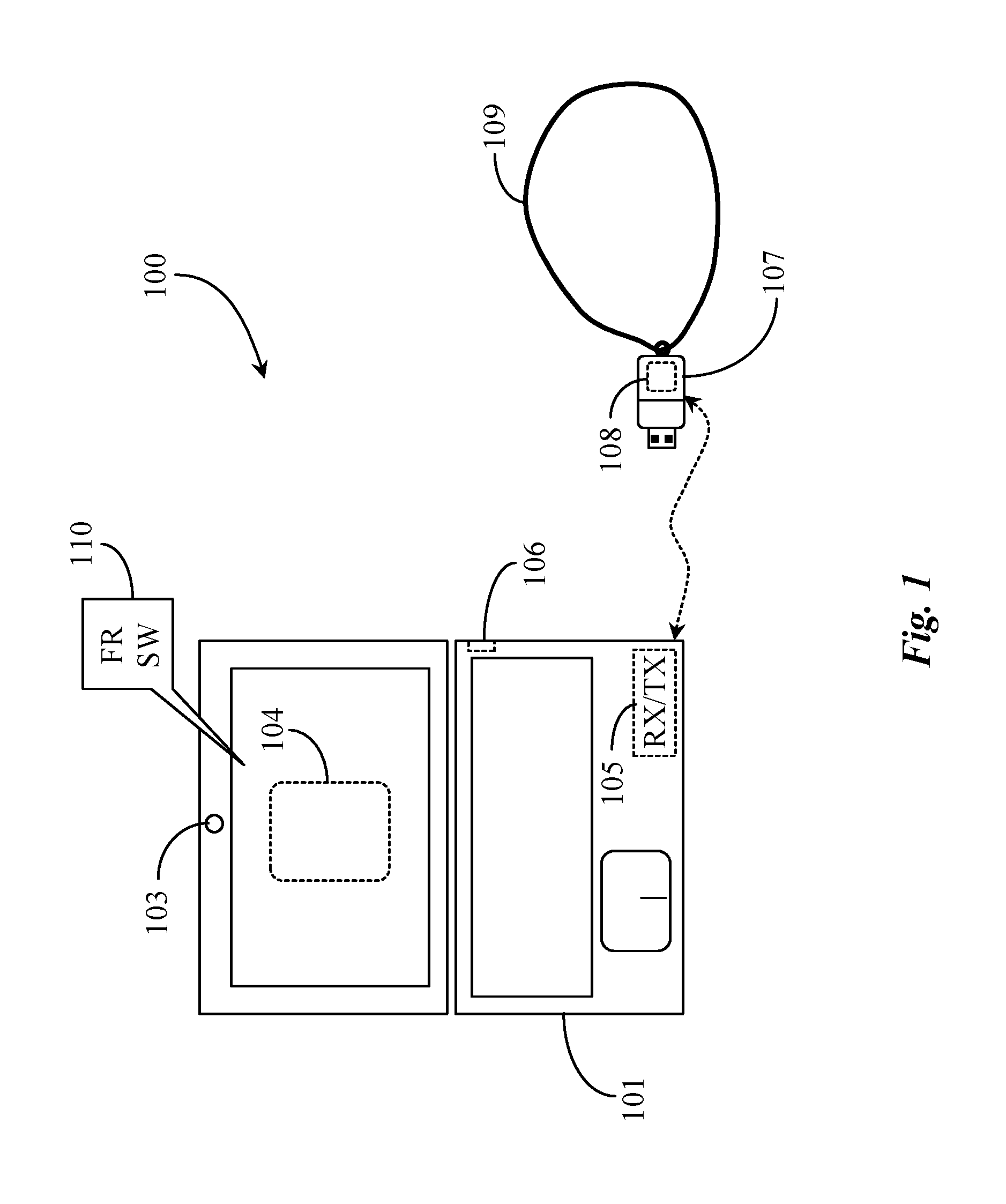
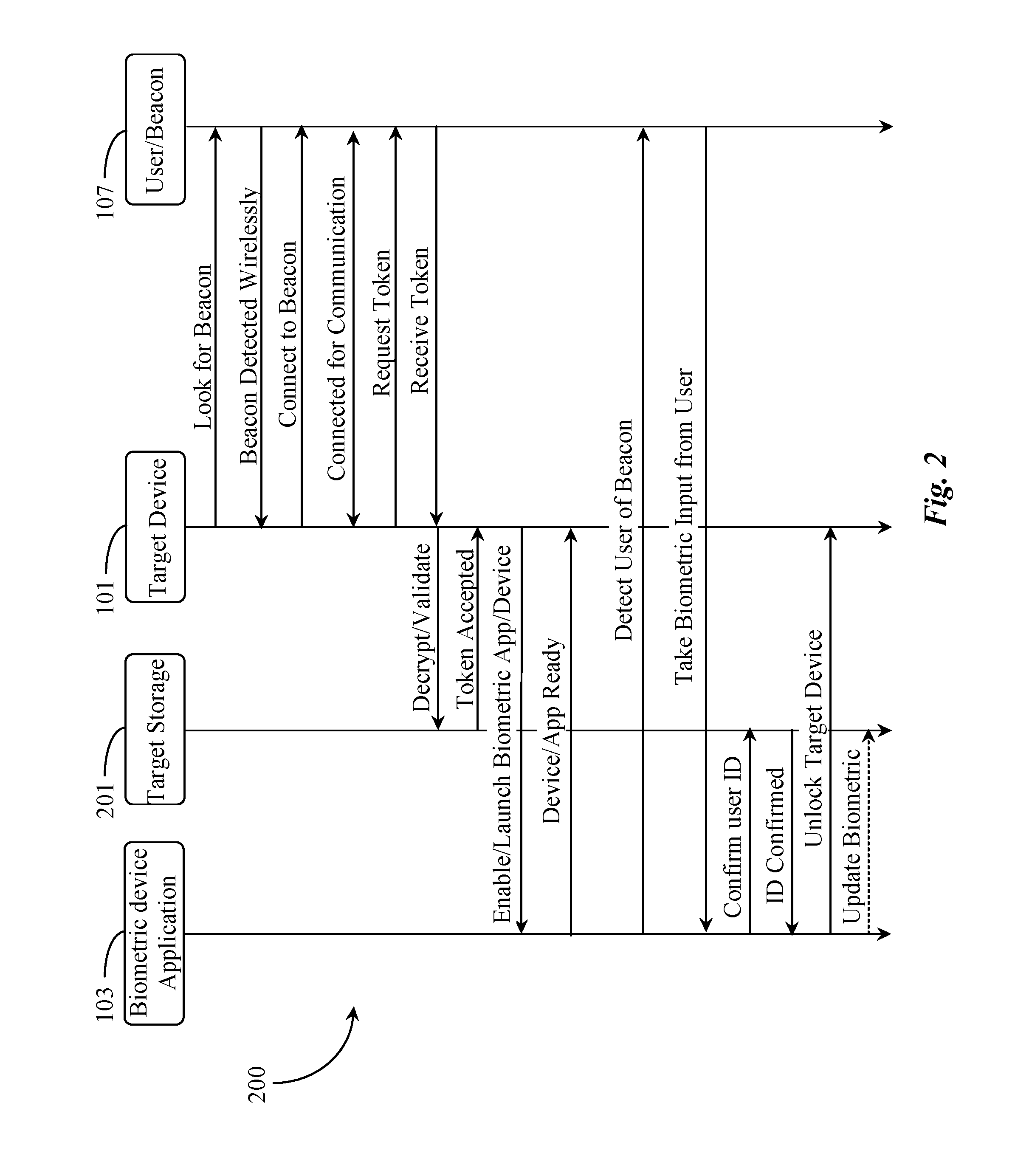
The present system and method enables the automatic detection and identification of authorized users within proximity of a computing apparatus and, after verifying, using biometric detection and analysis, that the user is authorized to access the target, providing the user with such access. The system comprises a computer appliance target requiring authentication of a user in order to access the target, including software stored on and executing from the target, a biometric input device, and a transceiver enabling short-range wireless communication with other wireless capable devices; a database accessible to the target; and a beacon device associated with the user, including at least a transceiver and a locally stored encrypted identity token associating the device with the identity of the user; wherein the transceiver on the target periodically scans for the beacon device within the short-range, and upon detection, establishes communication with the beacon device and requests the identity token, the beacon device receives the request and sends the identity token back to the target which decrypts and validates the token by comparing token data with stored token data in the database and upon successful decryption and validation of the identity token, the software initializes a biometric test input to positively identify the user in possession of the beacon, wherein the software of the target attempts to match the biometric input with second biometric input of the user stored in the database and upon a successful match, unlocks the target and allows the user to operate the target.
Owner:LEOW CHON HOCK
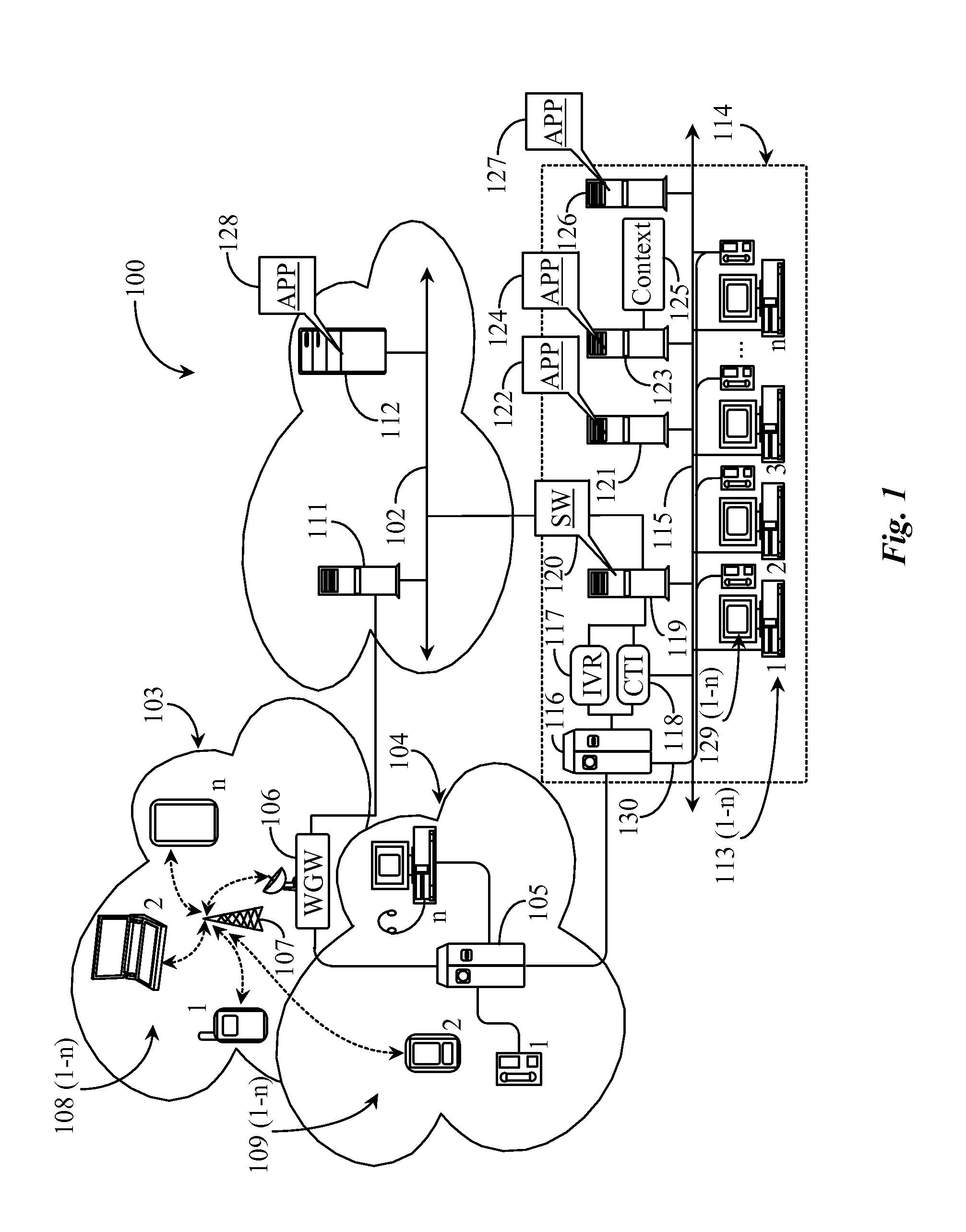
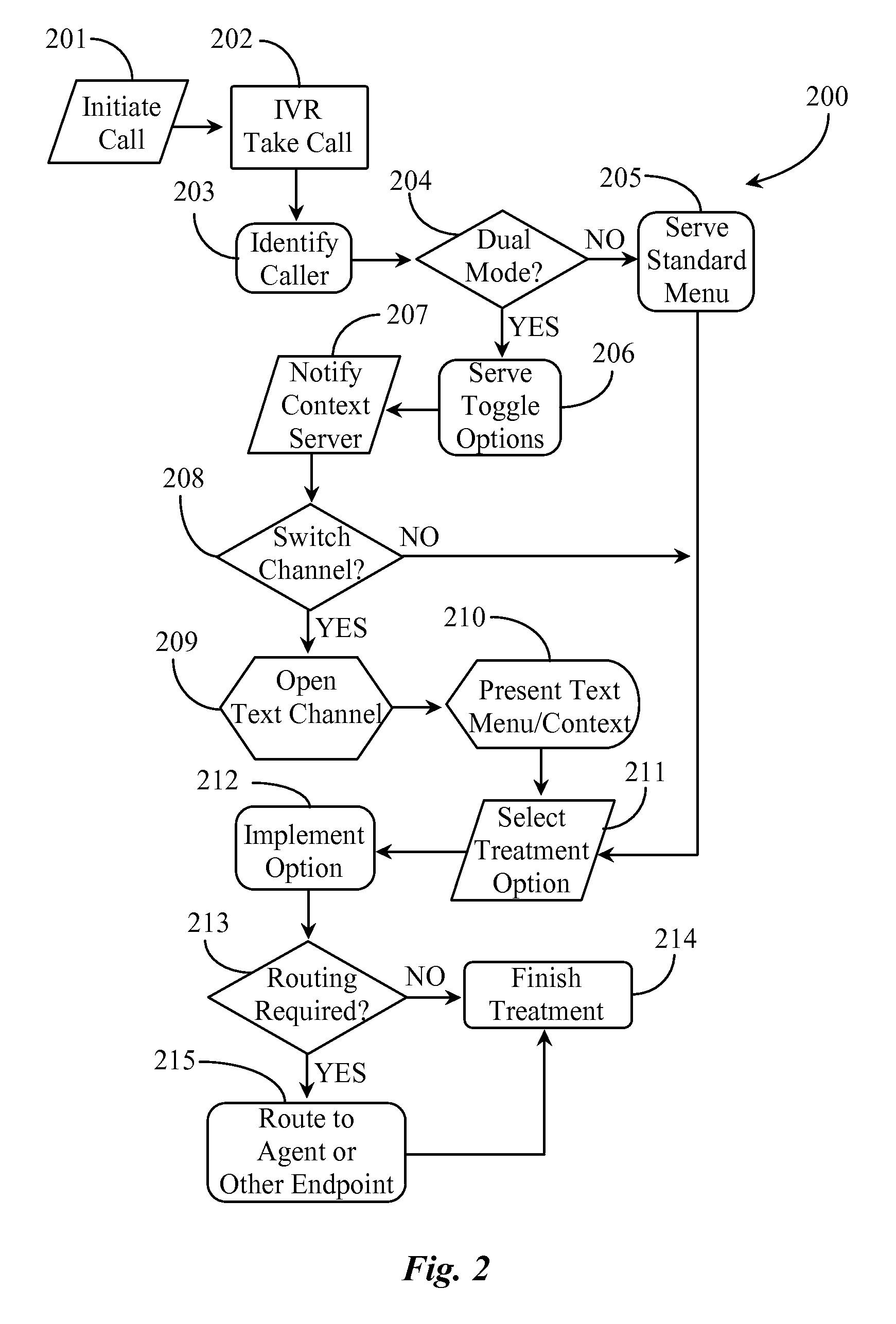
Media channel management apparatus for network communications sessions
ActiveUS20160028891A1Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersNetwork communicationMedia channel
A system includes: a computerized appliance having a processor; and software executing on the computerized appliance from a non-transitory physical medium, the software providing: establishment of a communication session over a network between two or more end communications appliances; detection and recording of at least media channel capabilities on individual end communications appliances connected in the session; service of media channel toggle options to end communications appliances; detection of media channel toggle option selections made by users operating the end communications appliances; and implementation of the media channel toggle option or options selected for individual communications sessions.
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC
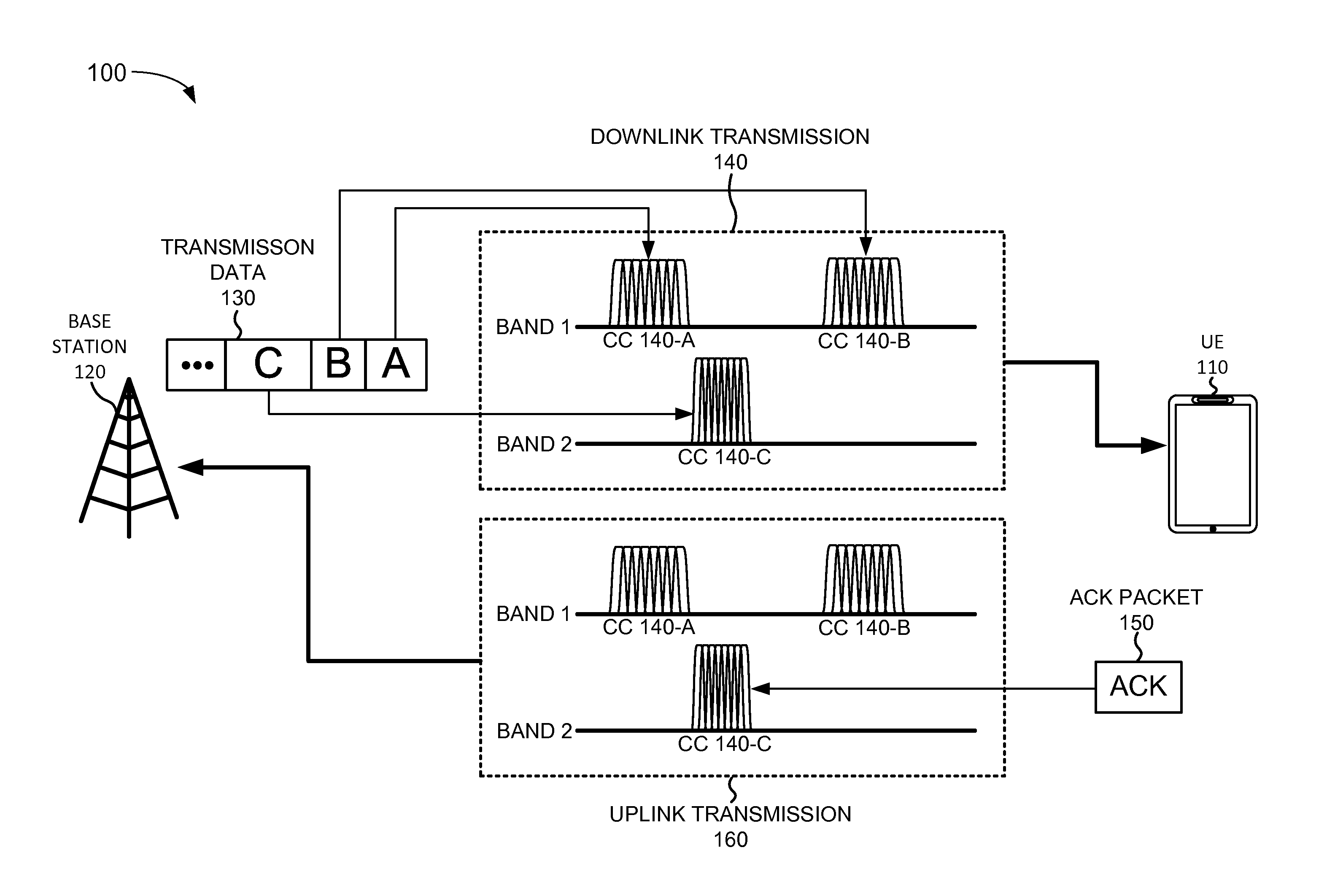
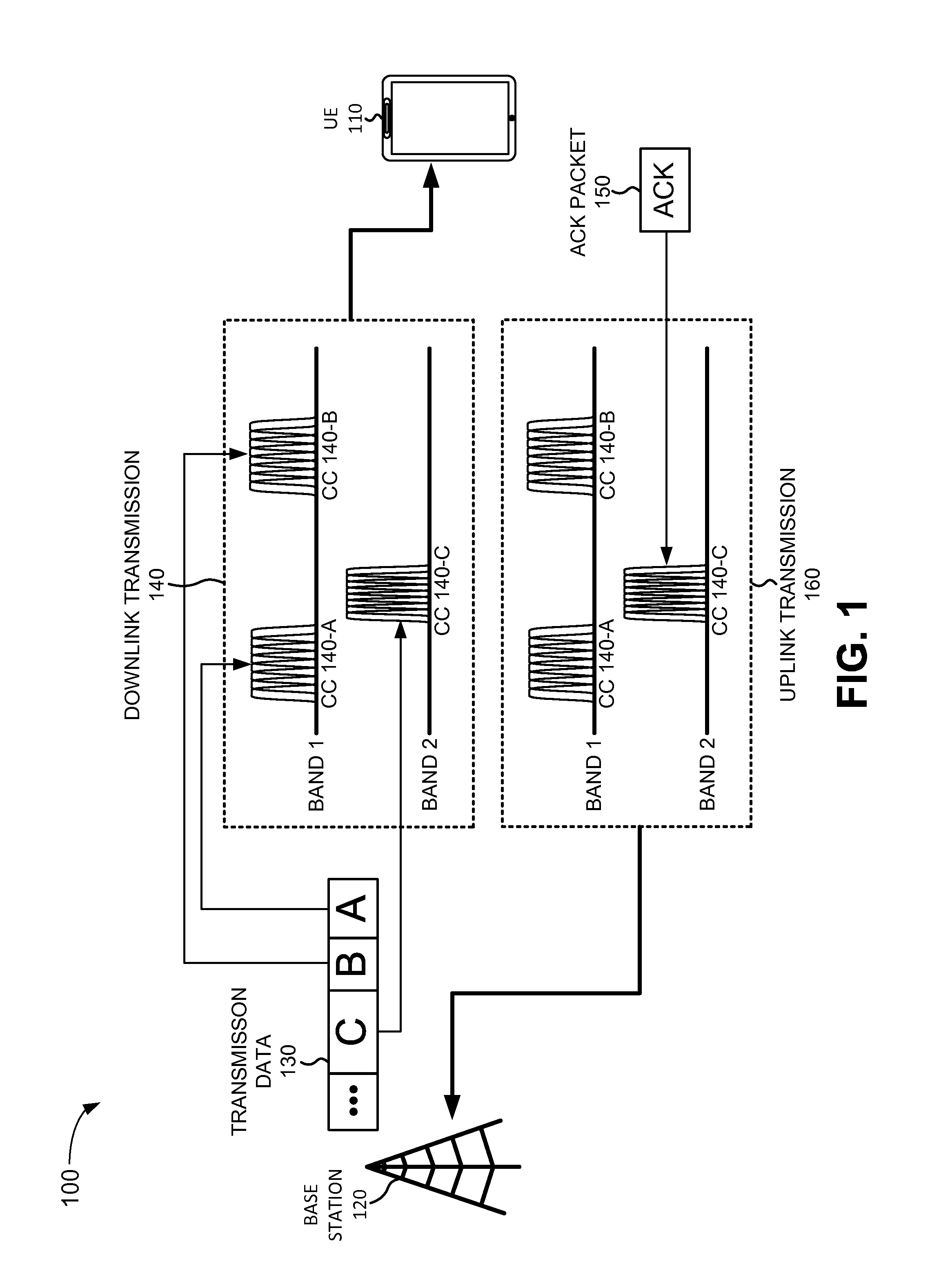
Carrier aggregation management
ActiveUS20150341945A1Transmission path divisionWireless commuication servicesComputer applianceCarrier signal
A computer device may include logic configured to configure carrier aggregation for a user equipment serviced by the base station device; activate a secondary component carrier for the user equipment; determine that a quality level for the secondary component carrier is lower than a quality threshold; and de-activate the secondary component carrier for the user equipment, in response determining that the quality level is lower than the quality threshold. The logic may be further configured to detect a problem associated with the primary component carrier for the user equipment; determine whether a better primary component carrier is available, in response to detecting the problem; switch to the better primary component carrier, when the better primary component carrier is available; and de-configure carrier aggregation for the user equipment, when the better primary component carrier for the user equipment is not available.
Owner:VERIZON PATENT & LICENSING INC
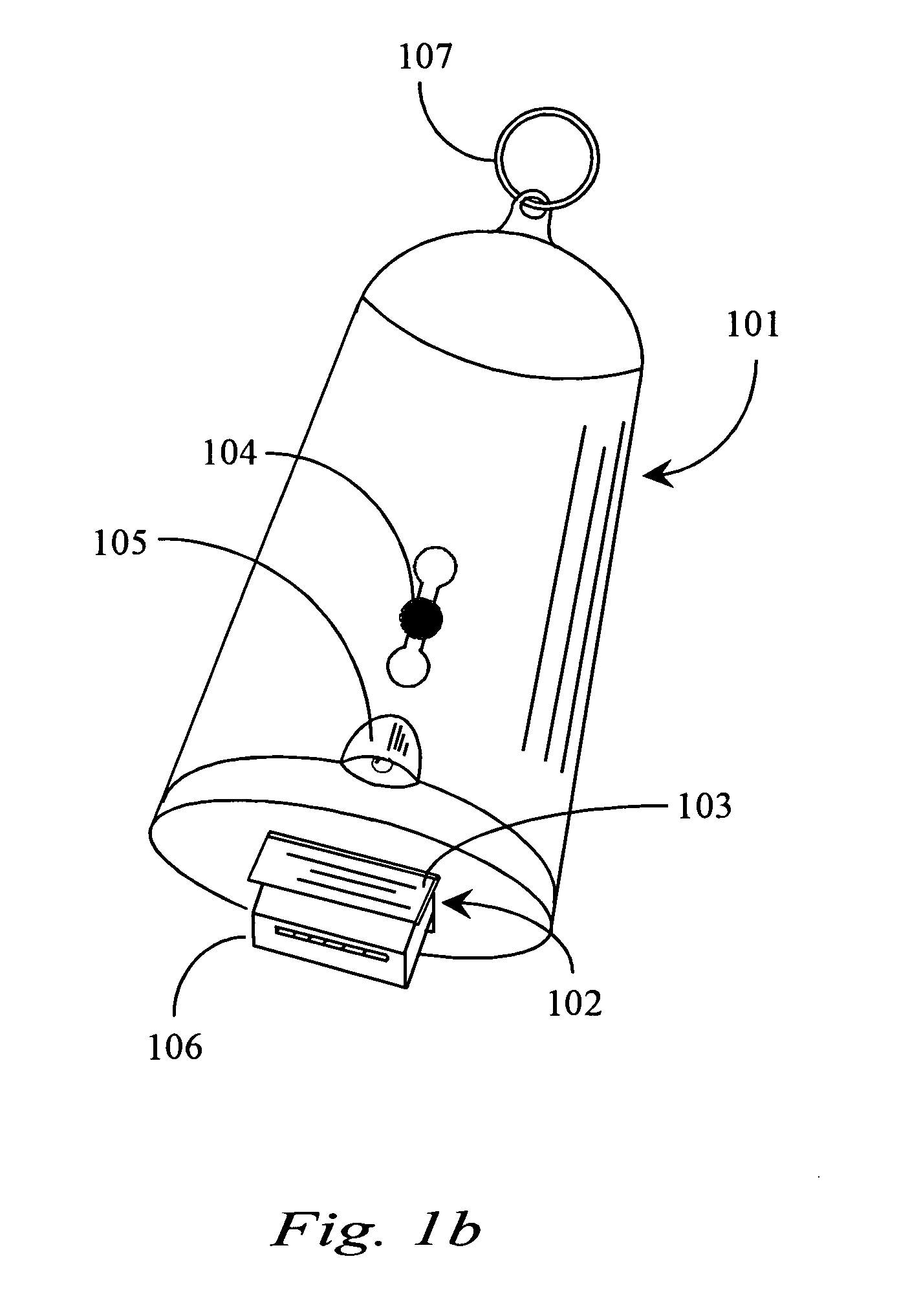
Thumb drive with retractable USB connector
InactiveUS20050130471A1Live contact access preventionElectrical apparatus casings/cabinets/drawersOn boardDisplay device
A thumb drive comprises on-board memory for storing digital information, a male USB connector coupled to the on-board memory for connecting to a USB port of a computer appliance, internal control elements for managing MP3 player functions for the thumb drive, a display for displaying downloaded song titles, user-operable controls for selecting and playing songs recorded as audio files in the on-board memory as audio output at an output connector, a Bluetooth™ compatible transmitter for transmitting selected data and audio output to external Bluetooth™ compatible devices, and an extension / retraction mechanism coupled to the connector for extending the connector from an enclosure of the drive and for retracting the connector when not in use.
Owner:ANU IP
Network distribution method and apparatus, storage medium, terminal and home appliance
InactiveCN107466086ASolve the problem of repeated operation of the distribution network processReduce operation timeAssess restrictionSecurity arrangementDistribution methodComputer terminal
Owner:GREE ELECTRIC APPLIANCES INC
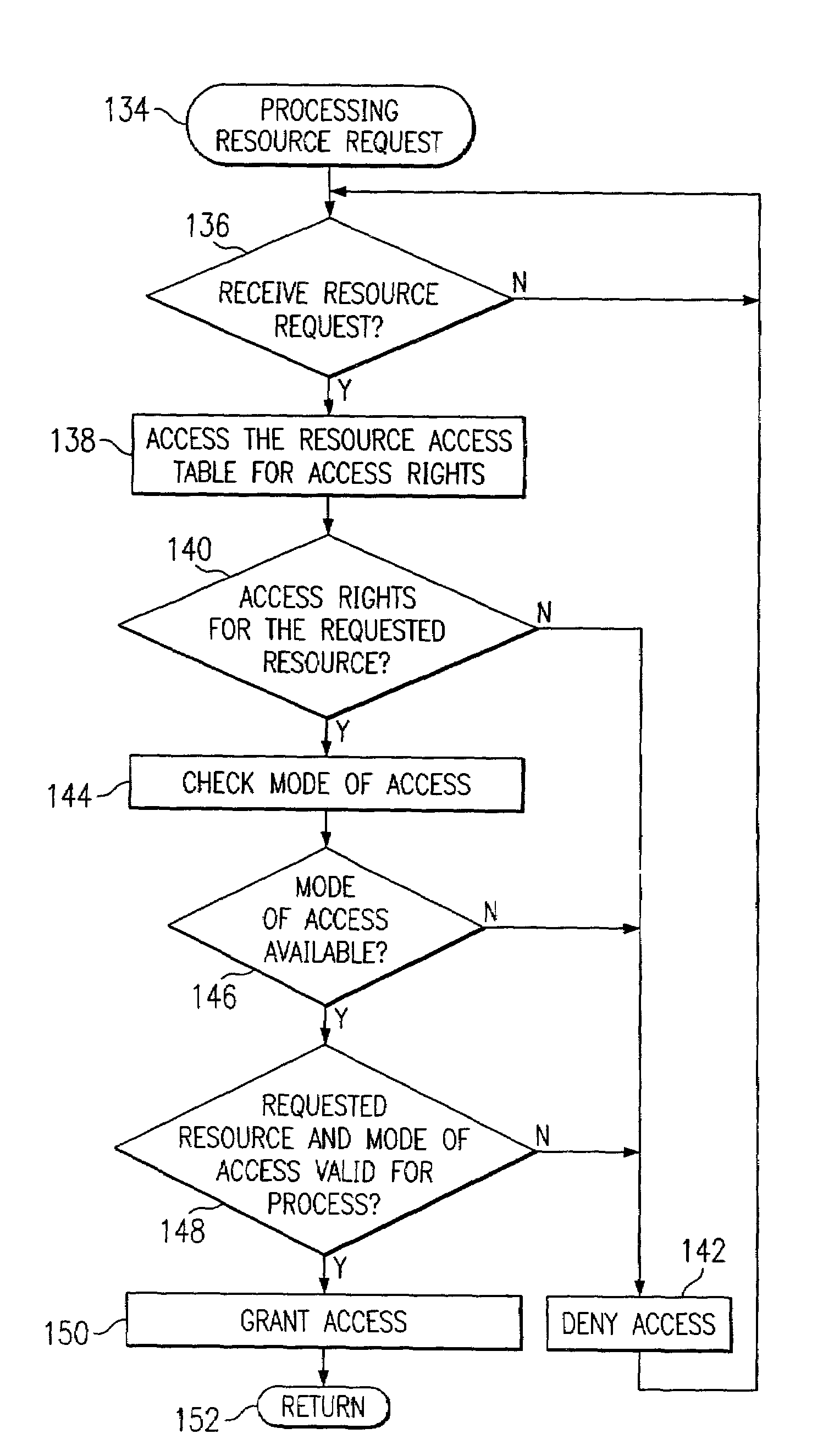
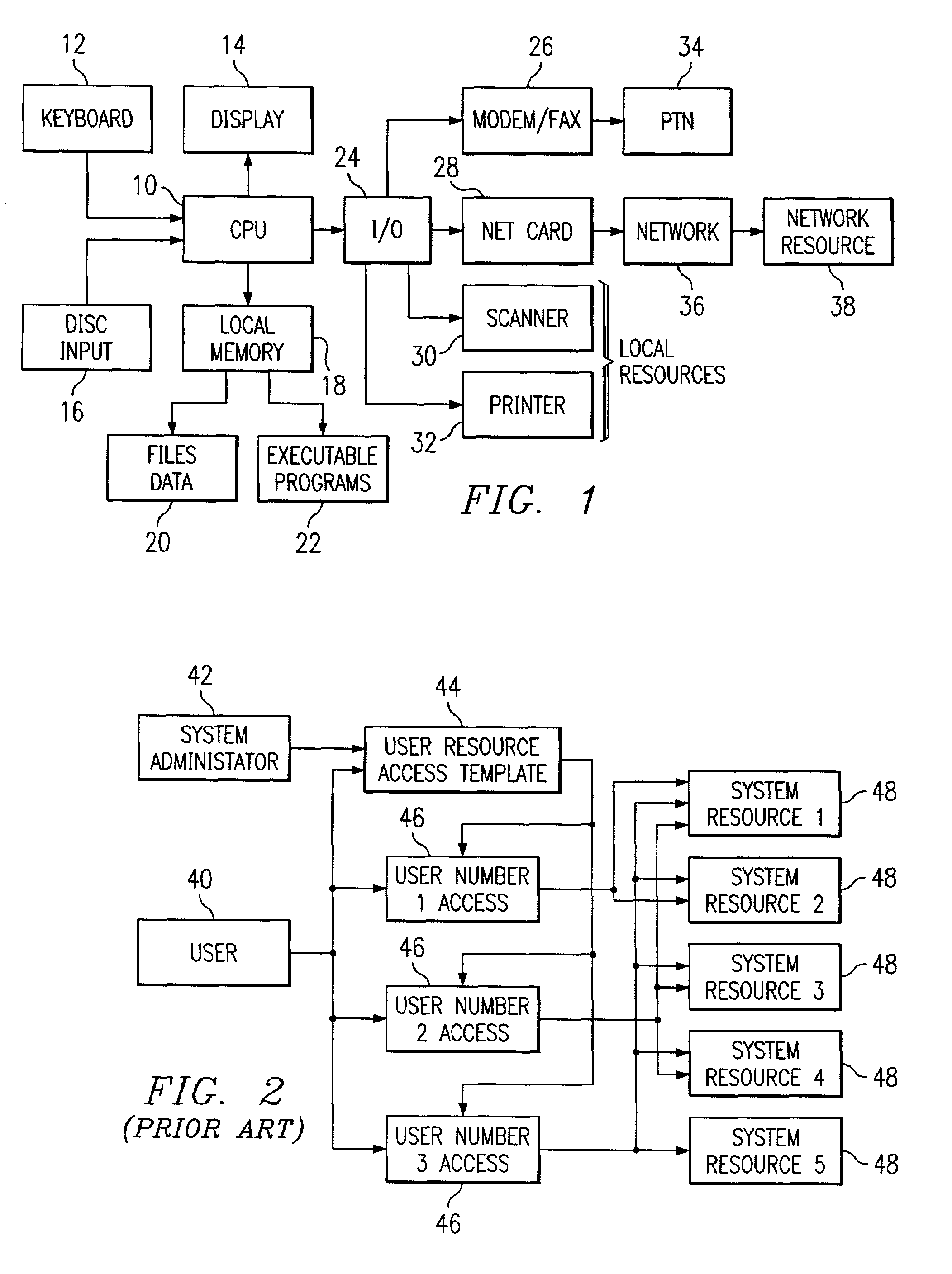
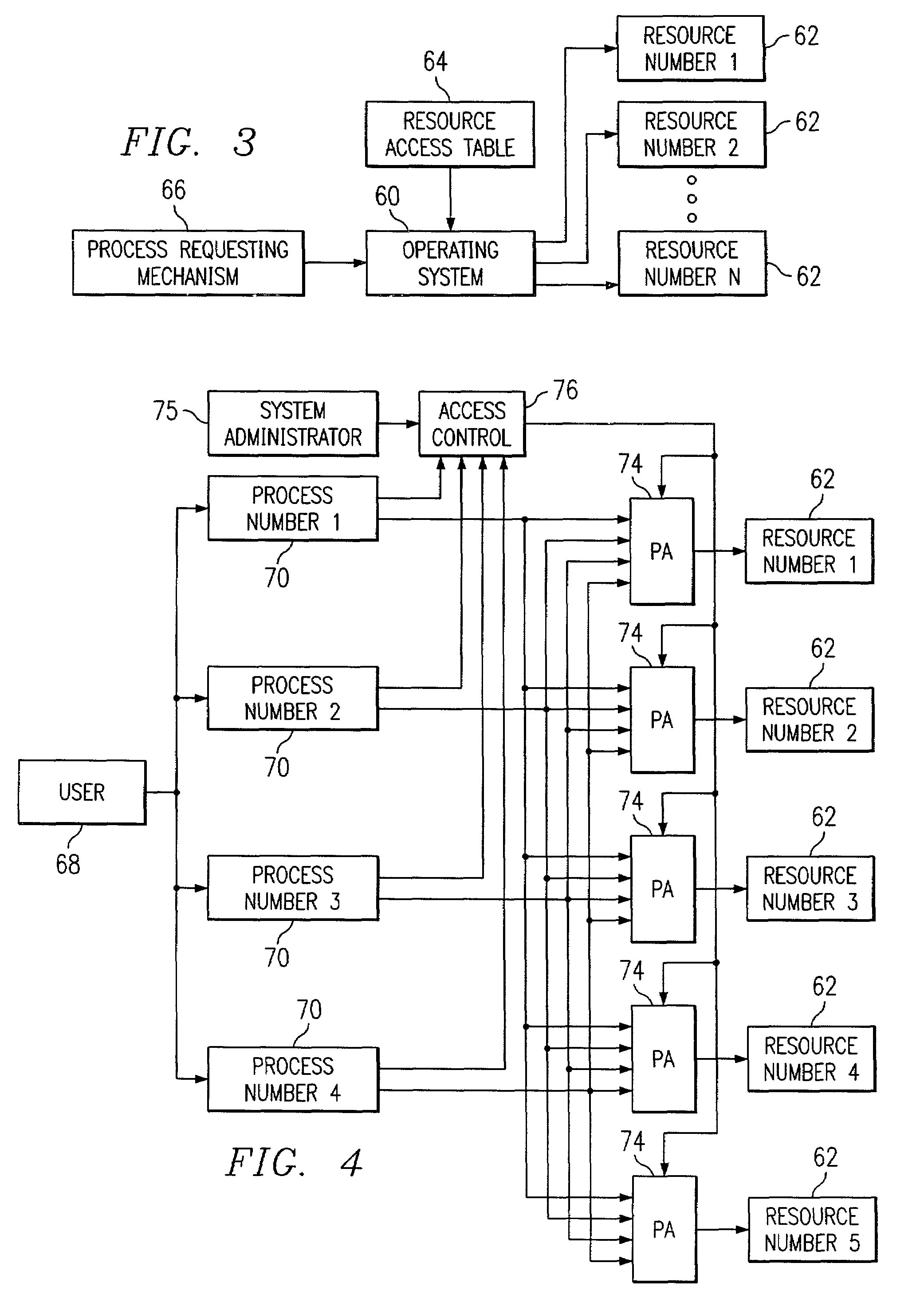
Method and apparatus for implementing process-based security in a computer system
A method is disclosed for providing process-based security in a special purpose computer system, comprising the steps of: configuring the special purpose computer with an operating system and at least one application for operation as a computer appliance; associating a resource access table with the at least one application, addressable by the at least one application, containing statements corresponding to predetermined requests for access to at least a one specified resource during running of the at least one application wherein the resource access table statements include information defining an execution path for the at least one application; interpreting the resource access table statements upon a request for the specified resource by the at least one application, wherein at least one of the statements in the resource access table provides for performing a security check prior to granting access to the specified resource; and causing the execution of the at least one application, upon granting access to the requested resource, including the use of the requested resource according to the execution path statements in the resource access table.
Owner:SAGEFIRST INC
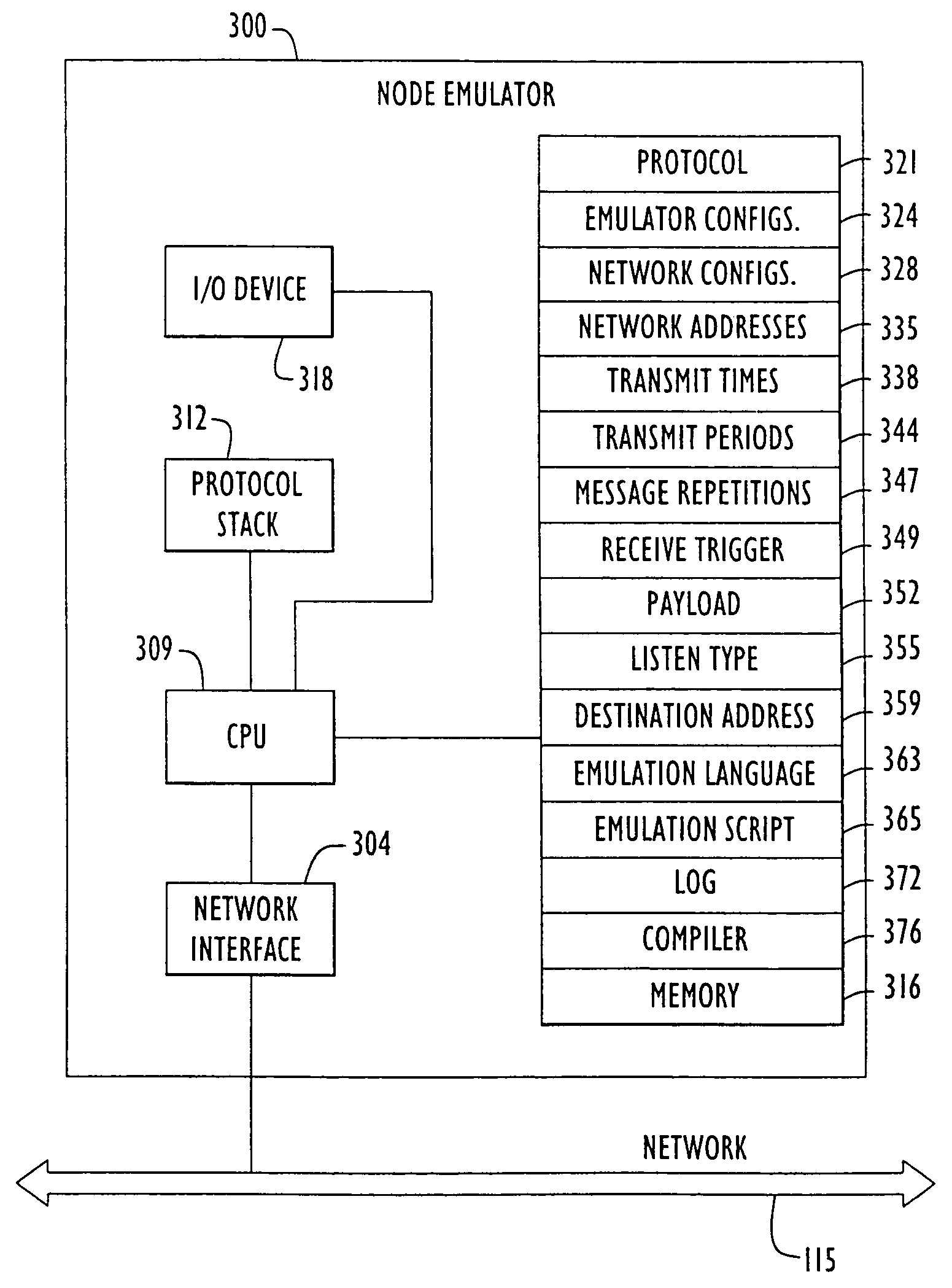
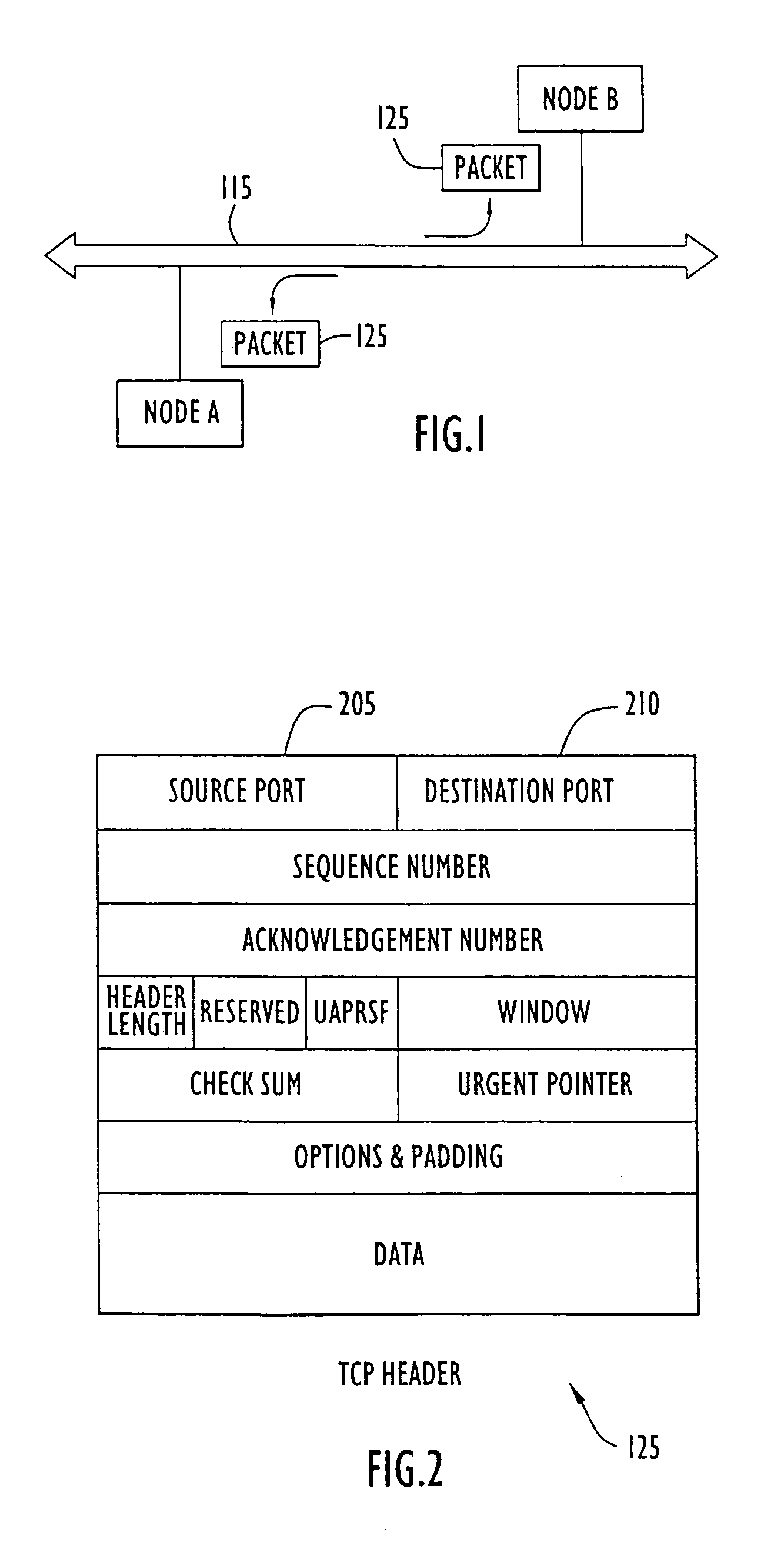
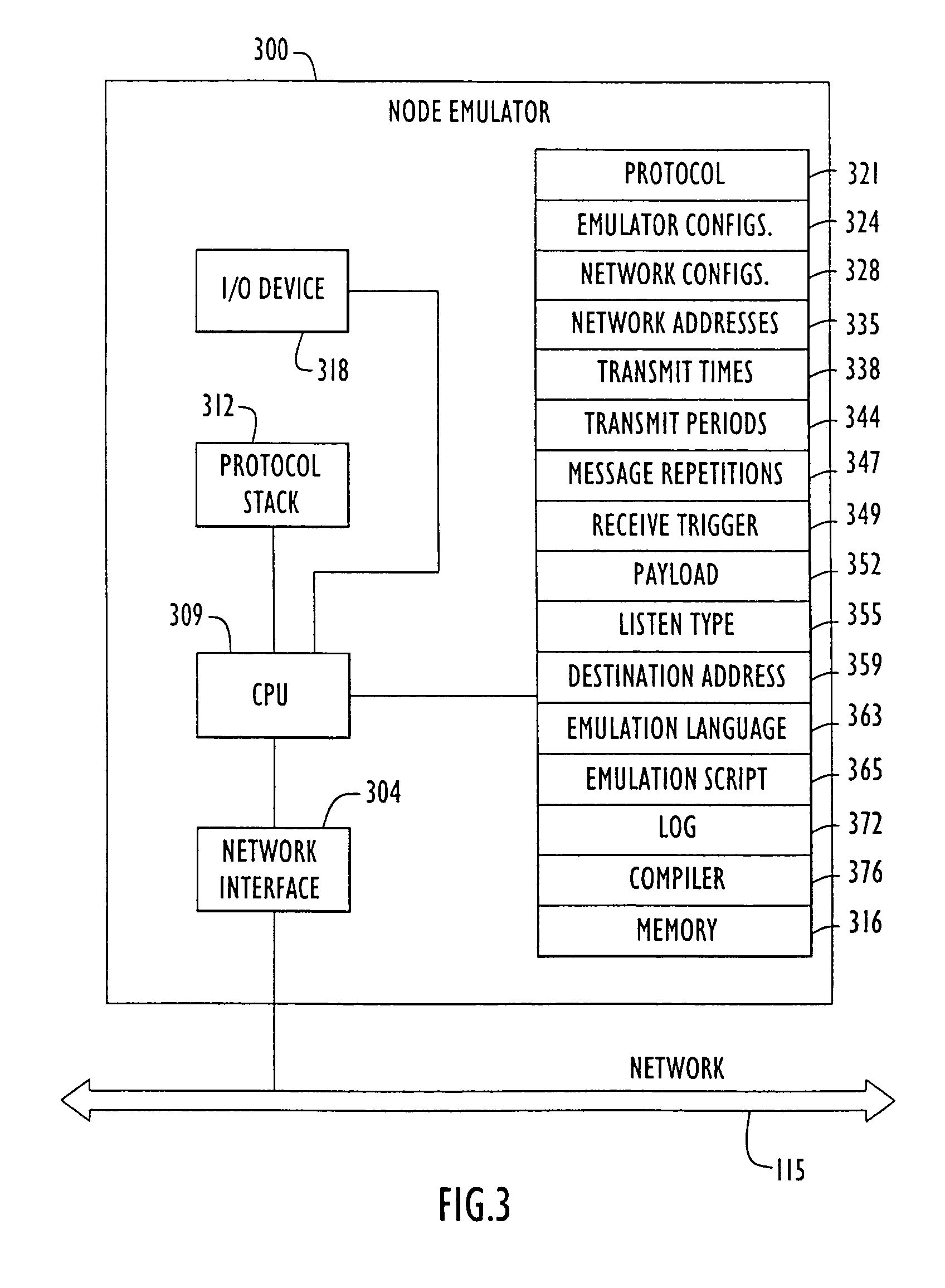
Network node emulator and method of node emulation
A method and apparatus is provided for network node emulation, including a node emulator, comprising a node interface, a memory, and a CPU. A method of generating an emulated network node includes the steps of generating an emulation script using a network node emulation language and operating a computer device according to the emulation script in order to transmit and receive data packets in the computer device. The method comprises receiving an incoming message, transmitting an outgoing message, and recognizing a response requirement in the incoming message. The method comprises responding to the incoming message by transmitting a response outgoing message if the incoming message includes a response requirement.
Owner:HARRIS CORP
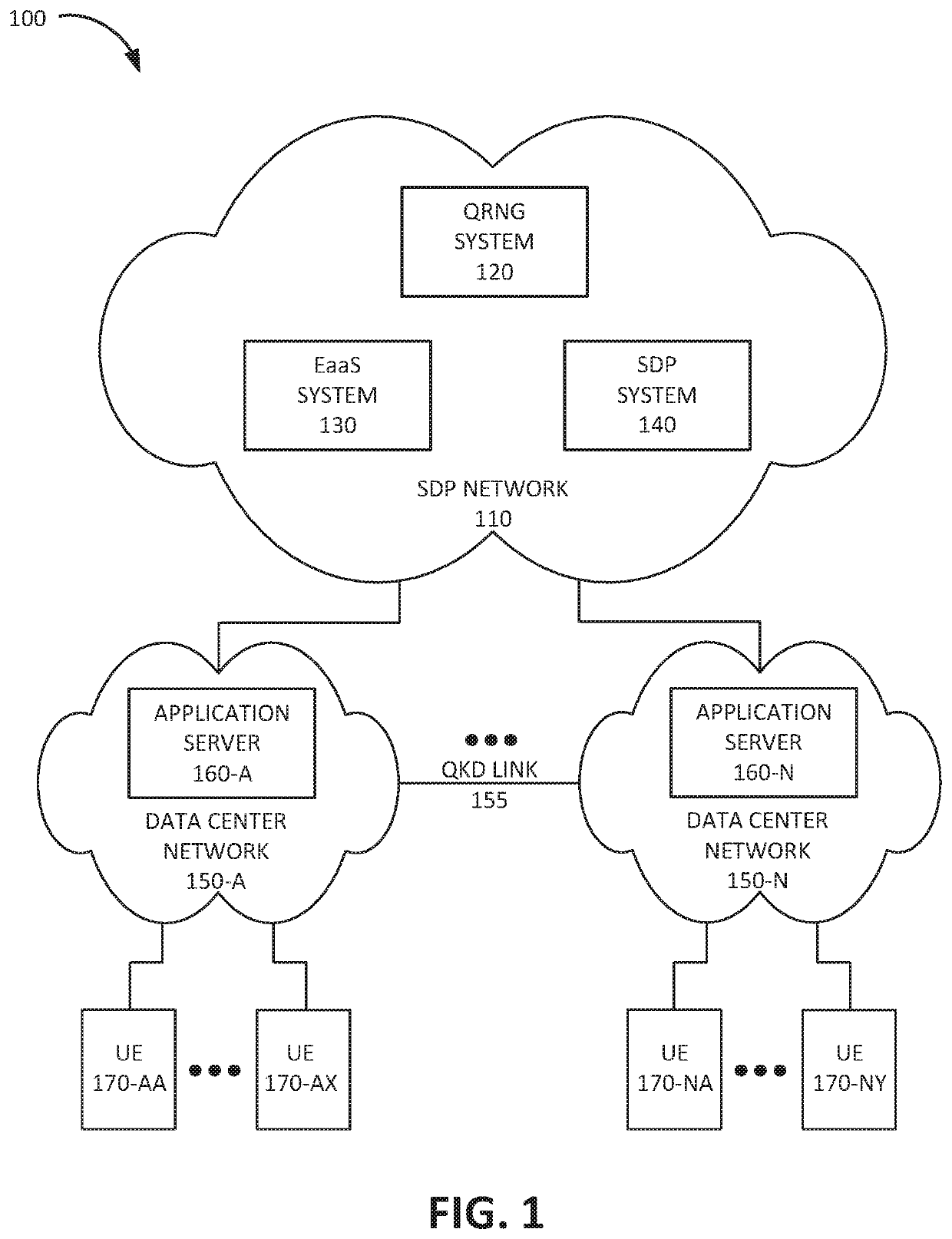
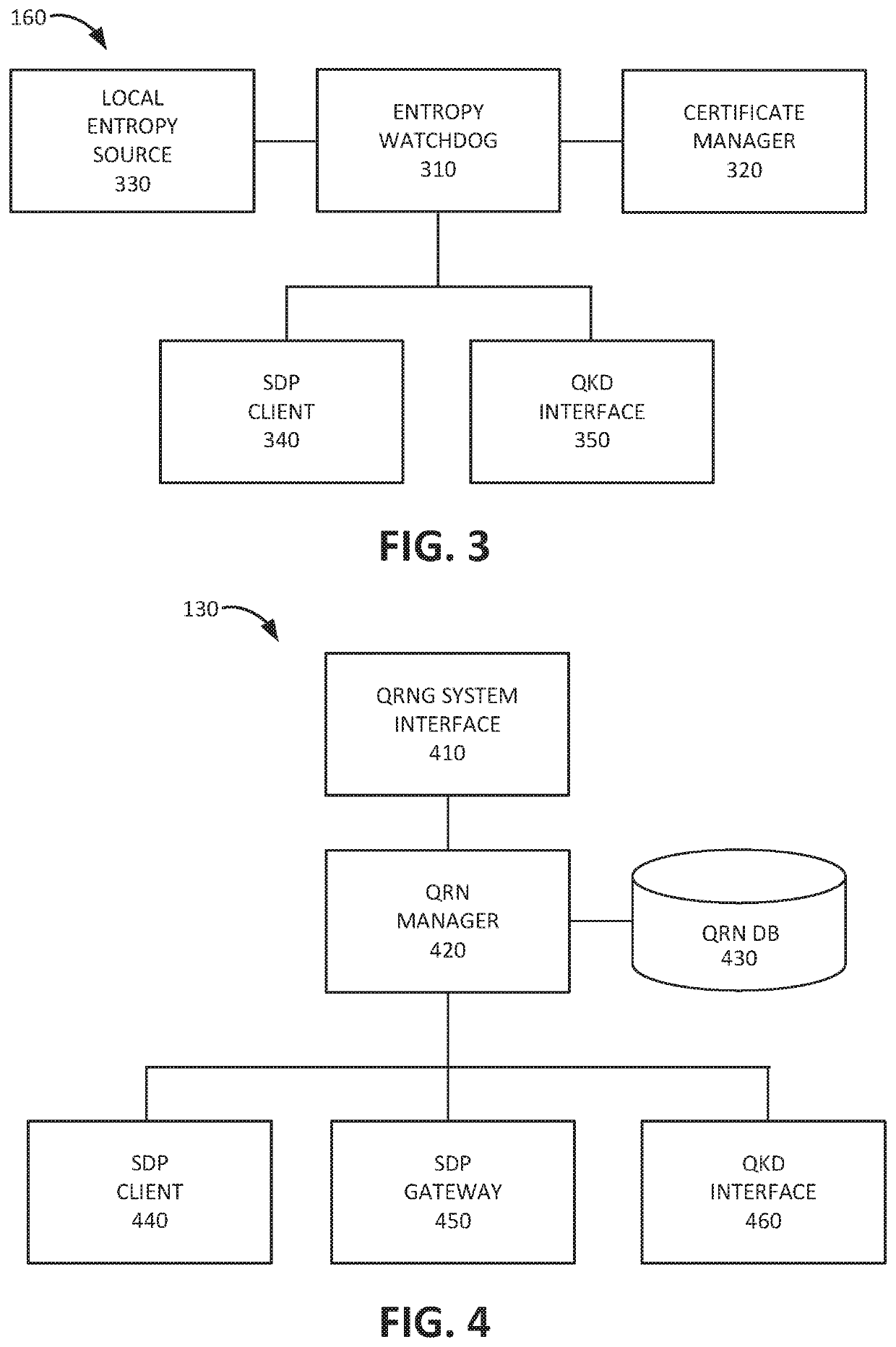
Quantum entropy distributed via software defined perimeter connections
ActiveUS20200403787A1Key distribution for secure communicationRandom number generatorsSecure communicationNumber generator
A computer device may include a memory storing instructions and processor configured to execute the instructions to receive a request for quantum random numbers from a client device. The processor may be further configured to establish a secure communication channel with the client device; obtain a stream of quantum random numbers from a quantum random number generator appliance; and provide a set of quantum random numbers from the obtained stream of quantum random numbers to the client device via the established secure communication channel.
Owner:VERIZON PATENT & LICENSING INC
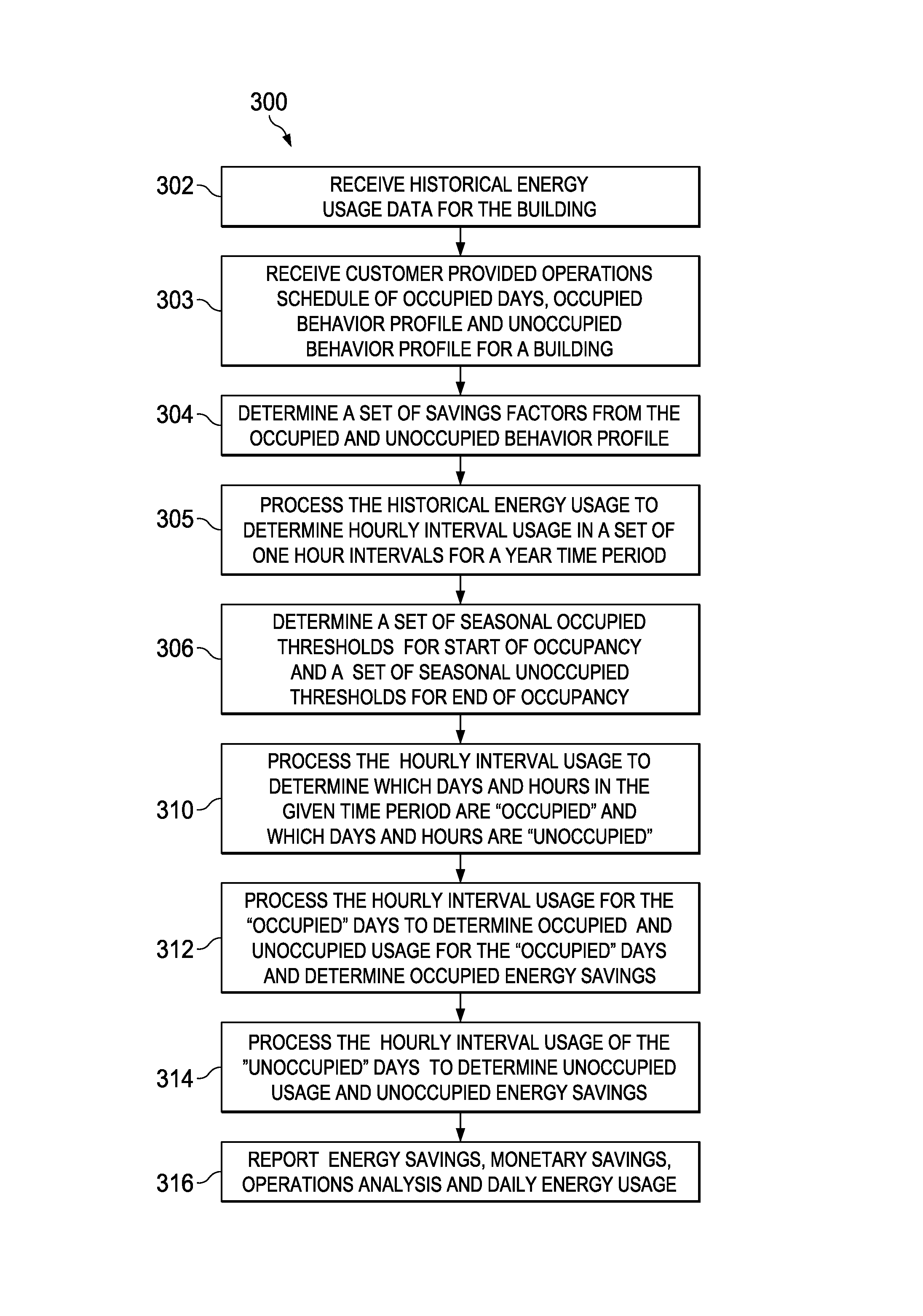
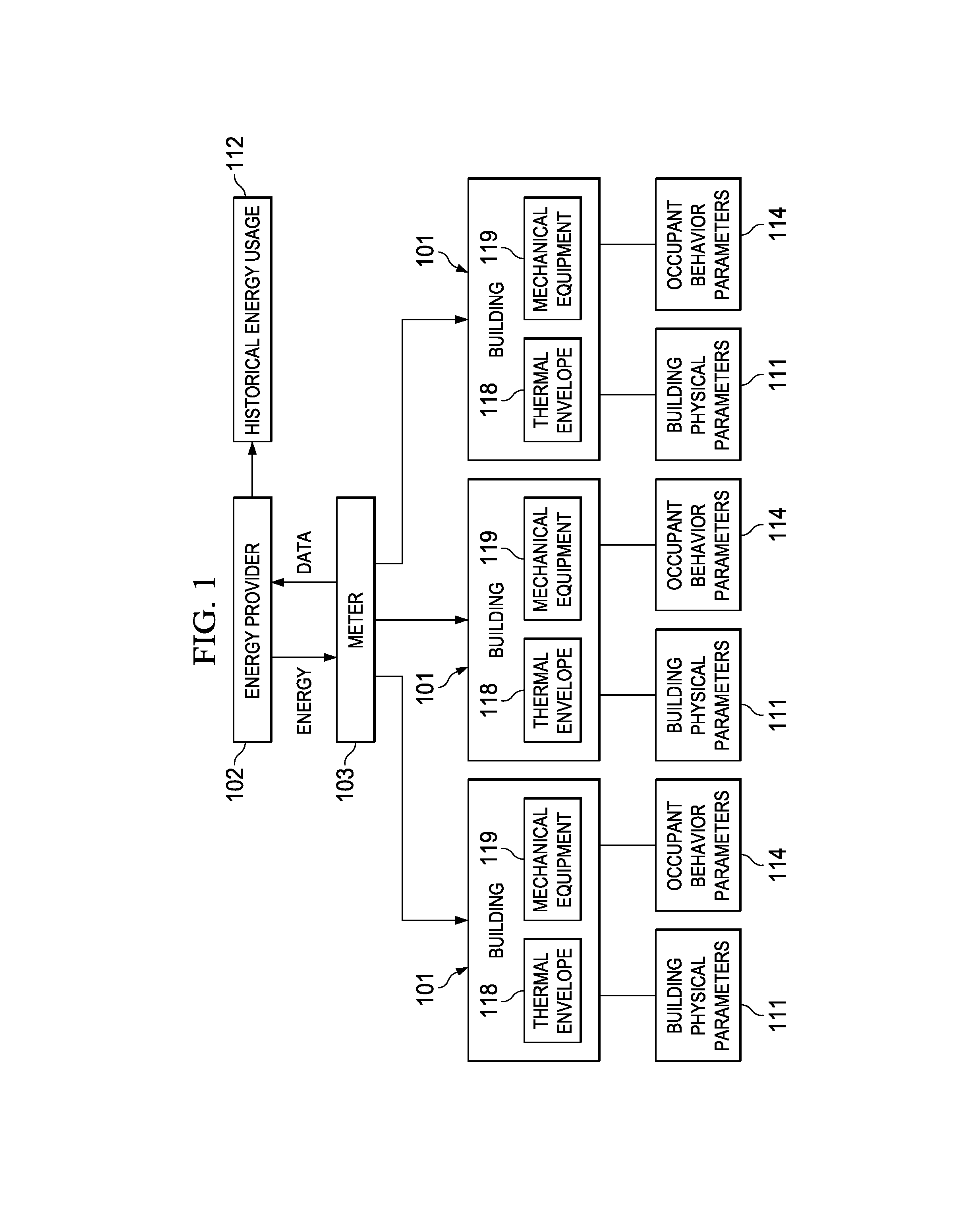
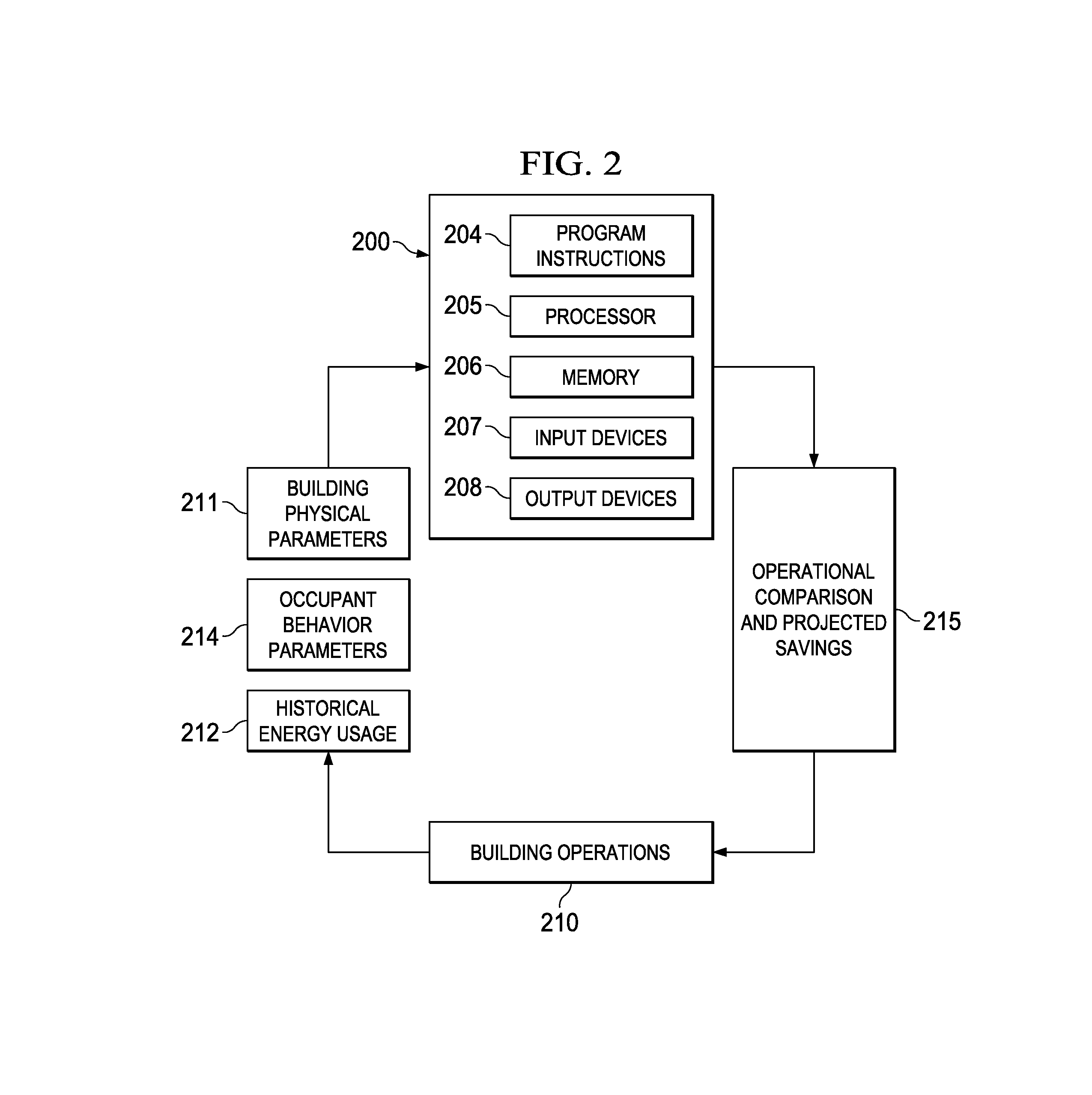
Interval analysis tool for energy consumption
A system and method for analyzing energy savings for a building is provided. The method includes receiving a schedule of occupied days, an occupancy behavior profile and historical energy usage data from which an hourly interval usage is determined. A set of occupancy thresholds is determined by season. Occupied days are determined from the set of occupancy thresholds and the hourly interval usage. The hourly interval usage is analyzed to determine occupied energy consumption in hourly intervals, occupied start and stop time savings, mechanical equipment savings and temperature setpoint savings during an occupied day. The hourly interval usage is also analyzed to determine unoccupied energy consumption in the hourly intervals and refrigeration savings, mechanical equipment savings, computer equipment savings, parking lot lighting savings, hallway lighting savings and temperature setpoint savings during an unoccupied day. Energy consumption, energy savings, operational comparisons and monetary savings are reported.
Owner:CENERGISTIC LLC
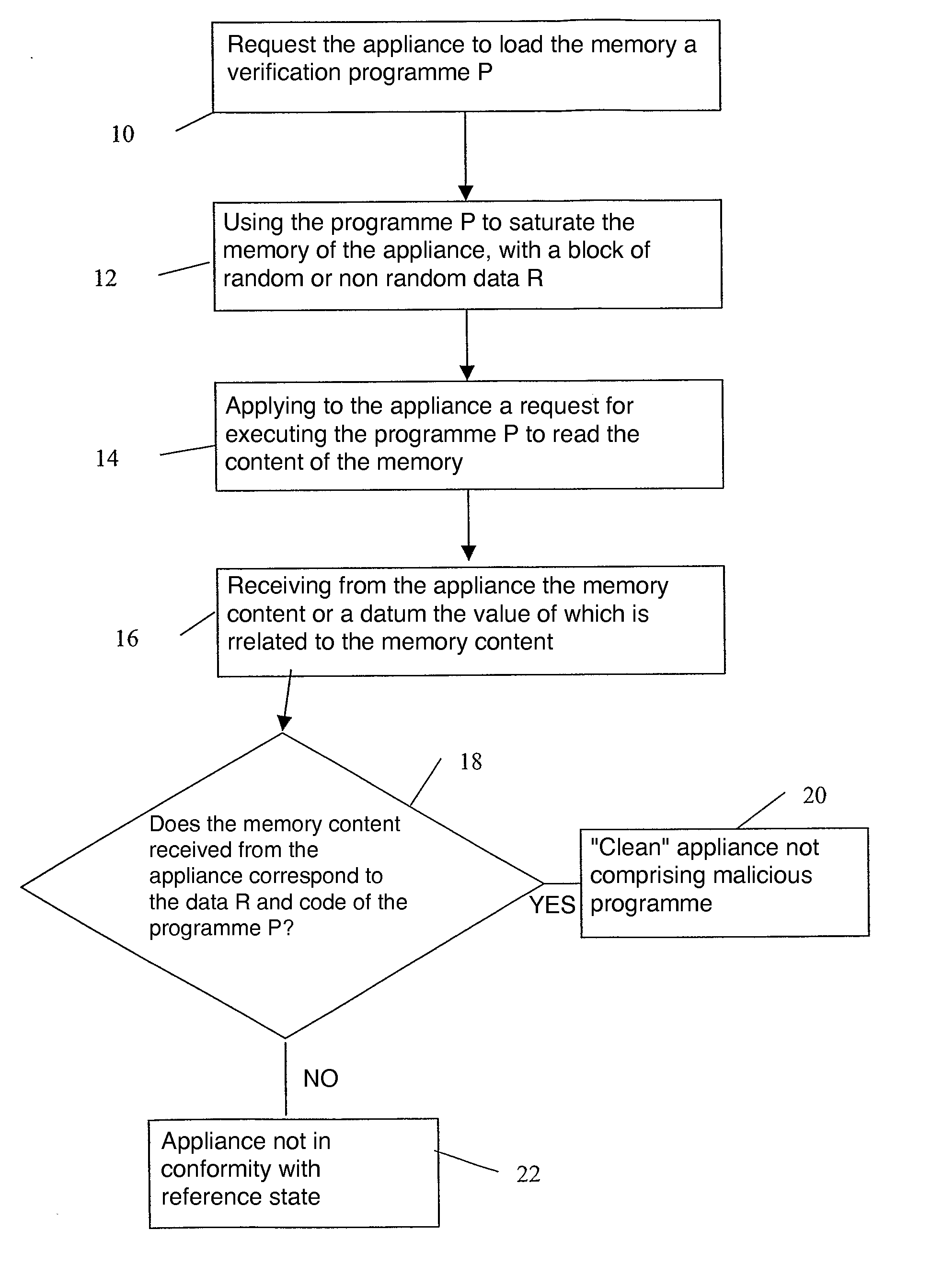
Method for verifying conformity of the logical content of a computer appliance with a reference content
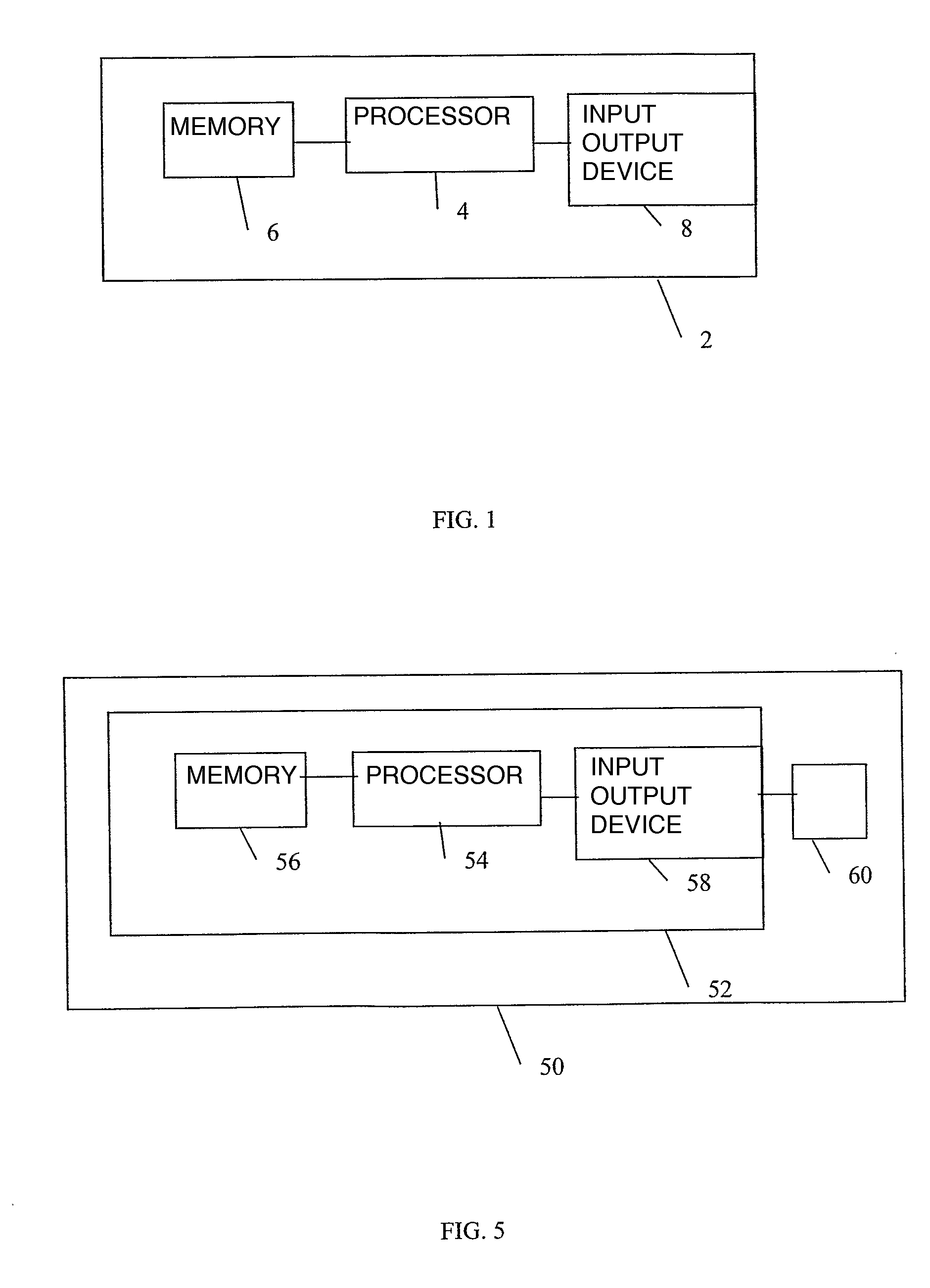
InactiveUS20090260084A1High activityMemory loss protectionError detection/correctionOutput deviceComputer appliance
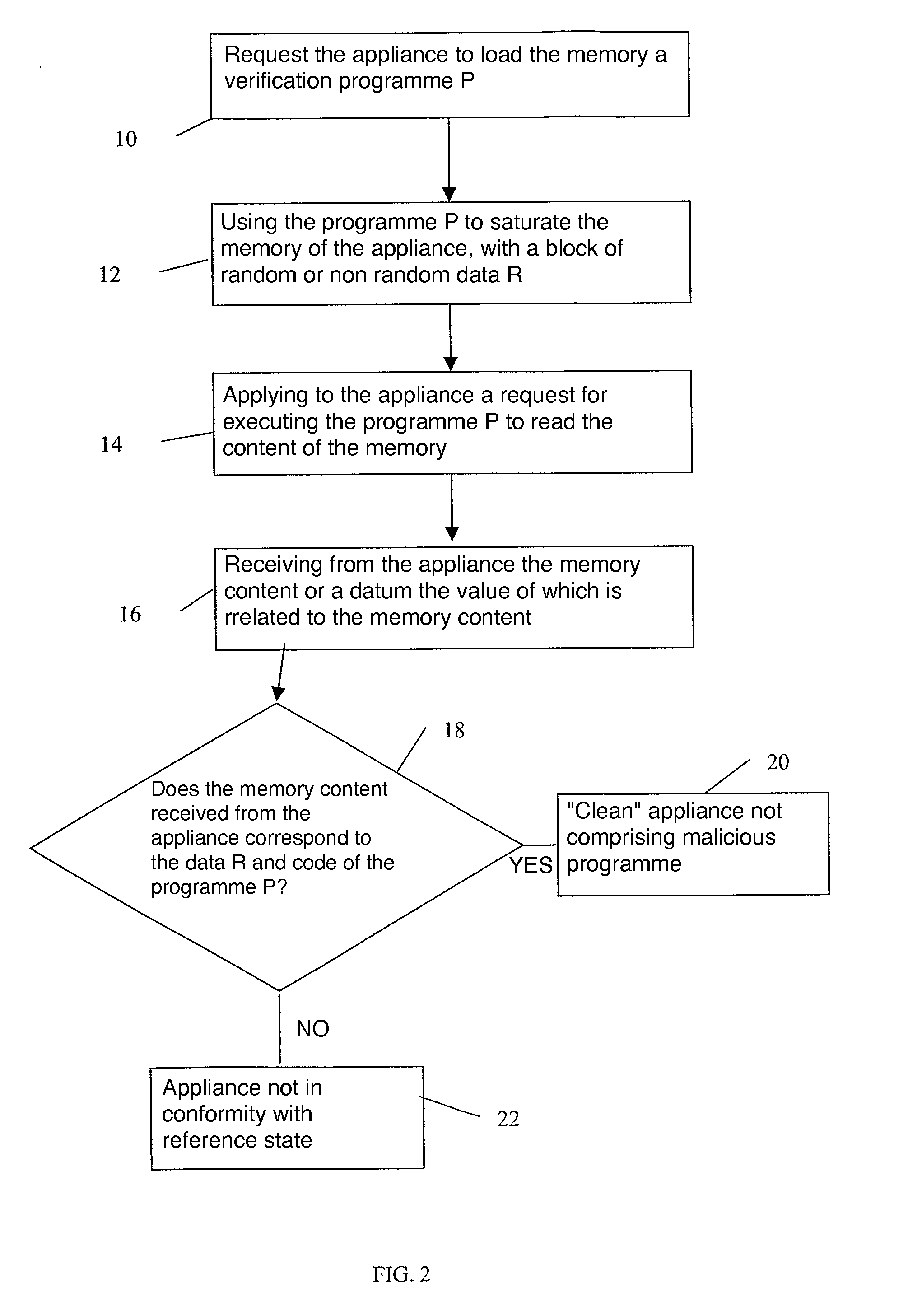
A computer appliance and method are provided. The computer appliance includes a processor, a memory in which the processor can read and write, and an input / output device for interfacing the appliance processor with the outside world. In order to verify conformity of the logical content of the appliance with the reference content, the method includes sending to the appliance a request for loading into the memory and executing a verification program. The verification program is capable or writing data into the memory of the appliance and of reading data in the memory to send them to the input / output device. Then, the method includes sending to the appliance a request for executing the program to saturate the memory available not taken up by the program. Finally, it includes exchanging messages with the appliance by executing the program. Based on the exchanged messages, the conformity of the logical content of the appliance is verified.
Owner:CIE IND & FINANCIERE DINGENIERIE (INGENICO)
Credit and transaction systems
Owner:INTELLECTUAL ADVANCE
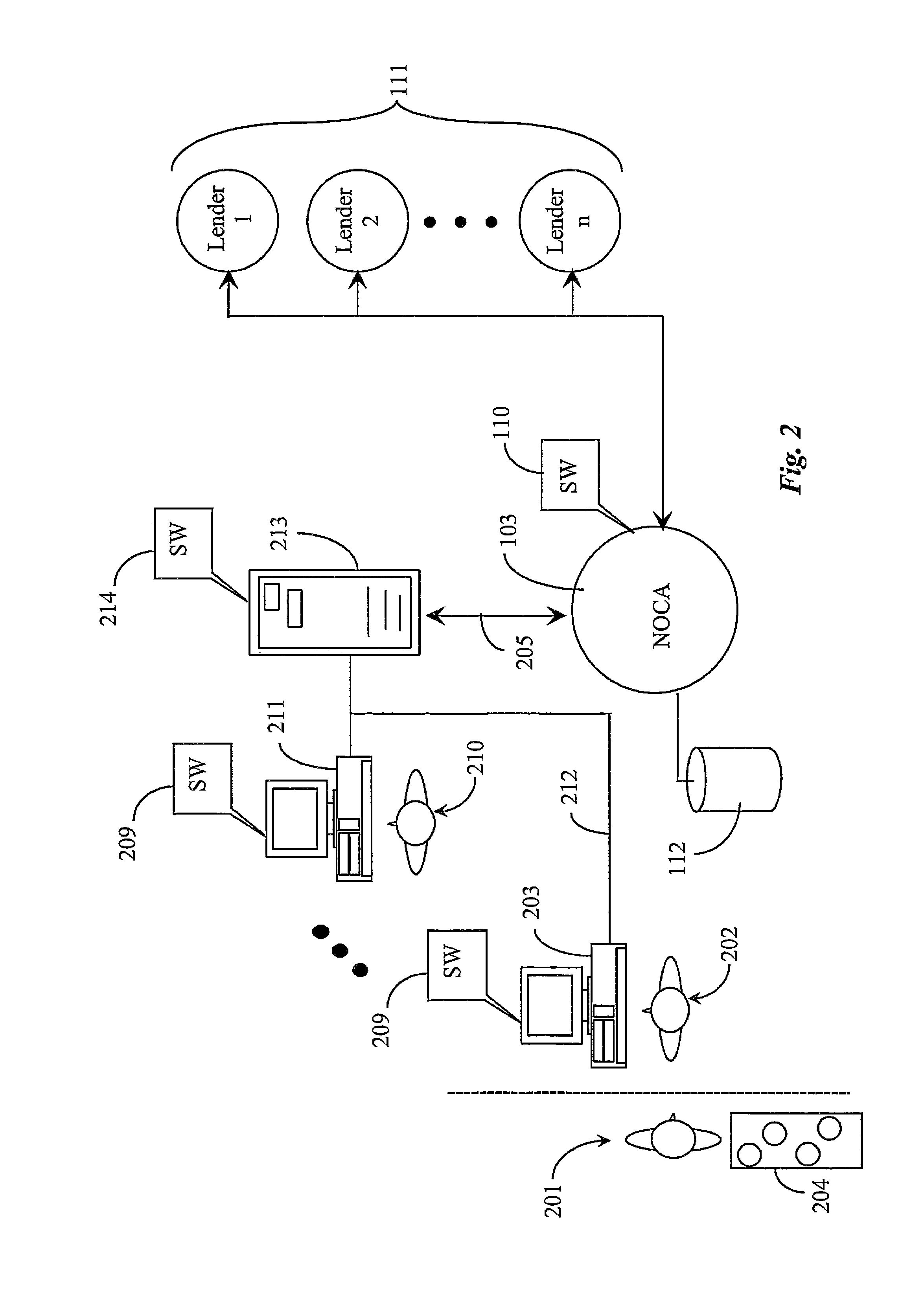
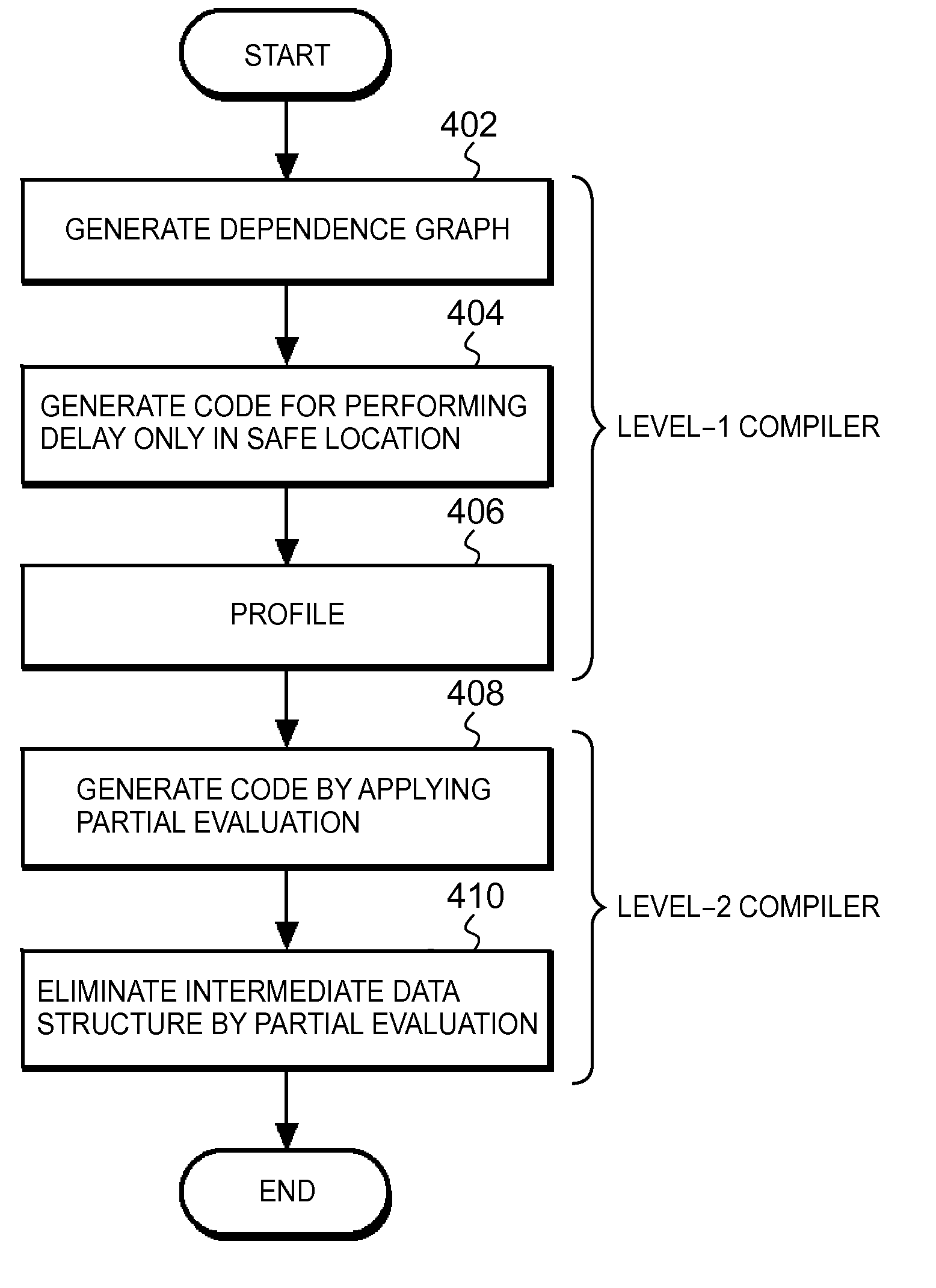
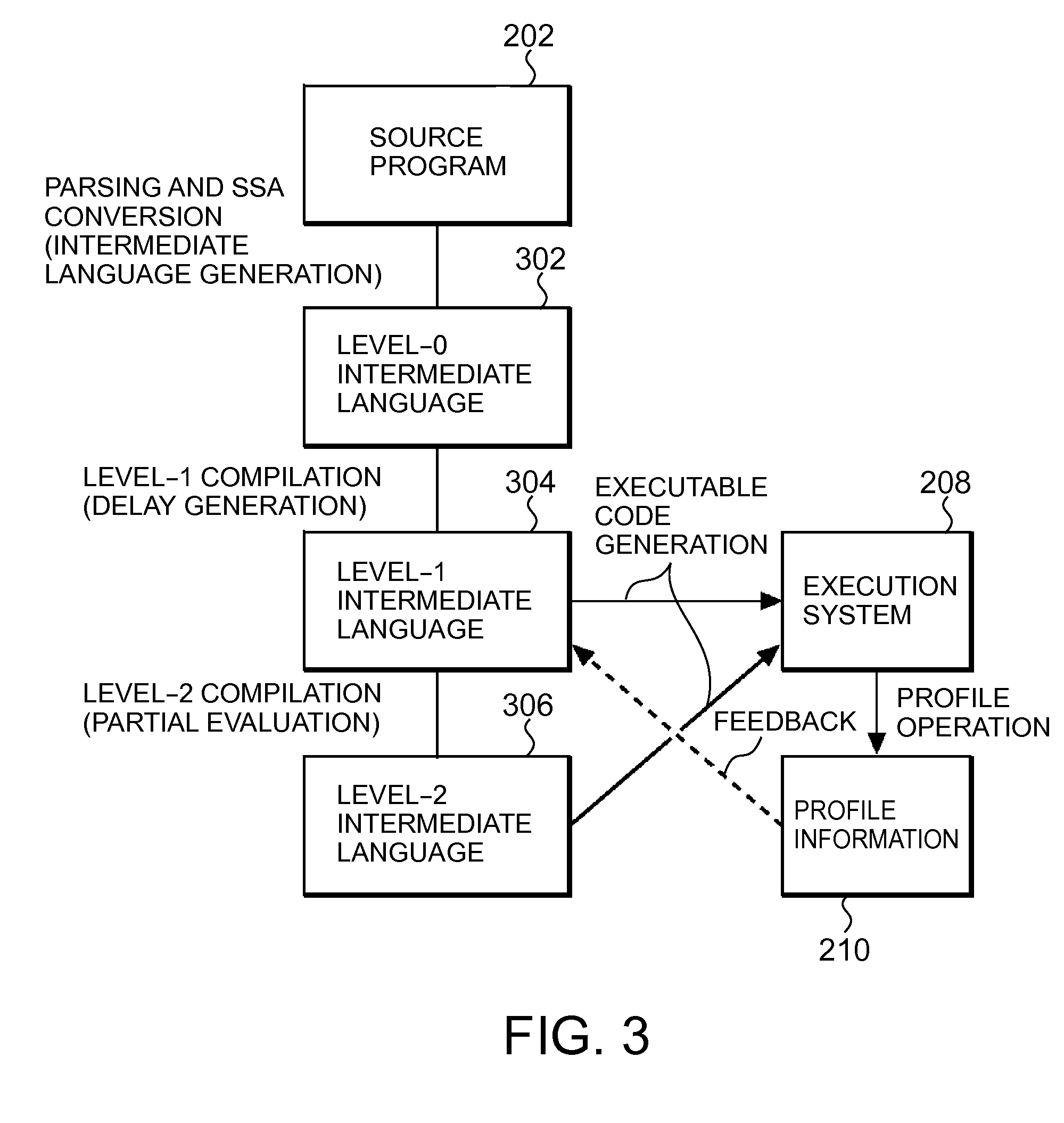
Compiler program, compilation method, and computer system
InactiveUS20110067018A1Improve programming performanceHigh frequencySoftware engineeringProgram controlCompilation errorCompiler
A method, computer program product and system for improving performance of a program during runtime. The method includes reading source code; generating a dependence graph with a dependency for (1) data or (2) side effects; generating a postdominator tree based on the dependence graph; identifying a portion of the program able to be delayed using the postdominator tree; generating delay closure code; profiling a location where the location is where the delay closure code is forced; inlining the delay closure code into a frequent location in which the delay closure code has been forced with high frequency; partially evaluating the program; and generating fast code which eliminates an intermediate data structure within the program, where at least one of the steps is carried out using a computer device so that performance of the program during runtime is improved.
Owner:IBM CORP
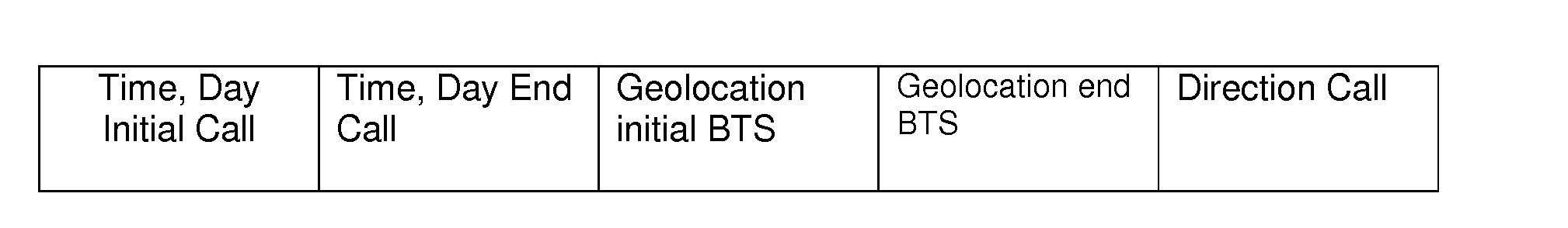
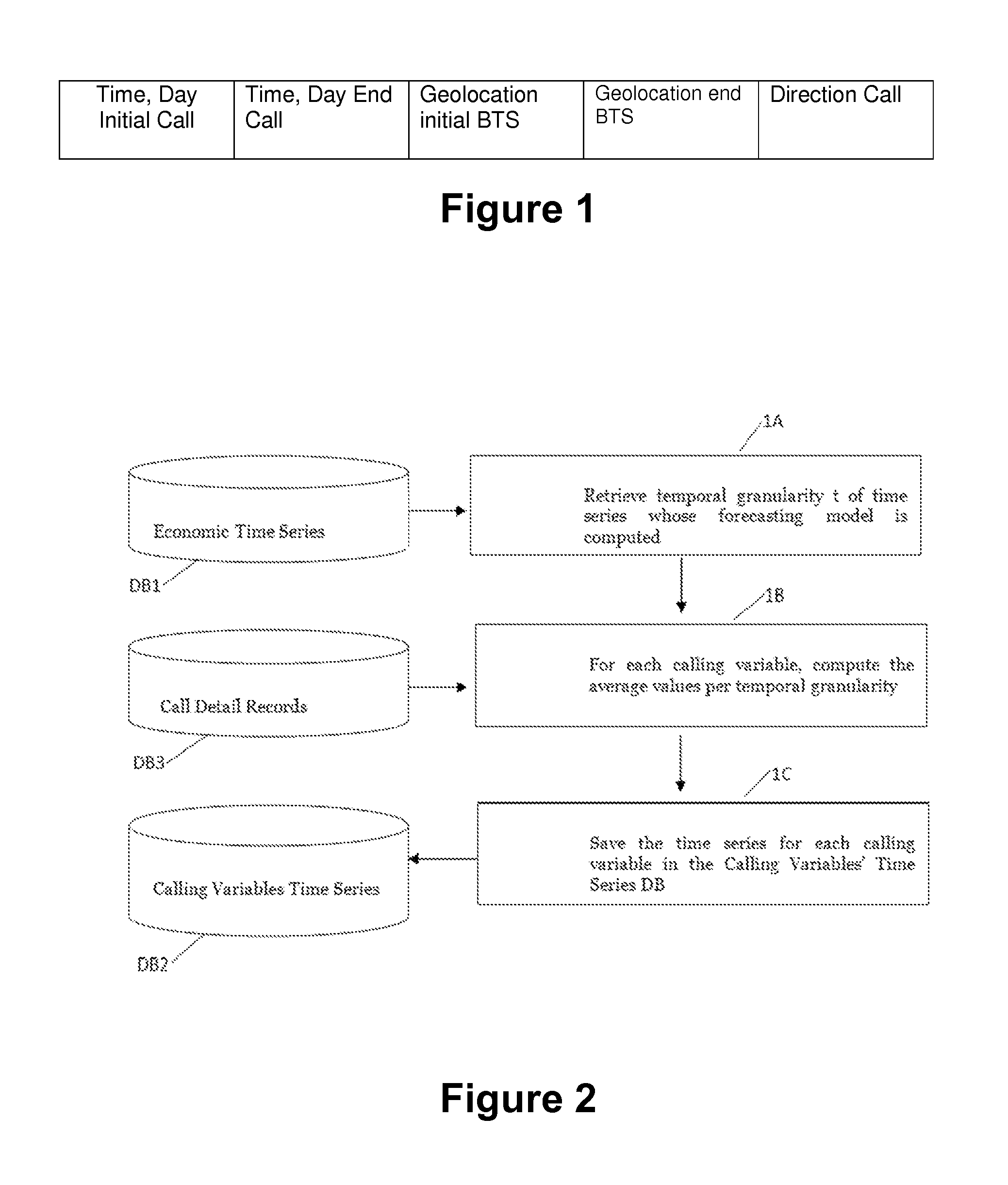
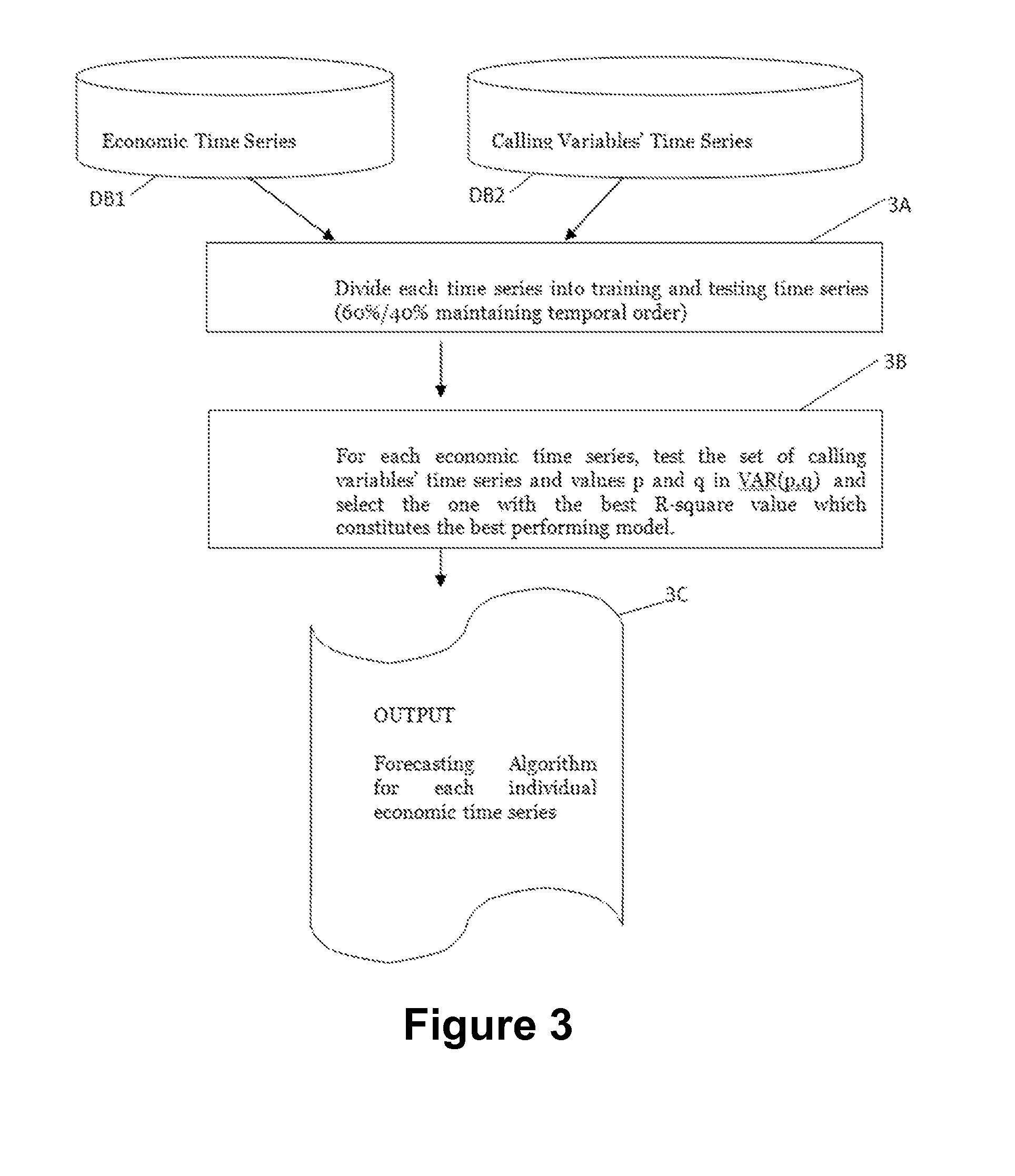
Method and computer system to forecast economic time series of a region and computer program thereof
The method uses a computer device to receive as inputs socio-economic data of a region during a definite time period representing an economic time series that are stored in a first database, comprising: computing, during the same definite time period, the average values of each of a plurality of anonym and aggregated call records generated by individuals using a plurality of base stations of said region obtaining calling variables and computing from said calling variables calling variables' time series representing average temporal usage statistics that are stored in a second database; and building from said economic time series and said computed calling variables time series a model to forecast future values of the economic time series of said region.
Owner:TELEFONICA DIGITAL ESPANA
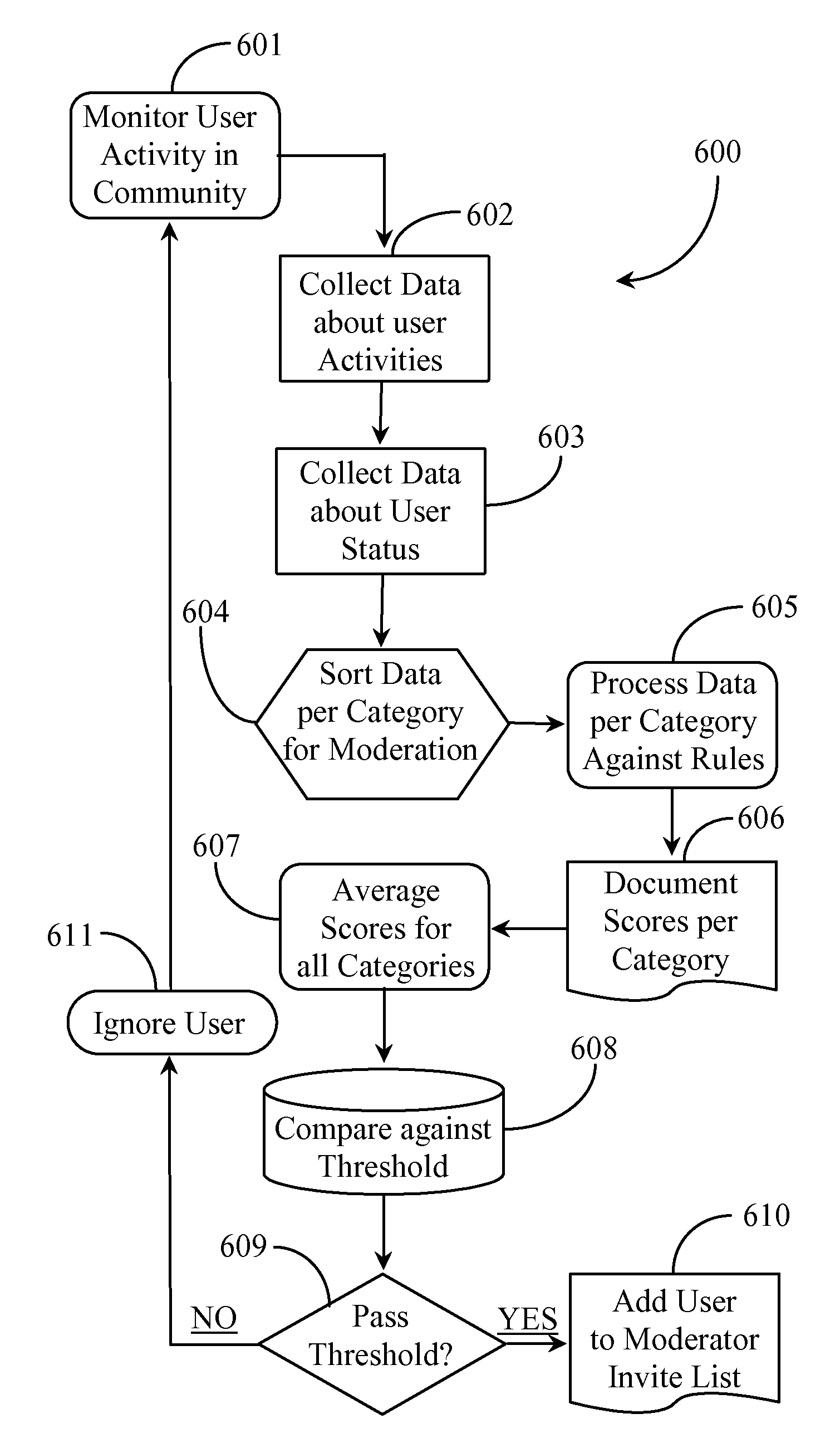
Community-Based Moderator System for Online Content
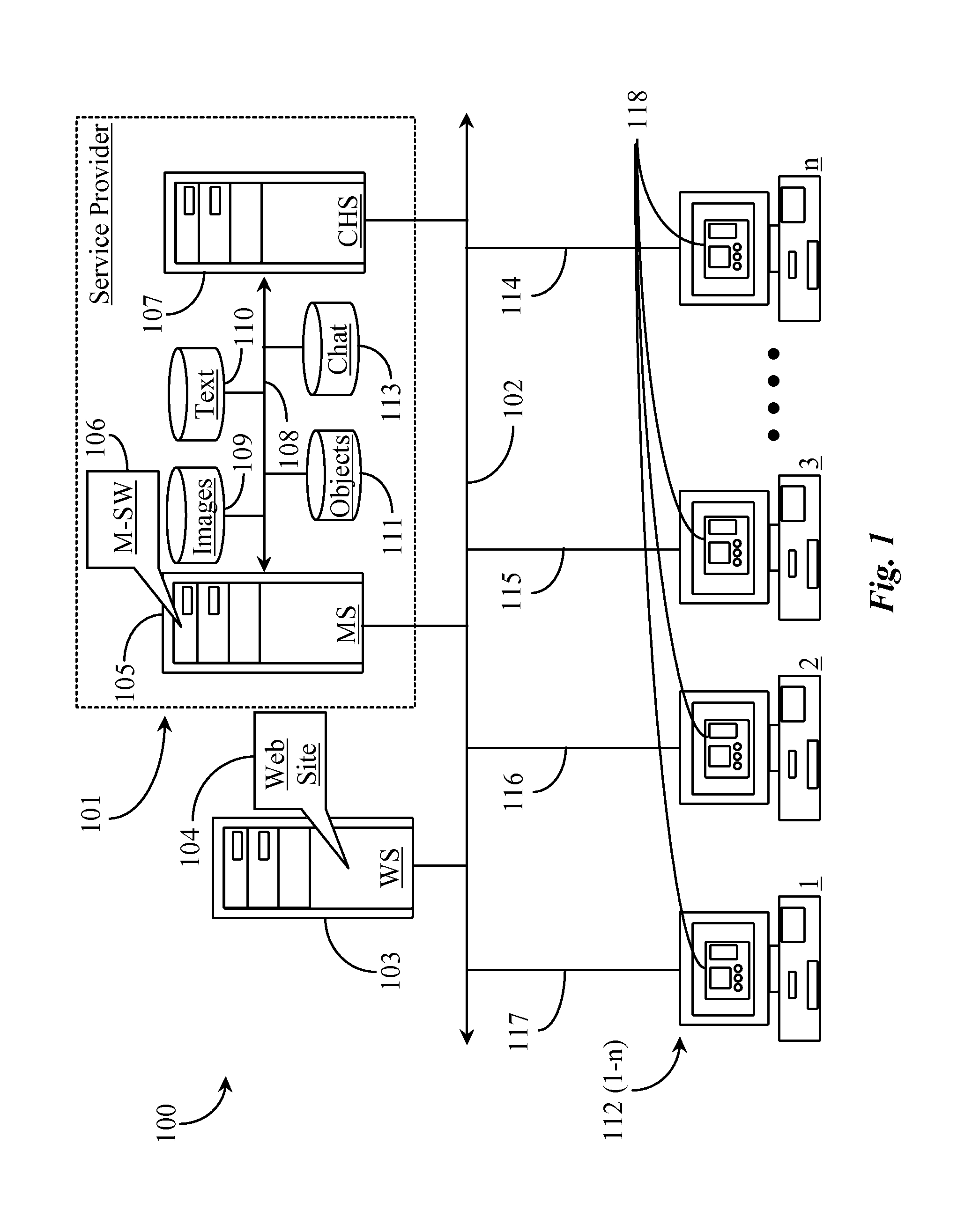
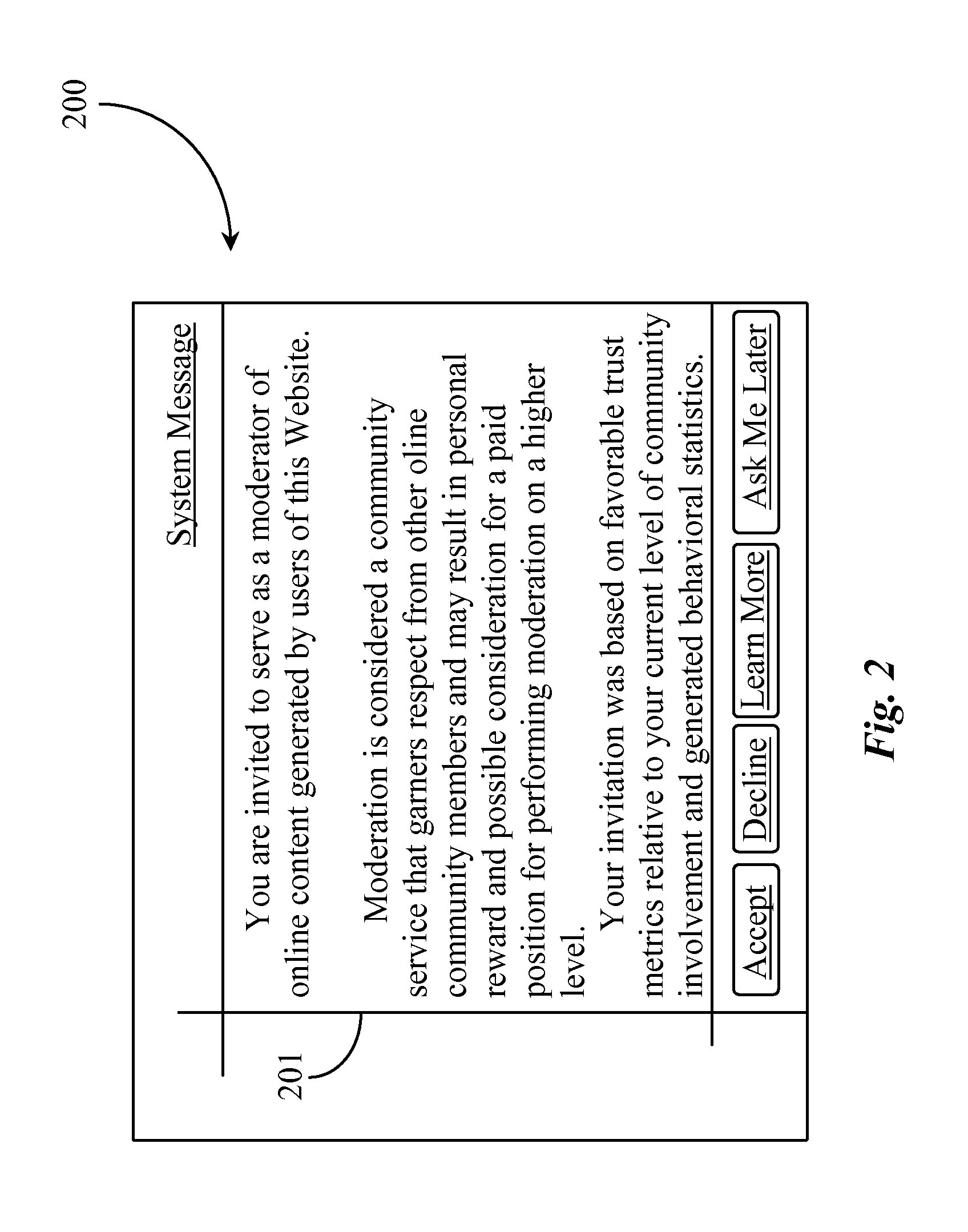
InactiveUS20110289432A1Low costInput/output for user-computer interactionWebsite content managementComputer applianceMachine-readable medium
A community-based moderation system for online content has a computerized server connected to the Internet network and executing software (SW) from a machine-readable medium, a queuing function of the SW for queuing items for moderation, a recruiting function of the SW for recruiting potential moderators from an online community via the Internet, an interactive interface generated by the SW and displayable on computer appliances of recruited moderators, for displaying items for moderation and controls for carrying out moderation, and a reporting function associated with the interactive display enabling the moderator to report results of moderation.
Owner:ROBLOX CORP
Computer systems and method for educational use
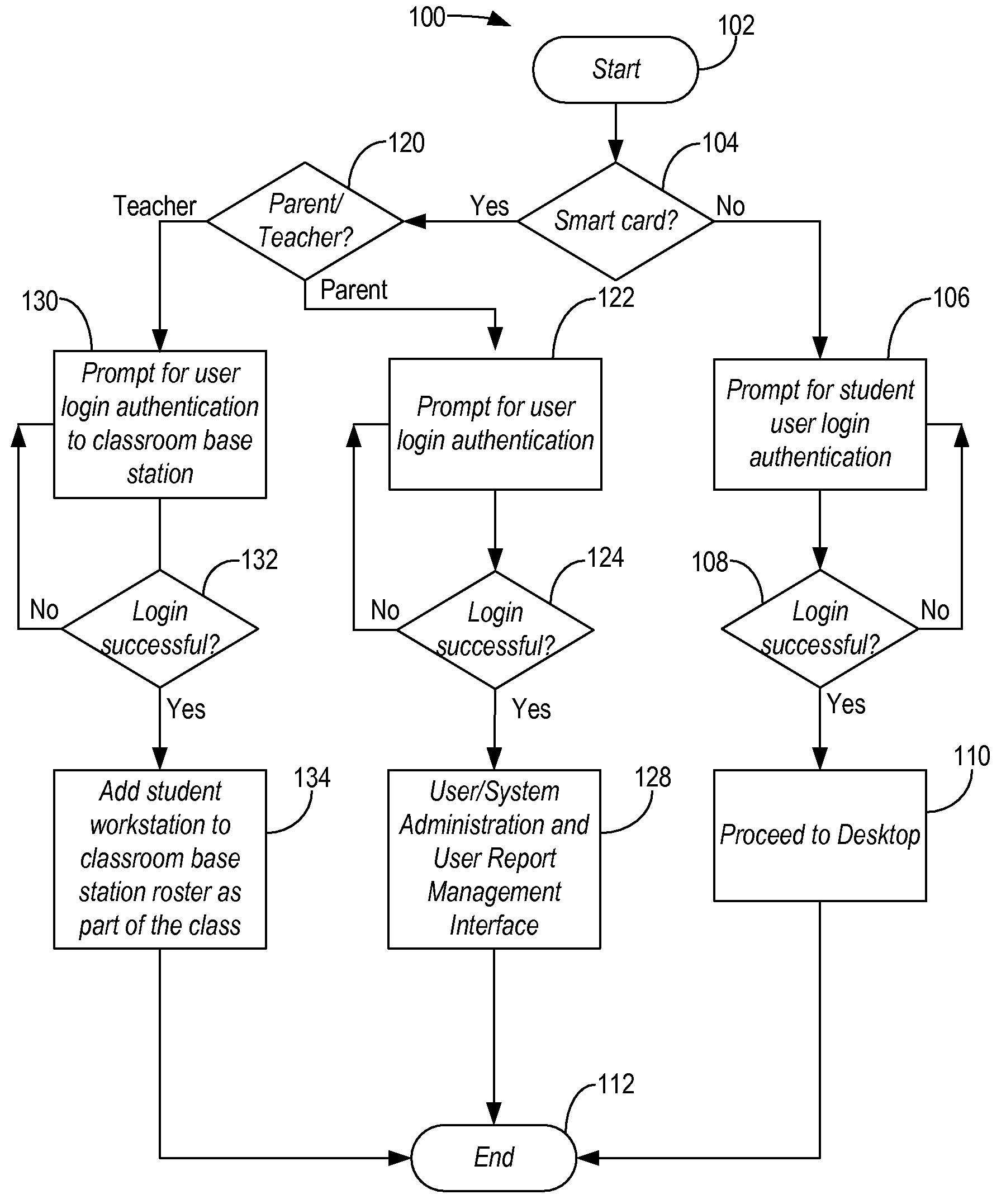
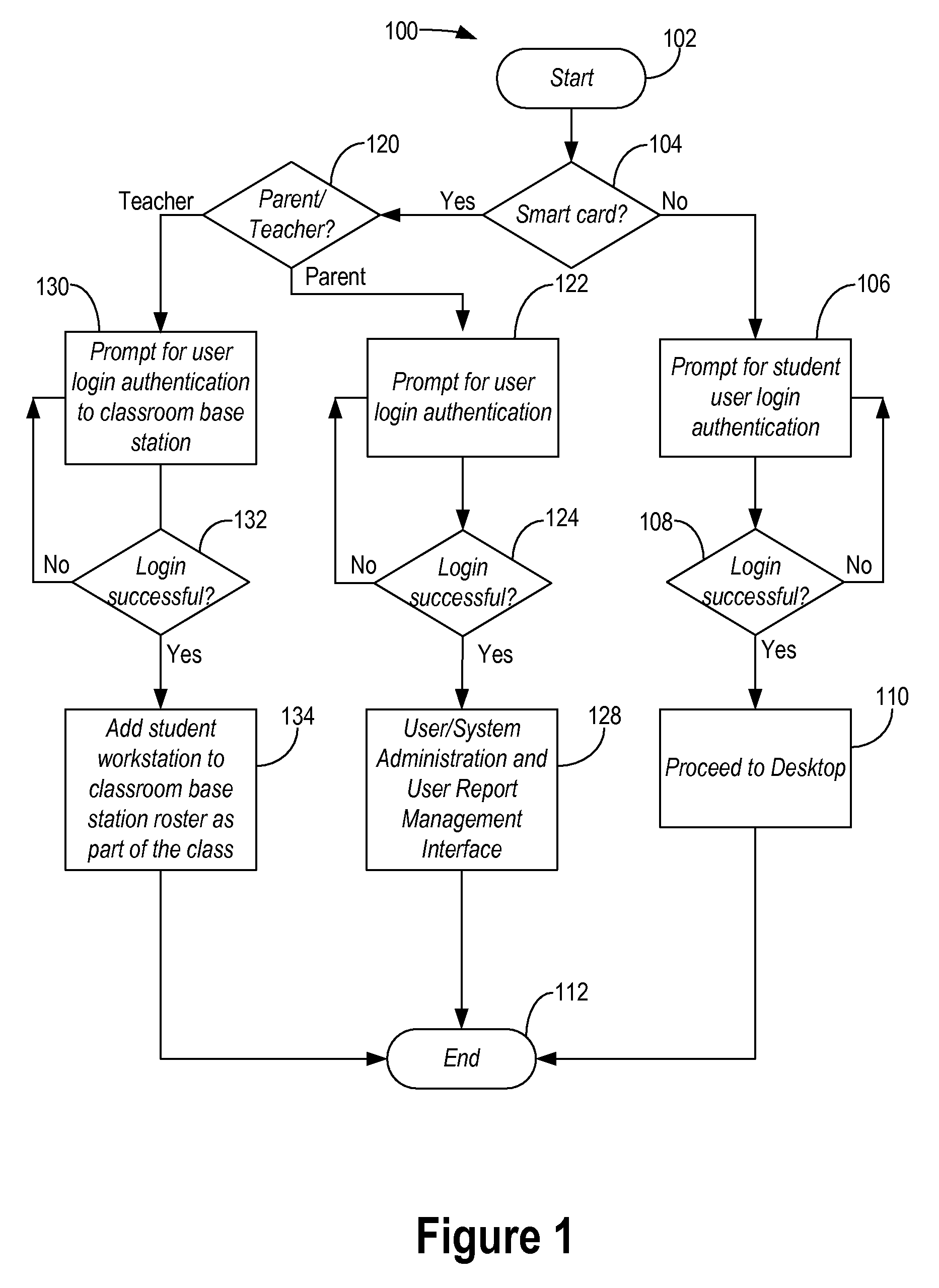
InactiveUS20080318199A1Secure and focusedElectrical appliancesMechanical appliancesComputerized systemComputer science
The present disclosure provides a computer system and associated usage method solely for educational purposes. The computer system is a computer appliance focused solely for educational use operating only educationally approved programs and loading only educationally approved content. Advantageously, such appliance provides a secure and focused platform for learning that can be used at home by parents and students and in class by teachers, parents, and students.
Owner:MANCHESTER SKY
Alternative user-interface
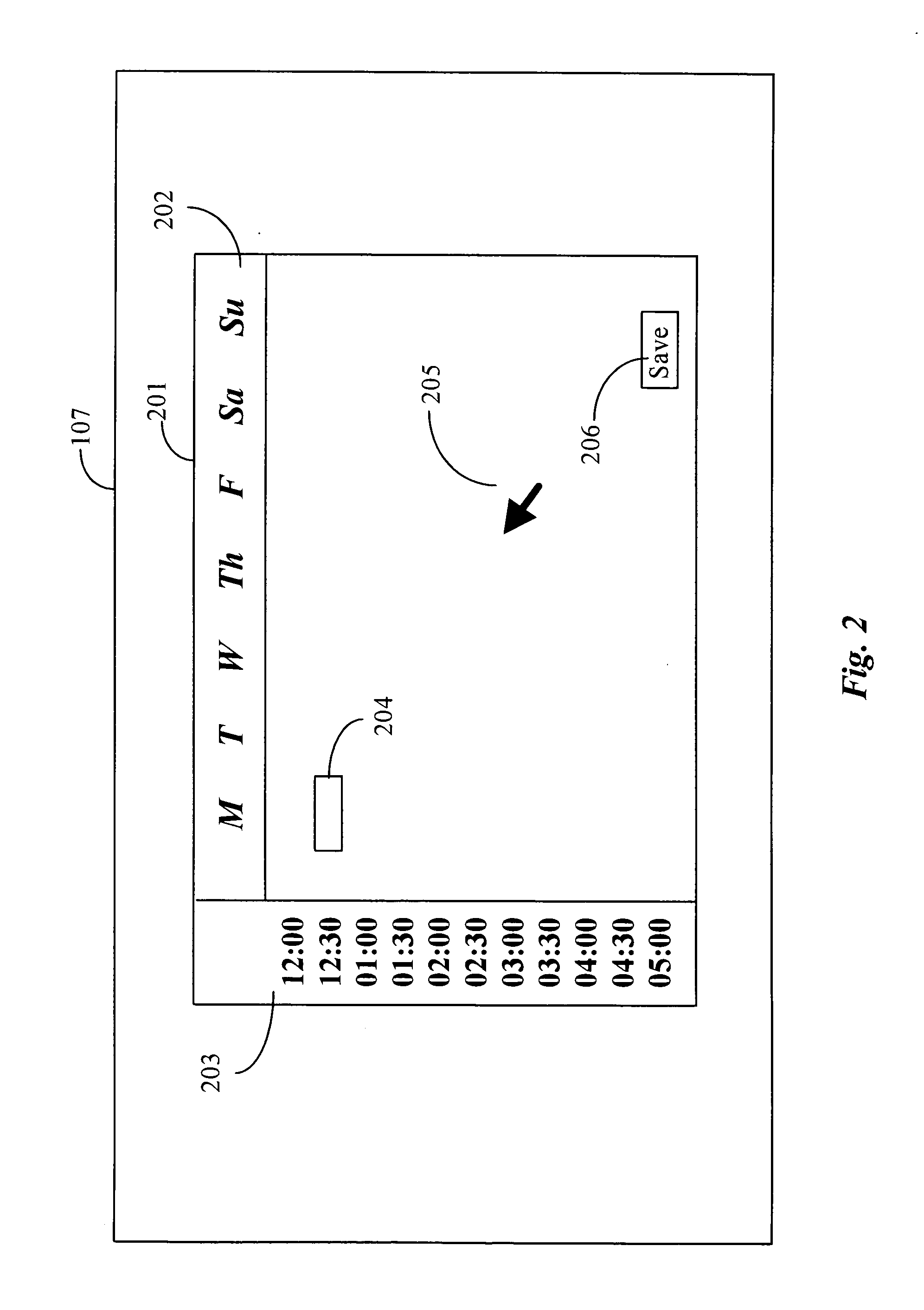
InactiveUS20050172075A1Sampled-variable control systemsCredit registering devices actuationUser interfaceComputer appliance
A system for programming a programmable device having an interface for a portable memory medium has an interactive interface executable on a stand-alone computer appliance for creating a program for the programmable device, a portable memory medium, and a downloading mechanism for transferring the created program to the portable memory medium.
Owner:CENT COAST PATENT AGENCY
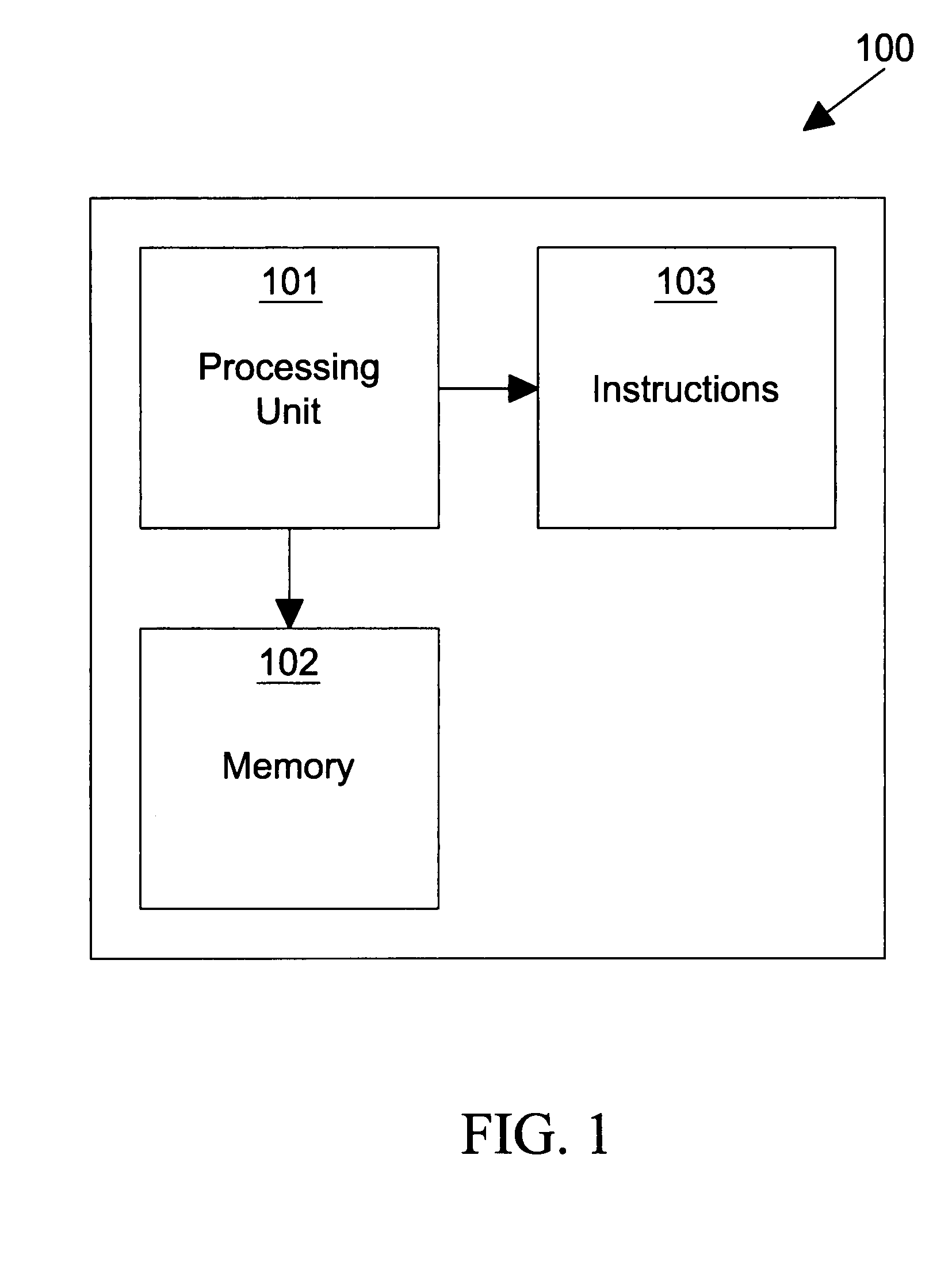
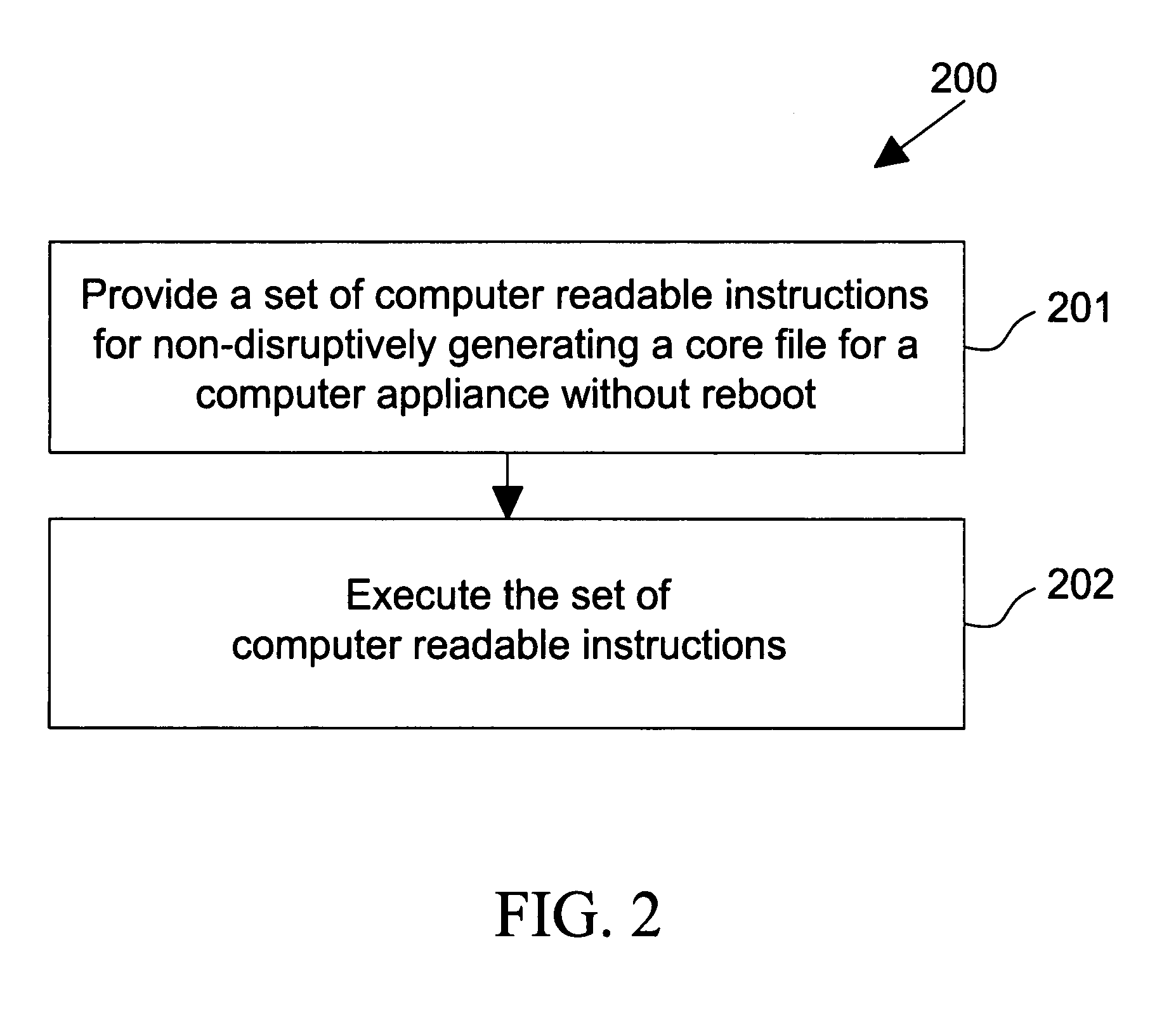
Non-disruptive generation of core files without reboot
ActiveUS7707462B1Useful in diagnosing potential problemLess disruptiveNon-redundant fault processingComputer appliance
The present invention is directed to non-disruptive generation of core files for a computer appliance without rebooting the computer appliance. In an embodiment of the invention, the computer appliance is analyzed. A determination is made as to what core file generation options will be non-disruptive to the computer appliance. The tradeoff is evaluated between options that will generate core files which are more useful in diagnosing potential problems with the computer appliance and options which will generate core files which are less disruptive. A procedure is determined which will generate the core file without disrupting the computer appliance. Resources are allocated to utilize in generation of the core file. The procedure is then executed and a core file is generated without disrupting the computer appliance.
Owner:NETWORK APPLIANCE INC
Automatic generation of core files and automatic generation of support information with generation of core files
The present invention is directed to an automatic generation of a support collateral as well as to an automatic generation of core files. In one embodiment, a support collateral is automatically generated when a core file is generated. The support collateral is information used to support diagnosis of potential problems. A computer appliance further includes a framework of rules organized by a subsystem. A subsystem is a functional component of the computer appliance. Rules are evaluated when an inflection point is encountered. An inflection point is a critical point in processing where processing is interrupted. A core file is generated for the computer appliance when indicated to do so by a rule.
Owner:NETWORK APPLIANCE INC
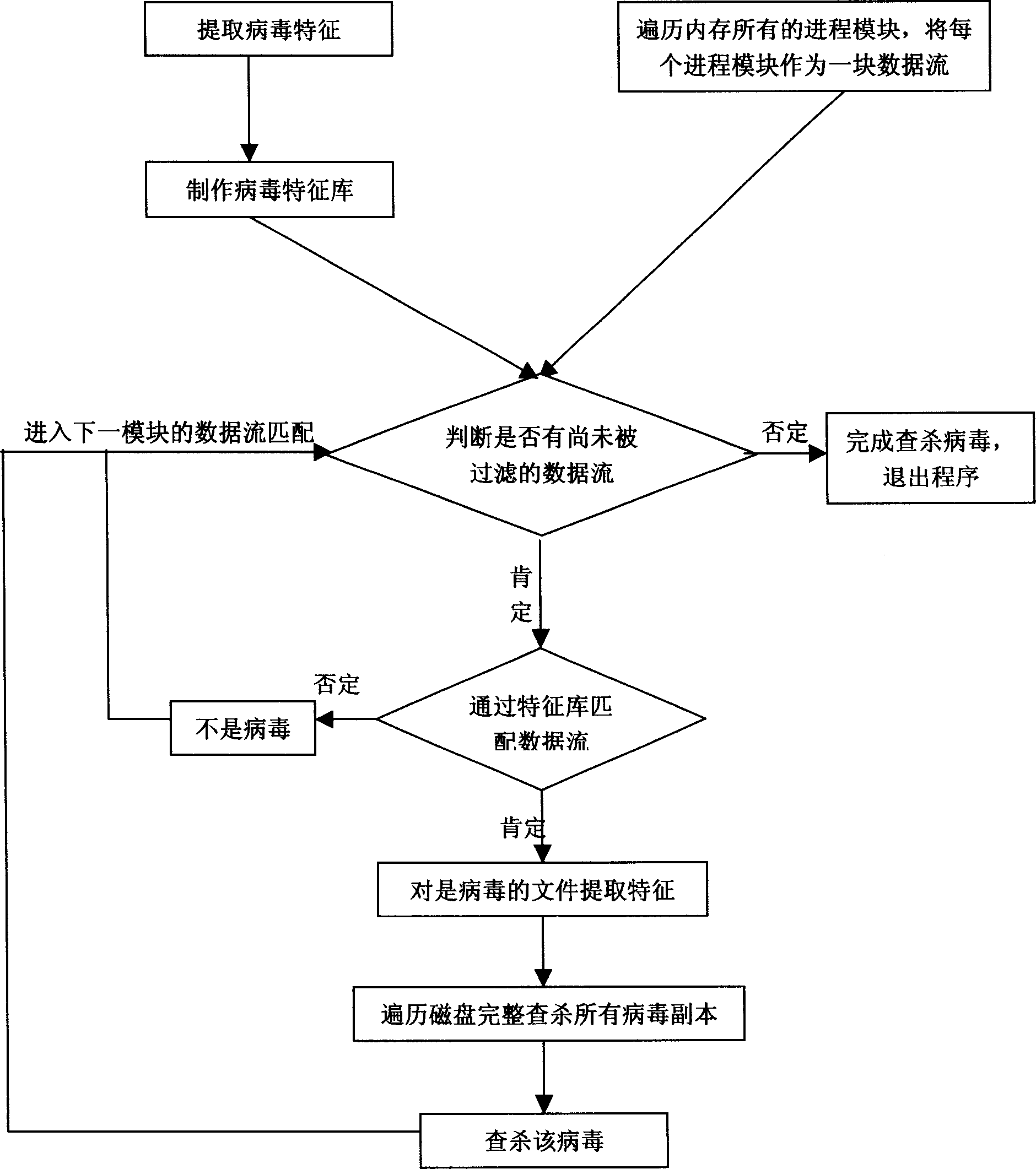
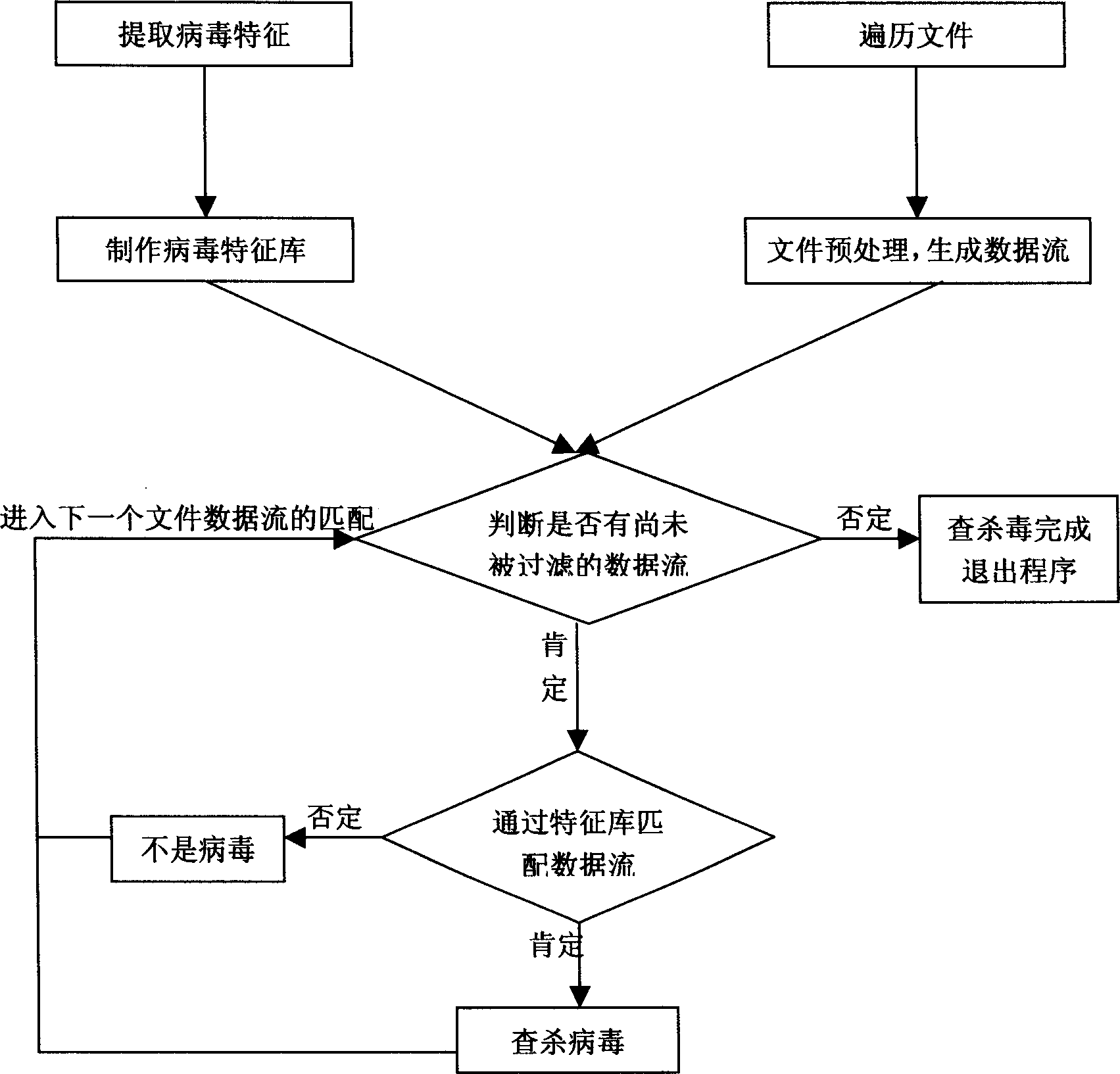
Computer virus checking and killing method based on data stream
The invention discloses a checking and diminishing method of computer virus in the computer appliance domain, which is characterized by the following: basing on computer virus checking and diminishing method of data flow through matching the virus feature data with the checked and diminished data flow (internal memory mode or file generation data flow); containing internal memory checking and diminishing virus method and file checking and diminishing virus method; providing the identification of new variant of known virus or partial new virus without updating or less updating; analyzing and extracting binary code of known virus as virus feature to find new variant of virus or new virus in the internal memory mode or file; extracting the file feature automatically (if the internal memory mode corresponds to the file)to generate new file virus feature; updating the virus database automatically; finishing checking and diminishing task through scanning the new variant of known virus and partial new virus and other all duplicates.
Owner:ZHUHAI BAOQU TECH CO LTD
Storage, transfer and compresson of next generation sequencing data
InactiveUS20180152535A1Increase the compression ratioProcessing speedCode conversionSequence analysisData fileApplication software
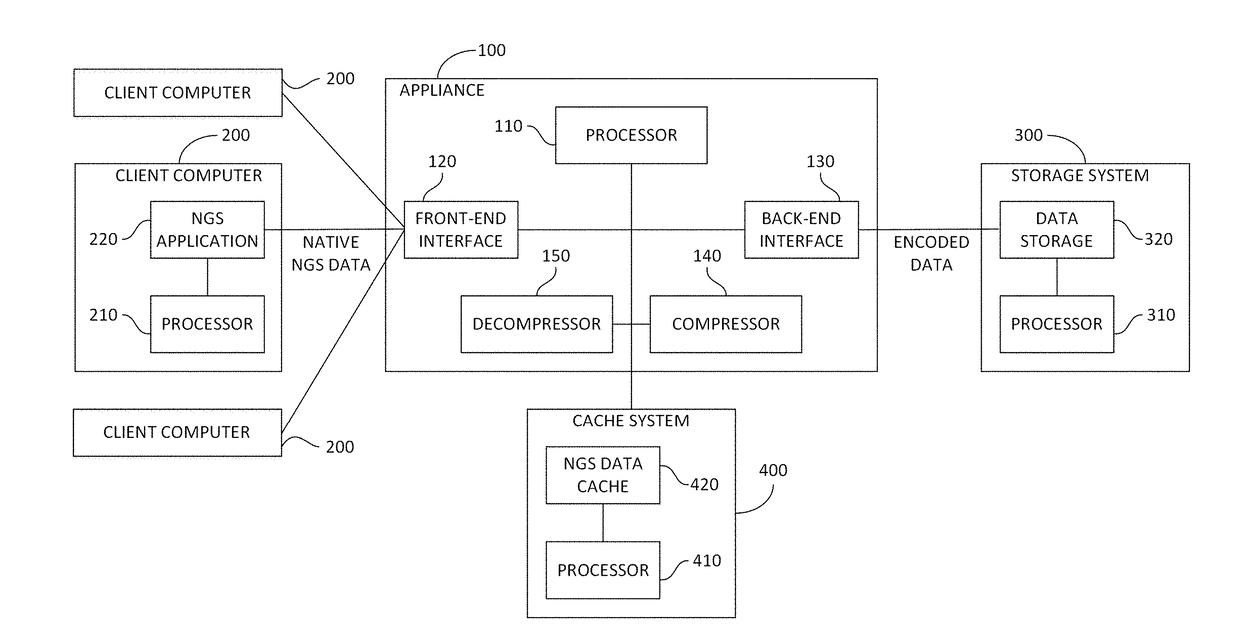
A computer appliance including a front-end interface communicating with a client computer, a back-end interface communicating with a storage, a compressor receiving native next generation sequencing (NGS) data from an application running on the client computer via the front-end interface, the application being programmed to process native NGS data, adding a compressed form of the native NGS data into a portion of an encoded data file or data object, and storing the portion of the encoded data file or data object in the storage via the back-end interface, and a decompressor receiving a portion of an encoded data file or data object from the storage via the back-end interface, decompressing the portion of the encoded data file or data object to generate therefrom native NGS data, and transmitting the native NGS data to the client via the front-end interface, for use by the application running on the client.
Owner:GENEFORMICS DATA SYST LTD
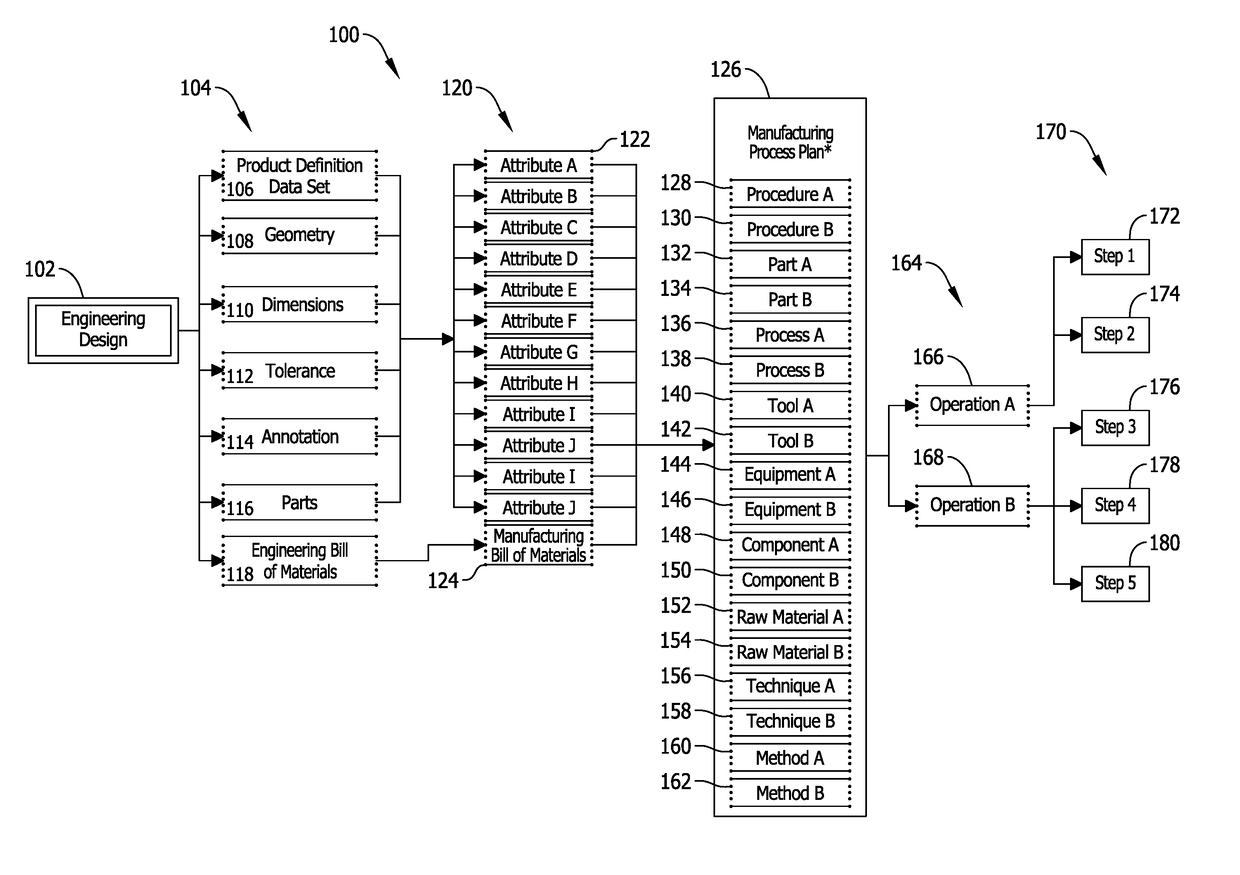
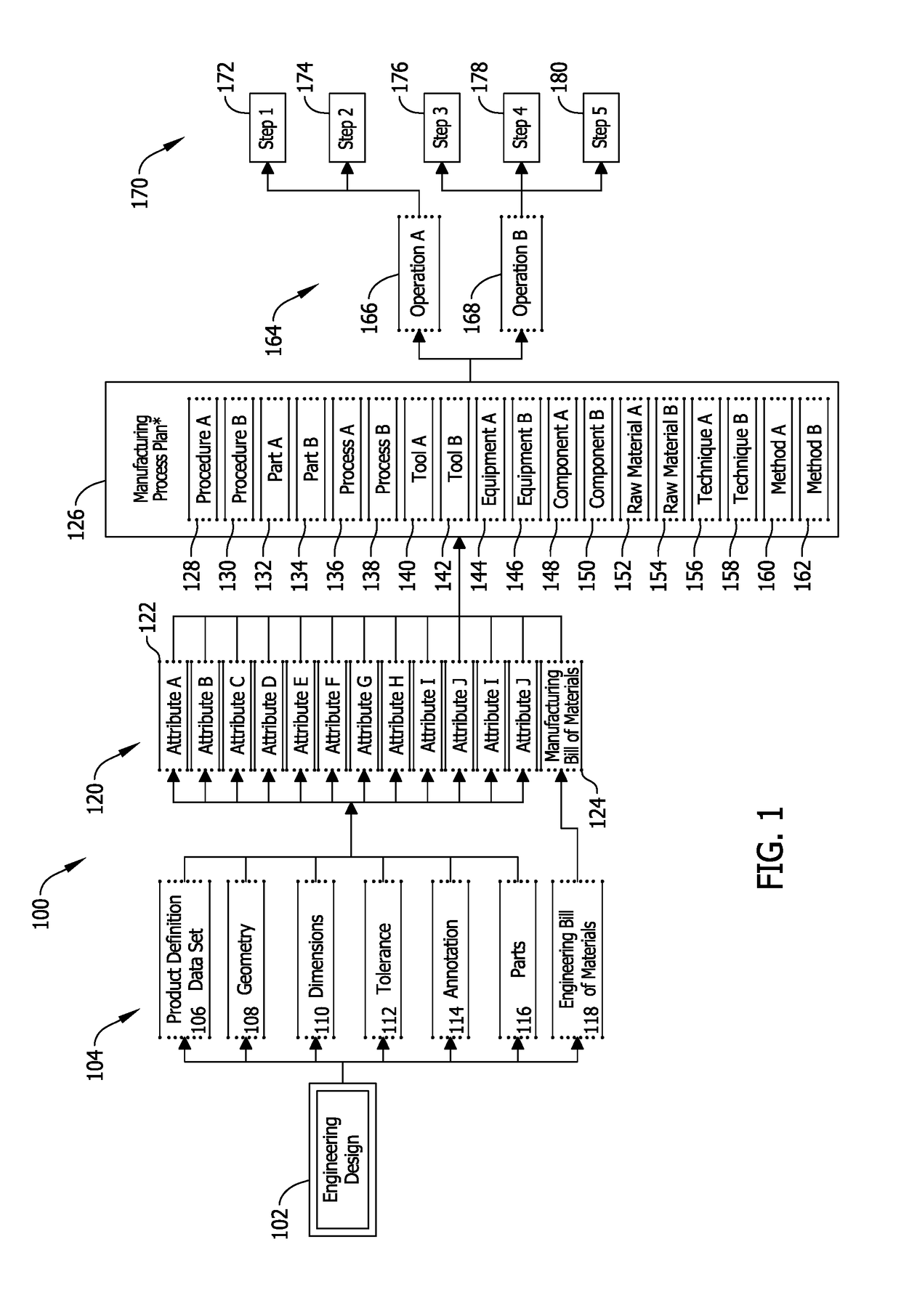
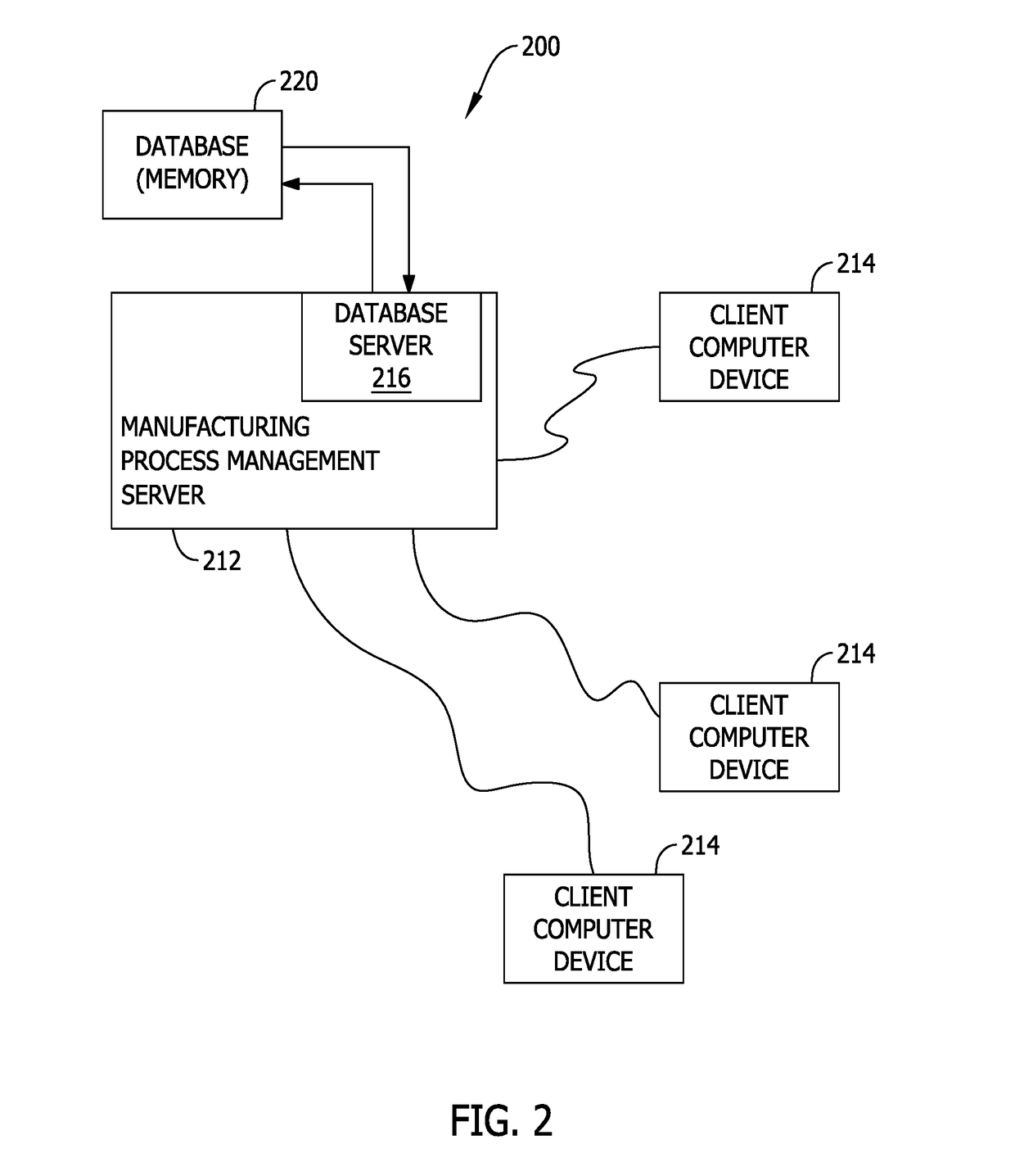
System and methods for managing changes to a product in a manufacturing environment including conversion of an engineering bill of material to a manufacturing bill of material
A manufacturing process management (MPM) computer device is provided. The MPM computer device is configured to store an engineering bill of materials for a product to be assembled including a first plurality of parts, store a manufacturing bill of materials for the product to be assembled including a second plurality of parts and a status, receive a request from a user to change the status of the manufacturing bill of materials, compare the first plurality of parts with the second plurality of parts, determine whether the first plurality of parts matches the second plurality of parts based on the comparison, if the comparison matches, change the status of the manufacturing bill of materials, and if the comparison does not match, prevent the status of the manufacturing bill of materials from changing.
Owner:THE BOEING CO
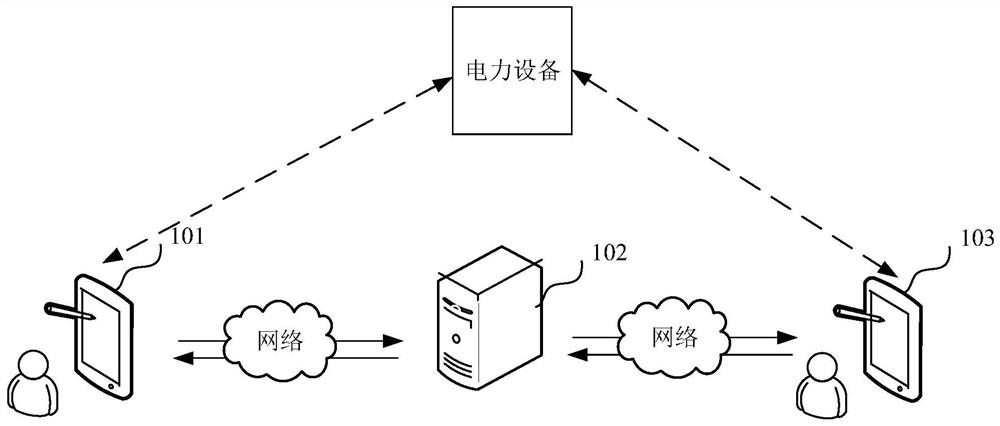
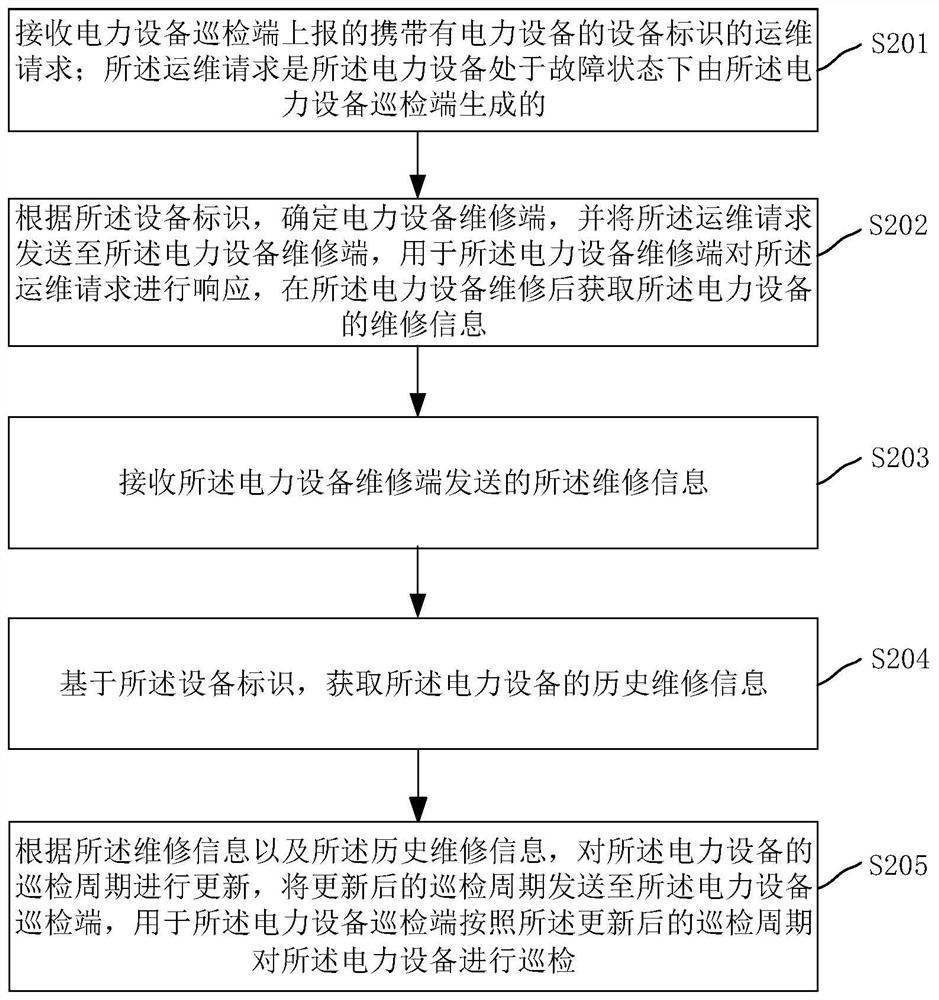
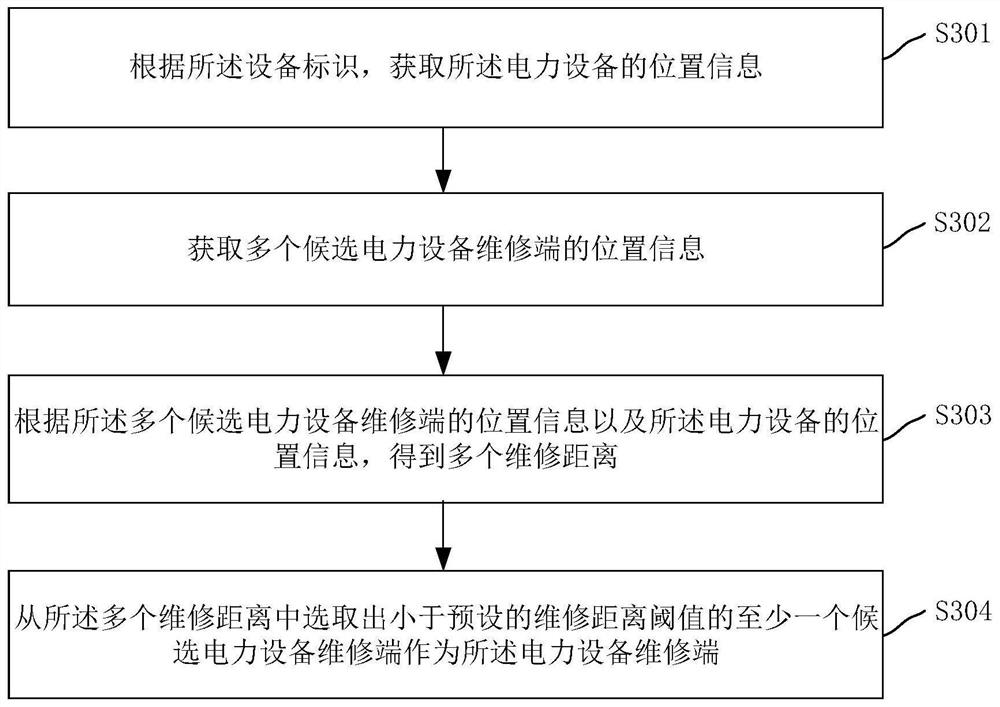
Operation and maintenance method, system and device for power equipment, equipment and storage medium
InactiveCN111626443AImprove operation and maintenance efficiencyChecking time patrolsData processing applicationsElectric power equipmentPower equipment
The invention relates to an operation and maintenance method, system and device of power equipment, computer equipment and a storage medium. The method comprises the following steps: an operation andmaintenance server receives an operation and maintenance request carrying an equipment identifier of power equipment reported by a power equipment inspection terminal; determining a power equipment maintenance end according to the equipment identifier, and sending the operation and maintenance request to the power equipment maintenance end for the power equipment maintenance end to respond to theoperation and maintenance request to obtain maintenance information; receiving maintenance information sent by the power equipment maintenance terminal; acquiring historical maintenance information ofthe power equipment based on the equipment identifier; and according to the maintenance information and the historical maintenance information, updating the inspection period of the power equipment,and sending the updated inspection period to the power equipment inspection end, so that the power equipment inspection end inspects the power equipment according to the updated inspection period. Byadopting the method, relevant adjustment can be performed on the inspection period according to the maintenance information of the power equipment and the historical maintenance information, so that the operation and maintenance efficiency is improved.
Owner:GUANGDONG POWER GRID CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com