Patents
Literature
506 results about "Opcode" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, an opcode (abbreviated from operation code, also known as instruction syllable, instruction parcel or opstring) is the portion of a machine language instruction that specifies the operation to be performed. Beside the opcode itself, most instructions also specify the data they will process, in the form of operands. In addition to opcodes used in the instruction set architectures of various CPUs, which are hardware devices, they can also be used in abstract computing machines as part of their byte code specifications.
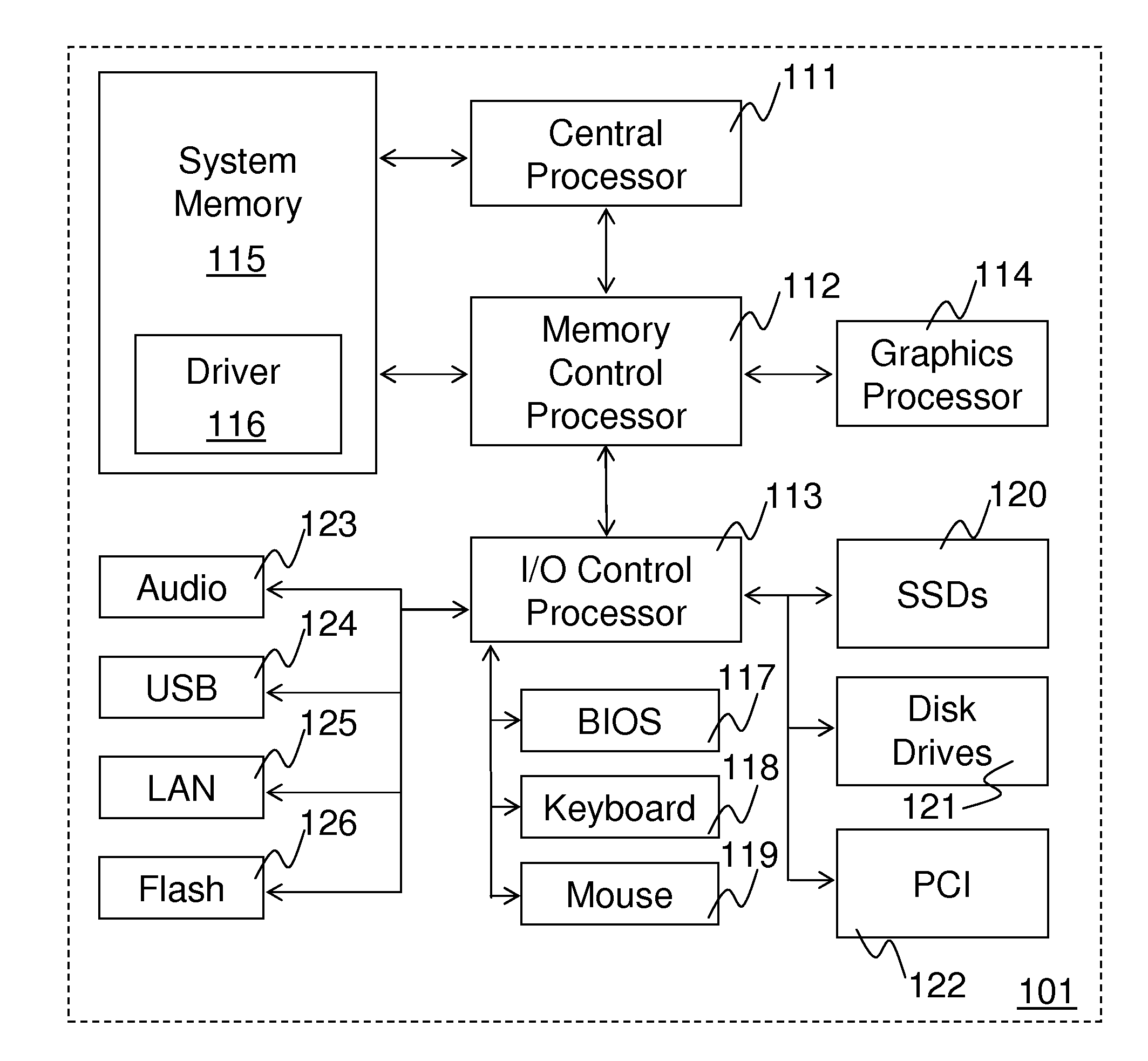
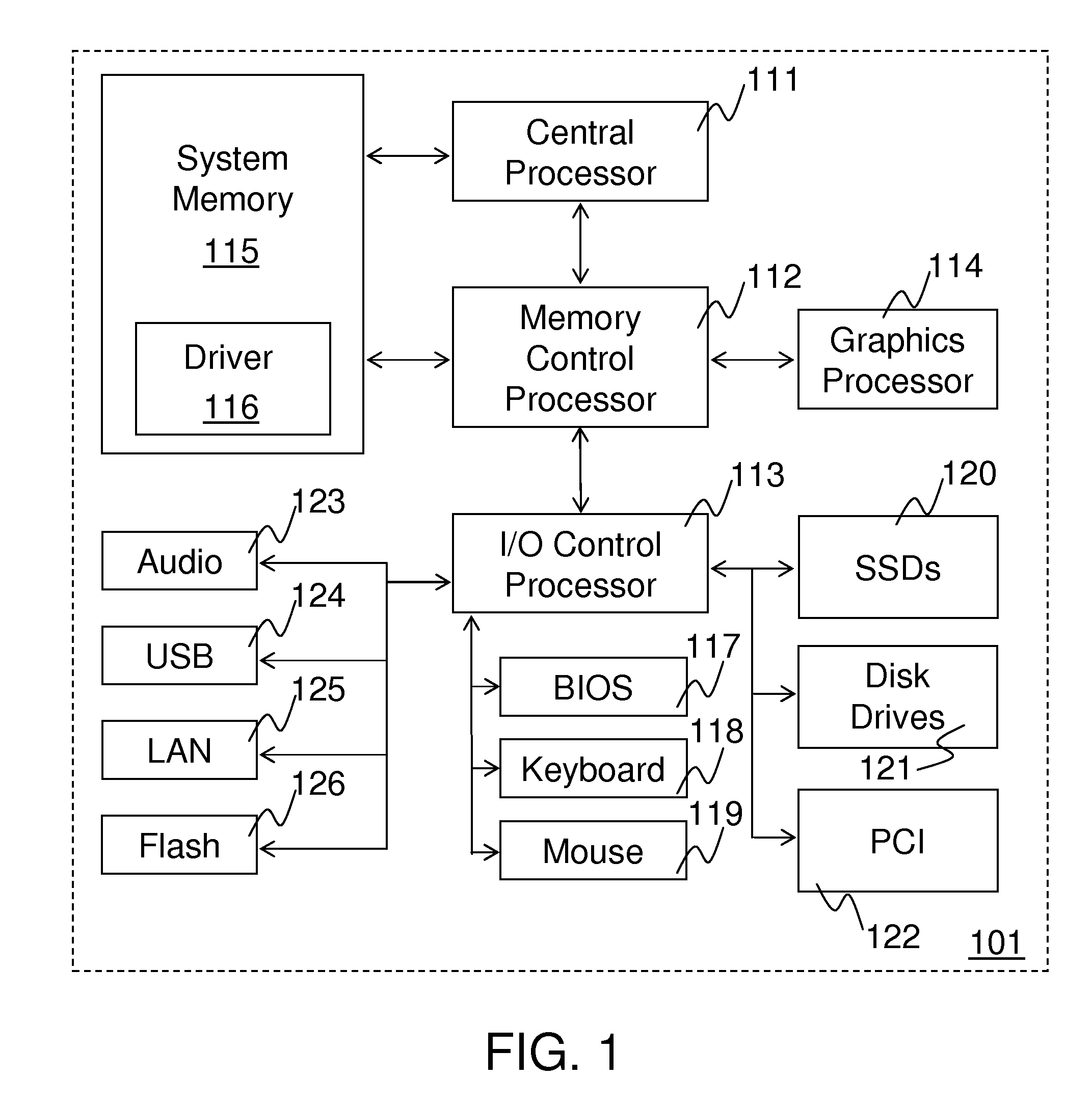
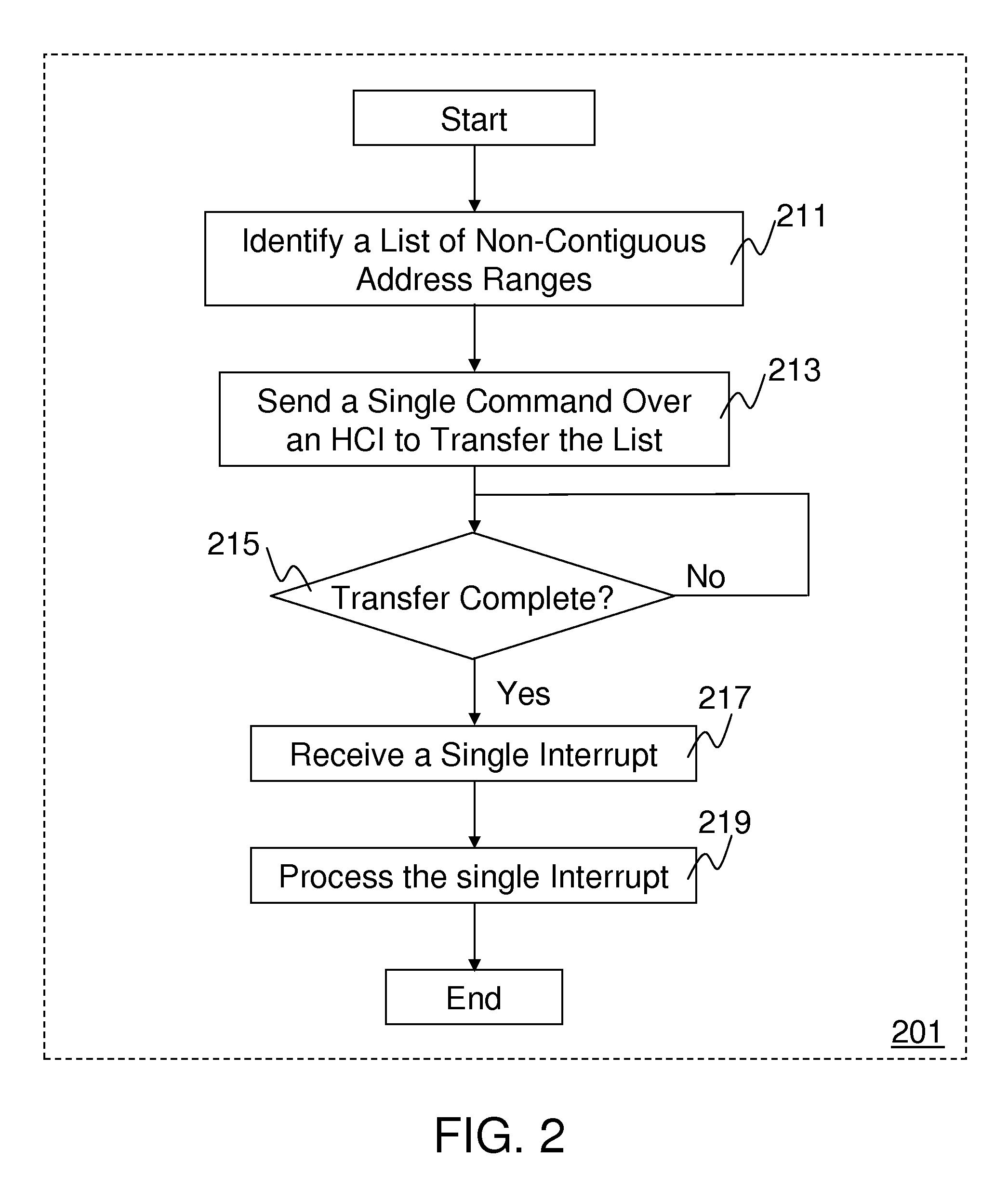
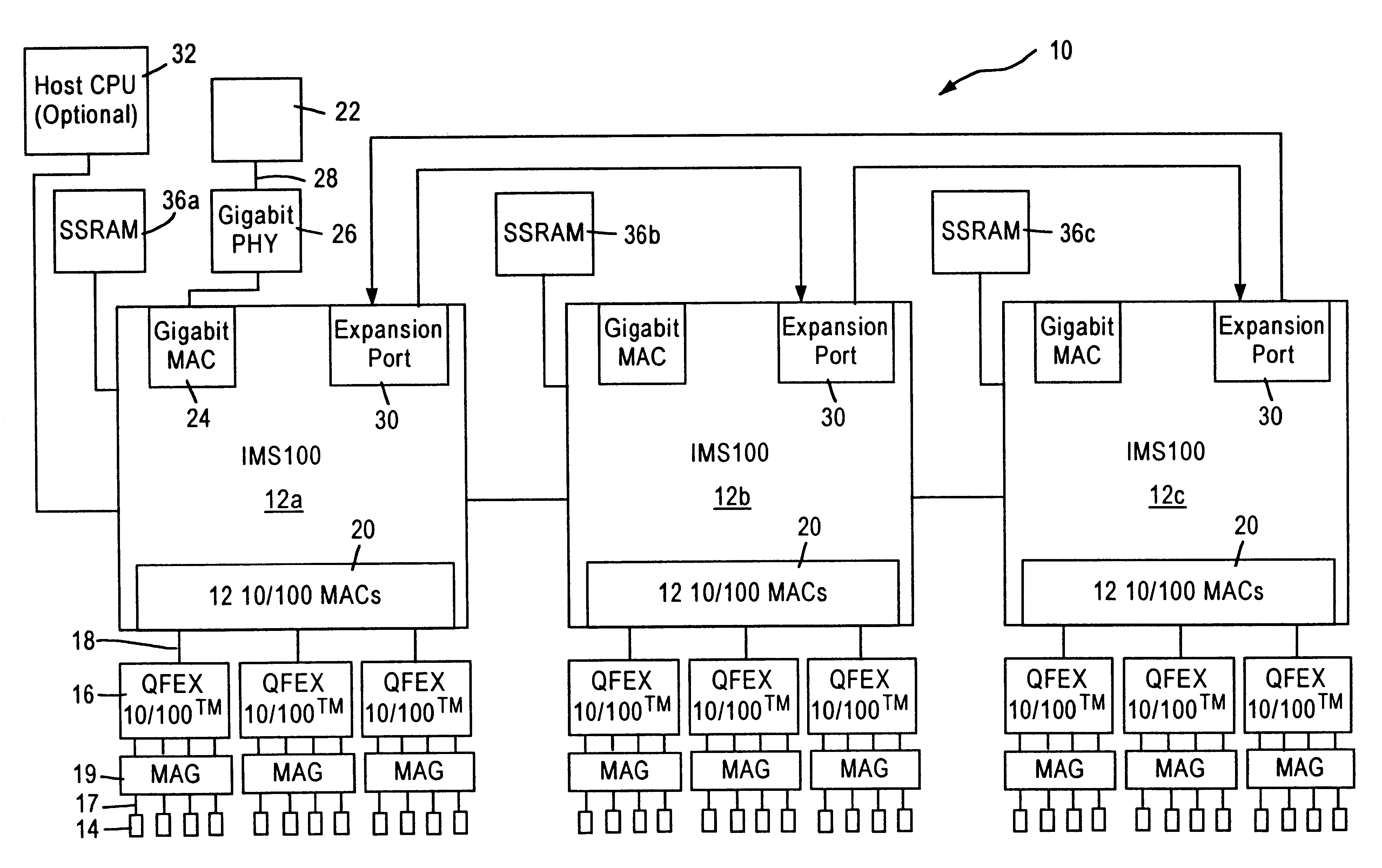
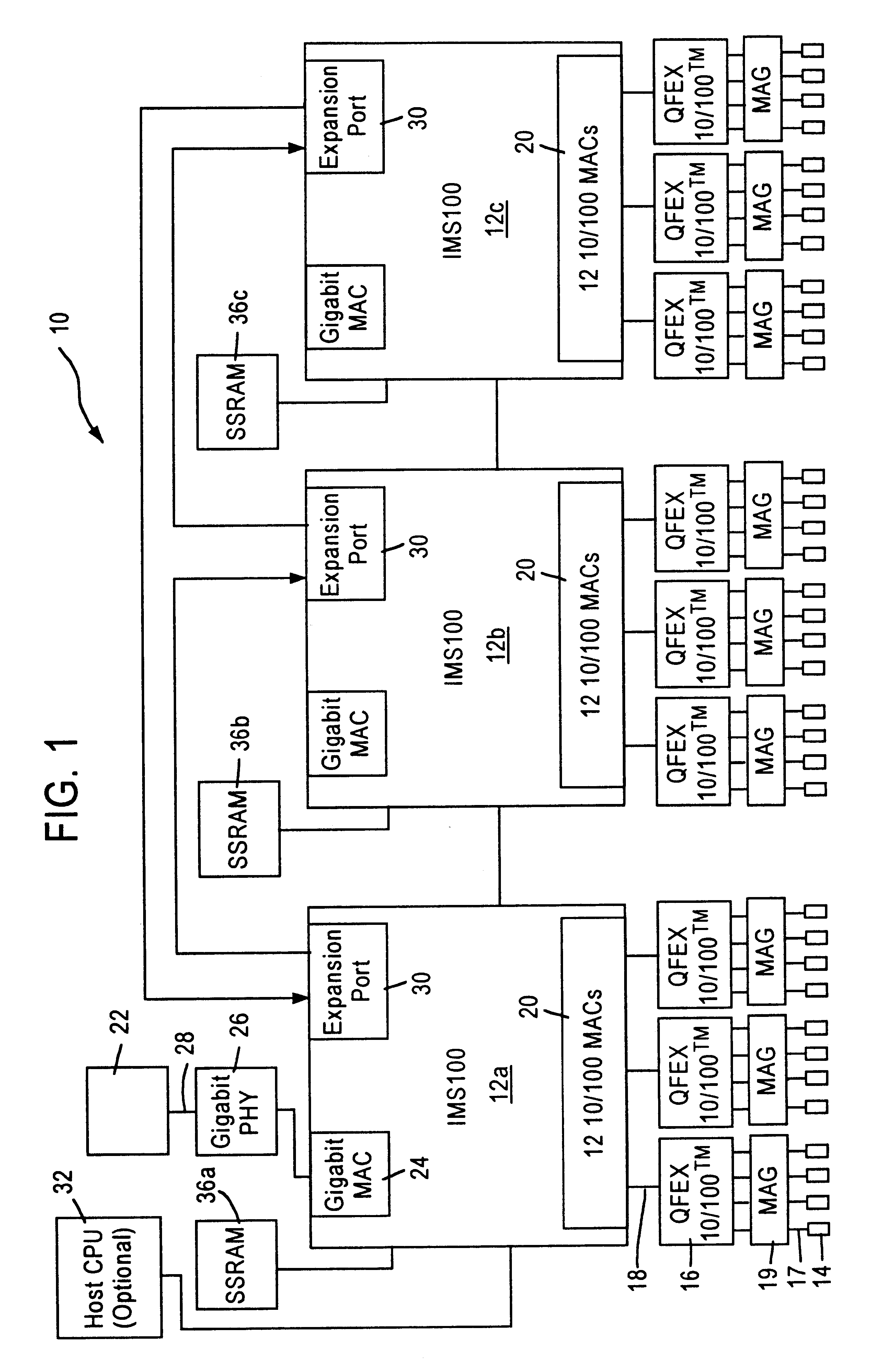
Method and system for queuing transfers of multiple non-contiguous address ranges with a single command
ActiveUS20100161936A1Input/output to record carriersProgram control using stored programsHost controller interfaceSoftware
Methods and systems for queuing transfers of multiple non-contiguous address ranges within a single command are disclosed. Embodiments of systems include system processors, memory to store data and executable software, and storage devices to receive transfer commands stored in system memory. A host controller interface driver is executed by one or more system processors and collects multiple non-continuous address ranges from storage-device transfer requests and records starting addresses and quantities of data to transfer for each non-continuous range in a tagged command list. It records the number of address ranges in the tagged command list, and a tagged-transfer opcode in a command, and stores the command and the tagged command list in a command table for the storage device. It records a base address for the command table in memory and an offset for the tagged command list into a command header, which is stored in a command queue.
Owner:INTEL CORP
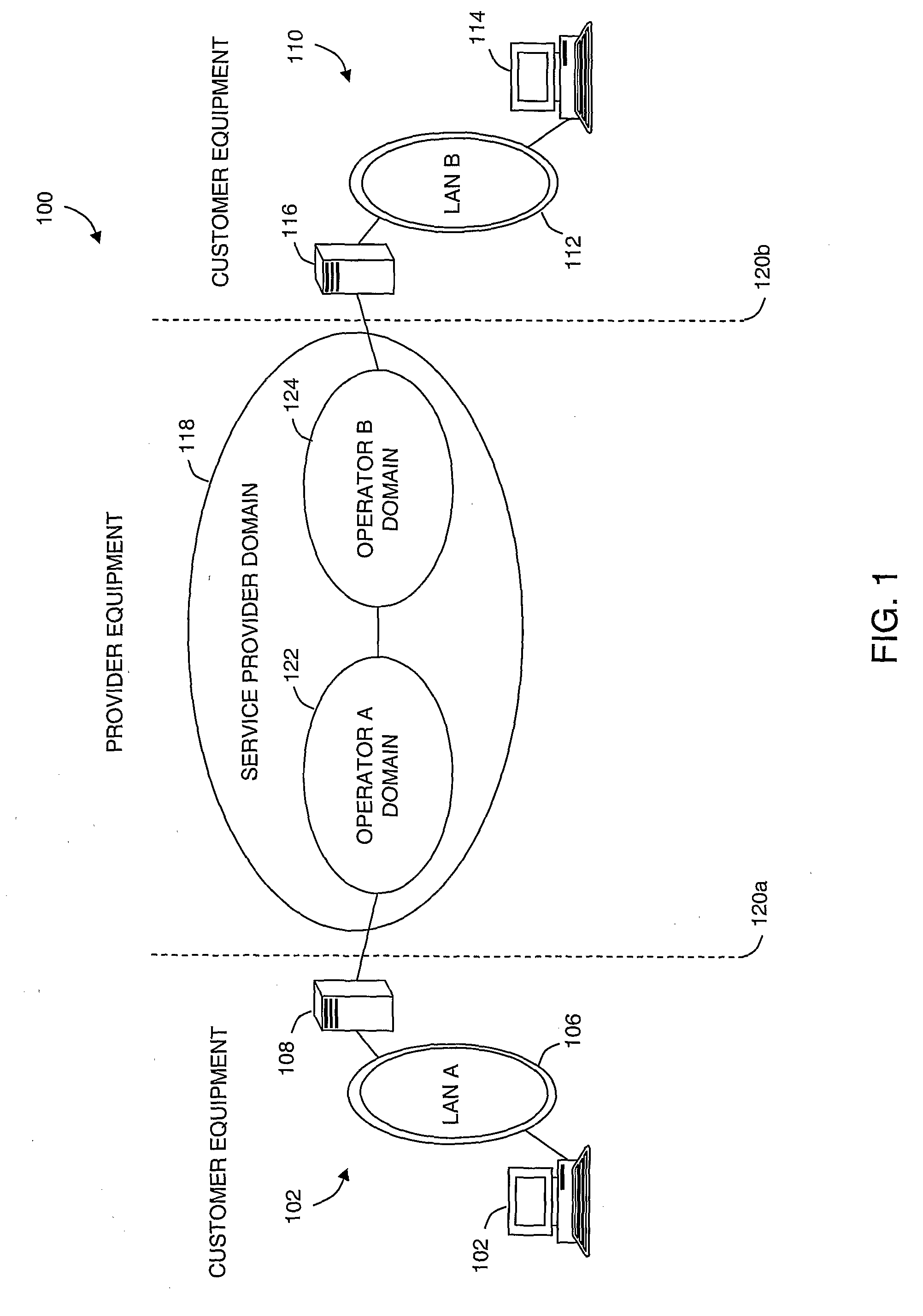
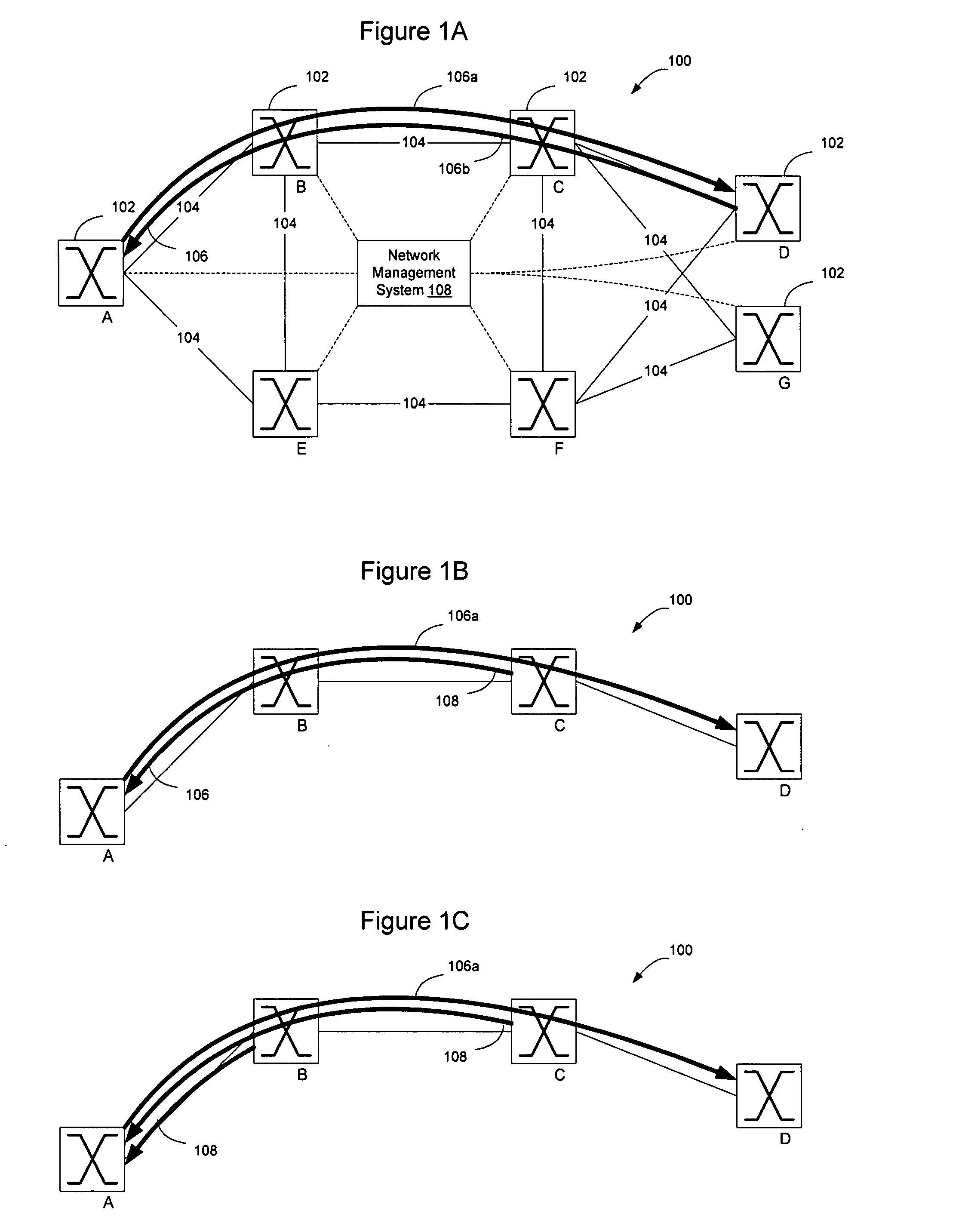
Forwarding Plane Data Communications Channel for Ethernet Transport Networks
InactiveUS20080219172A1Error preventionFrequency-division multiplex detailsEthernet protocolA domain
Described is a process and system for providing an extensible forwarding plane data communications channel adapted to selectively support operations, administration and maintenance (OAM) activity within one or more different domains of an Ethernet transport network. The data communication channel is established using Ethernet protocol data units forwarded within the forwarding plane, between network elements. The Ethernet protocol data units can be Ethernet OAM frames modified to include an OpCode indicative of a maintenance communication channel. The OAM frames are generated at a selected one of the network elements (source), forwarded along the same network path as the Ethernet frames, and terminate at another network element (destination) associated with a maintenance level identified within the OAM frame. The source and destination network elements can reside on a domain boundary using the Ethernet OAM frames flowing therebetween to relay maintenance communications channel messages.
Owner:RPX CLEARINGHOUSE
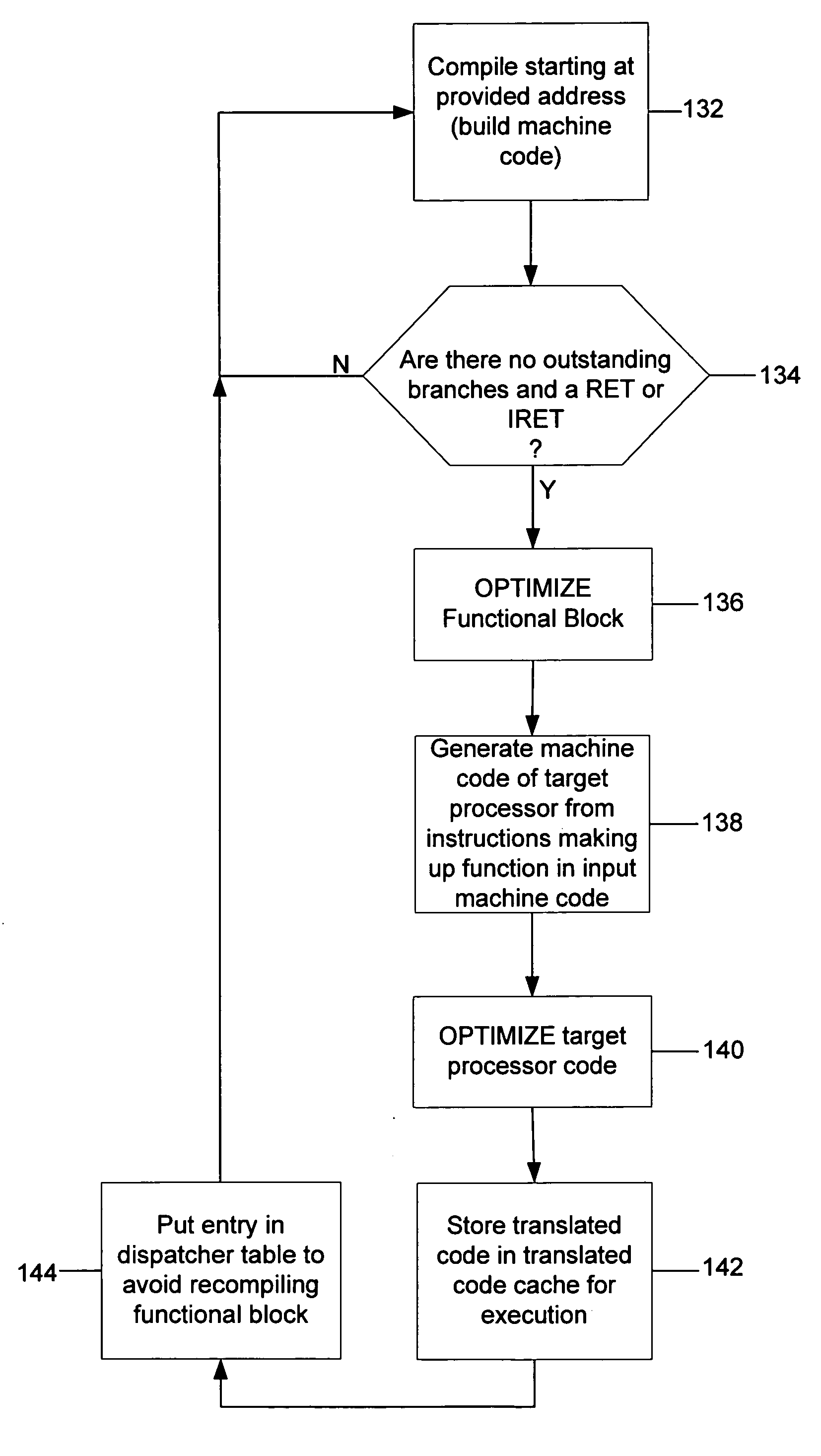
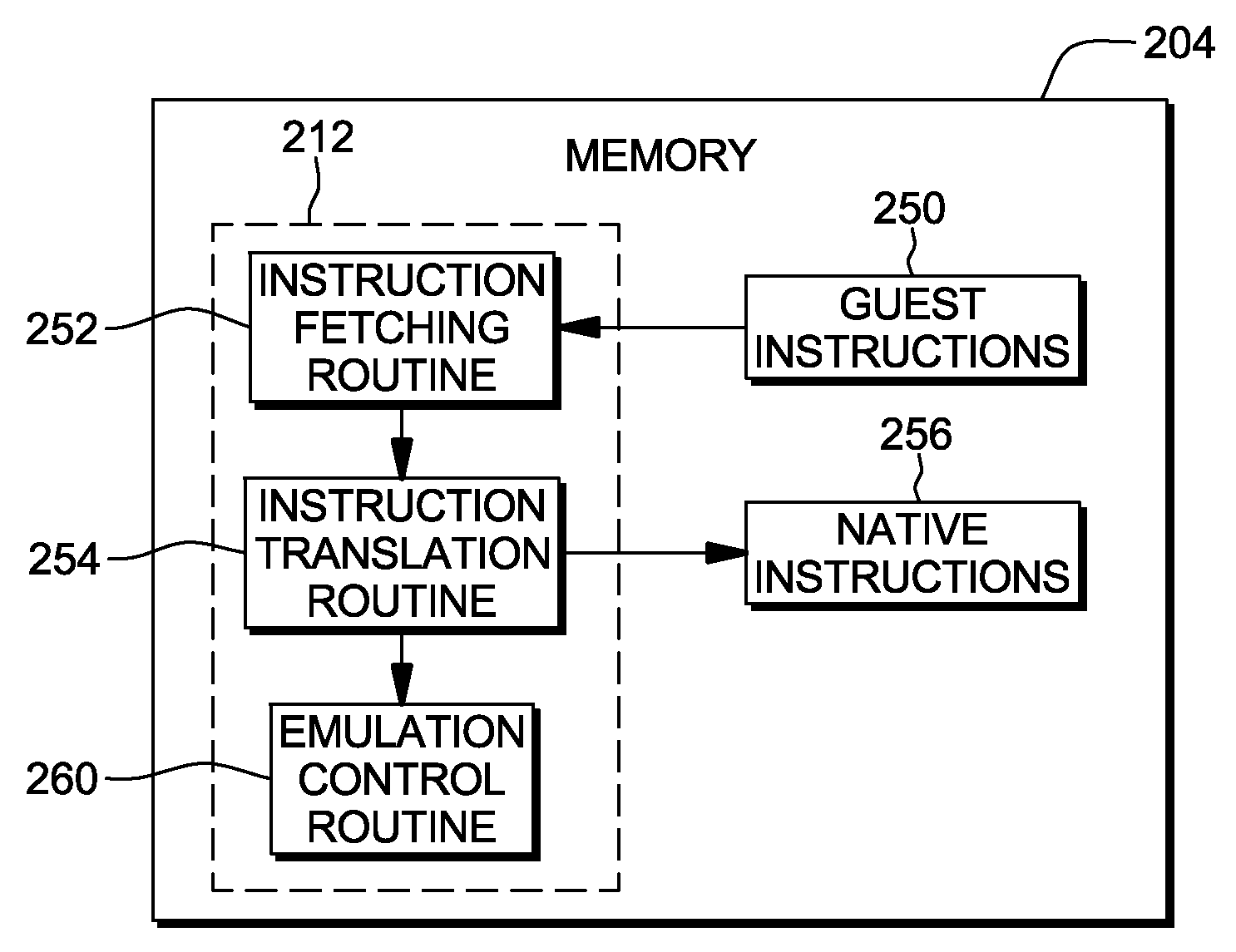
Function-level just-in-time translation engine with multiple pass optimization
InactiveUS20070006178A1Improve translationReduce context switchingBinary to binaryProgram controlCode TranslationSoftware emulation
A JIT binary translator translates code at a function level of the source code rather than at an opcode level. The JIT binary translator of the invention grabs an entire x86 function out of the source stream, rather than an instruction, translates the whole function into an equivalent function of the target processor, and executes that function all at once before returning to the source stream, thereby reducing context switching. Also, since the JIT binary translator sees the entire source code function context at once the software emulator may optimize the code translation. For example, the JIT binary translator might decide to translate a sequence of x86 instructions into an efficient PPC equivalent sequence. Many such optimizations result in a tighter emulated binary.
Owner:MICROSOFT TECH LICENSING LLC
Coprocessor opcode division by data type
InactiveUS6247113B1Easy to scaleReduced hardware coprocessorRegister arrangementsGeneral purpose stored program computerData processing systemCoprocessor
A data processing system having a main processor and a coprocessor. The main processor responsds to coprocessor instructions within its instruction stream by issuing the coprocessor instructions upon a coprocessor bus and detecting if the coprocessor accepts them by returning an accept signal. The coprocessor instructions include a coprocessor number and the coprocessor checks this number to see if it matches its own number(s) to determine whether or not it should accept the coprocessor instruction. A data type field within the coprocessor number in the coprocessor instruction also serves to specify one of multiple data types to be used in the coprocessor operation; particular coprocessors can interpret this part of the coprocessor number to determine data type. If the coprocessor supports multiple data types, then it has multiple coprocessor numbers for which it will issue accept signals and then uses the data type field to control the data type used. If a coprocessor does not support a particular data type then it will not issue an accept signal for coprocessor instructions that specify that data type. The main processor can then use emulation code to provide support for that coprocessor instruction.
Owner:ARM LTD
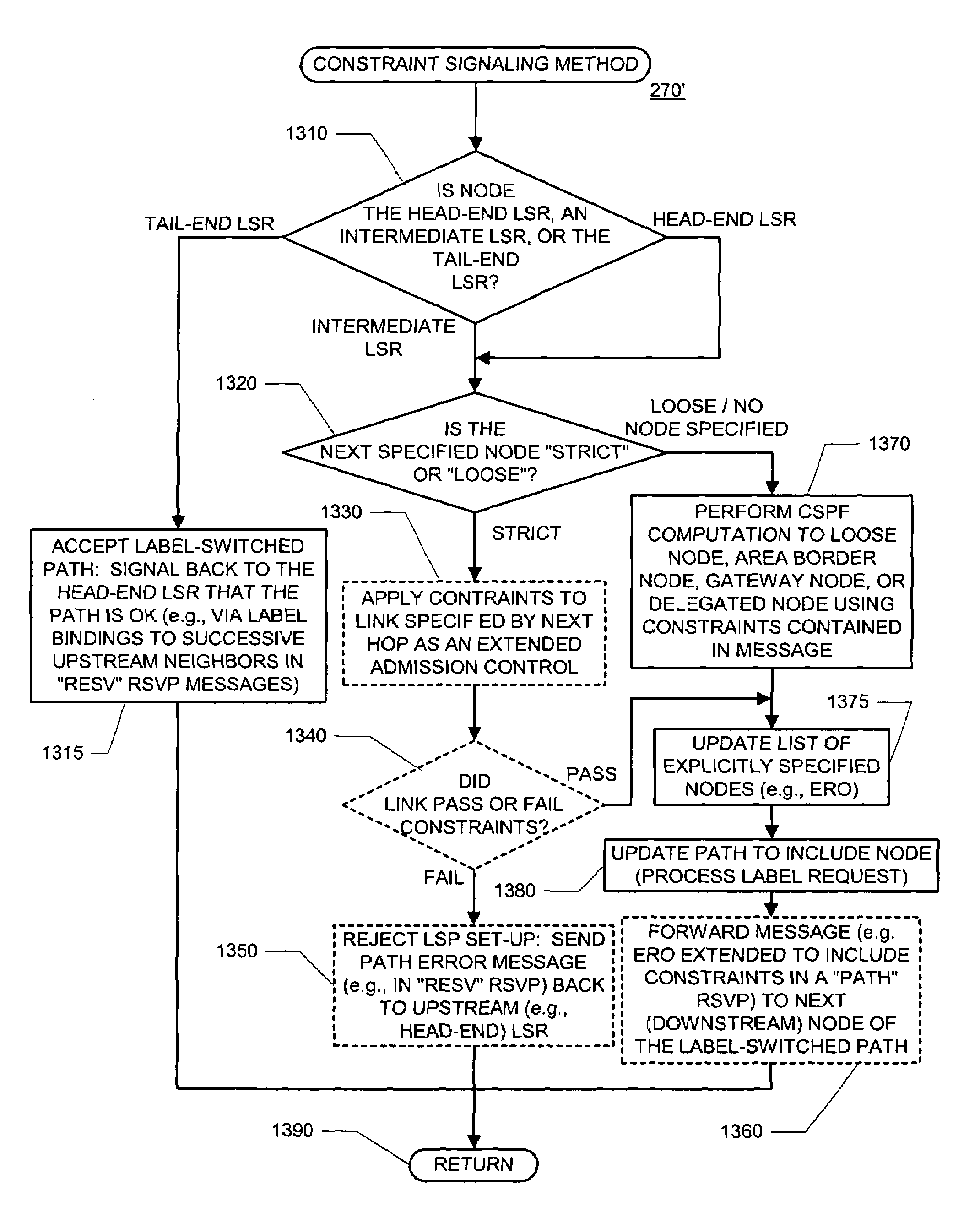
Communicating constraint information for determining a path subject to such constraints
InactiveUS7319700B1Error preventionFrequency-division multiplex detailsPathPingDistributed computing
Path determination constraints may be encoded in the form of a program having one or more instructions. Each of instructions may include an operation code, and operands (or pointers to locations where operands are stored). In this way, an extensible, interoperable way for a nodes (e.g., label-switching routers) to communicate constraints within a network is provided. Such constraints may be inserted (e.g., as one or more CONSTRAINT objects) into signaling messages (e.g., a PATH RSVP message). By enabling the signaling of constraints, the determination of constraint-based (label-switched) paths can be distributed among a number of (label-switching) routers or other nodes. Upon receiving a message with constraints (e.g., a CONSTRAINT object(s)), a node may (i) ignore the constraints if the node is a tail-end node (label-switching router), (ii) apply the constraints to a link if the next hop in the (label-switched) path is strict, and / or (iii) perform a constraint-based path determination to a next hop if the next hop is loose.
Owner:JUMIPER NETWORKS INC
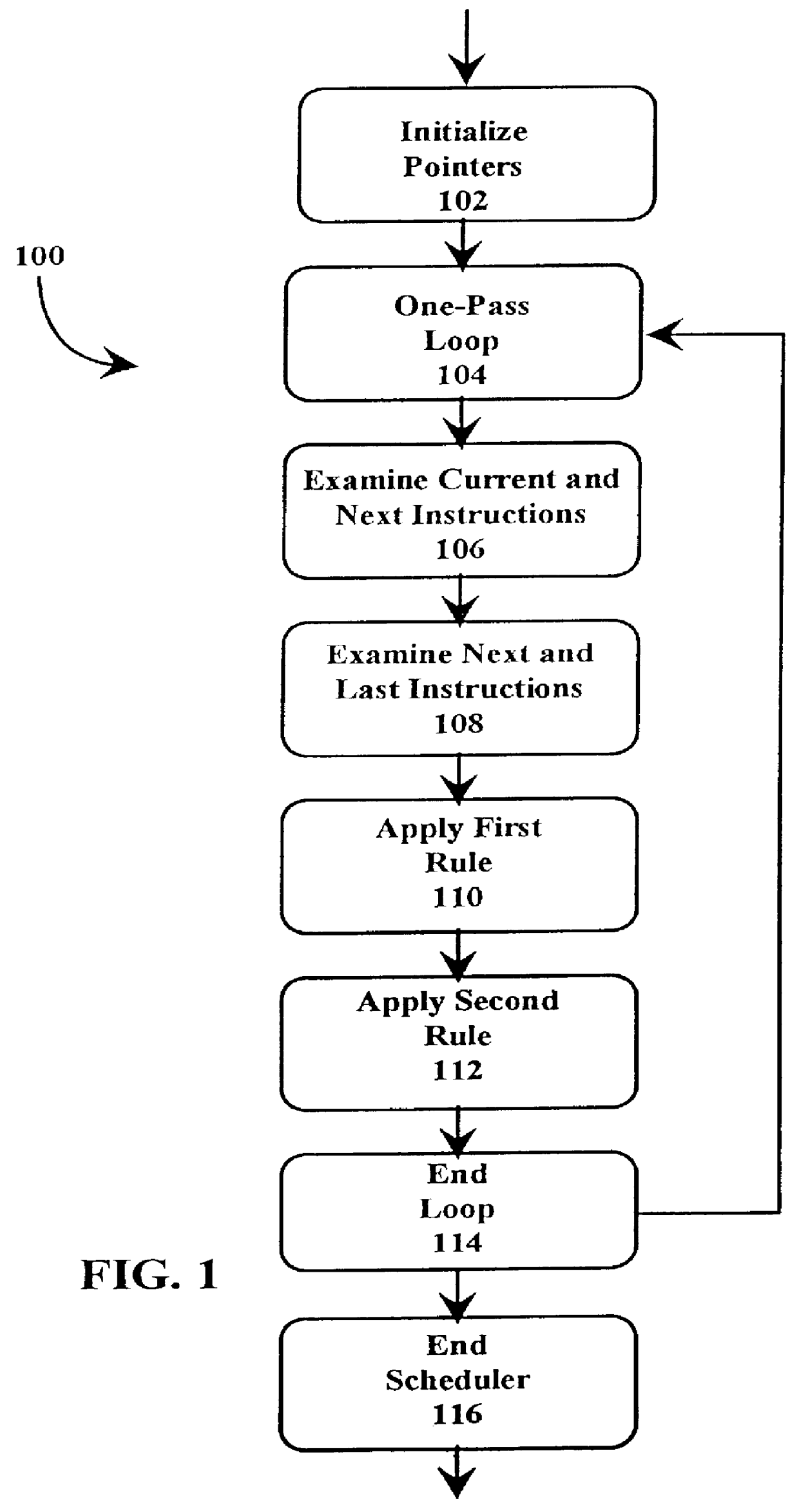
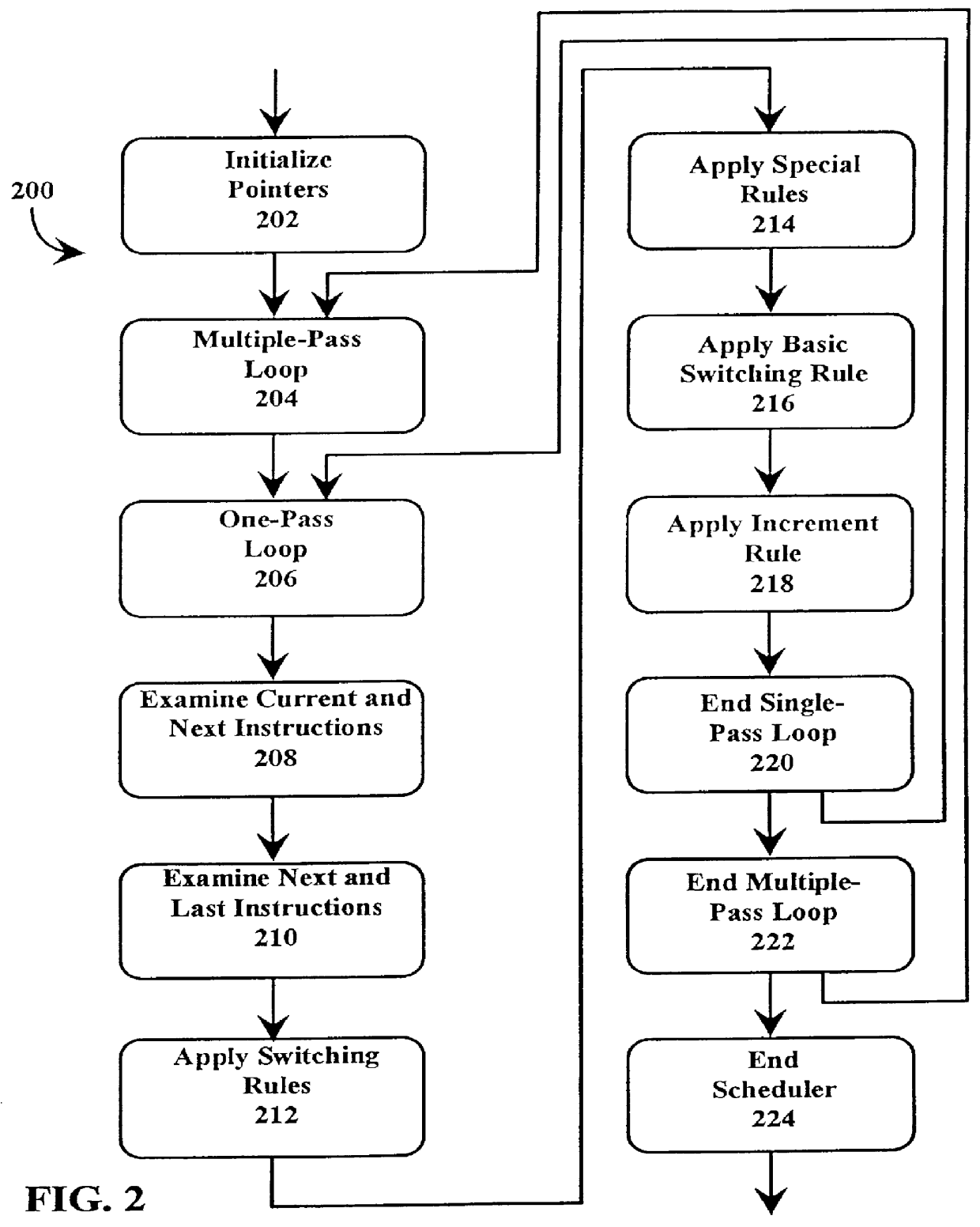
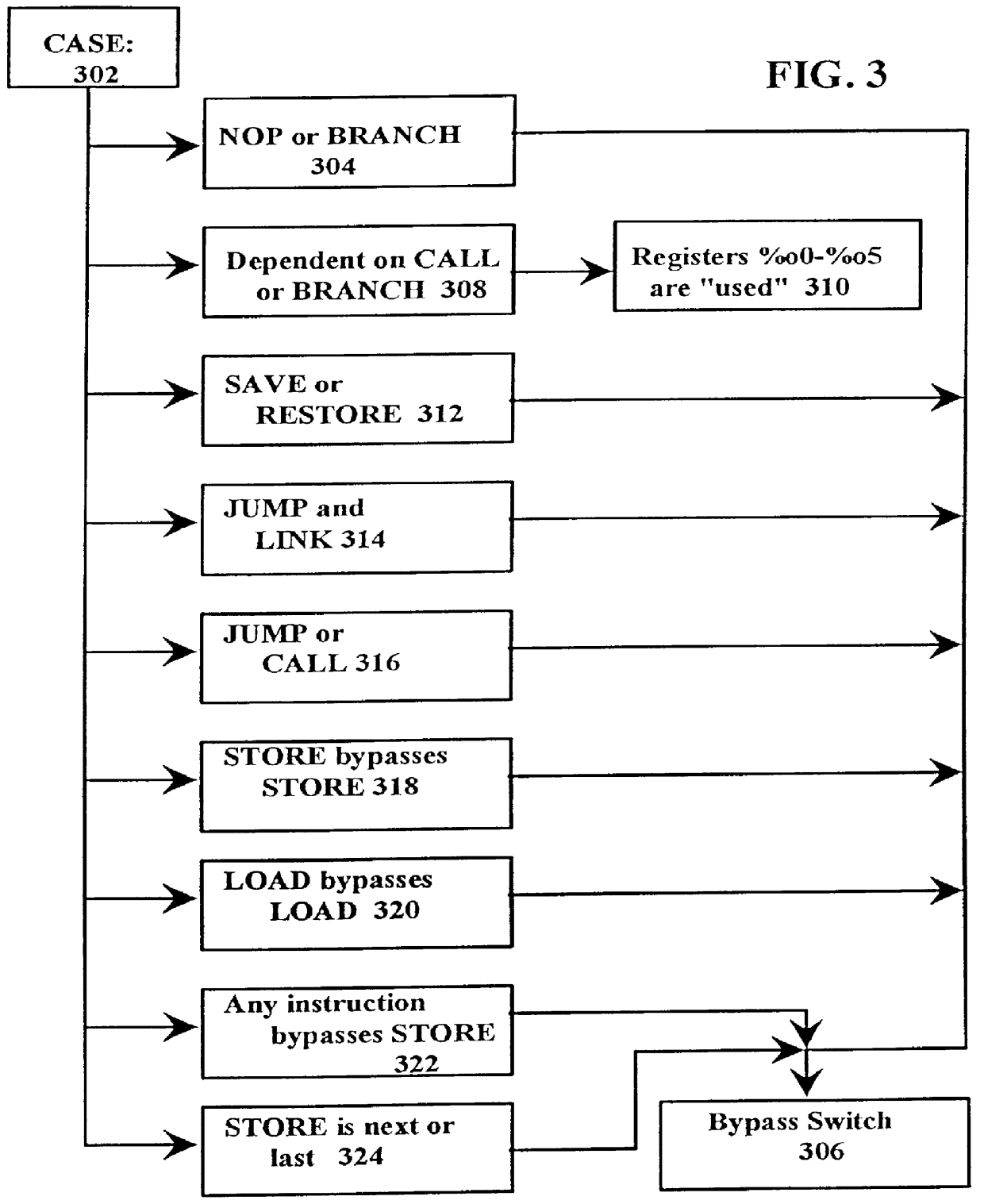
Fast just-in-time (JIT) scheduler
A just-in-time (JIT) compiler typically generates code from bytecodes that have a sequence of assembly instructions forming a "template". It has been discovered that a just-in-time (JIT) compiler generates a small number, approximately 2.3, assembly instructions per bytecode. It has also been discovered that, within a template, the assembly instructions are almost always dependent on the next assembly instruction. The absence of a dependence between instructions of different templates is exploited to increase the size of issue groups using scheduling. A fast method for scheduling program instructions is useful in just-in-time (JIT) compilers. Scheduling of instructions is generally useful for just-in-time (JIT) compilers that are targeted to in-order superscalar processors because the code generated by the JIT compilers is often sequential in nature. The disclosed fast scheduling method has a complexity, and therefore an execution time, that is proportional to the number of instructions in an instruction block (N complexity), a substantial improvement in comparison to the N2 complexity of conventional compiler schedulers. The described fast scheduler advantageously reorders instructions with a single pass, or few passes, through a basic instruction block while a conventional compiler scheduler such as the DAG scheduler must iterate over an instruction basic block many times. A fast scheduler operates using an analysis of a sliding window of three instructions, applying two rules within the three instruction window to determine when to reorder instructions. The analysis includes acquiring the opcodes and operands of each instruction in the three instruction window, and determining register usage and definition of the operands of each instruction with respect to the other instructions within the window. The rules are applied to determine ordering of the instructions within the window.
Owner:ORACLE INT CORP
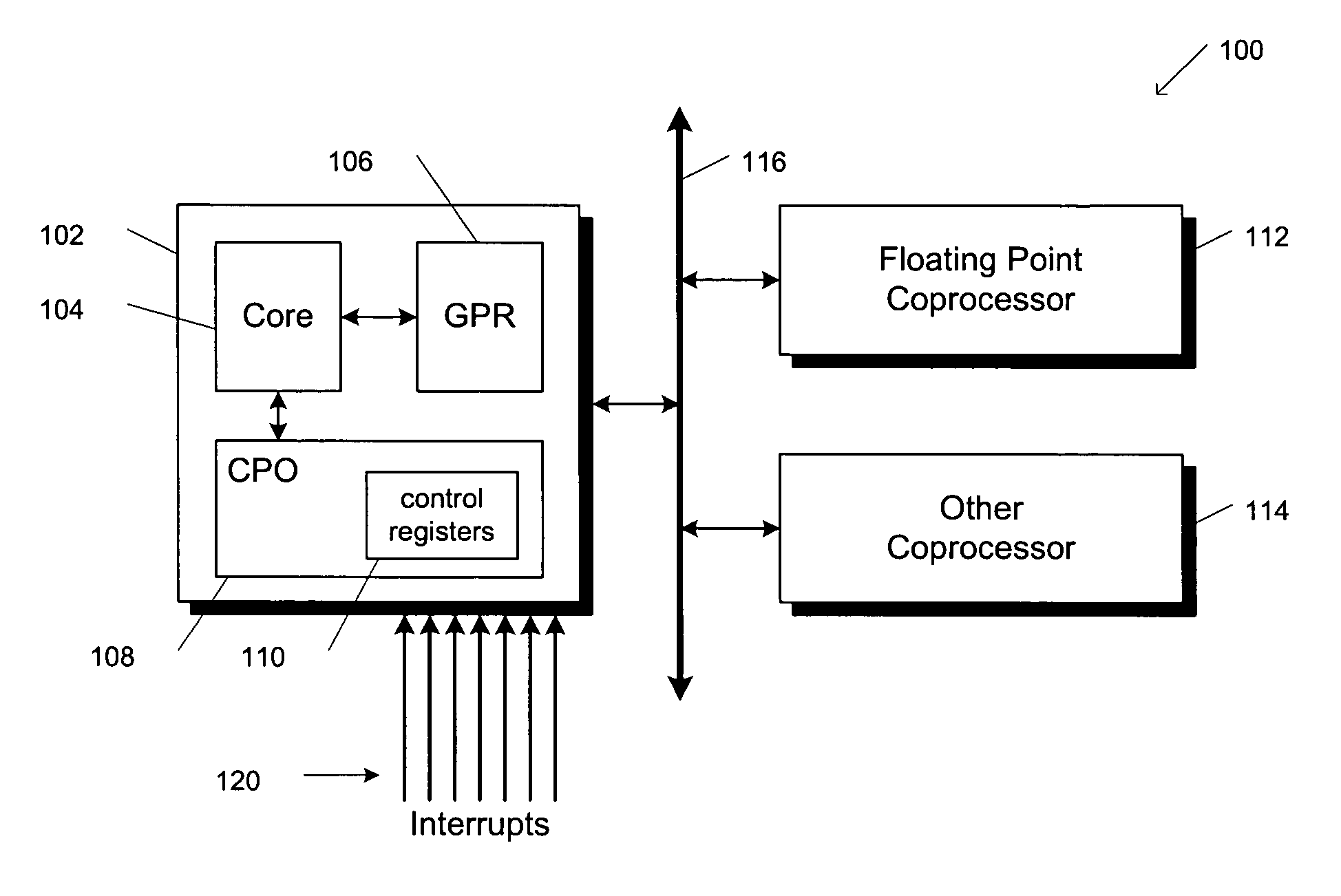
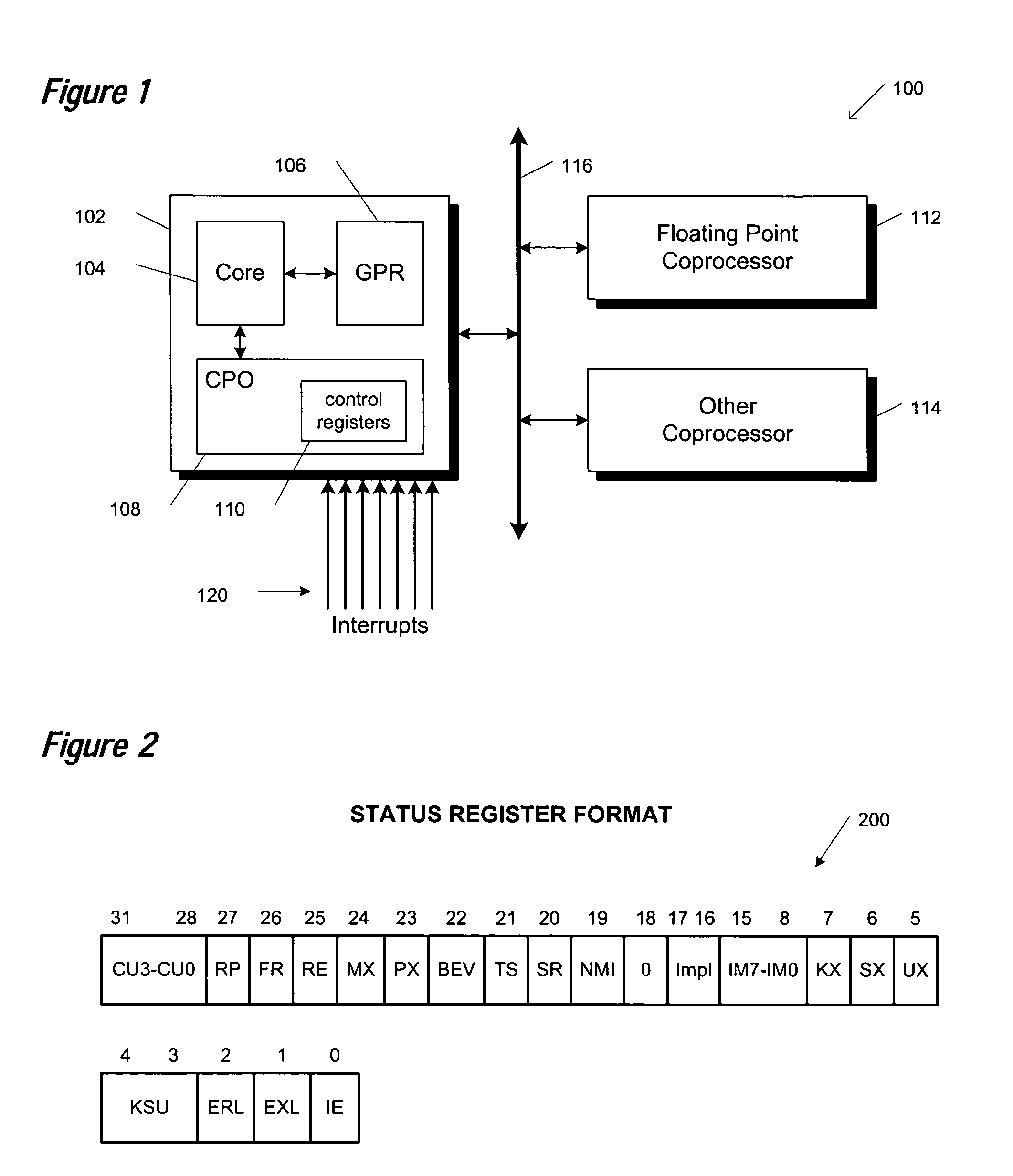
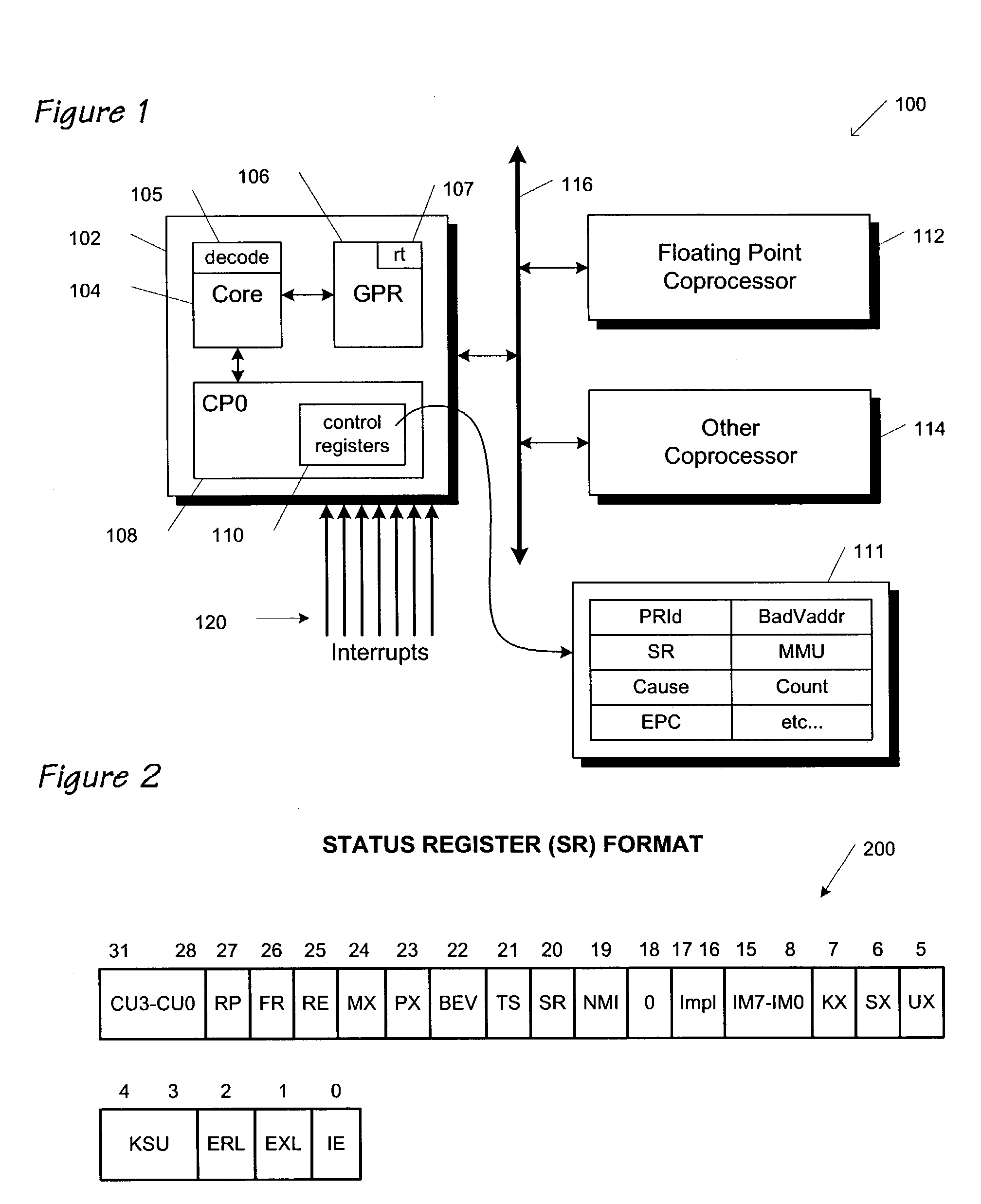
Atomic update of CPO state
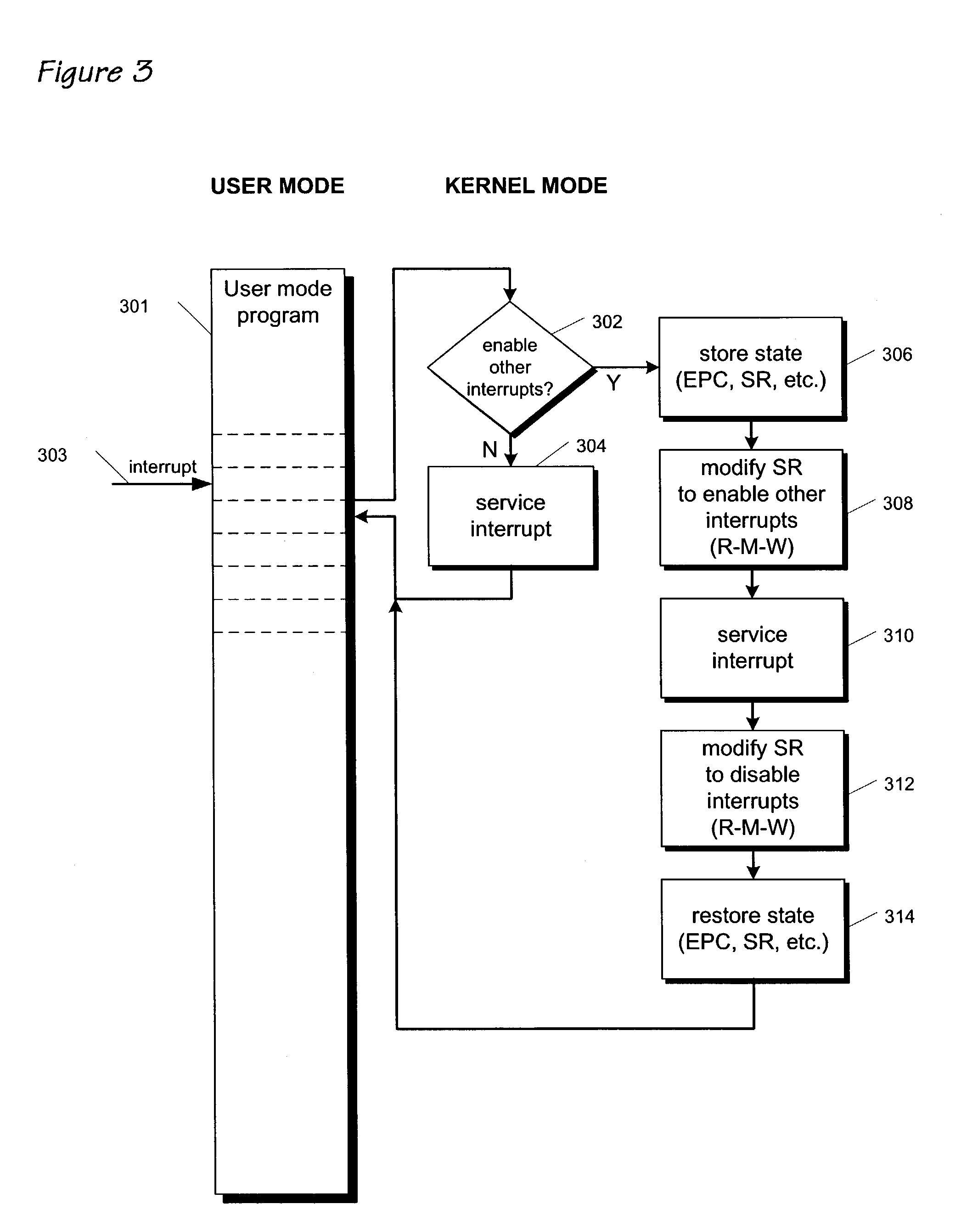
A group of bit set and bit clear instructions are provided for a microprocessor to allow atomic modification of privileged architecture control registers. The bit set and bit clear instructions include an opcode that designates to the microprocessor that the instructions are to execute in privileged (kernel) state only, and that the instructions are to communicate with privileged control registers. Two operands are provided for the instructions, the first designating which of the privileged control registers is to be modified, the second designating a general purpose register that contains a bit mask. The bit set instructions set bits in the designated control register according to bits set in the bit mask. The bit clear instructions clear bits in the designated control register according to bits set in the bit mask. By atomically modifying privileged control registers, a requirement for strict nesting of interrupt routines is eliminated.
Owner:MIPS TECH INC
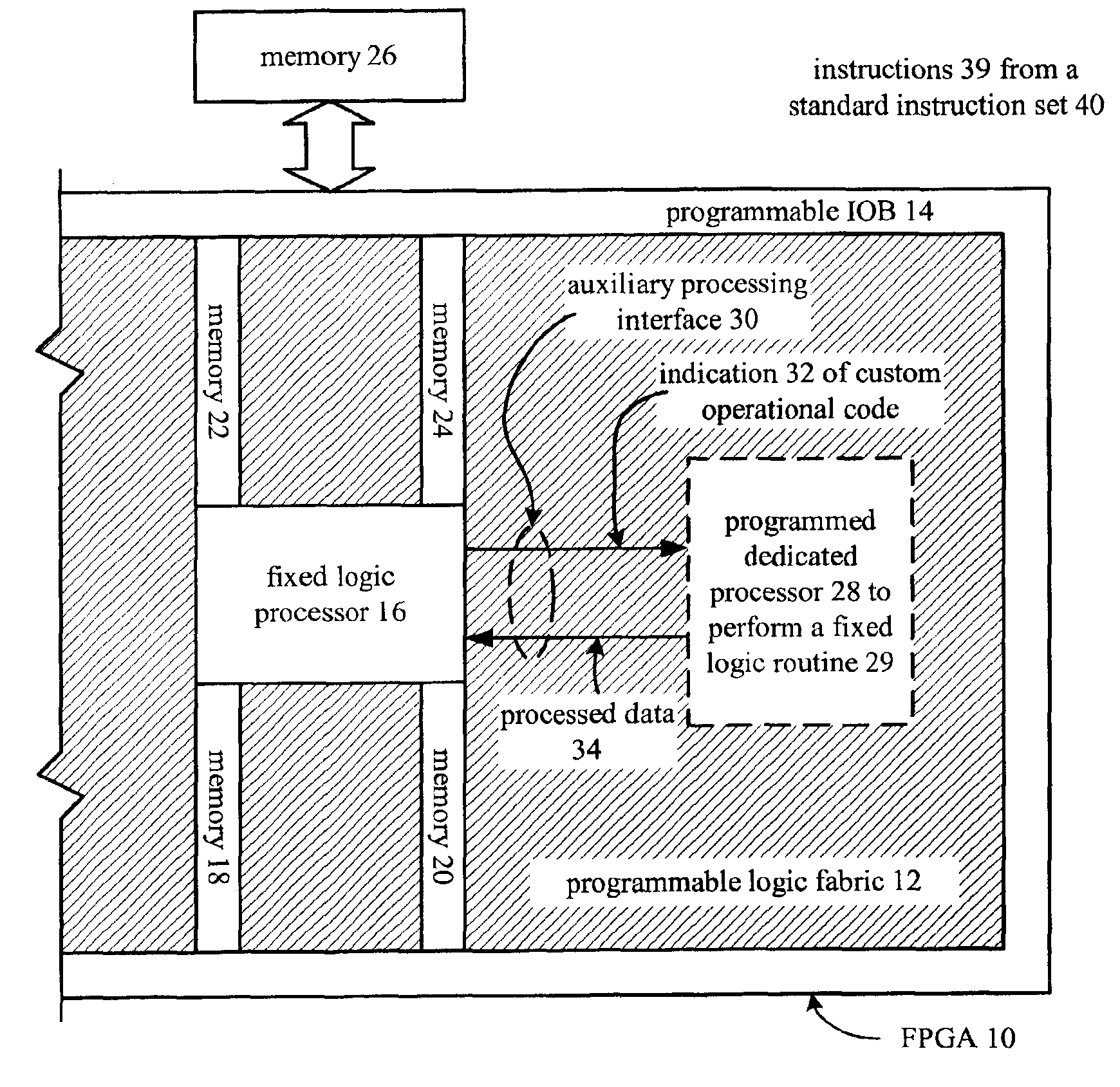
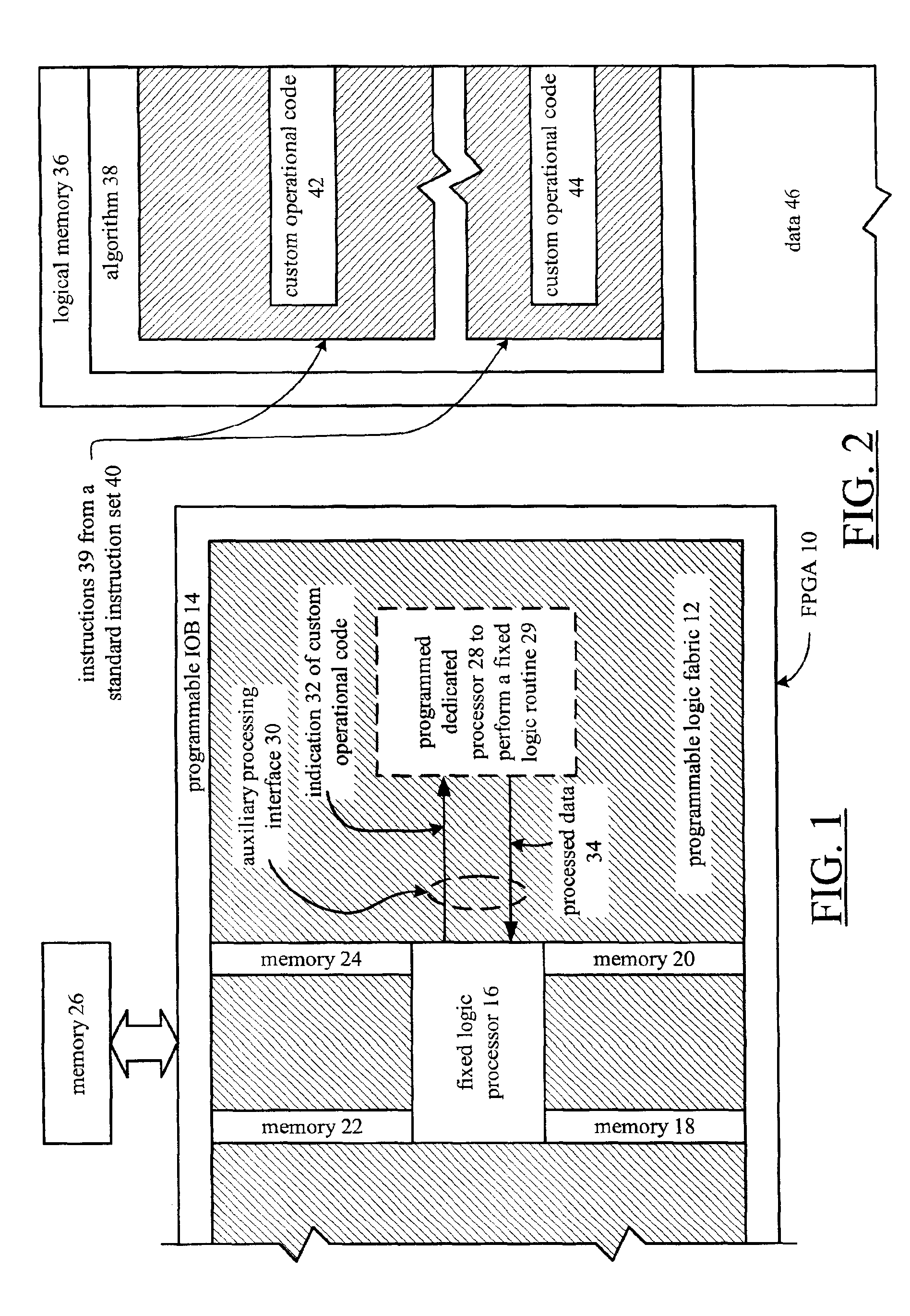
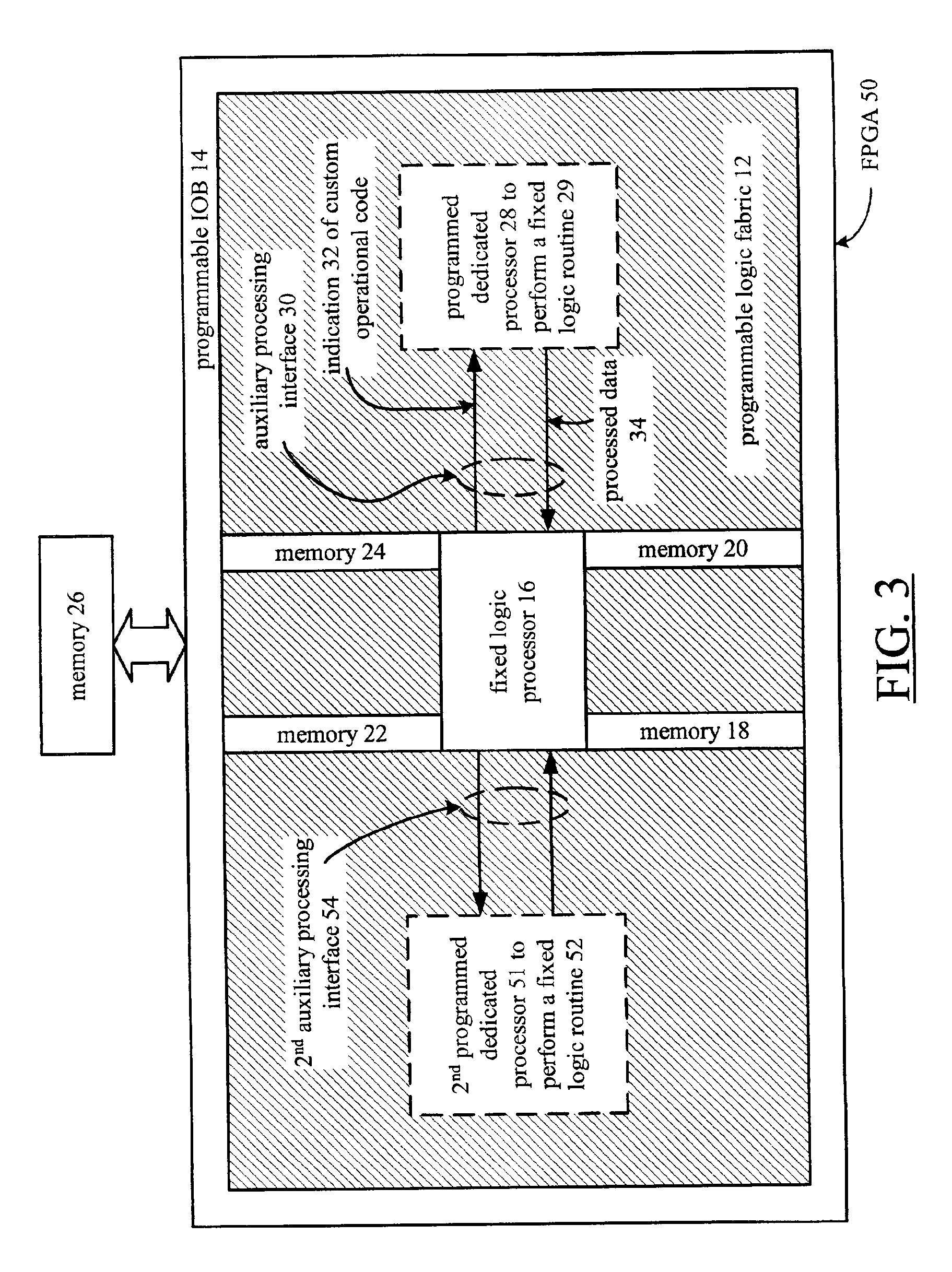
Custom code processing in PGA by providing instructions from fixed logic processor portion to programmable dedicated processor portion
A method and apparatus for processing data within a programmable gate array begins when a fixed logic processor that is embedded within the programmable gate array detects a custom operation code. The processing continues when the fixed logic processor provides an indication of the custom operational code to the programmable gate array. The processing continues by having at least a portion of the programmable gate array, which is configured as a dedicated processor, performing a fixed logic routine upon receiving the indication from the fixed logic processor.
Owner:XILINX INC
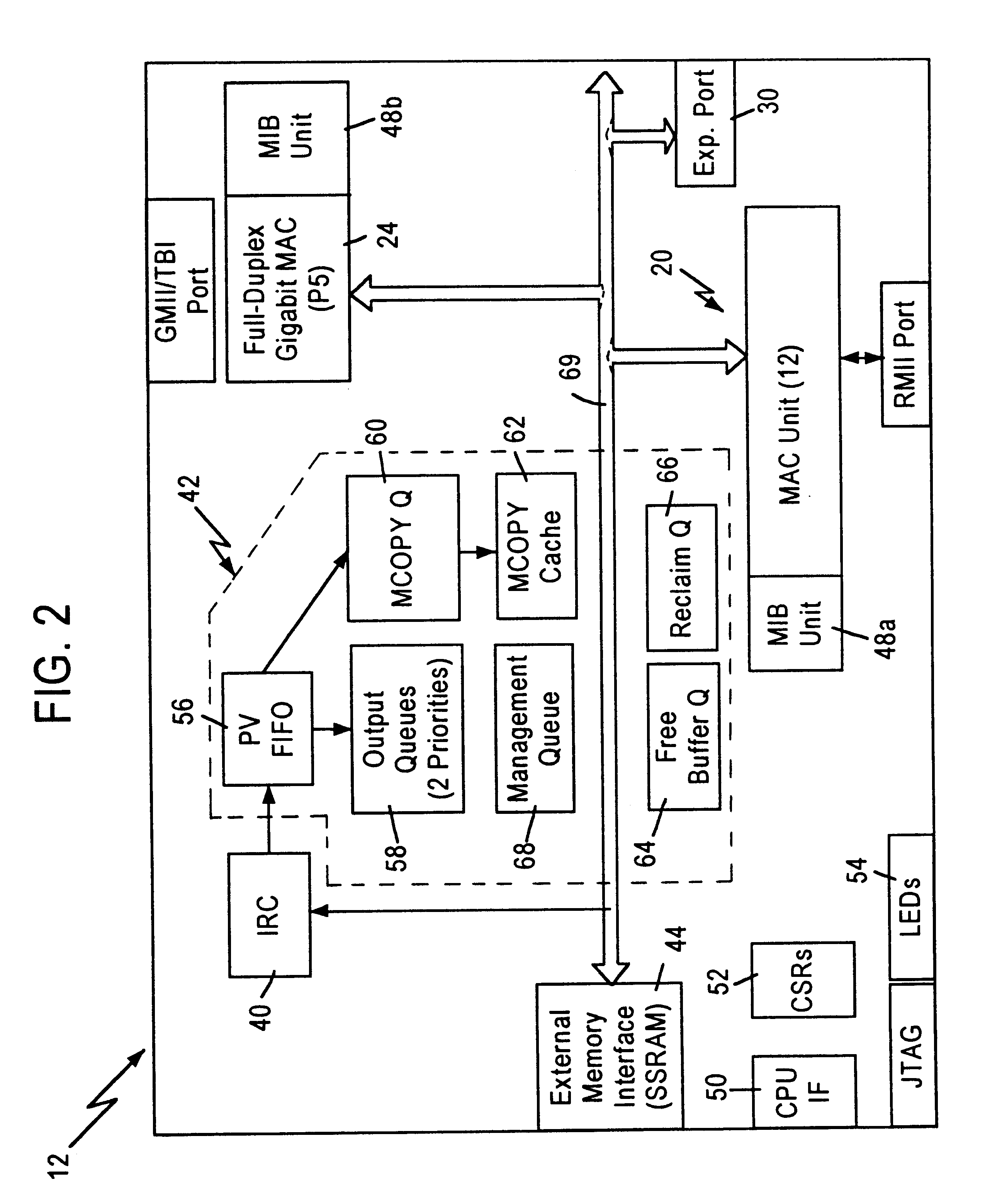
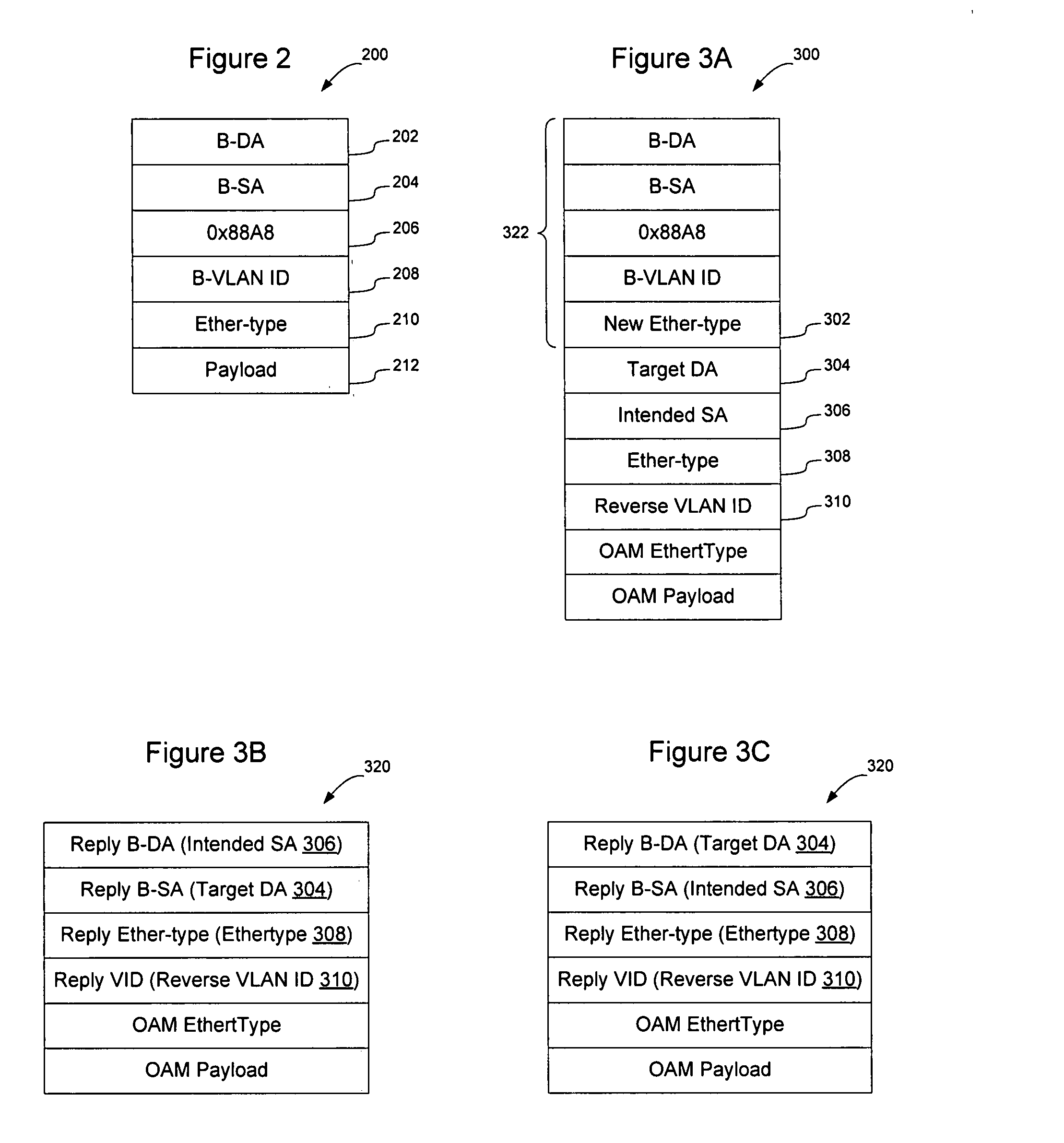
Method and apparatus for manipulating VLAN tags
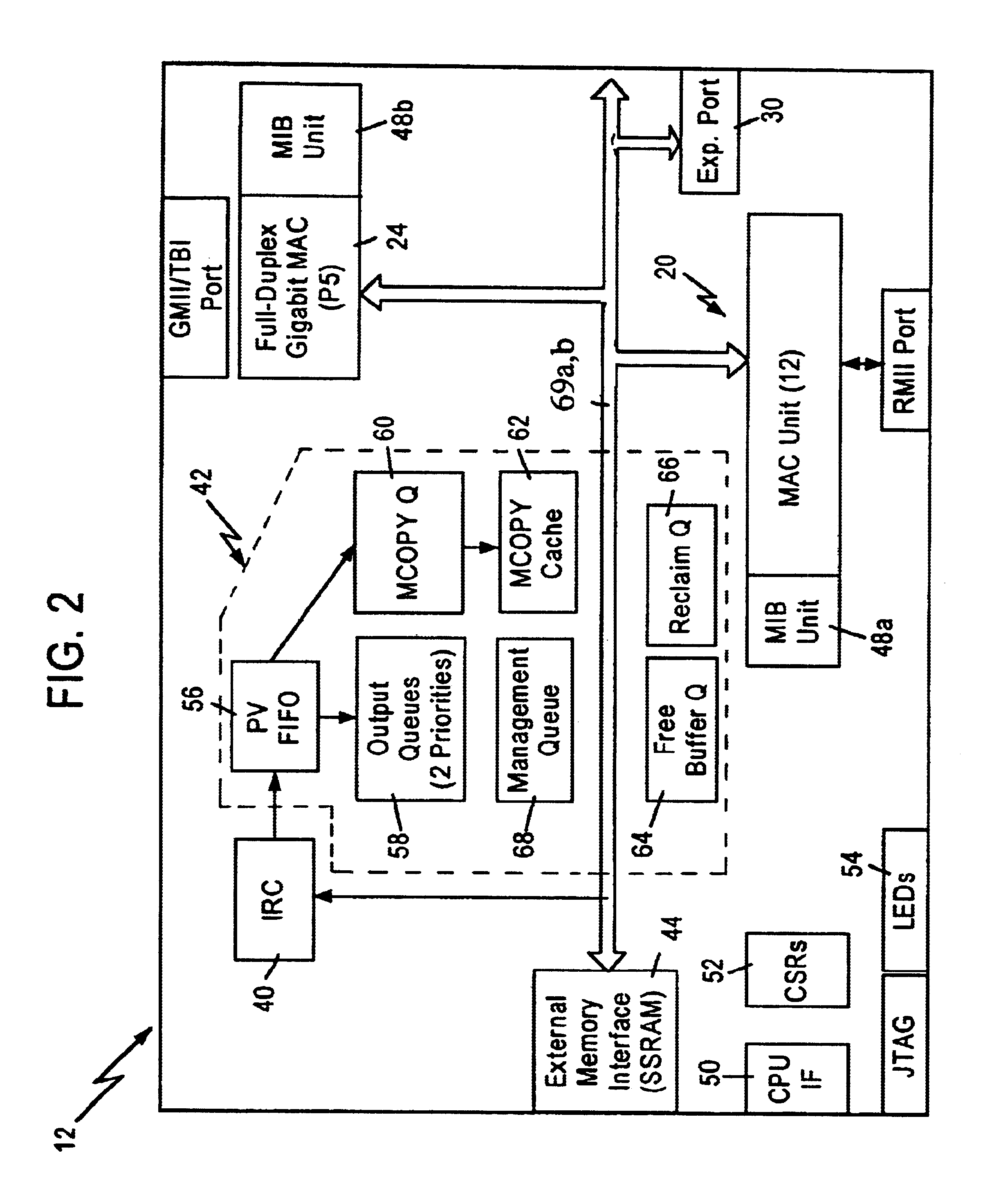
An integrated multiport switch operating in a packet switched network provides the capability to alter VLAN tags on a port by port basis. An internal rules checker (IRC) analyzes the header of a data frame to determine the frame type: untagged, VLAN-tagged, or priority-tagged. The IRC searches the untagged set table for the set of ports that are untagged for a particular VLAN. The IRC passes a forwarding descriptor that includes the frame type and a operational code (opcode) to a Port Vector FIFO logic (PVF). The PVF is responsible for creating a new opcode that instructs a dequeuing logic to add, remove, modify the VLAN tag, or send the frame unmodified. The opcodes generated by the PVF are individualized for each output port.
Owner:GLOBALFOUNDRIES INC
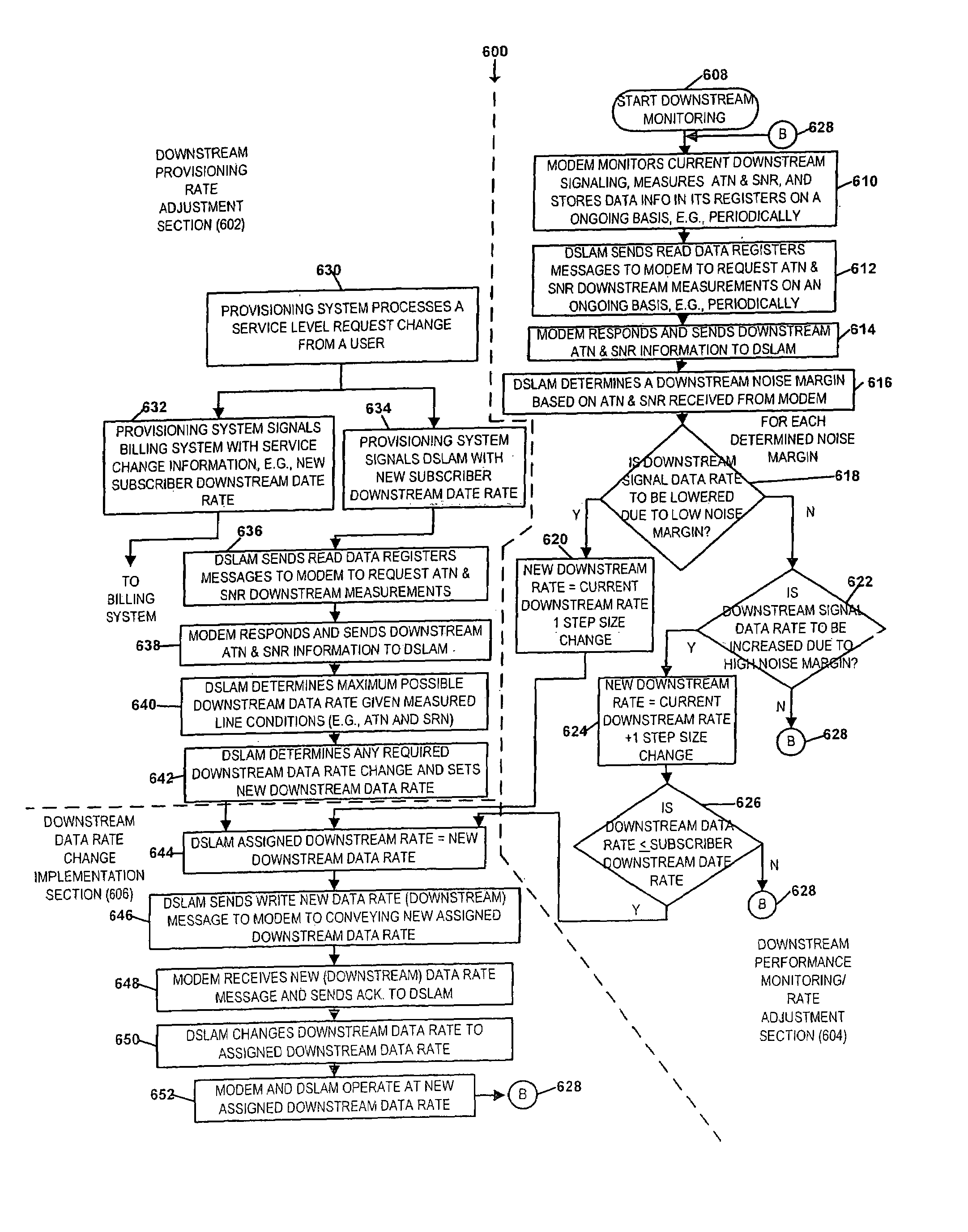
Rate agile rate-adaptive digital subscriber line
ActiveUS7317754B1Line rate can be increasedHigh achievable data rateEnergy efficient ICTSignal allocationModem deviceRate change
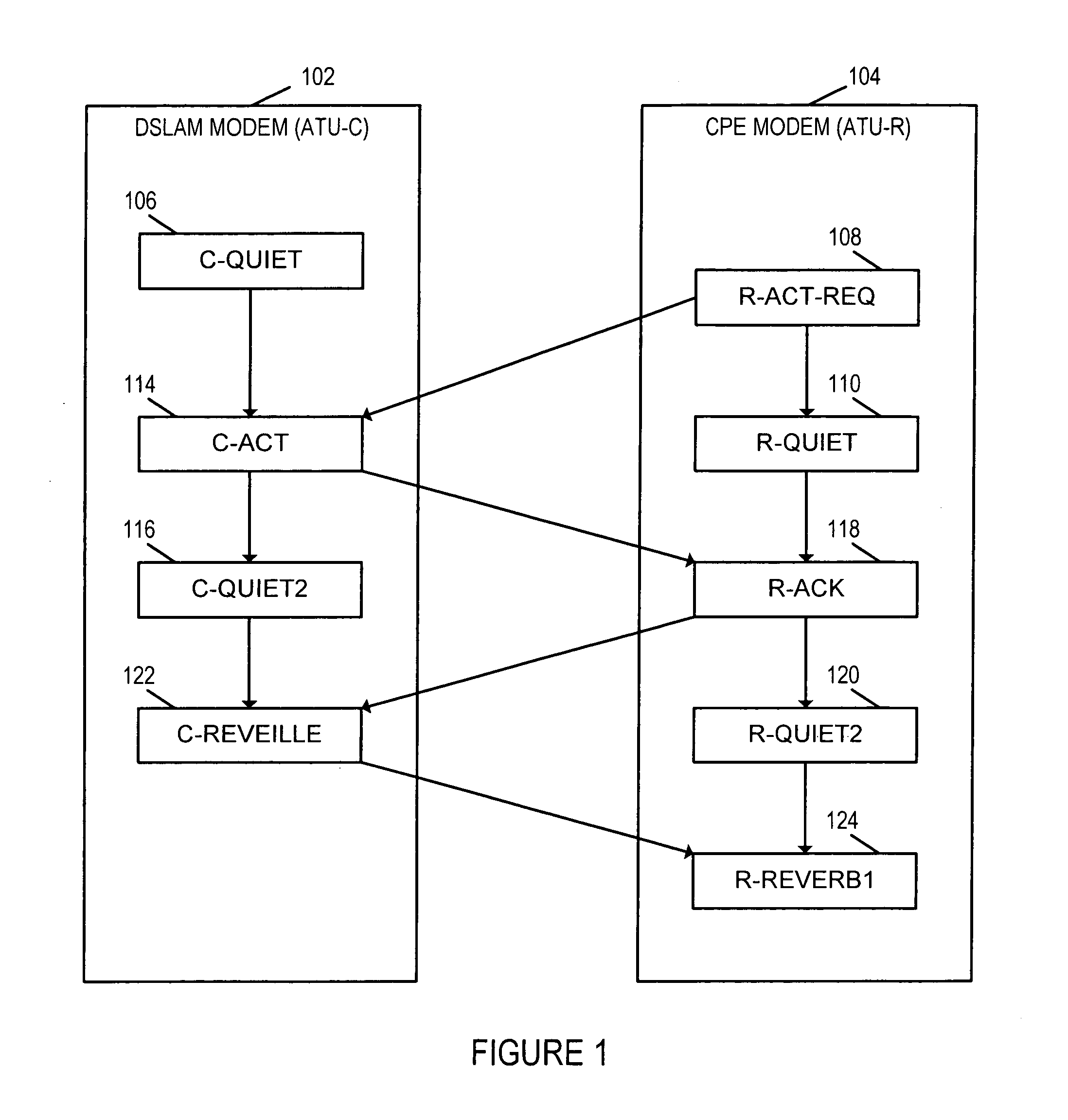
Methods and apparatus for maintaining the maximum achievable data rate on a DSL line, up to and including a rate to which a user subscribes is described. Performance monitoring is conducted on the DSL line on an ongoing basis to determine noise margins in each direction. Each noise margin is compared against pre-determined decreasing / increasing thresholds to determine whether the line characteristics dictate a data rate change without loss of synchronization. The invention supports dynamic provisioning changes including application driven service level change requests, e.g., new bandwidth-on demand services. In some embodiments, a combination of existing and new embedded operations channel (EOC) messages are used to implement the modem data rate changes. New EOC messages may be implemented using some of the reserved and / or vendor proprietary Opcodes currently permitted. Modem assigned data rate changes are implemented without a disruption of service, e.g., without the need for re-initialization and / or re-synchronization.
Owner:INTELLECTUAL VENTURES II
Method and apparatus for support of tagging and untagging per VLAN per port
An integrated multiport switch operating in a packet switched network provides the capability via distributed egress logic to alter VLAN tags on a port by port basis. An internal rules checker (IRC) analyzes the header of a data frame to determine the frame type: untagged, VLAN-tagged, or priority-tagged. The IRC searches the untagged set table for the set of ports that are untagged for a particular VLAN. The IRC passes a forwarding descriptor that includes the frame type and a operational code (opcode) to a Port Vector FIFO logic (PVF). The PVF is responsible for creating a new opcode that instructs a dequeuing logic to add, remove, modify the VLAN tag, or send the frame unmodified. The opcodes generated by the PVF are individualized for each output port.
Owner:GLOBALFOUNDRIES INC
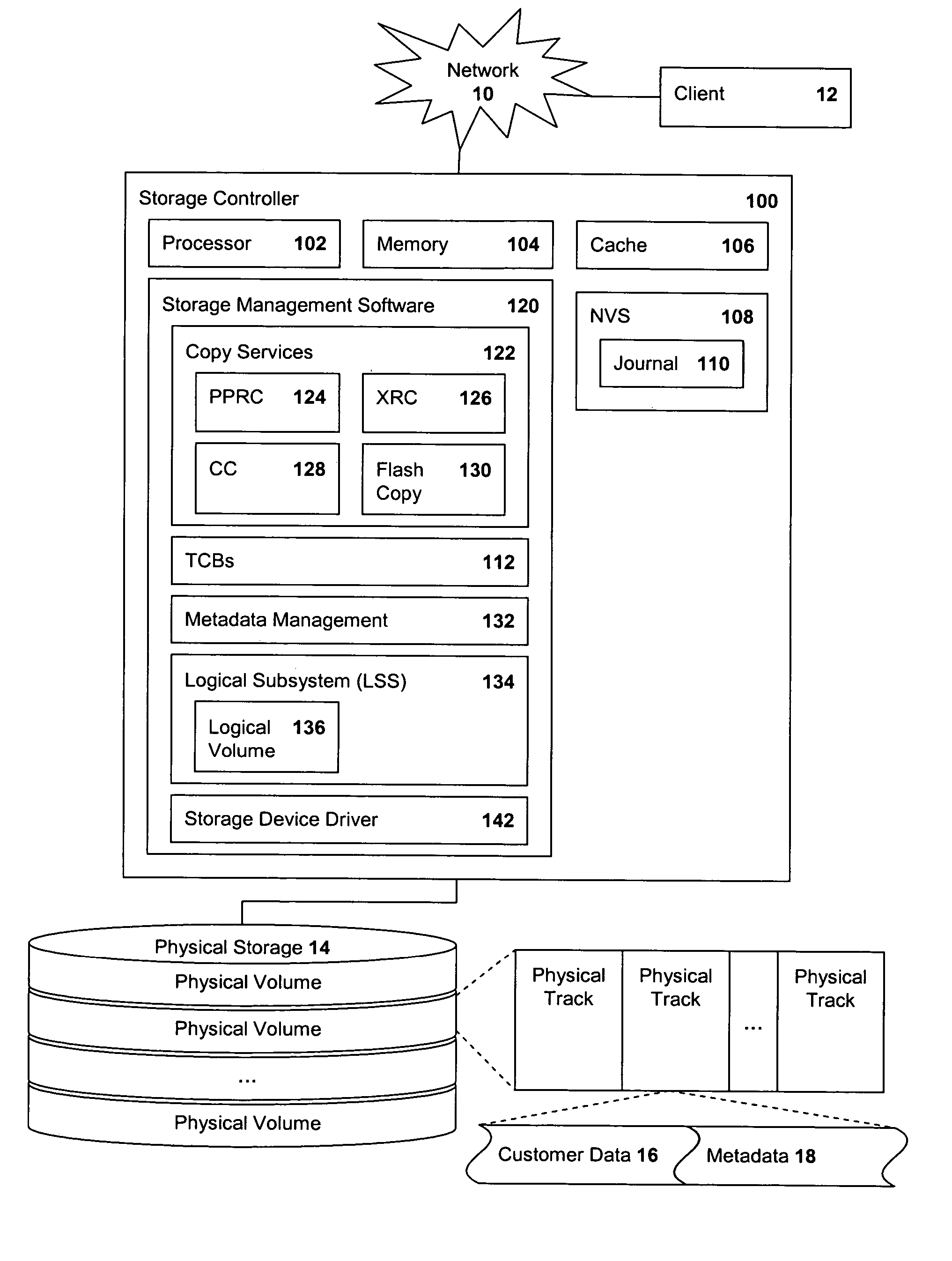
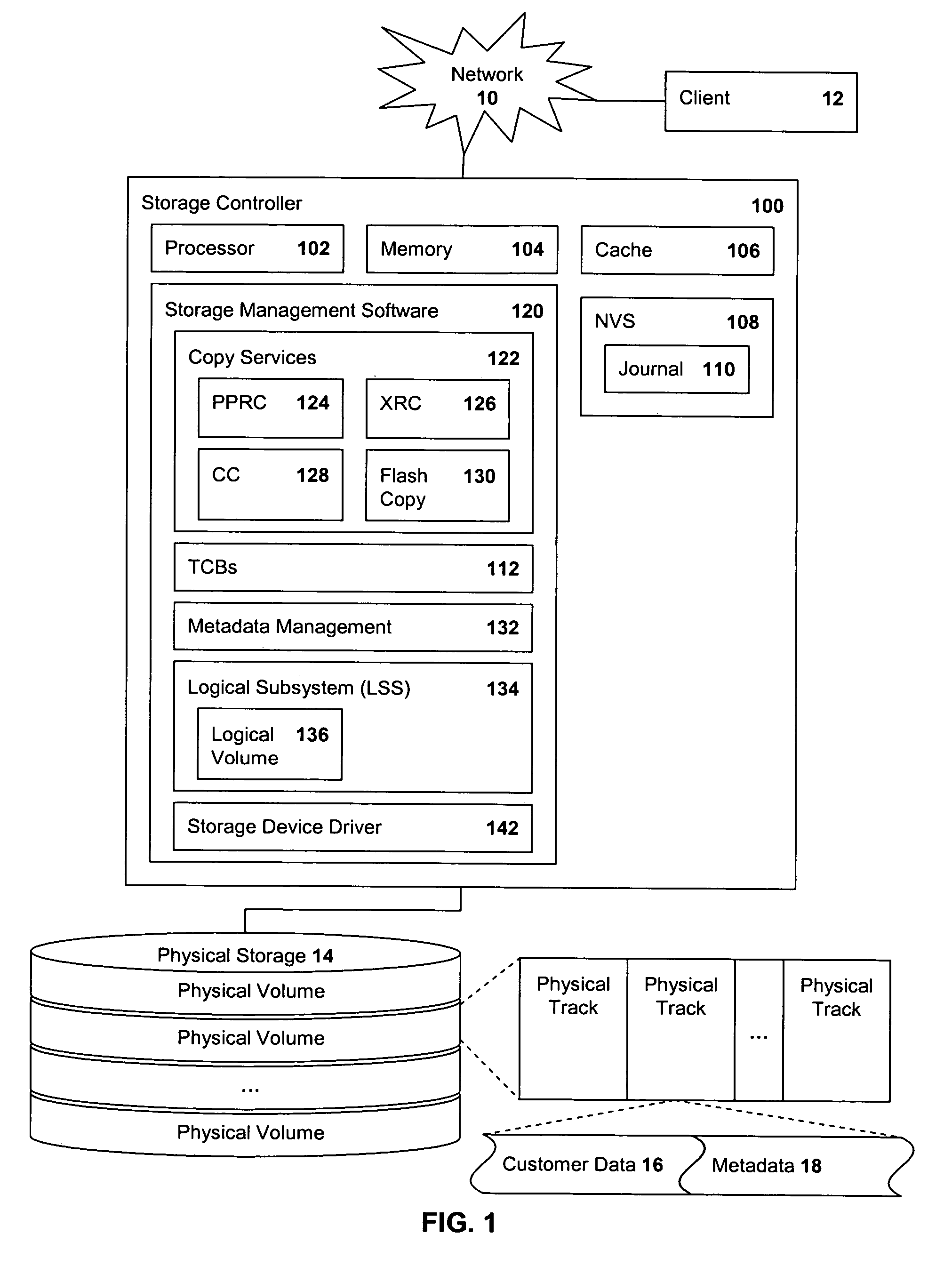
Managing atomic updates on metadata tracks in a storage system
InactiveUS20060106891A1Digital data processing detailsSpecial data processing applicationsData operationsMetadata
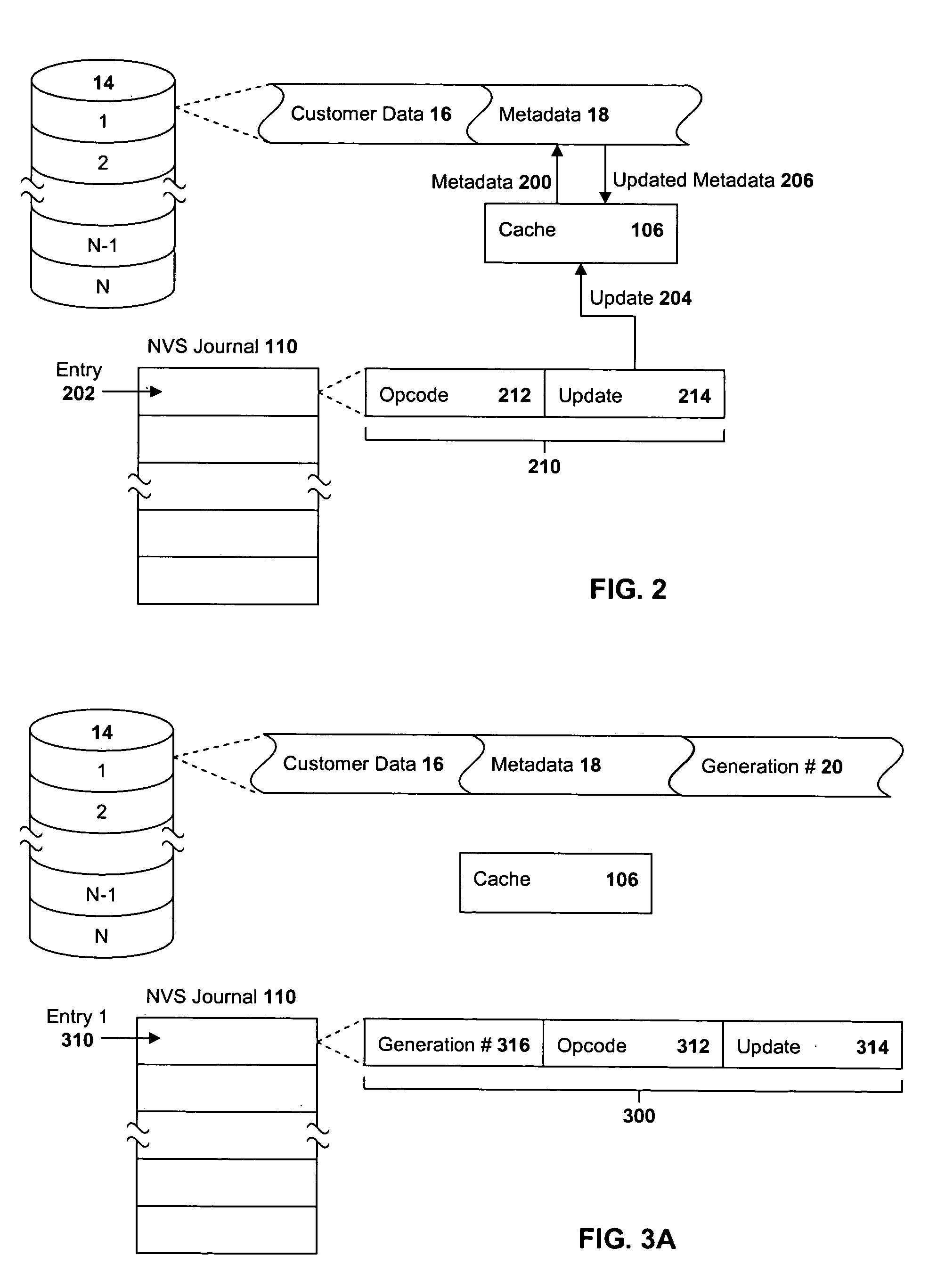
Methods, systems, computer program products and methods for deploying computing infrastructure for managing metadata in a storage subsystem are provided. A first metadata track is staged from disk storage to a cache storage after which a journal entry is stored in a nonvolatile storage (NVS). The journal entry includes an opcode and update data for the track. The opcode identifies the type of update to be performed and the number of tracks to be updated in the operation. Each of the other metadata tracks is staged and a corresponding journal entry stored. The journaled updates are then applied to the respective metadata track in the cache storage and the tracks destaged from cache to the disk storage.
Owner:IBM CORP
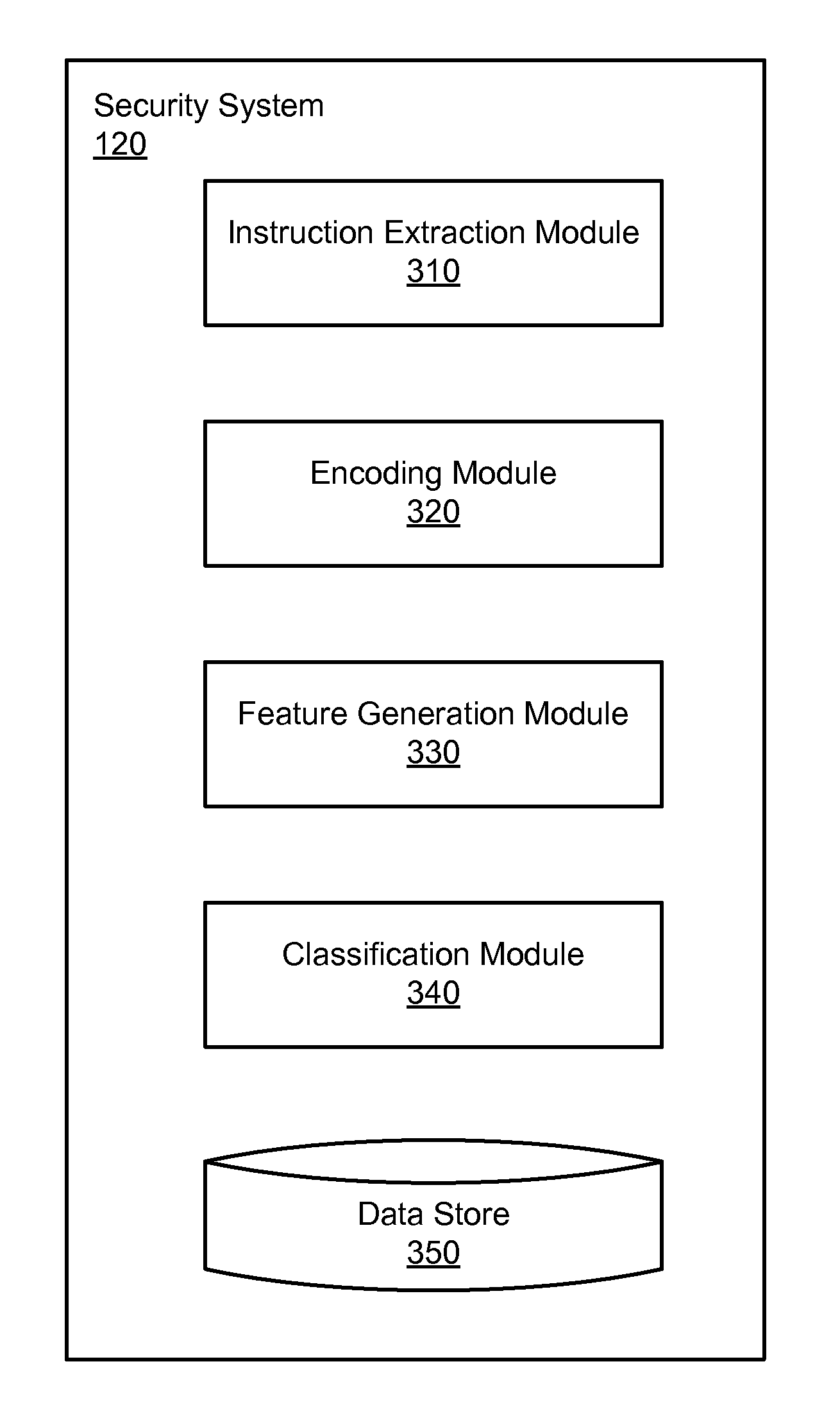
Encoding machine code instructions for static feature based malware clustering
Machine language instruction sequences of computer files are extracted and encoded into standardized opcode sequences. The standardized opcodes in the sequences are of the same length and do not include operands. A multi-dimension vector is generated as a static feature for each computer file, where each element in the vector corresponds to the number of occurrences of a unique N-gram (i.e., unique sequence of N consecutive standardized opcodes) in the standardized opcode sequence for that computer file. The computer files are clustered into clusters of similarly classified files based on similarities of their static features. An unknown computer file can be classified by first grouping the file into a cluster of files with similar static features (e.g., into the cluster with the shortest average distance), and then determining the classification of that file based on the classifications of other files that belong to the same cluster.
Owner:NORTONLIFELOCK INC
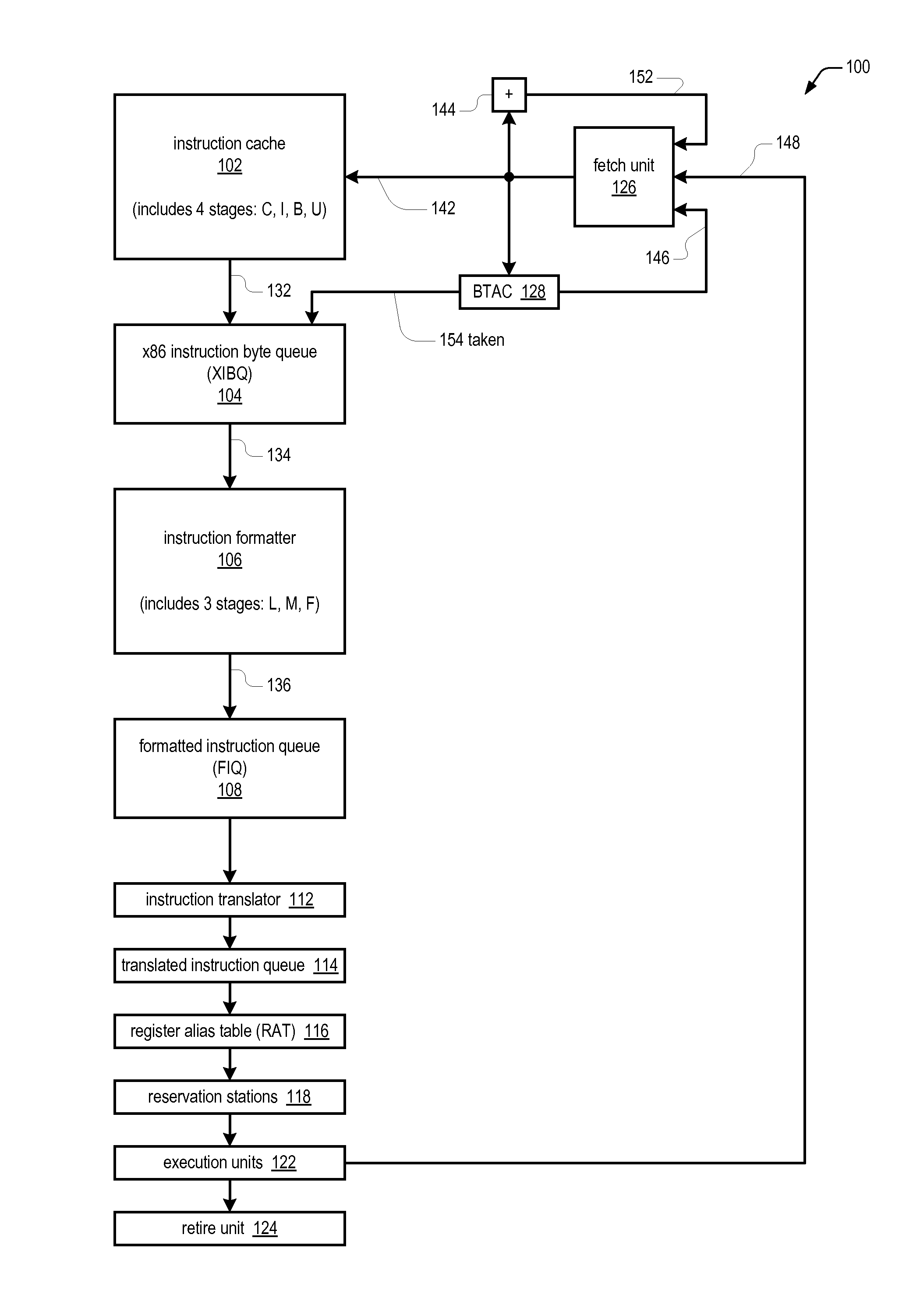
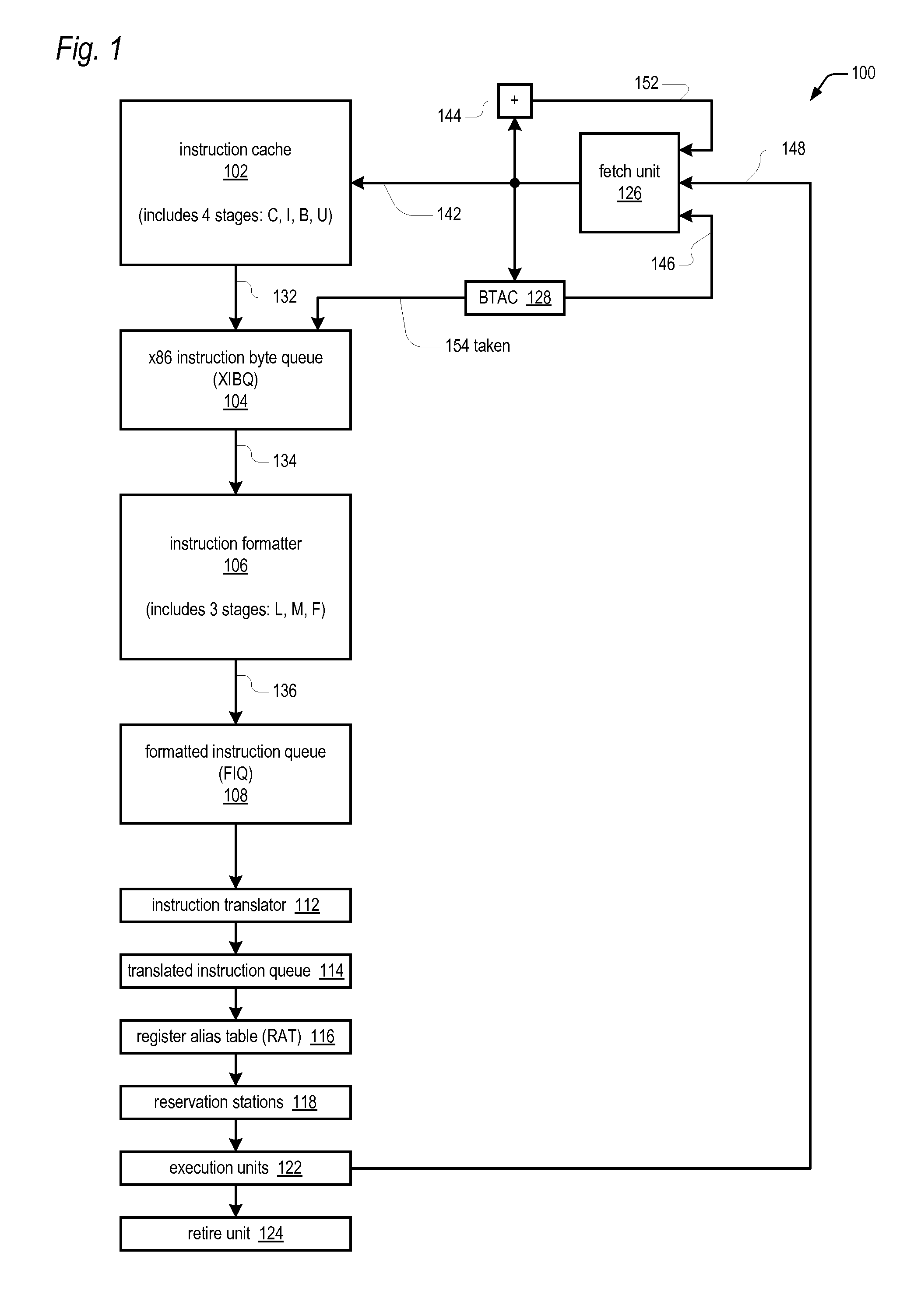
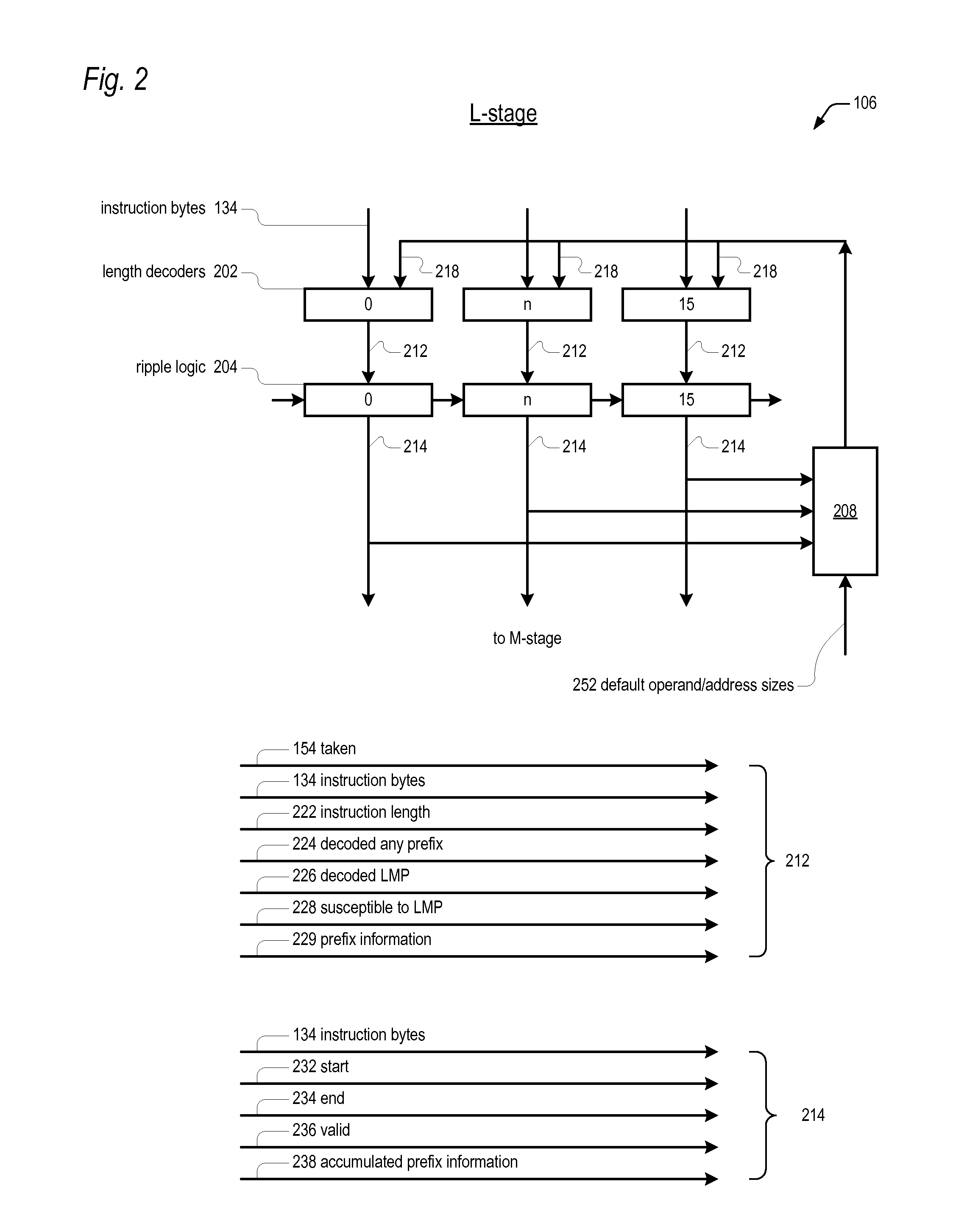
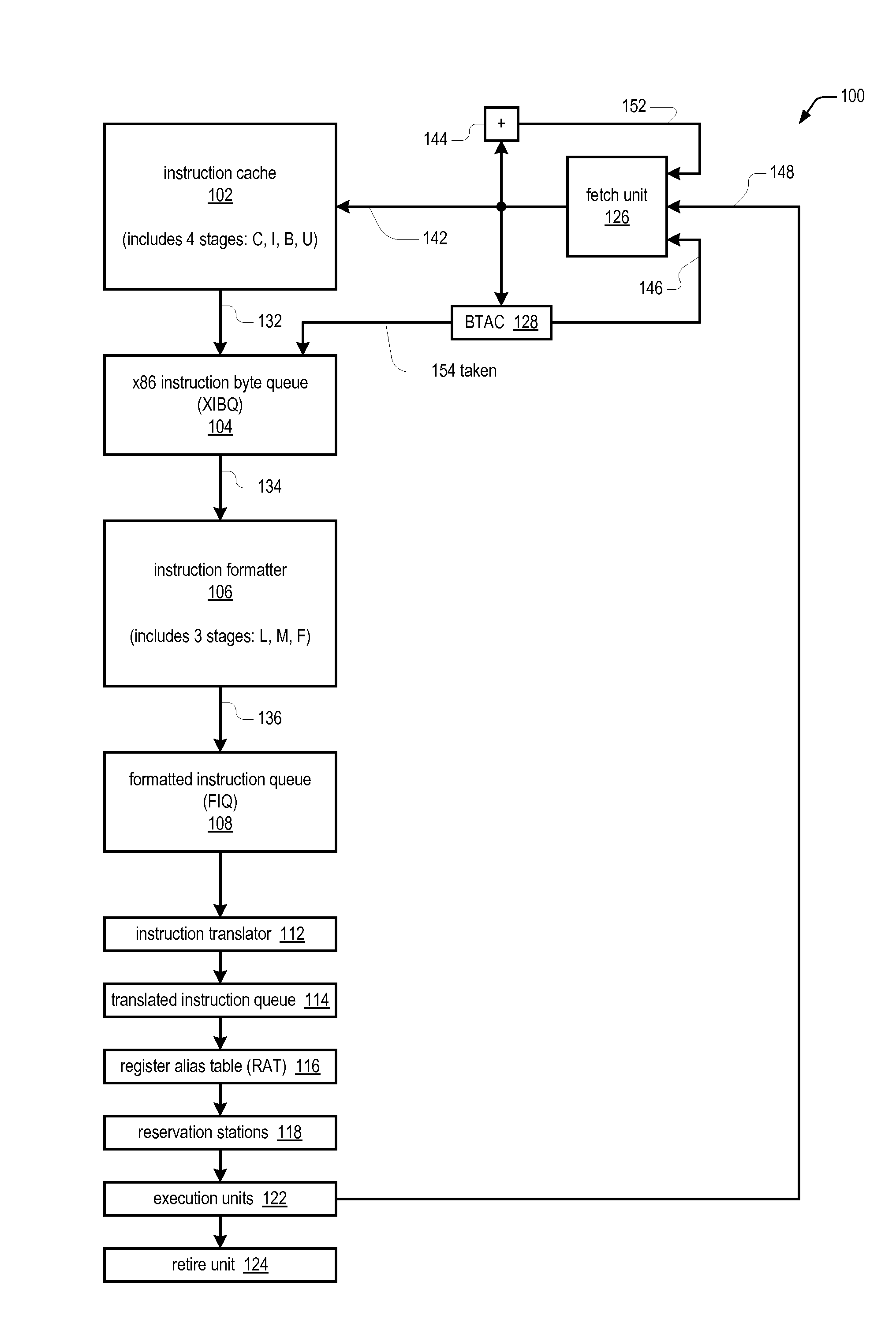
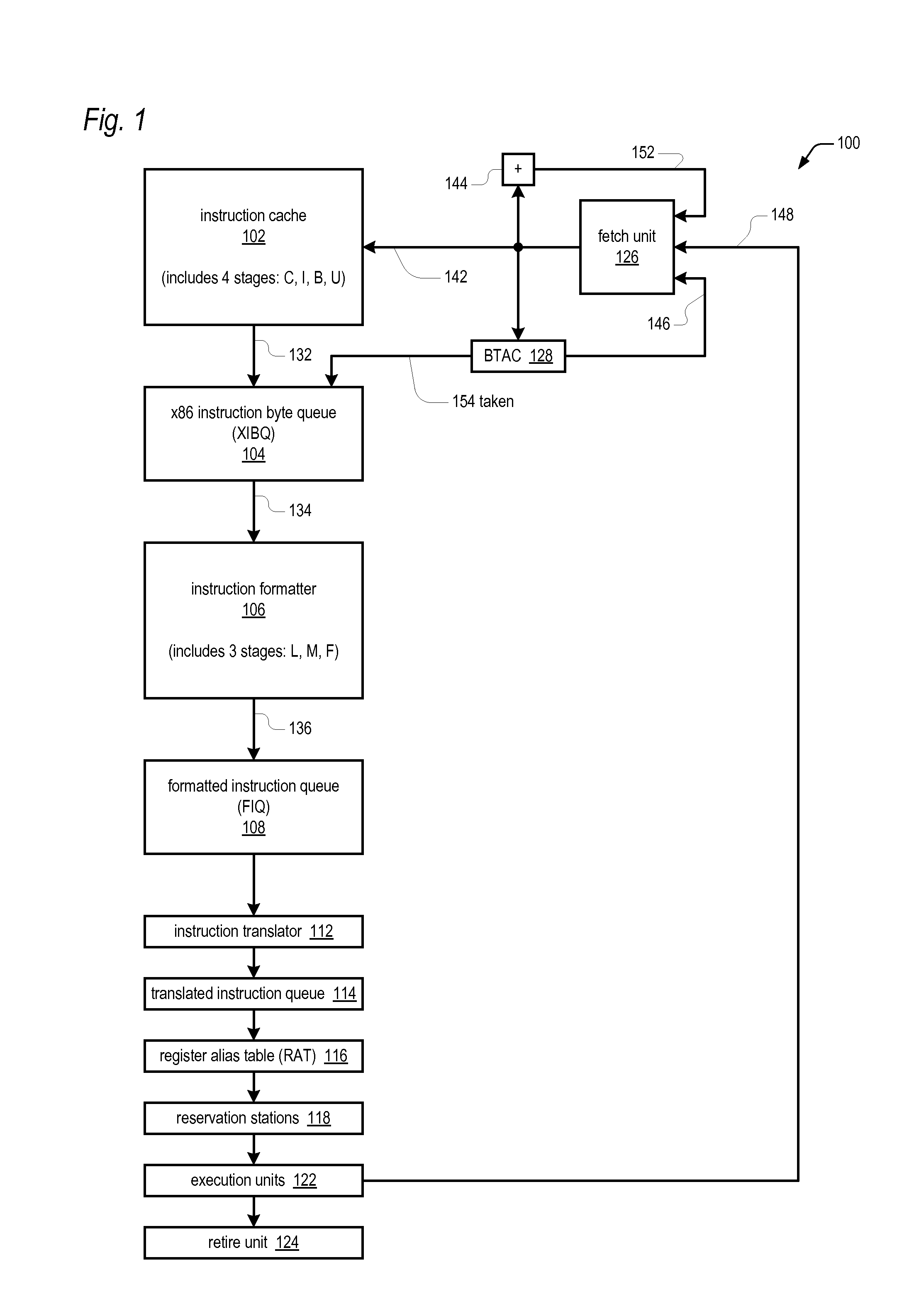
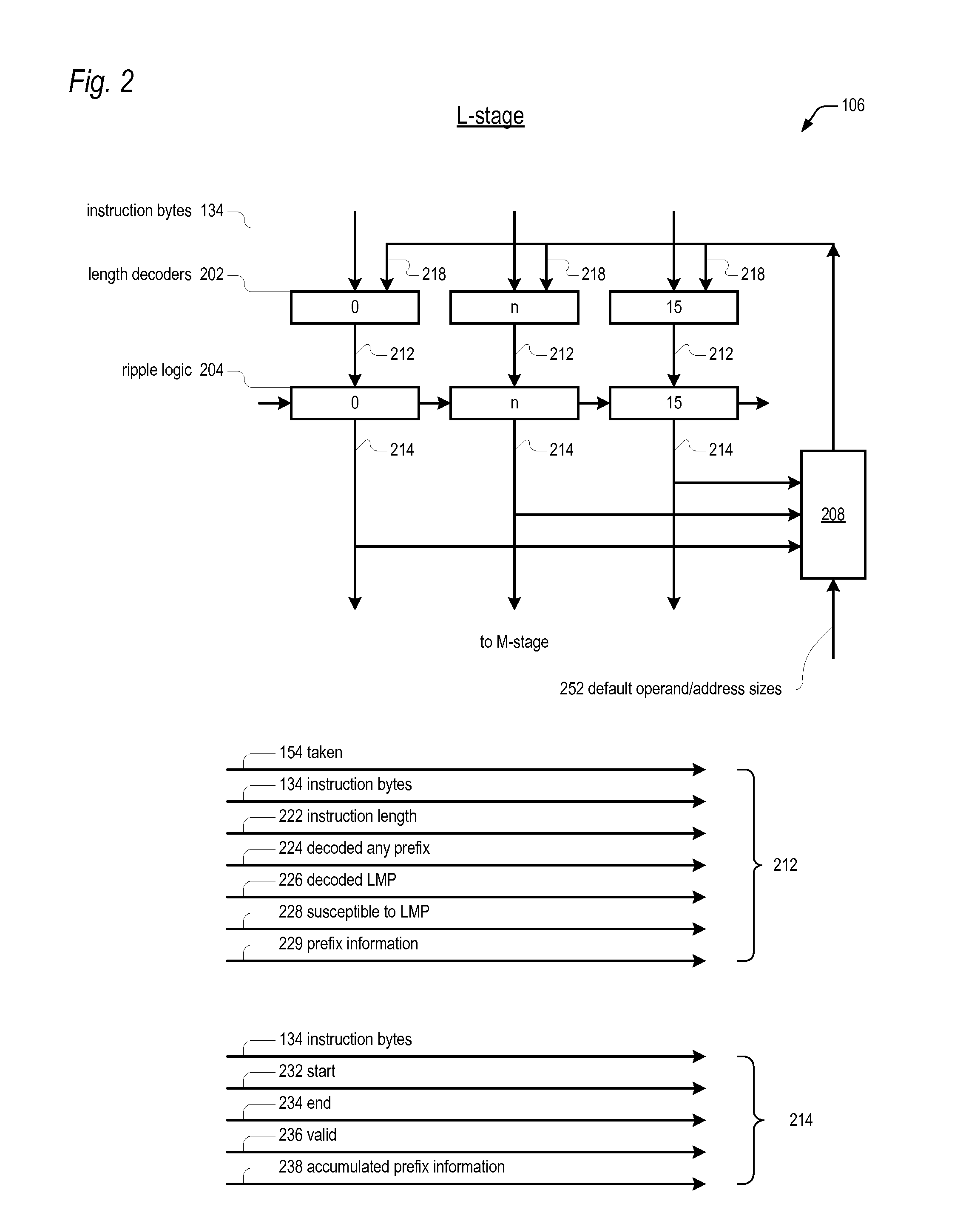
Prefix accumulation for efficient processing of instructions with multiple prefix bytes
ActiveUS20100299500A1Efficient extractionMemory architecture accessing/allocationDigital computer detailsByteInstruction set
In a microprocessor that has an instruction set architecture in which the instructions may include a variable number of prefix bytes, an apparatus for efficiently extracting instructions from a stream of undifferentiated instruction bytes. Decode logic determines which byte is an opcode byte for each instruction of a plurality of instructions within the stream of undifferentiated instruction bytes. The opcode byte is the first non-prefix byte of the instruction. The decode logic accumulates prefix information onto the opcode byte of the instruction for each instruction of the plurality of instructions. A queue holds the stream of undifferentiated instruction bytes and the accumulated prefix information. Extraction logic extracts the plurality of instructions from the queue in one clock cycle independent of the number of prefix bytes included in each of the plurality of instructions.
Owner:VIA TECH INC
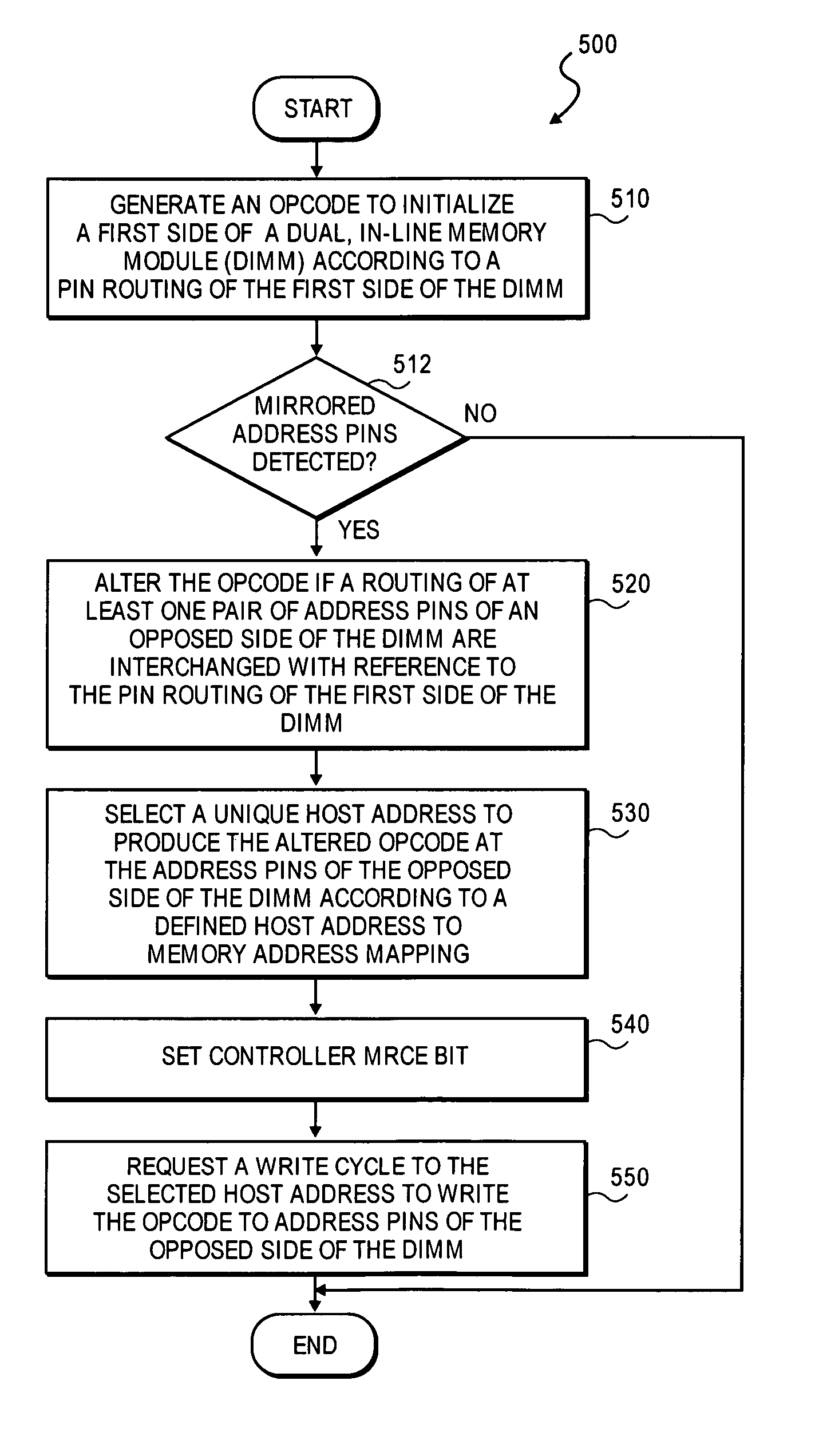
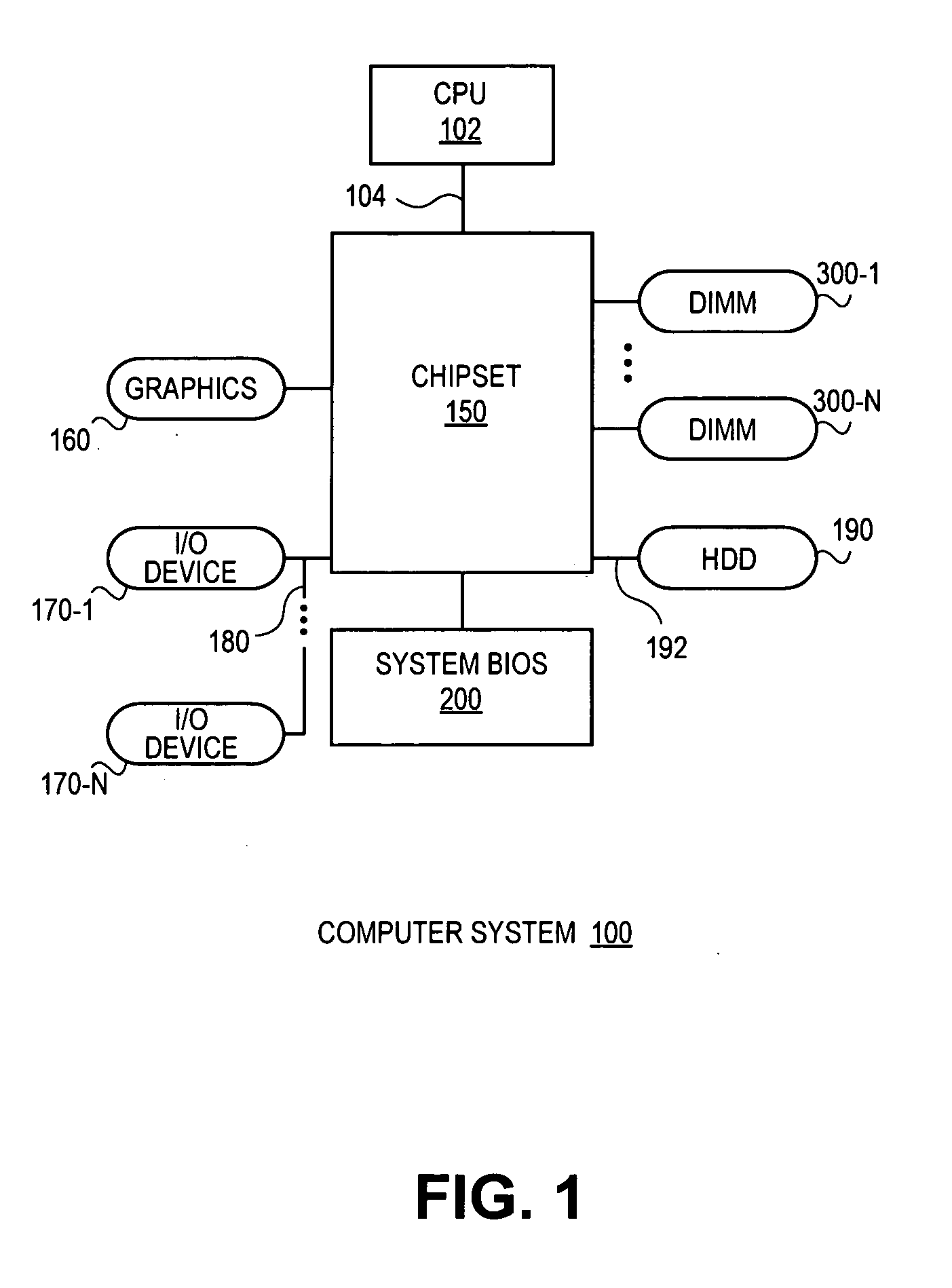
Apparatus and method for initialization of a double-sided dimm having at least one pair of mirrored pins
A method and apparatus for initialization of a double-sided memory module having a least one pair of mirrored pins. In one embodiment, the method includes the generation of an opcode to initialize a first side of the memory module according to a first side pin routing. In one embodiment, the opcode is written to a host address selected for the first side of the memory module according to a system host address to memory address mapping. In one embodiment, the opcode is altered if a routing of address pins of the opposed side of the memory module are interchanged with reference to the first side pin routing. Subsequently, a unique host address is selected to produce the altered opcode at the address pins of the opposed side of the memory module according to a defined host address to memory address mapping. Other embodiments are described and claimed.
Owner:INTEL CORP
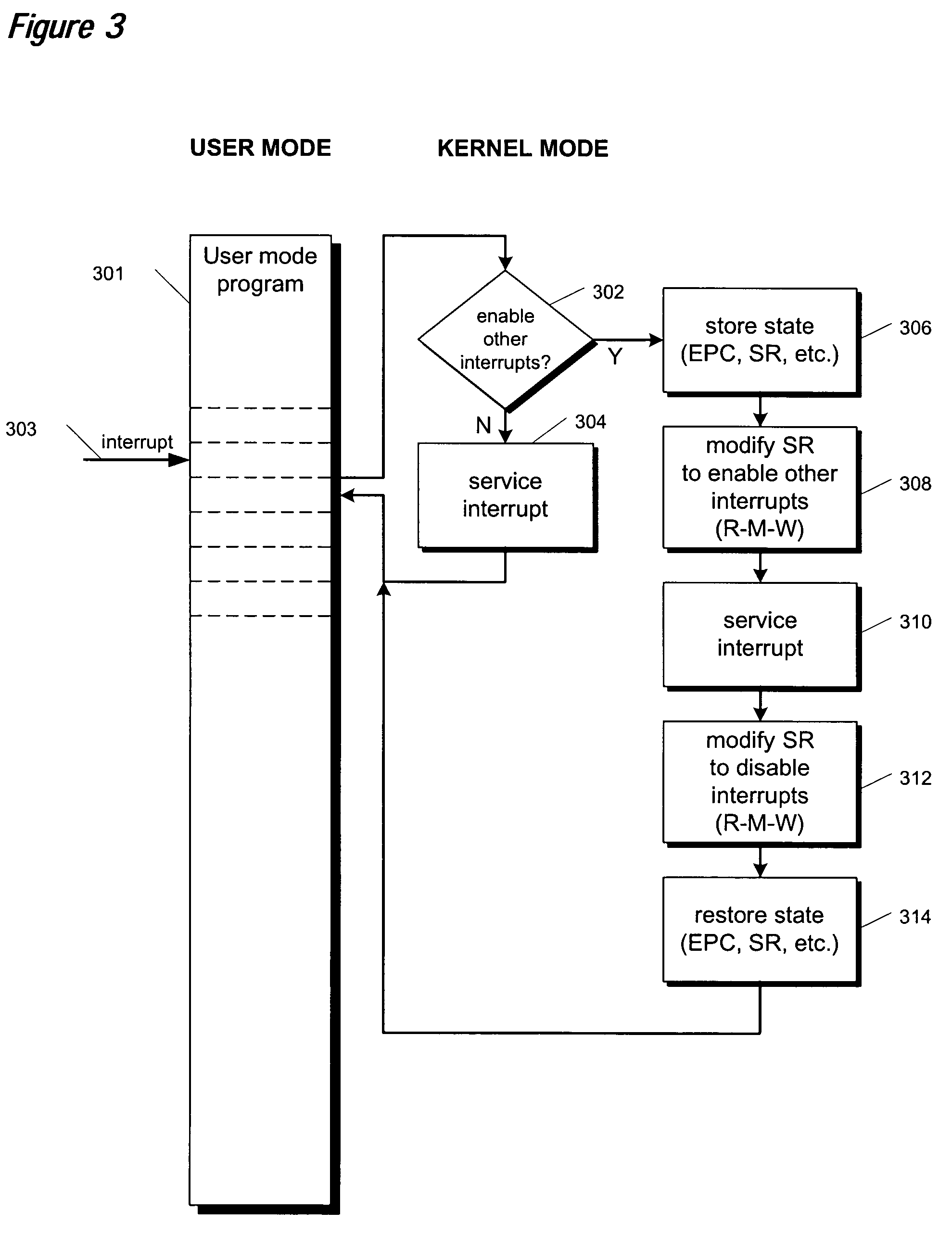
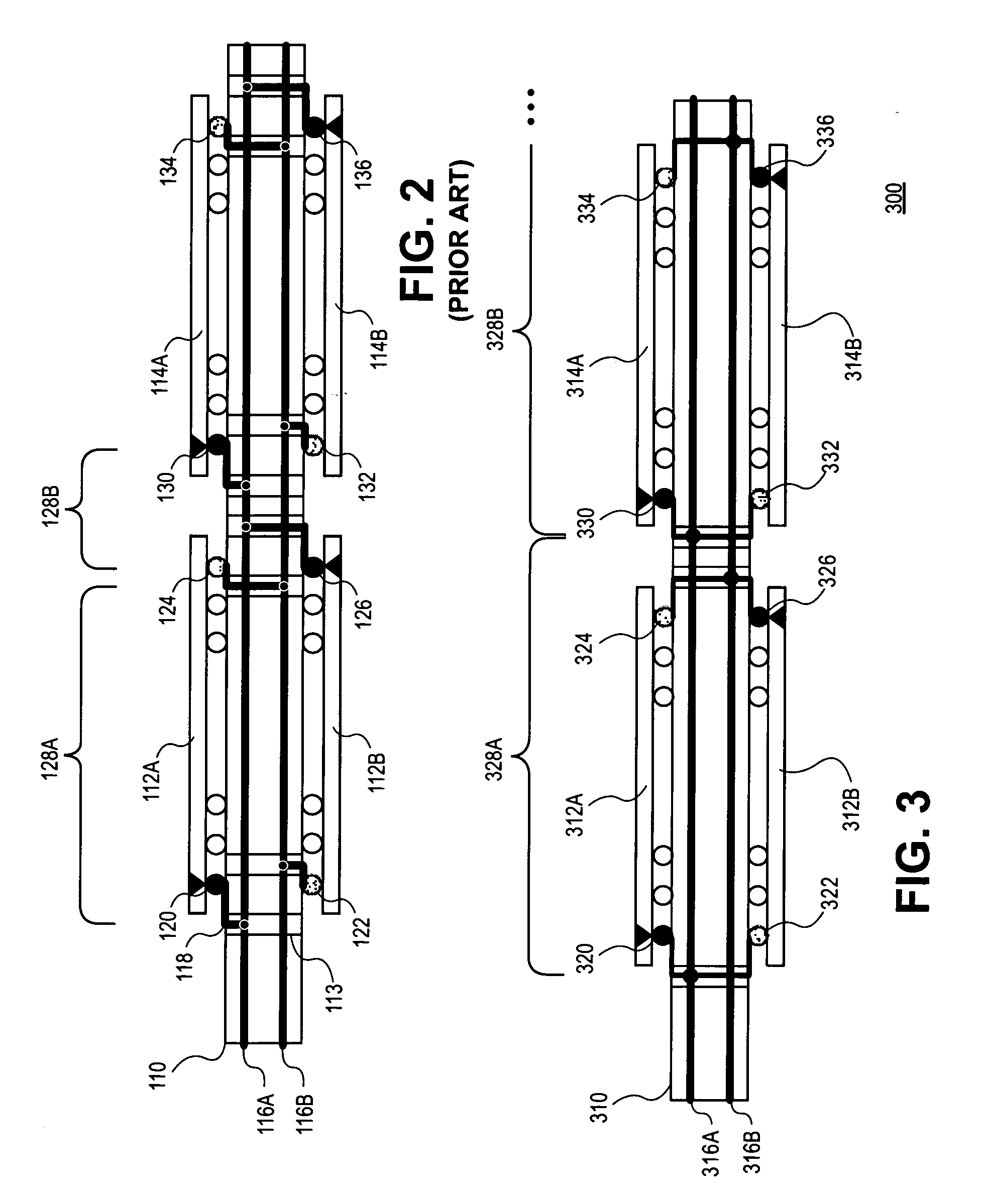
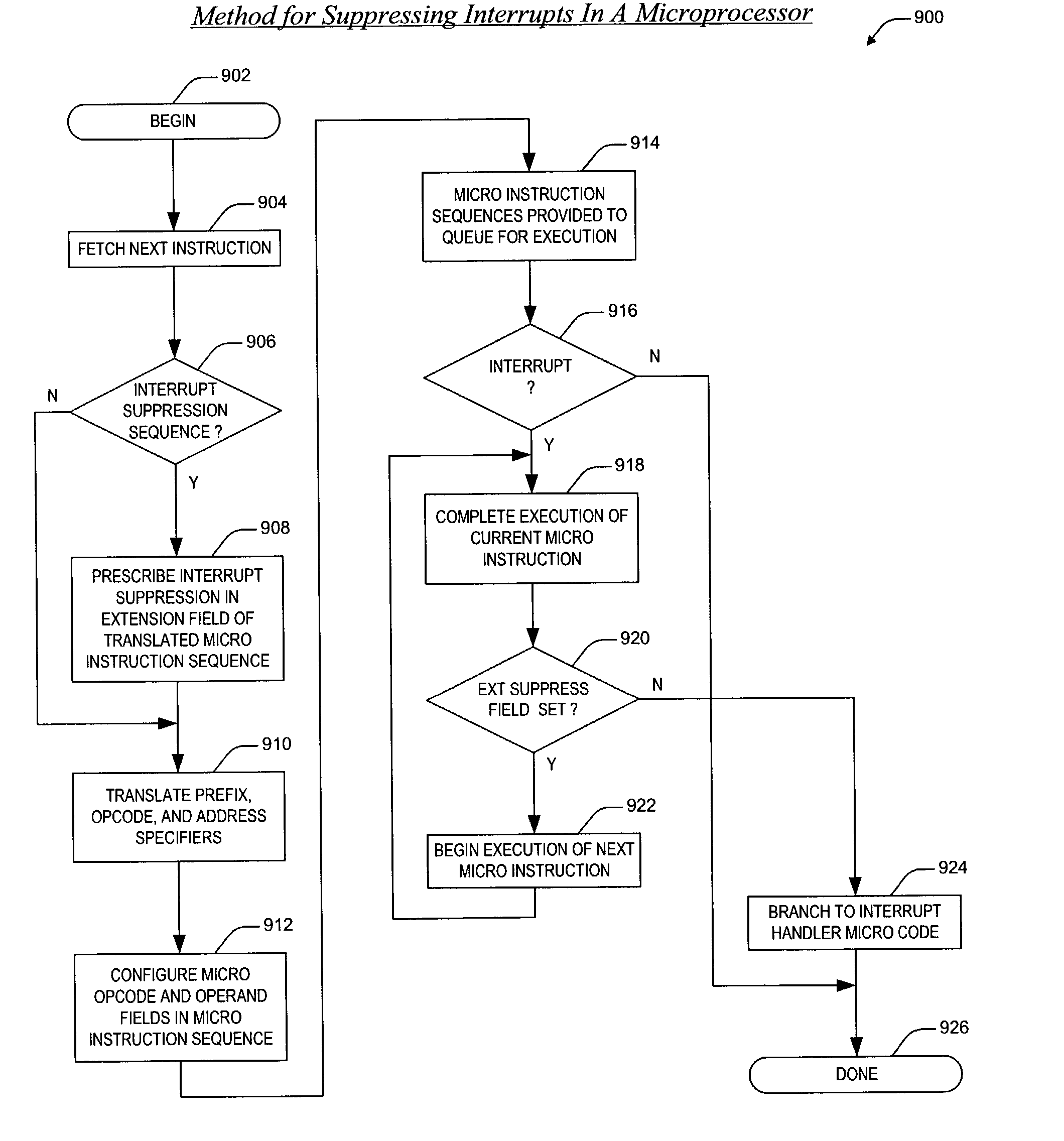
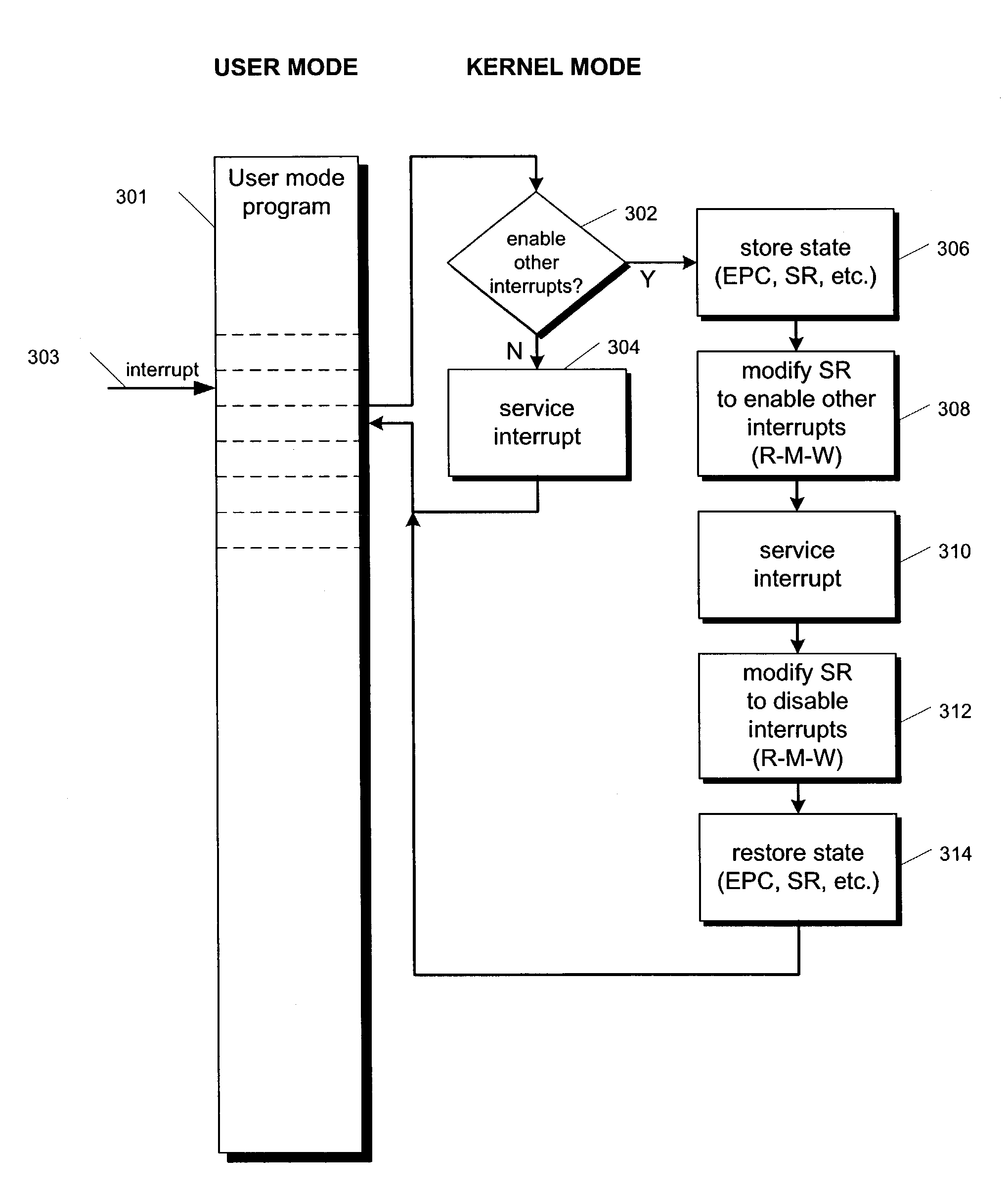
Selective interrupt suppression
ActiveUS7546446B2Good techniqueDigital computer detailsSpecific program execution arrangementsInstruction setMicroprocessor
An apparatus and method are provided for extending a microprocessor instruction set to allow for selective suppression of interrupts at the instruction level. The apparatus includes translation logic and extended execution logic. The translation logic translates an extended instruction into corresponding micro instructions. The extended instruction has and extended prefix and an extended prefix tag. The extended prefix specifies that interrupt processing be suppressed until execution of the extended instruction is completed, where the extended instruction prescribes an operation to be performed according to an existing instruction set. The extended prefix tag is an otherwise architecturally specified opcode within an existing instruction set. The extended execution logic is coupled to the translation logic. The extended execution logic receives the corresponding micro instructions, and completes execution of the corresponding micro instructions prior to processing a pending interrupt.
Owner:IP FIRST
Bad branch prediction detection, marking, and accumulation for faster instruction stream processing
ActiveUS20100299502A1Memory architecture accessing/allocationDigital computer detailsVariable lengthByte
An apparatus for extracting instructions from a stream of undifferentiated instruction bytes in a microprocessor having an instruction set architecture in which the instructions are variable length. Decode logic decodes the instruction bytes of the stream to generate for each a corresponding opcode byte indictor and end byte indicator and receives a corresponding taken indicator for each of the instruction bytes. The taken indicator is true if a branch predictor predicted the instruction byte is the opcode byte of a taken branch instruction. The decode logic generates a corresponding bad prediction indicator for each of the instruction bytes. The bad prediction indicator is true if the corresponding taken indicator is true and the corresponding opcode byte indicator is false. The decode logic sets to true the bad prediction indicator for each remaining byte of an instruction whose opcode byte has a true bad prediction indicator. Control logic extracts instructions from the stream and sends the extracted instructions for further processing by the microprocessor. The control logic foregoes sending an instruction having both a true end byte indicator and a true bad prediction indicator.
Owner:VIA TECH INC
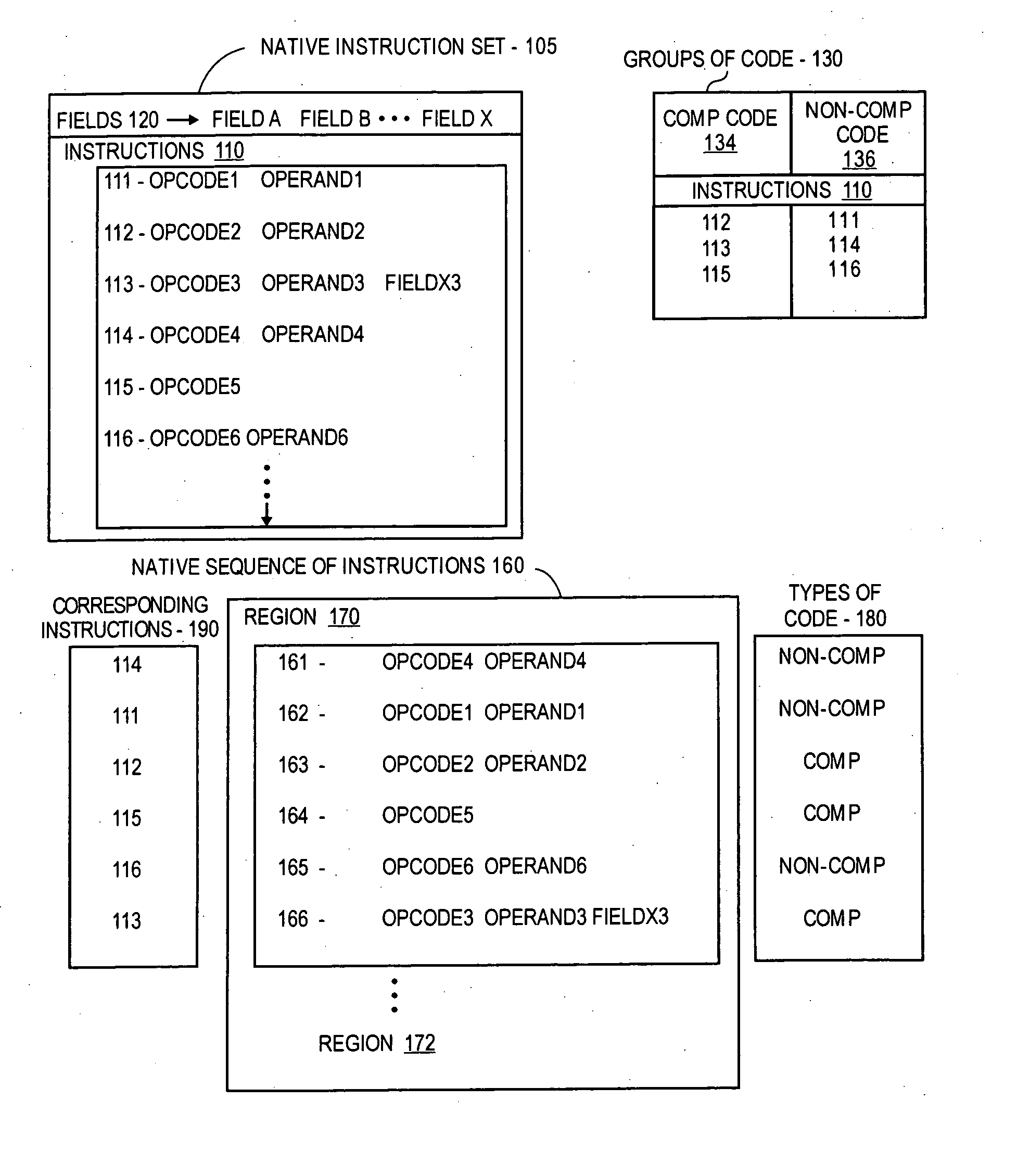
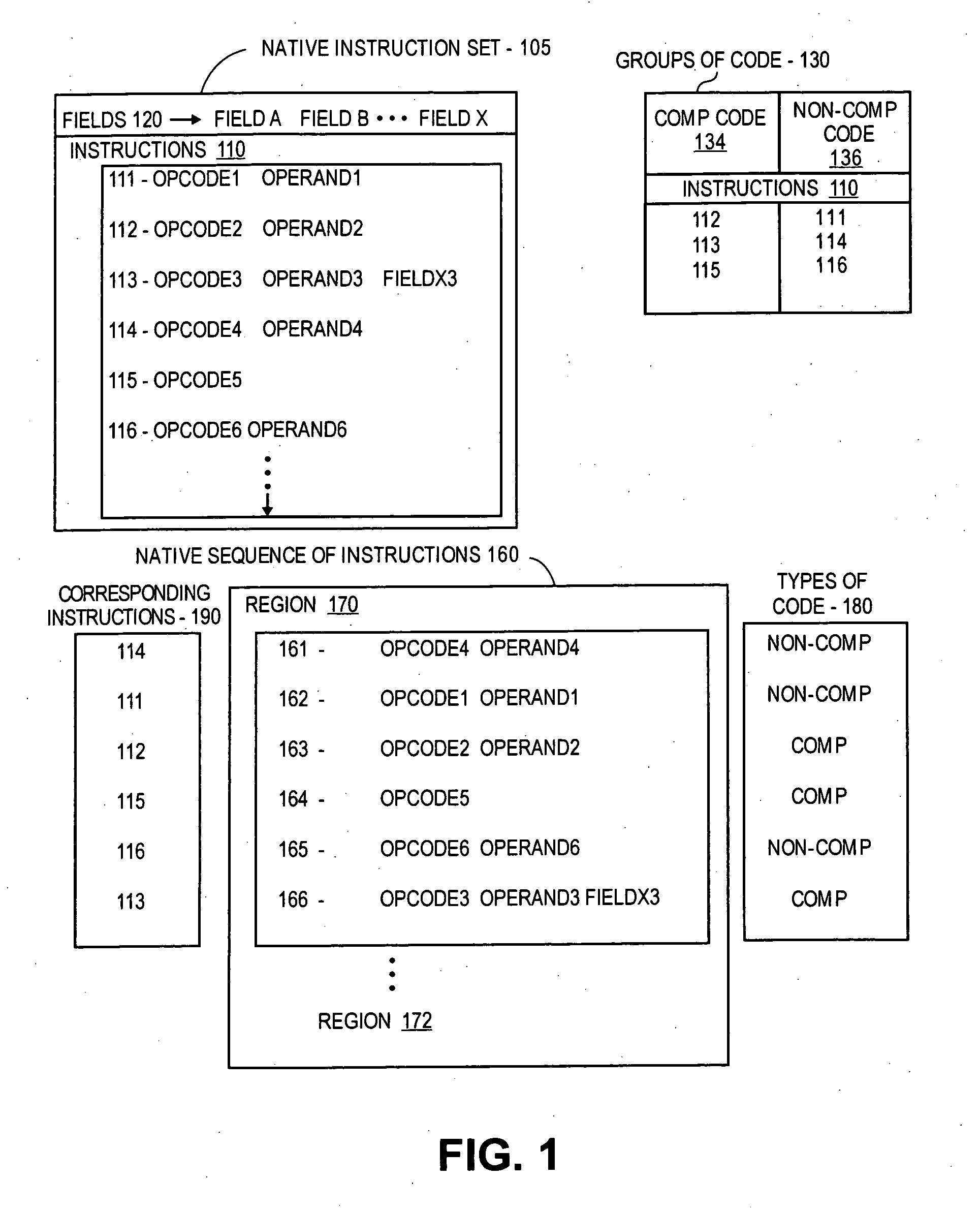
Compressing "warm" code in a dynamic binary translation environment
Selected regions of native instructions translated in a DBT environment from non-native instructions are compressed based on the independent compression of different fields of selected instructions using compression tables to reduce a length of selected fields. The regions of compressed instructions are stored and de-compressed into the native instructions during subsequent execution using de-compression tables. Specifically, for native instructions of a selected region, selected types of opcodes and / or operands may be compressed independently. The types may be selected by profiling the opcodes using benchmark programs and creating an opcode conversion table prior to compression, and scanning of the operands and creating an operand conversion table during compression of the opcodes.
Owner:INTEL CORP
Instruction encoding for system register bit set and clear
ActiveUS7634638B1Digital computer detailsSpecific program execution arrangementsGeneral purposeComputer architecture
An instruction encoding architecture is provided for a microprocessor to allow atomic modification of privileged architecture registers. The instructions include an opcode that designates to the microprocessor that the instructions are to execute in privileged (kernel) state only, and that the instructions are to communicate with privileged control registers, a field for designating which of a plurality of privileged architecture registers is to be modified, a field for designating which bit fields within the designated privileged architecture register is to be modified, and a field to designate whether the designated bit fields are to be set or cleared. The instruction encoding allows a single instruction to atomically set or clear bit fields within privileged architecture registers, without reading the privileged architecture registers into a general purpose register. In addition, the instruction encoding allows a programmer to specify whether the previous content of a privileged architecture register is to be saved to a general purpose register during the atomic modification.
Owner:MIPS TECH INC
Apparatus and method for processing data having a mixed vector/scalar register file
InactiveUS6282634B1Easy to useLarger register bankRegister arrangementsInstruction analysisProcessor registerFloating-point unit
A floating point unit is provided with a register bank comprising 32 registers that may be used as either vector registers of scalar registers. A data processing instruction includes at least one register specifying field pointing to a register containing a data value to be used in that operation. An increase in the instruction bit space available to encode more opcodes or to allow for more registers is provided by encoding whether a register is to be treated as a vector or a scalar within the register field itself. Further, the register field for one register of the instruction may encode whether another register is a vector or a scalar. The registers can be initially accessed using the values within the register fields of the instruction independently of the opcode allowing for easier decode.
Owner:ARM LTD
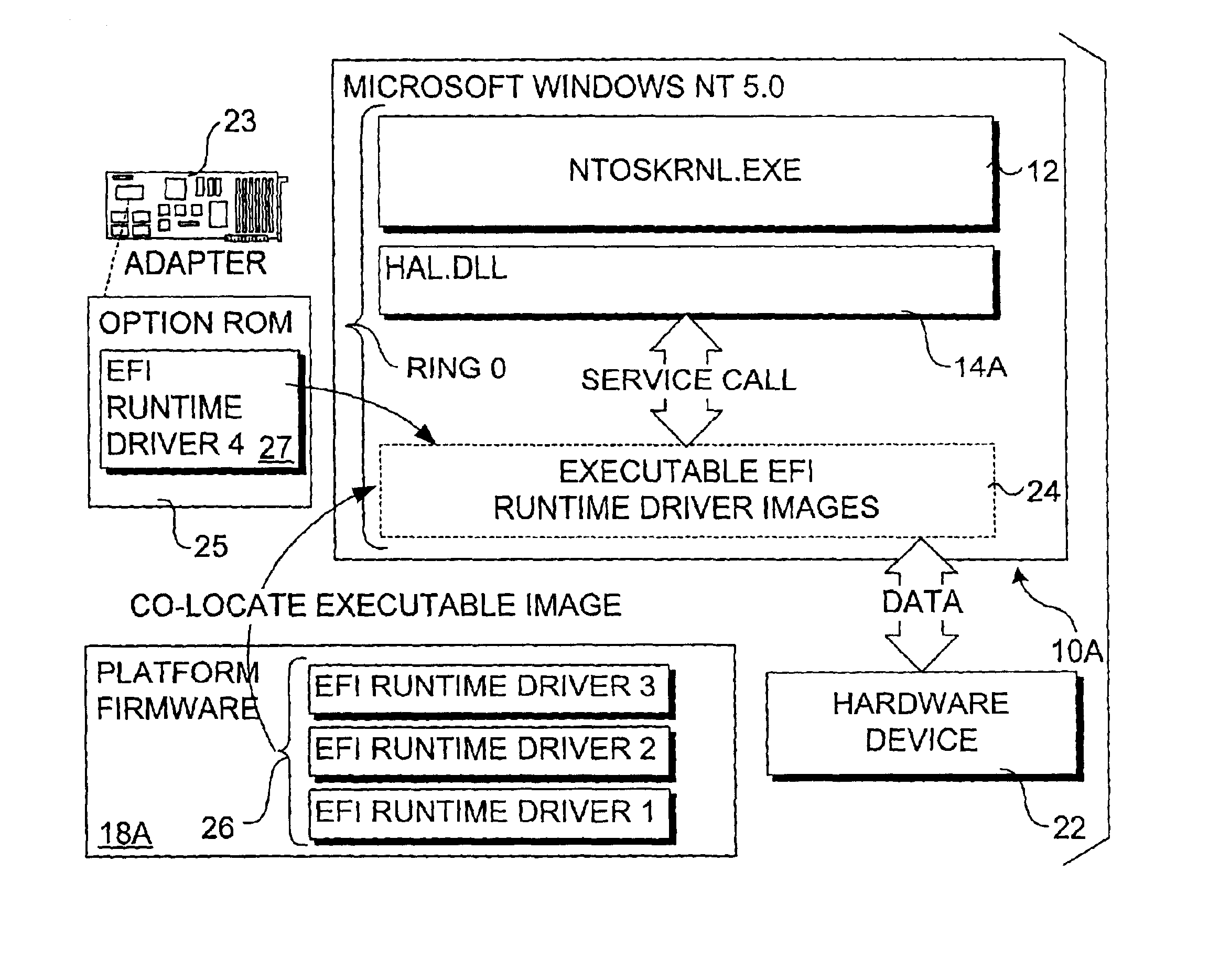
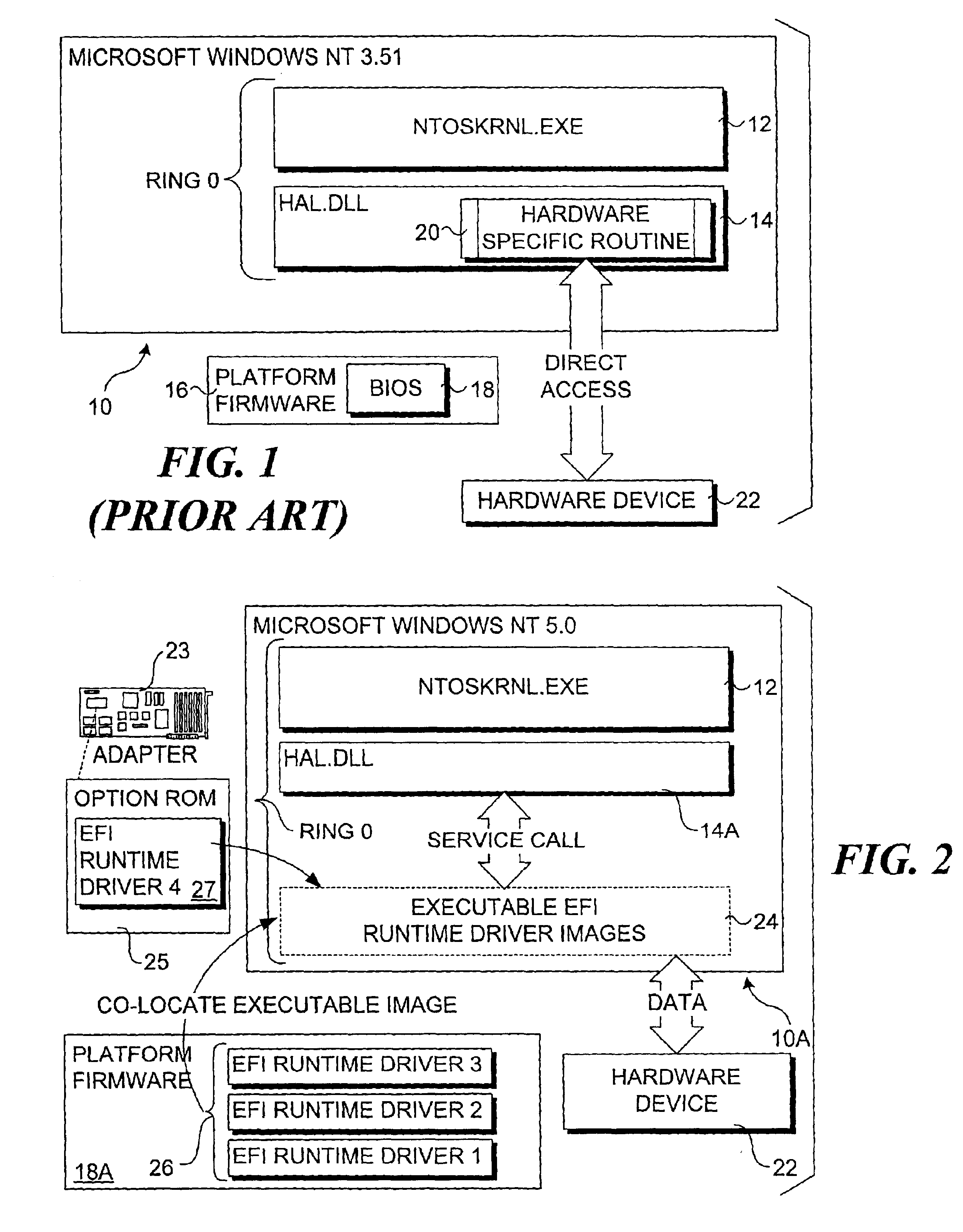
Technique to support co-location and certification of executable content from a pre-boot space into an operating system runtime environment
InactiveUS6978018B2Public key for secure communicationDigital data processing detailsOption ROMOperational system
Techniques to support co-location and certification of executable content from a pre-boot space into an operating system kernel mode runtime environment. The invention enables platform firmware runtime drivers to be loaded into memory as executable images during a pre-boot process and subsequently mapped into an operating system's runtime environment when the operating system is booted so as to enable runtime services provided by the platform firmware runtime drivers to be called via operating system interfaces. Prior to loading the executable images, a type certification check that compares type structure information corresponding to a runtime driver's opcode with type structure information corresponding to an operating system interface used to call the runtime driver may be performed. Additionally, a runtime driver file integrity verification may also be performed using a digital signature and associated key. The runtime driver may be loaded from various platform storage devices, including flash devices and option ROMs.
Owner:INTEL CORP
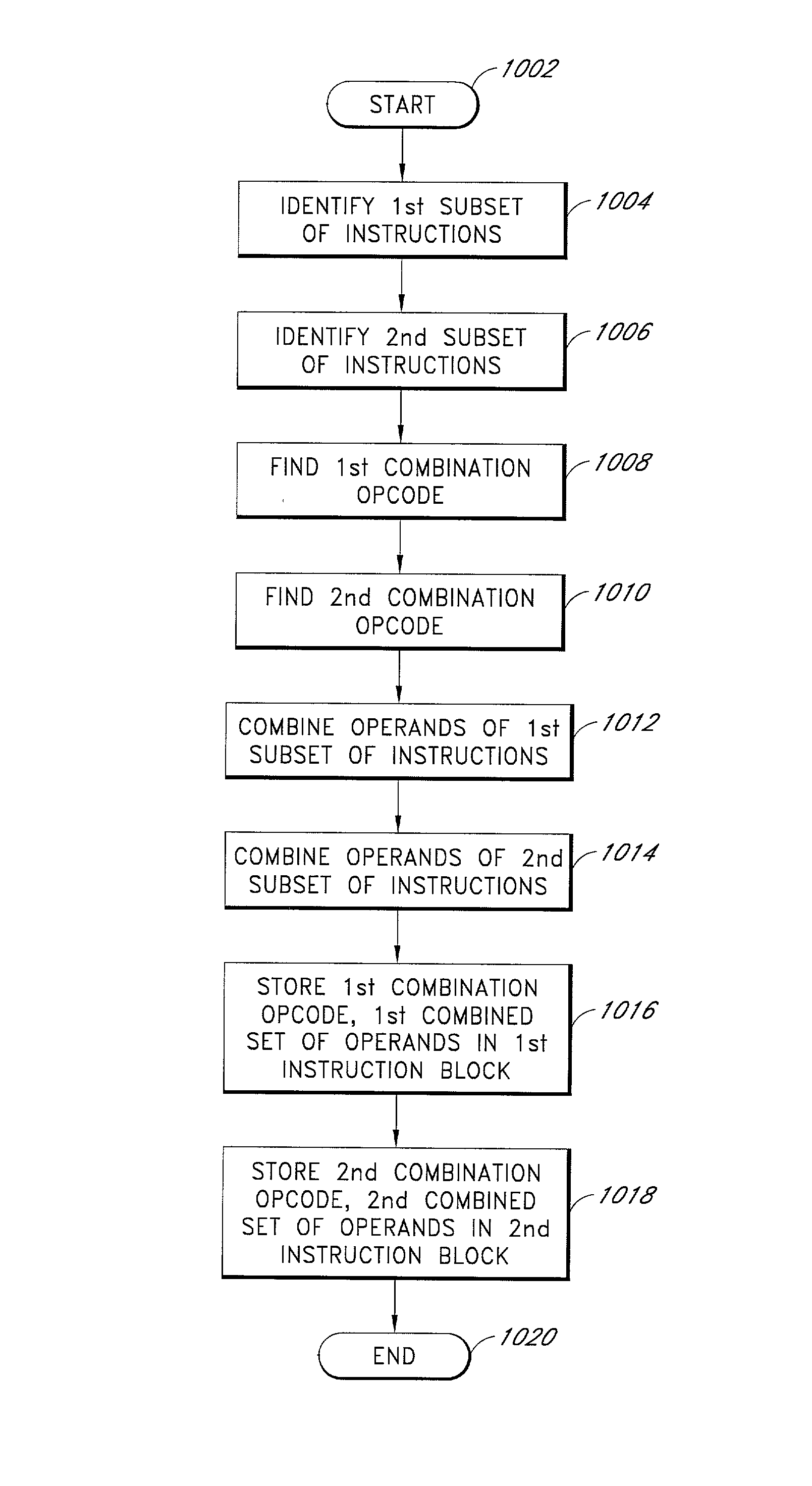
Microprocessor instruction format using combination opcodes and destination prefixes
The present application discloses an instruction format for storing multiple microprocessor instructions as one combined instruction. The instruction format includes a combination opcode field for storing a combination opcode that identifies a combination of the multiple instructions. The application also discloses an instruction format that uses prefix fields to specify the destination functional block for each combined instruction stored in an execute packet. A compiler program or an assembler program obtains from a table a combination opcode that corresponds to a combination of the multiple instructions. The table stores combination opcodes and their corresponding combinations of instructions. The compiler program or assembler program then assigns the found combination opcode to an opcode field of the combined instruction. In a trivial scenario, a single instruction can also be stored as a combined instruction. The compiler program or assembler program also uses prefix fields to identify the destination functional block of each combined instruction in an execute packet. A dispatcher identifies the prefix fields and sends each combined instruction in the execute packet to its destination functional block. An instruction decoder identifies the combination opcode of the combined instruction, separates the combined instruction into the multiple individual instructions, and sends each individual instruction to its respective functional unit for execution.
Owner:AVAZ NETWORKS
Parallel Pattern Detection Engine
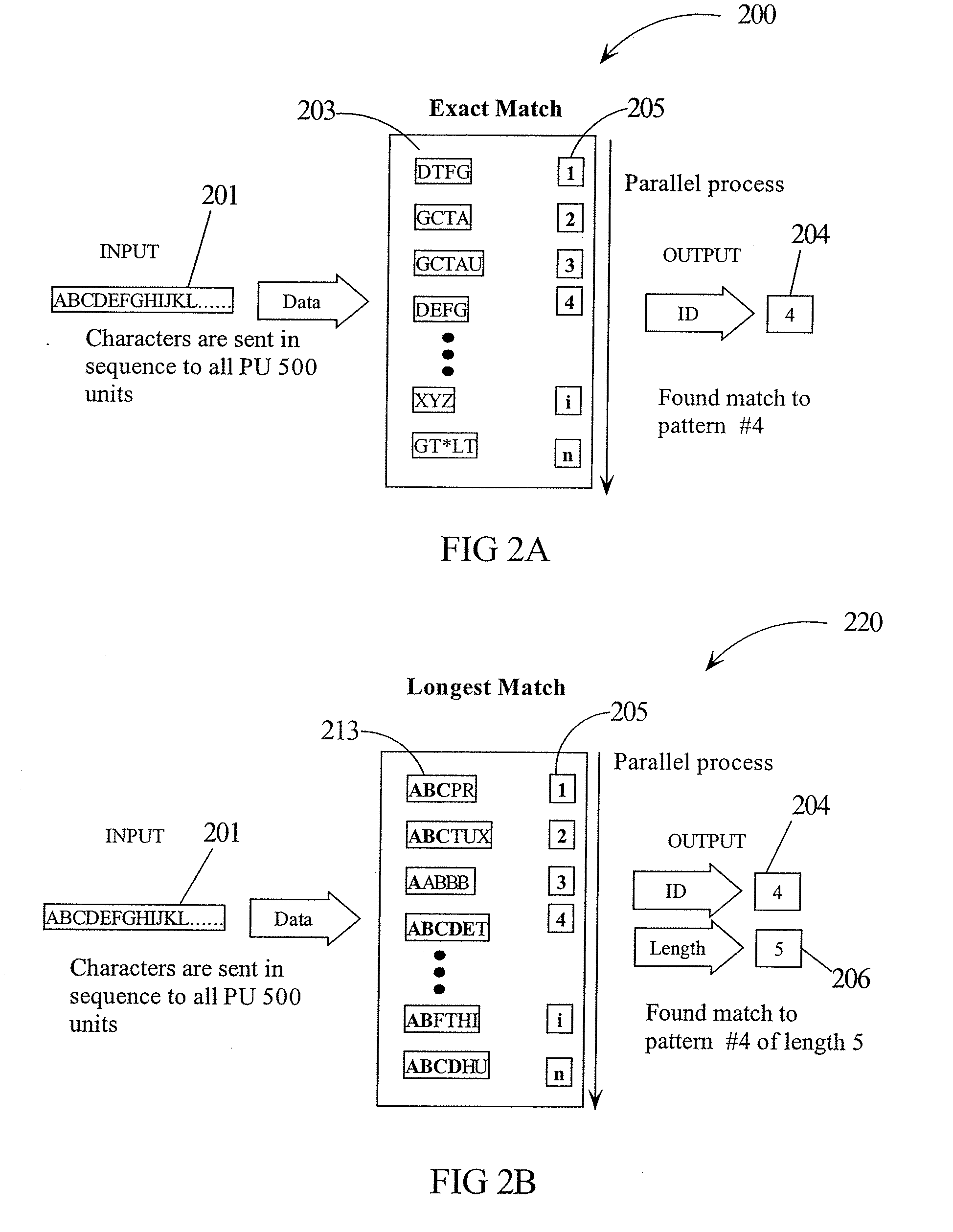
InactiveUS20070150623A1Character and pattern recognitionInput/output processes for data processingData matchingData stream
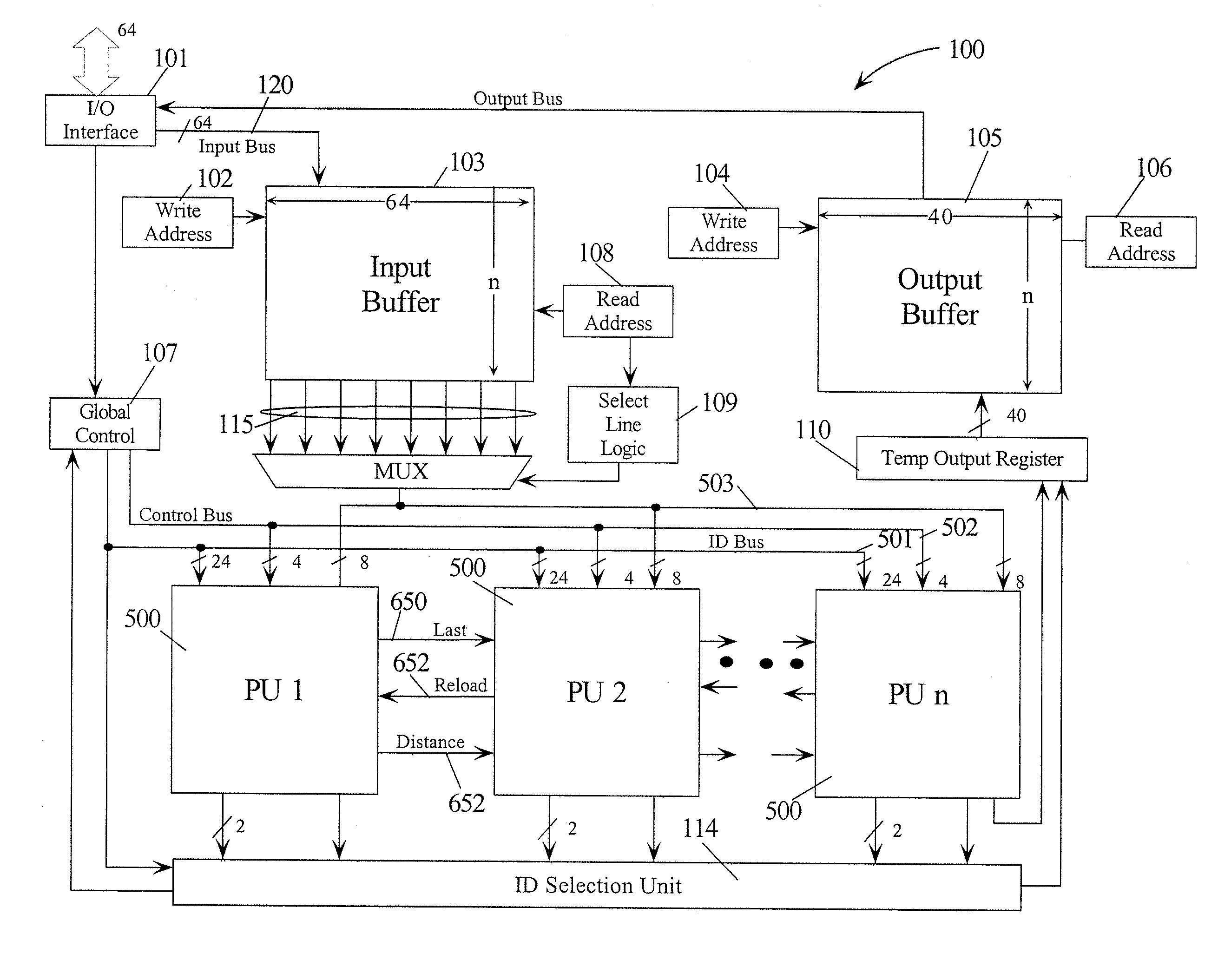
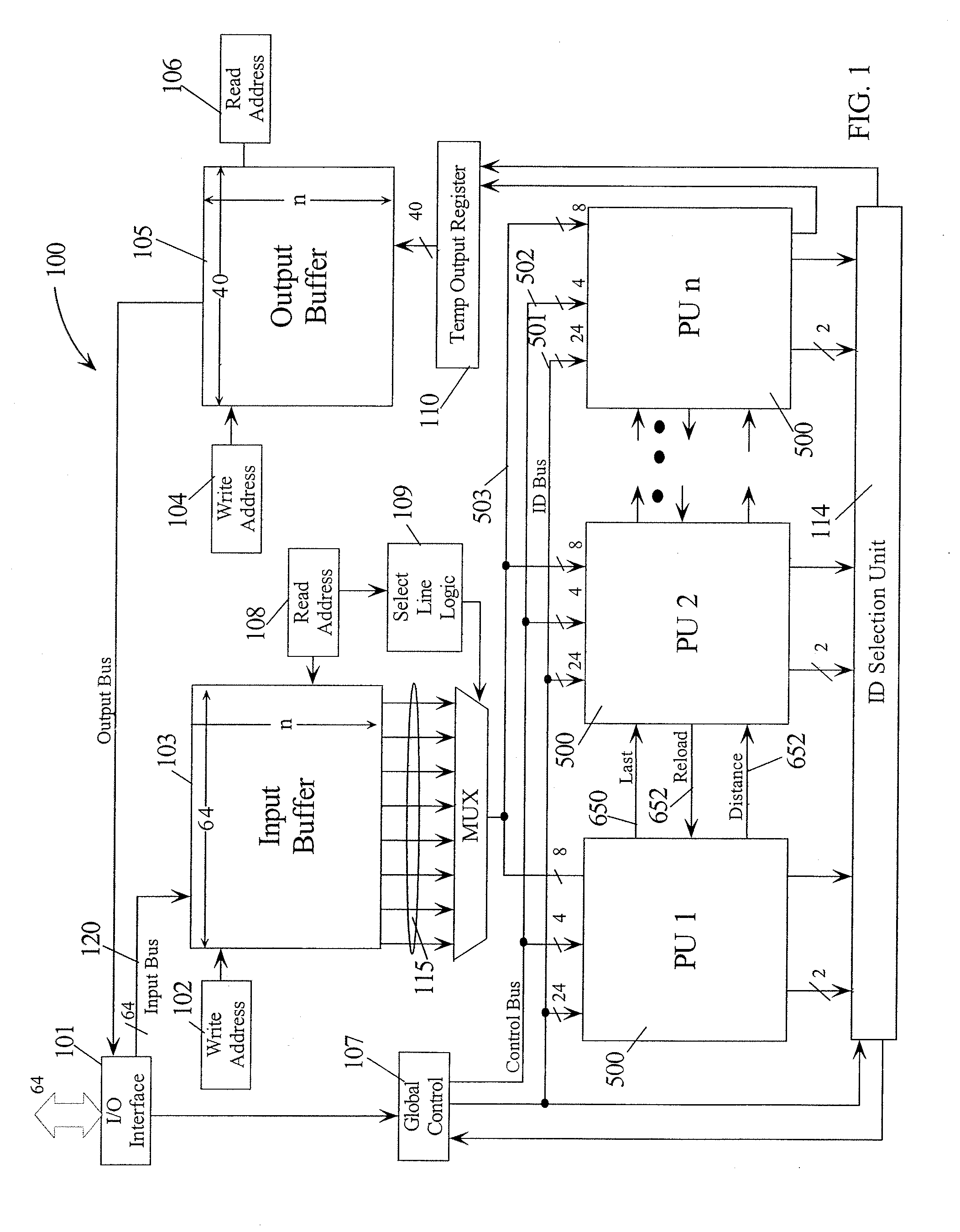
A parallel pattern detection engine (PPDE) comprise multiple processing units (PUs) customized to do various modes of pattern recognition. The PUs are loaded with different patterns and the input data to be matched is provided to the PUs in parallel. Each pattern has an Opcode that defines what action to take when a particular data in the input data stream either matches or does not match the corresponding data being compared during a clock cycle. Each of the PUs communicate selected information so that PUs may be cascaded to enable longer patterns to be matched or to allow more patterns to be processed in parallel for a particular input data stream.
Owner:KRAVEC KERRY A +3
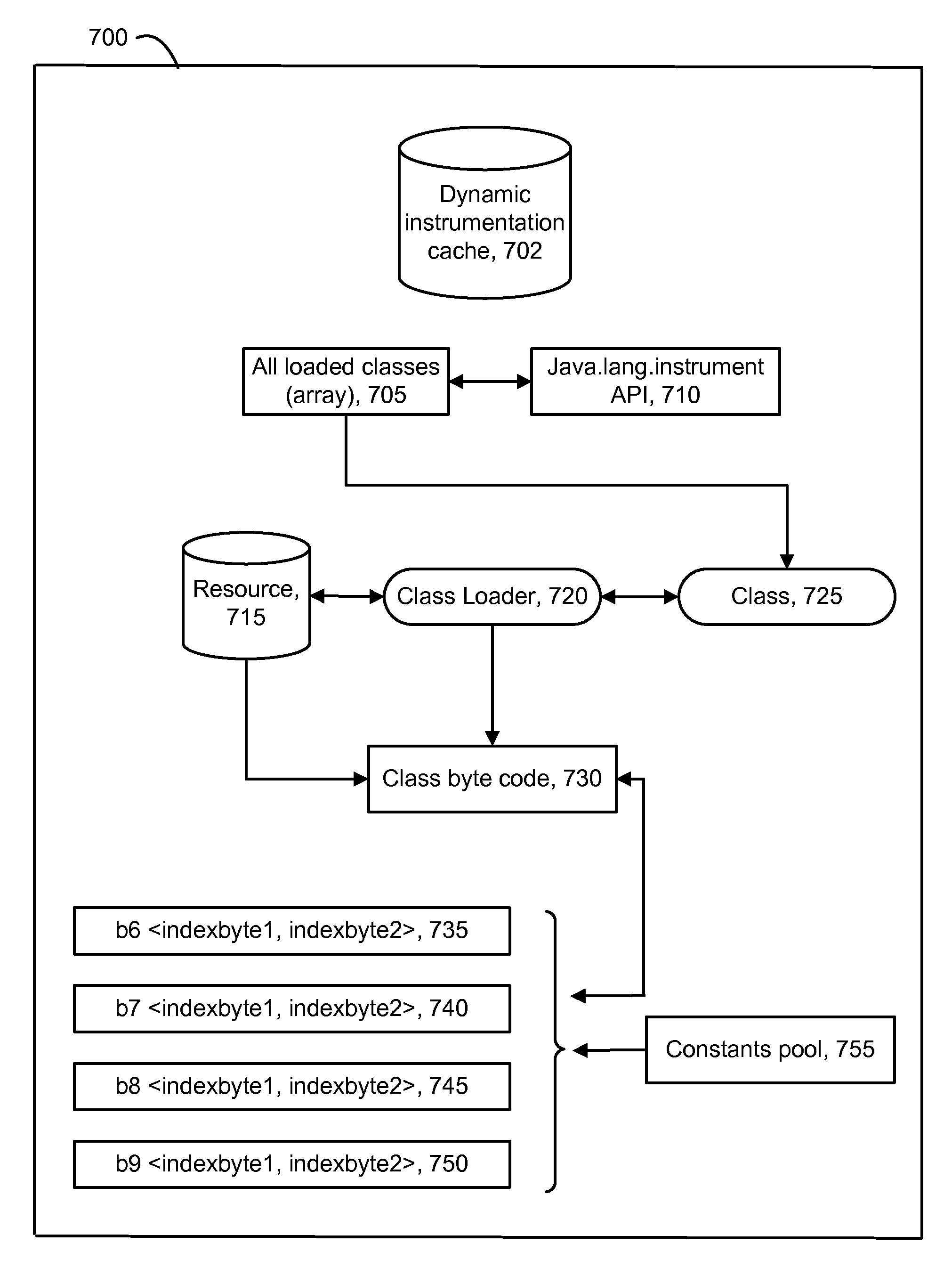
Detection of method calls to streamline diagnosis of custom code through dynamic instrumentation
A technique for analyzing software in which un-instrumented components can be discovered and dynamically instrumented during a runtime of the software. Initially, an application configured with a baseline set of instrumented components such as methods. As the application runs, performance data is gathered from the instrumentation, and it may be learned that the performance of some methods is an issue. To analyze the problem, any methods which are callable from a method at issue are discovered by inspecting the byte code of loaded classes in a JAVA Virtual Machine (JVM). Byte code of the class is parsed to identify opcodes which invoke byte code to call other methods. An index to an entry in a constants pool table is identified based on an opcode. A decision can then be made to instrument and / or report the discovered methods.
Owner:CA TECH INC
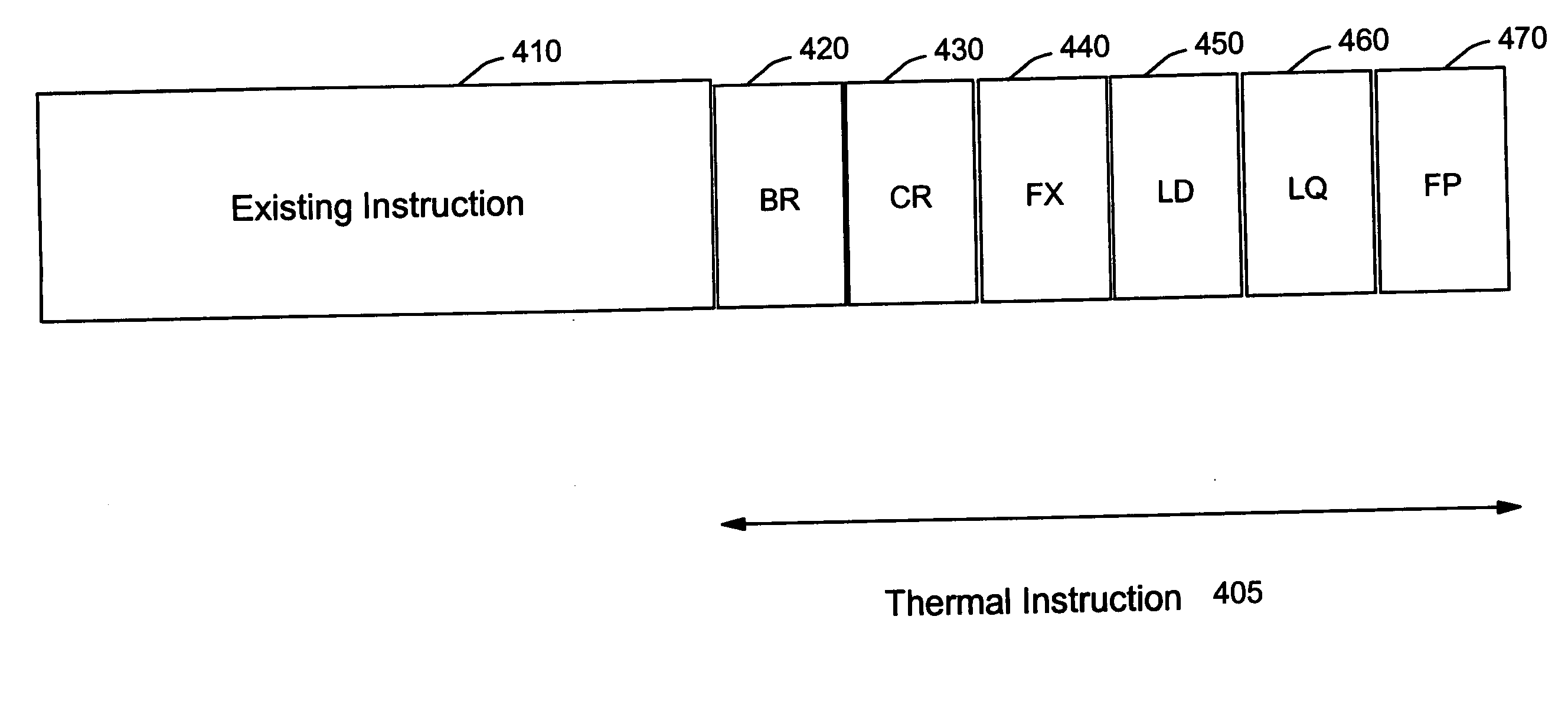
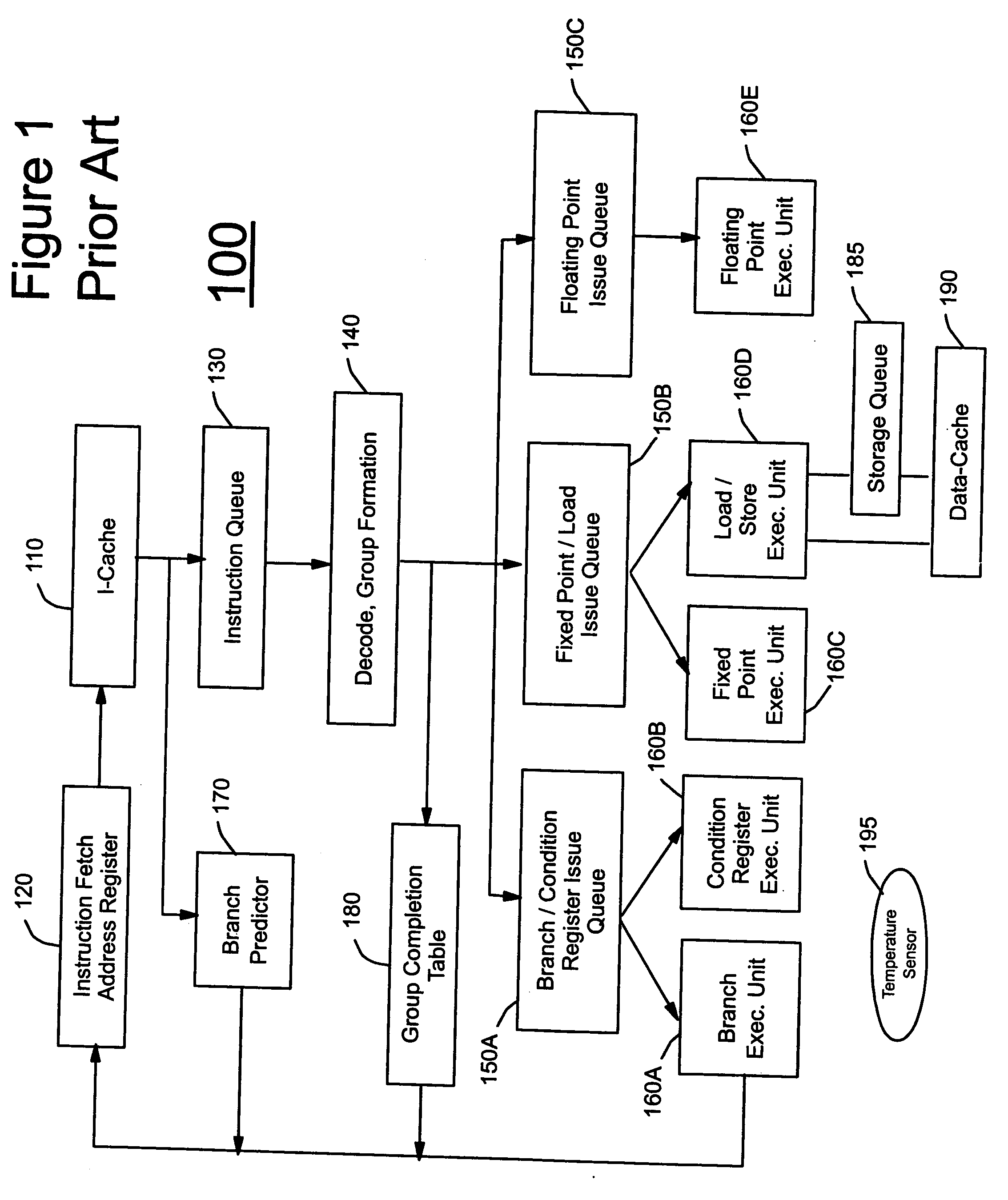
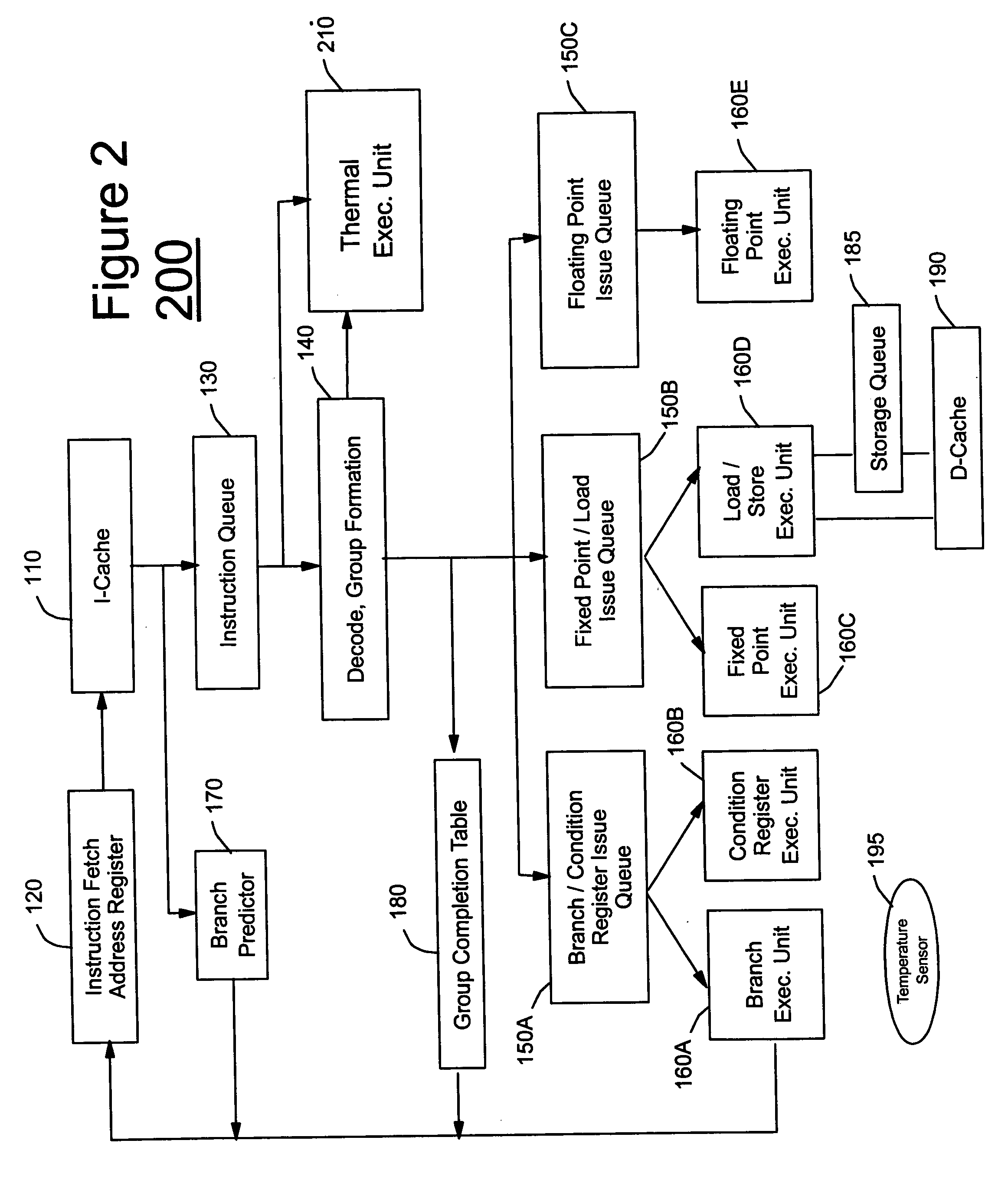
Instruction set with thermal opcode for high-performance microprocessor, microprocessor, and method therefor
InactiveUS20060101289A1Avoid problemsImprove protectionEnergy efficient ICTInstruction analysisHeat loadInstruction set
Owner:IBM CORP
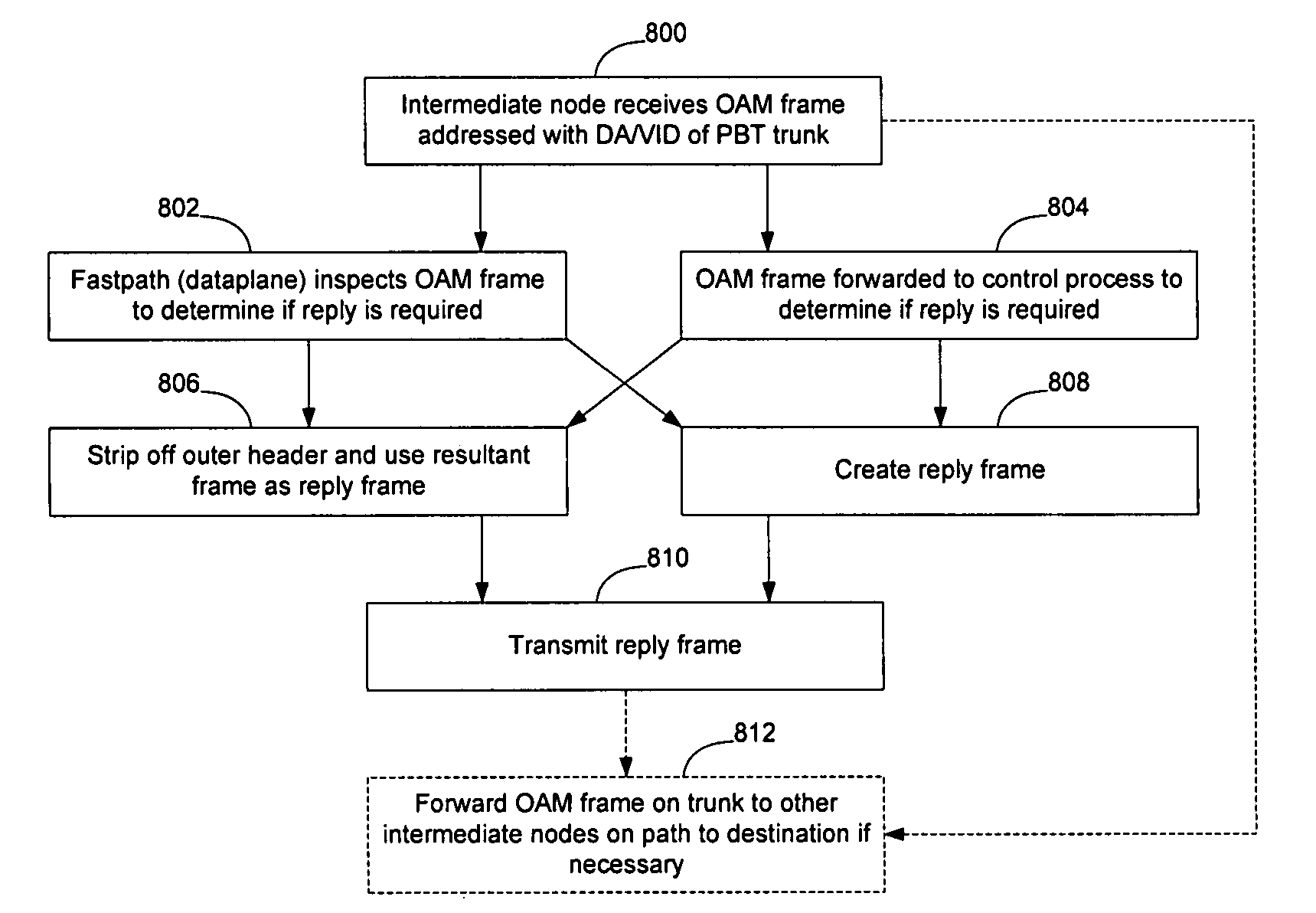
Ethernet OAM at intermediate nodes in a PBT network
OAM may be implemented at an intermediate node on a PBT trunk in an Ethernet network by causing OAM frames to be addressed to the PBT trunk endpoint but causing the OAM frames to carry an indicia (Ether-type, OpCode, TLV value or combination of these and other fields) that the OAM frames are intended to be used for intermediate node OAM functions. The Ether-type, OpCode, and TLV values may be standardized values, or vendor specific values such as OpCode=51 or TLV=31 may be used. Addressing the OAM frames to the PBT trunk end point enables the OAM frames to follow the PBT trunk through the network. The OAM indicia signals to the intermediate nodes that the OAM frames are intended to be used to perform an intermediate node OAM function. The OAM frames may contain reverse trunk information to prevent the intermediate nodes from being required to store correlation between forward and reverse PBT trunks.
Owner:RPX CLEARINGHOUSE
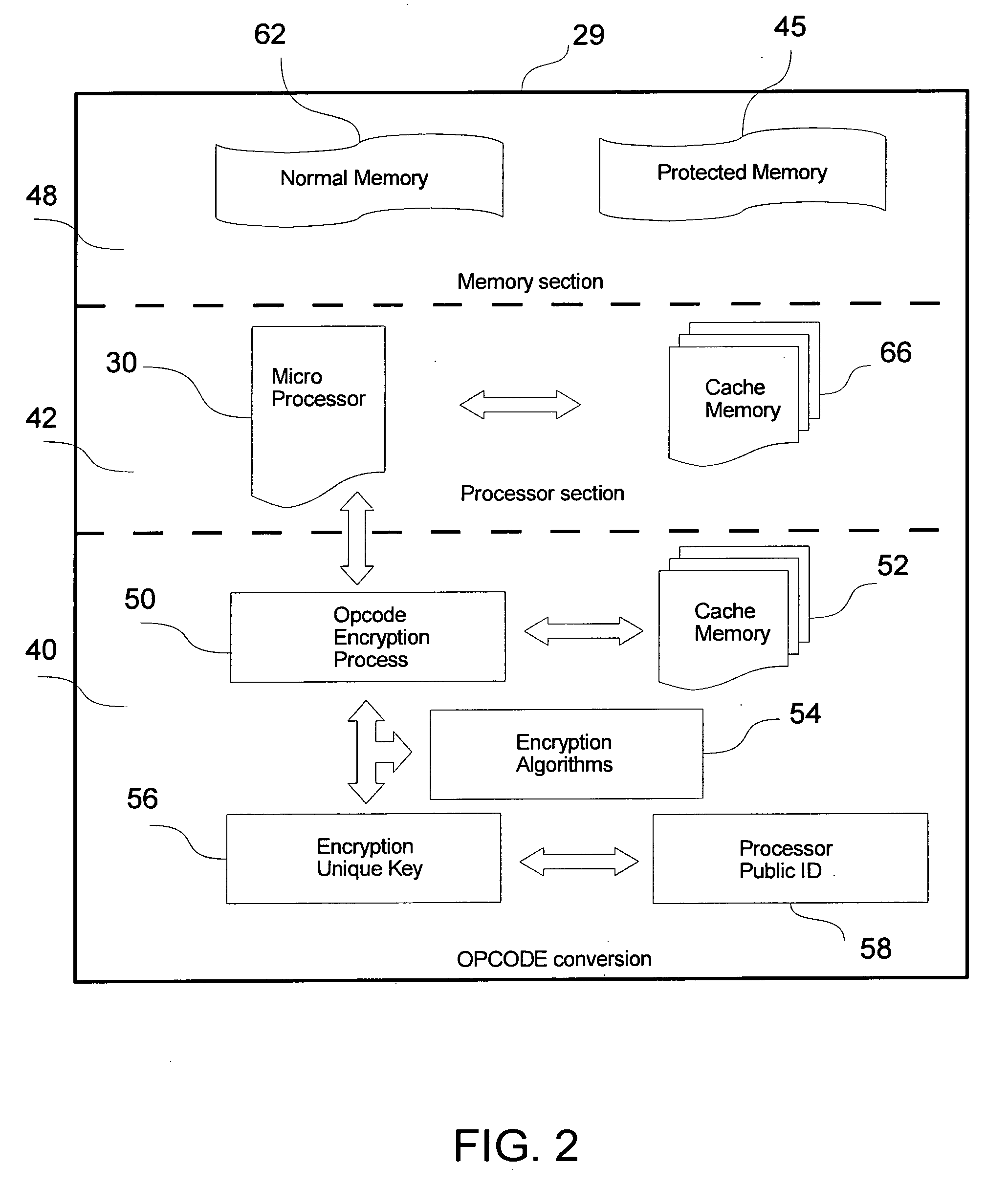
Secure microprocessor and method
InactiveUS20070074046A1Avoid accessUnauthorized memory use protectionHardware monitoringData setSource code
A method and reconfigurable computer architecture protect binary opcode, or other data and instructions by providing an encryption capability integrated into an instruction issue unit of a protected processor. Opcodes are encrypted at their source, and encrypted opcodes are then delivered to the CPU and decrypted “inside” the CPU. Access into the CPU is prevented. Each form of code or data selected for protection is protected from unauthorized viewing or access. Commonly, the binary executable, or object, code is selected for protection. However, protected information could also include source code or data sets or both. Encrypting opcodes will result in making unique opcodes for each processor. Encryption keys and hidden opcode algorithms provide further security.
Owner:CZAJKOWSKI DAVID R +1
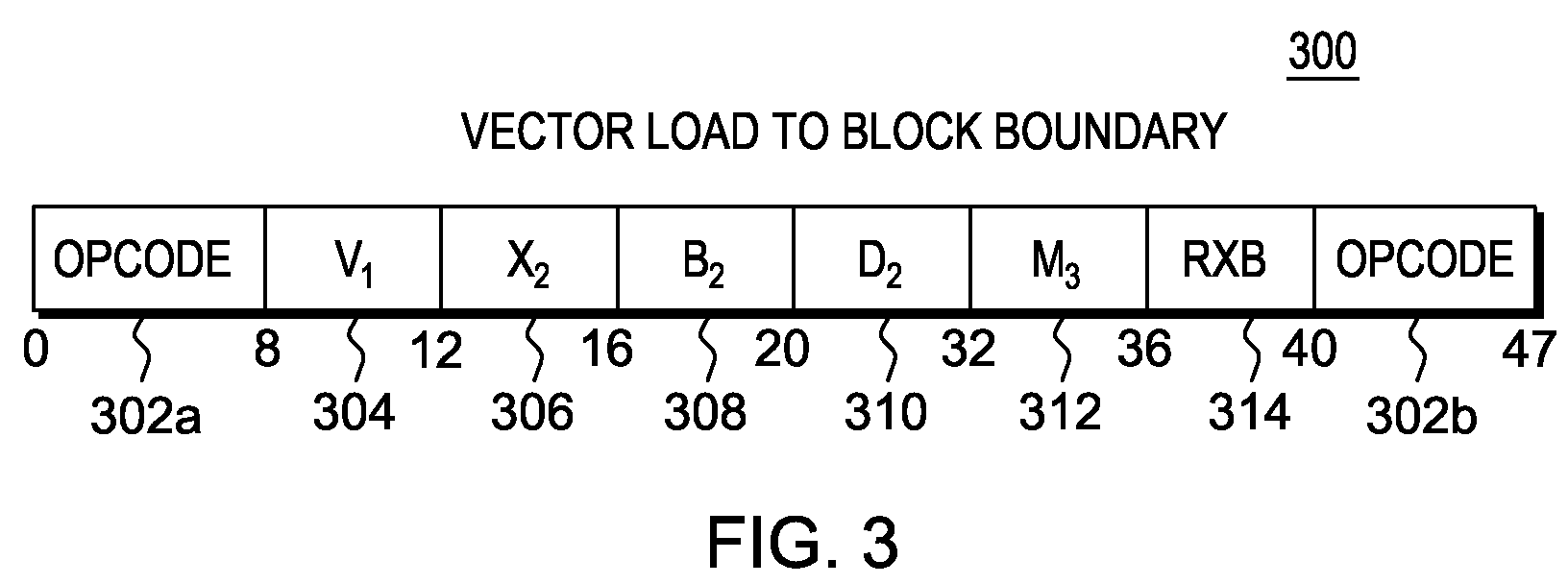
Instruction to load data up to a specified memory boundary indicated by the instruction
ActiveUS20130246764A1Quick conversionAccurate operationRegister arrangementsInstruction analysisProcessor registerParallel computing
A Load to Block Boundary instruction is provided that loads a variable number of bytes of data into a register while ensuring that a specified memory boundary is not crossed. The boundary may be specified a number of ways, including, but not limited to, a variable value in the instruction text, a fixed instruction text value encoded in the opcode, or a register based boundary.
Owner:IBM CORP
Methods and apparatus for extending mac control messages in epon
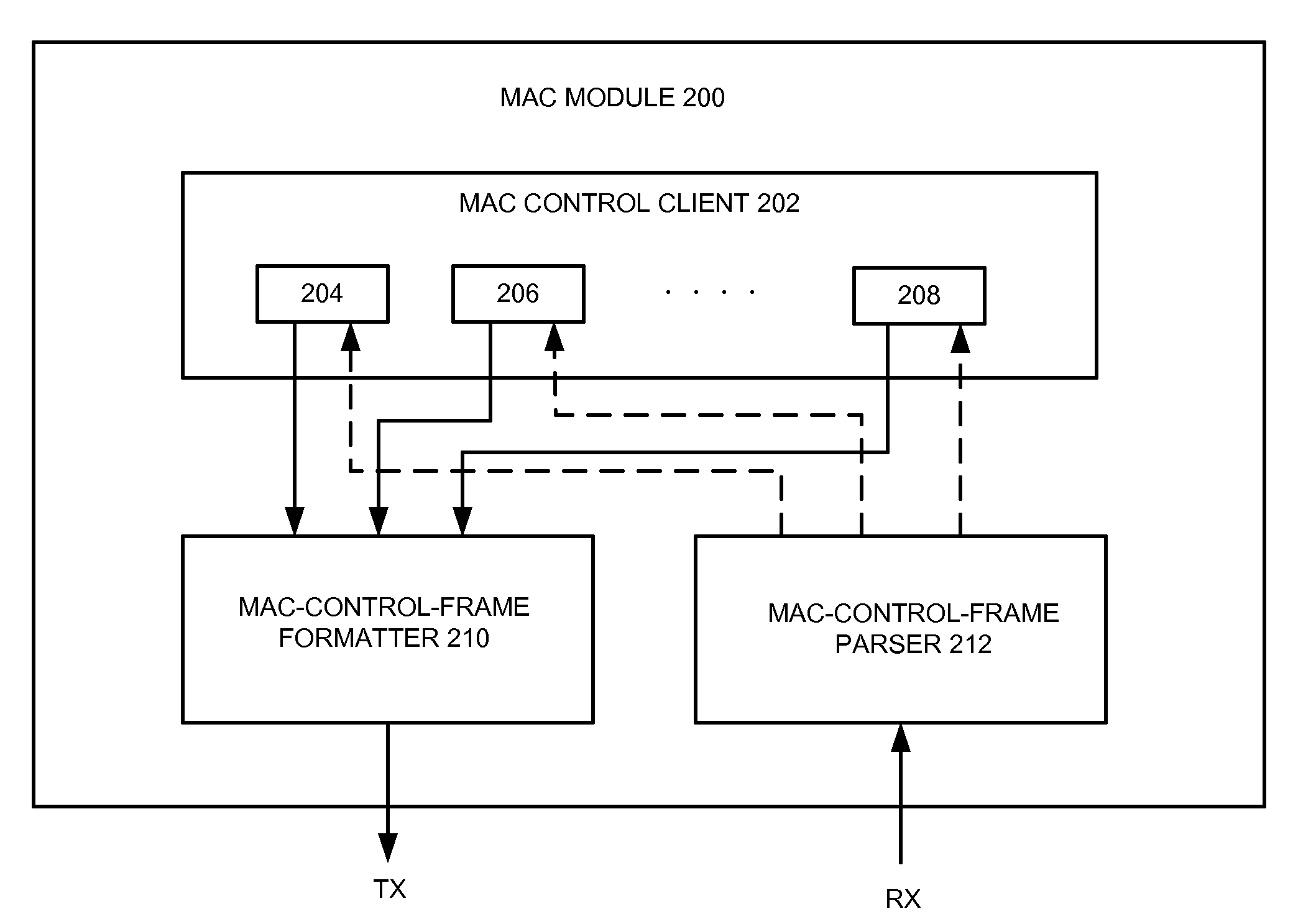
ActiveUS20100239252A1Easy to implementEasy to operateMultiplex system selection arrangementsSynchronisation arrangementAction CodeUnique identifier
One embodiment provides a media access control (MAC) module facilitating operations of an Ethernet passive optical network (EPON). The MAC module includes a frame formatter configured to generate a MAC control frame. The generated MAC control frame includes at least one of: an organizationally unique identifier (OUI) field, an OUI-specific operation code (opcode) field, and a number of fields associated with the OUI-specific opcode. Transmission of the MAC control frame facilitates realization of an EPON function based on the fields associated with the OUI-specific opcode.
Owner:AVAGO TECH INT SALES PTE LTD
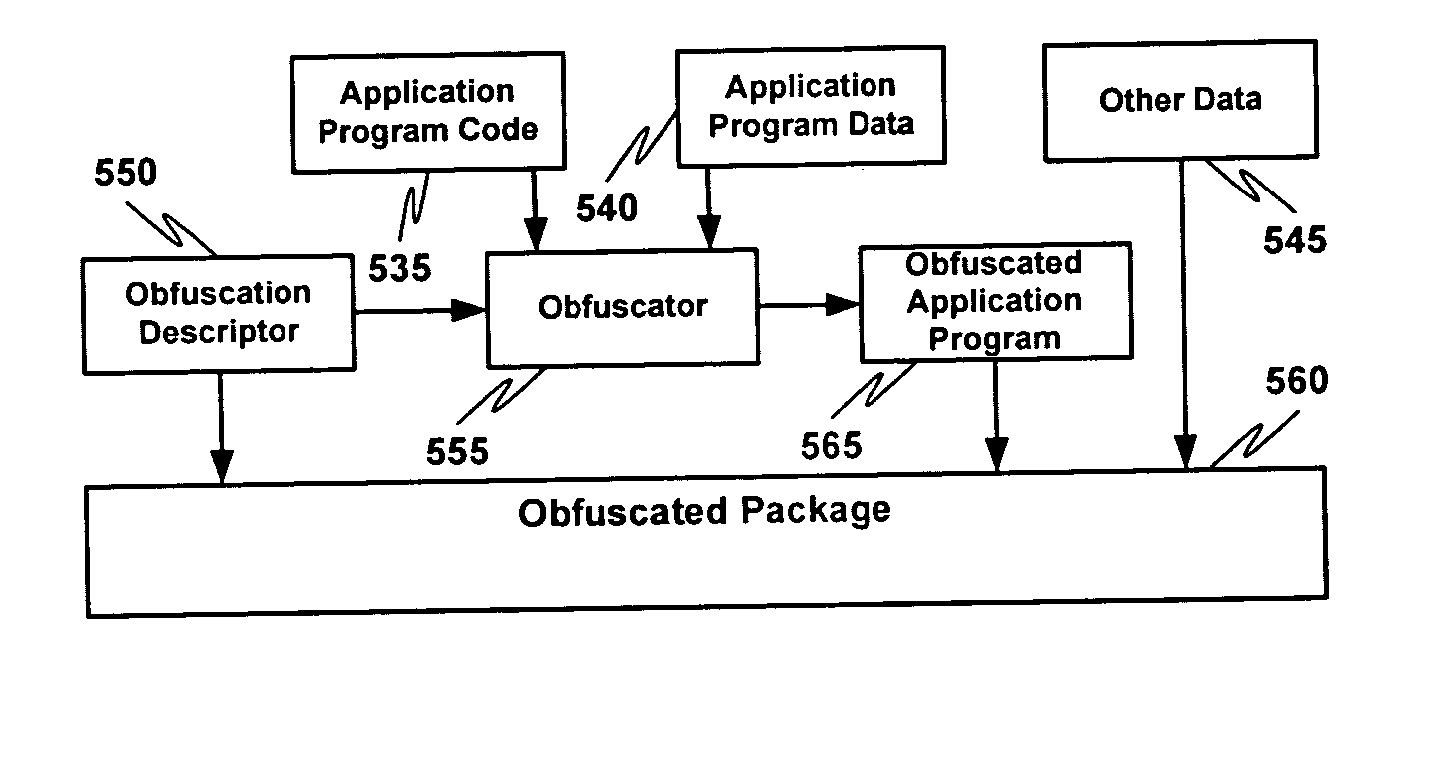
Multiple instruction dispatch tables for application program obfuscation
ActiveUS20050071652A1Key distribution for secure communicationDigital data processing detailsProgram instructionInstruction set
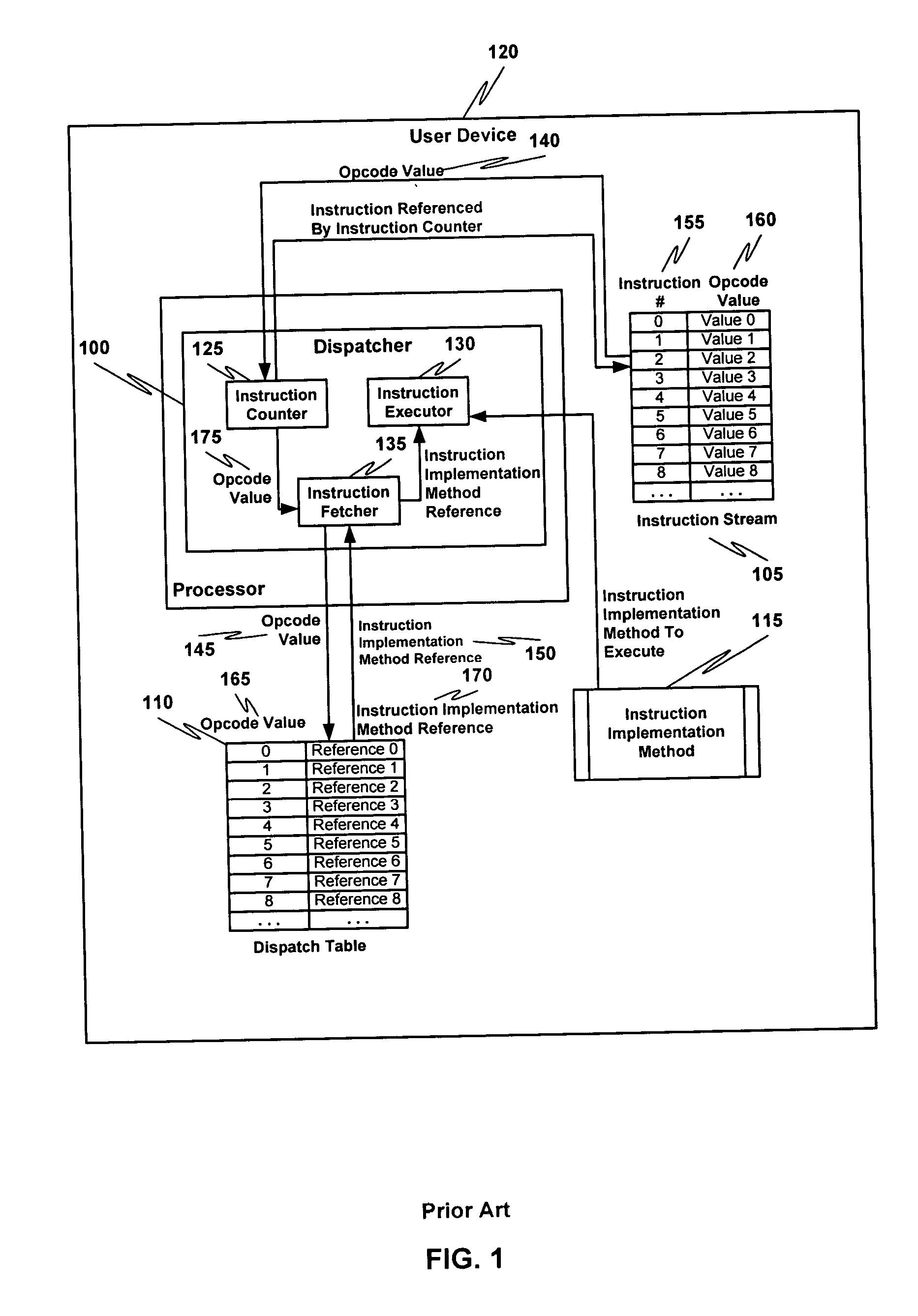
Obfuscating an application program comprises reading an application program comprising code, determining multiple dispatch tables associated with the application program, transforming the application program into application program code configured to utilize the dispatch tables during application program execution to determine the location of instruction implementation methods to be executed based at least in part on a current instruction counter value, and sending the application program code. Executing an obfuscated application program comprises receiving an obfuscated application program comprising at least one instruction opcode value encoded using one of multiple instruction set opcode value encoding schemes, receiving an application program instruction corresponding to a current instruction counter value, selecting an instruction dispatch table based at least in part on the current instruction counter value, and executing the application program instruction using the selected instruction dispatch table.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com