Secure microprocessor and method
a microprocessor and microprocessor technology, applied in the field of secure microprocessors and methods, can solve the problem that the cpu cannot install programs not encoded in the system, and achieve the effect of preventing access to the cpu
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
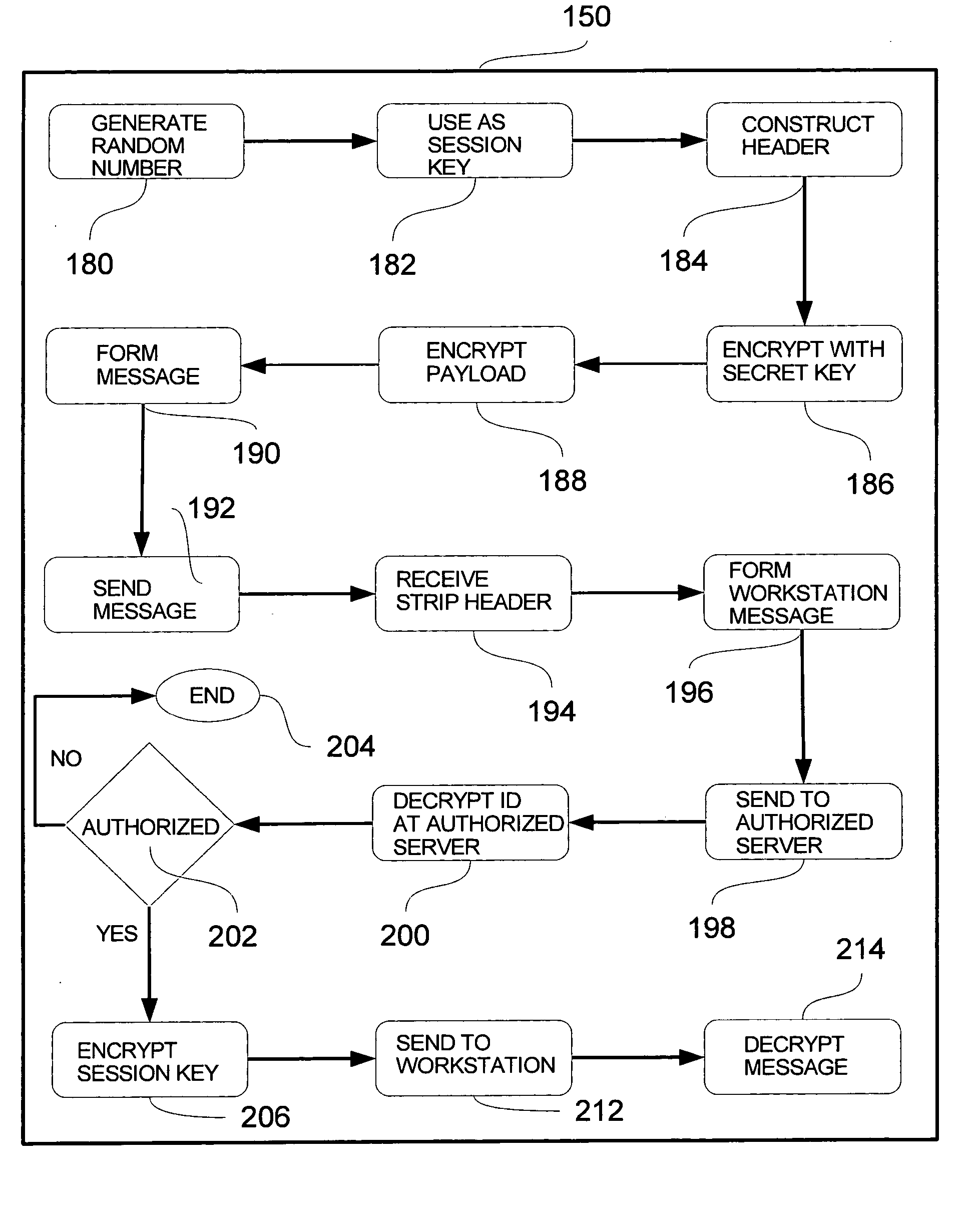
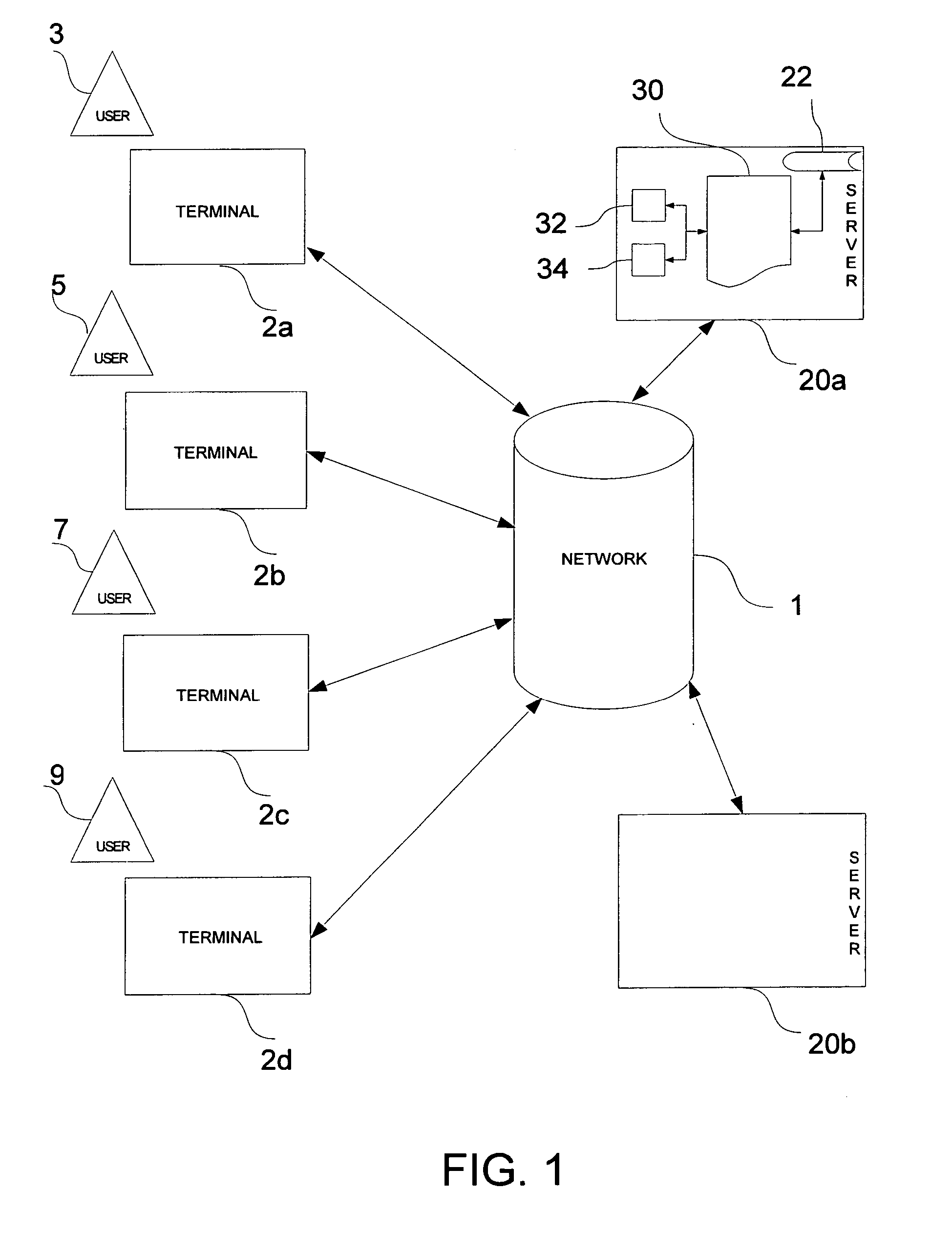
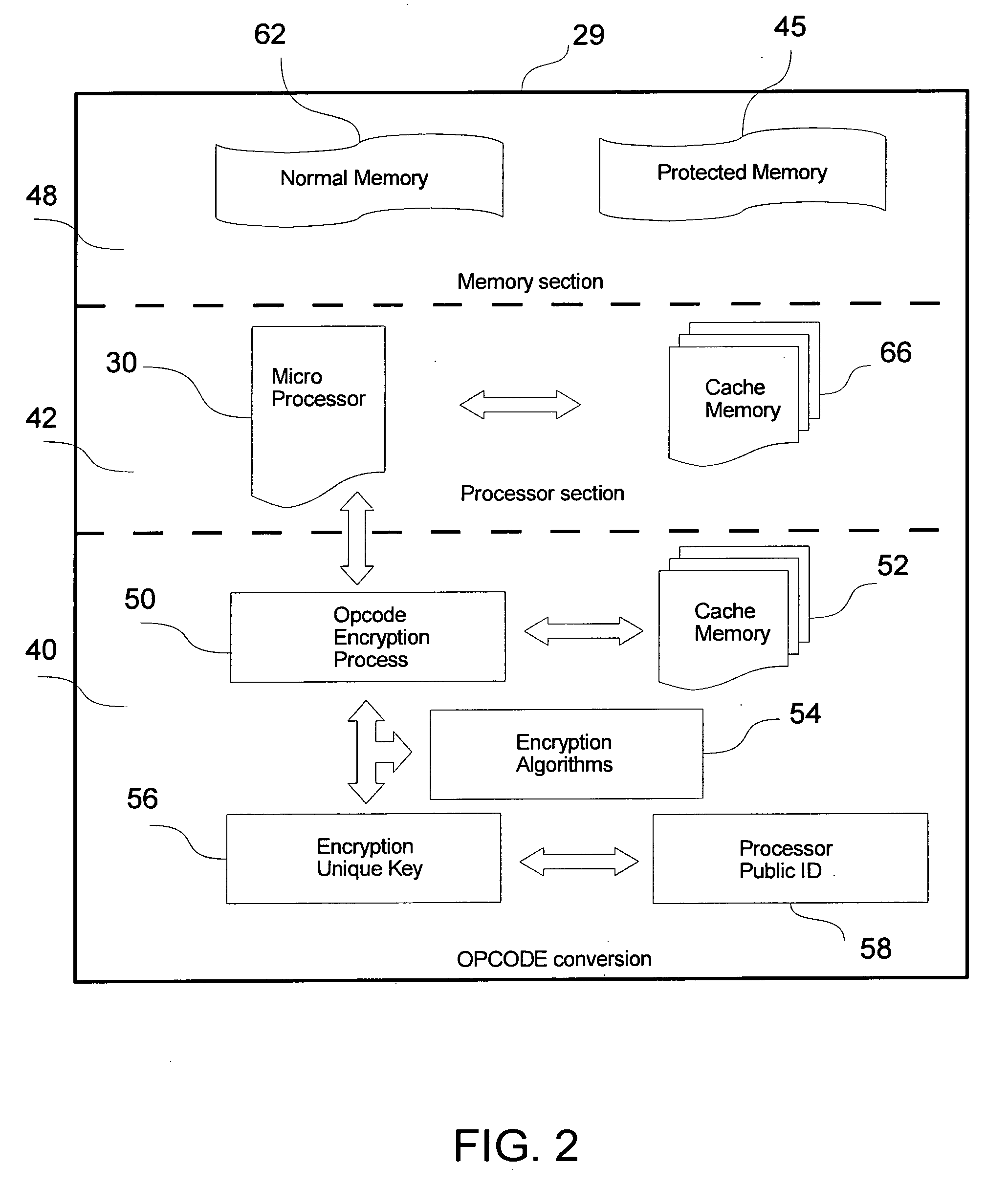
[0028] Embodiments of the present invention will provide for processors which can safely store code and which are protected from reverse engineering. Processors may also be programmed by code transmitted by a developer at a remote location, and software may be maintained by an administrator at a remote location. The protected processor may be made accessible to a user either on a users own server or via a hosted service accessed through the Internet or other network.
[0029] This is particularly significant in the context of reconfigurable computer architecture. A reconfigurable computing system compiles program source code to an intermediate code suitable for programming runtime processors or reconfigurable field-programmable gate arrays, enabling a software design to be implemented directly in hardware. Since many different hardware-implemented programs can potentially perform in parallel, a reconfigurable computing system can be considered an advanced parallel processing architect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com