Patents
Literature
680results about How to "Eliminate operation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method for separating air flows in a cooling system
InactiveUS6034873AGreat and great efficiencyImprove efficiencyHeat exchange apparatusCooling/ventilation/heating modificationsMulti materialEngineering
A cooling system and method employing separation chutes and baffles is disclosed. The separation chutes separate the cooled air descending from a heat exchanger positioned above heat-generating equipment in an equipment room from heated air ascending from the heat-generating equipment. Separation of the airflows reduces turbulence and increases cooling efficiencies. The separation chutes are made of a variety of materials, both rigid and flexible, for a variety of applications.
Owner:VERTIV CORP
Panel Array
ActiveUS20100066631A1Low insertion lossEliminate needAntenna arrays manufactureModular arraysHemt circuitsChipset
A mixed-signal, multilayer printed wiring board fabricated in a single lamination step is described. The PWB includes one or more radio frequency (RF) interconnects between different circuit layers on different circuit boards which make up the PWB. The PWB includes a number of unit cells with radiating elements and an RF cage disposed around each unit cell to isolate the unit cell. A plurality of flip-chip circuits are disposed on an external surface of the PWB and a heat sink can be disposed over the flip chip components.
Owner:RAYTHEON CO
Method and system for detecting wireless access devices operably coupled to computer local area networks and related methods
InactiveUS7440434B2Easy to usePrevent unauthorized wireless accessMemory loss protectionError detection/correctionAir spaceReal-time computing
Owner:ARISTA NETWORKS
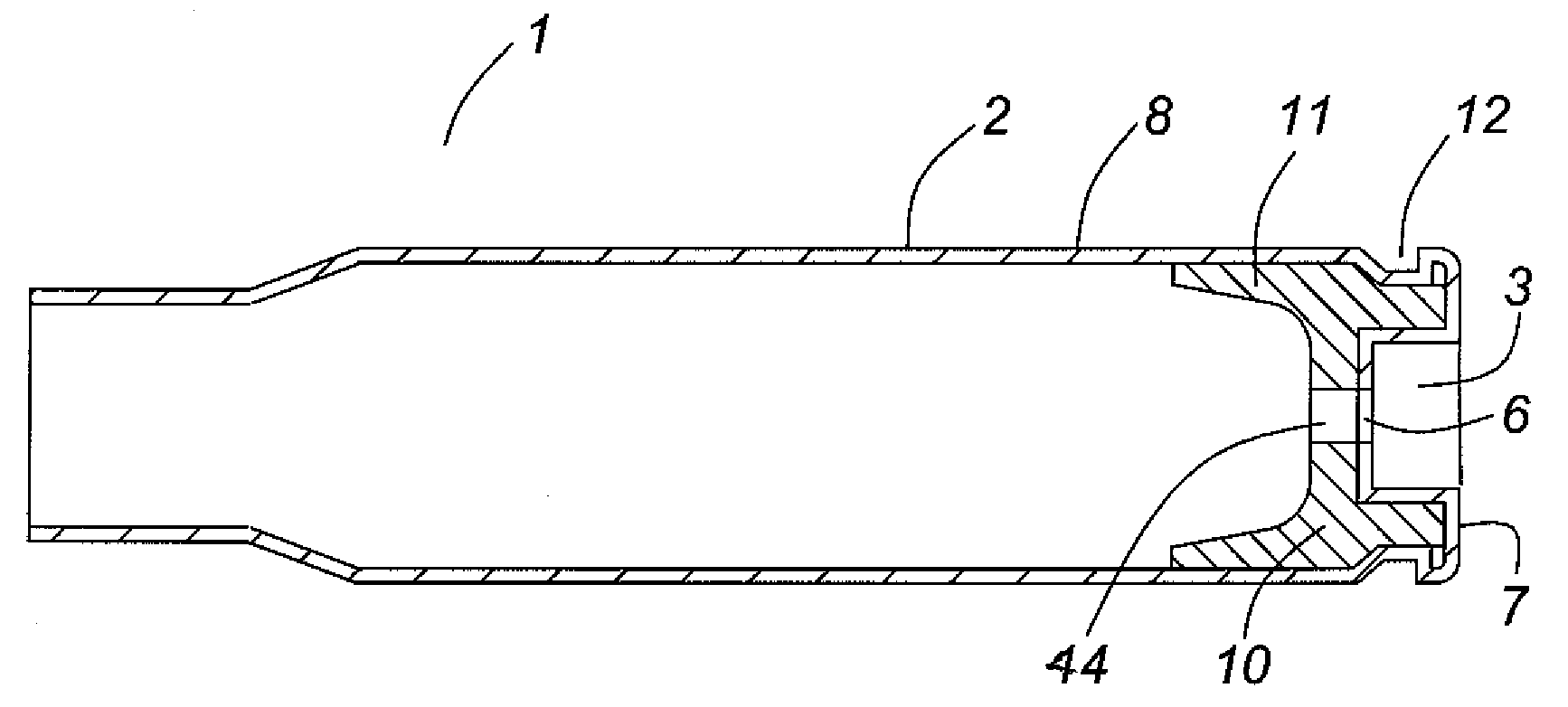
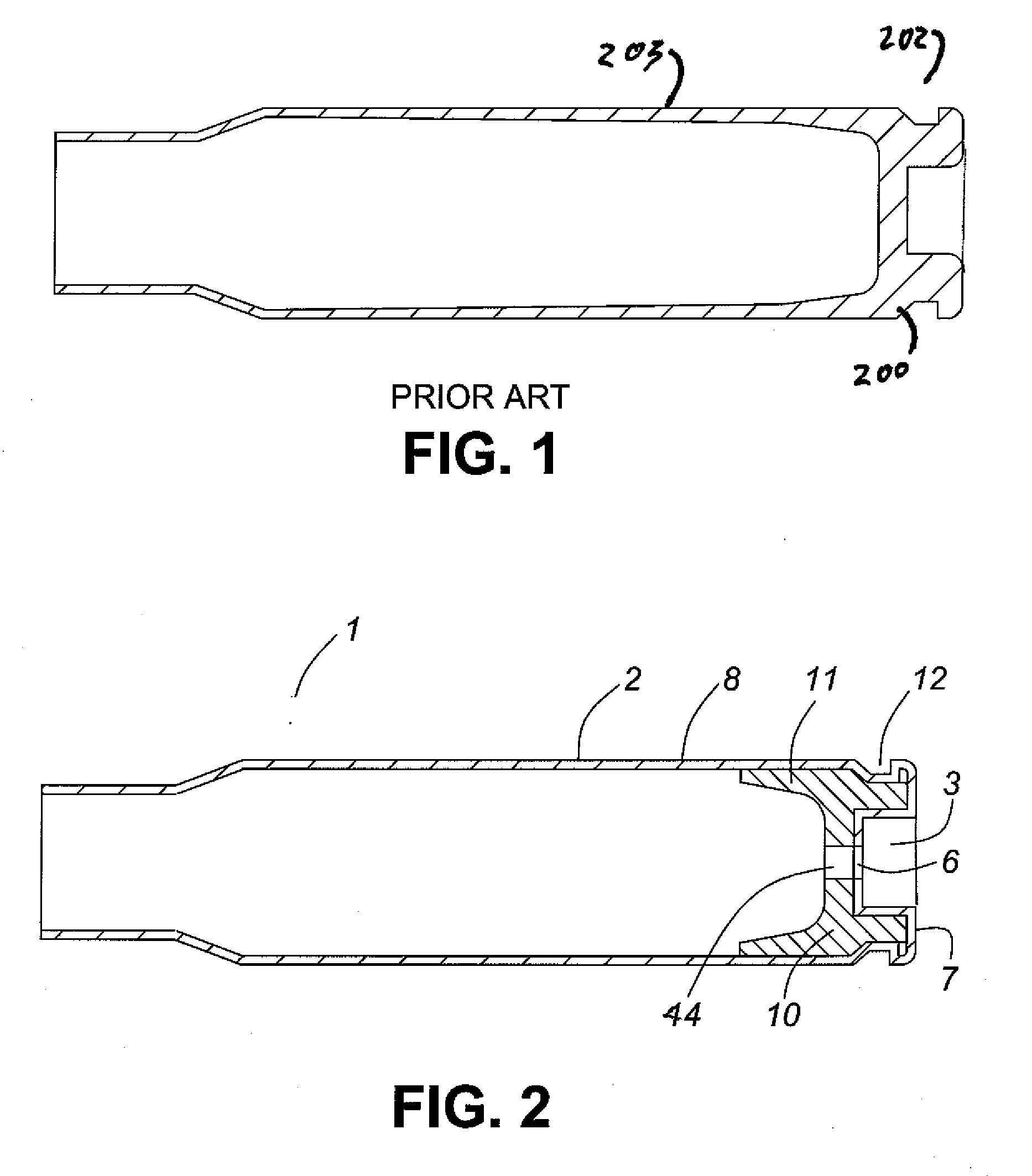
Thin walled, two component cartridge casing
A cartridge or ammunition casing is made of two components, one forming the outer casing sleeve and head end and the other comprising a plug seated within the head end to protect the outer casing material from propellant gases. The outer cylindrical sidewall and end panel of the casing may be made of a material selected from the group consisting of stainless steel, steel, pre-coated carbon steel, brass or brass-type alloys, aluminum, hardened aluminum alloys, and suitable polymeric plastic material such as nylon derivatives and VECTRA™. The inner plug may be made of a material selected from the group consisting of aluminum, brass, steel, stainless steel, and suitable polymeric materials.
Owner:TECH CORPORATION CO LTD
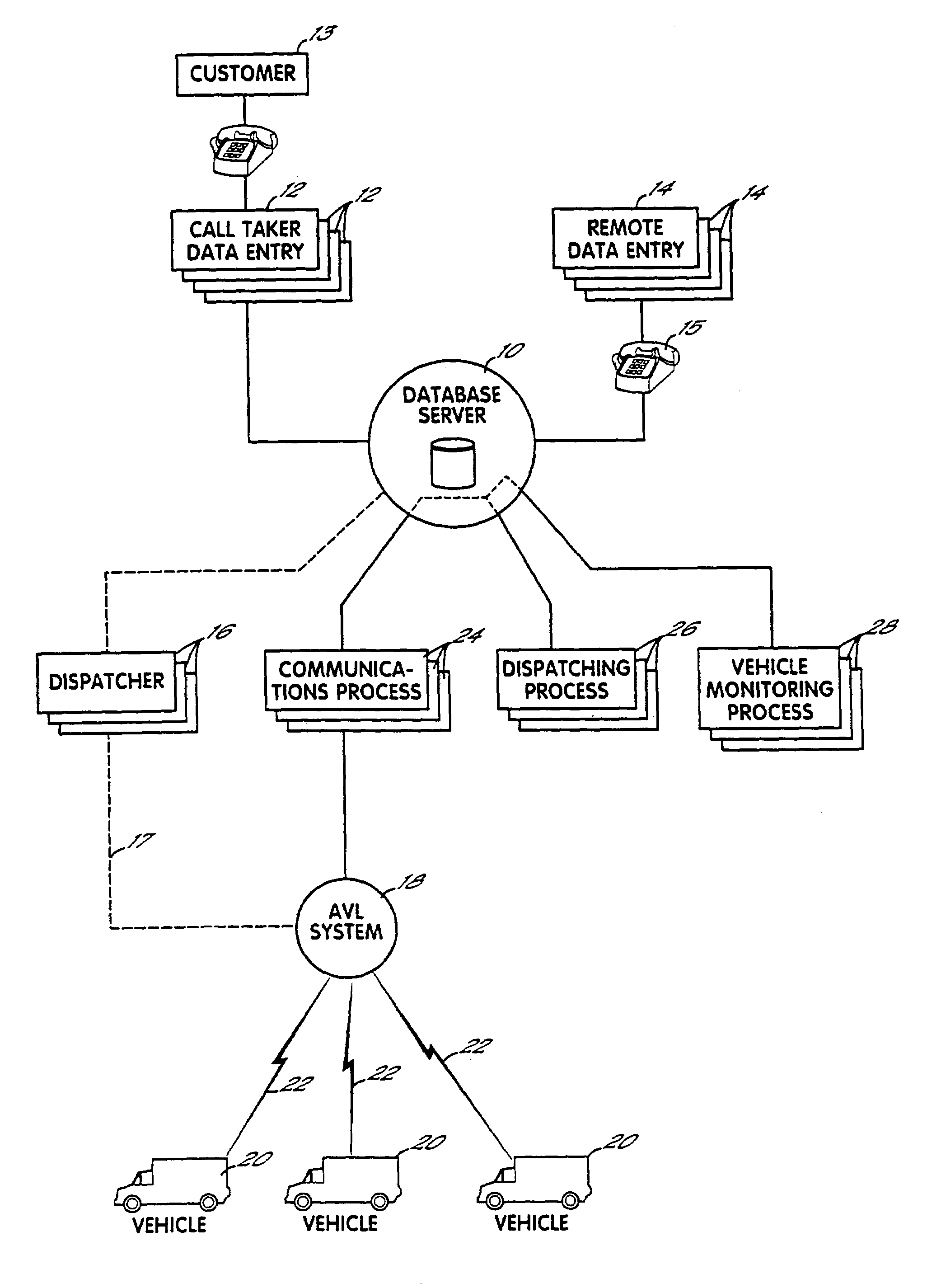
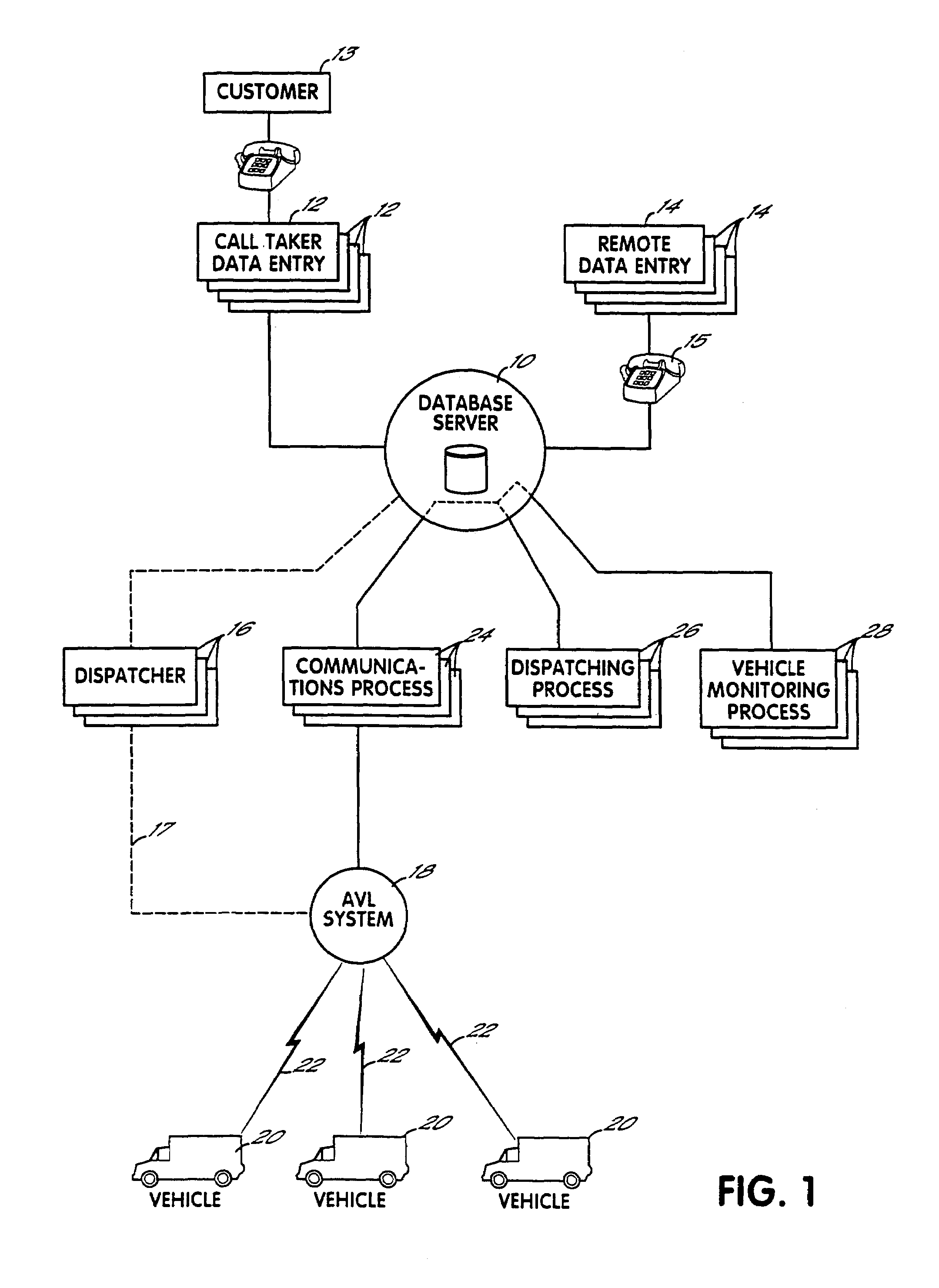
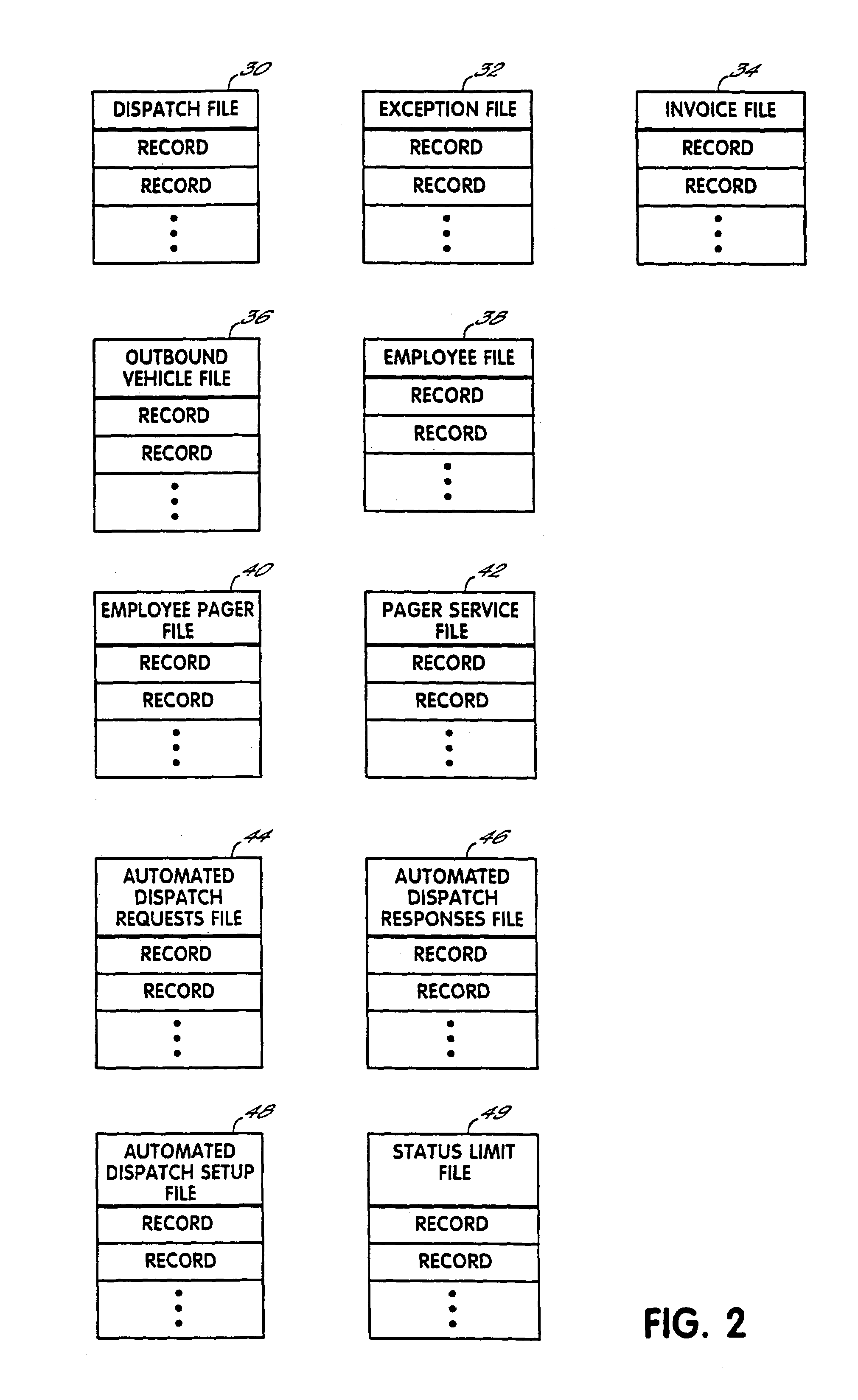
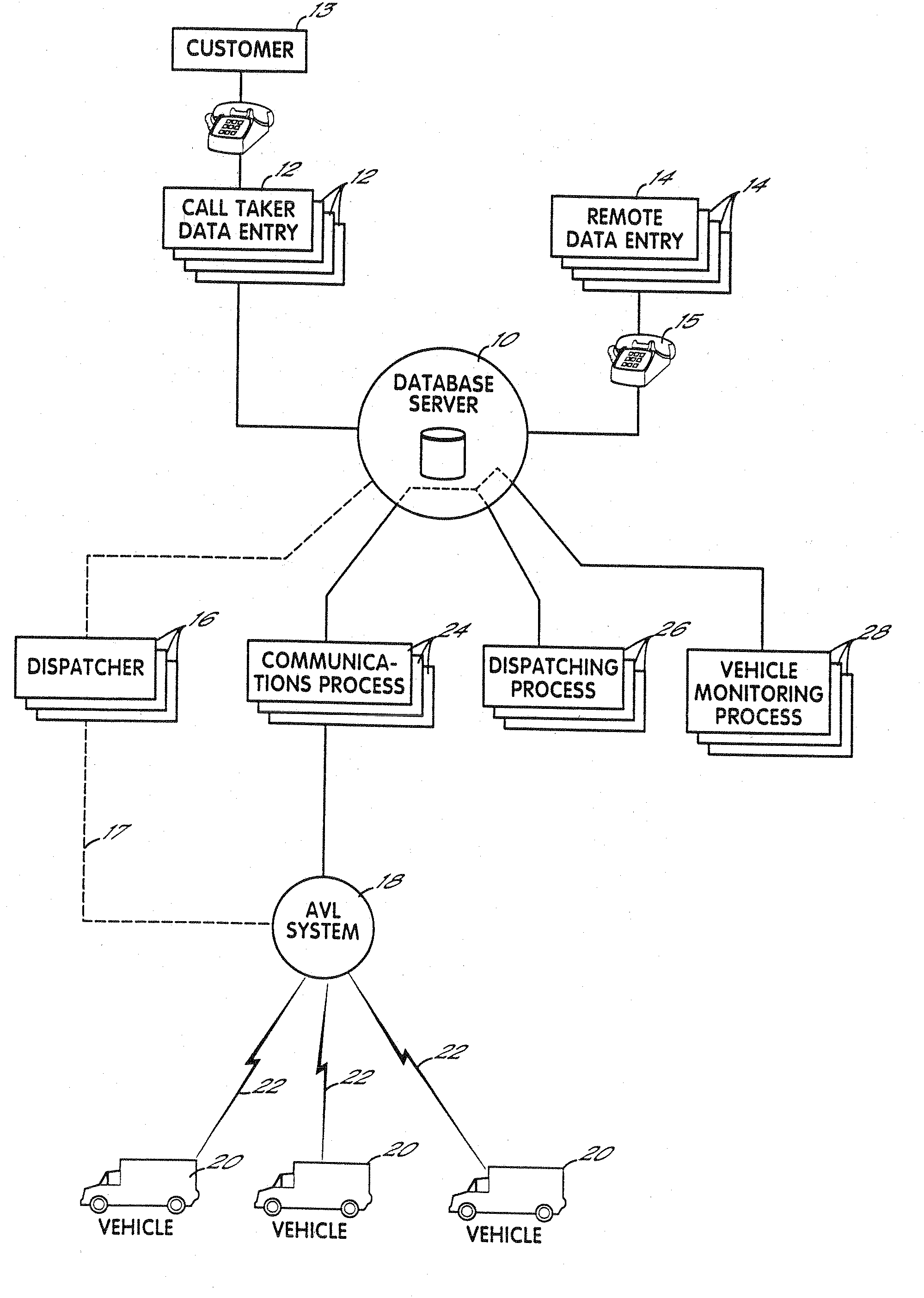
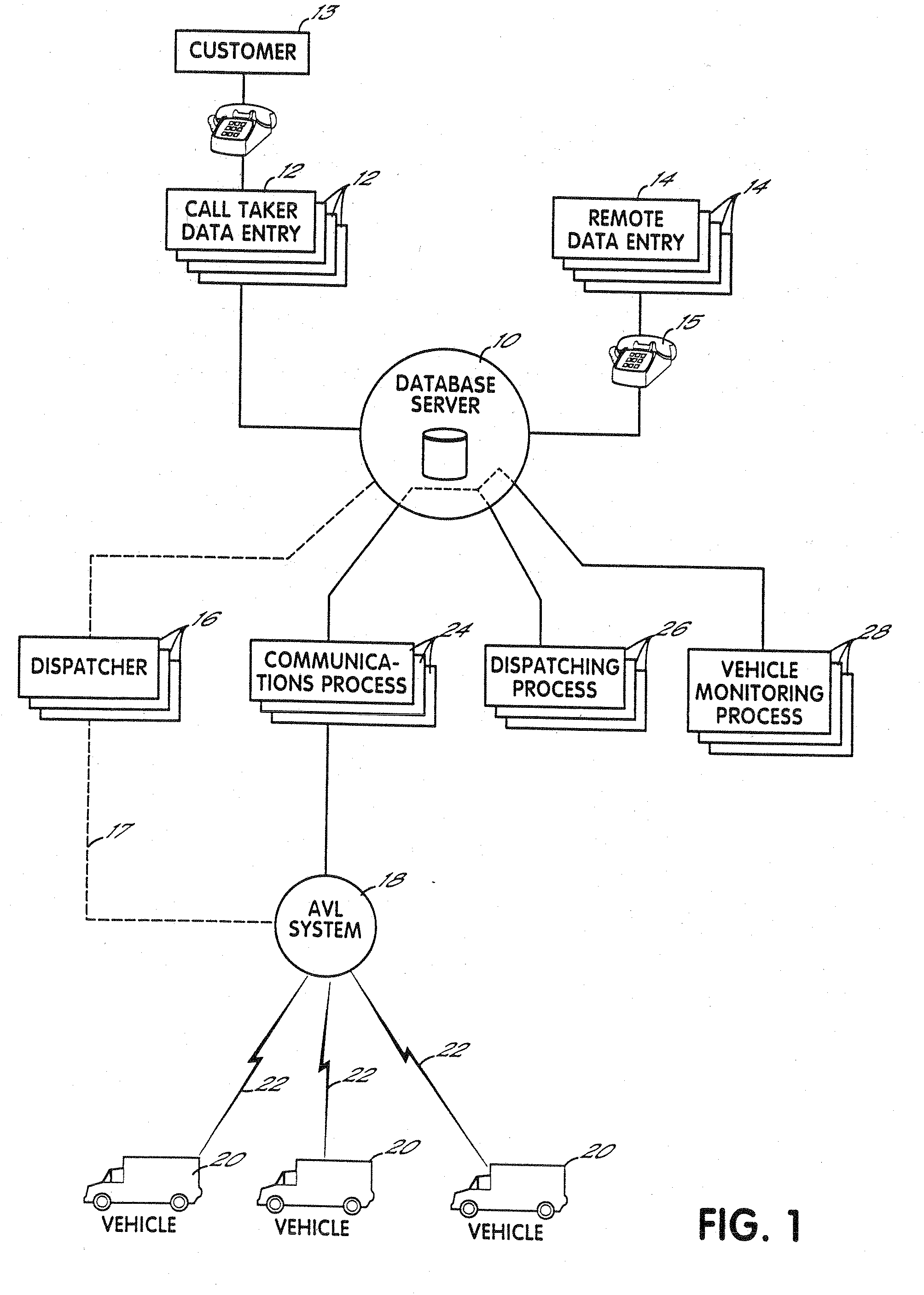
Fully automated vehicle dispatching, monitoring and billing
InactiveUS7113864B2Minimize future delayEasy to meetAnalogue computers for vehiclesAnalogue computers for trafficTransport engineeringFully automated
A system for controlling vehicles to provide transportation services without need for human intervention. A database stores records each documenting needed transportation services. Processing circuitry (which may be one or several networked computers) reviews these records, locates records indicating a need for immediate transportation service, and instructs vehicles to provide the service. The processing circuitry also monitors vehicle activities by reviewing the records, and automatically obtained vehicle activity information, to identify transportation services which are not being adequately provided, and refer these to human dispatchers for special attention. A variety of methods for obtaining and updating vehicle activity information are disclosed, as are various applications for the system.
Owner:TOTAL TECH CO LTD
Fluid processing apparatus
ActiveUS8535525B2Need is eliminated and minimisedEliminate needSettling tanks feed/dischargeDialysis systemsSterile waterEngineering
A machine is provided with a slot to releasably receive and retain a cartridge in which dialysis is effected. The machine is configured for supplying to the cartridge, at a controlled temperature and rate, sterile water for use in haemodialysis and is operable to maintain, in a sterile condition, residual water contained therein after completion of a haemodialysis treatment.
Owner:QUANTA DIALYSIS TECH LTD
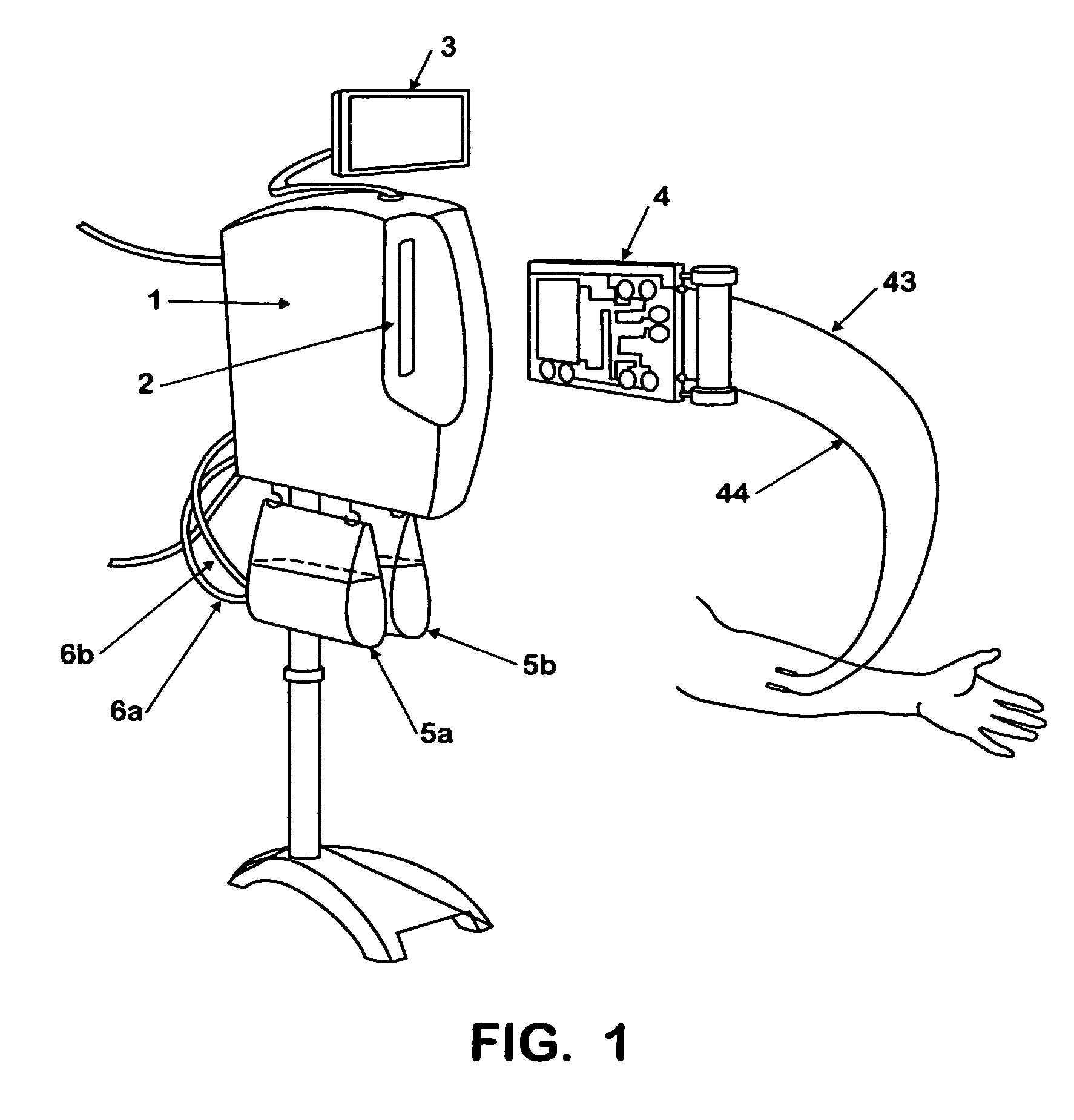
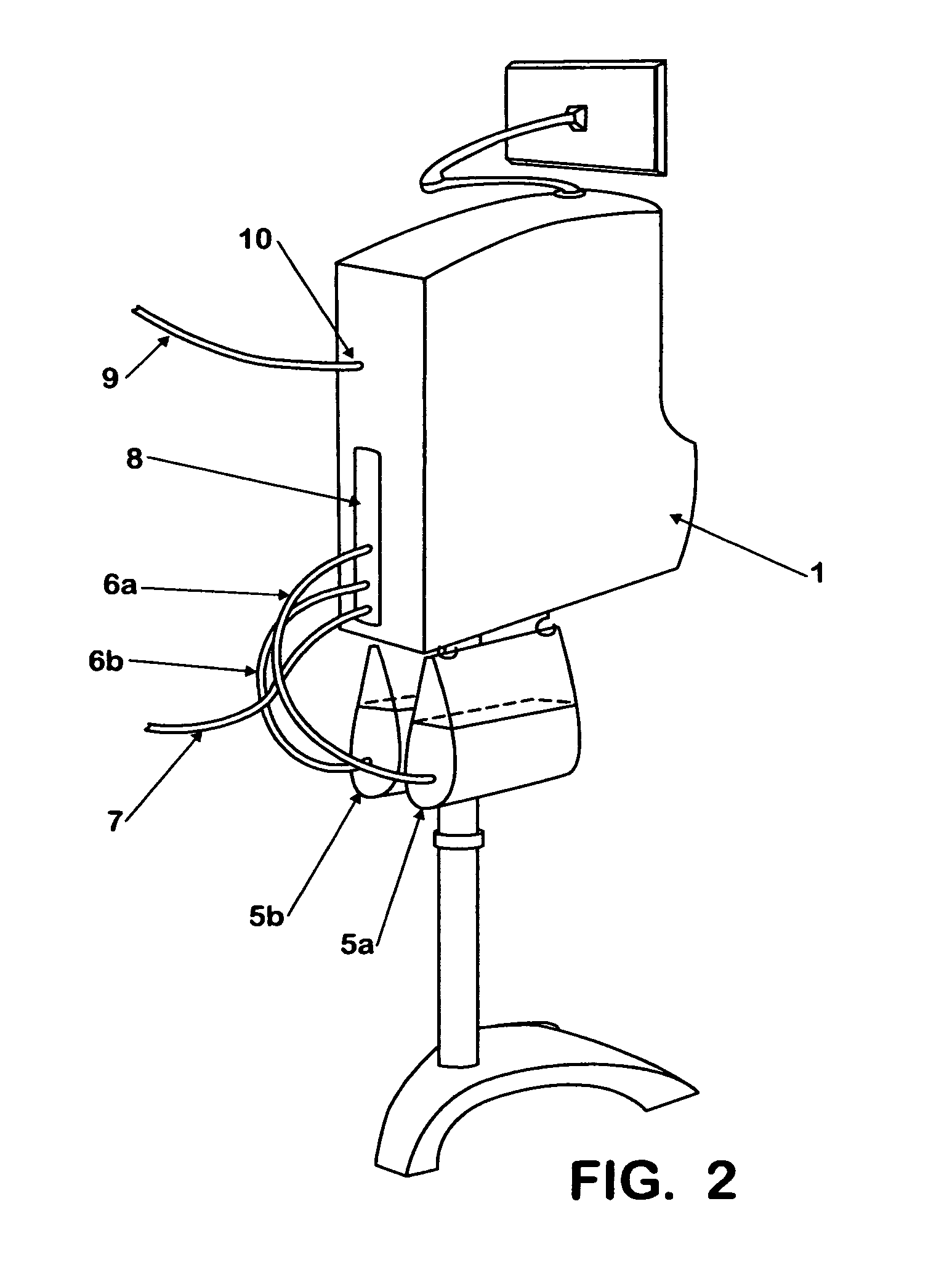
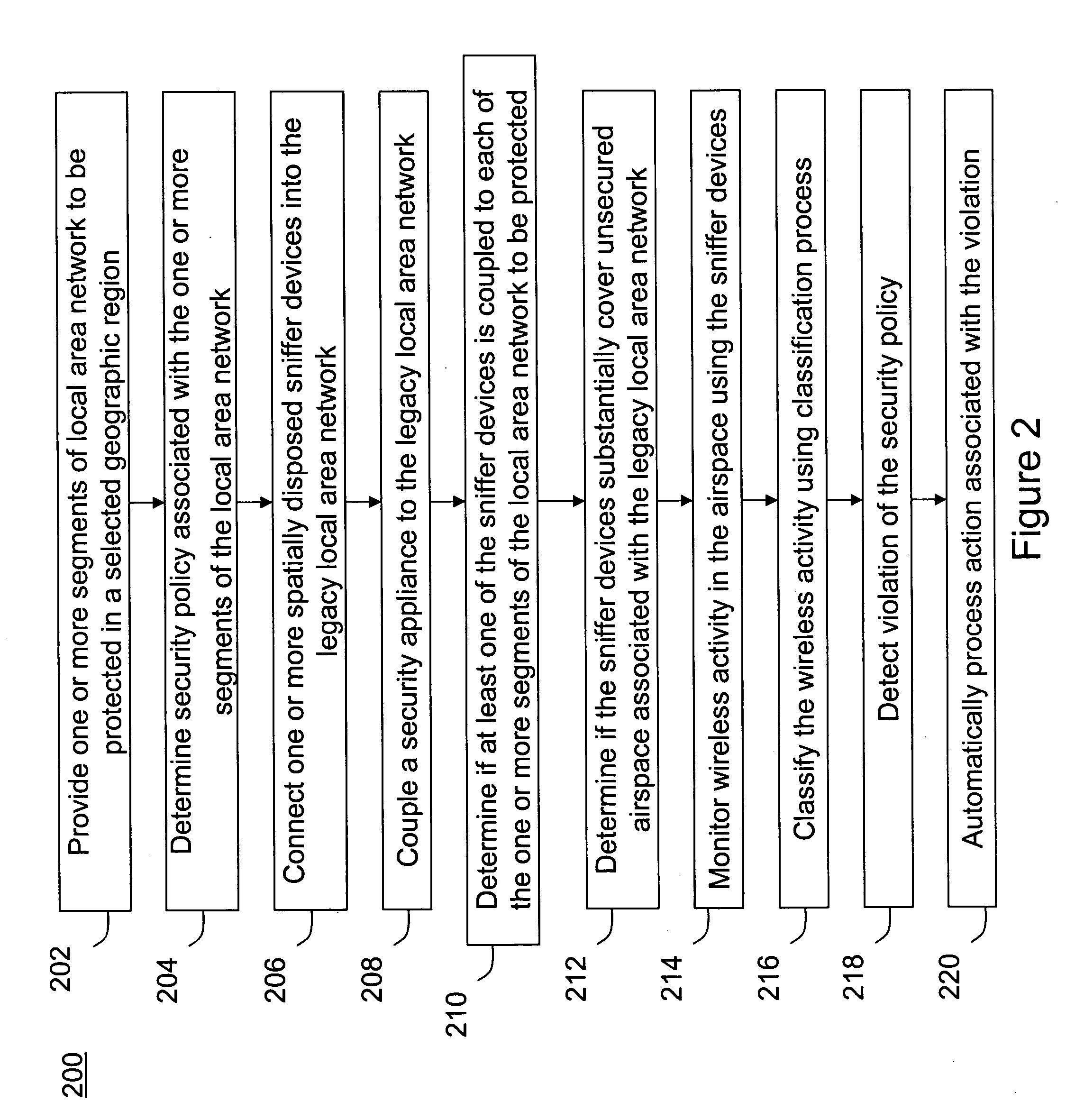
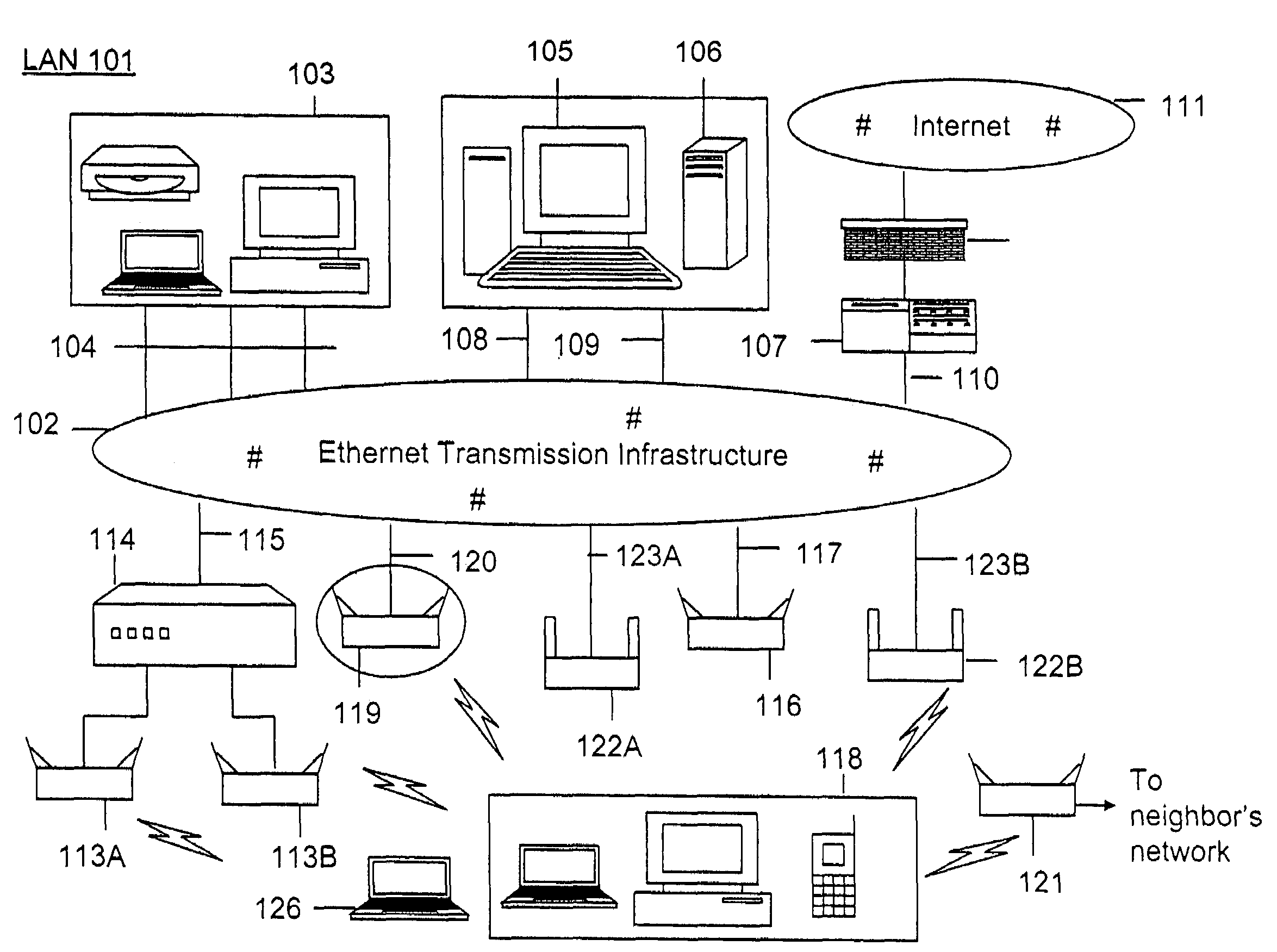
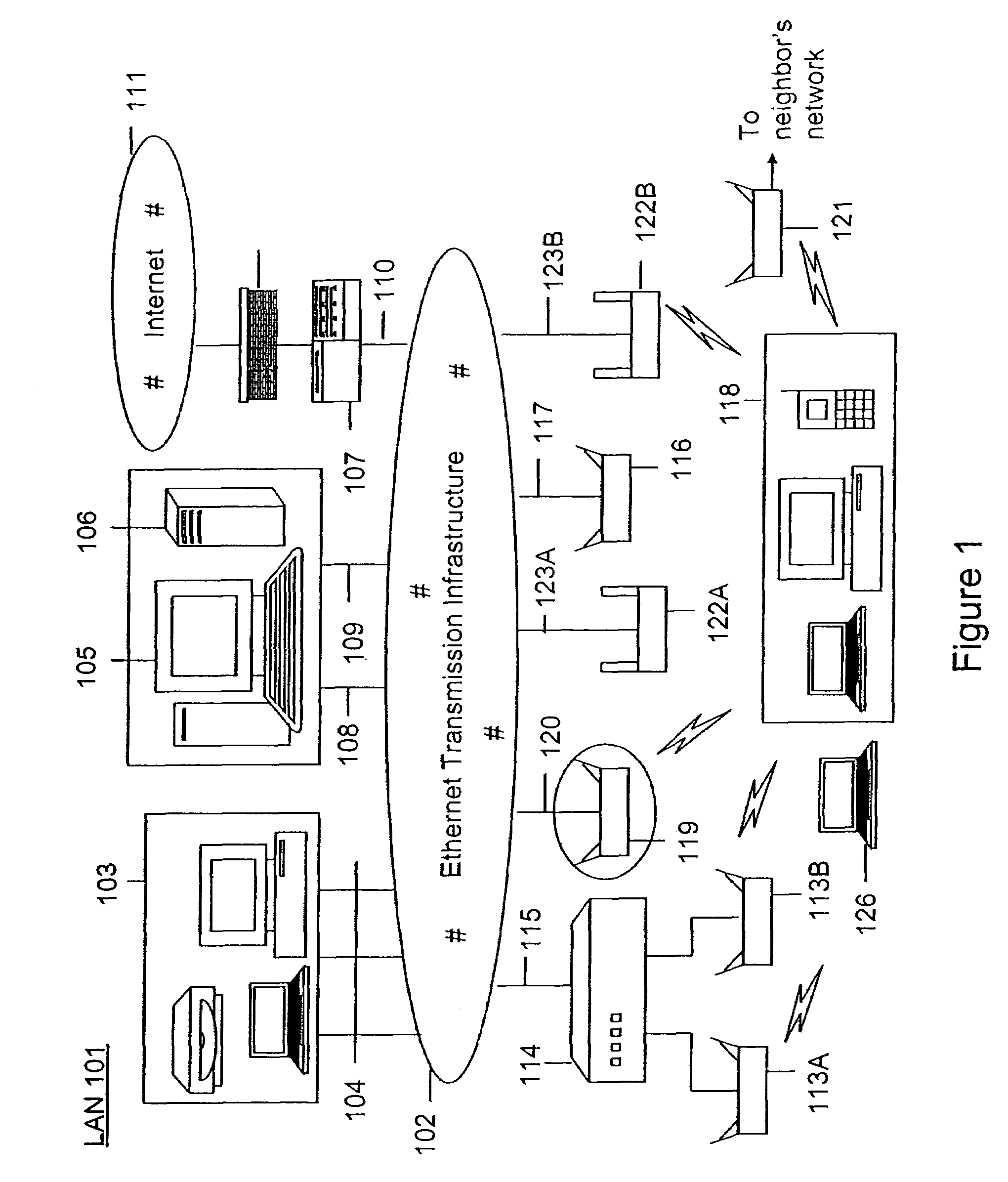
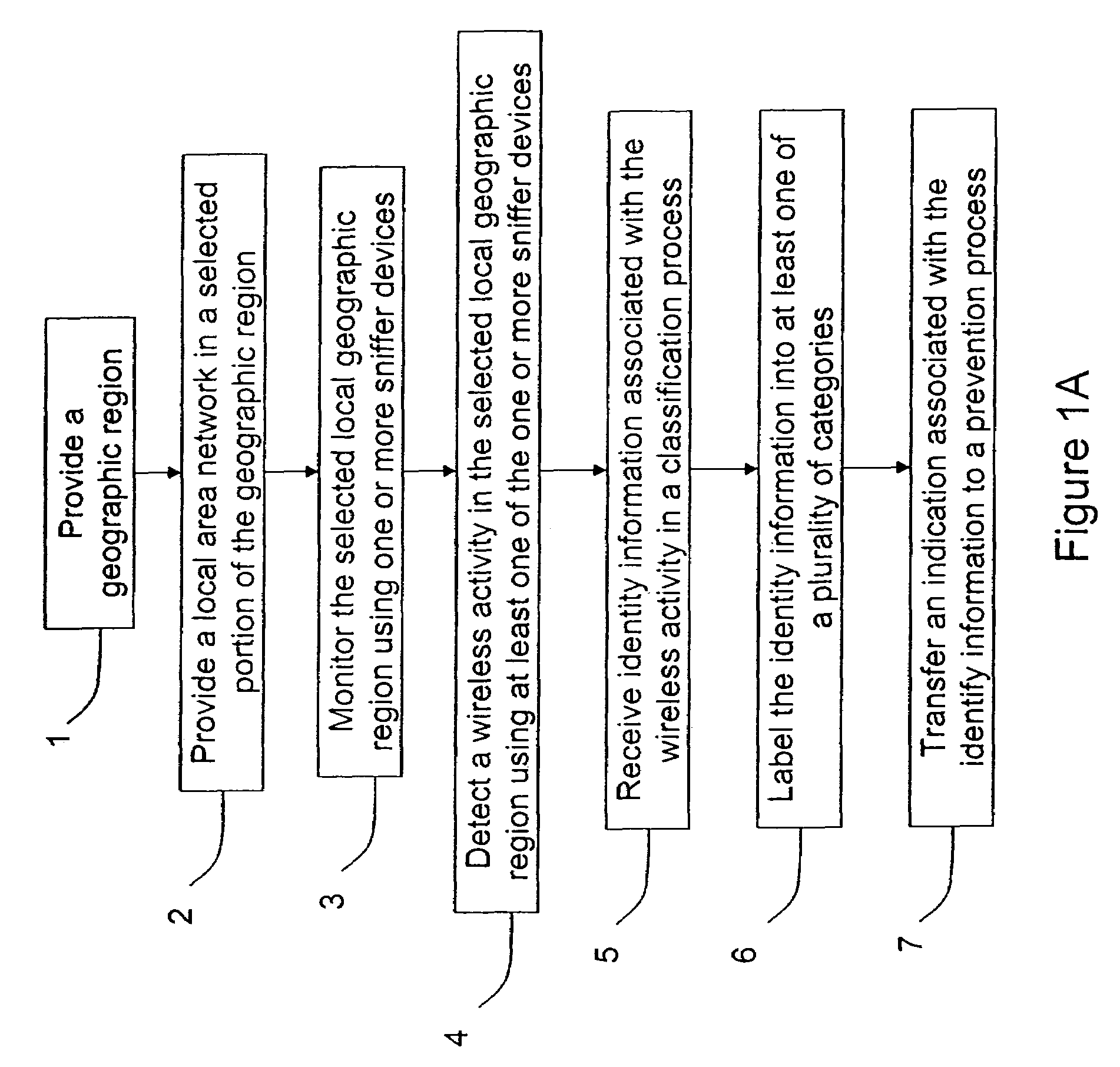
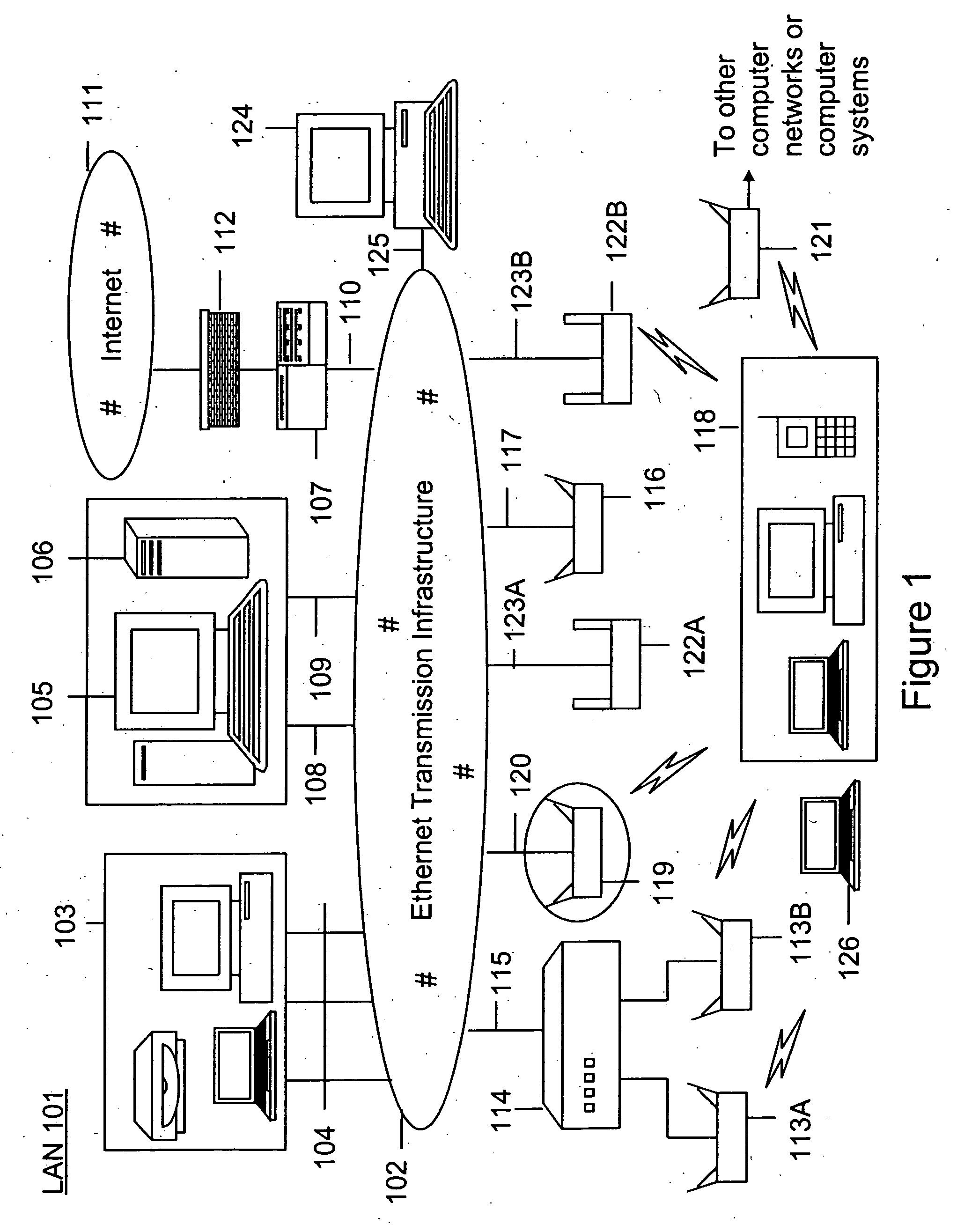
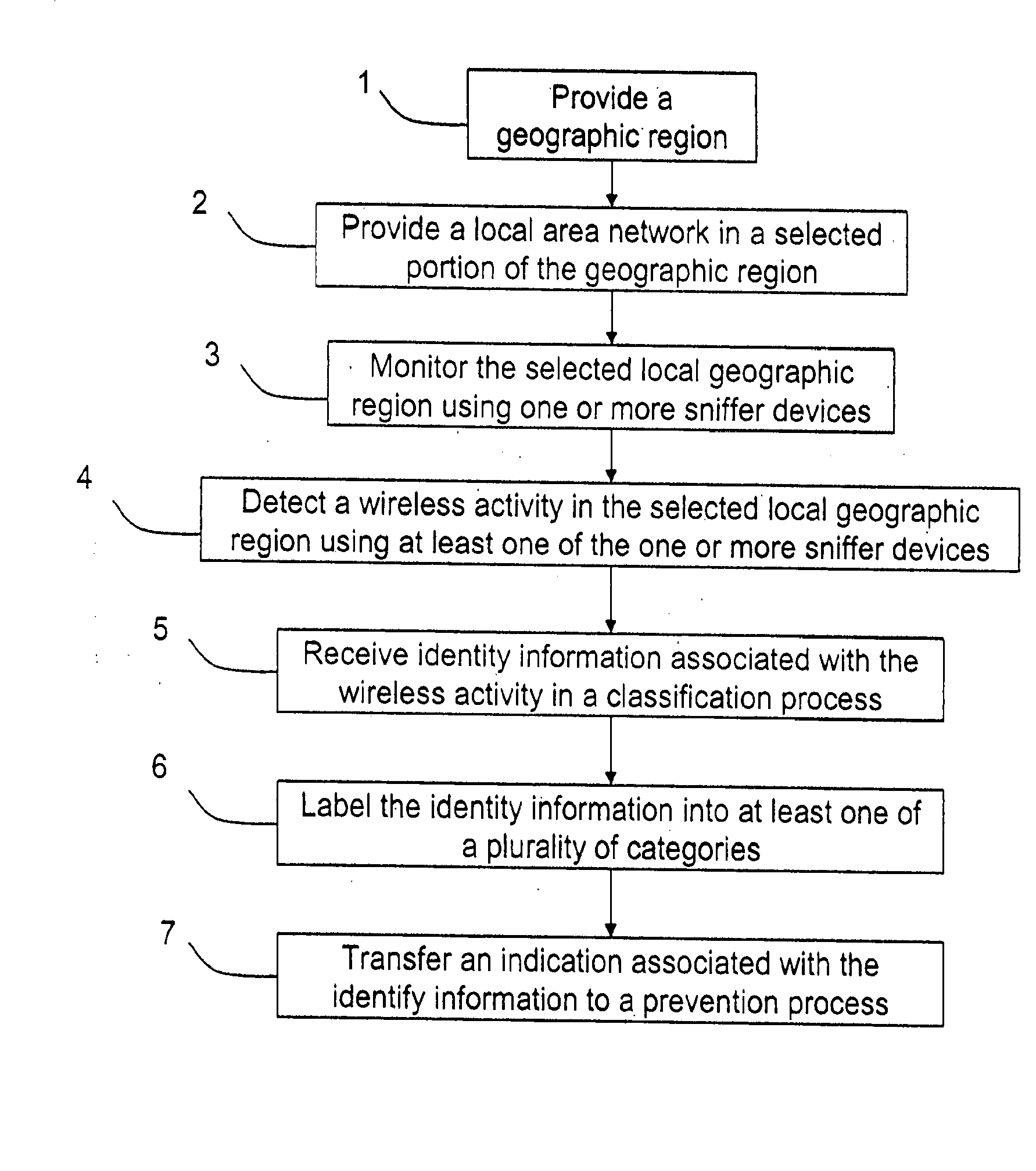
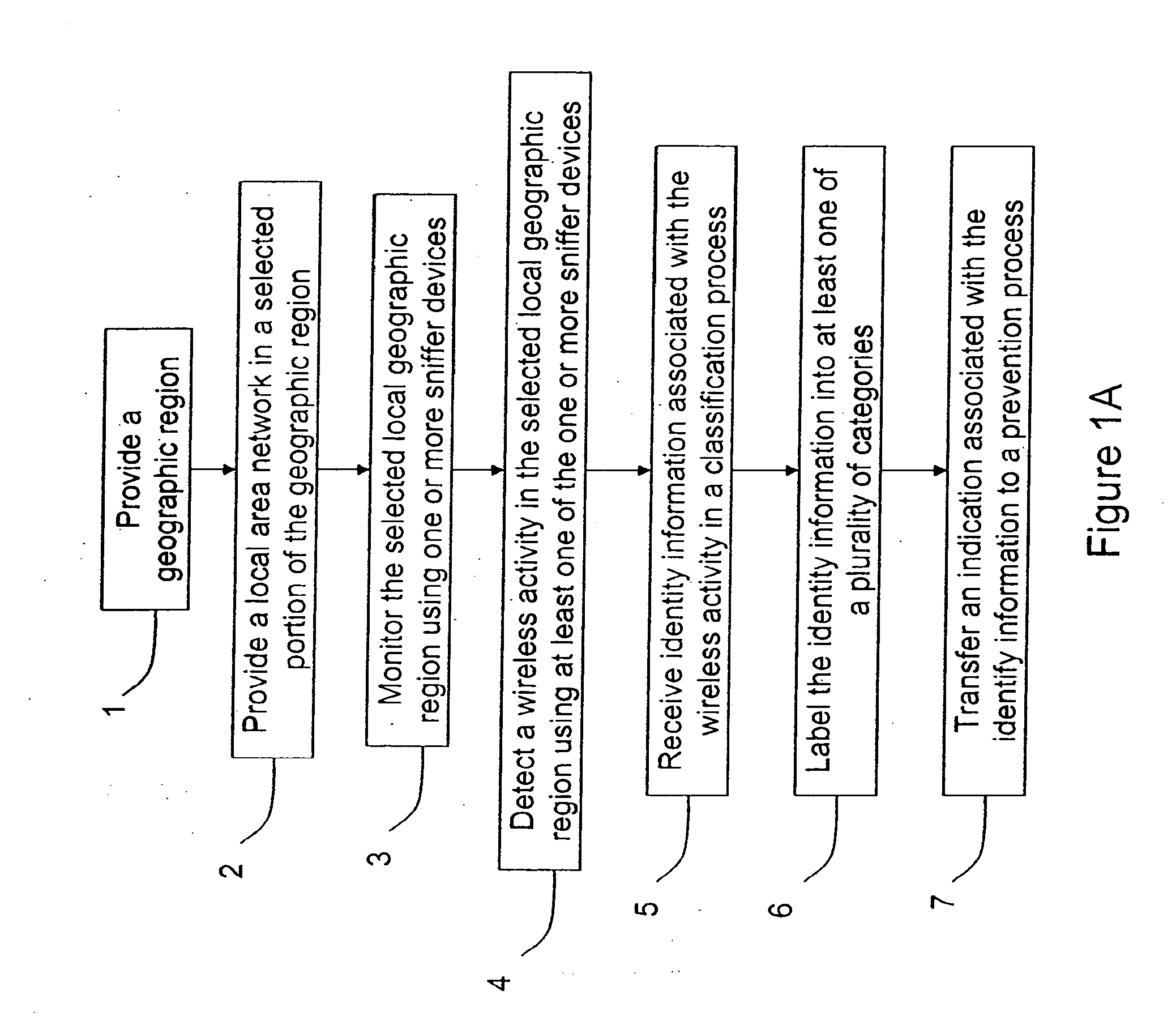
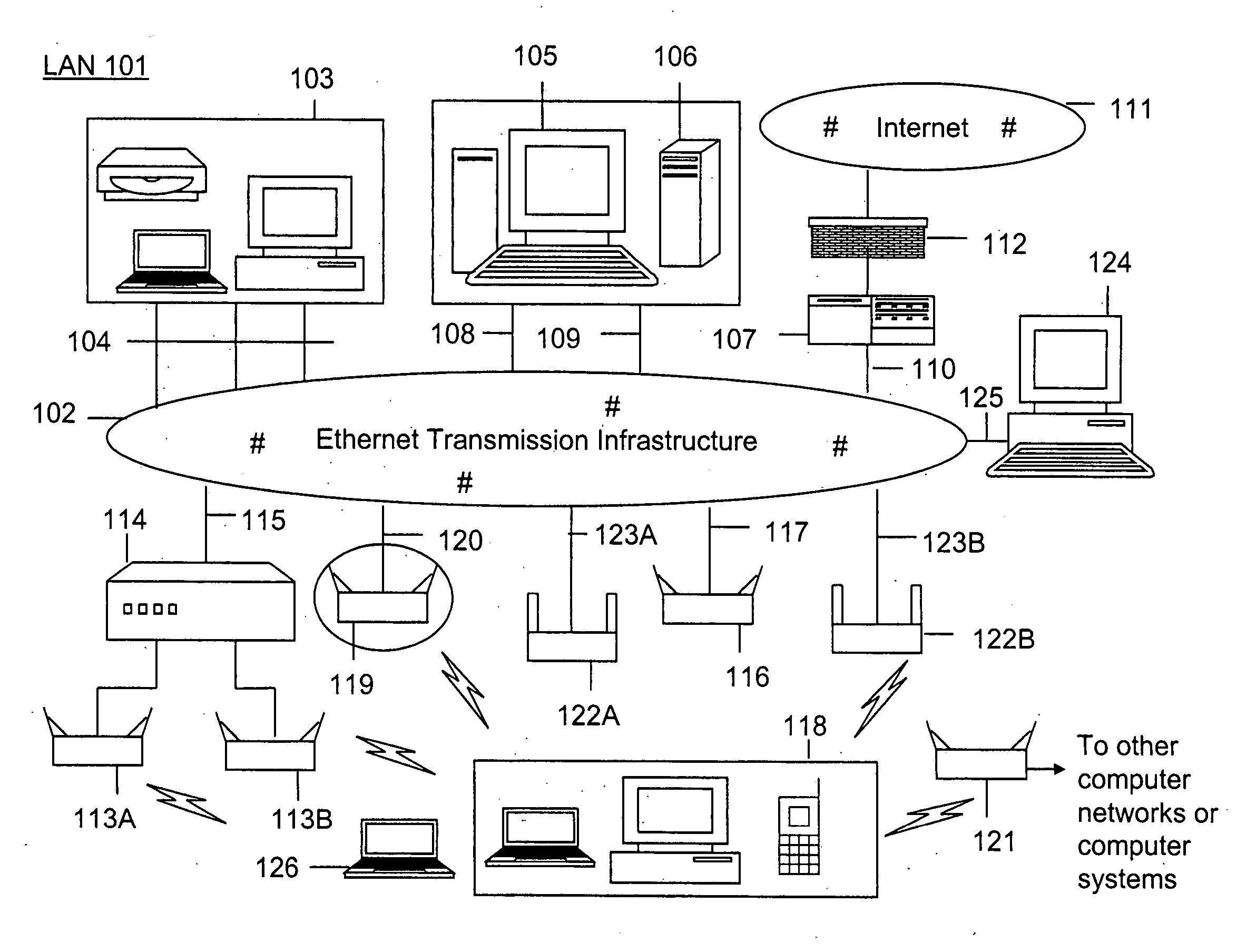
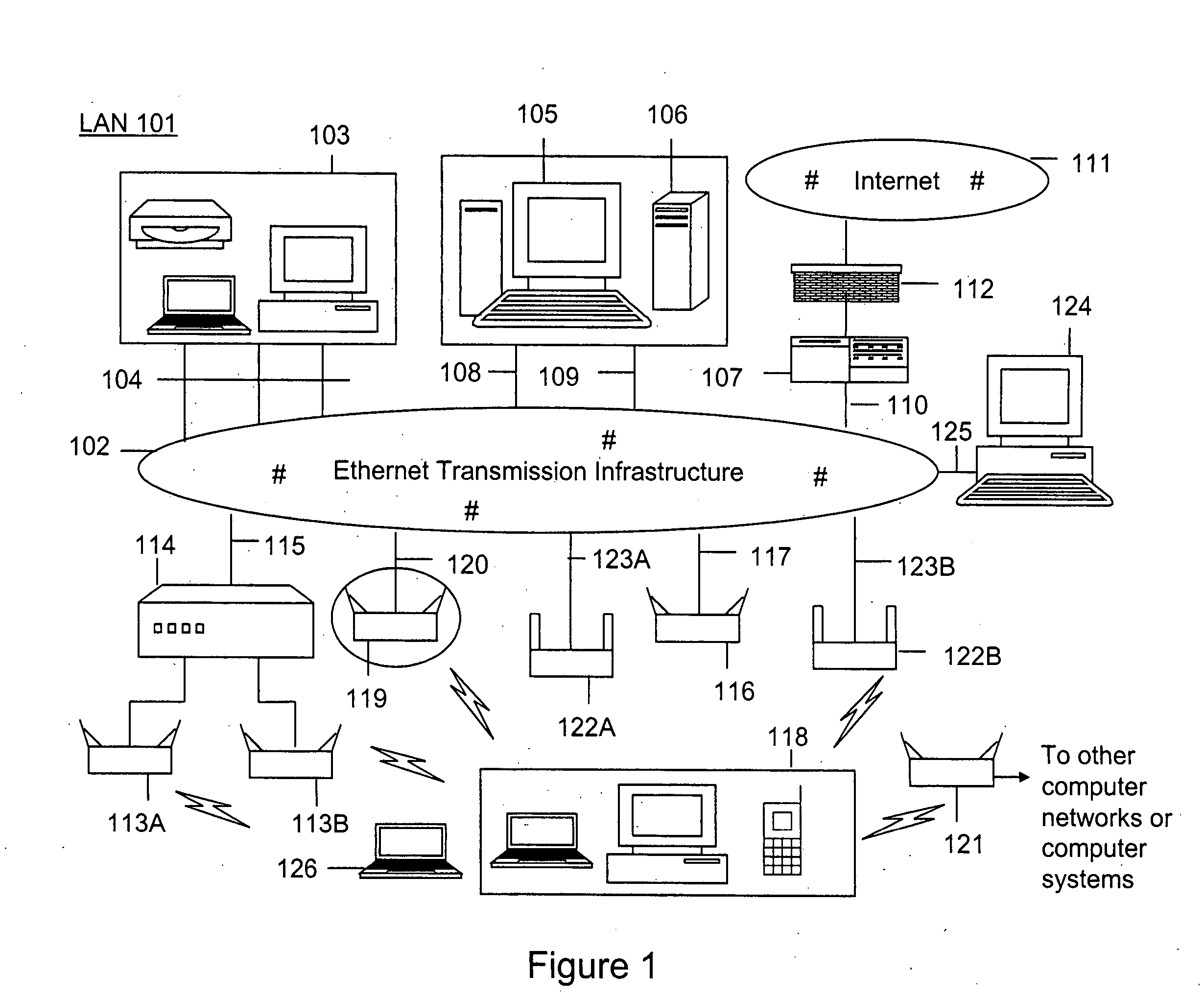
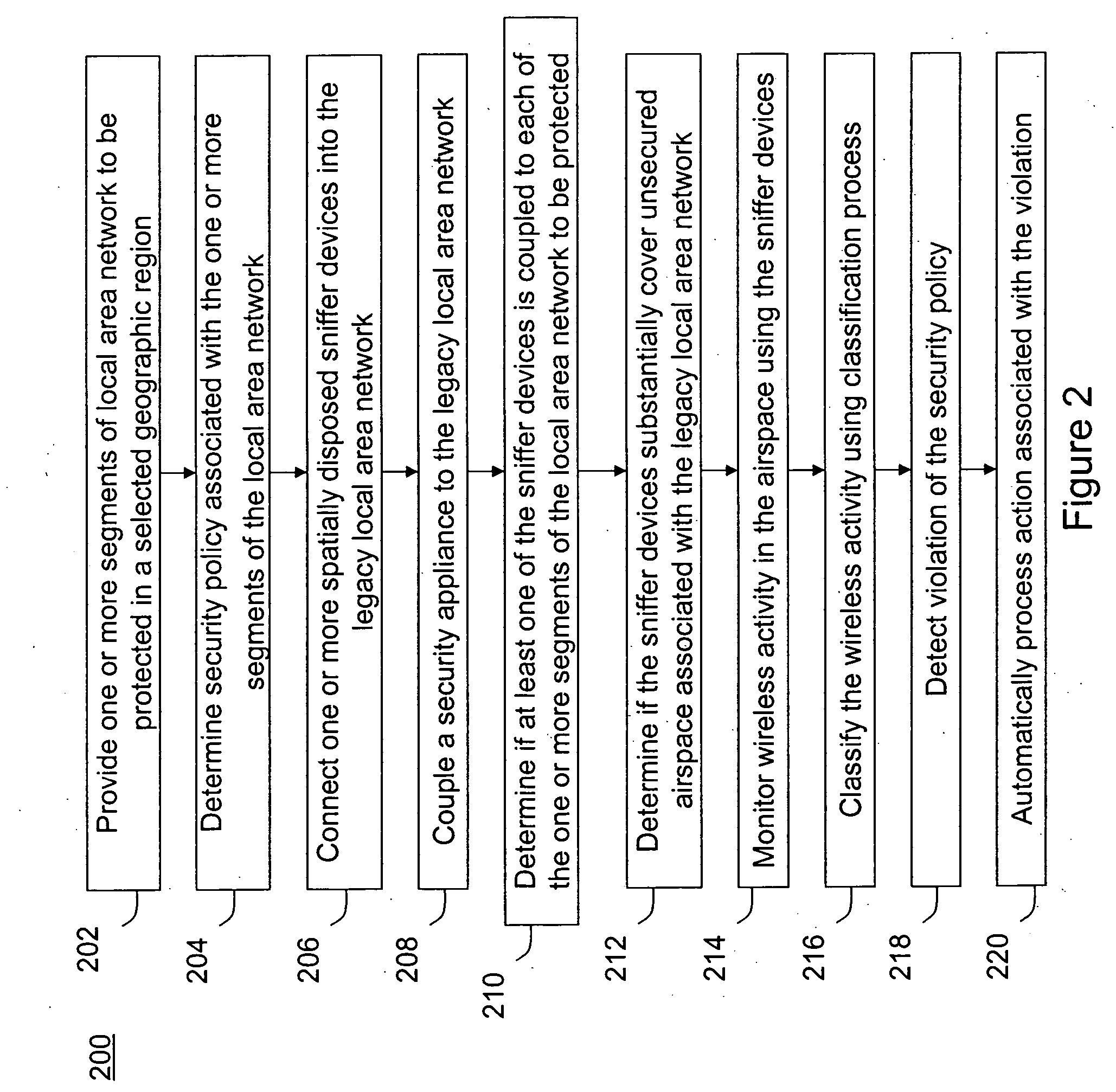
Method and system for monitoring a selected region of an airspace associated with local area networks of computing devices
ActiveUS7002943B2Easy to usePrevent unauthorized wireless accessWave based measurement systemsData switching by path configurationBody area networkGeographic regions
A method for monitoring a selected region of an airspace associated with local area networks of computing devices is provided. The method includes providing one or more segments of a legacy local area network to be protected in a selected geographic region. The legacy local area network is characterized by an unsecured airspace within the selected geographic region. The method includes determining a security policy associated with the one or more segments of the legacy local area network. The security policy at least characterizes a type of wireless activity in the unsecured airspace to be permitted, denied, or ignored. Additionally, the method includes connecting one or more sniffer devices into the legacy local area network. The one or more sniffer devices are spatially disposed within the selected geographic region to cause at least a portion of the unsecured airspace to be secured according to the security policy.
Owner:ARISTA NETWORKS
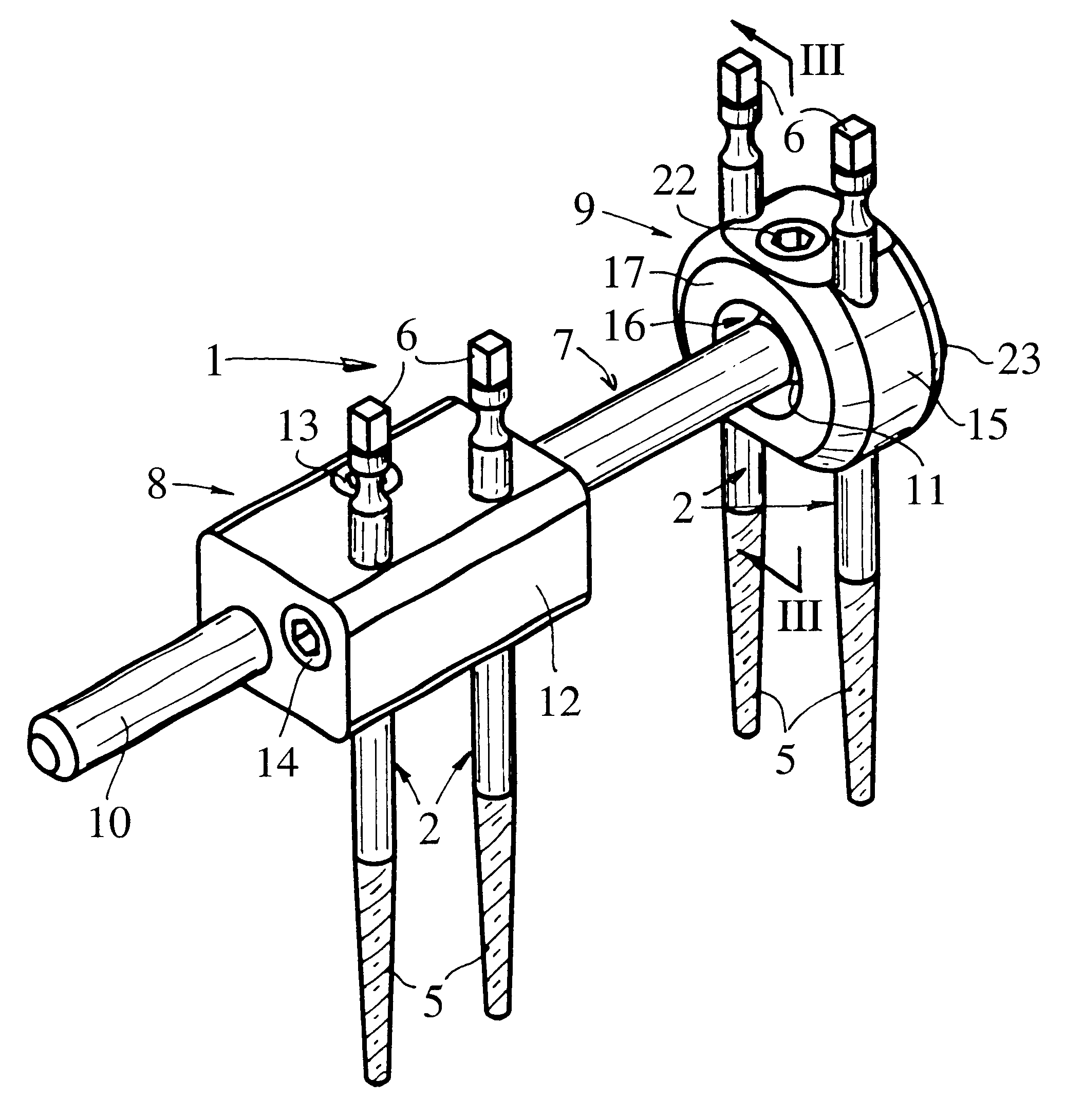
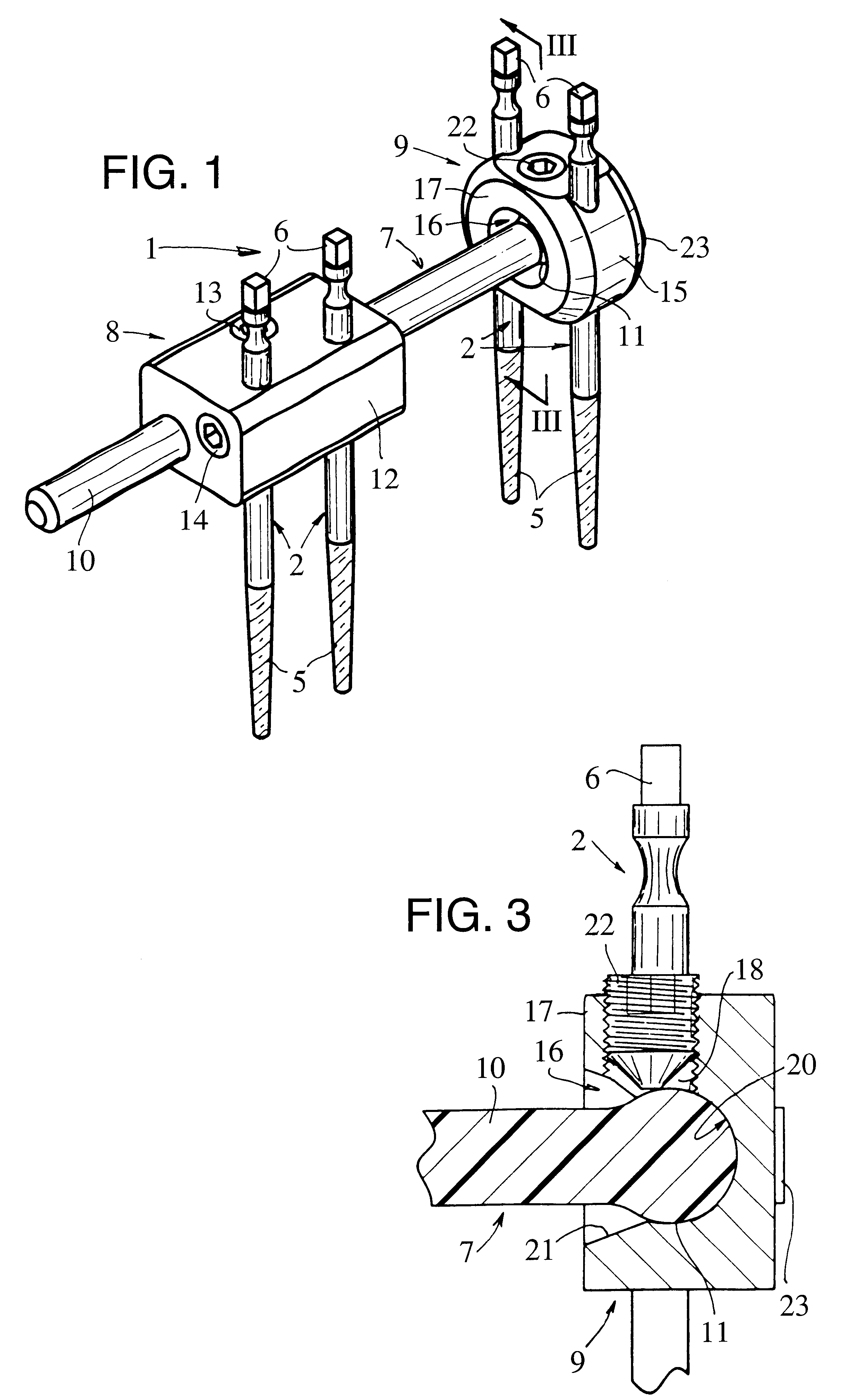
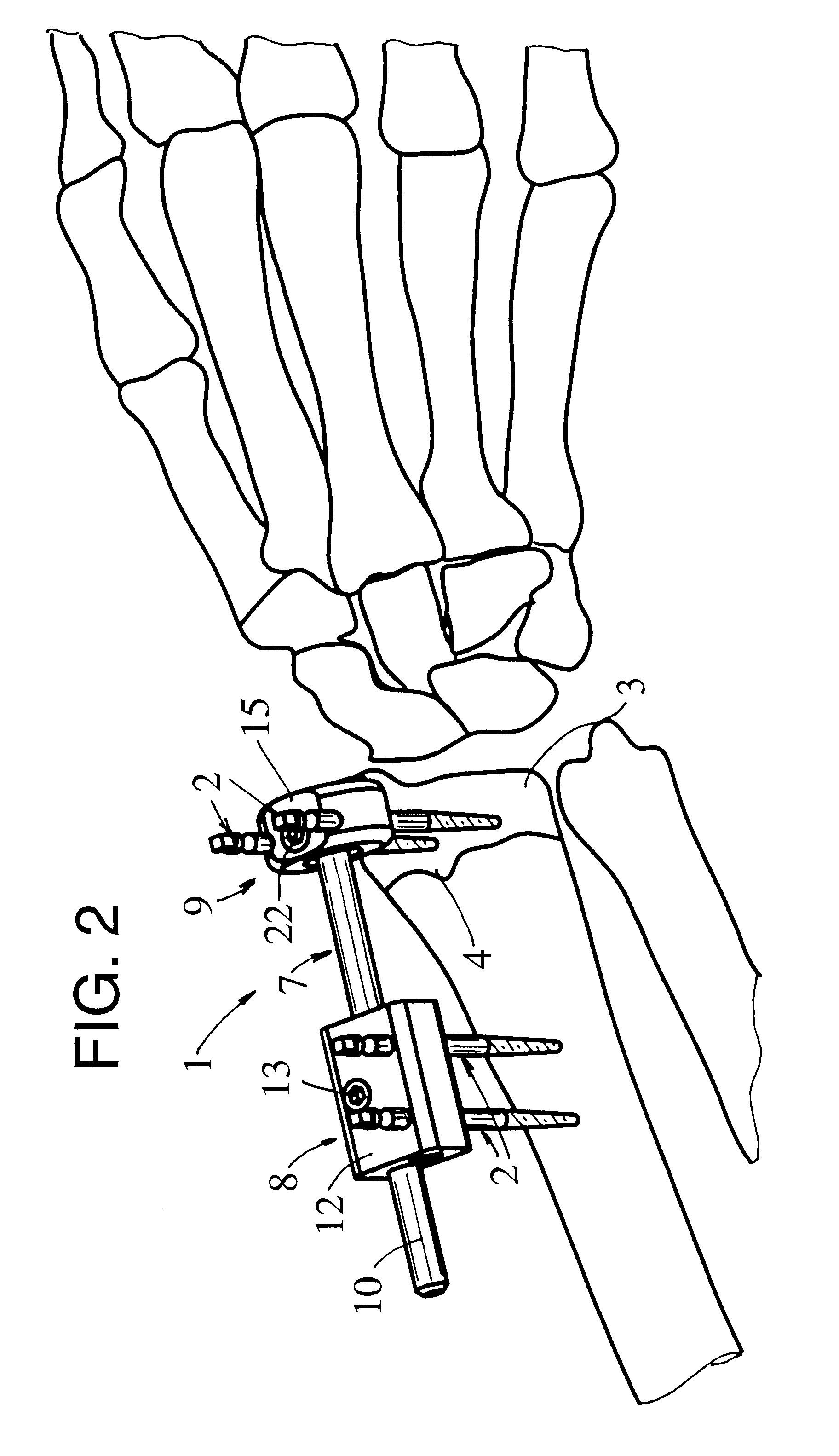
External fixator for immobilizing bone fragments, particularly in the area of the wrist
InactiveUS6530925B2Simple structureEasy to manufactureFractureInvalid friendly devicesExternal fixatorSpherical shaped
This fixator (1) comprises a rigid bar (7), two pin-holder assemblies (8, 9) which can be moved relative to this bar (7), and means (13, 22) with which it is possible to immobilize each pin-holder assembly (8, 9) in a defined position relative to the bar (7).According to the invention:the bar (7) has a cylindrical main part (10) and a spherical part (11) at one end;a first pin-holder assembly (8) comprises a one-piece body (12) with a bore passing through it to permit its engagement by sliding on the cylindrical part (10) of the bar (7); andthe second pin-holder assembly (9) comprises a one-piece body (15) in which a recess (16) is formed, this recess (16) having a zone of partially spherical shape with a radius slightly greater than that of said spherical part (11), this zone being such that it can receive this spherical part (11) with pivoting, without lateral play, and with a possibility of articulation of said second pin-holder assembly (9).
Owner:STRYKER EURO OPERATIONS HLDG LLC
Drive transmission mechanism and image forming device
InactiveUS20070264048A1Absorb evenlyProcess stabilityYielding couplingElectrographic process apparatusCouplingEngineering
A direction in which a drive transmission acts on a driving member and a coupling member at a coupling portion is perpendicular or substantially perpendicular to a direction in which the drive transmission acts on the coupling member and a driven member at a coupling portion. In both of the coupling portions, spaces are provided so that the driving member and the coupling member, and the coupling member and the driven member, can be respectively coupled to each other under a state in which mutual displacement is permitted in a direction that is perpendicular or substantially perpendicular to each drive transmission action direction.
Owner:MURATA MASCH LTD
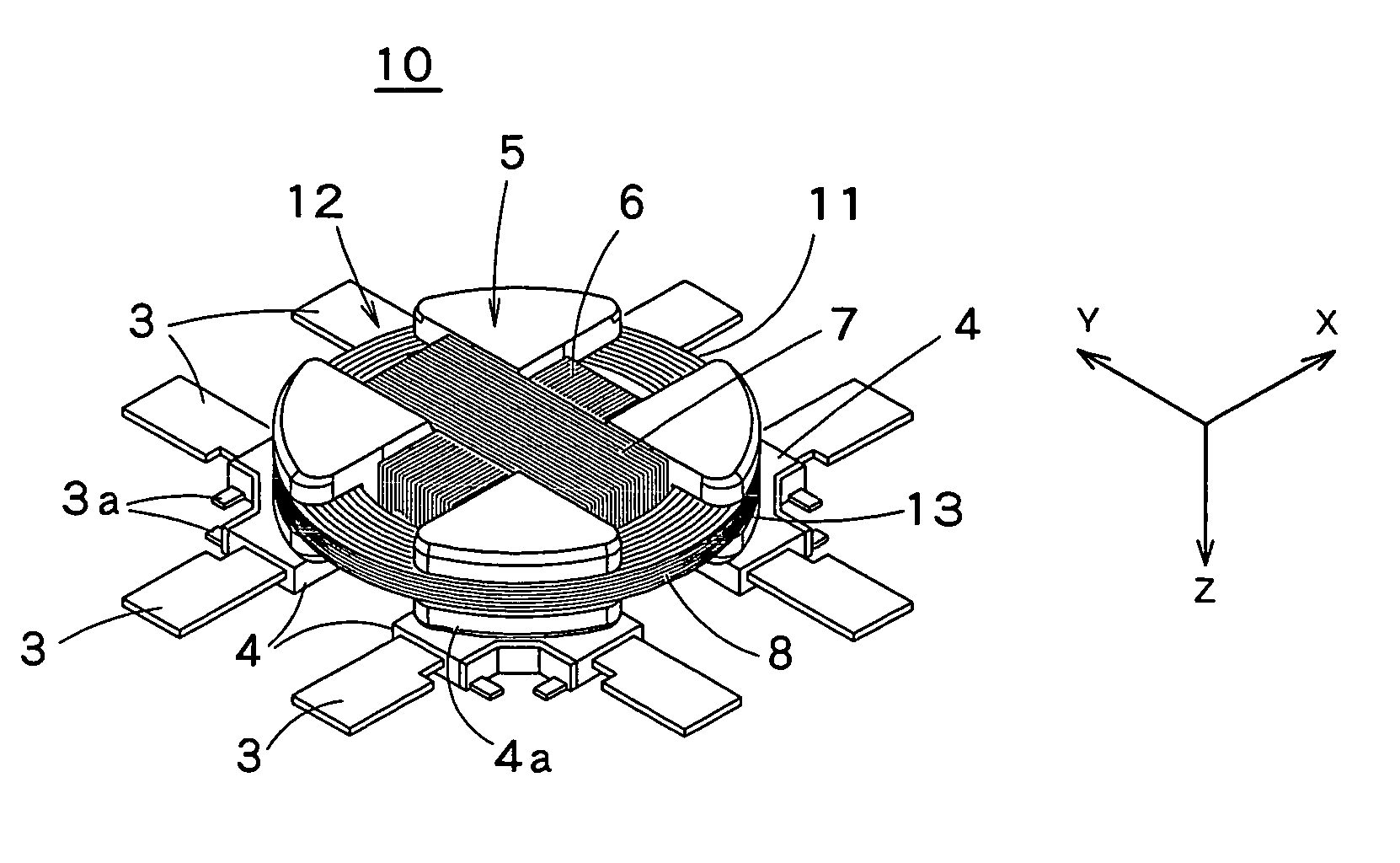
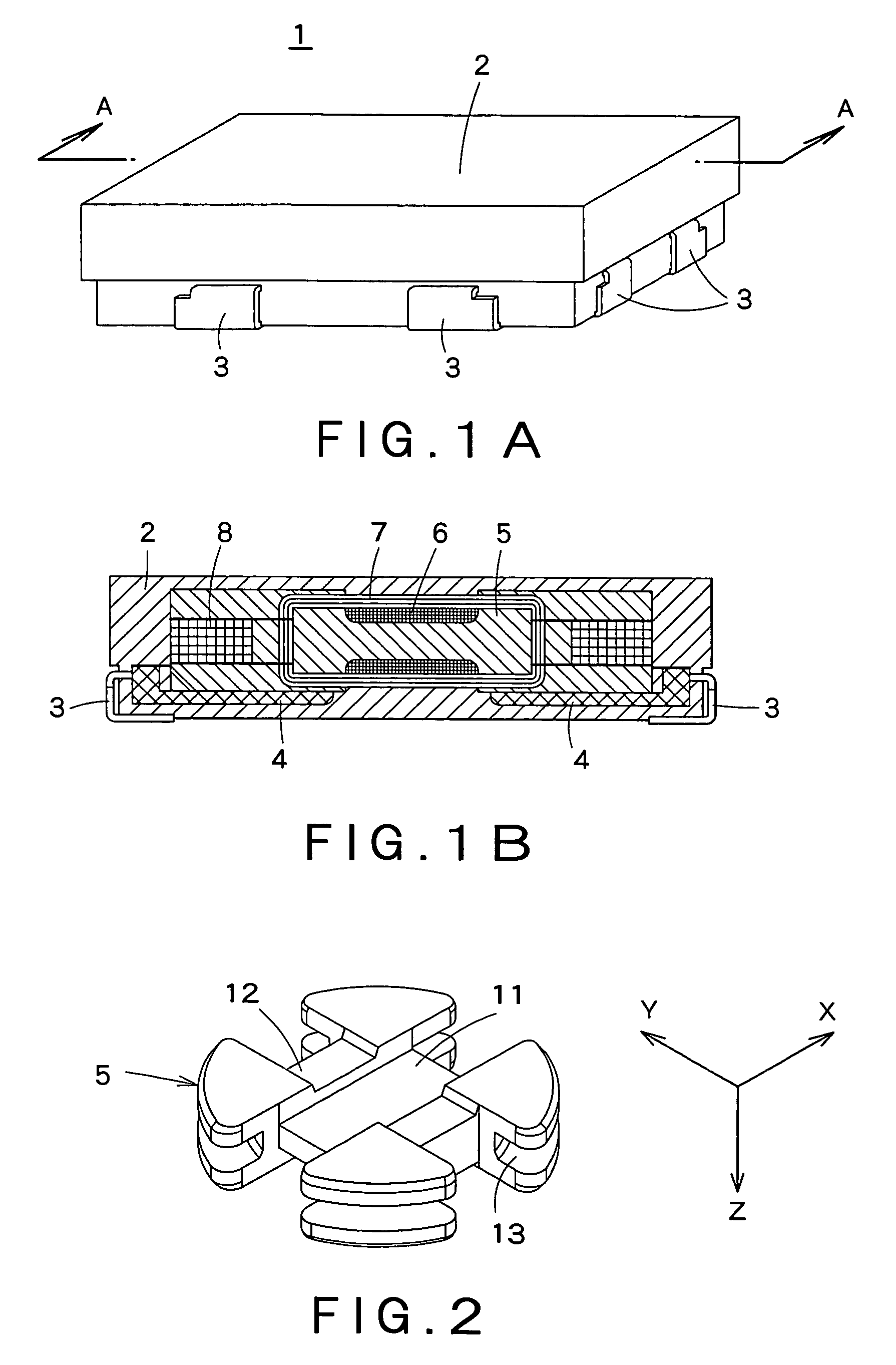
Transmit/Receive Daughter Card With Integral Circulator
ActiveUS20150015453A1Low insertion lossEliminate needSolid-state devicesAntenna arrays manufactureRadio frequencyDaughterboard
A mixed-signal, multilayer printed wiring board fabricated in a single lamination step is described. The PWB includes one or more radio frequency (RF) interconnects between different circuit layers on different circuit boards which make up the PWB. The PWB includes a number of unit cells with radiating elements and an RF cage disposed around each unit cell to isolate the unit cell. A plurality of flip-chip circuits are disposed on an external surface of the PWB and a heat sink can be disposed over the flip chip components.
Owner:RAYTHEON CO
Fully Automated Vehicle Dispatching, Monitoring and Billing
InactiveUS20080228562A1Minimize future delayEasy to meetTicket-issuing apparatusRoad vehicles traffic controlTransport engineeringFully automated
A system for controlling vehicles (20) to provide transportation services without need for human intervention. A database (10) stores records each documenting needed transportation services. Processing circuitry (which may be one or several networked computers) performs a dispatching process (26) which reviews these records, locates records indicating a need for immediate transportation service, and instructs vehicles to provide the service. The processing circuitry also performs a monitoring process (28) which monitors vehicle activities by reviewing the records, and automatically obtained vehicle activity information, to identify transportation services which are not being adequately provided, and refer these to human dispatchers (16) for special attention. A variety of methods for obtaining and updating vehicle activity information are disclosed, as are various applications for the system.
Owner:TOTAL TECH CO LTD
Fluid processing apparatus
ActiveUS20130037465A1Need is eliminated and minimisedEliminate needDialysis systemsMedical devicesSterile waterEngineering
A machine is provided with a slot to releasably receive and retain a cartridge in which dialysis is effected. The machine is configured for supplying to the cartridge, at a controlled temperature and rate, sterile water for use in haemodialysis and is operable to maintain, in a sterile condition, residual water contained therein after completion of a haemodialysis treatment.
Owner:QUANTA DIALYSIS TECH LTD
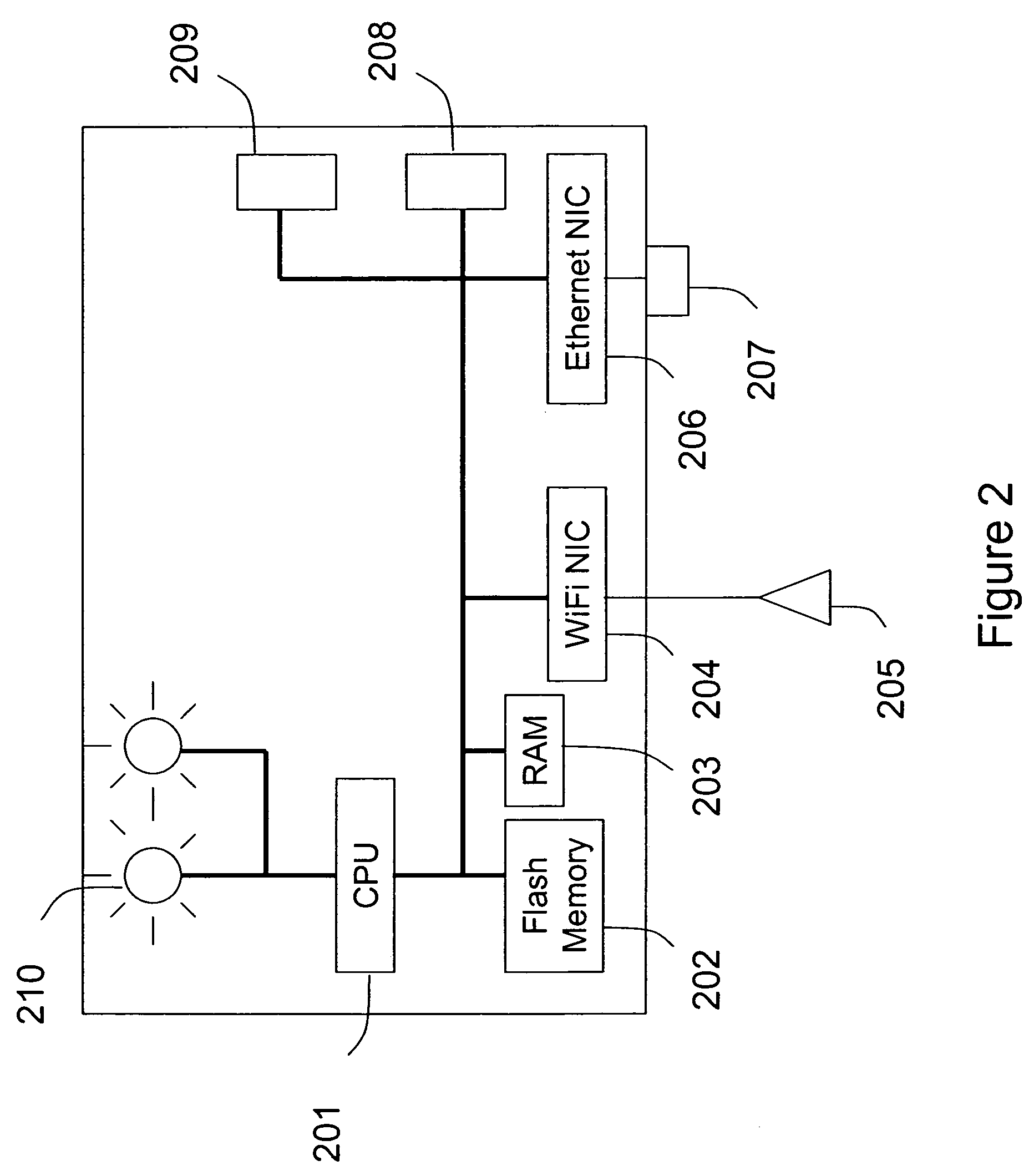
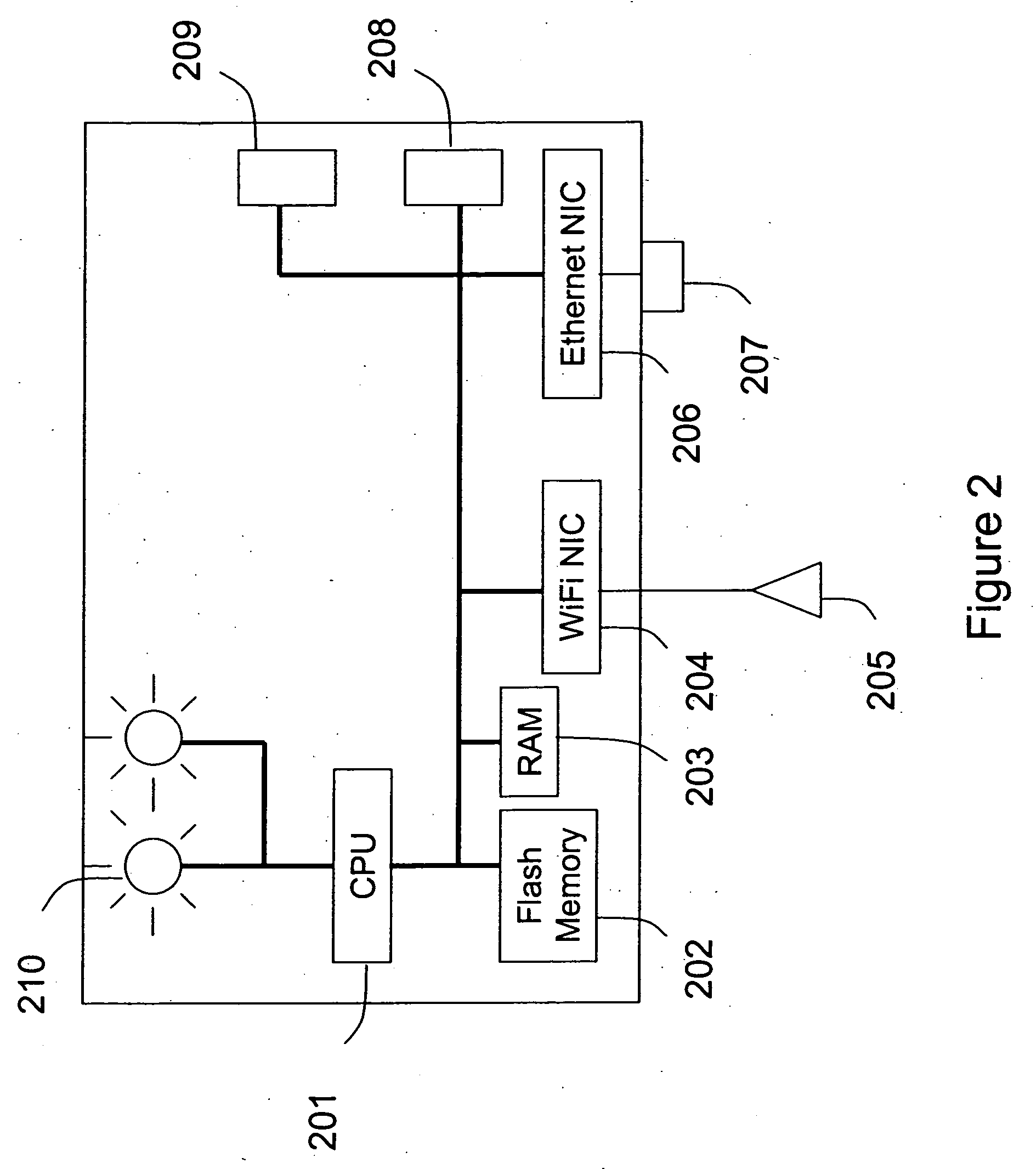
Automated sniffer apparatus and method for monitoring computer systems for unauthorized access
ActiveUS7339914B2Easy to usePrevent unauthorized wireless accessMemory loss protectionError detection/correctionGeographic regionsNetwork connection
An apparatus for wireless communication including an automated intrusion detection process is provided. The apparatus has a portable housing, which may have a length no greater than 1 meter, a width no greater than 1 meter, and a height of no greater than 1 meter. A processing unit (e.g., CPU) is within the housing. One or more wireless network interface devices are within the housing and are coupled to the processing unit. The apparatus has an Ethernet (or like) network interface device within the housing and coupled to the processing unit. A network connector is coupled to the Ethernet network device. One or more memories are coupled to the processing unit. A code is directed to perform a process for detection of a wireless activity within a selected local geographic region. According to a specific embodiment, the wireless activity is derived from at least one authorized device or at least an other device. A code is directed to receiving at least identity information associated with the wireless activity from the detection process in a classification process. A code is directed to labeling the identity information into at least one of a plurality of categories in the classification process. Depending upon the embodiment, other codes may exist to carry out the functionality described herein.
Owner:ARISTA NETWORKS
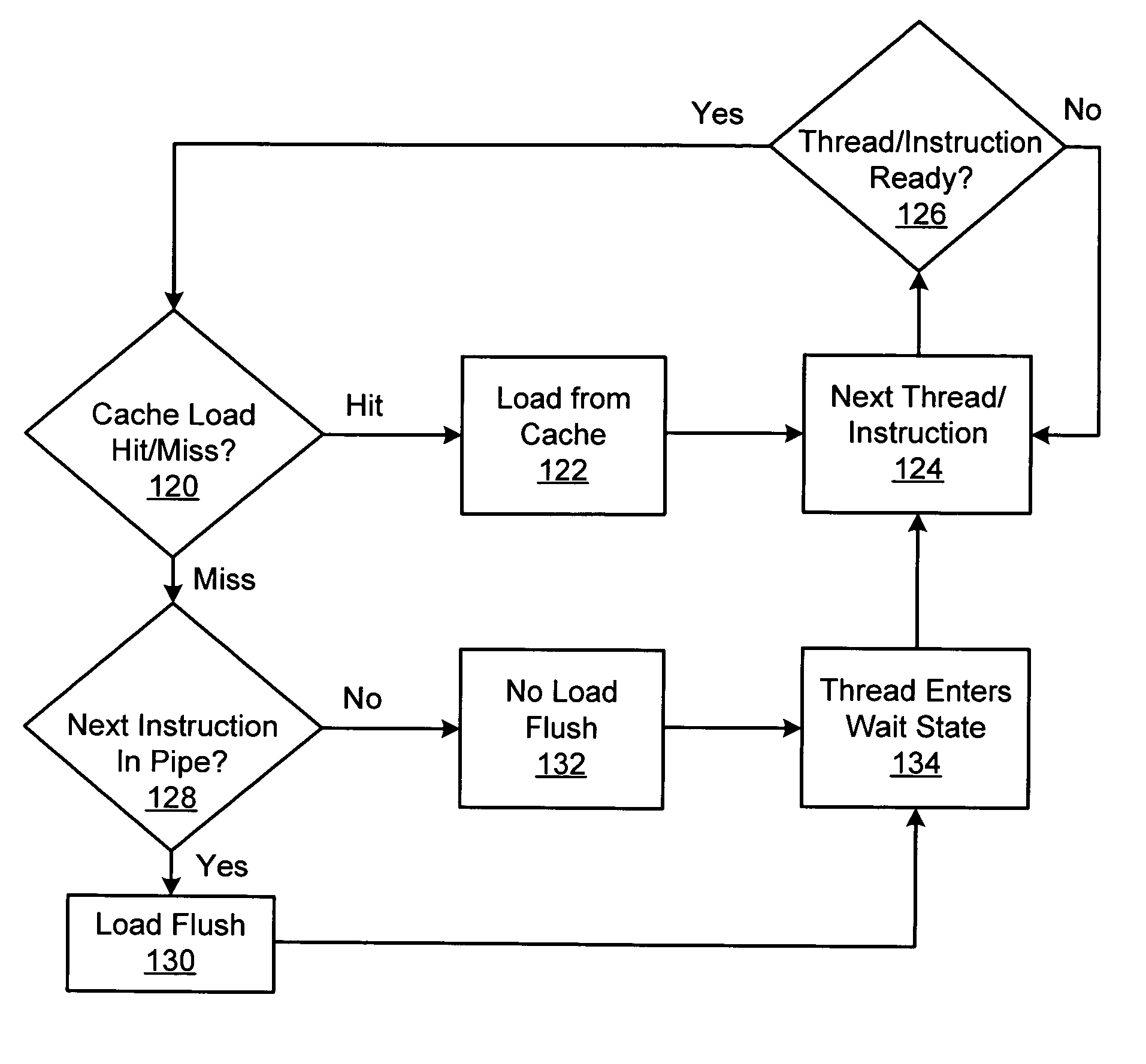
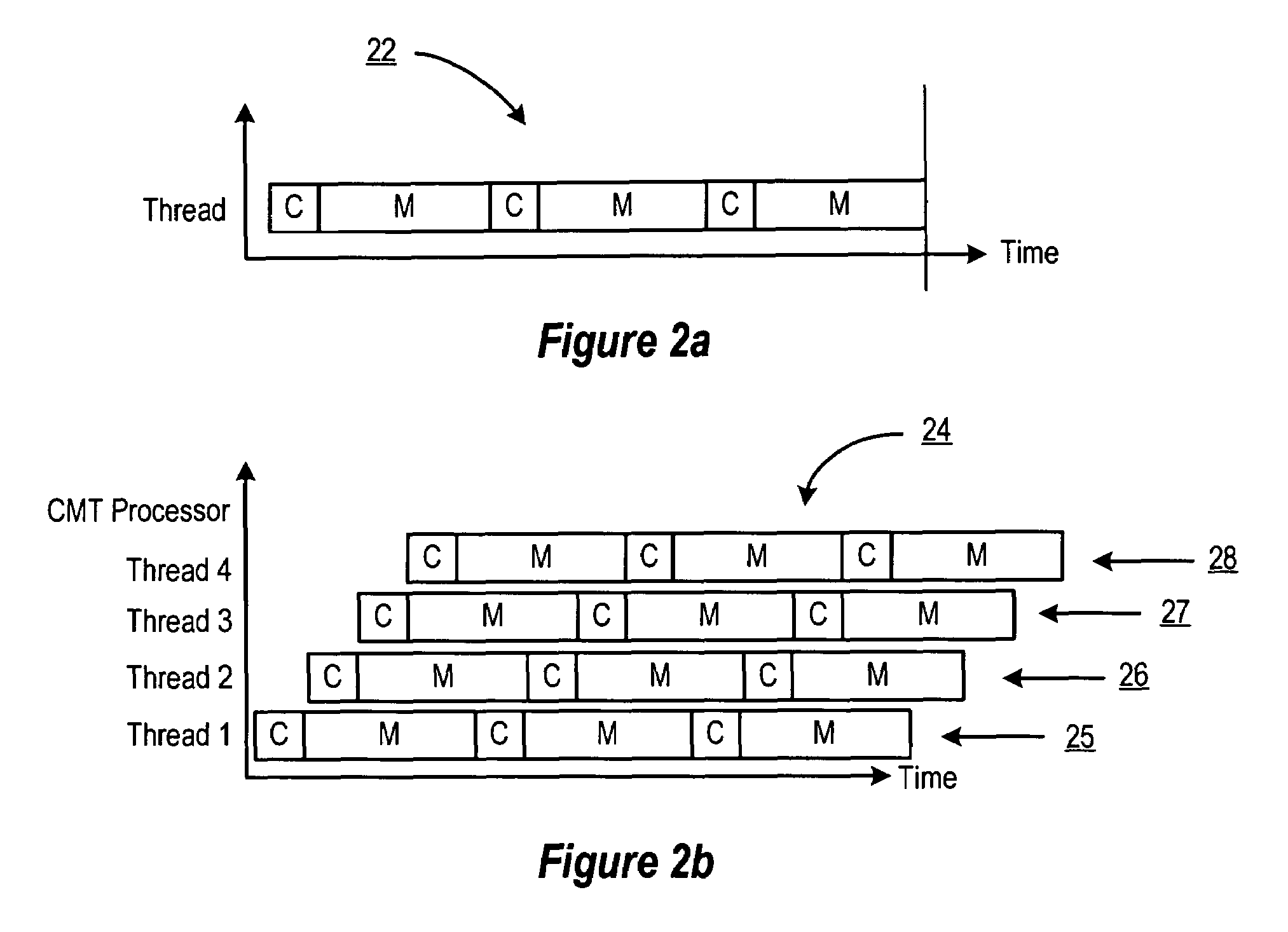
Handling cache misses by selectively flushing the pipeline
ActiveUS7509484B1Eliminate operationHigh bandwidthDigital computer detailsSpecific program execution arrangementsLoad instructionParallel computing
An apparatus and method for efficiently managing data cache load misses is described in connection with a multithreaded, pipelined multiprocessor chip. A CMT processor keeps track of load misses for each thread by issuing a load miss signal each time a load instruction to the data cache misses. A detection logic functionality in the IFU responds the load miss signal to determine if a valid instruction from the thread is at the one of the pipeline stages. If no instructions from the thread are detected in the pipeline, then no flush is required and the thread is placed in a wait state until the requested data is returned from higher order memory. If any instruction from the thread is detected in the pipeline, the thread is flushed and the instruction is re-fetched.
Owner:ORACLE INT CORP
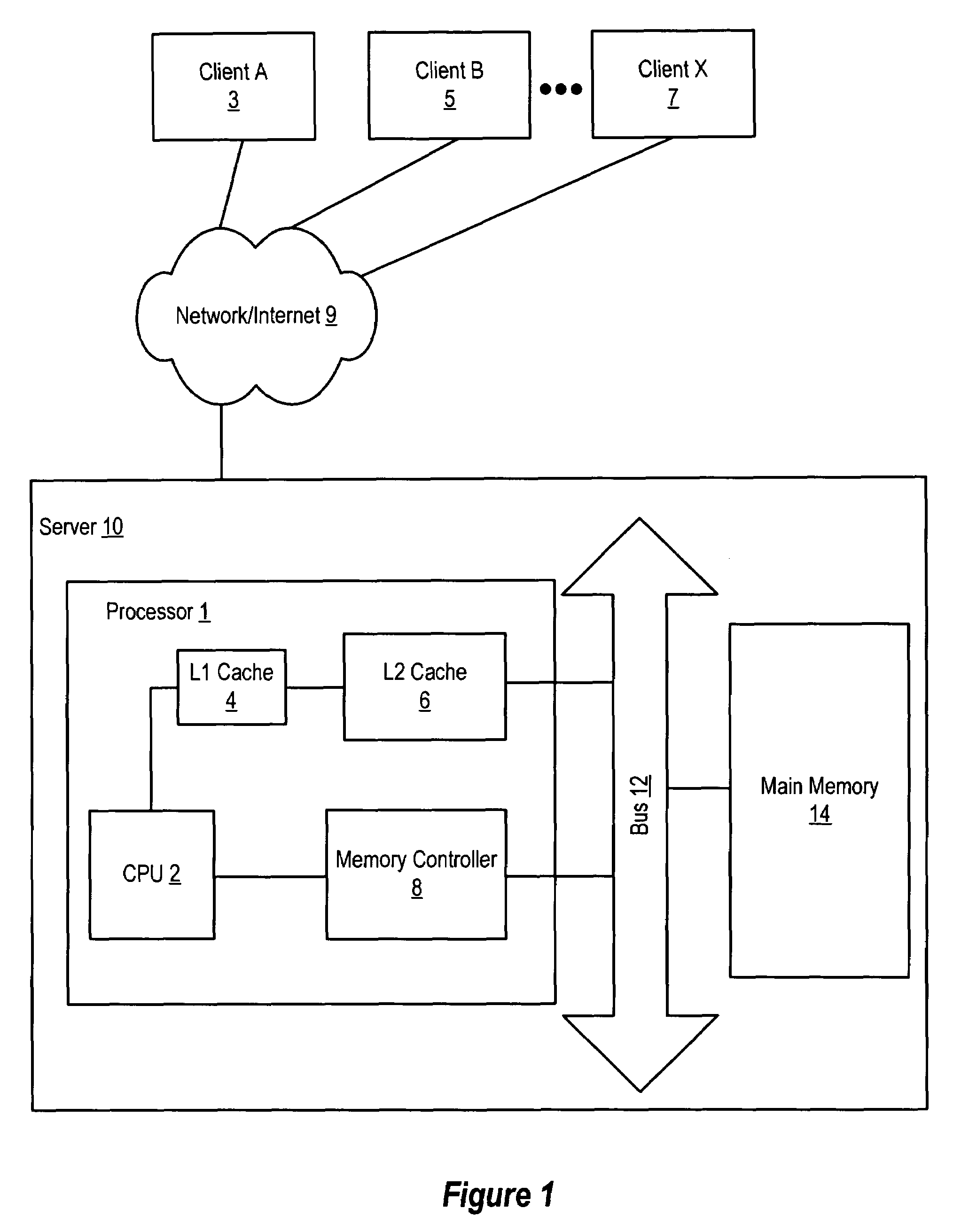
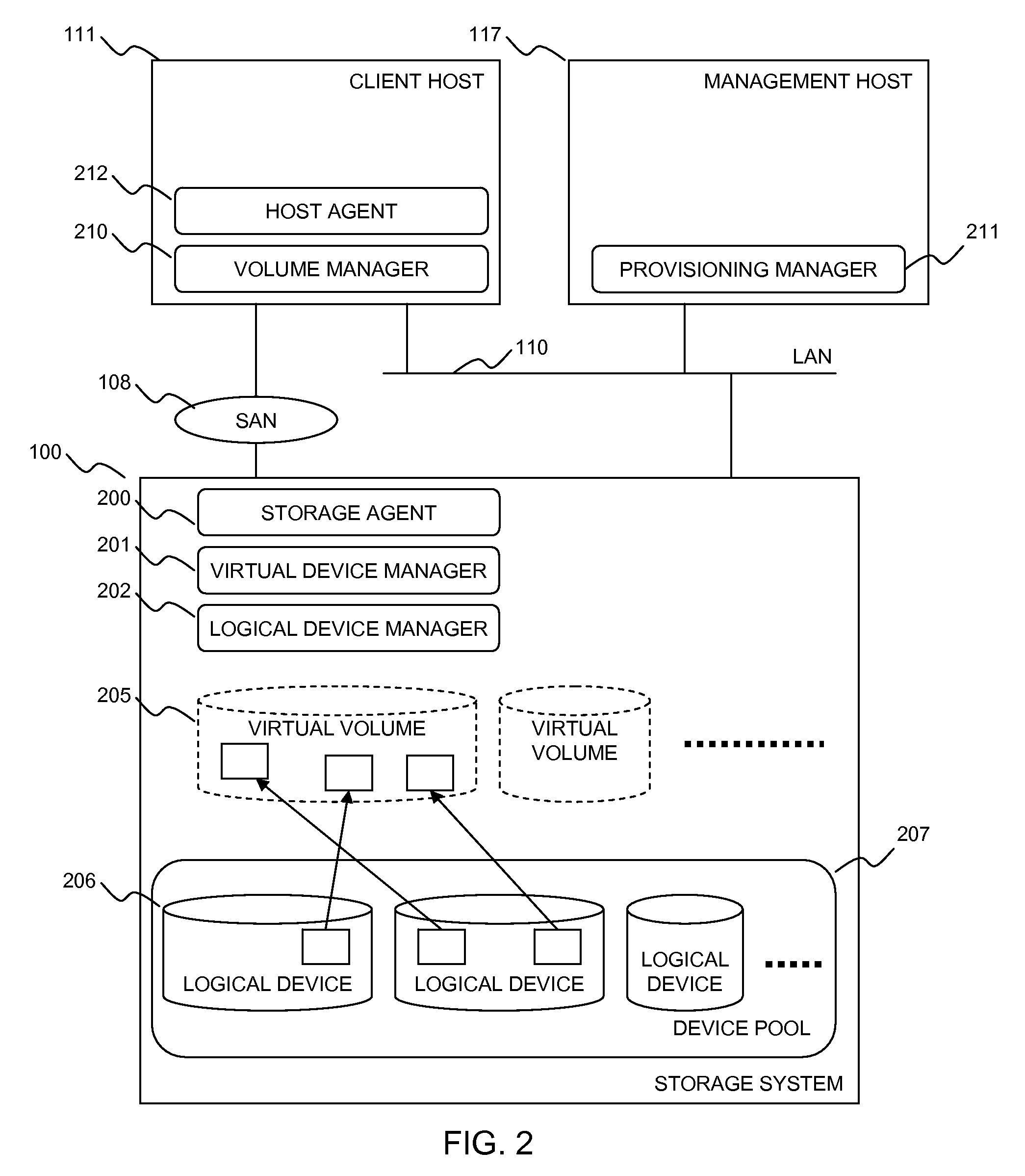
Method and Apparatus for Provisioning Storage Volumes
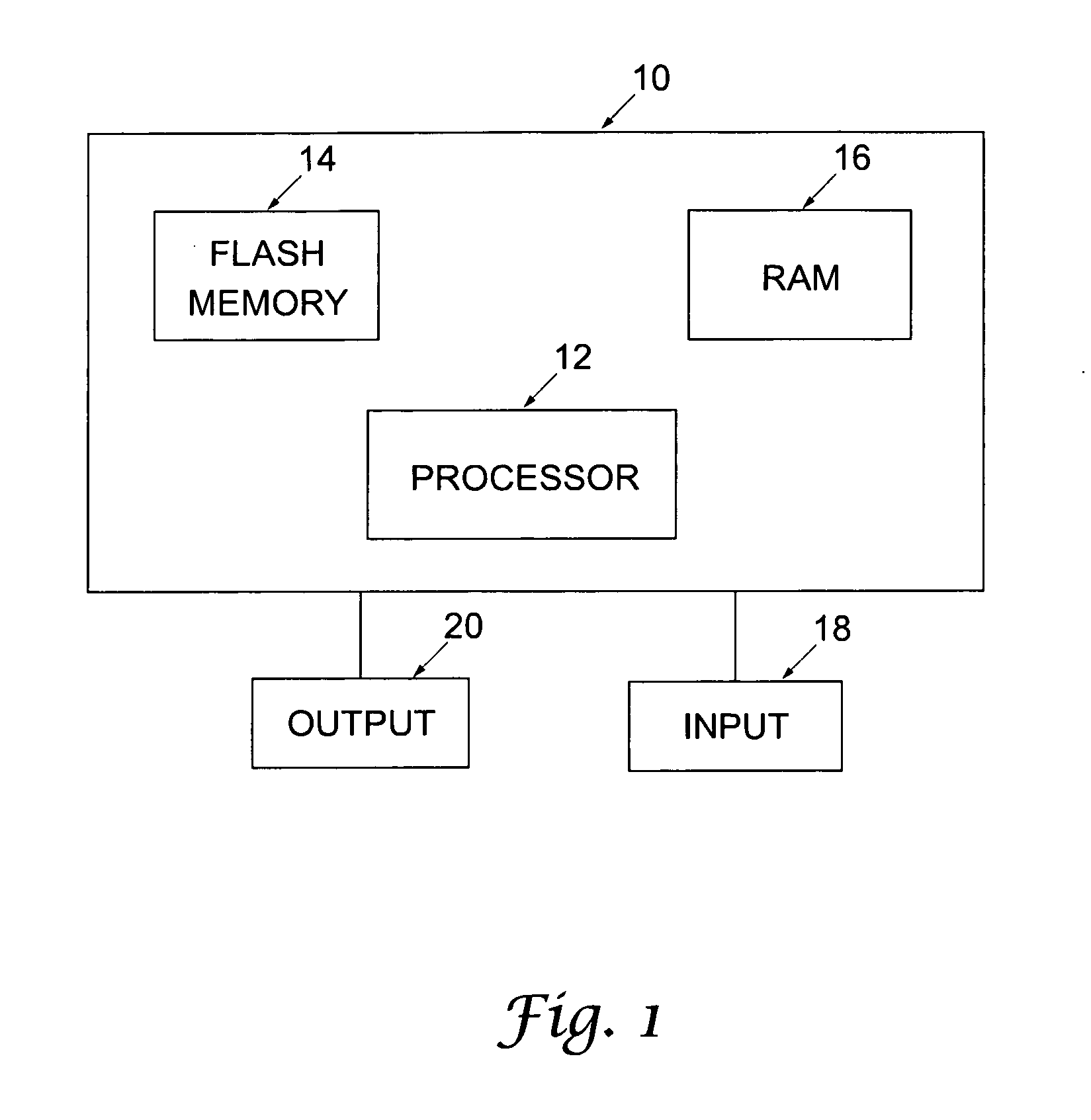
InactiveUS20080201535A1Eliminate operationMemory systemsInput/output processes for data processingClient-sideHost machine
A method for determining volume size in a storage system, comprising the steps of receiving a request for a volume assignment from a client host; obtaining client host specification; obtaining storage system specification; based on the client host specification and storage system specification selecting a proper volume size; and assigning a virtual volume to the client host, the virtual volume having the selected proper volume size.
Owner:HITACHI LTD
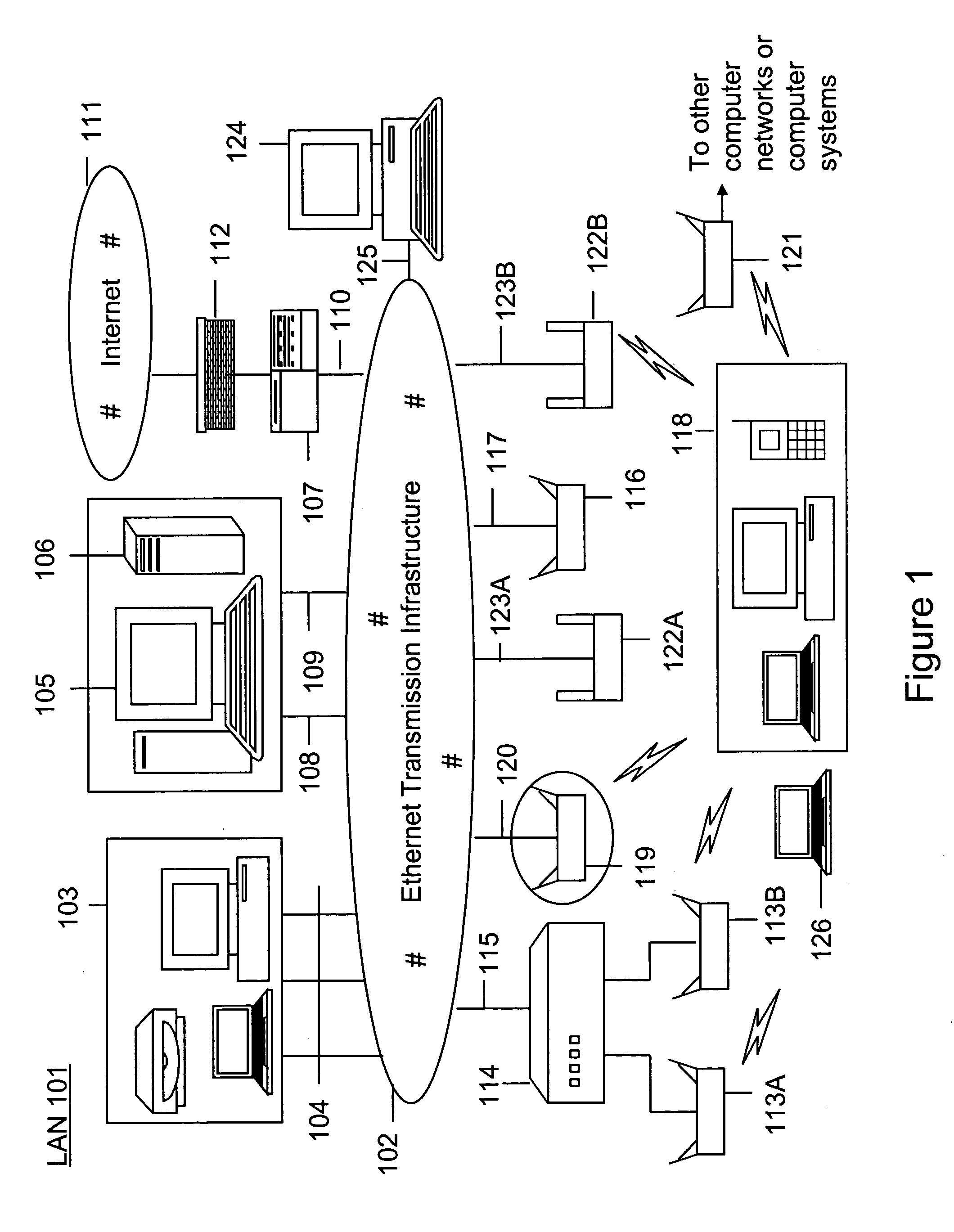
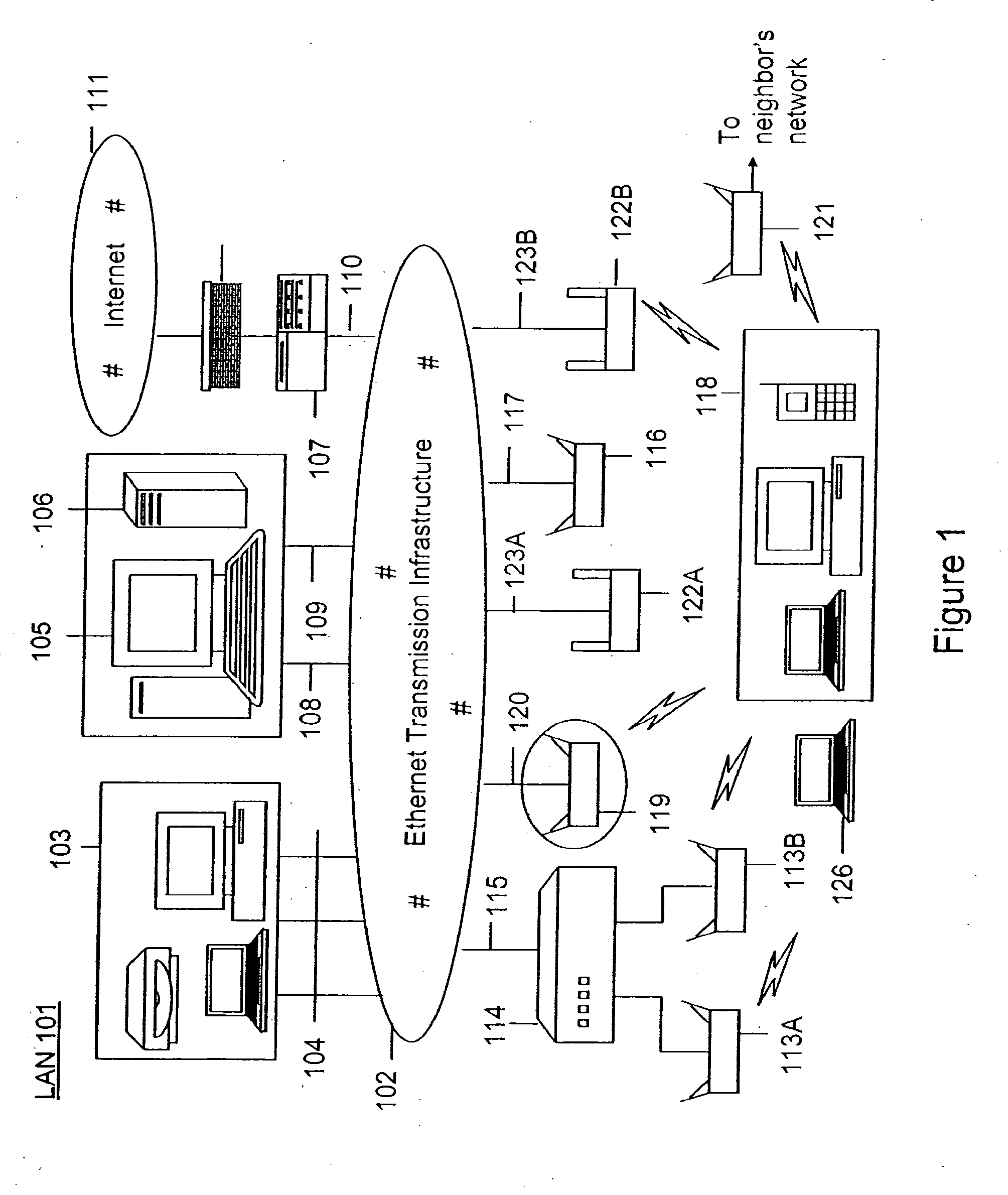
Method and apparatus for monitoring multiple network segments in local area networks for compliance with wireless security policy
InactiveUS20060193300A1Prevent unauthorized wireless accessMinimizes human effortNetwork topologiesRadio/inductive link selection arrangementsGeographic regionsComputer science
Method and system for monitoring a plurality of network segments in a local area network within a selected geographic region is provided. The monitoring is performed to check compliance with one or more wireless security policies. The method comprises providing a network monitoring device and coupling the network monitoring device to a connection port of the local are network. Moreover, the method includes providing one or more sniffers that are adapted to interact with a wireless medium. The sniffers are spatially disposed within and / or in a vicinity of the selected geographic region. The method includes determining a connectivity status of at least one wireless access device to the local area network.
Owner:AIRTIGHT NETWORKS
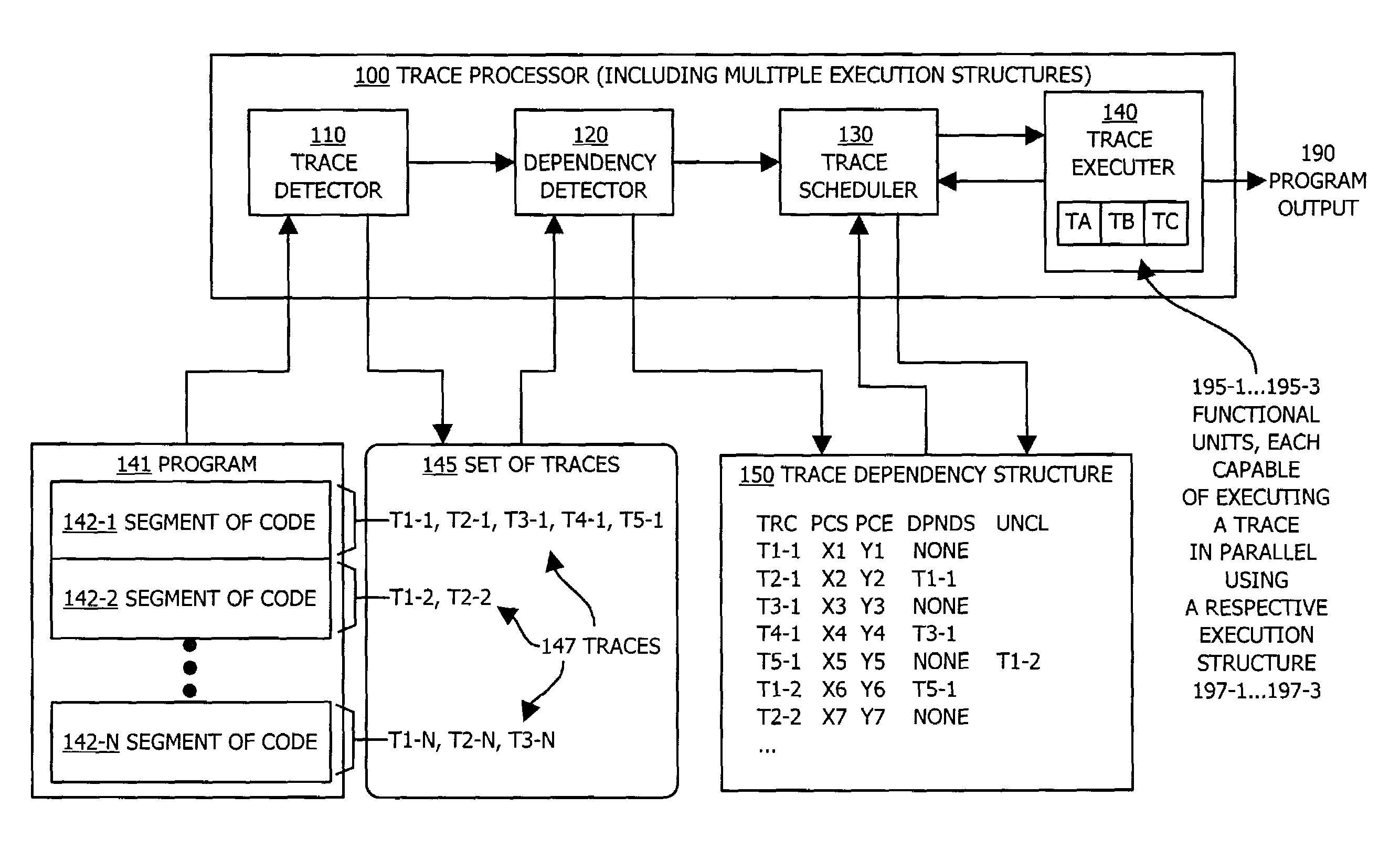
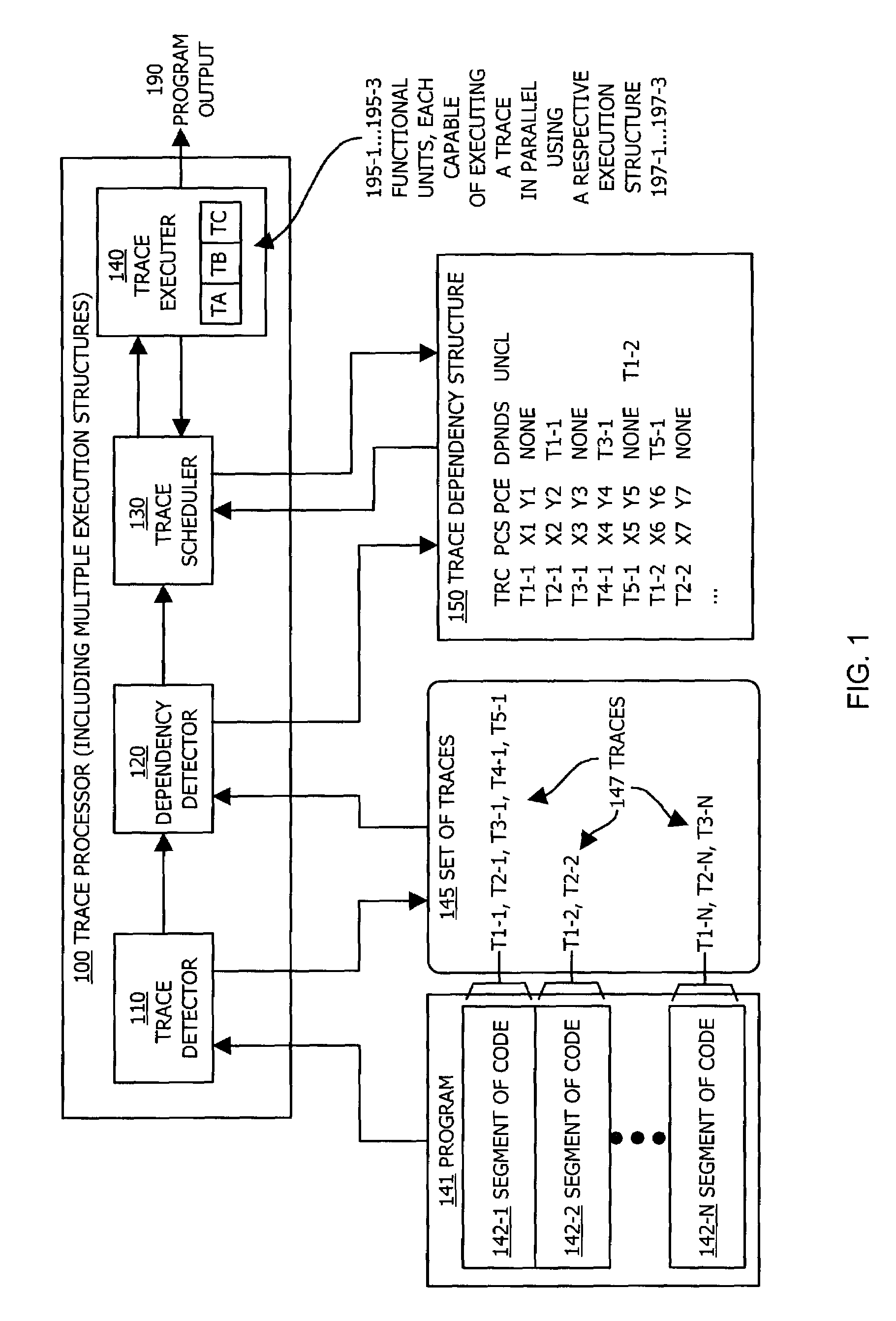
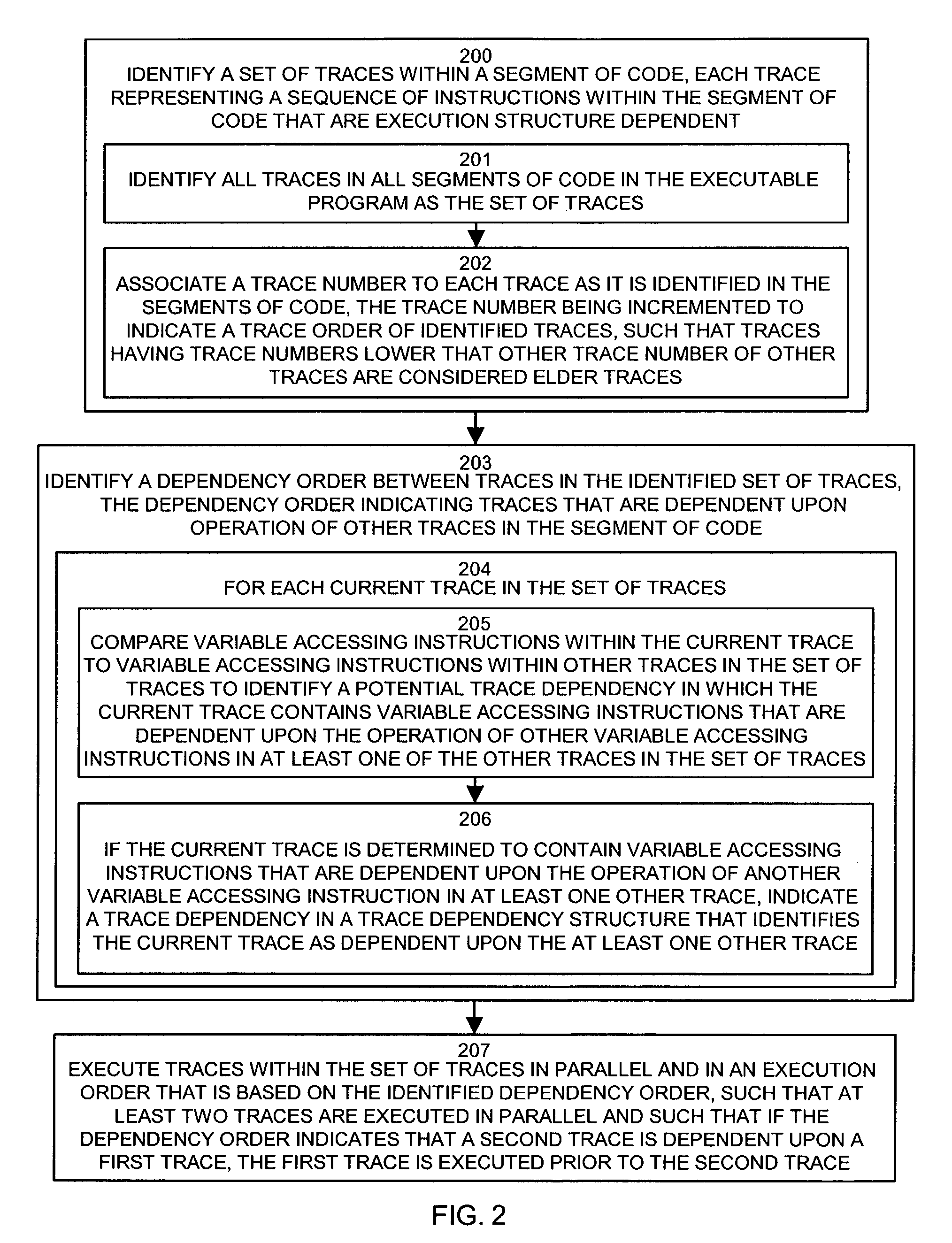
Methods and apparatus for executing instructions in parallel
ActiveUS7210127B1Eliminate operationLimited abilitySpecific program execution arrangementsMemory systemsParallel computingJava bytecode
A system, method and apparatus for executing instructions in parallel identify a set of traces within a segment of code, such as Java bytecode. Each trace represents a sequence of instructions within the segment of code that are execution structure dependent, such as stack dependent. The system, method and apparatus identify a dependency order between traces in the identified set of traces. The dependency order indicates traces that are dependent upon operation of other traces in the segment of code. The system, method and apparatus can then execute traces within the set of traces in parallel and in an execution order that is based on the identified dependency order, such that at least two traces are executed in parallel and such that if the dependency order indicates that a second trace is dependent upon a first trace, the first trace is executed prior to the second trace. This system provides bytecode level parallelism for Java and other applications that utilize execution structure-based architectures and identifies and efficiently eliminates Java bytecode stack dependency.
Owner:ORACLE INT CORP
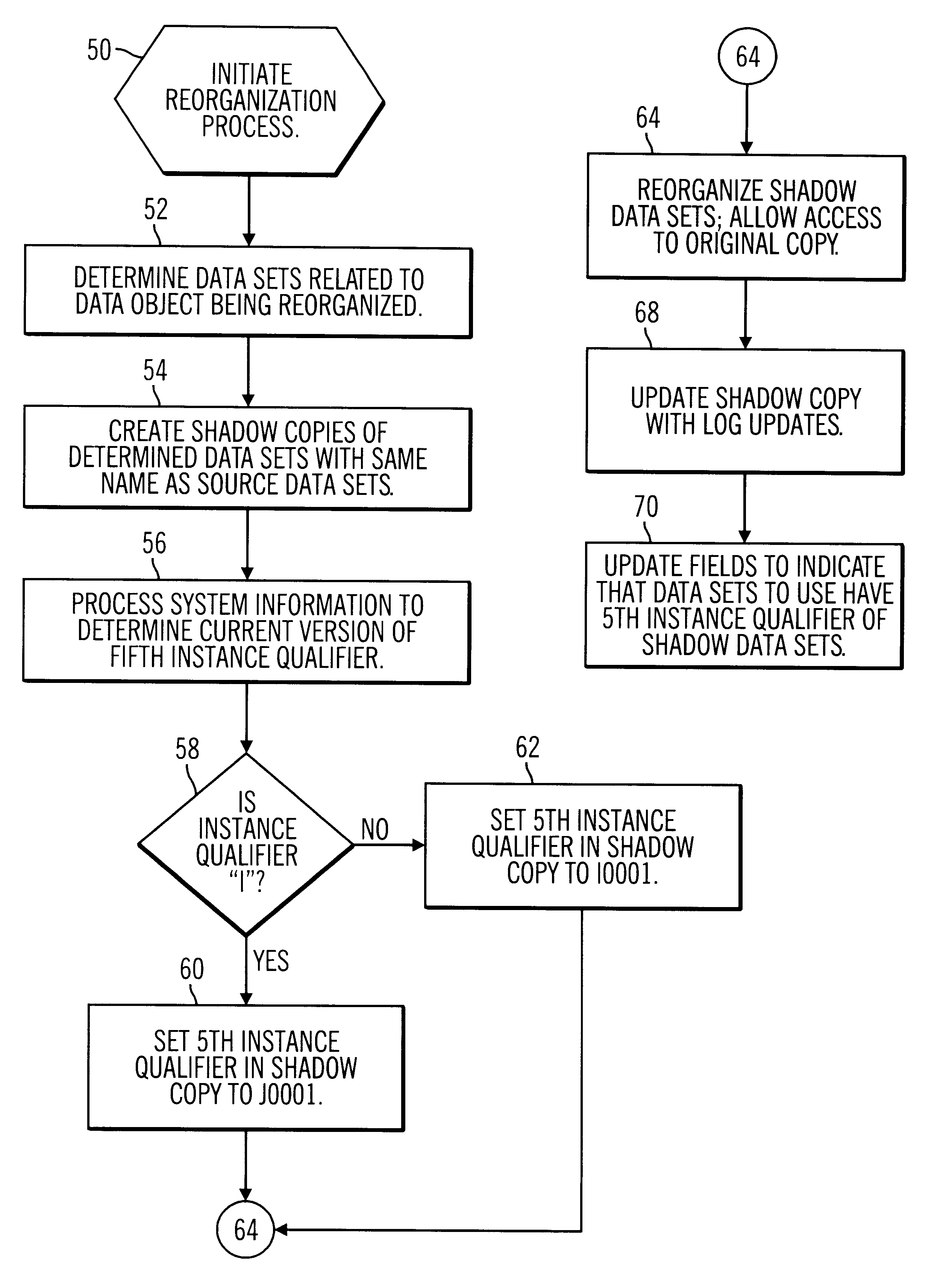
Method, system, and program for managing file names during the reorganization of a database object
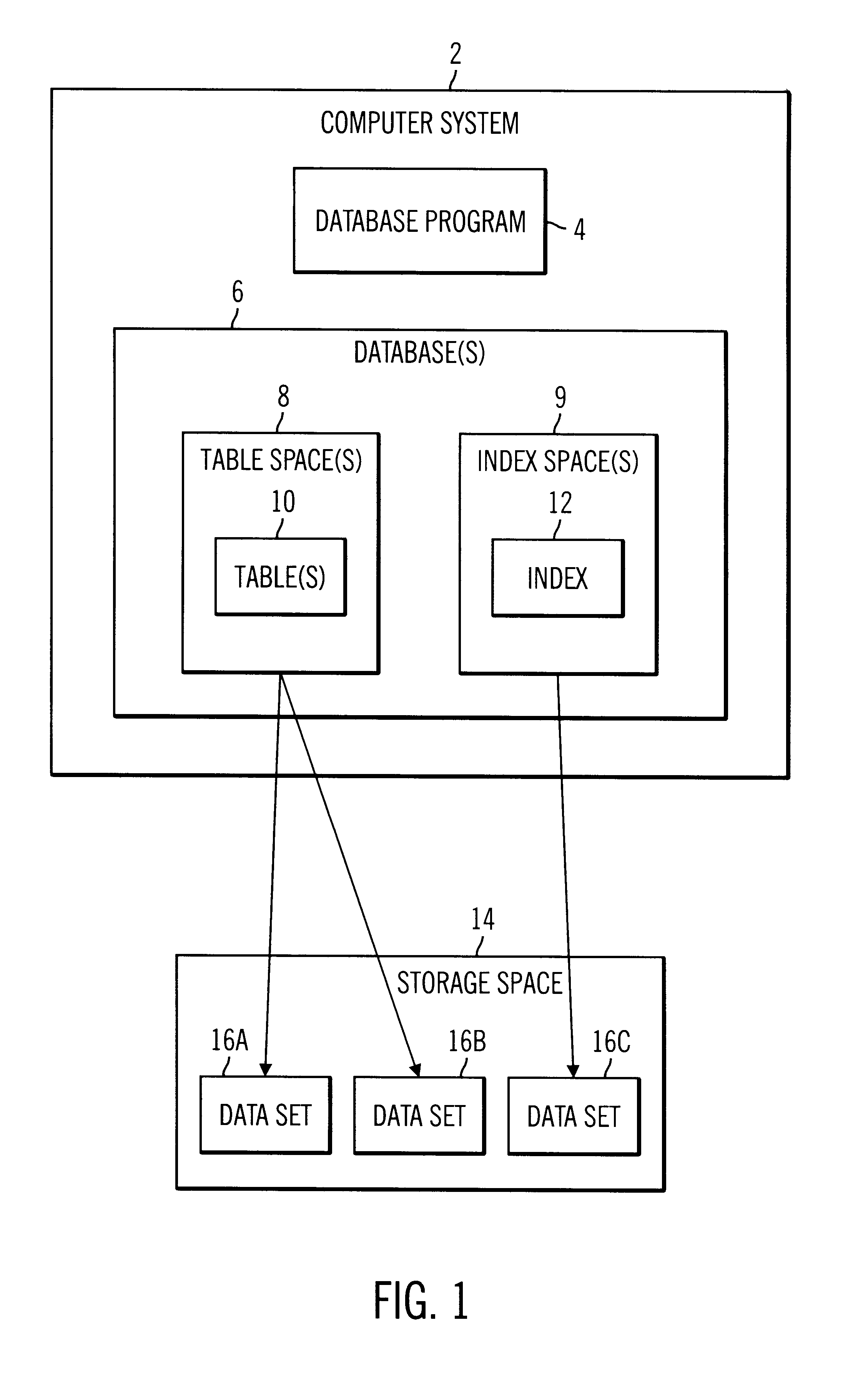
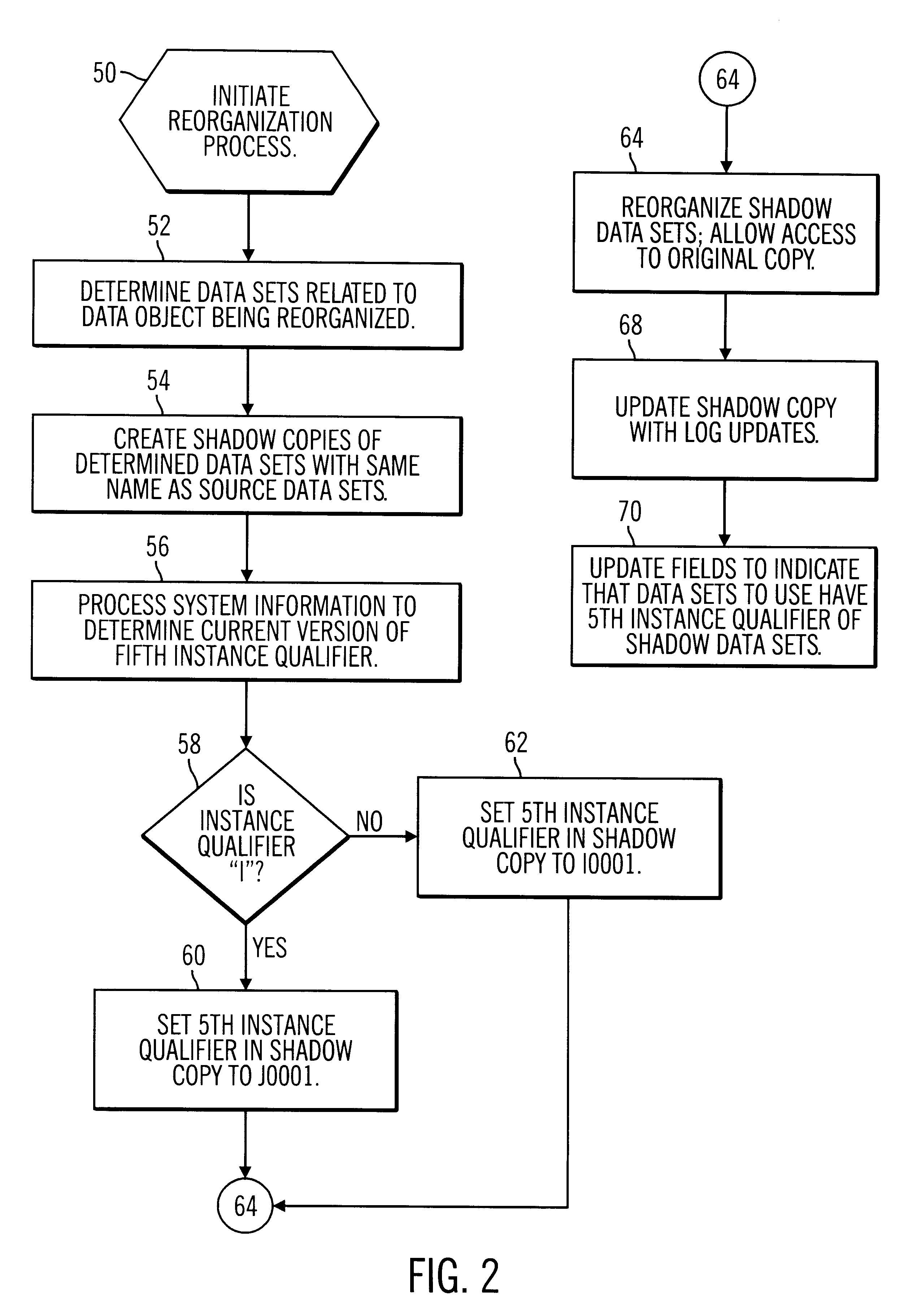
InactiveUS6460048B1Minimize the time the database objects are unavailable for accessEliminate operationData processing applicationsDigital data processing detailsDatabase fileDatabase object
Disclosed is a system, method, and program for reorganizing at least one database object. The database object is comprised of at least one database file. Each database file has a name. Source database files including data for the database objects subject to the reorganization have source names. Shadow copies of the source database files are created and shadow names for the shadow copies are generated, such that the source names and corresponding shadow names are different. The data in the shadow copies is reorganized. After the reorganization, the shadow names are used to access the database files for the reorganized database objects.
Owner:IBM CORP
Method and apparatus for equalization and decoding in a wireless communications system including plural receiver antennae
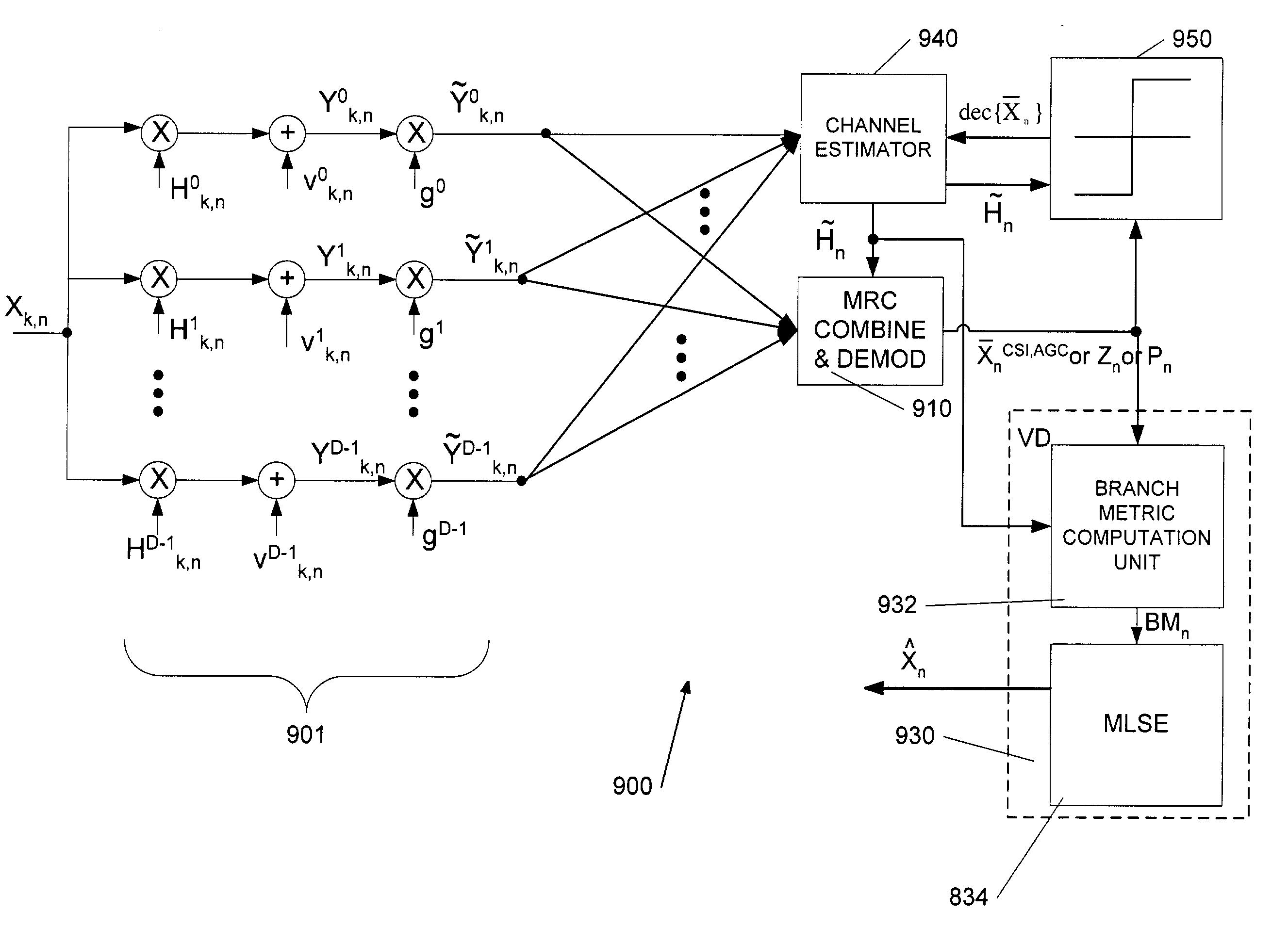
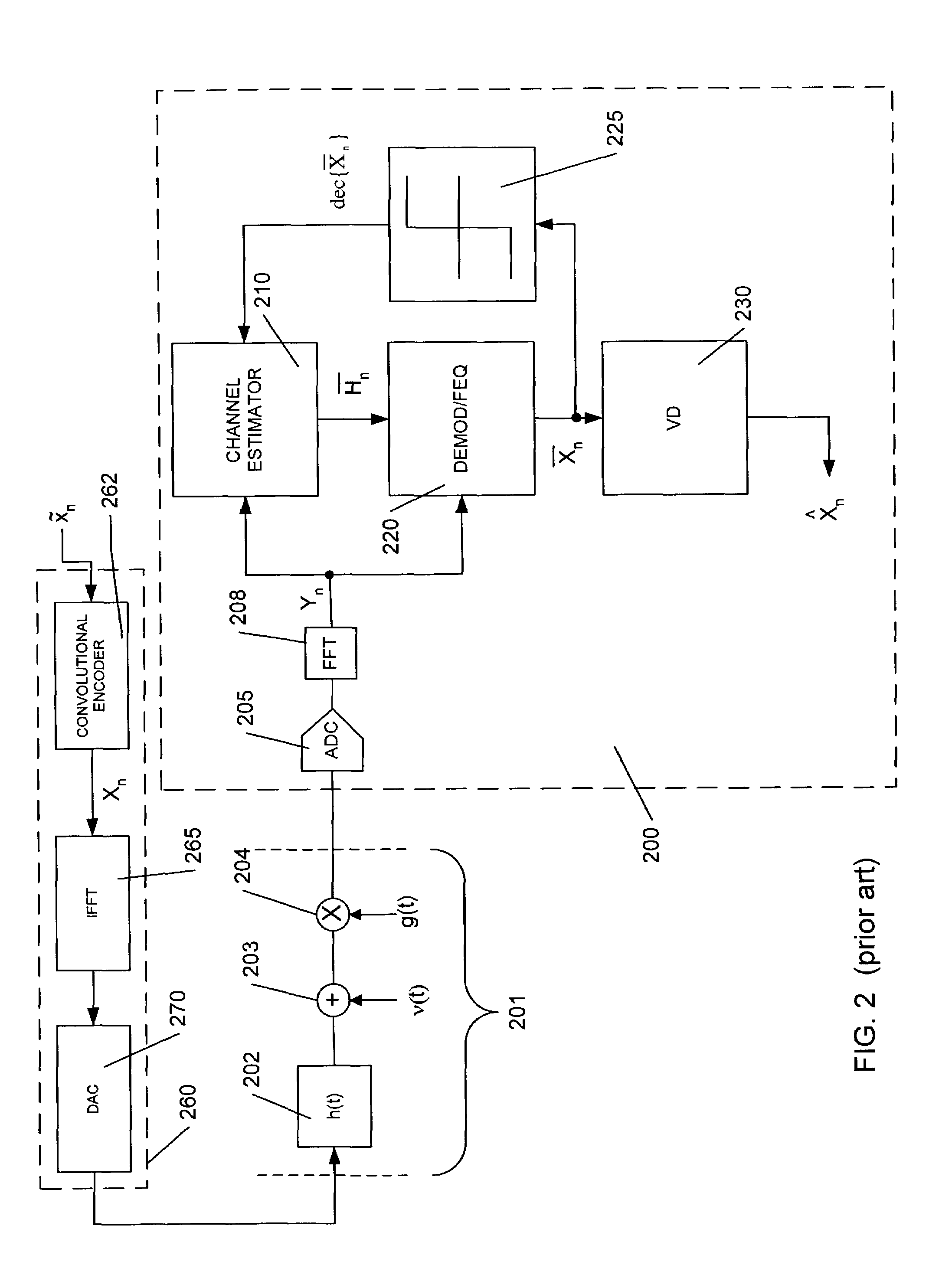
ActiveUS7065146B1Amplified equalizationSimplify complexityAmplitude-modulated carrier systemsDiversity/multi-antenna systemsChannel state informationCommunications system
Joint equalization and decoding techniques to eliminate the division operations in the Frequency domain Equalizer (FEQ) of an Orthogonal Frequency Division Modulation (OFDM) receiver by incorporating the magnitude of the channel impulse response estimates into the decision metrics in the decoder. This includes methods for both hard-decision symbol-by-symbol detection and soft-decision decoding using the Viterbi algorithm. Further, Channel State Information (CSI) is incorporated to improve the performance of the receiver. The disclosure also introduces a computationally efficient bit-by-bit piecewise approximation technique incorporating CSI to implement decoder decision metrics. Finally, an efficient implementation technique for multiple receiver antennae using Maximum Ratio Combining (MRC) and Viterbi decoding with CSI is disclosed.
Owner:MARVELL ASIA PTE LTD
Automated sniffer apparatus and method for monitoring computer systems for unauthorized access
InactiveUS20080109879A1Easy to usePrevent unauthorized wireless accessDigital data processing detailsError detection/correctionGeographic regionsNetwork interface device
An apparatus for wireless communication including an automated intrusion detection process is provided. The apparatus has a portable housing, which may have a length no greater than 1 meter, a width no greater than 1 meter, and a height of no greater than 1 meter. A processing unit (e.g., CPU) is within the housing. One or more wireless network interface devices are within the housing and are coupled to the processing unit. The apparatus has an Ethernet (or like) network interface device within the housing and coupled to the processing unit. A network connector is coupled to the Ethernet network device. One or more memories are coupled to the processing unit. A code is directed to perform a process for detection of a wireless activity within a selected local geographic region. According to a specific embodiment, the wireless activity is derived from at least one authorized device or at least an other device. A code is directed to receiving at least identity information associated with the wireless activity from the detection process in a classification process. A code is directed to labeling the identity information into at least one of a plurality of categories in the classification process. Depending upon the embodiment, other codes may exist to carry out the functionality described herein.
Owner:AIRTIGHT NETWORKS
Method of making a heat exchanger
ActiveUS7810552B2Increased complexity of componentReduce manufacturing costAdditive manufacturing apparatusPhotomechanical apparatusEngineeringDesign data
Owner:THE BOEING CO
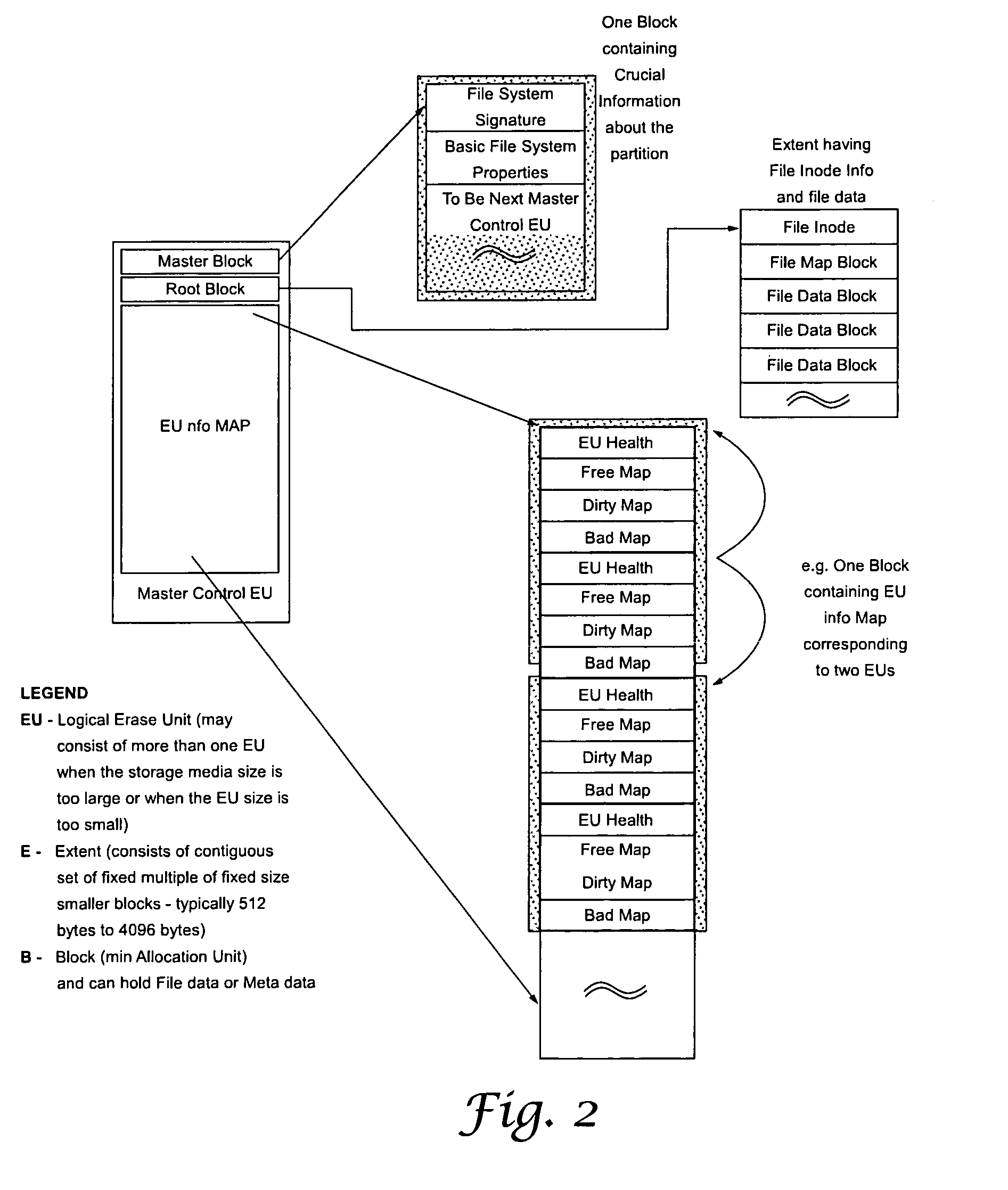
Efficient journaling and recovery mechanism for embedded flash file systems
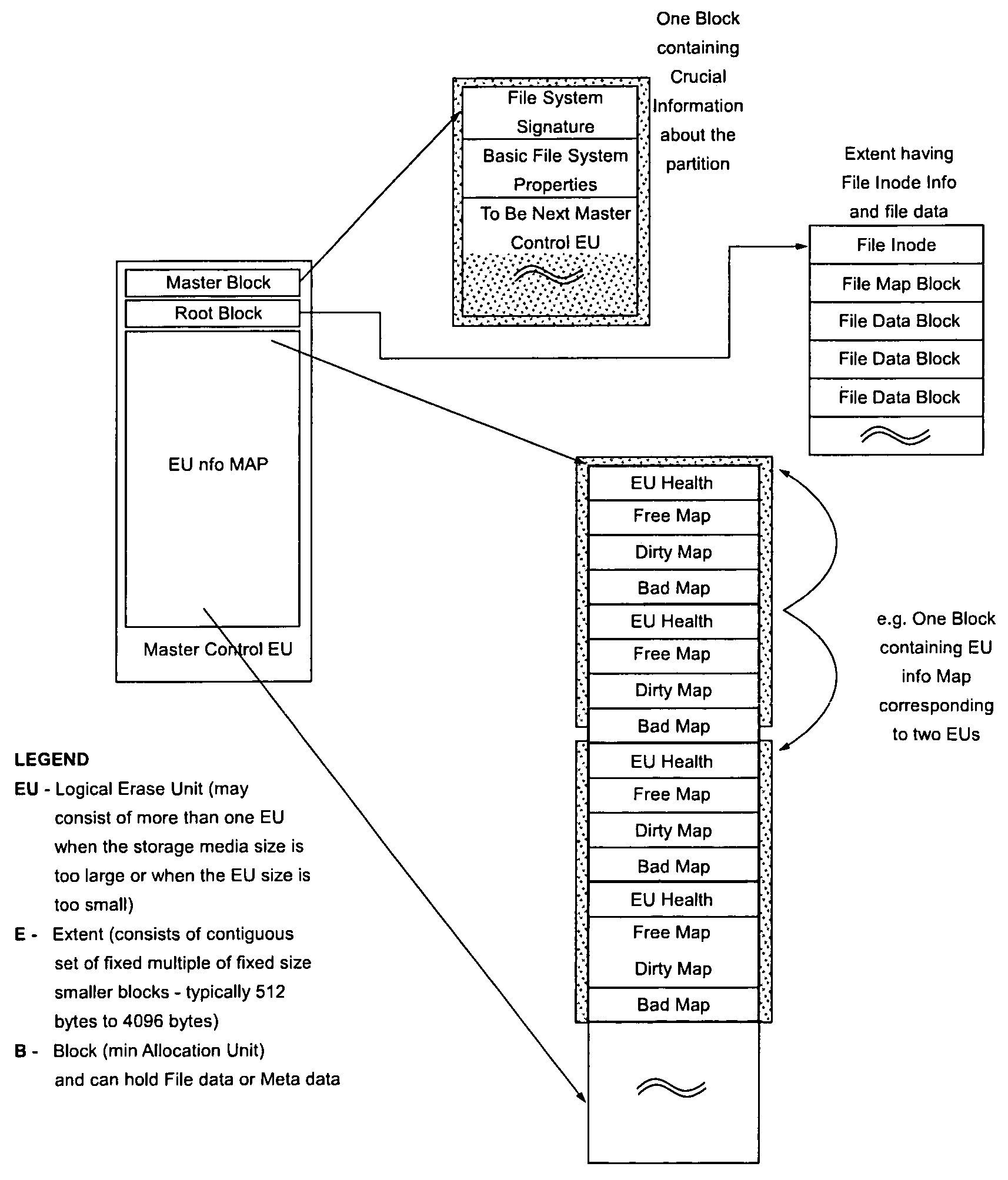
InactiveUS20080077590A1Eliminate incomplete file operationEliminate operationDigital data information retrievalError detection/correctionStable stateFlash file system
Implicit journaling of a file operation relating to a file stored in a flash memory is performed by locking a semaphore corresponding to the file on which a file operation is to be performed, by initializing journaling of the file operation using the file map, by performing the file operation on the file, by completing journaling of the file operation using a file map corresponding to the file, and unlocking the semaphore. Additionally or alternatively, a file system is placed in a stable state following an interruption occurring during a file operation by scanning File Maps corresponding to the files, determining whether a file operation is incomplete based on validity flags contained in the file maps, and performing remediation so as to eliminate the incomplete file operation.
Owner:HONEYWELL INT INC
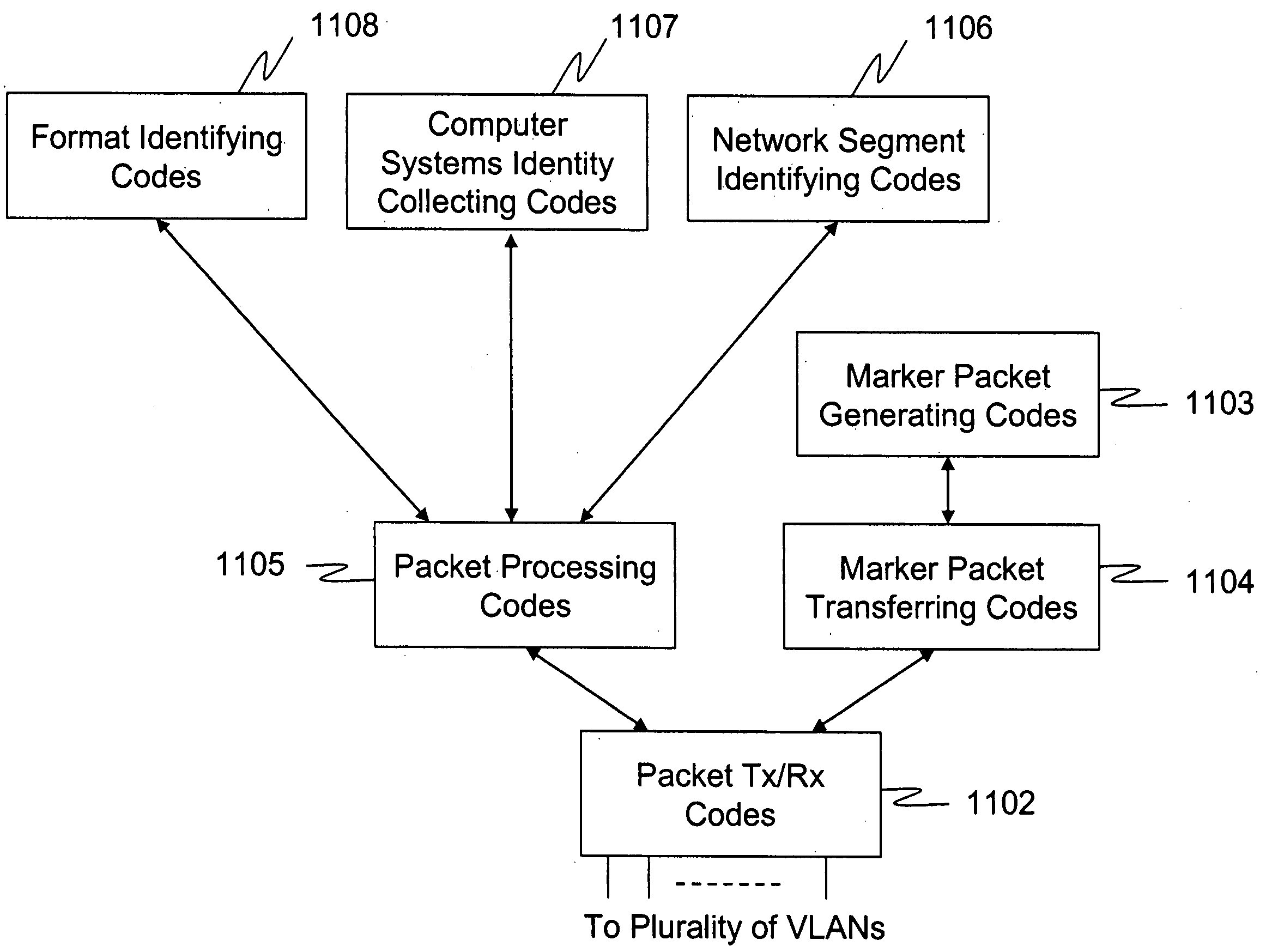
Method and system for monitoring of wireless devices in local area computer networks
ActiveUS7970894B1Easy to usePrevent unauthorized wireless accessUser identity/authority verificationNetwork topologiesPointing deviceAuthentication
A method and a system for detecting access point devices that provide unauthorized wireless access to local area computer networks is provided. The method includes transferring one or more marker packets to the wired portion of the local area network. The one or more marker packets include an authentication data that is computed based at least upon identify of the wirelessly active access point device and a secret key. The method includes processing one or more wireless frames transmitted from the wirelessly active access point device to extract and to verify at least a portion of the authentication data.
Owner:ARISTA NETWORKS
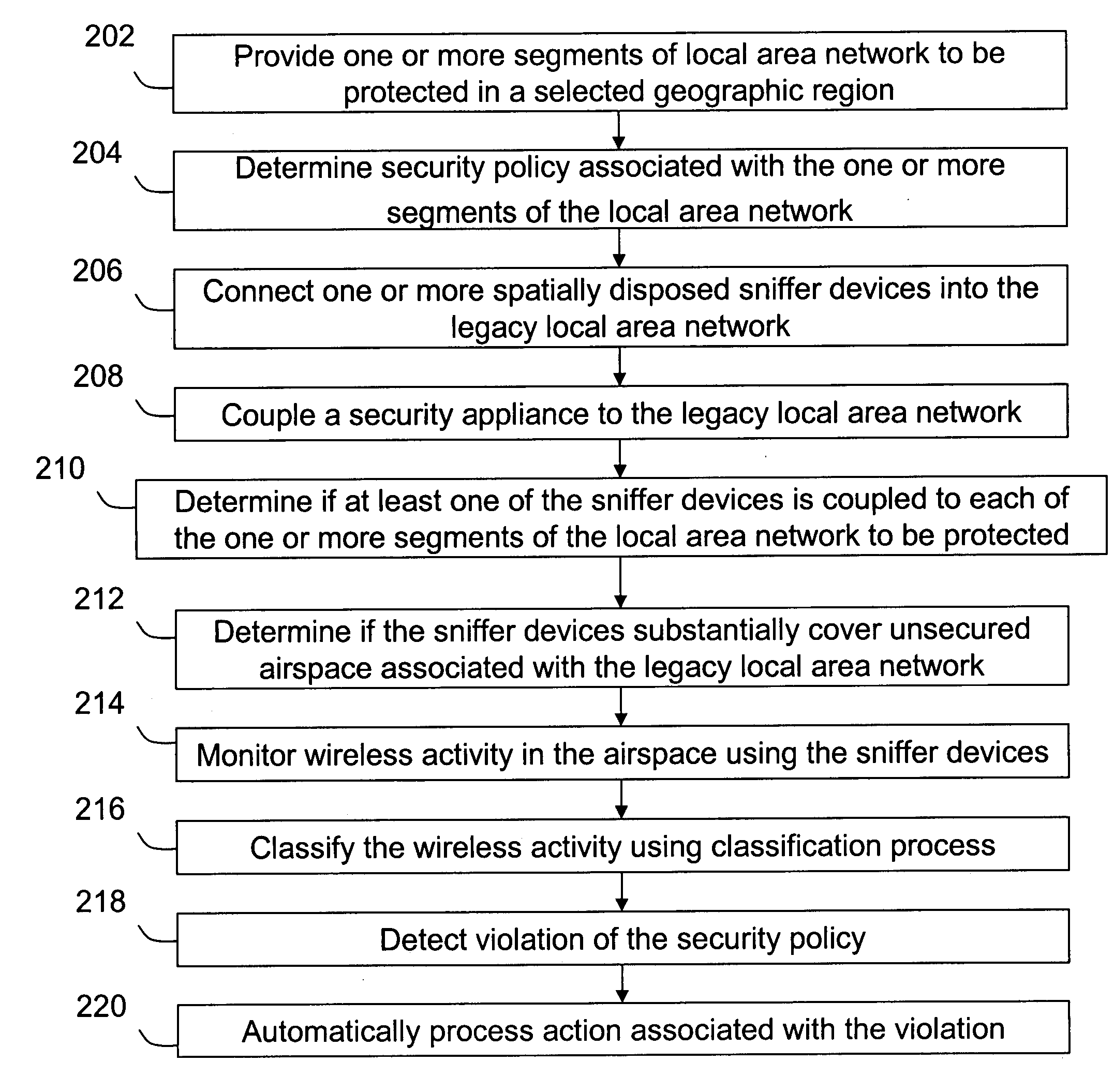
Method and system for monitoring a selected region of an airspace associated with local area networks of computing devices
ActiveUS20060153153A1Easy to usePrevent unauthorized wireless accessDigital data processing detailsData switching by path configurationBody area networkGeographic regions
A method for monitoring a selected region of an airspace associated with local area networks of computing devices is provided. The method includes providing one or more segments of a legacy local area network to be protected in a selected geographic region. The legacy local area network is characterized by an unsecured airspace within the selected geographic region. The method includes determining a security policy associated with the one or more segments of the legacy local area network. The security policy at least characterizes a type of wireless activity in the unsecured airspace to be permitted, denied, or ignored. Additionally, the method includes connecting one or more sniffer devices into the legacy local area network. The one or more sniffer devices are spatially disposed within the selected geographic region to cause at least a portion of the unsecured airspace to be secured according to the security policy. Moreover, the method includes coupling a security appliance to the legacy local area network. The method also includes determining if at least one of the sniffer devices is coupled to each of the one or more segments of the legacy local area network to be protected and determining if the one or more sniffer devices substantially covers the portion of the unsecured airspace to be secured. The method additionally includes monitoring wireless activity in the airspace using the one or more sniffer devices, and automatically classifying, using a classification process, a portion of information associated with the monitoring of the wireless activity to at least determine if the wireless activity communicates to at least one of the one or more segments to be protected. Further, the method includes detecting a violation of the security policy based upon at least the classifying of the portion of the information from the monitoring of the wireless activity, and automatically processing an action associated with the violation in accordance to the security policy for the one or more segments in the legacy local area network to be protected.
Owner:ARISTA NETWORKS
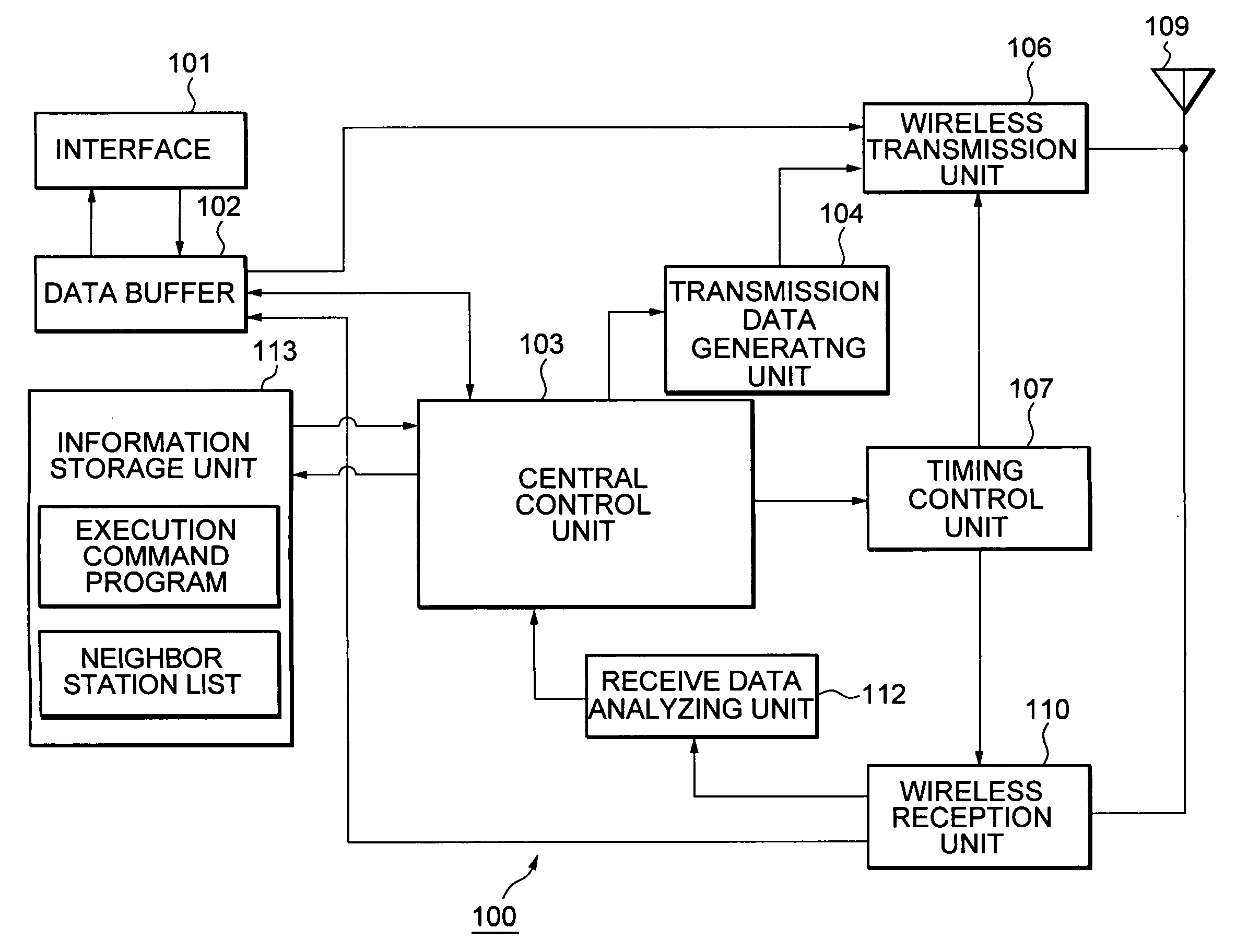
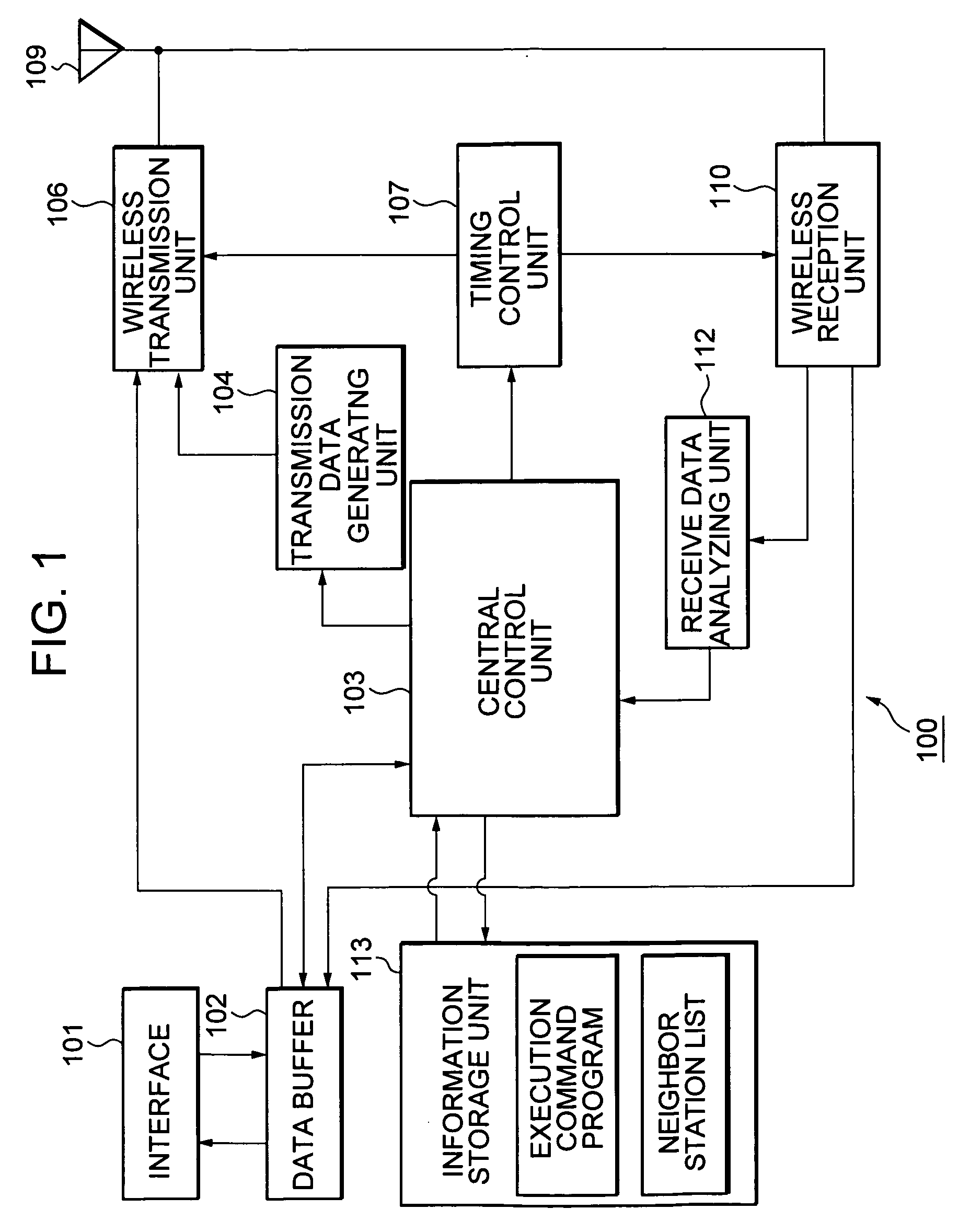
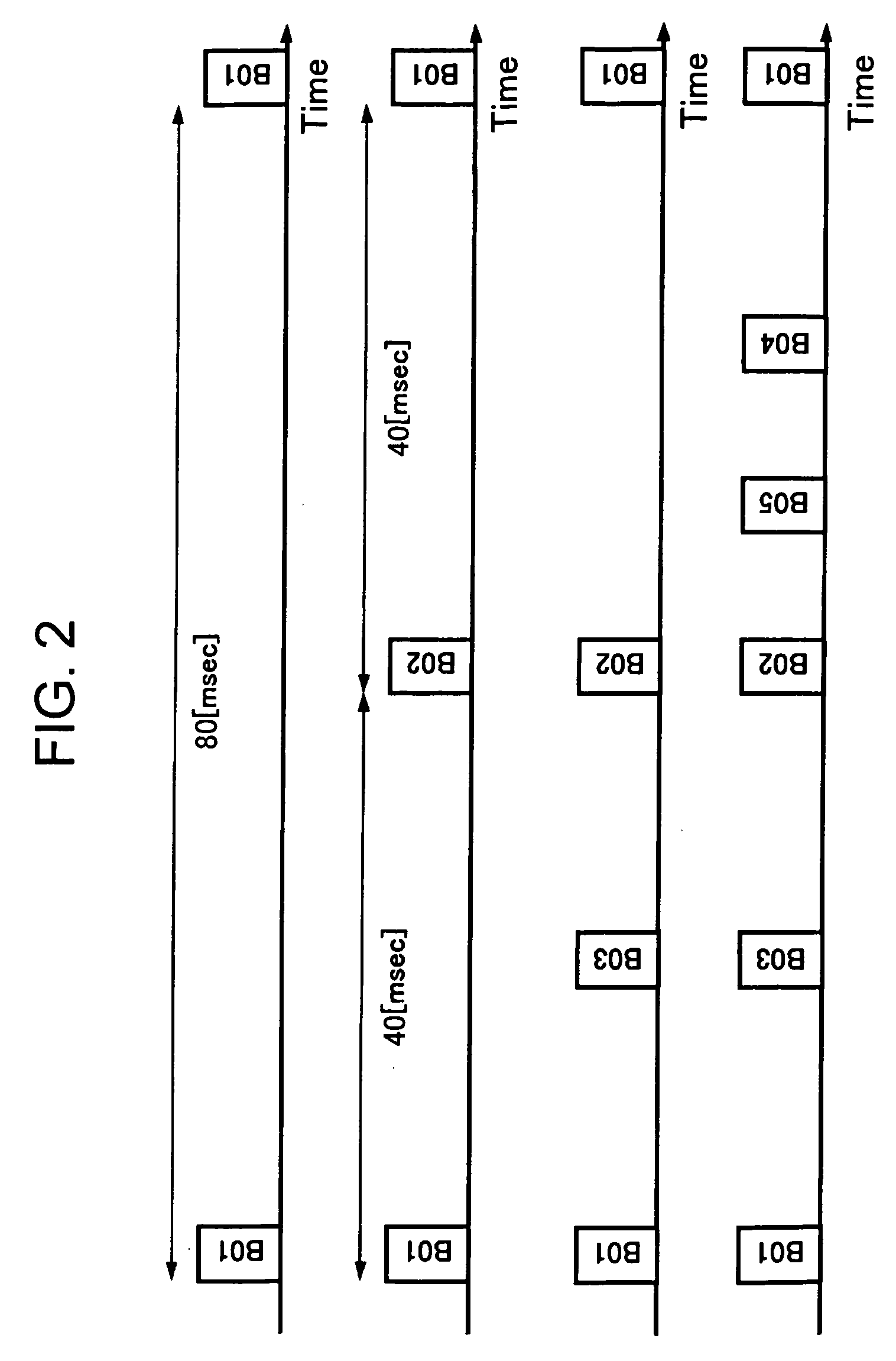
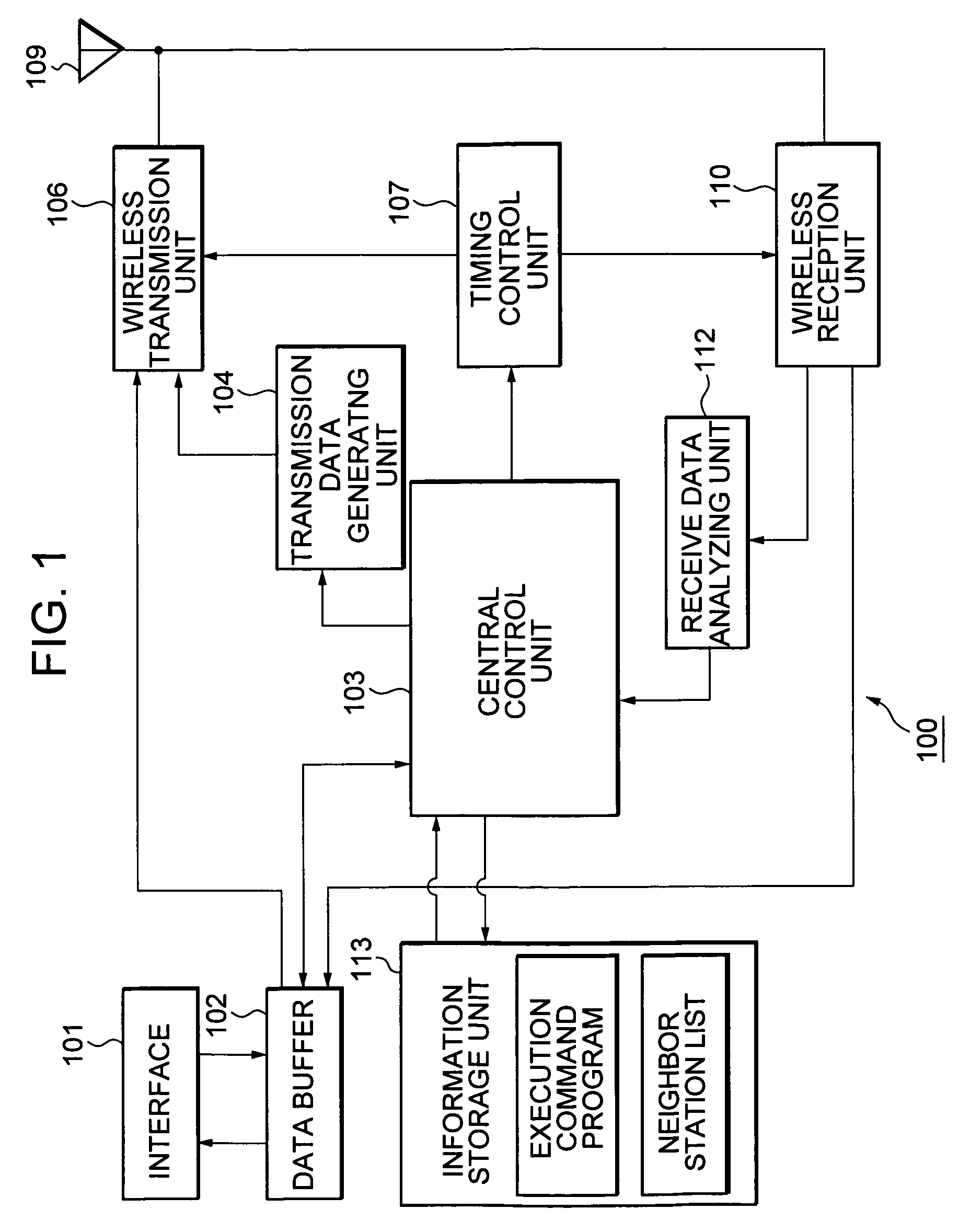
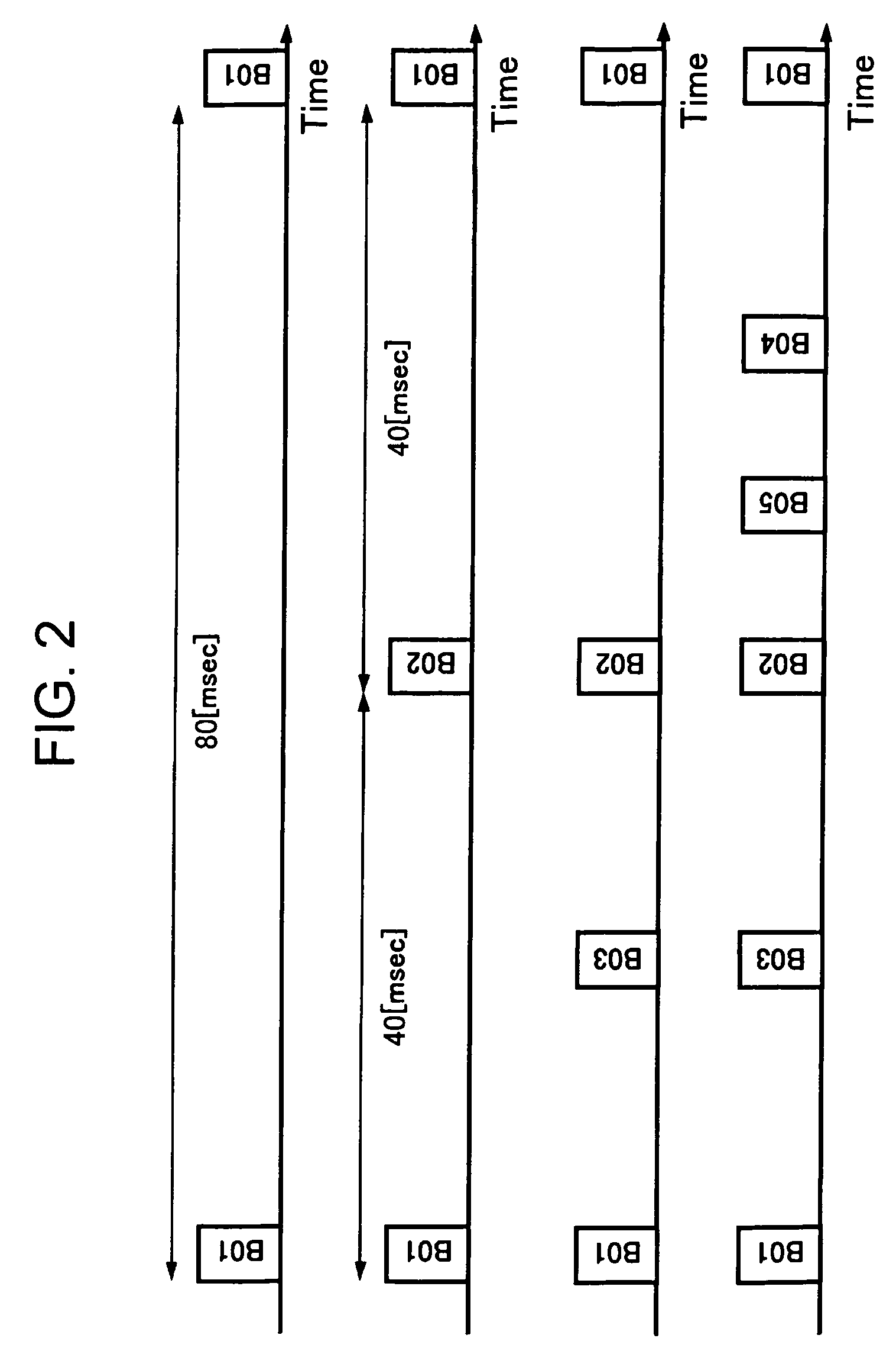
Wireless communication system, wireless communication apparatus, wireless communication method and computer program
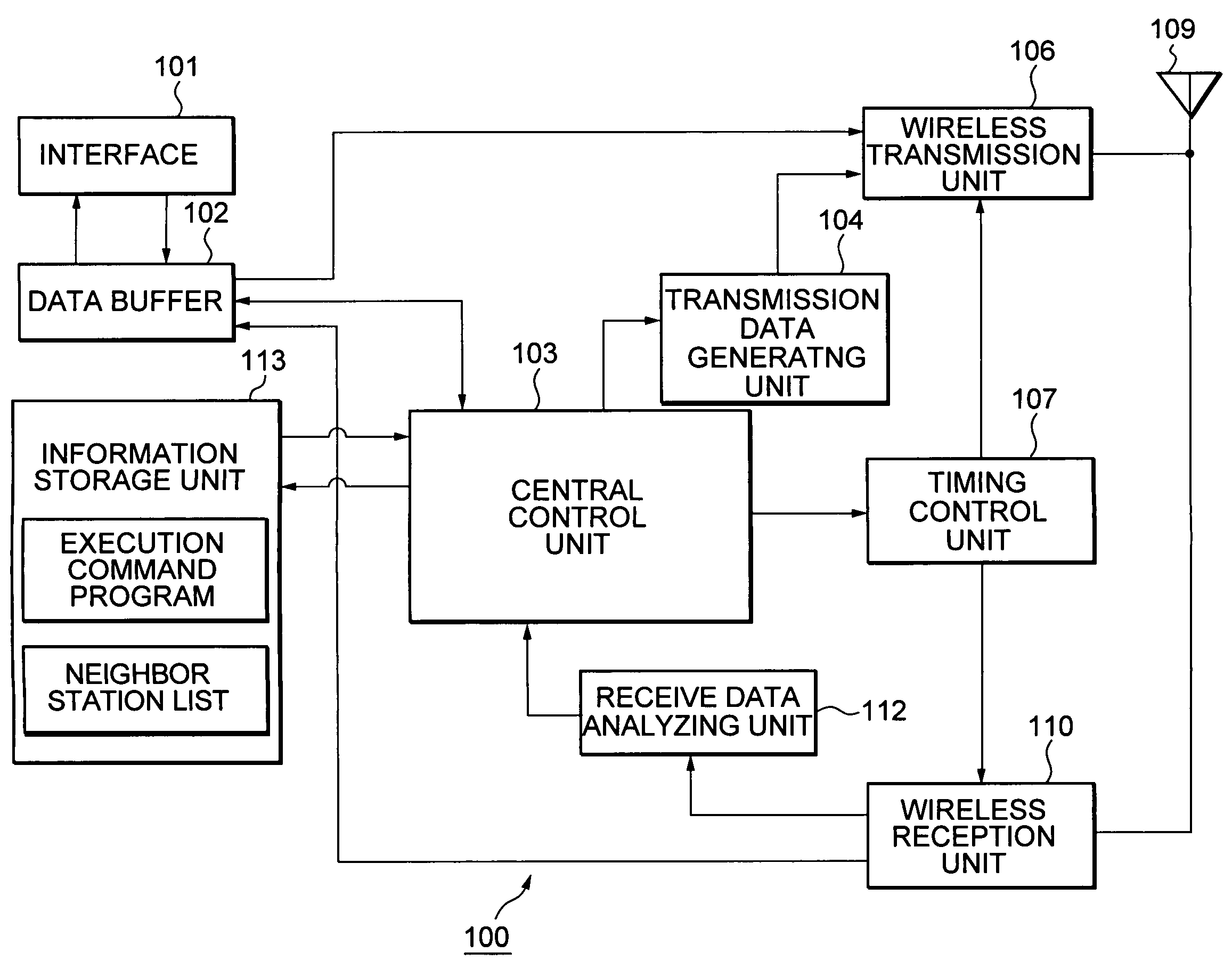
ActiveUS20050243782A1Avoid mutual interferenceGuaranteed bandwidthNetwork traffic/resource managementAssess restrictionCommunications systemTime zone
The present invention eliminates a transmission-waiting operation which is unnecessary while accommodating a prioritized traffic. Although a communication station enters a transmission-disallowed state in response to detection of a signal addressed to another station in accordance with medium access control based on CSMA, if the communication station receives a frame transmitted with priority to a local station during the transmission waiting, it cancels the transmission-disallowed state, sends back a frame responding the frame transmitted with priority and effectively operates a transmission prioritized period. The communication station starts a search procedure to perform a processing of evading duplication of the transmission prioritized periods if it judges a possibility of a problem occurring in a time zone in which reception with priority is possible.
Owner:REDWOOD TECHNOLOGIES LLC
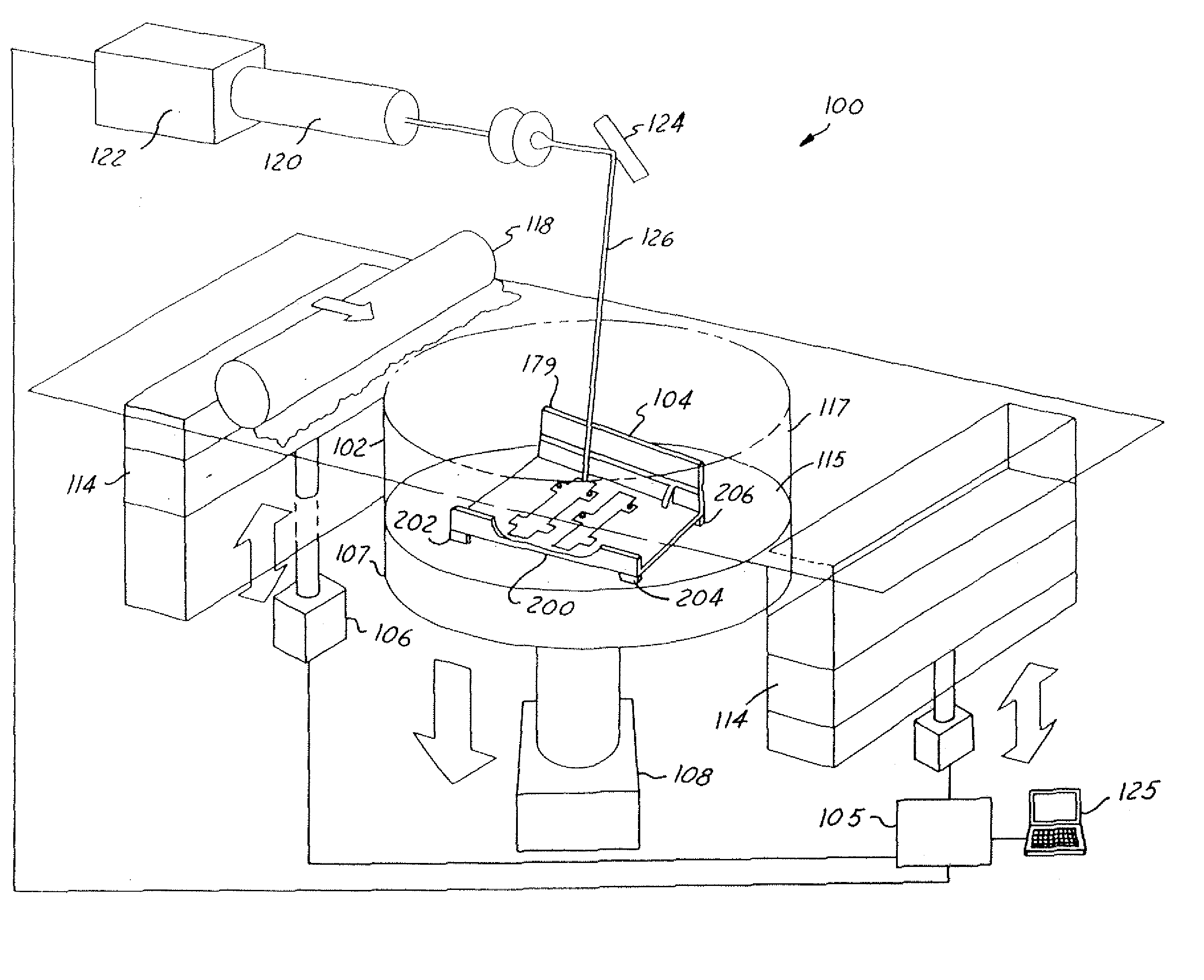
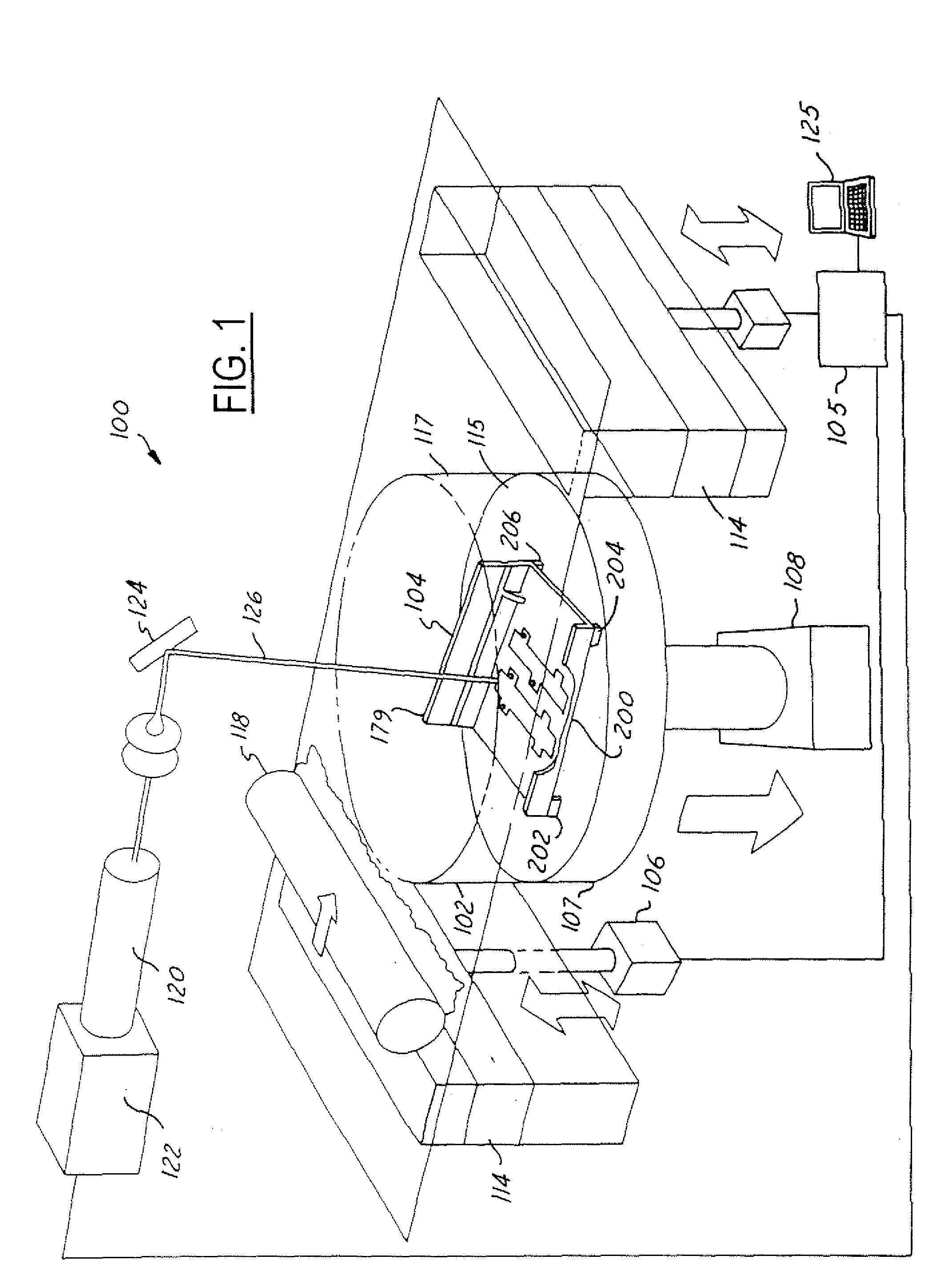
Joint Design For Large SLS Details
InactiveUS20050278933A1Reduce cost timeShorten cycle timeProgramme controlAdditive manufacturing apparatusLaserManufacturing engineering
A system for manufacturing a tool within a laser sintering system includes a chamber enclosing a sinter material. The laser sintering system grows or sinters the tool from the sinter material in response to signals from a controller, which generates the signals as a function of a predetermined tool design. The predetermined tool design includes several sections that are grown separately and are later coupled together.
Owner:THE BOEING CO
Optical recording medium and method for making
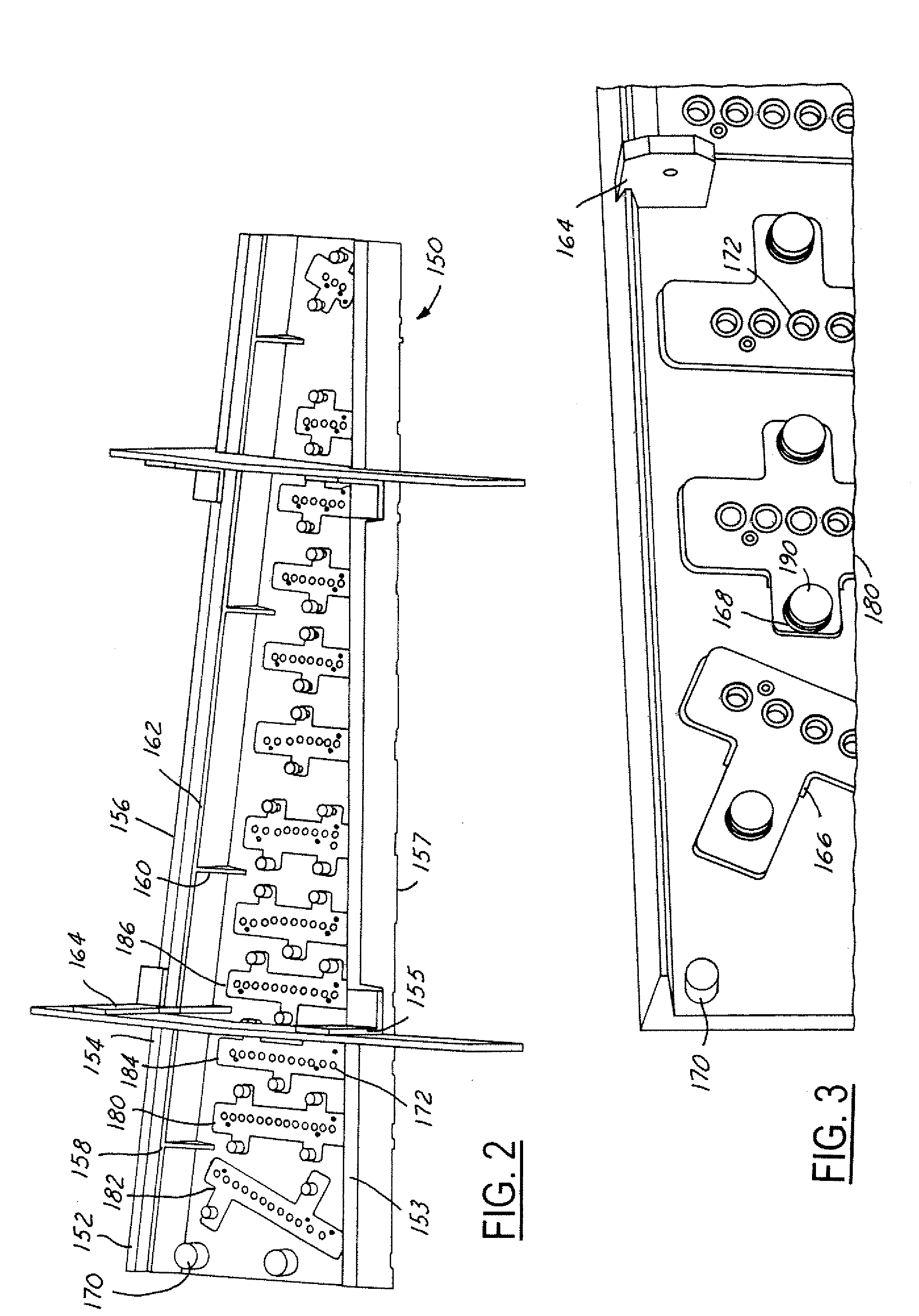
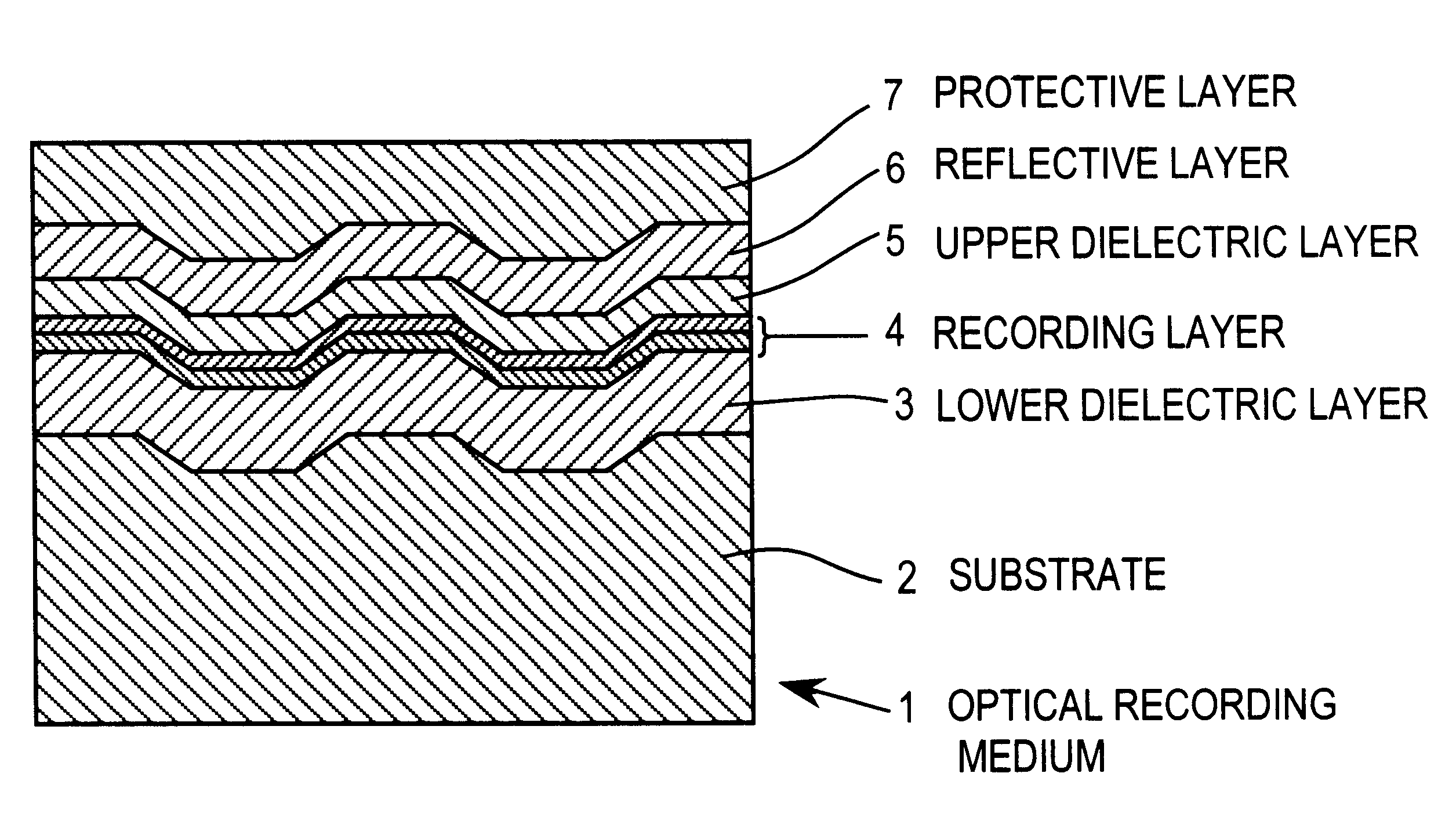
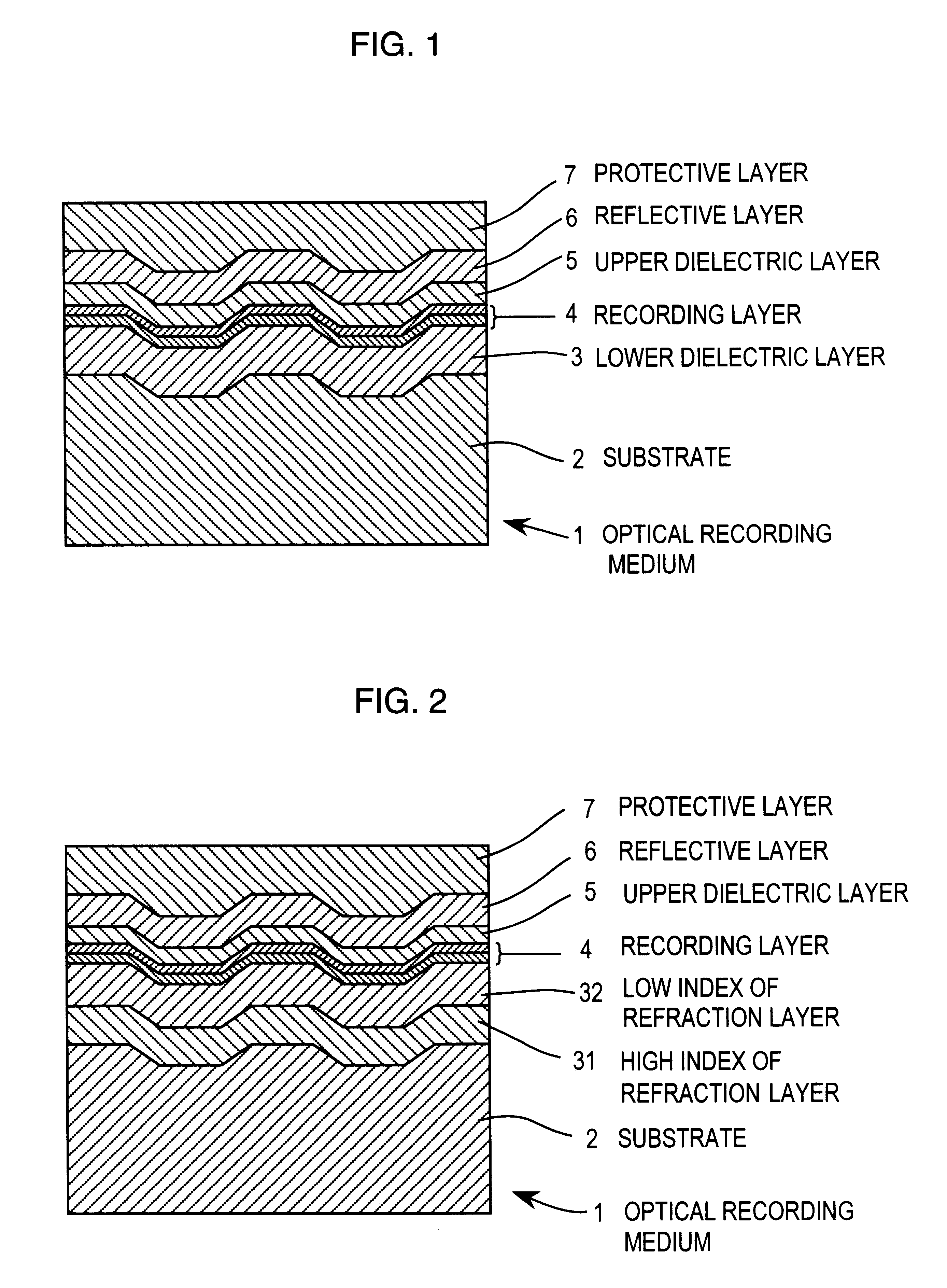
InactiveUS6242157B1Eliminate operationRadiation applicationsLayered productsOptical recordingPhase change
A phase change optical recording medium has on a substrate a recording layer consisting essentially of a Sb base thin film and a reactive thin film. The Sb base thin film is formed by depositing a Sb base material containing at least 95 at % of Sb to a thickness of 70-150 Å. The reactive thin film is formed of a material which forms a phase change recording material when mixed with Sb. The reactive thin film is typically formed of an In-Ag-Te or Ge-Te material. Stable write / read characteristics are accomplished at the first overwriting, initializing operation is eliminated, and rewriting is impossible at the same linear velocity as recording.
Owner:TDK CORPARATION
Wireless communication system, wireless communication apparatus, wireless communication method and computer program
ActiveUS7664130B2Eliminate operationEffective bandwidthNetwork traffic/resource managementAssess restrictionCommunications systemTime zone
Owner:REDWOOD TECHNOLOGIES LLC
Triaxial antenna coil
ActiveUS7042411B2Avoid breakingImprove productivityLoop antennas with ferromagnetic corePolarised antenna unit combinationsEngineeringConductor Coil
Owner:MURATA MFG CO LTD
Digital camera with reduced image buffer memory and minimal processing for recycling through a service center
InactiveUS20100020199A1Minimizes complexity and amountEasy to processTelevision system detailsTelevision system scanning detailsImaging processingComputer graphics (images)
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com