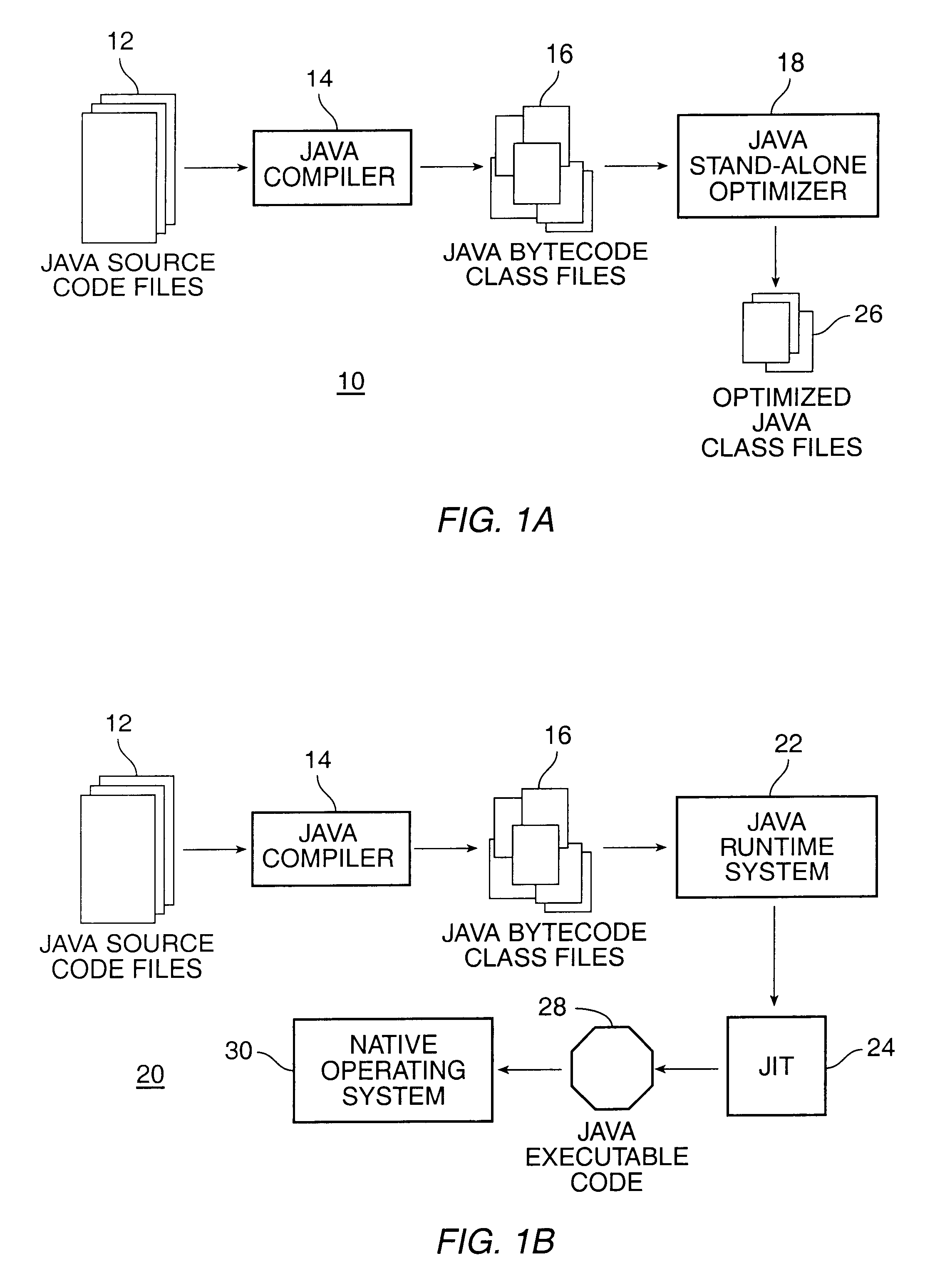
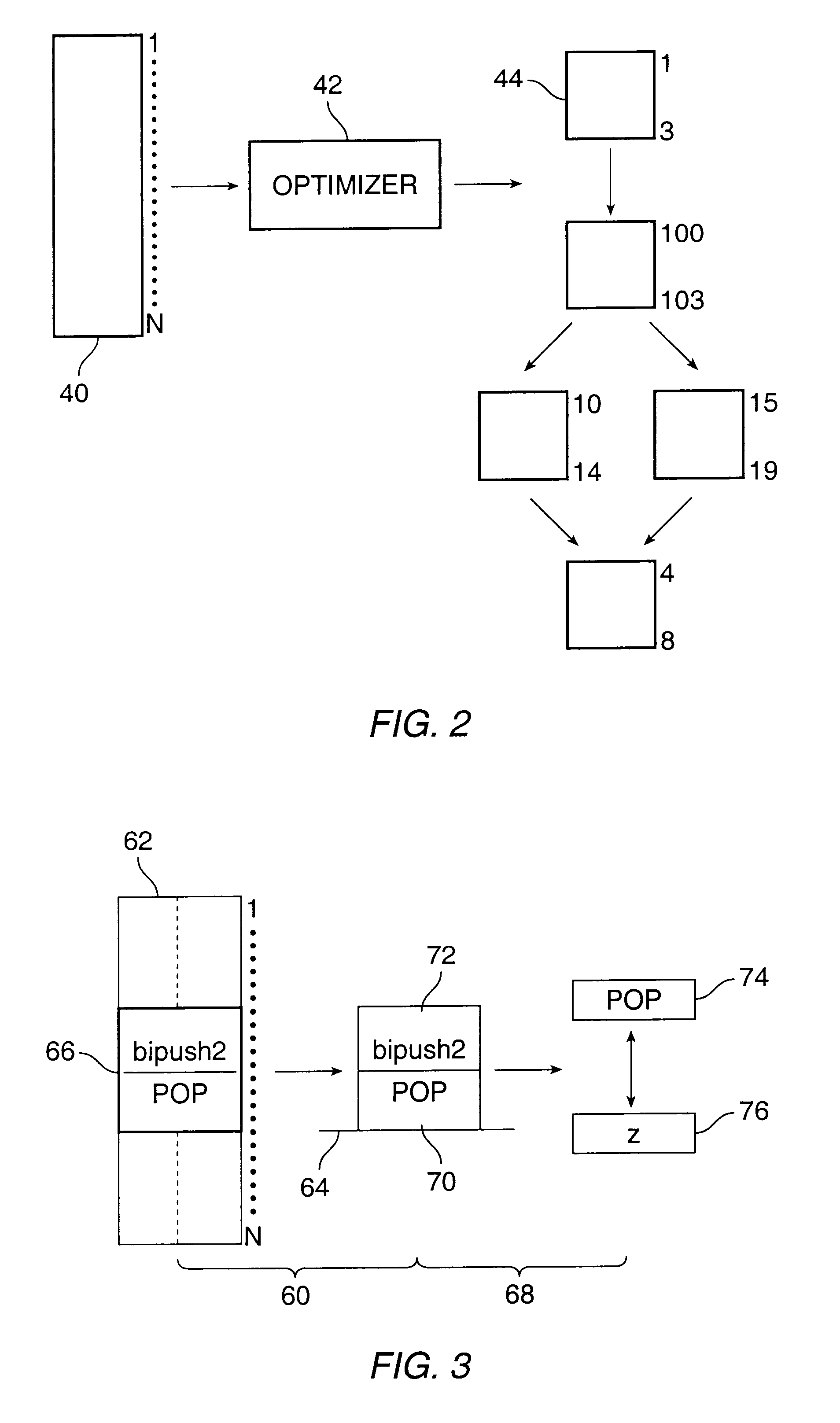
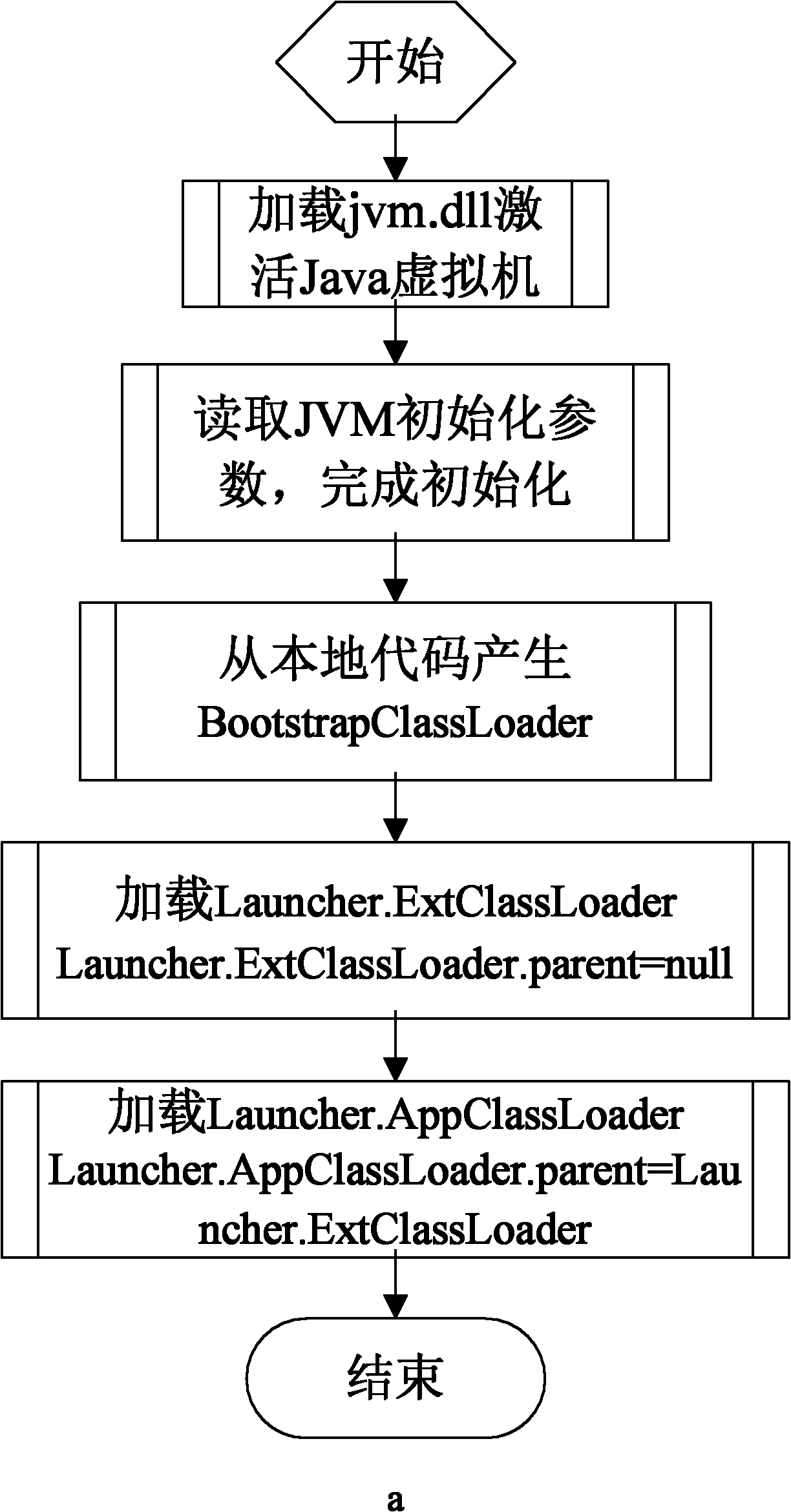
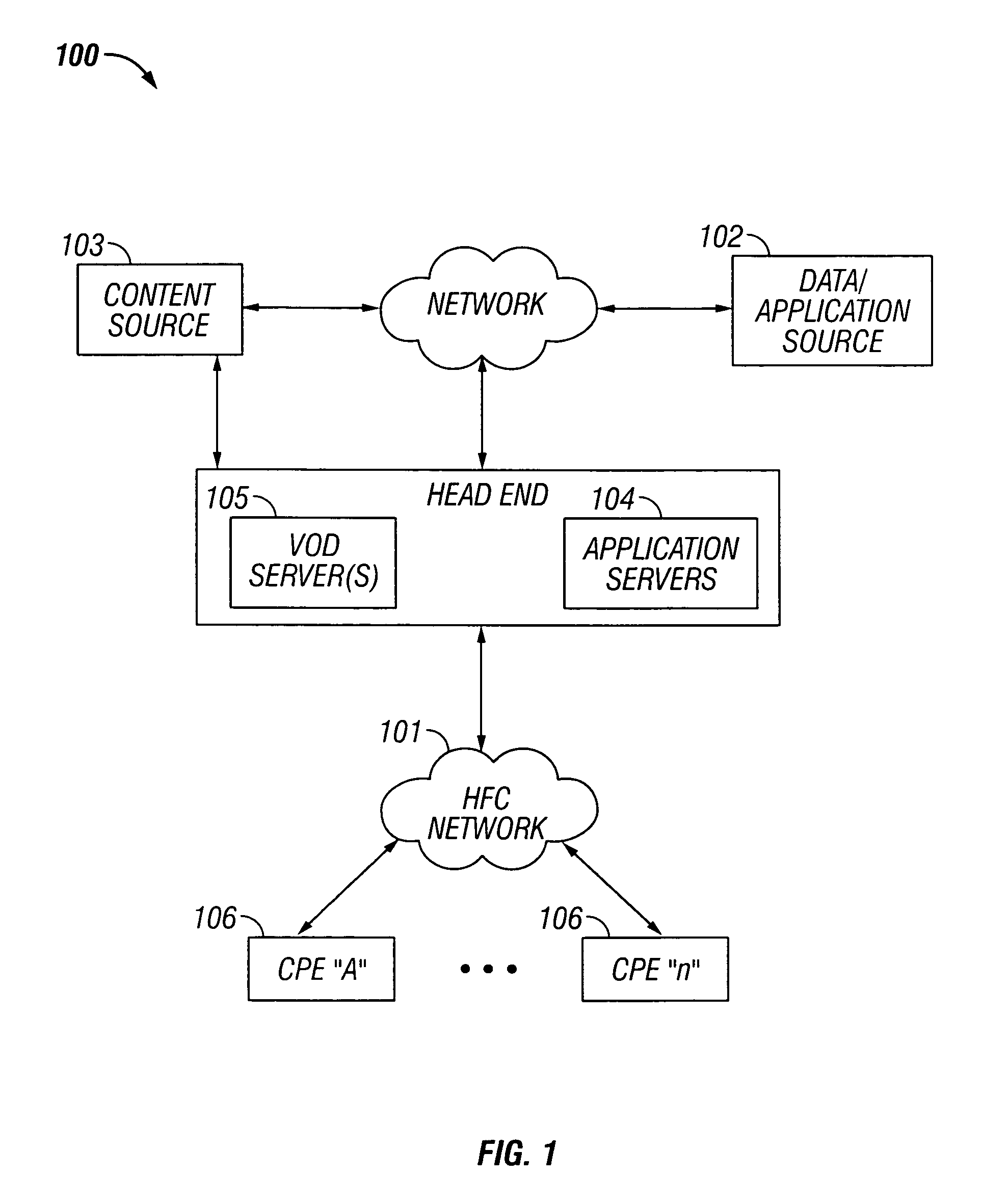
Patents
Literature
104 results about "Java bytecode" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
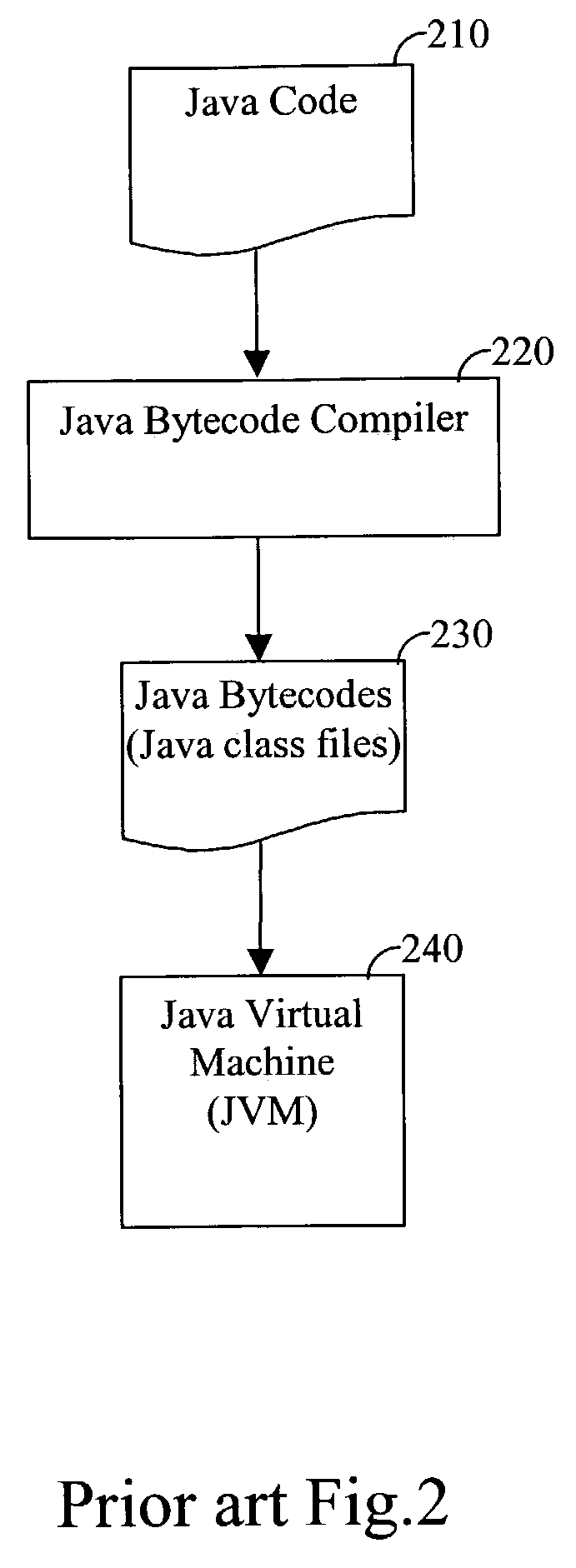
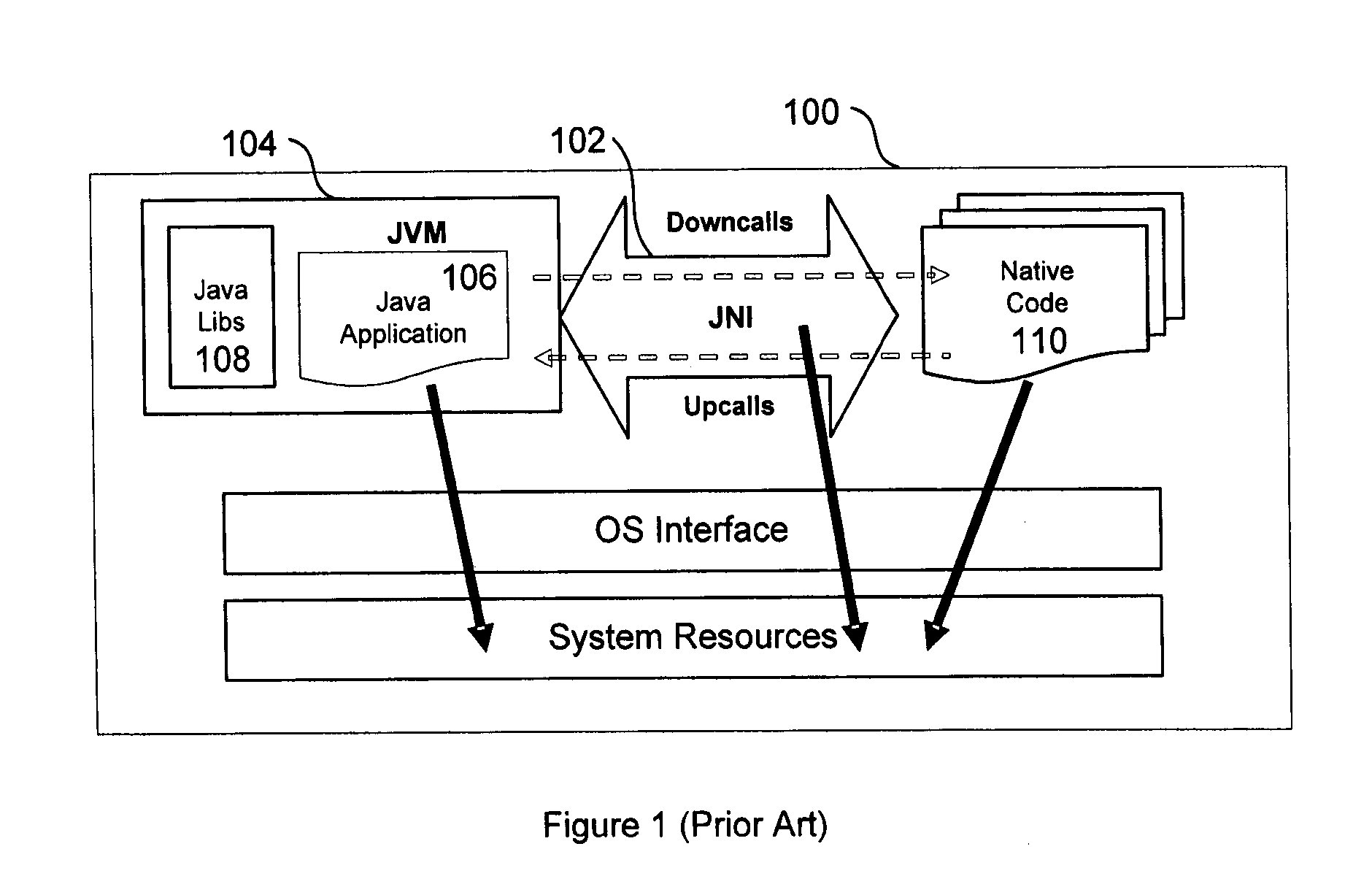
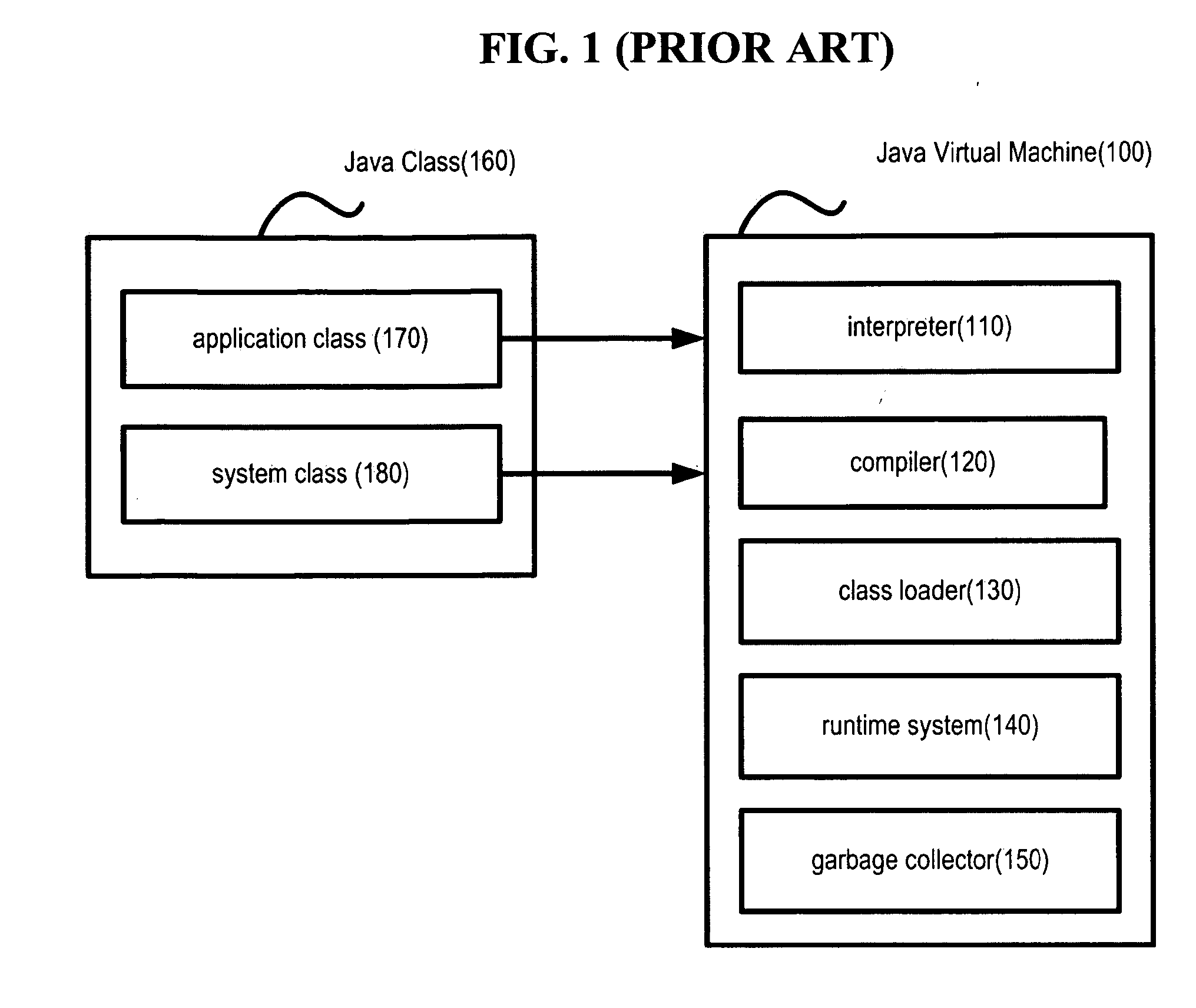
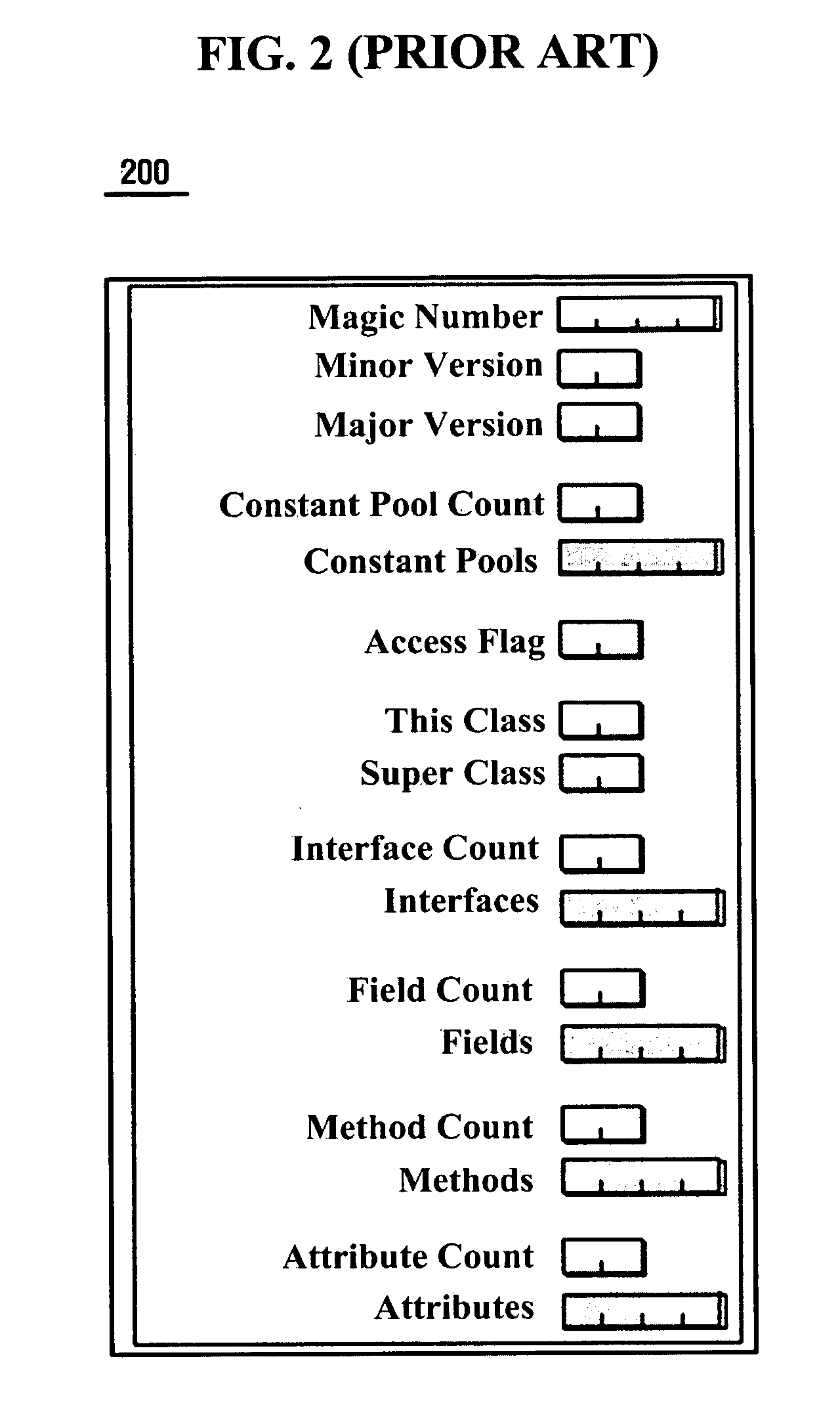
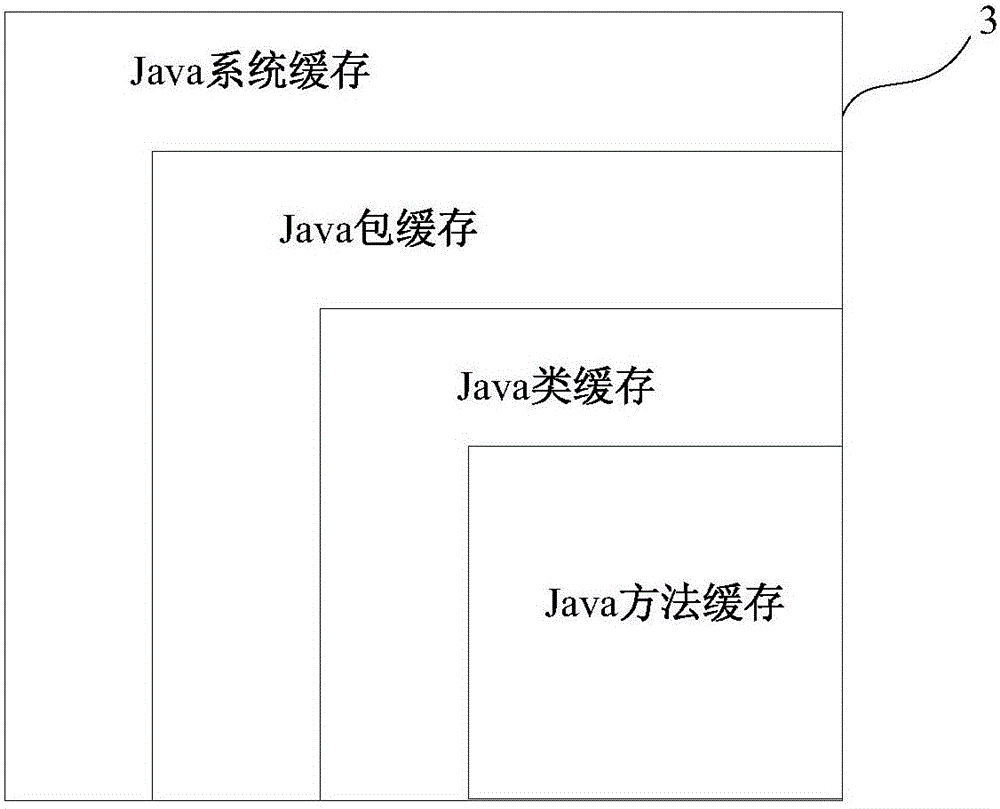
Java bytecode is the instruction set of the Java virtual machine (JVM).
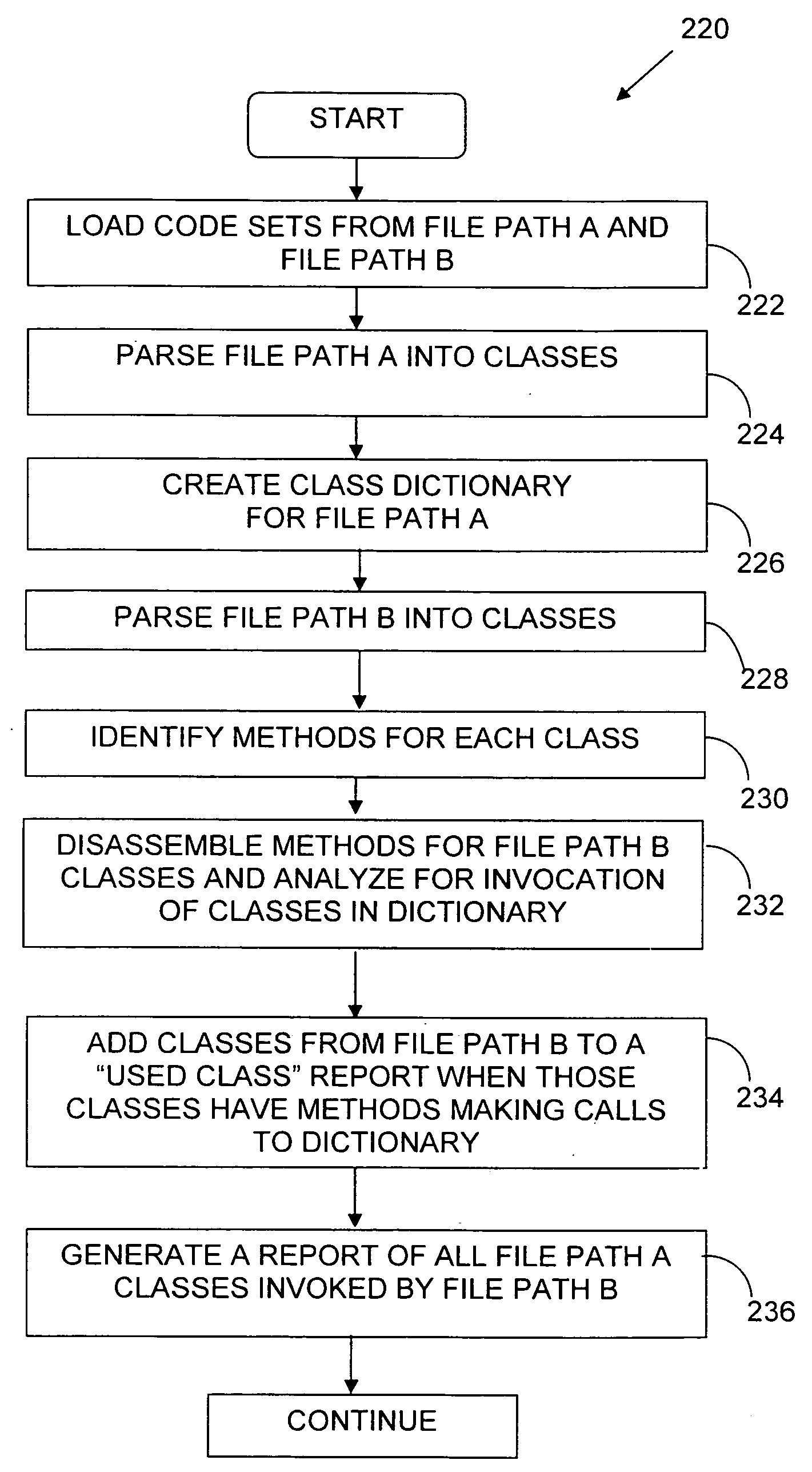
Methods and apparatus for analyzing software interface usage
ActiveUS20080134156A1Effective convenient meanEasy to analyze and useProgram documentationProgram controlApplication programming interfaceApplication software
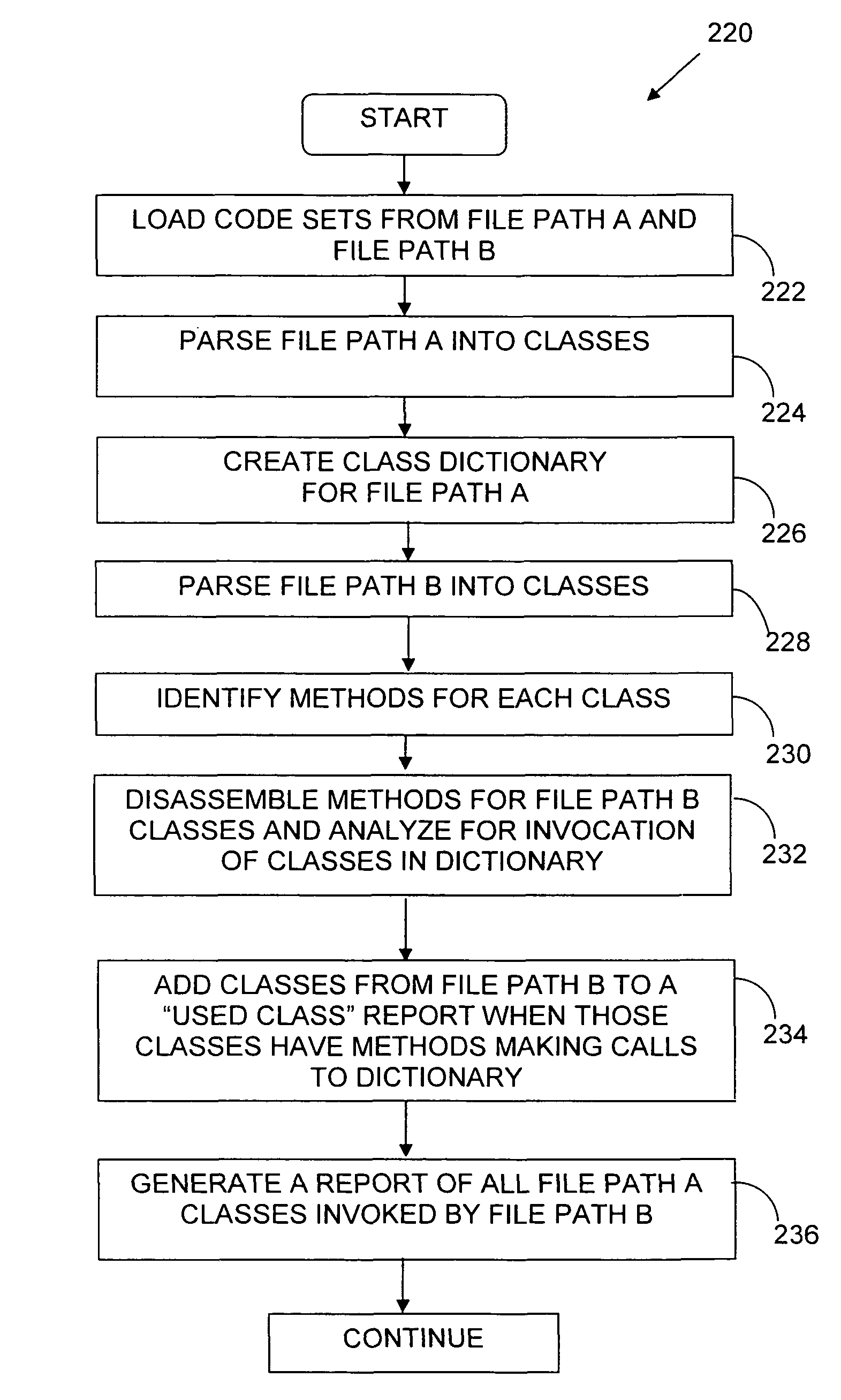
Methods and apparatus for analyzing the interface usage and requirements within software applications. In one embodiment, the interfaces comprise application programming interfaces (APIs) used with Java-based software, and the apparatus comprises a computer program that analyzes file paths (or classpaths) containing one or more files comprising Java bytecode. The names of the classes are extracted and placed into a class dictionary. The different classes listed in the dictionaries are broken down into their individual methods. Each method is then dissembled and analyzed for method or field invocations on other classes found in the dictionary. Methods called are added to a “used class” report. The used class report preferably contains the name of the class, method and the instruction information.
Owner:TIME WARNER CABLE ENTERPRISES LLC
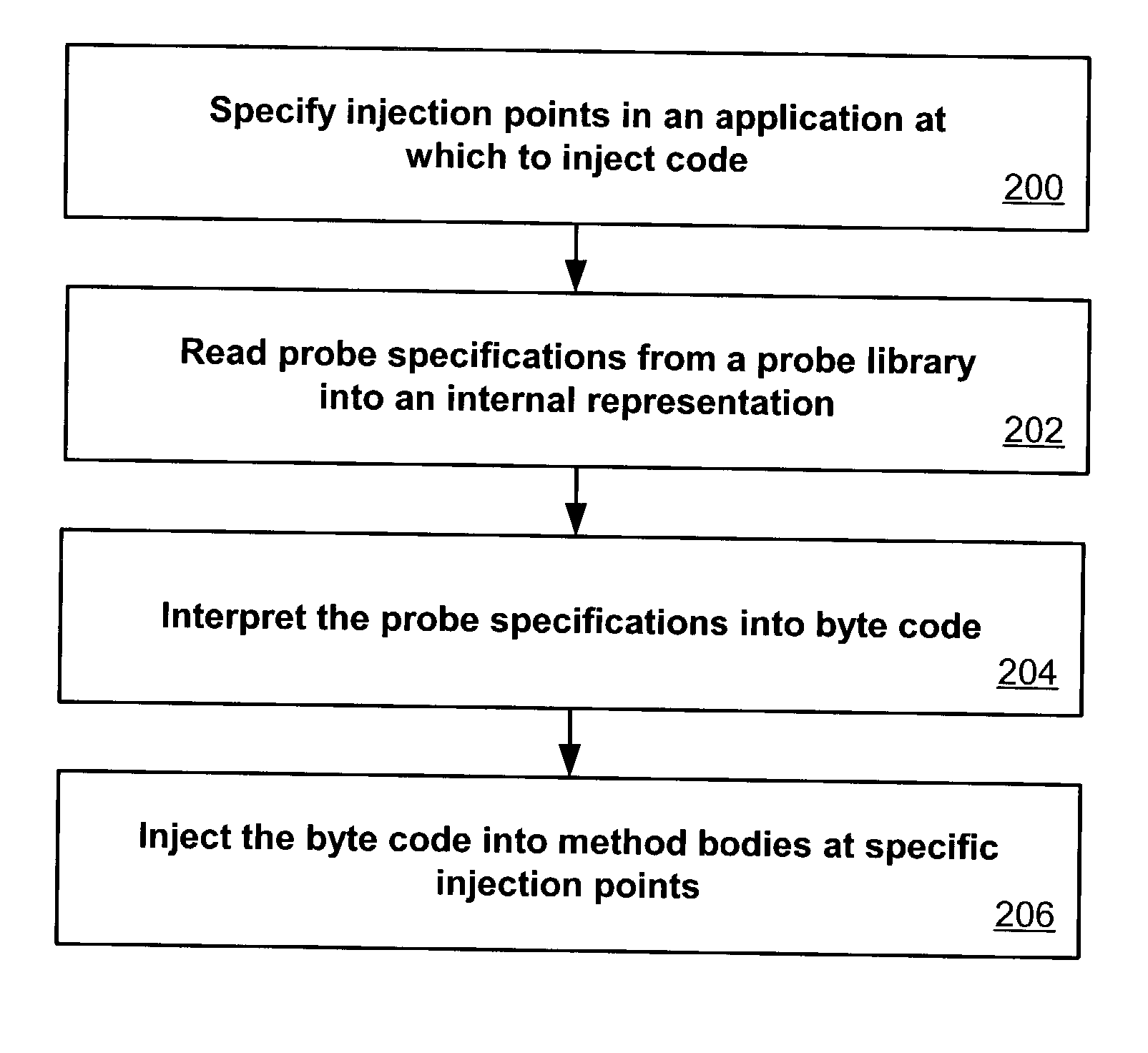
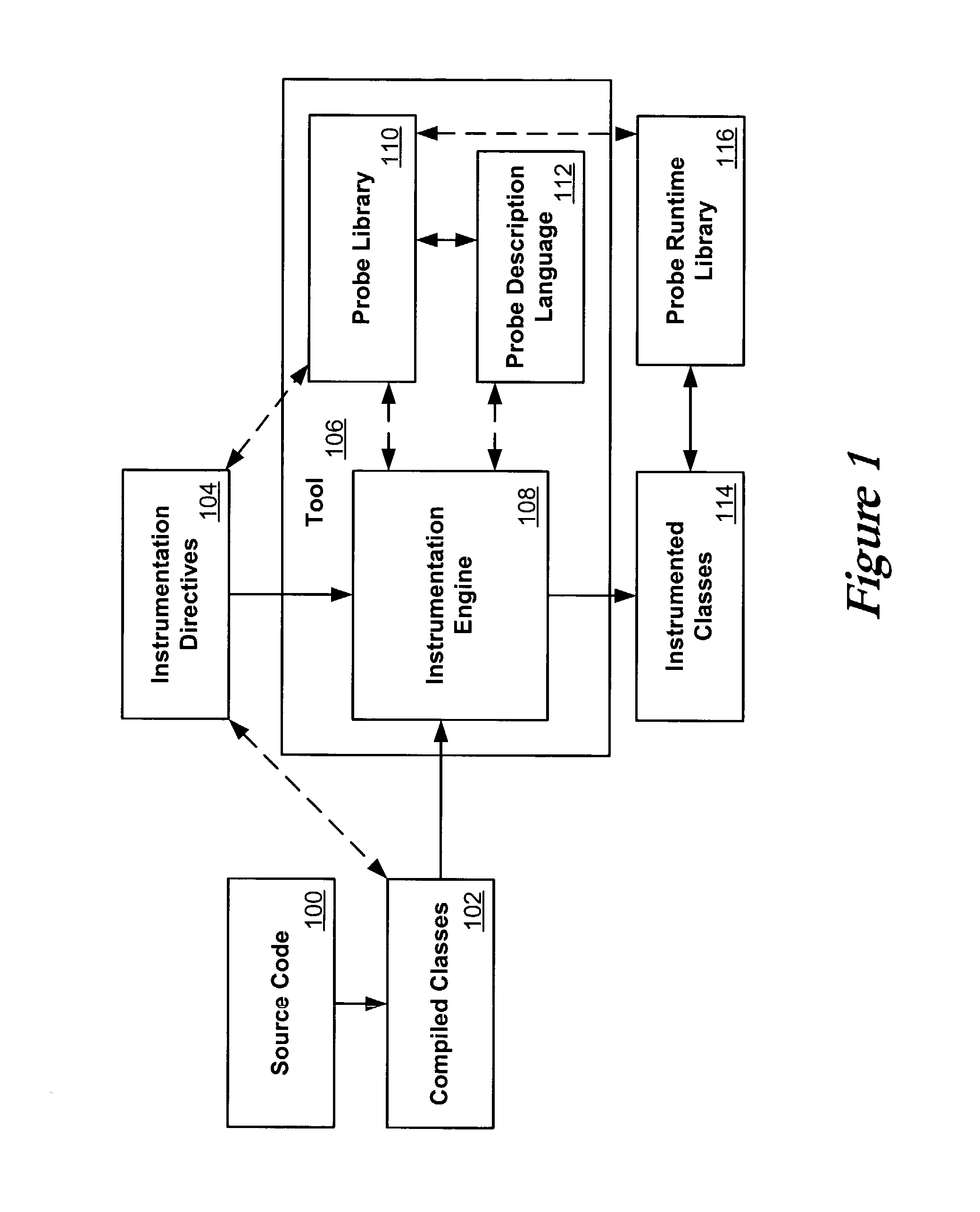
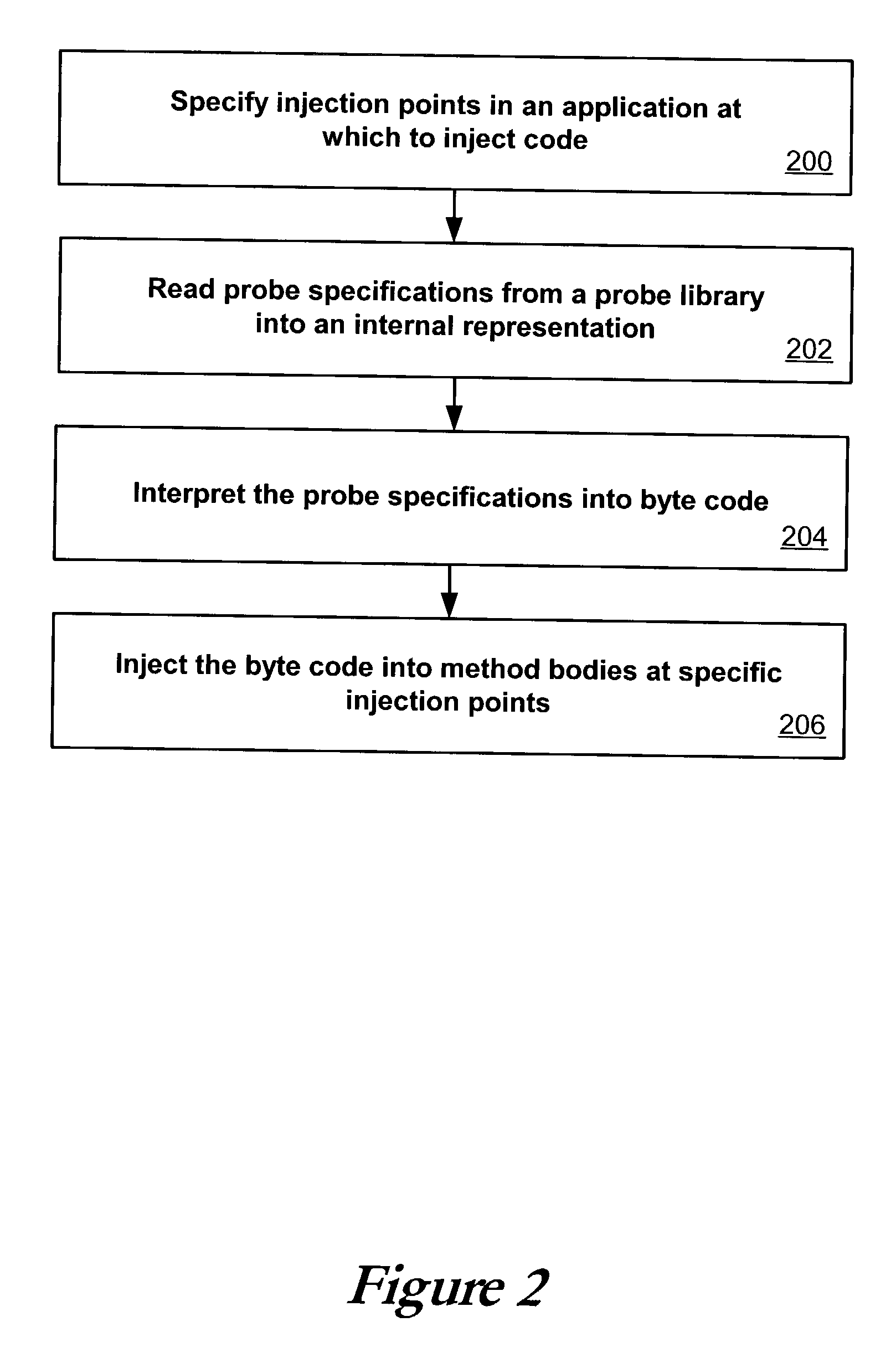
Flexible and extensible java bytecode instrumentation system
ActiveUS20030149960A1Error detection/correctionDigital computer detailsInjection pointCode injection
Code can be injected into a compiled application through the use of probes comprised of instrumentation code. Probes can be implemented in a custom high level language that hides low level instruction details. A directive file contains instructions on injecting a probe into a compiled application. An instrumentation engine reads these instructions and injects the probe into the compiled application at the appropriate injection points. Multiple probes can be used, and can be stored in a probe library. Each probe can inject code into the application at, for example, a package, class, method, or line of the compiled application. Calls can also be made to external runtime libraries. This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:ORACLE INT CORP
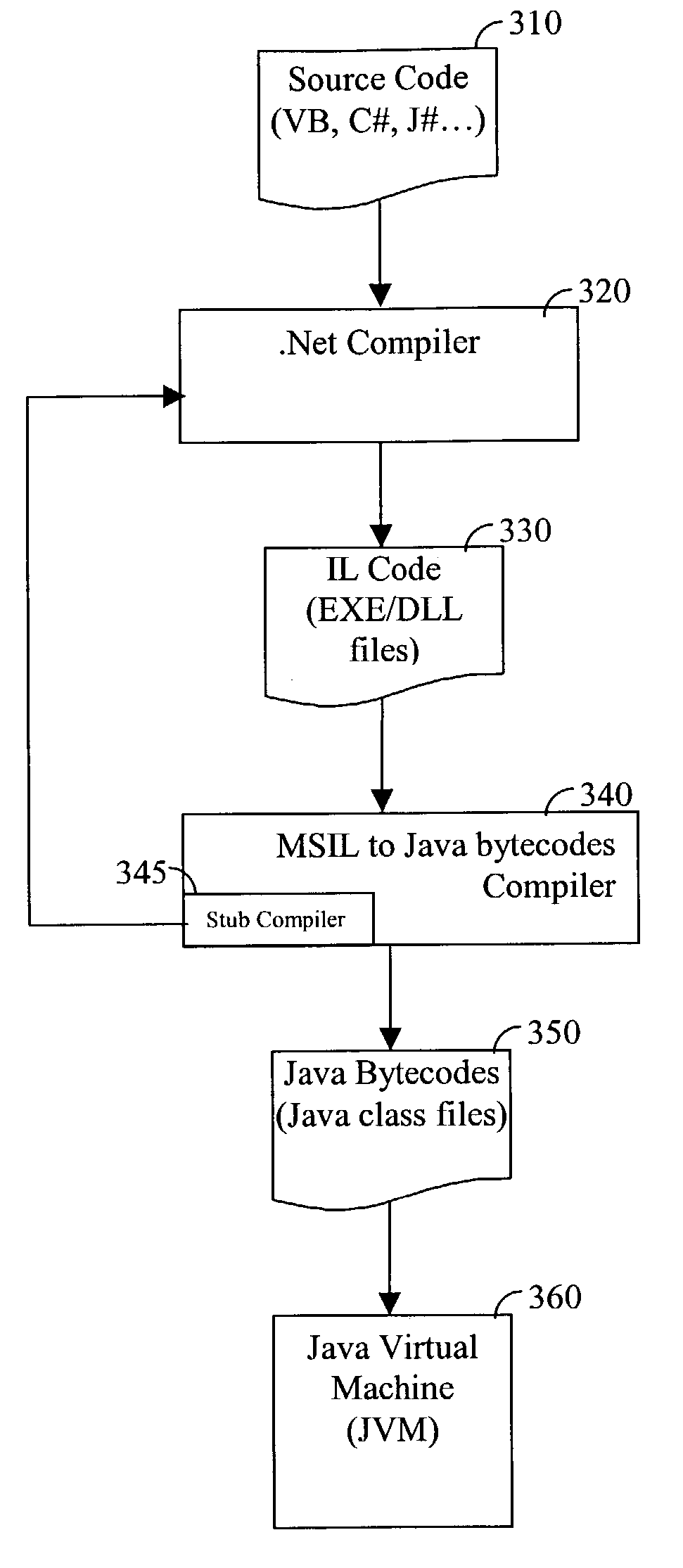
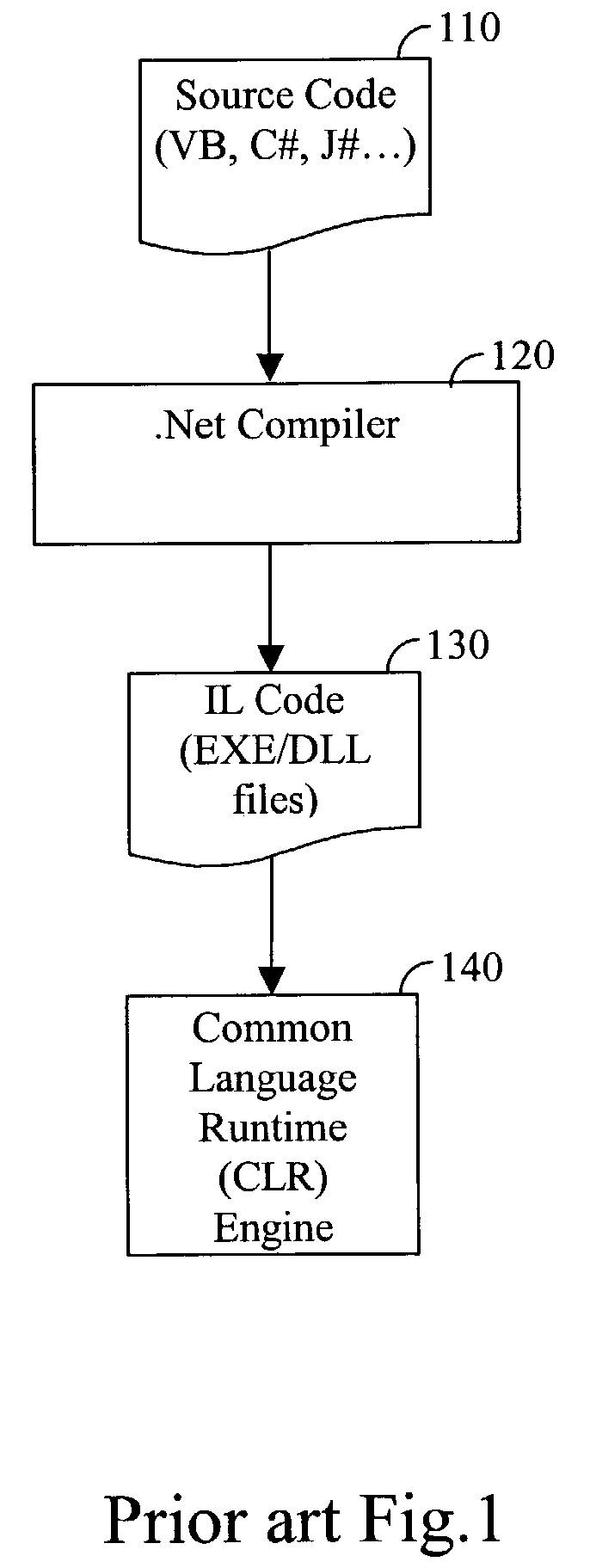
Compiler and software product for compiling intermediate language bytecodes into Java bytecodes
InactiveUS7380242B2Simple to executeSoftware engineeringSpecific program execution arrangements.NET FrameworkApplication software
Compiler and software product for compiling intermediate language (IL) bytecodes, such as Microsoft IL (MSIL) instructions into Java bytecodes, are provided. The provided compiler decodes the IL instructions, generates the stack content, and produces Java bytecodes based on the stack content. Furthermore, the compiler is specially designed to allow a programmer to develop software applications using the .Net framework that could be easily executed using a Java runtime environment.
Owner:HARMON IE R&D
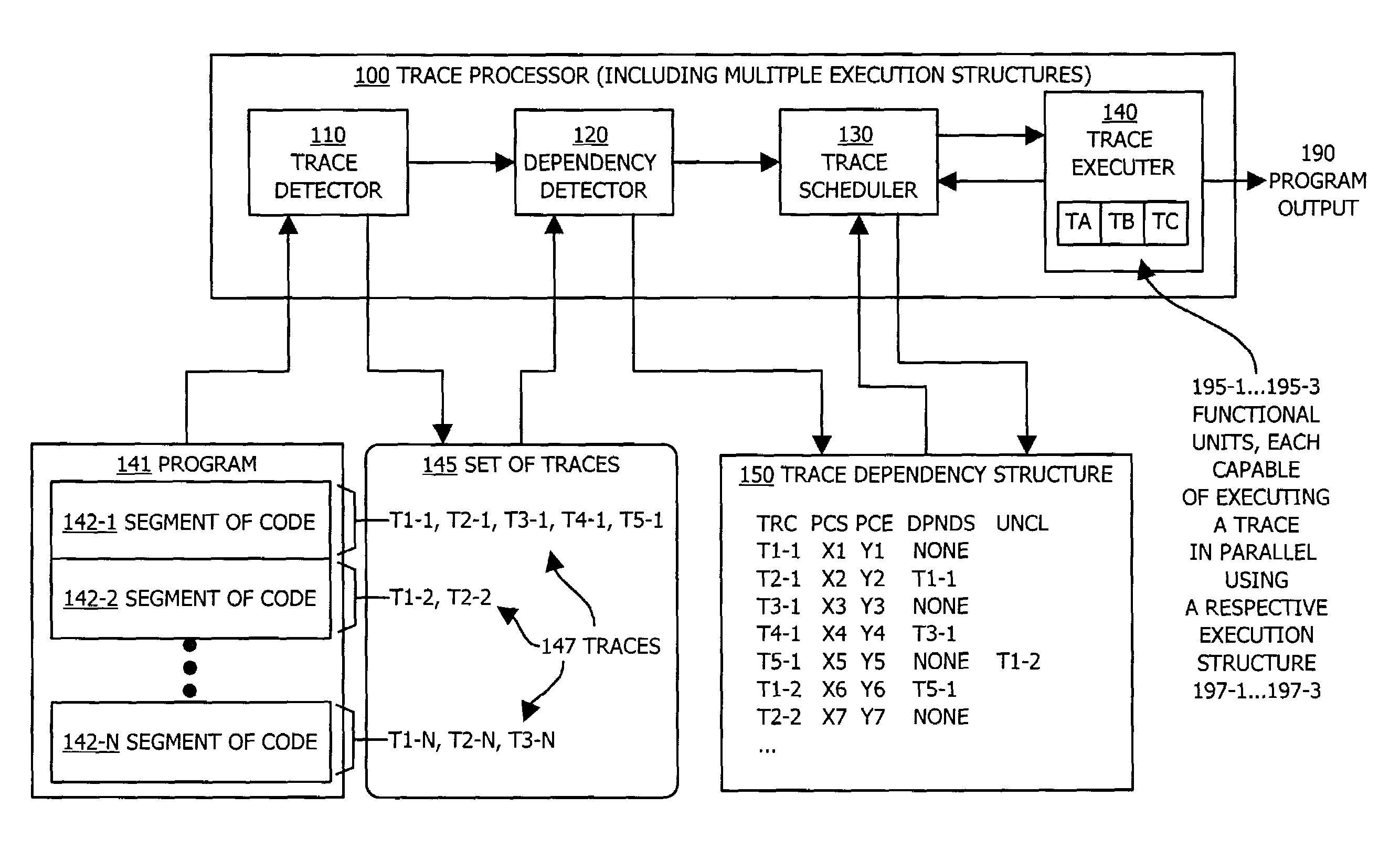
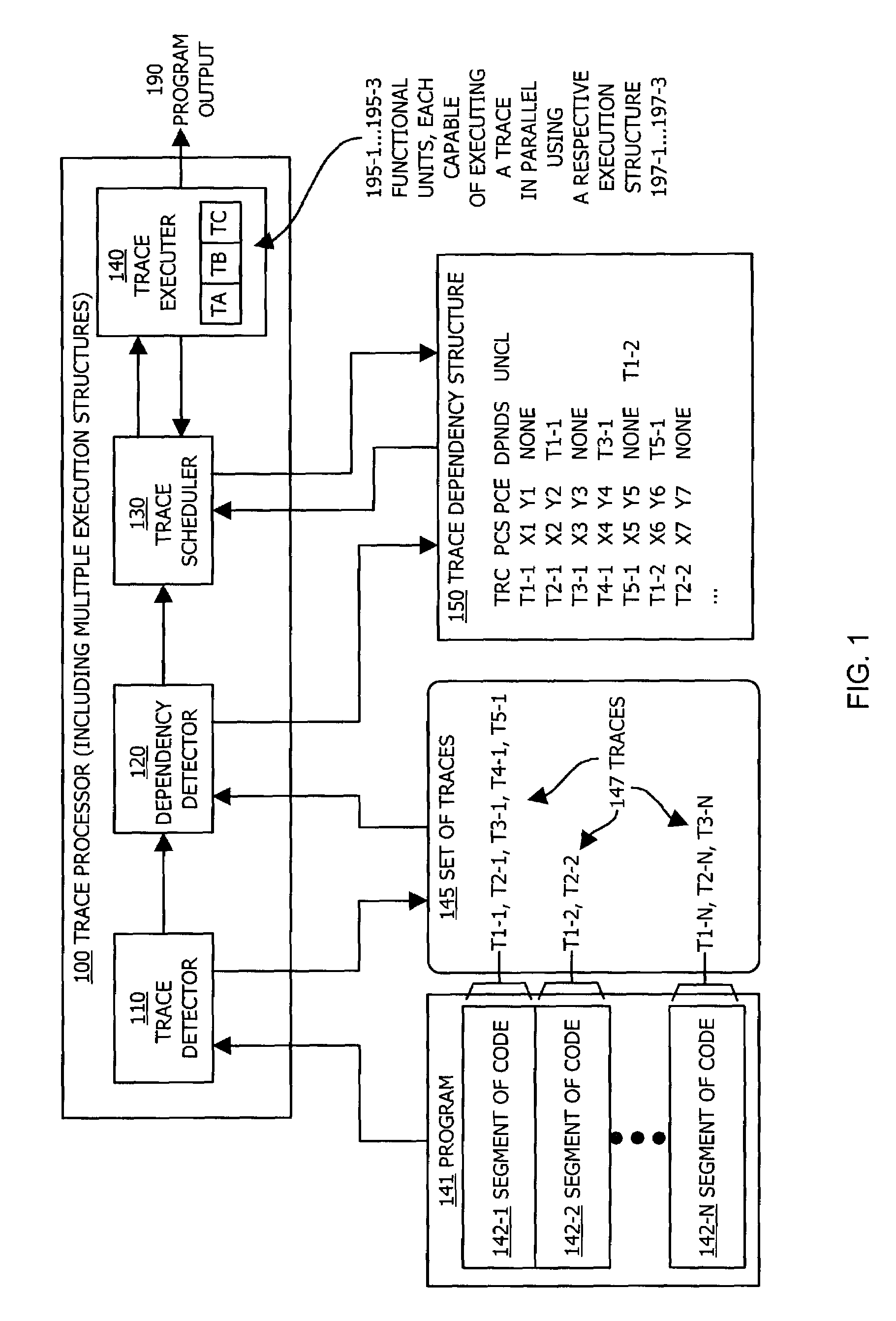
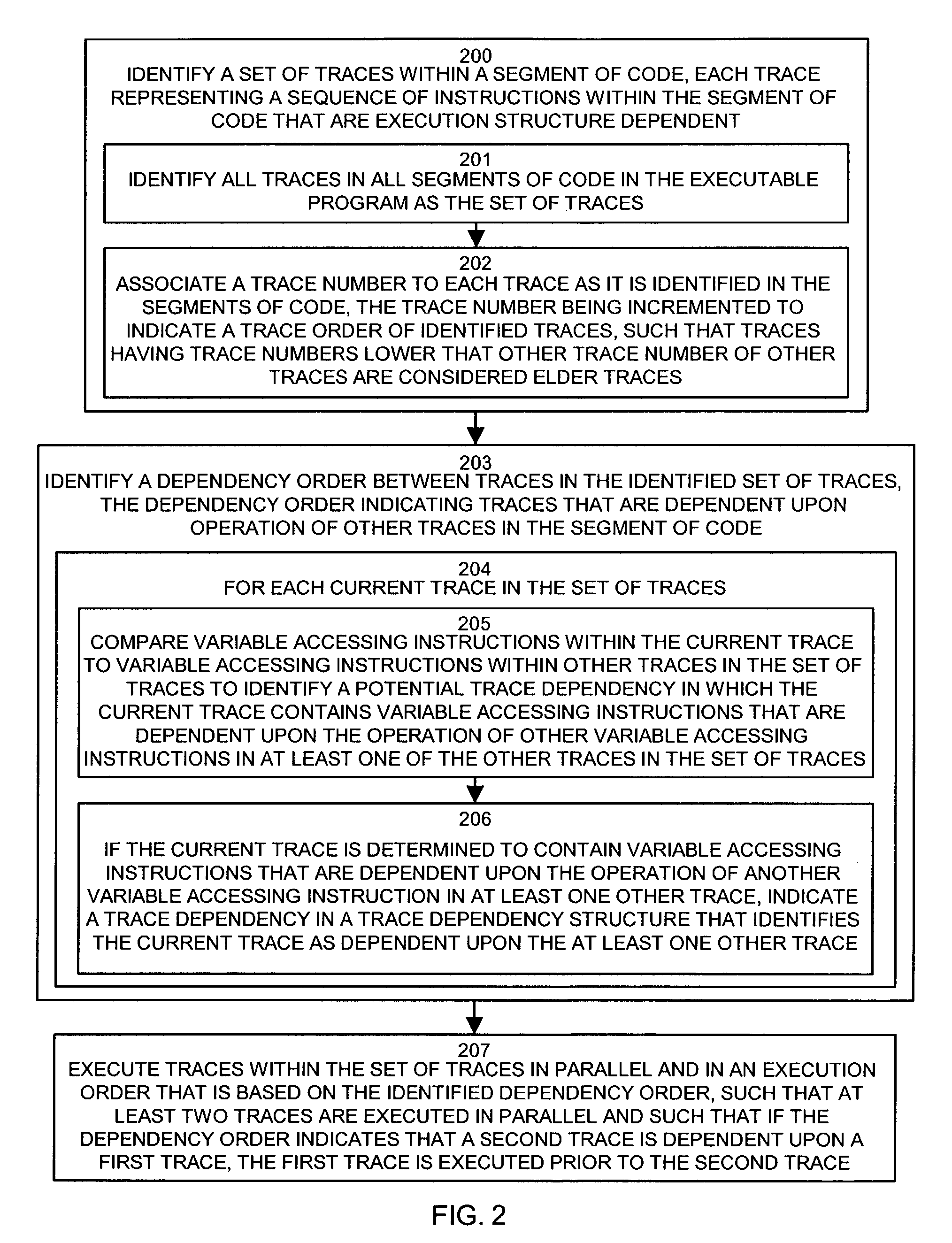
Methods and apparatus for executing instructions in parallel
ActiveUS7210127B1Eliminate operationLimited abilitySpecific program execution arrangementsMemory systemsParallel computingJava bytecode
A system, method and apparatus for executing instructions in parallel identify a set of traces within a segment of code, such as Java bytecode. Each trace represents a sequence of instructions within the segment of code that are execution structure dependent, such as stack dependent. The system, method and apparatus identify a dependency order between traces in the identified set of traces. The dependency order indicates traces that are dependent upon operation of other traces in the segment of code. The system, method and apparatus can then execute traces within the set of traces in parallel and in an execution order that is based on the identified dependency order, such that at least two traces are executed in parallel and such that if the dependency order indicates that a second trace is dependent upon a first trace, the first trace is executed prior to the second trace. This system provides bytecode level parallelism for Java and other applications that utilize execution structure-based architectures and identifies and efficiently eliminates Java bytecode stack dependency.
Owner:ORACLE INT CORP
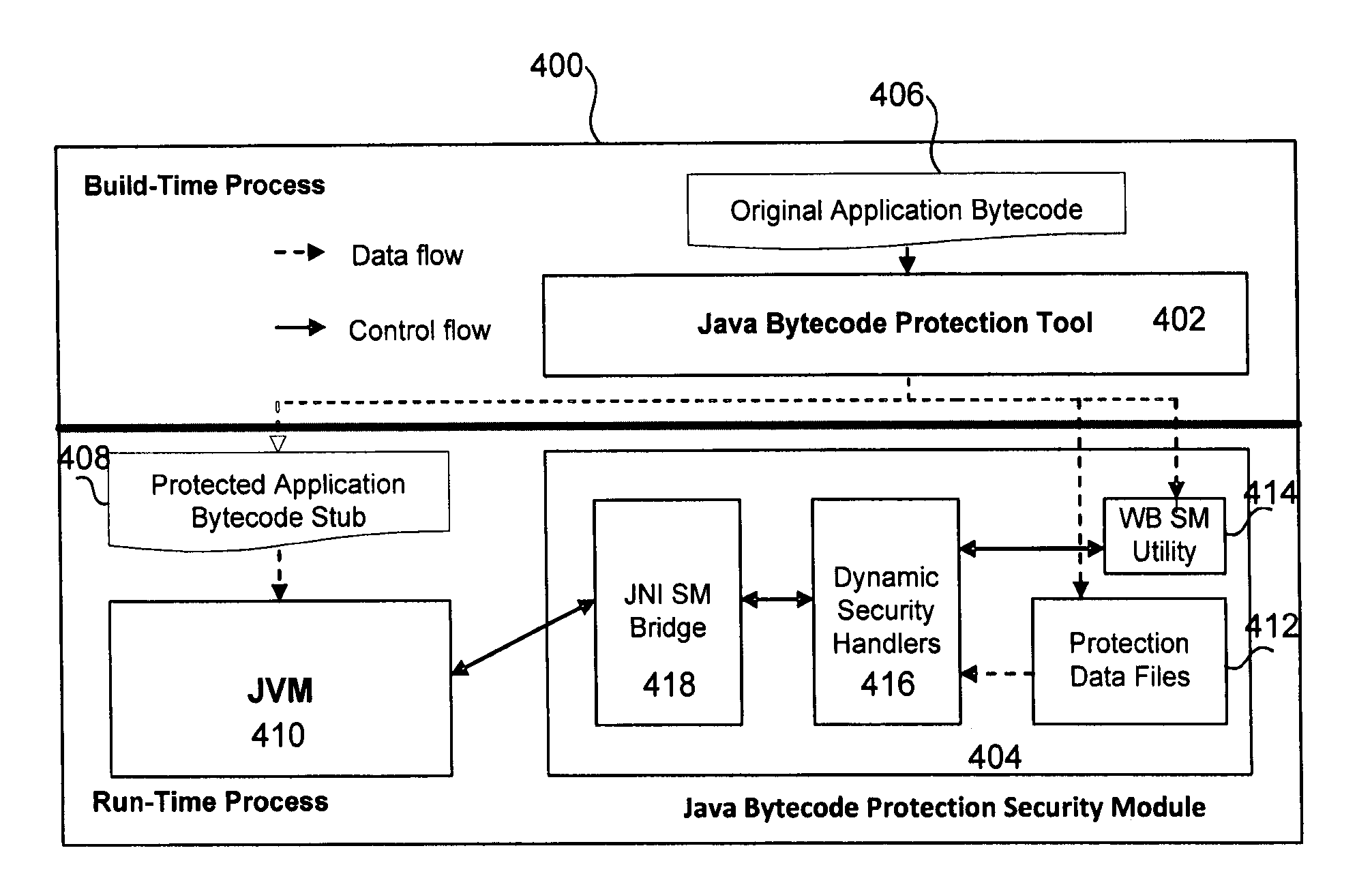
System and Method to Protect Java Bytecode Code Against Static And Dynamic Attacks Within Hostile Execution Environments
ActiveUS20120246487A1Enhancing traditional application building processesAvoid attackDigital data processing detailsUnauthorized memory use protectionJava bytecodeSoftware
A method and system that provides secure modules that can address Java platform weaknesses and protect Java bytecode during execution time. The secure modules are implemented in C / C++ as an example. Because implementation of the security modules is made in C / C++, this enables use of security technology that secures C / C++ software code.
Owner:IRDETO ACCESS
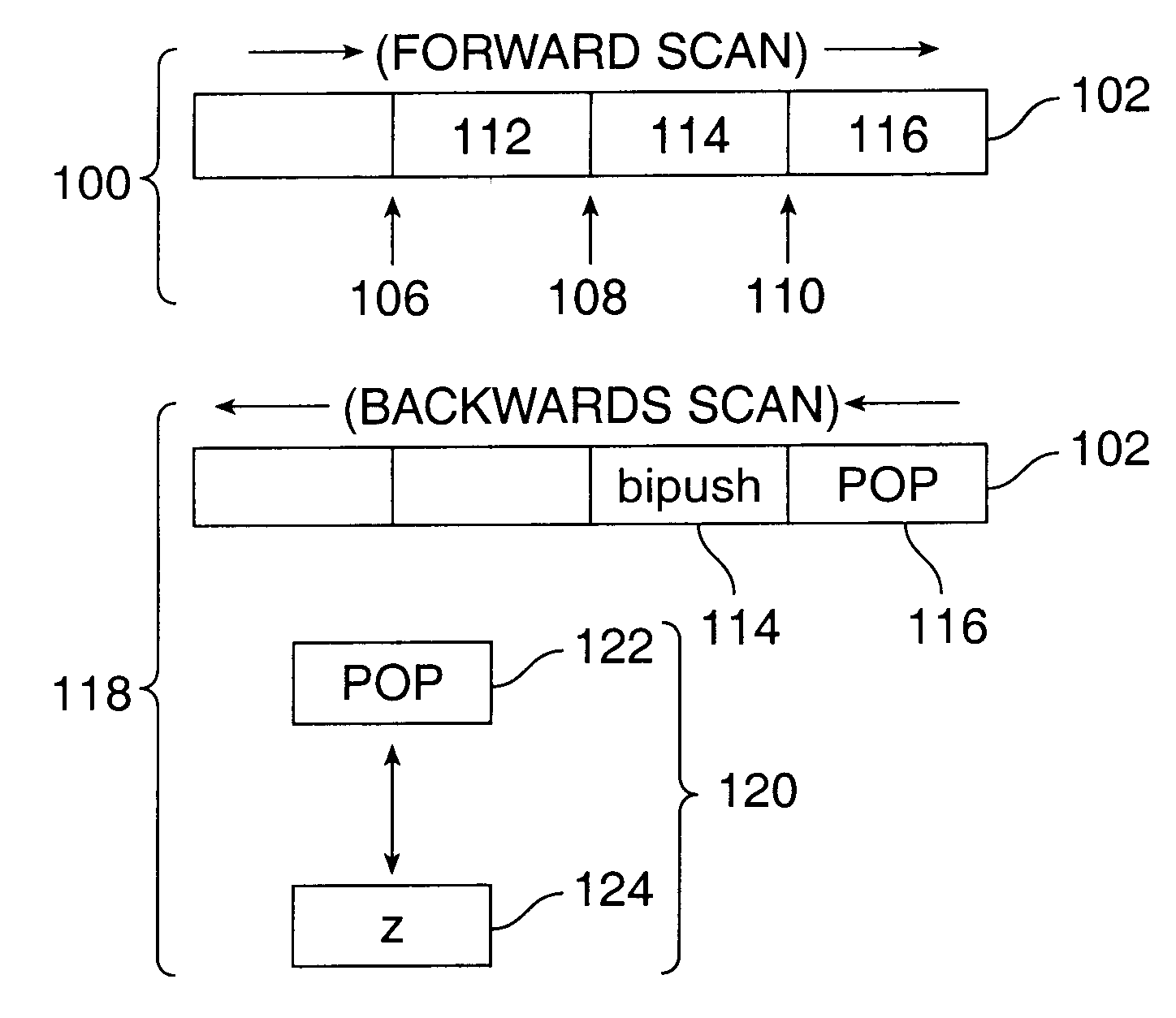
Method for generating a Java bytecode data flow graph
InactiveUS6233733B1Software engineeringSpecific program execution arrangementsParallel computingJava bytecode
According to a first aspect of the present invention, a method for linking bytecodes of an uninterrupted block of bytecodes in the formation of a data flow graph comprises the steps of scanning the uninterrupted block of bytecodes in a forward manner to identify the start of each of the bytecodes, scanning in a backward manner bytecodewise each of the bytecodes in the uninterrupted block of bytecodes, and generating a link in the data flow graph that links each of the bytecodes to all other of the bytecodes used by the each of the bytecodes.According to a second aspect of the present invention, a method for linking bytecodes between uninterrupted blocks of bytecodes in the formation of a data flow graph, the uninterrupted blocks of bytecodes having links according to an order of execution of the uninterrupted blocks and wherein a stack state has been generated for each of the uninterrupted blocks of bytecodes, comprises the steps of stepping through a first path of a plurality of paths of the order of execution that terminates in a join to generate a link in the data flow graph between each bytecode producing a value in one of the uninterrupted blocks and each bytecode consuming the value in another of the uninterrupted blocks in the first path, and duplicating each link in the first path with a link for each bytecode in all of the plurality of paths other than the first path for each bytecode producing a value having a similar stack location to each bytecode producing a value in one of the uninterrupted blocks in the first path.
Owner:ORACLE INT CORP
Method for preventing Java program from being decompiled
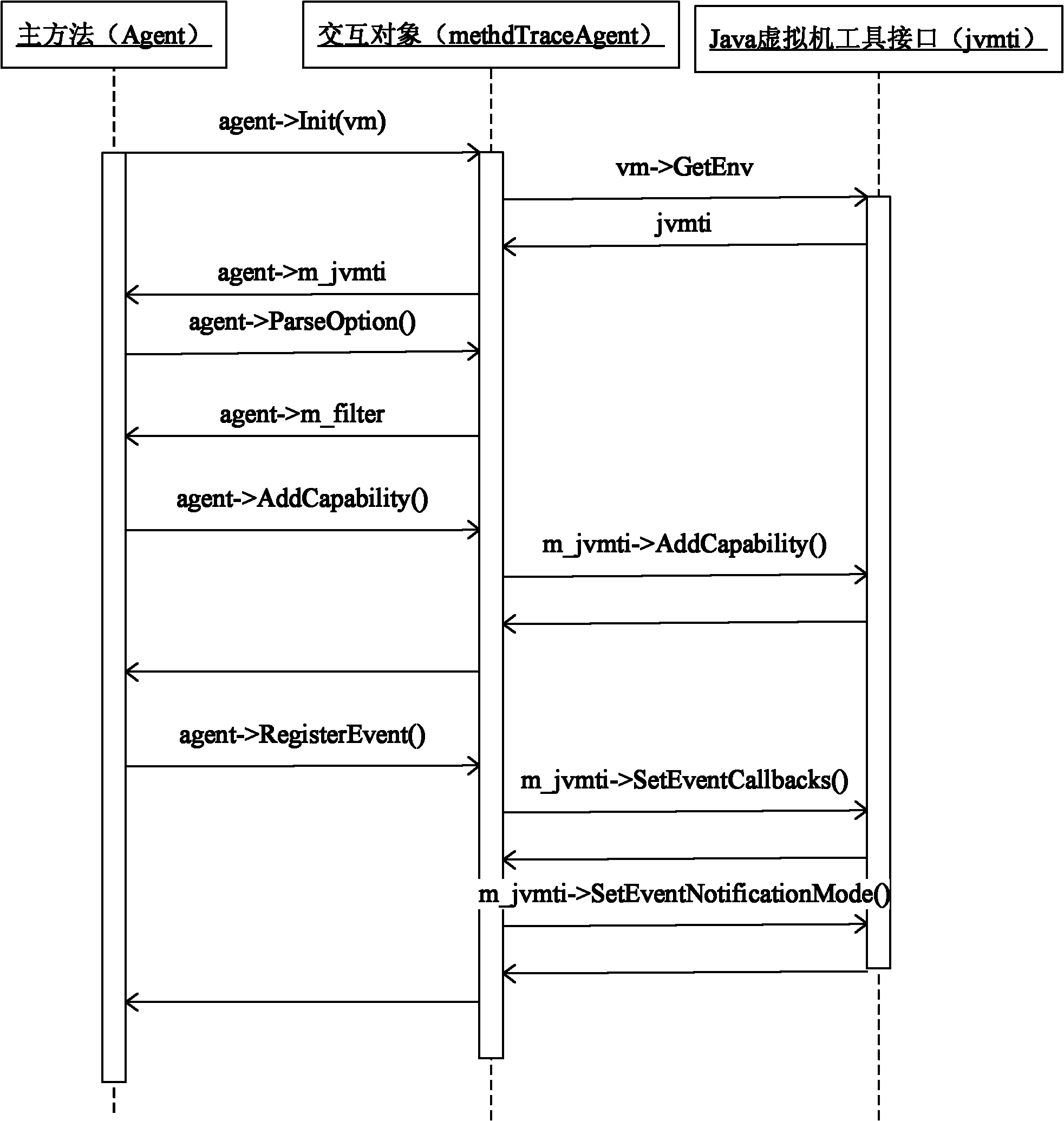
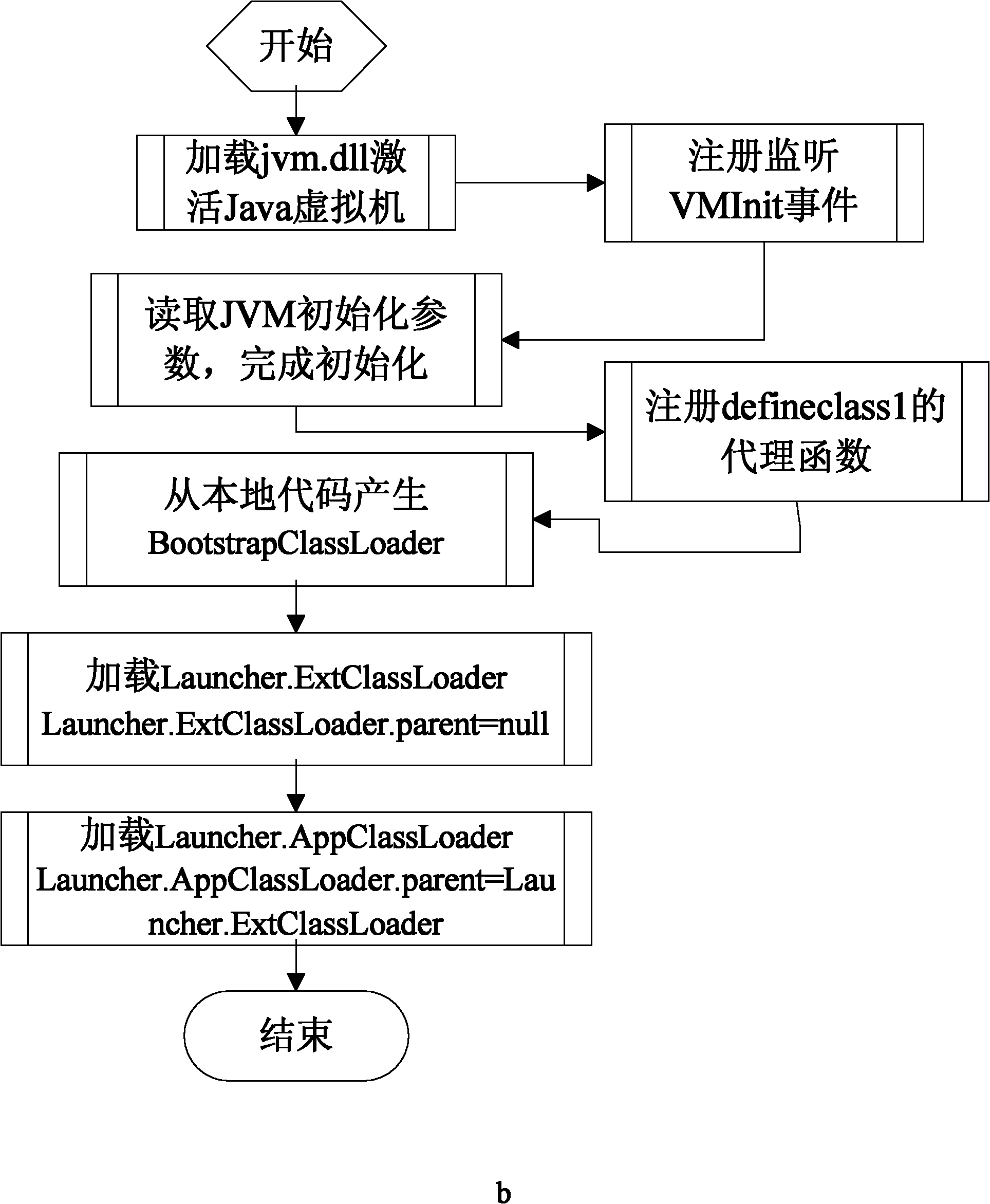
ActiveCN102043932AKeep it cross-platformGuaranteed versatilityProgram/content distribution protectionJava bytecodeJava virtual machine
The invention relates to a method for preventing a Java program from being decompiled, which comprises the following steps: 1) encrypting a Java bytecode file to be issued; 2) using a Java virtual machine tool interface to monitor an initialization event of a Java virtual machine; 3) designating a Hook function for the initialization event of the Java virtual machine; 4) when the initialization of the Java virtual machine is finished, automatically calling the Hook function, and using a Java local interface in the Hook function to register a function called by the Java virtual machine for generating class objects as a self-defined agent function; 5) when the Java virtual machine generates a certain class object, calling the self-defined agent function, and decrypting the encrypted Java bytecode file in the self-defined agent function; and 6) generating a class object corresponding to the decrypted Java bytecode file, and returning to the Java virtual machine. The invention solves the technical problem of the limited application range of the method for preventing a Java bytecode file from being decompiled in the prior art, keeps the cross-platform characteristics of the Java program and maintains the universality of the Java virtual machine.
Owner:AVIC NO 631 RES INST
JAVA hardware accelerator using microcode engine
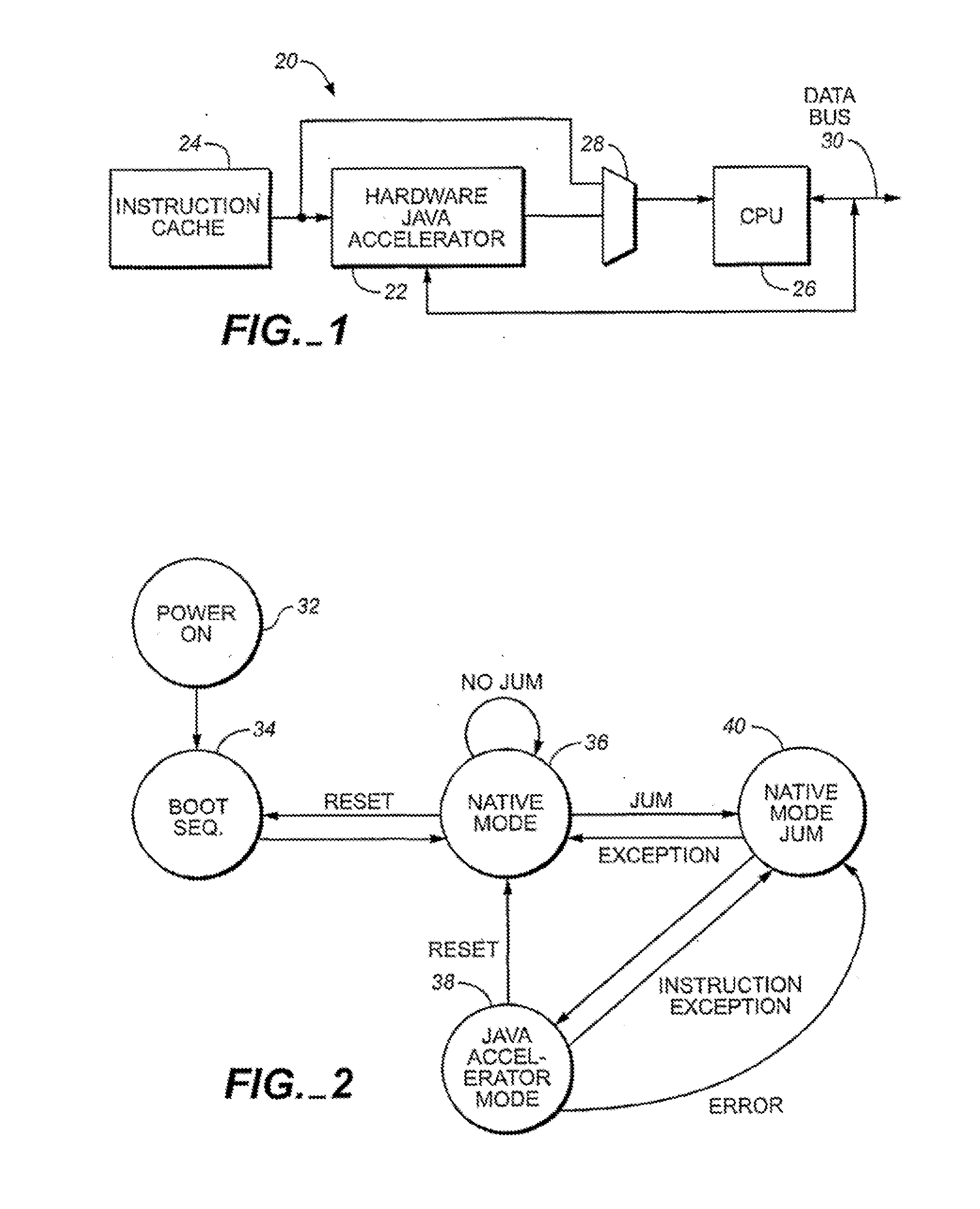
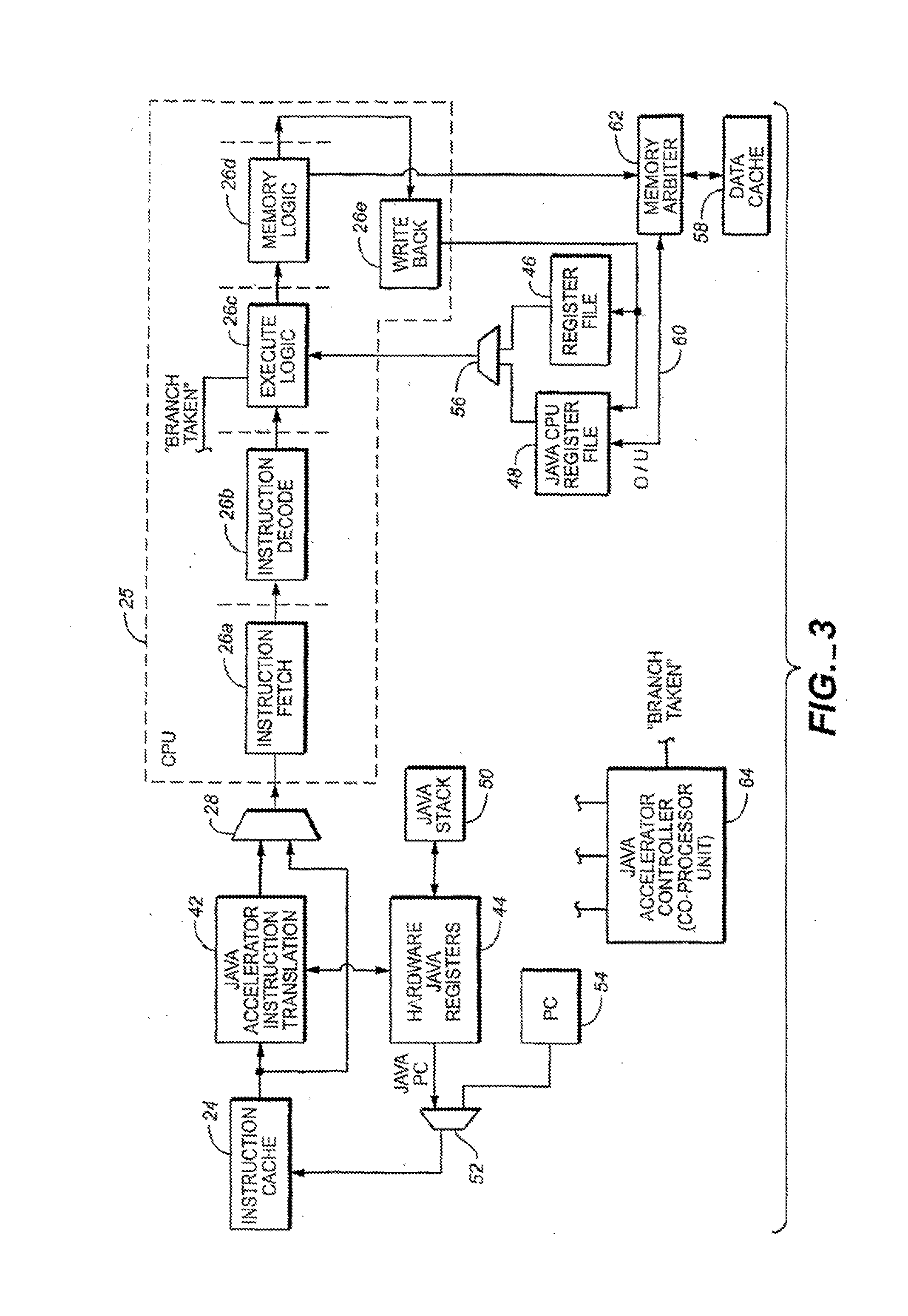
InactiveUS20070118724A1Easy to handleOperational speed enhancementTransformation of program codeJava bytecodeHardware acceleration
A hardware Java accelerator is comprised of a decode stage and a microcode stage. Separating into the decode and microcode stage allows the decode stage to implement instruction level parallelism while the microcode stage allows the conversion of a single Java bytecode into multiple native instructions. A reissue buffer is provided which stores the converted instructions and reissues them when the system returns from an interrupt. In this manner, the hardware accelerator need not be flushed upon an interrupt. A native PC monitor is also used. While the native PC is within a specific range, the hardware accelerator is enabled to convert the Java bytecodes into native instructions. When the native PC is outside the range, the hardware accelerator is disabled and the CPU operates on native instructions obtained from the memory.
Owner:NAZOMI COMM
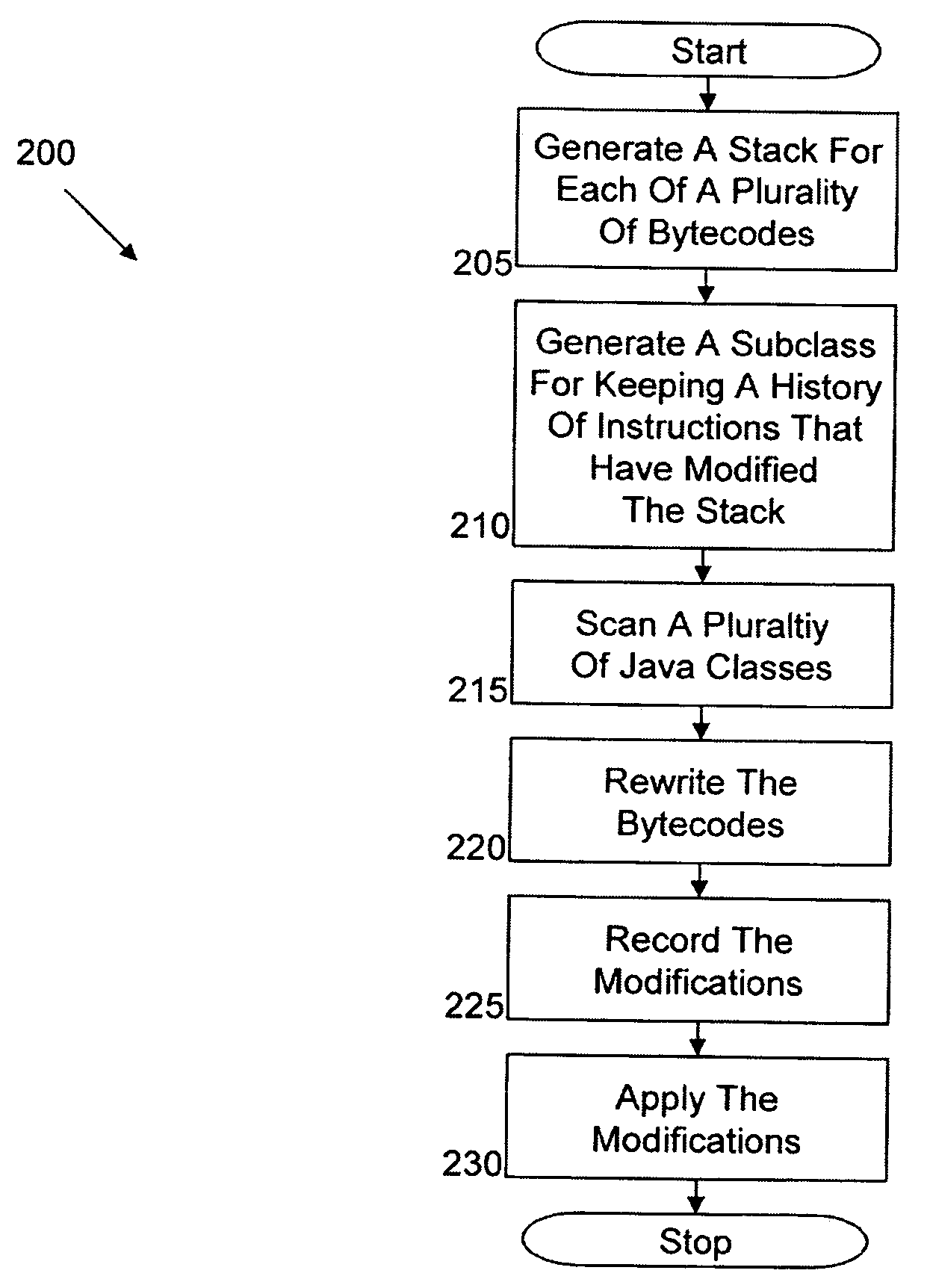
Systems, methods, and computer products for automated injection of JAVA bytecode instructions for JAVA load time optimization via runtime checking with upcasts
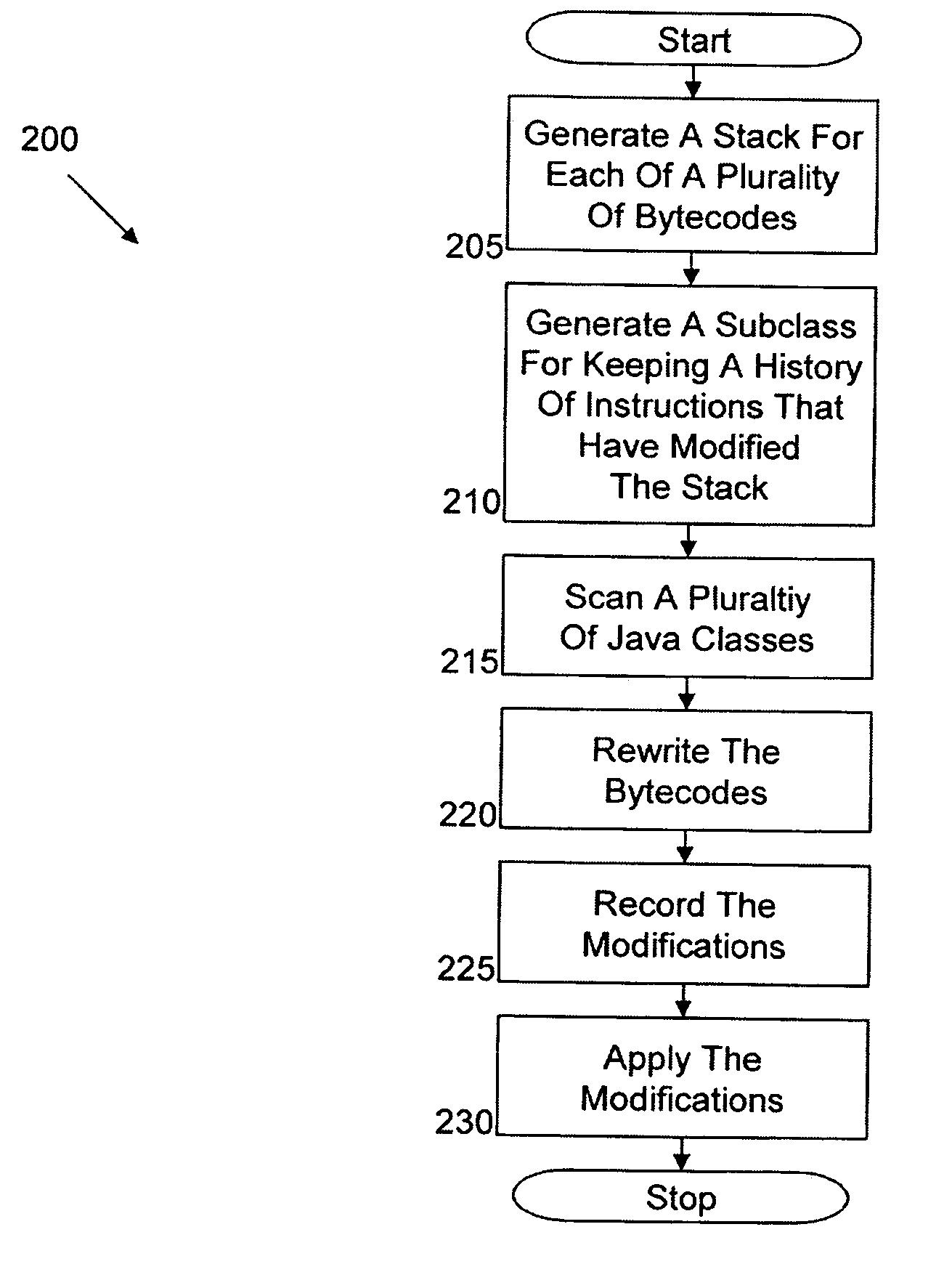
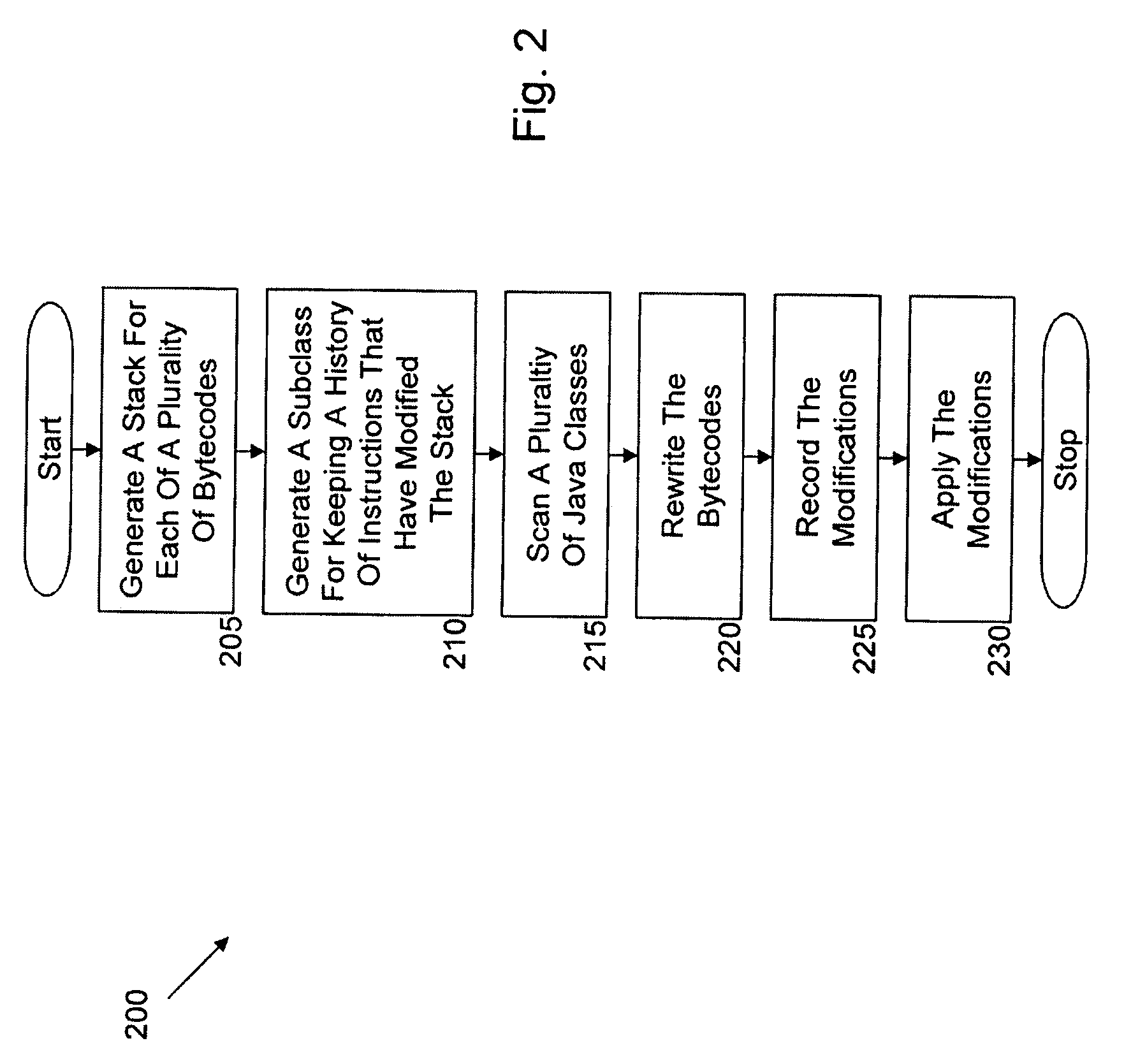
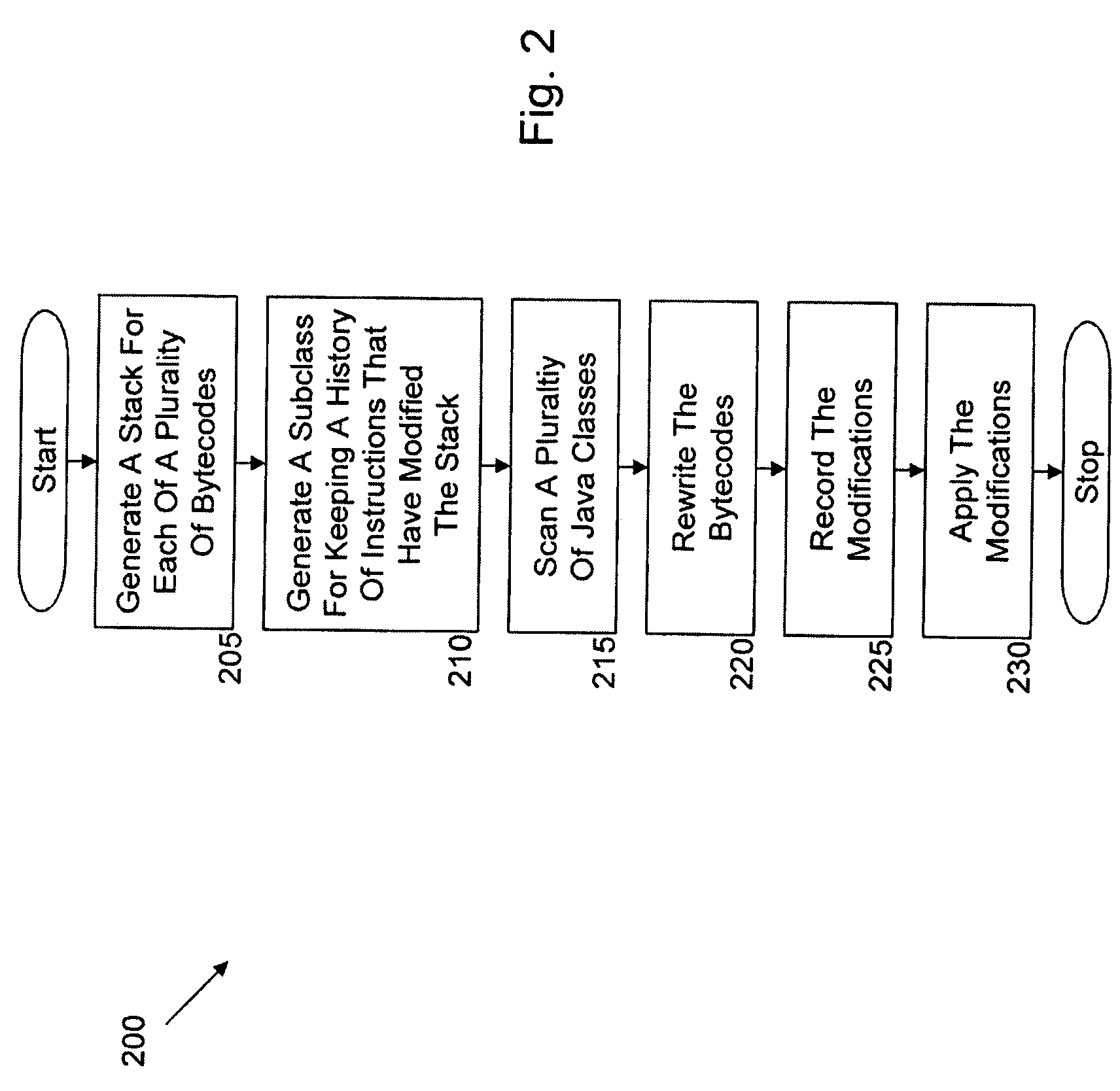
Automated injection of Java bytecode instructions for Java load time optimization via runtime checking with upcasts. Exemplary embodiments include a method including generating a stack for each of a plurality of bytecodes, generating a subclass configured to keep a history of instructions that have modified the stack, statically scanning a plurality of Java classes associated with the plurality of bytecodes to locate class file configurations and bytecode patterns that cause loading of additional classes to complete a verification of each of the classes in the plurality of Java classes, rewriting the bytecodes to delay the loading of the additional classes until required at a runtime, recording modifications that have been made to the stack by the instructions, and applying the modifications to each of the bytecodes in the plurality of bytecodes.
Owner:IBM CORP
Methods and apparatus for analyzing software interface usage
ActiveUS8370818B2Facilitates development and testingEasy to modifyProgram documentationProgram controlApplication programming interfaceApplication software
Methods and apparatus for analyzing the interface usage and requirements within software applications. In one embodiment, the interfaces comprise application programming interfaces (APIs) used with Java-based software, and the apparatus comprises a computer program that analyzes file paths (or classpaths) containing one or more files comprising Java bytecode. The names of the classes are extracted and placed into a class dictionary. The different classes listed in the dictionaries are broken down into their individual methods. Each method is then dissembled and analyzed for method or field invocations on other classes found in the dictionary. Methods called are added to a “used class” report. The used class report preferably contains the name of the class, method and the instruction information.
Owner:TIME WARNER CABLE ENTERPRISES LLC
Framework for Control Flow-Aware Processes
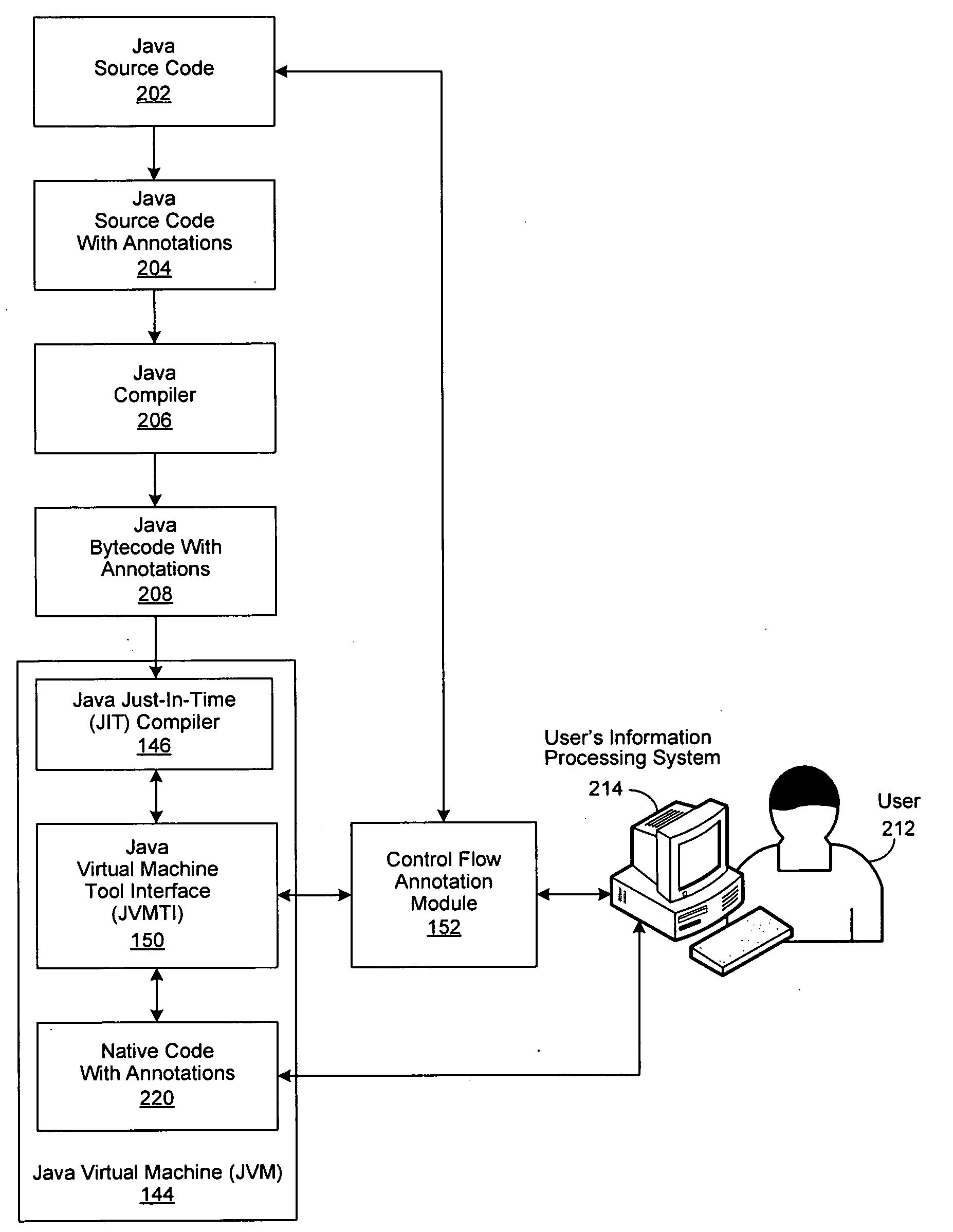
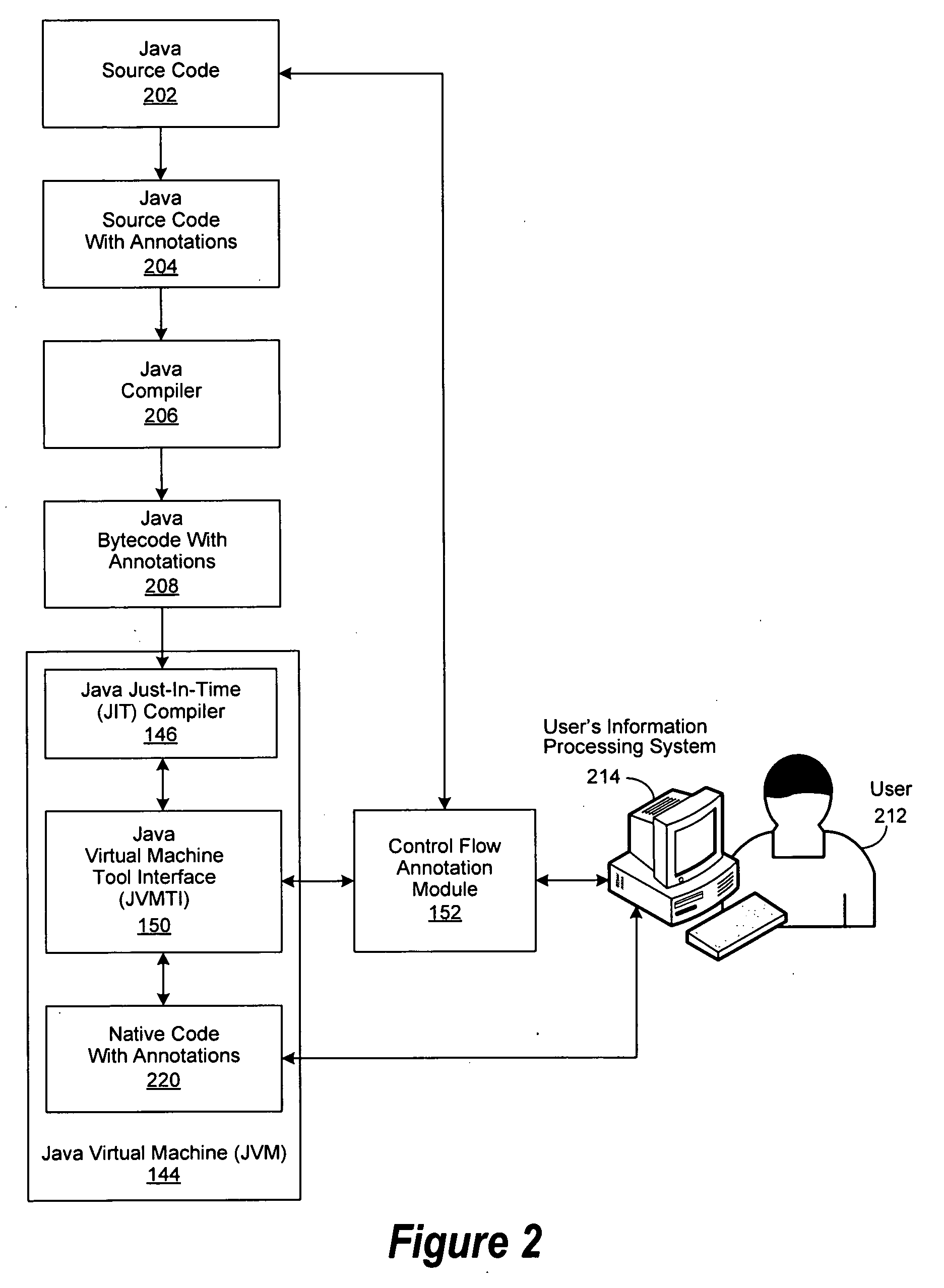
InactiveUS20100138820A1Error detection/correctionProgram controlJust-in-time compilationControl flow
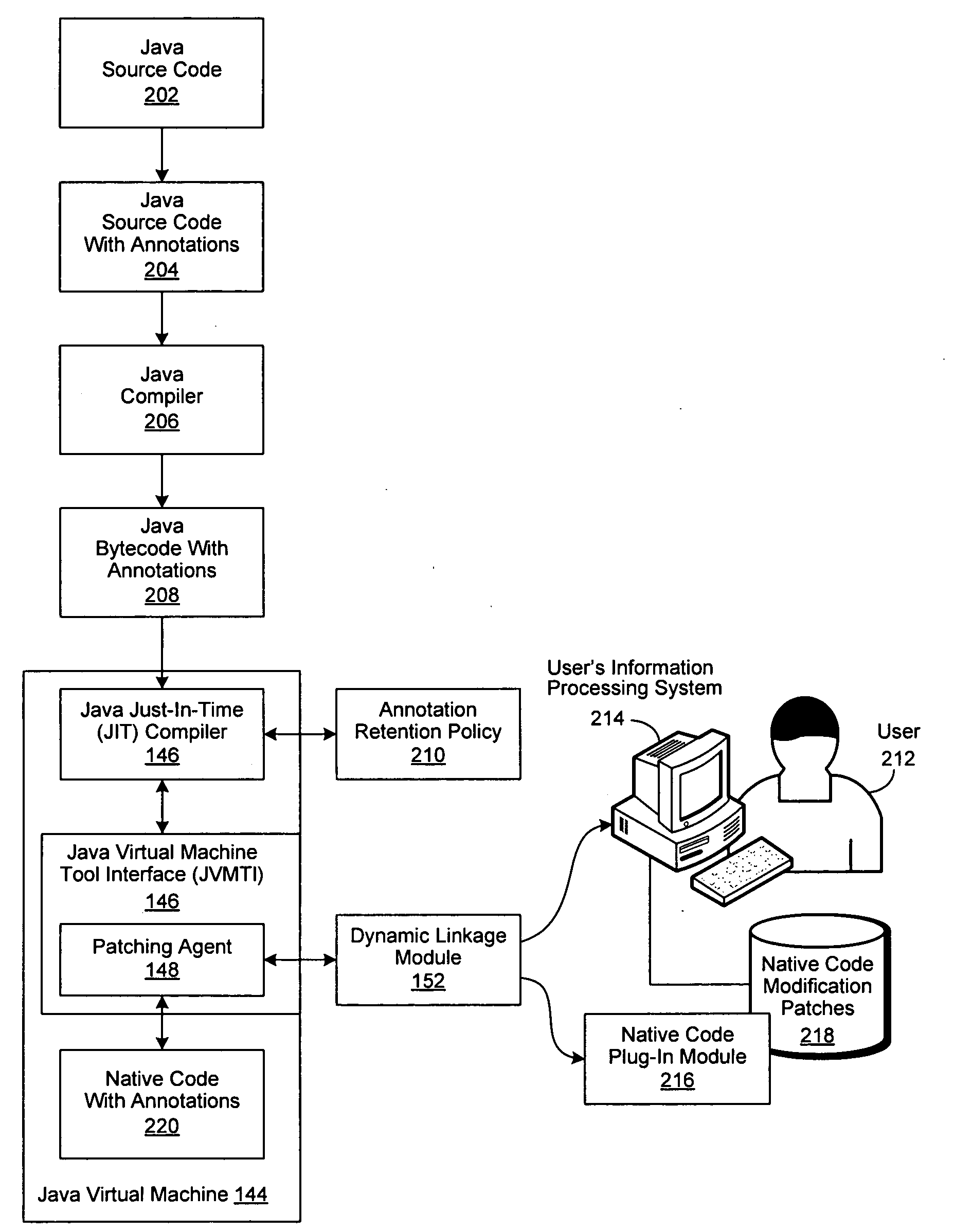
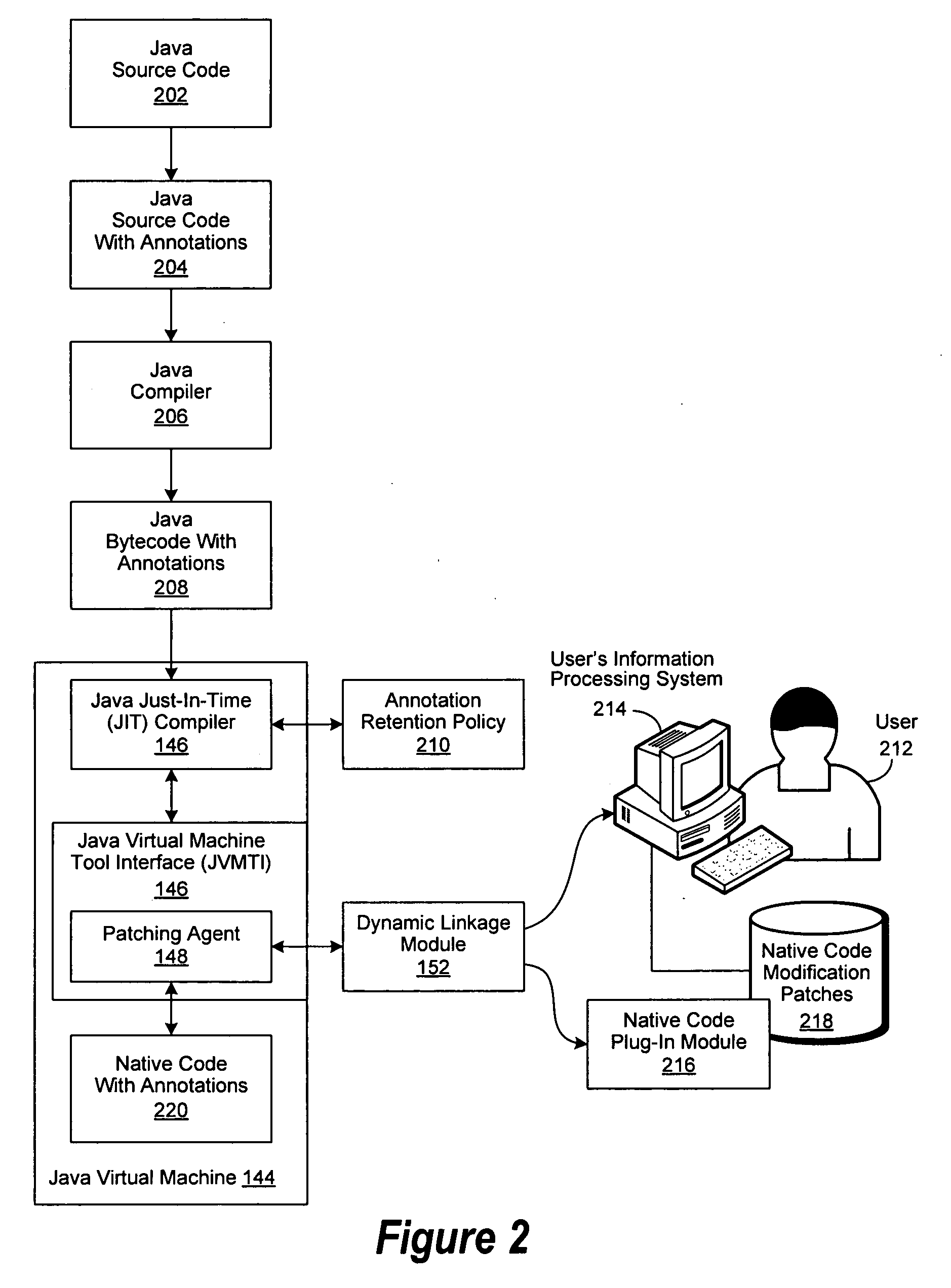
An improved system and method are disclosed for processing Java program code. Java source code is annotated with a Module or a ControlFlow annotation. The Java source code is then compiled to produce Java bytecode, which in turn is compiled by a just-in-time compiler to produce native code, which retains the annotations. The native code with annotations is then executed. If a bug is identified during the execution of the native code, an associated Module is selected for debugging, followed by determining associated Java source code segments within the responsible control flow path. Debugging operations are then performed on the associated Java source code segments.
Owner:GLOBALFOUNDRIES INC
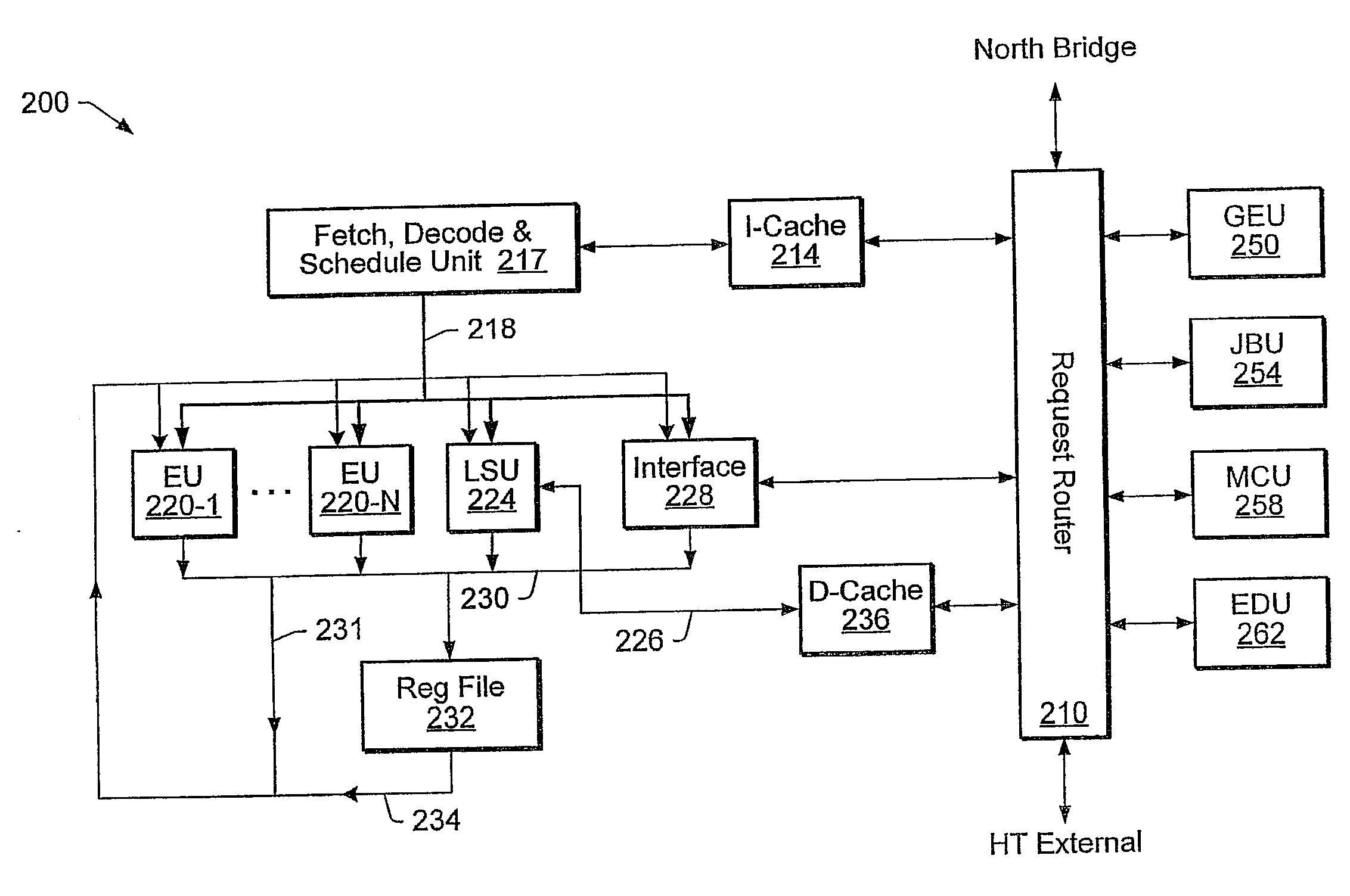
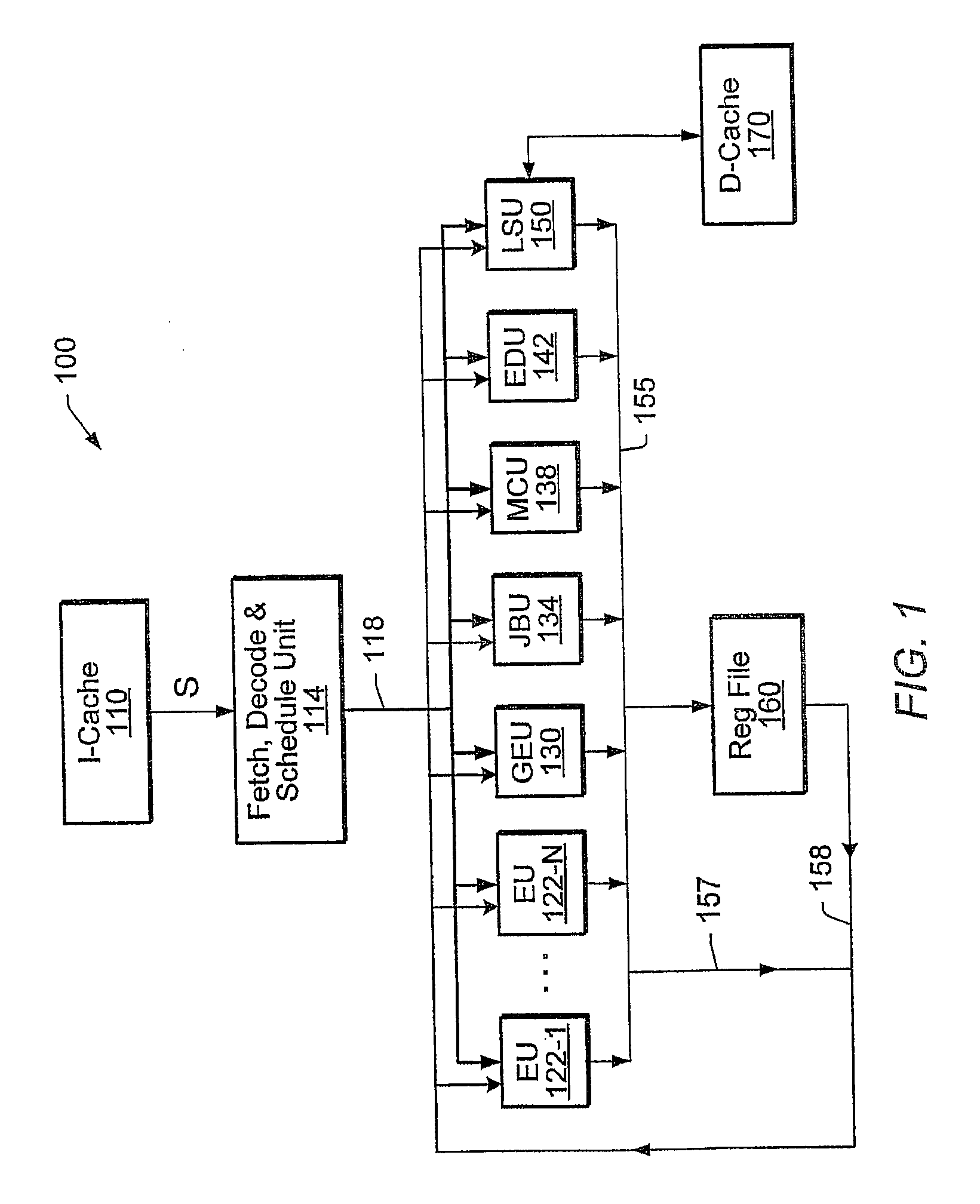
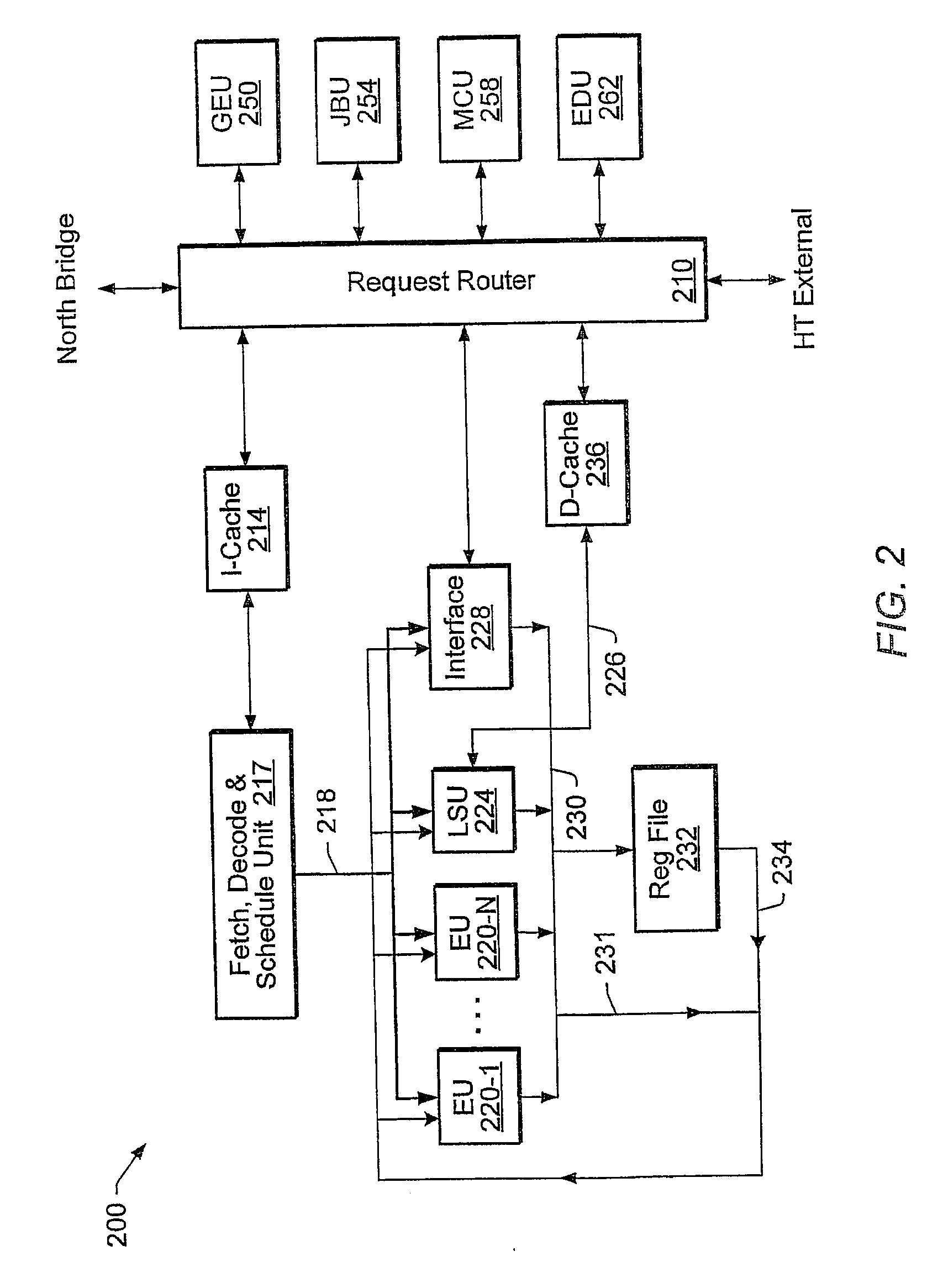
Unified Processor Architecture For Processing General and Graphics Workload
A processor comprising one or more control units, a plurality of first execution units, and one or more second execution units. Fetched instructions that conform to a processor instruction set are dispatched to the first execution units. Fetched instructions that conform to a second instruction set (different from the processor instruction set) are dispatched to the second execution units. The second execution units may be configured to performing graphics operations, or other specialized functions such as executing Java bytecode, managed code, video / audio processing operations, encryption / decryption operations etc. The second execution units may be configured to operate in a coprocessor-like fashion. A single control unit may handle the fetch, decode and scheduling for all the executions units. Alternatively, multiple control units may handle different subsets of the executions units.
Owner:GLOBALFOUNDRIES INC
Java source code protection method based on dynamic link library
InactiveCN107992723APrevent decompilationProgram loading/initiatingProgram/content distribution protectionThird partyJava Classloader
The invention discloses a Java source code protection method based on a dynamic link library. A function declaration port and a function implementation main body are extracted and separated from a Java source code file, a port declaration file extracted from the source codes is obtained, the source codes are compiled into a Java bytecode file, and the Java bytecode file is processed to obtain bytecode content information and to generate a dynamic link library file; the extracted port declaration file is compiled to obtain a publication-quality port call file, and the publication-quality port call file can be published to permit a third party to use; the dynamic link library file is deployed to a running environment, a loader corresponding to Java type is used for dynamically loading the bytecode information in the dynamic link library file content into a JVM virtual machine, and the operation of protected codes is completed. The method effectively protects core codes, controls the operation of the core codes, and increases the protection of the Java source codes.
Owner:NANJING LES INFORMATION TECH
Data processing using multiple instruction sets
InactiveUS6965984B2Easily set under software controlFacilitate and speed processingSoftware engineeringDigital computer detailsData processing systemProbable Case
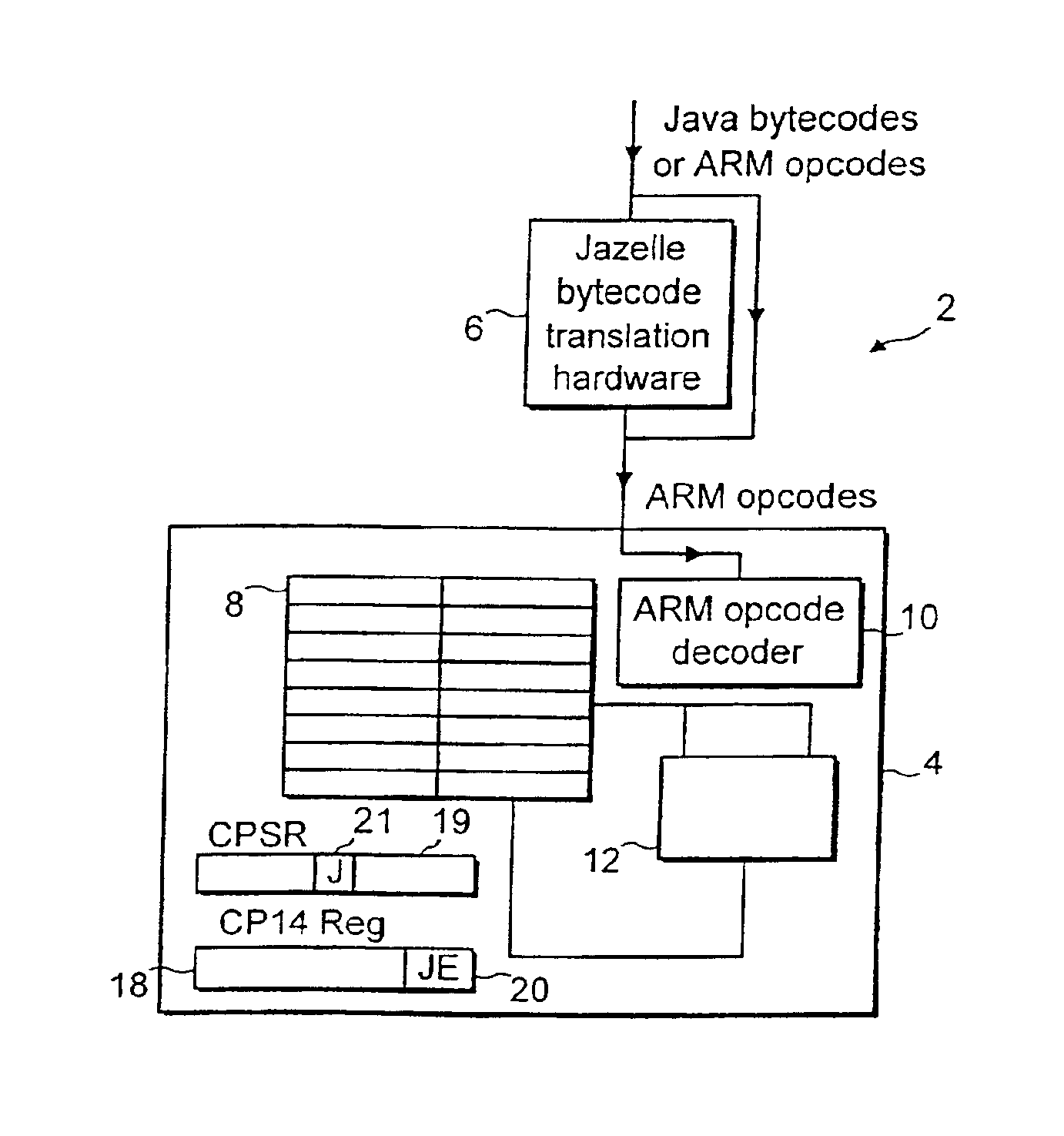
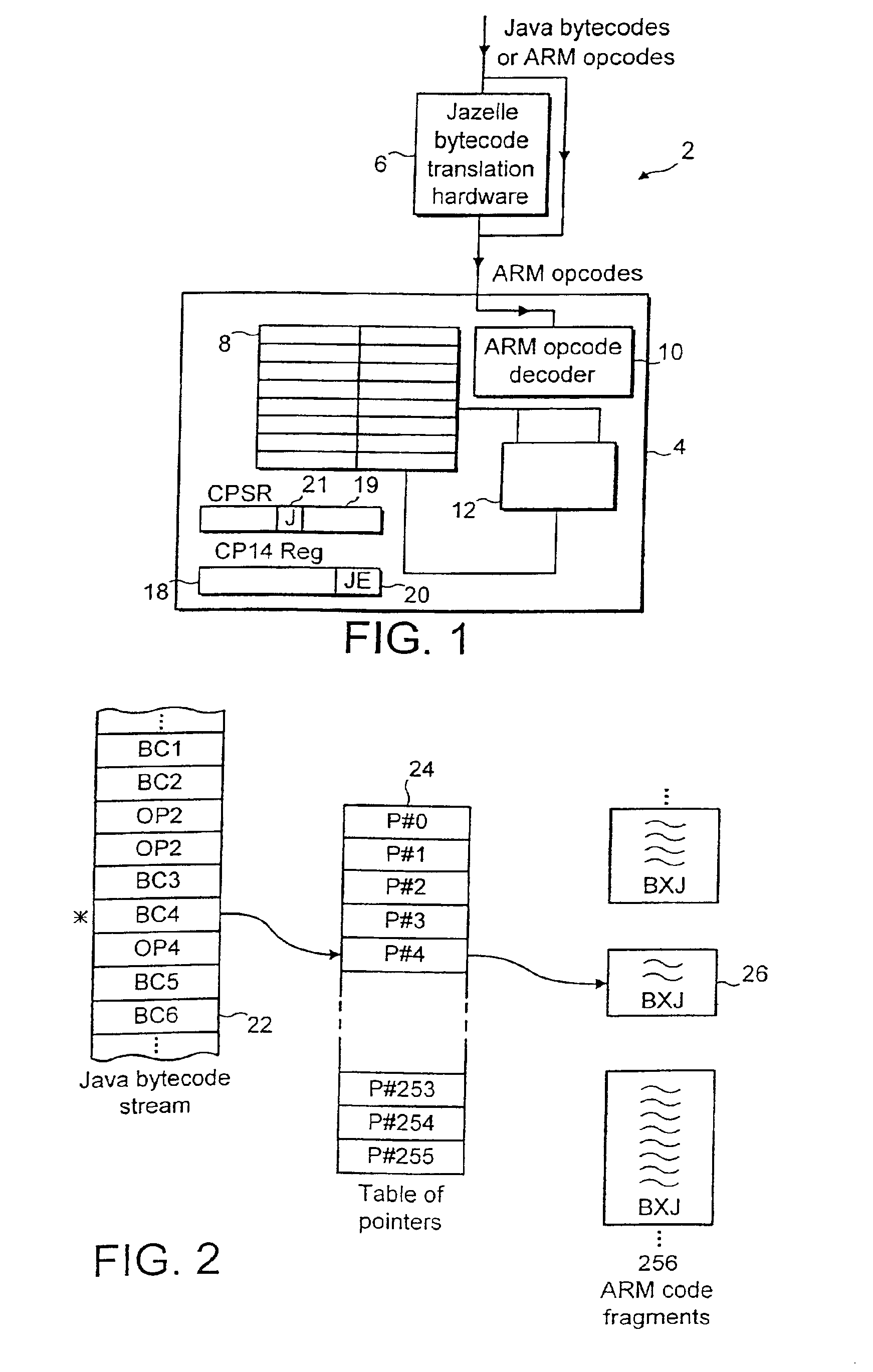
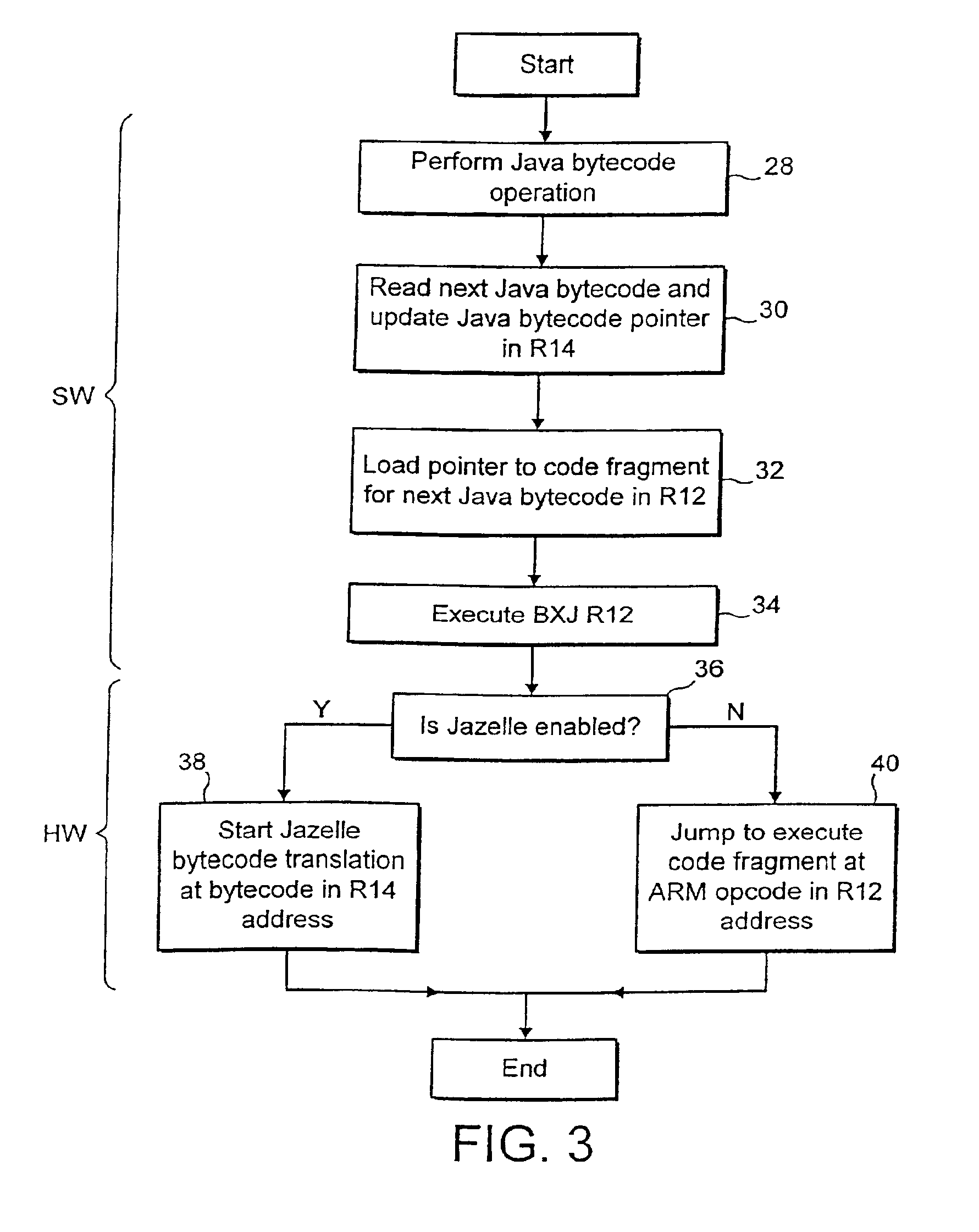
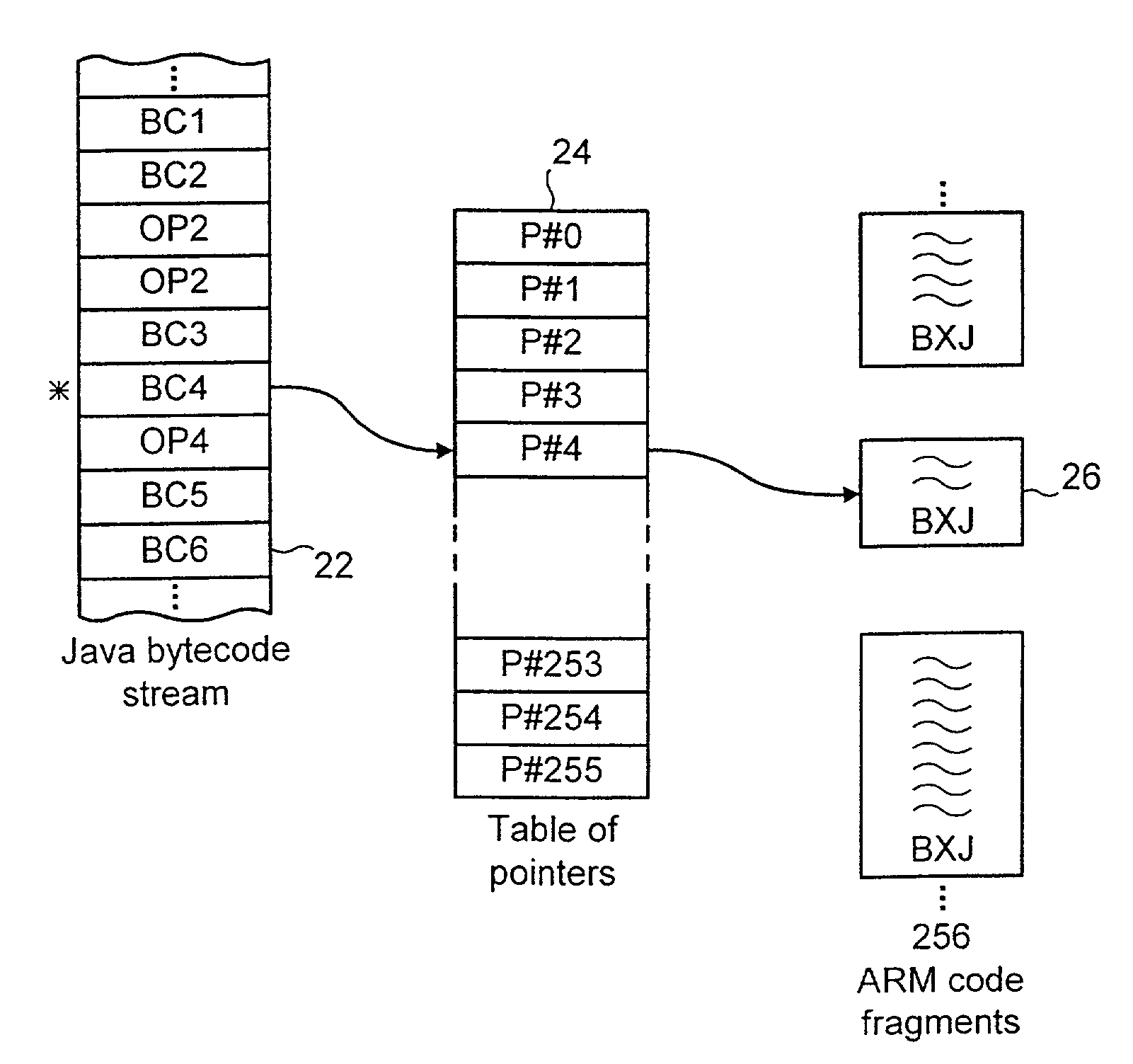
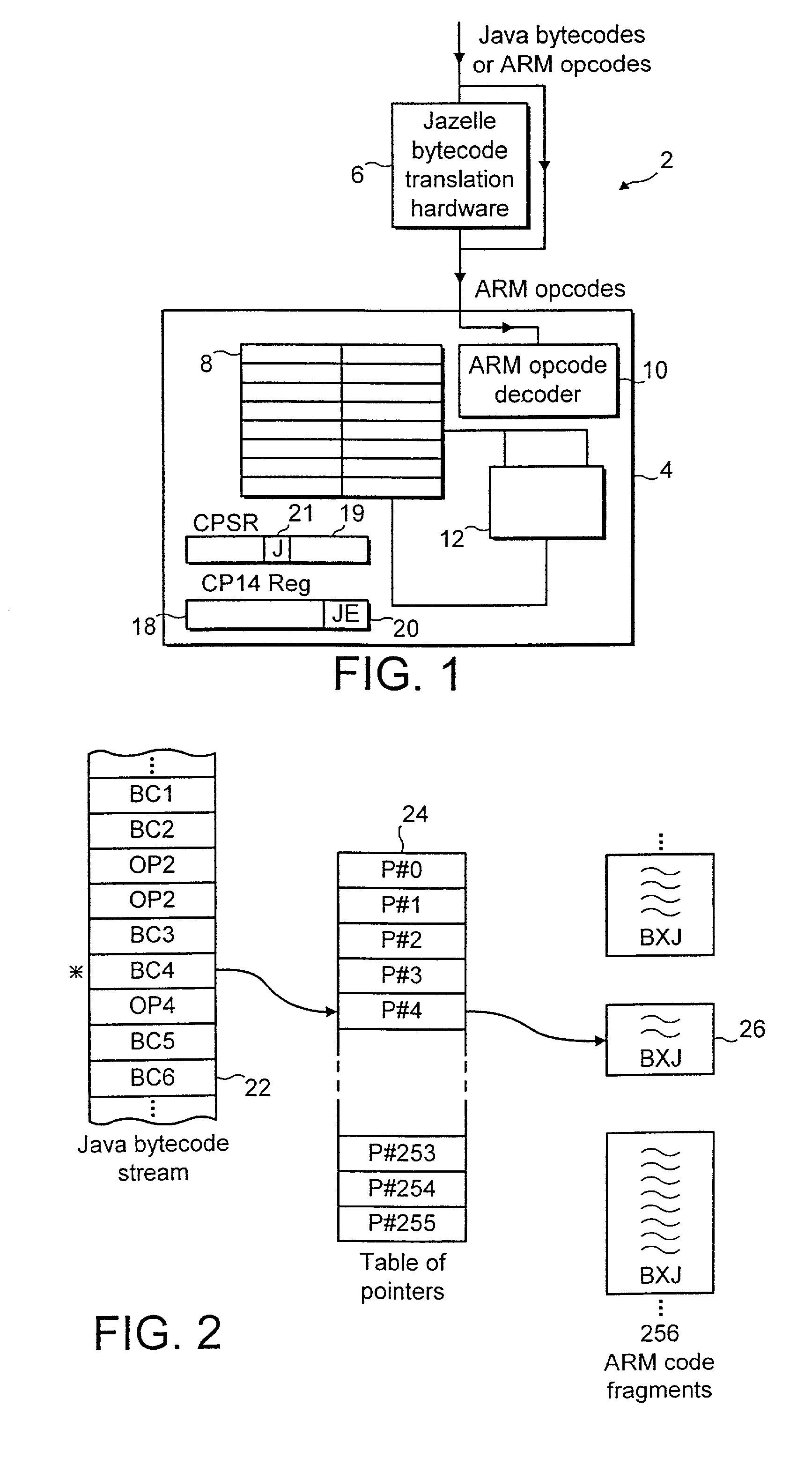
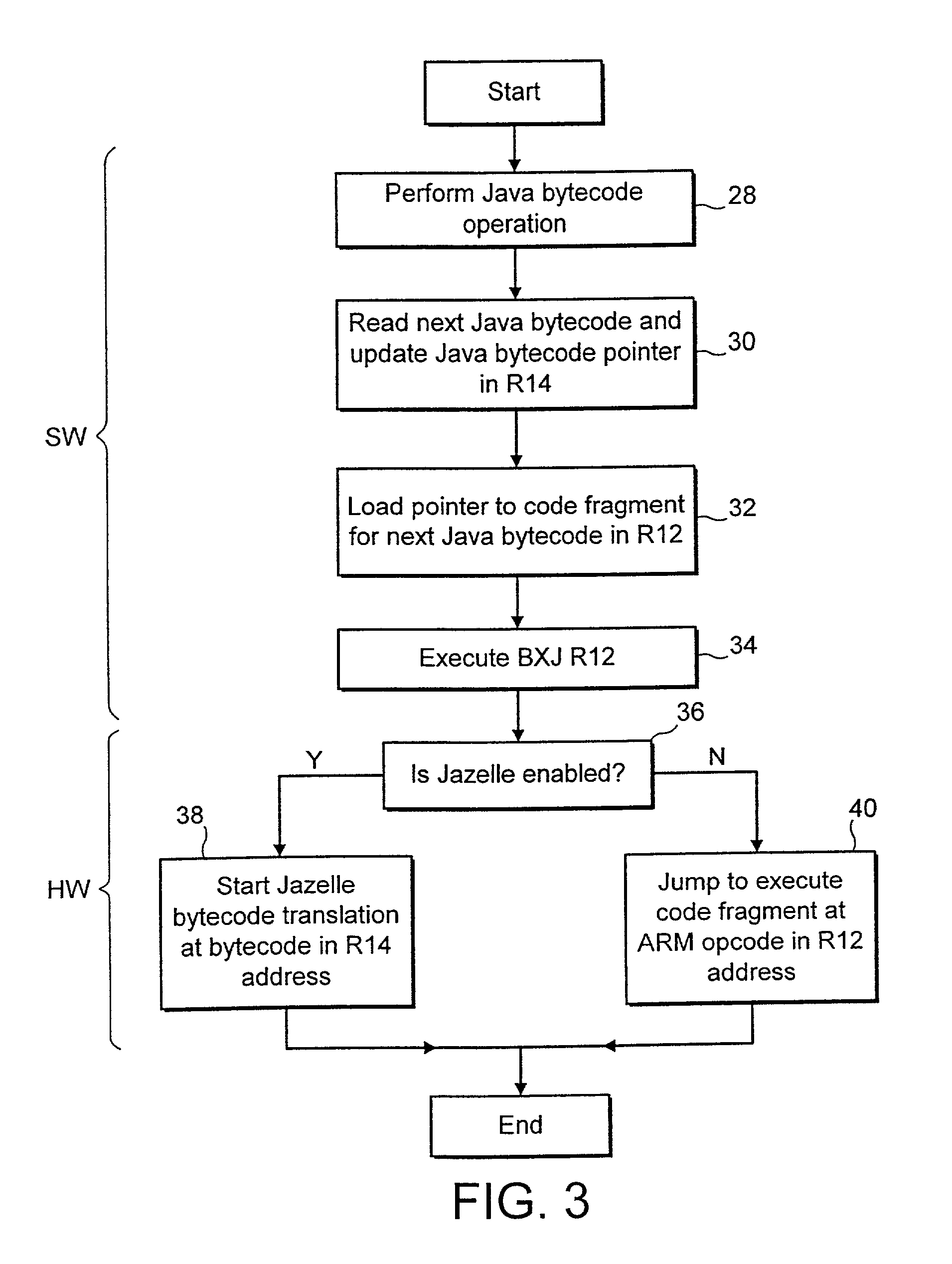
A data processing system supports execution of both native instructions and Java bytecodes using a hardware executer for the Java bytecodes where possible and a software instruction interpreter for the Java bytecodes where these are not supported by the hardware. The sequences of native instructions 26 within the software instruction interpreter that perform the processing for the Java bytecodes being interpreted terminate within a sequence terminating instruction BXJ that acts differently depending upon whether or not an enabled hardware executer 6 is detected to be present. If an enabled hardware executer is detected as present, then the execution of the next Java bytecode is attempted with this. If an active hardware executer is not present, then the next Java bytecode is passed directly to the software instruction interpreter.
Owner:ARM LTD
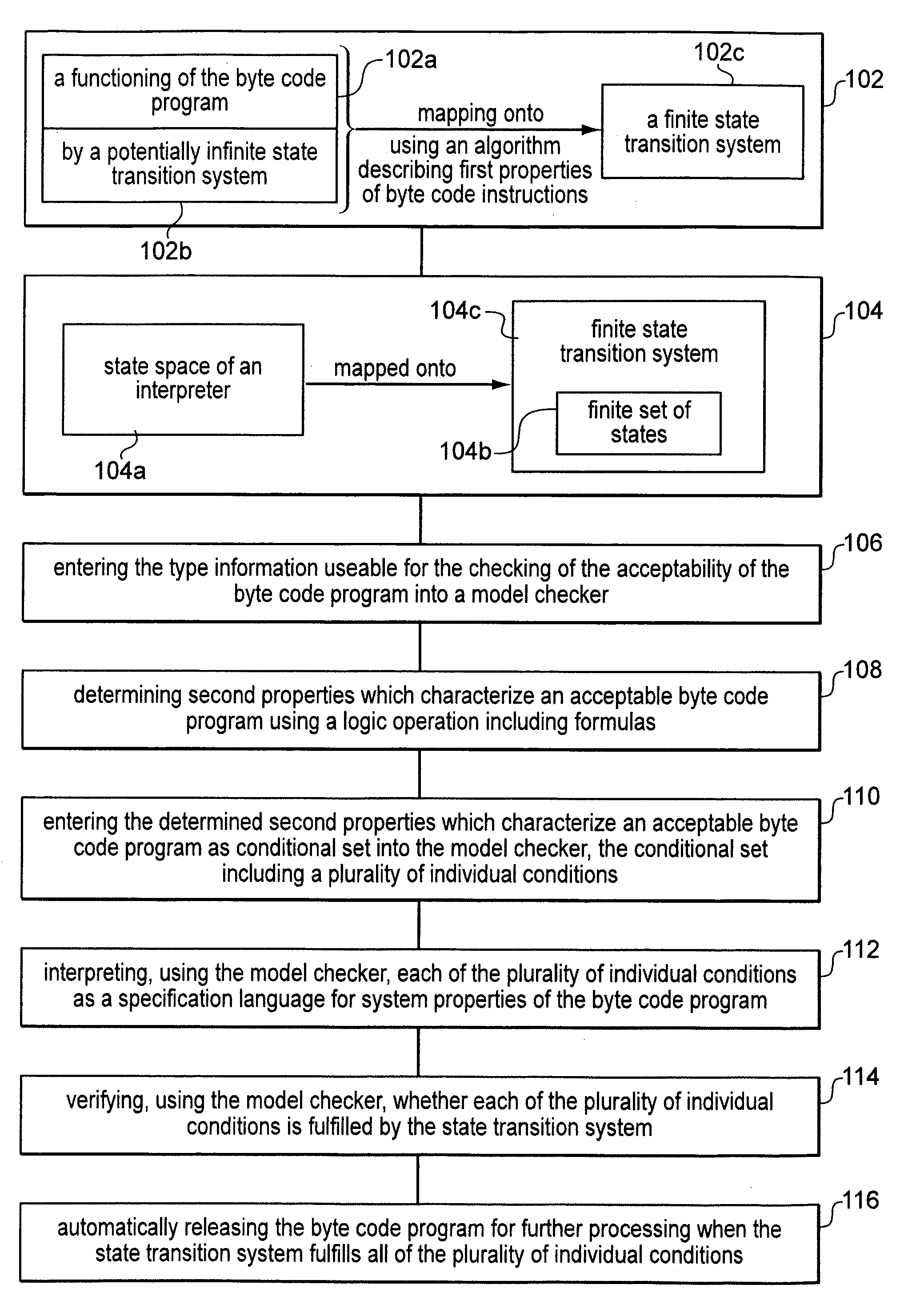
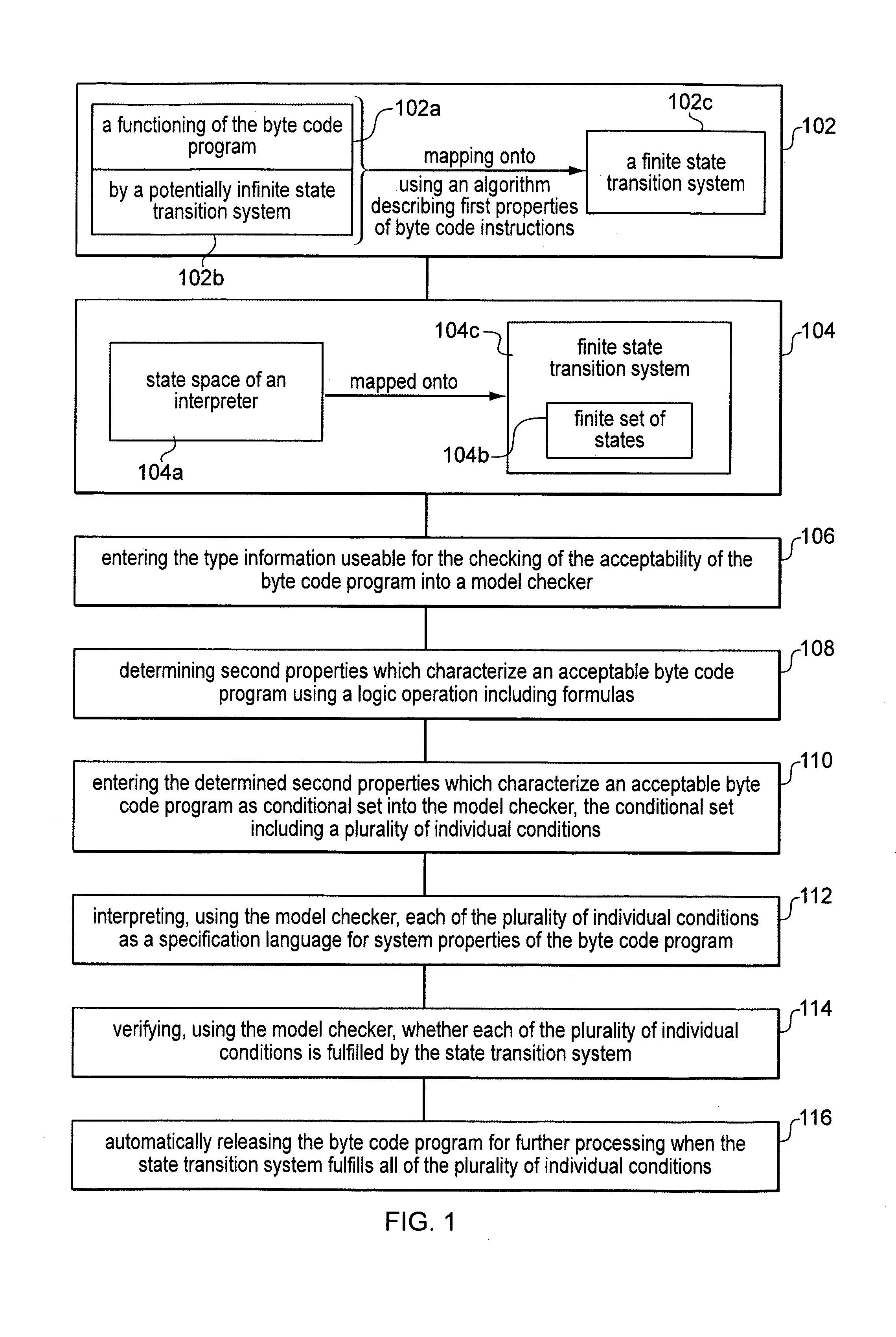
Method for verifying safety properties of java byte code programs
InactiveUS7181725B1Raise security concernsSoftware testing/debuggingProgram loading/initiatingState spaceSecurity properties
In a method for verifying the safety properties of Java byte code programs, the functioning of the byte code program to be verified is modeled on a finite state transition system M, and the state space of the Java Virtual Machine (JVM) on a finite set of states in M. Once entered into a model checker, the data of finite state transition system M are compared to the data entered in the model checker as conditional set S to determine properties characterizing an acceptable byte code program. The byte code program to be checked is released for further processing only when the state transition system M fulfills all conditions of conditional set S.
Owner:JOLLY SEVEN SERIES 70 OF ALLIED SECURITY TRUST I +1
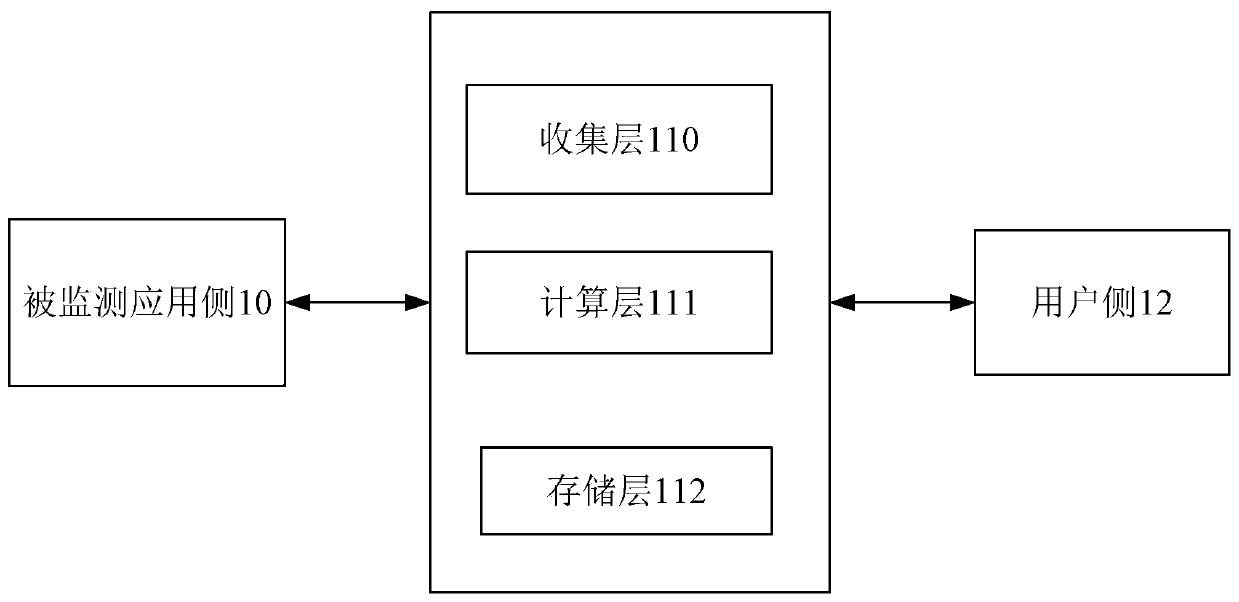
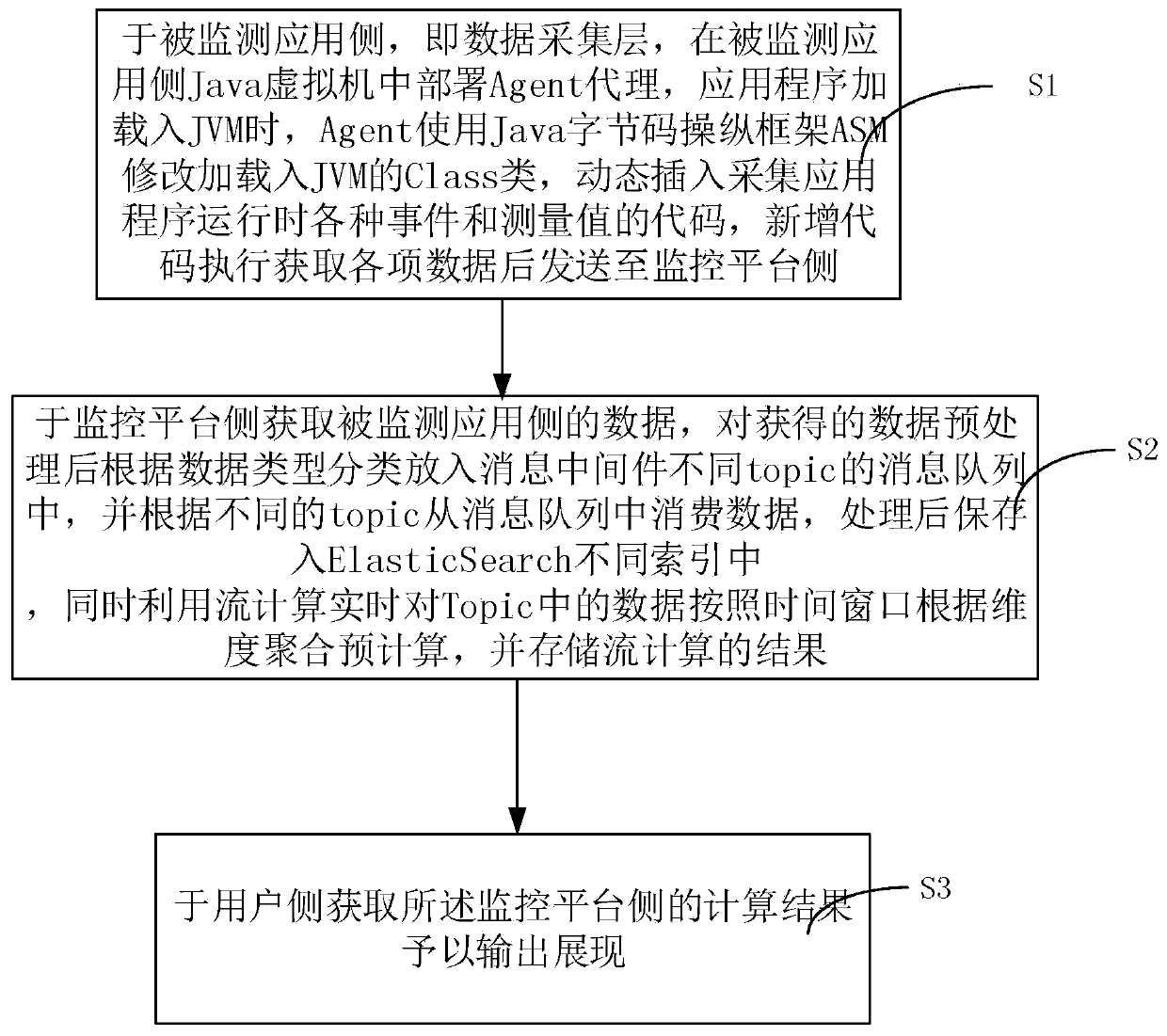
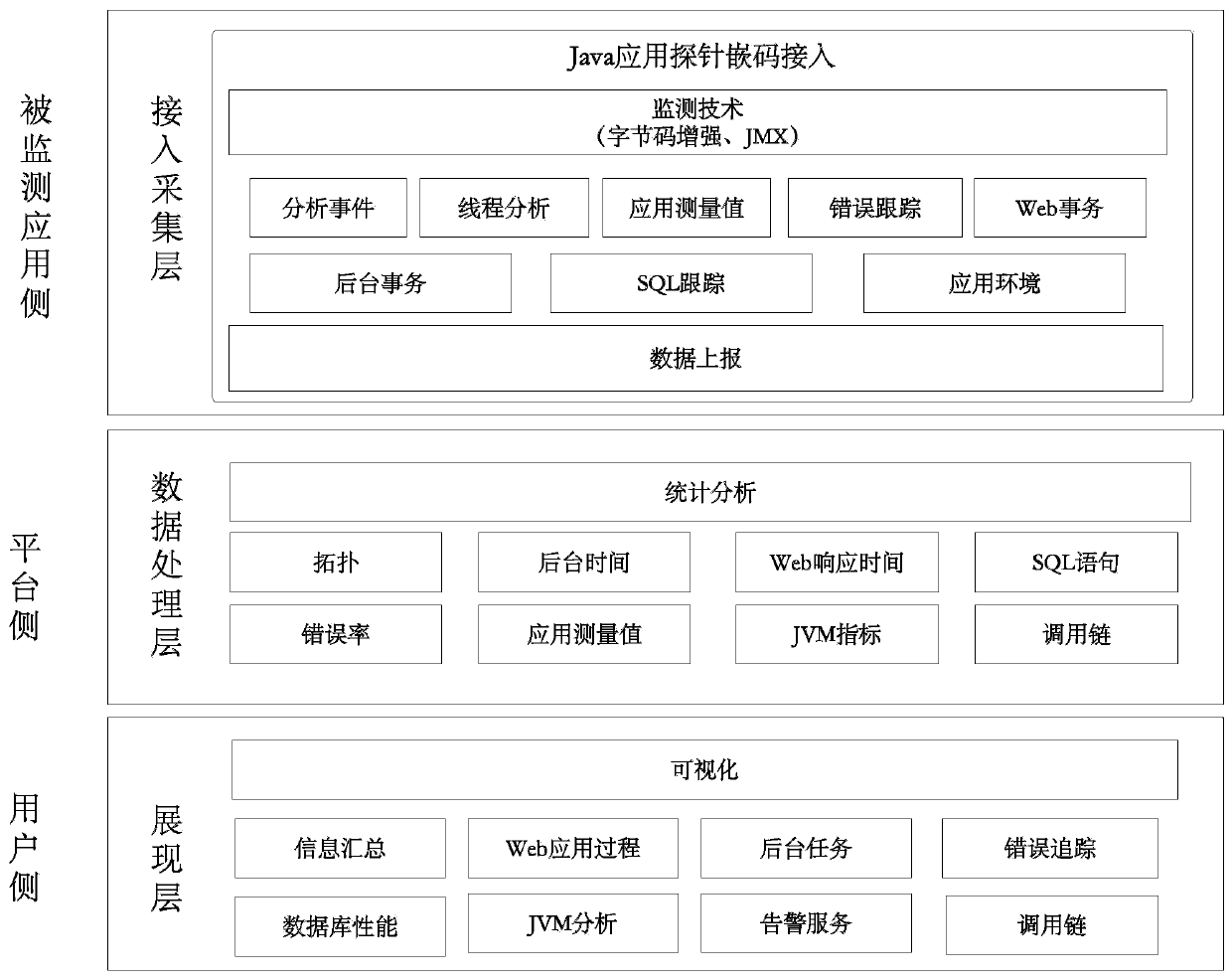
Service data real-time monitoring system and method based on Java byte code enhancement technology
PendingCN110083436AReduce workloadAutomatically obtain health indicatorsSoftware simulation/interpretation/emulationMessage queueMonitoring system
Owner:CHINA TELECOM SHANGHAI IDEAL INFORMATION IND GRP
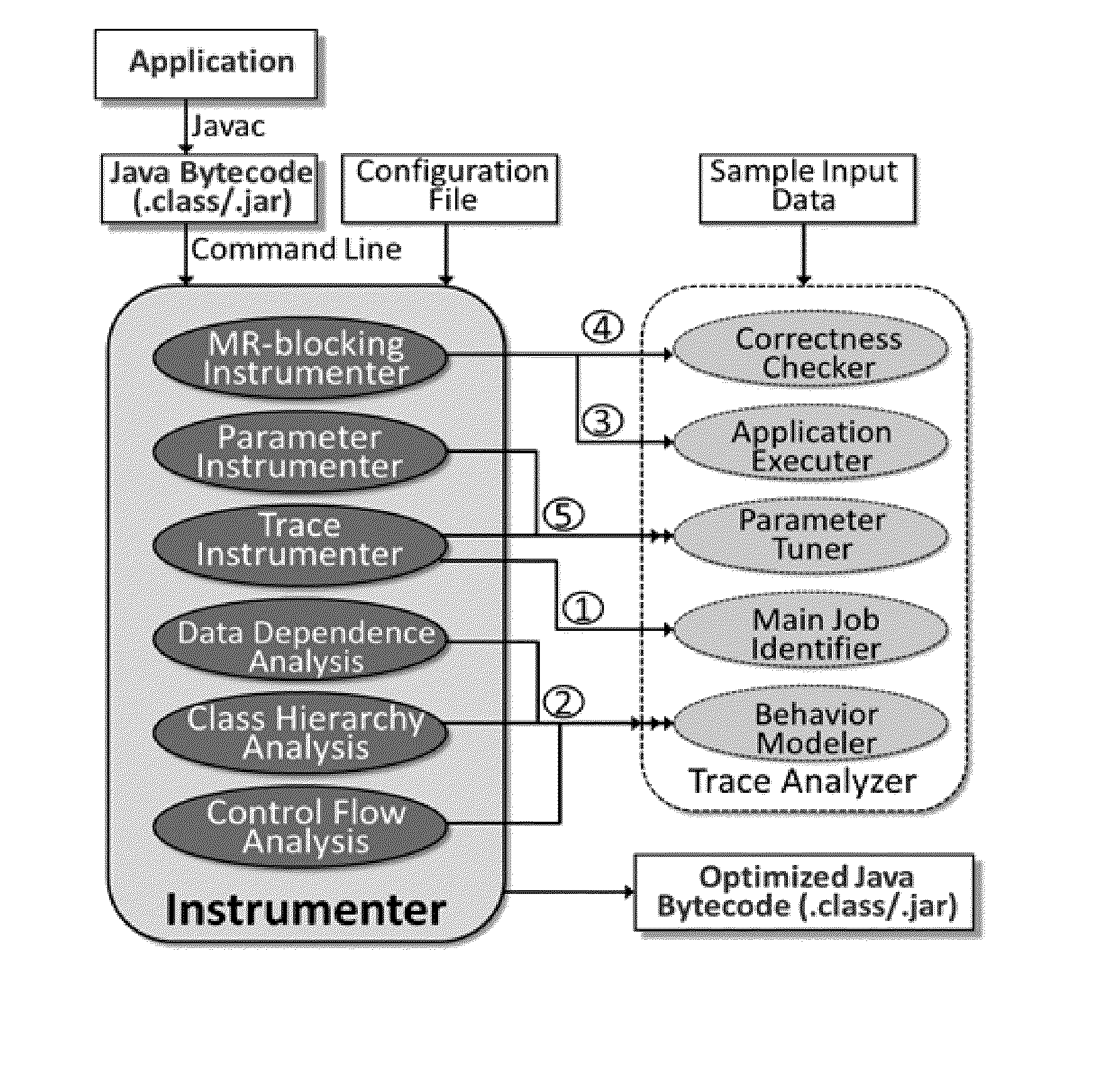
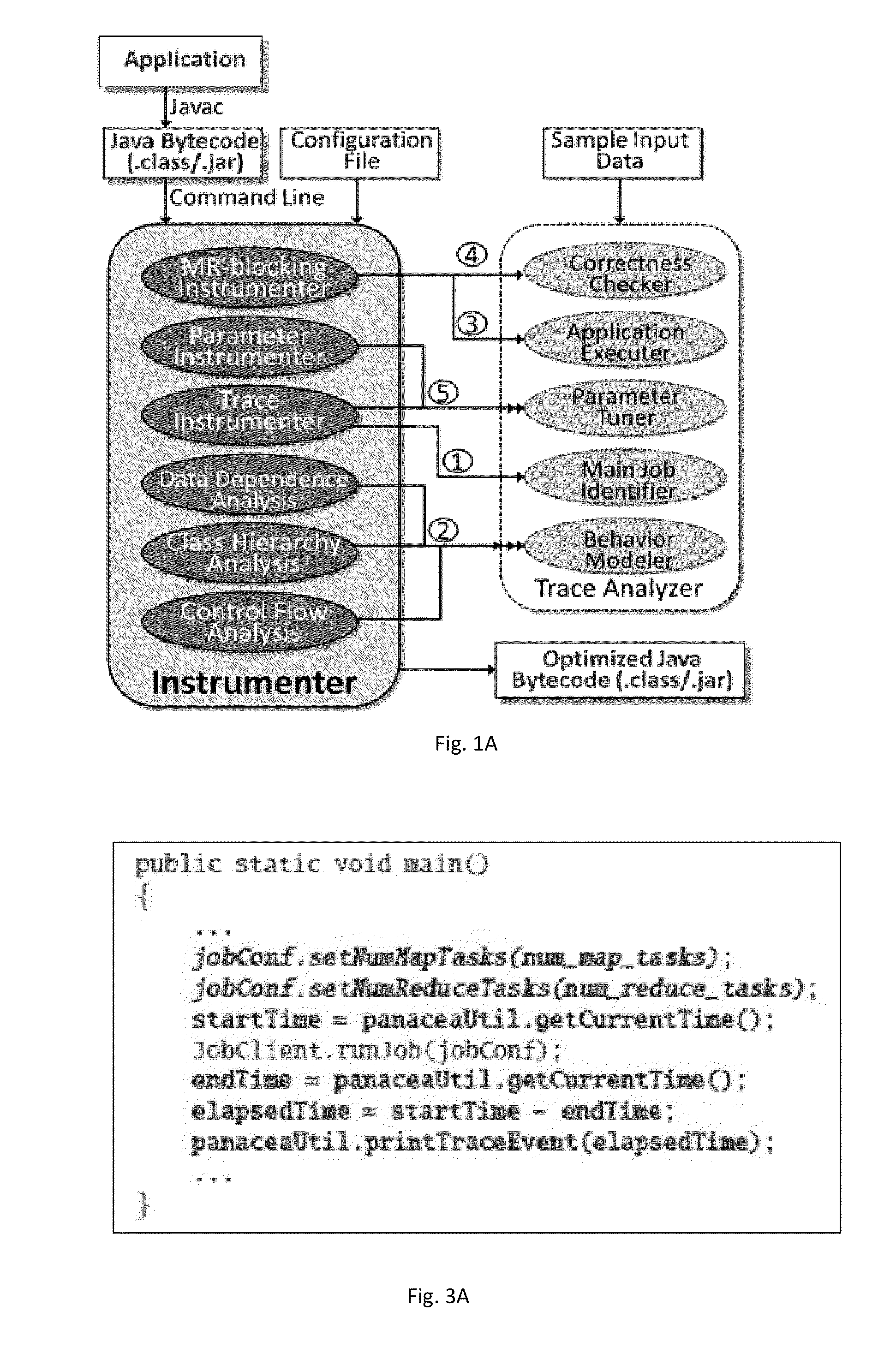
Computer-guided holistic optimization of MapReduce applications
InactiveUS8793674B2Software engineeringSpecific program execution arrangementsTheoretical computer scienceApplication software
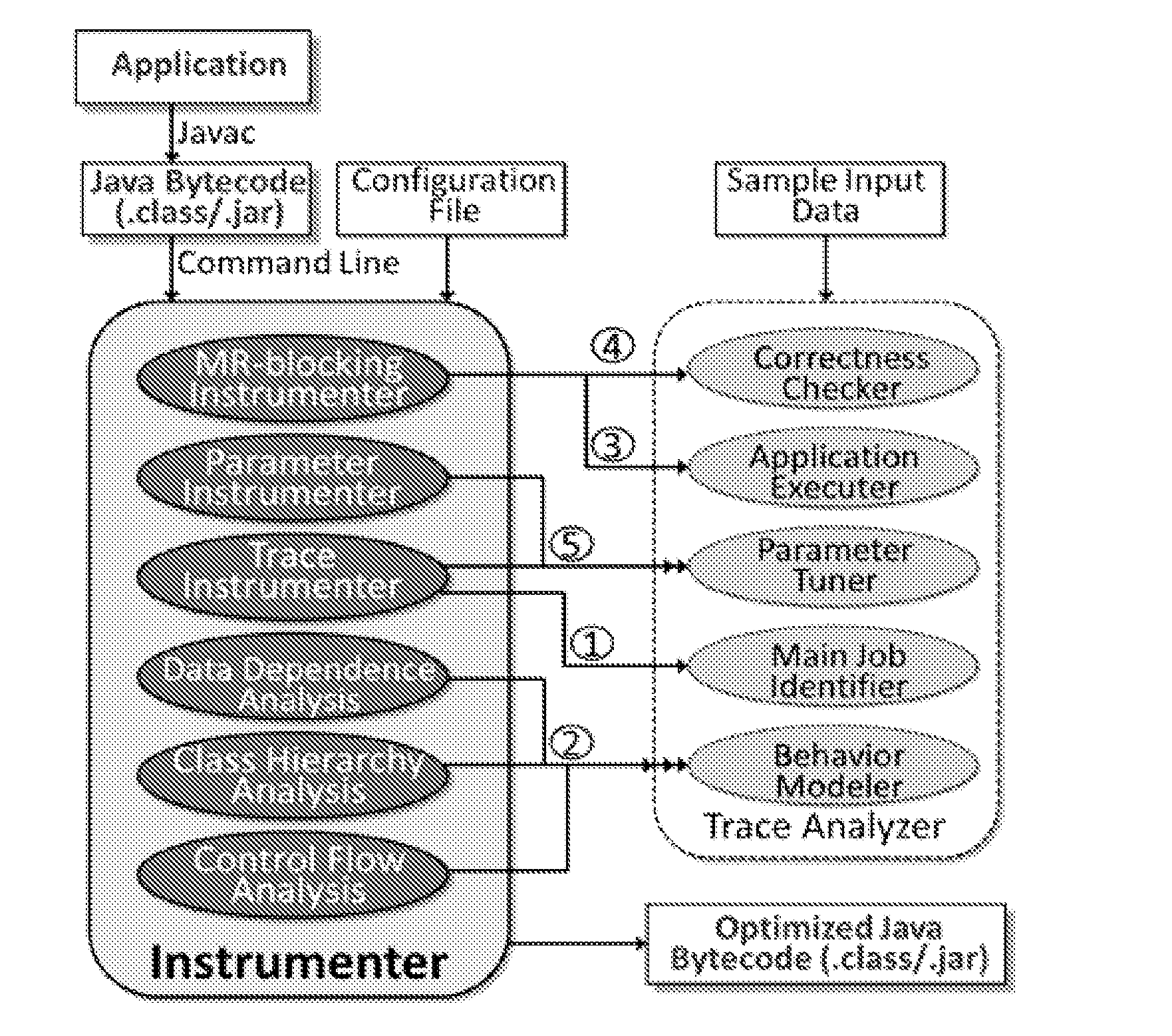
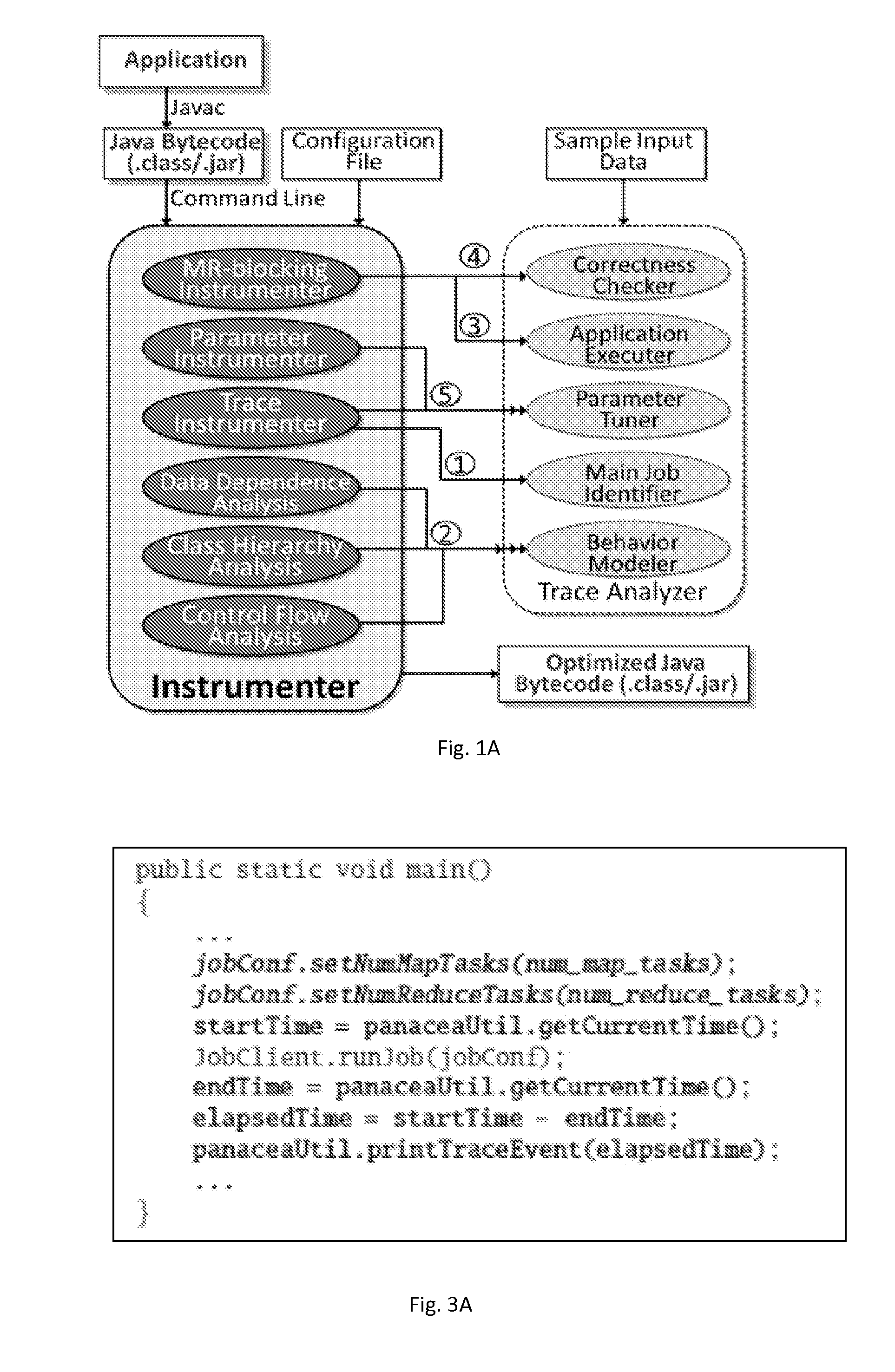
A method for compiler-guided optimization of MapReduce type applications that includes applying transformations and optimizations to JAVA bytecode of an original application by an instrumenter which carries out static analysis to determine application properties depending on the optimization being performed and provides an output of optimized JAVA bytecode, and executing the application and analyzing generated trace and feeds information back into the instrumenter by a trace analyzer, the trace analyzer and instrumenter invoking each other iteratively and exchanging information through files.
Owner:NEC CORP
Large-scale application regression testing information processing method based on Java bytecode
InactiveCN103425584AImprove test qualityLow costSoftware testing/debuggingInformation processingRegression testing
The invention relates to a large-scale application regression testing information processing method based on Java bytecode. The large-scale application regression testing information processing method based on Java bytecode comprises a plug-in step of injecting an object code; a step of acquiring an operating path of the object code at high efficiency, a mapping and storing step of an established relationship between the object code and a testing case; a step of comparing an object code in a new version and an object code in a cold version; an involved analysis step of automatically selected cases which need to be subjected to regression testing; a step of continuously improving the regression testing based on a version stream; a step of automatically generating all code structures and calling relationship of an object application; a step of carrying out data comparison based on a program structure and code semantic; a step of plugging exploration logic in the object application bytecode so as to dynamically acquire a complete code-operating path and coverage data; a step of controlling regression testing trigger of testing cases; and a step of representing a mapping relationship and an involvement relationship between the testing case and the code on a friendly interface. According to the large-scale application regression testing information processing method, the testing case is subjected to deep analysis, an original progress black-box state is converted into a semitransparent state, so that testing personnel can implement testing better.
Owner:SHANGHAI FAIRYLAND INFORMATION TECH CO LTD
Program instruction interpretation
InactiveUS7089539B2Low hardware requirementsSignificant performance gainDigital computer detailsSoftware simulation/interpretation/emulationProgram instructionJava bytecode
Program instructions in the form of Java bytecodes may be subject to fixed mappings to processing operations or programmable mappings to processing operations. A system is provided with a fixed mapping hardware interpreter, a programmable mapping hardware interpreter and a software interpreter. The fixed mapping hardware interpreter is able to provide high speed interpretation of the common and simple bytecodes. The programmable mapping hardware interpreter is able to provide high speed interpretation of the simple and performance critical programmable bytecodes with the remaining bytecodes and more complicated bytecodes being handled by the software interpreter.
Owner:ARM LTD
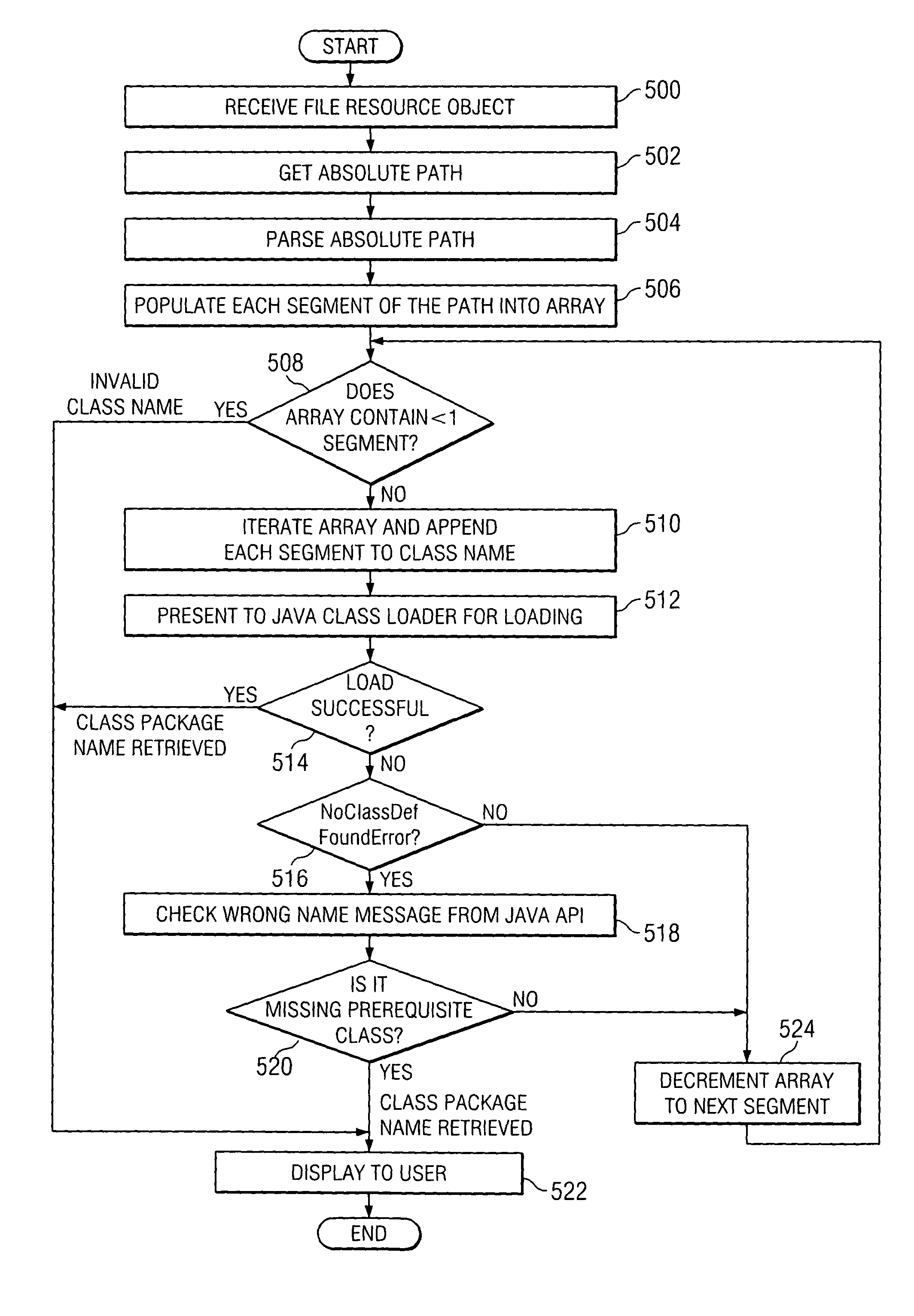
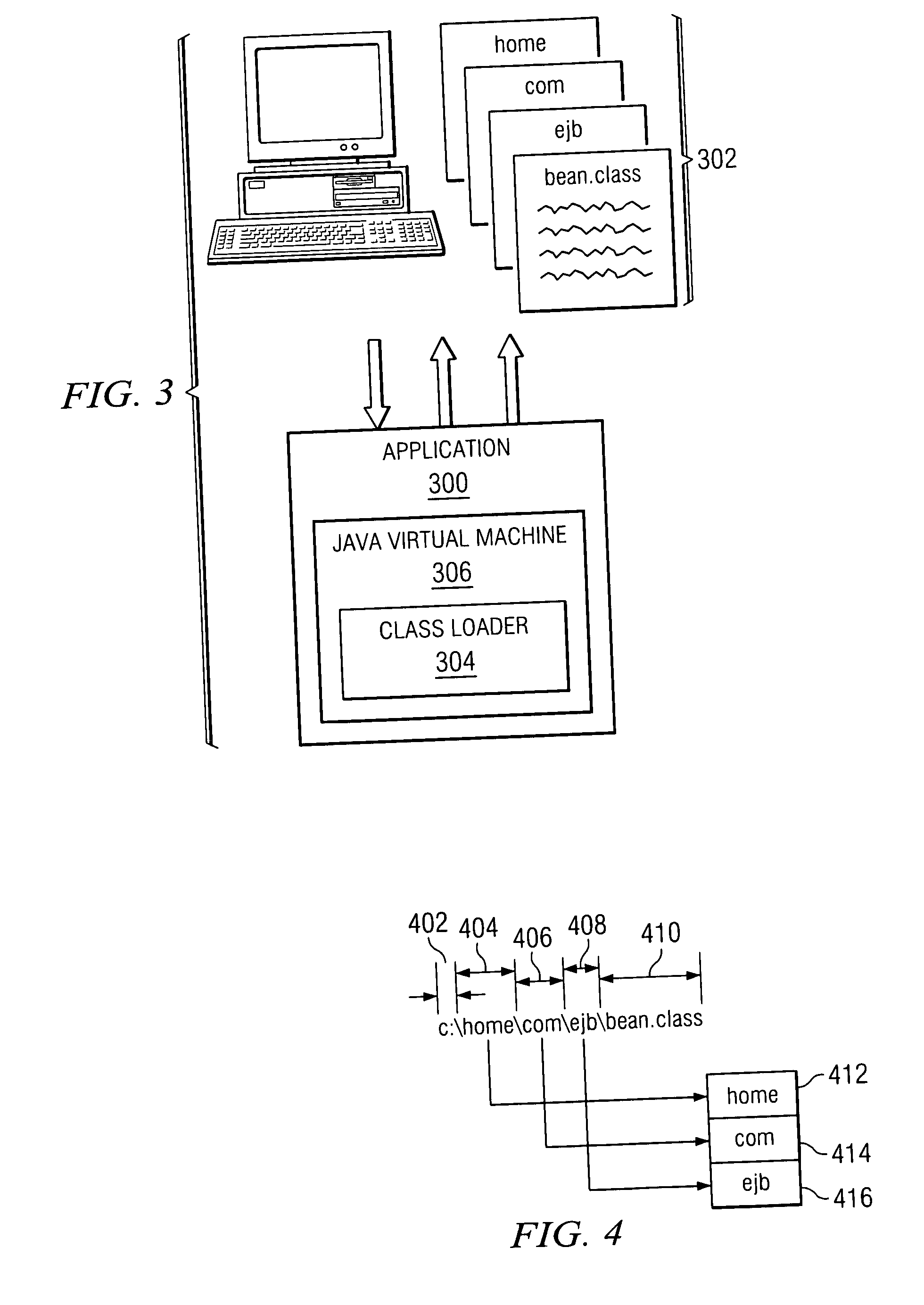
Method and apparatus for identifying a Java class package name without disassembling Java bytecodes
A system and method for retrieving class package name from a class file if not known or found by the Java class loader of the Java virtual machine at load time. An algorithm is derived which uses the class file to obtain the class package name by iterating the directory names of the class file in the user's current operating system. An output is provided to the user when the class package name is found and it is loaded by the Java class loader; when an error occurs after which the error message indicates that the prerequisite class of the class file is missing; or when the class package name itself is invalid.
Owner:IBM CORP
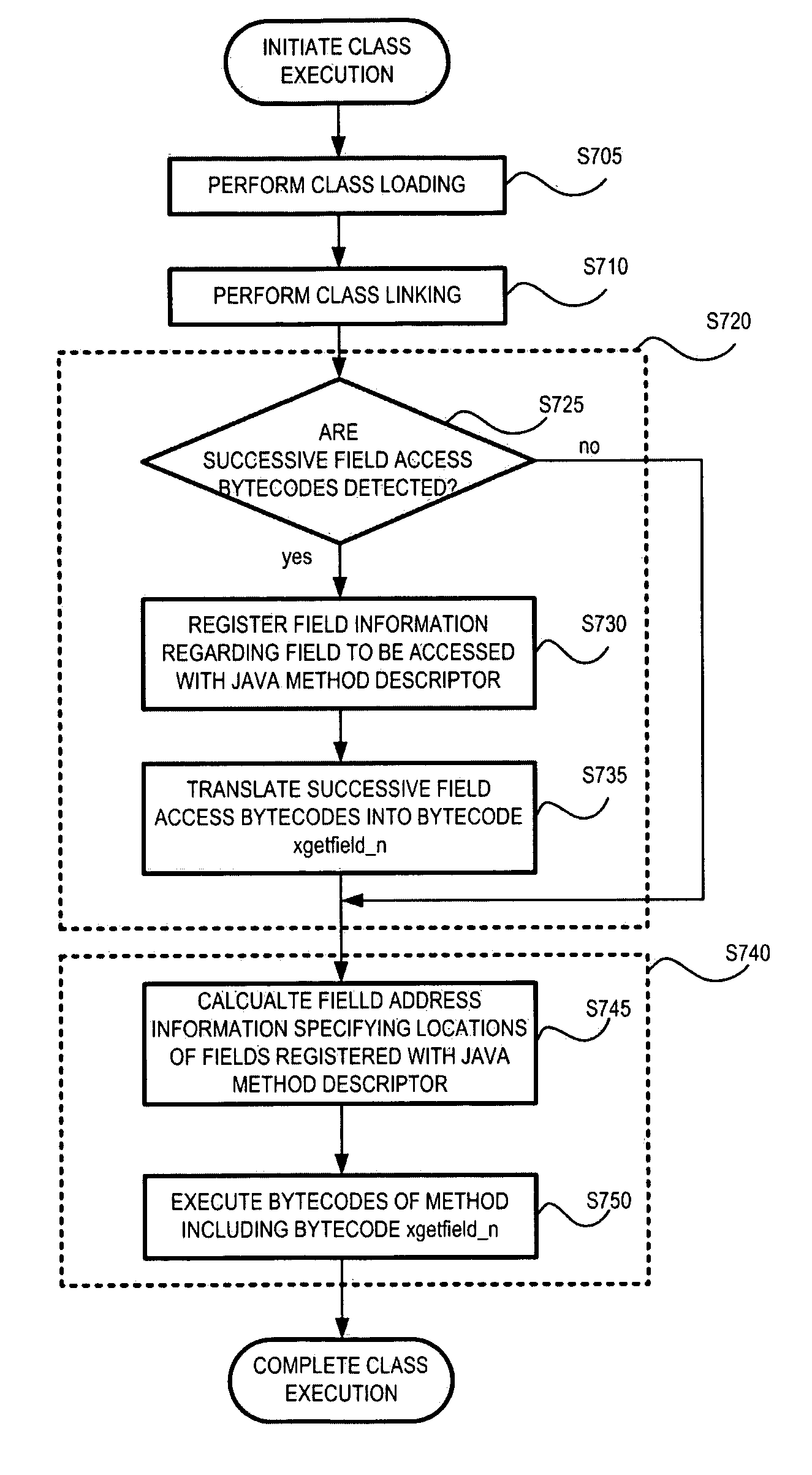
Java bytecode translation method and Java interpreter performing the same
A Java bytecode translation method and a Java interpreter performing the Java bytecode translation method are provided. The Java bytecode translation method includes extracting a number of successive Java bytecodes from a Java class, determining whether the extracted successive Java bytecodes are successive field access bytecodes for accessing a field in the Java class and translating the extracted successive Java bytecodes into predefined bytecode if the extracted successive Java bytecodes are determined to be the successive field access bytecodes, and executing the predefined bytecode.
Owner:SAMSUNG ELECTRONICS CO LTD
Per thread buffering for storing profiling data
InactiveUS20070074171A1Error detection/correctionSpecific program execution arrangementsSoftware engineeringJava bytecode
A method, system and computer program product for collecting profiling information during runtime of a multithreaded program. According to the method, a plurality of instructions of the program for execution in an application thread are first received; a plurality of variable size profiling records are then stored in a buffer assigned exclusively to the application thread during execution of the plurality of instructions; and the plurality of profiling records in the buffer are then processed. The program may be written in Java bytecode for execution in a Java virtual machine with the processing of profiling buffers performed by a component of a JIT compiler for insertion into a repository in internal JIT format, e.g. a hash table, for later optimization processing.
Owner:LINKEDIN
Post Processing of Dynamically Generated Code
InactiveUS20100115502A1Improve performanceSoftware engineeringProgram controlApplication softwareJava bytecode
A system and method are disclosed for improving the performance of compiled Java code. Java source code is annotated and then compiled by a Java compiler to produce annotated Java bytecode, which in turn is compiled by a just-in-time (JIT) compiler into annotated native code. The execution of the annotated native code is monitored with a patching agent, which captures the annotated native code as it is being executed. The captured native code is then provided through an application program interface to a dynamic linkage module, which in turn provides the captured native code to a user or to an application plug-in module for modifications. The modifications are saved as a patch. The annotated native code is then re-executed and the modifications to the annotated native code are applied as a patch by the patching agent.
Owner:GLOBALFOUNDRIES INC
Java bytecode debugger and debugging method
ActiveCN106201893AImprove debugging efficiencyRealize the debugging functionSoftware testing/debuggingData informationJava bytecode
Owner:HENGBAO
Systems, methods, and computer products for automated injection of java bytecode instructions for java load time optimization via runtime checking with upcasts
Automated injection of Java bytecode instructions for Java load time optimization via runtime checking with upcasts. Exemplary embodiments include a method including generating a stack for each of a plurality of bytecodes, generating a subclass configured to keep a history of instructions that have modified the stack, statically scanning a plurality of Java classes associated with the plurality of bytecodes to locate class file configurations and bytecode patterns that cause loading of additional classes to complete a verification of each of the classes in the plurality of Java classes, rewriting the bytecodes to delay the loading of the additional classes until required at a runtime, recording modifications that have been made to the stack by the instructions, and applying the modifications to each of the bytecodes in the plurality of bytecodes.
Owner:IBM CORP
Device and method for implementing dynamic analog remote interface
ActiveCN102955714AWill not cause hidden dangerMultiprogramming arrangementsSoftware simulation/interpretation/emulationEnd systemJava bytecode
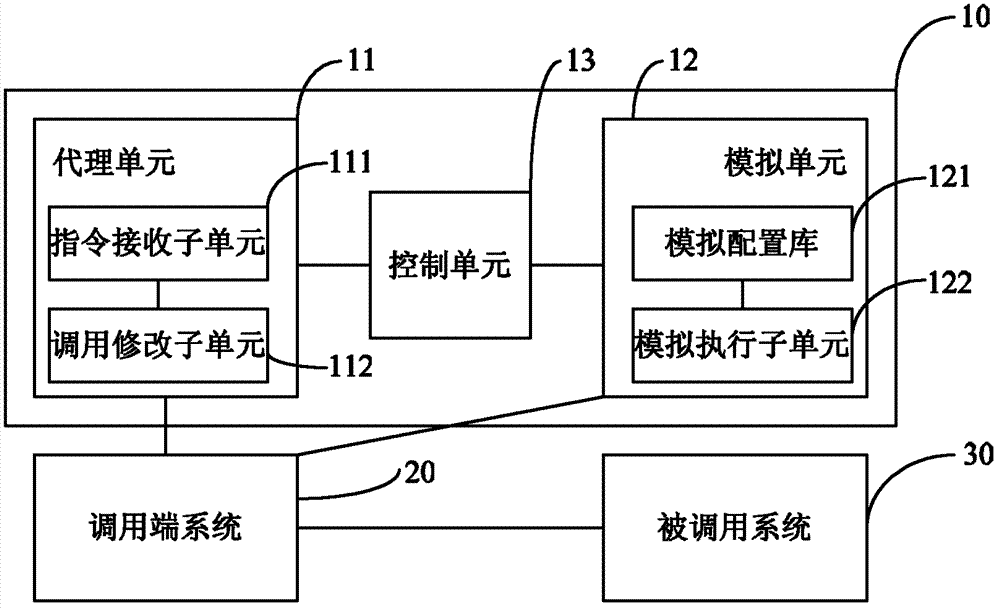
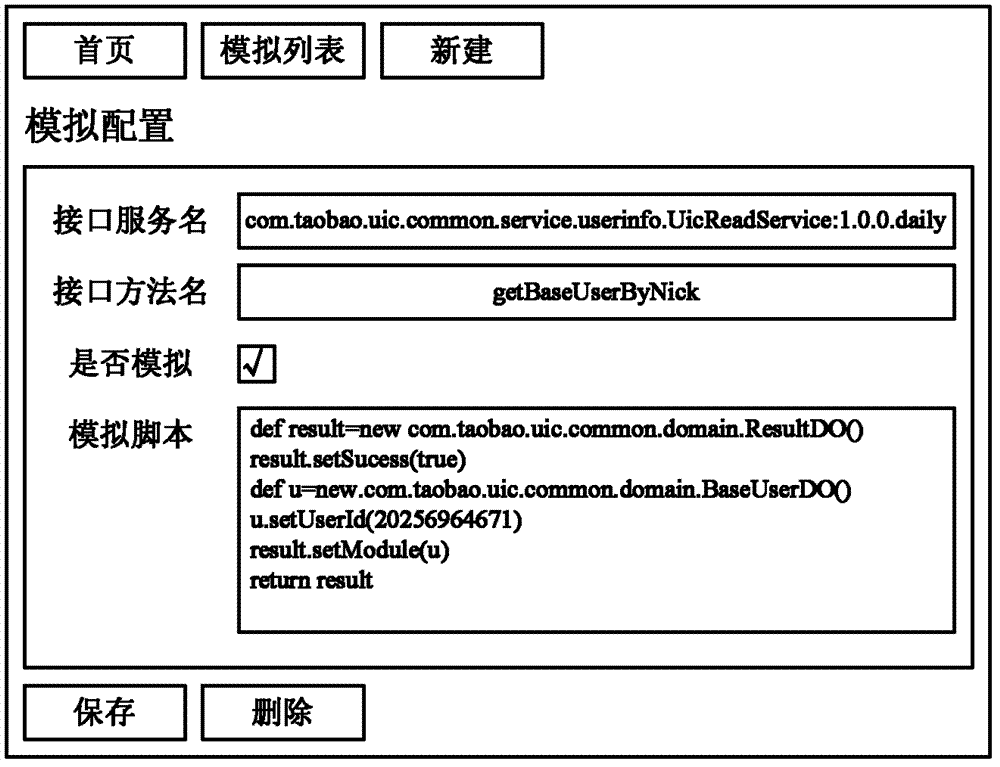
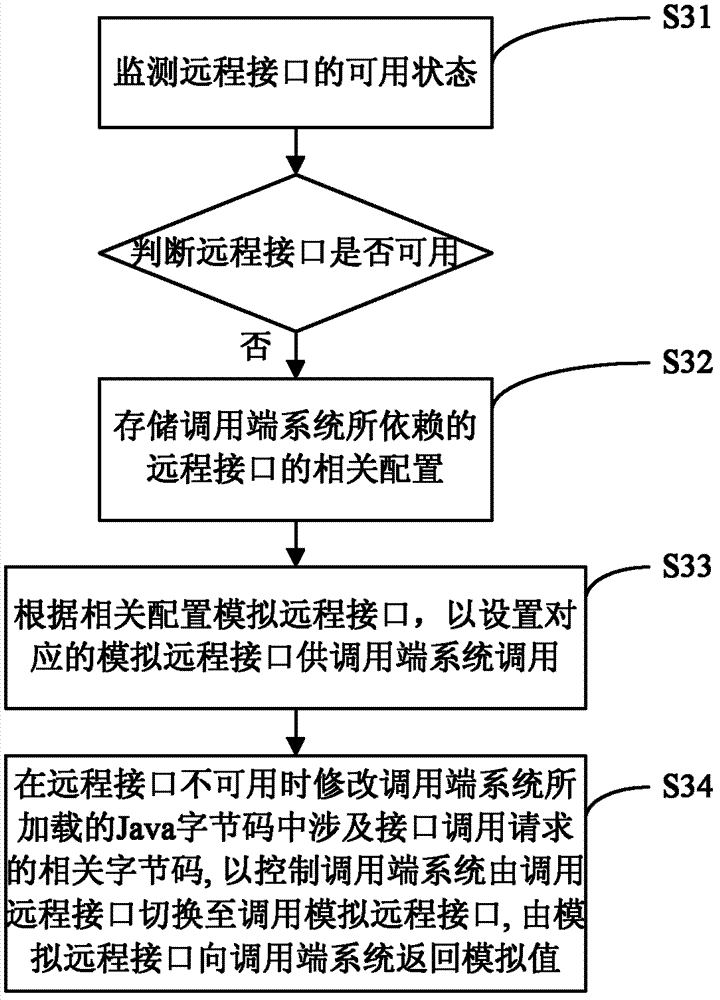
The invention discloses a device for implementing a dynamic analog remote interface. The device is connected to a calling end system for calling a remote interface of a called system, and the calling end system runs in a Java virtual machine. The device comprises an agent unit, an analog unit and a control unit, the agent unit is used for modifying relevant byte-codes involved in an interface calling request in Java byte-codes loaded in the calling end system, the analog unit is used for setting an analog remote interface according to the remote interface of the called system, and the control unit is used for controlling the agent unit to modify the relevant byte-codes when the remote interface is determined to be unusable, so that the calling end system calls the analog remote interface instead of the remote interface. The invention further correspondingly discloses a method for implementing the dynamic analog remote interface. In an embodiment of the invention, the calling end system is modified by means of dynamically modifying the Java byte-codes, codes are not required to be added into an original system, and potential hazards caused by surfing in formal environments to the system are prevented.
Owner:ALIBABA GRP HLDG LTD
Computer-Guided Holistic Optimization of MapReduce Applications
A method for compiler-guided optimization of MapReduce type applications that includes applying transformations and optimizations to Java bytecode of an original application by an instrumenter which carries out static analysis to determine application properties depending on the optimization being performed and provides an output of optimized Java bytecode, and executing the application and analyzing generated trace and feeds information back into the instrumenter by a trace analyzer, the trace analyzer and instrumenter invoking each other iteratively and exchanging information through files.
Owner:NEC CORP
Tamper-proof response scheme of Java program
InactiveCN101872393ATamper ResistancePositioning is not easyPlatform integrity maintainanceProgram/content distribution protectionTamper resistanceResponse type
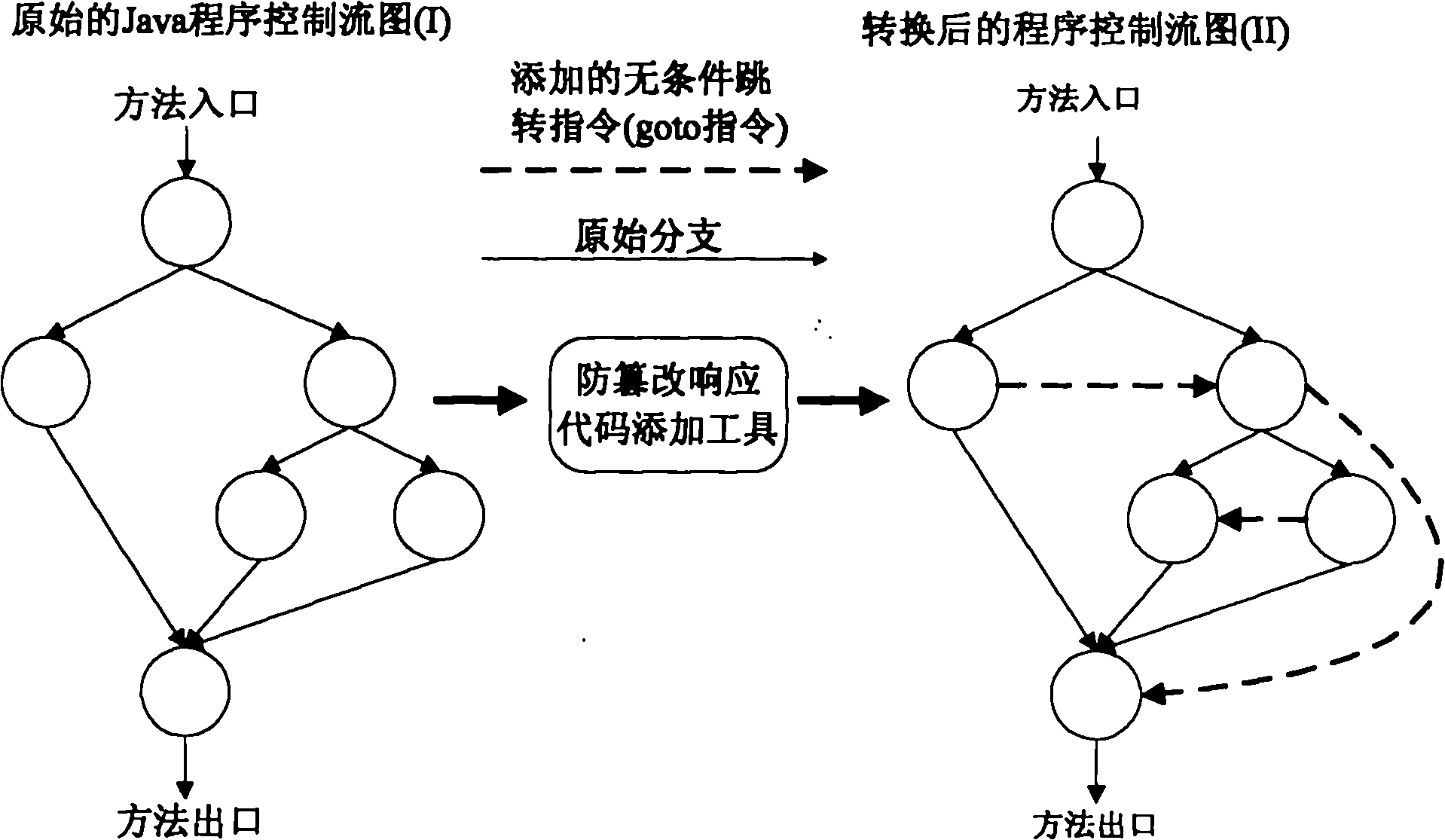
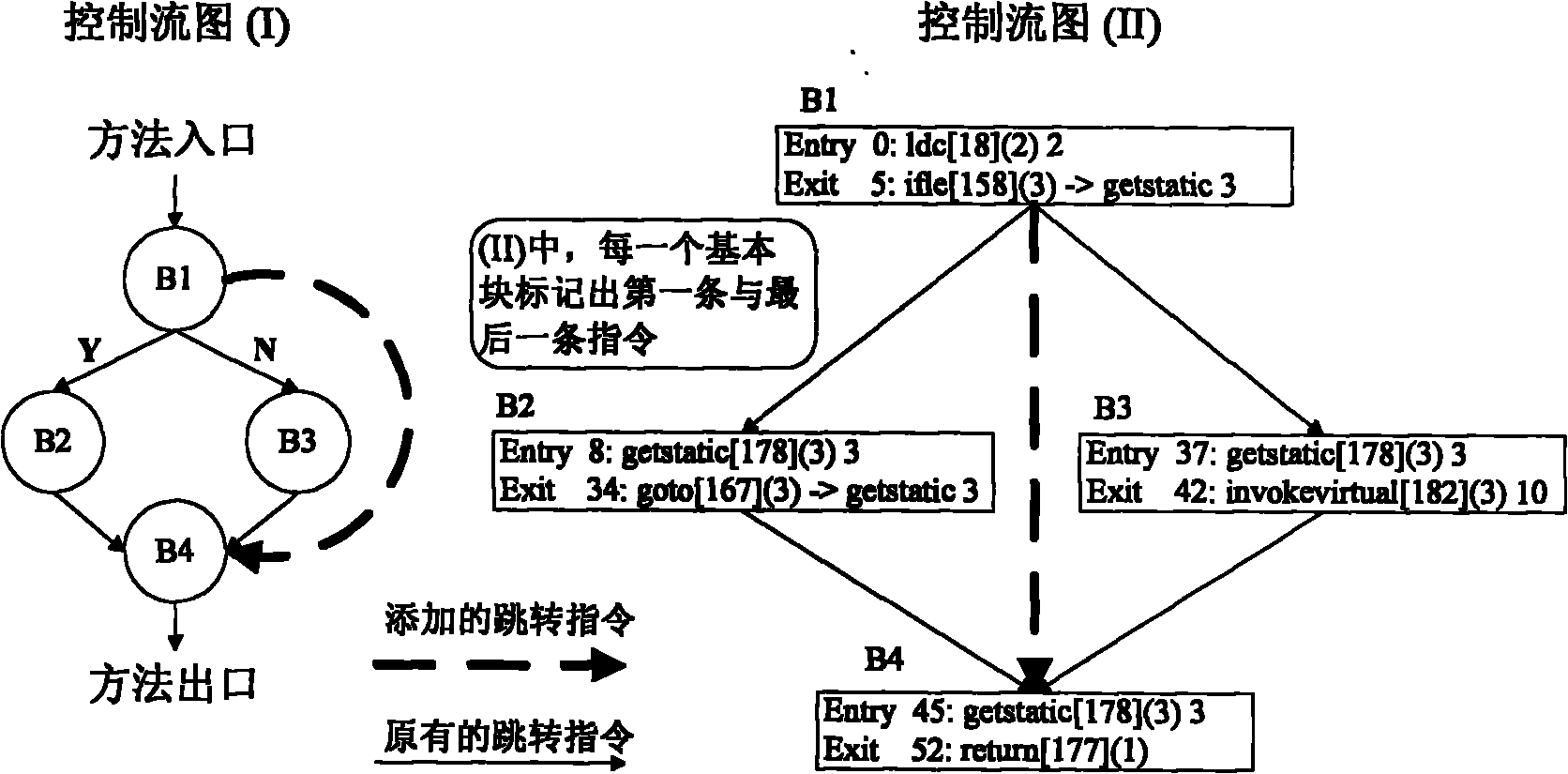
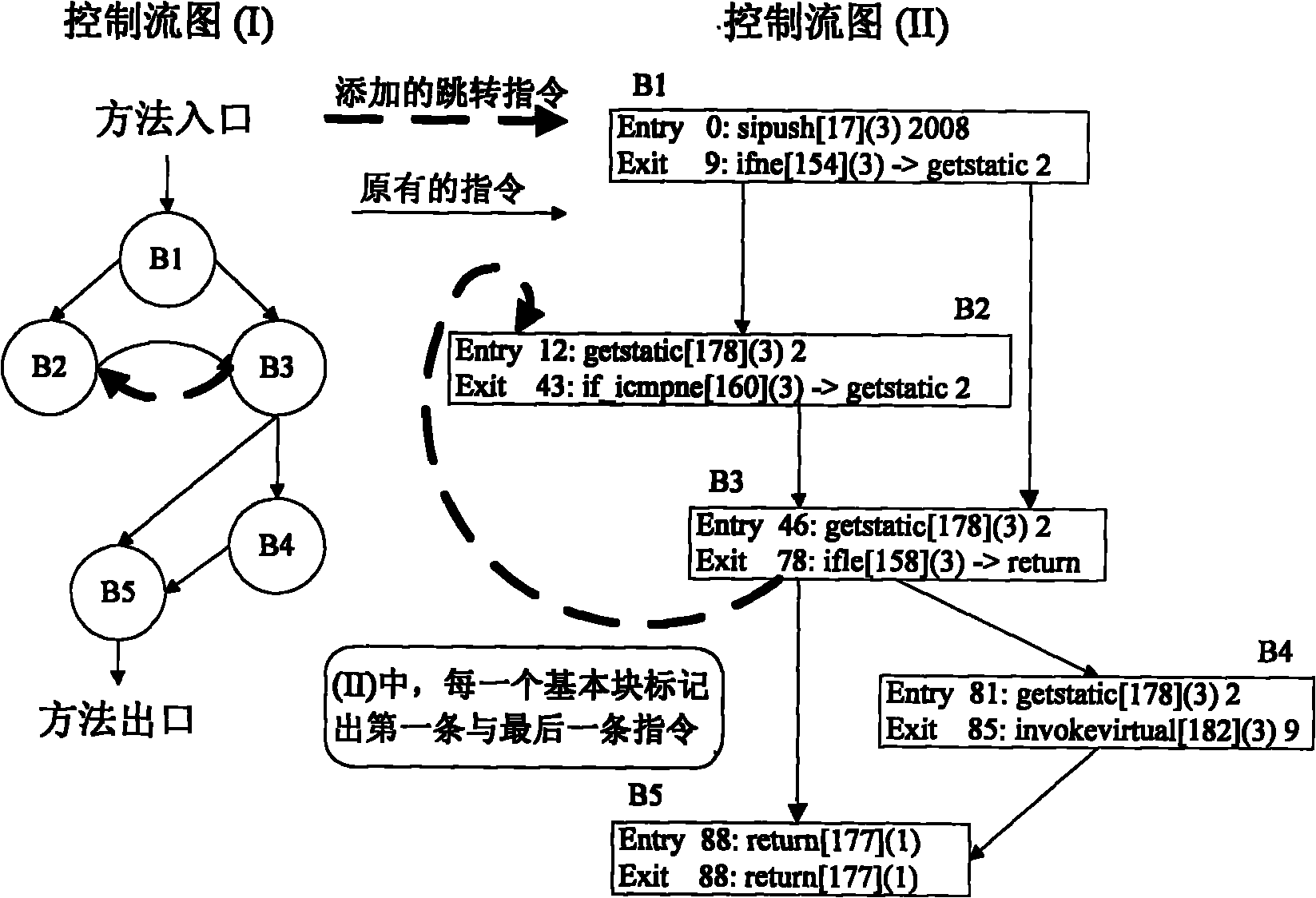
The invention relates to a software protection technique of a Java program, which belongs to a software tamper-proof branch in the technical field of software protection. In the technical scheme, an unconditional jump command is added to a byte code file which corresponds to the Java program after that the Java program is tampered is detected to modify a programmed control flow graph, and the unconditional jump command is used as response to disturb the normal running of the program and effectively resist the tampering behaviour of an attacker. The method is a self-response type and can influence the executing track of the program in three ways: interrupting the program in advance, lowering the performance of the program and leading the program to generate an error result. Implementing the scheme needs low consumption, and the self characteristic of the format of the Java program are utilized to control Java byte codes; and the added response codes have similarity with the Java byte codes. The scheme has high privacy.
Owner:李嘉 +1
Operation method of Java program and electronic terminal
InactiveCN101944042AAchieve securityImplemented security at the binary levelComputer security arrangementsSoftware simulation/interpretation/emulationSoftware engineeringComputer terminal
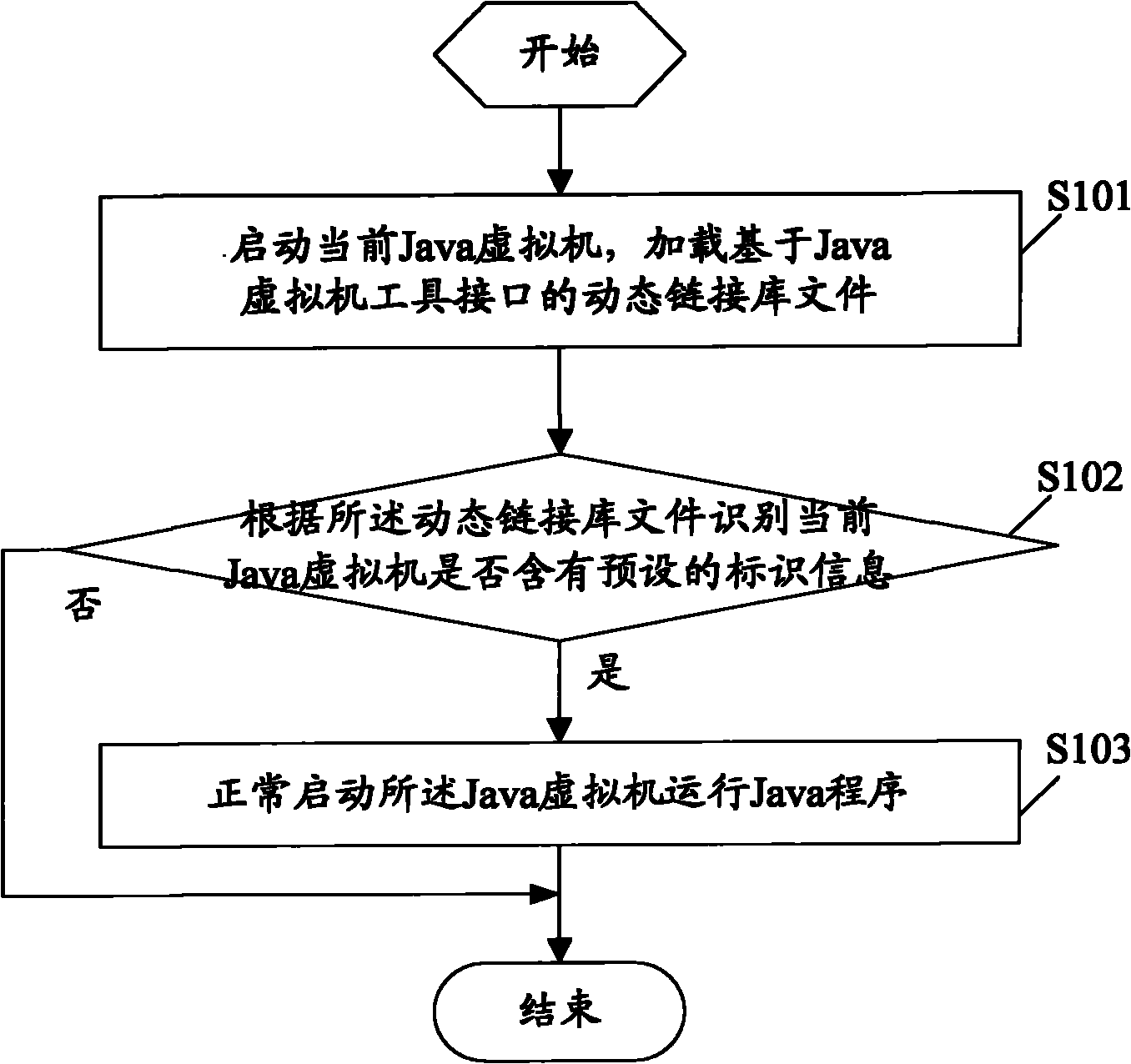
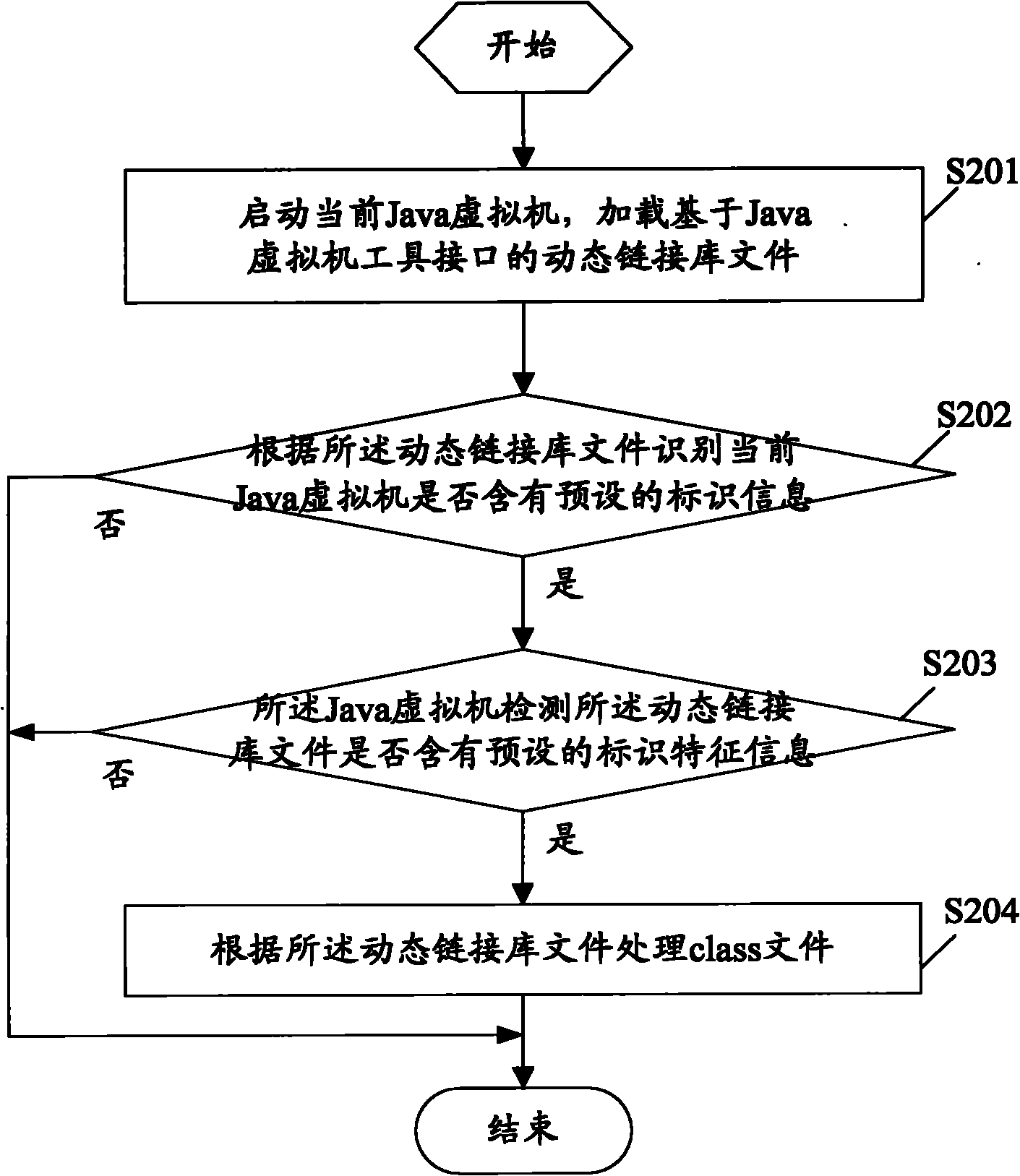
The embodiment of the invention discloses an operation method of a Java program, which comprises the following steps of: starting a current Java virtual machine, and loading a Java virtual machine tool interface-based dynamic link base file; identifying whether the current Java virtual machine contains preset identification information according to the dynamic link base file; when an identification result is yes, normally starting the Java virtual machine to run the Java program; and when the identification result is no, exiting from a startup program. Correspondingly, the invention also discloses an electronic terminal. When the operation method of the Java program and the electronic terminal are used, the security of Java byte codes is guaranteed in a binary system grade and an attacker cannot acquire the byte codes, so that a source code of business software is radically protected against stealing and the core algorithm and trade secrets of the business software are more securely protected; and when the technical scheme of the invention is adopted, the characteristics of any Java do not lose, the protection of cross-platform Java byte codes is realized, deployment is simple and cost is low.
Owner:深圳市拜特科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com