Patents
Literature
295 results about "Package.name" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
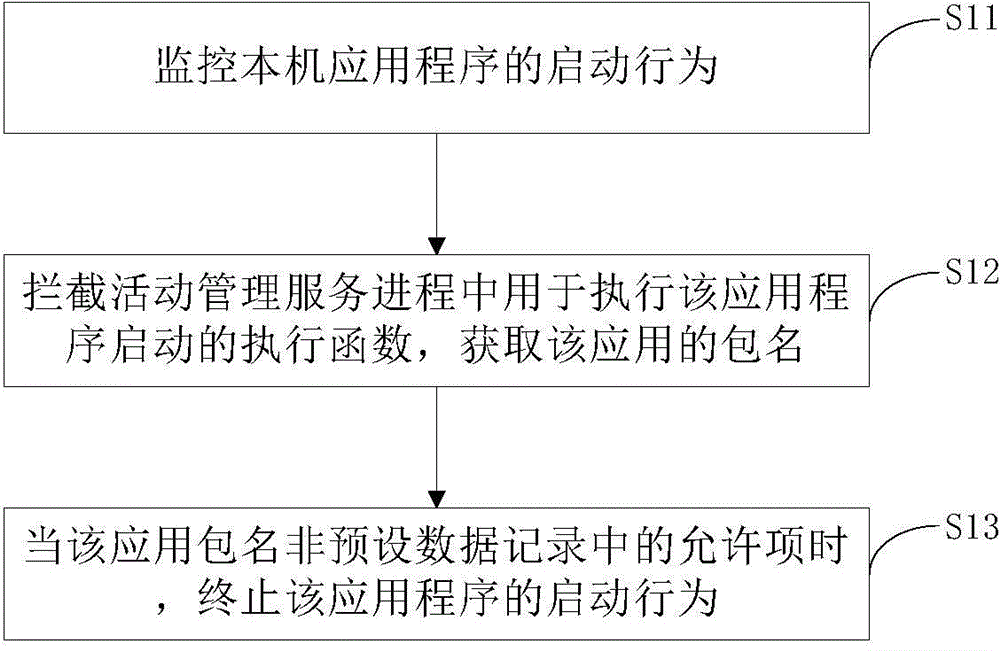
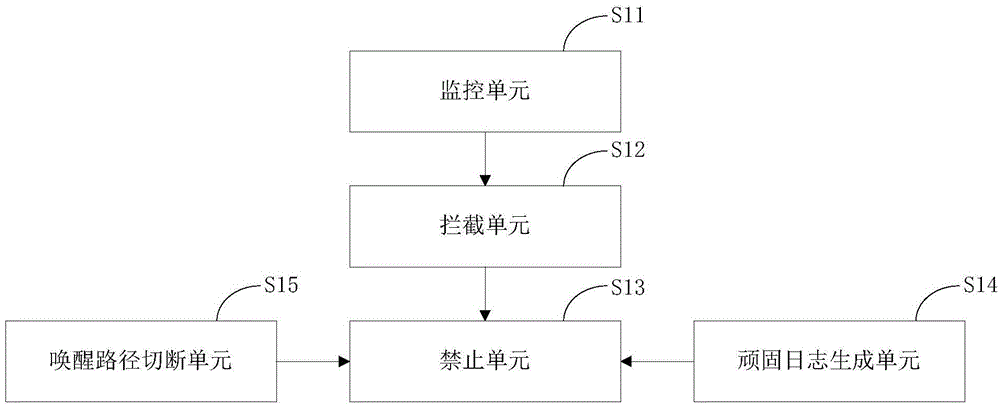
Method and device for preventing self-starting of application
ActiveCN104462952ADisable self-startRealize self-startComputer security arrangementsElectricityOperating system
The invention provides a method for preventing self-starting of an application. The method comprises the steps of monitoring the starting behavior of the application of a native machine, intercepting an execution function used for executing the application starting task in the activity management service progress and obtaining the package name of the application, and stopping the starting behavior of the application when the package name of the application is not an allowable item in a preset data record. Correspondingly, the invention provides a device for preventing self-starting of the application. By the adoption of the method and device for preventing self-starting of the application, the self-starting behavior and stubborn self-starting behavior of the application can be prevented, so that electricity consumption of a mobile terminal is reduced and operating speed is increased.
Owner:BEIJING QIHOO TECH CO LTD
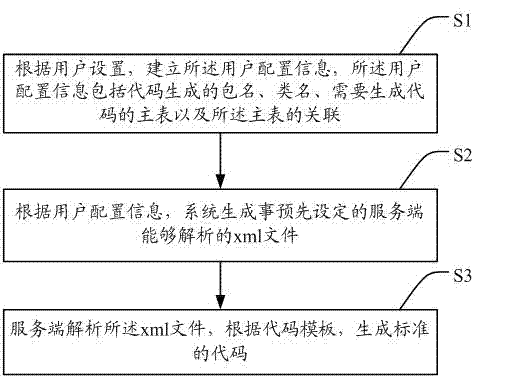
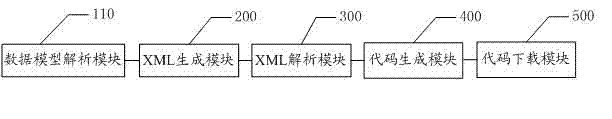
Method and system for automatically generating code based on data model drive
ActiveCN102968306AImprove efficiencyImprove readabilitySpecific program execution arrangementsMaintainabilityXML
The invention discloses a method and a system for automatically generating a code based on a data model drive. The method comprises the steps as follows: firstly, establishing user configuration information according to user settings, wherein the user configuration information comprises a package name generated by the code, a class name, a primary table required to generate the code and an association of the primary table; secondly, generating an xml (extensive markup language) file capable of being parsed by a preset server side by the system according to the user configuration information; and lastly, parsing the xml file by the server side, and generating the standard code according to a code template. Compared with the prior art, the method has the advantages of high efficiency, standard and uniform code, high readability, strong maintainability and the like; and meanwhile, the operation is visualized, convenient and quick, errors are not easily caused, and the technical requirements are lowered.
Owner:QTONE EDUCATION GROUP (GUANGDONG) CO LTD
Display method and related device
ActiveCN110471639AReduce areaImprove experienceCathode-ray tube indicatorsDevices with bluetooth interfacesInteraction systemsLarge screen
The embodiment of the invention provides a display method and a related device. The display method is applied to the information interaction system. The information interaction system comprises an electronic device and a large-screen device. The method comprises the steps that the electronic device obtains preset information. The preset information comprises information of applications installed in the electronic device. The information of the applications comprises at least one of names, icons and package names of the applications. The electronic equipment generates a first window according to the preset information, wherein the first window comprises any one of a plurality of desktops of the electronic equipment. The electronic equipment sends the first window to the large-screen equipment, so that the large-screen equipment displays a first user interface. The first user interface comprises the first window. By adopting the embodiment of the invention, the area of a large-screen equipment display screen occupied by the mapping window of the electronic equipment can be reduced. The user experience is improved.
Owner:HUAWEI TECH CO LTD
Self-configurable distributed system
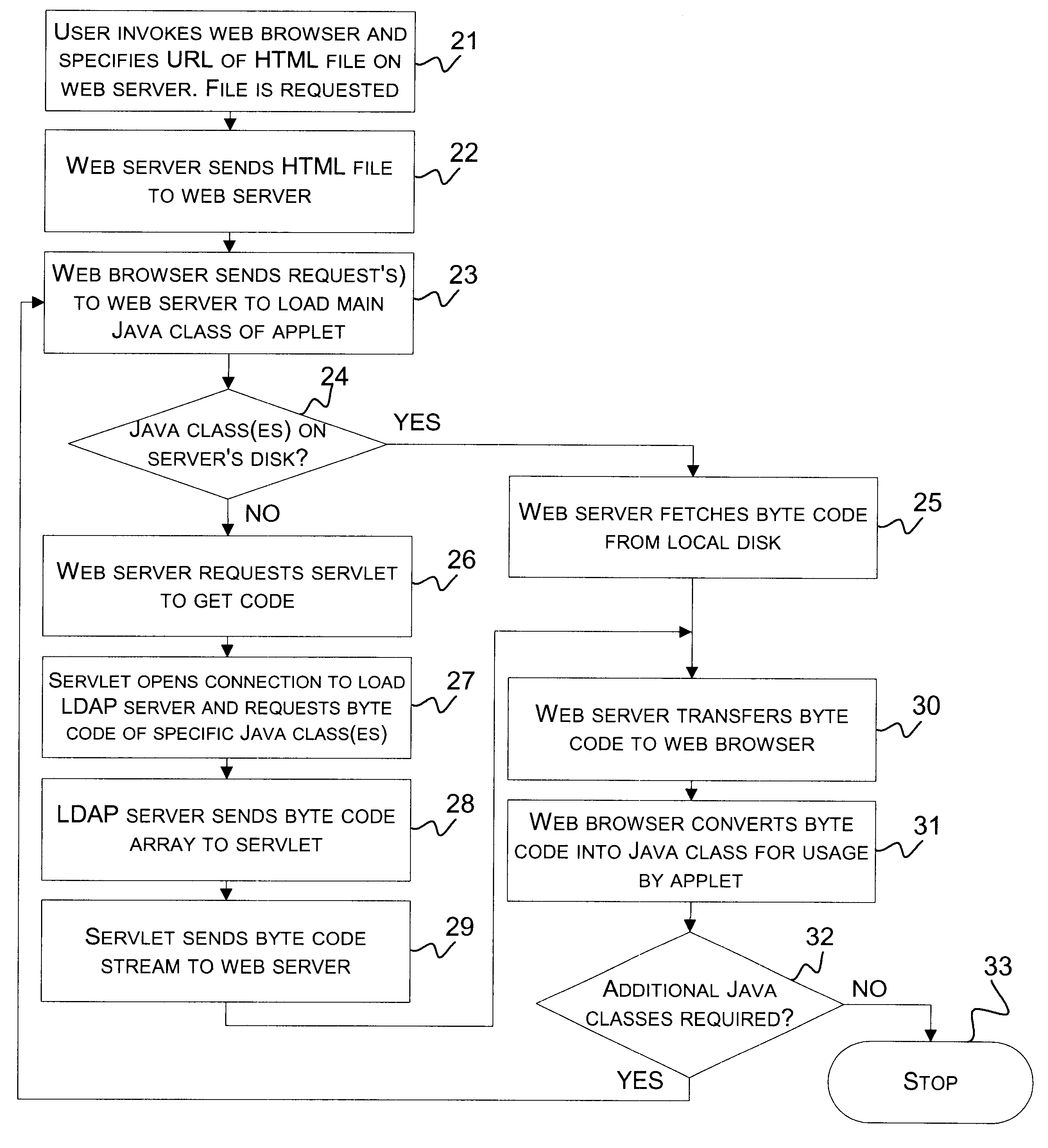
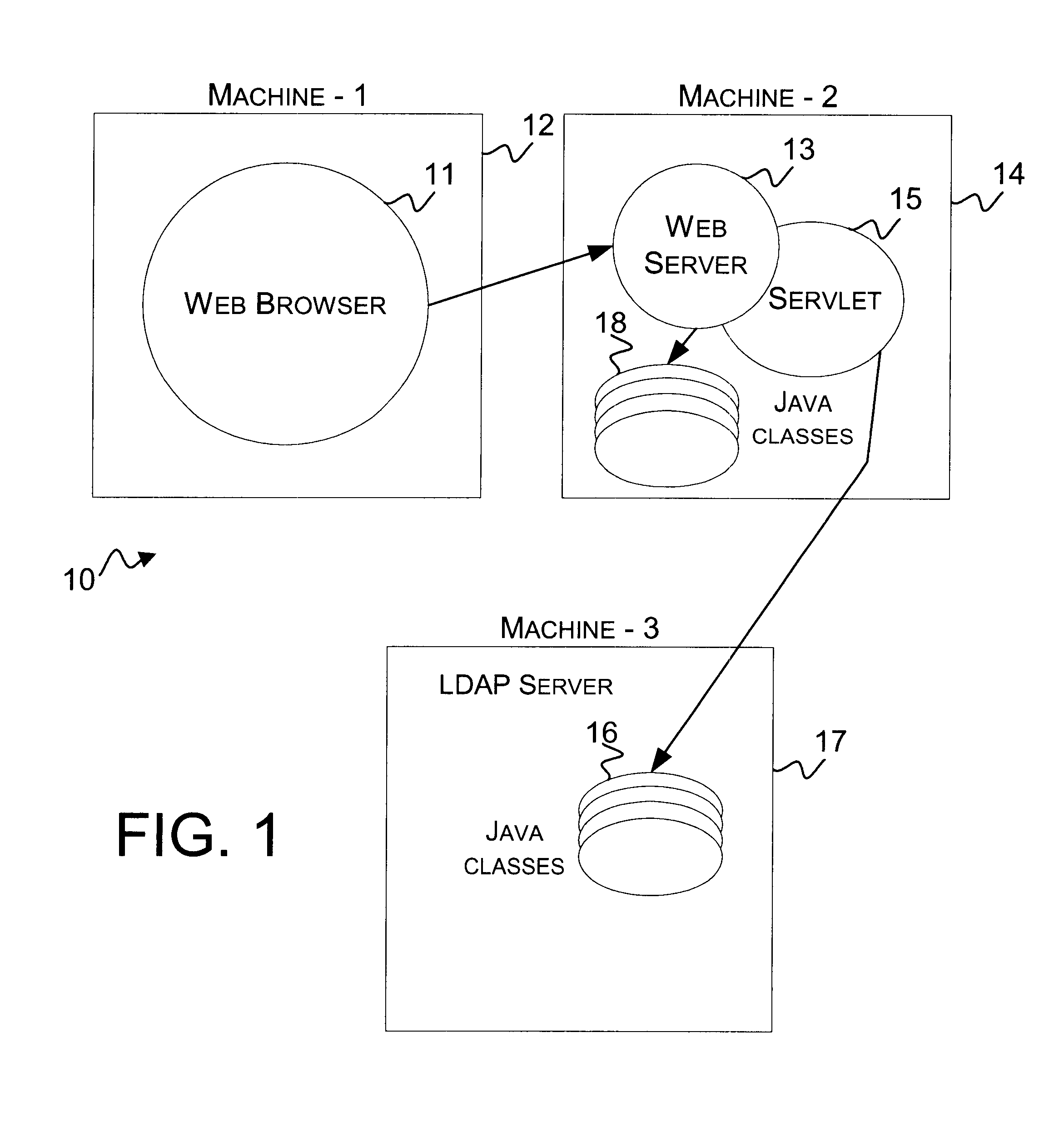
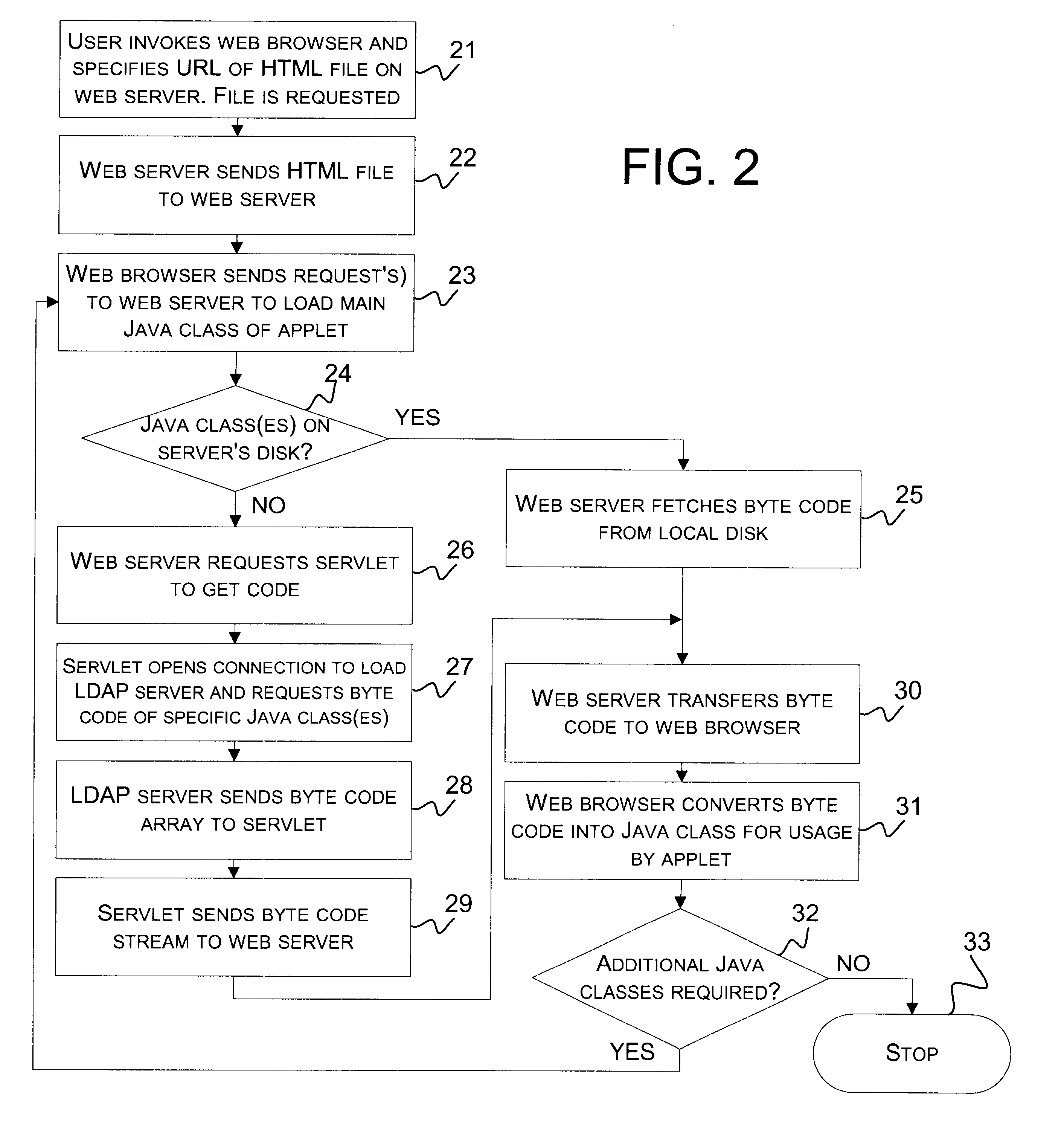
A self-configurable distributed computer software system and a method of enabling an applet running on a Web browser in the system to obtain needed software code in the form of Java classes from a machine that is not hosting the applet's originating Web server. A Lightweight Directory Access Protocol (LDAP) server stores Java classes utilized by a plurality of applets distributed throughout the system. The applet's Web server is connected to the Web browser and to the LDAP server, and includes a servlet for retrieving Java classes from the LDAP server. When the Web browser requests a needed Java class from the Web server, the Web server determines from the package name of the requested Java class whether or not the requested class is stored on the Web server's local storage disk. If not, the Web server requests the servlet to retrieve the Java class from the LDAP server. The servlet retrieves the byte code corresponding to the requested Java class, and the Web server provides it to the Web browser. The Web browser then converts the code to a Java class for use by the applet.
Owner:TELEFON AB LM ERICSSON (PUBL)
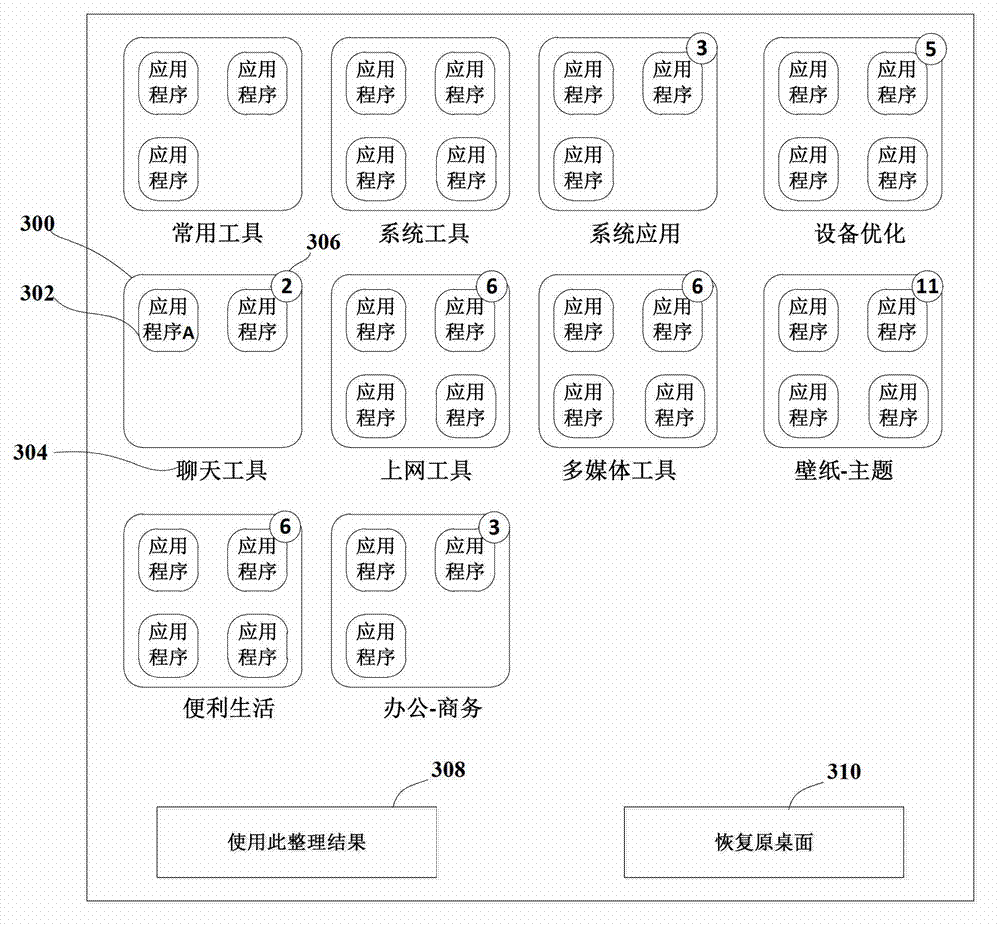
Application program classification method and device
ActiveCN103092604AFast and Accurate Classification ProcessingSolve the problem that classification will be more cumbersomeSpecific program execution arrangementsInput/output processes for data processingClassification methodsApplication software
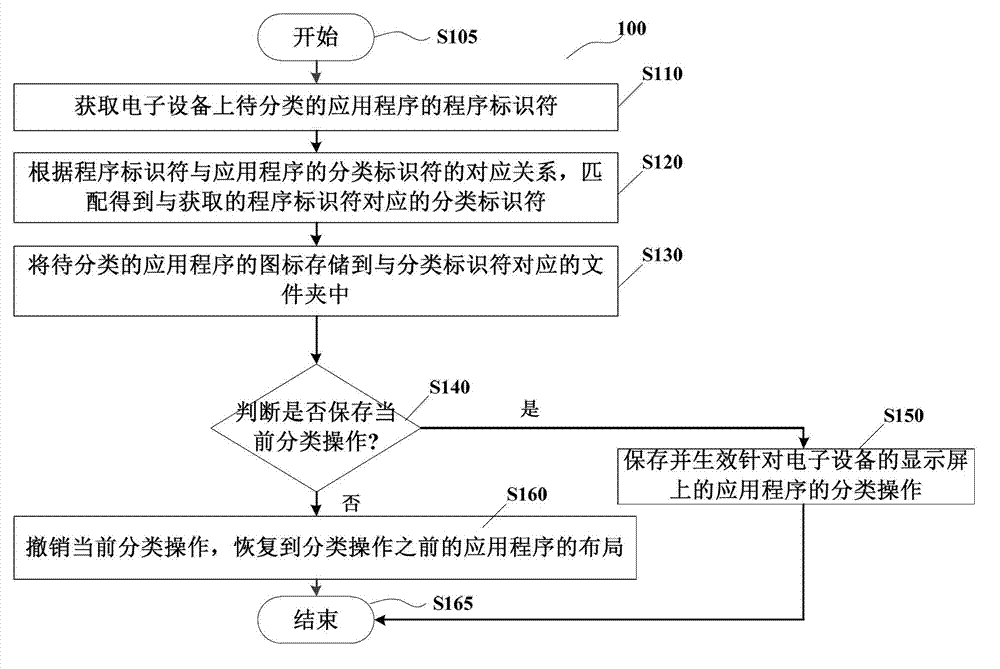
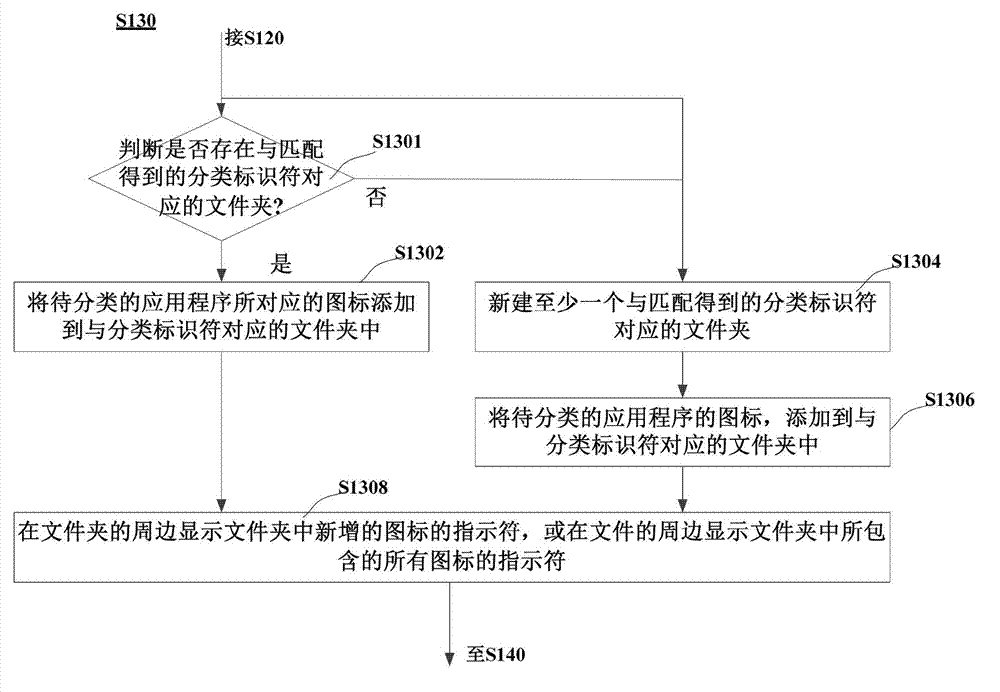
The invention discloses an application program classification method and an application program classification device. The device comprises a storage module, an acquiring module, a matching module and a classification module, wherein the storage module is used for storing a corresponding relationship between a program identifier and a classification identifier; the acquiring module is used for acquiring a program identifier of an application program to be classified; the matching module is used for obtaining a classification identifier which corresponds to the acquired program identifier; the classification module is used for storing icons of the application program to be classified into a folder which corresponds to the classification identifier; the acquiring module comprises a first acquiring unit and a second acquiring unit; the first acquiring unit is used for acquiring the package name of an application program installation package which corresponds to an application program to be classified on electronic equipment; and the second acquiring unit is used for acquiring a program identifier which corresponds to the package name of the application program installation package according to the package name of the application program installation package. By adoption of the technical scheme, the application program on the electronic equipment can be rapidly and accurately classified, so that a user can rapidly find the application program, and a user-friendly interface can be represented.
Owner:BEIJING QIHOO TECH CO LTD
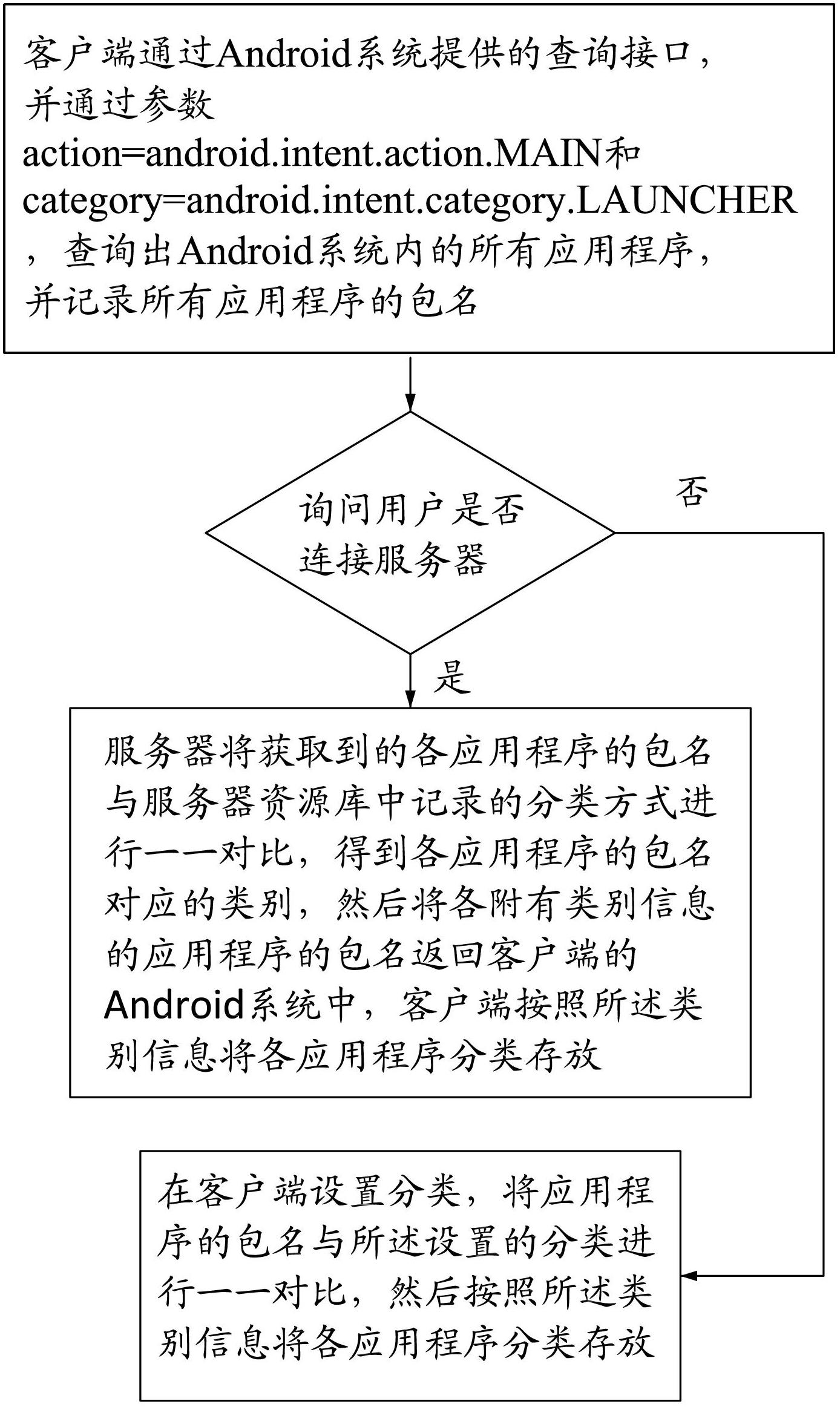
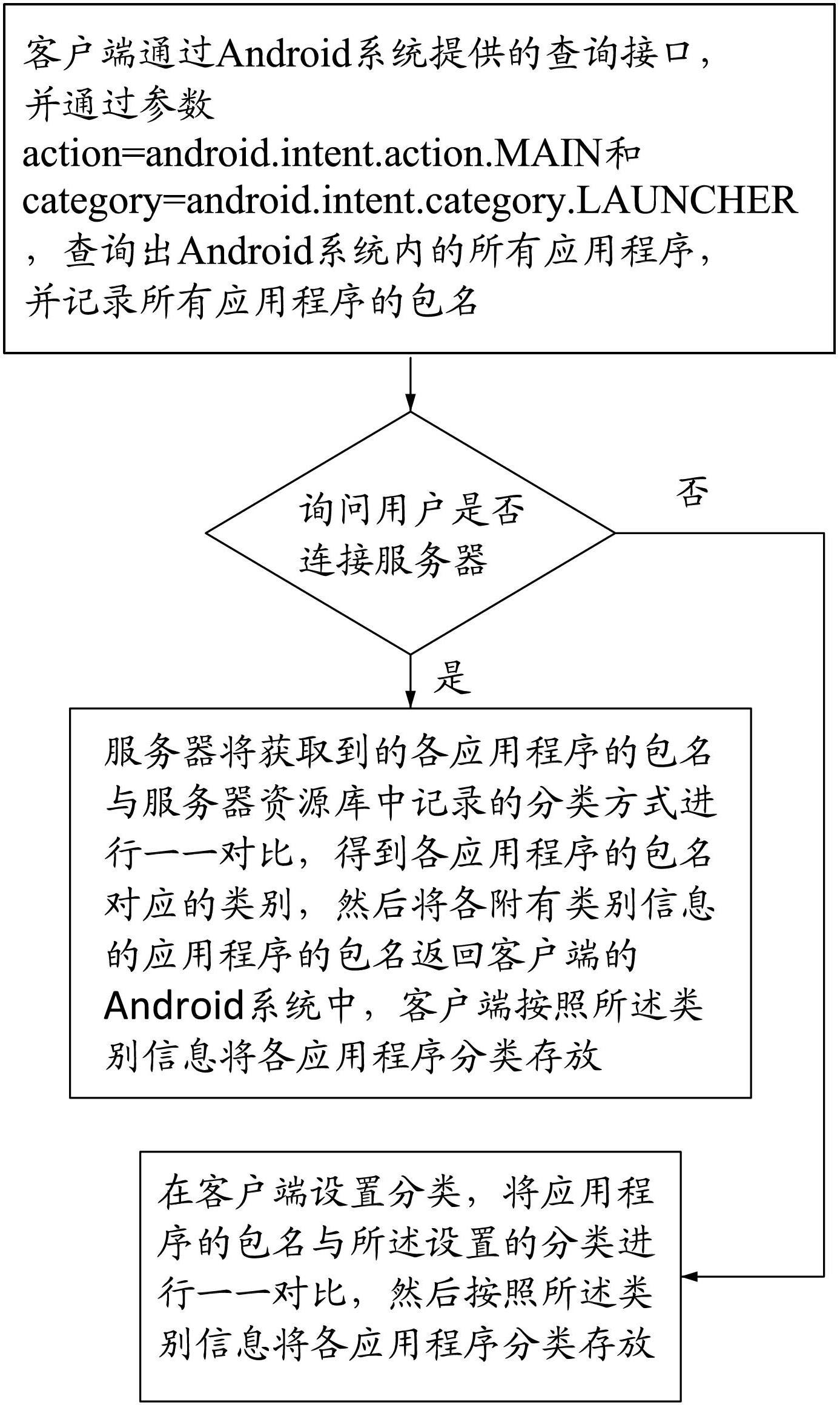
Method for automatically sorting application program based on Android
InactiveCN102693132AEasy to findFlexible classificationSpecial data processing applicationsSpecific program execution arrangementsProgramming languageClassification methods
The invention provides a method for automatically sorting application program based on Android. The method comprises the steps of: inquiring and recording package names of all application programs by a client side through an inquiry interface provided by an Android system and parameters, comparing the package names of the application programs with a sorting mode recorded in a server resource library one by one by connecting a server by the client side so as to obtain the class corresponding to the package names of each application program, then returning the package name of the application program with class information to the Android system of the client side; storing each application program in class by the client side according to the class information; and adopting another mode: setting classes on the client side, comparing the package names of the application programs with set classes one by one, and then storing each application program in class according to the class information. The method disclosed by the invention has the advantages of flexible selection mode, sorting accuracy and convenience for searching the application program.
Owner:FUZHOU BOYUAN WIRELESS NETWORK TECH
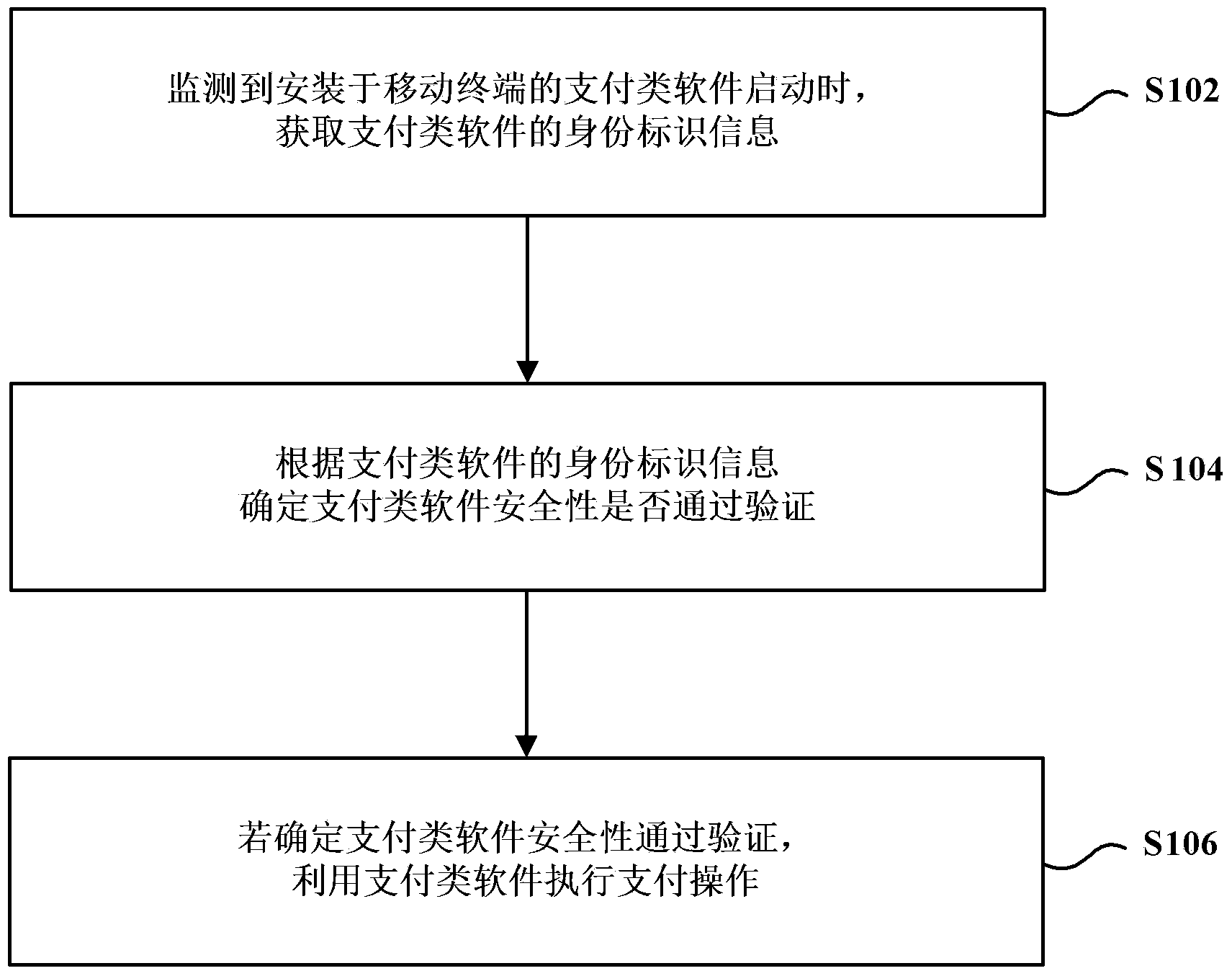
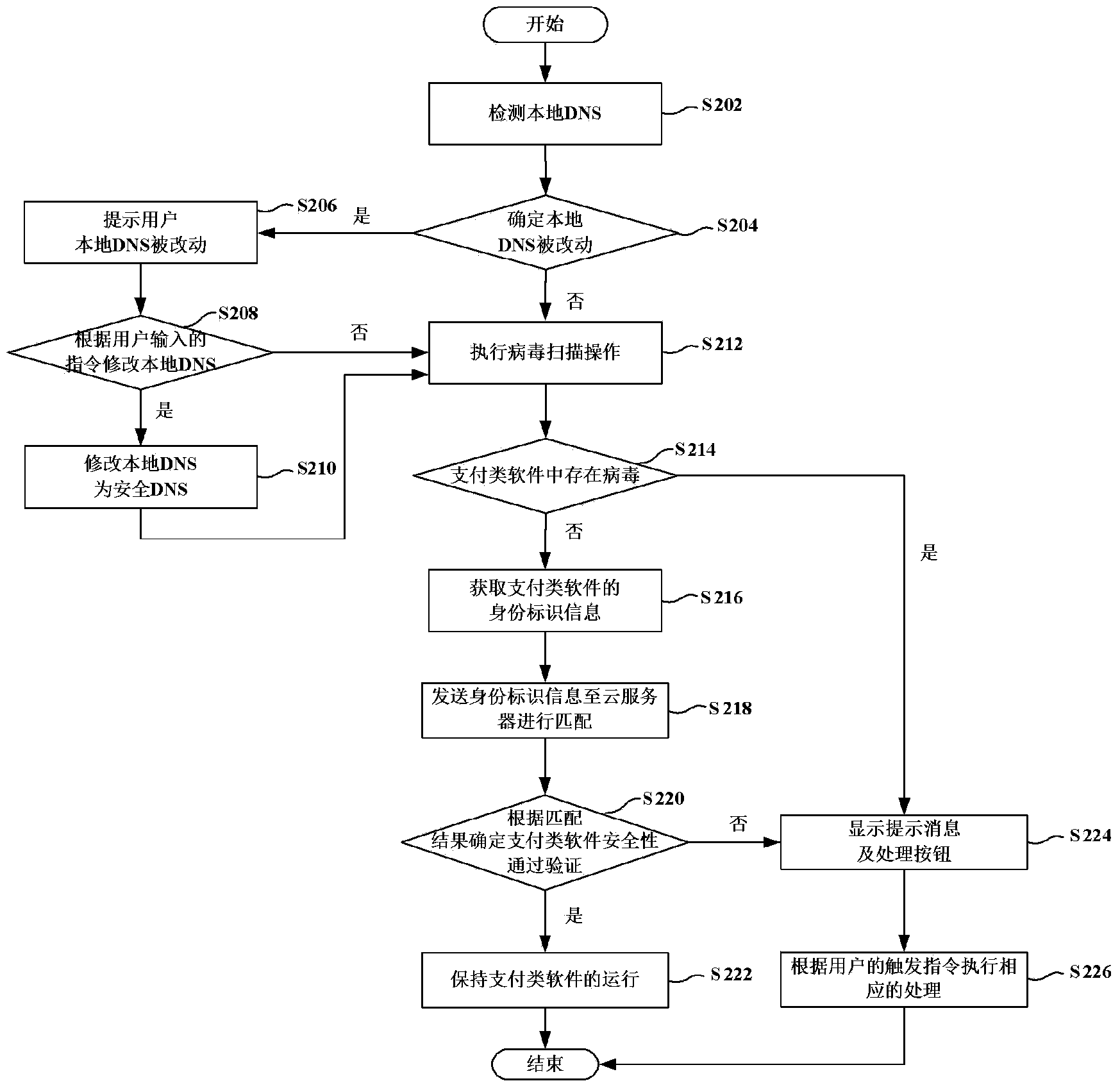
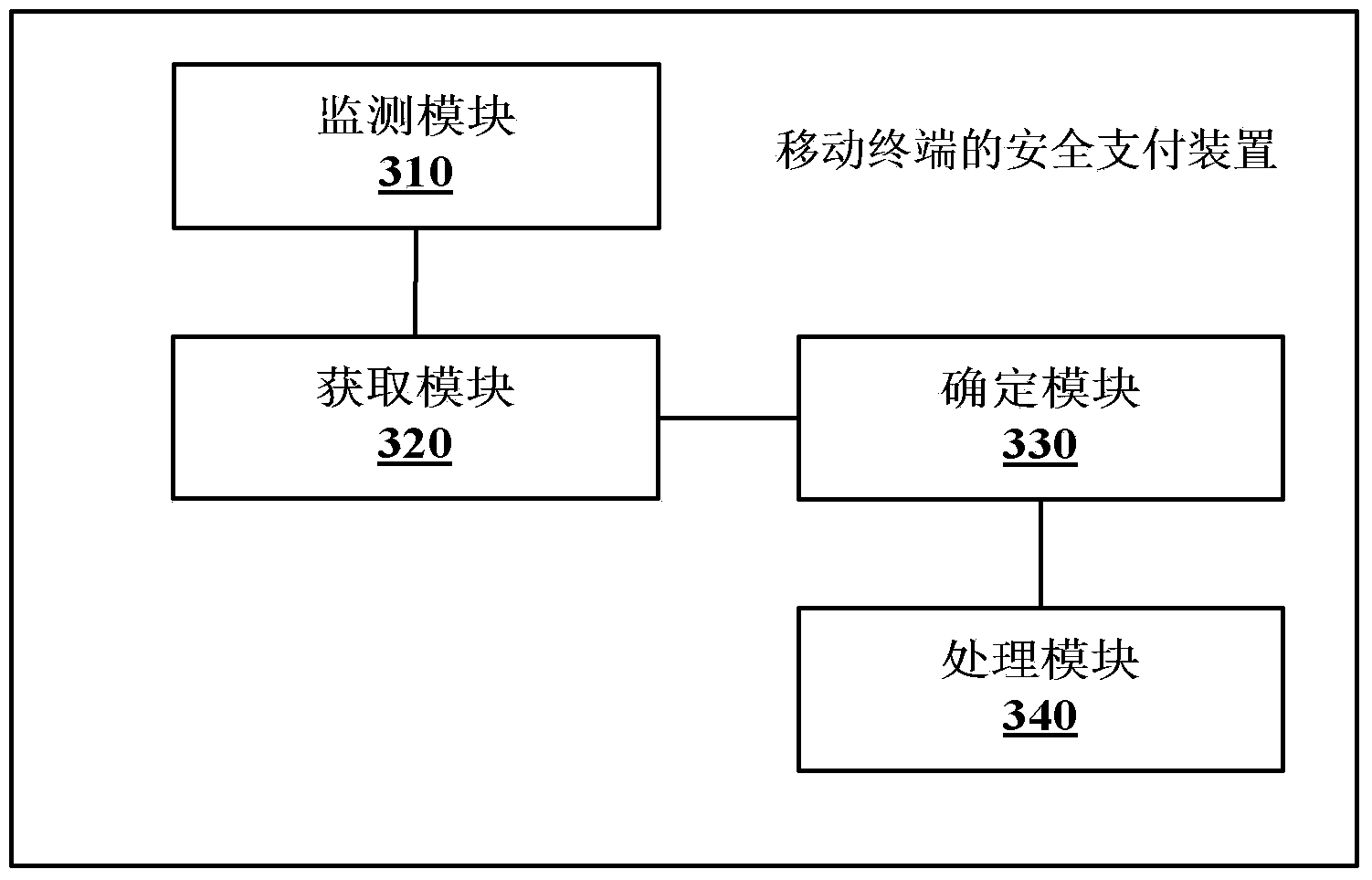
Safety payment method and device for mobile terminal
InactiveCN104021339APrevent leakageProtection securityPayment protocolsPlatform integrity maintainancePaymentSoftware engineering
The invention provides a safety payment method and device for a mobile terminal. The method includes the steps that when payment software installed in the mobile terminal is monitored to be started, identity label information of the payment software is obtained, wherein the identity label information includes one of package name information of the payment software, version information of the payment software and signing messages of the payment software; whether the safety of the payment software passes verification or not is determined according to the identity label information of the payment software; if yes, the payment software is used for executing payment operation. According to the embodiment, the problem that the safety of the payment software cannot be verified in the prior art can be solved.
Owner:BEIJING QIHOO TECH CO LTD +1
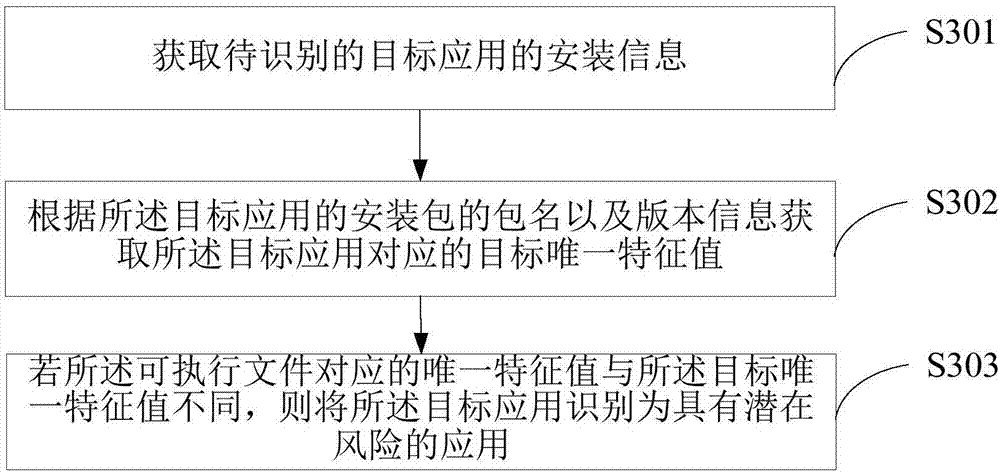
Method and server for identifying risk application
InactiveCN107480519AEfficient identificationImprove securityPlatform integrity maintainanceSoftware engineeringPotential risk
The embodiment of the invention discloses a method and server for identifying a risk application. The method comprises the steps of obtaining installation information of a to-be-recognized target application, wherein the installation information of the target application includes the package name of an installation package of the target application, edition information, and a sole feature value corresponding to an executable file; obtaining a target sole feature value corresponding to the target application according to the package name of the installation package of the target application and the edition information, wherein the target sole value is the pre-stored sole feature value, corresponding to the executable file, of the target application; identifying the target application as an application which has a potential risk if the sole feature value corresponding to the executable file is different from the target sole feature value. According to the embodiment, by executing the executable file which is falsified in the installation package, the falsified installation package can be effectively identified, thus the risk application can be effectively identified, and the safety of terminal information is then improved.
Owner:SHENZHEN GIONEE COMM EQUIP
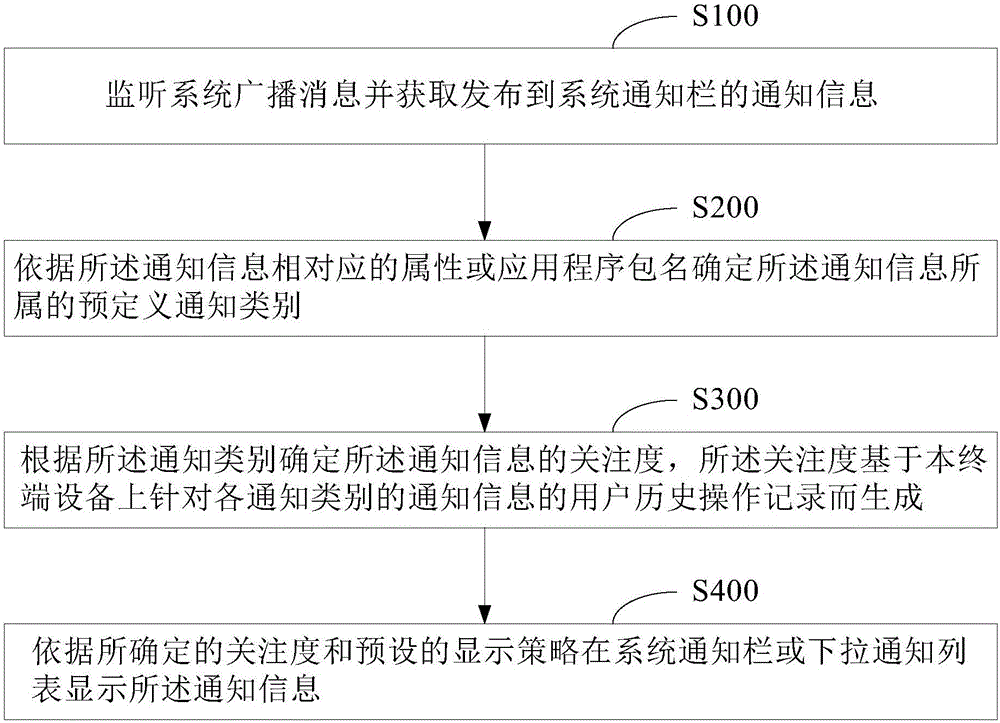
Method and device for processing notification information of mobile terminal system notification bar and mobile terminal
ActiveCN106557330AFind quicklyImprove experienceExecution for user interfacesTerminal equipmentApplication software
The invention provides a method and a device for processing notification information of a mobile terminal system notification bar. The method comprises the steps of monitoring a system broadcast message and obtaining the notification information released to the system notification bar; according to an attribute or an application program package name corresponding to the notification information, determining a predefined notification type to which the notification information belongs; according to the notification type, determining a concern degree of the notification information, wherein the concern degree is generated based on a user history operating record for each notification type of the notification information on a terminal device; and according to the determined concern degree and a preset display strategy, displaying the notification information in the system notification bar or a pull-down notification list. The system can display the notification information according to the user history operating record and the preset display strategy, so that the notification information with the high user concern degree can attract an attention of a user at a relatively conspicuous position, and the user can be guaranteed to quickly find the notification information concerned by himself / herself; the operating efficiency of the terminal device is improved, and the experience of the user is promoted; and in addition, the invention further provides a mobile terminal.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
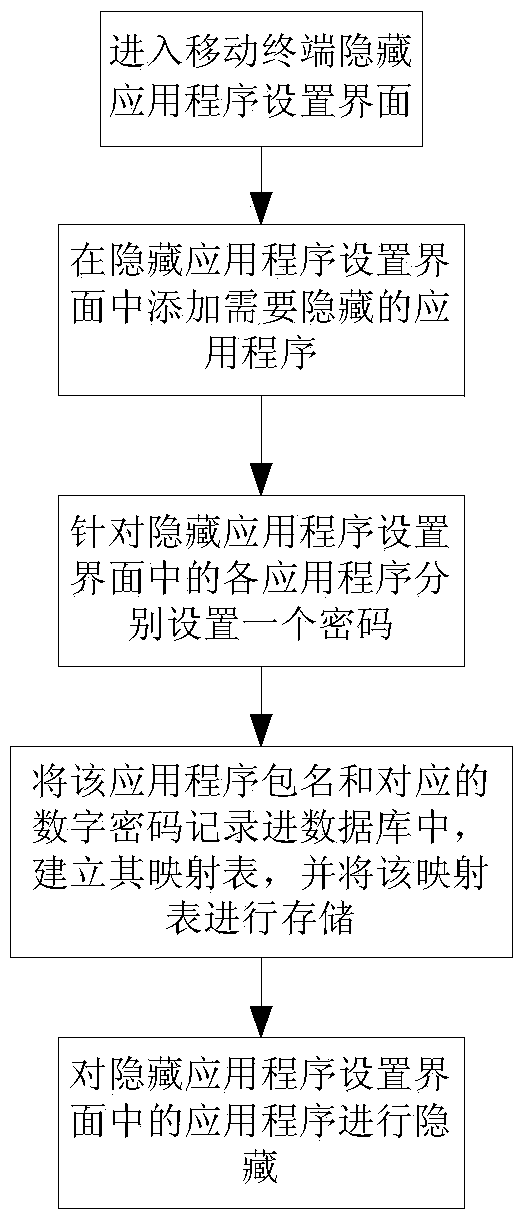
Mobile terminal, system and method for hiding and starting hidden application programs
InactiveCN104182662AImprove securityEasy to operateDigital data authenticationProgram/content distribution protectionPasswordComputer terminal
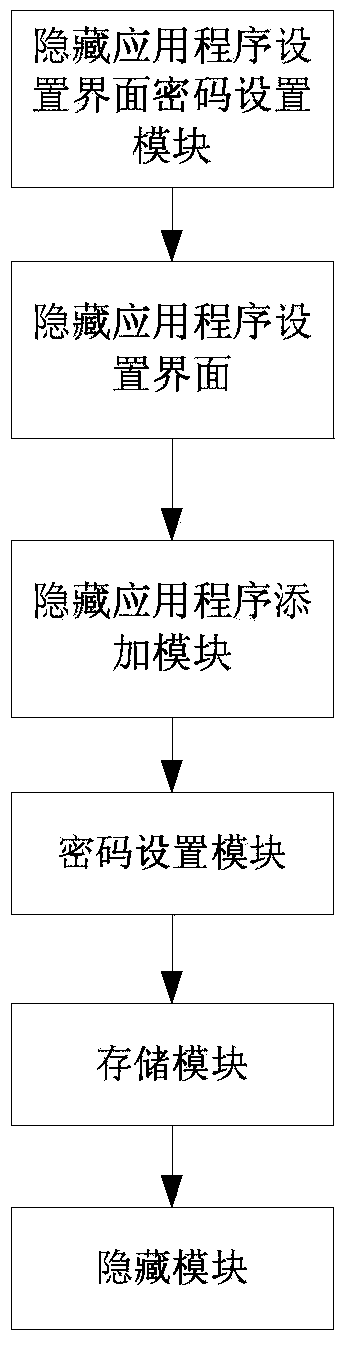
The invention discloses a mobile terminal, a system and a method for hiding and starting hidden application programs. When hiding of the application programs is required, passwords are set for the application programs needed to be hidden, package names of the application programs needed to be hidden and the corresponding passwords are stored, and then the application programs are hidden. When starting of the application programs is required, the passwords set for the application programs are directly input through a dial to find the corresponding package names of the application programs through the passwords, the hidden application programs can be directly started through the package names, and displaying the hidden application programs or accessing to setup interfaces of the hidden application programs is not needed. Therefore, the hidden application programs can never be displayed on a main menu, safety of privacy of users is improved, and simplicity and convenience in operation are achieved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
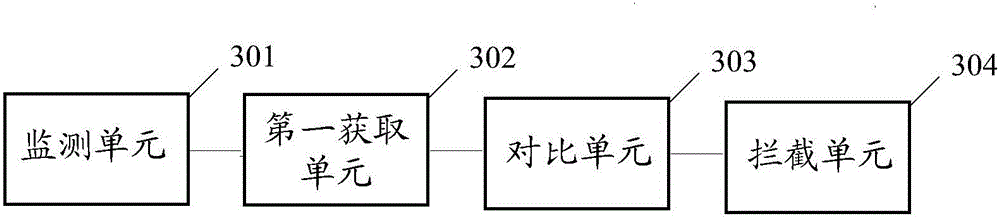
Popup window interception method and terminal
ActiveCN106126562AEffective interceptionSpecial data processing applicationsComputer terminalComputer engineering
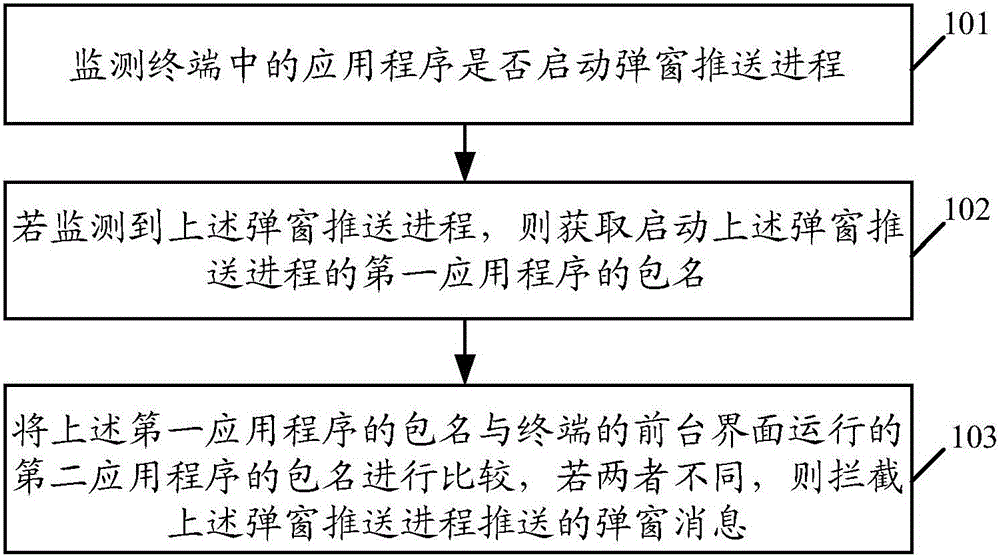
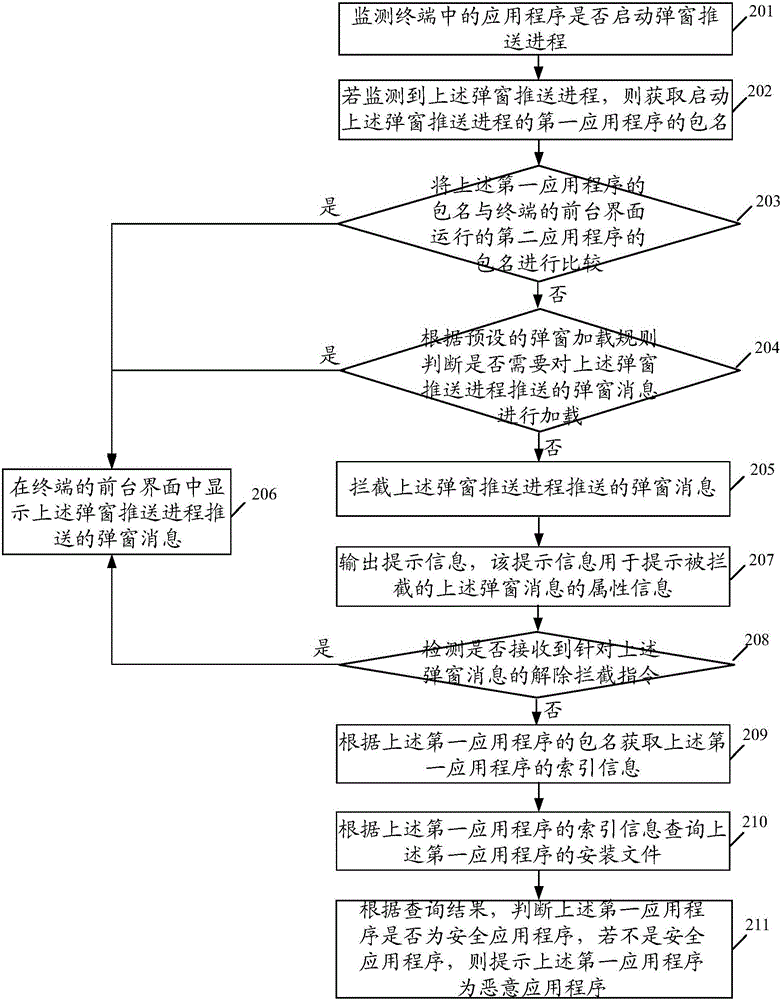
Embodiments of the invention disclose a popup window interception method and a terminal. The method is applied to the technical field of terminals. The method is implemented by comprising the steps of monitoring whether an application in the terminal starts a popup window pushing process or not; if the popup window pushing process is monitored, obtaining a package name of a first application starting the popup window pushing process; and comparing the package name of the first application with that of a second application running in a foreground interface of the terminal, and if the package name of the first application is different from that of the second application, intercepting a popup window message pushed by the popup window pushing process. By implementing the embodiments of the method and the terminal, popup window interference information pushed by a background application can be effectively intercepted.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
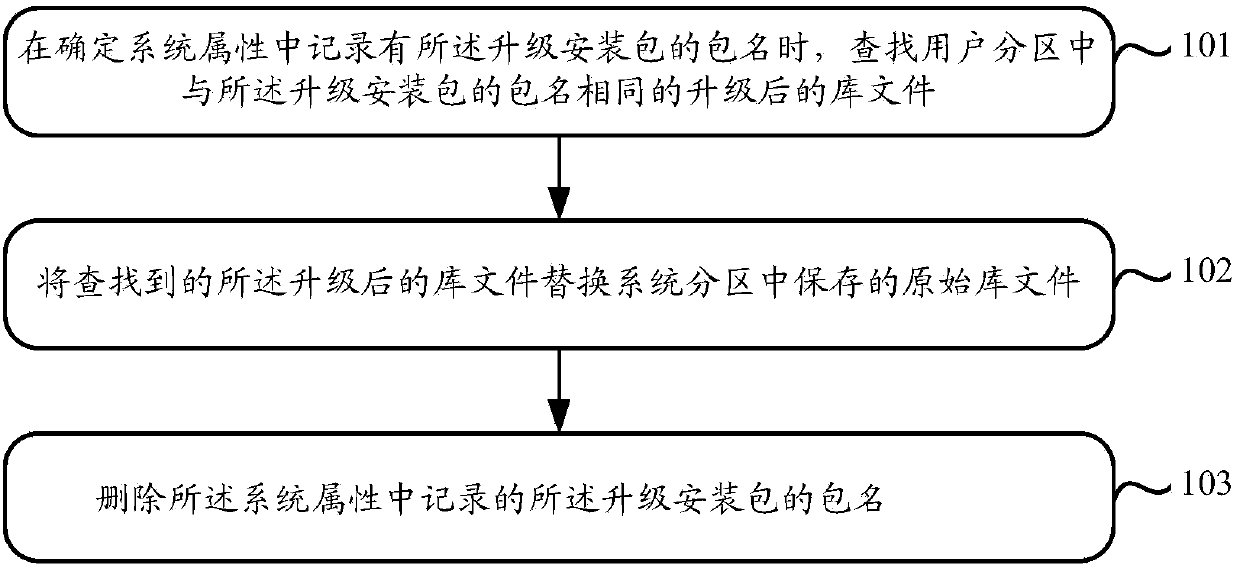
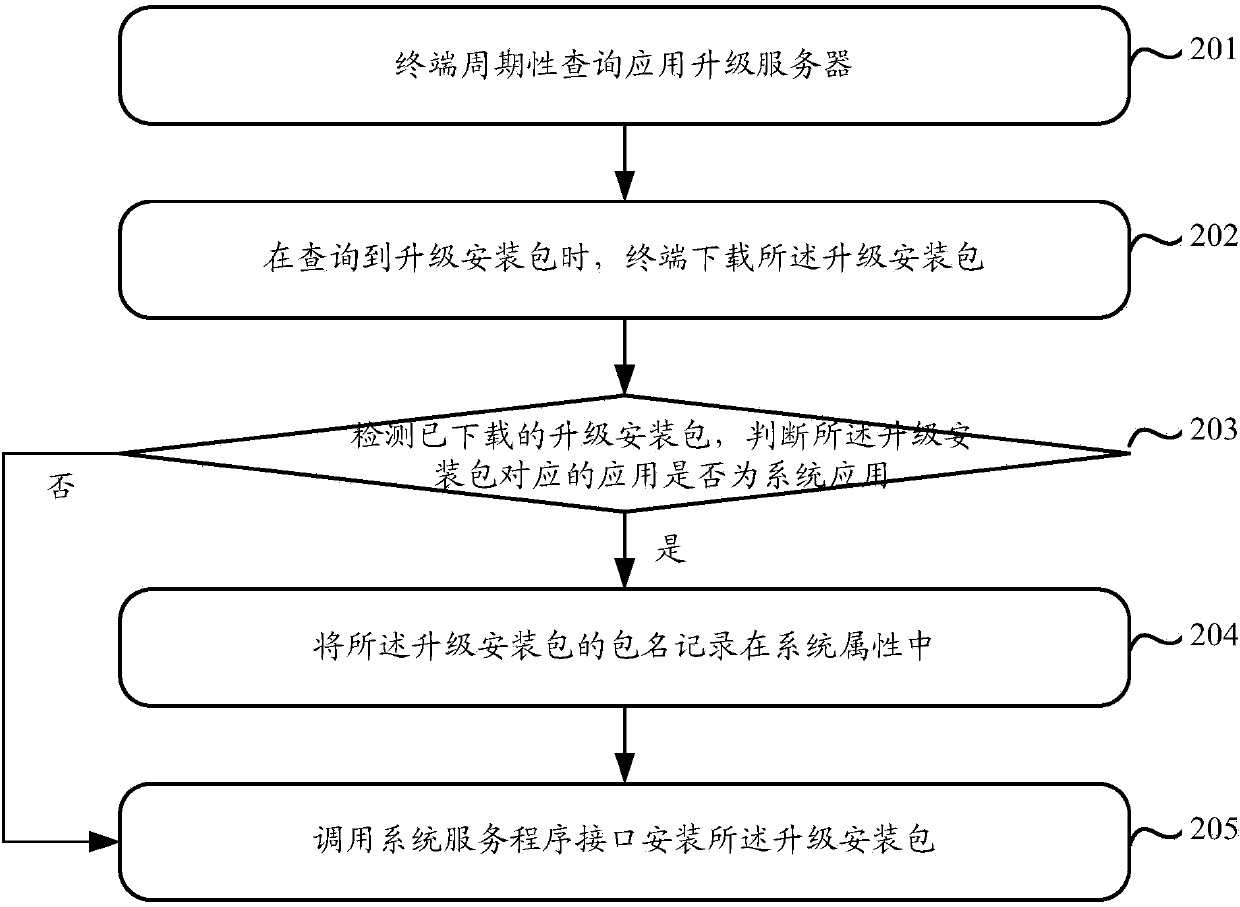
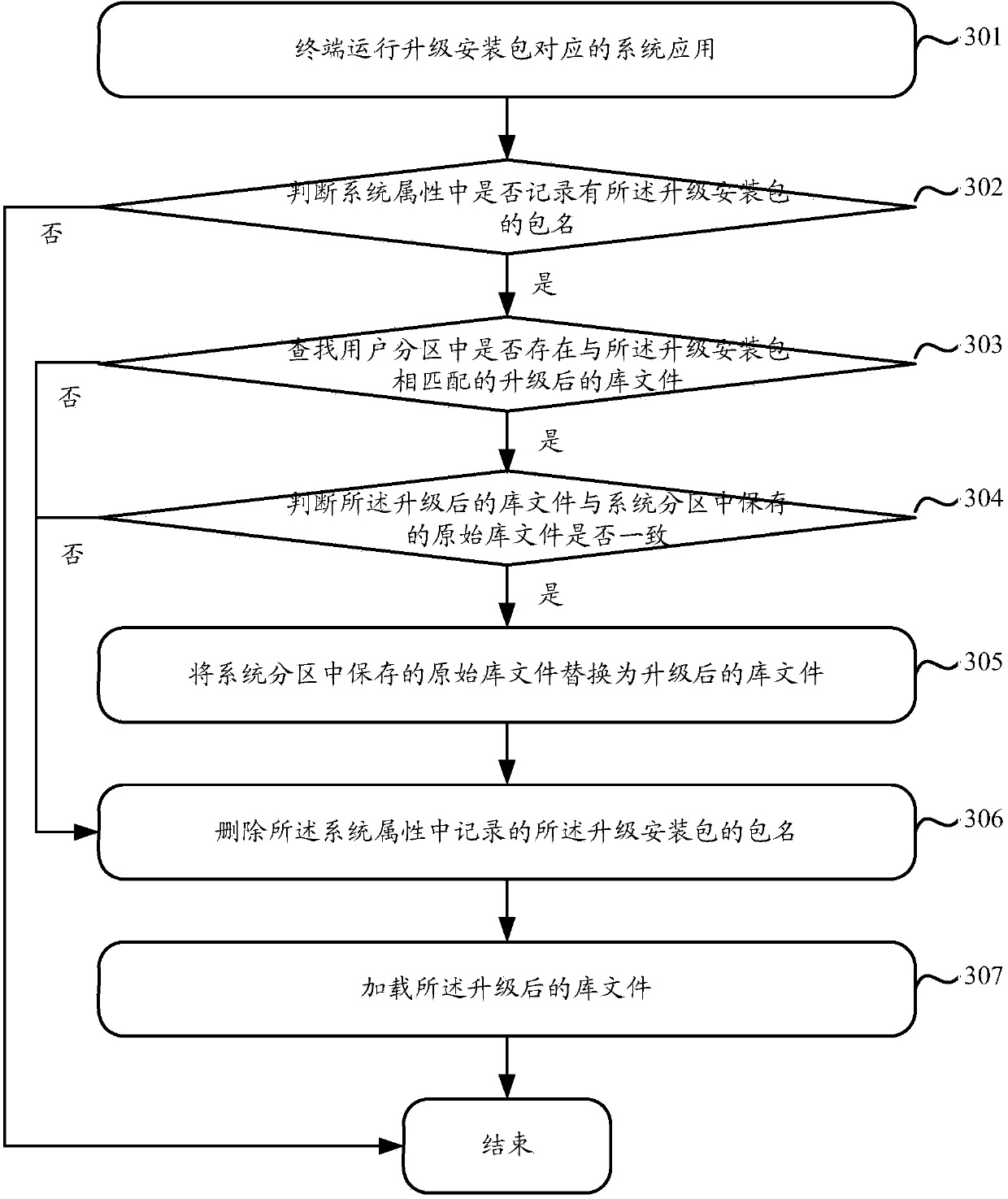
Method and terminal for upgrading library files of system application
ActiveCN104182255AImprove experienceTimely updateProgram loading/initiatingTransmissionSoftware engineeringUpgrade
The invention discloses a method and a terminal for upgrading library files of system application. The method mainly includes searching upgraded library files in user partitions according to package names of upgrade installation packages when the package names of the upgrade installation packages are recorded in system properties; replacing original library files stored in system partitions by the found upgraded library files; deleting package names, which are recorded in the system properties, of the upgrade installation packages. The upgraded library files correspond to the upgrade installation packages. The package names of the upgrade installation packages are recorded in the system properties when application corresponding to the upgrade installation packages is determined to be the system application. According to the scheme, the method and the terminal have the advantages that the problem that upgraded library files cannot be loaded when system application corresponding to upgrade installation packages is individually upgraded can be solved; the problem that an integral system is upgraded due to individual upgrading of certain system application can be solved, accordingly, system overhead can be reduced, the system application upgrading efficiency can be improved, and the user experience can be enhanced to a certain extent.
Owner:HISENSE BROADBAND MULTIMEDIA TECH
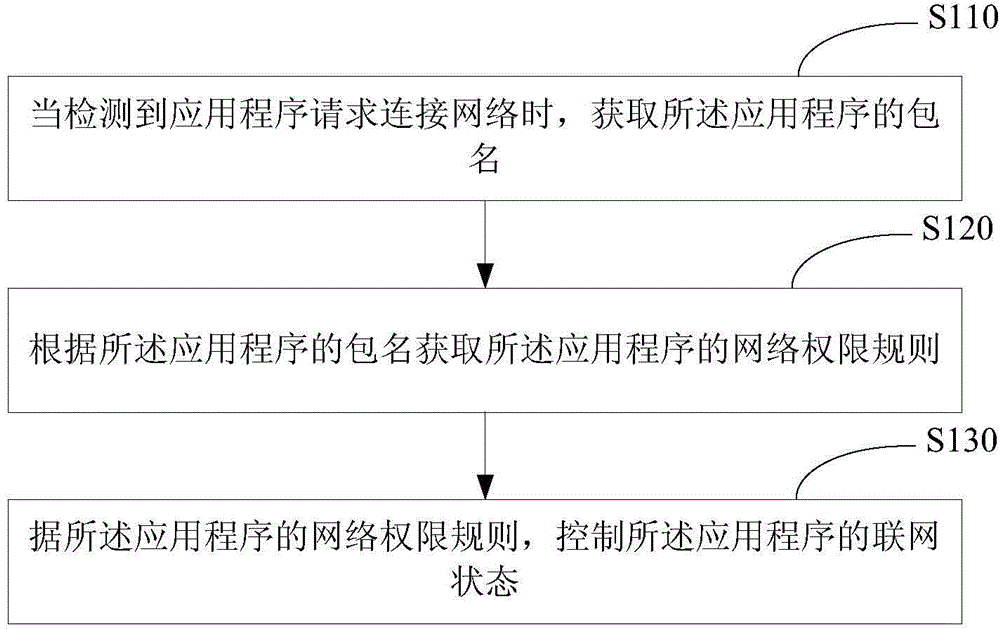
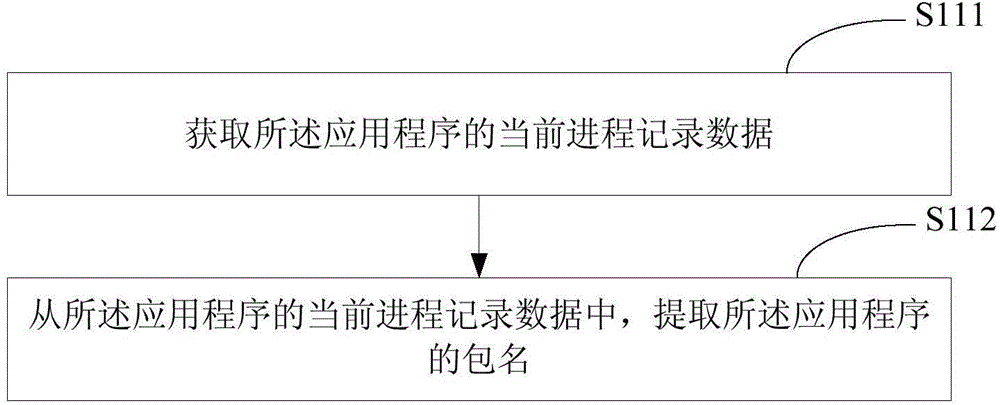
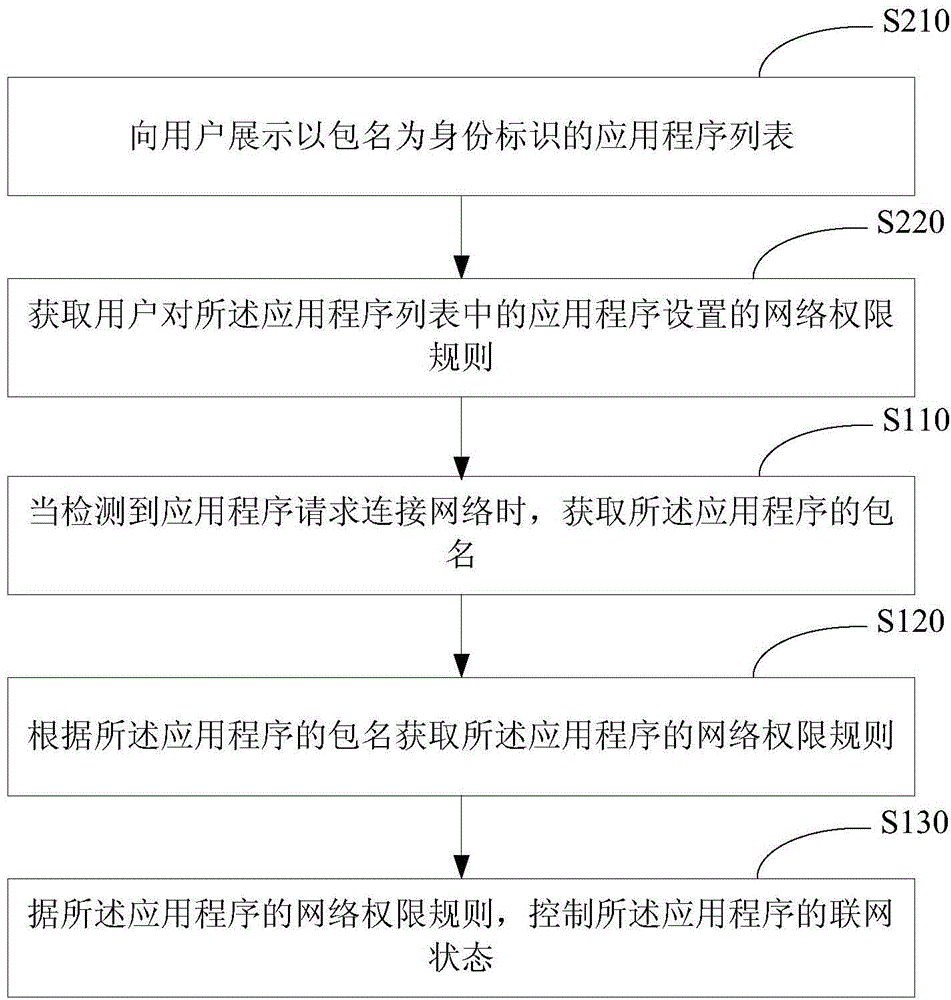
Network permission control method and apparatus of application program
InactiveCN104869569AThere will be no phenomenon that cannot be controlled separatelyHigh control precisionSecurity arrangementNetwork connectionApplication software
The embodiments of the disclosure disclose a network permission control method and apparatus of an application program. When an application program makes a request of network connection, a package name corresponding to the application program is obtained, and a network permission rule corresponding to the application program is obtained according to the package name of the application program; and on the basis of the network permission rule corresponding to the application program, a networking state of the application program is controlled. The package name is a unique identification mark of the application program; different application programs have different corresponding package names; and thus the various application programs can be distinguished by the package names. Because the networking states of the application programs are controlled based on the package names of the appliction programs, a phenomenon that networking states of application programs sharing the same UID can not be controlled respectively can be prevented and a phenomenon that the network permission rule can not be backed up to another intelligent terminal can also be avoided. Therefore, the networking states of the application programs can be controlled by using the package names of the application programs as the identity marks of the application programs, so that the control precision is improved.
Owner:XIAOMI INC
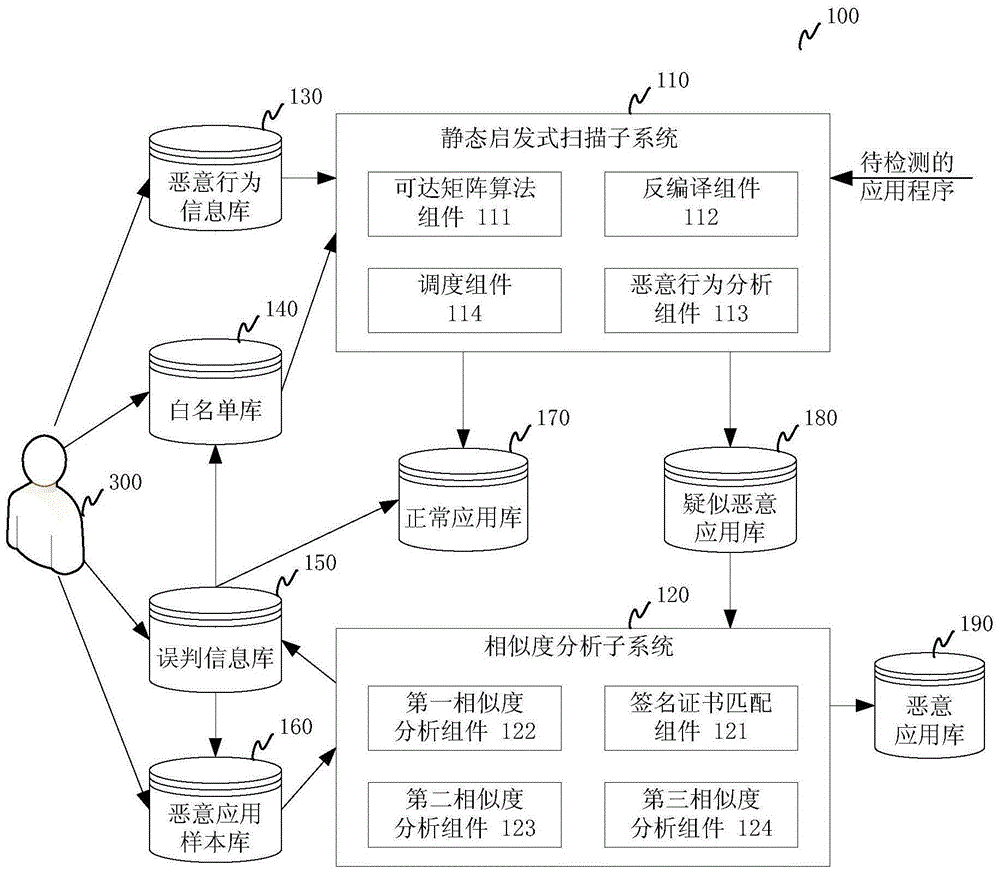
Malicious application detection method and system
ActiveCN106557695AAvoid performance bottlenecksSolve the false positive ratePlatform integrity maintainanceInformation repositorySimilarity analysis
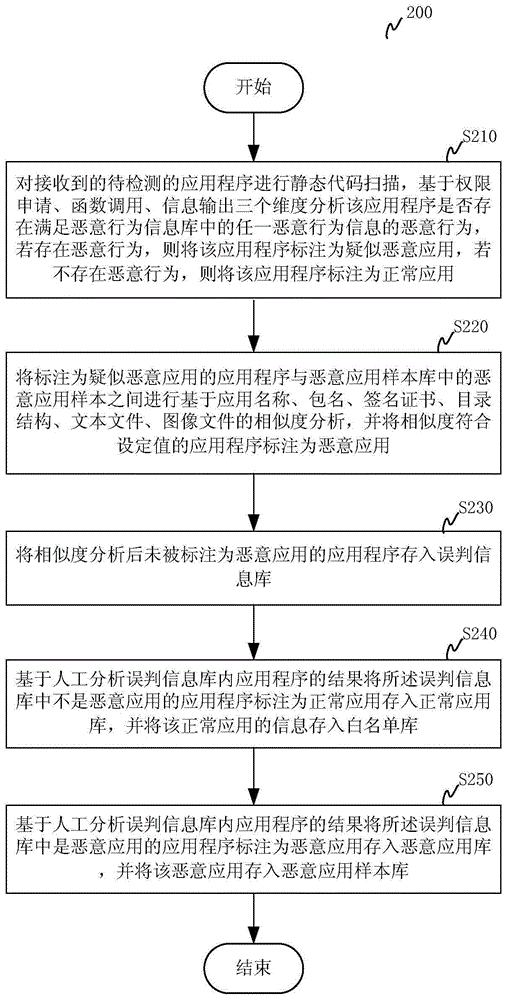
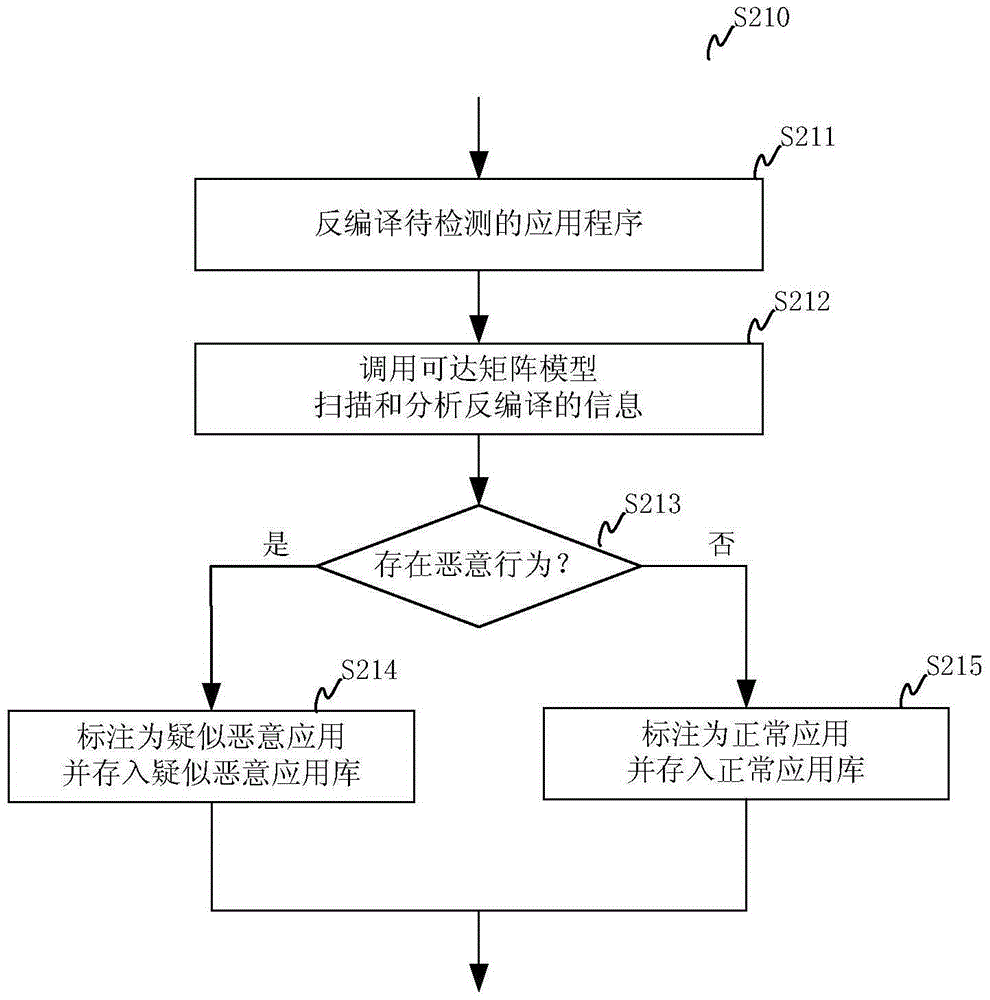
The invention relates to a malicious application detection method and system. The method comprises the steps of S1, performing static code scanning on a received to-be-detected application, analyzing whether the application has a malicious behavior conforming to any malicious behavior information in a malicious behavior information library or not based on three dimensions of right application, function call and information output, if the malicious behavior exists, marking the application as a suspected malicious application, and if the malicious behavior does not exist, marking the application as a normal application; and S2, performing application name, package name, signature certificate, directory structure, text file and image file-based similarity analysis between the application marked as the suspected malicious application and a malicious application sample in a malicious application sample library, and marking the application with the similarity conforming to a set value as a malicious application. According to the method and the system, the performance bottleneck of loading the application through a virtual machine for execution and analysis is avoided, the false alarm rate is effectively reduced, and the accuracy of identification is improved.
Owner:卓望数码技术(深圳)有限公司
Managing package dependencies
An illustrative embodiment provides a computer implemented method for managing package dependencies for an application installation. The computer implemented method identifies a set of used files for the application and a package for a respective file in the set of used files to form identified packages, adding names of the identified packages to an original package list of package names for the application, wherein the original package list defines package dependencies, and determines whether the identified packages can be located. The computer implemented method, responsive to a determination that the identified packages can be located, determines whether files within the identified packages can be found, responsive to a determination that the files within the identified packages can be found, determines whether files within the identified packages were used, and responsive to a determination that the files within the identified packages were used, updates the original list of package names for the application to form an updated list of managed package dependencies. The computer implemented method further creates a difference list between the updated list and the original list of package names and selectively installs the application using a combination of the original list of package names and the difference list according to the package dependencies.
Owner:IBM CORP
Application program update notification method and device
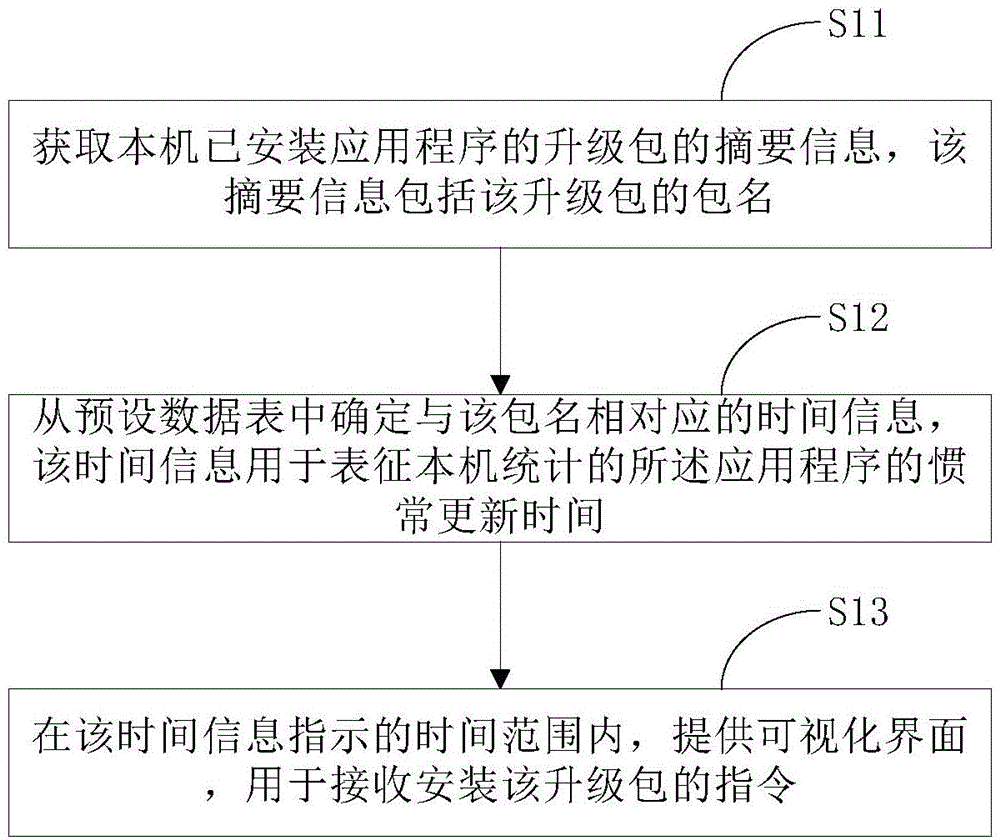
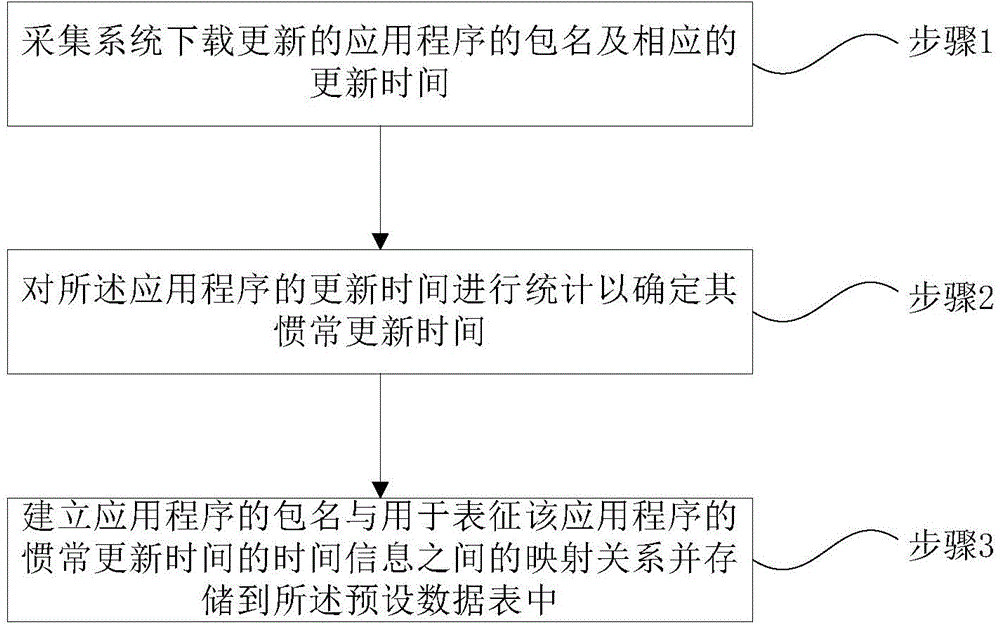
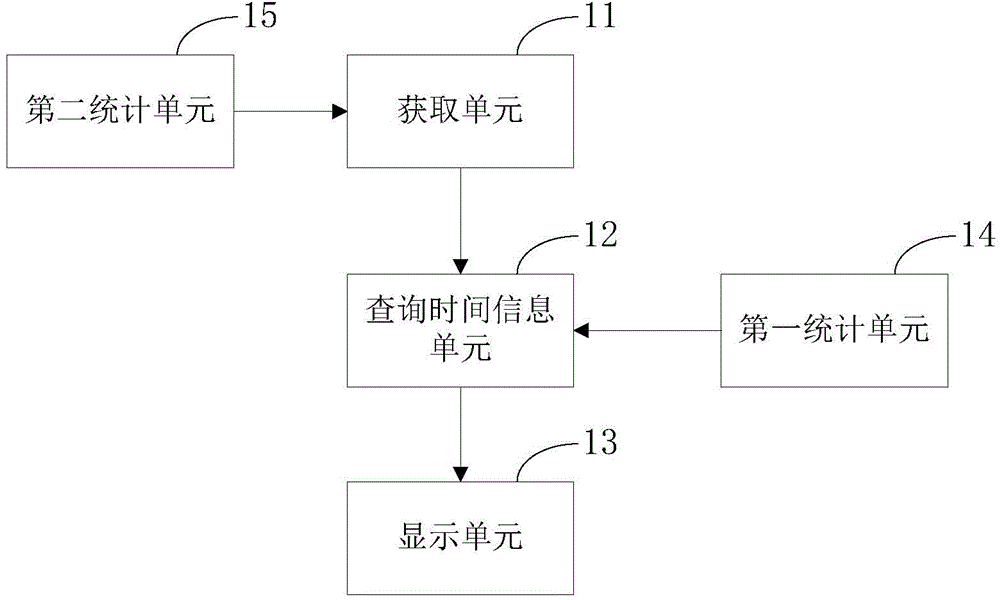
InactiveCN104793980AImprove experienceAvoid consumptionProgram loading/initiatingDatasheetTime information
The invention provides an application program update notification method which comprises the following steps: obtaining abstract information of an upgrade package of an application program installed in a local computer, wherein the abstract information includes a package name of the upgrade package; determining time information corresponding to the package name from a default datasheet, wherein the time information is used for representing usual update time of the application program counted by the local computer; and within the time range indicated by the time information, providing a visual interface used for receiving a command of installing the upgrade package. The invention further provides an application program update notification device for a mobile phone. According to the method provided by the invention, the usual update time of a user can be counted and determined through a self-learning algorithm, and the application update version is pushed in the time period, so that the user is intelligently promoted to perform update upgrade, and the user's experience degree is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
Method for root authority management and control in Android platform
ActiveCN105045625AImprove convenienceEnsure safetyPlatform integrity maintainanceProgram loading/initiatingSoftware engineeringInit
The present invention provides a method for root authortity management and control in an Android platform. The management and control method comprises: establishing and storing a rootagent executable file that is added with a package name of an application program allowed to be granted a root authority; an Android init process enabling a rootagent service corresponding to the rootagent executable file by reading a configuration file; before the application program applies for the root authority, judging whether a rootagent service process is running or not first; and the rootagent service process matching a process ID of the application program that submits an application with a process ID corresponding to the package name of the application program allowed to be granted the root authority in the rootagent service process, and if the matching is successful, then granting the application program, that submits the application, the root authority, or otherwise, rejecting. By using the method, the fact that only individual application is subjected to root authorization can be accurately limited, and at the same time, opening and closing operations of the root authority can be performed conveniently and quickly by setting system attributes.
Owner:湖州帷幄知识产权运营有限公司
Class dependency graph based Android application similarity detection method
ActiveCN103984883AEfficient extractionProgram/content distribution protectionSpecific program execution arrangementsConfusionByte
The invention belongs to the mobile Internet technical field and particularly relates to a class dependency graph based Android application similarity detection method. The class dependency graph based Android application similarity detection method specifically comprises step 1, decompiling an Android application and obtaining Dalvik byte codes of the Android application; step 2, obtaining package names and class names in the Android application according to a decompiled file directory and Dalvik byte code file names of the Android application; step 3, establishing a dependency relation graph between classes according to the package names, the class names and Dalvik byte code files; step 4, repeating the step 1 to the step 3 until class dependency graphs of Android application which need to be compared are obtained; step 5, performing comparison on similarities of the Android applications by a graph similarity comparison method according to the class dependency graphs of the Android applications. According to the class dependency graph based Android application similarity detection method, the structured information in the Android applications can be effectively extracted and the influences on the detection rate of the similar applications from an Android application confusion and deformation technology can be resisted.
Owner:XIANGTAN UNIV
APK (Android Package) downloading method and system based on Android system
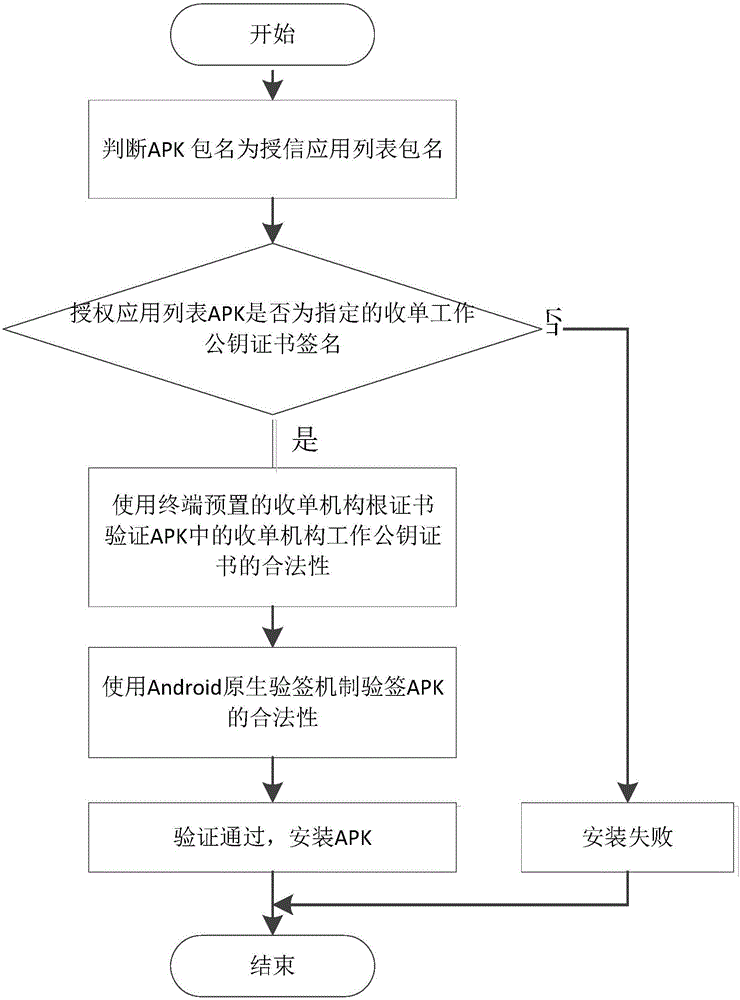
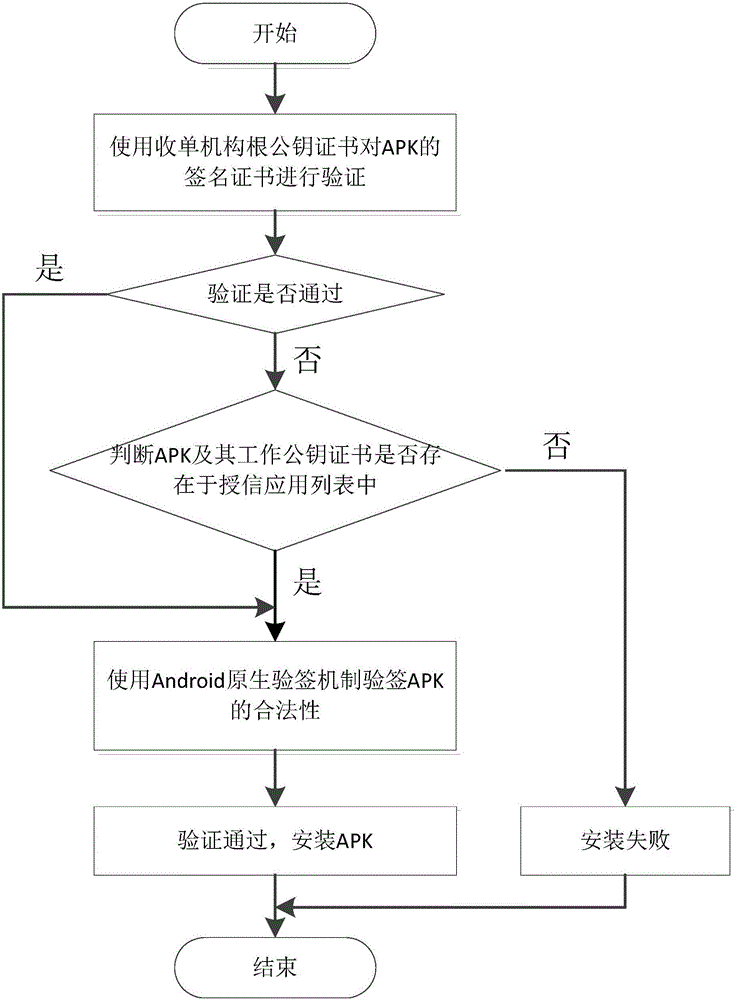
ActiveCN105787357AReliable sourceSimplify the update and upgrade processComputer security arrangementsProgram loading/initiatingPublic key certificateComputer science
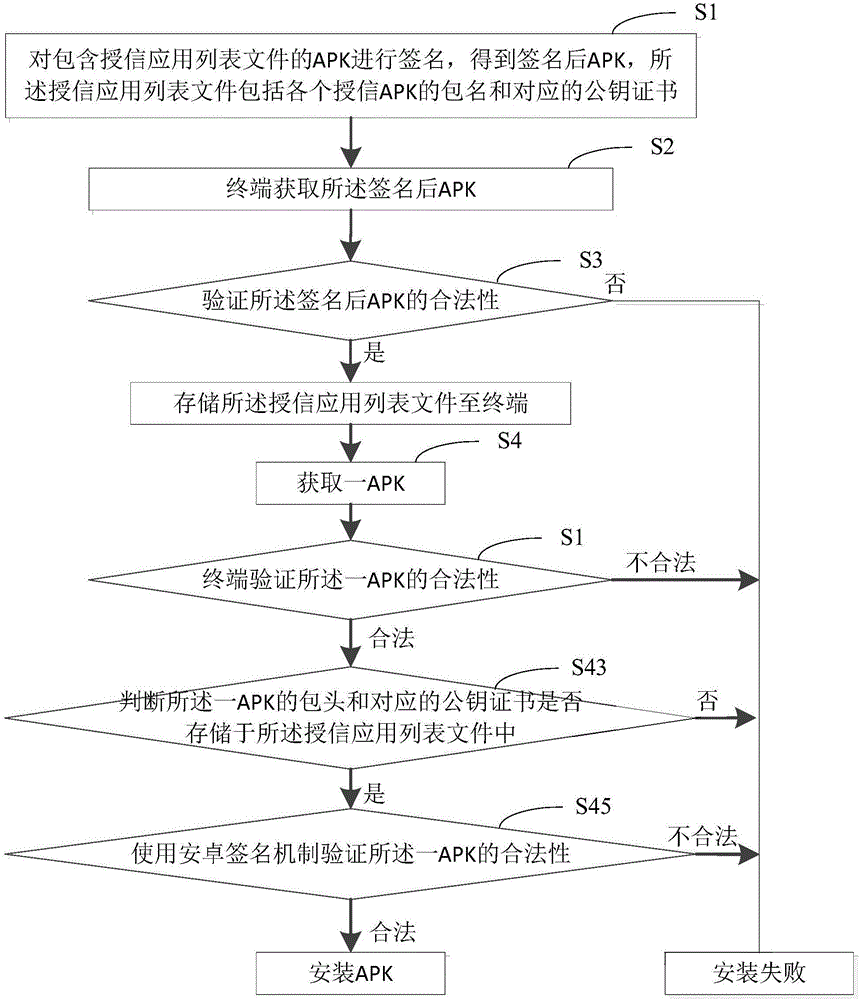
The invention provides an APK (Android Package) downloading method and system based on the Android system. The method comprises steps as follows: APKs containing credit-granted application list files are signed, the signed APKs are obtained, and each credit-granted application list file comprises package names of each credit-granted APK and a corresponding public key certificate; a terminal acquires the signed APKs; the legality of the signed APKs is verified, and the credit-granted application list files are stored after verification is passed; one APK is acquired, and the legality of the APK is verified; if the verification isn't passed, whether a package head of the APK and the corresponding public key certificate are stored in the credit-granted application list files is judged; if yes, the legality of the APK is verified by continuously using an Android signature mechanism. The credit-granted application list files are added, the credit-granted APK downloading and installing process is simplified, and the updating and upgrading process of the credit-granted APKs is further simplified; influence of application update and upgrade to normal work of the terminal is reduced.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
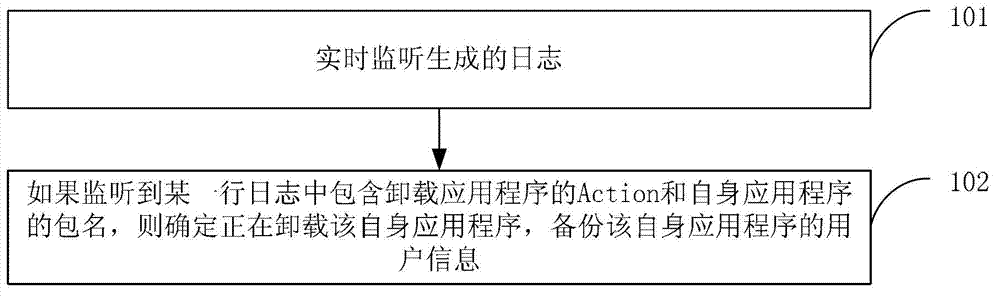
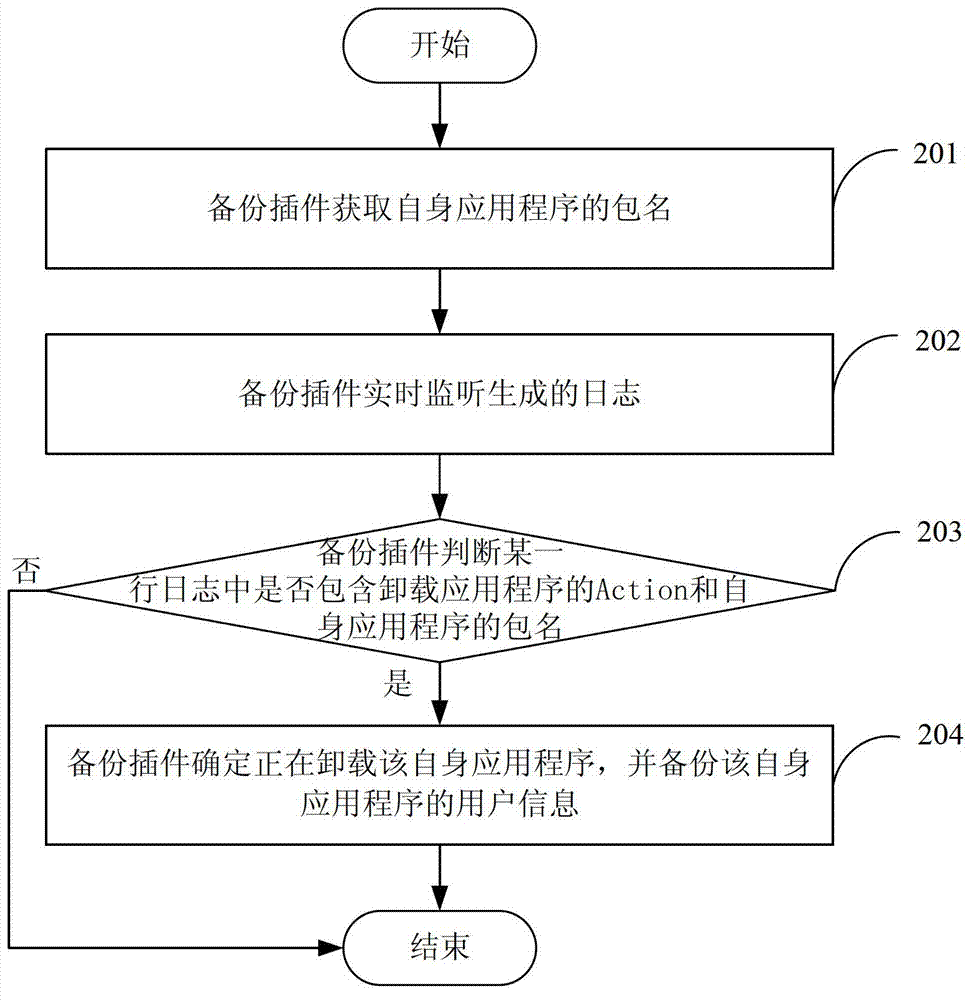
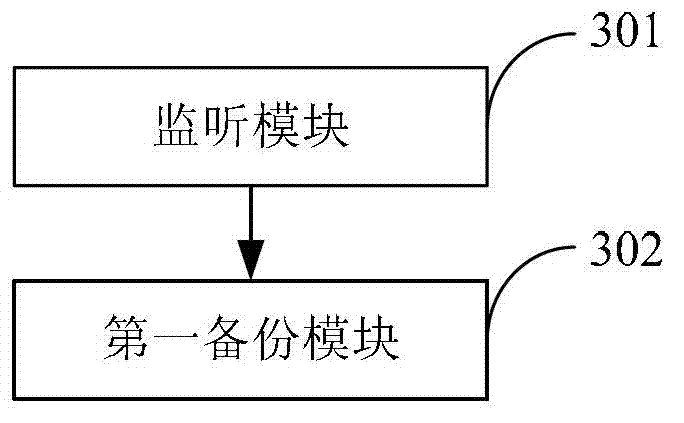
Information backup method and device
ActiveCN102831035AImprove experienceImprove friendlinessRedundant operation error correctionSoftware deploymentApplication softwareComputers technology
The invention discloses information backup method and device and belongs to the field of computer technology. The method includes: monitoring a generated log in real time; if a certain line of the monitored log includes an action of uninstalling an application program and a package name of the application program, confirming the application program being uninstalled, and backuping user information of the application program. The device comprises a monitoring module and a first backup module. The generated log is monitored in real time. If the certain line of the monitored log includes the action of uninstalling the application program and the package name of the application program, the application program being uninstalled is confirmed and the user information of the application program is backuped. Therefore, the user information of the application program is backuped so as to facilitate re-installation of the application program for the user and improve user experience.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
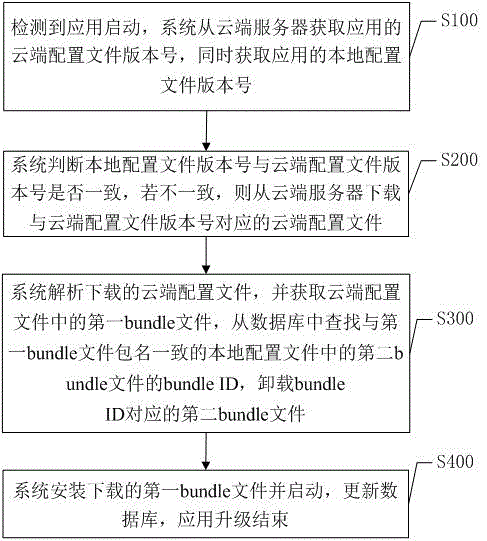
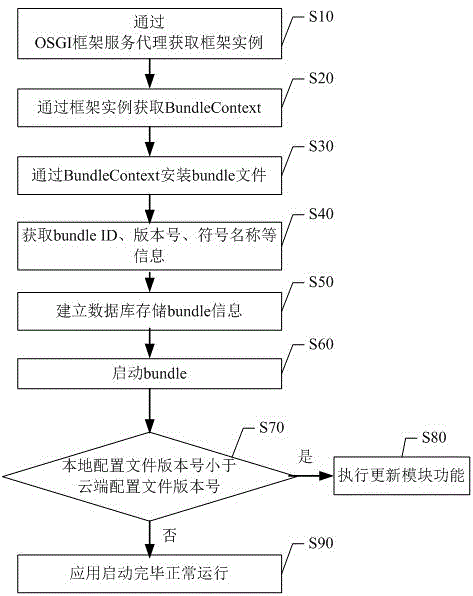
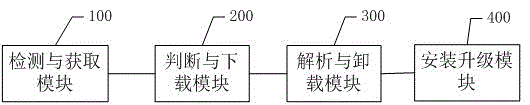
Application increment upgrading method and system based on Android system
ActiveCN105657191ASave upgrade stepsIncremental upgrade is convenientSubstation equipmentProgram loading/initiatingOperating systemData library
The invention discloses an application increment upgrading method and system based on an Android system. The method includes the steps that application starting is detected, and a cloud configuration file version number and a local configuration file version number of an application are obtained; a system judges whether the local configuration file version number is coincident with the cloud configuration file version number, if the local configuration file version number is not coincident with the cloud configuration file version number, a corresponding cloud configuration file is downloaded from a cloud server; the downloaded cloud configuration file is analyzed through the system, a first bundle file in the loud configuration file is obtained, and a second bundle file coincident with the first bundle file in the file-package name in a local configuration file is found and unloaded from a database; the downloaded first bundle file is installed and started through the system, and the database is updated. According to the application increment upgrading method and system, when some module and / or a plurality of modules are updated, the corresponding bundle file only needs to be updated, the upgrading step is saved, and application increment upgrading is convenient.
Owner:TCL CORPORATION
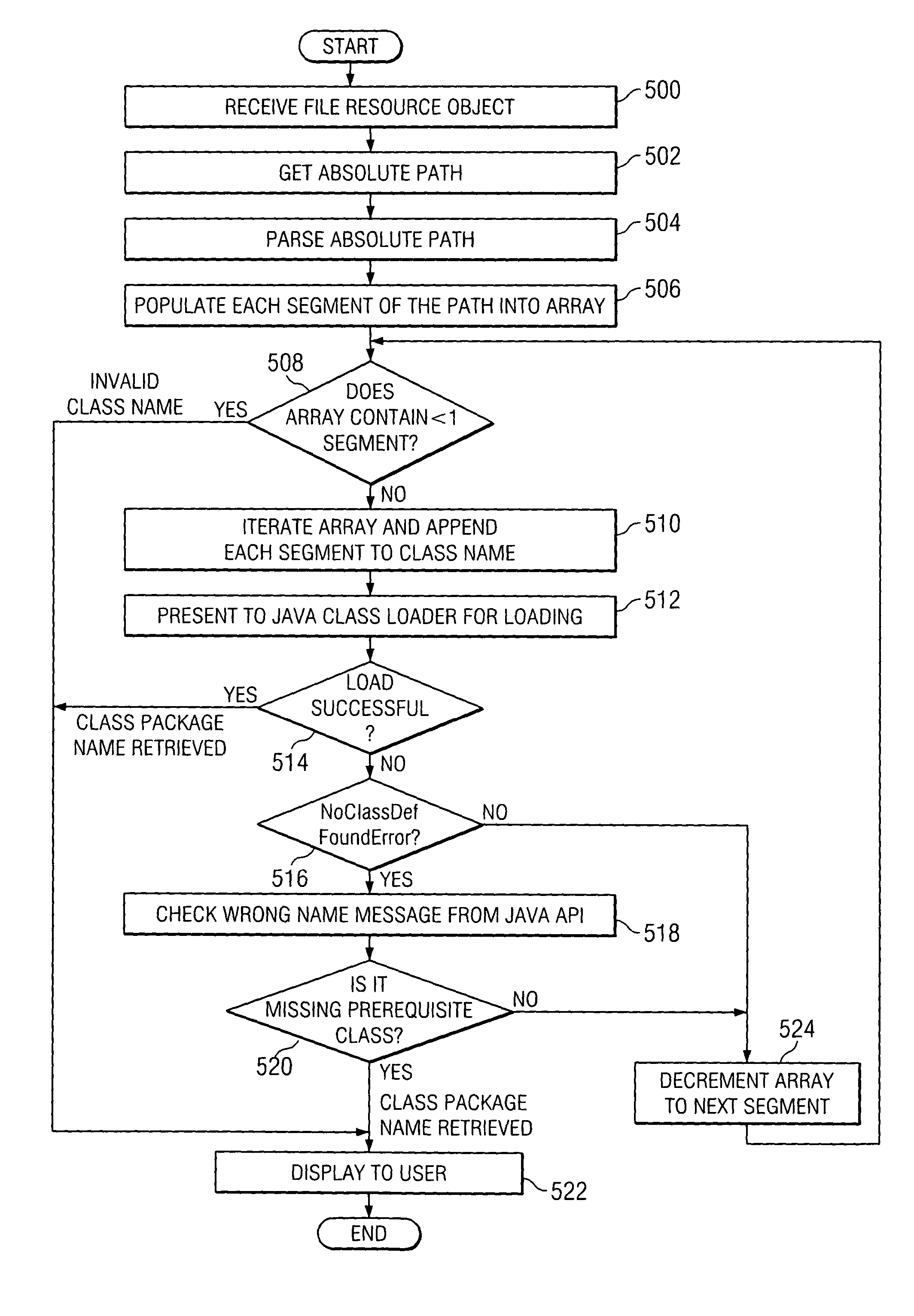
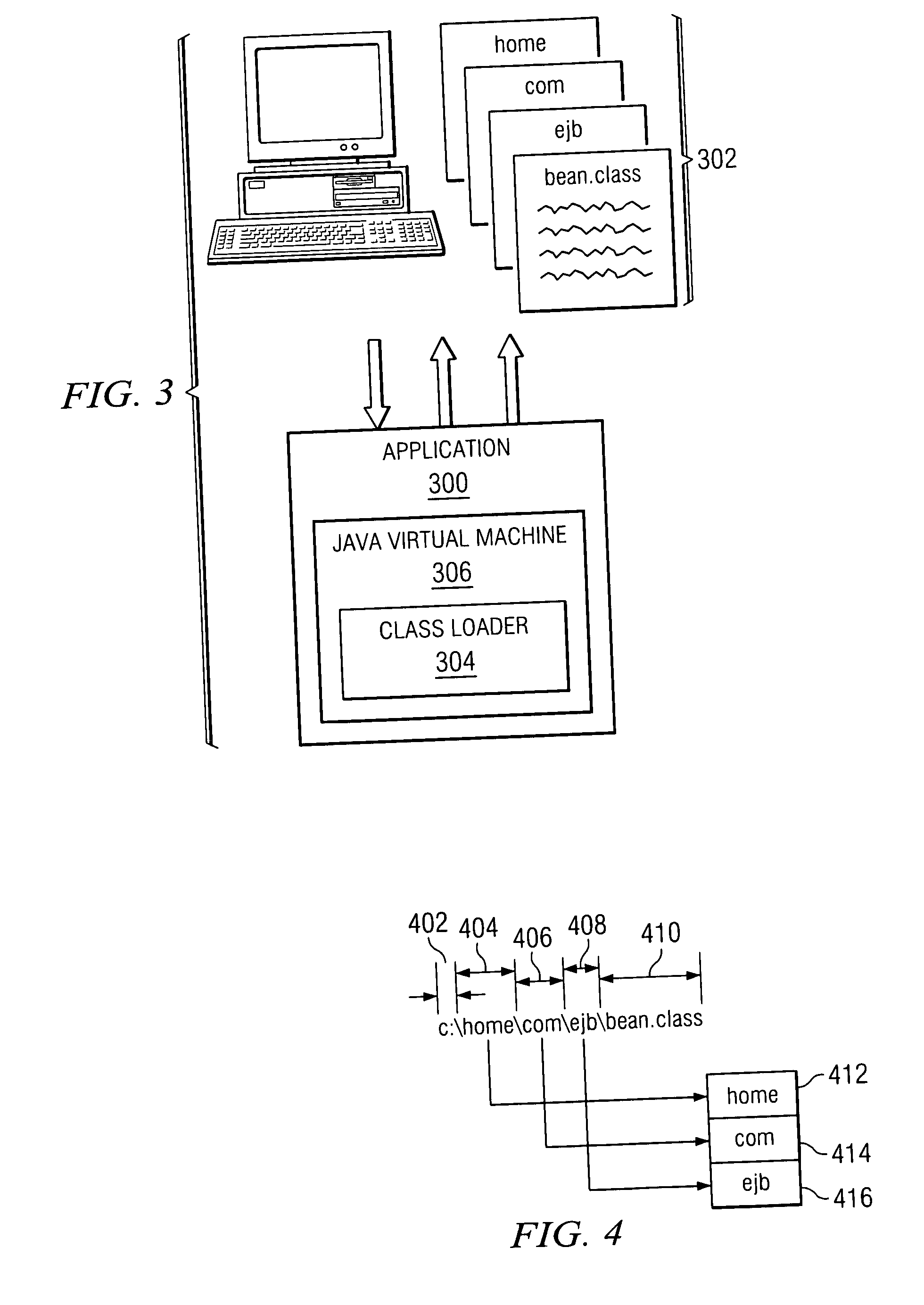
Method and apparatus for identifying a Java class package name without disassembling Java bytecodes
A system and method for retrieving class package name from a class file if not known or found by the Java class loader of the Java virtual machine at load time. An algorithm is derived which uses the class file to obtain the class package name by iterating the directory names of the class file in the user's current operating system. An output is provided to the user when the class package name is found and it is loaded by the Java class loader; when an error occurs after which the error message indicates that the prerequisite class of the class file is missing; or when the class package name itself is invalid.
Owner:IBM CORP
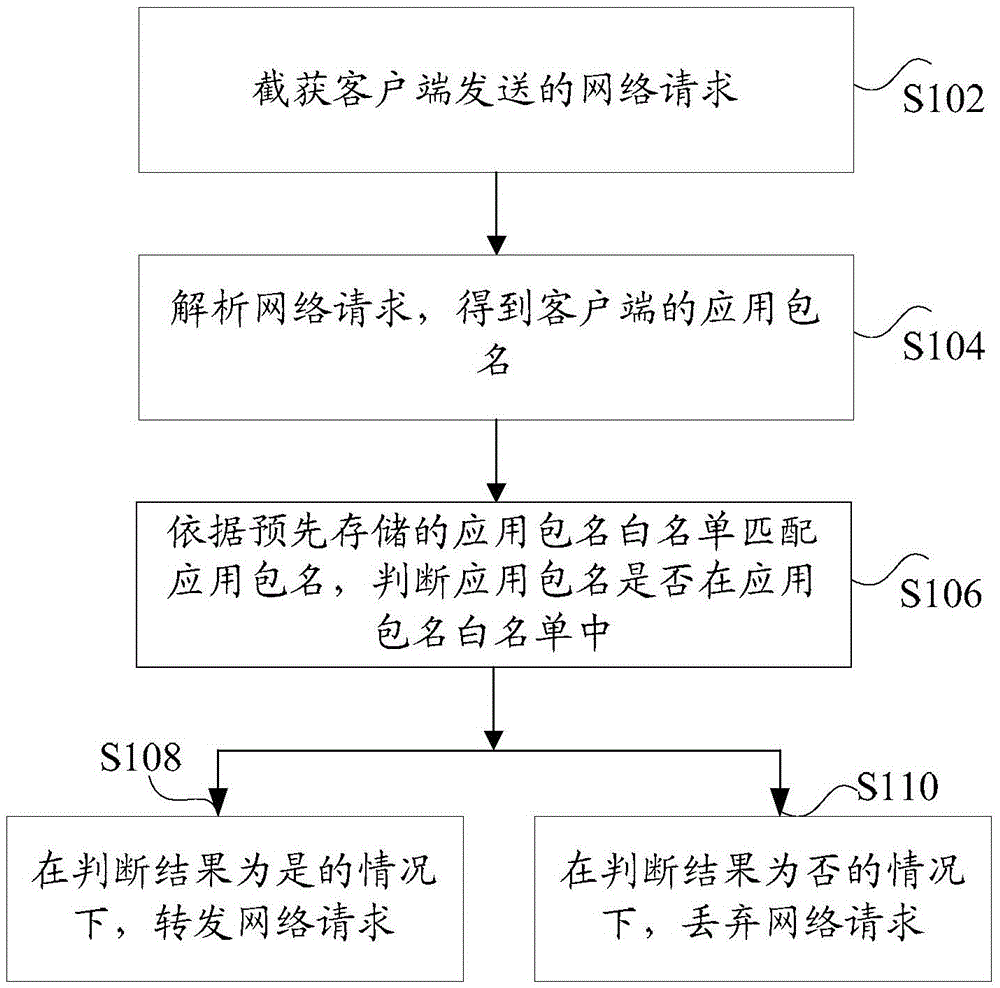
Method and device for verifying request data
ActiveCN105530255ASolve technical problems usedEffective supervisionTransmissionClient-sideComputer science
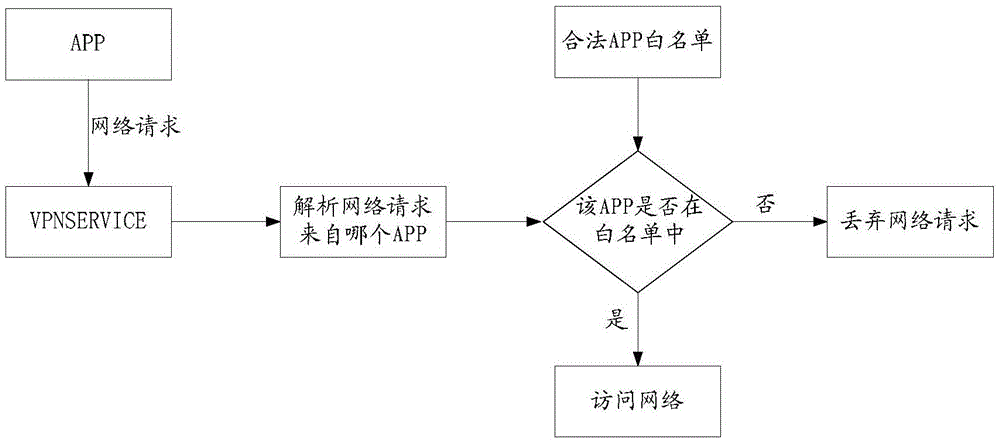
The invention discloses a method and a device for verifying request data. The method comprises the following steps: intercepting a network request sent by a client; analyzing the network request to obtain an application package name of the client; matching the application package name according to a pre-stored application package name white list, and judging whether the application package name is in the application package name white list; discarding the network request when the judgment result is negative; and forwarding the network request, when the judgment result is positive. The method disclosed by the invention is used for solving the technical problem that an illegal television client APP is used because there is no technology for effectively monitoring smart TVs and / or TV boxes in related technologies exists.
Owner:CHINANETCENT TECH
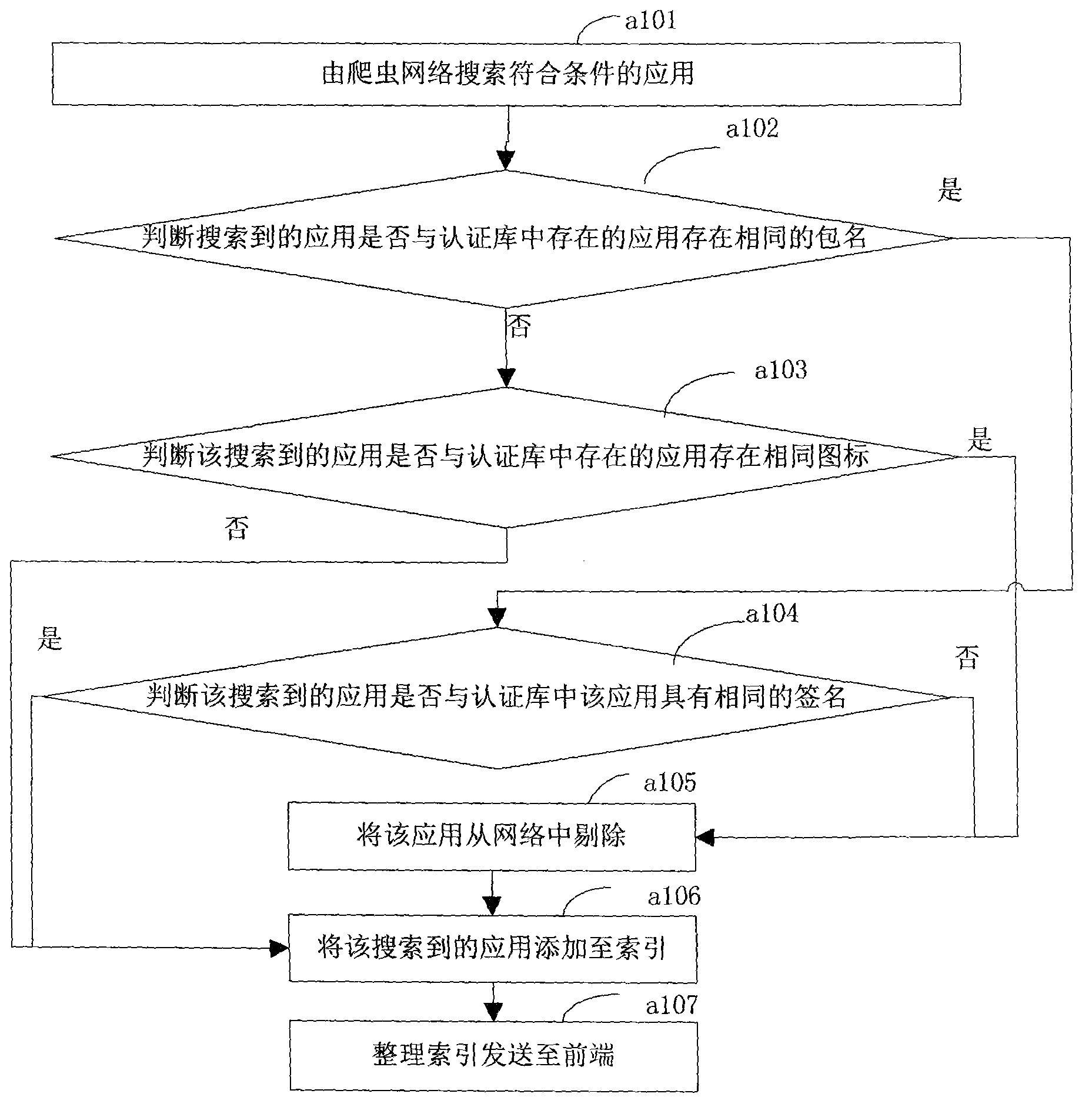
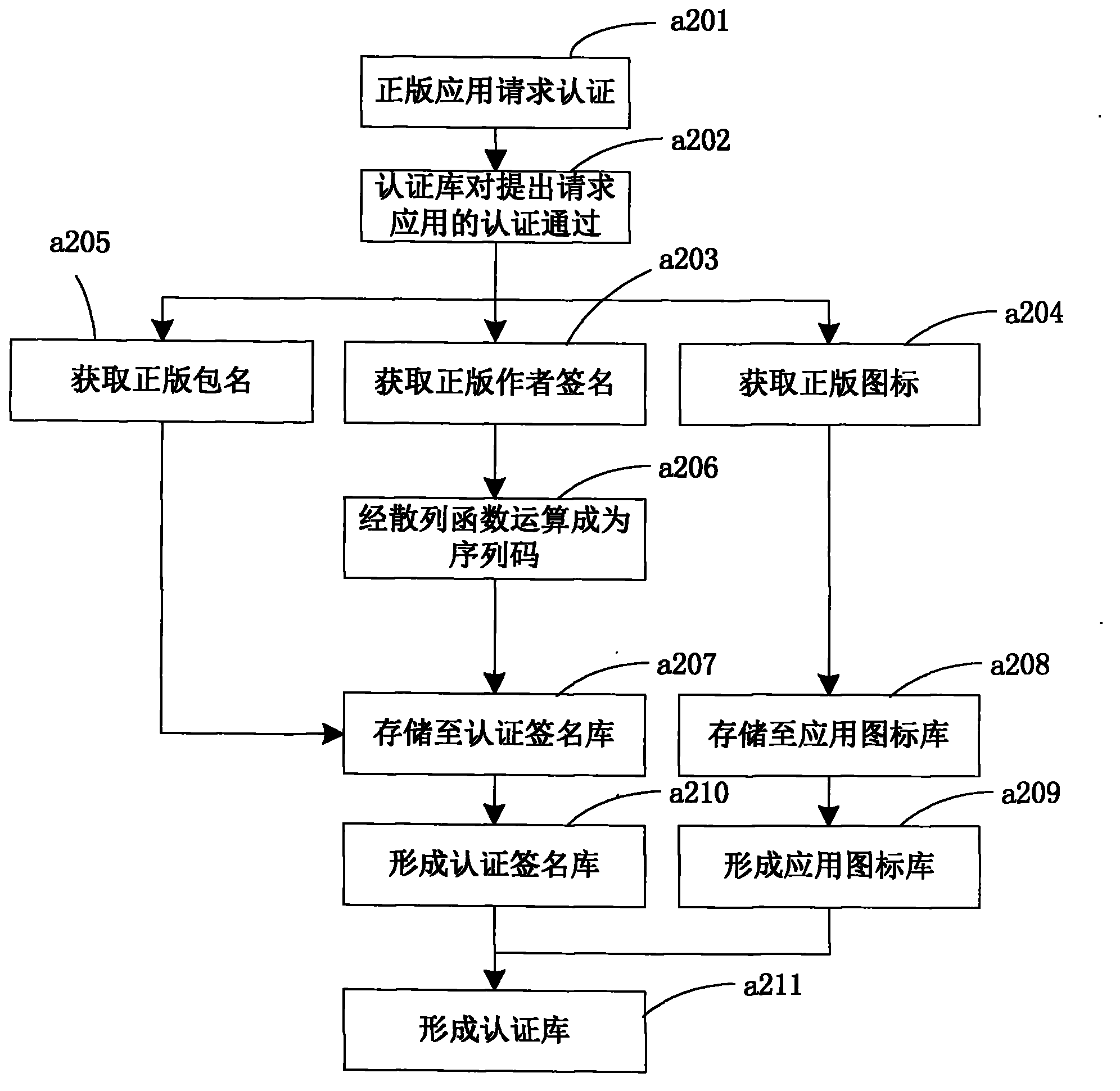
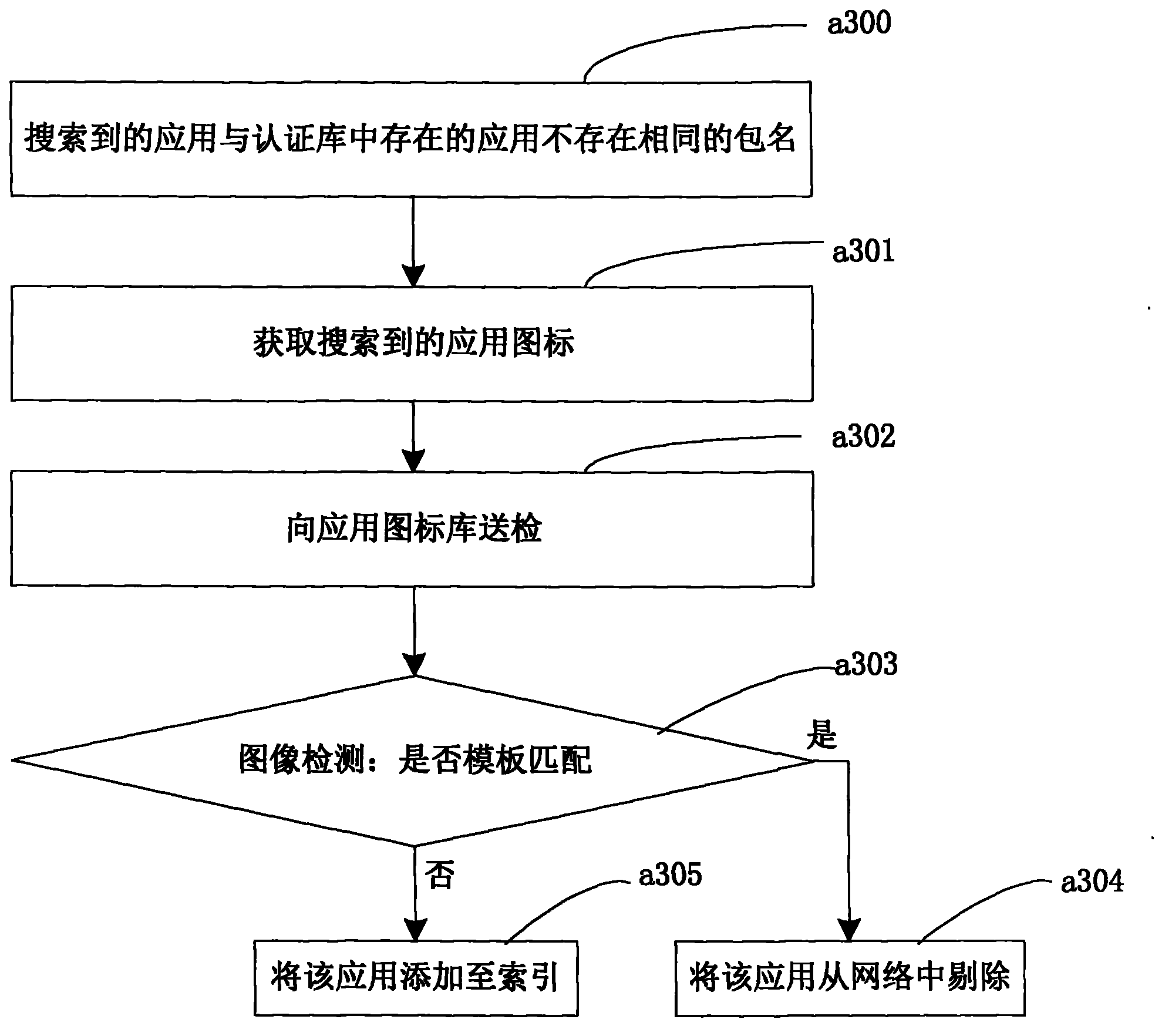
Method for removing copycatting applications in android application search and based on icon contrast
ActiveCN103324697AAccurate removalEfficient identificationSpecial data processing applicationsAuthenticationAndroid application
The invention relates to a method for removing copycatting applications in android application search. The method includes the following steps: capturing eligible applications through a crawler network, judging whether the captured eligible applications have identical icons with applications stored in an authentication database, judging the captured applications as copycatting applications if the applications with package names different from that of the captured applications but with icons identical with that of the captured applications exist in the database, judging the eligible applications as new applications otherwise; judging whether the captured eligible applications have identical signatures with the applications in the authentication database; judging the applications as an authorized edition on yes judgment and judging the applications as the copycatting applications on no judgment. The modes of package names, signatures and icon authentication are adopted in the method, and the copycatting applications in the search process are effectively removed.
Owner:北京掌汇天下科技有限公司
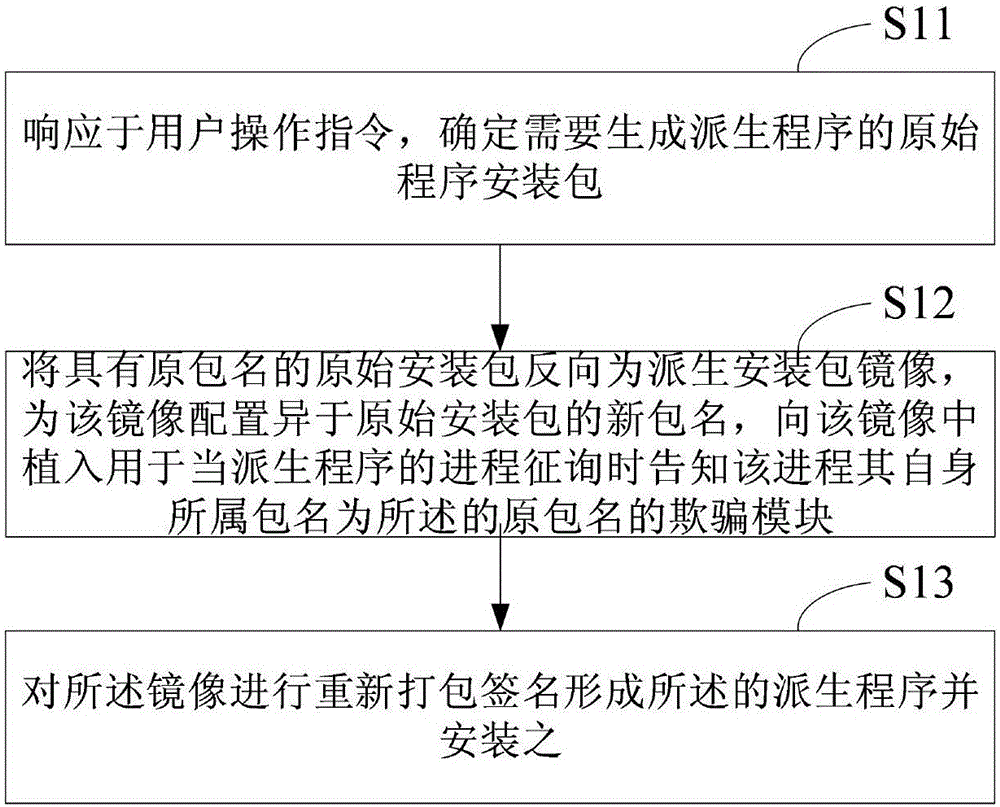
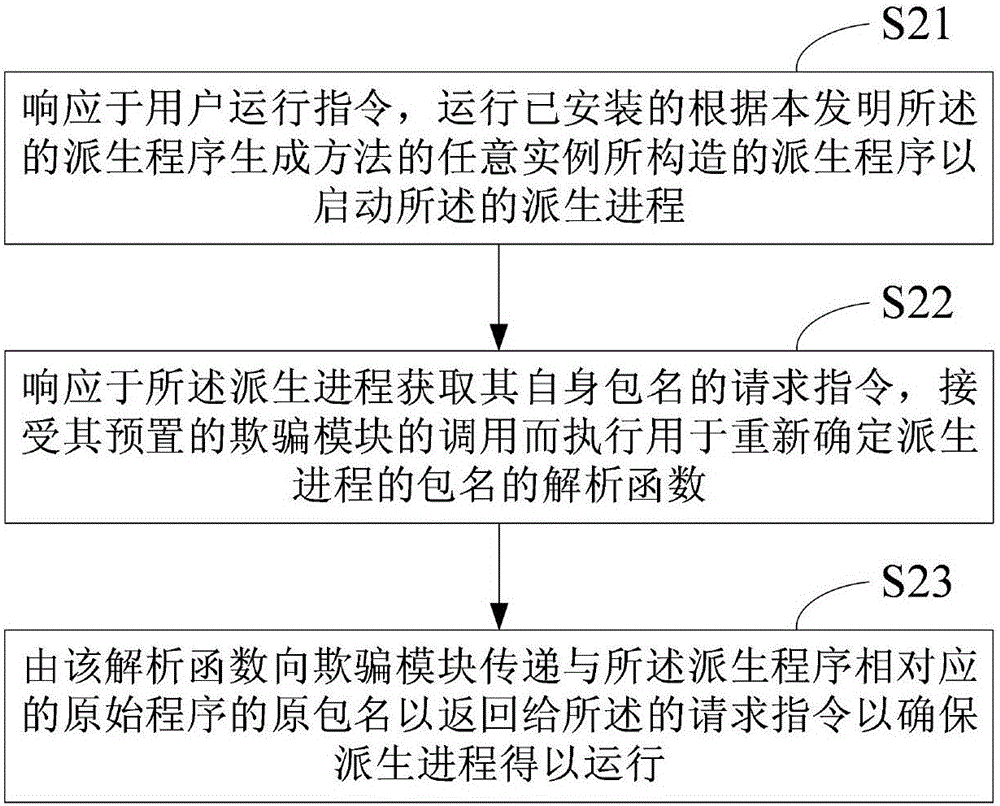
Derived process staying-resident method, derived program generating method and corresponding device
ActiveCN105843668AExperience without hindranceSimplify technical difficultyProgram loading/initiatingSoftware simulation/interpretation/emulationApplication softwareMirror image
The invention discloses a derived program generating method. The derived program generating method comprises following steps: responding to a user operation instruction, and determining an original program installation package where a derived program needs to be generated; reversing the original installation package with an original package name into an installation package mirror image, configuring a new package name different from that of the original installation package for the mirror image and implanting a resetting module in the mirror image, wherein the resetting module is used for informing the process that the package name of itself is the original package name during the consultation of the process of the derived program; and performing repackaging and signing on the mirror image so as to form and store the derived program. In addition, the invention also discloses a derived process staying-resident method for describing the operation control technology of the derived program generated by the derived program generating method. According to the invention, a scheme that processes of an original program and a copy thereof stay resident simultaneously is achieved through a simpler technology; and on the premise of following an application program copyright control technology, a blockade on the technology of an Android system is broken and user experience is improved.
Owner:北京世界星辉科技有限责任公司
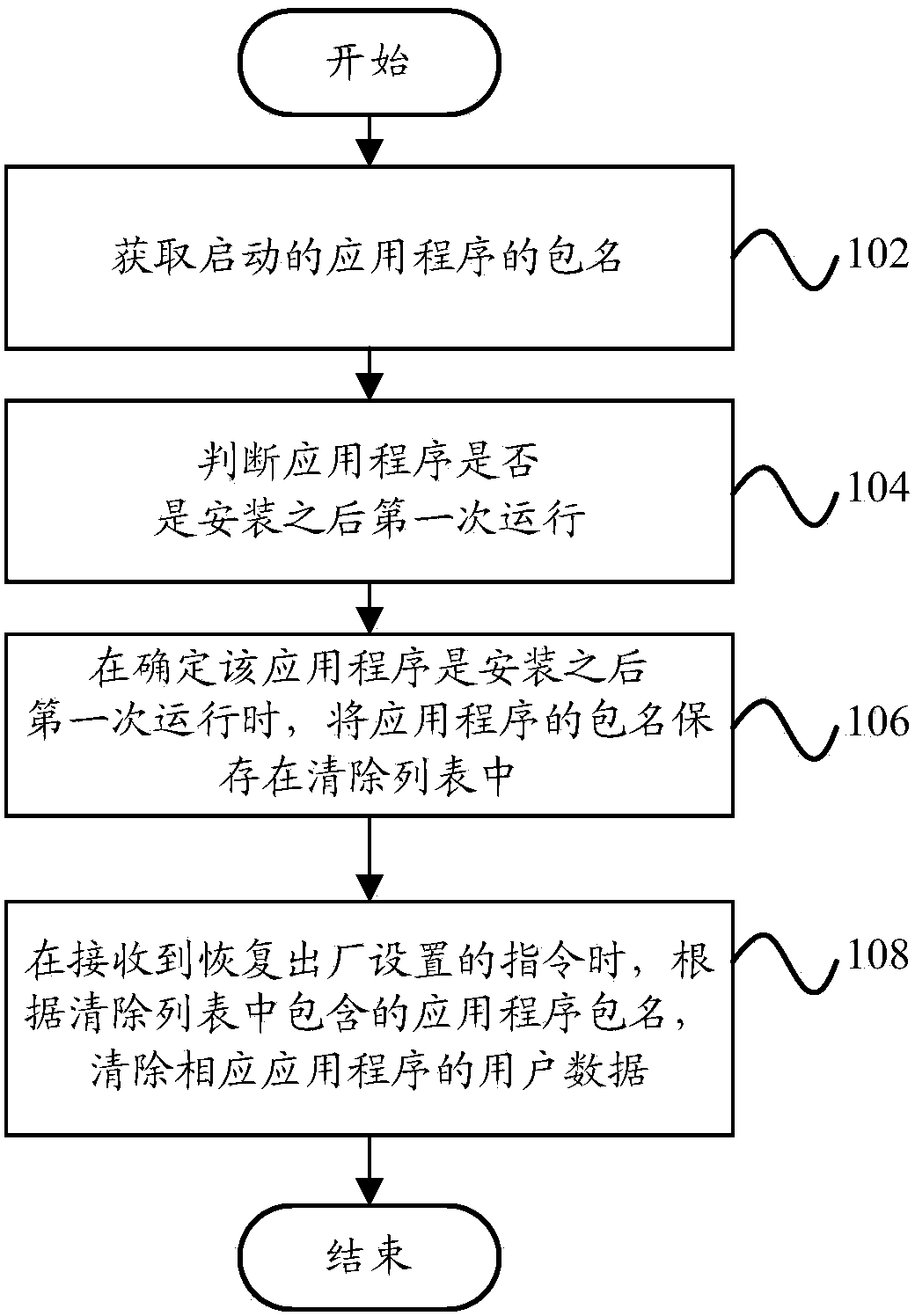
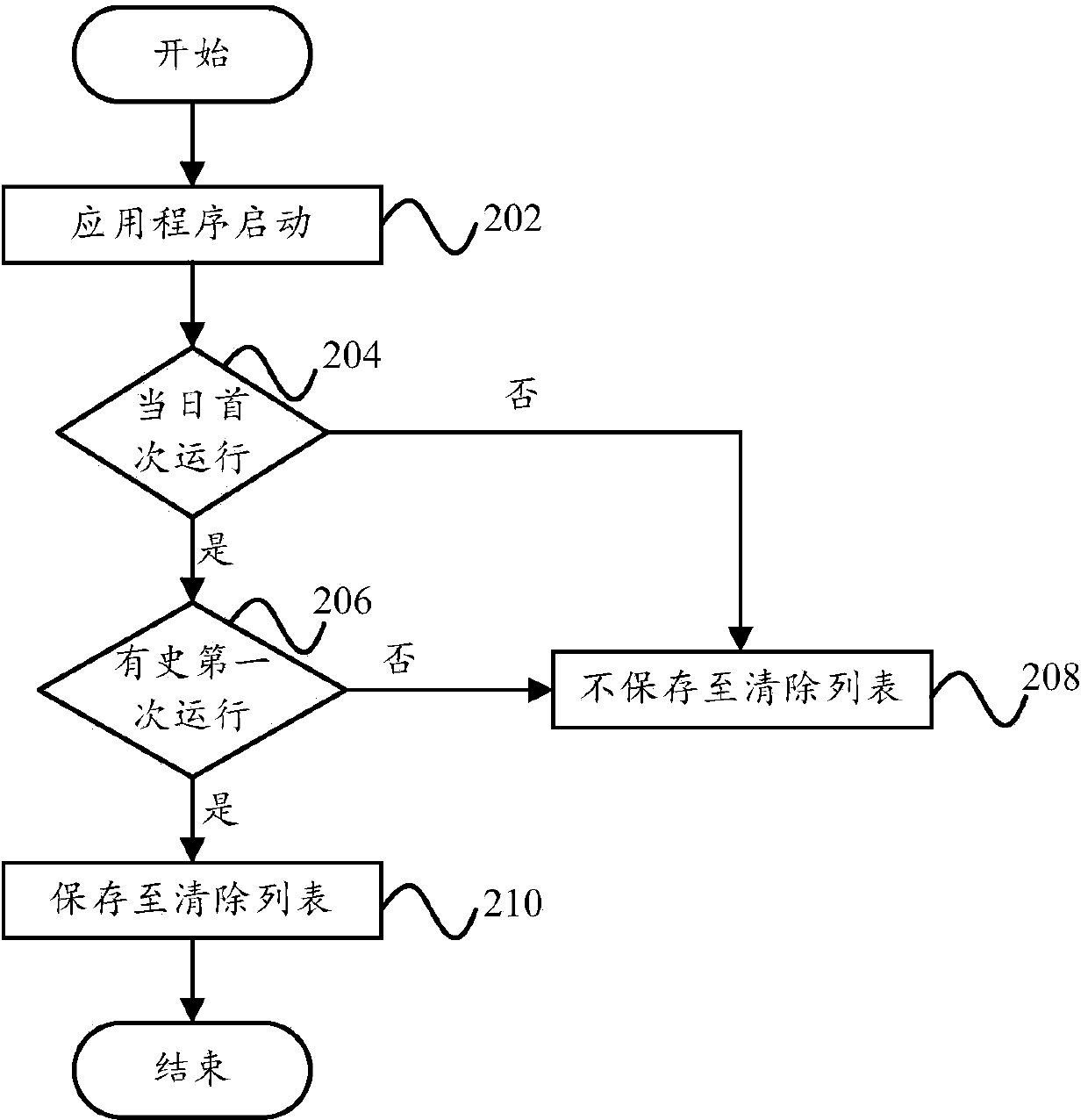
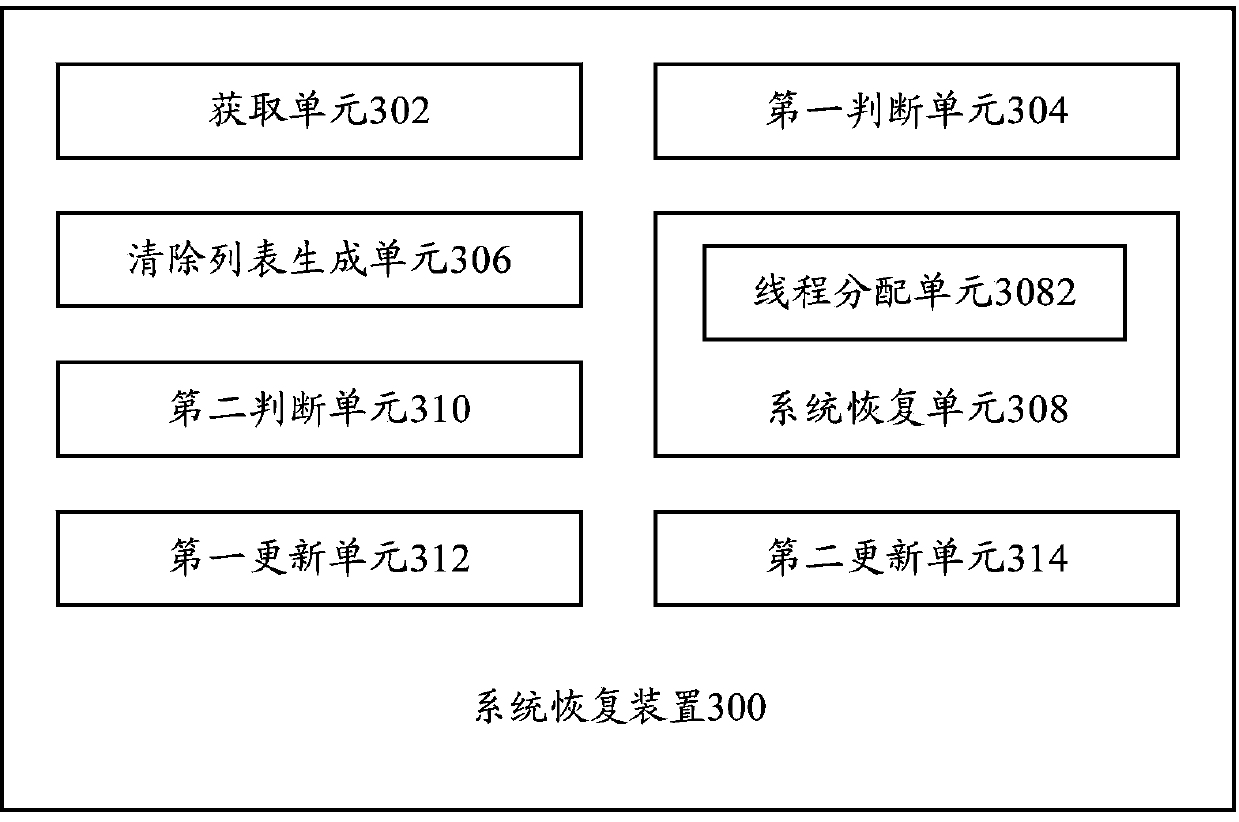
System recovery method and system recovery device
ActiveCN103699420AWill not repeatSimplify the build processProgram loading/initiatingRecovery methodRestoration method
The invention provides a system recovery method and a system recovery device. The system recovery method includes acquiring package names of started application programs; judging whether the application programs are started for first time or not; if yes, storing the package names of the application programs in a clear list; after receiving a command of recovering factory settings, clearing user data of the corresponding application programs according to the application program package names contained in the clear list. By the system recovery method and the system recovery device, operation of the application programs can be tracked dynamically and a list of application programs in need of data clearing can be generated so as to clear traces and user data of the application programs during factory setting recovery, and factory setting recovery can be completed without restart of a system and formatting of data partitions, so that time for recovering the factory settings is reduced.
Owner:HISENSE
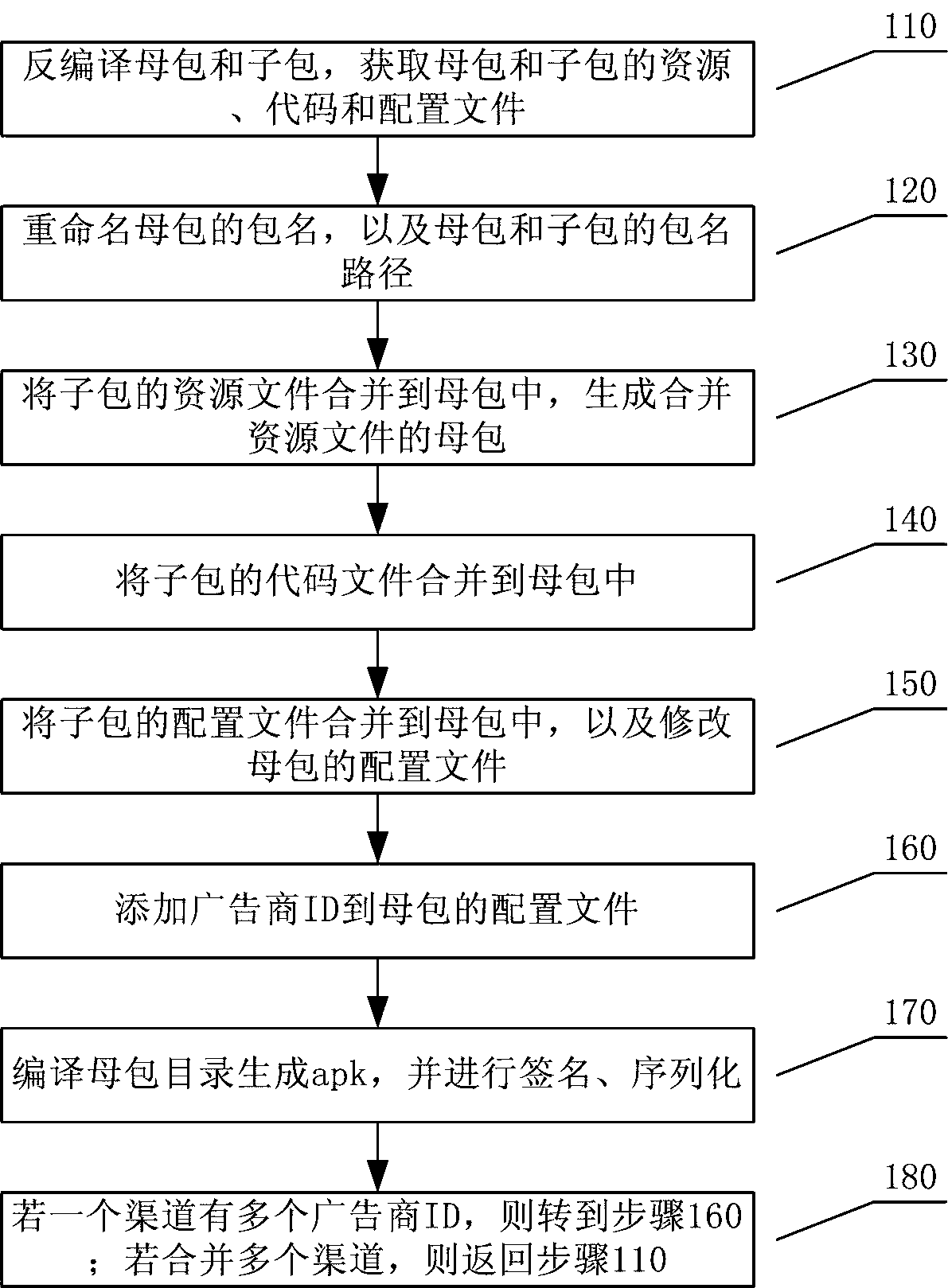
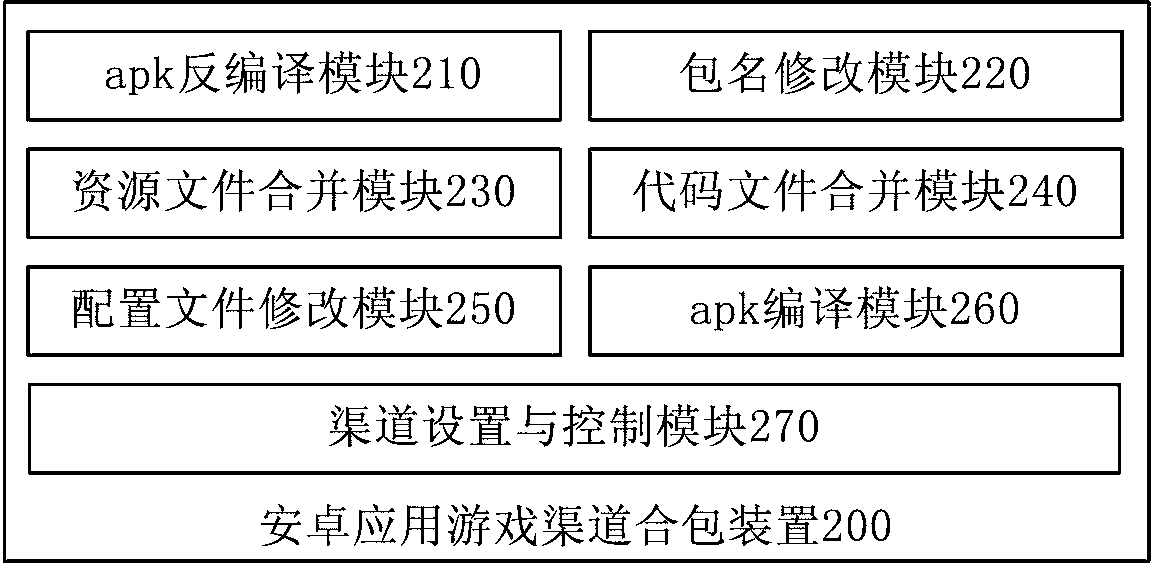
Android application channel packing method and device
InactiveCN107844301ASimplify the promotion processShorten development timeDecompilation/disassemblyCode compilationPackage.namePacking method
The invention discloses an android application channel packing method and device. The method comprises following steps: obtaining resource, codes and configuration files of mother packages and sub-packages; renaming the mother packages and the package name paths of the mother packages and the sub-packages; merging the resource files of the sub-packages into the mother packages to generate mother packages with merged resource files; merging the code files of the sub-packages into the mother packages; merging the configuration files of the sub-packages into the mother packages; modifying the configuration files of the mother packages; compiling mother package directory to generate apk and performing signing and sequencing. The Android application channel packing method and device of the present invention can simplify the channel promotion process and greatly save development time with a low error rate.
Owner:SNAIL GAMES
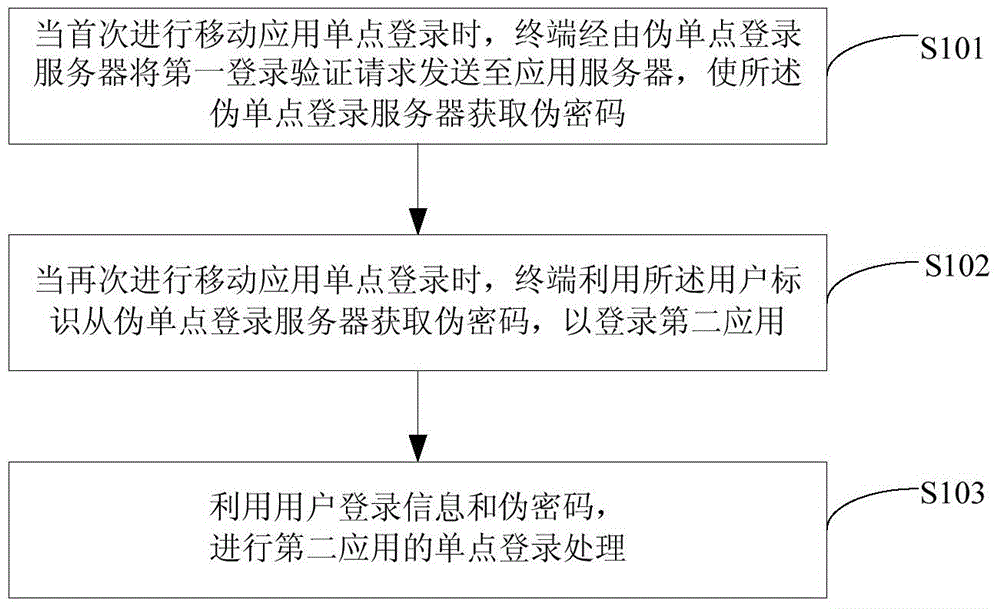
Mobile application single sign-on method and device
ActiveCN106209726AAvoid typing username multiple timesAvoid the hassle of user login information such as passwordsSecuring communicationApplication serverPackage.name
The invention discloses a mobile application single sign-on method and device. The method comprises the following steps: when mobile application single sign-on is carried out for the first time, a terminal sends a first sign-on verification request carrying user sign-on information, a package name of a first application and user identification to an application server through a pseudo single sign-on server to enable the pseudo single sign-on server to acquire a pseudo password after the application server verifies the first sign-on verification request; and when the mobile application single sign-on is carried out again, the terminal acquires the pseudo password from the pseudo single sign-on server by using the user identification to sign on a second application; and the terminal performs second application single sign-on processing by using the user sign-on information and the pseudo password, wherein the user sign-on information of the first application is the same as that of the second application, and the first application and the second application are associated with each other through the user identification. Through adoption of the method provided by the invention, single sign-on of multiple mobile applications and single sign-on of cross-terminal applications are realized.
Owner:ZTE CORP
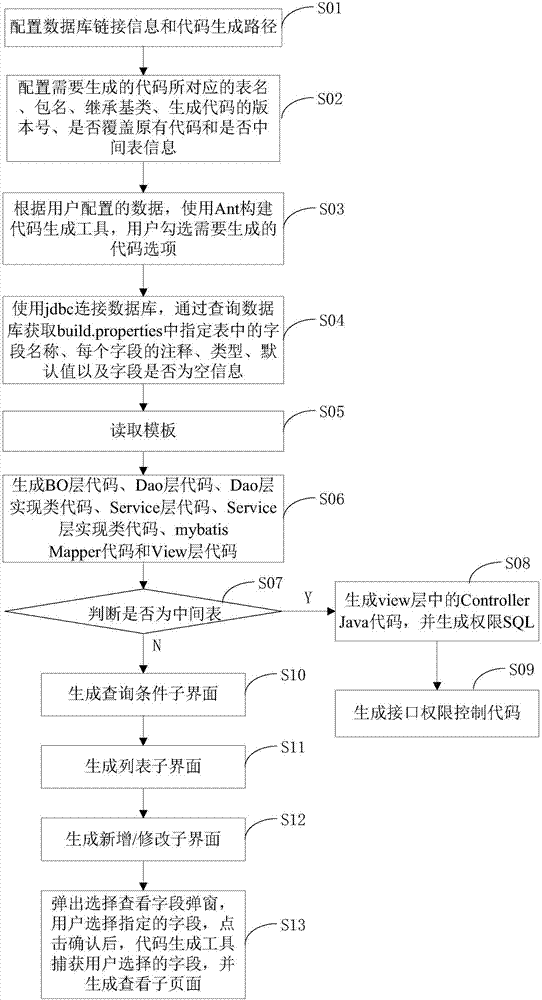
Method for generating code by frame-based code generation tool
ActiveCN107273116AImprove robustnessReduce duplicationSpecific program execution arrangementsCreation/generation of source codeFrame basedLayer interface
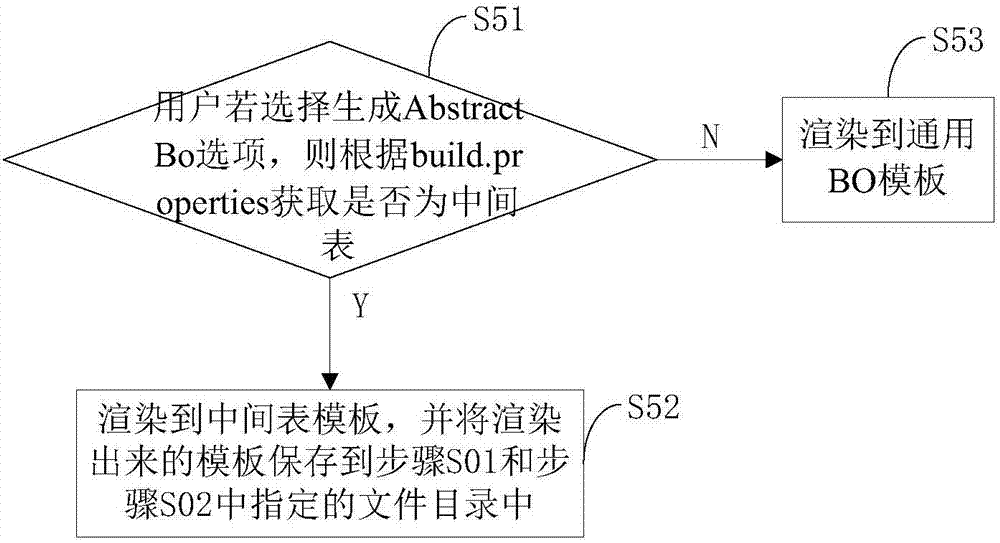
The invention discloses a method for generating a code by a frame-based code generation tool. The method comprises the following steps that: configuring database link information and a code generation path; configuring a table name and a package name corresponding to the code, and configuring whether the table name and the package name are intermediate table information or not; checking a code option to be generated; connecting with database information; reading a template; generating a BO layer, a Dao layer, a Dao layer implementation class, a Service layer, a Service layer implementation class, mybatis, Mapper and a View layer code; when the table name and the package name are the intermediate table, generating a view layer interface code; generating an interface permission control code; if the table name and the package name are not the intermediate table, generating a query condition sub interface; generating a list sub interface; generating a new / revised sub interface; and generating a checking sub interface. The code generation process is simple, efficiency is high, parameter verification is carried out on a front side and a service side, code robustness is good, code development cost is lowered, a development cost is shortened, and the repeated coding and the difference of the code can be reduced.
Owner:深圳互联天下信息技术有限公司
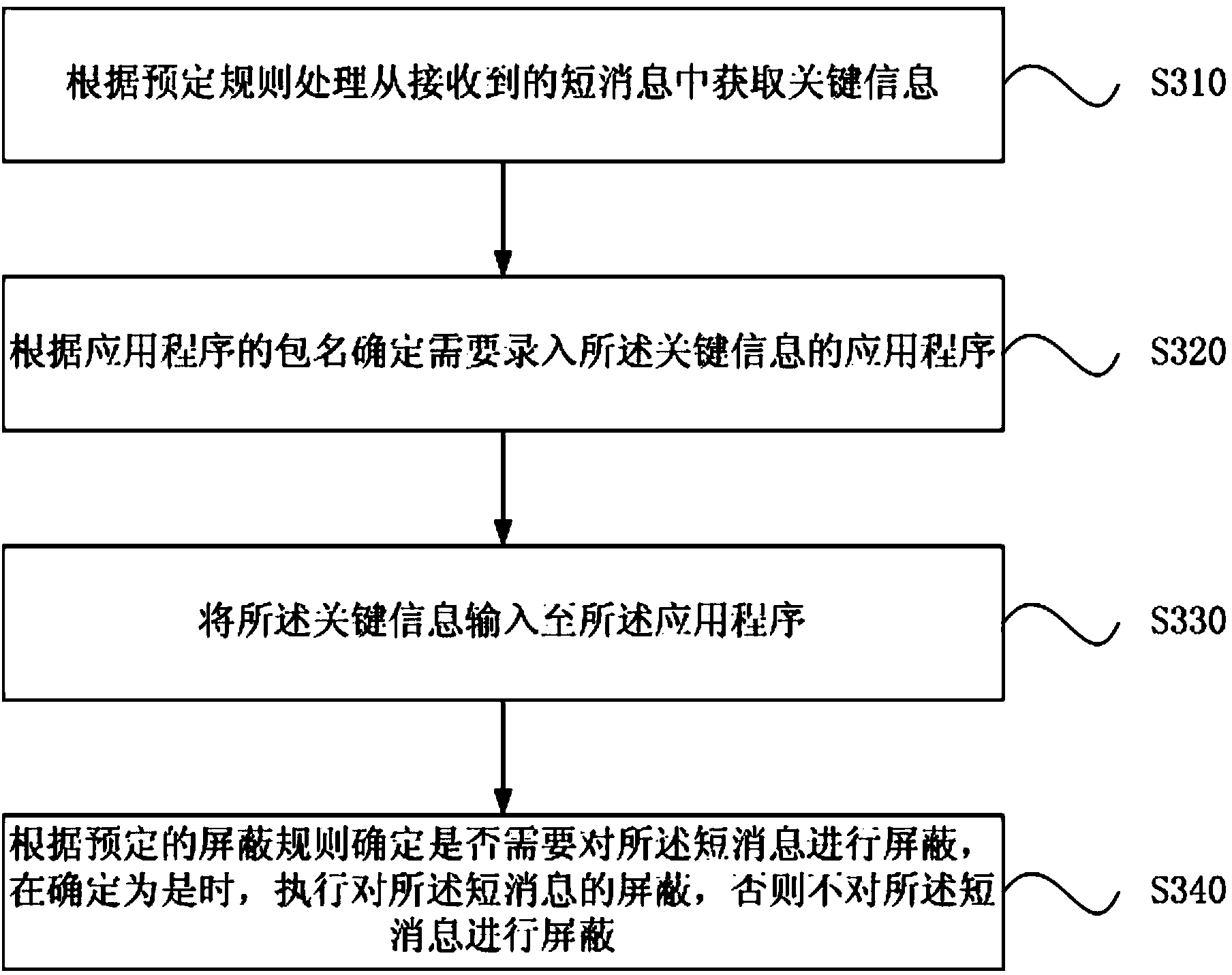
Short message processing method and device
ActiveCN104301875AImprove processing efficiencyMessaging/mailboxes/announcementsMessage processingInformation needs
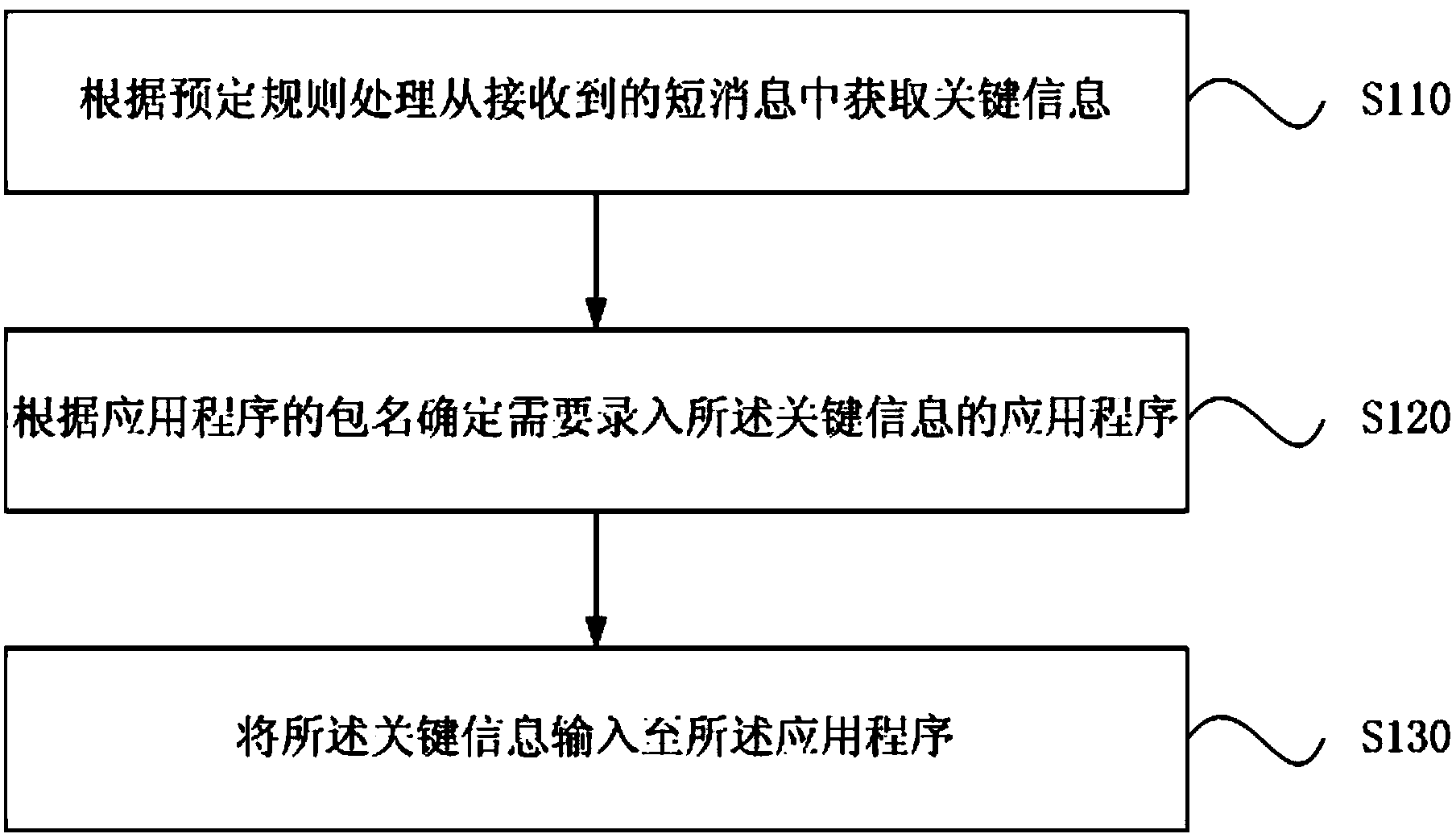
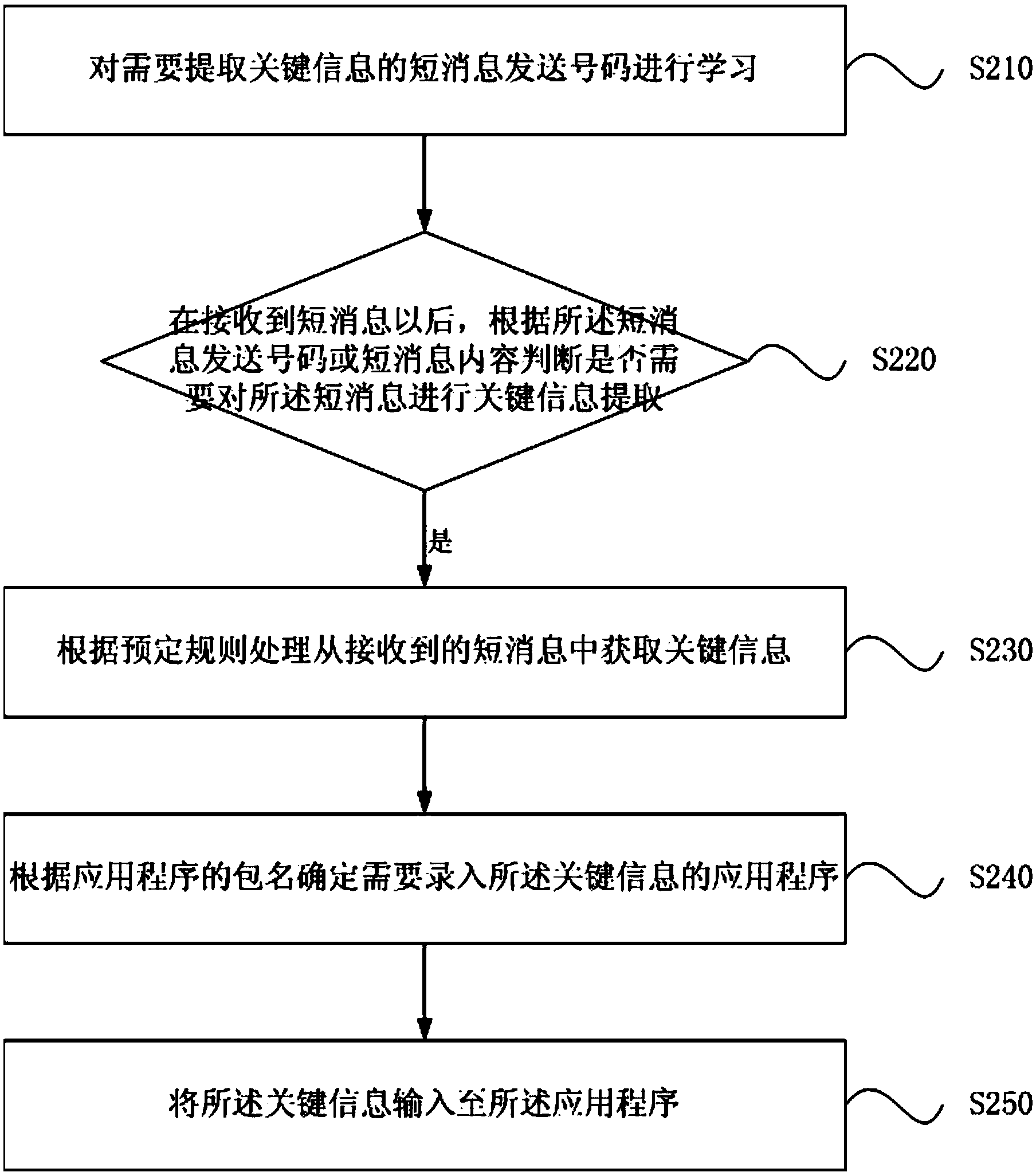
The embodiment of the invention discloses a short message processing method and device. The short message processing method comprises the steps that key information is acquired from a received short message according to a preset processing rule; an application program in which the key information needs to be input is determined according to the package name of the application program; the key information is input to the application program. According to the short message processing method and device, the efficiency for processing the short message including the key information is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com