Patents
Literature
3201 results about "Restoration method" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
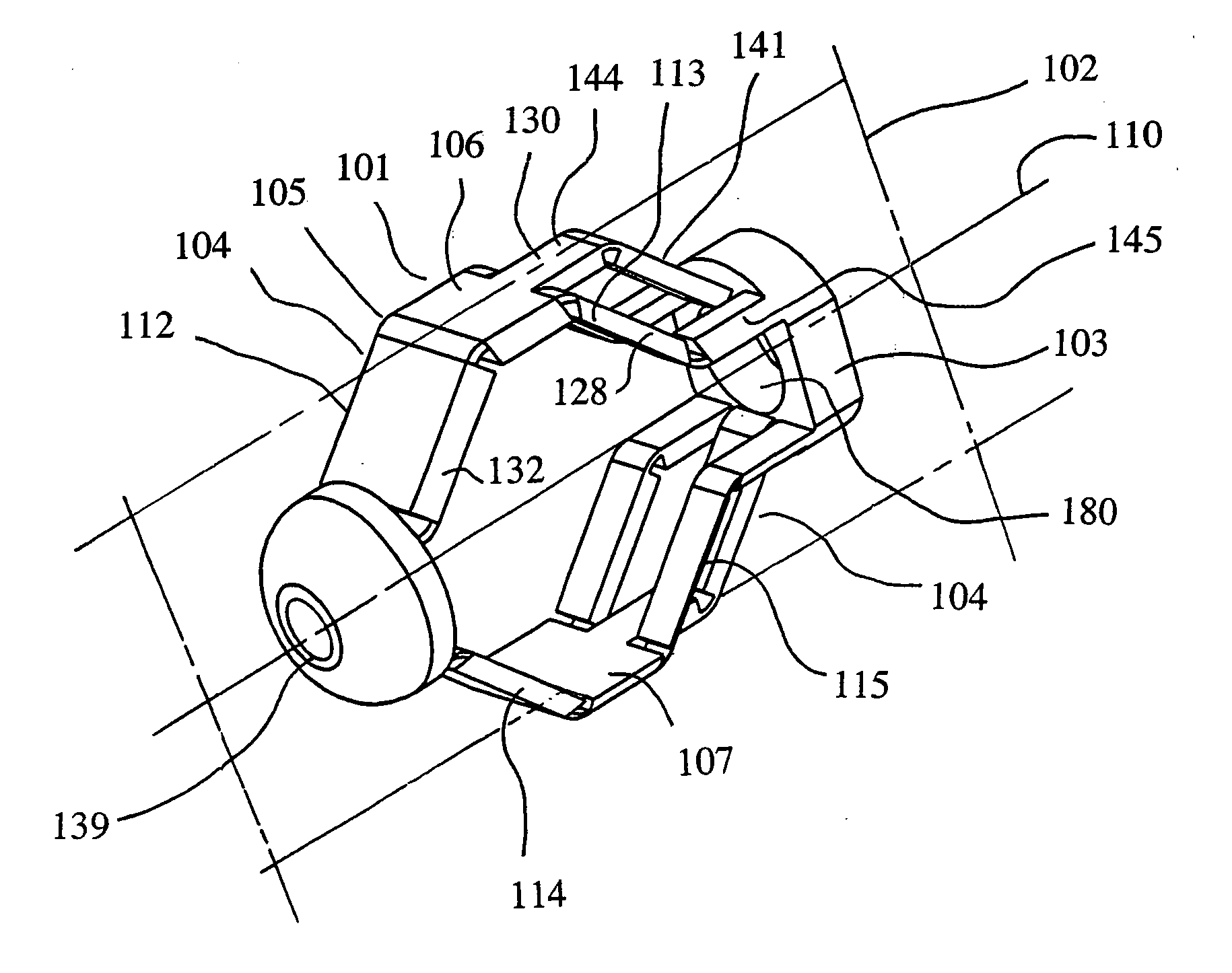
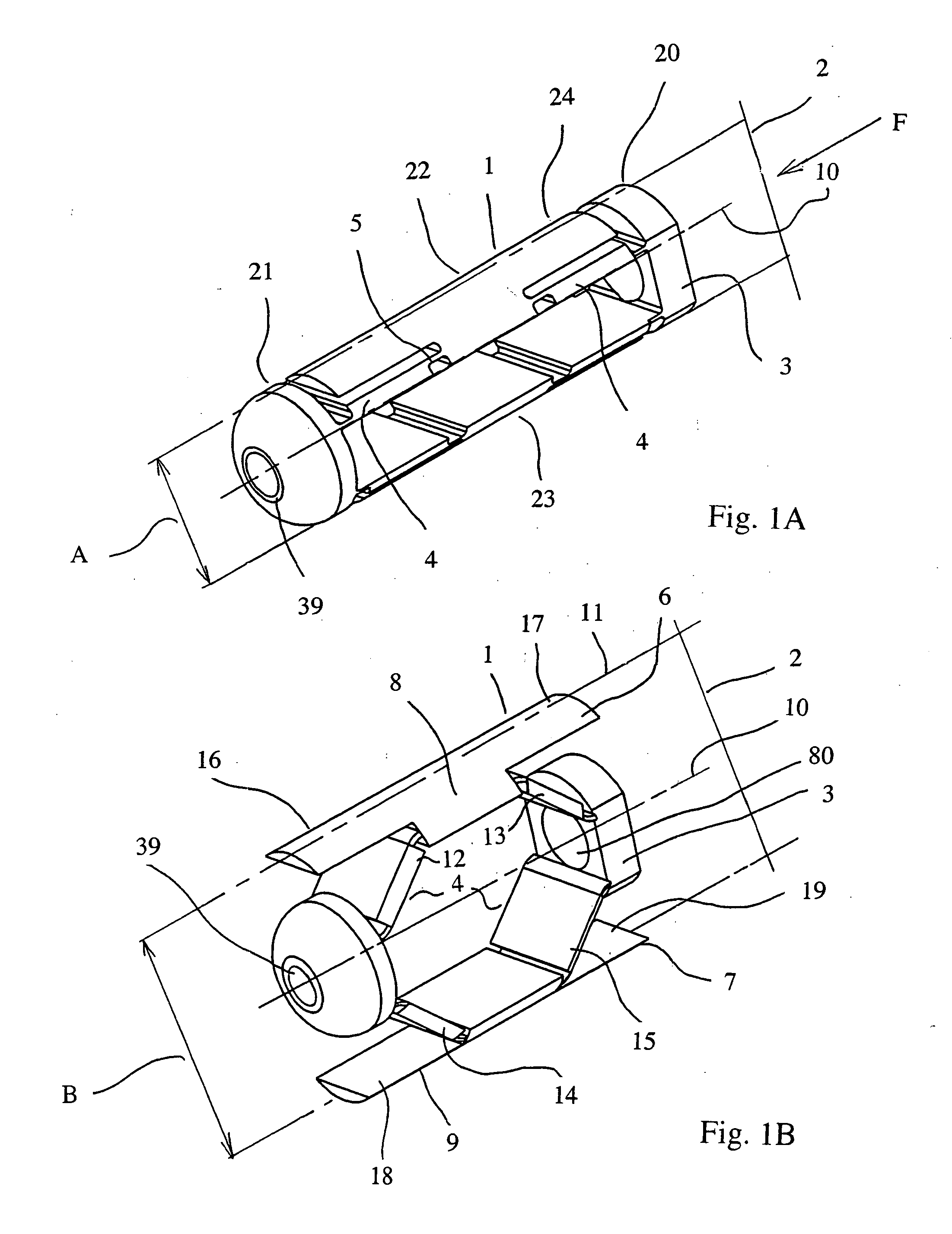
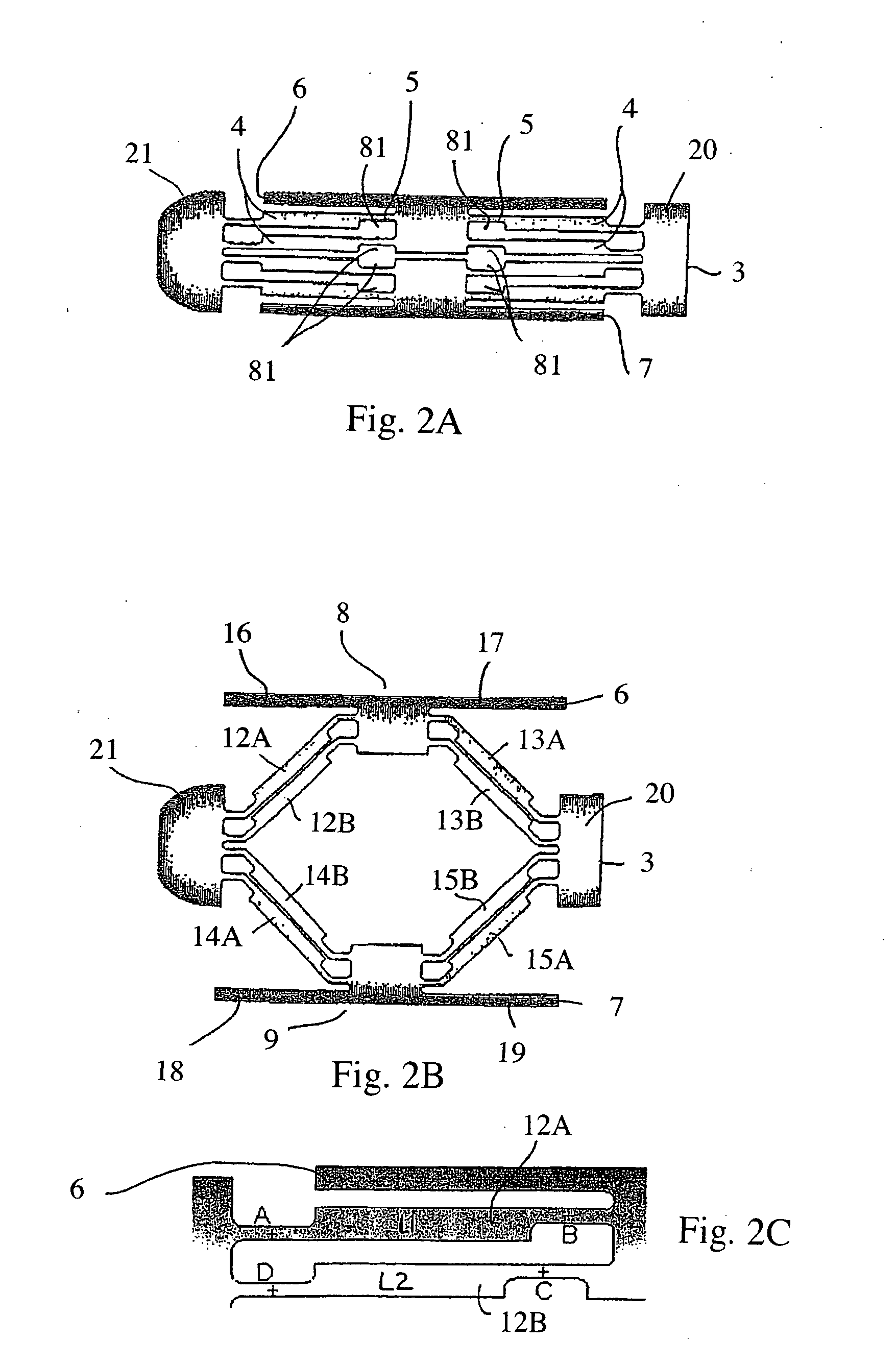
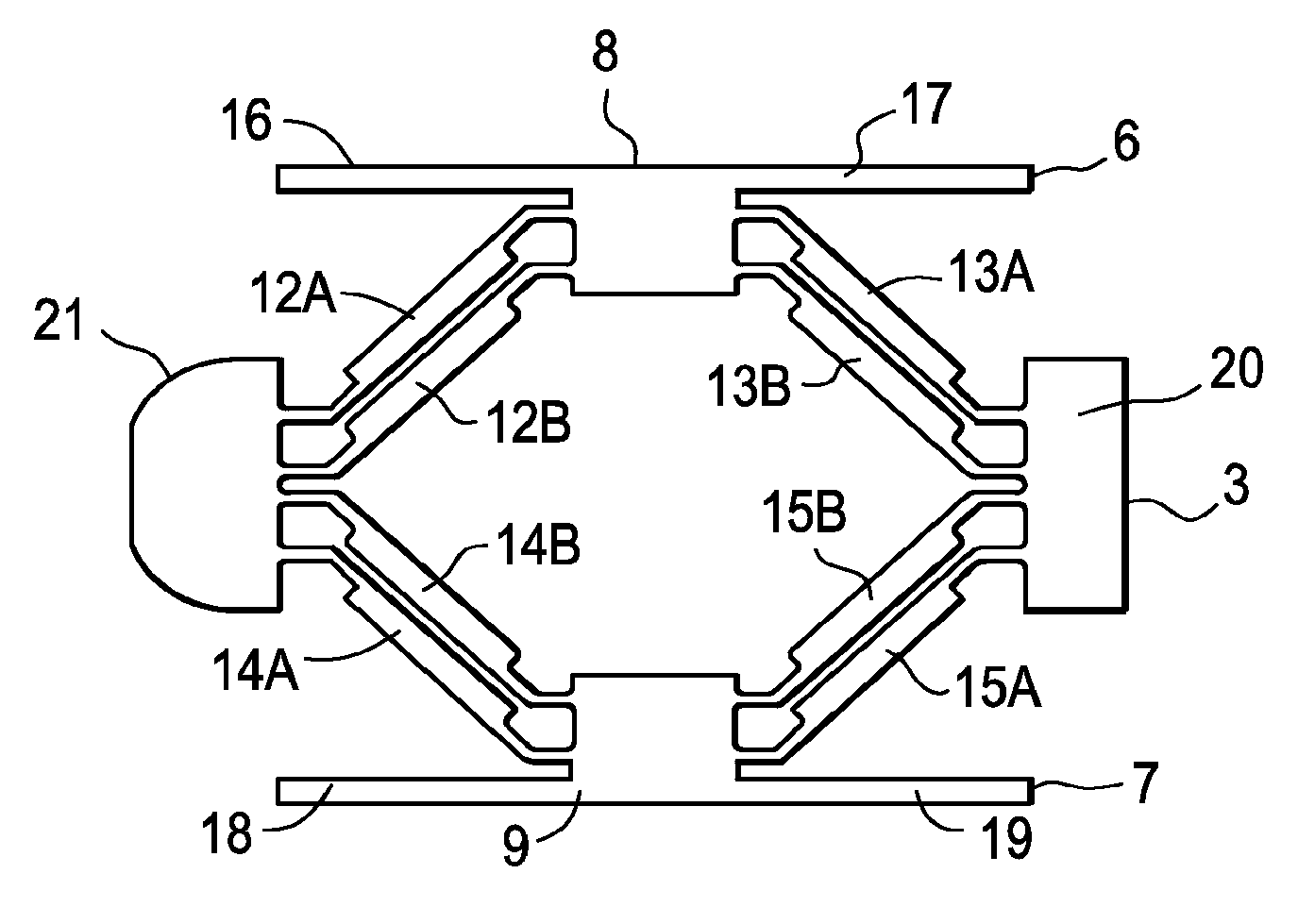
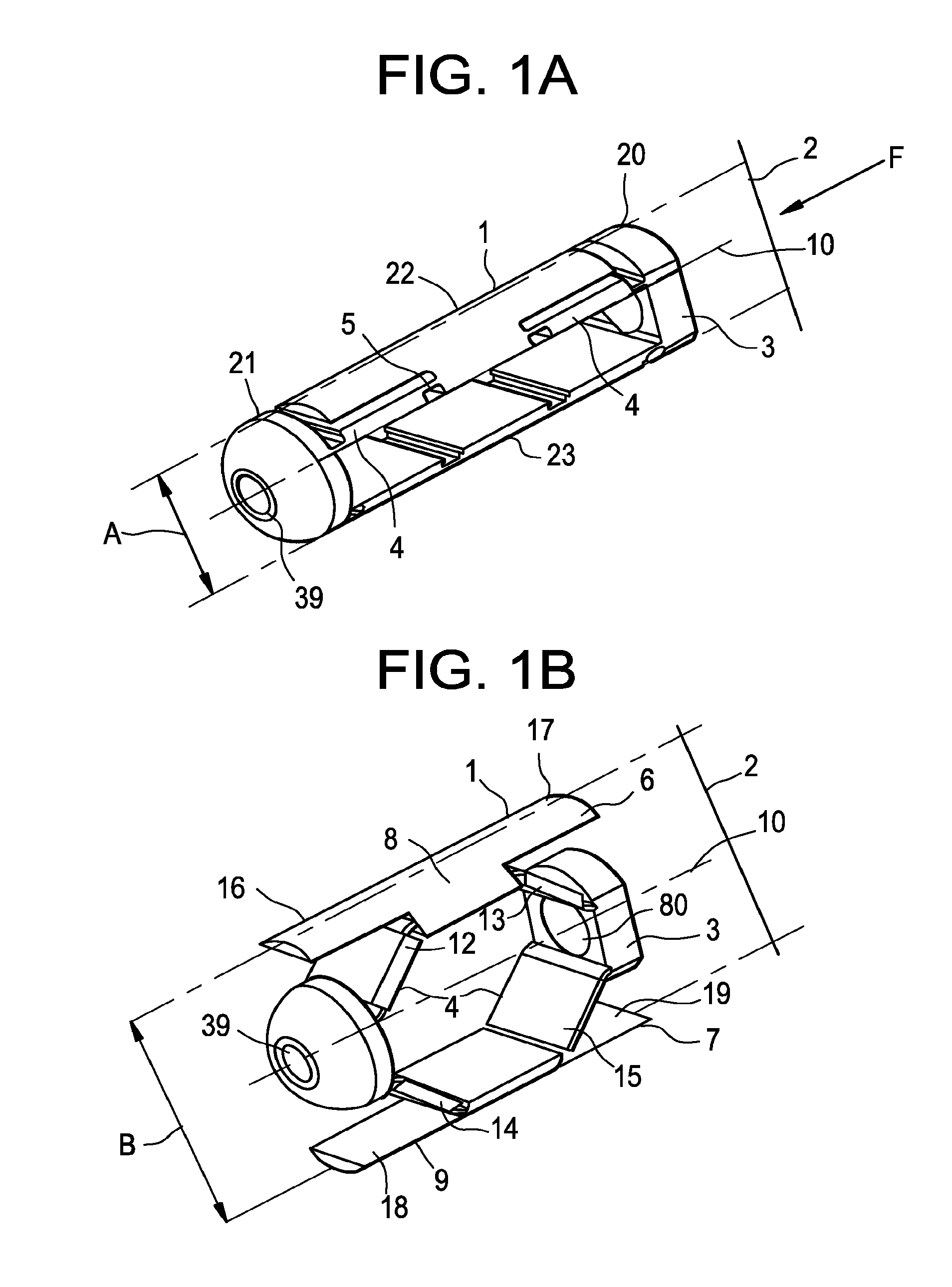
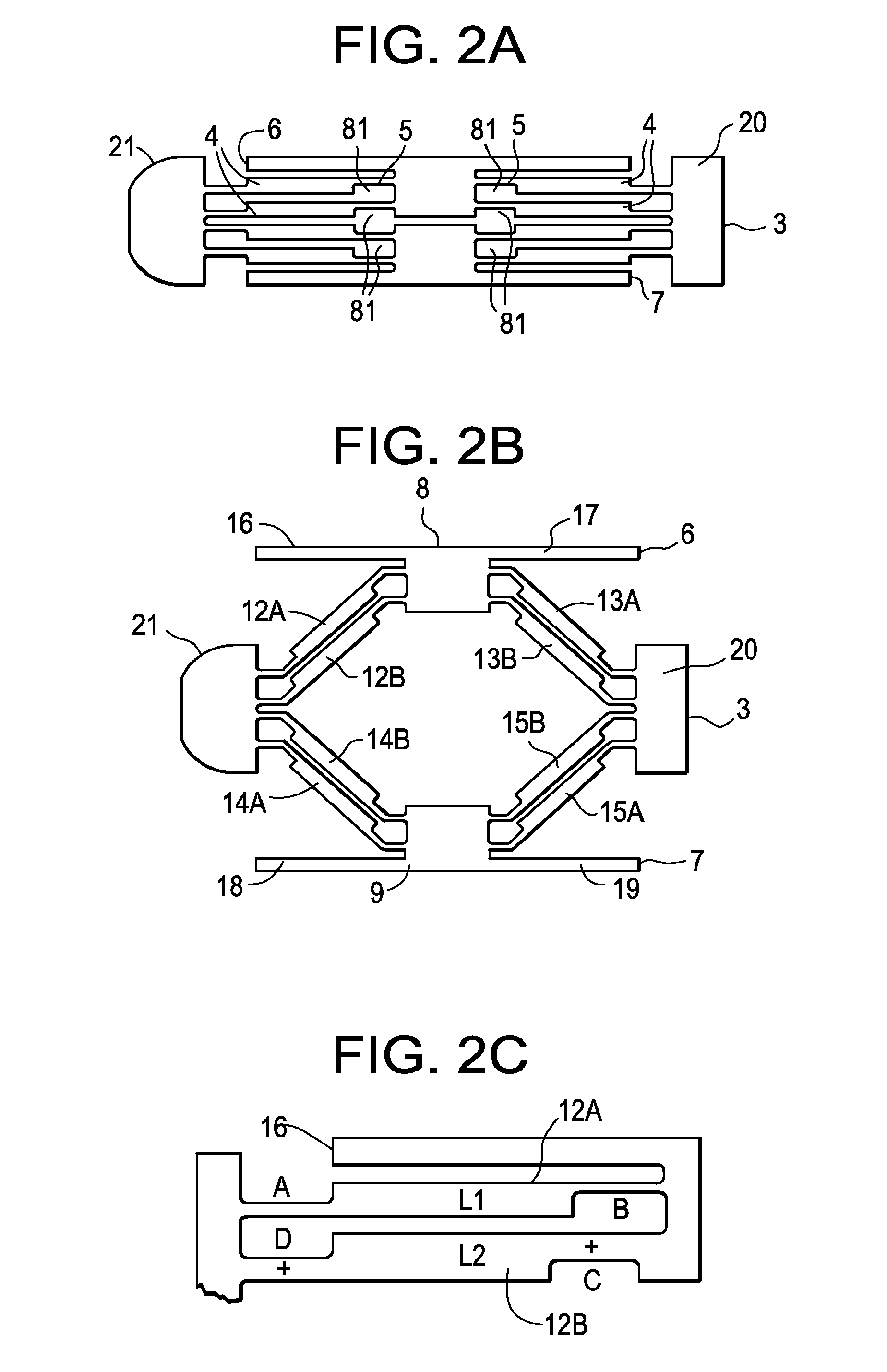
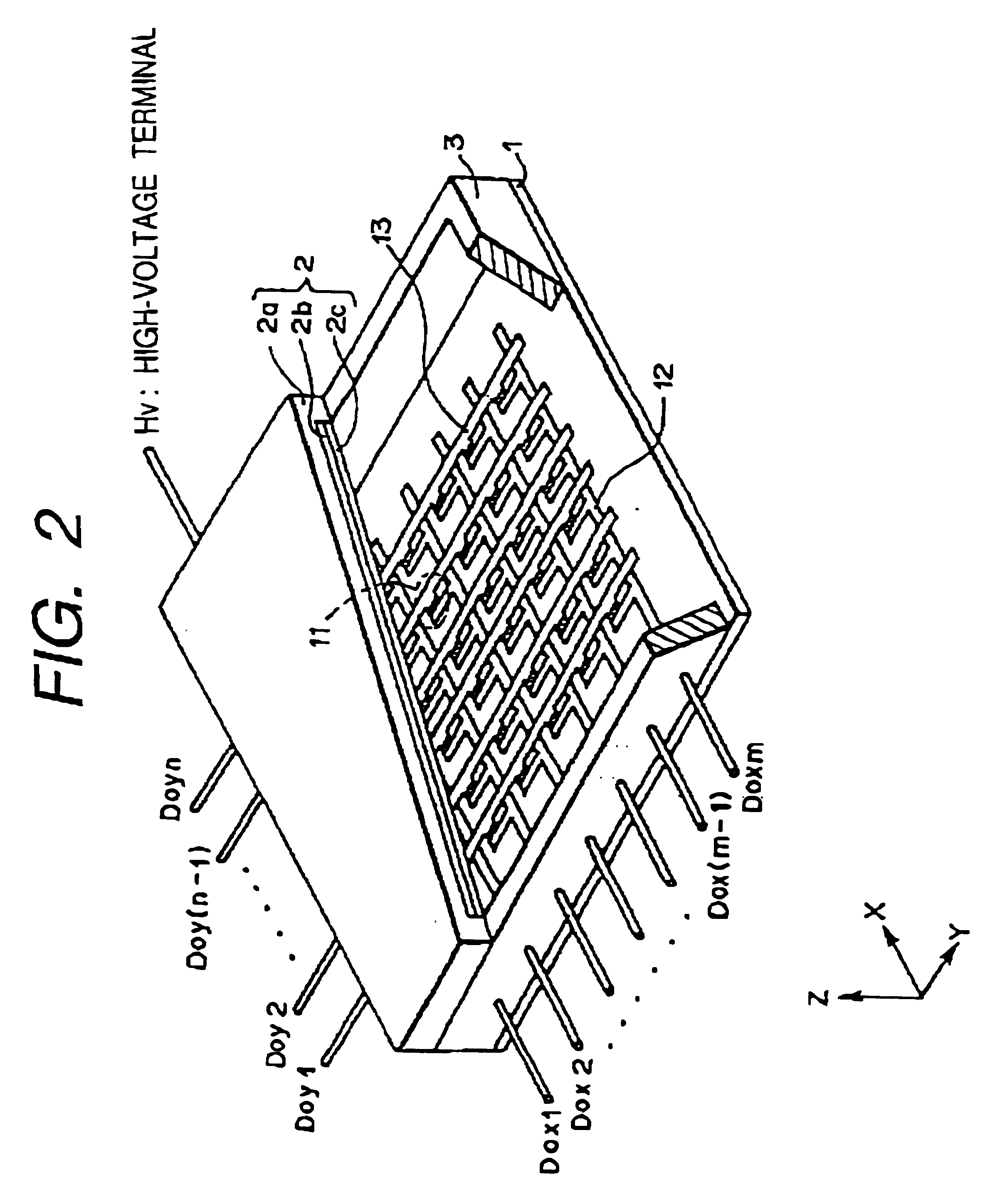
Methods and apparatuses for bone restoration
ActiveUS20060004455A1Reduce stressReduce injection pressureInternal osteosythesisBone implantRestoration methodBiomedical engineering
Methods and apparatuses for restoration of human or animal bone anatomy, which may include introduction, into a bone of an expansible implant capable of expansion in a single determined plane, positioning the expansible implant in the bone in order to correspond the single determined plane with a bone restoration plane and opening out the expansible implant in the bone restoration plane. A first support surface and a second support surface spread tissues within bone. The embodiments of the invention may also include injecting a filling material around the implant.
Owner:STRYKER EUROPEAN OPERATIONS LIMITED
Methods and apparatuses for bone restoration
ActiveUS7846206B2Reduce stressReduce injection pressureInternal osteosythesisBone implantAnatomical structuresRestoration method
Methods and apparatuses for restoration of human or animal bone anatomy, which may include introduction, into a bone of an expansible implant capable of expansion in a single determined plane, positioning the expansible implant in the bone in order to correspond the single determined plane with a bone restoration plane and opening out the expansible implant in the bone restoration plane. A first support surface and a second support surface spread tissues within bone. The embodiments of the invention may also include injecting a filling material around the implant.
Owner:STRYKER EUROPEAN OPERATIONS LIMITED
Disk failure restoration method and disk array apparatus
InactiveUS20080178040A1Reduce processing timeRedundant hardware error correctionRestoration methodDisk array
If a disk fails, another disk is used to rebuild the data of the failed disk on a first spare disk. When finishing being rebuilt, the first spare disk is separated from the disk array apparatus. Data to be updated while the first spare disk separated is written in another disk and managed by a bit map. The first spare disk is connected to the disk array apparatus at the position of the failed disk, then only the updated data is rebuilt on the first spare disk using another disk.
Owner:FUJITSU LTD
Method, system, and program for recovery from a failure in an asynchronous data copying system
InactiveUS20050071708A1Application downtime is minimizedMemory loss protectionUnauthorized memory use protectionRecovery methodDevice form
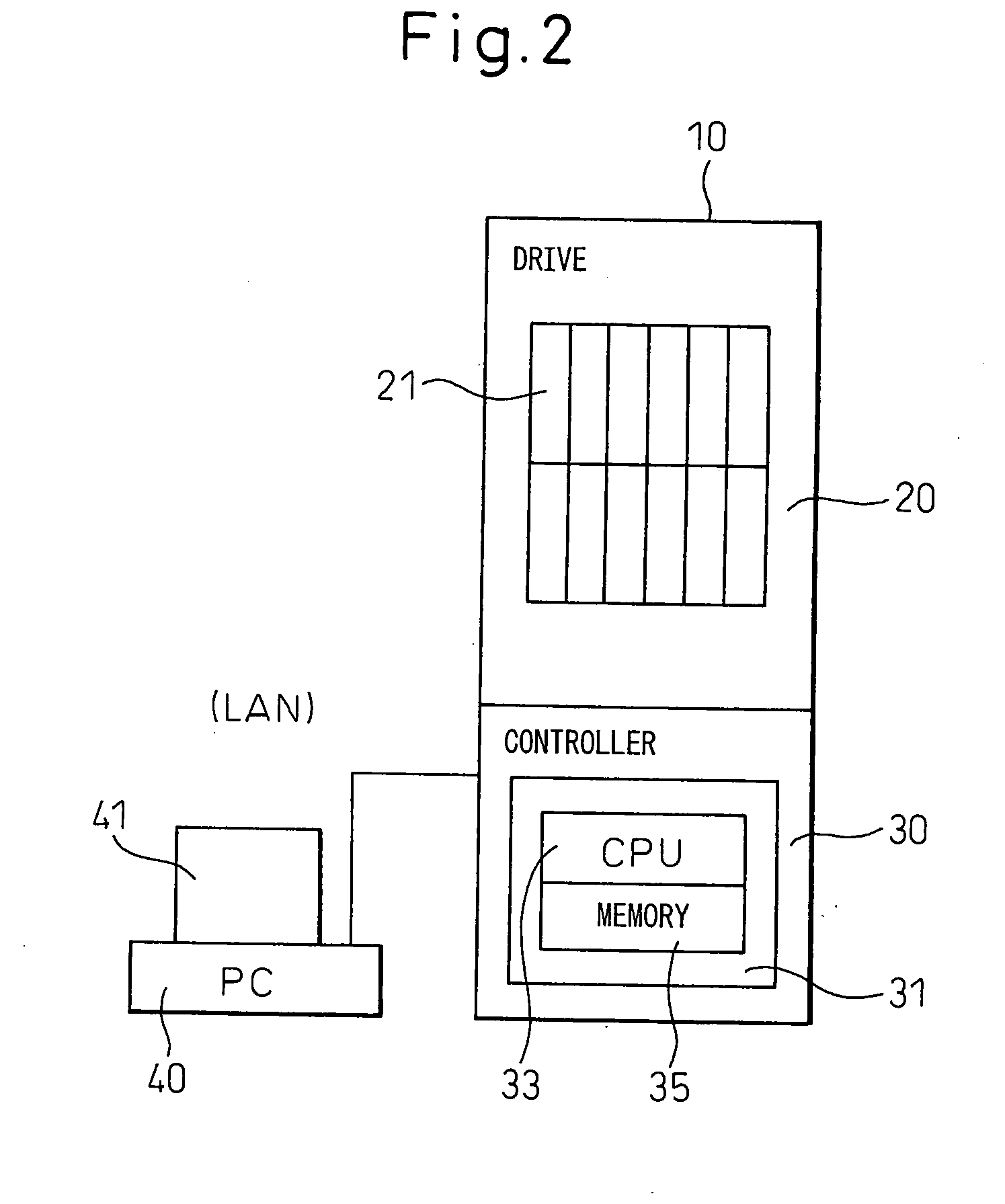
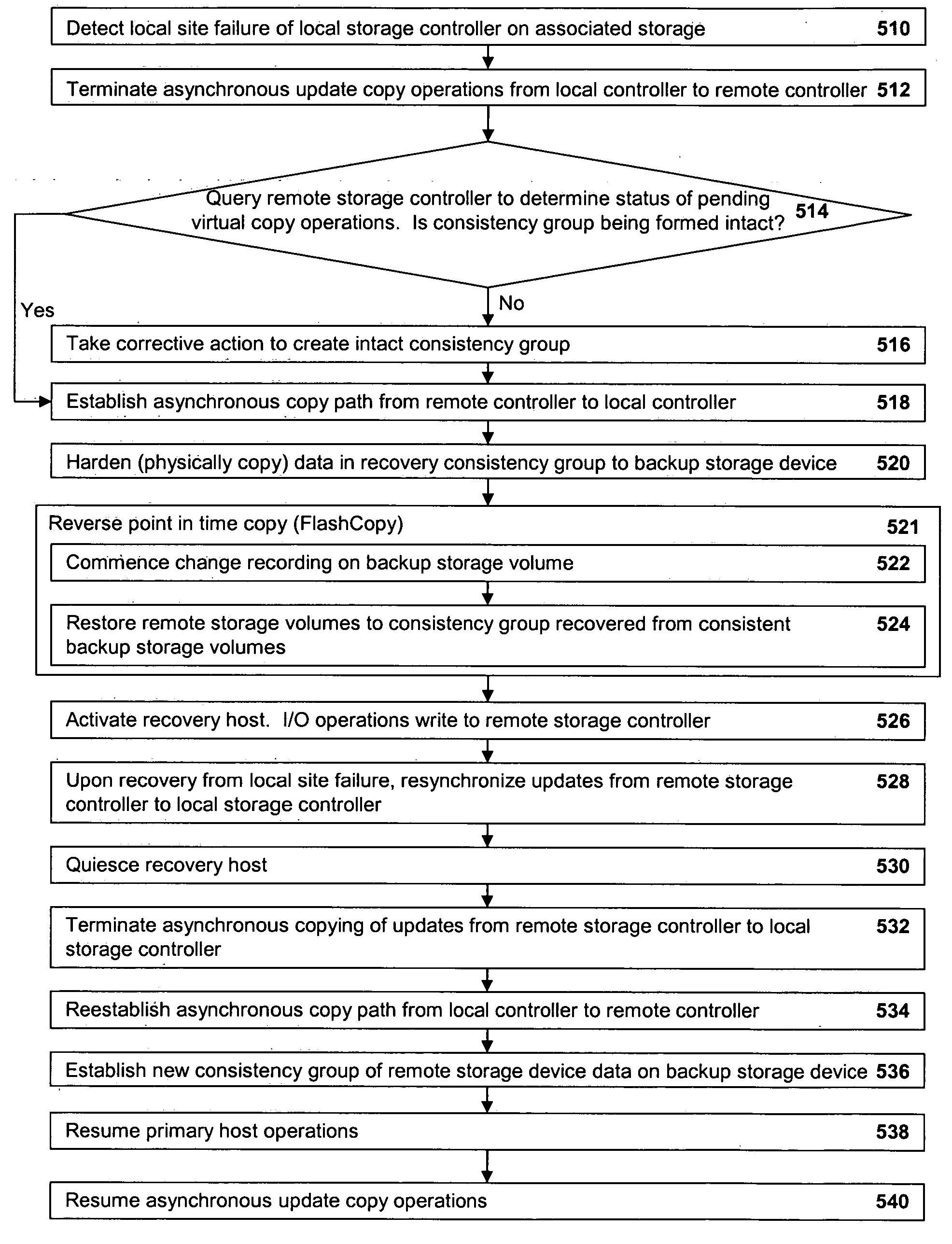
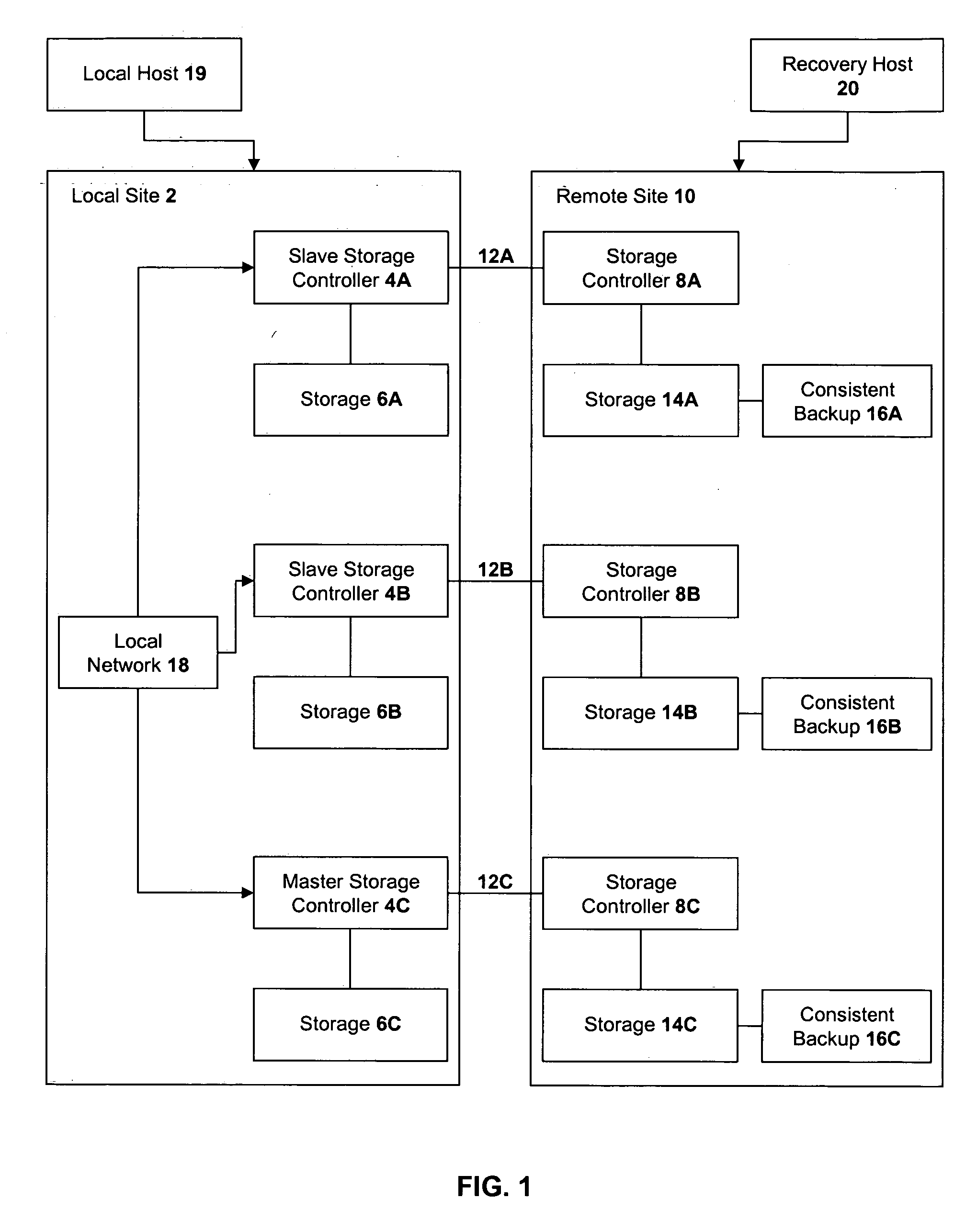
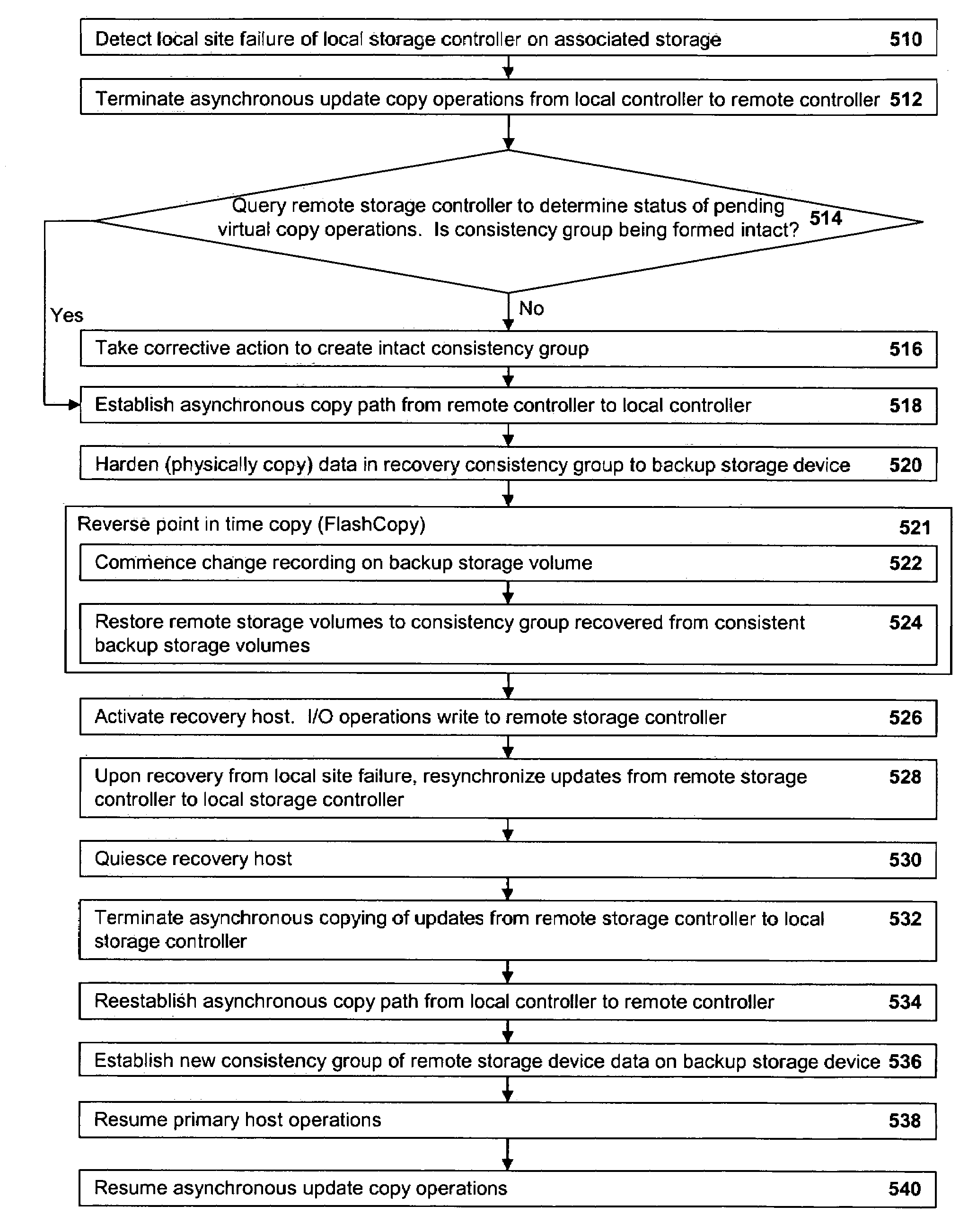
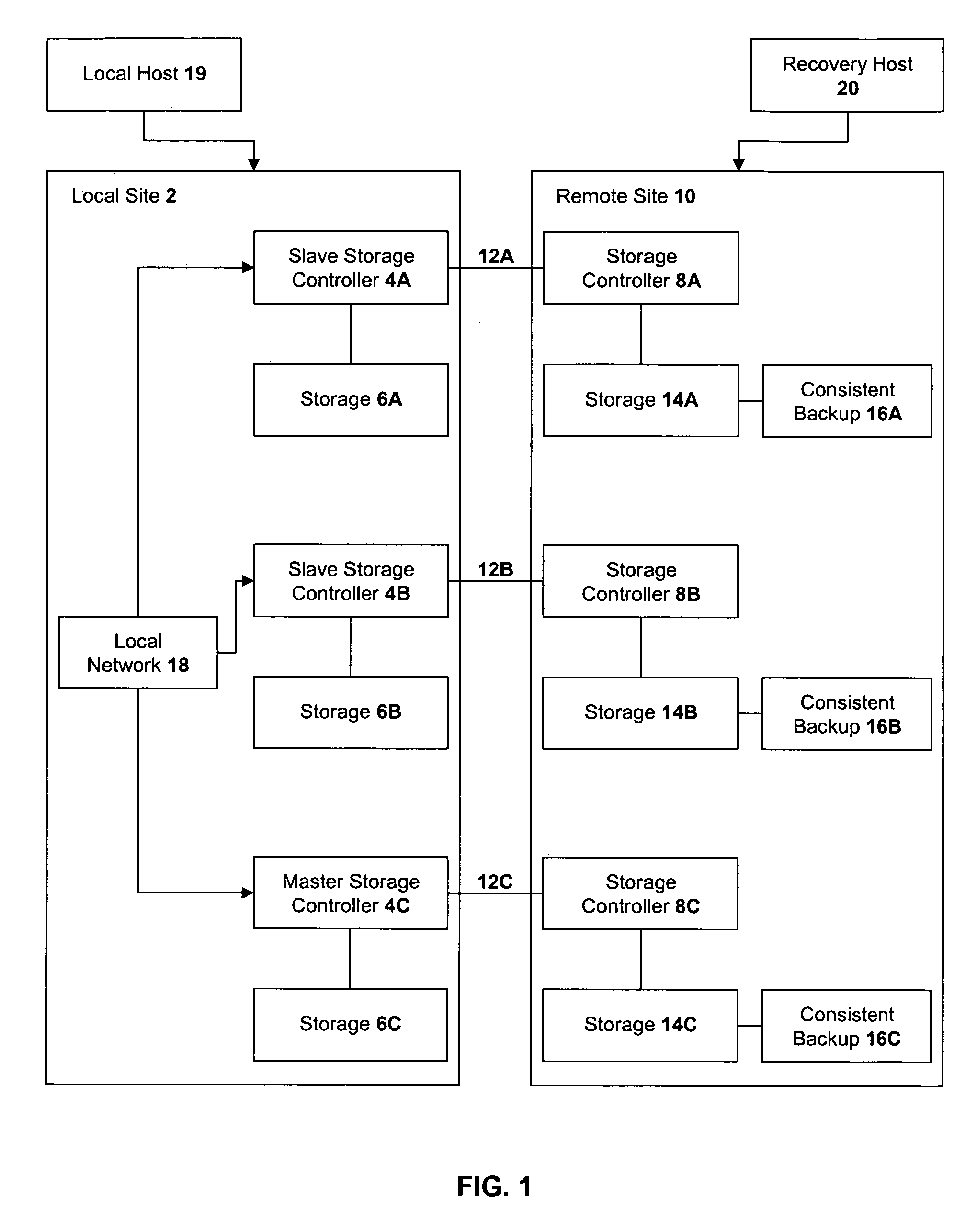
A method of recovery from a data storage system failure in a data storage system having a host computer writing data updates to a local storage controller at a local site. The local controller is associated with a local storage device. The local storage controller is also configured to asynchronously copy the updates to a remote storage controller associated with a remote storage device at a remote site. In addition, the remote storage controller is configured to store a consistent point in time copy of the updates on a backup storage device. The consistent point in time copy is known as a consistency group. Upon detection of a failure associated with the local site, a determination is made whether a group of updates pending for storage on the backup storage device form an intact consistency group. If an intact consistency group has not formed, corrective action may be taken to create an intact consistency group. The recovery method further consists of synchronizing the remote storage device, initiating recovery operations and, upon recovery of the local site, resynchronization of the local storage device and the backup storage device to recovery consistency group without the need for full volume storage copies and while minimizing application downtime.
Owner:IBM CORP
Block chain key trusteeship and recovery method and device based on secrecy sharing technology
InactiveCN107623569ASafekeepingSafe recoveryKey distribution for secure communicationRecovery methodRestoration method
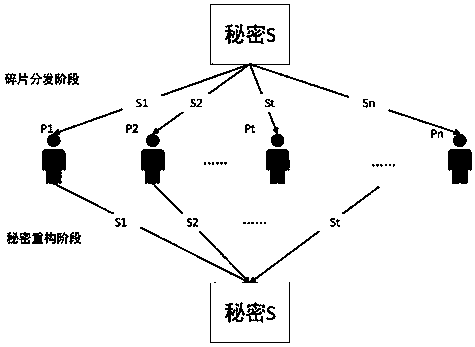
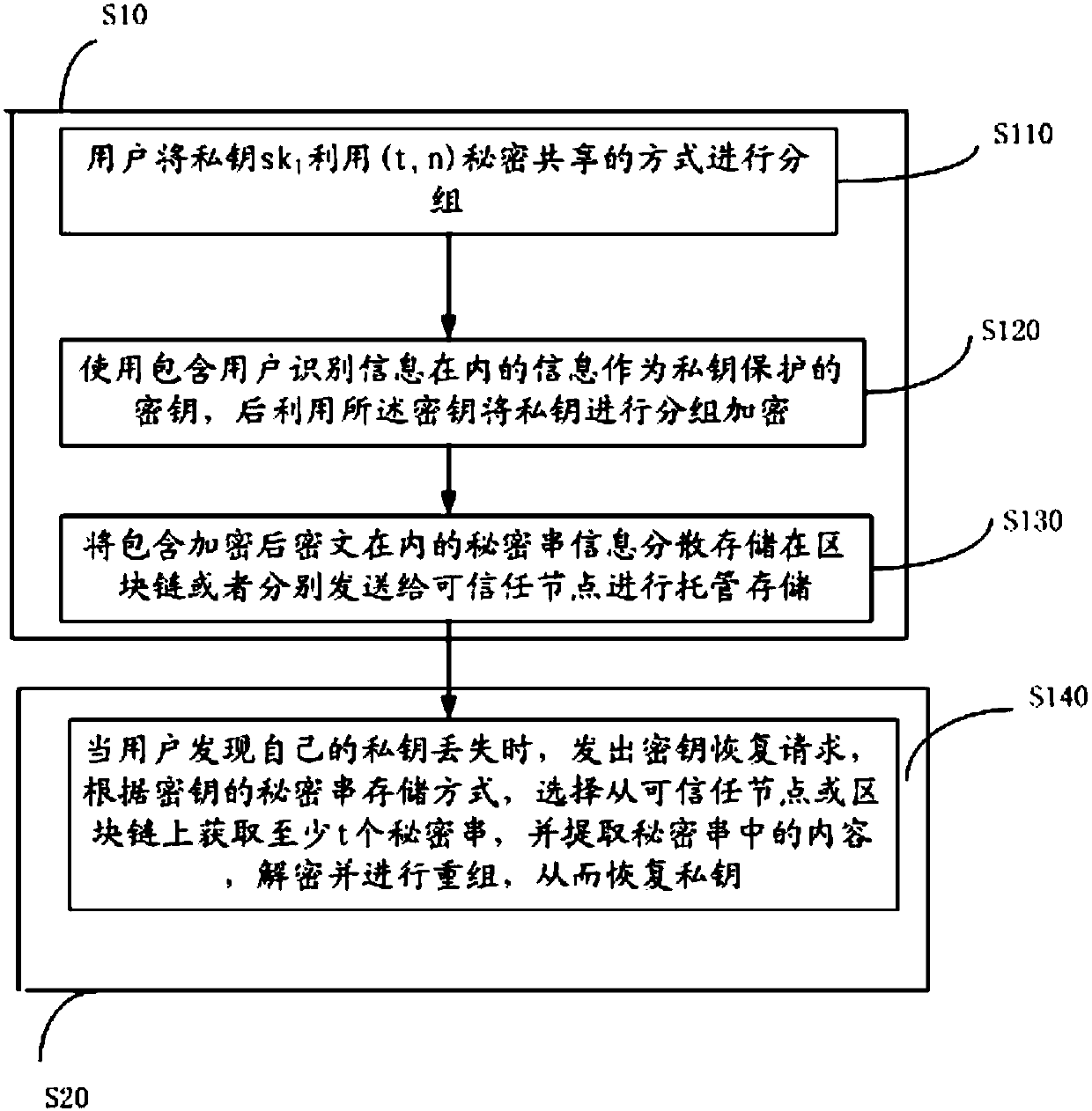
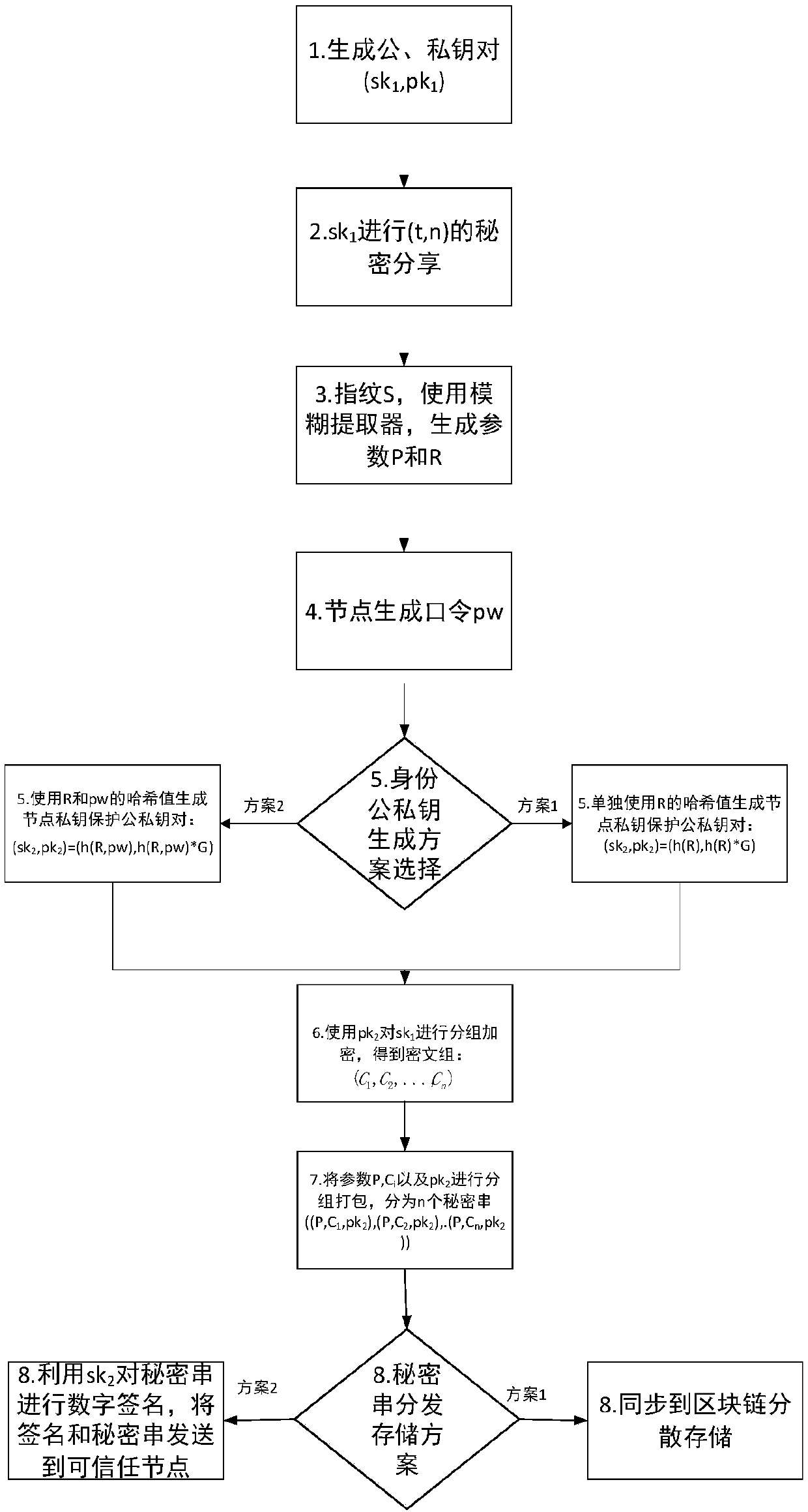
The invention discloses a block chain key trusteeship and recovery method and device based on a secrecy sharing technology. The method comprises the steps that A1, a user groups a private key sk1 in a(t, n) secrecy sharing mode, wherein the n is the number of fragments of shared secrecies obtained by splitting the private key, the t is the minimum number of the fragments for recovery of the private key, and the t is greater than or equal to 2 and is smaller than or equal to the n; A2, information containing user identification information is taken as a private key protection key, and then grouping encryption is carried out on the private key through utilization of the key; and A3, secrecy string information containing encrypted ciphertexts is dispersely stored to a block chain or is sentto trusted nodes for trusteeship and storage, when the user discovers that own private key is lost, a key recovery request is generated, at least t secrecy strings are obtained from the trusted nodesor the block chain in a secrecy string storage mode of the key, and the content in the secrecy strings is extracted, decrypted and recombined, so the private key is recovered. According to the methodand the device, the secrecy sharing technology is applied to a block chain scene for the first time, thereby solving the private key trusteeship and recovery security problem.
Owner:JUZIX TECH SHENZHEN CO LTD
Information Processing Device, Recovery Device, Program and Recovery Method
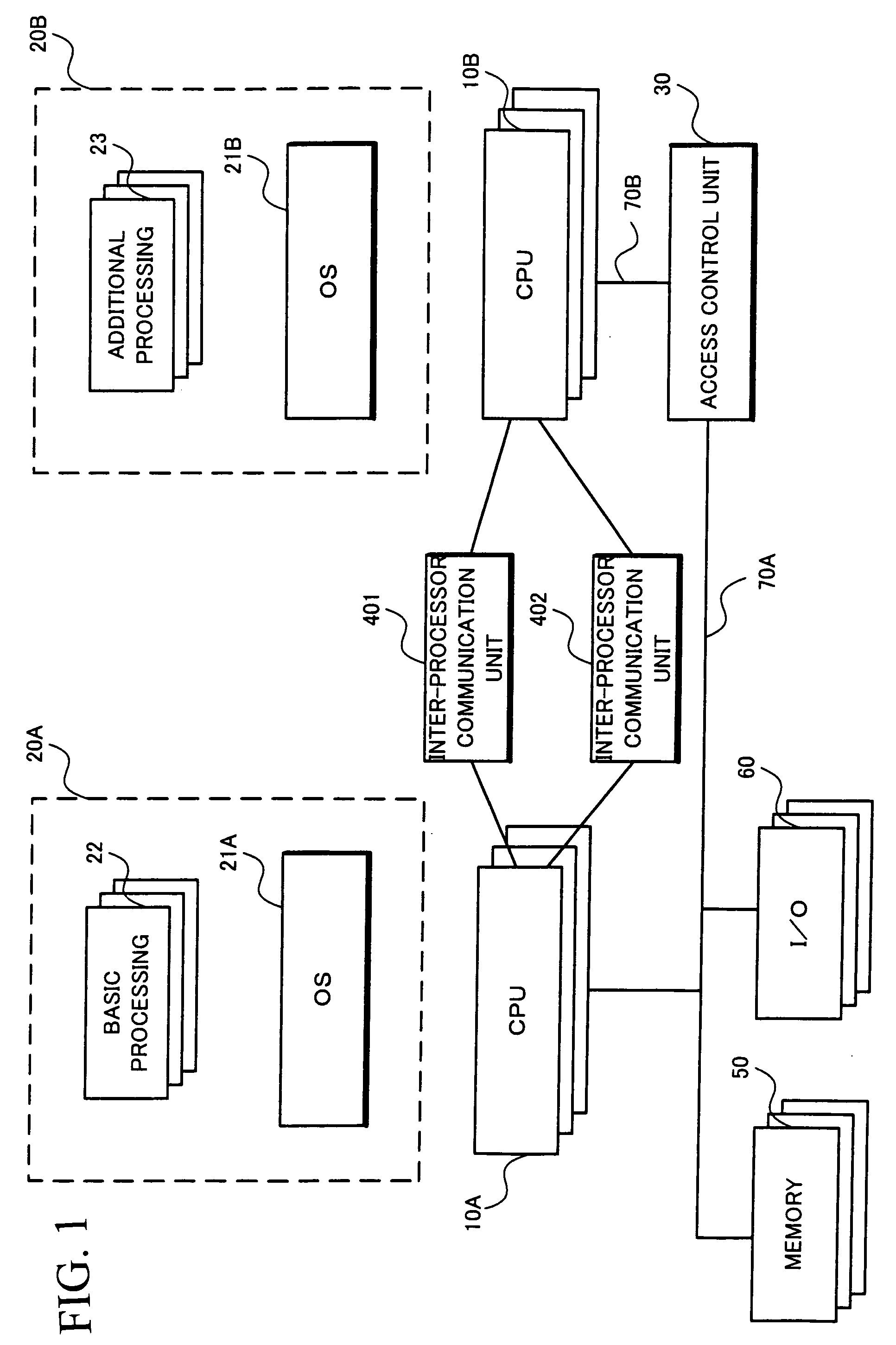
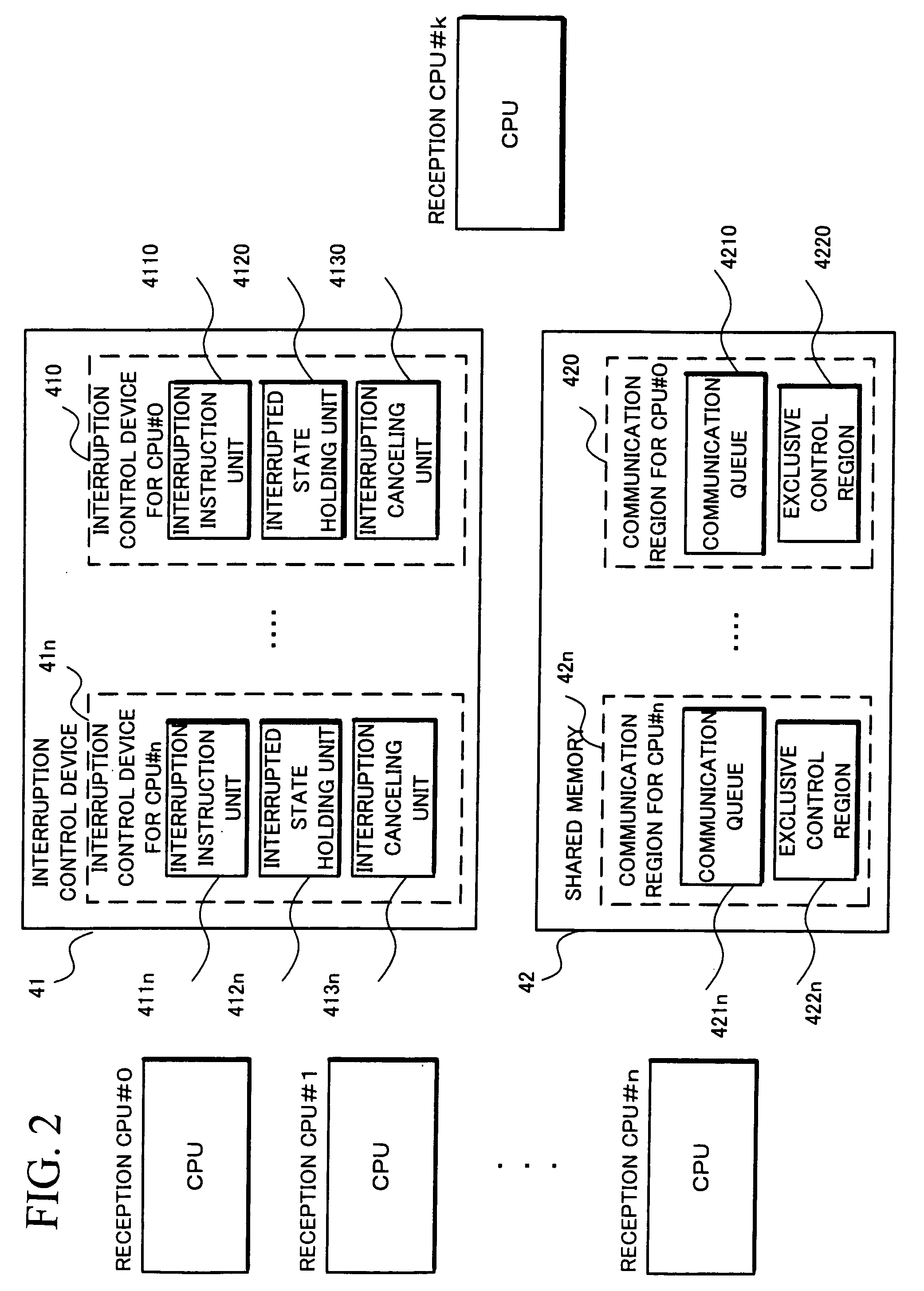
ActiveUS20090119541A1Fault responseDigital data processing detailsRecovery methodInformation processing
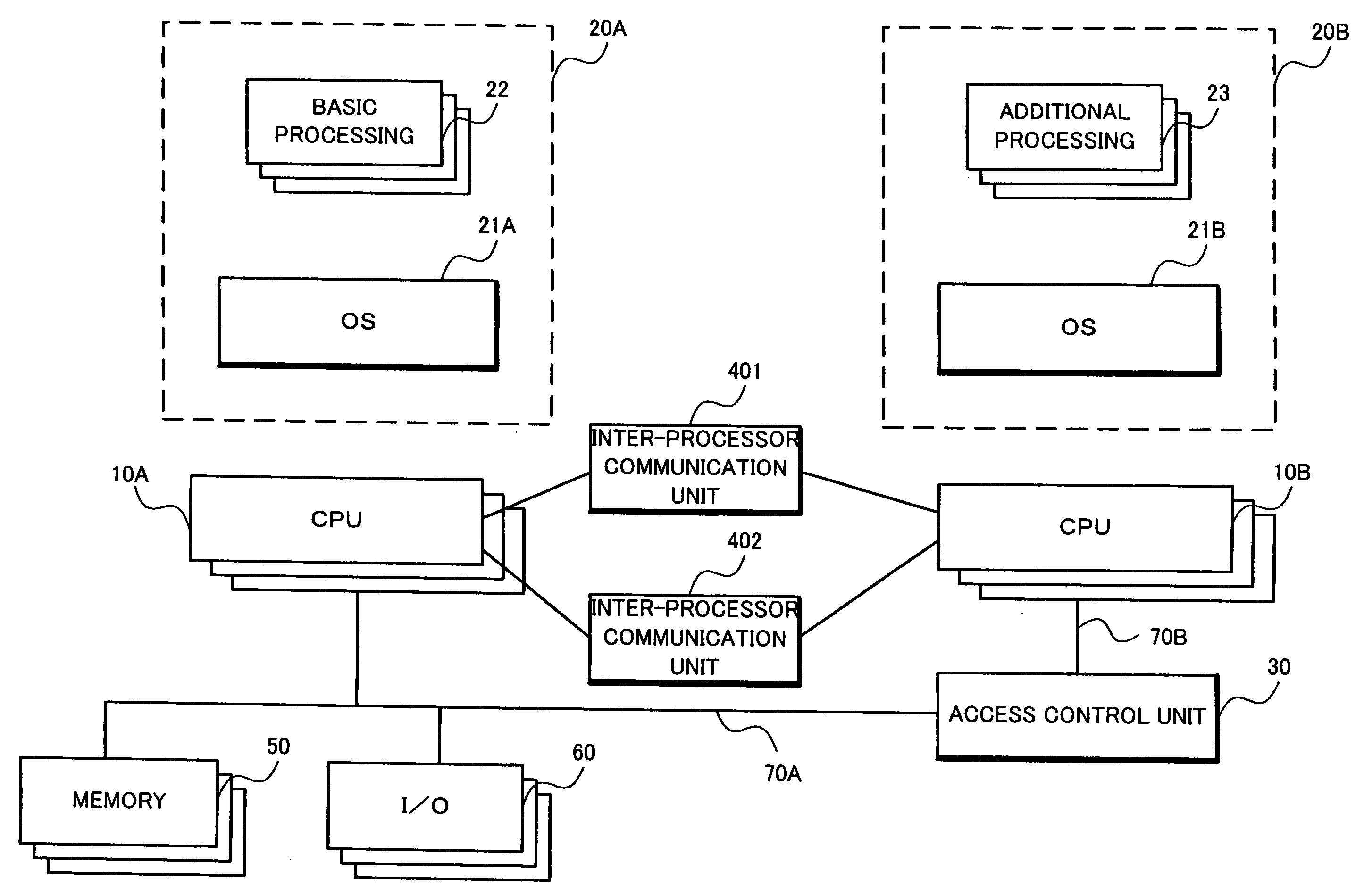
The information processing device which recovers a domain developing a fault caused by added application and device driver while maintaining security and reliability includes a plurality of processors, wherein the plurality of processors form a plurality of domains according to processing contents to be executed, and the processors in different domains communicate with each other through a communication unit, and which further includes a recovery unit for executing, for a domain developing a fault, failure recovery processing based on a failure recovery request notified by the domain and a recovery condition set in advance for each domain.
Owner:NEC CORP
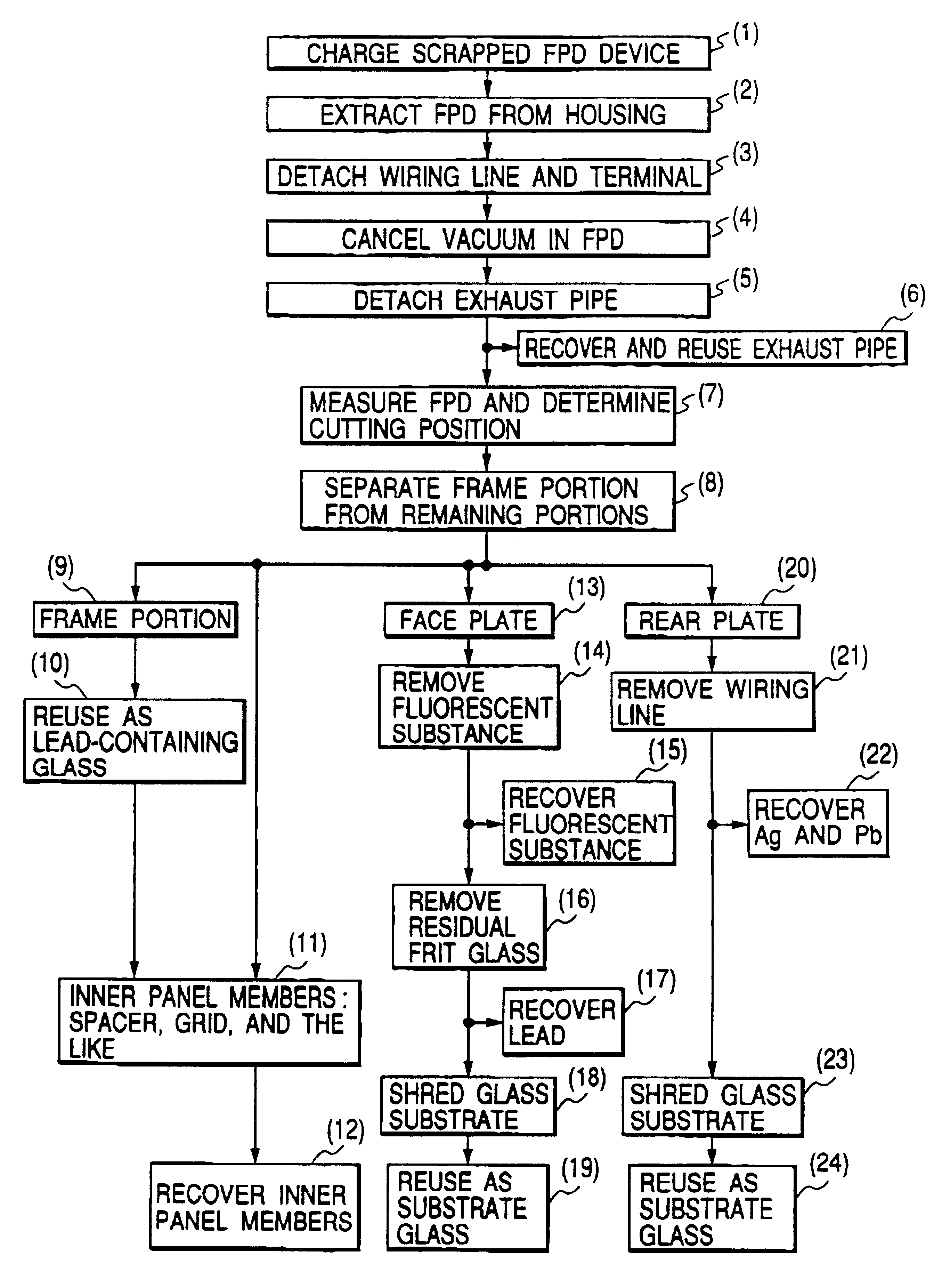
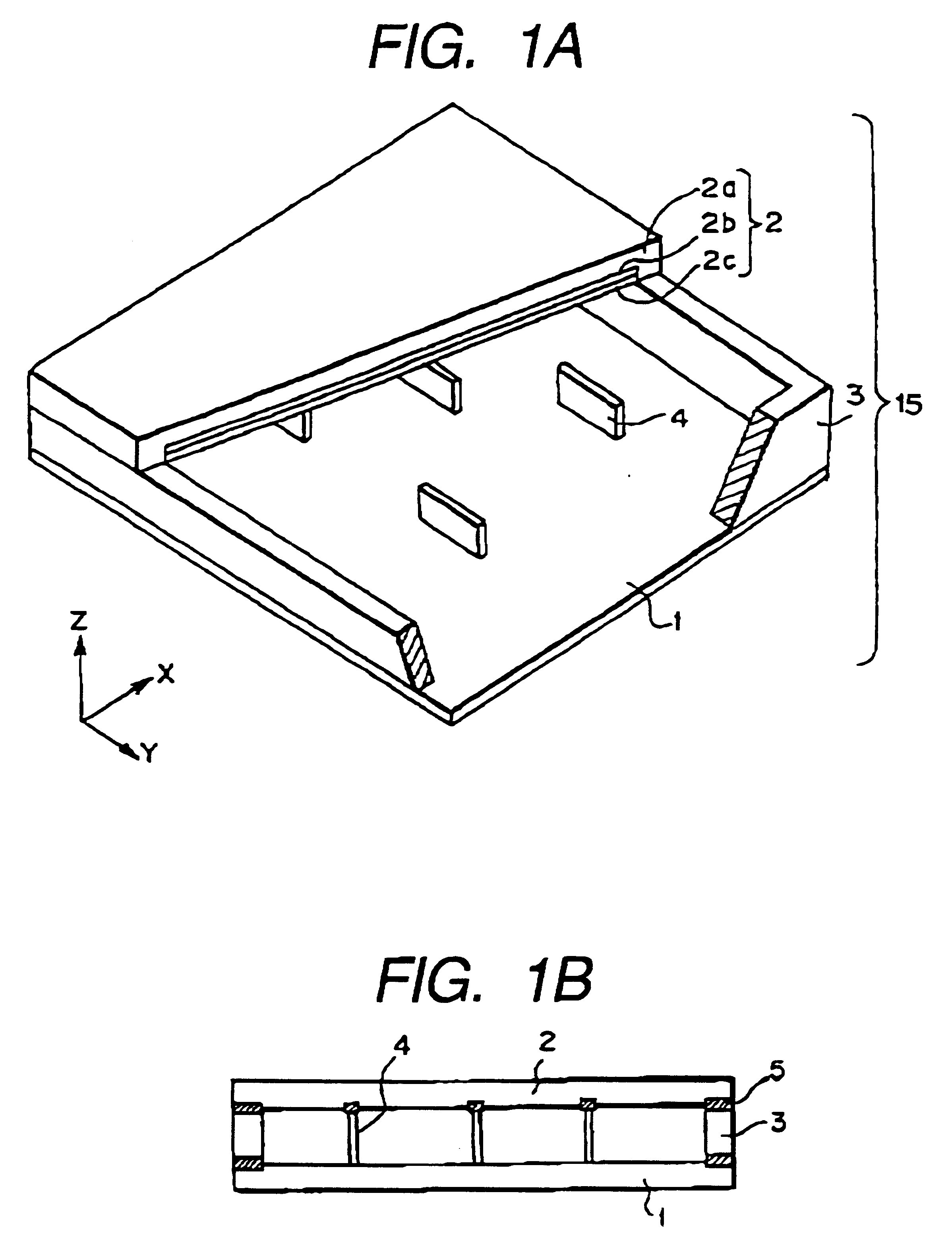
Image display apparatus, disassembly processing method therefor, and component recovery method
InactiveUS6632113B1No pressureAvoid secondary damageElectric discharge tubesGlass recyclingRecovery methodFrit
To reuse glass used in a flat panel display, processing suitable for global environment such as processing of separating a lead component must be realized. A disassembly processing method for a flat panel display having a structure in which a face plate and rear plate mainly containing glass are airtightly joined via a frame with frit glass is characterized by including the step of separating the face plate and rear plate joined with the frit glass. The separation step is characterized by separating the face plate and rear plate by cutting, dissolution, or melting.< / PTEXT>
Owner:CANON KK
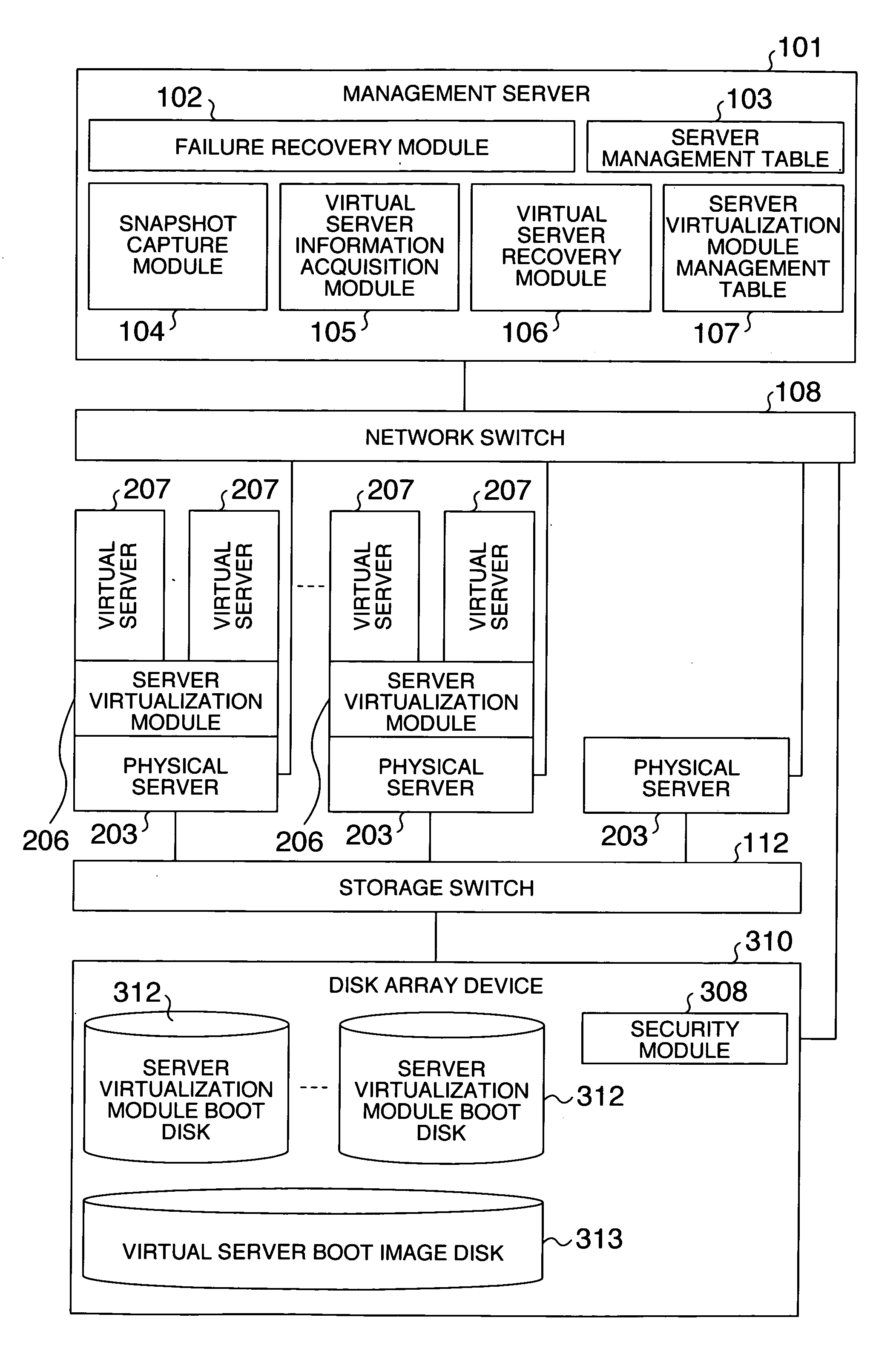
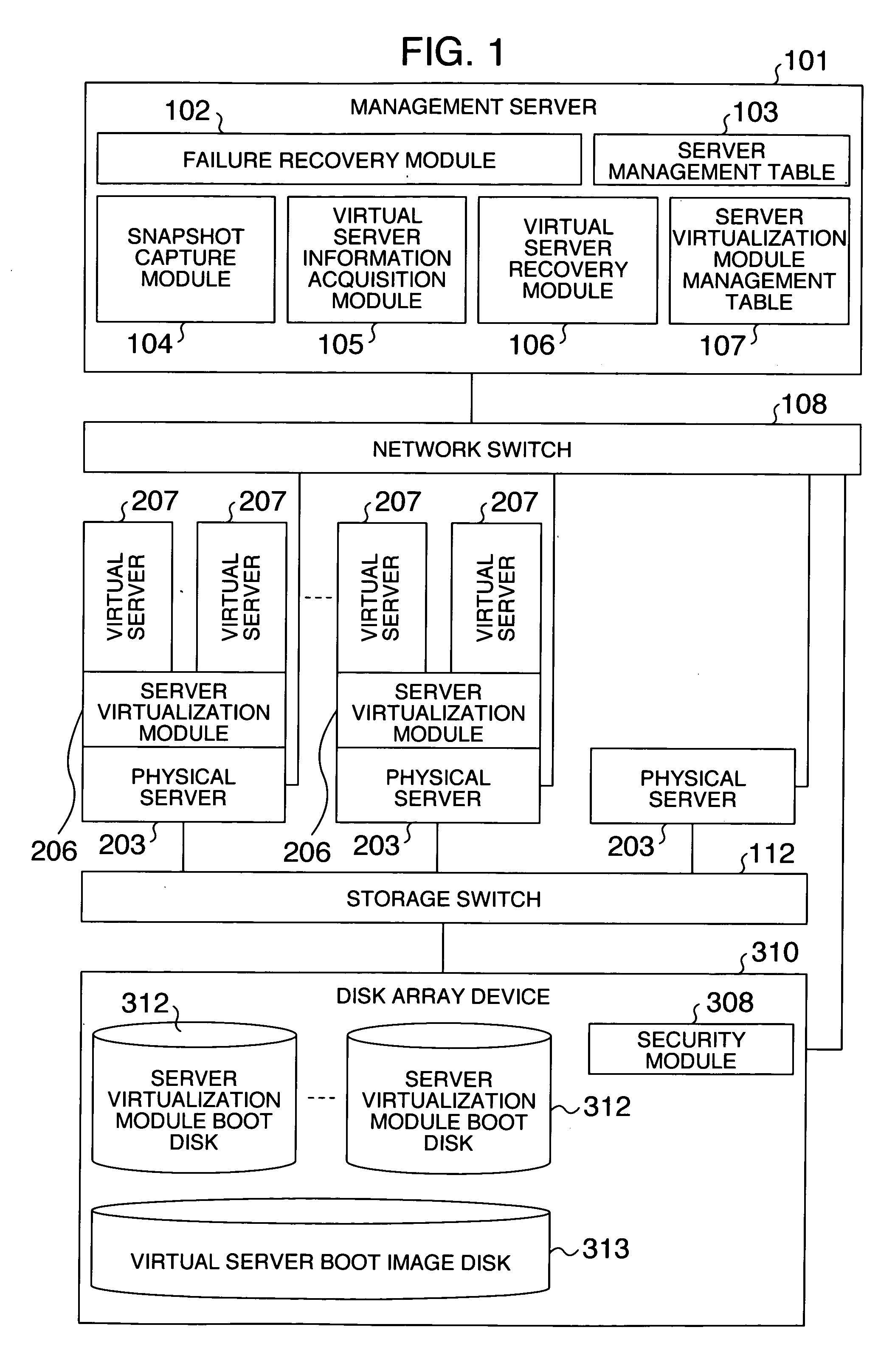
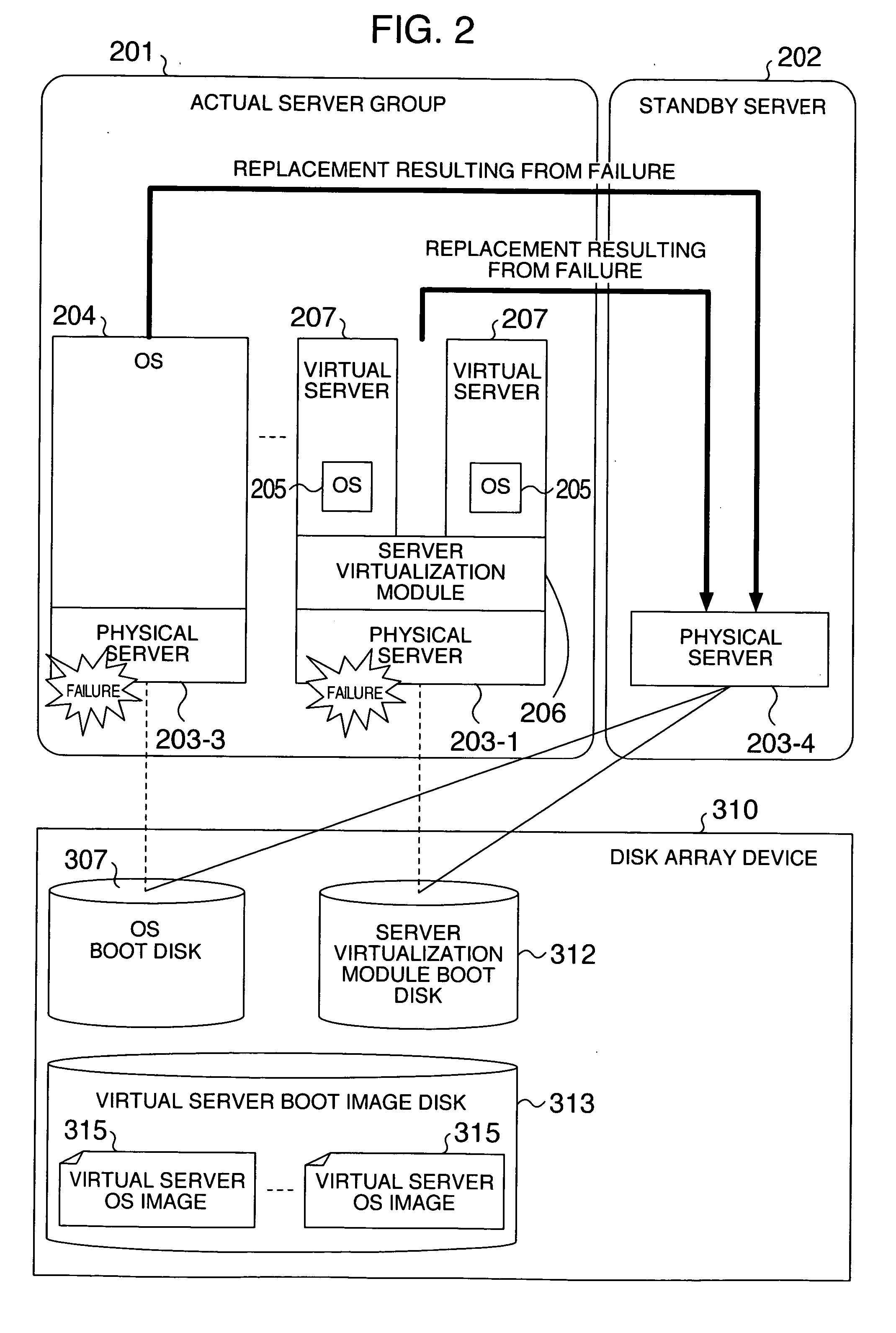
Failure recovery method
InactiveUS20070174658A1Reduce in quantityImprove reliabilityTransmissionRedundant hardware error correctionVirtualizationRecovery method
The reliability is improved at a low cost even in a virtualized server environment. The number of spare servers is reduced for improving the reliability and for saving a licensing fee for software on the spare servers. A server system comprises a plurality of physical servers on which a plurality of virtual servers run, a single standby server, a module for detecting an active virtual server, and a module for switching the correspondence of boot disks of virtualization modules for controlling virtual servers to the physical servers. When a physical server fails, the boot disk of the associated virtualization module is connected to a spare server to automatically activate on the spare server those virtual servers which have been active upon occurrence of the failure.
Owner:HITACHI LTD
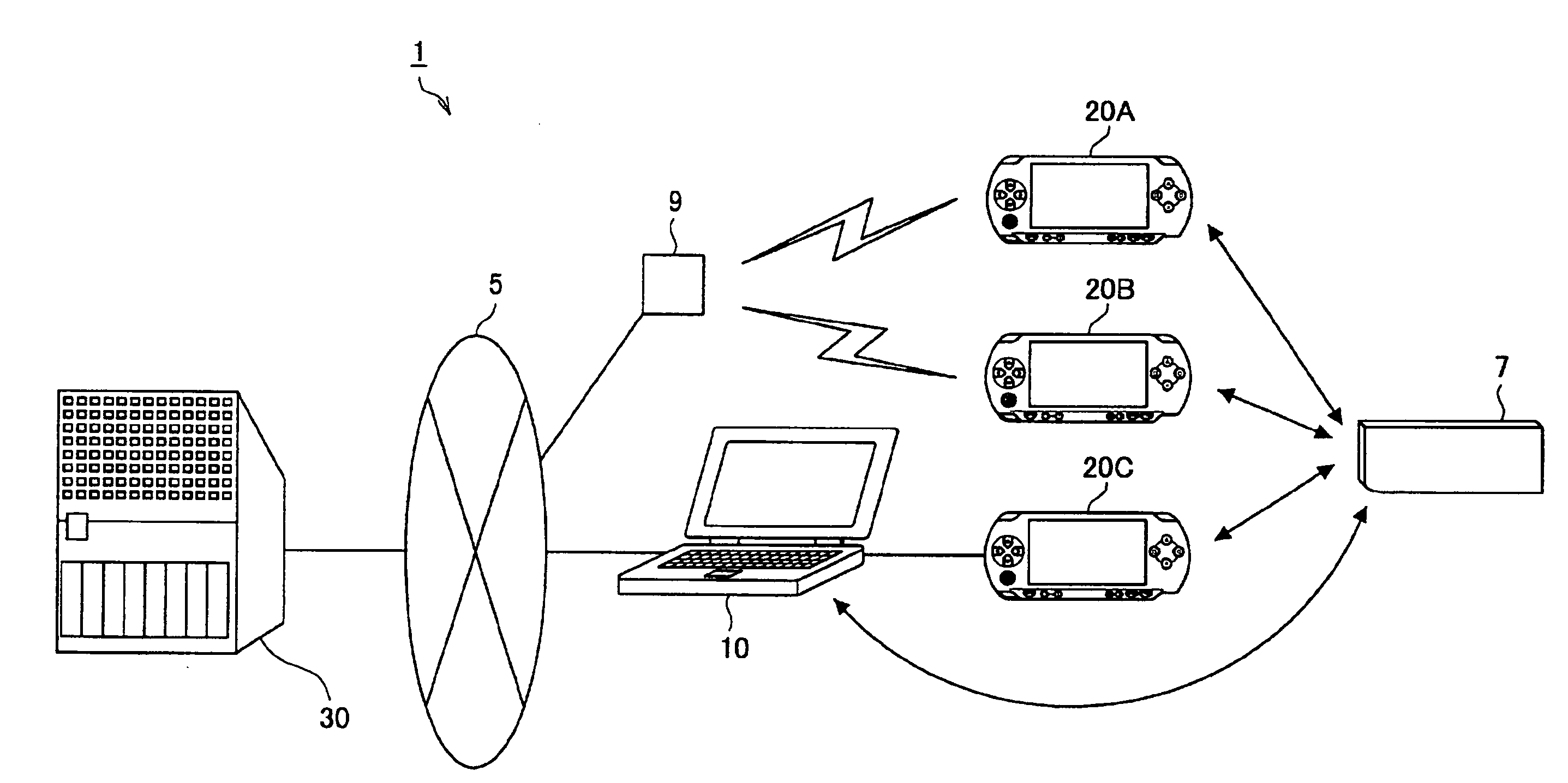
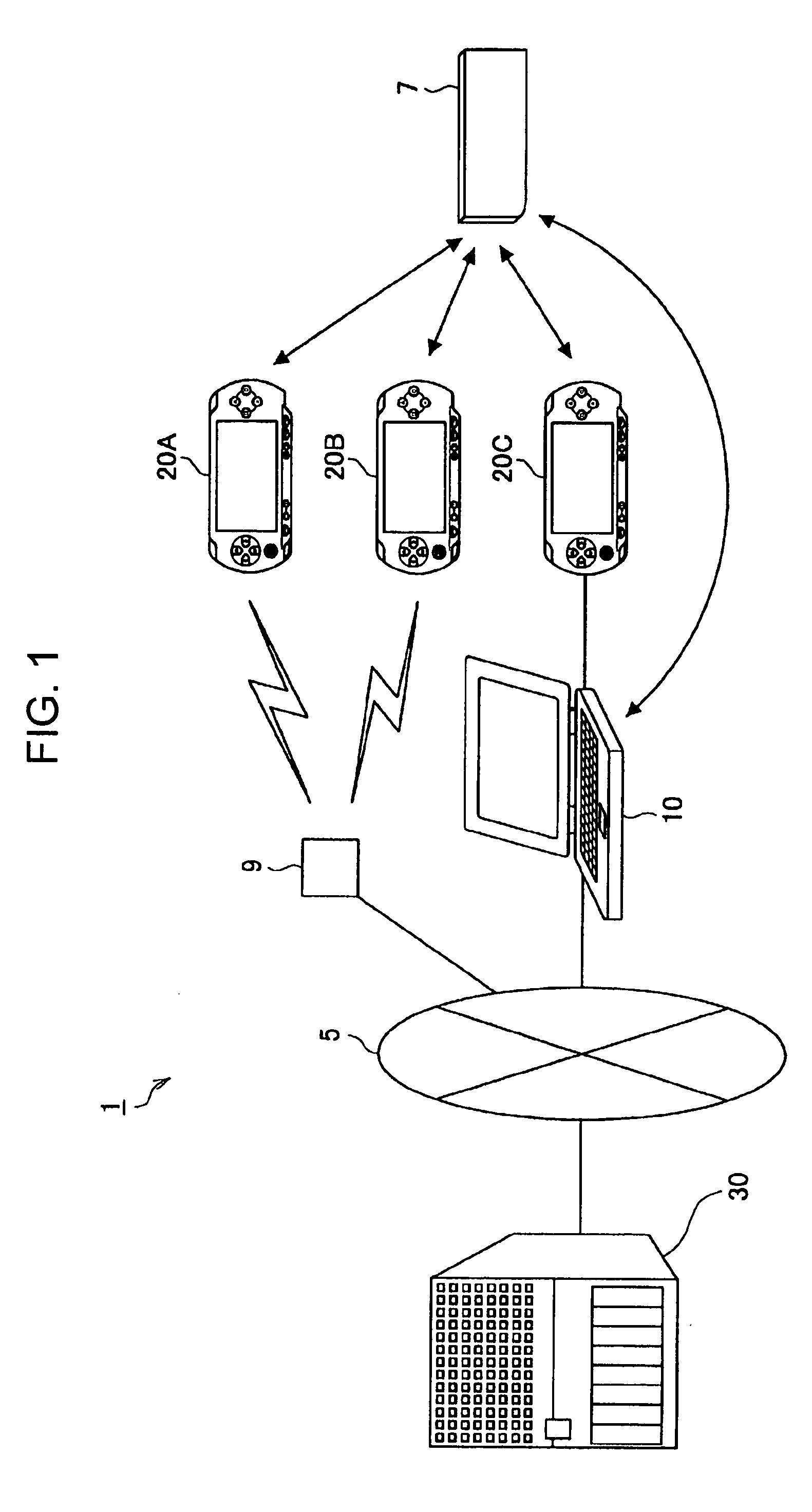
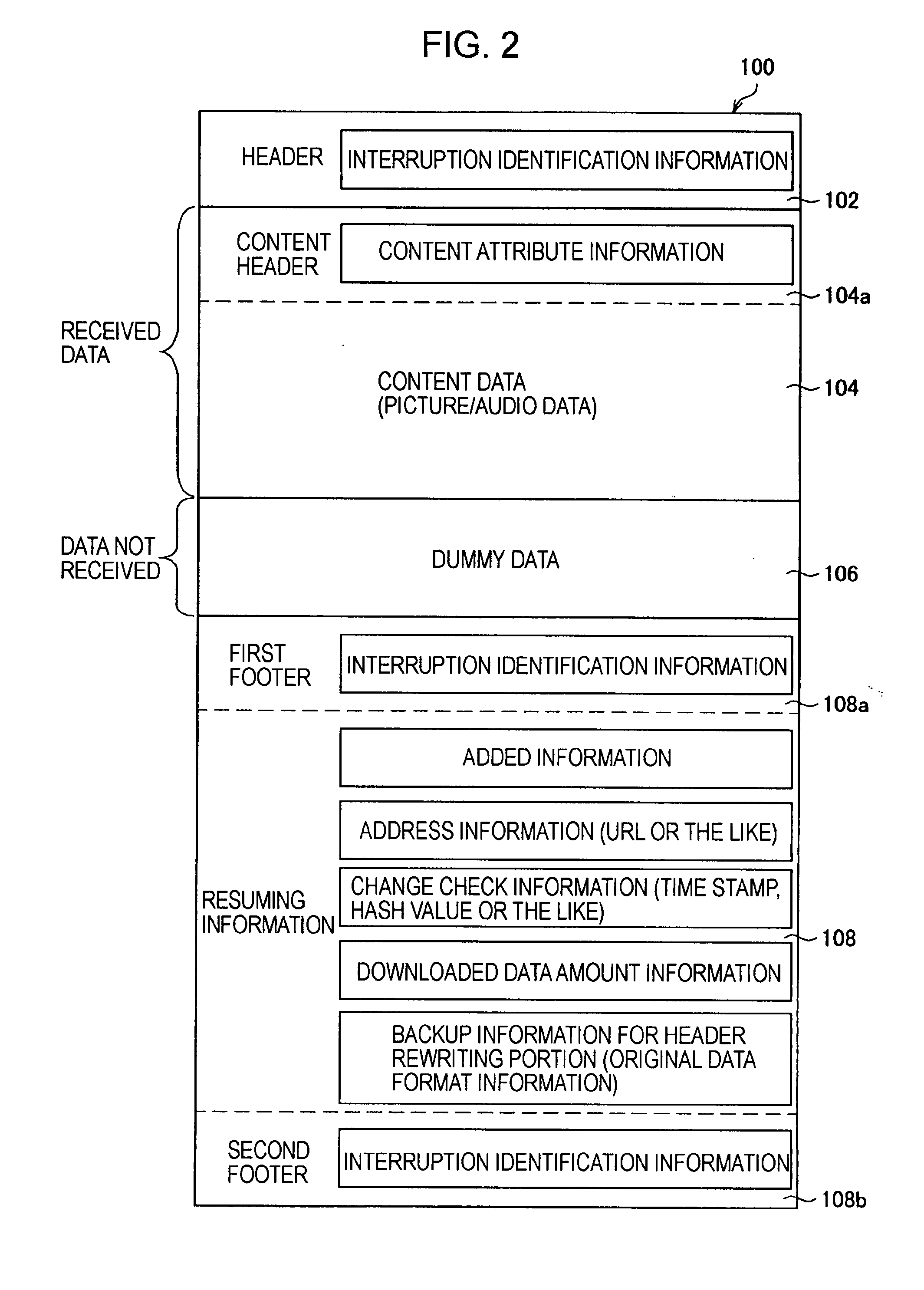
Information processing device, download method, download interruption method, download resuming method, and program
InactiveUS20080162666A1Improve compatibilityData processing applicationsMultiple digital computer combinationsInformation processingContent distribution
An information processing device for downloading content from a content distribution server via a network includes a mounting unit configured such that a storage media is detachably mounted thereto, a downloading unit arranged to receive content to be downloaded from the content distribution server, and to record the received content on the storage media, an interruption processing unit arranged to record resuming information necessary for resuming an interrupted content download on the storage media in the event that the reception for the content from the content distribution server by the downloading unit is interrupted, and a resuming processing unit arranged to read the resuming information from the storage media in the event of resuming the reception of the interrupted content, and to transmit a transmission request for the interrupted content to the content distribution server, based on the read resuming information.
Owner:SONY CORP
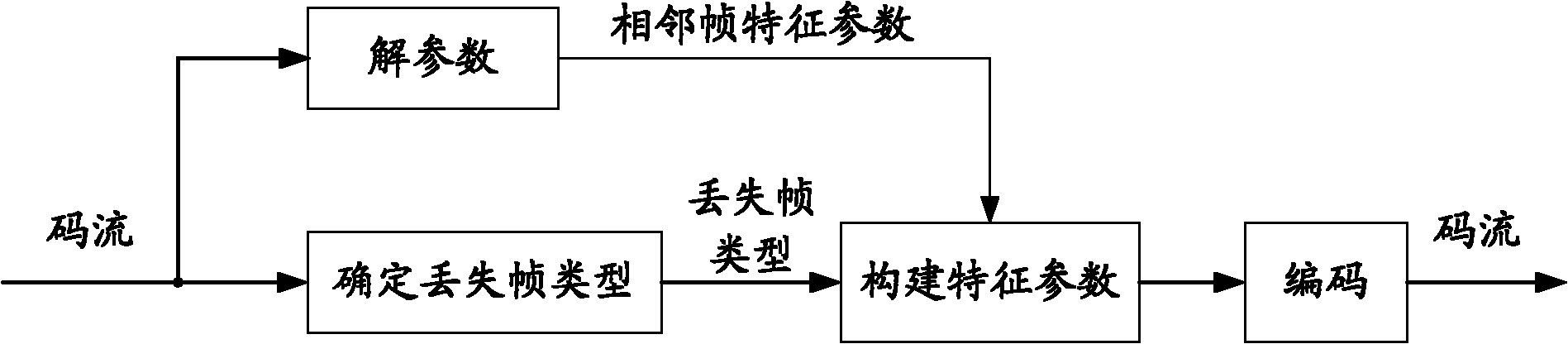
Lost frame recovering method and equipment as well as speech enhancing method, equipment and system
InactiveCN101894558AReduce consumptionSave resourcesSpeech analysisRestoration methodFeature parameter
The embodiment of the invention discloses lost frame recovering method and equipment as well as speech enhancing method, equipment and system, wherein the lost frame recovering method comprises the following steps of: determining the type of a lost frame according to the type of an adjacent frame adjacent to the lost frame; obtaining a characteristic parameter obtained after unlocking the parameter of the adjacent frame, wherein the characteristic parameter is used for determining the characteristic information of coded data in the frame; constructing the characteristic parameter conforming to the type of the lost frame according to the correlation between the characteristic parameter of the adjacent frame and the characteristic information of the coded data in each frame; and recovering the lost frame according to the constructed characteristic parameter of the lost frame. Through the method, the lost frame recovery of a parameter domain can be realized, and system resources consumed in the recovering process are reduced.
Owner:HUAWEI TECH CO LTD
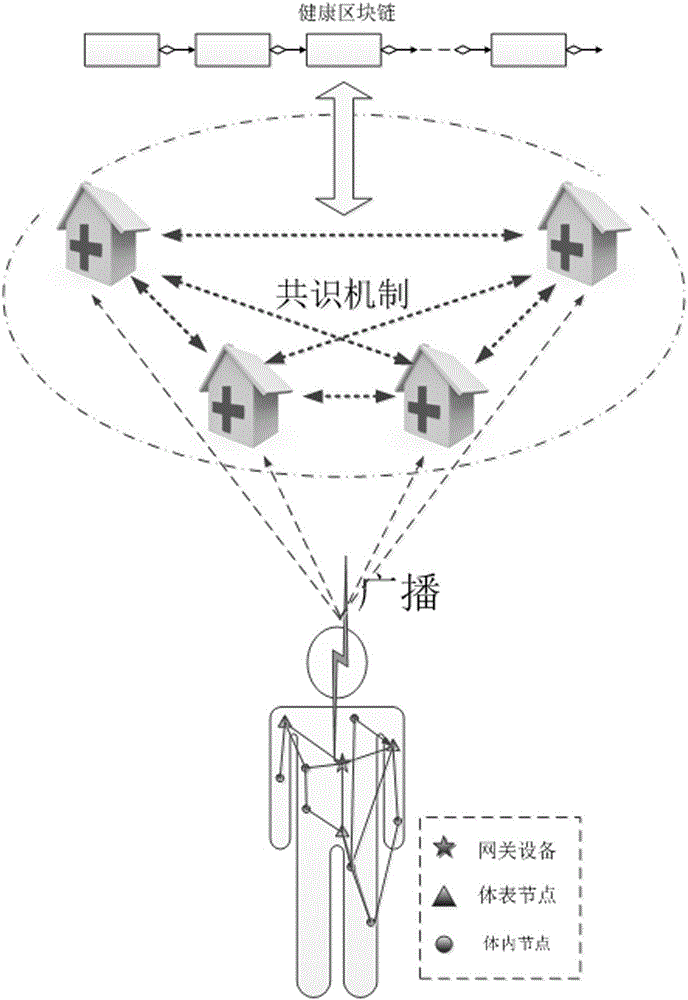
Lightweight back-up and efficient restoration method of health block chain data encryption keys
InactiveCN105812126AReduce management complexityAvoid heavy burdenKey distribution for secure communicationBody area networkRestoration method
The invention provides a lightweight back-up and efficient restoration method of health block chain data encryption keys.Body area networks achieve physiological parameters acquisition of healthy body health, health block chains are produced by a group of credible IT devices appointed by multiple health institutions and used for receiving and storing health data of the body area networks, the health block chain data encryption keys are produced by utilizing a fuzzy technology fuzzy vault and physiological signals acquired by the body area networks, human physiological data acquired in different time periods is encrypted by utilizing different data encryption keys and then is saved in the block chains of the IT devices without storage of historical data encryption keys; historical secret keys are restored by utilizing the health data acquired by the body area networks in real time.The lightweight back-up and efficient restoration method integrates the body area networks with the health block chains, avoids huge burden brought by secret key splitting related in a traditional secret key restoration method and safe storage and retrieval of shadow secret keys and greatly reduces management complexity of the health block chain data encryption keys.
Owner:QILU UNIV OF TECH
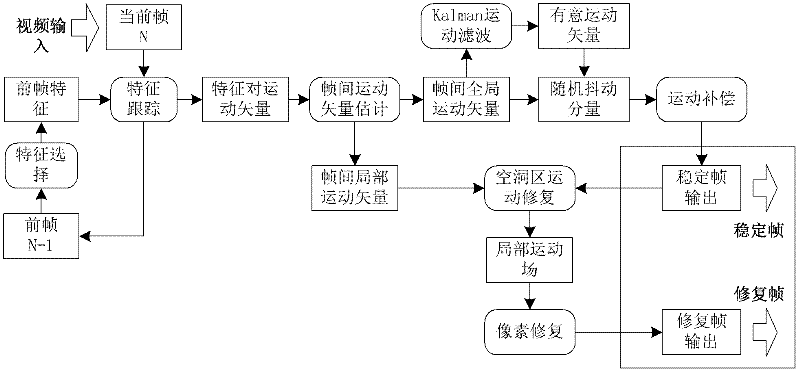
Electronic image stabilization method based on characteristic coupling
InactiveCN102231792AReduce time and space complexityReduce distractionsTelevision system detailsImage analysisVideo restorationMotion vector
The invention provides an electronic image stabilization method based on characteristic coupling. The method comprises the following steps: (1) motion estimation: estimating motion parameters of a present frame and a previous frame to obtain a global motion vector and a local motion vector; (2) motion filtering: employing a Kalman filter to carry out filtering on the global motion vector, and obtaining a willful scan vector, wherein difference between the global motion vector and the willful scan vector is a vibration parameter needs to compensate; (3) motion compensation: utilizing a compensation parameter obtained by filtering carrying out frame by frame compensation; (4) video restoration: by utilizing space-time redundant information of video, carrying out restoration on the local motion vector with a motion restoration method and guiding pixel point filling. In order to solve motion carrier vibration influence on video shooting effect, the invention provides the electronic image stabilization method based on characteristic coupling. The method has the advantages of high accuracy, good anti-noise performance, strong tracking performance, good boundary consistency and the like.
Owner:NANJING HUICHUAN IND VISUAL TECH DEV
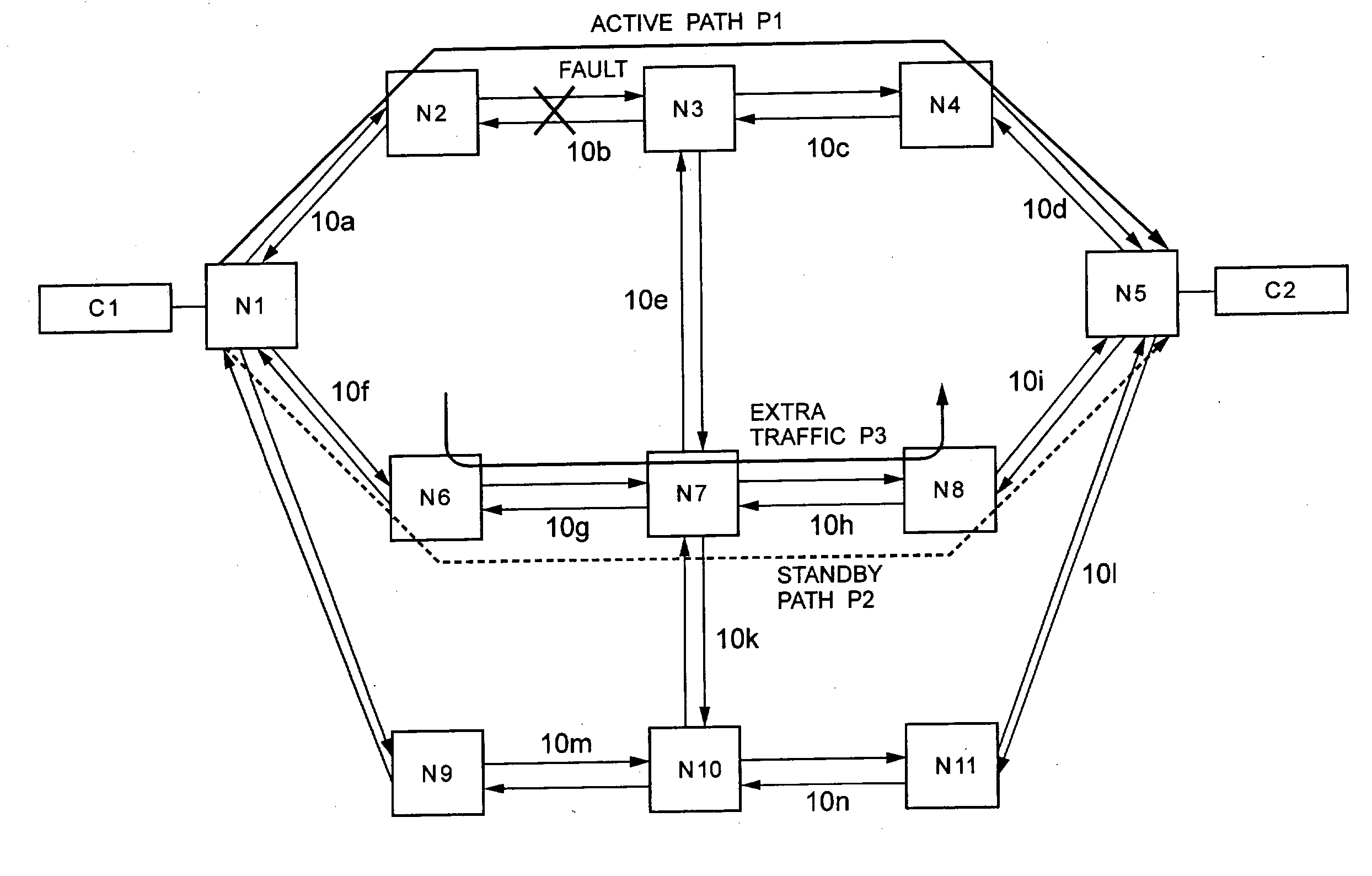
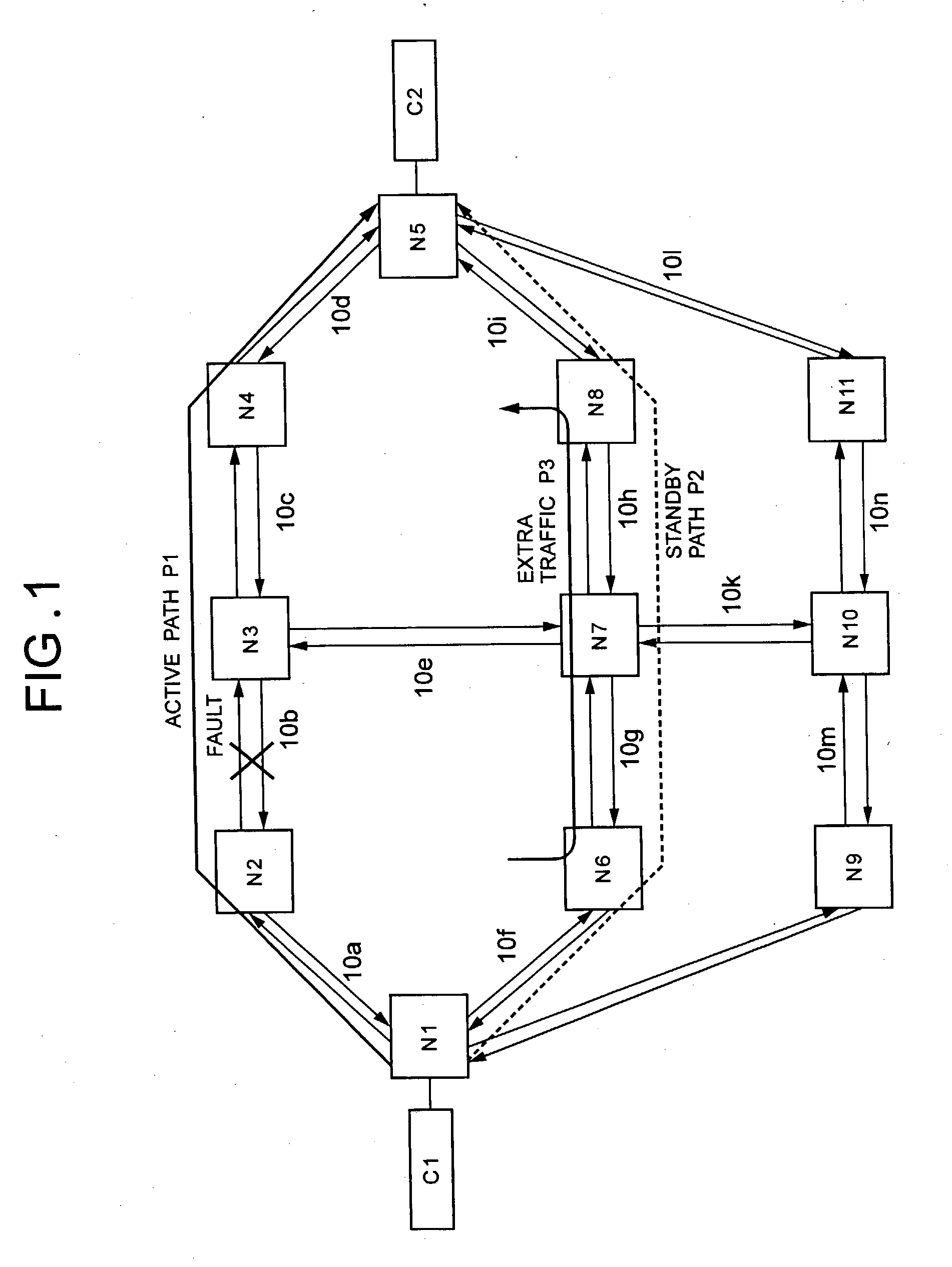
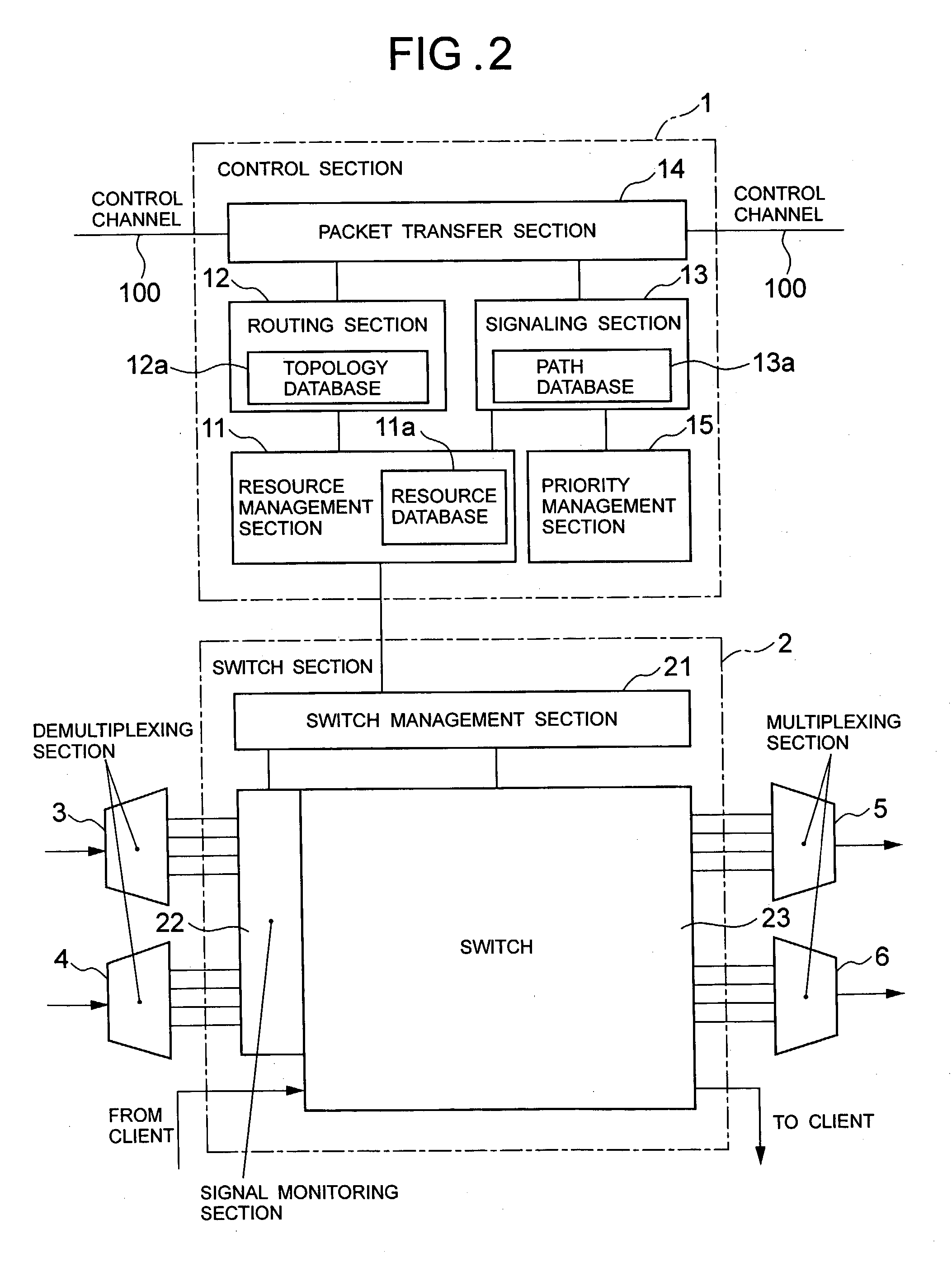
Path fault recovery method, switching-back method after recovery from fault, and node using the same
InactiveUS20030137932A1Improve reliabilityError preventionTransmission systemsRecovery methodRestoration method
This invention provides another optical path fault recovery method by which when the resources of a standby path are used by extra traffic, the standby path can be set quickly and an active path can be switched to the standby path without any improper connection in the event of a fault on the active path. An end point node of a path having received fault notification issues a resource securing request message transferred hop by hop to a start point node along the standby path. In the case where resources of the standby path are secured, when the resources are used by the extra traffic, the nodes on the standby path and the start point node that have received the message release the extra traffic and then secure the resources. When the resource securing request message reaches the start point node, the start point node issues a switch changeover request message, and the end point node, the start point node, and the nodes on the standby path set switches according to the secured resources.
Owner:NEC CORP
System and method for camera navigation
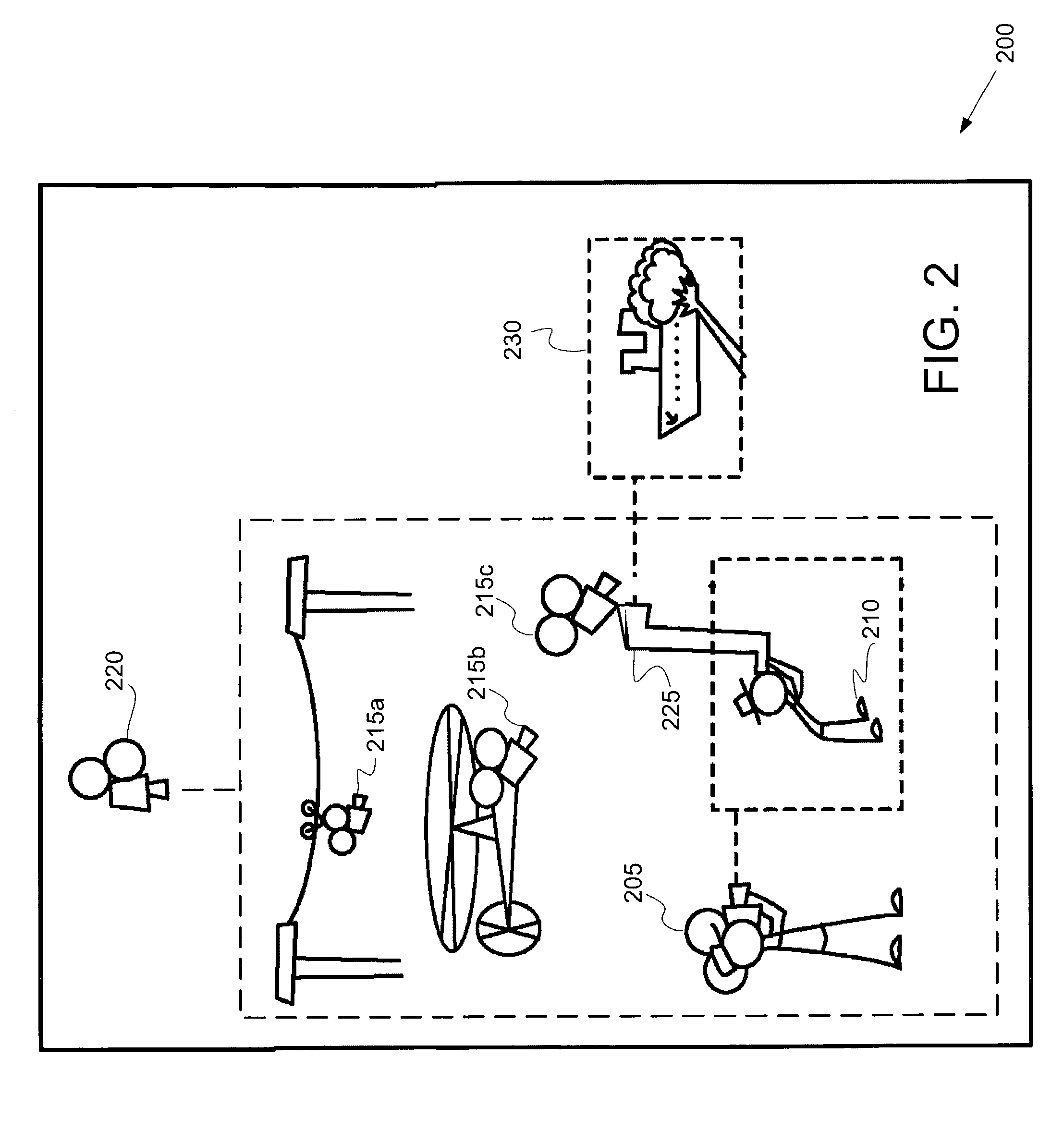
A system and method for camera navigation that provides a player with an unobstructed, non-disorienting view of a target. The system includes a memory for storing a camera navigation / control model, a central processing unit for executing the camera navigation / control model to provide unobstructed and non-disorienting target character views, and a graphics processing unit configured to render the unobstructed views of the target in an image for display. In addition, the camera navigation / control model includes an object detection model, line-of-sight restoration models to restore a line-of-sight view of an obstructed target, and a camera navigation path model. In the method, a collision probe is sent on a straight line path between a camera and a target whereby line-of-sight obstructions are detected if the probe intersects with polygonal sides of an object. A line-of-sight restoration method is used to move the camera to provide an unobstructed view of the target.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
Farmland soil heavy metal pollution restoration method through coupling activating and passivating
ActiveCN104550208AReduce concentrationImprove repair efficiencyContaminated soil reclamationRestoration methodCoupling
The invention provides a farmland soil heavy metal pollution restoration method through coupling activating and passivating, belonging to the technical field of environmental technology. According to a technical scheme adopted by the invention, the farmland soil heavy metal pollution restoration method comprises the following steps: a step I, planting heavy metal hyper-accumulation plant, applying a heavy metal activator into the soil, collecting plant which is enriched with heavy metals; a step II, applying a heavy metal passivator into the soil, planting and harvesting crops with heavy metal content reaching the safety standard. By two different coupling technologies in the two government stages, on one hand, the concentration of heavy metals in the farmland soil is lowered with high efficiency, on the other hand, the farmland can be put into safety production as early as possible, so that the heavy metal pollution farmland soil restoration efficiency is improved generally, and the method can be applied to farmland soil with large-area heavy metal pollution.
Owner:中环循环境技术有限责任公司
In-situ restoration method for heavy metal polluted soil
The invention discloses an in-situ restoration method for heavy metal polluted soil, which comprises the following steps of: uniformly mixing submicron or nano iron, coal ash, a magnesium-containing preparation and bentonite in proportion by weight of (5-25): (40-50): (1-10): (15-50) to obtain a heavy metal polluted soil restoration agent, after applying the heavy metal polluted soil restoration agent on the surface of the heavy metal polluted soil at the thickness of 1-4cm, uniformly mixing a 20cm thick polluted soil surface layer with the applied restoration agent by plowing, and after 3-6 months, reducing heavy metals such as cadmium, chromium, mercury, lead, arsenic, nickel, zinc, copper, magnesium and vanadium in the heavy metal polluted soil into low-valence immobilized heavy metals to lose biological effectiveness and realize the in-situ restoration for the heavy metal polluted soil. However, the environmental quality of restored soil satisfies the requirements of second-level standard values in Environmental Quality Standards for Soils (GB 15618-1995) in China.
Owner:刘阳生
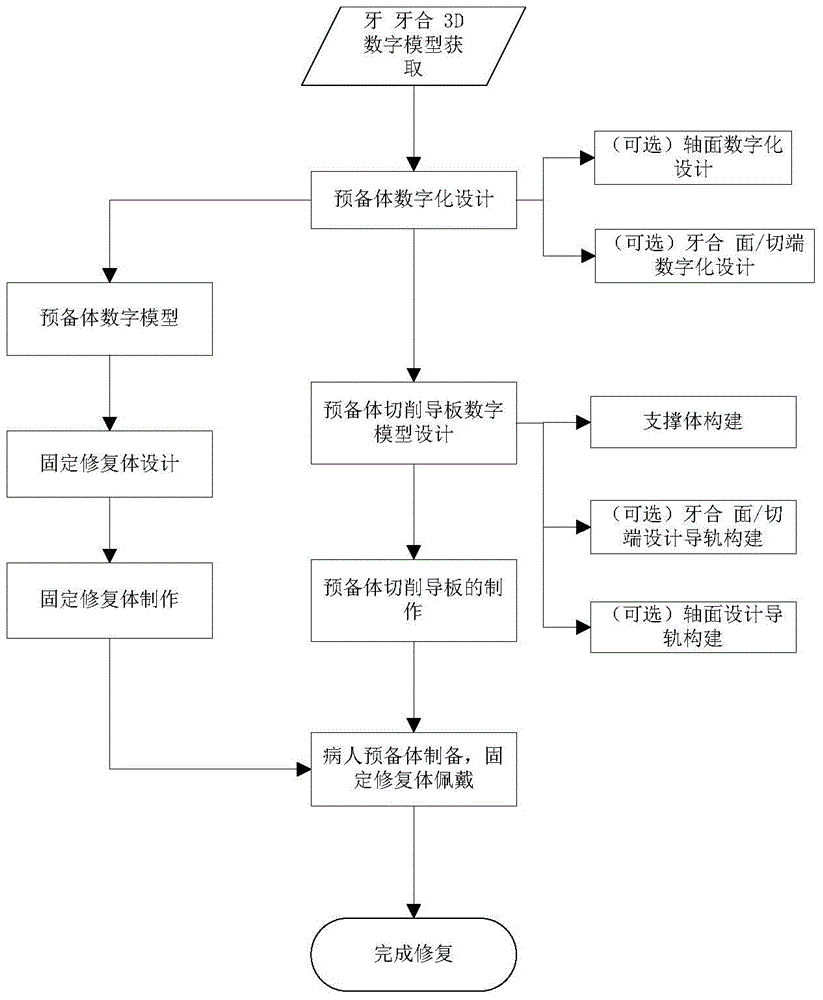
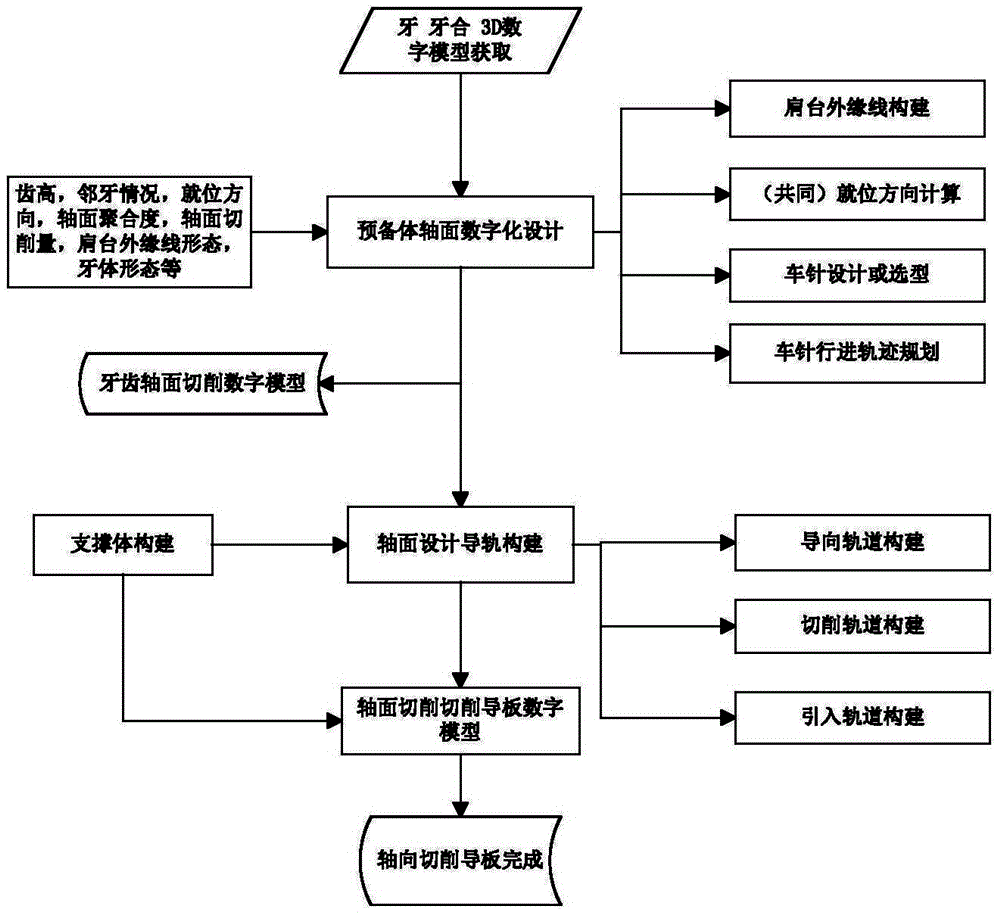
Digital oral fixed restoration method and device
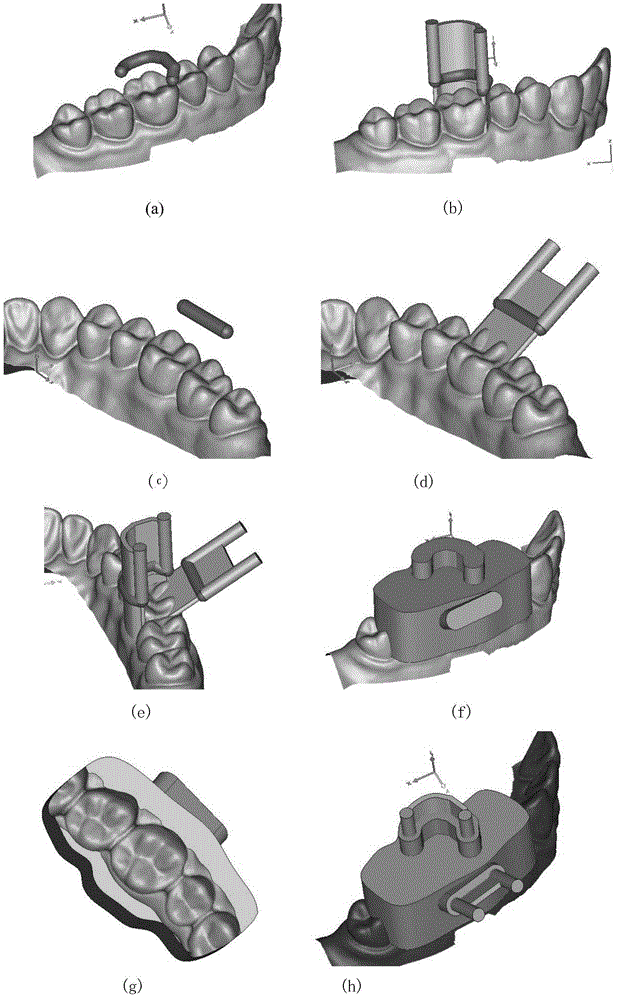
ActiveCN104699865AQuality improvementImprove efficiencyArtificial teethSpecial data processing applicationsRestoration methodTooth Preparations
The invention provides a digital oral fixed restoration method and device. Preparing and planning of a tooth preparation are completed by obtaining a three-dimensional digital model of an oral cavity of a patient before a dentist prepares the tooth preparation, and the tooth preparation is cured on a specially-made cutting guide plate, thereby greatly improving the quality of the tooth preparation prepared by the dentist and improving the efficiency of preparing the tooth preparation prepared by the dentist by the cutting guide plate. Furthermore, the invention can provide a complete set of digital scheme for oral fixed restoration, namely, simulation cutting of the three-dimensional digital model of teeth of the patient is completed in a computer, thereby acquiring a three-dimensional digital model of the tooth preparation of the patient; the oral fixed restoration body can be directly and digitally designed and manufactured on the basis. By virtue of the digital oral fixed restoration method and device, the tooth preparation cutting guide plate of the patient and the restoration body can be delivered to the dentist and the patient together; the patient can directly wear the individually designed and manufactured restoration body during accurate preparing of the tooth preparation; the efficiency and the effect of oral fixation can be greatly improved.
Owner:南京易形信息科技有限公司 +1
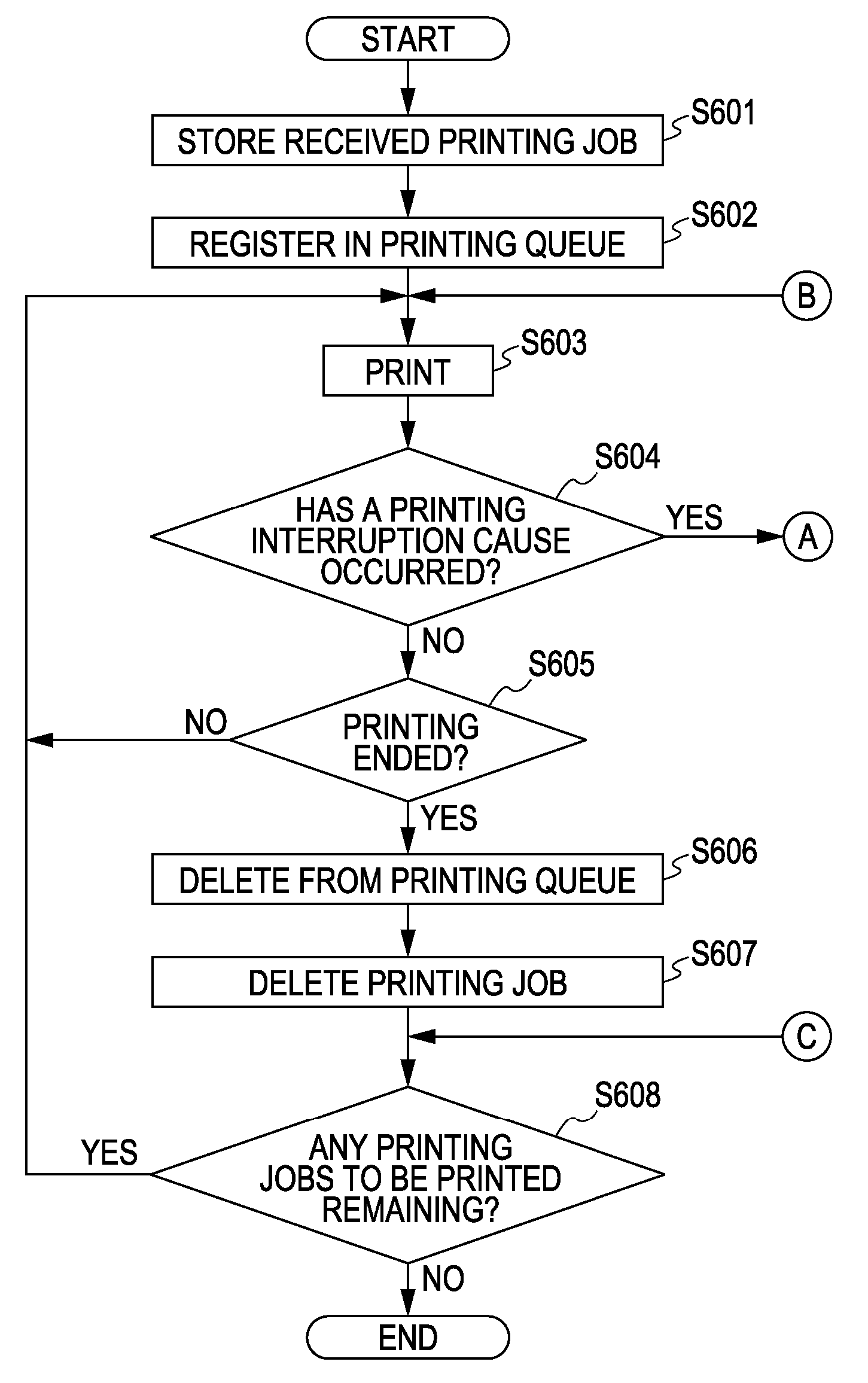
Printing system, job processing method, storage medium, and printing apparatus
InactiveUS20070109586A1Improve productivityEfficient processingVisual presentationPictoral communicationRestoration methodComputer science
In the event that the printing operations of a printing job have been interrupted by an interruption cause, and the cause of interruption for the interruption job is removed, resuming of the printing operations of the interrupted job is enabled with a resuming method corresponding to a user request, received from a user via a user interface, for a selection option that has been selected from multiple selection operations relating to resuming methods of the printing operations. This enables job resuming processing of a job regarding which printing has been interrupted to be suitably executed even under a printing environment such as a POD environment.
Owner:CANON KK
Heavy-metal polluted soil united directional restoration method by using plant-microorganism
InactiveCN101181715AImprove repair effectLow costContaminated soil reclamationMicroorganismResistant bacteria
The invention relates to a method for remediation of heavy metals contaminated soil by a plant-microorganism joint direction method. The detailed steps of the method of the invention are that: firstly, resistant bacteria of plant and microorganism is sifted, so as to obtain plant and microorganism bacteria strains with heavy metal resistance; and then the seeds of the resistant plant is soaked and coated in microorganism resistant bacteria solution; finally, the seeds are planted in the soil contaminated by heavy metal, therefore the soil can be remedied. The method has the advantages of good remediation effect, low cost, easy management and operation, no secondary pollution and broad application prospect, therefore, the method is the most important development direction of soil remediation technique.
Owner:SHANGHAI UNIV
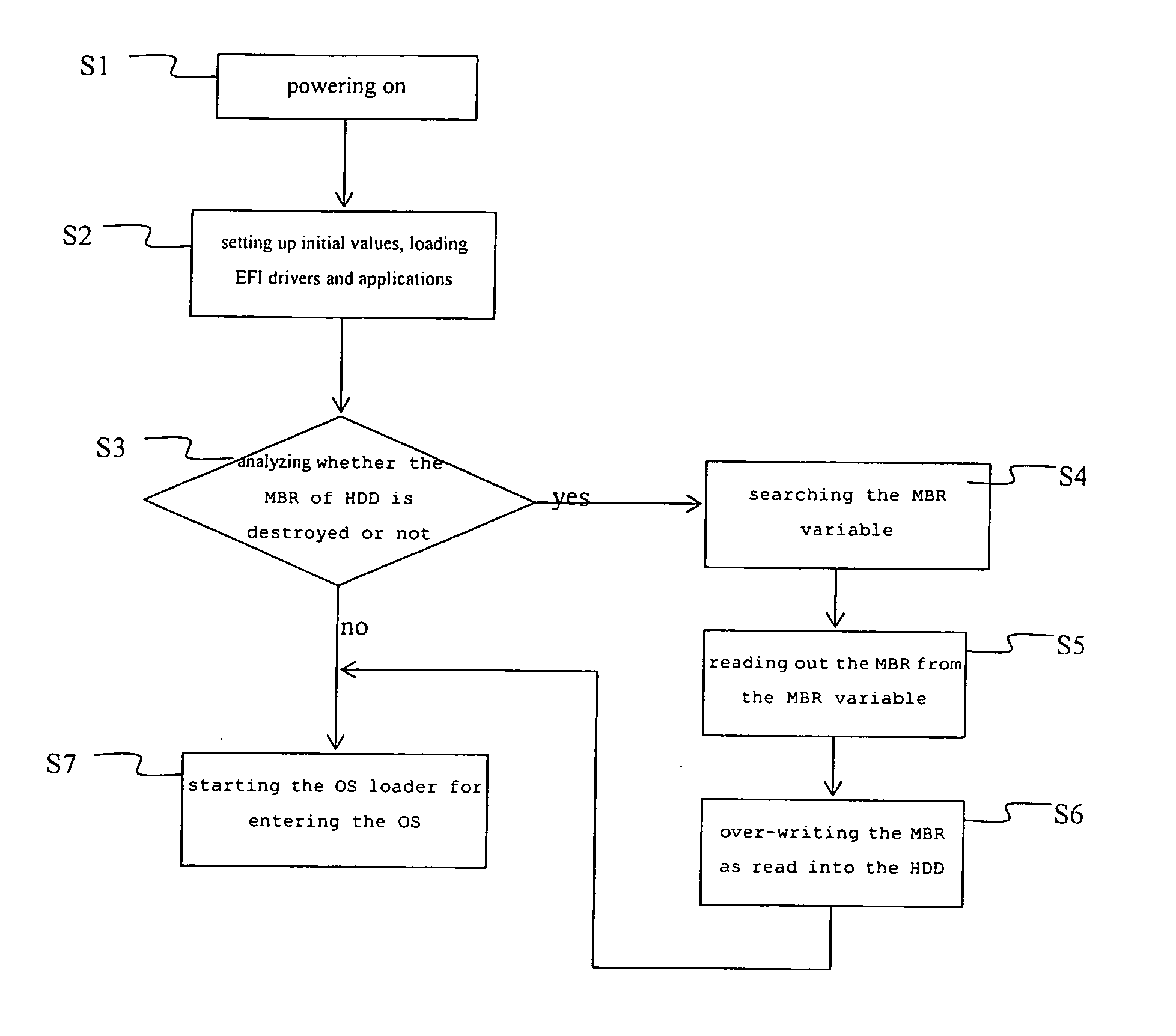
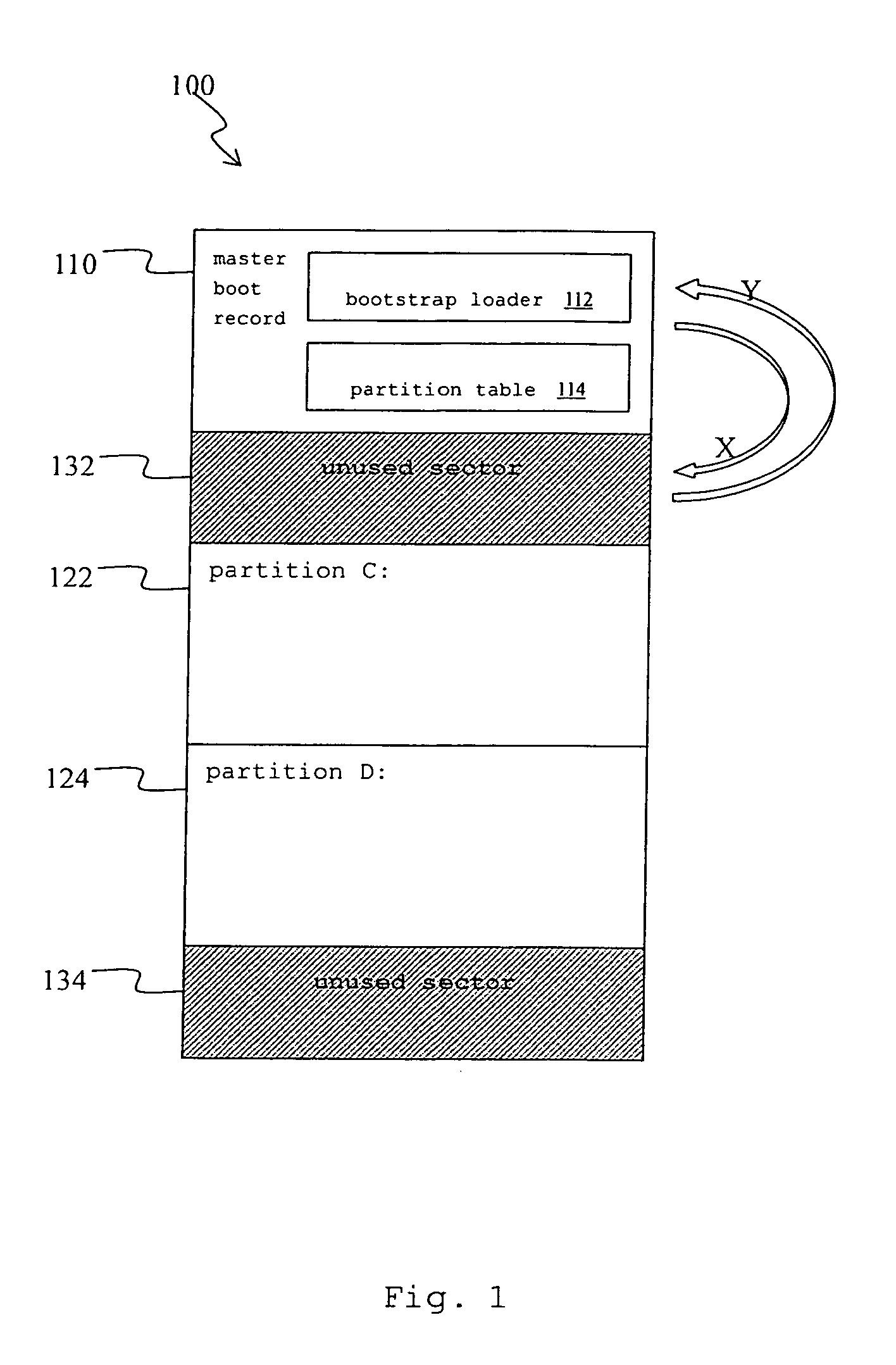
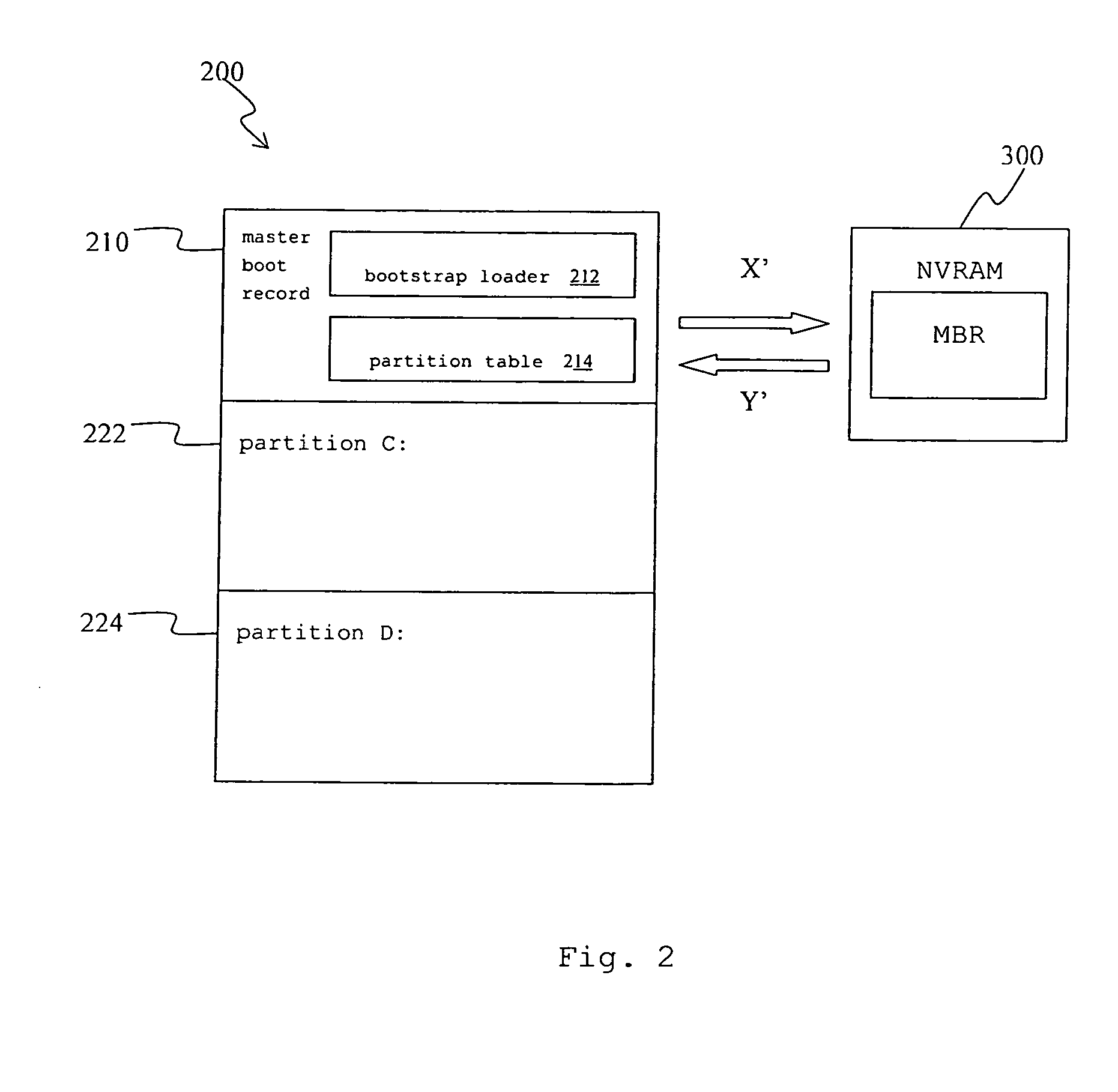
Recovery method for master boot record of hard disk drive
InactiveUS20060041738A1Avoid backupAvoid damageError detection/correctionDigital computer detailsRecovery methodHard disc drive
A recovery method for a master boot record of a hard disk drive is adapted to a computer system incorporating extensible firmware interface (EFI). When modification occurs in the master boot record, the extensible firmware interface stores the master boot record in an NVRAM (Non-volatile Random Access Memory) as a backup. The backup is read out for recovery of the hard disk driver if the master boot record is destroyed. The NVRAM is write-protected during runtime and the backup data stored therein is therefore free from destruction.
Owner:INSYDE SOFTWARE CORP
Data relay apparatus and failure recovery method
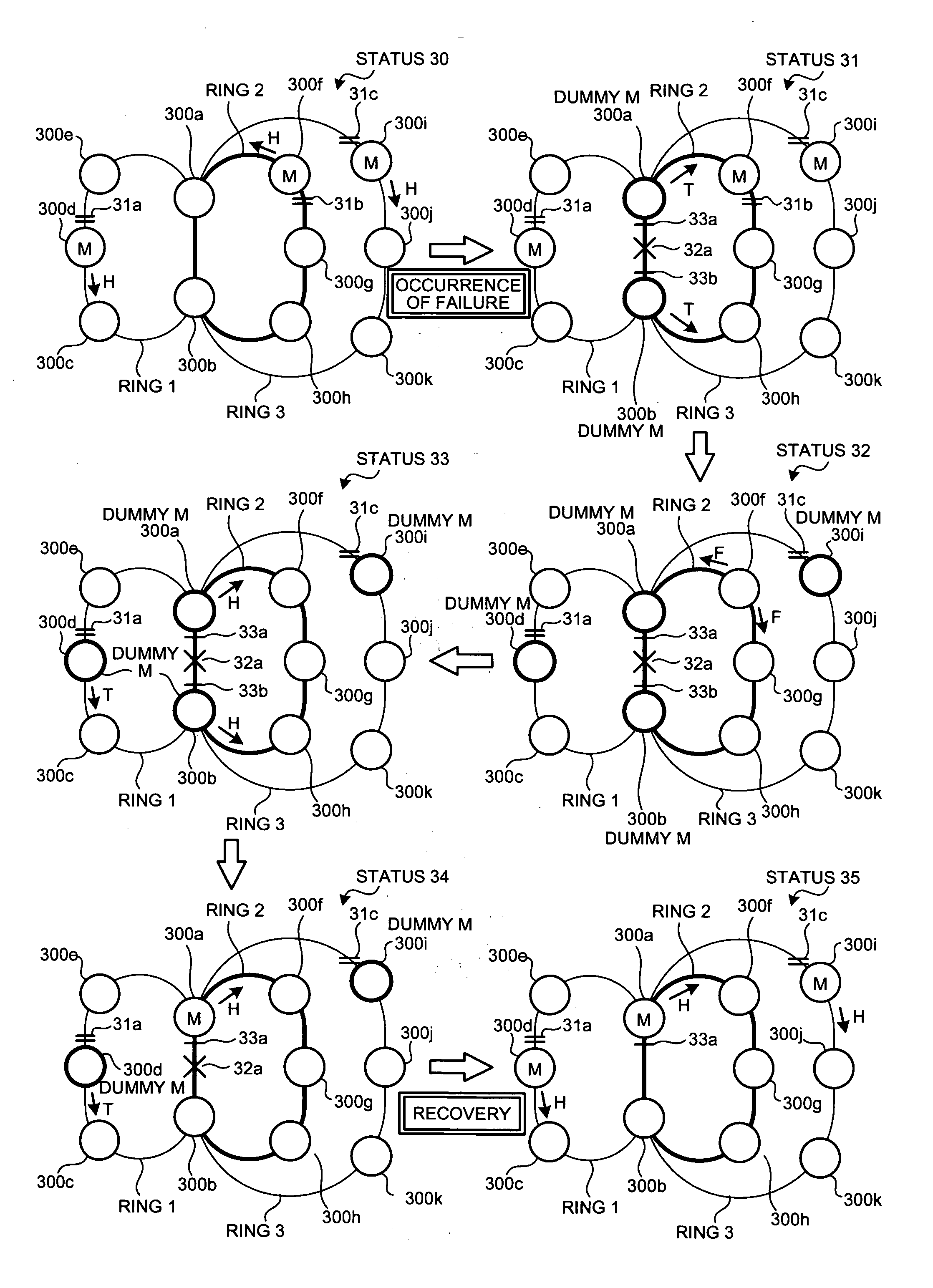
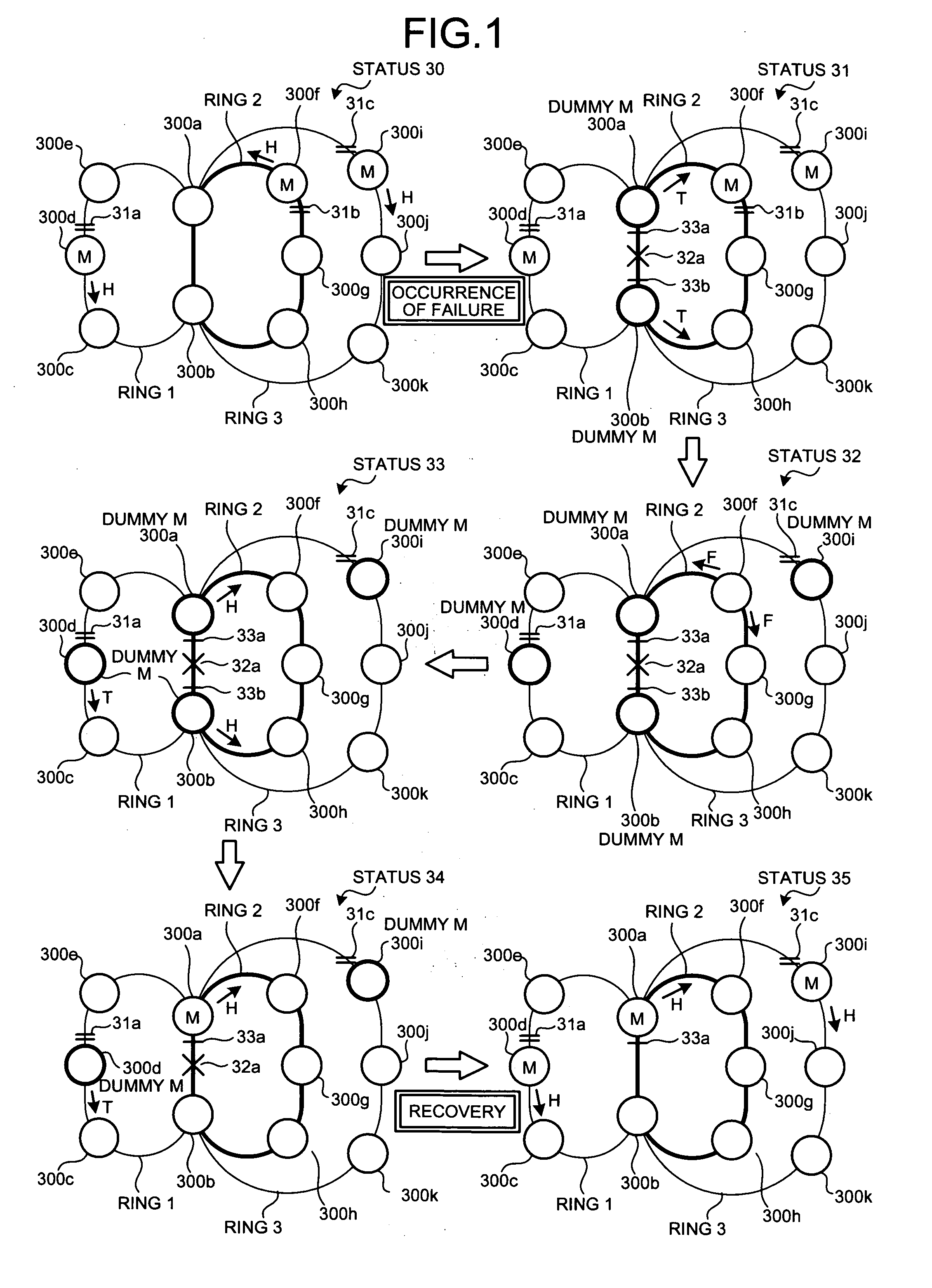
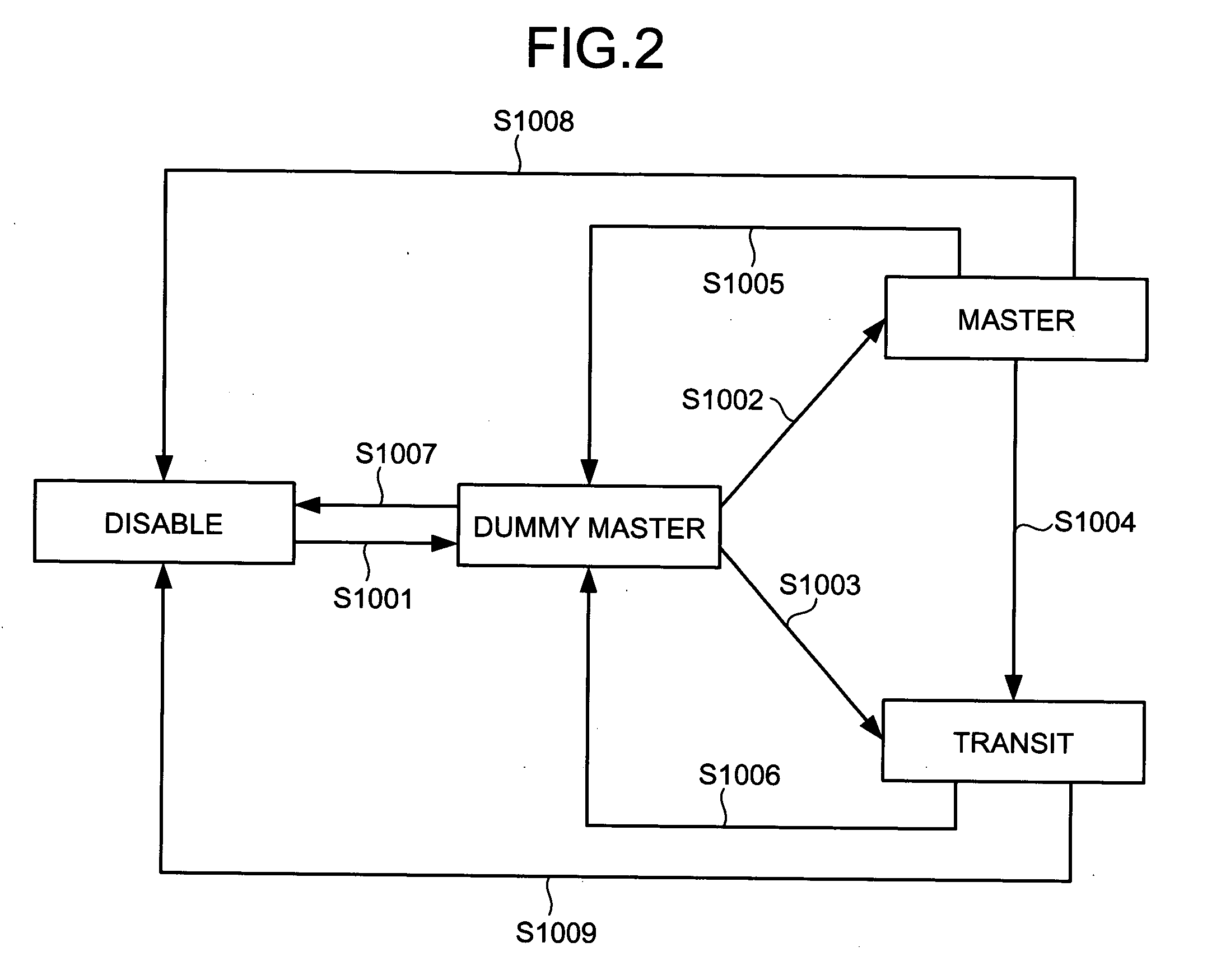
InactiveUS20060215546A1Solve problemsError preventionTransmission systemsRecovery methodRestoration method
A data relay apparatus that recovers a failure in a network that shares a part of a plurality of rings and avoids occurrence of a loop path by providing a block in each of the rings includes a failure-notification-packet transmitting unit that transmits, when a failure is detected in a shared portion of a ring, a failure notification packet to a predetermined redundancy-providing ring; and a block setting unit that sets a block that blocks a main signal by passing through a control packet at a port where the failure is detected.
Owner:FUJITSU LTD
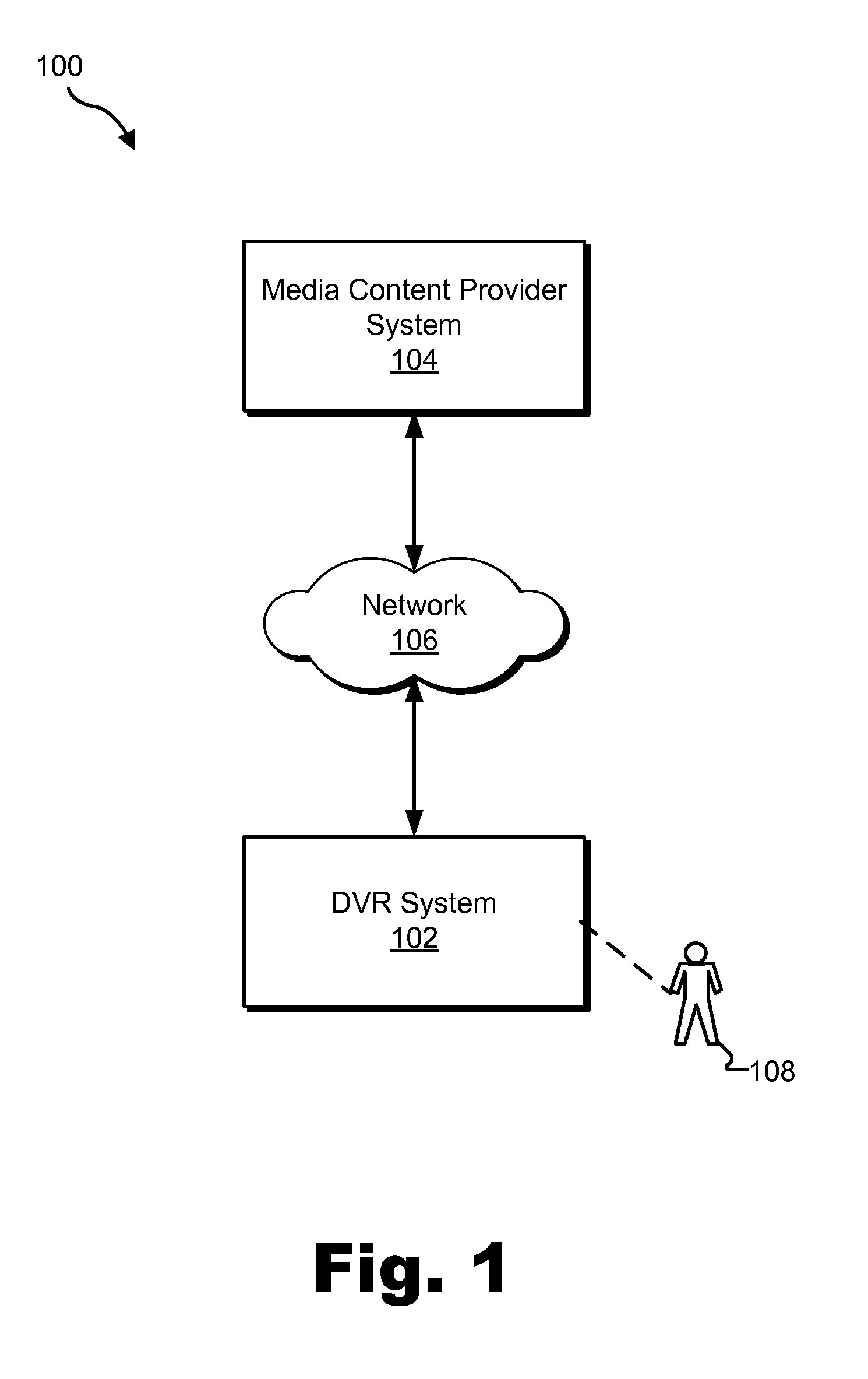
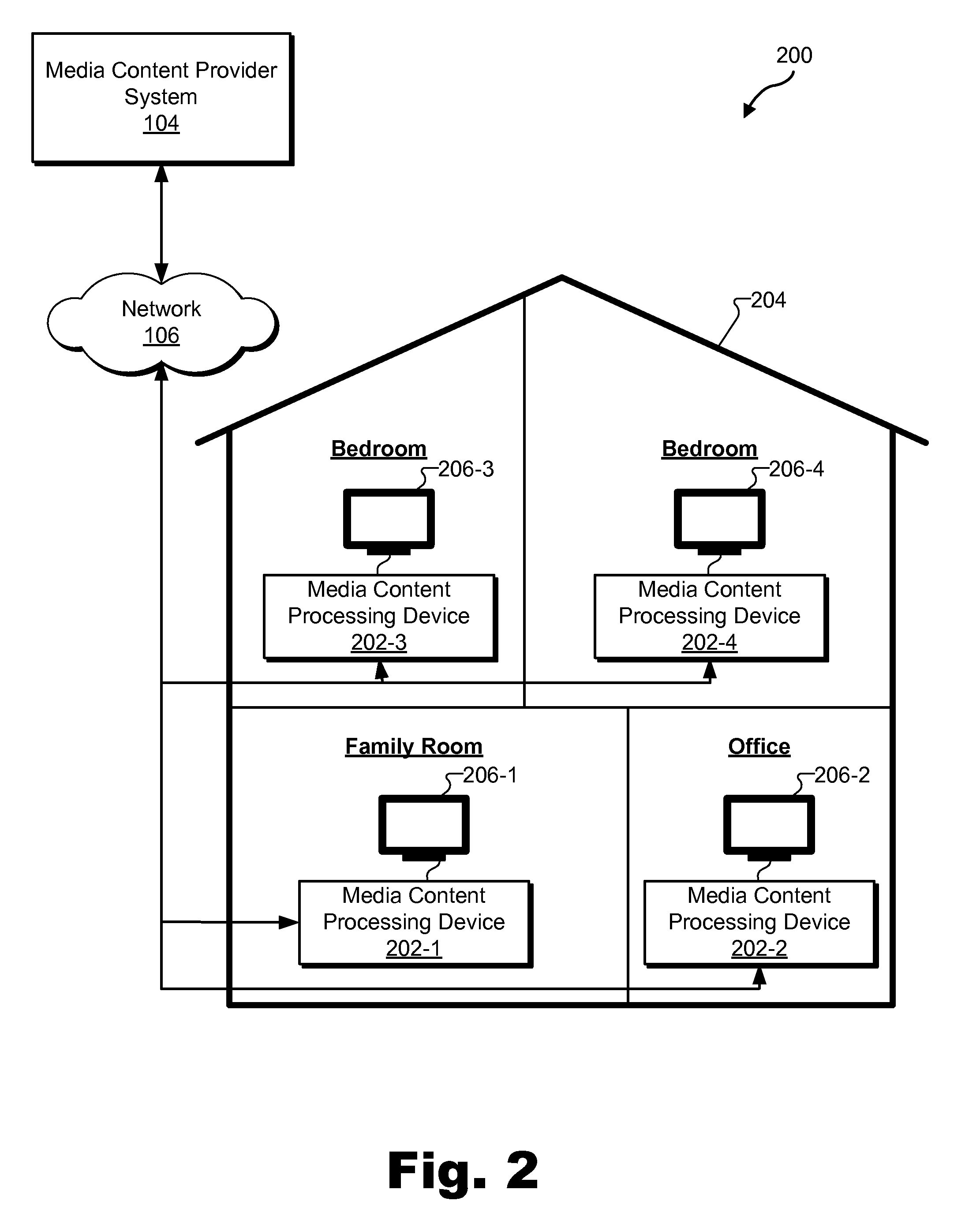
Media Content Asset Recovery Methods and Systems
ActiveUS20140186001A1Television system detailsColor television detailsRecovery methodRestoration method
An exemplary method includes a media content asset recovery system 1) detecting a migration of a user account from being associated with a first DVR system to being associated with a second DVR system, 2) identifying, in response to the detecting, a media content asset included within a library of one or more media content assets stored by the first DVR system at a time associated with the migration, 3) selecting, in accordance with a source selection heuristic, a media content source other than the first DVR system and that is configured to distribute the media content asset, and 4) directing the second DVR system to acquire the media content asset from the selected media content source for storage by the second DVR system.
Owner:VERIZON PATENT & LICENSING INC
Packet restoration method, packet restoration system, and mobile terminal and intermediate device used in the method
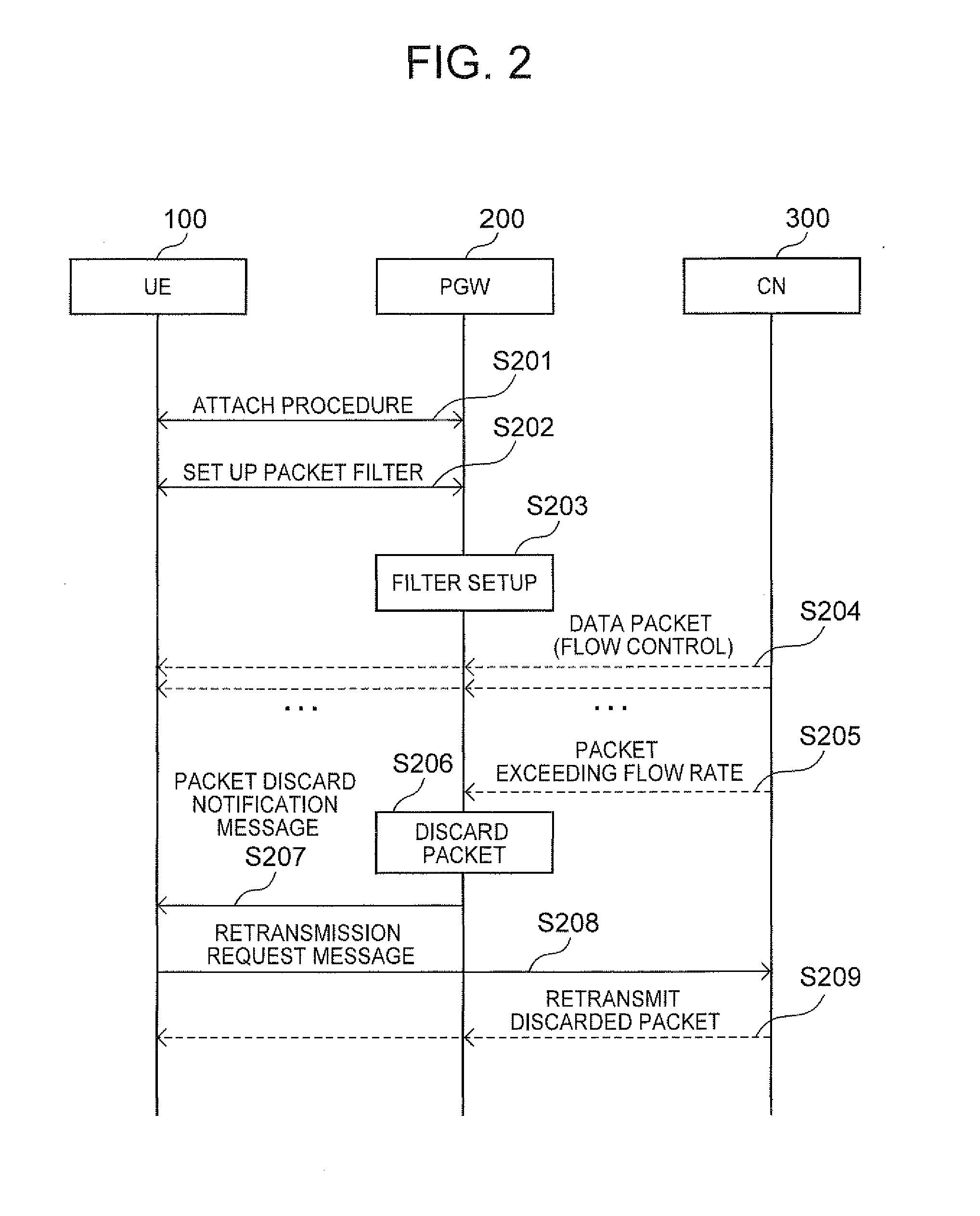
ActiveUS20120182859A1Improve communication efficiencyError preventionTransmission systemsRecovery methodCommunication quality
The present invention discloses a technique for providing a packet recovery method, and the like, capable of starting packet recovery processing without waiting for a wasteful latency (time-out) at a mobile terminal by giving notice of information on a packet discard in a gateway device in real time, thereby enabling improvement in communication quality and communication efficiency. According to the technique, there is provided a packet recovery method for recovering a packet discarded by an intermediate device positioned on a communication path between a mobile terminal and a correspondent node of the mobile terminal among packets exchanged between the mobile terminal and correspondent node, the method including: a step of causing the intermediate device to transmit a discard notification message to the mobile terminal based on information on a communication flow for which transmission of the discard notification message indicating that the packet has been discarded is required; and a step of causing the mobile terminal to transmit the correspondent node a retransmission request message for requesting retransmission of the discarded packet based the discard notification message.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Edge information-based multi-scale blurred image blind restoration method
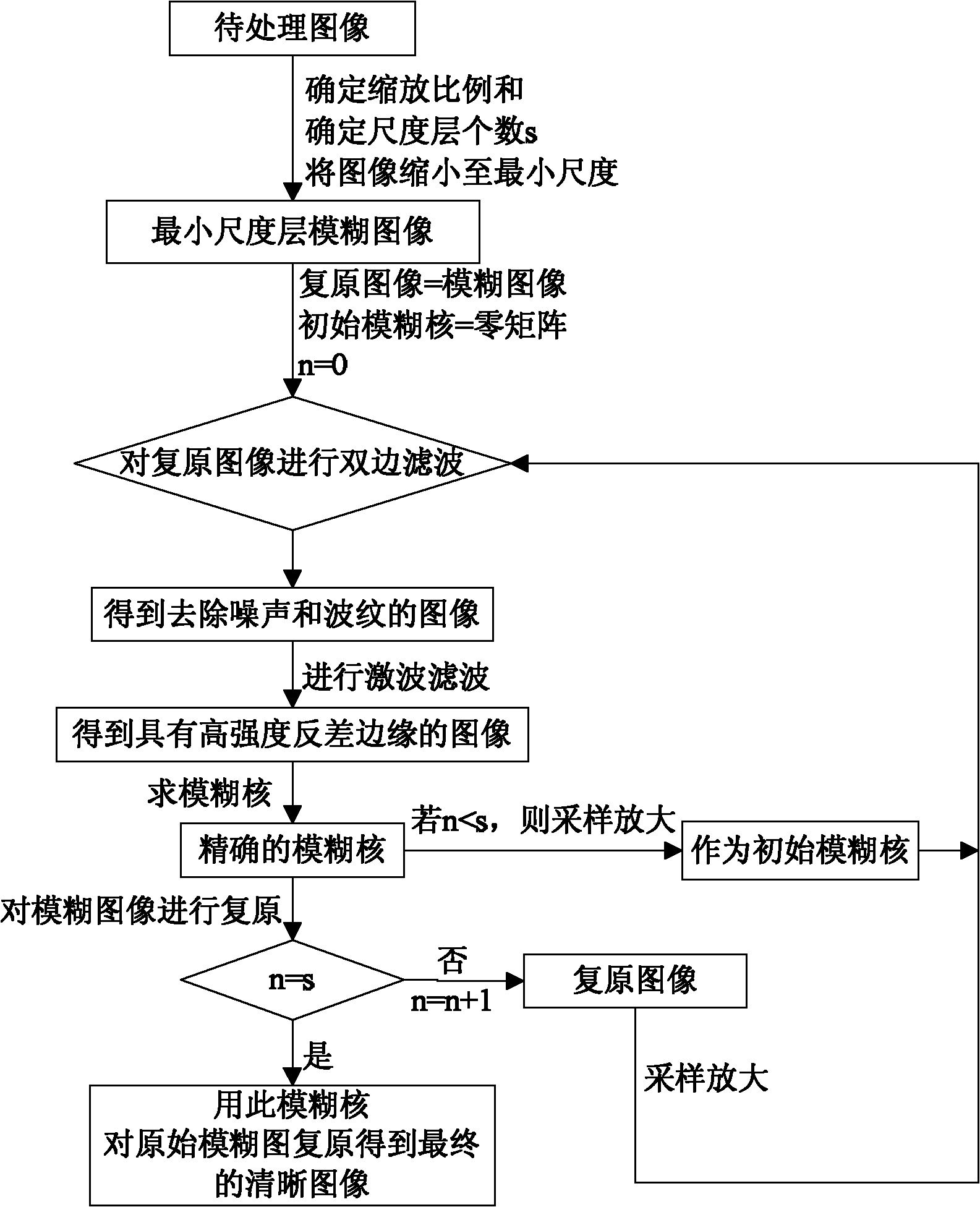
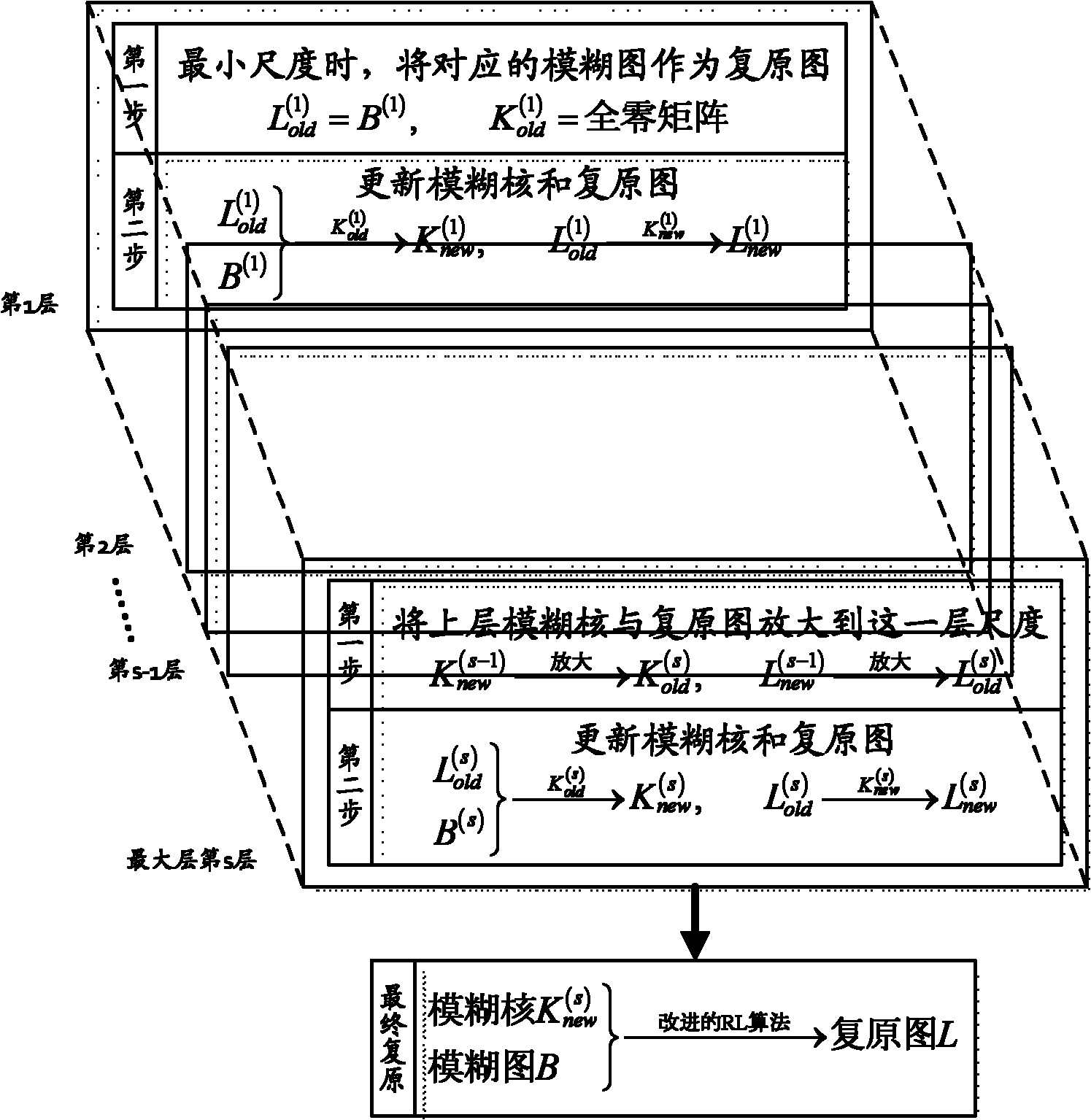
InactiveCN101930601AEffective convergenceReduce computational complexityImage enhancementShock wavePattern recognition
The invention discloses an edge information-based multi-scale blurred image blind restoration method, which comprises the following steps of: circularly and gradually restoring an image from a small scale layer to a large scale layer, setting self-adaptive parameters at different scales, and processing each scale layer, namely bilaterally filtering the restored image to obtain an image of which the noise and ripple are removed; performing shock wave filtering to obtain an image with high-strength contrast edges; solving the edges, and combining a fuzzy core initial value and a fuzzy graph to obtain an accurate fuzzy core; restoring a fuzzy image at the current scale to obtain a clear restored image by using the solved fuzzy core; sampling and amplifying in the current scale layer to obtain the restored image and a fuzzy core initial value of an adjacent large scale layer, and performing cycle operation on the adjacent large scale layer. The edge information-based multi-scale blurred image blind restoration method can effectively converge various images in different fuzzy degrees, and compared with a general blind restoration method which directly solves the energy minimization, the blurred image blind restoration method has the advantages of low computational complexity and high noise suppression capacity.
Owner:ZHEJIANG UNIV
Ecological restoration method for city watercourse
InactiveCN103882828AHas the ability to resist external interferenceEasy to viewWater resource protectionStream regulationEcological environmentRestoration method
The invention relates to an ecological restoration method for a city watercourse. The ecological restoration method for the city watercourse is characterized in that the polluted city watercourse is comprehensively restored with the combination of physical, biological and ecological technologies, the ecological theory is used for reference in the treatment process, the ecological idea is used as the guiding thought, a complex water ecosystem structure is constructed and restored, the original natural state of the watercourse is restored, the self-cleaning capacity of a river system is improved, the environment is beautified, and the local city microclimates are improved at the same time. The ecological restoration method mainly comprises the steps of (1) controlling a pollution source, (2) modifying the river bank, (3) optimizing the environment of the river bottom, (4) modifying the watercourse, (5) conducting aeration and oxygenation, (6) constructing an aquatic plant community, (7) constructing a fish and macrobenthos community, and (8) maintaining the system. The watercourse ecological system restored through the ecological restoration method has the certain anti-interference capacity, on the premise that a large amount of exogenous pollution is cut off, the certain-strength interference can be resisted, and the good ecological environmental effect is obtained. After one-time input, the better ecological benefit can be obtained only with a small number of maintenance costs.
Owner:深圳市益水生态科技有限公司
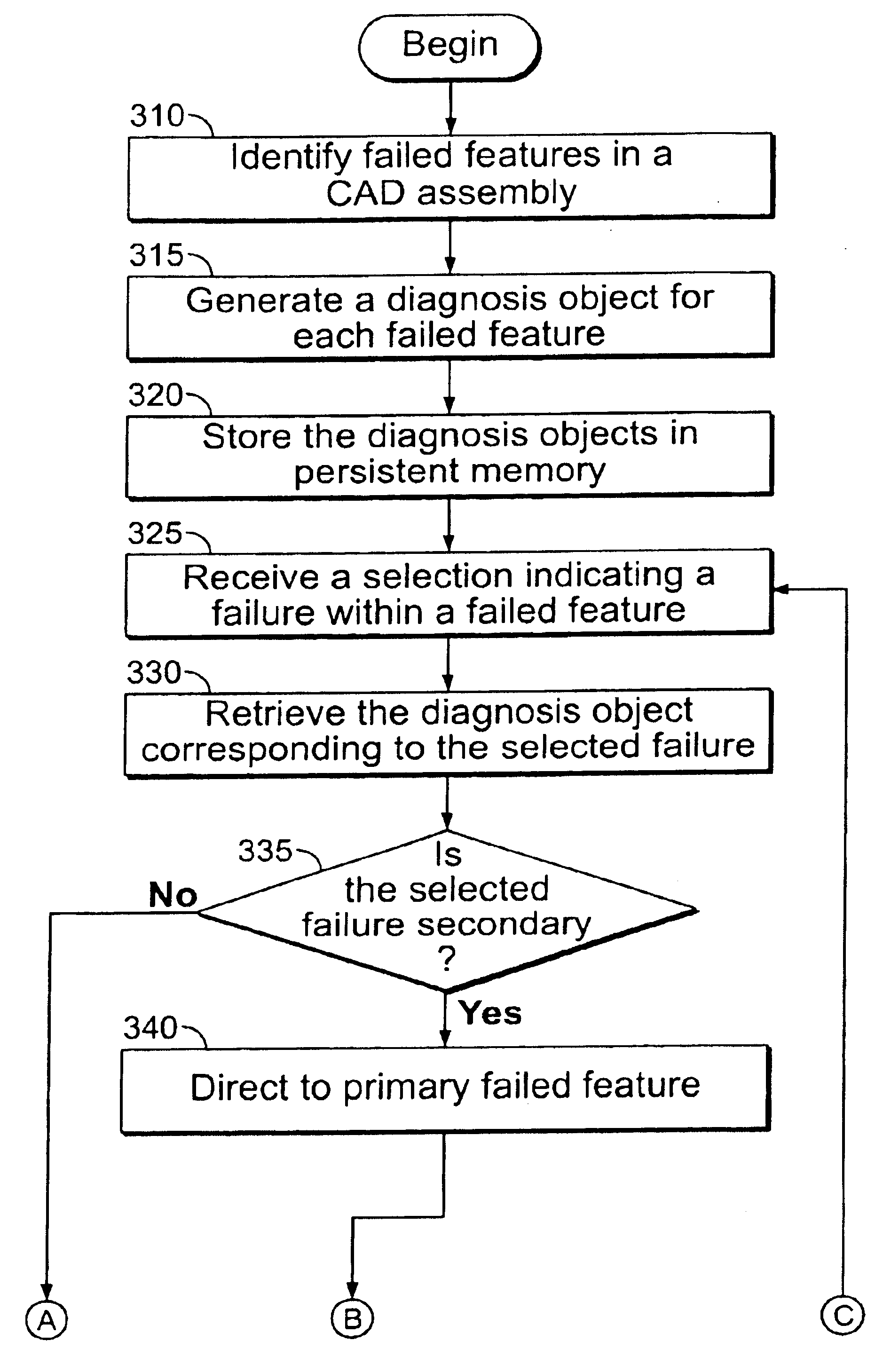
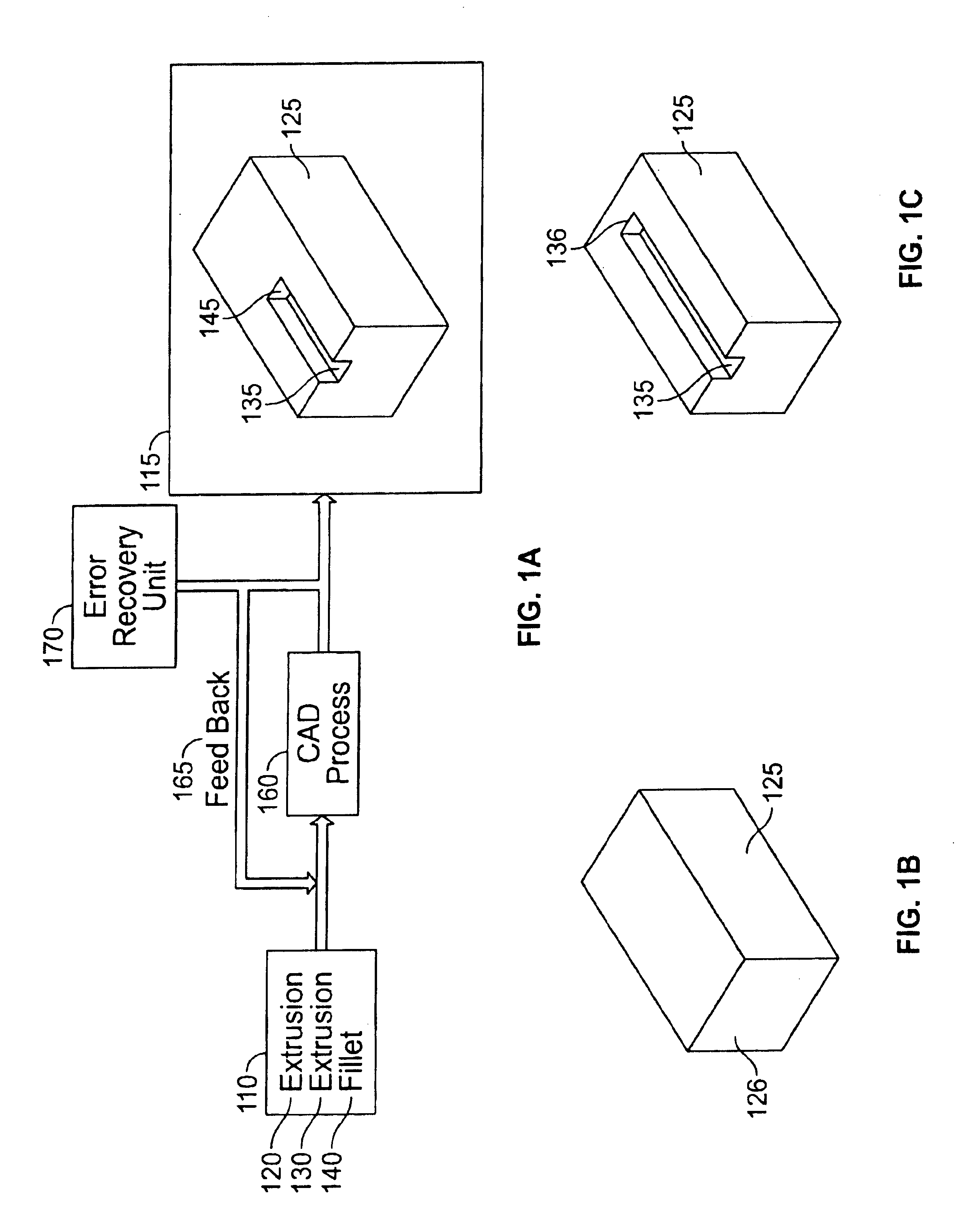
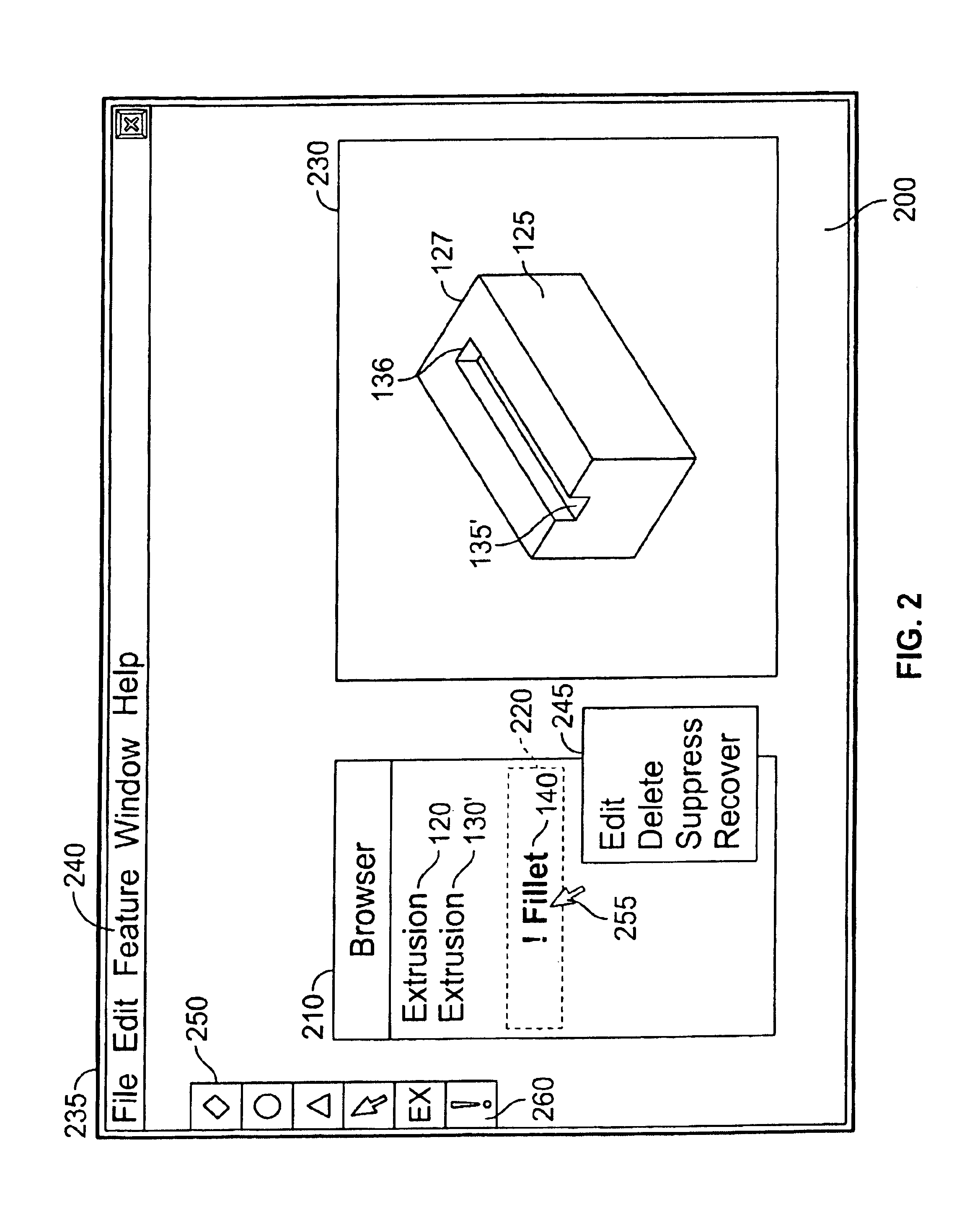
Error recovery in a computer aided design environment
The present invention provides an improved error recovery method and apparatus for computer aided design (CAD) environments. When a failure is identified in a feature of a CAD assembly, a set of treatments is automatically provided for the failure from which to select. The set of treatments is based, at least in part, on the particular failure. In one embodiment, information to identify and / or illustrate one or more failures within a particular feature is collected and stored in persistent memory. Then, when the particular feature is indicated, the information can be retrieved and provided in various formats, including text, graphics, and / or procedures, to assist a user in better understanding the failures. In another embodiment, when a treatment is selected from a set of treatments for a particular failure, the selected treatment is automatically initiated.
Owner:AUTODESK INC
Method, system, and program for recovery from a failure in an asynchronous data copying system
InactiveUS7278049B2Application downtime is minimizedMemory loss protectionUnauthorized memory use protectionRecovery methodDevice form
A method of recovery from a data storage system failure in a data storage system having a host computer writing data updates to a local storage controller at a local site. The local controller is associated with a local storage device. The local storage controller is also configured to a synchronously copy the updates to a remote storage controller associated with a remote storage device at a remote site. In addition, the remote storage controller is configured to store a consistent point in time copy of the updates on a backup storage device. The consistent point in time copy is known as a consistency group. Upon detection of a failure associated with the local site, a determination is made whether a group of updates pending for storage on the backup storage device form an intact consistency group. If an intact consistency group has not formed, corrective action may be taken to create an intact consistency group. The recovery method further consists of synchronizing the remote storage device, initiating recovery operations and, upon recovery of the local site, resynchronization of the local storage device and the backup storage device to recovery consistency group without the need for full volume storage copies and while minimizing application downtime.
Owner:INT BUSINESS MASCH CORP
Data replication and recovery method in asymmetric clustered distributed file system
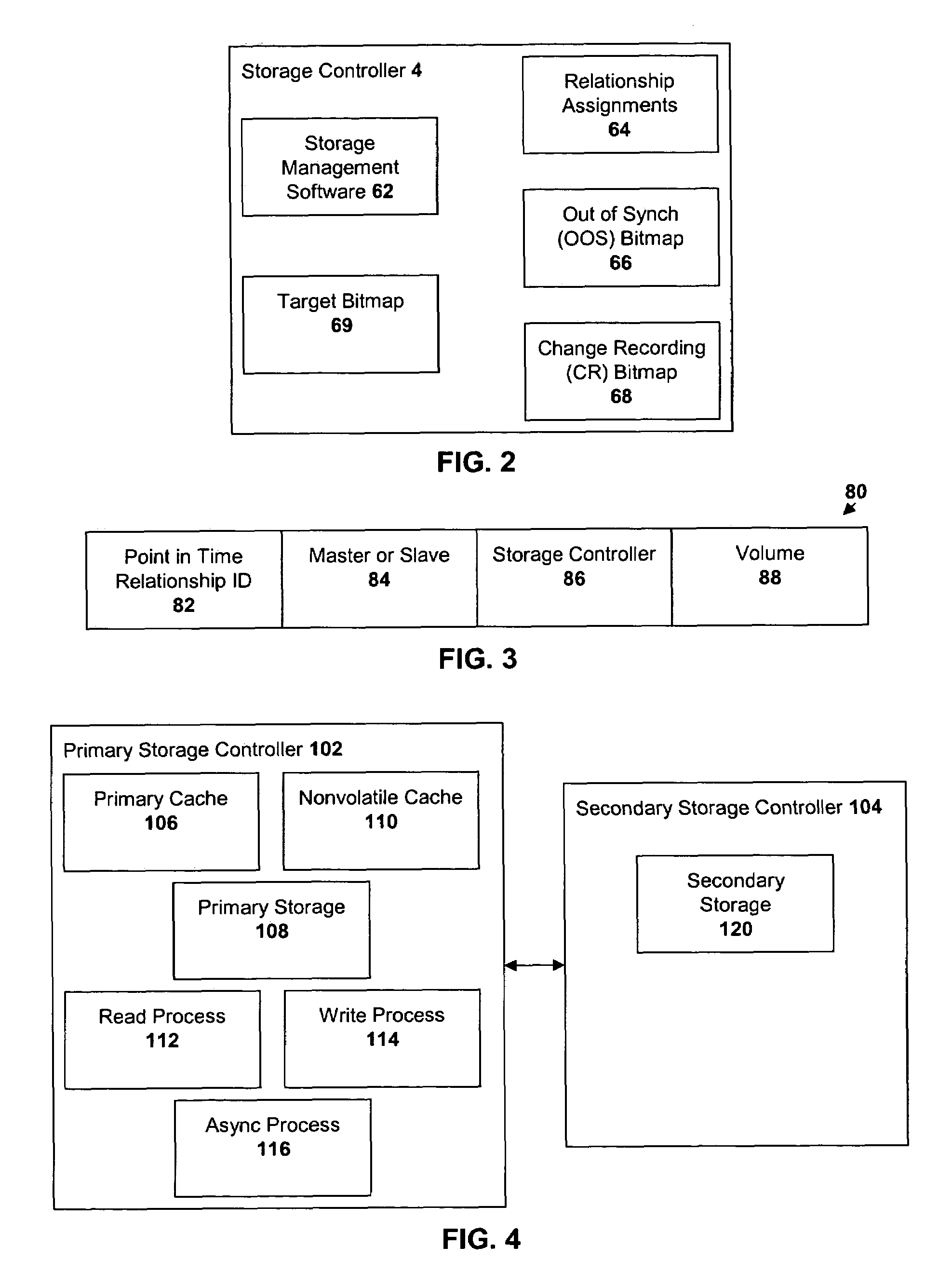
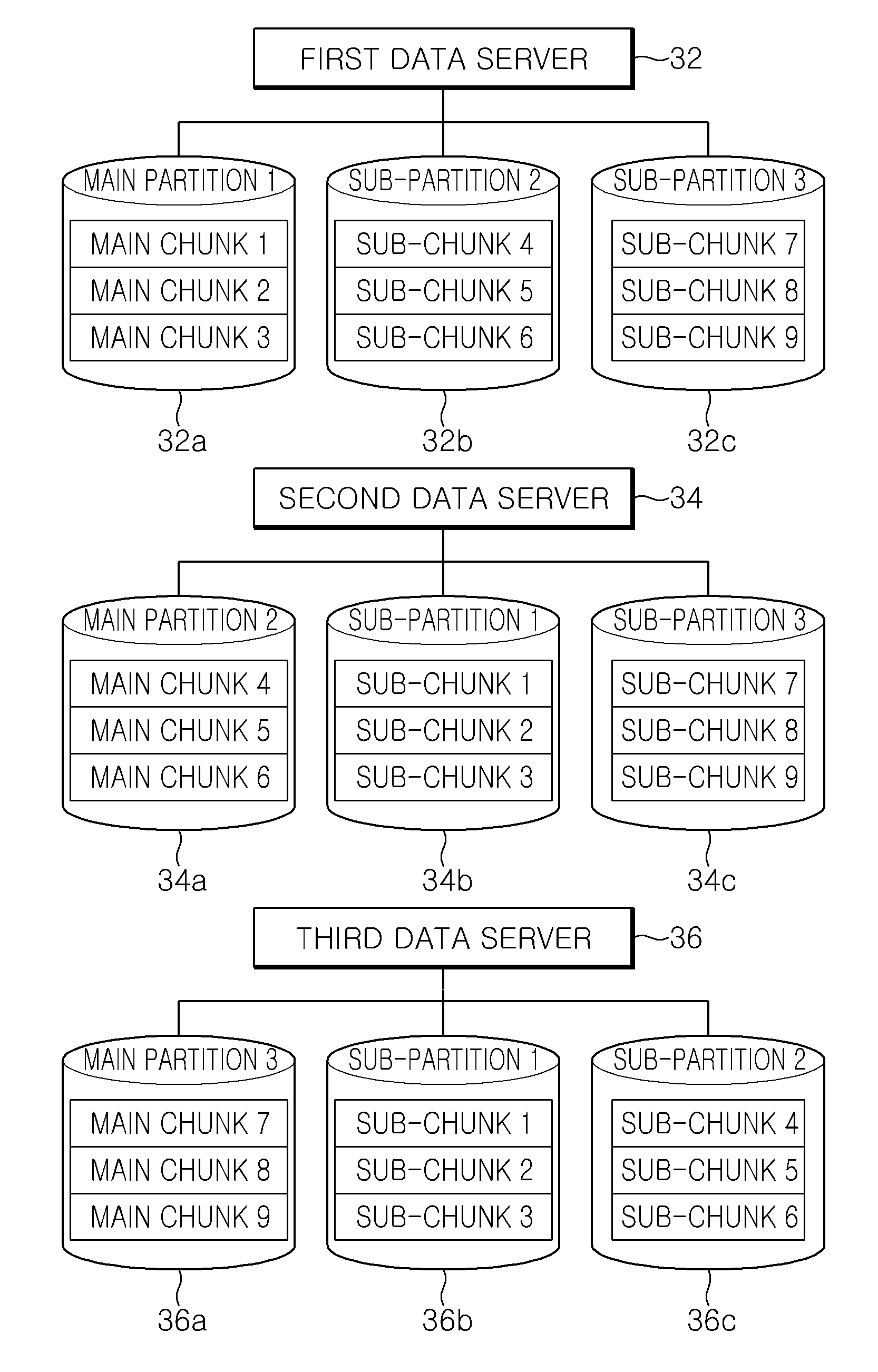
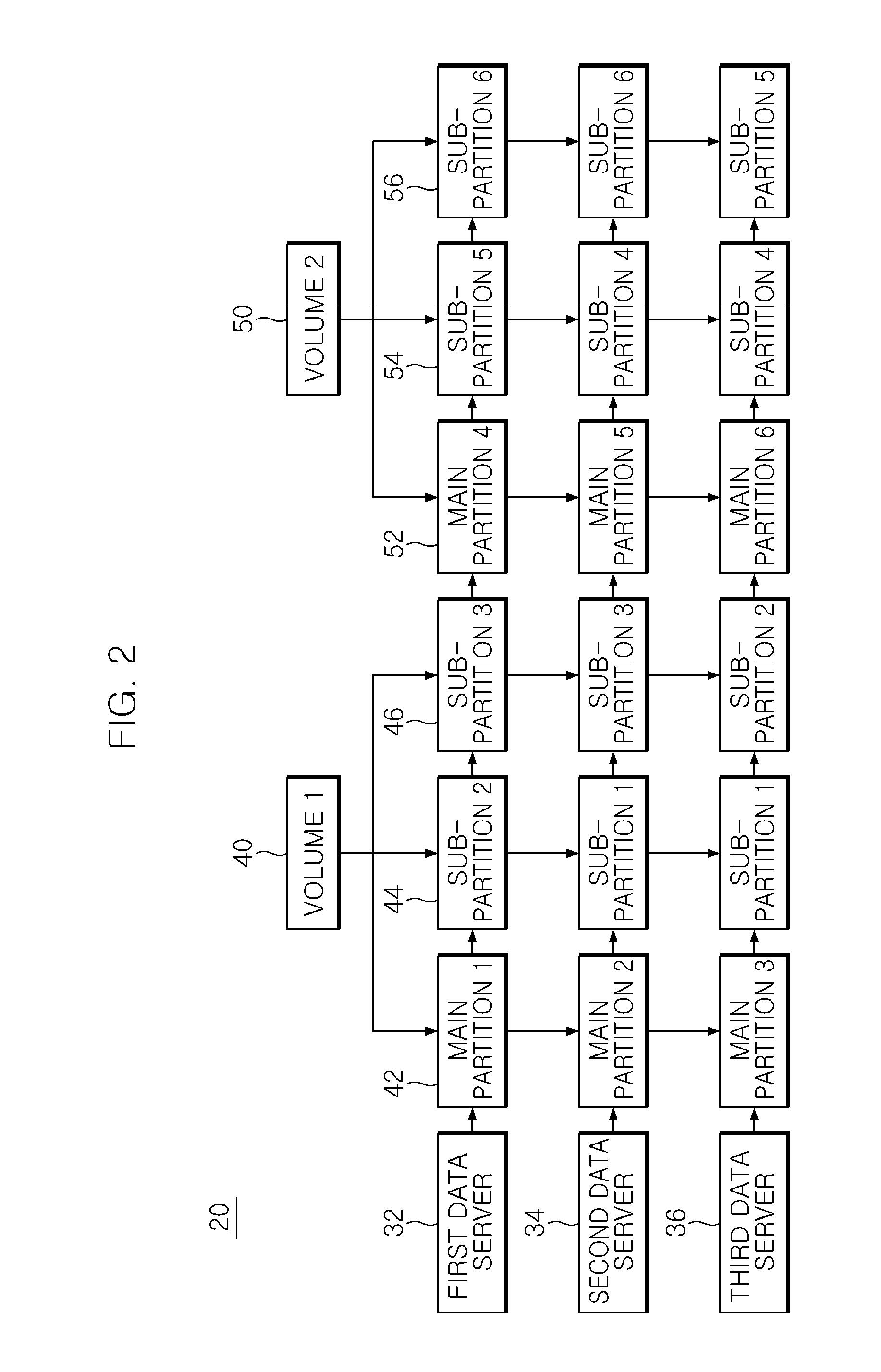
InactiveUS20110153570A1Efficiently processing chunk replicationEffective recoveryDigital data information retrievalMemory loss protectionRecovery methodSpatial partition
Disclosed herein is data replication and recovery method in an asymmetric clustered distributed file system, which divides the storage space of a data server into main partitions and sub-partitions, and separately manages main chunks and sub-chunks in the main partitions and the sub-partitions, thus efficiently processing chunk replication and recovery. In the disclosed method, when a failure occurs in a data server in an asymmetric clustered distributed file system, a failed partition is reported to all data servers including other partitions of a volume to which the partitions of the failed data server belong. Accordingly, other data servers can simultaneously perform the recovery of chunks using the information of their own main chunks and sub-chunks. As a result, when a failure occurs in a data server, all related data servers can simultaneously participate in data recovery, thus more promptly and efficiently coping with the failure.
Owner:ELECTRONICS & TELECOMM RES INST
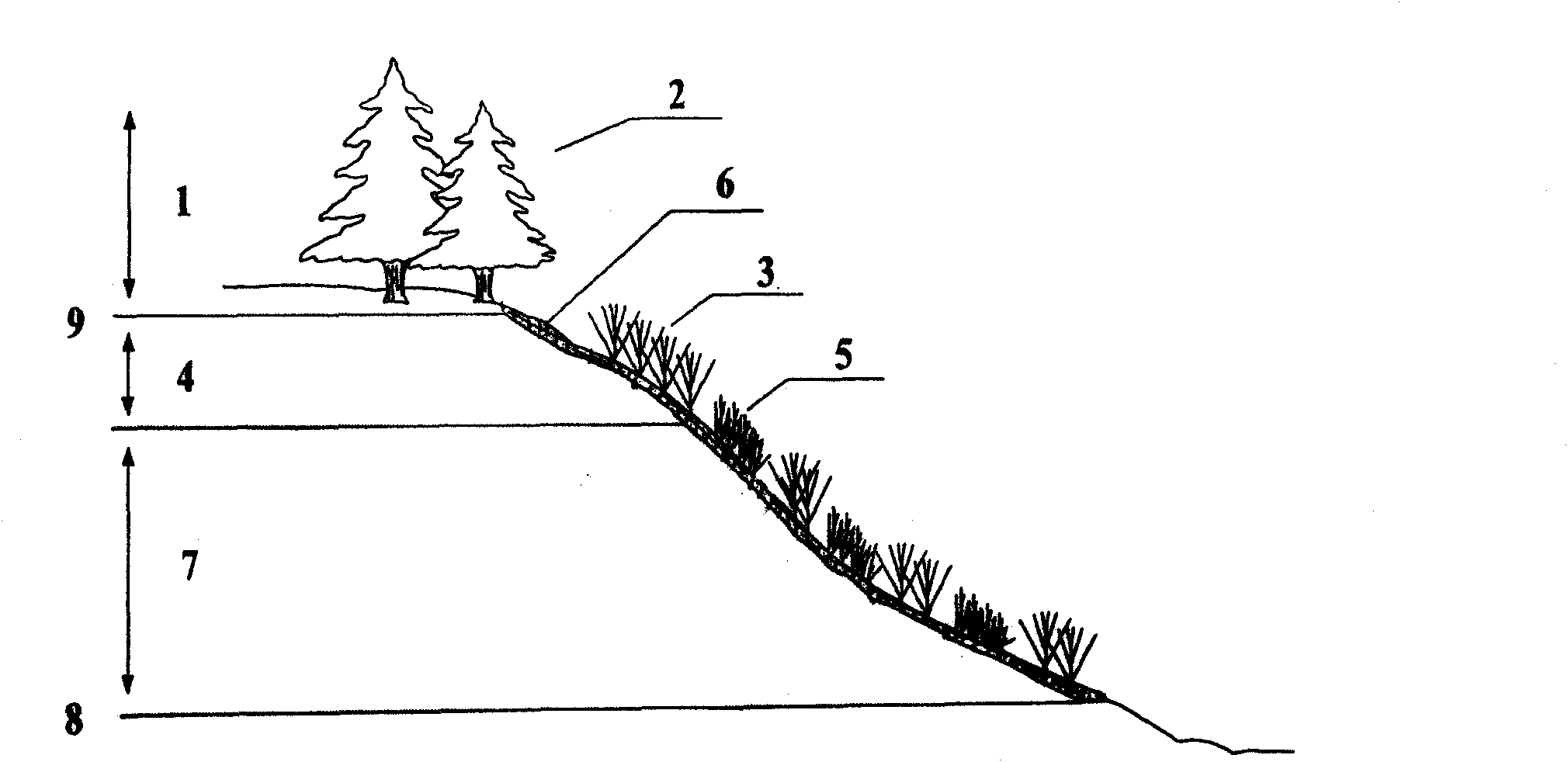
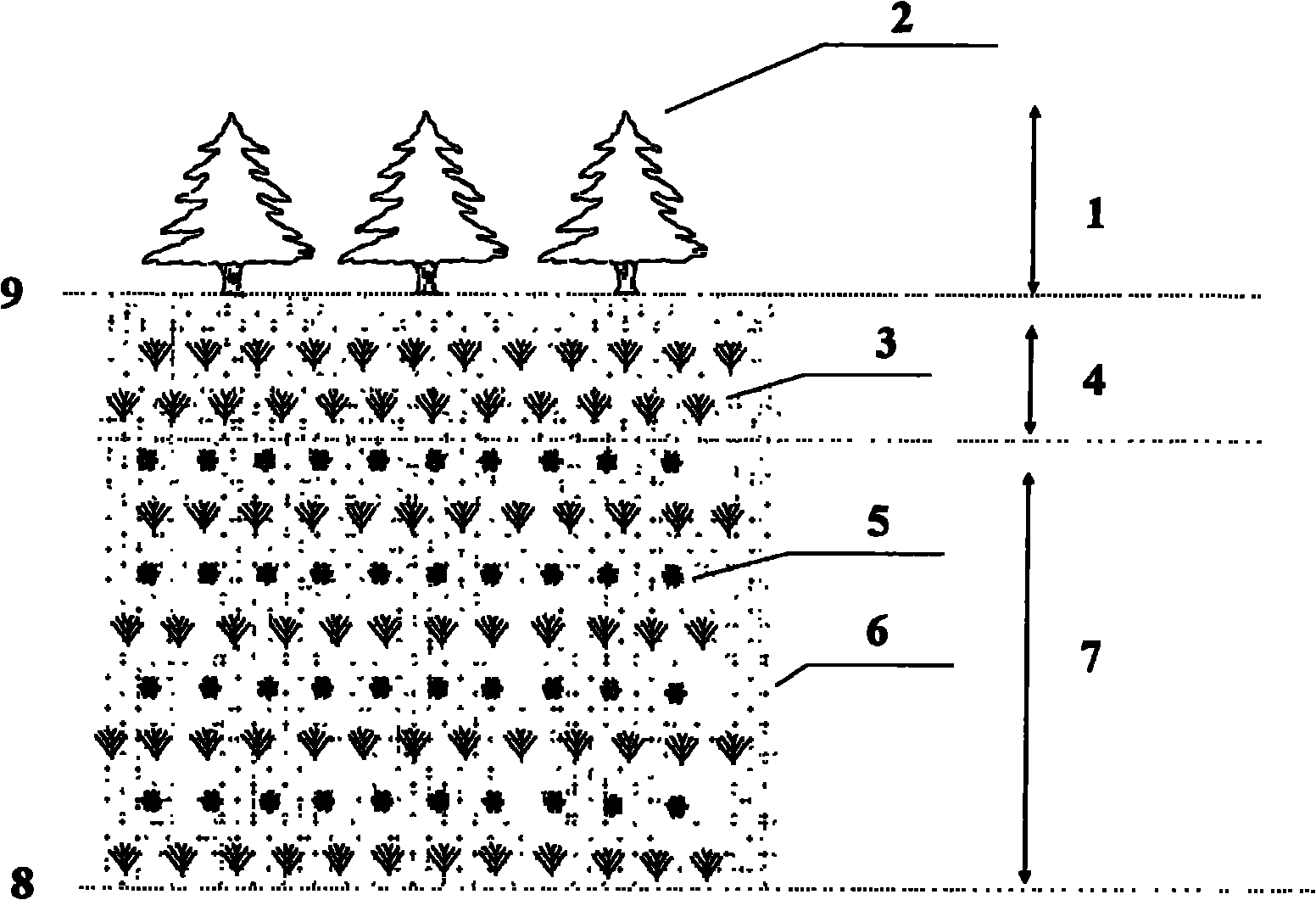
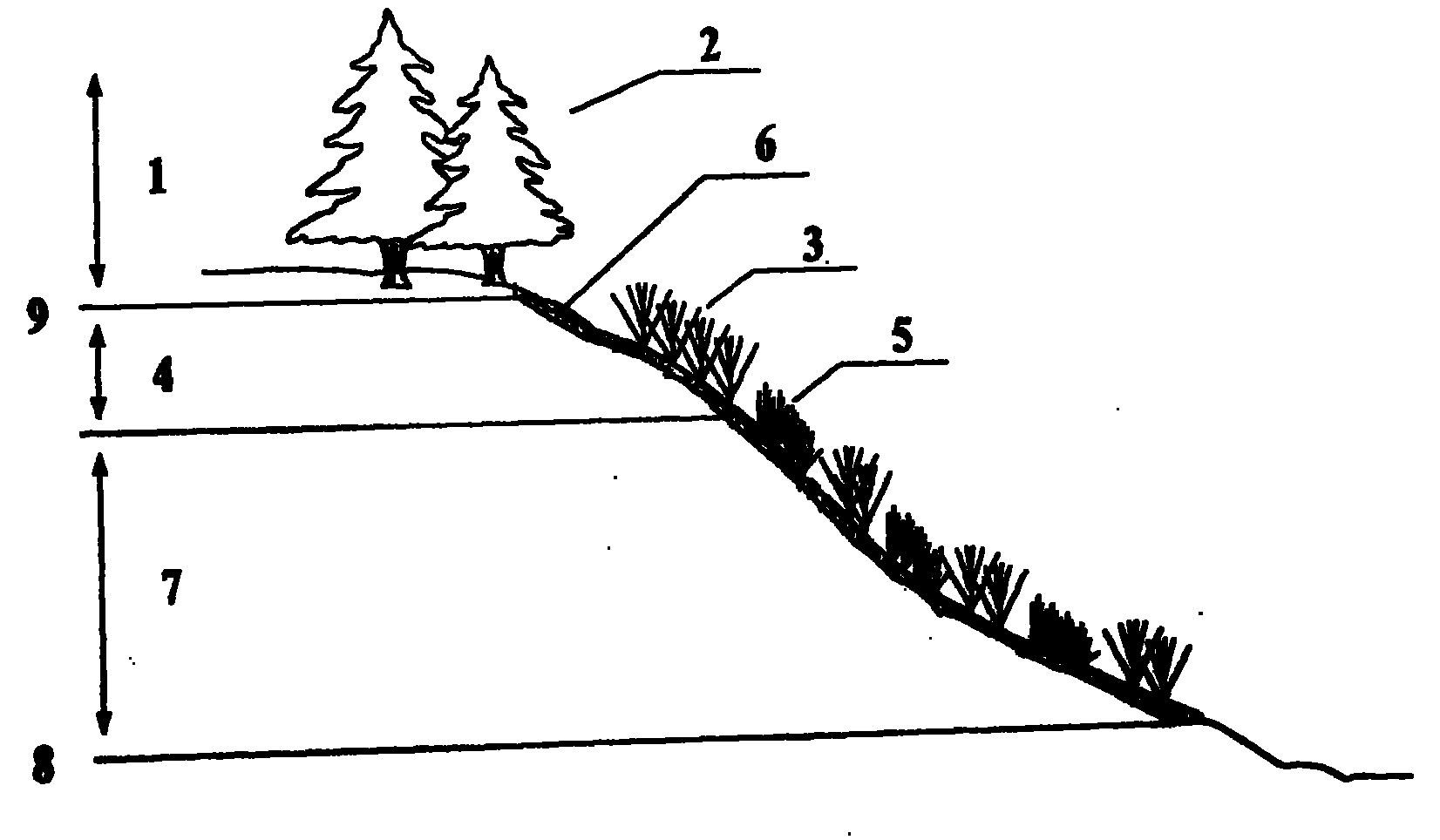
Restoration method for damaged ecosystem in steep-slope area in water-level-fluctuating zone of reservoir
InactiveCN101790931AAvoid erosionStable growth environmentAgriculture gas emission reductionHorticultureTerrainRestoration method
The invention relates to a restoration method for a damaged ecosystem in a steep-slope area in a water-level-fluctuating zone of a reservoir. The method comprises the following steps:when the impounded water level is at the lowest point, cleaning the upstream slope in the water-level-fluctuating zone, and manually tamping; digging planting holes at the top of the slope, and planting Chinese red pines and the like to form a multifunctional protective forest belt; digging planting grooves and planting holes within the range of the water-level-fluctuating zone, laying jute geotextile, planting vetiver within the range with the water-level-fluctuating depth of 2m to form a hedgerow; and mixedly planting vetiver and wire grass within the range with the water-level-fluctuating depth of 2-10m to form a combined vegetation slope restoration belt. The protective forest belt, the hedgerow and the combined vegetation slope restoration belt form a three-dimensional restoration space together, thereby ensuring that plants can take roots and restore in the steep-slope area in the water-level-fluctuating zone. By restoring the vegetation in large area, the invention effectively reduces the overland flow and the soil erosion, and improves the fertility and the properties of the soil, thereby restoring the damaged ecosystem. The invention has the advantages of convenient construction and less investment, can not be easily damaged by water, and is applicable to the water-level-fluctuating zone of a reservoir with large water-level-fluctuating range and precipitous topography.
Owner:HUAZHONG AGRI UNIV
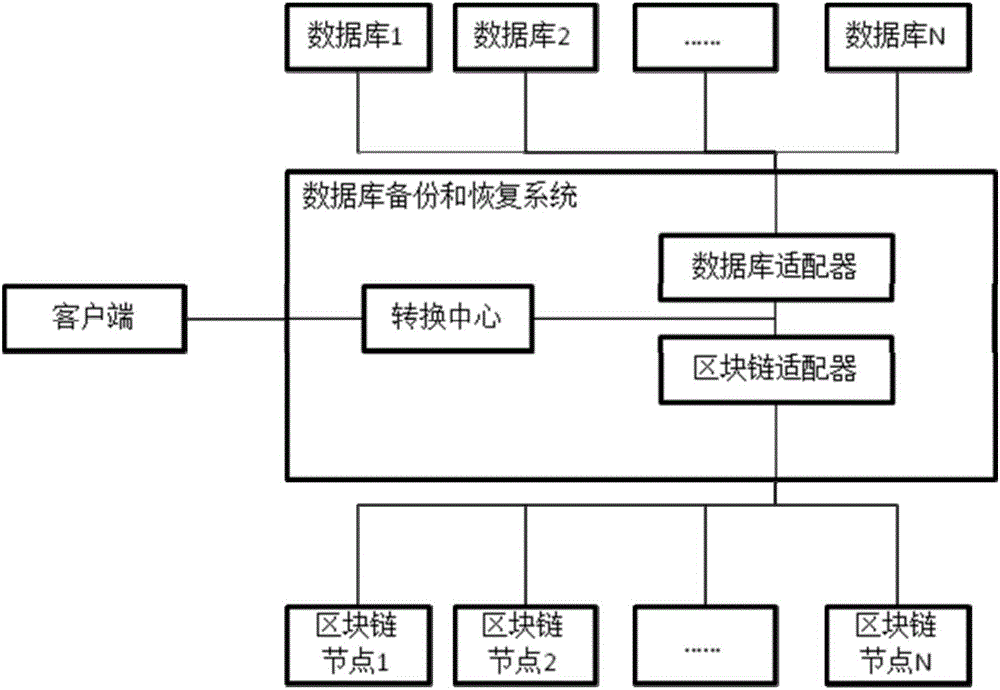
Database backup and recovery system based on block chain technology, and database backup method based on block chain technology, and database recovery method based on block chain technology
InactiveCN106383754ASafe and reliable backupEfficient deploymentRedundant operation error correctionSpecial data processing applicationsRecovery methodDatabase backup
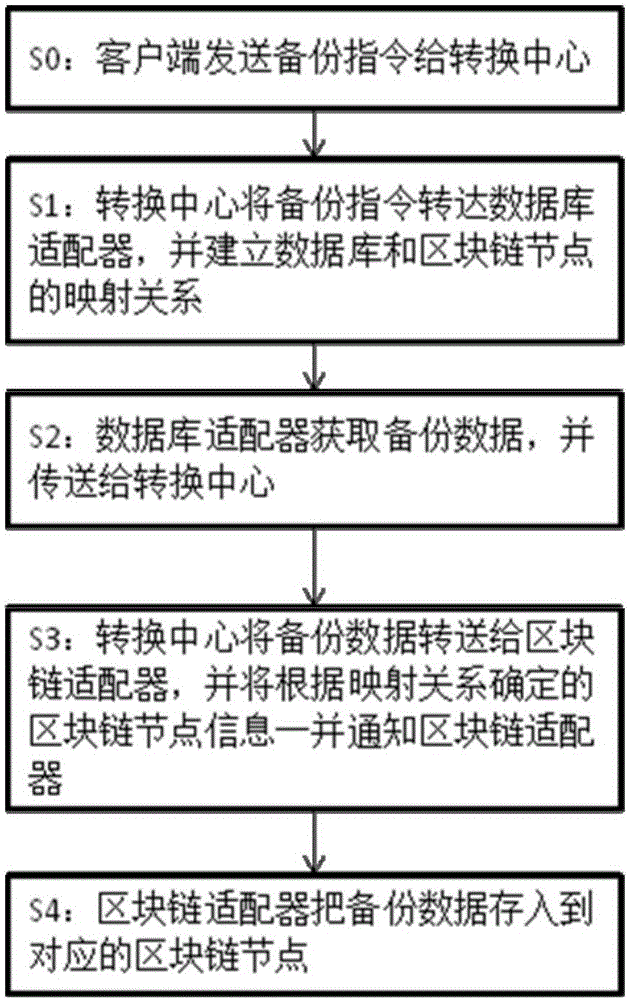
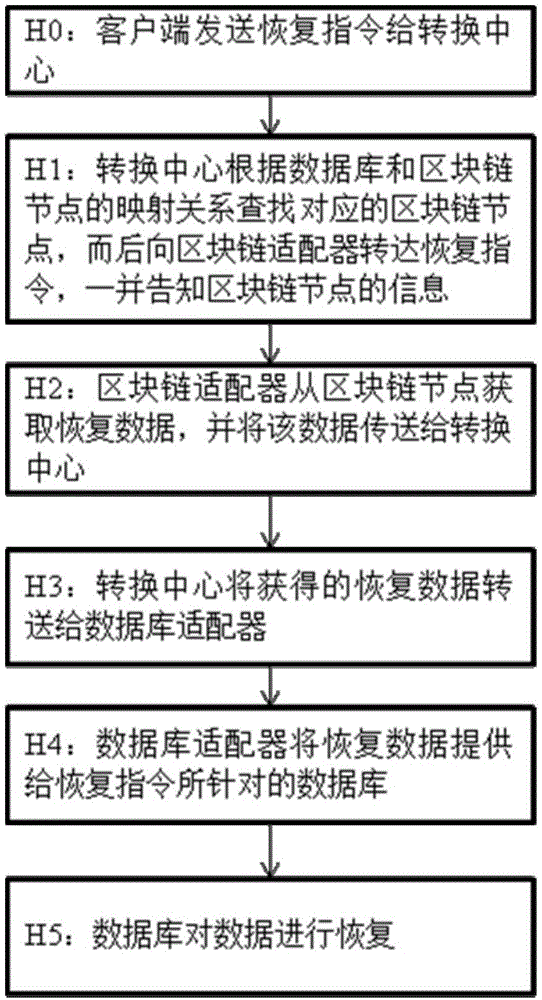
The invention provides a database backup and recovery system based on a block chain technology. The database backup and recovery system comprises a switching center, wherein the switching center is connected with a client side, is connected with one or a plurality of databases and is connected with one or a plurality of block chain nodes through a block chain adapter, and the switching center manages mapping relationships between the plurality of databases and the plurality of block chain nodes for data backup and recovery. The invention also provides a database backup method based on the block chain technology, and a database recovery method based on the block chain technology. The block chain technology is used, the characteristics that the block chain technology can not be tampered and can be permanently stored are utilized, meanwhile, data is distributed in the block chain nodes, overall failure caused by the faults of a center point can be avoided, so that safe and reliable database backup is realized, most of organizations can properly control cost and effectively deploy a backup scheme in existing environment to enable the requirements of most of organizations to be met, and the methods and the system can be generally implemented and have a very wide application scene.
Owner:BEIJING ZHONGXIANG BIT TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com