Patents
Literature
50results about How to "Avoid backup" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
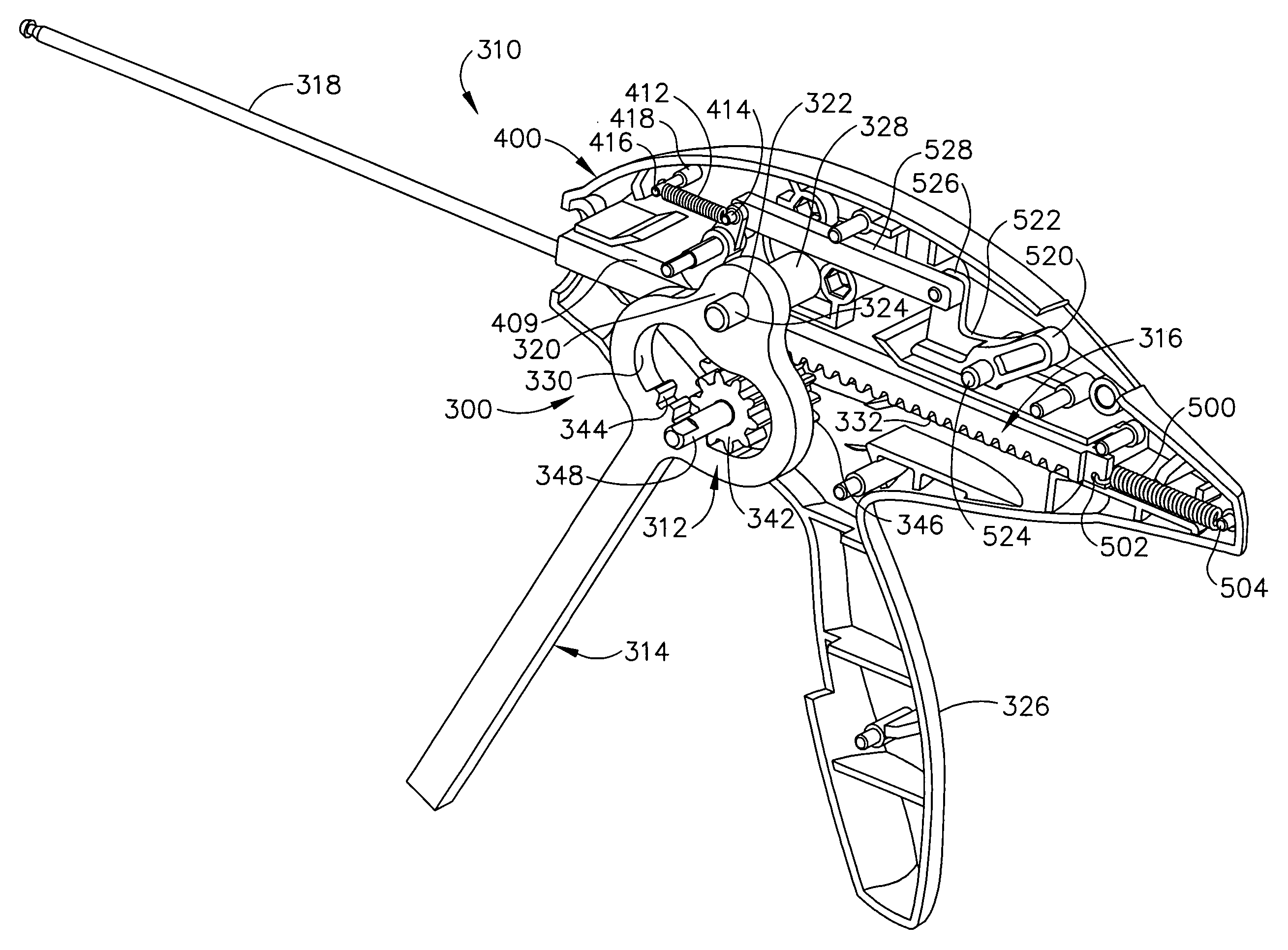
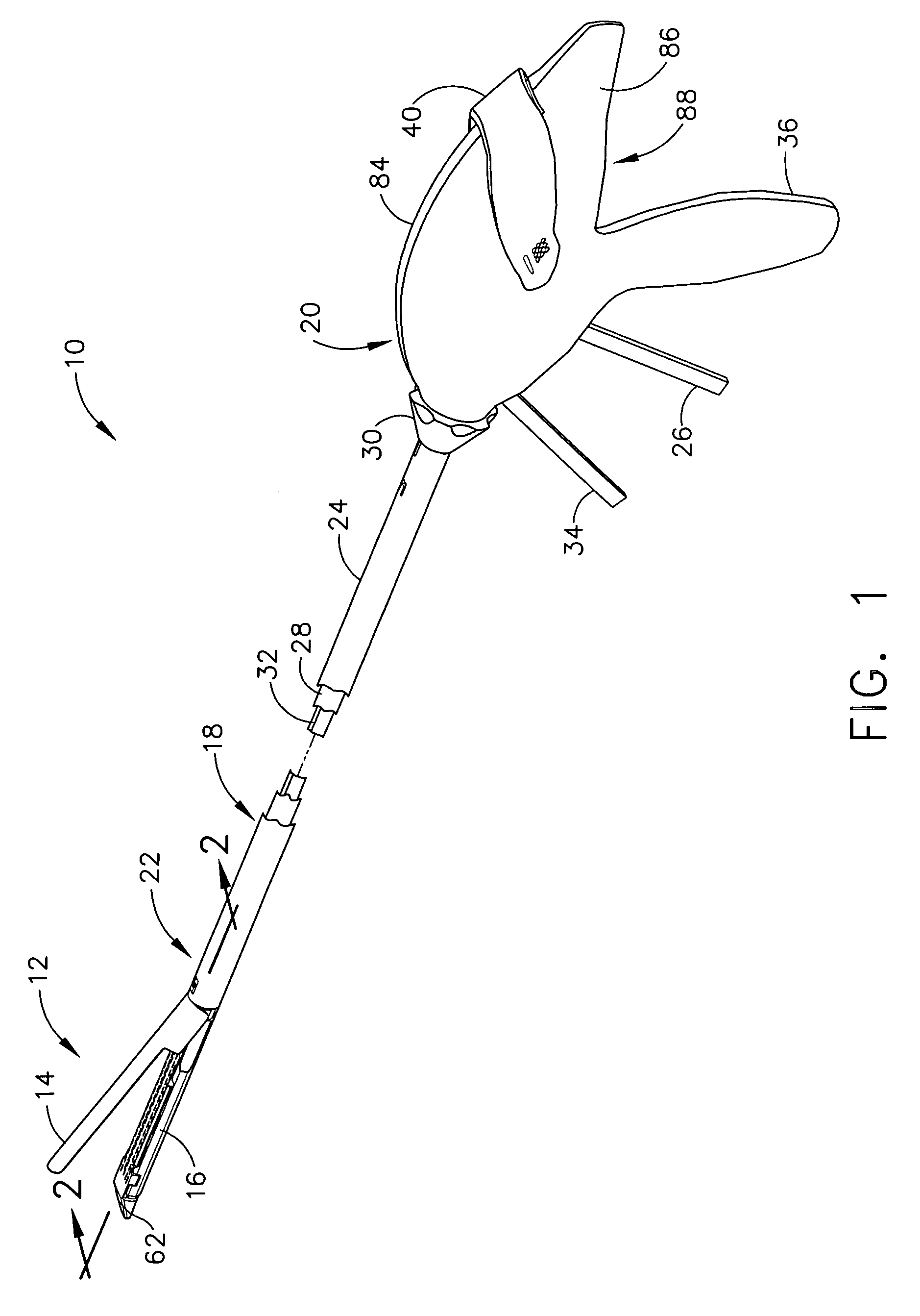
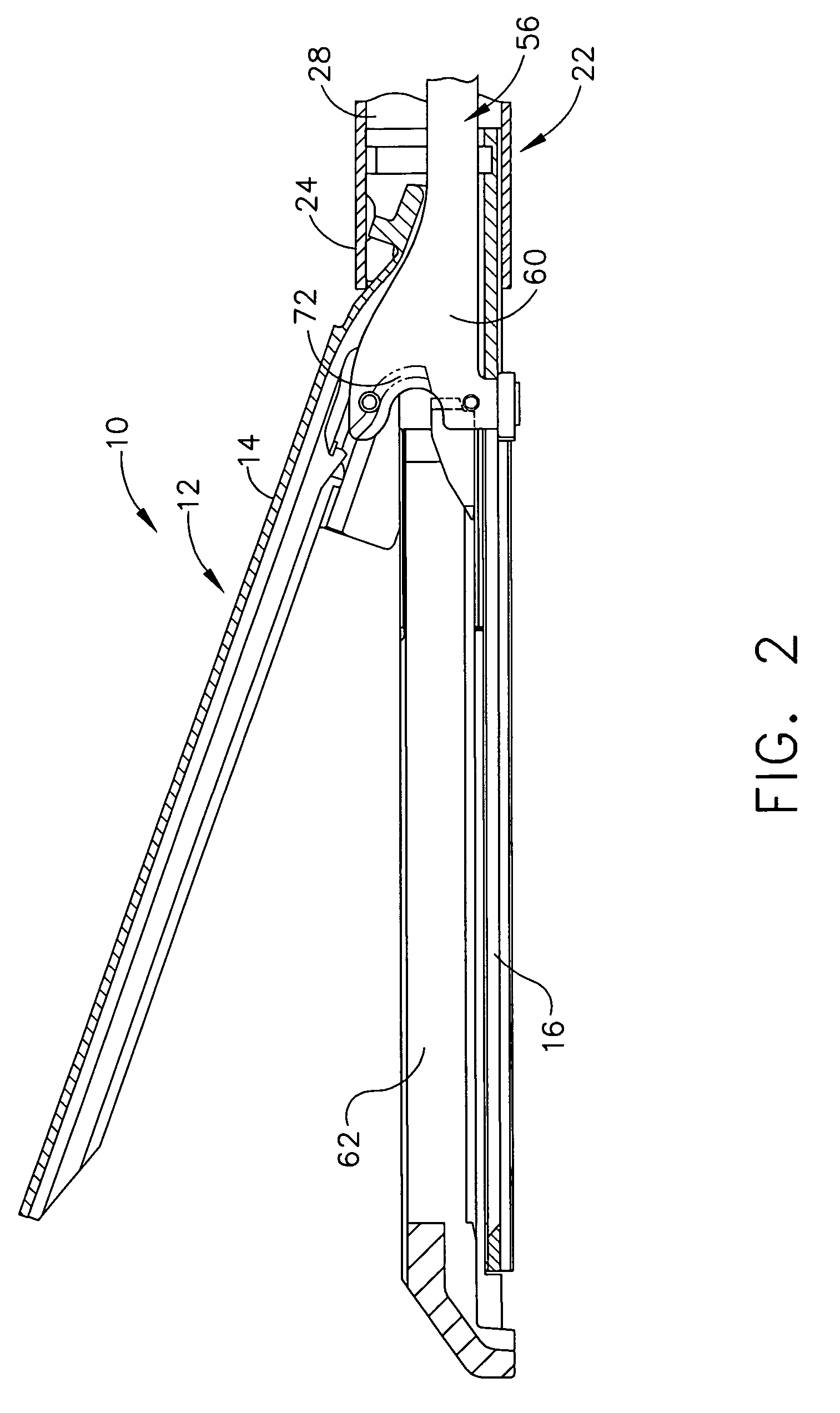
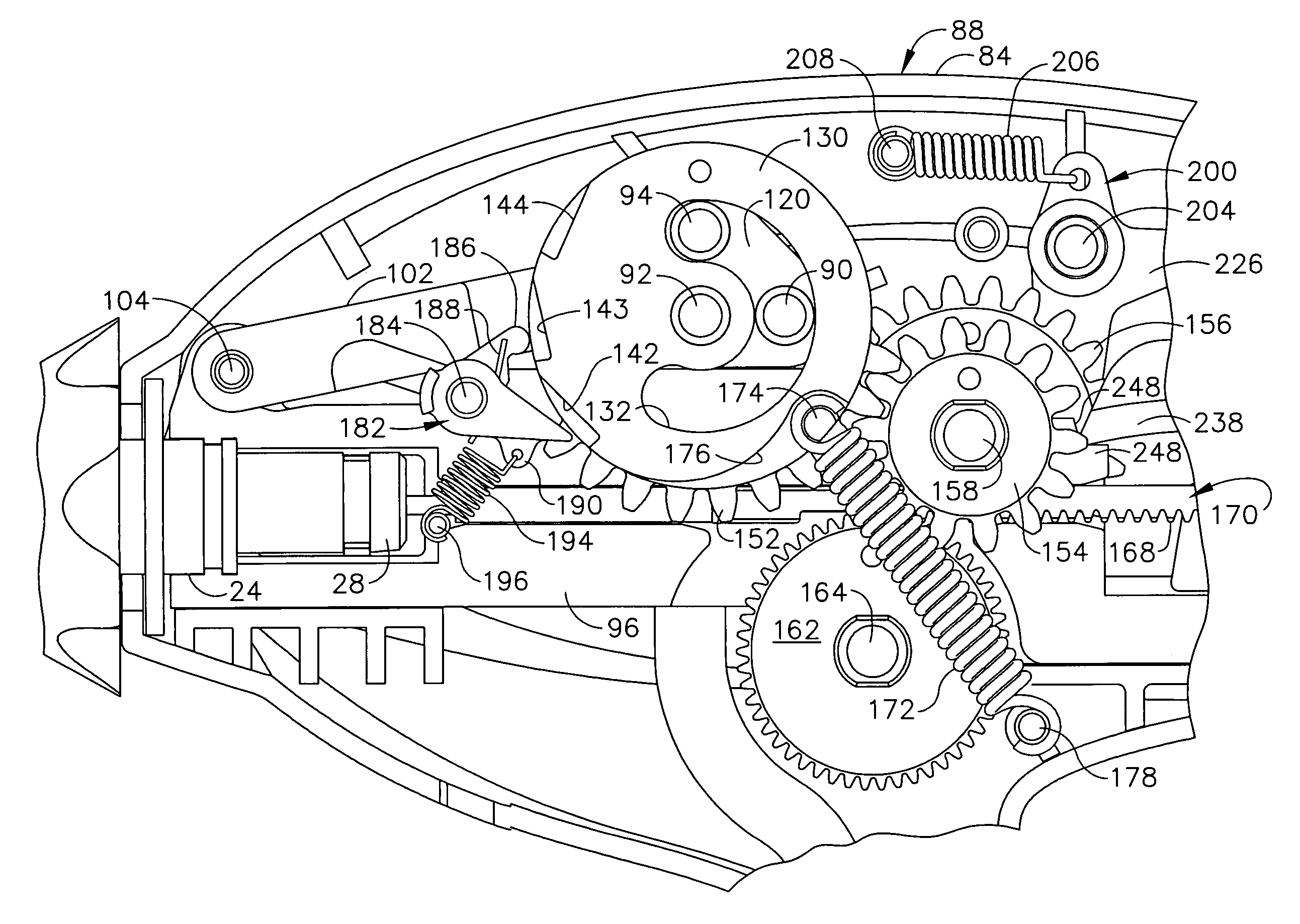
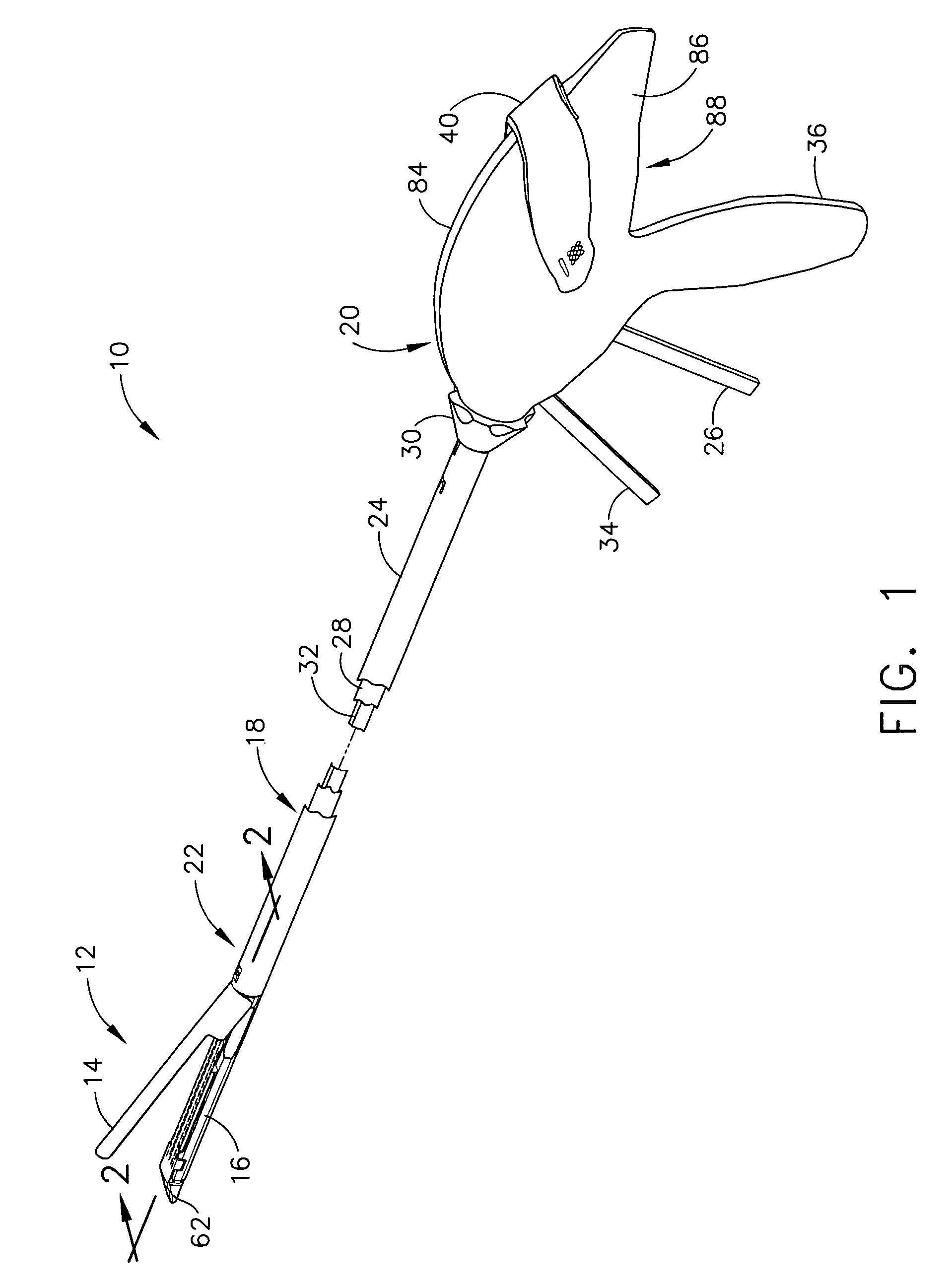
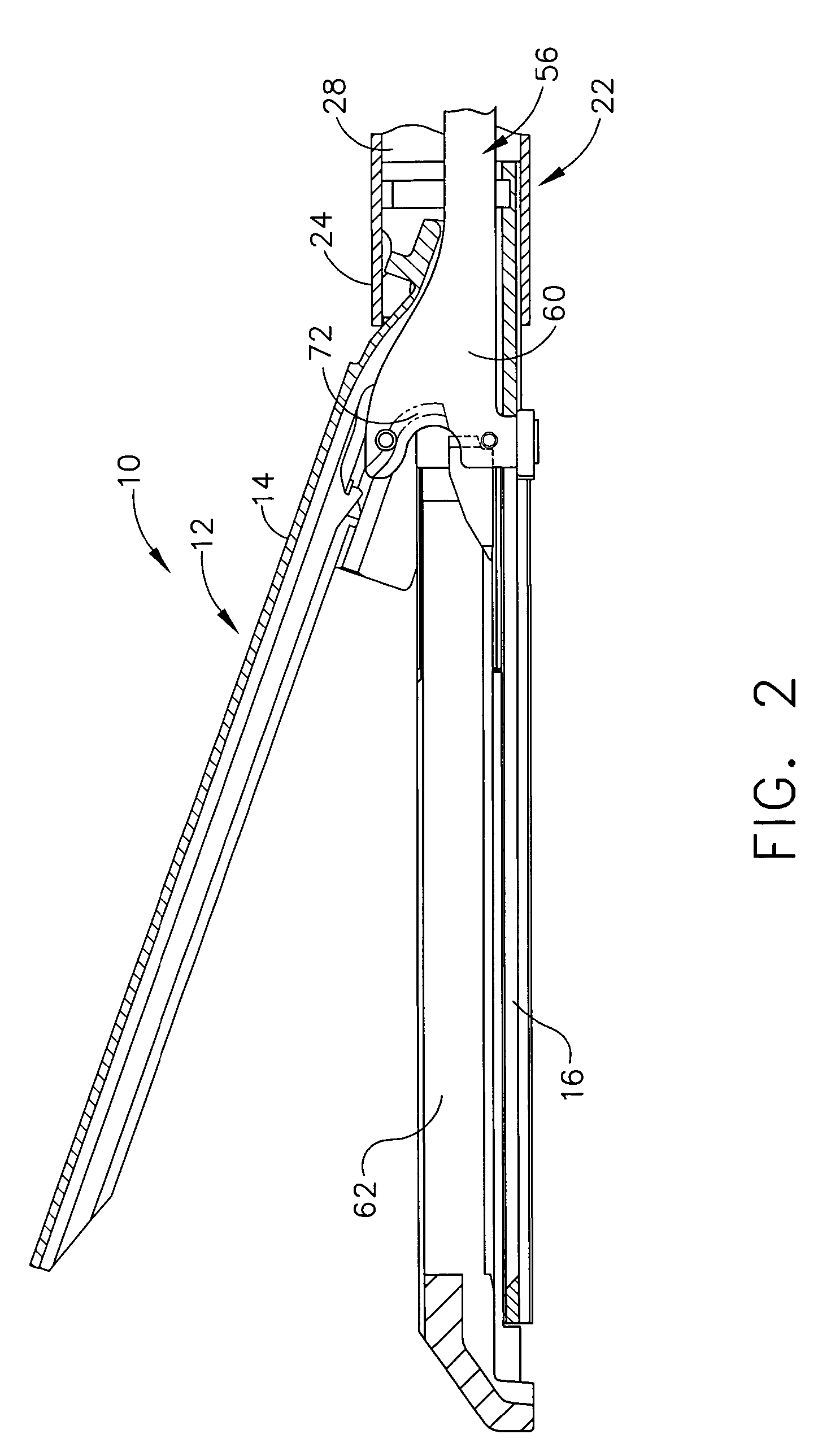
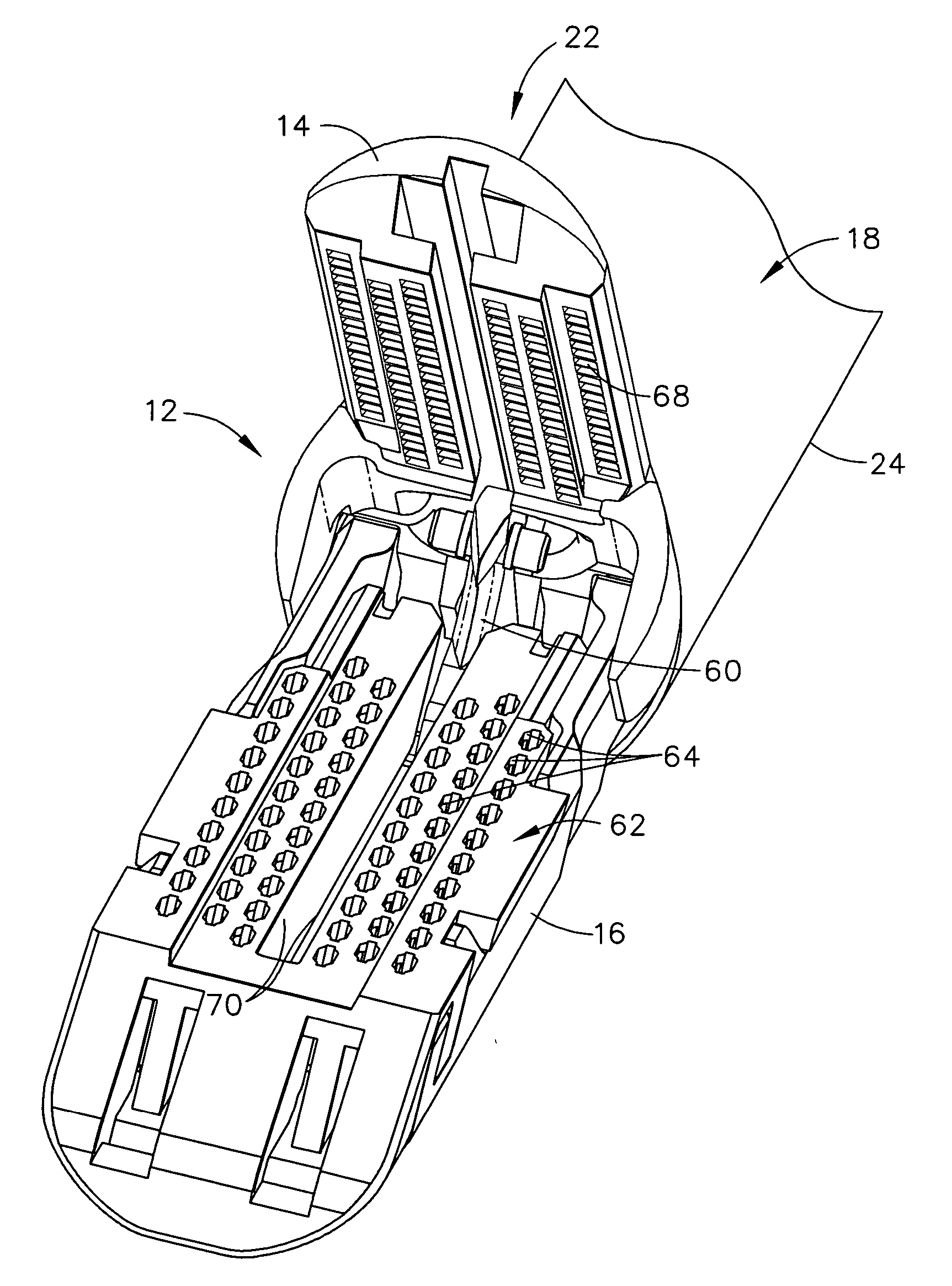
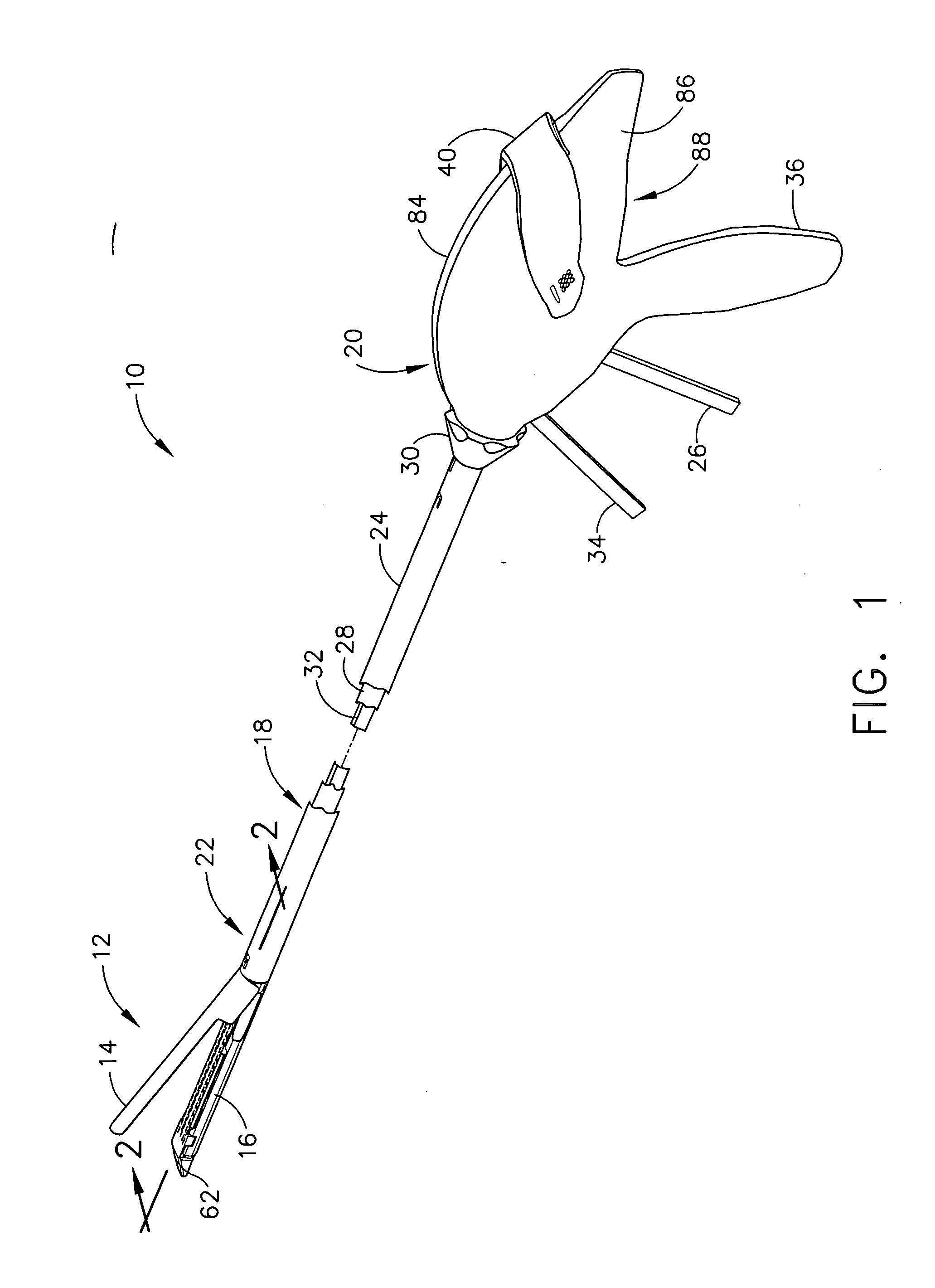
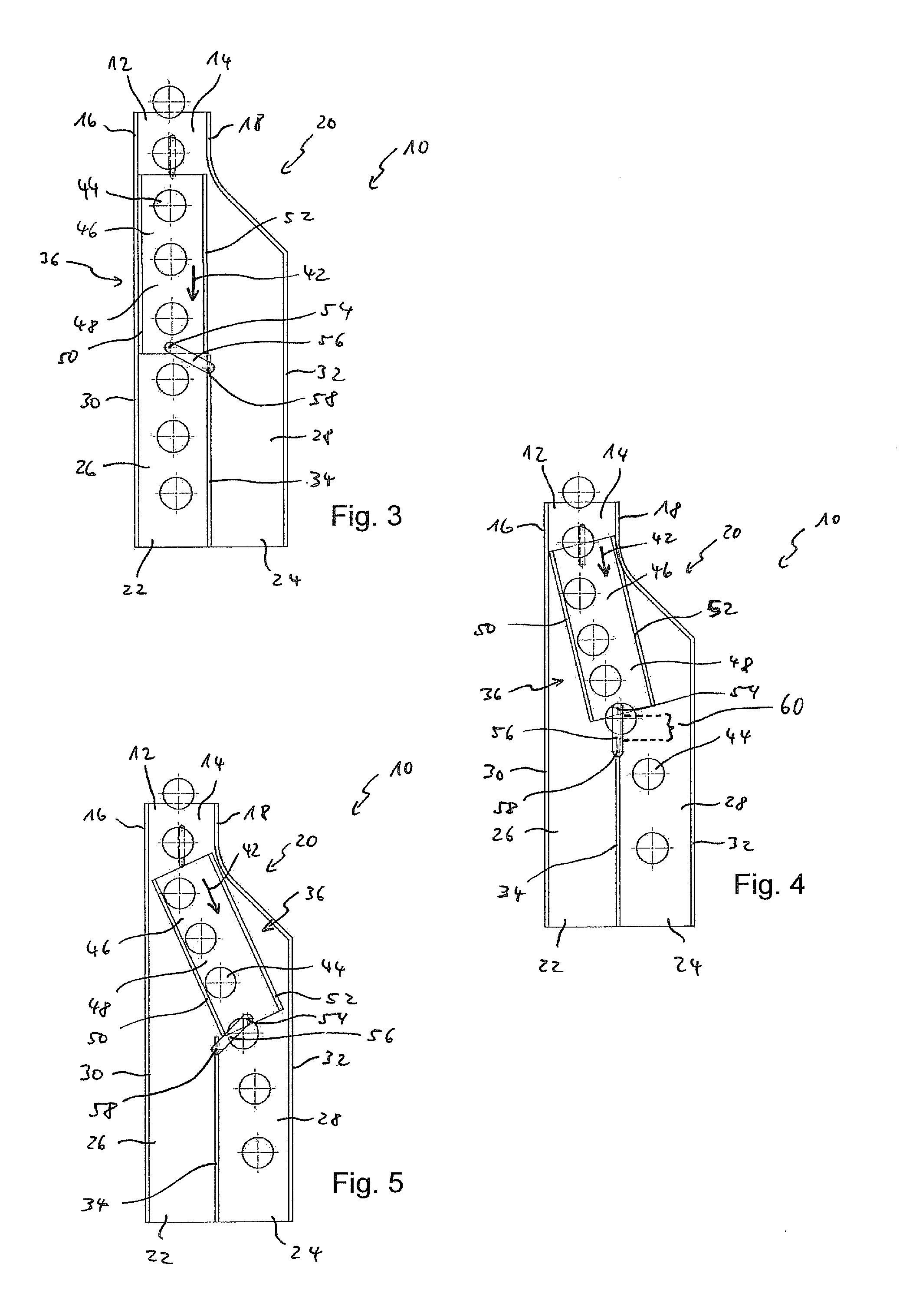
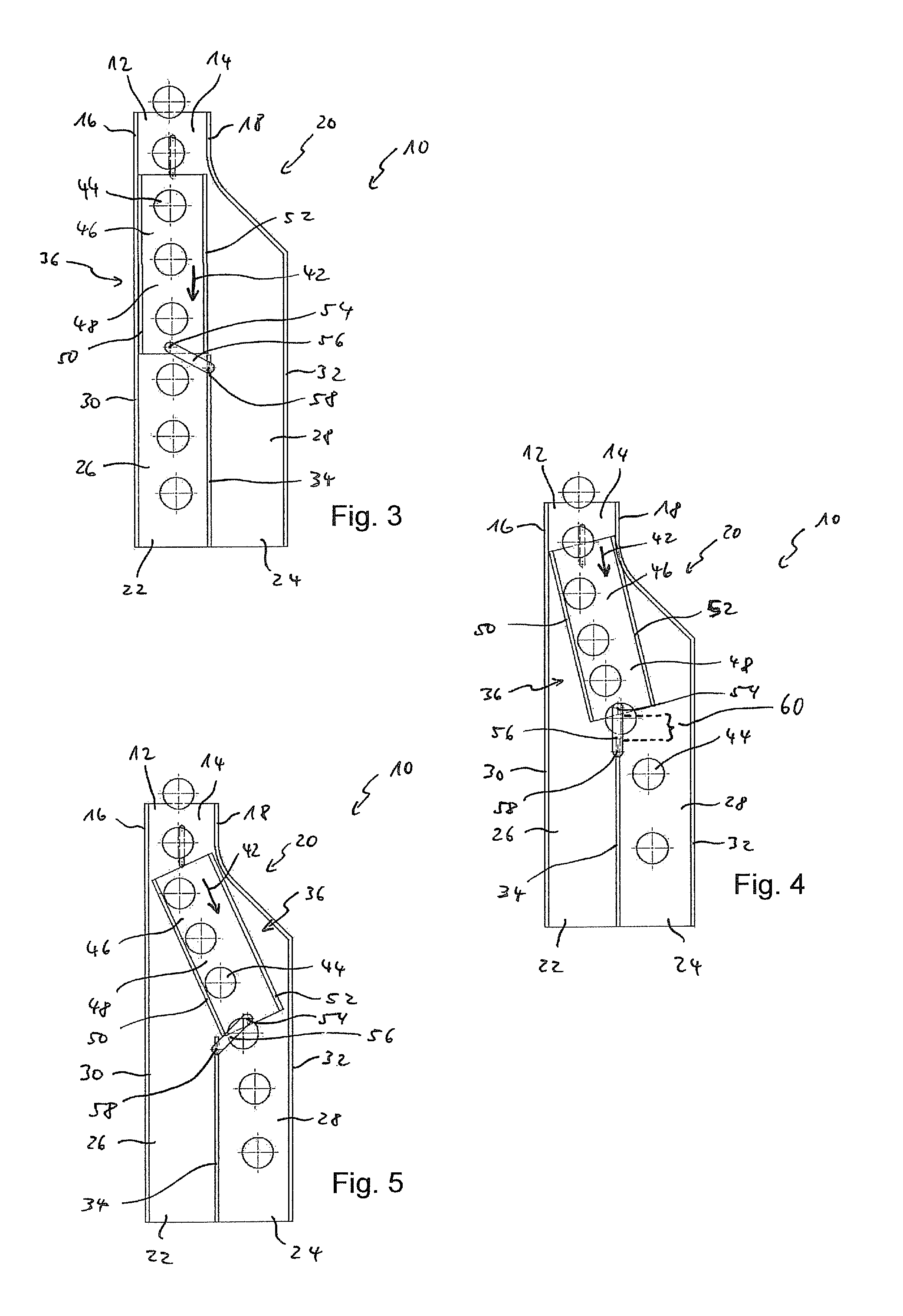
Surgical stapling instrument incorporating a multistroke firing mechanism having a rotary slip-clutch transmission
ActiveUS7128254B2Promote fireIncrease forceSuture equipmentsStapling toolsSurgical stapleEngineering
A surgical stapling and severing instrument particularly suited to endoscopic procedures incorporates a handle that produces separate closing and firing motions to actuate an end effector. In particular, the handle produces multiple firing strokes in order to reduce the required amount of force required to fire (i.e., staple and sever) the end effector.
Owner:CILAG GMBH INT
Surgical stapling instrument incorporating a multistroke firing mechanism having a rotary transmission
ActiveUS7367485B2Promote fireIncrease forceSuture equipmentsStapling toolsSurgical stapleEngineering
A surgical stapling and severing instrument particularly suited to endoscopic procedures incorporates a handle that produces separate closing and firing motions to actuate an end effector. In particular, the handle produces multiple firing strokes in order to reduce the required amount of force required to fire (i.e., staple and sever) the end effector.
Owner:CILAG GMBH INT
Surgical stapling instrument incorporating a multistroke firing mechanism having a rotary slip-clutch transmission
ActiveUS20060049230A1Promote fireIncrease forceSuture equipmentsStapling toolsSurgical stapleEngineering
A surgical stapling and severing instrument particularly suited to endoscopic procedures incorporates a handle that produces separate closing and firing motions to actuate an end effector. In particular, the handle produces multiple firing strokes in order to reduce the required amount of force required to fire (i.e., staple and sever) the end effector.
Owner:CILAG GMBH INT
Surgical stapling instrument incorporating a multistroke firing mechanism having a rotary transmission
ActiveUS20060000868A1Promote fireIncrease forceSuture equipmentsStapling toolsSurgical stapleEndoscopic Procedure
A surgical stapling and severing instrument particularly suited to endoscopic procedures incorporates a handle that produces separate closing and firing motions to actuate an end effector. In particular, the handle produces multiple firing strokes in order to reduce the required amount of force required to fire (i.e., staple and sever) the end effector.
Owner:CILAG GMBH INT
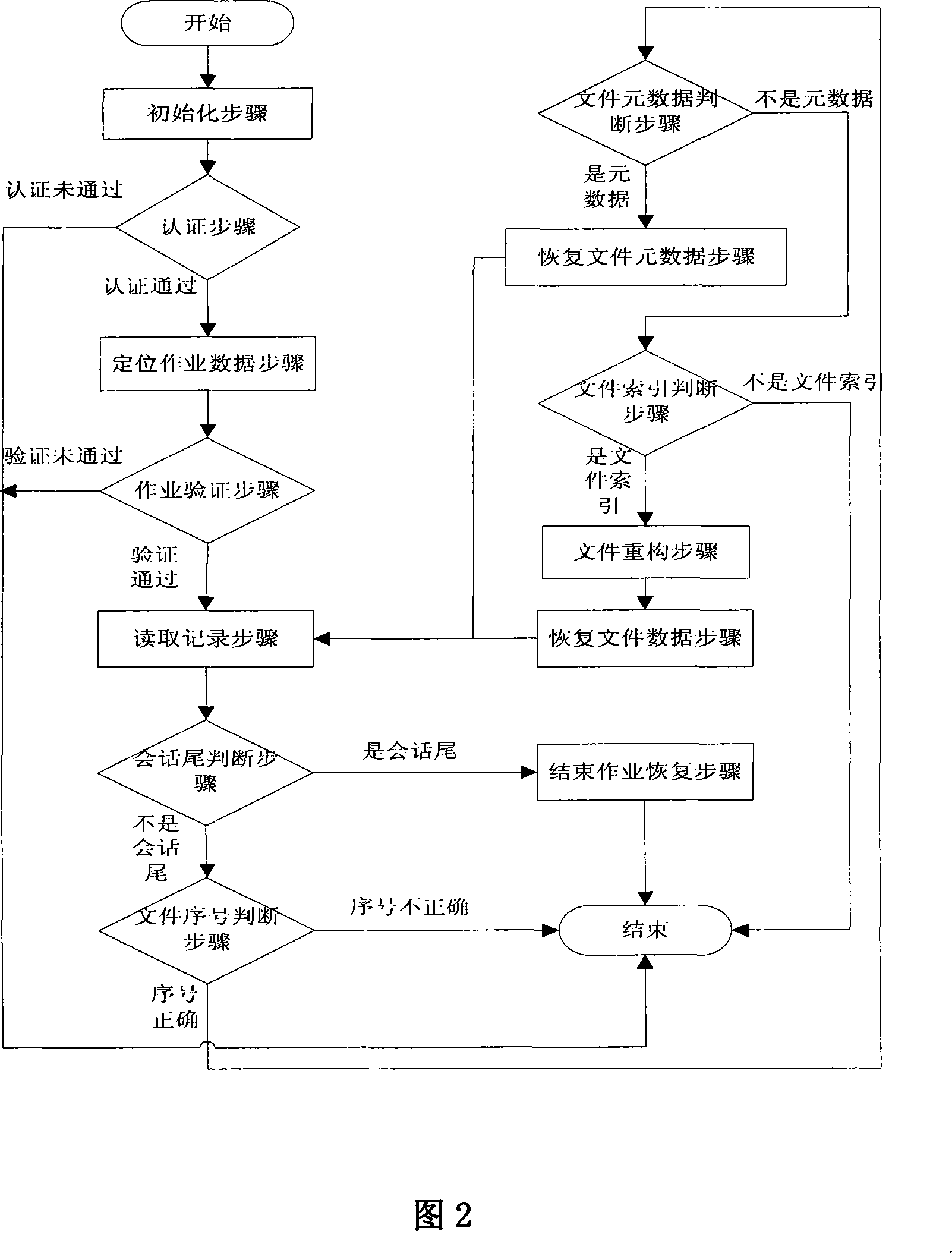
Recovery method for master boot record of hard disk drive
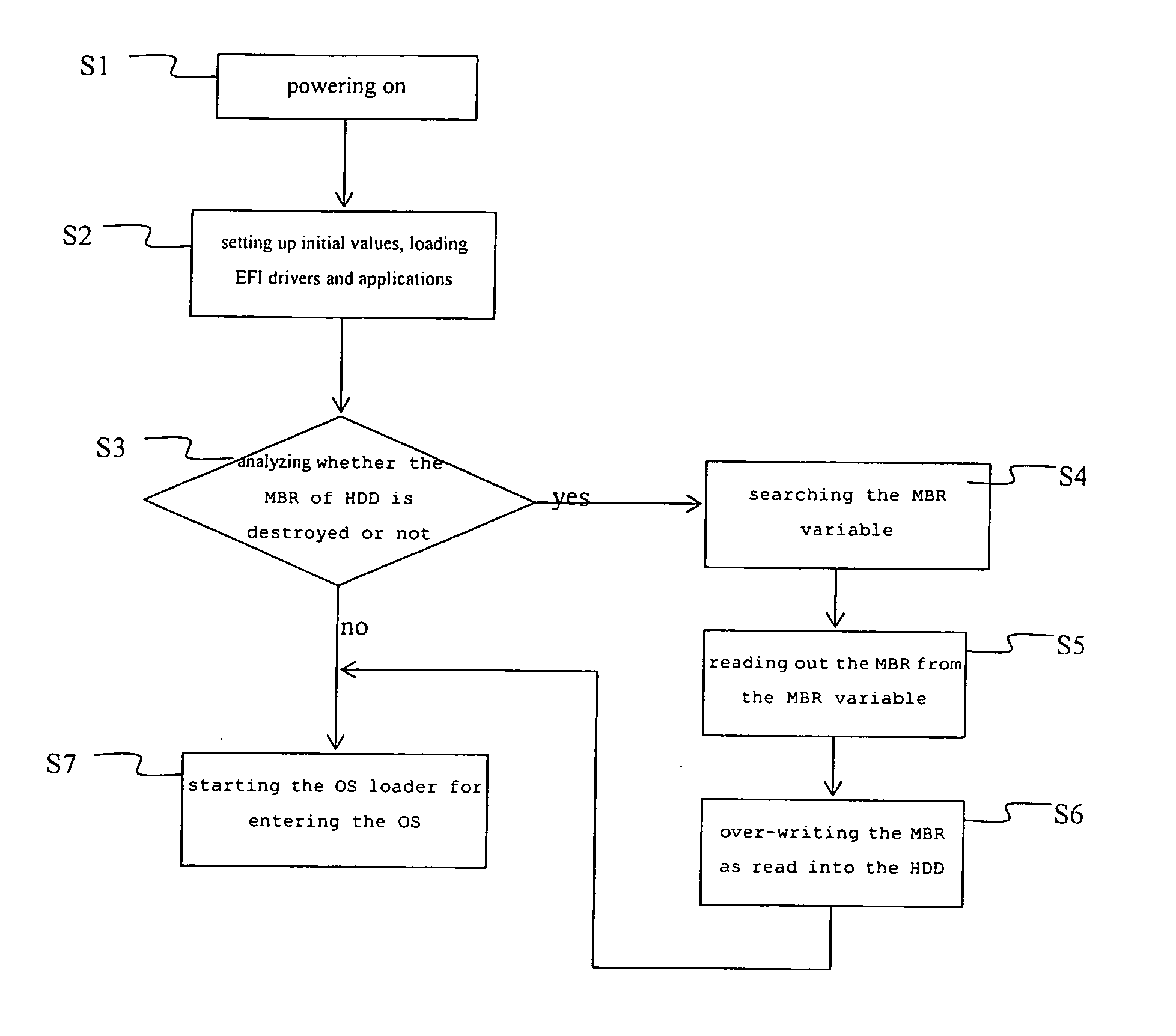
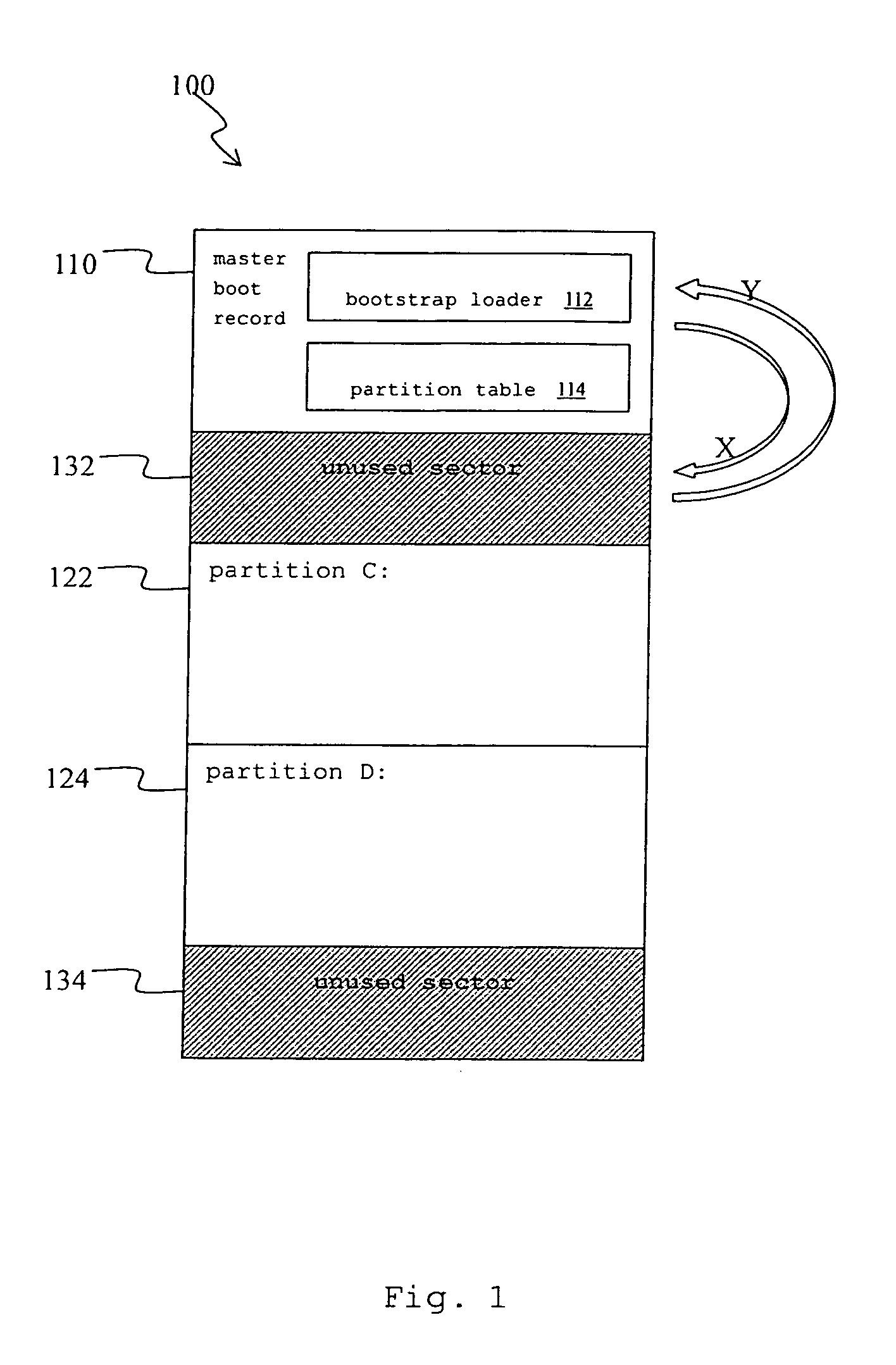
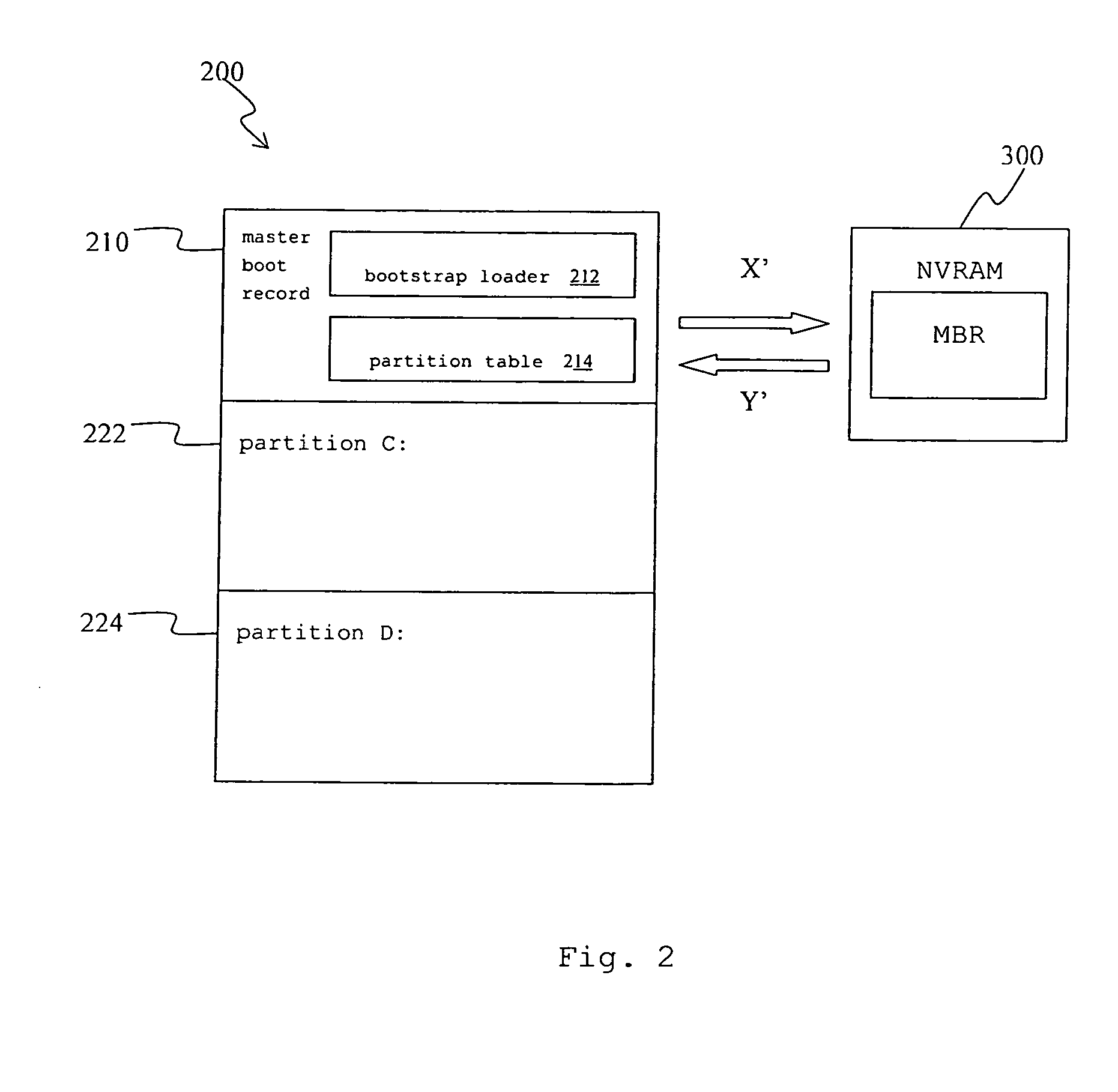
InactiveUS20060041738A1Avoid backupAvoid damageError detection/correctionDigital computer detailsRecovery methodHard disc drive
A recovery method for a master boot record of a hard disk drive is adapted to a computer system incorporating extensible firmware interface (EFI). When modification occurs in the master boot record, the extensible firmware interface stores the master boot record in an NVRAM (Non-volatile Random Access Memory) as a backup. The backup is read out for recovery of the hard disk driver if the master boot record is destroyed. The NVRAM is write-protected during runtime and the backup data stored therein is therefore free from destruction.
Owner:INSYDE SOFTWARE CORP
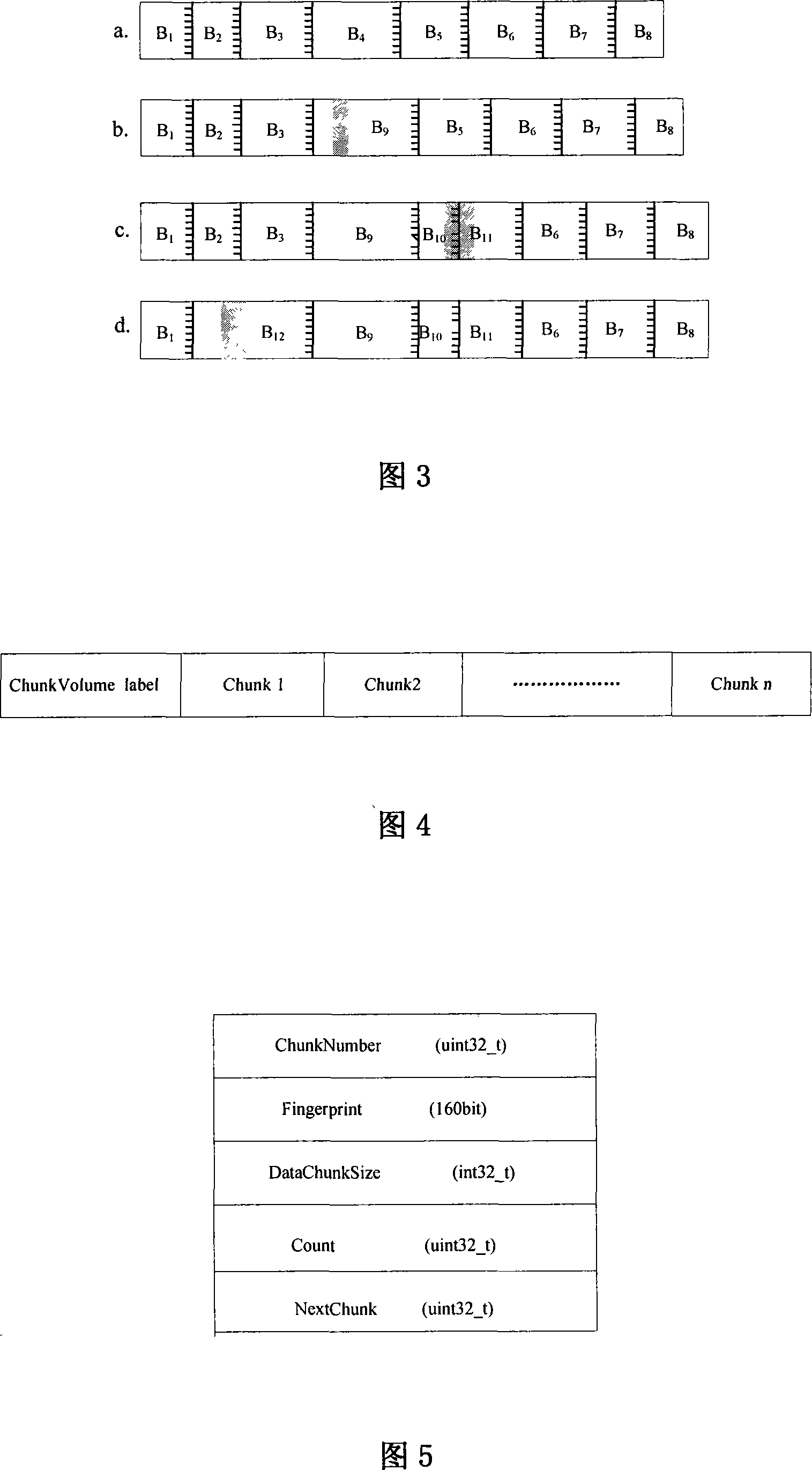
File backup method based on fingerprint
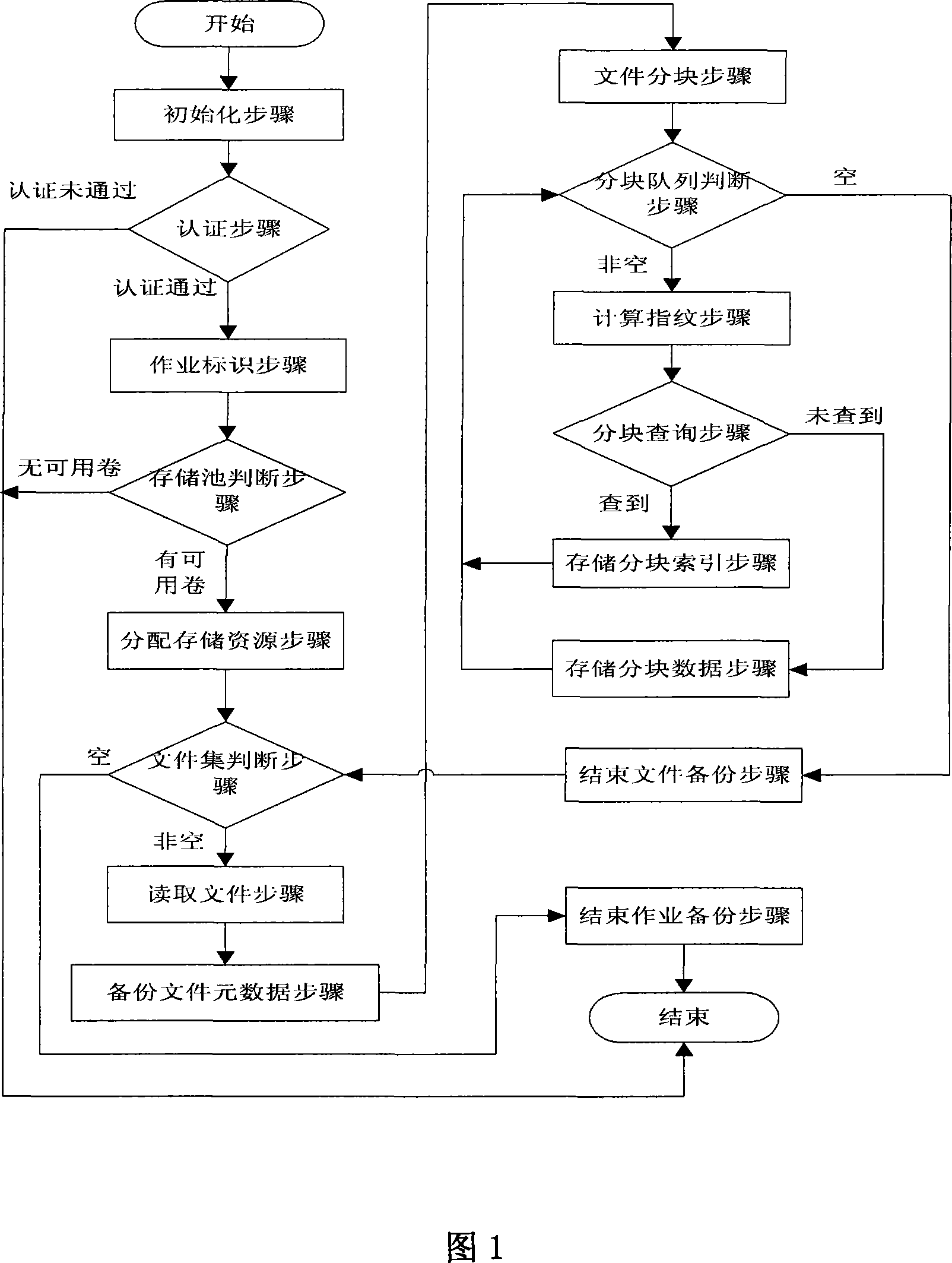
InactiveCN101216791AReduce overall backupSave bandwidthRedundant operation error correctionSpecial data processing applicationsFile sharingComputer science
The invention relates to a file backup method based on fingerprints, belonging to the technical field of storage backup in a computer. The invention is amied at reducing the backup of duplicated data, saving the cost of network bandwidth and storage needed by backup, and improving the backup efficiency. The invention comprises a backup process and a recovery procedure. The invention adopts the file blocking technology based on an anchorage to identify the redundant data of the backup file, the modification is stable, and the computation cost is low; data blocking of the file is memorized in a blocking volume in a storage server by using the fingerprints thereof as an identifier, thereby avoiding the backup of the duplicated data, and facilitating the data blocking to be shared by different files; file metadata and file blocking index are memorized in a storage volume in the storage server, thereby facilitating a user to organize a storage pool, and realizing the personalized management to logical objects.
Owner:HUAZHONG UNIV OF SCI & TECH
Storm water treatment apparatus employing dual vortex separators
ActiveUS20050184007A1Avoid backupImprove liquidityReversed direction vortexLiquid displacementSuspended particlesEddy current separator
A stormwater treatment device for removing floatables, solids and suspended particles and the like from stormwater run off, whereby a removable assembly is provided for installation into a manhole basin, the assembly including a pass-through member which receives stormwater from an incoming drainage system, and diverts low flows to at least one or more vortex separators, while allowing for high flows to bypass the separators and flow through the assembly untreated to exit the basin without diversion.
Owner:OLDCASTLE PRECAST
Storm water treatment apparatus employing dual vortex separators
ActiveUS7182874B2Avoid backupImprove liquidityReversed direction vortexLiquid displacementSuspended particlesEddy current separator
A stormwater treatment device for removing floatables, solids and suspended particles and the like from stormwater run off, whereby a removable assembly is provided for installation into a manhole basin, the assembly including a pass-through member which receives stormwater from an incoming drainage system, and diverts low flows to at least one or more vortex separators, while allowing for high flows to bypass the separators and flow through the assembly untreated to exit the basin without diversion.
Owner:OLDCASTLE PRECAST
Data backup method and device
ActiveCN106407356ASupport recoveryReduce storage spaceSpecial data processing applicationsRedundant operation error correctionBackupLogfile
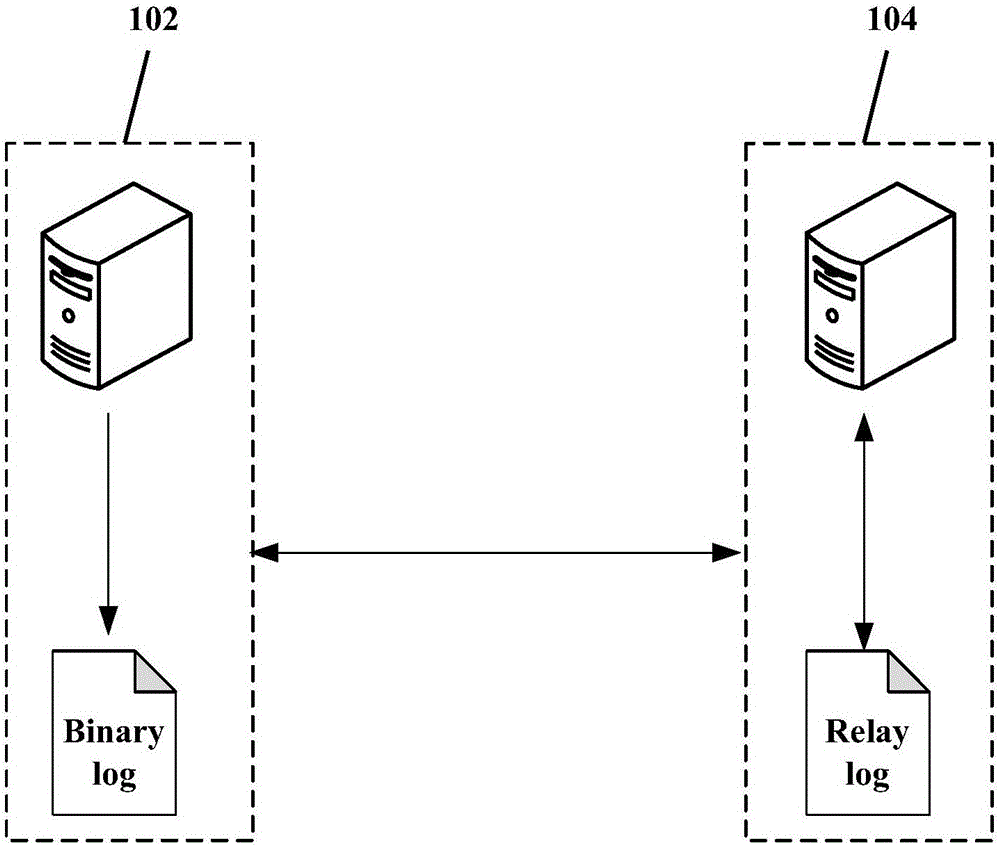
The embodiment of the invention provides a data backup method and device. The method comprises the steps of acquiring a final copy position of copied data in a binary system log file of a main database from a database during data backup in the database from the database based on a GTID (Global Transaction Identifier) mode; and acquiring a target binary system log file where the final copy position is located and a binary system log file behind the target binary system log file from the main database. According to the data backup method, during backup in the database based on the GTID mode, the backup data volume is reduced, the storage space occupied by the backup data is reduced, the backup time is reduced, and meanwhile, PIT (Point-In-time) recovery is effectively supported. Moreover, the embodiment of the invention provides a data backup device.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Guide bushing
The invention relates to a guide bushing between two components axially movable relative to each other, especially for guiding a piston rod subjected to longitudinal and transverse forces in the region of a piston rod seal of a hydropneumatic vibration damper. The guide bushing encompasses the piston rod, is held axially in a piston rod guide and is made of a material having good gliding characteristics. The guide bushing is arranged in the piston rod guide with a radial clearance having a gap with a changeable width when the piston rod is subjected to transverse forces created between the receptacle diameter of the piston rod guide and the outer diameter of the guide bushing.
Owner:ZF FRIEDRICHSHAFEN AG
Access hard switchover method and system of high speed downlink packet
ActiveCN1870591AAvoid invalid retransmission problemsAvoid large transmission delaysRadio/inductive link selection arrangementsData switching networksSource areaData transmission
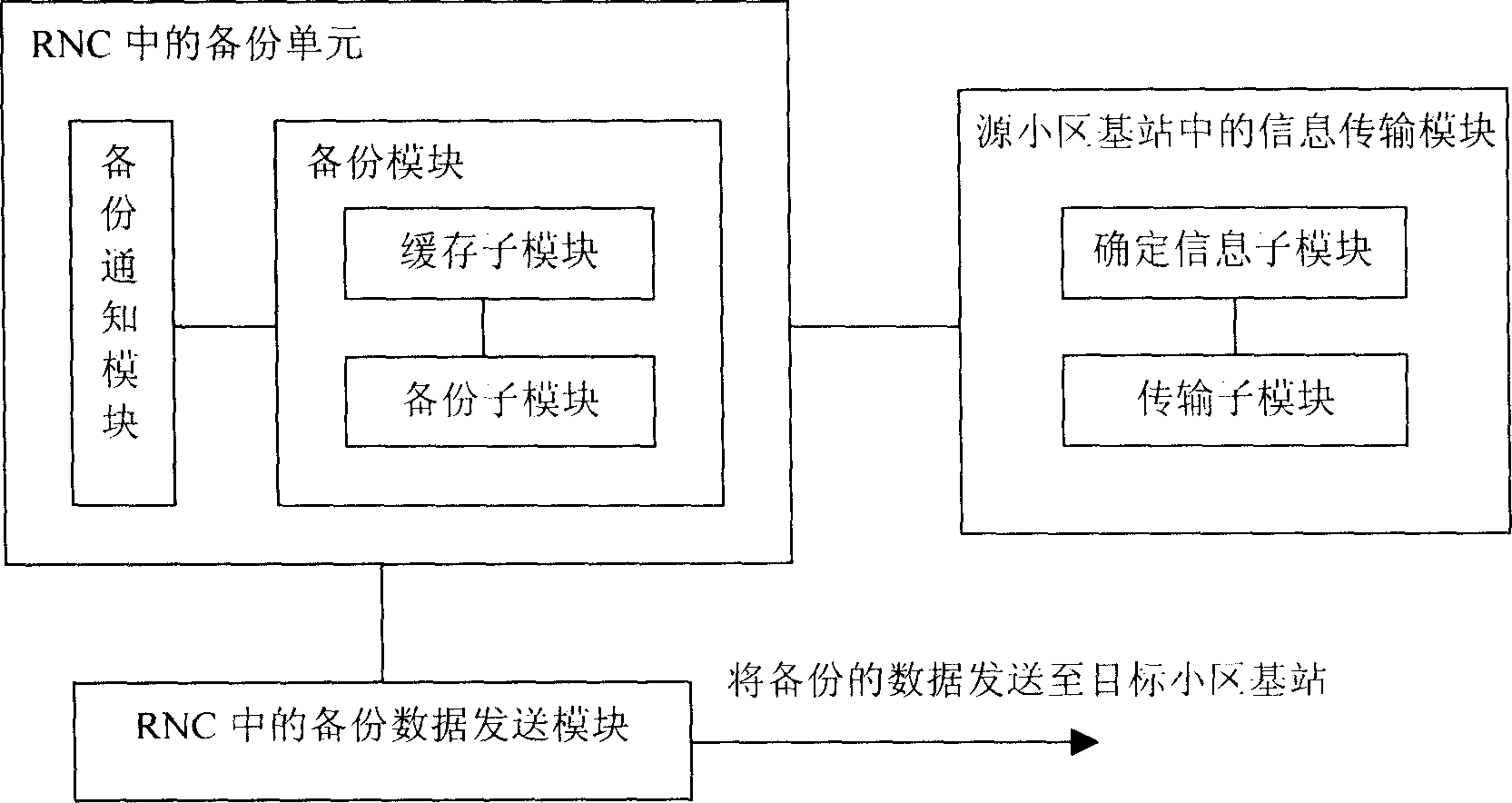
This invention provides a hard switchover method and a system for accessing high speed down packets, in which, the RNC backs up the HS-DSCH data of services of the UE when the UE is going to carrying out high speed down packet access hard switch and sends the backed up related data to a base station of the target area based on the information of deleted data of a base station of the source area, which avoids the re-transmission process of the RLC layer to the AM service and further avoids the invalid re-transmission process that UE tests data lost and sends re-transmission requests repeatedly and the RLC continuously sends re-transmission data and avoids data lost since the RLC sends the data deleted by the base station of the source area to the target area directly.
Owner:XFUSION DIGITAL TECH CO LTD
Tablet Flow
ActiveUS20110233027A1Avoid downtimeJamming of tablets is avoidedMetal-working feeding devicesPower-operated mechanismTablet computerGear drive
Tablet flow for the conveying away of tablets pressed in a tablet press, with a main flow channel, which has at least one branching into at least one first flow channel and at least one second flow channel separated from the first flow channel by at least one separating wall, wherein a separator is provided at the branching, which can be actuated such that tablets are directed out of the main flow channel alternatively into the first flow channel or into the second flow channel, characterized in that the separator has a guide channel for the tablets and in that a guide gear drive is provided, with which the guide channel is moveable between a first position connecting the main flow channel with the first flow channel and a second position connecting the main flow channel with the second flow channel.
Owner:FETTE COMPACTING GMBH
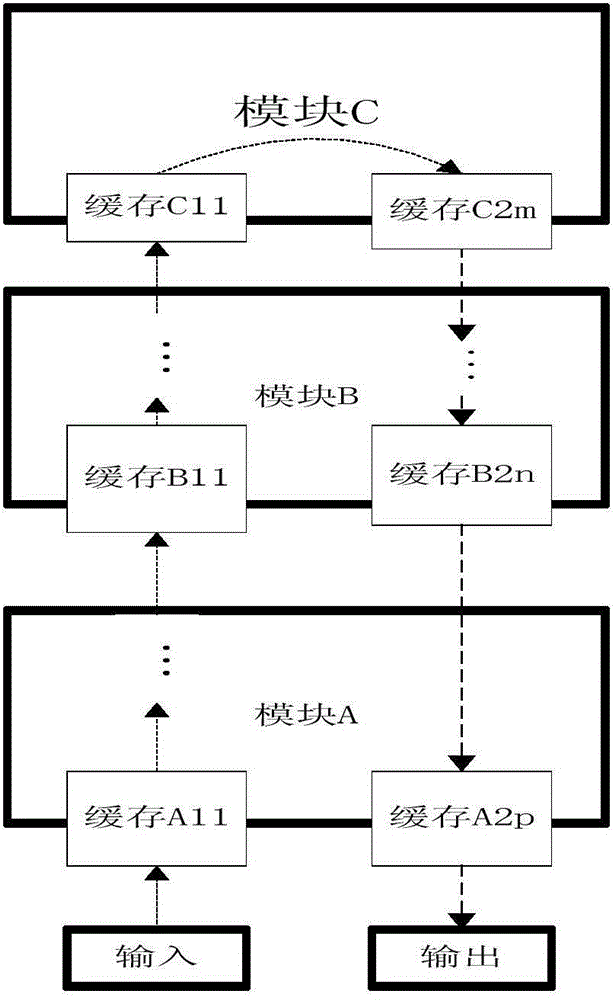
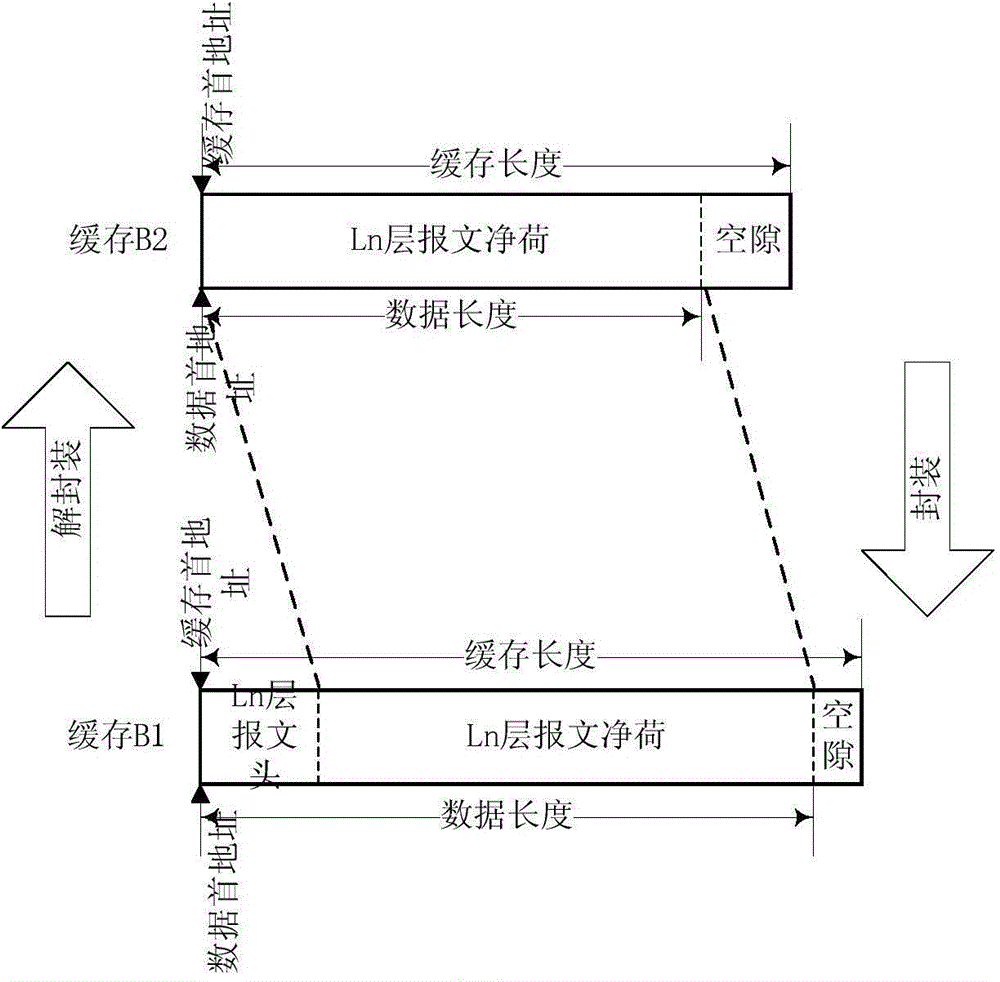
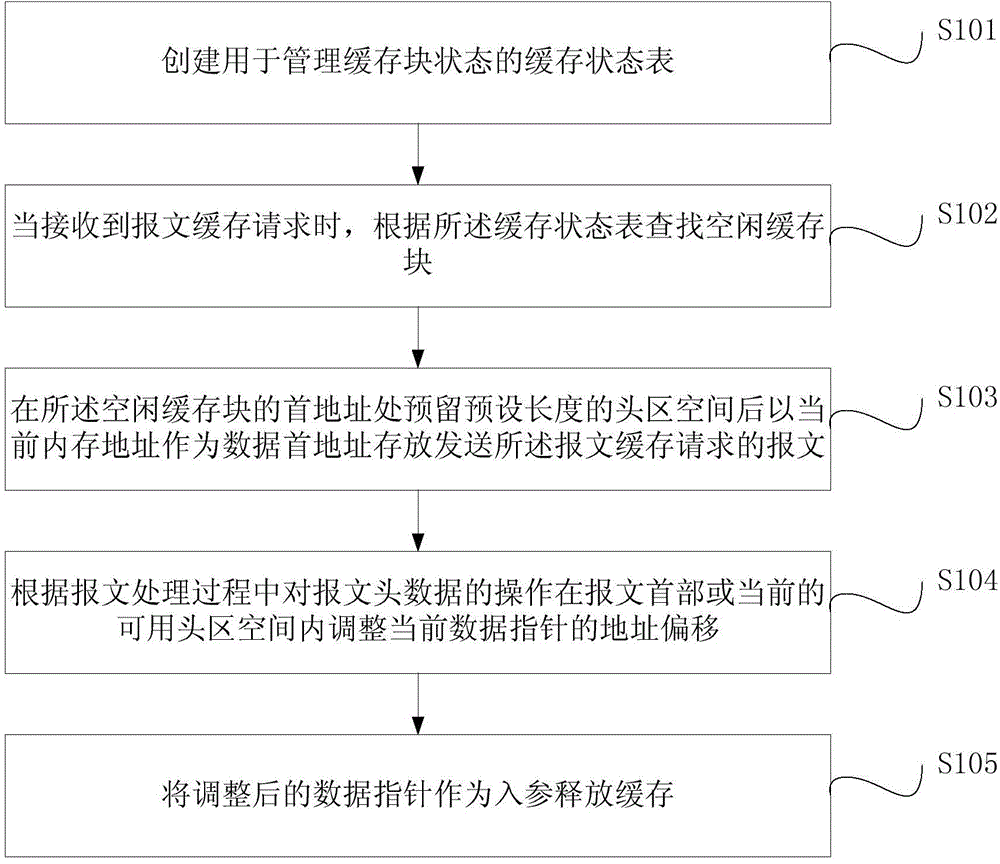
Message buffer management method and message buffer management device
ActiveCN104133784AImplement zero-copy transferAvoid backupMemory adressing/allocation/relocationMemory addressZero-copy
The invention provides a message buffer management method and a message buffer management device. The method comprises the following steps that: a buffer state table used for managing a buffer block state is created; when a message buffer request is received, an idle buffer block is found according to the buffer state table; a preset length of head region space is reserved in a position of the first address of the idle buffer block, then, the current memory address is used as a data first address for storing a message for sending the message buffer request; the address offset of a current data pointer is adjusted at a message header or a current available head region space according to the operation on the message header data in the message processing process; and the adjusted data pointer is used as an input parameter for buffer releasing. From the angle of the whole TTL (Time-to-Live) of the message, the method and the device provided by the invention realize the zero copying transmission of the message among all modules inside a central processing unit; the package throughput performance is improved; and meanwhile, the backup on an original address by a buffer user and the memory resource waste due to the backup can be avoided.
Owner:DATANG MOBILE COMM EQUIP CO LTD
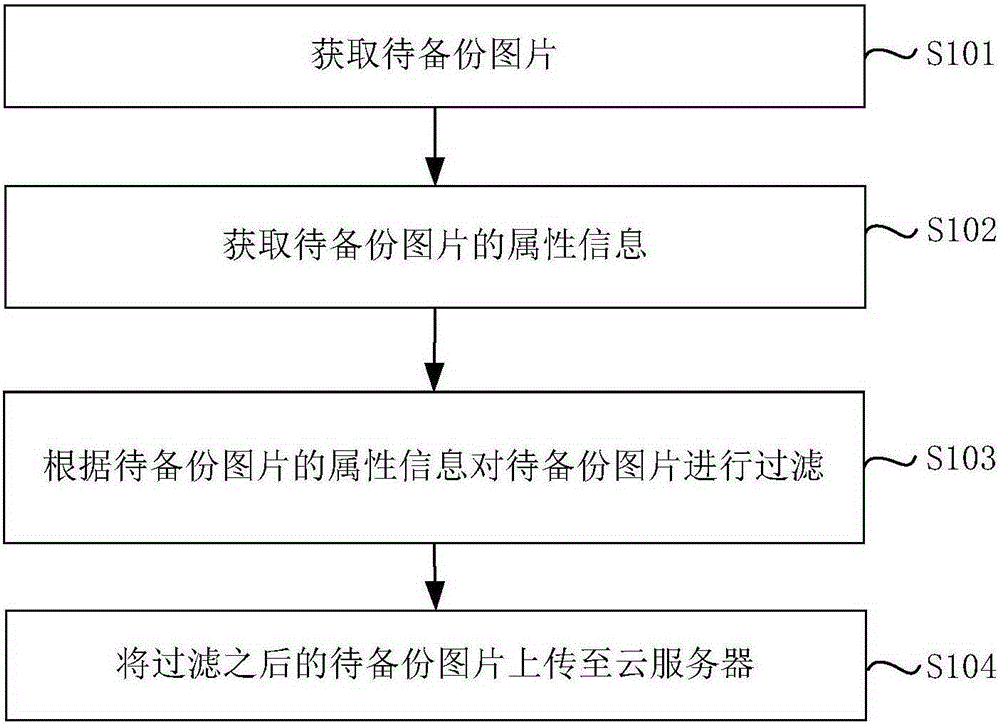
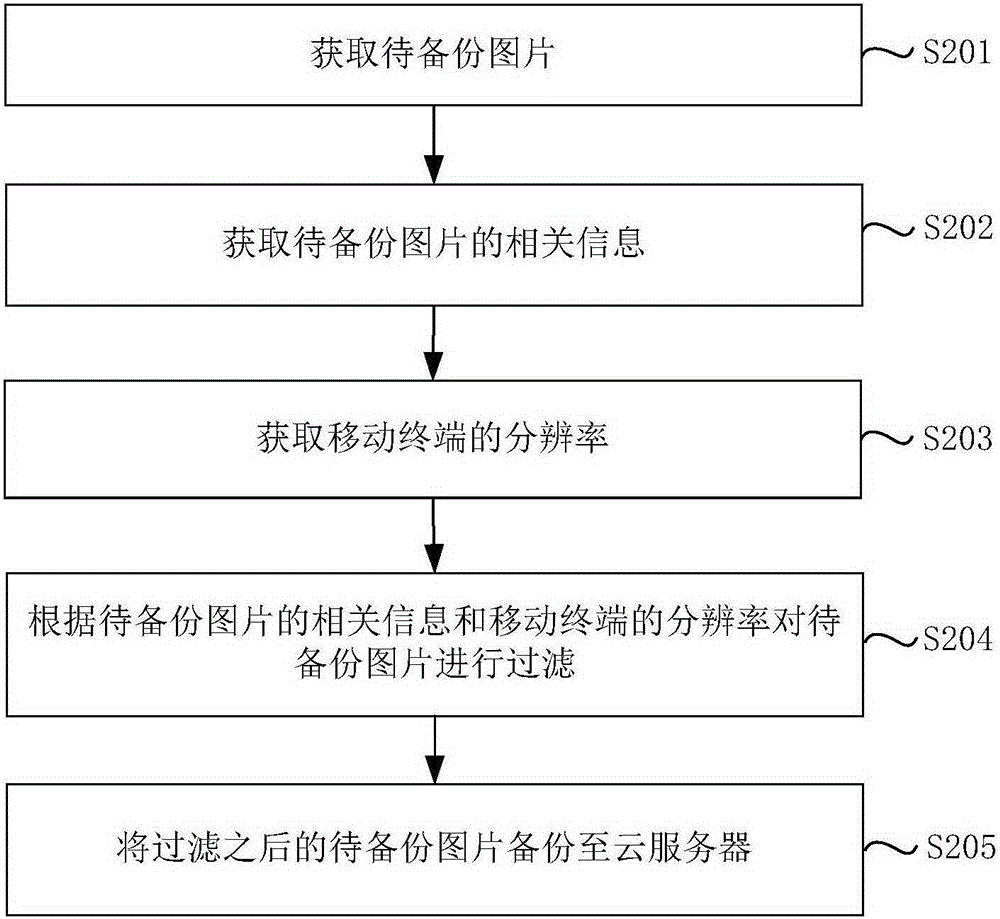
Picture cloud backup method, device and electronic equipment
The invention discloses a picture cloud backup method, a device and electronic equipment. The picture cloud backup method comprises steps that, to-be-backuped pictures are acquired; attribute information of the to-be-backuped pictures is acquired; the to-be-backuped pictures are filtered according to the attribute information of the to-be-backuped pictures; and the filtered to-be-backuped pictures are uploaded to a cloud server. According to the cloud backup method, the device and the electronic equipment, the to-be-backuped pictures are acquired, the attribute information of the to-be-backuped pictures is acquired, the to-be-backuped pictures are filtered according to the attribute information of the to-be-backuped pictures, the filtered to-be-backuped pictures are uploaded to the cloud server, pictures without backup values can be identified and are filtered, filtering the large-scale pictures without the backup values can be avoided, backup time is shortened, and backuped pictures in the cloud server can be conveniently and rapidly queried by users.
Owner:BEIJING KINGSOFT INTERNET SECURITY SOFTWARE CO LTD
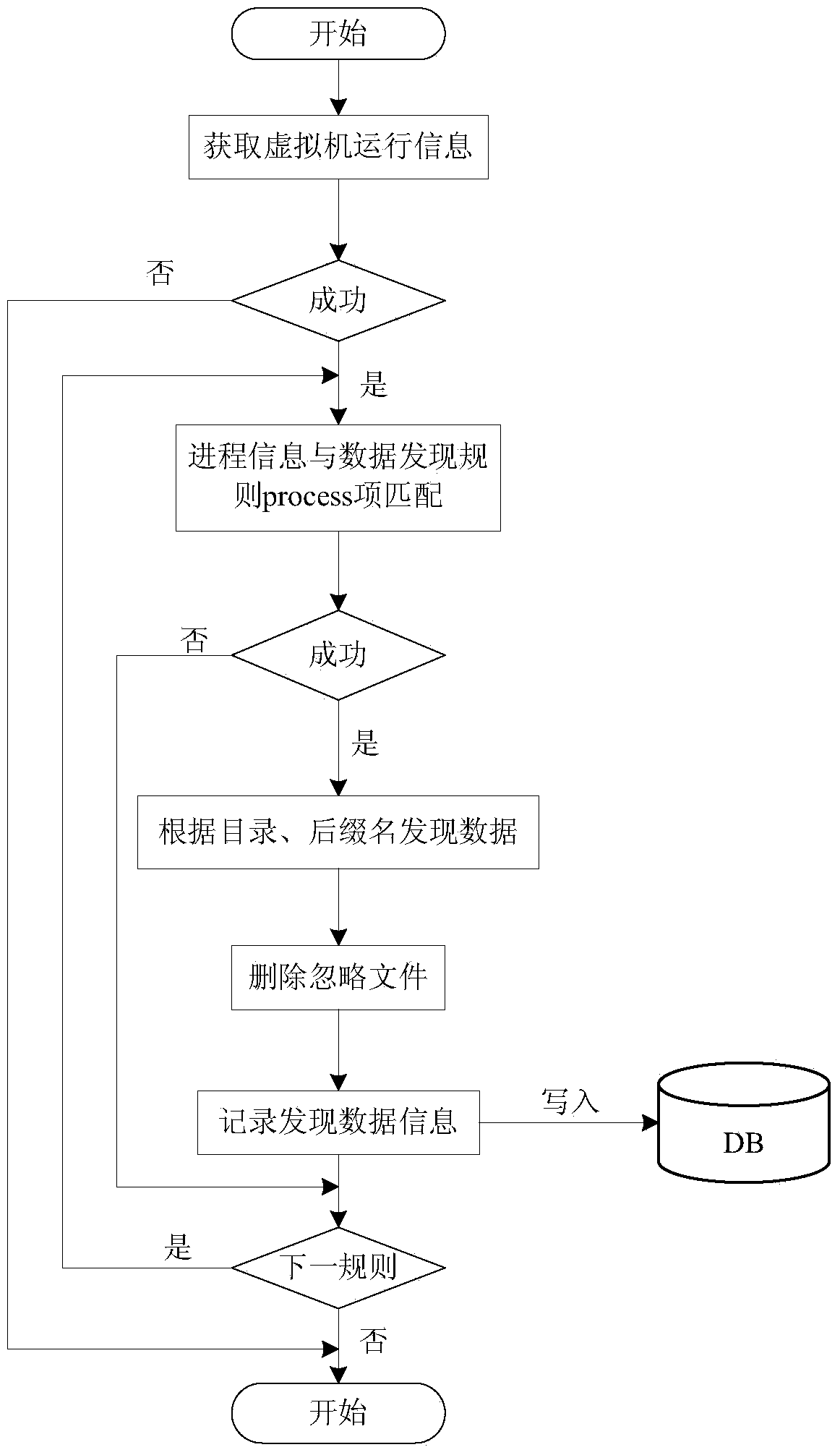
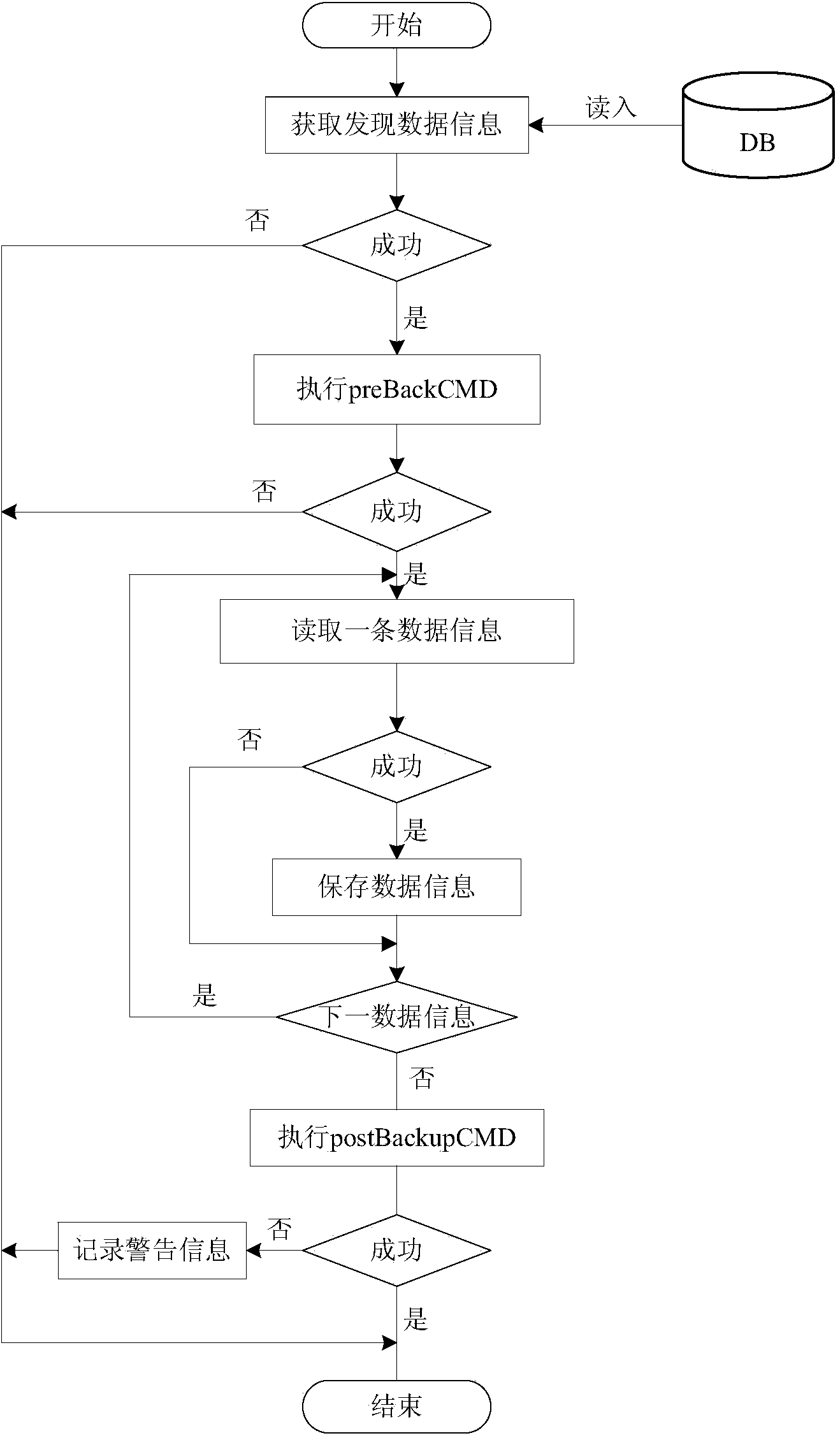
Backup method based on virtual machine operation information data finding
ActiveCN103678036ASave memorySave storage spaceSoftware simulation/interpretation/emulationRedundant operation error correctionVirtual machineResource consumption
The invention relates to a backup method based on virtual machine operation information data finding. The backup method comprises the following steps that a data cache unit obtains the progress information produced when a virtual machine operates; a pre-stored data finding rule is matched with the progress information through a data backup processing unit, and the production data position of an application program needing to be backed up is obtained and stored according to the data finding rule; the corresponding virtual machine production data are backed up according to the production data position and are mapped to the data backup storing unit. Compared with the prior art, the backup method has the advantages of being high in backup efficiency and speed, small in resource consumption and the like.
Owner:EISOO SOFTWARE
Information safety protection system of application system based on database and information safety protection method
ActiveCN102799831AAvoid backupPrevent core secretsComputer security arrangementsSpecial data processing applicationsInformation securityProtection system
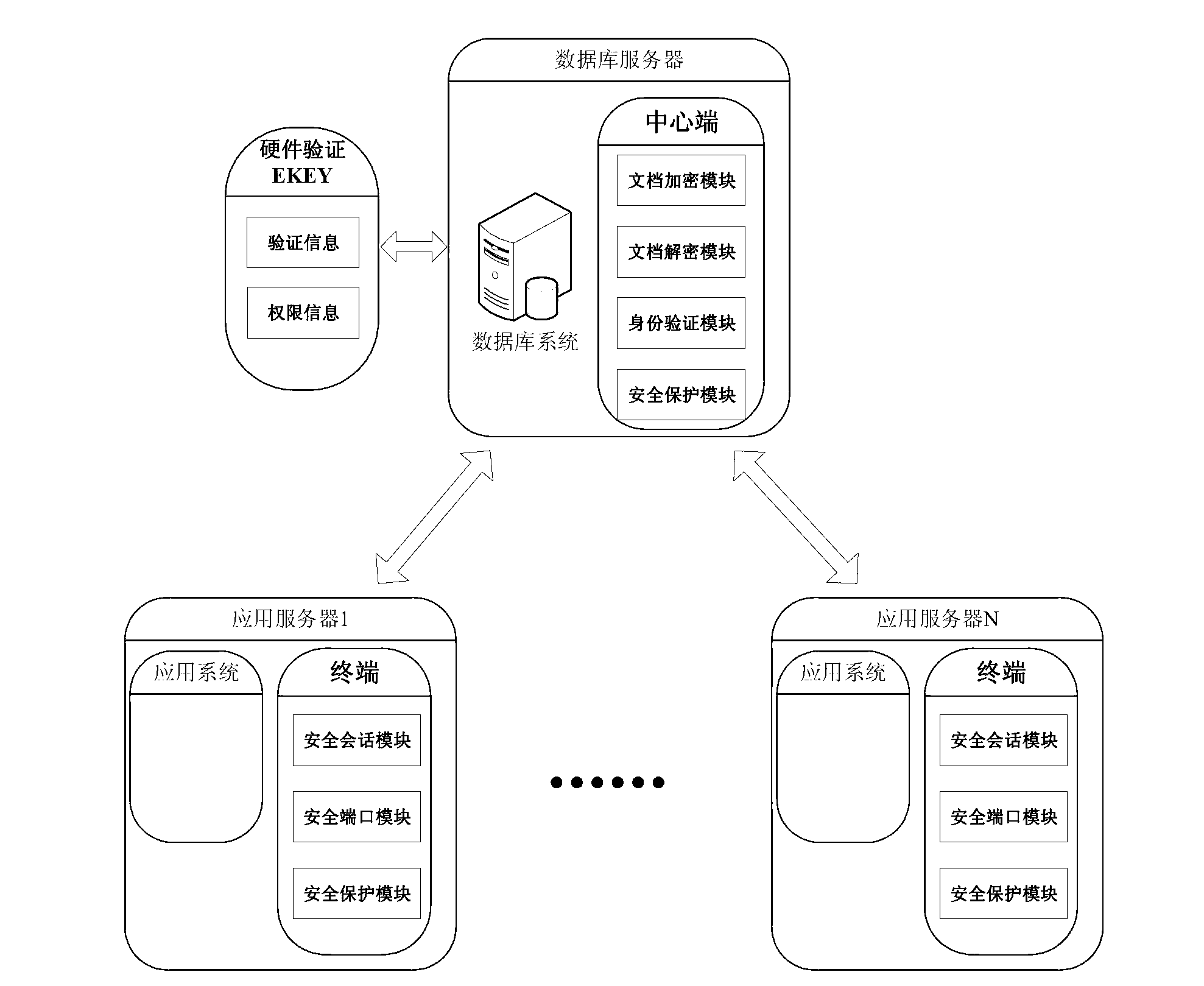
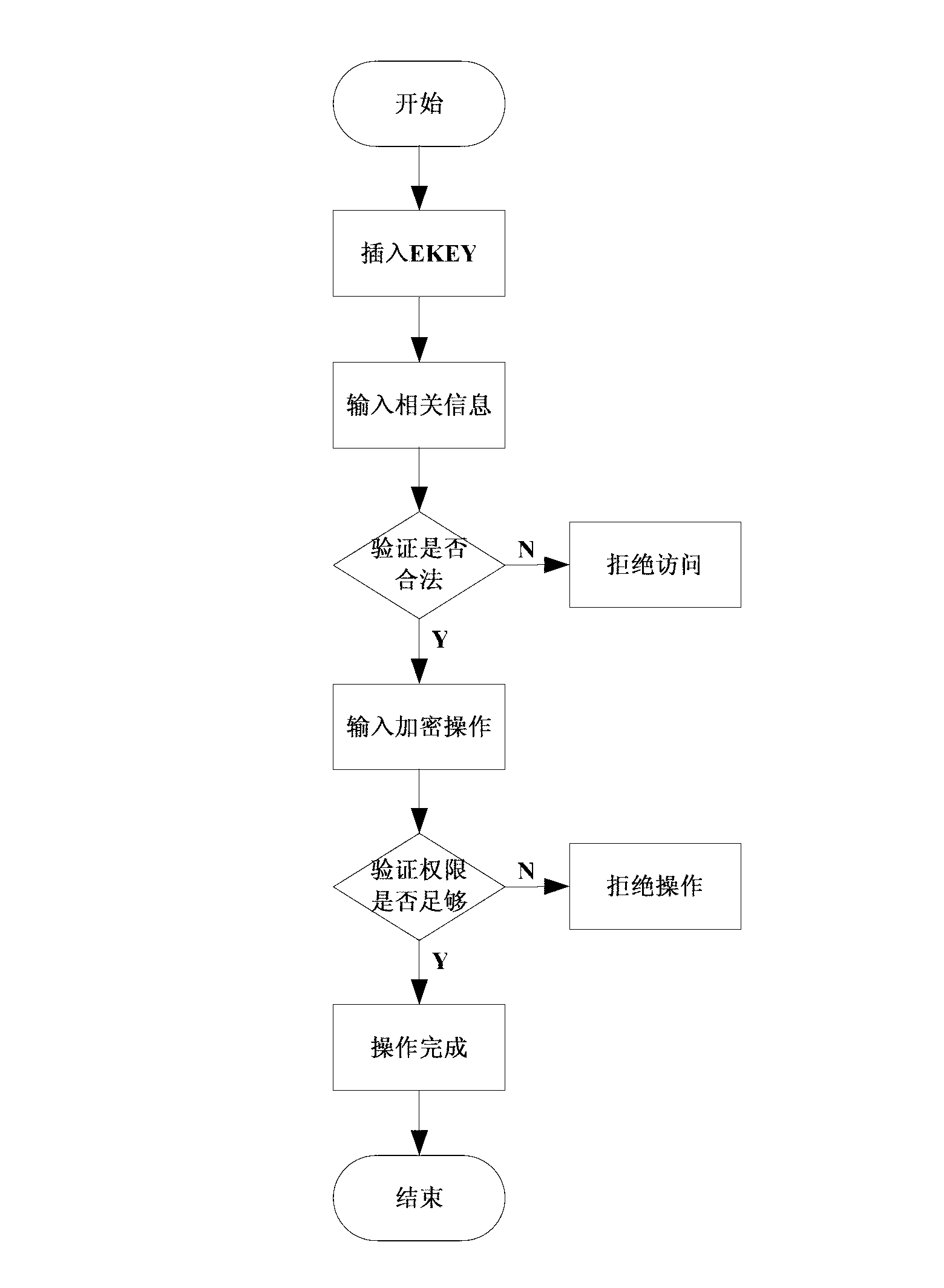
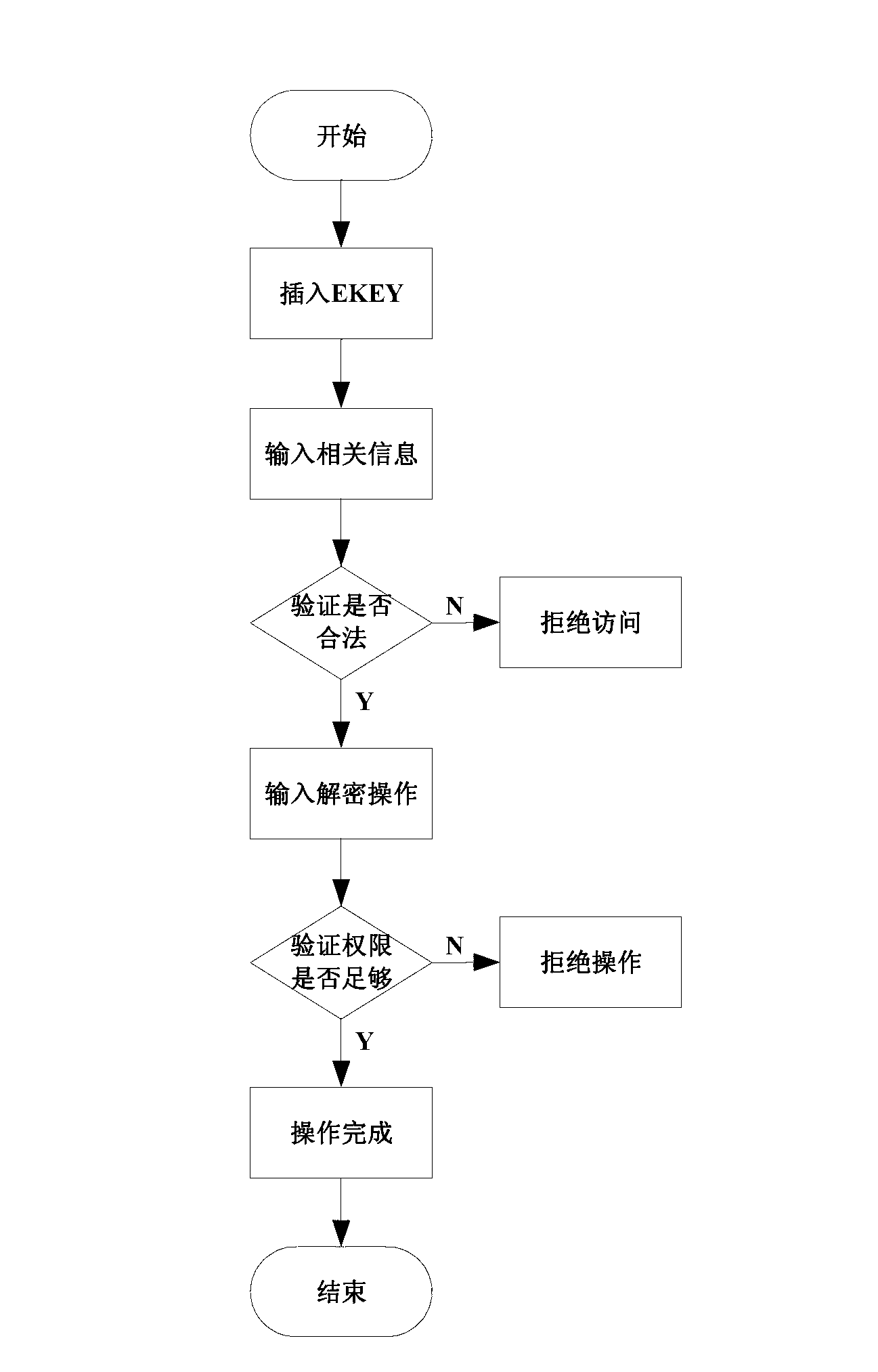
The invention discloses an information safety protection system of an application system based on a database and an information safety protection method. The system comprises a central terminal based on a database system terminal, a terminal based on an application system terminal, and a hardware verification electronic key for the central terminal, wherein the central terminal comprises a document encryption module, a document decryption module, an identity authentication module and a safety protection module; the terminal comprises a secure session module, a secure port module and a safety protection module; and the hardware verification electronic key comprises verification information and authority information. Because the connection is established between the database system terminal and the application system terminal, an illegal user or an unauthorized user is forbidden to carry out operations including backup or export, etc. on the database. The invention provides a secure interaction method aiming at the database and the application system to guarantee the safety of the whole session process. According to the information safety protection system of the application system based on the database and the information safety protection method, the safety dead angle of the application system based on the database can be well remedied, and the leakage of core secrets of an enterprise can be avoided.
Owner:WUXI CINSEC INFORMATION TECH
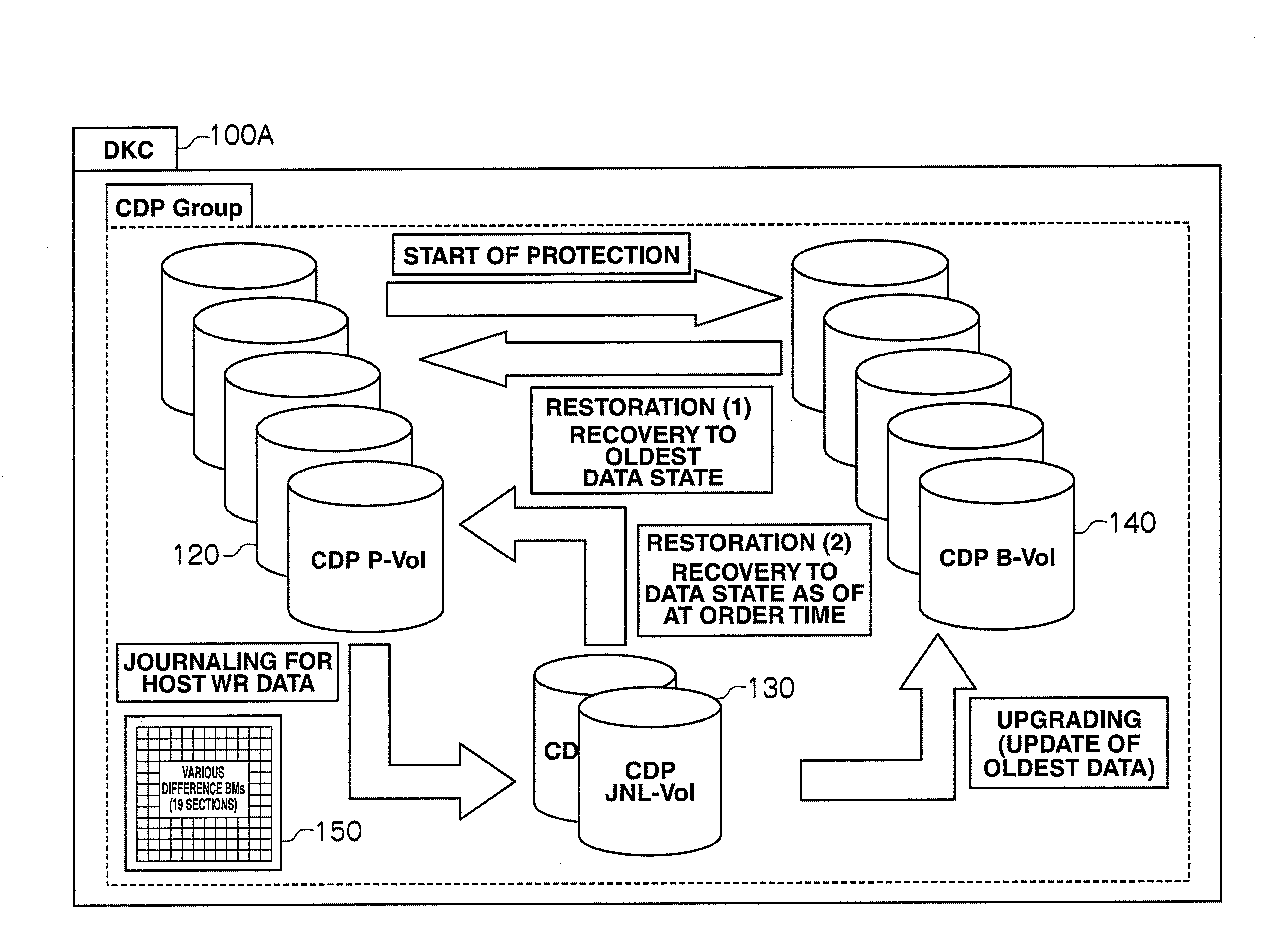
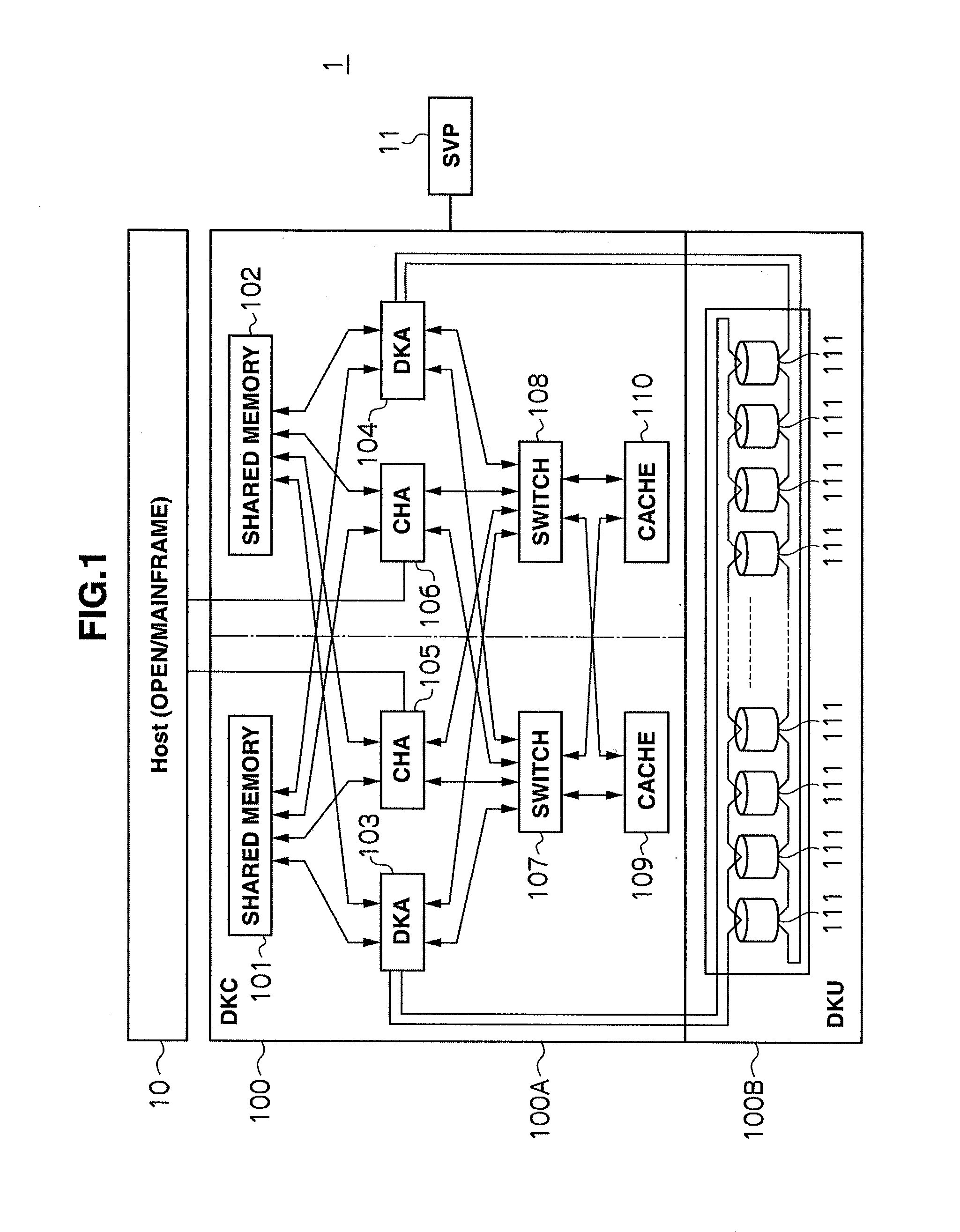
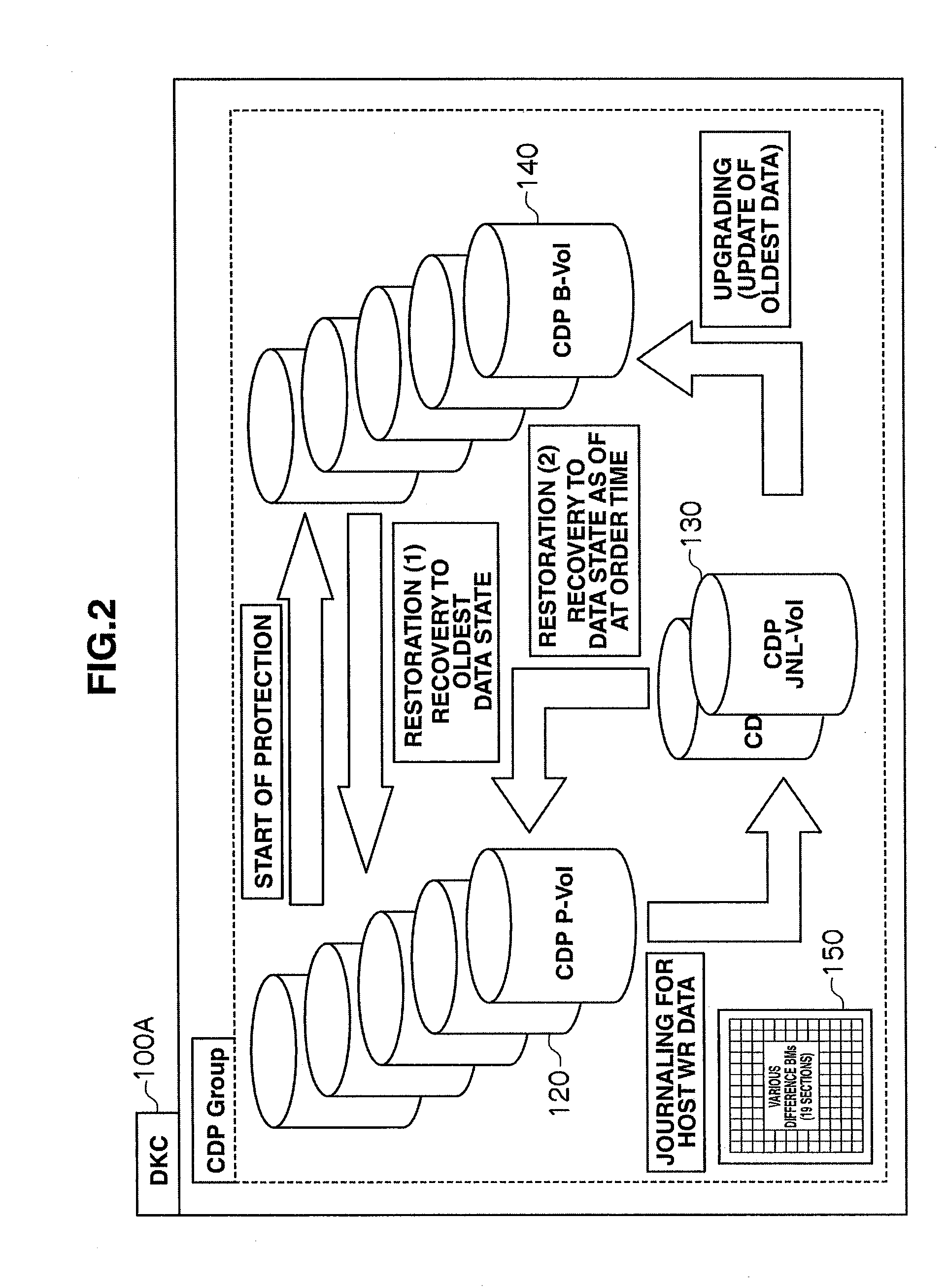
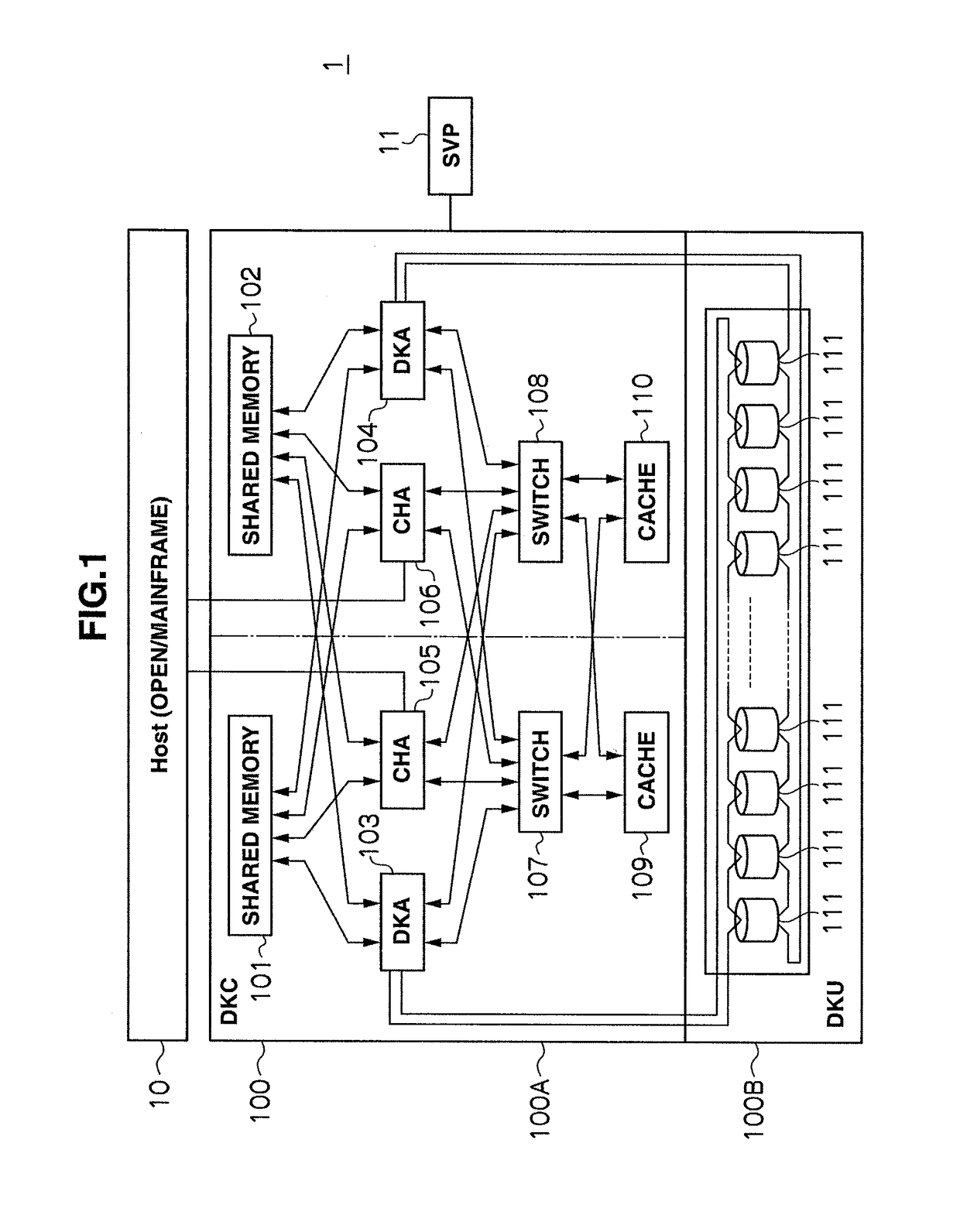
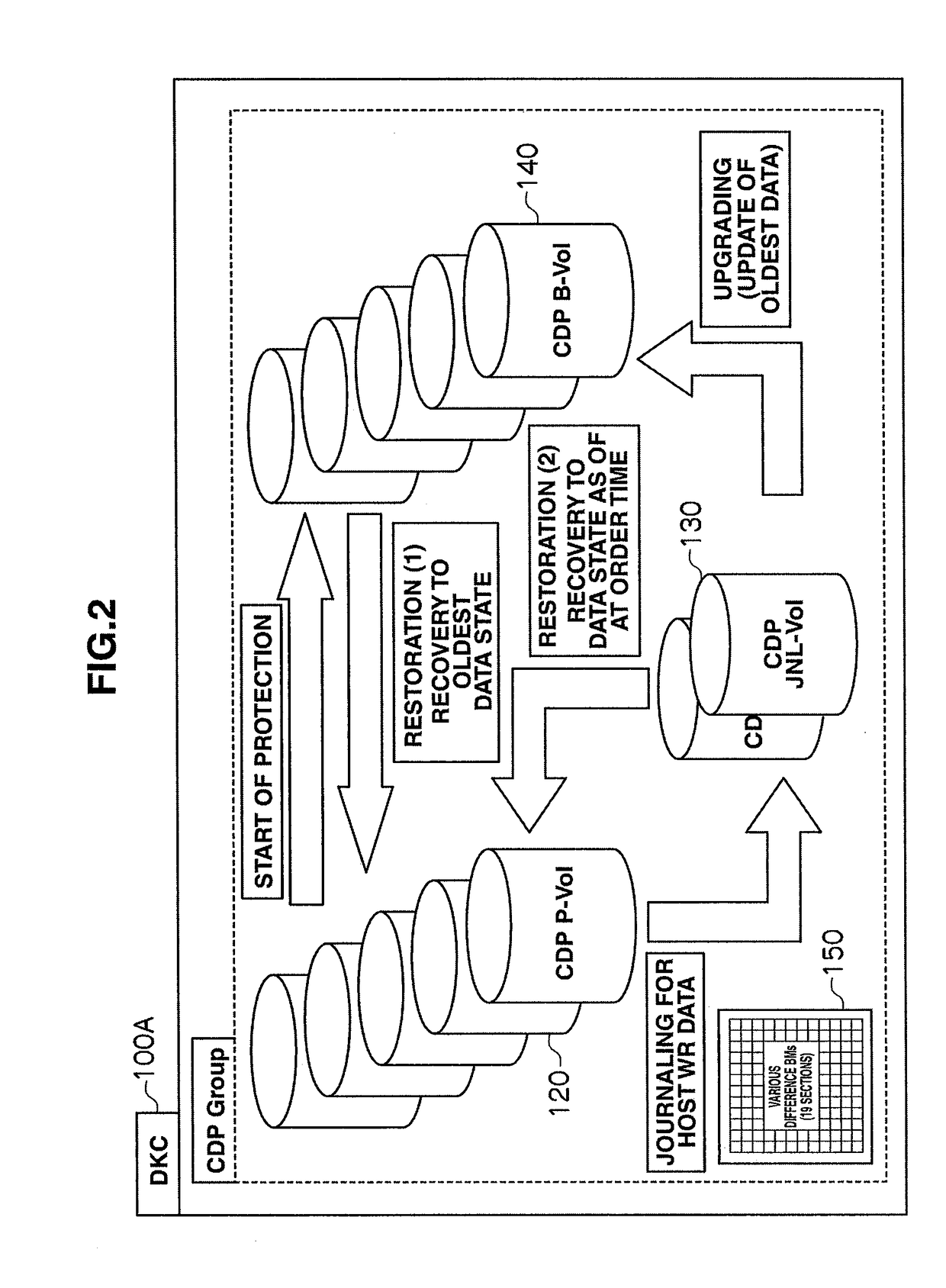
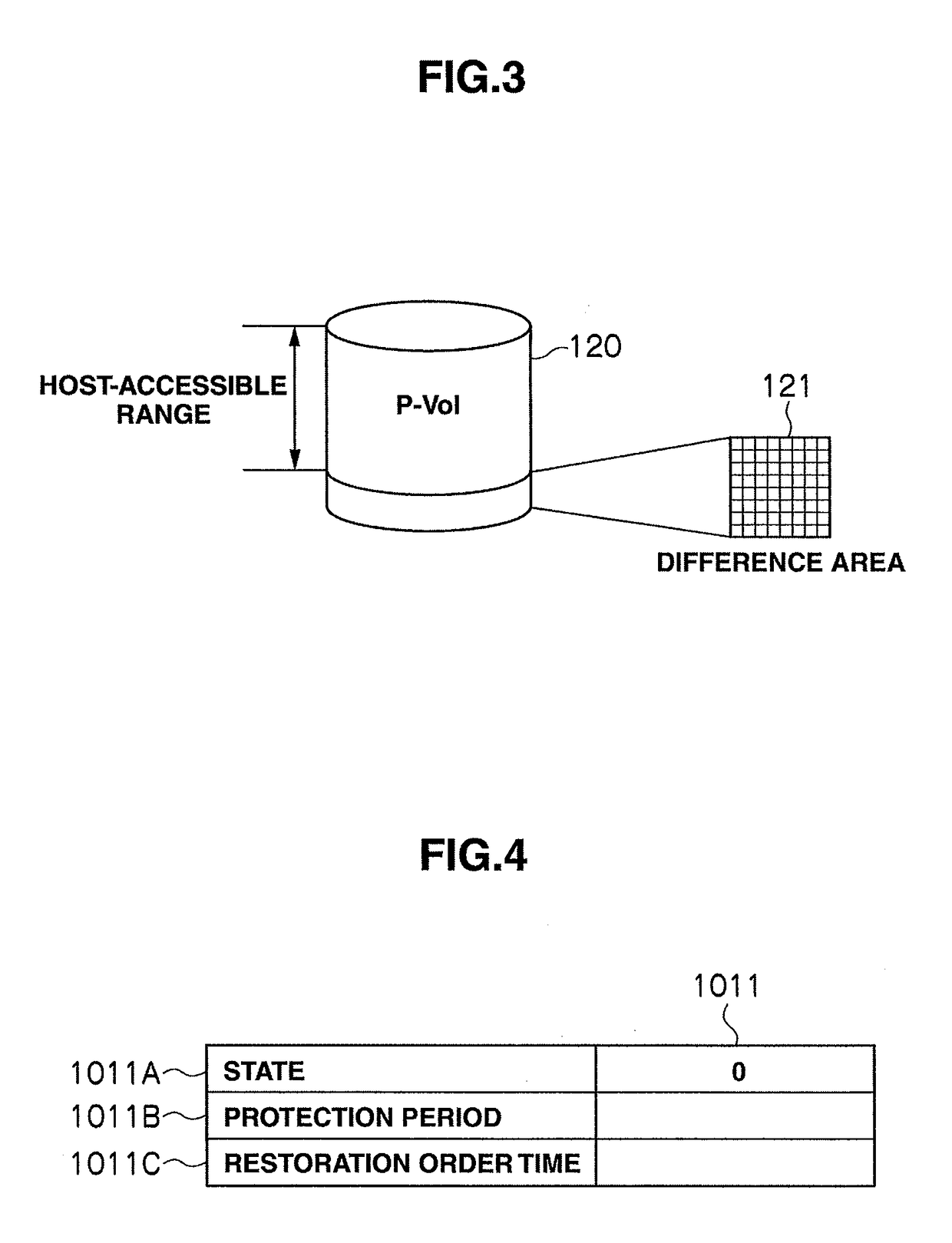
Storage apparatus and volume restoration method
InactiveUS20090254721A1Reduce amount of dataReduce restore timeMemory loss protectionError detection/correctionRestoration methodOperating system
A storage apparatus conducts, in a protection period, data protection processing for protecting, in a third logical volume, data stored in a first logical volume by using backup data stored in a second logical volume, and suspends the data protection processing in a no-protection period, during which backup relative to the second logical volume is suspended, in the protection period. Then, upon receiving an external order for restoring the first logical volume to its state as of at a time not in the no-protection period within the protection period, the storage apparatus restores the first logical volume to its state as of at a time of the order by using the data backed up in the second logical volume and the data protected in the third logical volume.
Owner:HITACHI LTD
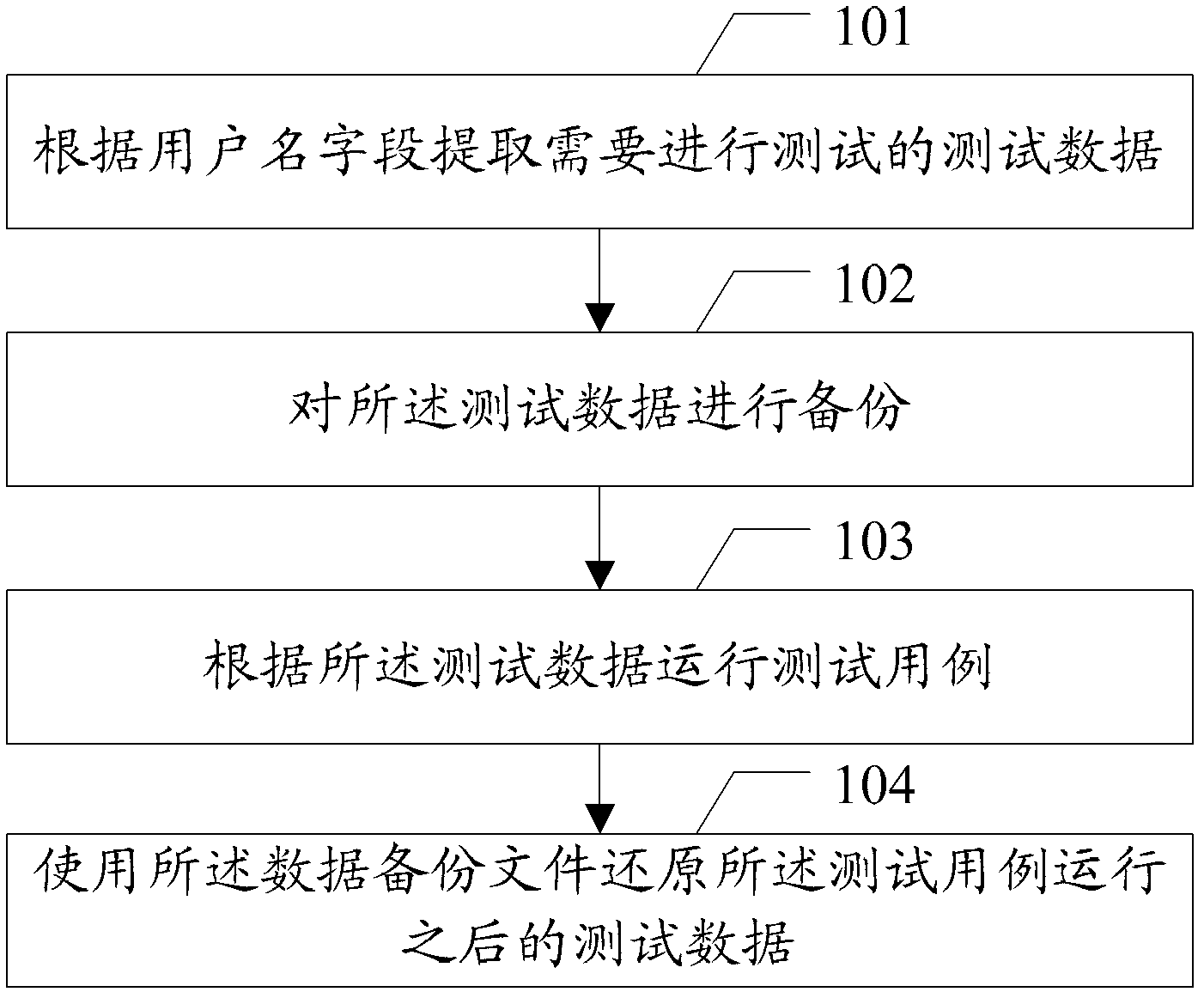
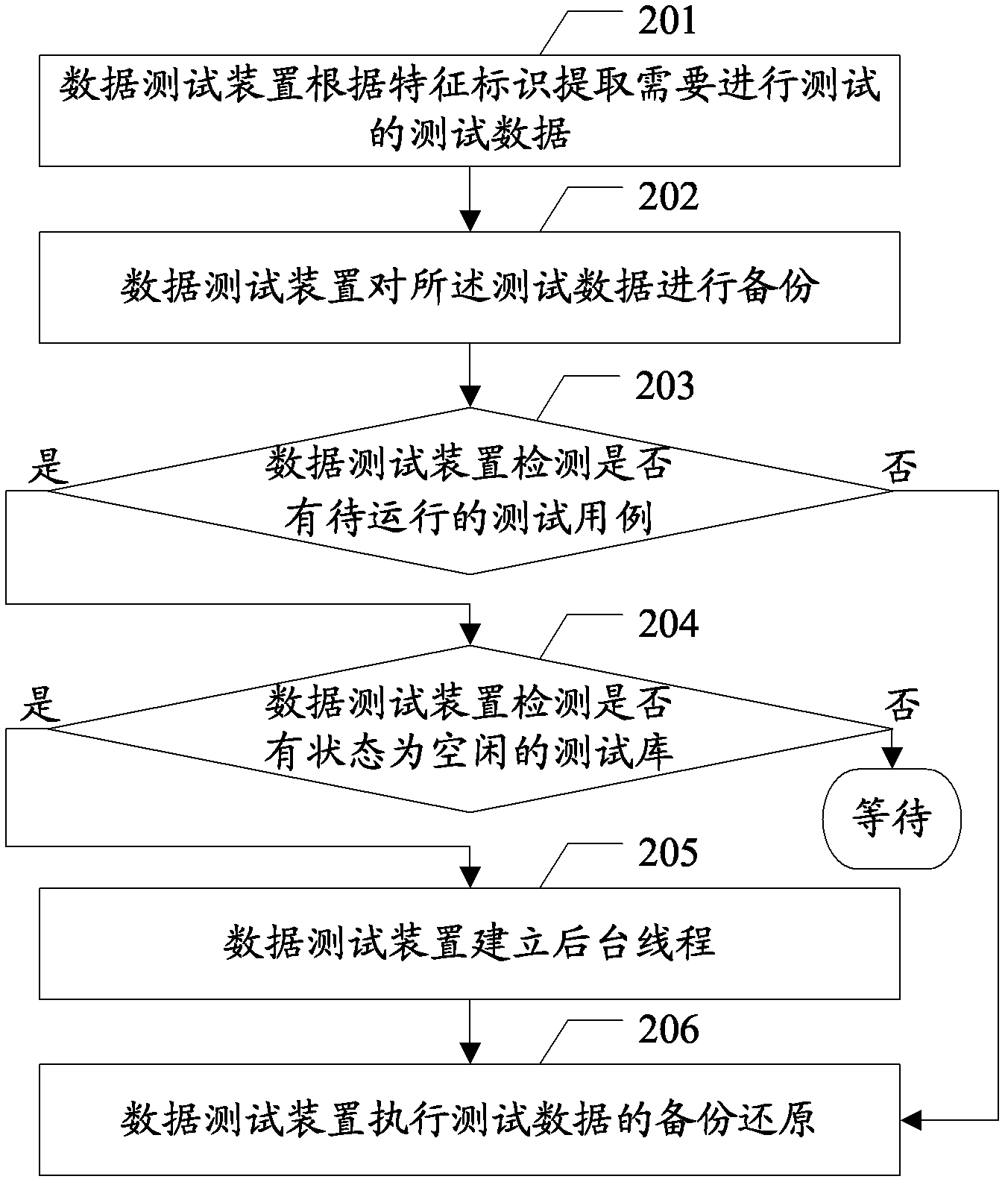
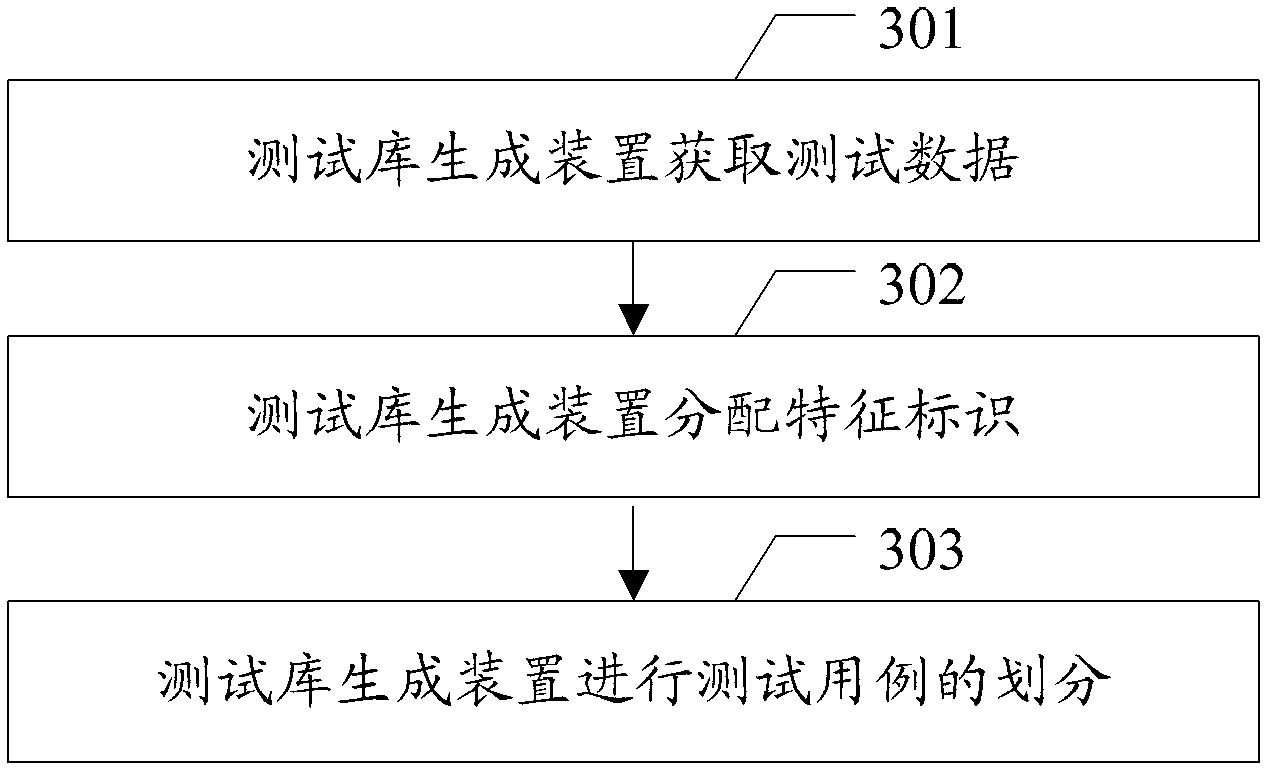
Data test method, test library generating method and related device
InactiveCN103186561AAvoid backupImprove the efficiency of data testingSpecial data processing applicationsRedundant operation error correctionLab test methodAutomatic testing
The embodiment of the invention discloses a data test method, a test library generating method and a related device, which are used for performing automatic test on data efficiently. The method provided by the embodiment of the invention comprises the following steps of: extracting test data which are required to be tested according to a characteristic identifier; backing up the test data to obtain a data backup file; operating a test case according to the test data; and restoring the test data which is obtained after the test case is operated by using the data backup file.
Owner:深圳市金蝶精斗云网络科技有限公司
Method for achieving multi-point integration monitoring based on mobile terminal
ActiveCN103561231ARealize remote managementRealize monitoring and managementTelevision system detailsColor television detailsVideo monitoringComputer terminal
The invention discloses a method for achieving multi-point integration monitoring based on a mobile terminal, and aims to achieve one hundred percent unattended automatic video monitoring management. Automatic integration monitoring management is conducted on multiple sets of videos, monitoring management is conducted on a video specific region or specific objects, and the monitoring time density of the different objects in a same monitoring plane is set according to requirements. Significant technical innovation and inventions of self-service monitoring management and the like achieved through terminal encryption and decoding, especially remote monitoring self-service management achieved through the mobile terminal have significant application innovation and invention value in the security and protection monitoring technology.
Owner:CHONGQING ZHITAO INFORMATION TECH CENT
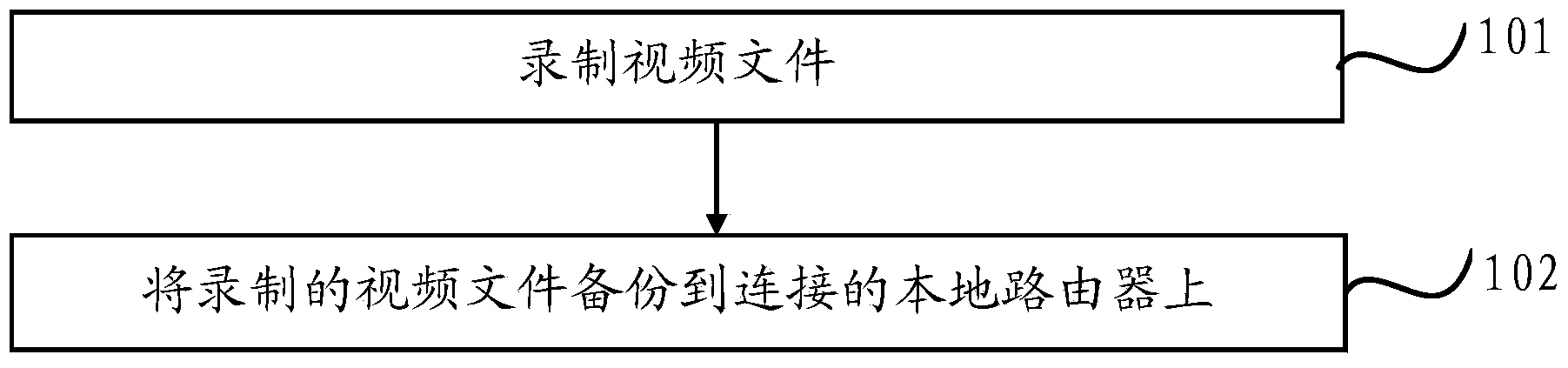
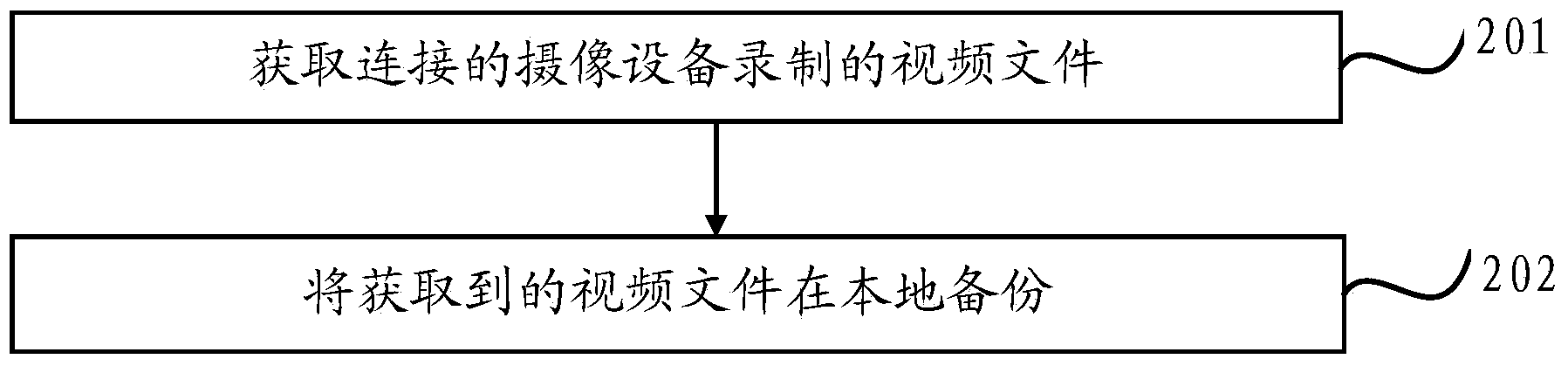
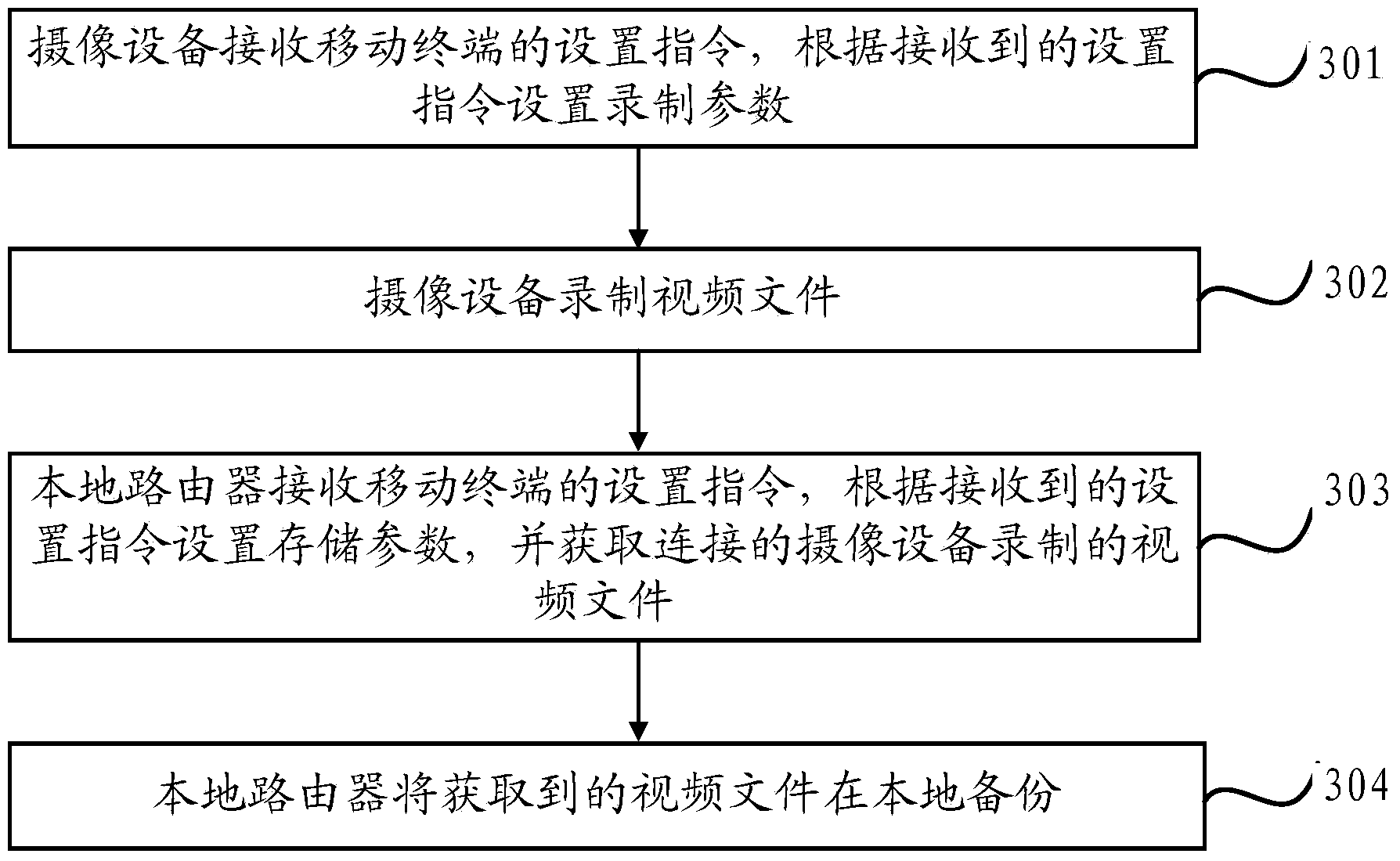
Video backup method and device
InactiveCN104166604AImprove securityMultiple storage spacesTelevision system detailsColor television signals processingComputer terminalComputer engineering
The invention provides a video backup method. The video backup method comprises the steps that a shooting device receives a setting order of a mobile terminal, and recording parameters are set according to the received setting order; the shooting device records a video file; a local router receives a setting order of the mobile terminal, saving parameters are set according to the received setting order, and the video file recorded by the shooting device connected with the local router is obtained; the local router backs up the obtained video file locally. According to the video backup method, the recorded video file is backed up to the local router connected with the shooting device, more memory space can be provided, rapid search and rapid preview can be facilitated, and the security of the saved video file is higher.
Owner:XIAOMI INC
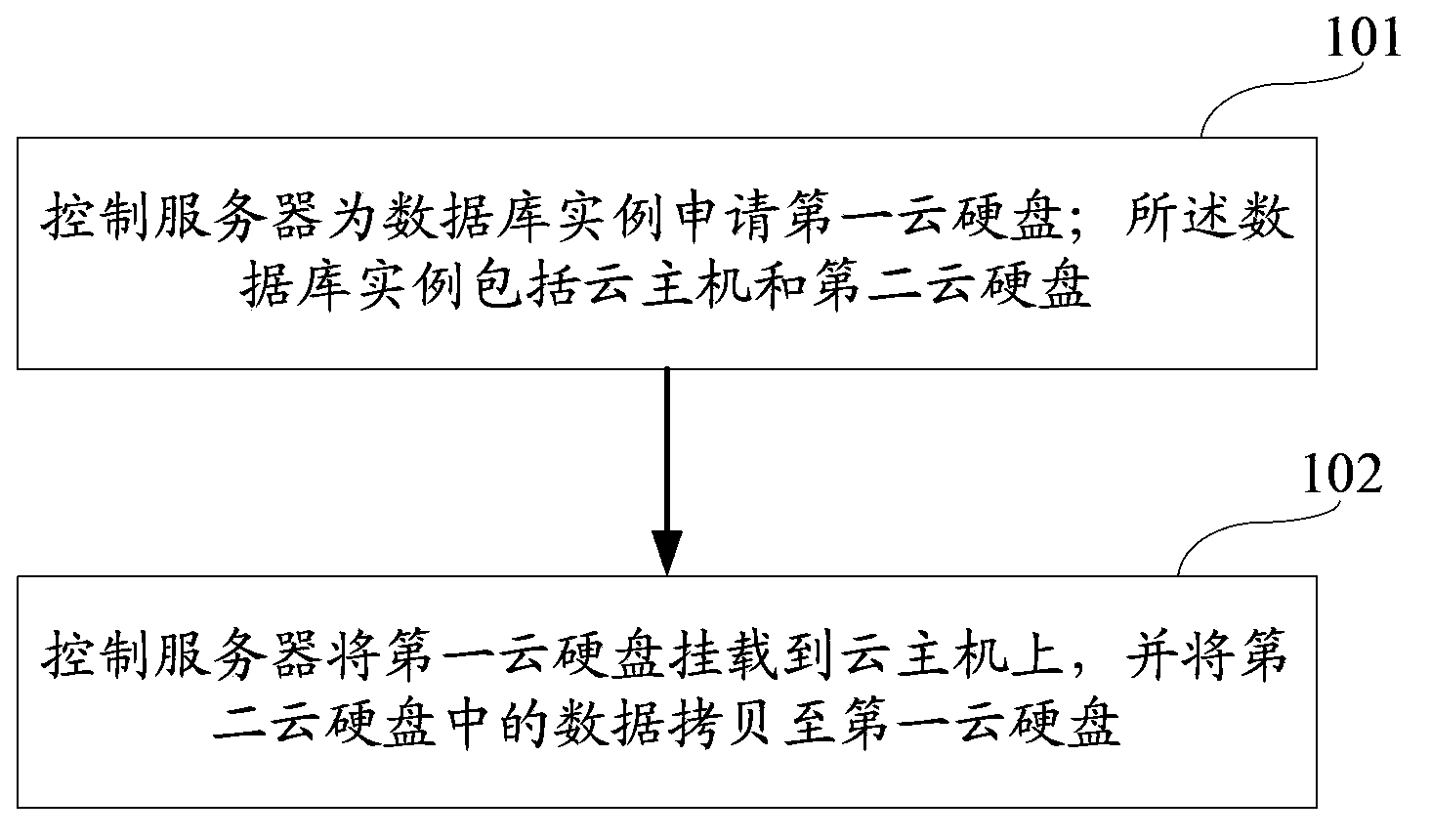
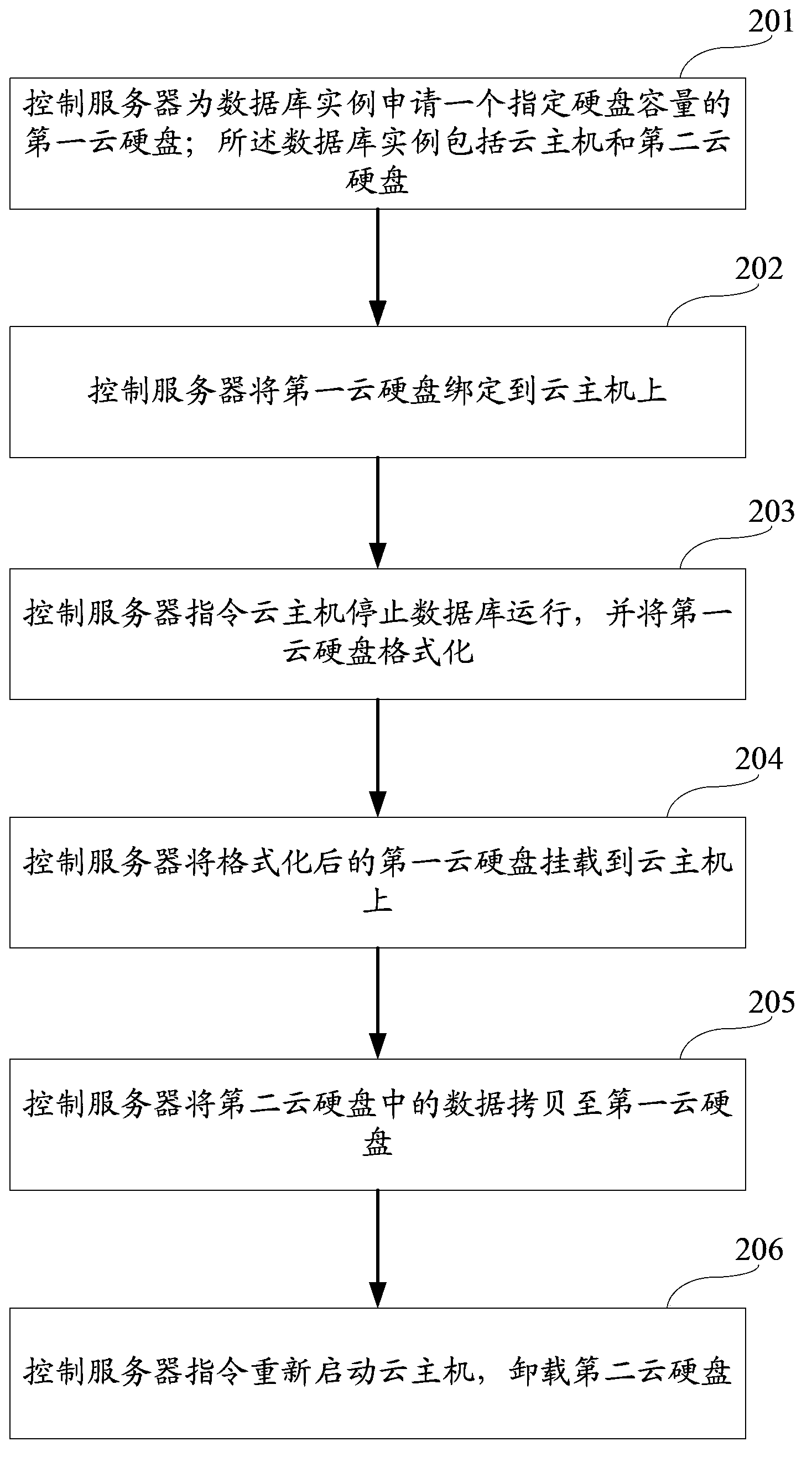
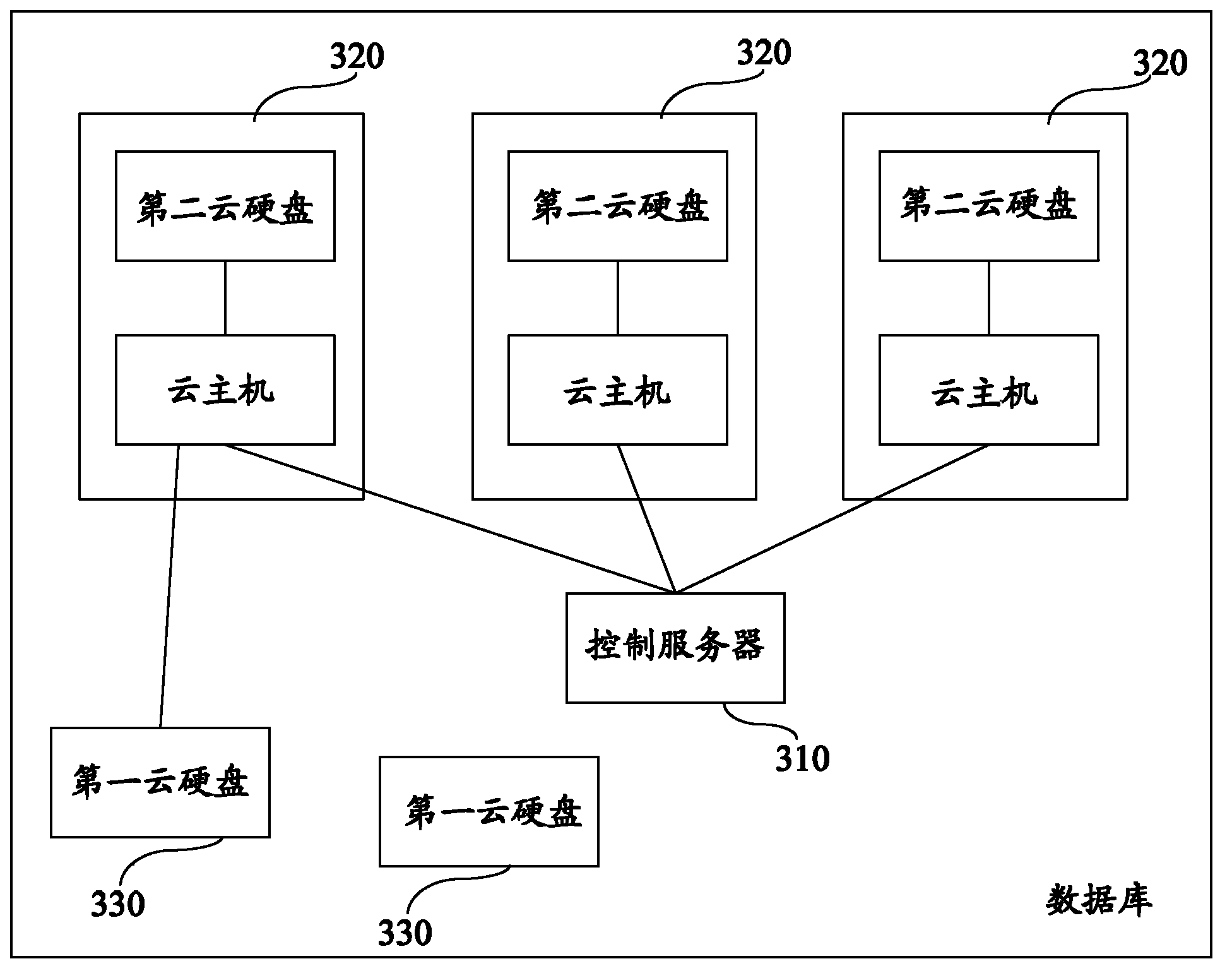
Database expansion method and database
ActiveCN104142943AFlexible mountAvoid backupSpecial data processing applicationsInput/output processes for data processingOperating systemData library
The embodiment of the invention provides a database expansion method and a database, the method comprises the following steps that: a control server applies a first cloud hard disk for a database instance; the database instance comprises a cloud host and a second cloud hard disk; the control server mounts the first cloud hard disk on the cloud host and copies data in the second cloud hard disk to the first cloud hard disk; the database comprises the control server used for applying expansion for the database instance, mounting the first cloud hard disk on the cloud host, and copying data in the database instance to the first cloud hard disk, the database instance used for storing and managing the data, and expanding according to the instruction of the control server, and the first cloud hard disk used for being mounted to the database instance, and expanding the database instance.
Owner:上海盛霄云计算技术有限公司
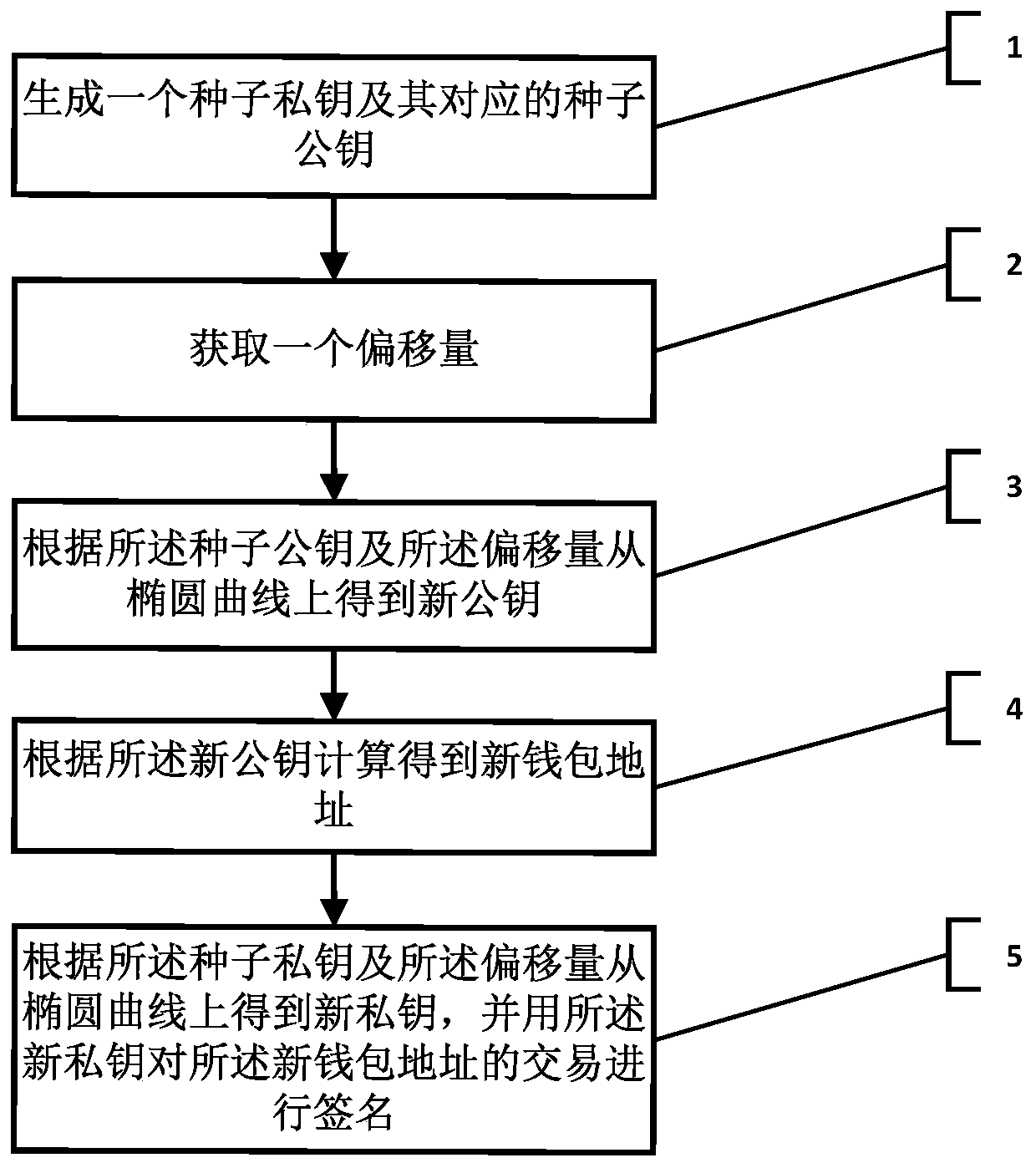
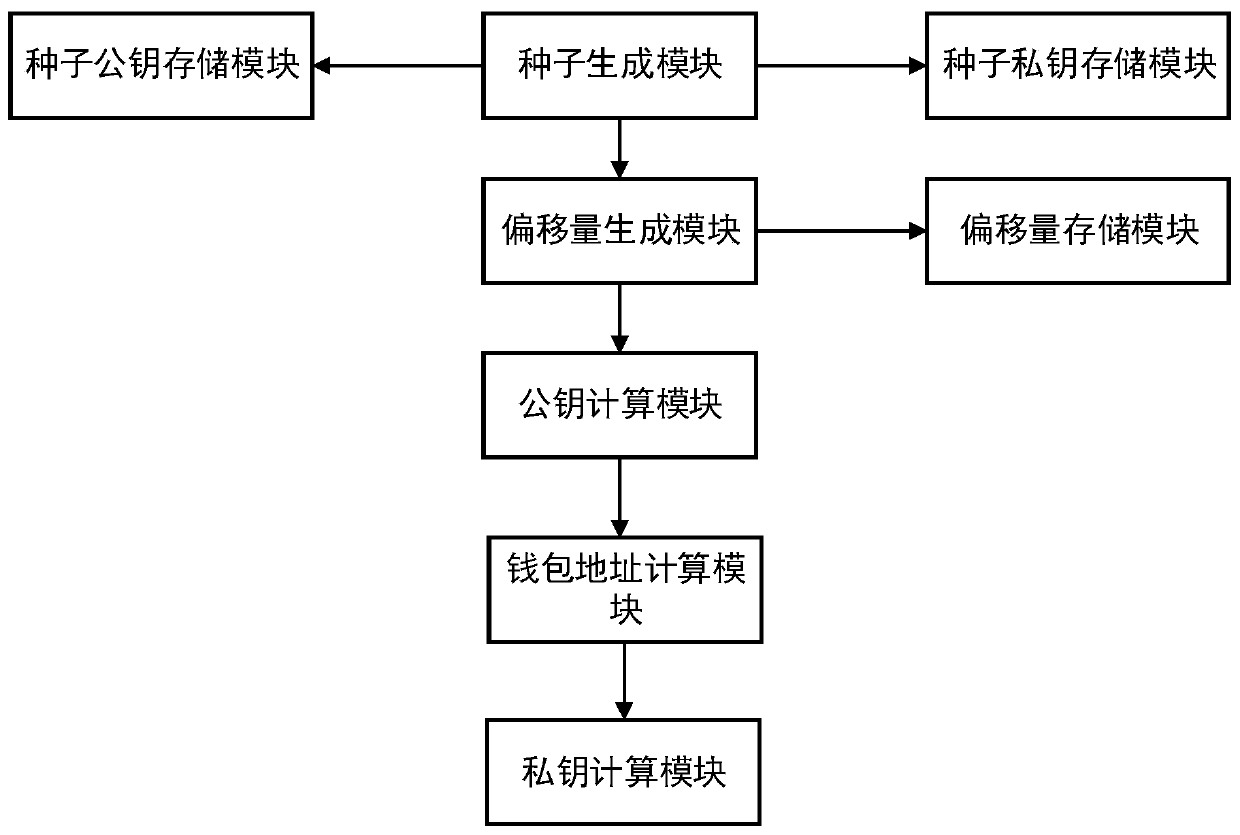
Block chain private key management method and system based on elliptic curve offset, and storage medium
PendingCN111325535AImprove securityAvoid storageFinancePayment protocolsComputer networkFinancial transaction
The invention relates to the technical field of block chains, in particular to a block chain private key management method and system based on elliptic curve offset and a storage medium. The method comprises the following steps: generating a seed private key and a seed public key corresponding to the seed private key; obtaining an offset; obtaining a new public key from an elliptic curve accordingto the seed public key and the offset; calculating to obtain a new wallet address according to the new public key; and obtaining a new private key from the elliptic curve according to the seed private key and the offset, and signing the transaction of the new wallet address by using the new private key. According to the method, generation of the private key of the wallet address depends on the seed private key and the offset, and leakage of the private key of the wallet address cannot be caused by independent leakage of the seed private key and the offset, so that the safety of the wallet isgreatly improved, and meanwhile, the problem that a common wallet needs to create a public and private key pair for each address for storage and backup is avoided.
Owner:福州博泉网络科技有限公司
Tablet flow
ActiveUS8490773B2Jamming of tablets is avoidedMinimize production downtimeMetal-working feeding devicesPower-operated mechanismTablet computerGear drive
Tablet flow for the conveying away of tablets pressed in a tablet press, with a main flow channel, which has at least one branching into at least one first flow channel and at least one second flow channel separated from the first flow channel by at least one separating wall, wherein a separator is provided at the branching, which can be actuated such that tablets are directed out of the main flow channel alternatively into the first flow channel or into the second flow channel, characterized in that the separator has a guide channel for the tablets and in that a guide gear drive is provided, with which the guide channel is moveable between a first position connecting the main flow channel with the first flow channel and a second position connecting the main flow channel with the second flow channel.
Owner:FETTE COMPACTING GMBH
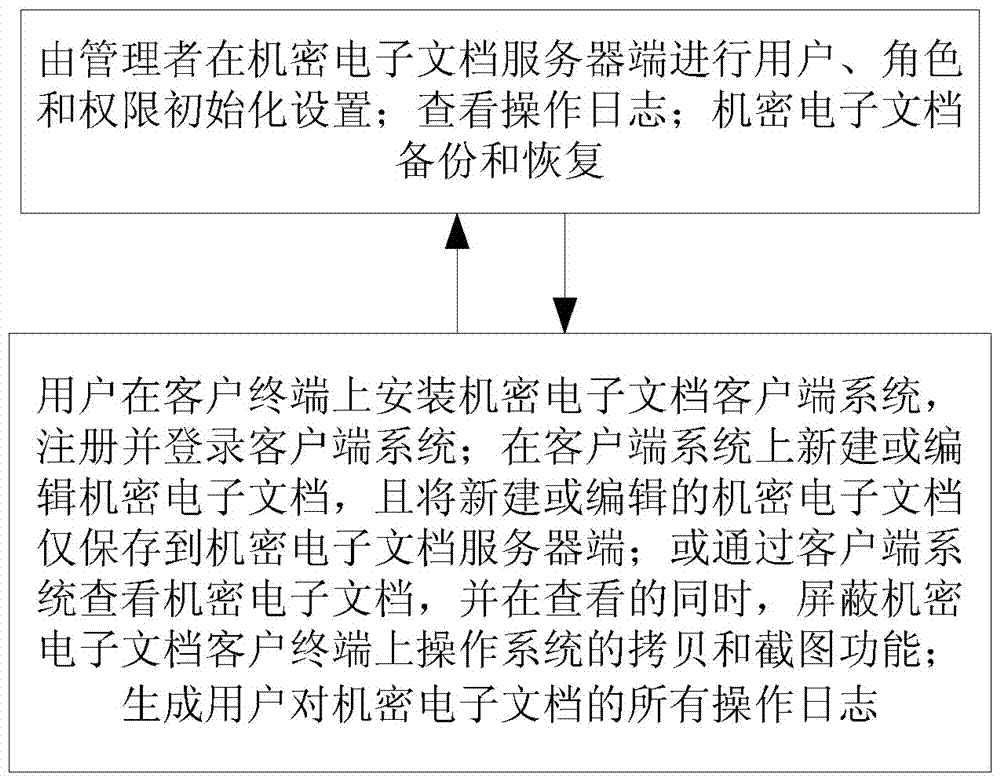
Secret electronic document full life cycle management method
InactiveCN107368710AAvoid backupPrevent leakageDigital data protectionProgram/content distribution protectionElectronic documentFull life cycle
The invention provides a secret electronic document full life cycle management method. The method comprises the steps of performing permission initialization setting in a secret electronic document server by a manager; installing a client system program in a secret electronic document client by a user, and registering and logging in a client system; newly creating or editing a secret electronic document in the client system, and storing the newly created or edited secret electronic document to the secret electronic document server only; or viewing the secret electronic document by utilizing the client system, and while the secret electronic document is viewed, shielding a copy function and a screenshot function of an operation system in the secret electronic document client. The method has the advantages that the secret electronic document is subjected to full life cycle management and protection through the management method, so that the secret electronic document can be effectively prevented from being leaked.
Owner:福建星瑞格软件有限公司
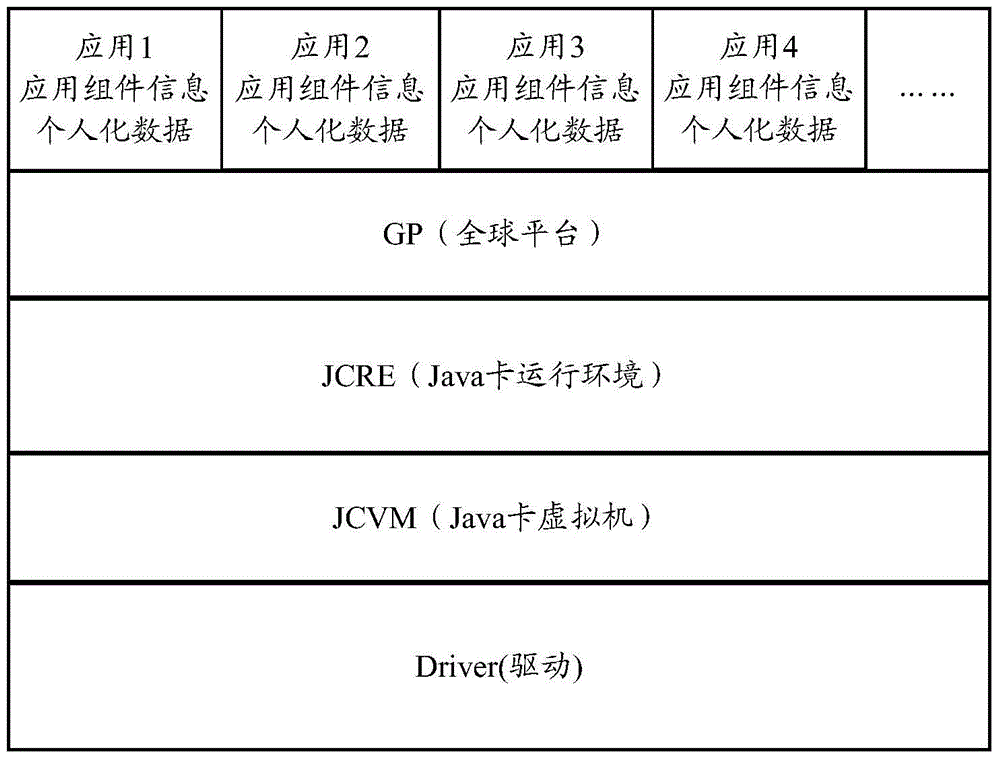
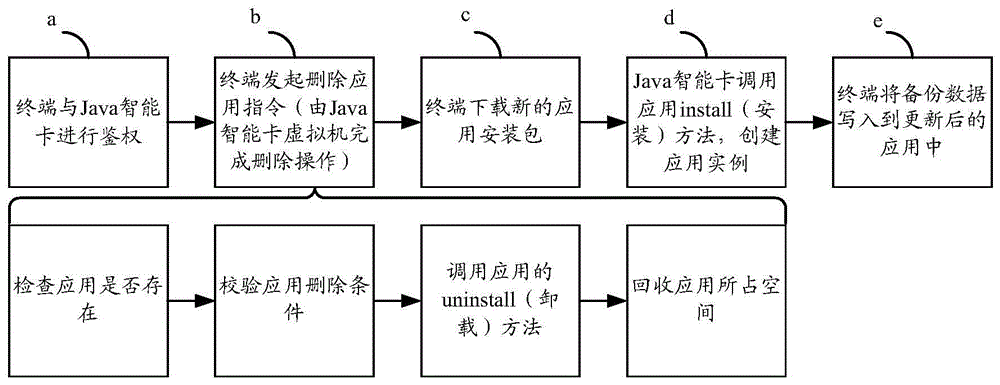
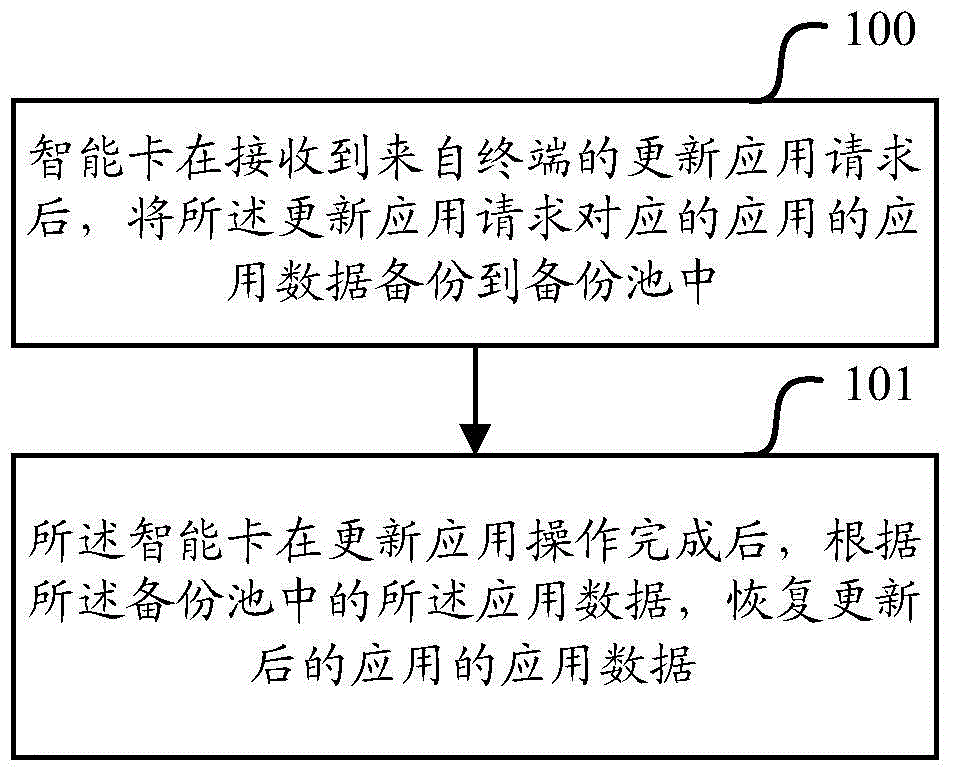
Method, equipment and intelligent card for back-upping and recovery of intelligent card application data
ActiveCN105786641AImprove backup efficiencyImprove recovery efficiencyProgram loading/initiatingRedundant operation error correctionSmart cardData recovery
The invention provides a method, equipment and intelligent card for back-upping and recovery of intelligent card application data and aims to solve the problem in the prior art that data back-upping operations and data recovery operations are complicated during back-upping of data of a to-be-updated application on the intelligent card and during data recovery of the updated application based on the backup data. The method provided by the invention comprises the steps that after receiving an application update request sent by a terminal, the intelligent card backups the application data of an application corresponding to the application update request to a backup pool; and after completion of application update operations, the intelligent card recovers the application data of the updated application according to the application data in the backup pool. According to the embodiment of the invention, the back-upping and recovery operations to the application data carried out by an application publisher or a remote reliable service platform are avoided, and complexity in the back-upping and recovery operations of the application data is reduced, so that the efficiency for the data back-upping and recovery is further increased.
Owner:SUMAVISION TECH CO LTD
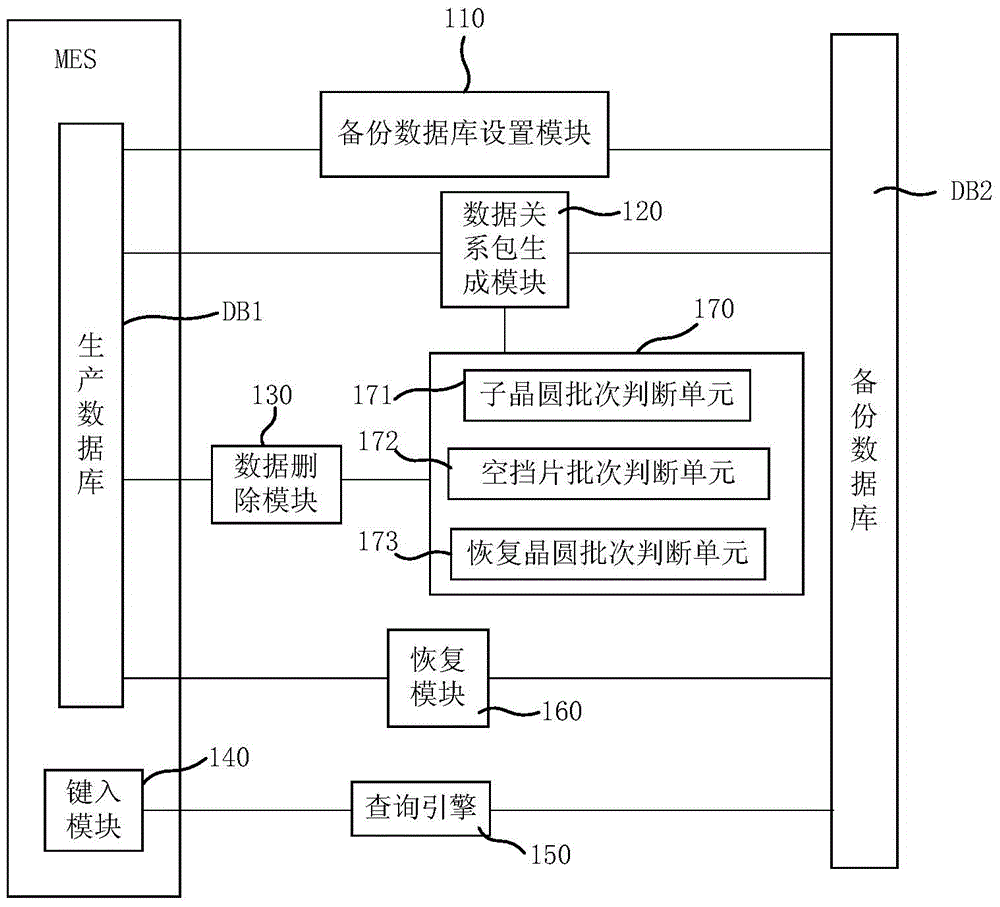
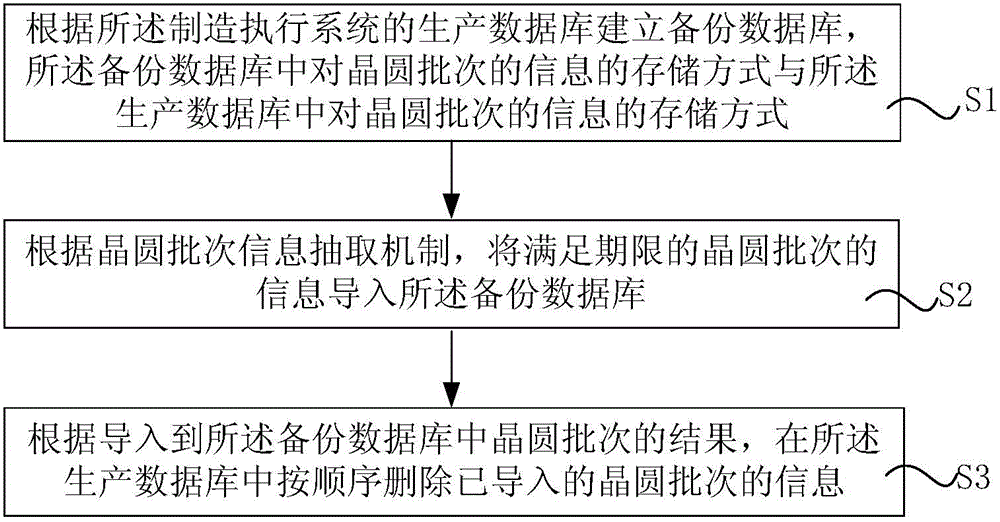
Data backup system and method of manufacturing execution system
ActiveCN106293995AAvoid backupAvoid manual backupsRedundant operation error correctionSpecial data processing applicationsManufacture execution systemTime cost
The invention discloses a data backup system of a manufacturing execution system. The data backup system comprises a backup database setting module for establishing a backup database based on a production database of the manufacturing execution system, wherein the storage mode for wafer batch information in the backup database is same as that for the wafer batch information in the production database; a data relation package generating module for importing the wafer batch information meeting the deadline into the backup database based on a wafer batch information extraction mechanism; and a data deleting module for deleting the imported wafer batch information in the production database according to an order based on the wafer batch result imported in the backup database. The invention also discloses a data backup method of the manufacturing execution system. The data backup system and method of the manufacturing execution system provided by the invention can efficiently reduce consumption cost of hardware resources, human cost of database maintenance personnel and time cost.
Owner:SEMICON MFG INT (SHANGHAI) CORP
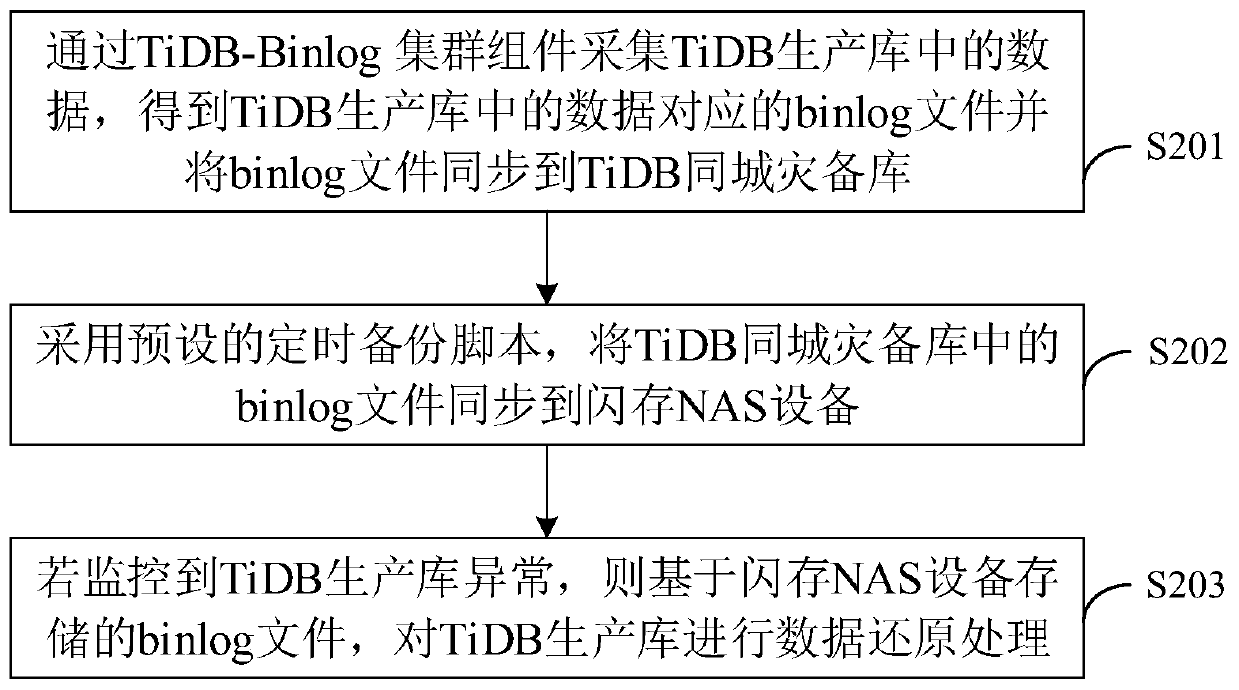
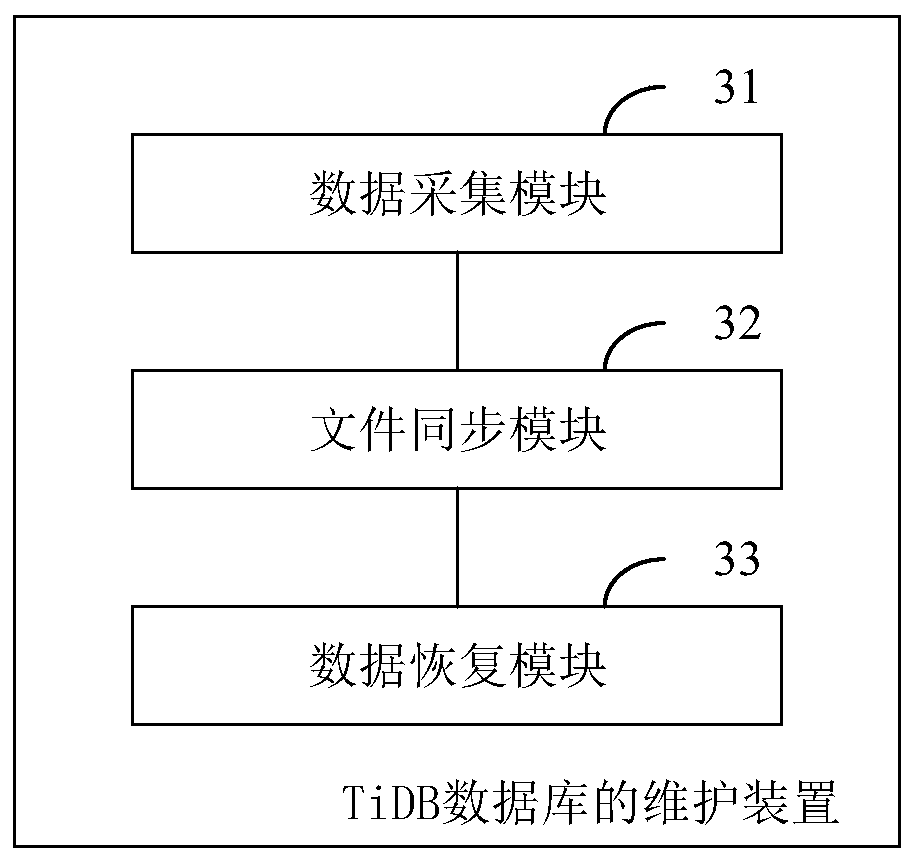
TiDB database maintenance method and device, computer equipment and storage medium
PendingCN111475334AImprove maintenance efficiencyAvoid backupDatabase updatingDatabase distribution/replicationFile synchronizationMagnetic tape
The invention discloses a TiDB database maintenance method and device, computer equipment and a storage medium. The method comprises the following steps of: acquiring data in a TiDB production librarythrough a TiDB-Binlog cluster component; obtaining a binlog file corresponding to the data in the TiDB production library; synchronizing the binlog file to a TiDB city-wide disaster recovery database; then, a preset timed backup script is adopted; synchronizing the binlog file in the TiDB city-wide disaster recovery database to a flash memory NAS device; when monitoring that the TiDB production library is abnormal, carrying out data recovery processing on the TiDB production library based on the binlog file stored in the flash memory NAS equipment, so that the problem of low backup and recovery speed due to the fact that data in the production library is directly stored in an archiving magnetic tape in a traditional mode is solved, and the maintenance efficiency of the TiDB database is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
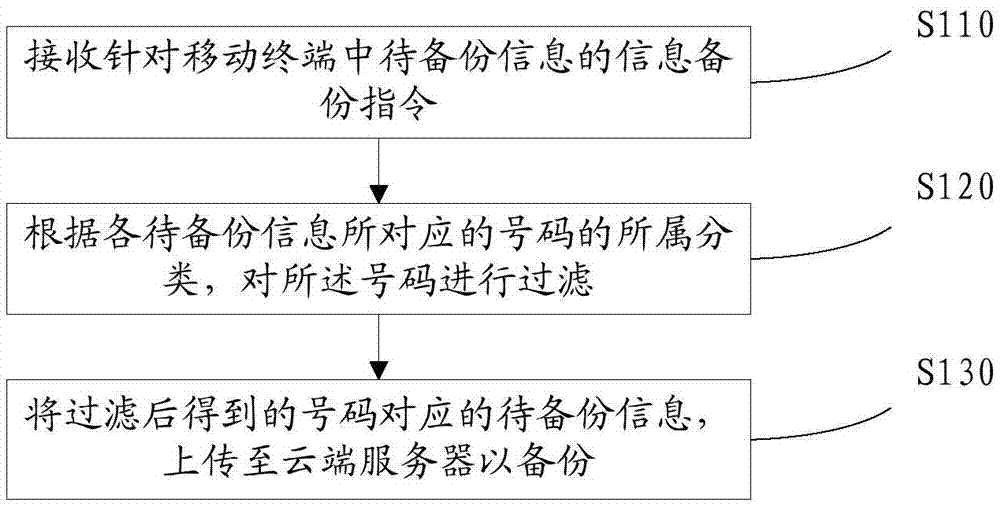
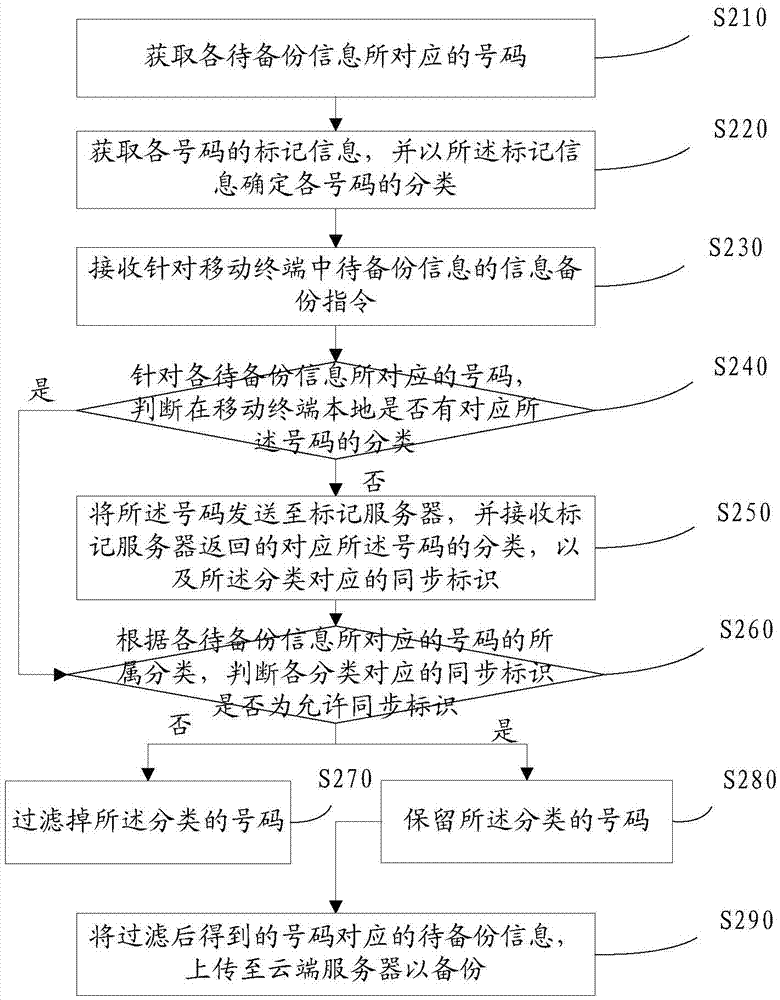
Mobile terminal information backup method and device
InactiveCN106921691AImprove backup efficiencyReduce cumbersome operationsSubstation equipmentTransmissionComputer scienceCloud server
The invention discloses a mobile terminal information backup method and device and relates to the technical field of information. The method provided by the invention comprises the steps of receiving an information backup instruction for to-be-backed up information in a mobile terminal; and filtering numbers according to types to which the numbers corresponding to the to-be-backed up information belong, and uploading the to-be-backed up information corresponding to the numbers obtained through filtering to a cloud server for backup. According to the method and the device, before the information is backed up, a user can automatically filter the information of which storage value is very low for the user, the user only carries out one-time backup operation, the information of which storage value is very low is prevented being backed up, the tedious operation of the user is reduced, and moreover, the mobile terminal information backup efficiency is improved.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
Storage apparatus and volume restoration method
InactiveUS7908447B2Reduce data volumeShorten recovery timeMemory loss protectionError detection/correctionRestoration methodData storing
A storage apparatus conducts, in a protection period, data protection processing for protecting, in a third logical volume, data stored in a first logical volume by using backup data stored in a second logical volume, and suspends the data protection processing in a no-protection period, during which backup relative to the second logical volume is suspended, in the protection period. Then, upon receiving an external order for restoring the first logical volume to its state as of at a time not in the no-protection period within the protection period, the storage apparatus restores the first logical volume to its state as of at a time of the order by using the data backed up in the second logical volume and the data protected in the third logical volume.
Owner:HITACHI LTD
Mineral oil infusion of polypropylene
InactiveUS7807731B1Accurately infuseAccurately pump correct amountSpecial tyresDyeing processEngineeringPolypropylene
A biodegradable plastic used for disposable packaging and other product which will degrade when disposed of in a land fill. The biodegradation begins in about 10 years after disposal. The shelf life of the disposable products is about 90 to 120 days before the infused mineral oil will begin to weep out of the plastic. The shelf life will be decreased if the plastic is stored at above 50 degrees Centigrade. The biodegradable plastic is made from a mixture of about 11.5% by weight of medical grade mineral oil to polypropylene. A mixing device having a feed chamber with polypropylene and mineral oil added to the feed chamber at a rate coordinated with the movement of the mixing and infusion screw delivers infused mineral oil in the polypropylene at a desired mixture ratio to a mold.
Owner:BILSKI DAVID A
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com