Data backup method and device
A data backup and data technology, which is applied in the direction of electrical digital data processing, special data processing applications, and redundant data error detection in calculations. , the large amount of backup data, etc., to achieve the effect of reducing the amount of backup data and supporting PIT recovery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
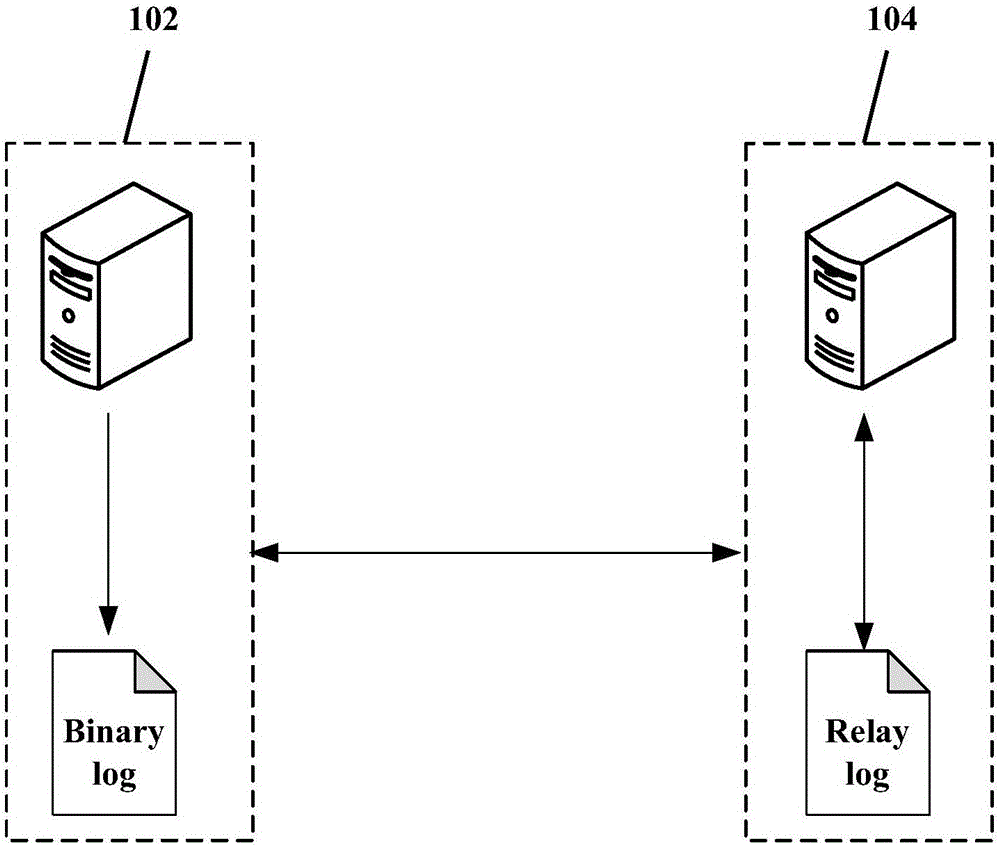
[0075] Embodiment 1. After obtaining the pre-configured target time to which the data of the database to be restored is restored, when sending the data copied from the slave database during the backup and the binary log files obtained from the master database during the backup to the database to be restored, according to The time stamp in the binary log file is used to send all binary log files whose time stamp identifies the time before the target time to the database to be restored, and control the database to be restored to use the received binary log file to process the received data Make changes.
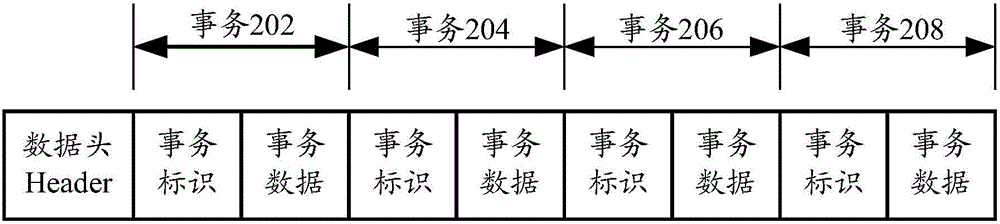
[0076] Specifically, the time tag in each binary log file records the time of the first change operation record and the time of the last change operation record in the binary log file, and each change operation record in the binary log file has a corresponding Therefore, after obtaining the pre-configured target time to which the data of the database to be restored is restored,...
Embodiment approach 2
[0078] Embodiment 2: After acquiring the pre-configured target moment to which the data of the database to be restored is restored, the data copied from the database during the backup and the binary log files obtained from the master database during the backup are sent to the database to be restored, and then the control When the recovery database uses the received binary log file to change the received data, control the database to be recovered to use the received binary log file to change the received data, and restore the data in the to-be-restored database to the target time to the same data as the primary database at the target time.
[0079] Specifically, control the database to be restored to use the received binary log file to change the received data, restore the data in the database to be restored to the target time to be the same as the data in the primary database at the target time, including: according to the binary log The time tag in the file controls the datab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com