Patents
Literature
177 results about "Business software" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Business software (or a business application) is any software or set of computer programs used by business users to perform various business functions. These business applications are used to increase productivity, to measure productivity and to perform other business functions accurately.
Method and systems for generating and using tokens in a transaction handling system
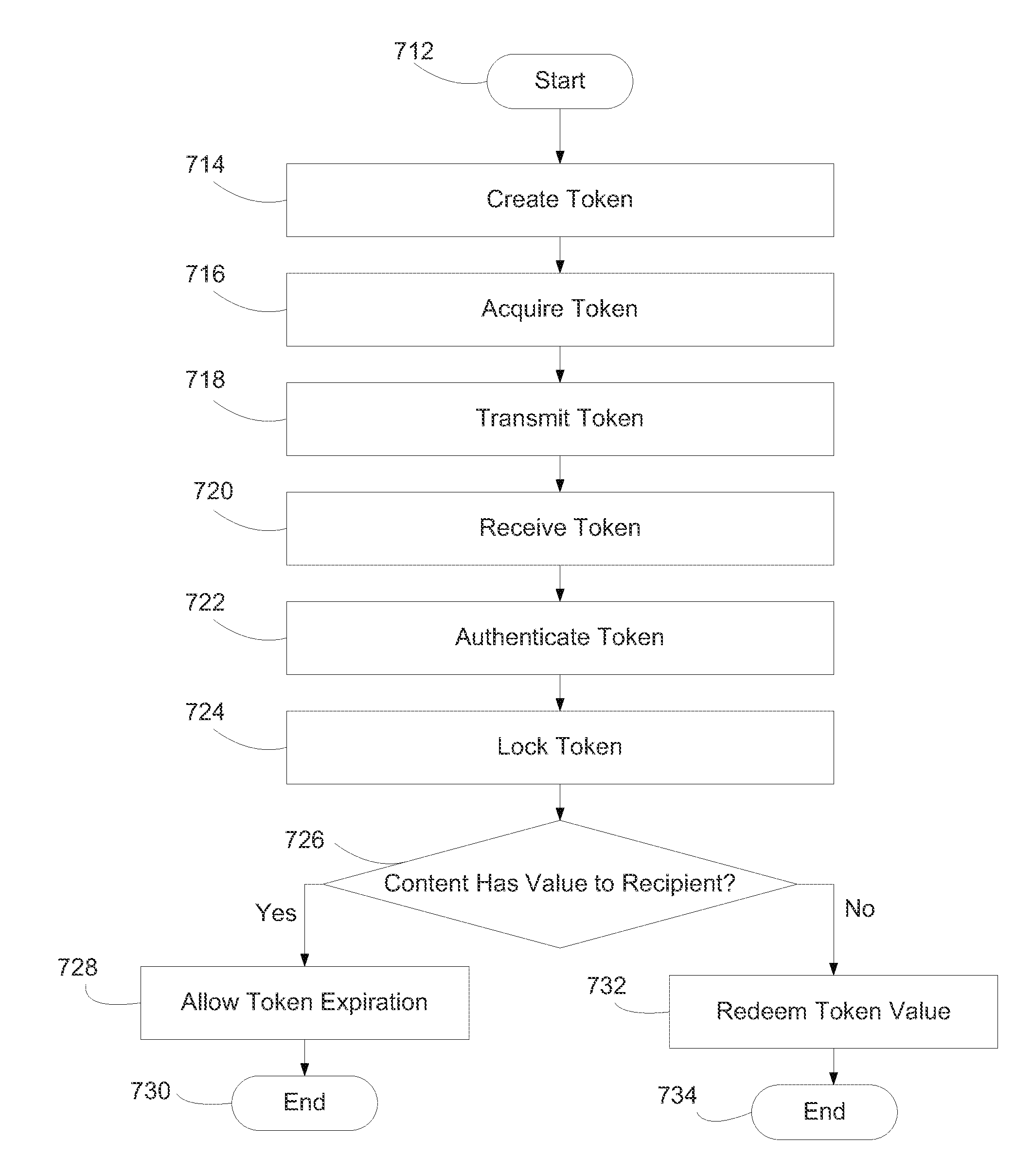
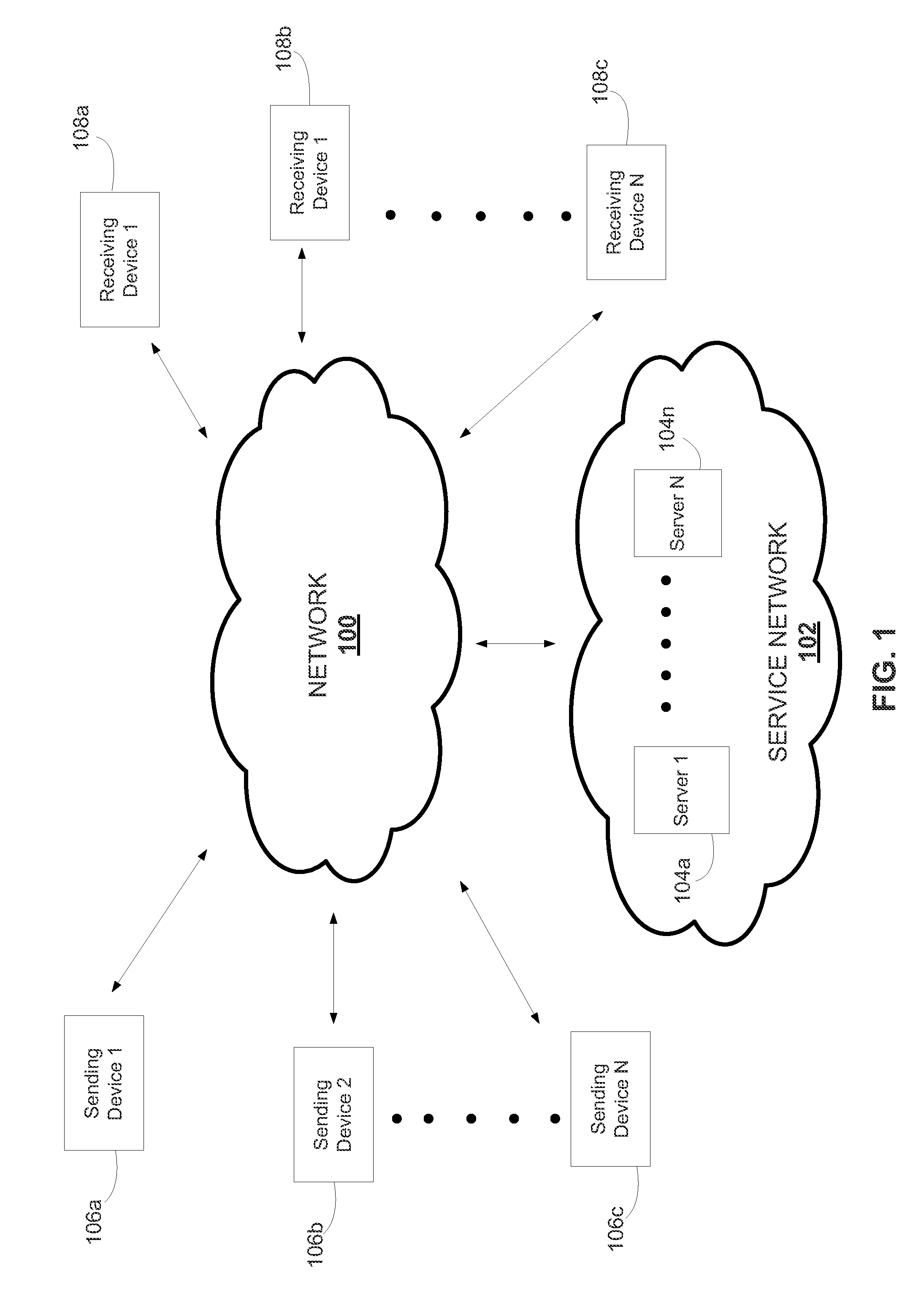
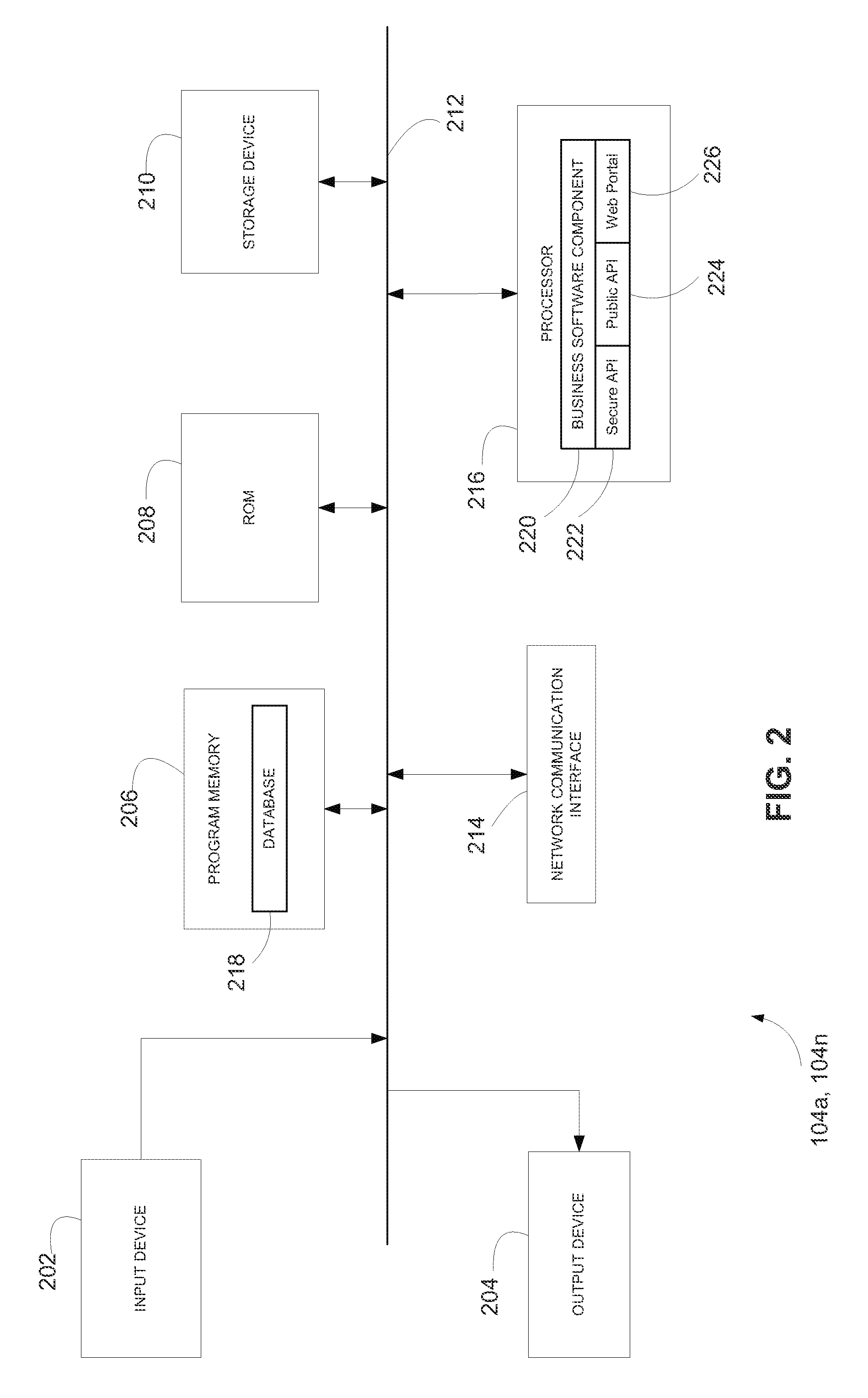
A method and systems for generating and using transaction tokens including a plurality of interfaces for communication over a network, the plurality of interfaces communicatively coupled to a plurality of information sending devices and a plurality of information receiving devices, at least one database including a token data table and a user profile table, the token data table storing at least one token, the at least one token having a user-defined value and a plurality of data fields, and a business software component communicatively coupled to the plurality of interfaces and the at least one database that is operative to receive at least one request from the plurality of interfaces, generate at least one token in response to the at least one request received from the plurality for interfaces, lock the at least one token generated in response to the received at least one request, and redeem the user-defined value of the locked at least one token.
Owner:GIDAH
E-commerce development intranet portal
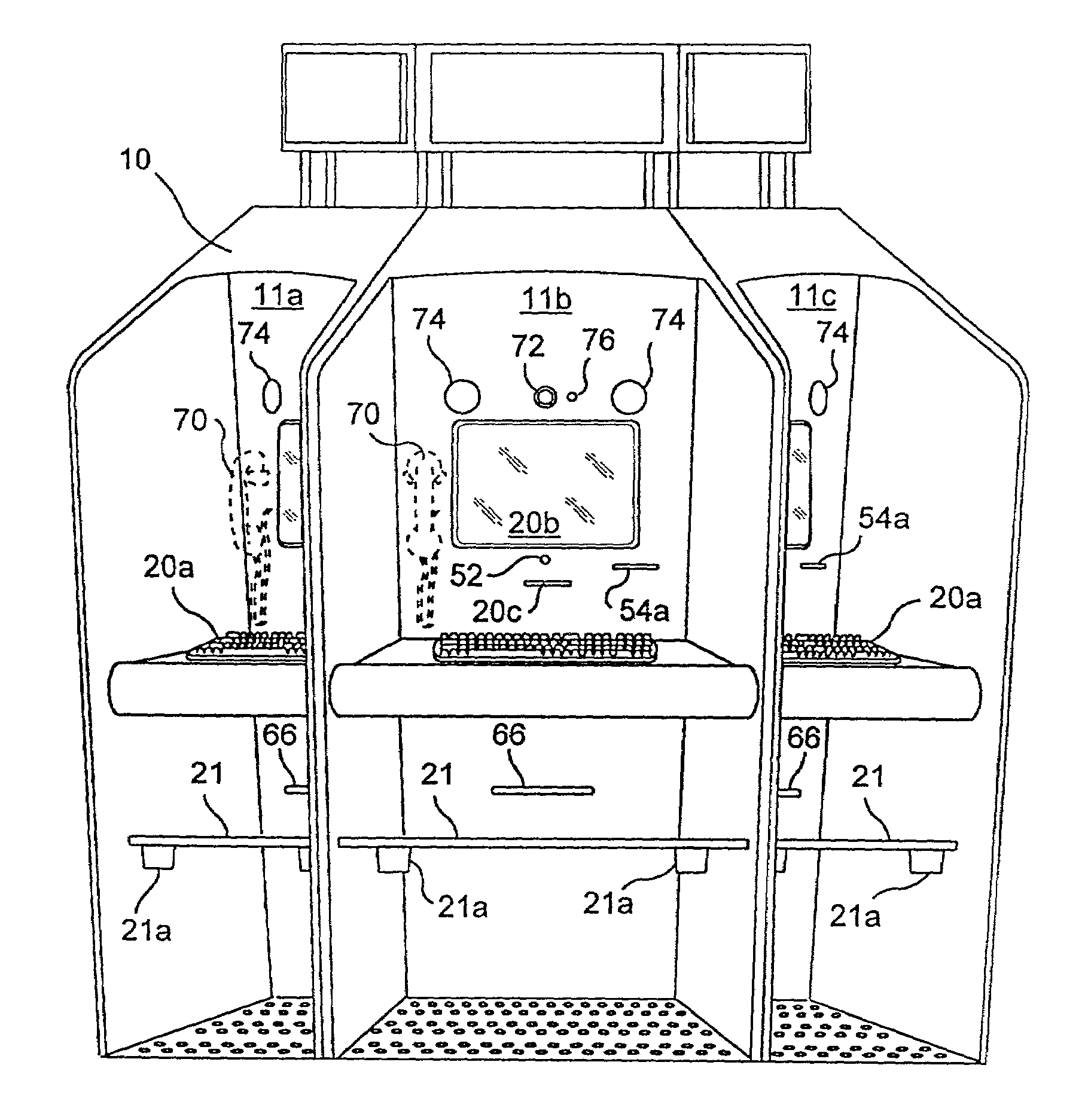
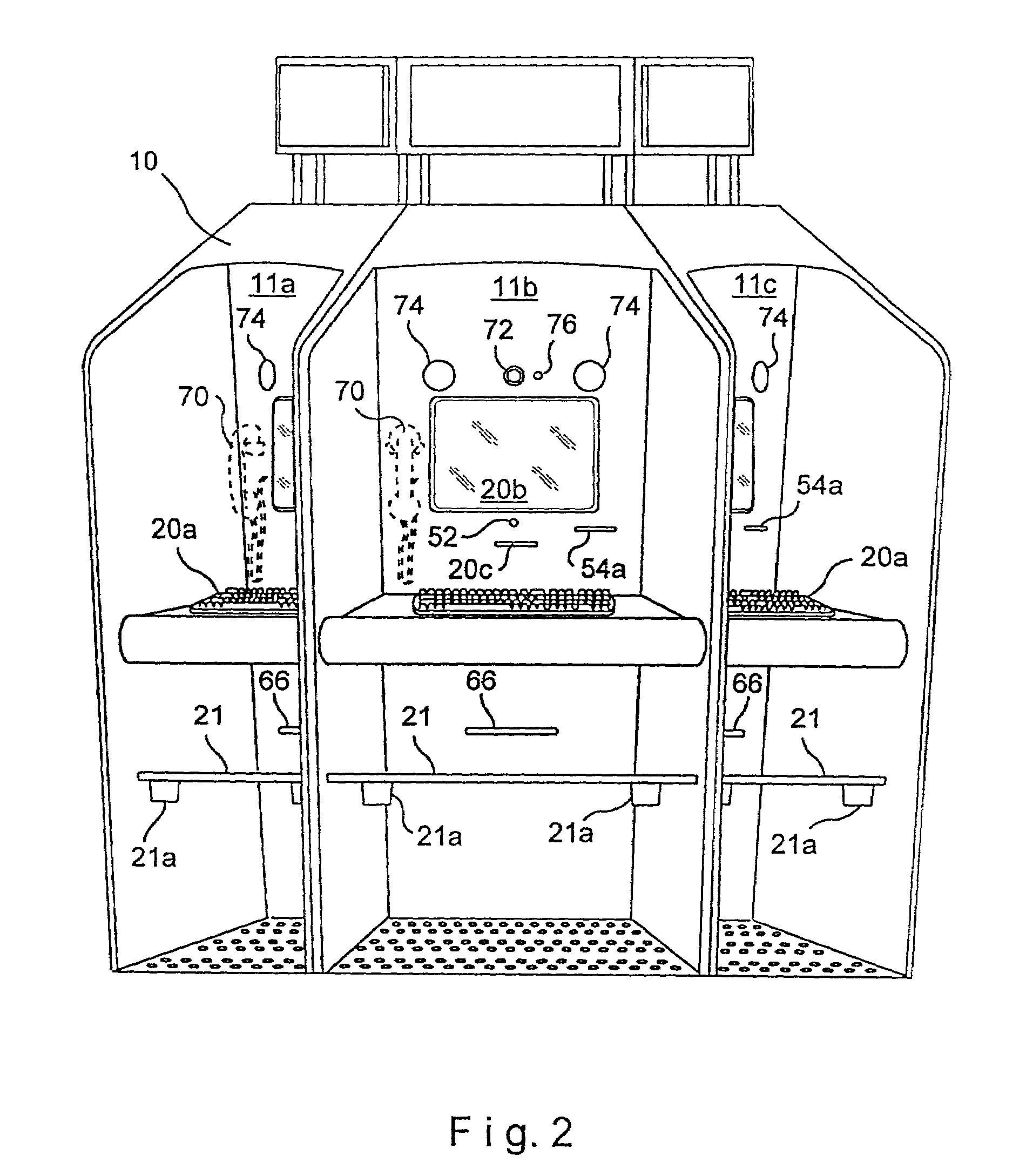
An intranet providing a multiple-carrel public-access kiosk is disclosed. The intranet provides free access to foreign and domestic informational e-commerce intranet sites as well as e-mail and public service educational and informational materials. The kiosk accepts anonymous pre-paid cards issued by a local franchisee of a network of c-commerce intranets that includes the local intranet. The franchisee owns or leases kiosks and also provides a walk-in e-commerce support center where e-commerce support services and goods, such as pre-paid accounts for access to paid services at a kiosk, can be purchased. The paid services provided by the carrel include video-conference and chat room time, playing and / or copying audio-visual materials such as computer games and music videos, and international e-commerce purchase support services such as customs and currency exchange. The third-party sponsored public service materials include audio-visual instructional materials in local dialects introducing the user to the use of the kiosks services and providing training for using standard business software programs. Sponsors include pop-up market research questions in the sponsored public service information and receive clickstream date correlated with the user's intranet ID and answers to the original demographic questions answered by the user.
Owner:DE FABREGA INGRID PERSCKY
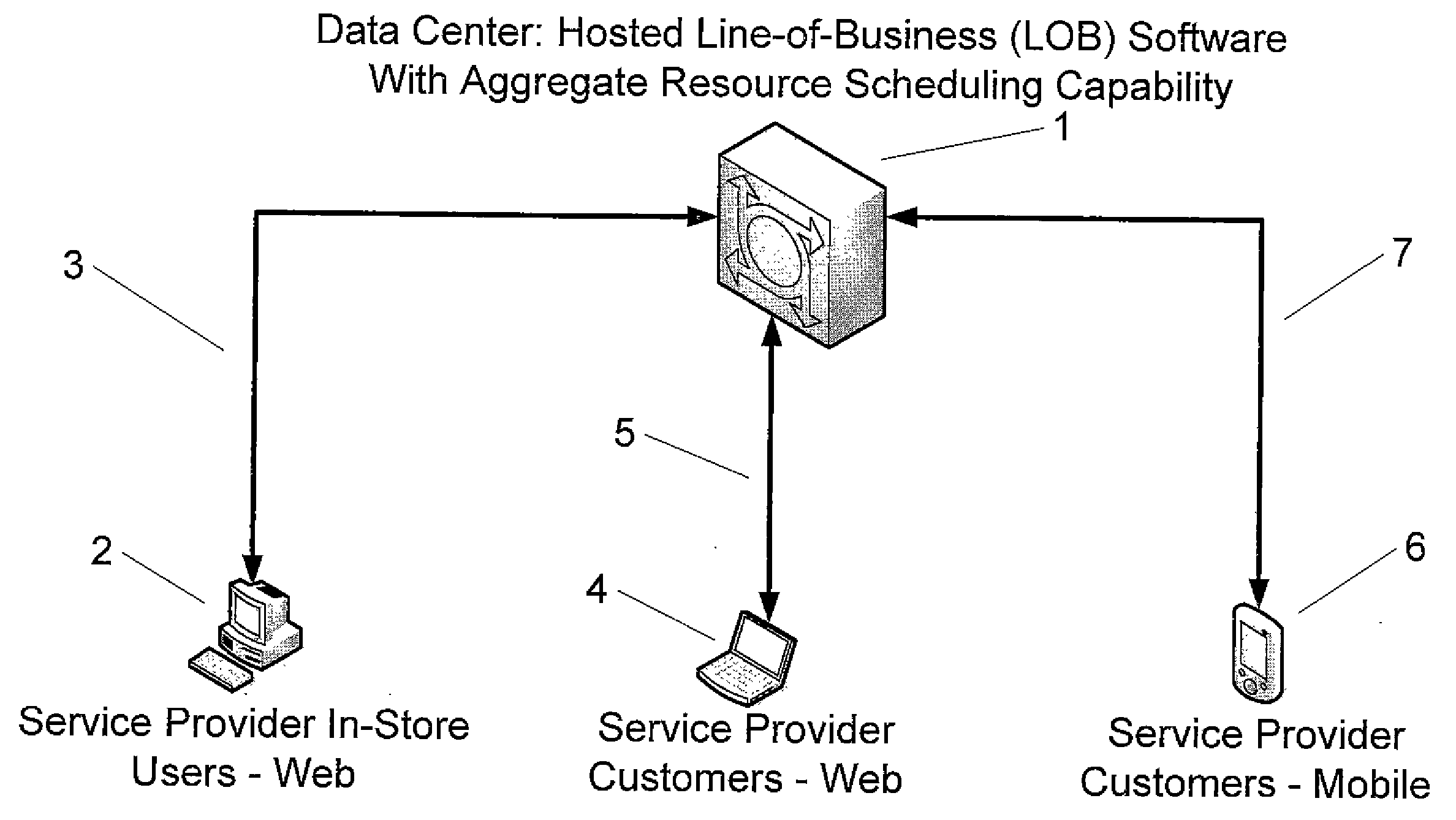
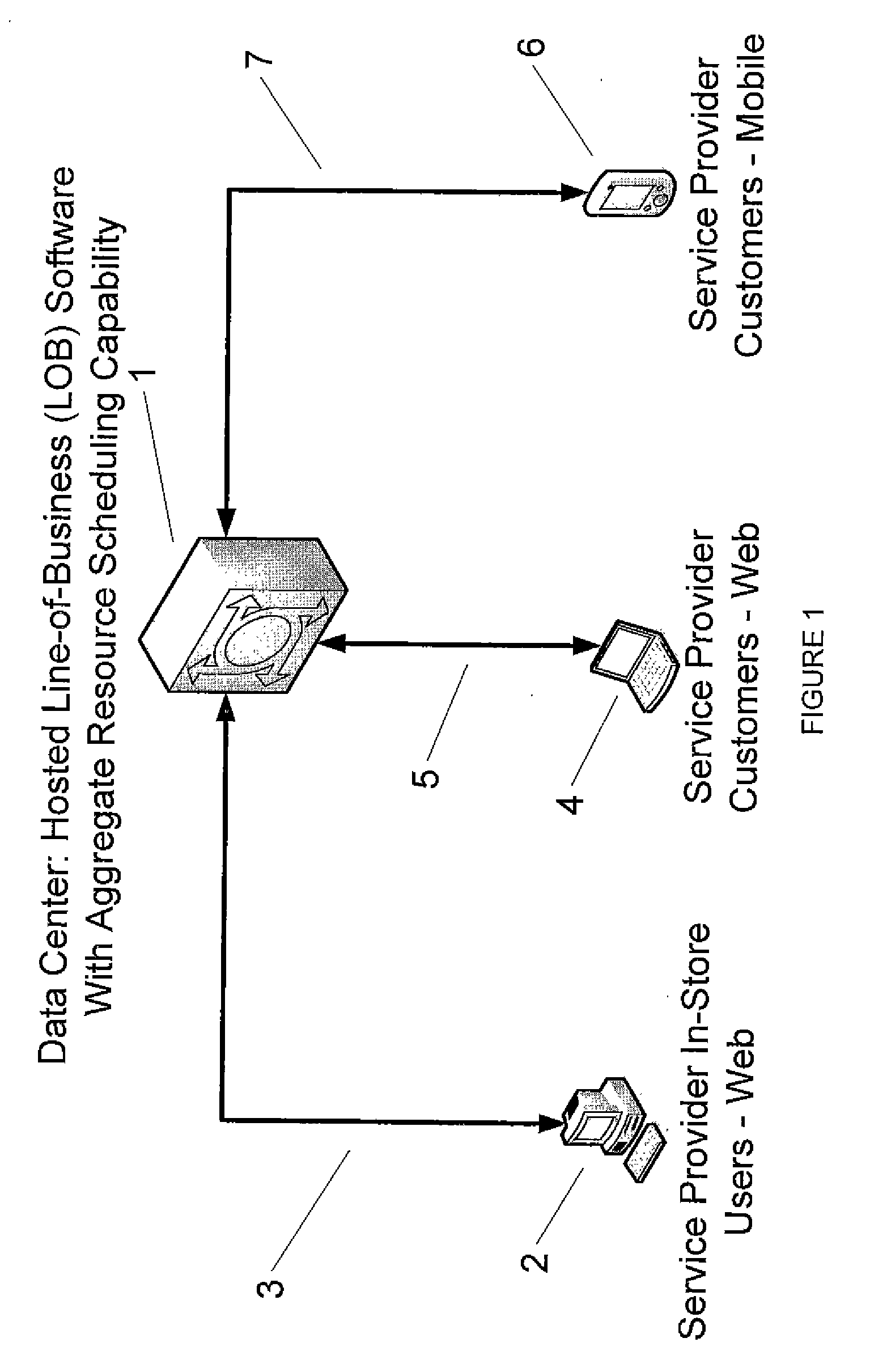
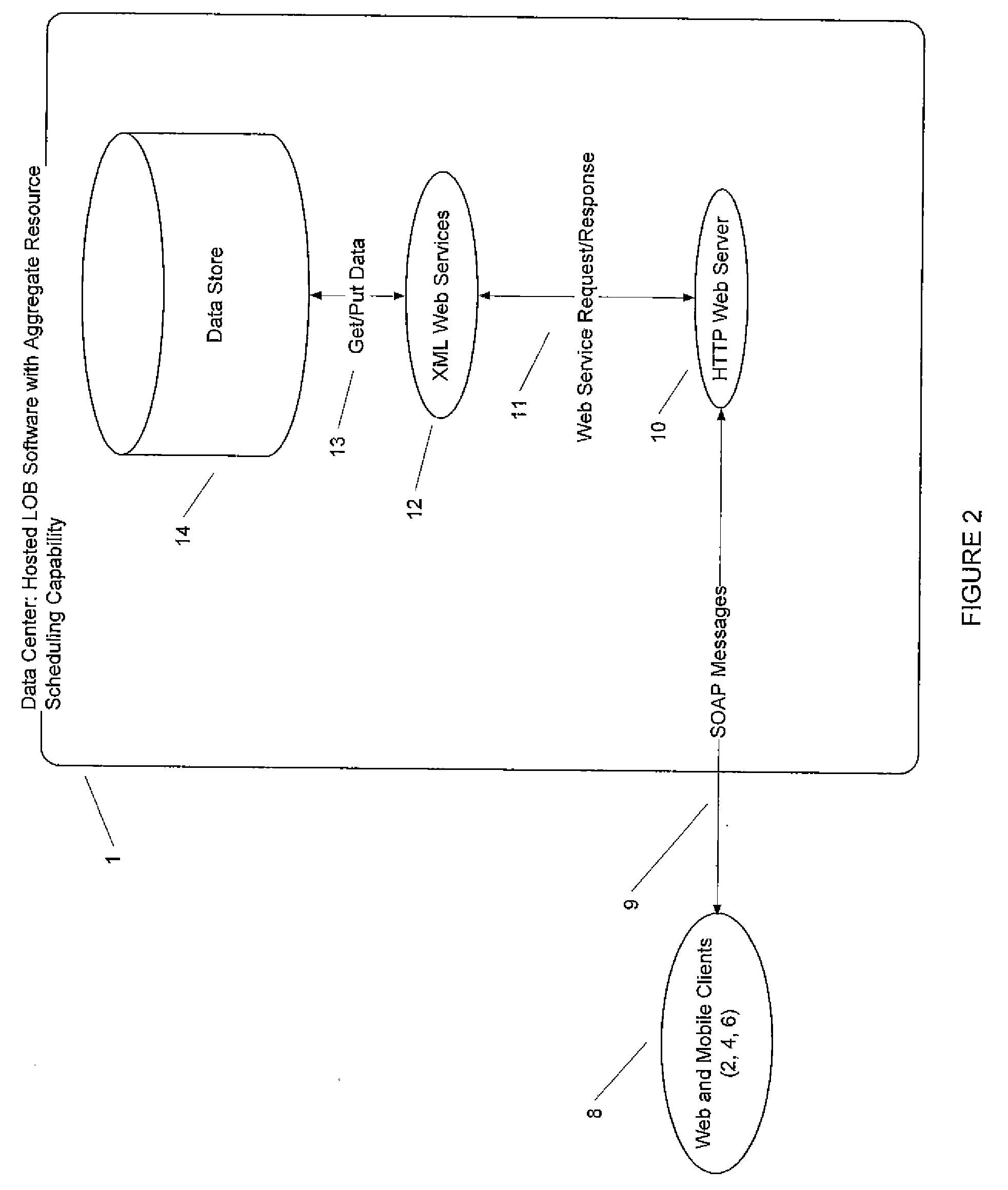
System and method for real-time scheduling of human and non-human resources
InactiveUS20080313005A1Eliminating double-bookingDelayed notificationResourcesData acquisition and loggingService provisionData center
A system for real-time resource scheduling comprising a hosted line-of-business software application for service providers operating in various industry verticals; a central data center; an in-store web-based calendar for service provider employees; a web-based calendar for service provider customers; and a mobile customer scheduling interface; wherein the central data center comprises a data store that comprises a master database and a plurality of service provider chain databases; the master database contains metadata of all service provider chain databases housed in the data store; the master database contains user accounts for customers who make reservations with any of the service providers; each service provider has a service provider chain database that is specific to that service provider; each service provider creates and maintains all resource scheduling information for its own human and non-human resources; and no data is shared between service providers.
Owner:SCHEDULICITY
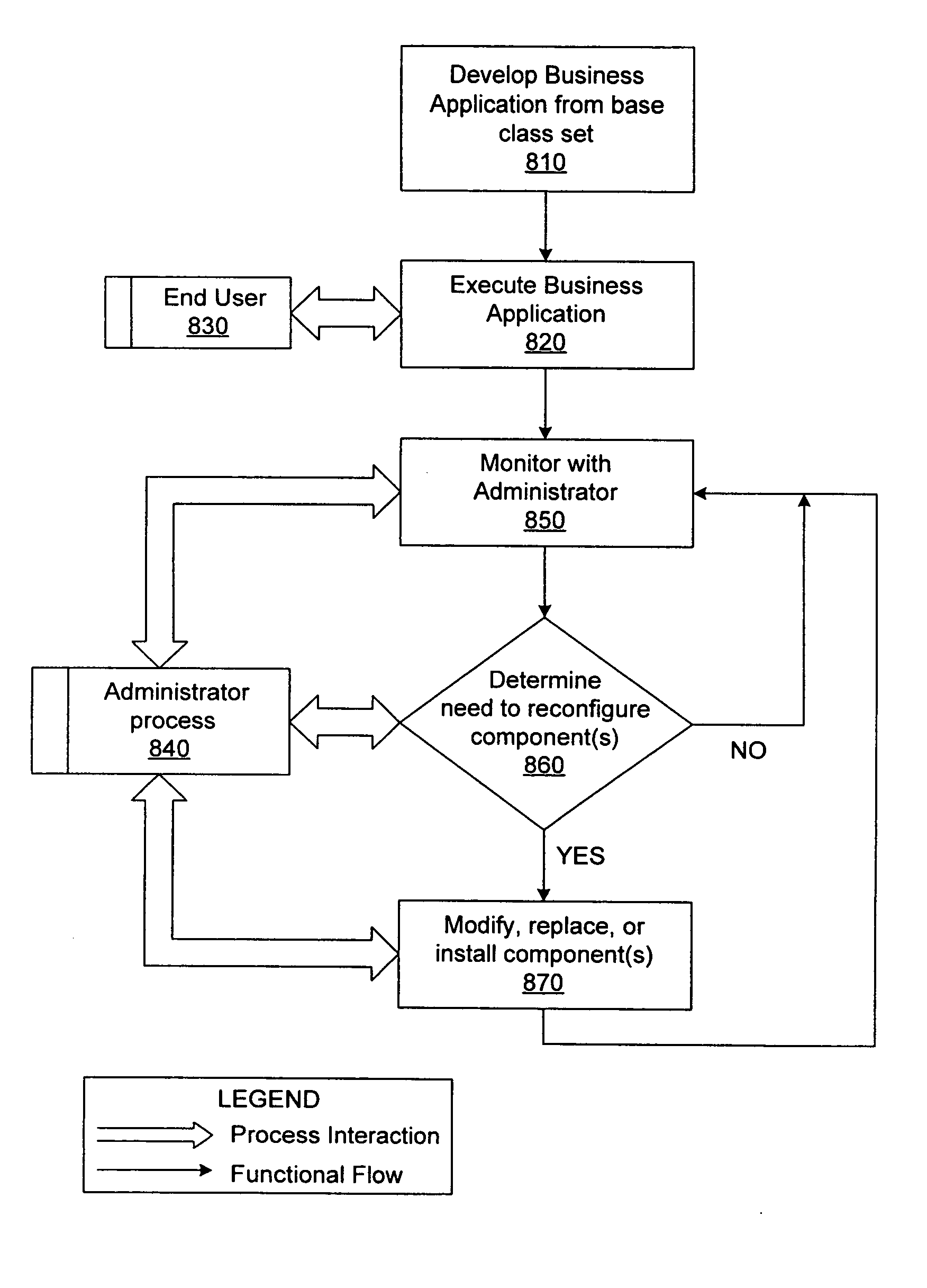
Method of administering software components using asynchronous messaging in a multi-platform, multi-programming language environment
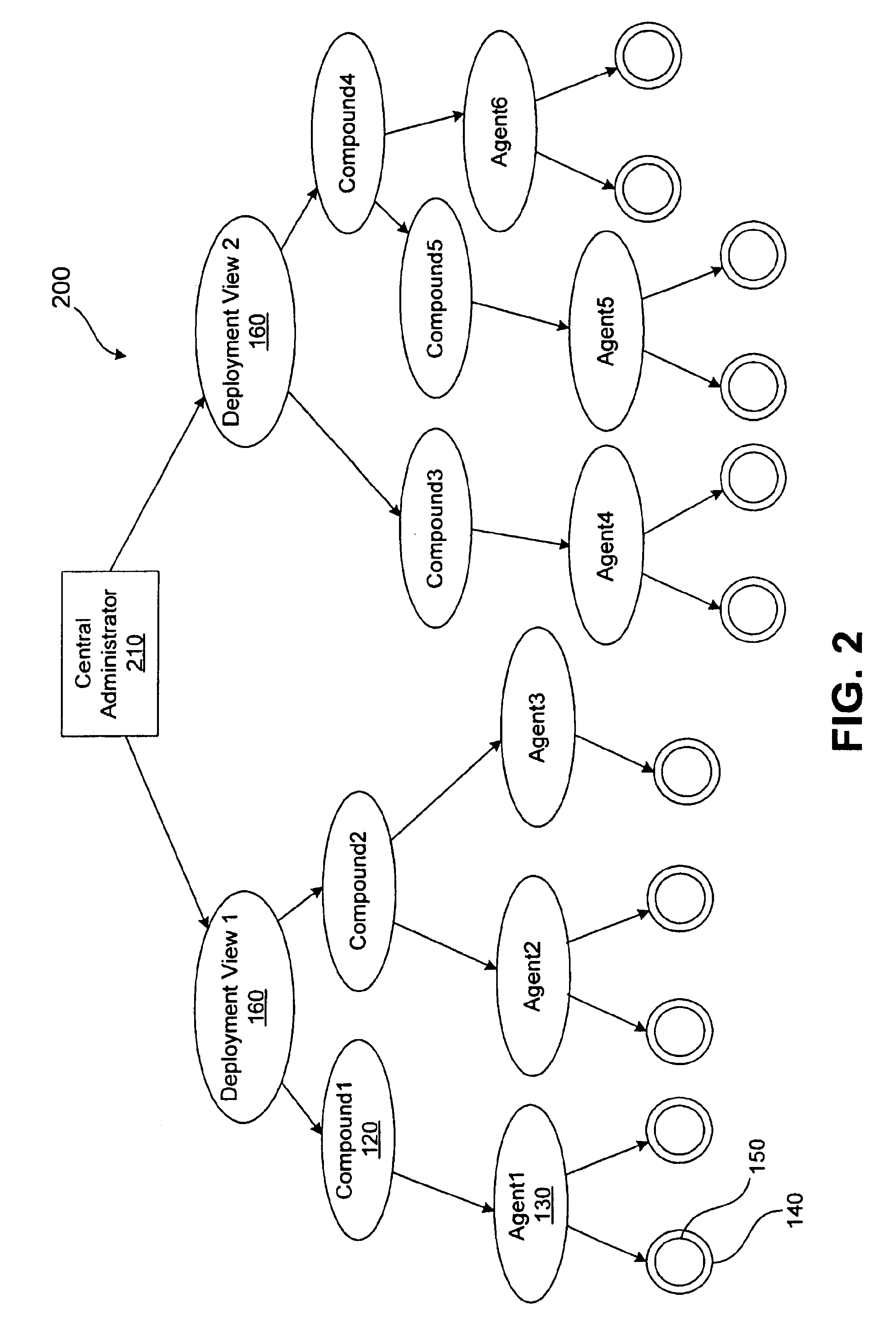
A method for performing life cycle management of business software applications and their components across a multiple-platform, multiple-language network. The method takes advantage of the inheritance properties of object-oriented programming (OOP) by developing all components of a business application from a set of base classes, thus deploying a common set of methods across all application components. The Central Administrator then determines when a need to reconfigure one or more components of the business application has arisen. The Central Administrator then modifies or replaces existing components of the business application or installs entirely new components over the network without end user interaction. In one embodiment of the present invention, the Central Administrator is aided by a set of Distributed Administrators located on each virtual node server / host computer of a business application operating over a network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Apparatus, method and article for direct slicing of step based nurbs models for solid freeform fabrication
InactiveUS20060155418A1Reduce eliminateImprove modeling accuracyProgramme controlTotal factory controlFeasibility studyGrating
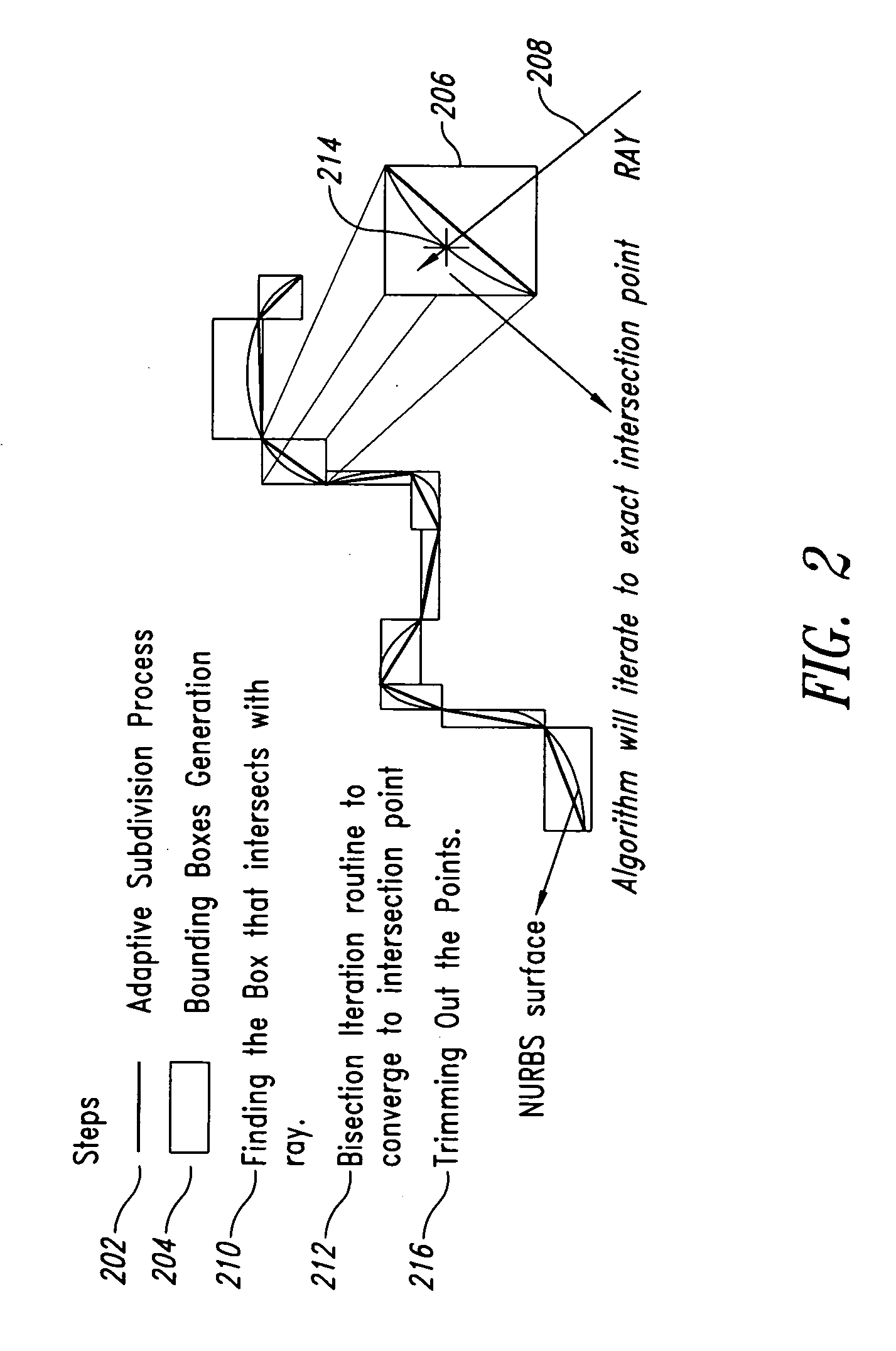
Direct slicing of CAD models to generate process planning instructions for solid freeform fabrication may overcome inherent disadvantages of using STL format in terms of the process accuracy, ease of file management, and incorporation of multiple materials. This paper will present the results of our development of a direct slicing algorithm for layered freeform fabrication. The direct slicing algorithm was based on a neutral, international standard (ISO 10303) STEP-formatted NURBS geometric representation and is intended to be independent of any commercial CAD software. The following aspects of the development effort will be presented: 1) Determination of optimal build direction based upon STEP-based NURBS models; 2) Adaptive subdivision of NURBS data for geometric refinement; and 3) Ray-casting slice generation into sets of raster patterns. Feasibility studies applying the direct slicing algorithm to example models and the generation of fabrication planning instructions involving multi-material structures will also be presented.
Owner:THERICS
Business software application generation system and method
InactiveUS20050154742A1Reduce decreasePowerful ERP optimizationSoftware engineeringDigital data processing detailsSoftware engineeringApplication software
Owner:GARPAC CORP
Component based software system
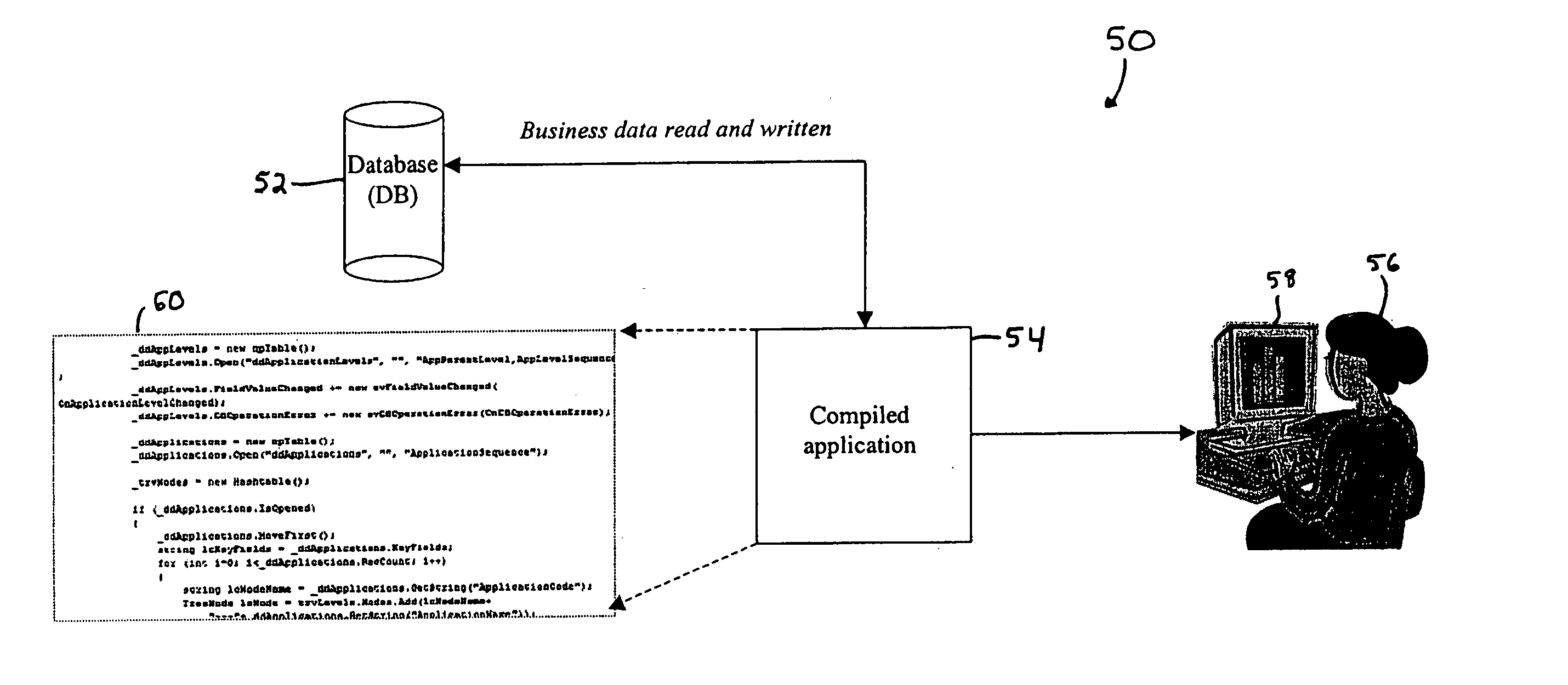
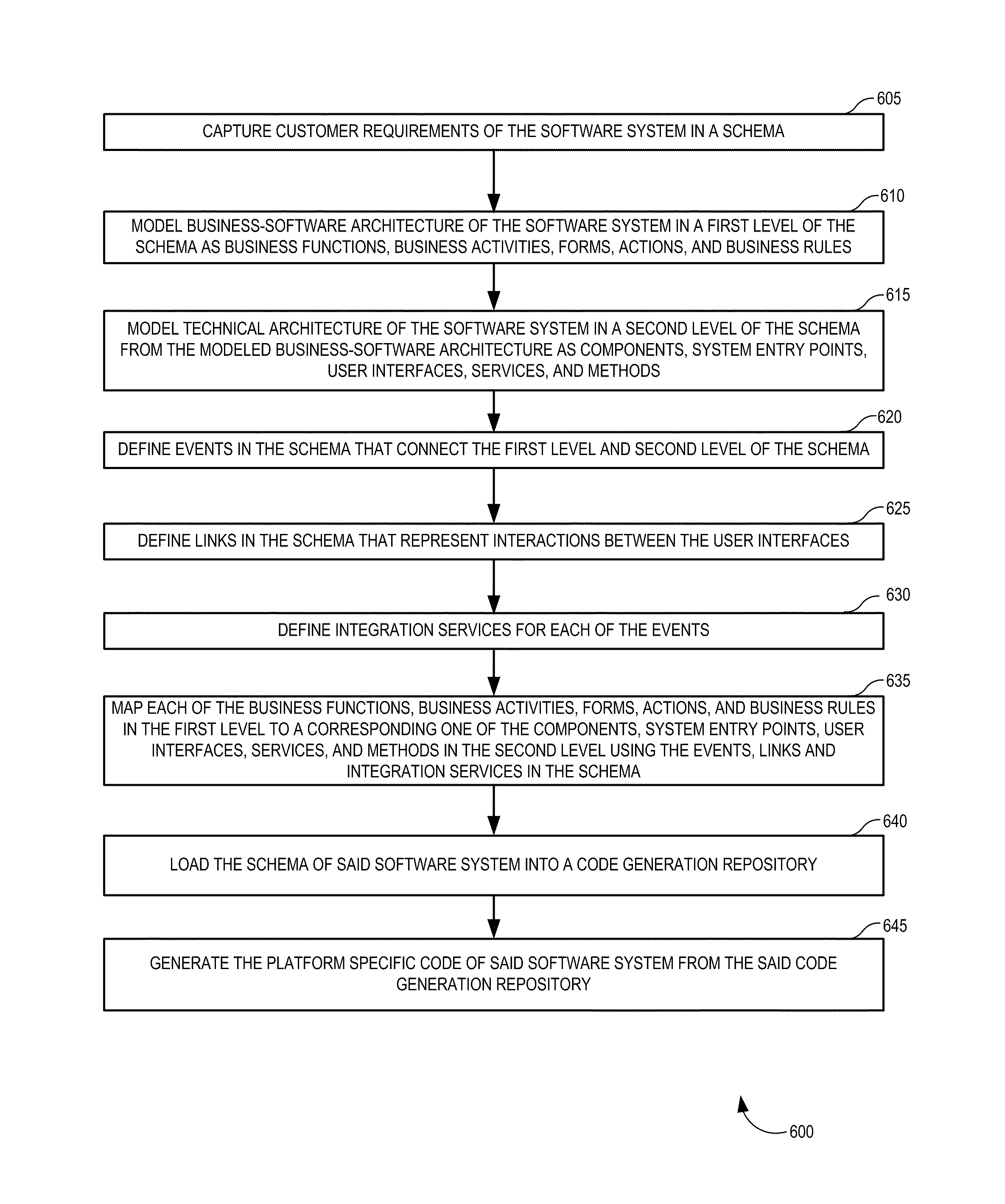
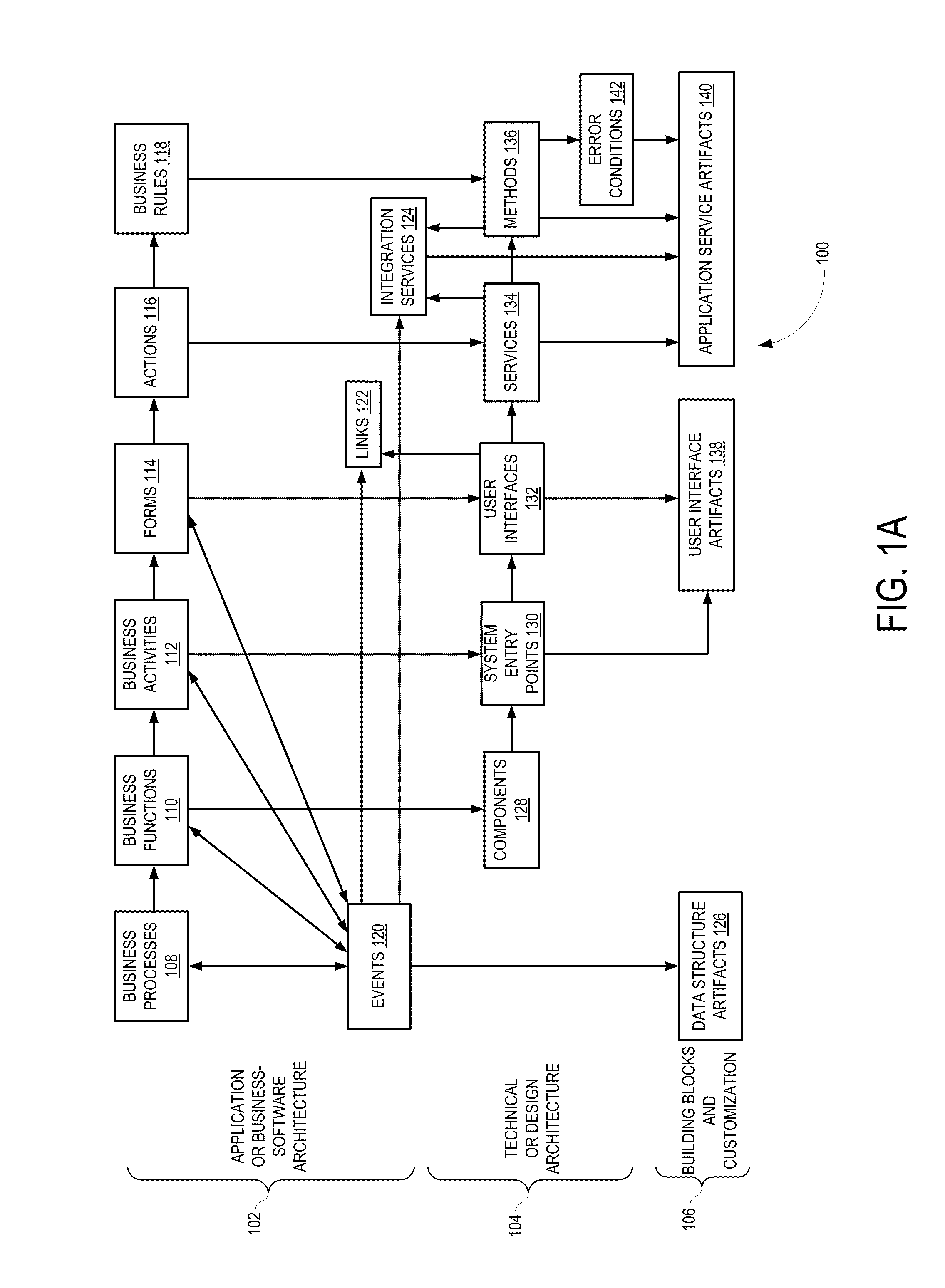
ActiveUS20100325606A1Model driven codeRequirement analysisCOLA (software architecture)Customer requirements
A computer implemented model-driven method to generate platform specific code for a user interface is disclosed. In one embodiment, the method includes, capturing customer requirements of the software component in a schema, modeling business-software architecture of the software component in a first level of the schema, modeling technical architecture of the software system from the modeled business-software architecture in a second level of the schema, defining events in the schema that connect the first level and the second level of the schema, defining links in the schema that represent interactions between the user interfaces, defining integration services in the schema for each of the events, mapping each element in the first level to a corresponding one of the elements in the second level using the events, links, and integration services in the schema, loading the schema of the software component into a code generation repository.
Owner:RAMCO SYSTEMS
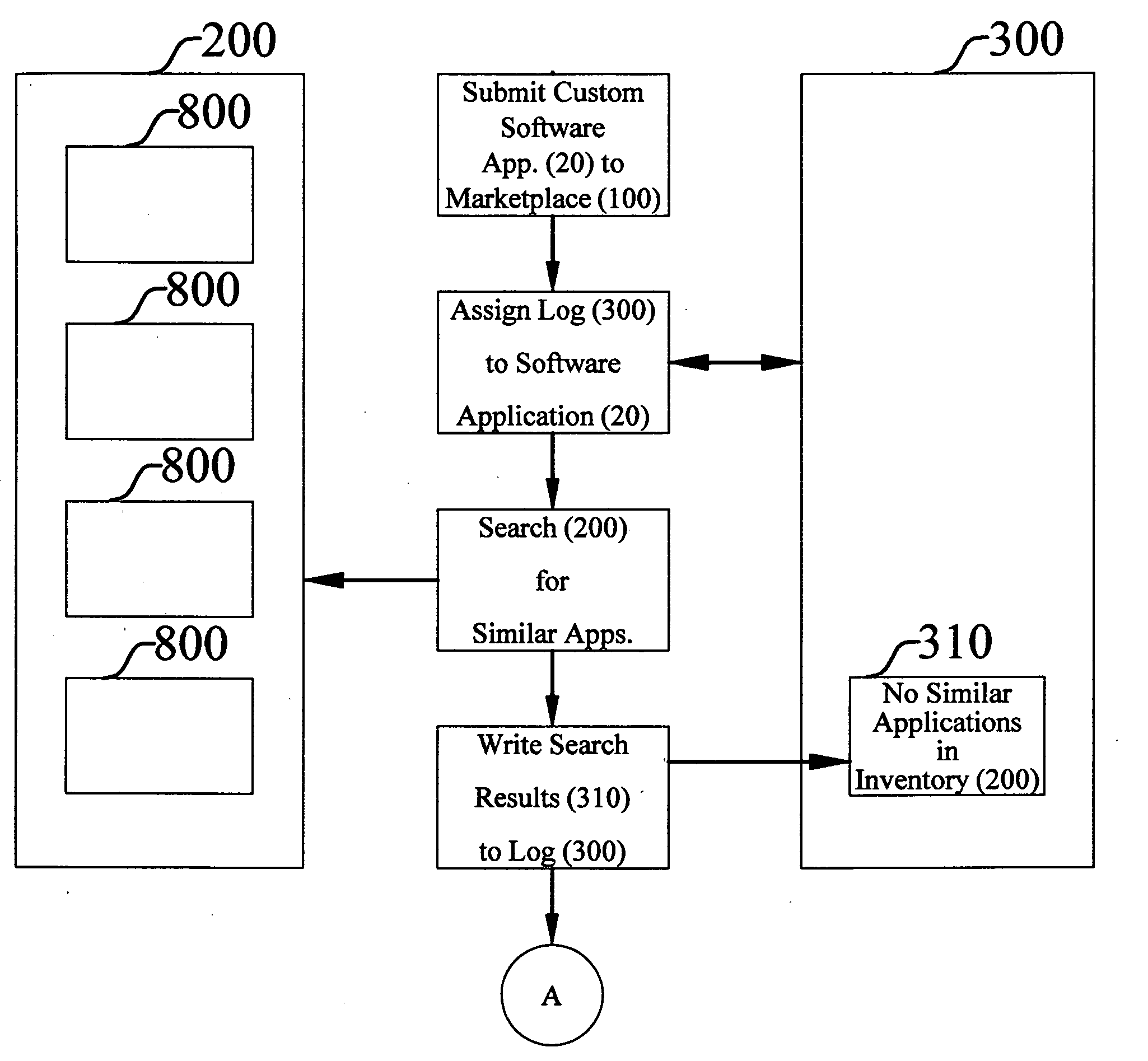
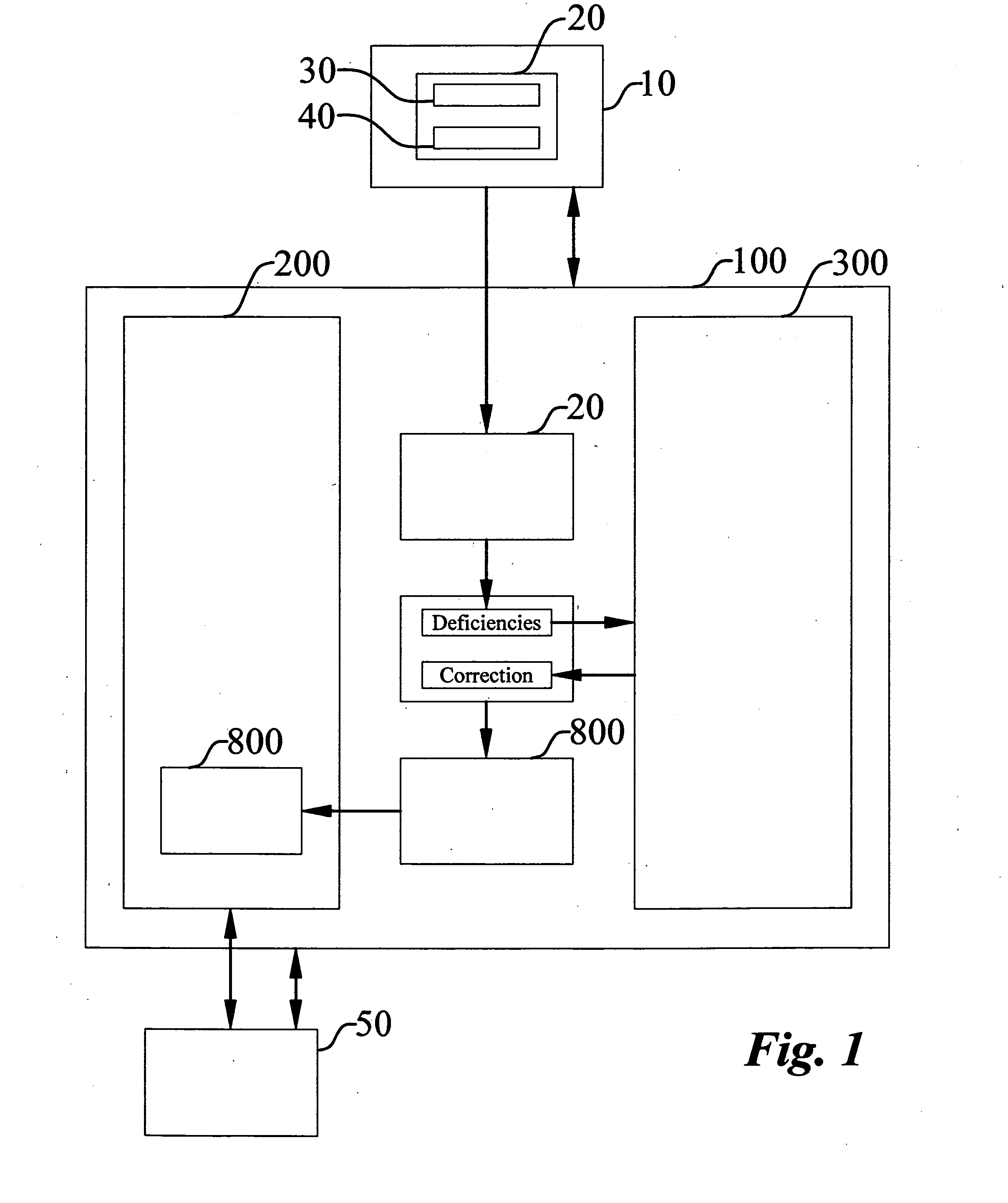
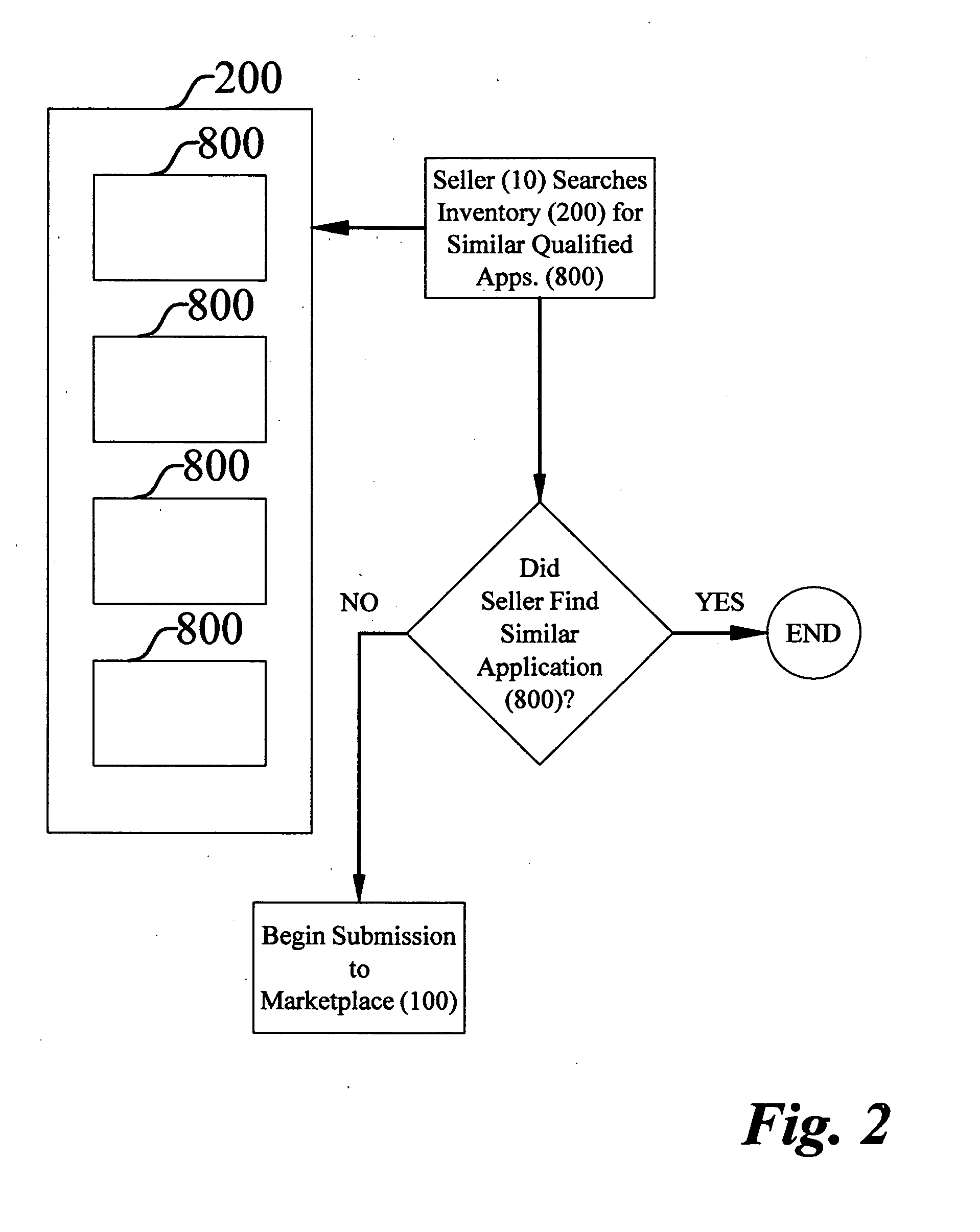
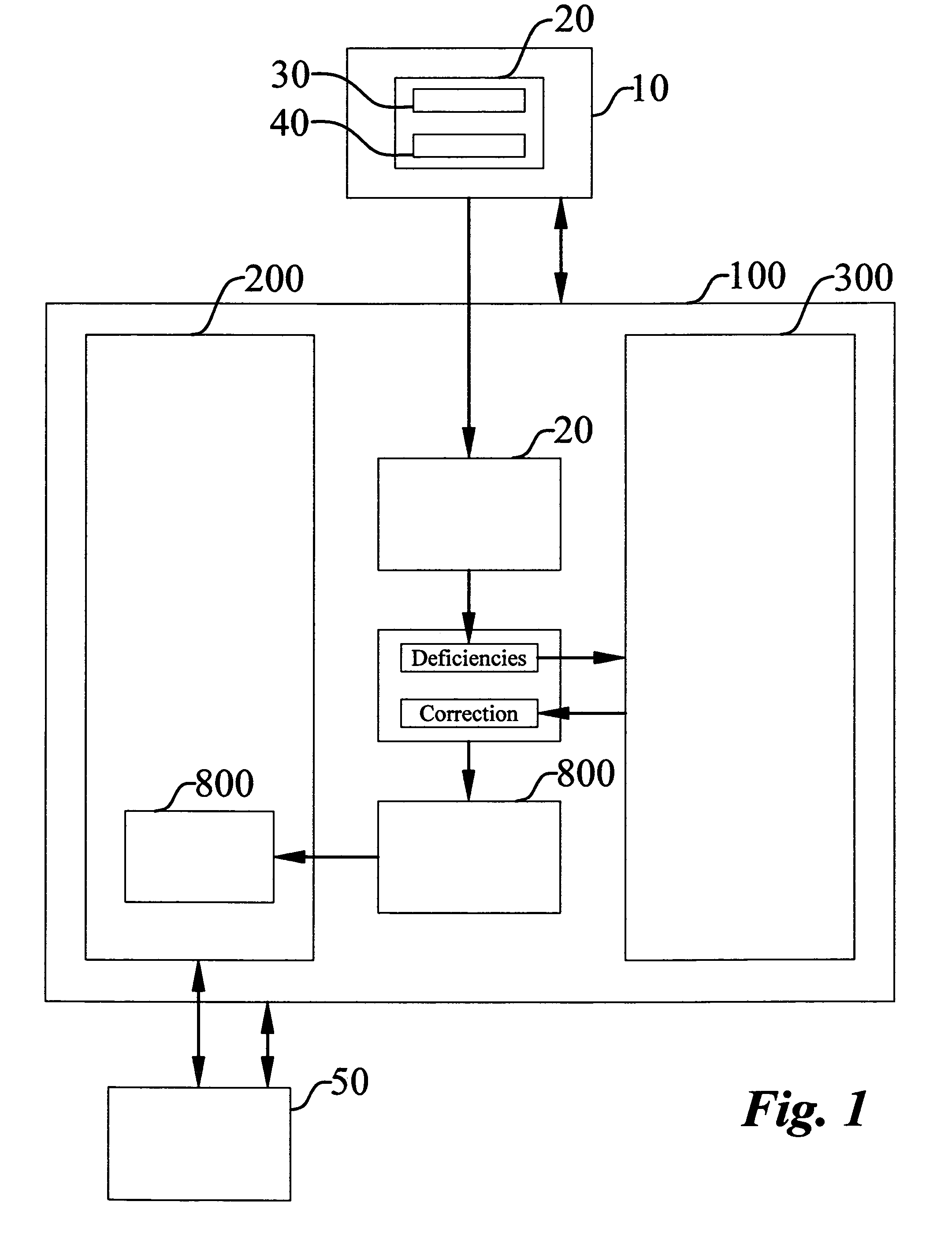
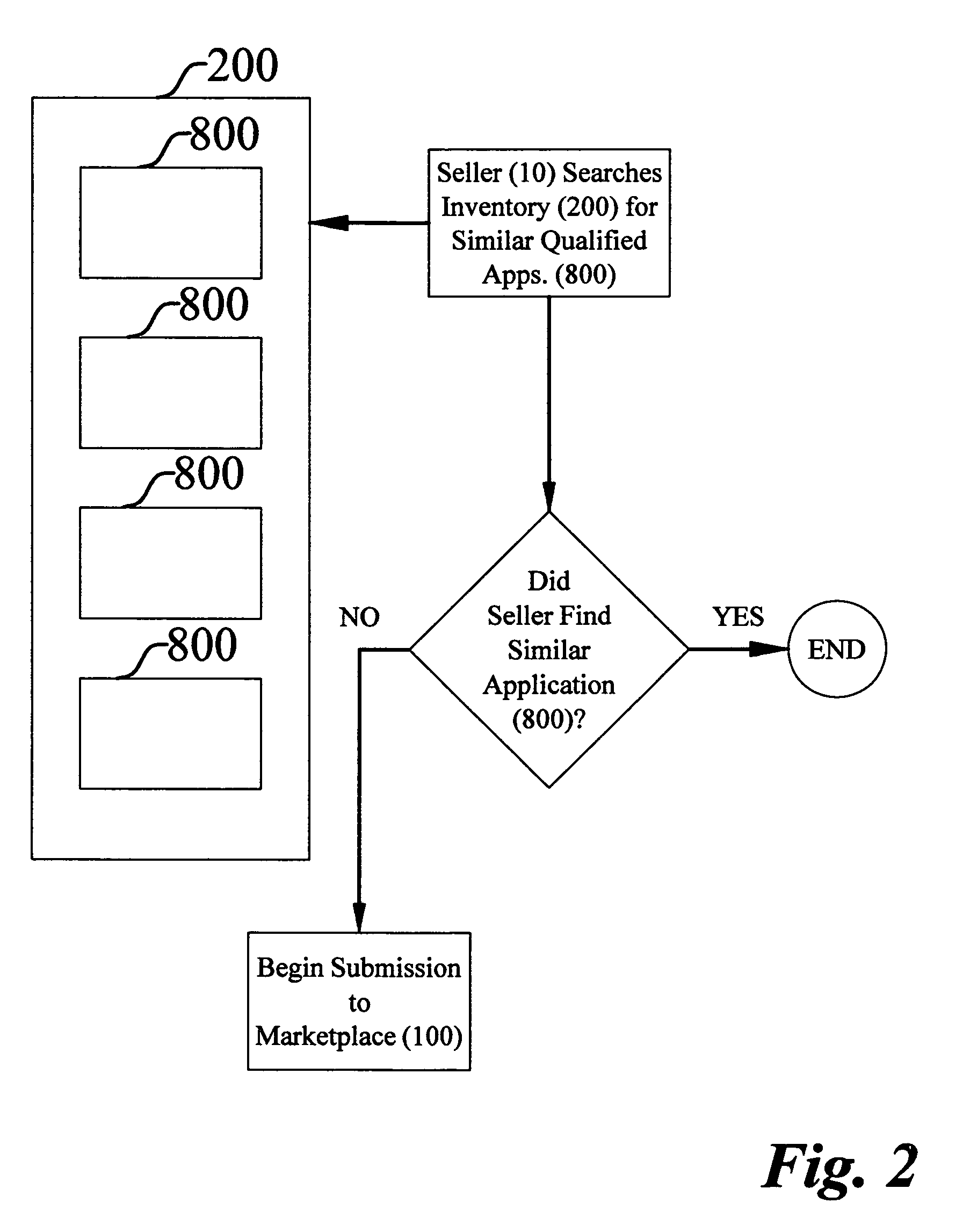
Method for selling custom business software and software exchange marketplace
InactiveUS20080140537A1Overcomes shortcomingDigital data processing detailsBuying/selling/leasing transactionsSoftware engineeringSoftware documentation
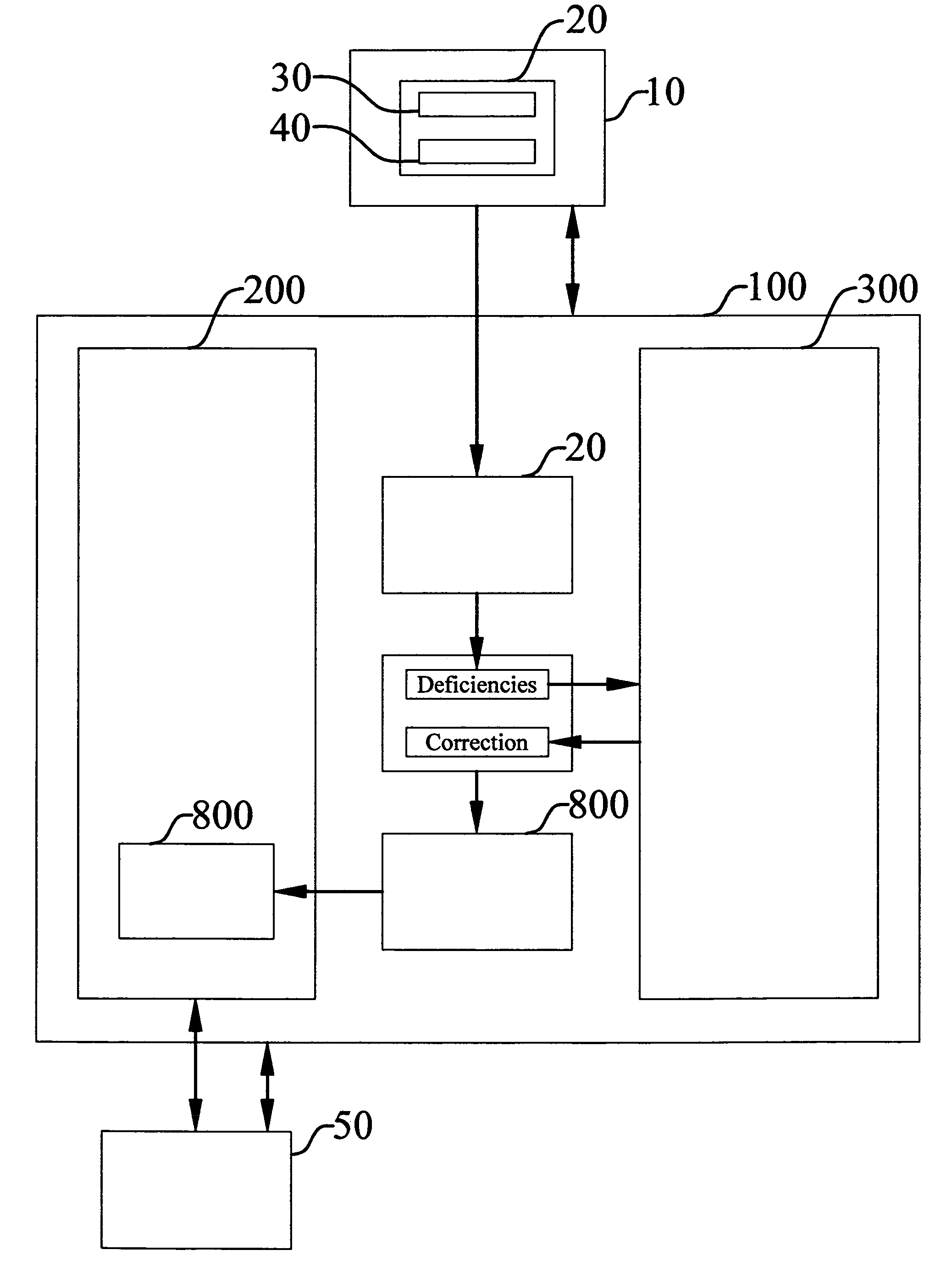
A method of selling custom business software and a software exchange marketplace enables a software seller to offer a custom software application for sale. The method includes receiving the custom software application from the software seller. The marketplace includes a qualified application inventory and a custom software application submission log. A prospective software buyer may search the qualified software application inventory. The method includes associating the custom application with the custom software application submission log. The method identifies deficiencies with a software source code by comparing the software source code to a source code qualification standard. The method identifies deficiencies with a plurality of software documents by comparing them to a document qualification standard. The method compares the submission log with a final review standard. The method qualifies the software source code and software documents before listing them in the qualified software application inventory.
Owner:POWELL NORMAN
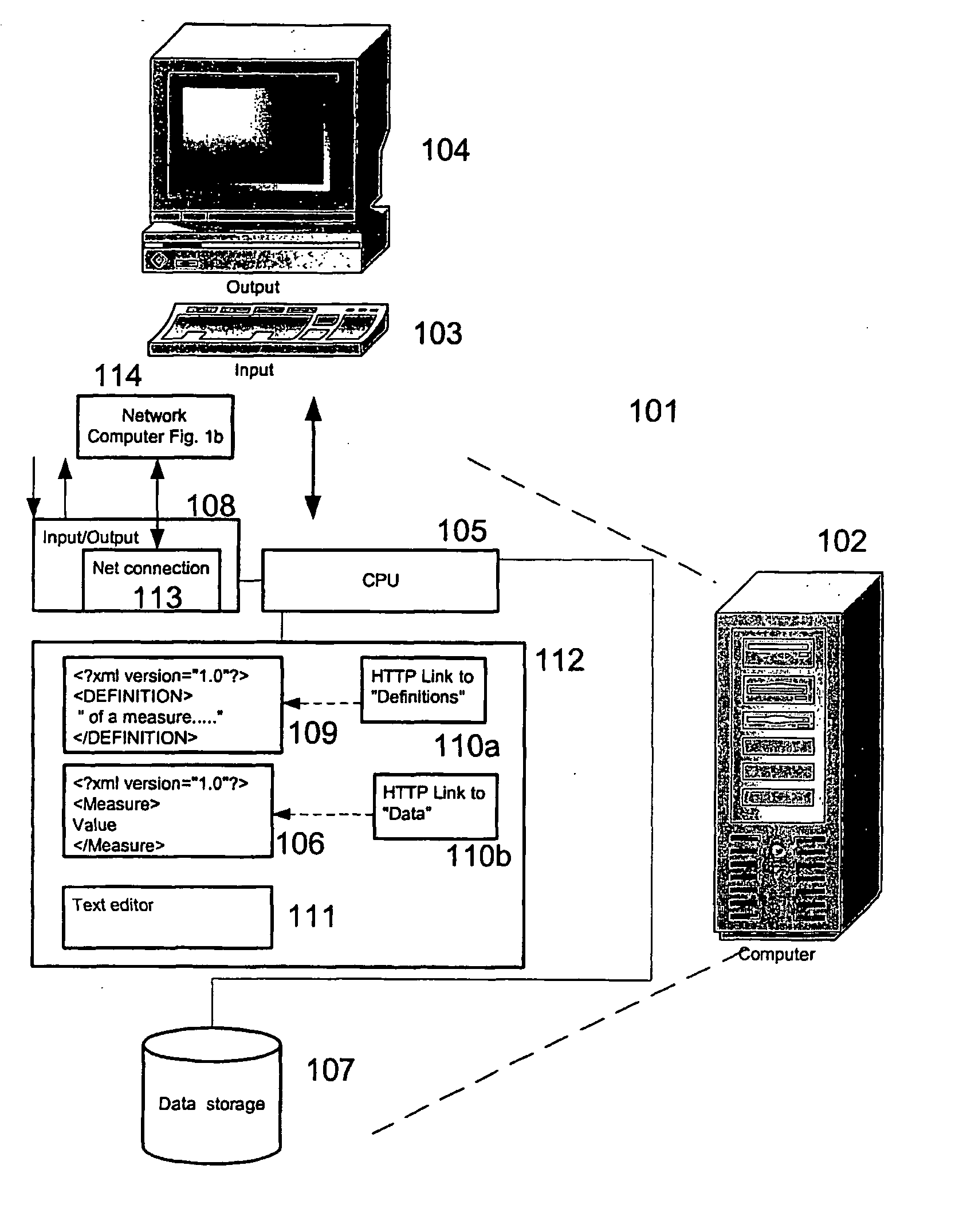
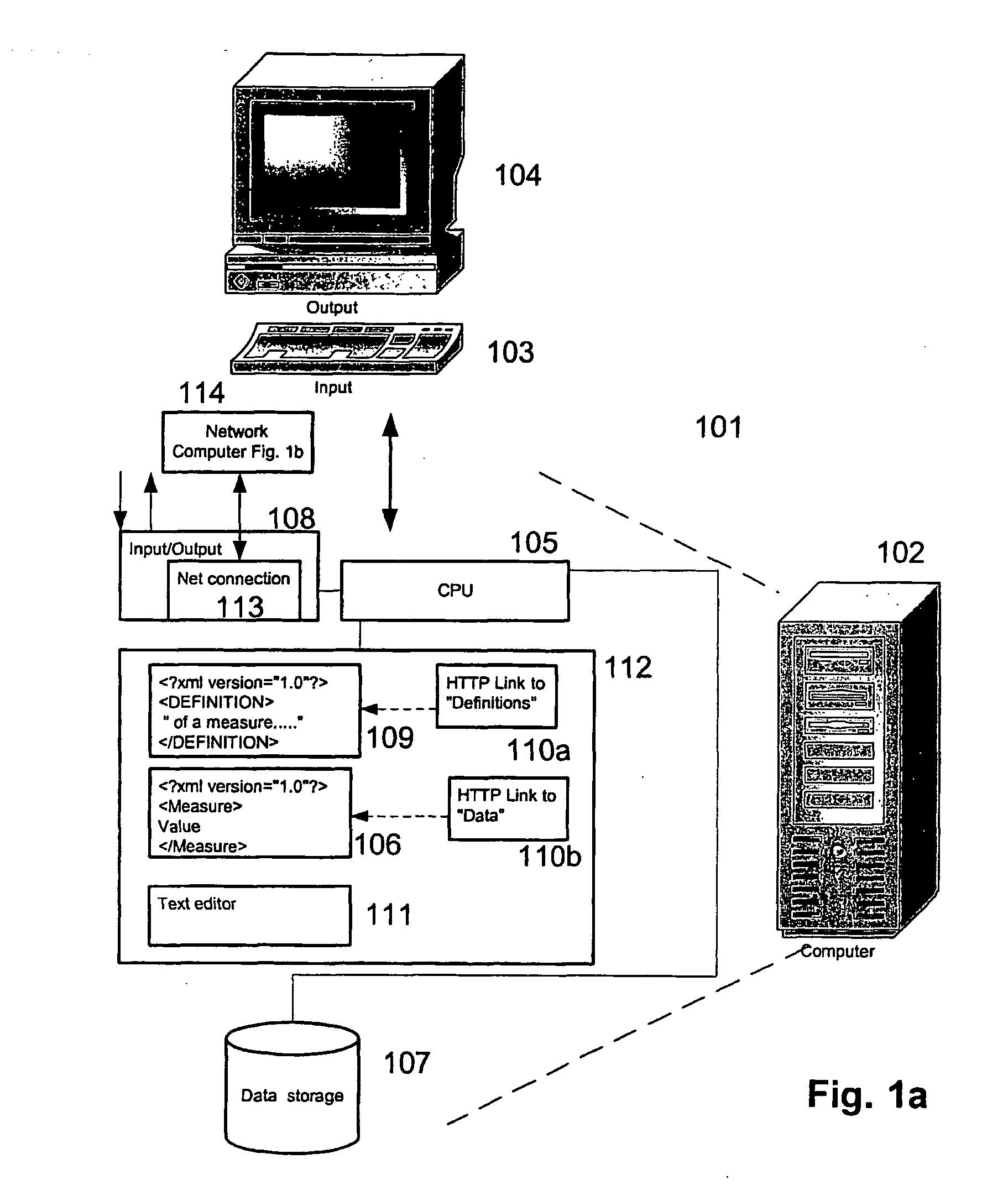
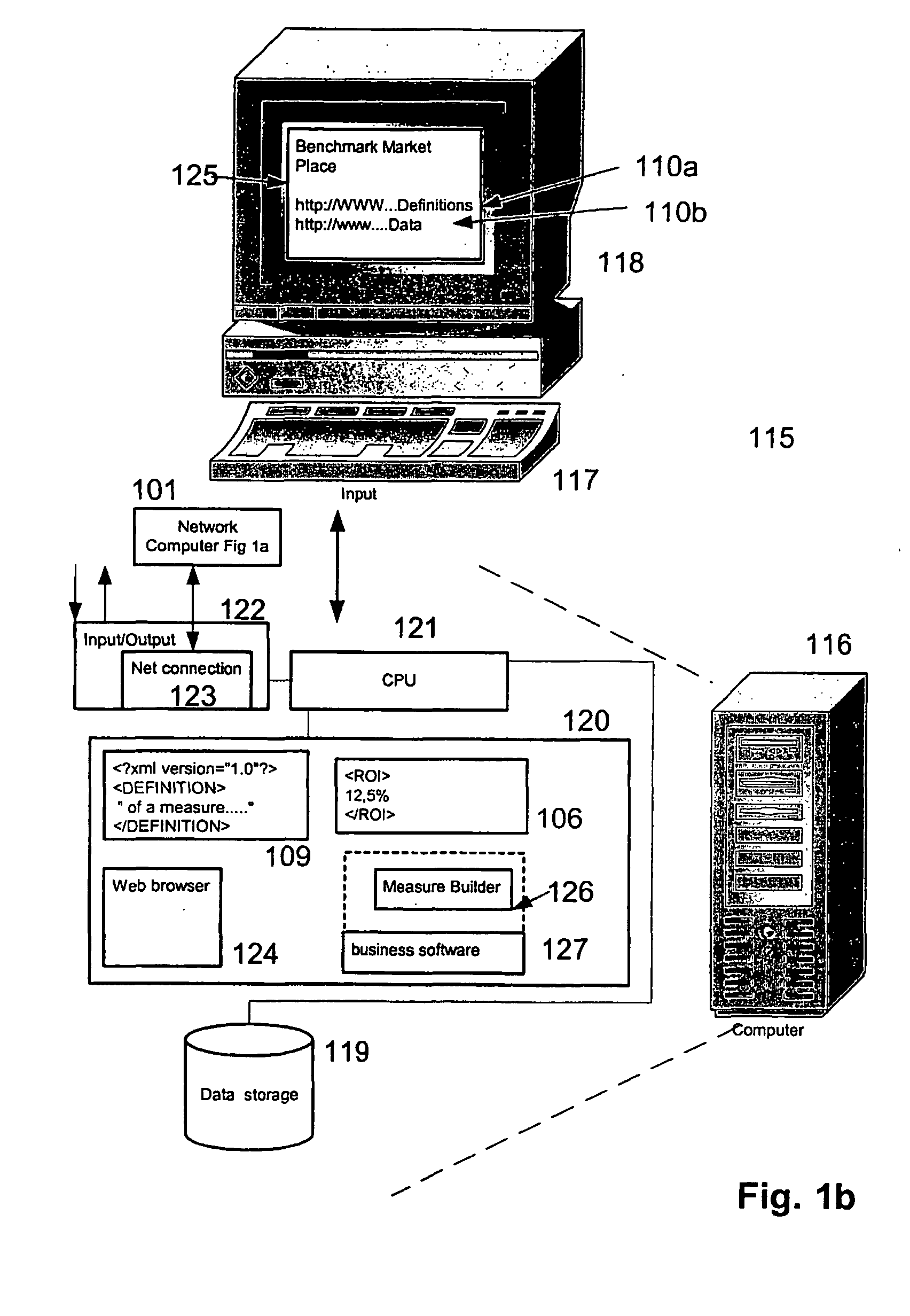
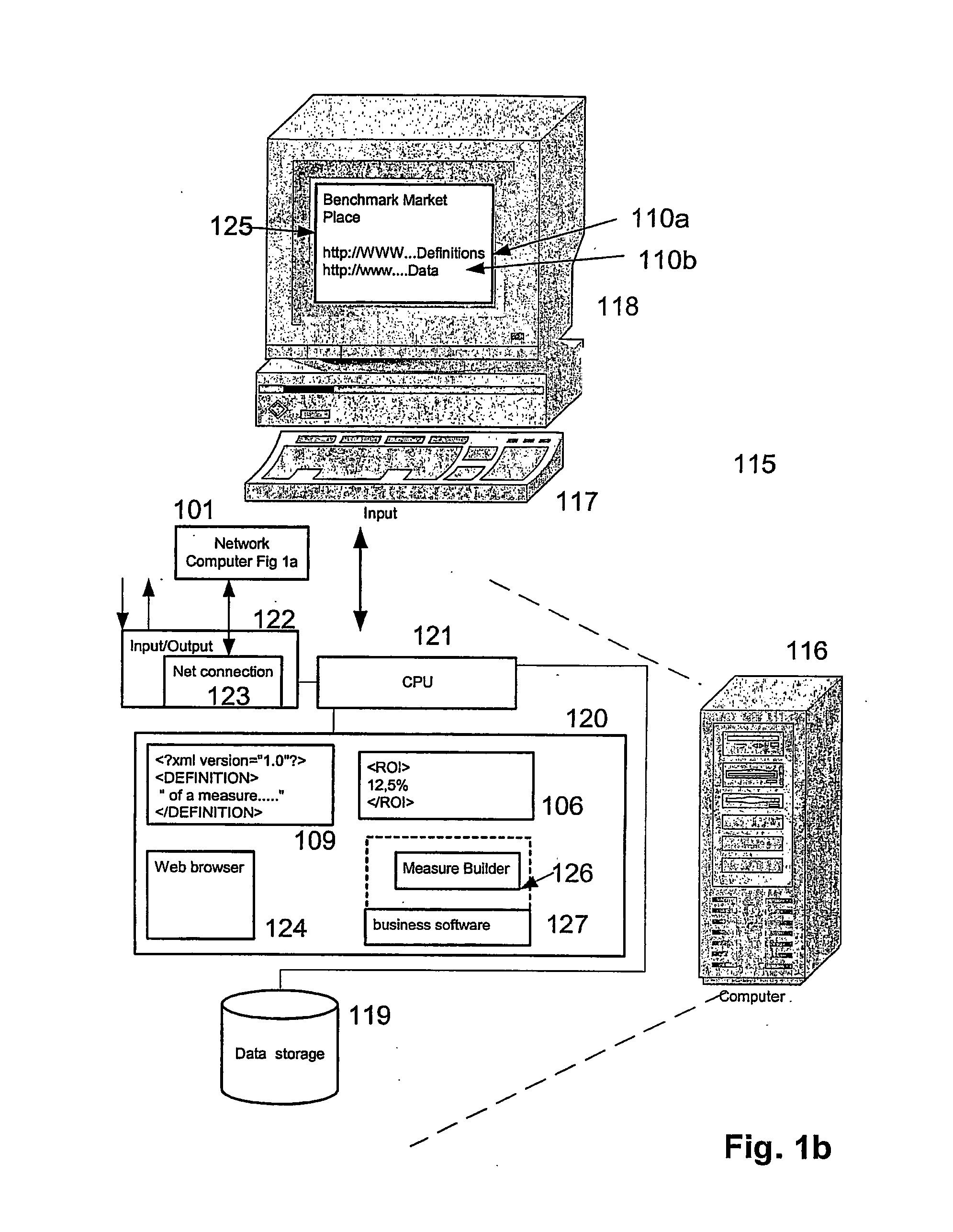
Method software application and system for incorporating benchmarks into a business software application
InactiveUS20050160057A1Promote exchangeDigital data processing detailsDigital computer detailsElectronic dataDatabase
Methods and systems are provided for processing and storing data objects by means of one or more processes running in a computer system having one or more electronic data structures. The electronic data structures may include benchmark definitions and may be in a format readable by a SGML-based language. In one exemplary implementation, the methods and systems present one or more of the electronic data structures to second parties by electronic means.
Owner:SAP AG
Deep code obfuscation method for Android system applications
ActiveCN103544414AImprove securityGuaranteed confidentialityProgram/content distribution protectionBase codeObfuscation
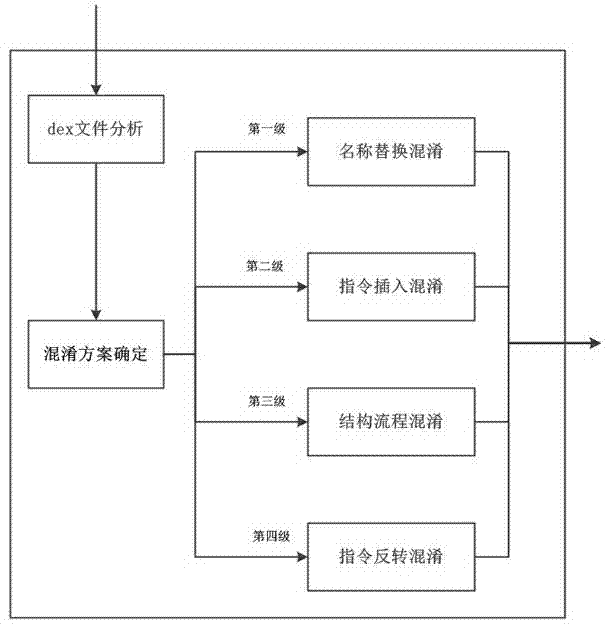
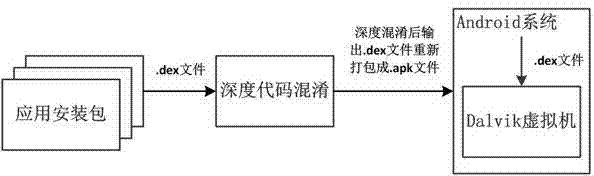
The invention discloses a deep code obfuscation method for Android system applications. The method uses graded code obfuscation. The graded code obfuscation includes first-grade name replacement obfuscation, second-grade command insertion obfuscation, third-grade structure process obfuscation, and fourth-grade command inversion obfuscation. For an application installation package developed and to be released, the method includes: extracting a DEX file, analyzing the file structure, a Dalvik instruction set and a program running process, determining an obfuscation scheme of corresponding grade or multiple combined grades to perform deep code obfuscation on the DEX file, generating a new DEX file, and re-packaging the file. The deep code obfuscation method according to the technical scheme has the advantages that the limitations of the traditional source-code-based code obfuscation scheme can be broken through, the DEX executable files are directly obfuscated in terms of element name, instruction and process structure, applications can be effectively protected from illegal cracking or inversion, safety of applications in the Android system is improved, and confidentiality of business software is guaranteed.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
Method, software application and system for incorporating benchmark data into a business software application
InactiveUS20050216479A1Promote exchangeDigital data processing detailsResourcesComputerized systemApplication software
The Invention relates to an electronic data structure comprising benchmark data, said electronic data structure being a file having a format readable by a SGML-based language. The invention further relates to a method for processing and storing data objects by means of one or more processes running in a computer system having one or more of the electronic data structures comprising a step of incorporating one or more of the benchmark data or benchmark definition contained in said one or more electronic data structures into data structure or into a software for support of business processes.
Owner:SAP AG
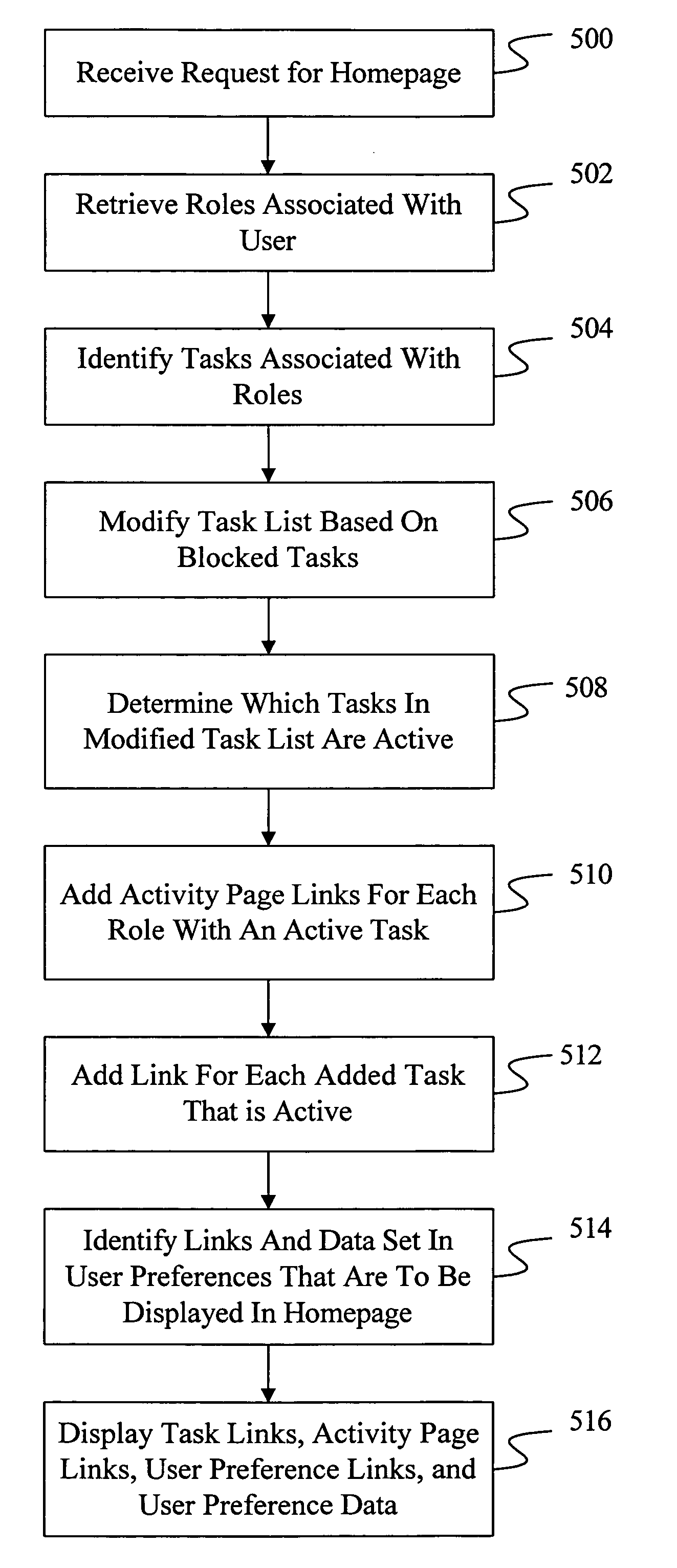
Adaptable user interface for business software
InactiveUS20060200771A1Well formedOffice automationProgram controlHuman–computer interactionUser interface
An adaptable user interface is formed based on a role assumed by a user and the identification of tasks in a process that need to be performed. For each role assumed by the user, a set of tasks assigned to the role is identified. Each task is evaluated to determine if it is an active task that needs to be performed in one or more processes. For each active task, an element is added to the user interface.
Owner:MICROSOFT TECH LICENSING LLC
Method of evaluating business components in an enterprise
A method of evaluating architectural fit of business software applications employed in an enterprise. The method comprises providing a computer tool with a defined rating system for each one of a set of business technology factors and with a set of defined keys having respective key values, inputting into the computer tool data for a plurality of business components using the respective key values, ranking one or more of the set of business technology factors according to the defined rating system, and conducting an analysis to evaluate architectural fit of the business software applications based on the data inputted using the respective key values and the ranked set of business technology factors. The conducting step further comprises providing at least one business or technology objective and executing an algorithm corresponding to the one business or technology objective provided to conduct the analysis.
Owner:KYNDRYL INC
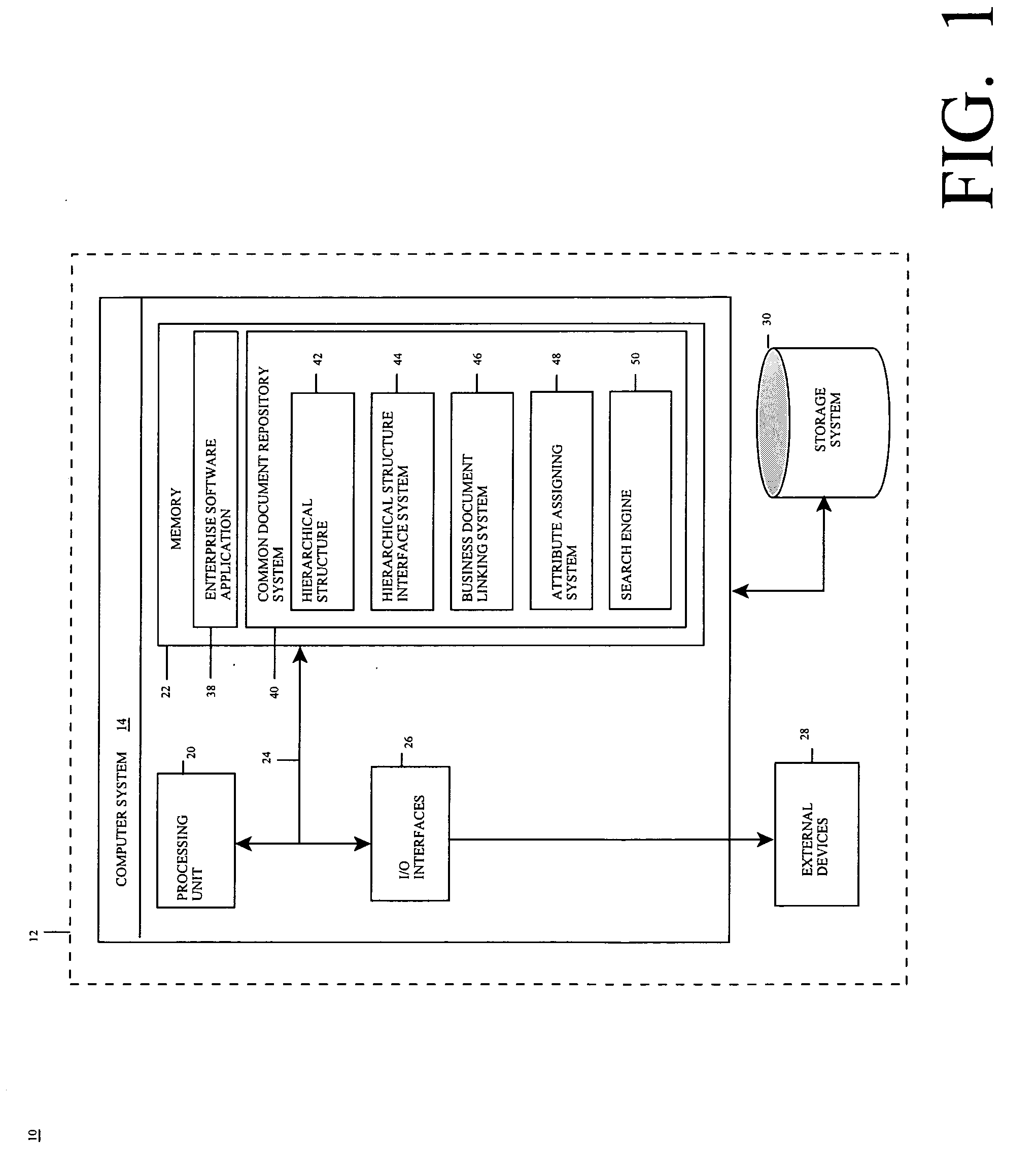
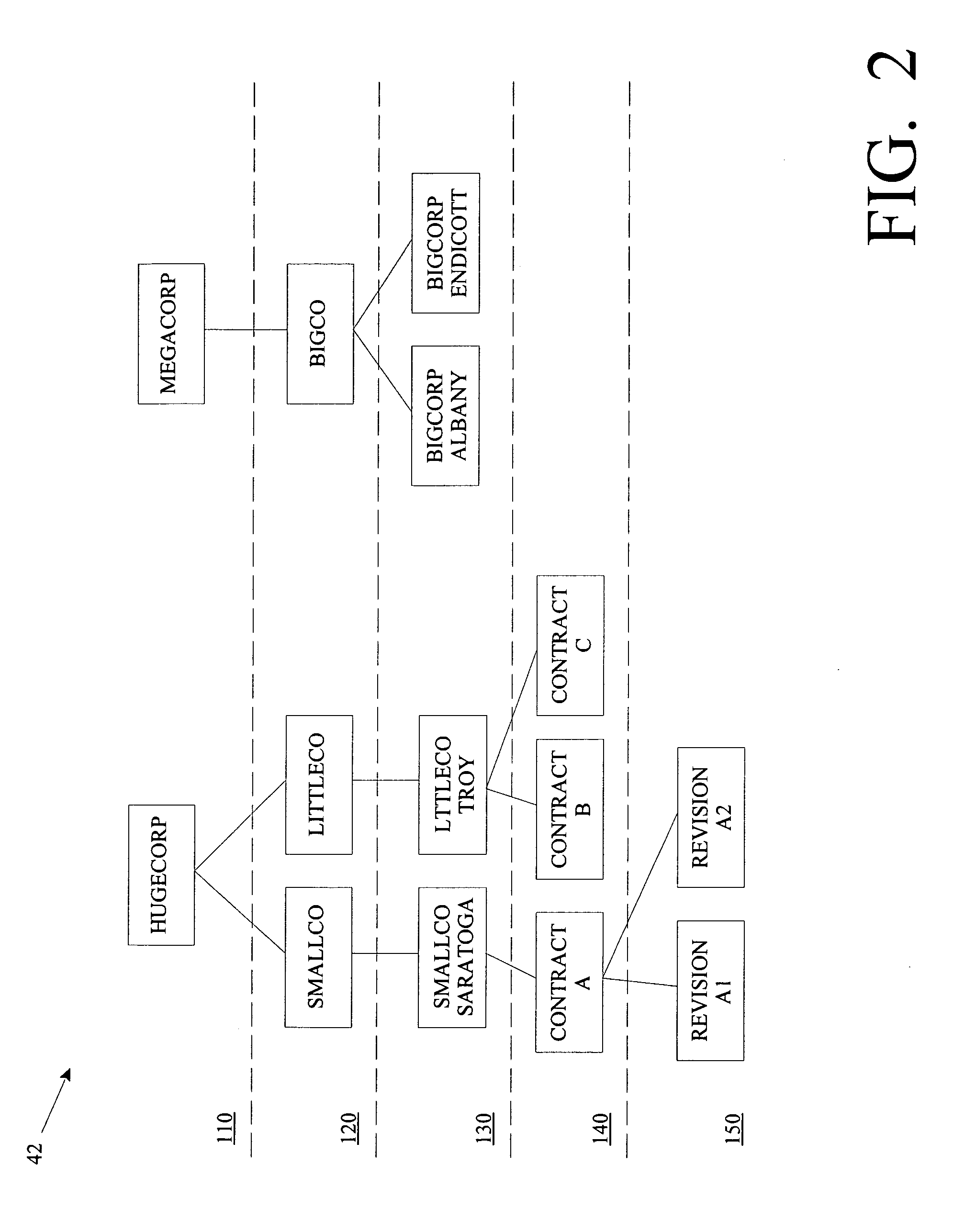
Computer-implemented method, tool, and program product for storing a business document in an enterprise software application environment
InactiveUS20070100857A1Digital data processing detailsOffice automationSelection criterionPaper document
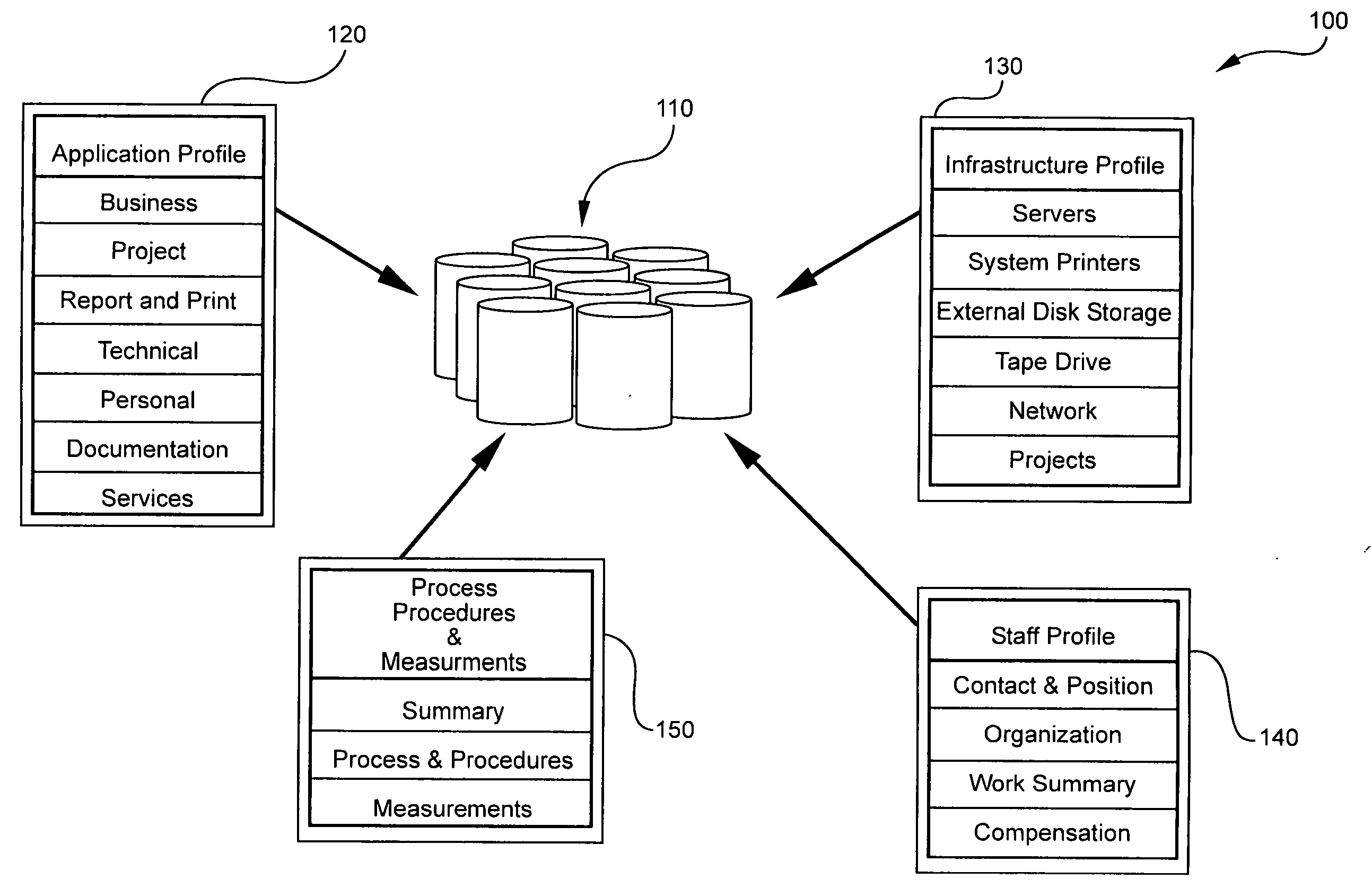
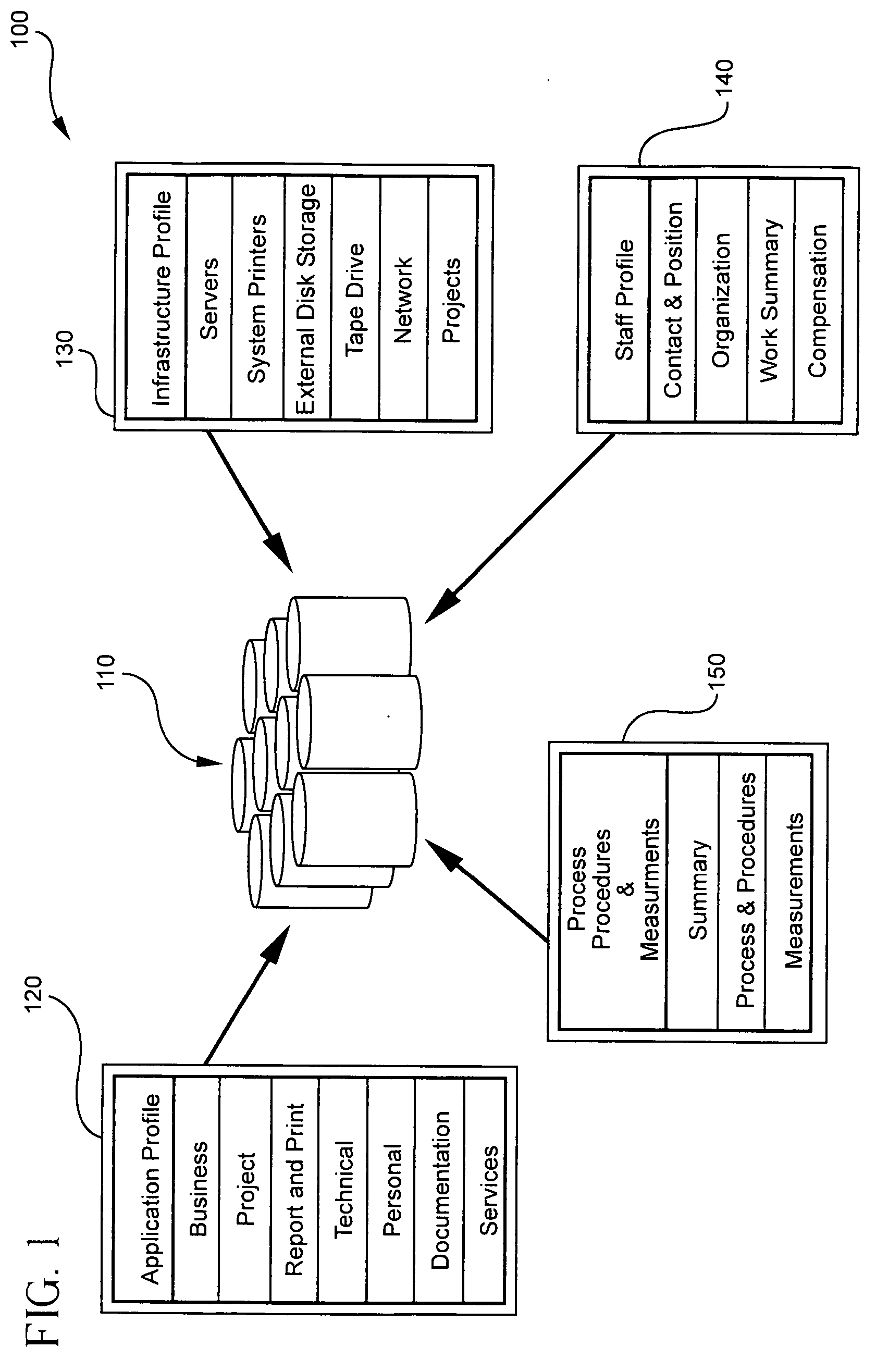
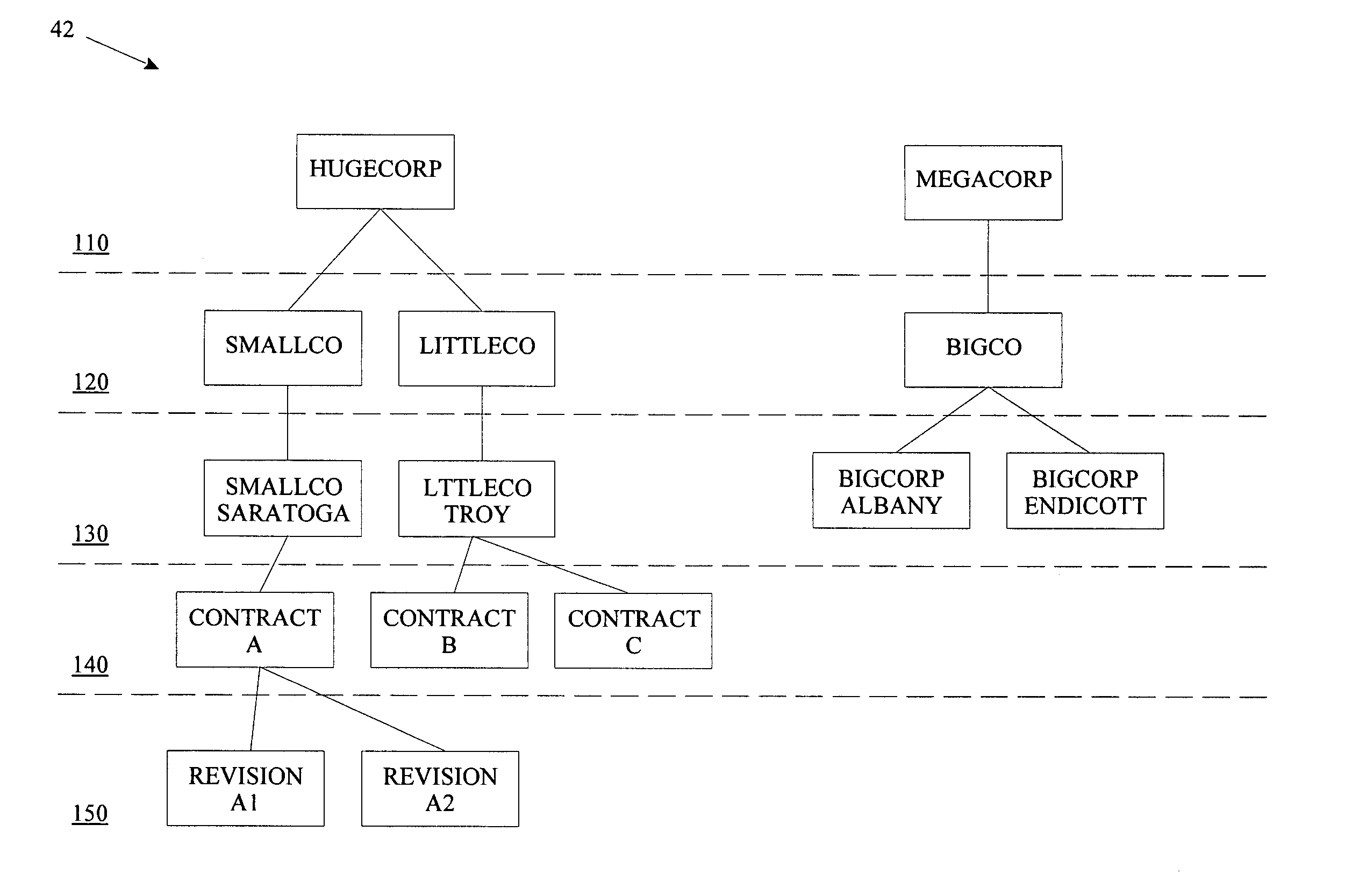
In general, the present invention provides a computer-implemented method, system, tool, and program product for storing a document in an enterprise software environment, such as SAP. Specifically, under the present invention, a hierarchical structure is provided for linking a business document. The hierarchical structure includes a plurality of levels that each represent a business entity level such as enterprise, company, customer, contract and revision. Additionally, standardized attributes may be chosen for association with the business document. The invention also provides a search engine for searching for a document that has previously been linked to the hierarchical structure. These searches may be performed using such factors as the level in the hierarchy and / or the specified attributes.
Owner:IBM CORP
Automated business software application integration
InactiveUS7395540B2Easy to useEasy to operateComplete banking machinesFinanceSoftware systemTechnical standard
Automatic business software application is provided. Aspects of business, including objects and activities are classified and described in a comprehensive, standard manner. When a business software component is installed, a discovery manager identifies capabilities and requirements of the software based upon information describing the software in accordance with the standardized classification. The software component is selectively bound to one or more roles of a model-driven bus. In some aspects, a standardized software adapter is able to facilitate use of embodiments of the present invention with prior art software systems. Additional software layers and overhead facilitate the management and operation of multiple software components.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for an information systems improvement planning and management process
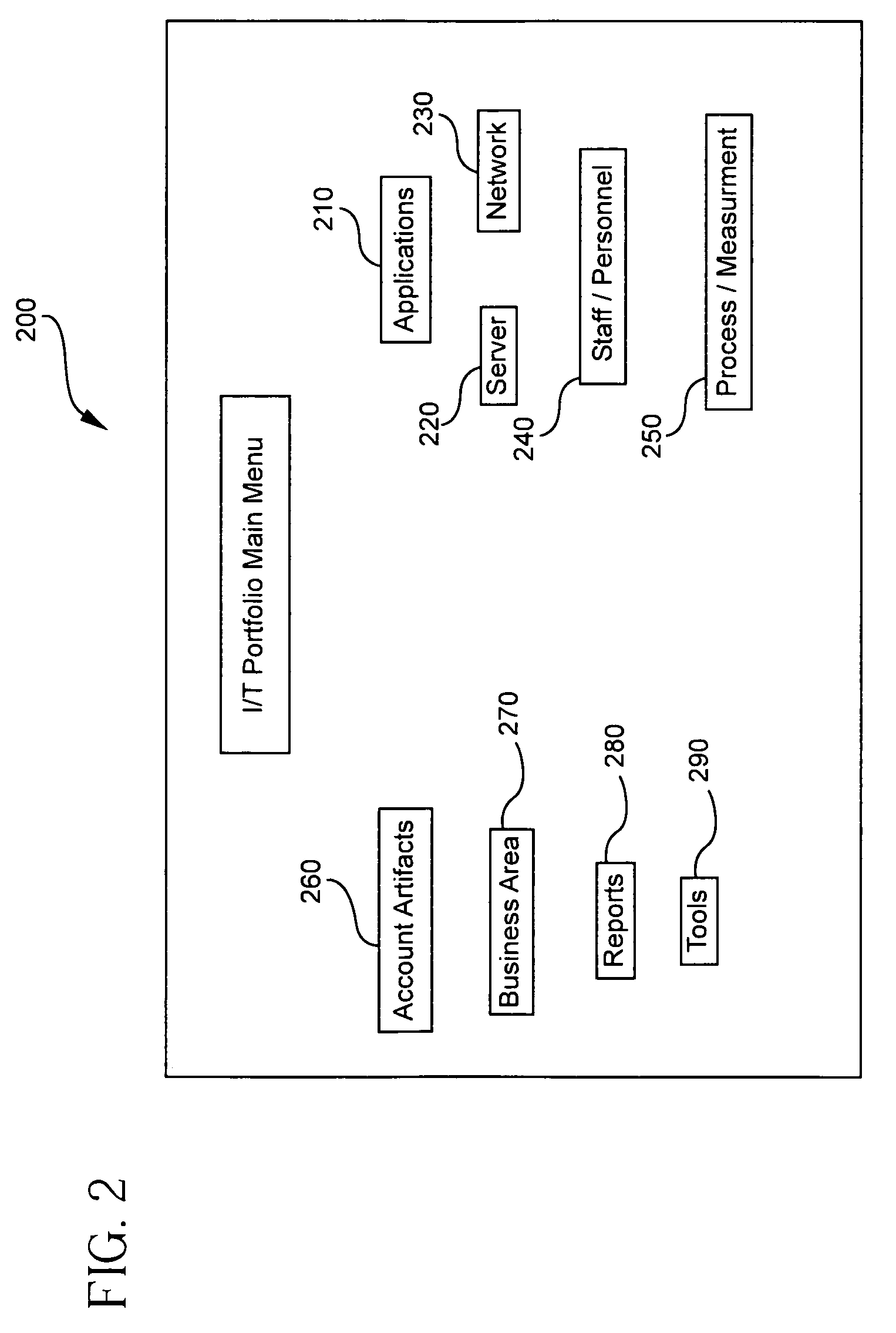
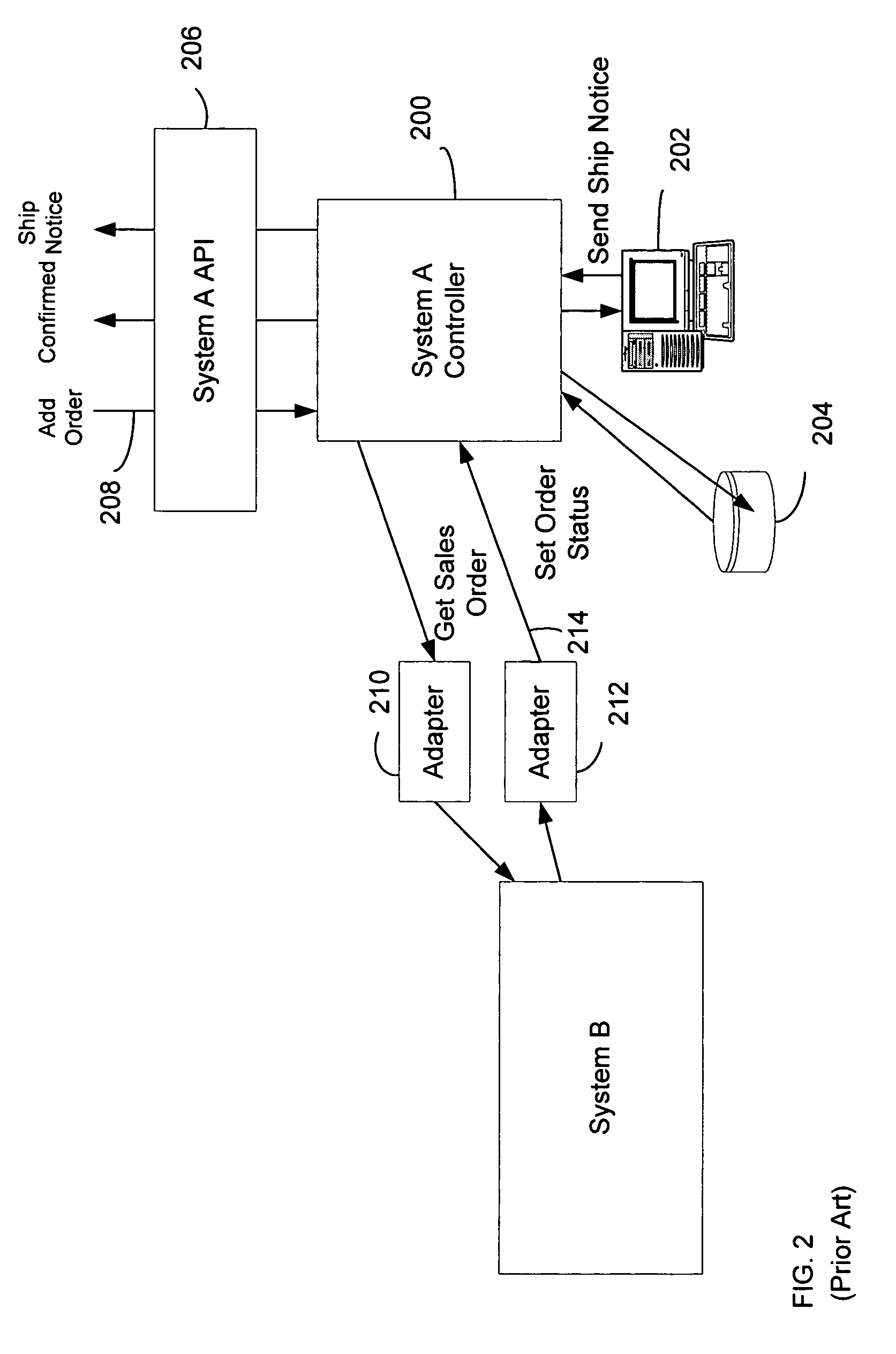
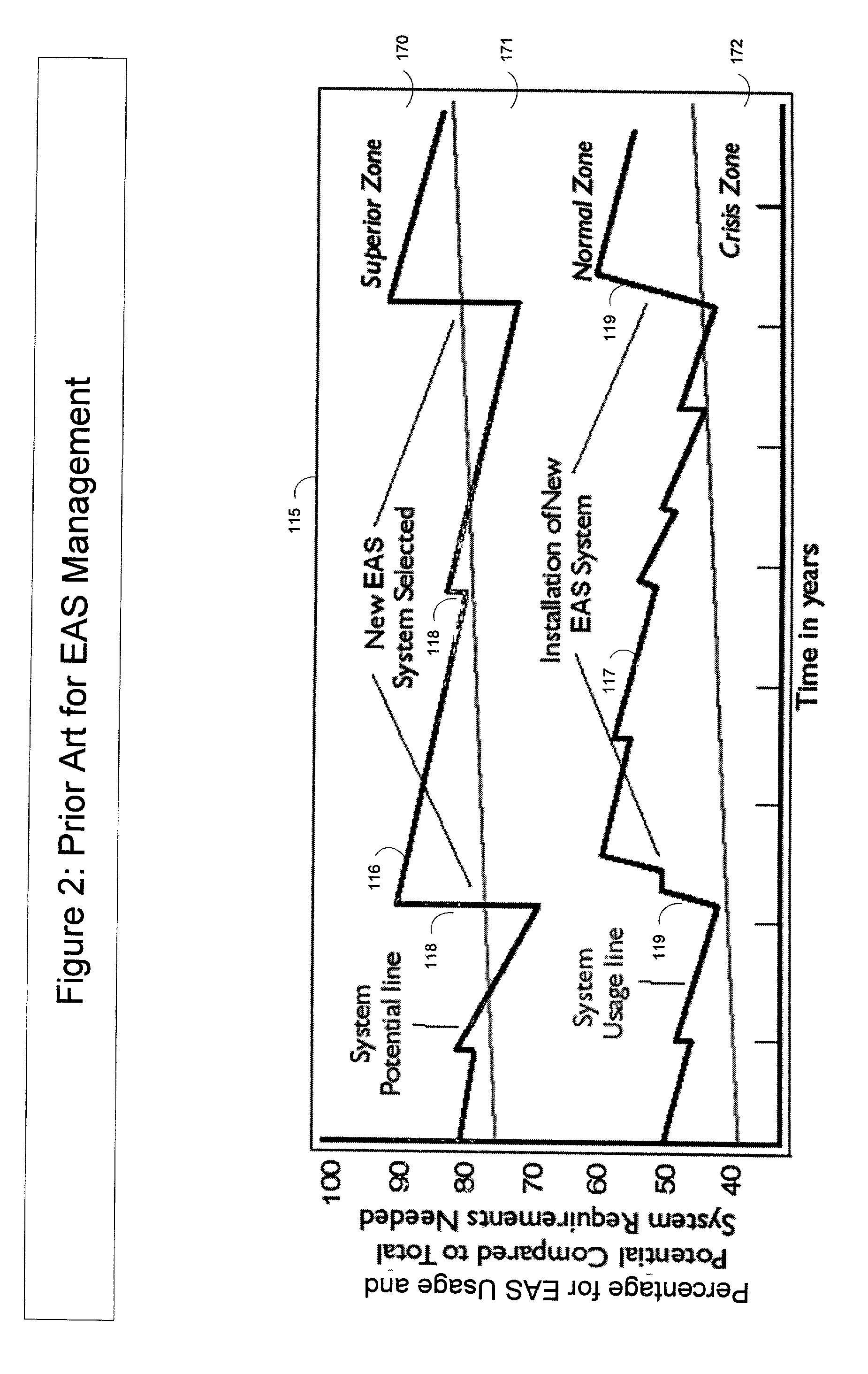
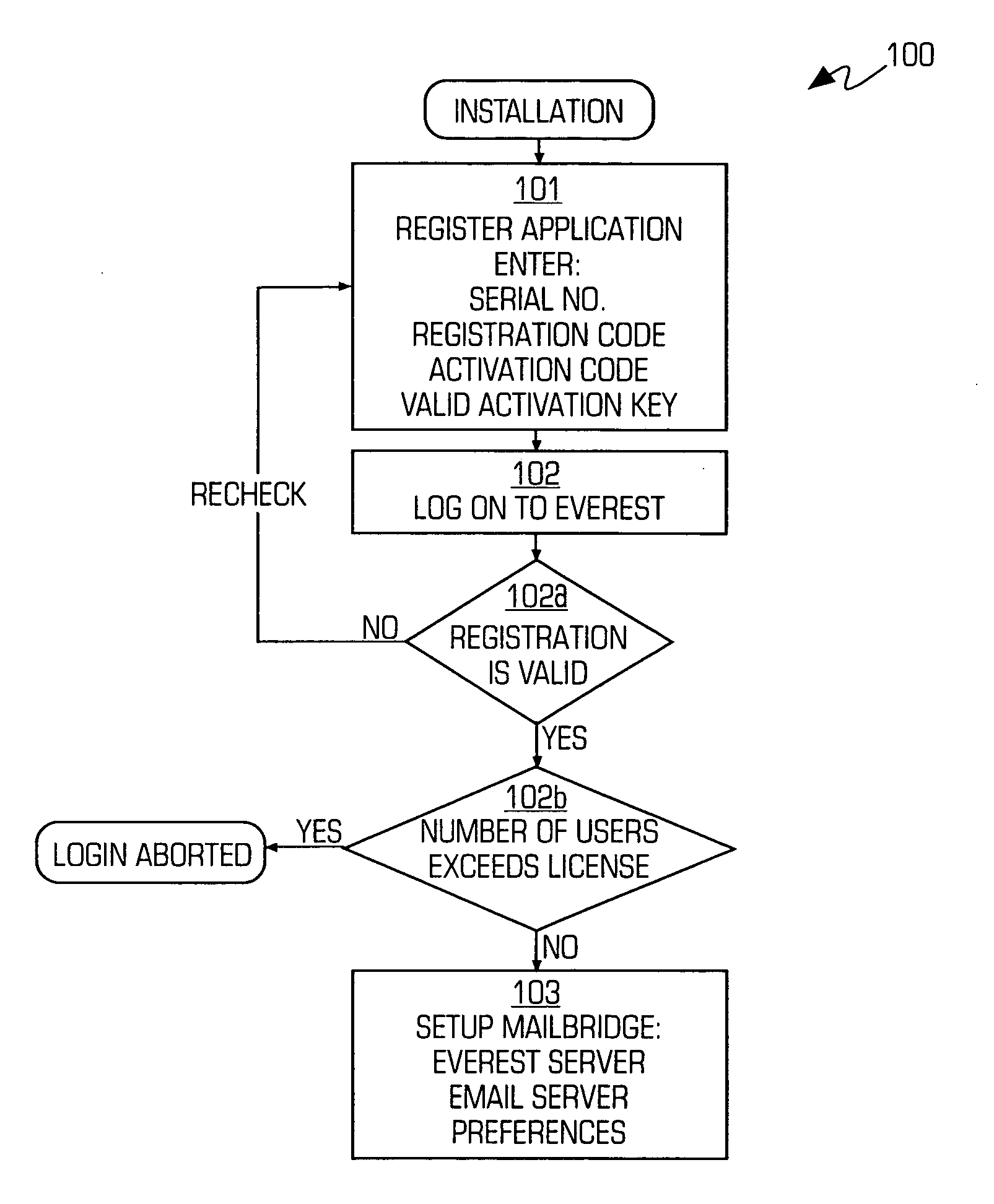
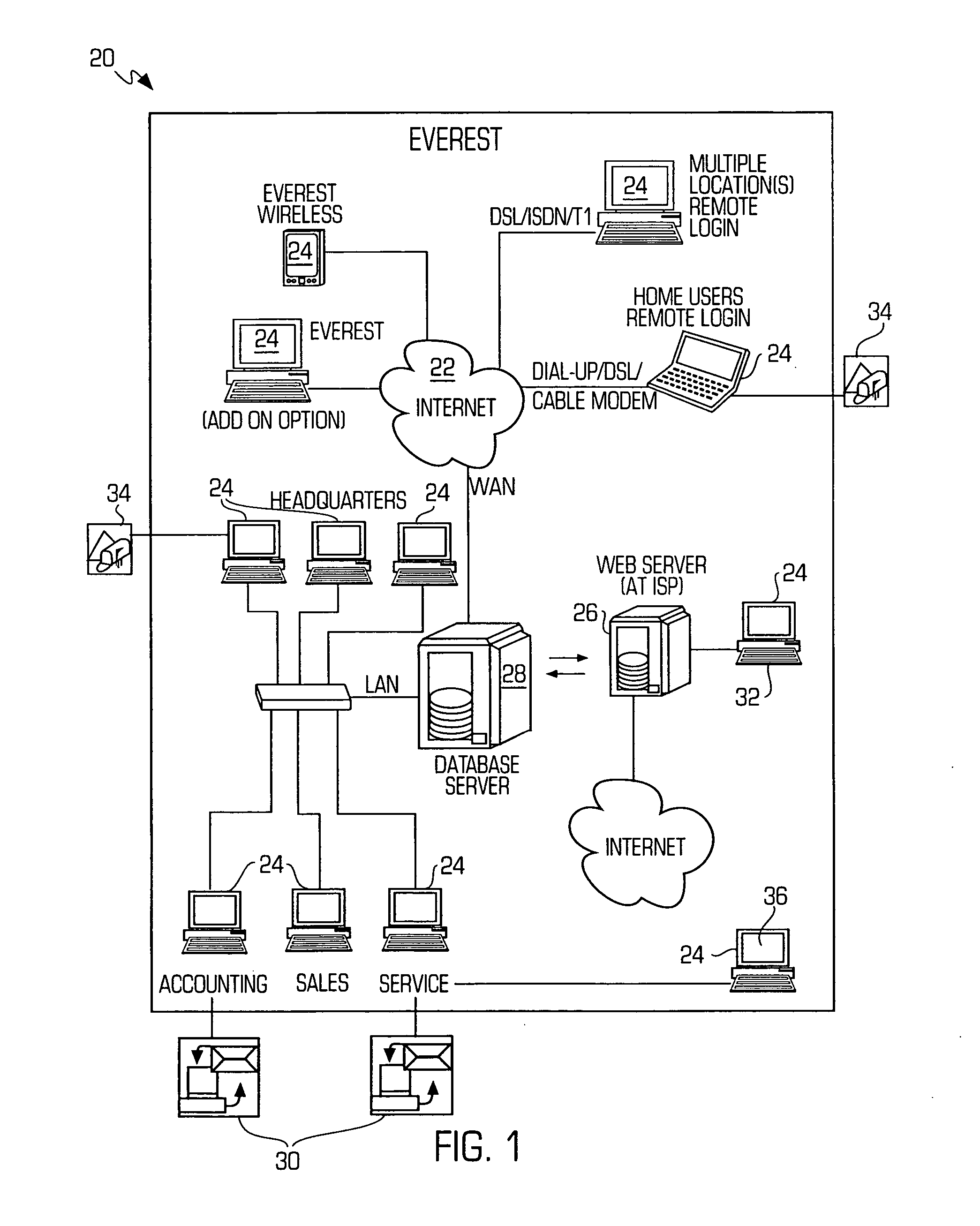
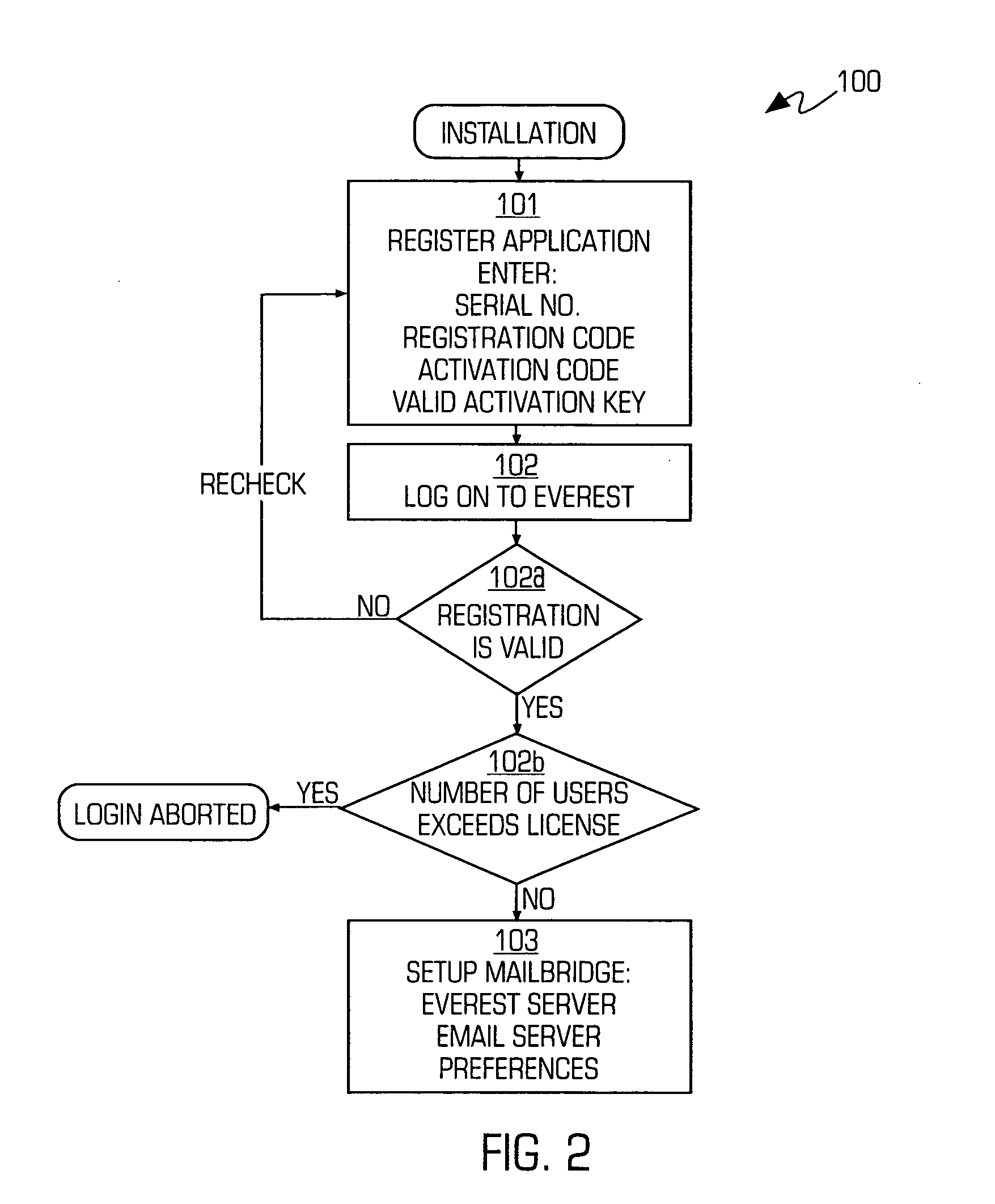
A system for comprehensively managing business software (referred to as: enterprise application software-EAS) that runs companies and organizations. Includes methods (100), software application (108), trained personnel (110 and 112) and team collaboration structure (FIG. 7) for developing an EAS plan, improving existing EAS systems and selecting and implementing new EAS systems. The system includes an EAS research component that provides businesses EAS software research, industry and peer group comparisons, and best practices. The EAS research function is comprised of trained personnel, methodology and software applications (291 and 293).
Owner:SOFTSELECT SYST
System and method for data storage and retrieval
InactiveUS20120179779A1Avoid the needMultiple digital computer combinationsTransmissionRepresentational state transferApplication server
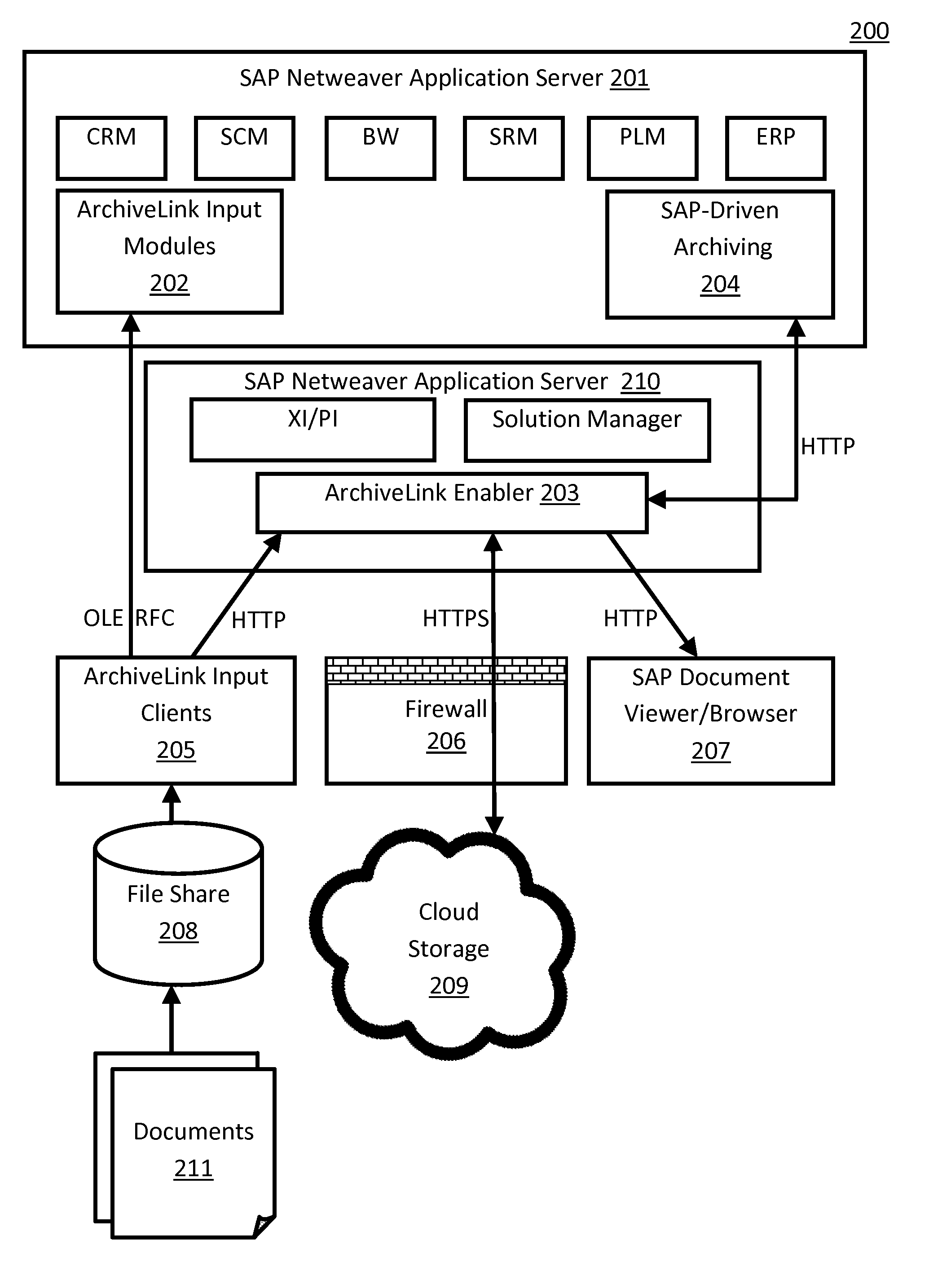
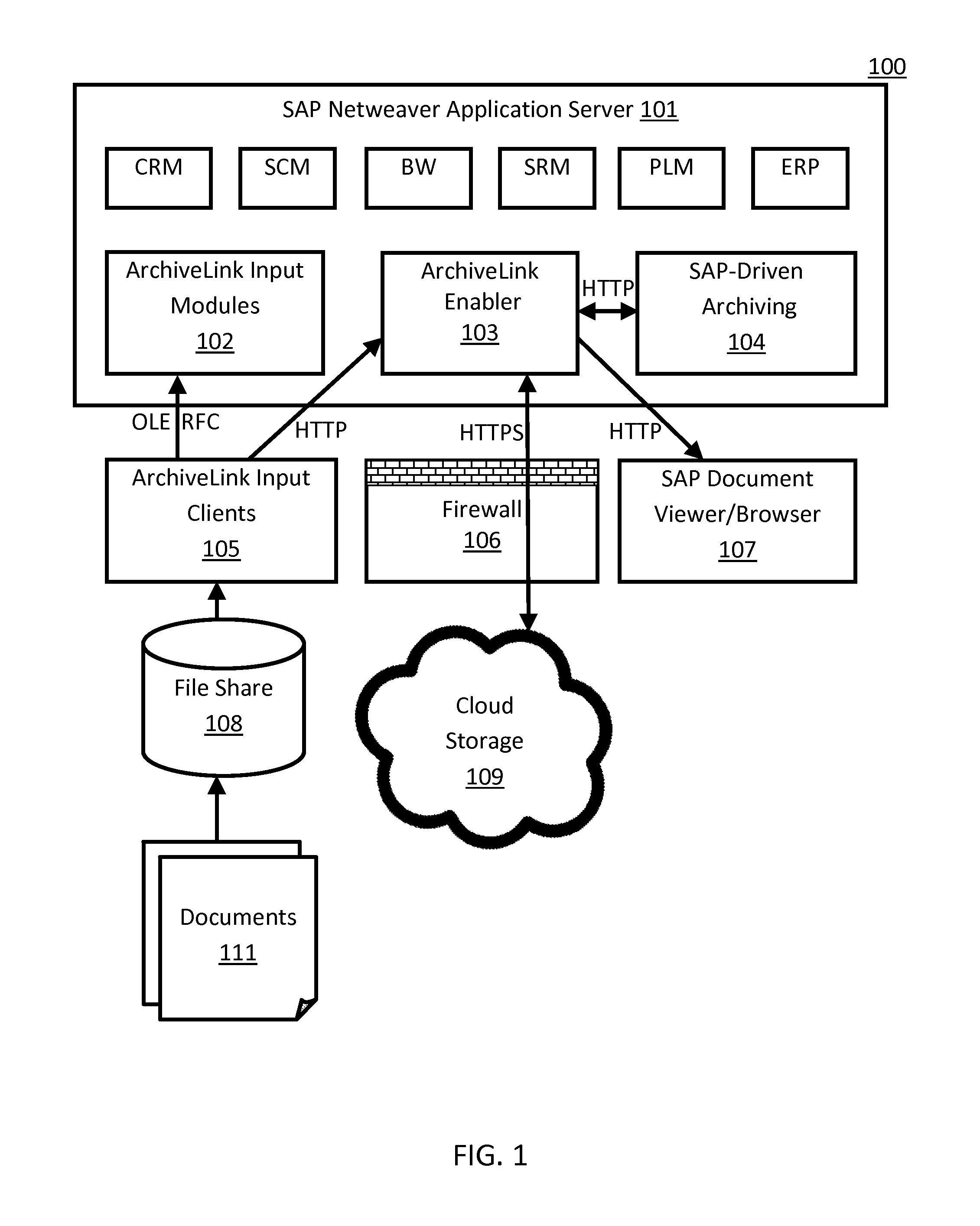
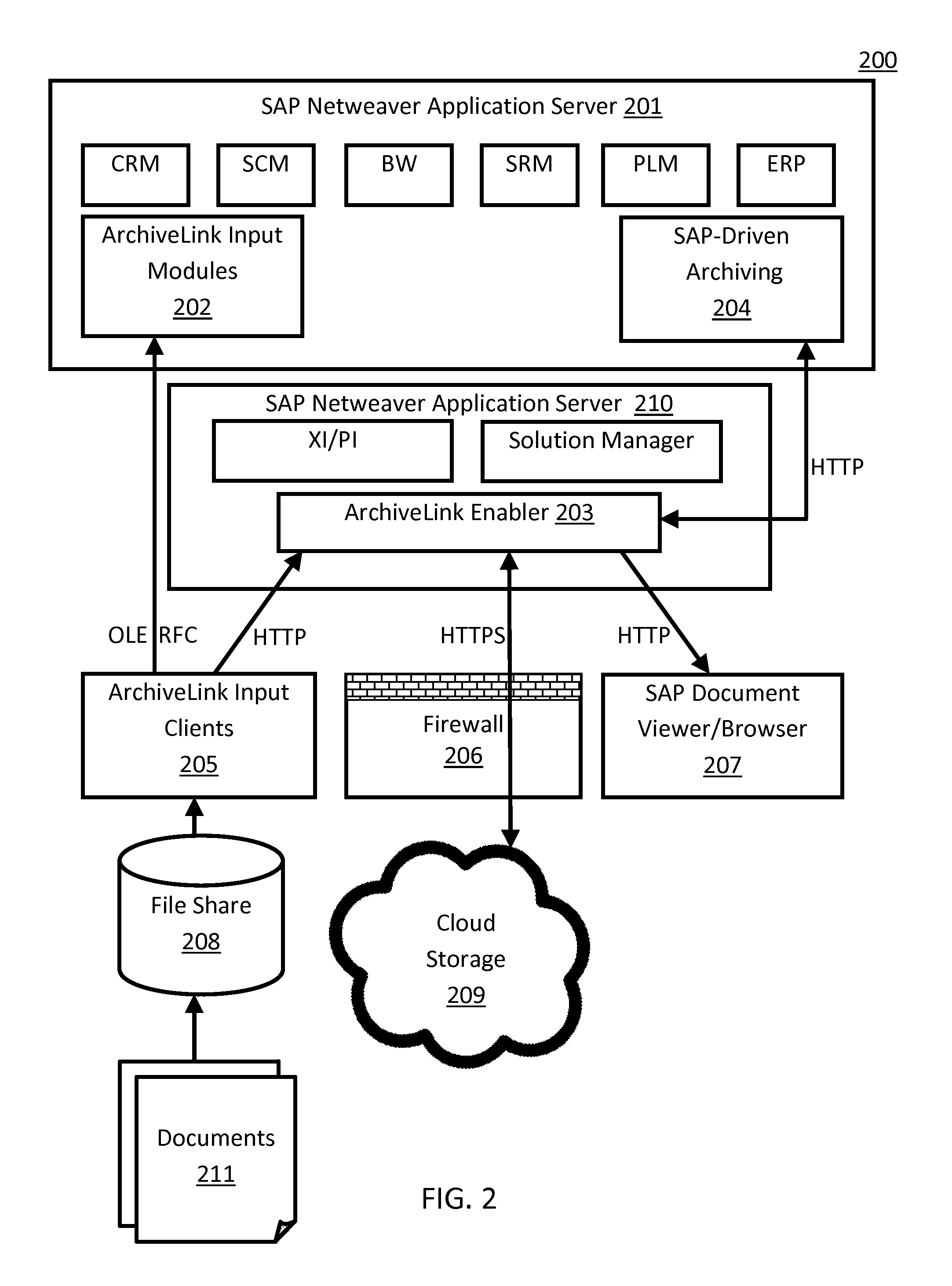
A scheme for a business-software application system (e.g., SAP) to access cloud storage (e.g., AT&T Synaptic Storage-as-a-Service) by means of an add-on enabler software module, where applications can use cloud storage as an archive (e.g., ArchiveLink) repository. In one embodiment, a business-software application system includes an application server and an enabler. The application server is configured to execute a plurality of applications and includes an archiving module. The enabler is adapted to exchange application data with (i) the archiving module, and, (ii) via a secure connection, a cloud-storage repository. In one embodiment, the enabler employs the SAP ArchiveLink protocol to communicate with the archiving module and is adapted to make signed Representational State Transfer (REST) HTTP calls through the ABAP language.
Owner:DOLPHIN ENTERPRISE SOLUTIONS
Method for selling custom business software and software exchange marketplace
InactiveUS7739256B2Digital data processing detailsBuying/selling/leasing transactionsSoftware engineeringSoftware documentation
A method of selling custom business software and a software exchange marketplace enables a software seller to offer a custom software application for sale. The method includes receiving the custom software application from the software seller. The marketplace includes a qualified application inventory and a custom software application submission log. A prospective software buyer may search the qualified software application inventory. The method includes associating the custom application with the custom software application submission log. The method identifies deficiencies with a software source code by comparing the software source code to a source code qualification standard. The method identifies deficiencies with a plurality of software documents by comparing them to a document qualification standard. The method compares the submission log with a final review standard. The method qualifies the software source code and software documents before listing them in the qualified software application inventory.
Owner:POWELL NORMAN
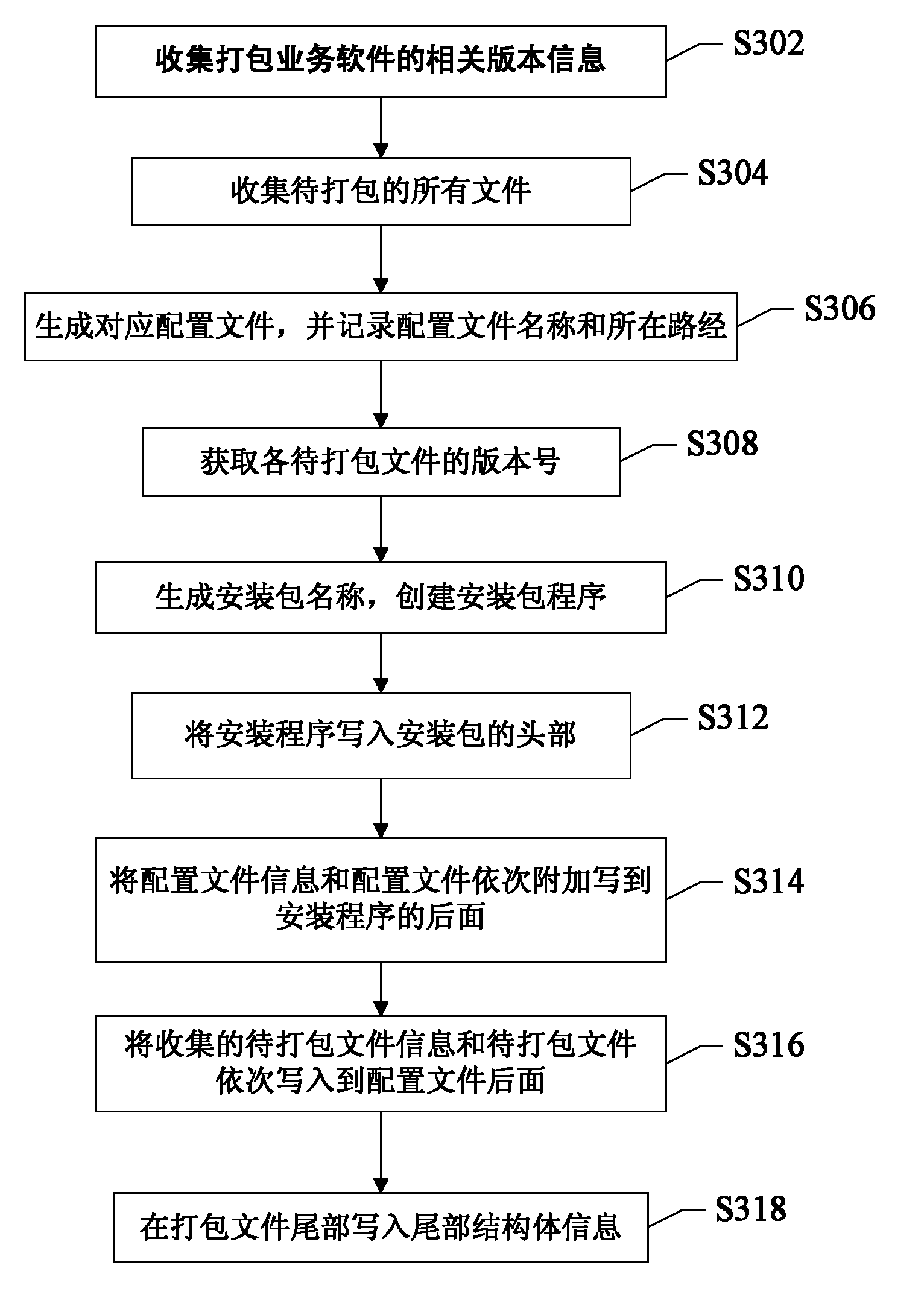
Method and device for generating and unloading software installation package
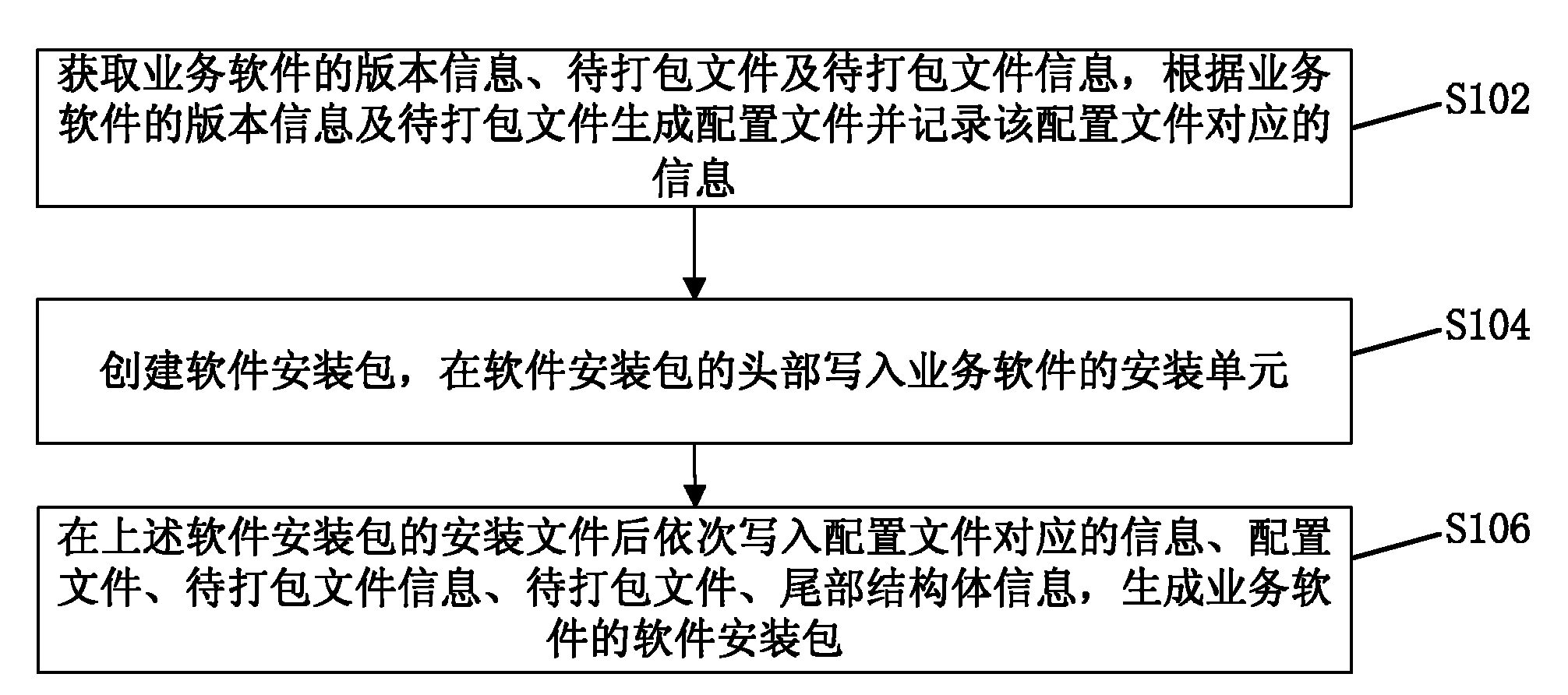
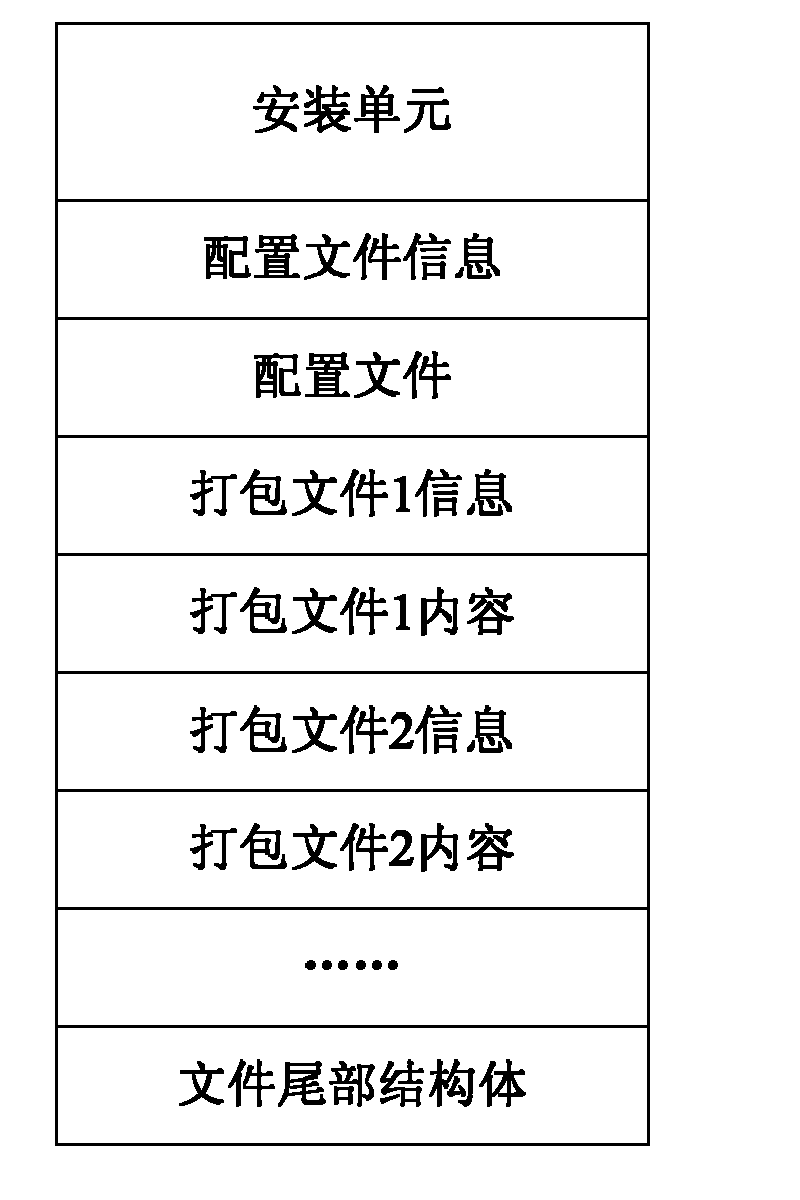
ActiveCN101984410AIncrease flexibilityGuaranteed CompatibilityProgram loading/initiatingSoftware deploymentSoftware engineeringComputer compatibility
The invention discloses a method and device for generating and unloading a software installation package. The method comprises the following steps: acquiring the version information of business software, a file to be packed and information of the file to be packed, generating a configuration file according to the version information of the business software and the file to be packed and recording information corresponding to the configuration file; creating a software installation package and writing a business software installation unit into the header of the software installation package; and writing the information corresponding to the configuration file, the configuration file, the information of the file to be packed, the file to be packed and the tail structure information into the installation file of the software installation package in turn, and generating the software installation package of the business software. Through the technical scheme of the invention, the entire installation process can be automatically processed by the installation unit; therefore, the invention ensures normal use of all installed business software and can realize matching between the platform software and the business software and guarantee the compatibility of all installed business software and the switch flexibility among various versions of the business software.
Owner:南京浦口科创投资集团有限公司
Method of administering software components using asynchronous messaging in a multi-platform, multi-programming language environment
InactiveUS20050177827A1Specific program execution arrangementsMemory systemsBase classSoftware engineering
A method for performing life cycle management of business software applications and their components across a multiple-platform, multiple-language network. The method takes advantage of the inheritance properties of object-oriented programming (OOP) by developing all components of a business application from a set of base classes, thus deploying a common set of methods across all application components. These methods enable monitoring by a Central Administrator element without interdependence between any of the business application components and the Central Administrator. The Central Administrator then determines when a need to reconfigure one or more components of the business application has arisen. The Central Administrator then modifies or replaces existing components of the business application or installs entirely new components over the network without end user interaction. In one embodiment of the present invention, the Central Administrator is aided by a set of Distributed Administrators located on each virtual node server / host computer of a business application operating over a network. The business application can thus reconfigured without terminating the application's business function in a scaleable, extensible manner without regard to platform or language.
Owner:VERIFONE INTERMEDIATE HLDG INC & VERIFONE
Mail management system and method
InactiveUS20050050146A1Efficient and cost-effective and accurateCost-effectiveMultiple digital computer combinationsOffice automationCost effectivenessClient-side
A mail management method and system are described that tracks correspondence exchanged with external entities such as customers and vendors, through e-mail messages, and the internal users of the system. The e-mail messages are then desirably imported into business software (of various types) and linkages created to such external entities within business software, from the E-mail Clients. In more detail, correspondence in the form of e-mail is automatically imported into business software and Tasks created in accordance with the invention. In the process, a repository of external e-mail correspondence is maintained within the business software. The mail management system in accordance with the invention is efficient, cost-effective and accurate, that would otherwise not be possible manually.
Owner:ICODE
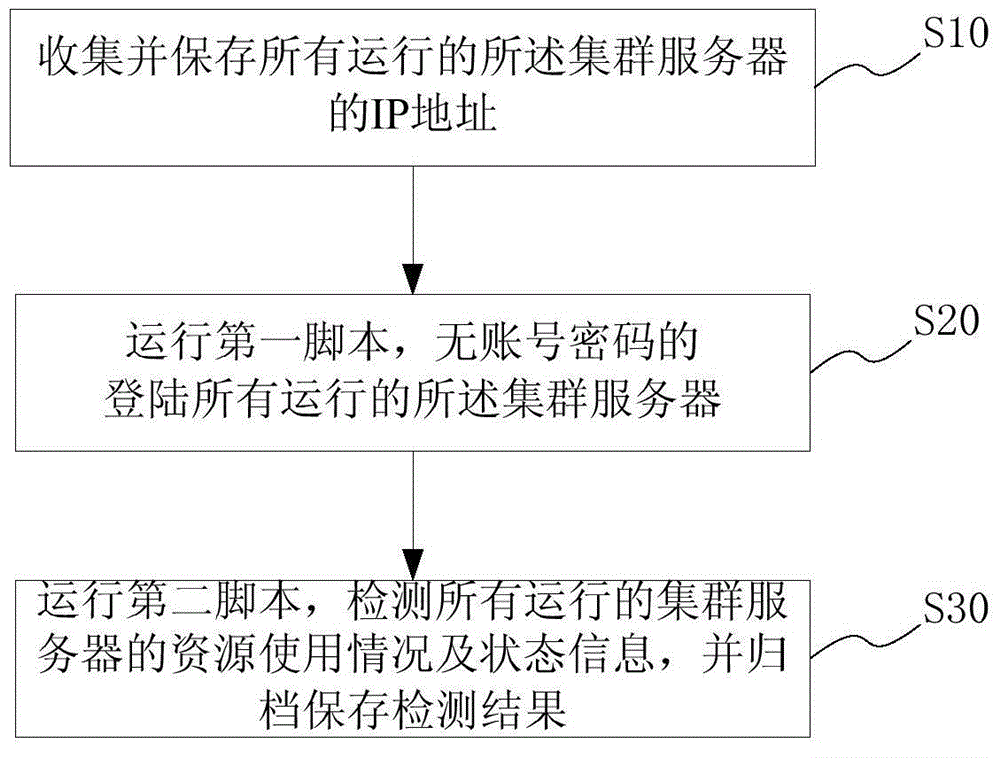
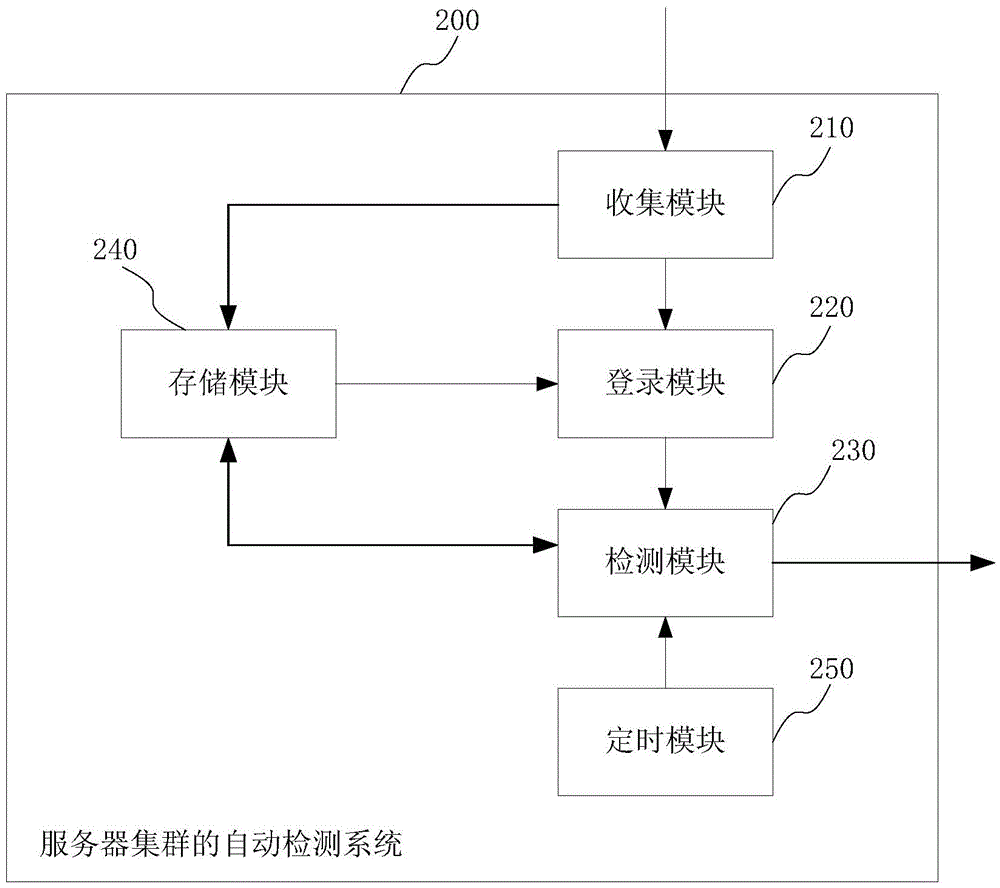
Automatic server cluster detecting method and system
The invention provides an automatic server cluster detecting method and system. The method comprises steps as follows: IP addresses of all operating cluster servers are collected and saved; a first script is operated according to the collected IP addresses, and all the cluster servers are logged in without account passwords; a second script is operated, the resource use condition and the state information of all the operating cluster servers are detected, and a detecting result is filed and saved. The first script is used for logging in the cluster servers without passwords and is pre-written with an SSH (secure shell) remote login authentication method; the second script is used for detecting the operating cluster servers and is pre-written through SHELL. According to the method and the system, no server is required to be purchased alone for deployment, no third-party business software is adopted, automatic detection is used to replace manual operation, the workload of a system administrator is reduced, the working efficiency is improved, and the cost is lower.
Owner:PHICOMM (SHANGHAI) CO LTD
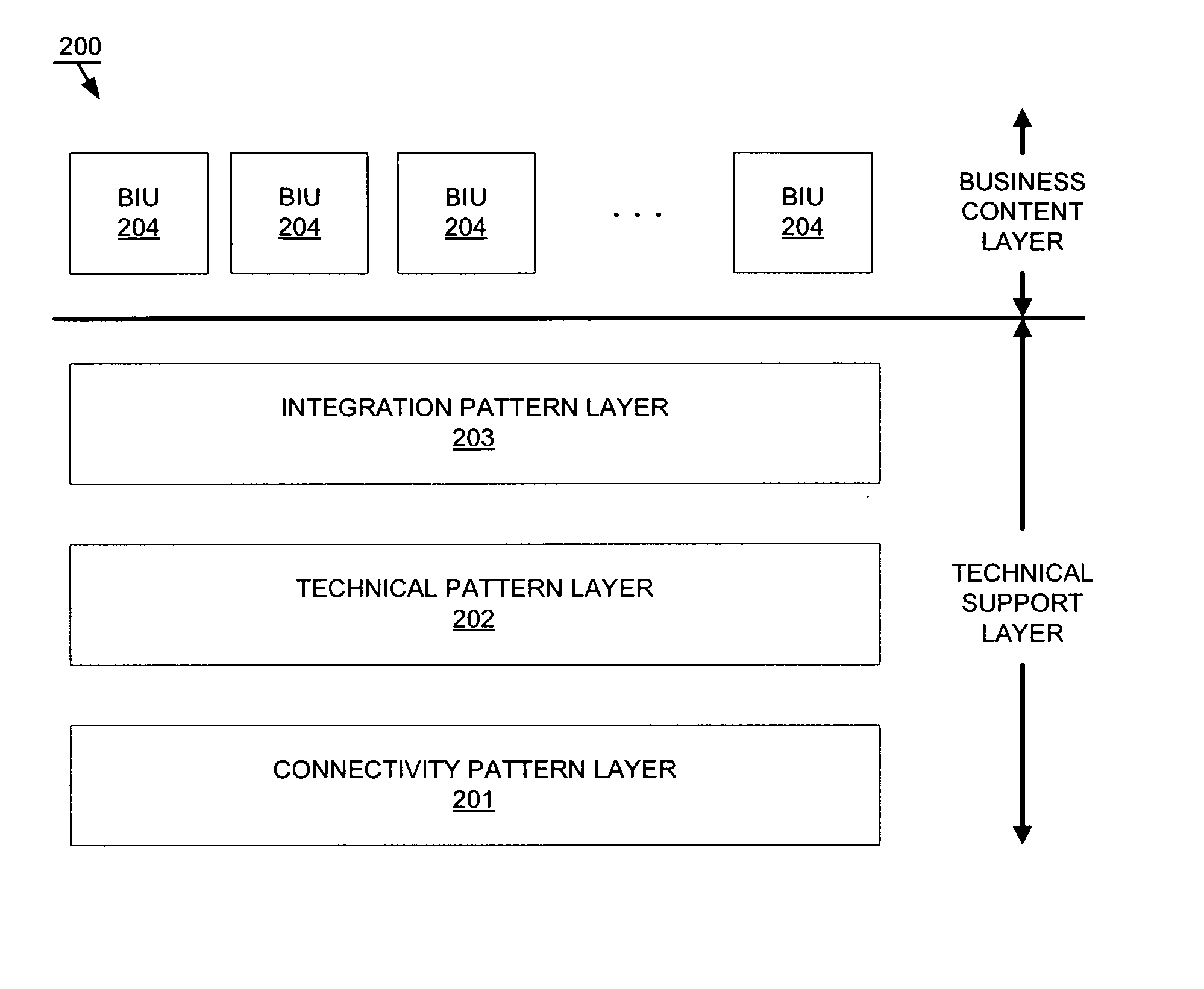
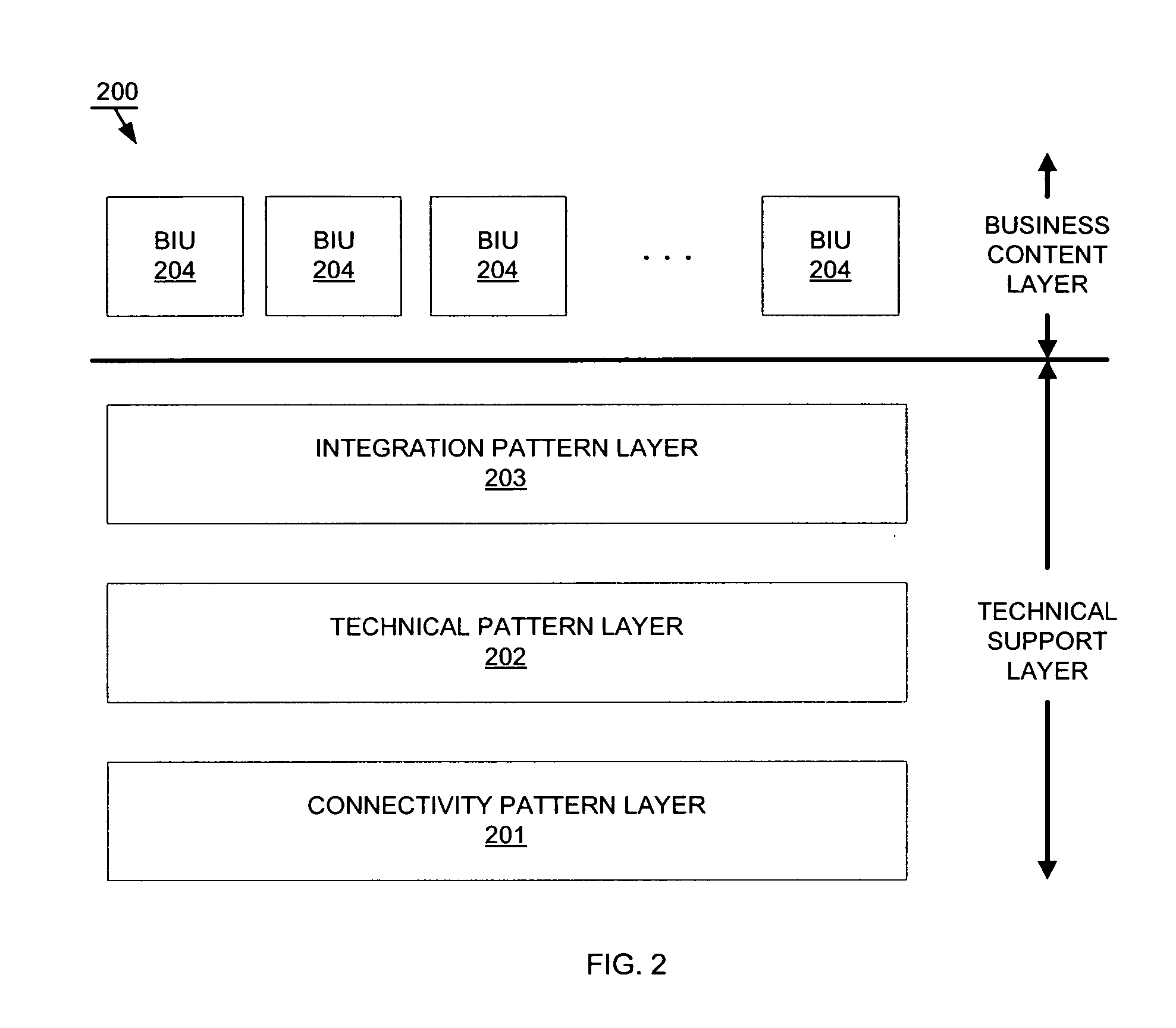
System and method for business software integration
Layering techniques are applied to business software integration, in order to provide an integration package that is usable “out of the box,” i.e., substantially upon installation thereof and after a brief configuration process. Accordingly, embodiments may comprise a technical support layer and a business content layer, where the technical support layer and the business content layer are substantially separate and distinct from each other. The technical support layer may comprise a plurality of predefined connectivity and integration patterns that can be configured to support precoded business logic in the business content layer. The layering helps to avoid “monolithic” structures that can prolong integration and be difficult to maintain.
Owner:SAP AG
Indoor integrated positioning platform and positioning method
InactiveCN107249167AReduce power consumptionLow costPosition fixationWireless commuication servicesHoneycombComputer science
The invention relates to an indoor integrated positioning platform and a positioning method. The indoor integrated positioning platform includes a system software layer, a device access layer, a service layer, a business integrated layer, a business software layer, and a presentation layer. The subsystem in each layer processes the data thereof through the service layer. An optical fiber communication network system and an RFID-based signal acquisition system import the data of different subsystems and realize data interaction between the subsystems and the indoor integrated positioning platform through the device access layer. The indoor integrated positioning platform adopts a honeycomb networking structure. Each device communicates with a gateway in a plurality of directions, and each device has a wireless signal relay function.
Owner:沈磊
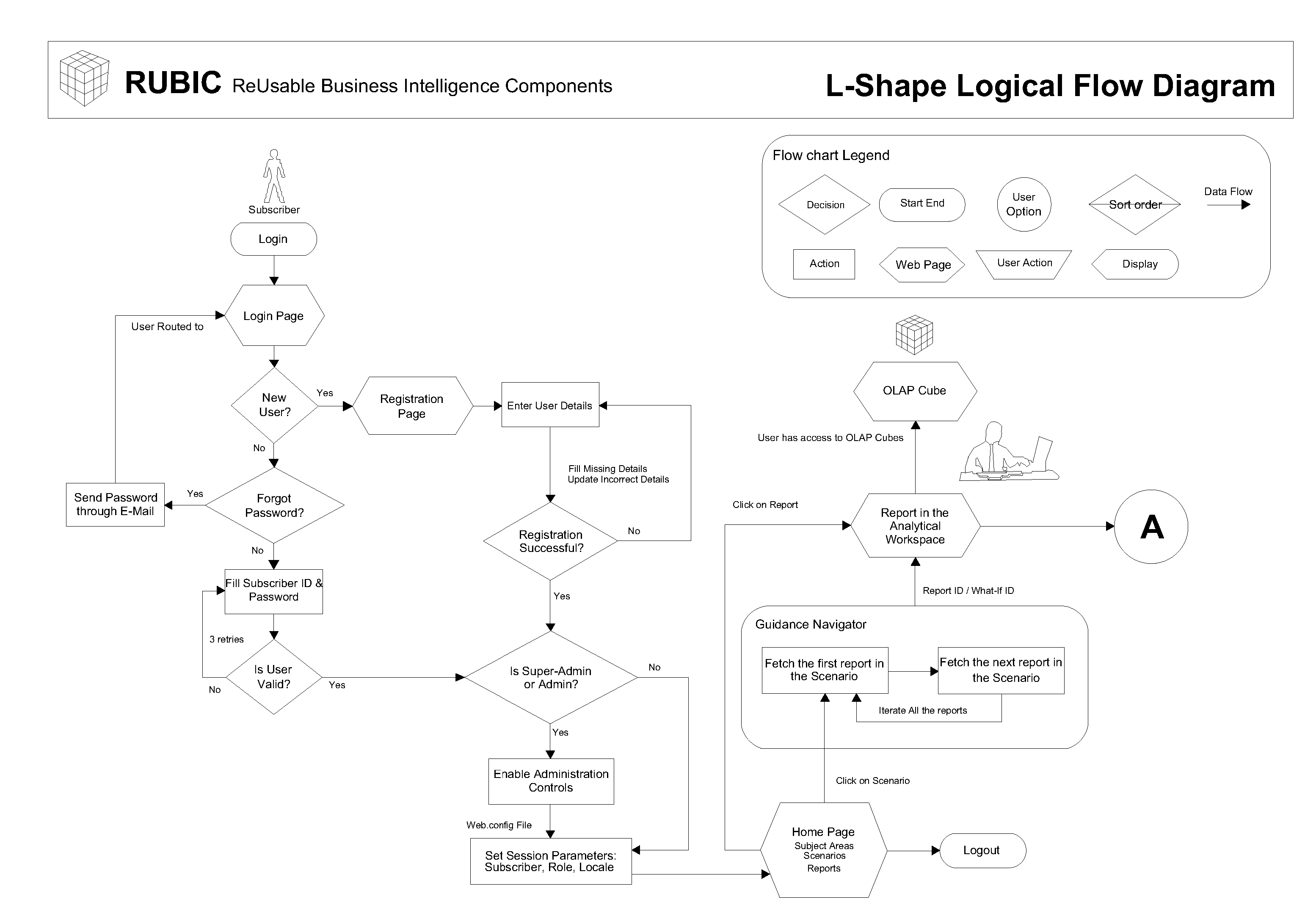
Method and system for generating an analytical report including a contextual knowledge panel
InactiveUS20070250466A1Digital data information retrievalSpecial data processing applicationsDisplay deviceData science
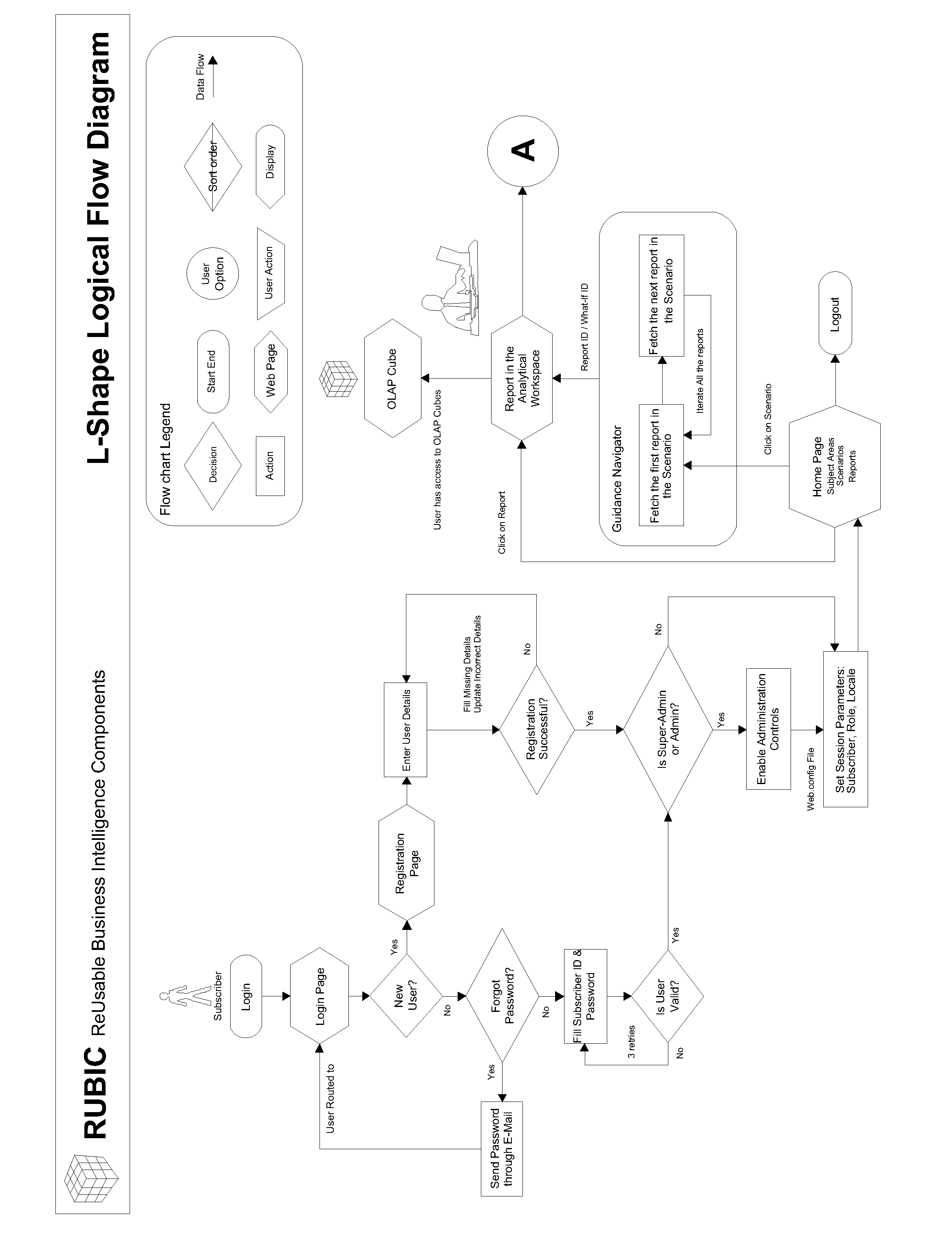
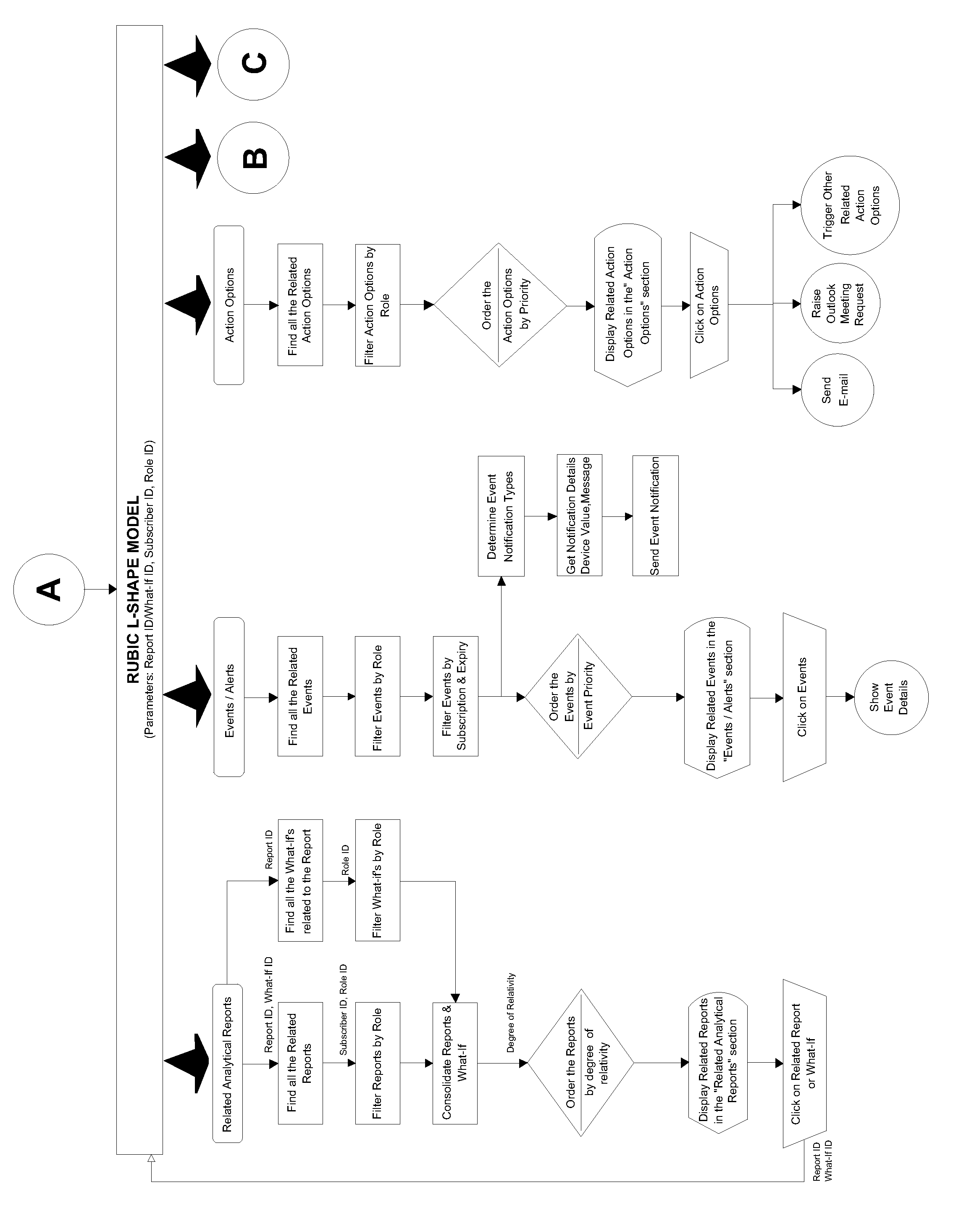
Described is a method and system for producing and displaying a required analytical report based on user-determined rule-set, selectively including contextual information that is specifically linked to the analytical report. Certain report-attributes, e.g., role ID, subscriber ID, and report ID / what-if ID, which are characteristic of the required report, are inputted into a user's system / framework to obtain outputs specific to the required analytical report by narrowing down / filtering the selection from available contextual information to obtain specific contextual information used for selective display. The method includes specific steps to use filter / narrow-down choices, considering what-if and different possible scenarios. The method can be part of commercial software that is tailored to the user's requirements and sold as a package. The analytical report might include contextual metadata, associated analytics for a particular analysis scenario, event alerts and operational metadata as part of a contextual knowledge panel. The display may have an L shaped configuration.
Owner:MINDTREE CONSULTING PVT
Data flow distributing method, mobile terminal and data flow distributing system
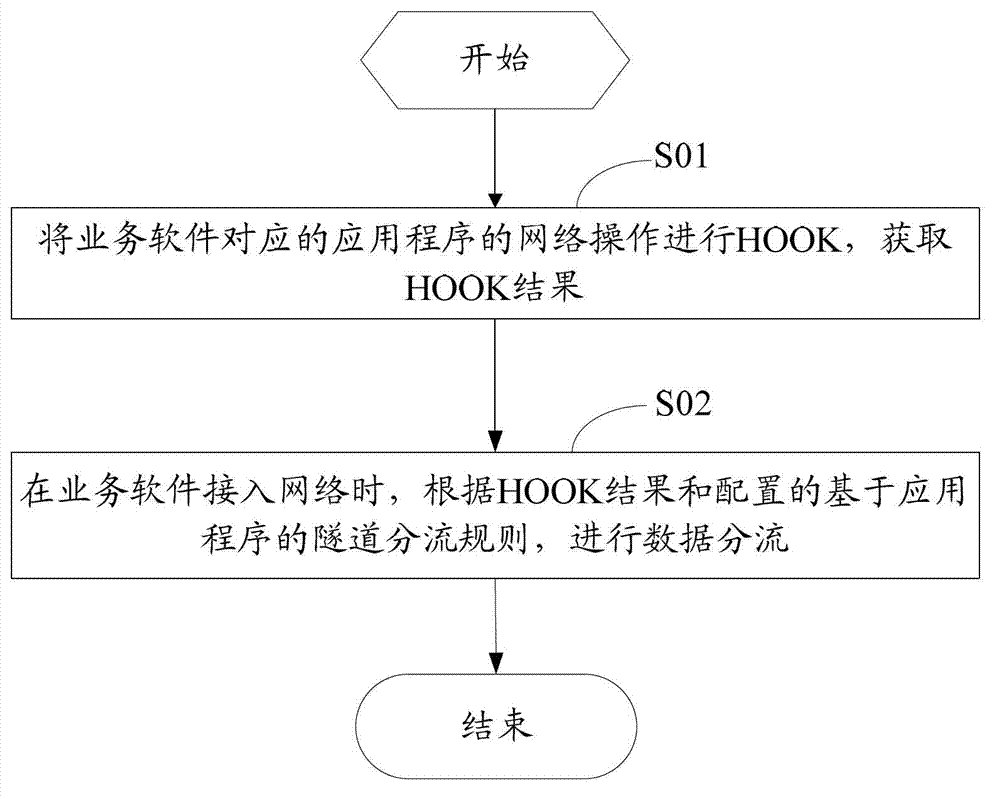
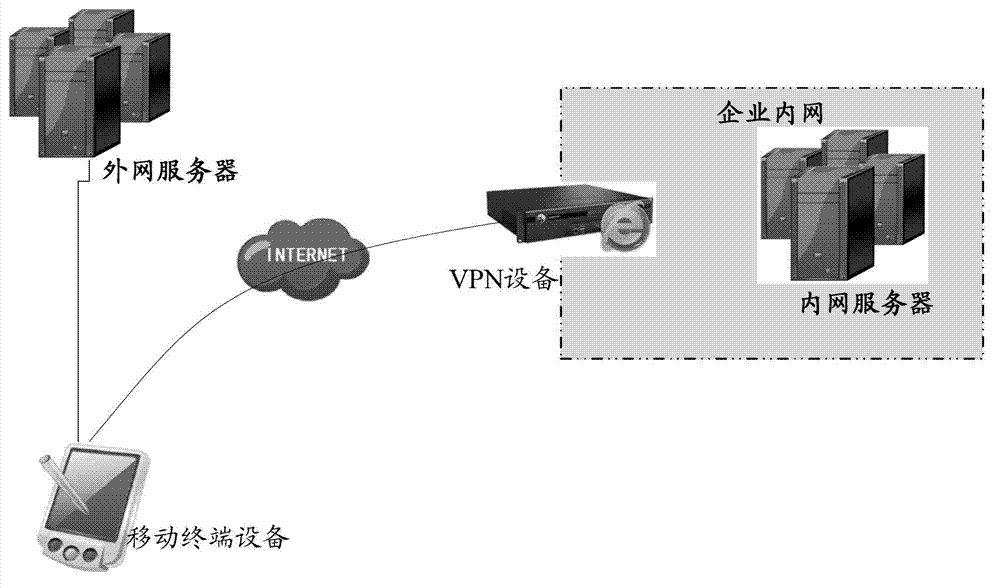
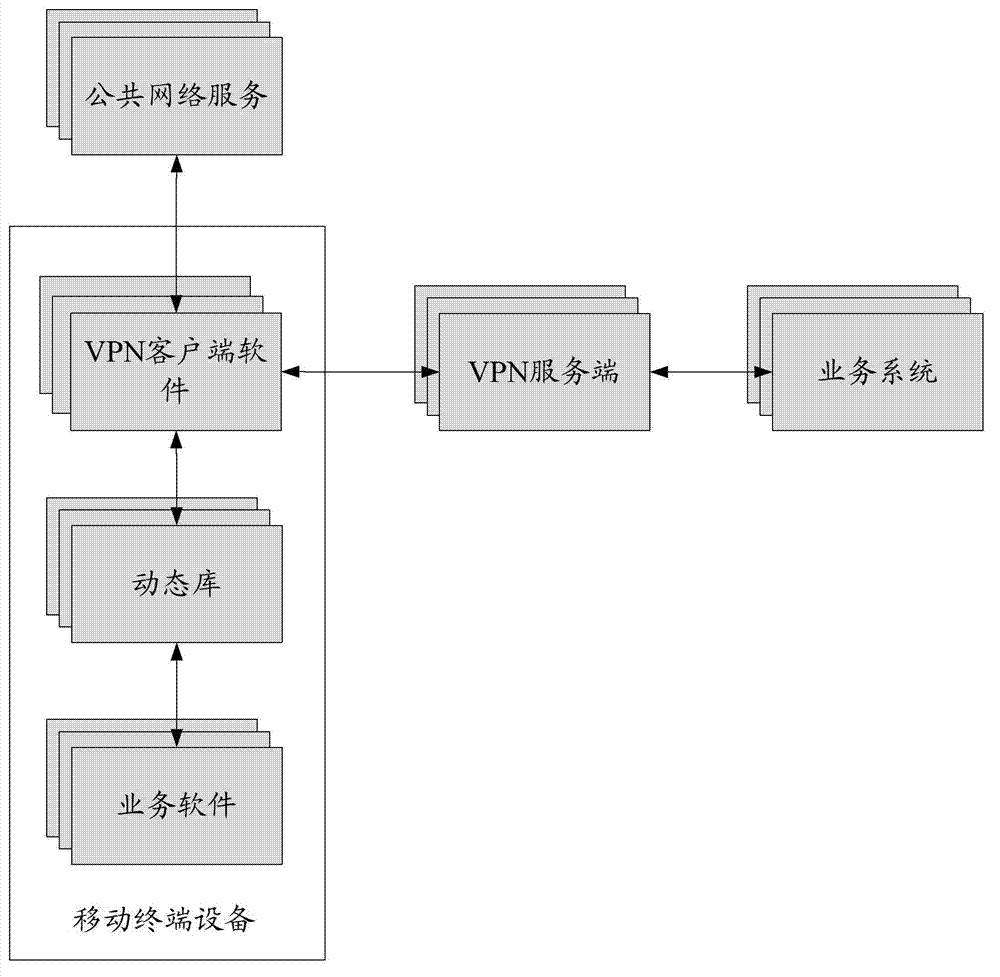
ActiveCN102891802ADoes not affect accessTunnel split rules do not affectNetworks interconnectionComputer terminalApplication software
The invention discloses a data flow distributing method. The data flow distributing method comprises the steps: carrying out HOOK on network operation of an application program corresponding to business software to acquire a HOOK result; and when the business software accesses a network, carrying out data flow distribution according to the HOOK result and the configured application-program-based tunnel flow distributing rules. The invention further discloses a mobile terminal and a data flow distributing system comprising the mobile terminal. Through carrying out HOOK on network operation of the application program corresponding to business software to acquire the HOOK result and carrying out data flow distribution according to the HOOK result and the configured application-program-based tunnel flow distributing rules when the business software accesses the network, the method has the beneficial effect that the mobile terminal can still access the network without the influence on access to enterprise intranet resources when the IP (Internet Protocol) segment distributed by WiFi (Wireless Fidelity) and the enterprise intranet segment are the same network segment, the configured tunnel flow distributing rules are not influenced no matter how a background server is modified, and a large amount of labor force is saved.
Owner:SANGFOR TECH INC
Method and system for mobile terminal parameter configuration
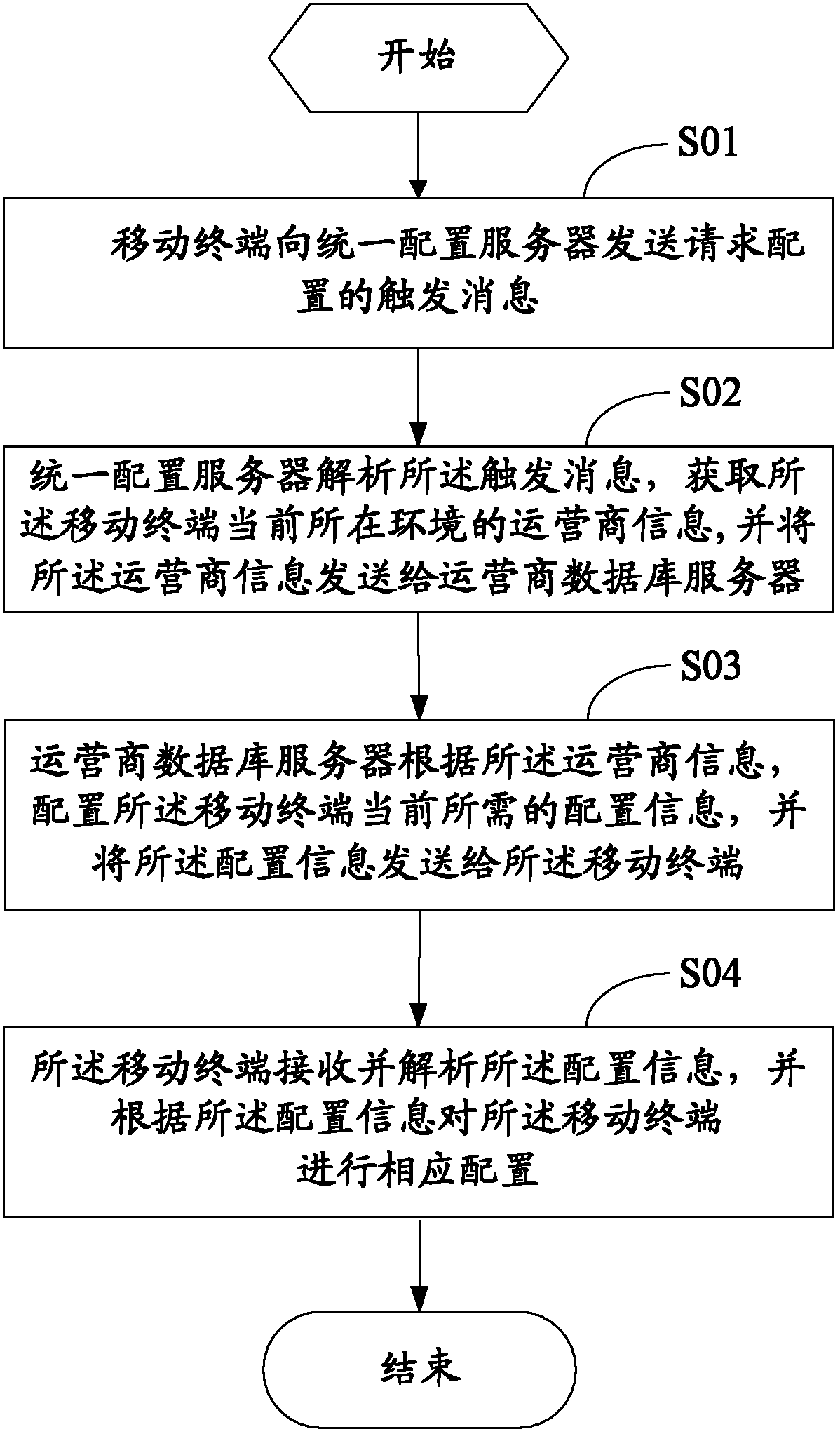
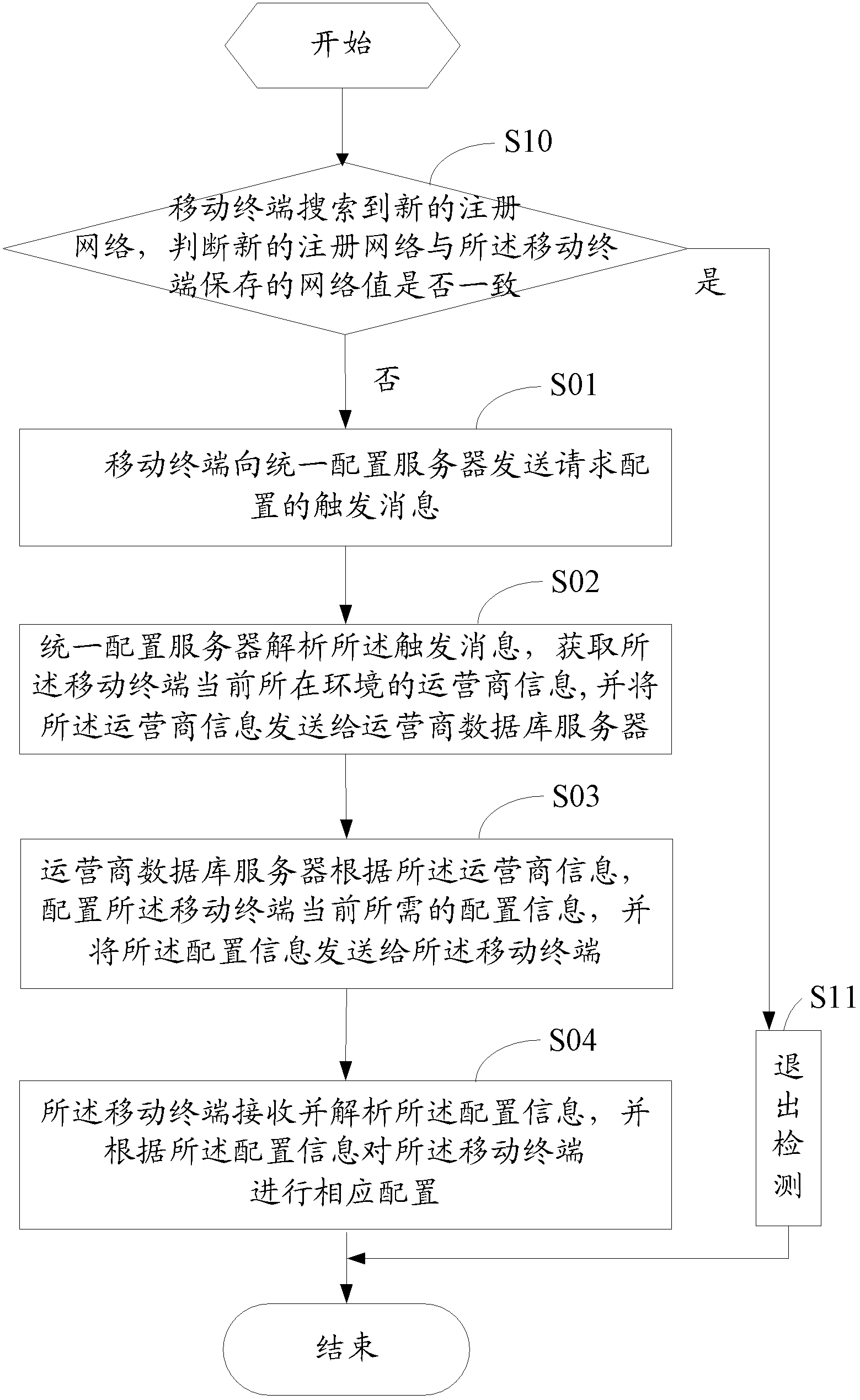
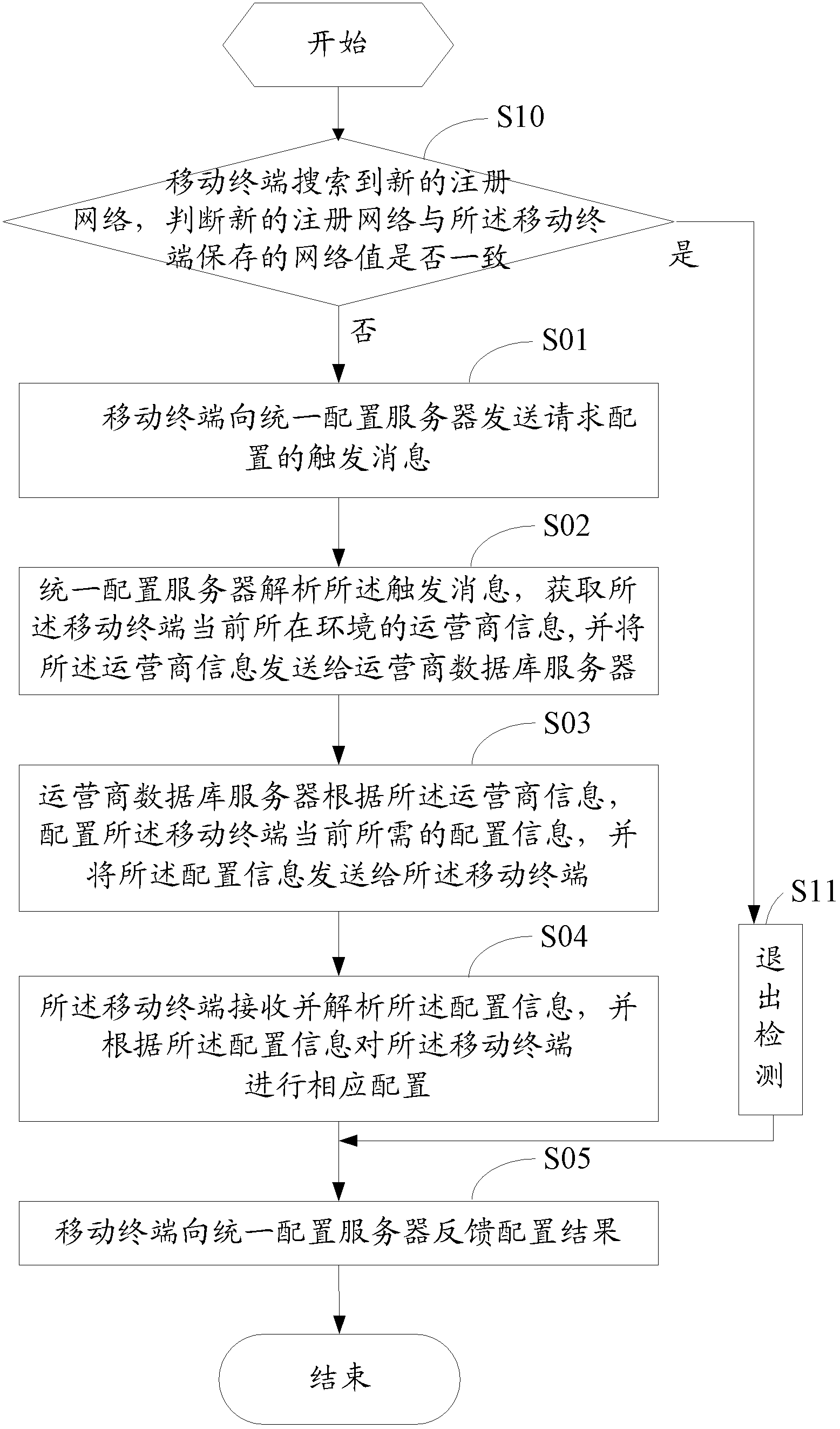
ActiveCN102647705AImprove experienceConvenient lifeService provisioningAssess restrictionDatabase serverComputer terminal
The invention discloses a method and a system for mobile terminal parameter configuration. The method comprises that a mobile terminal sends a trigger message of a configuration request to a unified configuration server; the unified configuration server analyzes the trigger message, acquires operator information of the mobile terminal in the current environment, and sends the operator information to an operator database server; according to the operator information, the operator database server configures configuration information which is required by the mobile terminal currently and sends the configuration information to the mobile terminal; and the mobile terminal receives and analyzes the configuration information and performs corresponding configuration for the mobile terminal in accordance with the configuration information. The terminal mobile actively requests client parameter configuration and modification of servers in some areas where functions are not available, so that business software can be used normally when the mobile terminal is in any environments, user experience is improved, and normal life of users in the area is improved.
Owner:ZTE CORP
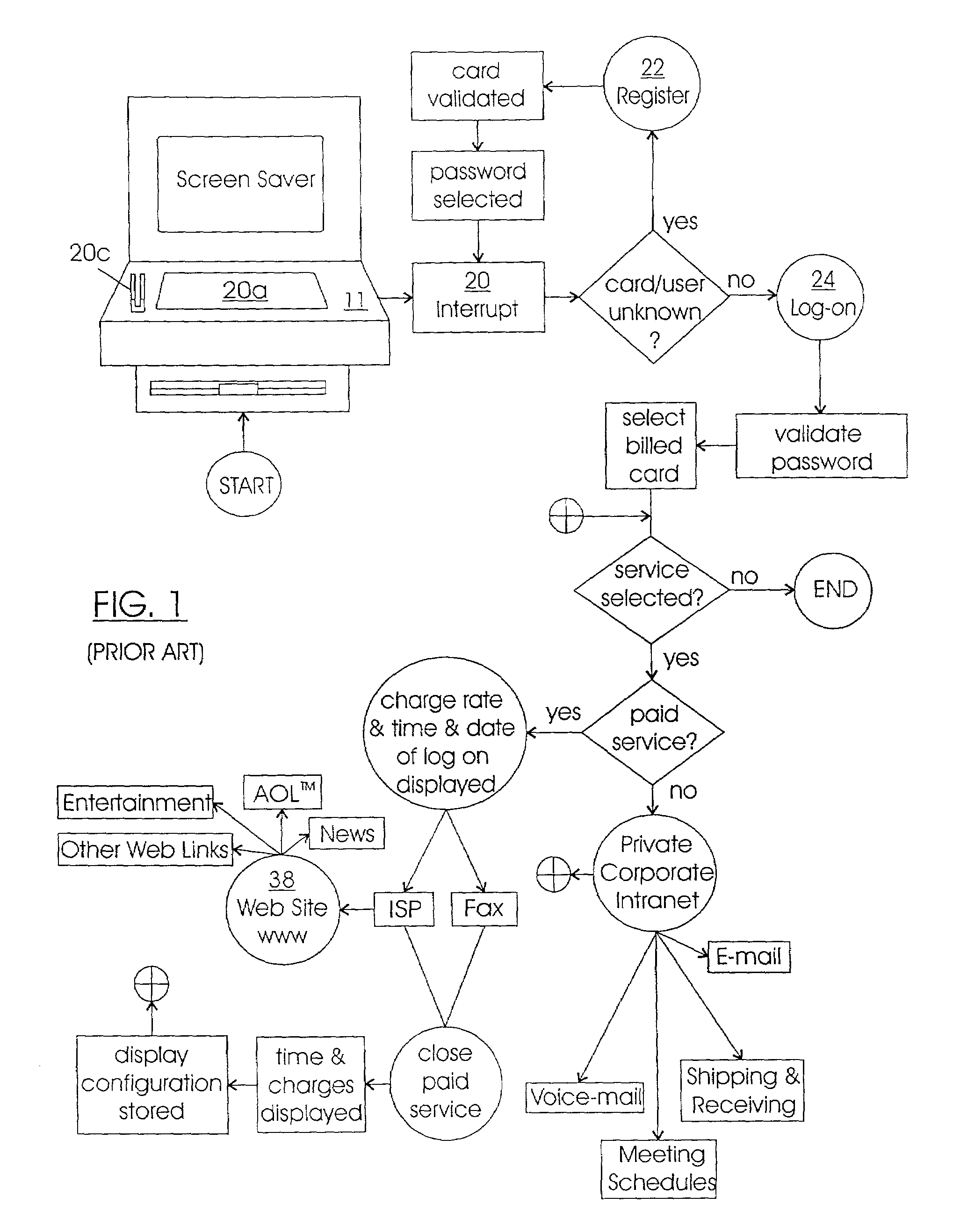
E-commerce development intranet portal
InactiveUS7647259B2Improve performanceSolve low usageCredit registering devices actuationFinanceFree accessSelf-service
An intranet providing a multiple-carrel public-access kiosk provides free access to foreign and domestic informational e-commerce intranet sites as well as e-mail and public service educational and informational materials. The kiosk accepts anonymous pre-paid cards issued by a local franchisee of a network of e-commerce intranets that includes the local intranet. The paid services provided by each carrel may include video-conference and chat room time, playing and / or copying audio-visual materials such as computer games and music videos, and international e-commerce purchase support services such as customs and currency exchange. Third-party sponsored public service materials may include audio-visual instructional materials in local dialects introducing the user to the use of the kiosk's services and providing training for using standard business software programs.
Owner:DE FABREGA INGRID PERSCKY
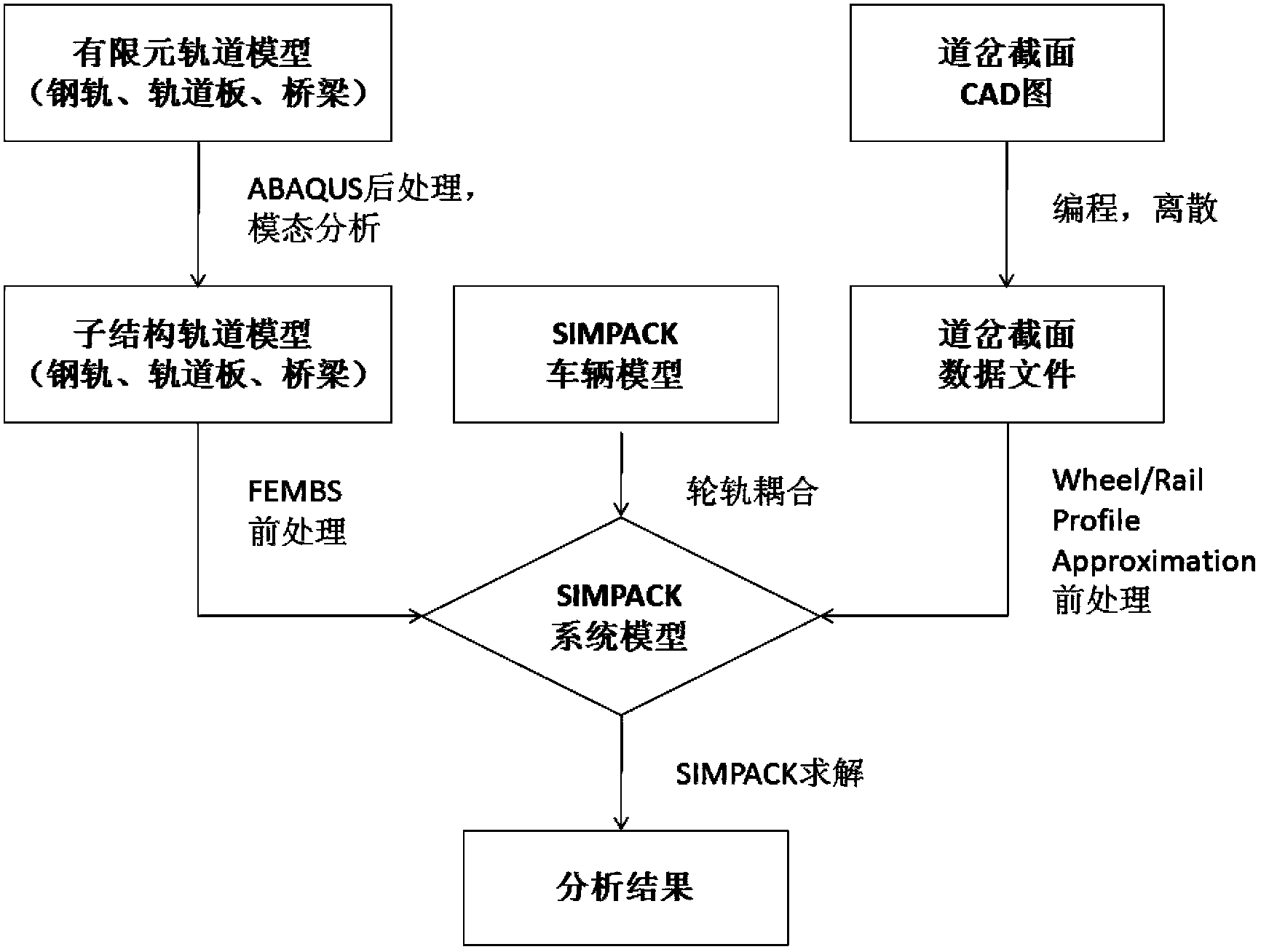
Joint-simulation-based on-bridge ballastless turnout structure system and dynamic analysis method thereof
InactiveCN103488805AGood modelingGuaranteed meticulousSpecial data processing applicationsSimulationCoupling system
The invention relates to a joint-simulation-based on-bridge ballastless turnout structure system and a dynamic analysis method thereof. The dynamic analysis method of the joint-simulation-based on-bridge ballastless turnout structure system comprises the following steps of firstly finishing the model establishment of a balastless track and bridge structure by utilizing the ABAQUS software; secondly finishing the model establishment of a vehicle and a turnout by utilizing the SIMPACK software; finally establishing rigid-flexible coupled wheel-track contact relationship in the SIMPACK software to form a vehicle-turnout-bridge coupling system model, and realizing the connection and the coupled solution of a vehicle model, a turnout model and a bridge model. According to the joint-simulation-based on-bridge ballastless turnout structure system and the dynamic analysis method thereof, which are disclosed by the invention, the complex wheel-track contact relationship of a turnout zone is fully considered, and the model establishment of a turnout and bridge structure is finished according to the actual state to the greatest extent so as to ensure the detailedness, the completion and the accuracy of the model; the model establishment is finished by utilizing the business software, so that the production, the design and the application are convenient, and the improvement is remarkable by comparing the modeling method provided by the invention with the traditional modeling method.
Owner:BEIJING JIAOTONG UNIV
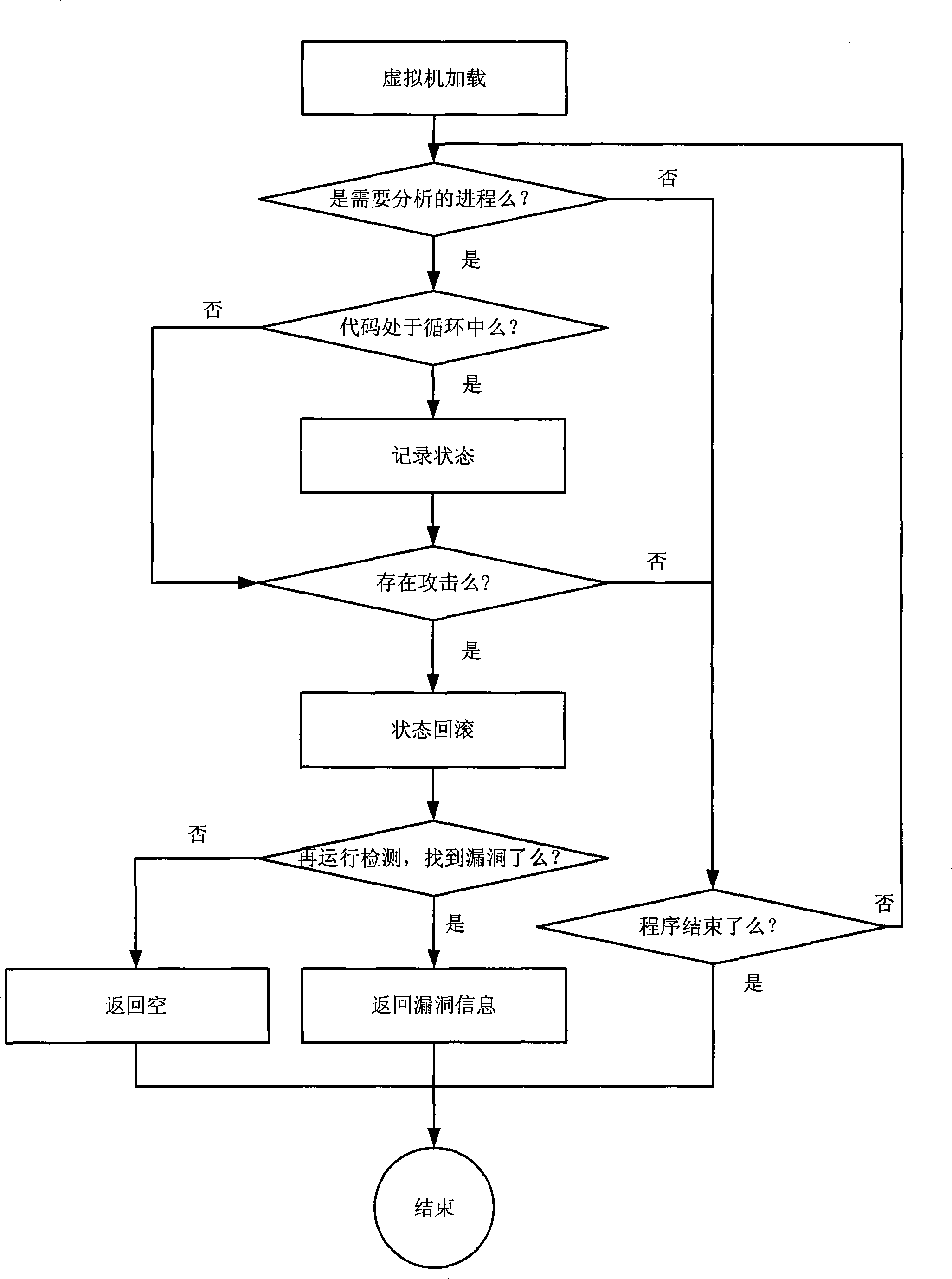
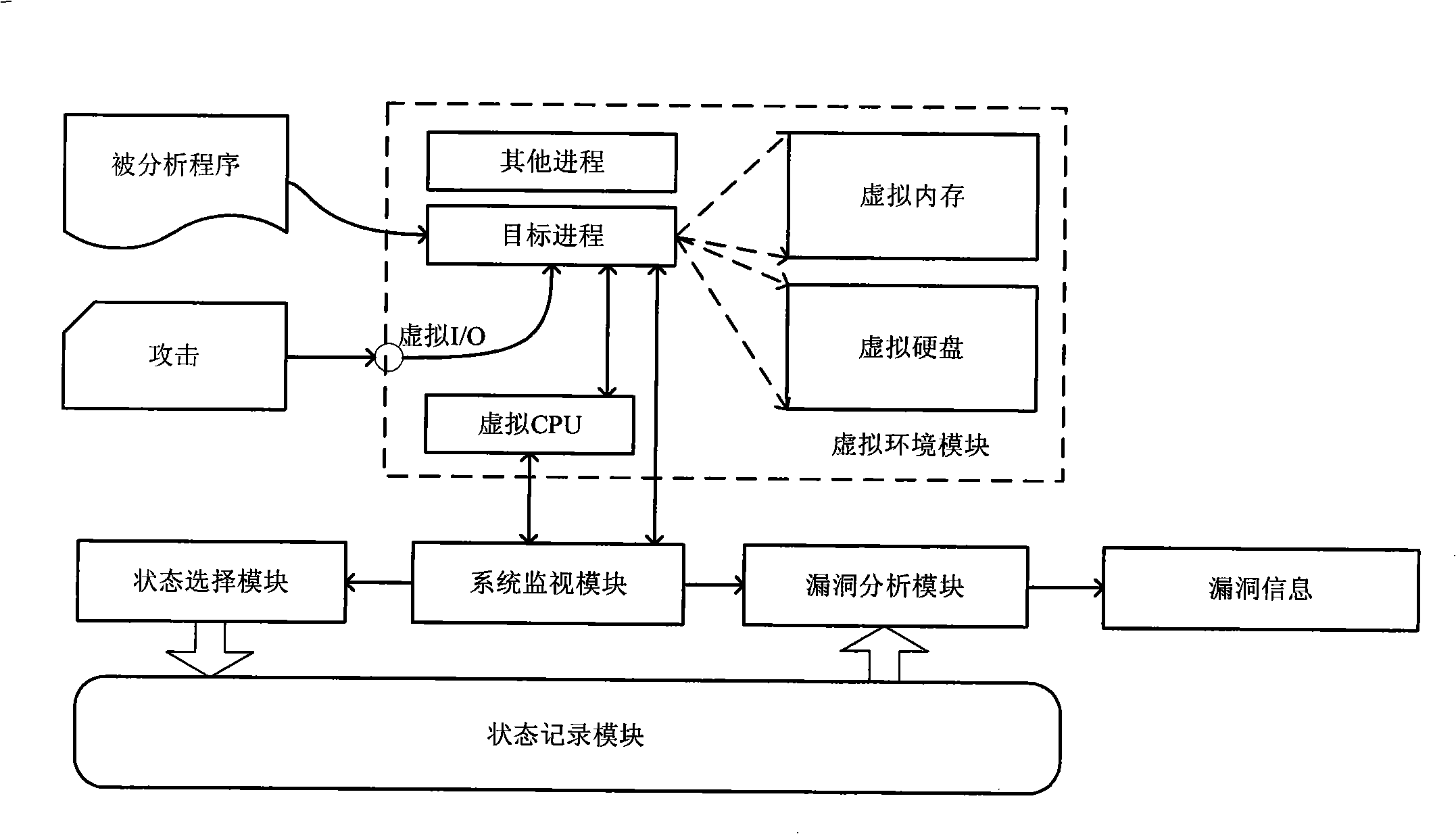
Vulnerability testing method in attack and system thereof
ActiveCN101515320AAvoid unanalyzable problemsReduce usagePlatform integrity maintainanceTransmissionRecord statusComputer module
The invention discloses a vulnerability testing method in attack and a system thereof, belonging to the field of network security. The method comprises: after programs which are analyzed is loaded into a virtual machine, whether the current running process of the virtual machine belongs to the analyzed program is recognized; if yes, whether the current code is in circulation is judged, the current status information is recorded when in circulation; if not, whether the current program is in attack is judged; if being in attack, the state s before variable which is depended by the last time program pointer can be looked for from the current recorded status information; the status information saved in the s is restored, and the program starts to run again from the state s; the concrete command which modifies the variable depended by the program pointer is found out, and the position of the command is returned; the system of the invention comprises a virtual environment module, a state selection module, a system monitoring module, a vulnerability-analysis module and a status record module. The invention has good maneuverability and high detection efficiency, and solves the problem that business software lacks a source code and can not be analyzed.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com