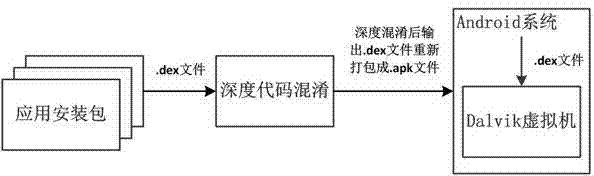
Deep code obfuscation method for Android system applications
A code obfuscation and system application technology, applied in the field of deep code obfuscation of Android system applications, can solve problems such as confusion, failure to handle program control structure and calling structure well, affecting the normal operation of programs, etc., to prevent illegal cracking or reverse, The effect of improving security and ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
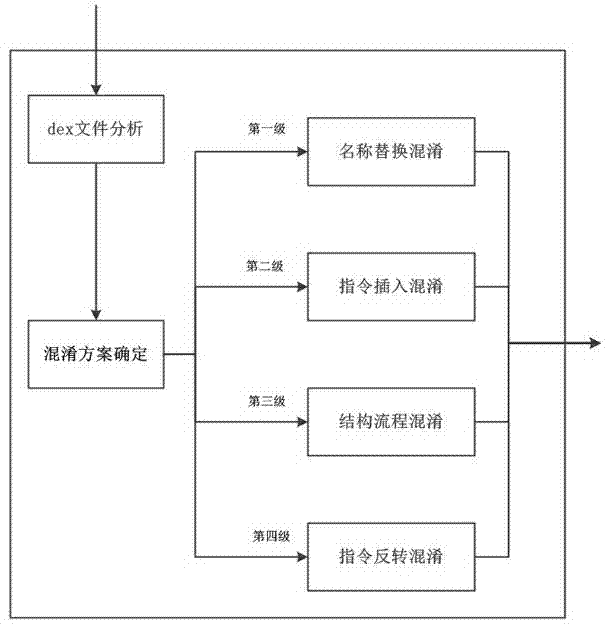
[0026] Embodiment 1: After a hacker obtains the installation package that has been obfuscated by the deep code obfuscator of the present invention, if the existing decompilation tool is used to decompile, the decompiled file can be obtained, but all the files in the obtained file Variables, classes, and method names will all become meaningless character or number sequences, increasing the workload of their static analysis.
Embodiment 2
[0027] Embodiment 2: When a hacker obtains the installation package that has been obfuscated by the second level of the deep code obfuscator of the present invention, using the decompilation tool for decompilation will directly cause the decompilation tool to collapse, resulting in no useful files being obtained; If the hacker manually analyzes the dex file, the various invalid instructions inserted in it and the combination of valid instructions and invalid data will cause great obstacles to the analysis process, causing the workload of its reverse work to soar.
Embodiment 3
[0028] Embodiment 3: When a hacker gets the third-level obfuscated installation package of the deep code obfuscator of the present invention, no matter whether he uses a decompilation tool or manually analyzes the dex file by himself, he can only see fake ones on the surface. The program flow and the real execution flow are hidden. Although it cannot completely prevent reverse analysis, it also achieves the purpose of increasing the complexity of reverse analysis.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com