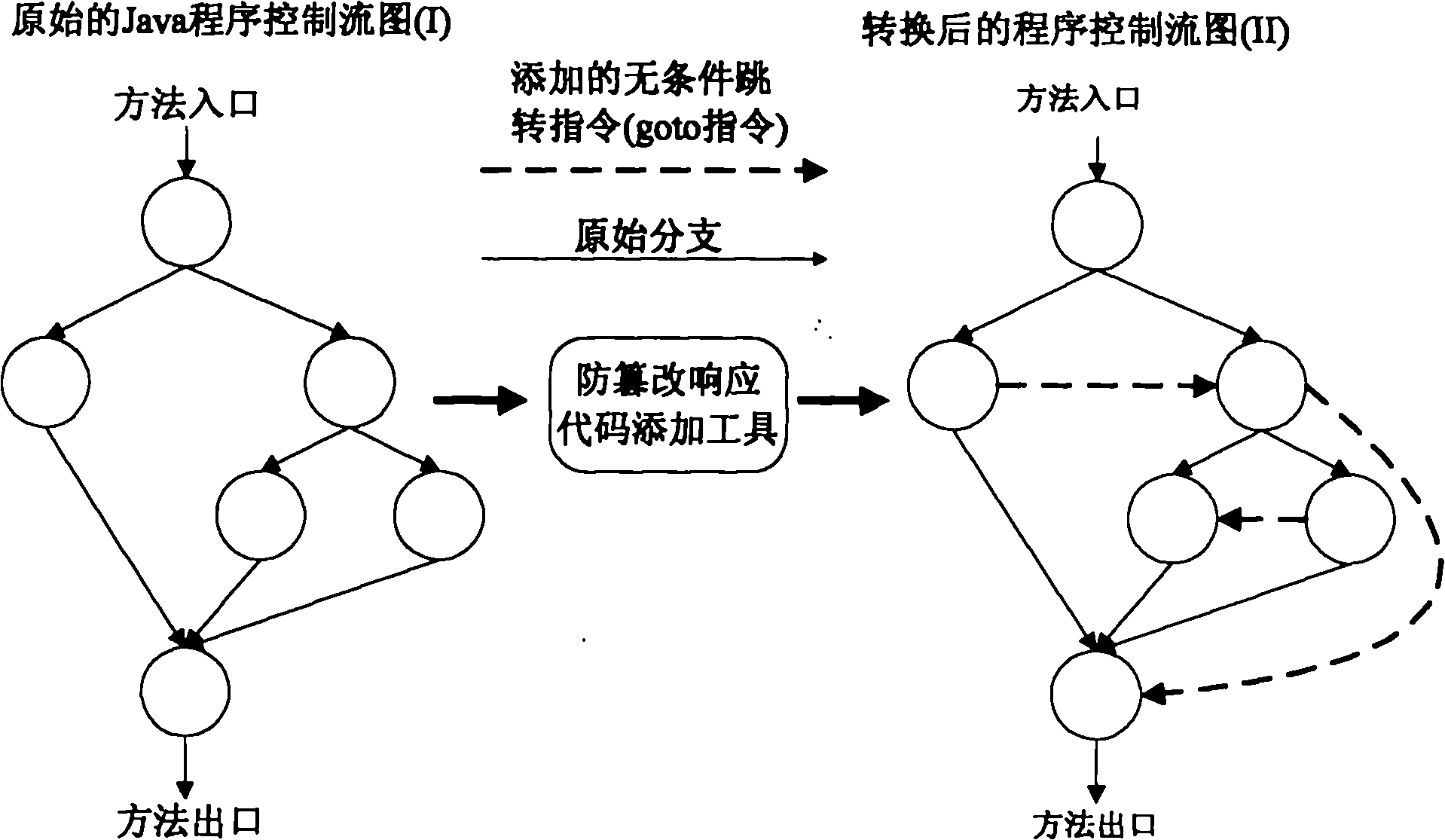
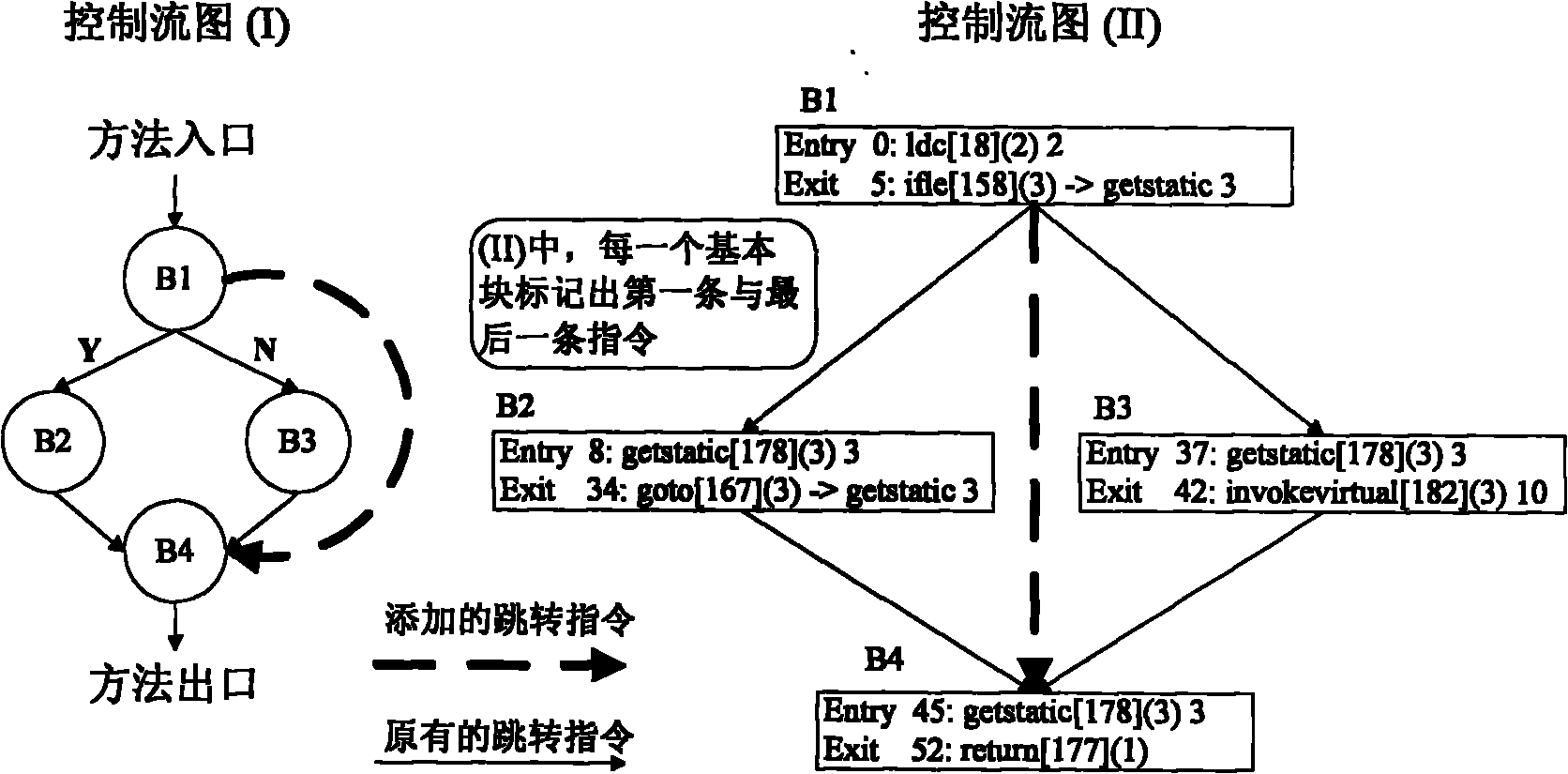
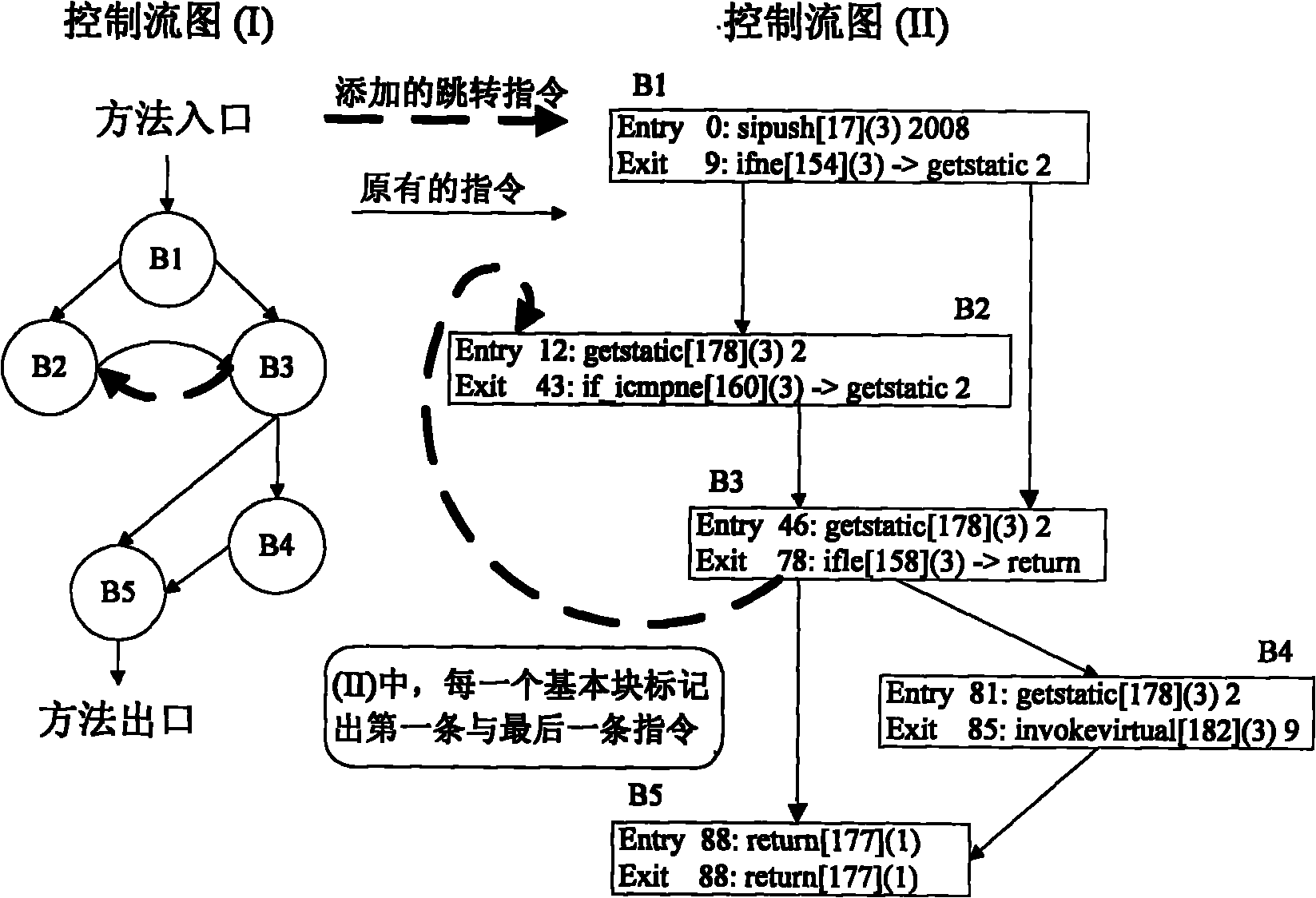
Tamper-proof response scheme of Java program
An anti-tampering and program technology, which is applied in program/content distribution protection, instruments, electrical digital data processing, etc., can solve problems such as difficult positioning and hindering the effectiveness of response schemes, and achieve the effects of easy implementation, reduced performance, and low consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] in Figure 4 In the Control Flow Analysis module, the user selects the Java program path, that is, enters the path name of a Jar package; selects the folder where the program corresponds to the control flow graph information, and the control flow graph information corresponding to all methods of a class file is stored in a file in. The module analyzes each class file in turn according to the input Jar package: creates a corresponding file storing control flow graph information according to the class file name, the format of the file is *.CIF (abbreviation of control flow graphinformation file); calculates control flow Figure and save its information to the corresponding CIF file, which records the path name of the corresponding class file.
[0047] in Figure 4 In the Data FlowAnalysis module, the user selects the path name of the folder where the control flow graph information is stored. The module parses each *.CIF file in the selected folder in turn: obtains the contro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com