Patents
Literature
342 results about "Java program" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
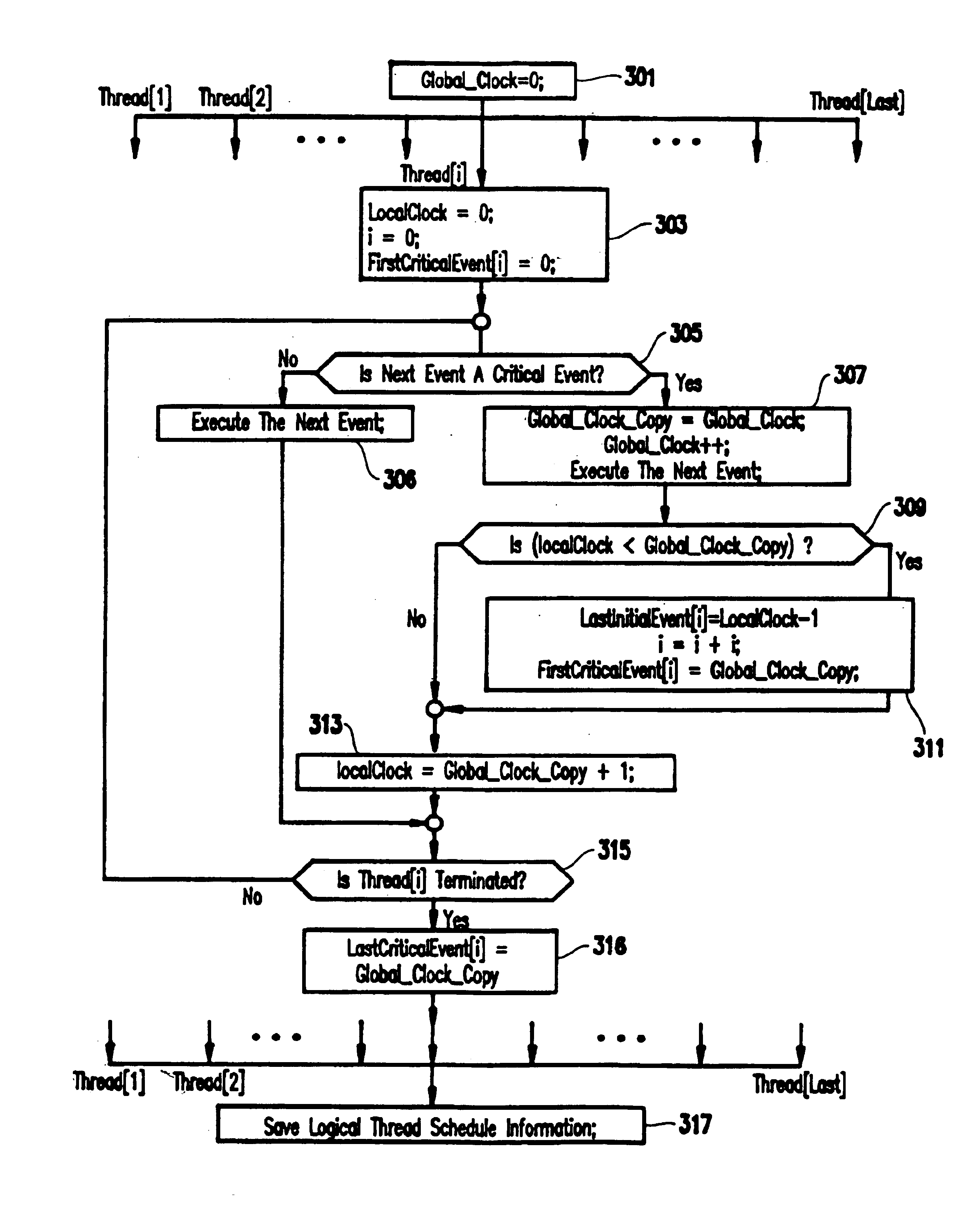
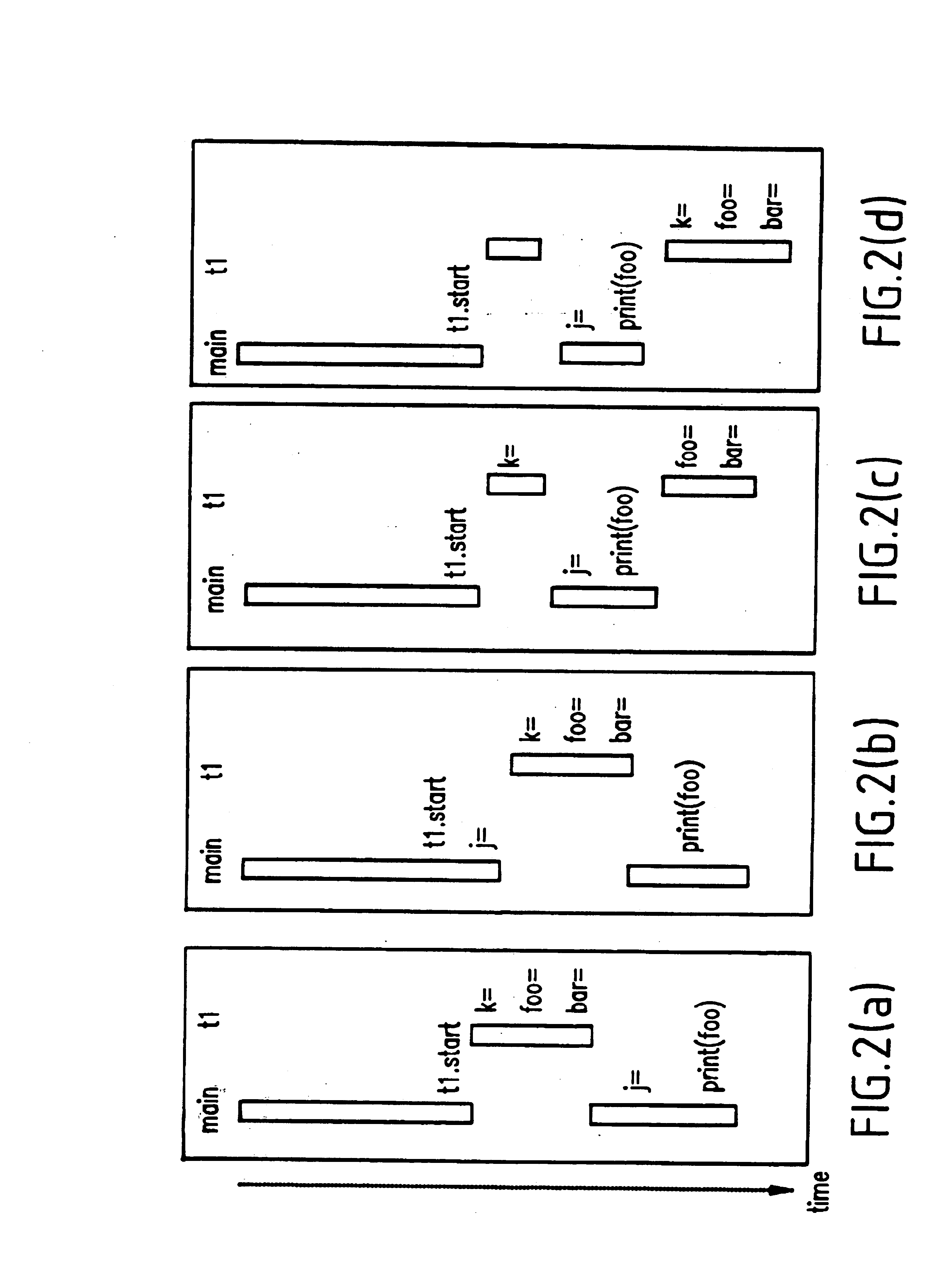
Method and system for recording and replaying the execution of distributed java programs
InactiveUS6832367B1Easy to copyGuaranteed orderError detection/correctionSpecific program execution arrangementsStream socketThread scheduling
A method for recording and replaying execution of distributed programs on a computer system in a distributed environment, includes identifying an execution order of critical events of a program, generating groups of critical events of the program, wherein for each group, critical events belonging to the group belong to a common execution thread, and generating for each execution thread a logical thread schedule that identifies a sequence of the groups so as to allow deterministically replaying a non-deterministic arrival of stream socket connection requests, a non-deterministic number of bytes received during message reads, and a non-deterministic binding of stream sockets to local ports.
Owner:IBM CORP
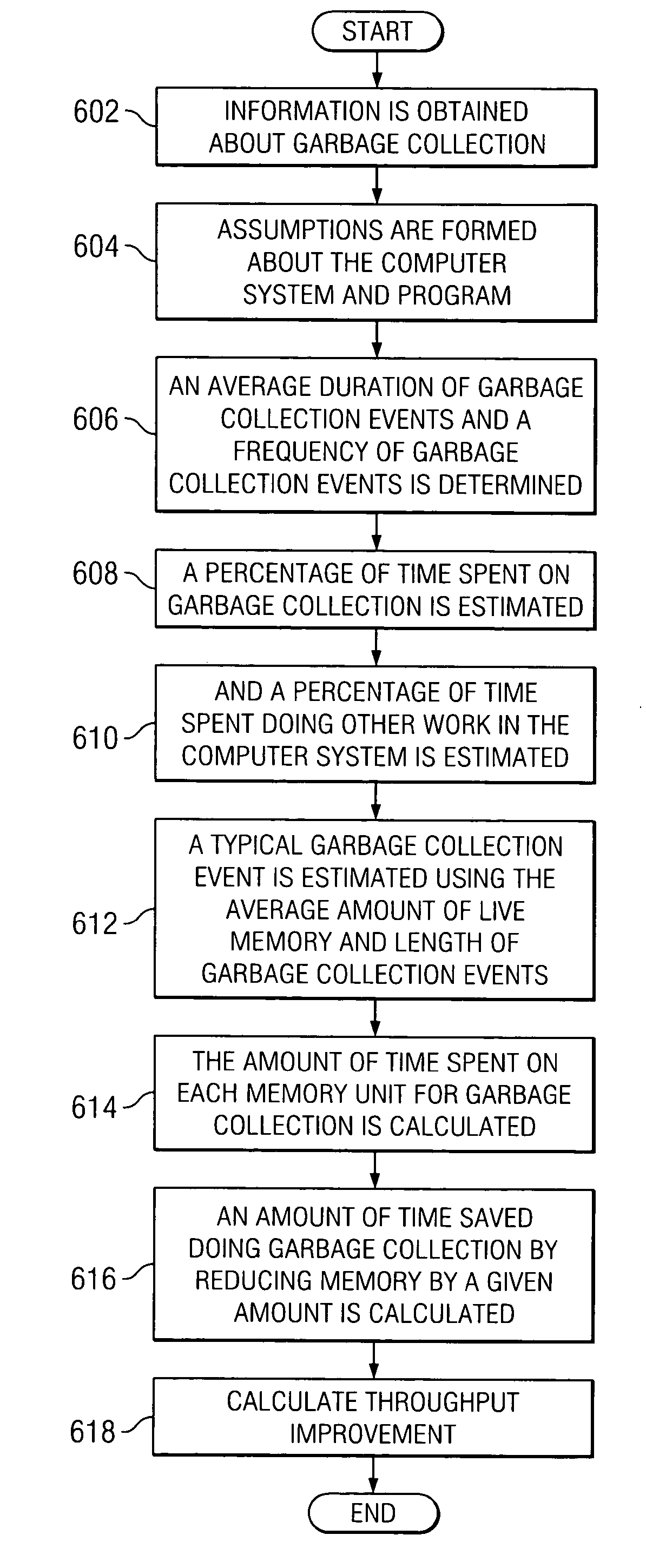
Method for determining a close approximate benefit of reducing memory footprint of a Java application
InactiveUS20050160416A1Improve performanceData processing applicationsSoftware engineeringMemory footprintParallel computing
Changes in performance in a Java program are deduced from information related to garbage collection events of the program. Assumptions are made about the system, the application and garbage collection, and changes in performance that will result from modifying the program are deduced.
Owner:IBM CORP
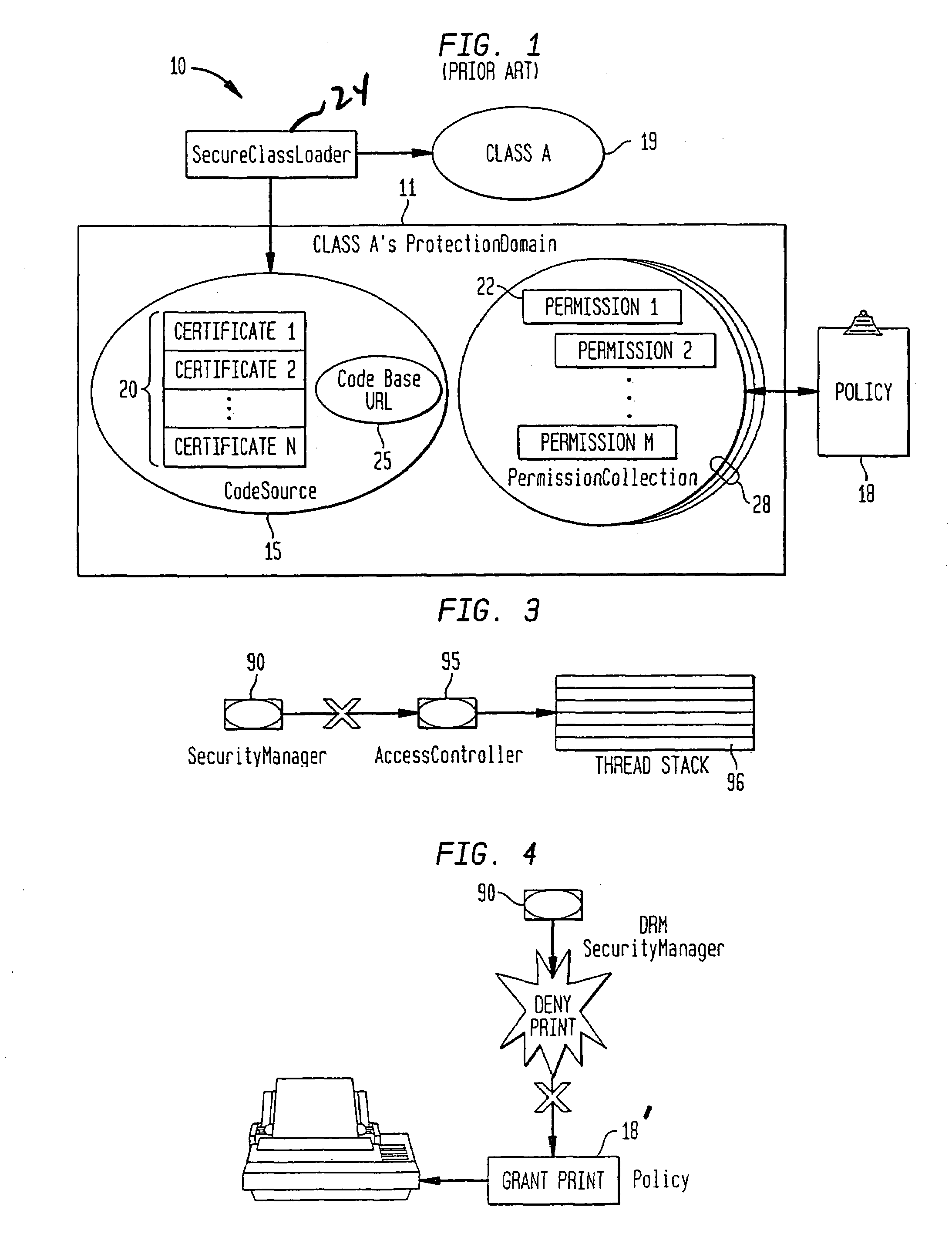
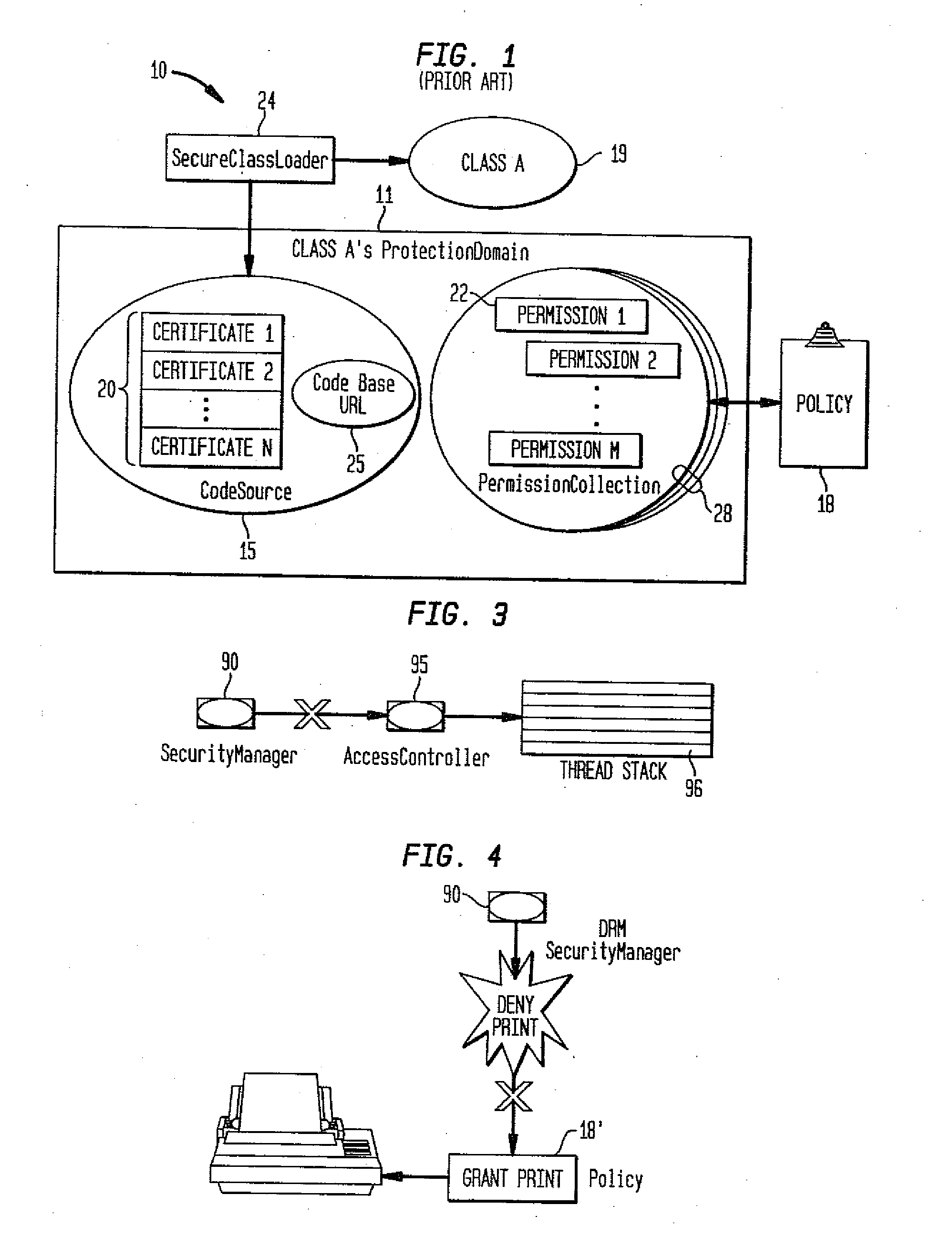
Integrating operating systems and run-time systems
InactiveUS6546546B1Specific access rightsMemory adressing/allocation/relocationOperational systemApplication software
The Virtual Machine is viewed by many as inherently insecure despite all the efforts to improve its security. This invention provides methods, apparatus, and computer products to implement a system that provides operating system style protection for code. Although applicable to many language systems, the invention is described for a system employing the Java language. Hardware protection domains are used to separate Java classes, provide access control on cross domain method invocations, efficient data sharing between protection domains, and memory and CPU resource control. Apart from the performance impact, these security measures are all transparent to the Java programs, even when a subclass is in one domain and its superclass is in another, when they do not violate the policy. To reduce the performance impact, classes are grouped and shared between protection domains and map data lazily as it is being shared. The system has been implemented on top of the Paramecium operating system used as an example of an extensible operating system application.
Owner:IBM CORP
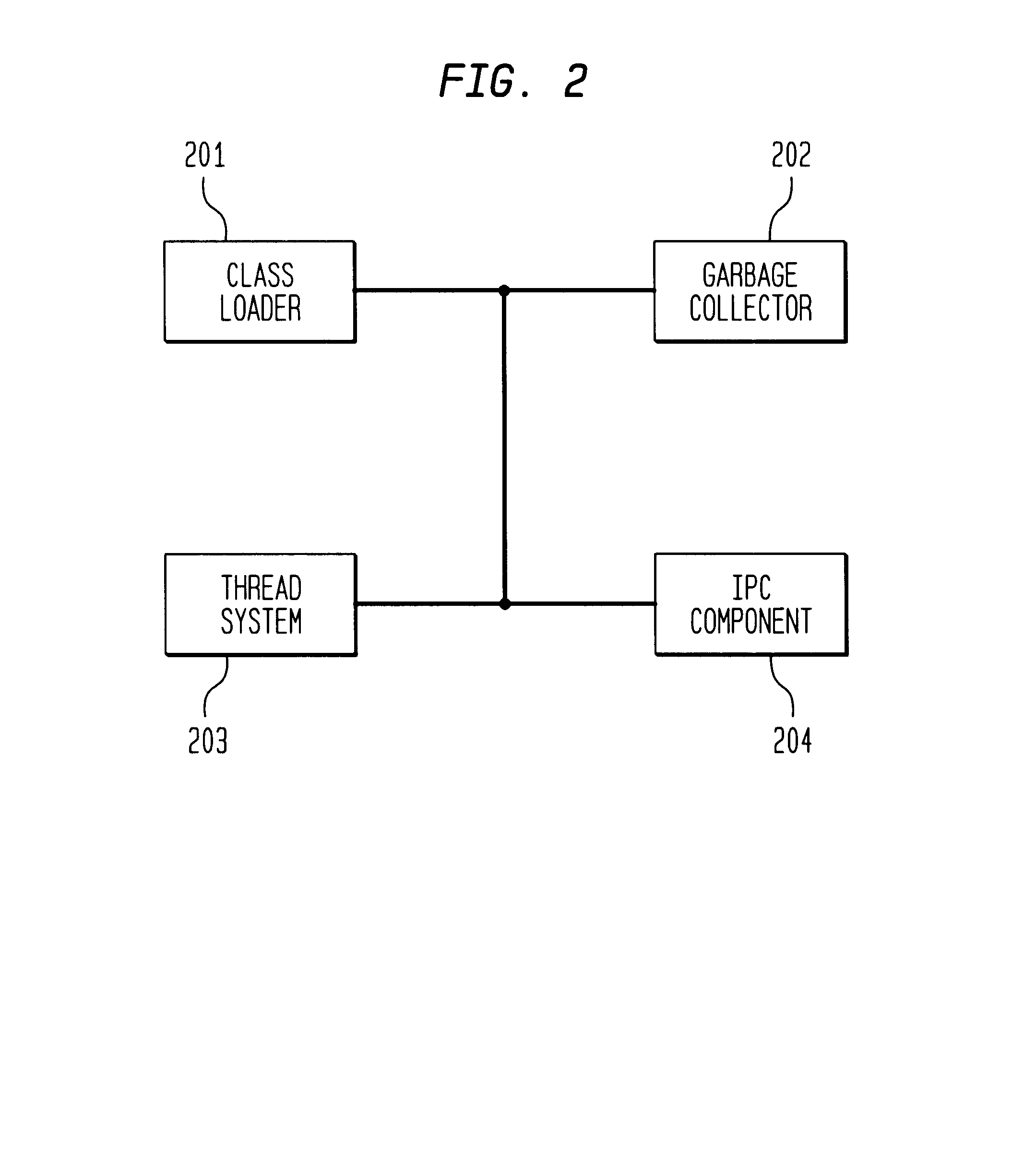
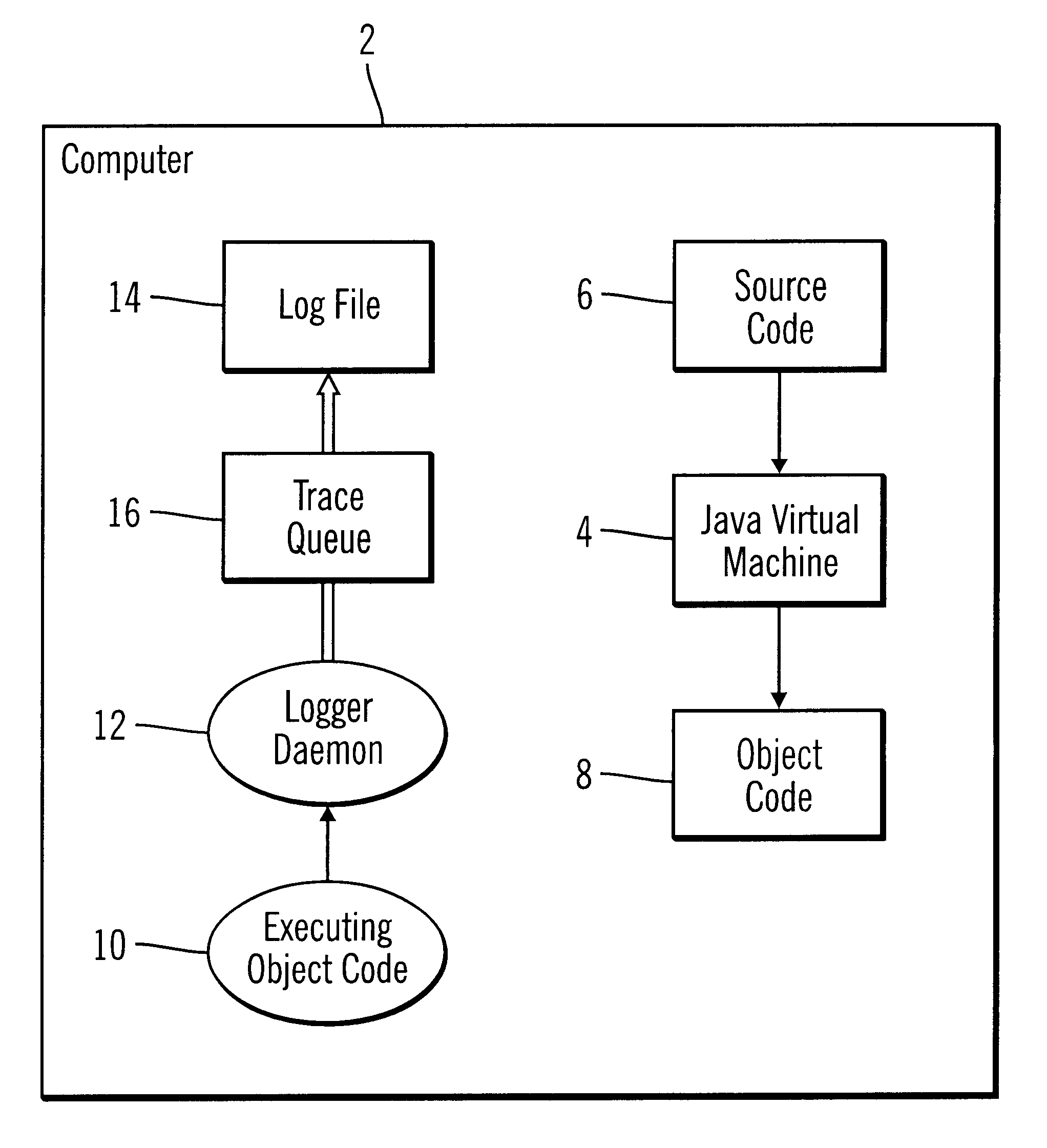
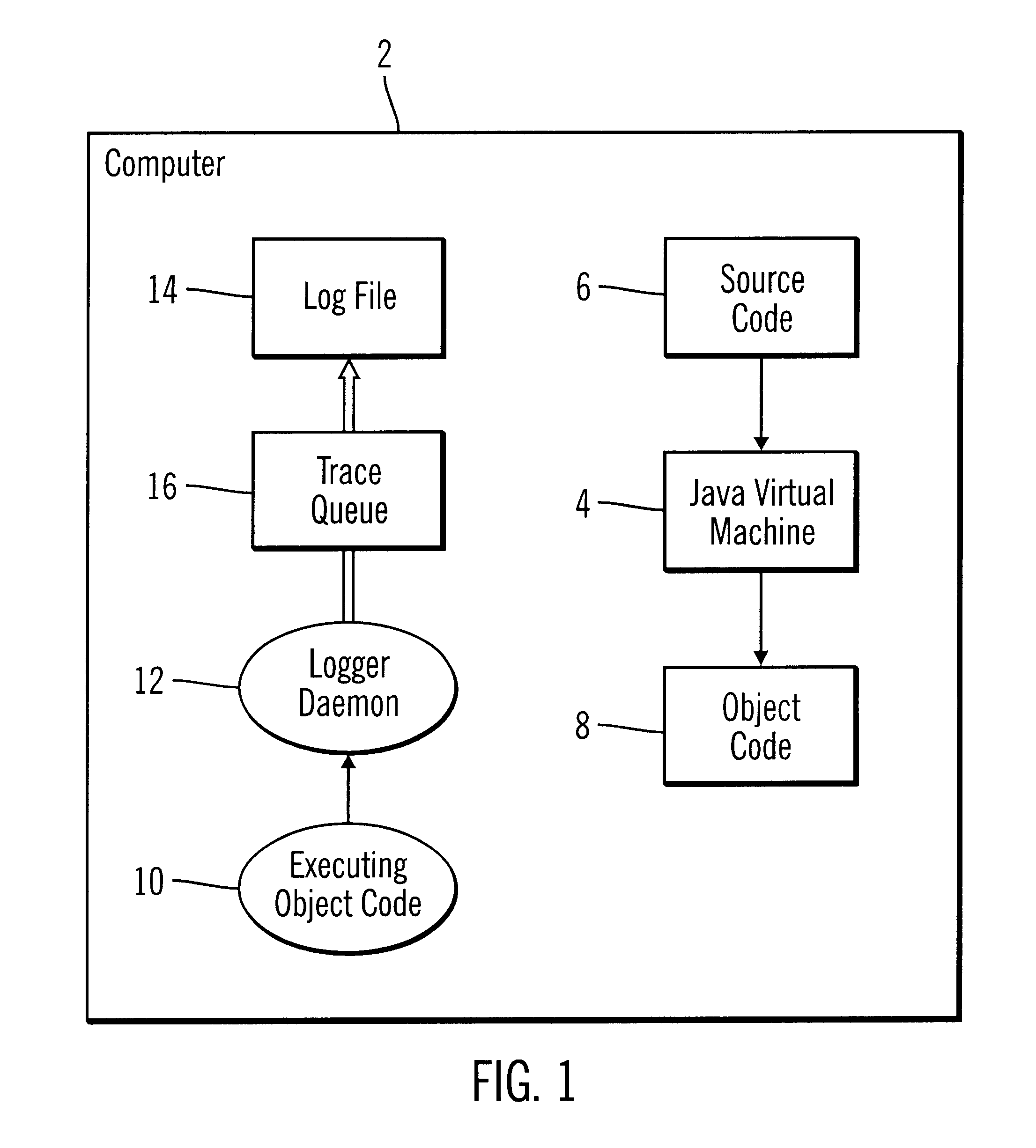
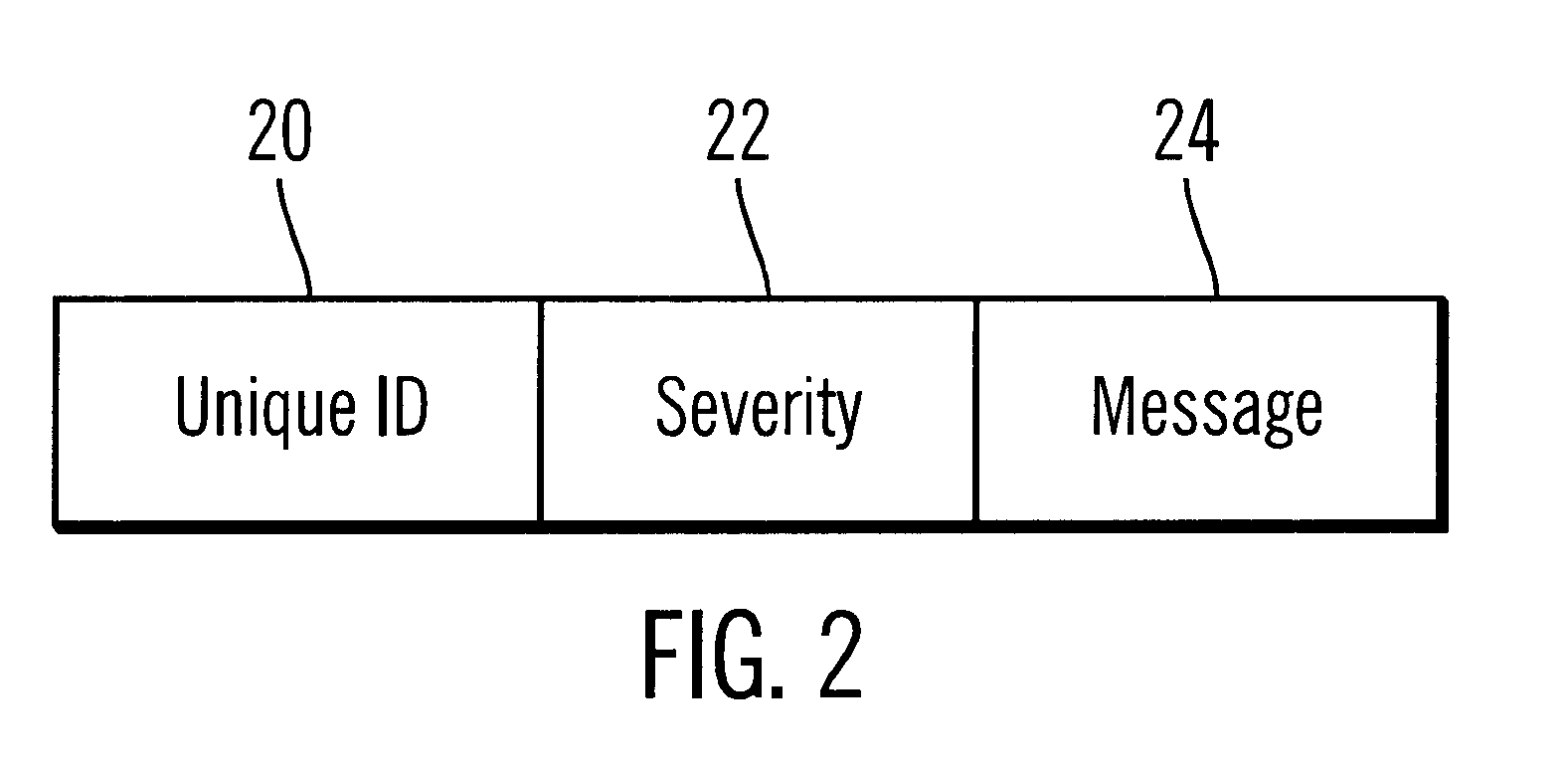
Method, system, and program for logging statements to monitor execution of a program
InactiveUS6539501B1Shorten the timeImprove space utilizationHardware monitoringSoftware testing/debuggingProgramming languageLogfile
Disclosed is a system, method, and program for generating trace statements to a log file. A log method in a program, such as a Java program, including an identifier parameter is processed. The program includes multiple instances of the log method to trace the execution of the program during debugging operations. A determination is made as to whether a variable indicates that log methods called with the identifier parameter should be processed. The class and method from which the log method was called is determined if the variable indicates that log methods called with the identifier parameter should be processed. Information on the identifier parameter and determined class and method are written to the log file.
Owner:IBM CORP
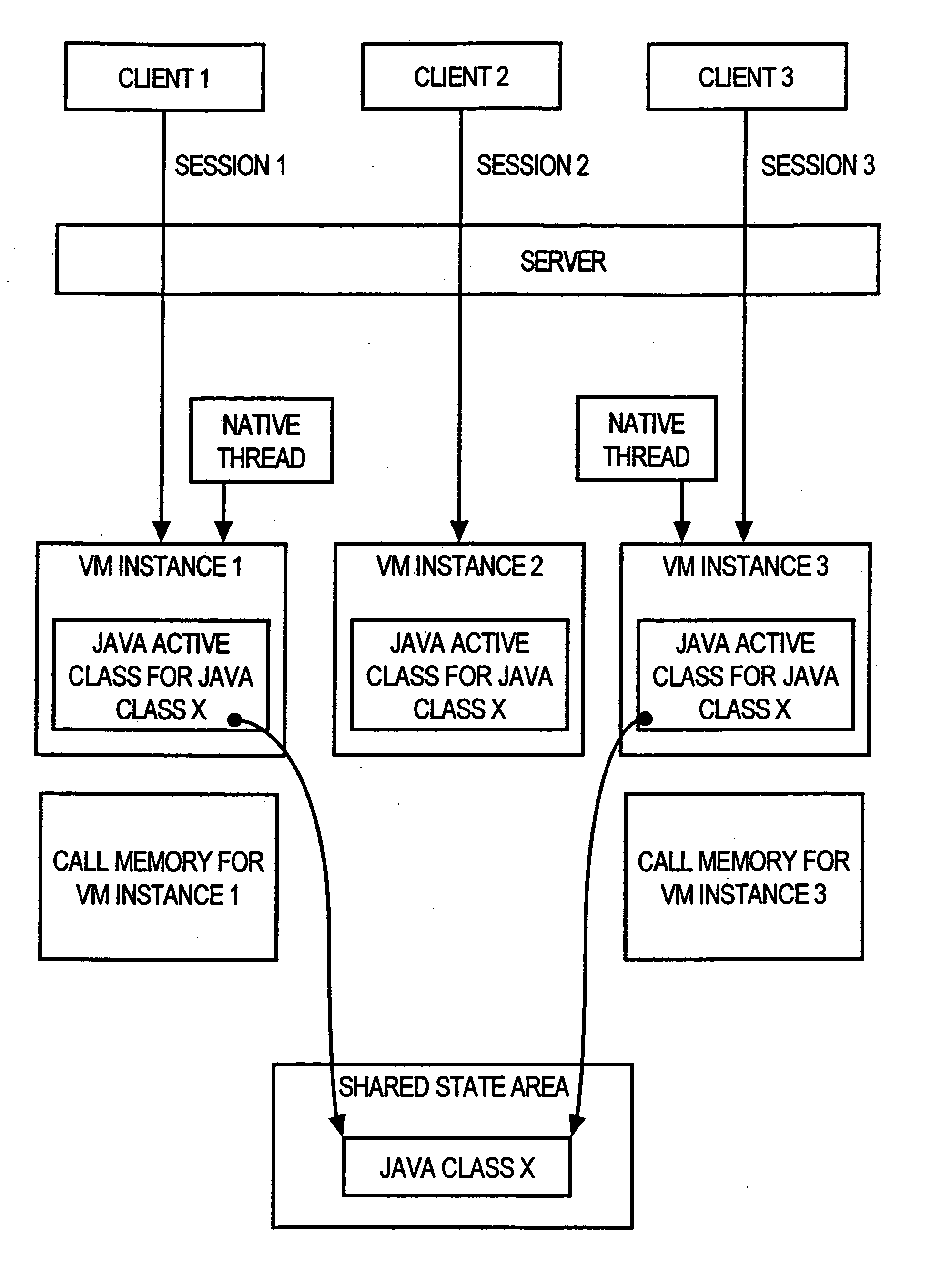
Using a virtual machine instance as the basic unit of user execution in a server environment
InactiveUS20050132368A1Data processing applicationsMultiple digital computer combinationsOperational systemExecution unit
Techniques are provided for instantiating separate Java virtual machines for each session established by a server. Because each session has its own virtual machine, the Java programs executed by the server for each user connected to the server are insulated from the Java programs executed by the server for all other users connected to the server. The separate VM instances can be created and run, for example, in separate units of execution that are managed by the operating system of the platform on which the server is executing. For example, the separate VM instances may be executed either as separate processes, or using separate system threads. Because the units of execution used to run the separate VM instances are provided by the operating system, the operating system is able to ensure that the appropriate degree of insulation exists between the VM instances.
Owner:ORACLE INT CORP
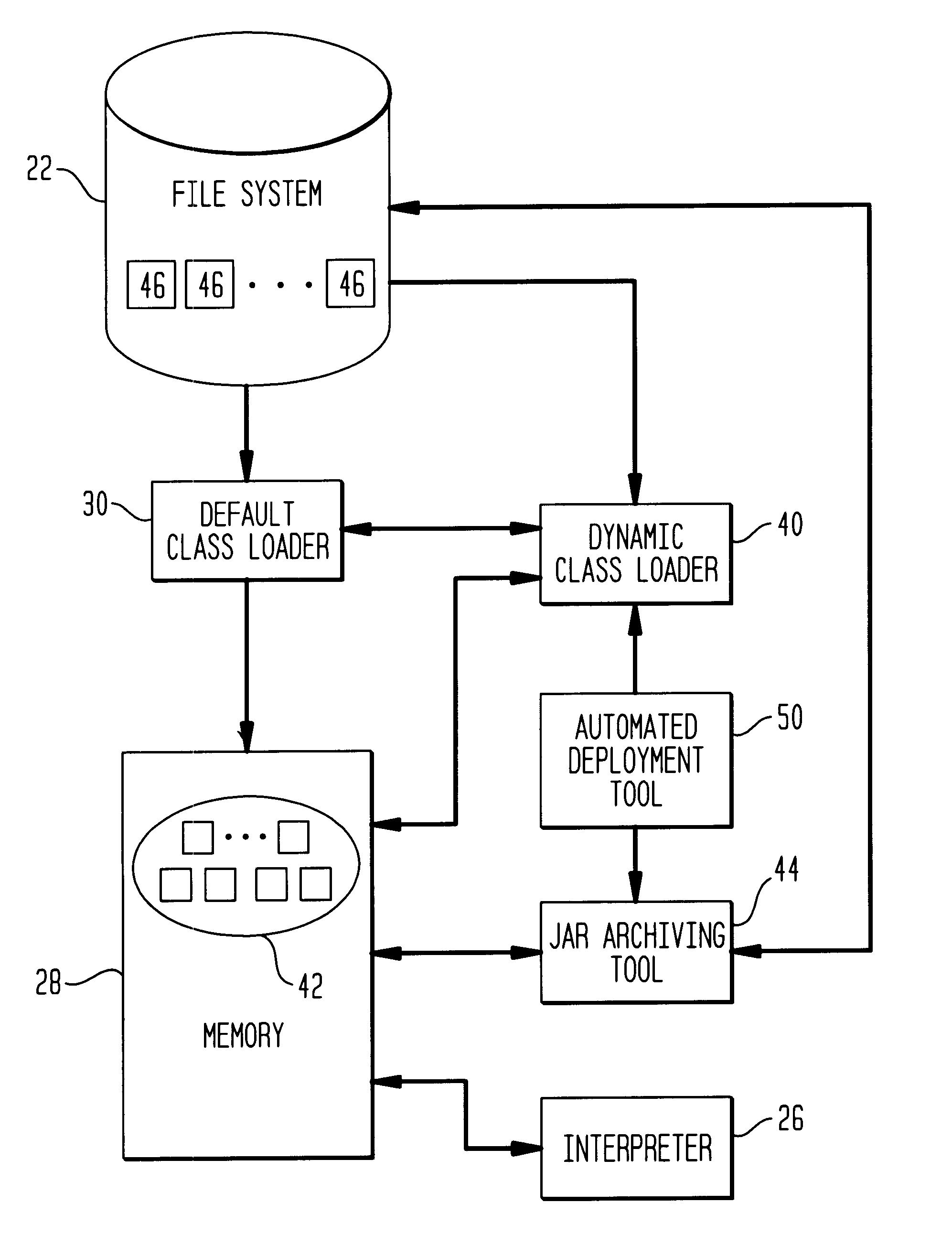
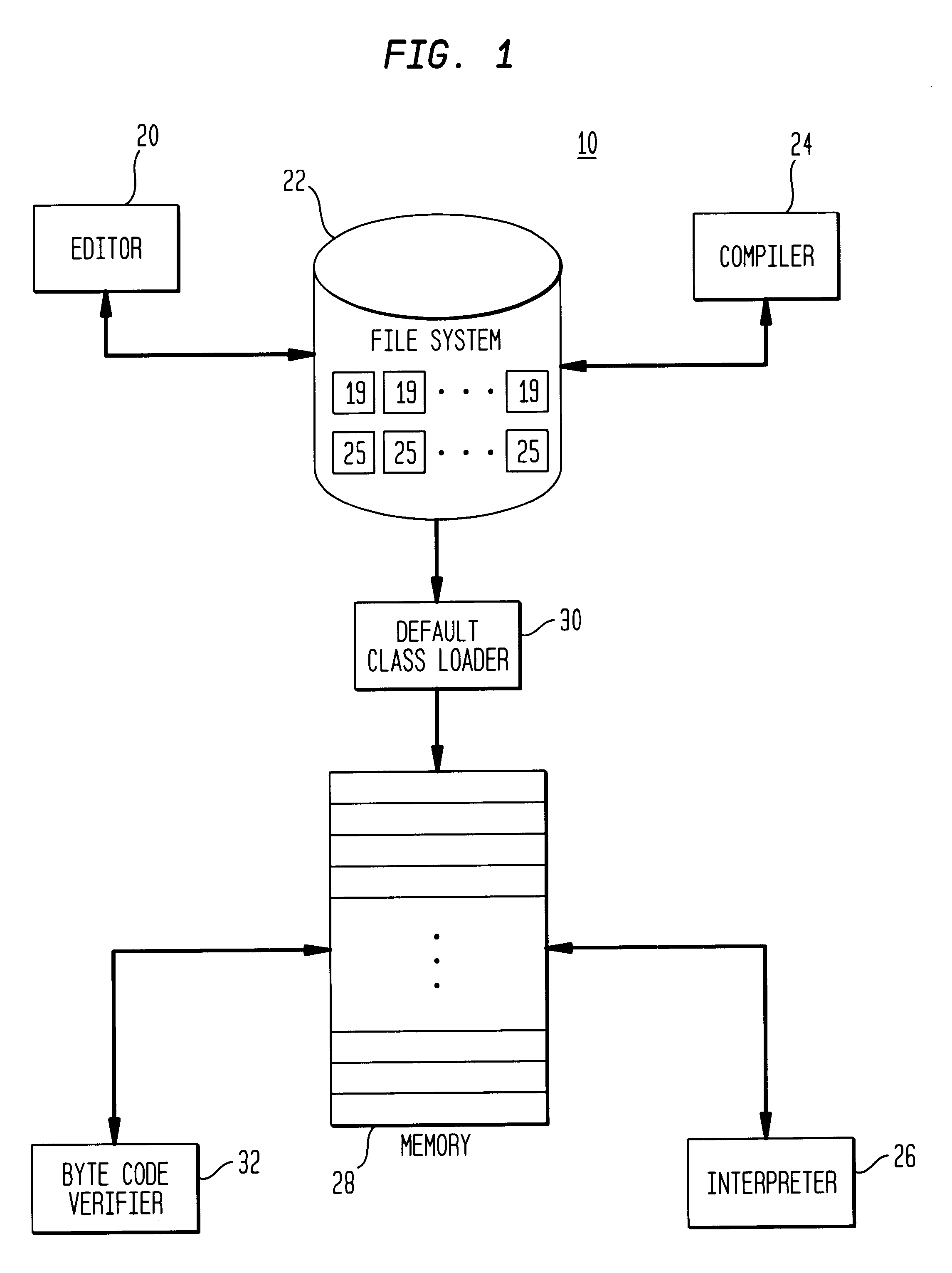
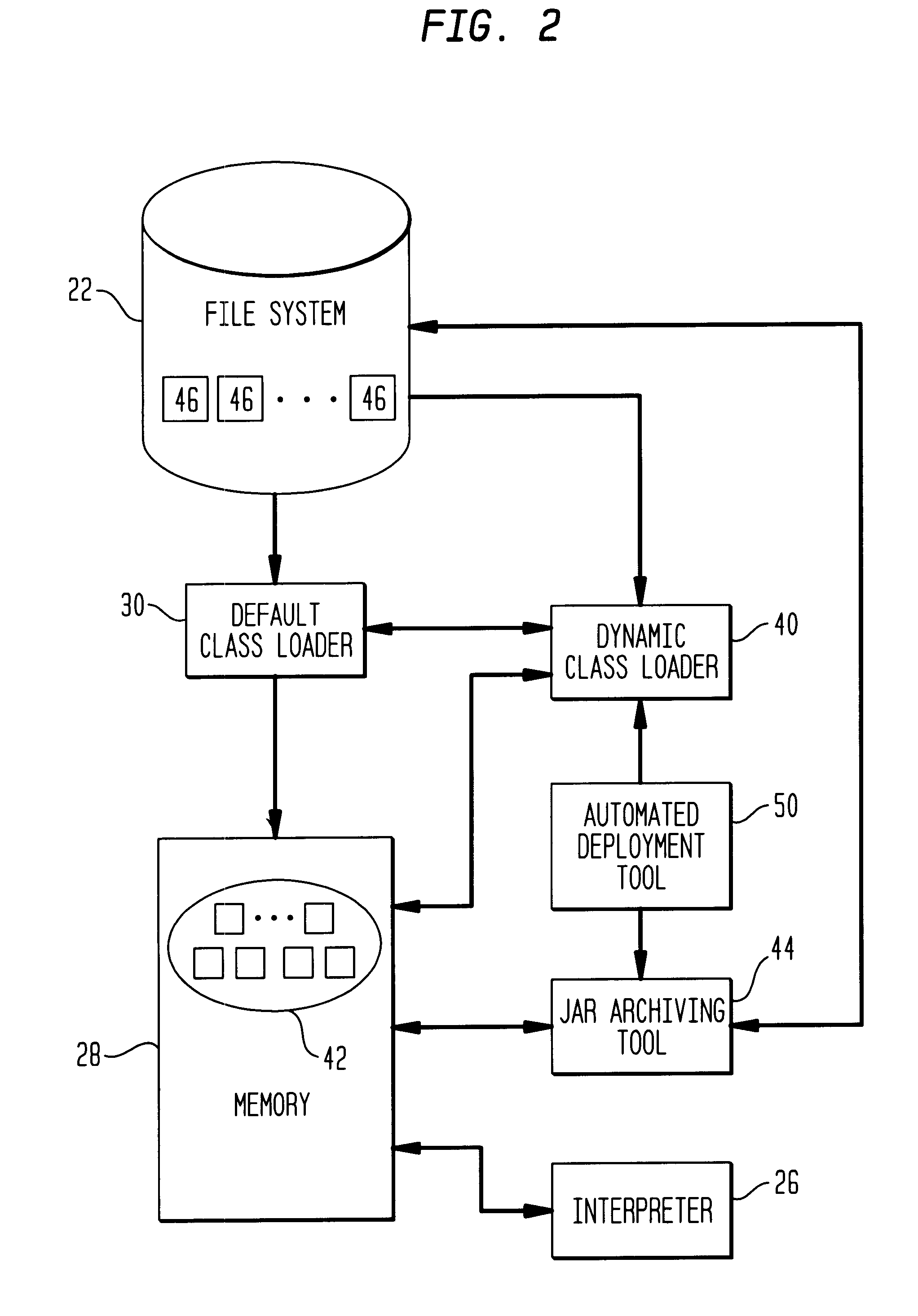
Class loader
This invention relates to the loading of classes in programming environments, and in particular, Java programming environments. This invention discloses a system and method that permits dynamic loading of classes during the execution of Java programs. This invention allows for classes to be loaded despite the fact that such classes may not reside in the current path or working directory within a Java programming environment. This invention also discloses a system and method for archiving files in an archive file that provides customized entry names for the archived files.
Owner:IBM CORP
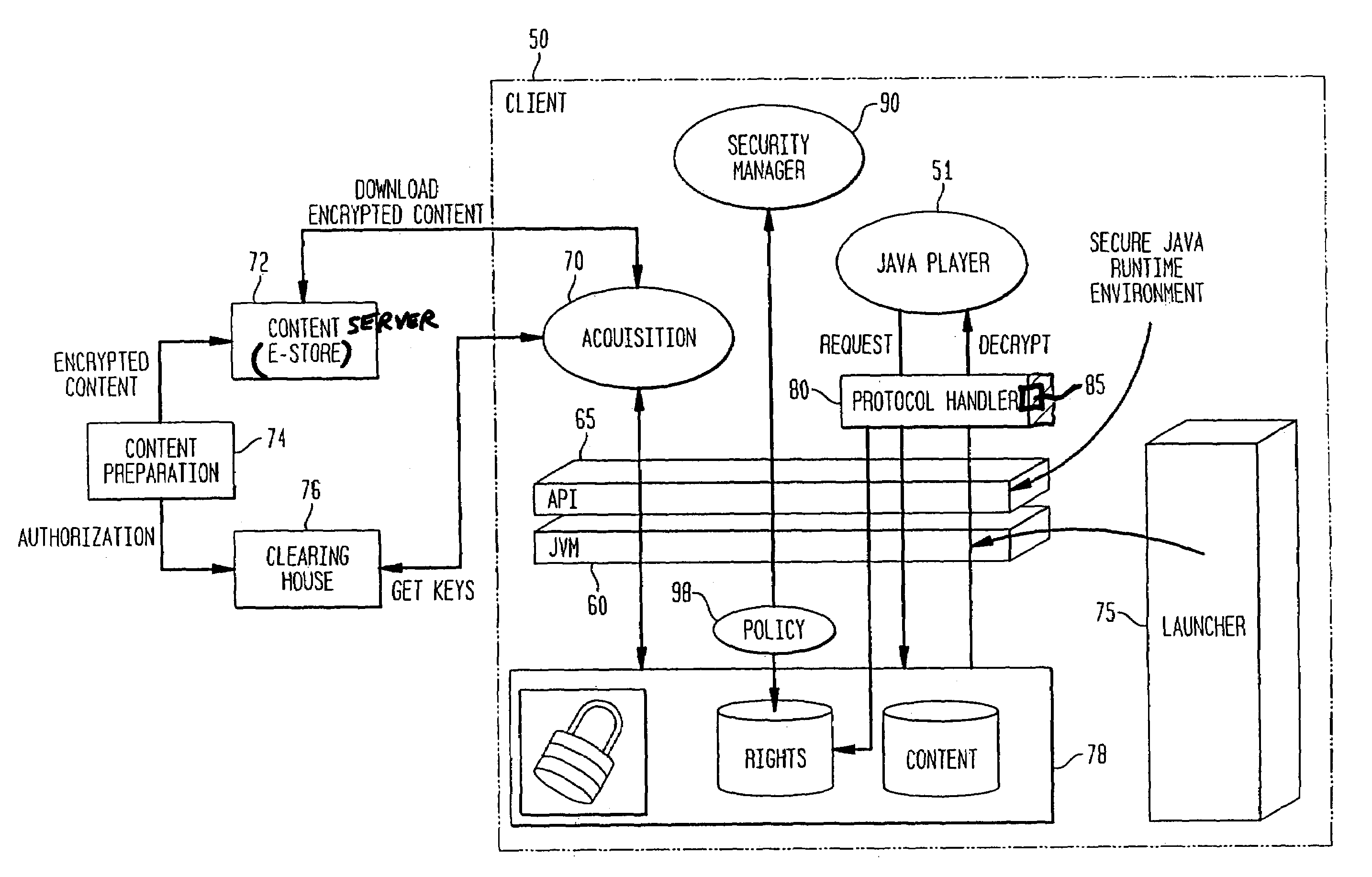
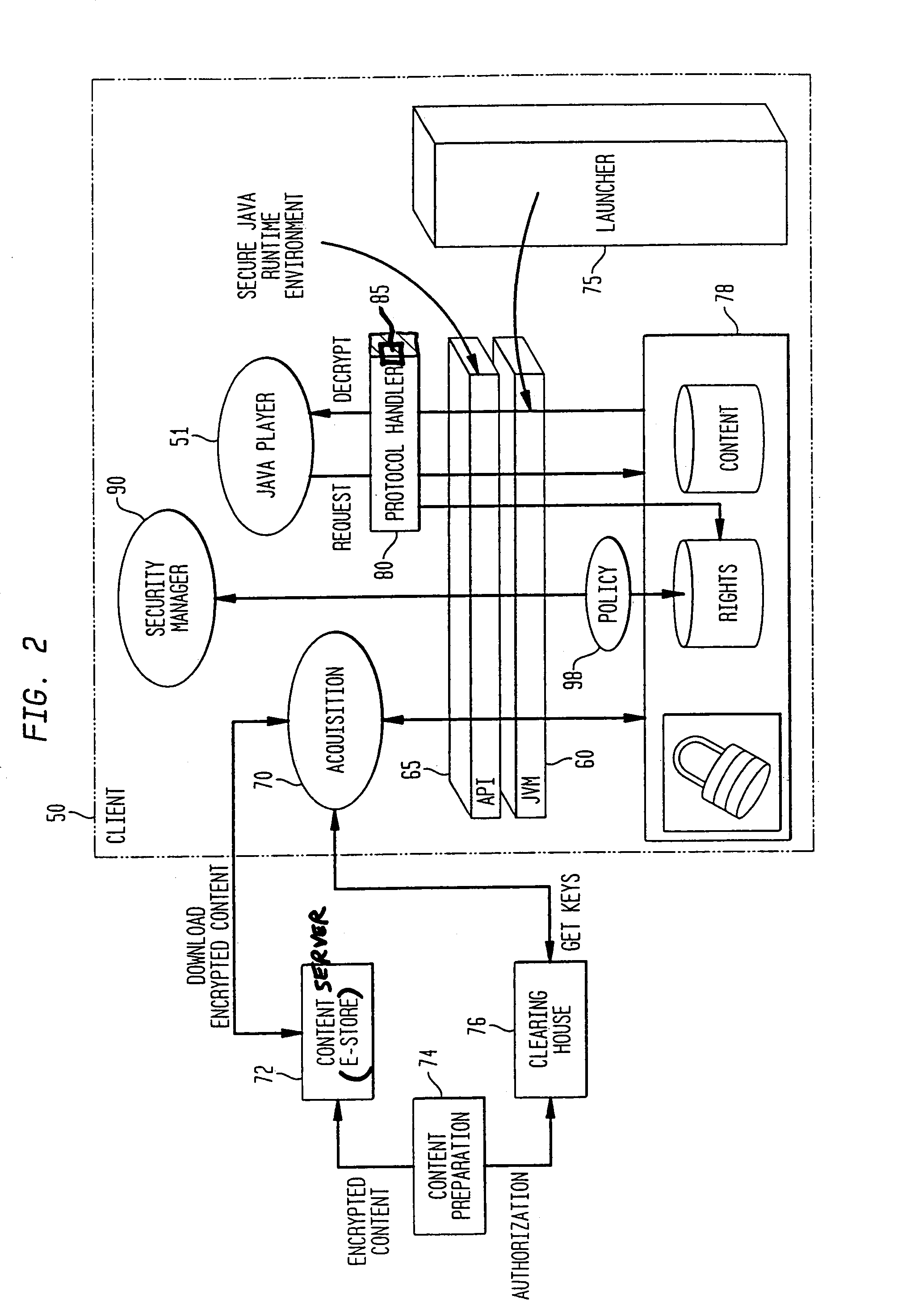
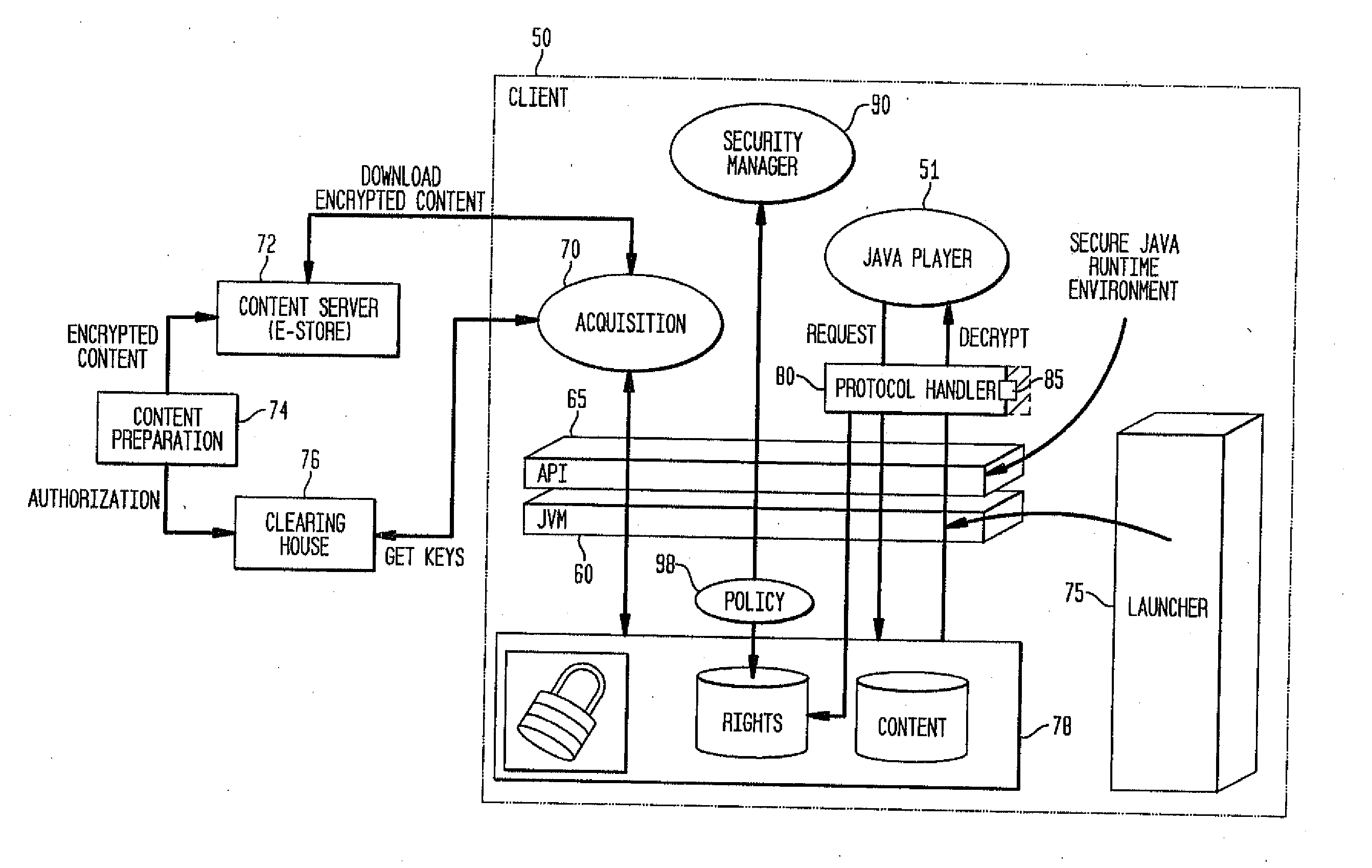
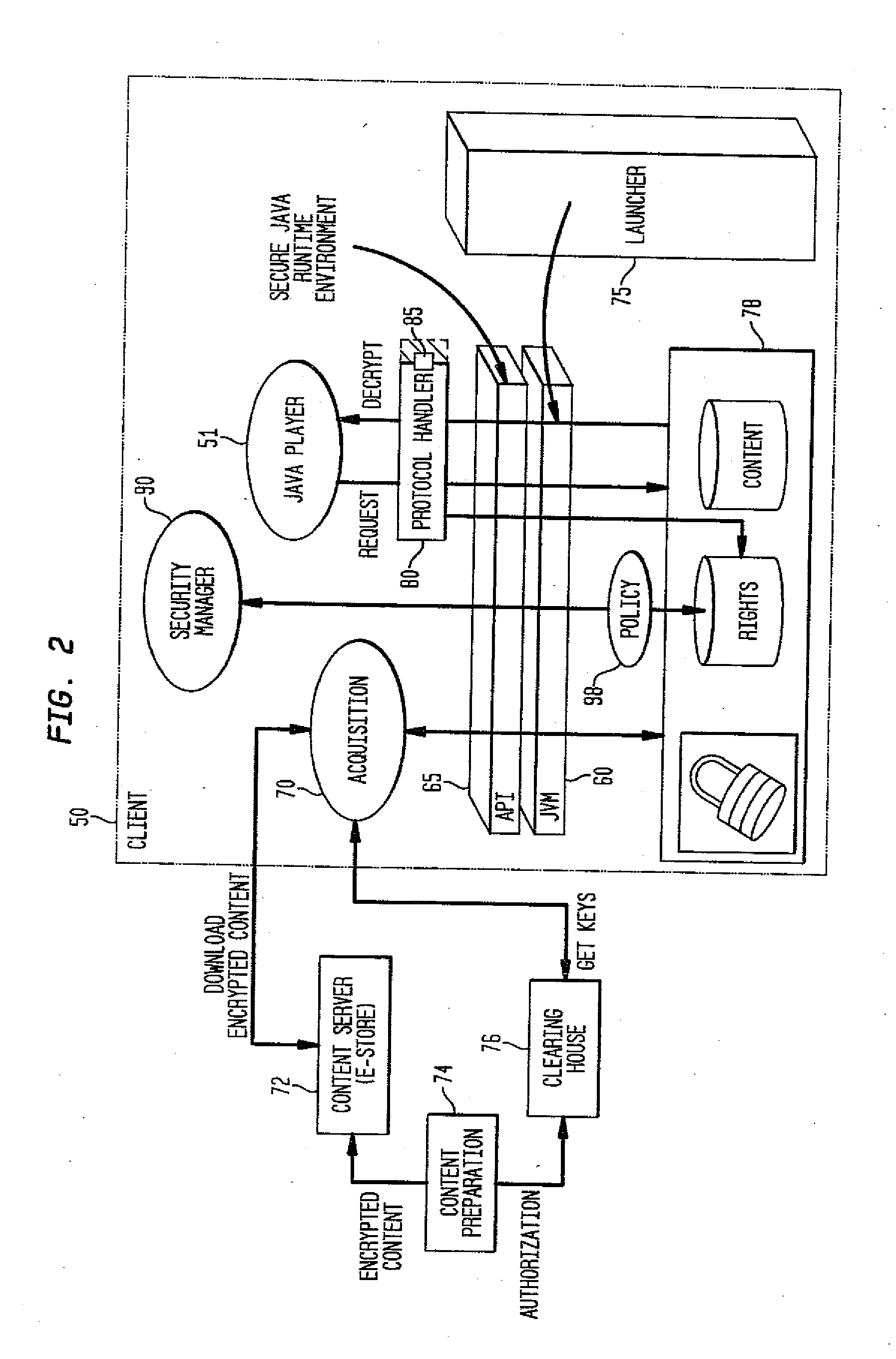
System and method for supporting digital rights management in an enhanced Java™ 2 runtime environment
InactiveUS7308717B2Provide protectionDigital data processing detailsAnalogue secracy/subscription systemsDigital rights management systemSoftware engineering
A digital rights management (DRM) system and methodology for a Java client implementing a Java Runtime Environment (JRE). The JRE comprises a Java Virtual Machine (JVM) and Java runtime libraries components and is capable of executing a player application for presenting content that can be presented through a Java program (e.g., a Java application, applet, servlet, bean, etc.) and downloaded from a content server to the client. The DRM system includes an acquisition component for receiving downloaded protected contents; and a dynamic rights management layer located between the JRE and player application for receiving requests to view or play downloaded protected contents from the player, and, in response to each request, determining the rights associated with protected content and enabling viewing or playing of the protected contents via the player application if permitted according to the rights. By providing a Ad DRM-enabled Java runtime, which does not affect the way non-DRM-related programs work, DRM content providers will not require the installation of customized players. By securing the runtime, every Java™ player automatically and transparently becomes a DRM-enabled player.
Owner:IBM CORP
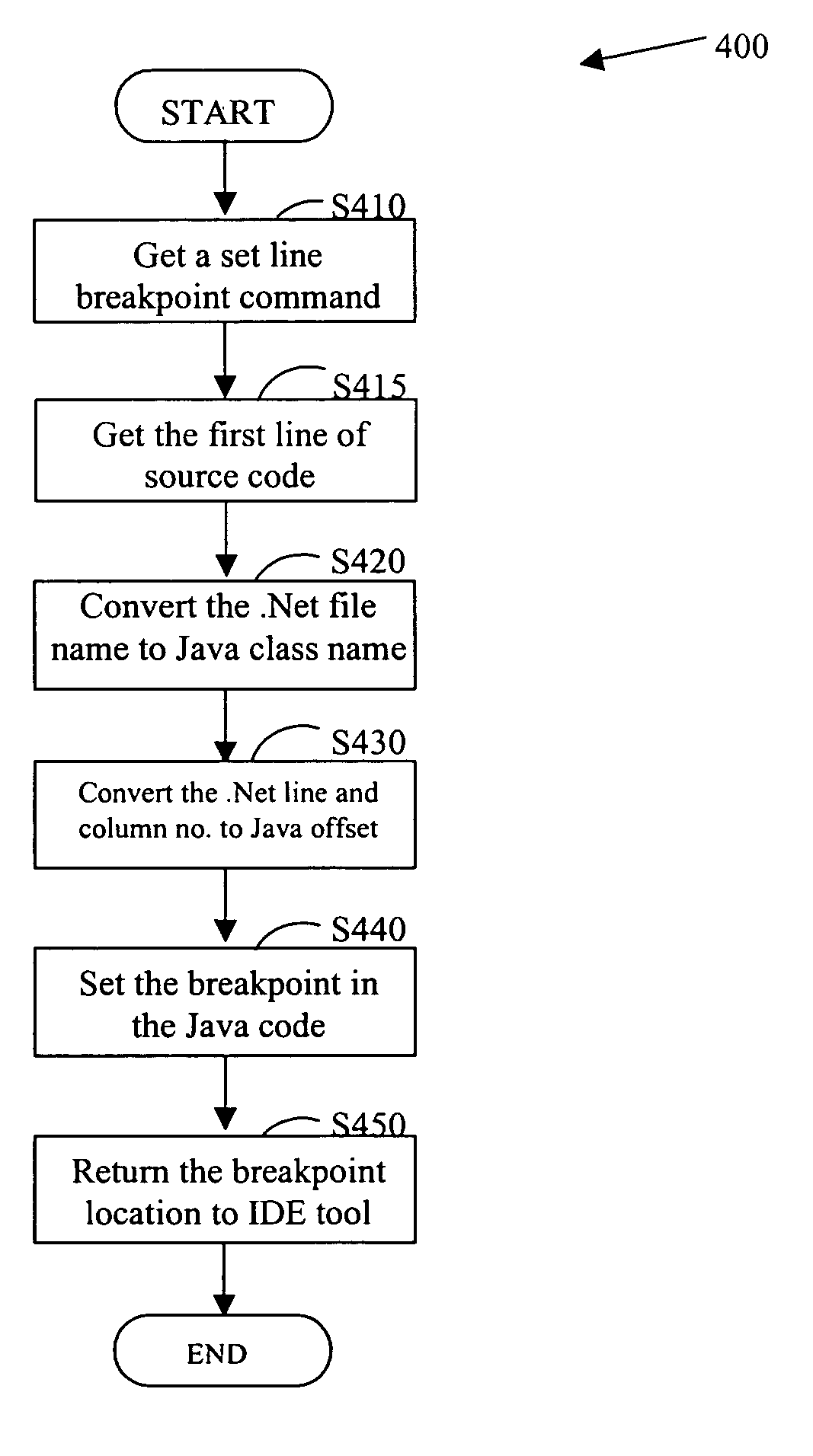
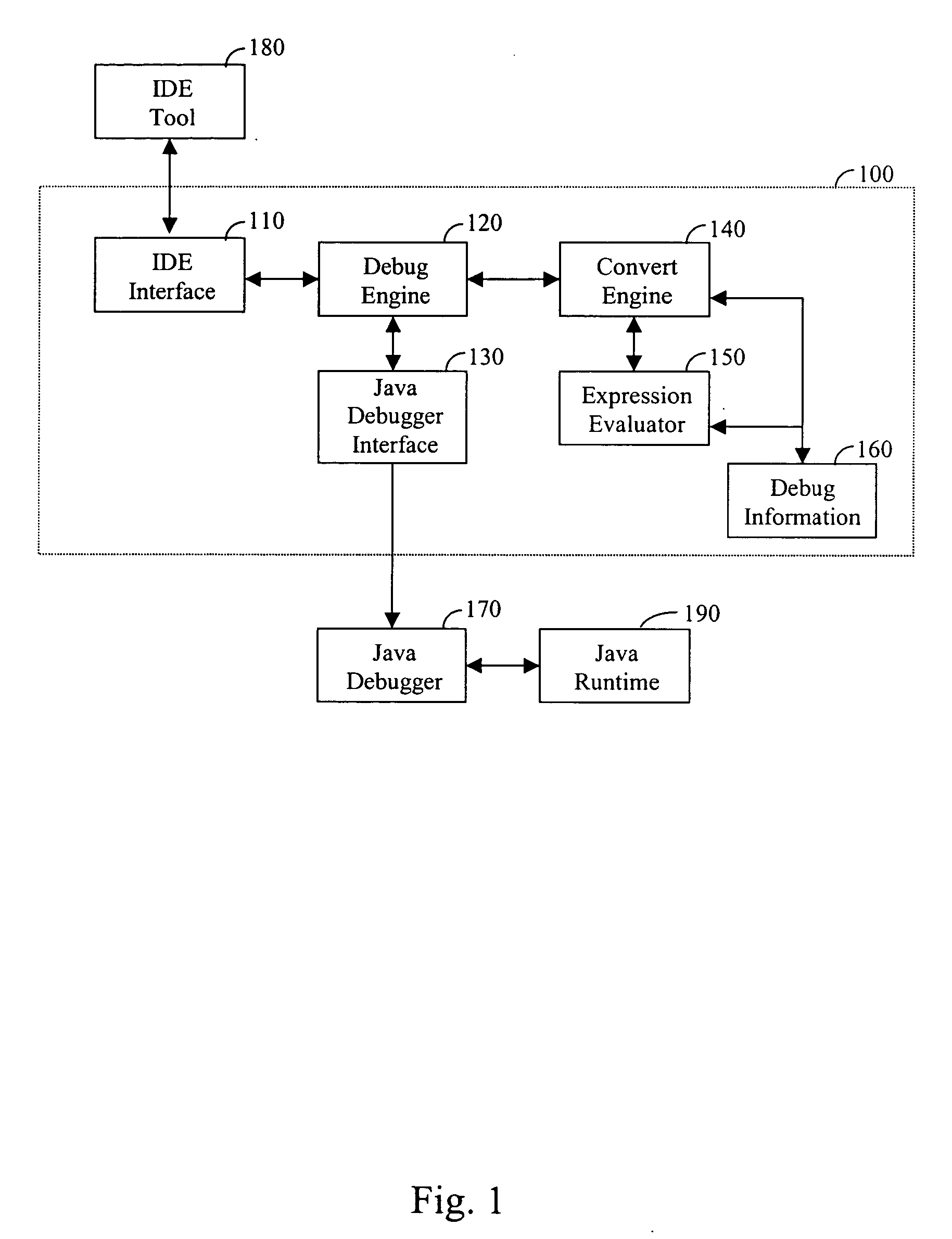
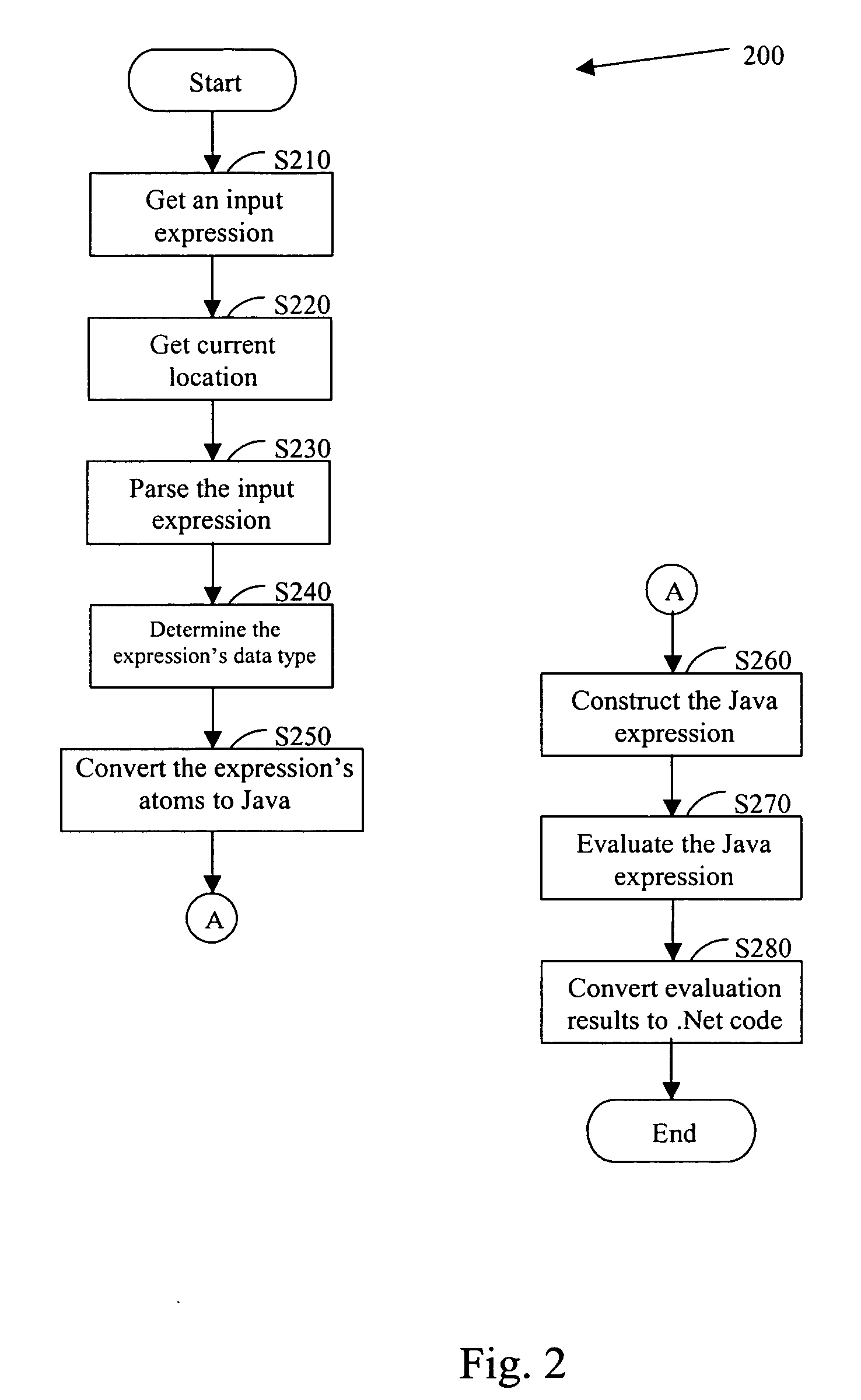
Debugger and method for debugging computer programs across multiple programming languages
InactiveUS20060064677A1Error detection/correctionSpecific program execution arrangementsCall stackSoftware development
A debugger and method for debugging computer programs across multiple programming languages are provided. The debugging is performed at a source level of a computer program written in any programming language supported by the .Net® platform, while the program is executed over a Java runtime environment. The debugger disclosed provides a call stack display and an expression evaluator. Furthermore, the debugger allows software developers to step through Java source code and follow the execution flow of the Java program. One exemplary embodiment of the disclosed debugger is an extension of the Microsoft® Visual Studio .Net®.
Owner:HARMON IE R&D
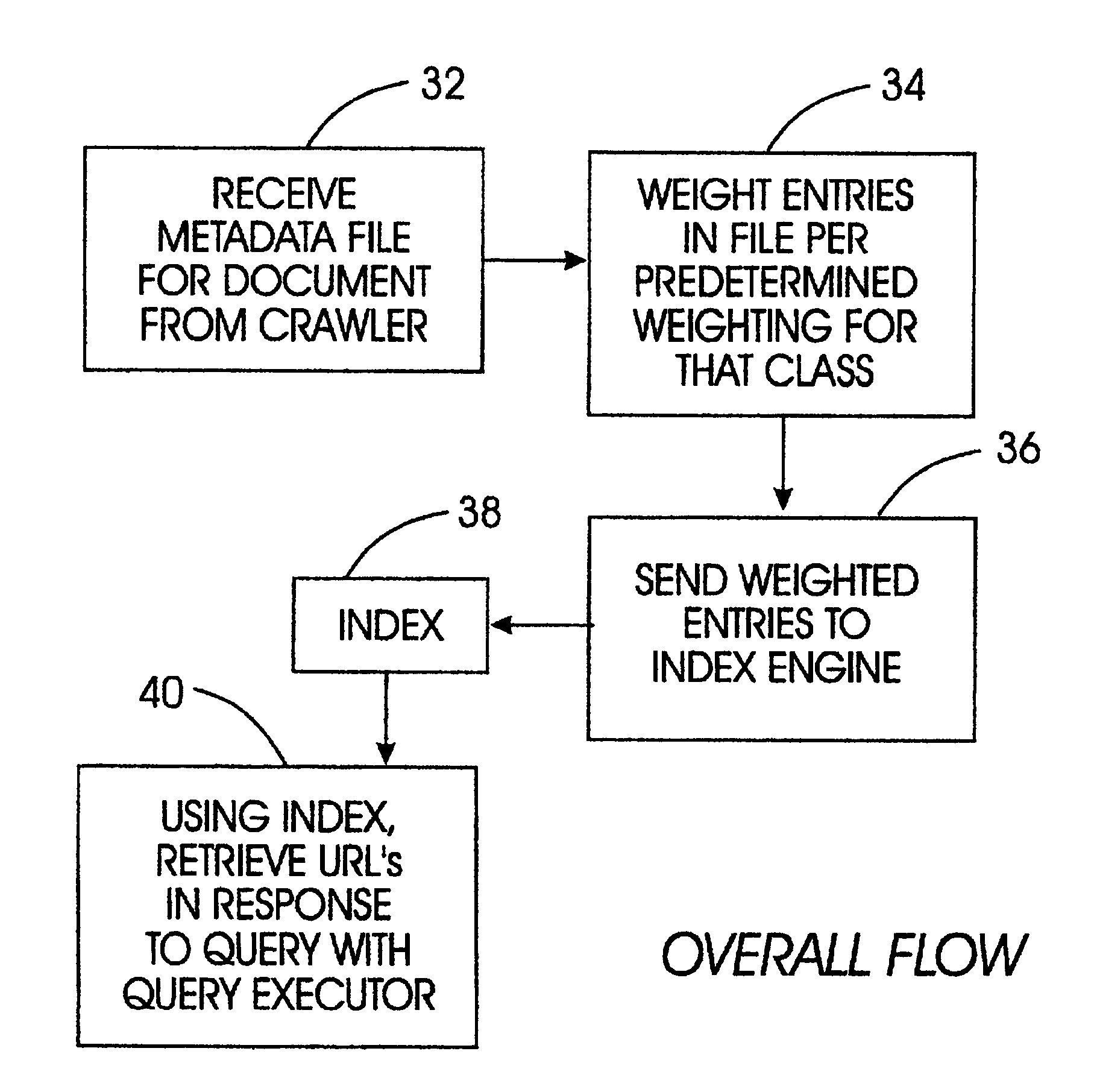
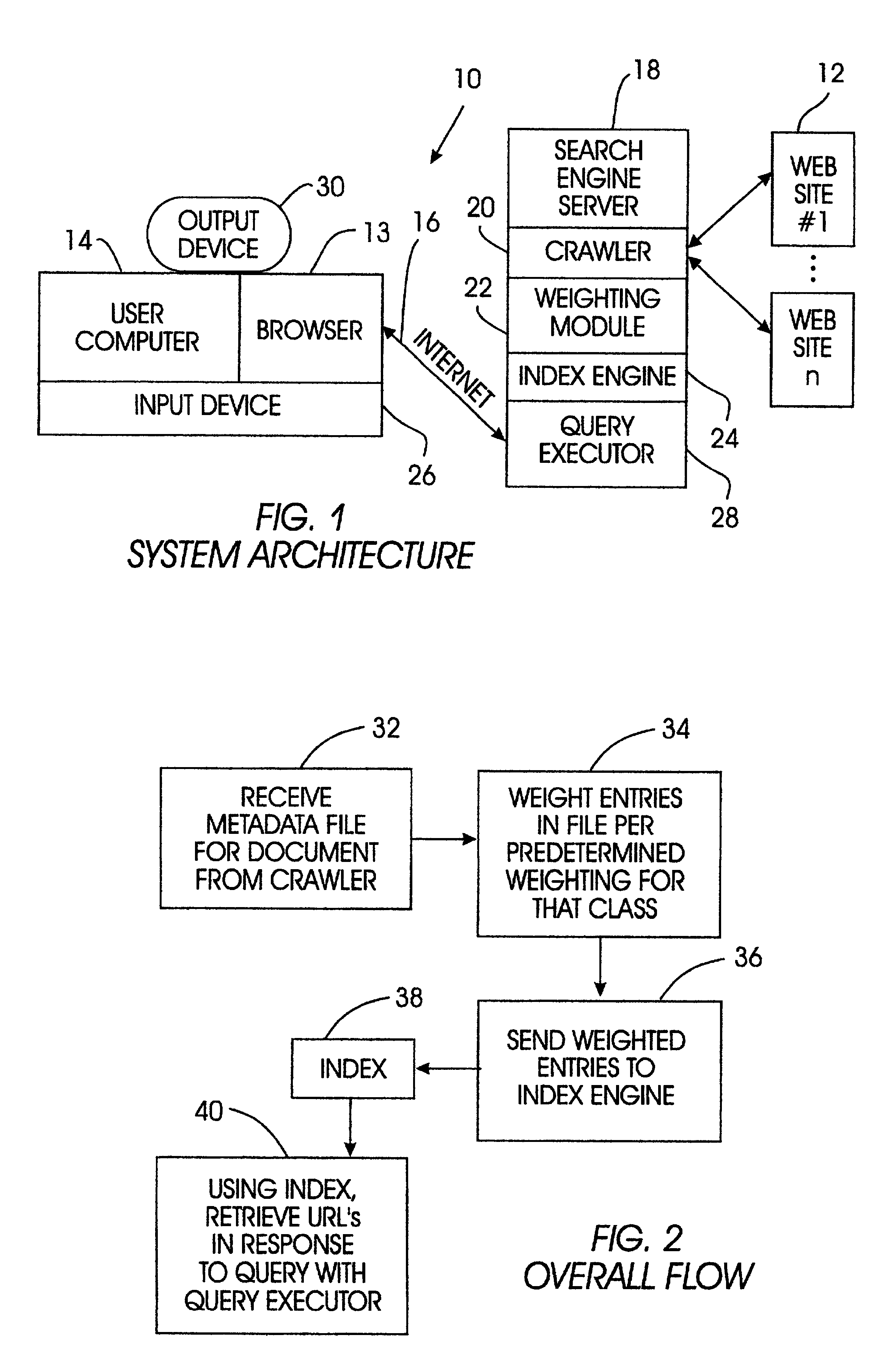
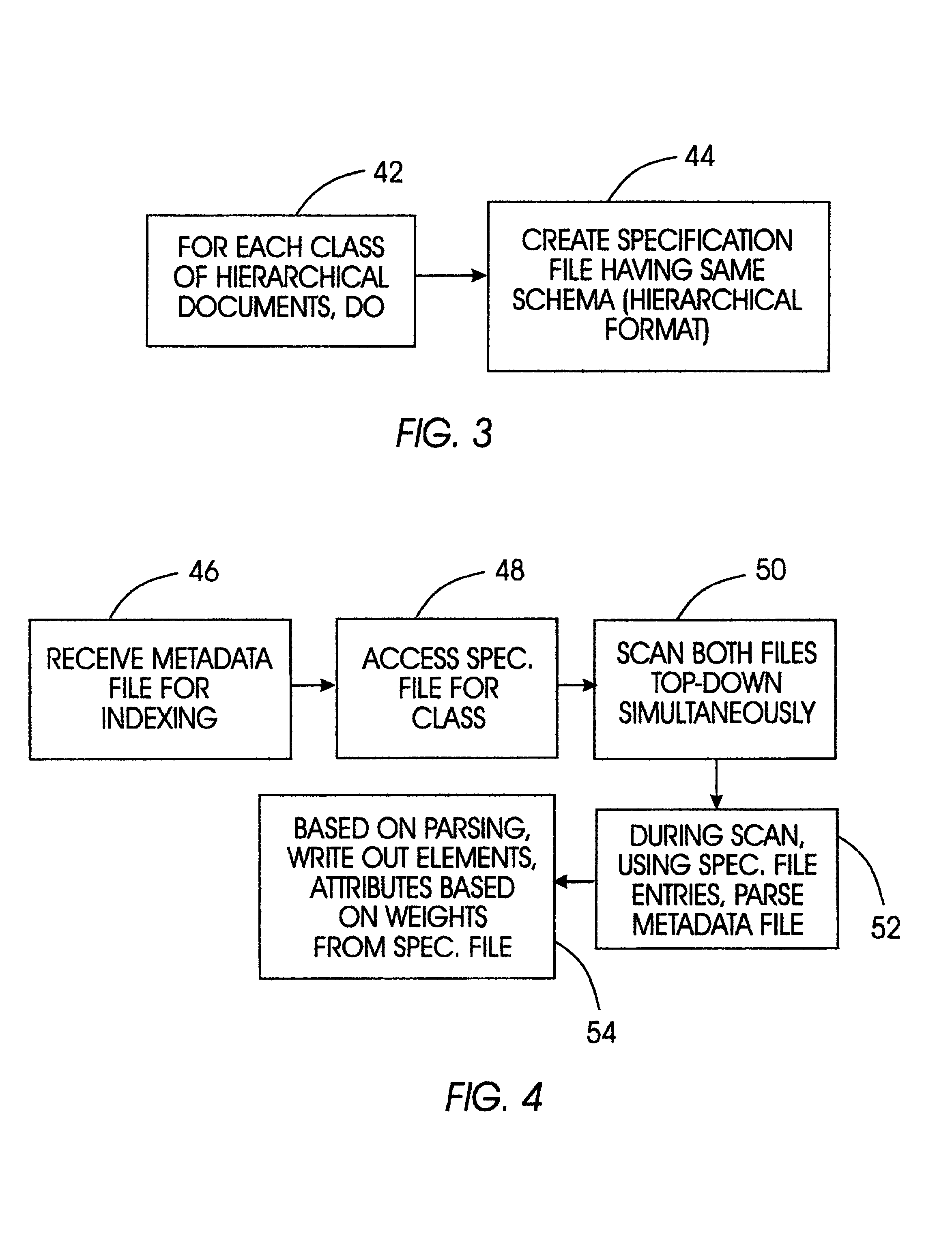
System for weighted indexing of hierarchical documents
Metadata files representing Web document content are parsed in accordance with a specification file, with a specification file being generated for each class of documents, e.g., HTML pages, newsgroup articles, and JAVA programs. Each specification file has the same format, i.e., schema, as a metadata file for the associated document class. Within each specification file, each element in the hierarchy is associated with a weight. When a metadata file is received, both the metadata file and the specification file are walked through top-down to parse data out of the metadata file into an index file in accordance with the weights in the specification file, e.g., a data element having a weight of zero is not written to the index file, an element with a weight of two is written out twice to the index file, and so on. Importantly, the tags in the metadata file are not written out to the index file. The index file is then used by an index engine to build an index, which can then be accessed by a query executor to respond to a user query for Web documents without having to search through an index containing tags and other data that is irrelevant to the search.
Owner:IBM CORP
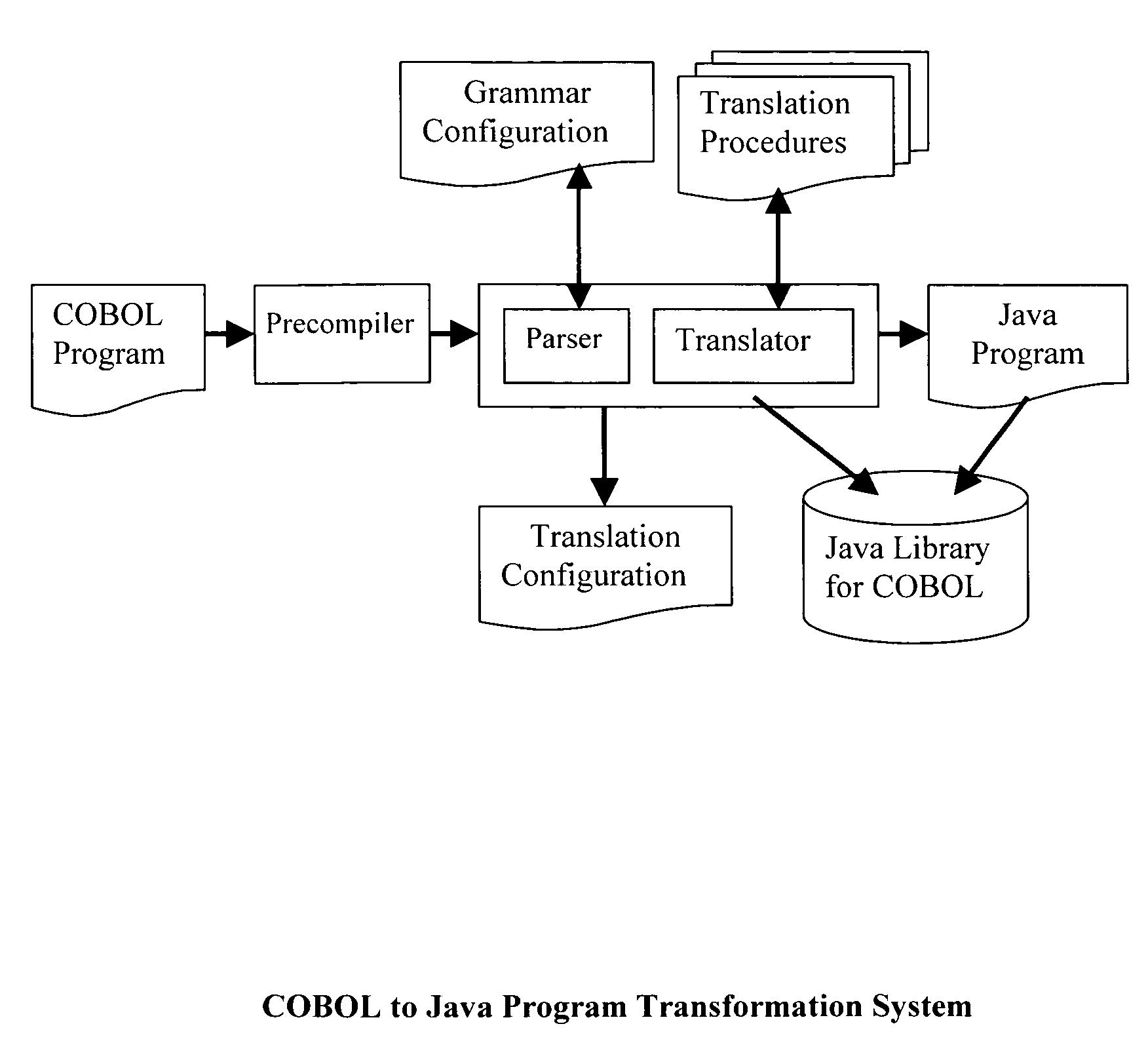
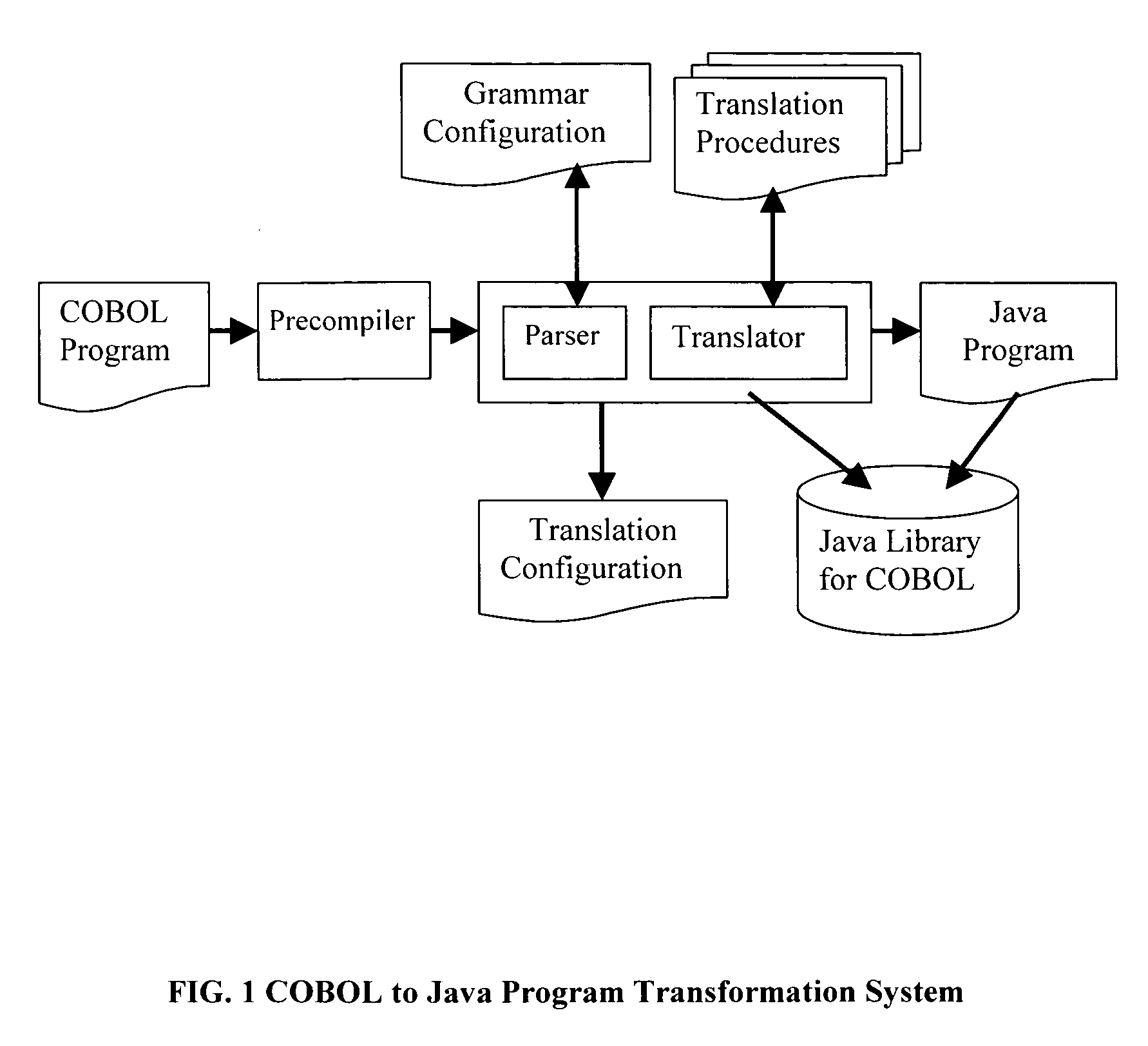
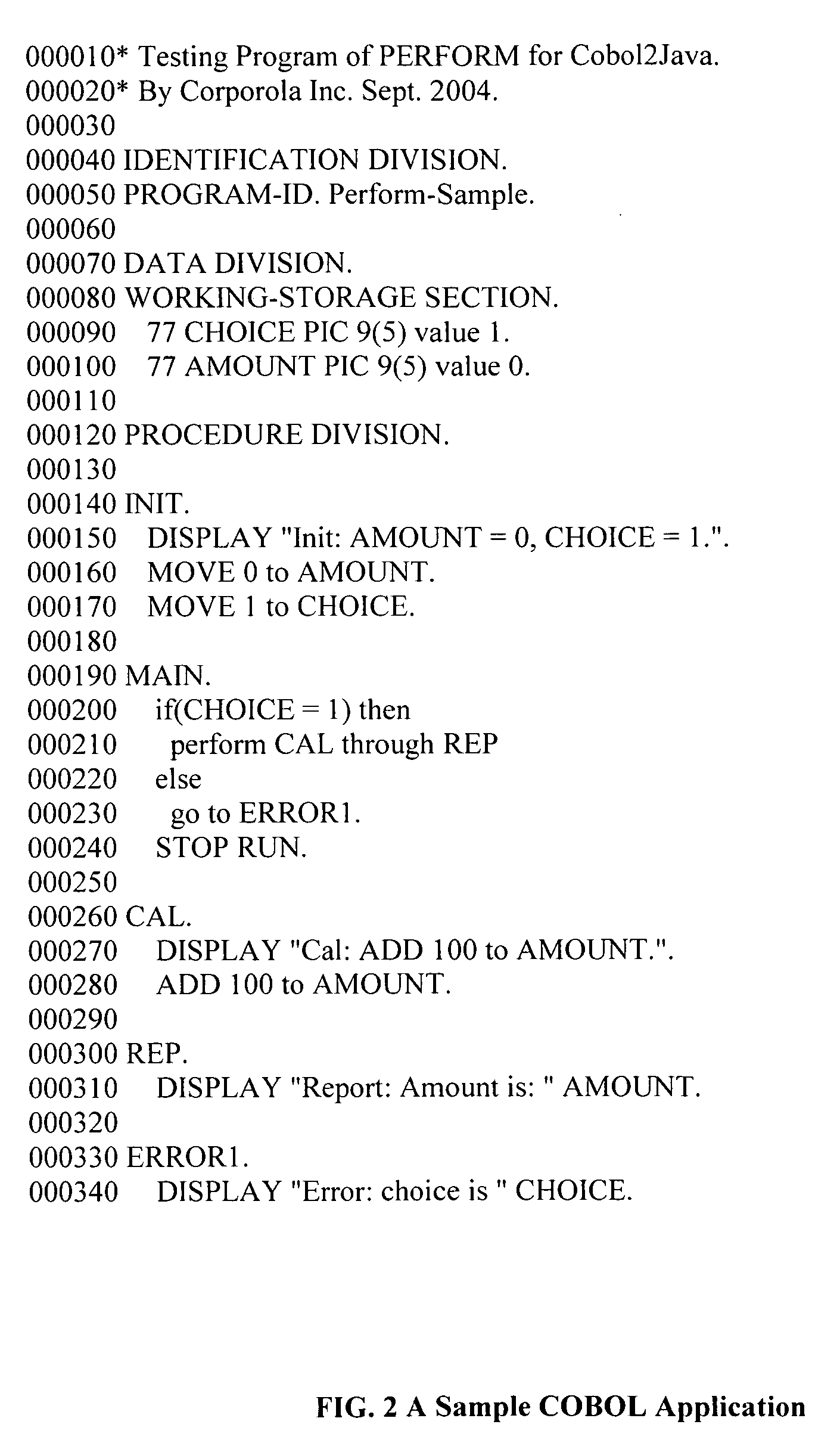
Method for program transformation and apparatus for COBOL to Java program transformation
InactiveUS20060031820A1Maintain maintainabilityImprove maintainabilityProgram controlMemory systemsTime complexityGoto
The present invention relates to a method for program transformation and an apparatus for COBOL to Java program transformation. The method consists of: (1) a new approach for statement-to-statement program transformation, facilitated by a predefined target language library, which keeps original comments, program control flow, functionality, and time complexity; (2) a new approach for goto statement elimination, which uses existing exception handling mechanism in target language and its implementation is hidden in a super class in a library; (3) a new extended BNF to distinguish different occurrences of the same term in a BNF production; (4) a new approach for embedded statement as a special marker statement and a comment, (5) in the description of the above, a program transformation specification language is defined to describe relationship between comments in two languages. (6) an apparatus, as the preferred embodiment of the method, is a COBOL to Java program transformation system Cobol2Java; a sample COBOL application and its Cobol2Java translation are given.
Owner:LI AIZHONG
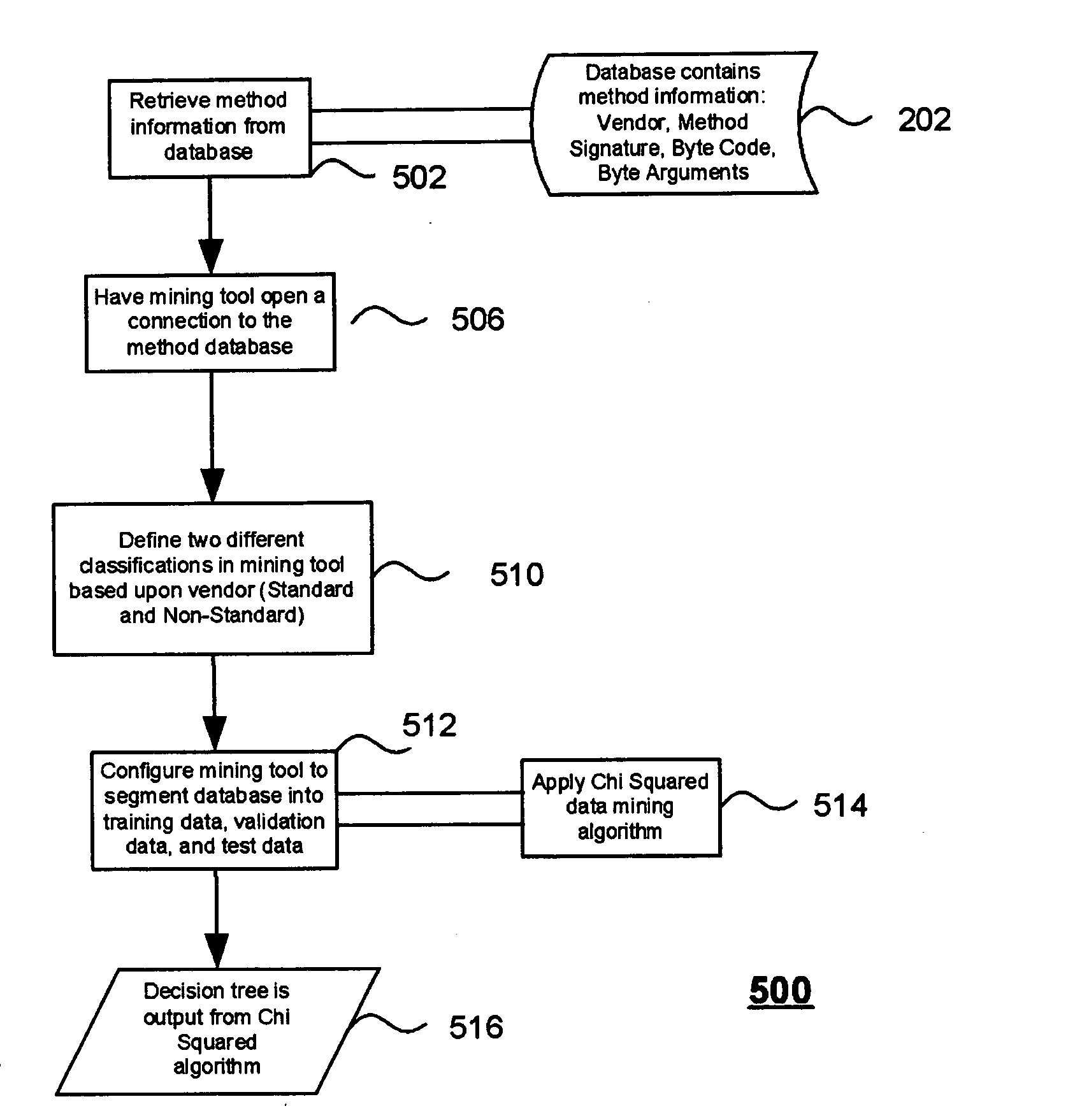
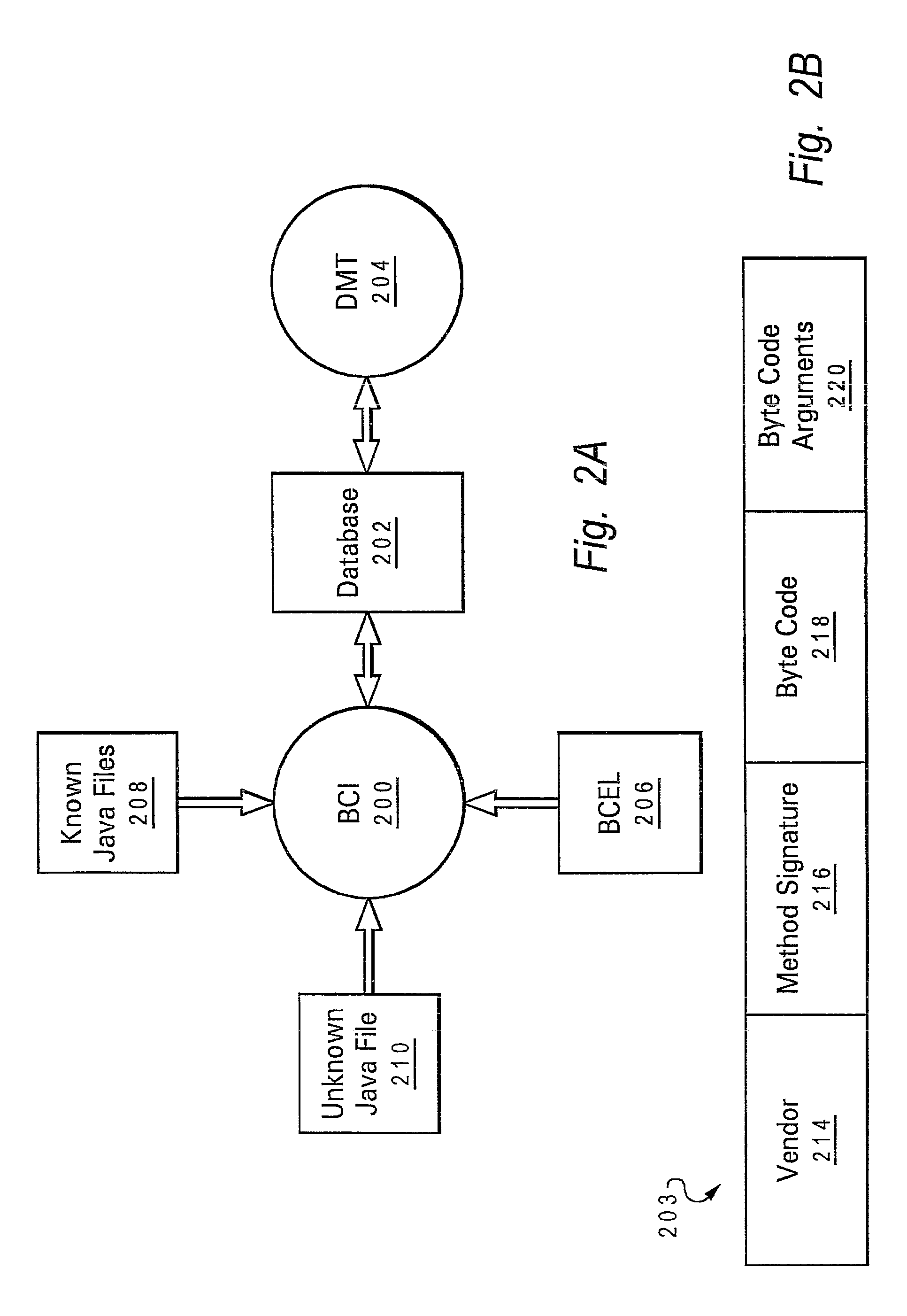
Method, system and program product for optimizing java application performance through data mining
InactiveUS20060005177A1Program documentationSpecific program execution arrangementsGood practiceJava classes
Metadata describing common Java classes is extracted and utilized to optimize a Java program's performance based on the code requirements of the application. Data mining techniques extract metadata and other information about different sets of JVM byte code written by multiple vendors to determine the design choices and optimizations made by each vendor in implementing their JVM. Then, byte code in a Java application being programmed is analyzed in comparison to each vendor's JVM metadata and information. Based upon the application's requirements (for example footprint, performance, etc.), recommendations are generated that yield a newly compiled rt.jar that combines the best practices of each vendor together or recommends a particular vendor's standard JVM that is best suited for the application.
Owner:IBM CORP
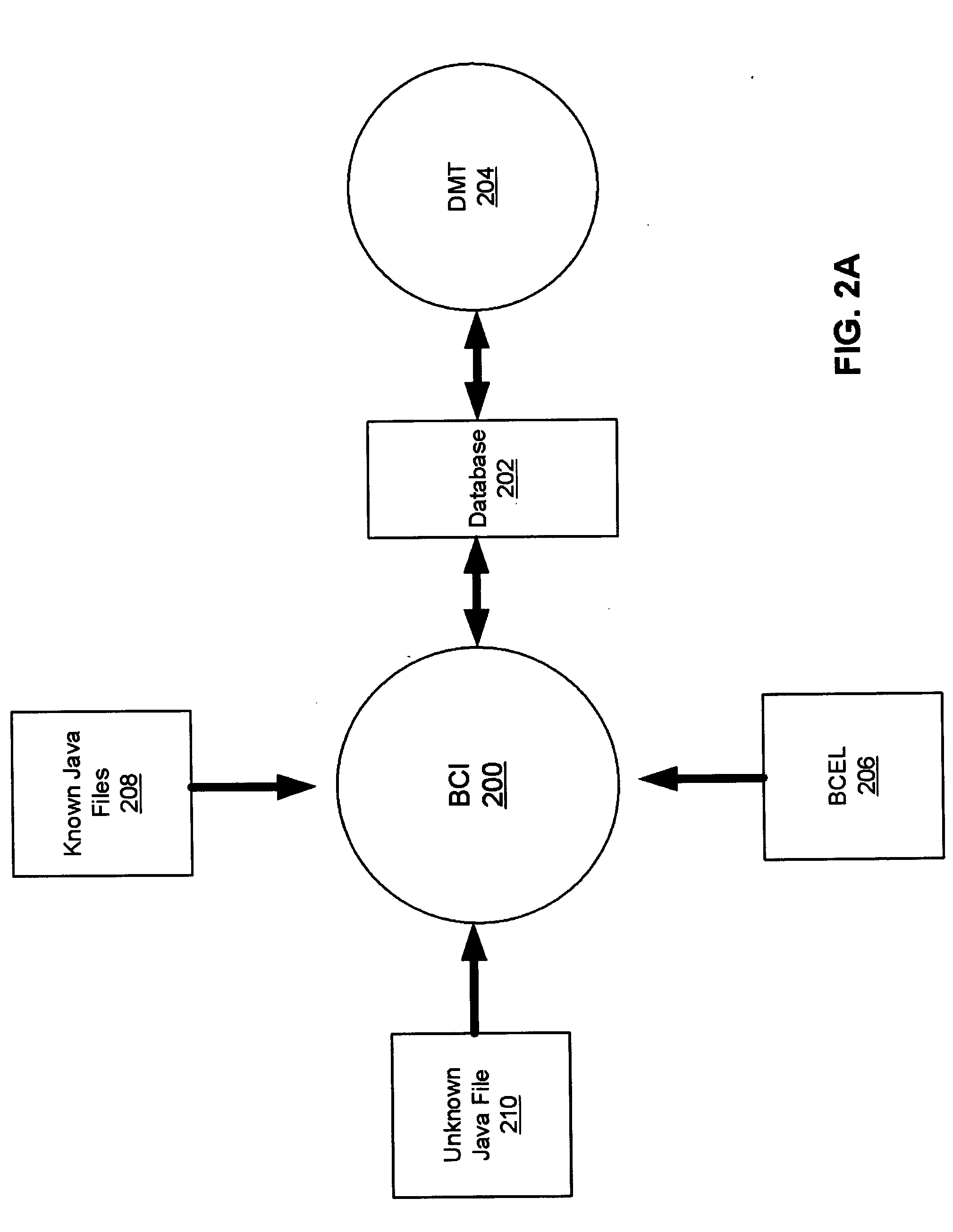
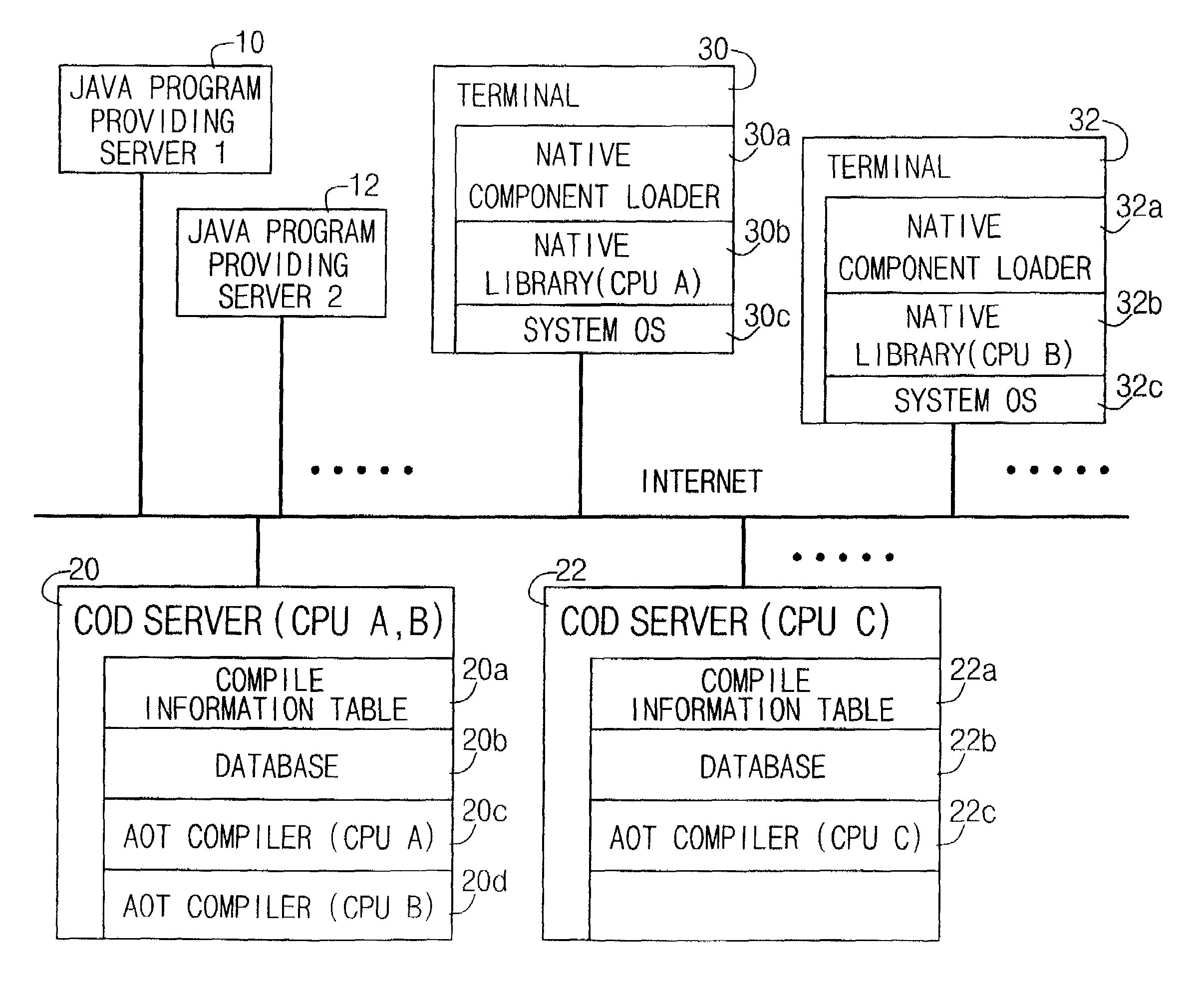
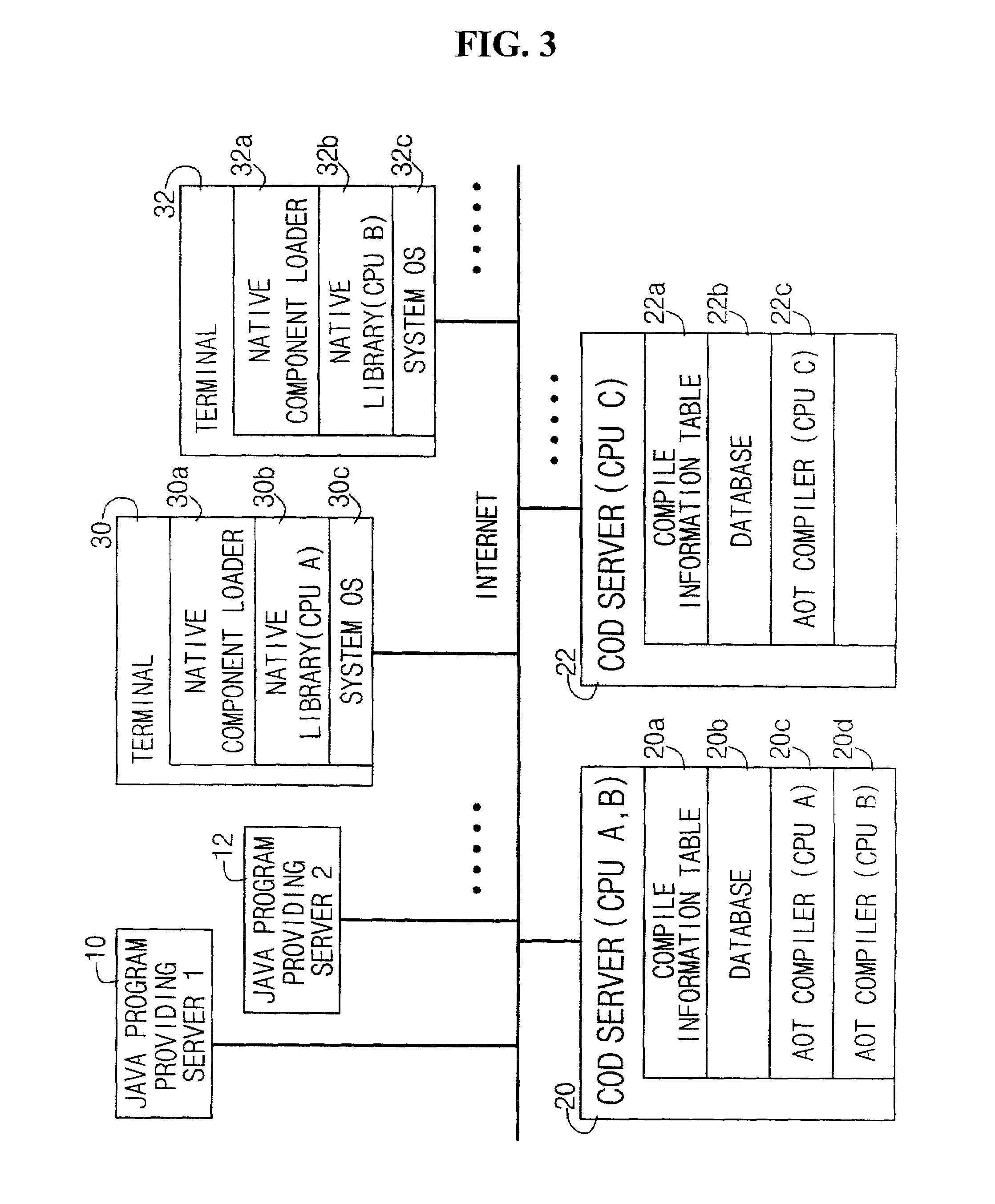
JAVA compile-on-demand service system for accelerating processing speed of JAVA program in data processing system and method thereof
ActiveUS7174544B2Reduce performanceHigh speedData processing applicationsProgram loading/initiatingData processing systemProgramming language
A JAVA program language compile-on-demand service system and method for accelerating a processing speed of a JAVA program in a data processing system having a relatively low performance is provided. The JAVA COD service system compiles a JAVA class file to be executed in a data processing system into a pattern which can be executed more speedily on the data processing system, and then transmits the compiled result, upon a request of the data processing system connected via a network in order to execute the JAVA program at a relatively faster speed. The system includes JAVA program providing servers, data processing systems, and a compile-on-demand server for receiving a service request, downloading a requested JAVA class file, compiling the downloaded JAVA class file, and transmitting the compiled result.
Owner:9FOLDERS INC
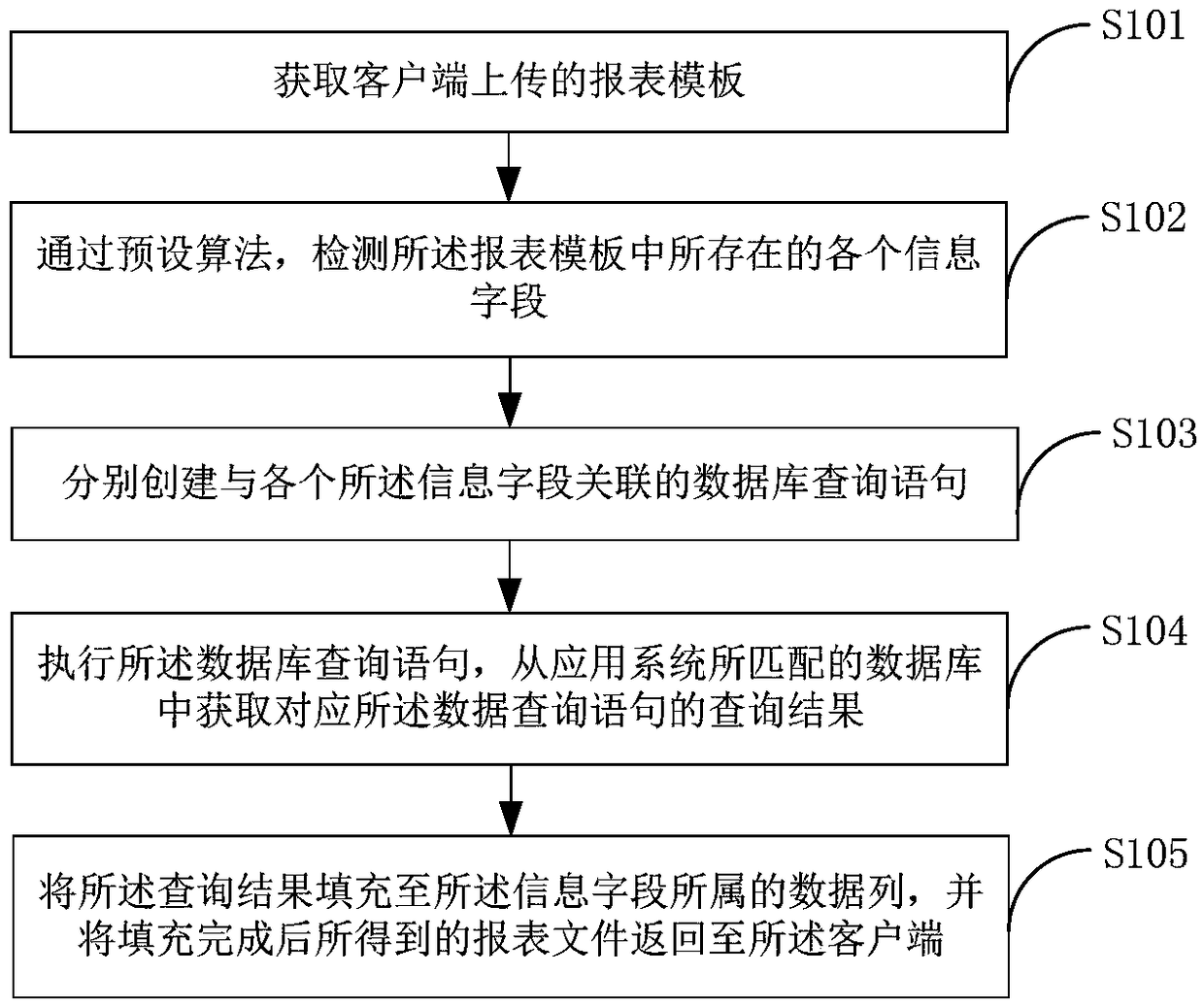
Method for generating report file, terminal device and medium
PendingCN109471890AFlexible replacementFlexible uploadDigital data information retrievalText processingDatabase queryTerminal equipment
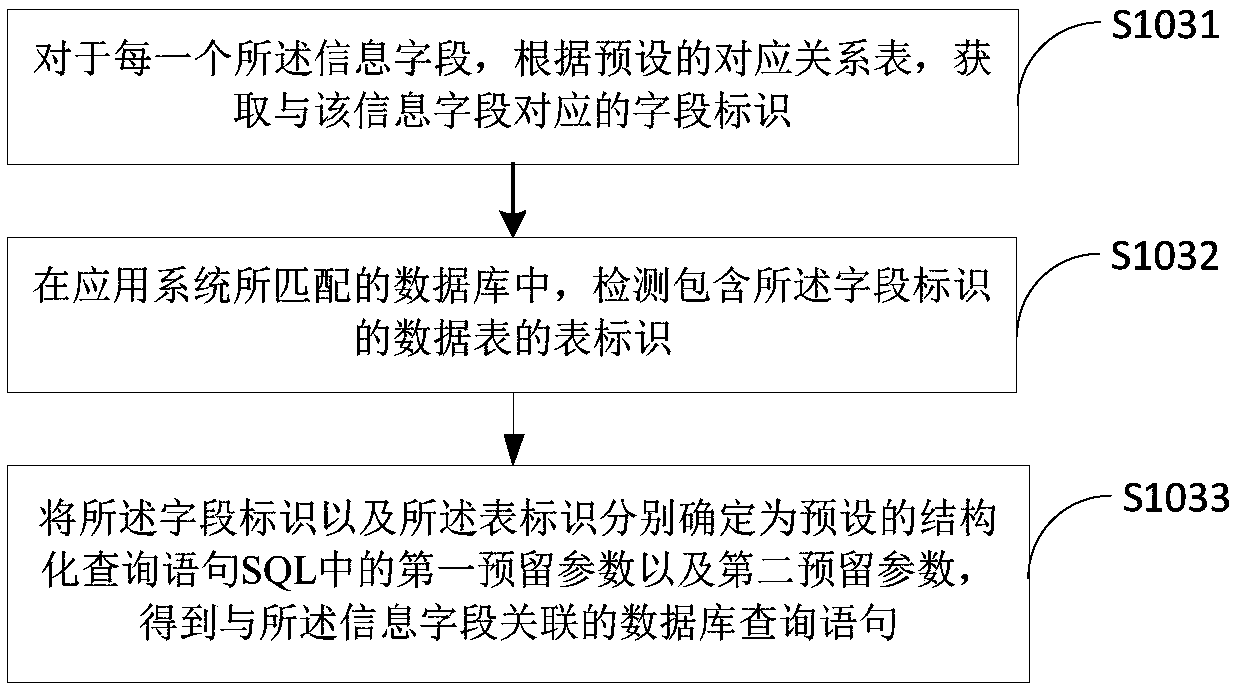
The invention is applicable to the technical field of data processing, and provides a report file generation method, a terminal device and a medium. The method comprises the following steps: obtaininga report template uploaded by a client; Detecting each information field existing in the report template by a preset algorithm; Creating database query statements associated with each information field; Executing a database query statement to obtain a query result of a corresponding data query statement from a database matched by an application system; Populates the query results to the data column to which the information field belongs, and returns the resulting report file to the client when the population is complete. In the invention, the report file is only related to the report templateuploaded by the client, therefore, the developer does not need to manually change the Java program code of the application system, and the operation complexity is reduced. Users do not have to wait for a long code update cycle to obtain their own report files, thus improving the efficiency of report file export.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
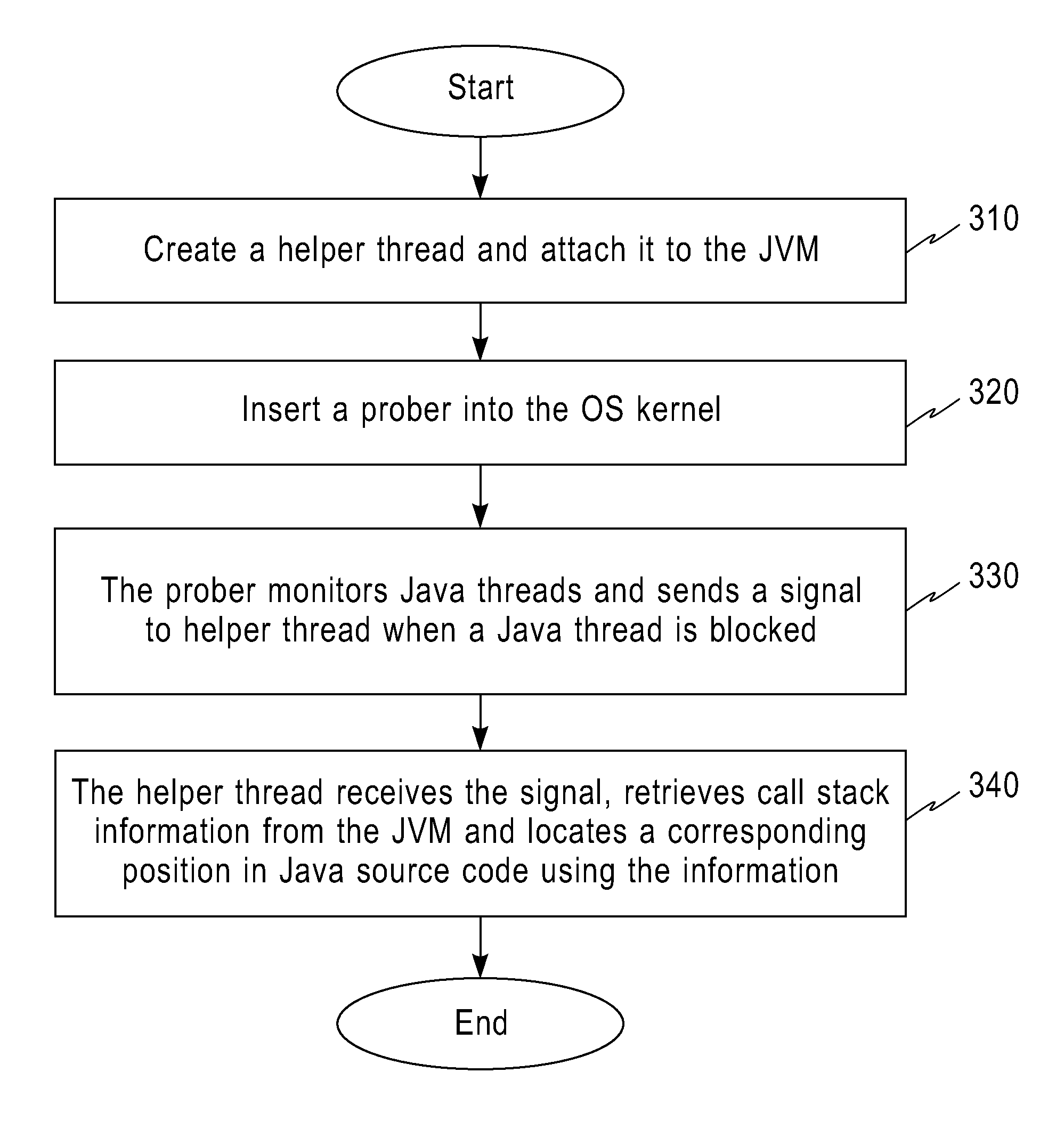
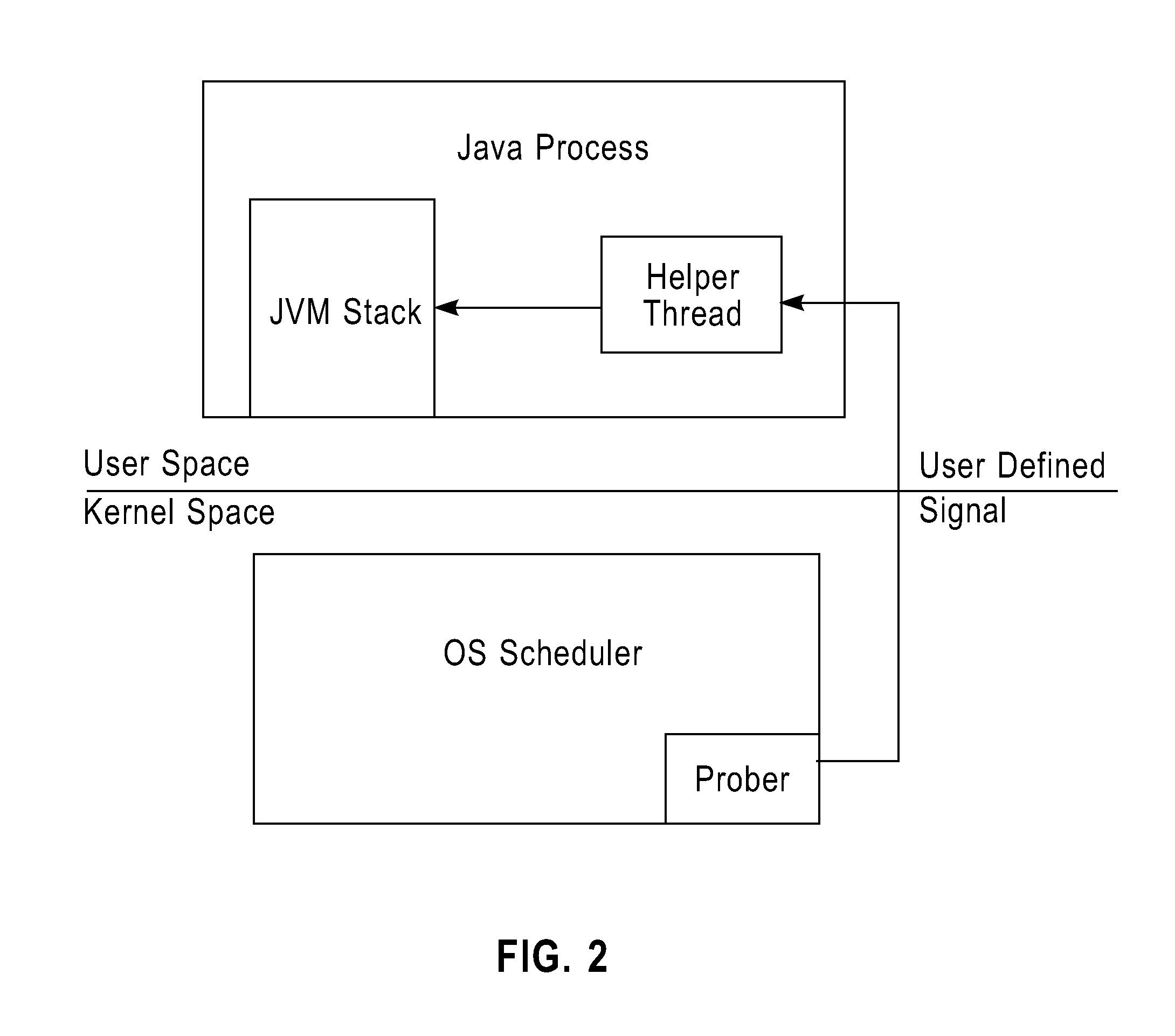
Method and apparatus to locate bottleneck of JAVA program
InactiveUS20110258608A1No obvious performance overheadLinked very accuratelyError detection/correctionSpecific program execution arrangementsCall stackOperational system
A method and an apparatus to locate a bottleneck of a Java program. The method to locate a bottleneck of a Java program includes the steps of: creating a helper thread in a Java process corresponding to the Java program, and attaching the helper thread to a Java virtual machine (JVM) created in the Java process; inserting a prober into an operating system kernel; monitoring states in the operating system kernel of Java threads in the Java process and sending a signal to the helper thread in response to detect that a Java thread is blocked; and retrieving call stack information from the JVM in response to receive the signal from the operating system kernel and locating the position in source code of the Java program that causes the block using the retrieved call stack information.
Owner:IBM CORP
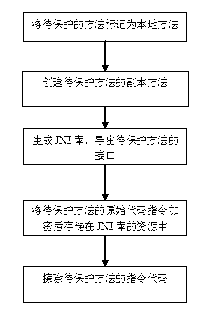
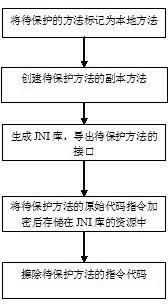
Method for protecting JAVA application programs in Android system
ActiveCN102708322APrevent piracyProgram/content distribution protectionSpecific program execution arrangementsApplication softwareJava classes
The invention relates to the field of computer safety, in particular to a method for protecting application programs in an Android system. By carrying out encryption transformation on a plurality of method instruction codes of JAVA objects to be protected, encrypted method codes are subjected to real-time decryption operation according to the calling requirement when the programs operate, so that the application programs are difficult to subject to decompilation and static analysis, and therefore, the effective protection on the JAVA programs in the Android system is implemented.
Owner:BEIJING SENSESHIELD TECH
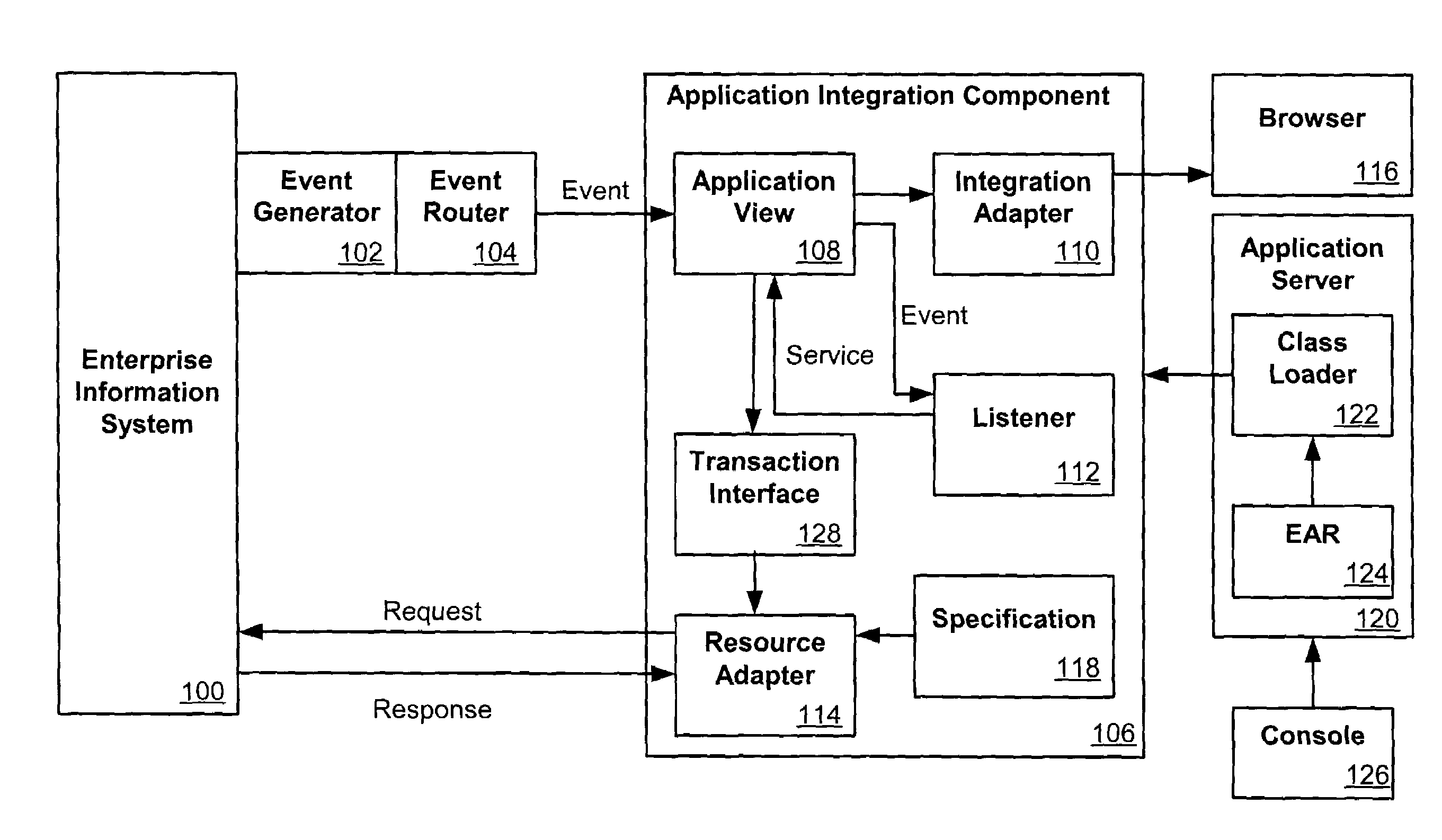
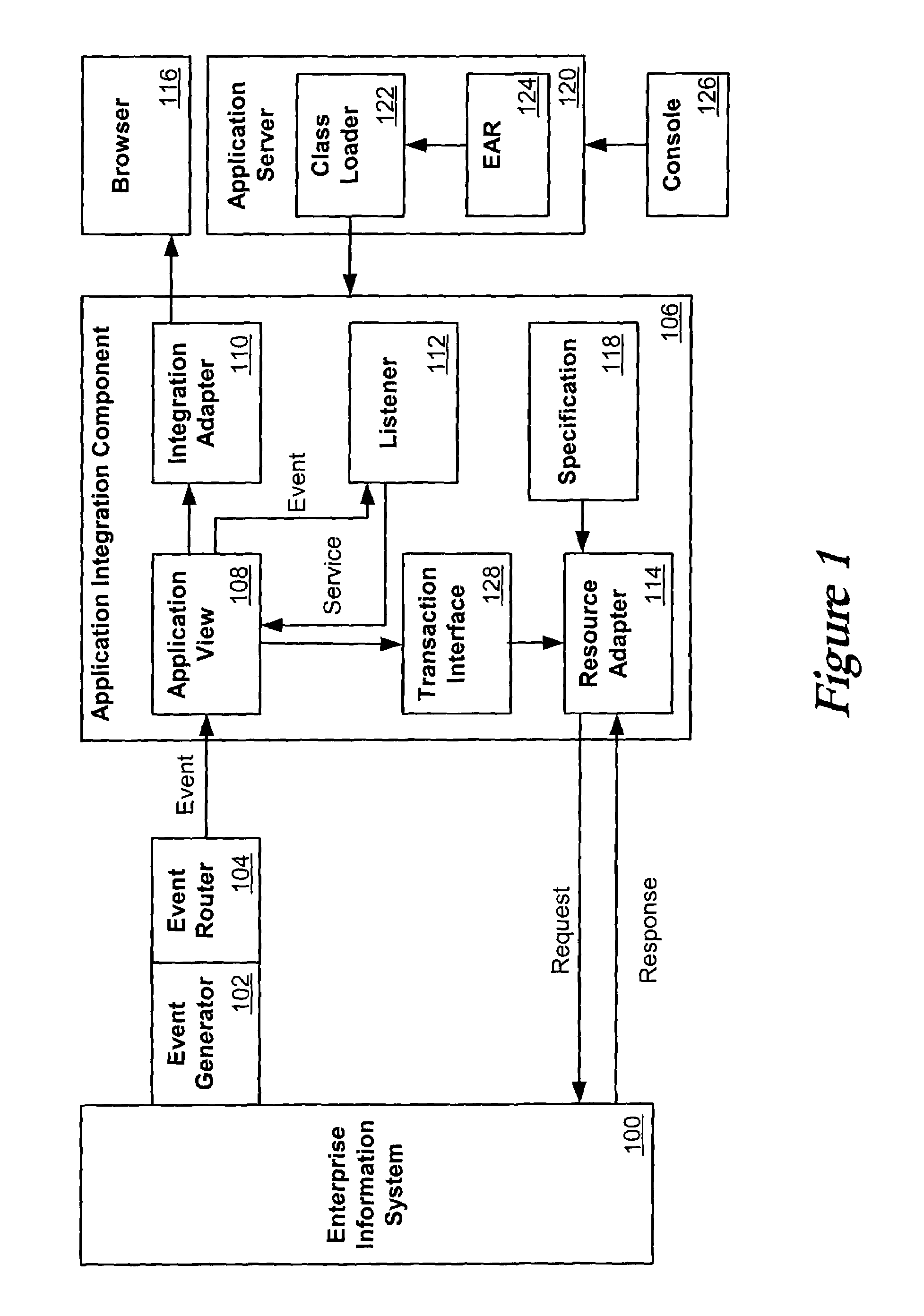
System and method for enterprise application interactions
ActiveUS7350184B2Digital data processing detailsMultiprogramming arrangementsApplication softwareClient-side
An application view control can allow users of a software tool to interact with Enterprise applications using simple Java APIs. This can allow a user who is not an expert in the use of a given Enterprise system to utilize its capabilities in a manner a Java programmer can understand. A developer can invoke application view services both synchronously and asynchronously, and can subscribe to application view events. The developer can use simple Java objects in both the service and event cases. The developer need not understand XML, or the particular protocol or client API for the Enterprise application, such as an Enterprise Information System (EIS).
Owner:ORACLE INT CORP
Method for preventing Java program from being decompiled
ActiveCN102043932AKeep it cross-platformGuaranteed versatilityProgram/content distribution protectionJava bytecodeJava virtual machine
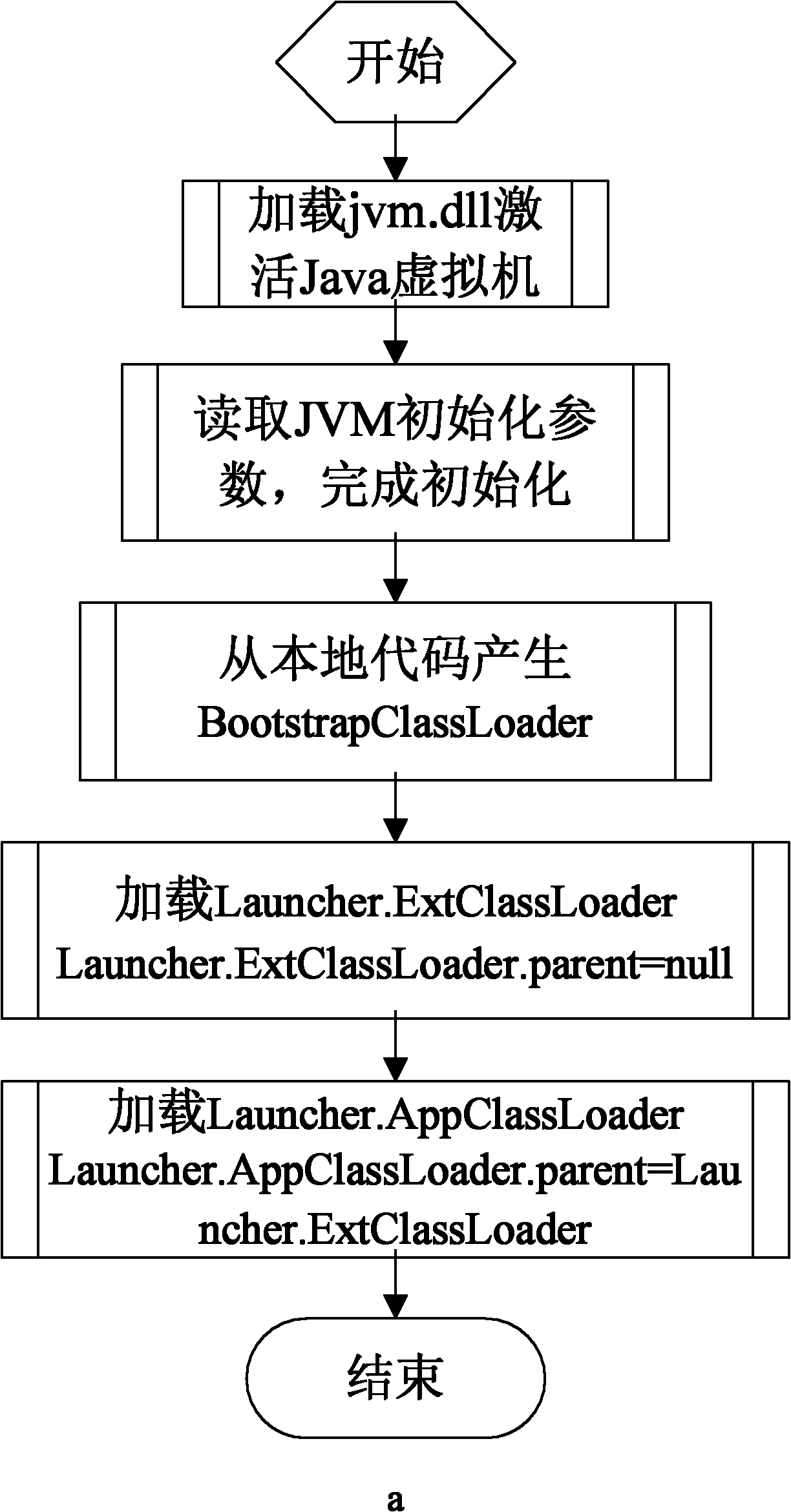
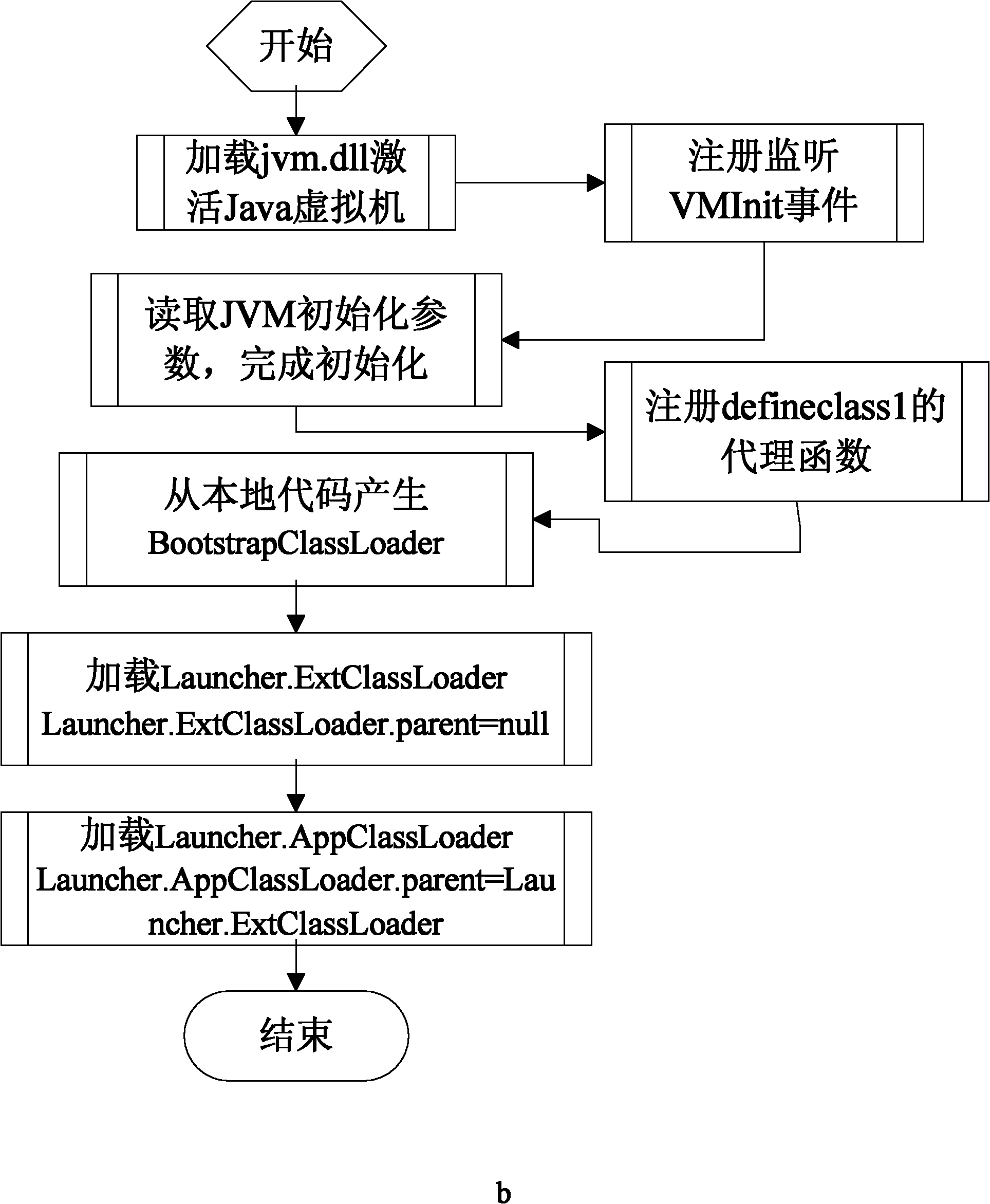
The invention relates to a method for preventing a Java program from being decompiled, which comprises the following steps: 1) encrypting a Java bytecode file to be issued; 2) using a Java virtual machine tool interface to monitor an initialization event of a Java virtual machine; 3) designating a Hook function for the initialization event of the Java virtual machine; 4) when the initialization of the Java virtual machine is finished, automatically calling the Hook function, and using a Java local interface in the Hook function to register a function called by the Java virtual machine for generating class objects as a self-defined agent function; 5) when the Java virtual machine generates a certain class object, calling the self-defined agent function, and decrypting the encrypted Java bytecode file in the self-defined agent function; and 6) generating a class object corresponding to the decrypted Java bytecode file, and returning to the Java virtual machine. The invention solves the technical problem of the limited application range of the method for preventing a Java bytecode file from being decompiled in the prior art, keeps the cross-platform characteristics of the Java program and maintains the universality of the Java virtual machine.
Owner:AVIC NO 631 RES INST
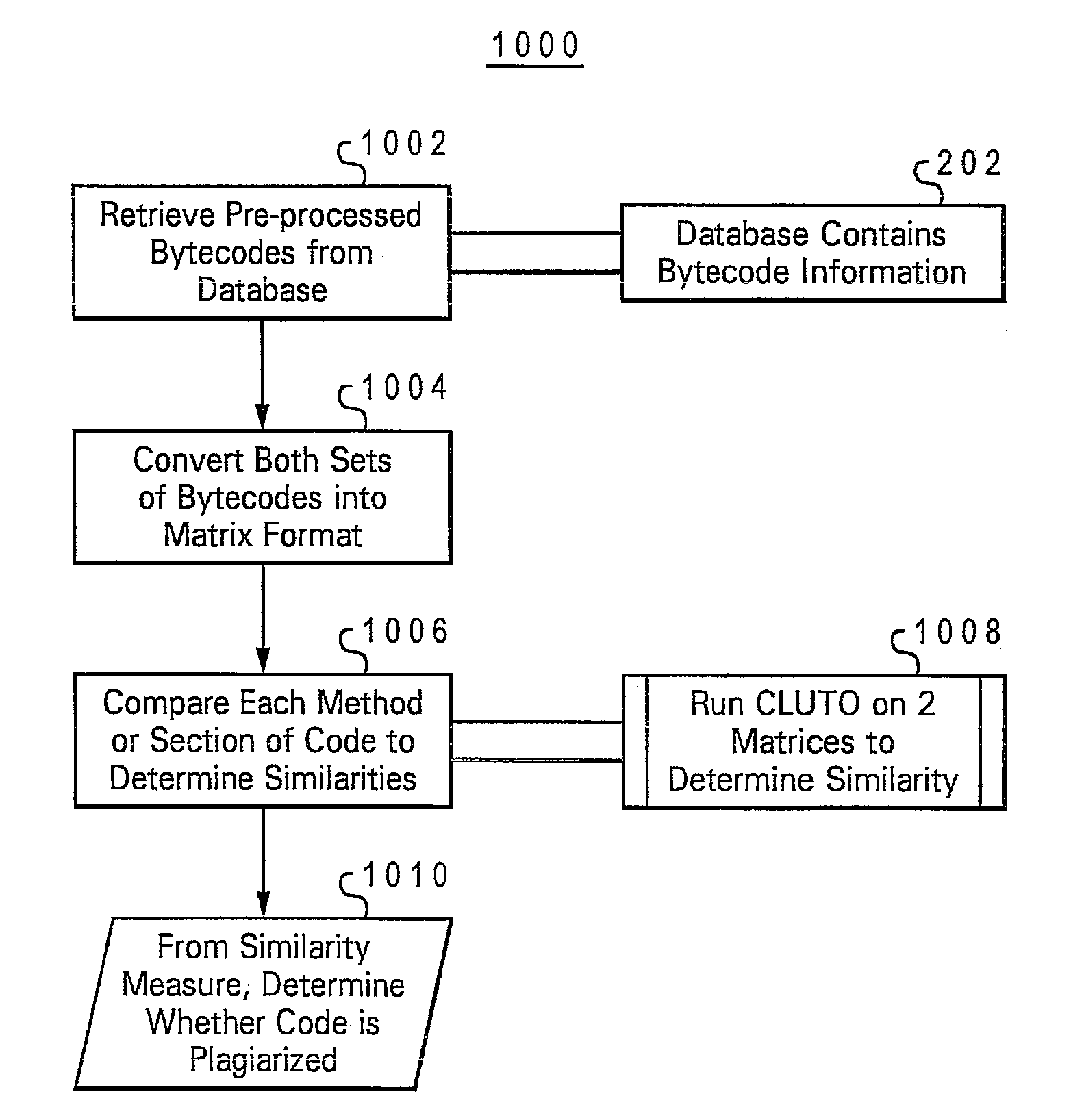
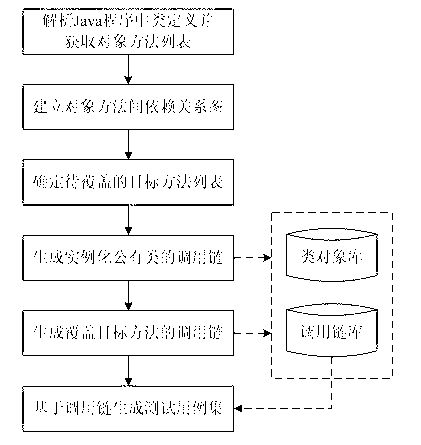
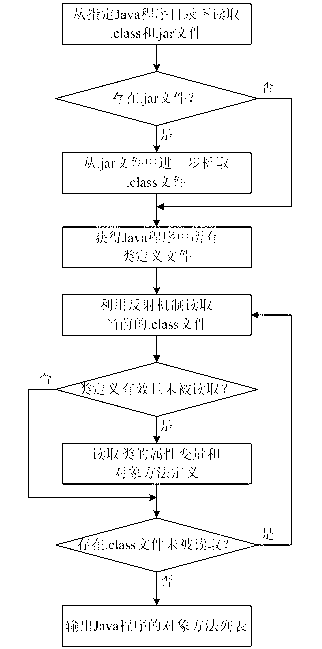
Method, system and program product for determining java software code plagiarism and infringement
An analysis tool extracts class data from Java objects within a potential plagiarizing Java program and the original Java program, and then compares classes common to the potential plagiarizing program and the original across various performance metrics. Similarities disclosed by the analysis tool are output for user or programmatic comparison of the matches between the potentially plagiarizing Java program byte code and the original program's byte code.
Owner:INT BUSINESS MASCH CORP
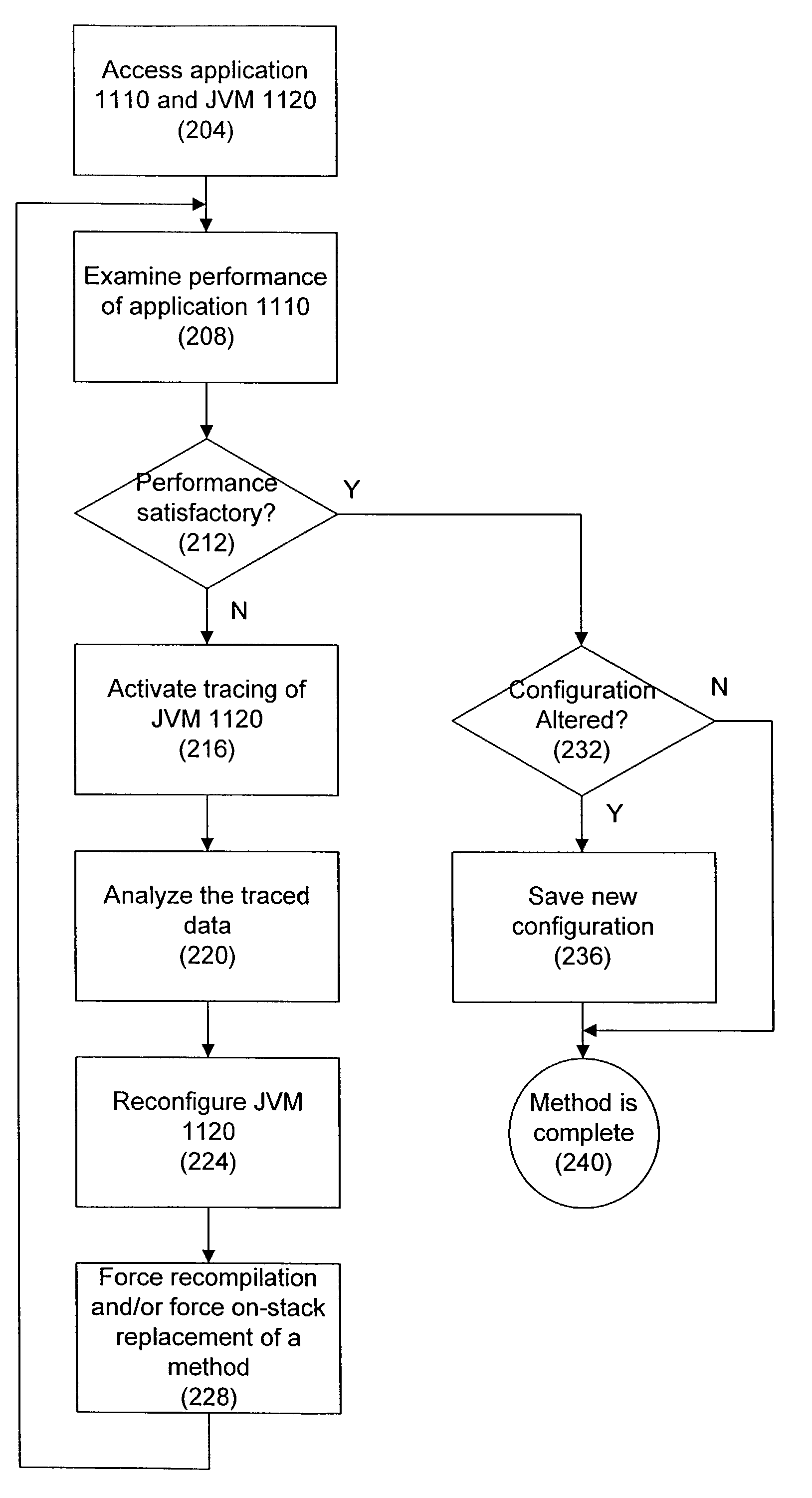
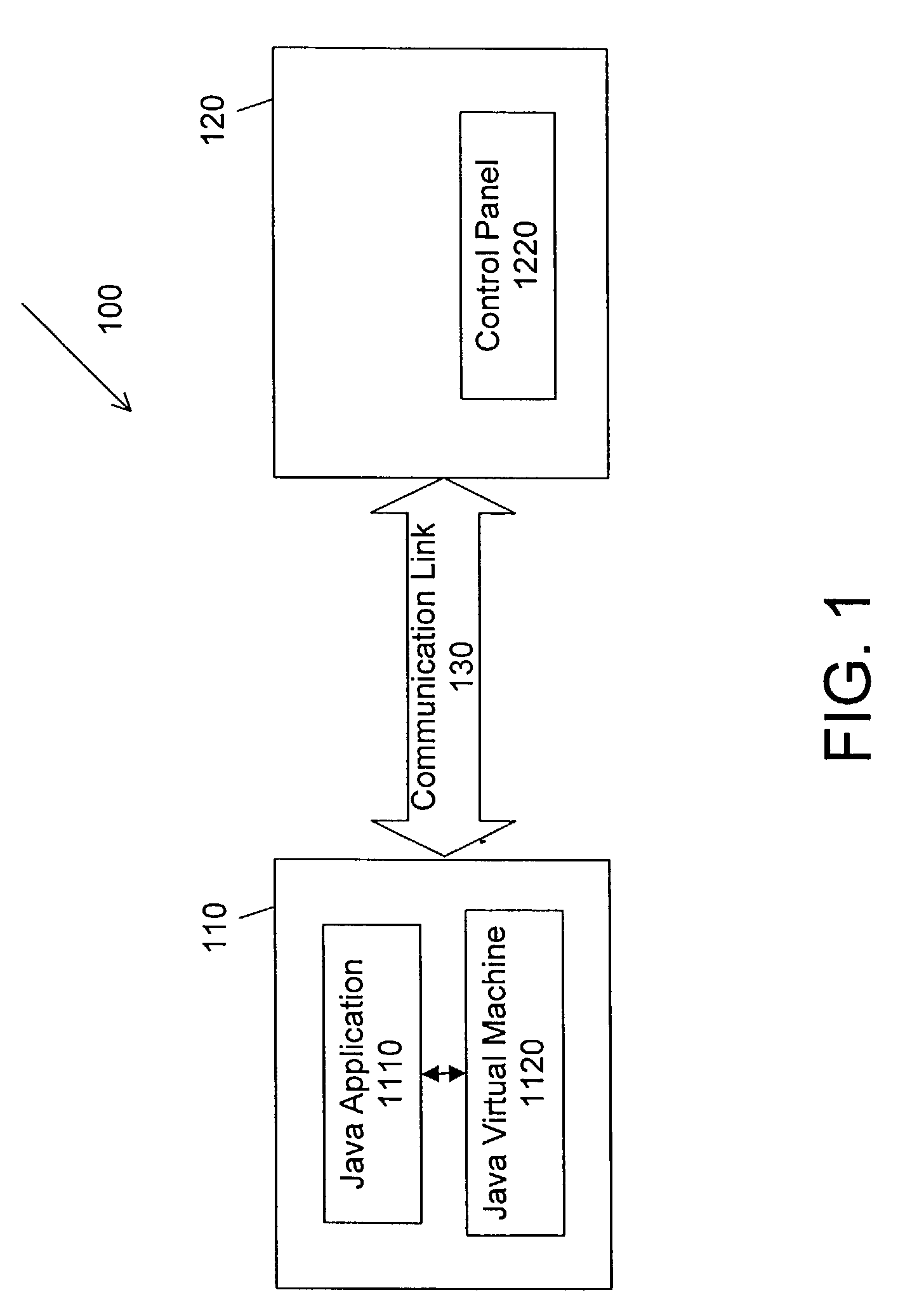
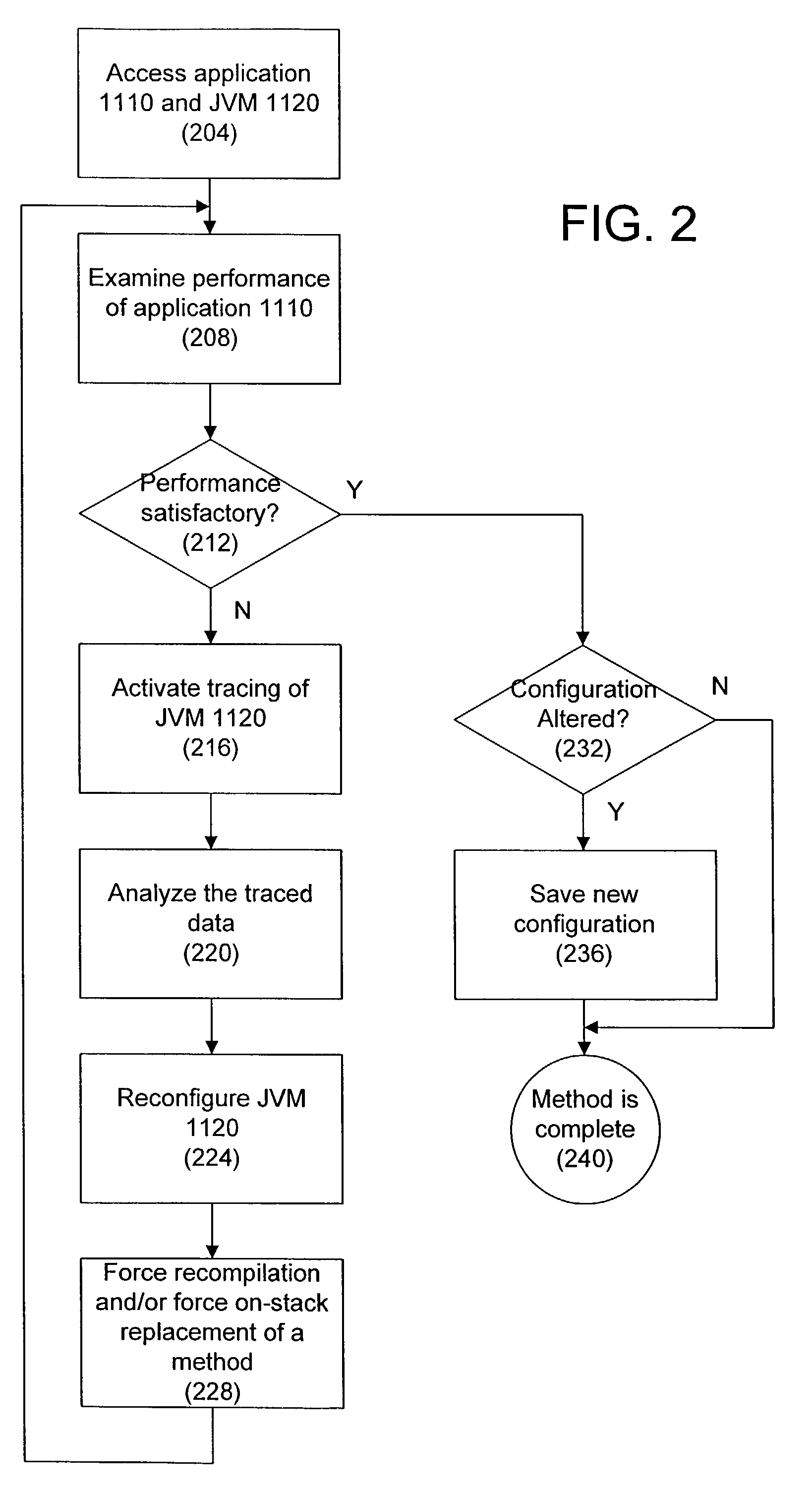
Performance of computer programs while they are running
ActiveUS7577951B2Improve performanceSoftware simulation/interpretation/emulationMemory systemsHuman languageRe optimization
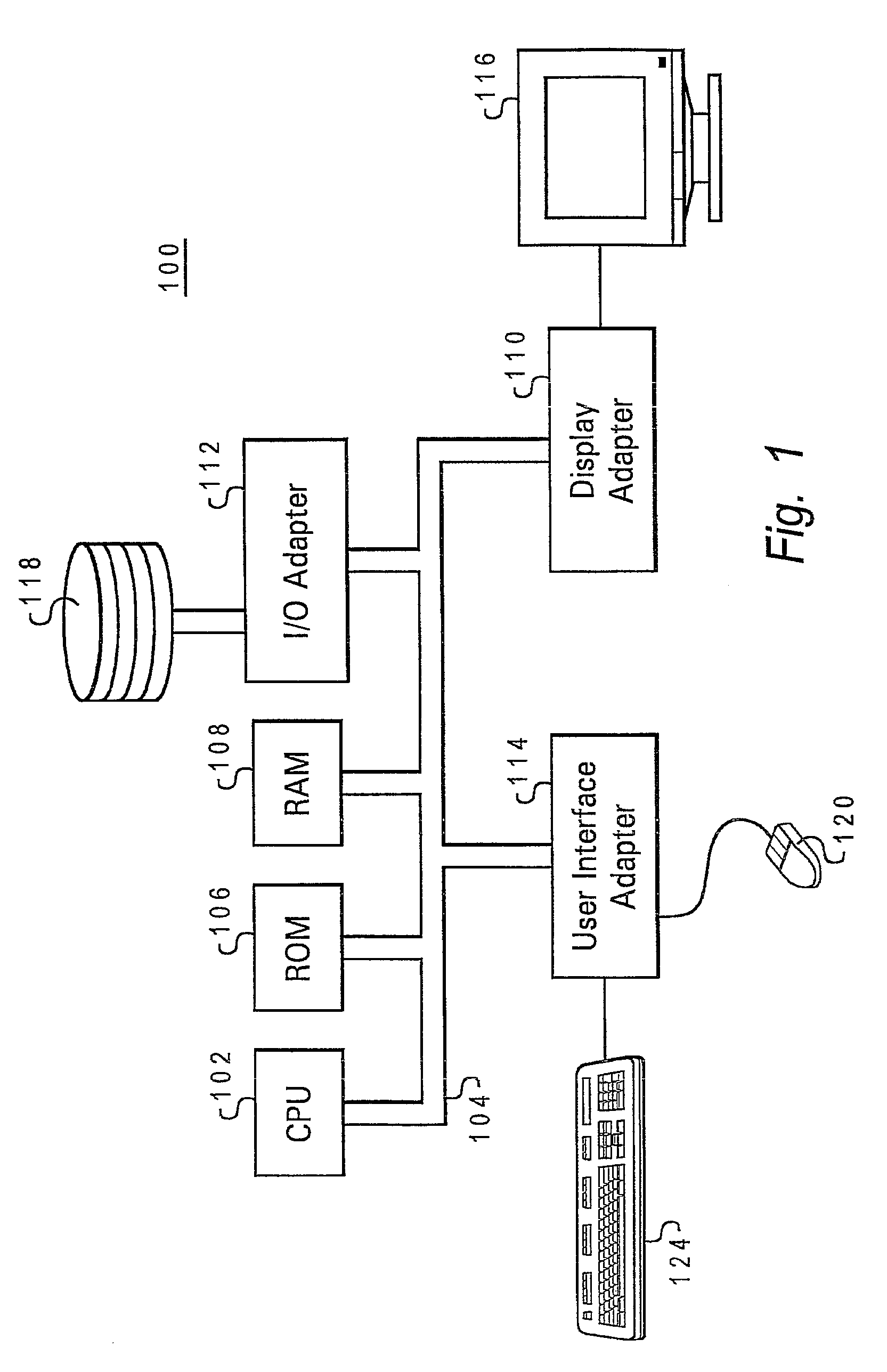
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
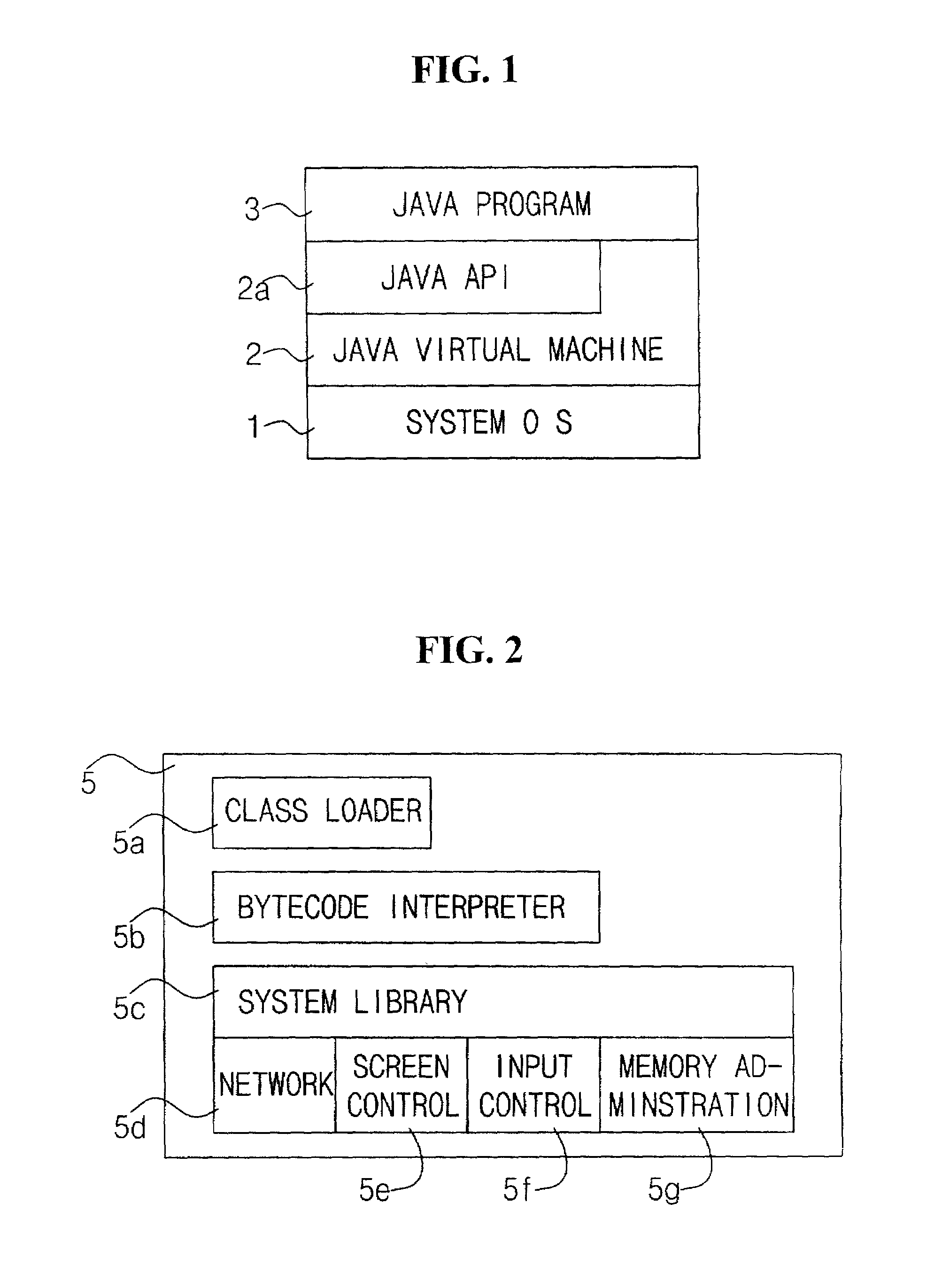
System for hiding runtime environment dependent part
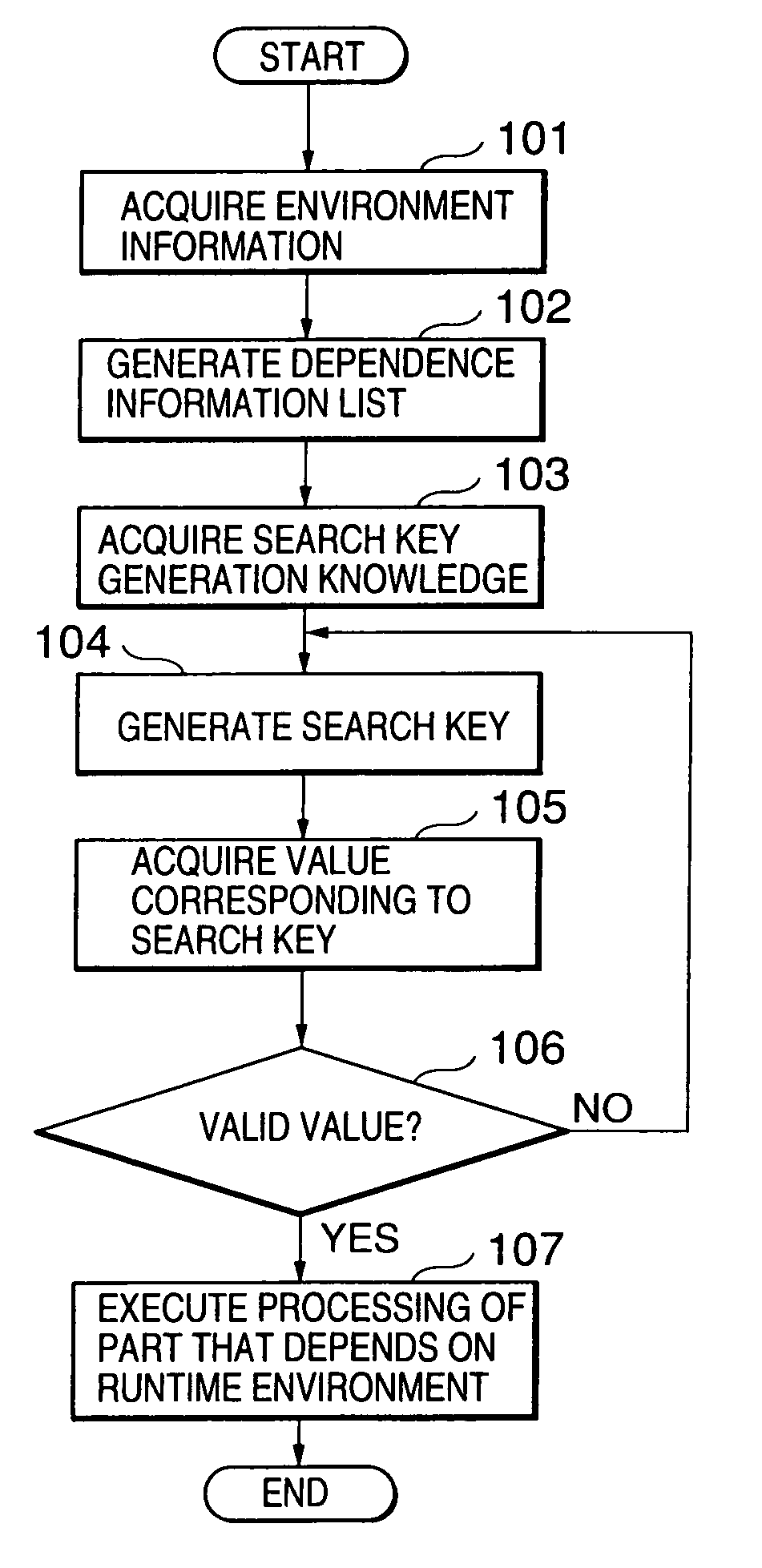
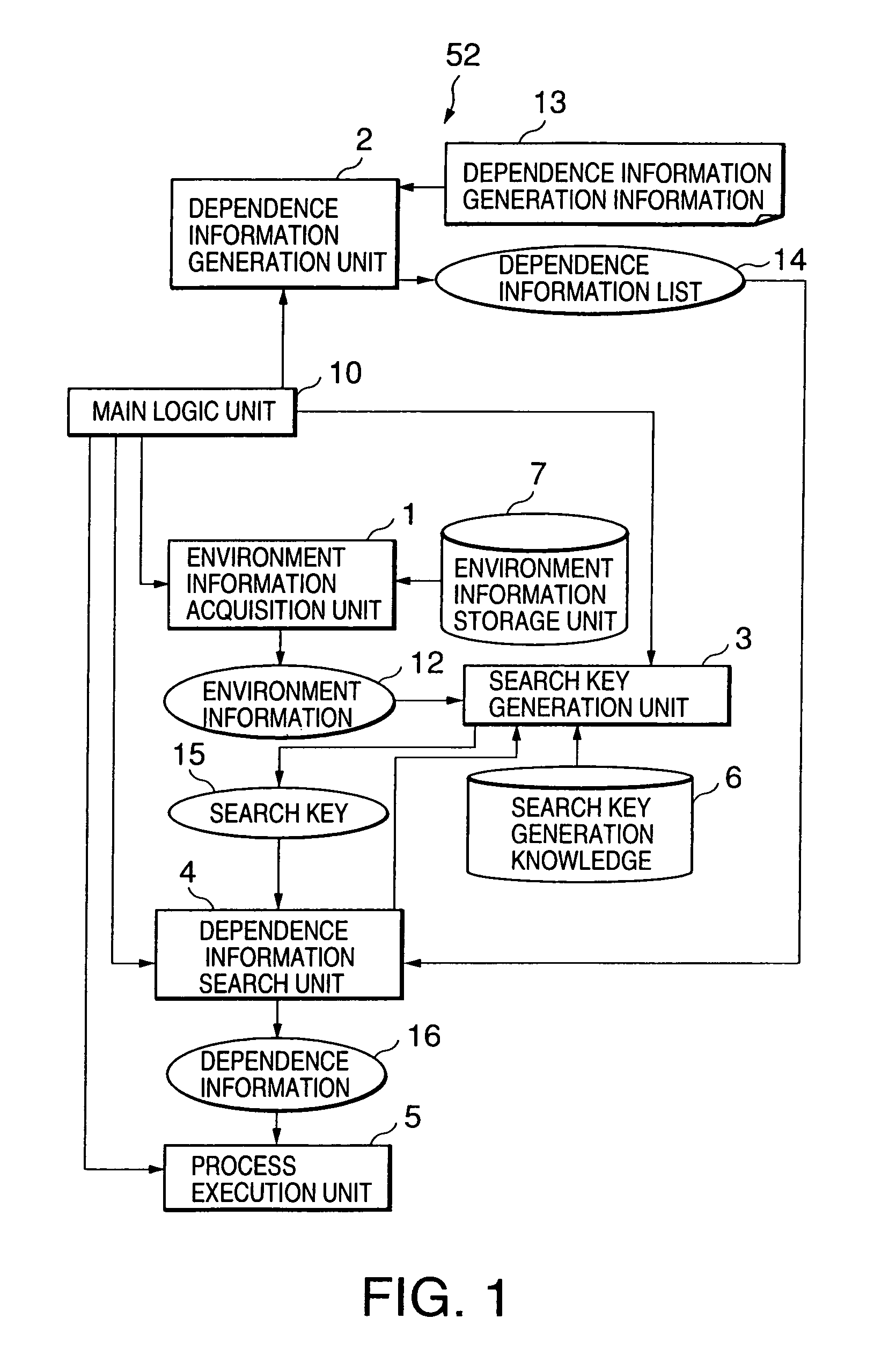
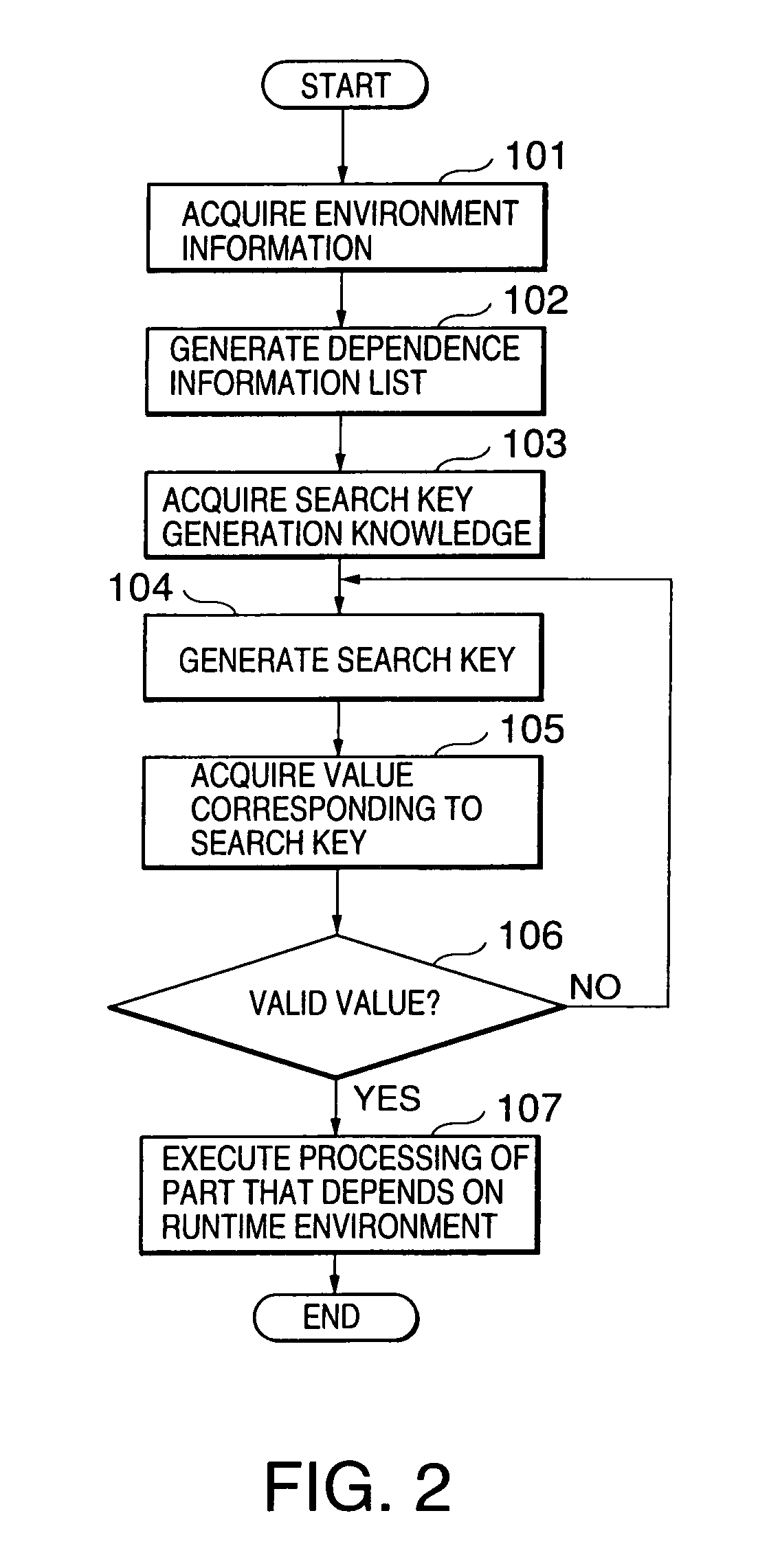
InactiveUS7076765B1Easy to changeEasy maintenanceSoftware simulation/interpretation/emulationMemory systemsExecution unitInformation searching
This invention provides a runtime environment dependency hiding apparatus and the like, which hides a part that depends on the runtime environment in software which runs on a plurality of runtime environments having different specifications. An environment information acquisition unit acquires environment information that pertains to the runtime environment of a Java program from standard properties and the like. A dependence information generation unit generates a dependence information list required for processing the part that depends on the runtime environment in the Java program on the basis of dependence information generation information. A search key generation unit generates a search key in accordance with search key generation knowledge on the basis of the environment information acquired by the environment information acquisition unit. A dependence information search unit searches the dependence information list generated by the dependence information generation unit for dependence information corresponding to the current runtime environment on the basis of the search key generated by the search key generation unit. A process execution unit executes the processing of the part that depends on the runtime environment on the basis of the dependence information obtained by the dependence information search unit.
Owner:KK TOSHIBA
Method and system for dynamically converting telecommunications service data
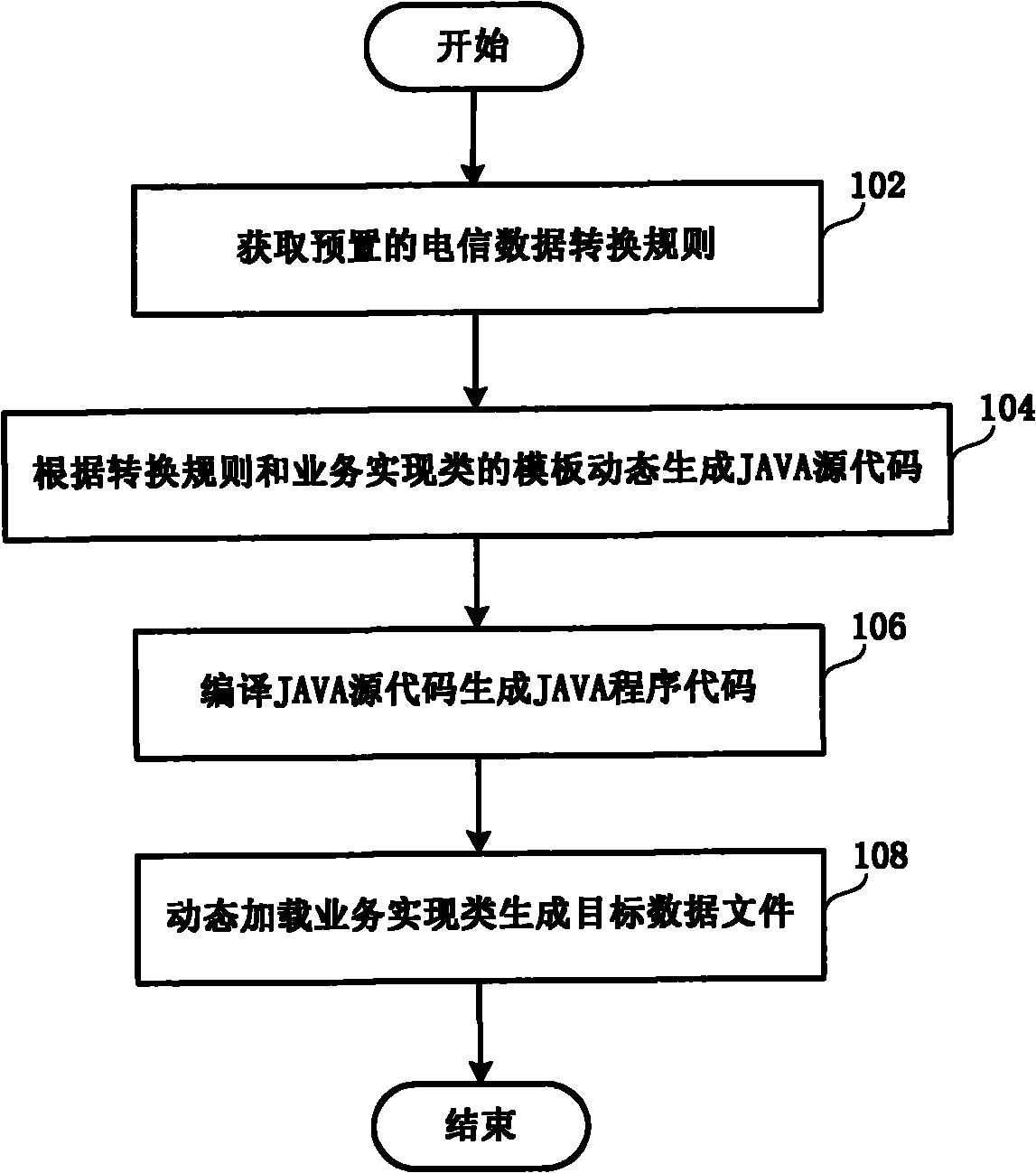
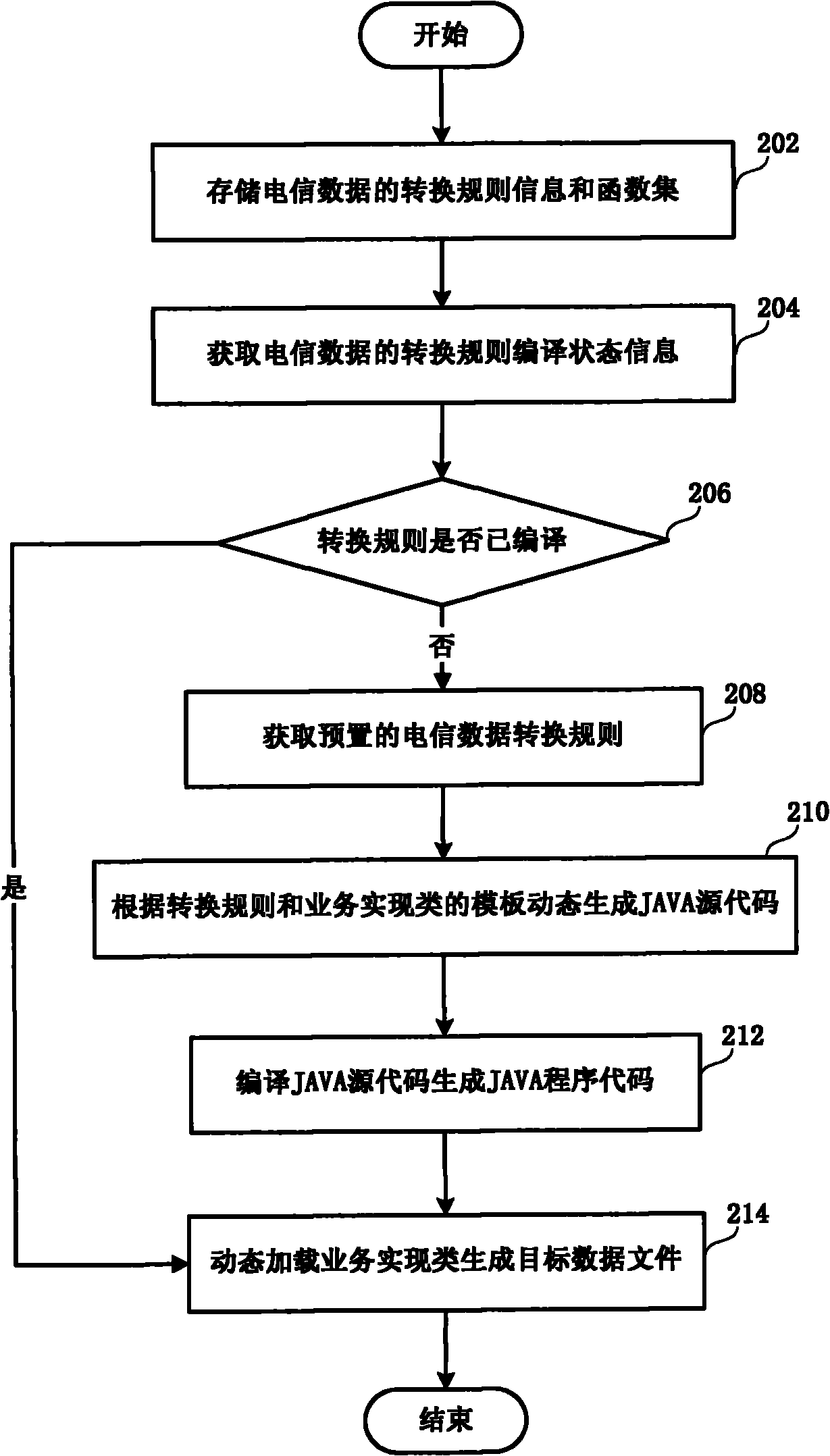
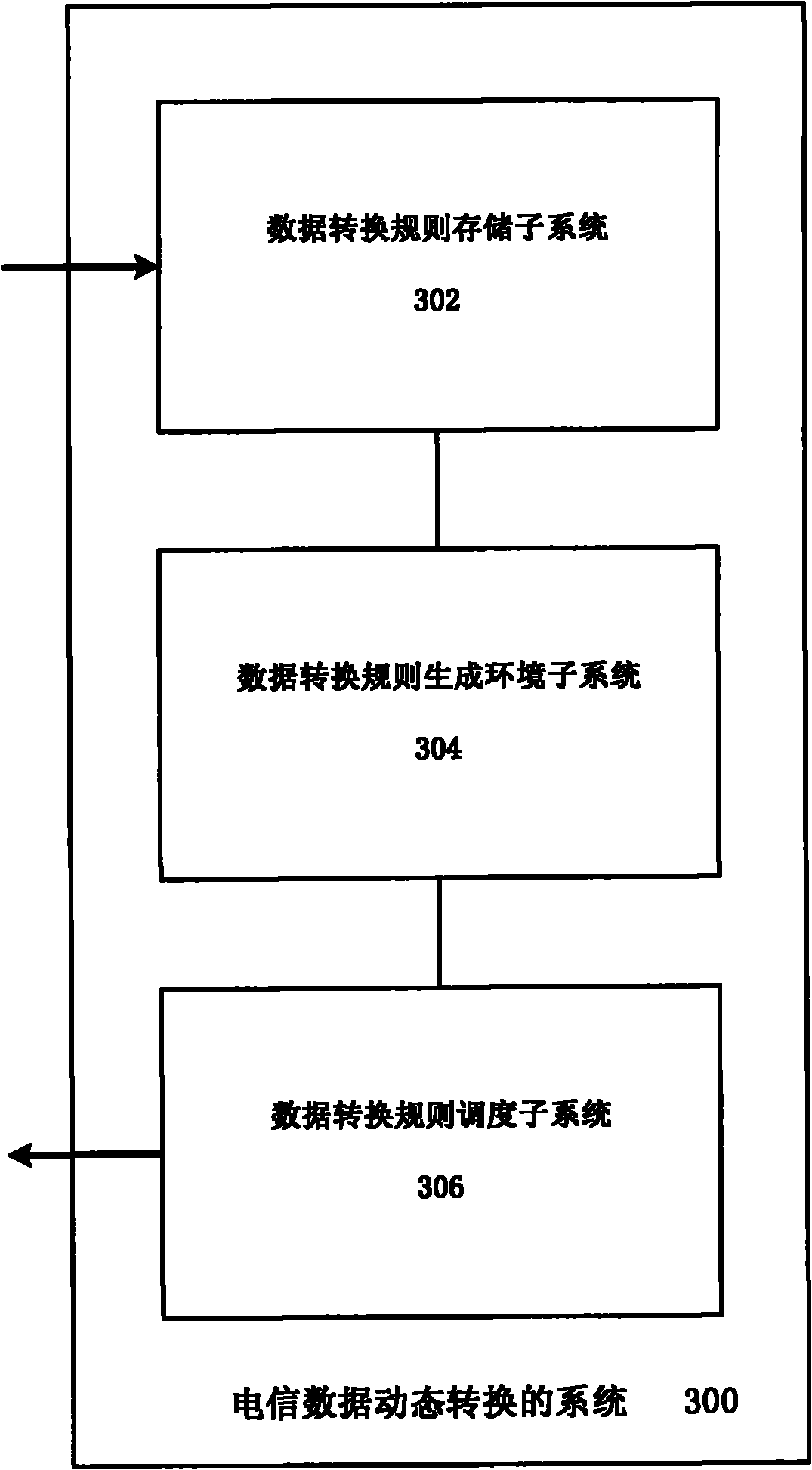
ActiveCN101958987AImprove scalabilityConversion dynamic implementationSupervisory/monitoring/testing arrangementsData fileJava code
The invention discloses a method and a system for dynamically converting telecommunications service data. The method comprises the following steps of: obtaining a preset telecommunications service data converting rule; dynamically generating a JAVA source code in a service realizing type according to the data converting rule and a preset service realizing type template; compiling and generating aJAVA program code; dynamically loading and executing the service realizing type; and generating a source data file into an object data file. The invention aims at the characteristics of the telecommunications service data to establish a rich function set, provides a function self-defining interface at the same time and is convenient to user self definition and function set expansion. Different from the current script interpretative type ETL (Extract-Transform-Load) tool, the invention adopts dynamic compiling, dynamic loading and a JAVA reflection technology, increases data conversion efficiency and has stronger cross-platform property and application flexibility.
Owner:CHINA TELECOM CORP LTD
Method for implementing dynamic update of Java program
InactiveCN101174217AGuaranteed to compile onceWill not interfere with each otherSpecific program execution arrangementsSoftware updateData field
The invention relates to a method for realizing dynamic update of Java program in the computer technical field, which comprises the following steps: firstly, modifying the class definitions that need dynamic update in the passive dynamic update program, and adding update support method for realizing judgment to the subobjects of the class objects one by one, wherein the parameter is class loader; secondly, modifying the update class definitions in the dynamic update program, and adding update method for realizing initialization to the variables under the update class objects, wherein, the input parameter is class loader and old object; thirdly, modifying part of the method invocation, data field memory, and object set of the updated program with the Java reflection to realize running recovery of the program; finally, adding update support method to the main class and adding update checkpoint in the main method circulation. The invention has the advantages of avoiding software update that needs halt, update and reboot and avoiding loss caused by halt.
Owner:SHANGHAI JIAO TONG UNIV
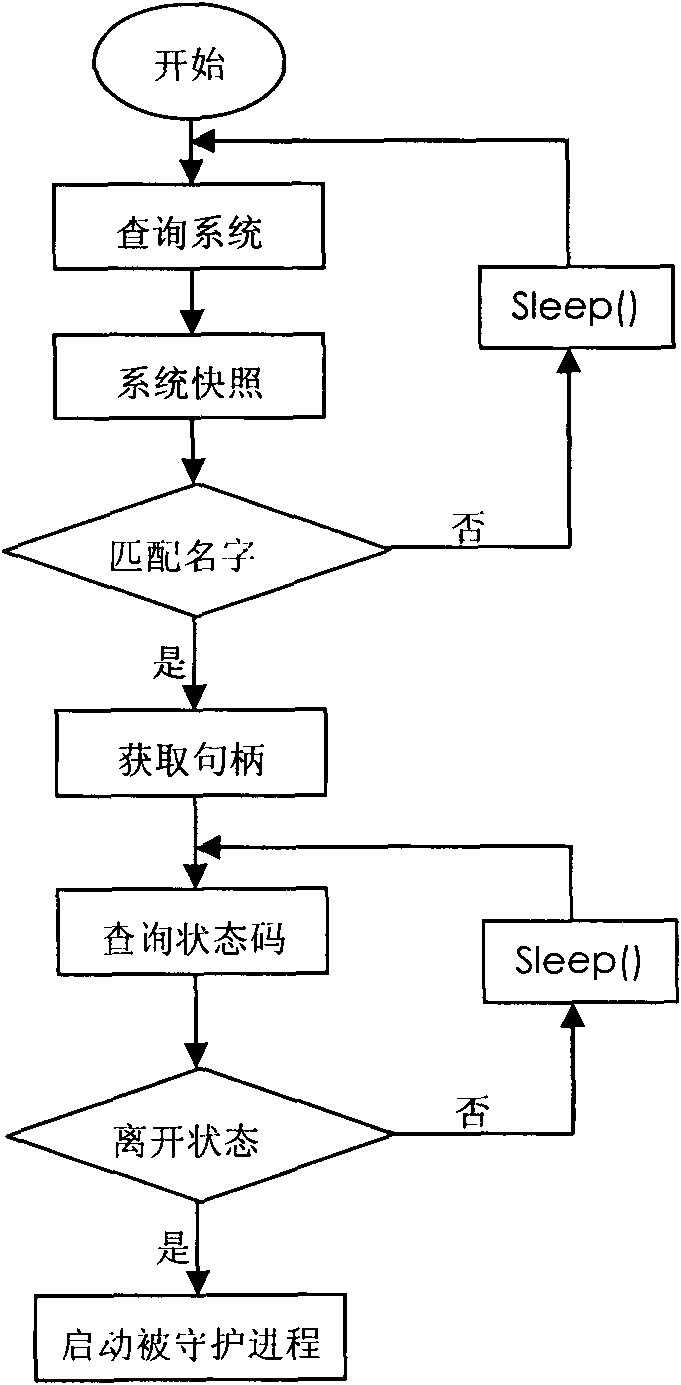
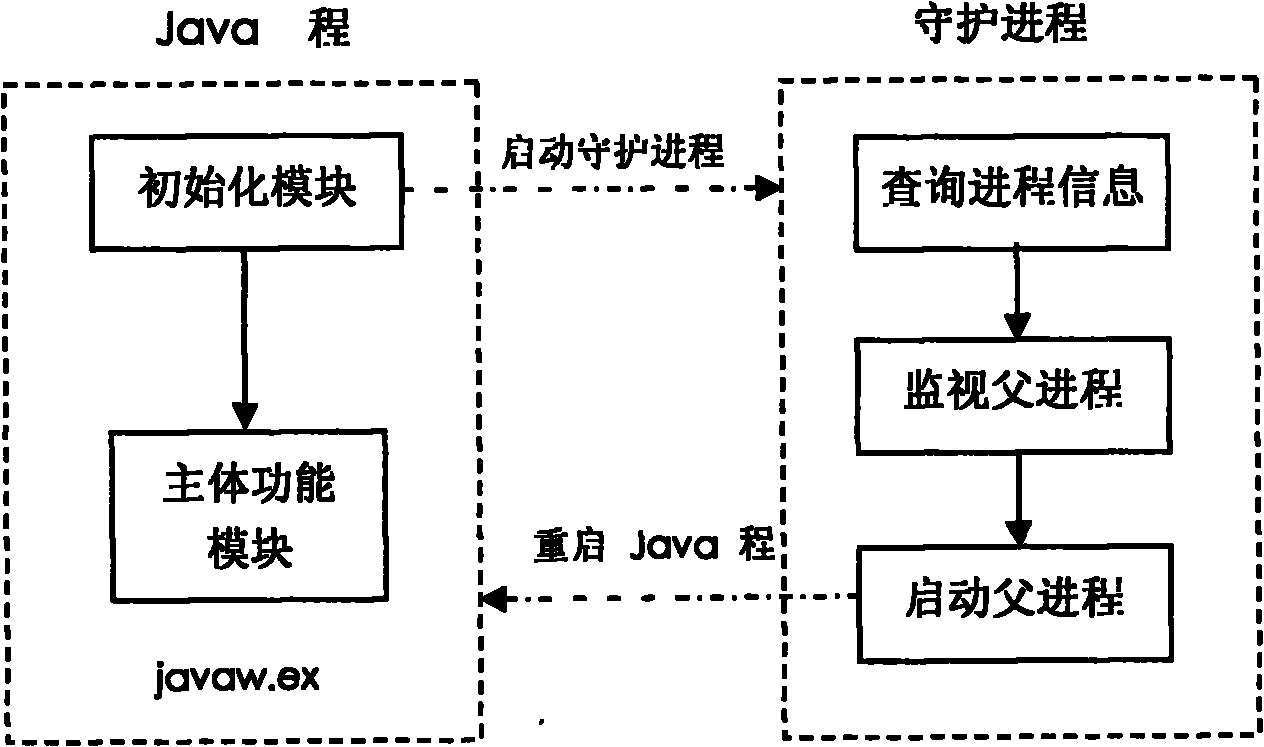
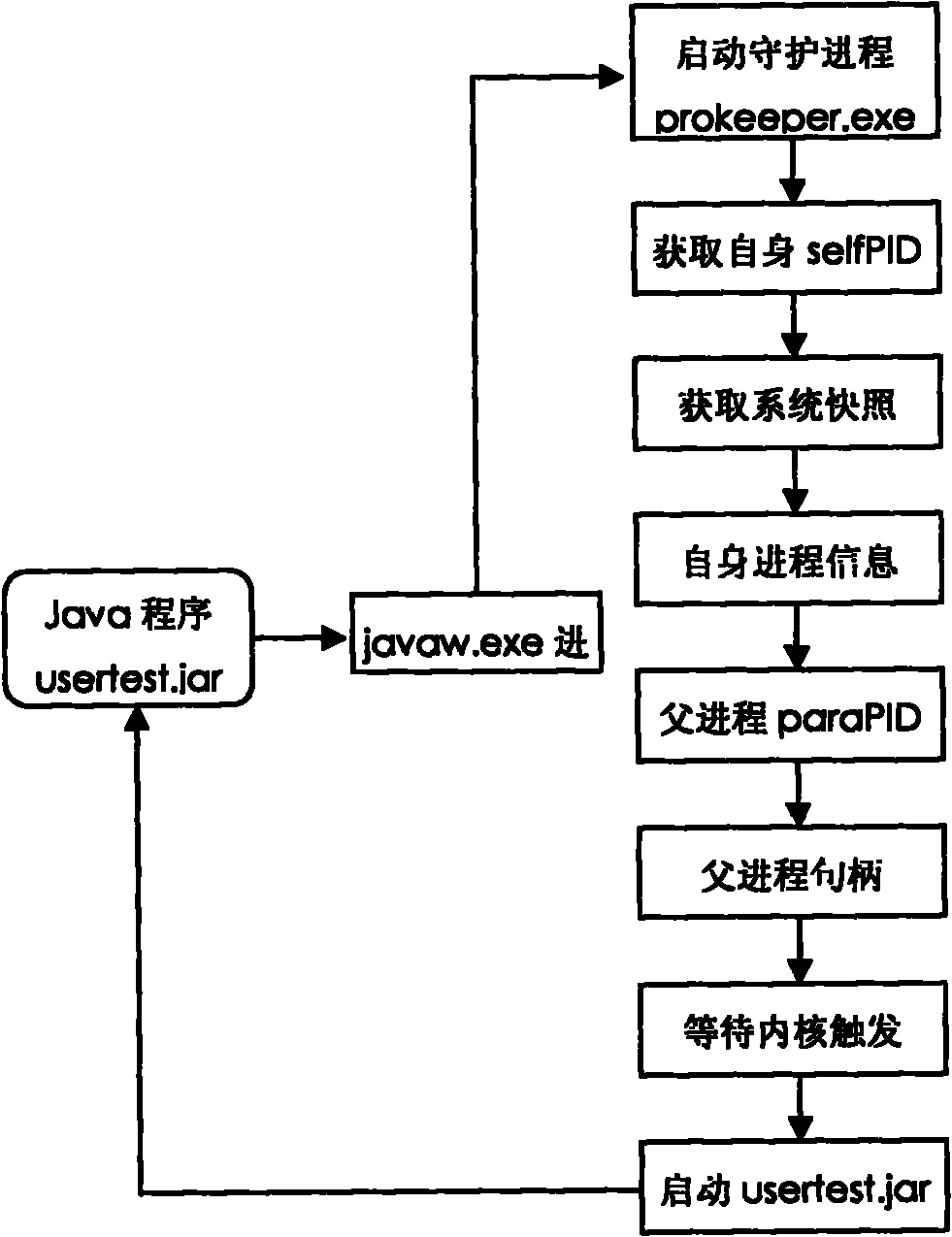
Method for protecting Java program progress based on inheritance relationship among progresses
InactiveCN102103676AOvercoming the drawbacks of matching to determine the daemonized processAccurately determinePlatform integrity maintainanceOperational systemRelationship - Father
The invention provides a method for protecting Java program progress based on an inheritance relationship among the progresses, wherein the method is used for protecting the Java program (the program developed by the Java programming language, hereinafter referred to as Java program) in a windows system (a name of an operating system). The method is mainly used for solving the authentication and determination of the protected Java program progress, monitoring the operating state of the Java program, and preventing the unexpected ending of the operation. The method establishes a father and soninheritance relationship between the protected Java program progress and the protecting program progress, uniquely determines the protected Java program progress by the protecting program progress based on the inheritance relationship and determines the operating state of the protected Java progress based on the inner core object state of the protected Java program progress.
Owner:NANJING UNIV OF POSTS & TELECOMM
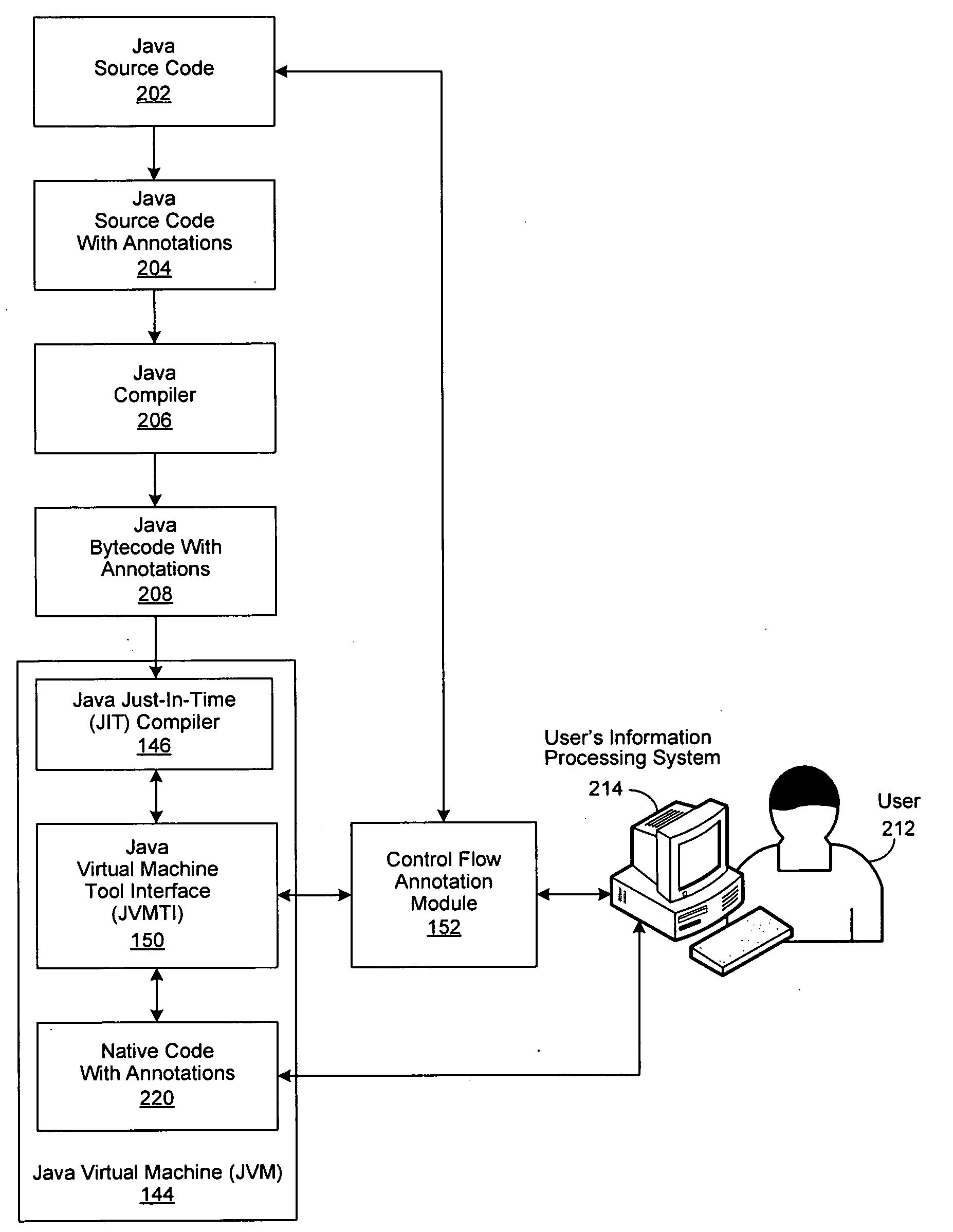
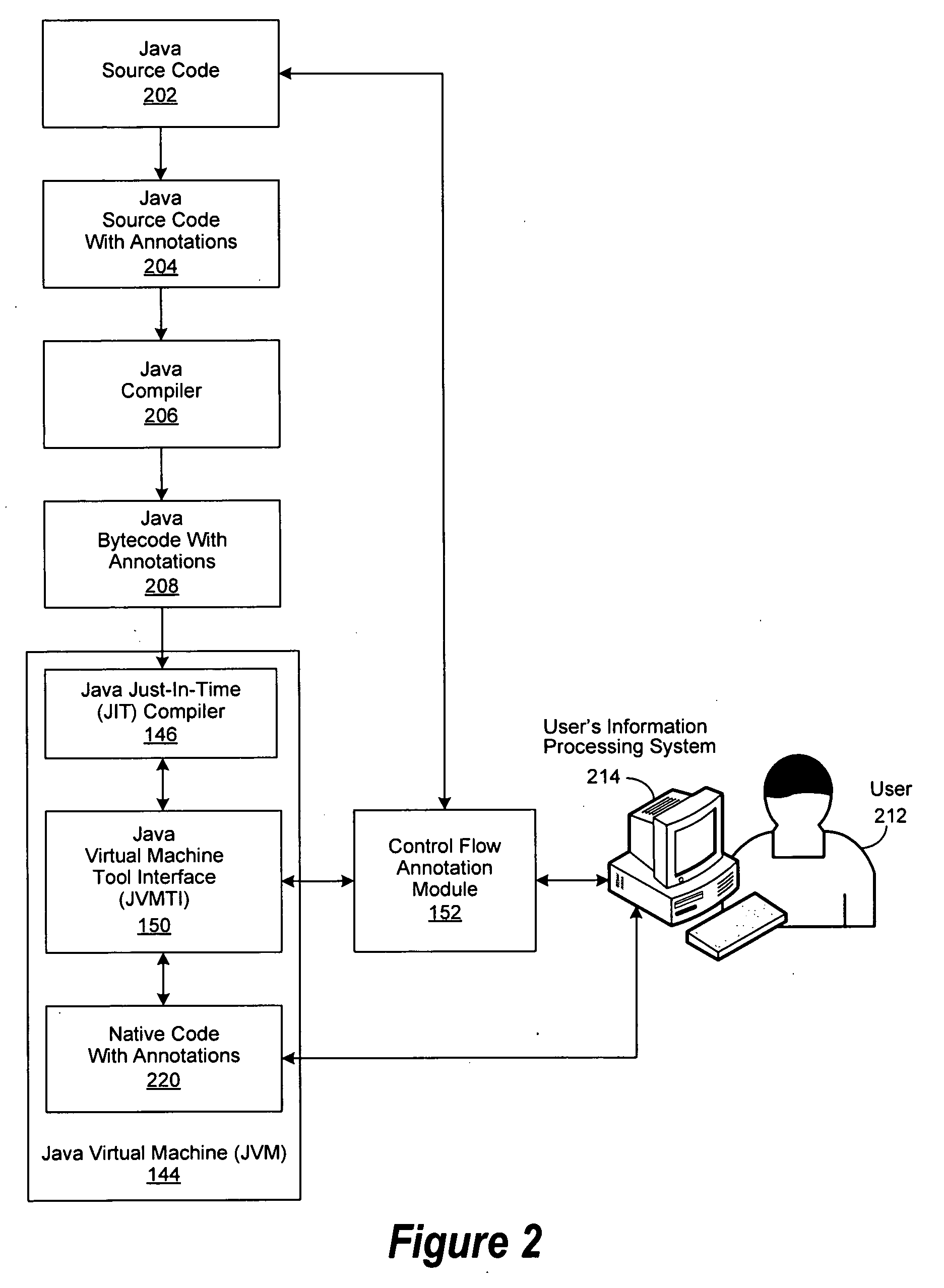
Framework for Control Flow-Aware Processes
InactiveUS20100138820A1Error detection/correctionProgram controlJust-in-time compilationControl flow
An improved system and method are disclosed for processing Java program code. Java source code is annotated with a Module or a ControlFlow annotation. The Java source code is then compiled to produce Java bytecode, which in turn is compiled by a just-in-time compiler to produce native code, which retains the annotations. The native code with annotations is then executed. If a bug is identified during the execution of the native code, an associated Module is selected for debugging, followed by determining associated Java source code segments within the responsible control flow path. Debugging operations are then performed on the associated Java source code segments.
Owner:GLOBALFOUNDRIES INC
Random test case generation method facing Java program
The invention discloses a random test case generation method facing a Java program. The random test case generation method comprises the following steps of: (1) resolving a class definition of the Java program, and acquiring an object method list; (2) establishing a dependency relation graph comprising a method calling graph and a property dependency graph among object methods; (3) determining a target method list to be covered; (4) generating a calling chain by aiming at instantiation for public classes, and maintaining a class object base; (5) generating a calling chain by aiming at covering target methods, and maintaining a calling chain base; and (6) generating a test case set for the Java program based on the calling chain base. The method can be widely applied to automatic test work of medium-and large-size Java software systems and can automatically generate test cases completely; the highest code coverage rate is achieved by the least number of test cases; complicated data structures can be processed; test assertion can be automatically generated; and the test case generation method is simple and effective, and has high applicability and expandability.
Owner:NANJING UNIV
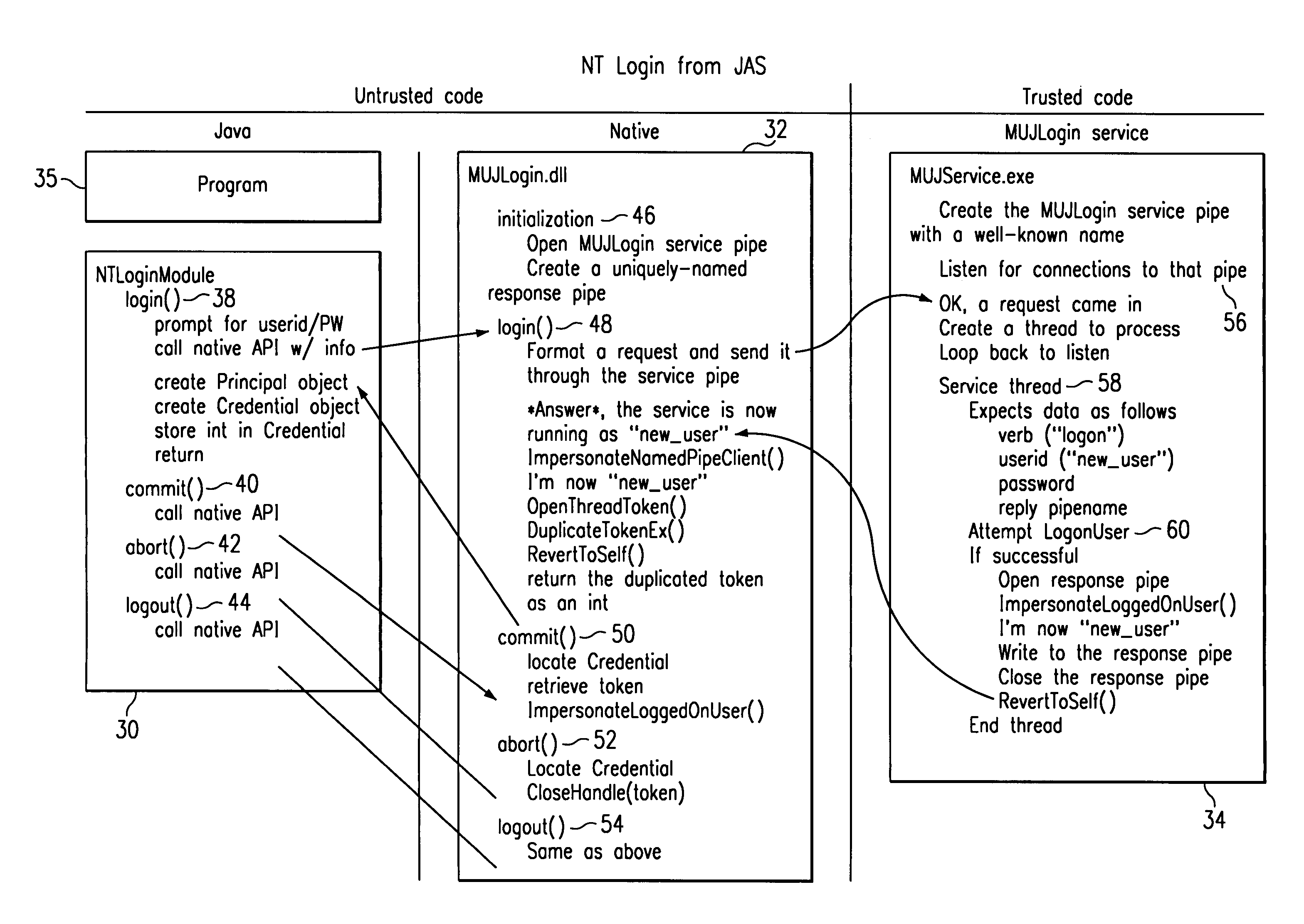
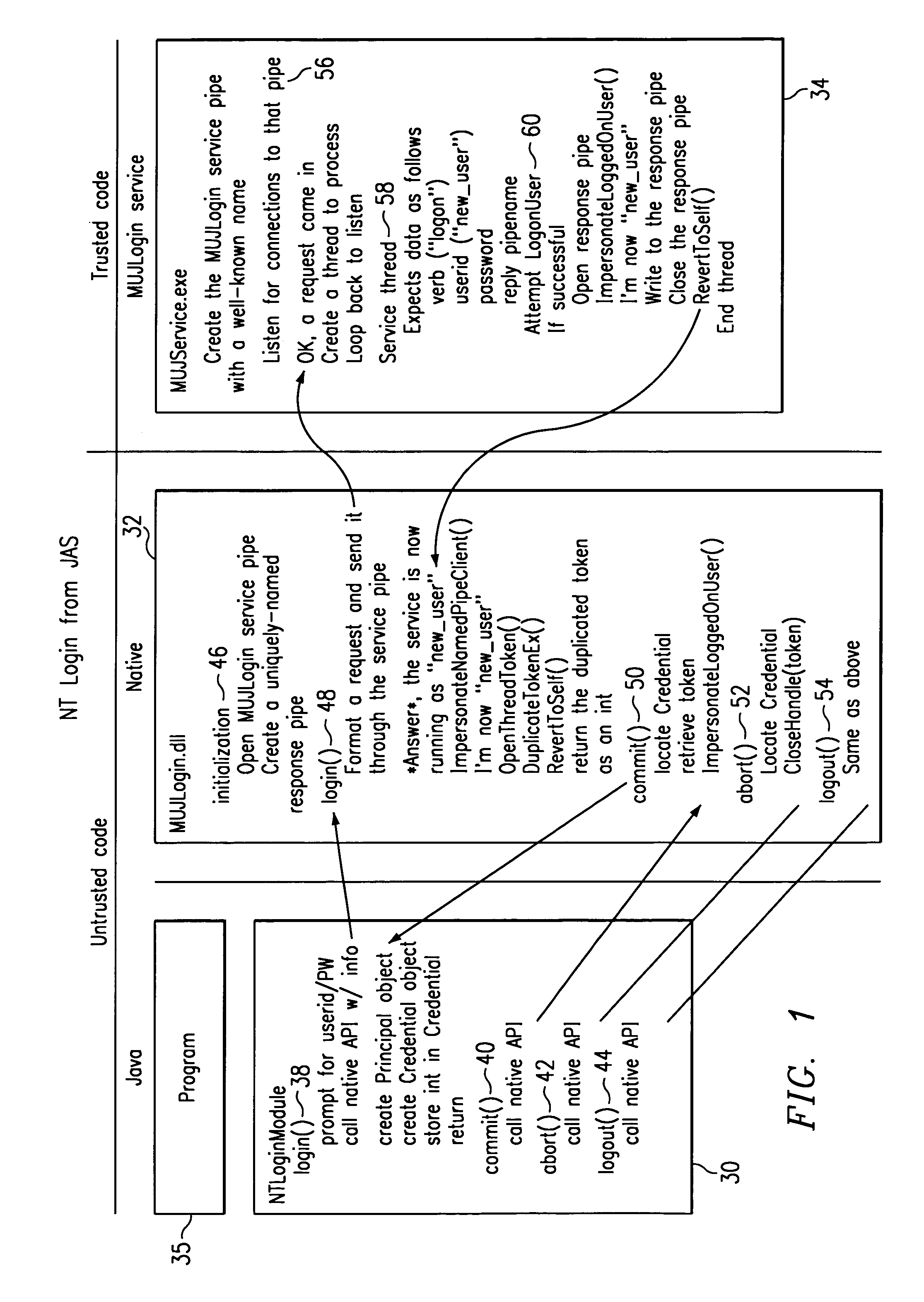
Method for enabling a program written in untrusted code to interact with a security subsystem of a hosting operating system
InactiveUS7451484B1Digital data processing detailsUnauthorized memory use protectionOperational systemSystem identifier
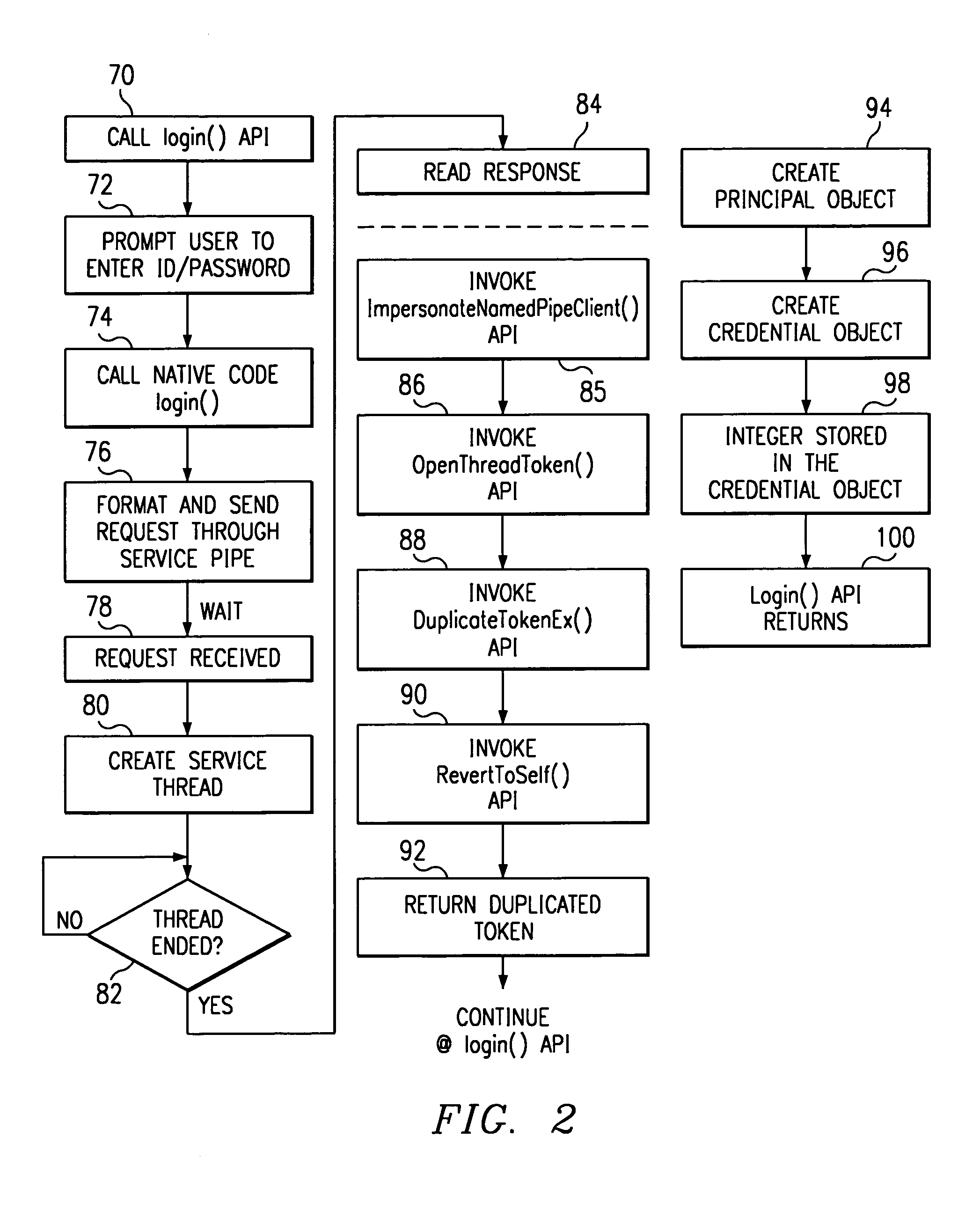
A program written in untrusted code (e.g., JAVA) is enabled to access a native operating system resource (e.g., supported in WINDOWS NT) through a staged login protocol. In operation, a trusted login service listens, e.g., on a named pipe, for requests for login credentials. In response to a login request, the trusted login service requests a native operating system identifier. The native operating system identifier is then sent to the program. Using this identifier, a credential object is then created within an authentication framework. The credential object is then used to login to the native operating system to enable the program to access the resource. This technique enables a JAVA program to access a WINDOWS NT operating system resource under the identity of the user running the JAVA program.
Owner:IBM CORP
Byte-code file reconstruction-based Java type online updating method
ActiveCN101963914AReduce overheadImprove update efficiencyProgram loading/initiatingSoftware deploymentJava classesMachine code
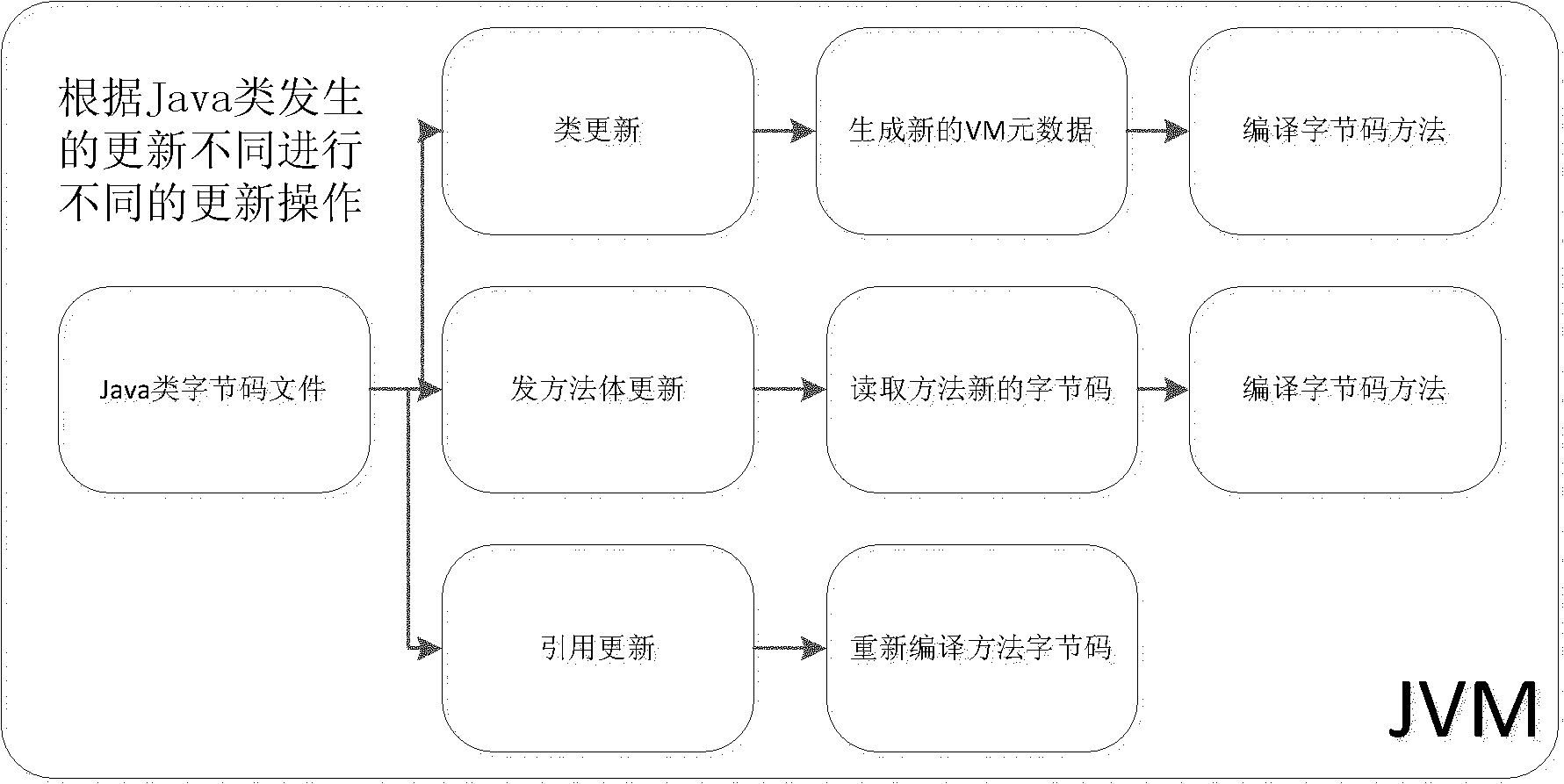
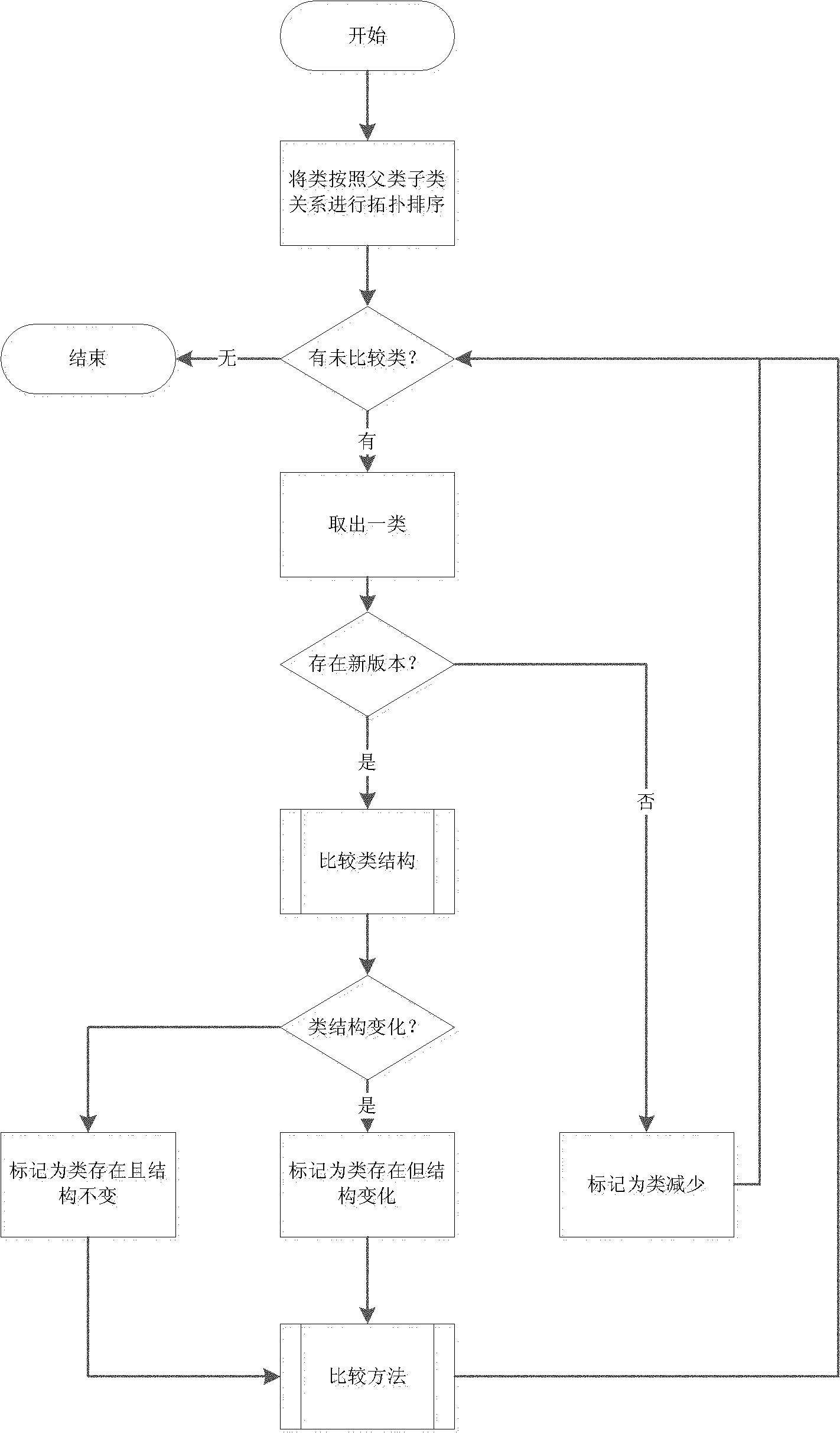
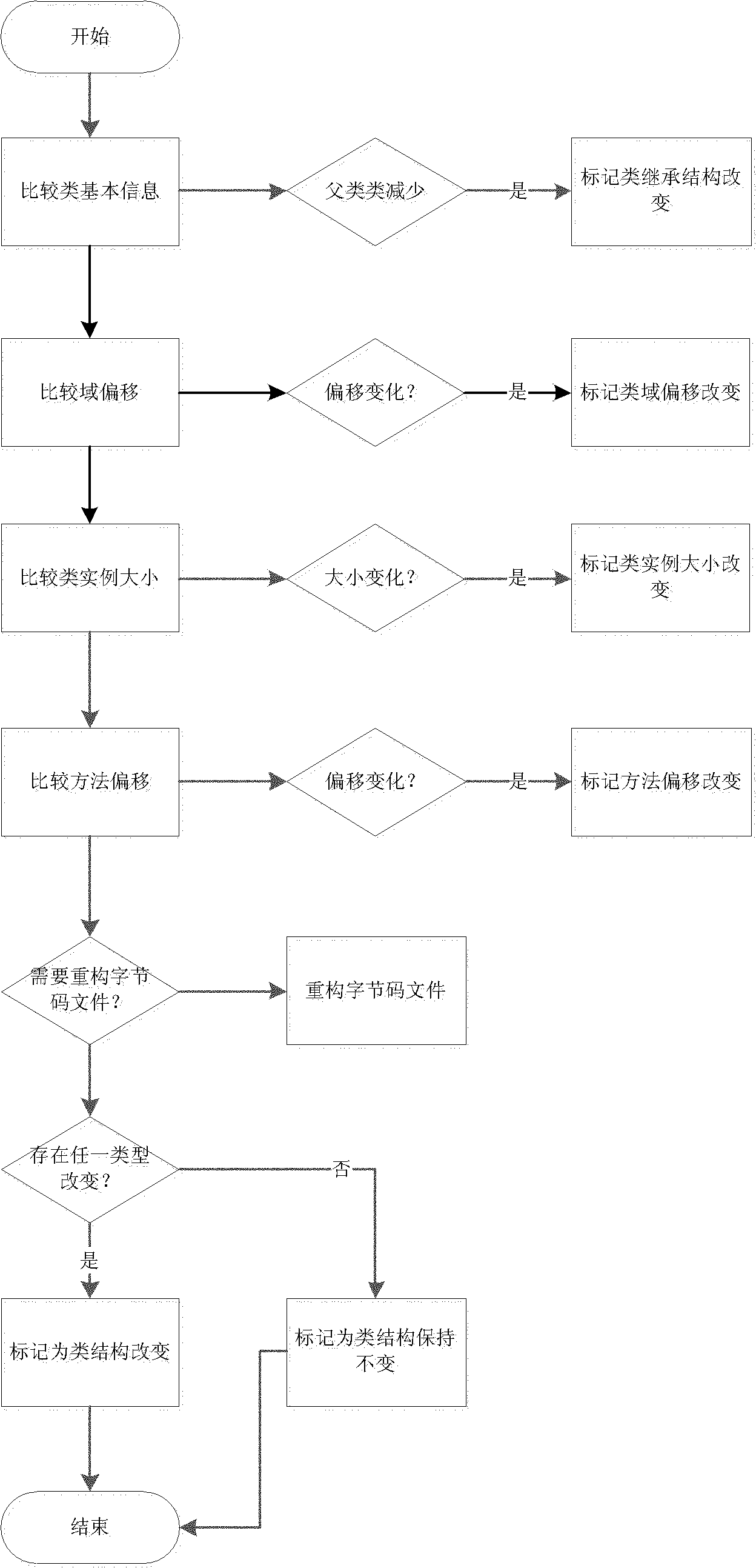
The invention discloses a byte-code file reconstruction-based Java type online updating method. In the method, when Java programs are updated dynamically, binary files are analyzed and reconstructed; and the method is combined with a new VM dynamic loading type mechanism to reduce the expense caused by recompiling a machine code by the dynamic updating during the time of running, and improve the updating efficiency.
Owner:山东中创软件商用中间件股份有限公司
System and method for supporting digital rights management in an enhanced javatm 2 runtime environment
InactiveUS20080060083A1Provide protectionDigital data processing detailsAnalogue secracy/subscription systemsDigital rights management systemRights management
A digital rights management (DRM) system and methodology for a Java client implementing a Java Runtime Environment (JRE). The JRE comprises a Java Virtual Machine (JVM) and Java runtime libraries components and is capable of executing a player application for presenting content that can be presented through a Java program (e.g., a Java application, applet, servlet, bean, etc.) and downloaded from a content server to the client. The DRM system includes an acquisition component for receiving downloaded protected contents; and a dynamic rights management layer located between the JRE and player application for receiving requests to view or play downloaded protected contents from the player, and, in response to each request, determining the rights associated with protected content and enabling viewing or playing of the protected contents via the player application if permitted according to the rights. By providing a DRM-enabled Java runtime, which does not affect the way non-DRM-related programs work, DRM content providers will not require the installation of customized players. By securing the runtime, every Java™ player automatically and transparently becomes a DRM-enabled player.
Owner:INT BUSINESS MASCH CORP
Business object and xml message mutual conversion method and system
InactiveCN105138613AImprove portabilityImprove execution efficiencySemi-structured data mapping/conversionSpecial data processing applicationsDatabaseJava program
The invention relates to a business object and xml message mutual conversion method and system. The method specifically comprises the following steps of: step 1: establishing a message node mapping table, and introducing message node and business object mapping information into the mapping table; step 2: receiving a reading request for reading the message node and business object mapping information into a buffer; step 3: performing format verification on a message node and a business object; and step 4: the system, according to a mapping relationship, converting the XML message into the business object; or the system, according to the mapping relationship, converting the business object into XML message data. The business object and xml message mutual conversion method adopts java programming, so that the code execution efficiency and reliability are relatively high and the program portability is good; and configuration is simple and flexible, mutual conversions between XML messages in different formats and business objects with different structures are supported, and the maintainability is good.
Owner:北京思特奇信息技术股份有限公司
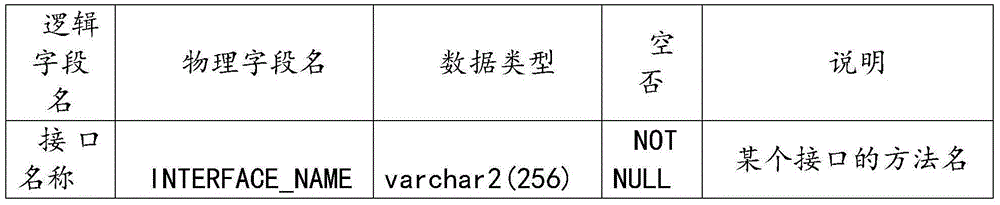
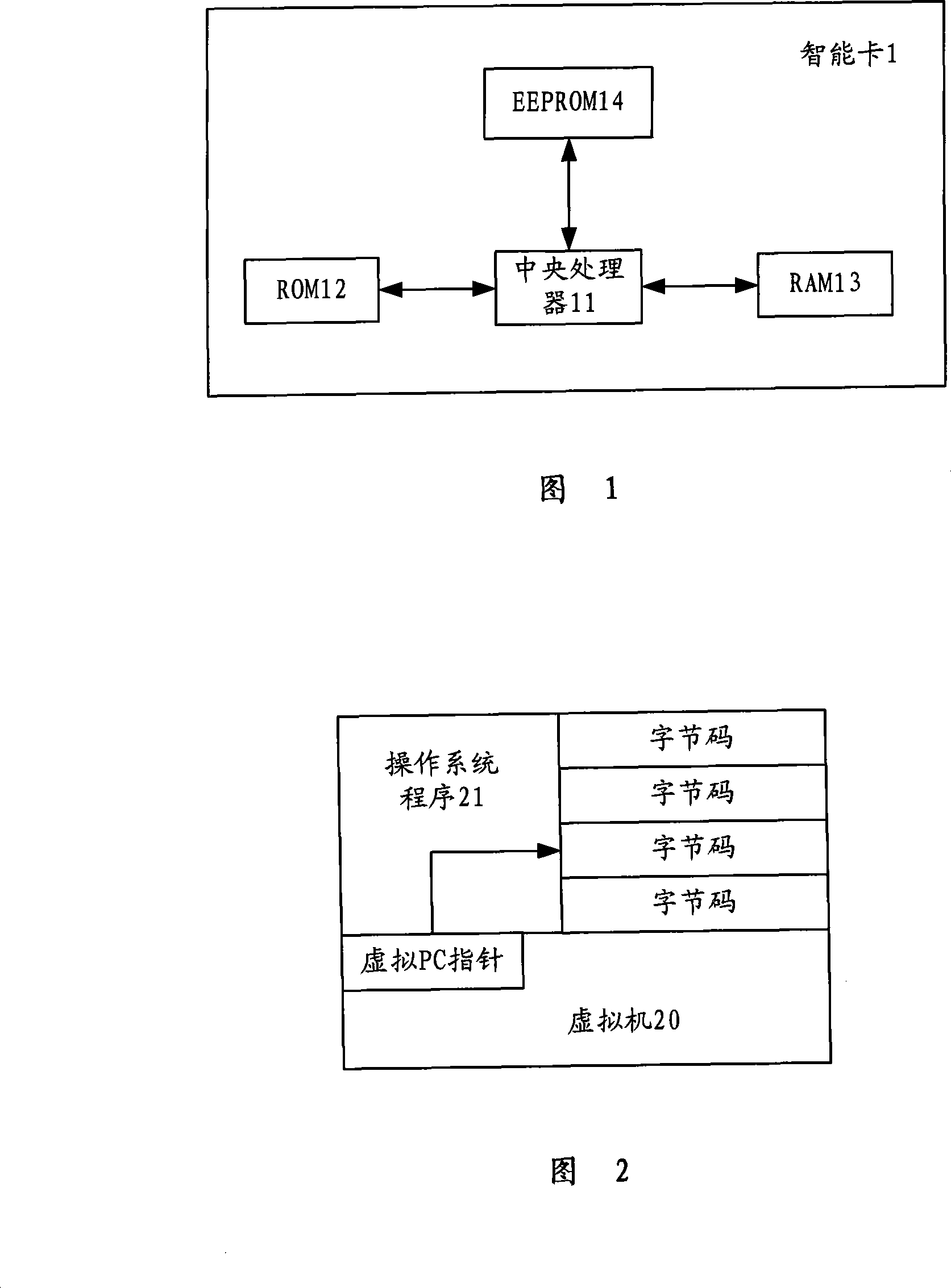
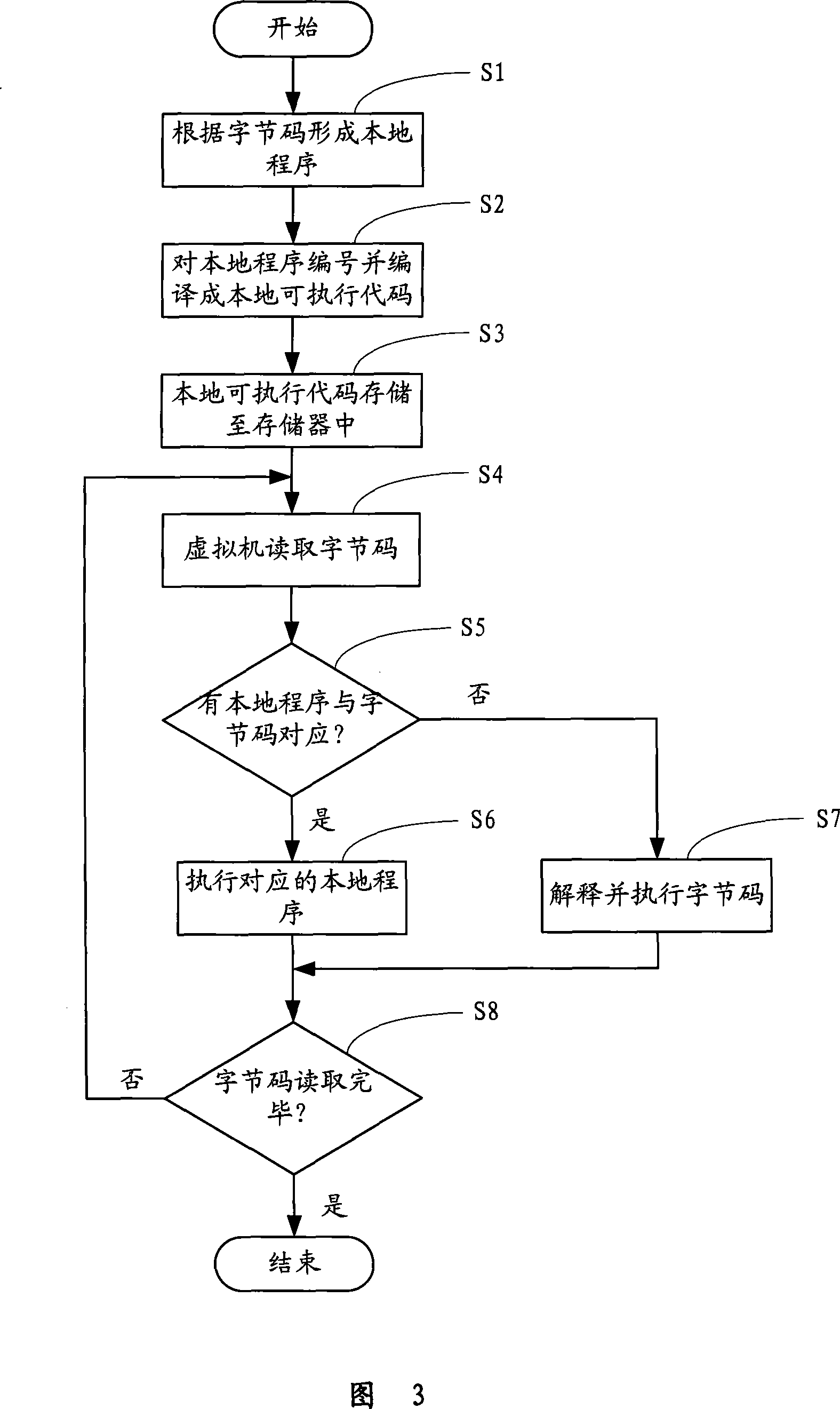
Method for execution of JAVA program instruction in smart card
InactiveCN101231597AEasy to identifyEnsure correct executionProgram controlRecord carriers used with machinesSmart cardByte
The invention provides an implementing method for the JAVA program instruction in a smart card. A virtual computer which can execute the JAVA program, as well as a central processing unit and a memory which can be visited by the central processing unit are arranged in the smart card, and the bytecode of the JAVA program is stored in the memory. The method comprises the following steps that: the bytecode is changed into a series of callings to the native code, so as to from a native program; the native program is compiled into a native executable code, and the native executable code is stored in the memory of the smart card; a virtual computer reads the byte code, and judges whether the native program which corresponds to the read byte code exists, if yes, the corresponding program is executed, if no, the read byte code is explained and executed. By utilizing the method of the invention to execute the JAVA program, the executing time of the JAVA program is greatly reduced, and the running speed of the smart card is improved.
Owner:EASTCOMPEACE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com