Patents
Literature
108 results about "Long code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
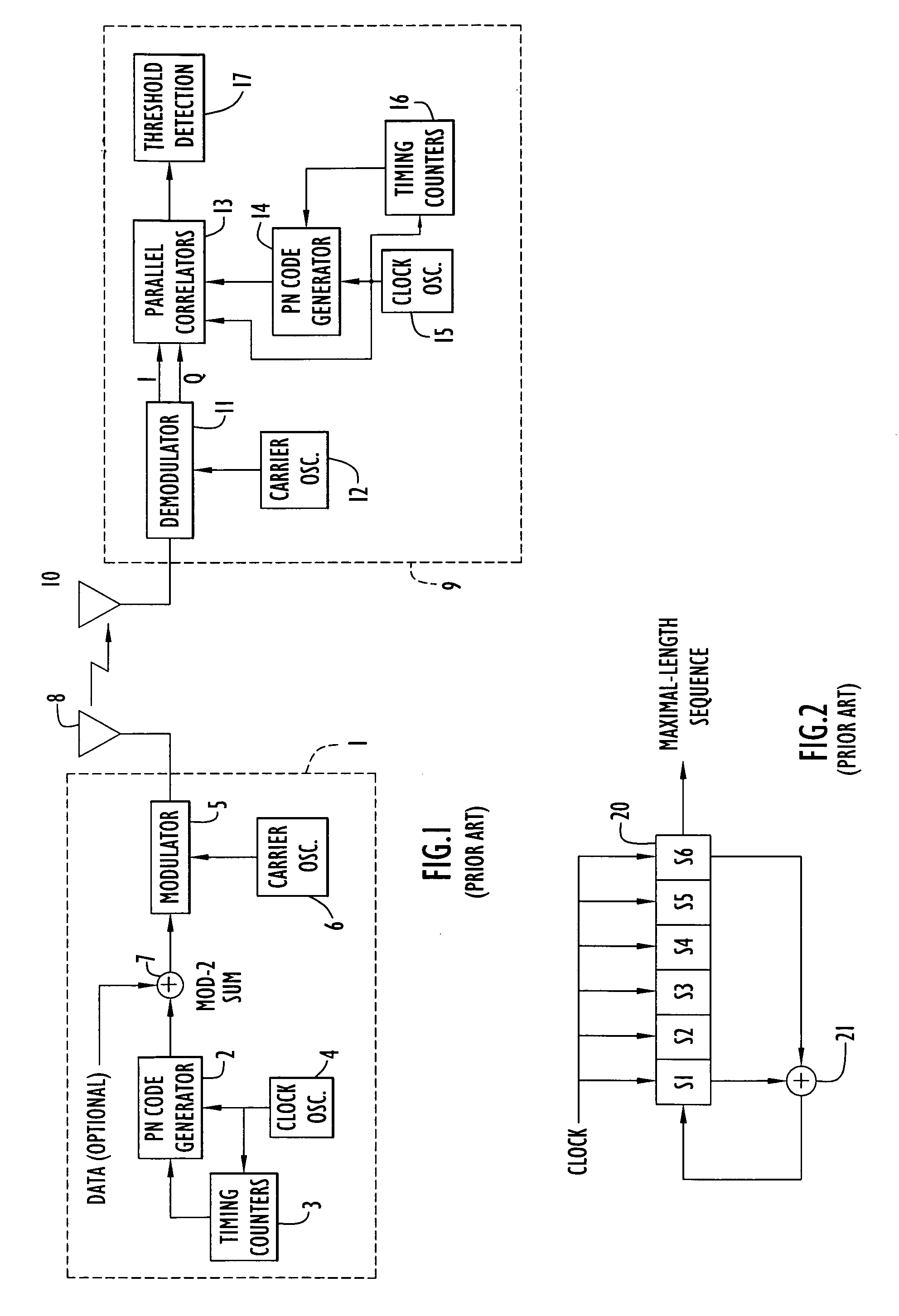
In theoretical computer science and coding theory, the long code is an error-correcting code that is locally decodable. Long codes have an extremely poor rate, but play a fundamental role in the theory of hardness of approximation.
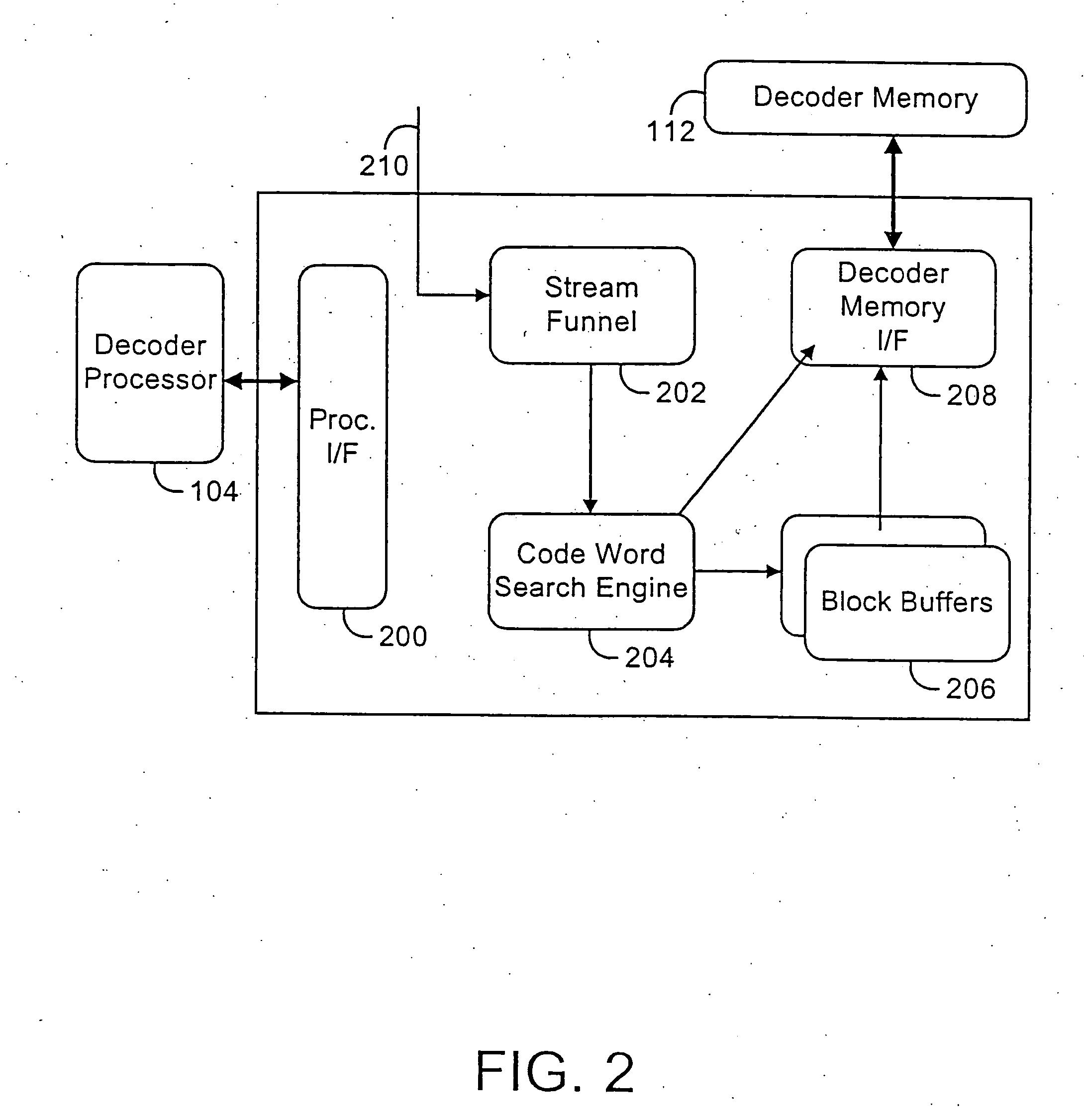
Method and apparatus for encoding a plurality of pre-defined codes into a search key and for locating a longest matching pre-defined code
InactiveUS20050157724A1Precise positioningEliminate needData processing applicationsCode conversionBit arrayTheoretical computer science
A method and apparatus for locating in a list of pre-defined codes, a longest code matching a given code. The method and apparatus involve producing a search mask encoding at least one portion of said given code and comparing the search mask to a search key having a Prefix Node Bit Array (PNBA) in which a bit is set active in at least one of a plurality of bit positions corresponding to possible bit combinations of bits in a bit string having a length equal to or less than the longest predefined code in the plurality of pre-defined codes and arranged by the lengths of possible bit combinations and by numeric values of the bit combinations, to identify a common active bit position in the search key and the search mask corresponding to one of the pre-defined codes having a length greater than all others of said pre-defined codes which correspond to common active bit positions.
Owner:RPX CLEARINGHOUSE
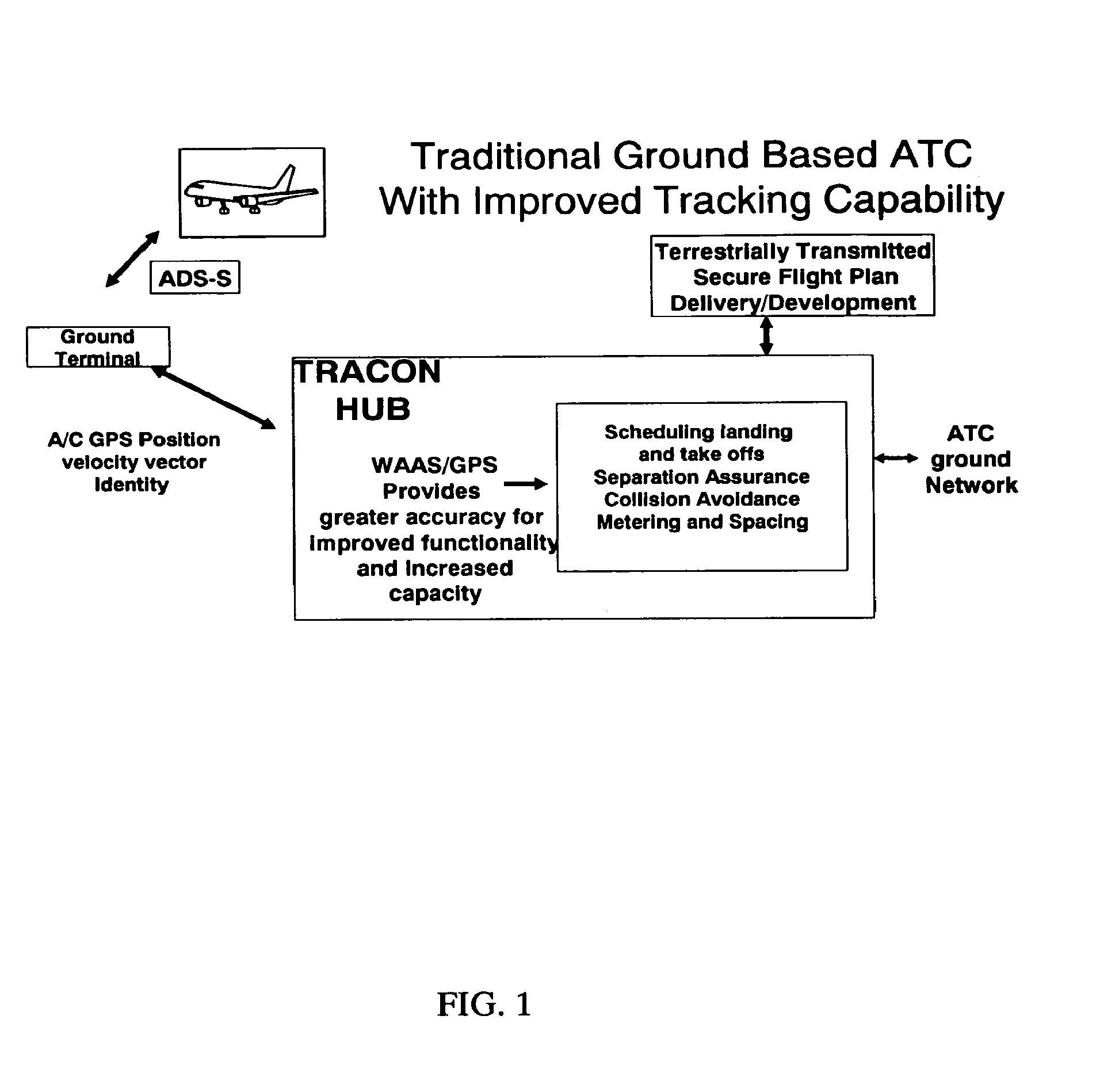
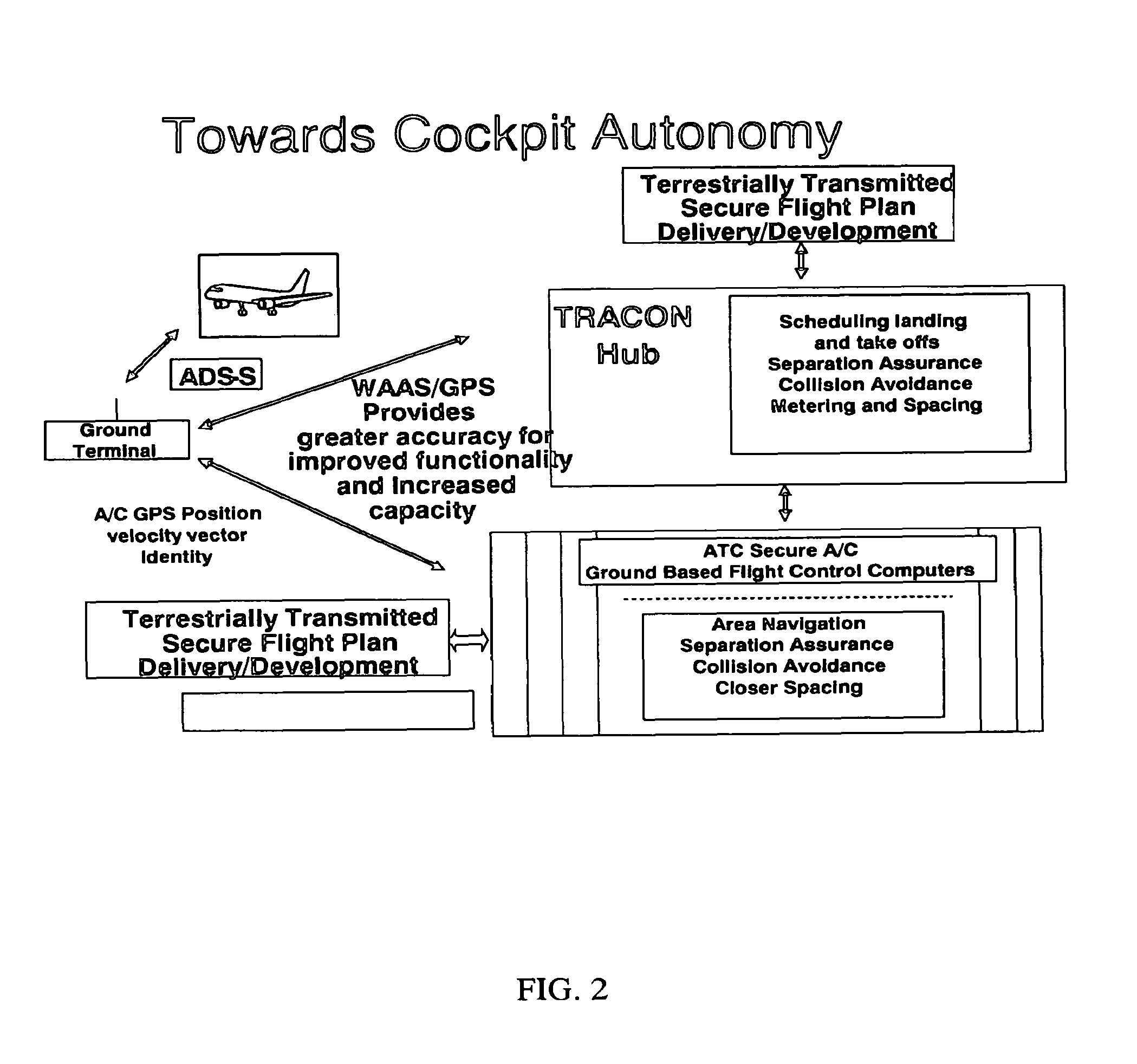
Automatic dependent surveillance system secure ADS-S
InactiveUS7876259B2Analogue computers for vehiclesAnalogue computers for trafficSystem capacityFrequency spectrum
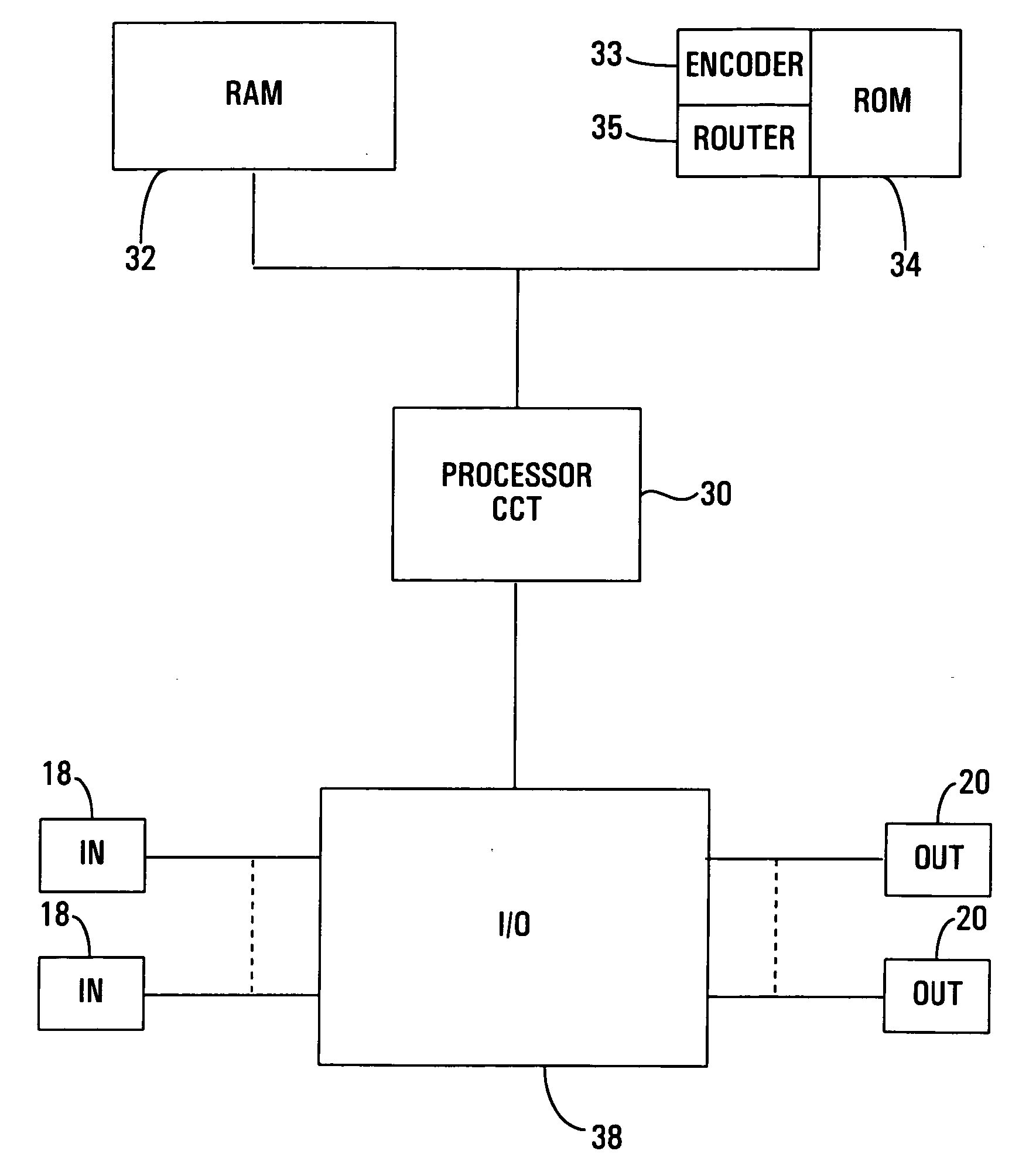
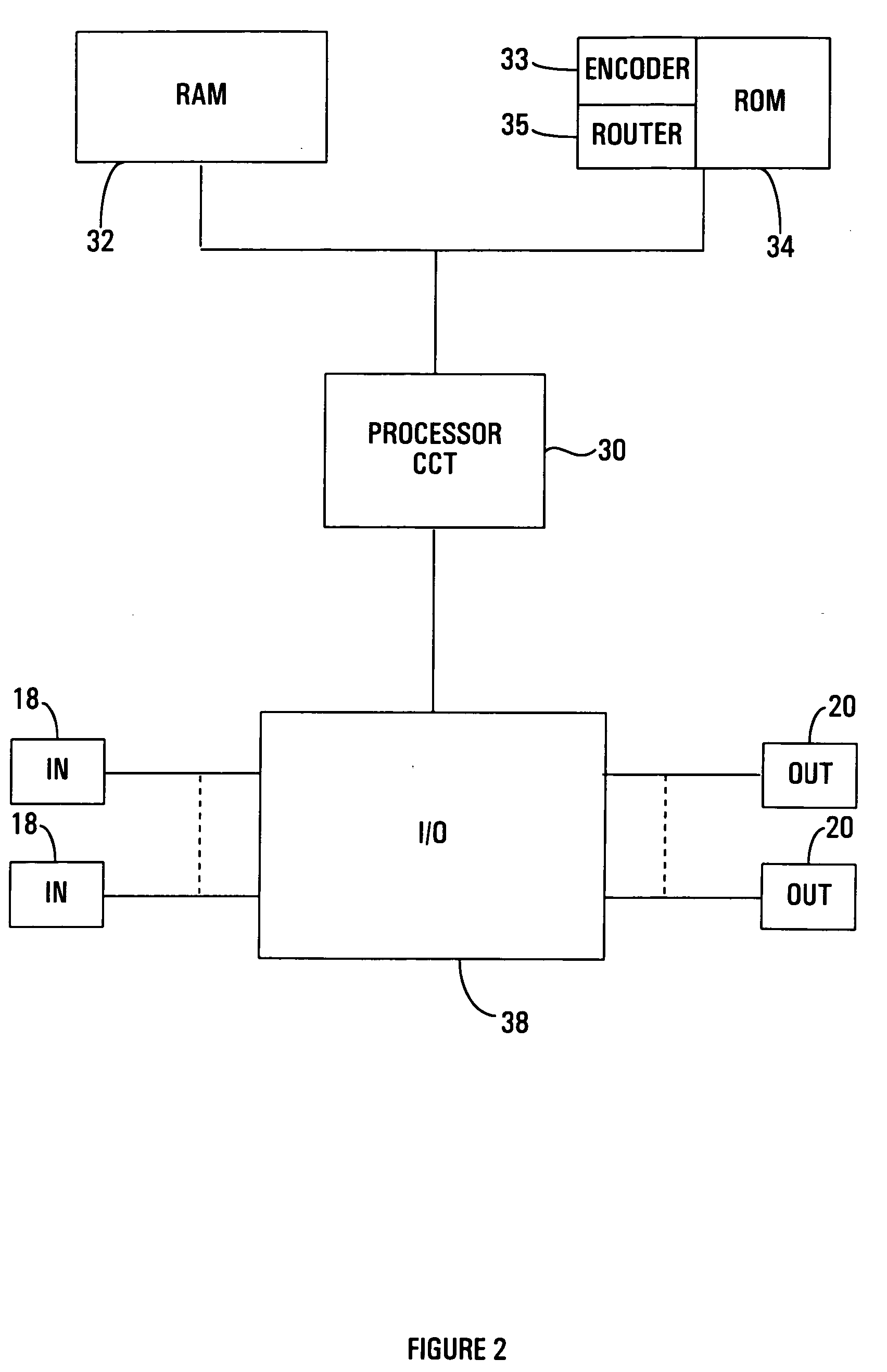
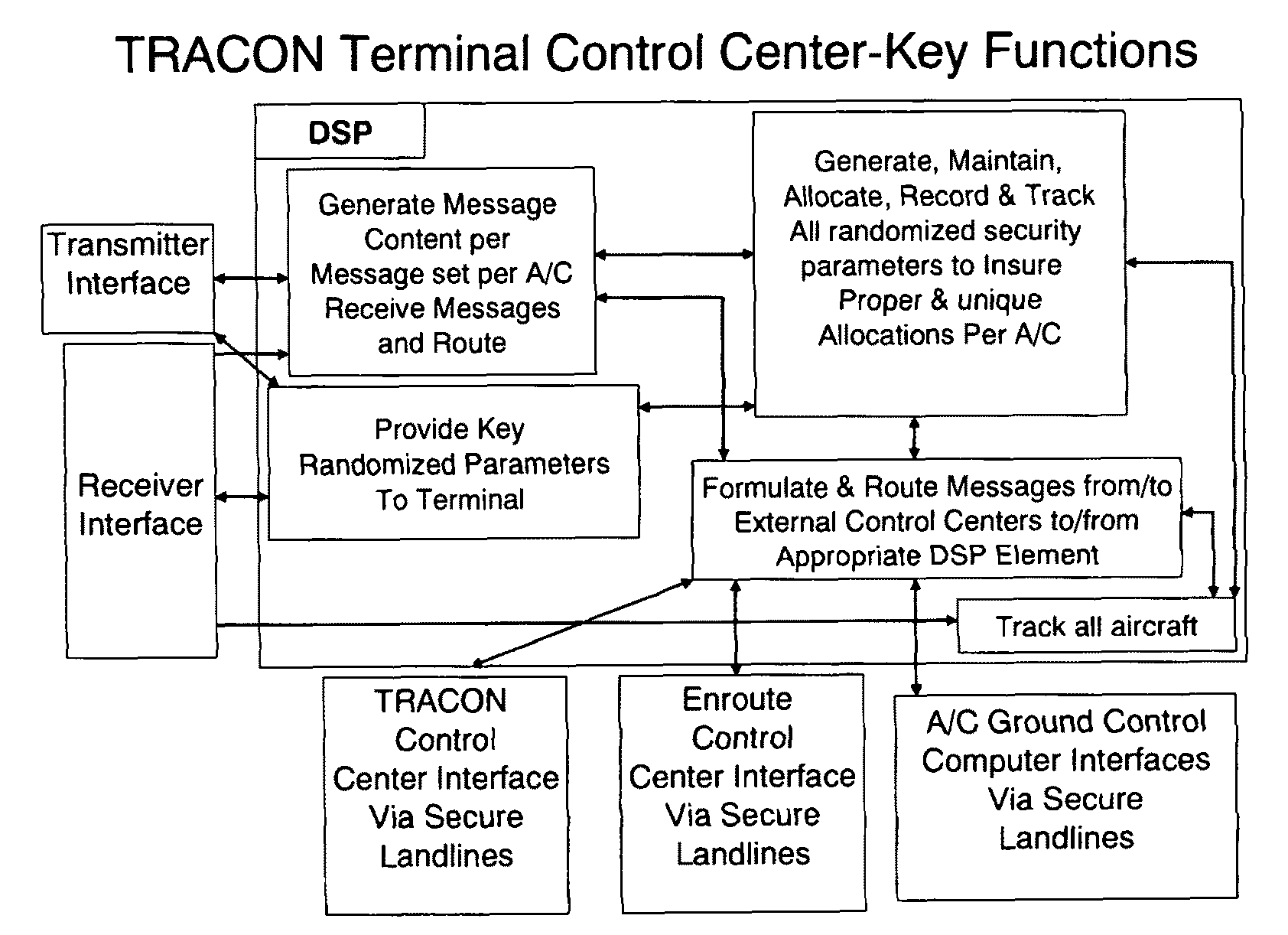
An air traffic control automatic dependent, WAAS / GPS based, surveillance system (ADS), for operation in the TRACON airspace. The system provides encryption protection against unauthorized reading of ADS messages and unauthorized position tracking of aircraft using multilateration techniques. Each aircraft has its own encryption and long PN codes per TRACON and transmit power is controlled to protect against unauthorized ranging on the ADS-S aircraft transmission. The encryption and PN codes can be changed dynamically. Several options which account for available bandwidth, burst data rates, frequency spectrum allocations, relative cost to implement, complexity of operation, degree of protection against unauthorized users, system capacity, bits per aircraft reply message and mutual interference avoidance techniques between ADS-S, ADS-B Enroute and Mode S / ATCRBS TRACON are disclosed. ADS messages are only transmitted as replies to ATC ground terminal interrogations (no squittering). Derivative surveillance backup systems provide an anti-spoofing capability.
Owner:SCHUCHMAN LEONARD
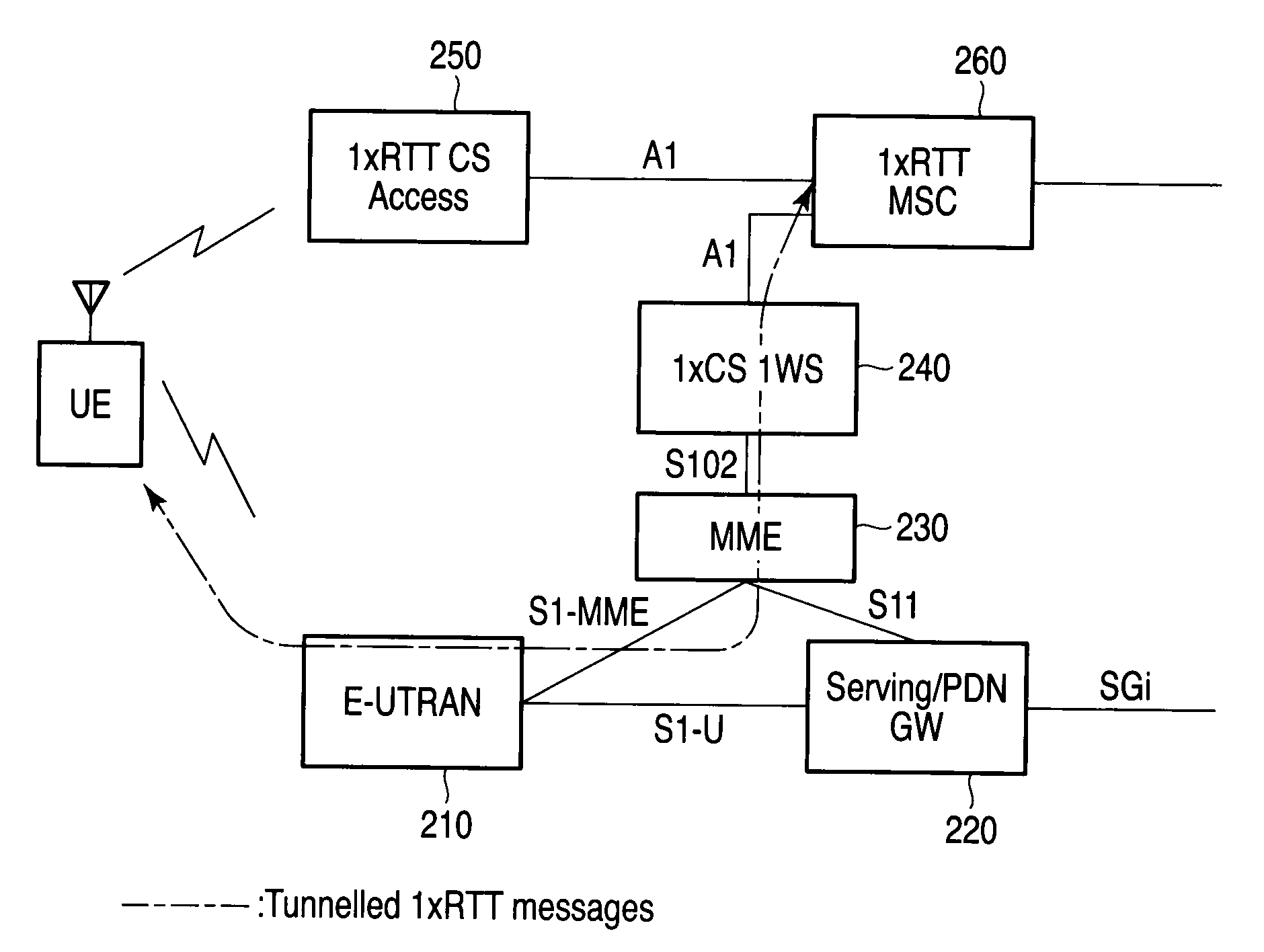
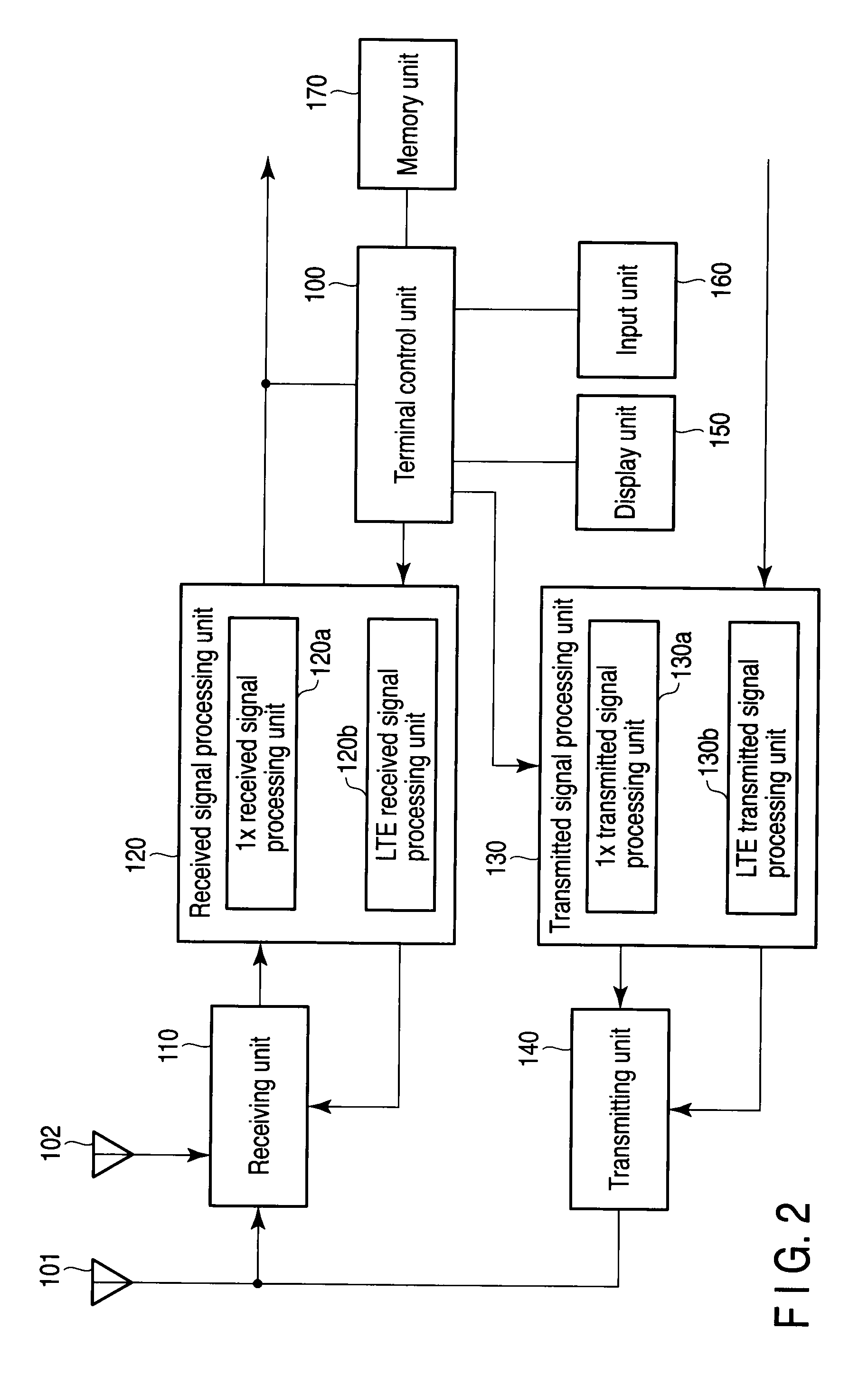
Mobile radio terminal and radio communication method
InactiveUS20100195568A1Short timeAssess restrictionCode division multiplexMobile radioMobile wireless
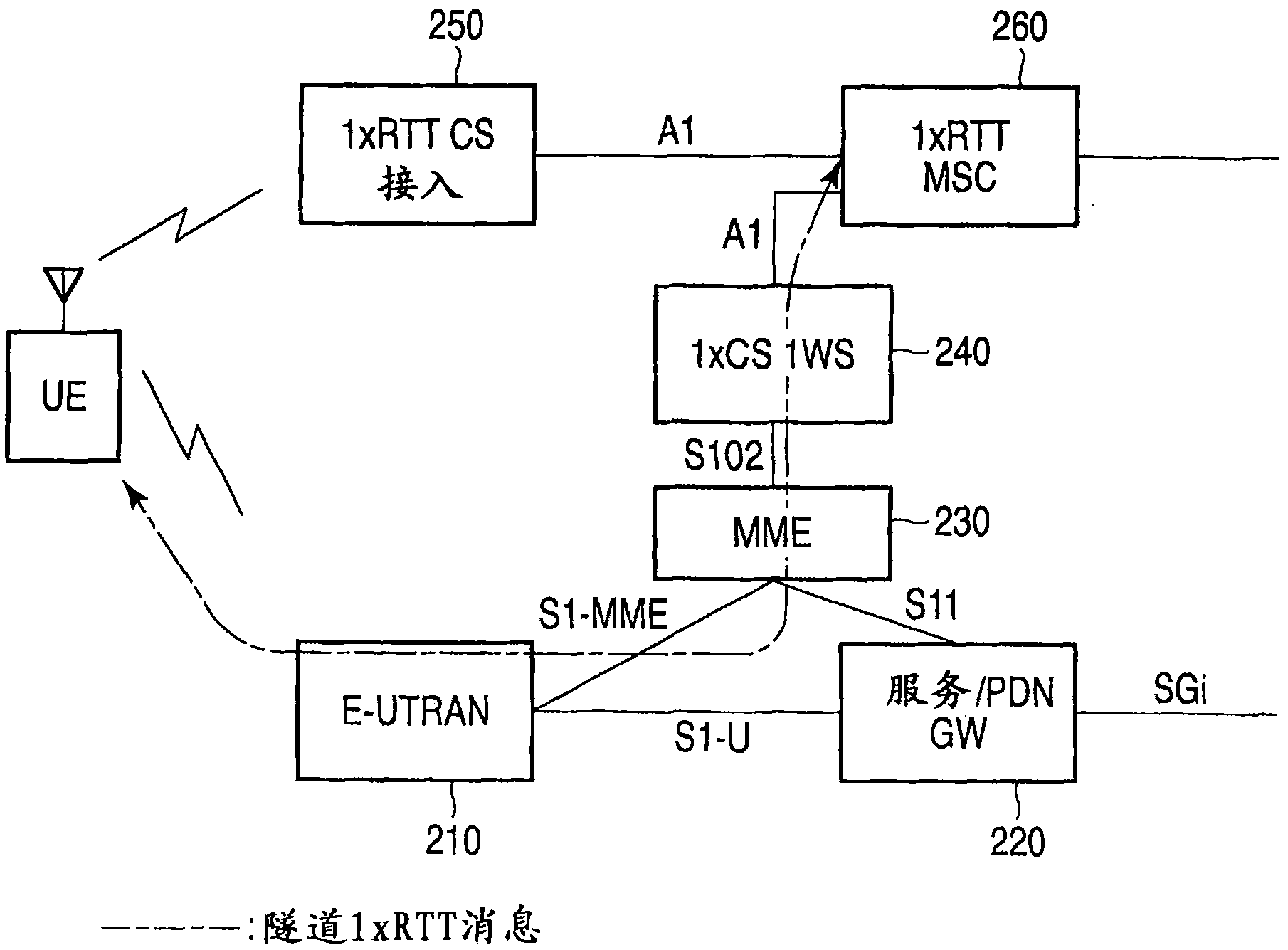
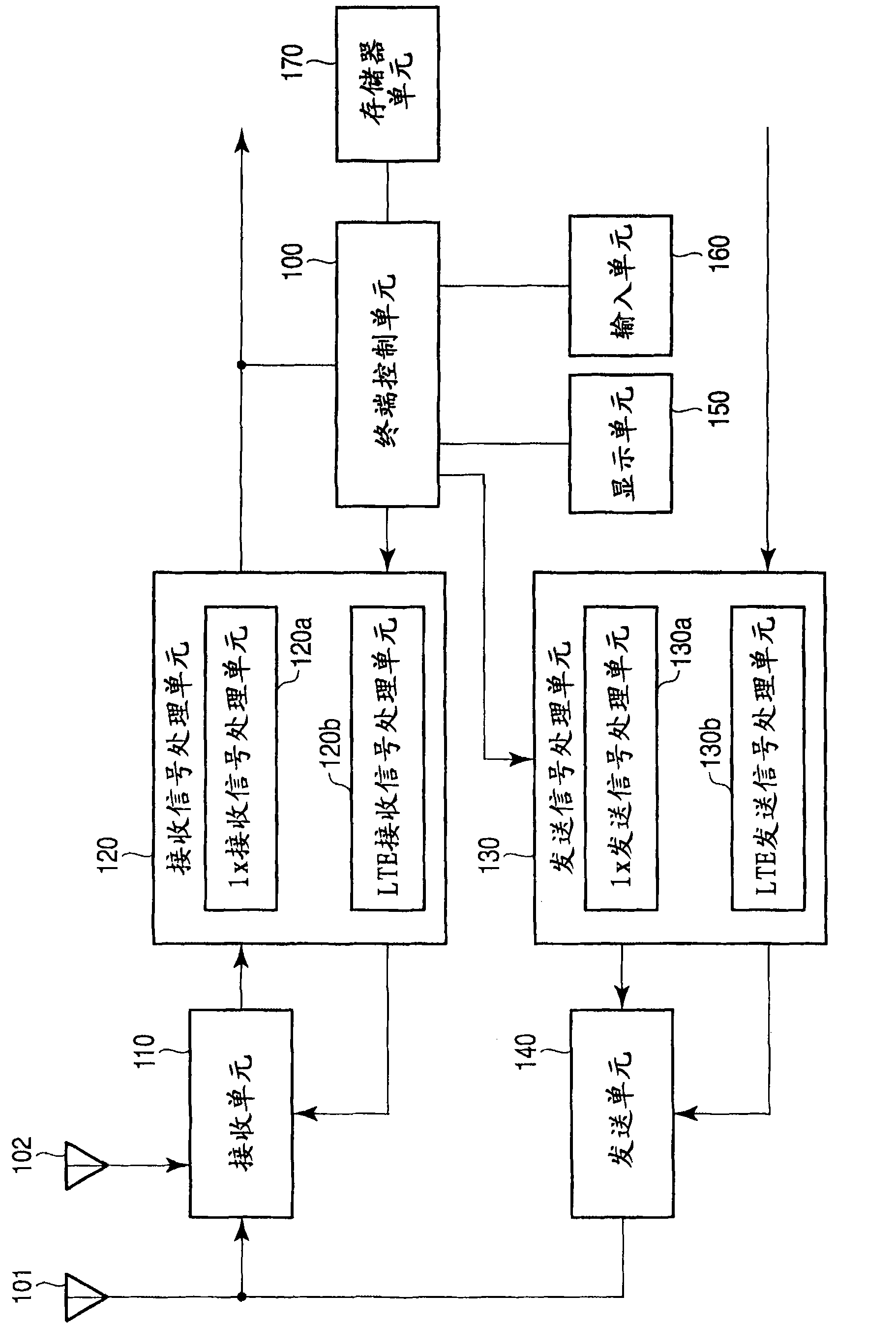
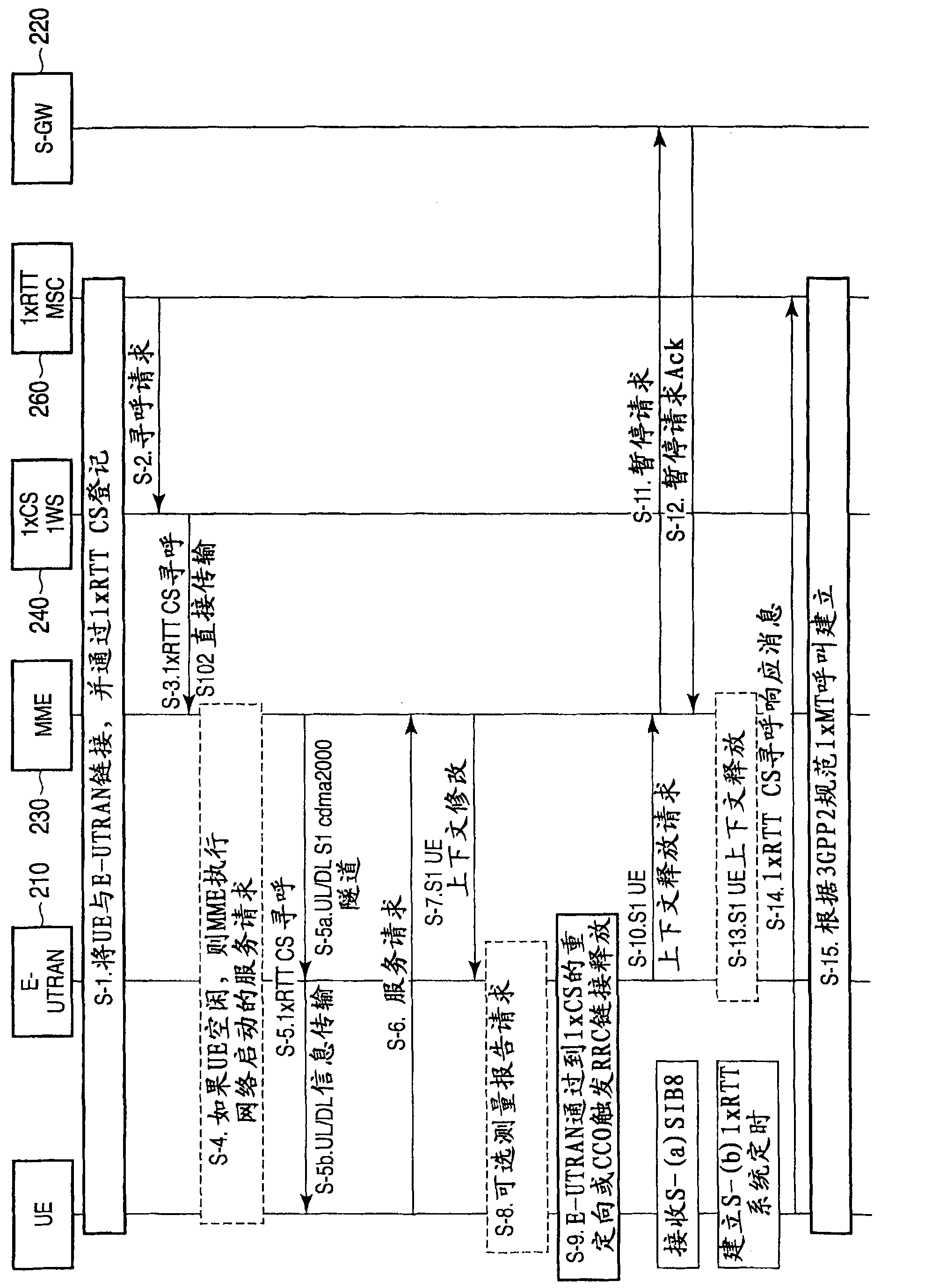
A mobile radio terminal UE performs starting PNG, detecting a best cell, and starting generation of Long Code and receives various types of messages from a 1×RTT CS Access on the basis of System Information supplied from an E-UTRAN.
Owner:FUJITSU TOSHIBA MOBILE COMM LTD
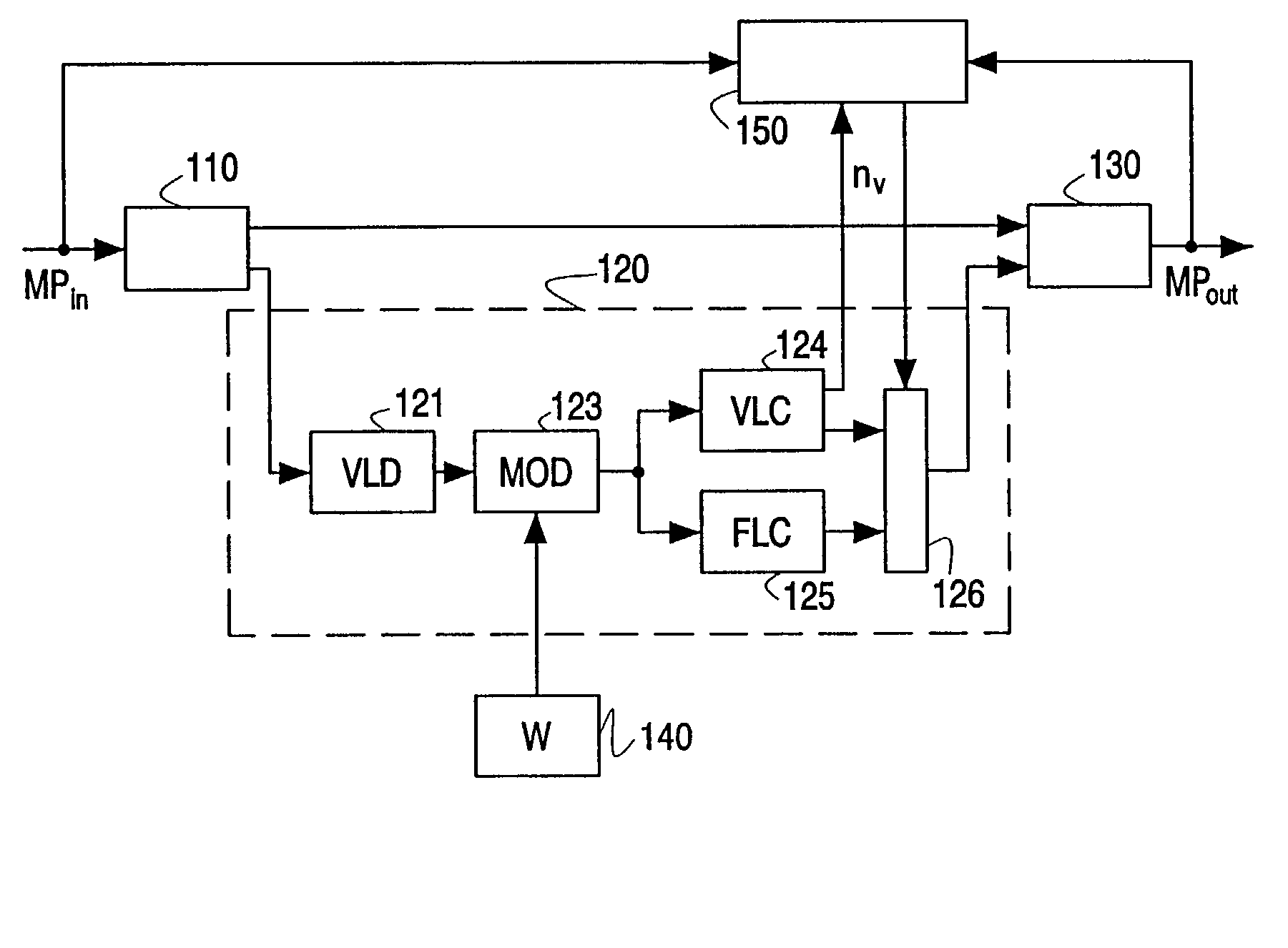
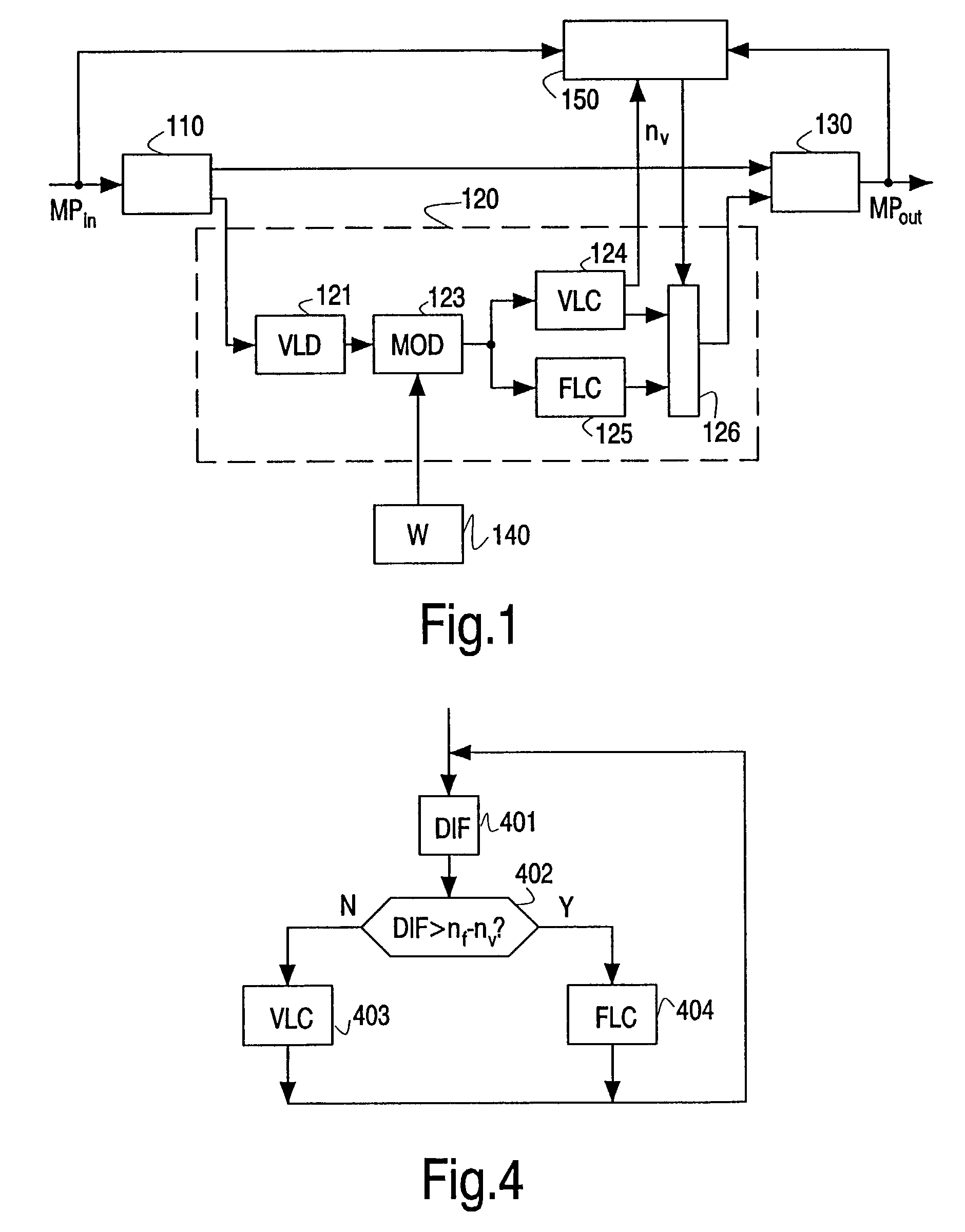
Processing a compressed media signal
InactiveUS20030016756A1Reduce bitratePicture reproducers using cathode ray tubesCode conversionVariable lengthSpatial noise
A method and arrangement are disclosed for processing a compressed media signal, for example, embedding a watermark in an MPEG2 video signal. The watermark, a spatial noise pattern (140), is embedded (123) by selectively discarding the smallest quantized DCT coefficients. The discarded coefficients are subsequently merged in the runs of other run / level pairs. To compensate for a too large reduction of the bit rate, some of the new run / level pairs are not variable-length encoded (124) but represented by longer code words according to further coding rule (125) providing such longer code words, for example, MPEG's "Escape coding".
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
System for direct acquisition of received signals
ActiveUS7224721B2High degree of parallelismQuick alignmentAmplitude-modulated carrier systemsSatellite radio beaconingTime correlationData acquisition
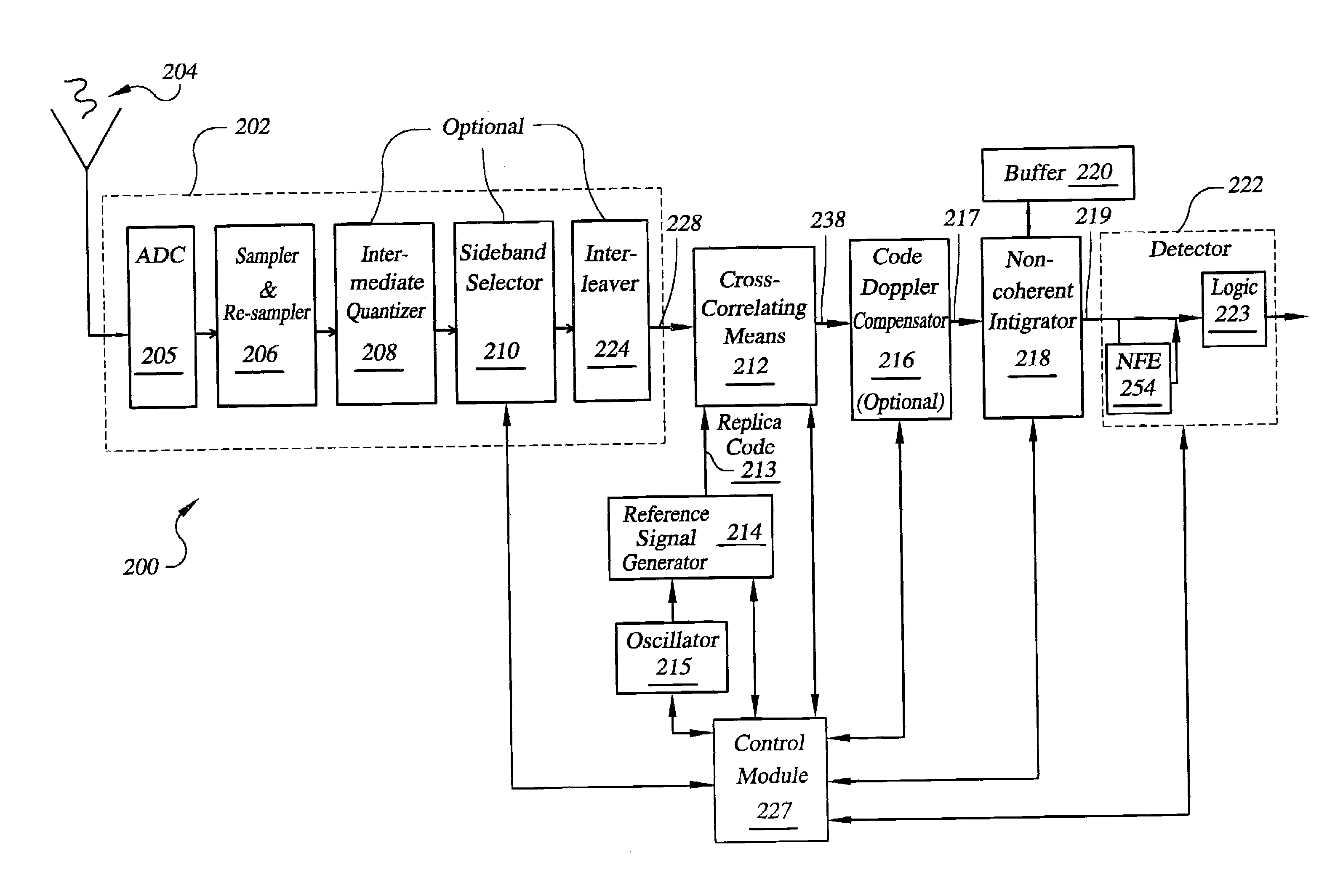
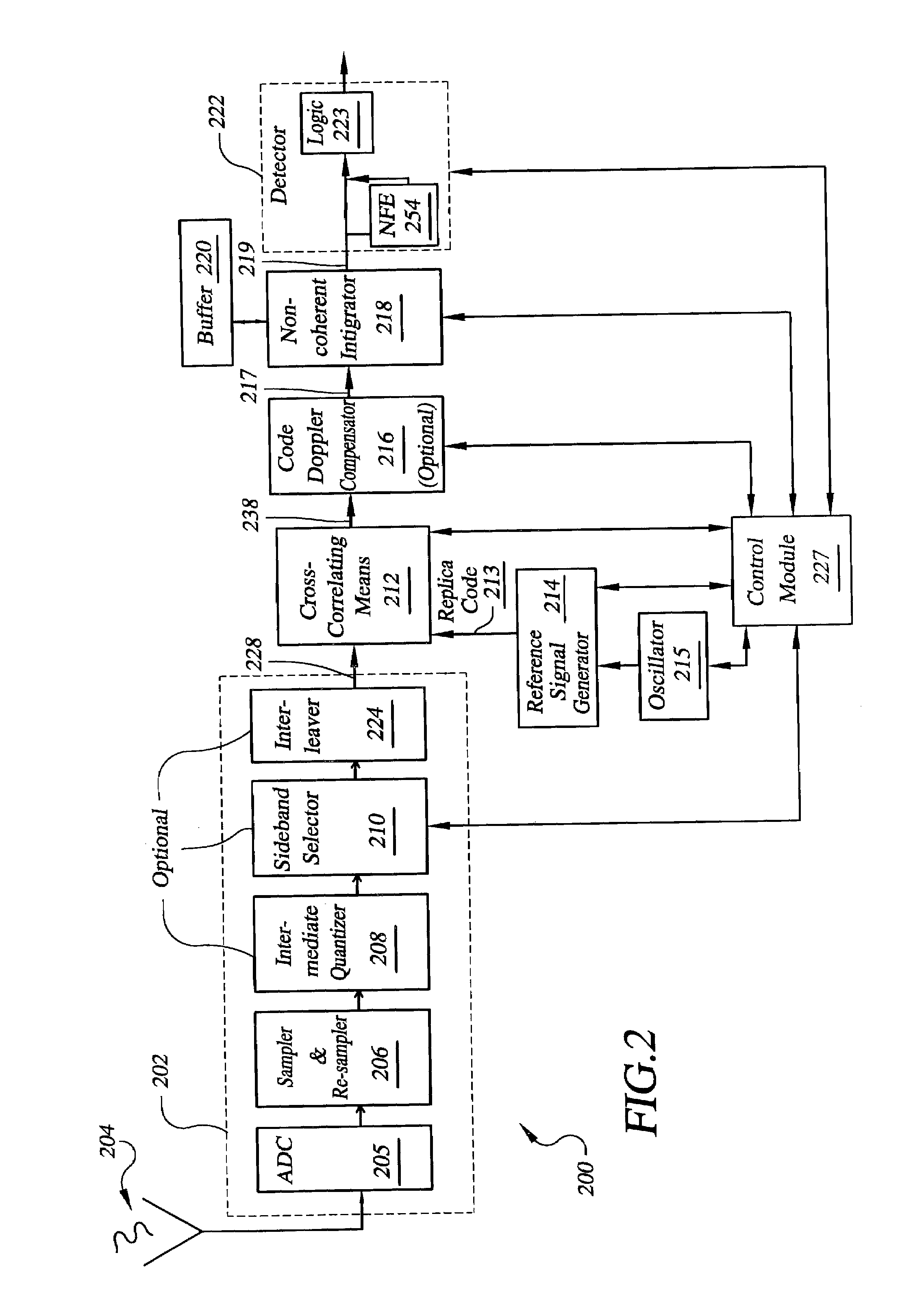
Signal processing architectures for direct acquisition of spread spectrum signals using long codes. Techniques are described for achieving a high of parallelism, employing code matched filter banks and other hardware sharing. In one embodiment, upper and lower sidebands are treated as two independent signals with identical spreading codes. Cross-correlators, in preferred embodiments, are comprised of a one or more banks of CMFs for computing parallel short-time correlations (STCs) of received signal samples and replica code sequence samples, and a means for calculating the cross-correlation values utilizing discrete-time Fourier analysis of the computed STCs. One or more intermediate quantizers may optionally be disposed between the bank of code matched filters and the cross-correlation calculation means for reducing word-sizes of the STCs prior to Fourier analysis. The techniques described may be used with BOC modulated signals or with any signal having at least two distinct sidebands.
Owner:MITRE SPORTS INT LTD
Transmitter, transmitting method, receiver, and receiving method for MC-CDMA communication system
InactiveUS7130293B2Accurate detectionTime-division multiplexMultiplex code generationCarrier signalMulti carrier
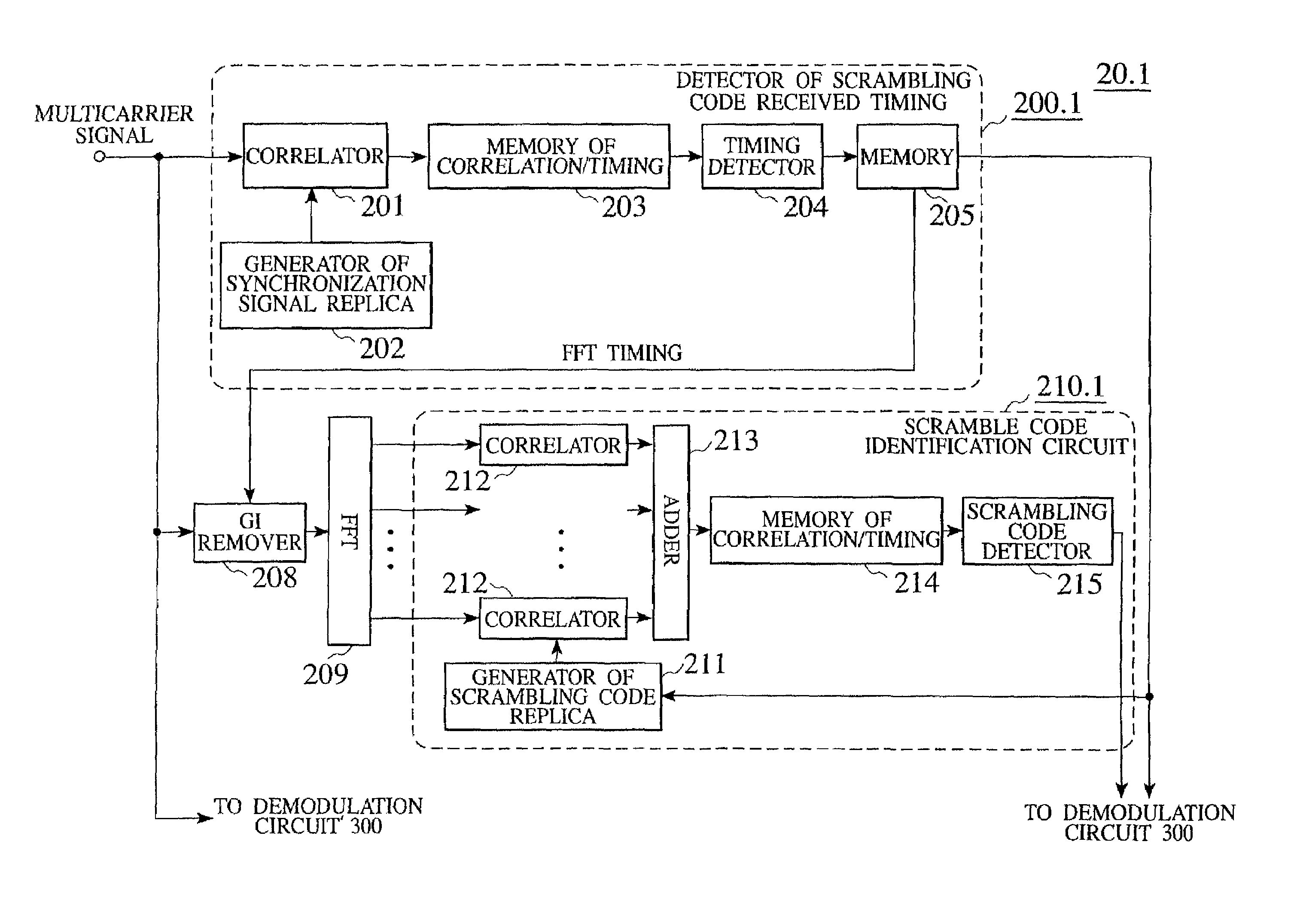
A reception step receives a multicarrier signal containing subcarriers, at least one of which a synchronization signal is transmitted therein, multiplied only by a synchronization signal spreading code, a correlation detection step detects correlation values between the received multicarrier signal and replicas of the synchronization signal, and a timing detection step detects a FFT timing and a long code received timing according to the correlation values.
Owner:NTT DOCOMO INC
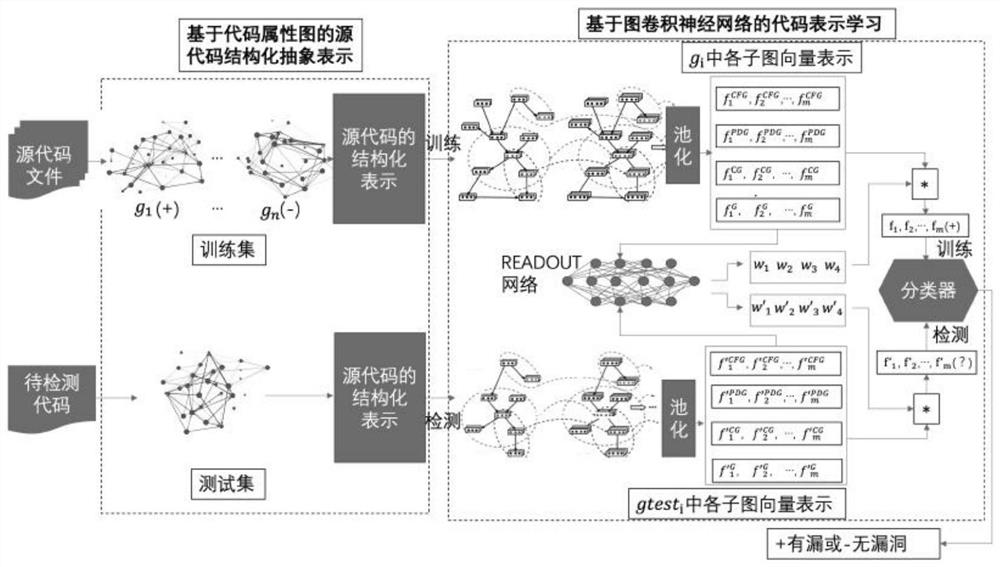
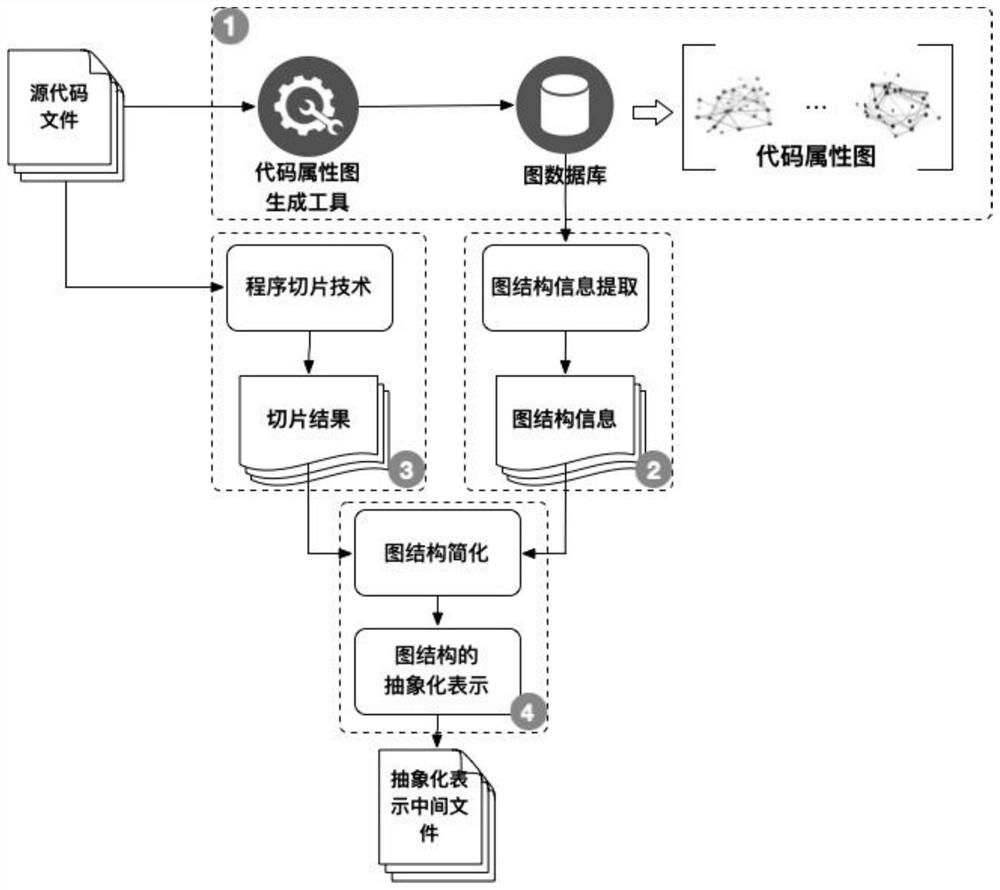
Source code vulnerability detection method for code graph representation learning based on graph convolution network
ActiveCN111783100ASmall scaleIncrease training speedPlatform integrity maintainanceNeural architecturesAlgorithmTheoretical computer science
The invention discloses a source code vulnerability detection method for code graph representation learning based on a graph convolution network. The method comprises the following steps: generating acode attribute graph; adding a function calling relationship and an inter-process dependency relationship into the code attribute graph; obtaining code slices according to the vulnerability key points; deleting nodes in the graph by utilizing slices, and extracting graph structure information related to vulnerabilities; learning vector representation of each node by using a graph convolution network; dividing the sub-graphs according to the types of the edges, and obtaining vector representation of the graphs through a READOUT model based on an attention mechanism; adjusting network parameters according to the vector representation and the label of the graph; and detecting the code vulnerability by using the trained model. According to the method, the structure and attribute information of the vulnerability code can be fully utilized and learned, the problems that code structure information is easy to lose when a traditional deep network learns code representation and long code context information is lost due to the fact that the code needs to be represented as a fixed length sequence are avoided, and false alarm and missing alarm of vulnerability detection are reduced.
Owner:HARBIN INST OF TECH
Initial synchronization method in DS-CDMA inter-base station asynchronous cellular scheme
InactiveUS6965586B1Increase speedImprove processing efficiencySynchronisation arrangementAssess restrictionComputer scienceBase station
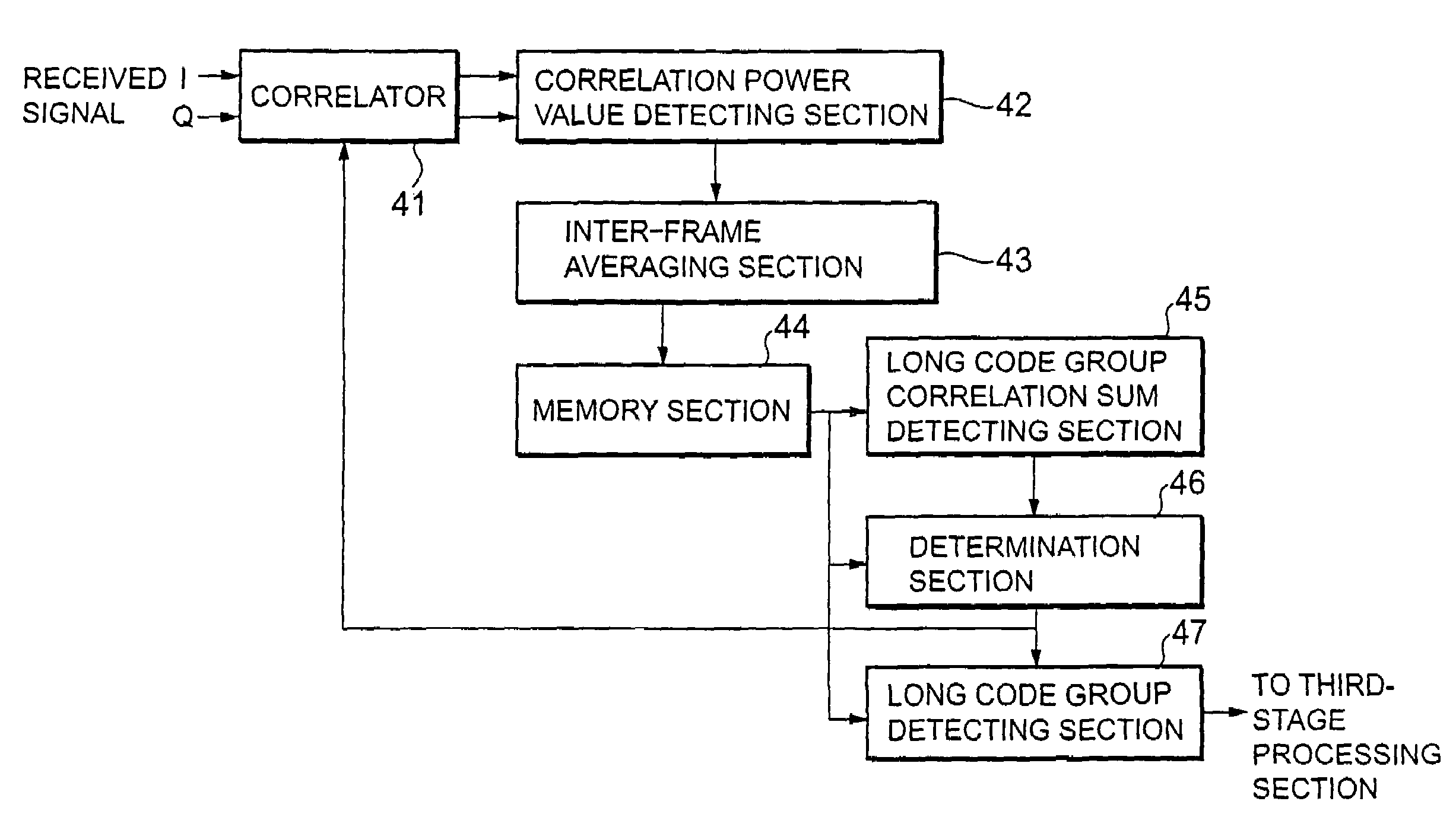
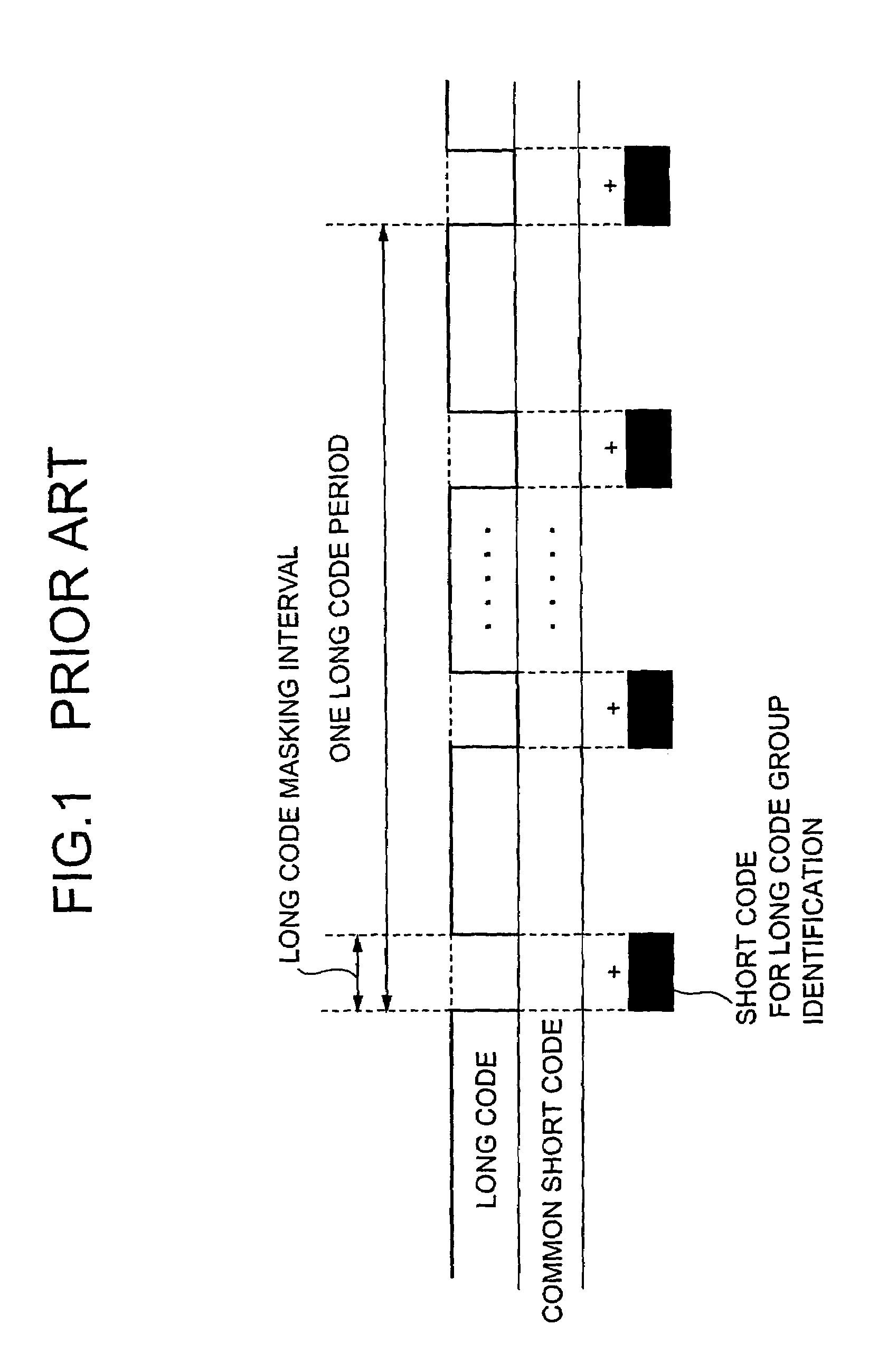
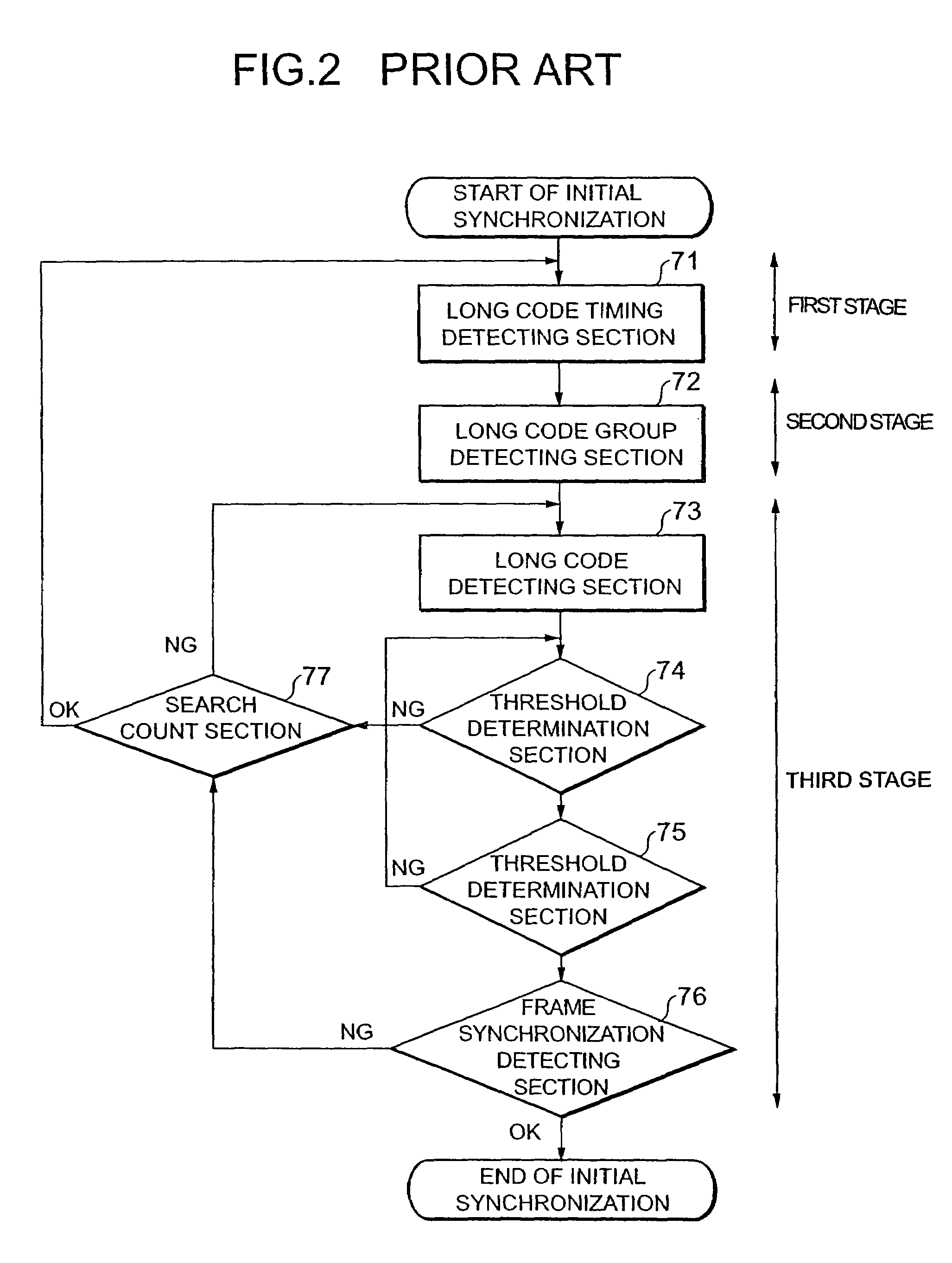
An initial synchronization method in a DS-CDMA inter-base station asynchronous cellular scheme of transmitting a spreading code sequence, includes: a first stage that detects correlation power values between the common identification code and a received signal by using a correlator and performs a threshold determination; a second stage that detects a correlation value between the received signal and each long code group identification short code, sets a group having a maximum correlation sum as a group, detects a slot in which a head of the pattern is obtained as a start slot of a frame, and compares an arbitrarily set threshold with the maximum correlation sum; and a third stage that sequentially generates replica codes of long codes and short codes, performs correlation detection for the obtained synchronization timing, and performs long code correlation detection.
Owner:NEC CORP
Method and apparatus for detecting an interleaved code
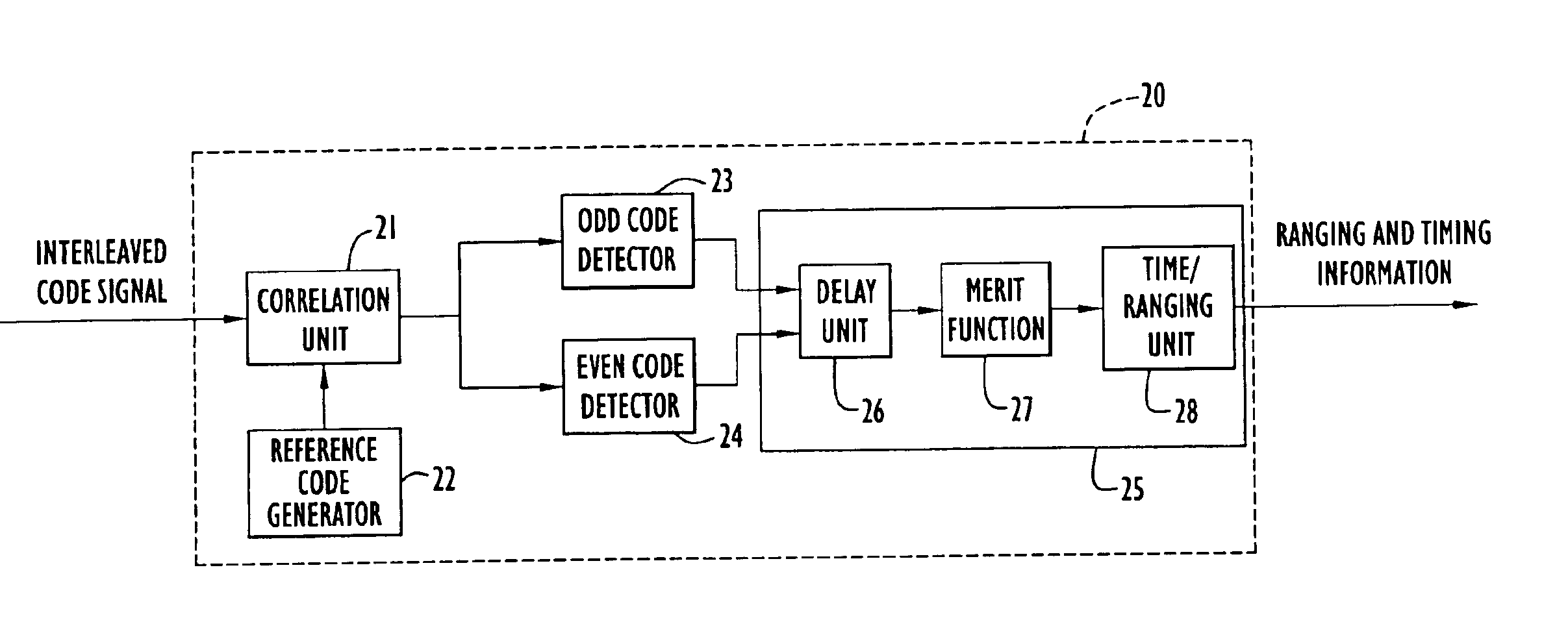
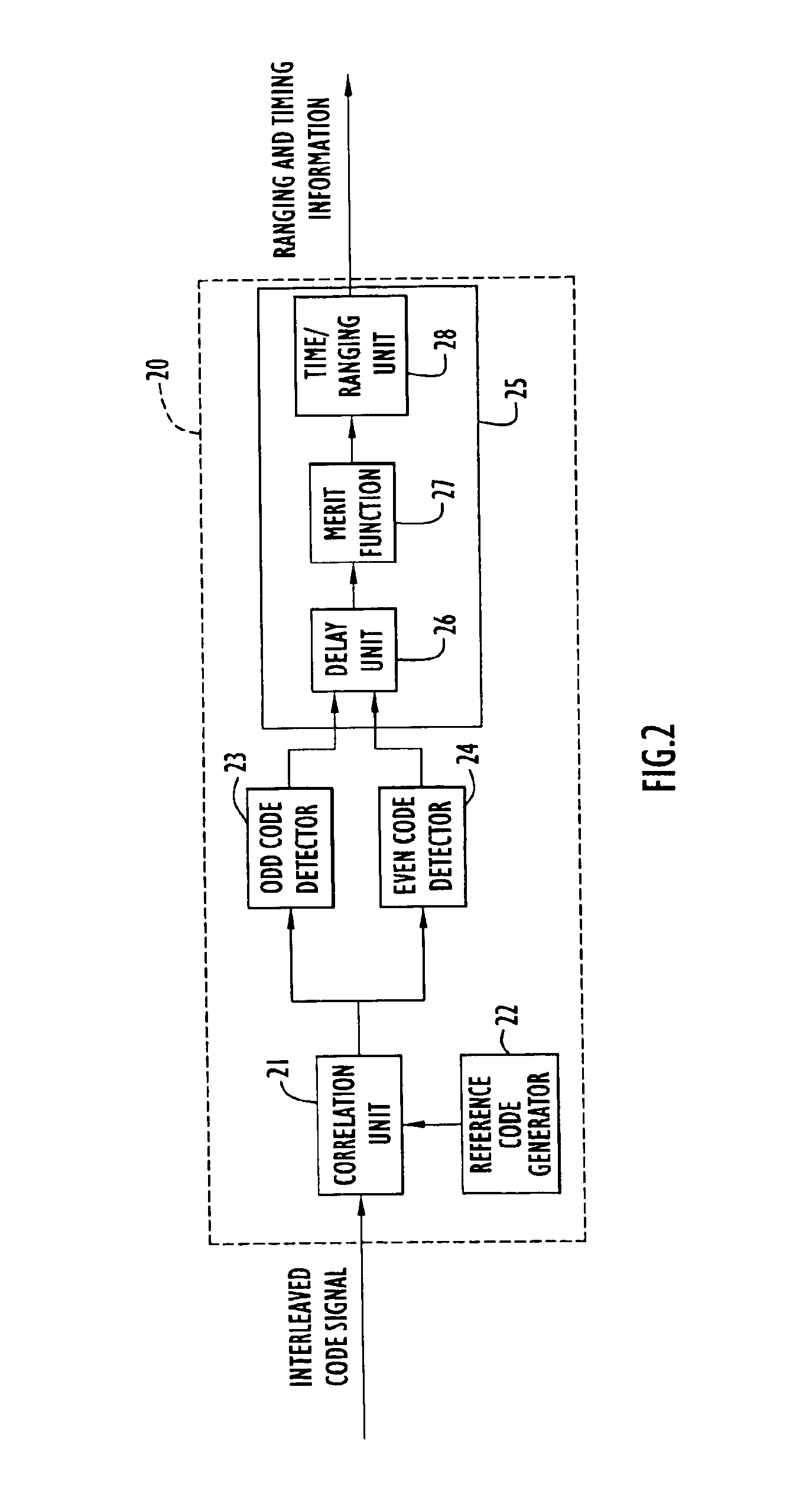
InactiveUS6873664B1Inexpensively detectingLower requirementAmplitude-modulated carrier systemsCode division multiplexEven codeComputer science
A receiver that receives a long pseudonoise (PN) code signal composed of two shorter codes interleaved with one another, includes a correlator unit that correlates the received signal with one or more reference codes corresponding to the two interleaved codes, respectively, and generates correlation signals. The receiver also includes an even code detector coupled to the correlator unit, for detecting from the correlation signals one of the two shorter codes, and an odd code detector coupled to the correlator unit, for detecting from the correlation signals the short code that is not detected by the even detector. A delay unit is coupled to the even and odd code detectors, and delays the even or the odd correlation signals so as to align the correlation signals. The aligned signals are combined and evaluated by a merit function. If the combined signals exceed a threshold value the short codes are determined to be aligned, the phase of each code can be determined, and the phase of the longer code can be determined from the determined phases of the shorter codes. The receiver can detect two short PN codes that have been combined, such as by interleaving the short codes, to create a long PN code. Hence, the receiver can inexpensively detect the two short codes which allows the receiver to detect the long code with high gain.
Owner:EXCELIS INC
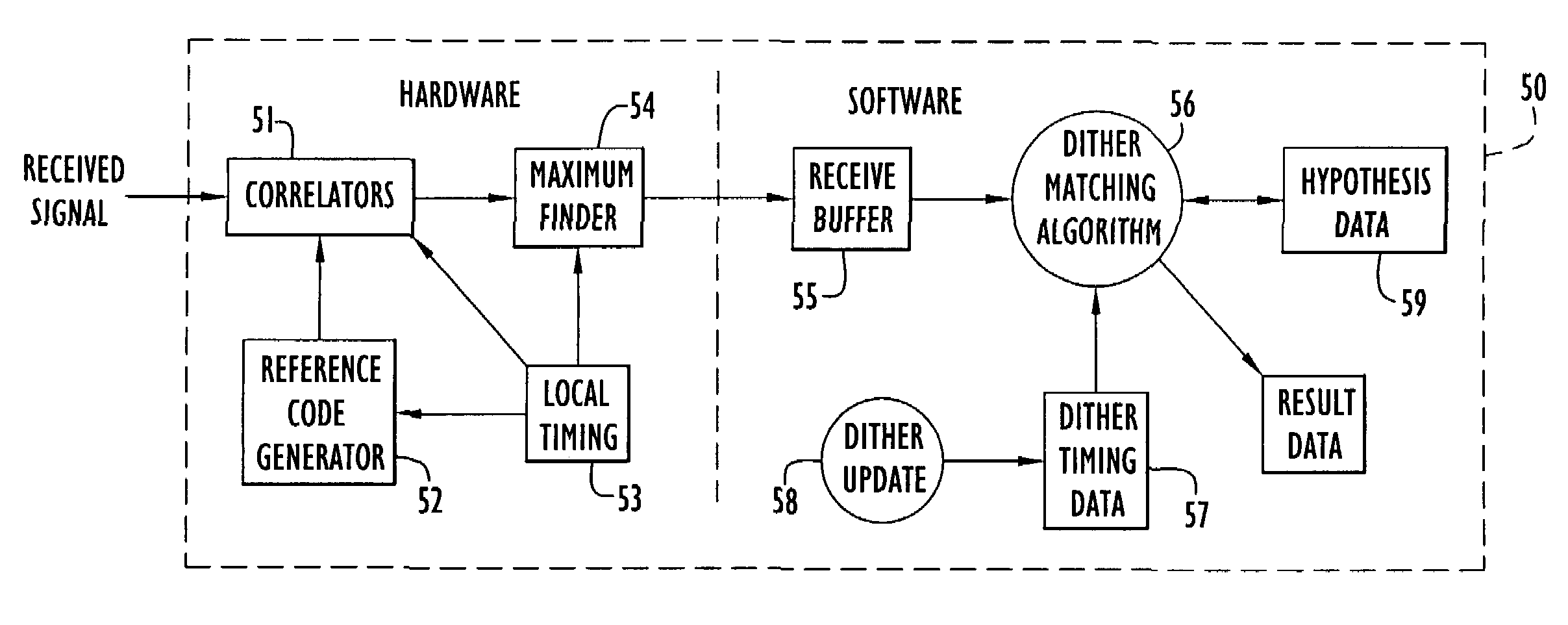
Non-stationary dither code generation and detection
A detector receives a signal and detects from it a long code composed from shorter codes, where the shorter codes are dithered according to a non-repeating dither pattern. The received signal is correlated with a reference code, the correlation sums are ranked, and short codes detected from the ranked sums. Because of a high jamming to signal (J / S) ratio, all the transmitted short codes may not be detected. A dither matching algorithm determines an interval between the detected codes and matches it with a previously stored dither pattern. If there is a strong match, the correlation sums and respective receive times are stored in a hypothesis data structure. If enough subsequent correlation pair have similar matches to exceed a threshold, the match is declared correct and the results are output. The time difference between received and matched pairs can be a measure of a pseudorange between transmitter and receiver.
Owner:HARRIS CORP
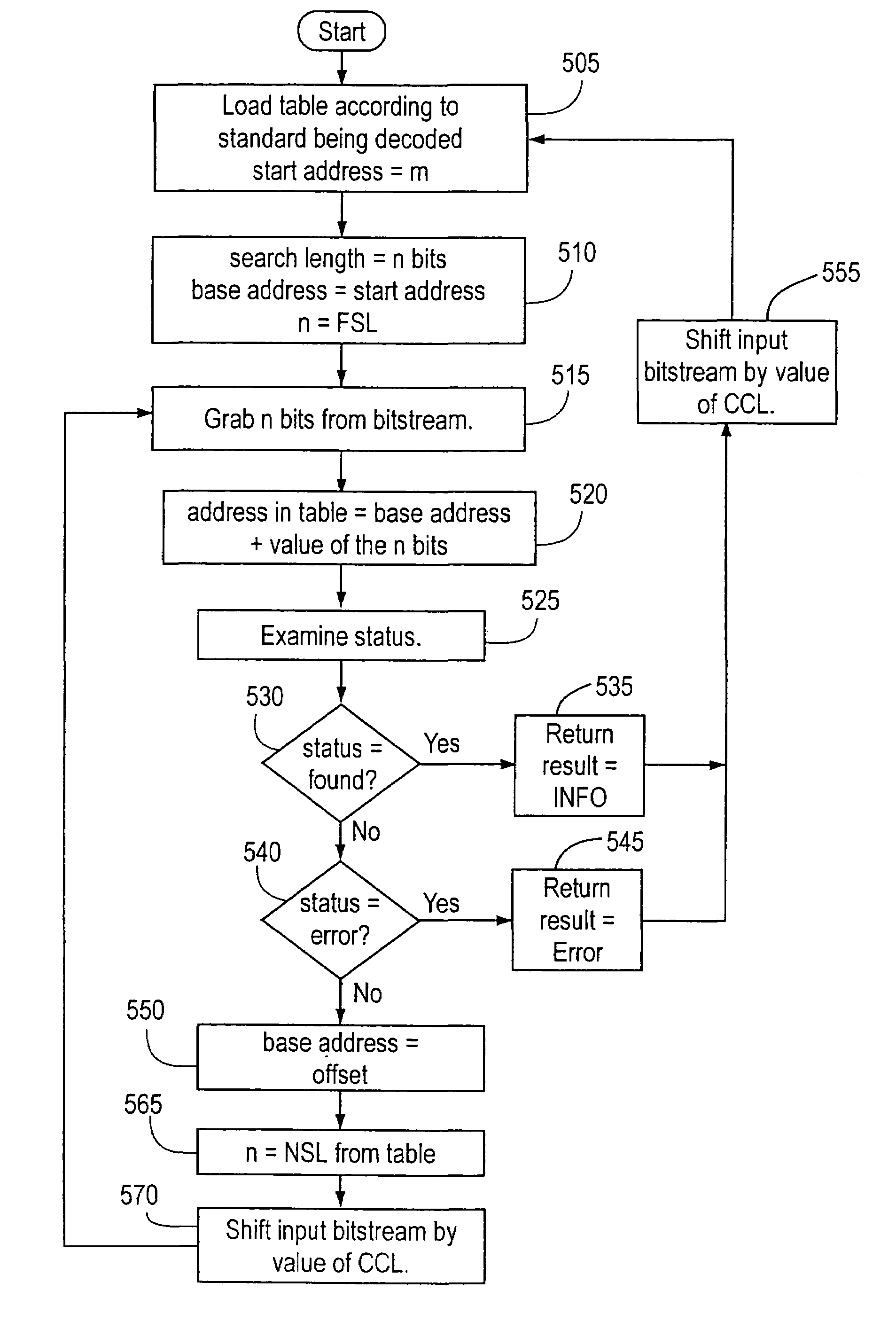
Programmable variable-length decoder
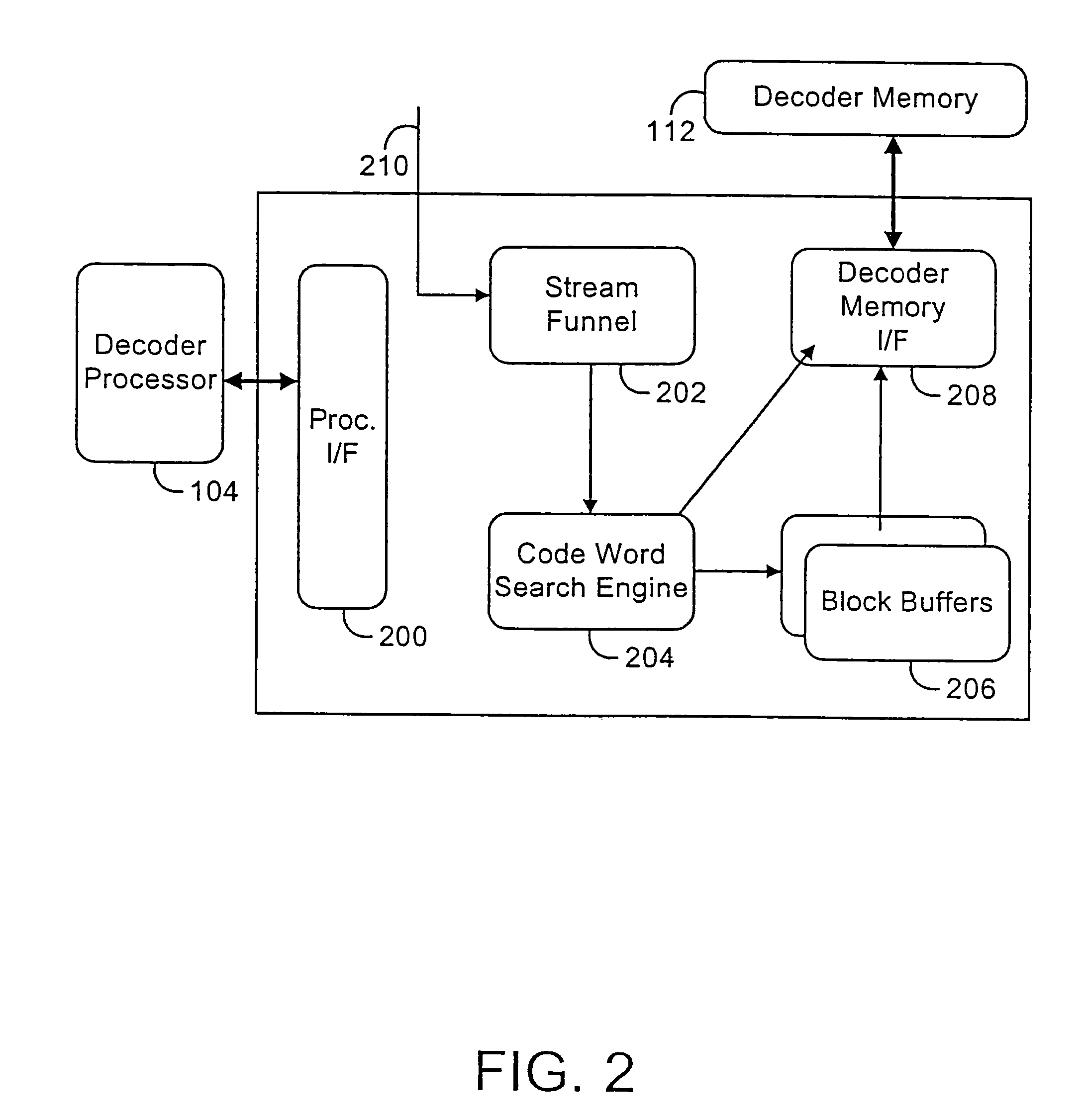
InactiveUS20050007264A1Speedily and efficiently decodeSimple and flexibleColor signal processing circuitsCode conversionAddress generatorLong code
System and method for decoding variable-length codes. A variable-length decoder includes an address generator and a local memory unit. The local memory stores a variable-length code look-up table. The local memory can be programmed to include a look-up table supporting substantially any decoding algorithm. In one embodiment, a decoder memory unit and a system memory unit are employed together with the local memory to store a codeword look-up table. The shortest codes are stored in local memory, the next shortest in decoder memory, and the longest codes are stored in system memory. A multistage search algorithm is employed to search for the longest codes. The address generator generates the address of the code table to be searched by adding the value of the bits to be searched to a base address.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
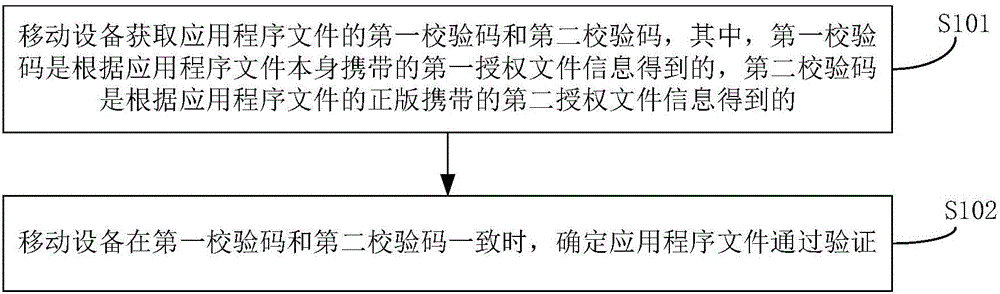
Application file verification method and system
InactiveCN106096381ADetermine securityDigital data authenticationComputer hardwareApplication software
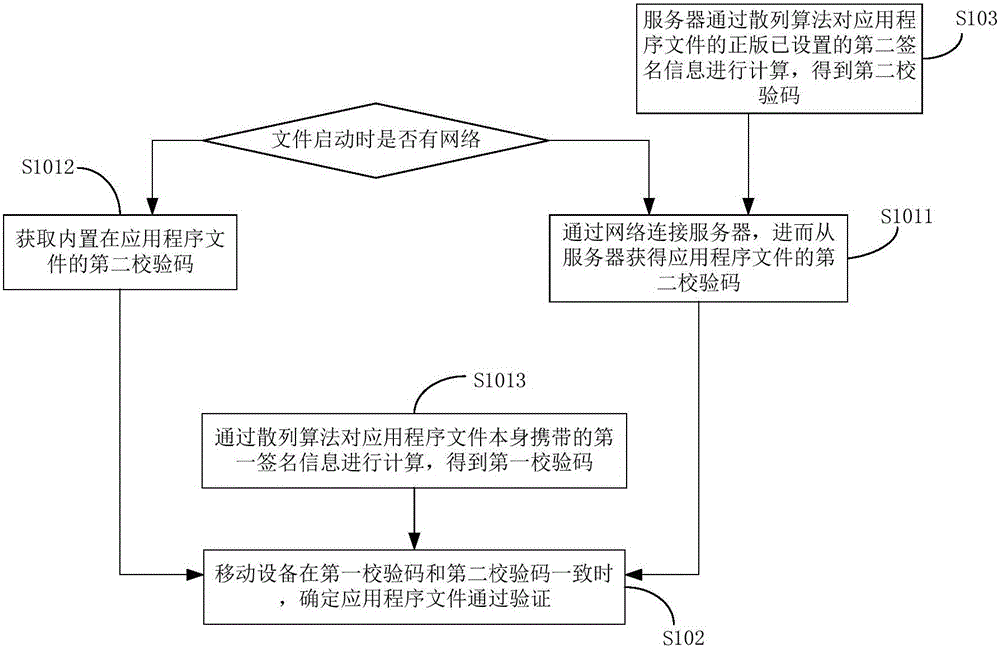
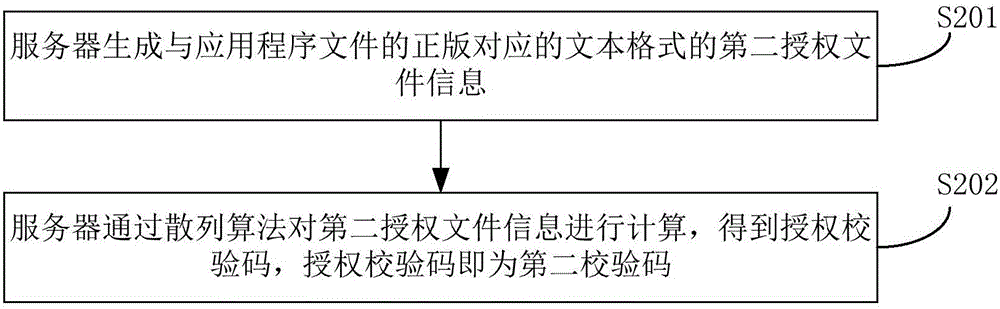
The invention discloses an application file verification method and system. The method comprises the steps that a mobile device obtains a first check code and a second check code of an application file, wherein the first check code is obtained according to first authorization file information carried by the application file, and the second check code is obtained according to second authorization file information carried by an authorized edition of the application file; and the mobile device determines that the application file passes the verification when the first check code is consistent with the second check code. Through the method and the system, the security of the application file can be determined at a mobile terminal and relatively long codes do not need to be input.
Owner:BEIJING ERENEBEN INFORMATION TECH
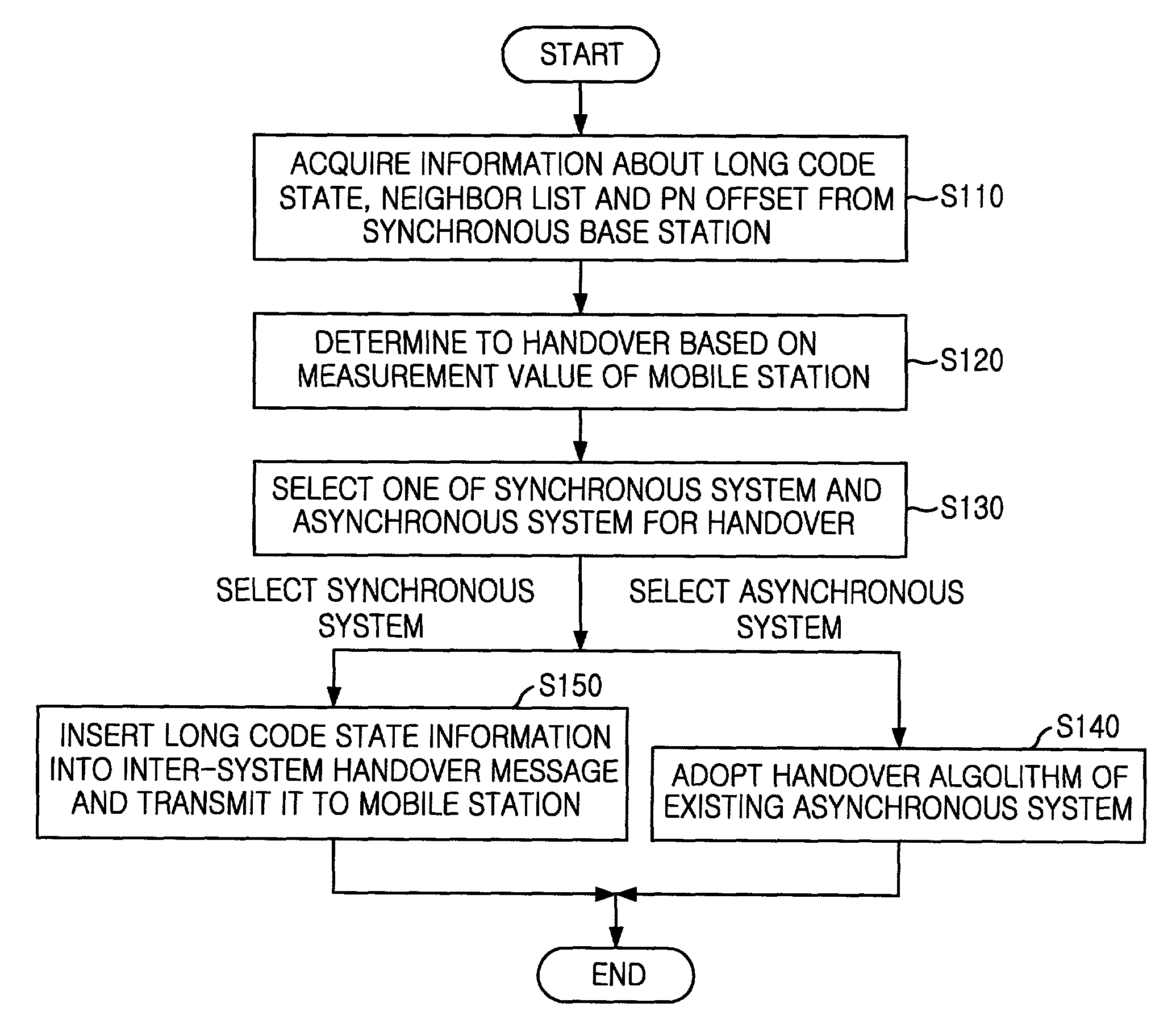
Method for transmitting long code state information in asynchronous mobile communication system
In a handover from an asynchronous radio network to a synchronous system, long code state information and activation time are transmitted. The method of transmitting long code state information and activation time includes the step of acquiring handover-related information from a neighboring synchronous system by the asynchronous radio network. In the handover, the synchronous system transmit a first message including activation time information and long code state information to the mobile station by the asynchronous radio network and after receiving the activation time information and the long code state information, makes use of the long code state information based on the activation time information by the mobile station.
Owner:YAMAZAKI HLDG
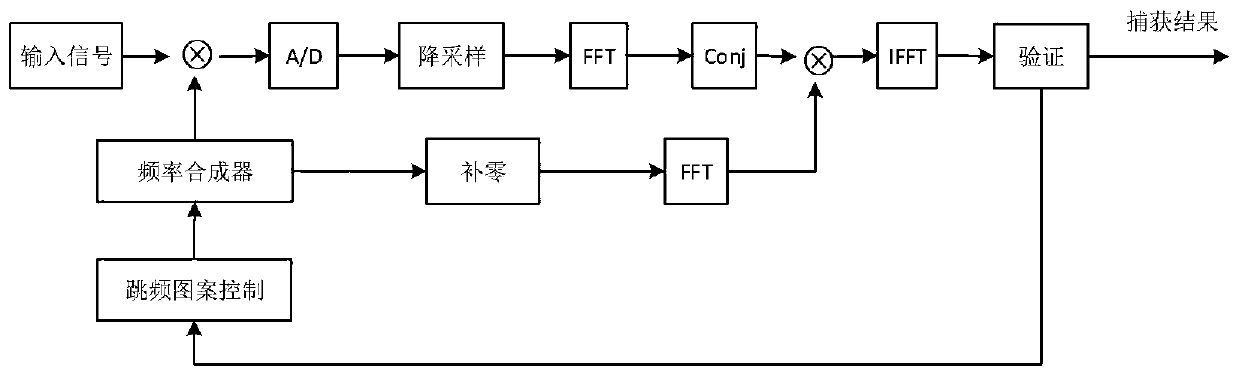
DS/FH frequency-hopping spectrum-spreading data transmission signal capturing method based on long code phase assistance
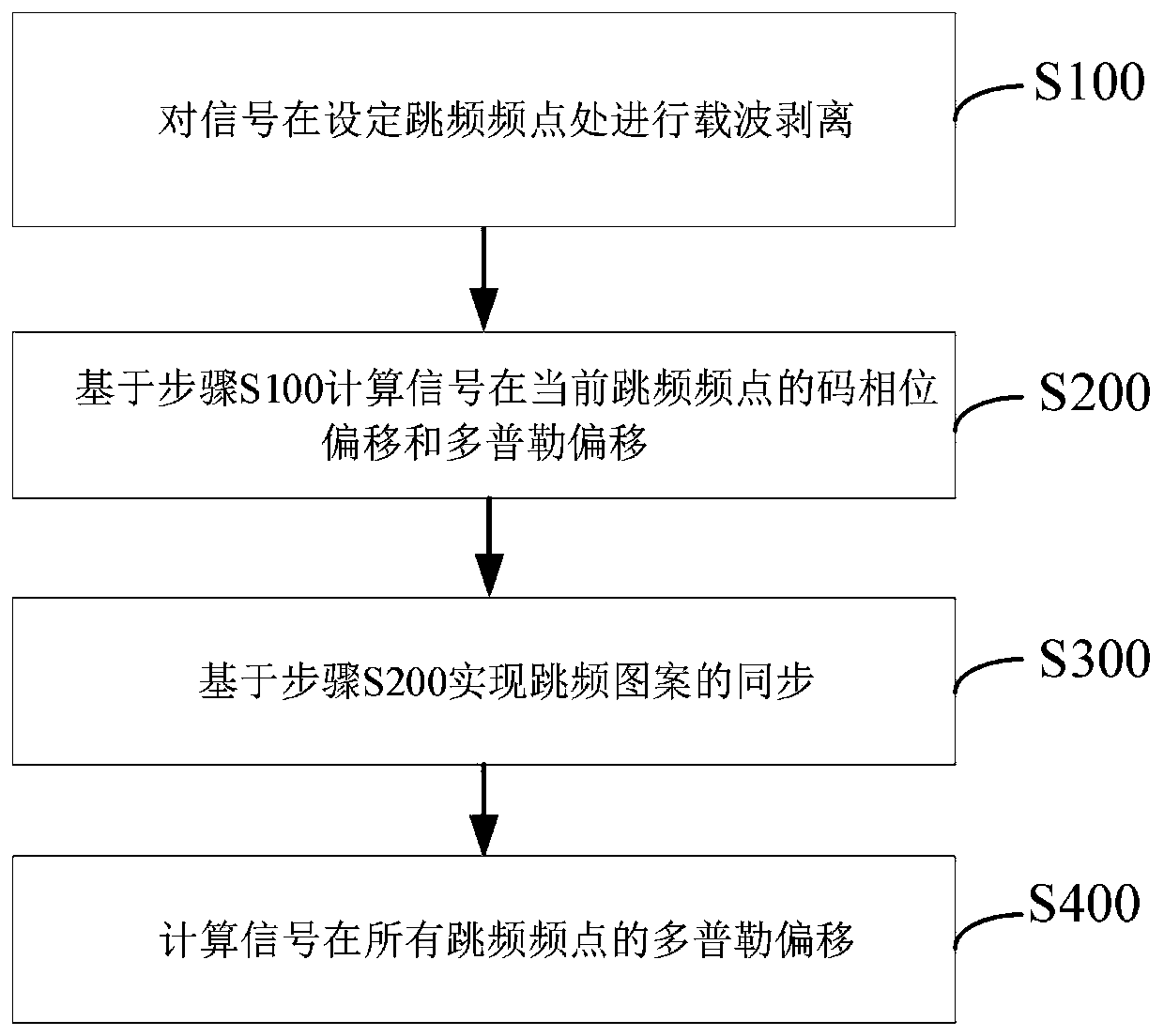
ActiveCN110474658ASolve the costSolve efficiency problemsTransmissionInterference resistancePhase shifted
The invention discloses a DS / FH frequency-hopping spectrum-spreading data transmission signal capturing method based on long code phase assistance, capable of solving the technical problems of relatively high cost and low efficiency of an existing method for keeping system synchronization for a DS / FH frequency-hopping spectrum-spreading hybrid system. Based on a local oscillator, the following steps are implemented: S100, carrying out carrier stripping on a signal at a set frequency hopping frequency point; S200, calculating code phase shift and Doppler shift of the signal at the current frequency hopping frequency point based on the step S100; S300, realizing synchronization of frequency hopping patterns based on the step S200; and S400, calculating Doppler shift of the signal at all frequency hopping points. According to the DS / FH frequency-hopping spectrum-spreading data transmission signal capturing method, the problem that receivers cannot be synchronized due to inconsistent Doppler shift of different frequency hopping points is solved; the DS / FH frequency-hopping spectrum-spreading data transmission signals based on long code phase assistance are captured, and the complexityis low, and implementation is flexible. The DS / FH frequency-hopping spectrum-spreading data transmission signal capturing method can effectively reduce the calculation amount and average capture time,improves the capture speed, can be used for capturing spectrum-spreading signals, and is higher in anti-interference capability.
Owner:HEFEI INNOVATION RES INST BEIHANG UNIV
Programmable variable-length decoder
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Information recording medium, information recording/reproducing apparatus and information management method
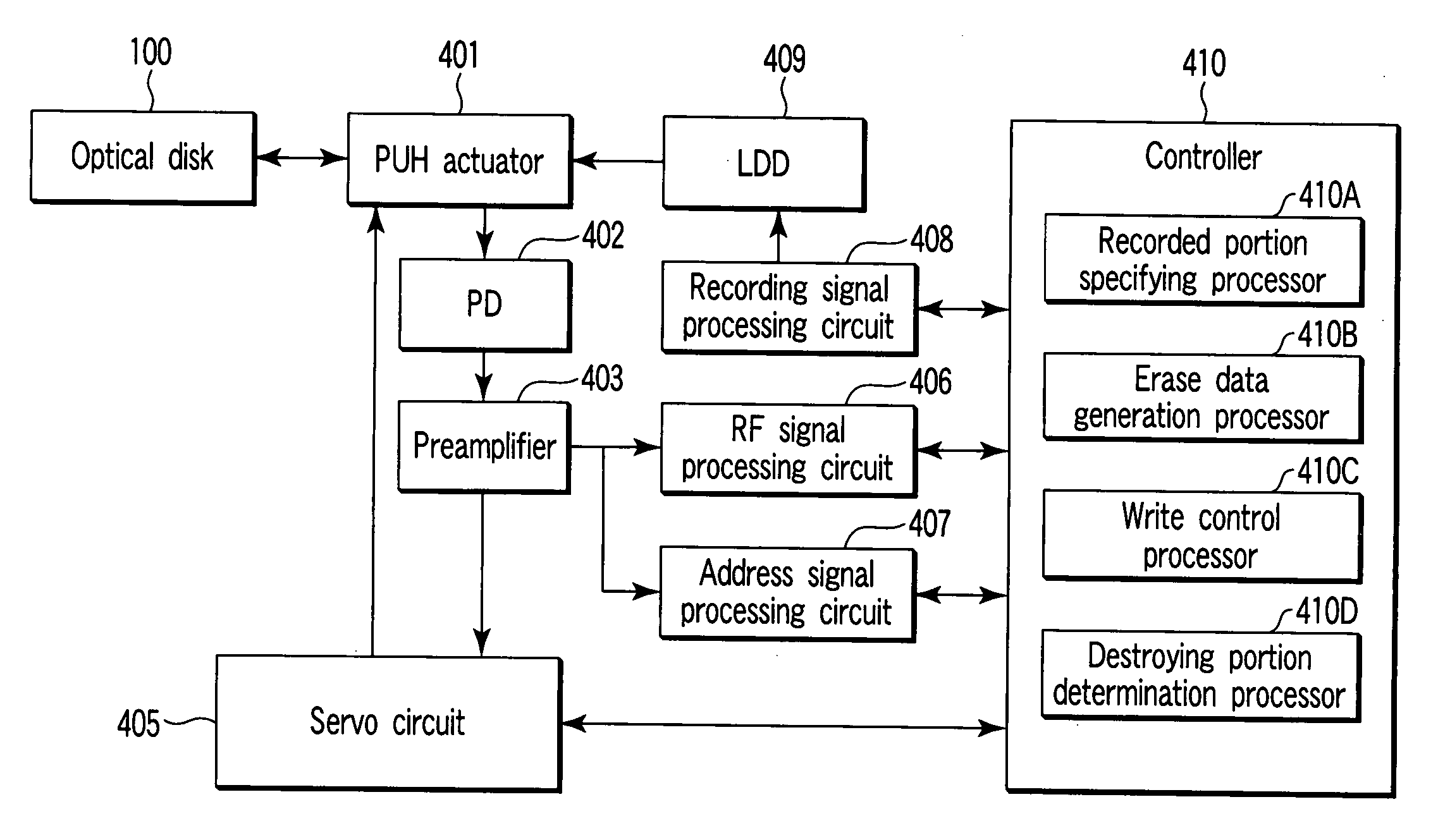
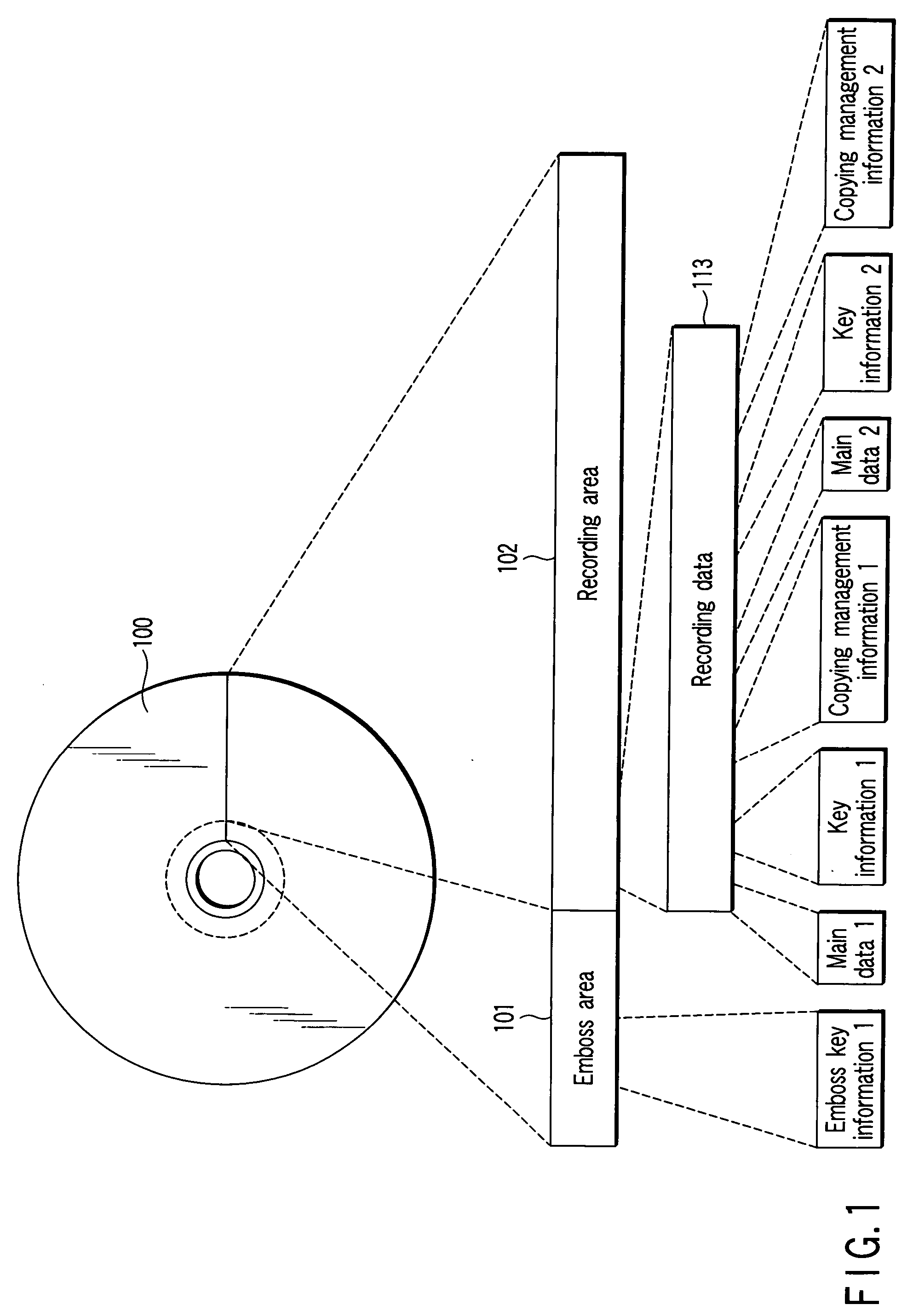
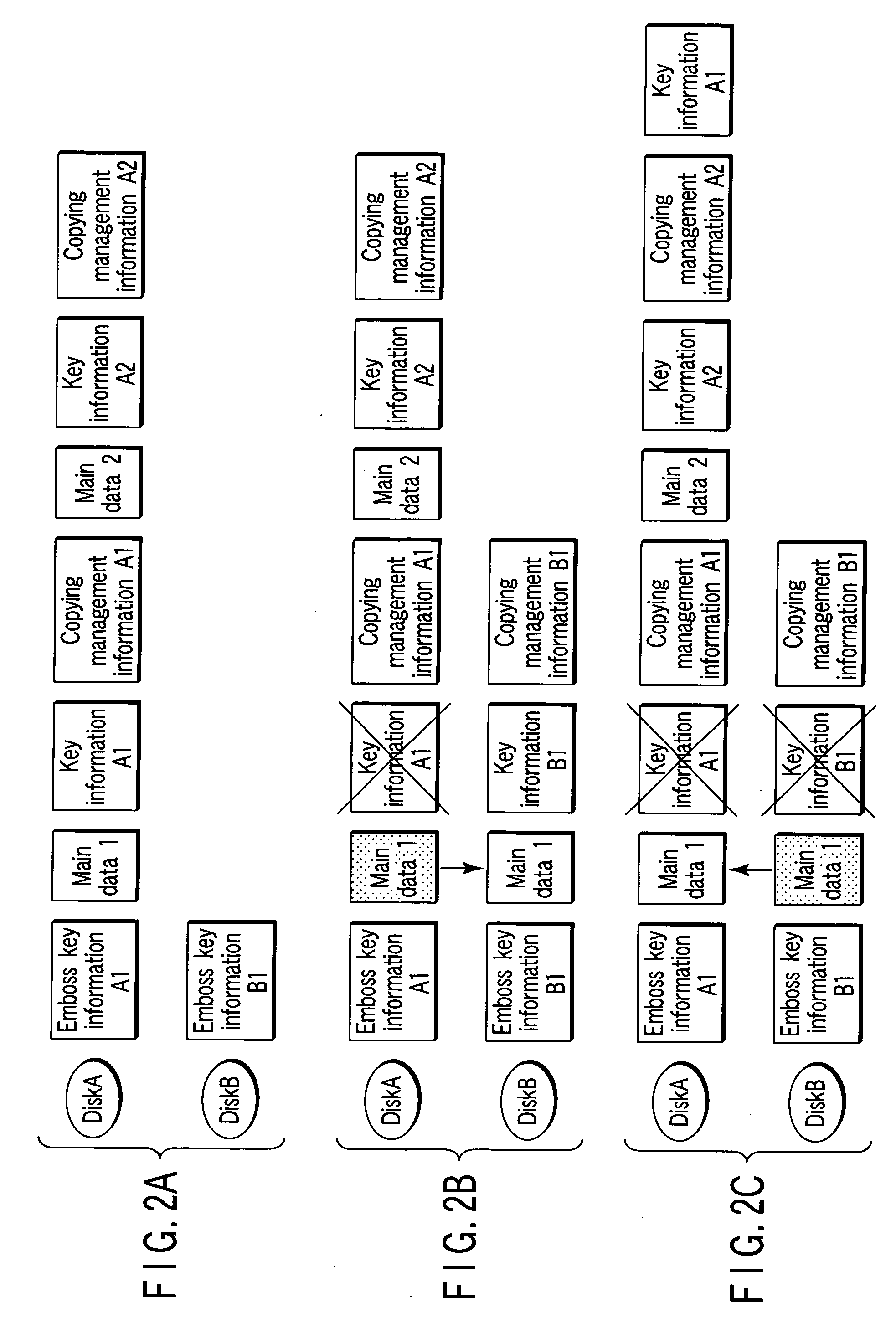
InactiveUS20060023596A1Improve practicalityEnhanced informationCombination recordingTelevision system detailsComputer hardwareFrequency of occurrence
There is provided an information management apparatus which can make it impossible to read out data recorded on a write-once type recordable optical disk as required and the usefulness thereof is enhanced. When recorded data is destroyed on the write-once type recordable optical disk, data modulated by a modulation system of the same run length restriction as run length restriction of a modulation system used for recording data is overwritten and recorded, data is overwritten and recorded by use of patterns in which the frequency of occurrence of spaces of the longest code is higher than the frequency of occurrence of the modulation system used for recording data, or data is overwritten and recorded by use of successive patterns of the shortest code in the run length restriction of the modulation system used for recording data.
Owner:KK TOSHIBA
LDPC decoding method and system, electronic device and storage medium
PendingCN110830050AHigh precisionEasy to implementError correction/detection using multiple parity bitsCode conversionParity-check matrixLong code
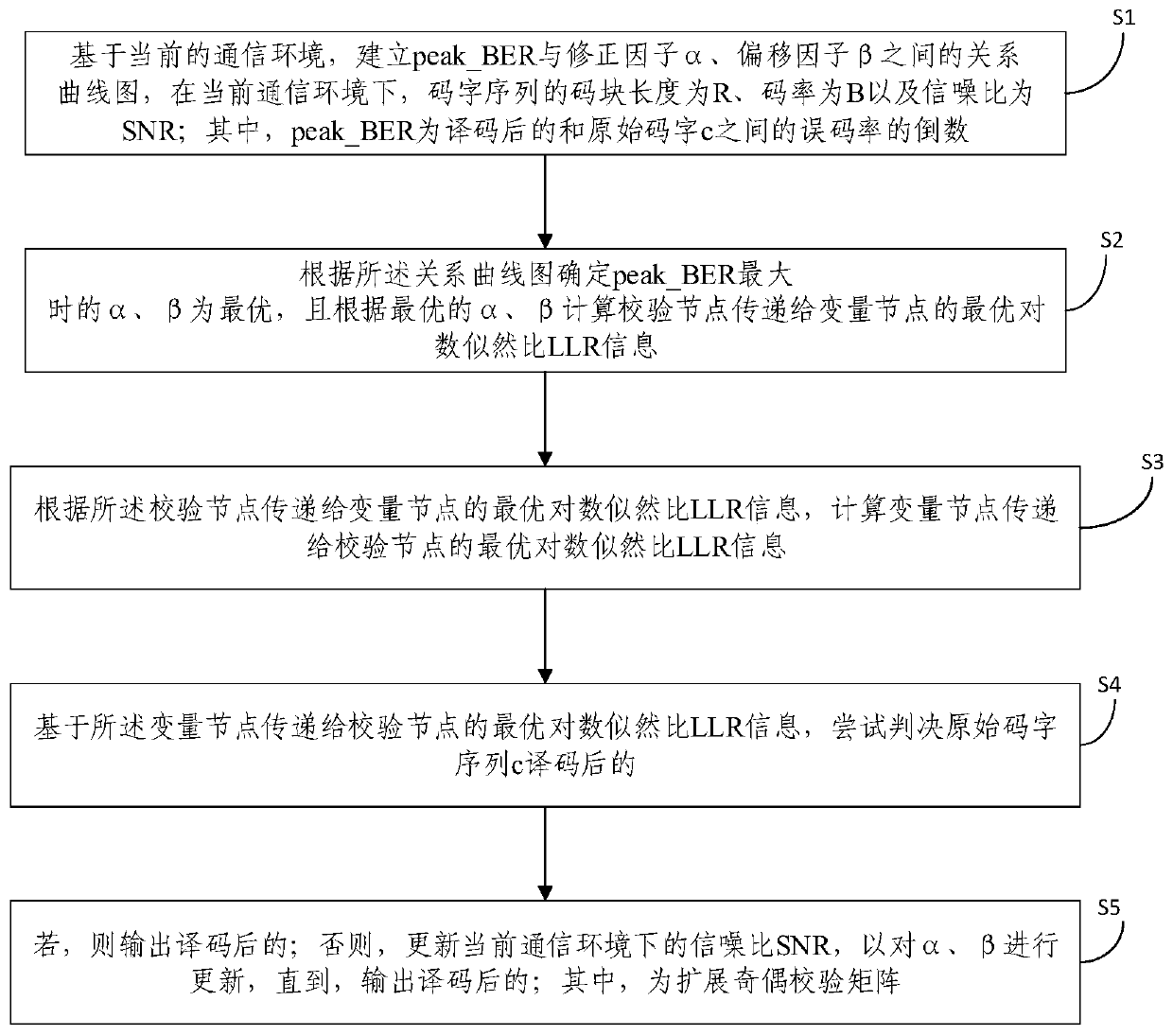
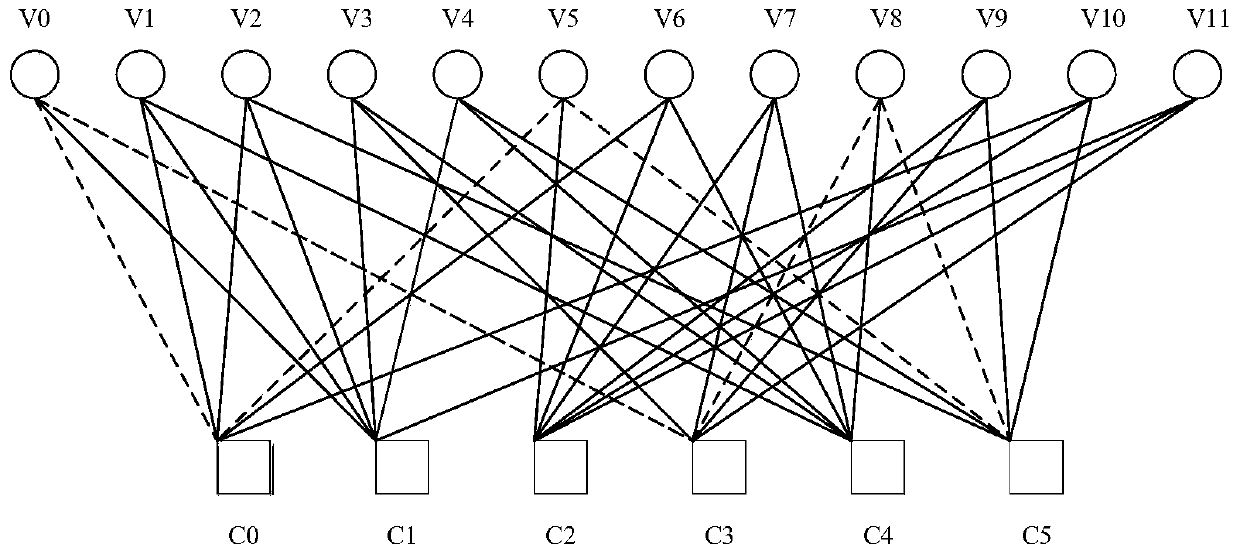
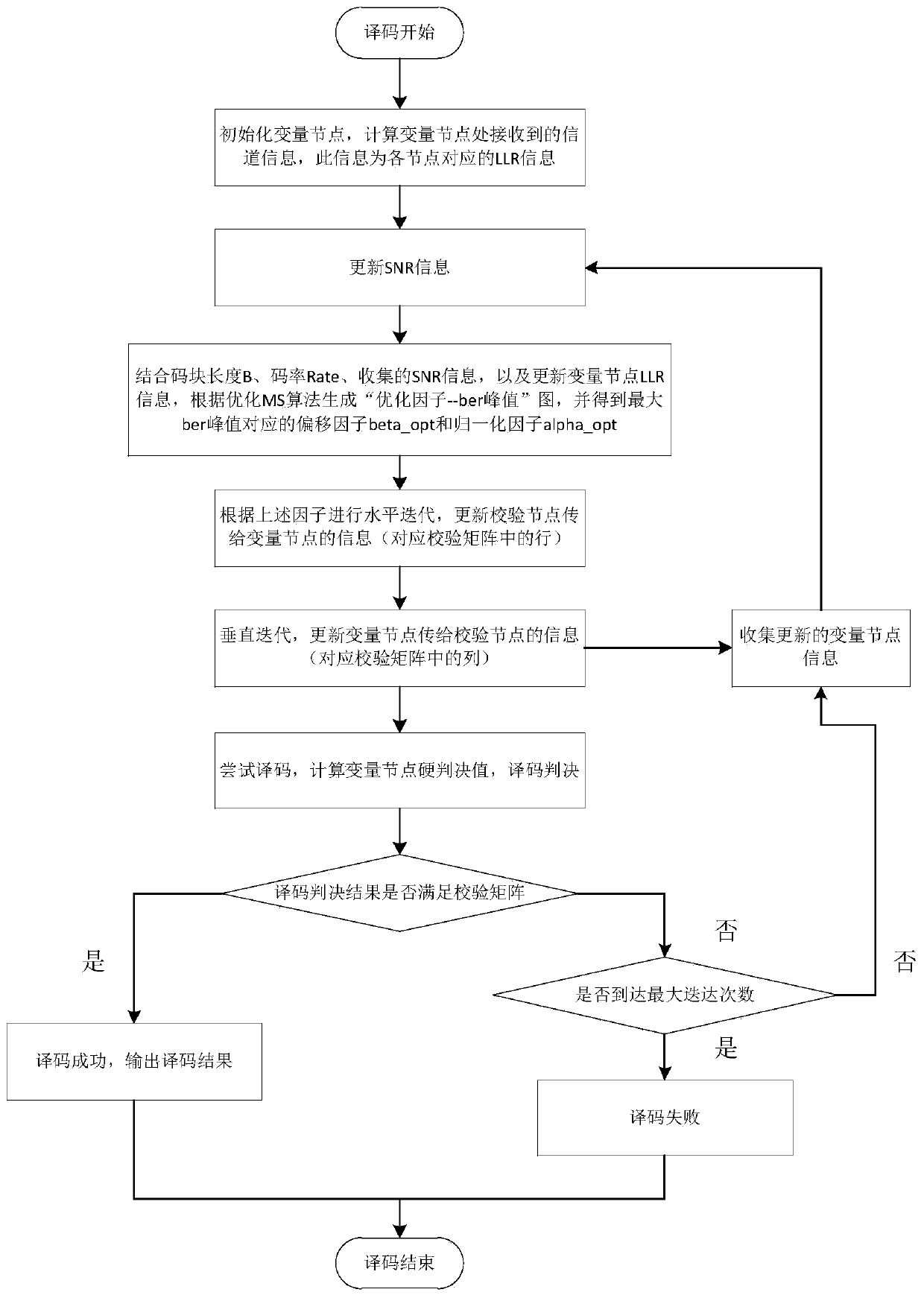
The embodiment of the invention provides an LDPC decoding method and system, an electronic device and a storage medium. The method comprises the following steps of establishing a relation curve graphbetween the peak _ BER and a correction factor alpha and an offset factor beta; determining that alpha and beta are optimal when peak _ BER is maximum, calculating the optimal log-likelihood ratio (LLR) information transmitted to a variable node by a check node according to the optimal alpha and beta, and further calculating the optimal log-likelihood ratio (LLR) information transmitted to the check node by the variable node; and trying to judge a coded parameter in an original code word sequence c, if a formula is satisfied, outputting the coded parameter, otherwise updating the SNR in the current communication environment so as to update alpha and beta until the formula is satisfied, and outputting the coded parameter, wherein H is an extended parity check matrix. According to the embodiment of the invention, the offset factor beta and the normalization factor alpha are adjusted dynamically by combining the parameters, such as the signal-to-noise ratio SNR, a long code block length B, a code rate R, etc. and further the optimal decoding sequence is obtained.
Owner:WUHAN HONGXU INFORMATION TECH
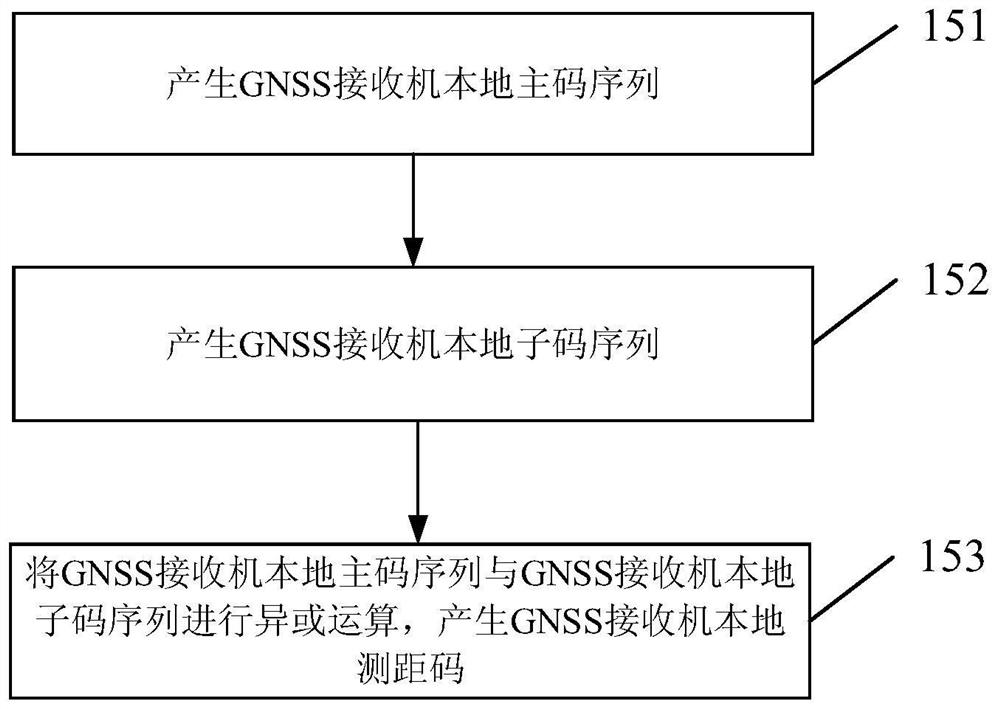
GNSS long code signal capturing method and device assisted by low earth orbit satellite
PendingCN112327334AImprove capture sensitivityIncrease processing gainSatellite radio beaconingLong codeLow earth orbit
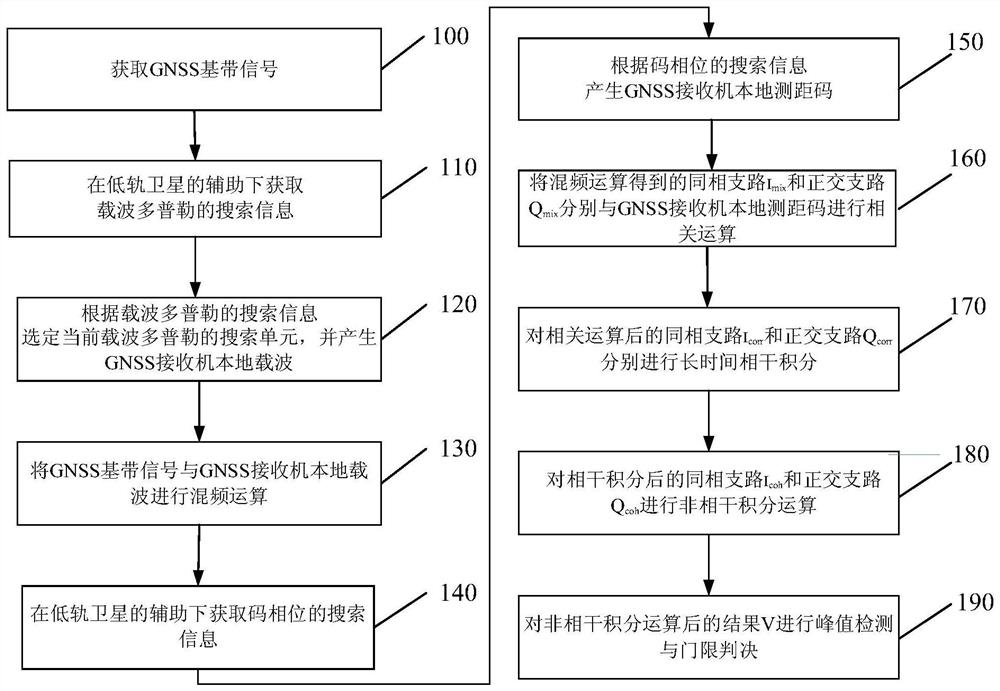
The invention provides a GNSS long code signal capturing method and device assisted by a low earth orbit satellite. The GNSS long code signal capturing method assisted by the low earth orbit satellitecomprises the following steps: acquiring GNSS baseband signals; performing frequency mixing operation; performing segment correlation operation; performing long-time coherent integration; carrying out incoherent integral operation; and performing peak detection and threshold judgment. The method and the device have the advantages that GNSS navigation signal auxiliary information, including roughDoppler information and rough code phase information, is acquired under the assistance of a low-orbit satellite, so that on one hand, the rough code phase information is used for generating sub-codesof local ranging codes and participating in related operation; it is guaranteed that the influence of bit hopping on coherent integration time is eliminated after correlation operation, high-sensitivity capturing of long codes is achieved through long-time coherent integration, and the long code signal capturing performance in the low signal-to-noise ratio environment is improved; and on the otherhand, rough Doppler information and rough code phase information of the GNSS navigation signals are utilized, the searching time of the signals in the frequency dimension and the code dimension is shortened, the capturing efficiency is improved, and rapid capturing of GNSS long code signals is achieved.
Owner:SPACE STAR TECH CO LTD
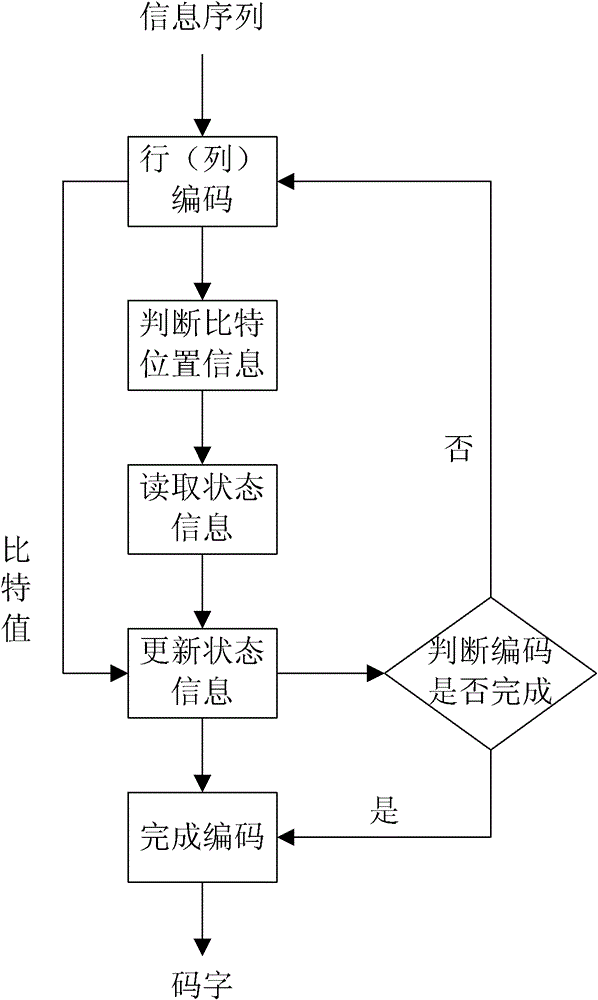
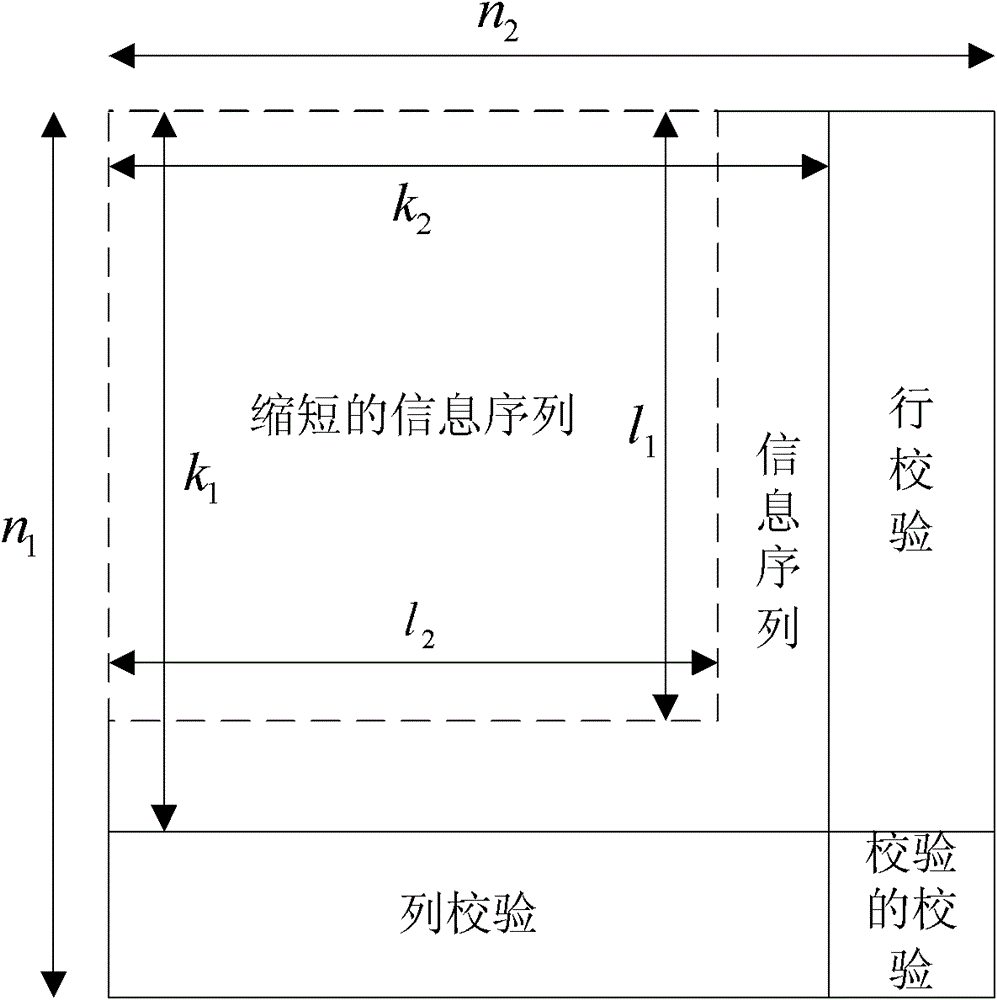
Encoding and decoding methods for shortening Turbo product code
InactiveCN101958720BIncrease storage resourcesImprove data throughputError correction/detection by combining multiple code structuresParallel encodingTheoretical computer science
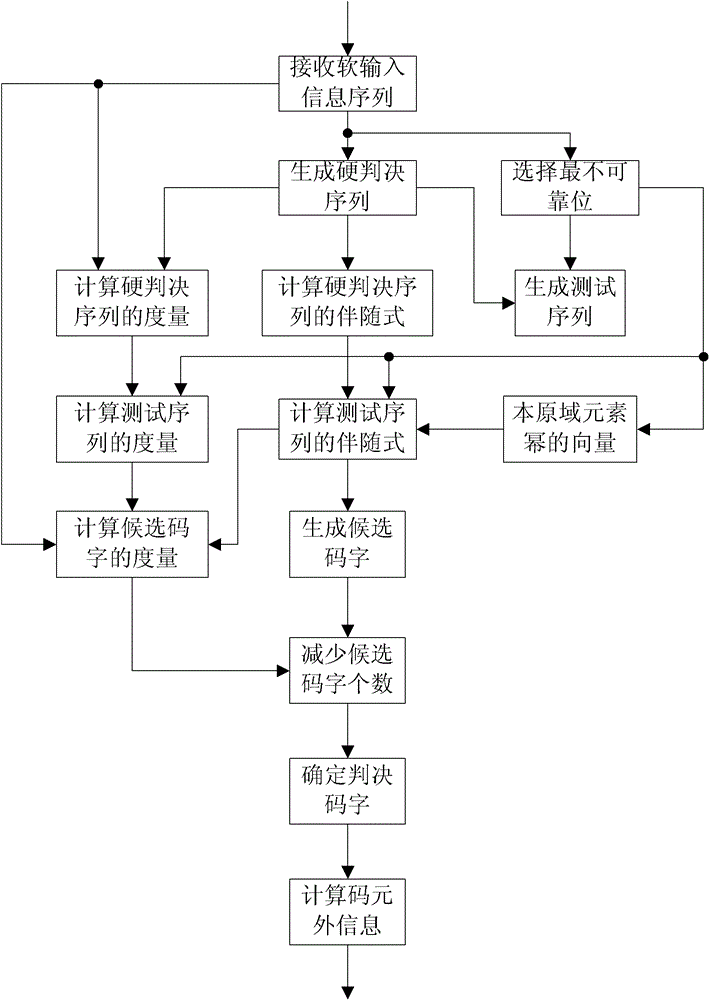
The invention relates to encoding and decoding methods for shortening a Turbo product code. The encoding method comprises the following steps of: performing row or column encoding on an information sequence to be encoded; performing parallel encoding on code words of row or column component codes generated by the row or column encoding; and judging whether the encoding is finished. The decoding method comprises the following steps of: generating a hard decision sequence of a soft-input information sequence; selecting the least reliable bits in the soft-input information sequence; generating a test sequence according to the hard decision sequence and the least reliable bits; decoding the test sequence to generate candidate code words; calculating the measurement of the candidate code words and the soft-input information sequence; reducing the number of the candidate code words; determining decision code words according to the measurement of the candidate code words; and calculating external information of each code element in the decision code words. The encoding method has the advantages of improving data throughput and reducing encoding delay; and the decoding method has the advantages of saving a mass of logical resources and storage resources, particularly well balancing decoding complexity and data throughput under the condition of longer code length of component codes.
Owner:XIDIAN UNIV
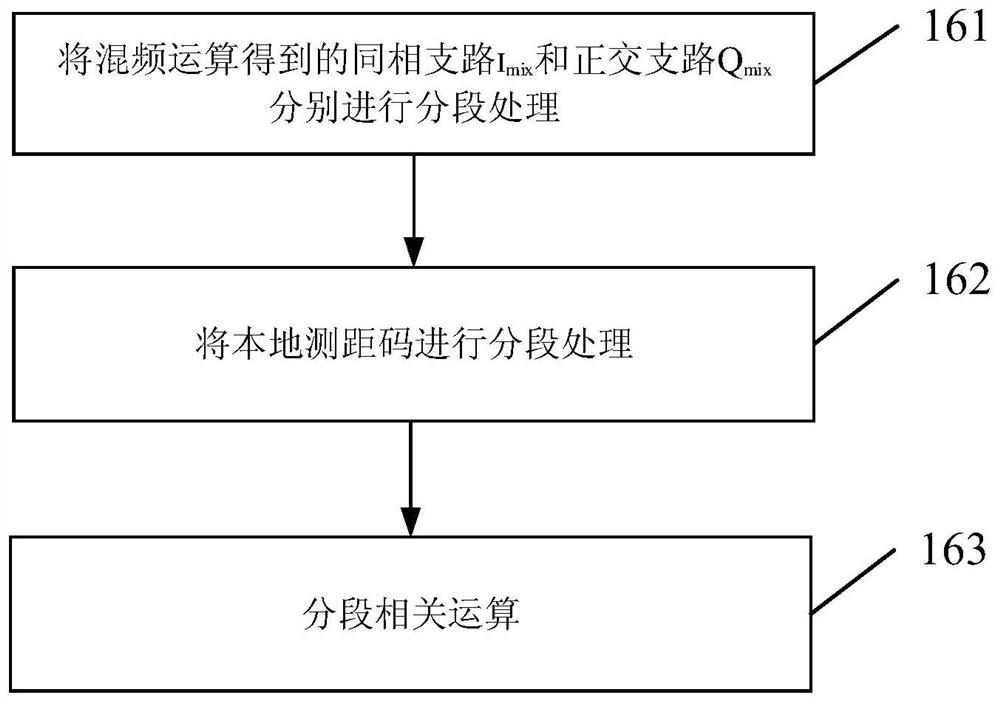
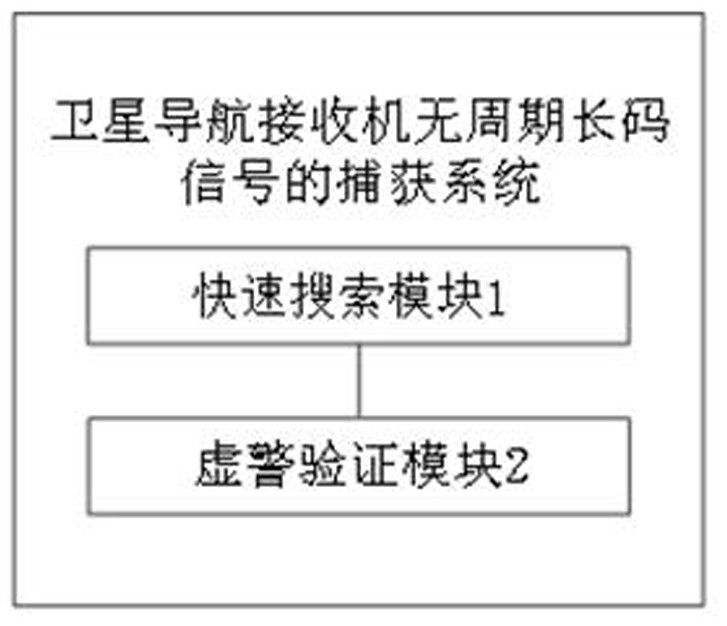
Method and system for capturing aperiodic long code signal of satellite navigation receiver
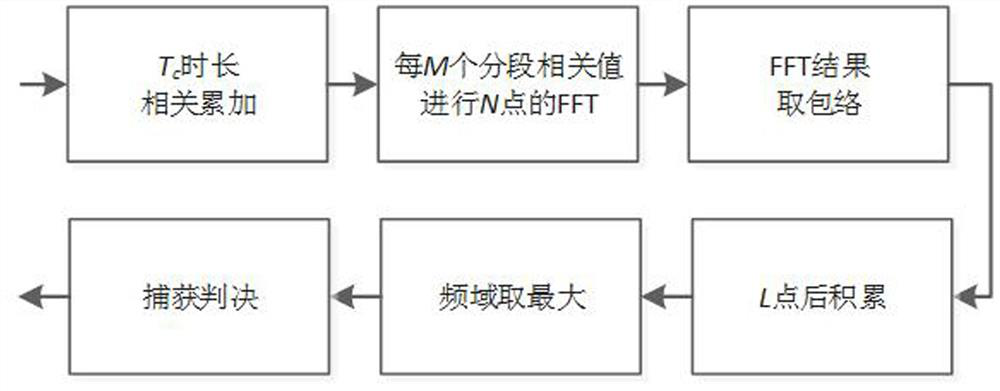
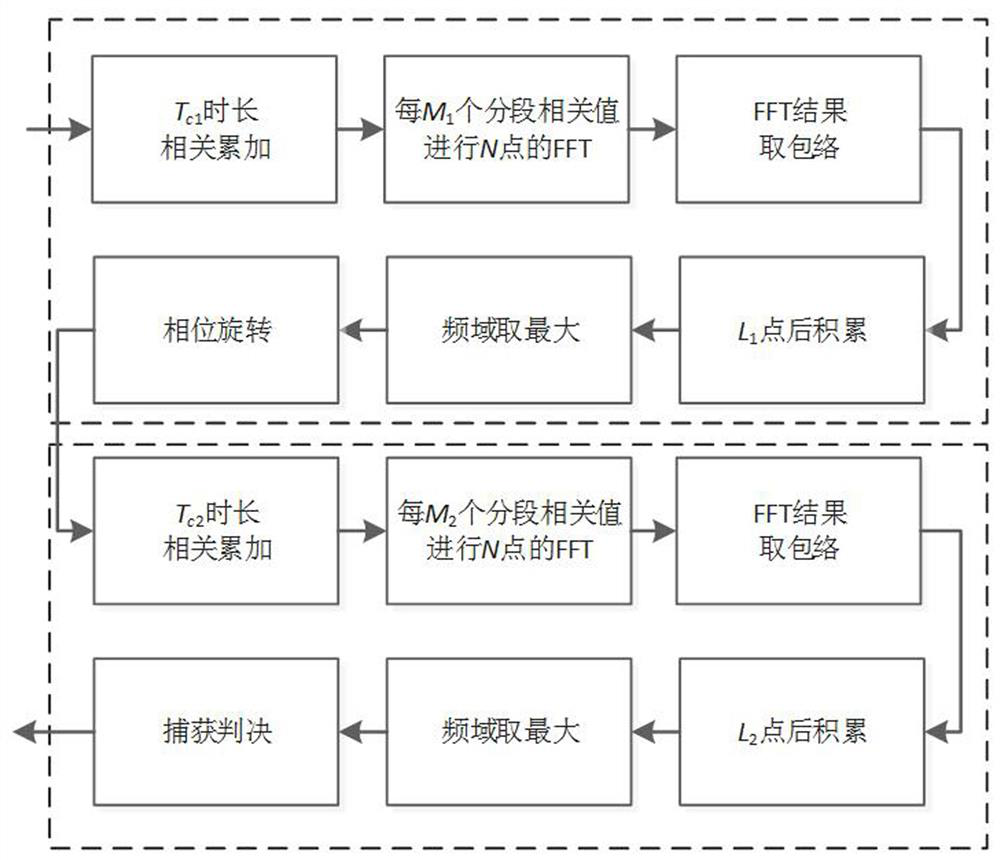
ActiveCN113820731AImplement two-level detectionEasy to detectSatellite radio beaconingFrequency spectrumCoherent integration
The invention discloses a method and a system for capturing an aperiodic long code signal of a satellite navigation receiver. The method comprises the following steps: S1, in a rapid search stage, carrying out segmented correlation accumulation by using relatively short coherent integration time, carrying out rapid Fourier transform, envelope taking and post-accumulation processing on a segmented correlation value, and maximizing a frequency spectrum envelope to obtain a Doppler frequency initial estimation value under a current code phase; s2, a false alarm verification stage: accumulating a plurality of segmented correlation values after phase rotation in the fast search stage to obtain a segmented correlation value with longer coherent integral time, similarly performing fast Fourier transform, envelope taking and post-accumulation processing, performing capture judgment by using a spectrum envelope maximum value, and when the envelope maximum value exceeds a capture threshold, performing false alarm verification, outputting the current code phase and Doppler frequency as a signal capturing result. Under the condition that the Doppler search range is guaranteed, high detection performance can be achieved, and two-stage detection is achieved under the condition that correlator resources are not increased.
Owner:湖南跨线桥航天科技有限公司
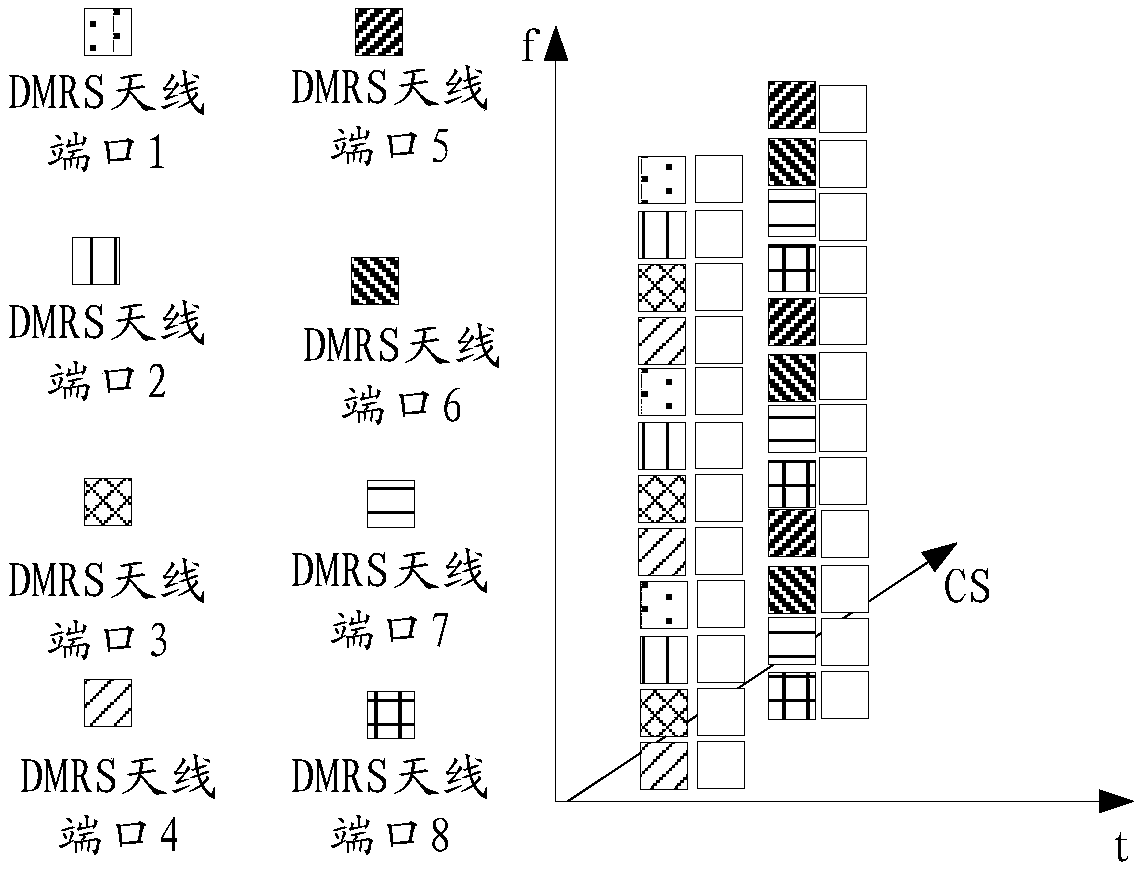
Demodulation reference signal transmission method, network side equipment and user equipment
The invention provides a demodulation reference signal transmission method, network side equipment and user equipment. The method comprises the following steps: configuring a mode of mapping a DMRS sequence to a frequency domain resource position; and according to a mode of mapping the configured DMRS sequence to the frequency domain resource position, DMRS transmission is carried out. According to the transmission method, configuration is carried out by mapping the DMRS sequence to the frequency domain resource position, so that the problem that the number of configured ports cannot meet thescene requirement of relatively large NOMA overload rate or relatively long code length in DMRS transmission in the prior art can be solved.
Owner:CHINA MOBILE COMM LTD RES INST +1
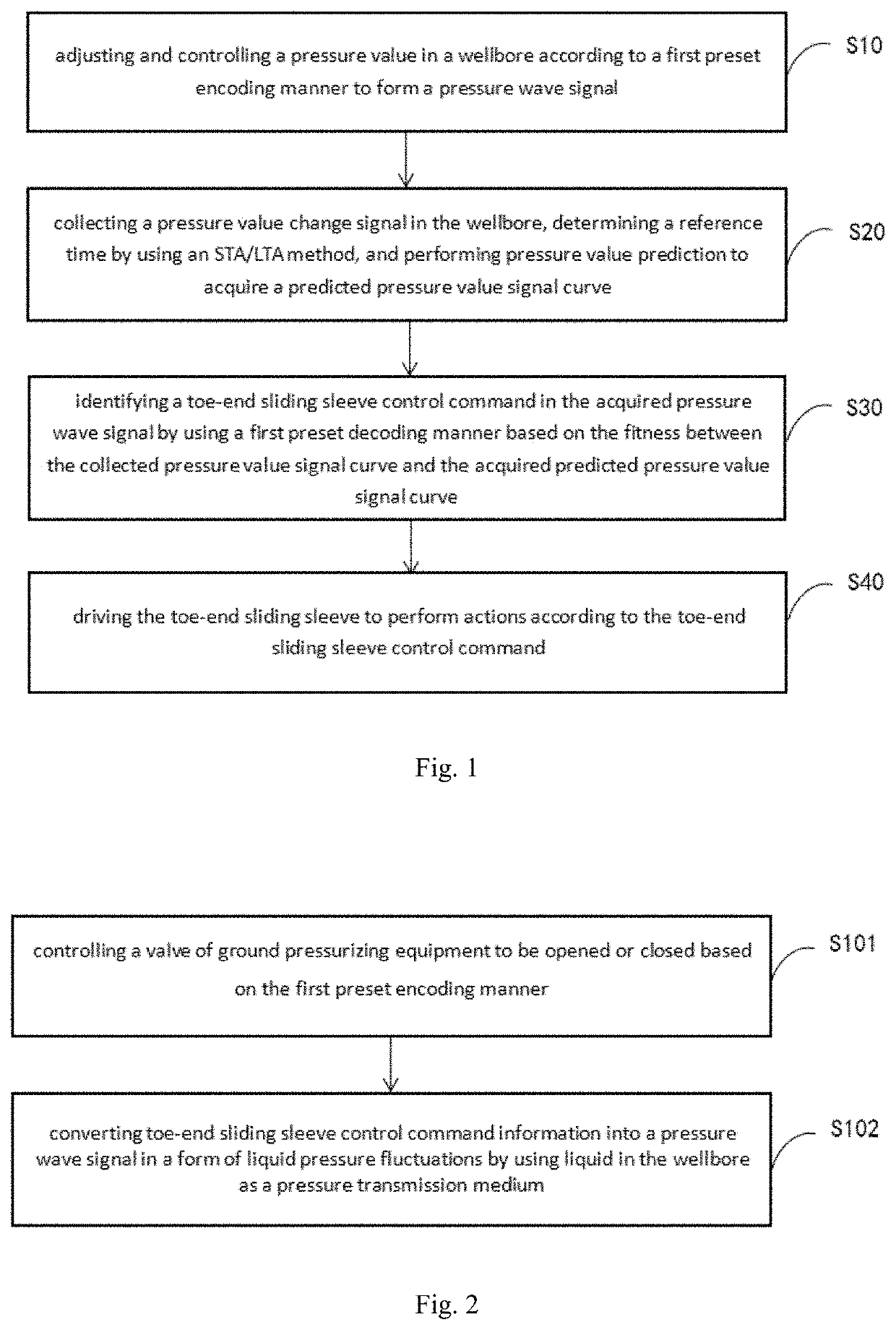
Method for controlling toe-end sliding sleeve of horizontal well based on efficient decoding communication
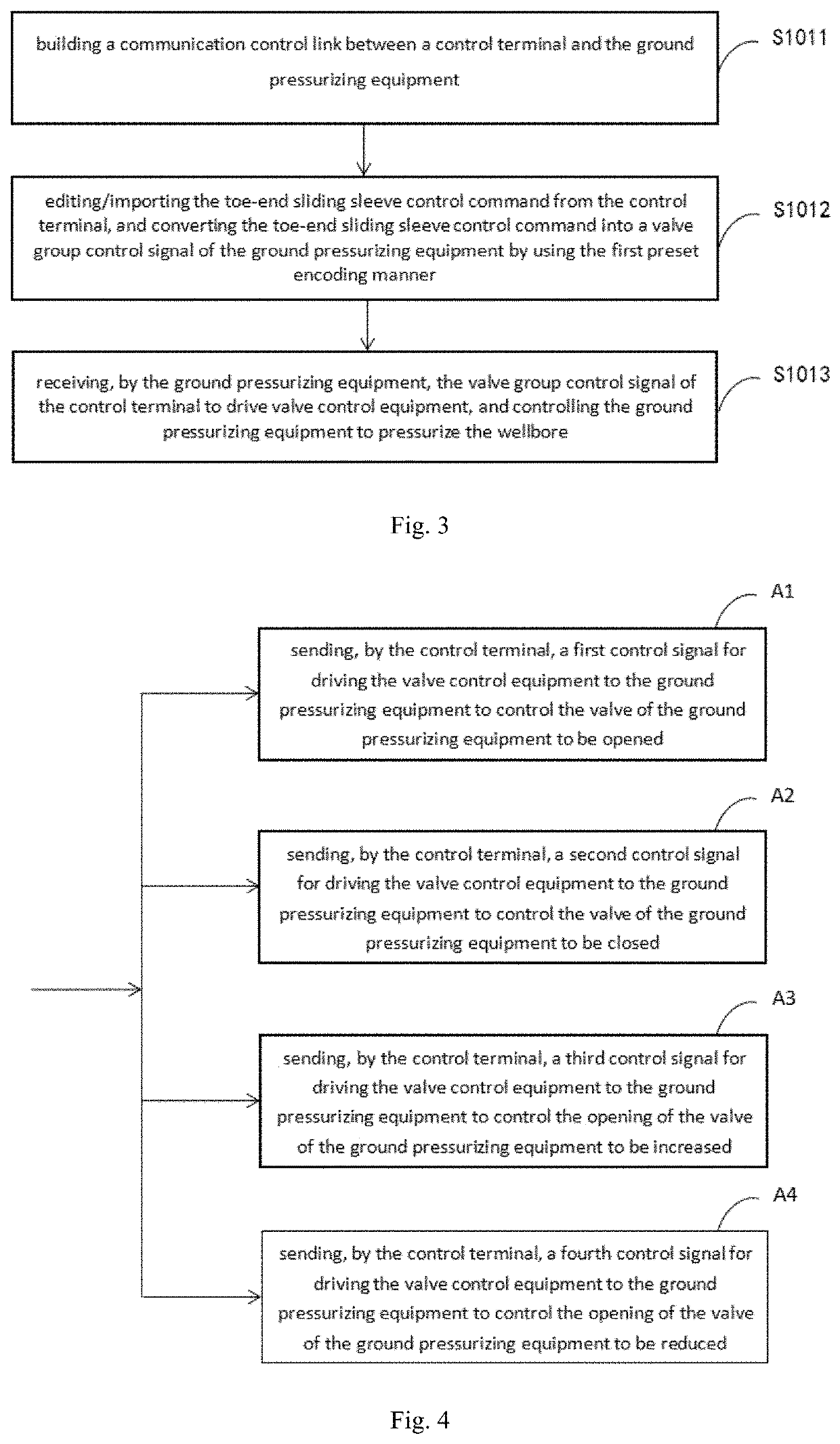
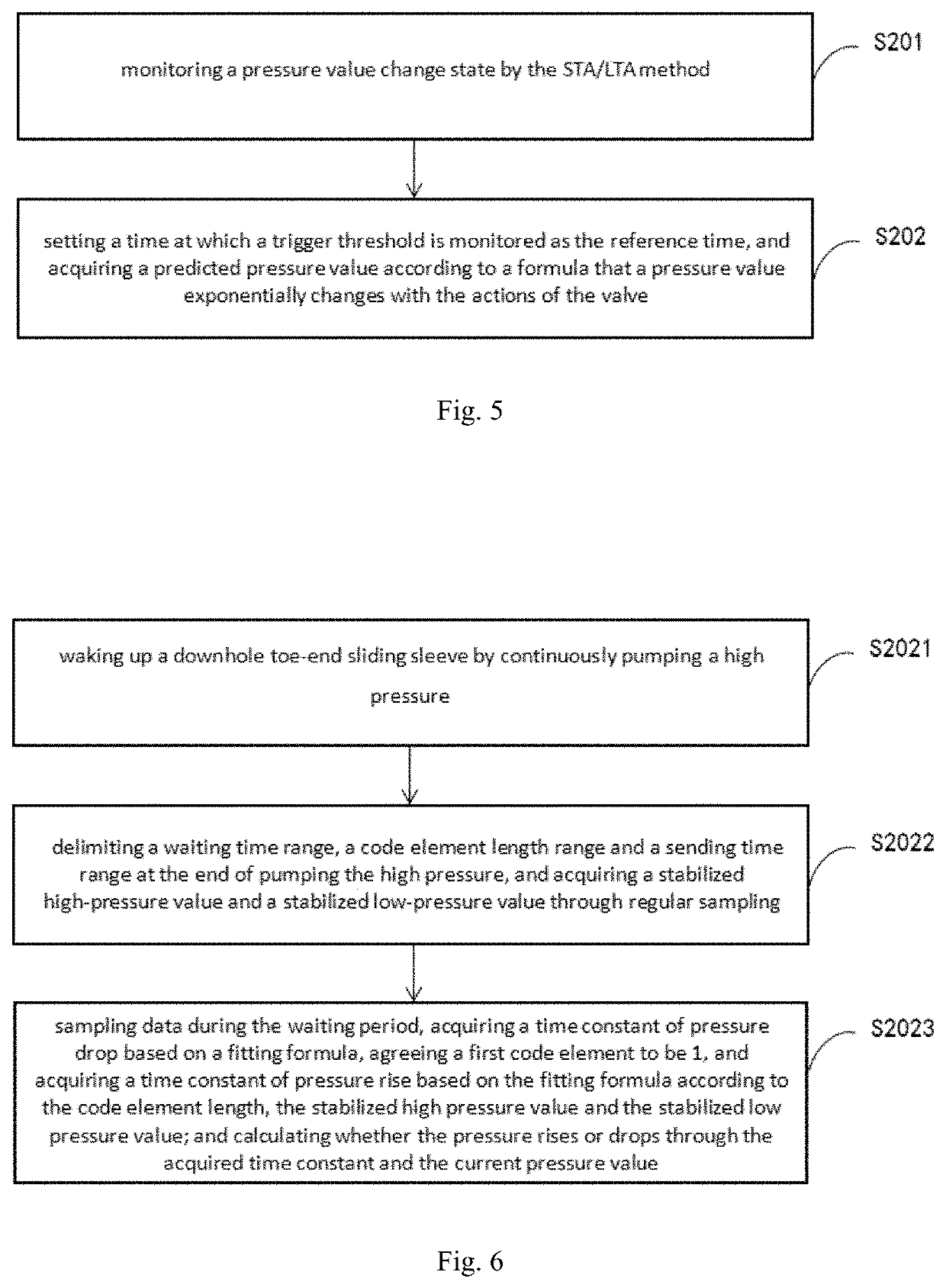
The present invention discloses a method for controlling a toe-end sliding sleeve in a horizontal well based on efficient decoding communication. The method comprises the following steps: forming a pressure wave signal by adjusting and controlling a pressure value in a wellbore according to a first preset encoding manner; acquiring a pressure value change signal in the wellbore, determining a reference time by using an STA / LTA method, and predicting pressure value to acquire a predicted pressure value signal curve; identifying a toe-end sliding sleeve control command in the acquired pressure wave signal by using a first preset decoding manner based on the fitness between the acquired pressure value signal curve and the predicted pressure value signal curve; and driving the toe-end sliding sleeve to perform actions according to the toe-end sliding sleeve control command. The method disclosed by the present invention is simple to operate, low in communication error rate, and aimed to solve the technical problems of complicated system of wellbore pressure test and sliding sleeve joint operation, high operation complexity, high bit error rate of pressure pulse communication, and long code element transmission time in the existing solutions in the prior art.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
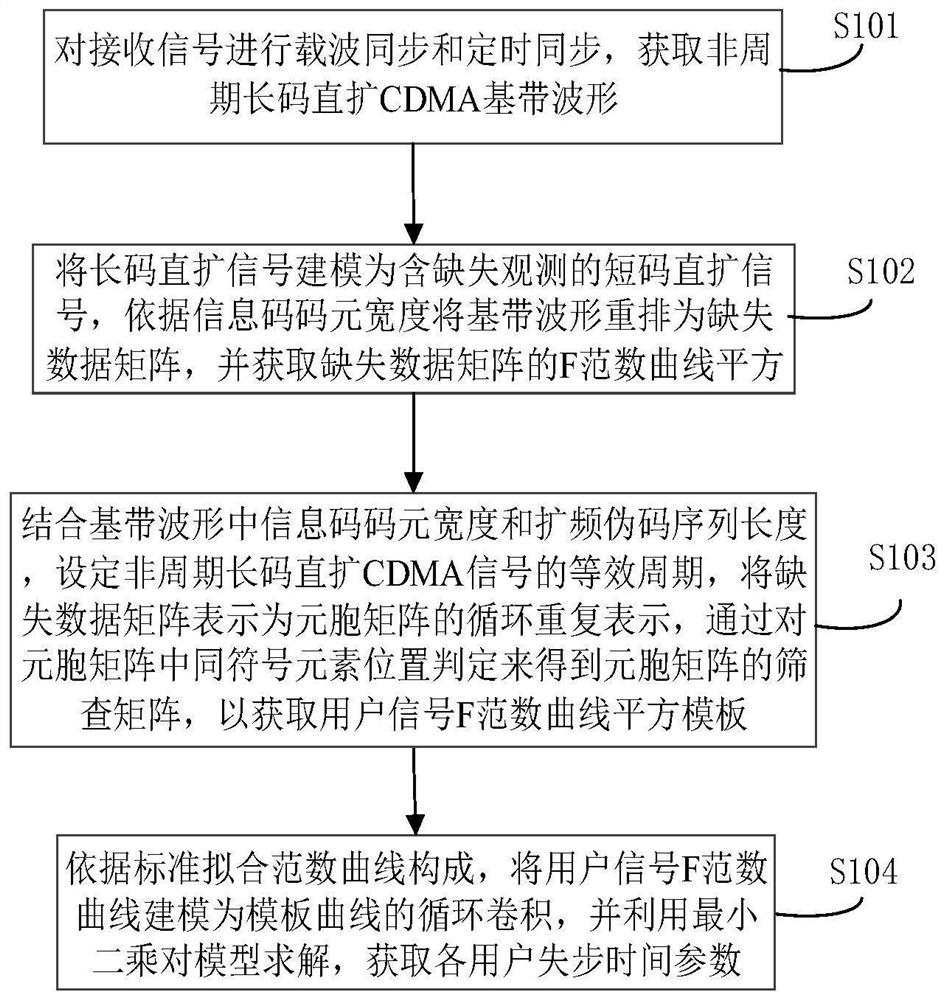
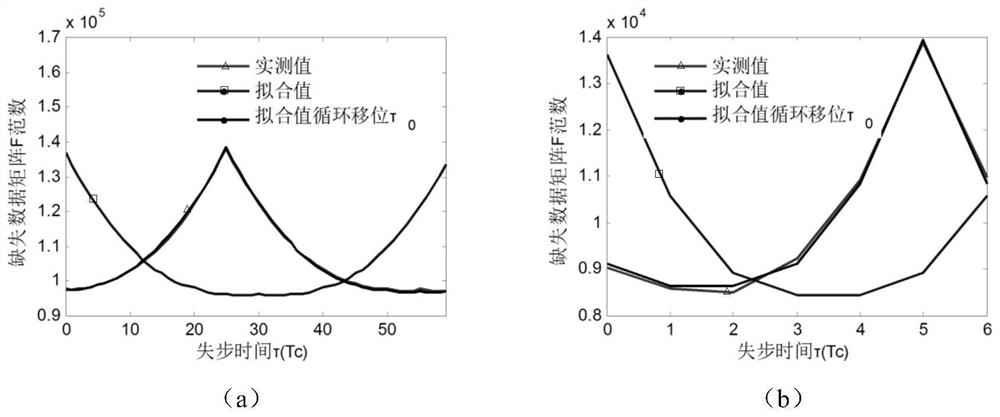
Aperiodic long-code direct sequence spread spectrum signal time delay estimation method and system based on norm fitting
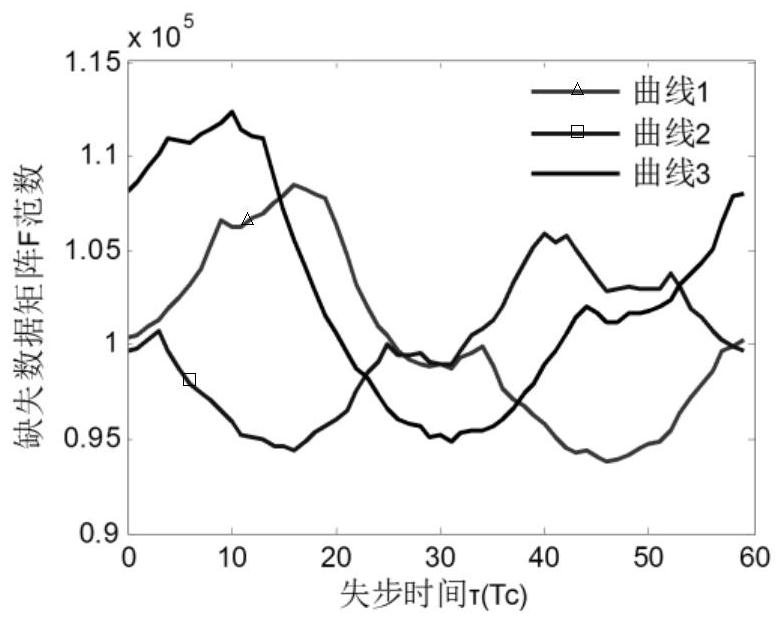
ActiveCN111953380AImprove estimation accuracyReduce operational complexityTransmissionMissing dataCarrier signal
The invention belongs to the technical field of signal processing, and particularly relates to an aperiodic long-code direct sequence spread spectrum signal time delay estimation method and system based on norm fitting, and the method comprises the steps: carrying out the carrier synchronization and timing synchronization of a received signal, and obtaining an aperiodic long-code direct sequence spread spectrum CDMA baseband waveform; modeling the long code direct sequence spread spectrum signal into a short code direct sequence spread spectrum signal containing missing observation, rearranging the baseband waveform into a missing data matrix according to the code element width of the information code, and obtaining an F norm curve of the missing data matrix; setting an equivalent period,representing the missing data matrix as cyclic repeat representation of a cellular matrix, and obtaining a user signal F norm curve square template according to the cellular matrix and the screening matrix; and modeling the multi-user signal F norm curve as cyclic convolution of a template curve, and solving the model by using a least square method to obtain an out-of-step time parameter of each user. According to the method, the time delay estimation of the high-capacity asynchronous NPLCDSSSCDMA system under the non-cooperative receiving condition can be realized, and the operation complexity of the system is effectively reduced while the good estimation precision is ensured.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
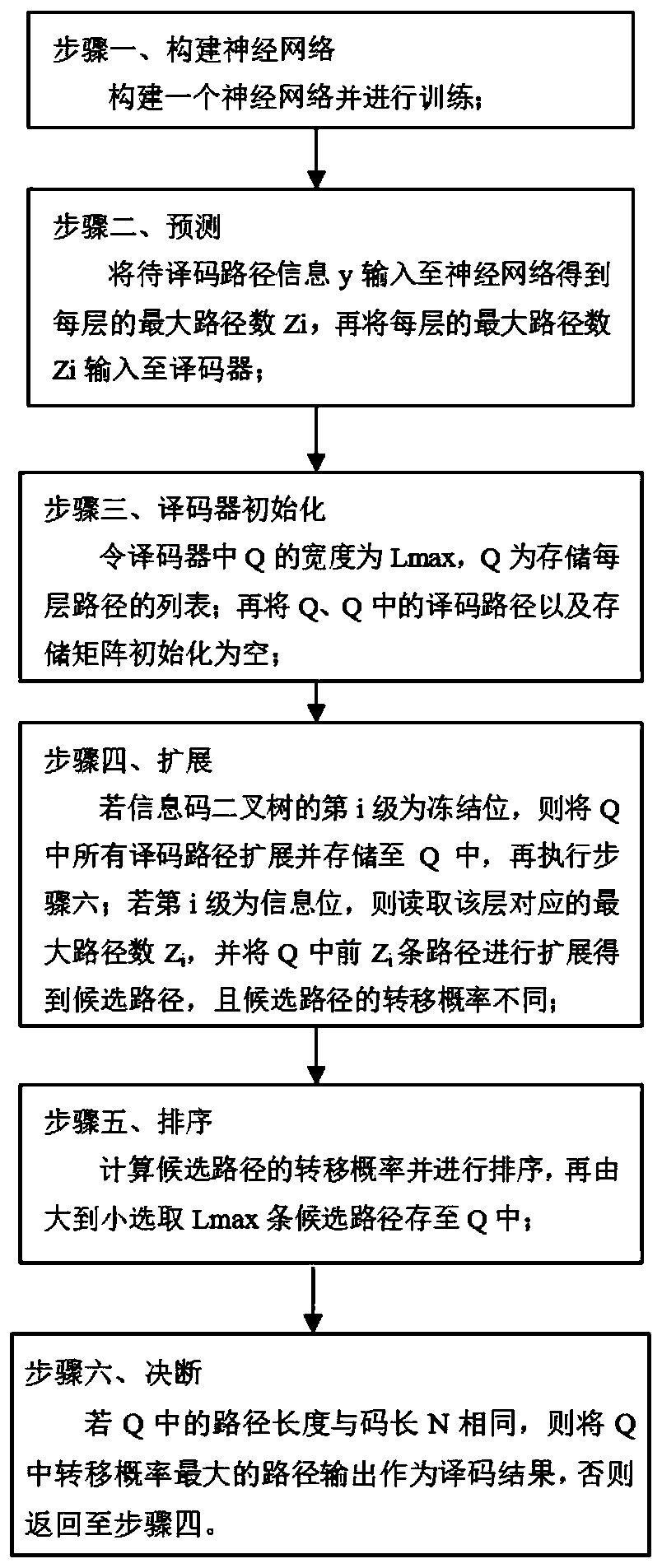
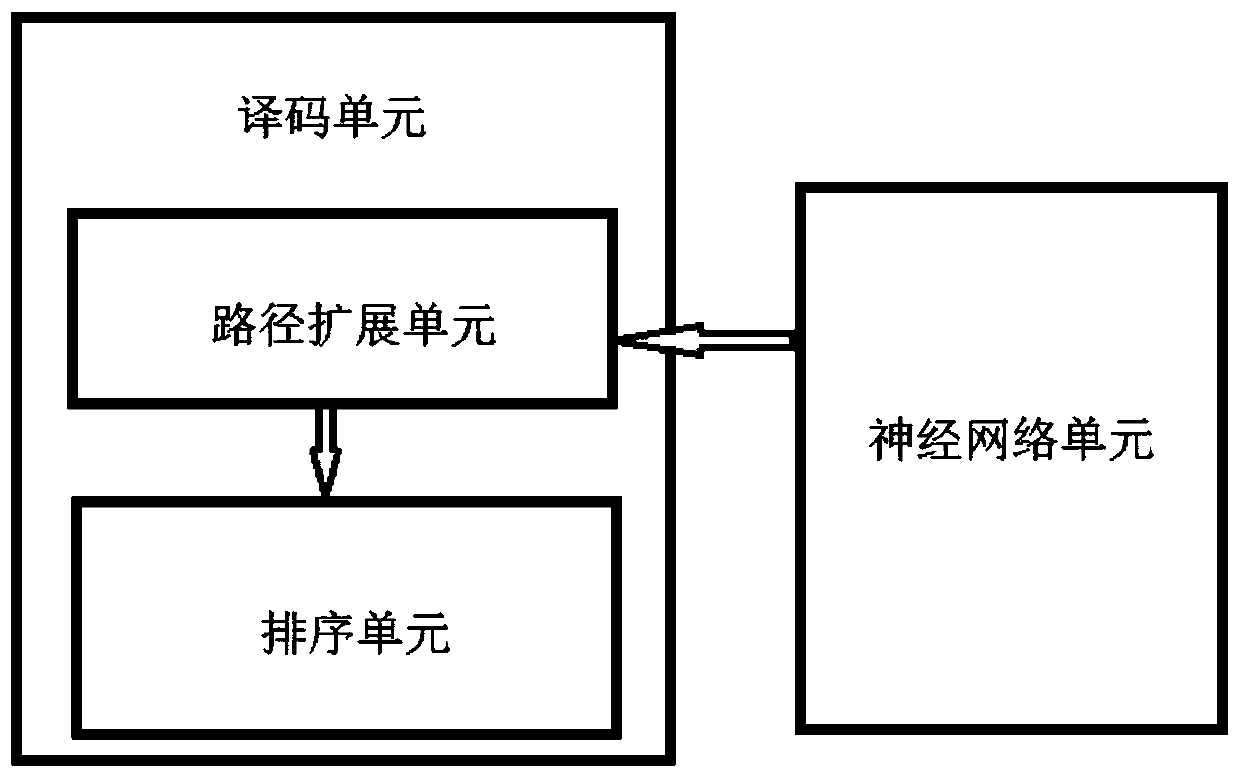
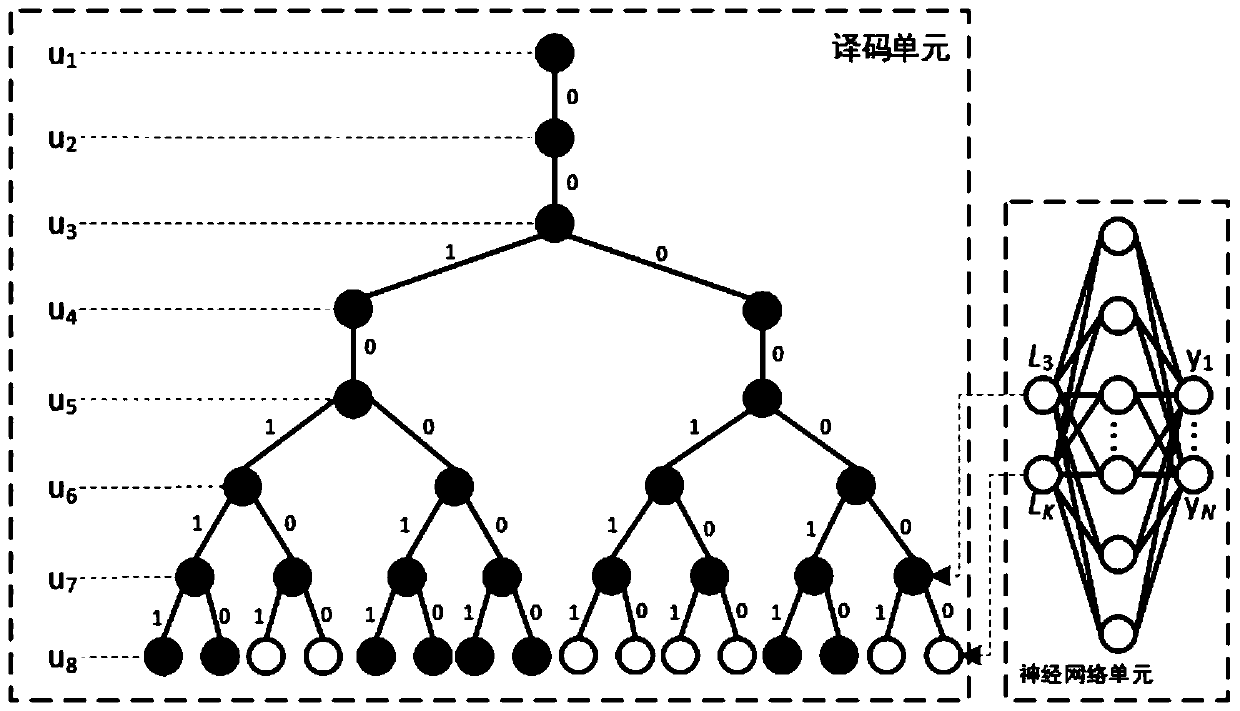
Polar code adaptive decoding method and system
ActiveCN110212922AReduce time complexityReduce space complexityError preventionError correction/detection using linear codesElectricityDecoding methods
The invention discloses a polar code adaptive decoding method and system, and belongs to the field of wireless communication. The method comprises the following steps: firstly constructing and training a neural network, and inputting to-be-decoded path information into the neural network to obtain the maximum path number of each layer; and inputting the maximum path number of each layer into a decoder, and decoding the path information to be decoded by using the decoder to obtain a decoding result. The system comprises a neural network unit and a decoding unit, wherein the neural network unitis electrically connected with the decoding unit; the decoding unit comprises a path expansion unit and a sorting unit, the path expansion unit is electrically connected with the sorting unit, and thepath expansion unit is electrically connected with the neural network unit. The invention aims to overcome the defects that in the prior art, a decoding algorithm based on deep learning is high in training complexity and not suitable for long code application, the decoding complexity can be reduced, and different channel environments and configuration requirements of a communication system can bemet.
Owner:南京宁麒智能计算芯片研究院有限公司
A method for implementing multi access channel in HRPD communication system
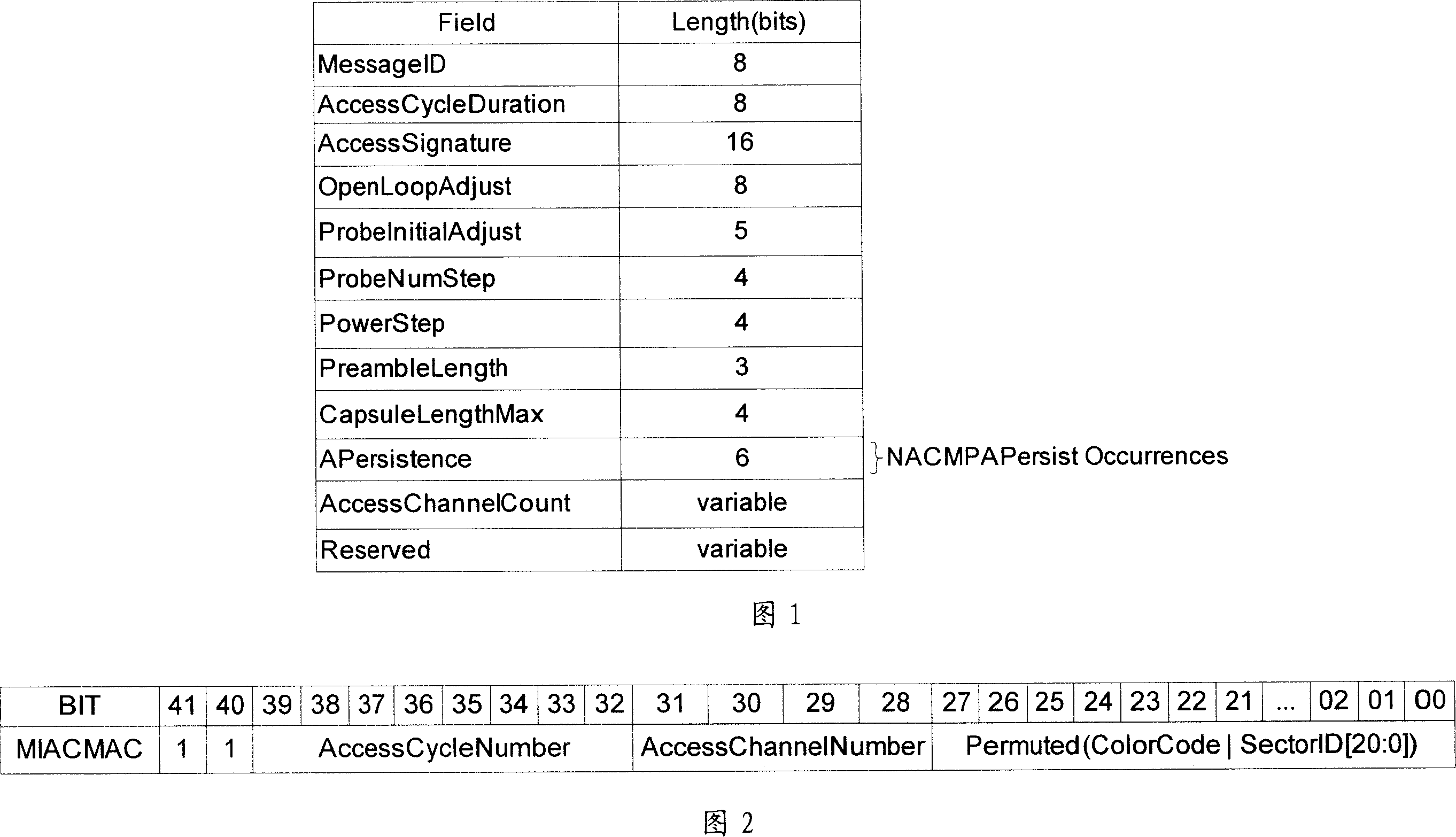
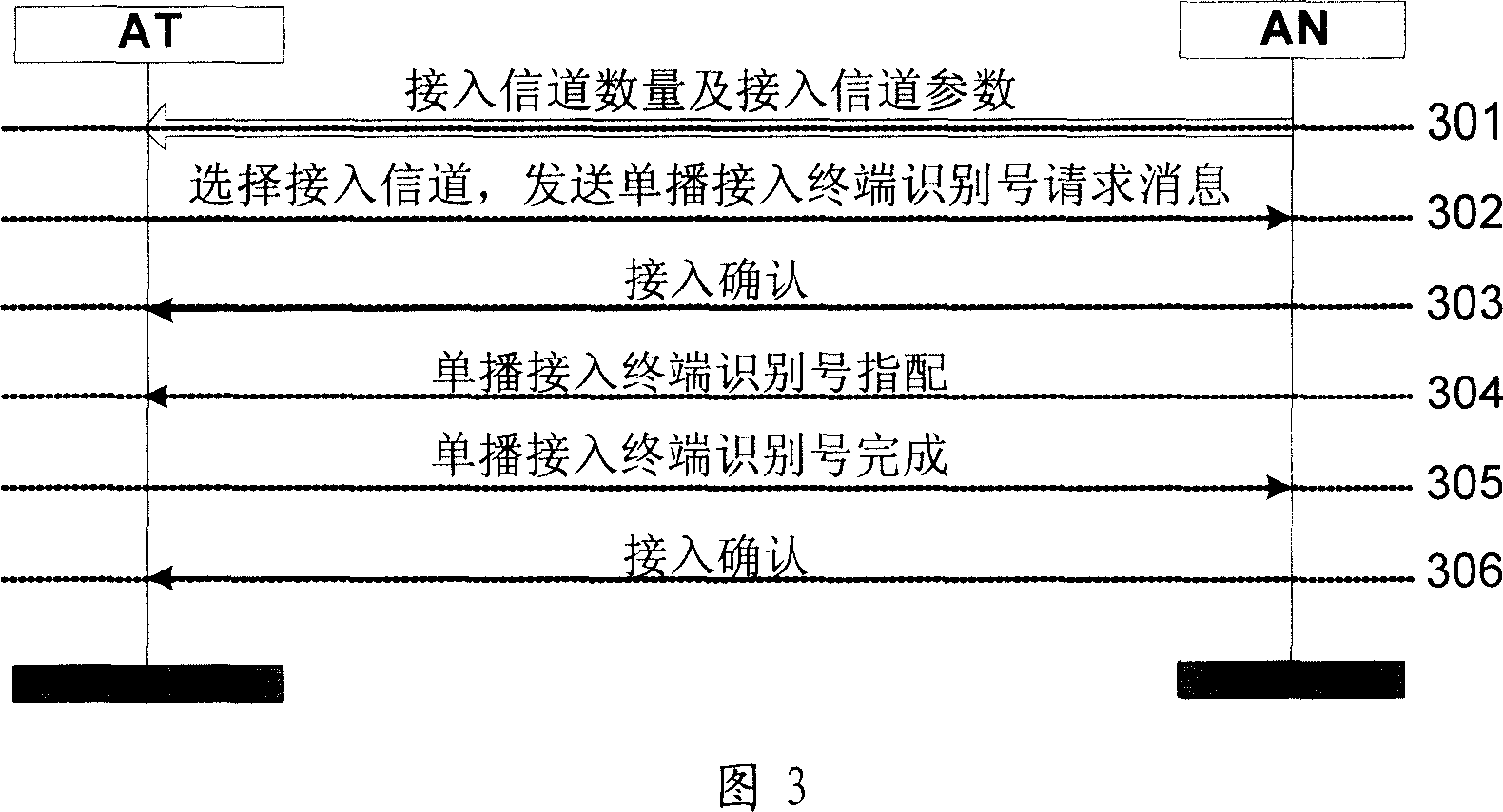
InactiveCN1972498AReduce the probability of collisionAssess restrictionRadio/inductive link selection arrangementsChannel parameterMulti access
This invention discloses one method to realize multiple interface signal channel on HRPD communication system, which comprises the following steps: a, establishing signal channels in the system; b, the system is connected with parameters through area composed of area interface signal channel parameters and number; c, AT receives parameters information to compute one interface channel by Harsh formula to get signal long code mask and to connect long signal channel by HRFD agreement and to add one interface section; d, sending reverse signals in channel to compute one signal channel to send reverse signals by step c.
Owner:ZTE CORP
Method and system for generating plcm for bcmcs in a mobile communication system
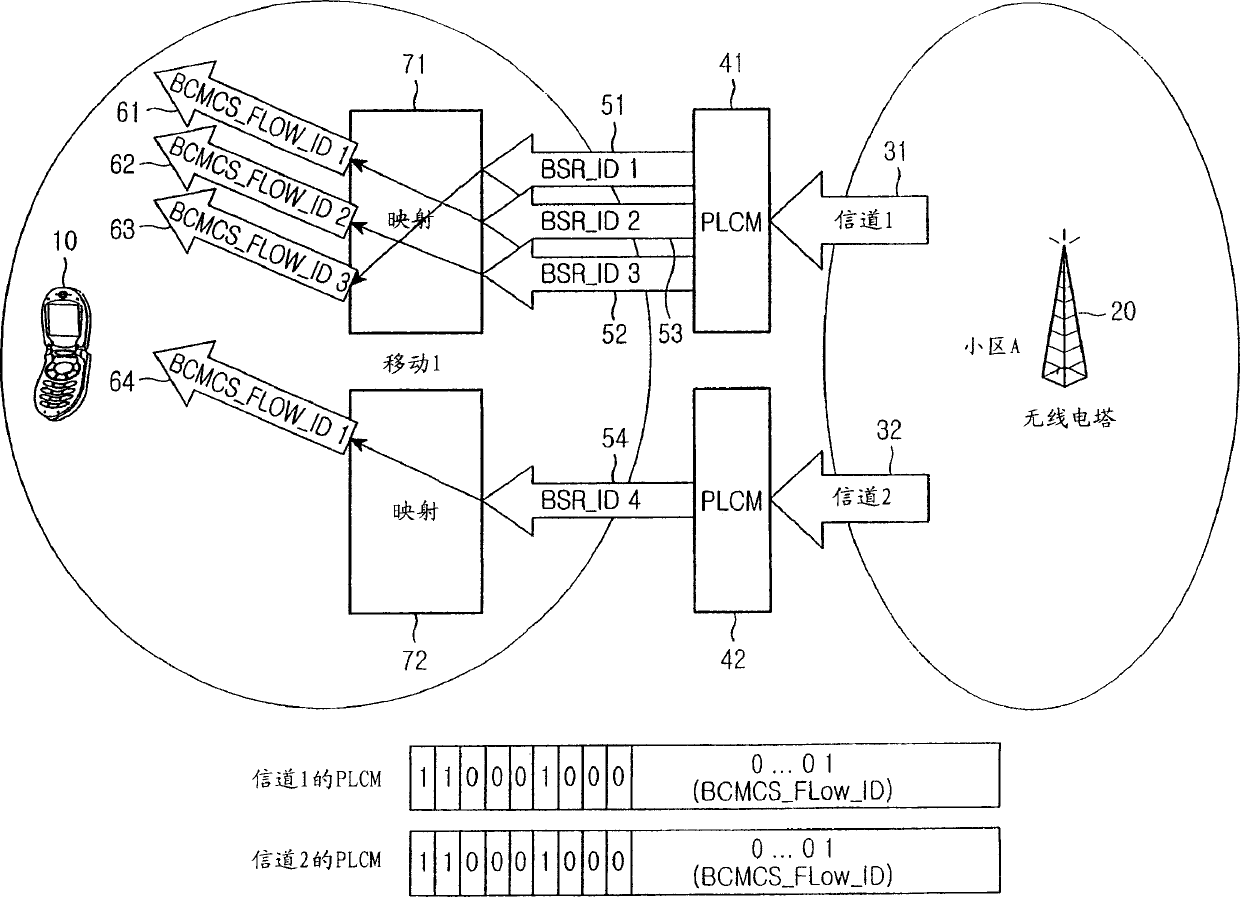
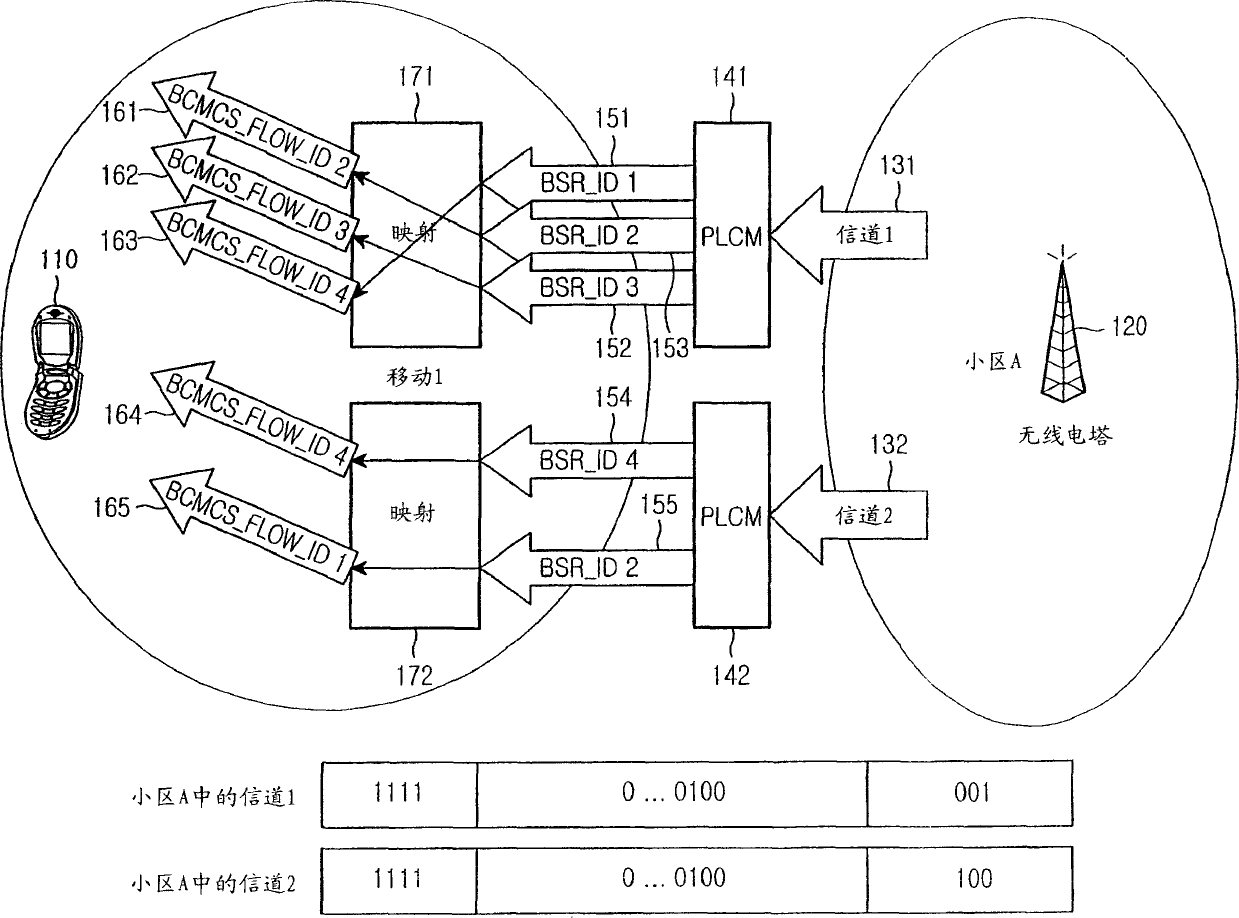
InactiveCN1762109AConnection managementBroadcast service distributionMobile stationMobile communication systems
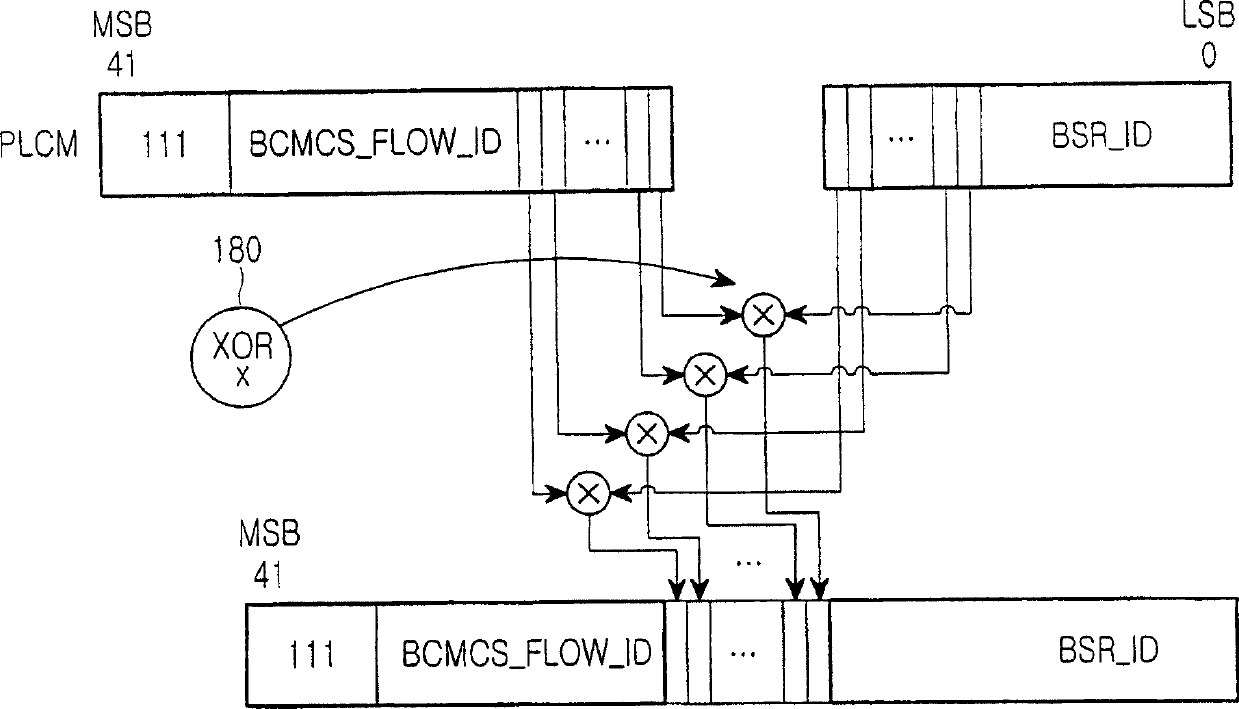
Disclosed is a method for generating a public long code mask (PLCM) so that a mobile station can receive a Broadcast / Multicast Service (BCMCS), in a mobile communication system including a base station and at least one mobile station located in a cell occupied by the base station, the BCMCS being provided from the base station to the mobile station. The PLCM is created by a combining a BCMCS flow identifier (BCMC FLOW ID) and a BCMC service reference identifier (BSR ID) matched thereto from a BCMCS service parameter message (BSPM) including information related to the BCMC FLOW IDs indicating individual flow IDs for identifying flows from respective broadcasting stations and BSR IDs matched to the BCMC FLOW IDs, the BSPM being transmitted from the base station to the mobile station over at least one channel.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for detecting a stationary dither code
An apparatus and method of detecting a transmission code from a received signal, where the transmission code is composed of a plurality of dithered codes. The codes can be dithered either by varying the length of the code or varying the phase of the code according to a dither pattern and can be a stationary dither pattern that is fixed and generally known. The method includes detecting the plurality of dithered codes, and detecting the long code based on the detected dithered codes. A detection signal is generated for each detected dither code, the detection signals are combined, and the long code is detected based on the combination of detection signals. If the composite code includes M dithered codes, the correlation signals are combined by summing the M correlation sums to generate a present final sum. The long code is detected by determining a largest final sum from among the present final sum and previously generated final sums, and associating a time of the largest final sum with the time of the transmission code.
Owner:EXCELIS INC
Method for recognizing malicious codes in host software after infection by malware
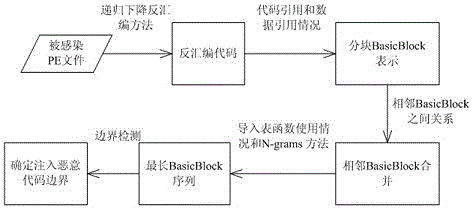
A method for recognizing malicious codes in host software after infection by malware comprises steps as follows: firstly, disassembling codes of the host software are acquired with a recursive descent disassembling method, wherein disassembling codes corresponding to a machine instruction, various citation information in the codes and import table function information are required to be acquired; then, breaking points among code sequences are determined according to the citation condition, and a code sequence between two breaking points forms a code block; then, merging is performed according to the relationship of adjacent code blocks; the longest code block sequence which doesn't employ an import table function is sought according to the import table function use condition; finally, a starting software block and an ending software block of malicious codes are determined according to the calling relation between the malicious codes and host software codes, and accordingly, a required malicious code sequence is obtained. The method can be taken as a universal method for recognizing malicious codes in the host software, and specific code position information is provided for further restoration of the software.
Owner:HENAN POLYTECHNIC UNIV
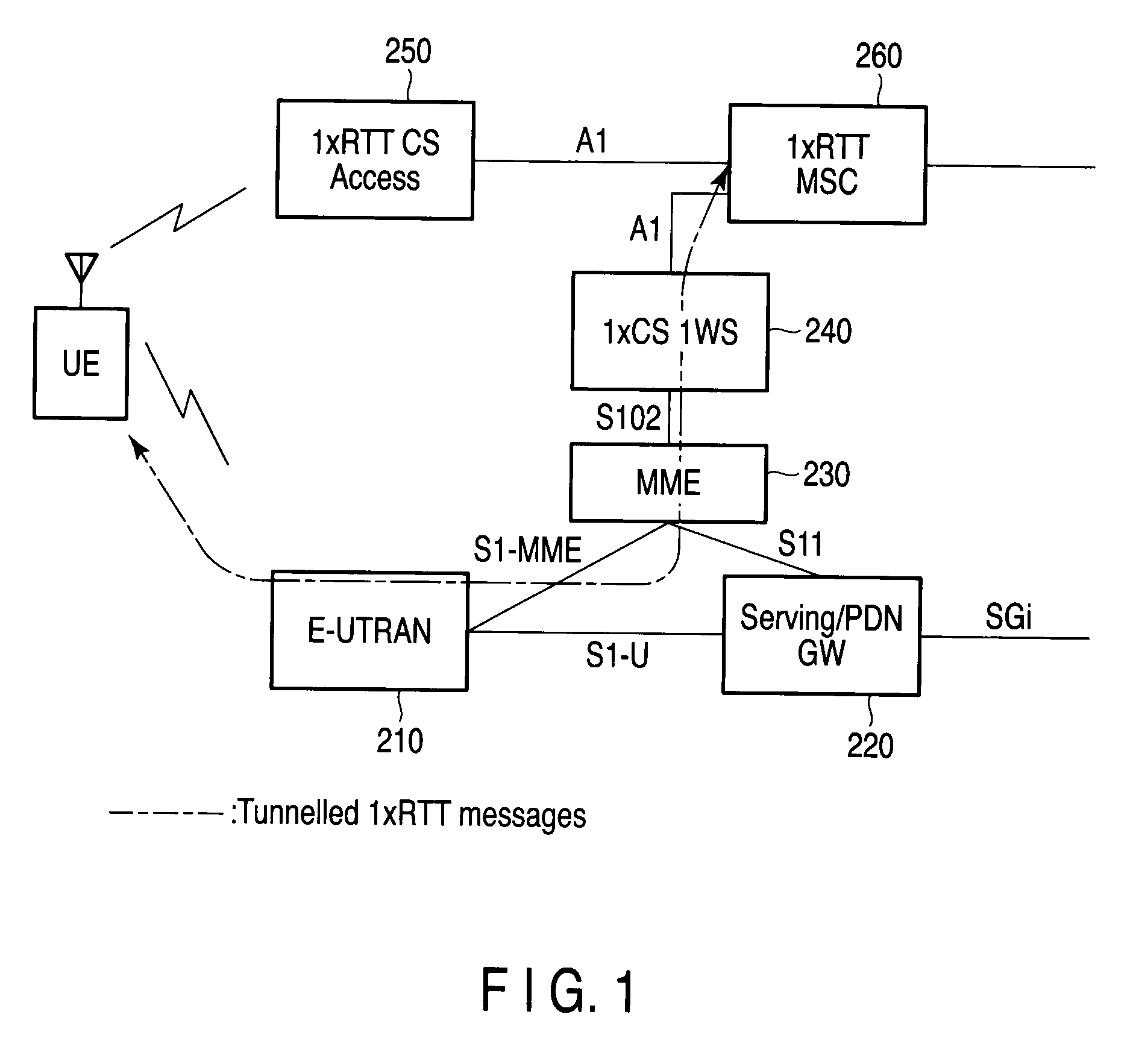
Mobile wireless electric terminal and wireless electric communication method
A mobile radio terminal UE performs starting PNG, detecting a best cell, and starting generation of Long Code and receives various types of messages from a 1xRTT CS Access on the basis of System Information supplied from an E-UTRAN.
Owner:FUJITSU TOSHIBA MOBILE COMM LTD
Compact representation and time series segment retrieval through deep learning
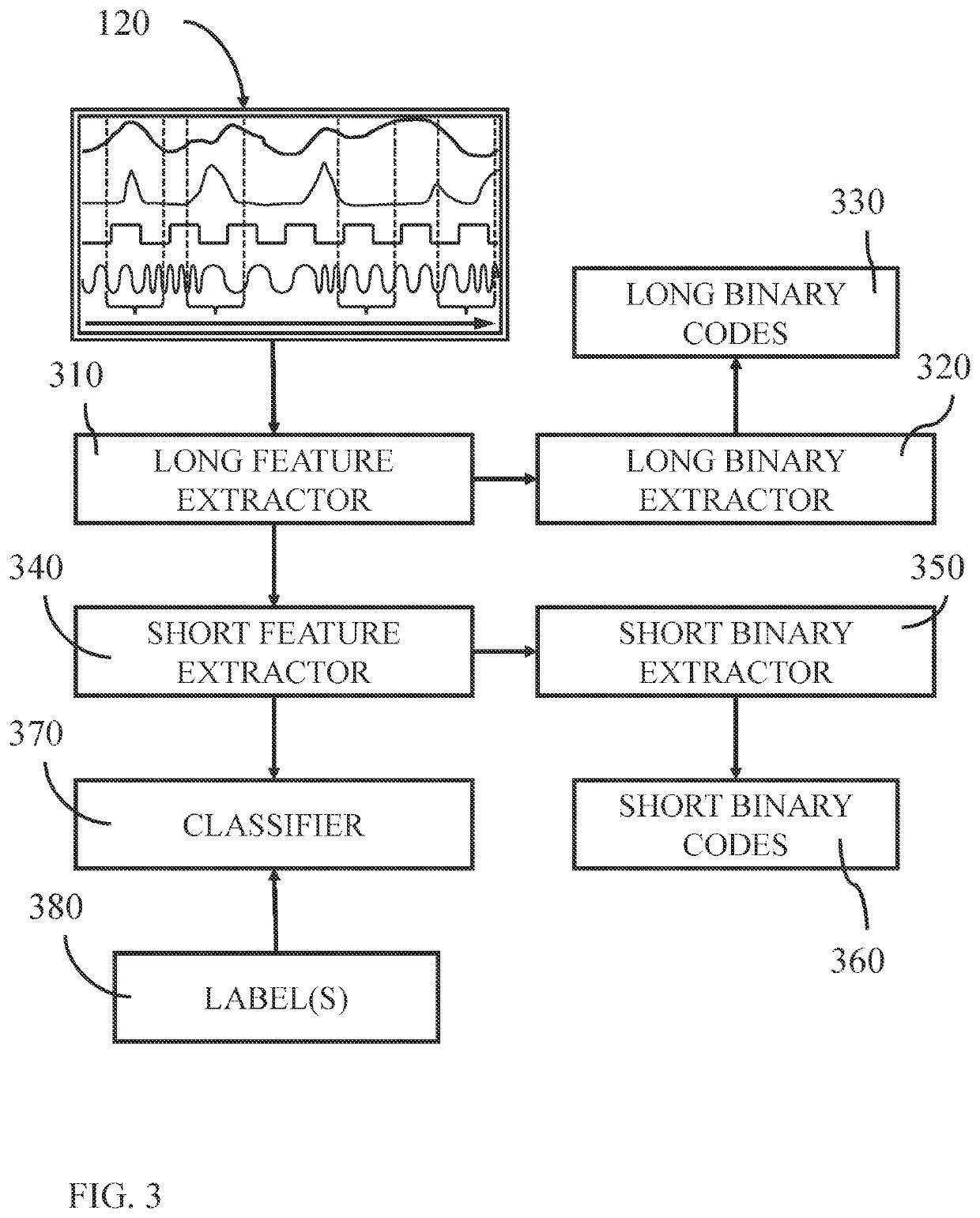
Systems and methods for retrieving similar multivariate time series segments are provided. The systems and methods include extracting a long feature vector and a short feature vector from a time series segment, converting the long feature vector into a long binary code, and converting the short feature vector into a short binary code. The systems and methods further include obtaining a subset of long binary codes from a binary dictionary storing dictionary long codes based on the short binary codes, and calculating similarity measure for each pair of the long feature vector with each dictionary long code. The systems and methods further include identifying a predetermined number of dictionary long codes having the similarity measures indicting a closest relationship between the long binary codes and dictionary long codes, and retrieving a predetermined number of time series segments associated with the predetermined number of dictionary long codes.
Owner:NEC LAB AMERICA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com