Method for recognizing malicious codes in host software after infection by malware
A malicious code and malicious software technology, applied in the identification field of malicious code injected into host software after being infected, can solve problems such as inability to directly call functions and difficulty in knowing the logical address of the import table.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
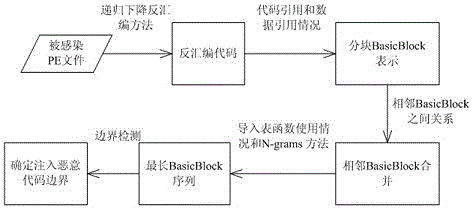
[0026] according to figure 1 The process introduced in , the specific implementation method is 5 steps:
[0027] Step 1. The recursive descent disassembly method obtains the disassembly code of the host software. The method of recursive descent is to disassemble the software according to the control flow executed by the machine code in the binary software. During the disassembly process, some functions with complete structure and the import table functions defined by the system can be identified.
[0028] Step 2. Determine breakpoints between code sequences based on references. According to the jump instructions and call instructions in the disassembled code, determine where code references and data references occur, and where they are referenced, and these locations can be used as breakpoints. Specifically, the instructions whose operators are "jmp", "call" and "retn" must be able to cause the transfer of control flow, and an instruction after these instructions is used as ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com