Patents
Literature
317 results about "File verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
File verification is the process of using an algorithm for verifying the integrity of a computer file. This can be done by comparing two files bit-by-bit, but requires two copies of the same file, and may miss systematic corruptions which might occur to both files. A more popular approach is to generate a hash of the copied file and comparing that to the hash of the original file.
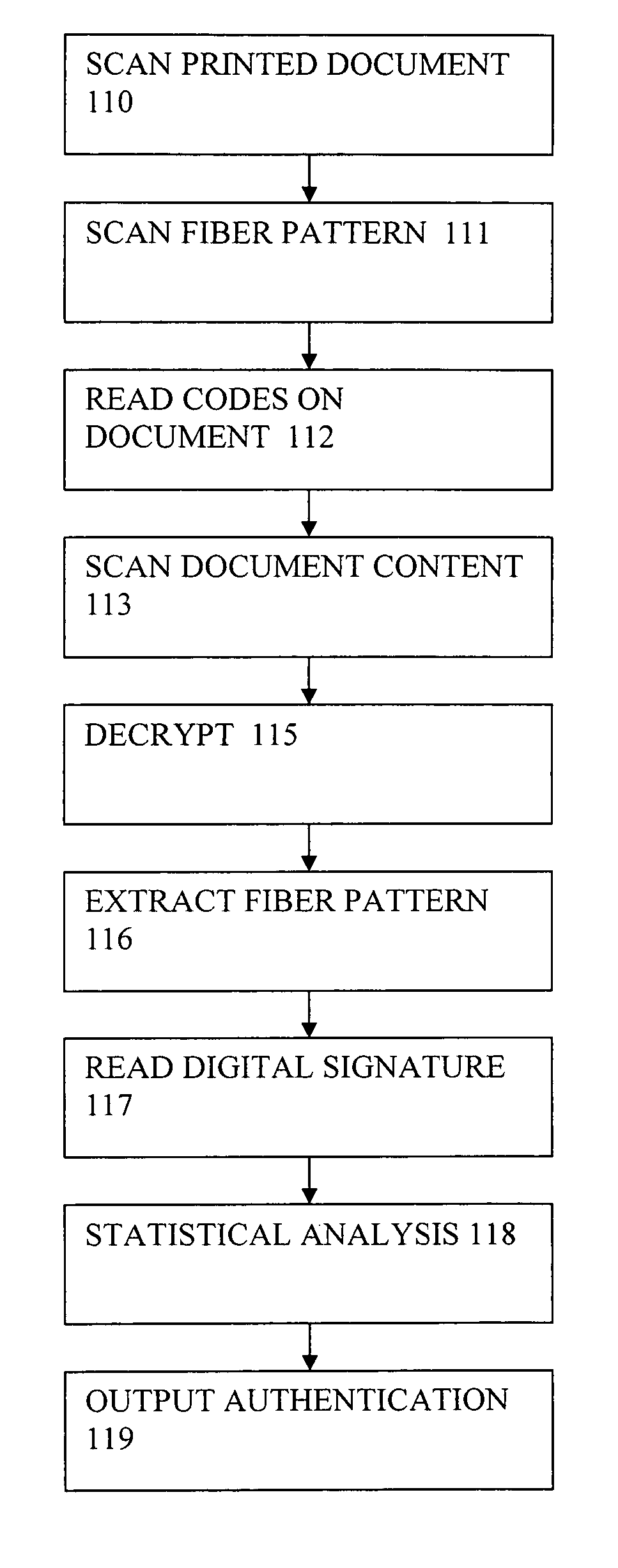
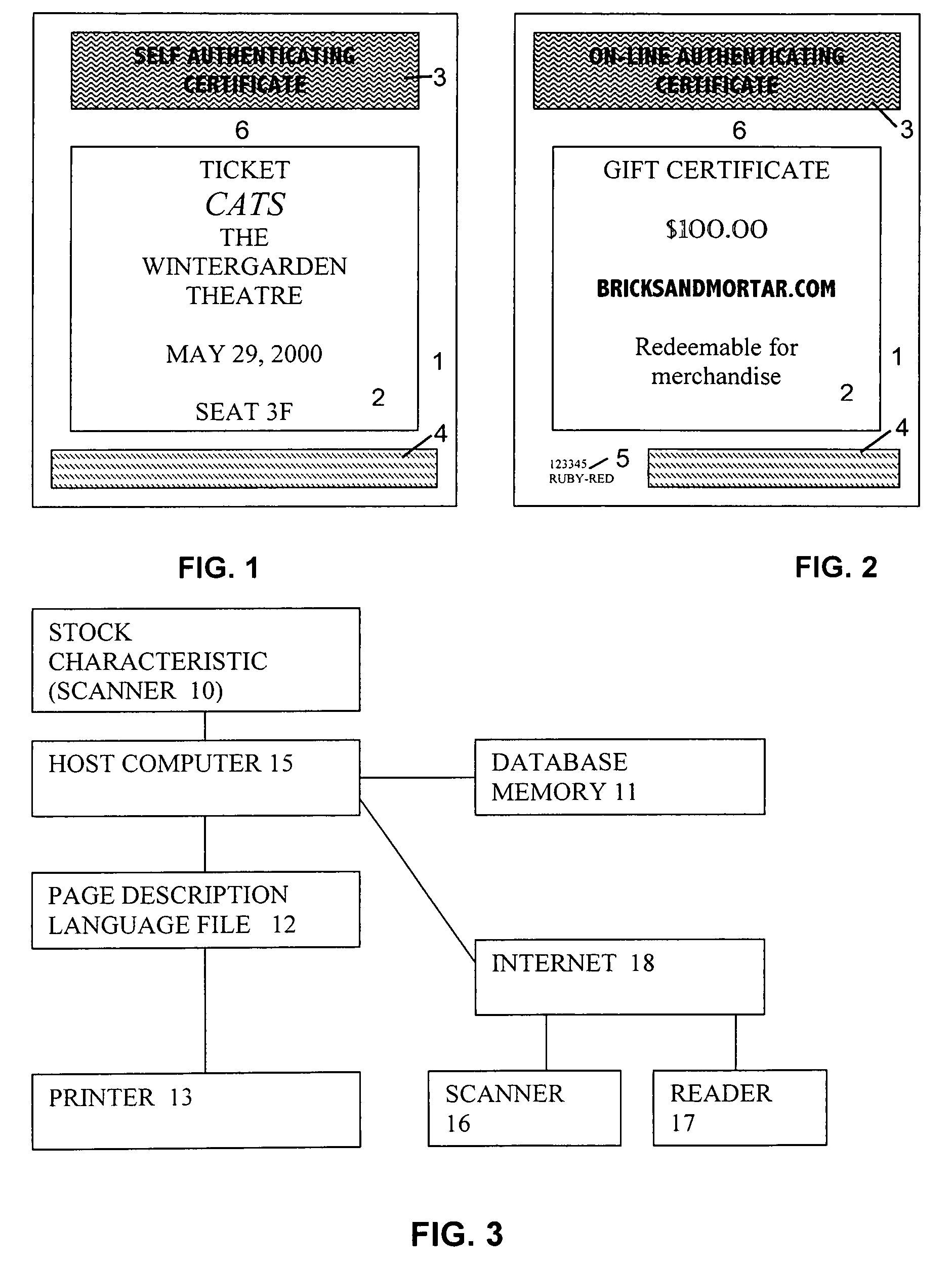
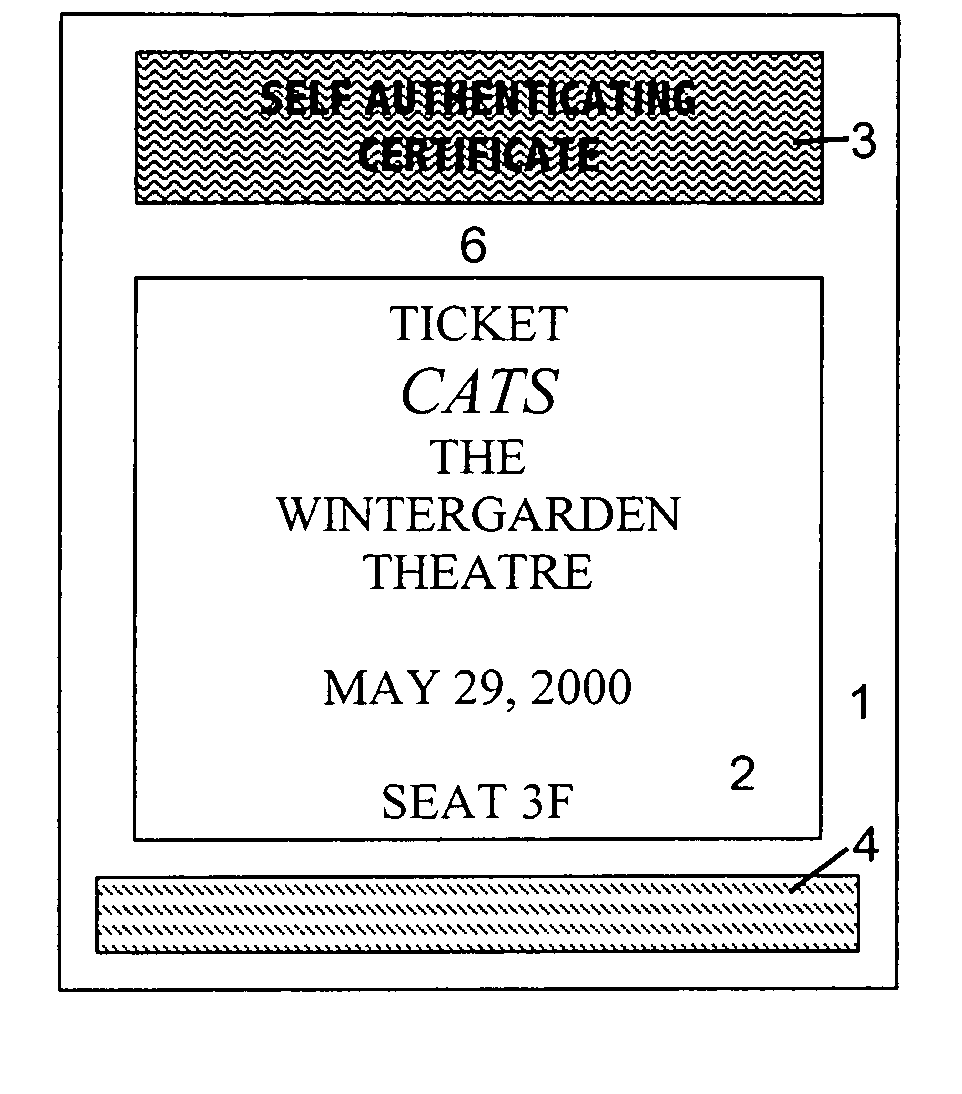
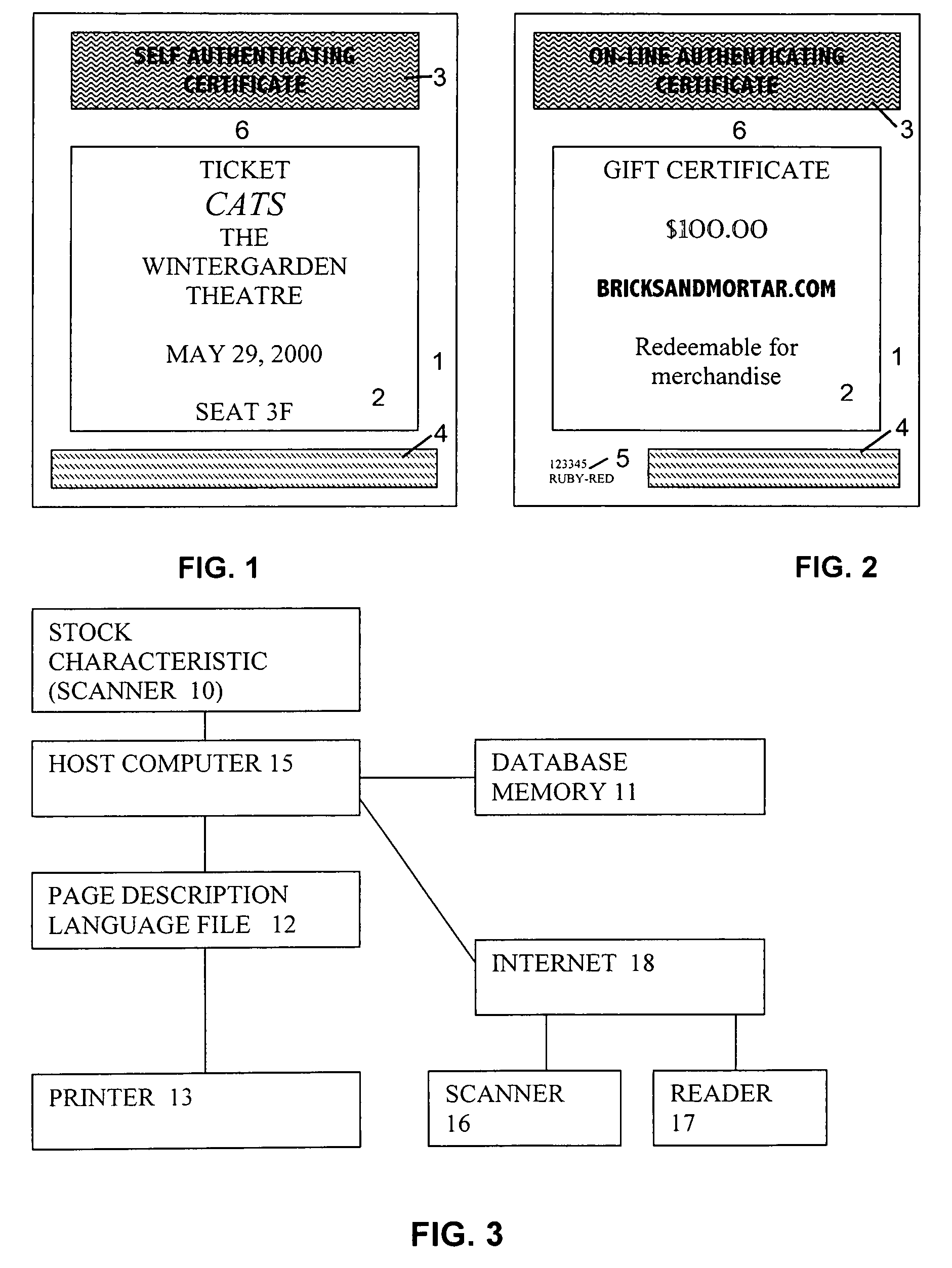
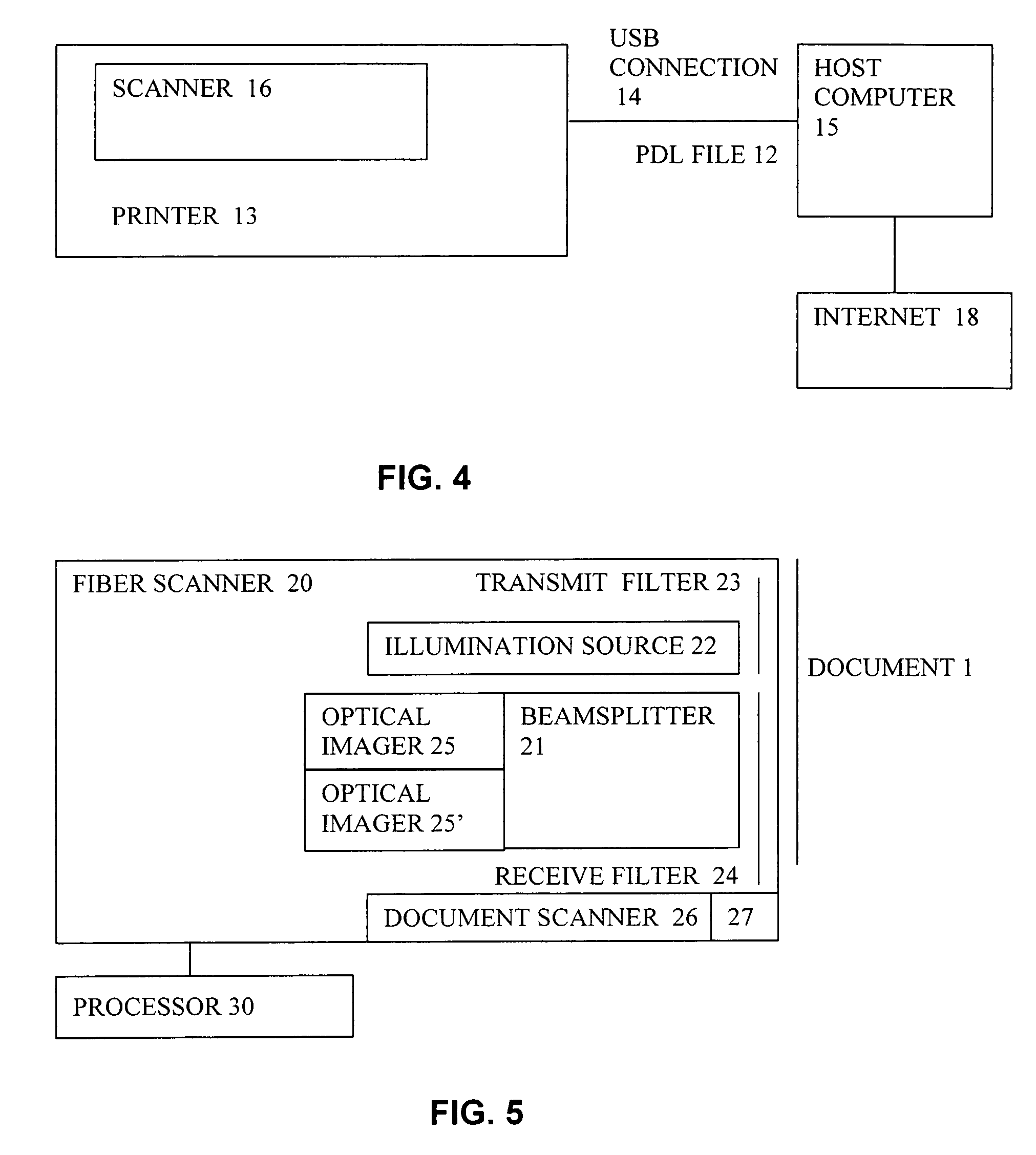
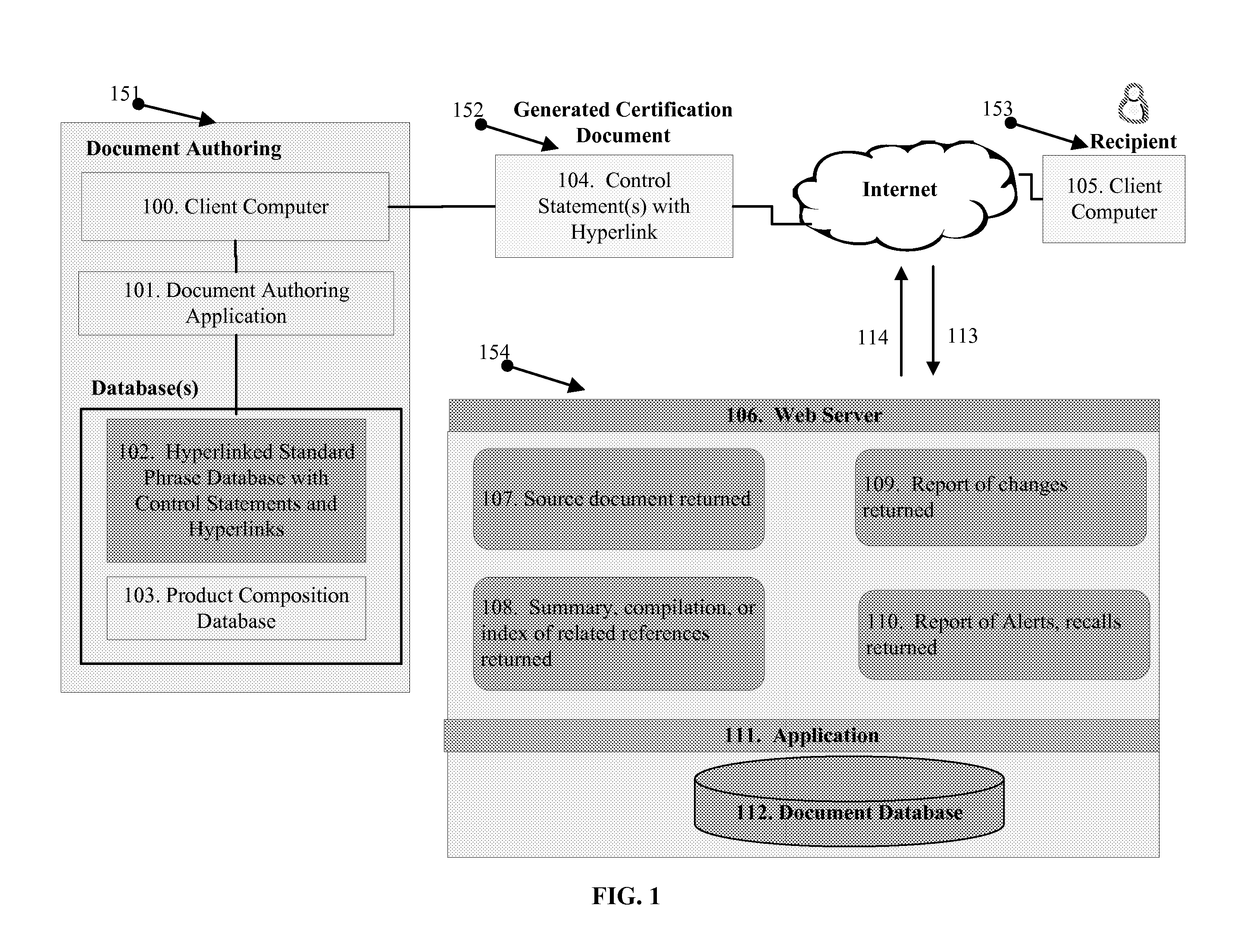
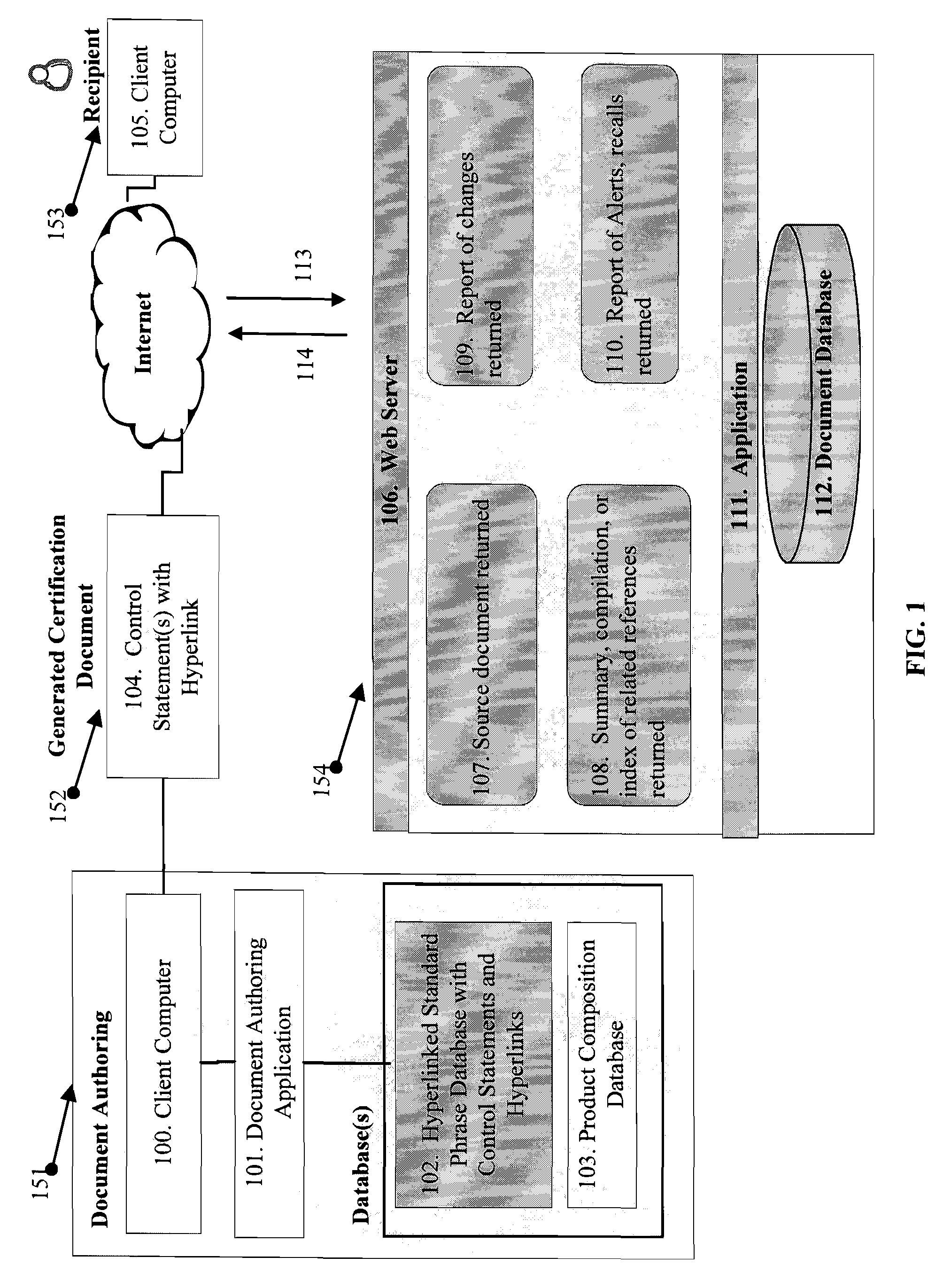
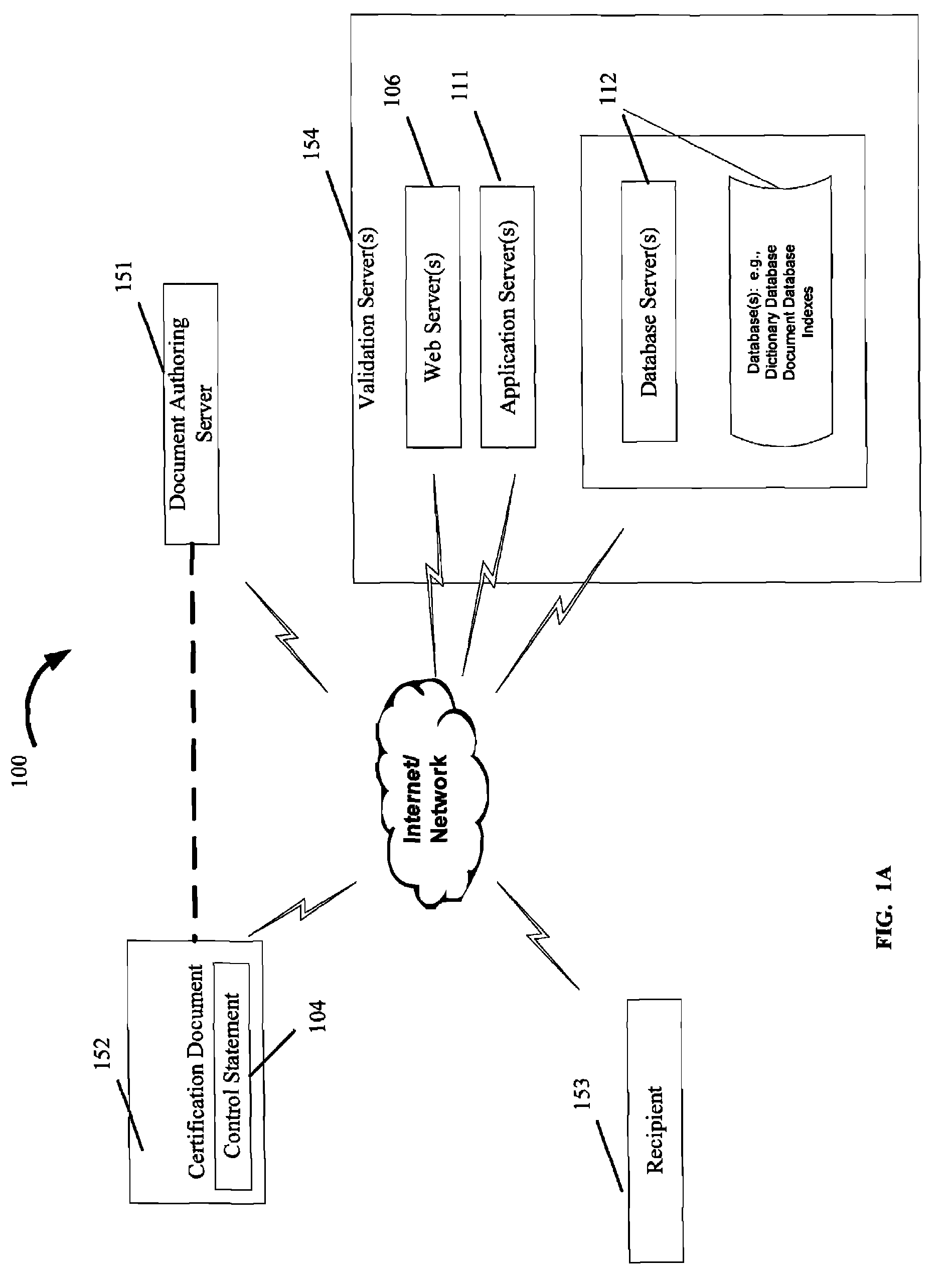
System and method for production and authentication of original documents
InactiveUS7080041B2Improve shielding effectImprove accuracyOther printing matterUser identity/authority verificationDocument IdentifierLogical security
A system and method for authenticating documents and content thereof. A counterfeit resistant document recording medium is provided, having thereon a predefined unique document identifier and at least one security feature. The recording medium is thereafter imprinted with document content, which typically varies between documents. The document content is stored in a database, indexed by an associated document identifier. The document may then be authenticated by checking the security feature and comparing the stored document content with a perceived document content. The system provides a number of opportunities for commercial exploitation, including sales of identified recording media, recording of information in a database, on-line authentication transactions, differential accounting for document validations and counterfeit identifications, imprinting devices, authentication devices, and the like. The system prevents counterfeiting of valuable documents through casual means by providing both physical and logical security.
Owner:ESECUREDOCS
System and method for production and authentication of original documents
InactiveUS20050038756A1Improve shielding effectImprove accuracyOther printing matterUser identity/authority verificationDocument IdentifierPaper document
A system and method for authenticating documents and content thereof. A counterfeit resistant document recording medium is provided, having thereon a predefined unique document identifier and at least one security feature. The recording medium is thereafter imprinted with document content, which typically varies between documents. The document content is stored in a database, indexed by an associated document identifier. The document may then be authenticated by checking the security feature and comparing the stored document content with a perceived document content. The system provides a number of opportunities for commercial exploitation, including sales of identified recording media, recording of information in a database, on-line authentication transactions, differential accounting for document validations and counterfeit identifications, imprinting devices, authentication devices, and the like. The system prevents counterfeiting of valuable documents through casual means by providing both physical and logical security.
Owner:ESECUREDOCS
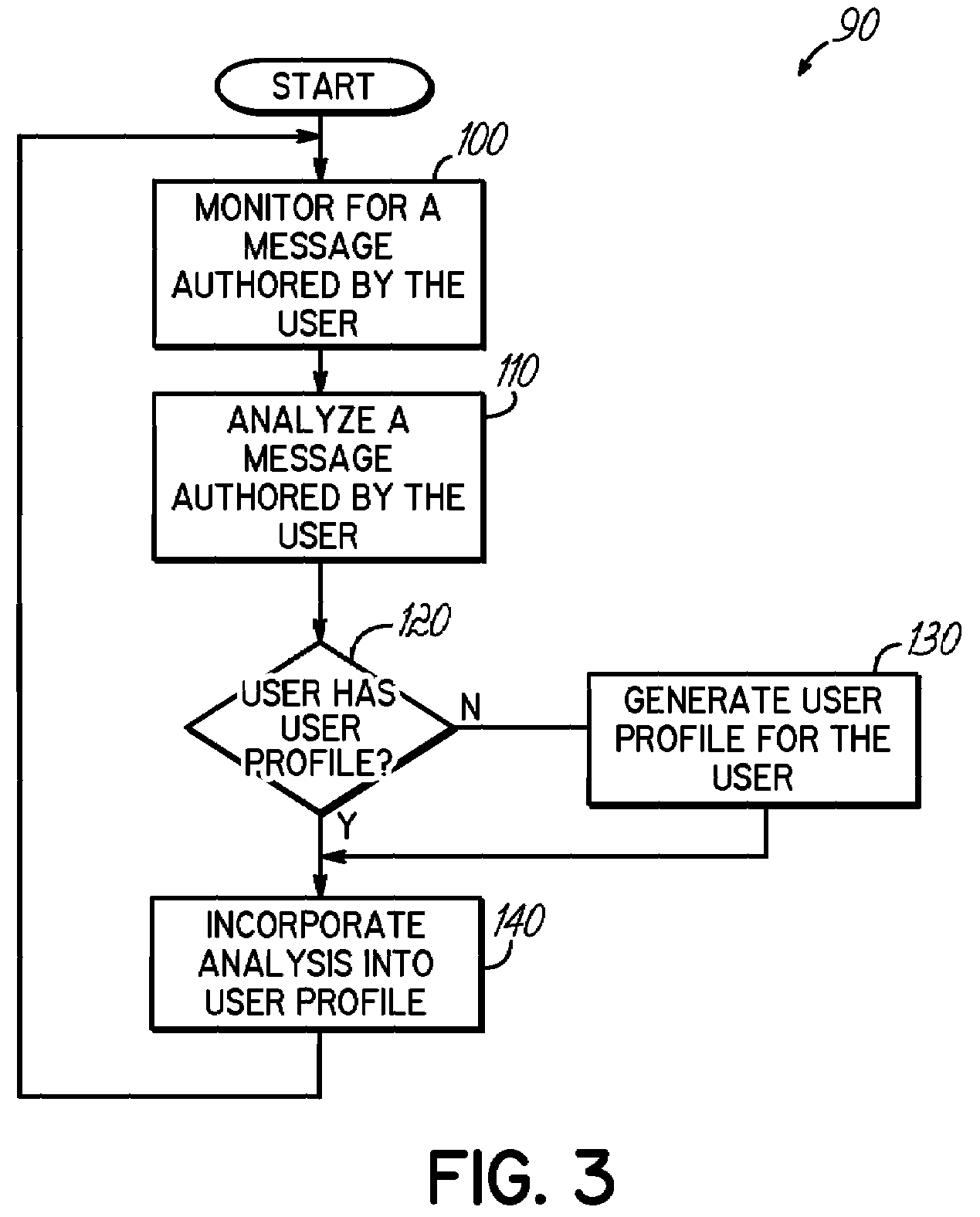
Verifying that a message was authored by a user by utilizing a user profile generated for the user
InactiveUS20080084972A1Automatic call-answering/message-recording/conversation-recordingData switching networksInternet privacyUser profile
An apparatus, program product and method that generate a user profile and verify the authorship of a second message against the user profile. As such, messages inconsistent with the user profile, which may be indicative of authorship by another user, may be detected primarily from one side of a communication, generally resulting in safer instant messaging and / or emailing. Additionally, reauthentication and / or blocking capabilities may be utilized to handle messages inconsistent with the user profile.
Owner:IBM CORP
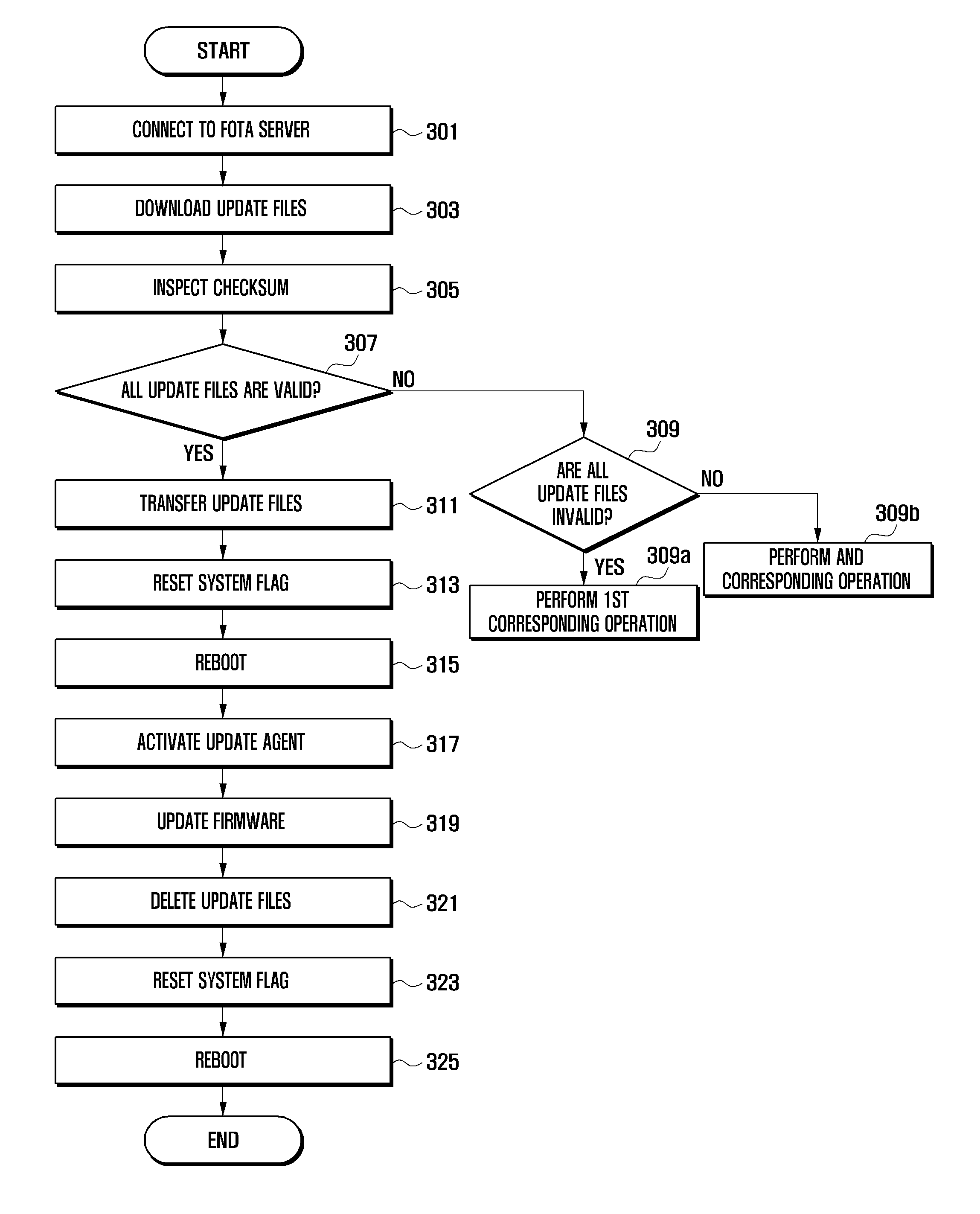
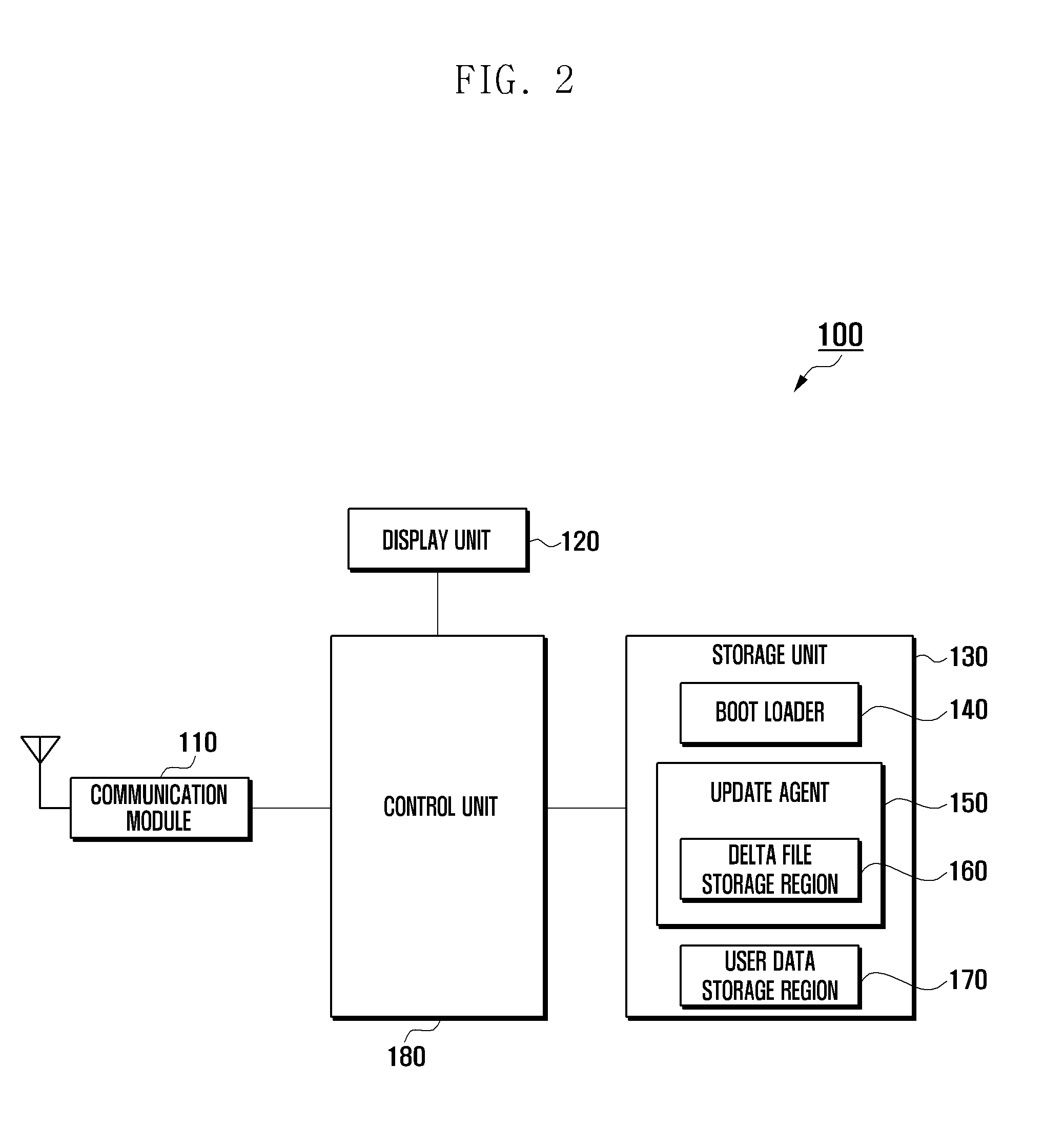
Firmware update method and apparatus for a mobile device
InactiveUS20120102477A1Improve usabilityImprove user convenienceData resettingSpecific program execution arrangementsChecksumMobile device
A method and apparatus for updating firmware of a mobile device based on the result of verification of integrities of a plurality of update files is provided. The firmware update method includes downloading a plurality of update files corresponding to the firmware and checksums corresponding to each of the update files in a user data storage region upon detecting a firmware update event; verifying whether each of the update files is valid; and updating the firmware using at least one valid update file from among the plurality of update files.
Owner:SAMSUNG ELECTRONICS CO LTD
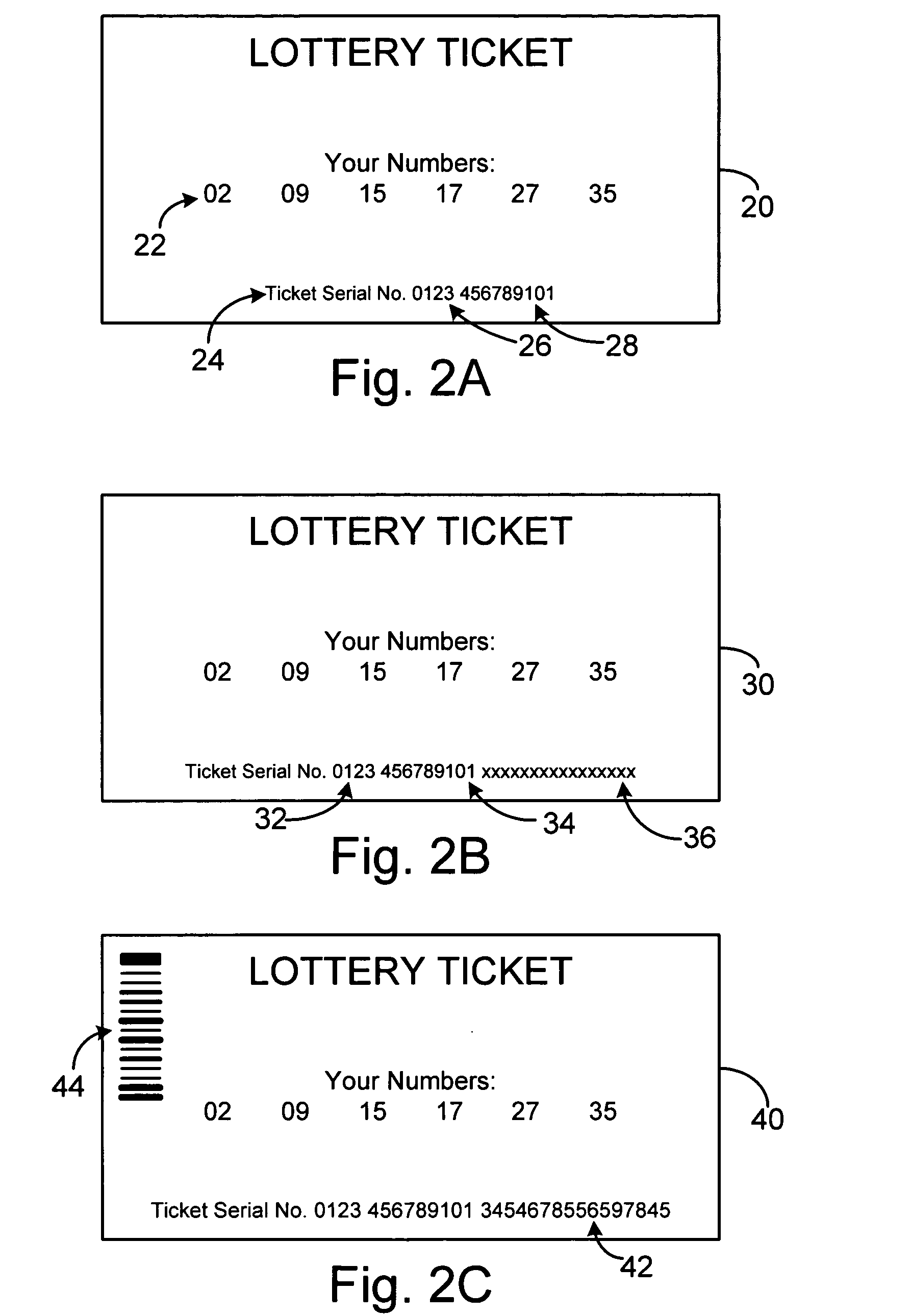
System and method for securing on-line documents using authentication codes
ActiveUS20050262338A1Low costReduce needPaper-money testing devicesUser identity/authority verificationPaper documentDocument preparation
A system method for providing an authentication code across a network for use in authentication of documents, such as printed lottery tickets. The system includes document-printing terminals that create a first key and a second key, with the first key used to generate an authentication code for printing on the document, and the second key is sent to a central server and usable to verify that the first key created the authentication code. The central server can also provide ticket serial numbers for tickets being dispensed at the terminals and the first key can be combined with the serial number and other secondary data to create the authentication code.
Owner:SCI GAMES LLC
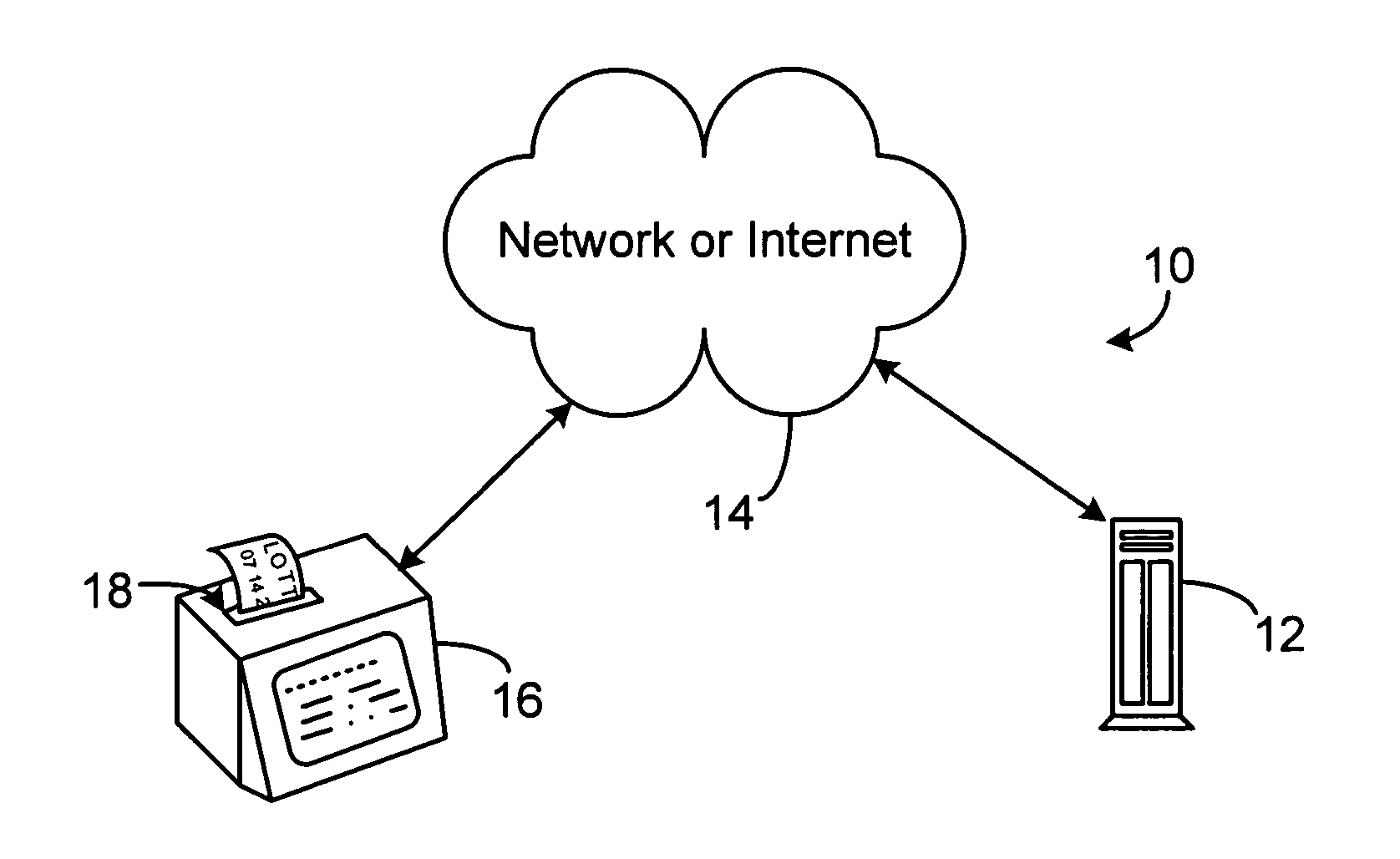
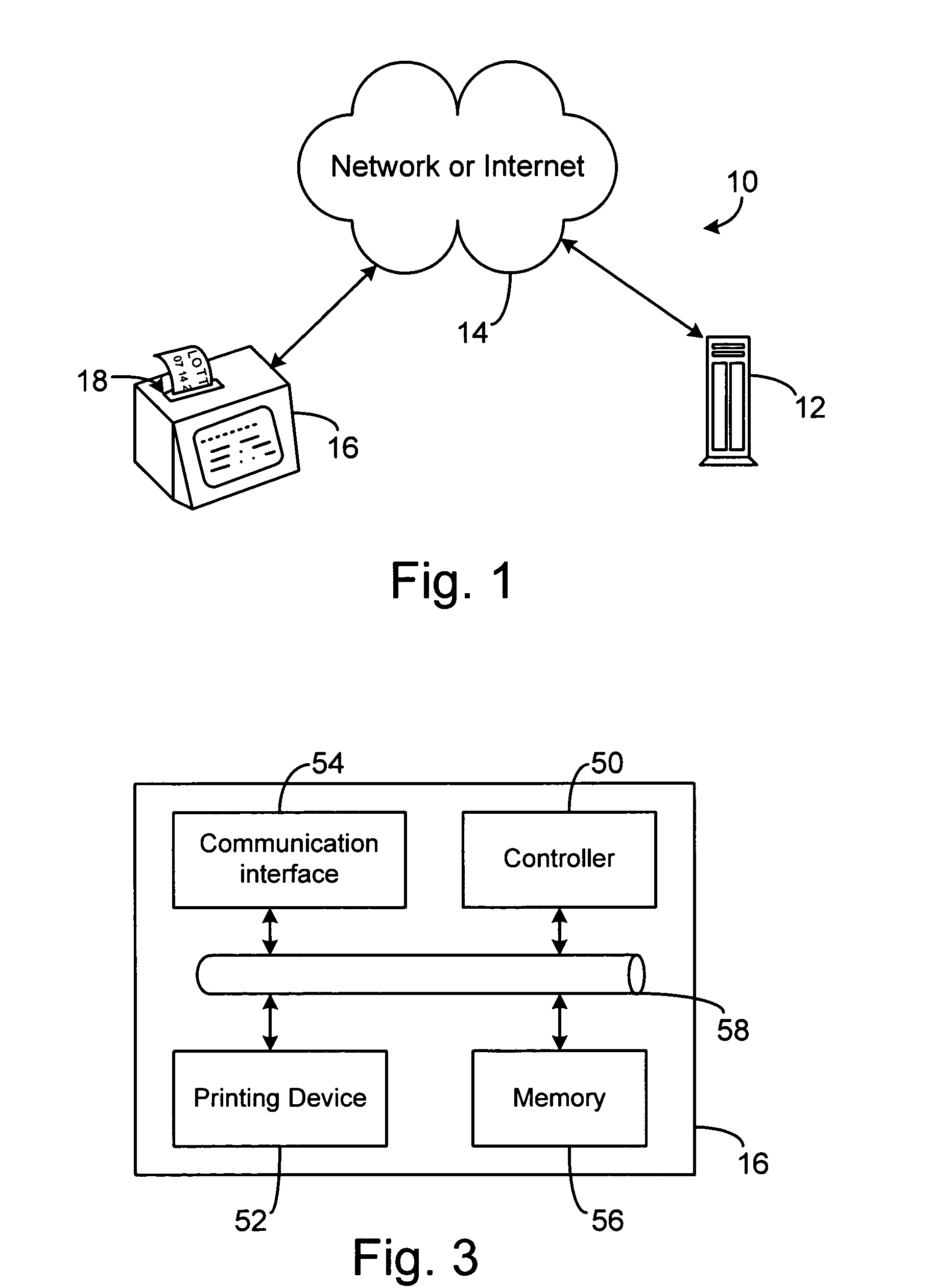
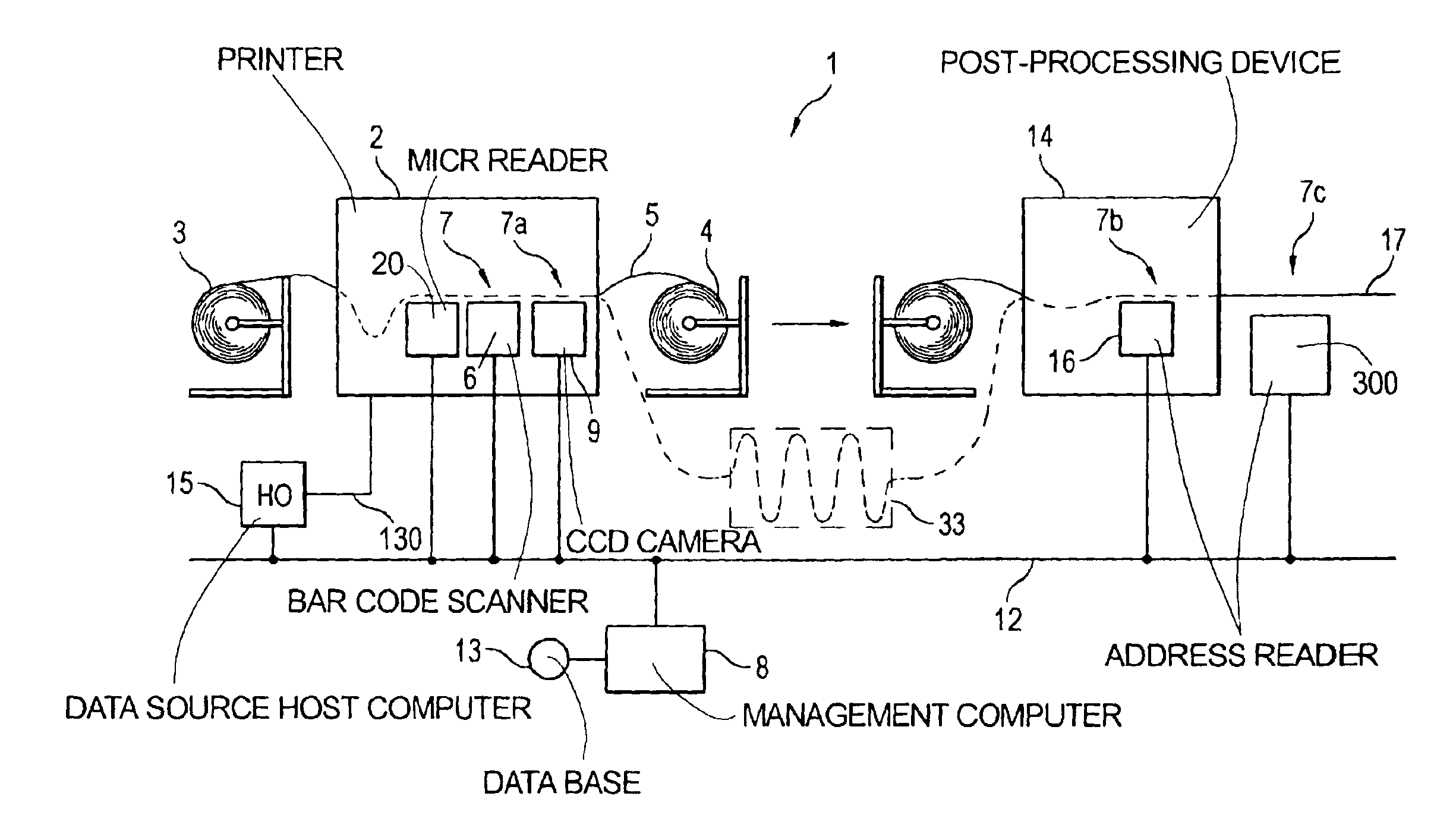
Document verification and tracking system for printed material
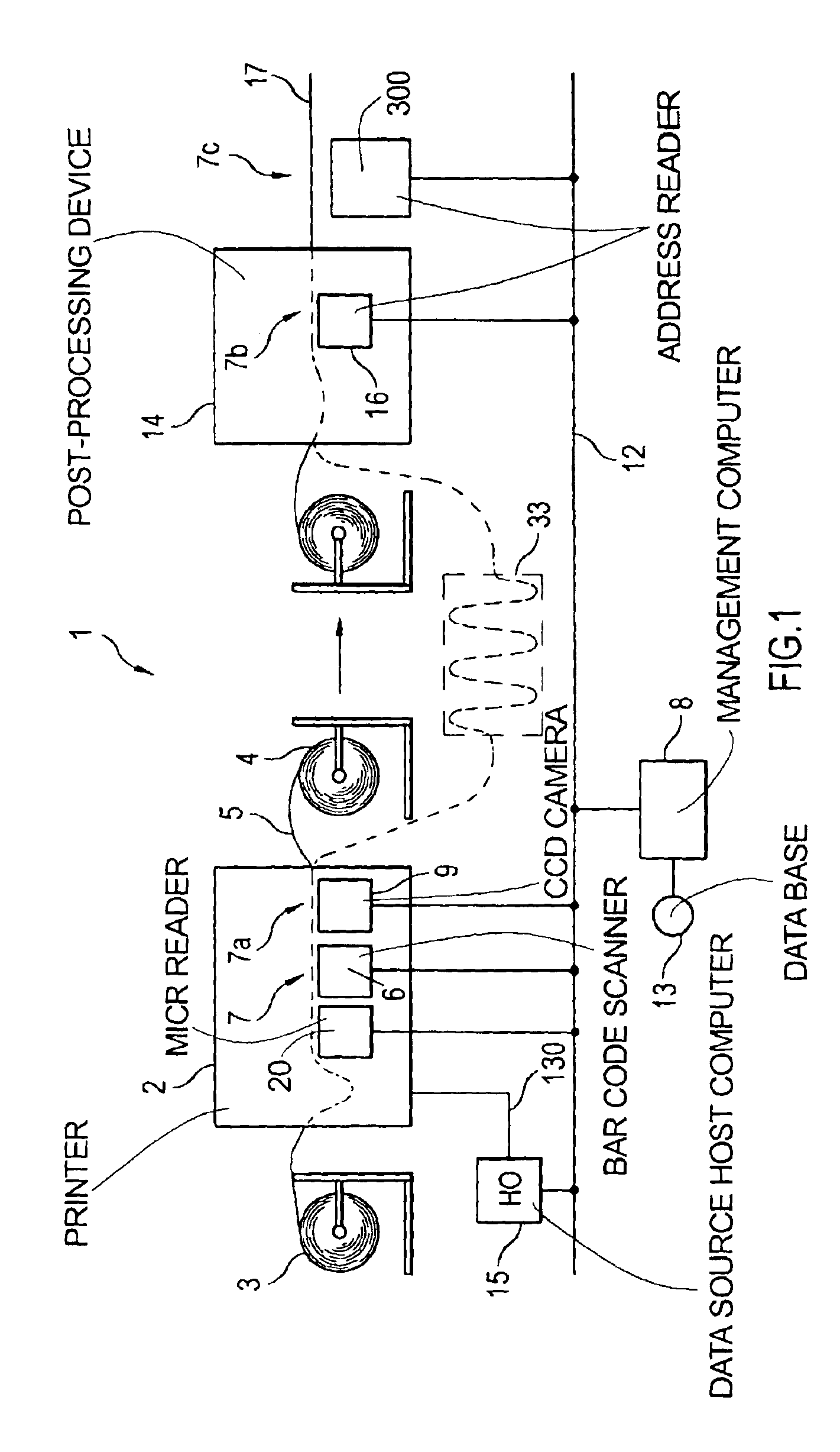
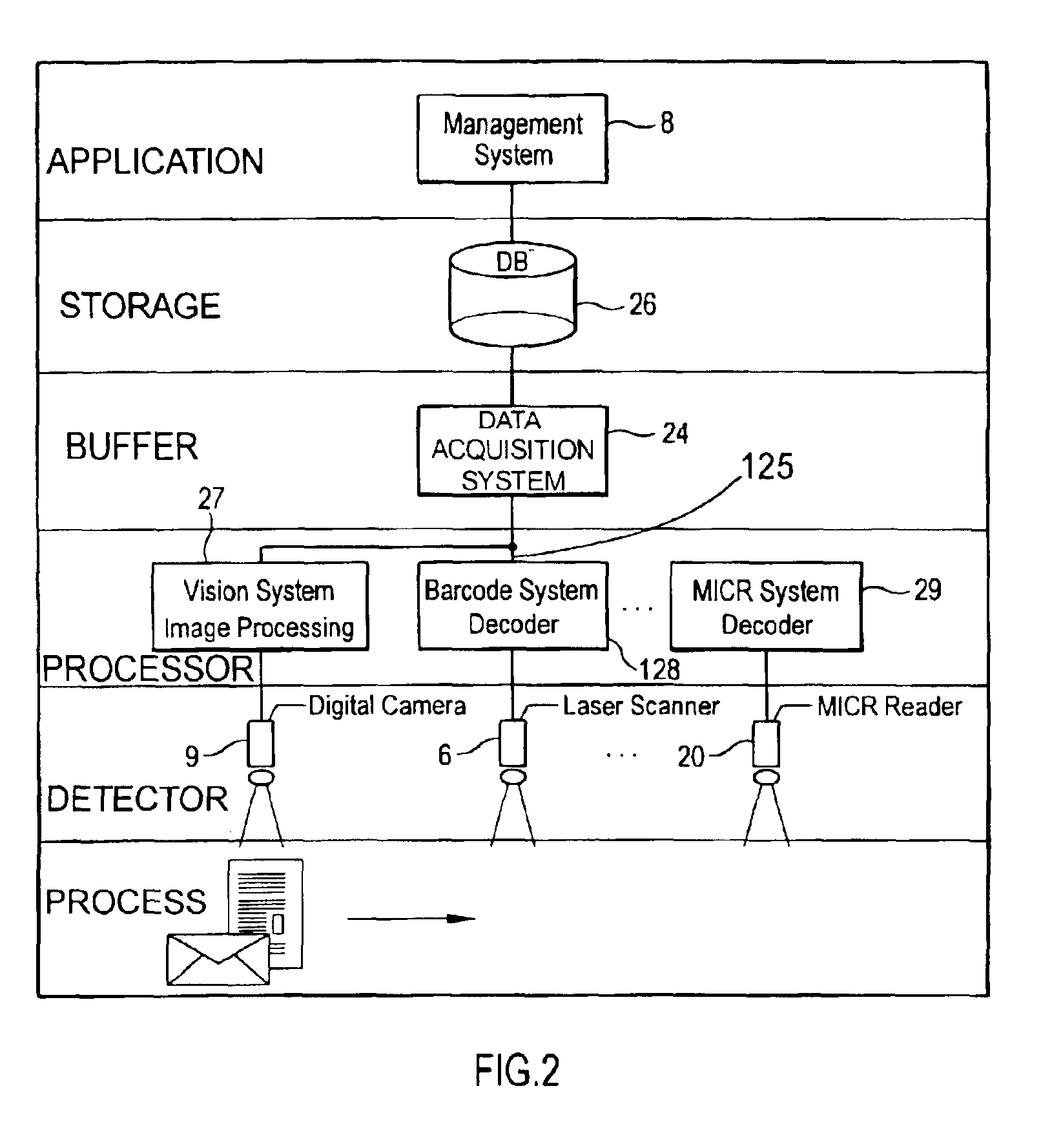
InactiveUSRE38957E1Co-operative working arrangementsCharacter and pattern recognitionOptical testBarcode
In a multifunctional printing method and printing system, printed material is checked, verified and tracked. For that purpose different test equipments are located in-line with a printing line. Magnetic information being printed by a printing station onto the recording carrier using magnetic ink character readable toner may be in-line tested by a magnetic test equipment, which reads information from the magnetic recording zone on the carrier. Optical information may be tested by an in-line mounted optical test equipment, respectively. Further in-line test equipment is proposed such as a leaser bar code scanner and an address reader. The printing line may have additional devices such as print preprocessing unwinders or print postprocessing stackers, folders or cutters.
Owner:OCE PRINTING SYST
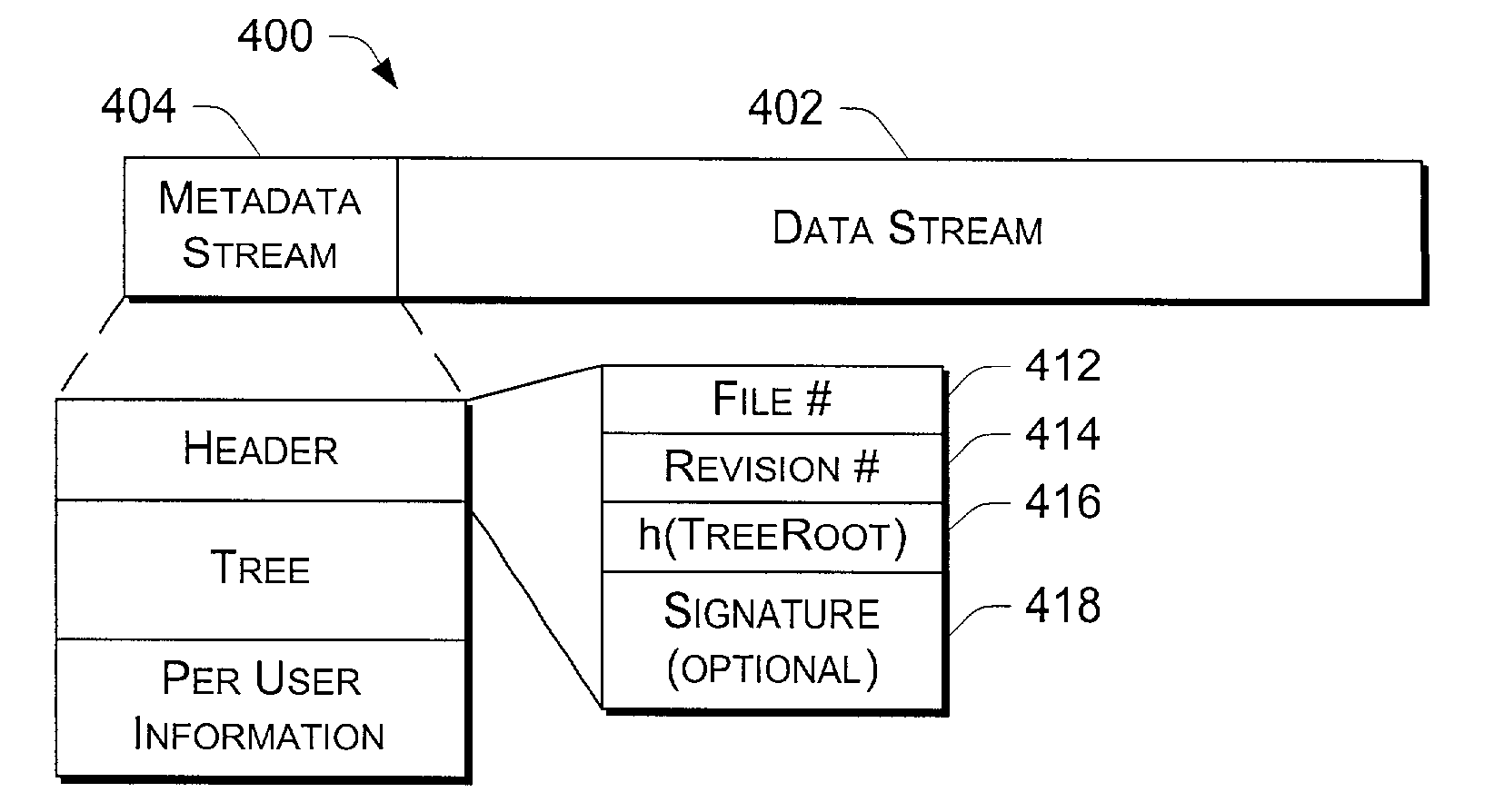
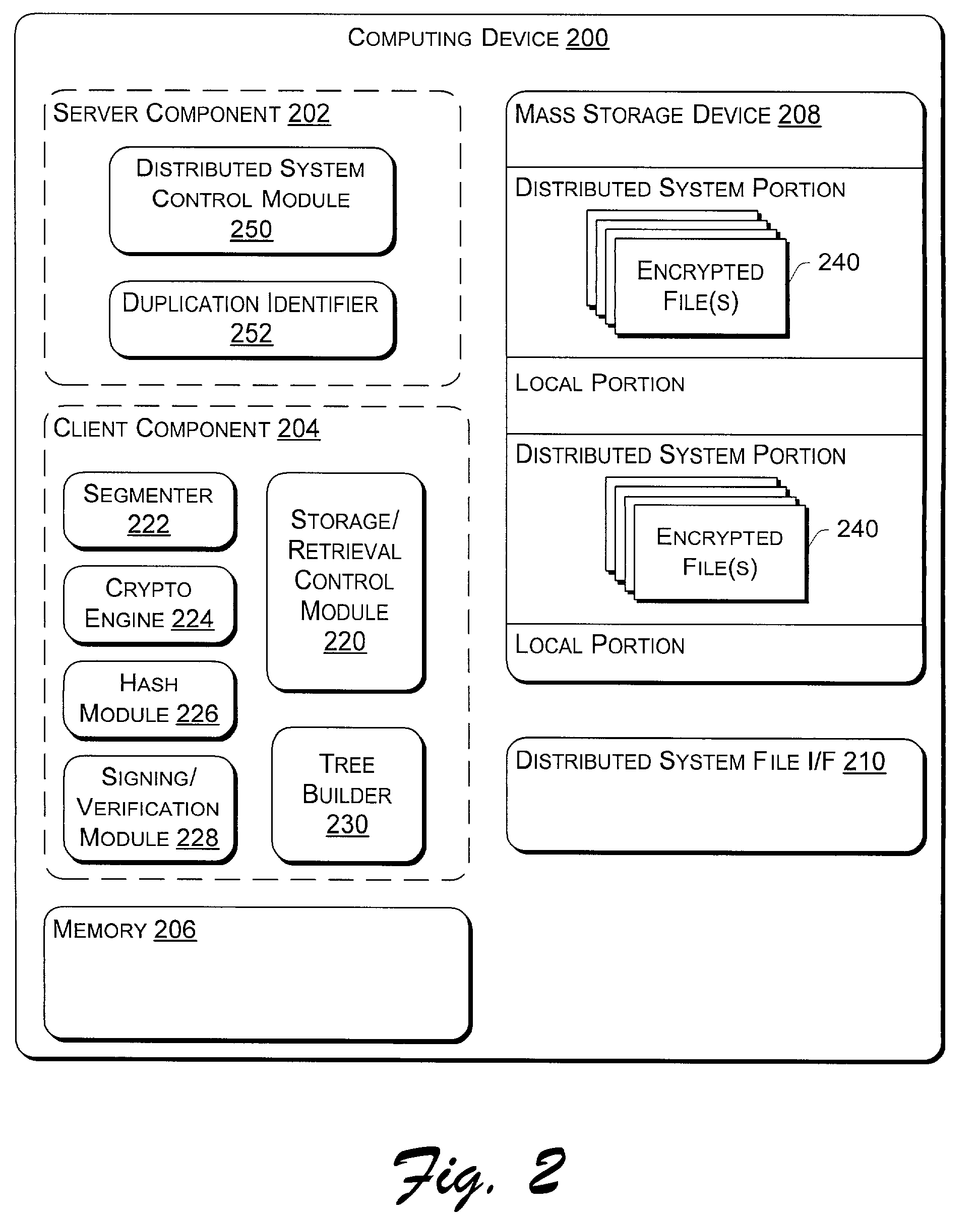
On-disk file format for serverless distributed file system with signed manifest of file modifications
InactiveUS7478243B2Error preventionUser identity/authority verificationSignature fileDistributed File System
In a serverless distributed file system, the writer of a file can provide file authentication information to a verifying machine without having to compute a new digital signature every time a written file is closed. Periodically, the writer compiles a list of the hash values of all files that have been written over a recent interval, computes a hash of the list, and signs the hash. This signed list of hash values is known as a manifest, akin to a shipping manifest that enumerates the items in a shipment. The advantage of using a signed manifest is that the writer need only perform a single signature computation in order to authenticate the writes to multiple files, rather than having to compute a separate signature for each file, as it would if a signature were embedded in each file.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for providing a document which can be visually authenticated
InactiveUS20050289345A1Authenticated quickly and easilyPaper-money testing devicesUser identity/authority verificationPaper documentDocument preparation
A method of providing a document which can be visually authenticated includes providing a document that is valid for a predetermined period of validity; randomly selecting visual authentication indicia just prior to the period of validity, the visual authentication indicia providing visual indication of validity during the period of validity; and transferring the visual authentication indicia to the document to visually authenticate the validity of the document during the period of validity. The method can be implemented using a system for creating a document which can be visually authenticated disclosed herein. The system includes a plurality of possible visual authentication indicia; a computer capable of executing instructions for randomly selecting one of the plurality of possible visual authentication indicia just prior to a predetermined period of validity; and at least one document validation station for transferring the selected visual authentication indicia to a document to visually authenticate the validity of the document during the period of validity.
Owner:BRADY WORLDWIDE INC
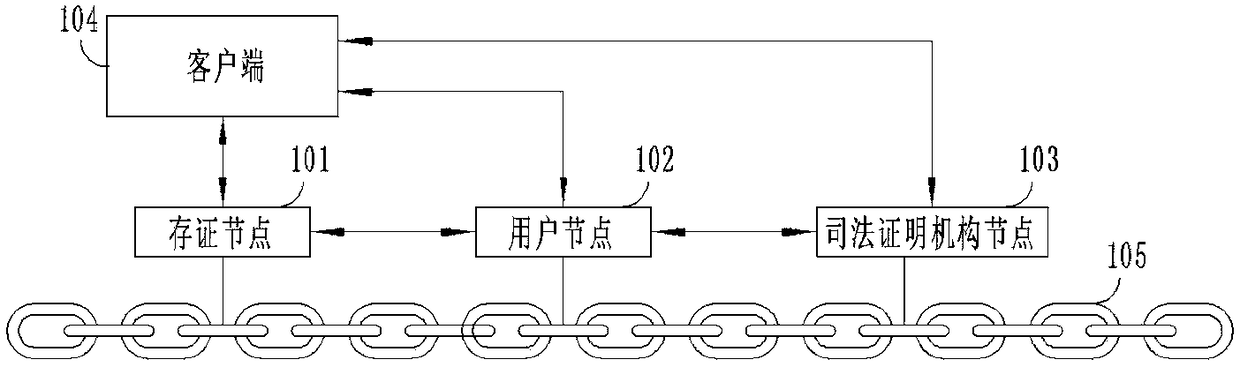
File attesting method and device, file verification method and device and file proof method and device
InactiveCN108549825ASolve the problem of low credibilityAvoid the risk of data tamperingDigital data protectionComputer scienceFile verification
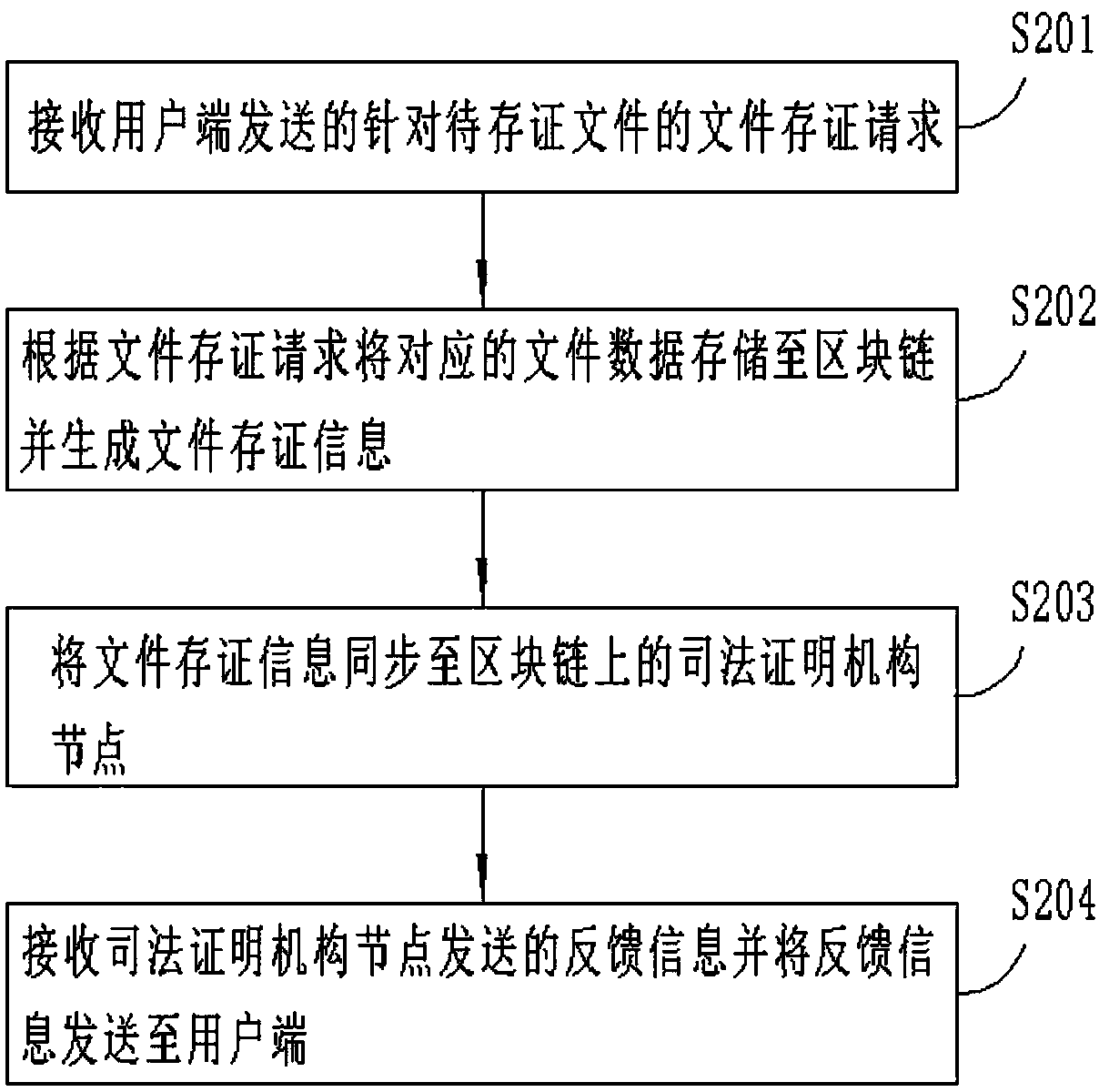
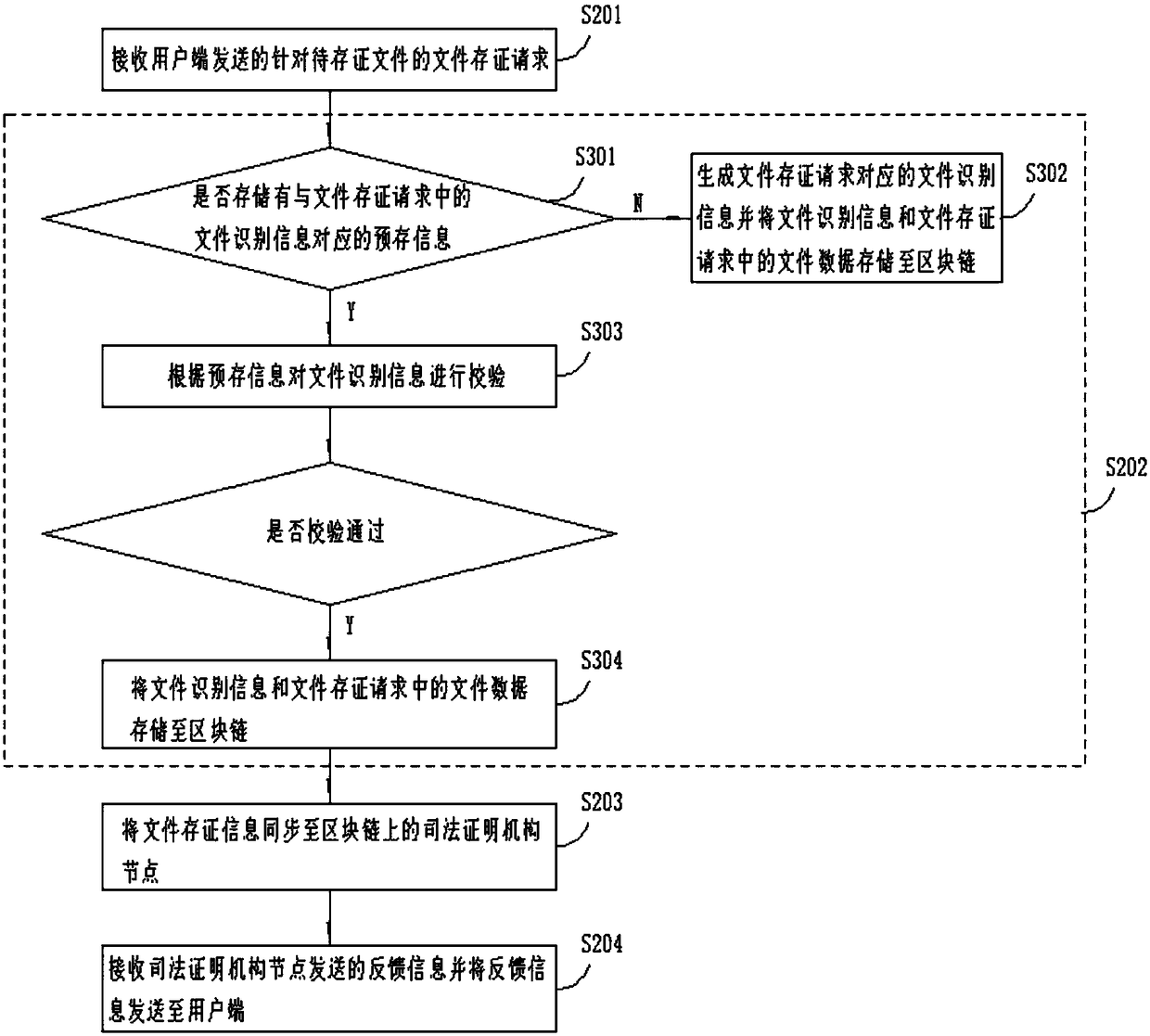
The invention discloses a file attesting method and device, a file verification method and device and a file proof method and device. The file attesting method comprises the following steps of: receiving a file attesting request, aiming at a to-be-attested file, sent by a user side; storing corresponding file data to a block chain according to the file attesting request and generating file attesting information; synchronizing the file attesting information to a judicial proof mechanism node on the block chain; and receiving feedback information sent by the judicial proof mechanism node and sending the feedback information to the user side. According to the file attesting method and device, the file verification method and device and the file proof method and device, the judicial proof mechanism node is imported into the block chain for attesting files, and block chain storage process of digital information such as electronic evidences and the like is filed and supervised through the judicial proof mechanism node, so that the problem that the prior art is relatively low in credibility in the aspects of data preservation and attesting of digital information is solved.
Owner:苏州朗润创新知识产权运营有限公司
Method and system for uploading files
ActiveCN102868765AOptimize upload methodSupport automatic identification functionTransmissionSpecial data processing applicationsFile verificationSynonym
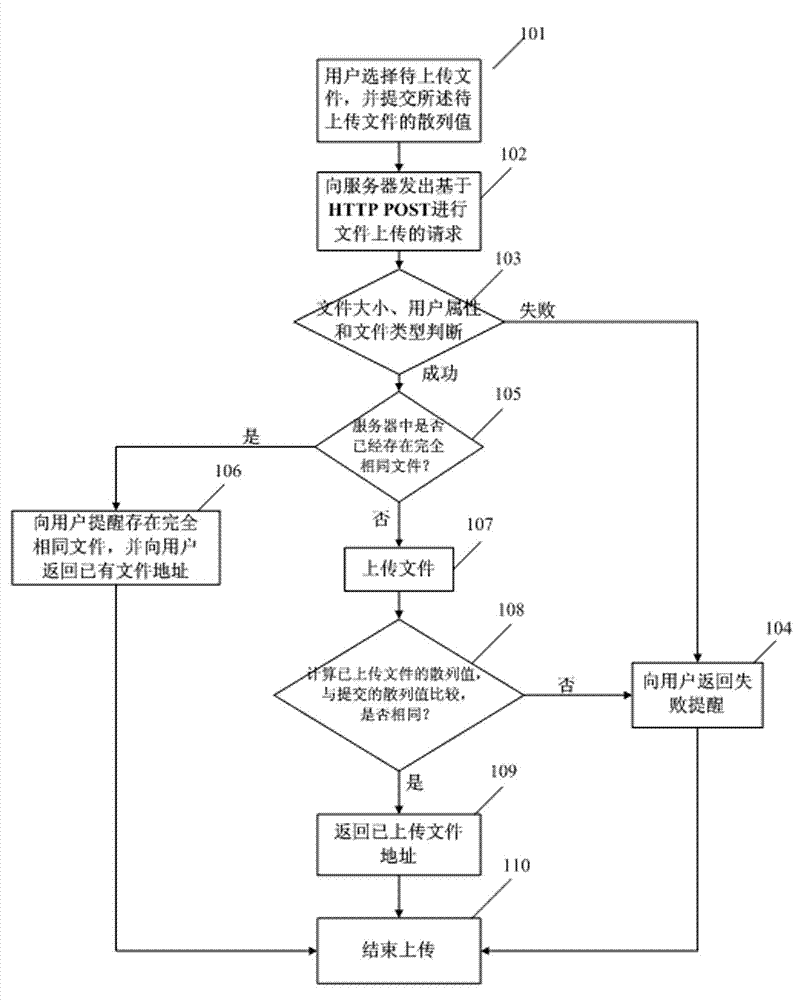
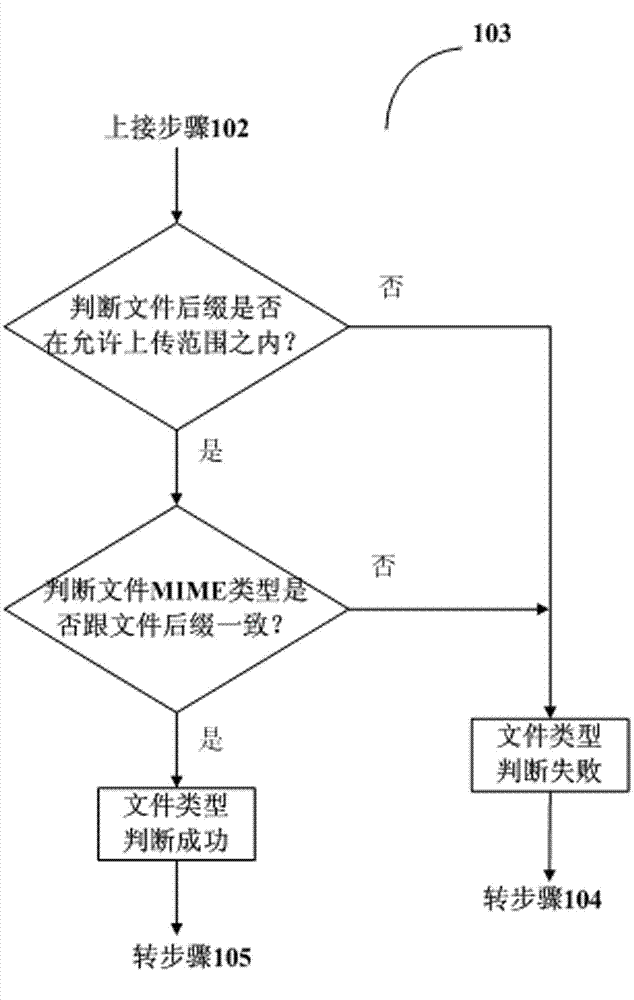
The invention relates to a method and a system for uploading files. The method includes that a user selects files to be uploaded and submits hashed value of the files to be uploaded. A request for file uploading and based on HTTPOST is sent to a server. File type of the files to be uploaded is judged, the next step is conducted on yes judgment, and failure warning is returned to the user to finish uploading on no judgment. The method further includes recognizing content of the files to the uploaded, reminding the user that identical files exist, returning pre-existing file address and finishing uploading if identical files exist in the server, starting uploading if no identical files exist in the server, calculating the hashed value of the uploaded files, comparing the hashed value with submitted hashed value, reminding that file uploading succeeds, returning the file address to the user and finishing uploading if the values are identical, and returning the uploading failure warning and finishing uploading if the values are not identical. The method and the system resolve the problems of synonym file re-uploading, file type judgment, file verification and the like.
Owner:LETV CLOUD COMPUTING CO LTD
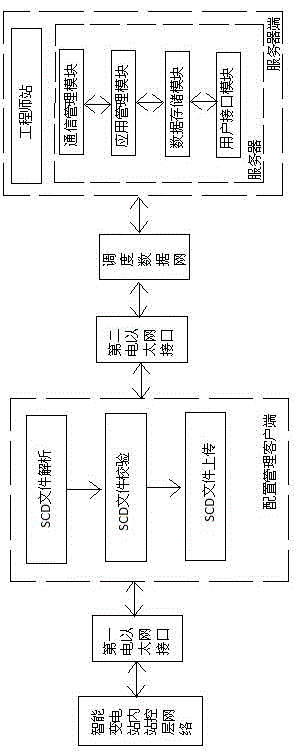
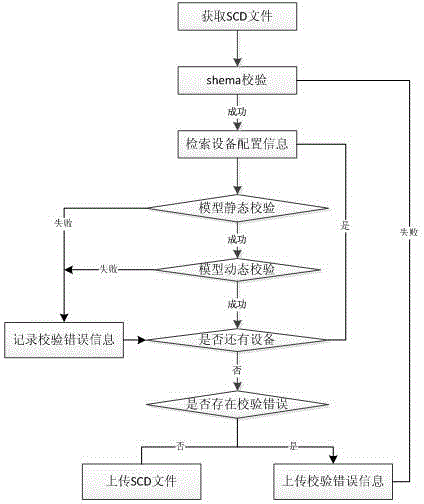
Intelligent transformer station configuration file standardized management system and file verification method
ActiveCN104036429AGuaranteed correctnessGuaranteed reasonablenessData processing applicationsInformation technology support systemModel dynamicsTransformer
The invention discloses an intelligent transformer station configuration file standardized management system comprising a server terminal which is arranged in a scheduling department and configuration management client-terminals which are arranged in all intelligent transformer stations. The multiple configuration management client-terminals are communicated with the server terminal via a scheduling data network. Management flow of an SCD file is standardized, the intelligent transformer station SCD file can be locally analyzed, and the SCD file can be verified via auxiliary verification functions like shema verification, model static verification and model dynamic verification so that correctness, rationality and integrity of the SCD file are ensured. Besides, the SCD file of each intelligent transformer station is uploaded to the server terminal to be managed in a unified way so that an effective tool for managing and inspecting a configuration file is provided for a transformer station operation maintenance unit, proper use of the configuration file in the processes of construction, acceptance, operation maintenance and enlargement of the intelligent transformer stations is facilitated for basic technical personnel, reliable operation of the intelligent transformer stations is ensured, and thus the system can be widely applied to all levels of electric power scheduling centers.
Owner:STATE GRID HENAN ELECTRIC POWER ELECTRIC POWER SCI RES INST +2
Document verification system
ActiveUS6948657B2Low costSlow verificationImage analysisOther printing matterFeature vectorAlgorithm
The present invention provides a document verification system capable of verifying whether a document is an original at low cost and with ease. A terminal device acquires, as a registered feature vector feature information indicating a feature of a nonreproducible disorder portion in a printing region on a document serving as the original, and stores the registered feature vector on a hard disk via the Internet. A server acquires, as a calculated feature vector the same information as the registered feature vector in a document to be verified as to whether the document is the original, reads out the registered feature vector from the hard disk, compares the acquired calculated feature vector with the read out registered feature vector, and verifies whether the document to be verified is the original on the basis of a result of the comparison.
Owner:FUJIFILM BUSINESS INNOVATION CORP
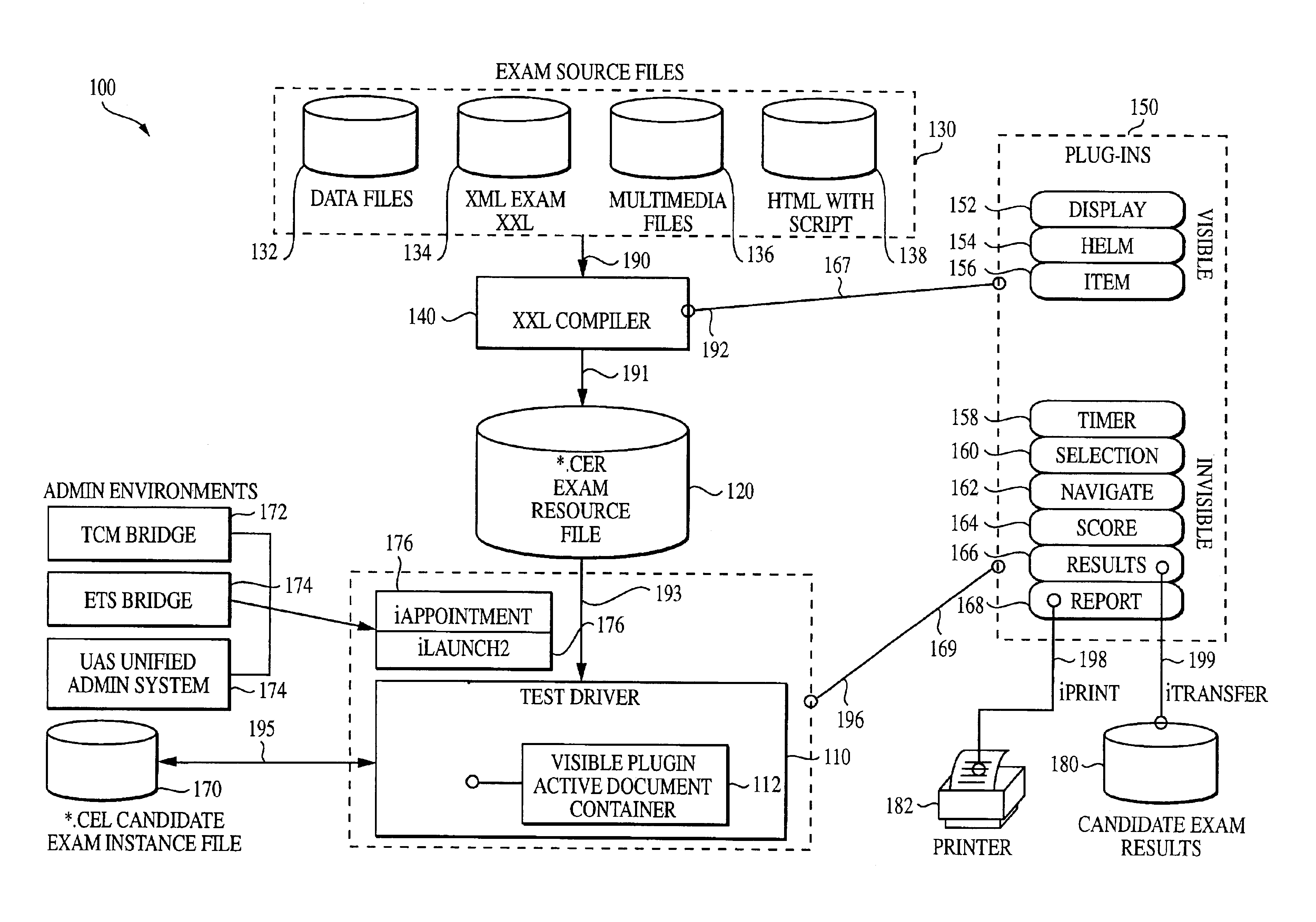
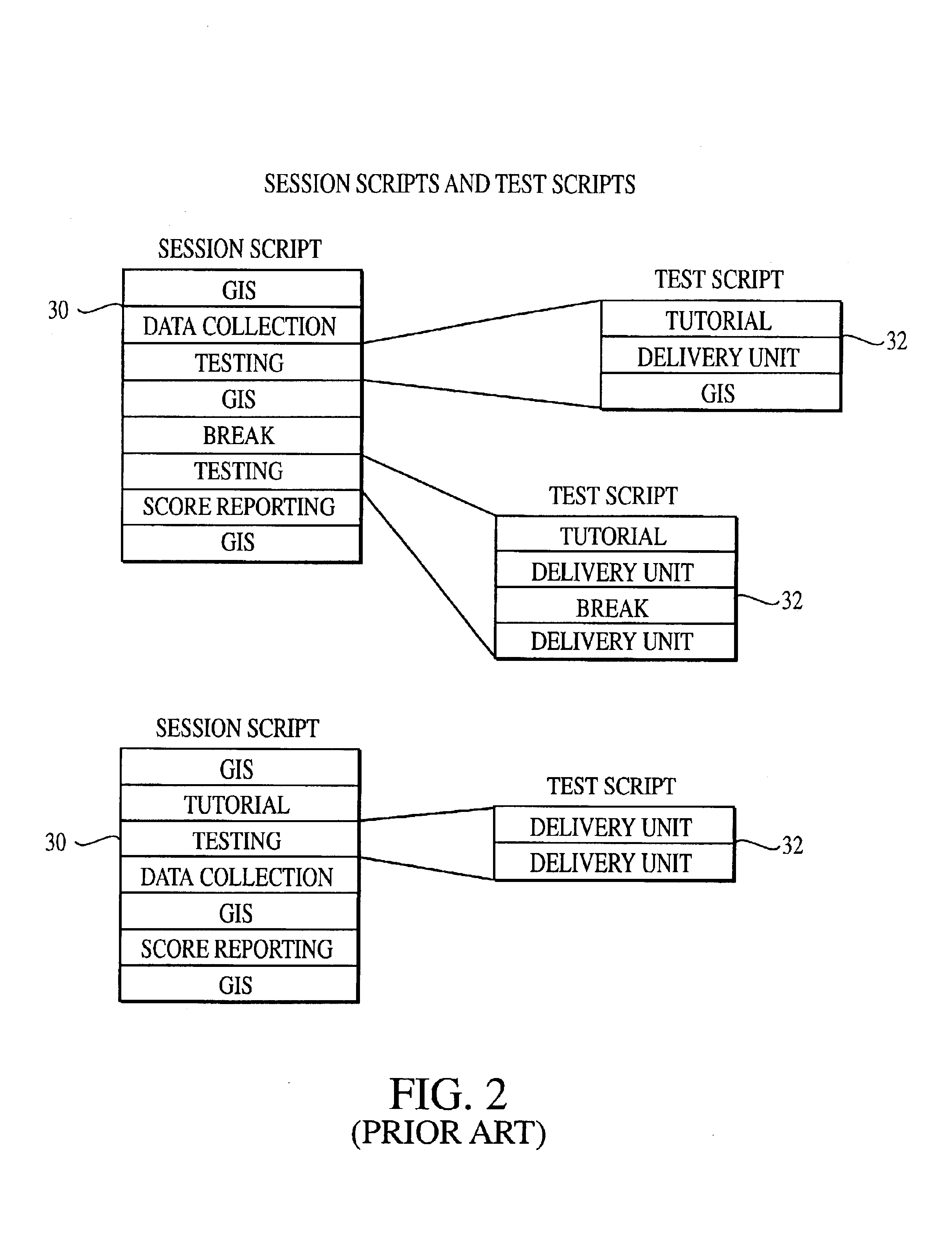
Method and system for computer based testing using a non-deterministic exam extensible language (XXL) protocol
InactiveUS6966048B2Natural language data processingSoftware testing/debuggingProgramming languageFile verification
A system for computer-based testing for producing and delivering a test to an examinee includes a test driver, a storage device that stores the test definition language as a plurality of segments, and a validation expansion module that validates the plurality of segments of the test definition language and writes the at least one of the plurality of segments directly to the storage device. A method of computer-based testing includes instantiating a validation expansion module during a test production cycle and validating the plurality of segments from the source file. The method also includes instantiating the validation expansion module and loading the plurality of segments of the test definition language into the validation expansion module during a test delivery cycle.
Owner:PROMETRIC LLC
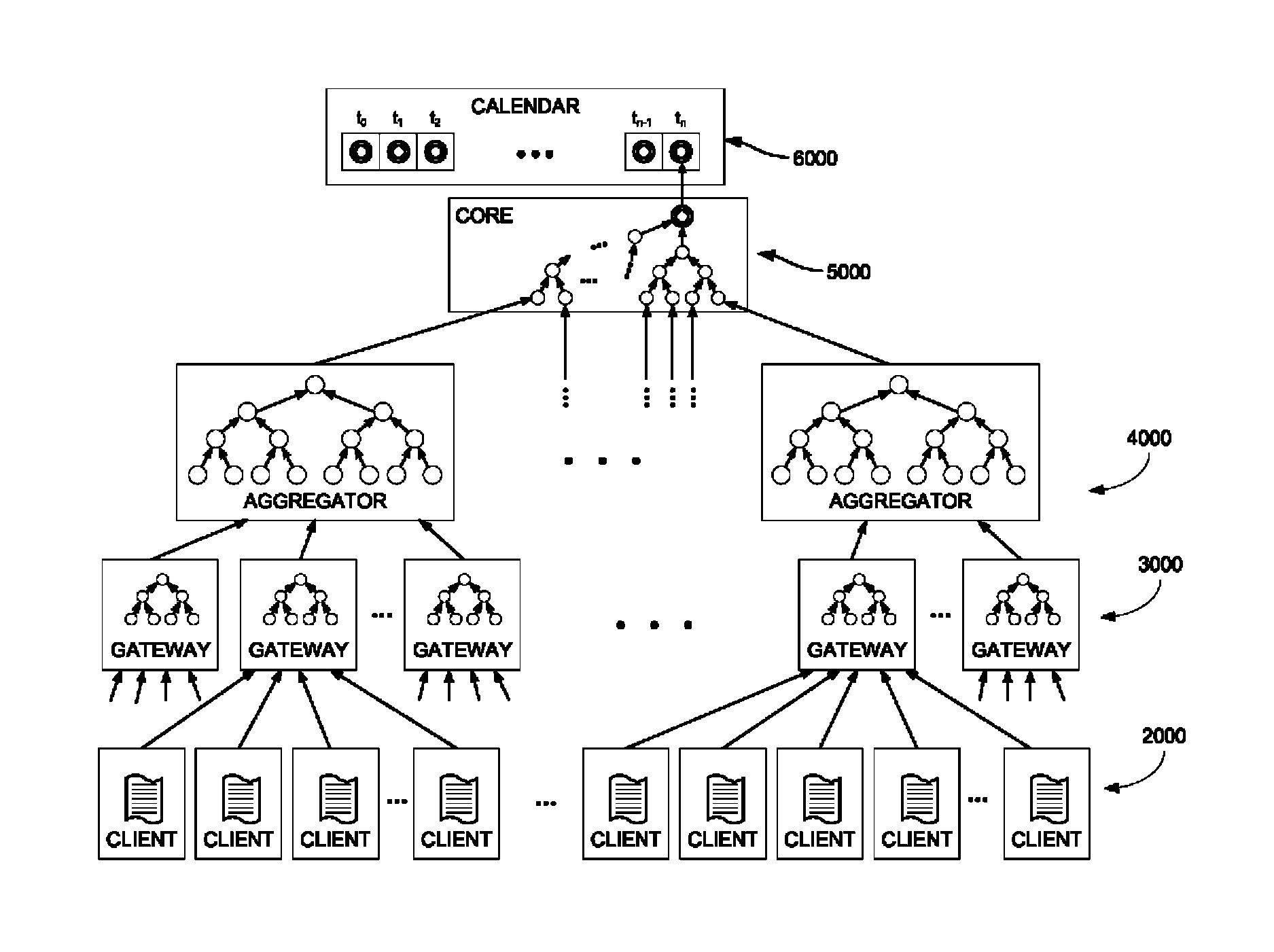
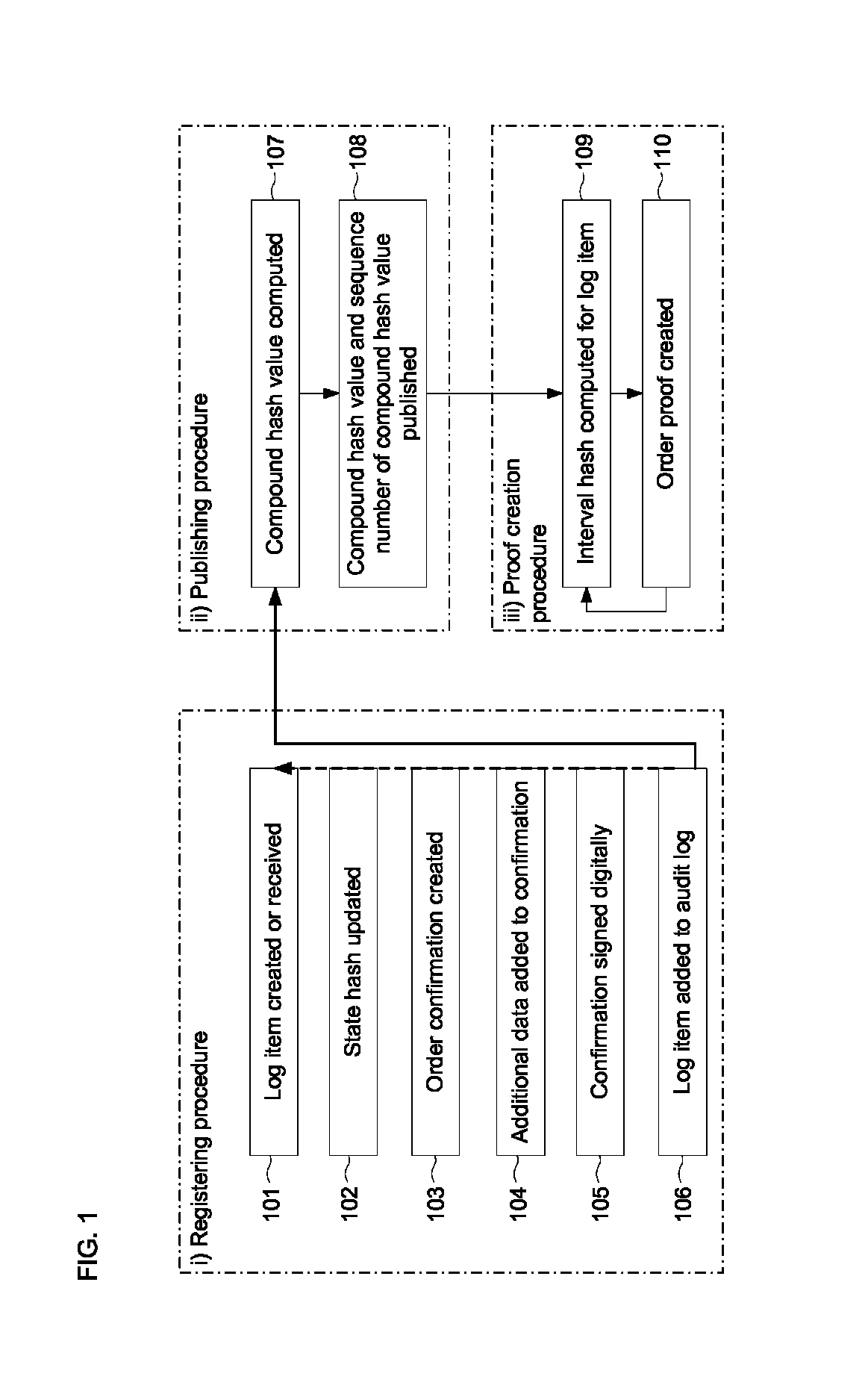
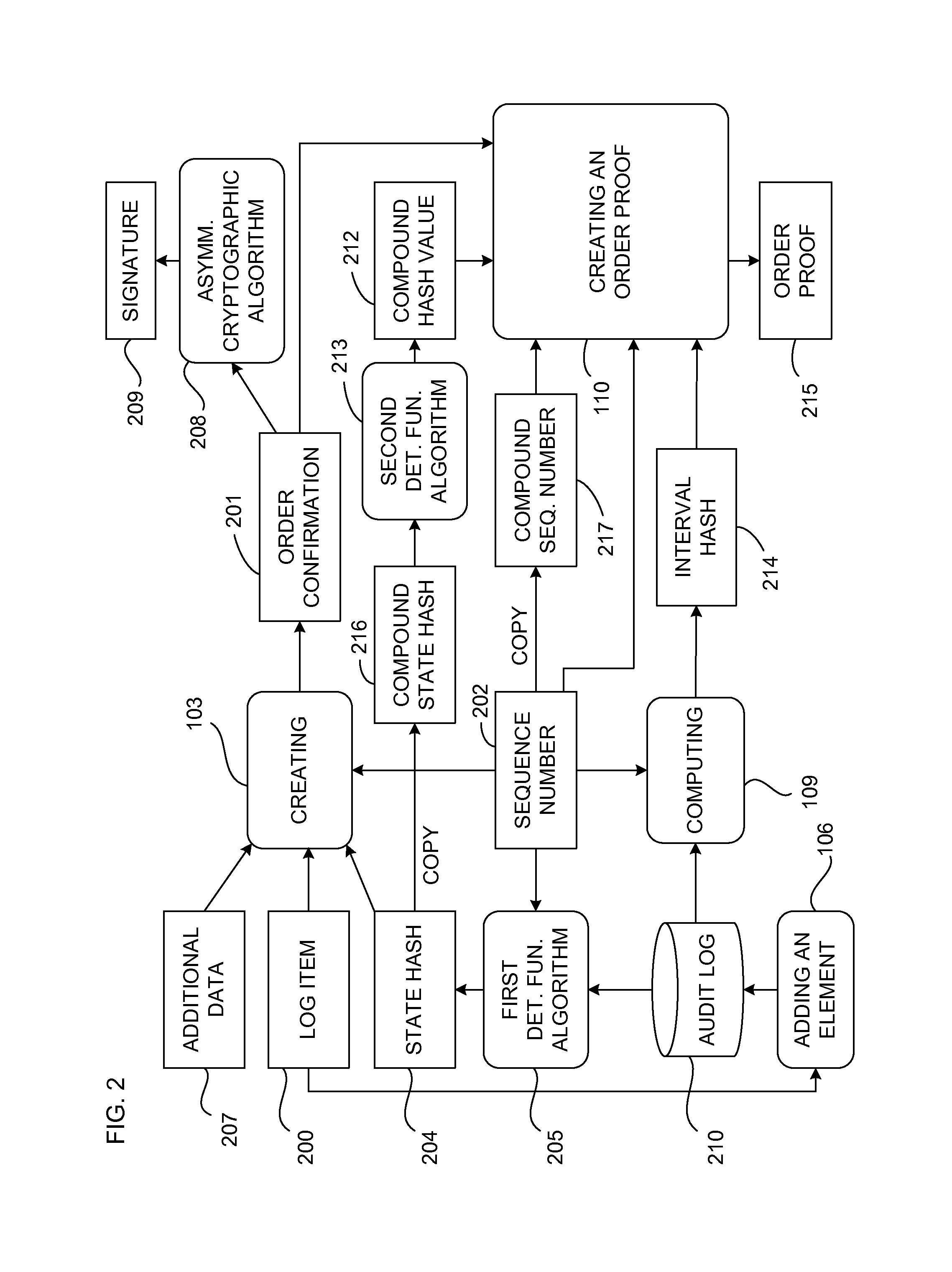
Document verification with distributed calendar infrastructure
ActiveUS8719576B2Digital data processing detailsUser identity/authority verificationTheoretical computer scienceTree (data structure)
Transformations of digital records are used as lowest level inputs to a tree data structure having a root in a core system and having nodes computed as digital combinations of child node values. A combination of root values is published in a permanent medium. Signature vectors are associated with the digital records and have parameters that enable recomputation upward through the tree data structure to either a current root value or to the published value. Recomputation yields the same value only if a candidate digital record is an exact version of the original digital record included in the original computation of the value.
Owner:GUARDTIME SA
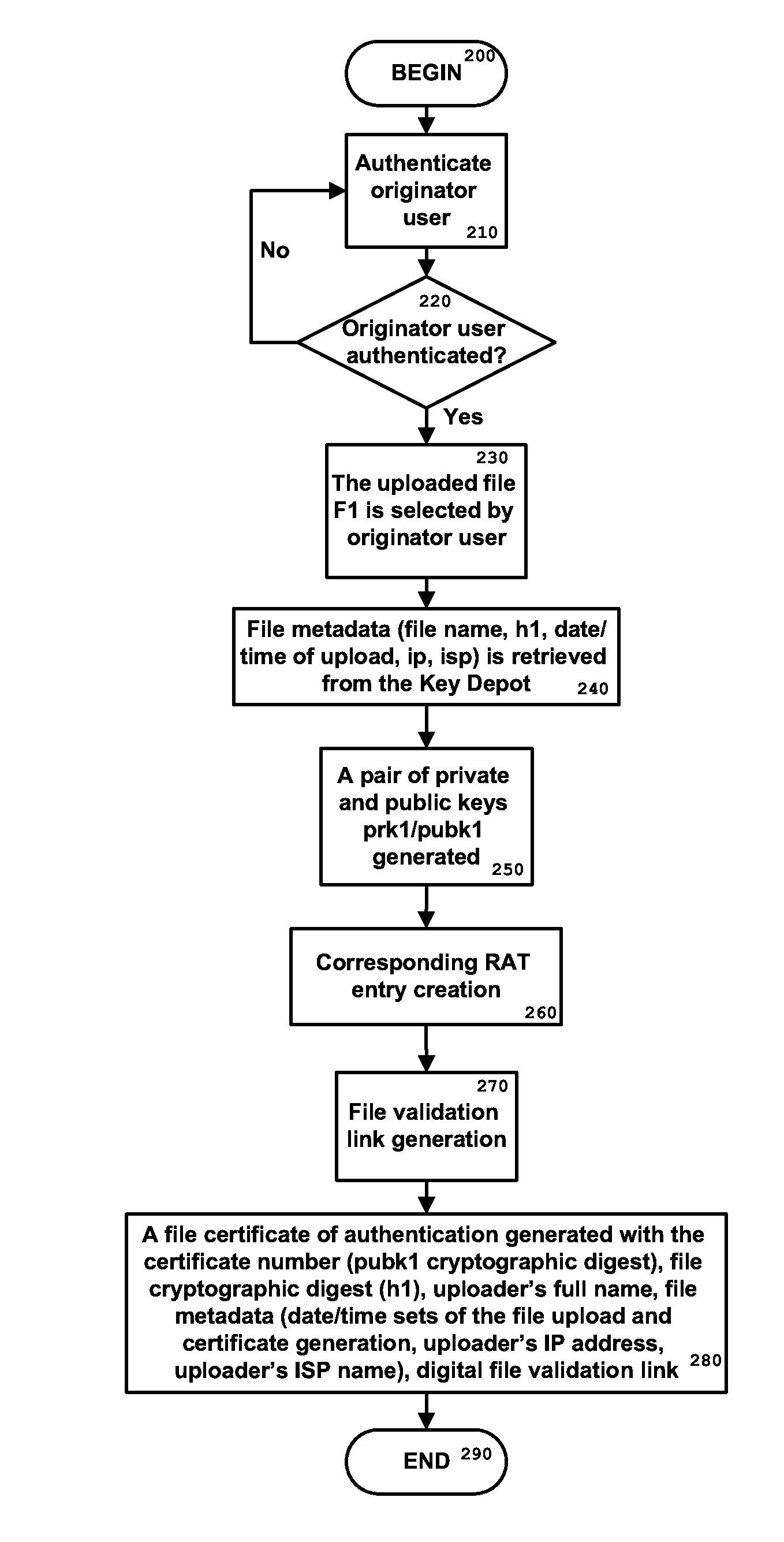
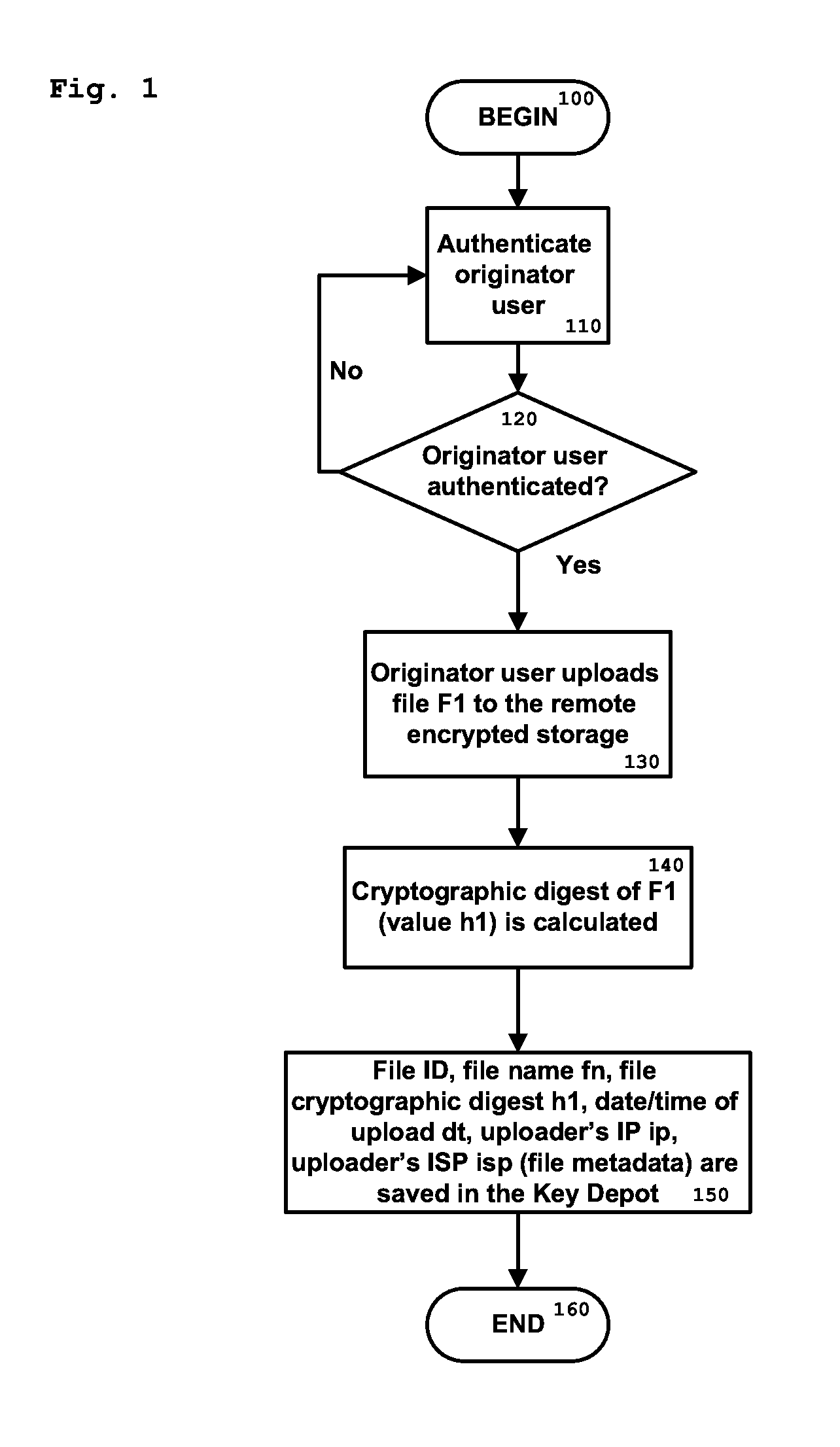
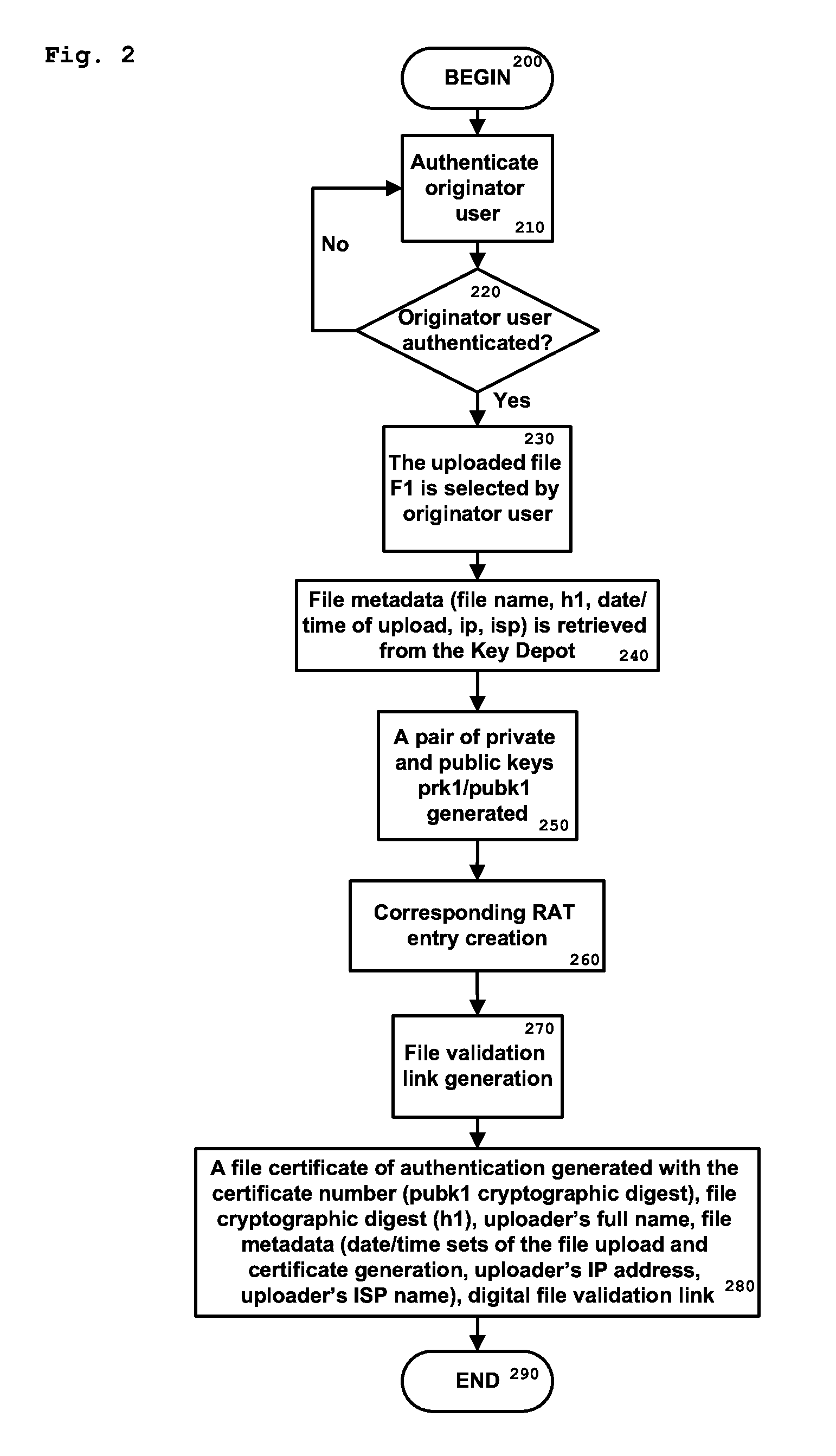
Method and system for authenticating and preserving data within a secure data repository
InactiveUS20140304512A1Eliminate CollisionsRemove threatMultiple keys/algorithms usageUser identity/authority verificationDigital signatureData source
A computer implemented method for identifying and linking a data originator and a data file or data batch from the originator through one or more data source systems. The system stores the data files and batches on a permanent basis for subsequent verification purposes, verifying the identity of the data file originator through originator-specific information from the data source system; and generating unique data entries associated with the originator identity, the file identity and / or a file verification cryptographic digest, and a unique originator signature. The data entries and signature are stored in encrypted form in a Relay Access Table (RAT), as are the public and private keys associated with both the data file and the originator. A certificate for verification of the data file is generated, that contains a digital signature, as well as a file cryptographic digest and metadata associated with filing conditions.
Owner:PRONIN SERGEI +3
Verifying method for network file transmission
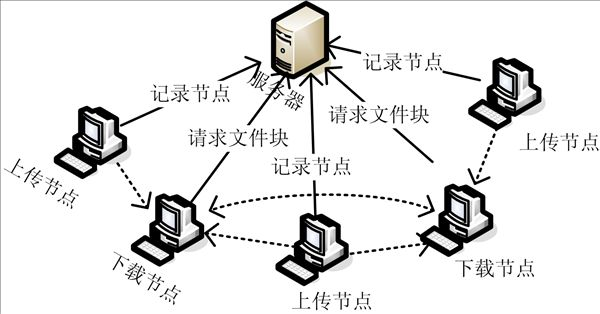
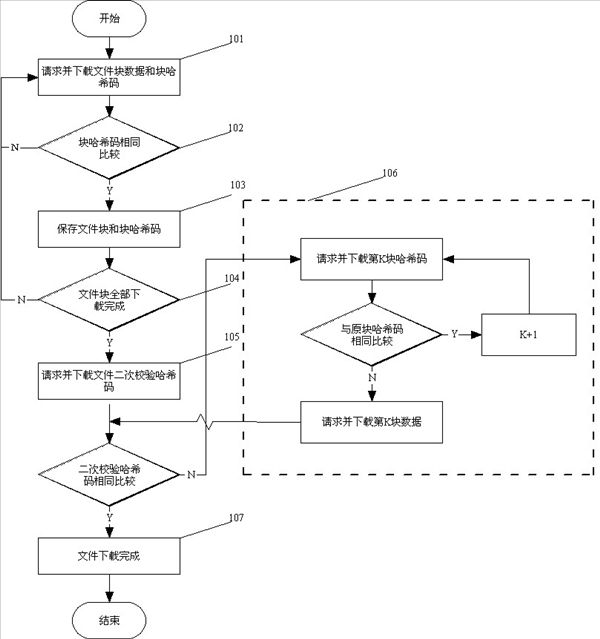
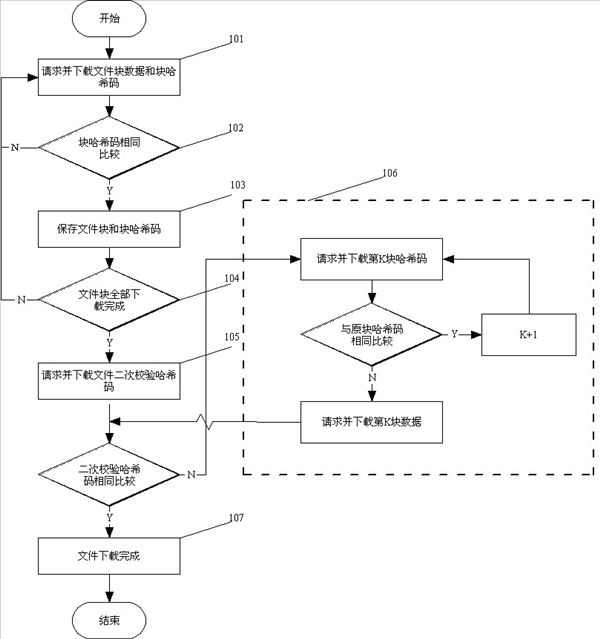
InactiveCN102325167AGuaranteed correctnessImprove reliabilityTransmissionComputer hardwareFile transmission
The invention provides a verifying method for network file transmission. File block transmission data and block hash codes are adopted in the method. The method comprises the following steps of: after block transmission finishes, extracting the block hash codes and comparing the extracted block hash codes with the value acquired by transmission, if an error happens, retransmitting the value from another data source, otherwise, preserving the block data and the block hash codes in a file; after the file is transmitted, acquiring secondary verification hash codes of file blocks from a server, performing secondary verification hash code extraction on the file preserving the block hash codes, comparing, if different, newly requesting the server for the addresses of other file servers, and retransmitting; and repeating the processes till the secondary verification hash codes of the file blocks are compared successfully. Compared with the prior art, the method has the advantages that: besides hash code verification of the file blocks, secondary verification of the hash codes of the file blocks is performed, so that the complete accuracy of file verification is ensured and the reliability of file transmission is improved. The secondary verified hash codes of the file blocks are acquired by secondary hash calculation of the hash codes of the file blocks, the number of the file blocks is limited, and the advantage is obvious compared with massive time consumption in hash calculation of the whole file. When the secondary verified hash codes of the file blocks are different, error file blocks of the file can be quickly found by using the block hash codes; and compared with a mode of directly downloading the file blocks, massive broadband resources are saved.
Owner:HANGZHOU MICORUNIT TECH
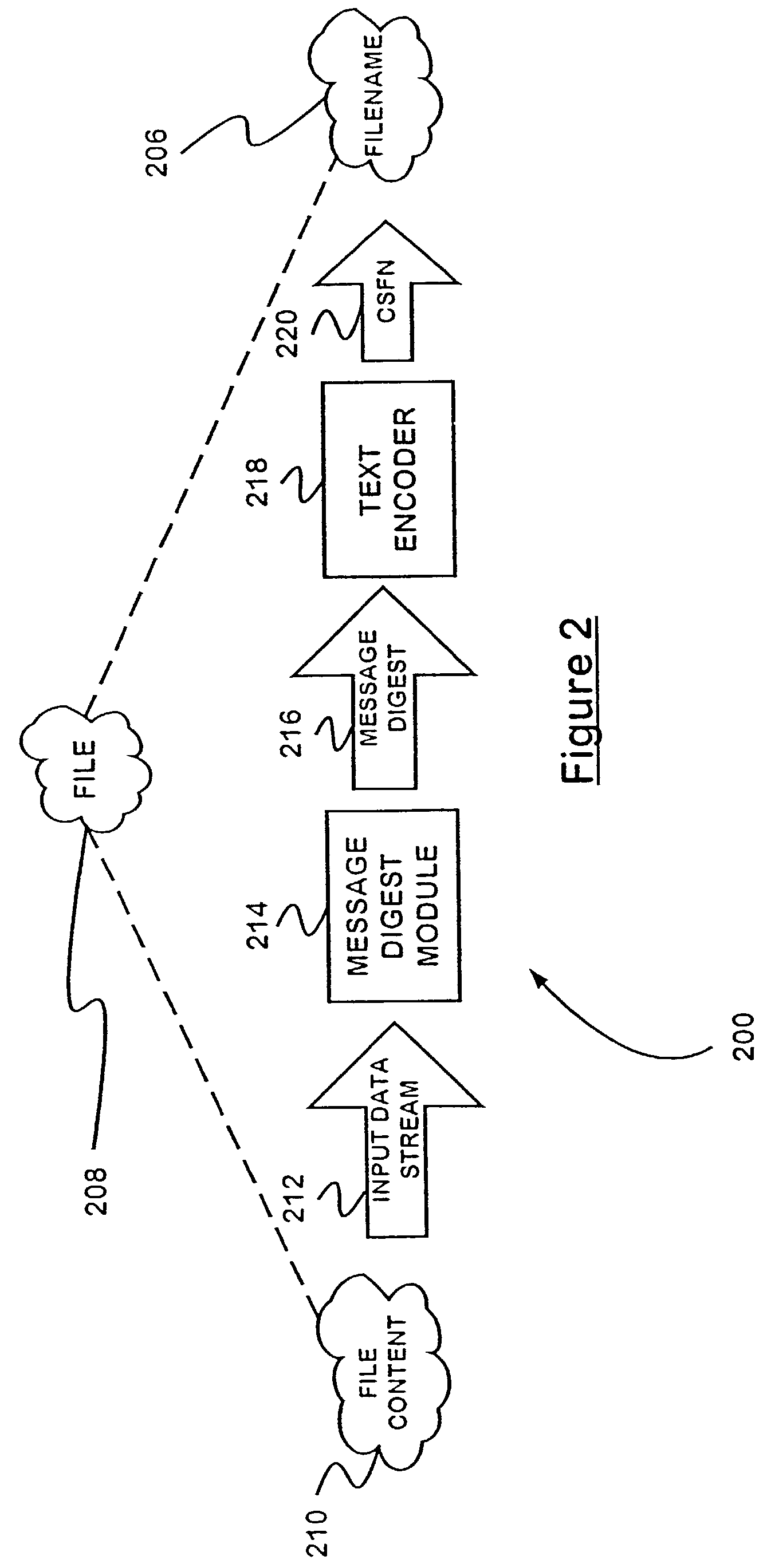
Installing content specific filename systems
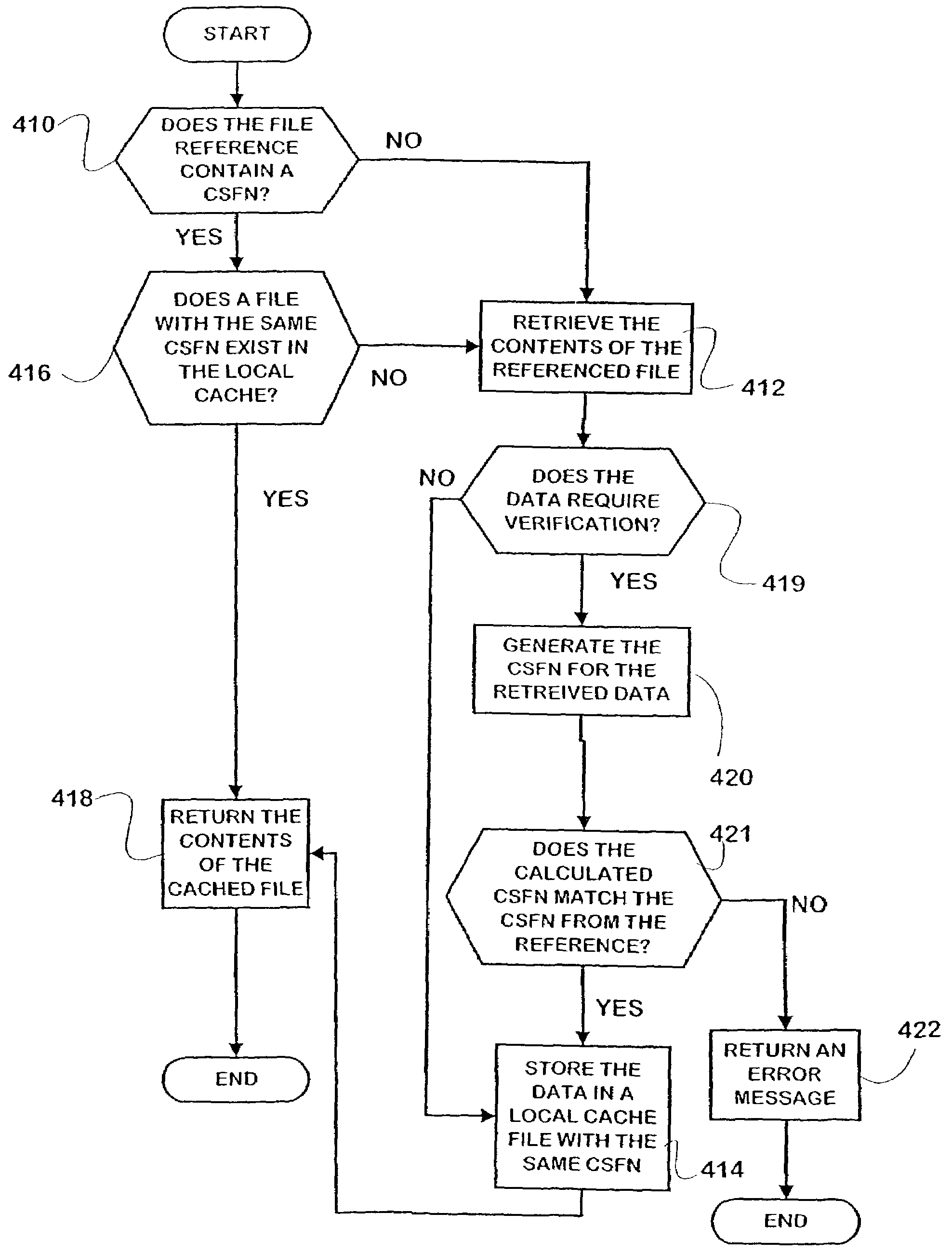
InactiveUS7284243B2Eliminating potentialEliminate for referenceDigital data information retrievalProgram loading/initiatingWeb browserFile system
A computer file naming technique employs content-specific filenames (CSFN's) that represent globally-unique identifiers for the contents of a file. Since file references incorporating the CSFN's are not location-specific, they offer unique advantages in the areas of file caching and file installation. Particularly, web browsers enabled to recognize CSFN's inherently verify the content of files when they are retrieved from a local cache, eliminating the need for comparison of file data or time stamps of the cached file copy and the server copy. Thus, file verification occurs solely in the local context. The invention includes caching and software installation systems that incorporate the benefits of CSFN's.
Owner:MICROSOFT TECH LICENSING LLC
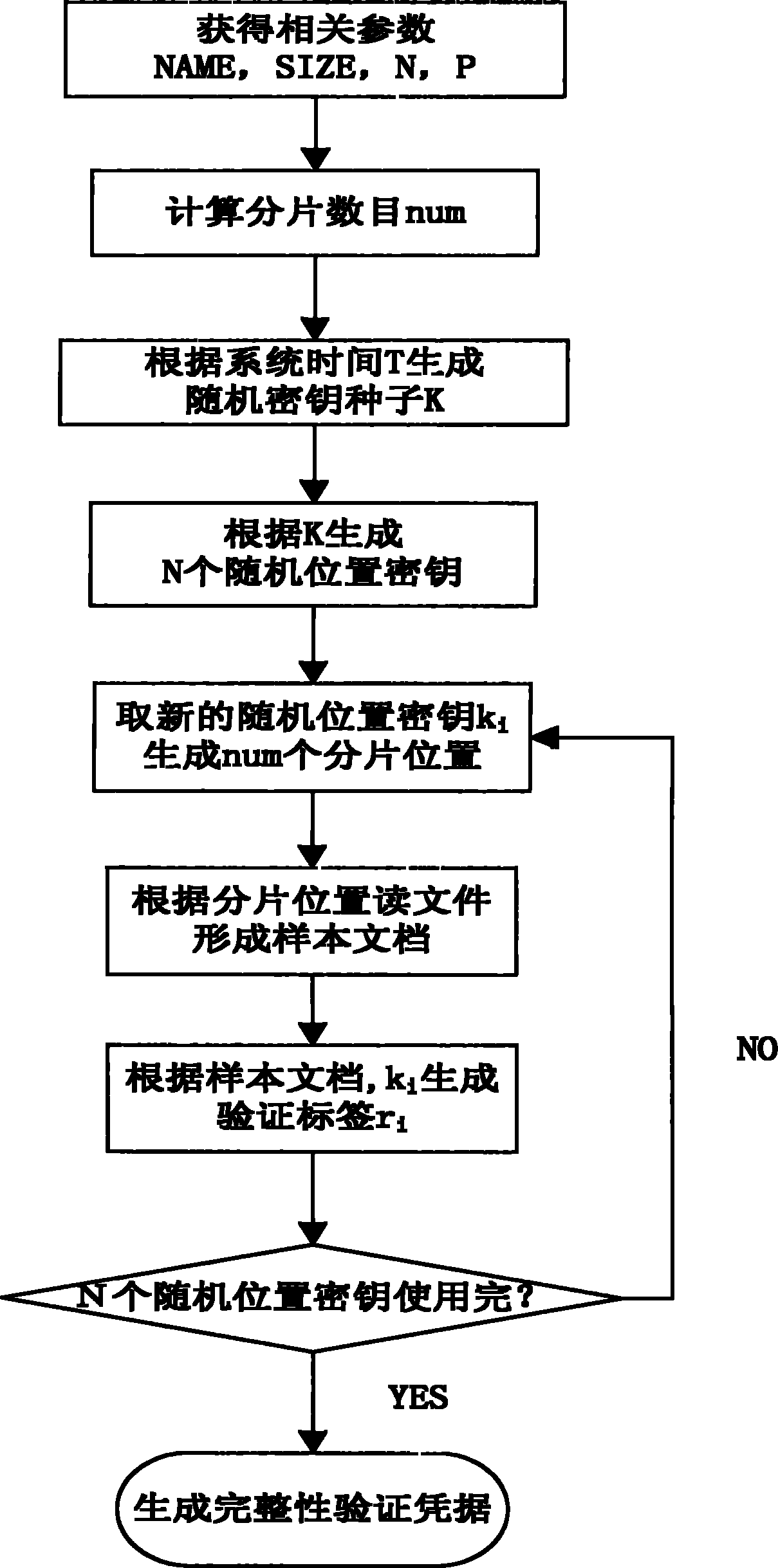
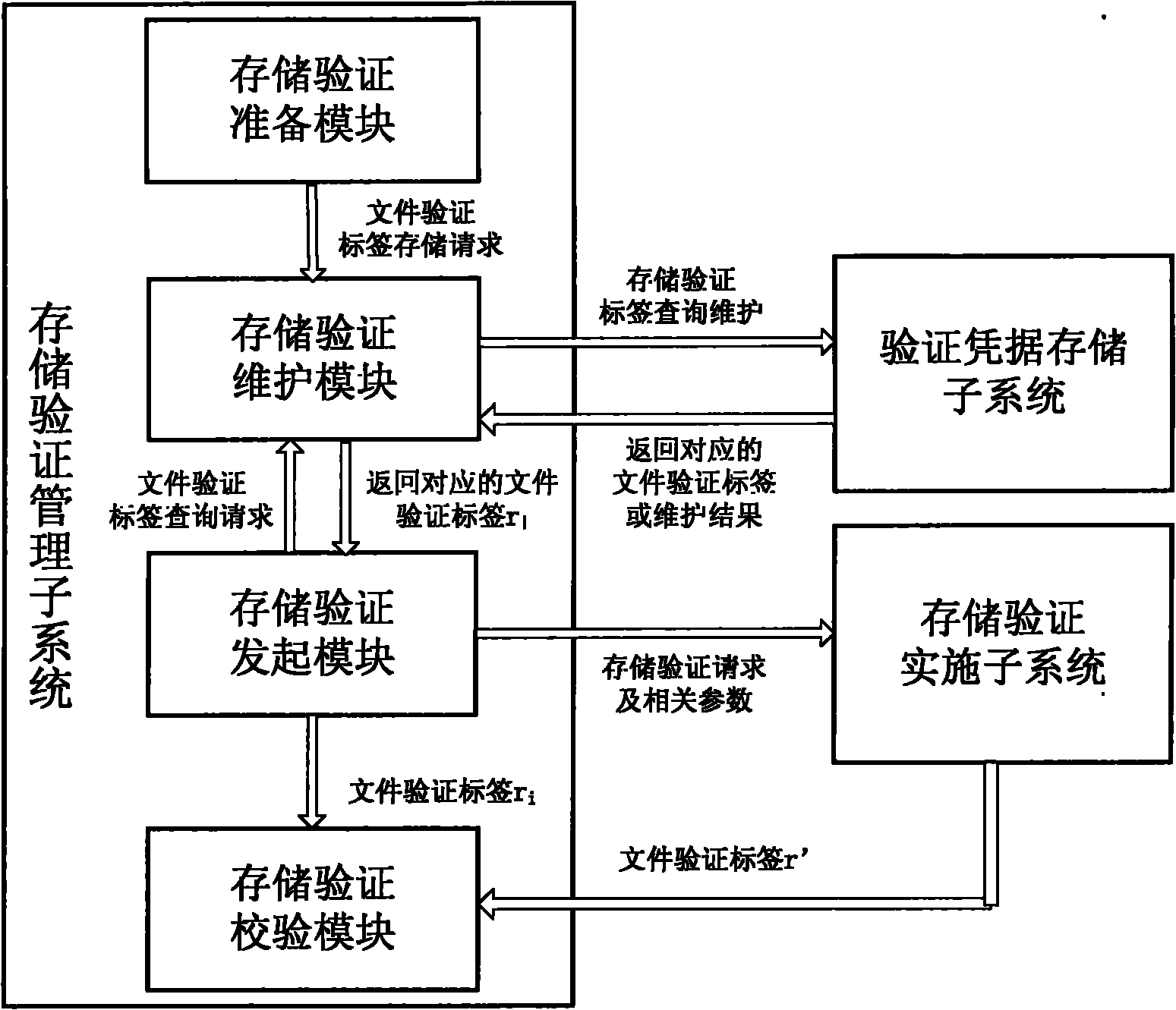
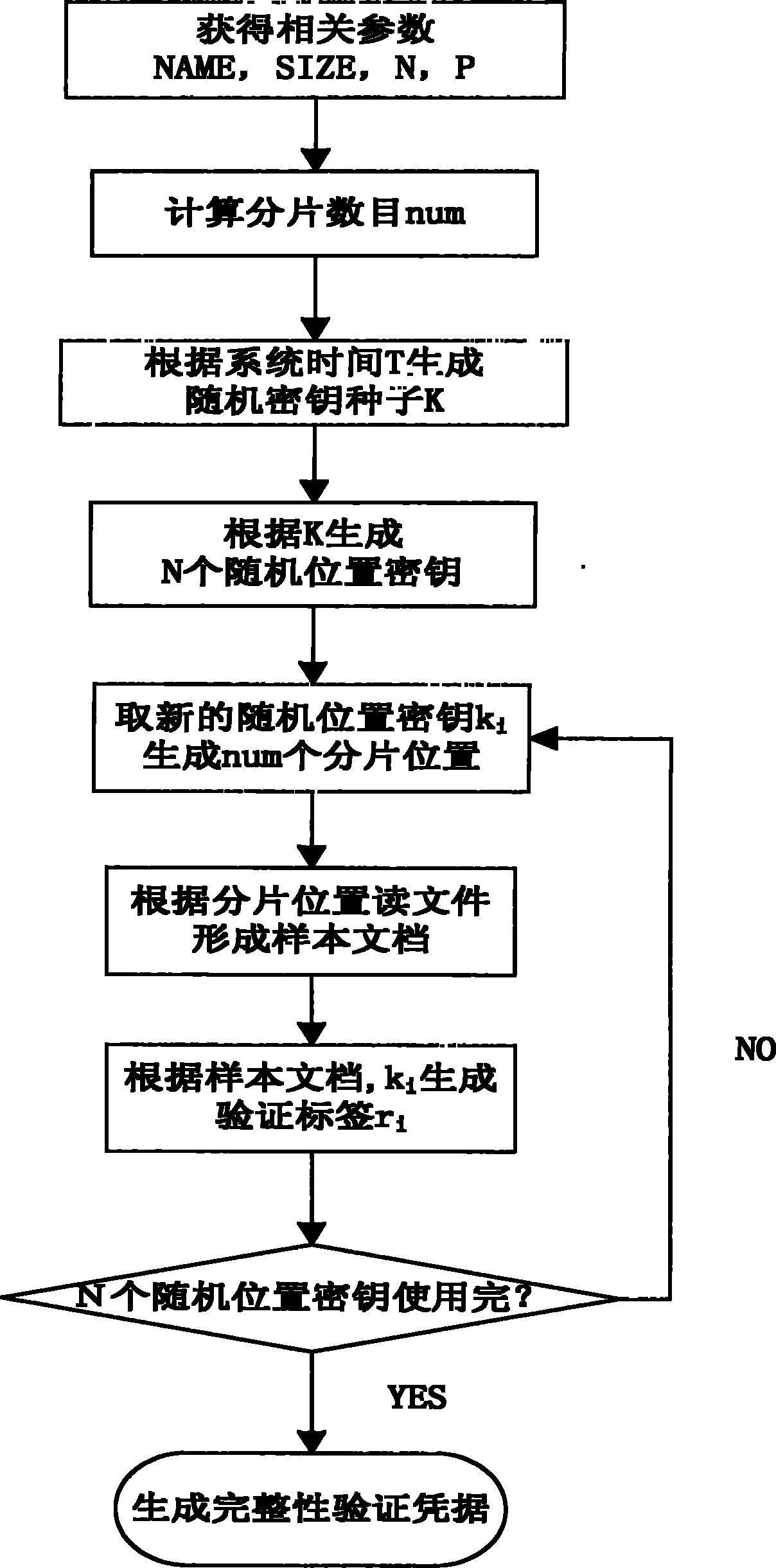
Cloud-storage-oriented trusted storage verification method and system
ActiveCN102045356AAvoid consumptionReduce consumptionTransmissionValidation methodsCloud storage system
The invention discloses a trusted storage verification method and a trusted storage verification system for cloud storage and belongs to the technical field of computer software. In the method and the system, before a file is transmitted to an untrusted cloud storage server, a series of random positions are generated according to the key held by a user and other generated related verification parameters, the contents at the random positions in the file are read, a plurality of verification labels are generated for the file, and all necessary parameters are stored and maintained; and when the storage state of the file is required to be checked, a user can initiate an interaction process with a cloud storage system according to related parameters, and the cloud storage system can generate new verification labels again according to parameters corresponding to the verification. In the method disclosed by the invention, a higher verification reliability can be acquired at a lower computingcost, the contents at different positions in the file are selected at each time of generation of the file verification labels, and different keys are adopted to prevent a server from generating a correct signature by using a stored correct signature or by storing the file contents at a specific position.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
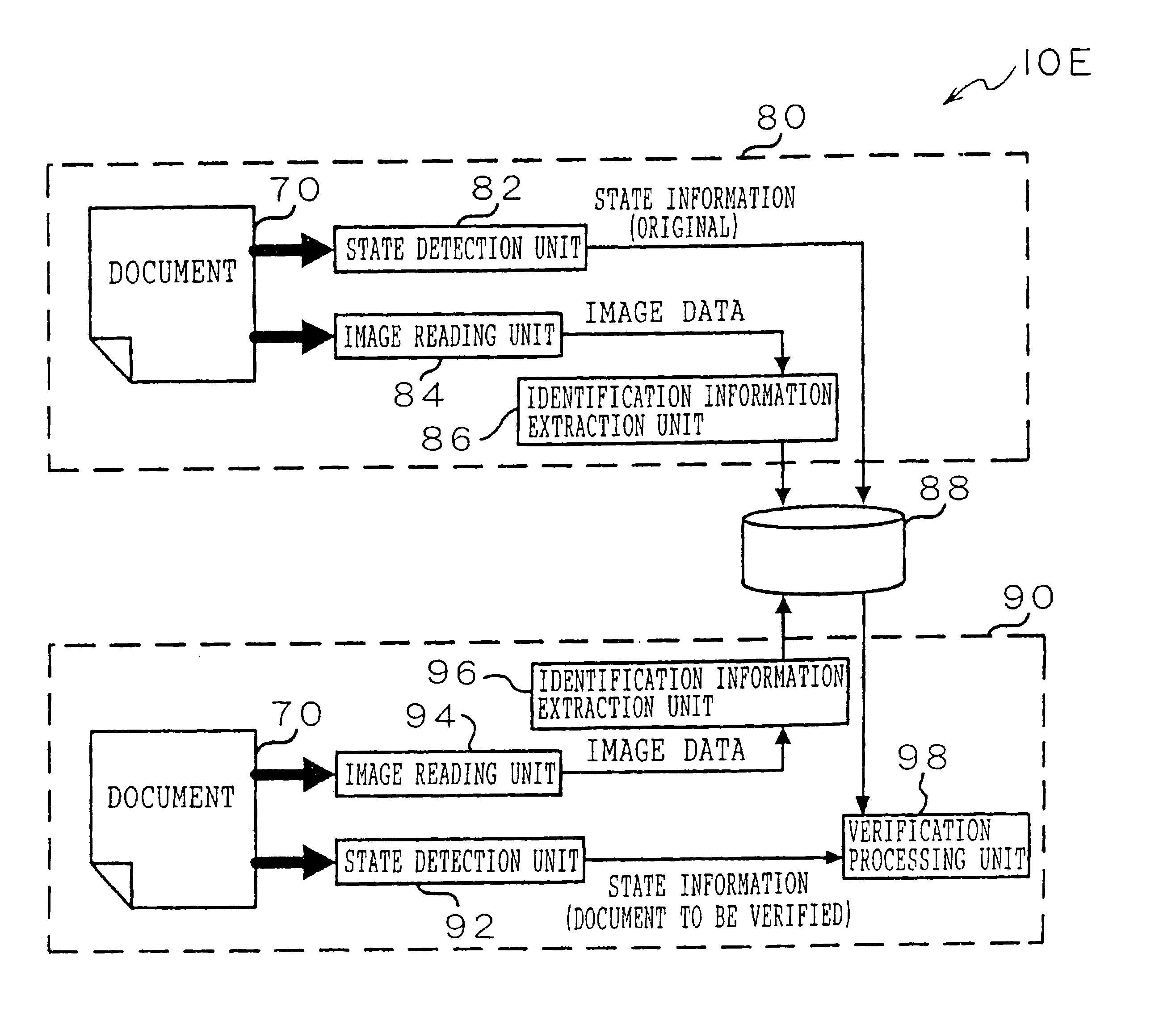
Document Verification Method And System
A method of and system for verifying a document, the method comprising generating verification information for the document, comparing the verification information with authentic verification information, and identifying differences between the document and an authentic document.
Owner:HEWLETT PACKARD DEV CO LP
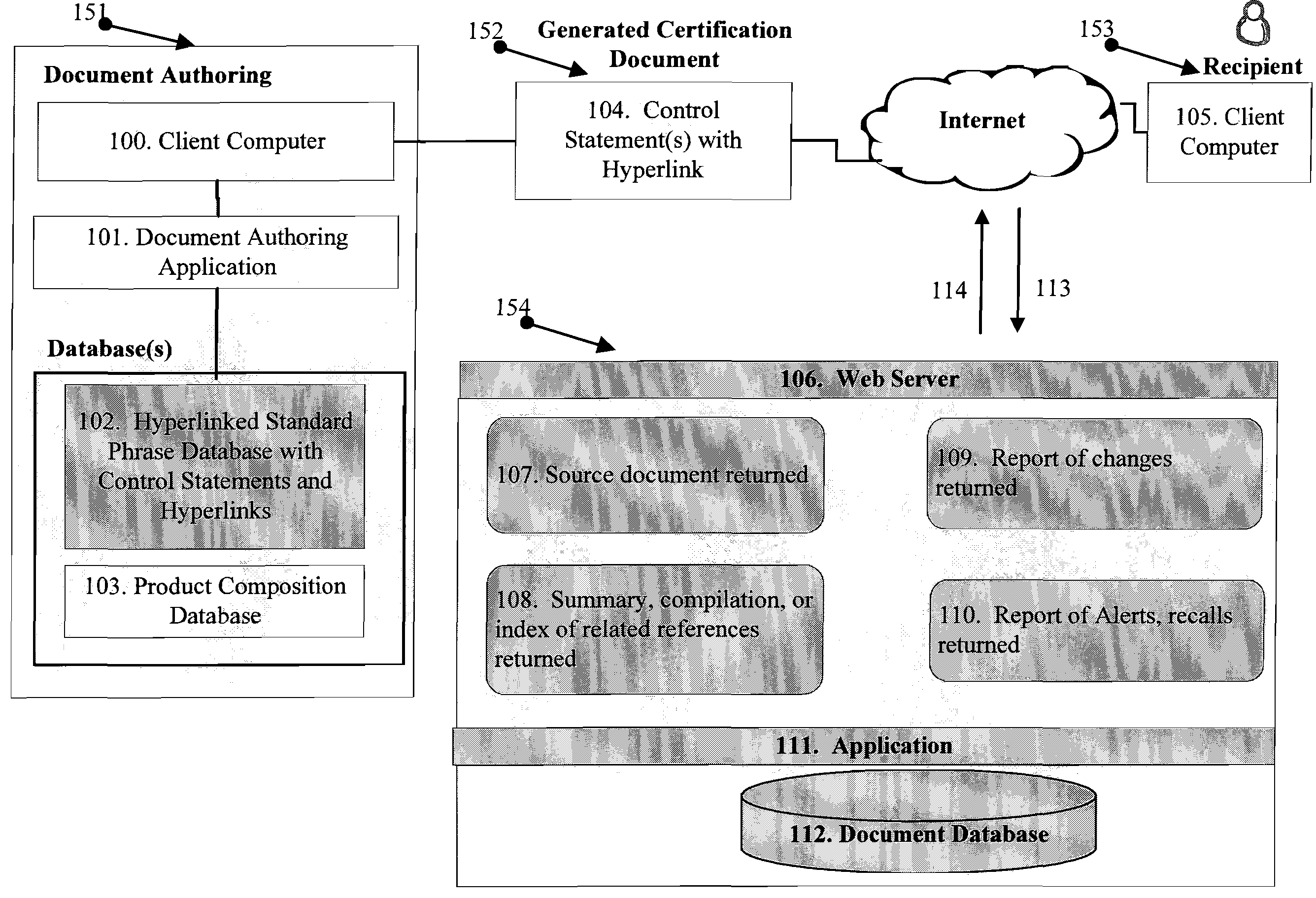
Document Validation System and Method
ActiveUS20070172062A1Free and flexibleImprove operational efficiencyDigital data processing detailsNatural language data processingDocumentation procedurePaper document
The present invention relates generally to the field of self-validating documents in supply chain management, documentation services and method for creating the same.
Owner:DECERNIS
Internet of things big data fast calibration method
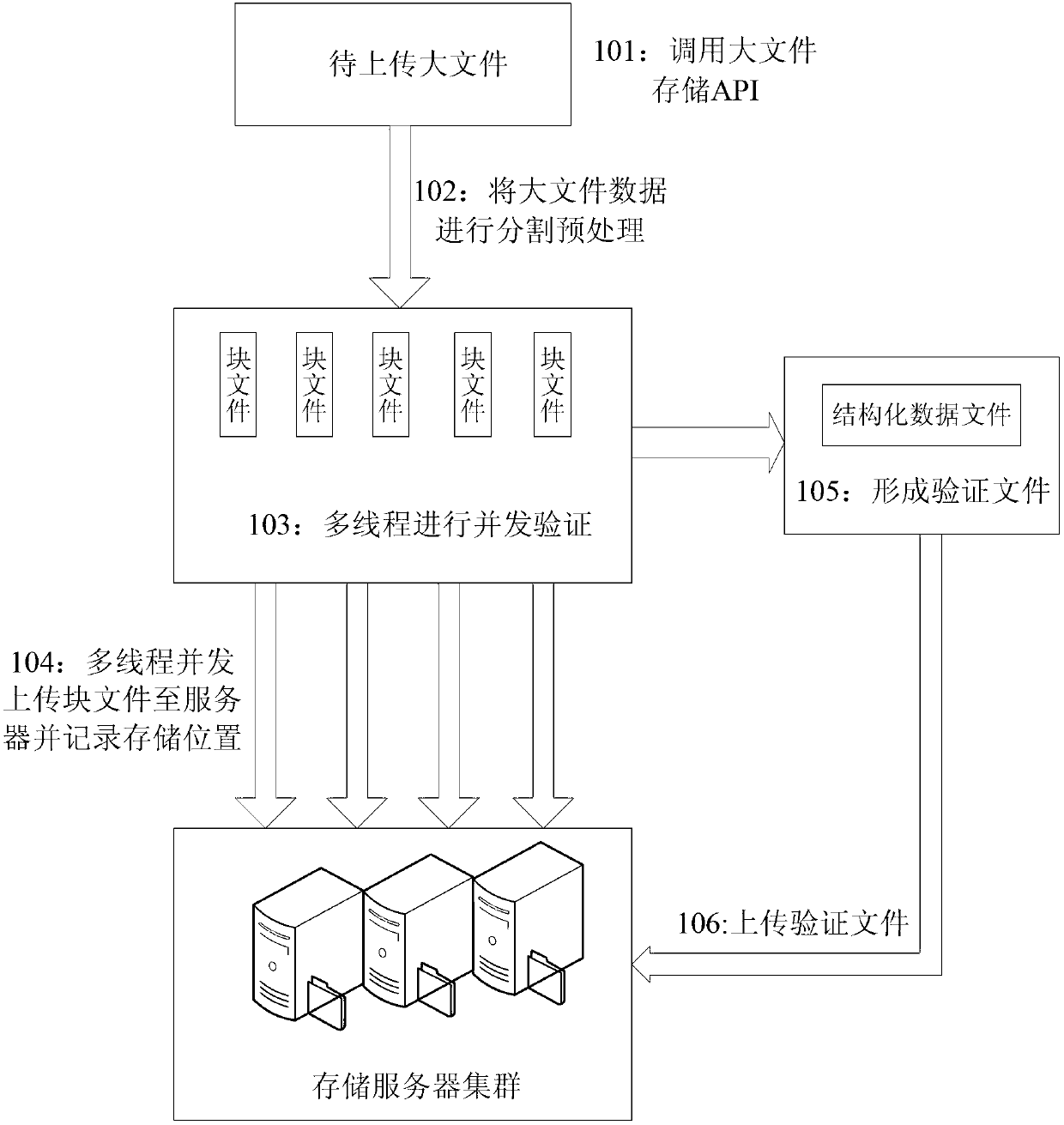
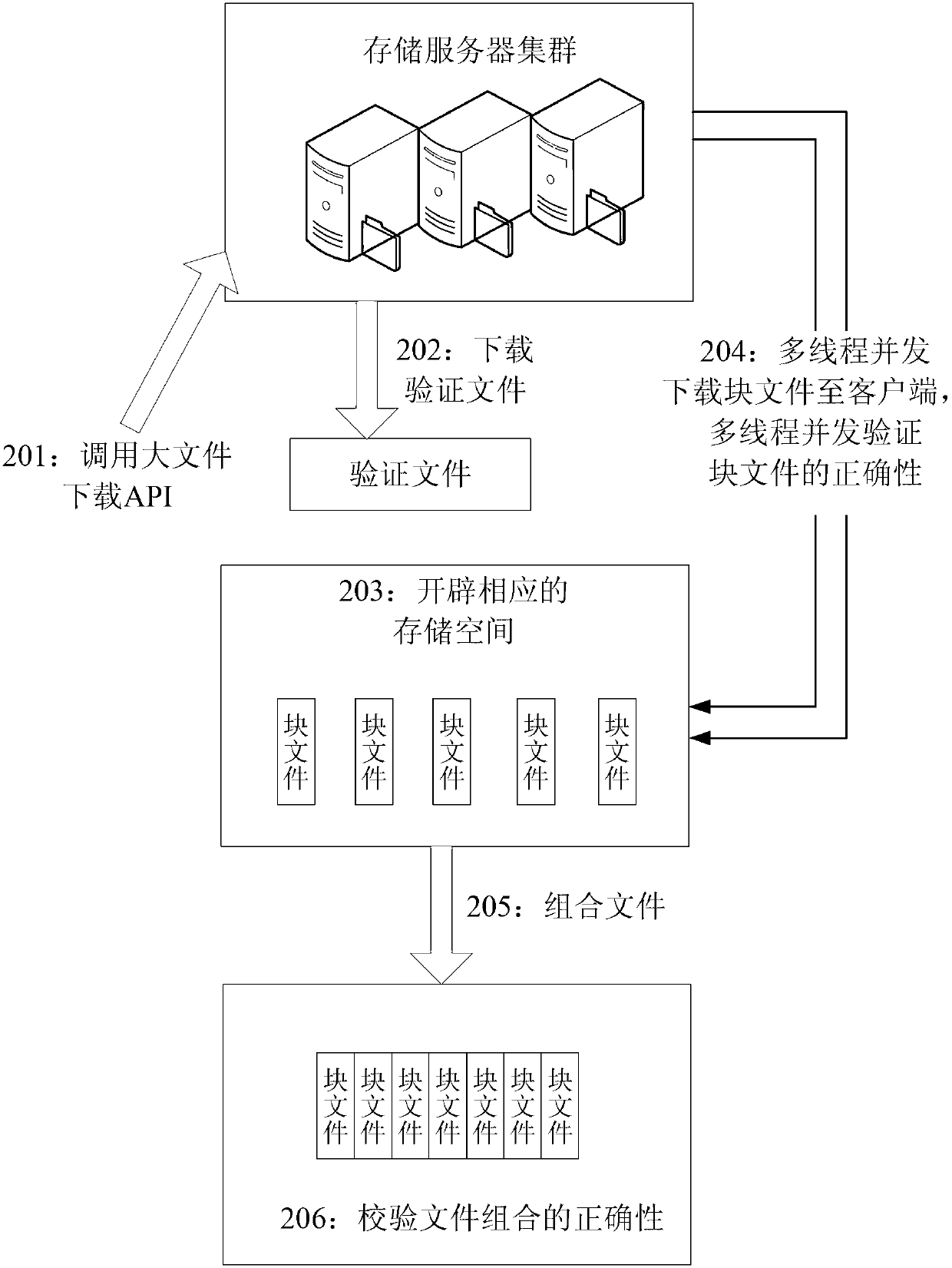
ActiveCN103106068AImprove verification speedVerified and reliableConcurrent instruction executionRedundant data error correctionValidation methodsThe Internet
The invention provides an internet of things big data fast calibration method which comprises a big file upload verification method and a big file download calibration method. The big file upload verification method comprises steps of carrying out segmentation preprocessing on big files, verifying a block file and joint nodes in a multithreading mode, uploading in a multithreading mode, forming verified files, uploading verified files and the like. The big file download calibration method comprises steps of downloading the verified files, downloading a block file in multithreading and complicated modes, verifying accuracy of the verified files in multithreading and complicated modes, combining the files, calibrating whole accuracy of the combination of the files and the like. The method is used for fast verifying the big data formed in the internet of things, and the bottleneck problem of speed of big file verification in the process of processing the big data in the internet of things is effectively solved.
Owner:无锡市源通电子有限公司
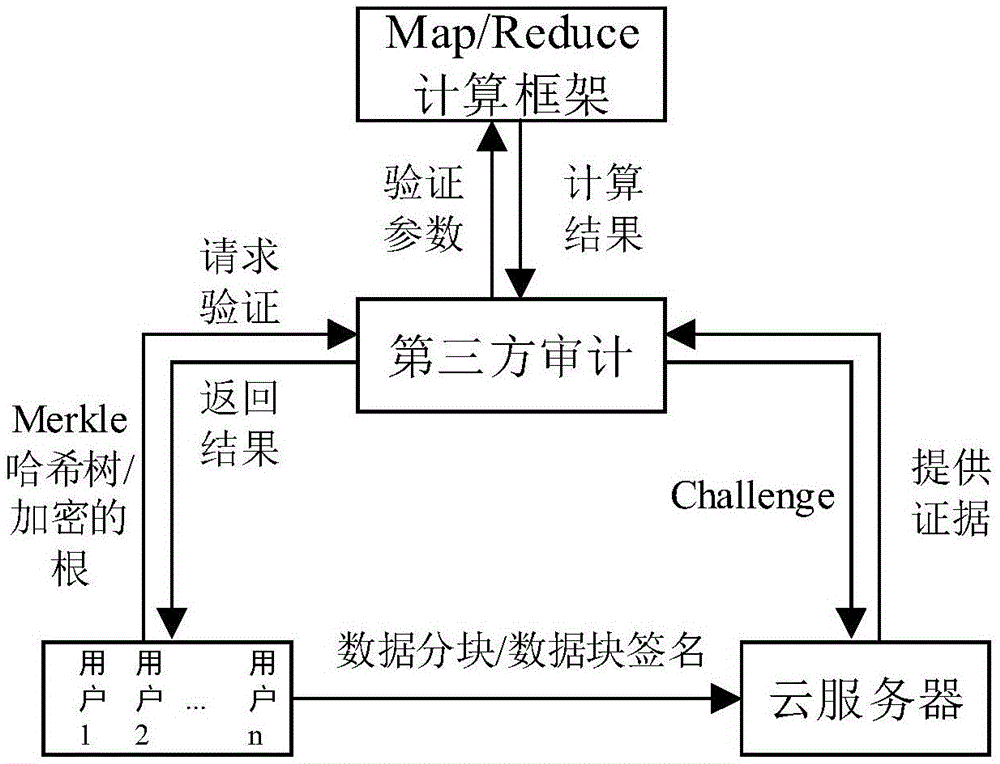
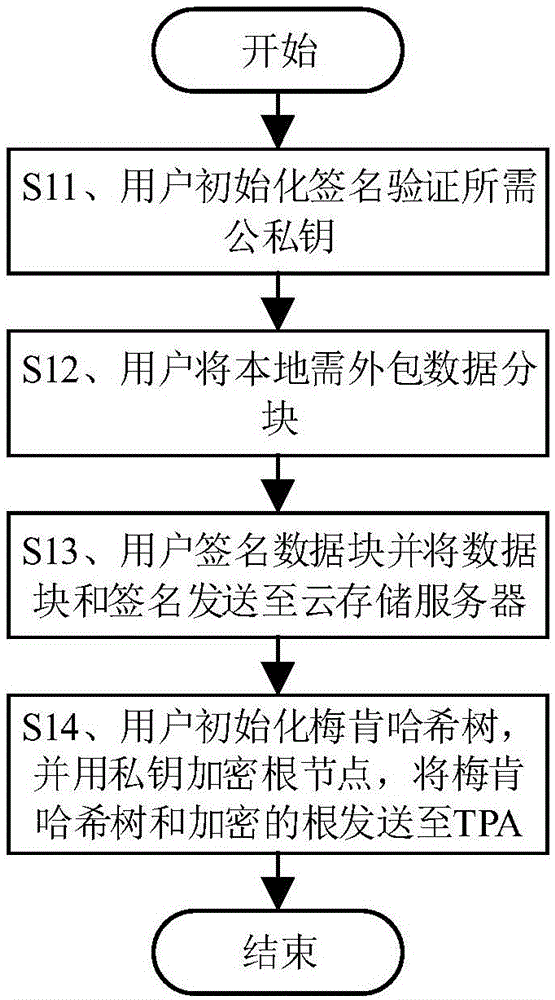
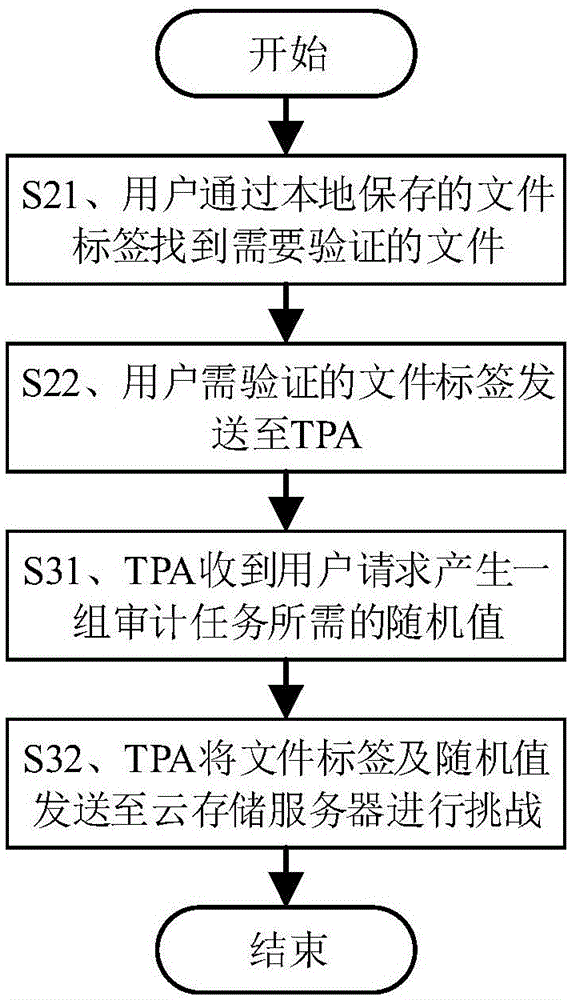
Cloud-storage batch auditing method based on MapReduce
The invention discloses a cloud-storage batch auditing method based on MapReduce, and the method comprises the steps that a user carries out the initialization of a local file; a request is sent to a TPA when the user wants to verify the integrity of packaged data; the TPA challenges a cloud storage server at each time when the request is received, and the cloud storage server returns an evidence corresponding to the file verification; the TPA verifies the data integrity after receiving the evidence; the TPA gathers the received verification evidences in each time period, and carries out one-time unified verification of data. The method can greatly improve the efficiency of batch auditing under the condition of batch auditing failures, solves a problem that a centralized auditing system is poor in adaptability, and reflects the availability of a distributed-type auditing system.
Owner:WUHAN UNIV OF SCI & TECH
Webpage privilege control system and method
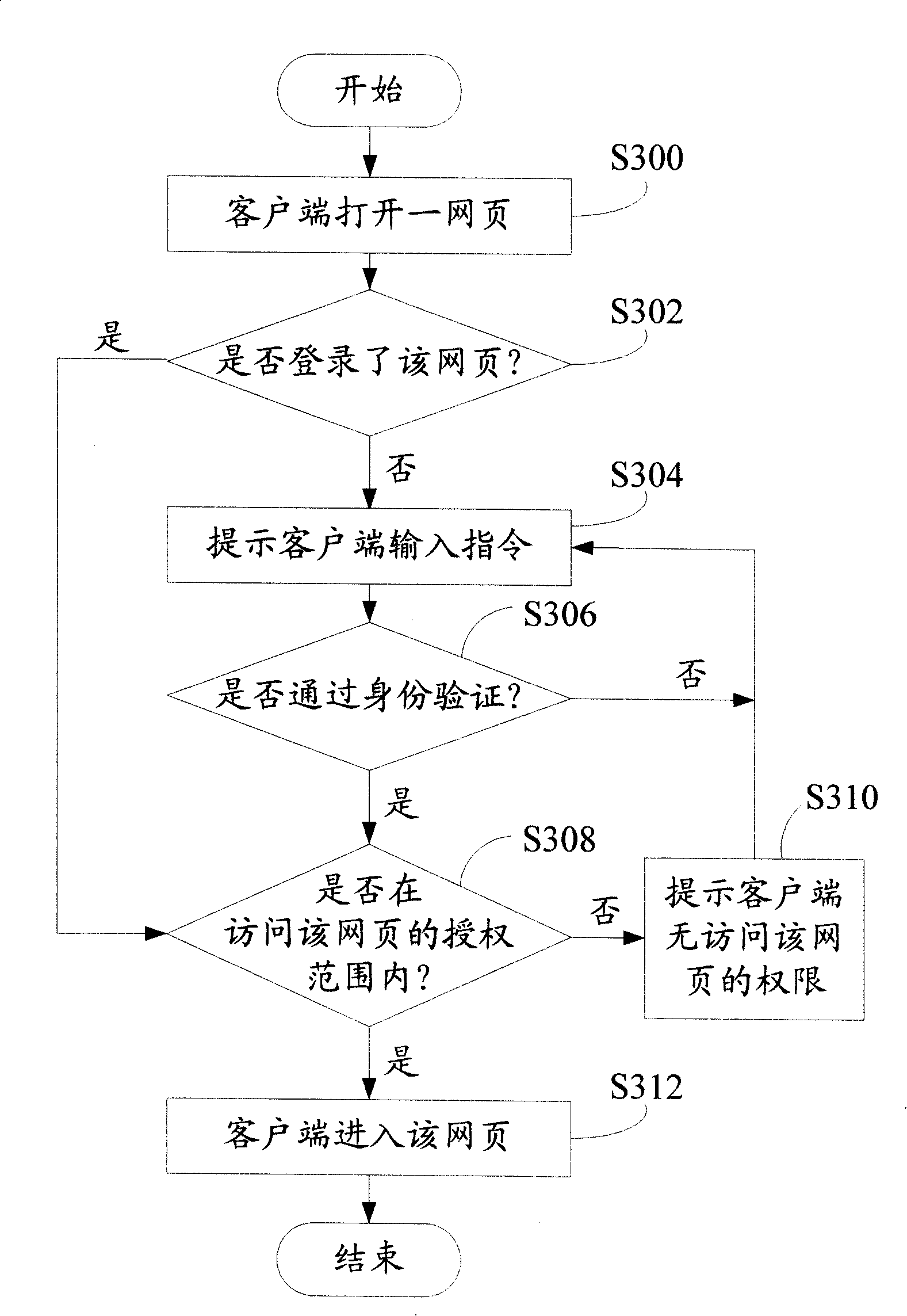
InactiveCN101212457AAuthority control reachesThe method is simple and flexibleDigital data authenticationTransmissionApplication serverControl system
The invention provides a method for managing and controlling webpage rights. The method verifies and manages the rights of accessing the webpage by a user end through an amounted configuration file in an application server. The method comprises the following steps: whether the user end log in the webpage is detected; if the user end dose not log in the webpage, a login dialogue frame is introduced; when the inputted instruction in the user end is received, an identity code and an identification code matching with the instruction are looked for in a database server for determining whether the user end passes through the identity verification; if the user end passes through the identity verification, the webpage access rights corresponding to the user end identity code is read out from the database server so as to determine whether the access rights of the user end is in the webpage authorization range. Besides, the invention also provides a system for managing and controlling the webpage rights.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
File verification method and a related device
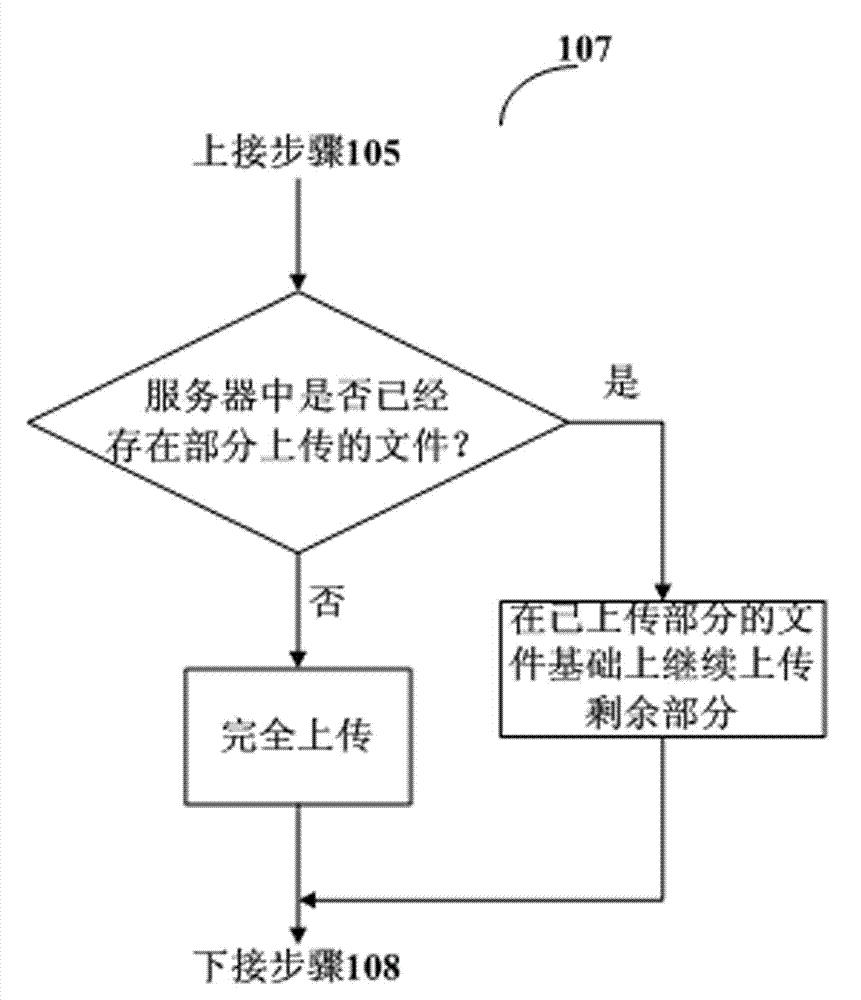
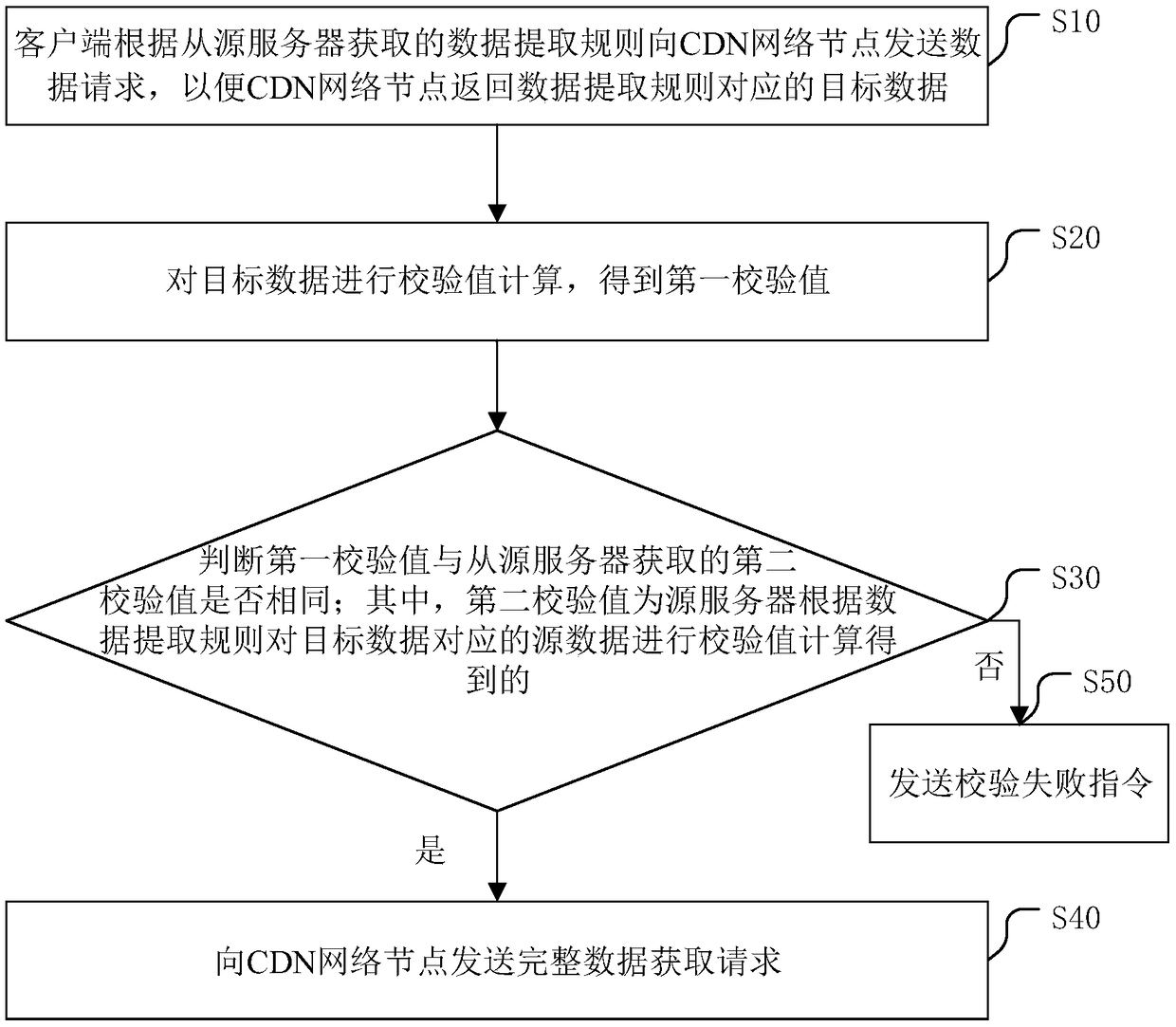
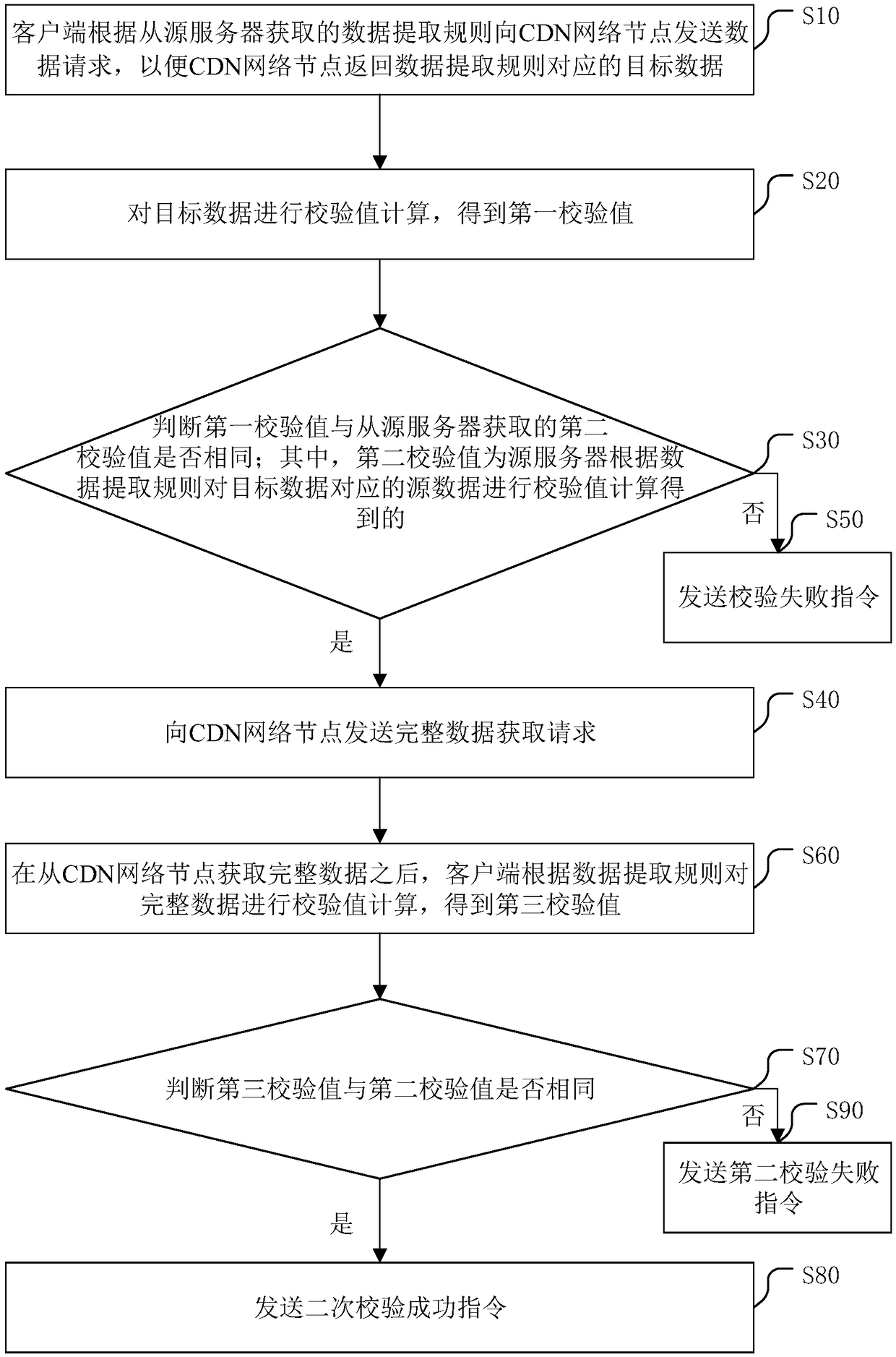
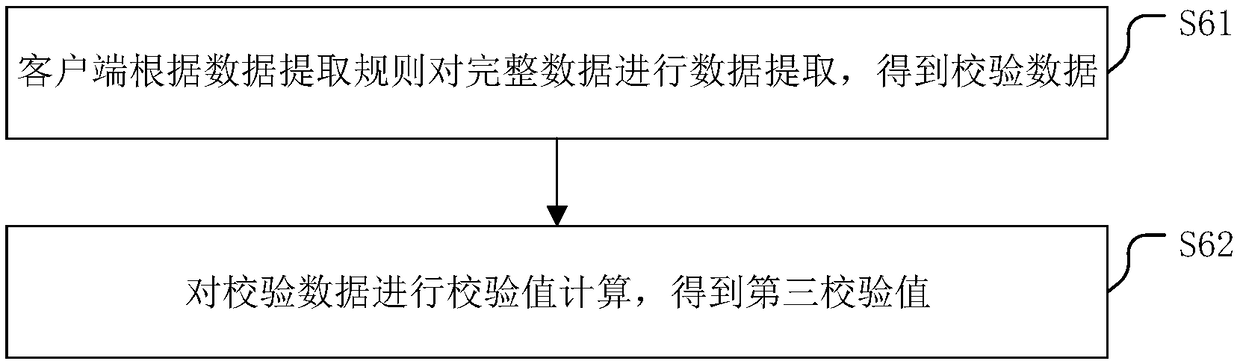
PendingCN109492436ASmall amount of calculationImprove performanceEncryption apparatus with shift registers/memoriesDigital data protectionComplete dataData acquisition
The invention discloses a file verification method, which comprises the following steps that: a client sends a data request to a CDN (Content Delivery Network) network node according to a data extraction rule obtained from a source server, so that the CDN network node returns target data corresponding to the data extraction rule; performing check value calculation on the target data to obtain a first check value; judging whether the first check value is the same as a second check value obtained from a source server or not; wherein the second check value is obtained by performing check value calculation on the source data corresponding to the target data by the source server according to the data extraction rule; and if yes, sending a complete data acquisition request to the CDN network node. The invention further discloses a file verification device, a file verification system, a computer readable storage medium and a computer program product. By verifying the target data, the calculation amount of verification calculation is reduced, the calculation efficiency is improved, and the hardware performance is improved.
Owner:SHENZHEN ONETHING TECH CO LTD
Method and system for identifying and conducting inventory of computer assets on a network
InactiveUS20080021984A1Error detection/correctionDigital computer detailsClient-sideFile verification
A system that includes one or more clients, databases and servers. The clients communicate with the servers using hyper-text transfer protocol. Each client includes a scheduling and monitoring agent. Each server includes several components. A first server component performs a plurality of functions, including receiving requests from the client(s) for configuration file verification information and storing in the database(s) a log of the requests. A second server component is capable of performing a plurality of functions, including receiving hardware and software inventory information, as well as software metering statistics, and storing the inventory information in at least one of the databases.
Owner:BARCLAYS CAPITAL INC
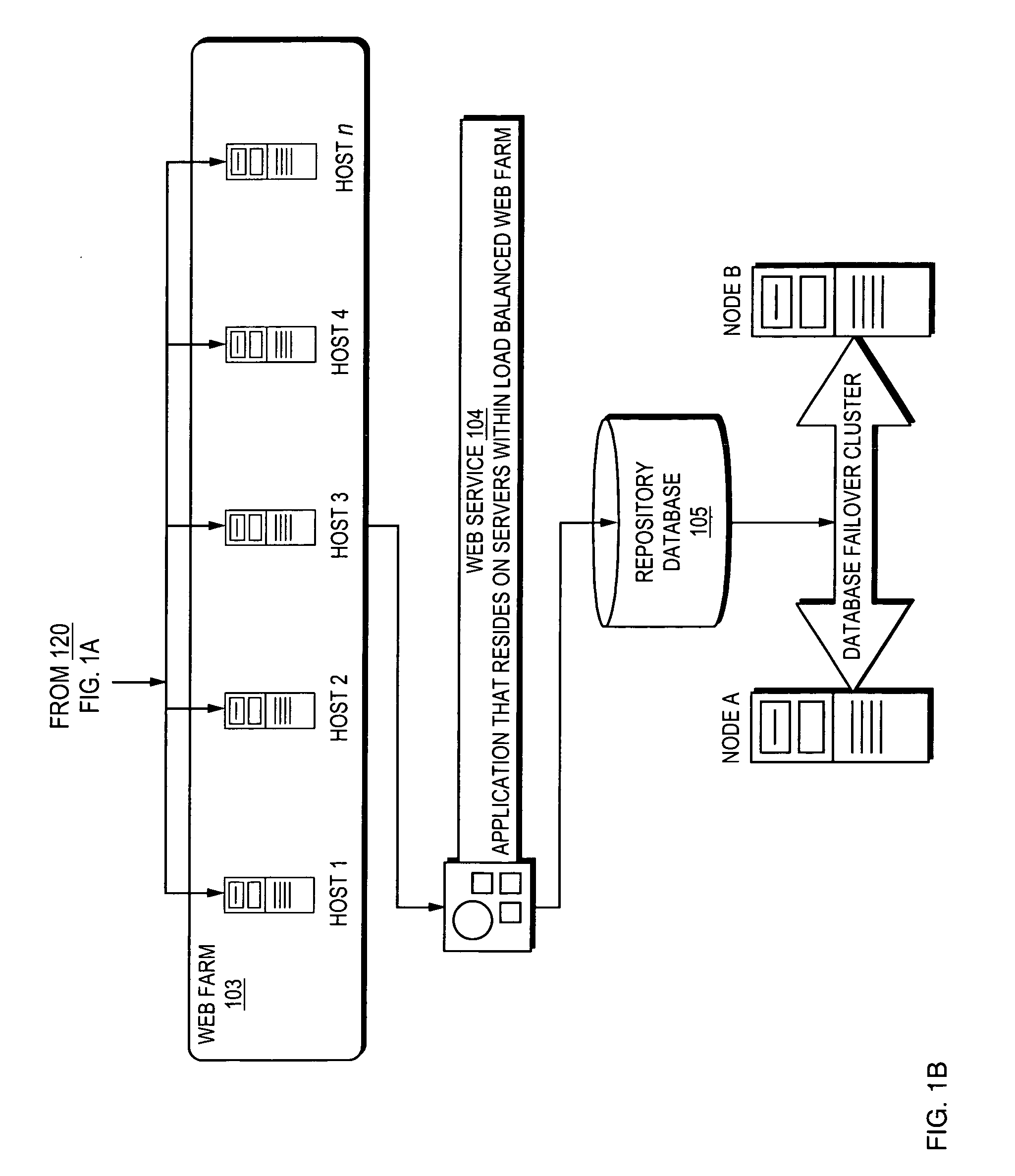
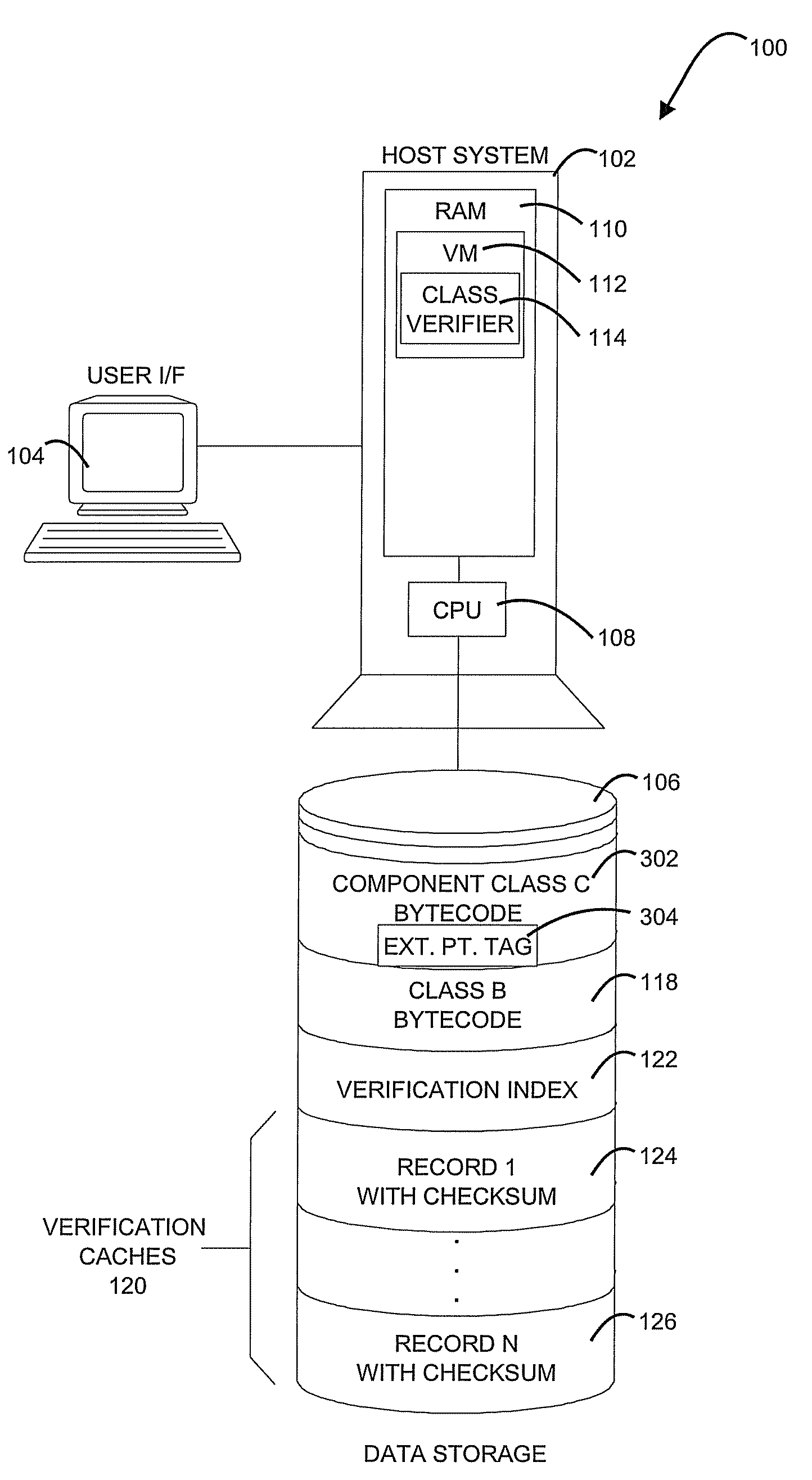
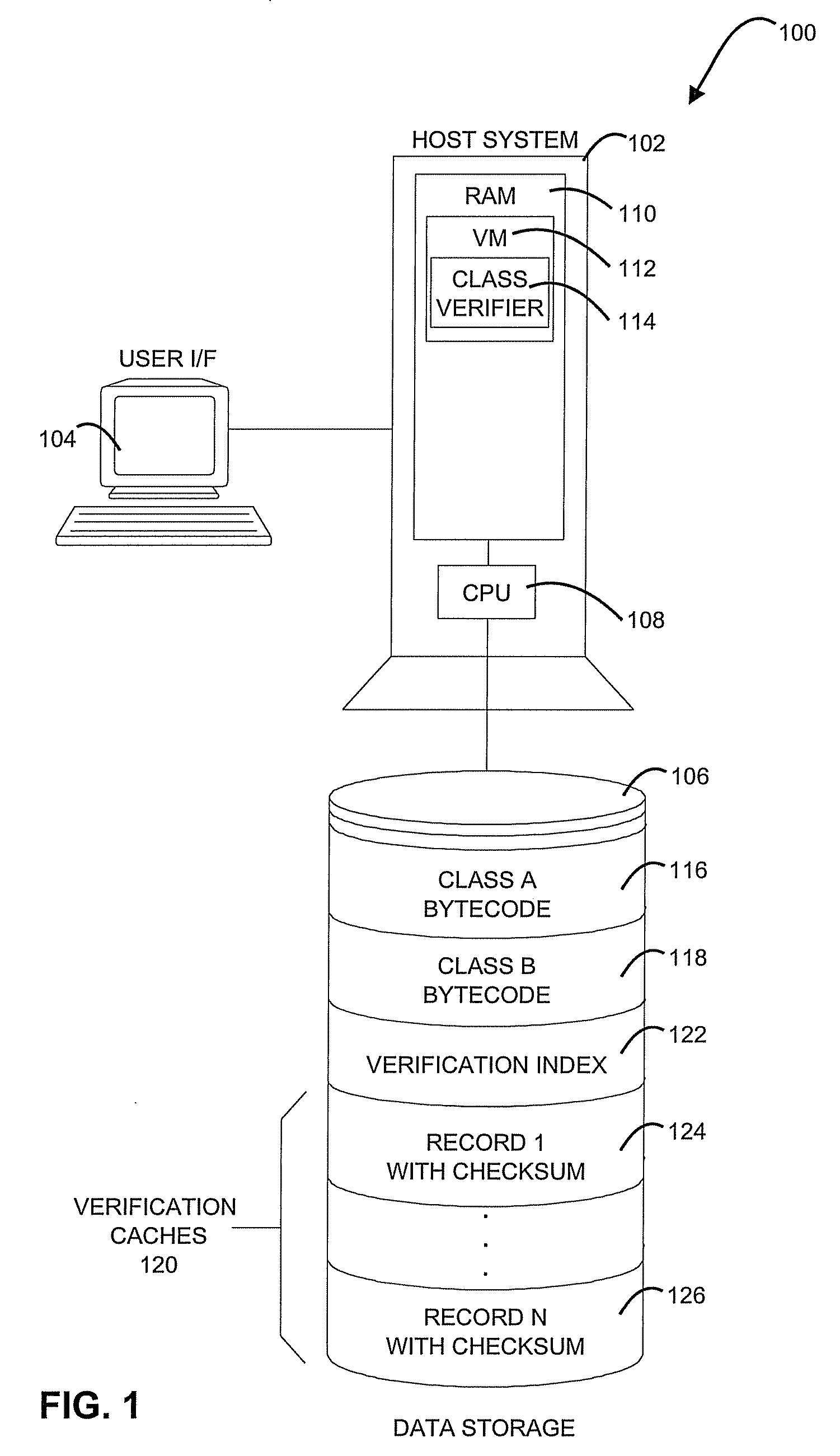
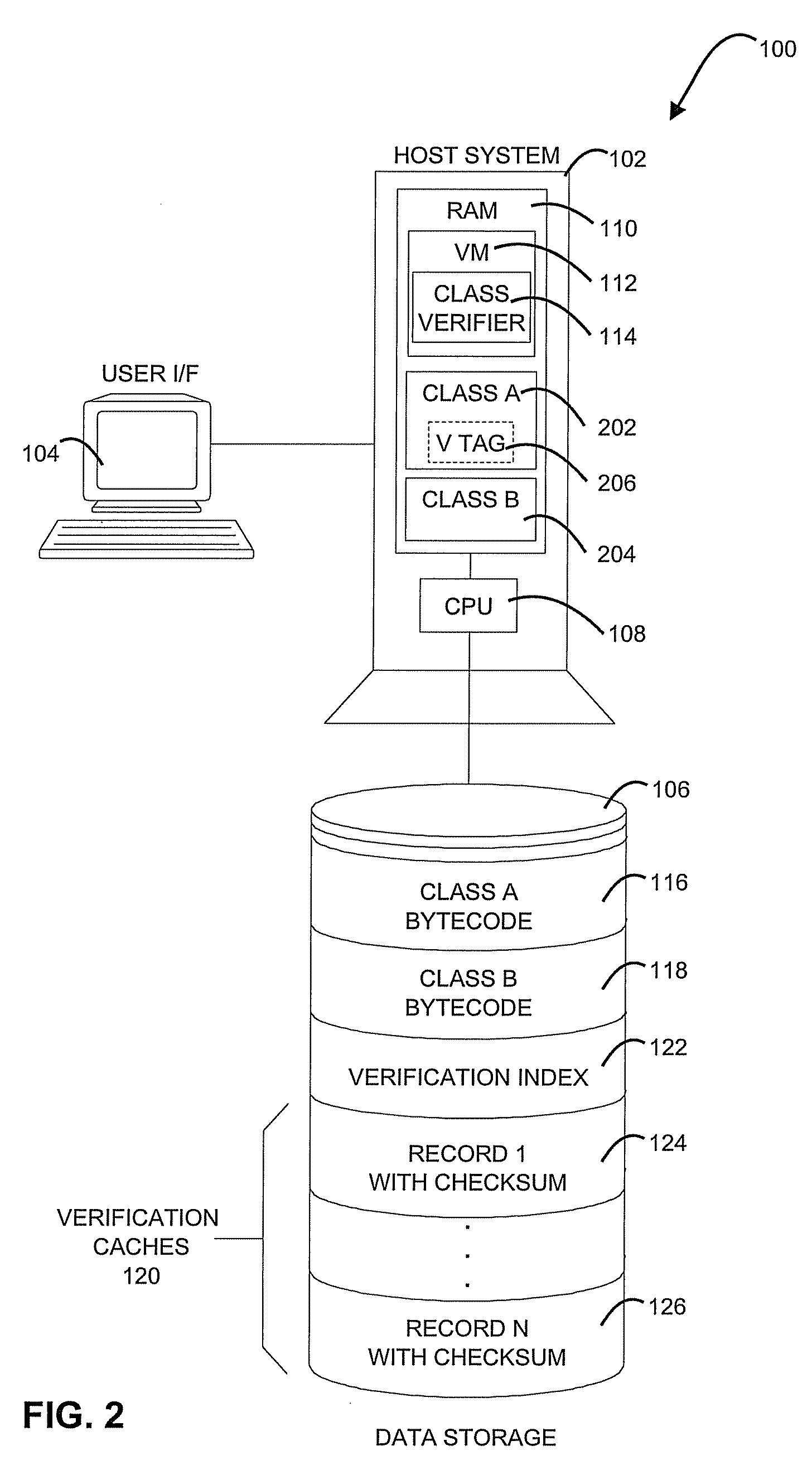
Methods, Systems, and Computer Program Products for Class Verification
A method, system, and computer program product for class verification are provided. The method includes initiating loading of a class, and searching for the class in verification caches. A record from the verification caches, including a checksum, is returned upon locating the class. The method further includes comparing the checksum in the record to a checksum of the class being loaded, and completing the loading of the class when the checksums match. The method additionally includes performing bytecode verification of the class upon one of: a checksum comparison mismatch, and a failure to locate the class in the verification caches. The method also includes calculating a new checksum of the class upon a successful bytecode verification, and storing the new checksum in the verification caches.
Owner:IBM CORP
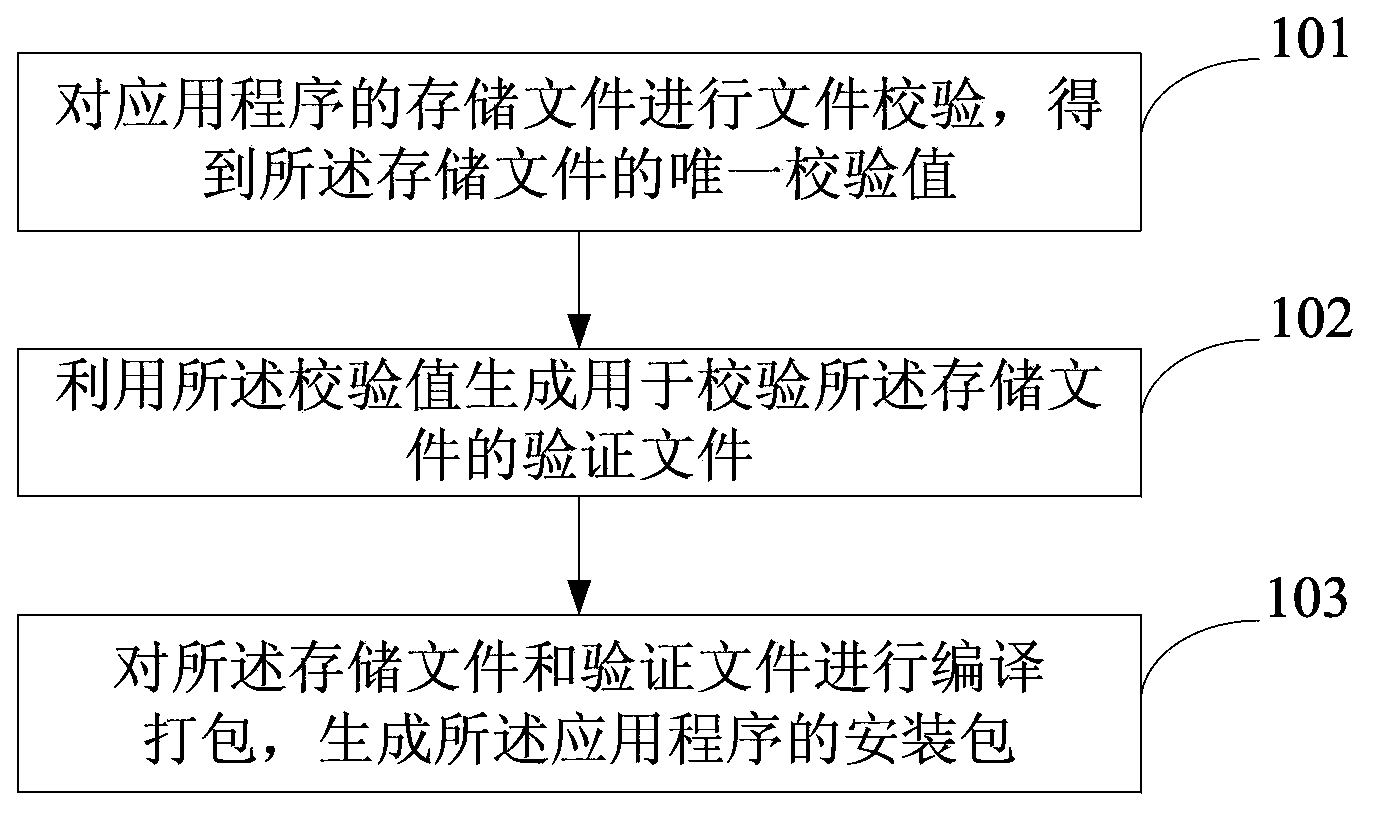
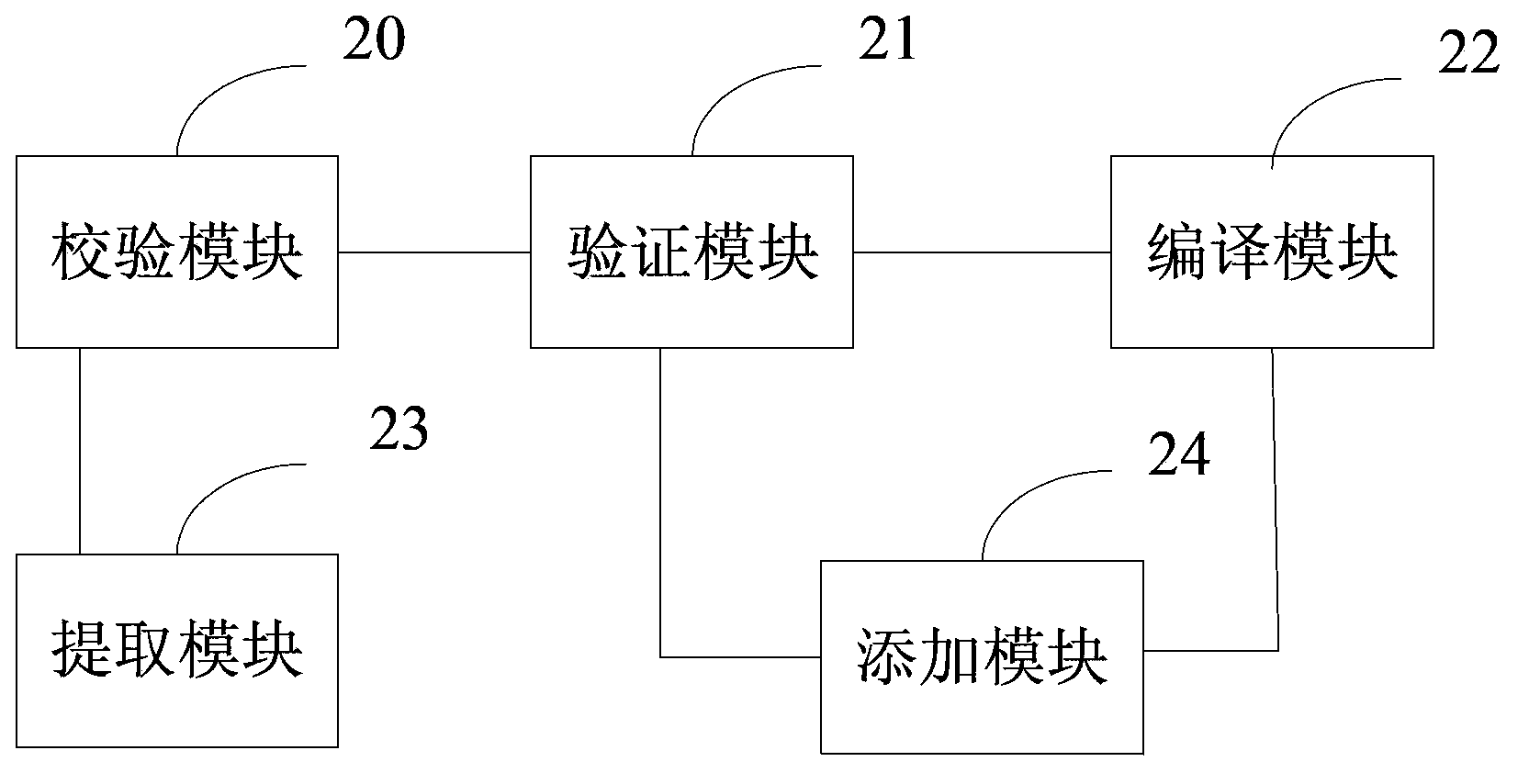
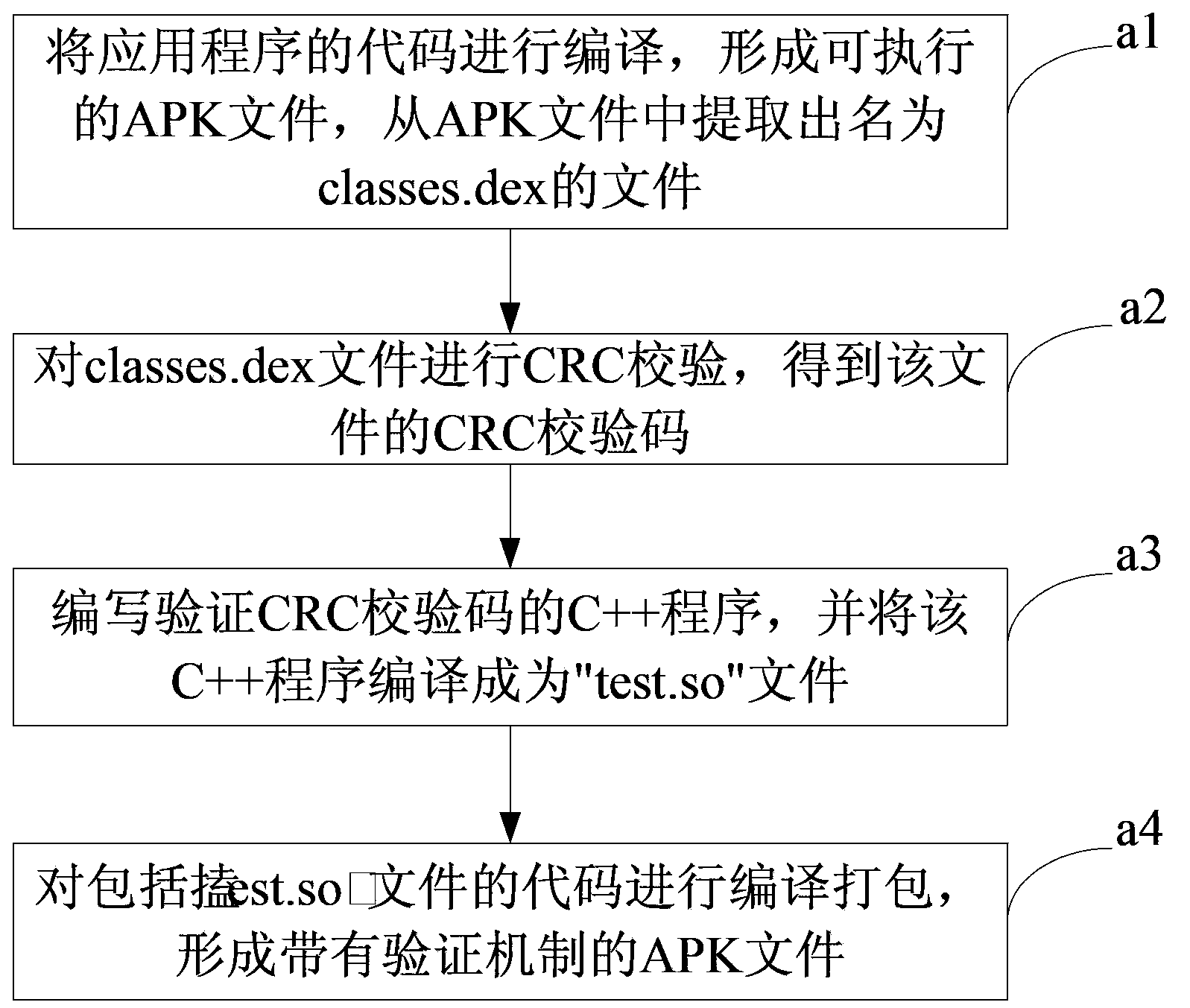
Method and device for preventing application program from being tampered
InactiveCN104123481AImprove securityPlatform integrity maintainanceProgram/content distribution protectionComputer terminalFile verification
The invention provides a method and device for preventing an application program from being tampered, and belongs to the field of safety of intelligent mobile terminals. The method for preventing the application program from being tampered is applied to a mobile terminal with the Android system. The method comprises the steps that file verification is carried out on a storage file of the application program, so that a unique verification value of the storage file is obtained; the verification value is used for generating a verification file used for verifying the storage file; compiling and packaging are carried out on the storage file and the verification file, so that an installation package of the application program is generated. According to the technical scheme, the method and device can verify whether the application program is tempered or not, so that safety of the application program is improved.
Owner:BEIJING CHEETAH MOBILE TECH CO LTD +4
Document validation system and method
ActiveUS7769712B2Free and flexibleImprove operational efficiencyDigital data processing detailsOffice automationDocumentation procedureFile verification
The present invention relates generally to the field of self-validating documents in supply chain management, documentation services and method for creating the same.
Owner:DECERNIS
Flow method for automatically verifying correctness of electric rule file
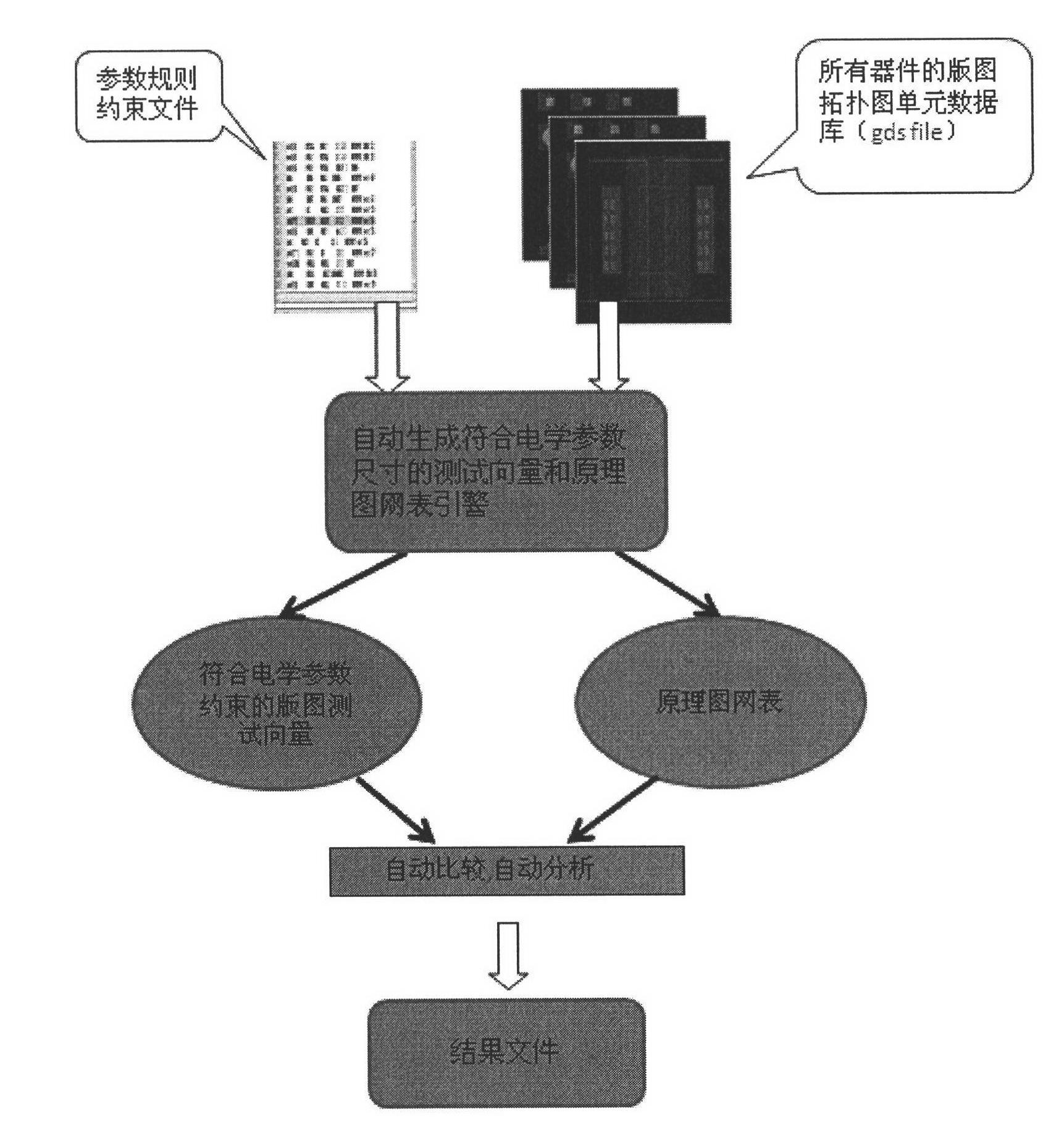
The invention discloses a method for automatically generating a device test vector and a schematic diagram net list corresponding to the device test vector and automatically performing consistency check and error analysis of a layout and a schematic diagram, namely an optimization method for increasing the verification efficiency of an electric rule file in an integrated circuit aided design software tool, and belongs to the field of the consistency verification of the layout and the schematic diagram in the integrated circuit aided design software tool. The conventional manual layout drawing, schematic diagram test vector, one-by-one net list extraction and one-by-one manual verification of the correctness of the electric rule file have large flow workload and long development time and require that engineers have better design capacity and integrally master the verification flow of a process rule file better, so that the design threshold is high, and the development period is long. The invention provides a flow method for automatically verifying the correctness of the electric rule file. Compared with the conventional manual drawing, comparison and result analysis flows in the industry, the method is easy to operate, the development efficiency is greatly increased, and subsequent frequent amendment and maintenance are facilitated.
Owner:MIRCOSCAPE TECH
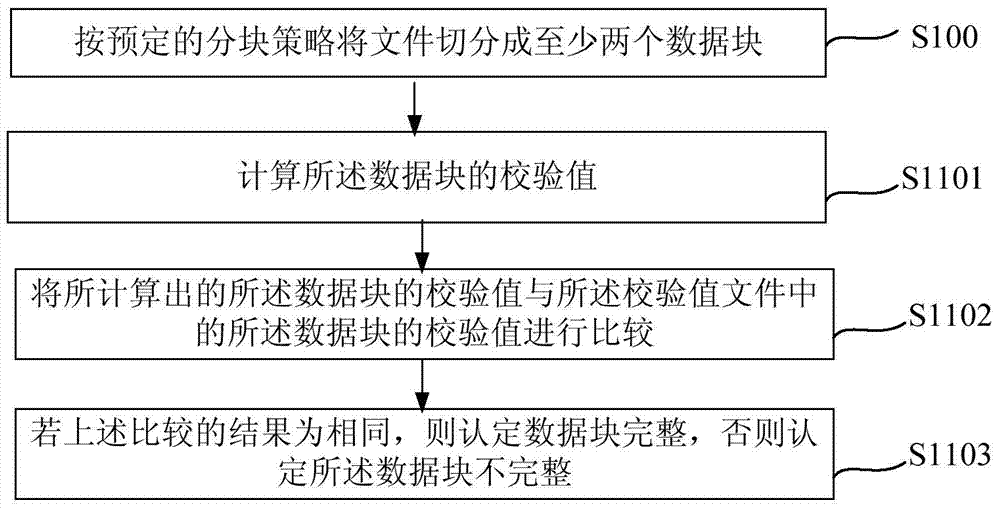
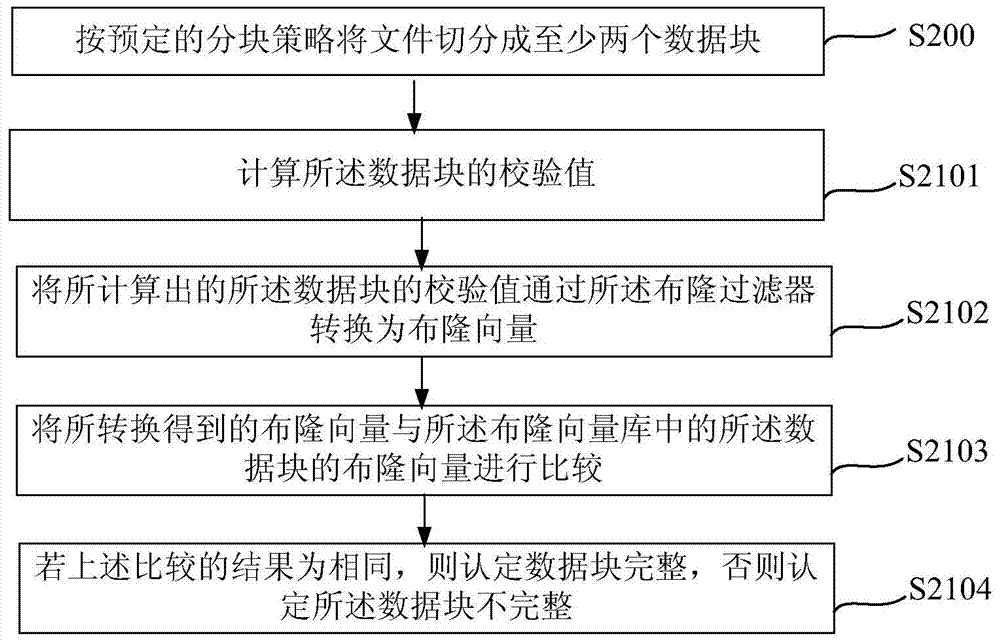
File integrity verification method and file processor
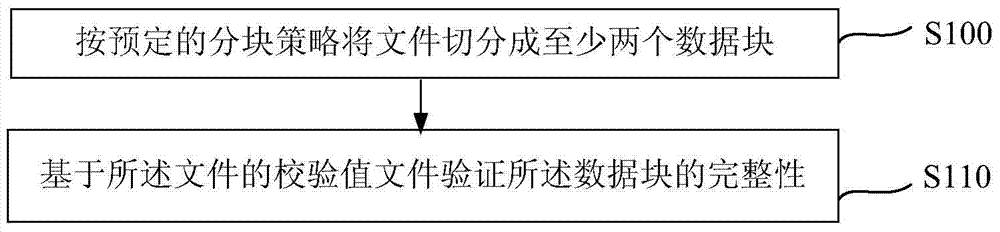
ActiveCN103488952AShorten the integrity check processShorten the timeDigital data protectionSpecific program execution arrangementsDocument handlingFile verification
The invention relates to a file integrity verification method and a file processor. The file integrity verification method includes the steps that a file is segmented into at least two data blocks according to a preset blocking strategy; the integrity of the data blocks is verified based on a verification value file of the file, wherein the verification value file comprises respective verification values of the at least two data blocks, and if any data block is identified as not integral, the file is judged as not integral, and verification is stopped. By the adoption of the file integrity verification method and the file processor, time for extracting the verification value of the file and verifying the integrity of the file can be shortened, and inherent falsification characteristic of a file integrity verification method in the prior art is avoided.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com