Verifying method for network file transmission
A network file and verification method technology, applied in the field of computer networks, can solve the problems of not completely guaranteeing the correctness of file verification, consuming a lot of time and bandwidth resources, etc., to save bandwidth resources, improve reliability, and ensure complete accuracy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The details of the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
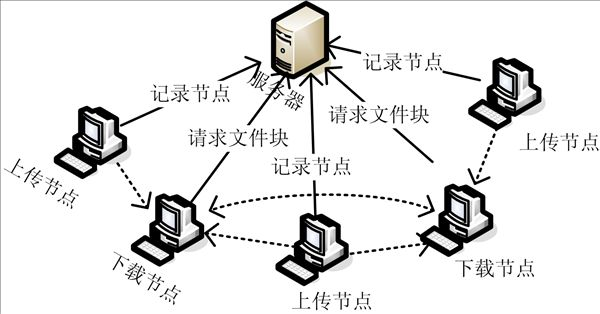
[0021] figure 1 Server and terminal download structure diagram.
[0022] The server is the resource allocation center and acts as a link in the entire network file transfer. The server is also a large database, which records all terminal node information, including terminal IP address, terminal serial number, terminal path, secondary verification hash code of all file blocks, etc., and establishes a terminal node information table, which can be accessed and queried at any time.
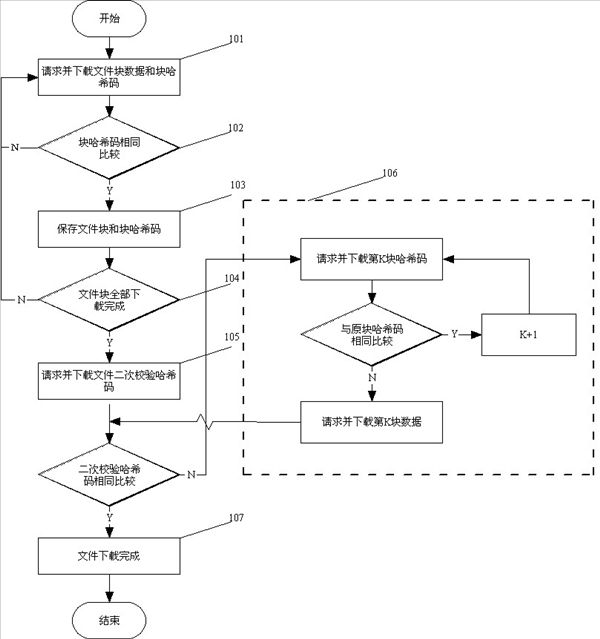
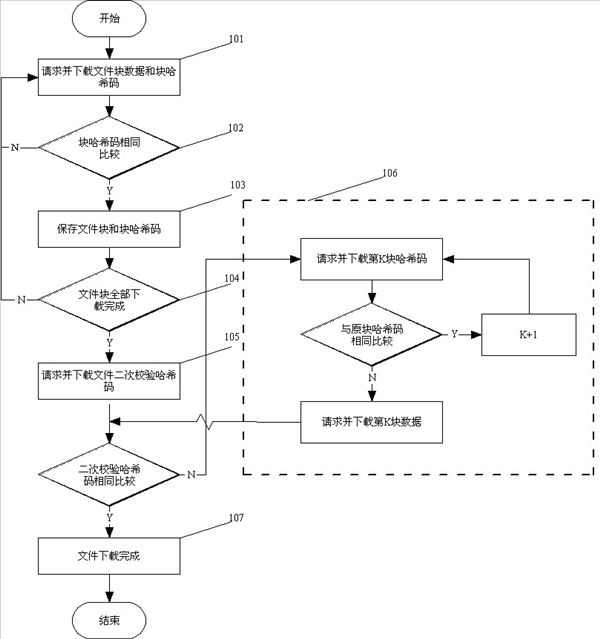
[0023] When a file is uploaded legally and correctly for the first time, the server records the file ID, file size, file block size, file block hash code, file block secondary check hash code and other file information when the file is uploaded. In particular, the file block secondary verification hash code is the value obtained by re-hash calculati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com