Safe network information transmission method
A technology of network information and transmission method, which is applied in the direction of transmission system, electrical components, user identity/authority verification, etc. It can solve the problems of network security hidden dangers that cannot be eradicated, security accidents occur continuously, etc., and achieve fast encryption speed, slow encryption speed, Guarantee the effect of safe exchange
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
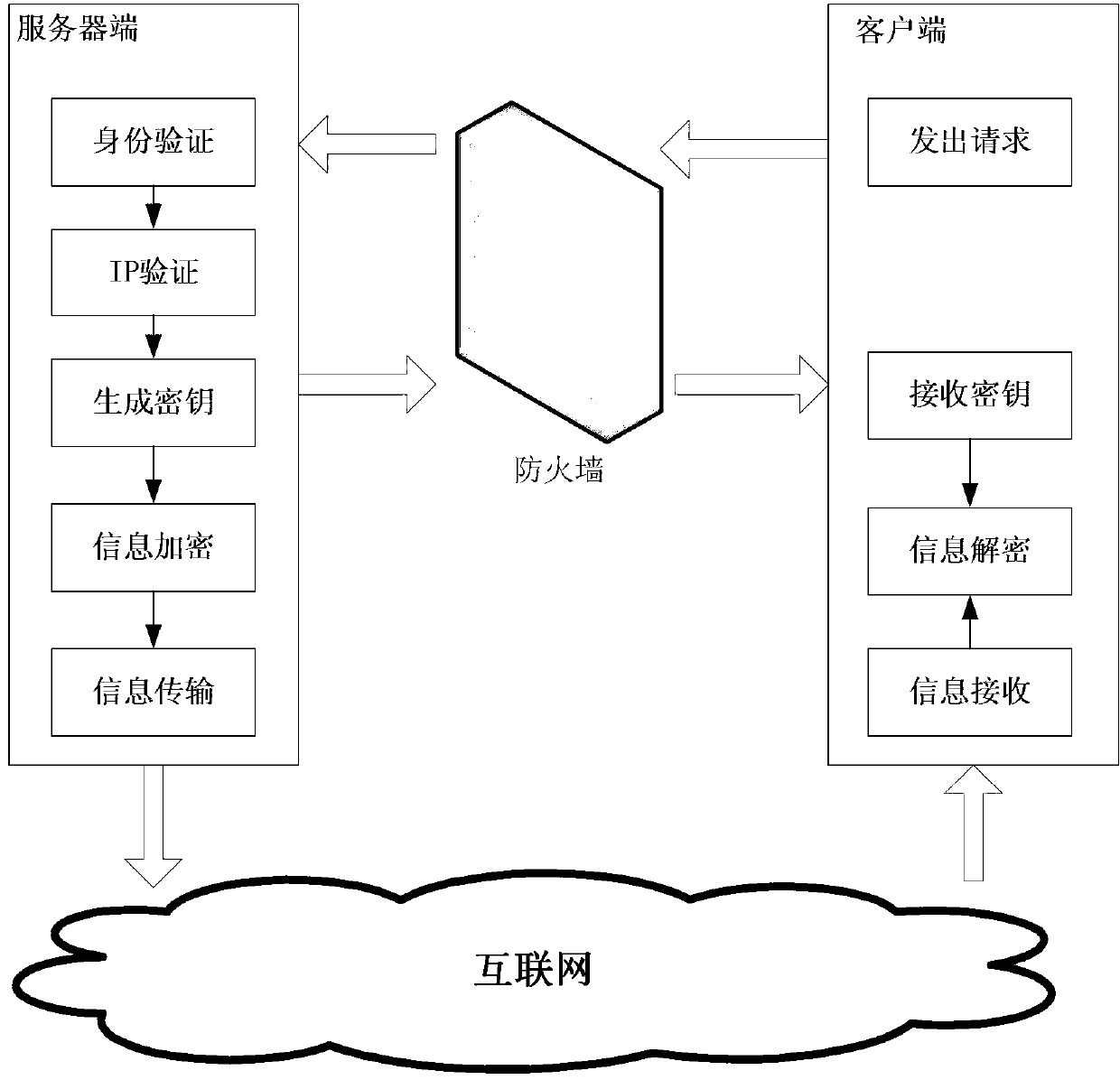
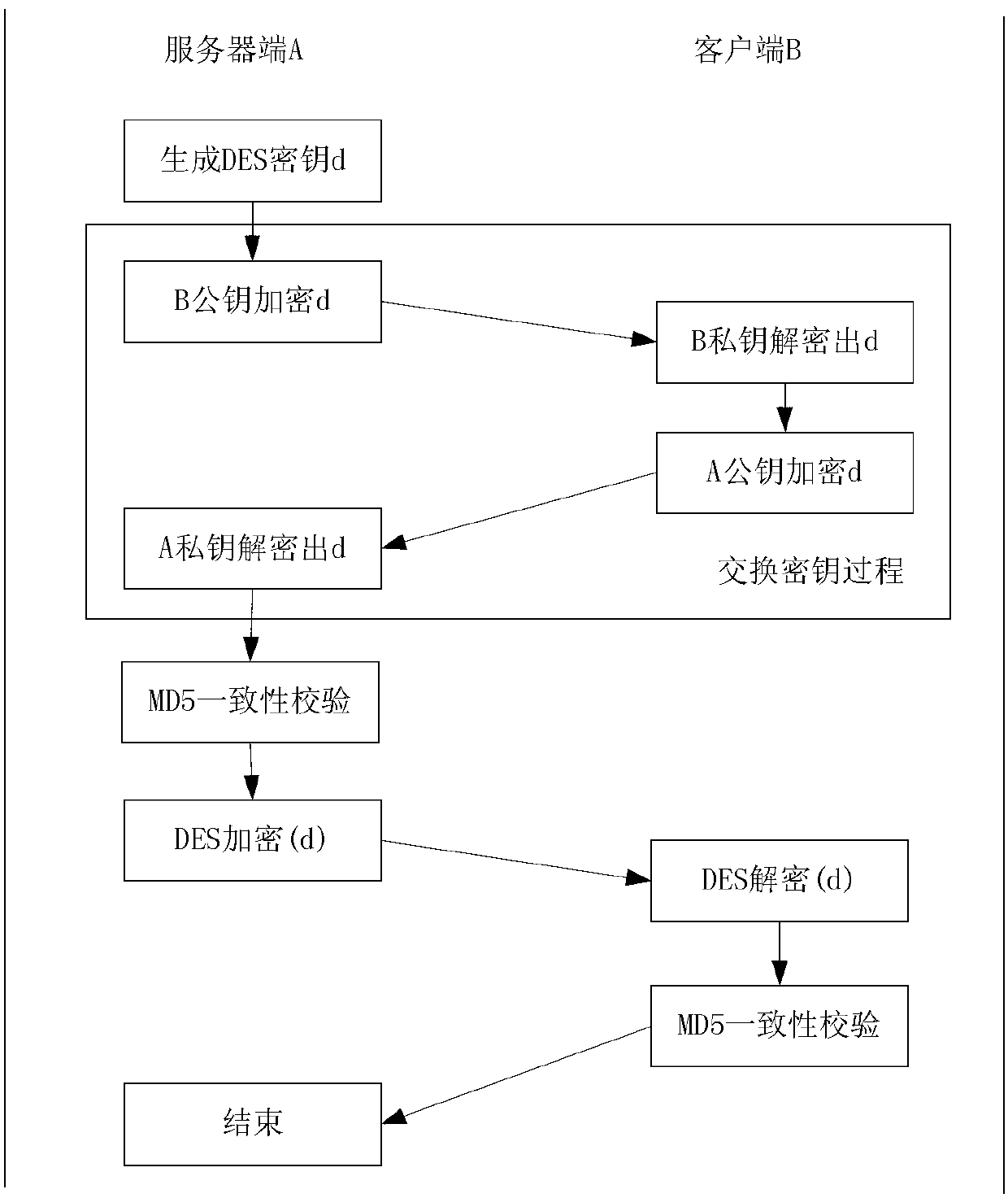
[0039] The data transmission server end of the present invention publishes on the server in the form of Web Services, and the client sends a data transmission request to the server end regularly through threads. The asymmetric encryption algorithm is realized through the RSA algorithm, the symmetric encryption algorithm is realized through the DES algorithm, and the information signature is realized through the MD5 algorithm. Algorithm implementation, the entire data encryption process is as follows: figure 2 shown. The server side initializes the client user information and the RSA algorithm public key and private key information (the key is composed of 5 decimal prime numbers and 308 decimal prime numbers), and the server side public key information is simultaneously saved to the client database.
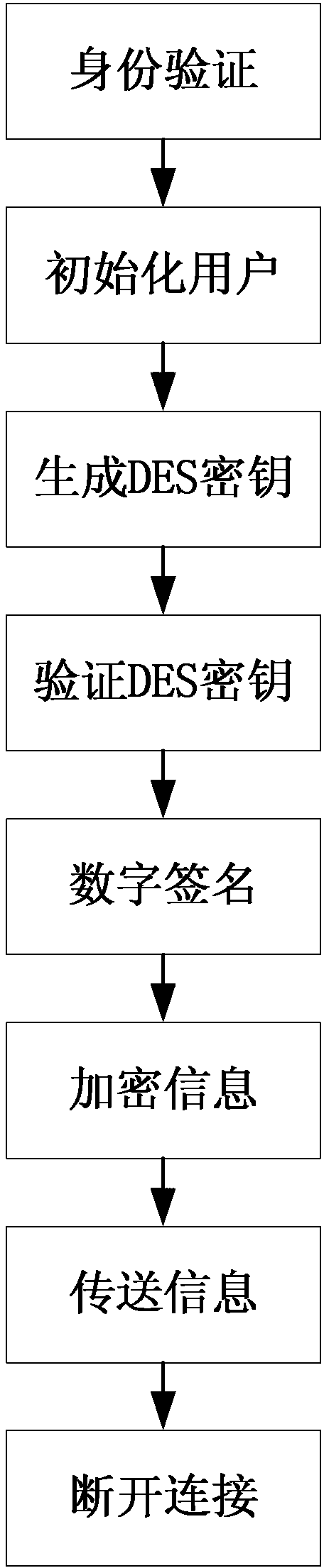
[0040] 1. Server-side information processing (such as image 3 shown)
[0041] (1) Identity verification
[0042] The server-side firewall intercepts user request information,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com