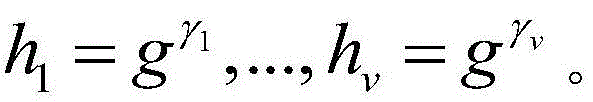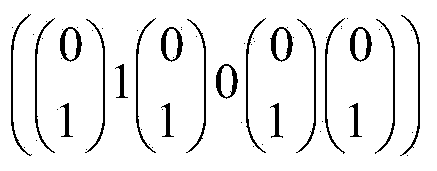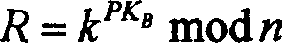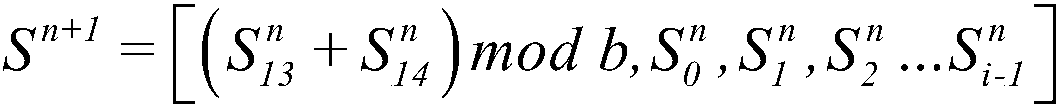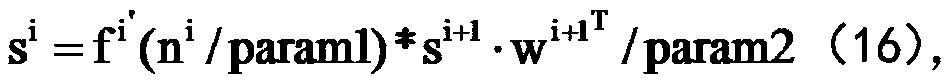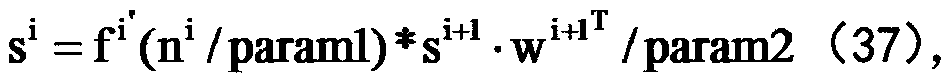Patents
Literature
245results about How to "Fast encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
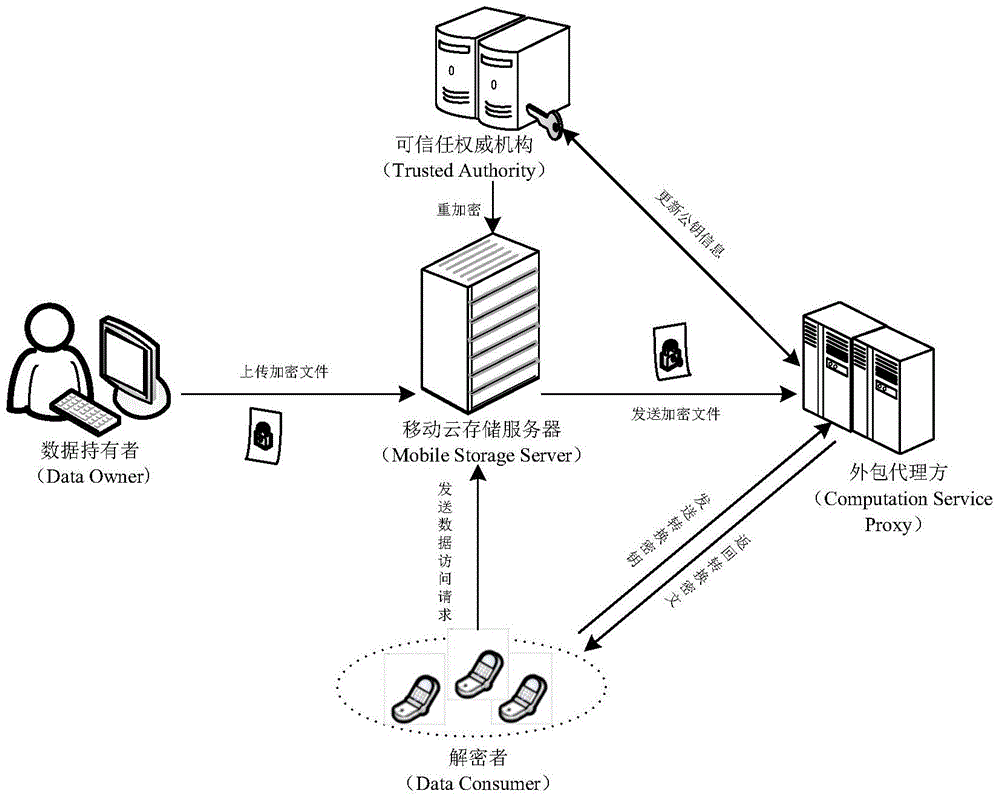
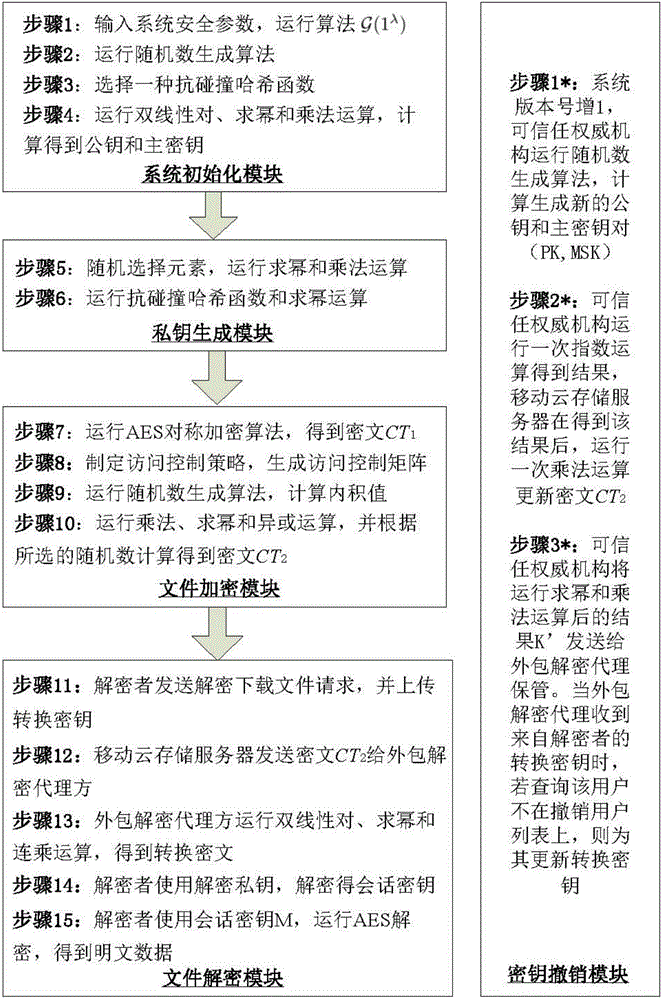
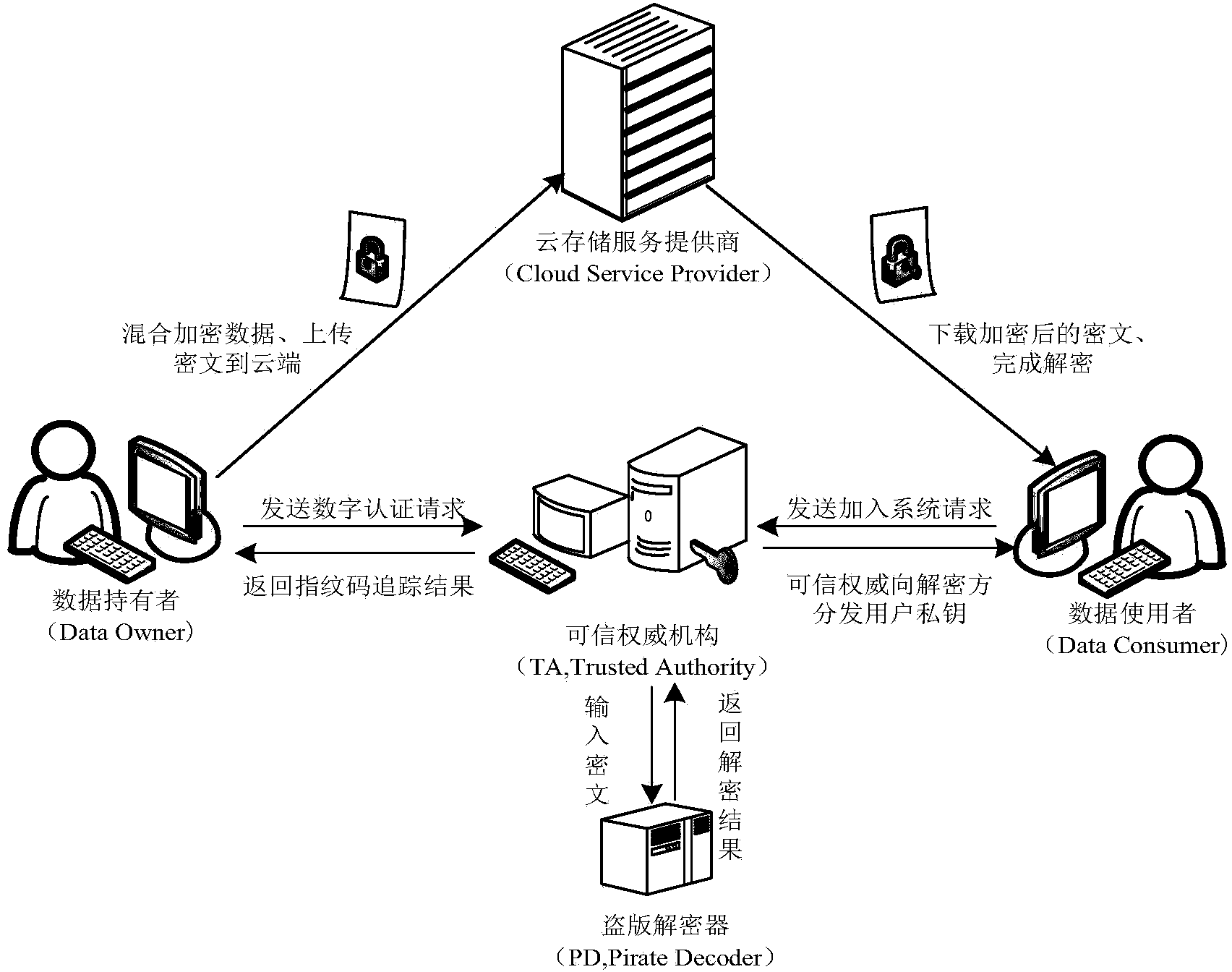
Revocable key external package decryption method based on content attributes
ActiveCN104486315APrevent unauthorized accessProtection securityUser identity/authority verificationComputer hardwareTrusted authority
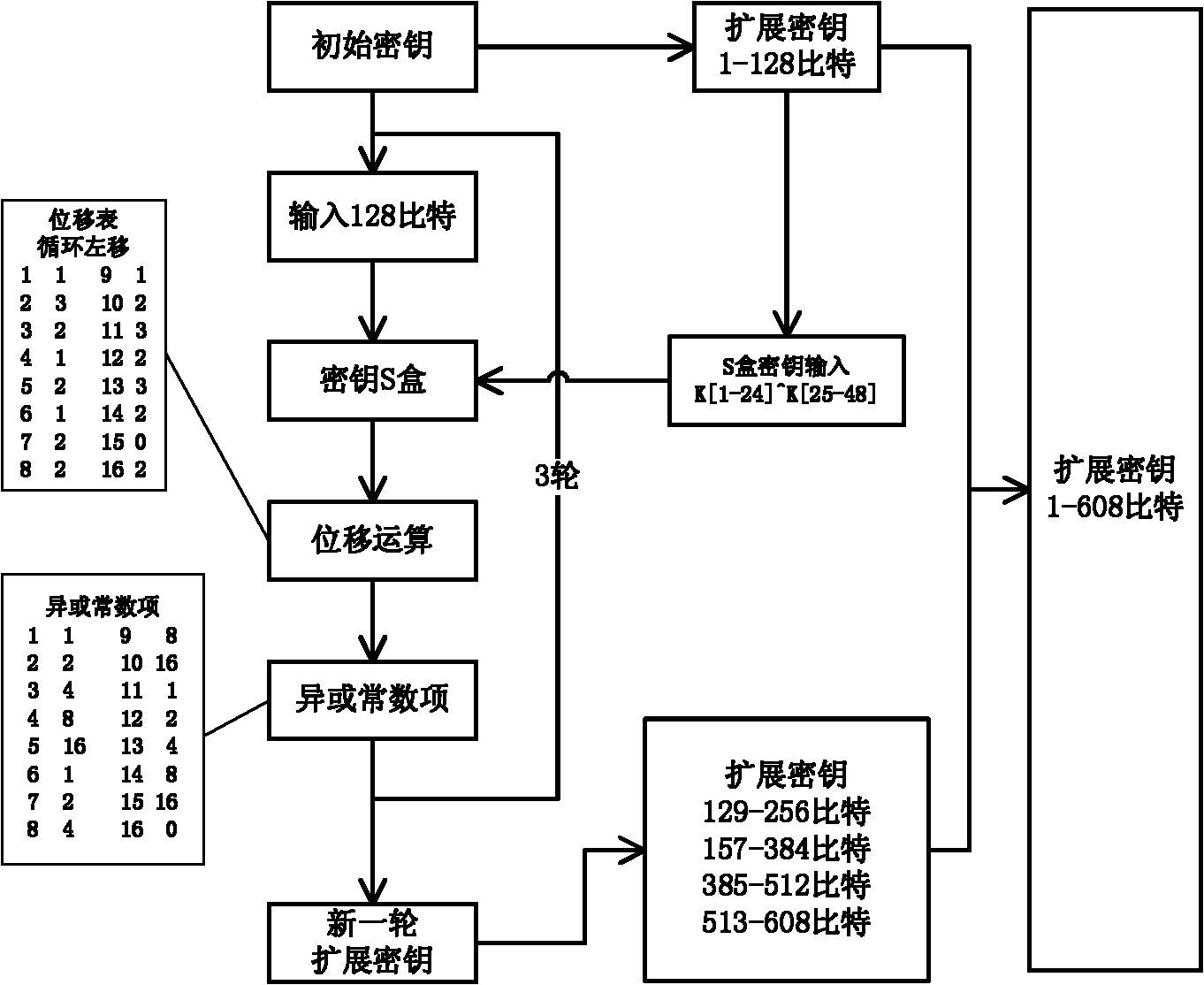
The invention relates to a revocable key external package decryption method based on content attributes. For a trusted authority, 1, initialization is carried out, and system parameters are output; 2, a random number generation algorithm operates; 3, a collision-resistant Hash function is selected, and the Hash value is calculated; 4, a public key and a main key are calculated; 5, the random number is selected, and exponentiation calculation and multiplication are carried out; 6, the collision-resistant Hash function operates, the exponentiation operation is carried out, and a decryption key is obtained. For a data holder, 7, AES data encryption is carried out; 8, an access control matrix is generated; 9, a random number is selected, and an inner product is calculated; 10, multiplication, exponentiation and exclusive-or operation is operated, and ciphertexts are obtained. For a decryption operator, 11, a decryption request and a transformation key are sent. For a mobile storage serve provider, 12, CT2 is sent to an external package decryption agency. For the external package decryption agency, 13, the transformation key is utilized, and the transformation ciphertext is calculated. For the decryption operator, 14, a conversation key is obtained through calculation; 15, AES data decryption is carried out.
Owner:HANGZHOU INNOVATION RES INST OF BEIJING UNIV OF AERONAUTICS & ASTRONAUTICS
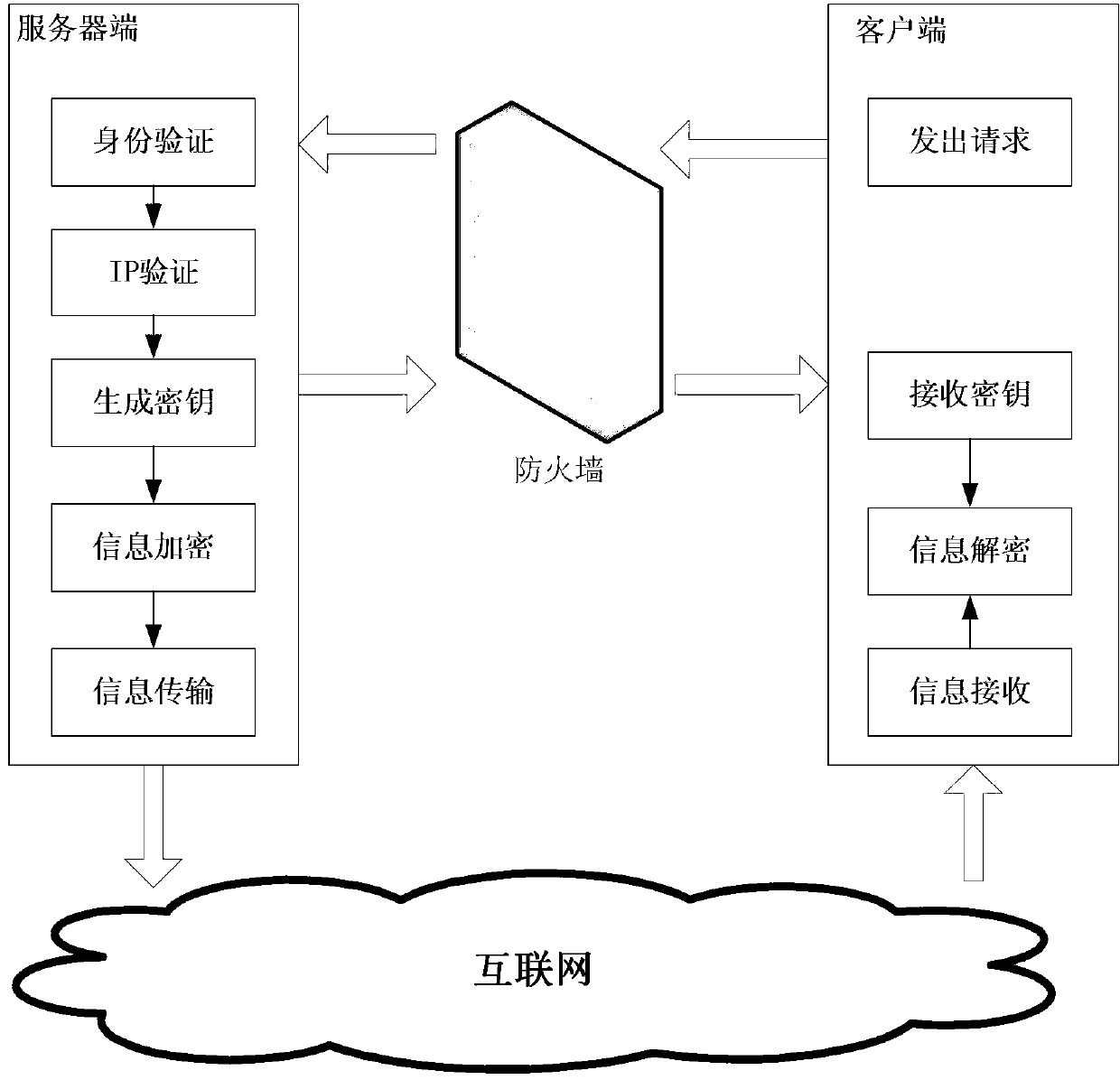
Safe network information transmission method
InactiveCN103001976AReduce the possibilityEnsure safetyUser identity/authority verificationEngineeringServer-side
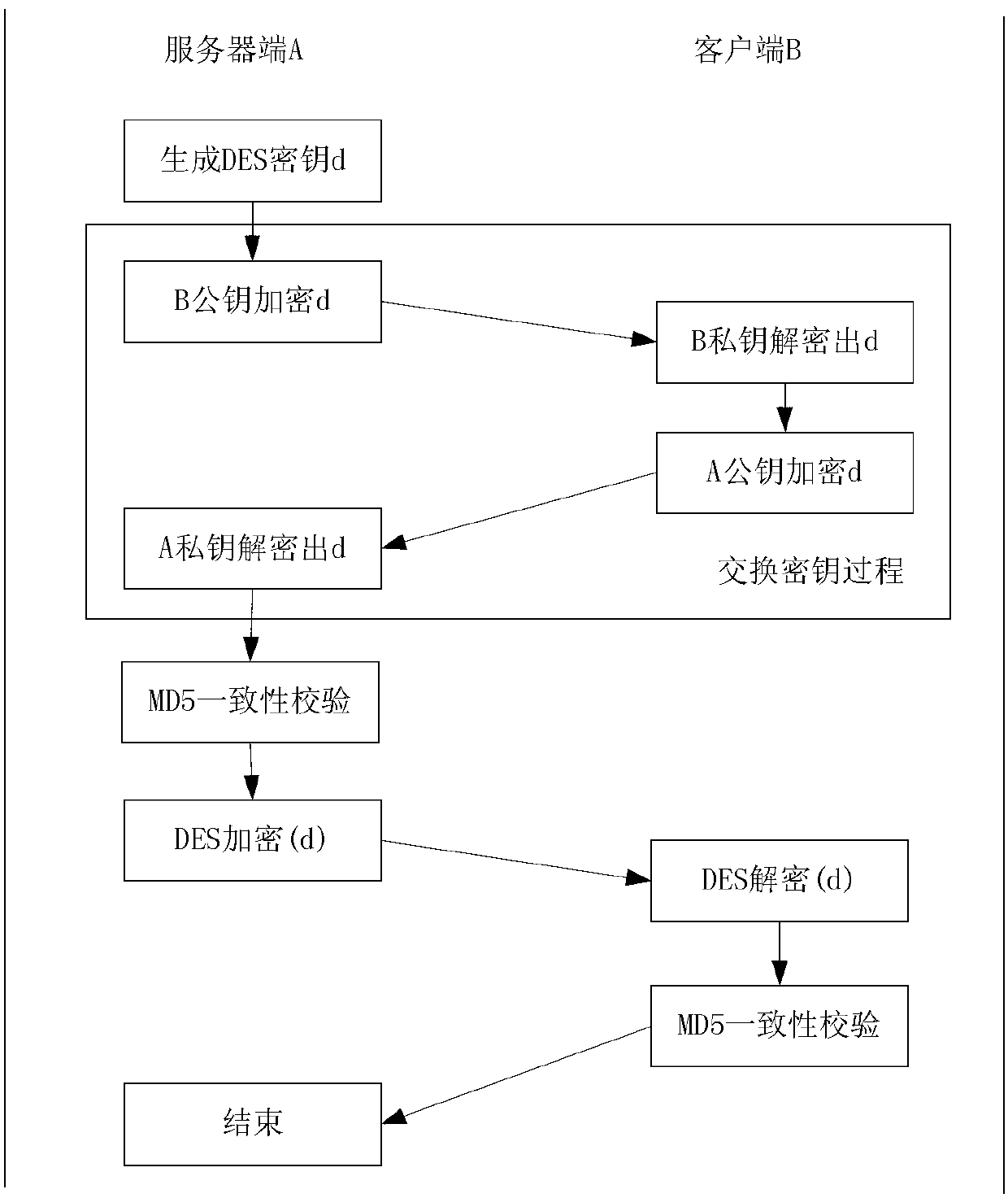
The invention discloses a safe network information transmission method. The method includes that a client sends a service request to a server; a server side verifies a user message in the service request and a client internet protocol (IP) address, and the server side establishes a session with the client if the verification passes; the server side generates a secret key, encrypts the secret key through a public key of the client and sends the secret key to the client; the client decrypts secret key information through a private key, encrypts decrypted secret key information through a public key of the server side and sends the secret key information to the server side; the server side performs digital signature to data of the service request, encrypts the data and digital signature information through the secret key and sends the data and the digital signature information to the client; and the client decrypts the data and performs consistent verification, the information which doesn't pass the consistent verification is discarded, the server side is applied for retransmission, and the information which passes the verification is stored into a local data base. By means of the safe network information transmission method, safety of information transmission is greatly improved.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Block cipher encryption and decryption method
InactiveCN102025484AIncreased confusionImprove throughputEncryption apparatus with shift registers/memoriesS-boxAdvanced Encryption Standard
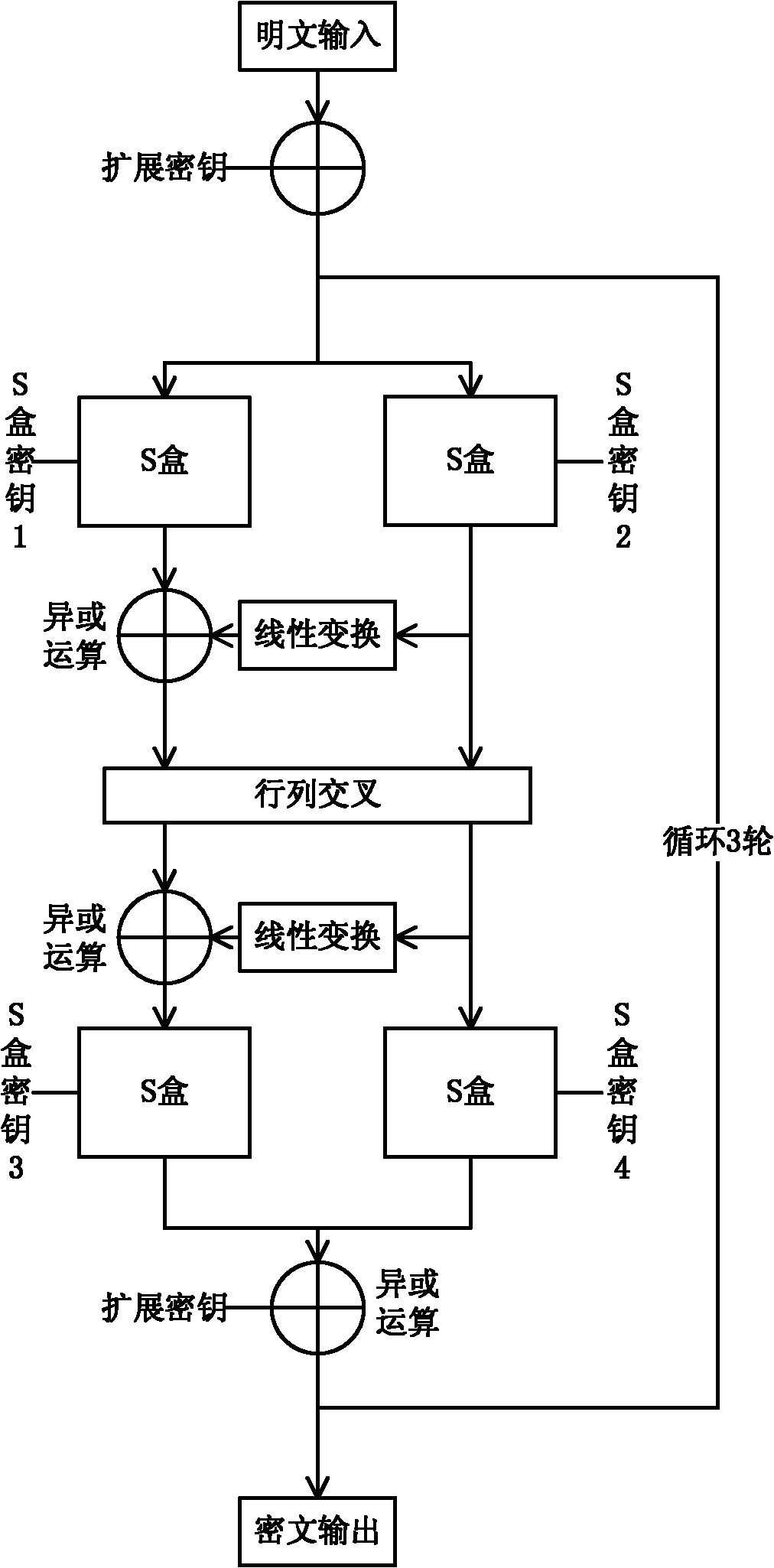
The invention provides a block cipher encryption and decryption method belonging to the field of data encryption and decryption. The algorithm of the invention designs a symmetric encryption structure, especially the S-box design in the invention can configure S transformation required for encryption and S inverse transformation required for decryption without additional circuit resources, thereby being beneficial to the implementation of an encryption / decryption integrated hardware circuit and consuming fewer area resources compared with the AES (advanced encryption standard) encryption / decryption integrated circuit. The complicated S box structure of the algorithm can resist the traditional known attack methods. In case of a small number of encryption rounds (three rounds), a high encryption speed can be provided, and decryption can be carried out at the same speed by using the same encryption and decryption hardware. The algorithm is especially suitable for realizing an ASIC (application specific integrated circuit), and can realize an ASIC chip based on the encryption and decryption special-purpose algorithm. Besides, the invention can be also used for the design of IP cores on FPGA (field programmable gate array). Compared with the AES algorithm, the invention consumes fewer resources on FPGA and has higher speed.
Owner:BEIHANG UNIV
Method for efficiently, parallelly and safely encrypting and decrypting high-capacity data packets
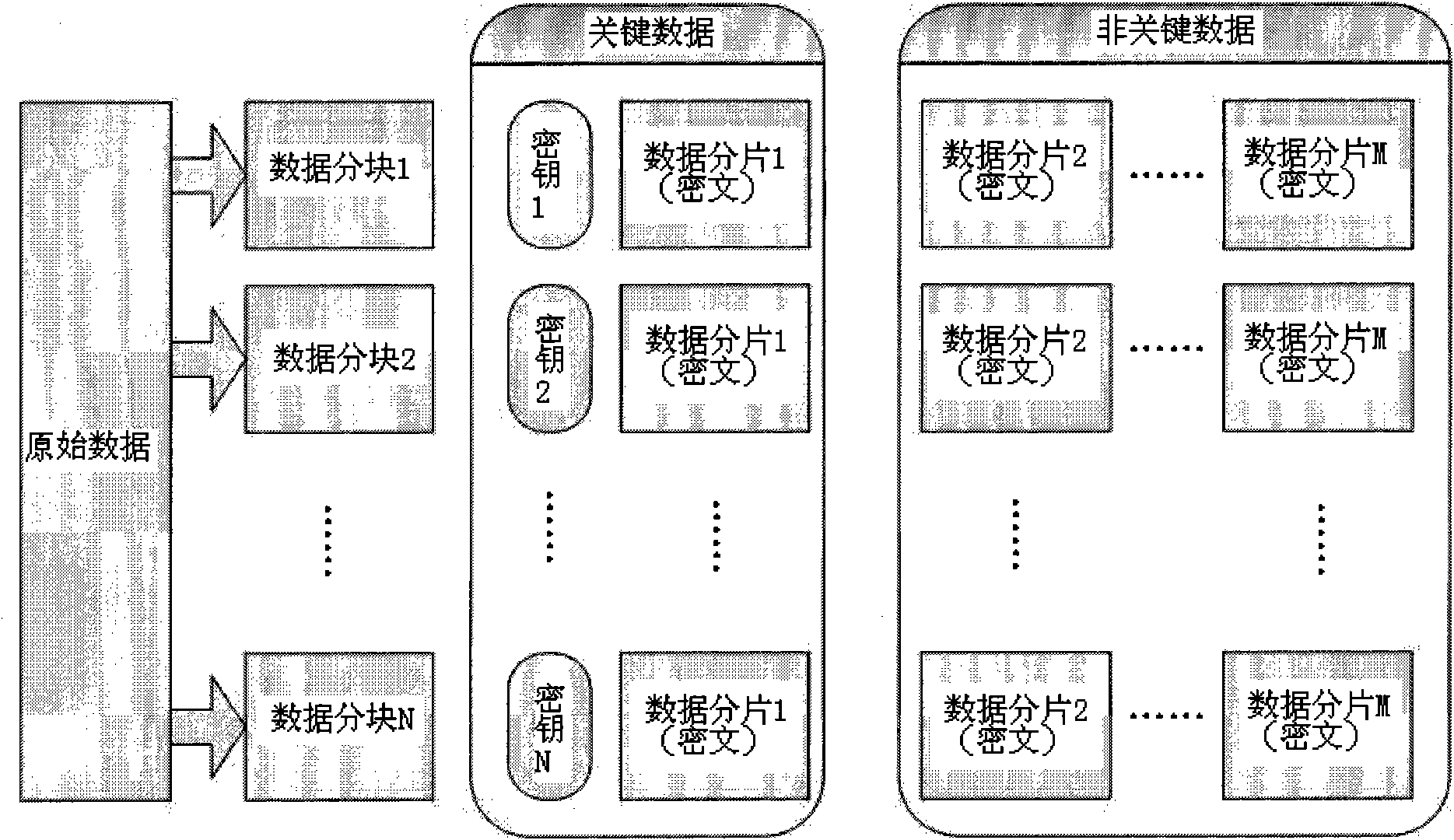
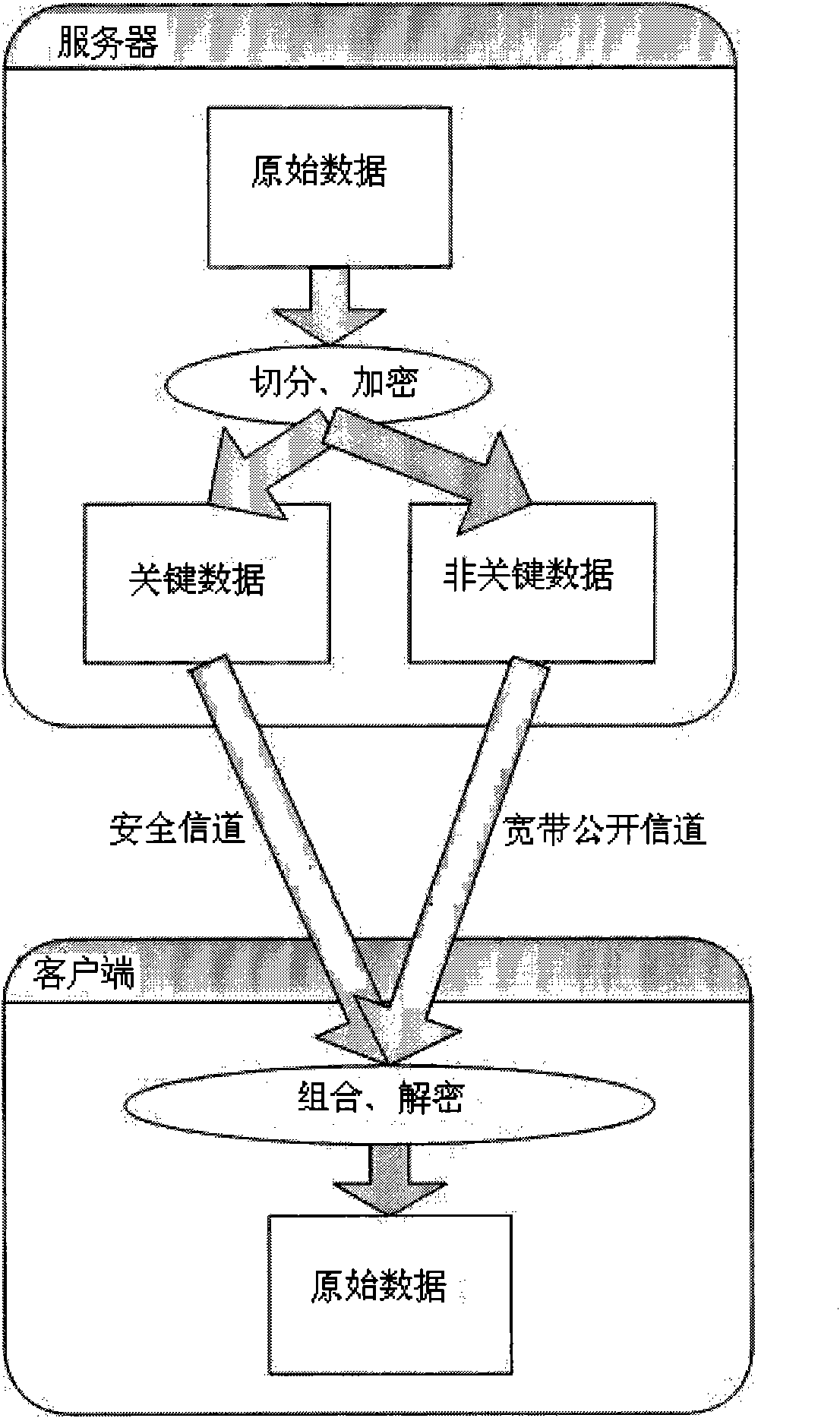
The invention discloses a method for efficiently, parallelly and safely encrypting and decrypting high-capacity data packets, comprising the steps as follows: 1, after a server acquires the high-capacity data packets, the data packets are divided into a fixed number of sub-blocks, and all data sub-blocks are decomposed into the data fragments with a fixed volume; 2, each data fragment is encrypted with randomly generated symmetric encryption keys, and the encryption result of the former data fragment is required to be used when the next data fragment is encrypted; 3, after the encryption is finished, all the symmetric encryption keys and first data fragment ciphertext of each data sub-block are stored together (called key data); and ciphertexts beginning from the second data fragment of each data sub-block are stored together (called non-key data); 4, when a client-side requests for the high-capacity data packets, the server issues the non-key data through public channels and the key data through safe channels; and 5, the client-side carries out decryption in accordance with the opposite encryption sequence. The method provided by the invention is high in safety and transmission efficiency.
Owner:上海盛轩网络科技有限公司
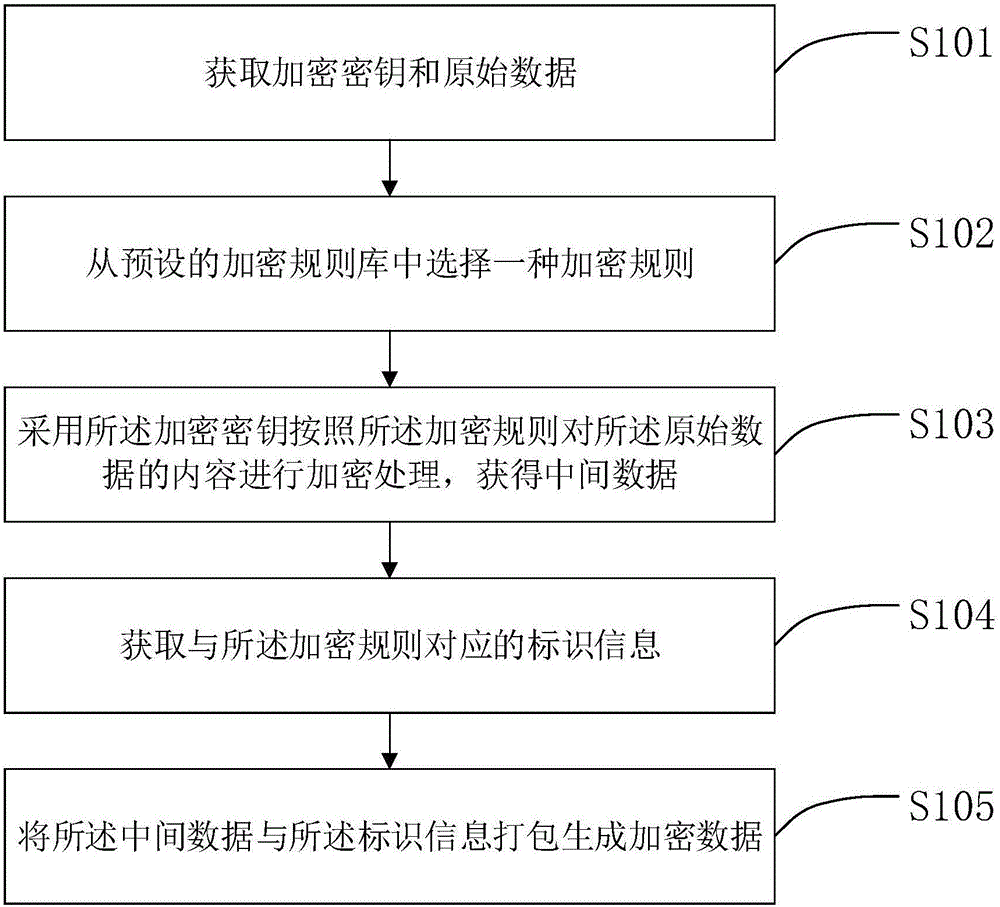
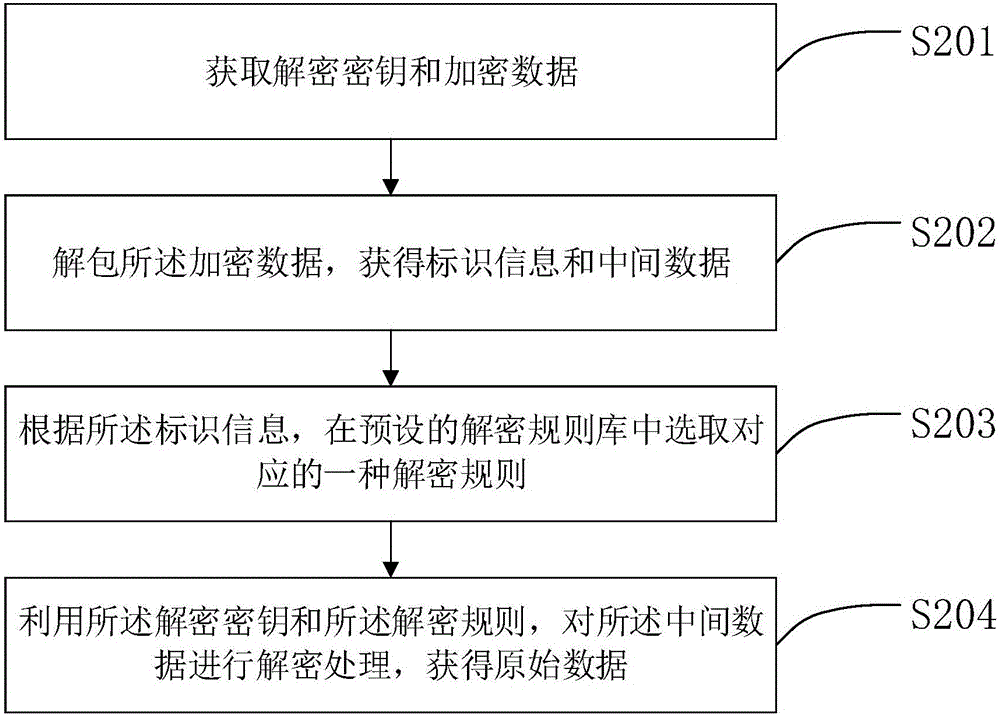
Data encrypting method and device and data decrypting method and device
ActiveCN105760765ARealize multi-dimensional encryptionAvoid crackingEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareOriginal data
The invention relates to the field of data encrypting and decrypting, in particular to a data encrypting method and device and a data decrypting method and device.The data encrypting method comprises the steps that at first, an encryption key and original data are obtained; then, an encryption rule is selected from a preset encryption rule base; the encryption key is adopted for encrypting the original data according to the encryption rule to obtain intermediate data; then, identification information corresponding to the encryption rule is obtained; finally, the intermediate data and the identification information are packaged to generate encrypted data.Compared with the prior art, encryption information does not only depend on the carrier key, the encryption rule is selectively used, and the encryption rule is encrypted; meanwhile, in the file transmitting process, only the identification information of the encryption rule exists in the transmission information, and the specific content of the encryption rule does not exist, so that multi-dimensional encryption is achieved, the encryption means is more complex, the key can not be decrypted easily, and encryption safety is higher.
Owner:BEIJING SEEYON INTERNET SOFTWARE CORP
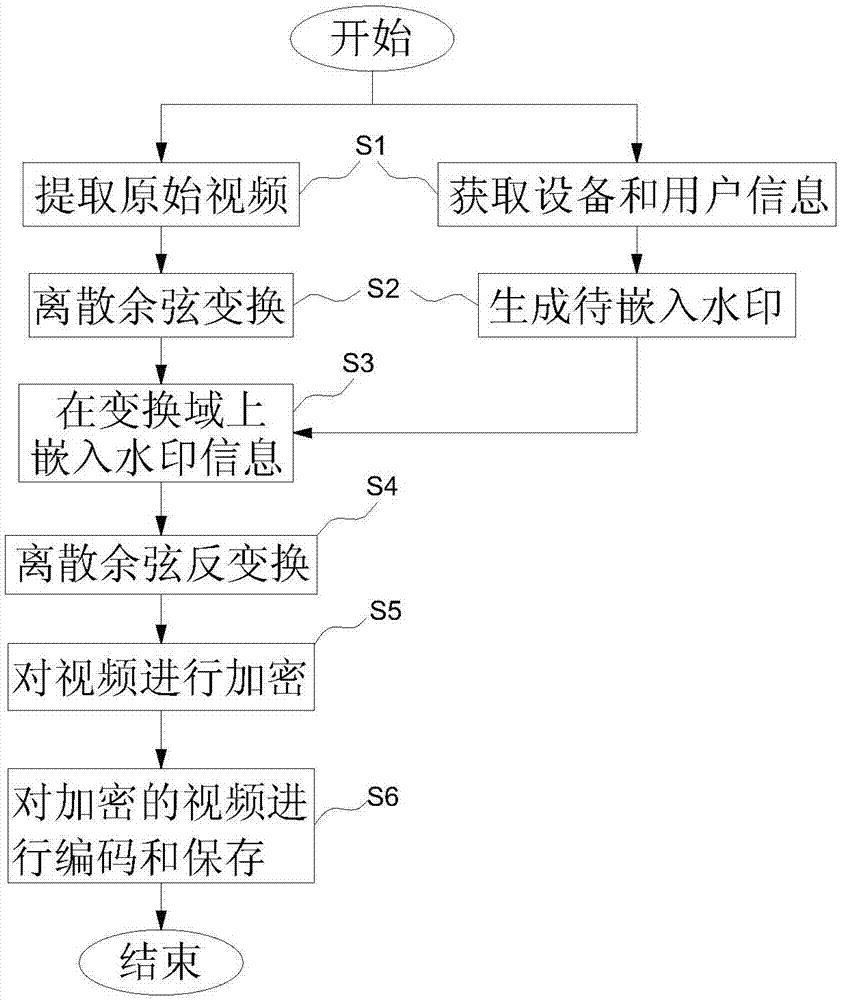
Video source tracing and encryption method based on watermark technology
InactiveCN107027055AAvoid damageGuaranteed video qualityDigital video signal modificationSelective content distributionSource tracingExtraction algorithm
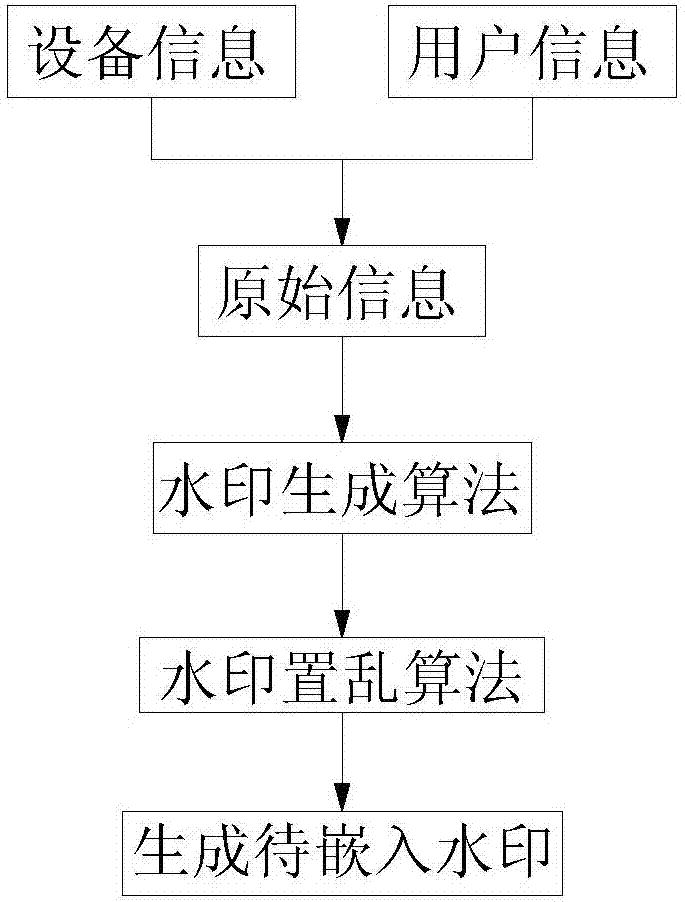
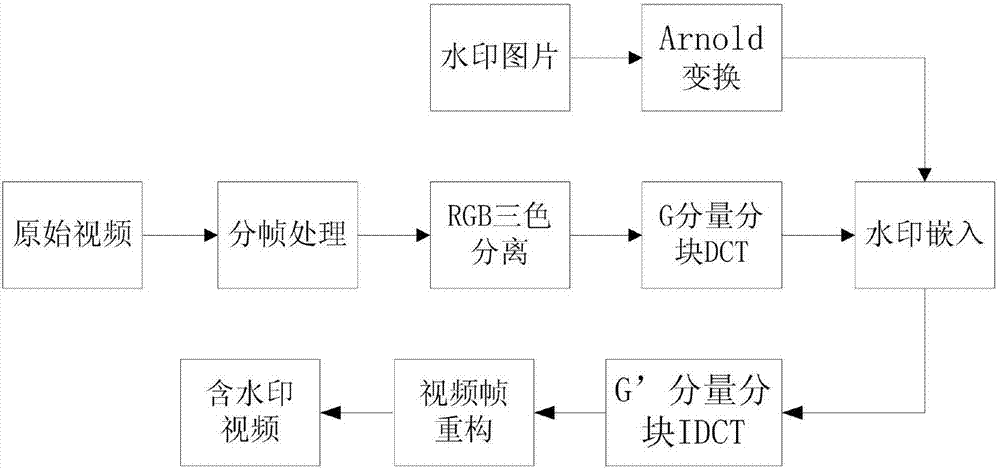
The invention relates to a video source tracing and encryption method based on a watermark technology. The method comprises the steps of extracting an original video and obtaining device information and user information; transforming the original video from a time domain to a frequency domain through adoption of a discrete cosine transform algorithm, and generating a to-be-embedded watermark through adoption of a watermark generation algorithm; embedding the to-be-embedded watermark through adoption of a watermark embedding algorithm, thereby generating the video containing the watermark; generating a time domain video containing the watermark through adoption of an inverse transform algorithm; carrying out encryption through adoption of a key frame extraction algorithm and a video head information encryption algorithm, thereby forming an encrypted video file; and coding and storing the encrypted video file. According to the method, the generated video containing the watermark is good in quality, high in concealment and security and good in video sensuality; the method is good in encryption effect and high in security; relatively good source tracing and encryption effects are achieved; the video sharing security and circulation traceability are realized.
Owner:ANHUI SUN CREATE ELECTRONICS
Single-point login method under point-to-point model
ActiveCN101286843AReduce the burden onImprove operational efficiencyPublic key for secure communicationUser identity/authority verificationService modeSecure channel
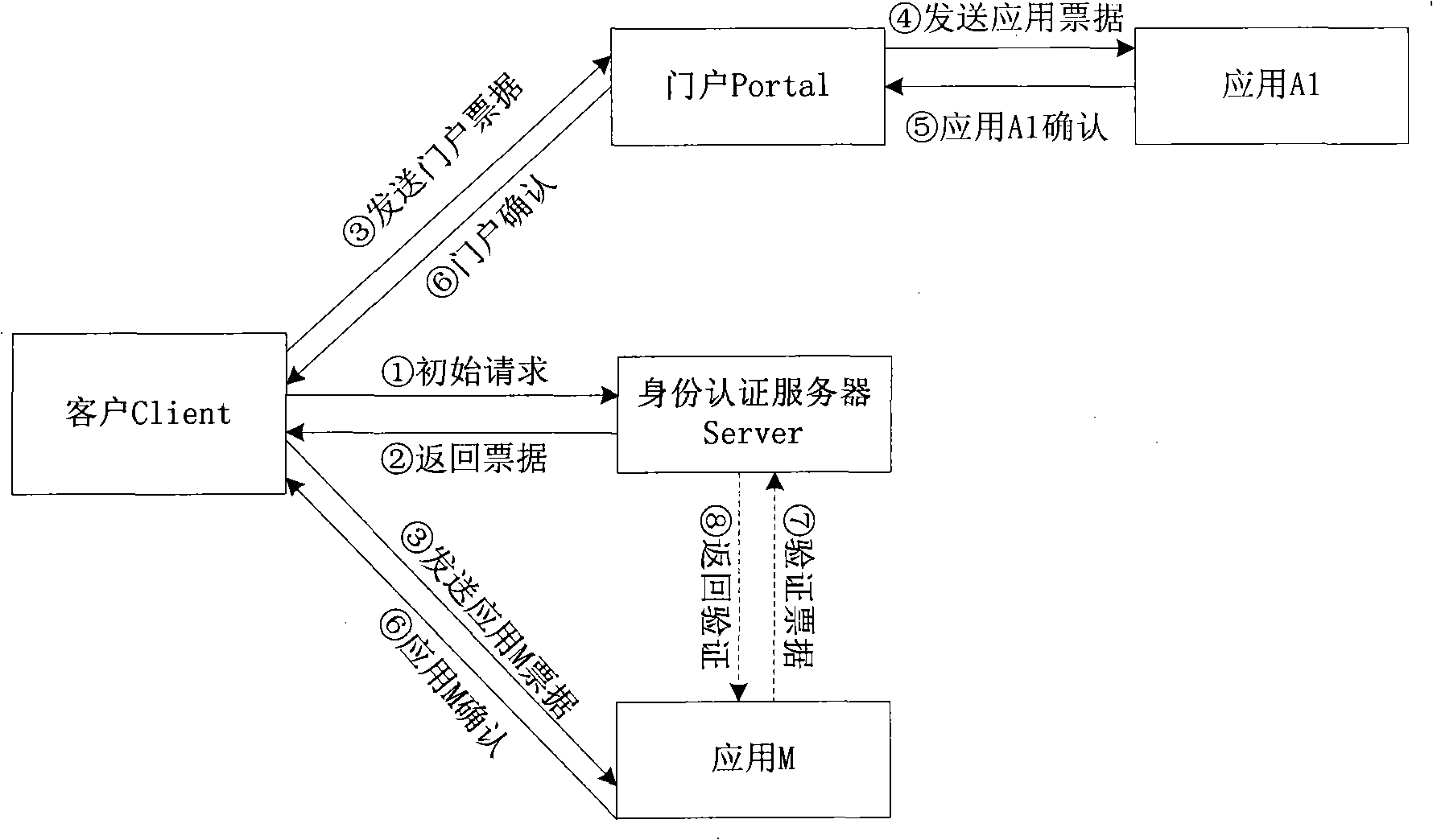
The invention relates to a single sign-on method in a point to point mode. Being different from the existing single sign-on method based on a customer server mode, the method manages the single sign-on life cycle of a customer by using valid period of certificate of the customer, and the customer can sign on for a plurality of times with single certification. The method completes the cross-certification of an application system and an identity certification server; the shared encryption key of communication parties is initialized, and a safe channel between the customer and the application system is established. Through the the identity certification server and the cross-certification of the application system, any application system can independently carry out identity certification, thus weakening the status of a central identity certification server, avoiding the defect of single-point failure in traditional customer / service mode and being characterized by low cost for system operation, high efficiency and good safety performance.
Owner:江西省电力信息通讯有限公司
Homomorphic encryption-based position privacy querying method
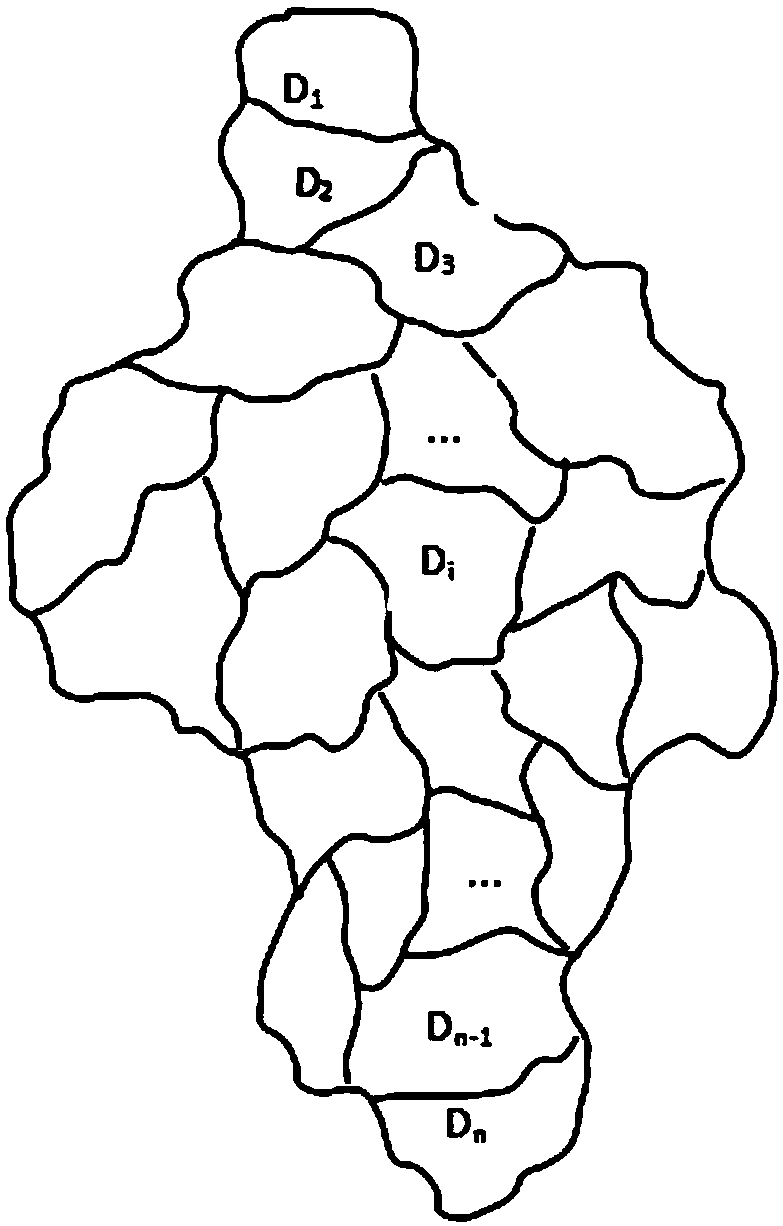
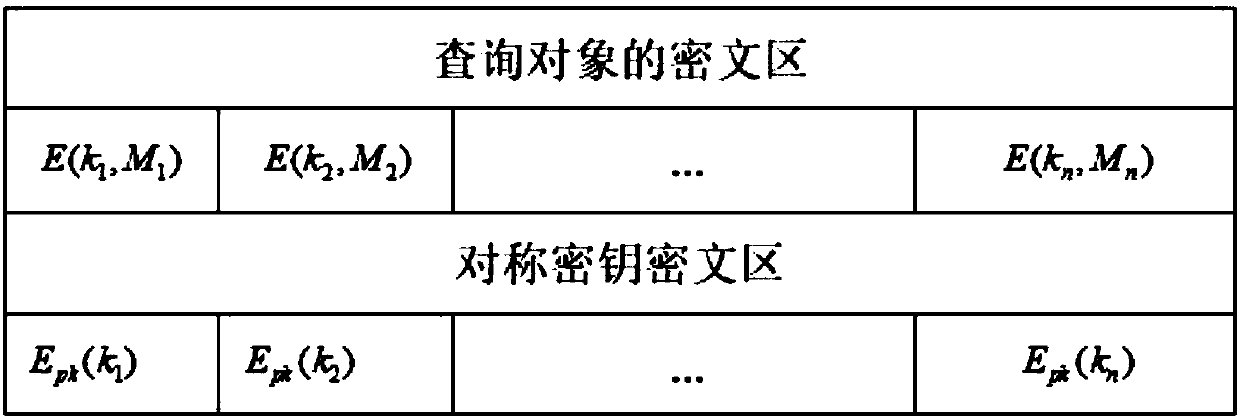
ActiveCN107749865AGuaranteed privacyFast encryptionKey distribution for secure communicationCommunication with homomorphic encryptionPlaintextCiphertext
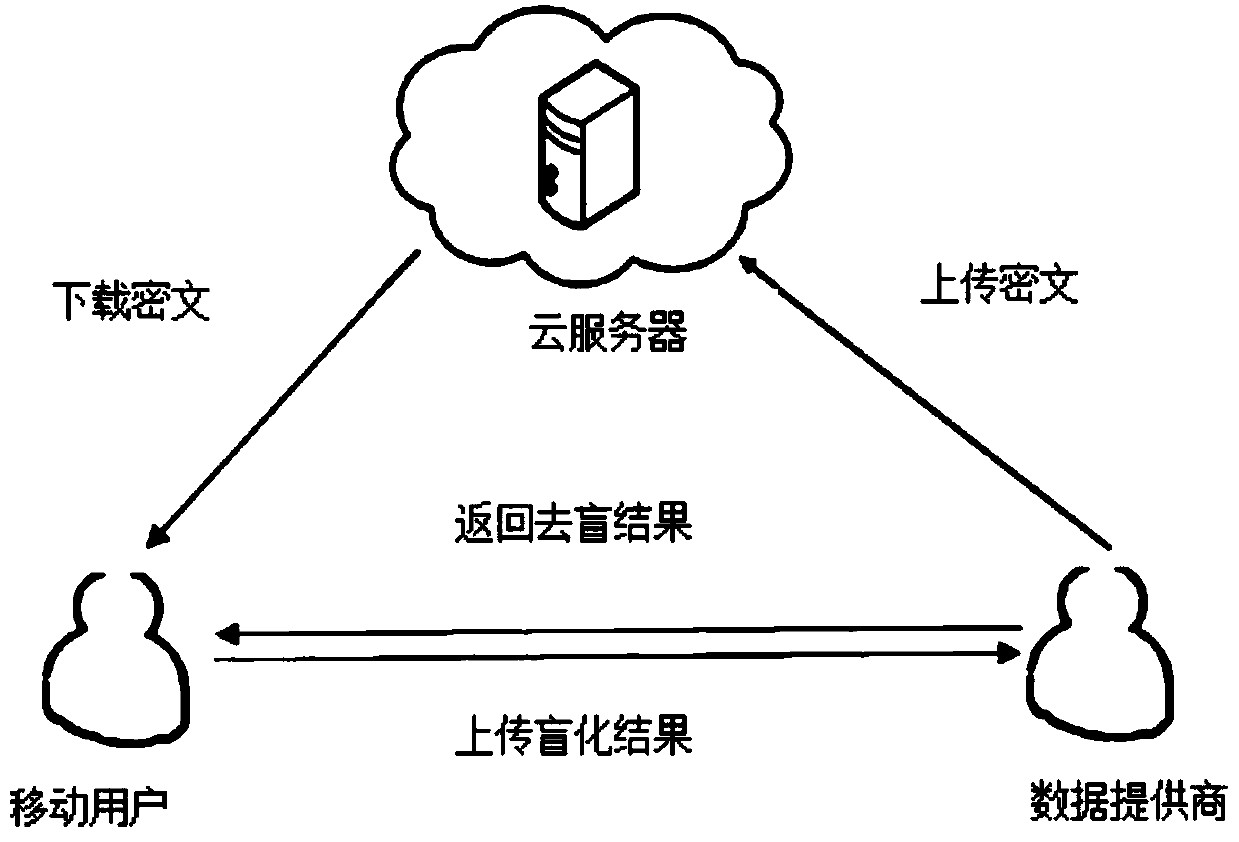
A homomorphic encryption-based position privacy querying method disclosed by the present invention comprises a cloud server, a data service provider and a plurality of mobile users. The data service provider SP partitions the areas in a map according to the intensity of the querying objects, then encrypts the querying objects in the partitions via a symmetric encryption algorithm, and encrypts thesymmetric secret keys via a homomorphic encryption algorithm, and finally stores all ciphertexts in the cloud server, thereby secretly saving the private keys of the homomorphic encryption. Users download the ciphertexts of the querying objects and the corresponding symmetric secret key ciphertexts from the cloud server according to the own positions, and further carry out the blind processing onthe symmetric secret key ciphertexts and transmit to the data service provider, and the data service provider transmits the decrypted blind plaintexts to the users, and finally, users decrypt the corresponding querying objects to obtain the final query results. According to the present invention, the position information of the users is not leaked during the whole process, thereby protecting theposition privacy.
Owner:安徽迪科数金科技有限公司
Improved SM4 parallel encryption and decryption communication method based on GPU (Graphics Processing Unit)
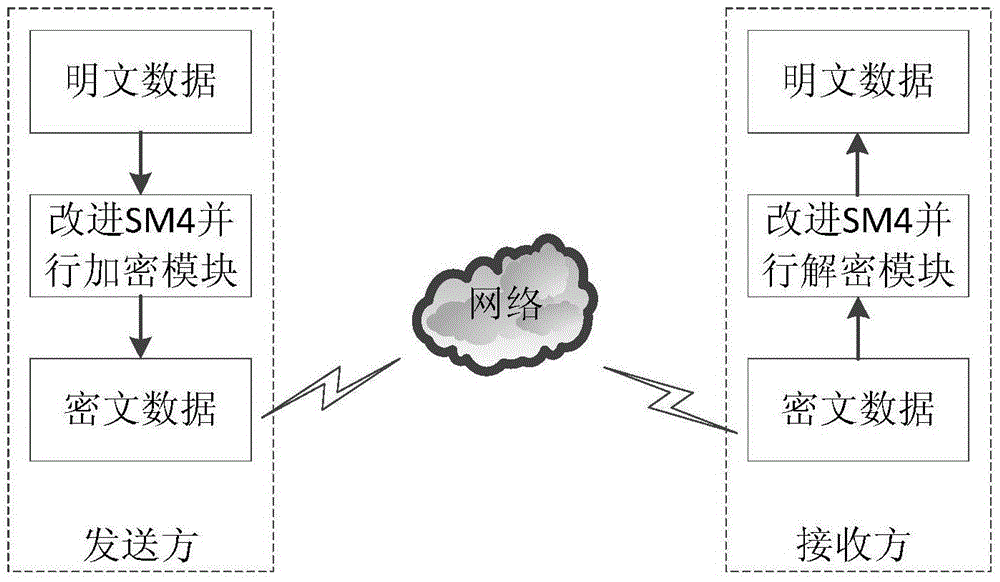
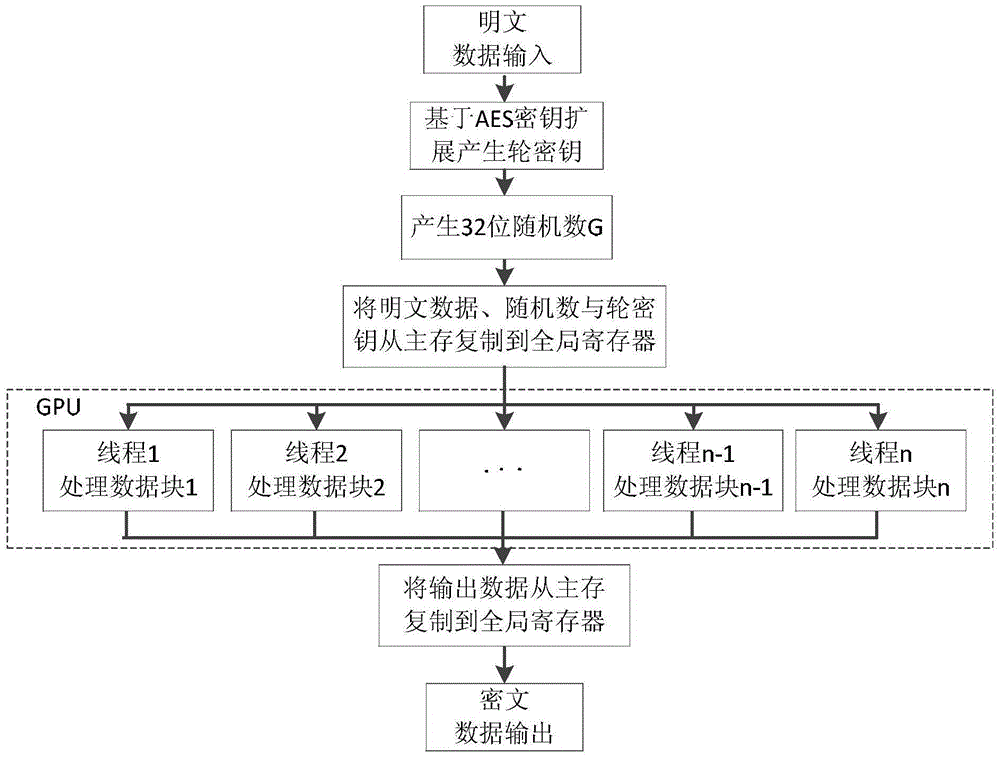
ActiveCN105490802AFast implementationImprove securityEncryption apparatus with shift registers/memoriesComputer hardwareData stream
The invention discloses an improved SM4 parallel encryption and decryption communication method based on a GPU (Graphics Processing Unit). The encryption and decryption method comprises the following steps: using an AES (Advanced Encryption Standard)-128 key expansion algorithm to generate an expanded subkey needed by an SM4 encryption algorithm; improving a round function in the SM4 encryption algorithm; and using the parallel computing power of the GPU, improving the SM4 encryption algorithm into a form of parallel encryption. By adopting the encryption and decryption communication method of the invention, the security and the speed of implementation can be effectively improved, real-time and parallel encryption can be performed on data, and the encryption speed can be improved, so that normal transmission of data flow can be guaranteed and the processing delay can be reduced.
Owner:桂林蓝港科技有限公司
Attribute-based hybrid encryption method capable of tracing leaked secret key
ActiveCN104168108AEnsure safetyAvoid destructionEncryption apparatus with shift registers/memoriesUser identity/authority verificationTrusted authorityHash function
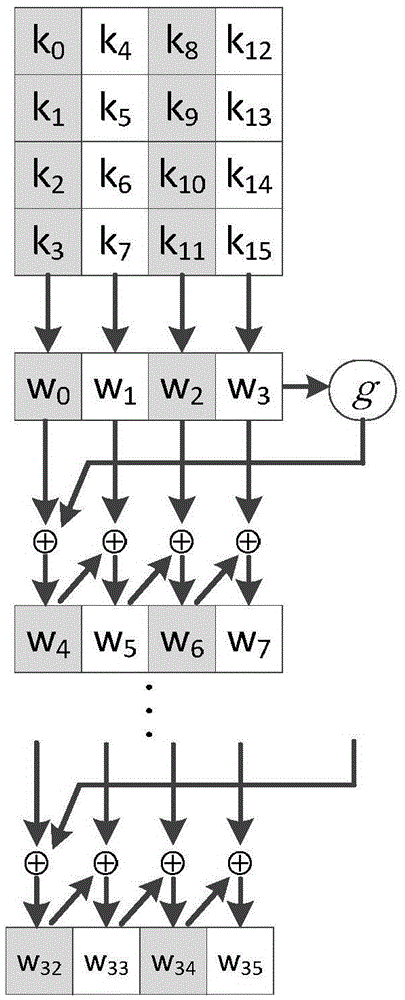
Disclosed is an attribute-based hybrid encryption method capable of tracing a leaked secret key. The method comprises the following steps: a trusted authority: 1, inputting a coefficient lambda, and outputting a system parameter; 2, running a randomized number generation algorithm; 3, selecting one anti-bump Hash function, and calculating a Hash value; 4, running a fingerprint code generation algorithm GenFC; 5, calculating a bilinear pair exponentiation operation; 6, distributing a fingerprint code to a user, and specifying an attribute set S; 7, running the randomized number generation algorithm, multiplication and exponentiation operation; and 8, embedding the fingerprint code in a user private key; a data holder: 9, carrying out AES data encryption; 10, generating an access control matrix; 11, running an attribute-based hybrid encryption algorithm Encapsulate, and encrypting an AES session secret key; and 12, running a bilinear pair and multiplication and division operation to obtain a session secret key; a data user: 13, running an AES data decryption algorithm; and the trusted authority: 1*, searching for an adaptability code word; 2*, calculating pj and Z; and 3, calculating a weight sum, and outputting a set C.
Owner:BEIHANG UNIV
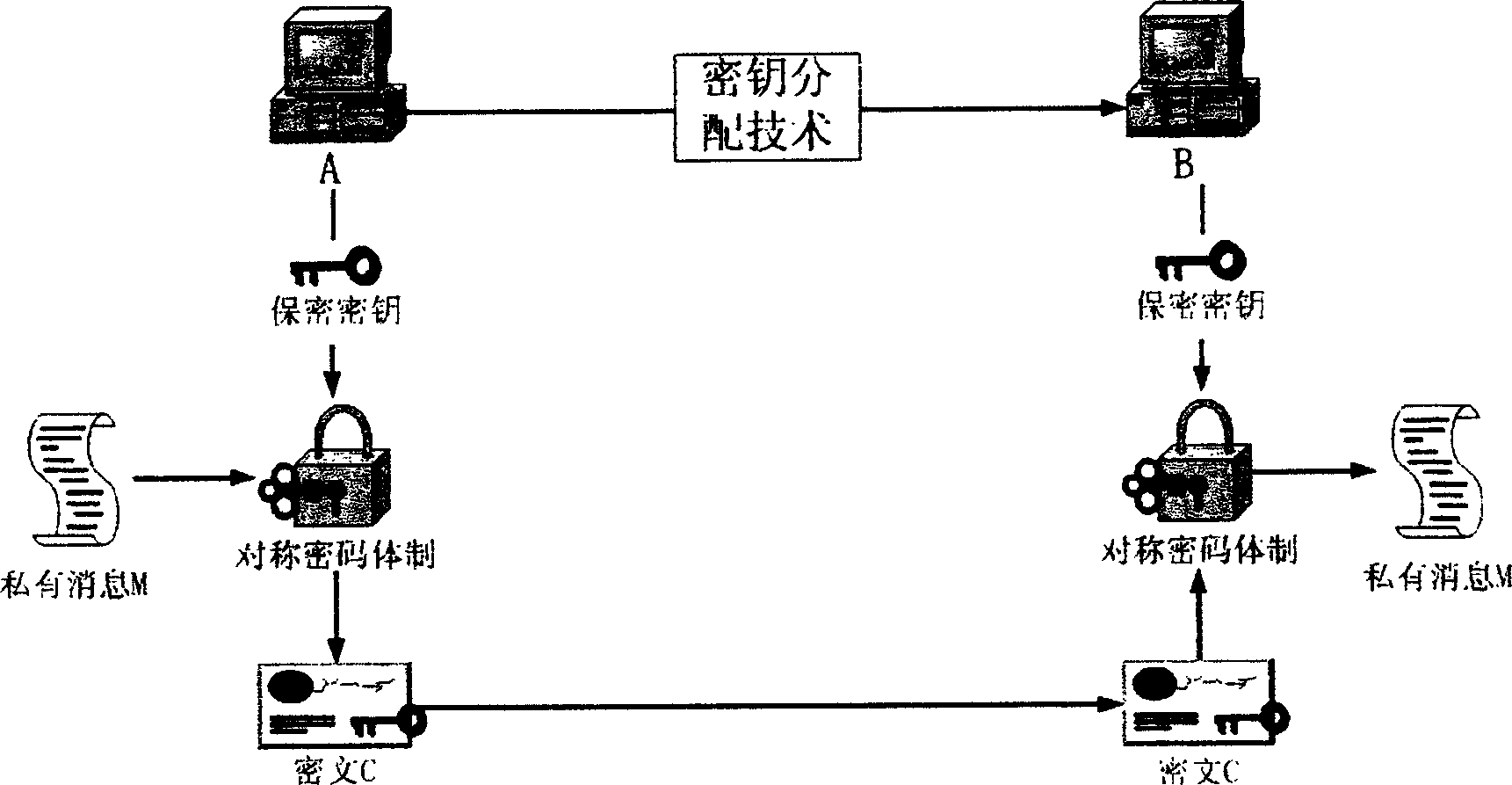
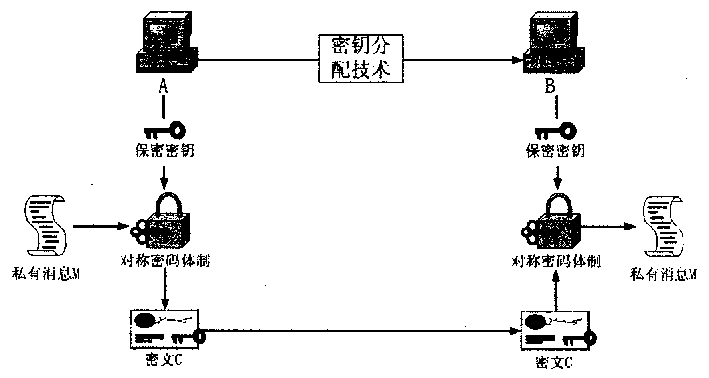
High performance and quick public pin encryption
The present invention relates to a fast and high efficient public key encrypting method. The two parties of communication are A and B, they have the private keys and public keys respectively, which are stored in the trustable verification center of the third party. 1. A produces randomly one of some temporary secret-key and encrypts the private information using the symmetric secret-code encrypting system to acquire encrypted file; 2. A converts the secret-key selected presently into an assigned file using the secret-key assigning technique of the public key secret-code system and using the public key of the receiving part B, and then transmits the secret-key assigning file and encrypted file to the receiving party; 3. The receiving party acquires the secret-key assigned by the transmitting party using his own private key.
Owner:WUHAN UNIV OF TECH
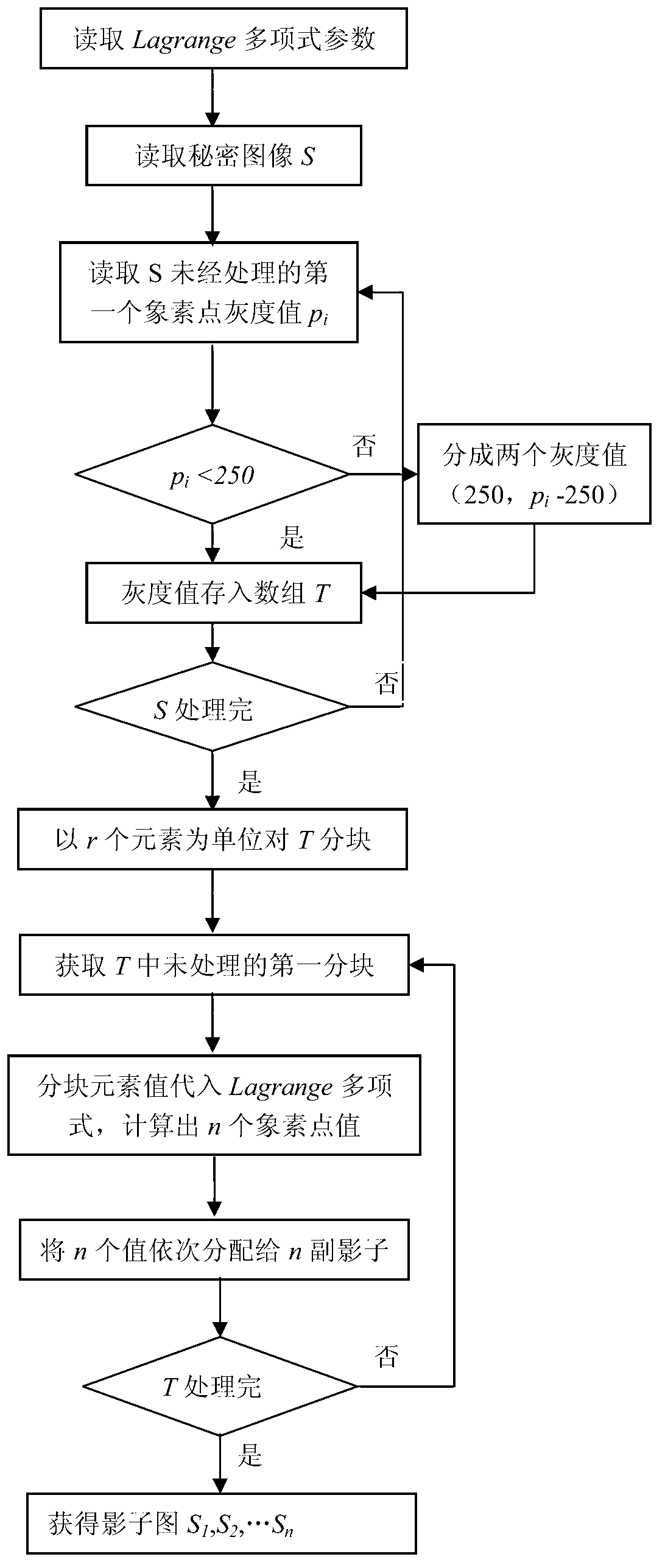
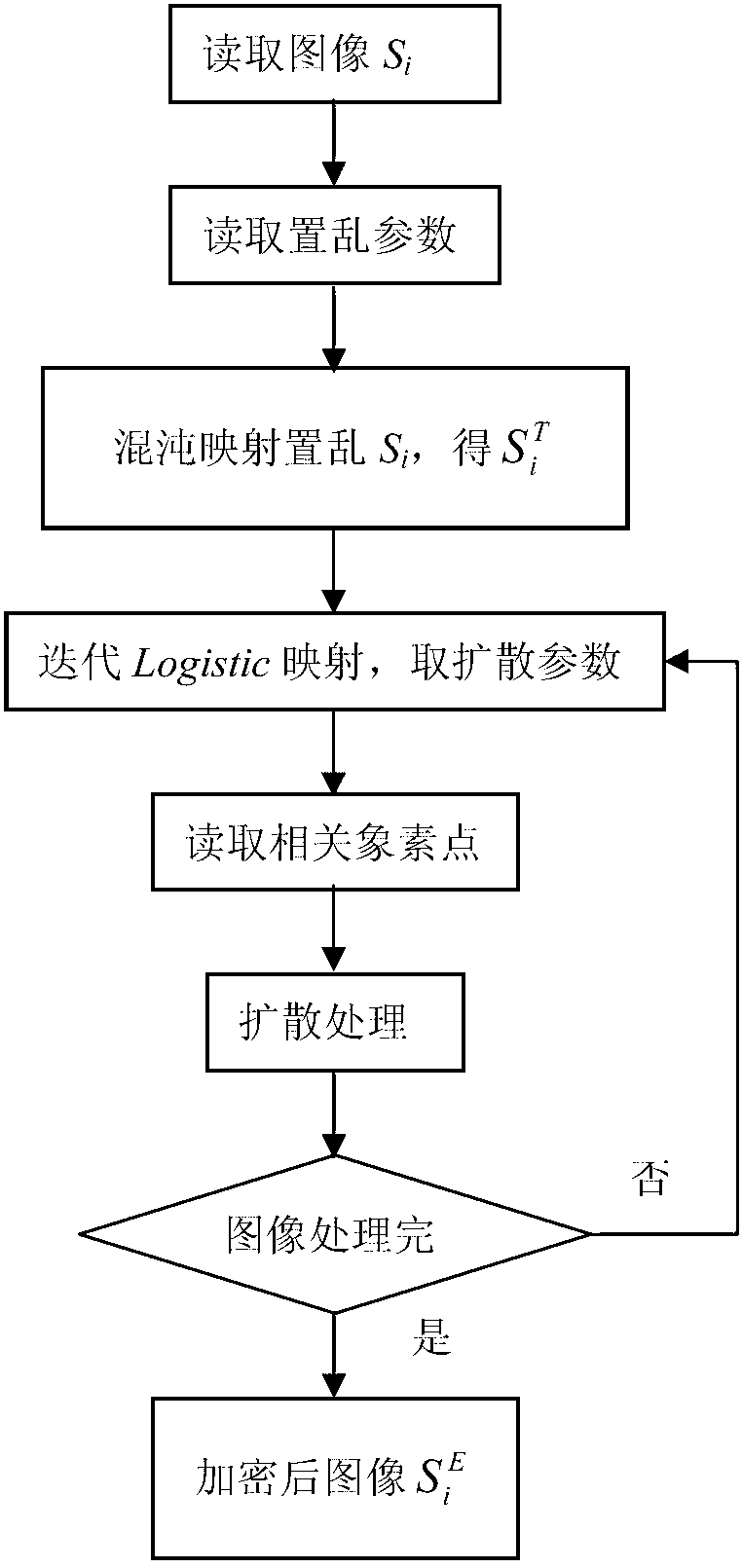
Chaotic-encryption-based medical image share method
ActiveCN103226802AImplement integrity verificationMeet confidentiality requirementsImage data processing detailsSecret shareConfidentiality
The invention discloses a chaotic-encryption-based medical image share method which comprises a secret image breakdown step, a chaotic image encryption step, a chaotic image decryption step and a secret image recovery step. According to the invention, a threshold secret share scheme is utilized to divide an image into n shadow images, the chaos principle is utilized to encrypt the n shadow images, the encrypted shadow images have the statistical property of white noise, and the collected r shadow images are utilized to recover the secret image. The chaotic-encryption-based medical image share method facilitates data storage and transmission, ensures confidentiality and integrity of significant images, and has strong anti-attack capacity.
Owner:CENT SOUTH UNIV
Medical image encryption method based on uniform scrambling and chaotic mapping
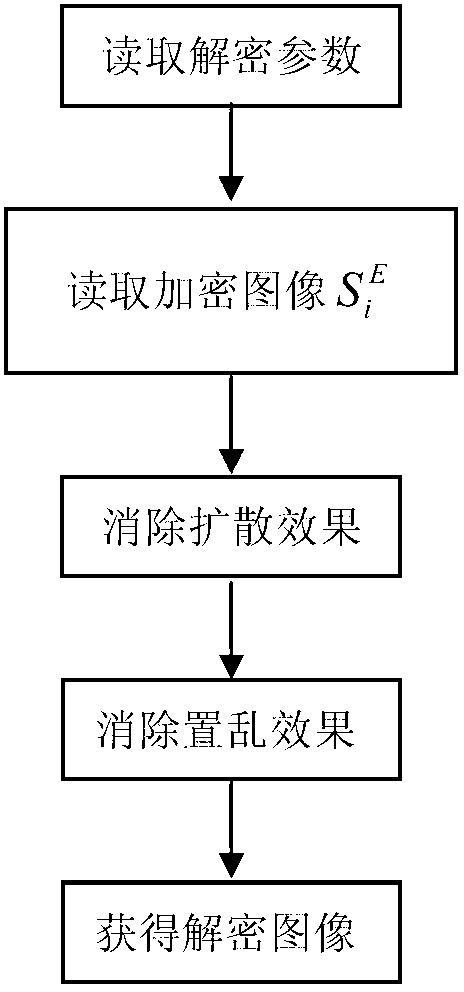
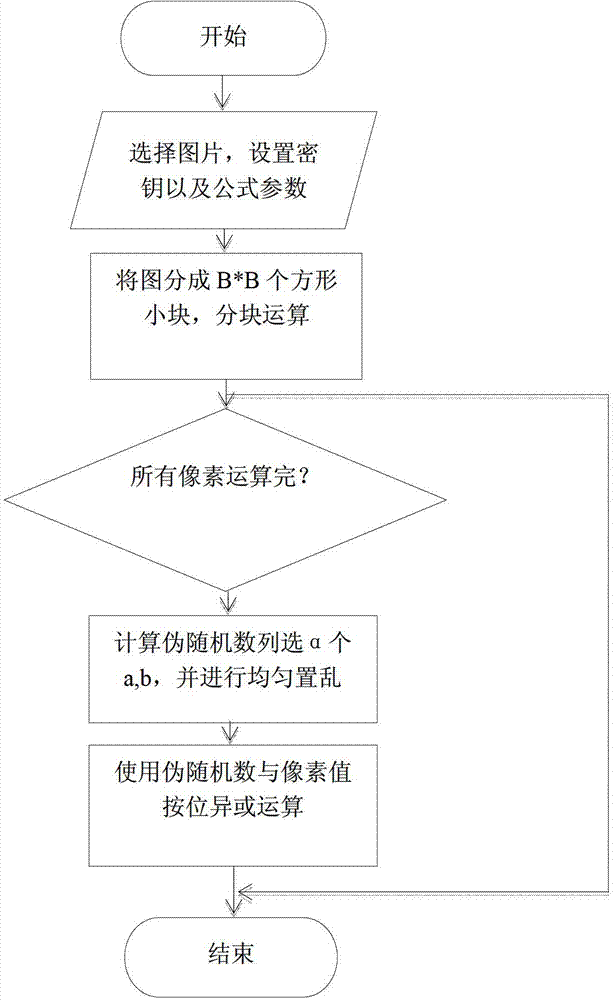
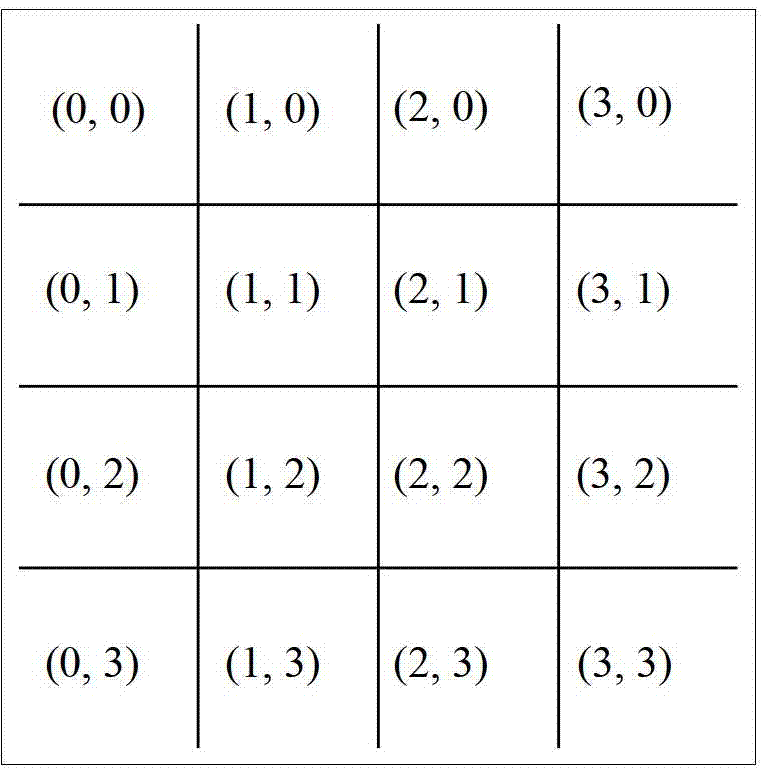
ActiveCN103248854AFast encryptionEasy to coverTelevision system detailsColor television detailsPasswordEncryption
A medical image encryption method based on uniform scrambling and chaotic mapping, belongs to the technical field of network image communication, and includes the following steps: 1, arranging a secret key and generating a random number sequence; 2, dividing a medical image into a plurality of small squares; 3, performing uniform scrambling operation to the medical image; 4, multiplying the generated pseudo random number by a pixel factor, 5, performing round-off and then performing xor with the original pixel; and performing the steps 1 to 5 repeatedly for all the pixels, traversing the medical image and summarizing all the pixels, and finally finishing the image encryption. The medical image encryption method based on uniform scrambling and chaotic mapping, provided by the invention, is simpler and quicker in encryption compared with the conventional method, can better cover the two-dimensional information of the image compared with the dimensional flow password encryption method, and lays emphasis on misdiagnose danger caused by falsification attack and has better falsification attack resistance especially in the field of medical image encryption.
Owner:辽宁然辉科技有限公司
An audio coding selective cryptographic method
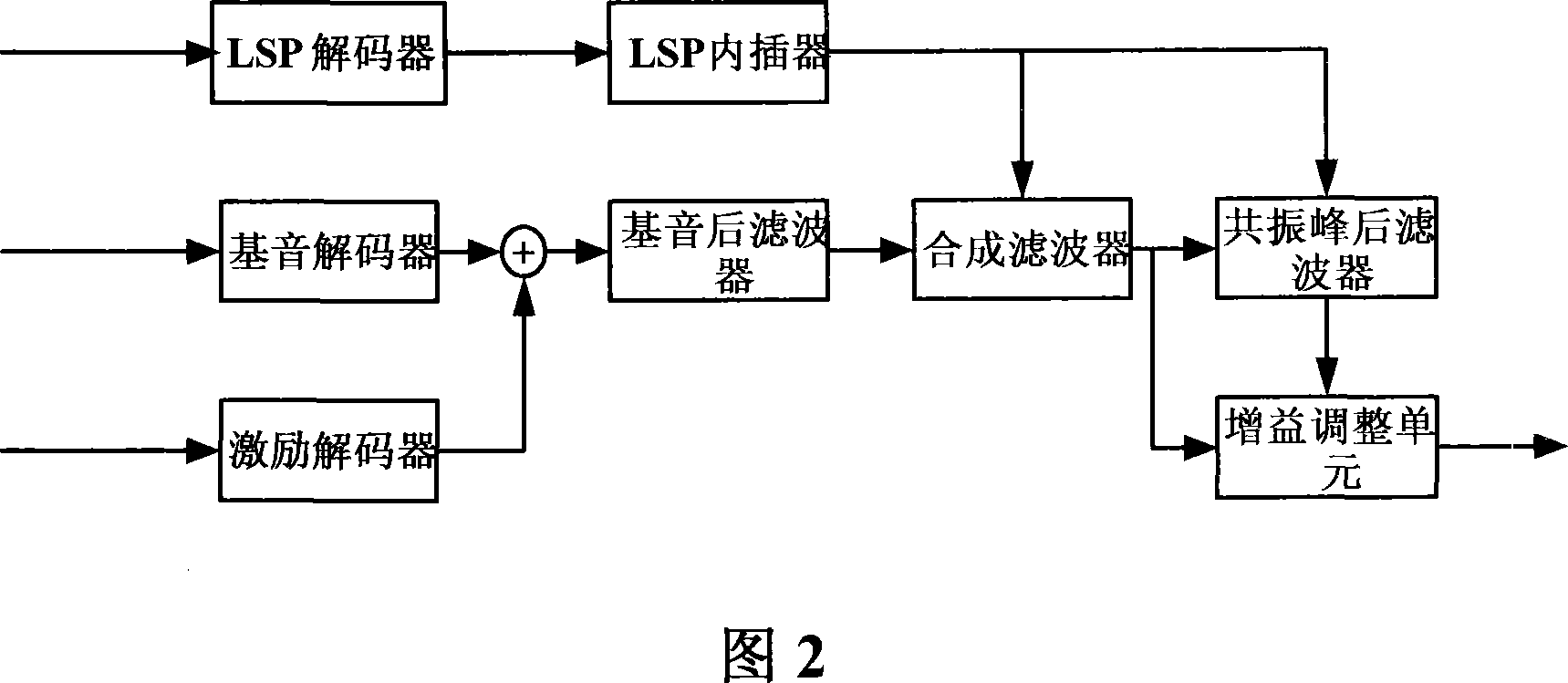
InactiveCN101059957AImprove real-time performanceReduce in quantityMultiple keys/algorithms usageSpeech analysisByteSpeech sound
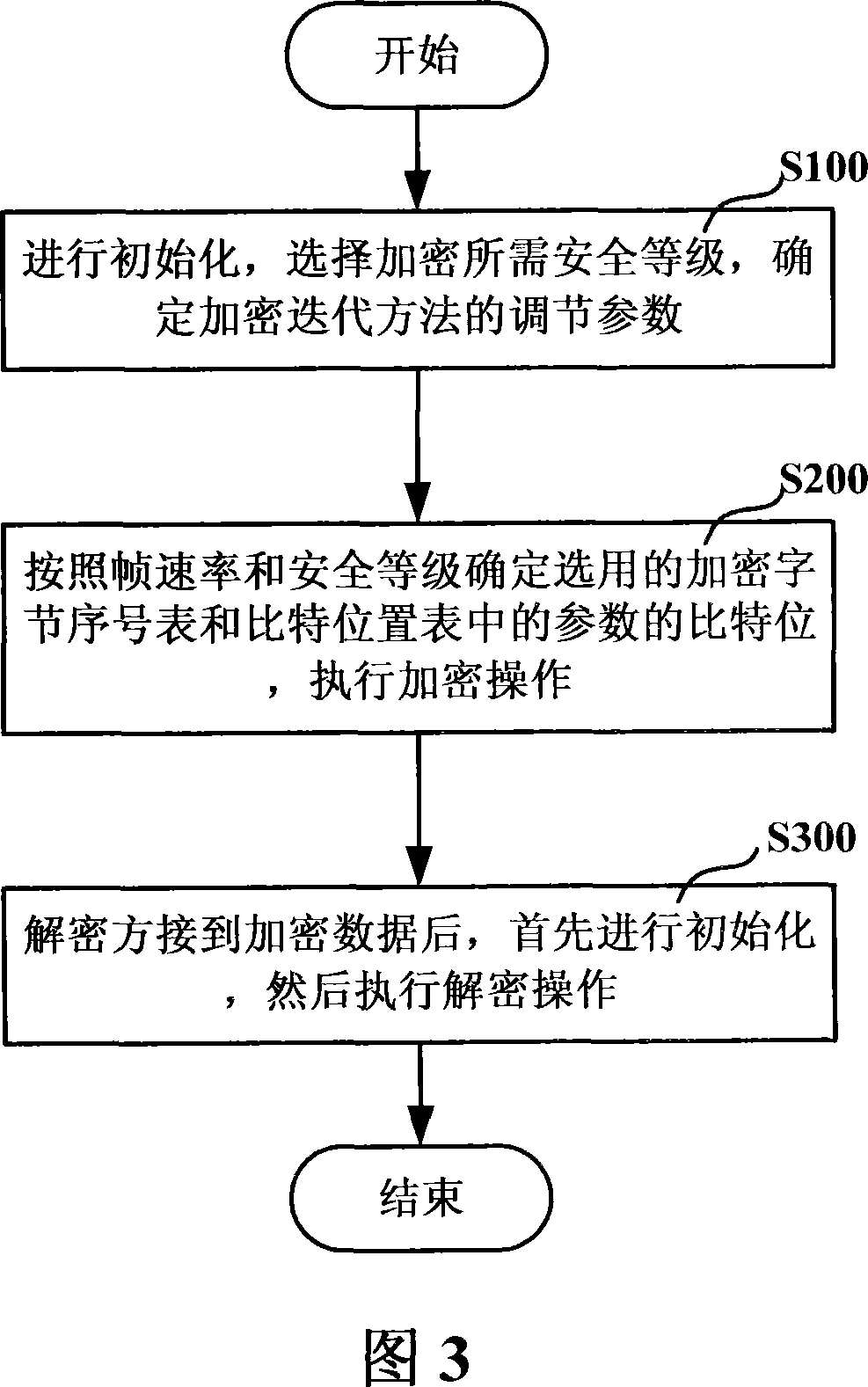
The invention discloses a sound code selective encrypt method, comprising A, first initialization, selecting encrypt safe level, finding the adjust parameters of chaotic encrypt method, B, finding the bit positions of encrypt bit serial number list and bit position list according to the frame speed and safe level, using chaotic encrypt method to encrypt, or even composed of step C that the decrypt user receives the encrypt data, to initialize and decrypt. The invention sets object data bit of sound code according to safe level, to improve real-time property, reduce system energy consumption and meet the demands of different levels.
Owner:HUAZHONG UNIV OF SCI & TECH
Encryption and decryption system based on medium security protection of IPTV platform
InactiveCN101521818AEnsure safetyStrengthen security managementKey distribution for secure communicationPulse modulation television signal transmissionMD5Value of information
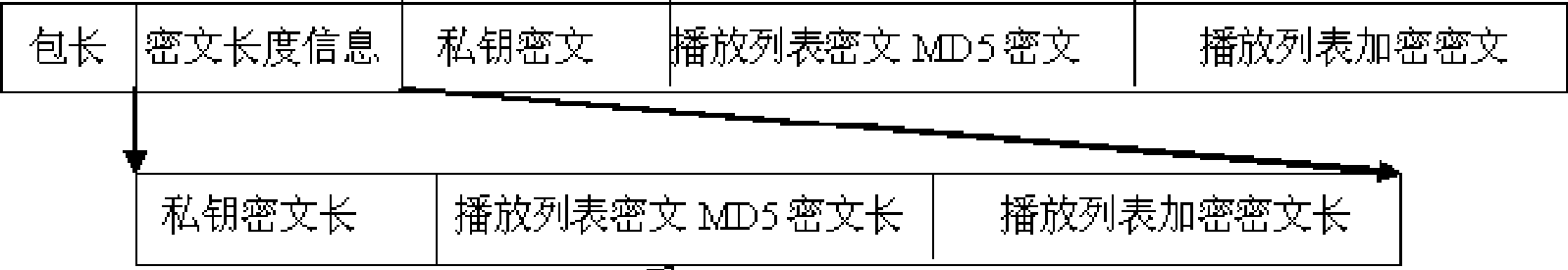
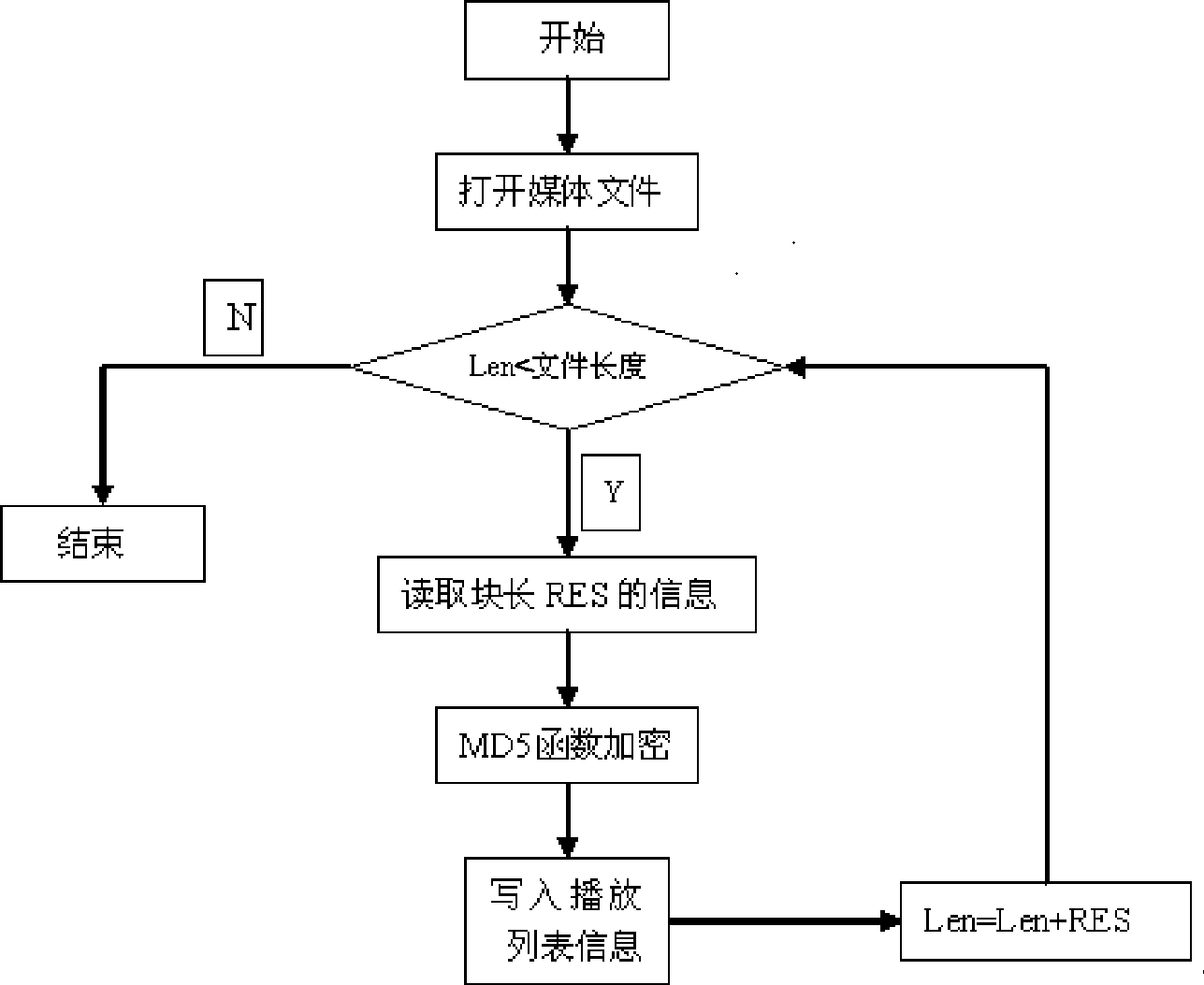
The invention discloses an encryption and decryption system based on the medium security protection of an IPTV platform. On a platform end in the method, each sub-block of a media file is firstly carried out with MD5 operation, then a section of information is combined by the MD5 values obtained from the sub-blocks, the information is carried out with MD5 operation again, an obtained result is placed in a playlist, and finally, the playlist is encrypted. On a terminal, firstly, the playlist is decrypted, MD5 values of information abstracts of the media file, which are obtained from the playlist, are compared with the MD5 of information abstracts combined by all the sub-blocks of an operation file; if the two MD5 values are not identical, the play is prohibited; if the two MD5 values are identical, the MD5 of each sub-block is compared, if identical, the information is placed in a buffer area to by played; and if else, the play is stopped. The method has high speed and high safety factor.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
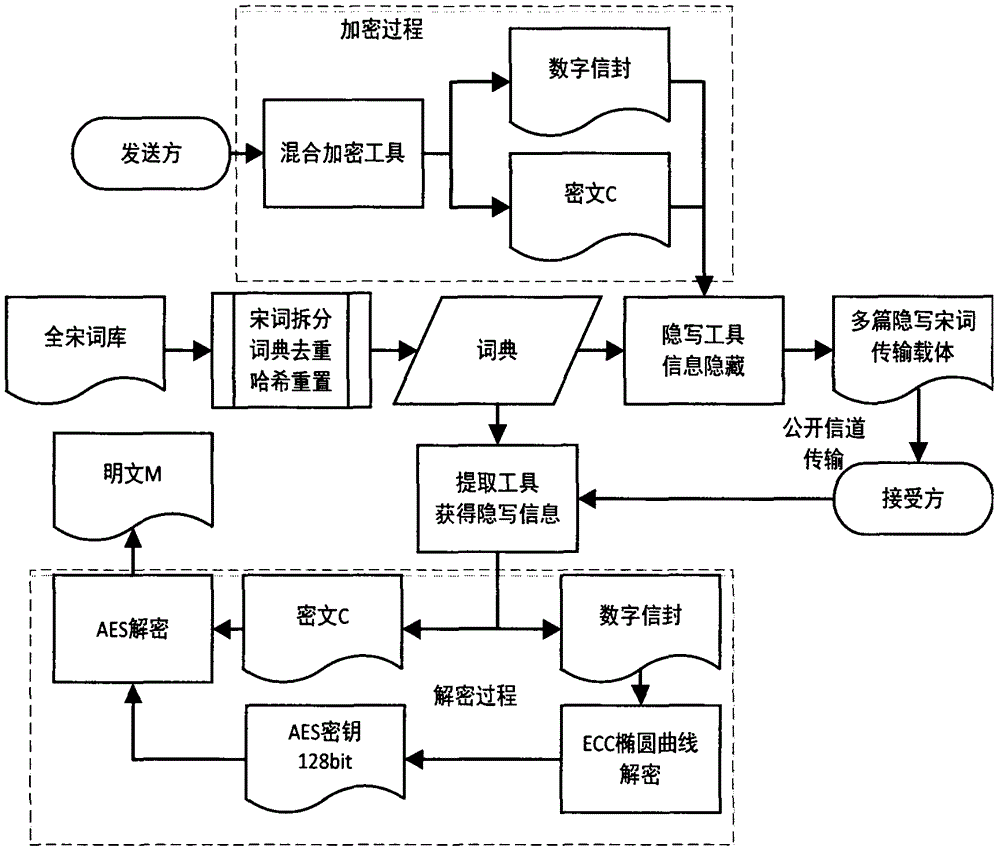
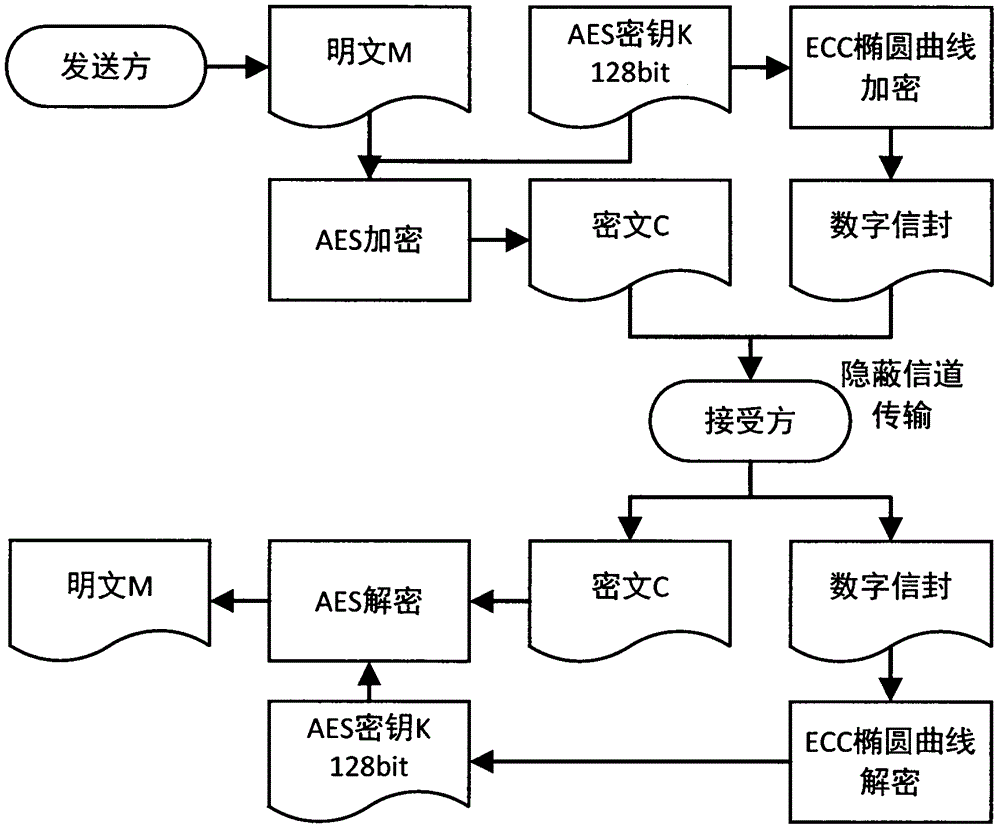
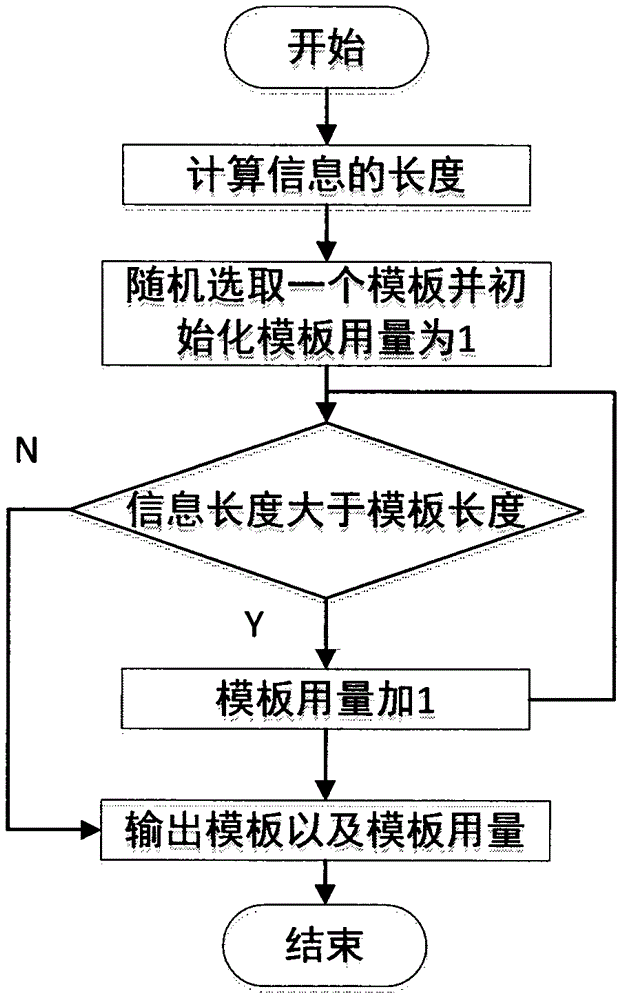
Song ci poetry text message hiding technology based on hybrid encryption
InactiveCN106254074AAchieve covert communicationSafety managementEncryption apparatus with shift registers/memoriesPublic key for secure communicationCiphertextXML Encryption
The invention provides a Song ci poetry text message hiding technology based on hybrid encryption, which belongs to the information hiding and data security directions in the field of computers. The Song ci poetry text message hiding technology comprises the steps of encrypting secret information to be hidden by using an advanced encryption standard (AES) in a hybrid manner, encrypting an AES secret key by using an elliptic curve cryptography (ECC) algorithm, passing all information after encryption processing through a 140 tune name template library of the complete collection of Song ci poetry, and hiding the information by means of the system which is composed of templates, a dictionary, a steganographic device and an extractor, wherein the system can generate steganographic Song ci poetry through a random selection or template designation method according to the length of a cryptograph, and the sentence length, grammatical style and intonation sentence pattern of the steganographic Song ci poetry conform to the original Song ci poetry completely, thereby achieving the purposes of obfuscating attackers and ensuring secure transmission of the hidden information. The Song ci poetry text message hiding technology disclosed by the invention can solve the security problem of data transmission in channels, can provide double security measures of information hiding and data encryption, and has high practical application value.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method of processing soft foundation by quick low position high vacuum layering pre-compacting consolidation
The invention relates to a quick ''low level high-vacuum hierarchical precompression compaction' method for soft ground, the concretely processes are: 1) a sand layer is laid on the ground before filling, then the plastic water discharging boards are inserted vertically, a high vacuum precompression system is arranged transversely in the sand layer, and a layer of plastic air isolating film is covered; 2) the high vacuum precompressing system carries on vacuum and precompression; 3) the sand blowing high vacuum compacting system is arranged on the film transversely or vertically; 4) fills sand on the film to the set height; 5) the high vacuum precompression system carries on precompressing to the set boding rate, the system carries on the first time of vacuuming and discharge, then carries on the first time of compacting or vibration compacting the sand on the film; 6) carries on the second time or several times of 'high vacuum compacting' to the sand to the overconsolidation state. The invention is short period, low price, and the quality is controllable.
Owner:SHANGHAI HARBOUR SOFT SOIL TREATMENT ENG CO LTD
Novel symmetric key algorithm for high speed encryption
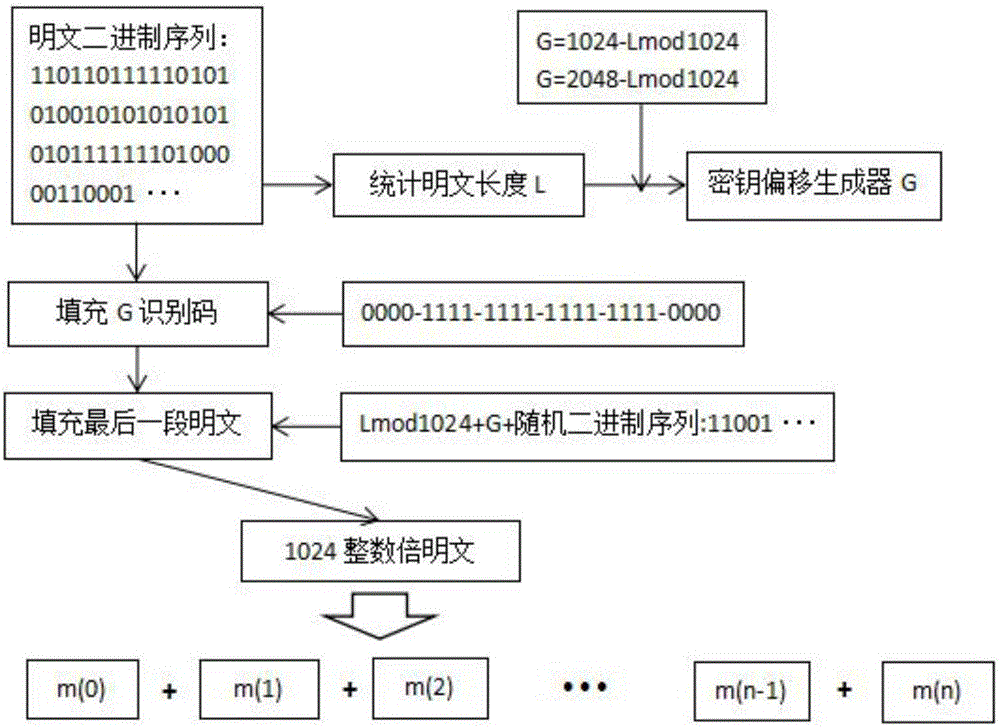
ActiveCN106656475AReduce repetition rateImprove securityEncryption apparatus with shift registers/memoriesPlaintextCiphertext
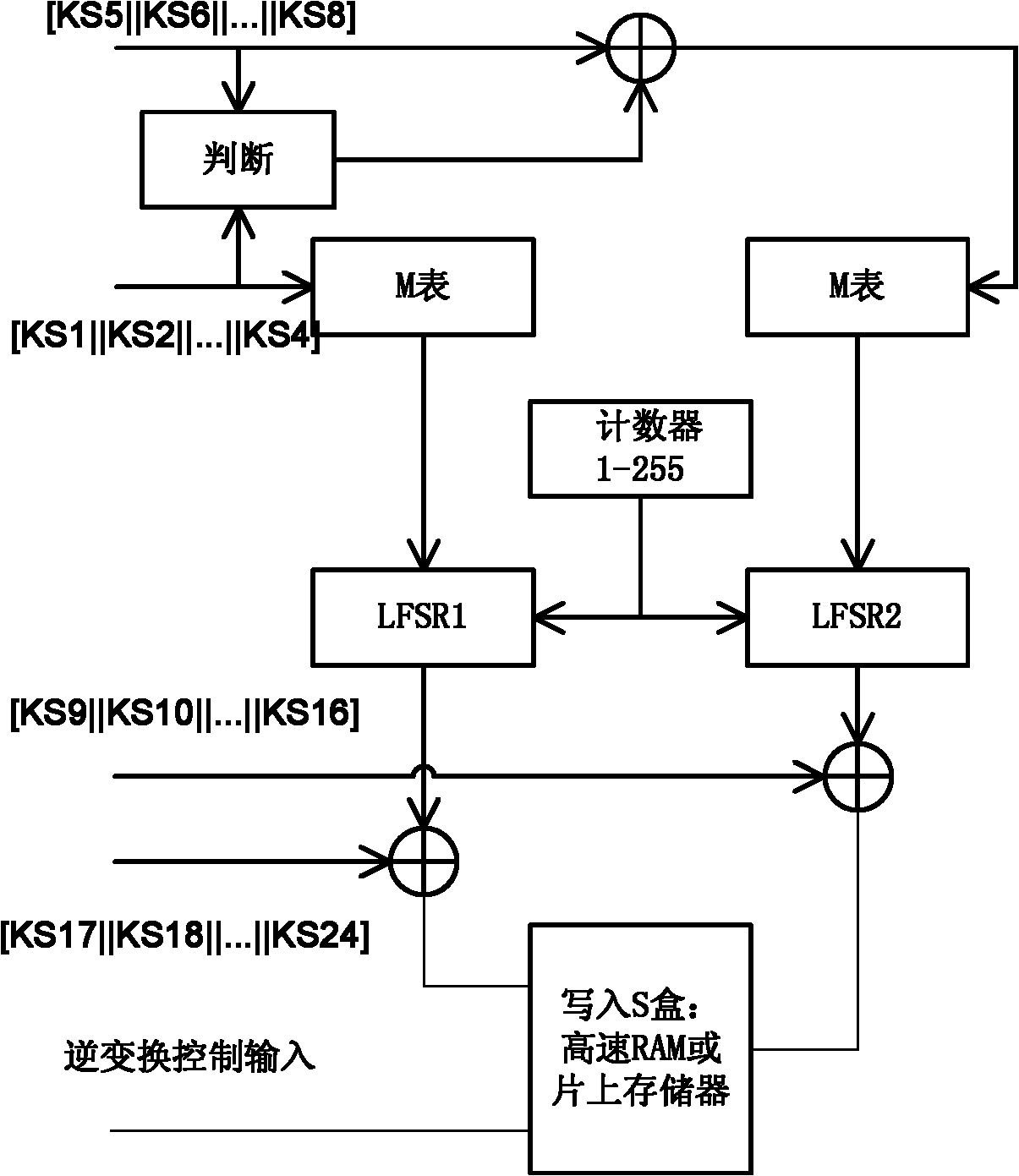
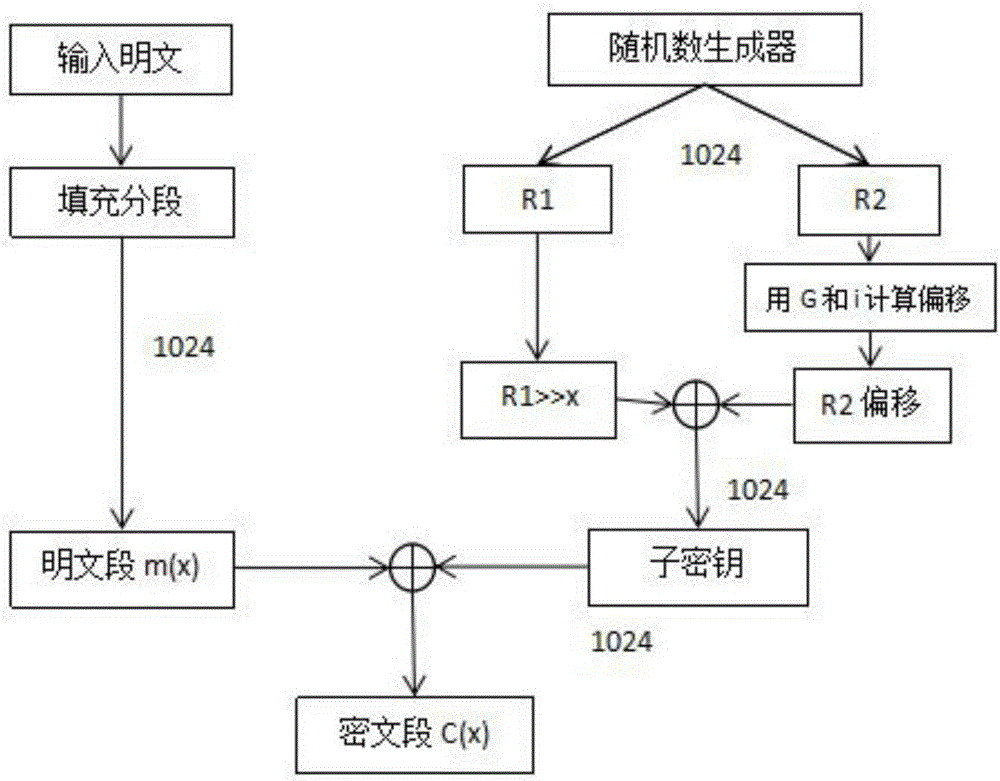
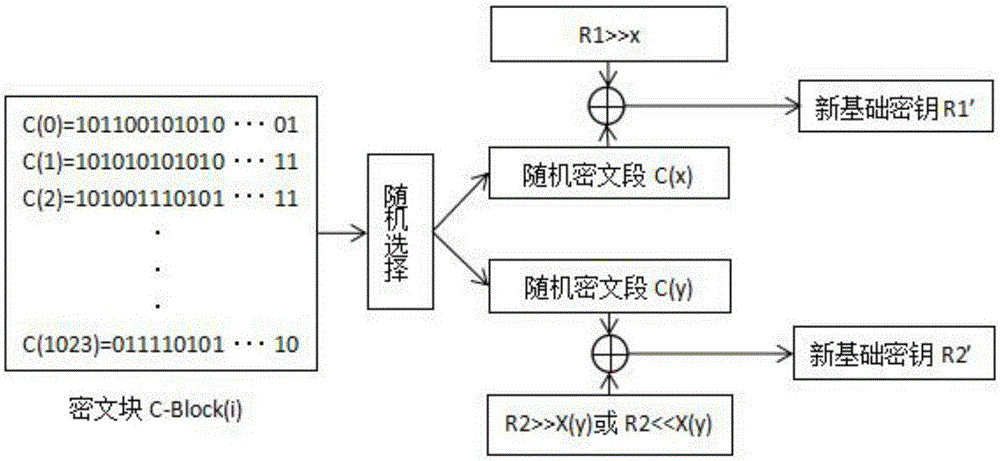
A novel symmetric key algorithm for high speed encryption comprises an encryption algorithm and a decryption algorithm, wherein the encryption algorithm comprises the following steps: grouping plaintexts M to obtain Mi; generating basic keys R1 and R2 by using a random number generator; collecting statistics about a plaintext length L, and filling Mn-1 with plaintext, that is, firstly filling a binary key generator identification code, calculating remaining bits, and filling with random binary code; getting a key offset generator G; encrypting a Mn-1 plaintext group; obtaining an encrypted key Keyi; encrypting all the plaintext groups; encrypting the basic keys R1 and R2, to obtain a cipher key CR; and completing the encryption, and transmitting the obtained ciphertext. The novel symmetric key algorithm has the advantages that the probability of key repetition is zero, and the encryption subkey of each plaintext segment is unique and random, so that the security is high; and the encryption speed is fast, that is, only two offsets, two modular operations, one multiplication, two additions, one judgment, two different or same 10-step basic operations are needed.
Owner:上海同态信息科技有限责任公司
SP network structure lightweight LBT block cipher realizing method with consistent encryption and decryption
ActiveCN107707343AFast encryptionEasy to implementEncryption apparatus with shift registers/memoriesKey sizePlaintext
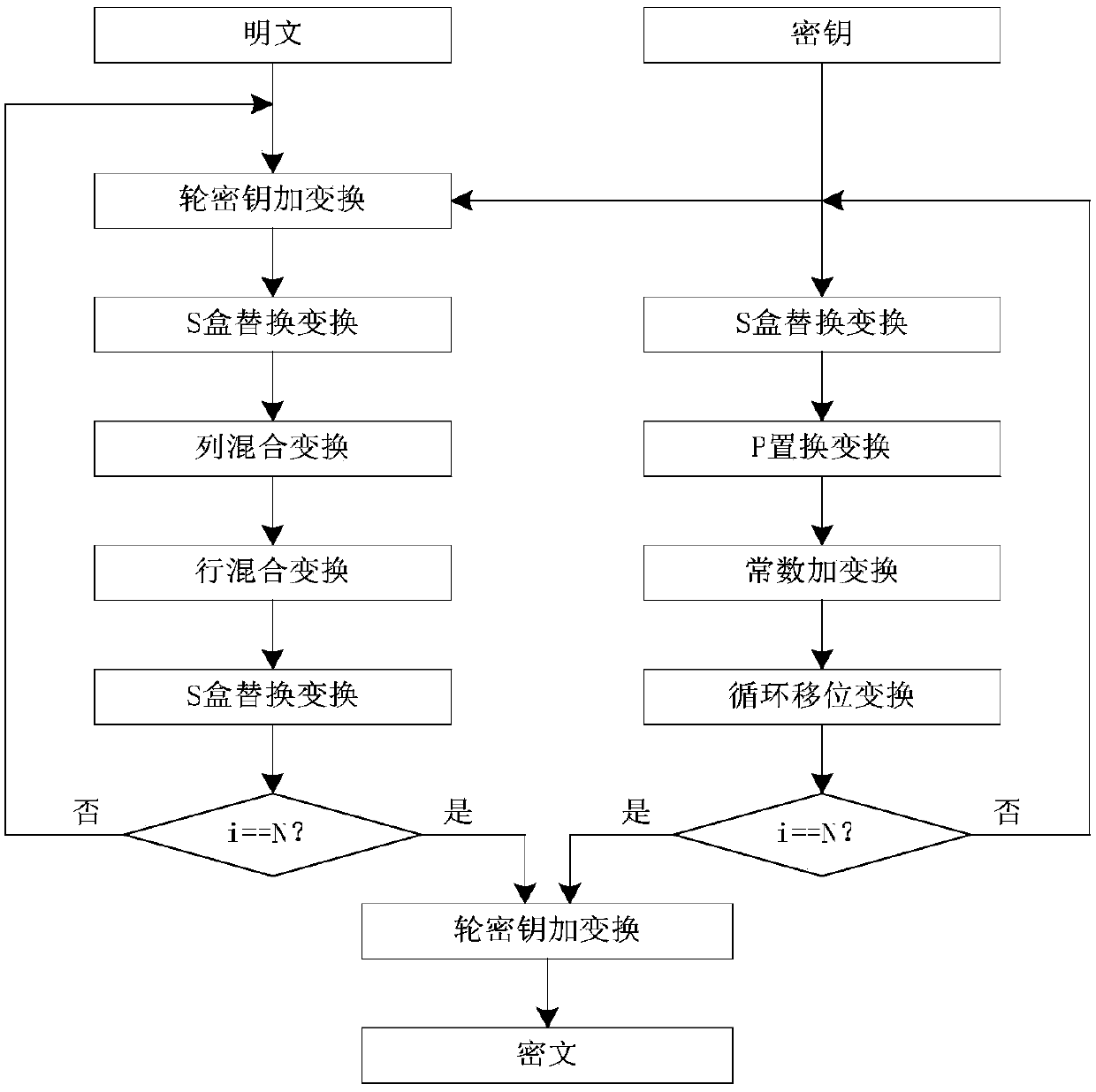
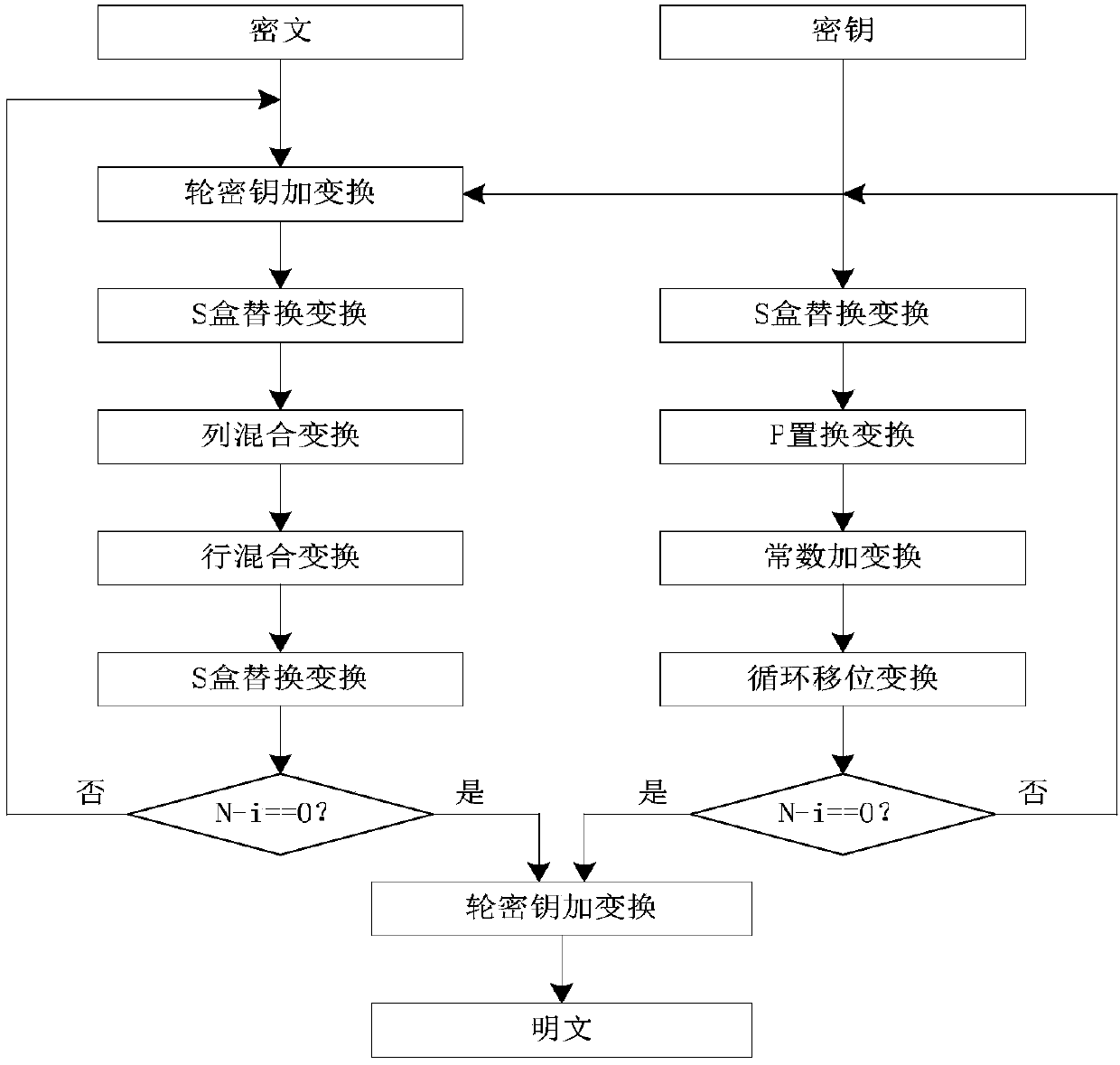
The invention discloses an SP network structure lightweight LBT block cipher realizing method with consistent encryption and decryption. The invention provides an SP network cipher structure with consistent encryption and decryption. The cipher structure is same with a Feistel network cipher structure. One algorithm is utilized in encryption and decryption, and designing of a special decryption algorithm is not required. According to the cipher structure, a plaintext data input direction for encryption is same with a cipher text data input direction for decryption. The designed cipher structure is realized as a lightweight LBT block cipher algorithm. A user selects different secret key length cipher algorithms according to an application occasion requirement. The SP network structure lightweight LBT block cipher realizing method has advantages of settling a bottleneck of high difficulty of realizing consistent encryption and decryption based on the SP network structure password, realizing high encryption speed and high decryption speed of the LBT cipher, facilitating software and hardware realization, reducing software resource and hardware resource, and realizing high suitabilityfor use as the lightweight block cipher.
Owner:GUIZHOU UNIV
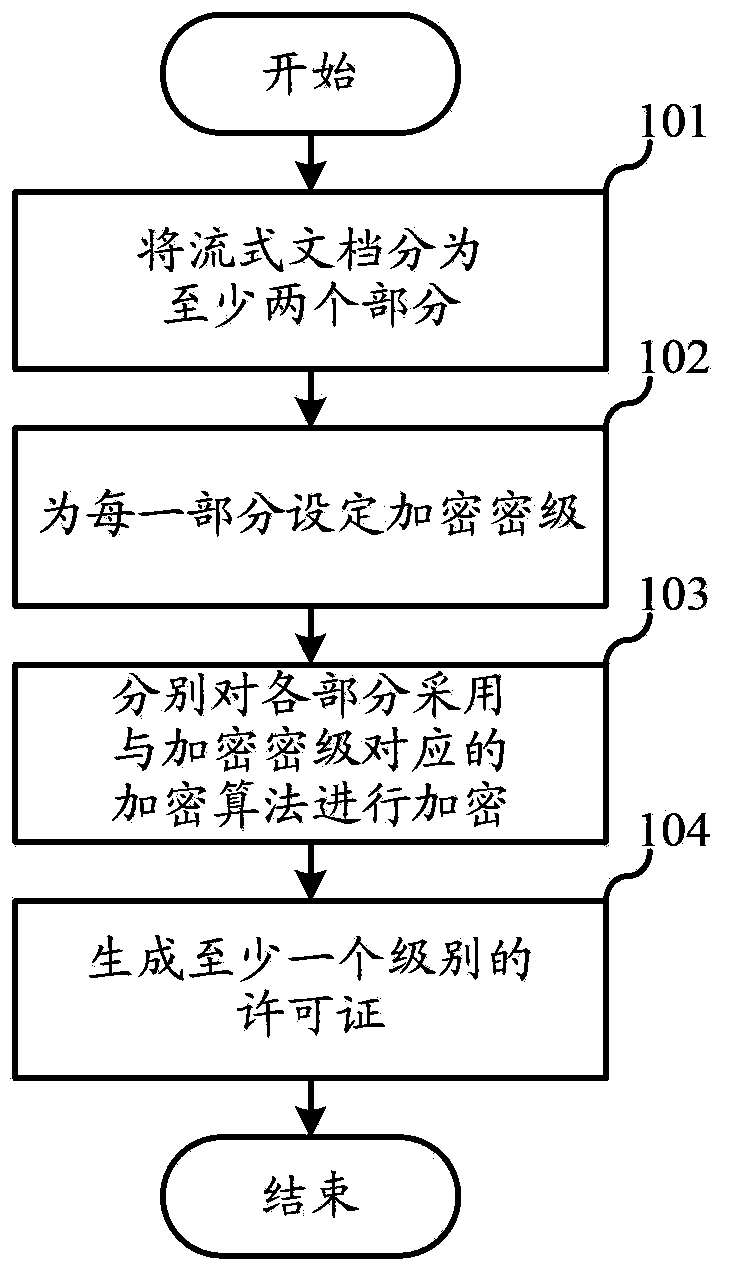
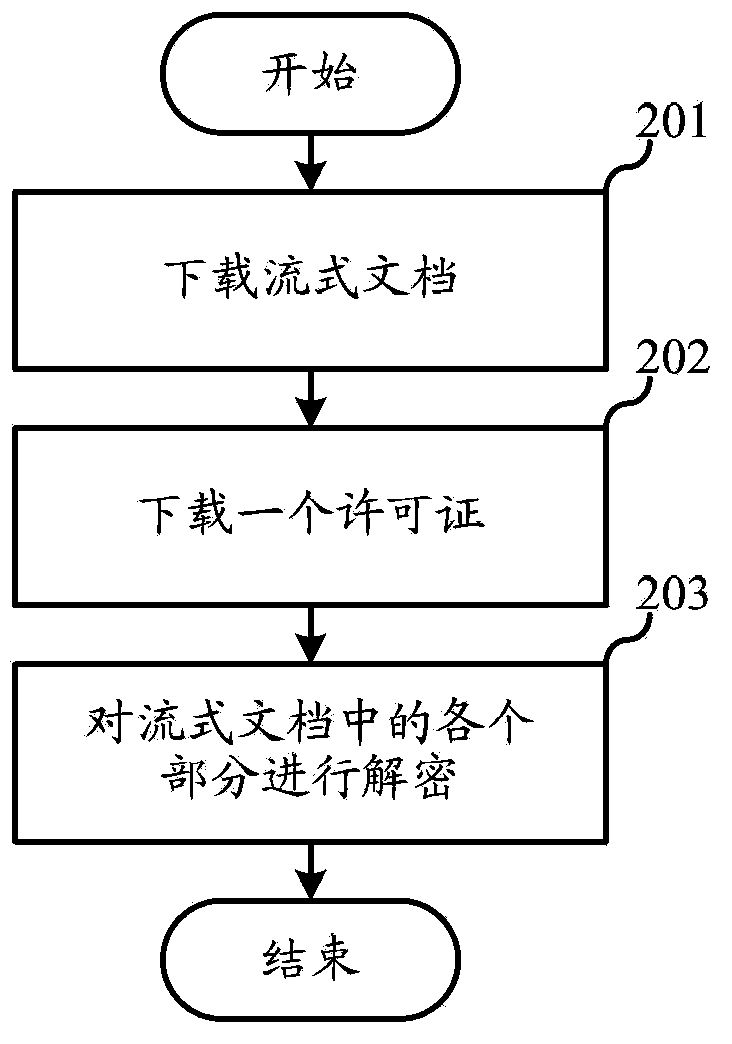
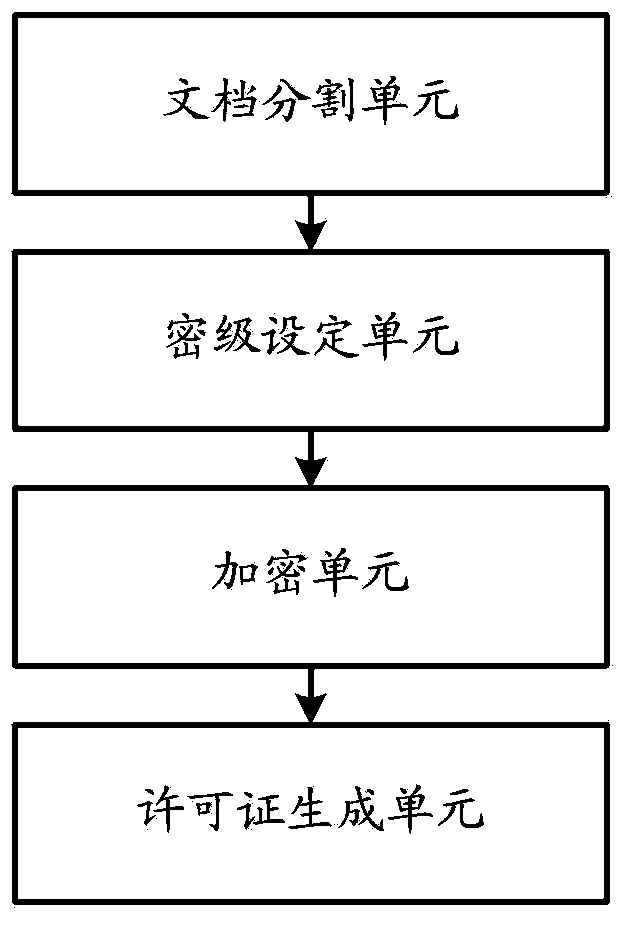
Method for encrypting and decrypting streaming document and device thereof
InactiveCN103577765AFast encryptionReduce the need for computing resourcesDigital data protectionComputer resourcesTerminal equipment
The invention relates to the field of digital publishing, and discloses a method for encrypting and decrypting a streaming document and a device thereof. According to the method, each part of one streaming document is encrypted at different encrypting grades, general contents can be encrypted by adopting a low-security-level rapid encryption algorithm, and important contents are encrypted by adopting a high-security-level safety encryption algorithm, so that the overall encryption speed of the document is increased, the demand on computing resources in a computer system is lowered, and the security of the important contents is ensured. Each part of one streaming document is encrypted by adopting different encrypting grades, and the contents of a low encryption security level can be decrypted rapidly, so that the overall decryption speed of the document is increased. At a lowest encryption security level, encryption is not performed, so that computer resources needed by encryption can be further reduced; parts of contents of the streaming document do not need to be decrypted during use, so that the demand of terminal equipment on computing resources is lowered; the method and the device are particularly suitable for trial reading of parts of chapters.
Owner:JIEFANG DAILY NEWSPAPER GRP
Quantum key classification providing method for improving electric power data transmission security
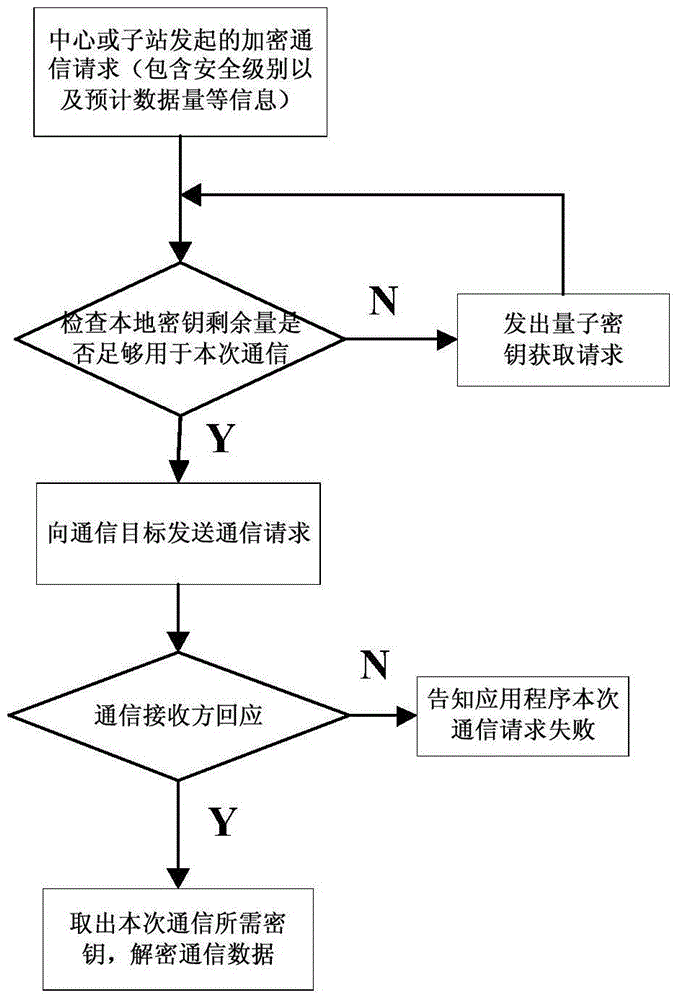
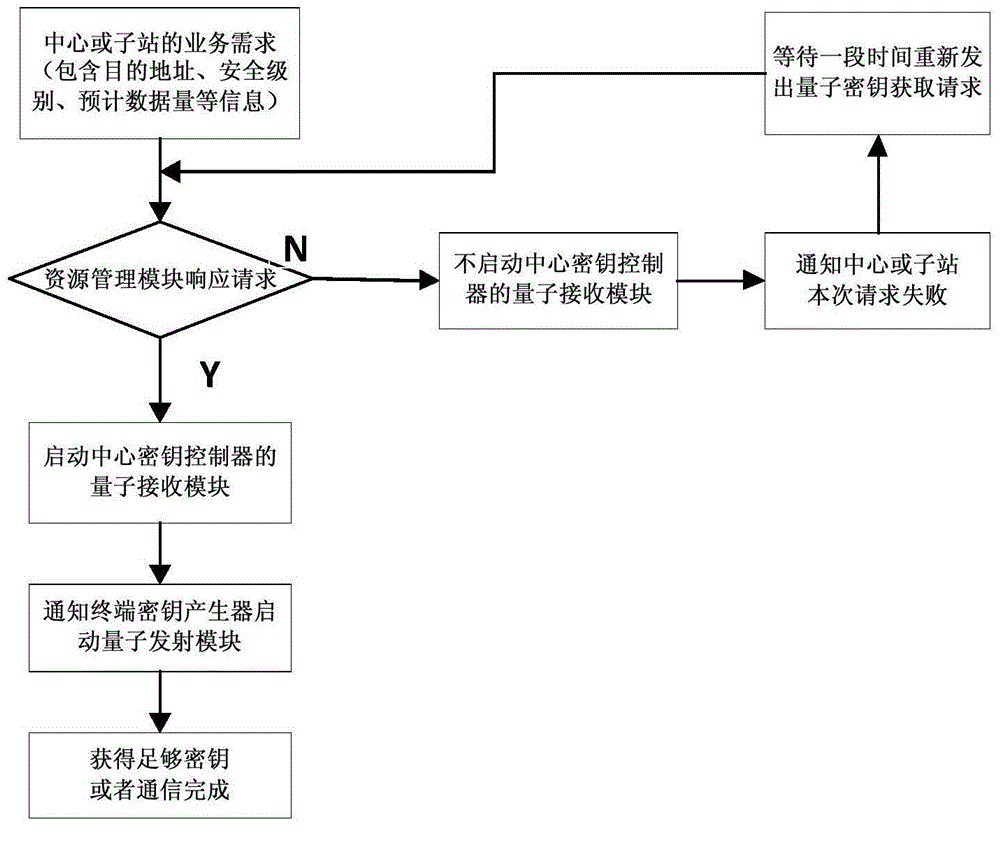
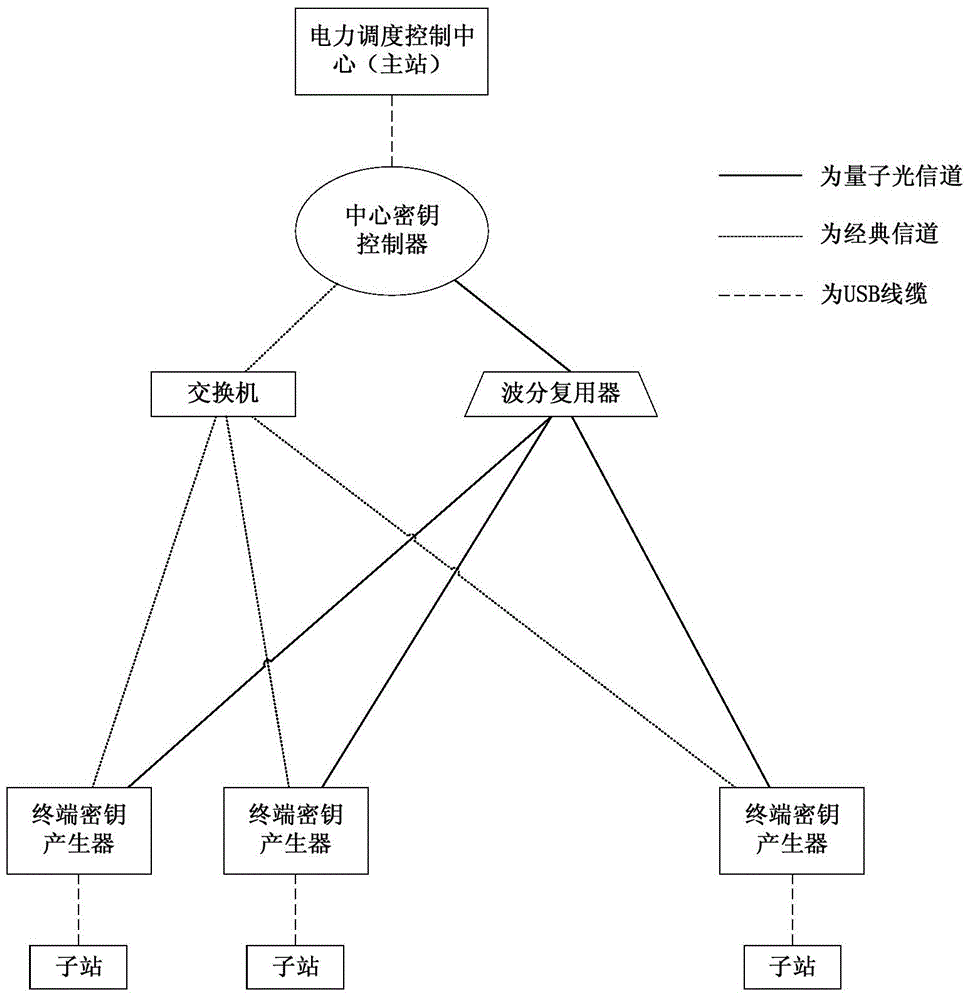
ActiveCN104486316AImprove practicalityResistance to Frequency AttacksKey distribution for secure communicationData transmissionTransmission security
The invention provides a quantum key classification providing method for improving electric power data transmission security. The method comprises the following steps that a communication initiating party judges whether a local key length meets the present communication requirement or not; a communication receiving party judges whether the own residual local key length meets the present communication requirements or not after receiving the present communication request; the communication receiving party starts the quantum key encryption communication; the communication initiating party starts the quantum key encryption communication. According to the quantum key classification providing method for improving the electric power data transmission security provided by the invention, while the problem that the quantum key distribution speed is unmatched with the service requirement speed is relieved, an encryption service, which meets the respective security requirements, is provided for data transmission of an electric power system with different security levels, and the practicability of the quantum encryption technology in the electric power system is greatly improved.
Owner:STATE GRID CORP OF CHINA +3
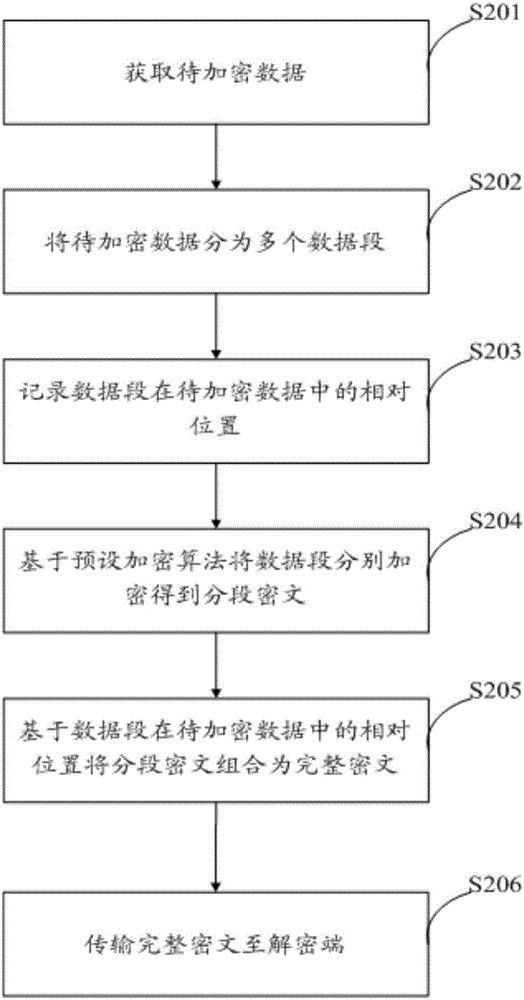
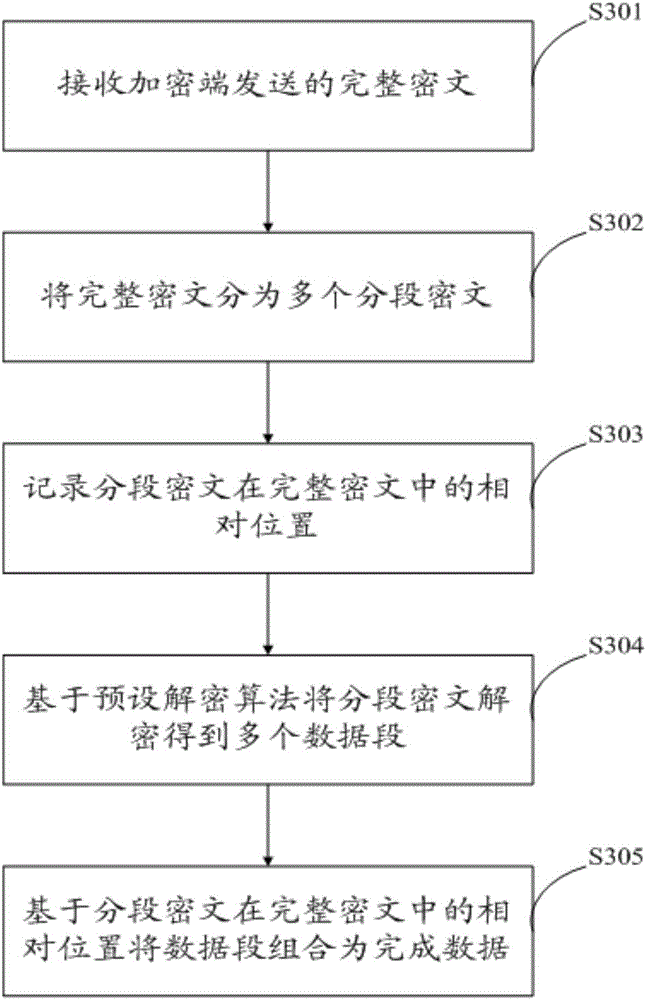
Sectional encryption transmission method and device
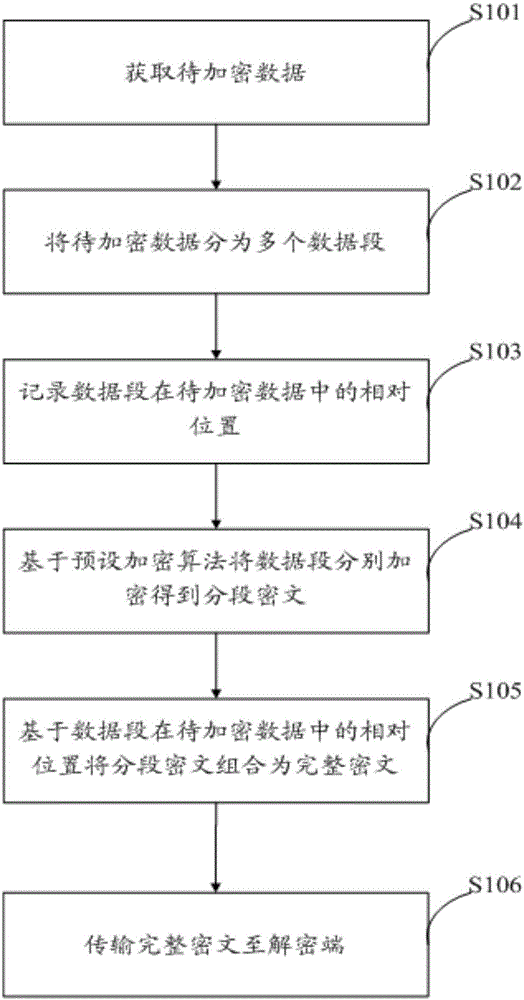
InactiveCN106788982ALower requirementReduce data volumeData stream serial/continuous modificationComputer hardwareData segment
The invention provides a sectional encryption transmission method, comprising: acquiring data to be encrypted; dividing the data to be encrypted into multiple data sections; recording relative positions of the data sections in the data to be encrypted; encrypting the data sections respectively based on a preset encryption algorithm to obtain sectional cyphertexts; combining the sectional cyphertexts into a complete cyphertext according to the relative positions of the data sections in the data to be encrypted; transmitting the complete cyphertext to a decoding terminal. Compared with the prior art where data to be encrypted is encrypted and transmitted directly, the method provided herein has a greatly reduced amount of data to be encrypted each time, may have lowered requirements on hardware and has lower cost of data encryption transmission.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
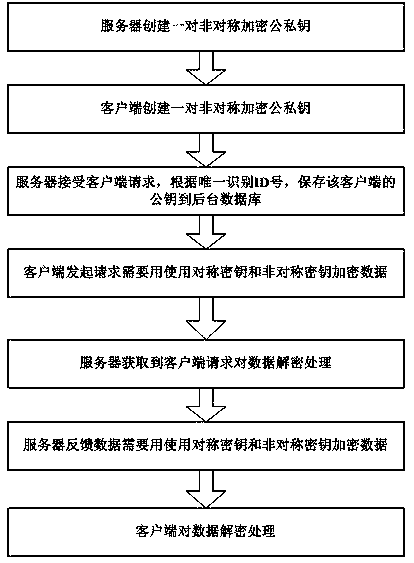
Hybrid encryption-based network transmission data security processing method
InactiveCN109150923AIncreased complexityEnsure safetyKey distribution for secure communicationPublic key for secure communicationClient-sideNumber generator
The invention discloses a network transmission data security processing method based on mixed encryption, which comprises the following steps: creating a pair of asymmetric encrypted public and private keys by a server; creating a pair of asymmetric encryption public and private keys by a client. accepting the request of the client by the server and saving the public key of the client to the background database according to the unique identification ID number, wherein the client needs to encrypt the data with symmetric key and asymmetric key to initiate the request; obtaining the request of the client to decrypt the data by the server, wherein the server needs to be encrypted with symmetric and asymmetric keys for data feedback; and decrypting the data by the client. According to the method, the data transmitted by the network are encrypted through the combination of asymmetrical encryption and symmetrical encryption, thereby realizing high safety and high reliability. The pseudo-random number generator is unique in generating process and troublesome to crack, which makes the symmetric encryption key more complex and improves the security effect. The method is unique, the design isclever and has good application prospects.
Owner:JIANGSU ETOWN DIGITAL TECH CO LTD
Digital image feedback encryption method based on image network
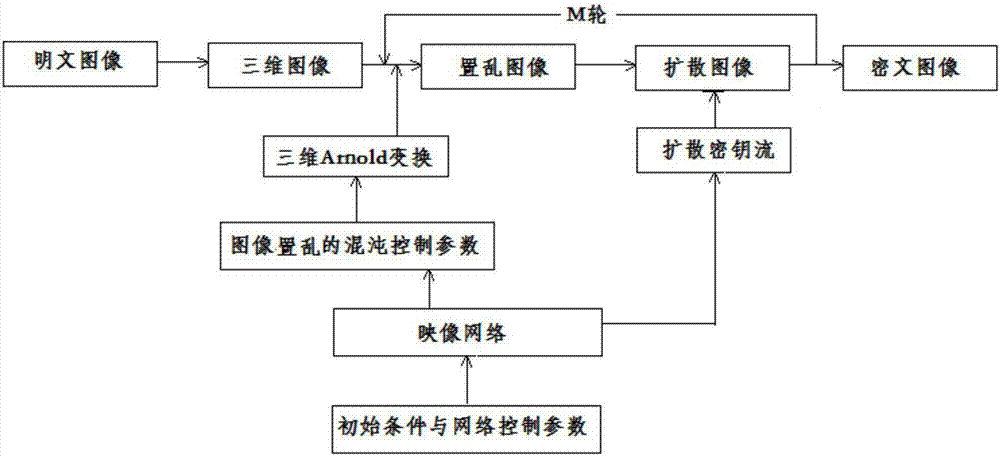
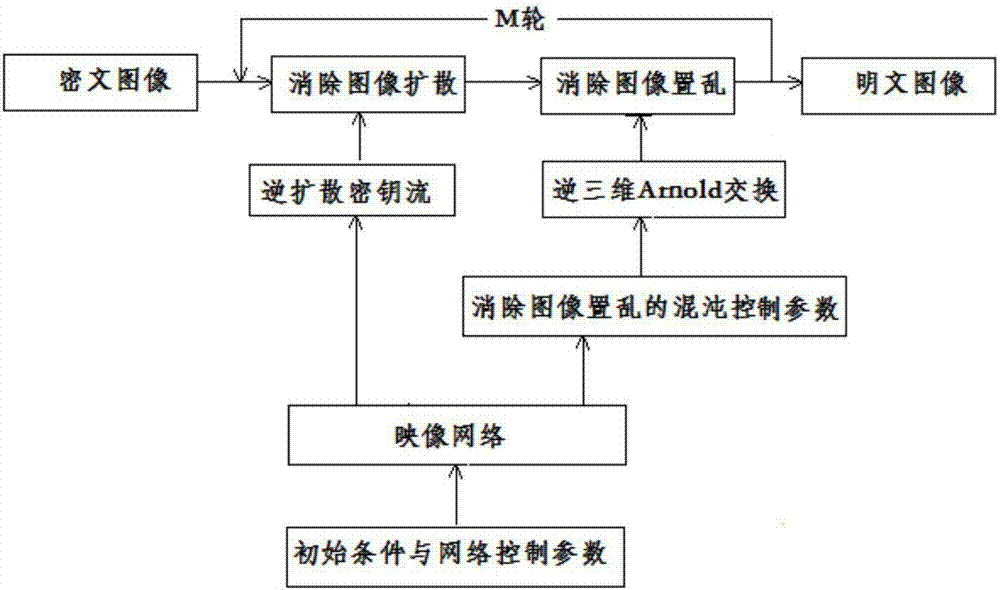
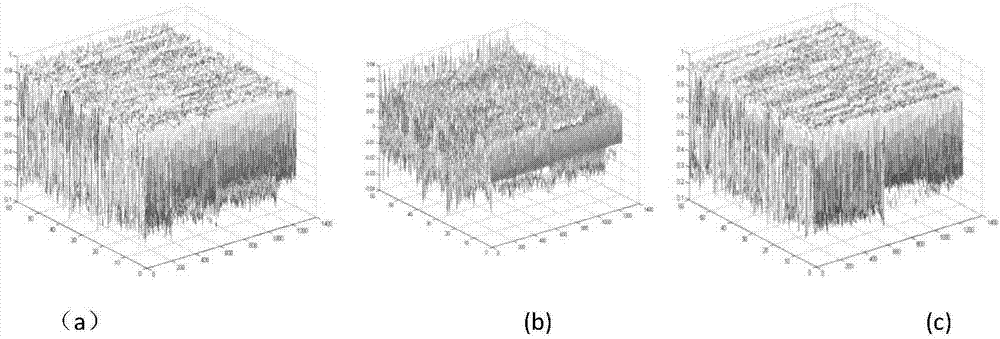
ActiveCN107220923AIncreased complexityStrong pseudo-randomnessImage data processing detailsPlaintextDiffusion
The invention discloses a digital image feedback encryption method based on an image network. The method comprises the following steps of processing a digital plaintext image; constructing the image network in which a node is a super-chaotic system and a non-neighbor connection mode is possessed; through three-dimensional Arnold, converting a scrambling image, wherein a scrambling matrix is driven by image-network space-time chaotic display and a current plaintext image; combining feedback information of the current plaintext image and a cryptograph image and carrying out image diffusion processing; alternatively operating scrambling and diffusion multiple times and acquiring the cryptograph image. In an encryption system, a scrambling-diffusion alternative-operated loop iteration structure is designed; during an encryption process, plaintext and cryptograph feedback mechanisms are introduced; and during each encryption, the used scrambling matrix and a secret key flow are dynamically changed and are different. An experiment result shows that the encryption method possesses high safety and high efficiency; and a capability of resisting various plaintext attacks, statistics attacks, violence attacks and difference attacks is high.
Owner:SHAANXI NORMAL UNIV
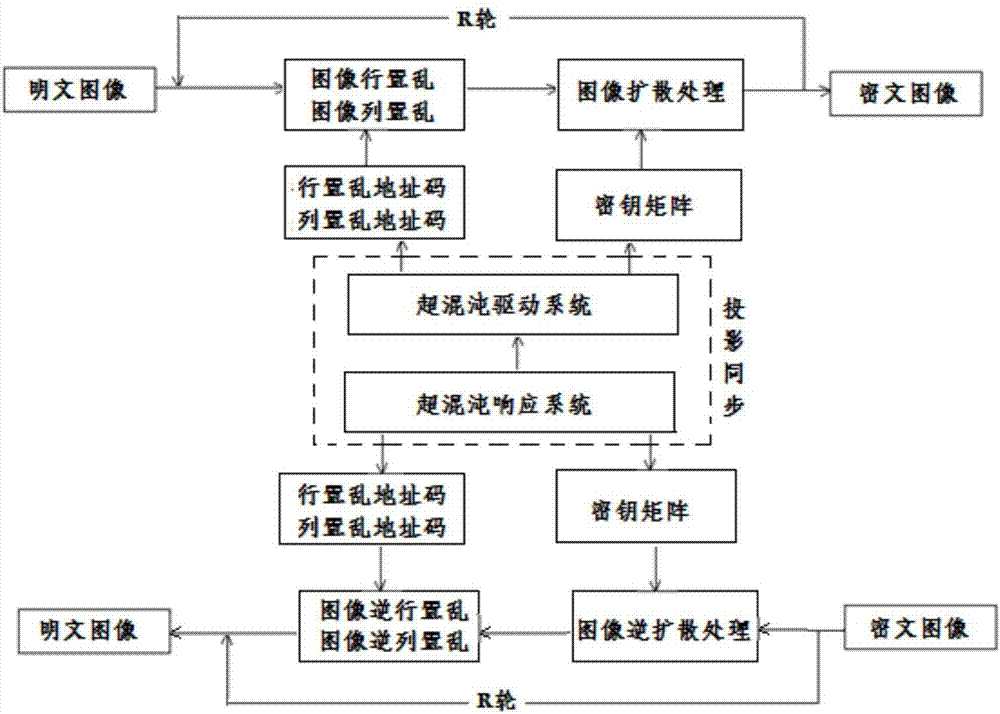
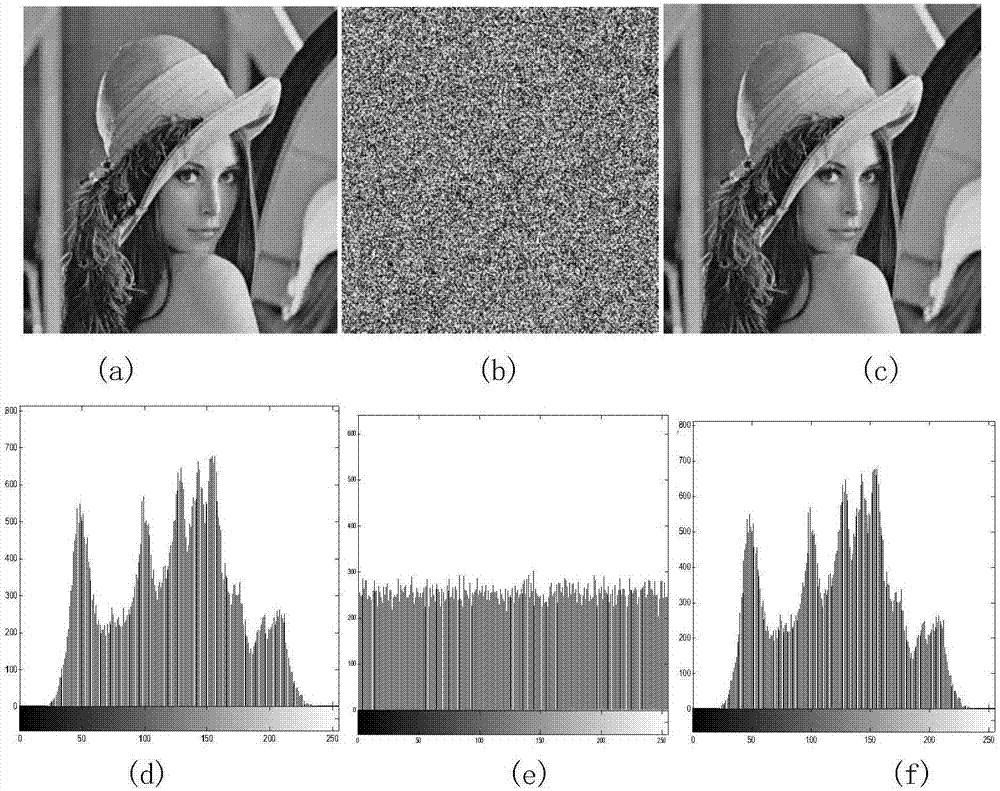
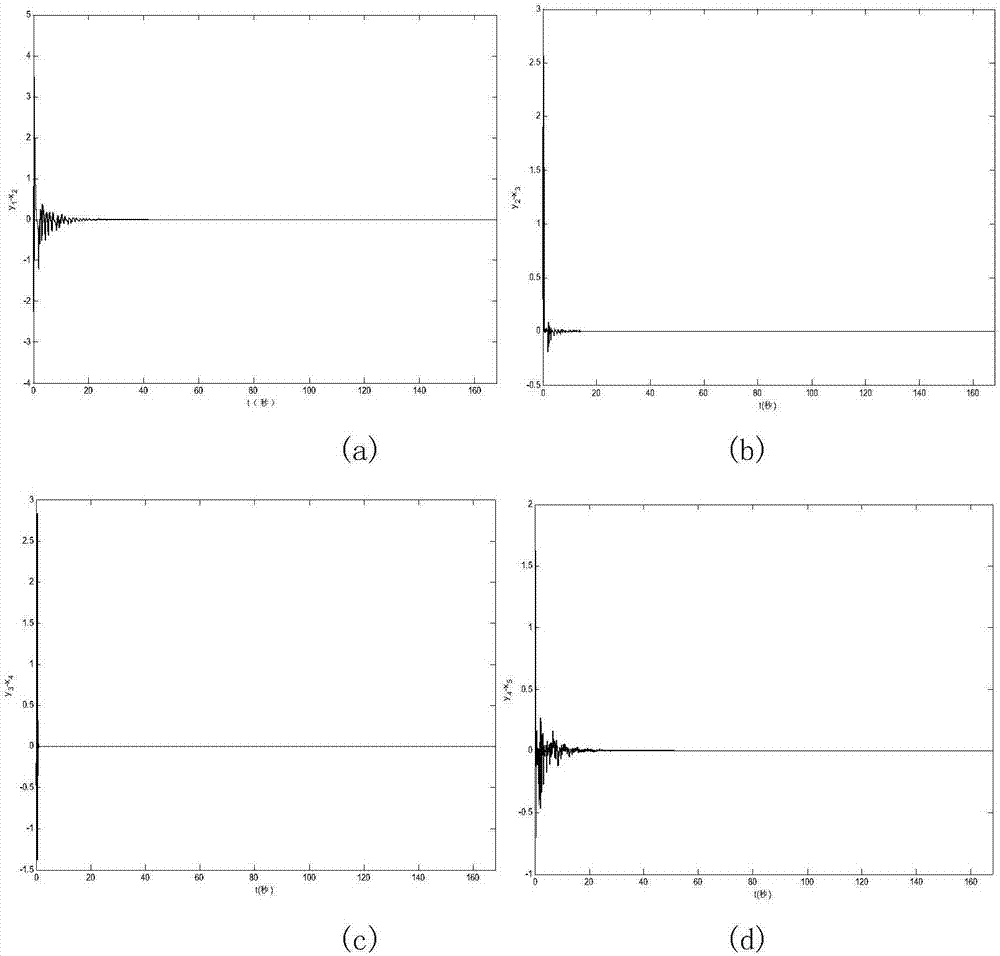
Image encryption method based on projection synchronization of hyperchaotic system
ActiveCN106997606AHas cryptographic propertiesIncreased complexityImage codingSecuring communication by chaotic signalsChosen-plaintext attackChaotic systems
The invention discloses an image encryption method based on the projection synchronization of a hyperchaotic system. The method comprises the steps of plaintext image quantifying and ciphertext image quantifying. The first step comprises generating of a hyperchaotic sequence of a hyperchaotic driving system, image row scrambling, image column scrambling, image diffusing, circulation image row scrambling, image column scrambling, multiple rounds of image diffusing, and a ciphertext image is acquired. The second step comprises ciphertext image quantifying, generating of a hyperchaotic sequence of a hyperchaotic response system, time acquiring, column scrambling index and line scrambling index valuing, image inverse diffusing, image inverse column scrambling, image inverse row scrambling, circulation image inverse diffusing, image inverse column scrambling, multiple rounds of image inverse row scrambling, and a decrypted image is acquired. According to the invention, a feedback mechanism with the current image is introduced; the row (column) scrambling address code and the key matrix are dynamically changed in each round of encryption; experiments show that the method has the advantages of good encryption effect, high security and large key space, can resist selected plaintext attacks, known plaintext attacks and various statistical attacks.
Owner:SHAANXI NORMAL UNIV
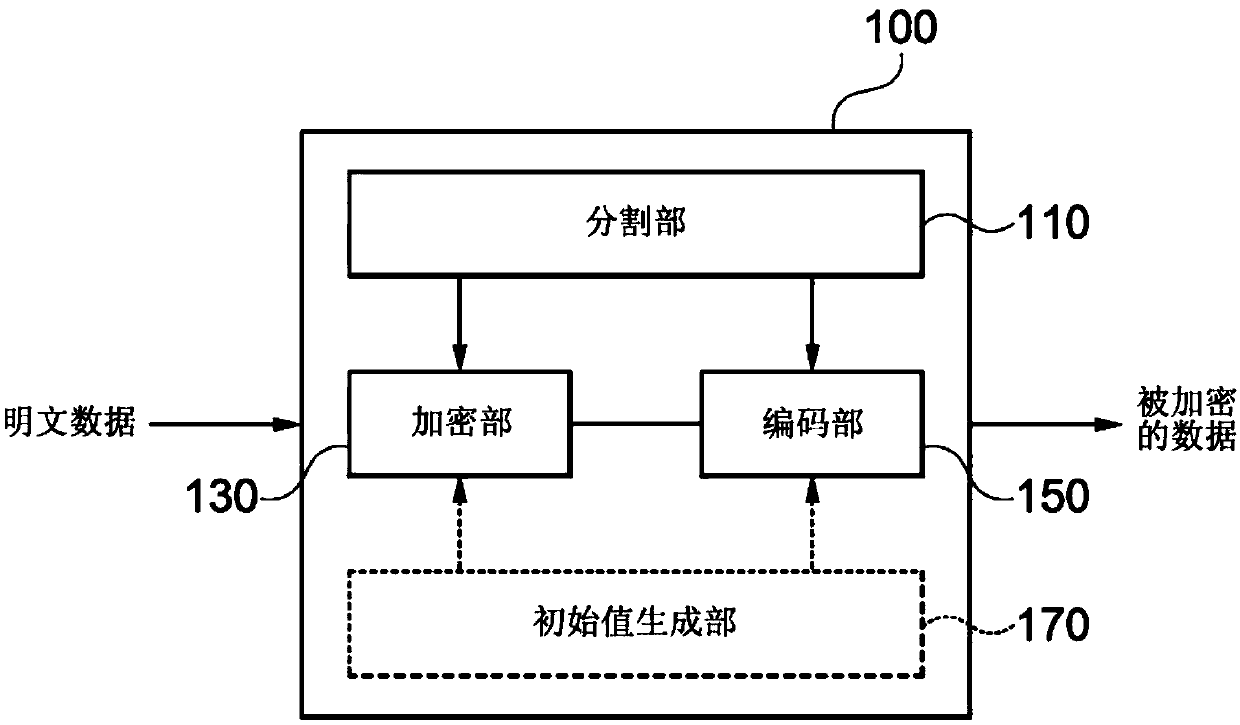
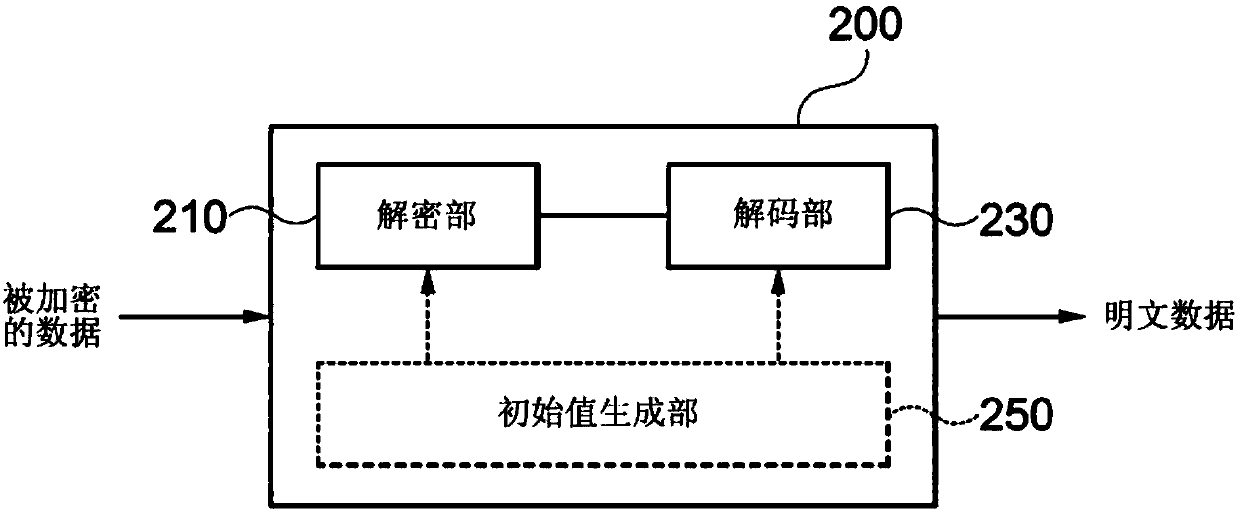
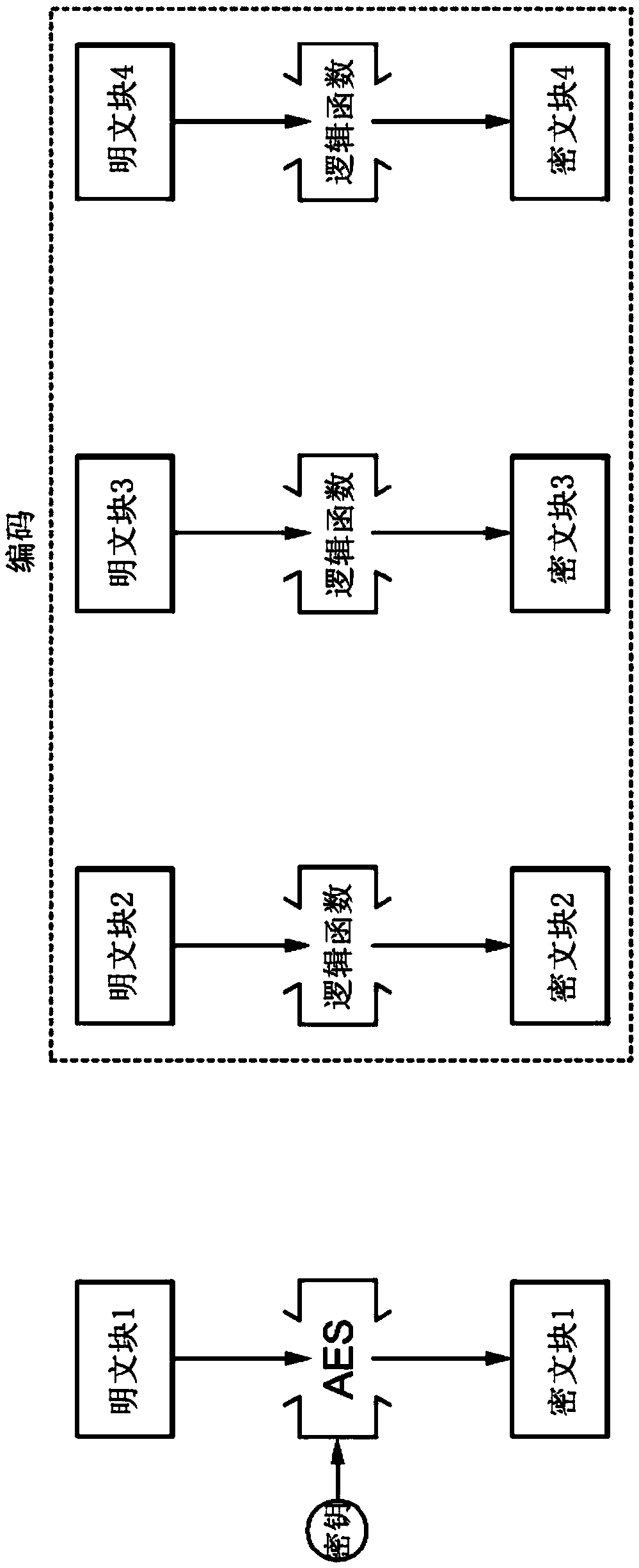
Data encryption apparatus and method, and data decryption apparatus and method
ActiveCN107637010AReduce computationFast encryptionMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesComputer hardwareData decryption
A data encryption apparatus and method, and a data decryption apparatus and method are disclosed. A data encryption apparatus according to one embodiment of the present invention comprises: a divisionunit for dividing data into a plurality of plaintext blocks; an encryption unit for encrypting at least one of initial values for encryption of data and some blocks among the plurality of plaintext blocks, using a cryptographic key-based block encryption scheme; and an encoding unit for encoding the remaining blocks among the plurality of plaintext blocks, which have not been encrypted by a predetermined block encryption scheme, using a non-cryptographic key-based encoding scheme.
Owner:SAMSUNG SDS CO LTD
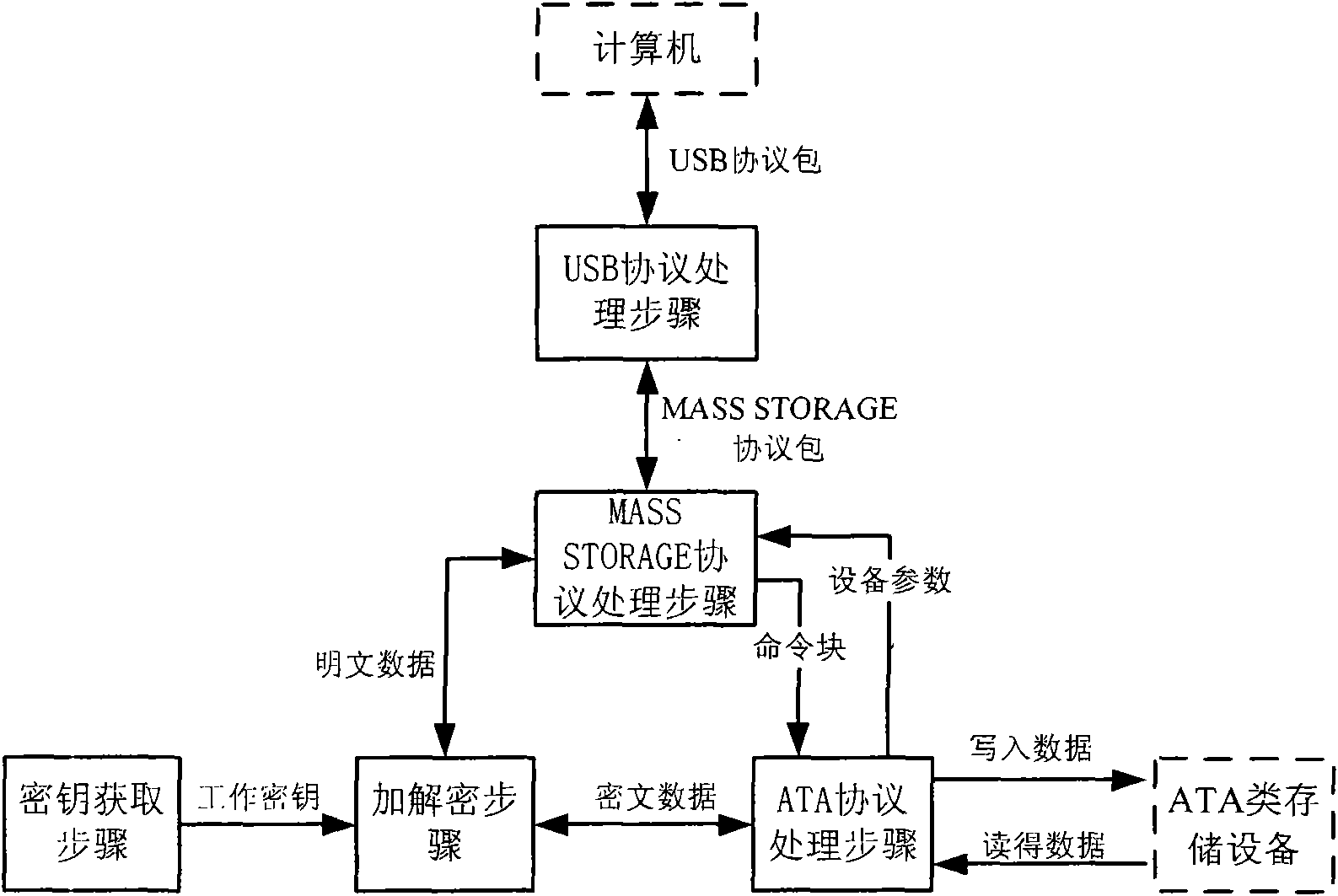
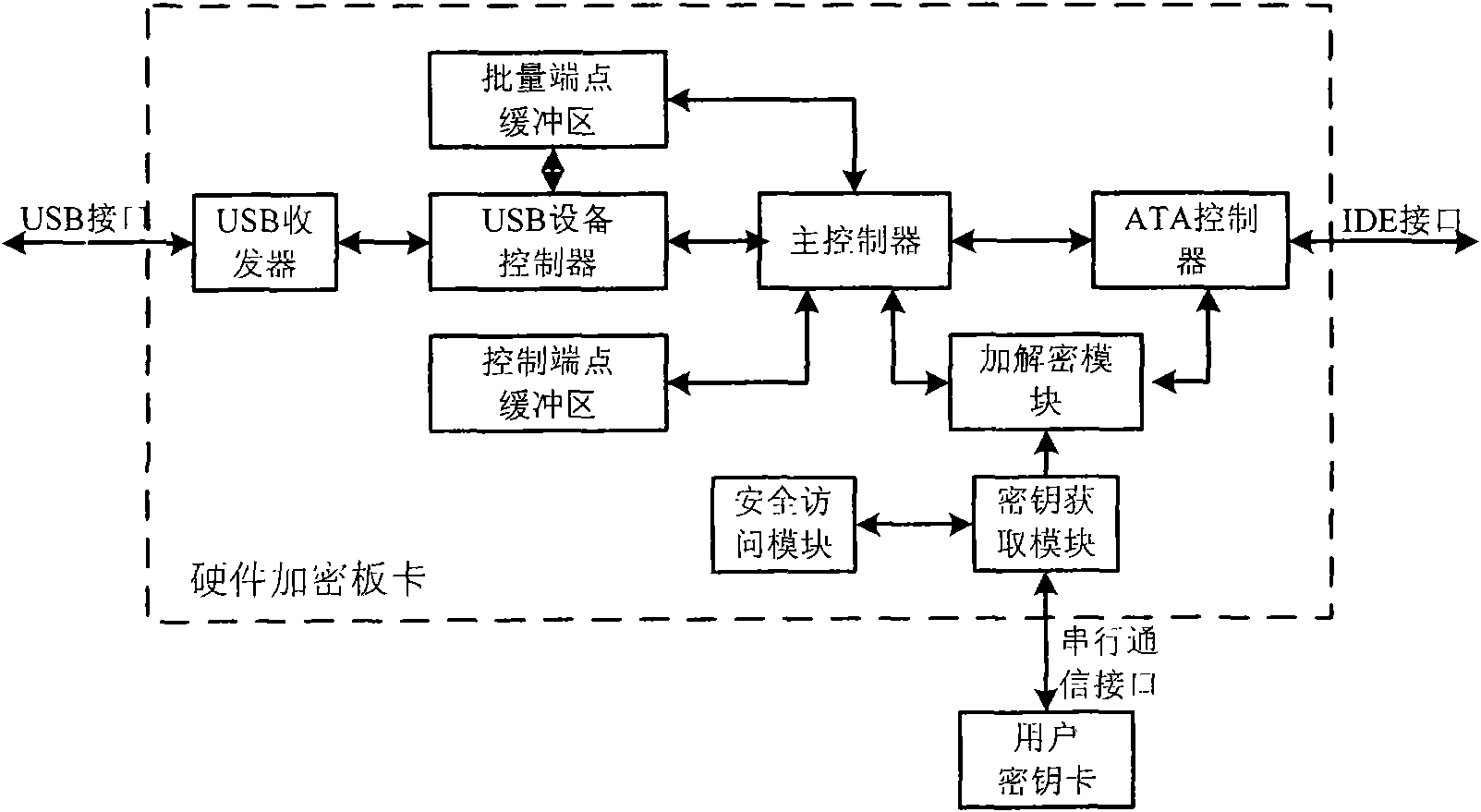
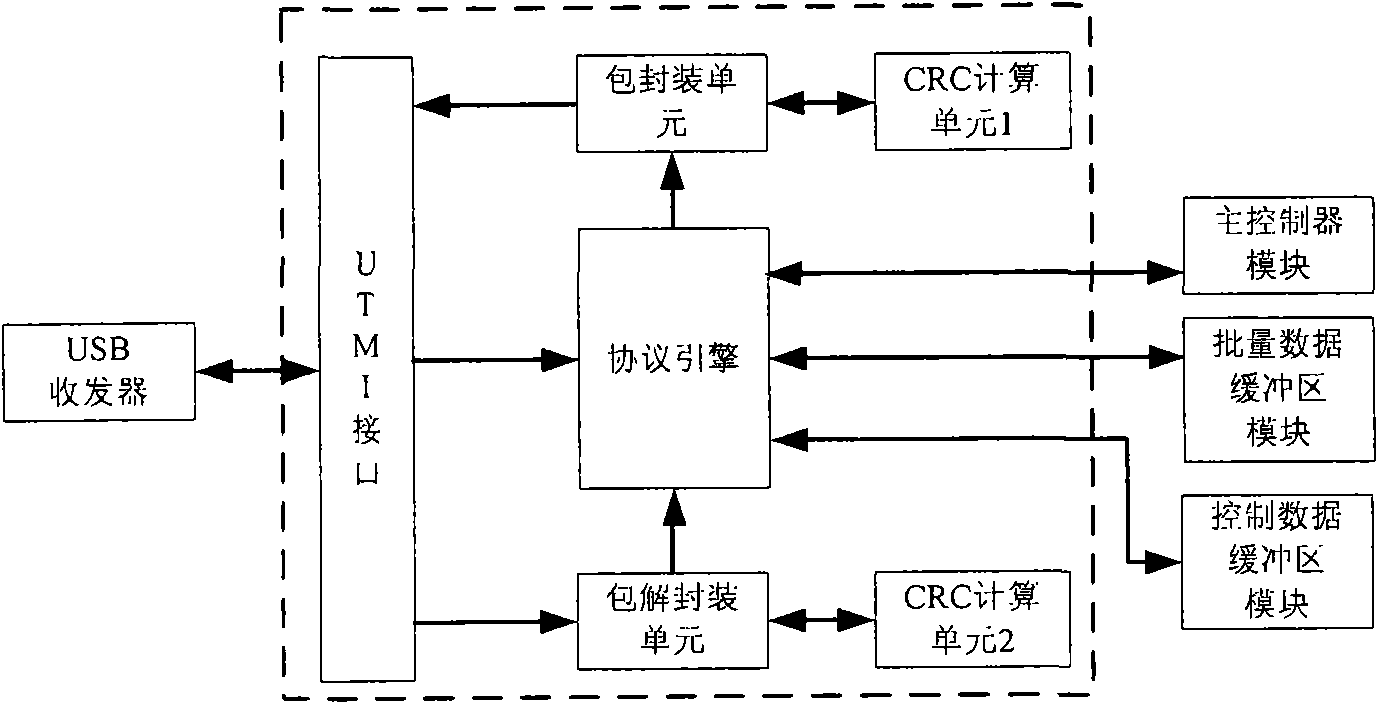
Method and device for encrypting data in ATA memory device with USB interface
InactiveCN101551784AFast encryption and decryptionImprove securityUnauthorized memory use protectionOperational systemEncryption decryption
The invention relates to a method and a device for encrypting data in an ATA memory device with a USB interface. Based on the conventional ATA memory device, the device for encrypting data consisting of a user card and a hardware encryption board card encrypts data transmitted between the memory device and a USB host, thereby achieving the aim for encrypting the data in the memory device. The device for encrypting data consists of a user secret key card and a hardware encryption bard card; and the hardware encryption bard card consist of a USB transreceiver, a USB equipment controller, a control endpoint buffer area, a batch endpoint buffer area, a main controller, an encryption-decryption module, an ATA controller, a secret key acquisition module and a safe access module. The invention has the advantages that the secret key is directly read by the encryption device, without using a computer connected with the memory, thereby ensuring high security; in addition, the data can be encrypted and decrypted at high speed without using an operation system; and moreover, the secret key is stored in a special hardware secret key memory card, and the secret key and the protected data are independently stored, thereby ensuring the security of the data.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
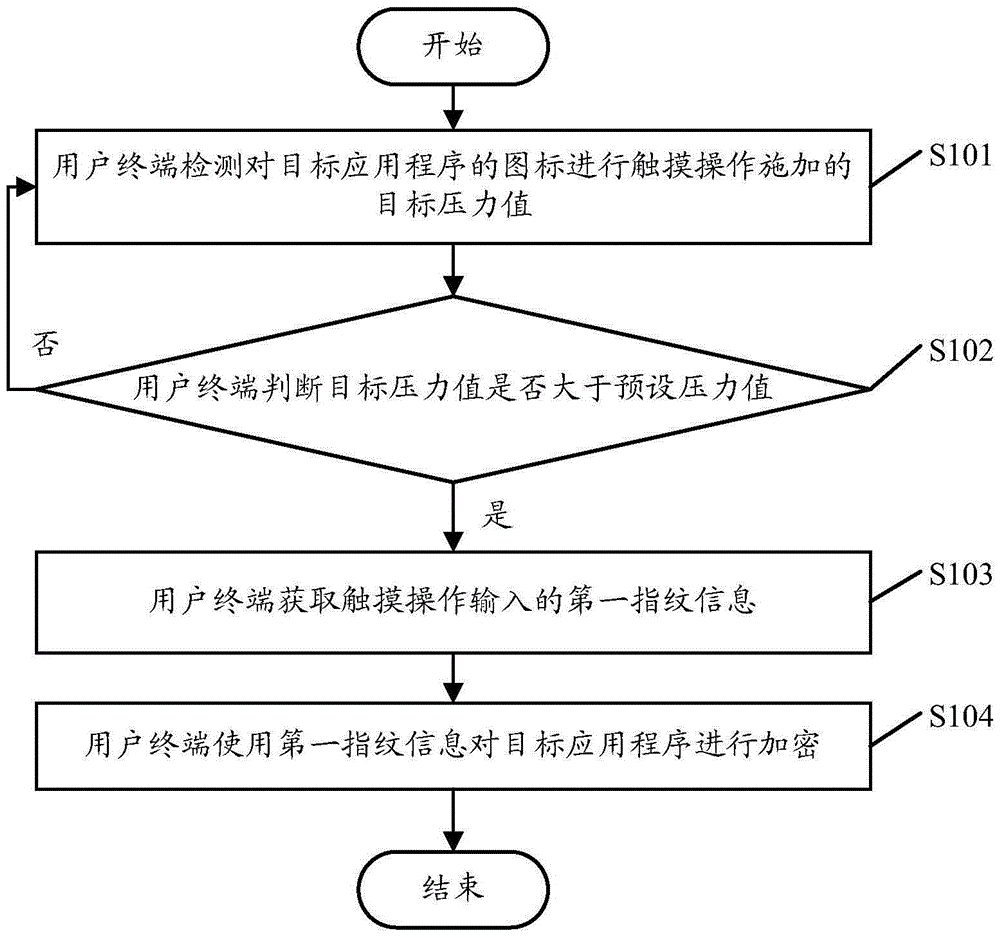
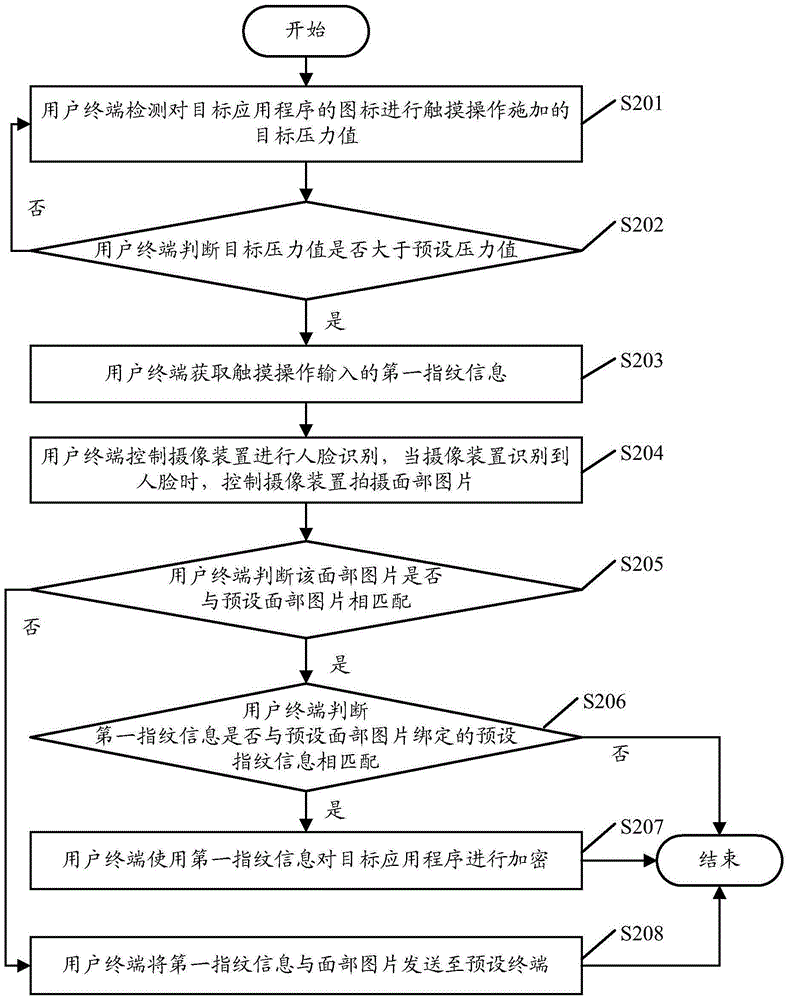
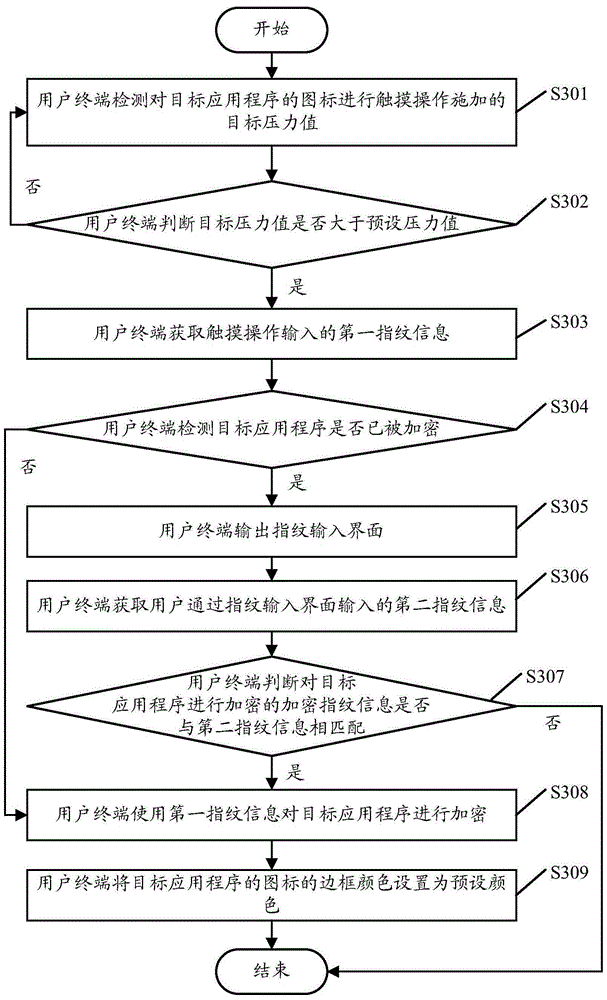
Application program encrypting method and user terminal
InactiveCN105205374AFast encryptionGood encryptionDigital data authenticationMultiple biometrics useComputer terminalApplication software
An embodiment of the invention discloses an application program encrypting method and a user terminal. The method comprises steps as follows: a target pressure value of touch operation on an icon of a target application program is detected; whether the target pressure value is larger than a preset pressure value is judged; when the target pressure value is larger than the preset pressure value, first fingerprint information input during touch operation is acquired; the first fingerprint information is used for encrypting the target application program. Accordingly, with the adoption of the application program encrypting method and the user terminal, the application program can be encrypted quickly and conveniently.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
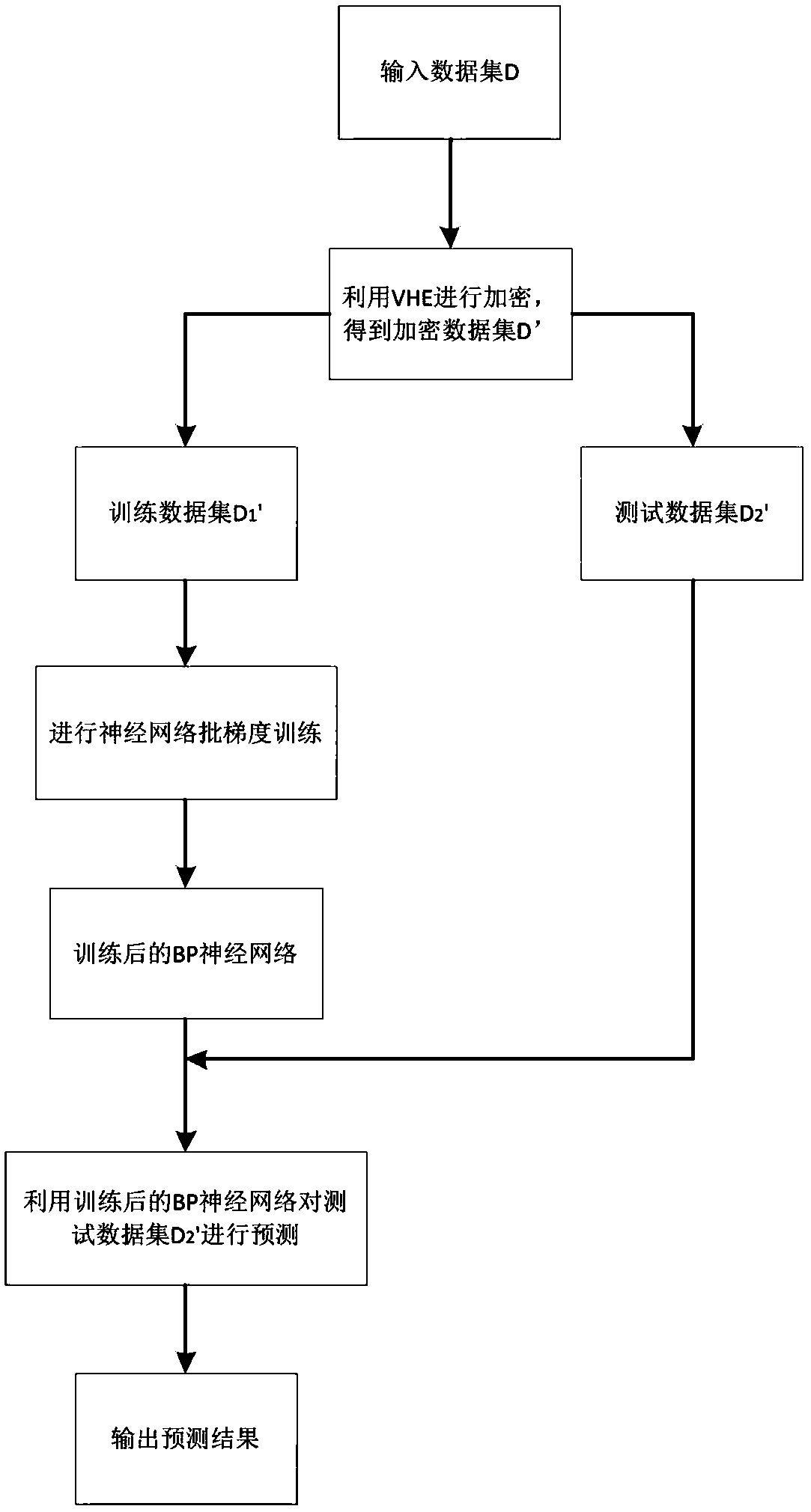
VHE-based privacy protection neural network training and predicting method
InactiveCN108776836ARealize computing outsourcingFast encryptionDigital data protectionNeural learning methodsData setPrivacy protection
The invention discloses a VHE-based privacy protection neural network training and predicting method. The method comprises the following steps of: encrypting a data set D by utilizing a VHE homomorphic encryption algorithm so as to obtain an encrypted data set D', wherein the encrypted data set D' comprises a training data set D'1 and a test data set D'2; carrying out BP neural network batch gradient training on the training data set D'1 so as to obtain a trained BP neural network; and predicting the test data set D'2 by utilizing the trained BP neural network. According to the method, an encryption algorithm and a BP neural network method are combined to realize the training and prediction of BP neural networks under a cyphertext domain, namely, BP neural network training and prediction also can be carried out on data under encryption protection when clouds are not credible, so that real computing outsourcing is realized.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
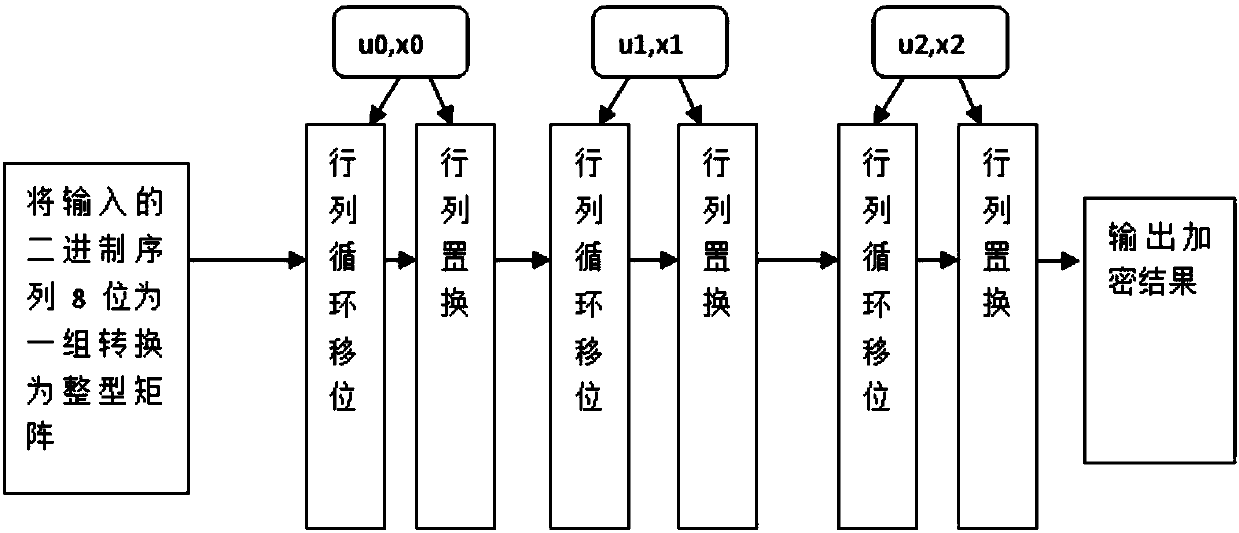
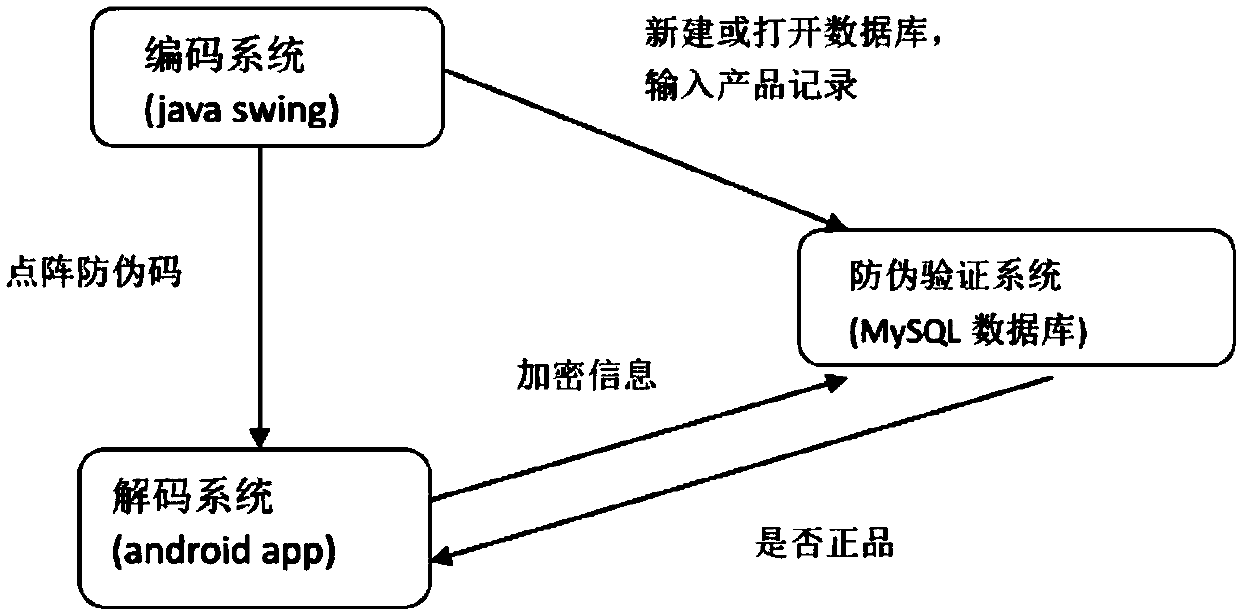
Chaotic encryption-based lattice anti-fake code design method and application system thereof
ActiveCN107609621AImprove securityMake up for the defect of not being able to resist scan-forgery attacksCo-operative working arrangementsCommercePlaintextDiffusion
The invention discloses a chaotic encryption-based lattice anti-fake code design method and an application system thereof. According to the method and the application system, the safety of lattice anti-fake codes is improved by utilizing a chaotic encryption technology, and chaotic encryption sequences are generated by using a worm population model and different initial values and control parameters so as to be applied to the diffusion and scrambling processes of chaotic encryption. According to the method and the application system, a ciphertext of a designed is as long as a plaintext, concise, efficient, high in encryption speed and suitable for commercialized production. The invention furthermore discloses the chaotic encryption-based lattice anti-fake code application system. Accordingto the method and the application system, a counter method is utilized to fill the gap that lattice anti-fake codes cannot resist scanning-counterfeiting attack, and a decryption function is deployedat a server, so that the pressure of an android app client is lightened, benefit is brought to the relative independence of the server, passwords are not easy to leak and the safety coefficient is relatively high.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com