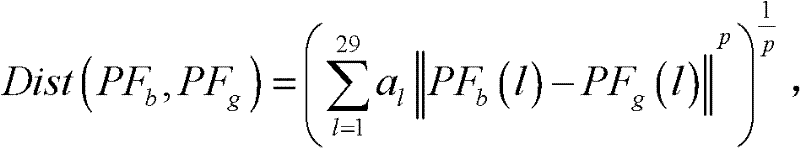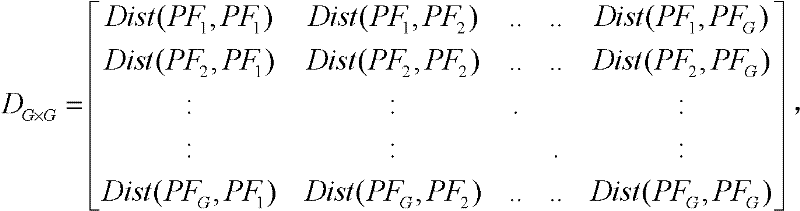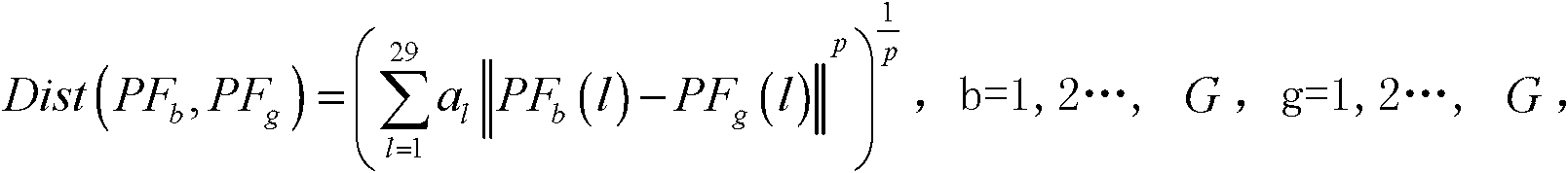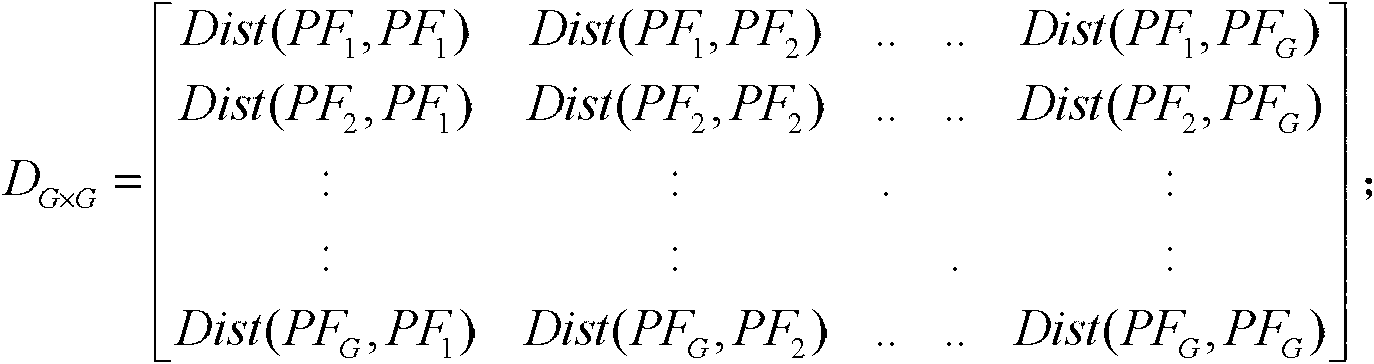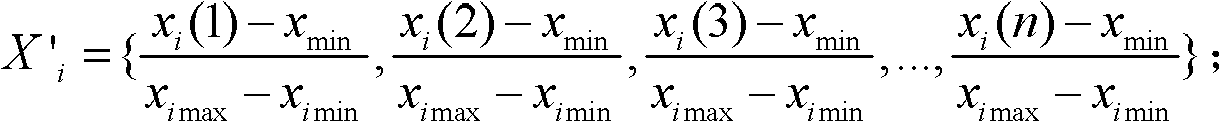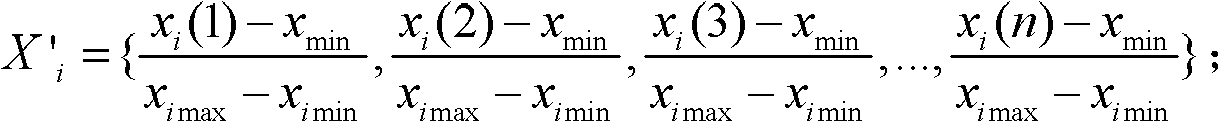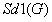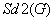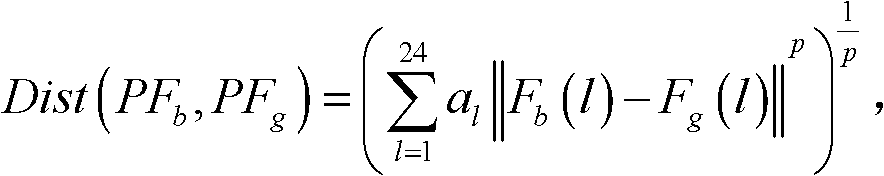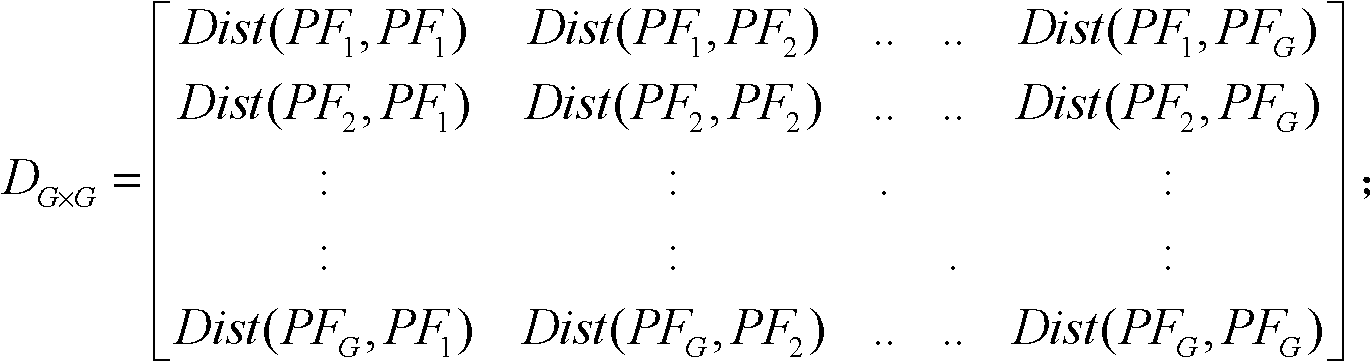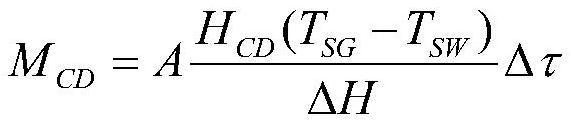Patents
Literature
65results about How to "Reduce the need for computing resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
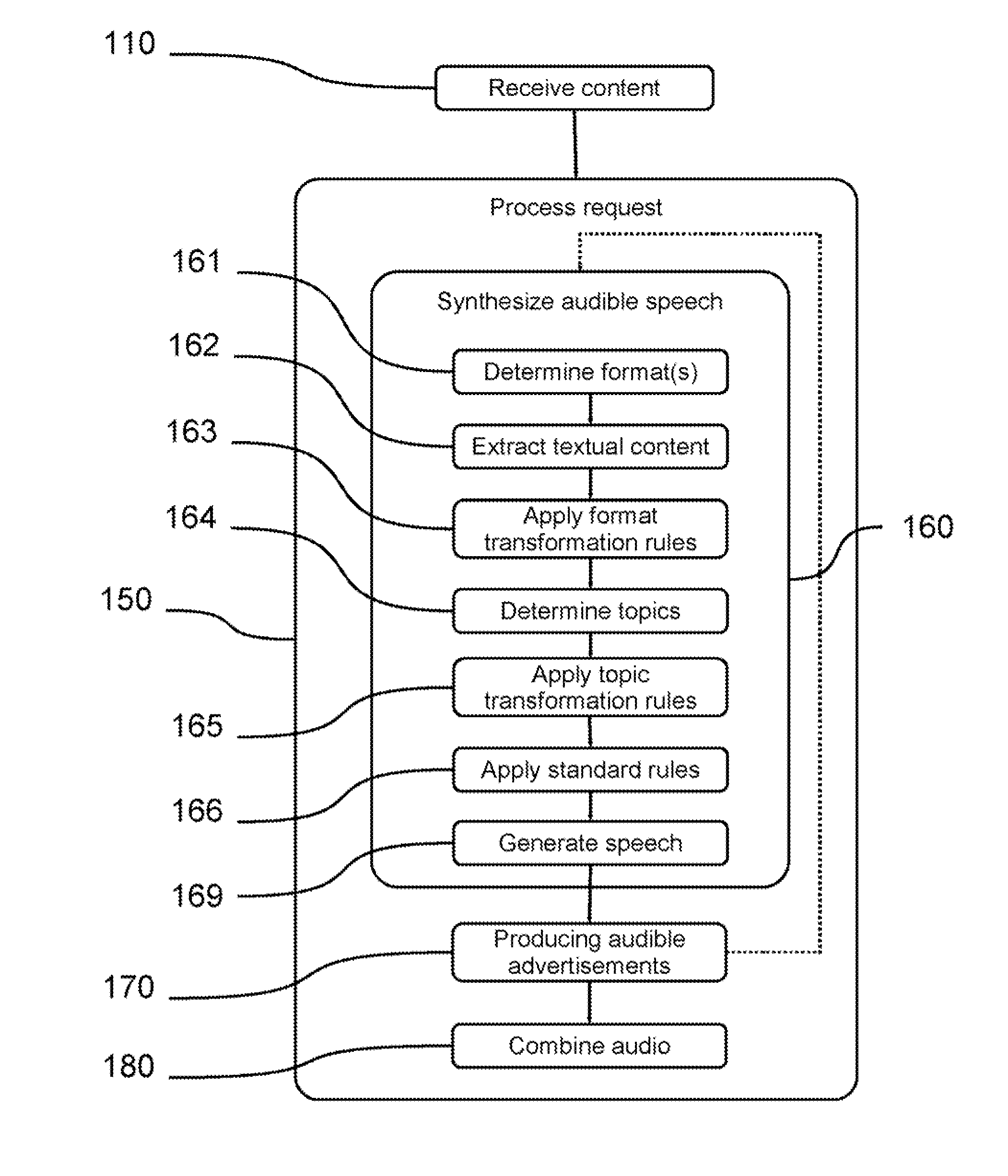
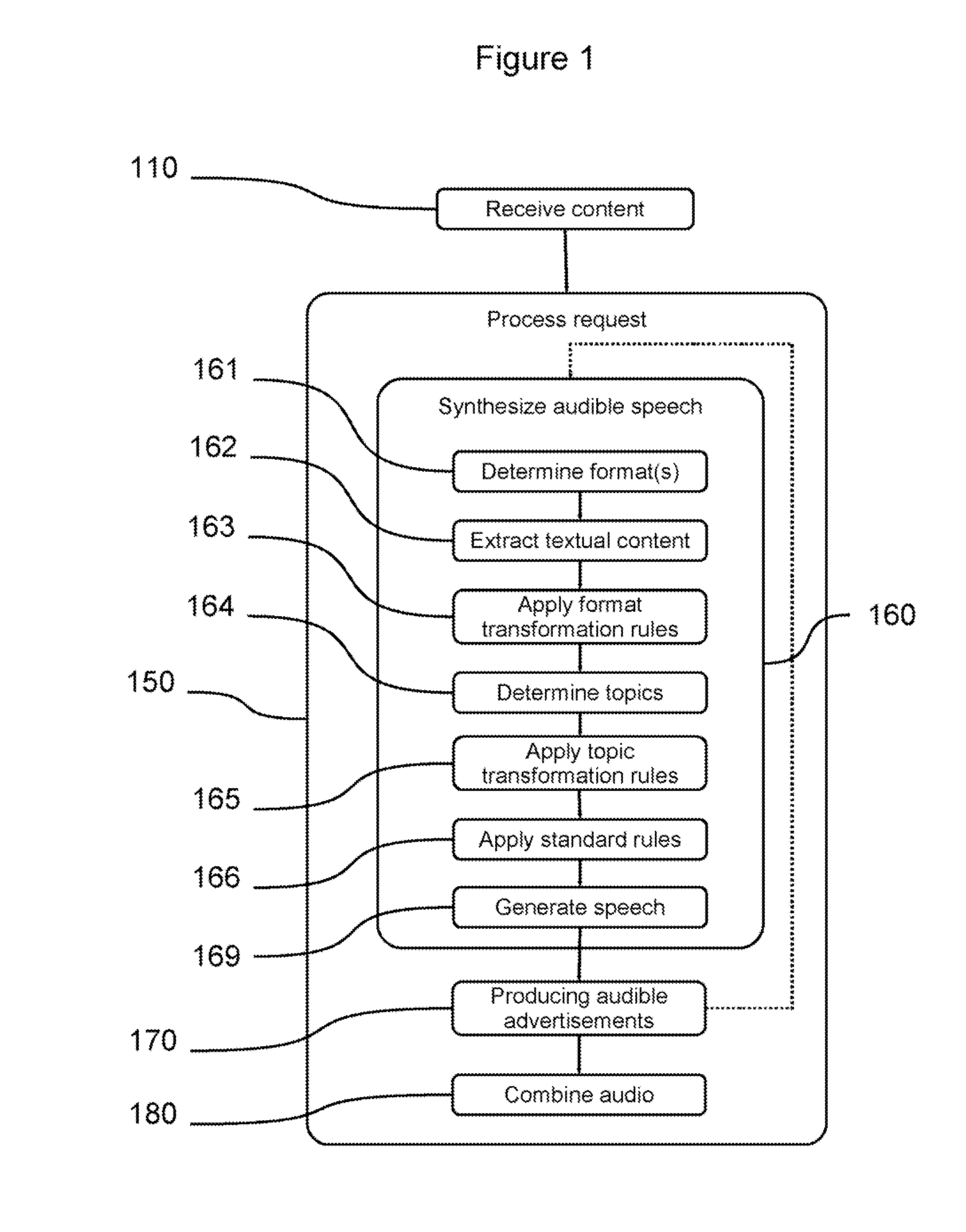
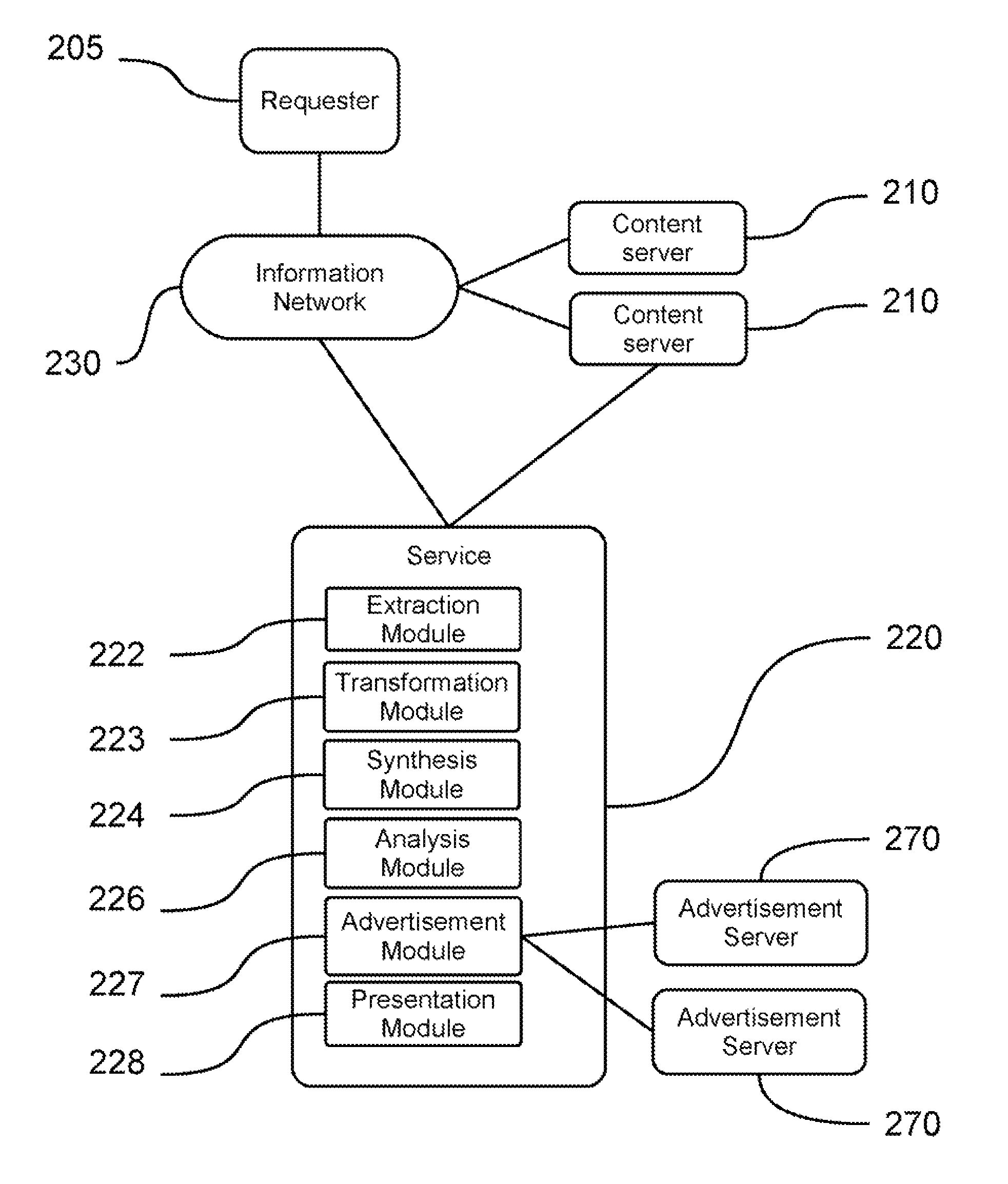
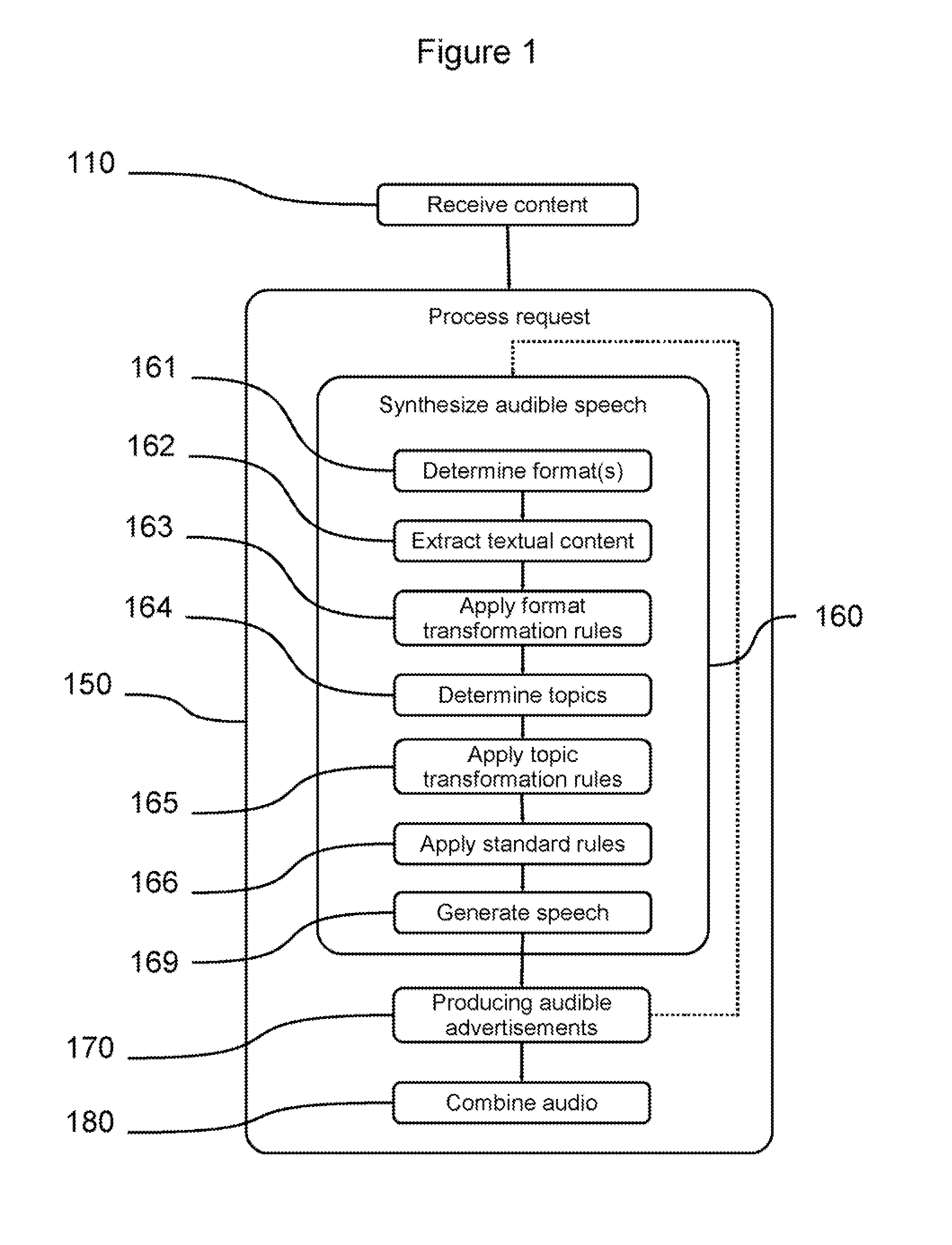
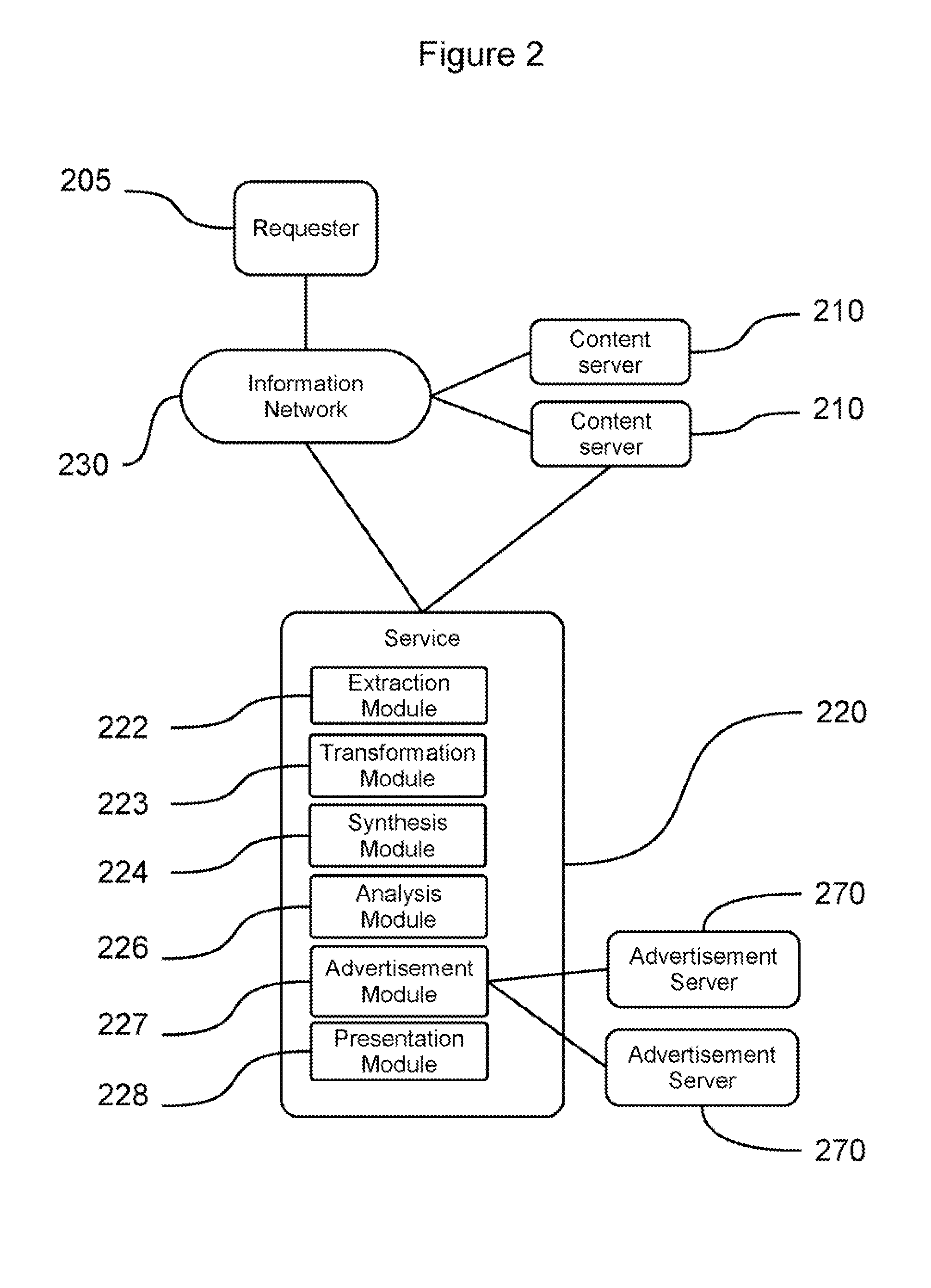
Method and System for a Speech Synthesis and Advertising Service
ActiveUS20080059189A1Reduce the need for computing resourcesReduce deploymentAutomatic call-answering/message-recording/conversation-recordingMultiple digital computer combinationsText to speech synthesisSpeech sound
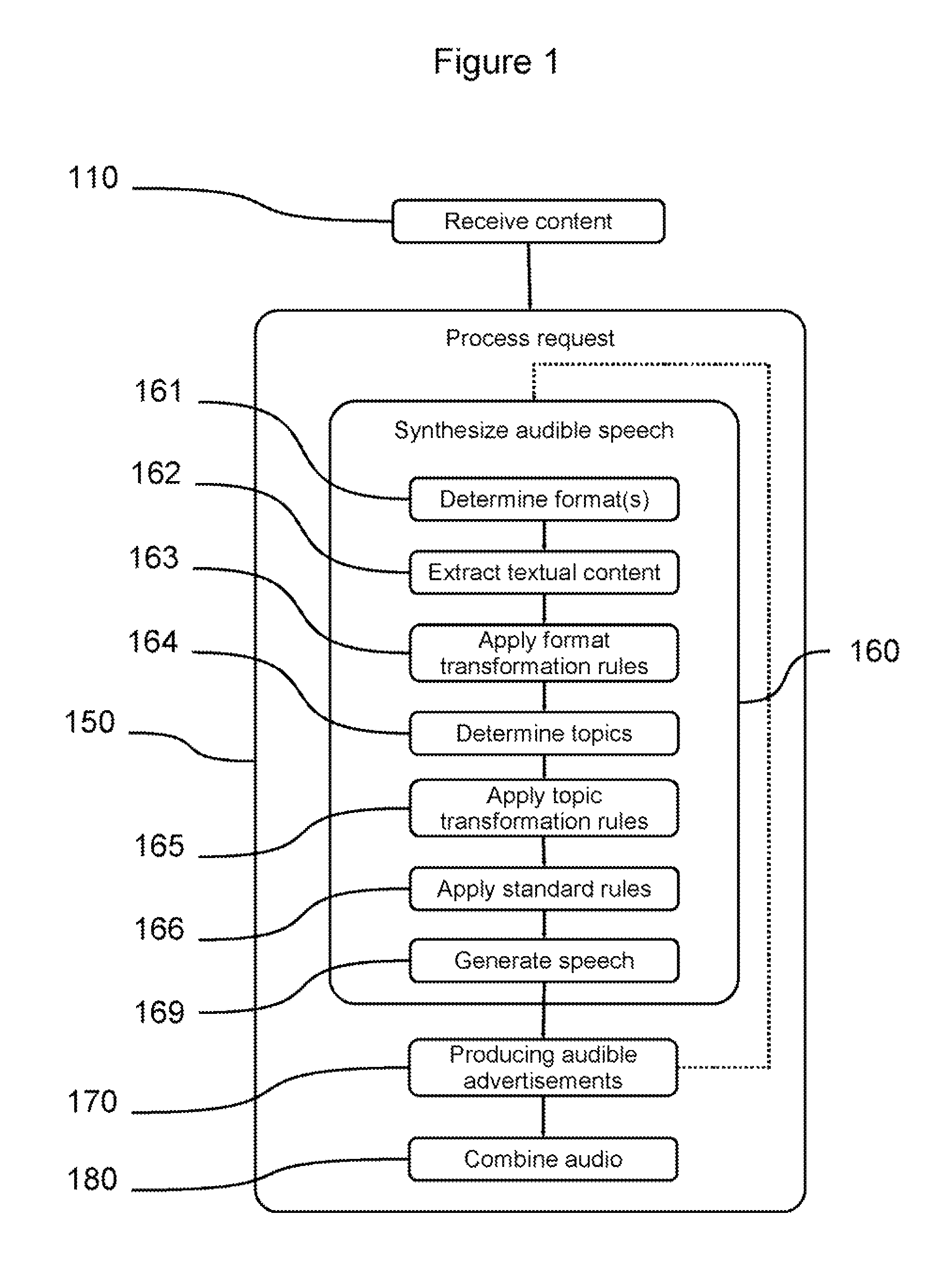
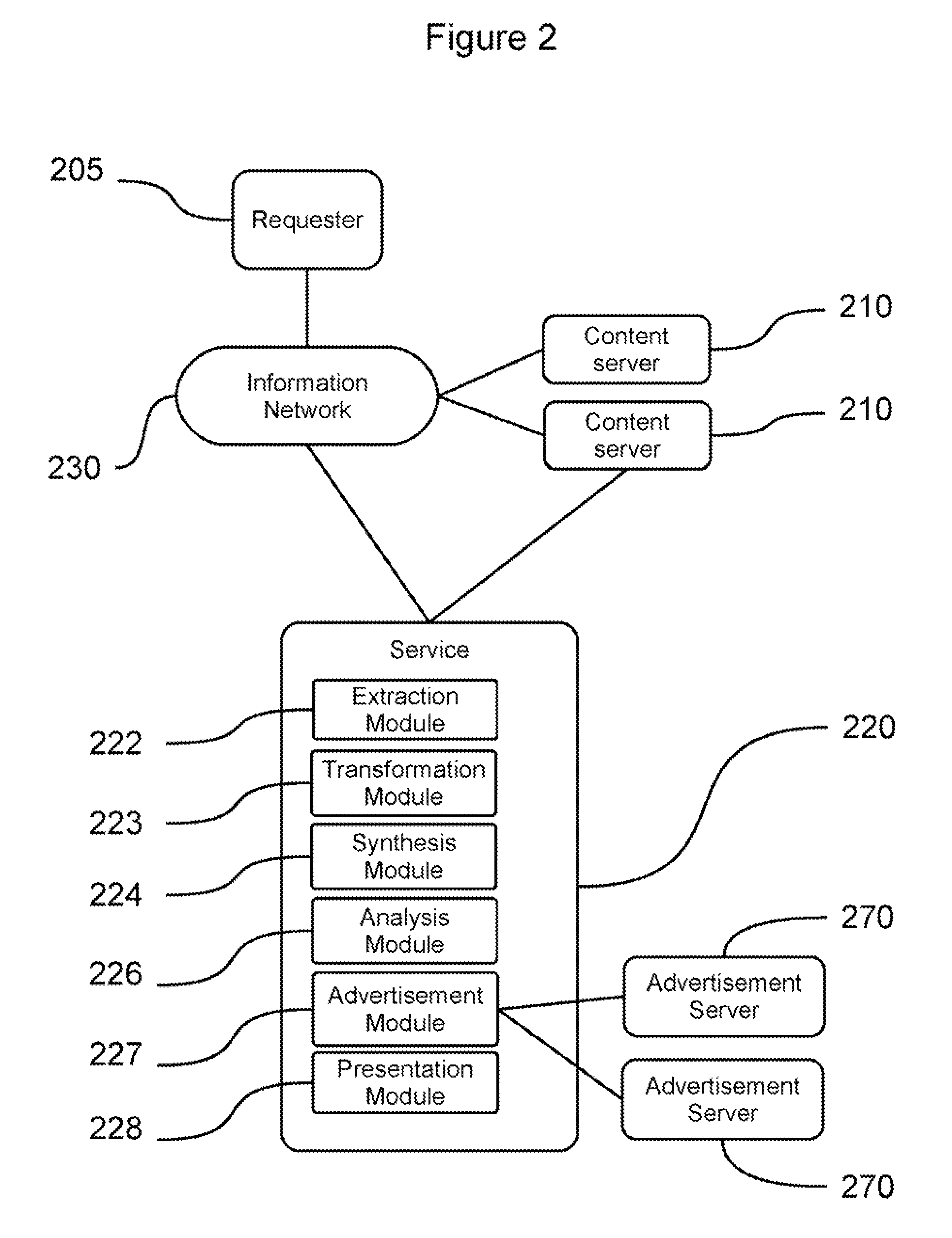
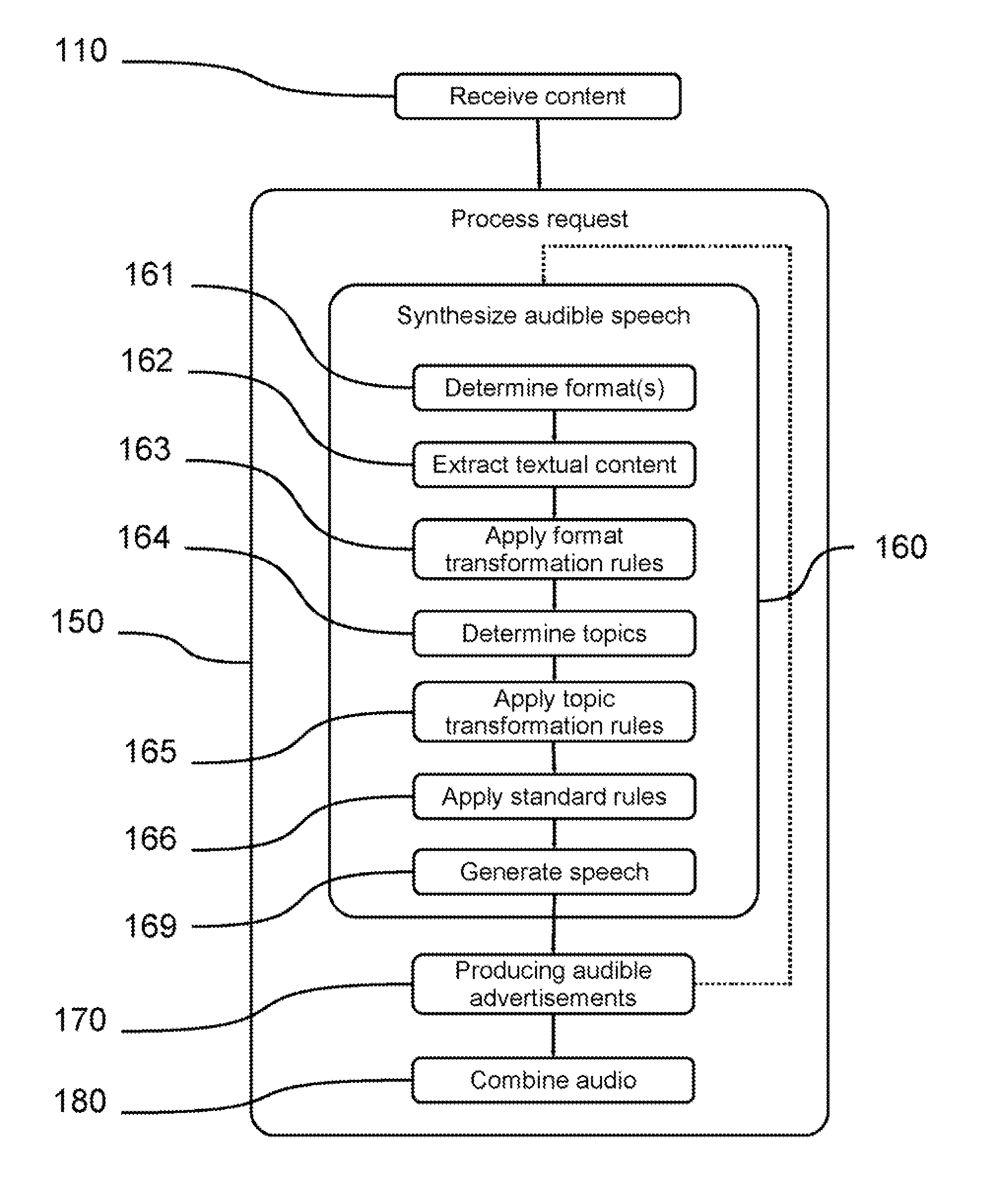
Methods and systems for providing a network-accessible text-to-speech synthesis service are provided. The service accepts content as input. After extracting textual content from the input content, the service transforms the content into a format suitable for high-quality speech synthesis. Additionally, the service produces audible advertisements, which are combined with the synthesized speech. The audible advertisements themselves can be generated from textual advertisement content.
Owner:CHEMTRON RES
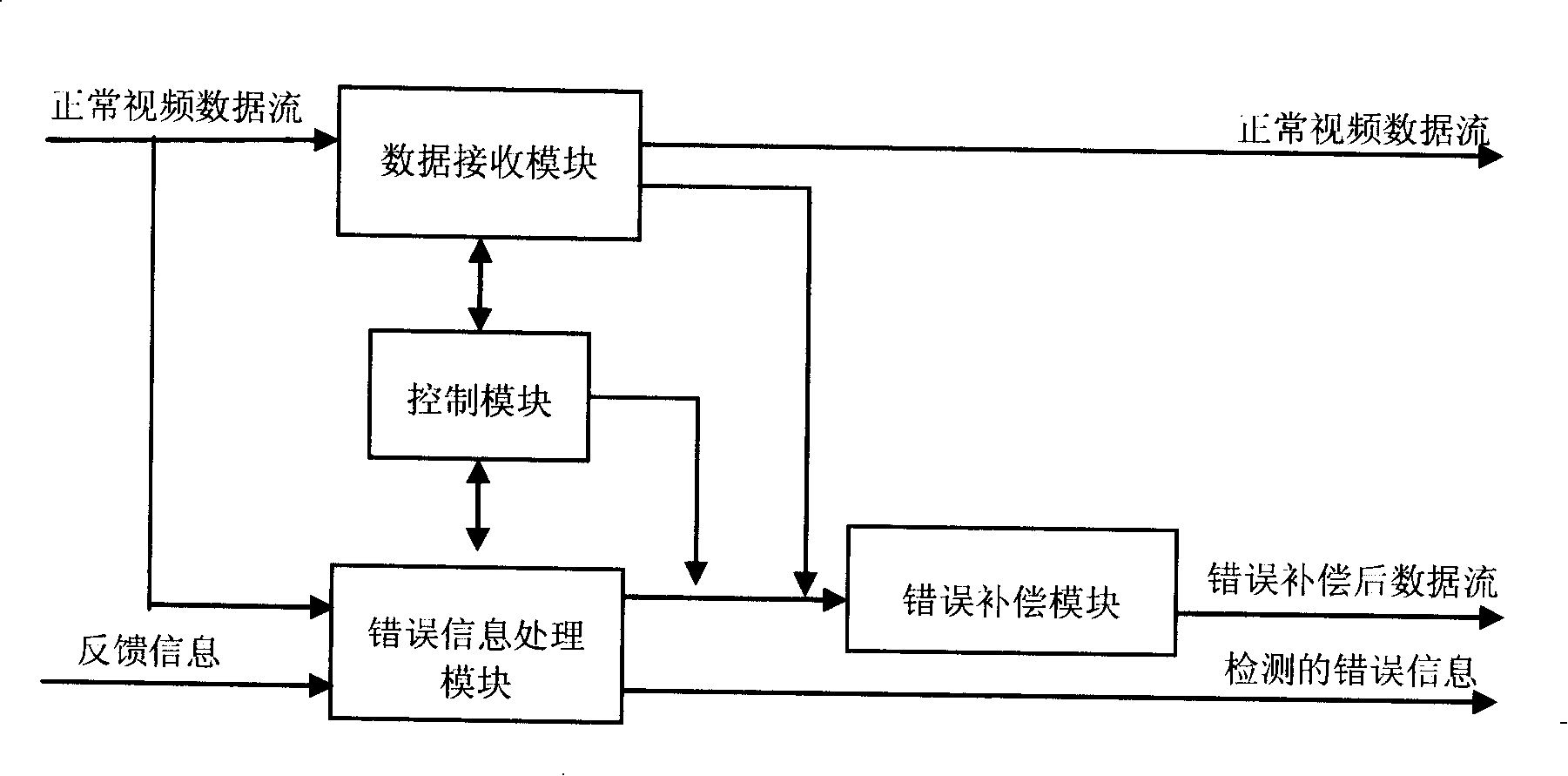
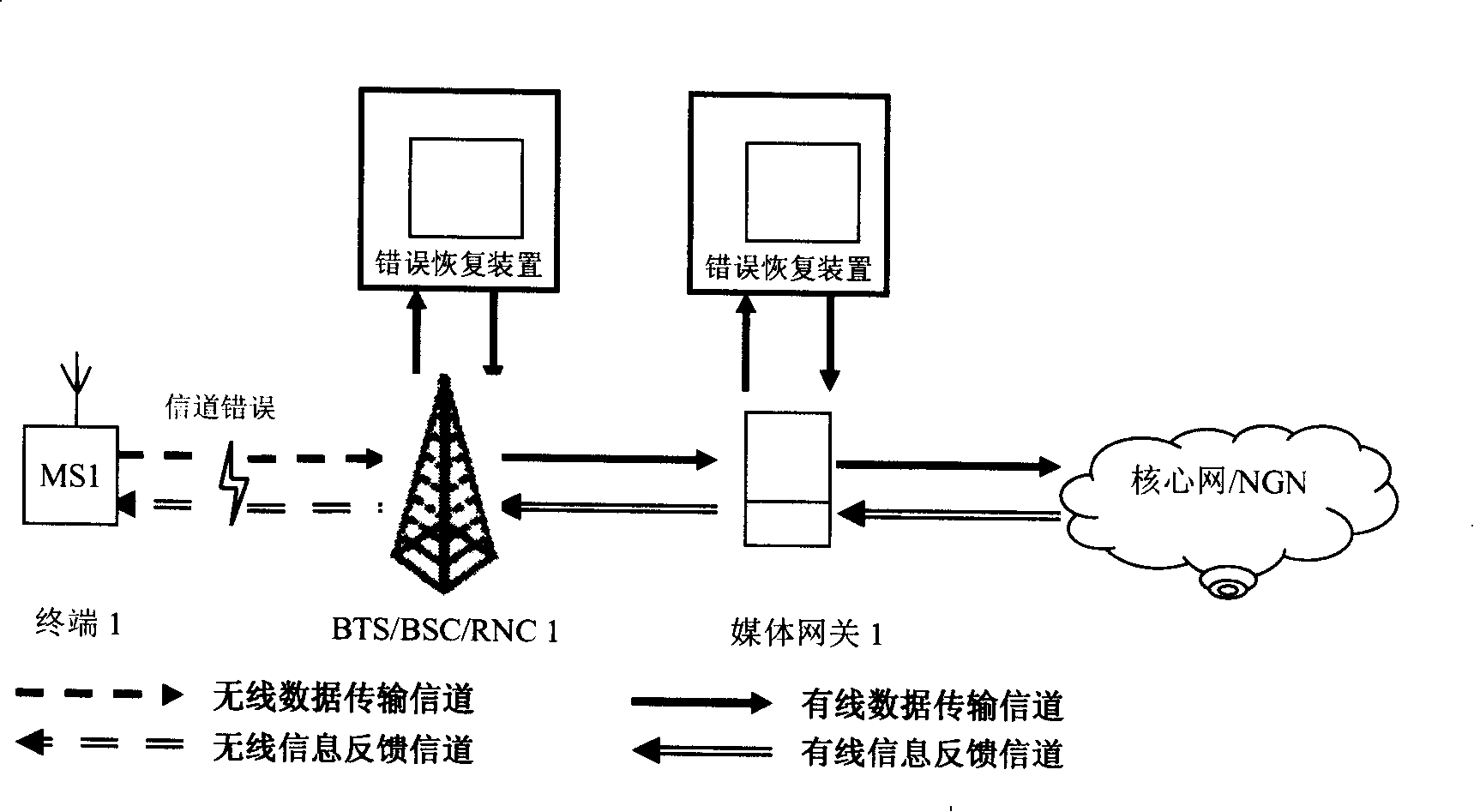
Self-adapted error recovery device, video communication system and method based on feedback
ActiveCN101193312ARestoring damaged image qualityReduce the need for computing resourcesTelevision systemsDigital video signal modificationSelf adaptiveVideo communication system
The invention discloses a self-adaptive error recovery device based on feedback, a video communication system and a method thereof. In the video communication system, the self-adaptive error recovery device based on feedback is added. A data receiving module in the error recovery device receives data; a wrong information processing module detects whether the received data is correct or not, or detects whether the wrong information exists in a feed back channel. If the wrong information exists, a controlling module starts an error compensating module to compensate the received wrong data and outputs the compensated data. Otherwise, the data receiving module directly outputs the normal data. The error recovery device can operate the error recovery processing within a relatively small feedback delay so as to recover the quality of damaged images of a video decoding terminal at the highest speed. The error recovery device and the method thereof can separate fault tolerance processing operation which needs relatively large computing resource from terminal decoding / encoding so as to reduce the demand on computing resources by the terminal.
Owner:ZTE CORP
Compressed image steganography encoding method based on AMBTC high and low average optimization
InactiveCN104284190ASimple calculationEasy to implementDigital video signal modificationPattern recognitionTwo step
The invention discloses a compressed image steganography encoding method based on AMBTC high and low average optimization. According to the compressed image steganography encoding method disclosed by the invention, after the smoothness of an image block is evaluated, data are embedded in smooth blocks one by one to obtain a stego image, wherein the data embedding comprises two steps: replacing a binary bitmap by the data, and optimizing high and low averages according to the embedded data and an original bitmap. With the adoption of the compressed image steganography encoding method, the computing is simple, the method is easy to realize, and a receiving side only needs to directly take out a bitmap of a receiving side, namely the embedded data, by discriminating the smooth blocks according to a secrete key; in addition, requirements on computing resources are low, and the use is convenient, so that the compressed image steganography encoding method has a good application prospect in the real-time field, mobile terminals with limited computing resources, and the like.
Owner:ANHUI UNIVERSITY
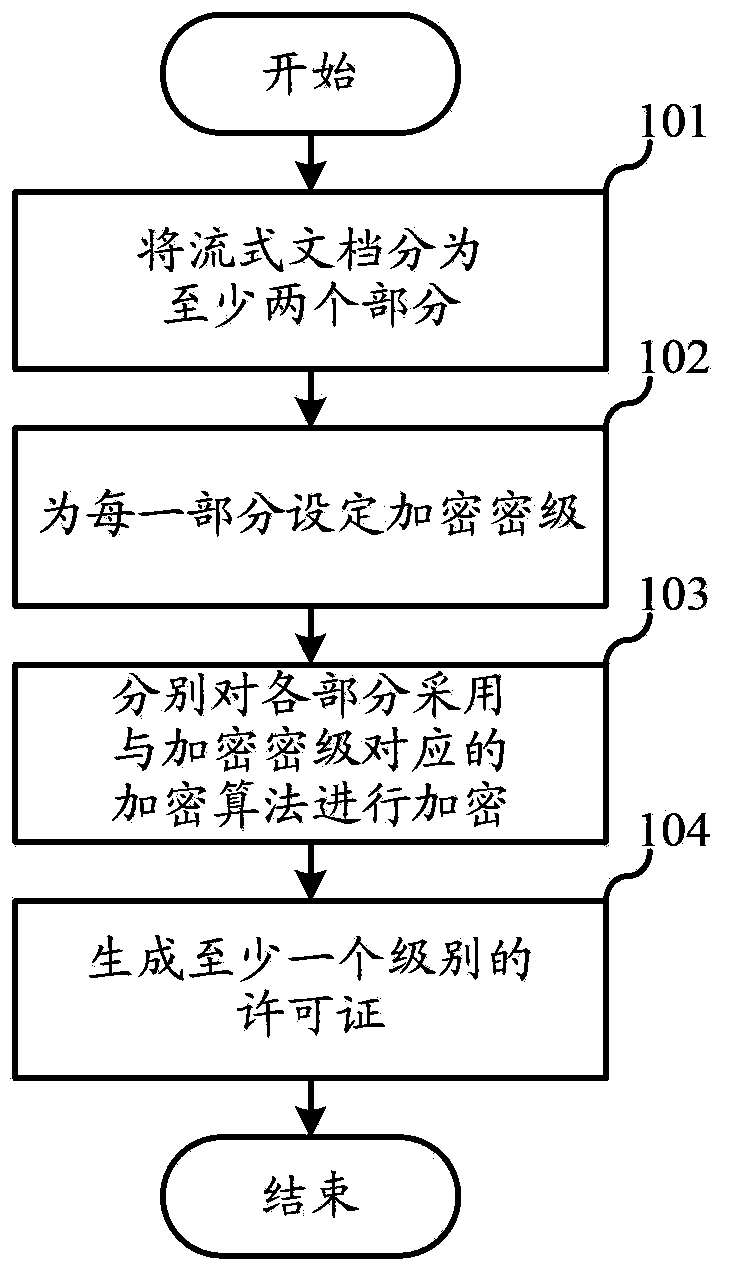
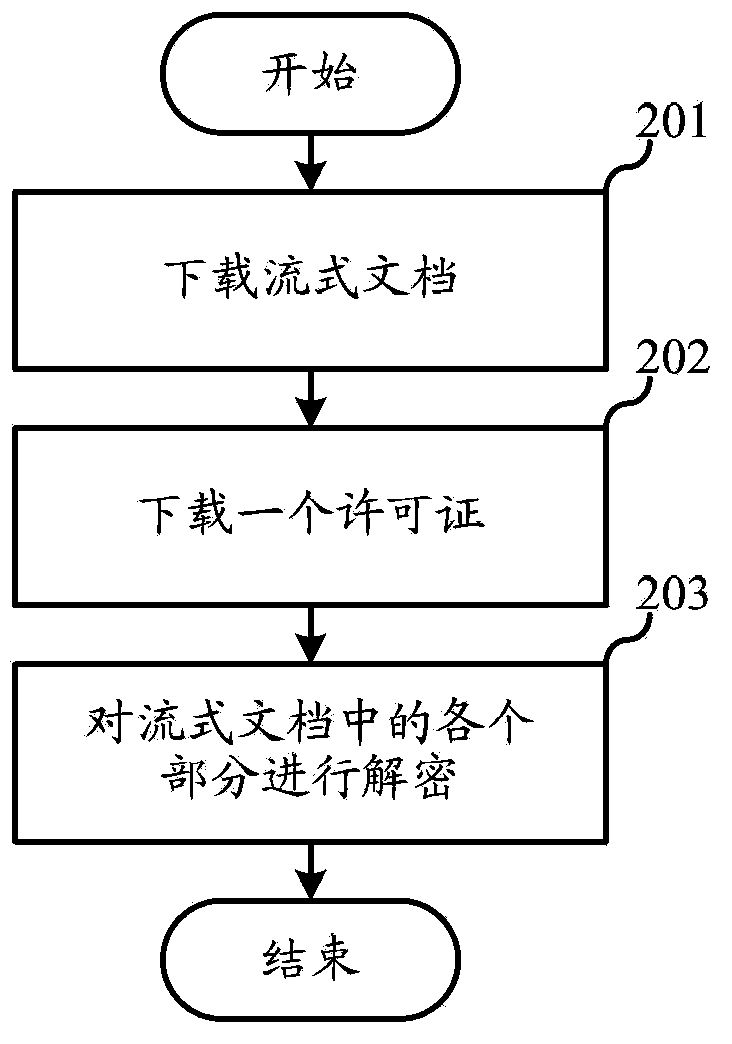
Method for encrypting and decrypting streaming document and device thereof
InactiveCN103577765AFast encryptionReduce the need for computing resourcesDigital data protectionComputer resourcesTerminal equipment
The invention relates to the field of digital publishing, and discloses a method for encrypting and decrypting a streaming document and a device thereof. According to the method, each part of one streaming document is encrypted at different encrypting grades, general contents can be encrypted by adopting a low-security-level rapid encryption algorithm, and important contents are encrypted by adopting a high-security-level safety encryption algorithm, so that the overall encryption speed of the document is increased, the demand on computing resources in a computer system is lowered, and the security of the important contents is ensured. Each part of one streaming document is encrypted by adopting different encrypting grades, and the contents of a low encryption security level can be decrypted rapidly, so that the overall decryption speed of the document is increased. At a lowest encryption security level, encryption is not performed, so that computer resources needed by encryption can be further reduced; parts of contents of the streaming document do not need to be decrypted during use, so that the demand of terminal equipment on computing resources is lowered; the method and the device are particularly suitable for trial reading of parts of chapters.
Owner:JIEFANG DAILY NEWSPAPER GRP
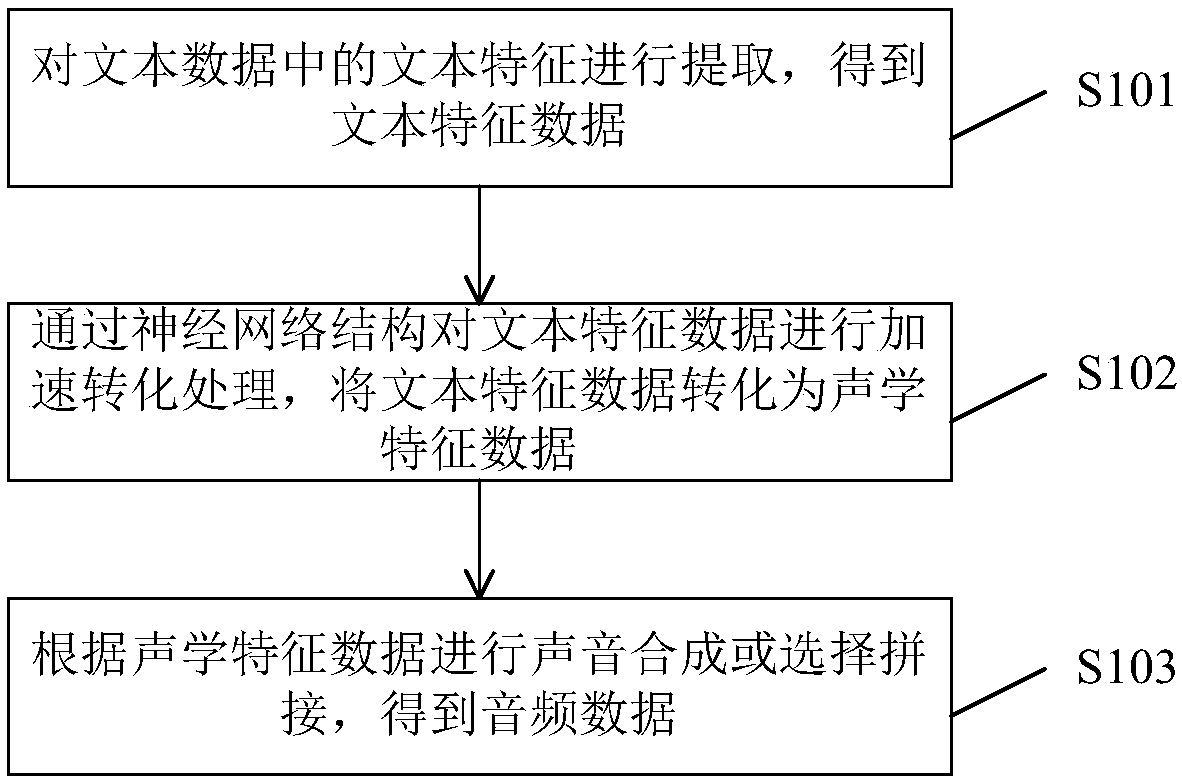
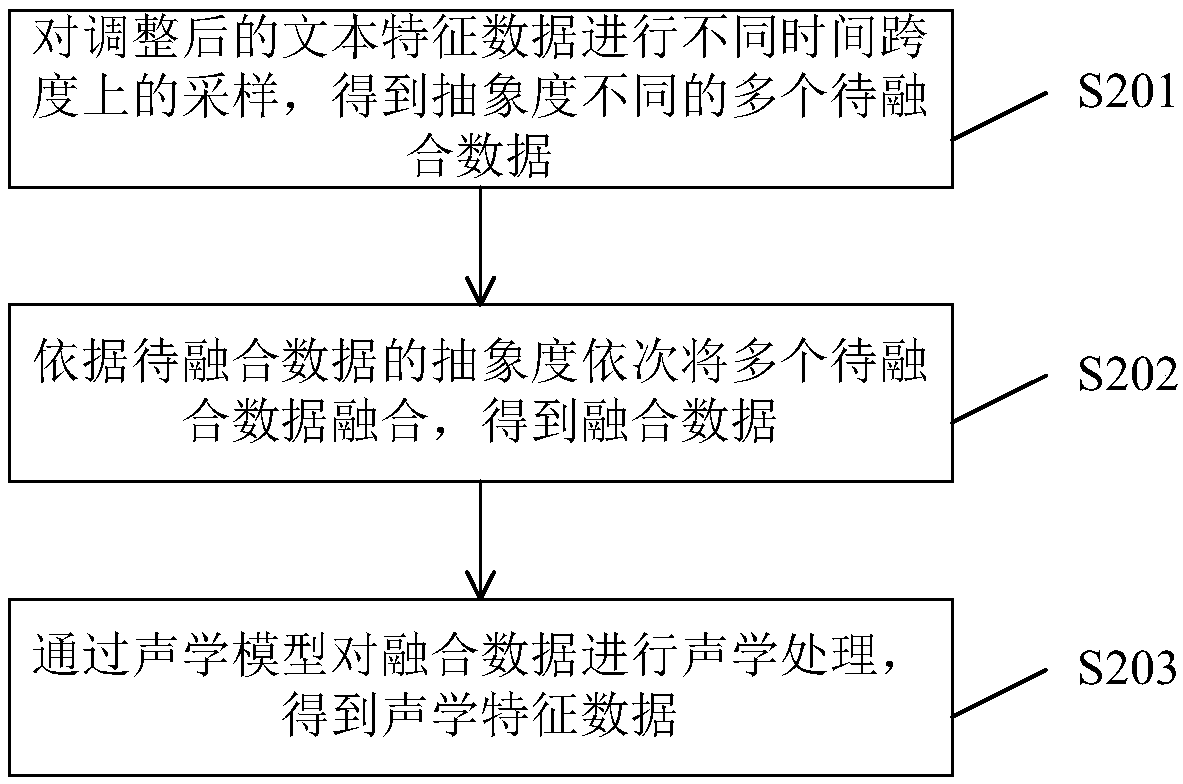
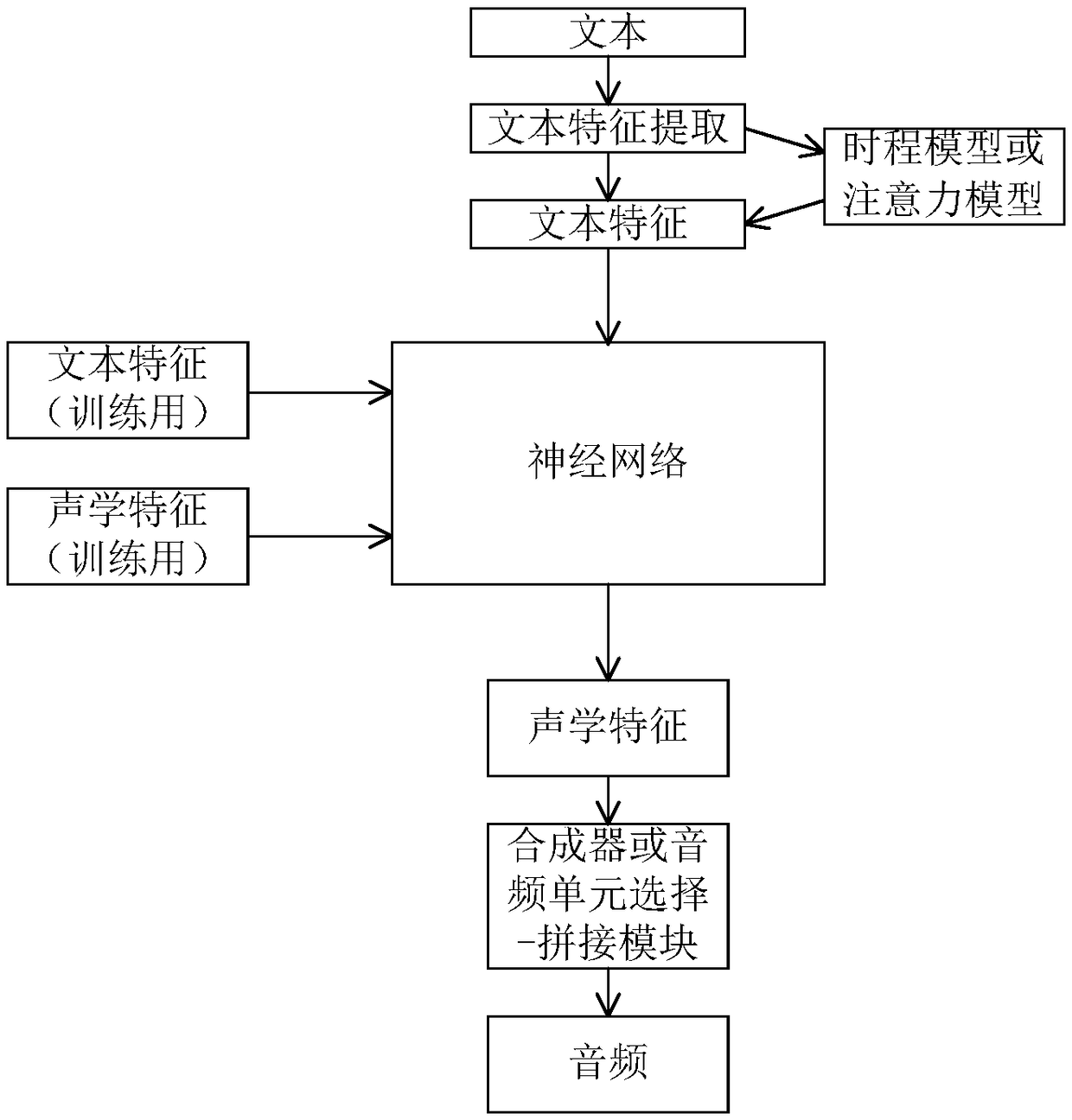
Audio data generating method and system for voice synthesis
ActiveCN109036371AGuaranteed prediction accuracyImprove interactive experienceSpeech synthesisNetwork structureFeature data
The invention provides an audio data generating method for voice synthesis. The audio data generating method comprises the following steps: extracting the text features in the text data to obtain textfeature data; carrying out the acceleration conversion processing on the text feature data through a neural network structure, and converting the text feature data into acoustic feature data; performing sound synthesis or selected splicing according to the acoustic feature data to obtain audio data. According to the invention, through the special anti-convolution structure is adopted, a good voice synthesis effect can be achieved on the premise that no any auto-regressive structure is included and few parameters are used, the calculation delay can be reduced while the prediction precision ofthe acoustic features can be guaranteed through the neural network structure, and the requirement for computing resources is reduced, the concurrent quantity is increased, the voice synthesis speed isincreased, and contribution is made to improvement of human-computer interaction experience.
Owner:BEIJING GUANGNIAN WUXIAN SCI & TECH
Data processing method and related equipment
PendingCN112288075AAchieving multi-task learningReduce the need for computing resourcesDigital data processing detailsNeural architecturesAlgorithmTerminal equipment
The invention relates to the field of artificial intelligence, and discloses a data processing method comprising the steps of acquiring to-be-processed data and a target neural network model, whereinthe target neural network model comprises a first transformer layer, the first transformer layer comprises a first residual error branch and a second residual error branch, the first residual error branch comprises a first attention head, and the second residual error branch comprises a target feedforward layer FFN; performing target task related processing on the to-be-processed data according toa target neural network model to obtain a data processing result, the target neural network model being used for performing target operation on the output of the first attention head and the first weight value to obtain the output of the first residual branch, and / or using the target neural network model for performing target operation on the output of the target FFN and the second weight value to obtain the output of the second residual branch. According to the embodiment of the invention, for different tasks, the weight value for controlling the output of the residual branch is set, so thatthe computing resource requirement of the terminal equipment for operating the target neural network model is reduced.
Owner:HUAWEI TECH CO LTD
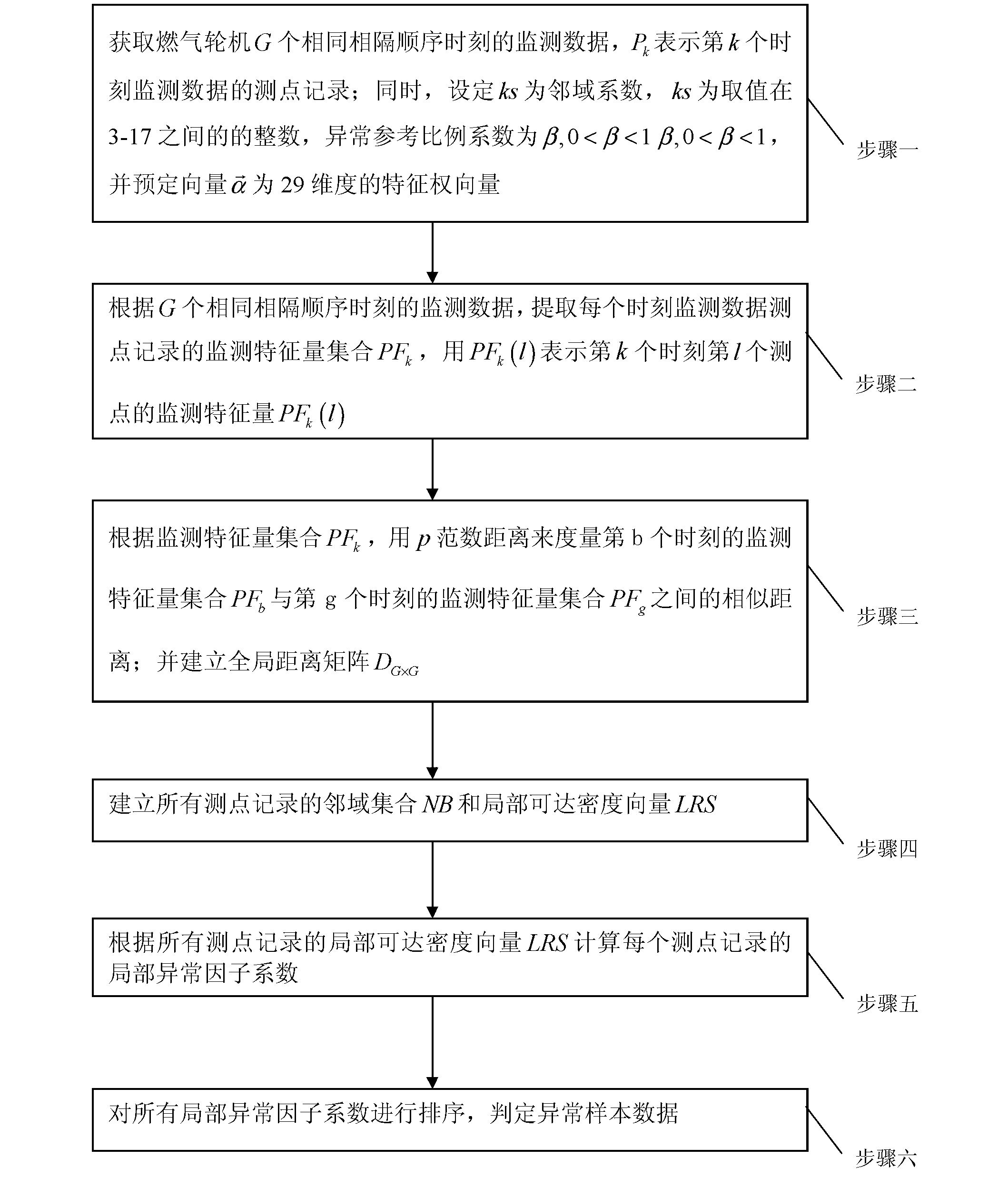
Cluster anomaly detection method of combustion gas turbine
InactiveCN102607641AReduce the need for computing resourcesShorten the timeMeasurement devicesClustered dataCombustion
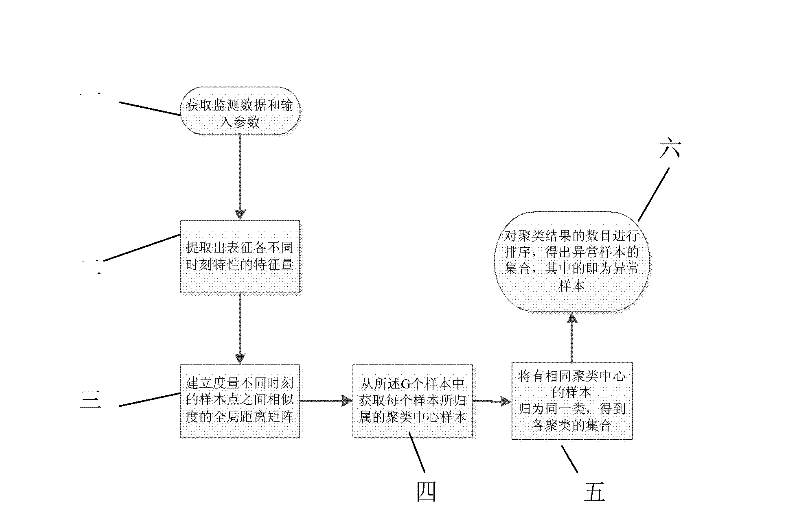
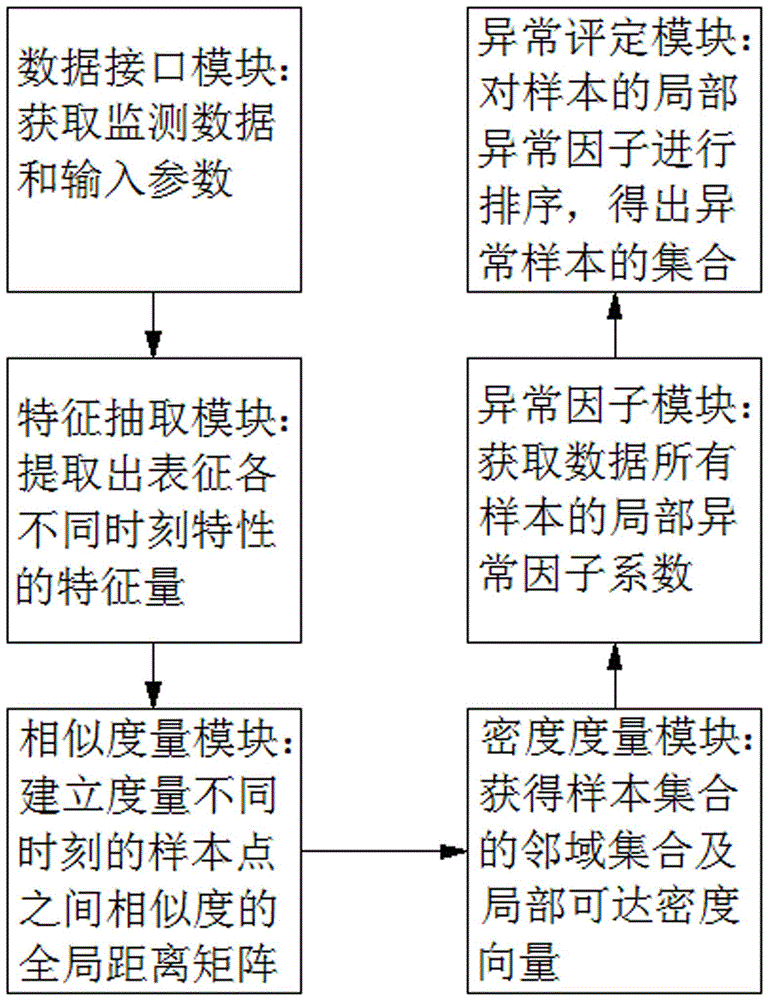
The invention provides a cluster anomaly detection method of a combustion gas turbine, which solves the problems of insufficient early warming, simple and limited fault monitoring level and high misjudgment degree, caused by that the conventional combustion gas turbine has the defects of large quantity of data collected by a sensor and excessively large information amount. The cluster anomaly detection method disclosed by the invention has special processes as follows: obtaining monitoring data and input parameters; extracting characteristic quantities for representing characteristics at different moments; establishing an overall distance matrix for measuring similarities among sample points at the different moments; obtaining a cluster center sample which each sample belongs to from G samples; sorting the samples with the same cluster center as one type, so as to obtain sets of clusters; and ordering the quantity of cluster results, so as to obtain a set of abnormal samples. The cluster anomaly detection method disclosed by the invention has a small calculation resource demand, and low time and space costs. The cluster anomaly detection method is used for finally representing abnormal data points by rapidly clustering data based on a linear clustering manner, and has very strong accountability.
Owner:HARBIN INST OF TECH
Embedded platform recognition method for large vocabulary quantity of voice command words
InactiveCN101751924AEfficient use ofReduce the need for computing resourcesSpeech recognitionPruningTree shaped
The present invention discloses an embedded platform recognition method for a large vocabulary quantity of voice command words, belonging to the technical field of voice recognition. The method comprises the following steps: preprocessing voice signals, extracting voice recognition parameters, building a voice acoustic model, training the voice model, building a tree-shaped recognition network and applying rapid recognition search algorithm. The voice acoustic model is an inter diphonia subsidiary model based on right context dependent words of initial consonants. The tree-shaped recognition network is made by that a tree-shaped recognition network is built based on the same consonant syllables and merged with the nodes of the same consonant syllables. The rapid recognition search algorithm adopts a state level pruning strategy and a frame-synchronous word level pruning strategy for the dynamic adjustment of window width according to the tree-shaped recognition network based on the same consonant syllables. The method is improved on the traditional embedded voice recognition method. The memory and the central processing unit (CPU) resources are fully utilized, and the speed for recognizing a large vocabulary quantity of voice command words is accelerated.
Owner:TSINGHUA UNIV
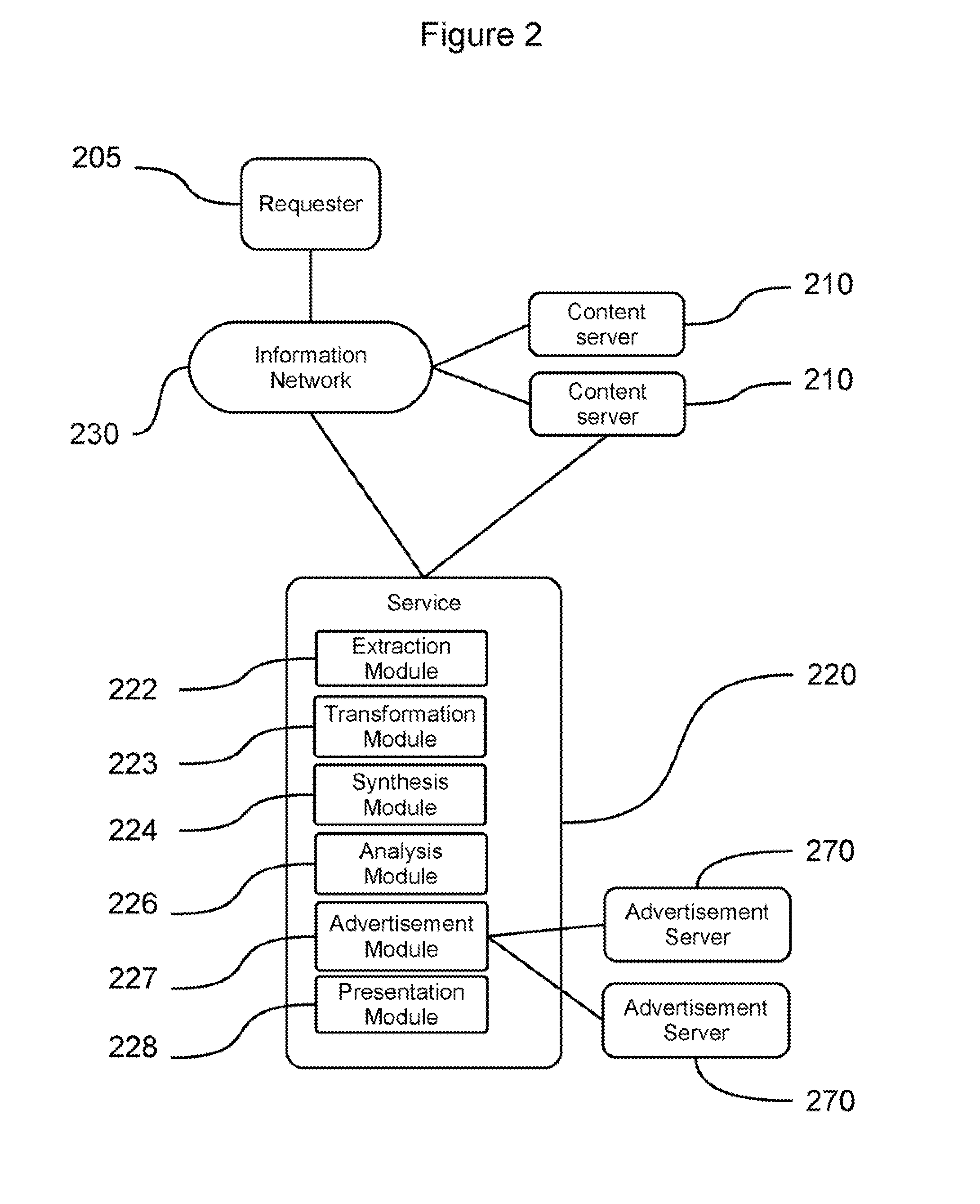
Content and advertising service using one server for the content, sending it to another for advertisement and text-to-speech synthesis before presenting to user
ActiveUS8032378B2Reduce the need for computing resourcesReduce deploymentAutomatic call-answering/message-recording/conversation-recordingMultiple digital computer combinationsText to speech synthesisSpeech sound
Owner:CHEMTRON RES
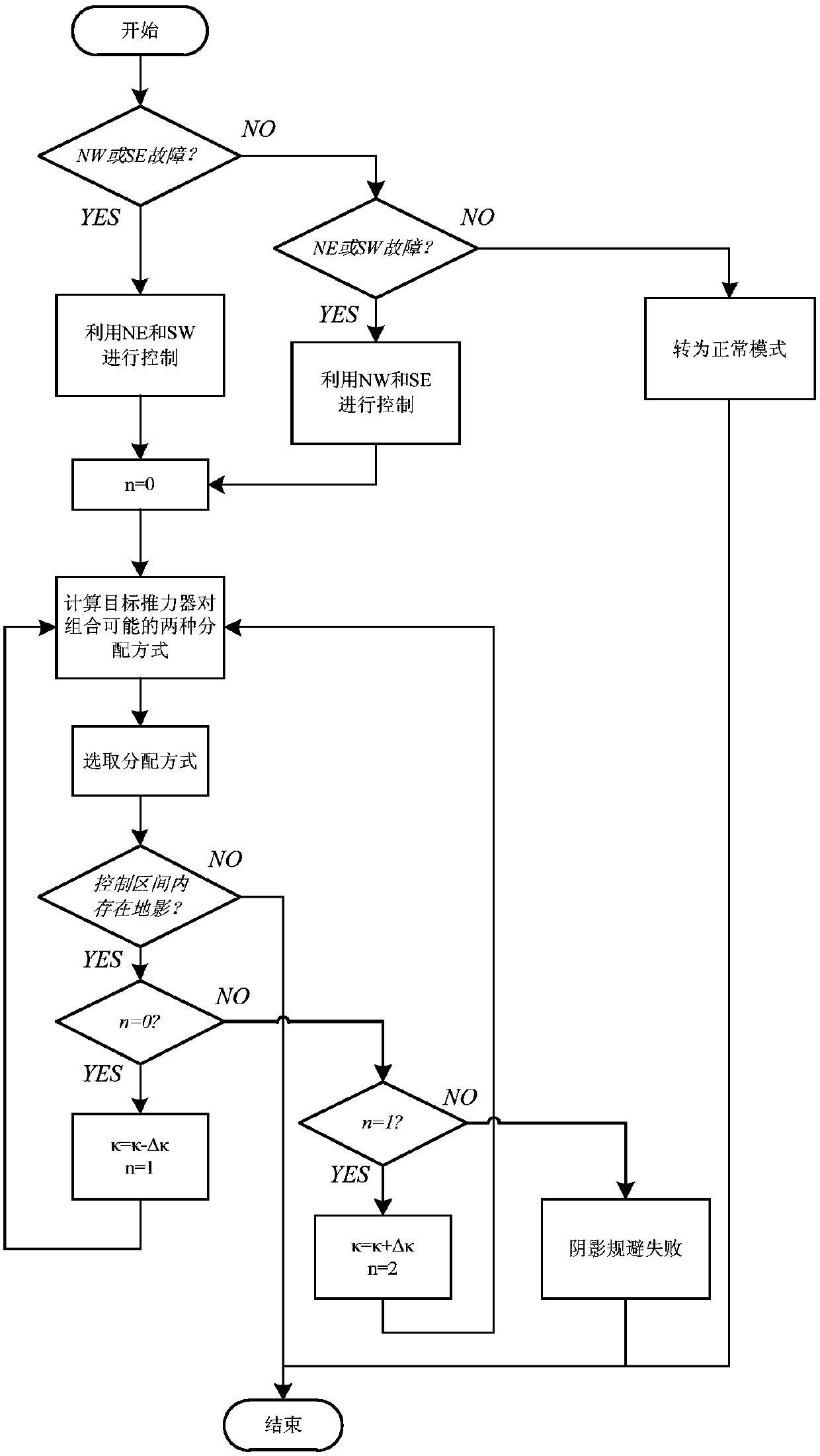
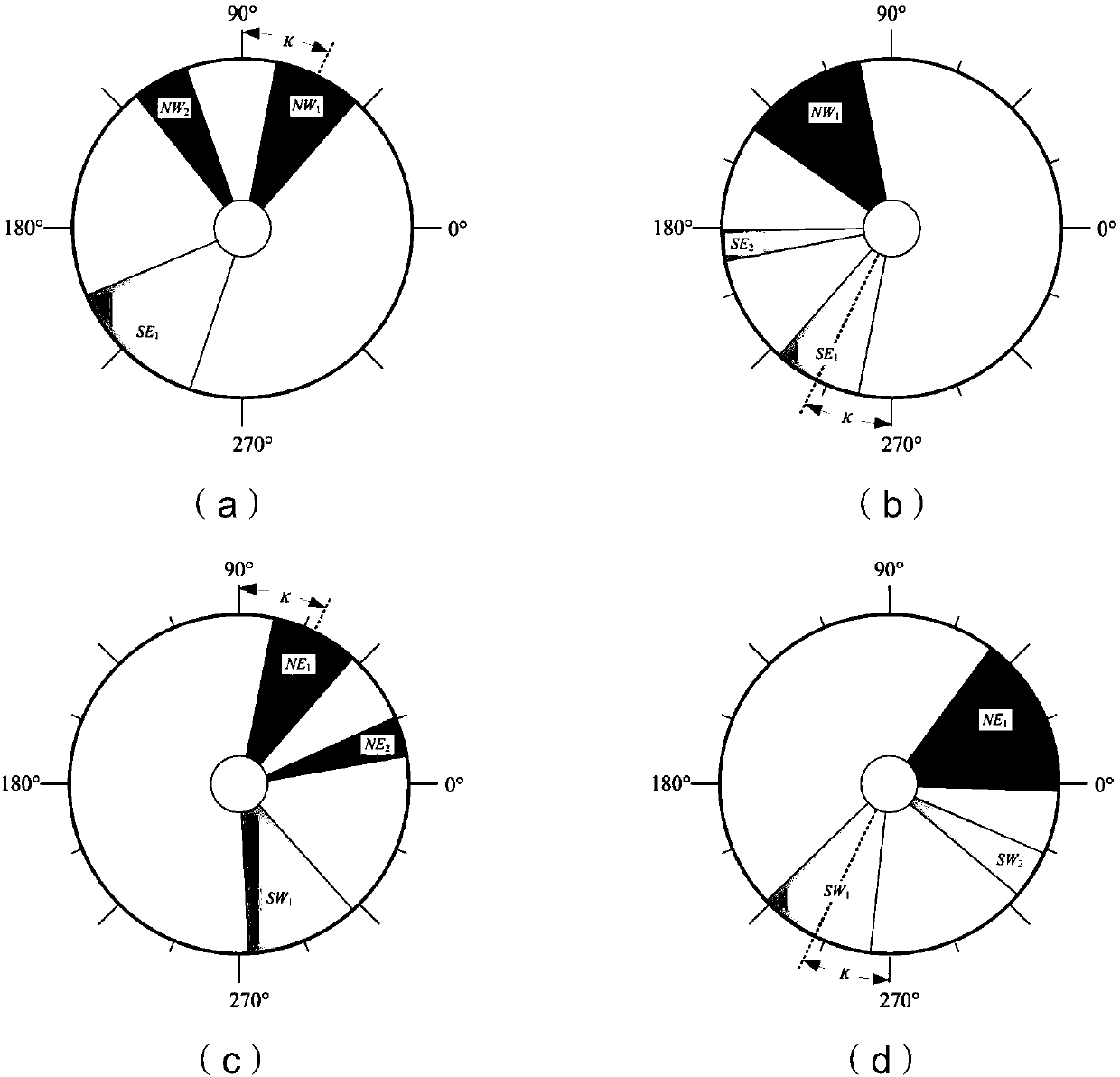
Method for optimum thrust distribution of position keeping of conical layout electric propulsion satellite in fault mode
ActiveCN107891997AReduce consumptionExtend your lifeCosmonautic vehiclesCosmonautic propulsion system apparatusElectricityOrbital period
The invention provides a method for optimum thrust distribution of position keeping of a conical layout electric propulsion satellite in a fault mode. According to the method, an analytical method isadopted for conducting position keeping control distribution of electric thrusters in a conical layout fault mode; firstly, a pair of thrusters which have no faults and are used for position keeping control are selected according to a thruster with faults; secondly, two different distribution modes of the thruster pair are obtained and selected; finally, the startup time of the electric thrustersis changed to avoid a shadow zone. According to the method, the completely analytical mode is adopted, and the distribution purpose of the electric propulsion position keeping thrusters in the fault mode is achieved, so that the fuel consumption is optimized, the startup frequency of the thrusters within an orbital period is reduced at the same time, and therefore the effective thruster distribution method is provided for electric propulsion position keeping of the geostationary orbit satellite in the fault mode.
Owner:BEIJING INST OF CONTROL ENG
Detection method for neighbor abnormities of gas turbine
InactiveCN102706563AReduce the need for computing resourcesShorten the timeEngine testingSpecial data processing applicationsDistance matrixVolumetric Mass Density
The invention discloses a detection method for neighbor abnormities of a gas turbine, and belongs to the technical field of state detection of the gas turbine. By adoption of the detection method, the problem that as the existing gas turbine adopts a plurality of sensors to acquire operating state data, the analysis efficiency for the health condition of the gas turbine is low due to more data quantity is solved. The detection method comprises the following steps of: firstly acquiring point measuring records of monitoring data; then extracting monitoring characteristic quantity sets representing different time characteristics; establishing a global distance matrix for measuring the similar distance among sample points at different times; acquiring local reachable density of each sample and a set of neighbourhood sample points from G samples; comparing the local reachable density of all the samples with that of other samples in the neighbourhood and calculating abnormal scores of all the samples; and carrying out sequencing on the number of abnormal score results of the samples, thus obtaining an abnormal sample set. The detection method disclosed by the invention is applicable to detection of neighbor abnormities of the gas turbine.
Owner:HARBIN INST OF TECH
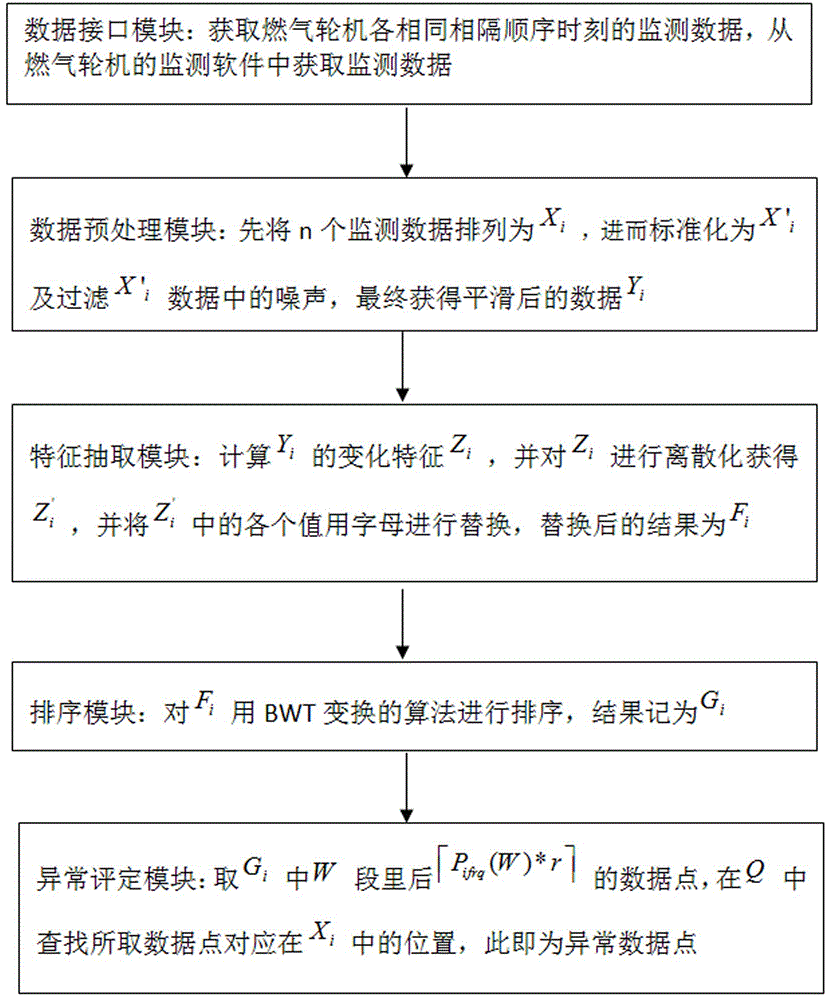
Method for detecting abnormal sequencing of gas turbine engine
ActiveCN102393303AStrong descriptiveReduce the need for computing resourcesEngine testingData informationEngineering
The invention relates to a method for detecting abnormal sequencing of a gas turbine engine, and aims to solve the problems that the data information collected by the sensor of the conventional gas turbine engine is large, the data quality is poor, the analysis efficiency of the sensor is low, and the misjudgement possibility is high. The method is as follows: acquiring monitoring data from a monitoring software of the gas turbine engine; arranging n monitoring data with the sampling time interval into Xi; normalizing the Xi into X'I; filtering noise in the X'I, and further obtaining the smooth data Yi; calculating the variation characteristic of Yi and marking the variation characteristic with Zi; performing the discretization of Zi to get Z'i; replacing all the values in the Z'i with letters, and obtaining Fi as the result after the replacement; sequencing the Fi through the BWT alternation algorithm, and recording the result with Gi; acquiring [Pifrq(W)*r]data points in the W section of Gi; finding the corresponding positions in the Xi of the acquired data points in Q, and therefore obtaining the abnormal data point. The invention has low computing resource requirement and lower time and space cost, and the abnormal data point expressed through frequentness is strongly illustrative.
Owner:NANJING POWER HORIZON INFORMATION TECH CO LTD
Method and System for Speech Synthesis and Advertising Service
ActiveUS20120010888A1Reduce the need for computing resourcesReduce deploymentSpeech synthesisText to speech synthesisSpeech sound
Owner:CHEMTRON RES
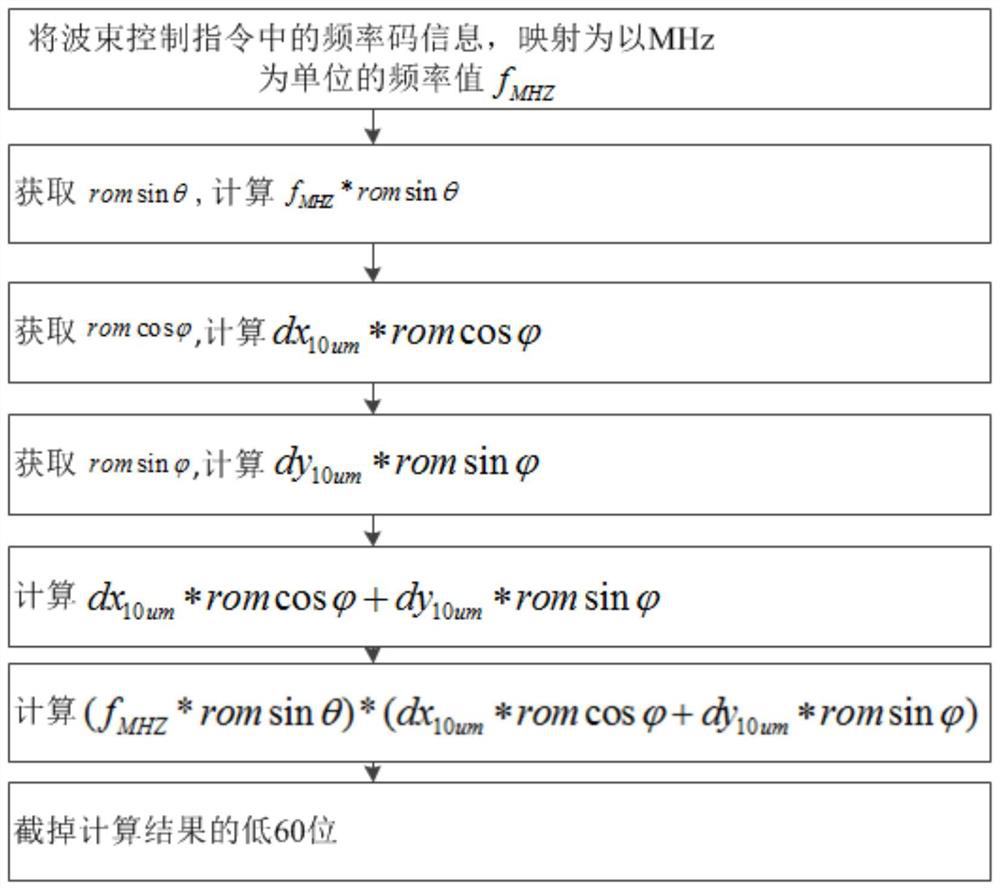
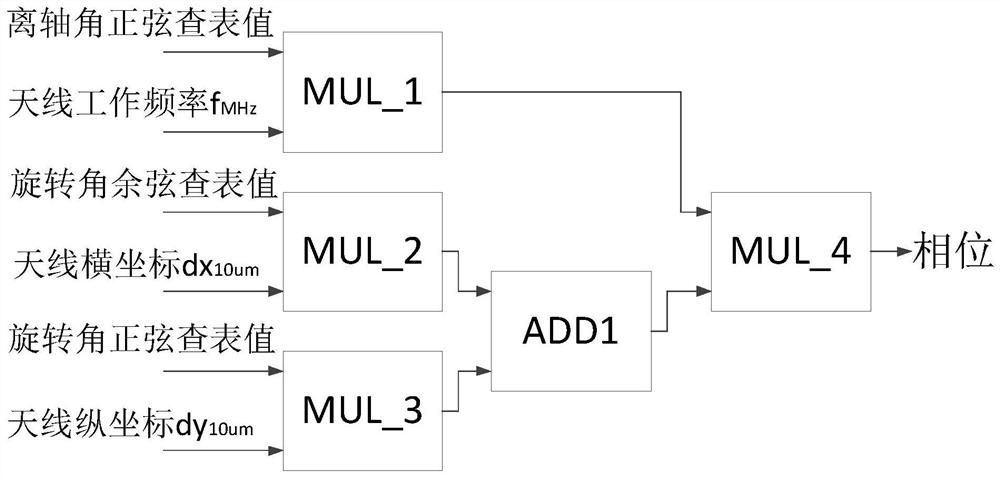
Phased array antenna wave control angle resolving method and system and storage medium
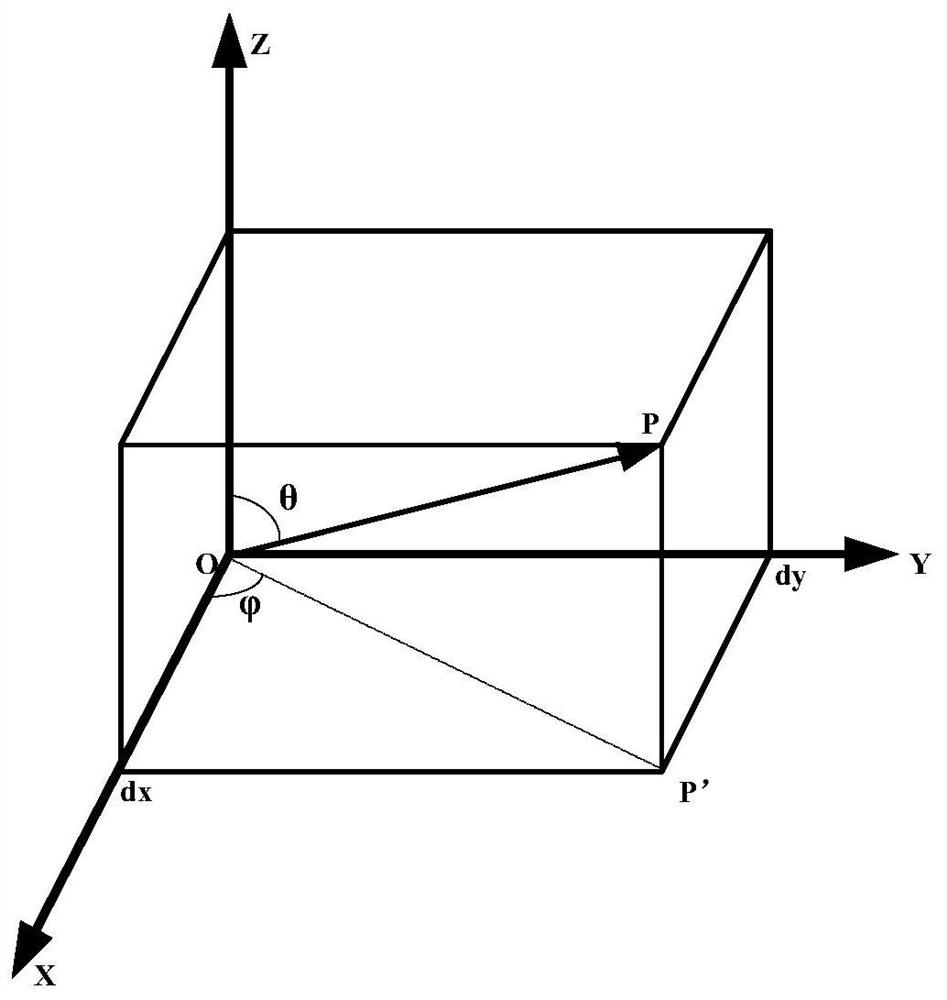
PendingCN111859269AAvoid calculationQuickly get valuesComputation using non-contact making devicesOther databases indexingBinary multiplierPhase shifted
The invention relates to the technical field of phased-array antennas, and discloses a phased-array antenna wave control angle resolving method and system and a storage medium. The resolving method isshown in the description, wherein dx<10[mu]m> and dy<10[mu]m> are calculated and stored in advance, romsinx (x belongs to [0-90 degrees]) in the range of 0-90 degrees is calculated and stored in advance, and romsin[theta], romsin[psi] and romcos[psi] are directly obtained or obtained through calculation by inquiring pre-stored data. The formula is calculated through calling of a multiplier and anadder and through pre-stored calculation parameters matched with the actual angle. Only fixed-point number multiplication operation and fixed-point number addition operation need to be carried out, the requirement for operation resources of a processor is lowered, phase shift code calculation can be rapidly achieved, and the calculation time is greatly shortened.
Owner:成都雷电微力科技股份有限公司
Neighbor abnormal detection system of gas turbine
InactiveCN106053090AReduce the need for computing resourcesShorten the timeGas-turbine engine testingCharacter and pattern recognitionPattern recognitionDistance matrix
The invention belongs to the technical field of gas turbine equipment and specifically relates to a neighbor abnormal detection system of a gas turbine. The system comprises the implementation steps of: obtaining monitoring data and input parameters; extracting characteristic quantities representing different moment characteristics; establishing a global distance matrix measuring similarity among the sample points at different moments; obtaining a local reachable density of each sample from G samples and a set of neighbor sample points; comparing the local reachable density of each sample with that of other samples in a neighbor domain, and calculating an abnormal score of each sample; and ordering the amounts of the abnormal score results of the samples, and obtaining a set of abnormal samples. According to the invention, the requirement on calculation resources is low, the time and space cost is relatively low, the data is rapidly calculated based on a linear calculation mode, the abnormal data points are finally expressed, and the accountability is high.
Owner:中国船舶重工集团公司第七〇三研究所
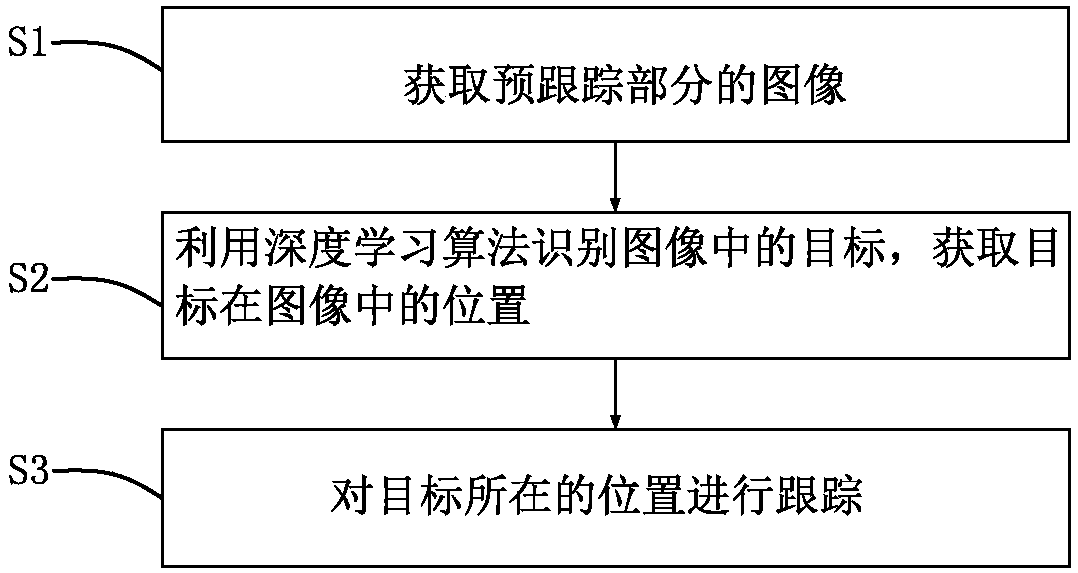
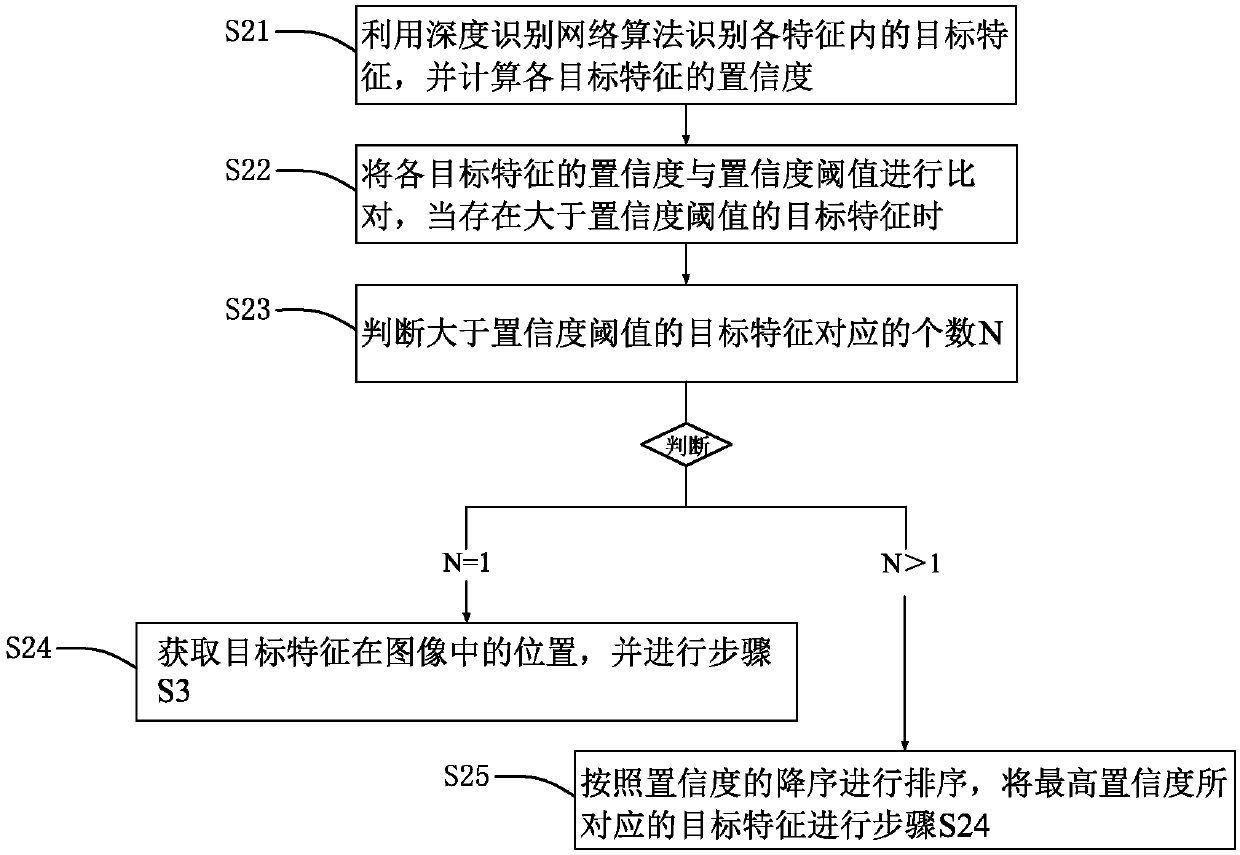
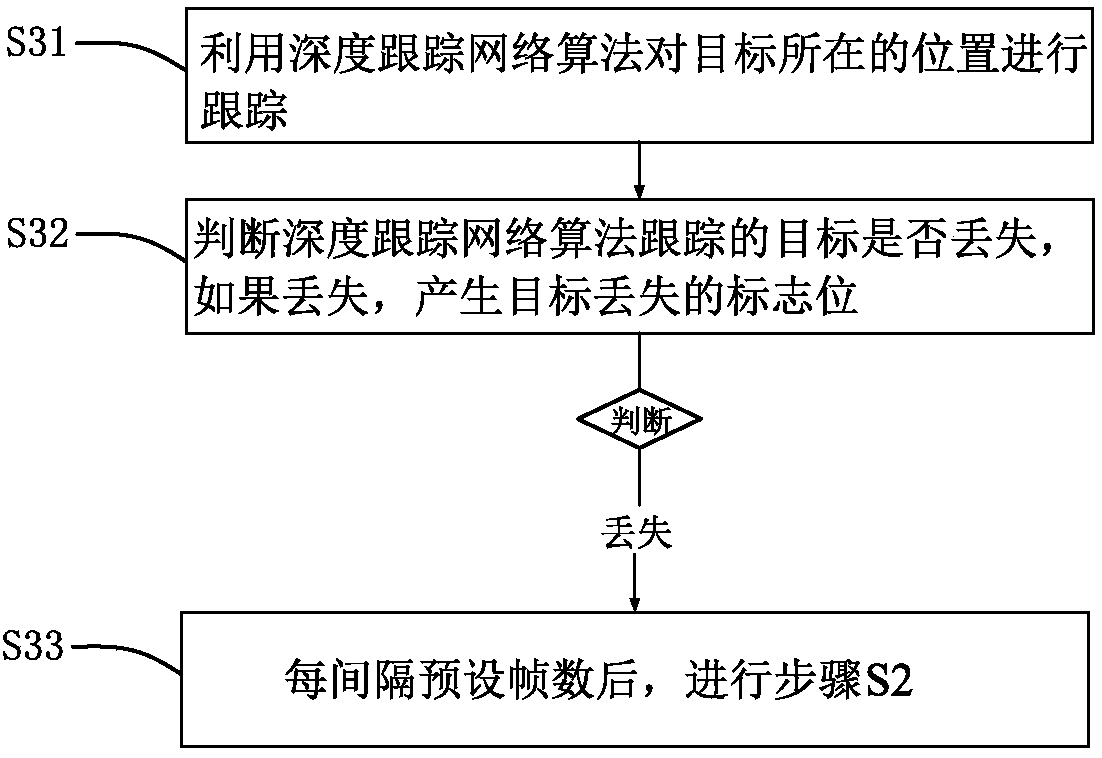
Fruit recognition tracking method and system based on deep learning algorithm
ActiveCN108564601AAccurate picking and positioningNot easy to loseImage enhancementImage analysisPattern recognitionNatural environment
The invention provides a fruit recognition tracking method and system based on a deep learning algorithm. The method comprises the following steps: obtaining the image of a pre-tracking part, using the deep learning algorithm to recognize a target in the image, and obtaining the position of the target in the image; and tracking the position of the target. According to the method and the system provided by the invention, the recognition and tracking of fruits in the image are realized in combination with a deep recognition network algorithm and a deep tracking network algorithm, the accuracy oftarget recognition and the correctness of tracking under complicated natural environments are guaranteed, the tracked target is unlikely to lose, accurate picking positioning is provided for pickingoperation, and the efficiency of picking operation is improved.
Owner:北京禾泽方圆智能科技有限公司
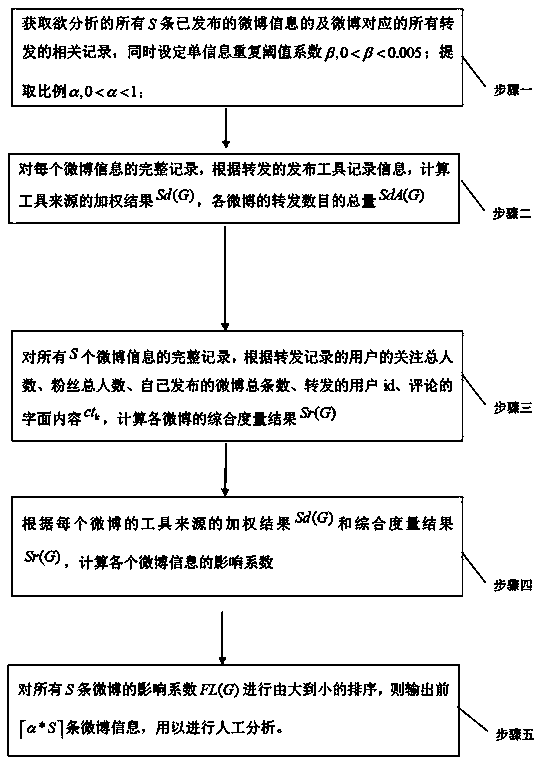
Method for extracting high-influence information of social network
InactiveCN103279472AReduce the need for computing resourcesShorten the timeSpecial data processing applicationsQuality dataMicroblogging
The invention provides an information extraction method based on transmission and distribution statistics and validity evaluation on the basis of intrinsic characteristics of a social network. The method includes the steps of carrying out initial qualitative evaluation on information distribution according to information source tools and establishing valid quadratic characteristics based on user information in the process of validity processing to carry out quantitative evaluation. In the process of calculation, a linear complexity algorithm is used for carrying out analysis, the demand for computing resources is low, and time cost and space cost are low. In the process of association, comparison processing is carried out, and MicroBlog information which is really high in exposure rate is output at last. The information extraction method has higher practical value in reality, effectively achieves analysis on influence and exposure rates of public opinion information of the social network and can filter out low-quality data and reserve true and valid information for use in follow-up manual analysis.
Owner:北京宏博知微科技有限公司 +1
Method for identifying abnormality of customers in futures market
InactiveCN102496127AEfficient clusteringReduce the need for computing resourcesFinanceInformation technologyData science
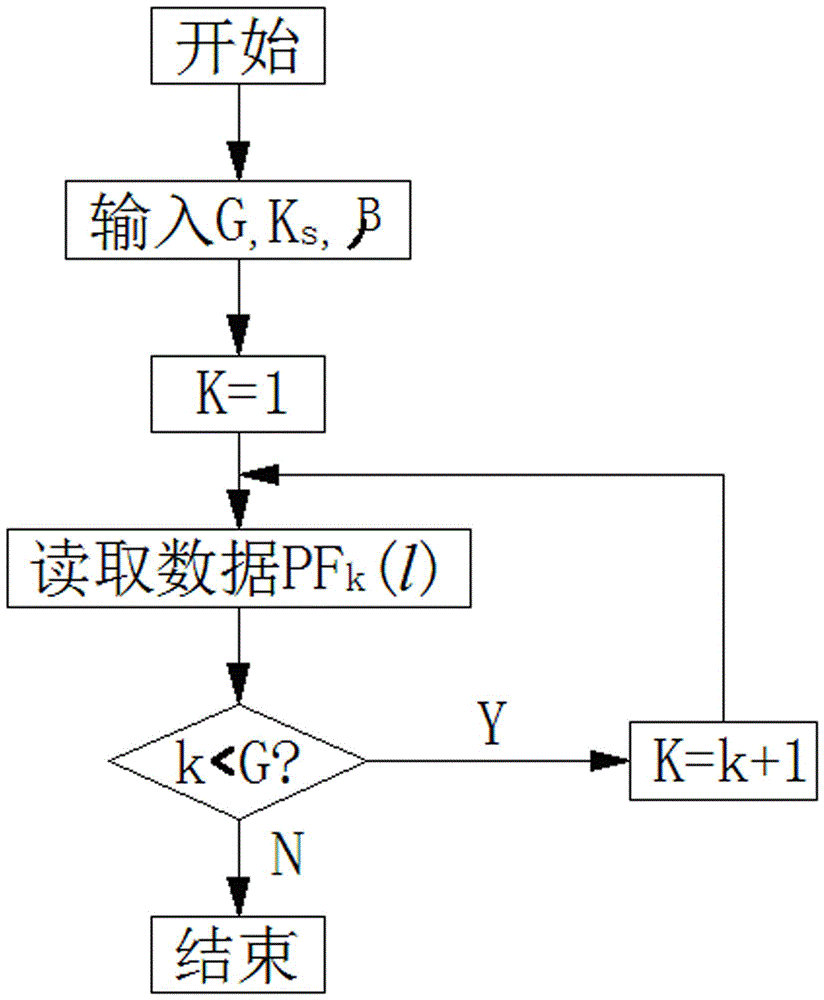
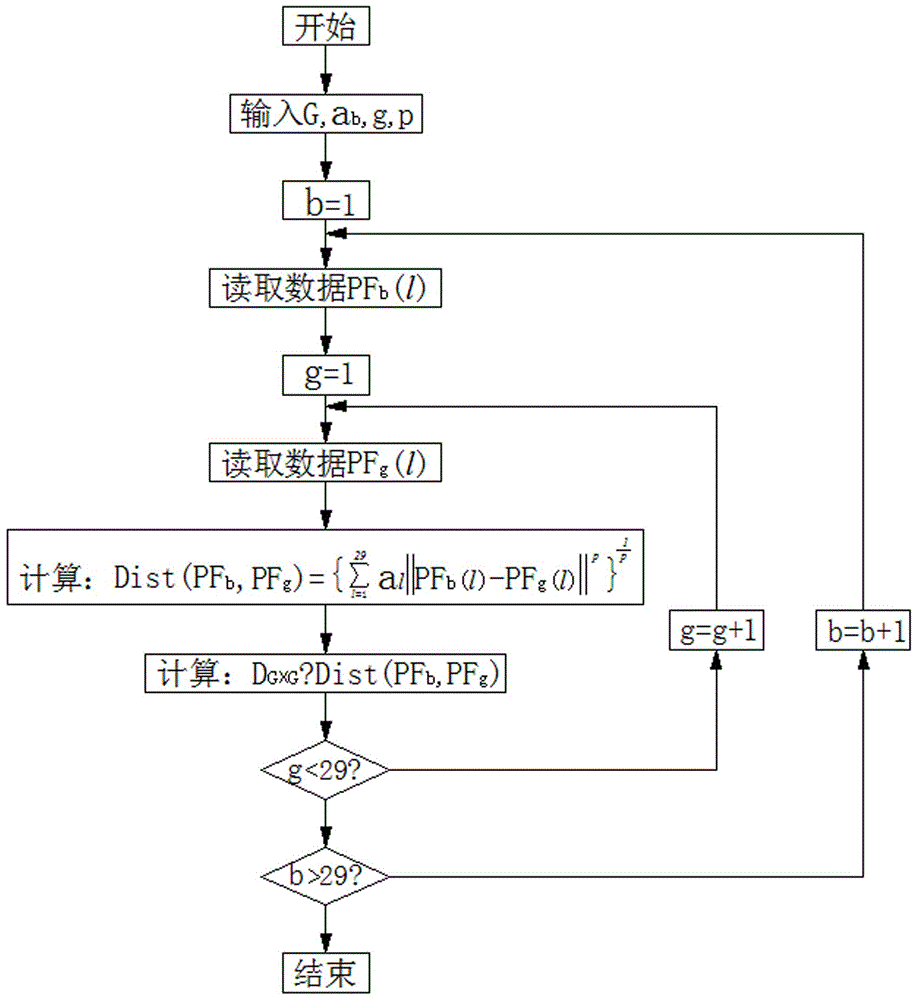
The invention discloses a method for identifying the abnormality of customers in a futures market, belongs to the technical field of information, and solves the problems of low efficiency and high mal-judgment degree in manual analysis of the credit risk of the customers. The method comprises the following steps of: acquiring the registration information and transaction data of G customers; according to the registration information and transaction data of the G customers, extracting the characteristic quantity Fk (1) of each customer; according to the characteristic quantity Fk (1) of each customer, establishing a global distance matrix D(G*G); establishing an active matrix A(G*G) and a feedback matrix R(G*G), and acquiring a cluster center sample fck of each customer PFk according to a similar distance Dist (PFb, PFg) between a customer PFb and a customer PFg; and gathering the customers PFk with the same cluster center samples fck into a customer cluster, and determining that the customer cluster having minimum customers is abnormal. The method is applicable to identification of the customers in the futures market.
Owner:HARBIN INST OF TECH
A method for extracting high-influence information from social networks
InactiveCN103279472BReduce the need for computing resourcesShorten the timeSpecial data processing applicationsMicrobloggingQuality data
The invention provides an information extraction method based on transmission and distribution statistics and validity evaluation on the basis of intrinsic characteristics of a social network. The method includes the steps of carrying out initial qualitative evaluation on information distribution according to information source tools and establishing valid quadratic characteristics based on user information in the process of validity processing to carry out quantitative evaluation. In the process of calculation, a linear complexity algorithm is used for carrying out analysis, the demand for computing resources is low, and time cost and space cost are low. In the process of association, comparison processing is carried out, and MicroBlog information which is really high in exposure rate is output at last. The information extraction method has higher practical value in reality, effectively achieves analysis on influence and exposure rates of public opinion information of the social network and can filter out low-quality data and reserve true and valid information for use in follow-up manual analysis.
Owner:北京宏博知微科技有限公司 +1
Ordering abnormal detection system of gas turbine
InactiveCN106053089AReduce the need for computing resourcesShorten the timeGas-turbine engine testingCharacter and pattern recognitionDiscretizationData interface
The invention belongs to the technical field of gas turbine equipment and specifically relates to an ordering abnormal detection system of a gas turbine. A data interface module of the system is used for obtaining monitored data from monitoring software of the gas turbine. A data pre-processing module firstly arranges n pieces of monitored data as Xi, further standardizes Xi into X'i and filters the noise in the X'i data, and finally the data Yi after smoothing is obtained; a characteristic extracting module calculates change characteristics Zi of Yi and carries out discretization on Zi to obtain Z'I, each value in Z'I is replaced by a letter, and the result after replacing is Fi; an ordering module orders Fi with a BWY conversion algorithm, and the result is Gi; and an abnormal evaluation module takes the data points shown in the specification and searches Q for the corresponding positions in Xi of the taken data points, and the positions are the abnormal data points. According to the invention, the requirement on the calculation resources is low, the time and space cost is relatively low, the abnormal data points are expressed by a frequentness mode, and the accountability is high.
Owner:中国船舶重工集团公司第七〇三研究所
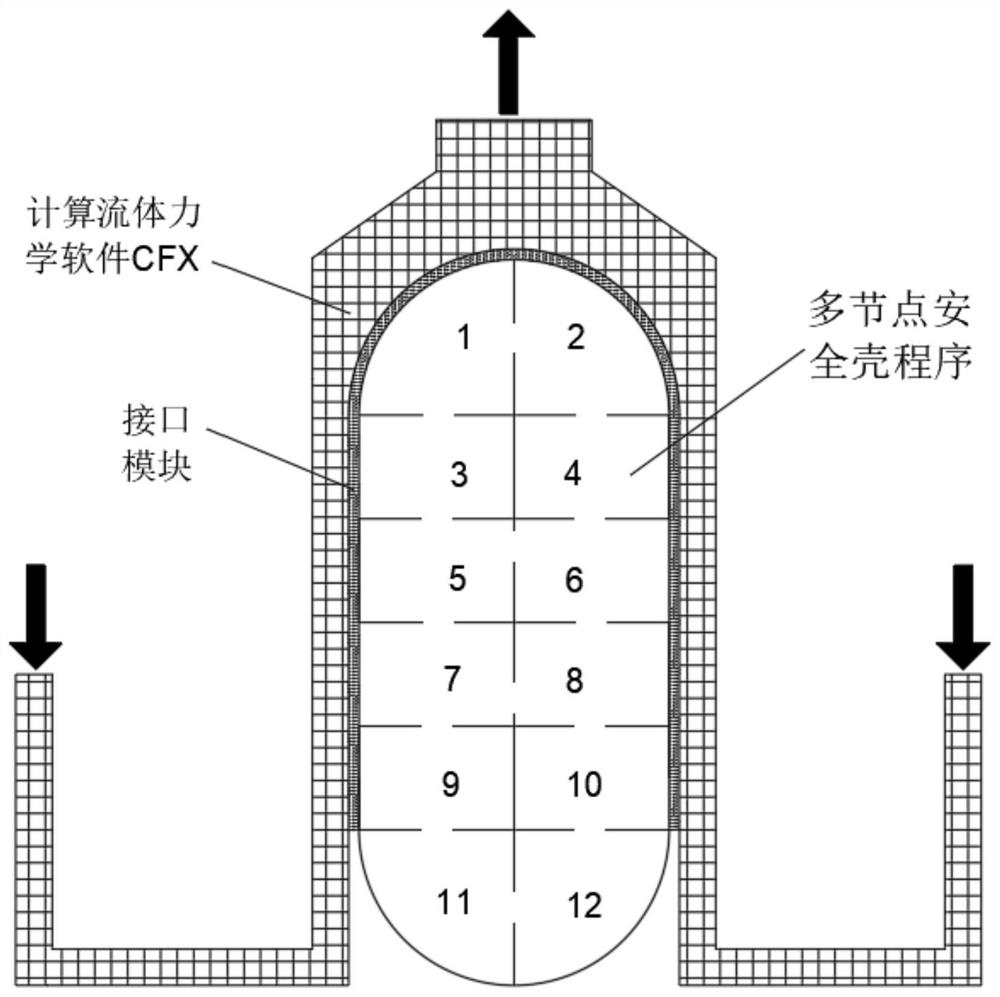
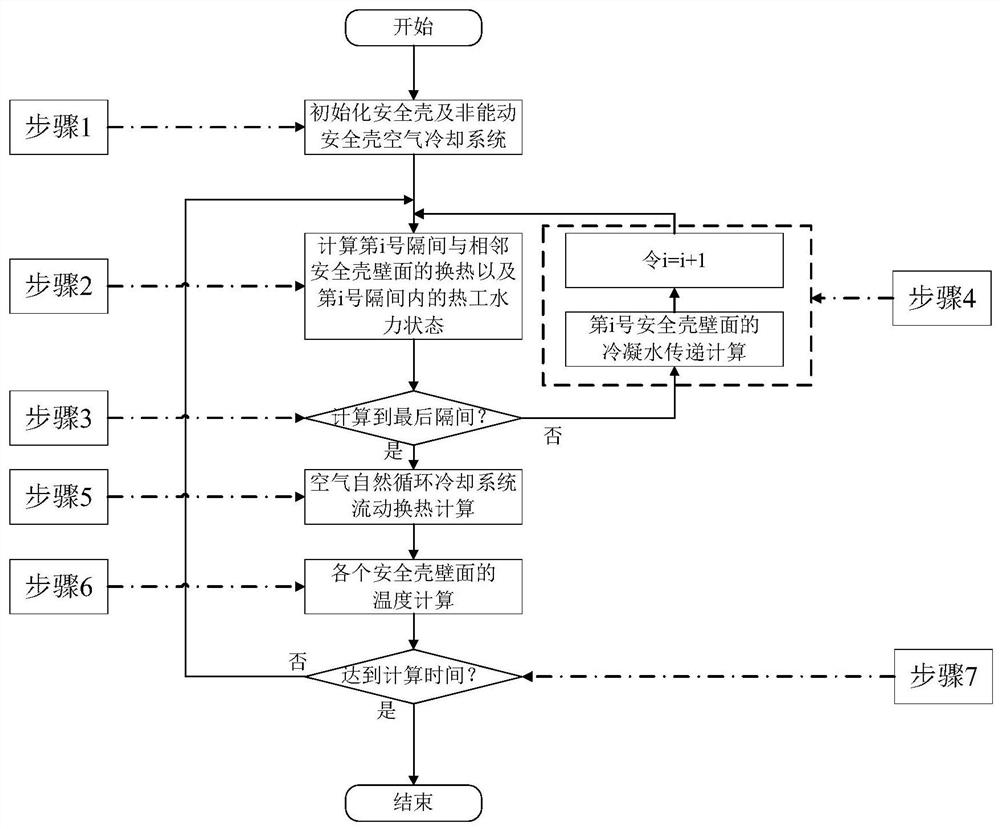
Cross-dimension coupling analysis method for containment and passive containment air cooling system
ActiveCN113283189AAccelerateReduce computing resource requirementsDesign optimisation/simulationAir cooling systemThermal hydraulics
The invention discloses a cross-dimension coupling analysis method for a containment and a passive containment air cooling system. The method comprises the following steps: 1, initializing the containment and the passive containment air cooling system; 2, utilizing a multi-node containment program to calculate the heat exchange between the compartment and the wall surface of the adjacent containment and the thermal hydraulic state in the compartment in the accident process; 3, judging whether the last compartment is calculated or not, if so, going to the step 5, and otherwise, going to the step 4; 4, calculating the condensate water transfer process of the wall surface of the containment, and performing calculation in the step 2 on the next compartment; 5, calculating flow heat exchange of the passive containment air cooling system by utilizing three-dimensional computational fluid mechanics software; 6, calculating the temperature of the wall surface of the containment; and 7, repeating the steps 1-6 until the appointed calculation time is reached. The flow heat exchange of the passive containment air cooling system and the influence of the flow heat exchange on the thermal hydraulic state of the containment can be quickly and accurately calculated, and the method is of great significance to the integrity analysis of the pressurized water reactor containment.
Owner:XI AN JIAOTONG UNIV
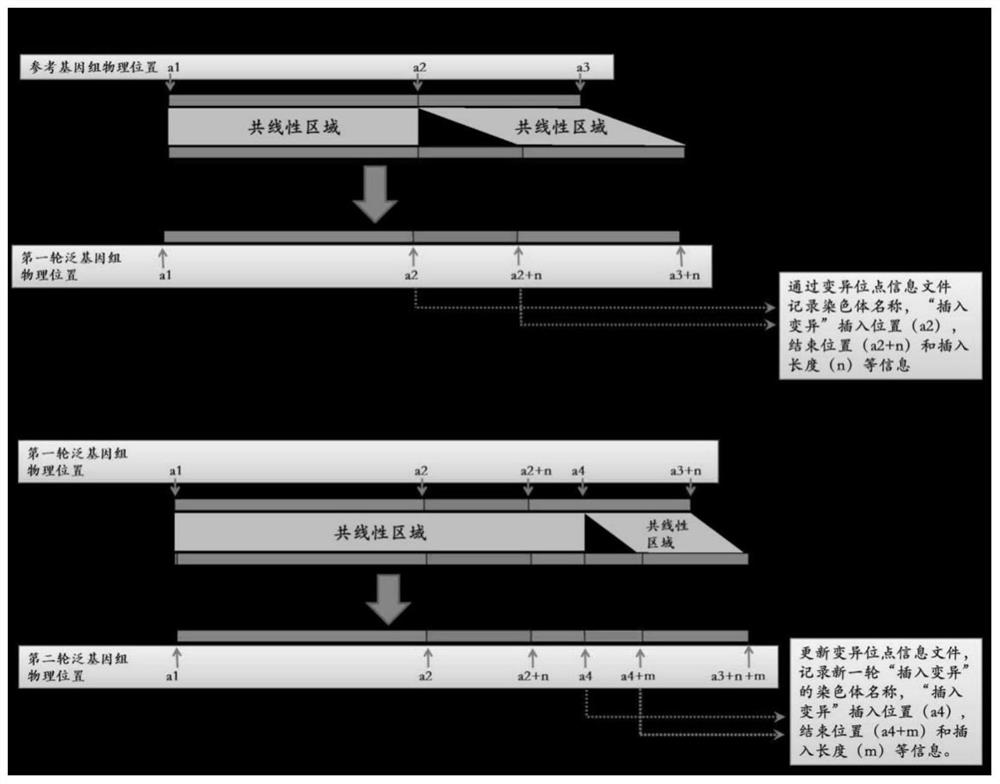
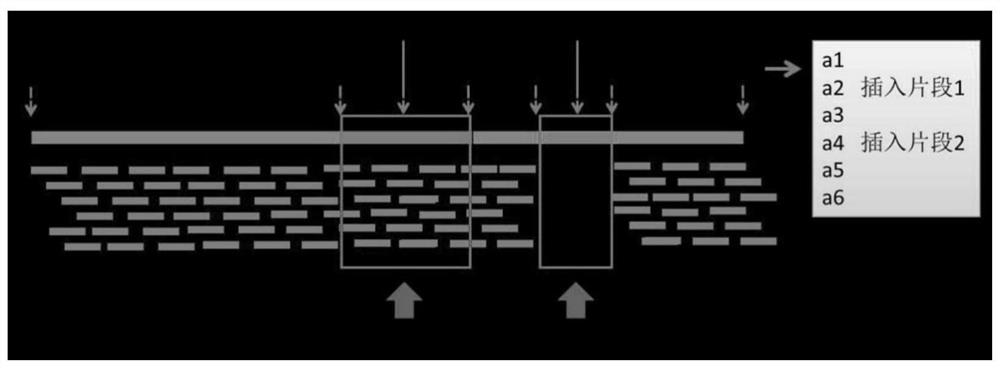
Generic genome construction method and corresponding structural variation mining method thereof
ActiveCN113571131AQuality improvementAchieve large-scale applicationBiostatisticsProteomicsTheoretical computer scienceEngineering
The invention belongs to the technical field of genome data analysis, and particularly relates to a generic genome construction method and a corresponding structural variation mining method thereof, structural variation obtained through genome comparison is put back to a linear genome, meanwhile, a structural variation site information file is added, and an efficient analysis generic genome which is linearized in the form and considers various structure variation forms is constructed. The generic genome not only can capture more brand-new structural variations which are not found by a reference genome, but also better displays the captured structural variations by combining a linearization method with a variation site information file, so that the constructed generic genome is easier to understand and analyze, and is more beneficial to subsequent application; according to the method and the process for analyzing the genome structure variation based on the generic genome and the second-generation sequencing data, a complete program code is compiled, and the efficient and accurate mining of the structure variation based on the relatively low-cost second-generation sequencing data is realized.
Owner:RICE RES INST GUANGDONG ACADEMY OF AGRI SCI
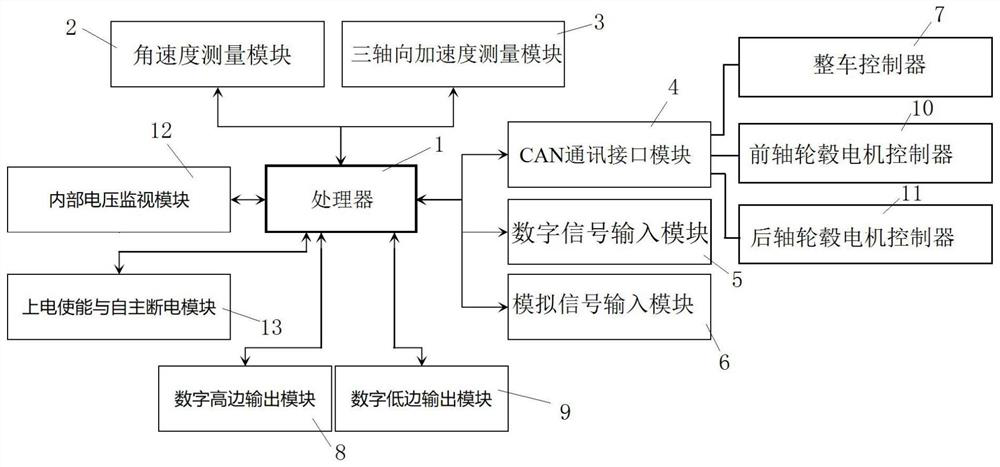
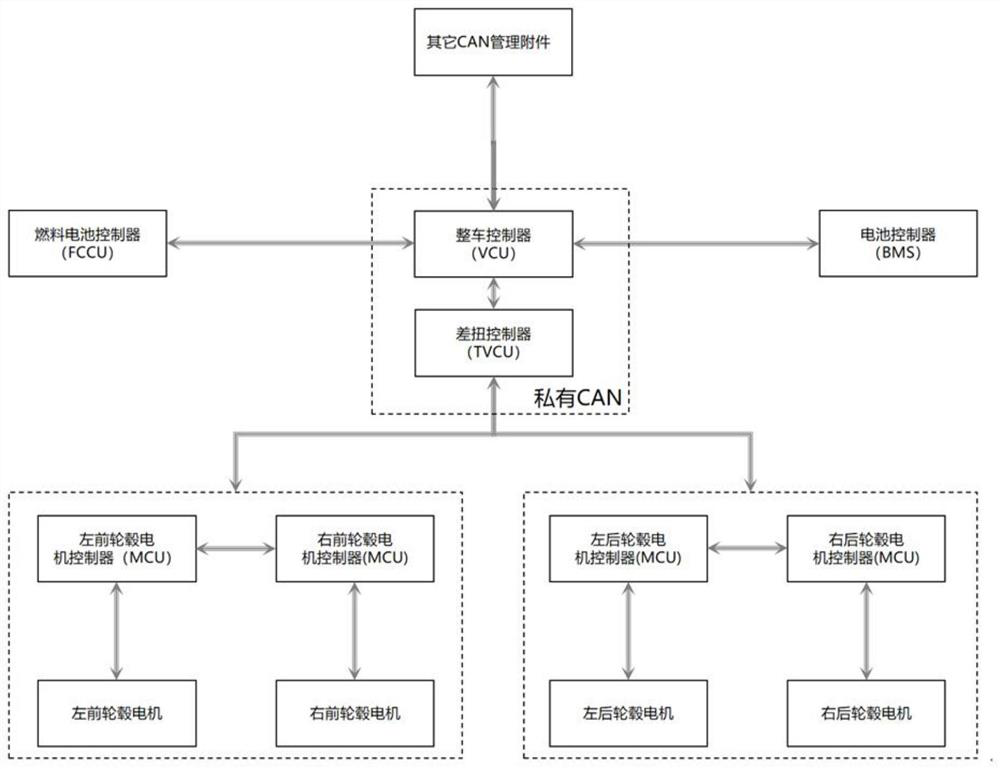
Hydrogen fuel cell four-wheel hub motor drive external controller and control method
ActiveCN112606707AReduce the need for computing resourcesLow costSpeed controllerElectric devicesElectric machineryControl function
The invention discloses a hydrogen fuel cell four-wheel hub motor drive external controller which comprises a processor, an angular velocity measurement module, a three-axial acceleration measurement module, a digital signal input module, an analog signal input module and a digital high-side output module, and is characterized in that the functions of a hub motor differential torque control TVCU and a vehicle control unit VCU are separated; the requirement for computing resource consumption of a controller chip is reduced, and the cost of the differential torque controller is saved; the functions of the controller are separated, so that the load unbalance risk on the CAN network is reduced; the control containing two control functions does not need to be developed again, and the development period is shortened; and the differential torque control of a hydrogen fuel cell full-power four-wheel hub motor driven automobile and a control function of the seamless integration of a whole automobile controller are realized for the first time.
Owner:DONGFENG MOTOR CORP HUBEI
Control method, device and system for numerical-control machine tool
InactiveCN108268011AReduce the need for computing resourcesProgramme controlComputer controlMachine toolEmbedded system
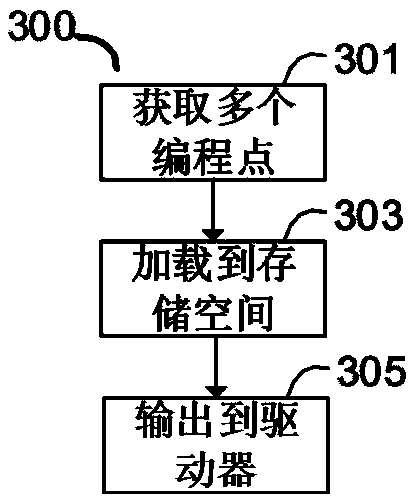
The invention relates to a control method and device for a numerical-control machine tool. The control method comprises that programming points related to a first program are obtained, the first program is used to execute a numerical control system of the numerical-control machine tool so that an operation including processing of a first interpolation track is completed, and the programming pointscomprise position information representing the first interpolation track; the programming points are loaded in a storage space associated with the numerical control system; and in response to a programming point feeding start instruction in the first program, programming points are obtained from the storage space, an interpolation program in the numerical control system is skipped, and the obtained programming points are output to a driver of the numerical control system according to a predetermined period. The invention also describes a corresponding device, a computer system and a readablestorage medium.
Owner:HUAZHONG UNIV OF SCI & TECH
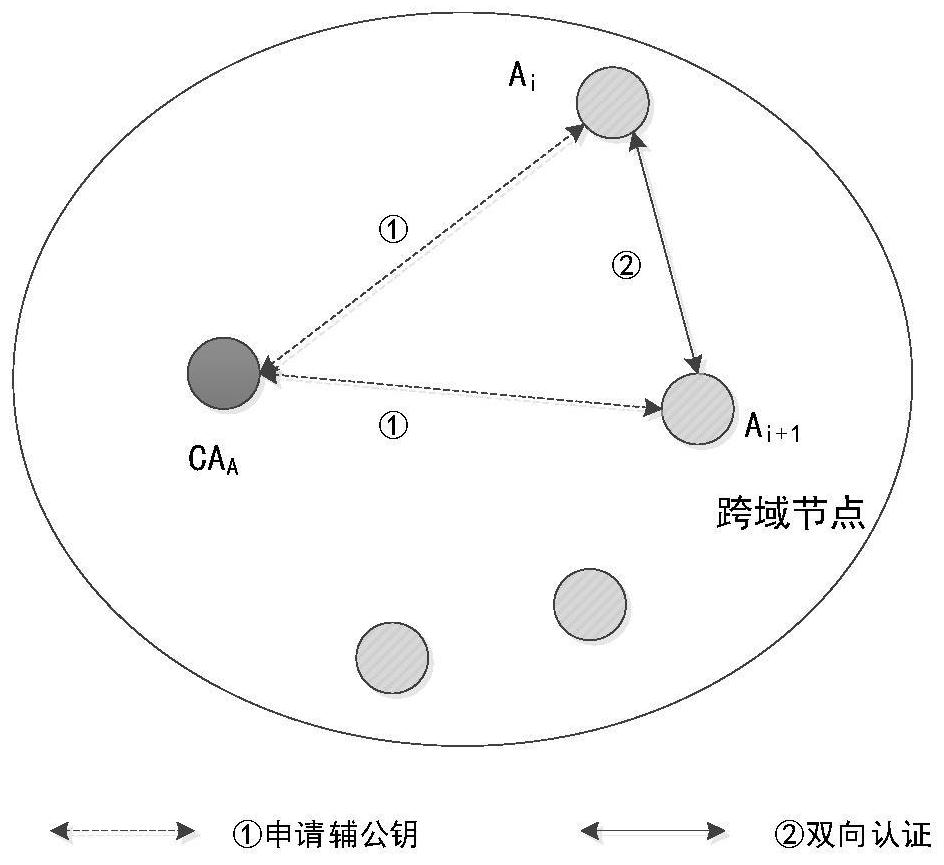
Bidirectional identity authentication method based on lightweight CA, computer program and storage medium
InactiveCN112654042AEnsure safetyPrivacy protectionUser identity/authority verificationSecurity arrangementInternet privacyPassword
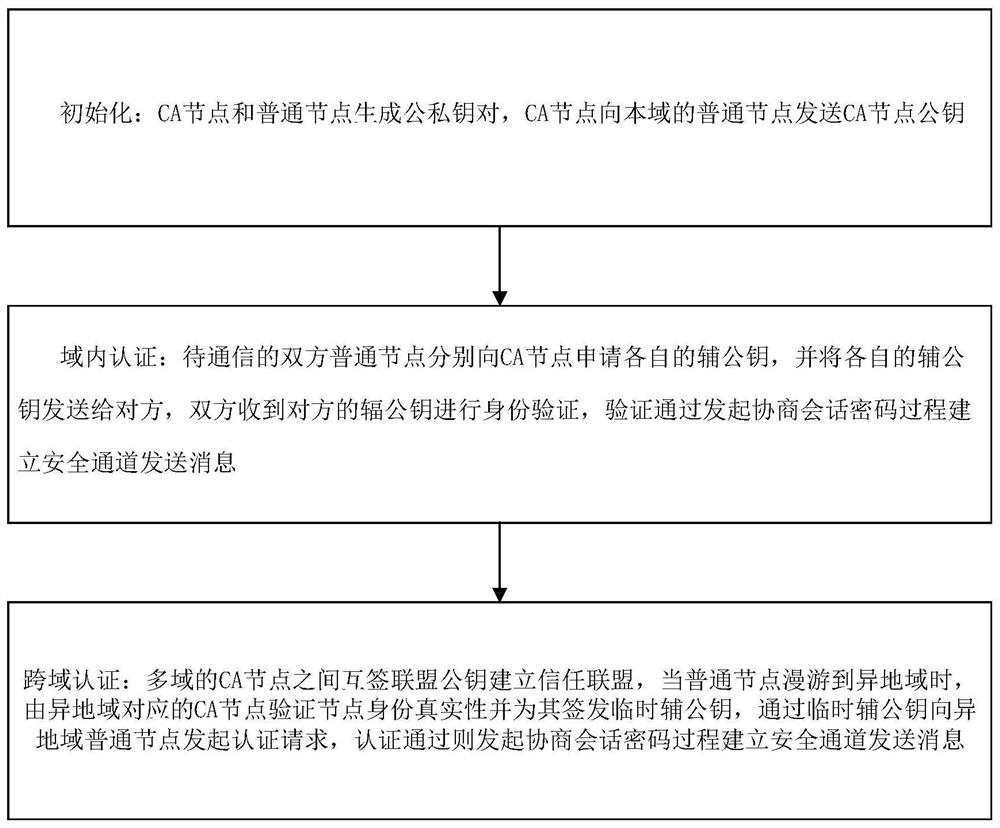
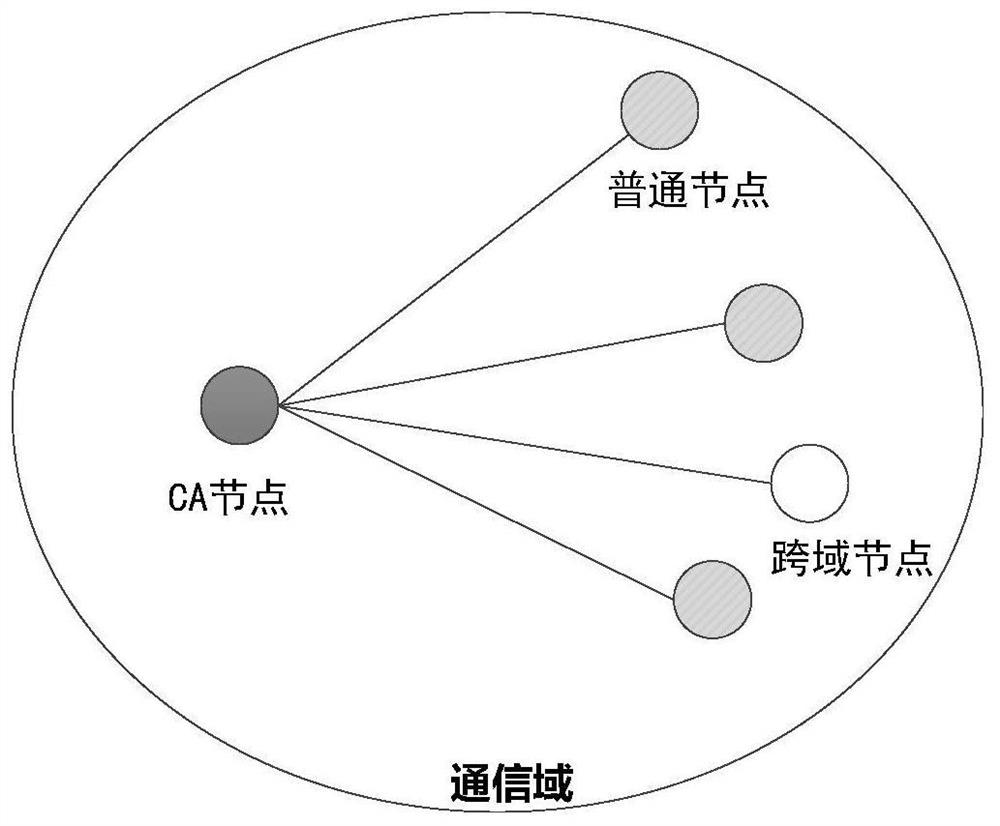
The invention relates to a bidirectional identity authentication method based on lightweight CA, which comprises the following steps: initialization: a CA node and a common node generating a public and private key pair, and the CA node sending a CA node public key to the common node in the domain; intra-domain authentication: the common nodes of the two parties to be communicated respectively applying for respective auxiliary public keys from the CA node and sending the respective auxiliary public keys to the opposite parties, and the two parties receiving the auxiliary public keys of the opposite parties to perform identity authentication and establishing a secure channel to send messages by initiating a negotiation session password process; cross-domain authentication: establishing a trust alliance by mutual signing of alliance public keys among CA nodes of multiple domains, verifying the authenticity of node identities by the CA nodes corresponding to different regions and signing and issuing temporary auxiliary public keys for the CA nodes when the common nodes roam to the different regions, and initiating an authentication request to the common nodes in the different regions through the temporary auxiliary public keys, and if the authentication is passed, initiating a negotiation session password process to establish a secure channel to send a message.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
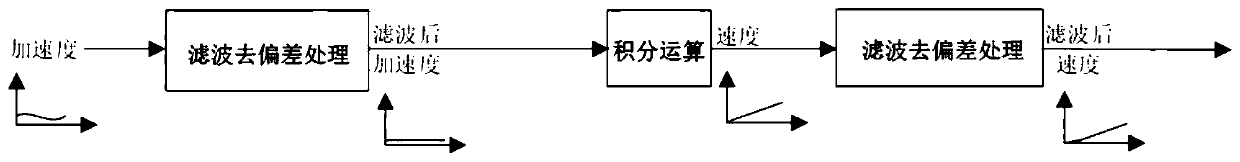
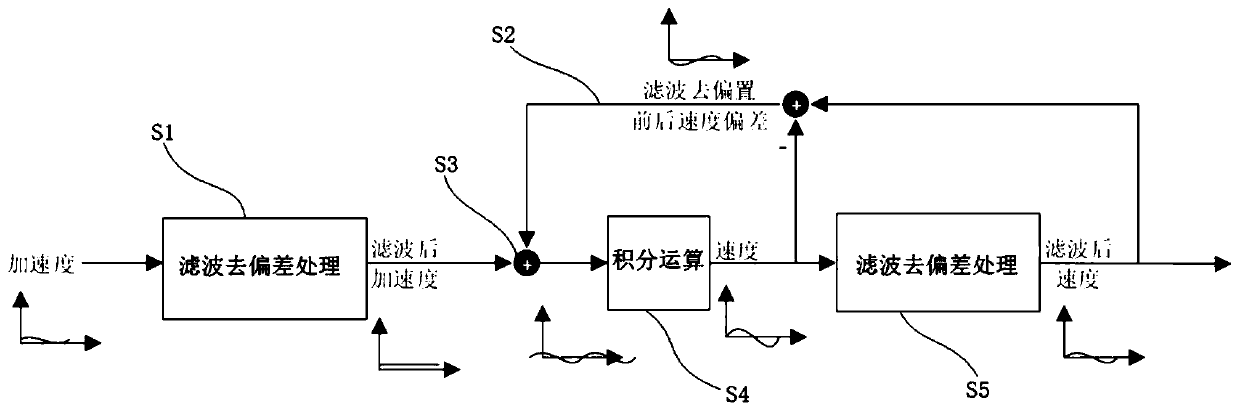
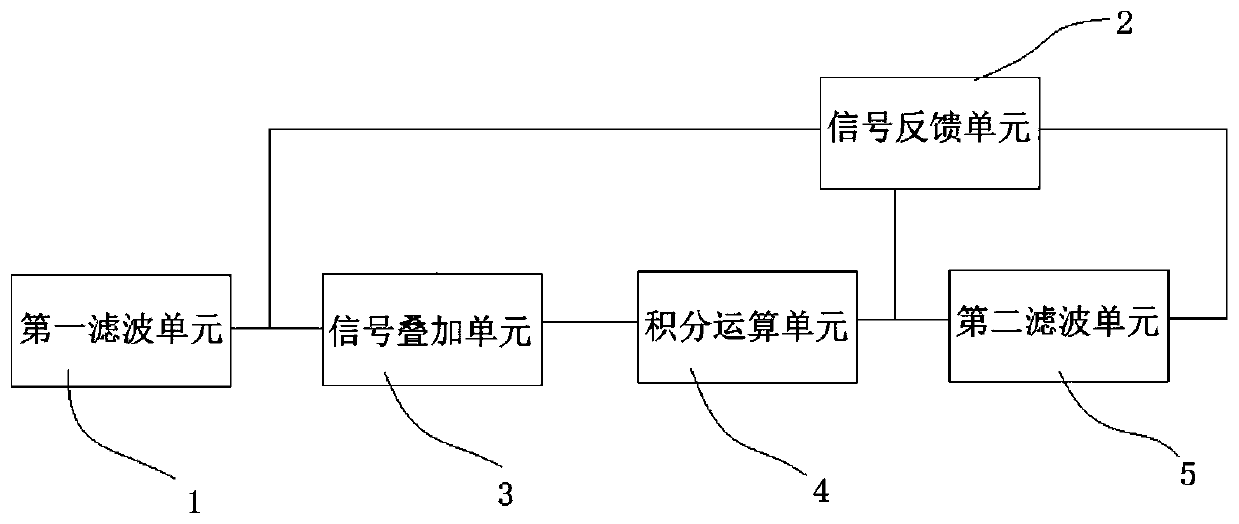
Signal integral deviation removing method and system and electronic device
ActiveCN111294014AReduce signal noiseReduce the need for computing resourcesDigital technique networkControl theoryComputer program
The invention provides a signal integral deviation removing method and system and an electronic device. The method comprises the following steps: receiving an acceleration characteristic signal, and performing filtering deviation removing processing on the acceleration characteristic signal to obtain a filtered deviation-removed acceleration signal; receiving a speed characteristic signal deviation feedback calculated amount in real time; superposing the filtered and deviated acceleration characteristic signal and the speed characteristic signal deviation feedback calculated amount to obtain asuperposed signal; performing integral operation on the superposed signal to obtain a first speed characteristic signal; and carrying out filtering and deviation removing processing on the first speed characteristic signal to obtain a second speed characteristic signal. The system is used for executing the method, and a computer program is stored in the electronic device to execute the method. Byimplementing the method, the real-time performance and the system application range can be improved, and the operation resource requirement is reduced.
Owner:GUANGZHOU AUTOMOBILE GROUP CO LTD
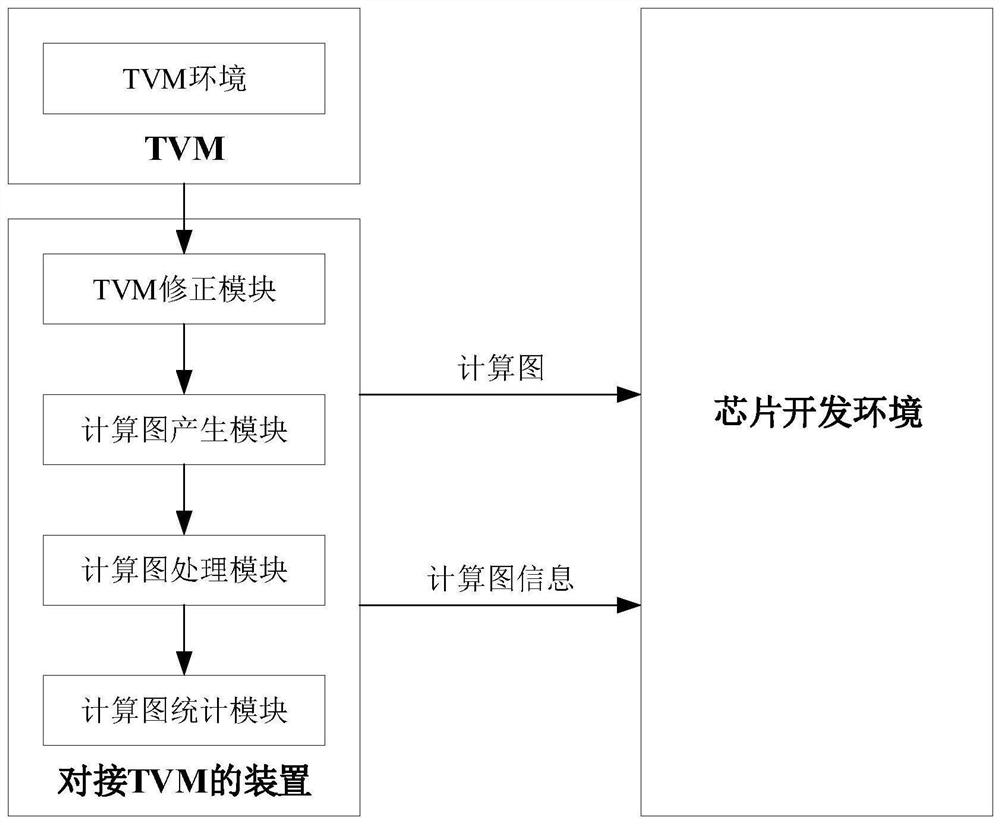
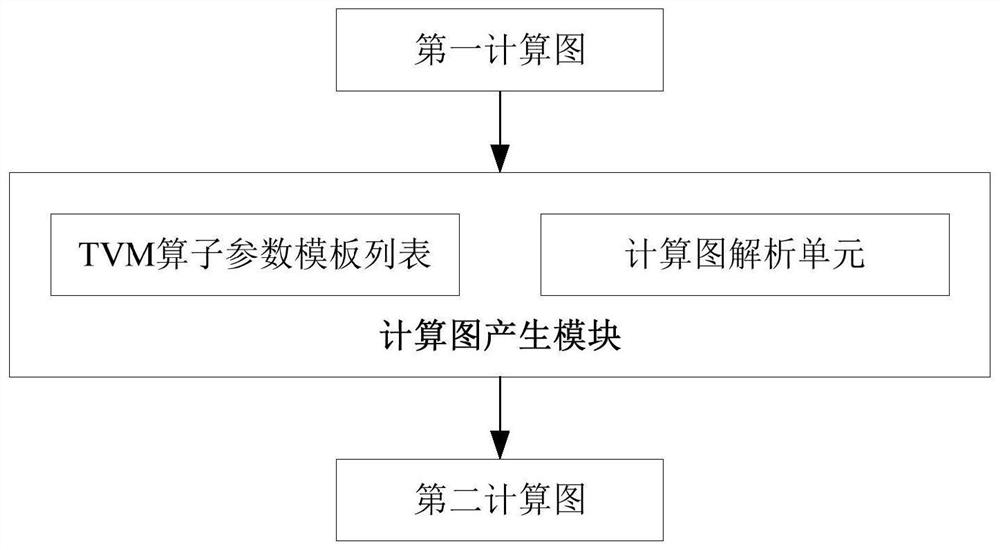
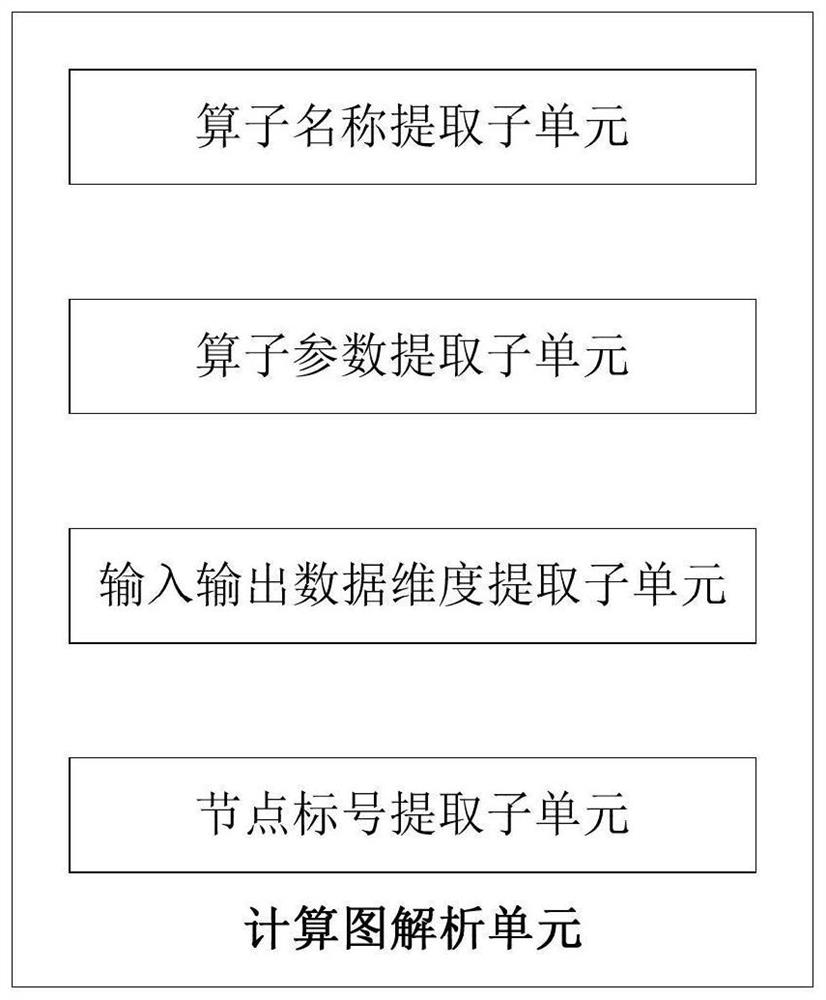
TVM docking method and related equipment
PendingCN112527272AReduce running timeComputing resource requirements are smallVisual/graphical programmingCompiler constructionTheoretical computer scienceComputer engineering
The embodiment of the invention provides a TVM docking method and related equipment, and the method comprises the steps: employing a TVM to generate a first calculation graph according to a target model which is used for the development of a chip; and generating a second calculation graph according to the first calculation graph, wherein the structure of the second calculation graph is a calculation graph structure used for chip development, and the second calculation graph is input of a chip development environment. By adopting the embodiment of the invention, the operation resource requirement of TVM introduction on the chip development environment can be reduced, the operation rate is improved, and the operation time of the chip development environment is reduced.
Owner:SHENZHEN INTELLIFUSION TECHNOLOGIES CO LTD +1
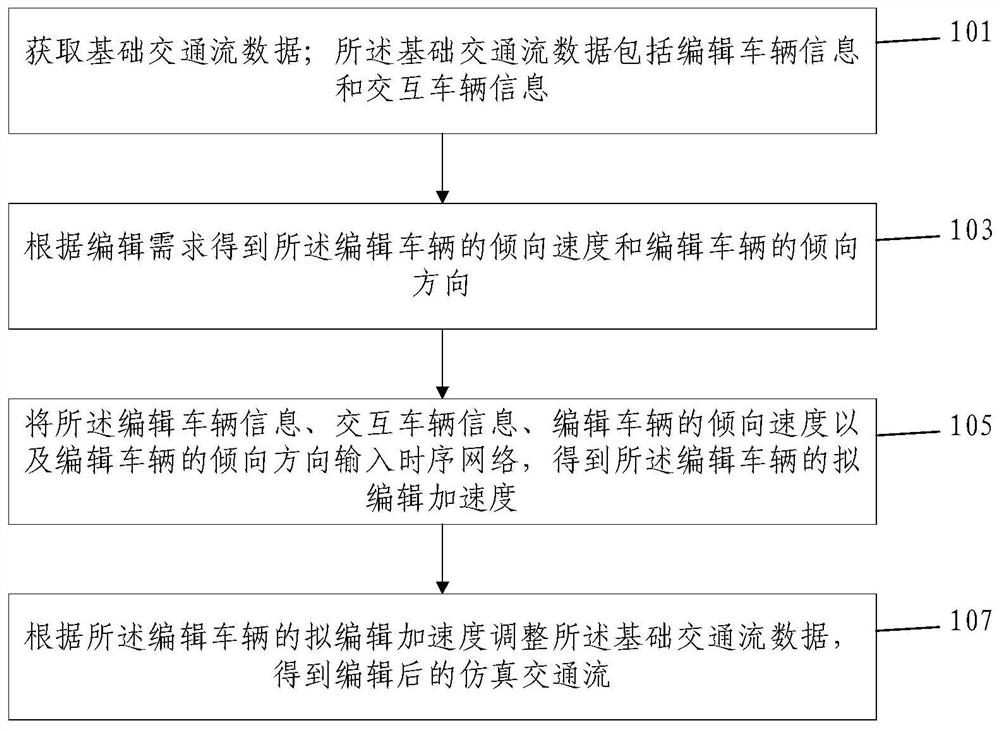
Simulation traffic flow editing method and system based on sequential network
PendingCN114117889ASimplify build difficultyReduce computing resource requirementsDesign optimisation/simulationNeural architecturesStreaming dataComputational resource
The invention relates to the technical field of traffic flow simulation, in particular to a simulation traffic flow editing method and system based on a sequential network. The method comprises the following steps: acquiring basic traffic flow data; obtaining a tendency speed and a tendency direction of the edited vehicle according to an editing demand; inputting the edited vehicle information, the interactive vehicle information, the tendency speed of the edited vehicle and the tendency direction of the edited vehicle into a sequential network to obtain a to-be-edited acceleration of the edited vehicle; and adjusting the basic traffic flow data according to the to-be-edited acceleration of the edited vehicle to obtain an edited simulated traffic flow. The invention provides the vehicle information editing method based on the basic traffic flow data, so that the construction difficulty of similar simulation scenes is effectively simplified, and the computing resource demand is reduced.
Owner:际络科技(上海)有限公司
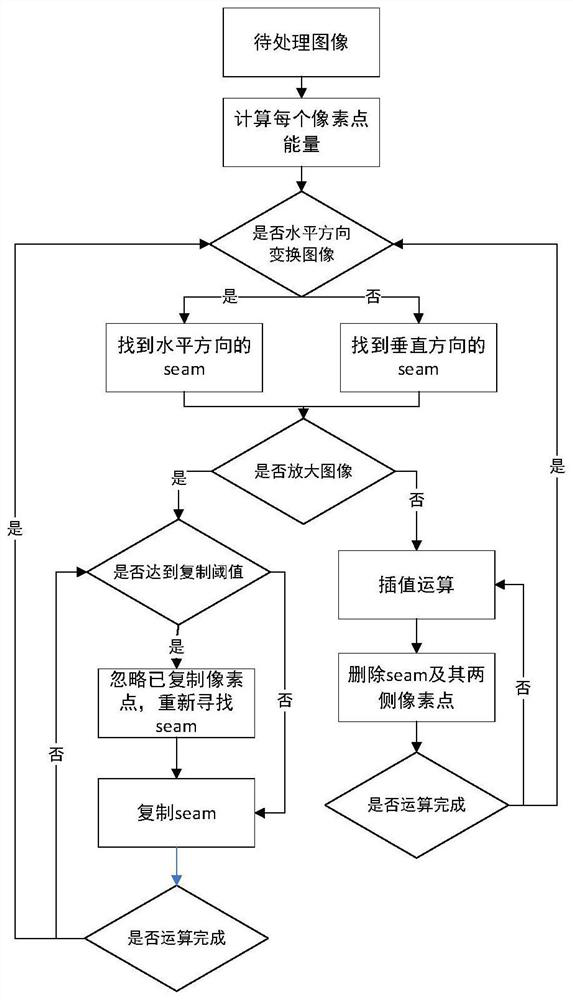
Real-time video seam clipping method and system based on microblaze
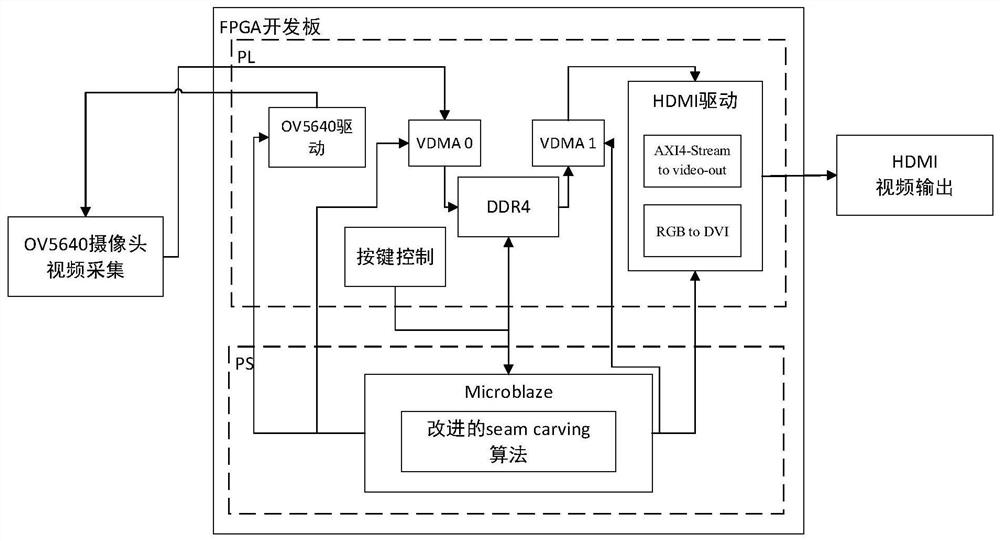
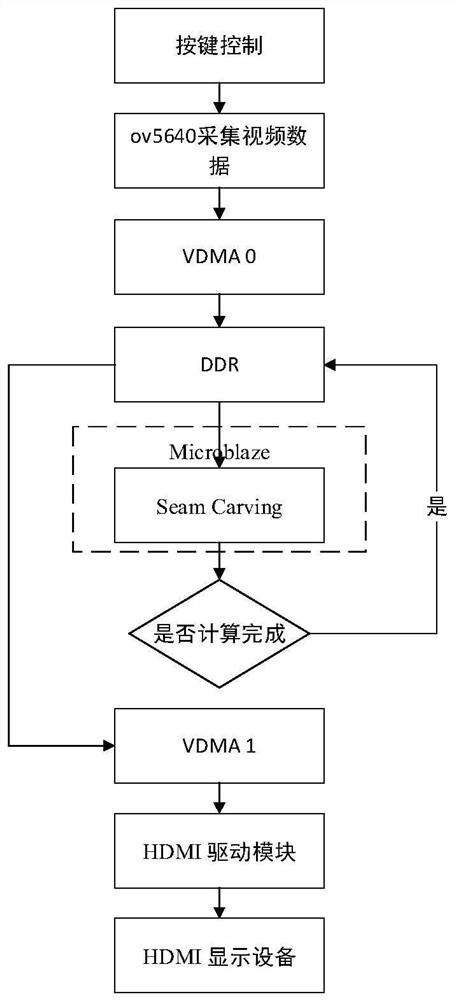
ActiveCN113727161AReduce occupancyImprove portabilitySelective content distributionComputer graphics (images)Processing
The invention provides a real-time video seam clipping method and system based on microblaze. The method and system can be used for performing seam clipping processing and real-time display after video acquisition. The system is jointly realized by a PL end and a PS end, an improved video seam clipping operation method is combined to process an image, and compared with an original Seam Carving algorithm, when the image is shrunk or magnified, video information is reserved, picture distortion is further reduced, and a user can obtain a better visual effect; on the other hand, the system provided by the invention is small in resource occupation and strong in portability, has the advantages of convenience in software programming debugging and high hardware calculation processing speed, improves the processing speed and reduces the time delay through the cooperative work of software and hardware, can randomly change the picture size while keeping the complete information of the displayed video, can be adapted to display equipment of various specifications, and is suitable for various live streaming or monitoring scenes.
Owner:NANJING UNIV
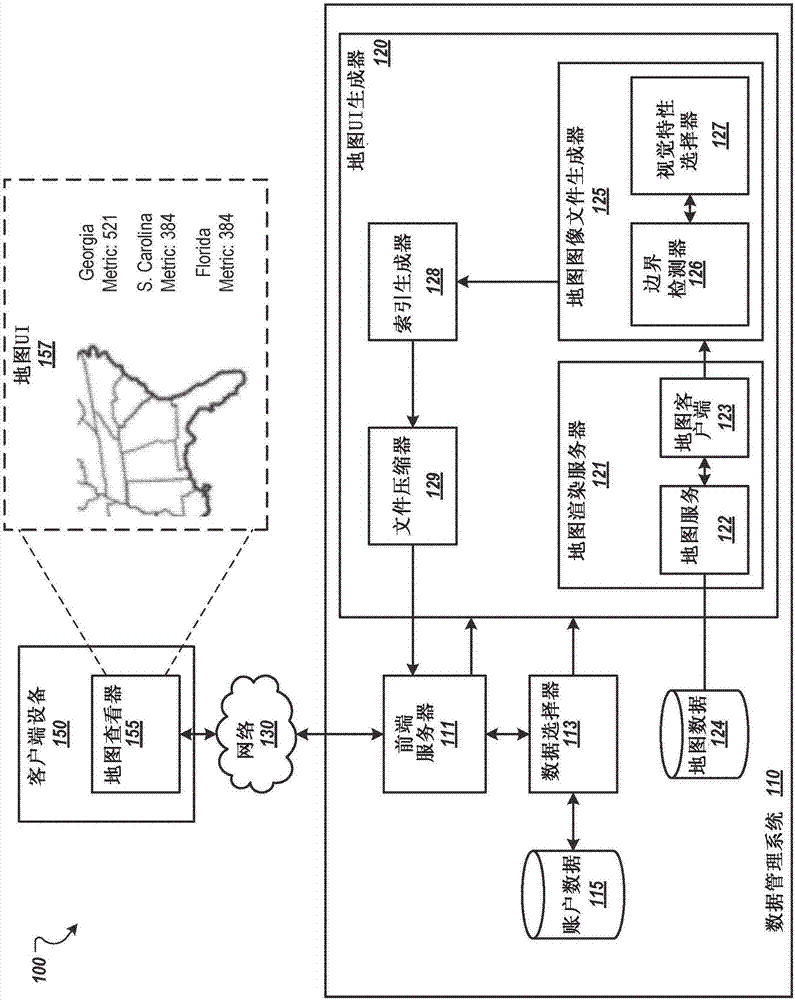
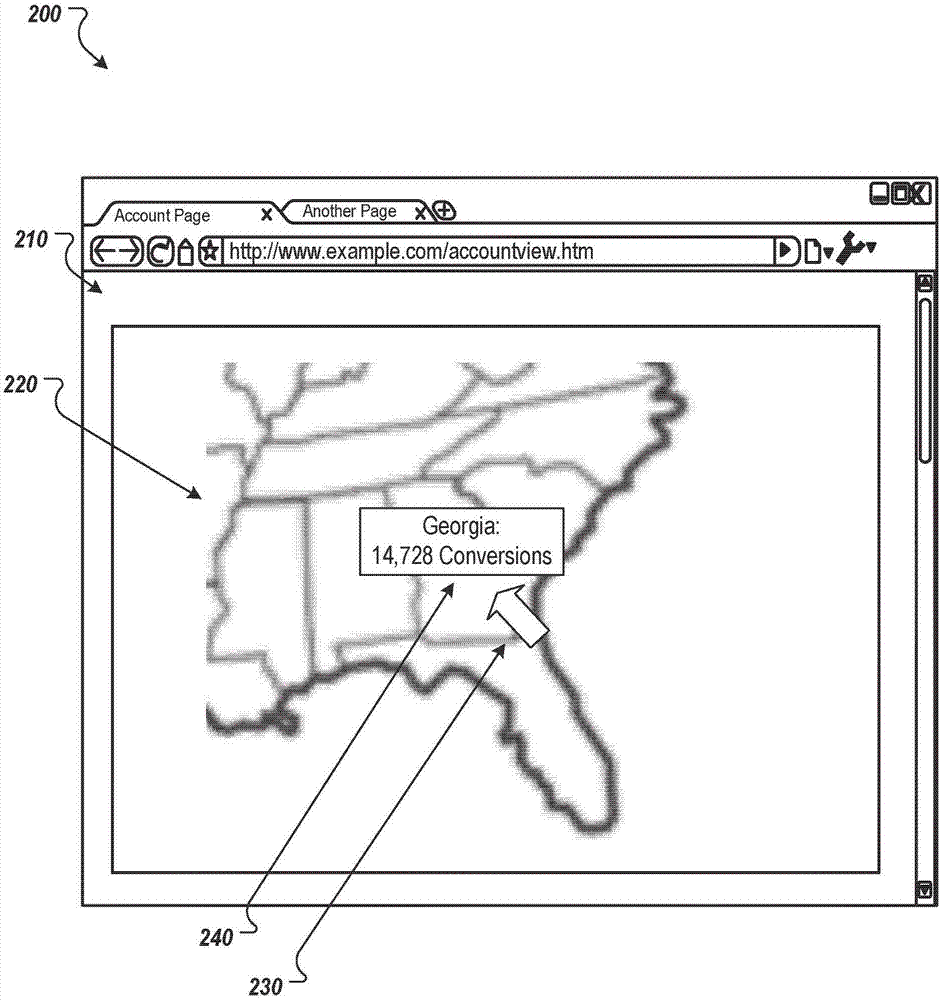
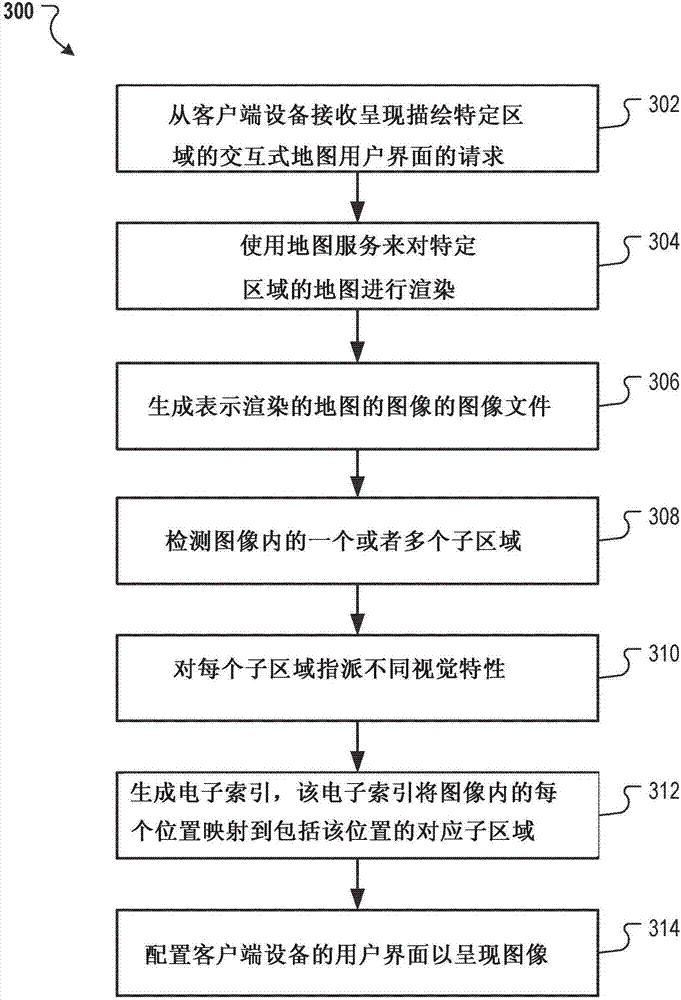
Reducing latency in map interfaces
PendingCN107231817AReduce latencyReduce the need for computing resourcesImage enhancementImage analysisComputer graphics (images)Human–computer interaction
Methods, systems, and apparatus, including computer programs encoded on a computer storage medium, for reducing latency in transmitting and presenting map user interfaces. In one aspect, a method includes receiving, from a client device, a request for presentation of an interactive map user interface that depicts (i) a region and (ii) data related to an account for sub-regions of the region. One or more servers render a map of the region. The server(s) generate an image file representing an image of the rendered map. A different visual characteristic is assigned to each different sub-region. The server(s) configure a user interface of the client device to present (i) the image with each of the different sub-regions being presented according to the different visual characteristics and (ii) account data related to a sub-region when the client device detects a user interaction with the sub-region.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com