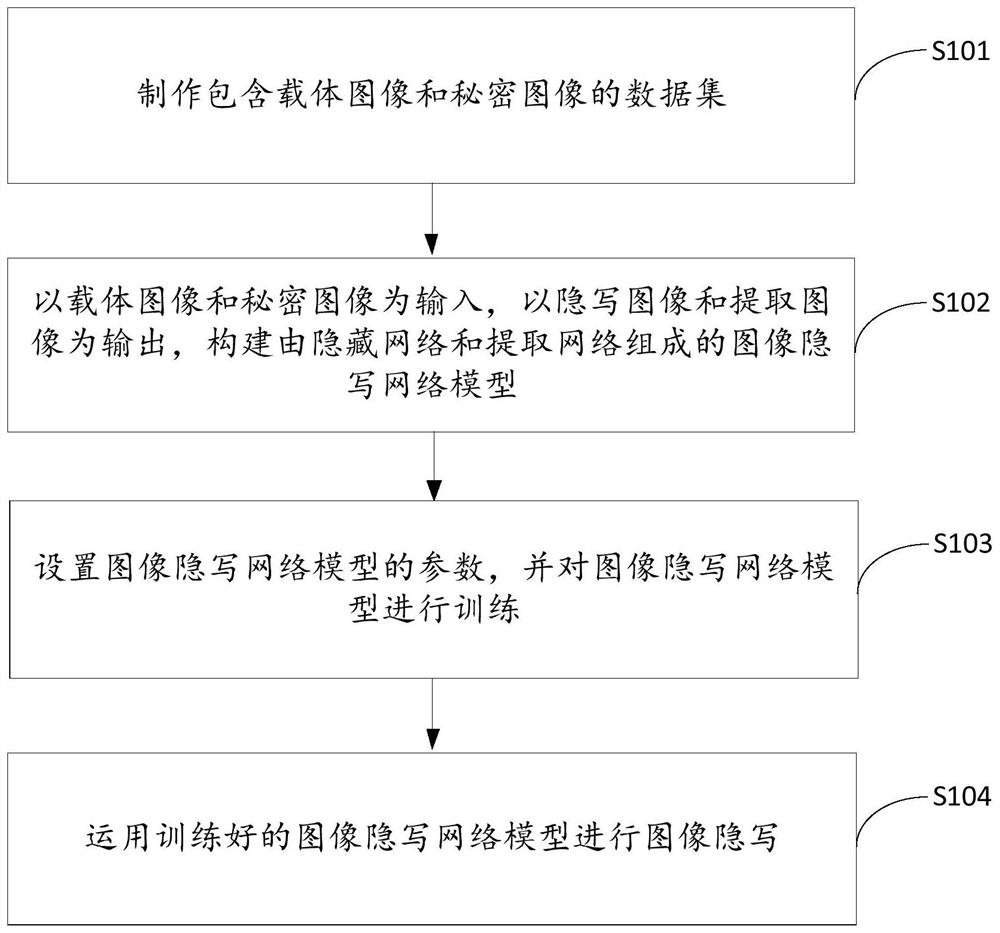
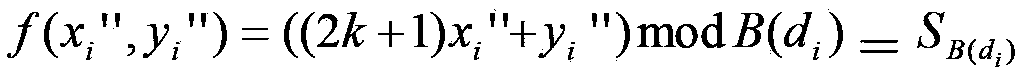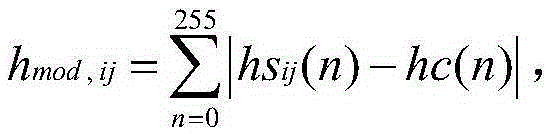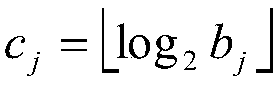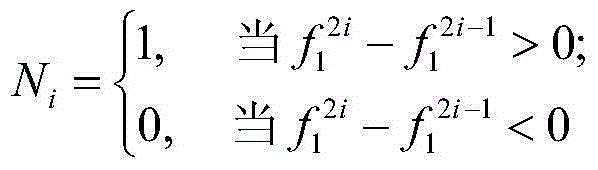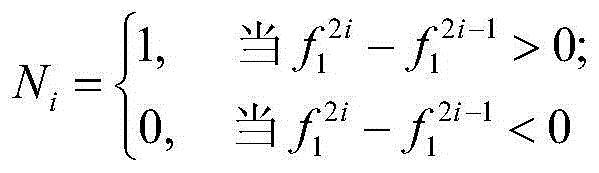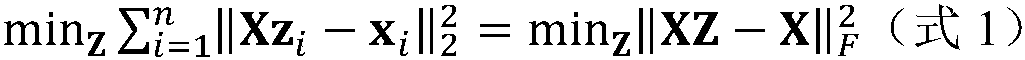Patents
Literature
124 results about "Image steganography" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
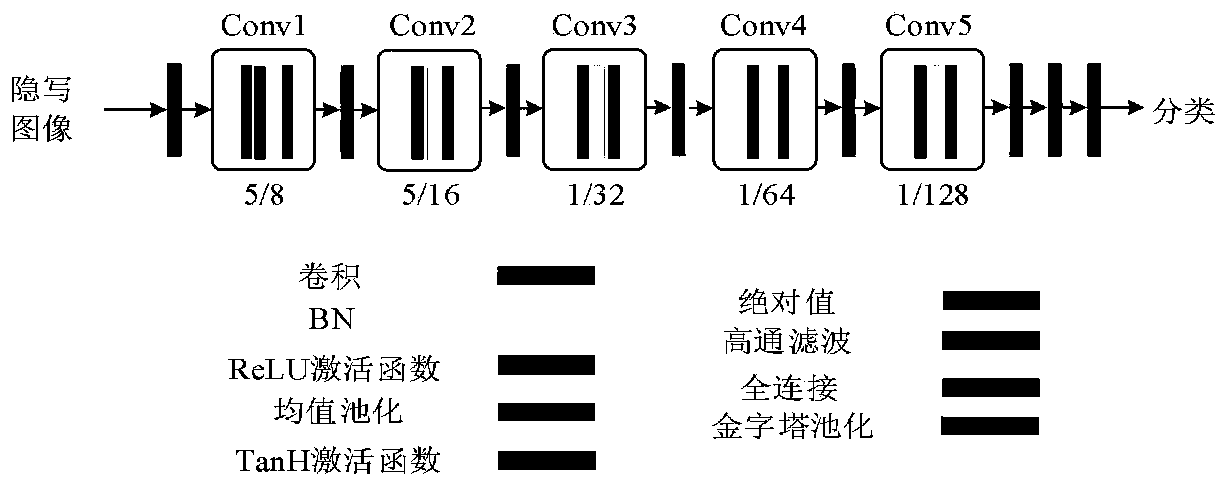
Image Steganalysis Based on Deep Learning
ActiveUS20180068429A1Highly universal image steganalysis modelAccurate identificationImage enhancementImage analysisSteganalysisFeature learning
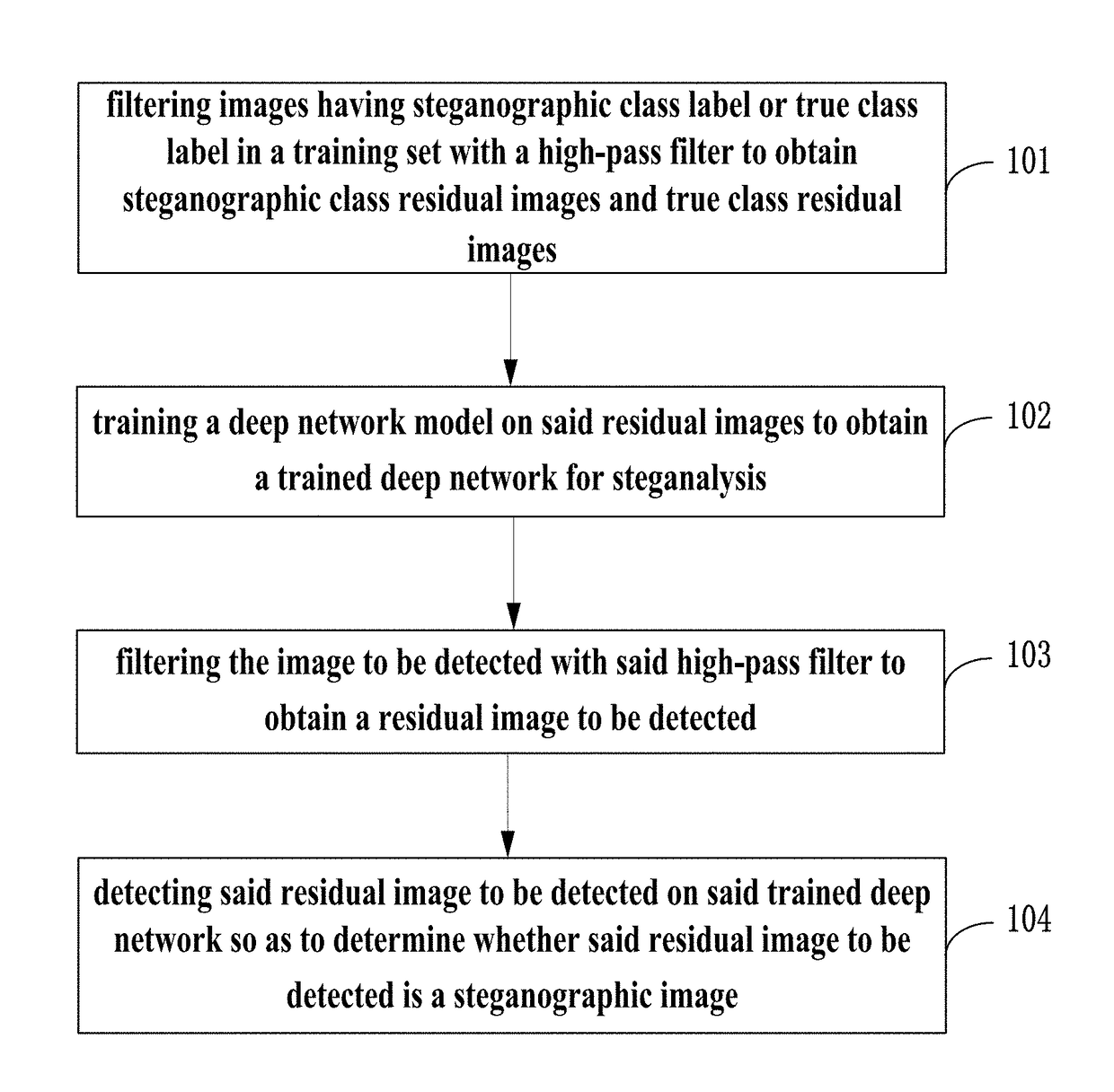
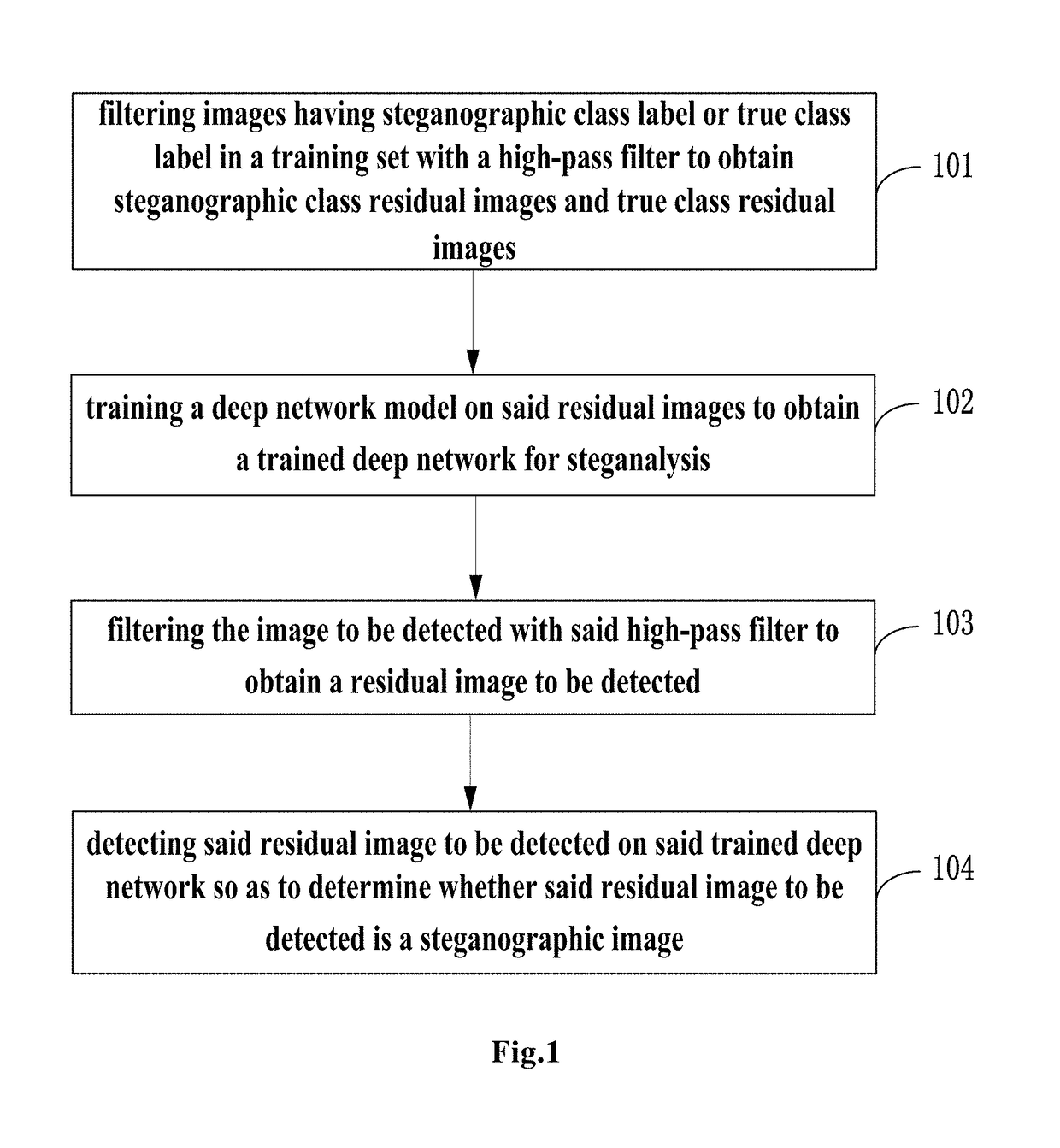
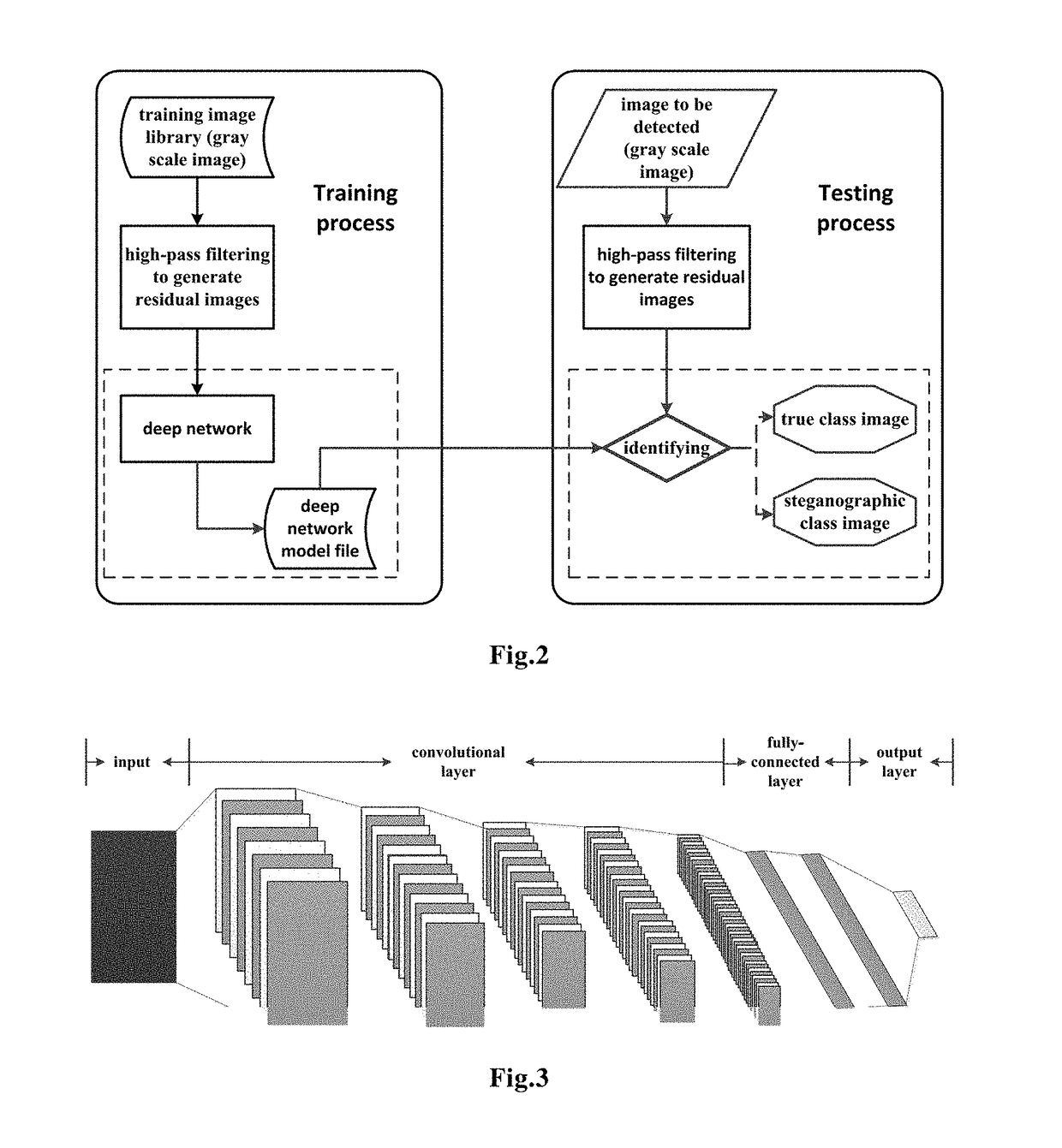
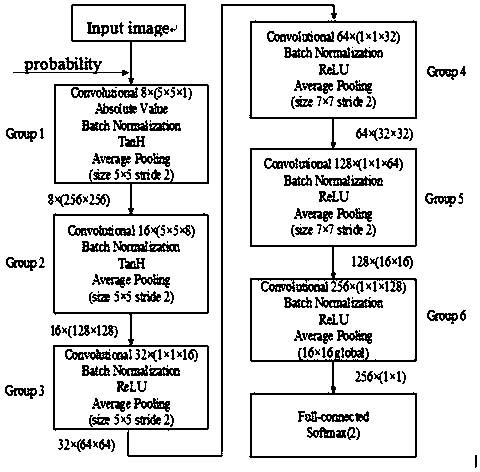
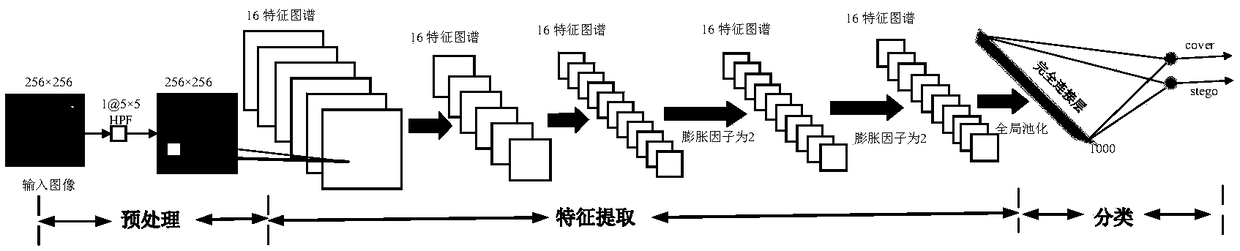
The present invention provides a method for detecting image steganography based on deep learning, which comprises: filtering images having steganographic class label or true class label in a training set with a high-pass filter to obtain a training set including steganographic class residual images and true class residual images; training a deep network model on said training set to obtain a trained deep model for steganalysis; filtering the image to be detected with said high-pass filter to obtain a residual image to be detected; detecting said residual image to be detected on said deep model so as to determine whether said residual image to be detected is a steganographic image. The method for detecting image steganography in the present invention can create an automatic blind steganalysis model through feature learning and can identify steganographic images accurately.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
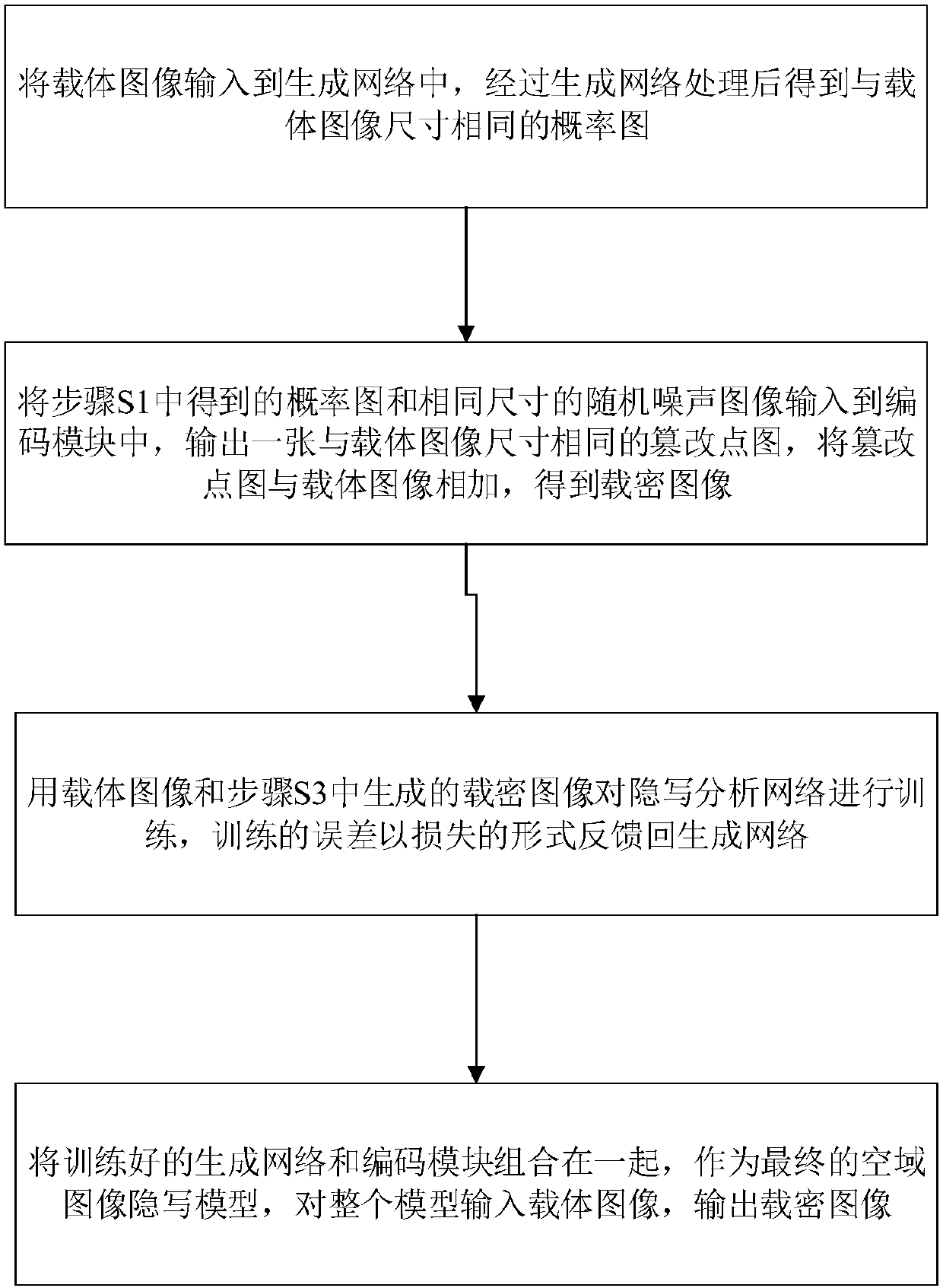
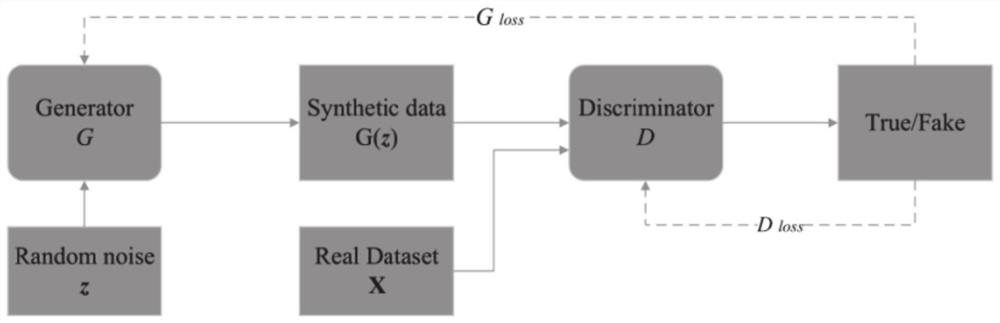
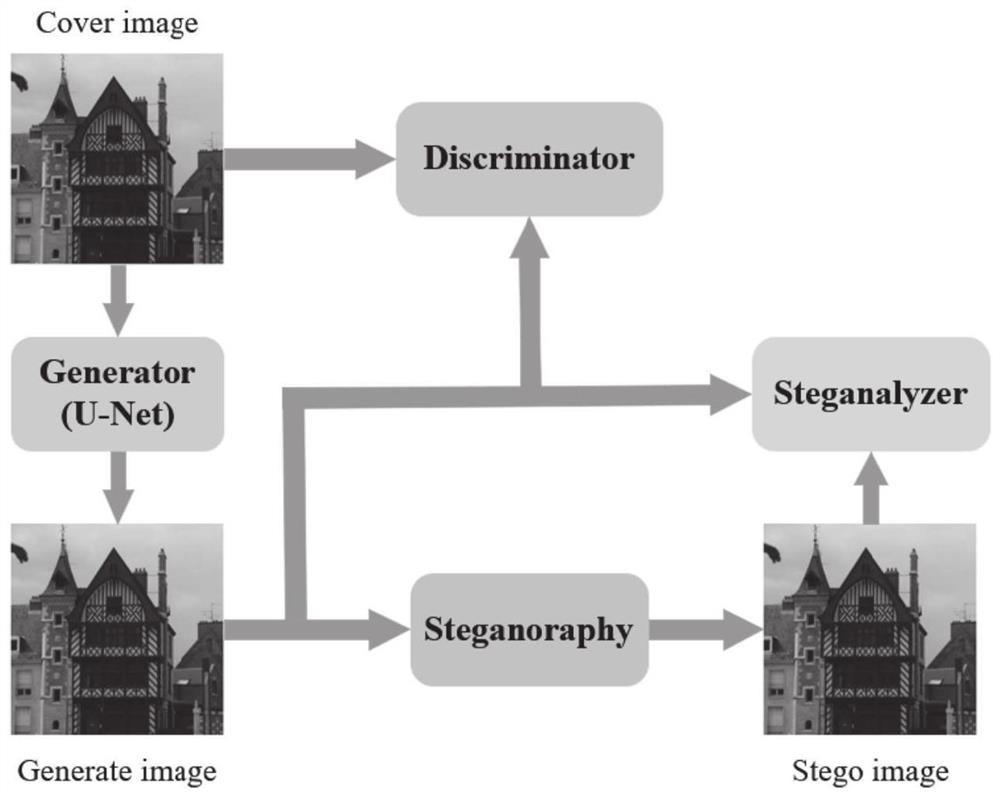
Spatial-domain image steganography method and system based on generative adversarial network
ActiveCN108346125ASimple designSmall number of structural parametersImage enhancementImage analysisCode moduleSteganalysis
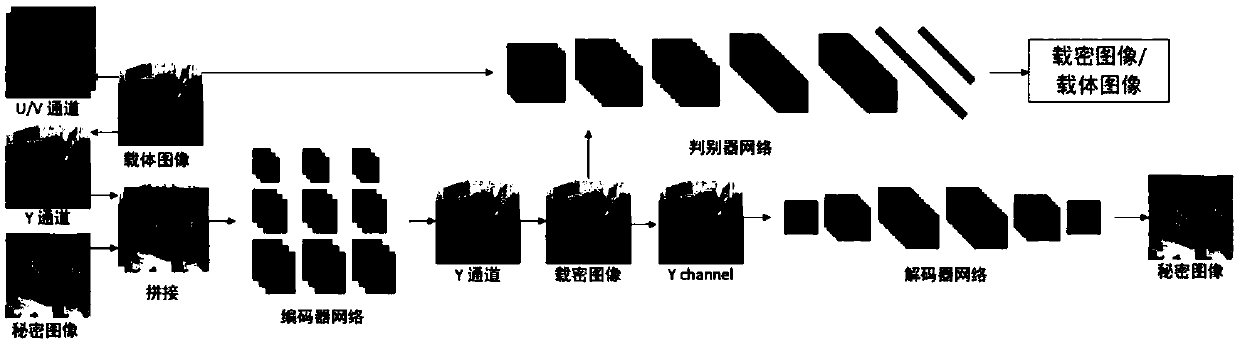
The invention discloses a spatial-domain image steganography method and system based on generative adversarial network. The carrier image is converted into a probability graph through the generation network of a U-shaped structure, and then the probability graph is coded by utilizing a hyperbolic tangent coding module, a tampering point graph is generated, and the carrier image and the tampering point graph are added to generate a secret-carrying image; and then a steganography analysis network is used for distinguishing the carrier image and the secret-carrying image, and the classification result is fed back to the generation network in an error mode; and finally, the trained generation network and the coding module are combined together, as a final spatial-domain image steganography model, the carrier image is input into the whole model, and the secret-carrying image is output. The invention further discloses a space-domain image steganography system based on the generative adversarial network, and the system includes a generation network module, an encoding module and an image steganography module. According to the spatial-domain image steganography method based on the generative adversarial network, the security is obviously improved, and the design is simple.
Owner:SUN YAT SEN UNIV
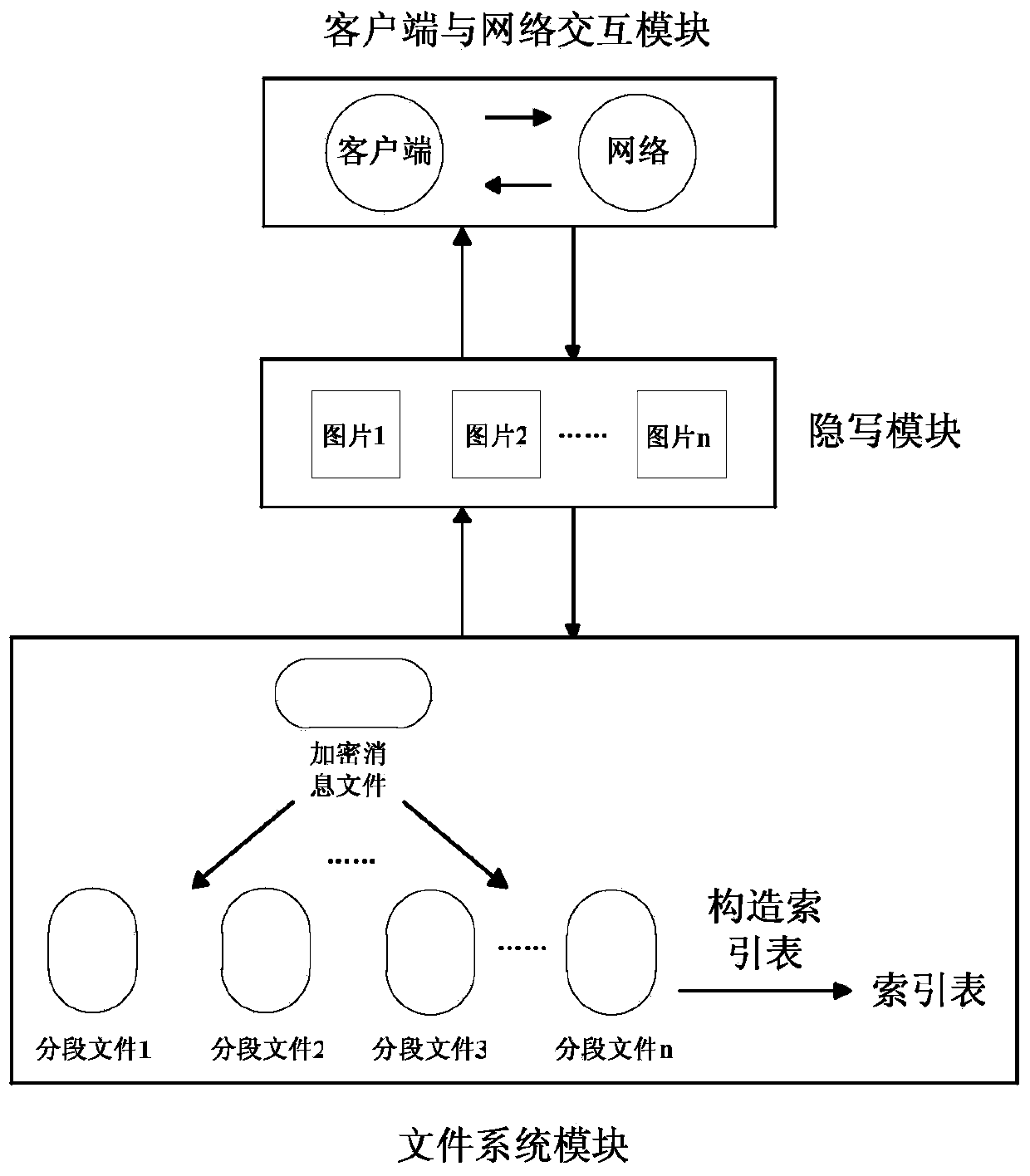
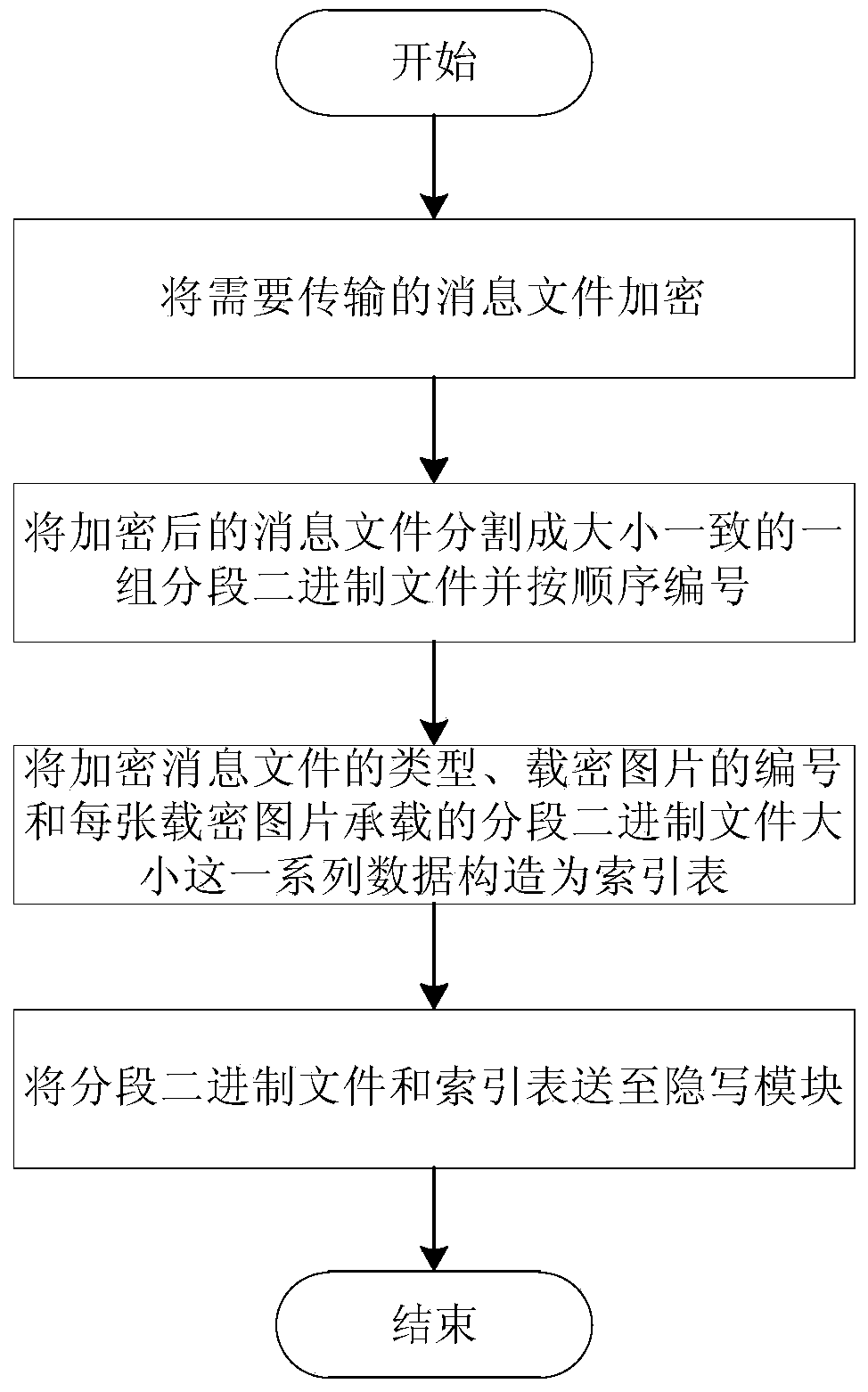
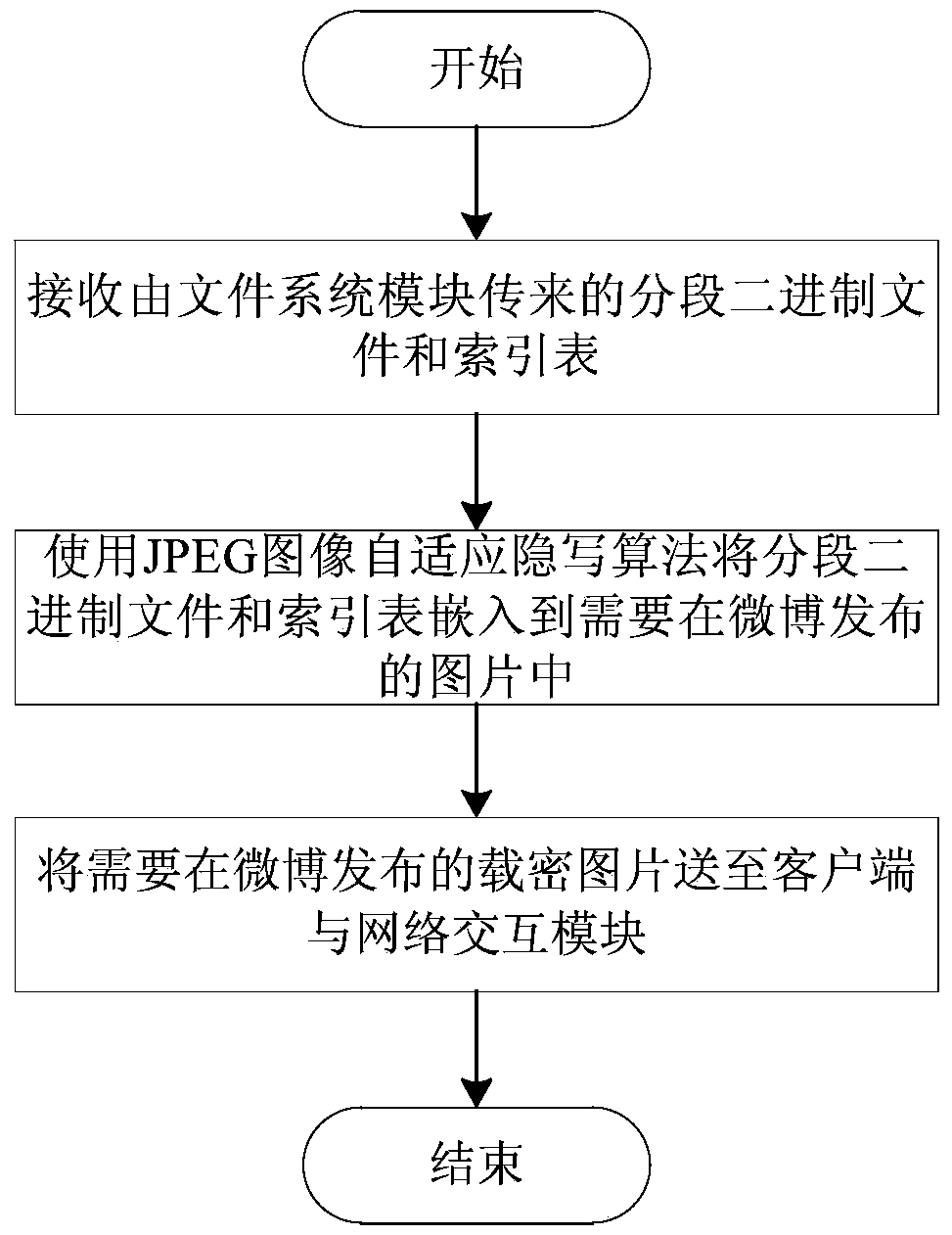
Privacy protection system and method based on social network
ActiveCN104052658AAchieving covert transmissionImprove securityImage data processing detailsData switching networksPrivate communicationMicroblogging
The invention discloses a privacy protection system and method based on a social network. The privacy protection method includes the steps that an information sender and an information receiver obtain the function of information interaction between the privacy protection system and a microblog based on the social network; the information sender logs in the privacy protection system and uses a self-adaptive JPEG image steganography for embedding information needing to be transmitted into an image needing to be published in the microblog after encrypting the information; the privacy protection system publishes the microblog containing the encrypted image and updates a microblog head portrait image of the information sender to finish sending the information; the information receiver logs in the privacy protection system and extracts and decrypts the encrypted information in the microblog image published by the information sender, and the information is pushed to the information receiver to finish receiving the information. By the adoption of the privacy protection system and method, it can be guaranteed that a safe and private communication channel is set up between the information sender and the information receiver which communicate in the Internet, and the privacy data of a user are effectively protected from illegal monitoring and stealing.
Owner:UNIV OF SCI & TECH OF CHINA
Invisible image steganography based on generative adversarial network
ActiveCN109587372ASolve the problem of color differenceResolve differencesNeural architecturesNeural learning methodsSteganalysisDiscriminator
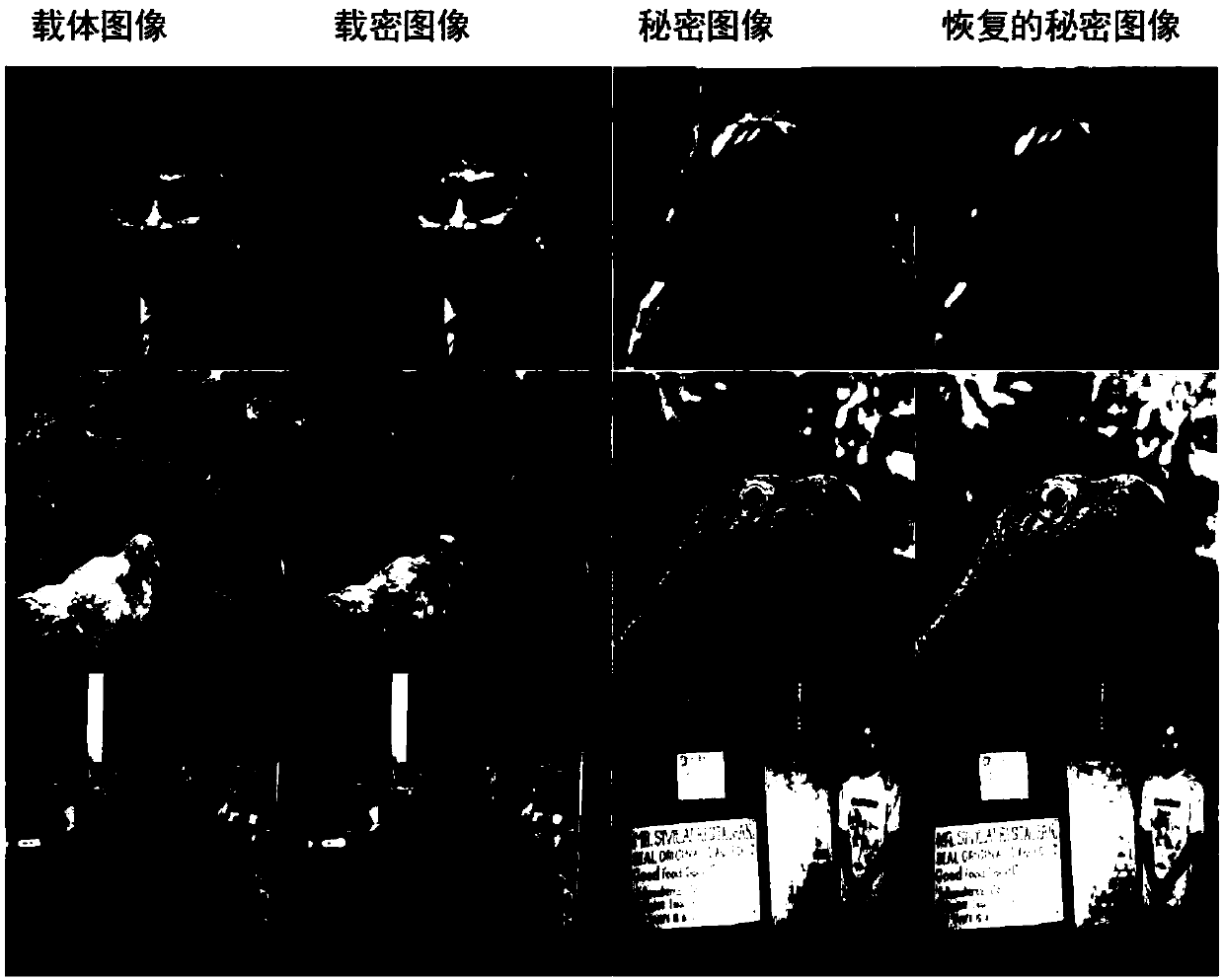
The invention discloses an invisible image steganography based on a generative adversarial network which can embed a grayscale secret image into a color carrier image to obtain a confidential image and can successfully recover a secret image from the payload image. The invisible image steganography comprises: an encoder network which is responsible for embedding a secret image into a carrier imageto generate a confidential image; a decoder network which is responsible for recovering a secret image from a loaded image; and a discriminator network which is responsible for performing steganalysis of a natural image and a confidential image to adjust the safety of the encoder network and decoder network. The invisible image steganography based on the generative adversarial network provides anew design idea for image information hiding.
Owner:BEIJING UNIV OF POSTS & TELECOMM
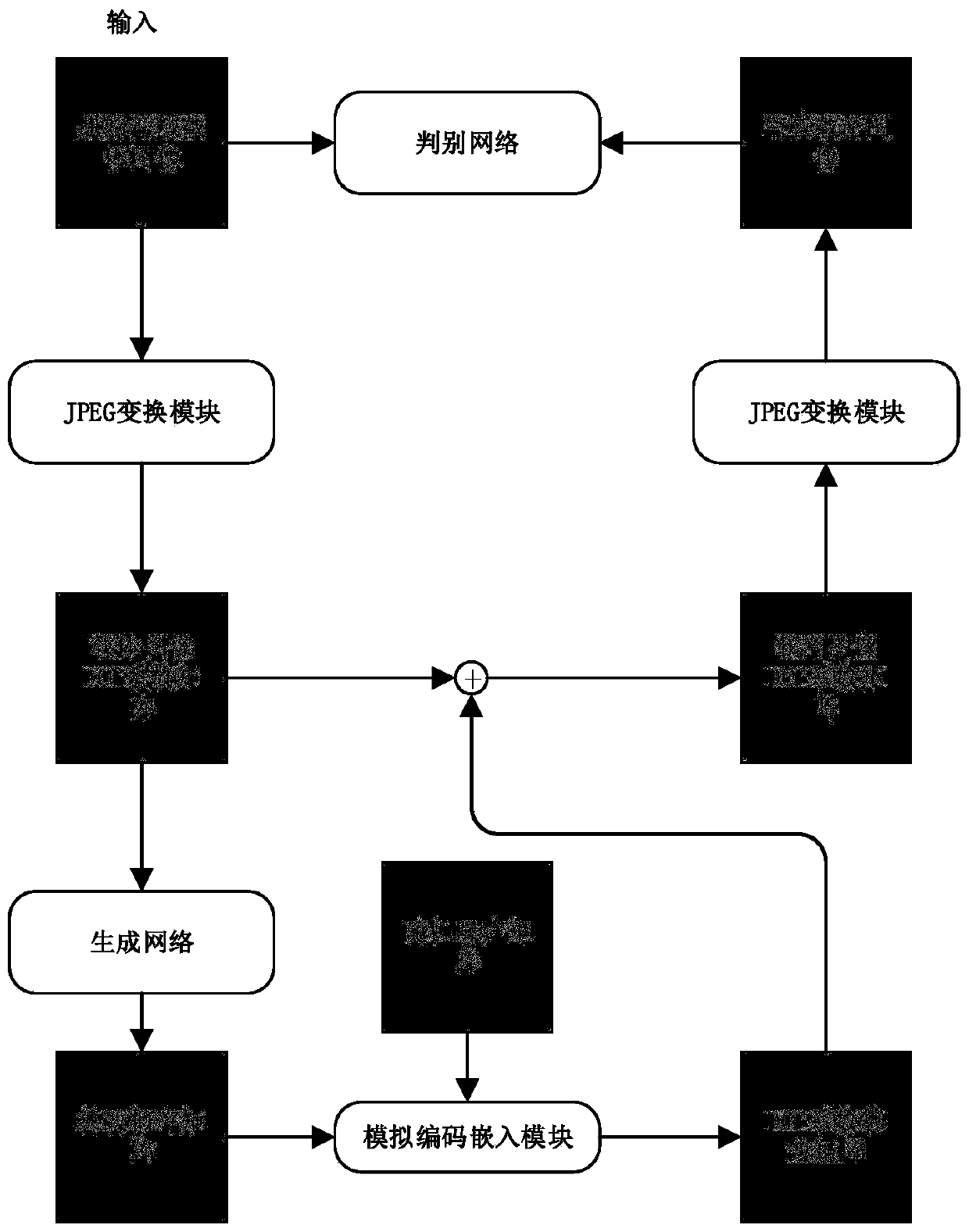
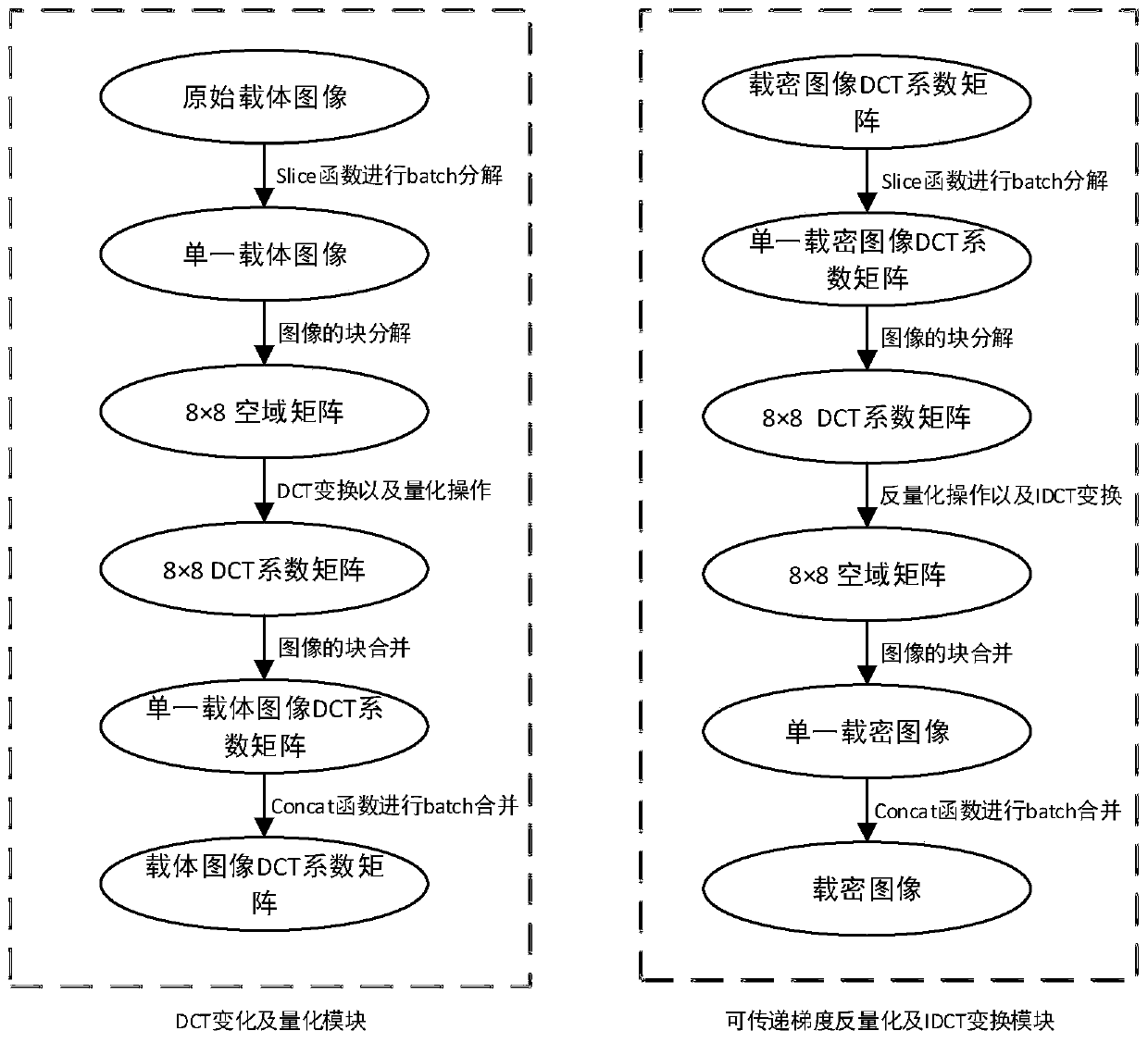
JPEG domain image steganography method and system based on generative adversarial network
ActiveCN110334805ASimple designEasy to implementImage codingDigital video signal modificationPattern recognitionCode module
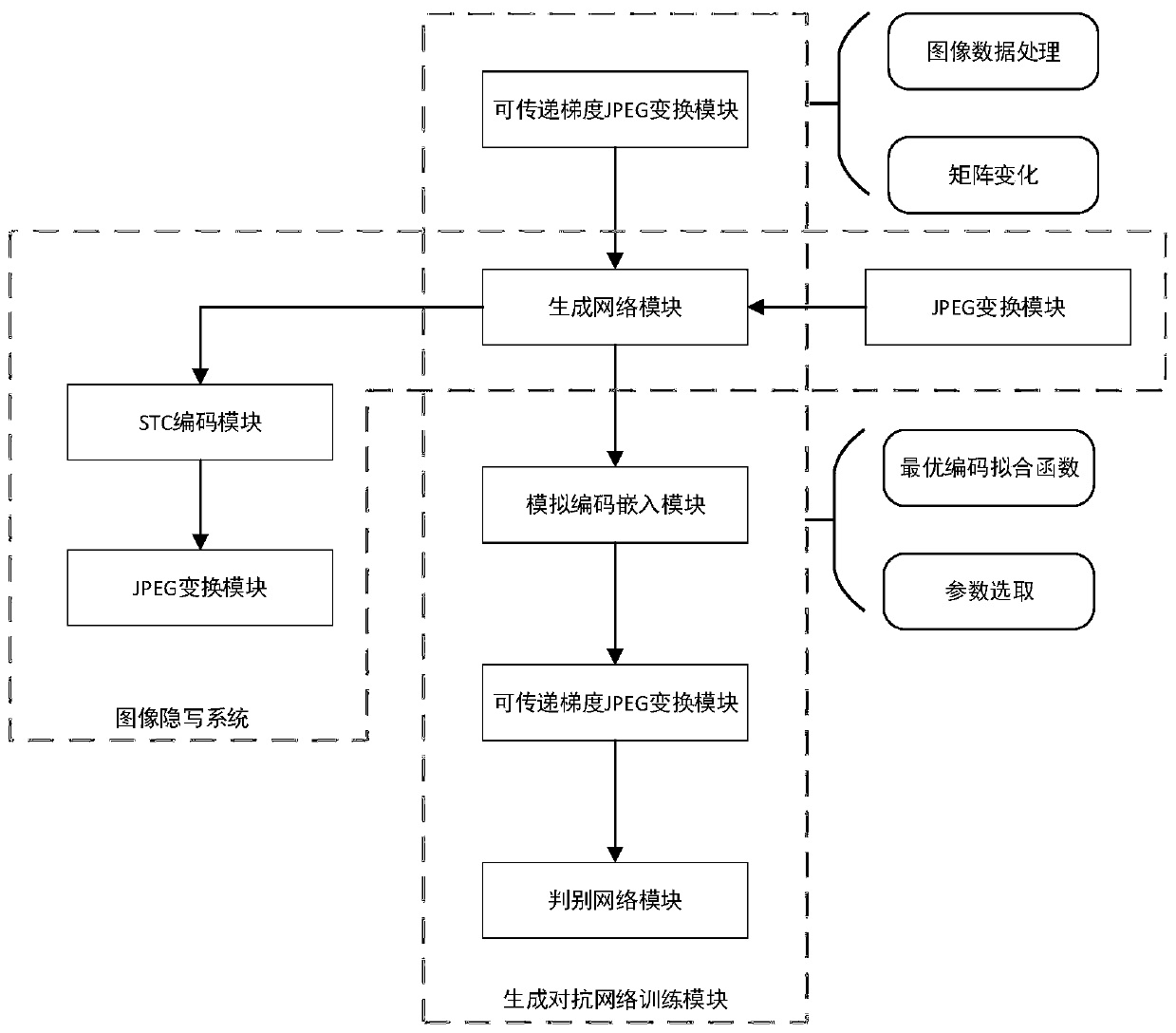
The invention discloses a JPEG domain image steganography method based on a generative adversarial network. The method comprises: generating a tampering probability matrix corresponding to a carrier image DCT coefficient matrix through a generation network; using an analog coding embedding module and a transmittable gradient JPEG transformation module for generating a corresponding secret carryingimage according to the tampering probability matrix; distinguishing the carrier image and the secret-carrying image through the discrimination network, using the classification error as a loss function to perform adversarial training on the generation network and the discrimination network, and finally obtaining the generation network model capable of generating the adaptive steganography cost value. Through combination of the model and a traditional information coding module, secret information is embedded into a carrier image to obtain a secret-carrying image. Compared with a traditional JPEG domain image steganography method, the method has the advantages of being simple in design, easy to implement, high in detection resistance and the like. The invention further discloses a JPEG domain image steganography system. The system comprises a generative adversarial network module, an information coding module and a JPEG transformation module which are obtained through the JPEG domain image steganography method based on the generative adversarial network.
Owner:SUN YAT SEN UNIV
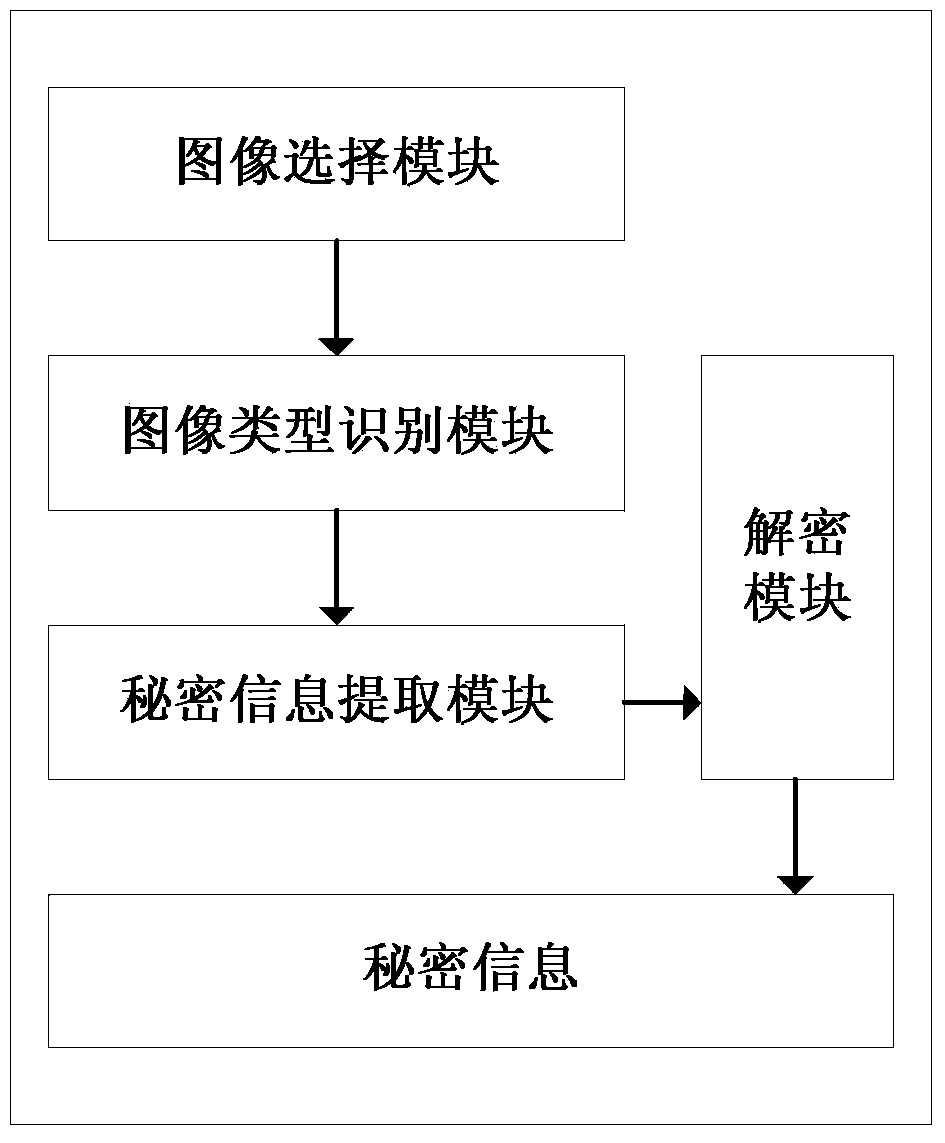
Image steganography method and secret information extraction method
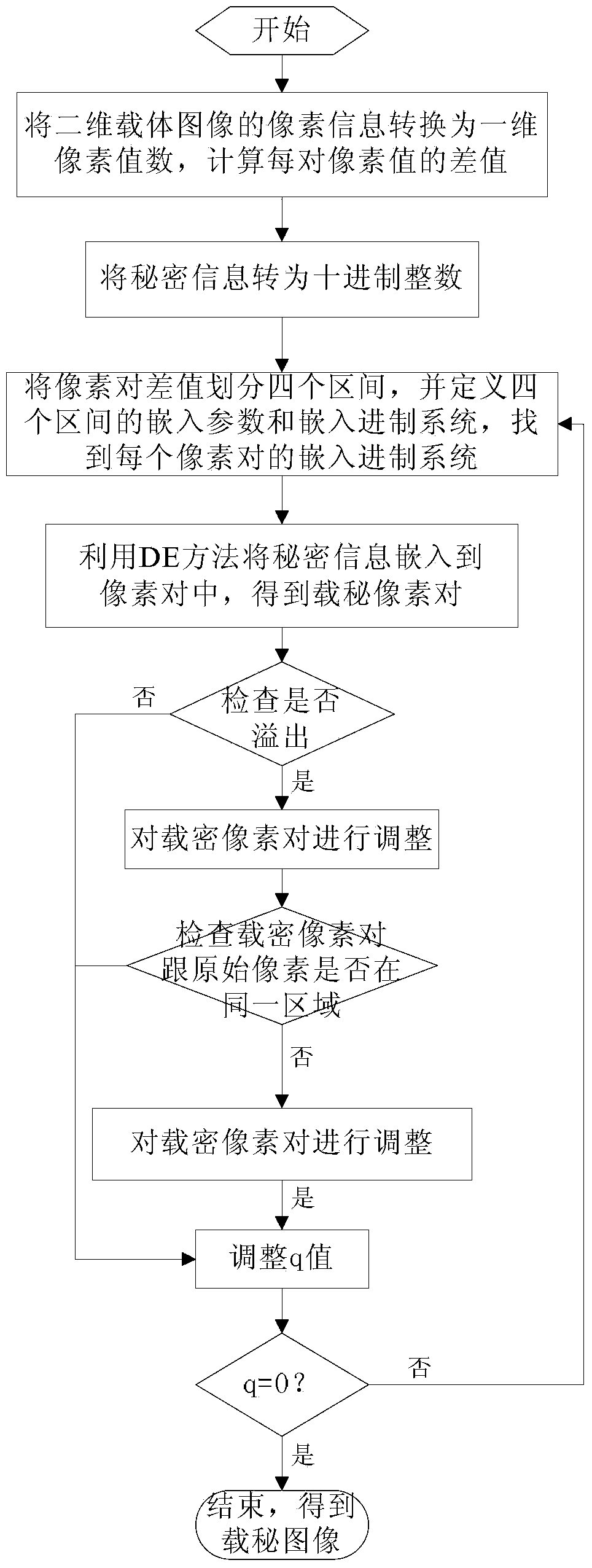
InactiveCN103413269AIncrease embedding capacityControl distortionImage data processing detailsSteganalysisComputer vision
The invention relates to an image steganography method and a secret information extraction method. The image steganography method comprises the steps: (1), converting pixel information of a two-dimensional carrier image I into a set of continuous and non-overlapping one-dimensional pixel value data, and computing a difference value of each pair of pixel values, wherein the size of the two-dimensional carrier image I is N1*N2; (2), performing DES encryption on secret information S, and transferring encrypted secret information S' into a decimal integer q; (3), dividing a di value computed in the step (1) into four sections Tj; (4), obtaining SB(di) according to the equation: SB(di)=qmodB(di), and inserting SB(di) into a pixel pair (xi, yi) through a DE method; (5), detecting whether overflowing occurs or not. Compared with the prior art, the image steganography method has the advantages of being capable of improving insertion capacity of the carrier image remarkably and controlling image distortion effectively. The image steganography method has the steganalysis abilities such as the certain safety performance and resistance to RS attack, and can operate efficiently on mainstream software and hardware platforms of a mobile intelligent terminal.
Owner:NINGBO UNIV
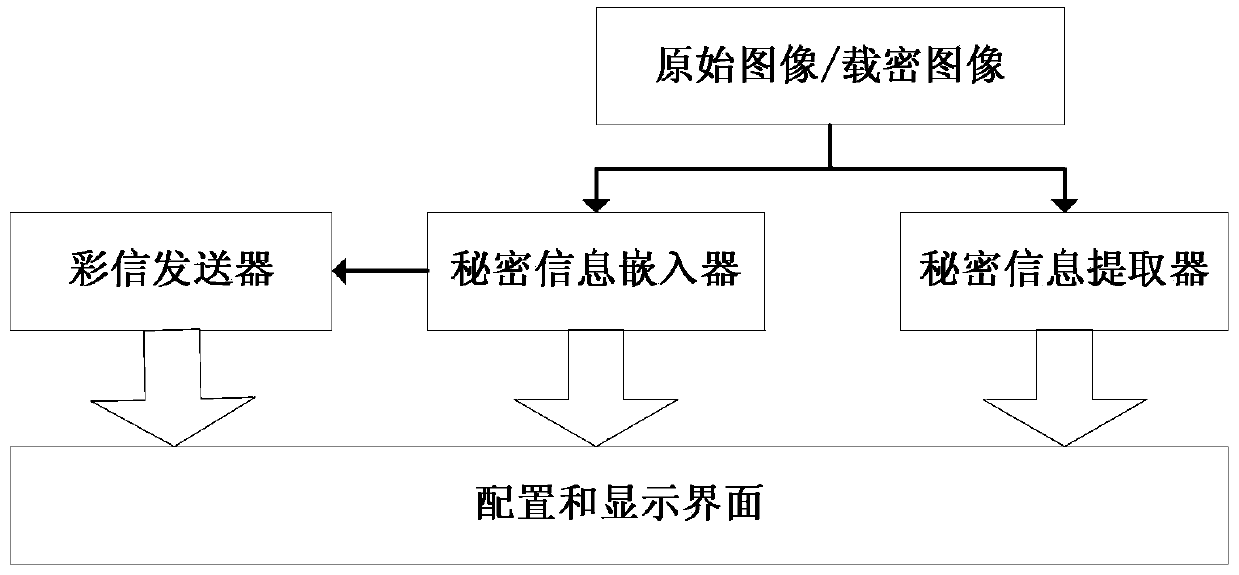
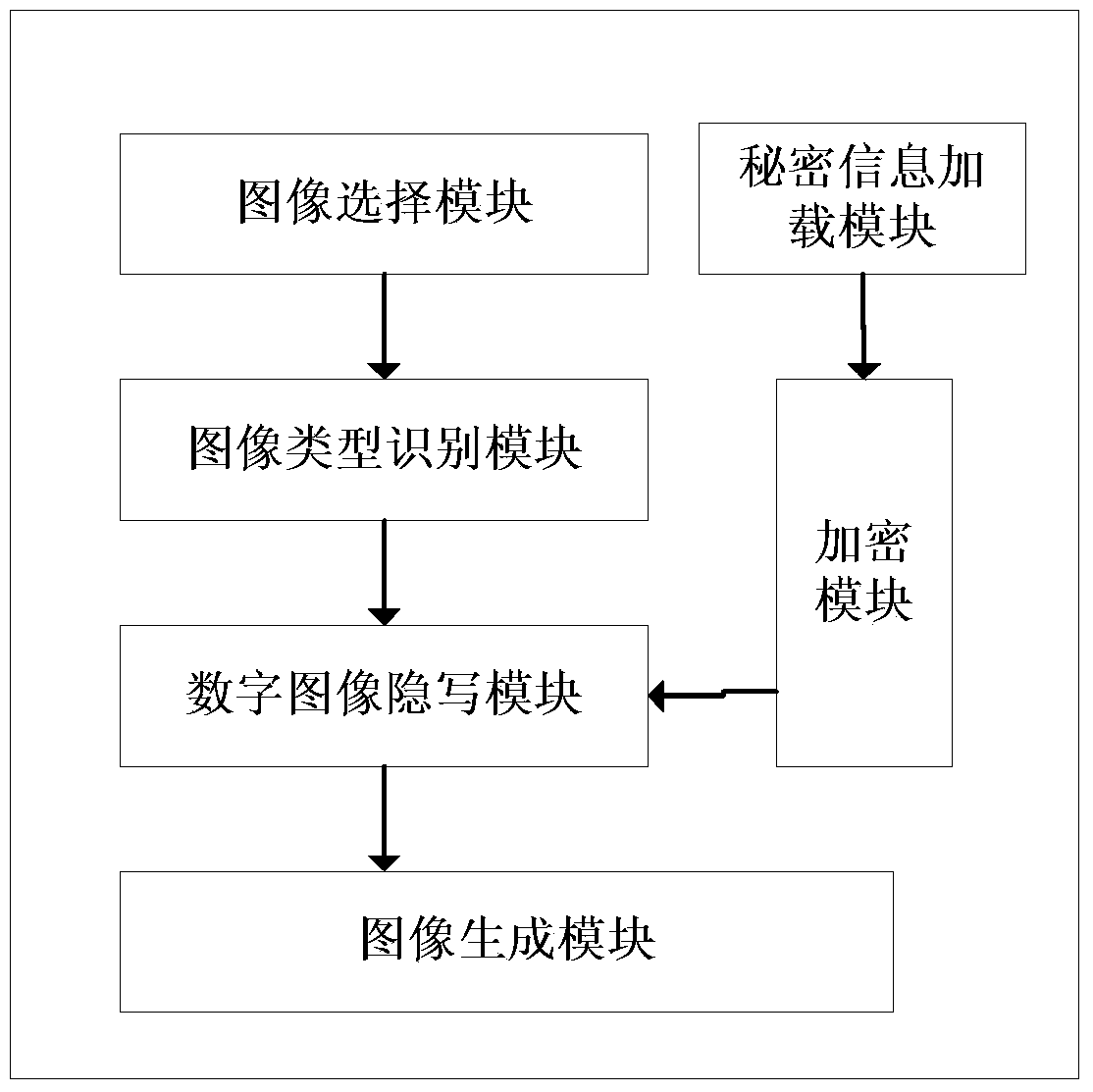
Image steganography and secret information extraction method based on intelligent mobile terminal
InactiveCN103442156AImprove sending efficiencyIncrease embedding capacityMessaging/mailboxes/announcementsPictoral communicationInformation embeddingSystem safety
The invention relates to an image steganography and secret information extraction method based on an intelligent mobile terminal. The intelligent mobile terminal comprises a secret information embedder, a secret information extractor and a multimedia message transmitter, and images are selected by the intelligent mobile terminal for different use purposes. If secret information needs to be embedded, original pictures are selected. If the secret information needs to be extracted, encrypted pictures are selected. The selected original pictures are uploaded into the secret information embedder for the secret information embedding operation, and the encrypted pictures are uploaded into the secret information extractor for the secret information extraction operation. If the current operation is the secret information embedding operation, the encrypted pictures embedded with the secret information are uploaded into the multimedia message transmitter, and are sent to a receiver in a multimedia message mode. Compared with the prior art, the image steganography and secret information extraction method has the advantages that the functions of secret information embedding, multimedia message sending and secret information extraction are achieved in the intelligent mobile terminal, system safety is enhanced, and meanwhile multimedia message sending efficiency is improved.
Owner:NINGBO UNIV
Compressed image steganography encoding method based on AMBTC high and low average optimization
InactiveCN104284190ASimple calculationEasy to implementDigital video signal modificationPattern recognitionTwo step
The invention discloses a compressed image steganography encoding method based on AMBTC high and low average optimization. According to the compressed image steganography encoding method disclosed by the invention, after the smoothness of an image block is evaluated, data are embedded in smooth blocks one by one to obtain a stego image, wherein the data embedding comprises two steps: replacing a binary bitmap by the data, and optimizing high and low averages according to the embedded data and an original bitmap. With the adoption of the compressed image steganography encoding method, the computing is simple, the method is easy to realize, and a receiving side only needs to directly take out a bitmap of a receiving side, namely the embedded data, by discriminating the smooth blocks according to a secrete key; in addition, requirements on computing resources are low, and the use is convenient, so that the compressed image steganography encoding method has a good application prospect in the real-time field, mobile terminals with limited computing resources, and the like.
Owner:ANHUI UNIVERSITY
A generative image steganography method based on an adversarial network
ActiveCN109818739AImprove securityEnhanced resistance to steganalysisKey distribution for secure communicationDigital video signal modificationPattern recognitionSteganalysis
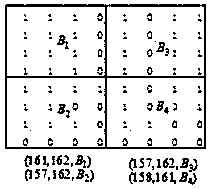
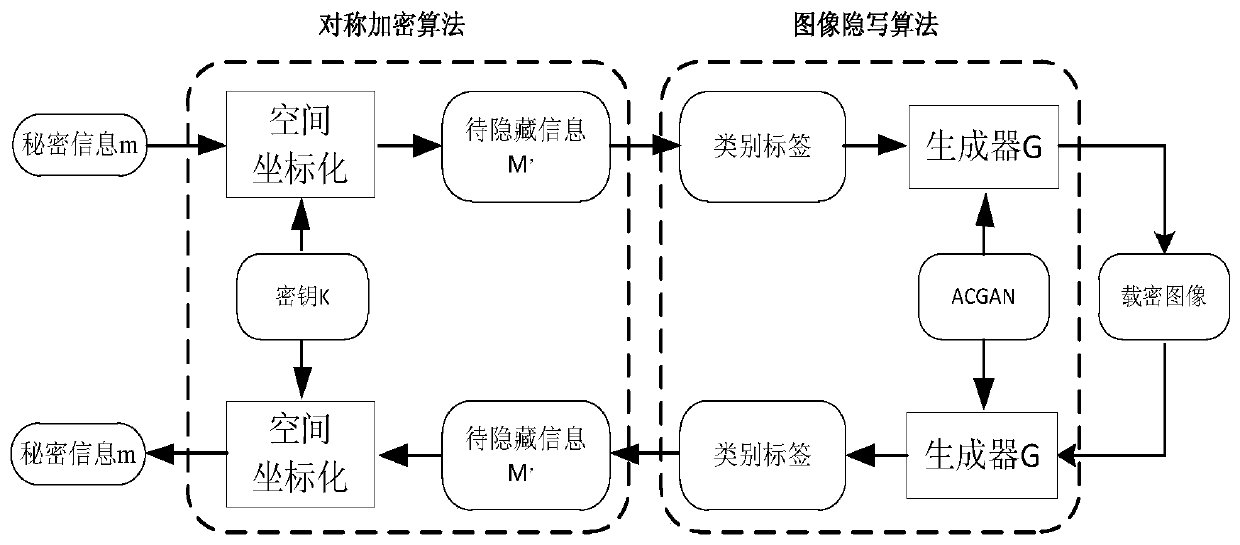
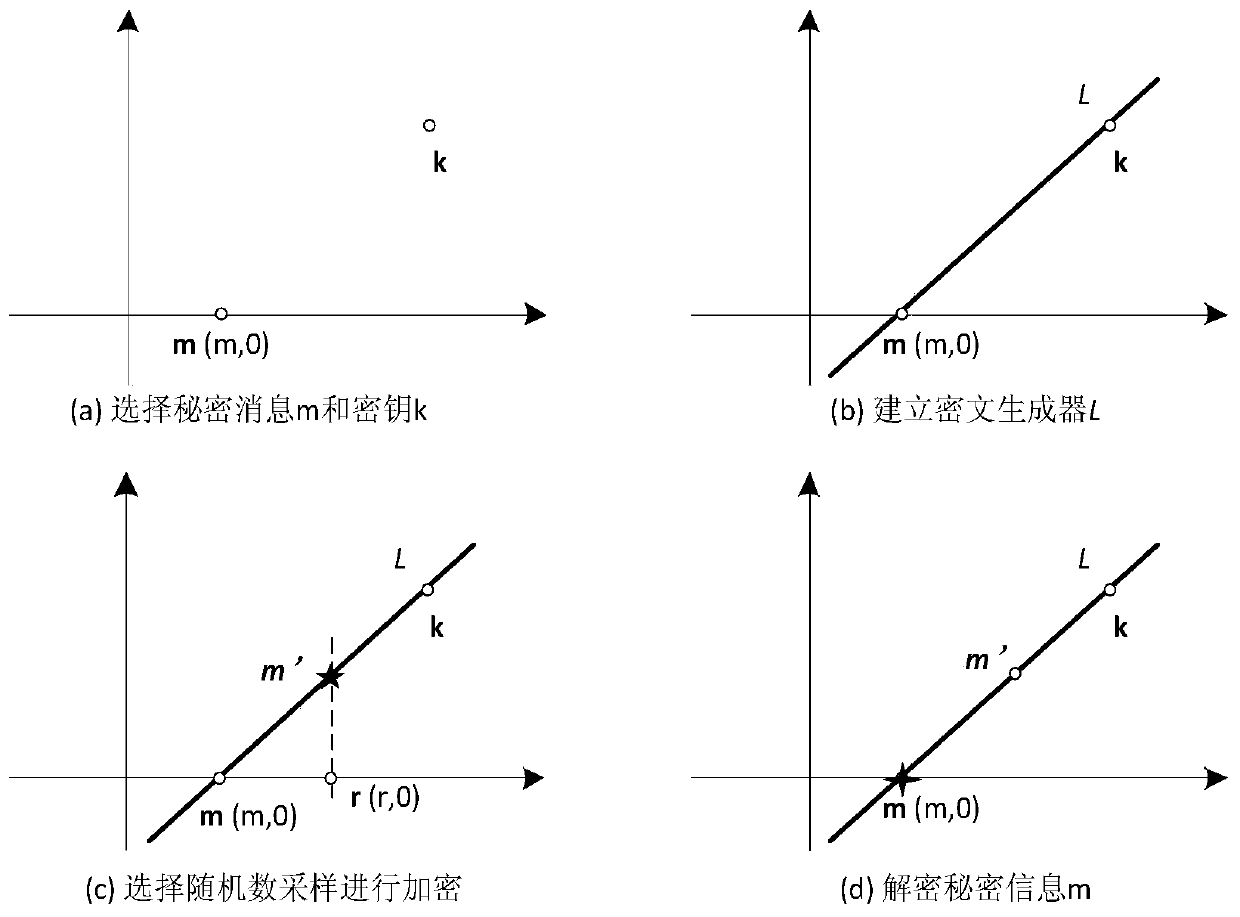
The invention particularly relates to a generative image steganography method based on an adversarial network, which comprises the following steps: a rule table is established, and secret informationto be hidden is converted into coordinate information according to the rule table; According to a two-point one-line principle, a ciphertext generator is established, and ciphertext coordinate point information is obtained; The sender randomly selects the ciphertext coordinate point information, replaces the label information with the ciphertext coordinate point information, inputs the ciphertextcoordinate point information into the generator, and generates a transfer image of a specified category; After receiving the transmission image, the receiver inputs the transmission image into a discriminator to obtain a category label, and then ciphertext information can be extracted; Decrypting is performed to obtain hidden coordinate information according to a two-point one-line principle; Andhidden secret information is obtained by comparing with the rule table, and information extraction is realized. According to the method, steganalysis detection based on statistics can be fundamentallyresisted, the safety of information transmission is improved, and meanwhile the steganalysis resisting capability is greatly enhanced.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Generative robust image steganography method
PendingCN111598762AUndetectableImprove practicalityImage watermarkingNeural architecturesPattern recognitionData set
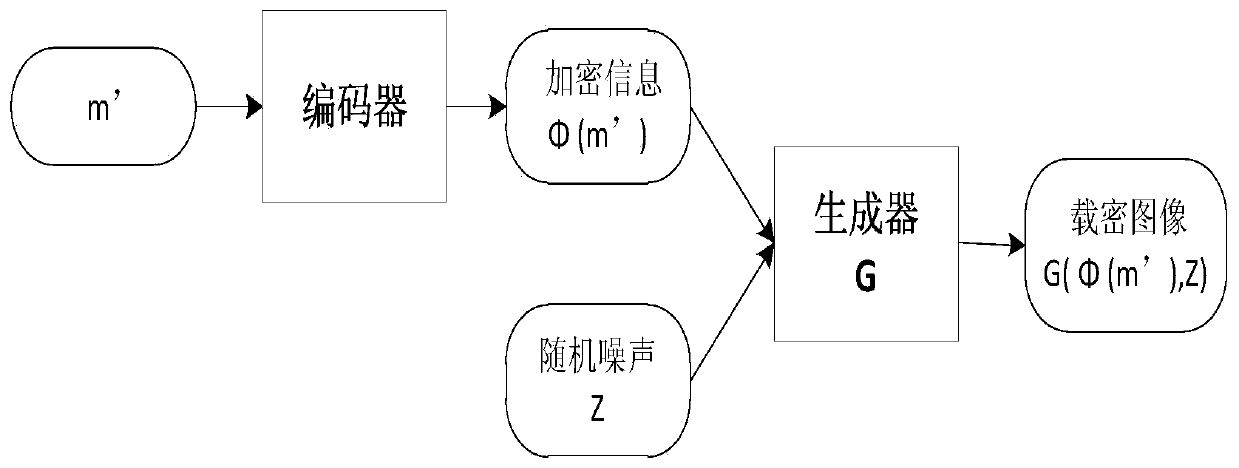
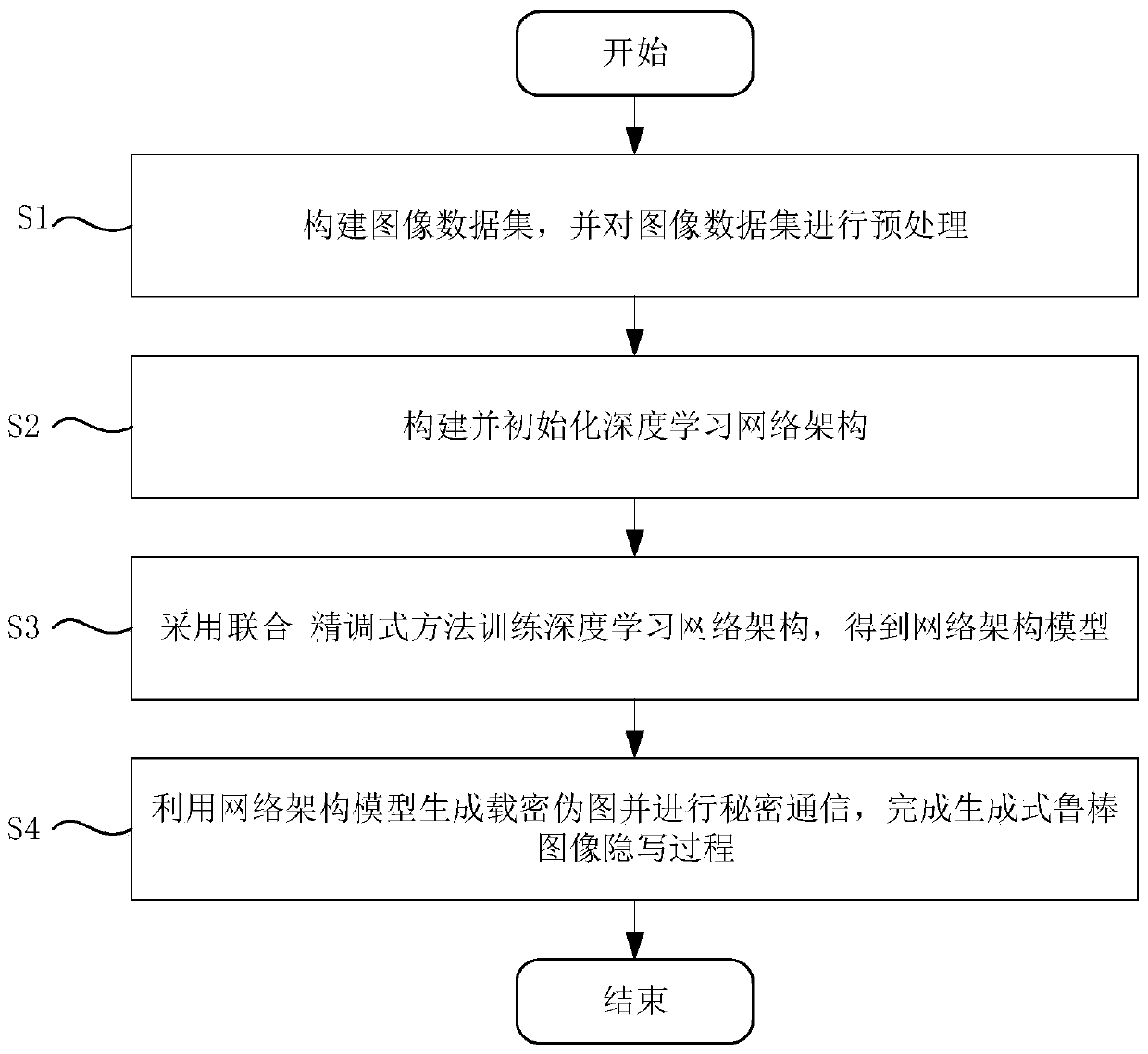
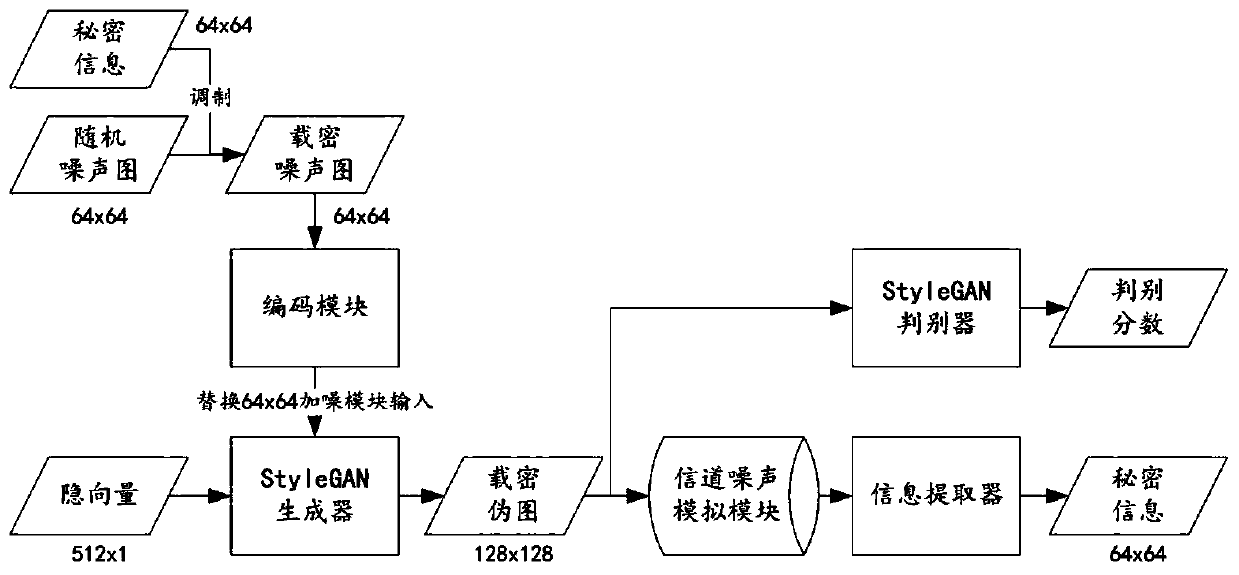
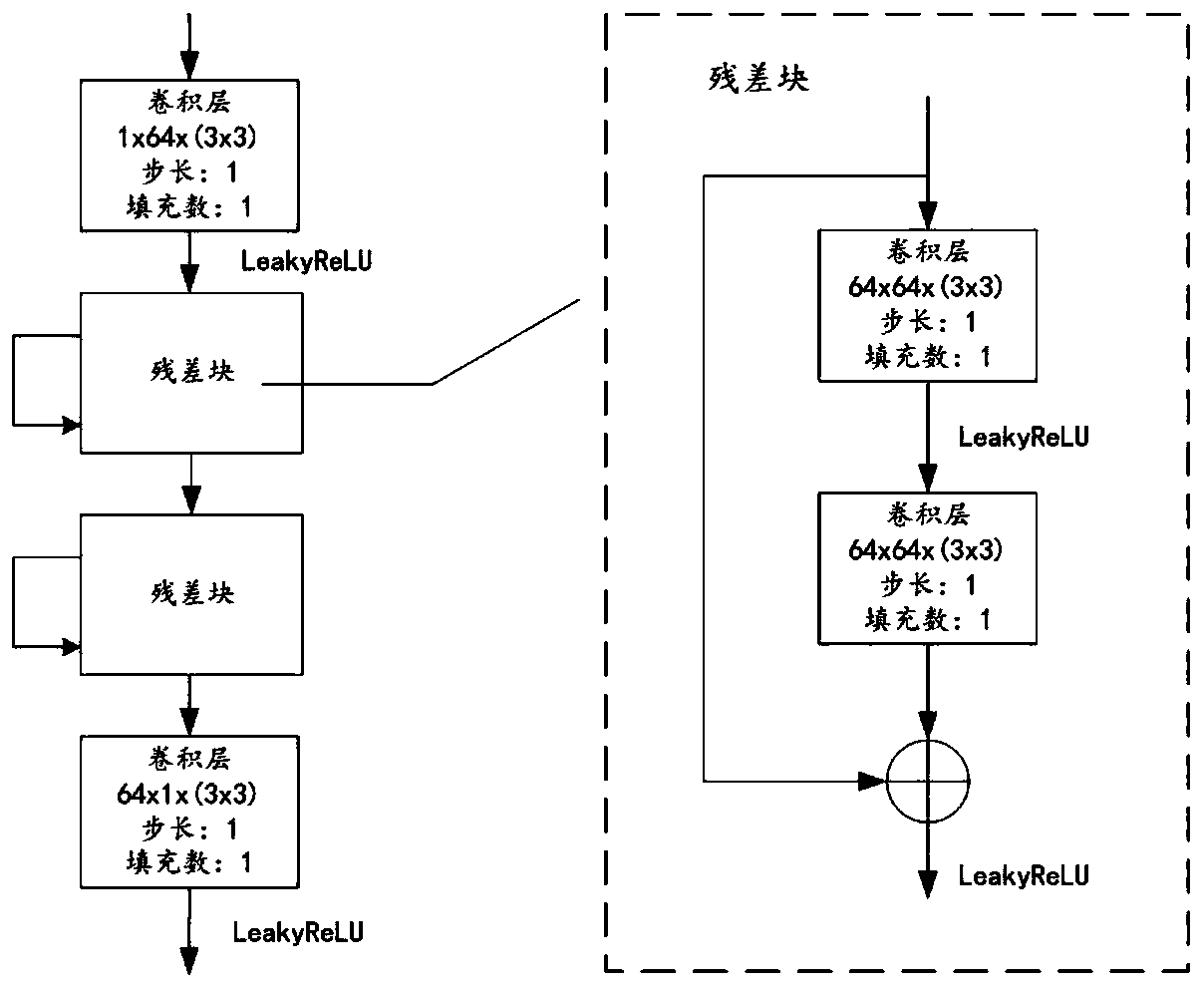
The invention provides a generative robust image steganography method, which comprises the following steps of: constructing an image data set, and preprocessing the image data set; constructing and initializing a deep learning network architecture; training a deep learning network architecture by adopting a joint-fine adjustment method to obtain a network architecture model; and generating a secret-carrying pseudo graph by using the network architecture model and carrying out secret communication to complete an image steganography process. According tothe image steganography method, a generative adversarial network StyleGAN is utilized to fuse the embedding process of the secret information into the generation process of the image; a generative image steganography architecture which can bear secret information with relatively large capacity and has certain robustness is constructed; therefore, the obtained generative image steganography method has the advantages of being large in embedded capacity, good in generated image quality, high in secret-loaded image statistics undetectability, high in practicability and the like, and the problems that an existing generative image steganography method is poor in secret-loaded image quality, low in embedded capacity, low in information extraction accuracy and the like are solved.
Owner:SUN YAT SEN UNIV
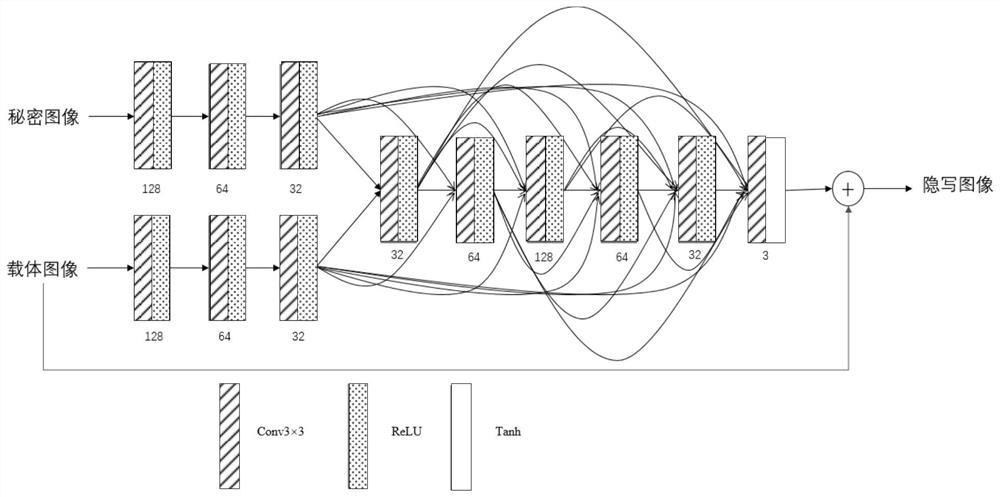
Color image steganography method based on convolutional neural network
ActiveCN112529758AQuality improvementImprove securityImage data processing detailsNeural architecturesColor imageData set
The invention discloses a color image steganography method based on a convolutional neural network. The method comprises the following steps: making a data set containing a carrier image and a secretimage; constructing an image steganography network model consisting of a hidden network and an extraction network by taking the carrier image and the secret image as input and taking the steganographyimage and the extraction image as output; setting parameters of the image steganography network model, and training the image steganography network model; and performing image steganography by usingthe trained image steganography network model. According to the color image steganography method based on the convolutional neural network, the color image is embedded and extracted through the imagesteganography network model composed of the hidden network and the extraction network, the generated steganography image has high quality and safety, and the steganography capacity is high.
Owner:HAINAN UNIVERSITY
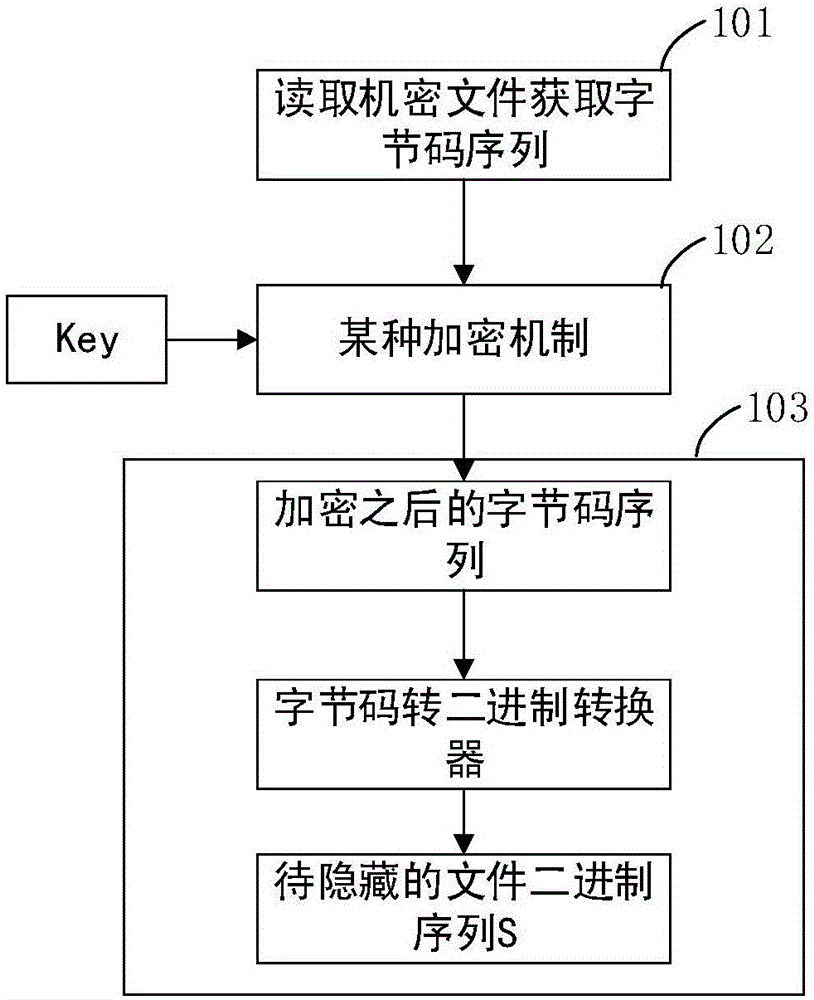
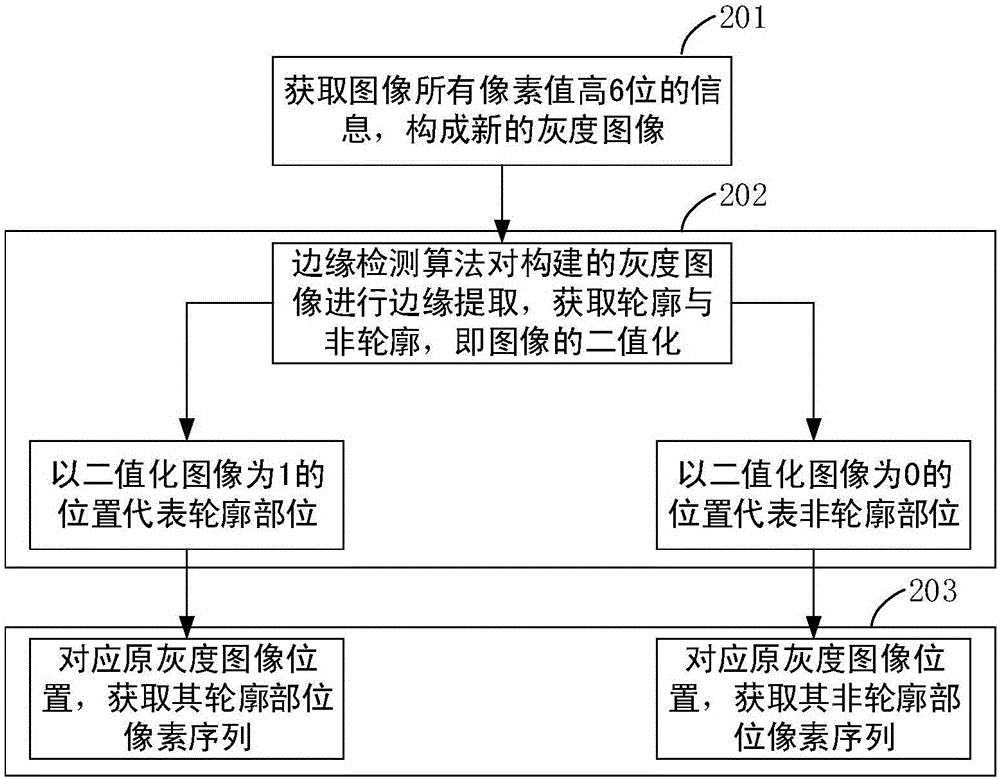
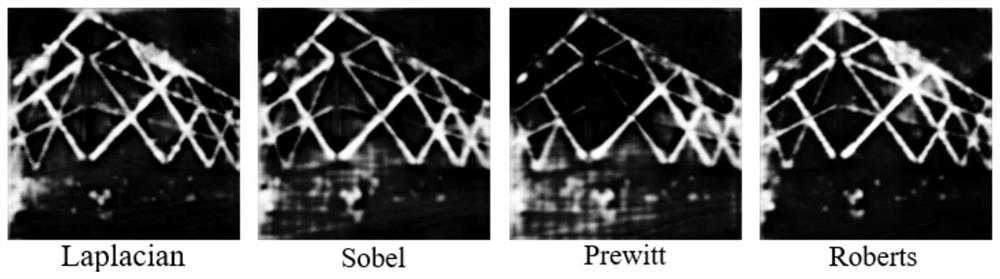
Edge detection-based grayscale image steganography method
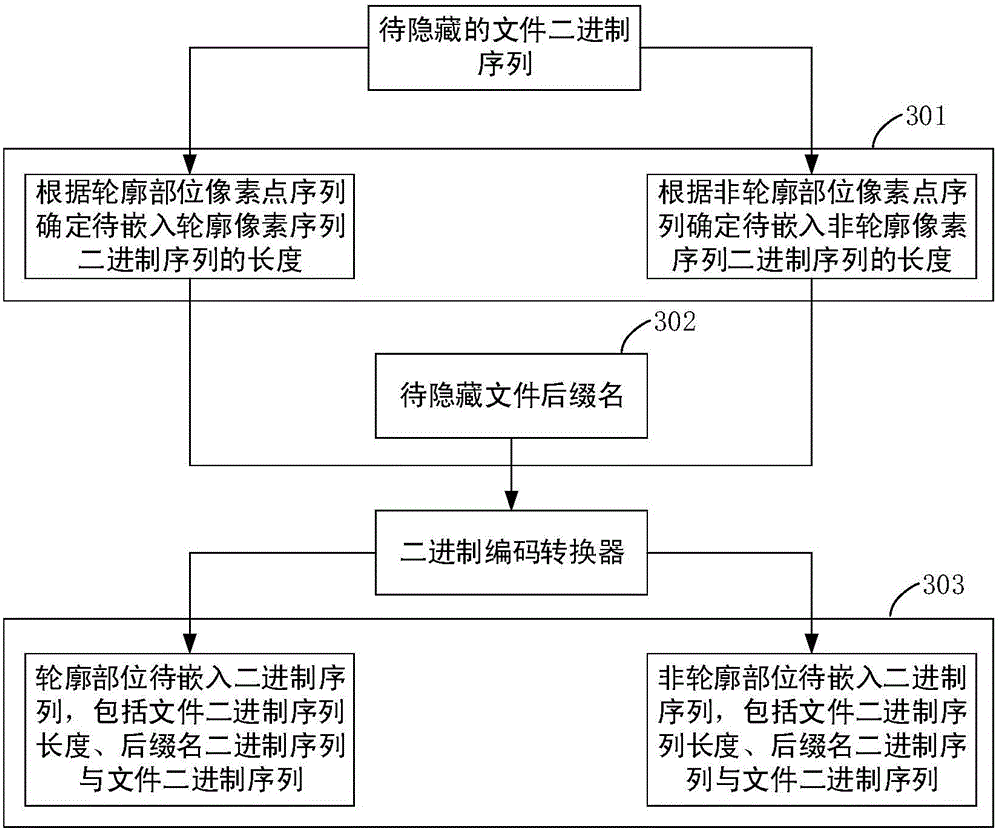
The present invention discloses an edge detection-based grayscale image steganography method. The objective of the invention is to carry out concealed communication in a public transport channel and prevent the theft and disclosure of confidential information. According to the method, a grayscale image is divided into two parts according to an edge detection method, namely a contour pixel sequence and a non-contour pixel sequence; based on different characteristics of the pixel sequence obtained through the image edge detection and other pixels, steganographic data are embedded into a contour part and a non-contour part according to different embedding rates; and therefore, high efficiency, reliability and concealment of an steganographic image can be improved in aspects such as image sensing and security. The method is divided into two stages, namely, the embedding stage and extraction stage of confidential information; in an embedding process, in order to ensure the integrity of the confidential information, contour extraction is performed by using the high bits of the pixel value of an image, and the embedding of the confidential information is performed by using the low bits of the pixel value of the image; in the embedding stage, the encryption of the confidential information and the conversion of a binary sequence are ensured, and then the binary sequence is embedded into the pixel value of the image; and in the extraction stage, it can be ensured that the binary sequence can be extracted from the steganographic image, and therefore, the confidential information can be obtained through decoding conversion and restoration.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Optimal coupling image steganography method based on packet replacement
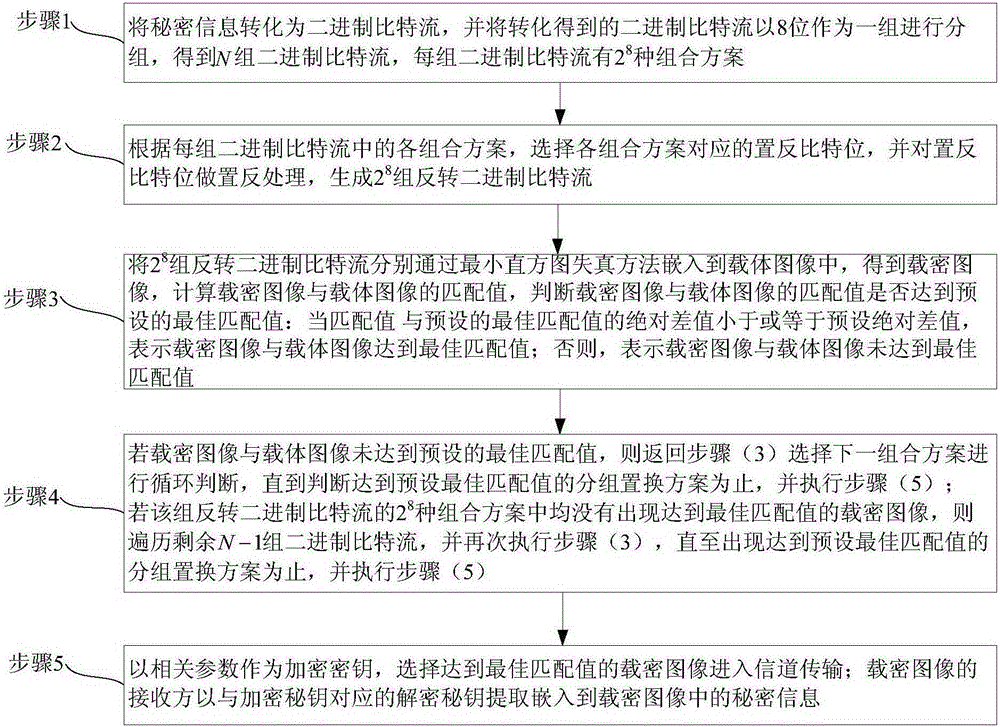
InactiveCN105260981AImprove concealmentImprove securityImage data processing detailsCouplingRecipient side
The invention relates to an optimal coupling image steganography method based on packet replacement. The method comprises steps that, secret information is converted into binary bit rates which are divided at 8 bits into sets to form N sets of binary bit streams, each set of binary bit streams has 28 types of combination schemes; according to each combination scheme of each set of binary bit streams, and bit position reversion processing for each combination scheme is carried out to generate 28 sets of counter-rotating binary bit streams; the 28 sets of counter-rotating binary bit streams are embedded into a carrier image through a least histogram distortion method to acquire a secret carrying image; through calculation and determination, when a coupling value of the secret carrying image and the carrier image reaches a preset optimal coupling value, relevant parameters are taken as an encryption key, the secret carrying image reaching the optimal coupling value is selected to enter channel transmission, otherwise, each combination scheme of other N-1 sets of binary bit streams is calculated till the secret carrying image having the optimal coupling value appears; secret information in the secret carrying image is extracted by a receiver by utilizing a decryption key corresponding to the encryption key.
Owner:NINGBO UNIV
High-capacity image steganography method and a secret information extraction method
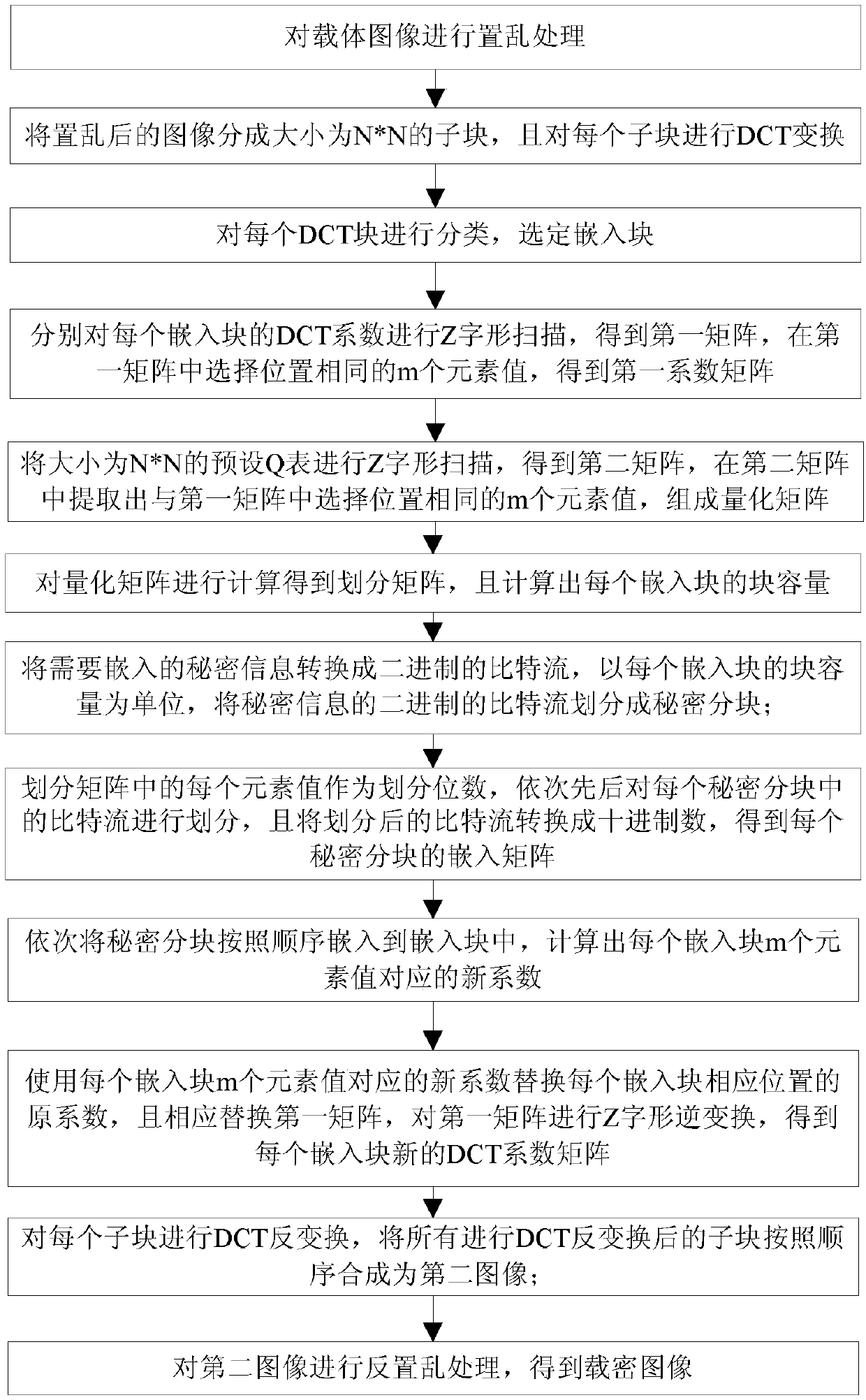
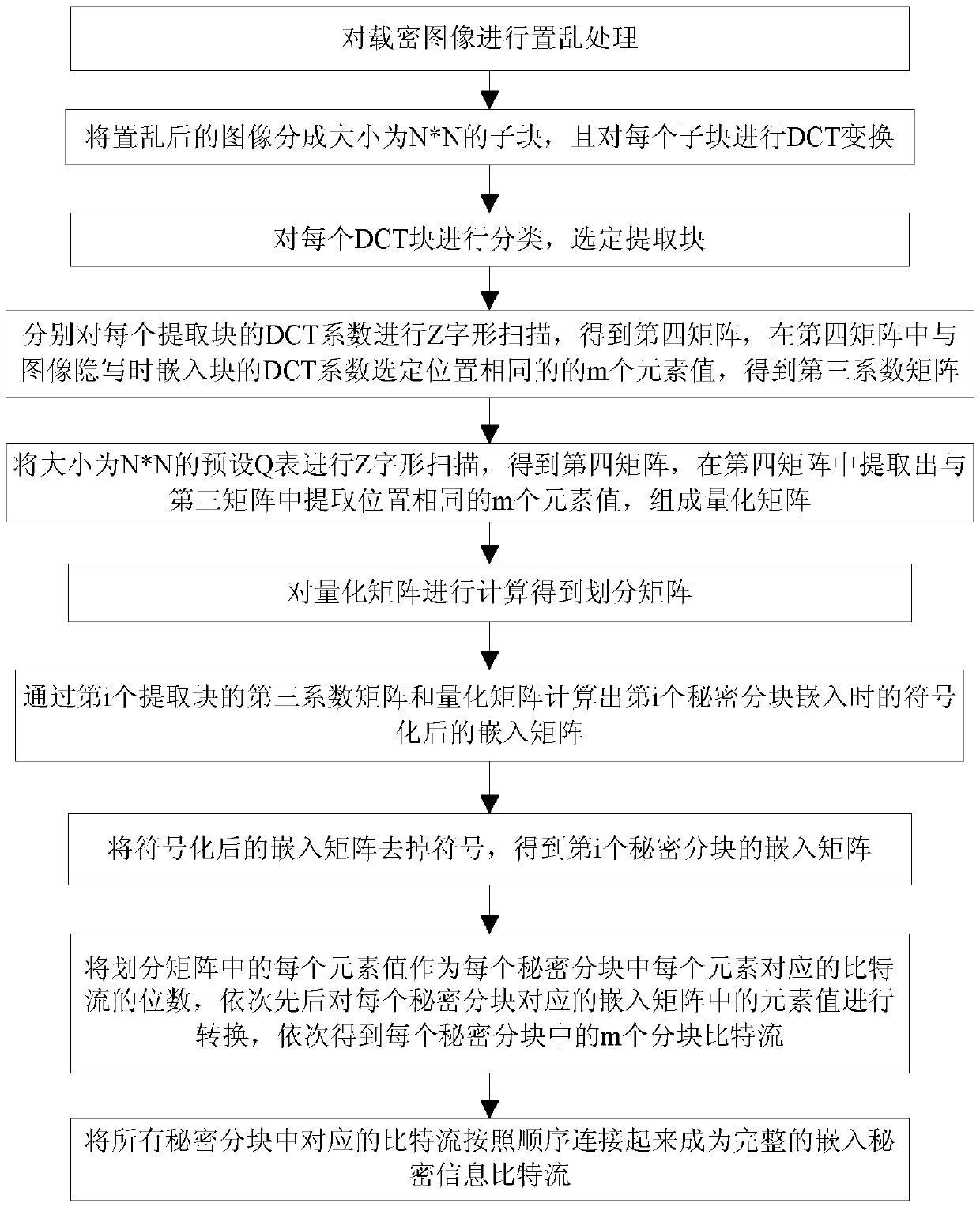
ActiveCN109658322AIncreased complexityImprove securityImage enhancementImage data processing detailsQuantization matrixInverse operation
The invention discloses a high-capacity image steganography method. The method comprises the following steps: carrying out scrambling processing on a carrier image; Dividing the scrambled image into N* N sub-blocks and carrying out DCT (Discrete Cosine Transform); Classifying each DCT block, and selecting an embedded block; Element values at selected positions are extracted from a matrix obtainedafter the DCT coefficient of each embedded block is scanned in a Z shape, and a coefficient matrix is obtained; Extracting element values which are the same as the element values at the selected positions from a matrix obtained after Z-shaped scanning of the Q table to form a quantization matrix; Calculating a division matrix and block capacity through the quantization matrix; Dividing the bit stream of the secret information according to the block capacity; Calculating an embedded matrix for the divided bit stream; Calculating a new coefficient matrix; Replacing the DCT coefficient with theelement value in the new coefficient matrix, and carrying out inverse operation of Z-shaped scanning to obtain a new DCT coefficient; And carrying out DCT inverse transformation on each sub-block andthen carrying out inverse scrambling processing. The invention also discloses a secret message extraction method. And the image complexity is high and the embedding capacity is large.
Owner:NINGBO UNIV
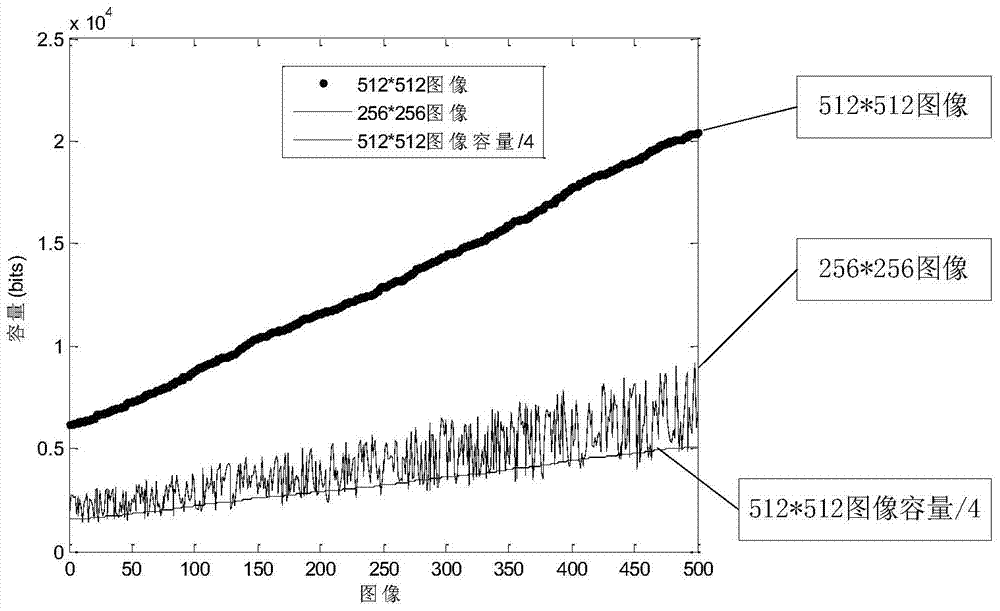
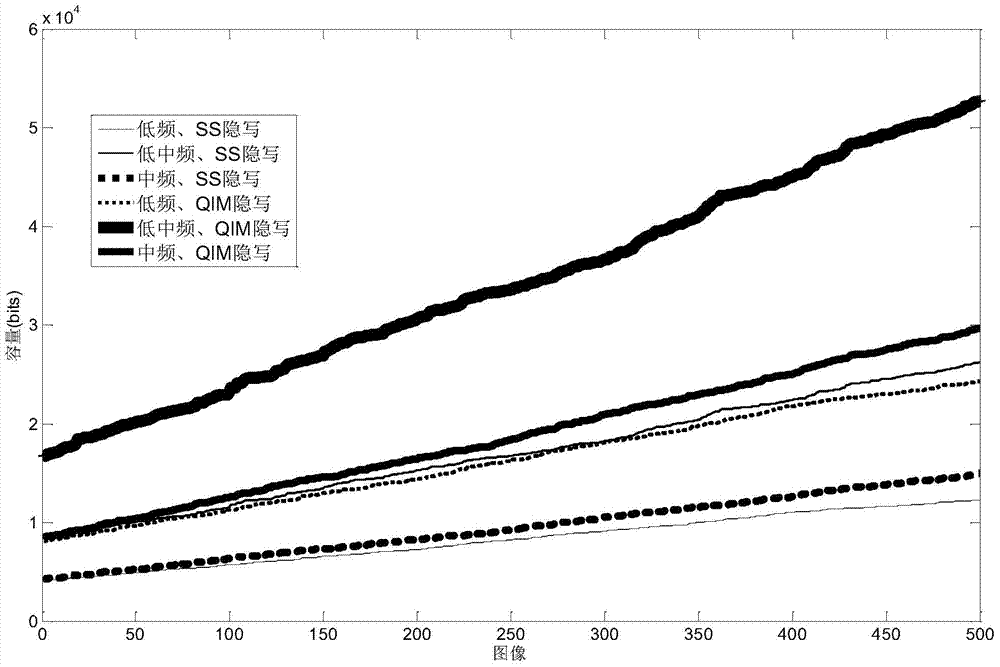
Method for assessing DCT-domain image steganography capacity based on MCUU model
ActiveCN103903214AImprove carrying capacityImage codingImage data processing detailsRelational modelJPEG
The invention discloses a method for assessing the DCT-domain steganography capacity of JPEG images based on a control model of maximizing capacity under undetectable (short for an MCUU model), so that the theory that the steganography capacity is not only related to the sizes of the images and the image complexity but also related to the factors such as specific bearing frequency bands, steganography operators and embedding strength is obtained. By the adoption of the method, the relation of the steganography capacity and the factors such as the image sizes, the bearing frequency bands, the steganography operators, the embedding strength and the image complexity can be analyzed, a rigorous experimental scheme is disclosed, and experiments verify the correctness of the relation model of the steganography capacity and the factors. Compared with other methods, the method has more theoretical value and practical engineering significance.
Owner:ZHEJIANG UNIV OF TECH
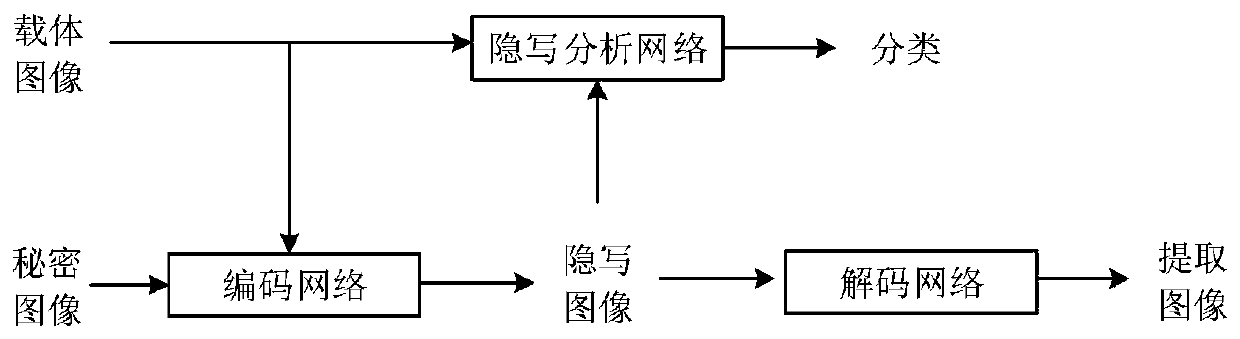
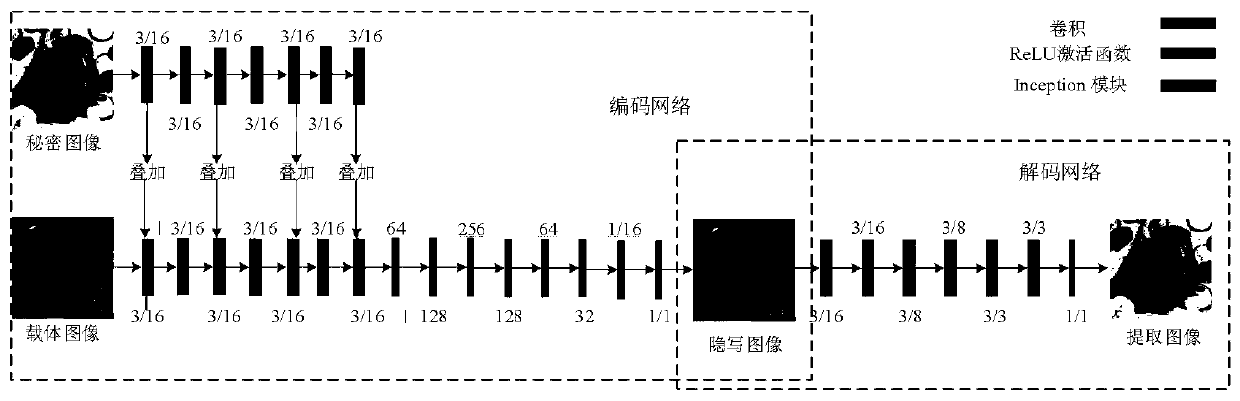
Safe and robust high-capacity image steganography method
PendingCN111292221ASolve the problem of steganographic image distortionImprove resistance to steganalysisCharacter and pattern recognitionImage watermarkingPattern recognitionSteganalysis
The invention discloses a safe and robust high-capacity image steganography method, which comprises the following steps: (1) making a data set which comprises a training image and a test image; (2) constructing a large-capacity image steganography network based on an adversarial network, wherein the steganography network comprises an encoding network, a decoding network and a steganography analysis network; (3) initializing parameters in the steganography network; and (4) training the constructed steganography network, and adjusting and optimizing the overall parameters of the network, so thatthe loss function of the model is as small as possible. According to the method, the problem of steganography image distortion in a large-capacity image steganography method is solved, and the steganalysis resistance is improved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
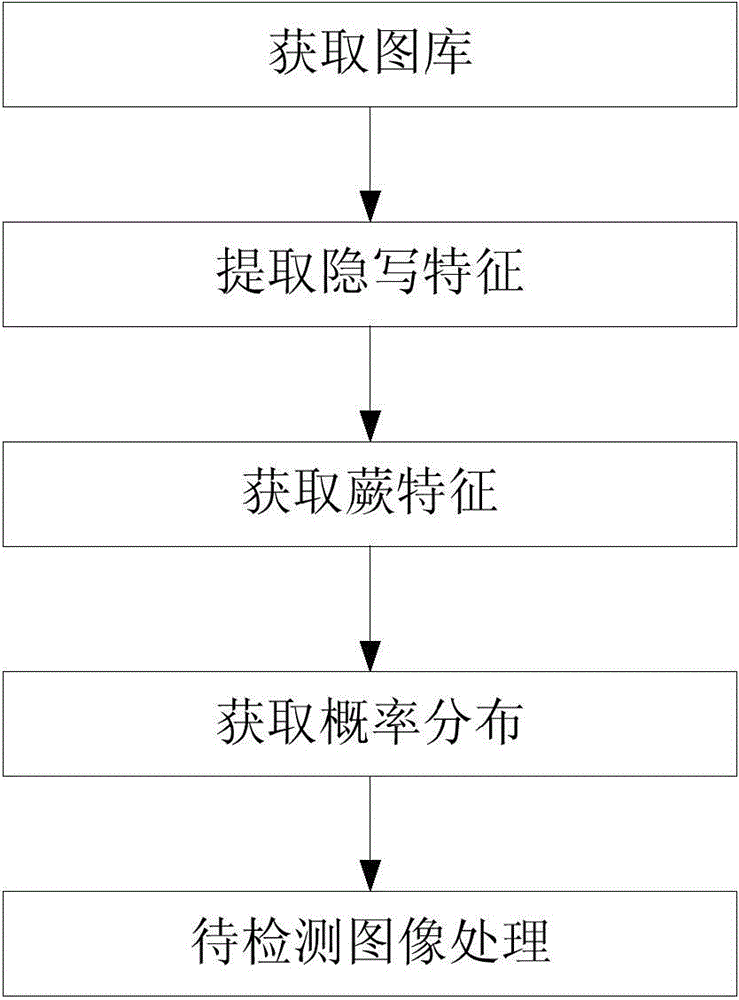
Image steganography analysis method and device
InactiveCN104636764AQuick checkVersatilityCharacter and pattern recognitionImage data processing detailsSteganalysisPattern recognition
The invention discloses an image steganography analysis method and device. The method comprises the following steps: (1) acquiring a gallery; (2) extracting steganography characteristics; (3) acquiring fern characteristics; (5) acquiring probability distribution, and establishing a probability control table; (6) processing images to be detected, acquiring corresponding occurrence probability of each fen value of each image to be detected in steganography images and corresponding occurrence probability of each fen value of each image to be detected in carrier images, and comparing the two corresponding probabilities, so as to obtain whether the corresponding image is a steganography image or not. According to the method and the device, the probability distribution of the steganography images and no-steganography images is obtained through training a database, and whether the images to be detected are the steganography images or not are judged through processing the images to be detected, so that the method has universality and can be applicable to different steganography ways.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Image steganography based on convolution neural network
PendingCN109472733AImprove robustnessImprove accuracyImage data processing detailsNeural architecturesSteganalysisImaging processing
The invention belongs to the field of image processing and computer vision technology, and is a method capable of effectively extracting steganographic features from steganographic images and improving image steganographic analysis effect on the premise of restraining original image detail features. For this purpose, the technical scheme adopted by the invention is that, according to the invention, By training convolution neural network, minimize network losses, The optimal parameter value P* is obtained to improve the detection performance of the network model. After the image is processed bythe convolution neural network preprocessing layer and the feature extraction layer, the extracted features are classified by the full connection layer, and the extracted features are classified by the softmax layer in the full connection layer. The invention is mainly applied to image processing occasions.
Owner:TIANJIN UNIV
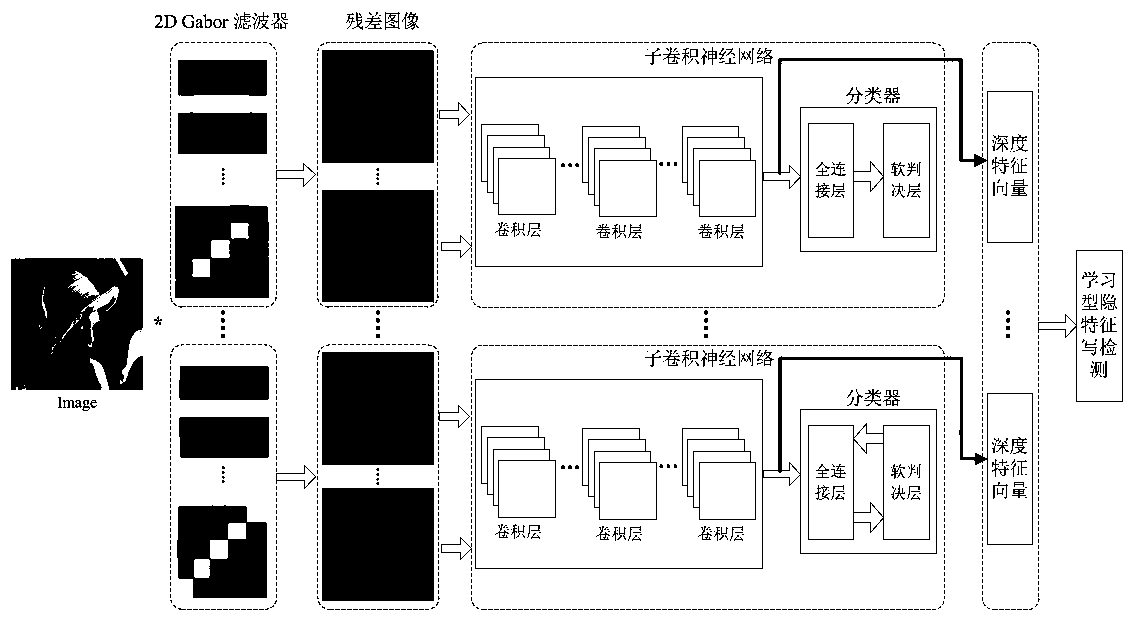
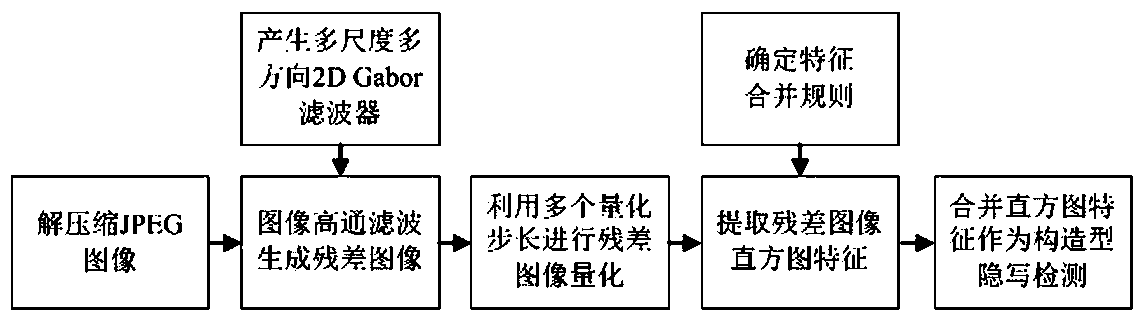
Image steganography detection method based on Gabor filtering and convolutional neural network
ActiveCN109859091AImplement extractionReduce detection error rateCharacter and pattern recognitionImage codingSteganalysisFeature learning
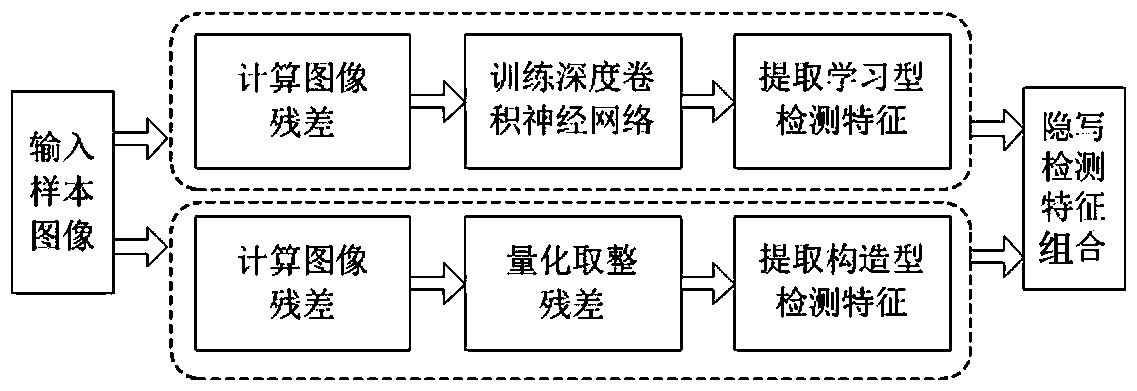
The invention provides an image steganography detection method based on Gabor filtering and a convolutional neural network, and belongs to the technical field of information hiding, and is characterized by comprising the following steps: selecting a carrier image and a secret-carrying image to generate a sample image; extracting steganography detection characteristics of the sample image; the steganalysis features and the class labels of the sample images are trained through an integrated classifier to obtain a steganalysis detector; and after steganography detection characteristics of the to-be-detected image are extracted, the steganography detection characteristics are input into the steganography detector for image steganography detection. Image filtering is performed by using a filterto construct a plurality of deep convolutional neural networks to carry out steganography detection feature learning, and the extraction of diversified learning type steganography detection characteristics is realized. Meanwhile, according to the method, the filtering coefficient is used for carrying out structural steganography detection feature extraction. Finally, the learning type steganography detection feature and the structural steganography detection feature are combined to serve as steganography detection features, steganography detection is carried out through an integrated classifier, and the steganography detection method remarkably reduces the detection error rate of image self-adaptive steganography.
Owner:NAT UNIV OF DEFENSE TECH
Image steganography method and system based on generative steganography confrontation
PendingCN113538202AImprove visual qualityImprove anti-detection abilityCharacter and pattern recognitionImage data processing detailsPattern recognitionSteganalysis
The invention discloses an image steganography method and system based on generative steganography confrontation, and the method comprises the steps: constructing a generative steganography confrontation model which comprises a generative network, a steganography device, a discrimination network and a steganalysis network, enabling the generative network to convert an original image into a carrier image, enabling the steganography device to embed a secret image into the carrier image, and obtaining a secret-carrying image, wherein the discrimination network judges the authenticity of the carrier image, and the steganalysis network judges whether the secret carrying image contains secret image information; respectively constructing loss functions of the generative network, the discrimination network and the steganalysis network according to judgment results of the discrimination network and the steganalysis network, and performing adversarial training on the generative network, the discrimination network and the steganalysis network according to the loss functions of the generative network, the discrimination network and the steganalysis network to obtain a trained generative steganalysis adversarial model; and obtaining a steganographic image corresponding to the original image based on the trained generative steganographic adversarial model. A carrier image with high visual quality is generated, and the security of carrier image information hiding is improved.
Owner:QILU UNIV OF TECH
Improved EMD image steganography embedding and extraction methods based on weight vector prevention
ActiveCN106791265AIncrease embedding capacityImprove securityPictoral communicationVisual perceptionExtraction methods
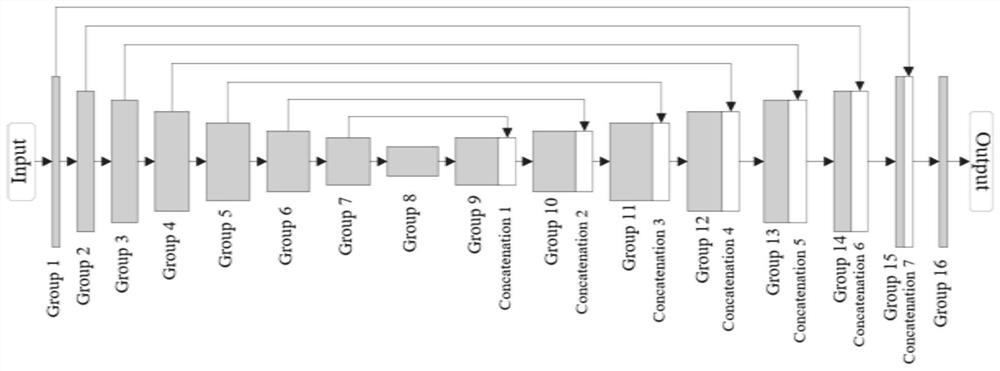
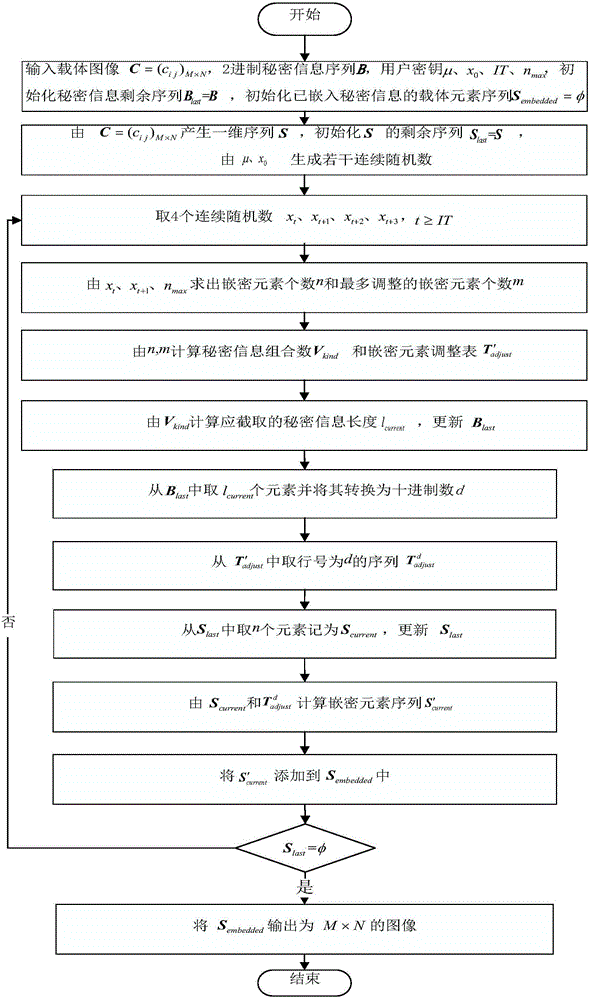
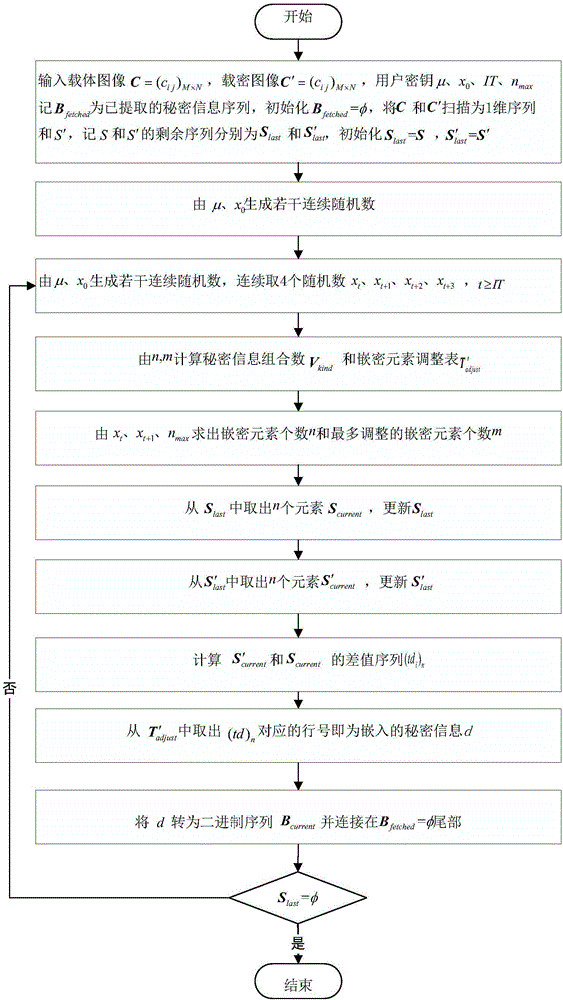
The invention provides improved EMD image steganography embedding and extraction methods based on weight vector prevention. The improved EMD image steganography extraction method comprises: a carrier image is scanned to form a one-dimensional element sequence; on the basis of combination of a user secret key with chaotic mapping, the secret embedding element number and the maximum adjusted secret embedding element number are designated randomly and a secret information combination number and a secret embedding adjusting table are generated; according to the secret embedding element number and the secret information combination number, a carrier element and a binary-system secret information bit are intercepted from a carrier element sequence and a binary system secret information sequence; and then table row adjustment is carried out on scrambled secret embedding elements mapped by the secret information bit to adjust the intercepted carrier element, thereby realizing secret information bit embedding. Compared with the existing EMD method, the provided methods have the following beneficial effects: the maximum embedding capacity can be realized on the premise that the equal embedded visual quality is kept, so that a problem of capacity restriction caused weight vector setting can be solved; and with an embedded extraction link associated with the carrier and the secret key, security of the embedded information can be enhanced.
Owner:SHAANXI NORMAL UNIV
Image adaptive steganalysis system and method based on saliency detection
ActiveCN111696021ATargeted optimizationGuaranteed validityImage data processing detailsSteganalysisData set
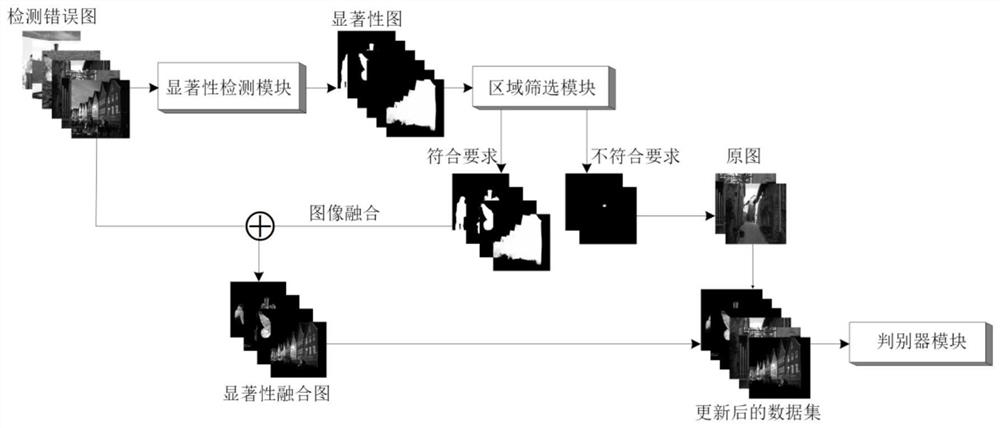
The invention belongs to the technical field of image processing, and particularly discloses an image adaptive steganalysis system based on saliency detection, which comprises a saliency detection module, a region screening module and a discriminator module. The invention also discloses an analysis method, which specifically comprises the following steps of: firstly, inputting an image detected tobe wrong by the discriminator module into the saliency detection module to form a saliency map; extracting a saliency map meeting requirements by the region screening module, and performing image fusion on the saliency map and a corresponding original image to form a saliency fusion map; and finally, replacing the saliency map which does not meet the requirements with the original image, combining the original image and the saliency fusion map to form an updated data set, and inputting the updated data set into the discriminator module for training to enable the discriminator to perform targeted feature learning on an area with relatively high overlap ratio with the steganography area. According to the method, the saliency detection technology is utilized to guide the steganalysis model to pay more attention to the characteristics of the image steganography area, so that the training effect and the detection accuracy of the model are improved.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
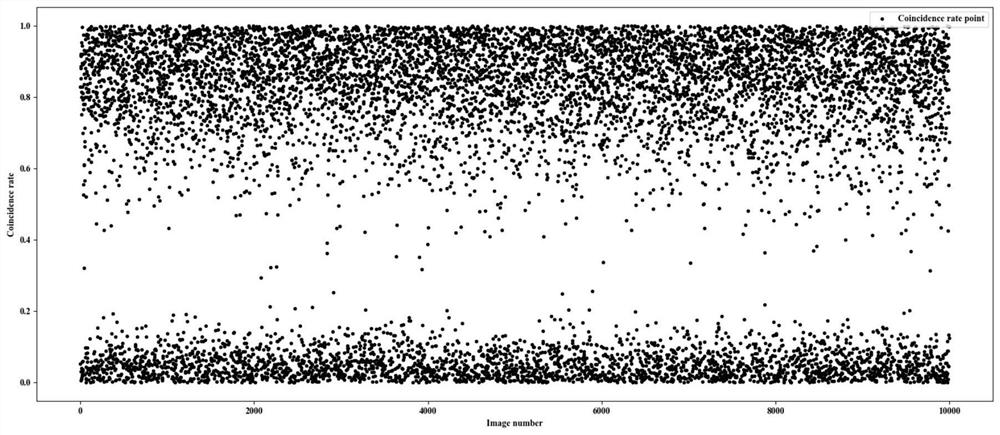
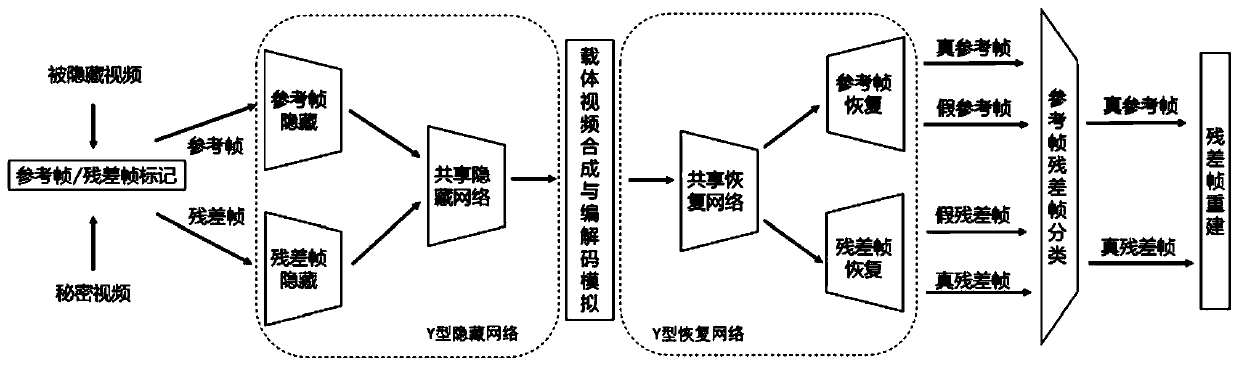
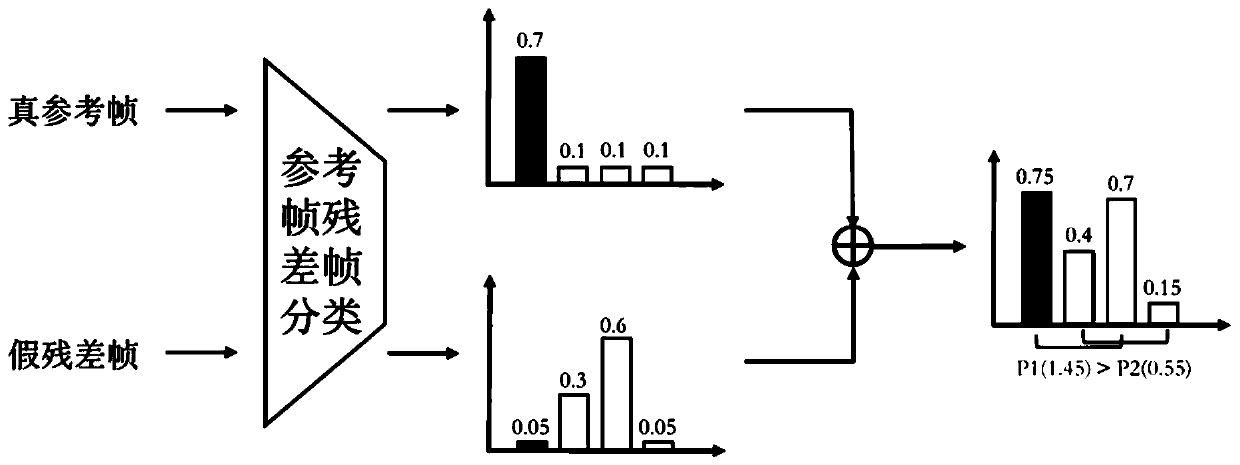
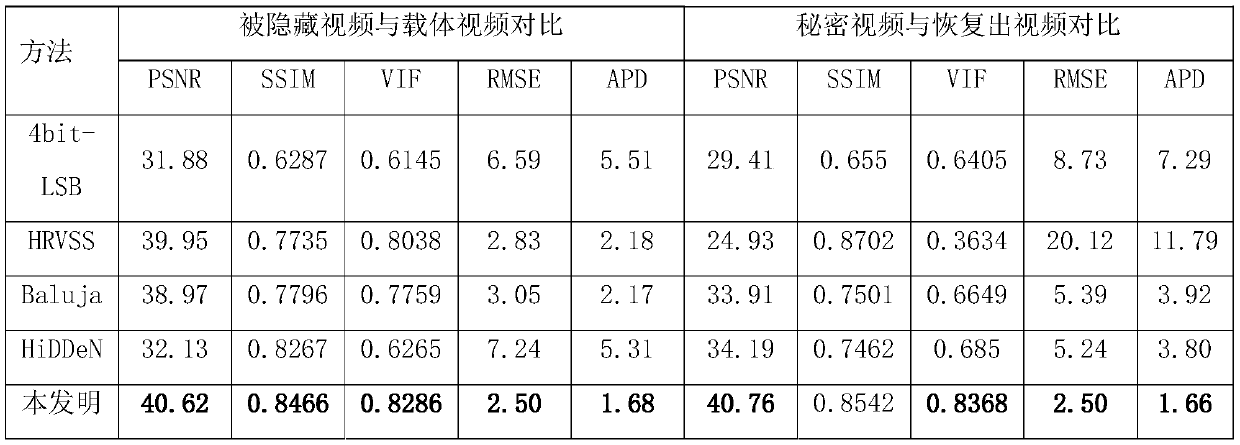
High-embedding-capacity video steganography method and system based on time sequence residual convolution modeling
ActiveCN110312138AGuaranteed imperceptibleEasy to embedDigital video signal modificationNeural architecturesConsecutive frameSteganographic algorithm
The invention relates to a high-embedding-capacity video steganography method and system based on time sequence residual convolution modeling. The method comprises the following steps: marking a reference frame and a residual frame of a secret video, simultaneously processing the reference frame and the residual frame by adopting a Y-shaped convolutional neural network to hide secret information and output a carrier video frame, and synthesizing the carrier video frame into a carrier video; and recovering secret information in the carrier video by adopting a Y-type convolutional neural network. Compared with a convolutional neural network-based image steganography algorithm which is directly applied to video steganography, the video steganography method has the advantages that the sparsityof a residual error between continuous frames is explored, two Y-type convolutional neural network structures are adopted, different endpoint processing is adopted for video frames with different properties, and part of convolutional layer parameters are shared at the same time. One video can be hidden in the other video with the same length, the hidden information amount can reach 24 bpp and ismuch larger than that of a traditional method, and the problem that the traditional method cannot be applied to high-embedding-capacity video steganography is solved to a great extent.
Owner:PEKING UNIV +1
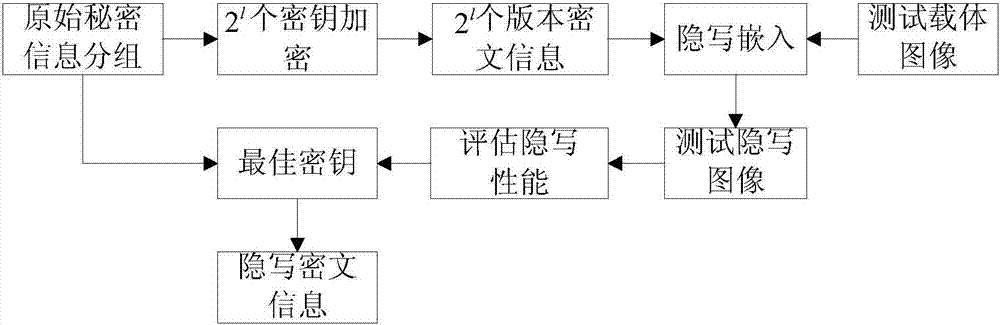
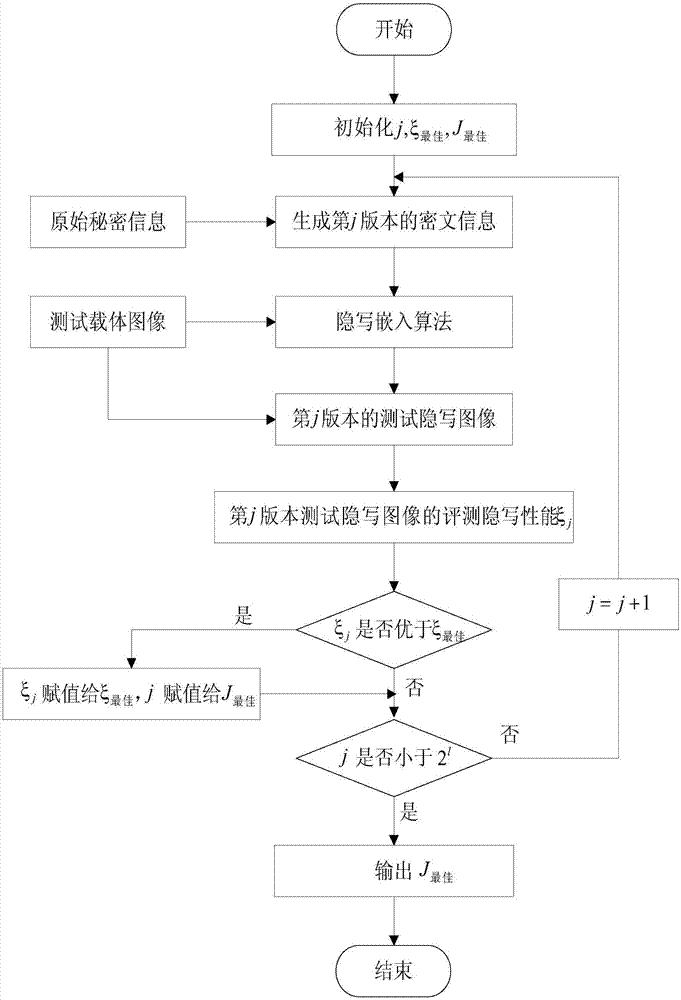
Ciphertext information generation method for image steganography
ActiveCN107169914AImprove universalityImprove steganographic performanceImage data processing detailsComputation complexityCiphertext
The invention relates to a ciphertext information generation method for image steganography. Through grouping original secret information, generated 2<l> cipher keys with the length to be l are used for XOR encryption, the obtained ciphertext information is embedded to a pre-selected test carrier image, and different test steganography images are obtained; according to the test carrier image and the different steganography images, the steganography performance is evaluated to obtain a cipher key used by the secret information when the steganography performance is the best, the cipher key is used as the best cipher key for the secret information, the original secret information and the best cipher key are subjected to XOR encryption, the ciphertext information of the original secret information is obtained, and the ciphertext information for steganography is finally acquired. Compared with the prior art, the method has the advantages that the performance of the steganography system after the best cipher key for the secret information is searched is enhanced, the encryption and decryption calculation complexity is low, and the method can be applicable to a mobile terminal.
Owner:NINGBO UNIV +1
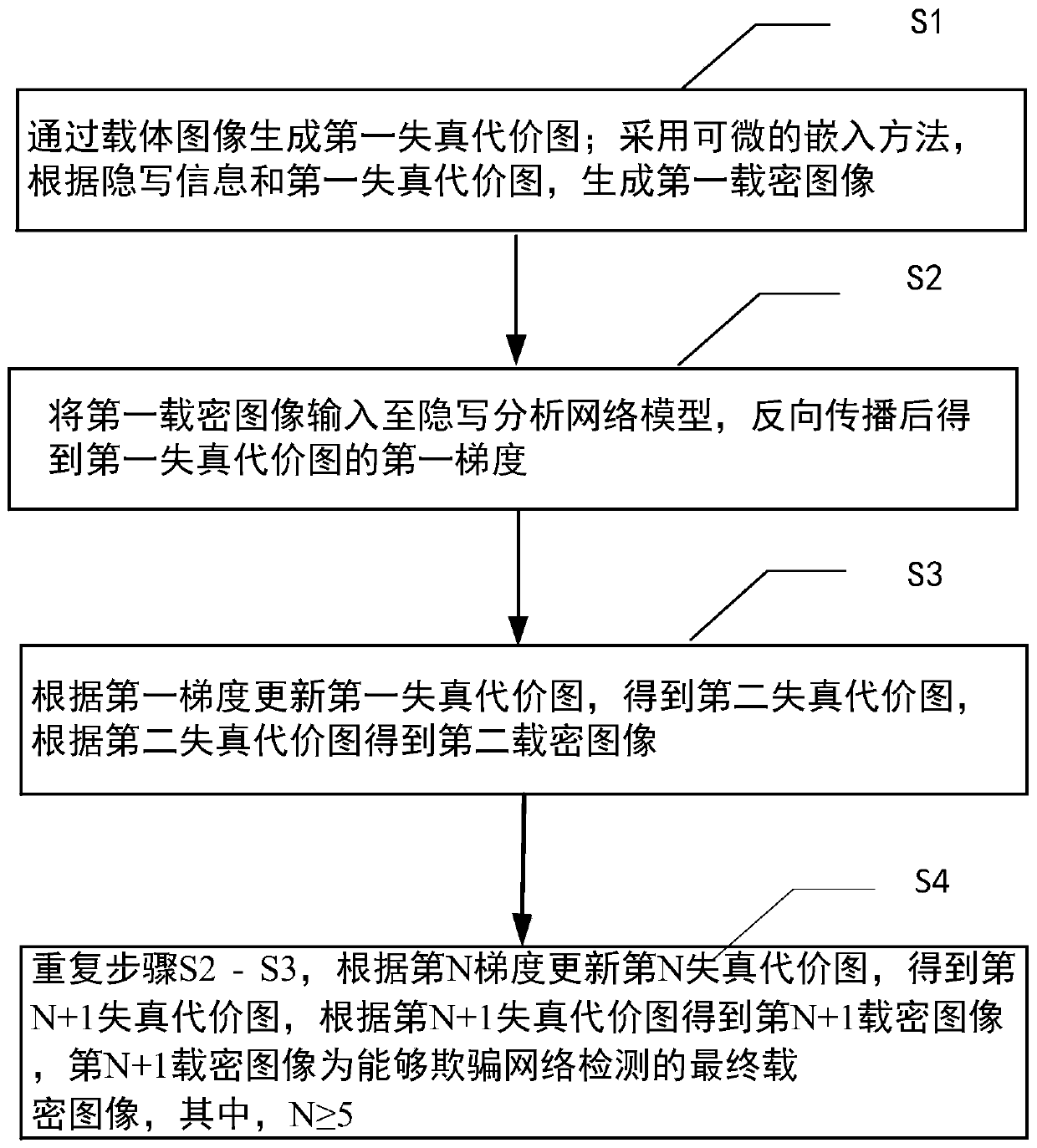
Image steganography method and device, electronic device and medium
The invention provides an image steganography method and device, an electronic device and a medium. The method comprises the steps of S1, generating a first distortion cost graph through a carrier image; generating a first secret-carrying image according to the steganography information and the first distortion cost graph by adopting a differentiable embedding method; s2, inputting the first secret-loaded image into a steganalysis network model, and performing back propagation to obtain a first gradient of a first distortion cost graph; s3, updating the first distortion cost graph according tothe first gradient to obtain a second distortion cost graph, and obtaining a second secret-carrying image according to the second distortion cost graph; and S4, repeating the steps S2-S3, updating the Nth distortion cost graph according to the Nth gradient, obtaining an (N + 1) th distortion cost graph, obtaining an (N + 1) th secret-carrying image according to the (N + 1) th distortion cost graph, the (N + 1) th secret-carrying image being a final secret-carrying image capable of spoofing network detection, and N is greater than or equal to 5. Through the image steganography method providedby the invention, the problem of low anti-detection capability of the secret-carrying image can be solved.
Owner:UNIV OF SCI & TECH OF CHINA +1
Image steganography algorithm using "controversial" pixels in RGB (Red, Green, Blue) color space
InactiveCN109547664AEmbedding Position OptimizationImprove anti-steganalysis performancePictoral communicationColor imageInformation embedding
The invention discloses an image steganography algorithm using "controversial" pixels in a RGB (Red, Green, Blue) color space, comprising the following steps: respectively extracting three color channels of red, green and blue of a color image in the RGB color space; using the steganography algorithm for respectively perform information embedding on the three color channels of red, green and blueto respectively obtain information embedding positions; formulating a "controversy" rule, giving the pixel points with different degrees of controversy different weights; performing grey scale processing on the color image to obtain a grayscale image, calculating the embedding loss values of each pixel in the grayscale image to obtain an initial grayscale loss value; using a mean filter to smooththe grayscale image loss value; selecting STC encoding to embed the secret information in the carrier image according to the grayscale image loss value to obtain a steganographic image. The algorithmimproves the anti-steganography analysis performance, thereby realizing the secure transmission of secret information in the image.
Owner:TIANJIN UNIV
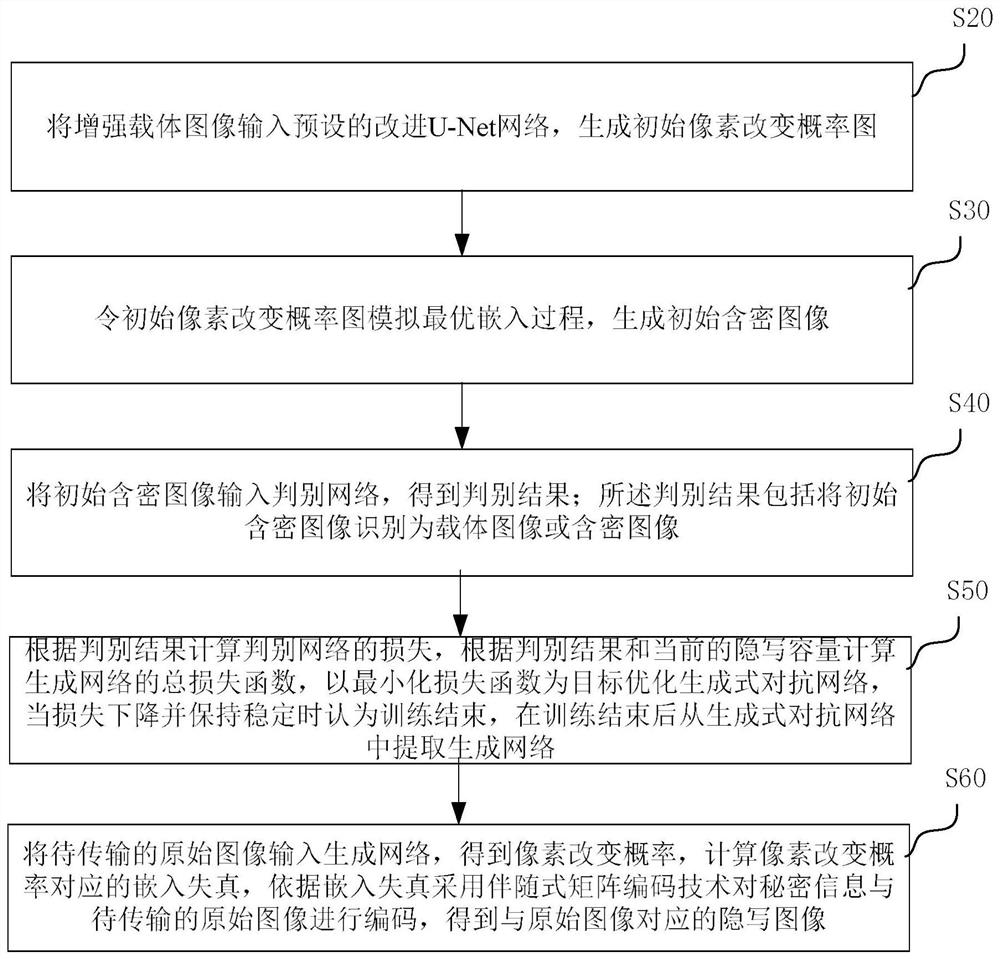
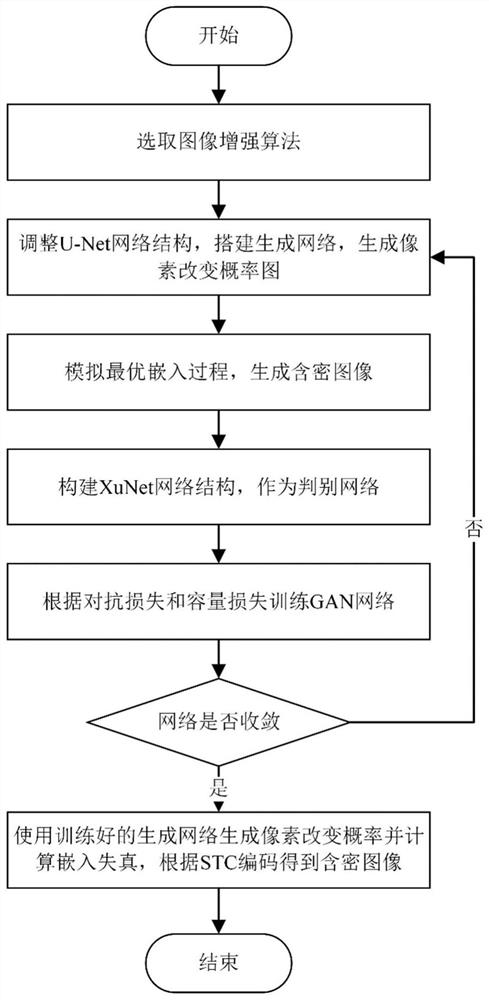
Image steganography method and system for automatically learning distortion based on GAN network structure
ActiveCN112767226ANarrow down the search spaceReduce training timeInternal combustion piston enginesImage codingPattern recognitionGenerative adversarial network
The invention discloses an image steganography method and system for automatically learning distortion based on a GAN network structure, and the method comprises the steps: inputting an enhanced carrier image into a preset improved U-Net network, sequentially generating an initial pixel change probability graph and an initial secret-containing image, inputting the initial secret-containing image into a discrimination network, and obtaining a discrimination result, calculating the loss of the discrimination network according to the discrimination result, calculating a total loss function of the generative network according to the discrimination result and the current steganography capacity, optimizing the generative adversarial network by taking minimization of the loss function as a target, when the loss is reduced and kept stable, considering that the training is ended, extracting the generative network from the generative adversarial network after the training is ended, and inputting a to-be-transmitted original image into the generative network to obtain a pixel change probability, calculating embedded distortion corresponding to the pixel change probability, and coding the secret information and the to-be-transmitted original image by adopting a syndrome matrix coding technology according to the embedded distortion to obtain a steganographic image corresponding to the original image.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
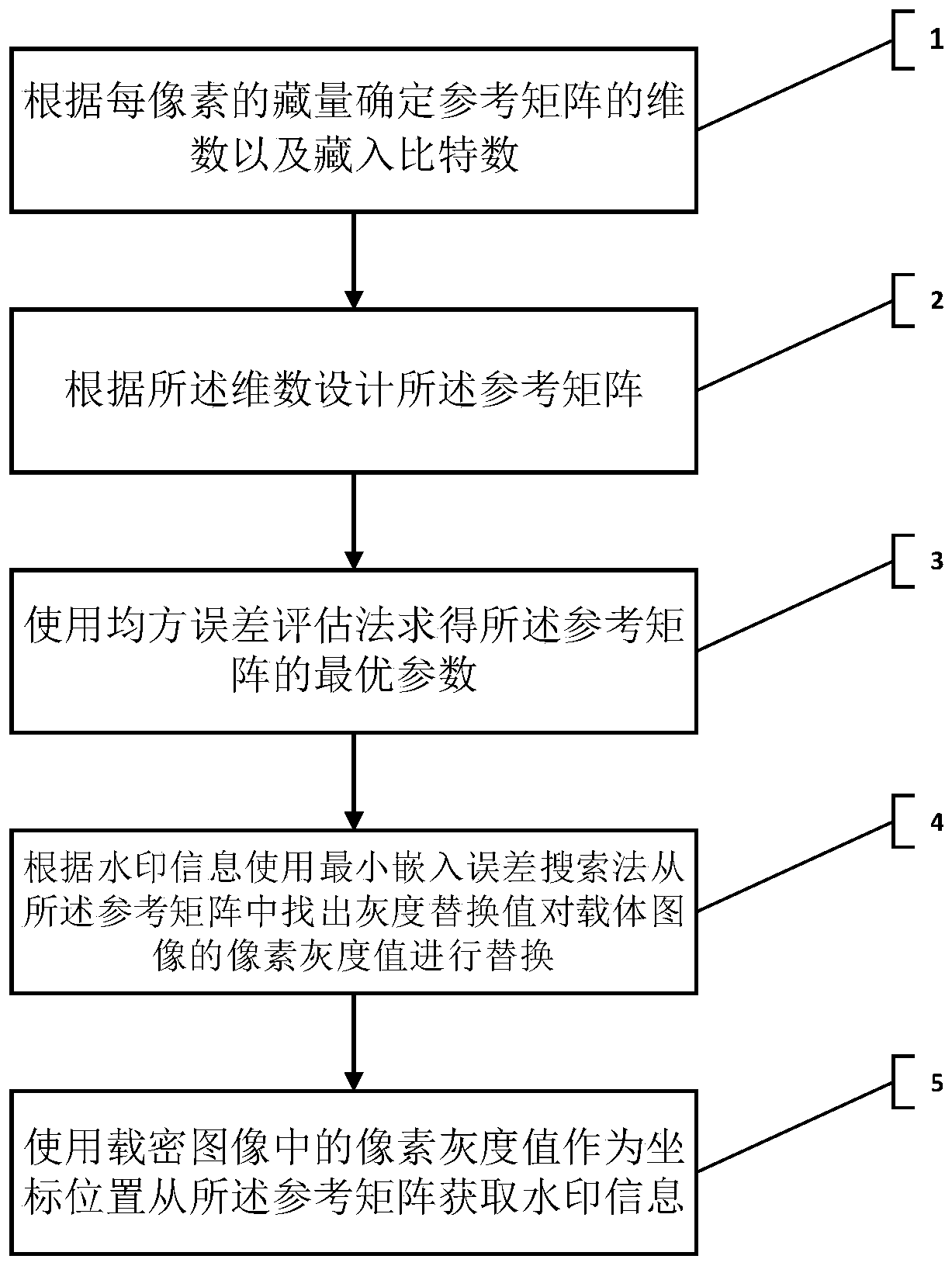
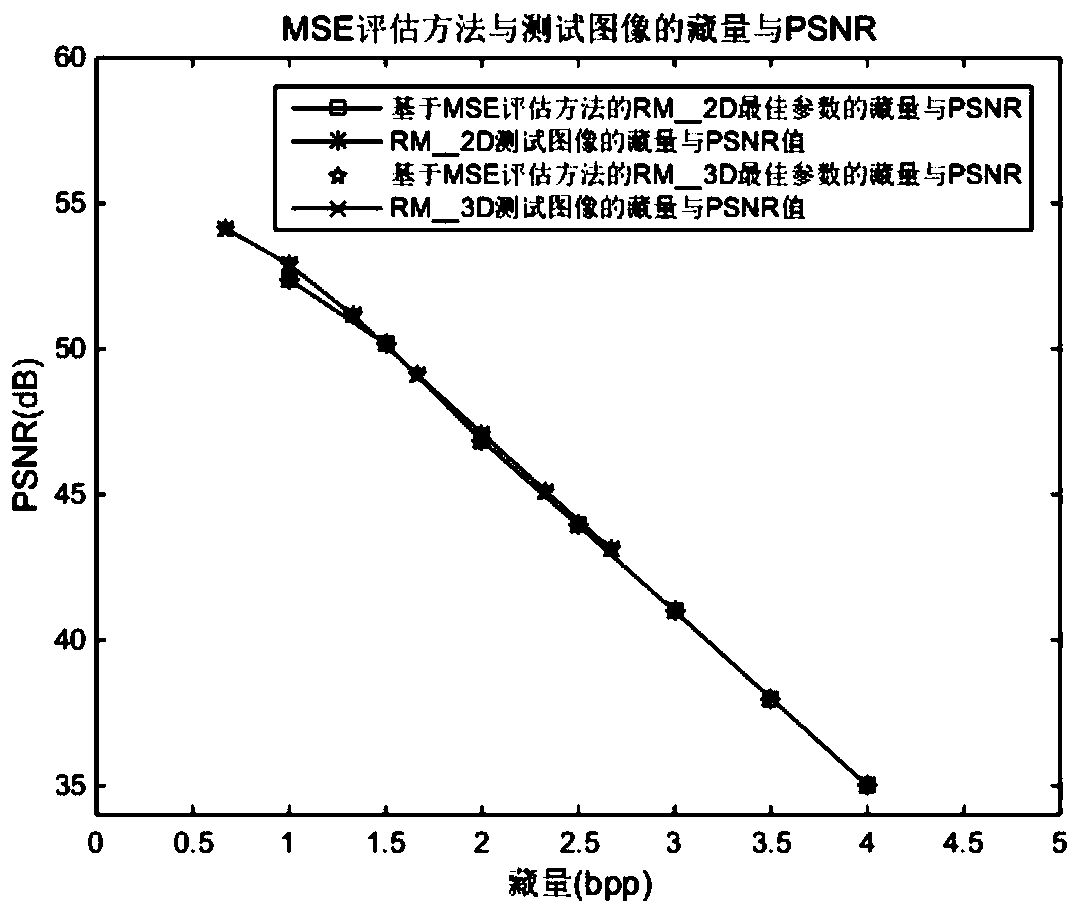
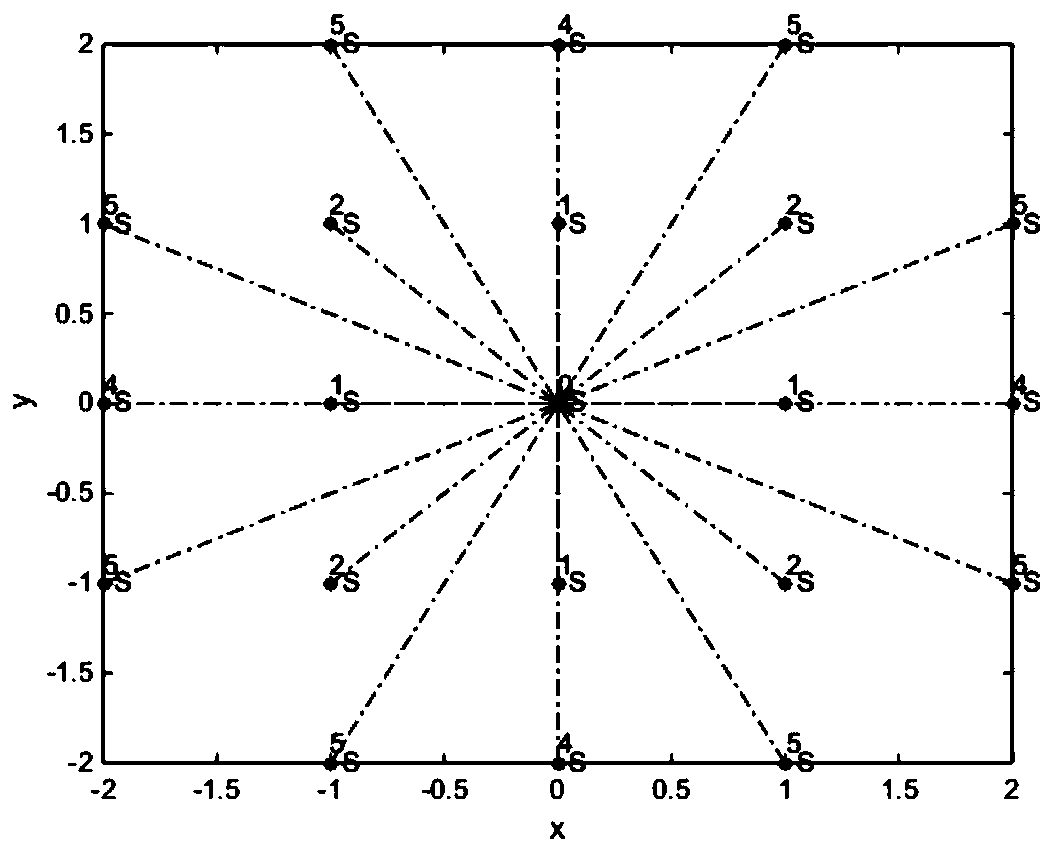
Image steganography method of reference matrix model based on mean square error evaluation
ActiveCN111161124AOvercome inherent flawsImage quality PSNR improvementsImage data processing detailsComputation complexityImaging quality
The invention belongs to the technical field of digital communication, and particularly relates to an image steganography method of a reference matrix model based on mean square error evaluation. Themethod comprises the following steps: 1, determining the dimension and the hidden bit number of a reference matrix according to the hidden quantity of each pixel; 2, designing the reference matrix according to the dimension; 3, solving an optimal parameter of the reference matrix by using a mean square error evaluation method; 4, finding out a gray replacement value from the reference matrix by using a minimum embedding error search method according to the watermark information to replace the pixel gray value of the carrier image. According to the method, a universal reference matrix design method is provided for watermark data with different storage capacities, the calculation complexity of the matrix MSE is greatly reduced, the calculation time is greatly shortened, and meanwhile under the condition of the same storage capacity, the image quality PSNR is obviously improved compared with an existing method.
Owner:FUQING BRANCH OF FUJIAN NORMAL UNIV
Self-adaptive cost sensitive feature learning method for unbalanced JPEG image steganography detection
ActiveCN111415289ASolve the imbalanceCharacter and pattern recognitionImage watermarkingSteganalysisFeature learning
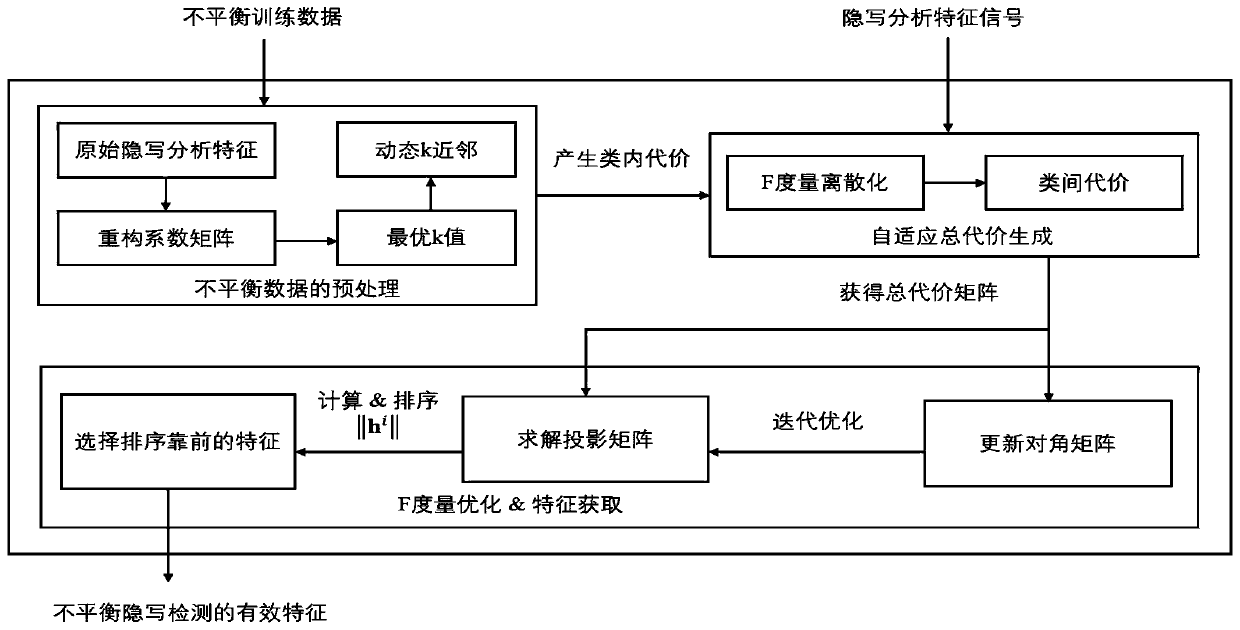
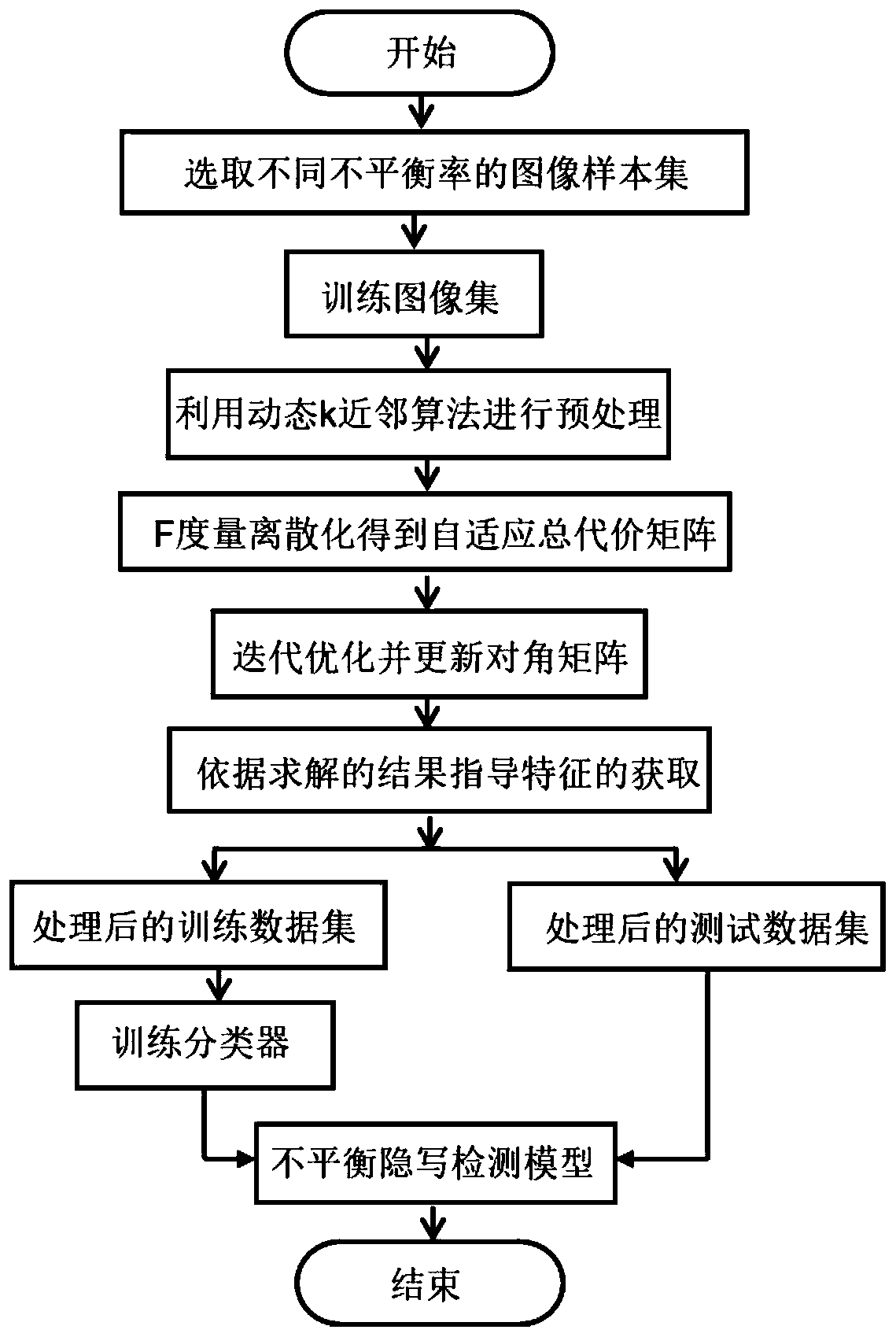
The invention discloses a self-adaptive cost sensitive feature learning method for unbalanced steganography detection. According to the method, for an unbalanced JPEG image steganography detection environment, in order to solve problem that the detection effectiveness of a traditional steganalysis method is greatly reduced under the condition of unbalanced data distribution, an unbalanced data set-oriented steganography detection scheme is realized mainly from the following three aspects: firstly, an unbalanced sample preprocessing method is provided, the optimal k value of a dynamic k nearestneighbor algorithm (DkNN) of each sample is determined, and the intra-class cost is obtained according to the proportion of classes; secondly, an adaptive cost sensitive classifier is generated basedon the intra-class and inter-class cost of each training sample; and finally, the feature corresponding to the maximum F metric is obtained through the F metric maximization and regularization logistic regression adaptive cost-sensitive classifier and the effective feature acquisition.
Owner:WUHAN UNIV
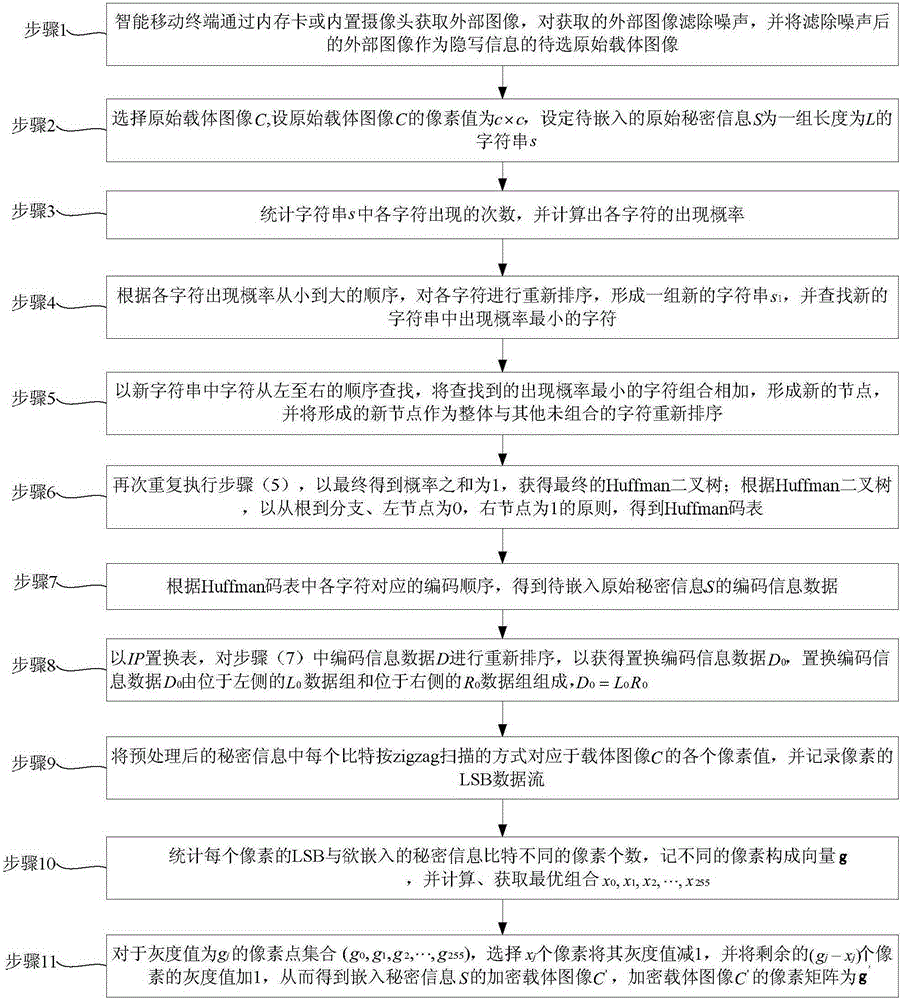
Intelligent mobile terminal image steganography method based on secret information encryption pretreatment
ActiveCN105279728AEnsure safetyGood visual concealmentImage data processing detailsPattern recognitionData stream
The invention relates to an intelligent mobile terminal image steganography method based on secret information encryption pretreatment: enabling an intelligent mobile terminal to select an external image after noise filtering as an original carrier image, carrying out the statistics of occurrence probability of characters in embedded secrete information, carrying out the reordering of all characters according to the occurrence probability of characters, and obtaining a new character string; enabling the characters, which are found in the new character string and has the lowest occurrence probability, to be combined and added to form a new node, enabling the new node to serve as a body and to participate the reordering with other non-combined characters, obtaining a final Huffman binary tree, a Huffman code table and coding information data of secrete information; carrying out the reordering of coding information data through an IP displacement table, and obtaining displacement coding information data; recording LSB data flows of all pixels of a carrier image, and the number of pixels with different bits in secret information; and obtaining an encrypted carrier image with embedded secret information through subtracting one from or adding one to the pixels.
Owner:NINGBO UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com