Invisible image steganography based on generative adversarial network
A steganography and network technology, applied in the field of image processing, can solve a large amount of prior knowledge and other problems, and achieve the effect of speeding up training and improving quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to make the above-mentioned features and advantages of the present invention more obvious and understandable, the present invention will be further described in detail below in conjunction with specific embodiments and the accompanying drawings.
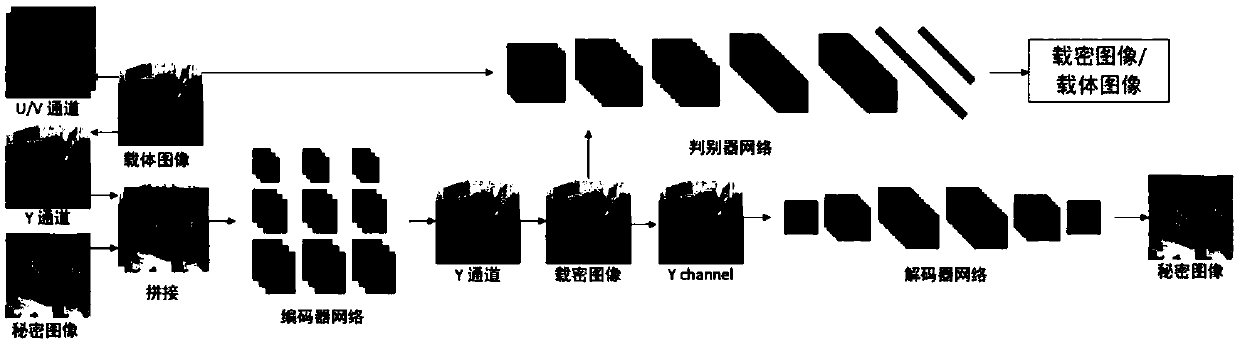
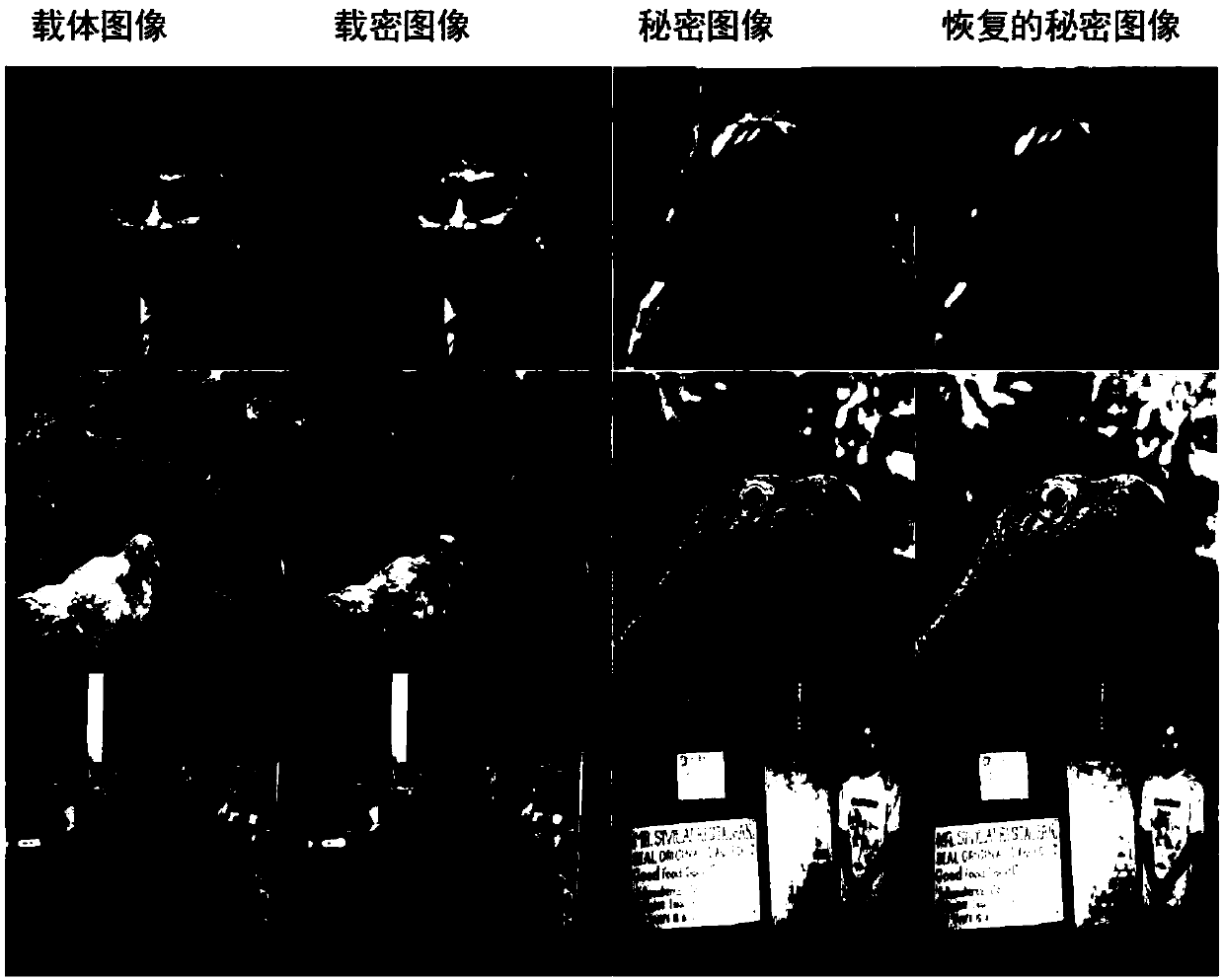
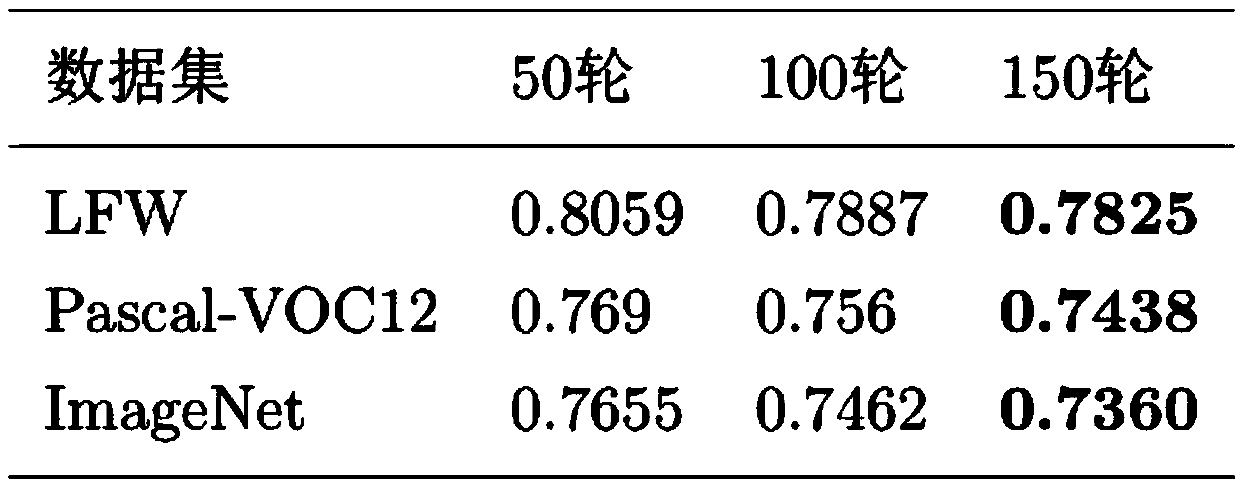
[0029] The image steganography method designed by the present invention is based on a generative confrontation network, and is suitable for embedding a gray-scale secret image into a color carrier image. This method uses the data set to train the model to obtain the optimal model parameters. The specific training process is as follows figure 1 As shown, the main steps include:
[0030] Step 101: Convert the color carrier image from the RGB color space to the YCrCb color space.
[0031] Step 102: Concatenate the Y channel of the color carrier image and the gray-scale secret image together and then output to the encoder network.
[0032] Step 103: The encoder network outputs a single-channel image after feature extraction and f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com