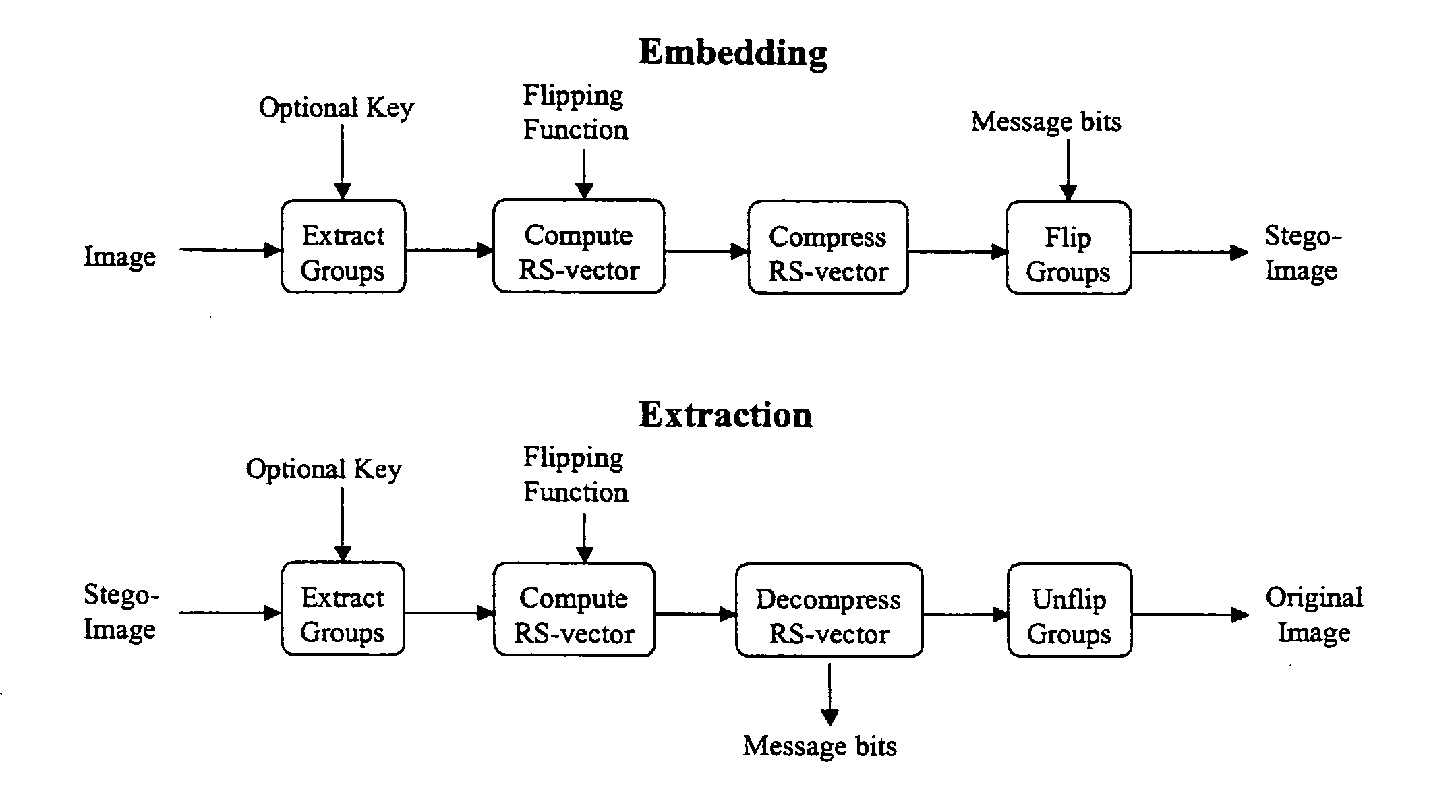
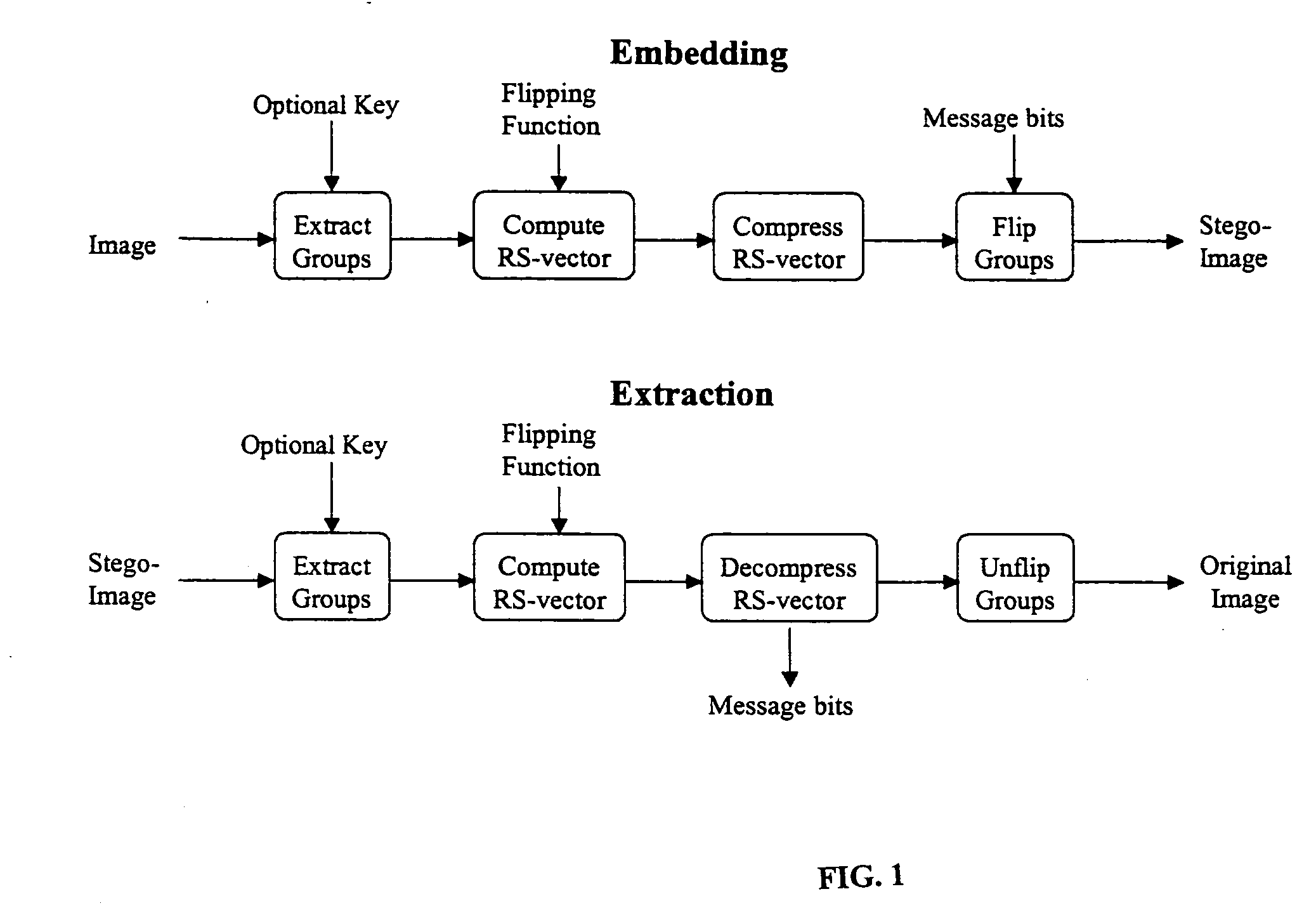
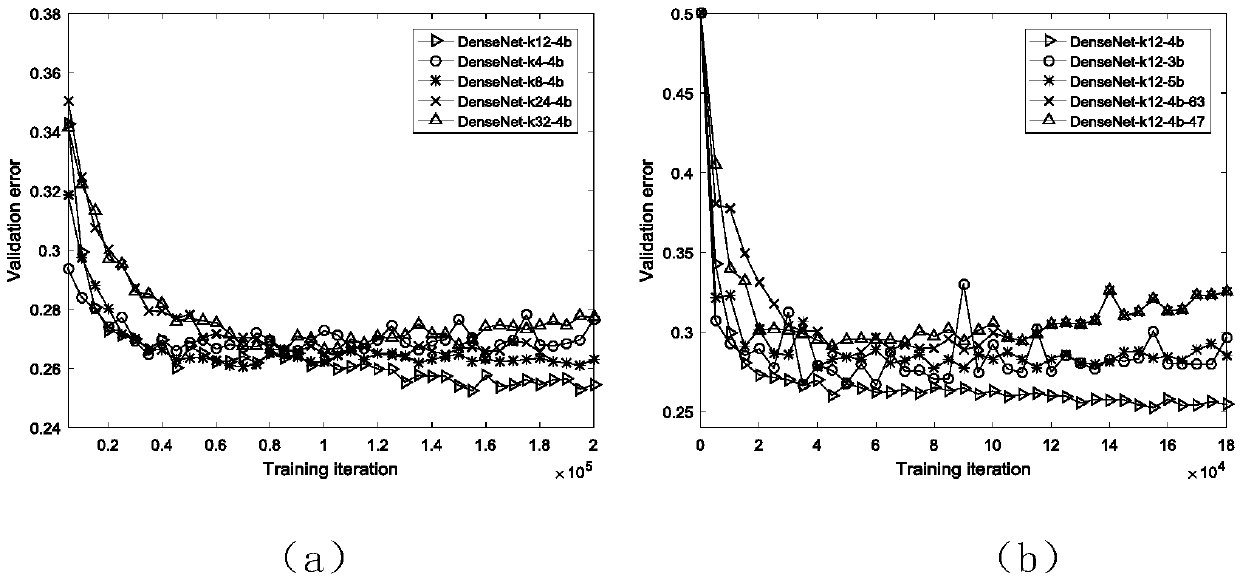
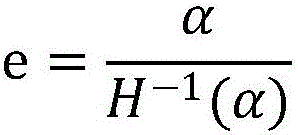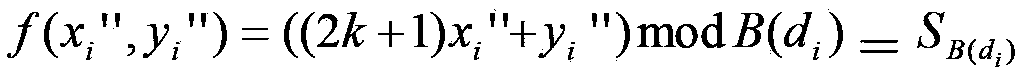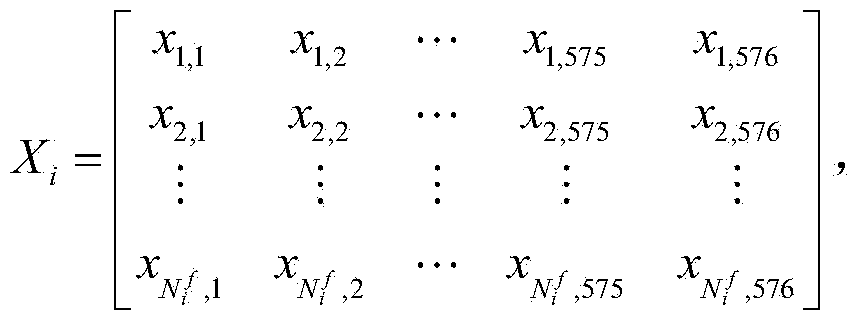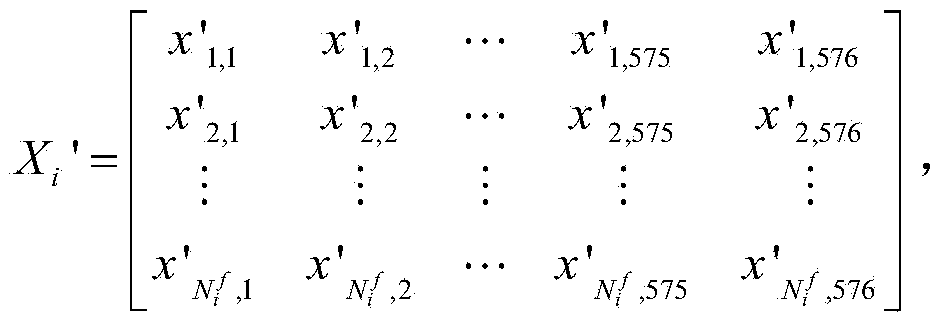Patents
Literature
229 results about "Steganalysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Steganalysis is the study of detecting messages hidden using steganography; this is analogous to cryptanalysis applied to cryptography.
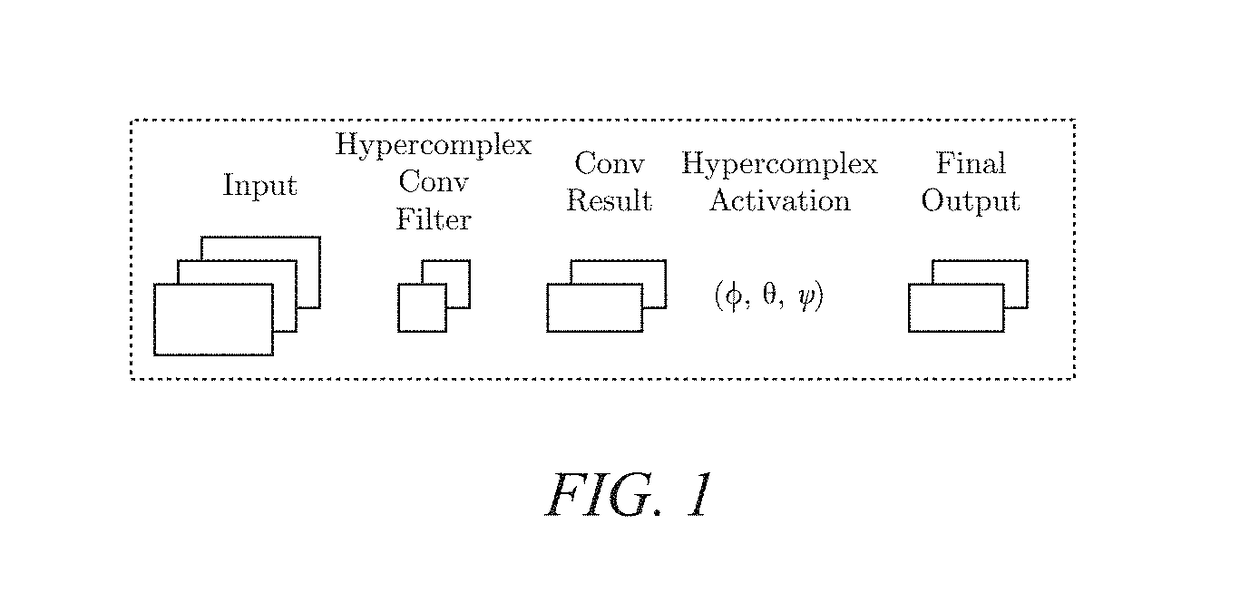
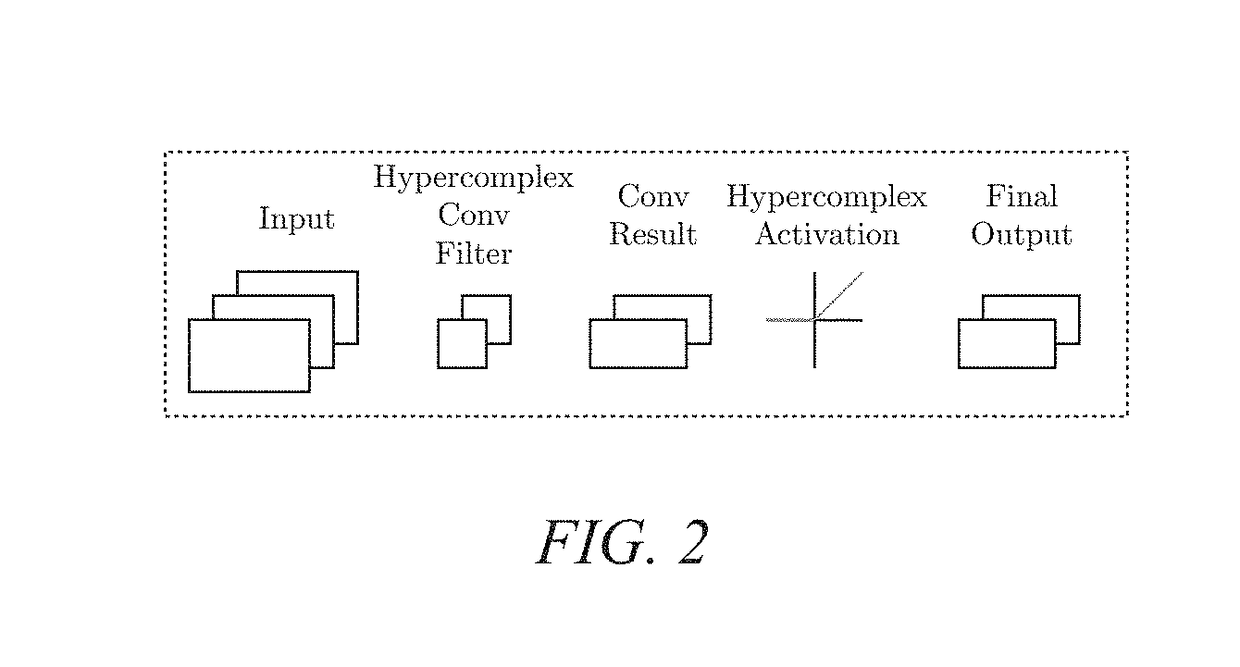
Hypercomplex deep learning methods, architectures, and apparatus for multimodal small, medium, and large-scale data representation, analysis, and applications
A method and system for creating hypercomplex representations of data includes, in one exemplary embodiment, at least one set of training data with associated labels or desired response values, transforming the data and labels into hypercomplex values, methods for defining hypercomplex graphs of functions, training algorithms to minimize the cost of an error function over the parameters in the graph, and methods for reading hierarchical data representations from the resulting graph. Another exemplary embodiment learns hierarchical representations from unlabeled data. The method and system, in another exemplary embodiment, may be employed for biometric identity verification by combining multimodal data collected using many sensors, including, data, for example, such as anatomical characteristics, behavioral characteristics, demographic indicators, artificial characteristics. In other exemplary embodiments, the system and method may learn hypercomplex function approximations in one environment and transfer the learning to other target environments. Other exemplary applications of the hypercomplex deep learning framework include: image segmentation; image quality evaluation; image steganalysis; face recognition; event embedding in natural language processing; machine translation between languages; object recognition; medical applications such as breast cancer mass classification; multispectral imaging; audio processing; color image filtering; and clothing identification.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
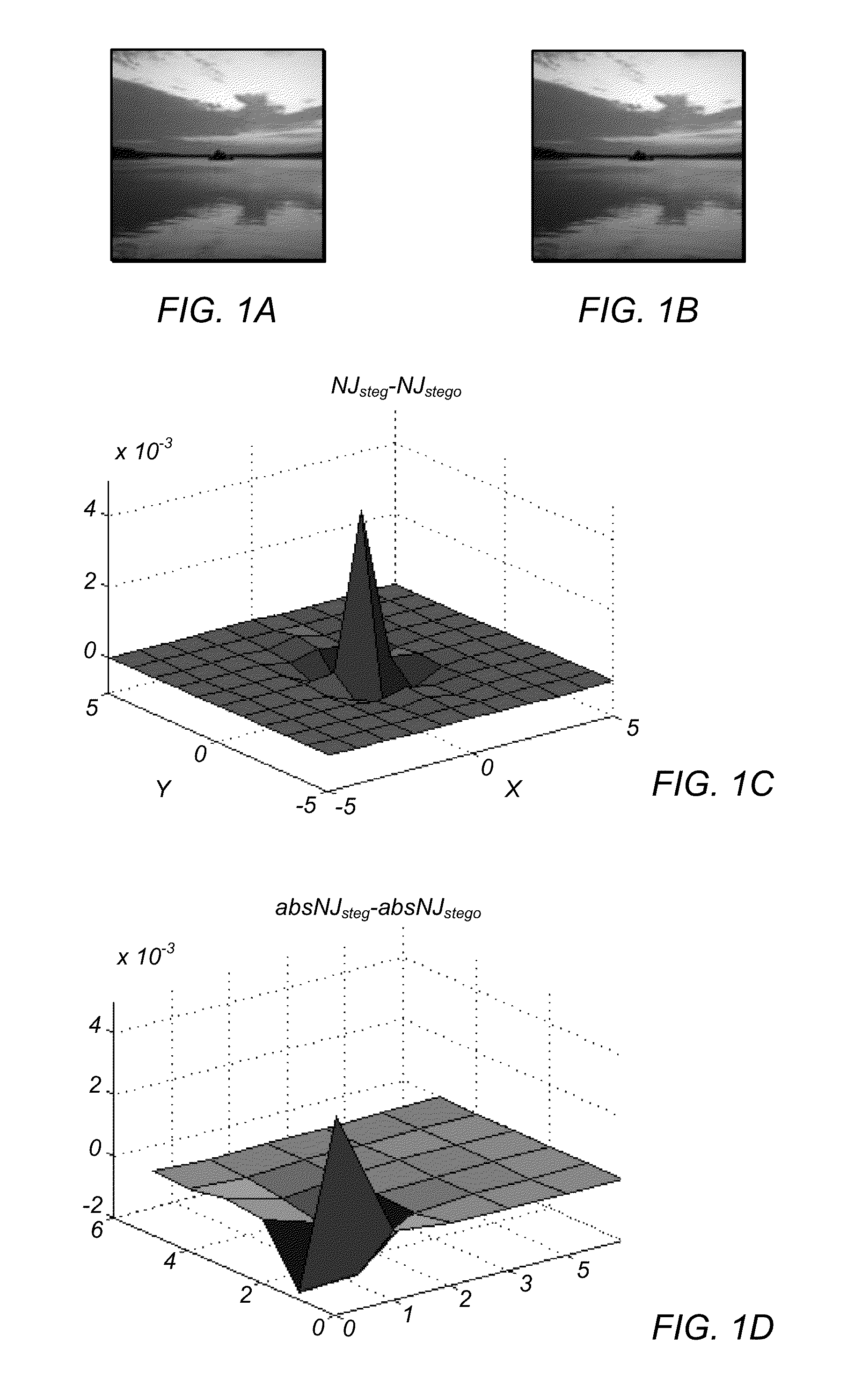
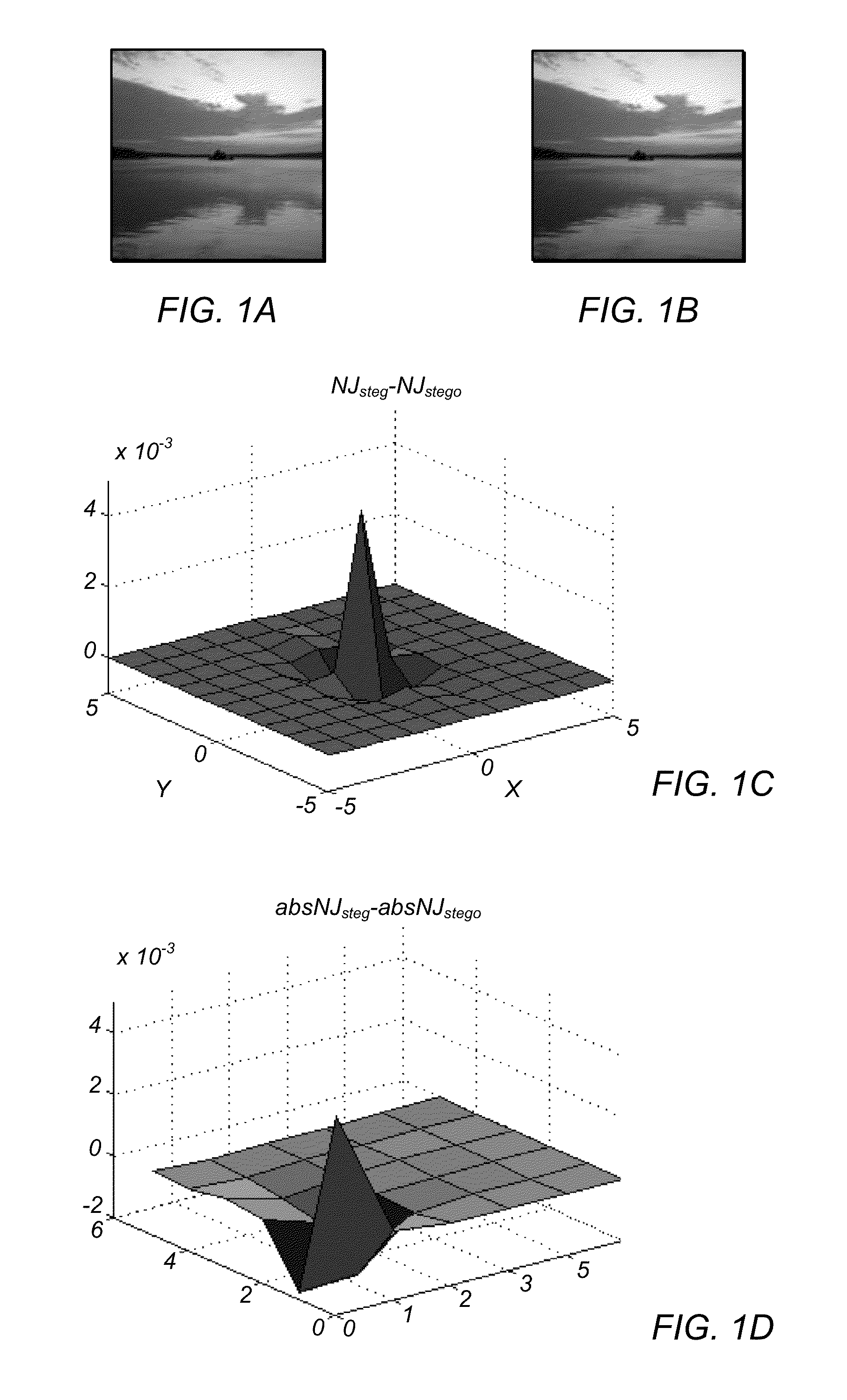
Steganalysis with neighboring joint density
ActiveUS20130208941A1Character and pattern recognitionImage watermarkingSteganalysisComputer graphics (images)
Systems and methods for detecting hidden messages and information in digital files are described. In an embodiment, a method of detecting steganography in a compressed digital image includes extracting neighboring joint density features from the image under scrutiny. Steganography in the image may be detected based on differences in a neighboring joint density feature of the image.
Owner:SAM HOUSTON STATE UNIVERSITY
Image Steganalysis Based on Deep Learning
ActiveUS20180068429A1Highly universal image steganalysis modelAccurate identificationImage enhancementImage analysisSteganalysisFeature learning
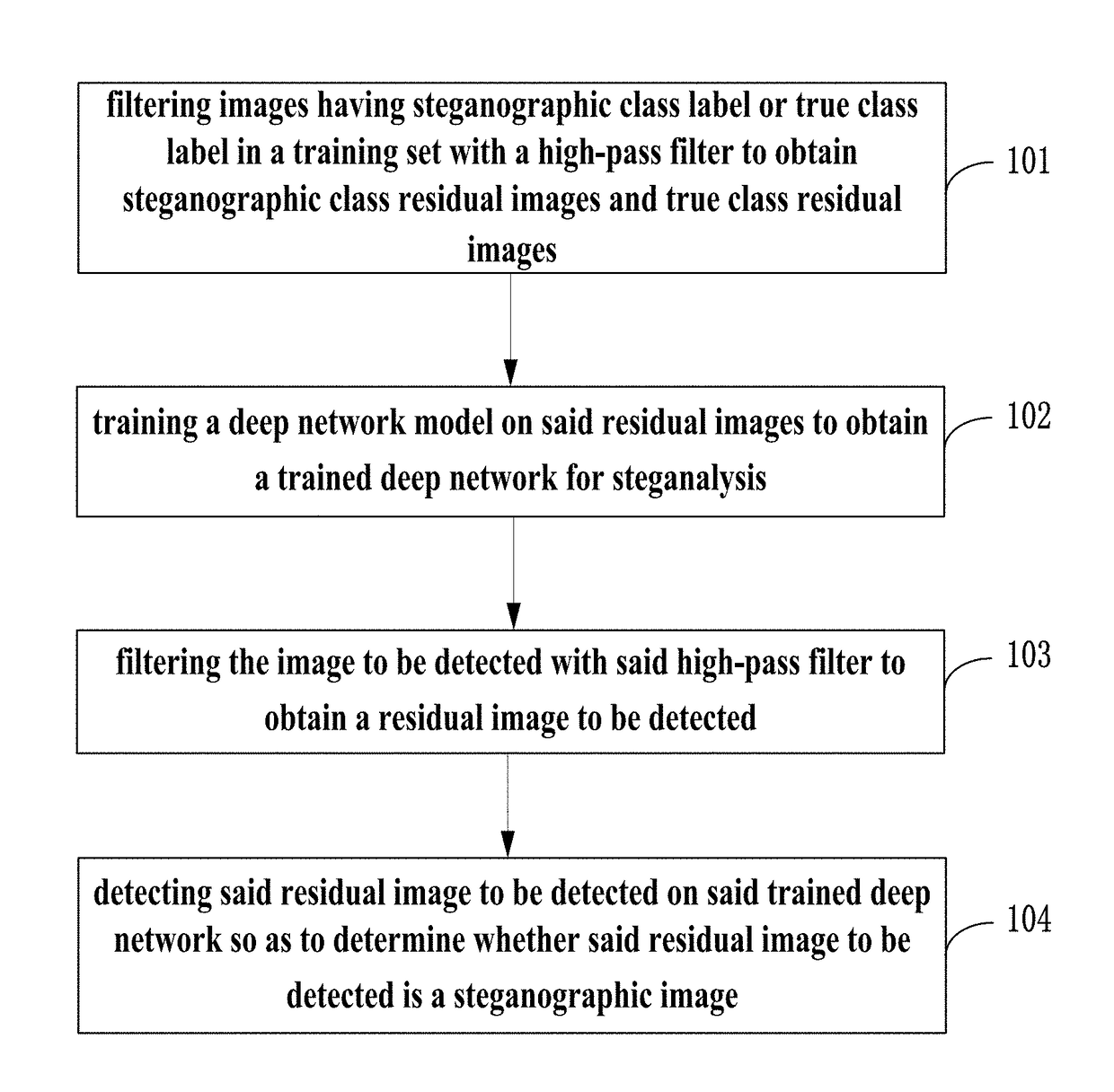
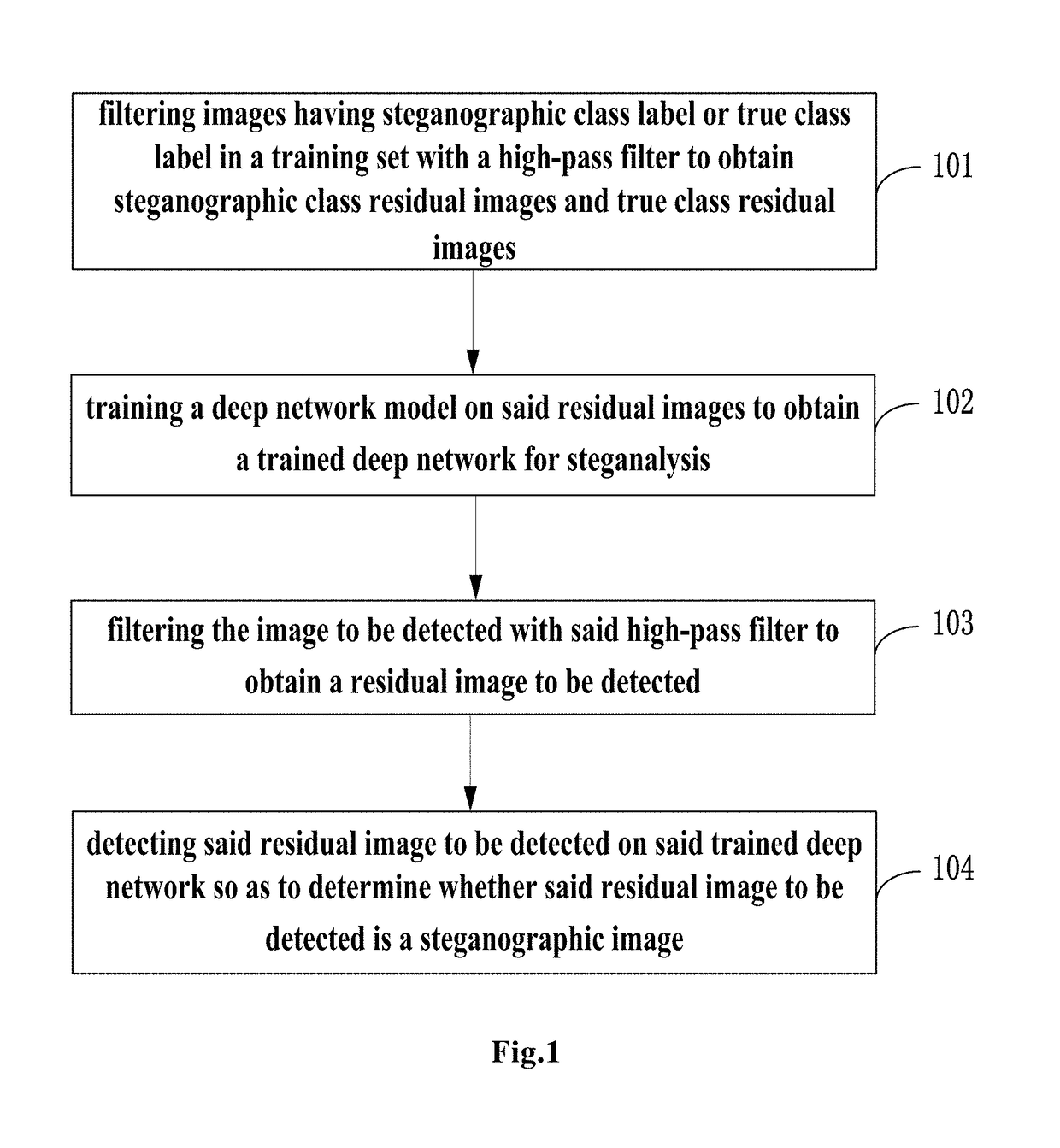
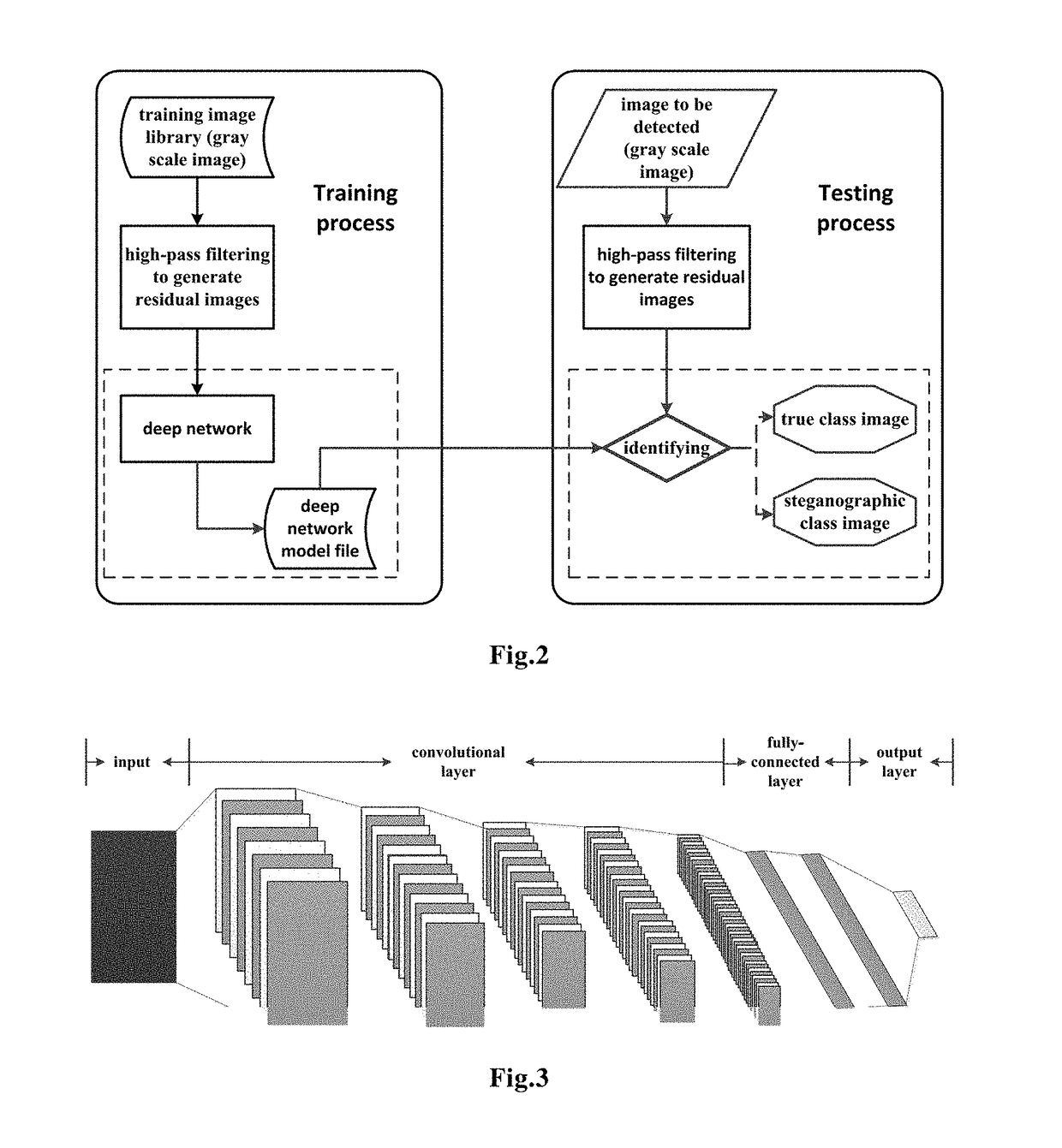
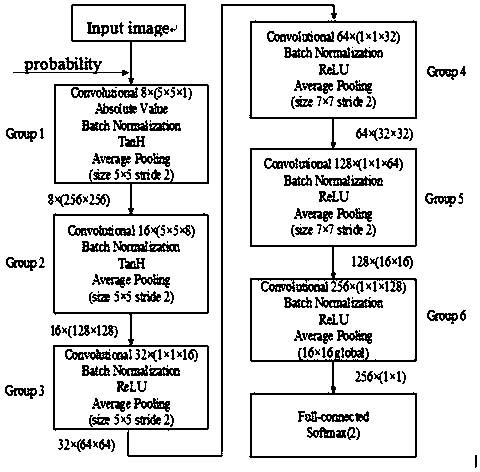
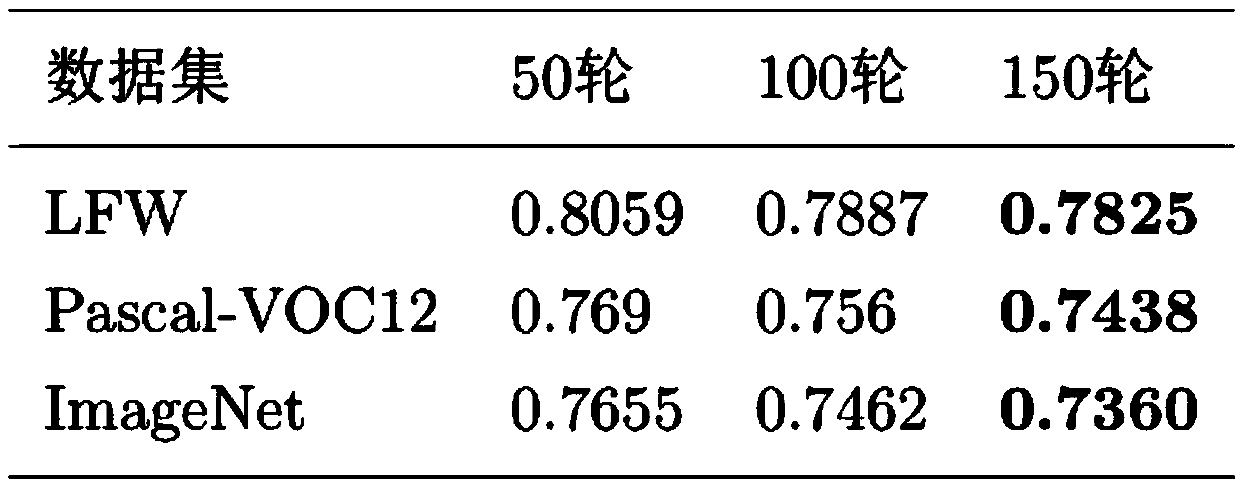
The present invention provides a method for detecting image steganography based on deep learning, which comprises: filtering images having steganographic class label or true class label in a training set with a high-pass filter to obtain a training set including steganographic class residual images and true class residual images; training a deep network model on said training set to obtain a trained deep model for steganalysis; filtering the image to be detected with said high-pass filter to obtain a residual image to be detected; detecting said residual image to be detected on said deep model so as to determine whether said residual image to be detected is a steganographic image. The method for detecting image steganography in the present invention can create an automatic blind steganalysis model through feature learning and can identify steganographic images accurately.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
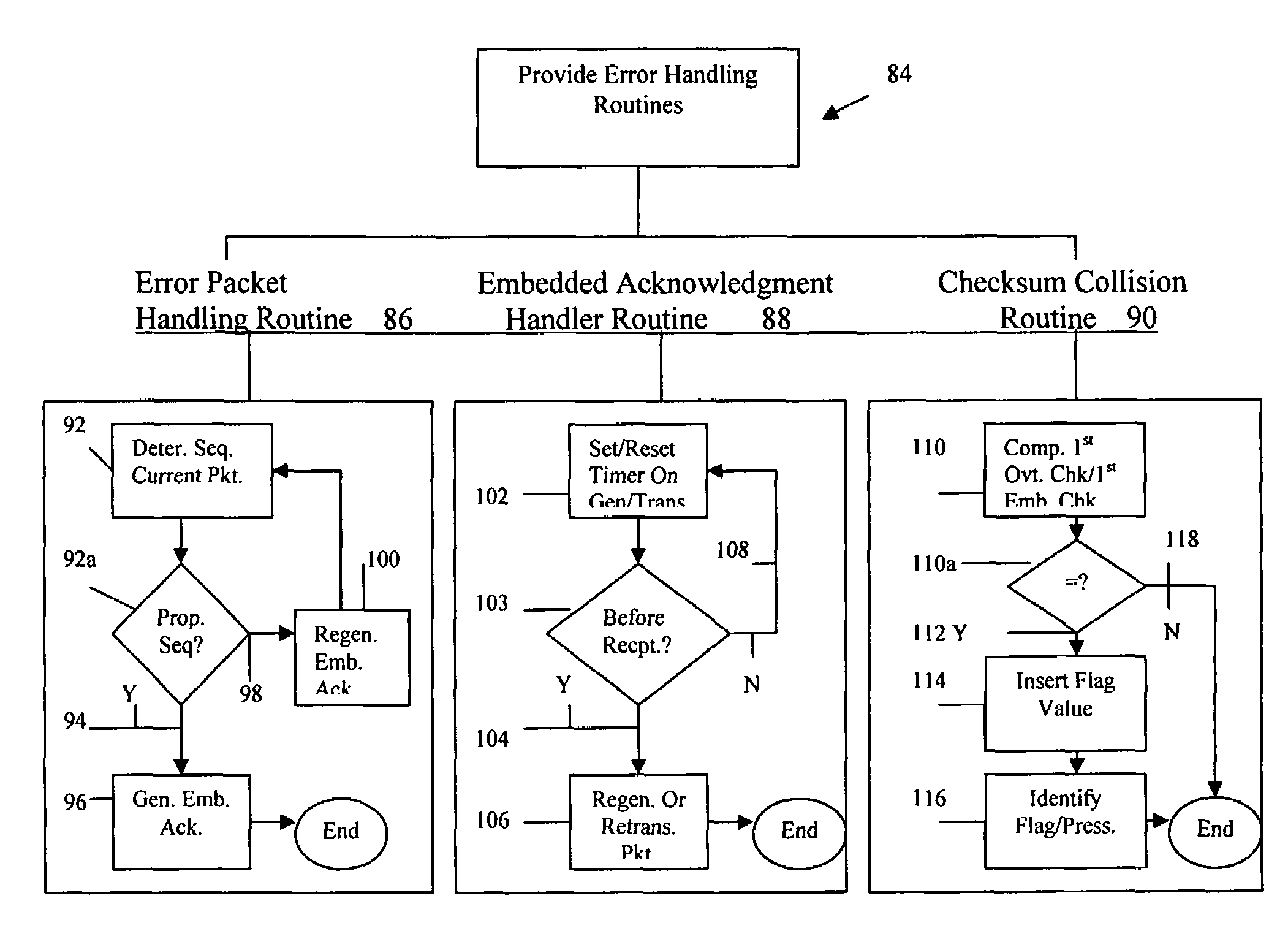
Embedded communications system and method
InactiveUS7725595B1Transmission systemsFrequency-division multiplex detailsSteganalysisCommunications system
A method and system for steganography and steganalytic techniques are provided for effecting embedded communications in a variety of communication environments. One aspect may include an embedded transmitter for inserting embedded data into a packet and an embedded receiver for receiving the packet via, for example, a packetized communication network such as the Internet. Various aspects of the present invention provide robust communications with optimized throughput and may include various error handlers to maximize performance and ensure transfer of incorrupt data. A method for identifying and blocking embedded communications is also provided.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
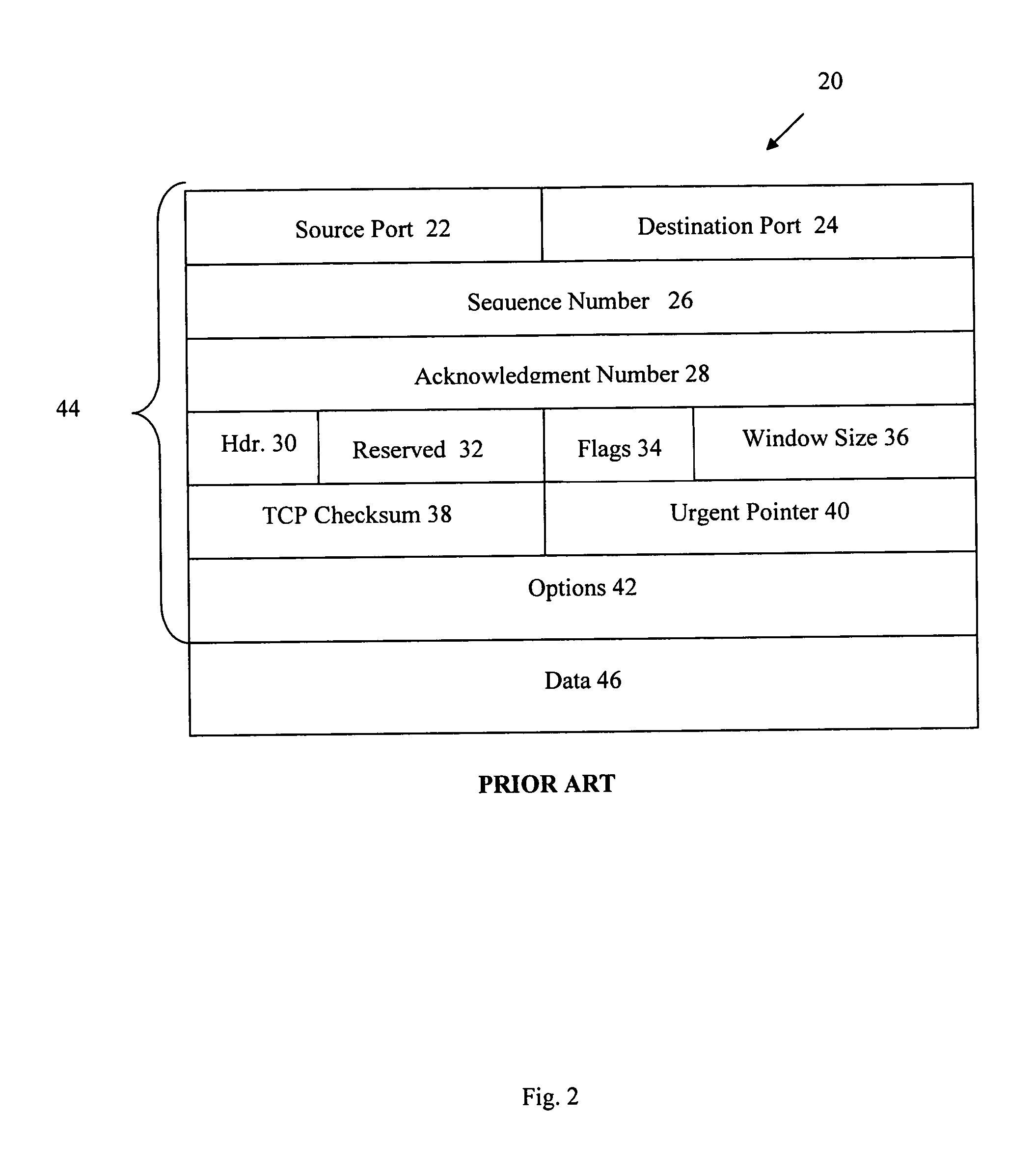
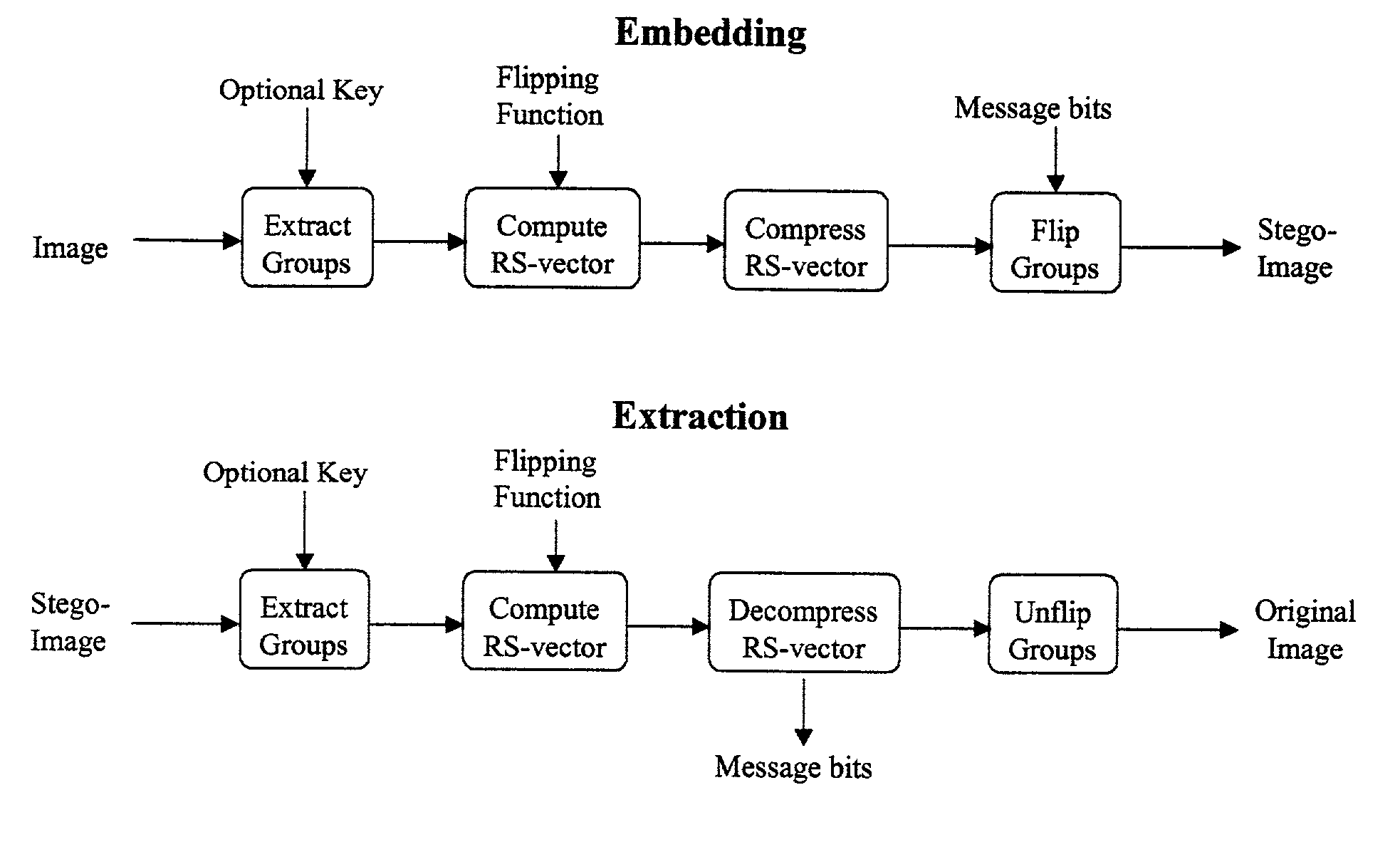
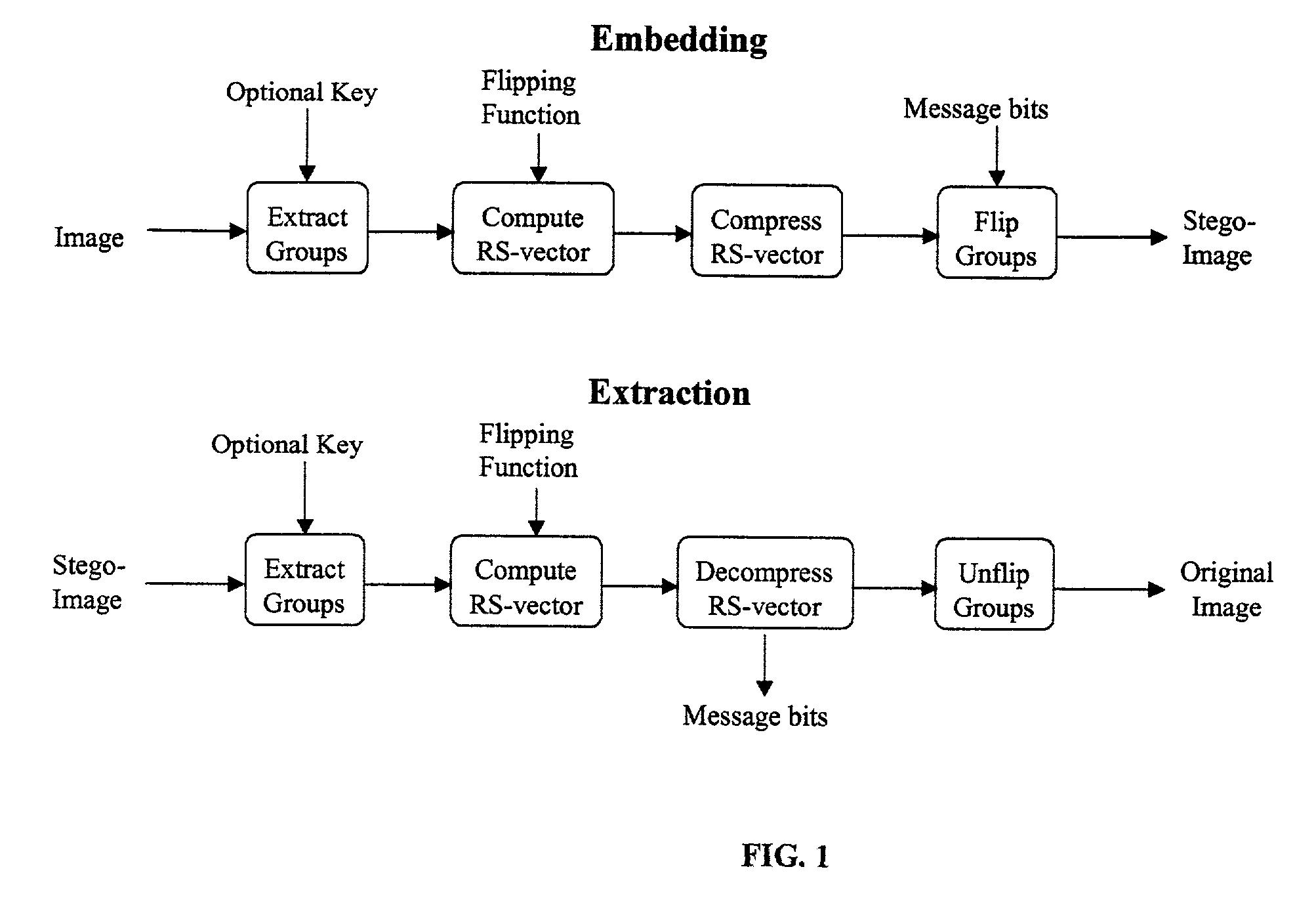
Lossless embedding of data in digital objects
ActiveUS7006656B2Simple and elegant lossless techniqueHeavy loadUser identity/authority verificationCharacter and pattern recognitionSteganalysisHidden data
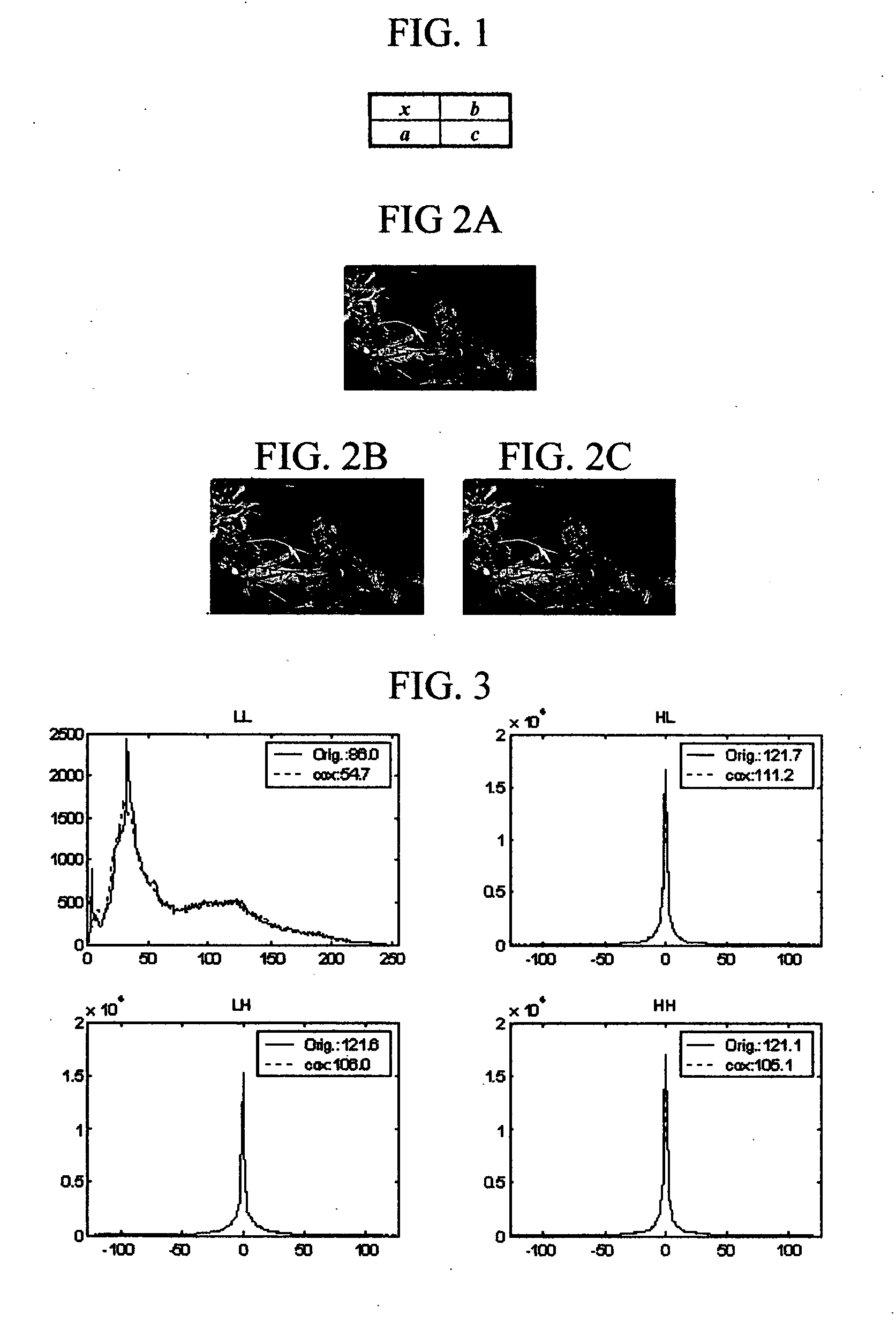
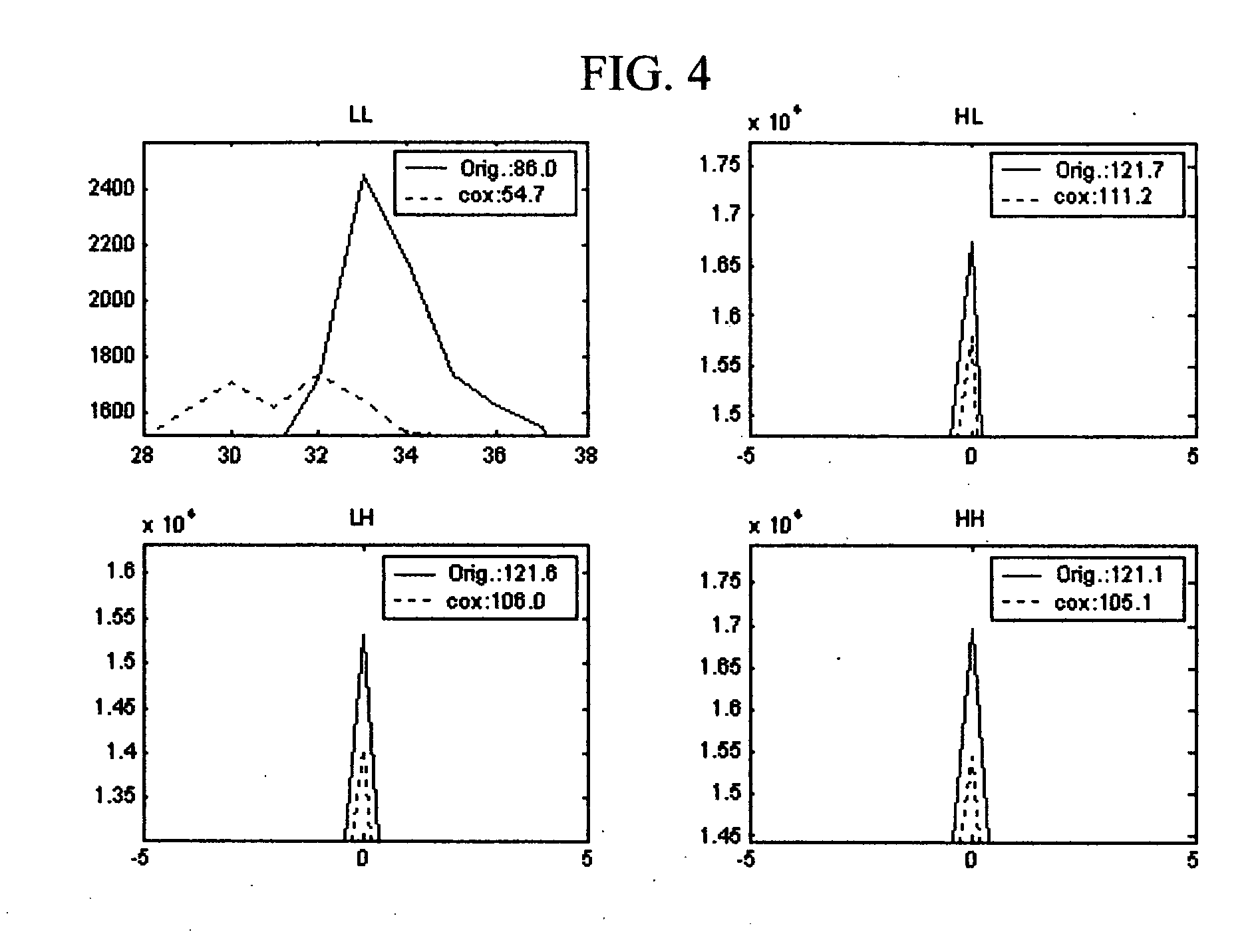
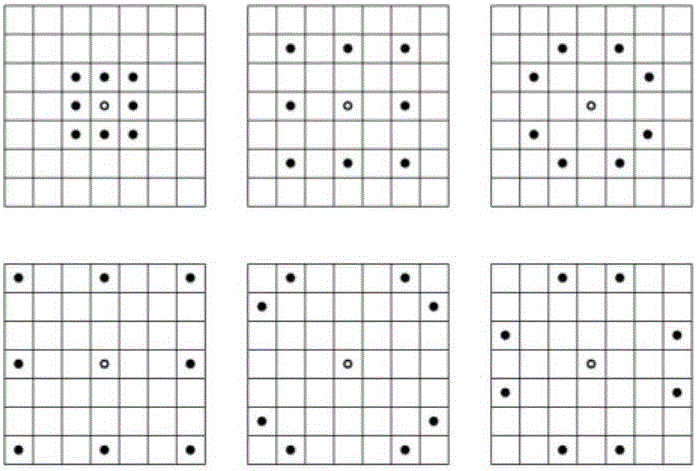
Current methods of embedding hidden data in an image inevitably distort the original image by noise. This distortion cannot generally be removed completely because of quantization, bit-replacement, or truncation at the grayscales 0 and 255. The distortion, though often small, may make the original image unacceptable for medical applications, or for military and law enforcement applications where an image must be inspected under unusual viewing conditions (e.g., after filtering or extreme zoom). The present invention provides high-capacity embedding of data that is lossless (or distortion-free) because, after embedded information is extracted from a cover image, we revert to an exact copy of the original image before the embedding took place. This new technique is a powerful tool for a variety of tasks, including lossless robust watermarking, lossless authentication with fragile watermarks, and steganalysis. The technique is applicable to raw, uncompressed formats (e.g., BMP, PCX, PGM, RAS, etc.), lossy image formats (JPEG, JPEG2000, wavelet), and palette formats (GIF, PNG).
Owner:RES FOUND OF SUNY THE +1
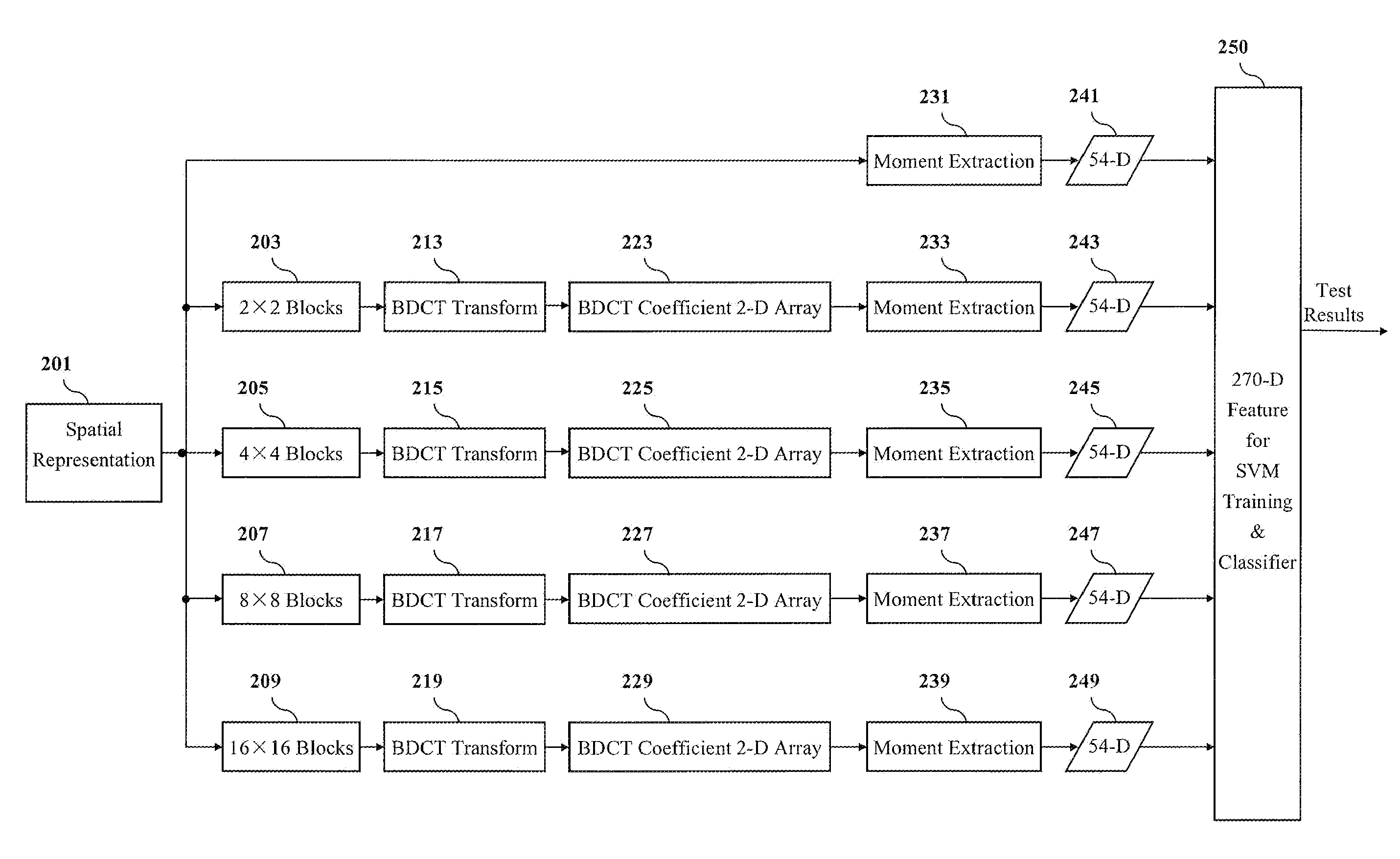
Method and apparatus for steganalysis for texture images
ActiveUS20080175429A1Simple methodImprove abilitiesCharacter and pattern recognitionImage watermarkingSteganalysisImage decompression
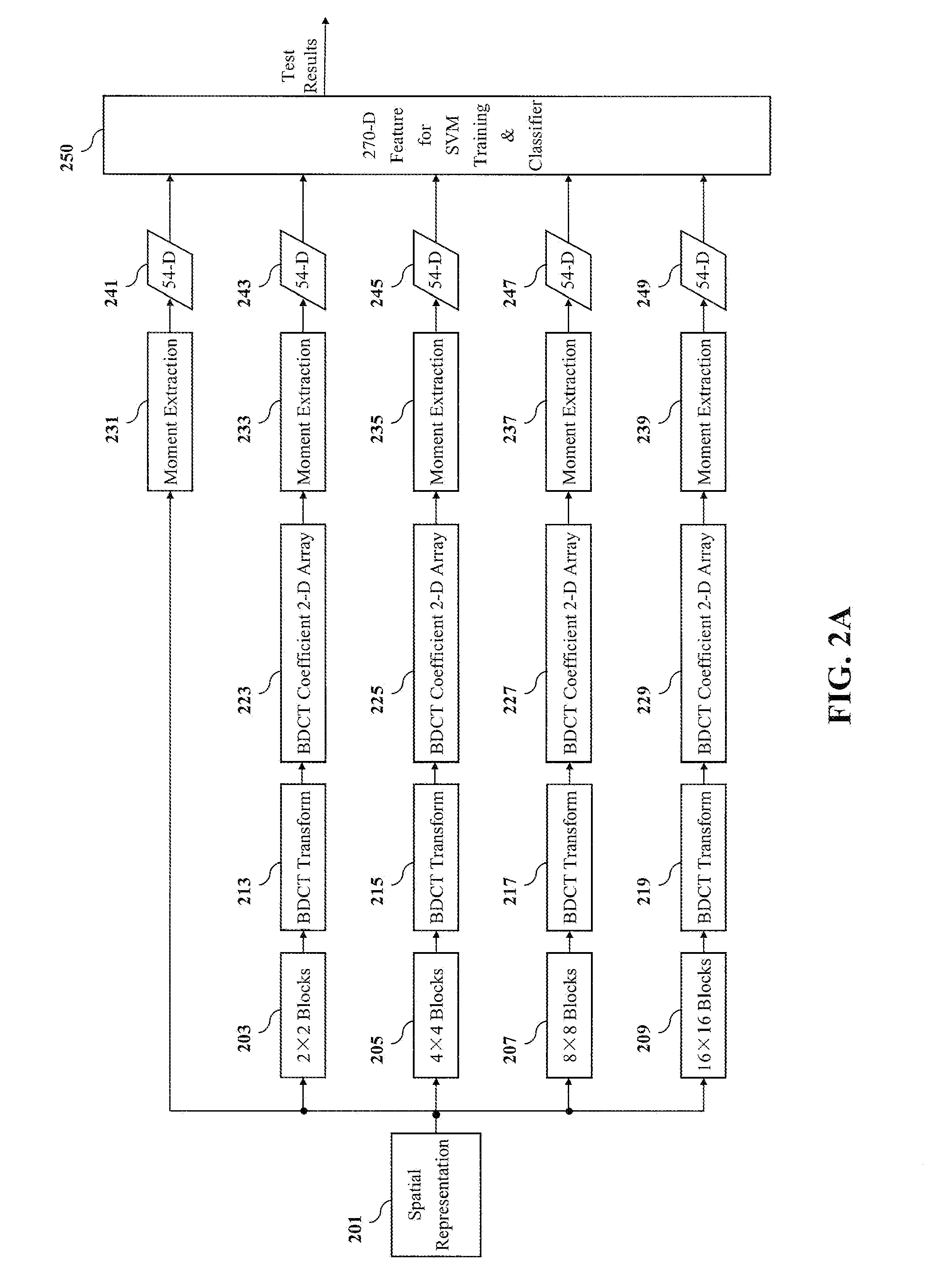
Embodiments of the invention are directed toward methods for steganalysis that improve the detection of steganography in texture images. The methods combine features extracted from the image spatial representation and from a block discrete cosine transform (BDCT) representation with multiple different block sizes (i.e., N×N) to improve detection of data hidden in texture images. Image data that is to undergo steganalysis can be provided to embodiments of the invention in at least one of spatial (pixel) and JPEG format. When JPEG format is provided, the image is first decompressed to spatial representation, from which the features are extracted when the block size is at least one 2×2, 4×4, and 16×16. When the block size is 8×8, the JPEG coefficients (JPEG quantized 8×8 BDCT coefficients) derived directly from the JPEG image are used to extract features. In addition, the method is also effective as a universal steganalyzer for both texture and smooth / non-texture images. Embodiments of the invention also (1) utilize moments of 1-D and 2-D characteristic functions; (2) Prediction-error; and (3) all wavelet subbands including the low-low subbands.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
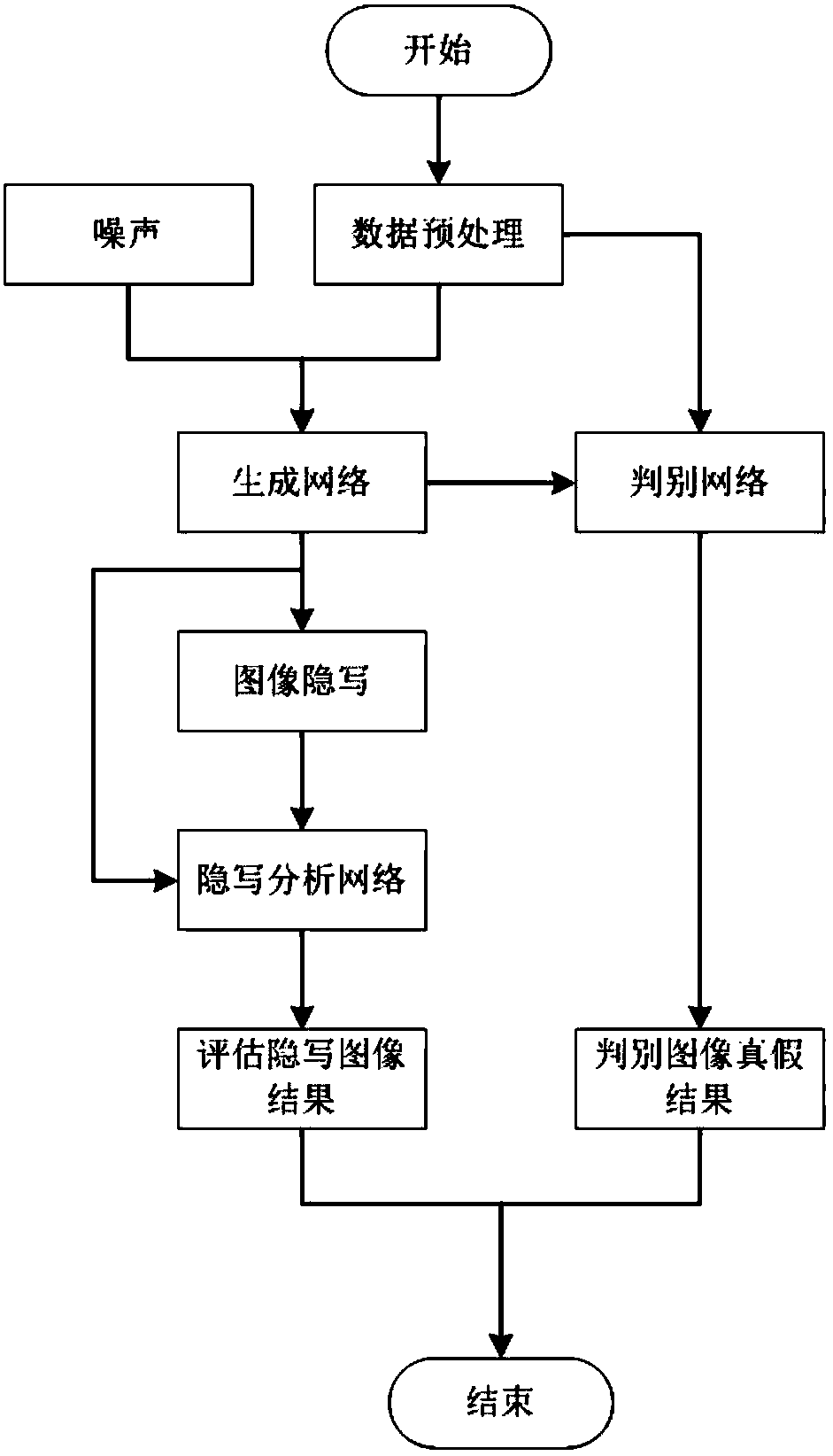
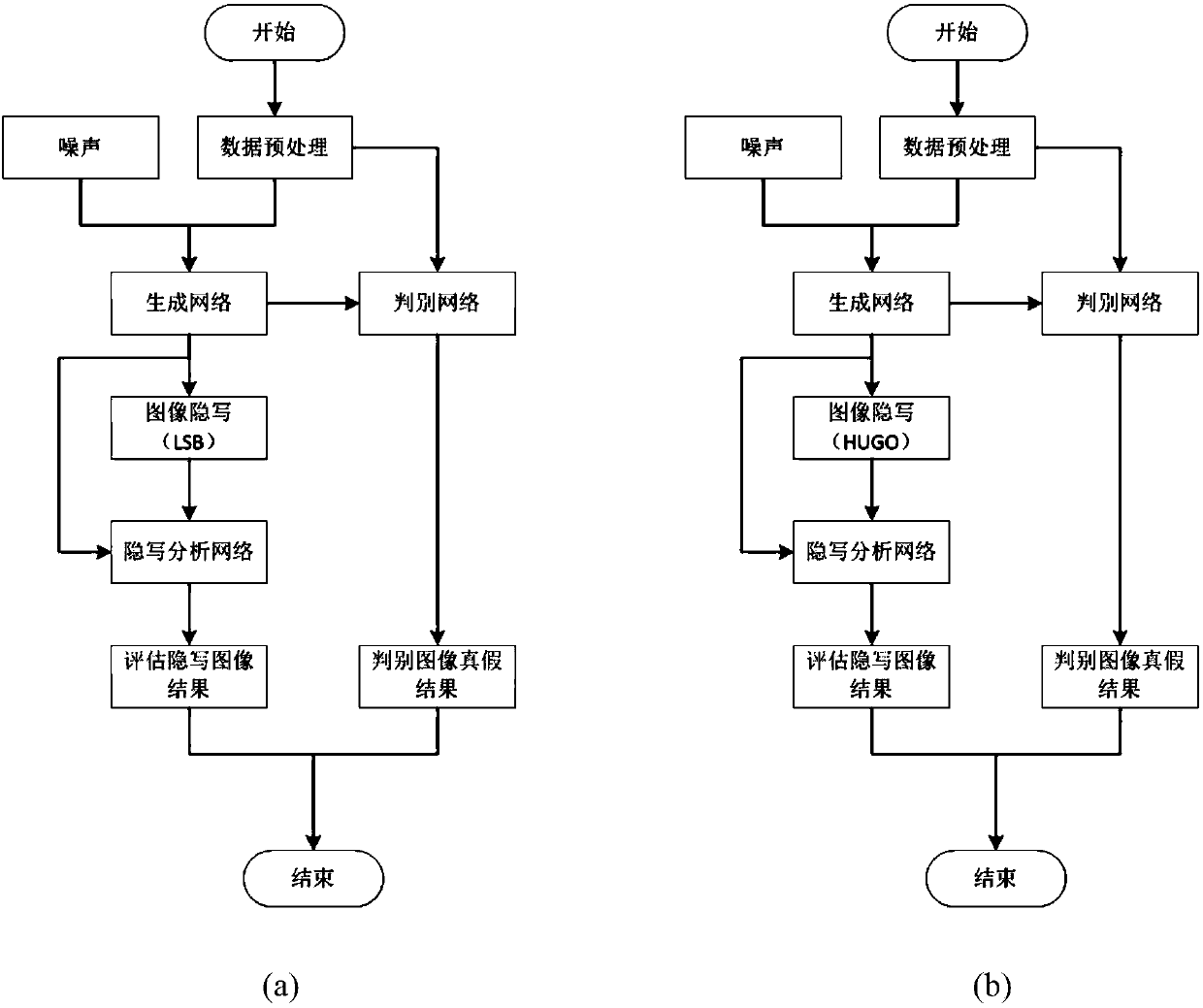
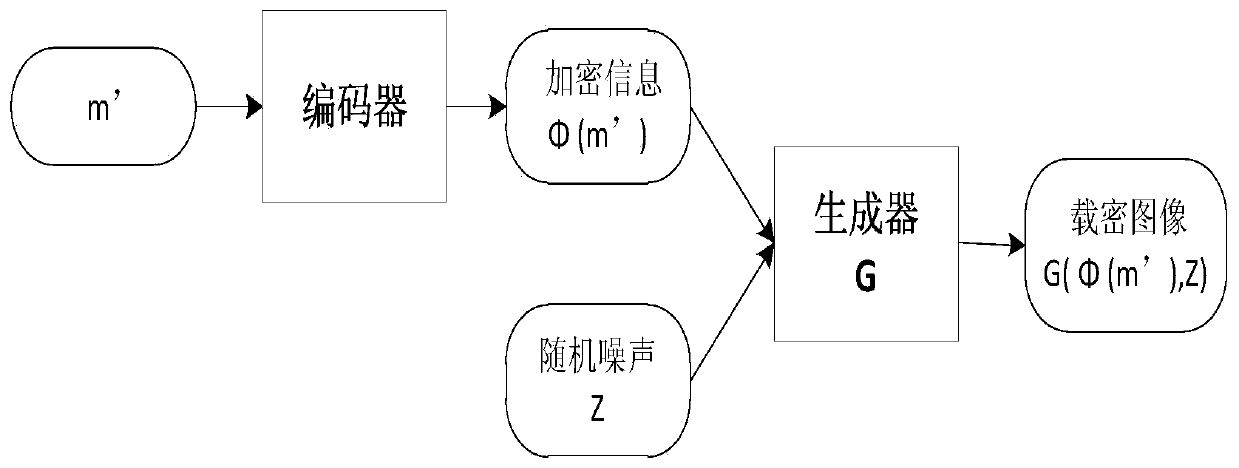
Spatial-domain image steganography method and system based on generative adversarial network
ActiveCN108346125ASimple designSmall number of structural parametersImage enhancementImage analysisCode moduleSteganalysis
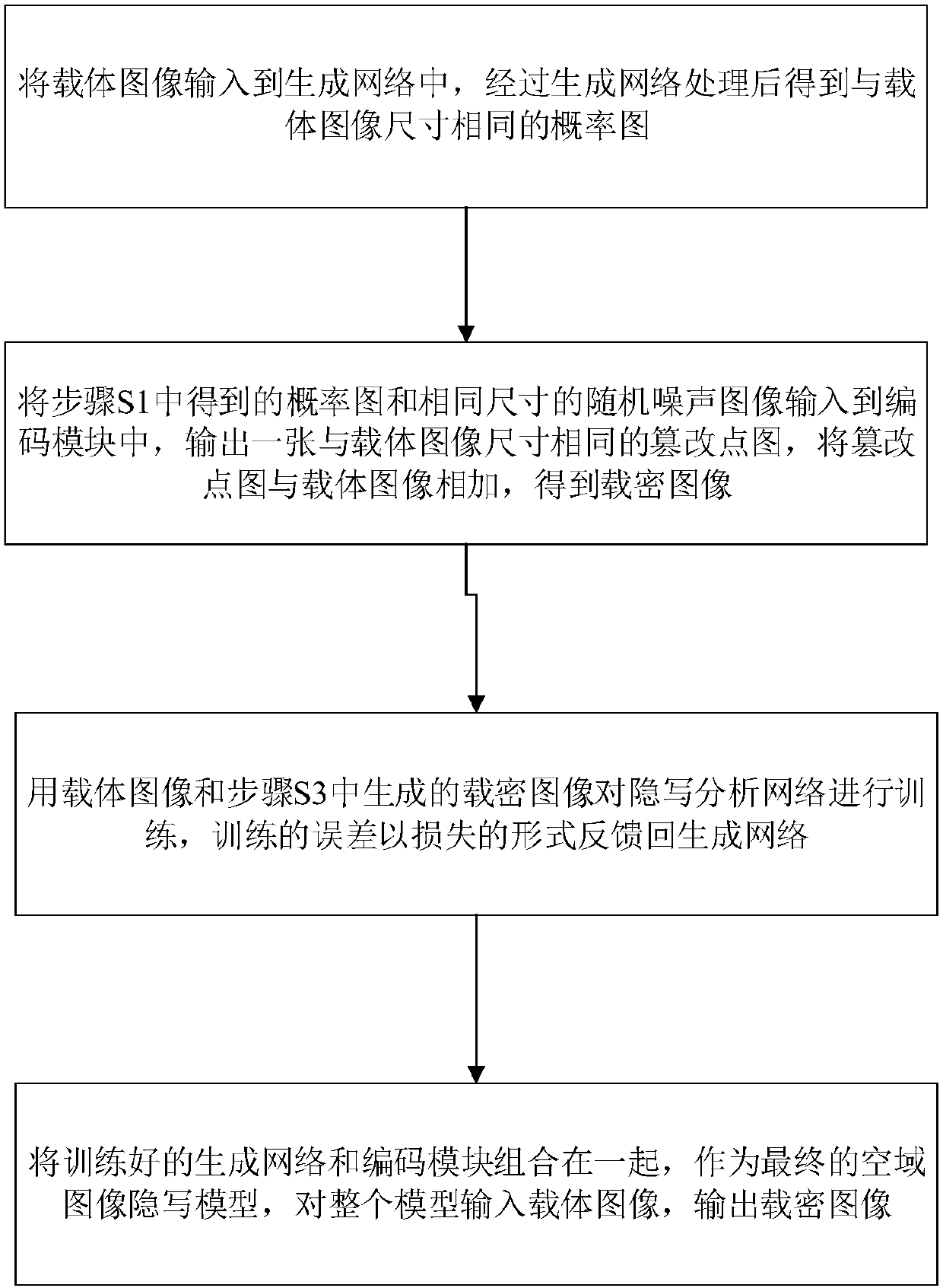
The invention discloses a spatial-domain image steganography method and system based on generative adversarial network. The carrier image is converted into a probability graph through the generation network of a U-shaped structure, and then the probability graph is coded by utilizing a hyperbolic tangent coding module, a tampering point graph is generated, and the carrier image and the tampering point graph are added to generate a secret-carrying image; and then a steganography analysis network is used for distinguishing the carrier image and the secret-carrying image, and the classification result is fed back to the generation network in an error mode; and finally, the trained generation network and the coding module are combined together, as a final spatial-domain image steganography model, the carrier image is input into the whole model, and the secret-carrying image is output. The invention further discloses a space-domain image steganography system based on the generative adversarial network, and the system includes a generation network module, an encoding module and an image steganography module. According to the spatial-domain image steganography method based on the generative adversarial network, the security is obviously improved, and the design is simple.
Owner:SUN YAT SEN UNIV
Invisible image steganography based on generative adversarial network
ActiveCN109587372ASolve the problem of color differenceResolve differencesNeural architecturesNeural learning methodsSteganalysisDiscriminator
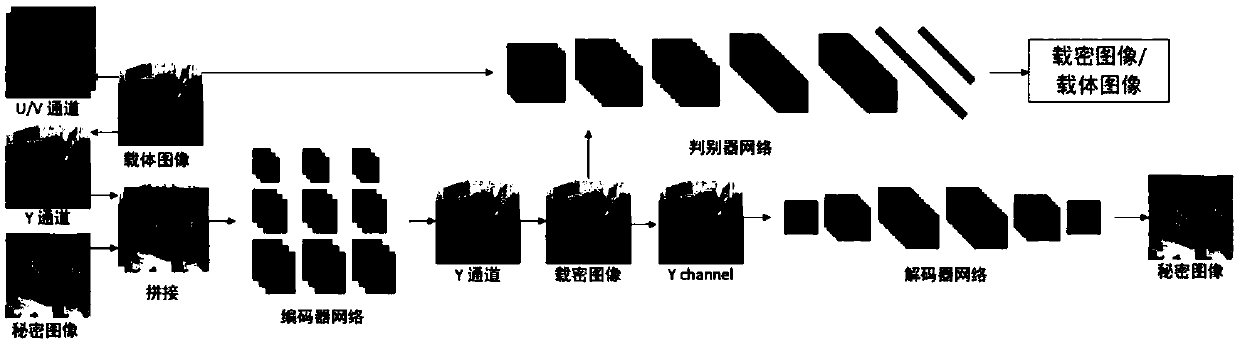
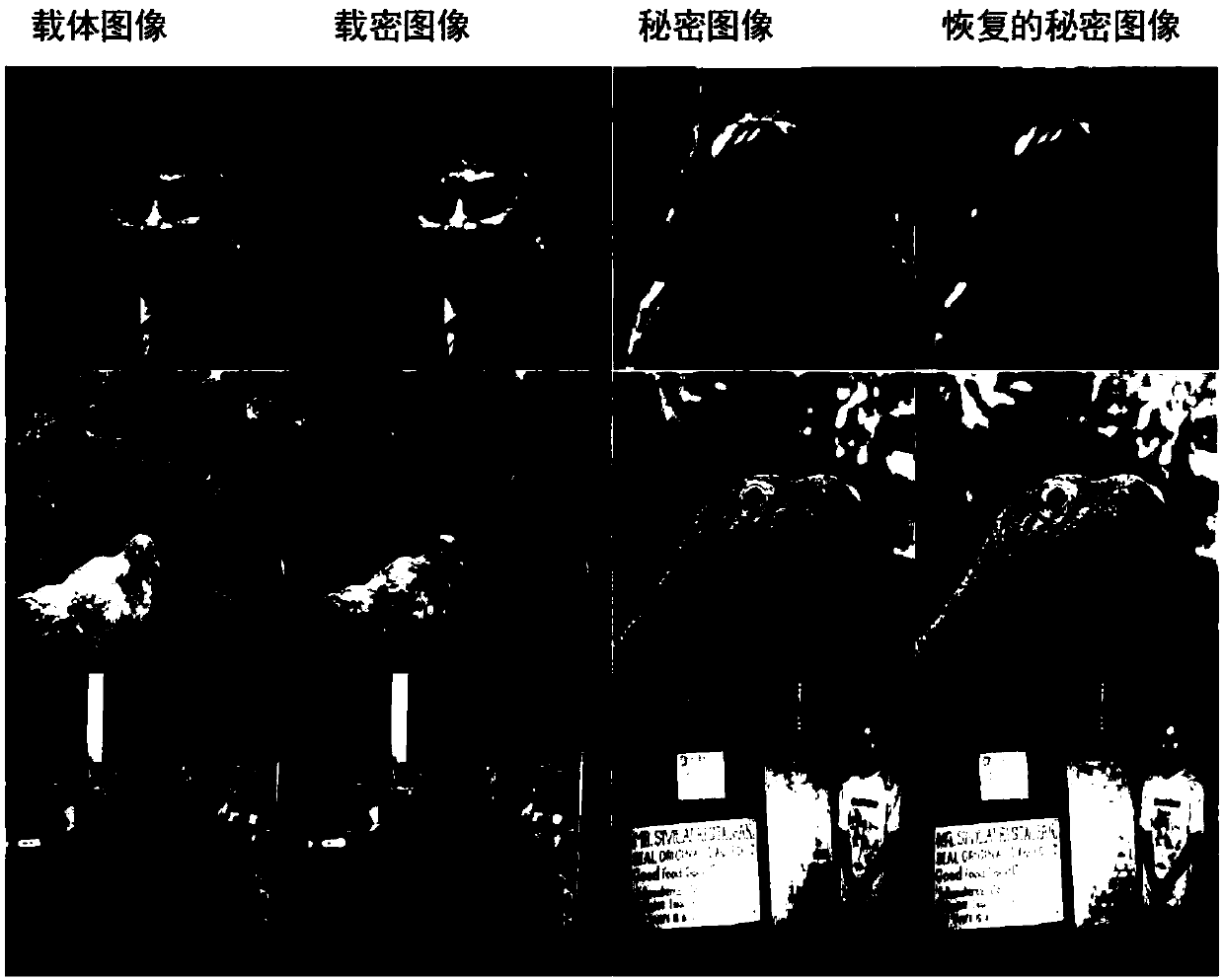
The invention discloses an invisible image steganography based on a generative adversarial network which can embed a grayscale secret image into a color carrier image to obtain a confidential image and can successfully recover a secret image from the payload image. The invisible image steganography comprises: an encoder network which is responsible for embedding a secret image into a carrier imageto generate a confidential image; a decoder network which is responsible for recovering a secret image from a loaded image; and a discriminator network which is responsible for performing steganalysis of a natural image and a confidential image to adjust the safety of the encoder network and decoder network. The invisible image steganography based on the generative adversarial network provides anew design idea for image information hiding.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Statistic supervision and structure supervision based hidden messages analysis system
InactiveCN1920877AImprove reliabilityComputer security arrangementsImage data processing detailsSteganalysisPattern recognition
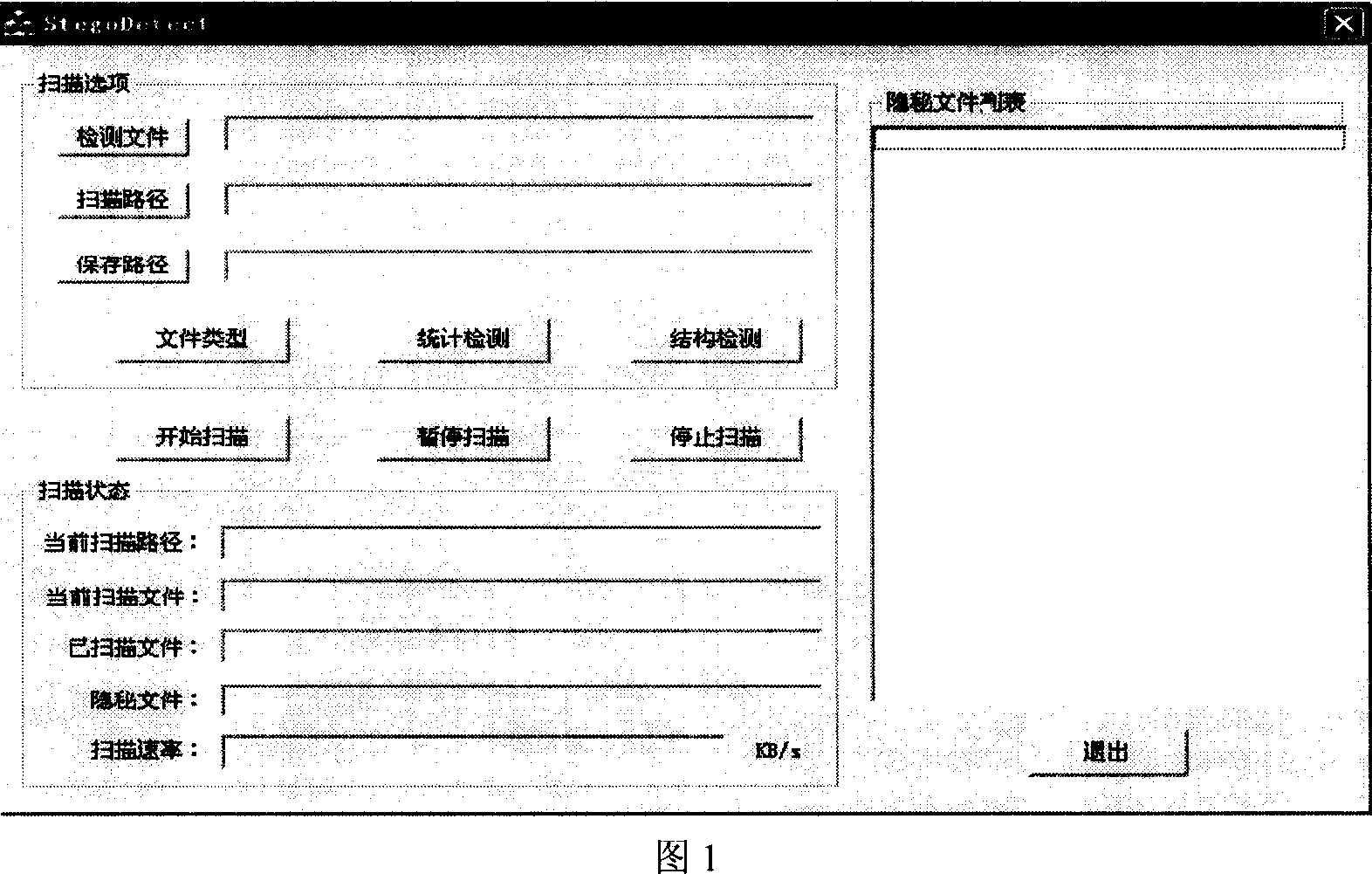
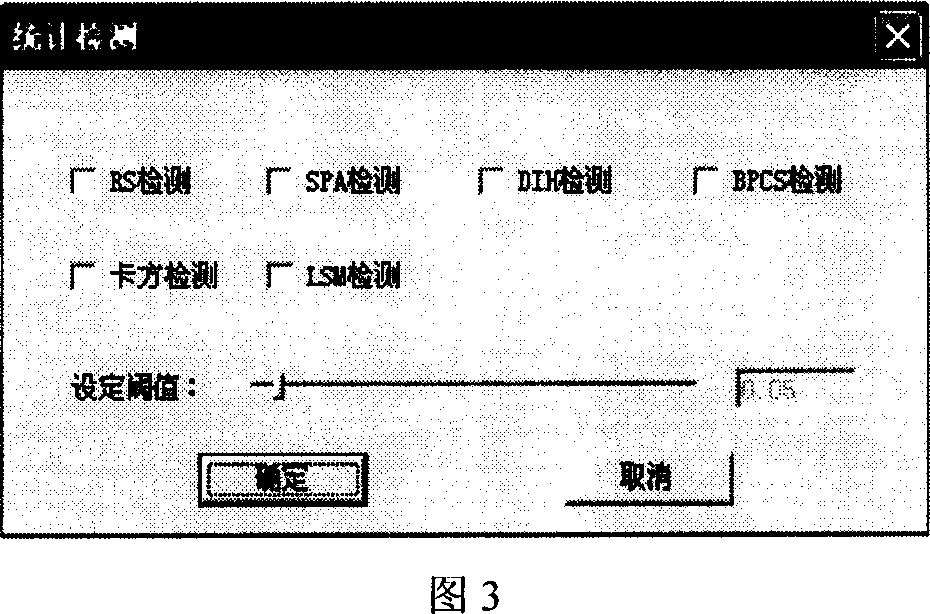
The invention relates to a hidden-writing analyze system, based on statistic detection and structural detection, wherein the core detecting module of system is integrated with six statistic detecting modules and two structure detecting modules, to user hidden-writing technique as LSB, BPCS and structure hidden-writing techniques of spatial region to detect the reliability of hidden encrypted document which uses common video and voice as carrier, as MBP image, JPEG image and WAVE voice. The invention combines the detecting results of several detecting modules to judge, with better adaptability on present hidden-writing method, to reduce average detecting rate and high false alarm rate, to detect variable carrier types and variable hidden-writing methods at high quality and high efficiency. And the invention has better expandable property, to integrate new detecting module to upgrade the detecting property of system.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Secure steganography method and device based on generative adversarial networks
ActiveCN107563155AImprove securitySolve the problem that the effect of steganalysis is not obviousDigital data protectionImage data processing detailsSteganalysisDiscriminator
The invention relates to a secure steganography method and device based on generative adversarial networks. The method includes: generating a carrier image, into which information needs to be embedded, through the generator network under a generative adversarial network framework, and judging authenticity of the generated carrier image through the discriminator network, enabling the carrier image,which is generated by the generator network, to be close to a real image through a dynamic game process of the generator network and the discriminator network; carrying out embedding of the information on the carrier image generated by the generator network; and then utilizing a steganalysis network to carry out binary classification on the input carrier image and a steganographed image to obtainaccuracy rates of classification into an original image and the steganographic image. According to the method, the generated carrier image is closer to the real image visually, a generation speed isfaster, and steganographic security can be improved.
Owner:INST OF INFORMATION ENG CAS
Video steganalysis method based on partial cost non-optimal statistics
InactiveCN103108188AGood and wide versatilityHigh-precision detectionTelevision systemsDigital video signal modificationLocal optimumPattern recognition
The invention provides a video steganalysis method based on partial cost non-optimal statistics. A fundamental principle of producing a motion vector is deeply excavated in the steganalysis method. The video steganalysis method based on the partial cost non-optimal statistics starts from the local optimum characteristics which should be kept and produced by the motion vector, and thereby the steganalysis method is enabled not to be limited to a particular video coding standard and a coding tool, is applicable to video encoding formats adopting interframe prediction technology such as moving picture expert group (MPEG)-2, MPEG-4 and H.264 and has good and wide generality and a high detection accurate rate. The video steganalysis method based on the partial cost non-optimal statistics can be applied to national security, army, government and enterprise sectors, achieves effective detection and monitoring of video content security, prevents illegal personnel from transferring intelligence information with a large data amount through video data and has important research significance and application values for ensuring the national intelligence safety, preventing enterprise confidential information from being revealed and the like.
Owner:WUHAN UNIV
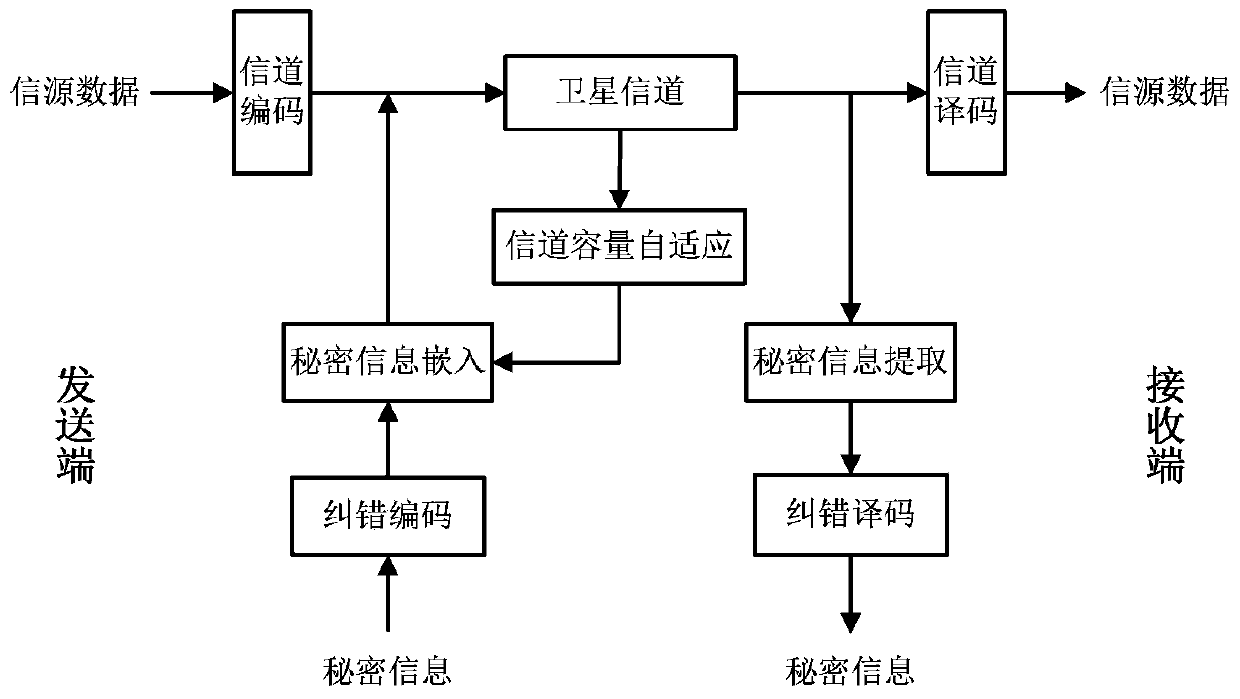
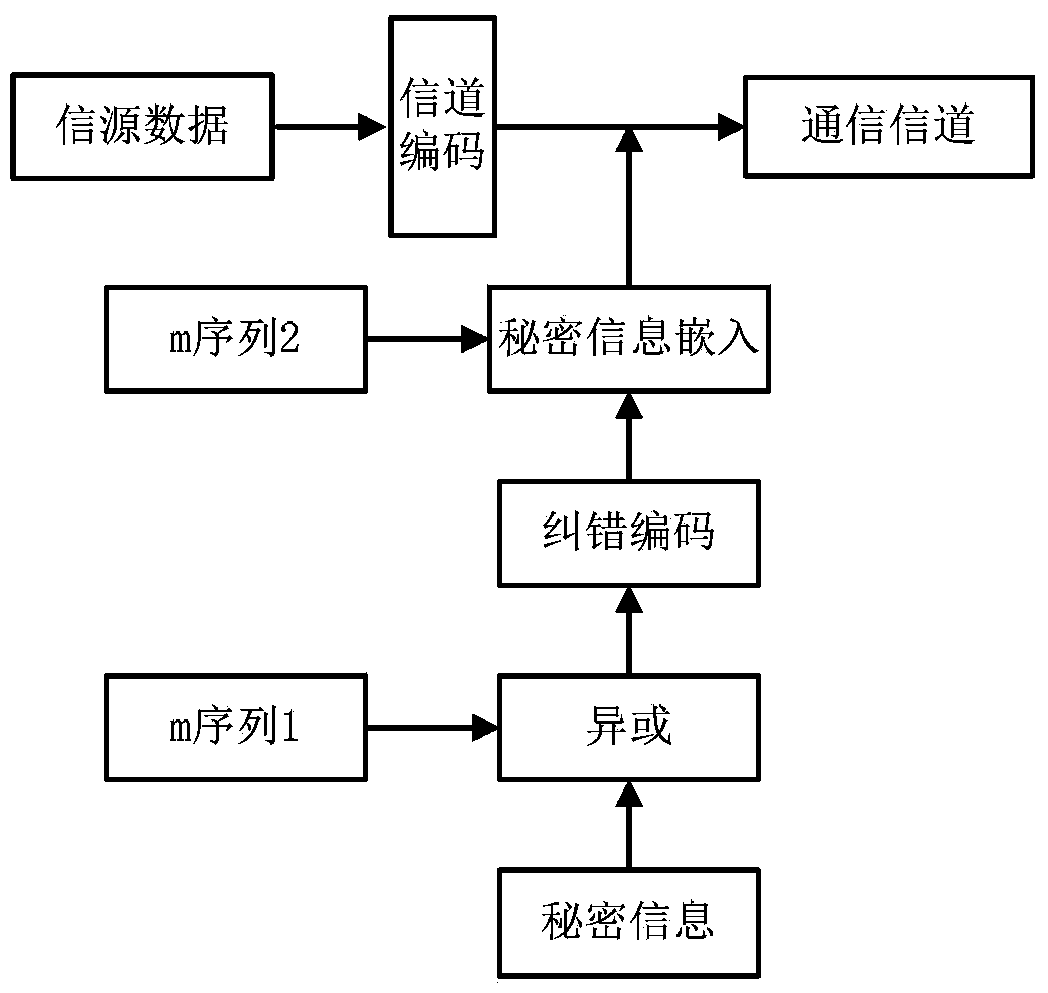
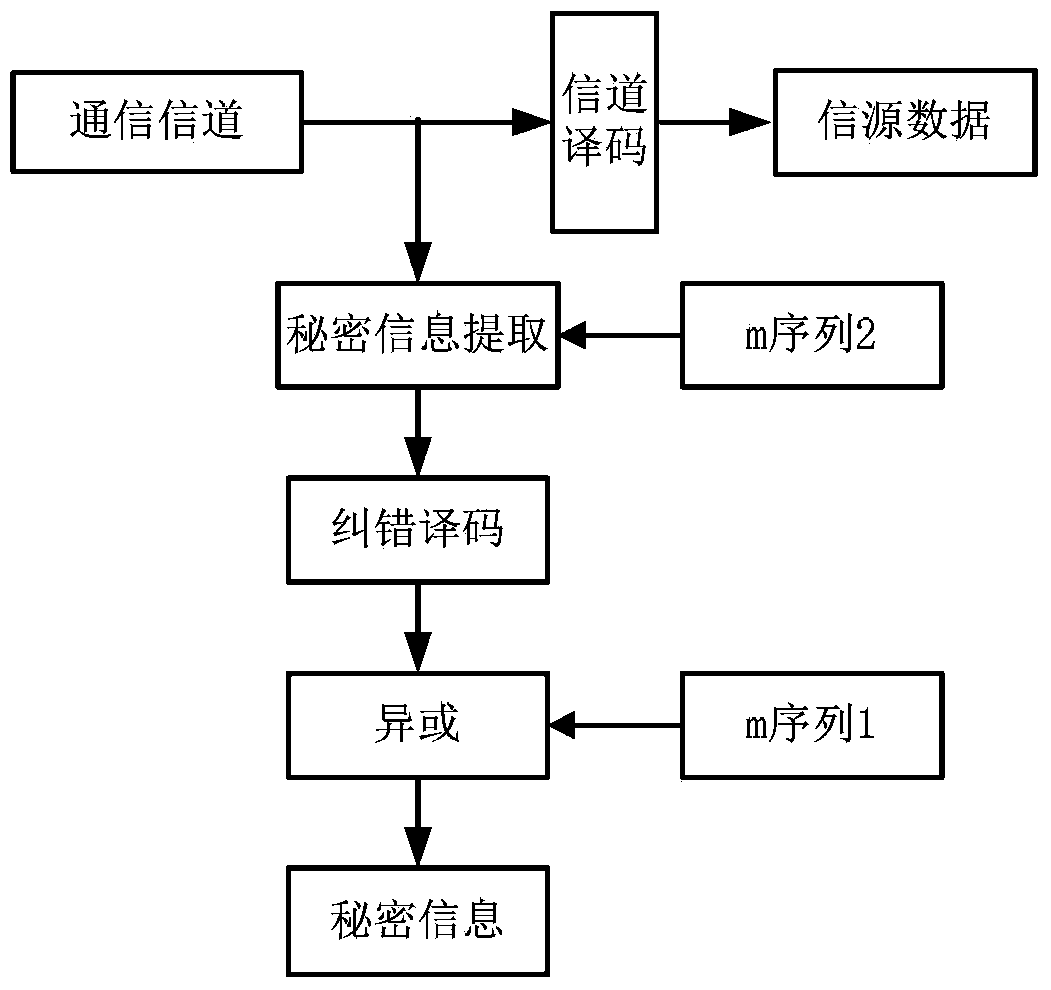
Self-adaption covert communication method based on satellite channel coding
InactiveCN103476026AAvoid bit errorsImprove securityError preventionSecurity arrangementBlock codeCovert communication
The invention provides a self-adaption covert communication method based on satellite channel coding, and directing at different channel encoding algorithms of block codes, RS codes, convolutional codes, serial concatenated code and the like, provides a capacity self-adaption method for secrete information embedding; further provides a channel encoding information embedding and extracting algorithm based on m sequences. By the utilization of the self-adaption covert communication method, the capacity of covert channels can be determined in a self-adaption mode according to different used channel encoding algorithms and different used communication environments; normal use of carriers containing secretes is not influenced, and main steganalysis attacks such as chi-square analysis attacks and RS analysis attacks can be resisted; under the condition that the satellite channel bit error rate is 10-3-10-5, quasi error-free transmission of secrete information can be realized.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
System and method for image steganalysis
InactiveCN106203492AIncrease training speedImprove classification effectCharacter and pattern recognitionImage data processing detailsSteganalysisFeature extraction
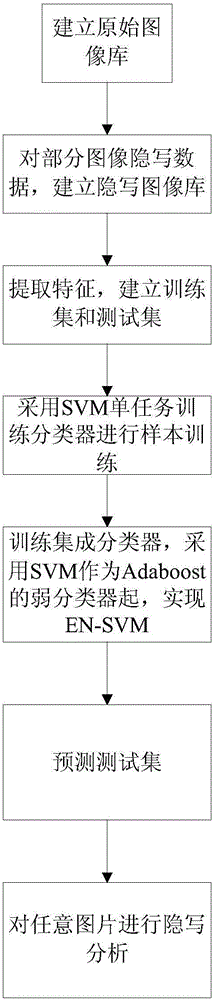
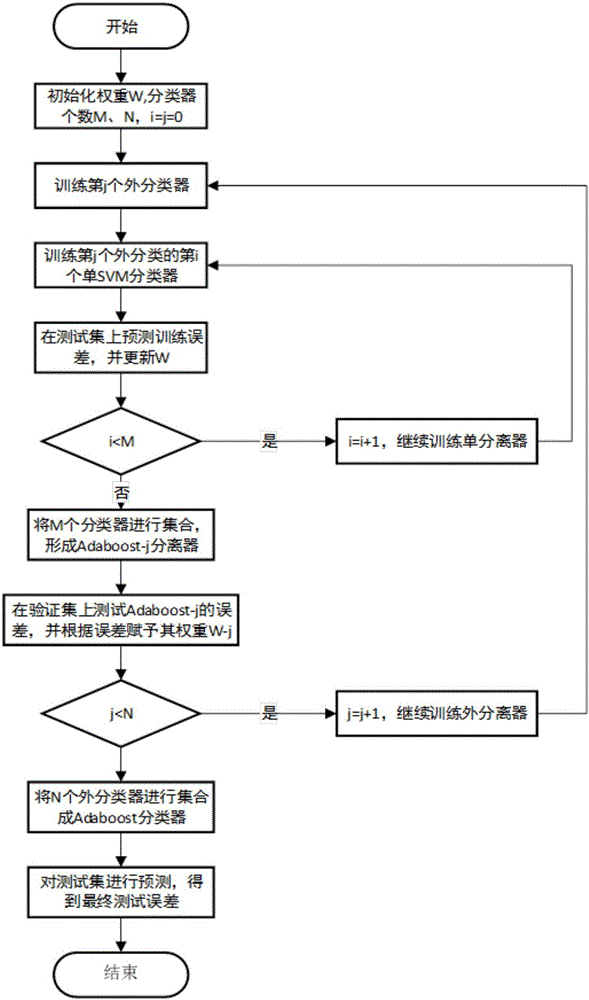
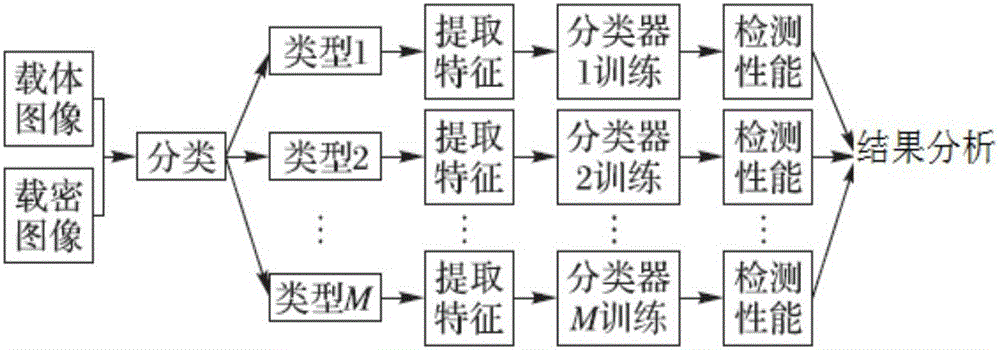
The present invention provides a system and method for image steganalysis, relating to the fields of network transmission, information security, digital image processing, machine learning and the like. The method comprises a step of establishing an original image database, generating a steganographic image database for the image hidden information in the original image database, extracting the characteristics of the original image database and the images in steganographic images, and generating multiple sample spaces, a step of carrying out sample training on the multiple sample spaces, generating multiple classifiers, combining the multiple classifiers to generate a new classifier through a voting mode, and carrying out steganalysis on the image uploaded by the user through the new classifier. According to the system and the method, different steganographic methods can be selected to carry out steganography on the image, the characteristic of an image set is extracted and is converted into vector data, and different characteristic extracting methods can be employed at the same time.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Image steganography method and secret information extraction method
InactiveCN103413269AIncrease embedding capacityControl distortionImage data processing detailsSteganalysisComputer vision
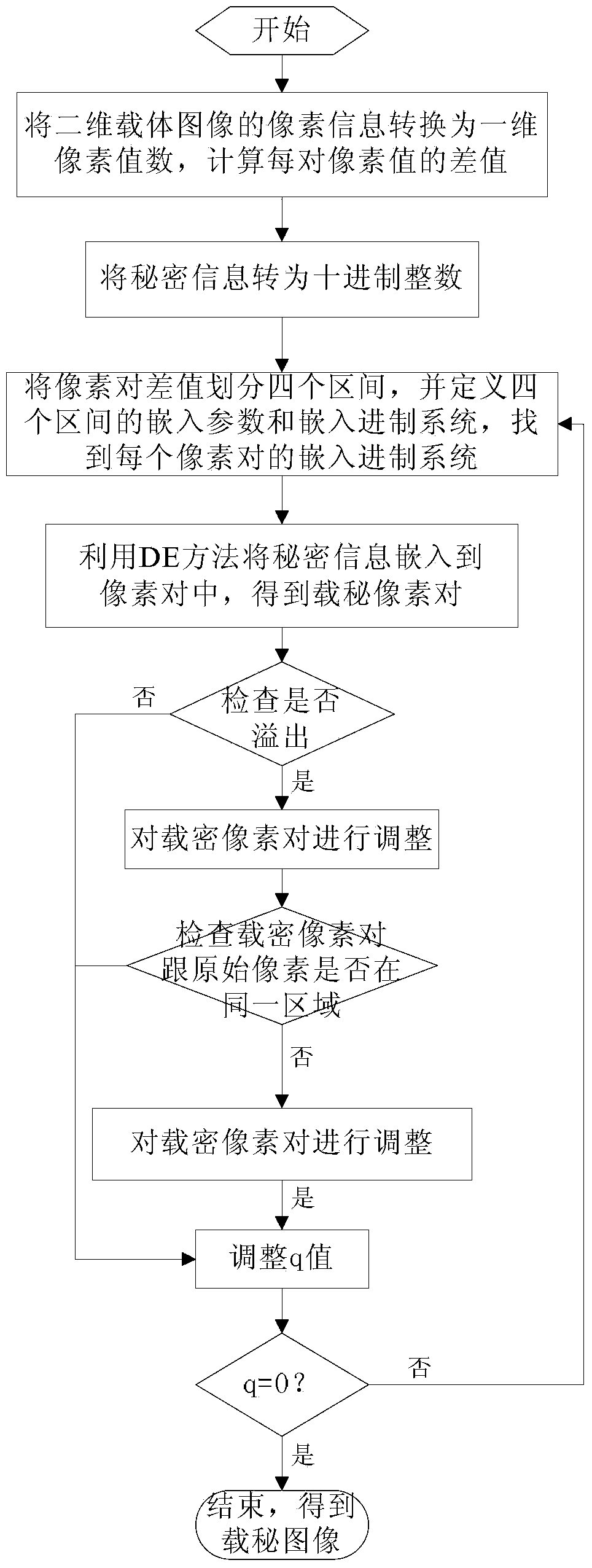
The invention relates to an image steganography method and a secret information extraction method. The image steganography method comprises the steps: (1), converting pixel information of a two-dimensional carrier image I into a set of continuous and non-overlapping one-dimensional pixel value data, and computing a difference value of each pair of pixel values, wherein the size of the two-dimensional carrier image I is N1*N2; (2), performing DES encryption on secret information S, and transferring encrypted secret information S' into a decimal integer q; (3), dividing a di value computed in the step (1) into four sections Tj; (4), obtaining SB(di) according to the equation: SB(di)=qmodB(di), and inserting SB(di) into a pixel pair (xi, yi) through a DE method; (5), detecting whether overflowing occurs or not. Compared with the prior art, the image steganography method has the advantages of being capable of improving insertion capacity of the carrier image remarkably and controlling image distortion effectively. The image steganography method has the steganalysis abilities such as the certain safety performance and resistance to RS attack, and can operate efficiently on mainstream software and hardware platforms of a mobile intelligent terminal.
Owner:NINGBO UNIV
Video steganographic method based on macro block partition mode disturbance
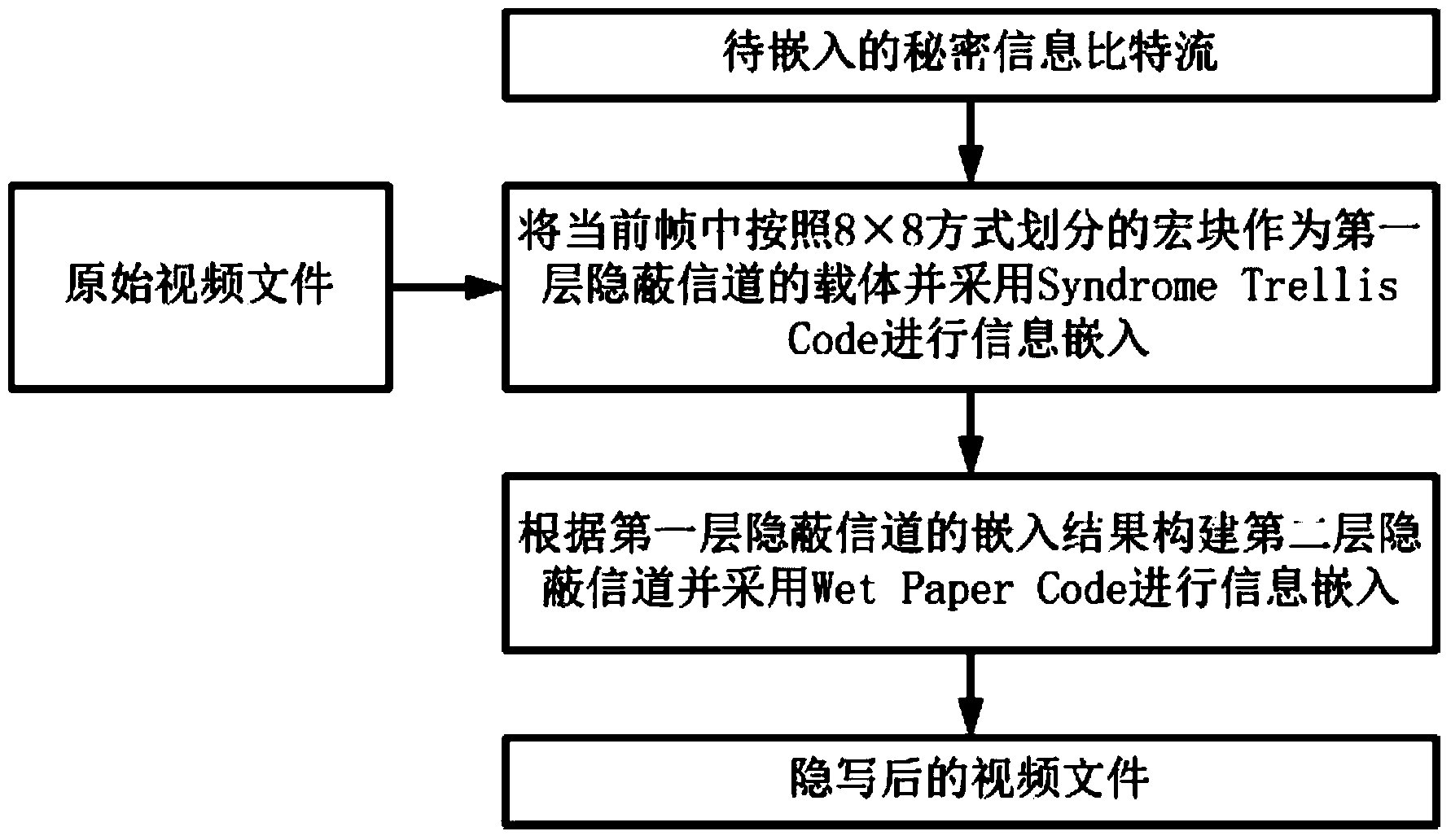
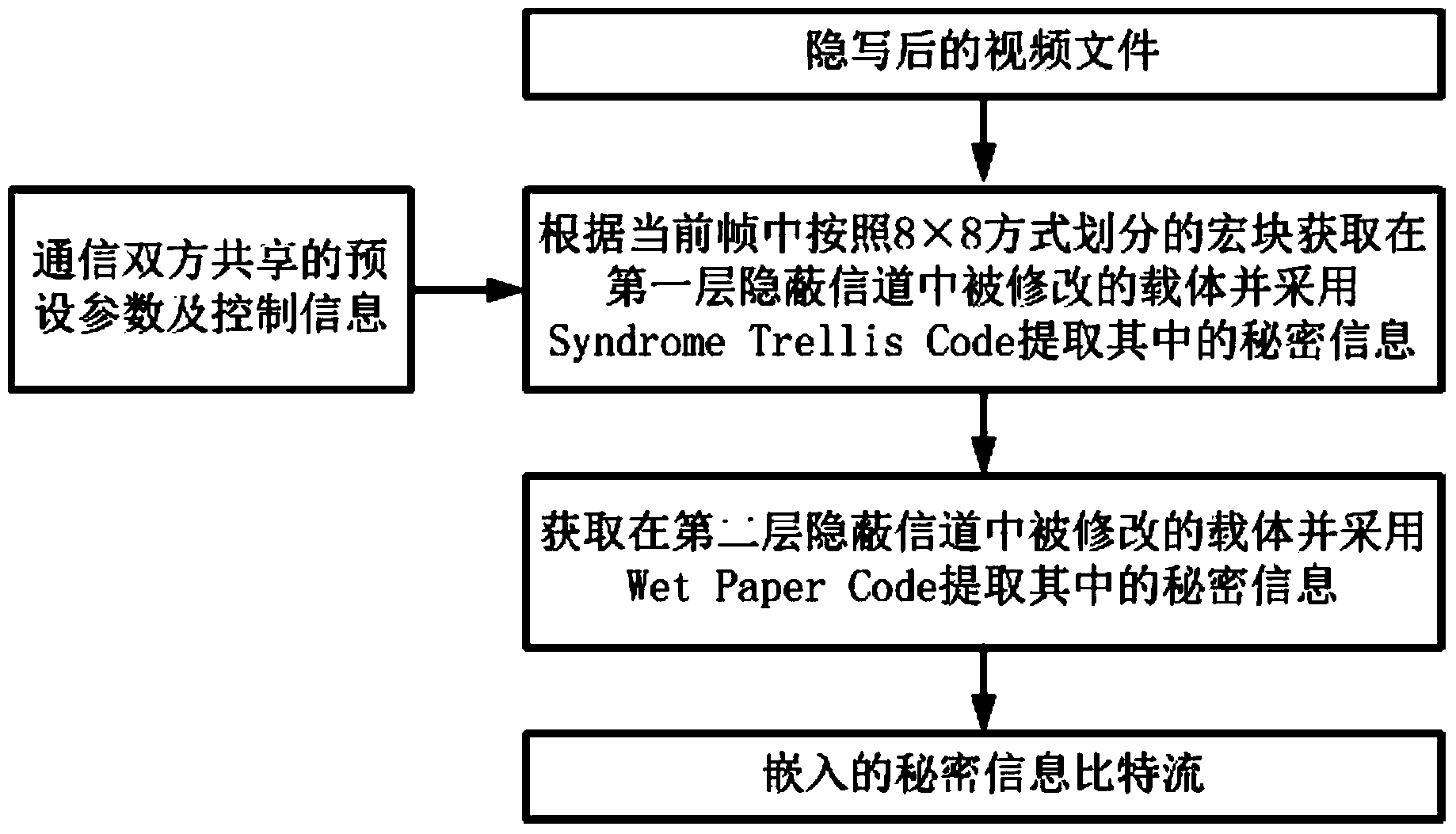
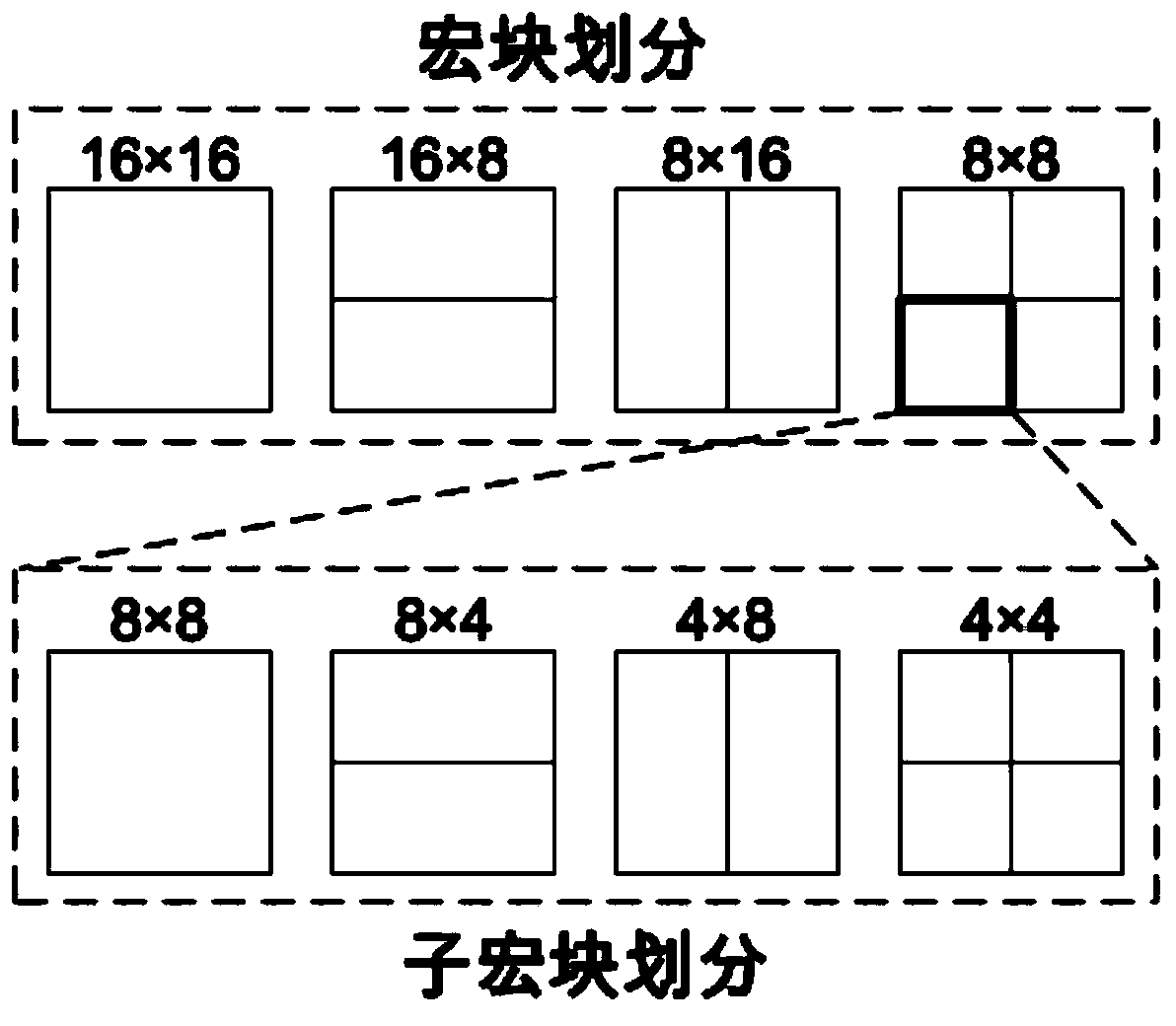
InactiveCN104010193AImprove securityChange load rateDigital video signal modificationSteganalysisAnalysis method
The invention relates to a video steganographic method based on macro block partition mode disturbance. The method includes an embedment process of secrete information and an extraction process of the secrete information. Two hidden channels are built in the embedment process of the secrete information, the secret information is embedded through different steganographic codes, and the secrete information is extracted from the two hidden channels sequentially in the extraction process of the secret information. Preferably, the two hidden channels are built through the steganographic codes including a Syndrome Trellis Code and a Wet Paper Code, and embedment and extraction of the secret information are carried out. Various steganographic codes are used comprehensively to carry out video steganography, high embedment efficiency is achieved, attack of an existing video steganographic analysis method can be resisted effectively, and the video steganographic method is especially suitable for high-safety hidden communication; different macro block division mode disturbance costs can be made according to different application scenes, and high flexibility is achieved.
Owner:INST OF INFORMATION ENG CAS
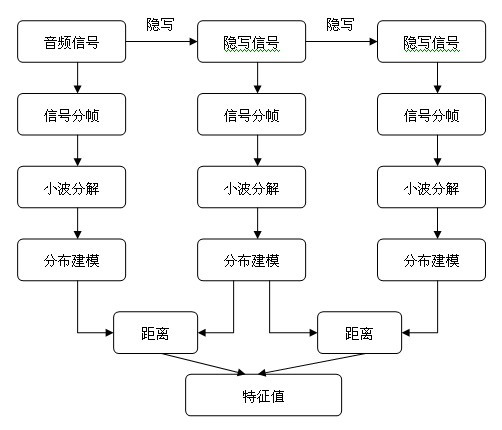
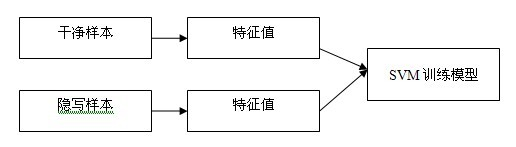
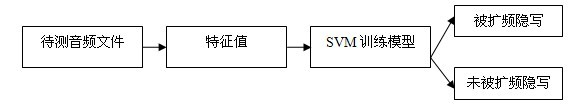
Steganalysis method for audio spread-spectrum steganography
InactiveCN102063907AImprove accuracyReduce false alarm rateSpeech analysisSupport vector machineSteganalysis
The invention relates to the technical field of information hiding detection, particularly a steganalysis method for audio spread-spectrum steganography. The method provided by the invention mainly aims at the statistic difference of signals caused by repeated embedding, and comprises the following steps: introducing a Gaussian hybrid model into a wavelet domain to establish a model for a wavelet sub-band coefficient, and calculating a signal and a first steganographic signal, wherein the statistic distance between the first steganographic signal and a second steganographic signal is used as a characteristic value; and finally, constructing a steganalysis algorithm for a categorizer by using a support vector machine. The method provided by the invention has the advantages of stable performance, high detection accuracy, low false alarm rate, low omission factor and low time complexity, is simple to use, can be applied to the field of hidden information detection, and has an important meaning for preventing illegal hidden communication.
Owner:WUHAN UNIV
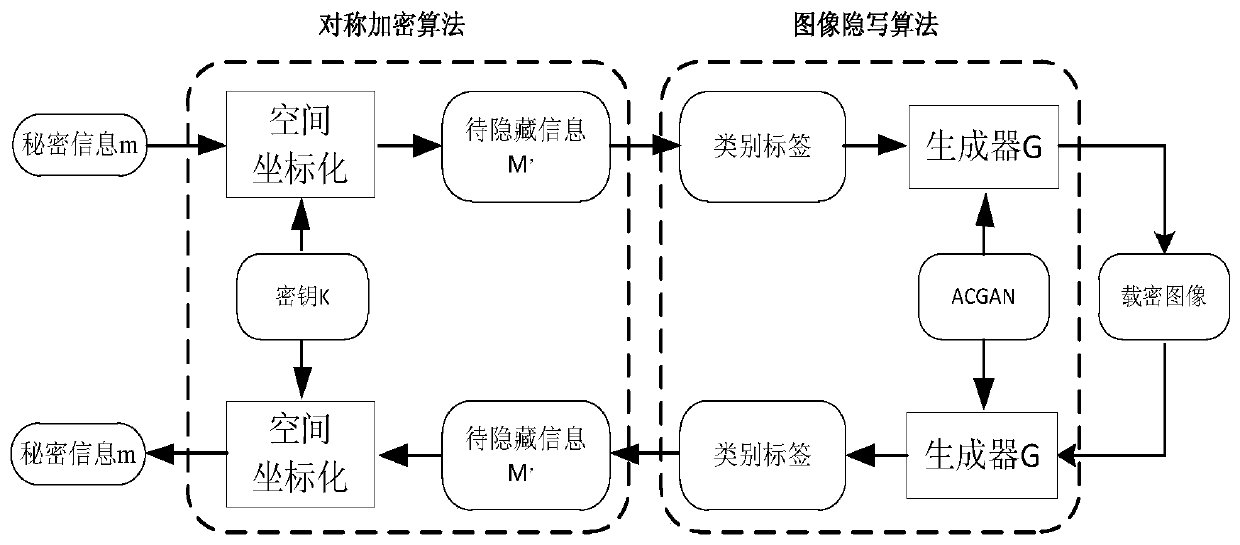
A generative image steganography method based on an adversarial network
ActiveCN109818739AImprove securityEnhanced resistance to steganalysisKey distribution for secure communicationDigital video signal modificationPattern recognitionSteganalysis
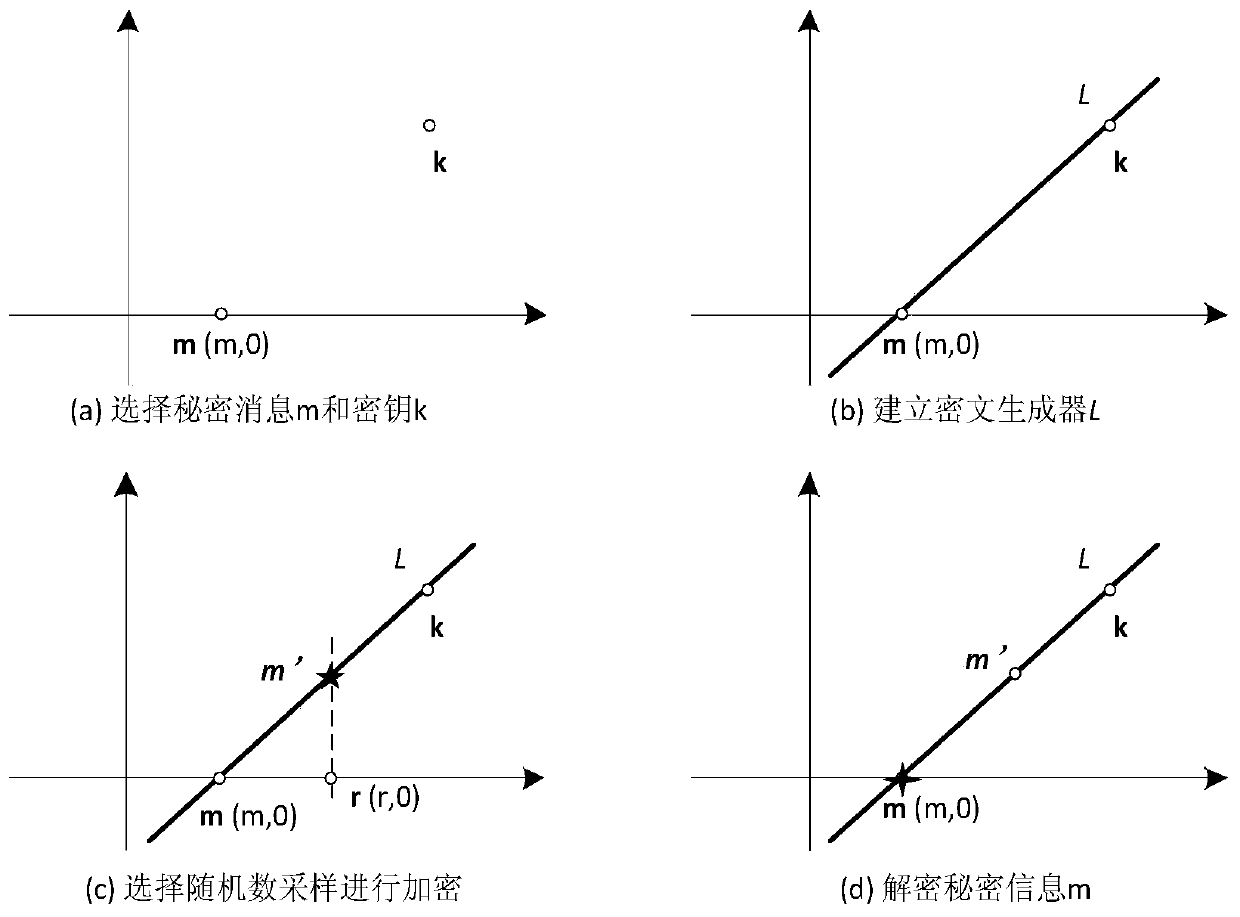
The invention particularly relates to a generative image steganography method based on an adversarial network, which comprises the following steps: a rule table is established, and secret informationto be hidden is converted into coordinate information according to the rule table; According to a two-point one-line principle, a ciphertext generator is established, and ciphertext coordinate point information is obtained; The sender randomly selects the ciphertext coordinate point information, replaces the label information with the ciphertext coordinate point information, inputs the ciphertextcoordinate point information into the generator, and generates a transfer image of a specified category; After receiving the transmission image, the receiver inputs the transmission image into a discriminator to obtain a category label, and then ciphertext information can be extracted; Decrypting is performed to obtain hidden coordinate information according to a two-point one-line principle; Andhidden secret information is obtained by comparing with the rule table, and information extraction is realized. According to the method, steganalysis detection based on statistics can be fundamentallyresisted, the safety of information transmission is improved, and meanwhile the steganalysis resisting capability is greatly enhanced.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
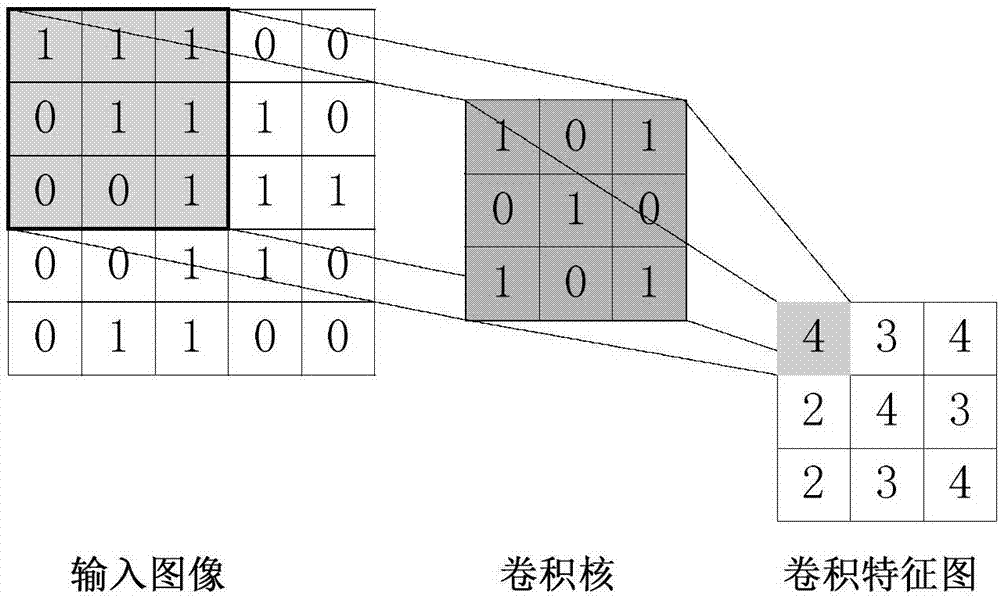
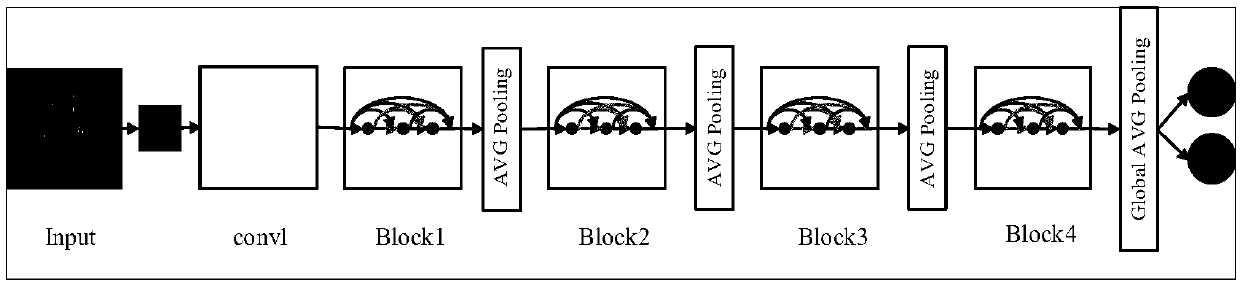
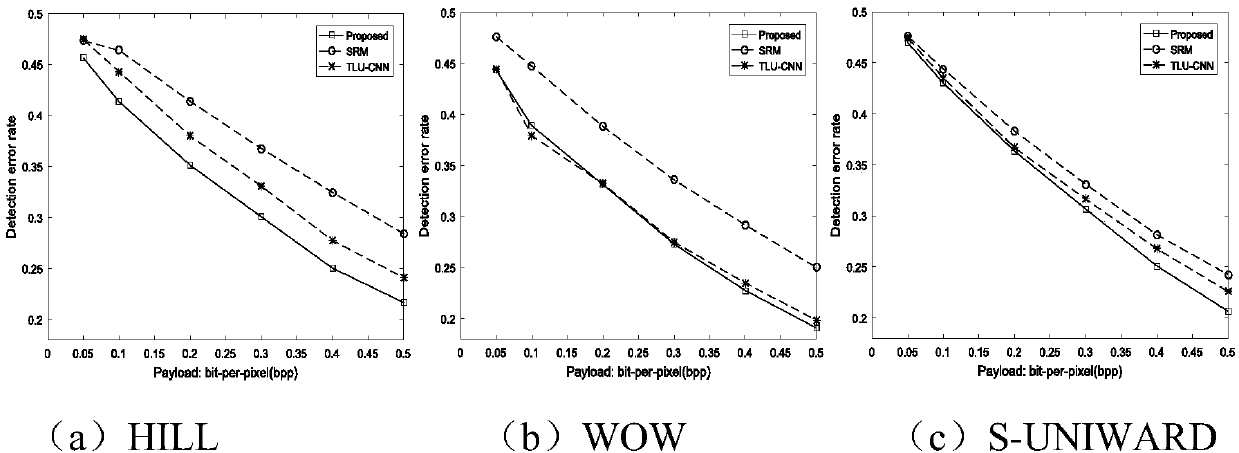
Convolutional neural network-based digital image steganalysis method
InactiveCN107330845AImprove performanceImprove accuracyImage data processing detailsNeural architecturesSteganalysisActivation function
The present invention designs a convolutional neural network-based digital image steganalysis method. The convolutional neural network-based digital image steganalysis method comprises the following steps of S1 constructing a convolutional neural network formed by connecting multiple convolutional layers in series; S2 for the first convolutional layer, adopting a high-pass filter to initialize a convolution kernel, and then adopting a truncation linear unit activation function as the activation function of the convolutional layer; S3 inputting a digital image in the convolutional neural network, and using the convolutional neural network to output a result of the digital image whether or not after the steganography.
Owner:SUN YAT SEN UNIV
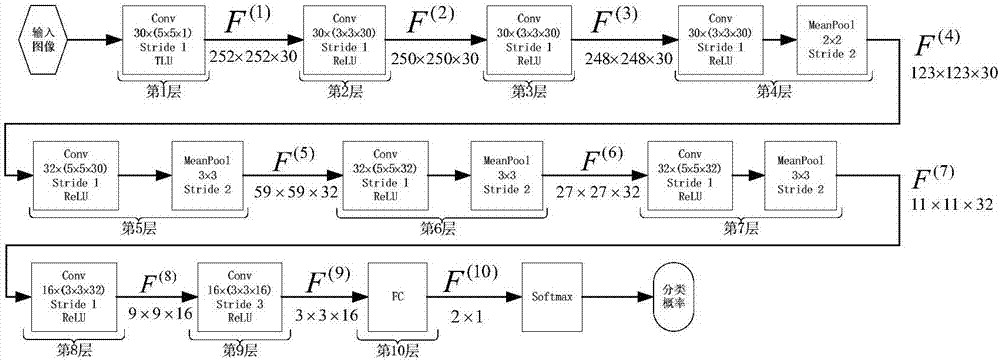
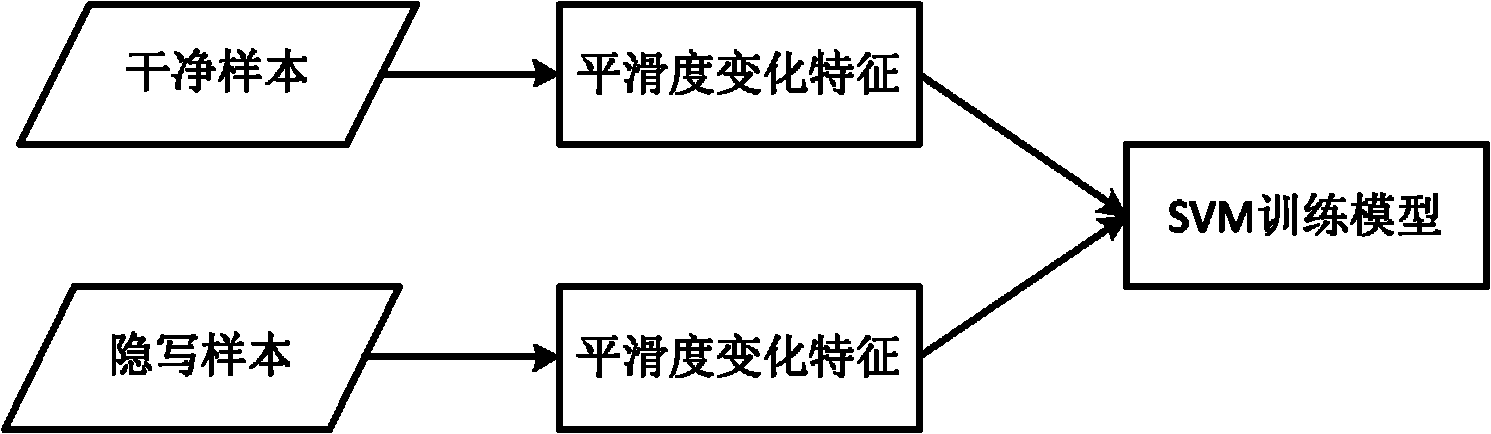
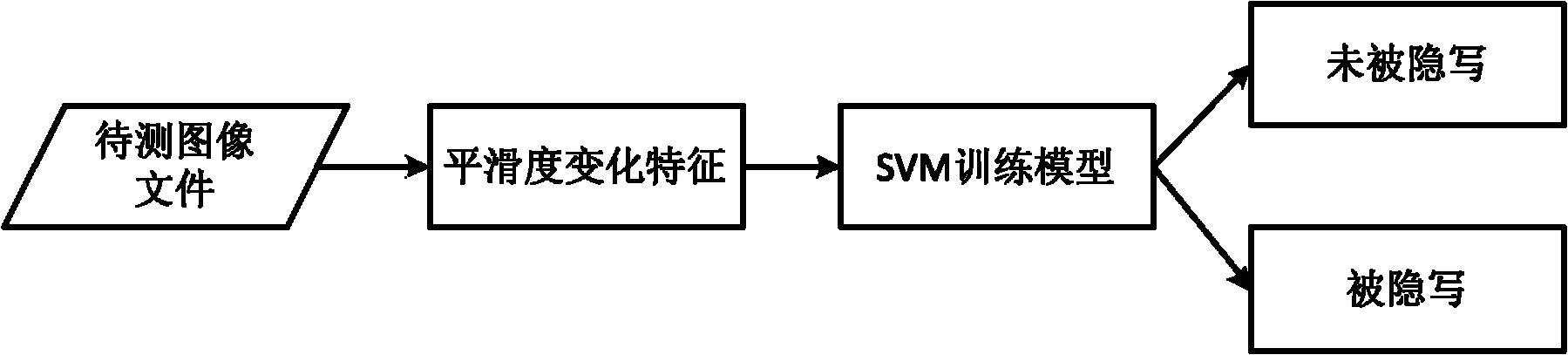
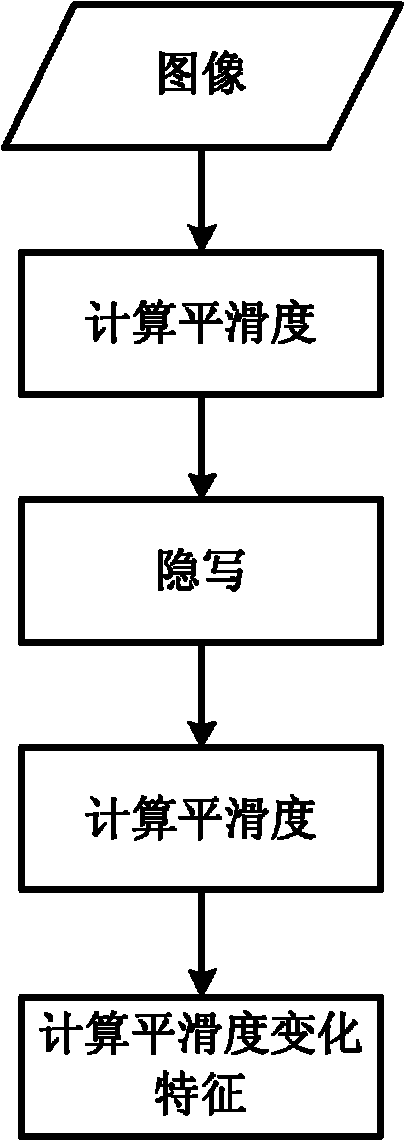
Steganalysis method based on image smoothness variation characteristics
InactiveCN102147913AAdaptableImprove accuracyImage data processing detailsSteganalysisFeature extraction
The invention discloses a steganalysis method based on image smoothness variation characteristics, which comprises a process for extracting image smoothness and a process for extracting image smoothness variation characteristics, wherein the process for extracting the image smoothness comprises a segment covering step and a smoothness calculating step; the segment covering step comprises: covering the segment in a zero-degree direction, covering the segment in a 45-degree direction, covering the segment in a 90-degree direction and covering the segment in a 135-degree direction, selecting parameters after the segments are covered and calculating the image smoothness; the process for extracting the image smoothness variation characteristics comprises the following four steps: calculating the image smoothness characteristics before writing hidden information, writing hidden information by using the steganography to be analyzed, calculating the image smoothness characteristics after writing hidden information and calculating the smoothness variation characteristics. In the method, the hidden information writing of a grey image based on least significant bit (LSB) and histogram modification can be analyzed and the accuracy of the method is high for the two steganographies.
Owner:BEIHANG UNIV
System and method for steganalysis
ActiveUS20060257018A1Character and pattern recognitionImage watermarkingSteganalysisComputer science
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
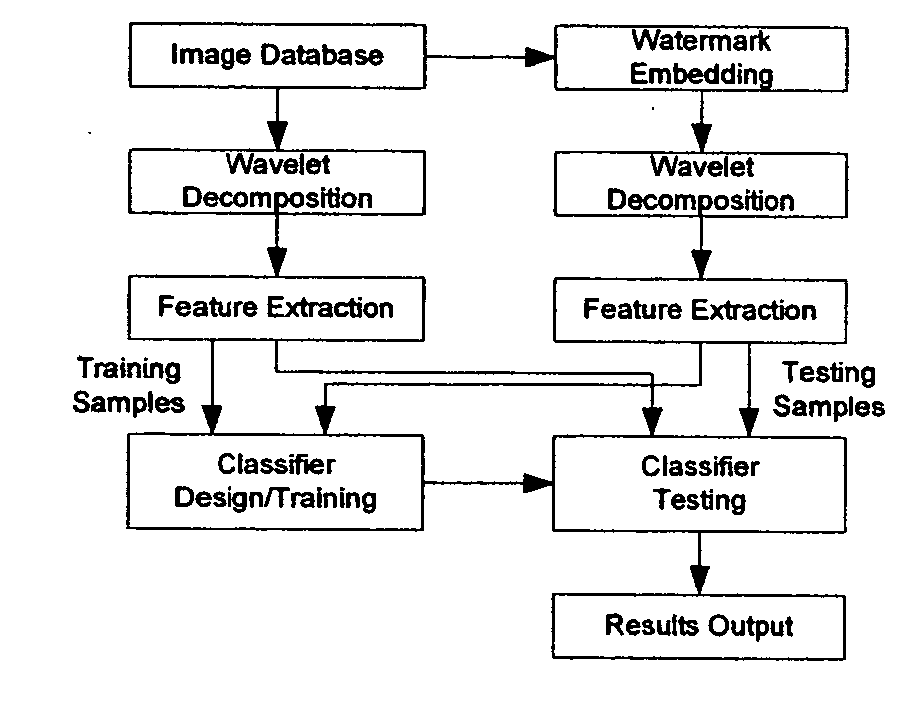
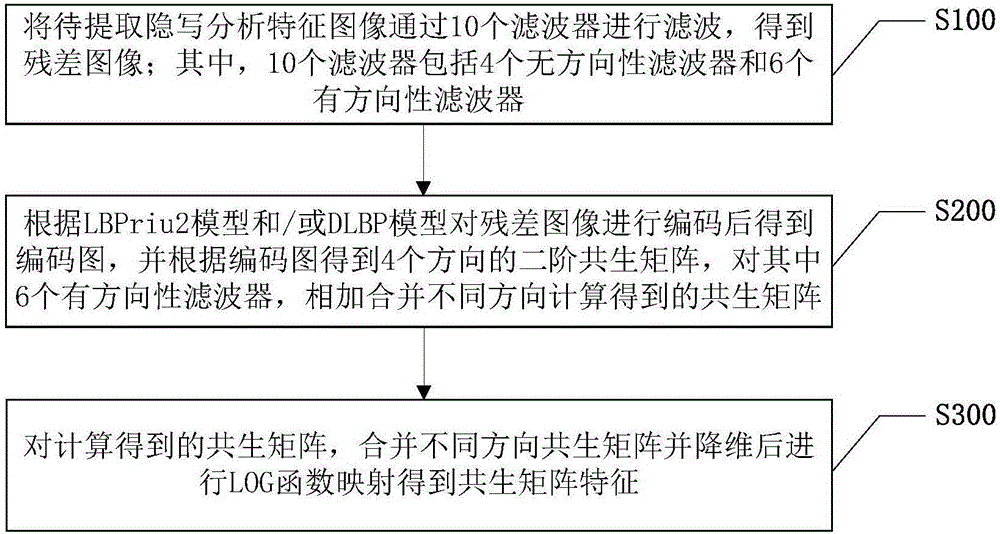
Feature extraction method and extraction system for digital image steganalysis
The invention discloses a feature extraction method and extraction system for digital image steganalysis. The method comprises the steps of filtering a steganalysis feature image to be extracted by ten filters to obtain residual images, the ten filters including four non-directional filters and six directional filters; encoding the residual images according to an LBPriu2 model and / or a DLBP model to obtain coding graphs, obtaining second-order co-occurrence matrices in four different directions according to the coding graphs, and for the six directional filters, adding the co-occurrence matrices calculated in different directions; for the calculated co-occurrence matrices, combining the co-occurrence matrices in different directions and decreasing the dimensions of the co-occurrence matrices, and then performing LOG function mapping to obtain co-occurrence matrix features. According to the invention, similar performance to the existing mainstream general steganalysis method SRM is gained, and the classification effect has higher accuracy than that of the SRM.
Owner:SHENZHEN UNIV
Lossless embedding of data in digital objects
InactiveUS20070071280A1Simple and elegant lossless techniqueHeavy loadUser identity/authority verificationCharacter and pattern recognitionSteganalysisHidden data
Current methods of embedding hidden data in an image inevitably distort the original image by noise. This distortion cannot generally be removed completely because of quantization, bit-replacement, or truncation at the grayscales 0 and 255. The distortion, though often small, may make the original image unacceptable for medical applications, or for military and law enforcement applications where an image must be inspected under unusual viewing conditions (e.g., after filtering or extreme zoom). The present invention provides high-capacity embedding of data that is lossless (or distortion-free) because, after embedded information is extracted from a cover image, we revert to an exact copy of the original image before the embedding took place. This new technique is a powerful tool for a variety of tasks, including lossless robust watermarking, lossless authentication with fragile watermarks, and steganalysis. The technique is applicable to raw, uncompressed formats (e.g., BMP, PCX, PGM, RAS, etc.), lossy image formats (JPEG, JPEG2000, wavelet), and palette formats (GIF, PNG).
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
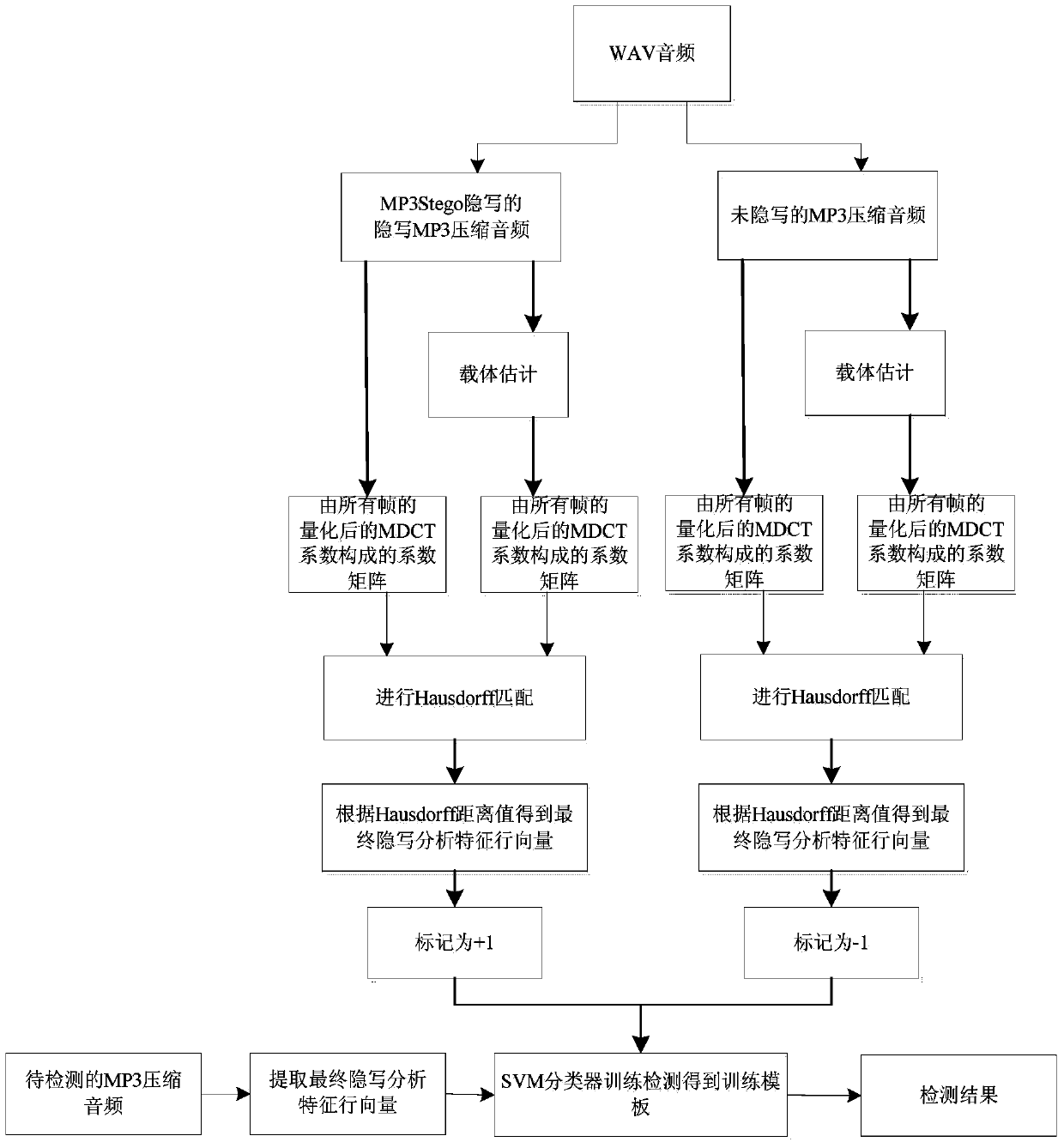
Steganography detection method for audio subjected to MP3Stego steganography
ActiveCN104282310AEliminate distractionsImprove detection efficiencySpeech analysisSteganalysisDouble compression
The invention discloses a steganography detection method for audio subjected to MP3Stego steganography. The method includes the steps of forming a sample library through MP3 compressed audio not subjected to steganography and MP3 compressed audio subjected to steganography, conducting double-compression coding on each sample to obtain carrier estimation of each sample, extracting a quantized MDCT coefficient of each frame in each sample to obtain a first coefficient matrix corresponding to the sample, extracting a quantized MDCT coefficient of each frame in the carrier estimation of each sample to obtain a second coefficient matrix corresponding to the carrier estimation, calculating a Hausdorff distance value between corresponding lines in each first coefficient matrix and the corresponding coefficient matrix to obtain the final steganography analysis characteristic line vector of each sample, obtaining a training template through SVM classifier training, and detecting the MP3 compressed audio to be detected through the training template. The method has the advantages that whether the MP3 compressed audio is subjected to MP3Stego steganography or not can be quite accurately determined, and particularly, the quite high detection efficiency can still be obtained under the condition that the steganography information embedment rate is low.
Owner:NINGBO UNIV
Steganalysis method based on adversarial net
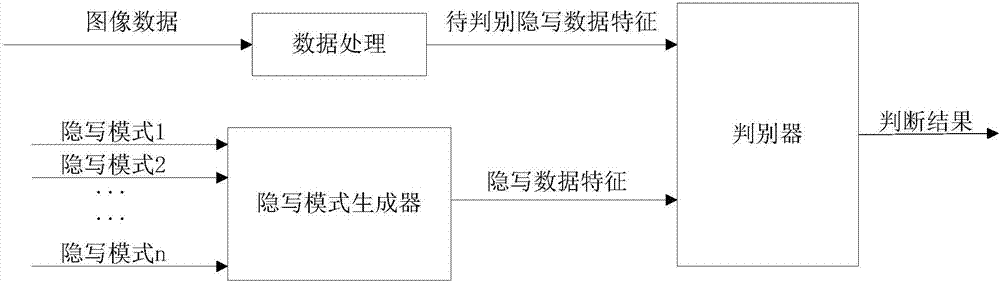
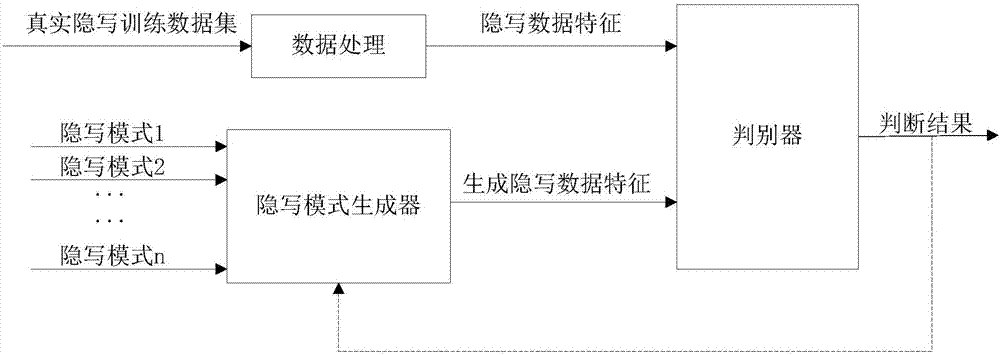
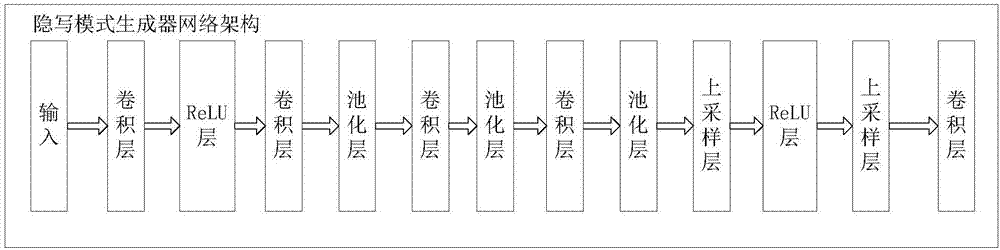
ActiveCN106920206AHigh precisionImprove universalityImage data processing detailsSteganalysisData treatment
The invention relates to a steganalysis method based on adversarial net. The method includes the following steps: A1. processing data in image data that is uploaded by a user, extracting to-be-determined steganalysis characteristics; A2. using a steganalysis mode generator of the adversarial net that is trained in advance to generate steganalysis data characteristics; A3. inputting the to-be-determined steganalysis characteristics and the generated steganalysis data characteristics to a determining machine of the adversarial net which is trained in advance, and comparing characteristics, on the basis of similarity from the comparison, identifying the type of the steganalysis mode of the image data that is uploaded. According to the invention, the method combines the adversarial net and the steganalysis, applies expandability, trainability, robustness and non-linear mapping capability of the adversarial net, and increases the precision and universality of steganalysis.
Owner:GUANGZHOU UNIVERSITY
A robust general steganalysis method for image content awareness
InactiveCN106228505AImprove processing efficiencyImprove judgment accuracyImage watermarkingSteganalysisPattern recognition
The invention aims to provide a robust general steganalysis method for image content awareness. The method of the invention can better utilize the advantage of the CS technology to process digital images, and further improve the data processing efficiency and the classification judgment precision of the steganalysis. The method comprises the following steps: (1) setting the size N, a block size B and a measured value M of a digital image X; (2) determining a 9 / 7-Haar DWT sparse matrix Psi; (3) determining a Hadamard measurement matrix PhiB of the BCS; (4) dividing a digital image into B*B blocks and calculating a measurement vector yi and the measurement data Y of the entire image X; calculating the measurement vector yi of the i-th image block and the measurement data Y of the entire image X according to the Hadamard measurement matrix PhiB ; and (5) dividing the image into a smooth part and a non-smooth part as a perceived result; (6) a training process; 7) a classification process; 8) a judgment and analysis process; and 9) repeating iterative search until the entire image data is detected.
Owner:GUANGDONG POLYTECHNIC NORMAL UNIV
Blind steganalysis method based on symmetric neighborhood information
The invention discloses a digital image steganalysis method based on airspace characteristics. The digital image steganalysis method comprises the following steps of: calculating pixel grey scale differential value information of a digital image (with marked class information) in a training set in a symmetric neighborhood in multiple directions; carrying out processing and rotational invariance encoding on the pixel grey scale differential value information; calculating a histogram of encoded information, and normalizing the histogram to be taken as a characteristic; carrying out training and classifying on the extracted characteristic to obtain a classifier model; calculating the neighborhood information of randomly inputted digital images to extract characteristics; and inputting the extracted characteristics into the classifier model to obtain class information of the inputted images. The digital image steganalysis method disclosed by the invention has the characteristic of no needing of analyzing specific steganography, and is a universal method so as to be capable of being widely applied to universal (blind) steganalysis of the digital images.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Digital steganography and steganalysis method for color image
InactiveCN103745479AImprove search matching speedGuaranteed Unique AuthenticationImage analysisColor imageSteganalysis
The invention relates to the technical field of information hiding and detection. A digital steganography and steganalysis method for a color image is characterized in that a secret information embedding step comprises the following small steps: generating a general image data buffer and data steganography factors; performing a series of function transformations on the color image and the data steganography factors to generate a steganography data-contained color image. A secret information extracting step comprises the following small steps: generating the general image data buffer, and performing a series of function transformations on the steganography data-contained color image to read out steganography data. According to the digital steganography and steganalysis method for the color image disclosed by the invention, by solidifying the steganography data, the steganography speed is increased, and the data steganography CPU (central processing unit) time and the steganography data reading CPU time are shortened. The digital steganography and steganalysis method for the color image supports various color image formats. By adopting the thread pool technique, the data steganography concurrence number is improved, and the robustness of data of preventing steganography attack is enhanced.
Owner:FUJIAN ZHONGGENG SHITONG INFORMATION TECH CO LTD
Steganalysis with neighboring joint density
Owner:SAM HOUSTON STATE UNIVERSITY
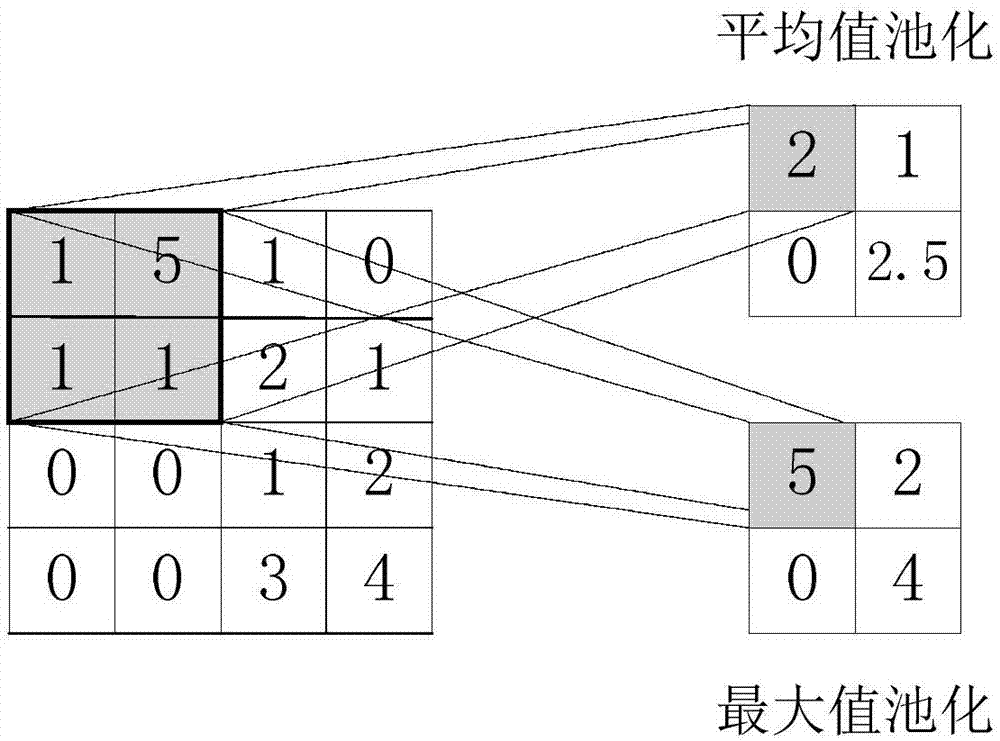
Airspace image steganalysis method based on full dense connection network
ActiveCN108717680AIncrease diversityExtensive Image Feature ReuseImage data processing detailsNeural architecturesFeature vectorSteganalysis
The invention provides an airspace image steganalysis method based on a full dense connection network. The method comprises the following steps of building the full dense connection network includinga plurality of dense connection blocks, wherein each dense connection block comprises a plurality of groups of convolution layers and one average pooling layer, the adjacent dense connection blocks are connected, and the network width of the dense connection blocks are increased in a way of being the multiples of 2 in a sequence from lower layers to high layers; obtaining an original feature graphof the airspace image to be recognized through convolution operation; inputting the original feature graph into the full dense connection network; performing multilayer convolution and pooling operation on the original feature graph to obtain a multi-dimensional feature vector; performing dimension reduction on the multi-dimensional feature vector into a two-dimensional feature vector through thefull connection layer; and inputting the two-dimensional feature vector into a softmax activation function to obtain a prediction probability value for predicting whether the airspace image is a steganalysis image or an ordinary image. The airspace image steganalysis method can accelerate the wider image feature reuse; the signal propagation of steganalysis weak signals in the network is reinforced; and the steganalysis analysis detection performance is improved.
Owner:BEIJING JIAOTONG UNIV
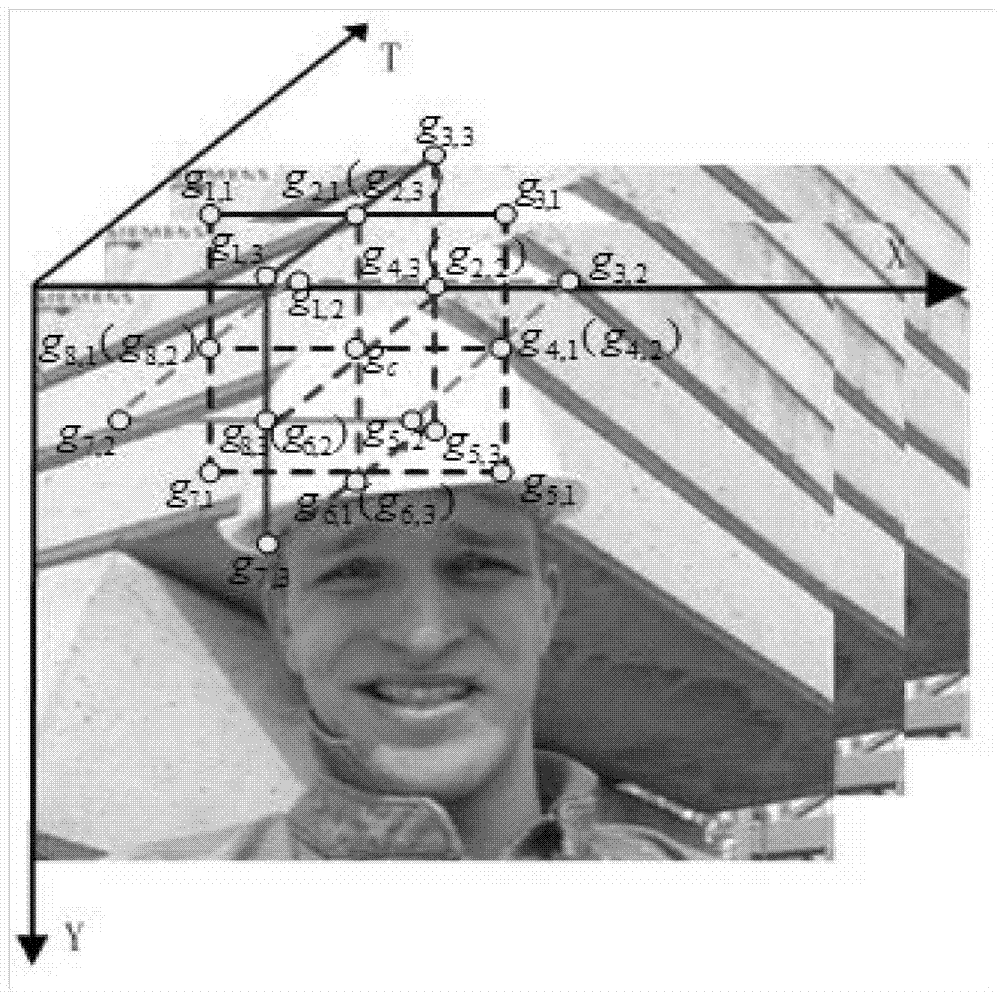
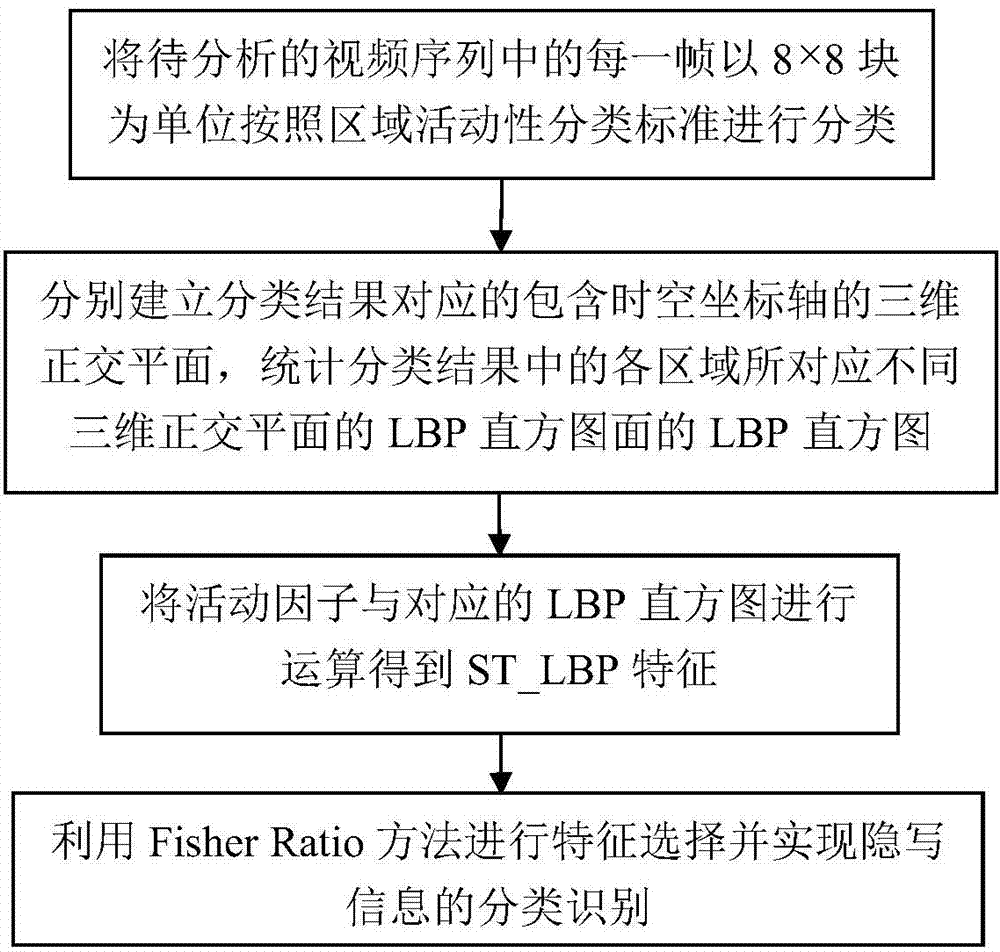
Video steganography analysis method based on space-time domain local binary pattern
InactiveCN104519361AReduce distractionsImprove detection effectivenessCharacter and pattern recognitionDigital video signal modificationFeature DimensionLiveness
The invention discloses a video steganography analysis method based on a space-time domain local binary pattern. The video steganography analysis method includes step 1, classifying each frame in a video sequence to be analyzed by taking 8x8 blocks as a unit according to regional activity classifying standards; step 2, respectively establishing three-dimensional orthogonal planes, containing time-space coordinate axis, corresponding to classifying result, and making statistic analysis on LBP histograms of different three-dimensional orthogonal planes corresponding to each area in the classifying result; step 3, introducing a concept of activity factor, and enabling the activity factor and the corresponding LBP histograms to be in operation to acquire ST_LBP features; step 4, utilizing a Fisher Ratio method for feature selection, and realizing classifying recognition of steganographic information. Compared with the prior art, the video steganography analysis method has the advantages that by introducing the activity factor, interference, on detection result, caused by movement of an activity area object can be lowered, so that detection effectiveness is improved effectively; limitation of feature dimension is avoided, and valuing of radius R and field point number P in an LBP definition can be further expanded, so that relevance of space-time domain of the video sequence is utilized more effectively.
Owner:TIANJIN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com